Page 1

User’s Guide
Page 2

Norton™ Personal Firewall User’s Guide
The software described in this book is furnished under a license agreement and may be
used only in accordance with the terms of the agreement.
Documentation version 6.0
PN: 10025076
Copyright Notice
Copyright • 2002 Symantec Corporation. All Rights Reserved.
Any technical documentation that is made available by Symantec Corporation is the
copyrighted work of Symantec Corporation and is owned by Symantec Corporation.
NO WARRANTY. The technical documentation is being delivered to you AS-IS and
Symantec Corporation makes no warranty as to its accuracy or use. Any use of the
technical documentation or the information contained therein is at the risk of the user.
Documentation may include technical or other inaccuracies or typographical errors.
Symantec reserves the right to make changes without prior notice.
No part of this publication may be copied without the express written permission of
Symantec Corporation, 20330 Stevens Creek Blvd., Cupertino, CA 95014.
Standard Template Library
This product utilizes the Standard Template Library, a C++ library of container classes,
algorithms, and iterators.
Copyright • 1996-1999. Silicon Graphics Computer Systems, Inc.
Permission to use, copy, modify, distribute and sell this software and its documentation for
any purpose is hereby granted without fee, provided that the above copyright notice
appears in all copies and that both that copyright notice and this permission notice appear
in supporting documentation. Silicon Graphics makes no representations about the
suitability of this software for any purpose. It is provided “as is” without express or
implied warranty.
Copyright • 1994. Hewlett-Packard Company
Permission to use, copy, modify, distribute and sell this software and its documentation for
any purpose is hereby granted without fee, provided that the above copyright notice
appears in all copies and that both that copyright notice and this permission notice appear
in supporting documentation. Hewlett-Packard Company makes no representations about
the suitability of this software for any purpose. It is provided “as is” without express or
implied warranty.
Trademarks
Symantec, the Symantec logo, Norton Personal Firewall, and LiveUpdate are U.S.
registered trademarks of Symantec Corporation.
Microsoft, MS-DOS, MSN, Windows and the Windows logo are registered trademarks of
Microsoft Corporation. AOL and CompuServe are registered trademarks of America
Online, Inc. Pentium is a registered trademark of Intel Corporation.
Other product names mentioned in this manual may be trademarks or registered
trademarks of their respective companies and are hereby acknowledged.
Printed in the United States of America.
10987654321
Page 3

SYMANTEC LICENSE AND WARRANTY
IMPORTANT: PLEASE READ THE TERMS AND
CONDITIONS OF THIS LICENSE AGREEMENT
CAREFULLY BEFORE USING THE SOFTWARE.
SYMANTEC CORPORATION AND/OR ITS SUBSIDIARIES
(“SYMANTEC”) IS WILLING TO LICENSE THE SOFTWARE
TO YOU AS THE INDIVIDUAL, THE COMPANY, OR THE
LEGAL ENTITY THAT WILL BE UTILIZING THE
SOFTWARE (REFERENCED BELOW AS “YOU” OR
“YOUR”) ONLY ON THE CONDITION THAT YOU ACCEPT
ALL OF THE TERMS OF THIS LICENSE AGREEMENT. THIS
IS A LEGAL AND ENFORCEABLE CONTRACT BETWEEN
YOU AND SYMANTEC. BY OPENING THIS PACKAGE,
BREAKING THE SEAL, CLICKING ON THE “AGREE” OR
“YES” BUTTON OR OTHERWISE INDICATING ASSENT
ELECTRONICALLY, OR LOADING THE SOFTWARE, YOU
AGREE TO THE TERMS AND CONDITIONS OF THIS
AGREEMENT. IF YOU DO NOT AGREE TO THESE TERMS
AND CONDITIONS, CLICK ON THE “I DO NOT AGREE” OR
“NO” BUTTON, OR OTHERWISE INDICATE REFUSAL,
MAKE NO FURTHER USE OF THE SOFTWARE, AND
RETURN THE FULL PRODUCT WITH PROOF OF
PURCHASE TO THE DEALER FROM WHOM IT WAS
ACQUIRED WITHIN SIXTY (60) DAYS OF PURCHASE,
AND YOUR MONEY WILL BE REFUNDED.
1. LICENSE:
The software which accompanies this license (collectively
the “Software”) is the property of Symantec or its licensors
and is protected by copyright law. While Symantec
continues to own the Software, you will have certain rights
to use the Software after your acceptance of this license.
This license governs any releases, revisions, or
enhancements to the Software that Symantec may furnish
to you. Except as may be modified by a Symantec license
certificate, license coupon, or license key (each a “License
Module”) which accompanies, precedes, or follows this
license, your rights and obligations with respect to the use
of this Software are as follows:
YOU MAY:
A. use one copy of the Software on a single computer. If a
License Module accompanies, precedes, or follows this
license, you may make that number of copies of the
Software licensed to you by Symantec as provided in your
License Module. Your License Module shall constitute
proof of your right to make such copies.
B. make one copy of the Software for archival purposes, or
copy the Software onto the hard disk of your computer and
retain the original for archival purposes;
C. use the Software on a network, provided that you have a
licensed copy of the Software for each computer that can
access the Software over that network; and
D. after written notice to Symantec, transfer the Software
on a permanent basis to another person or entity, provided
that you retain no copies of the Software and the transferee
agrees to the terms of this license.
YOU MAY NOT:
A. copy the printed documentation which accompanies the
Software;
B. sublicense, rent or lease any portion of the Software;
reverse engineer, decompile, disassemble, modify,
translate, make any attempt to discover the source code of
the Software, or create derivative works from the Software;
C. use a previous version or copy of the Software after you
have received a disk replacement set or an upgraded
version. Upon upgrading the Software, all copies of the
prior version must be destroyed;
D. use a later version of the Software than is provided
herewith unless you have purchased upgrade insurance or
have otherwise separately acquired the right to use such
later version;
E. use, if you received the software distributed on media
containing multiple Symantec products, any Symantec
software on the media for which you have not received a
permission in a License Module; or
F. use the Software in any manner not authorized by this
license.
2. CONTENT UPDATES:
Certain Symantec software products utilize content that is
updated from time to time (antivirus products utilize
updated virus definitions; content filtering products utilize
updated URL lists; firewall products utilize updated
firewall rules; vulnerability assessment products utilize
updated vulnerability data, etc.; collectively, these are
referred to as “Content Updates”). You may obtain Content
Updates for any period for which you have purchased a
subscription for Content Updates for the Software
(including any subscription included with your original
purchase of the Software), purchased upgrade insurance
for the Software, entered into a maintenance agreement
that includes Content Updates, or otherwise separately
acquired the right to obtain Content Updates. This license
does not otherwise permit you to obtain and use Content
Updates.
3. SIXTY DAY MONEY BACK GUARANTEE:
If you are the original licensee of this copy of the Software
and are dissatisfied with it for any reason, you may return
the complete product, together with your receipt, to
Symantec or an authorized dealer, postage prepaid, for a
full refund at any time during the sixty (60) day period
following the delivery to you of the Software.
4. LIMITED WARRANTY:
Symantec warrants that the media on which the Software
is distributed will be free from defects for a period of sixty
(60) days from the date of delivery of the Software to you.
Your sole remedy in the event of a breach of this warranty
will be that Symantec will, at its option, replace any
defective media returned to Symantec within the warranty
period or refund the money you paid for the Software.
Symantec does not warrant that the Software will meet
your requirements or that operation of the Software will be
uninterrupted or that the Software will be error-free.
THE ABOVE WARRANTY IS EXCLUSIVE AND IN LIEU OF
ALL OTHER WARRANTIES, WHETHER EXPRESS OR
IMPLIED, INCLUDING THE IMPLIED WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR
PURPOSE AND NONINFRINGEMENT OF INTELLECTUAL
Page 4

PROPERTY RIGHTS. THIS WARRANTY GIVES YOU
SPECIFIC LEGAL RIGHTS. YOU MAY HAVE OTHER
RIGHTS, WHICH VARY FROM STATE TO STATE AND
COUNTRY TO COUNTRY.
5. DISCLAIMER OF DAMAGES:
SOME STATES AND COUNTRIES, INCLUDING MEMBER
COUNTRIES OF THE EUROPEAN ECONOMIC AREA, DO
NOT ALLOW THE LIMITATION OR EXCLUSION OF
LIABILITY FOR INCIDENTAL OR CONSEQUENTIAL
DAMAGES SO THE BELOW LIMITATION OR EXCLUSION
MAY NOT APPLY TO YOU.
TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE
LAW AND REGARDLESS OF WHETHER ANY REMEDY
SET FORTH HEREIN FAILS OF ITS ESSENTIAL PURPOSE,
IN NO EVENT WILL SYMANTEC OR ITS LICENSORS BE
LIABLE TO YOU FOR ANY SPECIAL, CONSEQUENTIAL,
INDIRECT OR SIMILAR DAMAGES, INCLUDING ANY
LOST PROFITS OR LOST DATA ARISING OUT OF THE USE
OR INABILITY TO USE THE SOFTWARE EVEN IF
SYMANTEC HAS BEEN ADVISED OF THE POSSIBILITY OF
SUCH DAMAGES.
IN NO CASE SHALL SYMANTEC'S OR ITS LICENSORS’
LIABILITY EXCEED THE PURCHASE PRICE FOR THE
SOFTWARE. The disclaimers and limitations set forth
above will apply regardless of whether you accept the
Software.
6. U.S. GOVERNMENT RESTRICTED RIGHTS:
RESTRICTED RIGHTS LEGEND. All Symantec products
and documentation are commercial in nature. The software
and software documentation are “Commercial Items”, as
that term is defined in 48 C.F.R. section 2.101, consisting
of “Commercial Computer Software” and “Commercial
Computer Software Documentation”, as such terms are
defined in 48 C.F.R. section 252.227-7014(a)(5) and 48
C.F.R. section 252.227-7014(a)(1), and used in 48 C.F.R.
section 12.212 and 48 C.F.R. section 227.7202, as
applicable. Consistent with 48 C.F.R. section 12.212, 48
C.F.R. section 252.227-7015, 48 C.F.R. section 227.7202
through 227.7202-4, 48 C.F.R. section 52.227-14, and
other relevant sections of the Code of Federal Regulations,
as applicable, Symantec’s computer software and
computer software documentation are licensed to United
States Government end users with only those rights as
granted to all other end users, according to the terms and
conditions contained in this license agreement.
Manufacturer is Symantec Corporation, 20330 Stevens
Creek Blvd., Cupertino, CA 95014.
7. GENERAL:
If You are located in North America or Latin America, this
Agreement will be governed by the laws of the State of
California, United States of America. Otherwise, this
Agreement will be governed by the laws of England. This
Agreement and any related License Module is the entire
agreement between You and Symantec relating to the
Software and: (i) supersedes all prior or contemporaneous
oral or written communications, proposals and
representations with respect to its subject matter; and (ii)
prevails over any conflicting or additional terms of any
quote, order, acknowledgment or similar communications
between the parties. This Agreement may only be modified
by a License Module or by a written document which has
been signed by both You and Symantec. This Agreement
shall terminate upon Your breach of any term contained
herein and You shall cease use of and destroy all copies of
the Software. The disclaimers of warranties and damages
and limitations on liability shall survive termination.
Should You have any questions concerning this
Agreement, or if You desire to contact Symantec for any
reason, please write: (i) Symantec Customer Service, 555
International Way, Springfield, OR 97477, USA, or (ii)
Symantec Customer Service Center, PO BOX 5689, Dublin
15, Ireland.
This product utilizes the Standard Template Library, a C++
library of container classes, algorithms, and iterators.
Copyright • 1996-1999. Silicon Graphics Computer
Systems, Inc. Copyright • 1994. Hewlett-Packard
Company.
Page 5

Contents
Chapter 1 Responding to emergencies
If you think your computer is under attack ...................................... 11
Recover from an emergency ................................................................ 12
Prevent future problems ....................................................................... 13
Chapter 2 About Norton Personal Firewall
What’s new in Norton Personal Firewall 2003 ................................ 15
Norton Personal Firewall features ...................................................... 16
About Norton Personal Firewall .................................................. 17
Chapter 3 Installing Norton Personal Firewall
System requirements ............................................................................. 19
Supported email clients ................................................................. 20
Supported instant messenger clients ......................................... 21
Before installation .................................................................................. 21
Prepare your computer .................................................................. 21
Install Norton Personal Firewall ......................................................... 22
If the opening screen does not appear ....................................... 25
Register your software .......................................................................... 25
After installation ..................................................................................... 28
Restart your computer ................................................................... 28
Use the Security Assistant ............................................................ 28
If you have Norton SystemWorks installed ...................................... 33
If you need to uninstall Norton Personal Firewall ........................... 34
Page 6

Contents6
Chapter 4 Norton Personal Firewall basics
Access Norton Personal Firewall ........................................................ 35
Access Norton Personal Firewall from the system tray ......... 36
Work with Norton Personal Firewall .................................................. 37
Access Norton Personal Firewall protection features ............. 37
Use the Security Monitor .............................................................. 38
Respond to Norton Personal Firewall alerts ............................. 39
Use Alert Tracker ............................................................................ 41
Check your computer’s vulnerability to attack ........................ 42
Identify the source of communications ...................................... 43
Stop Internet communication with Block Traffic ..................... 44
Customize Norton Personal Firewall .................................................. 45
About General options ................................................................... 45
About LiveUpdate options ............................................................. 45
About Firewall options ................................................................... 45
About Web Content options .......................................................... 46
About Email options ....................................................................... 46
Password-protect options ...................................................................... 46
Reset options password ................................................................. 47
Temporarily disable Norton Personal Firewall ................................ 47
For more information ............................................................................. 48
Look up glossary terms ................................................................. 48
Use online Help ............................................................................... 48
Readme file and Release Notes .................................................... 49
Use the User’s Guide PDF ............................................................. 50
About Norton Personal Firewall on the Web ............................ 51
Explore online tutorials ................................................................. 51
Subscribe to the Symantec Security Response newsletter .... 52
Chapter 5 Keeping current with LiveUpdate
About program updates ......................................................................... 53
About protection updates ...................................................................... 54
About your subscription ........................................................................ 54
When you should update ...................................................................... 55
Request an update alert ................................................................. 55
If you run LiveUpdate on an internal network ................................. 55
If you can’t use LiveUpdate .................................................................. 56
Obtain updates using LiveUpdate ....................................................... 56
Set LiveUpdate to Interactive or Express mode ............................... 56
Turn off Express mode ................................................................... 57
Run LiveUpdate automatically ............................................................. 58
Page 7

