Page 1

3Com® Telecommuting Module
Installation Guide
Version 4.3
Page 2

3Com® Telecommuting Module Installation Guide: Version 4.3
Part Number BETA
Published December 2005
3Com Corporation, 350 Campus Drive, Marlborough MA 01752-3064
Copyright © 2005, 3Com Corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to
make any derivative work (such as translation, transformation, or adaptation) without written permission from 3Com Corporation.
3Com Corporation reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of
3Com Corporation to provide notification of such revision or change.
3Com Corporation provides this documentation without warranty, term, or condition of any kind, either implied or expressed, including, but not
limited to, the implied warranties, terms, or conditions of merchantability, satisfactory quality, and fitness for a particular purpose. 3Com may make
improvements or changes in the product(s) and/or the program(s) described in this documentation at any time.
If there is any software on removable media described in this documentation, it is furnished under a license agreement included with the product as a
separate document, in the hardcopy documentation, or on the removable media in a directory file named LICENSE.TXT or !LICENSE.TXT.If you
are unable to locate a copy, please contact 3Com and a copy will be provided to you.
UNITED STATES GOVERNMENT LEGEND
If you are a United States government agency, then this documentation and the software described herein are provided to you subject to the
following:
All technical data and computer software are commercial in nature and developed solely at private expense. Software is delivered as "Commercial
Computer Software" as defined in DFARS 252.227-7014 (June 1995) or as a "commercial item" as defined in FAR 2.101(a) and as such is provided
with only such rights as are provided in 3Com’s standard commercial license for the Software. Technical data is provided with limited rights only as
provided in DFAR252.227-7015(Nov1995)orFAR 52.227-14 (June 1987), whichever is applicable. You agree not to removeor defaceanyportion
of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this guide.
Unless otherwise indicated, 3Com registered trademarks are registered in the United States and may or may not be registered in other countries.
3Com, the 3Com logo, NBX, and SuperStack are registered trademarks of 3Com Corporation. NBX NetSet, pcXset, and VCX are trademarks of
3Com Corporation.
Adobe is a trademark and Adobe Acrobat is a registered trademark of Adobe Systems Incorporated. Microsoft, Windows, Windows 2000, Windows
NT,and Microsoft Word are registered trademarks of Microsoft Corporation.
All other company and product names may be trademarks of the respective companies with which they are associated.
Page 3

Table of Contents
Part I. Installation of the 3Com VCX IP Telecommuting Module......................................................................... i
1. Introduction .....................................................................................................................................................1
2. Overview of the Installation ............................................................................................................................3
3. Installing 3Com VCX IP Telecommuting Module..........................................................................................6
Part II. Configuring 3Com VCX IP Telecommuting Module...............................................................................14
4. Network Configuration..................................................................................................................................15
5. SIP Configuration ..........................................................................................................................................26
6. Administration of the Telecommuting Module .............................................................................................31
7. Firewall and Client Configuration .................................................................................................................36
Index..................................................................................................................................................................39
i
Page 4

Part I. Installation of the 3Com VCX IP
Telecommuting Module
This document will help you to get started with your 3Com VCX IP Telecommuting Module. It contains the
necessary information to configure your Telecommuting Module.
Additional information about managing your 3Com VCX IP Telecommuting Module can be found in the User
Manual.
These chapters contain an introduction to the 3Com VCX IP Telecommuting Module, descriptions of the various
models and information about how to install your Telecommuting Module.
Page 5
Chapter 1. Introduction
What is a Telecommuting Module?
A Telecommuting Module is a device which processes traffic under the SIP protocol (see RFC 3261). The
Telecommuting Module receives SIP requests, processes them according to the rules you have set up, and forwards
them to the receiver.
The Telecommuting Module connects to an existing enterprise firewall through a DMZ port, enabling the
transmission of SIP-based communications without affecting firewall security. SIP messages are then routed
through the firewall to the private IP addresses of authorized users on the internal network.
The Telecommuting Module can also be used as an extra gateway to the internal network without connecting to the
firewall, transmitting only SIP-based communications.
Configuration alternatives
The 3Com VCX IP Telecommuting Module can be connected to your network in three different ways, depending
on your needs.
Note that the interface which should receive traffic from the outside must have a public IP address (no NAT),
regardless of which Telecommuting Module Type was selected. For a DMZ or DMZ/LAN type, this means that
the interface connected to the DMZ of the firewall must have a public IP address.
DMZ Configuration
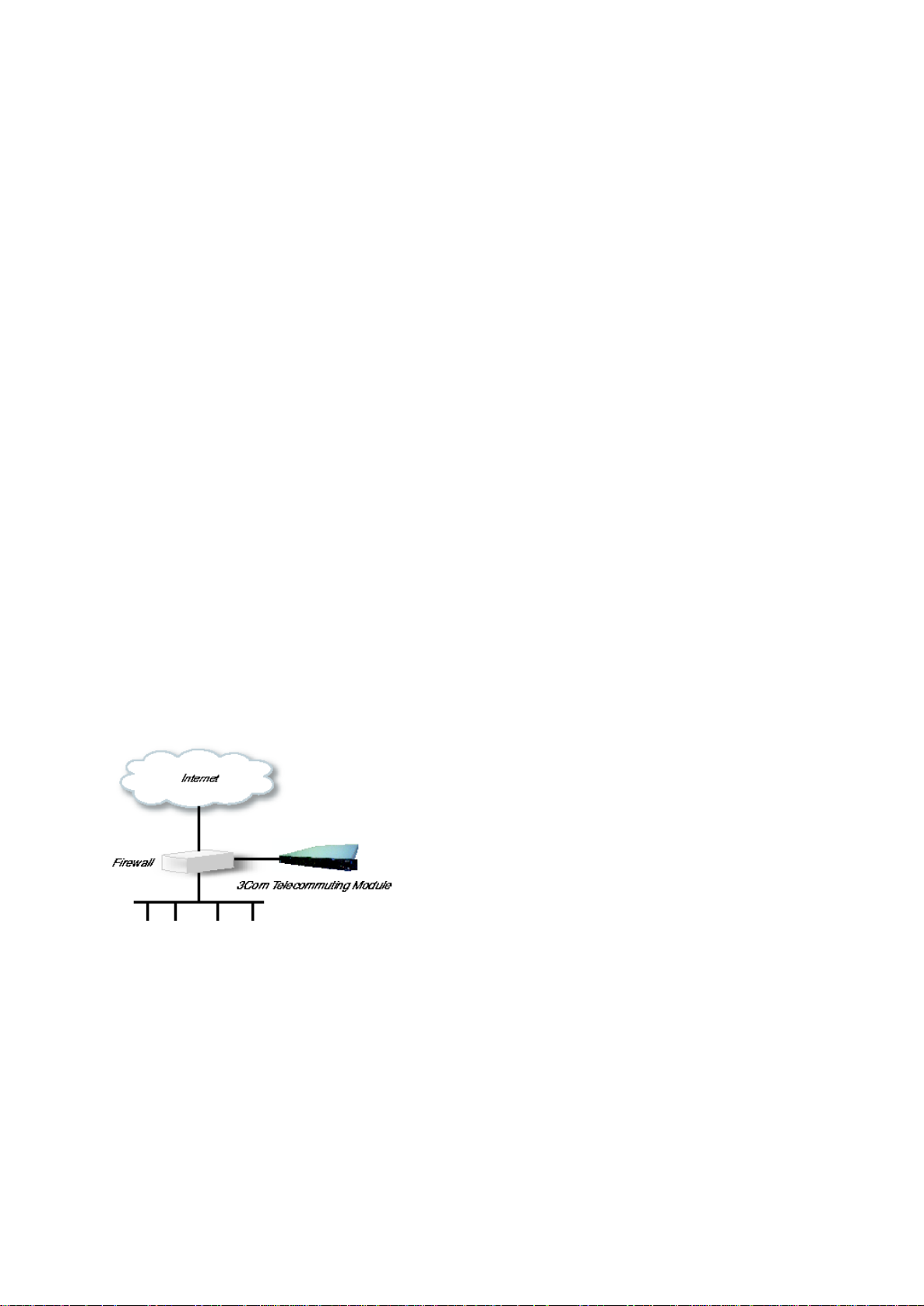
Using this configuration, the Telecommuting Module is located on the DMZ of your firewall, and connected to it
with only one interface. The SIP traffic finds its way to the Telecommuting Module using DNS or by setting the
Telecommuting Module as an outbound proxy on the clients.
This is the most secure configuration, since all traffic goes through both your firewall and your Telecommuting
Module. It is also the most flexible, since all networks connected to any of your firewall’s interfaces can be
SIP-enabled.
The drawback is that the SIP traffic will pass the firewall twice, which can decrease performance.
Fig 1. Telecommuting Module in DMZ configuration.
DMZ/LAN Configuration
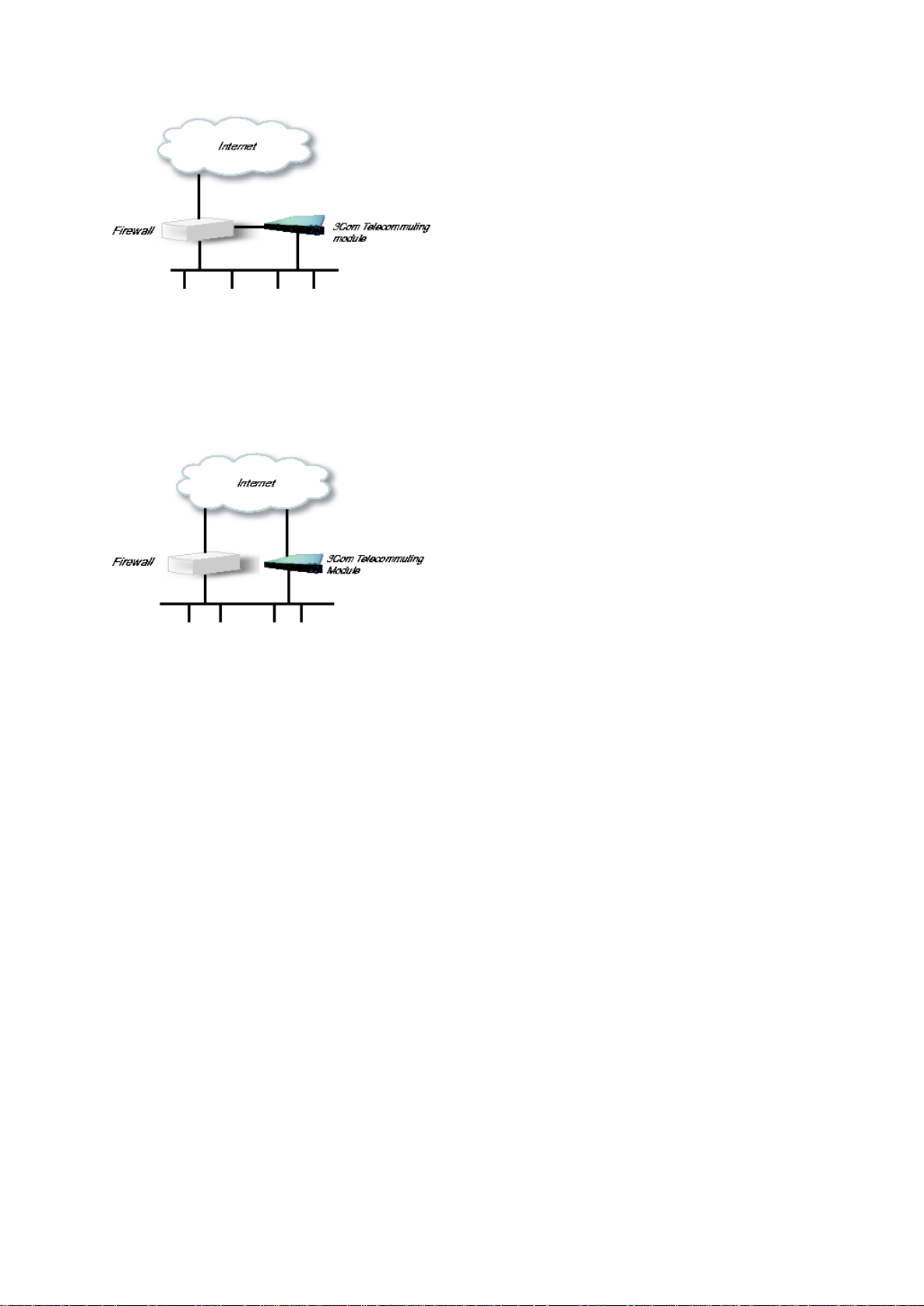
Using this configuration, the Telecommuting Module is located on the DMZ of your firewall, and connected to it
with one of the interfaces. The other interface is connected to your internal network. The Telecommuting Module
can handle several networks on the internal interface even if they are hidden behind routers. No networks on other
interfaces on the firewall can be handled.
This configuration is used to enhance the data throughput, since the traffic only needs to pass your firewall once.
This configuration can only support one local network.
1
Page 6
Chapter 1. Introduction
Fig 2. Telecommuting Module in DMZ/LAN configuration.
Standalone Configuration
Using this configuration, the Telecommuting Module is connected to your internal network on one interface and the
outside world on the other.
Use this configuration only if your firewall lacks a DMZ interface, or for some other reason cannot be configured
for the DMZ or DMZ/LAN alternatives.
Fig 3. Telecommuting Module in Standalone configuration.
2
Page 7

