Page 1

HP Data Protector A.06.10
Concepts guide
B6960-96035
Part number: B6960-96035
First edition: November 2008
Page 2

Legal and notice information
© Copyright 1999, 2008 Hewlett-Packard Development Company, L.P.
Confidential computer software. Valid license from HP required for possession, use or copying. Consistent
with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and
Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard
commercial license.
The information contained herein is subject to change without notice. The only warranties for HP products
and services are set forth in the express warranty statements accompanying such products and services.
Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for
technical or editorial errors or omissions contained herein.
Intel, Itanium, Pentium, Intel Inside, and the Intel Inside logo are trademarks or registered trademarks of
Intel Corporation or its subsidiaries in the United States and other countries.
Microsoft, Windows, Windows XP, and Windows NT are U.S. registered trademarks of Microsoft
Corporation.
Adobe and Acrobat are trademarks of Adobe Systems Incorporated.
Java is a US trademark of Sun Microsystems, Inc.
Oracle is a registered US trademark of Oracle Corporation, Redwood City, California.
UNIX is a registered trademark of The Open Group.
Printed in the US
Page 3

Contents
Publication history .............................................................. 21
About this guide ................................................................. 23
Intended audience ............................................................................................. 23
Documentation set ............................................................................................. 23
Guides ...................................................................................................... 23
Online Help ............................................................................................... 26
Documentation map .................................................................................... 27
Abbreviations ...................................................................................... 27
Map ................................................................................................... 28
Integrations ......................................................................................... 29
Document conventions and symbols ..................................................................... 31
Data Protector graphical user interface ................................................................. 32
General information .......................................................................................... 33
HP technical support .......................................................................................... 33
Subscription service ........................................................................................... 34
HP websites ...................................................................................................... 34
Documentation feedback .................................................................................... 34
1 About backup and Data Protector ...................................... 35
In this chapter ................................................................................................... 35
About Data Protector ......................................................................................... 35
Introducing backups and restores ......................................................................... 38
What is a backup? ..................................................................................... 38
What is a restore? ...................................................................................... 39
Backing up a network environment ................................................................ 39
Direct backup ............................................................................................. 40
Data Protector architecture .................................................................................. 40
Operations in the cell .................................................................................. 42
Backup sessions .......................................................................................... 43
Restore sessions ......................................................................................... 44
Enterprise environments ...................................................................................... 45
Splitting an environment into multiple cells ...................................................... 45
Concepts guide 3
Page 4

Media management .......................................................................................... 48
Backup devices ................................................................................................. 49
User interfaces .................................................................................................. 50
Data Protector GUI ...................................................................................... 50
Data Protector Java GUI ........................................................................ 52
Overview of tasks to set up Data Protector ............................................................ 55
2 Planning your backup strategy .......................................... 57
In this chapter ................................................................................................... 57
Backup strategy planning ................................................................................... 58
Defining the requirements of a backup strategy ............................................... 58
Factors influencing your backup strategy ........................................................ 60
Preparing a backup strategy plan ................................................................. 60
Planning cells .................................................................................................... 62
One cell or multiple cells? ............................................................................ 62
Installing and maintaining client systems ........................................................ 64
Creating cells in the UNIX environment .......................................................... 64
Creating cells in the Windows environment .................................................... 65
Windows domains ............................................................................... 65
Windows workgroups ........................................................................... 66
Creating cells in a mixed environment ........................................................... 66
Geographically remote cells ......................................................................... 66
Understanding and planning performance ............................................................ 67
The infrastructure ......................................................................................... 67
Network versus local backups ................................................................ 67
Network or server versus direct backups .................................................. 68
Devices ............................................................................................... 68
High performance hardware other than devices ........................................ 69
Advanced high performance configuration .............................................. 69
Using hardware in parallel .................................................................... 69
Configuring backups and restores ................................................................. 70
Software compression ........................................................................... 70
Hardware compression ......................................................................... 70
Full and incremental backups ................................................................. 71
Disk image versus filesystem backups ...................................................... 71
Object distribution to media ................................................................... 71
Disk performance ........................................................................................ 72
SAN performance ....................................................................................... 73
Online database application performance ..................................................... 73
Planning security ............................................................................................... 73
Cells ......................................................................................................... 74
Data Protector users accounts ....................................................................... 74
4
Page 5

Data Protector user groups ........................................................................... 75
Data Protector user rights ............................................................................. 75
Visibility of backed up data .......................................................................... 76
Data encryption .......................................................................................... 76
How Data Protector AES 256-bit encryption works ................................... 76
How Data Protector drive-based encryption works ..................................... 77
Restore from encrypted backups ............................................................. 78
What is backup ownership? ......................................................................... 78
Clustering ......................................................................................................... 79
Cluster concepts ......................................................................................... 79
Cluster support ........................................................................................... 82
Example cluster environments ....................................................................... 83
Cell Manager installed outside a cluster .................................................. 83
Cell Manager installed outside a cluster, devices connected to the cluster
nodes ................................................................................................. 85
Cell Manager installed in a cluster, devices connected to the cluster
nodes ................................................................................................. 87
Full and incremental backups .............................................................................. 91
Full backups ............................................................................................... 92
Synthetic backup .................................................................................. 92
Incremental backups .................................................................................... 92
Conventional incremental backup ........................................................... 93
Enhanced incremental backup ................................................................ 93
Types of incremental backups ................................................................. 93
Considering restore ..................................................................................... 96
Keeping backed up data and information about the data ....................................... 99
Data protection ........................................................................................... 99
Catalog protection .................................................................................... 100
Logging level ........................................................................................... 100
Browsing files for restore ............................................................................ 100
Enabling the browsing of files and quick restore ..................................... 101
Enabling the restore of files, but not browsing ......................................... 101
Overwriting backed up files with new data ............................................ 101
Exporting media from a cell ................................................................. 102
Backing up data ............................................................................................. 102
Creating a backup specification .................................................................. 103
Selecting backup objects .......................................................................... 103
Backup sessions ........................................................................................ 105
Object mirrors .......................................................................................... 105
Media sets ............................................................................................... 105
Backup types and scheduled backups .......................................................... 105
Scheduling, backup configurations, and sessions ........................................... 106
Scheduling tips and tricks ........................................................................... 106
Concepts guide 5
Page 6

When to schedule backups .................................................................. 107
Staggering full backups ....................................................................... 107
Optimizing for restore ......................................................................... 107
Automated or unattended operation ................................................................... 110
Considerations for unattended backups ....................................................... 110
Duplicating backed up data ............................................................................. 112
Copying objects ....................................................................................... 113
Why use object copy? ........................................................................ 116
Object mirroring ....................................................................................... 119
Copying media ........................................................................................ 122
Automated media copying ................................................................... 124
Smart media copying using VLS ........................................................... 124
Restoring data ................................................................................................ 125
Restore duration ........................................................................................ 125
Selection of the media set .......................................................................... 126
Selection of devices ................................................................................... 126
Operators are allowed to restore ................................................................ 127
End users are allowed to restore ................................................................. 128
Disaster recovery ............................................................................................. 128
Disaster recovery methods .......................................................................... 130
Alternative disaster recovery methods .................................................... 131
3 Media management and devices .................................... 133
In this chapter ................................................................................................. 133
Media management ........................................................................................ 133
Media life cycle .............................................................................................. 134
Media pools ................................................................................................... 135
Free pools ................................................................................................ 137
Media pool usage examples ...................................................................... 140
Implementing a media rotation policy .......................................................... 143
Media rotation and Data Protector ........................................................ 144
Media needed for rotation ................................................................... 144
Media management before backups begin ......................................................... 145
Initializing or formatting media ................................................................... 145
Labeling Data Protector media .................................................................... 145
Location field ............................................................................................ 146
Media management during backup sessions ....................................................... 147
Selecting media for backups ...................................................................... 147
Adding data to media during backup sessions .............................................. 148
Writing data to several media sets during backup ......................................... 150
Calculating media condition ....................................................................... 150
Media management after backup sessions .......................................................... 151
6
Page 7

Vaulting ................................................................................................... 151
Restoring from media in a vault ................................................................... 153
Devices .......................................................................................................... 153
Device lists and load balancing .................................................................. 155
How load balancing works .................................................................. 156
Device streaming and concurrency .............................................................. 156
Segment size ............................................................................................ 157
Block size ................................................................................................ 158
Number of disk agent buffers ..................................................................... 159
Device locking and lock names ................................................................... 159
Standalone devices .......................................................................................... 160
Small magazine devices ................................................................................... 161
Large libraries ................................................................................................. 162
Handling of media .................................................................................... 162
Size of a library ........................................................................................ 162
Sharing a library with other applications ..................................................... 163
Enter / eject mail slots ............................................................................... 163
Barcode support ....................................................................................... 163
Cleaning tape support ............................................................................... 164
Sharing a library with multiple systems ........................................................ 164
Data Protector and Storage Area Networks ......................................................... 170
Storage Area Networks ............................................................................. 171
Fibre Channel .......................................................................................... 172
Point-to-point topology ......................................................................... 173
Loop topology .................................................................................... 173
Switched topology .............................................................................. 174
Device sharing in SAN .............................................................................. 175
Configuring multiple paths to physical devices ........................................ 175
Device locking ................................................................................... 177
Indirect and Direct Library Access ............................................................... 178
Indirect Library Access ........................................................................ 178
Direct Library Access .......................................................................... 179
Device sharing in clusters ........................................................................... 180
Static drives ....................................................................................... 180
Floating drives ................................................................................... 181
4 Users and user groups ................................................... 183
In this chapter ................................................................................................. 183
Increased security for Data Protector users .......................................................... 183
Access to backed up data .......................................................................... 183
Users and user groups ..................................................................................... 184
Using predefined user groups ..................................................................... 185
Concepts guide 7
Page 8

Data Protector user rights ........................................................................... 185
5 The Data Protector internal database ............................... 187
In this chapter ................................................................................................. 187
About the IDB ................................................................................................. 187
The IDB on the Windows Cell Manager ....................................................... 188
The IDB on the UNIX Cell Manager ............................................................. 189
The IDB in the Manager-of-Managers environment ......................................... 189
IDB architecture ............................................................................................... 189
Media Management Database (MMDB) ...................................................... 190
Catalog Database (CDB) ........................................................................... 191
Detail Catalog Binary Files (DCBF) .............................................................. 192
Session Messages Binary Files (SMBF) ......................................................... 193
Serverless Integrations Binary Files (SIBF) ...................................................... 194
IDB operation ................................................................................................. 194
During backup .......................................................................................... 194
During restore ........................................................................................... 195
During object copying or object consolidation .............................................. 195
Exporting media ....................................................................................... 195
Removing the detail catalog ...................................................................... 196
Filenames purge ....................................................................................... 196
File versions purge .................................................................................... 196
Overview of IDB management ........................................................................... 196
IDB growth and performance ............................................................................ 197
Key IDB growth and performance factors ..................................................... 197
IDB growth and performance: key tunable parameters ................................... 198
Logging level as an IDB key tunable parameter ...................................... 199
Catalog protection as an IDB key tunable parameter ............................... 201
Recommended usage of logging level and catalog protection .................. 201
IDB size estimation ................................................................................... 203
6 Service management ..................................................... 205
In this chapter ................................................................................................. 205
Overview ....................................................................................................... 205
Data Protector and service management ...................................................... 206
Native Data Protector functionality ..................................................................... 207
Application Response Measurement version 2.0 (ARM 2.0 API) ....................... 208
Integration with HP Operations Manager software ........................................ 210
SNMP traps ............................................................................................. 210
The monitor .............................................................................................. 210
Reporting and notification .......................................................................... 211
Event logging and notification .................................................................... 212
8
Page 9

Data Protector log files ........................................................................ 213
Windows application log ........................................................................... 213
Java-based online reporting ....................................................................... 213
Data Protector checking and maintenance mechanism ................................... 214
Central management, distributed environment ............................................... 214
Using the data provided by Data Protector ................................................... 214
Service management integrations ...................................................................... 215
Data Protector OM-R integration ................................................................. 215
Data Protector OM SIP .............................................................................. 217
7 How Data Protector operates .......................................... 219
In this chapter ................................................................................................. 219
Data Protector processes or services ................................................................... 219
Backup sessions .............................................................................................. 220
Scheduled and interactive backup sessions ................................................... 221
Backup session data flow and processes ...................................................... 221
Pre-exec and post-exec commands .............................................................. 223
Queuing of backup sessions ....................................................................... 224
Mount requests in backup sessions .............................................................. 224
Backing up with disk discovery ................................................................... 225
Restore sessions ............................................................................................... 225
Restore session data flow and processes ...................................................... 226
Queuing of restore sessions ........................................................................ 227
Mount requests in a restore session .............................................................. 228
Parallel restores ......................................................................................... 228
Fast multiple single file restore .................................................................... 229
Object copy sessions ....................................................................................... 229
Automated and interactive object copy sessions ............................................ 230
Object copy session data flow and processes ............................................... 230
Queuing of object copy sessions ................................................................. 232
Mount requests in an object copy session ..................................................... 232
Object consolidation sessions ........................................................................... 233
Automated and interactive object consolidation sessions ................................ 233
Object consolidation session data flow and processes ................................... 233
Queuing of object consolidation sessions ..................................................... 234
Mount requests in an object consolidation session ......................................... 235
Media management sessions ............................................................................ 235
Media management session data flow ......................................................... 235
8 Integration with database applications ............................. 237
In this chapter ................................................................................................. 237
Overview of database operation ....................................................................... 237
Concepts guide 9
Page 10

Filesystem backup of databases and applications ................................................ 239
Online backup of databases and applications .................................................... 239
9 Direct backup ............................................................... 243
In this chapter ................................................................................................. 243
Overview ....................................................................................................... 243
Direct backup ........................................................................................... 244
Direct backup benefits ......................................................................... 245
How direct backup works ........................................................................... 245
Environment ....................................................................................... 246
About resolve ..................................................................................... 247
About XCopy ..................................................................................... 247
XCopy + Resolve ................................................................................ 248
Direct backup process flow ......................................................................... 248
Backup stages for data files ................................................................. 248
Restore .............................................................................................. 249
Requirements and support ................................................................................ 249
Supported configurations .................................................................................. 250
Three hosts: CM, application, Resolve .......................................................... 250
Two Hosts: Cell Manager/Resolve Agent and application .............................. 251
Basic configuration: single host ................................................................... 251
10 Disk backup ................................................................ 253
In this chapter ................................................................................................. 253
Overview ....................................................................................................... 253
Disk backup benefits ........................................................................................ 254
Data Protector disk-based devices ...................................................................... 255
11 Synthetic backup .......................................................... 257
In this chapter ................................................................................................. 257
Overview ....................................................................................................... 257
Synthetic backup benefits ................................................................................. 258
How Data Protector synthetic backup works ........................................................ 258
Synthetic backup and media space consumption ........................................... 260
Restore and synthetic backup ............................................................................ 260
How data protection periods affect restore from synthetic backup .................... 262
12 Split mirror concepts .................................................... 265
In this chapter ................................................................................................. 265
Overview ....................................................................................................... 265
Supported configurations .................................................................................. 269
10
Page 11

Local mirror - dual host .............................................................................. 269
Local mirror - single host ............................................................................ 270
Remote mirror ........................................................................................... 270
Local/remote mirror combination ................................................................ 272
Other configurations ................................................................................. 273
13 Snapshot concepts ....................................................... 275
In this chapter ................................................................................................. 275
Overview ....................................................................................................... 275
Storage virtualization ................................................................................. 275
Snapshot concepts .................................................................................... 276
Snapshot backup types .............................................................................. 278
Instant recovery ........................................................................................ 279
Replica set and replica set rotation .............................................................. 279
Types of snapshots .................................................................................... 279
Supported configurations .................................................................................. 281
Basic configuration: single disk array - dual host ........................................... 281
Other supported configurations ................................................................... 282
Other configurations ................................................................................. 286
14 Microsoft Volume Shadow Copy service .......................... 289
In this chapter ................................................................................................. 289
Overview ....................................................................................................... 289
Data Protector Volume Shadow Copy integration ................................................. 293
VSS filesystem backup and restore ..................................................................... 295
A Backup scenarios .......................................................... 297
In this appendix .............................................................................................. 297
Considerations ......................................................................................... 297
Company XYZ ................................................................................................ 299
Environment ............................................................................................. 299
Backup strategy requirements ..................................................................... 302
Proposed solution ...................................................................................... 303
Company ABC ................................................................................................ 313
Environment ............................................................................................. 313
Backup strategy requirements ..................................................................... 315
Proposed solution ...................................................................................... 317
B Further information ........................................................ 331
In this appendix .............................................................................................. 331
Backup generations ........................................................................................ 331
Concepts guide 11
Page 12

Examples of automated media copying .............................................................. 332
Example 1: automated media copying of filesystem backups ........................... 333
Incr1 backup ..................................................................................... 333
Full backup ........................................................................................ 335
Example 2: automated media copying of Oracle database backups ................ 338
Full backup ........................................................................................ 339
Internationalization .......................................................................................... 340
Localization .............................................................................................. 340
File name handling ................................................................................... 341
Background ....................................................................................... 341
File name handling during backup ........................................................ 342
Browsing file names ............................................................................ 342
File name handling during restore ......................................................... 342
Glossary ......................................................................... 345
Index .............................................................................. 403
12
Page 13