Chapter 6 Controlling access to protected computers
Control how people use your computer ............................................. 61
Connect to a network ..................................................................... 61
Enable file and printer sharing .................................................... 62
Organize computers into network zones ................................... 62
Identify computers to Norton Personal Firewall ...................... 64
Control how users access the Internet ............................................... 67
If you access the Internet via a cable or DSL router ............... 67
If multiple computers share a single Internet connection ..... 67
Control how outside users access your network ............................. 67
If you run Symantec pcAnywhere ............................................... 67
If you run a Virtual Private Network .......................................... 68
Chapter 7 Guarding against intrusion attempts
How Norton Personal Firewall protects against network
attacks ............................................................................................... 69
Norton Personal Firewall monitors communications ............. 70
Intrusion Detection analyzes communications ........................ 70
Visual Tracking locates attackers ............................................... 71
Customize firewall protection .............................................................. 72
Change the Security Level slider ................................................ 72
Change individual security settings ........................................... 73
Reset security settings to defaults .............................................. 75
Customize firewall rules ....................................................................... 75
How firewall rules are processed ................................................ 75
Create new firewall rules .............................................................. 76
Manually add a firewall rule ........................................................ 80
Change an existing firewall rule ................................................. 83
Reset firewall rules to the default settings ............................... 85
Customize Intrusion Detection ............................................................ 85
Exclude specific network activity from being monitored ...... 85
Enable or disable AutoBlock ......................................................... 87
Unblock computers ........................................................................ 87
Exclude computers from AutoBlock ........................................... 88
Restrict a blocked computer ......................................................... 88
Contents 7
Page 8

Contents8
Chapter 8 Protecting your privacy
Identify private information to protect .............................................. 89
Privacy Control and SSL ................................................................ 90
Add private information ................................................................ 90
Modify or remove private information ....................................... 91
Customize Privacy Control ................................................................... 91
Set the Privacy Level ...................................................................... 91
Adjust individual Privacy Control settings ............................... 92
Chapter 9 Blocking Internet advertisements
How Ad Blocking works ........................................................................ 95
Blocking by dimensions ................................................................ 95
Blocking by location ....................................................................... 96
Enable or disable Ad Blocking ............................................................. 96
Enable or disable Popup Window Blocking ...................................... 97
Enable or disable Flash blocking ......................................................... 98
Use the Ad Trashcan .............................................................................. 98
Use text strings to identify ads to block or permit .......................... 99
How to identify Ad Blocking strings ......................................... 100
Add an Ad Blocking string .......................................................... 100
Modify or remove an Ad Blocking string ................................. 101
Chapter 10 Monitoring Norton Personal Firewall
View the Status & Settings window .................................................. 104
View the Statistics window ................................................................104
Reset information in the Statistics window ............................105
Review detailed statistics ...................................................................105
Reset detailed statistics counters .............................................. 106
Set the statistics displayed in the Detailed Statistics
window .................................................................................... 106
View Norton Personal Firewall Logs ................................................ 107
View the logs ................................................................................. 108
Refresh the logs ............................................................................. 109
Clear the logs .................................................................................109
Change the size of the logs .........................................................110
Page 9

Appendix A Troubleshooting Norton Personal Firewall
Troubleshoot Norton Personal Firewall problems ......................... 112
What is wrong with this Web site? ........................................... 112
Why can’t I post information online? ....................................... 113
Why did an email message I sent never arrive? .................... 113
Why doesn’t Norton Personal Firewall notify me before
letting programs access the Internet? .............................. 114
Why can’t I print to a shared computer or connect to a
computer on my local network? ......................................... 114
Why can’t I connect to the Internet via my cable
modem? ................................................................................... 114
How can a Web site get my browser information? ................ 115
Appendix B About the Internet
How information is transmitted over the Internet ........................118
About UDP ...................................................................................... 120
About ICMP .................................................................................... 120
About IGMP .................................................................................... 120
How Web information is located on the Internet ........................... 120
Requesting a page ........................................................................ 121
Understanding URLs .................................................................... 121
How ports identify programs on servers ......................................... 122
How computers are identified on the Internet ............................... 123
Contents 9
Appendix C Understanding Internet risks
Risks from hackers ............................................................................... 125
The process of a hacker attack ................................................... 125
Risks from active content ................................................................... 128
Risks from inappropriate content and activities ............................ 129
Blocking site and newsgroup categories .................................129
Restricting access to programs .................................................. 129
Risks to your privacy ........................................................................... 129
Sending private information ...................................................... 129
Understanding cookies ................................................................ 130
Blocking cookies ........................................................................... 130
Tracking Internet use .................................................................. 131
Risks from Trojan horses and viruses .............................................. 131
The likelihood of being attacked .......................................................132
Page 10

Contents10
Glossary
Service and support solutions
Index
CD Replacement Form
Page 11

Responding to emergencies
If you have an emergency, these procedures can help you find the solution
to your problem.
If you think your computer is under attack
If your computer is behaving unpredictably, and you have determined that
the behavior is not due to a virus or a corrupted file, you may be the victim
of an Internet attack.
If you suspect that someone is attacking your computer, immediately
disconnect your computer from the Internet. If you have not yet installed
Norton Personal Firewall, install it now.
See “Stop Internet
communication
with Block Traffic”
on page 44.
If you have installed Norton Personal Firewall, you can use its security
tools to block the attack, investigate the attacker, and prevent this type of
attack in the future.
To block and investigate an attack
1 Open Norton Personal Firewall.
2 Click Block Traffic.
This immediately stops all incoming and outgoing communication
with other computers.
3 If you are using the Security Monitor, click Security Center.
4 In the Security Center, click Statistics.
5 Click Attacker Details.
Your browser opens the Visual Tracking Web page.
Page 12
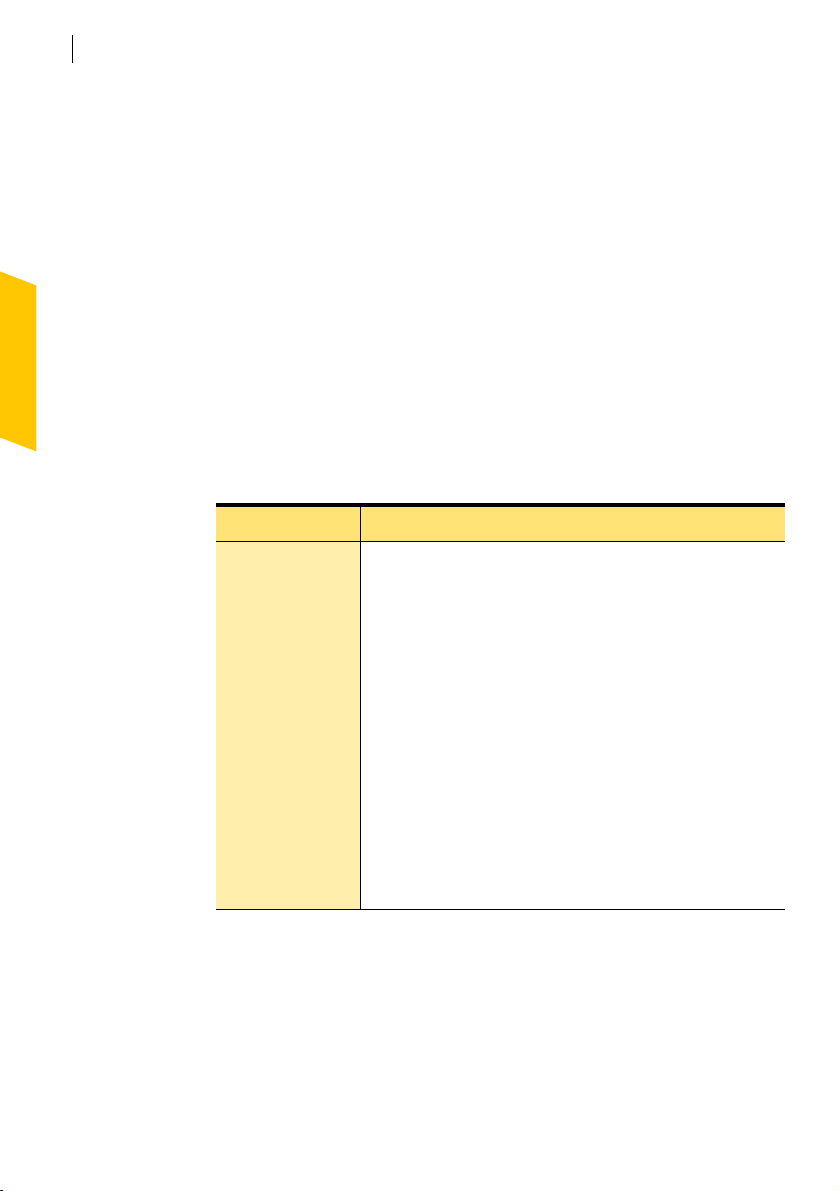
Responding to emergencies
12
Recover from an emergency
See “Identify the
source of
communications”
on page 43.
6 Use Visual Tracking to identify the IP address of the computer that the
attacker used.
You can use this information to report the attack to the ISP that owns
the IP address.
See “Restrict a
blocked computer”
on page 88.
7 To block all future connections from this IP address, add this computer
to your Restricted Zone.
If you suspect that the attacker has already compromised your computer,
install Norton Personal Firewall, then visit http://security.symantec.com
for tools to repair damage and eradicate any threats that the attacker may
have placed on your computer.
Recover from an emergency
Once you’ve dealt with the problem, you can install Norton Personal
Firewall and perform the following activities.
Action Description
Install Norton
Personal Firewall.
Update your
protection.
Norton Personal Firewall can keep your computer safe from
future attacks.
See “Installing Norton Personal Firewall” on page 19.
After installing, run LiveUpdate to ensure that you have the
most updated protection.
See “Keeping current with LiveUpdate” on page 53.
Configure your
firewall.
Periodically review
program logs and
statistics.
The default installation of Norton Personal Firewall should
provide sufficient protection for most users, but you can
customize protection by adjusting firewall settings.
See “Customize firewall protection” on page 72.
Norton Personal Firewall maintains extensive logs of all of
the actions that it takes to protect your computer. Check
these logs occasionally to identify potential problems.
See “Monitoring Norton Personal Firewall” on page 103.
Page 13

Prevent future problems
Norton Personal Firewall can protect your computer against most Internet
attacks.
To prepare your computer for emergencies:
1 Stay informed about security risks by visiting the Symantec Security
Response Web site (securityresponse.symantec.com).
1 Keep your browser up-to-date. Software publishers release new
versions to fix vulnerabilities in their browsers.
1 Use passwords intelligently. For important information, use complex
passwords that include uppercase and lowercase letters, numbers, and
symbols. Don’t use the same password in multiple places.
1 Don’t run software if you don’t trust the publisher and the source from
which you received the software.
1 Don’t open email attachments unless you are expecting an attachment
and you trust the sender.
1 Be sensible about providing personal information. Many sites ask for
more information than they need.
1 Review the privacy policies of the sites to which you are considering
sending information.
1 Tell children never to reveal details about themselves to people they
meet via instant messenger programs.
1 Back up files regularly and keep copies of the last few backups on
hand.
Responding to emergencies
Prevent future problems
13
Page 14

Responding to emergencies
14
Prevent future problems
Page 15

About Norton Personal Firewall
Norton Personal Firewall protects computers from Internet attacks, guards
your privacy, and speeds Web surfing by eliminating ads.
What’s new in Norton Personal Firewall 2003
Norton Personal Firewall 2003 now includes:
1 Security Monitor
Gives you fast access to the most-used Norton Personal Firewall tools
1 Visual Tracking
Identifies the source of attacks and other Internet communication
1 Password protection
Provides increased security for Norton Personal Firewall options
1 Block Traffic
Lets you immediately stop other computers’ ability to communicate
with your computer
1 Alert Assistant
Helps you understand alerts and potential security issues
1 Log Viewer
Improved version helps you see all of the actions Norton Personal
Firewall takes to protect your computer
1 Privacy Control
Enhanced version blocks private information in email and instant
messages
Page 16
About Norton Personal Firewall
16
Norton Personal Firewall features
Norton Personal Firewall features
Norton Personal Firewall includes a number of security tools that help keep
your computer safe. You can get fast access to all Norton Personal Firewall
tools from the new Security Monitor.
Internet security can be a complicated topic to understand, so Norton
Personal Firewall now includes the Alert Assistant, which helps you
understand security issues, suggests how you can resolve problems, and
advises you on avoiding future security problems.
Page 17
About Norton Personal Firewall
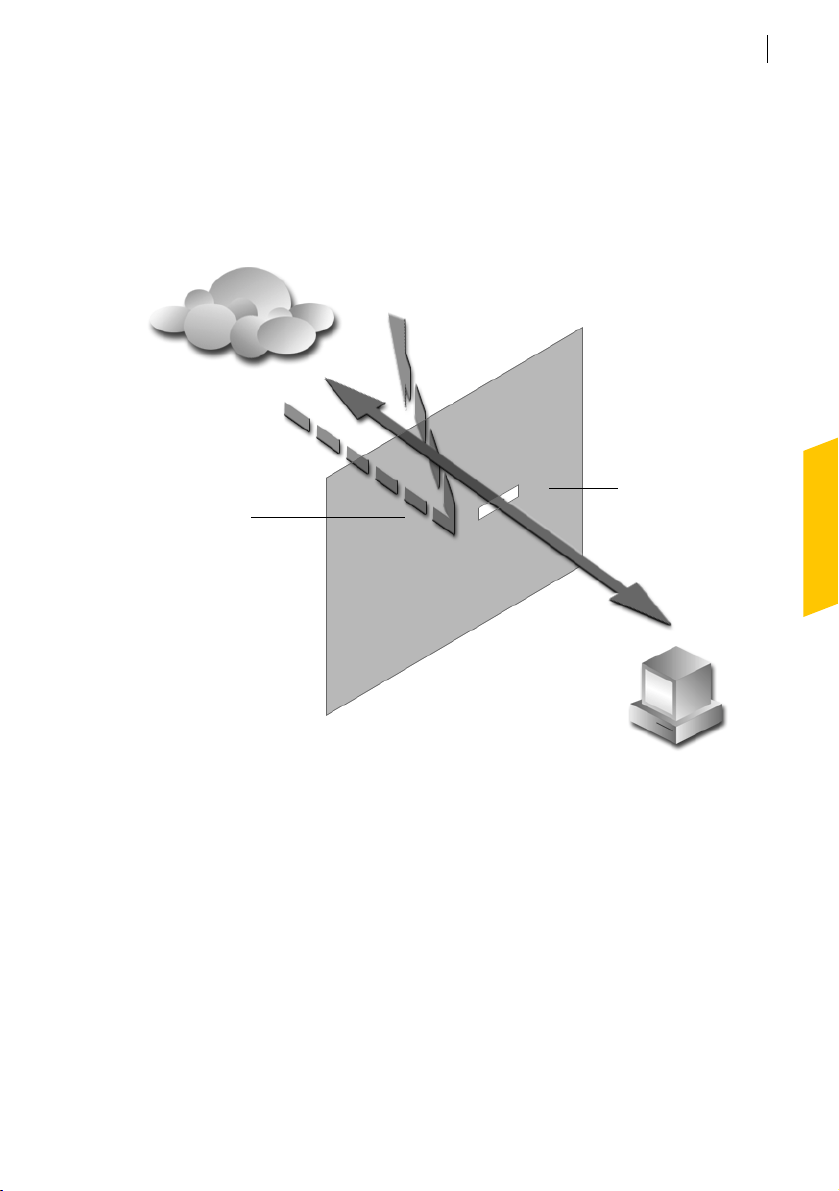
Norton Personal Firewall provides a barrier between your computer and
the Internet. A firewall prevents unauthorized users from accessing private
computers and networks connected to the Internet.
Internet
Norton Personal
Firewall blocks access
attempts from the
Internet
About Norton Personal Firewall
Norton Personal Firewall features
Attackers can’t see
your computer
behind the firewall
Norton Personal
Firewall allows
communications that
you initiate
17
Firewall
Home computer
Norton Personal Firewall includes features that prevent unauthorized
access to your computer when you are on the Internet, detect possible
Internet attacks, protect your personal information, and block Internet
advertisements to speed your Internet browsing.
Page 18