Chapter 2. Overview of the Installation
Quick guide to 3Com VCX IP Telecommuting Module installation
3Com VCX IP Telecommuting Module is easy to install:
• Select an IP address for the Telecommuting Module on your network.
• The network interfaces are marked with 1 and 2. These numbers correspond to the physical interfaces eth0 and
eth1 respectively, the latter which should be use in the installation program.
• Plug in the power cord and turn on the Telecommuting Module.
• Wait while the Telecommuting Module boots up.
• Connect the network cables to the network interfaces.
• Find out the MAC address of the Telecommuting Module’s Network Interface 1 (printed on the Telecommuting
Module label).
• Add a static entry in your local ARP table consisting of the Telecommuting Module’s MAC address and the IP
address it should have on Network Interface 1.
This is how to add a static ARP entry if you use a Windows computer:
Run the command command (or cmd).
In the Command window, enter the command arp -s ipaddress macaddress where ipaddress is the new IP
address for Network Interface 1, and macaddress is the MAC address printed on the Telecommuting Module, but
with all colons (:) replaced with dashes (-).
• Ping this IP address to give the Telecommuting Module its new IP address. You should receive a ping reply if the
address distribution was successful.
• Direct your web browser to the IP address of the Telecommuting Module. You will be prompted to set a
password for the Telecommuting Module admin user.
• Now you can see the top page of 3Com VCX IP Telecommuting Module. Click on the Telecommuting Module
Type link and select the configuration for your Telecommuting Module. The types are described on the web page.
• Go to the Network Interface 1 page and enter the necessary configuration. See also the Interface section. Note
that the Telecommuting Module must have at least one IP address which can be reached from the Internet.
• If one of the Telecommuting Module Types DMZ/LAN or Standalone was chosen, move on to the Network
Interface 2 page and give the Telecommuting Module at least one IP address on this interface and state the
networks connected to the interface. See also the Interface section.
• Go to the Networks and Computers page. Define the networks that will send and receive SIP traffic using the
Telecommuting Module. Usually, you need at least one network per interface of the firewall connected to the
Telecommuting Module (or, for the Standalone type, per interface of the Telecommuting Module). Some
computers should be handled separately, and they therefore need their own networks. See also the Networks and
Computers section.
• Go to the Basic Configuration page under Basic Configuration and enter a Default gateway and a DNS
server. See also the Basic Configuration section.
• Go to the Access Control page and make settings for the configuration of the Telecommuting Module. See also
the Access Control section.
• Go to the Surroundings page (for the DMZ Telecommuting Module Type) and state the networks connected to
the firewall. See also the Surroundings section in chapter 4, Network Configuration.
• Go to Basic under SIP Services and turn the SIP module on. See also the Basic section.
• Go to the Interoperability page. Turn Preserve username and SIP URL encryption on.
3
Page 8

Chapter 2. Overview of the Installation
• If you use a dialing domain which looks like an IP address, enter the dialing domain in the Translation
exceptions table. See also the Interoperability section.
• For this type of dialing domain, you also need to go to the Routing page. Enter the dialing domain in the DNS
Override For SIP Requests table and state the IP address of the SIP server(s) to handle the domain. See also the
Routing section.
• Go to the Save/Load Configuration page under. Select Apply configuration. Now you can test your new
configuration and save it permanently if you are satisfied with it. If the configuration is not satisfactory, select
Revert or restart the Telecommuting Module. The old configuration will remain.
When the Telecommuting Module is configured, the firewall connected to it must also be reconfigured (for the
DMZ and DMZ/LAN Telecommuting Module Types).
• Allow UDP and TCP traffic in the port interval used for media streams by the Telecommuting Module, and port
5060. This traffic must be allowed to all networks which should be reached by SIP traffic.
See also chapter 14, Firewall and Client Configuration, for information on configuring the firewall and the SIP
clients, and chapter 4 of the User Manual for Telecommuting Module configuration examples.
Before you start
You could do a rough sketch of your network to make the configuration simpler. Things to think of:
• Which IP addresses will the Telecommuting Module interfaces use? You can have more than one IP network on
one interface, each requiring a separate IP address for the Telecommuting Module.
• Which series of IP addresses will be used on the networks connected to the different interfaces?
• Are there networks behind routers?
• What is the default gateway for the Telecommuting Module?
About settings in 3Com VCX IP Telecommuting Module
3Com VCX IP Telecommuting Module uses two sets of Telecommuting Module configurations: preliminary and
permanent configuration. The permanent configuration is what is used in the active Telecommuting Module. The
preliminary configuration is where you change and set the configuration. See chapter 3 of the User Manual for
instructions.
The changes you make in the preliminary configuration are not stored in the permanent configuration until you click
on Apply configuration on the Save/Load Configuration page under Administration.
The password configuration and time setting are the exceptions to this rule; they are saved immediately. Change the
administrator passwords and create more administrator users on the User Administration page under
Administration.
3Com VCX IP Telecommuting Module displays serious errors in red, e.g., if mandatory information is not entered.
Blank fields are shown in red. Fields that you correct remain red until you select Save, Add new rows or update the
page in some other way.
If you have a web connection with the Telecommuting Module that is inactive for 10 minutes, it will ask for a
password again.
Always log out from the Telecommuting Module administration interface when you are not using it. Press the Log
out button on the left to log out.
The terms used in the book are explained in appendix C of the User Manual.
For a general description of how to configure and administer the Telecommuting Module, see chapter 3 of the User
Manual.
4
Page 9