Figures
Data Protector graphical user interface ............................................... 331
Backup process ............................................................................... 392
Restore process ............................................................................... 393
Network backup .............................................................................. 404
The Data Protector cell (physical view and logical view) ....................... 415
Backup or restore operation .............................................................. 436
Backup session ................................................................................ 447
Restore session ................................................................................ 448
Large Data Protector enterprise environment ........................................ 459
Single-point management of multiple cells ........................................... 4610
Manager-of-Managers environment .................................................... 4711
How backup specifications, devices, and media pools are related ......... 4912
Using the Data Protector user interface ............................................... 5013
Original Data Protector GUI .............................................................. 5214
Data Protector Java GUI ................................................................... 5215
Data Protector Java GUI architecture .................................................. 5316
Backup session with AES 256-bit encryption ........................................ 7717
Backup session with drive-based encryption ........................................ 7818
Typical cluster ................................................................................. 8019
Cell Manager installed outside a cluster ............................................. 8420
Cell Manager installed outside a cluster, devices connected to the cluster
21
nodes ............................................................................................ 86
Cell Manager installed in the cluster, devices connected to cluster
22
nodes ............................................................................................ 89
Concepts guide 13
Page 14

Incremental backups ........................................................................ 9523
Leveled incremental backups ............................................................. 9524
Media needed to restore from simple and leveled incremental
25
backups ......................................................................................... 98
Media needed to restore from leveled incremental backups ................... 9826
Backup session .............................................................................. 10227
Full backup with daily simple incremental backups ............................. 10828
Full backup with daily level 1 incremental backups ............................. 10929
Full backup with mixed incremental backups ..................................... 11030
Object copy concept .................................................................... 11431
Freeing media .............................................................................. 11732
Demultiplexing a medium ............................................................... 11833
Disk staging concept ..................................................................... 11934
Object mirroring ............................................................................ 12135
Free pools .................................................................................... 13836
A simple one device/one media pool relation ................................... 14037
Configuration of media pools for large libraries ................................. 14138
14
Multiple devices, single media pool ................................................. 14239
Multiple devices, multiple media pools ............................................. 14340
Multiple objects and sessions per medium, sequential writes ................ 14941
Multiple objects and sessions per medium, concurrent writes ............... 14942
Multiple media per session, multiple media per object ........................ 14943
Each object written on a separate medium ........................................ 15044
Data format .................................................................................. 15845
Device locking and device names .................................................... 16046
Connecting drives to multiple systems ............................................... 16547
Sharing a SCSI library (robotics attached to a Data Protector Client
48
System) ........................................................................................ 168
Sharing a SCSI library (robotics attached to an NDMP Server) ............ 16949
Page 15

Sharing an ADIC/GRAU or StorageTek ACS library ........................... 17050
Storage Area Network ................................................................... 17251
Loop initialization protocol .............................................................. 17452
Example multipath configuration ...................................................... 17653
Indirect Library Access ................................................................... 17954
Direct Library Access ...................................................................... 18055
IDB parts ...................................................................................... 19056
The influence of logging level and catalog protection on IDB growth .... 19957
Service management information flow .............................................. 20758
Example of an IT service provider environment with service management
59
access through the client portal ....................................................... 215
Data Protector Reporter example ..................................................... 21660
Operational error status report ........................................................ 21761
Direct SIP integration example ......................................................... 21862
Backup session information flow (1) .................................................. 22263
Backup session information flow - multiple sessions ............................. 22364
Restore session information flow ...................................................... 22765
Parallel restore session flow ............................................................. 22966
Object copy session information flow .............................................. 23267
Relational database ....................................................................... 23868
Data Protector integration with databases ......................................... 24069
Direct backup architecture .............................................................. 24670
Basic three host configuration .......................................................... 25171
Synthetic backup ........................................................................... 25972
Virtual full backup .......................................................................... 26073
Full and incremental backups .......................................................... 26174
Synthetic backup ........................................................................... 26175
Regular synthetic backup ................................................................ 26276
Synthetic backup and object copy .................................................... 26277
Concepts guide 15
Page 16

Split mirror backup concept ............................................................ 26678
Local mirror - dual host (full performance, Zero Downtime Backup) ....... 26979
Split mirror - remote mirror (LAN-free remote backup - data HA) ........... 27180
Local/remote mirror combination (disaster recovery integrated backup
81
[Service HA - HP-UX only]) .............................................................. 272
Snapshot backup ........................................................................... 27782
Single disk array - dual host (full performance, Zero Downtime
83
Backup) ........................................................................................ 281
Multiple disk arrays - dual host ........................................................ 28284
Multiple application hosts - single backup host .................................. 28385
Disk array(s) - single host ................................................................ 28486
LVM mirroring - HP StorageWorks Virtual Array only .......................... 28587
Campus Cluster with LVM Mirroring - HP StorageWorks Virtual Array
88
only ............................................................................................. 286
Actors of the traditional backup model ............................................. 29289
Actors of the VSS backup model ...................................................... 29290
Current XYZ backup topology .......................................................... 30091
Proposed XYZ backup topology ....................................................... 30592
16
Input parameters ........................................................................... 30693
Results .......................................................................................... 30694
Current ABC Cape Town backup topology ........................................ 31495
ABC enterprise environment ............................................................ 31896
ABC Cape Town enterprise backup environment ................................ 32197
Input parameters ........................................................................... 32298
Results .......................................................................................... 32299
Backup generations ....................................................................... 332100
Incr1 backup and automated media copying .................................... 335101
Full backup and automated media copying ....................................... 337102
Overview of backup and automated media copy sessions ................... 338103
Full database backup and automated media copying ......................... 339104
Page 17

Overview of backup and automated media copy sessions ................... 340105
Concepts guide 17
Page 18

Tables
Edition history ................................................................................. 211
Document conventions ...................................................................... 312
Backup behavior ............................................................................. 853
Backup behavior ............................................................................. 874
Backup behavior ............................................................................. 905
Comparison of full and incremental backup ........................................ 916
Relative referencing of backup runs .................................................... 957
The staggered approach ................................................................ 1078
Data Protector data duplication methods .......................................... 1129
Required Data Protector Media Agent for drive control ....................... 16610
Required Data Protector Media Agent for robotic control ..................... 16711
Data Protector predefined user groups .............................................. 18512
ARM functionality .......................................................................... 20913
Benefits of using VSS ..................................................................... 29314
18
Hardware and software environment of XYZ ...................................... 29915
Proposed environment .................................................................... 30316
The staggering approach ................................................................ 30817
Remote full backups to the HP DLT 4115 library .................................. 30918
Size of backup environment ............................................................ 31319
Maximum acceptable downtime for recovery .................................... 31520
How long data should be kept ........................................................ 31621
Amount of data to be backed up ..................................................... 31622
Amount of data to be backed up in five years ................................... 31723
ABC cell configuration ................................................................... 31924
Page 19

ABC’s Media Pool Usage ............................................................... 32525
The Staggering Approach for ABC Cape Town .................................. 32626
ABC’s backup specification configuration ......................................... 32727
Concepts guide 19
Page 20

20
Page 21

Publication history
Guide updates may be issued between editions to correct errors or document product
changes. To ensure that you receive updated or new editions, subscribe to the
appropriate product support service. See your HP sales representative for details.
Table 1 Edition history
ProductGuide editionPart number
Data Protector Release A.05.00August 2002B6960-90059
Data Protector Release A.05.10May 2003B6960-90080
Data Protector Release A.05.50October 2004B6960-90105
Data Protector Release A.06.00August 2006B6960-96001
Data Protector Release A.06.10November 2008B6960-96035
Concepts guide 21
Page 22

Publication history22
Page 23

About this guide
This guide describes Data Protector concepts. Read this manual to fully understand
the fundamentals and the model of Data Protector.
Intended audience
This guide is intended for users interested in understanding the concepts of Data
Protector operation and for people who plan company backup strategies. Depending
on the required level of detail, you can also use this manual together with the Data
Protector online Help.
Documentation set
Other documents and online Help provide related information.
Guides
Data Protector guides are available in printed format and in PDF format. Install the
PDF files during the Data Protector setup procedure by selecting the English
Documentation & Help component on Windows or the OB2-DOCS component
on UNIX. Once installed, the guides reside in the Data_Protector_home\docs
directory on Windows and in the /opt/omni/doc/C directory on UNIX.
You can find these documents from the Manuals page of the HP Business Support
Center website:
http://www.hp.com/support/manuals
In the Storage section, click Storage Software and then select your product.
• HP Data Protector concepts guide
This guide describes Data Protector concepts and provides background information
on how Data Protector works. It is intended to be used with the task-oriented
online Help.
Concepts guide 23
Page 24

• HP Data Protector installation and licensing guide
This guide describes how to install the Data Protector software, taking into account
the operating system and architecture of your environment. This guide also gives
details on how to upgrade Data Protector, as well as how to obtain the proper
licenses for your environment.
• HP Data Protector troubleshooting guide
This guide describes how to troubleshoot problems you may encounter when
using Data Protector.
• HP Data Protector disaster recovery guide
This guide describes how to plan, prepare for, test and perform a disaster
recovery.
• HP Data Protector integration guides
These guides describe how to configure and use Data Protector to back up and
restore various databases and applications. They are intended for backup
administrators or operators. There are four guides:
• HP Data Protector integration guide for Microsoft applications: SQL Server,
SharePoint Portal Server, Exchange Server, and Volume Shadow Copy Service
This guide describes the integrations of Data Protector with the following
Microsoft applications: Microsoft Exchange Server, Microsoft SQL Server, and
Volume Shadow Copy Service.
• HP Data Protector integration guide for Oracle and SAP
This guide describes the integrations of Data Protector with Oracle, SAP R3,
and SAP DB/MaxDB.
• HP Data Protector integration guide for IBM applications: Informix, DB2, and
Lotus Notes/Domino
This guide describes the integrations of Data Protector with the following IBM
applications: Informix Server, IBM DB2, and Lotus Notes/Domino Server.
• HP Data Protector integration guide for VMware Virtual Infrastructure, Sybase,
Network Node Manager, and Network Data Management Protocol Server
This guide describes the integrations of Data Protector with VMware Virtual
Infrastructure, Sybase, Network Node Manager, and Network Data
Management Protocol Server.
• HP Data Protector integration guide for HP Service Information Portal
This guide describes how to install, configure, and use the integration of Data
Protector with HP Service Information Portal. It is intended for backup
administrators. It discusses how to use the application for Data Protector service
management.
About this guide24
Page 25

• HP Data Protector integration guide for HP Reporter
This manual describes how to install, configure, and use the integration of Data
Protector with HP Reporter. It is intended for backup administrators. It discusses
how to use the application for Data Protector service management.
• HP Data Protector integration guide for HP Operations Manager for UNIX
This guide describes how to monitor and manage the health and performance of
the Data Protector environment with HP Operations Manager and HP Service
Navigator on UNIX.
• HP Data Protector integration guide for HP Operations Manager for Windows
This guide describes how to monitor and manage the health and performance of
the Data Protector environment with HP Operations Manager and HP Service
Navigator on Windows.
• HP Data Protector integration guide for HP Performance Manager and HP
Performance Agent
This guide provides information about how to monitor and manage the health
and performance of the Data Protector environment with HP Performance Manager
(PM) and HP Performance Agent (PA) on Windows, HP-UX, Solaris, and Linux.
• HP Data Protector zero downtime backup concepts guide
This guide describes Data Protector zero downtime backup and instant recovery
concepts and provides background information on how Data Protector works in
a zero downtime backup environment. It is intended to be used with the
task-oriented HP Data Protector zero downtime backup administrator's guide and
the HP Data Protector zero downtime backup integration guide.
• HP Data Protector zero downtime backup administrator's guide
This guide describes how to configure and use the integration of Data Protector
with HP StorageWorks Virtual Array, HP StorageWorks Enterprise Virtual Array,
EMC Symmetrix Remote Data Facility and TimeFinder, and HP StorageWorks
Disk Array XP. It is intended for backup administrators or operators. It covers the
zero downtime backup, instant recovery, and the restore of filesystems and disk
images.
• HP Data Protector zero downtime backup integration guide
This guide describes how to configure and use Data Protector to perform zero
downtime backup, instant recovery, and standard restore of Oracle, SAP R/3,
Microsoft Exchange Server, and Microsoft SQL Server databases. The guide also
describes how to configure and use Data Protector to perform backup and restore
using the Microsoft Volume Shadow Copy Service.
• HP Data Protector MPE/iX system user guide
Concepts guide 25
Page 26

This guide describes how to configure MPE/iX clients and how to back up and
restore MPE/iX data.
• HP Data Protector Media Operations user's guide
This guide provides tracking and management of offline storage media. It describes
the tasks of installing and configuring the application, performing daily media
operations and producing reports.
• HP Data Protector product announcements, software notes, and references
This guide gives a description of new features of HP Data Protector A.06.10. It
also provides information on supported configurations (devices, platforms and
online database integrations, SAN, and ZDB), required patches, and limitations,
as well as known problems and workarounds. An updated version of the supported
configurations is available at http://www.hp.com/support/manuals.
• HP Data Protector product announcements, software notes, and references for
integrations to HP Operations Manager, HP Reporter, HP Performance Manager,
HP Performance Agent, and HP Service Information Portal
This guide fulfills a similar function for the listed integrations.
• HP Data Protector Media Operations product announcements, software notes,
and references
This guide fulfills a similar function for Media Operations.
• HP Data Protector command line interface reference
This guide describes the Data Protector command-line interface, command options
and their usage as well as provides some basic command-line examples.
Online Help
Data Protector provides context-sensitive (F1) Help and Help Topics for Windows
and UNIX platforms.
You can access the online Help from the top-level directory on the installation
DVD-ROM without installing Data Protector:
•
Windows:
•
UNIX:
system through DP_help.htm.
Unzip DP_help.zip and open DP_help.chm.
Unpack the zipped tar file DP_help.tar.gz, and access the online Help
About this guide26
Page 27

Documentation map
Abbreviations
Abbreviations in the documentation map that follows are explained below. The guide
titles are all preceded by the words “HP Data Protector”.
GuideAbbreviation
Command line interface referenceCLI
Concepts guideConcepts
Disaster recovery guideDR
Getting started guideGS
Online HelpHelp
IG-IBM
IG-MS
IG-PM/PA
IG-Var
Integration guide for IBM applications: Informix, DB2, and Lotus
Notes/Domino
Integration guide for Microsoft applications: SQL Server, SharePoint
Portal Server, Exchange Server, and Volume Shadow Copy Service
Integration guide for Oracle and SAPIG-O/S
Integration guide for HP Operations Manager for UNIXIG-OMU
Integration guide for HP Operations Manager for WindowsIG-OMW
Integration guide for HP Performance Manager and HP Performance
Agent
Integration guide for HP ReporterIG-Report
Integration guide for HP Service Information PortalIG-SIP
Integration guide for VMware Virtual Infrastructure, Sybase, Network
Node Manager, and Network Data Management Protocol Server
Concepts guide 27
Page 28

GuideAbbreviation
Installation and licensing guideInstall
Media Operations getting started guideMO GS
Map
MO RN
Media Operations product announcements, software notes, and
references
Media Operations user guideMO UG
MPE/iX system user guideMPE/iX
Product announcements, software notes, and referencesPA
Troubleshooting guideTrouble
ZDB administrator's guideZDB Admin
ZDB concepts guideZDB Concept
ZDB integration guideZDB IG
The following table shows where to find information of different kinds. Shaded squares
are a good place to look first.
About this guide28
Page 29

Integrations
Look in these guides for details of the following integrations:
GuideIntegration
IG-OMU, IG-OMWHP Operations Manager for UNIX/for Windows
IG-PM/PAHP Performance Manager
IG-PM/PAHP Performance Agent
Concepts guide 29
Page 30

GuideIntegration
IG-RHP Reporter
IG-SIPHP Service Information Portal
all ZDBHP StorageWorks Disk Array XP
all ZDBHP StorageWorks Enterprise Virtual Array (EVA)
all ZDBHP StorageWorks Virtual Array (VA)
IG-IBMIBM DB2 UDB
IG-IBMInformix
IG-IBMLotus Notes/Domino
MO UserMedia Operations
MPE/iXMPE/iX system
IG-MS, ZDB IGMicrosoft Exchange Server
IG-MSMicrosoft Exchange Single Mailbox
IG-MS, ZDB IGMicrosoft SQL Server
IG-MS, ZDB IGMicrosoft Volume Shadow Copy Service (VSS)
IG-VarNDMP Server
IG-VarNetwork Node Manager (NNM)
IG-O/SOracle
ZDB IGOracle ZDB
IG-O/SSAP DB
IG-O/S, ZDB IGSAP R/3
About this guide30
Page 31
Document conventions and symbols
Table 2 Document conventions
ElementConvention
Cross-reference links and e-mail addressesBlue text: Table 2 on page 31
website addressesBlue, underlined text: http://www.hp.com
Text emphasisItalic text
• File and directory names
• System output
Monospace text
• Code
• Commands, their arguments, and
argument values
GuideIntegration
IG-VarSybase
all ZDBEMC Symmetrix
IG-VarVMware
Monospace, italic text
• Code variables
• Command variables
Emphasized monospace texttext
CAUTION:
Indicates that failure to follow directions could result in damage to equipment or data.
IMPORTANT:
Provides clarifying information or specific instructions.
Concepts guide 31
Page 32