About Norton Personal Firewall
18
Norton Personal Firewall features
Norton Personal Firewall features include:
Intrusion Detection Intrusion Detection helps keep your computer safe from
Privacy Control Privacy Control gives you several levels of control over the
Ad Blocking Ad Blocking speeds up your Web surfing by eliminating
Internet attacks by scanning each piece of information that
enters and exits your computer. If it identifies a potential
attack, Intrusion Detection alerts you and automatically
blocks the connection that contained the attack.
See “Guarding against intrusion attempts” on page 69.
kind of information that users can send via the Web, email,
and instant messenger programs. You can also control how
Privacy Control reacts when Web sites attempt to set and use
cookies or learn about your browser.
See “Protecting your privacy” on page 89.
banner ads and other slow-loading or intrusive content.
Norton Personal Firewall now also blocks ads made with
Macromedia Flash and prevents sites from opening pop-up or
pop-under ad windows.
See “Blocking Internet advertisements” on page 95.
Page 19

Installing Norton Personal Firewall
Before installing Norton Personal Firewall, take a moment to review the
system requirements listed in this chapter.
System requirements
To use Norton Personal Firewall, your computer must have one of the
following Windows operating systems installed:
1 Windows 98, 98SE
1 Windows Me
1 Windows 2000 Professional
1 Windows XP Professional or Windows XP Home Edition
Windows 95 and NT, the server editions of Windows 2000/XP, and the
Windows XP 64-bit edition are not supported.
Page 20

Installing Norton Personal Firewall
20
System requirements
Your computer must also meet the following minimum requirements.
Operating System Requirements
Windows 98/
98SE/Me
Windows 2000
Professional
Windows XP
Professional or
Home Edition
Supported email clients
Norton Personal Firewall can scan email messages for private information
in any POP3-compatible email client, including:
1 Microsoft
1 Microsoft Outlook 97/98/2000/XP
1 Netscape
1 Eudora
•
•
•
Light 3.0, Eudora Pro 4.0, Eudora 5.0
1 Intel Pentium processor (or compatible) at 150 MHz or
higher
1 48 MB of RAM (64 MB recommended)
1 25 MB of available hard disk space
1 Internet Explorer 5.01 or later (5.5 recommended)
1 CD-ROM or DVD-ROM drive
1 Intel Pentium processor (or compatible) at 150 MHz or
higher
1 48 MB of RAM (64 MB recommended)
1 25 MB of available hard disk space
1 Internet Explorer 5.01 or later (5.5 recommended)
1 CD-ROM or DVD-ROM drive
1 Intel Pentium II processor (or compatible) at 300 MHz or
higher
1 48 MB of RAM (64 MB recommended)
1 25 MB of available hard disk space
1 Internet Explorer 5.01 or later (5.5 recommended)
1 CD-ROM or DVD-ROM drive
Outlook• Express 4.0/5.X
Messenger 4.X, Netscape Mail 6.0
Page 21

Email scanning does not support the following email clients:
1 IMAP clients
1 AOL clients
1 POP3s that use SSL (Secure Sockets Layer)
1 Web-based email such as Hotmail and Yahoo!
1 Lotus Notes mail
Supported instant messenger clients
Norton Personal Firewall can scan for private information in the following
instant messengers:
1 AOL Instant Messenger, version 4.3 or later
1 MSN Instant Messenger, version 3.6 or later
1 Windows Messenger, version 4.0 or later
Before installation
Before you install Norton Personal Firewall, prepare your computer.
Installing Norton Personal Firewall
Before installation
21
Prepare your computer
See “If you need to
uninstall Norton
Personal Firewall”
on page 34.
If you’re using Windows XP
If you have an older version of Norton Personal Firewall, the new version
prompts you to remove the older version. If you have a recent version of
Norton Personal Firewall, you can transfer your existing settings to the
new version of the program.
Quit all other Windows programs before installing Norton Personal
Firewall. Other active programs may interfere with the installation and
reduce your protection.
Windows XP includes a firewall that can interfere with Norton Personal
Firewall protection features. You must disable the Windows XP firewall
before installing Norton Personal Firewall.
Page 22

Installing Norton Personal Firewall
22
Install Norton Personal Firewall
To disable the Windows XP firewall
1 On the Windows XP taskbar, click Start > Control Panel > Network
Connections.
2 If you have created more than one modem or network connection,
select the active connection.
3 Click Network Tasks.
4 Click Change settings of this connection.
5 On the Advanced tab, in the Internet Connection Firewall section,
uncheck Protect my computer and network by limiting or
preventing access to this computer from the Internet.
6 Click OK to close the settings window.
7 Click OK to close the Network Tasks window.
Install Norton Personal Firewall
Install Norton Personal Firewall from the Norton Personal Firewall CD.
Install a copy of Norton Personal Firewall on each computer that you want
to protect.
See “If the opening
screen does not
appear” on
page 25.
To install Norton Personal Firewall
1 Insert the Norton Personal Firewall CD into the CD-ROM drive.
2 In the Norton Personal Firewall CD window, click Install Norton
Personal Firewall.
If your computer is not set to automatically run a CD, you must
manually open it.
The first installation window reminds you to close all other Windows
programs.
Page 23
Installing Norton Personal Firewall
Install Norton Personal Firewall
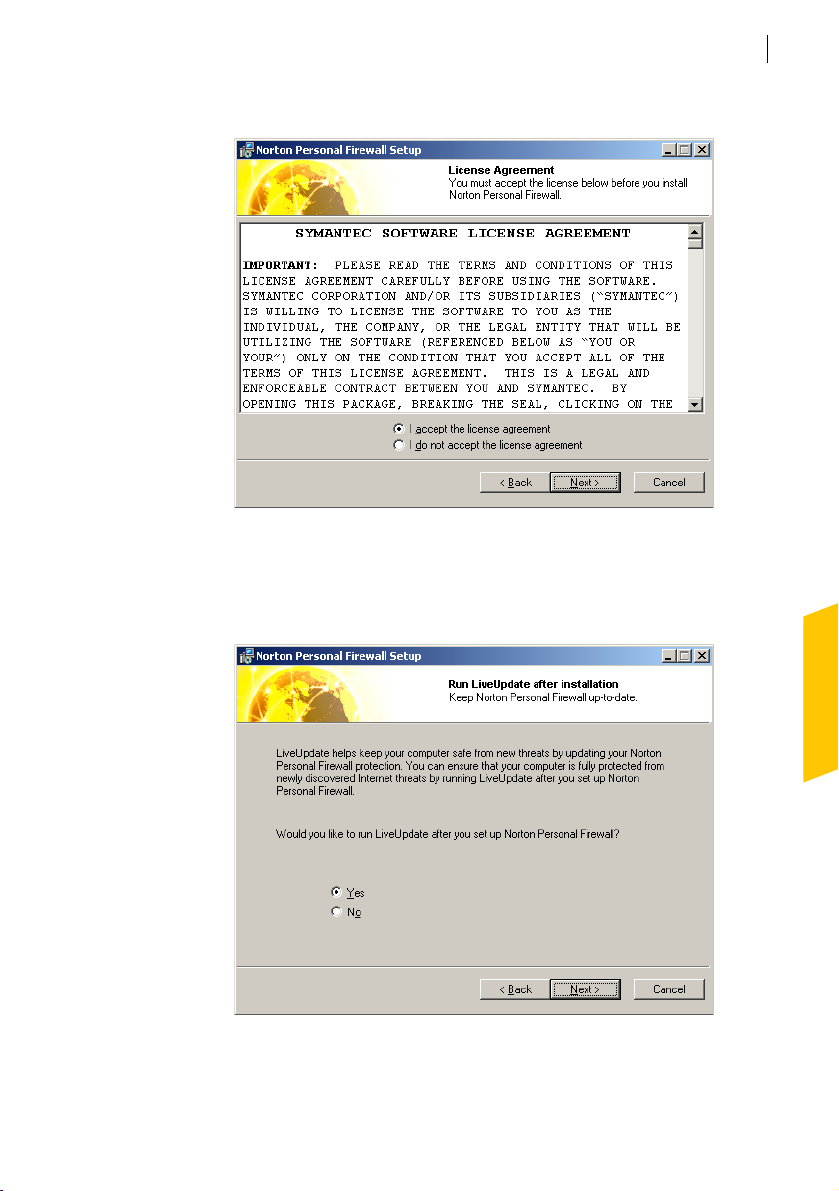
3 Click Next.
4 Read the License Agreement, then click I accept the license
agreement.
If you decline, you cannot continue with the installation.
5 Click Next.
23
6 In the Run LiveUpdate after installation window, select whether you
want to run LiveUpdate after the installation is done.
Page 24
Installing Norton Personal Firewall
24
Install Norton Personal Firewall
7 Click Next.
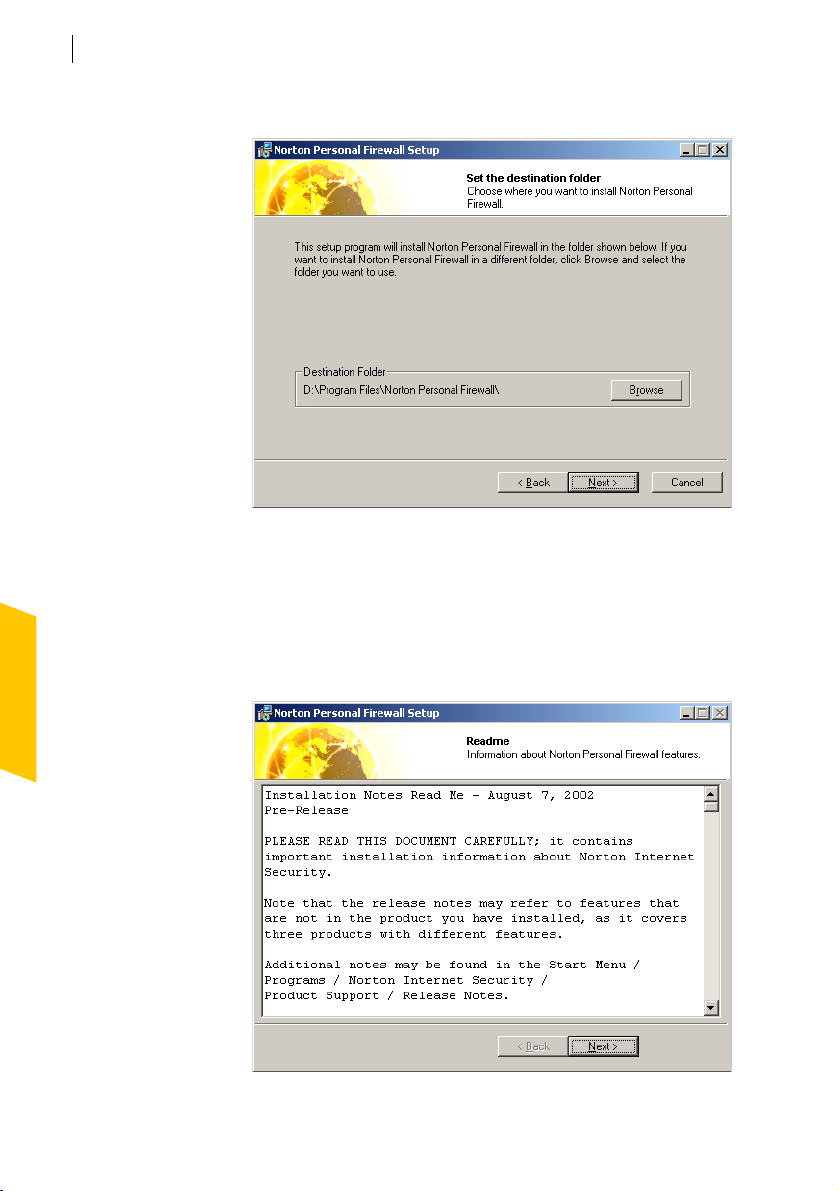
8 Click Browse to select a folder into which you want to install Norton
9 Click Next.
See “Register your
software” on
page 25.
10 Click Next to begin installing Norton Personal Firewall.
Personal Firewall, if it is other than the default location.
After Norton Personal Firewall is installed, the Registration Wizard
appears.
Page 25
11 Read the readme text, then click Next.
12 Click Finish to complete the installation.
If the opening screen does not appear
Sometimes a computer’s CD-ROM drive does not automatically run a CD.
To start the installation from the Norton Personal Firewall CD
1 On your desktop, double-click My Computer.
2 In the My Computer window, double-click the icon for your CD-ROM
drive.
3 In the list of files, double-click Cdstart.exe.
Register your software
Use the Registration Wizard to register your software online. If you skip
online registration, you can register your software later using the Product
Registration option on the Help menu.
To register your software
1 In the first Registration window, select the country from which you are
registering and the country in which you live (if different), then click
Next.
Installing Norton Personal Firewall
Register your software
25
Page 26
Installing Norton Personal Firewall
26
Register your software
2 If you would like information from Symantec about Norton Personal
3 Type your name, then click Next.
4 Type your address, then click Next.
Firewall, select the method by which you want to receive that
information, then click Next.
Page 27
Installing Norton Personal Firewall
Register your software
5 Do one of the following:
2 Answer the survey questions to help Symantec improve its
products and services, then click Next.
2 Skip the survey by clicking Next.
27
6 Select whether you want to register Norton Personal Firewall over the
Internet or by mail.
If you want to register by mail, your computer must be connected to a
printer that the Registration Wizard can use to print the registration
form. If you want to register using the Internet, you must be connected
to the Internet.
7 Click Next.
8 To get a copy of your registration information for future reference, do
one of the following:
2 Write down the serial number.
2 Click Print.
9 Click Next.
10 Select whether you want to use your existing profile the next time that
you register a Symantec product, or type the information as part of
registration.
11 Click Finish.
Page 28