Chapter 2. Overview of the Installation
License Conditions
To fulfill the license conditions, we must either attach the source code with the software, or send a written offer,
valid at least three years, to give a copy of the source code to anyone who wants it. According to 3b) of the license,
we are entitled to charge for the distribution of the source code.
3Com Corporation offer the source code for all third party software included in 3Com VCX IP Telecommuting
Module and licensed under GPL. This offer is valid for this version of 3Com VCX IP Telecommuting Module and
is valid for three years after deliverance of your 3Com VCX IP Telecommuting Module unit. Contact 3Com
Corporation for current information.
5
Page 10

Chapter 3. Installing 3Com VCX IP Telecommuting Module
Installation
There are three ways to install an 3Com VCX IP Telecommuting Module: using a serial cable, using a diskette or
perform a magic ping.
Installation with a serial cable or a diskette requires being at the same place as the Telecommuting Module, but will
give more options for the start configuration.
Installation with magic ping does not require being on the same place as the Telecommuting Module (but the
computer has to be connected to the same logical network as the Telecommuting Module), but restricts the start
configuration.
Installation with magic ping
You can use the magic ping to set an IP address for the Telecommuting Module. This is how to perform a magic
ping:
• Plug in the power cord and turn the Telecommuting Module on.
• Wait while the Telecommuting Module boots up.
• Connect the network cables to the network interfaces.
• Find out the MAC address of the Telecommuting Module (printed on the back of the Telecommuting Module).
This is the MAC address of Network Interface 1.
• Add a static entry in your local ARP table consisting of the Telecommuting Module’s MAC address and the IP
address it should have on Network Interface 1.
This is how to add a static ARP entry if you use a Windows computer:
Run the command command (or cmd).
In the Command window, enter the command arp -s ipaddress macaddress where ipaddress is the new IP address
for the Network Interface 1 interface, and macaddress is the MAC address printed on the Telecommuting
Module, but with all colons (:) replaced with dashes (-).
• Ping this IP address to give the Telecommuting Module its new IP address. You should receive a ping reply if the
address distribution was successful.
• Configure the rest through a web browser.
• Plug in the power cord and turn the Telecommuting Module on.
• Wait while the Telecommuting Module boots up.
• Connect the network cables to the network interfaces.
• Find out the MAC address of the Telecommuting Module (printed on the back of the Telecommuting Module).
This is the MAC address of Network Interface 1.
• Add a static entry in your local ARP table consisting of the Telecommuting Module’s MAC address and the IP
address it should have on Network Interface 1.
This is how to add a static ARP entry if you use a Windows computer:
Run the command command (or cmd).
In the Command window, enter the command arp -s ipaddress macaddress where ipaddress is the new IP address
for the Network Interface 1 interface, and macaddress is the MAC address printed on the Telecommuting
Module, but with all colons (:) replaced with dashes (-).
6
Page 11

Chapter 3. Installing 3Com VCX IP Telecommuting Module
• Ping this IP address to give the Telecommuting Module its new IP address. You should receive a ping reply if the
address distribution was successful.
• Configure the rest through a web browser.
Installation with a serial cable
These steps are performed when installing with a serial cable:
• Connect the Telecommuting Module to your workstation with a null modem serial cable.
• Plug in the power cord and turn the Telecommuting Module on.
• Wait while the Telecommuting Module boots up.
• Log on from your workstation.
• Run the installation program (see following instructions).
• Connect the network cables to the network interfaces.
• Configure the rest through a web browser.
Connect the Telecommuting Module to your workstation with a null modem serial cable, plug in the power cord
and turn the Telecommuting Module on. You will have to wait a few minutes while it boots up.
• If you use a Windows workstation, connect like this: Start Hyperterm. A Location dialogue will show, asking for
your telephone number and area. Click Cancel followed by Yes. Then you will be asked to make a new
connection. Type a name for this connection, select an icon and click OK. The Location dialogue will show
again, so click Cancel followed by Yes.
Now you can select Connect using COM1 and click OK. A Port settings dialogue will show, where you select
19200 as Bits per second. Use the default configuration for all other settings. Click OK and wait for a login
prompt. (In some cases you have to press Return to get the login prompt.)
• If you use a Linux workstation, connect like this: Make sure that there is a symbolic link named /dev/modem
which points to the serial port you connected the Telecommuting Module to. Connect using minicom with the bit
rate 19200 bits/s, and wait for a login prompt.
Log on as the user admin. The first time you log on, no password is required. You set the password when you run
the installation script, which starts automatically when you have logged on.
Each network interface is marked with a name (1 and 2), which corresponds to a tab under Network. All eth
interfaces belong to ethernet cards and should only be connected using ethernet cables.
Decide which computer(s) are allowed to configure 3Com VCX IP Telecommuting Module and enter the name of
the network interface to which they are connected, for example, Network Interface 1. You must use the physical
device name (eth0 and eth1).
Enter the IP address of the Telecommuting Module on this interface and the network mask for the network.
A network mask can be written in two ways in 3Com VCX IP Telecommuting Module:
• The first looks just like an IP address, for example 255.255.192.0 or 255.255.254.0.
• The other way is as a number between 0 and 32. An IP address has 32 bits, where the number of the network
mask indicates how many bits are used in the network’s addresses. The rest of the bits identifies the computer on
the network.
Now, you can select to deactivate any network interfaces. Select y to deactivate all interfaces but the one you just
configured. The remaining network interfaces can be activated later when you complete the configuration via the
web interface from your work station. This only applies to interfaces which was previously active; you can’t
activate interfaces with this setting.
Now enter the computer or computers from which the Telecommuting Module may be configured (the configuration
computers).
7
Page 12
Chapter 3. Installing 3Com VCX IP Telecommuting Module
Then enter a password for the Telecommuting Module. This is the password you use in your web browser to access
and change the Telecommuting Module’s configuration. Finally, you can reset all other configuration if you want to.
Following is a sample run of the installation program.
3Com VCX IP Telecommuting Module Administration
1. Basic configuration
2. Save/Load configuration
3. Become a failover team member
4. Leave failover team and become standalone
5. Wipe email logs
6. Set password
q. Exit admin
==>
Select 1 to install your 3Com VCX IP Telecommuting Module.
Basic unit installation program version 4.3
Press return to keep the default value
Network configuration inside:
Physical device name[eth0]:
IP address [0.0.0.0]: 10.47.2.242
Netmask/bits [255.255.255.0]: 255.255.0.0
Deactivate other interfaces? (y/n) [n]
Computers from which configuration is allowed:
You can select either a single computer or a network.
Configure from a single computer? (y/n) [y]
If you choose to allow only one computer to configure the Telecommuting Module, you are asked for the IP address
(the mask is set automatically).
IP address [0.0.0.0]: 10.47.2.240
If this IP address is not on the same network as the IP address of the Telecommuting Module, you are asked for the
router. Enter the IP address of the router on the network where the Telecommuting Module is connected. Then enter
the network address and mask of the network containing the configuring computer.
Static routing:
The computer allowed to configure from is not on a network local to
this unit. You must configure a static route to it. Give
the IP address of the router on the network the unit is on.
The IP address of the router [0.0.0.0]: 10.47.3.1
Network address [10.47.0.0]: 10.10.0.0
Netmask [255.255.255.0]:
You can choose to allow several computers to configure the Telecommuting Module, by answering no to the
question:
Configure from a single computer? (y/n) [y] n
8
Page 13
Chapter 3. Installing 3Com VCX IP Telecommuting Module
The installation program then asks for the network number. The network number is the lowest IP address in the
series of numbers that includes the configuration computers (see chapter 3 of the User Manual). The network mask
determines the number of computers that can act as configuration computers.
Network number [0.0.0.0]: 10.47.2.0
Netmask/bits [255.255.255.0]: 255.255.255.0
If the network or partial network is not directly connected to the Telecommuting Module, you must enter the IP
address of the router leading to that network. Then enter the network’s address and mask.
Static routing:
The network allowed to configure from is not on a network local to this
unit. You must configure a static route to it. Give the
IP address of the router on the network this unit is on.
The IP address of the router [0.0.0.0]: 10.47.3.1
Network address [10.47.0.0]: 10.10.0.0
Netmask [255.255.255.0]:
Then enter a password.
Password []:
Finally, you are asked if you want to reset other configuration.
Other configuration
Do you want to reset the rest of the configuration? (y/n) [n]
If you answer n, nothing is removed. If you answer y, you have three alternatives to select from:
1. Clear as little as possible. This is the alternative that is used if you answer n to the question above. Both the
preliminary and the permanent configurations will be updated with the configuration specified above.
2. Revert to the factory configuration and then apply the configuration specified above. This will affect the
permanent but not the preliminary configuration.
3. Revert to the factory configuration and empty all logs and then apply the configuration specified above. Both
the preliminary and the permanent configurations will be affected.
Select the update mode, which is what you want to remove.
Update mode (1-3) [1]:
All configuration is now complete. The installation program shows the configuration and asks if it is correct.
yes saves the configuration.
no runs the installation program over again.
abort ends the installation program without saving.
9
Page 14