NOTE:
Provides additional information.
TIP:
Provides helpful hints and shortcuts.
Data Protector graphical user interface
Data Protector provides a cross-platform (Windows and UNIX) graphical user
interface. You can use the original Data Protector GUI (Windows only) or the Data
Protector Java GUI. For information about the Data Protector graphical user interface,
see the online Help.
About this guide32
Page 33

Figure 1 Data Protector graphical user interface
General information
General information about Data Protector can be found at http://www.hp.com/go/
dataprotector.
HP technical support
For worldwide technical support information, see the HP support website:
http://www.hp.com/support
Before contacting HP, collect the following information:
• Product model names and numbers
• Technical support registration number (if applicable)
• Product serial numbers
• Error messages
• Operating system type and revision level
• Detailed questions
Concepts guide 33
Page 34

Subscription service
HP recommends that you register your product at the Subscriber's Choice for Business
website:
http://www.hp.com/go/e-updates
After registering, you will receive e-mail notification of product enhancements, new
driver versions, firmware updates, and other product resources.
HP websites
For additional information, see the following HP websites:
• http://www.hp.com
• http://www.hp.com/go/software
• http://www.hp.com/support/manuals
• http://www.hp.com/support/downloads
Documentation feedback
HP welcomes your feedback.
To make comments and suggestions about product documentation, please send a
message to DP.DocFeedback@hp.com. All submissions become the property of HP.
About this guide34
Page 35

1 About backup and Data Protector
In this chapter
This chapter provides an overview of backup and restore concepts. It introduces Data
Protector architecture, media management, user interfaces, backup devices, and
other features. The chapter concludes with an overview of Data Protector configuration
and other tasks needed to set up Data Protector.
It is organized as follows:
“About Data Protector” on page 35
“Introducing backups and restores” on page 38
“Data Protector architecture” on page 40
“Enterprise environments” on page 45
“Media management” on page 48
“Backup devices” on page 49
“User interfaces” on page 50
“Overview of tasks to set up Data Protector” on page 55
About Data Protector
HP Data Protector is a backup solution that provides reliable data protection and
high accessibility for your fast growing business data. Data Protector offers
comprehensive backup and restore functionality specifically tailored for enterprise-wide
and distributed environments. The following list describes major Data Protector
features:
• Scalable and Highly Flexible Architecture
Concepts guide 35
Page 36

Data Protector can be used in environments ranging from a single system to
thousands of systems on several sites. Due to the network component concept of
Data Protector, elements of the backup infrastructure can be placed in the topology
according to user requirements. The numerous backup options and alternatives
to setting up a backup infrastructure allow the implementation of virtually any
configuration you want. Data Protector also enables the use of advanced backup
concepts, such as synthetic backup and disk staging.
• Easy Central Administration
Through its easy-to-use graphical user interface (GUI), Data Protector allows you
to administer your complete backup environment from a single system. To ease
operation, the GUI can be installed on various systems to allow multiple
administrators to access Data Protector via their locally installed consoles. Even
multiple backup environments can be managed from a single system. The Data
Protector command-line interface allows you to manage Data Protector using
scripts.
• High Performance Backup
Data Protector enables you to perform backup to several hundred backup devices
simultaneously. It supports high-end devices in very large libraries. Various backup
possibilities, such as local backup, network backup, online backup, disk image
backup, synthetic backup, backup with object mirroring, and built-in support for
parallel data streams allow you to tune your backups to best fit your requirements.
• Data security
To enhance the security of your data, Data Protector lets you encrypt your backups
so that they become protected from others. Data Protector offers two data
encryption techniques: software-based and drive-based.
• Supporting Mixed Environments
As Data Protector supports heterogeneous environments, most features are common
to the UNIX and Windows platforms. The UNIX and Windows Cell Managers
can control all supported client platforms (UNIX, Windows, and Novell NetWare).
The Data Protector user interface can access the entire Data Protector functionality
on all supported platforms.
• Easy Installation for Mixed Environments
The Installation Server concept simplifies the installation and upgrade procedures.
To remotely install UNIX clients, you need an Installation Server for UNIX. To
remotely install Windows clients, you need an Installation Server for Windows.
The remote installation can be performed from any client with an installed Data
Protector GUI. For supported platforms for the Installation Server, see the HP Data
Protector product announcements, software notes, and references.
• High Availability Support
About backup and Data Protector36
Page 37

Data Protector enables you to meet the needs for continued business operations
around the clock. In today's globally distributed business environment,
company-wide information resources and customer service applications must
always be available. Data Protector enables you to meet high availability needs
by:
• Integrating with clusters to ensure fail-safe operation with the ability to back
up virtual nodes. For a list of supported clusters, see the HP Data Protector
product announcements, software notes, and references.
• Enabling the Data Protector Cell Manager itself to run on a cluster.
• Supporting all popular online database Application Programming Interfaces.
• Integrating with advanced high availability solutions like EMC Symmetrix, HP
StorageWorks Disk Array XP, HP StorageWorks Virtual Array, or HP
StorageWorks Enterprise Virtual Array.
• Providing various disaster recovery methods for Windows and UNIX platforms.
• Offering methods of duplicating backed up data during and after the backup
to improve fault tolerance of backups or for redundancy purposes.
• Easy Restore
Data Protector includes an internal database that keeps track of data such as
which files from which system are kept on a particular medium. In order to restore
any part of a system, simply browse the files and directories. This provides fast
and convenient access to the data to be restored.
• Automated or Unattended Operation
With the internal database, Data Protector keeps information about each Data
Protector medium and the data on it. Data Protector provides sophisticated media
management functionality. For example, it keeps track of how long a particular
backup needs to remain available for restoring, and which media can be (re)used
for backups.
The support of very large libraries complements this, allowing for unattended
operation over several days or weeks (automated media rotation). Additionally,
when new disks are connected to systems, Data Protector can automatically detect
(or discover) the disks and back them up. This eliminates the need to adjust backup
configurations manually.
• Service Management
Data Protector is the first backup and restore management solution to support
service management. The integration with Application Response Management
(ARM) and Data Source Integration (DSI) enables powerful support of Service
Level Management (SLM) and Service Level Agreements (SLA) concepts by
providing relevant data to management and planning systems.
Concepts guide 37
Page 38

The DSI integration provides a set of scripts and configuration files from which
users are able to see how to add their own queries using Data Protector reporting
capabilities.
• Monitoring, Reporting and Notification
Superior web reporting and notification capabilities allow you to easily view the
backup status, monitor active backup operations, and customize reports. Reports
can be generated using the Data Protector GUI, or using the omnirpt command
on systems running UNIX or Windows, as well as using Java-based online
generated web reports.
You can schedule reports to be issued at a specific time or to be attached to a
predefined set of events, such as the end of a backup session or a mount request.
In addition, the Data Protector auditing functionality enables you to collect a
subset of backup session information and provides an overview of backup
operations. Backup session information is recorded to the audit log files.
• Integration with Online Database Applications
Data Protector provides online backup of Microsoft Exchange Server, Microsoft
SQL Server, Oracle, Informix Server, SAP R/3, Lotus Notes/Domino Server, IBM
DB2 UDB, Sybase database objects, and VMware Virtual Infrastructure objects.
For a list of supported versions for a particular operating system, see the HP Data
Protector product announcements, software notes, and references.
• Integration with Other Products
Additionally, Data Protector integrates with EMC Symmetrix, Microsoft Cluster
Server, MC/ServiceGuard and other products.
For detailed documentation describing the features of Data Protector, including
integrations, as well as the latest platform and integration support information, consult
the HP Data Protector home page at http://www.hp.com/support/manuals.
Introducing backups and restores
This section explains basic backup and restore concepts.
What is a backup?
A backup is a process that creates a copy of data on backup media. This copy is
stored and kept for future use in case the original is destroyed or corrupted.
A high-level presentation of a backup is shown in Figure 2 on page 39.
About backup and Data Protector38
Page 39

Figure 2 Backup process
In most cases, the source is data on a disk, such as files, directories, databases, and
applications. If the backup is expected to be used for disaster recovery, it needs to
be consistent.
Software that actually copies data to the destination is a backup application. The
destination is a backup device, such as a tape drive, with media to which a copy of
the data is written.
What is a restore?
A restore is a process that recreates the original data from a backup copy. This
process consists of the preparation and actual restore of data, and some post-restore
actions that make that data ready for use.
Figure 3 Restore process
The source is a backup copy. A restore application is software that actually writes
data to a destination. The destination is usually a disk to which the original data is
written.
Backing up a network environment
During backups in a network environment, data is transferred over the network from
systems to be backed up to media on systems with backup devices, where the data
is stored.
Concepts guide 39
Page 40

Figure 4 Network backup
To accomplish backup of a network environment you need an application that allows
you to:
• Attach backup devices to any system in the network
This enables local backups of systems with large volumes of data and network
backups in order to reduce backup device costs.
• Route backup data flow to any network path
• Route backup data away from the LAN and onto a SAN when data volume or
network traffic makes LAN transfer inefficient
• Manage backup activities from any system
• Integrate into the IT management framework
• Support many different types of systems to be backed up
Direct backup
A direct backup is one in which you can send data directly from disk to tape in the
SAN without involving a dedicated backup server for the data movement.
The use of a filesystem-independent ability to resolve data is fully integrated with the
industry-standard XCOPY functionality that is embedded in supported disk arrays
and bridges, removing the need for a separate data mover appliance.
Data Protector architecture
The Data Protector cell, shown in Figure 5 on page 41, is a network environment
that has a Cell Manager, client systems, and devices. The Cell Manager is the central
control point where Data Protector software is installed. After installing Data Protector
software, you can add systems to be backed up. These systems become Data Protector
client systems that are part of the cell. When Data Protector backs up files, it saves
them to media in backup devices.
About backup and Data Protector40
Page 41

The Data Protector internal database (IDB) keeps track of the files you back up so
that you can browse and easily recover the entire system or single files.
Data Protector facilitates backup and restore jobs. You can do an immediate (or
interactive) backup using the Data Protector user interface. You can also schedule
your backups to run unattended.
Figure 5 The Data Protector cell (physical view and logical view)
NOTE:
The GUI and the Cell Manager systems can run on UNIX and Windows operating systems;
they do not have to run the same operating system. For a list of supported operating
systems for a particular Data Protector component, see the
announcements, software notes, and references
.
HP Data Protector product
Cell Manager
The Cell Manager is the main system in the cell. The Cell Manager:
• Manages the cell from a central point
• Contains the IDB
• Runs core Data Protector software
• Runs Session Managers that start and stop backup and restore sessions and write
The IDB contains information about backup details such as, backup durations,
media IDs, and session IDs
session information to the IDB
Concepts guide 41
Page 42

Systems to be backed up
Client systems you want to back up must have the Data Protector Disk Agent (DA),
also called Backup Agent, installed. To back up online database integrations, install
the Application Agent. In the rest of the manual, the term Disk Agent will be used for
both agents. The Disk Agent reads or writes data from a disk on the system and sends
or receives data from a Media Agent. The Disk Agent is also installed on the Cell
Manager, thus allowing you to back up data on the Cell Manager, the Data Protector
configuration, and the IDB.
Systems with backup devices
Client systems with connected backup devices must have a Data Protector Media
Agent (MA) installed. Such client systems are also called Drive Servers. A backup
device can be connected to any system and not only to the Cell Manager. A Media
Agent reads or writes data from or to media in the device and sends or receives data
from the Disk Agent.
Systems with a user interface
You can manage Data Protector from any system on the network on which the Data
Protector graphical user interface (GUI) is installed. Therefore, you can have the Cell
Manager system in a computer room while managing Data Protector from your
desktop system.
Installation Server
The Installation Server holds a repository of the Data Protector software packages
for a specific architecture. The Cell Manager is by default also an Installation Server.
At least two Installation Servers are needed for mixed environments: one for UNIX
systems and one for Windows systems.
Operations in the cell
The Data Protector Cell Manager controls backup and restore sessions, which perform
all the required actions for a backup or restore, respectively, as shown in Figure
6 on page 43.
About backup and Data Protector42
Page 43
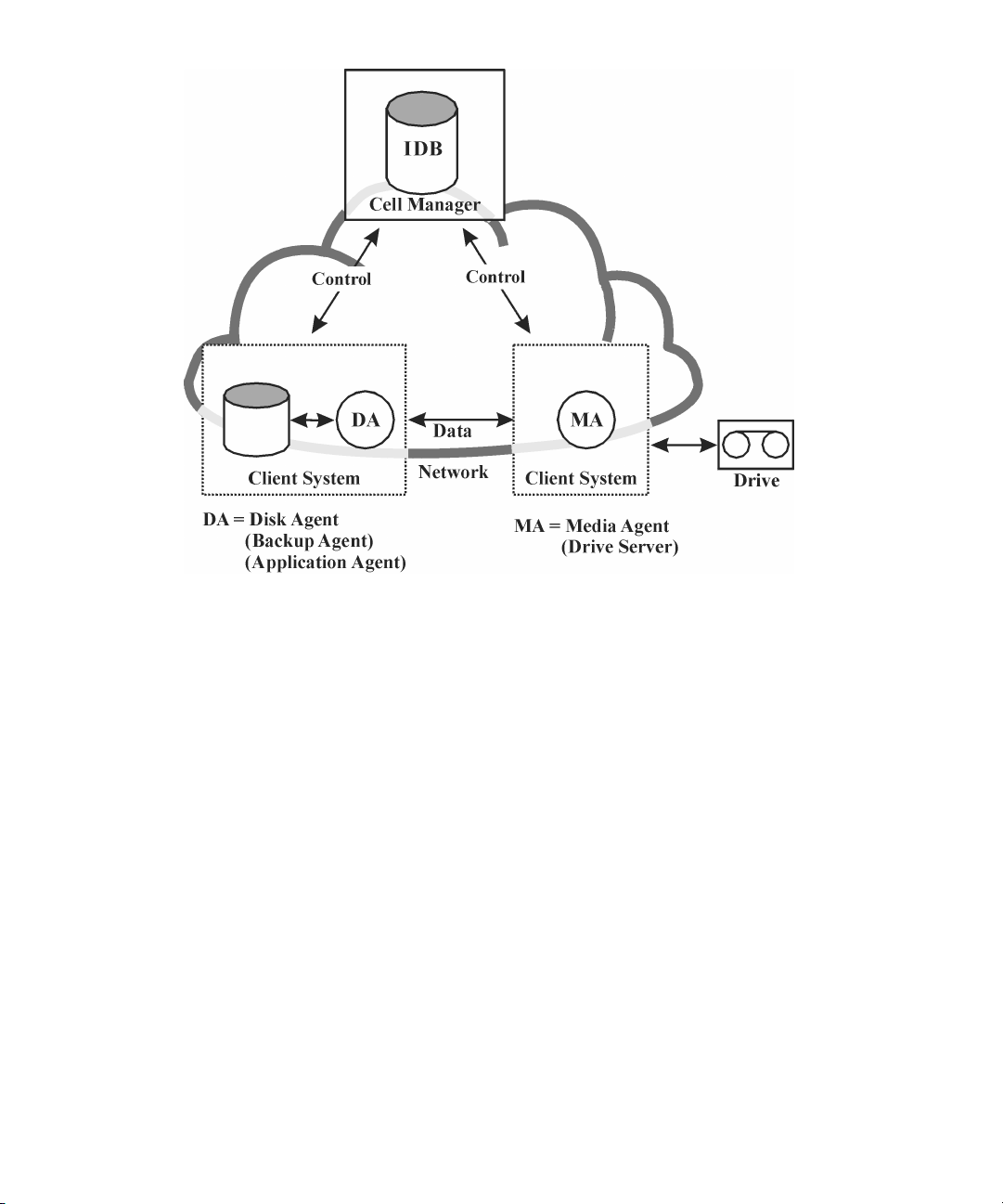
Figure 6 Backup or restore operation
Backup sessions
What is a backup session?
A backup session, shown in Figure 7 on page 44, is a process that creates a copy
of data on storage media. It is started either interactively by an operator using the
Data Protector user interface, or unattended using the Data Protector Scheduler.
How does it work?
The Backup Session Manager process starts Media Agent(s) and Disk Agent(s),
controls the session, and stores generated messages to the IDB. Data is read by the
Disk Agent and sent to a Media Agent, which saves it to media.
Concepts guide 43
Page 44