Installing Norton Personal Firewall
28
After installation
After installation
After Norton Personal Firewall is installed, a prompt appears giving you
the option to restart your computer immediately. After restarting, the
Security Assistant appears to guide you through the configuration of
Norton Personal Firewall.
Restart your computer
After installation, a prompt appears telling you that you must restart your
computer for the updates to take effect.
To restart your computer
4 In the Installer Information dialog box, click Yes.
Configuration of Norton Personal Firewall is not complete until you
restart your computer.
Use the Security Assistant
The Security Assistant helps you quickly configure your Norton Personal
Firewall protection. The Security Assistant is divided into four categories:
1 Home Networking
1 Program Control
1 Privacy Control
1 Password Protection
Set up Home Networking
See “Connect to a
network” on
page 61.
Use Home Networking to identify computers to which you want to grant
access to your computer and those to which you want to deny access. The
Home Network Wizard can automatically configure your network and add
computers to your Trusted Zone.
Page 29
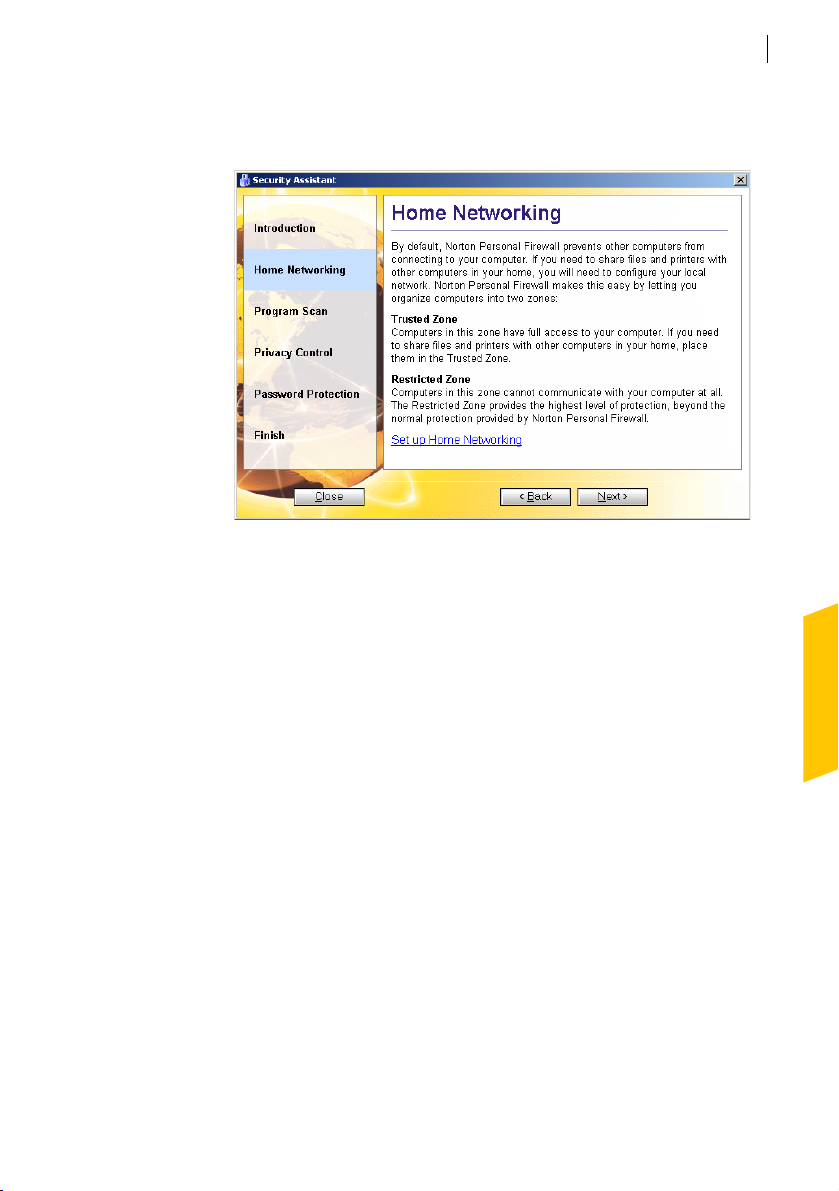
Installing Norton Personal Firewall
After installation
To set up Home Networking
1 In the Security Assistant Roadmap, click Home Networking.
2 In the Home Networking pane, click Set up Home Networking.
3 In the Home Networking Wizard, click Next.
4 Follow the on-screen instructions to configure your network.
29
Set up Program Control
See “Scan for
Internet-enabled
programs” on
page 77.
Norton Personal Firewall can scan your computer for Internet-enabled
programs and create access rules for them. When the scan is complete, you
can use the results to determine which programs should have access to the
Internet and, if desired, adjust their access rules.
Page 30
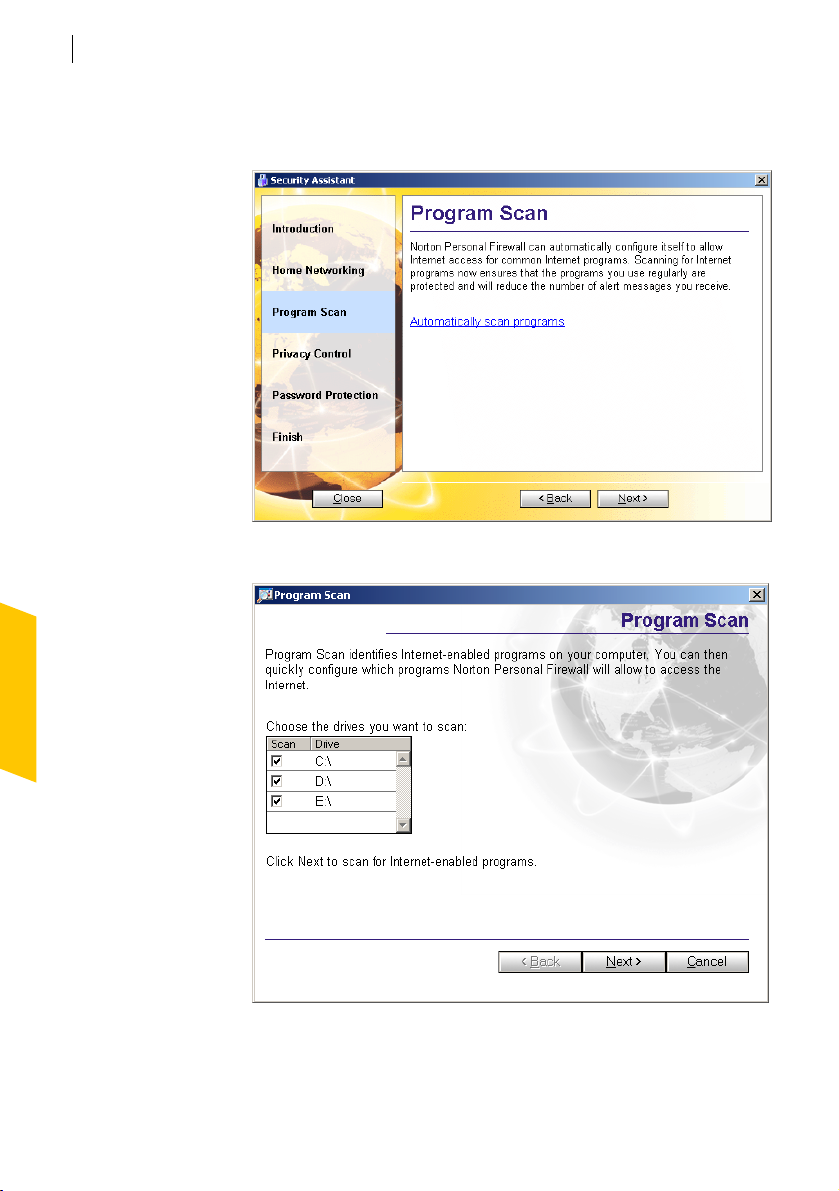
Installing Norton Personal Firewall
30
After installation
To set up Program Control
1 In the Security Assistant Roadmap, click Program Scan.
2 In the Program Scan pane, click Automatically scan programs.
Page 31

Installing Norton Personal Firewall
After installation
3 In the Program Scan window, click Next to begin the scan.
When the scan is complete, all Internet-enabled programs that were
found are listed.
31
4 To allow Internet access for a program, check the check box to the left
5 To change the Internet access rule or category of a program, in the
6 Click Finish when you are done.
Set up Privacy Control
See “Identify
private information
to protect” on
page 89.
Using Privacy Control, you can identify private information that should
have extra protection. Privacy Control can then prevent users from sending
this information to Web sites, in email messages and attached Microsoft
Office files, and through supported instant messenger programs.
of the program’s name.
Internet Access or Category drop-down lists, select the setting that you
want.
Page 32

Installing Norton Personal Firewall
32
After installation
To set up Privacy Control
1 In the Security Assistant Roadmap, click Privacy Control.
2 In the Privacy Control pane, click Add private information to
3 In the Add Private Information dialog box, under Type of information
4 In the Descriptive name text box, type a description to help you
5 In the Information to protect text box, type the last five or six
6 Click OK.
protect.
to protect, select a category.
remember why you are protecting the data.
characters of the information that you want to block from being sent
over nonsecure Internet connections.
By entering only partial information, you ensure that untrustworthy
people with physical access to your computer cannot steal entire
credit card numbers and other information.
Set up Password Protection
See “Use the
Security Monitor”
on page 38.
For maximum security, you can require a password before allowing anyone
to make a change to your Norton Personal Firewall settings. This ensures
that only the people you trust are able to disable your protection, turn off
your firewall and intrusion detection, or make changes to Norton Personal
Firewall options.
Page 33

Installing Norton Personal Firewall
If you have Norton SystemWorks installed
To protect Norton Personal Firewall options with a password
1 In the Security Assistant Roadmap, click Password Protection.
2 In the Password Protection pane, click Turn on password
protection.
3 In the Password and Confirm Password text boxes, type a password.
4 Click OK.
33
If you have Norton SystemWorks installed
If you have Norton SystemWorks installed on your computer when you
install Norton Personal Firewall, the installer adds a Norton Personal
Firewall tab to the Norton SystemWorks main window and a Norton
SystemWorks tab to the Security Center.
To open Norton Personal Firewall from Norton SystemWorks
1 Open Norton SystemWorks.
2 On the Norton Personal Firewall tab, click Launch Norton Personal
Firewall.
To open Norton SystemWorks from Norton Personal Firewall
1 Open Norton Personal Firewall.
2 In the Security Center, on the Norton SystemWorks tab, click Launch
Norton SystemWorks.
Page 34

Installing Norton Personal Firewall
34
If you need to uninstall Norton Personal Firewall
If you need to uninstall Norton Personal Firewall
If you need to uninstall Norton Personal Firewall from your computer, use
the Uninstall Norton Personal Firewall option on the Windows Start menu.
w During uninstall, Windows may indicate that it is installing software. This
is a standard Microsoft installation message and can be disregarded.
To uninstall Norton Personal Firewall
1 Do one of the following:
2 On the Windows taskbar, click Start > Programs > Norton
Personal Firewall > Uninstall Norton Personal Firewall.
2 On the Windows XP taskbar, click Start > More Programs >
Norton Personal Firewall > Uninstall Norton Personal
Firewall.
2 Click Next.
3 In the Installer Information dialog box, click Yes to restart your
computer.
If you have no other Symantec products on your computer, you should also
uninstall LiveReg and LiveUpdate.
To uninstall LiveReg and LiveUpdate
1 Do one of the following:
2 On the Windows taskbar, click Start > Settings > Control Panel.
2 On the Windows XP taskbar, click Start > Control Panel.
2 In the Control Panel, double-click Add/Remove Programs.
3 In the list of currently installed programs, click LiveReg.
4 Do one of the following:
2 In Windows 2000/Me, click Change/Remove.
2 In Windows 98, click Add/Remove.
2 In Windows XP, click Remove.
5 Click Yes to confirm that you want to uninstall the product.
6 To uninstall LiveUpdate, repeat steps 1 through 5, selecting
LiveUpdate in step 3.
Page 35