Chapter 3. Installing 3Com VCX IP Telecommuting Module
You have now entered the following configuration
Network configuration inside:
Physical device name: eth0
IP address: 192.168.150.2
Netmask: 255.255.255.0
Deactivate other interfaces: no
Computer allowed to configure from:
IP address: 192.168.128.3
Password: eeyore
The rest of the configuration is kept.
Is this configuration correct (yes/no/abort)? yes
Now, finish configuration of the Telecommuting Module from the computer/computers specified in the installation
program.
Installation with a diskette
These steps are performed when installing with a diskette:
• Select an IP address and store it on the installation diskette as described below.
• Insert the installation diskette into the Telecommuting Module’s floppy drive.
• Plug in the power cord and turn the Telecommuting Module on.
• Connect the network cables to the network interfaces.
• Wait while the Telecommuting Module boots up.
• Configure the rest through a web browser.
You must first insert the diskette into your PC. If the PC is running Windows, open a Command window and run the
finst-en script from the diskette. If the PC is running Linux, mount the diskette, change directory to the mounted
one, and run the finst-en script.
Decide which computer(s) are allowed to configure 3Com VCX IP Telecommuting Module and enter the name of
the network interface to which they are connected, for example, Network Interface 1. You must use the physical
device name (eth0 and eth1).
Enter the IP address of the Telecommuting Module on this interface and the network mask for the network.
A network mask can be written in two ways in 3Com VCX IP Telecommuting Module:
• The first looks just like an IP address, for example 255.255.192.0 or 255.255.254.0.
• The other way is as a number between 0 and 32. An IP address has 32 bits, where the number of the network
mask indicates how many bits are used in the network’s addresses. The rest of the bits identifies the computer on
the network.
Now, you can select to deactivate any network interfaces. Select y to deactivate all interfaces but the one you just
configured. The remaining network interfaces can be activated later when you complete the configuration via the
web interface from your work station. This only applies to interfaces which was previously active; you can’t
activate interfaces with this setting.
Now enter the computer or computers from which the Telecommuting Module may be configured (the configuration
computers).
Then enter a password for the Telecommuting Module. This is the password you use in your web browser to access
and change the Telecommuting Module’s configuration. Finally, you can reset all other configuration if you want to.
10
Page 15

Chapter 3. Installing 3Com VCX IP Telecommuting Module
Following is a sample run of the installation program on the diskette.
Basic unit installation program version 4.3
Press return to keep the default value
Network configuration inside:
Physical device name[eth0]:
IP address [0.0.0.0]: 10.47.2.242
Netmask/bits [255.255.255.0]: 255.255.0.0
Deactivate other interfaces? (y/n) [n]
Computers from which configuration is allowed:
You can select either a single computer or a network.
Configure from a single computer? (y/n) [y]
If you choose to allow only one computer to configure the Telecommuting Module, you are asked for the IP address
(the netmask is set automatically).
IP address [0.0.0.0]: 10.47.2.240
If this IP address is not on the same network as the inside of the Telecommuting Module, you are asked for the
router. Enter the IP address of the router on the network where the Telecommuting Module is connected. Now enter
the network address and mask of the network containing the configuring computer.
Static routing:
The computer allowed to configure from is not on a network local to
this unit. You must configure a static route to it. Give
the IP address of the router on the network the unit is on.
The IP address of the router [0.0.0.0]: 10.47.3.1
Network address [10.47.0.0]: 10.10.0.0
Netmask [255.255.255.0]:
You can choose to allow several computers to configure the Telecommuting Module, by answering no to the
question:
Configure from a single computer? (y/n) [y] n
The installation program then asks for the network number. The network number is the lowest IP address in the
series of numbers that includes the configuration computers (see chapter 3 of the User Manual). The network mask
determines the number of computers that can act as configuration computers.
Network number [0.0.0.0]: 10.47.2.0
Netmask/bits [255.255.255.0]: 255.255.255.0
If the network or partial network is not directly connected to the Telecommuting Module, you must enter the IP
address of the router leading to that network. Then enter the network’s address and mask.
11
Page 16

Chapter 3. Installing 3Com VCX IP Telecommuting Module
Static routing:
The network allowed to configure from is not on a network local to this
unit. You must configure a static route to it. Give the
IP address of the router on the network this unit is on.
The IP address of the router [0.0.0.0]: 10.47.3.1
Network address [10.47.0.0]: 10.10.0.0
Netmask [255.255.255.0]:
Then enter a password.
Password []:
Finally, you are asked if you want to reset other configuration.
Other configuration
Do you want to reset the rest of the configuration? (y/n) [n]
If you answer n, nothing is removed. If you answer y, you have three alternatives to select from:
1. Clear as little as possible. This is the alternative that is used if you answer n to the question above. Both the
preliminary and the permanent configurations will be updated with the configuration specified above.
2. Revert to the factory configuration and then apply the configuration specified above. This will affect the
permanent but not the preliminary configuration.
3. Revert to the factory configuration and empty all logs and then apply the configuration specified above. Both
the preliminary and the permanent configurations will be affected.
Select the update mode, which is what you want to remove.
Update mode (1-3) [1]:
All configuration is now complete. The installation program shows the configuration and asks if it is correct.
yes saves the configuration.
no runs the installation program over again.
abort ends the installation program without saving.
Now, eject the diskette from your PC and insert it into the Telecommuting Module’s floppy drive. Then power up
the Telecommuting Module and wait for it to boot. Then, finish configuration of the Telecommuting Module from
the computer/computers specified in the installation program.
Note that the diskette contains a command to erase certain parts of the configuration during boot when the
diskette is inserted. Make sure to eject it once the Telecommuting Module has booted up to avoid future loss of
data.
If you happen to forget the administrator password for the Telecommuting Module, you can insert the diskette into
the Telecommuting Module again and boot it. Note that if you selected anything but 1 as the update mode, you will
lose configuration when doing this.
Turning off a Telecommuting Module
Backup the Telecommuting Module configuration (just in case something should happen). You do this on the
Save/Load Configuration page under Administration. Once this is done, just turn the computer off. The computer
that runs 3Com VCX IP Telecommuting Module is specially designed so that you can switch it off without causing
any problems in the file structure.
12
Page 17

Chapter 3. Installing 3Com VCX IP Telecommuting Module
Remember to lock up the Telecommuting Module
The Telecommuting Module is a computer with special software, and must be protected from unauthorized physical
access just as other computers performing critical tasks. A locked up Telecommuting Module protects against:
• connecting to the console
• connecting a keyboard and monitor
• changing the administrator password using the installation diskette.
• changing BIOS configuration to allow the Telecommuting Module to be booted from a diskette
For more information about the necessary configuration, see chapter 3 of the User Manual.
13
Page 18

Part II. Configuring 3Com VCX IP
Telecommuting Module
These chapters contain information about how to configure your 3Com VCX IP Telecommuting Module, once it
has been installed. All configuration is made through the web interface of the Telecommuting Module.
The configuration described in these chapters is basic for making the Telecommuting Module work. For
descriptions of more advanced Telecommuting Module functions, please refer to the User Manual.
Page 19

Chapter 4. Network Configuration
First, the Telecommuting Module must be configured to be aware of the network in which it operates. This is
performed on the Network pages. The important pages for getting started are Telecommuting Module Type,
Interface (Network Interface 1 and 2), Networks and Computers and (for the DMZ Telecommuting Module
Type) Surroundings.
You will also need to add configuration on the Basic Configuration page under Basic Configuration.
Telecommuting Module Type
The Telecommuting Module can be connected to your network in different ways, depending on your needs. On this
page, you state what configuration you have.
The DMZ Configuration
Using this configuration, the Telecommuting Module is located on the DMZ of your firewall, and connected to it
with only one interface.
This is the safest configuration, since all traffic goes through both your firewall and your Telecommuting Module. It
is also the most flexible, since all networks connected to any of your firewall’s interfaces can be SIP-enabled.
On your firewall, you need to open the SIP port (normally UDP port 5060) and a range of UDP ports for RTP traffic
between the Telecommuting Module and the Internet as well as between the Telecommuting Module and your
internal networks. The SIP traffic finds its way to the Telecommuting Module using DNS or by setting the
Telecommuting Module as an outbound proxy on the clients.
The firewall mustn’t use NAT for the traffic between the Telecommuting Module and your internal networks or for
the traffic between the Telecommuting Module and the Internet. However, the Telecommuting Module can itself use
NAT for traffic to the Internet.
You need to declare your internal network topology on the Surroundings page.
The DMZ/LAN Configuration
Using this configuration, the Telecommuting Module is located on the DMZ of your firewall, and connected to it
with one of the interfaces.
This configuration is used to enhance the data throughput, since the traffic only needs to pass your firewall once.
15
Page 20