Figure 7 Backup session
A typical backup session is more complex than the one shown in Figure 7 on page 44.
A number of Disk Agents read data from multiple disks in parallel and send data to
one or more Media Agents. For more information on complex backup sessions, see
Chapter 7 on page 219.
Restore sessions
What is a restore session?
A restore session, shown in Figure 8 on page 44, is a process that restores data from
previous backups to a disk. The restore session is interactively started by an operator
using the Data Protector user interface.
How does it work?
After you have selected the files to be restored from a previous backup, you invoke
the actual restore. The Restore Session Manager process starts the needed Media
Agent(s) and Disk Agent(s), controls the session, and stores messages in the IDB.
Data is read by a Media Agent and sent to the Disk Agent, which writes it to disks.
Figure 8 Restore session
A restore session may be more complex than the one shown in Figure 8 on page 44.
For more information on restore sessions, see Chapter 7 on page 219.
About backup and Data Protector44
Page 45

Enterprise environments
What is an enterprise environment?
A typical enterprise network environment, shown in Figure 9 on page 45, consists
of a number of systems from different vendors with different operating systems. The
systems may be located in different geographical areas and time zones. All the
systems are connected with LAN or WAN networks operating at various
communication speeds.
When to use an enterprise environment
This solution can be used when several geographically separated sites require common
backup policies to be used. It can also be used when all departments at the same
site want to share the same set of backup devices.
Figure 9 Large Data Protector enterprise environment
Configuring and managing backups of such a heterogeneous environment is
challenging. Data Protector functionality has been designed to highly simplify this
task. For information about the Manager of Managers (MoM), see MoM on page 46.
Splitting an environment into multiple cells
You may decide to split large environments into multiple cells for a number of reasons:
Concepts guide 45
Page 46
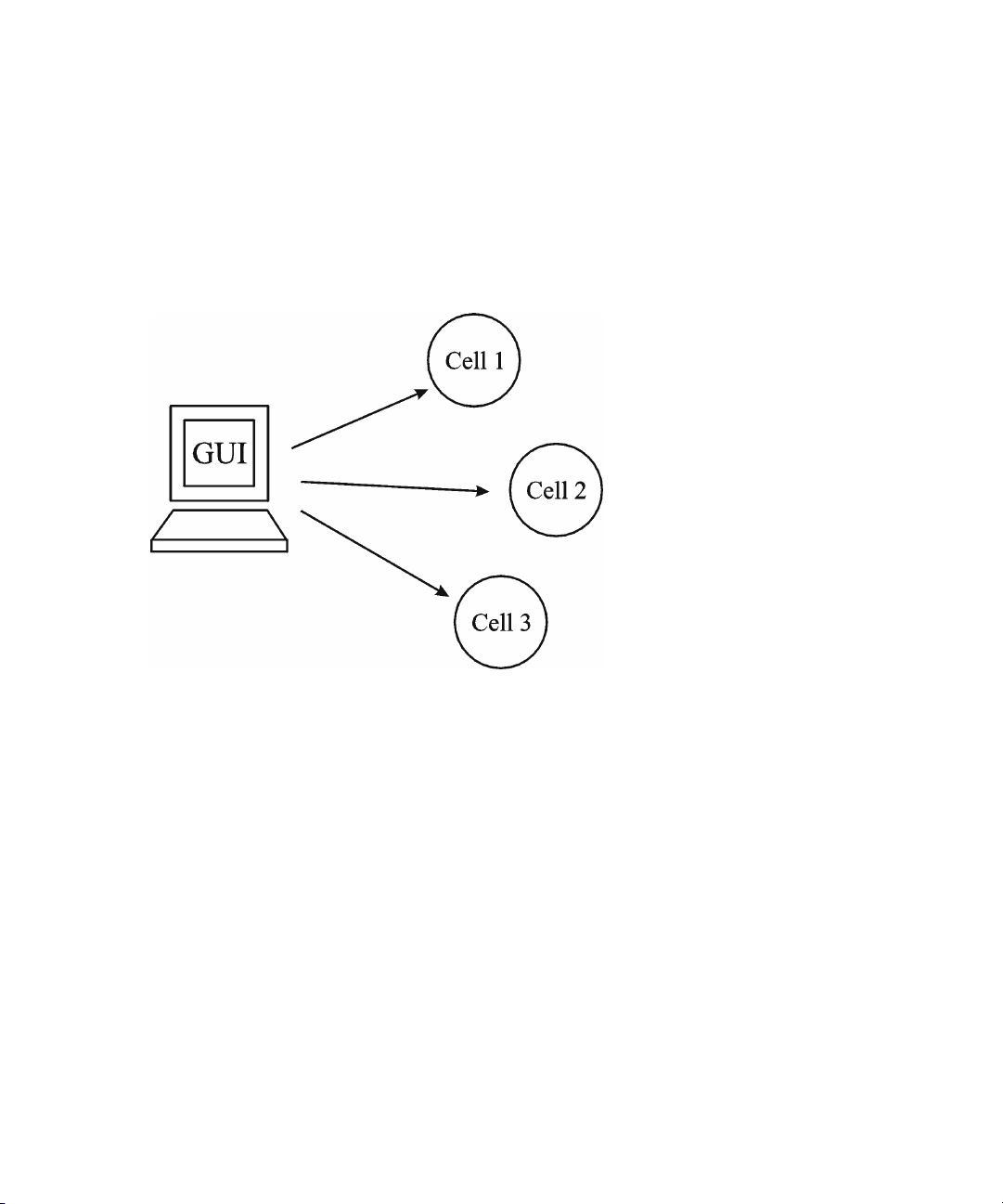
Why split large environments into multiple cells?
• Geographical grouping of systems.
• Logical grouping of systems, for example, departments.
• Slow network connection between some systems.
• Performance considerations.
• Separate administrative control.
For a list of considerations in planning your environment, see Chapter 2 on page 57.
Data Protector allows you to manage multiple cells from a single point.
MoM
Figure 10 Single-point management of multiple cells
Data Protector provides the Manager-of-Managers to manage large environments
with multiple cells. The MoM allows you to group multiple cells into a larger unit,
called a MoM environment that can be managed from a single point, as shown in
Figure 10 on page 46. The MoM enables virtually unlimited growth of your backup
environment. New cells can be added or existing ones split.
A MoM environment does not require a reliable network connection from Data
Protector cells to the central MoM cell, because only the controls are sent over the
long distance connections, however the backups are performed locally within each
Data Protector cell. Nevertheless, this is based on the assumption that each cell has
its own Media Management Database.
About backup and Data Protector46
Page 47
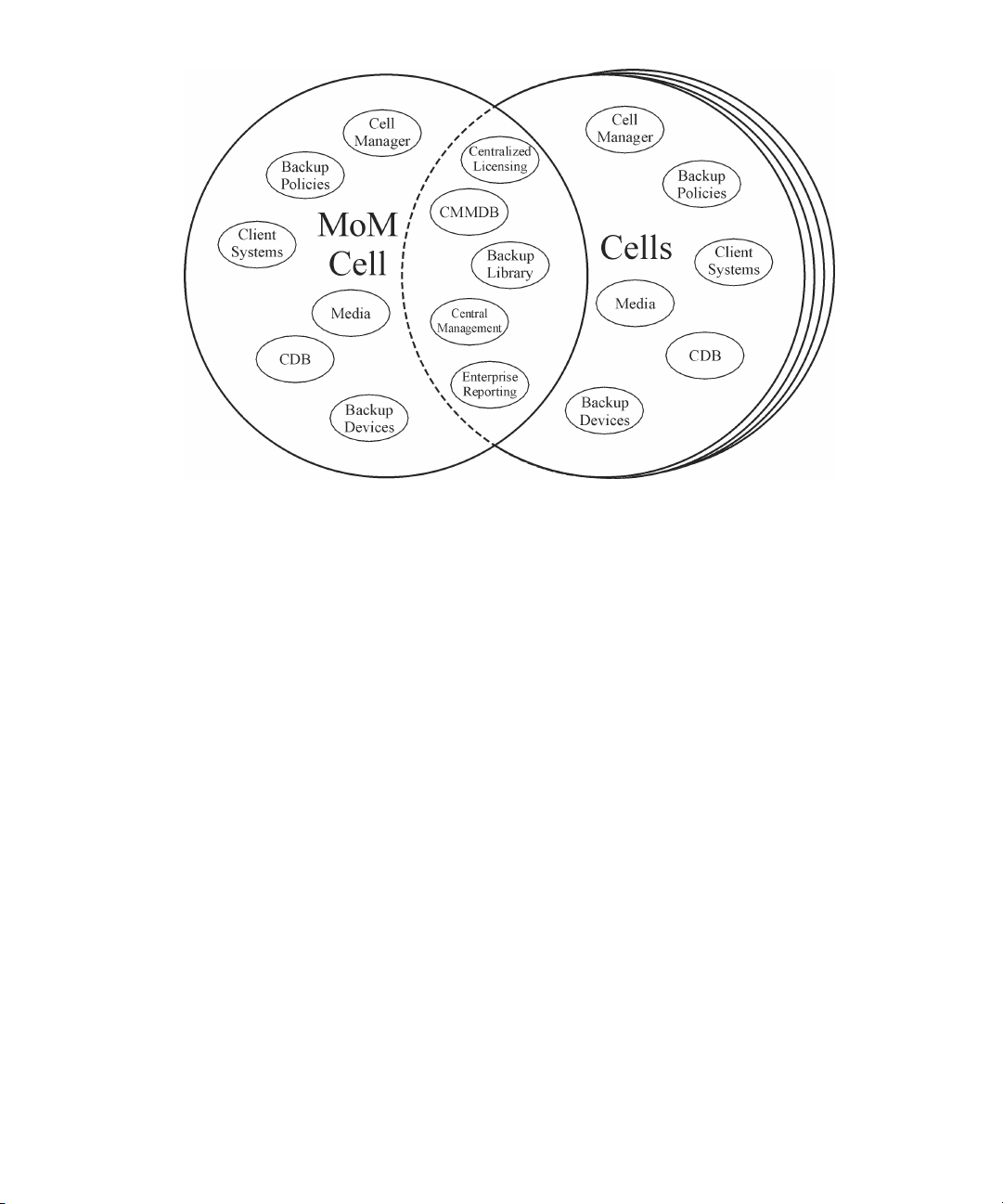
Figure 11 Manager-of-Managers environment
Manager-of-Managers provides the following features:
• Centralized licensing repository
This enables simplified license management. This is optional but useful for very
large environments.
• Centralized Media Management Database (CMMDB)
The CMMDB allows you to share devices and media across several cells in a
MoM environment. This makes devices of one cell (using the CMMDB) accessible
to other cells that use the CMMDB. The CMMDB, if used, must reside in the MoM
cell. In this case, a reliable network connection is required between the MoM cell
and the other Data Protector cells. Note that it is optional to centralize the Media
Management Database.
• Sharing libraries
With the CMMDB, you can share high-end devices between cells in the multi-cell
environment. One cell can control the robotics, serving several devices that are
connected to systems in different cells. Even the Disk Agent to Media Agent data
path can go across cell boundaries.
• Enterprise reporting
The Data Protector Manager-of-Managers can generate reports on a single-cell
basis as well as for the entire enterprise environment.
Concepts guide 47
Page 48

Media management
Data Protector provides you with powerful media management, which lets you easily
and efficiently manage large numbers of media in your environment in the following
ways:
Media management functionality
• Grouping media into logical groups, called media pools, which allows you to
think about large sets of media without having to worry about each medium
individually.
• Data Protector keeps track of all media and the status of each medium, data
protection expiration time, availability of media for backup, and a catalog of
what has been backed up to each medium.
• Fully automated operation. If Data Protector controls enough media in the library
devices, the media management functionality lets you run the backup sessions
without operator intervention.
• Automated media rotation policies that allow media selection for backups to be
performed automatically.
• Recognition and support of barcodes on large library devices and silo devices
with barcode support.
• Recognition, tracking, viewing, and handling of media used by Data Protector
in large library devices and silo devices.
• The possibility of having information about the media in a central place and the
sharing of this information among several Data Protector cells.
• Interactive or automated creation of additional copies of the data on the media.
• Support for media vaulting.
What is a media pool?
Data Protector uses media pools to manage large numbers of media. A media pool
is a logical collection of media of the same physical type with common usage policies
(properties). Usage is based on the data on the media. The structure and quantity of
the pools, as well as which pool contains what type of data on its media, depend
entirely on your preferences.
When a device is configured, a default media pool is specified. This media pool is
used if no other media pool is defined in the backup specification.
About backup and Data Protector48
Page 49

Backup devices
Data Protector defines and models each device as a physical device with its own
usage properties, such as the default pool. This device concept is used because it
allows you to easily and flexibly configure devices and use them in conjunction with
backup specifications. The definition of the devices is stored in the Data Protector
Media Management Database.
Figure 12 How backup specifications, devices, and media pools are
related
Figure 12 on page 49 shows the relationship among the backup specification,
devices, and media pools. The devices are referred to in the backup specification.
Each device is linked to a media pool; this media pool can be changed in the backup
specification. For example, backup specification 2 references the pool Dept_X
instead of the default pool.
Data Protector supports various devices. For more information, see the HP Data
Protector product announcements, software notes, and references.
Concepts guide 49
Page 50

User interfaces
Data Protector provides easy access to all configuration and administration tasks
using the Data Protector GUI on Windows and UNIX platforms. You can use the
original Data Protector GUI (on Windows) or the Data Protector Java GUI (on
Windows and UNIX). Both user interfaces can run simultaneously on the same
computer. Additionally, a command-line interface is available on Windows and UNIX
platforms.
The Data Protector architecture allows you to flexibly install and use the Data Protector
user interface. The user interface does not have to be used from the Cell Manager
system; you can install it on your desktop system. As depicted in Figure
13 on page 50, the user interface also allows you to transparently manage Data
Protector cells with Cell Managers on all supported platforms.
Figure 13 Using the Data Protector user interface
TIP:
In a typical mixed environment, install the Data Protector user interface on several systems
in the environment, thus providing access to Data Protector from several systems.
Data Protector GUI
Both, the original Data Protector GUI, depicted in Figure 14 on page 52, as well as
the Data Protector Java GUI, depicted in Figure 15 on page 52, are easy-to-use,
powerful interfaces providing the following functionalities:
About backup and Data Protector50
Page 51

• A Results Tab with all the configuration wizards, properties and lists.
• Easy configuration and management of the backup of online database applications
that run in Windows environments, such as Microsoft SQL Server, Microsoft
Exchange Server, SAP R/3, and Oracle or those that run in the UNIX environments,
such as SAP R/3, Oracle, and Informix Server.
• A comprehensive online Help system called the Help Topics, and context-sensitive
Help called the Help Navigator.
Concepts guide 51
Page 52

Figure 14 Original Data Protector GUI
Figure 15 Data Protector Java GUI
Data Protector Java GUI
The Data Protector Java GUI is a Java-based graphical user interface with a
About backup and Data Protector52
Page 53
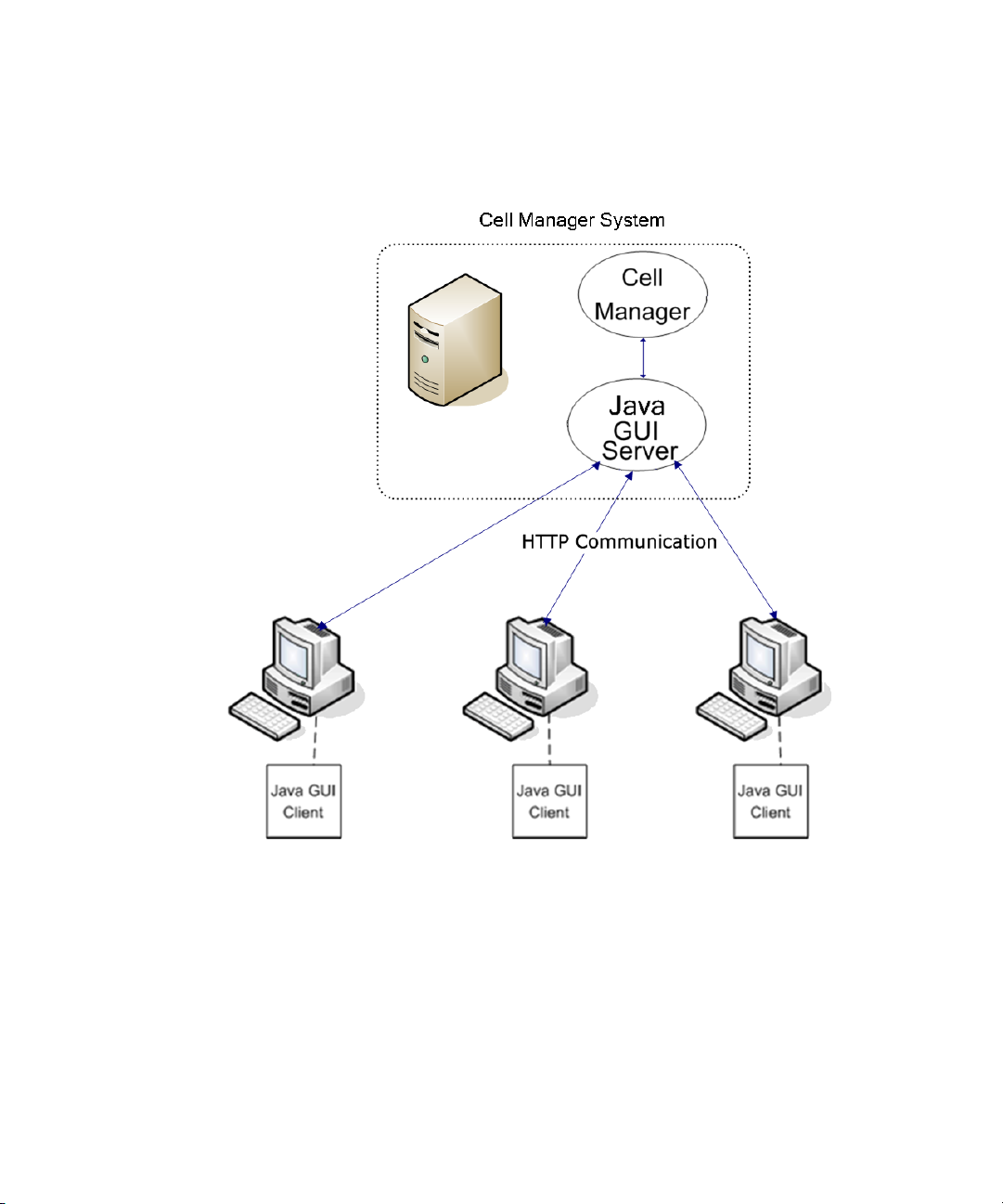
client-server architecture. It enables backup management with the same look and feel
as the original Data Protector GUI.
The Java GUI consists of two components: Java GUI Server and Java GUI Client.
Figure 16 on page 53 shows the relationship between these components.
Figure 16 Data Protector Java GUI architecture
The Java GUI Server is installed on the Data Protector Cell Manager system. The Java
GUI Server receives requests from the Java GUI Client, processes them and then
sends the responses back to the Java GUI Client. The communication is done through
Hypertext Transfer Protocol (HTTP) on port 5556.
The Java GUI Client contains only user interface related functionalities and requires
connection to the Java GUI Server to function.
Concepts guide 53
Page 54