Norton Personal Firewall basics
After installation, Norton Personal Firewall automatically protects any
computer on which it is installed. You do not have to start the program to
be protected.
Access Norton Personal Firewall
Launch Norton Personal Firewall to change protection settings or monitor
its activities.
To access Norton Personal Firewall
4 Do one of the following:
2 On the Windows taskbar, click Start > Programs > Norton
Personal Firewall > Norton Personal Firewall.
Page 36

Norton Personal Firewall basics
36
Access Norton Personal Firewall
2 On the Windows XP taskbar, click Start > More Programs >
Norton Personal Firewall > Norton Personal Firewall.
2 On the Windows desktop, double-click Norton Personal
Firewall.
Access Norton Personal Firewall from the system tray
Norton Personal Firewall adds an icon to the Windows system tray. On
most computers, the system tray is at the far right of the Windows taskbar
at the bottom of your screen. Click this icon to open a menu containing
frequently used Norton Personal Firewall tools.
To use the Norton Personal Firewall system tray menu
1 In the system tray, right-click the Norton Personal Firewall icon.
2 In the menu that appears, select an item. Items in the menu include:
Norton Personal
Firewall
Hide/View Alert
Tracker
Block Traffic Immediately stops all incoming and outgoing
Opens a Norton Personal Firewall window.
Displays or hides the Alert Tracker.
See “Use Alert Tracker” on page 41.
information.
See “Stop Internet communication with Block Traffic” on
page 44.
Page 37

Norton Personal Firewall basics
Work with Norton Personal Firewall
37
See “About Global
Settings” on
page 46.
About Norton
Personal Firewall
LiveUpdate Updates your protection.
Help Displays the Norton Personal Firewall online Help.
Disable Turns off all Norton Personal Firewall protection features.
Use the Norton Personal Firewall Options to add additional tools to the
menu.
Displays detailed information about Norton Personal
Firewall components.
See “Keeping current with LiveUpdate” on page 53.
See “Use online Help” on page 48.
See “Temporarily disable Norton Personal Firewall” on
page 47.
Work with Norton Personal Firewall
Norton Personal Firewall works in the background, so you may only
interact with the program when it alerts you of new network connections
and possible problems. You can choose to view the new Security Monitor or
the standard Security Center window, respond to security problems, and
control the number of alerts you receive and how the program resolves
potential security problems.
Access Norton Personal Firewall protection features
The default settings for Norton Personal Firewall provide a safe, automatic,
and efficient way of protecting your computer. If you want to change or
customize your protection, you can access all Norton Personal Firewall
tools from the Status & Settings window.
To change settings for individual features
1 Open Norton Personal Firewall.
2 If you have chosen to view the Security Monitor, click Security
Center.
Page 38

Norton Personal Firewall basics
38
Work with Norton Personal Firewall
3 In the Security Center, do one of the following:
2 Double-click a feature you want to customize.
2 Select a feature, then in the lower-right corner of the window,
4 Configure the feature.
5 When you are done making changes, click OK.
Use the Security Monitor
The Security Monitor collects the most-used Norton Personal Firewall tools
into a compact window. When you’re online, place the Security Monitor
window in an unused part of your screen. This lets you monitor your
connection, view information about security events, and personalize your
protection without requiring a lot of space on your screen.
When you start Norton Personal Firewall, it launches the Security Center.
You can then switch to the Security Monitor.
click Customize.
To view the Security Monitor
4 In the Security Center, in the upper-left corner, click Security
Monitor.
To view the Security Center
4 In the Security Monitor, in the upper-left corner, click Security
Center.
Page 39

Select a task with the Security Monitor
Use the Select a Task menu in the Security Monitor to quickly perform
common Norton Personal Firewall tasks. The Select a Task menu includes:
Tas k More information
Norton Personal Firewall basics
Work with Norton Personal Firewall
39
Test security
Edit private
information
View Log Viewer
Run LiveUpdate
Run Program Scan
Setup Home
Network
See “Check your computer’s vulnerability to attack” on page 42.
See “Protecting your privacy” on page 89.
See “View Norton Personal Firewall Logs” on page 107.
See “Keeping current with LiveUpdate” on page 53.
See “Scan for Internet-enabled programs” on page 77.
See “Organize computers into network zones” on page 62.
Respond to Norton Personal Firewall alerts
Norton Personal Firewall monitors communication activities to and from
your computer and lets you know when an activity that may compromise
your security is taking place.
When an alert appears, read it before you make a decision. Identify what
type of alert it is and the threat level. Once you understand the risks, you
can make a choice.
w Take as much time as you need to make your choice. Your computer is safe
from attack while the alert is active.
Norton Personal Firewall helps you decide on an appropriate action by
preselecting the recommended action if one exists. Norton Personal
Firewall cannot suggest recommended actions for all alerts.
Learn more with the Alert Assistant
Each Norton Personal Firewall alert includes a link to the Alert Assistant.
The Alert Assistant includes customized information about each alert,
including:
1 The type of alert
1 The threat level
1 The communication that triggered this alert
Page 40

Norton Personal Firewall basics
40
Work with Norton Personal Firewall
1 What these types of alerts indicate
1 How to reduce the number of these alerts you receive
To use the Alert Assistant
1 In any alert window, click the Alert Assistant button.
2 In the Alert Assistant window, review the information about this alert.
3 To respond to the alert, close the Alert Assistant.
Adjust the Alerting Level
The Alerting Level slider lets you control the amount of information that
Norton Personal Firewall logs and the number of alerts that it displays.
Your options are:
Alerting
Level
Information
provided
Alert
Tracker
Security
Alerts
messages
Minimal Critical
Internet
None Logged, not
displayed
events
Medium Important
Internet
Some Logged, not
displayed
events
High Important
Internet
Many Logged and
displayed
events and
complete
program
activities
To adjust the Alerting Level
1 Open Norton Personal Firewall.
2 In the Security Center, click Alerting Level.
3 Move the slider to choose an Alerting Level.
Notifies you when…
Program Control rules are
created automatically.
Port scans occur.
Confidential information
is blocked.
A remote access Trojan
horse program is
encountered.
Same notification as
Minimal, plus:
1 Programs access the
Internet.
Same notification as
Medium, plus:
1 Unused ports are
blocked.
1 Cookies and content
are blocked.
Page 41

Use Alert Tracker
Many of the Internet events that Norton Personal Firewall monitors are not
significant enough to trigger alerts. Alert Tracker provides an easy way to
monitor these less-important security events.
Alert Tracker displays the same information that appears in the Security
Event field on the Security Monitor. This allows you to monitor your
computer’s security without having to keep the Security Monitor visible at
all times. Alert Tracker also provides a quick way to remove ads from Web
pages.
If you choose to display Alert Tracker, it attaches to either side of the
screen on your primary monitor. When a security event occurs, Alert
Tracker displays a message for a few seconds and then returns to the side
of the screen. If you miss an Alert Tracker message, you can review a list of
recent messages.
Norton Personal Firewall basics
Work with Norton Personal Firewall
Alert Tracker rests on the
side of your screen
41
See “Use the Ad
Trashcan” on
page 98.
Alert Tracker opens for a few
seconds to display messages
Alert Tracker also contains the Ad Trashcan, which is part of the Norton
Personal Firewall Ad Blocking feature.
To view or hide Alert Tracker
1 Open Norton Personal Firewall.
2 In the Security Center, click Options > Internet Security.
3 On the General tab, do one of the following:
2 Check Show the Alert Tracker to view Alert Tracker.
2 Uncheck Show the Alert Tracker to hide Alert Tracker.
4 Click OK.
Page 42

Norton Personal Firewall basics
42
Work with Norton Personal Firewall
To review recent Alert Tracker messages
1 On the Windows desktop, double-click the Alert Tracker.
2 To the right of the first message, click the arrow if it appears.
See “Review
detailed statistics”
on page 105.
3 Double-click an entry to open the Log Viewer.
To move Alert Tracker
4 Drag the half globe to the side of the screen on which you want it to
appear.
To hide Alert Tracker from the system tray menu
4 In the Windows system tray, right-click the Norton Personal Firewall
icon, then click Hide Alert Tracker.
If you hide Alert Tracker, you will not be notified when your computer joins
a network. Information about the connection will still appear in the logs.
Check your computer’s vulnerability to attack
Use Security Check to test your computer’s vulnerability to security
intrusions. The Security Check link in Norton Personal Firewall connects
you to the Symantec Web site, where you can scan for vulnerabilities and
get detailed information about Security Check scans.
w You must be connected to the Internet to check your computer’s
vulnerability.
To check your computer’s vulnerability to attack
1 Open Norton Personal Firewall.
2 Do one of the following:
2 In the Security Center, click Security, then click Check
Security.
2 In the Security Monitor window, on the Select a Task menu, click
Test Security.
3 On the Security Check Web page, click Scan for Security Risks.
4 To learn more about the Security Check tests, click About Scan for
Security Risks.
When the scan is complete, the results page lists all of the areas that were
checked and your level of vulnerability in each one. For any area marked as
at risk, you can get more details about the problem and how to fix it.
Page 43

To get more information about an at-risk area
4 On the results page, next to the scan name, click Show Details.
Identify the source of communications
Visual Tracking helps you learn more about computers that attempt to
connect to your computer. Using Visual Tracking, you can identify the
location of the IP address used and contact information for the owner of the
address. You can use this information to identify the origin of an attack and
to learn more about intrusion attempts.
You can trace connection attempts from three places in Norton Personal
Firewall:
1 Statistics
1 Log Viewer
1 AutoBlock
To trace a connection attempt from Statistics
1 Open Norton Personal Firewall.
2 In the Security Center, click Statistics.
3 Click Attacker Details.
Your browser opens the Visual Tracking Web page.
Norton Personal Firewall basics
Work with Norton Personal Firewall
43
To trace a connection attempt from the Log Viewer
1 Open Norton Personal Firewall.
2 In the Security Center, click Statistics.
3 Click View Logs.
4 In the left column of the Log Viewer window, under Internet Security,
click Connections.
5 In the right column of the Log Viewer window, select a connection you
want to trace.
6 At the bottom of the Log Viewer window, click the computer’s IP
address or name.
Your browser opens the Visual Tracking Web page.
To trace a connection attempt from AutoBlock
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Intrusion Detection.
Page 44

Norton Personal Firewall basics
44
Work with Norton Personal Firewall
3 In the Intrusion Detection window, in the AutoBlock section, select a
connection you want to trace.
4 Click Attacker Details.
Your browser opens the Visual Tracking Web page.
When Visual Tracking is finished, it displays a visual representation of
where this communication originated and contact information for the
owner of the IP address.
Stop Internet communication with Block Traffic
The Security Center and the Security Monitor include a Block Traffic button
that lets you immediately halt any communication between your computer
and another. This can be a handy way to limit any damage to your
computer if it is attacked, if a Trojan horse is sending personal information
without your permission, or if you inadvertently allow an untrusted person
to access files on your computer.
When this option is active, Norton Personal Firewall stops all
communication to and from your computer. To the outside world, it appears
that your computer has completely disconnected from the Internet.
If you want to block all traffic into and out of your computer, Block Traffic is
more effective than simply using your Internet software to disconnect.
Most Internet programs can automatically connect without any input from
the user, so a malicious program could reconnect when you are away from
the computer.
w Block Traffic is meant to be used as a temporary measure while you
address a security problem. If you restart your computer, Norton Personal
Firewall automatically allows all incoming and outgoing communication. To
continue blocking traffic, click the Block Traffic button in the Security
Center or Security Monitor.
To avoid attack while fixing security problems
1 Open Norton Personal Firewall.
2 In the Security Center or the Security Monitor window, click Block
Traffic.
3 Use Norton Personal Firewall tools to address the security problem.
4 When you have fixed the problem, click Allow Traffic.
Page 45

Customize Norton Personal Firewall
Customize Norton Personal Firewall
The default Norton Personal Firewall settings should provide adequate
protection for most users. If you need to make changes, use the Options
menu to access Norton Personal Firewall options. The options let you
control more advanced settings.
w If you are using Windows 2000/XP and you do not have Local
Administrator access, you cannot change Norton Personal Firewall options.
To customize Norton Personal Firewall
1 Open Norton Personal Firewall.
2 At the top of the Security Center, click Options.
3 Select the tab on which you want to change options.
About General options
General options let you control when Norton Personal Firewall runs,
protect program settings with a password, and choose visual elements you
want to display.
Norton Personal Firewall basics
45
About LiveUpdate options
See “Keeping
current with
LiveUpdate” on
page 53.
LiveUpdate options let you enable and disable Automatic LiveUpdate,
which automatically checks for Norton Personal Firewall updates when you
are connected to the Internet. For maximum security, you should leave this
option checked.
You can choose the Norton Personal Firewall components you want
Automatic LiveUpdate to monitor. You can also choose whether Automatic
LiveUpdate updates the components in the background or alerts you that
there are updates available.
About Firewall options
Firewall options let you activate advanced protection features and
customize the ports your computer uses to view Web pages. Most people
will not need to make any changes to these settings.
Page 46

Norton Personal Firewall basics
46
Password-protect options
About Web Content options
Web Content options let you control how Norton Personal Firewall handles
interactive online content, ads, and possible privacy intrusions. Web
Content options are arranged on three tabs.
About Global Settings
Global Settings let you control the default actions Norton Personal Firewall
takes when Web sites attempt to get information about your browser or use
animated images, JavaScripts, and other active content.
About User Settings
User Settings let you customize cookie blocking, pop-up window blocking,
and ActiveX and Java settings for individual sites.
About Ad Blocking settings
Ad Blocking settings let you specify individual ad banners or groups of ad
images you want to block or allow on individual sites. See “Use text strings
to identify ads to block or permit” on page 99.
About Email options
Email options let you control how Norton Personal Firewall notifies you
when it is scanning email messages for private information.
Password-protect options
You can protect Norton Personal Firewall options with a password. This
ensures that only the people you trust are able to make changes to your
options.
To protect Norton Personal Firewall options with a password
1 Open Norton Personal Firewall.
2 At the top of the Norton Personal Firewall window, click Options >
Internet Security.
3 On the General tab, check Turn on Password Protection.
4 In the Password and Confirm Password text boxes, type a password.
5 Click OK.
Page 47