Chapter 4. Network Configuration
On your firewall, you need to open the SIP port (normally UDP port 5060) and a range of UDP ports for RTP traffic
between the Telecommuting Module and the Internet. The other interface is connected to your internal network.
The Telecommuting Module can handle several networks on the internal interface even if they are hidden behind
routers. No networks on other interfaces on the firewall can be handled.
Internal users have to configure the Telecommuting Module as outbound proxy, or an internal proxy has to use the
Telecommuting Module as outbound proxy.
The Telecommuting Module derives information about your network topology from the interface configuration.
The Standalone Configuration
Using this configuration, the Telecommuting Module is connected to your internal network on one interface and the
outside world on the other.
Use this configuration only if your firewall lacks a DMZ interface, or for some other reason cannot be configured
for the DMZ or DMZ/LAN alternatives.
Internal users have to configure the Telecommuting Module as outbound proxy, or an internal proxy has to use the
Telecommuting Module as outbound proxy. No change in the firewall configuration is needed.
The Telecommuting Module derives information about your network topology from the interface configuration.
Telecommuting Module Type configuration
Current Telecommuting Module Type
Shows which type is currently active.
Change Telecommuting Module Type to
Select a new Telecommuting Module Type here.
Change type
Press the Change type button to set the new Telecommuting Module Type. This setting, like others, must be
applied on the Save/Load Configuration page before it affects the Telecommuting Module functionality.
16
Page 21

Chapter 4. Network Configuration
Basic Configuration
On the Basic Configuration page, general settings for the Telecommuting Module are made. The most important
ones for getting started are the default gateway and, for SIP, the DNS server.
General
Name of this Telecommuting Module
Here, you can give your 3Com VCX IP Telecommuting Module a name. The name of the Telecommuting Module
is displayed in the title bar of your web browser. This can be a good idea if you administer several Telecommuting
Modules. The name is also used if you use SNMP and when you export log files into the WELF format.
Default domain
Here, you can enter a default domain for all settings. If a default domain is entered, the Telecommuting Module will
automatically assume that an incomplete computer name should be completed with the default. If, for example,
Default domain contains company.com, you could as the name of the computer axel.company.com use only
axel. If no default domain should be used, the Default domain field should contain a single dot (.).
IP policy
Here, you specify what will happen to IP packets which are neither SIP packets, SIP session media streams, or
Telecommuting Module administration traffic. Discard IP packets means that the Telecommuting Module ignores
the IP packets without replying that the packet did not arrive. Reject IP packets makes the Telecommuting Module
reply with an ICMP packet telling that the packet did not arrive.
Policy For Ping To the Telecommuting Module
Here, you specify how the Telecommuting Module should reply to ping packets to its IP addresses. You can choose
between Never reply to ping, Only reply to ping from the same interface and Reply to ping to all IP addresses.
Only reply to ping from the same interface means that the ping request should originate from a network which is
directly connected to the pinged interface of the Telecommuting Module or from a network to which there exists a
static route from the pinged interface, or the request will be ignored.
Ping is a way of finding out whether a computer is working. See appendix C of the User Manual for further
information on ping.
Default Gateways
A Default Gateway is the IP address of a router that is used to contact the outside world. This IP address is usually
the firewall. Default Gateway must be an IP address from one of the Directly Connected Networks of the
Telecommuting Module’s interfaces. See appendix C of the User Manual, for further description of
routers/gateways.
The Telecommuting Module must have at least one default gateway to work. You can enter more than one default
gateway. The Telecommuting Module will use one of them until it stops responding, and then switch to the next one.
17
Page 22

Chapter 4. Network Configuration
DNS name or IP address
Enter the DNS name or IP address for the default gateway. If an interface will receive its IP address from a DHCP
server, the Telecommuting Module will get its default gateway from the server, and Default Gateway must be set to
"*".
IP address
Shows the IP address of the DNS name or IP address you entered in the previous field.
Gateway Reference Hosts
The gateway reference hosts are used by the Telecommuting Module to check if the gateways are alive. For each
reference host, test ping packets are sent, using the different gateways.
Reference hosts are only needed when multiple default gateways are used.
DNS name or IP address
Enter the DNS name or IP address for the reference host. The reference host must be located on the other side of the
default gateway.
IP address
Shows the IP address of the DNS name or IP address you entered in the previous field.
DNS Servers
Here, you configure DNS servers for the Telecommuting Module. The servers are used in the order they appear in
this table, which means that the Telecommuting Module uses the top server to resolve DNS records until it doesn’t
reply. Only then is server number two contacted.
18
Page 23

Chapter 4. Network Configuration
No.
The DNS servers are used in the order they are presented in the table. To move a server to a certain row, enter the
number on the row to which you want to move it. You need only renumber servers that you want to move; other
servers are renumbered automatically. When you click on Save, the DNS servers are re-sorted.
DNS Name Or IP Address
The DNS name/IP address of the DNS server which the Telecommuting Module should use. Note that to use DNS
names here, there must exist a DNS server in the Telecommuting Module’s permanent configuration.
IP address
Shows the IP address of the DNS name or IP address you entered in the previous field.
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Save
Saves the Basic Configuration configuration to the preliminary configuration.
Cancel
Reverts all the above fields to their previous configuration.
Look up all IP addresses again
Looks up the IP addresses for all DNS names on this page in the DNS servers you entered above.
Interface (Network Interface 1 and 2)
There is a menu selection for each network interface (Network Interface 1 and 2) on the Telecommuting Module.
Select a page to make configuration for that interface. There is also a page where configuration for all interfaces can
be viewed and changed.
Here, you set the interface name, whether the interface is on or off, the IP address, alias, and static routing.
For each interface, go to Directly Connected Networks and state the IP address of the Telecommuting Module and
the size of the network connected to this interface.
General
Physical device name
This tells the physical device name of the network interface. The physical interface eth0 corresponds to Network
Interface 1, and eth1 corresponds to Network Interface 2.
19
Page 24

Chapter 4. Network Configuration
Status
Specify if this network interface is On or Off. If the interface is off, all configuration on this page is ignored, and
the Telecommuting Module will behave as if this interface wasn’t present (except when used for failover).
If the interface should be used for failover, you should select Off. In this case, it won’t be available for other traffic
than the synchronizing within the failover team. Read more about failover in chapter 12 of the User Manual.
Interface name
The network Interface name is only used internally in the Telecommuting Module, e. g. when configuring
Networks and Computers.
Directly Connected Networks
The Telecommuting Module must have an IP address on every network to which it is directly connected. This
applies to all networks on the same physical network to which this interface is connected.
Note that the interface which should receive traffic from the outside must have a public IP address (no NAT),
regardless of which Telecommuting Module Type was selected. For a DMZ or DMZ/LAN type, this means that
the interface connected to the DMZ of the firewall must have a public IP address.
Name
A name for this IP address. You can use this name when configuring the administration IP address. This name is
only used internally in the Telecommuting Module.
DNS name or IP address
The name/IP address of the Telecommuting Module on this network interface on this directly connected network.
IP address
Shows the IP address of the DNS name or IP address you entered in the previous field.
Netmask/bits
Enter the mask of the network where the DNS name or IP address applies.
Network address
The IP address of the network where the DNS name or IP address applies.
Broadcast address
Shows the broadcast address of the network in the Network address field.
VLAN id
VLANs are used for clustering IP ranges into logical networks.
A VLAN id is simply a number, which identifies the VLAN uniquely within your network.
Enter a VLAN id for this network. You don’t need to use a named VLAN (defined on the VLAN page).
VLAN name
If you entered the VLAN id of a named VLAN, the name will show here.
20
Page 25

Chapter 4. Network Configuration
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Alias
3Com VCX IP Telecommuting Module can use extra IP addresses, aliases, on its interfaces. All alias IP addresses
must belong to one of the Directly Connected Networks you have specified.
Aliases are necessary for setting up a STUN server.
Name
Enter the name of your alias. This name is only used internally in the Telecommuting Module.
DNS name or IP address
Enter the IP address of this alias, or a name in the DNS. If you enter a DNS name instead of an IP address, you must
enter the IP address of a DNS server on the Basic Configuration page.
IP address
Shows the IP address of the DNS name or IP address you entered in the previous field.
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Static routing
If there is a router between the Telecommuting Module and a computer network which the Telecommuting Module
is serving, you must name the router and the network here. The table is sorted by network number and network
mask.
The Default gateway, configured on the Basic Configuration page, will automatically be entered in this table on
the corresponding interface page, when added to the Default Gateways table.
21
Page 26