Benefits of Java GUI
The Data Protector Java GUI has the following advantages over the original Data
Protector GUI:
• Portability
The Data Protector Java GUI architecture enables you to install Java GUI Clients
on all platforms that support Java Runtime Environment (JRE).
• Easy firewall configuration
The Java GUI Client uses port 5556 to connect to the Java GUI Server. It is easier
to configure Java GUI in a firewall environment because only one port needs to
be opened. The communication between the Java GUI Client and the Java GUI
Server is done through HTTP, which is also firewall friendlier.
For details, see the Data Protector support matrices under specifications at http:/
/www.hp.com/support/manuals.
• Improved localization and internationalization
Only one installation package is needed for all locales. The Java GUI enables
better display in all locales, since controls are automatically resized to match the
size of the text.
• Non-blocking behavior
The Java GUI Server transmits only data for the current context, which reduces
the network traffic between the Java GUI Server and the Java GUI Client. Due to
its non-blocking behavior, you can work on different contexts while Java GUI
Server processes your requests in the background.
Differences from the Original Data Protector GUI
Due to the different underlying technologies used, there are also some visual and
minor functional differences between the two GUIs. These differences do not have
an important impact on the functionality of Data Protector.
For example, in the Clients context, if you view the Security tab in a client’s properties,
browsing the network behaves differently depending on the GUI used:
• The original Data Protector GUI (on Windows systems only) displays the network
neighborhood of the GUI client.
• The Data Protector Java GUI displays the network neighborhood of the Cell
Manager and not of the GUI client. Browsing is available only with a Windows
Cell Manager; however, it makes no difference if the GUI runs on a Windows
or UNIX system.
About backup and Data Protector54
Page 55

Overview of tasks to set up Data Protector
This section provides an overview of global tasks to set up your Data Protector backup
environment. Depending on the size and complexity of your environment, you may
not need to go through all these steps.
1. Analyze your network and organizational structure. Decide which systems need
to be backed up.
2. Check if there are any special applications and databases which you want to
back up, such as Microsoft Exchange, Oracle, IBM DB2 UDB, SAP R/3, or
others. Data Protector provides specific integrations with these products.
3. Decide on the configuration of your Data Protector cell, such as:
• the system to be your Cell Manager
• systems on which you want to install the user interface
• local backup versus network backup
• systems to control backup devices and libraries
• type of connections, LAN and/or SAN
4. Purchase the required Data Protector licenses for your setup. This way you obtain
the passwords you will need to install.
Alternatively, you can operate Data Protector using an instant-on password.
However, this is valid only for 60 days from the date of installation. For details,
see the HP Data Protector installation and licensing guide.
5. Consider security aspects:
• Analyze security considerations. See the HP Data Protector installation and
licensing guide.
• Consider which user groups you need to configure.
• Enhance security by writing data to media in an encrypted format.
6. Decide how you want to structure your backups:
• Which media pools do you want to have, and how will they be used?
• Which devices will be used, and how?
• How many copies of each backup do you want?
• How many backup specifications do you need, and how should they be
grouped?
• If you are planning to back up to disk, consider advanced backup strategies
such as synthetic backup and disk staging.
Concepts guide 55
Page 56

7. Install and configure your Data Protector environment.
• Install the Data Protector Cell Manager system and use the Data Protector
user interface to distribute Data Protector components to other systems.
• Connect devices (tape drives) to the systems that will control them.
• Configure backup devices.
• Configure media pools and prepare the media.
• Configure backup specifications, including backup of the IDB.
• Configure reports, if needed.
8. Become familiar with tasks such as:
• Handling failed backups
• Performing restores
• Duplicating backed up data and vaulting media
• Preparing for disaster recovery
• Maintaining the IDB
About backup and Data Protector56
Page 57
2 Planning your backup strategy
In this chapter
This chapter describes backup strategy planning. It focuses on planning Data Protector
cells, performance, and security, as well as backing up and restoring data. The
chapter also discusses basic backup types, automated backup operation, clustering,
and disaster recovery.
It is organized as follows:
“Backup strategy planning” on page 58
“Planning cells” on page 62
“Understanding and planning performance” on page 67
“Planning security” on page 73
“Clustering” on page 79
“Full and incremental backups” on page 91
“Keeping backed up data and information about the data” on page 99
“Backing up data” on page 102
“Automated or unattended operation” on page 110
“Duplicating backed up data” on page 112
“Restoring data” on page 125
“Disaster recovery” on page 128
Concepts guide 57
Page 58

Backup strategy planning
Data Protector is simple to configure and administer. However, if you work in a large
environment with diverse client systems and huge amounts of data to back up, plan
in advance. Planning simplifies subsequent configuration steps.
What is backup strategy planning?
Backup strategy planning is a process that includes the following steps:
1. Defining the requirements and constraints for backups, for example, how often
your data needs to be backed up or whether you need additional copies of the
backed up data on additional media sets.
2. Understanding the factors that influence your backup solution, such as the
sustained data transfer rates of the network and of backup devices. These factors
can affect how you configure Data Protector and the kind of backup -- network
or direct, for example -- that you choose. For instance, if you back up to disk,
you can take advantage of advanced backup strategies such as synthetic backup
and disk staging.
3. Preparing the backup strategy that shows your backup concept and how it is
implemented.
This section provides detailed information on the preceding steps. The rest of this
guide provides important information and considerations that help you plan your
backup solution.
Defining the requirements of a backup strategy
Defining objectives and constraints of your backup strategy includes answering
questions, such as:
• What are your organizational policies regarding backups and restores?
Some organizations already have defined policies on archiving and storing data.
Your backup strategy should comply with these policies.
• What types of data need to be backed up?
List all types of data existing in your network, such as user files, system files, Web
servers, and large relational databases.
• How long is the maximum downtime for recovery?
Planning your backup strategy58
Page 59

The allowed downtime has a significant impact on the investments into network
infrastructure and equipment needed for backups. For each type of data, list the
maximum acceptable downtime for recovery, that is, how long specific data can
be unavailable before recovered from a backup. For example, user files may be
restored in two days, while some business data in a large database would need
to be recovered in two hours.
Recovery time consists mainly of the time needed to access the media and the
time required to actually restore data to disks. A full system recovery takes more
time, because some additional steps are required. For more information, see
“Disaster recovery” on page 128.
• How long should specific types of data be kept?
For each type of data, list how long the data must be kept. For example, you may
only need to keep user files for three weeks, while information about company
employees may be kept for five years.
• How should media with backed up data be stored and maintained?
For each type of data, list how long the media with data must be kept in a vault,
a safe, external location, if you use one. For example, user files may not be stored
in a vault at all, while order information may be kept for five years, with
verification of each medium after two years.
• To how many media sets should the data be written during backup?
Consider writing critical data to several media sets during backup to improve the
fault tolerance of such backups, or to enable multi-site vaulting. Object mirroring
increases the time needed for backup.
• How much data needs to be backed up?
List the estimated amount of data to be backed up, for each type of data. This
influences the time needed for backup and helps you to choose the right backup
devices and media for backup.
• What is the projected future growth of the amount of data?
Estimate future growth, for each type of data. This will help you to come up with
backup solutions that will not be quickly outdated. For example, if your company
plans to hire 100 new employees, the amount of users’ data and client systems’
data will grow accordingly.
• How long can a backup take?
Estimate the time needed for each backup. This directly affects the amount of time
data is available for use. User files can be backed up at any time when the users
are not working on them, while some transactional databases may only have a
few hours available for backup.
Concepts guide 59
Page 60

The time needed for backup depends on the type of backup, full or incremental.
For more information, see “Full and incremental backups” on page 91. Data
Protector also backs up some popular online database applications. For more
information, see the HP Data Protector integration guide.
If you back up to disk, you can take advantage of synthetic backup and disk
staging. These advanced backup strategies significantly reduce the time needed
for backup. For more information, see Chapter 11 on page 257 and Disk
staging on page 118.
When there is a very fast and large disk to be backed up on a slower device,
consider the possibility of backing up one hard disk through multiple concurrent
Disk Agents. Starting multiple Disk Agents on the same disk speeds up the backup
performance considerably.
Also, if there is a large volume of information to be backed up and the available
time to complete the backup is limited, consider the possibility of using direct
backup to take advantage of SAN speed, reduced network traffic, and the lack
of the backup-server bottleneck.
• How often does data need to be backed up?
For each type of data, list how often the data needs to be backed up. For example,
user working files may be backed up on a daily basis, system data on a weekly
basis, and some database transactions twice a day.
Factors influencing your backup strategy
There are a number of factors that influence how your backup strategy is implemented.
Understand these factors before preparing your backup strategy.
• Your company’s backup and storage policies and requirements.
• Your company’s security policies and requirements.
• Your physical network configuration.
• Computer and human resources available at different sites of your company.
Preparing a backup strategy plan
The result of the planning is a backup strategy that must address the following areas:
• How critical system availability (and backup) is to the company
• The need to keep the backed up data at a remote location in case of a disaster.
• The level of business continuance
This includes the recovery and restore plan for all critical client systems.
• The security of backed up data
Planning your backup strategy60
Page 61

The need to guard premises to prevent unauthorized people from entering.
This also includes safeguarding all relevant data against unauthorized access,
using physical access prevention and electronic password protection.
• Types of data that need to be backed up
List the company’s types of data and how you want to combine them in backup
specifications, including the time frames available for backups. The company’s
data can be divided into categories like company business data, company
resource data, project data, and personal data, each with its own specific
requirements.
• Backup policy implementation
• How backups are done and the backup options that you use
This defines the frequency of full and incremental backups. It also defines the
backup options that are used and whether the backups are permanently
protected and the backup media stored at a security company.
• How the client systems are grouped into backup specifications
Consider how best to group backup specifications. This can be done on the
basis of departments, data types, or backup frequency.
• How the backups are scheduled
Consider using the staggered approach, whereby full backups are scheduled
for different clients (backup specifications) on different days to avoid network
load, device load, and time window issues.
• Retaining data on media, and information about backups
Consider protecting data from being overwritten by newer backups for a
specified amount of time. This protection, called data protection, is on a session
basis.
Define the period of time the Catalog Database should store information about
backup versions, the number of backed up files and directories, and messages
stored in the database. For as long as this catalog protection has not expired,
backed up data is easily accessible.
• Device configuration
Determine devices to use for backups, and the client systems they are connected
to. Connect the backup devices to client systems with the largest amount of data,
so that as much data as possible is backed up locally and not via the network.
This increases the backup speed.
If you need to back up large amounts of data:
• Consider using a library device.
Concepts guide 61
Page 62

• Consider backing up to a disk-based device. Besides other benefits, backup
to disk reduces the time needed for backup and enables the use of advanced
backup strategies such as synthetic backup and disk staging.
• Consider configuring your system for direct backup by attaching a library
device to the SAN through a fibre channel bridge. This is a solution when the
network impairs the backup speed.
• Media management
Determine the type of media to use, how to group the media into media pools,
and how to place objects on the media.
Define how media are used for backup policies.
• Vaulting
Decide whether to store media at a safe place (a vault), where they are kept for
a specific period of time. Consider duplicating backed up data during or after
the backup for this purpose.
• Backup administrators and operators
Determine the rights of users that can administer and operate your storage product.
Planning cells
One of the most important decisions in planning your backup strategy is whether
you want to have a single or multiple cell environment. This section describes the
following:
• Factors you should consider when planning cells
• How cells relate to a typical network environment
• How cells relate to Windows domains
• How cells relate to Windows workgroup environments
One cell or multiple cells?
When deciding whether to have a single cell or multiple cells in your environment,
consider the following items:
• Backup administration issues
The use of multiple cells gives you higher administration freedom within each cell.
You can apply completely independent media management policies for each
cell. If you have several administrative groups, you may, for security reasons, not
want a cell to span across these groups. A disadvantage of having multiple cells
Planning your backup strategy62
Page 63

is that it can require more administrative work or might even require a separate
administrator for each cell.
• Size of each cell
The size of a Data Protector cell affects backup performance and the ability to
manage the cell. The recommended maximum size for a Data Protector cell is
100 client systems. Cells with more than 200 client systems are less manageable.
• Network considerations
All client systems of a cell should be on the same LAN for maximum performance.
For more information about other network considerations such as your network
configuration, see the sections that follow.
• Geographical location
If the client systems you want to back up are geographically dispersed, it may
be difficult to manage them from a single cell and there may be networking
problems between the client systems. Additionally, the security of data may be
an issue.
• Time Zones
Each cell should be within one time zone.
• Security of data
Data Protector provides cell level based security. All Data Protector administrative
work is done in the context of a single cell: media, backup devices, and backed
up data belong to one cell. Note that Data Protector lets you share devices or
move media between cells, so physical access to media must be limited to
authorized personnel.
• Mixed environments
Data Protector allows you to back up client systems of diverse platforms in a single
cell. However, it may be convenient to group client systems in a cell based on
the platforms. For example, you may have one cell with the Windows client
systems and one with the UNIX client systems. This is especially useful if you have
separate administrators and policies for the UNIX and Windows environments.
• Departments and sites
You can group each department or site in a separate cell. For example, you may
have one cell for the accounting, one for the IT, and one for the manufacturing
department. Even if you choose to have several cells, Data Protector allows you
to easily configure common policies among the cells.
Concepts guide 63
Page 64