Reset options password
If you forget your options password you can reset it.
To reset your Norton Personal Firewall options password
1 Do one of the following:
2 On the Windows taskbar, click Start > Programs > Norton
Personal Firewall > Uninstall Norton Personal Firewall.
2 On the Windows XP taskbar, click Start > More Programs >
Norton Personal Firewall > Uninstall Norton Personal
Firewall.
2 In the Remove Application window, click Reset Password.
3 In the password reset dialog box, in the Reset Password Key text box,
type the Reset Password Key that appears above the text box.
The Reset Password Key is case-sensitive.
4 In the New Password and Confirm New Password text boxes, type a
new password.
5 Click OK.
6 In the Remove Application window, click Cancel.
7 In the Norton Personal Firewall alert, click Exit.
8 In the Setup Canceled alert, click OK.
Norton Personal Firewall basics
Temporarily disable Norton Personal Firewall
47
Temporarily disable Norton Personal Firewall
There may be times when you want to temporarily disable Norton Personal
Firewall or one of its features. For example, you might want to view online
ads or see if Norton Personal Firewall is preventing a Web page from
appearing correctly.
Disabling Norton Personal Firewall also disables all of the individual
features.
To temporarily disable Norton Personal Firewall
1 Open Norton Personal Firewall.
2 In the Security Center, click Security.
3 On the right side of the screen, click Turn Off.
Norton Personal Firewall is automatically turned back on the next time you
start your computer.
Page 48

Norton Personal Firewall basics
48
For more information
You can also disable individual security features. For example, you might
want to see if the Personal Firewall is preventing a program from operating
correctly.
To disable a protection feature
1 Open Norton Personal Firewall.
2 In the Security Center, select the feature that you want to disable.
3 On the right side of the screen, click Turn Off.
For more information
Norton Personal Firewall provides glossary terms, online Help, this User’s
Guide in PDF format, tutorials on the Web, and links to the Knowledge Base
on the Symantec Web site.
Look up glossary terms
Technical terms that are italicized in the User’s Guide are defined in the
glossary, which is available in both the User’s Guide PDF and Help. In both
locations, clicking a glossary term takes you to its definition.
Use online Help
Help is always available throughout Norton Personal Firewall. Help buttons
or links to more information provide information specific to the task you
are completing. The Help menu provides a comprehensive guide to all
product features and tasks you can complete.
To access Help
1 At the top of the Norton Personal Firewall main window, click Help.
Online Help table of
contents and index
Version, system, and
password reset
information
Link to Symantec
Web sites for more
information
Page 49

2 On the main Help menu, click Norton Personal Firewall Help.
3 In the left pane of the Help window, select one of the following tabs:
2 Contents: Displays the Help by topic.
2 Index: Lists Help topics in alphabetical order by key word.
2 Search: Opens a search field where you can enter a word or
phrase.
Window and dialog box Help
Window and dialog box Help provides information about the Norton
Personal Firewall program. This type of Help is context-sensitive, meaning
that it provides help for the dialog box or window that you are currently
using.
To access window or dialog box Help
4 Do one of the following:
2 Click the Tell Me More link if one is available.
2 In the dialog box, click Help.
Readme file and Release Notes
The Readme file contains information about installation and compatibility
issues. The Release Notes contain technical tips and information about
product changes that occurred after this guide went to press. They are
installed on your hard disk in the same location as the Norton Personal
Firewall product files.
Norton Personal Firewall basics
For more information
49
To read the Readme file
1 Do one of the following:
2 On the Windows taskbar, click Start > Programs > Norton
Personal Firewall > Product Support > Readme.txt.
2 On the Windows XP taskbar, click Start > More Programs >
Norton Personal Firewall > Product Support > Readme.txt.
The file opens in Notepad.
2 Close the word processing program when you are done reading the
file.
Page 50

Norton Personal Firewall basics
50
For more information
The Release Notes can be accessed from the Start menu.
To read the Release Notes
1 Do one of the following:
2 On the Windows taskbar, click Start > Programs > Norton
2 On the Windows XP taskbar, click Start > More Programs >
The file opens in Notepad.
2 Close the word processing program when you are done reading the
file.
Use the User’s Guide PDF
This User’s Guide is provided on the Norton Personal Firewall CD in PDF
format. You must have Adobe Acrobat Reader installed on your computer to
read the PDF.
To install Adobe Acrobat Reader
1 Insert the Norton Personal Firewall CD into the CD-ROM drive.
2 Click Browse CD.
3 Double-click the Manual folder.
4 Double-click the Acrobat folder.
5 Double-click ar500enu.exe.
6 Follow the on-screen instructions to select a folder for Adobe Acrobat
Reader and complete the installation.
Personal Firewall > Product Support > Norton Personal
Firewall Release Notes.
Norton Personal Firewall > Product Support > Norton
Personal Firewall Release Notes.
Once you have installed Adobe Acrobat Reader, you can read the PDF from
the CD.
To read the User’s Guide PDF from the CD
1 Insert the Norton Personal Firewall CD into the CD-ROM drive.
2 Click Browse CD.
3 Double-click the Manual folder.
4 Double-click NPF2003.pdf.
You can also copy the User’s Guide to your hard disk and read it from there.
It needs approximately 2.25 MB of disk space.
Page 51

Norton Personal Firewall basics
To read the User’s Guide from your hard disk
1 Open the location into which you copied the PDF.
2 Double-click NPF2003.pdf.
About Norton Personal Firewall on the Web
The Symantec Web site provides extensive information about Norton
Personal Firewall. There are several ways to access the Symantec Web site.
To access the Symantec Web site from the Norton Personal Firewall
main window
1 Click Help.
2 Select one of the following:
2 Technical Support Web site: Takes you to the Technical Support
page of the Symantec Web site, from which you can search for
solutions to specific problems, update your virus protection, and
read the latest information about antivirus technology.
2 Visit the Symantec Web site: Takes you to the home page of the
Symantec Web site, from which you can get product information
on every Symantec product.
51
For more information
You can always access the Symantec Web site through your Internet
browser.
To access the Symantec Web site in your browser
4 Type the Symantec Web site address, www.symantec.com.
Explore online tutorials
Symantec provides online tutorials that you can use to review many
common tasks that Norton Personal Firewall performs.
To explore the online tutorials
1 Point your browser to www.symantec.com/techsupp/tutorials.html
2 On the tutorials Web page, select the product and version for which
you want a tutorial.
3 Click continue.
4 In the list of available tutorials for your product, select the one that you
want to review.
Page 52

Norton Personal Firewall basics
52
For more information
Subscribe to the Symantec Security Response newsletter
Each month, Symantec publishes a free electronic newsletter that is
focused on the needs of Internet security customers. It discusses the latest
antivirus technology produced by Symantec Security Response, common
viruses, trends in virus workings, virus outbreak warnings, and special
virus definition releases.
To subscribe to the Symantec Security Response newsletter
1 Point your browser to securityresponse.symantec.com
2 On the security response Web page, scroll down to the reference area
of the page, then click Newsletter.
3 On the security response newsletter Web page, choose the language in
which you want to receive the newsletter.
4 On the subscribe Web page, type the information requested, then click
Subscribe.
Page 53

Keeping current with LiveUpdate
Symantec products depend on current information to protect your
computer from newly discovered threats. Symantec makes this information
available to you through LiveUpdate. Using your Internet connection,
LiveUpdate obtains program updates and protection updates for your
computer.
Your normal Internet access fees apply when you use LiveUpdate.
w If you are using Norton Personal Firewall on Windows 2000/XP, you must
have Administrator access rights to run LiveUpdate.
About program updates
Program updates are minor improvements to your installed product. These
differ from product upgrades, which are newer versions of entire products.
Program updates that have self-installers to replace existing software code
are called patches. Patches are usually created to extend operating system
or hardware compatibility, adjust a performance issue, or fix bugs.
LiveUpdate automates the process of obtaining and installing program
updates. It locates and obtains files from an Internet site, installs them, and
then deletes the leftover files from your computer.
Page 54

Keeping current with LiveUpdate
54
About protection updates
About protection updates
Protection updates are files available from Symantec, by subscription, that
keep your Symantec products up-to-date with the latest anti-threat
technology. The protection updates you receive depend on which product
you are using.
Norton AntiVirus,
Norton SystemWorks
Norton Internet
Security
Norton Personal
Firewall
About your subscription
See “Subscription
policy” on
page 142.
Your Symantec product includes a complimentary, limited-time
subscription to protection updates for the subscription services that are
used by your product. When the subscription is due to expire, you are
prompted to renew your subscription.
Users of Norton AntiVirus and Norton SystemWorks
receive virus definition service updates, which provide
access to the latest virus signatures and other technology
from Symantec.
In addition to the virus definition service, users of Norton
Internet Security also receive protection updates to the
Web filtering service, the intrusion detection service, and
Spam Alert.
The Web filtering service updates provide the latest lists of
Web site addresses and Web site categories that are used
to identify inappropriate Web content.
The intrusion detection service updates provide the latest
predefined firewall rules and updated lists of applications
that access the Internet. These lists are used to identify
unauthorized access attempts to your computer.
Spam Alert updates provide the latest spam definitions
and updated lists of spam email characteristics. These lists
are used to identify unsolicited email.
Users of Norton Personal Firewall receive intrusion
detection service updates for the latest predefined firewall
rules and updated lists of applications that access the
Internet.
If you do not renew your subscription, you can still use LiveUpdate to
obtain program updates. However, you cannot obtain protection updates
and will not be protected against newly discovered threats.
Page 55

When you should update
Run LiveUpdate as soon as you have installed your product. Once you know
that your files are up-to-date, run LiveUpdate regularly to obtain updates.
For example, to keep your virus protection current, you should use
LiveUpdate once a week or whenever new viruses are discovered. Program
updates are released on an as-needed basis.
Request an update alert
To ensure your protection updates are current, you can request to receive
an email alert whenever there is a high-level virus outbreak or other
Internet security threat. The email alert describes the threat, provides
detection and removal instructions, and includes advice on keeping your
computer safe. You should always run LiveUpdate after you receive one of
these alerts.
To request an update alert
1 From your Web browser, navigate to securityresponse.symantec.com/
avcenter
2 On the Security Response Web page, scroll to the bottom of the page,
then click Symantec security response Free subscription.
3 On the security alert subscription Web page, fill in the subscription
form.
4 Click Send me FREE Security Alerts.
Keeping current with LiveUpdate
When you should update
55
If you run LiveUpdate on an internal network
If you run LiveUpdate on a computer that is connected to a network that is
behind a company firewall, your network administrator might set up an
internal LiveUpdate server on the network. LiveUpdate should find this
location automatically.
If you have trouble connecting to an internal LiveUpdate server, contact
your network administrator.
Page 56

Keeping current with LiveUpdate
56
If you can’t use LiveUpdate
If you can’t use LiveUpdate
When new updates become available, Symantec posts them on the
Symantec Web site. If you can’t run LiveUpdate, you can obtain new
updates from the Symantec Web site.
w Your subscription must be current to obtain new protection updates from
the Symantec Web site.
To obtain updates from the Symantec Web site
1 Point your Web browser to securityresponse.symantec.com
2 Follow the links to obtain the type of update that you need.
Obtain updates using LiveUpdate
LiveUpdate checks for updates to all of the Symantec products that are
installed on your computer.
w If you connect to the Internet through America Online (AOL), CompuServe,
or Prodigy, connect to the Internet first, and then run LiveUpdate.
To obtain updates using LiveUpdate
1 Open your Symantec product.
2 At the top of the window, click LiveUpdate.
You might receive a warning that says that your subscription has
expired. Follow the on-screen instructions to complete the
subscription renewal.
3 In the LiveUpdate window, click Next to locate updates.
4 If updates are available, click Next to download and install them.
5 When the installation is complete, click Finish.
w Some program updates may require that you restart your computer after
you install them.
Set LiveUpdate to Interactive or Express mode
LiveUpdate runs in either Interactive or Express mode. In Interactive mode
(the default), LiveUpdate downloads a list of updates available for your
Symantec products that are supported by LiveUpdate technology. You can
then choose which product updates you want to install. In Express mode,
Page 57

LiveUpdate automatically installs all available updates for your Symantec
products.
To set LiveUpdate to Interactive or Express mode
1 Open your Symantec product.
2 At the top of the window, click LiveUpdate.
3 On the LiveUpdate welcome screen, click Configure.
4 On the General tab of the LiveUpdate Configuration dialog box, select
Interactive Mode or Express Mode.
5 If you selected Express Mode, select how you want to start checking
for updates:
2 To have the option of cancelling the update, select I want to
press the start button to run LiveUpdate.
2 To have any updates installed automatically whenever you start
LiveUpdate, select I want LiveUpdate to start automatically.
6 Click OK.
Turn off Express mode
Once you have set LiveUpdate to run in Express mode, you can no longer
access the LiveUpdate Configuration dialog box directly from LiveUpdate.
You must use the Symantec LiveUpdate control panel.
Keeping current with LiveUpdate
Set LiveUpdate to Interactive or Express mode
57
To turn off Express mode
1 On the Windows taskbar, click Start > Settings > Control Panel.
2 In the Control Panel window, double-click Symantec LiveUpdate.
3 On the General tab of the LiveUpdate Configuration dialog box, select
Interactive Mode.
4 Click OK.
Page 58

Keeping current with LiveUpdate
58
Run LiveUpdate automatically
Run LiveUpdate automatically
You can have LiveUpdate check for protection updates automatically, on a
set schedule, by enabling Automatic LiveUpdate. You must continue to run
LiveUpdate manually to receive product updates.
w Automatic LiveUpdate checks for an Internet connection every five
minutes until a connection is found, and then every four hours. If you have
an ISDN router that is set to automatically connect to your Internet service
provider (ISP), many connections will be made, with connection and phone
charges possibly being incurred for each connection. If this is a problem,
you can set your ISDN router to not automatically connect to the ISP or
disable Automatic LiveUpdate in the Norton Personal Firewall options.
To enable Automatic LiveUpdate
1 Start Norton Personal Firewall.
2 At the top of the Norton Personal Firewall main window, click
Options.
w If you set a password for Options, Norton Personal Firewall asks you
for the password before you can continue.
3 In the Norton Personal Firewall Options dialog box, on the LiveUpdate
tab, check Enable Automatic LiveUpdate.
4 If you want to be notified when updates are available, check Notify
me when Norton Personal Firewall updates are available.
5 Select the updates for which you want Automatic LiveUpdate to check.
6 For each type of update you want Automatic LiveUpdate to check for,
set how you want those updates to be applied by selecting one of the
following:
Automatically
update my
protection
Notify me LiveUpdate checks for protection updates and asks if you
LiveUpdate checks for and installs protection updates
without prompting you. LiveUpdate displays an alert when
a protection update has been downloaded. You should still
run LiveUpdate occasionally to check for program updates.
want to install them.
7 Click OK.
Page 59