Chapter 4. Network Configuration
Routed network
Enter the DNS name or IP address of the routed network under DNS name or network address.
The IP address of the routed network is shown under Network address.
In the Netmask field, enter the netmask of the network.
Router
The name or IP address of the router that will be used for routing to the network. If there are several routers
between the Telecommuting Module and the network, fill in the router closest to the Telecommuting Module.
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Save
Saves all Interface configuration to the preliminary configuration.
Cancel
Clears and resets all fields in new rows and resets changes in old rows.
Look up all IP addresses again
Looks up the IP addresses for all DNS names on this page in the DNS servers you entered on the Basic
Configuration page.
Networks and Computers
Here, you name groups of computers and networks. Sometimes it can be useful to give a group of computers a
network name, such as Administration. If you want to group some computers, this can be done here, even if they do
not have consecutive IP addresses. You can also include a subgroup when defining a new network group.
The names are used when you configure Surroundings and SNMP.
Every group of computers which can reach each other without having to pass through the firewall needs a separate
network group.
The rows are sorted in alphabetical order, except that all upper case letters are sorted before lower case letters (B
comes before a).
22
Page 27

Chapter 4. Network Configuration
When using an already defined group as a subgroup, select the name of the group under Subgroup. Set
Interface/VLAN to ’-’ and leave the other fields empty.
Name
Enter a name for the group of computers. You can use this name when you change configuration on the pages
mentioned above. A group can consist of several rows of IP addresses or series of IP addresses. By clicking on the
plus sign beside the name, you add more rows where you can specify more IP addresses for this group.
Subgroup
An already defined group can be used as a subgroup to new groups. Select the old group here and leave the fields
for DNS name empty. Select ’-’ as Interface/VLAN. If you don’t want to use a subgroup, select ’-’ here.
Lower Limit
DNS Name Or IP Address
Enter the DNS name or IP address of the network or computer. For computers in an IP range that you want to give a
network name, enter the first IP address in the range. DNS Name Or IP Address must not be empty if you are not
using a subgroup.
IP Address
The IP address of the object you entered in the DNS name or IP address field is displayed here. This field is not
updated until you click on Look up all IP addresses again or make changes in the DNS Name Or IP Address
field.
Upper Limit
DNS Name Or IP Address
Here, enter the last DNS name/IP address of the network or group. If the network contains a single computer, you
can leave this field empty. Then only the IP address in Lower Limit is used.
23
Page 28

Chapter 4. Network Configuration
For computers in an IP range that you want to give a network name, enter the last IP address in the range. The IP
address in Upper Limit must be at least as high as the one in Lower Limit. If you use a subgroup, leave this field
empty.
IP Address
The IP address of the object you entered in the DNS Name Or IP Address field is displayed here. This field is not
updated until you click on Look up all IP addresses again or make changes in the DNS Name Or IP Address
field.
Interface/VLAN
Here, you can select an interface or a VLAN to restrict the IP range.
If the interface ’-’ is chosen, the group will consist of all IP addresses in the interval between Lower limit and
Upper limit, regardless of what interface they are connected to. By selecting an interface or a VLAN, you constrain
the group to consist only of the IP addresses in the interval that really are connected to the selected interface/VLAN.
For example, if 10.20.0.0 - 10.20.0.255 are IP addresses behind the interface DMZ-1 and the lower and upper limits
are 10.10.10.20 and 255.255.255.255 respectively, choosing DMZ-1 as Interface will cause the group to consist of
the IP addresses 10.20.0.0 - 10.20.0.255, being the IP addresses in the interval actually connected to the selected
interface.
If you have selected a subgroup, the Interface/VLAN should be ’-’.
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new groups and rows you want to add to the table, and then click on Create.
Save
Saves the Networks and Computers configuration to the preliminary configuration.
Cancel
Clears and resets all fields in new rows and reset changes in old rows.
Surroundings
Settings on the Surroundings page are only required when the Telecommuting Module has been made the DMZ
type.
The Telecommuting Module must know what the networks around it looks like. On this page, you list all networks
which the Telecommuting Module should serve and which are not reached through the default gateway of the
firewall.
All computers that can reach each other without having to go through the firewall connected to the Telecommuting
Module should be grouped in one network. When you are finished, there should be one line for each of your
firewall’s network connections (not counting the default gateway).
One effect of this is that traffic between two users on different networks, or between one of the listed networks and
a network not listed here, is NAT:ed.
Another effect is that for connections between two users on the same network, or on networks where neither is
listed in Surroundings, no ports for RTP sessions will be opened, since the Telecommuting Module assumes that
they are both on the same side of the firewall.
24
Page 29

Chapter 4. Network Configuration
Normally, at least one network should be listed here. If no networks are listed, the Telecommuting Module will not
perform NAT for any traffic.
Network
Select a network. The alternatives are the networks you defined on the Networks and Computers page.
Delete Row
If you select this box, the row is deleted when you click on Add new rows or Save.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Save
Saves all Surroundings configuration to the preliminary configuration.
Cancel
Clears and resets all fields in new rows and resets changes in old rows.
25
Page 30

Chapter 5. SIP Configuration
SIP (Session Initiation Protocol) is a protocol for creating and terminating various media stream sessions over an IP
network. It is for example used for Internet telephone calls and distribution of video streams.
SIP takes care of the initiation, modification and termination of a session with one or more participants. The
protocol makes it possible for the participants to agree on what media types they should share. You can find more
information about SIP in appendix A of the User Manual and in RFC 3261.
You find examples on how to configure your 3Com VCX IP Telecommuting Module for SIP in chapter 4 of the
User Manual.
Basic SIP configuration is made on the Basic, User database, and possibly also Sessions and Media pages. If you
want to use an external SIP proxy, you must state this on the Routing page.
Basic
Here, you make basic settings for the Telecommuting Module SIP management.
General
Here, select whether the SIP module should be activated or not. If you select to turn the SIP module Off, no other
SIP settings will have any effect.
SIP media port range
State a port interval which the Telecommuting Module should use for SIP media streams. You can use any high
ports except 4500 (reserved for NAT-T) and 65097-65200 (reserved for RADIUS).
Enter the lower and upper limit of the port range that the TelecommutingModule should use for media streams. The
upper limit must be at least as high as the lower limit.
SIP Servers To Monitor
Your Telecommuting Module can be made to monitor SIP servers, to check that they are alive. The information is
used by the Telecommuting Module when SIP signaling should be passed on to the server in question. This is useful
when a domain resolves to several individual hosts; the Telecommuting Module will know immediately if one of
them is down, which will speed up the call connection.
26
Page 31
Chapter 5. SIP Configuration
Server
Enter the host name, domain name, or IP address of the server to be monitored.
Port
Enter the port to be monitored on that host. This should be the port to use for SIP signaling.
Transport
Select the transport to be monitored on that host. This should be the transport to use for SIP signaling.
Delete Row
If you select this box, the row is deleted when you click on Add new rows or Save.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Logging
The same settings can also be found on the Logging Configuration page under Logging.
Log class for SIP errors
The Telecommuting Module sends a message if there are any SIP errors. Select a log class for these log messages.
Log class for SIP signaling
For each SIP packet, the Telecommuting Module generates a message, containing the sender and receiver of the
packet and what type of packet it is. Select a log class for these log messages.
27
Page 32

Chapter 5. SIP Configuration
Log class for SIP packets
The Telecommuting Module logs all SIP packets (one SIP packet is many lines). Select a log class for the SIP
packets.
Log class for SIP debug messages
The Telecommuting Module logs a lot of status messages, for example the SIP initiation phase of a reboot. Select a
log class for these messages.
Save
Saves the Basic configuration to the preliminary configuration.
Cancel
Clears and resets all fields in new rows and resets changes in old rows.
Routing
DNS Override For SIP Requests
Here, you can register SIP domains to which the Telecommuting Module should be able to forward requests, but
which for some reason cannot be resolved in DNS. Enter an IP address and port to which the requests should be
forwarded. You can also select to use a specific protocol.
If you use a dialing domain that looks like an IP address, you must enter that dialing domain here along with the
SIP server for that domain.
You can enter more than one IP address or host name for a domain, and set weights and priorities for these.
Domain
Enter the domain name of the SIP domain.
Relay to
Enter the IP address for the SIP registrar handling the domain. You can also enter a DNS name for the SIP registrar,
if it has a DNS-resolvable host name, even if the SIP domain is not possible to look up in DNS.
Under Port, enter the port on which the SIP registrar listens for SIP traffic. The standard port is 5060 (5061 for
TLS).
You can select which transport protocol to use between the Telecommuting Module and the registrar. Under
Transport, select from UDP, TCP and TLS. You can also select "-", which means that the signaling is passed on
using the same transport as was used to reach the Telecommuting Module.
28
Page 33