Installing and maintaining client systems
If you have several UNIX and Windows client systems, an efficient mechanism for
the installation of Data Protector becomes important. Local installation on every client
is not feasible in large environments.
Installation Servers and the Cell Manager
The main system in a Data Protector cell is the Cell Manager. To conveniently distribute
(push) Data Protector components to client systems from a central location, a system
holding the Data Protector software repository is needed. This system is called the
Data Protector Installation Server. The Cell Manager is by default also an Installation
Server.
Each time you perform a remote installation, you access the Installation Server. The
advantage of using Installation Servers is that the time required for remote installation,
update, upgrade, and removal of Data Protector software is greatly reduced,
especially in enterprise environments.
There are certain hardware and software requirements that need to be met by
Installation Servers and Cell Managers before you start installing the software. A
dedicated port, generally port 5555, needs to be available throughout the cell. For
details, see the HP Data Protector installation and licensing guide.
The Cell Manager and Installation Servers are installed directly from the CD. After
you have installed the Cell Manager and Installation Servers you can then install the
components on various client systems using the Data Protector Installation GUI.
When you install Data Protector for the first time, it runs with an instant-on license,
valid for 60 days, that lets you use Data Protector before you acquire a permanent
license. During this time, purchase any required licenses.
Also during this time, you should set up and configure your Data Protector environment
and request your permanent license. To request a permanent password string, you
need to know which client systems belong in which Data Protector cell, the number
of devices connected to the client systems, and whether you need to use any of the
Data Protector integrations.
Creating cells in the UNIX environment
Creating cells in the UNIX environment is easy. Based on the considerations given
in this manual, decide which client systems you want to add to the cell and define
the Cell Manager system. During installation, root access is required to every client
system. An important prerequisite is to have a clean node name resolving setup, such
Planning your backup strategy64
Page 65

that each client system is accessible from every other client system using the same
fully qualified node name.
Creating cells in the Windows environment
Due to the different possible configurations (domain versus workgroup), the various
levels of support for Windows Administrators may have some impact on the setup
of Data Protector during installation. An important prerequisite is to have a clean
node name resolving setup, so that each client system is accessible from every other
client system using the same fully qualified node name.
Windows domains
A Windows domain can easily be mapped to a Data Protector cell. In a single
Windows domain, use a one-to-one mapping if the size of the domain does not
exceed the recommended size of the Data Protector cell. Otherwise, split it into two
or more cells and manage these cells using the Data Protector Manager-of-Managers.
Mapping a Data Protector cell into a Windows domain
Mapping a Data Protector cell into a Windows domain also eases administration
within Data Protector itself. To ease administration, distribute the software such that
all the client systems can be installed using a central Windows account in a domain
organization. Other operations, however, are not limited to a Windows domain
organization since all operations and security verifications are performed by the
Data Protector internal protocol and not by the Windows Security.
In general, there are no limitations on how and where Data Protector can be installed.
However, because of the structure of Windows and the most common configurations
that are domain environments, some operations are easier when Data Protector is
mapped to a single domain or a multiple domain model, where one of the domains
is a master domain, to allow a single user to manage all the client systems within the
environment (Software Distribution and User Configuration).
In a multiple cell environment with a Manager-of-Managers, this issue is more
significant because all the cells that are configured require a central administrator
that has access to the entire backup environment. When a single domain or multiple
domains with a master domain are configured, the same global master domain user
can be the administrator of all the cells and the Manager-of-Managers environment.
If multiple independent domains are used, you need to configure multiple users to
administer the environment.
Concepts guide 65
Page 66

Windows workgroups
Some of the configuration tasks require more steps in some cases, because there are
no global users as in a domain. Software distribution requires a unique logon for
every client system that you install the software on. This means that to install 100
client systems in a workgroup environment, you are required to enter 100 logons.
In such cases, use a domain environment, since installation and many other non-Data
Protector related administration tasks are much easier for a large-scale environment.
Using MoM in such an environment requires you to configure the administrators
separately for each cell, to manage the MoM environment from any of the cells.
Again, Data Protector is not limited to a Windows domain organization. However,
it takes advantage of and simplifies the administration procedures in the areas where
user authentication is required (Installation, User Management).
Creating cells in a mixed environment
In a mixed environment, take into account the factors described in “Creating cells in
the UNIX environment” on page 64. The more the environment is broken into multiple
domains and multiple workgroups, the more accounts and steps need to be considered
to distribute the software and to prepare the environment for administration.
Geographically remote cells
Data Protector allows you to easily administer geographically remote cells. For more
information, see “Splitting an environment into multiple cells” on page 45.
Considerations for geographically remote cells
When configuring geographically remote cells, remember the following:
• Data is not sent over a WAN.
The devices and the client systems that you are backing up are configured locally.
• The cells are configured in a MoM.
To manage geographically remote cells centrally, you need to configure the cells
in a MoM environment.
• Consider user configurations.
All the considerations that are mentioned regarding single domain, multiple
domain, and workgroup configurations need to be taken into account.
Planning your backup strategy66
Page 67

You can configure a single cell over geographically remote locations. In this case,
you need to ensure that data transfer from each client system to the corresponding
device is not done over a WAN. Because a WAN network is not a stable connection,
it is possible that connections are lost.
MoM environment
A MoM environment does not require a reliable network connection from cells to the
central MoM cell, because only controls are sent over the long distance connections,
and backups are performed locally within each Data Protector cell. However, this is
based on the assumption that each cell has its own media management database.
In such a case, use the Data Protector Reconnect broken connections backup option
so that connections are reestablished after they are broken.
Understanding and planning performance
In business-critical environments, it is a key requirement to minimize the time needed
for data recovery in case of a corrupt database or a disk crash. Therefore,
understanding and planning backup performance is extremely important. Optimizing
the time required for the backup of a number of client systems and large databases
that are all connected on different networks and different platforms is a challenging
task.
The following sections give an overview of the most common backup performance
factors. Due to the high number of variables it is not possible to give distinct
recommendations that fit all user requirements.
The infrastructure
The infrastructure has a high impact on the backup and restore performance. The
most important aspects are the parallelism of data paths and the use of high-speed
equipment.
Network versus local backups
Sending data over a network introduces additional overhead, as the network becomes
a component of performance consideration. Data Protector handles the data stream
differently for the following cases:
• Network datastream: Disk to Memory of Source System to Network to Memory
of Destination System to Device
• Local datastream: Disk to Memory to Device
Concepts guide 67
Page 68

To maximize performance, use local backup configurations for high volume
datastreams.
Network or server versus direct backups
Sending data over a network and through a server introduces additional overhead,
as the network and the server become performance considerations. Data Protector
handles the datastream differently for the following cases:
• Network datastream: Disk to Memory of Source System to Network to Memory
of Destination System to Device
• Direct datastream: Disk to Device
To maximize performance, use direct backup configurations for high volume
datastreams.
Devices
Device performance
Device types and models impact performance because of the sustained speed at
which devices can write data to a tape (or read data from it).
Data transfer rates also depend on the use of hardware compression. The achievable
compression ratio depends on the nature of the data being backed up. In most cases,
using high speed devices with hardware compression improves performance. This
is true, however, only if the devices stream.
At the start and at the end of a backup session backup devices require some time
for operations such as rewinding media and mount or unmount media.
Libraries offer additional advantages because of their fast and automated access to
a large number of media. At backup time, loading new or reusable media is needed,
and at restore time the media which contain the data to be restored need to be
accessed quickly.
Data in disk based-devices is accessed faster than that in conventional devices, as
there is no need to load and unload media. This reduces the amount of time spent
for backup and restore. Additionally, disk-based devices enable the use of advanced
backup strategies such as synthetic backup and disk staging, which also reduce the
backup and restore time.
Planning your backup strategy68
Page 69

High performance hardware other than devices
Performance of computer systems
The speed of computer systems themselves directly impacts performance. The systems
are loaded during backups by reading the disks, handling software compression,
and so on.
The disk read data rate and CPU usage are important performance criteria for the
systems themselves, in addition to I/O performance and network types.
Advanced high performance configuration
Data Protector Zero Downtime Backup solution provides a means of shortening the
application downtime or backup mode time and reduces the network overhead by
using locally attached backup devices instead of network backup devices. The
application downtime or backup mode time is limited to the time needed to create
a replica of data, which is then backed up on a backup system to a locally attached
device.
For more information on Zero Downtime Backup, see the HP Data Protector zero
downtime backup concepts guide.
Using hardware in parallel
Using several datapaths in parallel is a fundamental and efficient method to improve
performance. This includes the network infrastructure. Parallelism boosts performance
in the following situations:
When to use parallelism
• Several client systems can be backed up locally, that is, with the disk(s) and the
related devices connected on the same client system.
• Several client systems can be backed up over the network. Here the network
traffic routing needs to be such that datapaths do not overlap, otherwise the
performance is reduced.
• Several objects (disks) can be backed up to one or several (tape) devices.
• An object (disk or files) can be directly backed up to several (tape) devices using
several XCOPY engines.
• Several dedicated network links between certain client systems can be used. For
example, if system_A has 6 objects (disks) to be backed up, and system_B has
Concepts guide 69
Page 70

3 fast tape devices, consider using 3 dedicated network links between system_A
and system_B.
• Load Balancing
Using this Data Protector feature, Data Protector dynamically determines which
object (disk) should be backed up to which device. Enable this feature, especially
to back up a large number of filesystems in a dynamic environment. For more
information, see “How load balancing works” on page 156.
Note that you cannot predict to which media a particular object is written.
Configuring backups and restores
Any given infrastructure must be used efficiently to maximize performance. Data
Protector offers high flexibility to adapt to the environment and the desired way to
operate backups and restores.
Software compression
Software compression is done by the client CPU when reading data from a disk. This
reduces the data that is sent over the network, but it requires significant CPU resources
from the client.
By default, software compression is disabled. Use software compression only for
backups of many machines over a slow network, where data can be compressed
before sending it over the network. If software compression is used, hardware
compression should be disabled since trying to compress data twice actually expands
the data.
Hardware compression
Hardware compression is done by a device that receives original data from a Drive
Server and writes it to media in the compressed mode. Hardware compression
increases the speed at which a tape drive can receive data, because less data is
written to the tape.
By default, hardware compression is enabled. On HP-UX systems, enable hardware
compression by selecting a hardware compression device file. On Windows systems,
enable hardware compression during device configuration. Use hardware compression
with caution, because media written in compressed mode cannot be read using a
device in uncompressed mode and vice-versa.
Planning your backup strategy70
Page 71

Full and incremental backups
A basic approach to improve performance is to reduce the amount of data to back
up. Carefully plan your full and incremental backups. Note that you may not need
to perform all the full backups of all the client systems at the same time.
If you back up to disk, you can use advanced backup strategies such as synthetic
backup and disk staging.
Disk image versus filesystem backups
It used to be more efficient to back up disk images (raw volumes) rather than
filesystems. This is still true in some cases, such as heavily-loaded systems or disks
containing large numbers of small files. The general recommendation is to use
filesystem backups.
Object distribution to media
The following are examples of object/media backup configurations provided by
Data Protector:
• One object (disk) goes to one medium
The advantage is a known fixed relationship between an object and a medium
where the object resides. This can be of benefit for the restore process, since only
one medium needs to be accessed.
The disadvantage in a network backup configuration is the likely performance
limitation due to the network, causing the device not to stream.
• Many objects go to a few media, each medium has data from several objects,
one object goes to one device
The advantage here is the flexibility of datastreams at backup time, helping to
optimize performance, especially in a network configuration.
The strategy is based on the assumption that the devices receive enough data to
be able to stream, since each device receives data from several sources
concurrently.
The disadvantage is that data (from other objects) has to be skipped during the
restore of a single object. Additionally, there is no precise prediction as to which
medium will receive data from which object.
For more information on device streaming and backup concurrency, see “Device
streaming and concurrency” on page 156.
Concepts guide 71
Page 72

Disk performance
All data that Data Protector backs up resides on disks in your systems. Therefore, the
performance of disks directly influences backup performance. A disk is essentially a
sequential device, that is, you can read or write to it, but not both at the same time.
Also, you can read or write one stream of data at a time. Data Protector backs up
filesystems sequentially, to reduce disk head movements. It also restores files
sequentially.
Sometimes this is not visible because the operating system stores most frequently used
data in a cache memory.
Disk fragmentation
Data on a disk is not kept in the logical order that you see when browsing the files
and directories, but is fragmented in small blocks all over the physical disk. Therefore,
to read or write a file, a disk head must move around the whole disk area. Note that
this differs from one operating system to another.
TIP:
Backups are most efficient for large files with little fragmentation.
Compression
If data is compressed on a disk, the Windows operating system first decompresses
the data before sending it across the network. This reduces the backup speed and
uses CPU resources.
Disk image backups
Data Protector also allows you to back up UNIX disks as disk images. With a disk
image backup, a complete image of the disk is backed up without tracking the
filesystem structure. The disk head moves linearly across the surface. Thus a disk
image backup can be considerably faster than a filesystem backup.
Disk Agent performance on Windows systems
Disk Agent performance of Windows filesystem backup can be improved by enabling
asynchronous reading. Asynchronous reading improves performance of the Disk
Agent when backing up data on disk arrays, especially if large files are backed up.
It is recommended to perform test backups to establish if asynchronous reading will
Planning your backup strategy72
Page 73

improve performance in your specific environment and determine the optimum
asynchronous reading settings.
SAN performance
If large volumes of data need to be backed up in one session, the time needed to
transfer the data becomes significant. This consists of the time required to move the
data over a connection (LAN, local, or SAN) to a backup device.
Online database application performance
When you back up databases and applications, such as Oracle, SAP R/3, Sybase,
and Informix Server, the performance of the backups also depends on the applications.
Database online backups are provided so that backups can occur while the database
application remains online. This helps to maximize database up time but may impact
application performance. Data Protector integrates with all popular online database
applications to optimize backup performance.
For more information on how Data Protector integrates with various applications and
for tips on how to improve backup performance, see the HP Data Protector integration
guide.
Also see the documentation that comes with your online database application for
more information on how to improve backup performance.
Planning security
When you plan your backup environment, consider security. A well thought out,
implemented, and updated security plan prevents the unauthorized access, duplication,
or modification of data.
What is security?
Security in the backup context typically refers to:
• Who can administer or operate a backup application (Data Protector).
• Who can physically access client systems and backup media.
• Who can restore data.
• Who can view information about backed up data.
Data Protector provides security solutions on all these levels.
Concepts guide 73
Page 74

Data Protector security features
The following features allow and restrict access to Data Protector and the backed up
data. The items in this list are described in detail in the following sections.
• Cells
• Data Protector user accounts
• Data Protector user groups
• Data Protector user rights
• Visibility and access to backed up data
Cells
Starting sessions
Data Protector security is based on cells. Backup and restore sessions can only be
started from the Cell Manager unless you have the Data Protector
Manager-of-Managers functionality. This ensures that users from other cells cannot
back up and restore data from systems in your local cell.
Access from a specific Cell Manager
Additionally, Data Protector allows you to explicitly configure from which Cell
Manager a client system can be accessed, that is, configuring a trusted peer.
Restrict pre- and post-execution
For security reasons, various levels of restrictions can be configured for pre-exec and
post-exec scripts. These optional scripts allow a client system to be prepared for the
backup by, for example, shutting down an application to obtain a consistent backup.
Data Protector users accounts
Anyone using any Data Protector functionality, administering Data Protector, or
restoring personal data, must have a Data Protector user account. This restricts
unauthorized access to Data Protector and backed up data.
Who defines user accounts?
An administrator creates this account specifying a user login name, systems from
which a user can log in, and the Data Protector user group membership that defines
the user rights.
Planning your backup strategy74
Page 75

When is the account checked?
When a user starts the Data Protector user interface, Data Protector checks user rights.
User rights are also checked when specific tasks are performed by a user.
For more information, see Chapter 4 on page 183.
Data Protector user groups
What are user groups?
When a new user account is created, the user becomes a member of the specified
user group. Each user group contains defined Data Protector user rights. All the
members of the group have the user rights set for the group.
Why use user groups?
Data Protector user groups simplify user configuration. The administrator groups users
according to the access they need. For example, an end-user group could allow
members to restore personal data to a local system only, while the operator group
allows the starting and monitoring of backups, but not the creating of backups.
For more information, see Chapter 4 on page 183.
Data Protector user rights
What are user rights?
Data Protector user rights define the actions that a user can perform with Data
Protector. They are applied on the Data Protector user group level and not to each
user individually. Users added to a user group automatically gain the user rights
assigned to this user group.
Why use user rights?
Data Protector provides flexible user and user group functionality, which allows the
administrator to selectively define who can use a particular Data Protector functionality.
It is important to carefully apply the Data Protector user rights: backing up and
restoring data is essentially the same as copying data.
For more information, see Chapter 4 on page 183.
Concepts guide 75
Page 76