Keeping current with LiveUpdate
Run LiveUpdate automatically
To delete the schedule for Automatic LiveUpdate, disable Automatic
LiveUpdate.
To disable Automatic LiveUpdate
1 Start Norton Personal Firewall.
2 At the top of the Norton Personal Firewall main window, click
Options.
w If you set a password for Options, Norton Personal Firewall asks you
for the password before you can continue.
3 In the Norton Personal Firewall Options dialog box, click the
LiveUpdate tab.
4 In the LiveUpdate pane, uncheck Enable Automatic LiveUpdate.
5 Click OK.
59
Page 60

Keeping current with LiveUpdate
60
Run LiveUpdate automatically
Page 61

Controlling access to protected computers
You can configure Norton Personal Firewall to meet your needs in many
different situations. You can use the program to control your computer’s
access to both local computers and computers over the Internet. You can
also control how outside users access your computer.
Control how people use your computer
Norton Personal Firewall monitors all connections, including those made
among computers in your home. After installation, you may need to adjust
some settings to share files, printers, and other resources with other
computers.
Connect to a network
Every time that you use Windows file sharing to exchange files with
someone, print to a shared printer, or connect to the Internet using a
modem or broadband connection, your computer joins a network of other
computers. When you are part of a network, your computer is vulnerable to
attacks. Norton Personal Firewall automatically monitors all new network
connections to ensure that your computer is safe.
Normally, your computer connects to a network because of an action that
you take. Unexpected connections can be a sign that a malicious program
is attempting to send information over the Internet. Some wireless access
cards automatically scan for and connect to any network in range. If you
travel with a laptop that is equipped with a wireless access card, you may
discover that your computer joins wireless networks in airports and other
public places.
Page 62

Controlling access to protected computers
62
Control how people use your computer
See “Monitoring
Norton Personal
Firewall” on
page 103.
Whenever you join a network, Norton Personal Firewall automatically
begins monitoring the connection. You do not need to make any changes in
order to be protected. Norton Personal Firewall notifies you of the new
connection and records it in the Connections log.
Enable file and printer sharing
Microsoft networking provides file and printer sharing. By default, Norton
Personal Firewall prevents any computers from accessing these services on
a protected computer.
To share files and give access to printers on your local network, you can
enable file and printer sharing. If you enable these features on your local
network, they are still protected from malicious users on the Internet.
w Before enabling file and printer sharing on your local network, ensure that
each shared resource is protected by a secure password. To learn more
about securing shared resources, consult the Help file on your Start menu.
To enable file and printer sharing
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 In the Personal Firewall window, on the Advanced tab, click General
Rules.
4 In the General Rules window, select the entry for Windows file sharing
or printer sharing.
5 Click Modify.
6 In the Modify Rule dialog box, on the Action tab, click Permit
Internet access.
7 Click OK.
8 In the General Rules dialog box, click OK.
9 In the Advanced Firewall window, click OK.
Organize computers into network zones
Norton Personal Firewall lets you organize computers on your home
network and the Internet into Trusted and Restricted Zones.
If you have more than one computer in your home, you will likely want to
add all of these computers to your Trusted Zone. Only add external
Page 63

Controlling access to protected computers
Control how people use your computer
computers to your Trusted Zone if you know that their users can be trusted
and they have firewall software installed.
The Home Network Wizard is the fastest way to organize computers into
zones. You can also manually add individual computers to zones.
To open the Home Network Wizard from the Security Center
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 In the Personal Firewall window, on the Home Networking tab, click
Wizard.
To open the Home Network Wizard from the Security Monitor
1 Open Norton Personal Firewall.
2 In the Security Monitor, on the Select a Task menu, select Setup
Home Networking.
63
To organize computers into zones with the Home Network Wizard
1 In the Home Network Wizard, click Next.
2 In the resulting list, check the network adapters that you want Norton
Personal Firewall to configure automatically and add to your Trusted
Zone.
3 Click Next.
4 Click Finish to close the wizard.
Page 64

Controlling access to protected computers
64
Control how people use your computer
To manually add computers to zones
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 In the Personal Firewall window, on the Home Networking tab, select
the zone to which you want to add a computer.
4 Click Add.
See “Identify
computers to
Norton Personal
Firewall” on
page 64.
5 In the Specify Computers window, identify the computer.
6 When you have finished adding computers, click OK.
To remove computers from zones
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 Select the computer that you want to remove.
4 Click Remove.
5 When you have finished removing computers, click OK.
Identify computers to Norton Personal Firewall
You must identify computers to Norton Personal Firewall to manually
configure network zones, firewall rules, and other protection features. In
these cases, the Specify Computers dialog box appears.
The Specify Computers dialog box lets you specify computers in three
ways. In each, you can use IP addresses to identify computers.
Page 65

Find a computer’s IP address
There are two procedures for finding a computer’s IP address. On Windows
98/Me computers, you can use Winipcfg to find the IP address of a
computer. On Windows 2000/XP computers, you can use Ipconfig to find
the IP address of a computer.
To find an IP address with Winipcfg
1 On the Windows taskbar, click Start > Run.
2 In the Run dialog box, type winipcfg
3 Click OK.
4 Select the appropriate network adapter.
5 Record the IP address.
To find an IP address with Ipconfig
1 On the Windows taskbar, click Start > Run.
2 In the Run dialog box, type cmd
3 Click OK.
4 At the command prompt, type ipconfig
5 Click OK.
6 Record the IP address.
Controlling access to protected computers
Control how people use your computer
65
Specify an individual computer
The computer name that you type can be an IP address, a URL such as
service.symantec.com, or a Microsoft Network computer name, such as
Mojave. You can find the names of computers on your local network in
Network Neighborhood or Network Places on your Windows desktop.
w If you don’t have TCP/IP bound to Client for Microsoft Networks in
Windows Network Properties, you must use IP addresses instead of names
for the computers on your local network.
To specify an individual computer
1 In the Specify Computers dialog box, click Individually.
2 Type the name or IP address of a single computer.
3 Click OK.
Page 66

Controlling access to protected computers
66
Control how people use your computer
Specify a range of computers
You can enter a range of computers by specifying the starting (lowest
numerically) IP address and the ending (highest numerically) IP address.
All of the computers within that range of IP addresses are included.
In almost every case, the first three of the four numbers of the IP addresses
entered should be the same.
To specify a range of computers
1 In the Specify Computers dialog box, click Using a range.
2 In the Starting Internet Address text box, type the starting (lowest
numerically) IP address.
3 In the Ending Internet Address text box, type the ending (highest
numerically) IP address.
4 Click OK.
Specify computers using a network address
You can identify all of the computers on a single subnet by specifying an IP
address and a subnet mask. The IP address that you specify can be any
address in the subnet that you are identifying.
If you use DHCP
To specify computers using a network address
1 In the Specify Computers dialog box, click Using a network address.
2 In the Network Address text box, type the IP address of a computer on
the subnet.
3 In the Subnet Mask text box, type the subnet mask.
The appropriate subnet mask is almost always 255.255.255.0.
4 Click OK.
If your ISP uses a DHCP server to provide IP addresses to users’ computers,
you must be careful when entering IP addresses.
Instead of identifying a computer with a single IP address, which might
change at any time, enter a network address using a base IP address and a
subnet mask. Enter values that cover the range of addresses that might be
assigned to the computer.
Page 67

Controlling access to protected computers
Control how users access the Internet
Control how users access the Internet
Norton Personal Firewall supports most Internet connection methods
without needing additional configuration.
If you access the Internet via a cable or DSL router
Norton Personal Firewall works behind a cable or DSL router and adds to
the protection provided by the router. In some cases, you might want to
reduce the protection provided by the router so that you can use programs
like NetMeeting or Microsoft Messenger. Norton Personal Firewall also
provides features that might not be available with cable and DSL routers,
such as privacy protection.
If multiple computers share a single Internet connection
Norton Personal Firewall works with most Internet connection sharing
programs. To protect your network from many outside attacks, install
Norton Personal Firewall on the gateway computer. For maximum
protection against Trojan horses or other problem programs that initiate
outbound connections, install Norton Personal Firewall on all computers
that share the connection.
67
Control how outside users access your network
Norton Personal Firewall can protect computers while still allowing outside
users to access servers on your network. To run servers on protected
computers, you may have to create firewall rules that let outside users
connect to certain ports. For maximum security, only create these rules on
the computers running your servers.
If you run Symantec pcAnywhere
See “Change an
existing firewall
rule” on page 83.
You should have no problems using Symantec pcAnywhere as either a
client or host with Norton Personal Firewall. For maximum protection, if
you run a Symantec pcAnywhere host, edit the rule to limit its use to only
the computers with which you use it. This, and Symantec pcAnywhere
passwords, provide maximum security.
Page 68

Controlling access to protected computers
68
Control how outside users access your network
If you run a Virtual Private Network
Norton Personal Firewall works with the following Virtual Private
Networks (VPNs):
1 Nortel
1 VPNRemote
1 PGP
1 SecureRemote
With most VPNs, when the VPN client is active, you cannot see the Internet
or other computers on your local network. You can only see what is
available through the VPN server to which you are connected.
Page 69

Guarding against intrusion attempts
Internet attacks take advantage of the way that computers transfer
information. Norton Personal Firewall can protect your computer by
monitoring the information that comes into and out of your computer and
blocking any attack attempts.
How Norton Personal Firewall protects against network attacks
Norton Personal Firewall includes three tools that protect your computer
from intrusion attempts, malicious Web content, and Trojan horses:
1 Norton Personal Firewall
Monitors all Internet communication and creates a shield that blocks
or limits attempts to view information on your computer
1 Intrusion Detection
Analyzes all incoming and outgoing information for data patterns
typical of an attack
1 Visual Tracking
Identifies the computer responsible for the attack
Page 70

Guarding against intrusion attempts
70
How Norton Personal Firewall protects against network attacks
Norton Personal Firewall monitors communications
When Norton Personal Firewall is active, it monitors communications
among your computer and other computers on the Internet. It also protects
your computer from such common security problems as:
See “Customize
firewall
protection” on
page 72.
Improper connection
attempts
Trojan horses Notifies you when your computer encounters
Security and privacy
incursions by malicious
Web co nt en t
Port scans Cloaks inactive ports on your computer and detects port
Intrusions Detects and blocks malicious traffic and attempts by
You can control the level of protection that Norton Personal Firewall
provides by using the Security Level slider. You can also control how
Norton Personal Firewall reacts to improper connection attempts, Trojan
Warns you of any connection attempts from other
computers and attempts by programs on your computer
to connect to other computers
destructive programs that are disguised as something
useful
Monitors all Java applets and ActiveX controls and lets
you choose whether to run or block the program
scans
outside users to attack your computer
horses, and malicious Web content.
Intrusion Detection analyzes communications
Intrusion Detection scans each packet that enters and exits your computer
for attack signatures, arrangements of information that identify an
attacker’s attempt to exploit a known operating system or program
vulnerability.
Norton Personal Firewall protects your computer against most common
Internet attacks, including the following.
Bonk An attack on the Microsoft TCP/IP stack that can crash the
attacked computer
RDS_Shell A method of exploiting the Remote Data Services component
of the Microsoft Data Access Components that lets a remote
attacker run commands with system privileges
WinNuke An exploit that can use NetBIOS to crash older Windows
computers
Page 71

Guarding against intrusion attempts
How Norton Personal Firewall protects against network attacks
Because attacks may span packets, Intrusion Detection examines packets
in two different ways. It scans each packet individually looking for patterns
that are typical of an attack. It also monitors the packets as a stream of
information, which lets it identify attacks spread across multiple packets.
If the information matches a known attack, Intrusion Detection
automatically discards the packet and severs the connection with the
computer that sent the data. This protects your computer from being
affected in any way.
You can modify how Intrusion Detection responds to attacks by excluding
attack signatures from being monitored and by enabling or disabling
AutoBlock, which automatically blocks all communication with an
attacking computer. By excluding certain network behavior from blocking,
you can continue to be productive, even while your computer is under
attack.
Along with protecting your computer against attacks, Norton Personal
Firewall also monitors all of the information that your computer sends to
other computers. This ensures that your computer cannot be used to attack
other users or be exploited by zombies. If Norton Personal Firewall detects
that your computer is sending information that is typical of an attack, it
immediately blocks the connection and warns you about the possible
problem.
71
To reduce the number of warnings that you receive, Norton Personal
Firewall only monitors attacks that are targeted at ports that your computer
uses. If an attacker attempts to connect to your computer via an inactive
port or a port that has been blocked by the firewall, Norton Personal
Firewall will not notify you because there is no risk of an intrusion.
Norton Personal Firewall does not scan for intrusions by computers in your
Trusted Zone. However, Intrusion Detection does monitor the information
that you send to Trusted computers for signs of zombies and other remote
control attacks.
See “Keeping
current with
LiveUpdate” on
page 53.
Intrusion Detection relies on an extensive list of attack signatures to detect
and block suspicious network activity. Run LiveUpdate regularly to ensure
that your list of attack signatures is up to date.
Visual Tracking locates attackers
See “Identify the
source of
communications”
on page 43.
Norton Personal Firewall now includes Visual Tracking, which lets you get
information about the IP address used for a particular connection. This can
help you identify the source of an attack.
Page 72

Guarding against intrusion attempts
72
Customize firewall protection
Customize firewall protection
The default Norton Personal Firewall settings should provide adequate
protection for most users. If the default protection is not appropriate, you
can customize Norton Personal Firewall protection by using the Security
Level slider to select preset security levels, or by changing individual
security settings.
Change the Security Level slider
The Security Level slider lets you select Minimal, Medium, or High security
settings. When you change the slider position, the protection level changes.
Changing the Security Level slider does not affect the protection provided
by Intrusion Detection.
To change the Security Level slider
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
Page 73