Chapter 5. SIP Configuration
If you entered more than one IP address/host name for the same domain, you should also assign them Priority and
Weight. A low Priority value means that the unit should have a high priority. If more than one unit has the same
Priority, the signaling sent to them is distributed between them according to their Weight. If two units have the
same priority, and Unit 1 has weight 4, and Unit 2 has weight 9, 4/13 of the signaling will be sent to Unit 1, and
9/13 will be sent to Unit 2.
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new groups and rows you want to add to the table, and then click on Create.
Interoperability
Preserve username
When registering a SIP client on one side of the Telecommuting Module to a SIP server on the other side, the
Contact header is normally rewritten. By doing this, we make it possible for the SIP server to track when the same
user is registering multiple times from different places. It is possible to turn this rewriting off and preserve the
username in Contact headers passing through the Telecommuting Module, but that makes it impossible for the SIP
server to tell if registrations for a certain user belong to one or several clients (if a user has two registrations from
different clients and deregisters one of them, the SIP server will delete its only registration for him).
To make all calls work, you need to turn this On.
Select if usernames should be preserved or not. The recommended setting is to Preserveusername in Contact
header.
Translation exceptions
Usually, the Telecommuting Module rewrites IP addresses in the SIP signaling to hide it for the receiver. For some
reasons, you might want to except certain IP addresses from being rewritten. Enter those IP addresses in the table.
If you use a dialing domain that looks like an IP address (like 10.10.10.10), you need to enter that domain in this
table.
29
Page 34

Chapter 5. SIP Configuration
Except this from translation
Enter the DNS name or IP address to be excepted from IP address translation. If you enter a DNS name, the
corresponding IP address will be excepted from translation.
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Remote SIP Connectivity
Remote NAT Traversal
If your SIP client is not STUN-capable, you can use the built-in Remote NAT traversal feature of the
Telecommuting Module. The client must register on the Telecommuting Module (or through it).
The SIP client needs to re-REGISTER rather often for this to work. The exact period for this depends on the
NAT-ing device, but 20 seconds should be enough to get across most NAT boxes. It is not advisable to use
OPTIONS for 3Com SIP clients.
Remote NAT traversal
Turn this function on or off.
Re-REGISTER period for clients
Clients using this function will have to re-REGISTER very often, to keep the IP/port NAT binding. A
re-REGISTER interval of 20 seconds should be enough to ensure this.
If some clients are unable to handle short re-REGISTER intervals, the Telecommuting Module can send OPTIONS
messages instead, see below.
Use OPTIONS for registered clients
Select if the Telecommuting Module should use OPTIONS packets instead of short re-REGISTER intervals to keep
the NAT binding.
OPTIONS should not be used for 3Com phones, as they don’t respond to that.
OPTIONS interval
Enter the interval for the Telecommuting Module to send OPTIONS packets to the client.
30
Page 35

Chapter 6. Administration of the Telecommuting Module
You also need to configure who can access the Telecommuting Module web interface. This is done on the Access
Control page under Basic Configuration.
Remember that the configuration you see in the web interface (preliminary configuration) isn’t necessarily the work
configuration (permanent configuration) of the Telecommuting Module. When all configuration is made in the web
interface, it must be applied. This is done on the Save/Load Configuration page under Administration.
Access Control
On the Access Control page, settings are made which controls the access to the Telecommuting Module
administration web interface.
Select one or two configuration IP addresses for the Telecommuting Module. The configuration address is the IP
address to which you direct your web browser to access the web interface of the Telecommuting Module.
For each network interface, you also specify whether or not the Telecommuting Module can be configured via this
network interface.
You also select what kind of authentication will be performed for the users trying to access the web interface.
To further increase security, the Telecommuting Module can only be configured from one or a few computers that
are accessed from one of these interfaces. Enter the IP address or addresses that can configure the Telecommuting
Module. The IP addresses can belong to one or more computers.
Configuration Allowed Via Interface
Specify whether or not this interface can be used to configure the Telecommuting Module. The choices are On and
Off. This configuration is a complement to the Configuration Computers setting below.
User Authentication
Select where the administrator database is: Local users (administrator users are defined locally on the
Telecommuting Module), RADIUS (administrator users are defined on an external RADIUS server), or a choice
between the two alternatives at login (Local users or RADIUS database).
Local administrator users and their passwords are defined on the User Administration page under Administration.
If the authentication should be made by help of a RADIUS server, you must enter one on the RADIUS page.
Configuration Transport
Select one or two Telecommuting Module IP addresses. The Telecommuting Module web server will listen for web
traffic on the selected IP addresses and ports.
31
Page 36

Chapter 6. Administration of the Telecommuting Module
This is the IP address and port which should be entered in your web browser to connect to the Telecommuting
Module.
Configuration via HTTP
Select which IP address and port the Telecommuting Module administrator should direct her web browser to when
HTTP is used for Telecommuting Module configuration. You can select from the Telecommuting Module IP
addresses configured on the Interface pages under Network.
You can use different IP addresses for HTTP and HTTPS configuration.
Configuration via HTTPS
Select which IP address and port the Telecommuting Module administrator should direct her web browser to when
HTTPS is used for Telecommuting Module configuration. You can select from the Telecommuting Module IP
addresses configured on the Interface pages under Network.
You can use different IP addresses for HTTP and HTTPS configuration.
You also need to select a TLS certificate, which works as an ID card, identifying the Telecommuting Module to
your web browser. This will ensure that you are really communicating with your Telecommuting Module and not
somebody else’s computer. TLS uses an encryption method using two keys, one secret and one public. The secret
key is kept in the Telecommuting Module and the public key is used in the certificate. If any of the keys is changed,
the TLS connection won’t work.
The certificate is created on the Certificates page.
Configuration Computers
Enter the IP address or addresses that can configure the Telecommuting Module. The IP addresses can belong to
one or more computers.
Note that you must also allow configuration via the Telecommuting Module interface that the computers are
connected to. See Configuration Allowed Via Interface above.
DNS Name Or Network Address
Enter the DNS name or IP address of the computer or network from which the Telecommuting Module can be
configured. Avoid allowing configuration from a network or computer on the Internet or other insecure networks, or
use HTTPS or VPN to connect to the Telecommuting Module from these insecure networks.
32
Page 37

Chapter 6. Administration of the Telecommuting Module
Network Address
Shows the IP address of the DNS Name Or Network Address you entered in the previous field.
Netmask/Bits
Netmask/Bits is the mask that will be used to specify the configuration computers. See chapter 3 of the User
Manual, for instructions on writing the netmask. To limit access so that only one computer can configure, use the
netmask 255.255.255.255. You can also specify the netmask as a number of bits, which in this case would be 32. To
allow configuration from an entire network, you must enter the network address under Network address, and a
netmask with a lower number here. To allow configuration from several computers or networks, create several lines
for the information.
Range
The Range shows all IP addresses from which the Telecommuting Module can be configured. The range is
calculated from the configuration under DNS name or network address and Netmask/Bits. Check that the correct
information was entered in the DNS name or network address and Netmask/Bits fields.
Log Class
Here, you enter what log class the Telecommuting Module should use to log the configuration traffic to the
Telecommuting Module’s web server. Log classes are defined on the Log Classes page under Logging. See also
chapter 11 of the User Manual.
Log Rule No.
The Log Rule No. field determines the order of the lines. The order is important in deciding what is logged and
warned for. The Telecommuting Module uses the first line that matches the configuration traffic.
Perhaps you want to configure the Telecommuting Module so that configuration traffic from one specific computer
is simply logged while traffic from the rest of that computer’s network is both logged and generates alarms.
The rules are used in the order in which they are listed, so if the network is listed first, all configuration traffic from
that network is both logged and generates alarms, including the traffic from that individual computer. But if the
individual computer is listed on a separate line before the network, that line will be considered first and all
configuration traffic from that computer is only logged while the traffic from the rest of the computer’s network is
both logged and generates alarms.
Delete Row
If you select this box, the row is deleted when you click on Add new rows, Save, or Look up all IP addresses
again.
Create
Enter the number of new rows you want to add to the table, and then click on Create.
Save
Saves the Access Control configuration to the preliminary configuration.
Cancel
Reverts all the above fields to their previous configuration.
Look up all IP addresses again
Looks up the IP addresses for all DNS names on this page in the DNS servers you entered on the Basic
Configuration page.
33
Page 38

Chapter 6. Administration of the Telecommuting Module
Save/Load Configuration
Here, you work with the preliminary and permanent configurations, save them and load new configurations from
previously saved configurations.
Test Preliminary Configuration
When Apply configuration is pressed, the Telecommuting Module will test the configuration before you make it
permanent.
During test, the Telecommuting Module waits for you to press one of the three buttons displayed. If you never see
the three buttons, something in your preliminary configuration (now tested) is wrong, which makes it impossible for
you to access the configuration web interface.
Duration of limited test mode
Here, you enter the time limit for the testing. If you do not press any button within this time, the Telecommuting
Module will assume that some part of your preliminary configuration makes connecting impossible. When the
timeout is reached, the Telecommuting Module automatically reverts to the old permanent configuration. If this
occurs, you will be informed when trying to press a button.
Apply configuration
Saves the preliminary configuration to the permanent configuration and puts it into use. You can test your
preliminary configuration before finalizing it.
Three buttons are displayed during the test:
Save configuration saves your preliminary configuration to the permanent configuration and puts it into use.
Continue testing shows a new page with only the other two buttons.
Revert cancels this test of the preliminary configuration without saving.
If you do not press any button within the time limit, the Telecommuting Module will revert to the old permanent
configuration, just as if you had pressed Revert. This is useful if you happen to configure your Telecommuting
Module so it isn’t accessible from your browser.
After the timeout, pressing either of the three buttons will show a new page which will inform you that the test run
was aborted.
Restarting the Telecommuting Module by cycling the power also cancels the test.
Backup
All configurations can be saved to and loaded from diskette or file. This does not affect the permanent configuration.
34
Page 39