Visibility of backed up data
Backing up data means creating a new copy. Therefore, when you deal with
confidential information, it is important to restrict access to both the original data
and to the backup copy itself.
Hiding data from other users
When configuring a backup, you can decide whether during a restore the data is
visible to everyone (public) or only to the owner of the backup (private). For more
information about backup owners, see “What is backup ownership?” on page 78.
Data encryption
Open systems and public networking make data security in large enterprises essential.
Data Protector lets you encrypt backed-up data so that it becomes protected from
others. Data Protector offers two data encryption techniques: software-based and
drive-based.
Data Protector software encryption, referred to as AES 256-bit encryption, is based
on the AES-CTR (Advanced Encryption Standard in Counter Mode) encryption
algorithm that uses random keys of 256-bit length. The same key is used for both
encryption and decryption. With AES 256-bit encryption, data is encrypted before
it is transferred over a network and before it is written to media.
Data Protector drive-based encryption uses the encryption functionality of the drive.
The actual implementation and encryption strength depend on the drive's firmware.
Data Protector only turns on the feature and manages encryption keys.
The key management functionality is provided by the Key Management Server (KMS),
which is located on the Cell Manager. All encryption keys are stored centrally in the
key store file on the Cell Manager and administered by the KMS.
You can encrypt all or selected objects in a backup specification and also combine
encrypted and unencrypted sessions on the same medium.
In addition to the encryption functionality, Data Protector also offers the encoding
functionality that uses a keyless, built-in algorithm for this purpose.
How Data Protector AES 256-bit encryption works
The Backup Session Manager (BSM) reads the backup specification in which the AES
256-bit encryption option is selected and requests an active encryption key from the
Key Management Server (KMS). The key is transferred to the Disk Agent (DA), which
Planning your backup strategy76
Page 77
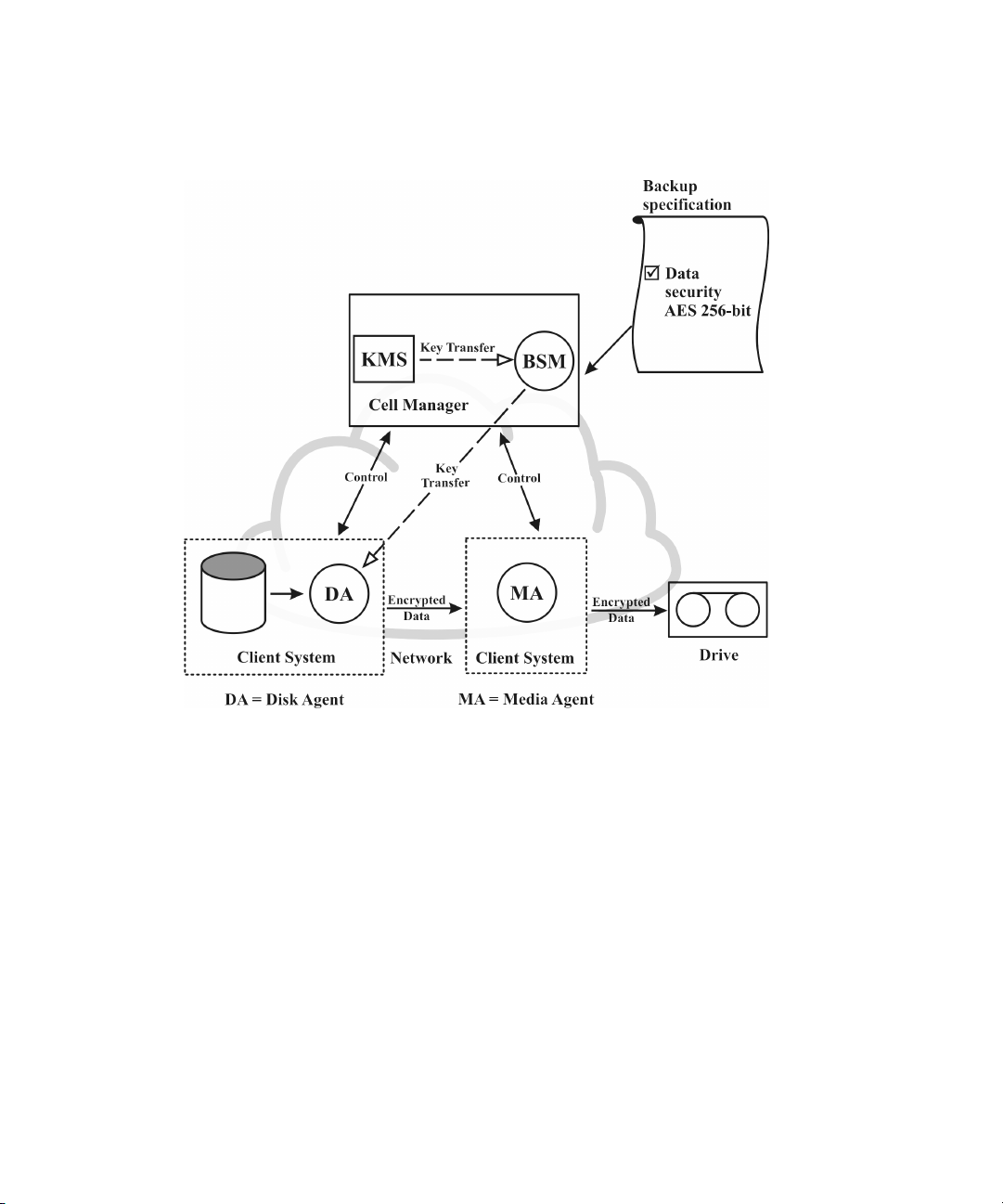
encrypts the data. Thus the backed up data is encrypted before it is transferred over
the network and written to media.
Figure 17 on page 77 shows a basic interaction during an encrypted backup session
with the AES 256-bit encryption option selected.
Figure 17 Backup session with AES 256-bit encryption
How Data Protector drive-based encryption works
The BSM reads the backup specification in which the Drive-based encryption option
is selected and requests an active encryption key from the KMS. The key is transferred
to the Media Agent (MA), which configures the drive for encryption and sets the
encryption key into the drive. The drive encrypts both the data and the meta-data
that is written to the medium.
In an object copy or object consolidation operation from an encrypted backup, the
data is decrypted by the source drives, transferred over the network and encrypted
by the destination drives.
Concepts guide 77
Page 78
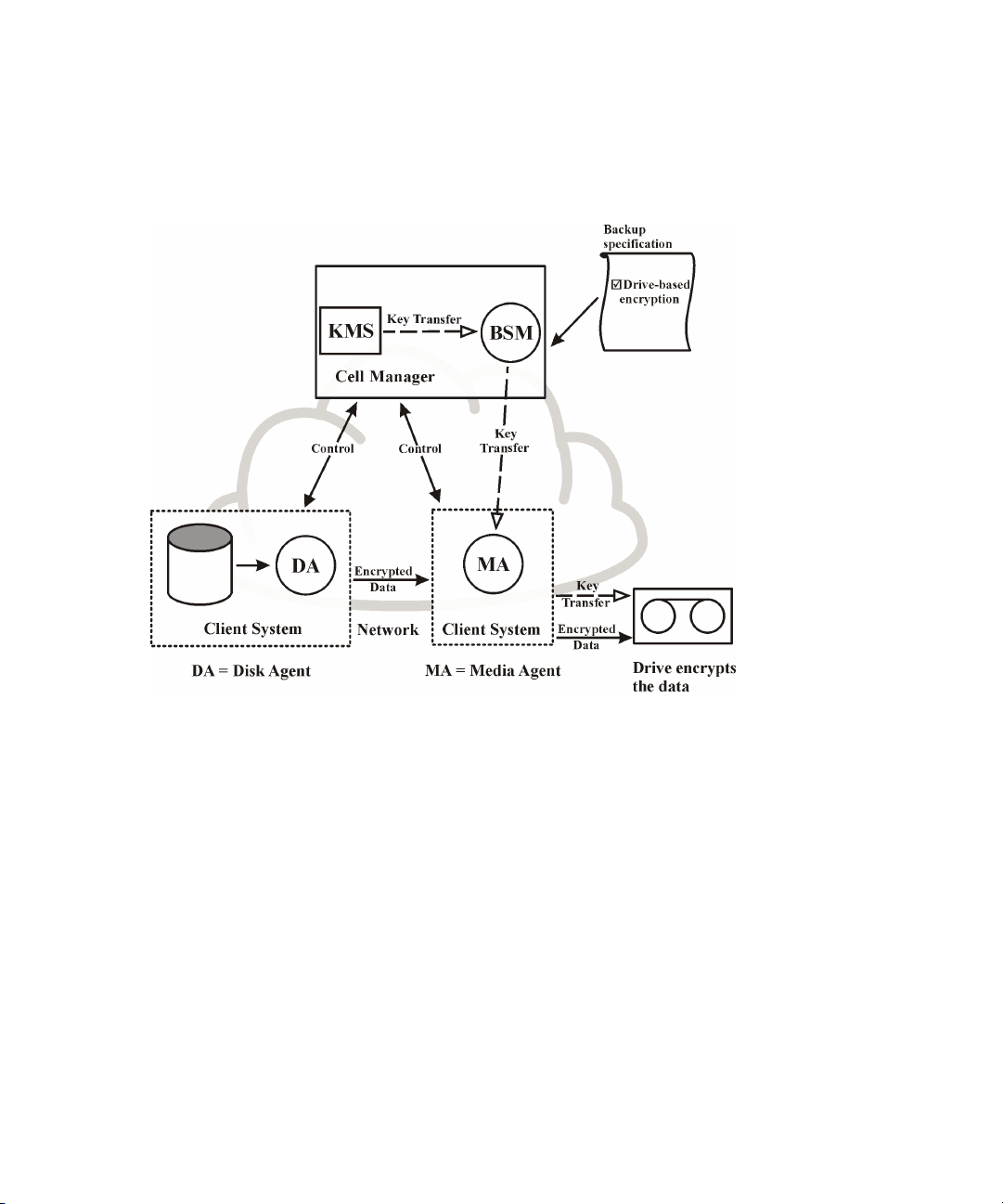
If a source medium involved in an automatic media copy session stores encrypted
as well as non-encrypted data, all data written to the corresponding target medium
will be either encrypted or non-encrypted, depending on current settings for
drive-based encryption.
Figure 18 on page 78 shows a basic interaction during an encrypted backup session
with the Drive-based encryption option selected.
Figure 18 Backup session with drive-based encryption
Restore from encrypted backups
No additional encryption related preparations are needed for restore of encrypted
backups, as Data Protector automatically obtains the appropriate decryption keys.
What is backup ownership?
Who owns a backup session?
Each backup session and all the data backed up within it is assigned an owner. The
owner can be the user who starts an interactive backup, the account under which
Planning your backup strategy78
Page 79

the CRS process is running, or the user specified as the owner in the backup
specification options. For instructions on how to specify a backup owner, see the
online Help index: "ownership".
Backup ownership and restore
Backup ownership affects the ability of users to see and restore data. Unless the
object is marked as Public, only the owner of the media set or an administrator can
see the data saved in the media set. The right to see and restore private objects can
be granted to groups other than admin as well. For instructions on who can see and
restore a private object and how this can be applied, see the online Help index:
"ownership".
Clustering
Cluster concepts
What is a cluster?
A cluster is a group of two or more computers that appear on the network as a single
system. This group of computers is managed as a single system and is designed to:
• Ensure that mission-critical applications and resources are as highly-available as
possible
• Tolerate component failures
• Support either the addition or subtraction of components
For clustering purposes, Data Protector integrates with Microsoft Cluster Server for
Windows Server, with MC/Service Guard for HP-UX, with Veritas Cluster for Solaris
and with Novell NetWare Cluster Services. For a list of supported clusters, see the
HP Data Protector product announcements, software notes, and references.
Concepts guide 79
Page 80

Figure 19 Typical cluster
Components:
• Cluster nodes (two or more)
• Local disks
• Shared disks (shared between nodes)
Cluster nodes
Cluster nodes are computers that compose a cluster. They are physically connected
to one or more shared disks.
Shared disks
The shared disks volumes (MSCS, Novell NetWare Cluster Services) or shared volume
groups (MC/SG, Veritas Cluster) contain mission-critical application data as well as
specific cluster data needed to run the cluster. In MSCS clusters, a shared disk is
exclusively active on only one cluster node at a time.
Cluster network
A cluster network is a private network that connects all cluster nodes. It transfers the
internal cluster data called heartbeat of the cluster. The heartbeat is a data packet
with a time stamp that is distributed among all cluster nodes. Each cluster node
compares this packet and determines the cluster node that is still operational so that
Planning your backup strategy80
Page 81

you can make an appropriate determination of the ownership of the package
(MC/SG, Veritas Cluster) or group (MSCS).
What is a package or group?
A package (MC/SG, Veritas Cluster) or a group (MSCS) is a collection of resources
that are needed to run a specific cluster-aware application. Each cluster-aware
application declares its own critical resources. The following resources must be
defined in each group or package:
• Shared disk volumes (MSCS, Novell NetWare Cluster Services)
• Shared volume groups (MC/SG, Veritas Cluster)
• Network IP names
• Network IP addresses
• Cluster-aware application services
What is a virtual server?
Disk volumes and volume groups represent shared physical disks. A network IP name
and a network IP address are resources that define a virtual server of a cluster-aware
application. Its IP name and address are cached by the cluster software and mapped
to the cluster node where the specific package or group is currently running. Since
the group or package can switch from one node to another, the virtual server can
reside on different machines in different time frames.
What is a failover?
Each package or group has its own “preferred” node where it normally runs. Such
a node is called a primary node. A package or group can be moved to another
cluster node (one of the secondary nodes). The process of transferring a package or
group from the primary cluster node to the secondary is called failover or switchover.
The secondary node accepts the package or group in case of failure of the primary
node. A failover can occur for many different reasons:
• Software failures on the primary node
• Hardware failures on the primary node
• The administrator intentionally transfers the ownership because of maintenance
on the primary node
In a cluster environment there can be more than one secondary node but only one
can be the primary.
Concepts guide 81
Page 82

A cluster-aware Data Protector Cell Manager that is responsible for running the IDB
and managing backup and restore operations has many major benefits over
non-cluster versions:
High availability of the Data Protector Cell Manager
All Cell Manager operations are always available since Data Protector services are
defined as cluster resources within the cluster and are automatically restarted when
a failover occurs.
Automatic restart of backups
Data Protector backup specifications that define the backup procedure can easily be
configured to be restarted in case of a failover of the Data Protector Cell Manager.
Restart parameters can be defined using the Data Protector GUI.
Load balancing at failover
A special command-line utility is provided for operations that allow backup sessions
to be aborted in case applications other than Data Protector perform a failover. The
Data Protector Cell Manager allows you to define what should happen in such
situations. If the backup is less important than the application, Data Protector can
abort running sessions. If the backup is more important or is just ending, Data Protector
can continue the sessions. For more information on how to define the criteria, see
the online Help index: "cluster, managing backups".
Cluster support
The Data Protector cluster support means the following:
• The Data Protector Cell Manager is installed in a cluster. Such a Cell Manager
is fault tolerant and can restart operations in the cell automatically after the failover.
NOTE:
If the Cell Manager is installed in the cluster, its cluster critical resources need to
be configured in the same cluster package or group as the application being
backed up, in order to automatically restart
due to a failover. Otherwise, the failed backup sessions must be restarted
manually.
Planning your backup strategy82
failed backup sessions
that failed
Page 83

• The Data Protector client is installed in a cluster. The Cell Manager (if not installed
in the cluster) in such a case is not fault tolerant; the operations in the cell must
be restarted manually.
The behavior of the Cell Manager after the failover is configurable as far as the
backup session (failed due to the failover) is concerned - the failed session can be:
• restarted as a whole
• restarted only for the failed objects
• not restarted at all
For more information on backup session behavior options on failover of the Data
Protector Cell Manager, see the online Help index: "cluster, backup specification
options".
Example cluster environments
This section gives three example cluster configurations.
Cell Manager installed outside a cluster
In the environment depicted below:
• The Cell Manager installed outside a cluster
• A backup device connected to the Cell Manager or one of the (non-clustered)
clients
Concepts guide 83
Page 84

Figure 20 Cell Manager installed outside a cluster
When creating a backup specification, you can see three or more systems that can
be backed up in the cluster.
• Physical Node A
• Physical Node B
• Virtual Server
Virtual server backup
If you select the virtual server in the backup specification, then the backup session
will back up the selected active virtual host/server regardless of the physical node
the package or group is currently running on.
For more information on how to define these options, see the online Help index:
"cluster, backup specification options".
Planning your backup strategy84
Page 85

The following is the expected backup behavior under this configuration.
Table 3 Backup behavior
ResultCondition
Successful backupFailover of the node before
a backup starts
Failover of the node during
backup activity
Filesystem/disk image backup: The backup session fails. The
completed objects from the session can be used for restore,
the failed (running and pending) objects need to be backed
up again by restarting the session manually.
Application backup: The backup session fails. The session
needs to be restarted manually.
Cell Manager installed outside a cluster, devices connected to the cluster nodes
In the environment depicted below:
• The Cell Manager installed outside a cluster
• Backup devices connected to the nodes in the cluster
Concepts guide 85
Page 86

Figure 21 Cell Manager installed outside a cluster, devices connected
to the cluster nodes
When creating a backup specification, you can see three or more systems that can
be backed up in the cluster.
• Physical Node A
• Physical Node B
• Virtual Server
Virtual server backup
If you select the virtual server in the backup specification, then the backup session
will back up the selected active virtual host/server regardless of the physical node
the package or group is currently running on.
Planning your backup strategy86
Page 87
NOTE:
The difference with the previous example is that each of the cluster nodes has a Data
Protector Media Agent installed. Additionally, you need to use the Data Protector load
balancing functionality. Include both devices in the backup specification. With load
balancing set to min=1 and max=1, Data Protector will only use the first available
device.
The following is the expected backup behavior under this configuration.
Table 4 Backup behavior
ResultCondition
Failover of the node before a backup starts
Failover of the node during backup activity
Successful backup due to automatic device
switching (load balancing)
Filesystem/disk image backup: The backup
session fails. The completed objects from the
session can be used for restore, the failed
(running and pending) objects need to be
backed up again by restarting the session
manually.
Application backup: The backup session fails.
The session needs to be restarted manually.
IMPORTANT:
If a failover during backup activity occurs in such a configuration, the MA may not be
able to properly abort the session. This results in the corruption of the medium.
Cell Manager installed in a cluster, devices connected to the cluster nodes
In the environment depicted below:
• The Cell Manager installed in a cluster.
With regard to the Data Protector application integrations, there are two possible
ways of configuring Data Protector and an application in such a configuration:
• The Data Protector Cell Manager is configured to run (both during the normal
operation and during the failover) on the same node as the application - the
Concepts guide 87
Page 88