Chapter 6. Administration of the Telecommuting Module
Save to diskette
Insert a formatted diskette into the Telecommuting Module’s floppy drive and press Save to diskette to save the
preliminary configuration. Do not remove the diskette until the light on the floppy drive goes out.
Check that you get a confirmation of the saving. If not, the diskette may be faulty.
Load from diskette
Insert the diskette with the saved configuration into the Telecommuting Module’s floppy drive and press Load from
diskette. Do not remove the diskette until the light on the floppy drive goes out. The contents of the diskette are
now loaded in the preliminary configuration.
Save to local file
Press Save to local file to save the preliminary configuration to the file you have selected. A new window is opened
where you enter the name of the file.
Load from local file
Press Load from local file to load a new preliminary configuration from the file you have selected.
Browse
Browse is used to scan your local disk. The web browser opens a new window where you can search among files
and directories. Go to the right directory and select the file you want to upload.
Revert to old configurations
You can revert to old configurations of the Telecommuting Module, either back to the last configuration
successfully applied, or to the configuration delivered with your Telecommuting Module from the factory.
Abort All Edits
Abort all edits copies the permanent configuration to the preliminary configuration. All changes made in the
preliminary configuration are deleted.
Reload Factory Configuration
The factory configuration is the standard configuration that is delivered with a Telecommuting Module. Click on
this button to load this configuration into the preliminary configuration. The permanent configuration is not affected.
35
Page 40

Chapter 7. Firewall and Client Configuration
Additional configuration for the firewall and the SIP clients is required to make the Telecommuting Module work
properly. The amount and nature of the configuration depends on which Telecommuting Module Type was
selected.
The DMZ type
Using the DMZ type, the network configuration should look like this:
The Firewall
The firewall to which the Telecommuting Module is connected should have the following configuration:
SIP over UDP
• Let through UDP traffic between the Internet (all high ports) and the Telecommuting Module (port 5060). You
must allow traffic in both directions.
• Let through UDP traffic between the internal networks (all high ports) and the Telecommuting Module (port
5060). You must allow traffic in both directions.
• Let through UDP traffic between the Internet (all high ports) and the Telecommuting Module (the port interval
for media streams which was set on the Basic page). You must allow traffic in both directions.
• Let through UDP traffic between the internal networks (all high ports) and the Telecommuting Module (the port
interval for media streams which was set on the Basic page). You must allow traffic in both directions.
• Let through UDP traffic between the Telecommuting Module (all high ports) and the Internet (port 53). You must
allow traffic in both directions. This enables the Telecommuting Module to make DNS queries to DNS servers on
the Internet. If the DNS server is located on the same network as the Telecommuting Module, you don’t have to
do this step.
• NAT between the Telecommuting Module and the Internet must not be used.
• NAT between the Telecommuting Module and the internal networks must not be used.
SIP over TCP/TLS
• Let through TCP traffic between the Internet (all high ports) and the Telecommuting Module (ports 1024-32767).
You must allow traffic in both directions.
• Let through TCP traffic between the internal networks (all high ports) and the Telecommuting Module (ports
1024-32767). You must allow traffic in both directions.
• Let through UDP traffic between the Internet (all high ports) and the Telecommuting Module (the port interval
for media streams which was set on the Basic page). You must allow traffic in both directions.
• Let through UDP traffic between the internal networks (all high ports) and the Telecommuting Module (the port
interval for media streams which was set on the Basic page). You must allow traffic in both directions.
• Let through UDP traffic between the Telecommuting Module (all high ports) and the Internet (port 53). You must
allow traffic in both directions. This enables the Telecommuting Module to make DNS queries to DNS servers on
the Internet. If the DNS server is located on the same network as the Telecommuting Module, you don’t have to
do this step.
36
Page 41

Chapter 7. Firewall and Client Configuration
• NAT between the Telecommuting Module and the Internet must not be used.
• NAT between the Telecommuting Module and the internal networks must not be used.
The SIP clients
SIP clients will use the Telecommuting Module as their outgoing SIP proxy and as their registrar (if they can’t be
configured with the domain only). If you don’t want to use the Telecommuting Module as the registrar, you should
point the clients to the SIP registrar you want to use.
Other
The DNS server used must have a record for the SIP domain, which states that the Telecommuting Module handles
the domain, or many SIP clients won’t be able to use it (if you don’t use plain IP addresses as domains).
The DMZ/LAN type
Using the DMZ/LAN type, the network configuration should look like this:
The Firewall
The firewall to which the Telecommuting Module is connected should have the following configuration:
SIP over UDP
• Let through UDP traffic between the Internet (all high ports) and the Telecommuting Module (port 5060). You
must allow traffic in both directions.
• Let through UDP traffic between the Internet (all high ports) and the Telecommuting Module (the port interval
for media streams which was set on the Basic page). You must allow traffic in both directions.
• Let through UDP traffic between the Telecommuting Module (all high ports) and the Internet (port 53). You must
allow traffic in both directions. This enables the Telecommuting Module to make DNS queries to DNS servers on
the Internet. If the DNS server is located on the same network as the Telecommuting Module, you don’t have to
do this step.
• NAT between the Telecommuting Module and the Internet must not be used.
SIP over TCP/TLS
• Let through TCP traffic between the Internet (all high ports) and the Telecommuting Module (ports 1024-32767).
You must allow traffic in both directions.
• Let through UDP traffic between the Internet (all high ports) and the Telecommuting Module (the port interval
for media streams which was set on the Basic page). You must allow traffic in both directions.
• Let through UDP traffic between the Telecommuting Module (all high ports) and the Internet (port 53). You must
allow traffic in both directions. This enables the Telecommuting Module to make DNS queries to DNS servers on
the Internet. If the DNS server is located on the same network as the Telecommuting Module, you don’t have to
do this step.
• NAT between the Telecommuting Module and the Internet must not be used.
37
Page 42

Chapter 7. Firewall and Client Configuration
SIP clients
The SIP clients on the internal network should have the Telecommuting Module’s IP address on that network as
their outgoing SIP proxy and registrar.
Other
The DNS server used must have a record for the SIP domain, which states that the Telecommuting Module handles
the domain, or many SIP clients won’t be able to use it (if you don’t use plain IP addresses as domains).
The Standalone type
Using the Standalone type, the network configuration should look like this:
The SIP clients
SIP clients will use the Telecommuting Module as their outgoing SIP proxy and as their registrar (if they can’t be
configured with the domain only). If you don’t want to use the Telecommuting Module as the registrar, you should
point the clients to the SIP registrar you want to use.
Other
The DNS server used must have a record for the SIP domain, which states that the Telecommuting Module handles
the domain, or many SIP clients won’t be able to use it (if you don’t use plain IP addresses as domains).
38
Page 43

Index
apply configuration, 34
authentication
of administrator, 31
backup, 34
Basic configuration
SIP, 26
configuration
apply, 34
IP address, 31
permanent, 4
preliminary, 4
use protocol, 31
via HTTPS, 32
configuration computers, 32
configuration interface, 31
default domain, 17
default gateway,17
directly connected networks, 20
DMZ type, 15
configuration of DNS server, 37
configuration of firewall, 36
configuration of SIP clients, 37
DMZ/LAN type, 15
configuration of DNS server, 38
configuration of firewall, 37
configuration of SIP clients, 37
factory configuration, 35
gateway, 17
HTTPS
for configuration, 32
installing 3Com VCX IP Telecommuting Module, 6
interface, 19
interface name, 20
IP policy, 17
limited test mode, 34
logging
of configuration, 33
SIP, 27
magic ping, 6
monitor SIP servers, 26
network interface, 19
network topology, 24
networks and computers, 22
permanent configuration, 4
physical device name, 19
ping policy, 17
port interval for media streams, 26
preliminary configuration, 4
router, 17, 21
save configuration, 34
SIP, 26
SIP basic configuration, 26
SIP domains
static, 28
SIP servers
monitored, 26
standalone type, 16
configuration of DNS server, 38
configuration of SIP clients, 38
static routing, 21
subgroup
networks, 23
surroundings, 24
TelecommutingModule name, 17
TelecommutingModule Type
configuration, 16
DMZ, 15
DMZ/LAN, 15
standalone, 16
test mode, 34
turn off the 3Com VCX IP Telecommuting Module, 12
version control, 17
39
 Loading...
Loading...