Data Protector cluster critical resources are defined in the same package
(MC/ServiceGuard) or group (Microsoft Cluster Server) as the application
cluster critical resources.
IMPORTANT:
Only in such a configuration, it is possible to define the automated action
concerning the Data Protector sessions aborted during the failover.
• The Data Protector Cell Manager is configured to run (both during the normal
operation and during the failover) on nodes other than the application node
- the Data Protector cluster critical resources are defined in some other package
(MC/ServiceGuard) or group (Microsoft Cluster Server) as the application
cluster critical resources.
• Backup device(s) connected to the cluster shared Fibre Channel bus via an
FC/SCSI MUX.
Planning your backup strategy88
Page 89

Figure 22 Cell Manager installed in the cluster, devices connected to
cluster nodes
When creating a backup specification, you can see three or more systems that can
be backed up in the cluster.
• Physical Node A
• Physical Node B
• Virtual Server
Virtual server backup
If you select the virtual server in the backup specification, then the backup session
will back up the selected active virtual host/server regardless of the physical node
the package or group is currently running on.
Concepts guide 89
Page 90
NOTE:
Clusters do not support a SCSI bus with shared tapes. To bring high availability also to
Media Agents, the Fibre Channel technology can be used as an interface to the device.
The device itself is not highly-available in this configuration.
This configuration allows the following features:
• Customizable automatic restart of backups in case of failover of the Cell Manager.
The Data Protector backup specifications can be configured to be restarted in
case of failover of the Cell Manager. Restart parameters can be defined using
the Data Protector GUI.
• System load control at failover.
Sophisticated control is provided to define Data Protector behavior at failover. A
special command, omniclus, is provided for this purpose. The Cell Manager
allows the administrator to define what should happen in such situations.
• If the backup is less important than the application that just switched to the
backup system, Data Protector can abort the running sessions.
• If the backup is more important or it is just pending, Data Protector continues
the sessions.
The following is the expected backup behavior under this configuration.
Table 5 Backup behavior
backup starts
Failover of the
application and the Cell
Manager during backup
activity (Cell Manager
runs on the same node
as the application).
Planning your backup strategy90
ResultCondition
Successful backupFailover before a
Filesystem/disk image backup The
backup session fails. The completed
objects from the session can be used
for restore, the failed (running and
pending) objects are backed up again
by restarting the session automatically.
Application backup The backup
session fails. The session is restarted
automatically.
IMPORTANT
To restart the session,
the appropriate Data
Protector option must be
selected. For information
on defining all possible
Data Protector actions in
case of failover of the
Cell Manager, see the
online Help index:
"cluster, managing
backups".
Page 91

ResultCondition
Failover of the
application during
backup activity without
Cell Manager failover
(Cell Manager runs on
other node than the
application).
Filesystem/disk image backup The backup session fails at failover
of the node where the filesystem is installed. The completed
objects from the session can be used for restore, the failed
(running and pending) objects need to be backed up again by
restarting the session manually.
Application backup The backup session fails. The session needs
to be restarted manually.
IMPORTANT:
If a failover during backup activity occurs in such a configuration, the MA may not be
able to properly abort the session. This results in the corruption of the medium.
Additionally, the Data Protector cluster Cell Manager/client can be integrated with
the EMC Symmetrix or HP StorageWorks Disk Array XP environment, producing a
very highly-available backup environment. For more information, see the HP Data
Protector zero downtime backup administrator's guide.
Full and incremental backups
Data Protector provides two basic types of filesystem backups: full and incremental.
A full backup saves all the files selected for backup in a filesystem. An incremental
backup saves only those files that have changed since the last full or incremental
backup. This section gives hints on how to choose the backup type and how this
influences your backup strategy.
Table 6 Comparison of full and incremental backup
Incremental backupFull backup
Resources
Device handling
Takes more time to complete than
incremental backup and requires
more media space.
If you use a standalone device with
a single drive, you need to change
the media manually if a backup
does not fit on a single medium.
Backs up only changes made since
a previous backup, which requires
less time and media space.
It is less likely that the backup will
require additional media.
Concepts guide 91
Page 92

Incremental backupFull backup
Data Protector can also make incremental backups of online database applications.
These vary from application to application. On Sybase, for instance, this type of
backup is referred to as a transaction backup (a backup of transaction logs modified
since the last backup).
Note that the incremental backup concept is not related to the log level concept,
which defines the amount of information written to the IDB.
NOTE:
A number of additional backup types (such as direct backup, split mirror backup, snapshot
backup, and data mover backup) are available with Data Protector application
integrations. For more information, see the respective
guides
Full backups
Full backups always back up all selected objects, even if there are no changes since
the previous backup.
Enables simple and quick restore.Restore
for more information.
A restore takes more time because
of the number of media needed.
Occupies less space in the IDB.Occupies more space in the IDB.IDB impact
HP Data Protector integration
Synthetic backup
Synthetic backup is an advanced backup solution that eliminates the need to run
regular full backups. Instead, incremental backups are run, and subsequently merged
with the full backup into a new, synthetic full backup. For more information, see
Chapter 11 on page 257.
Incremental backups
Incremental backups back up changes from a previous still protected (full or
incremental) backup. A full backup of an object (with identical client name, mount
point, and description) must exist before an incremental backup of this object is
possible.
Planning your backup strategy92
Page 93

Incremental backups depend on the last full backup. If you specify an incremental
backup and there is no protected full backup, a full backup is performed instead.
Conventional incremental backup
Before running an incremental backup of a specific backup object, Data Protector
compares the trees in the backup object with the trees in the valid restore chain of
this object. If the trees do not match (for example, an additional directory in the
backup object was selected for backup since the last backup or multiple backup
specifications with the same backup object and different trees exist), a full backup
is automatically performed. This ensures that all files that have changed since the last
relevant backup are backed up.
With conventional incremental backup, the main criterion for determining whether
a file has changed or not since a previous backup is the file's modification time.
However, if a file has been renamed, moved to a new location, or if some of its
attributes have changed, its modification time does not change. Consequently, the
file is not always backed up in a conventional incremental backup. Such files are
backed up in the next full backup.
Enhanced incremental backup
Enhanced incremental backup reliably detects and backs up also renamed and moved
files, as well as files with changes in attributes.
Enhanced incremental backup also eliminates unnecessary full backups of an entire
backup object when some of the trees selected for backup change. For example, if
an additional directory is selected for backup since the last backup, a full backup of
this directory (tree) is performed, whereas the backup of the rest is incremental.
Using enhanced incremental backup is a prerequisite for synthetic backup.
You can also perform enhanced incremental backup using the Windows NTFS Change
Log Provider. Change Log Provider queries the Windows Change Journal for a list
of changed files rather than performs a time-consuming file tree walk. As the Change
Journal detects and records all changes made to the files and directories on an NTFS
volume, Data Protector can use it as a tracking mechanism to generate a list of files
modified since the last full backup. This improves the incremental backup speed,
especially in environments containing millions of files only a few of which have
changed, and allows to eliminate unnecessary full backups.
Types of incremental backups
Data Protector provides incremental backups of different types:
Concepts guide 93
Page 94

Incr A simple incremental backup, shown in Figure
23 on page 95, is based on the last backup that is still
protected, which can be a full backup or an incremental
backup.
Incr1-9 A leveled incremental backup, shown in Figure
24 on page 95, depends on the last backup of the next lower
level that is still protected. For example, an Incr1 backup
saves all changes since the last full backup, while an Incr5
backup saves all changes since the last Incr4 backup. An
Incr1-9 backup never references an existing Incr backup.
Planning your backup strategy94
Page 95
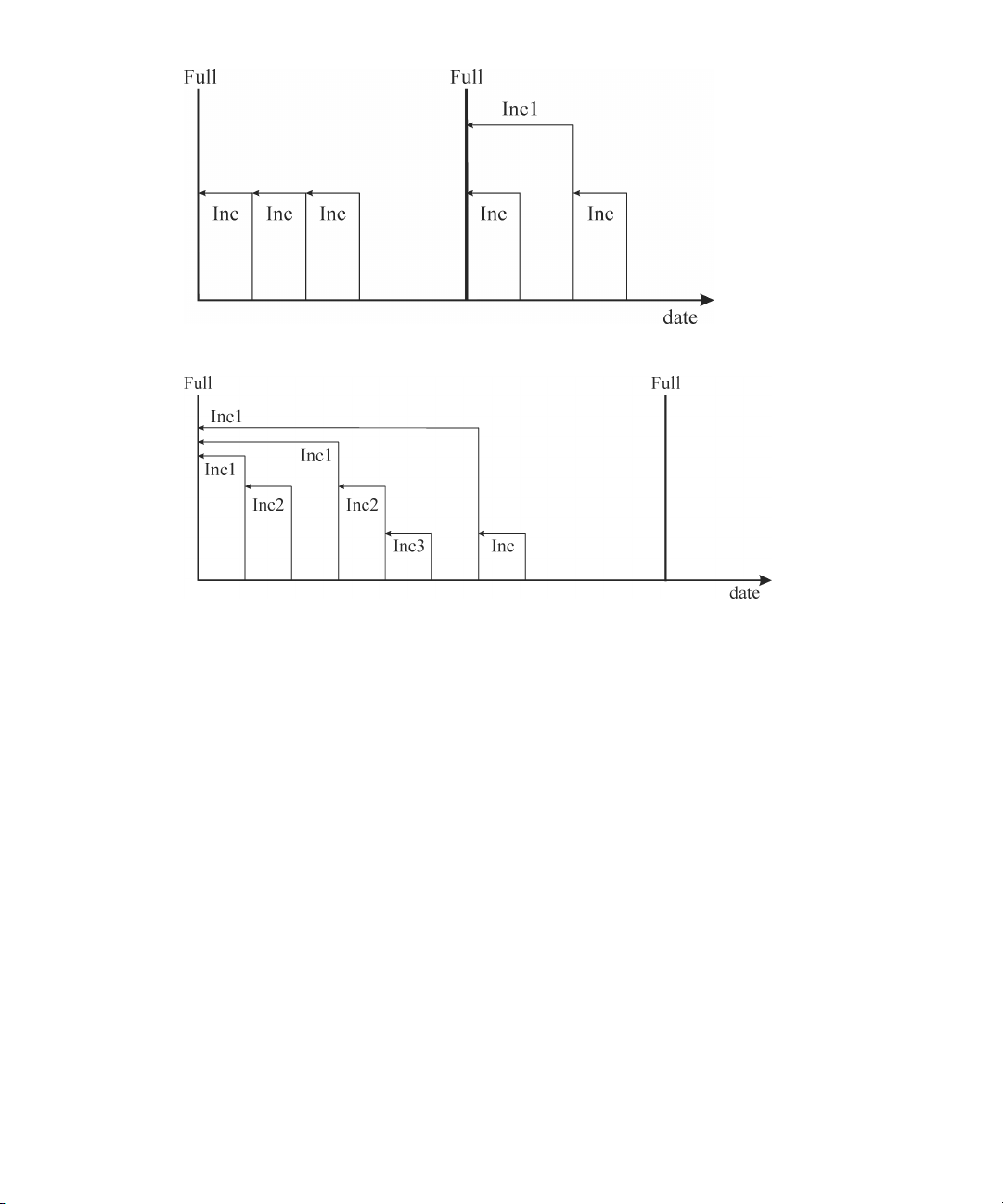
Figure 23 Incremental backups
Figure 24 Leveled incremental backups
Table 7 on page 95 shows the relative referencing of backup runs with various
backup types. See the text following the table for a full explanation.
Table 7 Relative referencing of backup runs
Incr1<----Full1
Incr2<----<----<----Full2
Incr2<----Incr1<----Full3
Incr<----Full4
Incr<----Incr1<----Full5
Incr<----Incr2<----Incr1<----Full6
Incr<----Incr<----Incr1<----Full7
Concepts guide 95
Page 96

How to read Table 7 on page 95
• The rows in Table 7 on page 95 are independent of each other and show different
situations.
• The age of the backups increases from right to left, so that the far left is the oldest
and the far right is the most recent backup.
• The full and IncrX represent still protected objects of the same owner. Any existing
IncrX that is not protected can be used for restore, but is not considered for
referencing on subsequent backup runs.
Examples
• In the second row, there is a full, still protected backup and an Incr2 is running.
There is no Incr1, so the backup is executed as an Incr1.
• In the fifth row, there is a full backup, an Incr1 and another incremental is running.
Data Protector references the currently running backup to the previous incremental,
that is Incr1.
• In the eighth row, the Incr3 is executed as Incr2, and in the eleventh row, the
Incr3 is executed as Incr1.
Incr3<----Incr1<----Full8
Incr3<----Incr2<----Incr1<----Full9
Incr3<----Incr2<----<----<----Full10
Incr3<----<----<----<----<----Full11
Considering restore
To restore the latest data, you need media from your last full backup and subsequent
incremental backups. Therefore, the more incremental backups you have, the more
media you need to handle. This is inconvenient if you use standalone devices, and
the restore can last long.
Using simple and leveled incremental backups, as indicated in Figure 25 on page 98,
will require access to all five previously completed media sets, up to and including
the full backup. The space needed on the media is lowest here, but the restore is
rather complex. The series of required media sets is also called a restore chain.
Planning your backup strategy96
Page 97

TIP:
Use the Data Protector Appendable on Incrementals Only option to keep data from full
and incremental backups (of the same backup specification) on the same media set.
Another common use of the incremental backup concept is indicated in Figure
26 on page 98. Here the required space on the media is slightly larger. Only two
media sets need to be accessed to restore to the desired point in time. Note that
there is no dependency on any previous Incr1 media set for this restore, unless the
desired restore point in time would be moved.
Concepts guide 97
Page 98

Figure 25 Media needed to restore from simple and leveled incremental
backups
Figure 26 Media needed to restore from leveled incremental backups
Note that you must set the appropriate data protection in order to get all needed full
and incremental backups for restore. If the data protection is not properly set, you
can get a broken restore chain. For more information, see Appendix B on page 331.
Planning your backup strategy98
Page 99

Keeping backed up data and information about the data
Data Protector lets you specify how long to keep your backed up data on the media
itself (data protection), how long to keep information about the backed up data in
the IDB (catalog protection), and what level of information to keep in the IDB (logging
level).
You can set the protection independently for backed up data and for backup
information about this data in the IDB. When copying media, you can specify a
different protection period for the copies than the protection of the original media.
Data Protector Internal Database
Restore performance depends, in part, on how fast the media required for a restore
can be found. By default, this information is stored in the IDB to enable the highest
restore performance as well as the convenience of being able to browse the files and
directories to be restored. However, putting all file names of all backups in the IDB
and keeping them for a long time can cause the IDB to grow to unmanageable levels.
Data Protector allows you to trade off IDB growth with the convenience of restore,
by letting you specify catalog protection independently of data protection. For example
you can implement a policy that enables an easy and fast restore within four weeks
after the backup, by setting catalog protection to four weeks. From then on restores
can still be done in a less convenient way until the data protection expires, say after
one year. This would considerably reduce the space requirements in the IDB.
Data protection
What is data protection?
Data Protector allows you to specify the amount of time data on media is protected
from being overwritten by Data Protector. You can specify the protection in absolute
or relative dates.
You can specify data protection in different parts of Data Protector. For details, see
the online Help index: "data protection".
If you do not change the Data Protection backup option when configuring a backup,
it is permanently protected. Note that if you do not change this protection, the number
of media needed for backup grows constantly.
Concepts guide 99
Page 100

Catalog protection
What is catalog protection?
Data Protector saves information about backed up data in the IDB. Since the
information about the backed up data is written to the IDB each time a backup is
done, the IDB grows with the number and the size of backups. Catalog protection
tells Data Protector how long the information about backed up data is available to
users browsing data during restore. Once catalog protection has expired, Data
Protector will overwrite this information in the IDB (not on the media) in one of the
subsequent backups.
You can specify the protection using absolute or relative dates.
If you do not change the Catalog Protection backup option when configuring your
backup, information about backed up data has the same protection duration as data
protection. Note that if you do not change this, the IDB grows constantly as new
information is added with each backup.
For more information on how catalog protection settings influence the IDB growth
and performance, see “Catalog protection as an IDB key tunable
parameter” on page 201.
The protection model used by Data Protector can be mapped to the concept of backup
generations, which is elaborated in Appendix B on page 331
Logging level
What is logging level?
Logging level determines the amount of details on files and directories written to the
IDB during backup. You can always restore your data, regardless of the logging
level used during the backup.
Data Protector provides four logging levels that control the amount of details on files
and directories written to the IDB. For more information, see “Logging level as an
IDB key tunable parameter” on page 199.
Browsing files for restore
The IDB keeps information about the backed up data. This information allows you to
browse, select and start the restore of files using the Data Protector user interface.
You can also restore data without this information as long as the media are still
Planning your backup strategy100
 Loading...
Loading...