Guarding against intrusion attempts
Customize firewall protection
3 Move the slider to the Security Level that you want. Your options are:
High The firewall blocks everything until you allow it. If you
have run a Program Scan, you should not be interrupted
frequently with Program Control alerts. See “Enable
Automatic Program Control” on page 76.
You are alerted each time that an ActiveX control or Java
applet is encountered. Unused ports do not respond to
connection attempts, giving them a stealth appearance.
73
Medium
(recommended)
Minimal Firewall blocks connection attempts by Trojan horse
The firewall blocks everything until you allow it. If you
have run a Program Scan, you should not be interrupted
frequently with Program Control alerts.
ActiveX controls and Java applets run without warning.
Unused ports do not respond to connection attempts,
giving them a stealth appearance.
programs. ActiveX controls and Java applets run
without warning.
Change individual security settings
If the Security Level options do not meet your needs, you can change the
settings for Norton Personal Firewall, Java, and ActiveX protection levels.
Changing an individual setting overrides the Security Level, but it does not
change the other security settings in that level.
To change individual security settings
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
Page 74

Guarding against intrusion attempts
74
Customize firewall protection
3 Click Custom Level.
4 Do one or more of the following:
2 On the Personal Firewall menu, select a level. Your options are:
High Blocks all communication that you do not specifically
allow. You must create firewall rules for every program
that requests Internet access.
Medium Blocks many ports that are used by harmful programs.
However, it can also block useful programs when they use
the same ports.
None Disables Norton Personal Firewall and allows all Internet
communications.
2 On the Java Applet Security or ActiveX Control Security menu,
select a level. Your options are:
High Blocks your browser from running any Java applets or
ActiveX controls over the Internet. This is the safest, but
most inconvenient, option. Some Web sites might not
operate properly using this setting.
Medium Prompts you when Java applets and ActiveX controls are
encountered. This lets you temporarily or permanently
allow or block each Java applet or ActiveX control that you
encounter. It can be bothersome to respond every time that
you encounter a Java applet or ActiveX control, but it lets
you decide which ones to run.
None Lets Java applets and ActiveX controls run whenever you
encounter them.
Page 75

2 To be notified whenever unknown programs access the Internet,
check Enable Access Control Alerts.
2 To be notified whenever a remote computer attempts to connect
to a port no program is using, check Alert when unused ports
are accessed.
5 Click OK.
Reset security settings to defaults
Setting a custom security level disables the Security Level slider. The slider
indicates the security level on which your custom level is based, but you
cannot use the slider to make changes to your settings. To use the slider to
choose a preset security level, you must reset the security level.
To reset security settings to defaults
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 Click Default Level.
See “Change the
Security Level
slider” on page 72.
This resets your security level to medium. Use the Security Level slider to
choose one of the other preset security levels.
Guarding against intrusion attempts
Customize firewall rules
75
Customize firewall rules
Firewall rules control how Norton Personal Firewall protects your
computer from malicious incoming traffic, programs, and Trojan horses.
The firewall automatically checks all data coming in or out of your
computer against these rules.
How firewall rules are processed
When a computer attempts to connect to your computer, or when your
computer attempts to connect to a computer on the Internet, Norton
Personal Firewall compares the type of connection with its list of firewall
rules.
Firewall rules are processed in a set order based on their types. System
rules are processed first, followed by program rules, and then Trojan horse
rules.
Once a rule that blocks or permits communications is matched, all
remaining rules are ignored. In other words, additional rules that match
Page 76

Guarding against intrusion attempts
76
Customize firewall rules
this type of communication are ignored if they appear below the first rule
that matches.
If no matching rule is found, the communication is blocked. Depending on
the Reporting level, an alert may appear.
Create new firewall rules
Norton Personal Firewall includes Program Control, which helps you create
firewall rules as you use the Internet.
There are four ways to create firewall rules with Program Control:
Enable Automatic
Program Control
Use Program Scan Finds and configures access for all Internet-enabled
Manually add
programs
Respond to alerts Norton Personal Firewall warns users when a program
Enable Automatic Program Control
When Automatic Program Control is active, Norton Personal Firewall can
automatically configure Internet access settings for programs the first time
that they run. Automatic Program Control only configures Internet access
for the versions of programs that Symantec has identified as safe.
If an unknown program or an unknown version of a known program
attempts to access the Internet, Norton Personal Firewall warns the user.
The user can then choose to allow or block Internet access for the program.
See “Keeping
current with
LiveUpdate” on
page 53.
Symantec regularly updates the list of recognized programs. You should
run LiveUpdate regularly to ensure that your list is up-to-date.
Automatically configures access for well-known programs
the first time that users run them. This is the easiest way to
set up firewall rules.
programs on a computer at once.
Closely manage the list of programs that can access the
Internet.
attempts to access the Internet for the first time. Users can
then allow or block Internet access for the program.
Page 77

Guarding against intrusion attempts
Customize firewall rules
To enable Automatic Program Control
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
77
3 In the Personal Firewall window, on the Program Control tab, check
Turn on Automatic Program Control.
4 Click OK.
Scan for Internet-enabled programs
Scanning for Internet-enabled programs is the quickest way to configure
the Personal Firewall. Norton Personal Firewall scans the computer for
programs that it recognizes and suggests appropriate settings for each
program.
You can scan for Internet-enabled programs from the Security Center or the
Security Monitor.
To scan for Internet-enabled programs from the Security Center
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
Page 78

Guarding against intrusion attempts
78
Customize firewall rules
3 In the Personal Firewall window, on the Program Control tab, click
4 Select the disk or disks on your computer that you want to scan.
5 Click OK.
6 In the Program Scan window, do one of the following:
7 Click Finish.
8 Click OK.
To scan for Internet-enabled programs from the Security Monitor
1 Open Norton Personal Firewall.
2 In the Security Monitor, on the Select a Task menu, click Program
3 Select the disk or disks on your computer that you want to scan.
4 Click OK.
5 In the Program Scan window, do one of the following:
6 Click Finish.
Program Scan.
2 Check programs that you want to add to the Program Control list.
2 To add all Internet-enabled programs at once, click Check All.
Scan.
2 Check programs that you want to add to the Program Control list.
2 To add all Internet-enabled programs at once, click Check All.
Manually add a program to Program Control
See “Customize
firewall
protection” on
page 72.
Users can add programs to Program Control to strictly control the
programs’ ability to access the Internet. This overrides any settings made
by Automatic Program Control.
To add a program to Program Control
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 In the Personal Firewall window, on the Program Control tab, click
Add.
4 Select the program’s executable file.
Executable file names typically end in .exe.
5 Click Open.
Page 79

Guarding against intrusion attempts
Customize firewall rules
6 In the Internet Access Control alert, select the access level you want
this program to have. Your options are:
79
Automatically
configure Internet
access
(Recommended)
Permit Allow all access attempts by this program.
Block Deny all access attempts by this program.
Manually configure
Internet Access
7 If you want to see any risks that this program could pose to your
computer, click Details.
8 Click OK.
Change Program Control settings
After using Norton Personal Firewall for a while, you may find that you
need to change access settings for certain programs. Any changes override
settings made by Automatic Program Control.
To change Program Control settings
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 In the Personal Firewall window, on the Program Control tab, in the
list of programs, click the program that you want to change.
4 Click Modify.
Use the default Norton Personal Firewall settings for
this program.
Create rules controlling how this program accesses the
Internet.
Page 80

Guarding against intrusion attempts
80
Customize firewall rules
5 In the Internet Access Control alert, select the access level you want
this program to have. Your options are:
Automatically configure
Internet access
Permit this program
access to the Internet
Block this program from
accessing the Internet
Customize Internet
access for this program
6 Click OK.
Manually add a firewall rule
While Norton Personal Firewall automatically creates most of the firewall
rules that you need, you may want to add specific rules. Only experienced
Internet users should create their own firewall rules.
There are three sets of firewall rules you can customize:
1 General Rules
1 Trojan Horse Rules
1 Program Rules
To add a General Rule
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 In the Personal Firewall window, on the Advanced tab, click General
Rules.
4 Follow the on-screen instructions.
See “Write a firewall rule” on page 81.
Use the default Norton Personal Firewall settings
for this program.
Allow all access attempts by this program.
Deny all access attempts by this program.
Create rules controlling how this program
accesses the Internet.
To add a Trojan Horse Rule
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
Page 81

3 In the Personal Firewall window, on the Advanced tab, click Trojan
4 Follow the on-screen instructions.
To add a Program Rule
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Personal Firewall.
3 In the Personal Firewall window, on the Program Control tab, in the
4 In the Select a program window, select a program’s executable file.
5 In the Internet Access Control alert, on the What do you want to do
6 Follow the on-screen instructions.
Write a firewall rule
Norton Personal Firewall leads you through the process of writing your
own firewall rules.
Guarding against intrusion attempts
Horse Rules.
See “Write a firewall rule” on page 81.
list of programs, click Add.
Executable file names typically end in .exe.
menu, select Create a firewall rule.
See “Write a firewall rule” on page 81.
81
Customize firewall rules
To write a firewall rule
1 In the General Rules, Trojan Horse Rules, or Program Rules window,
click Add.
2 In the Add Rule window, select the action that you want for this rule.
Your options are:
Permit Internet
Access
Block Internet
Access
Monitor Internet
Access
Allows communication of this type to take place.
Prevents communication of this type from taking place.
Updates the Firewall tab in the Event Log or shows a
message each time that communication of this type takes
place. This lets you monitor how often this firewall rule is
used.
w To monitor a permitted connection, you must create
both a monitor and a permit rule. The monitor rule must
precede the permit rule.
3 Click Next.
Page 82

Guarding against intrusion attempts
82
Customize firewall rules
4 Select the type of connection the rule should monitor. Your options are:
Connections to
other computers
Connections from
other computers
Connections to and
from other
computers
The rule applies to outbound connections from your
computer to another computer.
The rule applies to inbound connections from another
computer to your computer.
The rule applies to both inbound and outbound
connections.
5 Click Next.
6 Select the computers the rule should monitor. Your options are:
Any computer The rule applies to all computers.
Only computers
specified below
Adapters The rule applies to a specific network adapter in your
The rule applies only to the computers, sites, and
domains listed.
computer. This allows you to customize firewall rules for
each of your computer’s IP addresses. For example, if
your computer is connected to a home network and to
the Internet, you might want to set up a rule that
permits file sharing on the home network, while another
rule blocks file sharing over the Internet.
7 Click Next.
8 Select the protocols the rule should monitor. Your options are:
TCP The rule applies to TCP (Transmission Control Protocol)
communications.
UDP The rule applies to UDP (User Datagram Protocol)
TCP and UDP The rule applies to both TCP and UDP communications.
ICMP The rule applies to ICMP (Internet Control Message
communications.
Protocol) communications. This option is only available
when adding or modifying a General Rule.
Page 83

Guarding against intrusion attempts
Customize firewall rules
9 Select the ports the rule should monitor. Your options are:
83
All types of
communications (all
ports)
Only the types of
communications or
ports listed below
The rule applies to communications using any port.
The rule applies to the ports listed. You can add ports
to, or remove ports from, the list.
10 Click Next.
11 Choose if and how you want Norton Personal Firewall to track this
rule. Your options are:
Do not track this rule No record of the actions of this rule is made.
Create an Event Log
entry
Notify me with an
Alert Tracker
message
Display Security Alert A Security Alert dialog box appears when a network
An entry is created in the firewall Event Log when a
network communication event matches this rule.
An Alert Tracker message appears when a network
communication event matches this rule.
communication event matches this rule.
12 Click Next.
13 In the What do you want to call this rule? text box, type a name for
this rule.
14 Click Next.
15 Review the new rule settings, then click Finish.
16 When you have finished adding rules, click OK.
Change an existing firewall rule
You can change firewall rules if they are not functioning the way that you
want.
Page 84

Guarding against intrusion attempts
84
Customize firewall rules
To change an existing firewall rule
1 In the General Rules, Trojan Horse Rules, or Program Rules window,
click Add.
2 Select the rule that you want to change.
3 Click Modify.
See “Write a
firewall rule” on
page 81.
4 Follow the on-screen instructions to change any aspect of the rule.
5 When you have finished changing rules, click OK.
Change the order of firewall rules
See “How firewall
rules are
processed” on
page 75.
Norton Personal Firewall processes each list of firewall rules from the top
down. You can determine how Norton Personal Firewall processes firewall
rules by changing their order.
To change the order of a firewall rule
1 In the General Rules, Trojan Horse Rules, or Program Rules window,
select the rule that you want to move.
2 Do one of the following:
2 To have Norton Personal Firewall process this rule before the rule
above it, click Move Up.
2 To have Norton Personal Firewall process this rule after the rule
below it, click Move Down.
3 When you are done moving rules, click OK.
Temporarily disable a firewall rule
You can temporarily disable a firewall rule if you need to allow specific
access to a computer or program.
To temporarily disable a firewall rule
4 In the General Rules, Trojan Horse Rules, or Program Rules window,
uncheck the box next to the rule you want to disable.
Remember to re-enable the rule when you are done working with the
program or computer that required the change.
Remove a firewall rule
Remove firewall rules when they are no longer necessary.
Page 85

Guarding against intrusion attempts
To remove a firewall rule
1 In the General Rules, Trojan Horse Rules, or Program Rules window,
click Add.
2 Select the rule that you want to remove.
3 Click Remove.
4 When you are done removing rules, click OK.
Reset firewall rules to the default settings
Resetting the firewall rules returns the firewall to its default settings and
deletes any changes you have made to firewall rules.
w You should only use this procedure in an emergency. Before resetting your
firewall rules, try removing recently changed firewall rules.
To reset the firewall rules to the default settings
1 Close all Norton Personal Firewall windows.
2 In Windows Explorer, double-click My Computer.
3 Double-click the hard disk on which you installed Norton Personal
Firewall.
In most cases, this will be drive C.
4 Open Program Files > Common Files > Symantec Shared.
5 Drag firewall.rul to the Recycle Bin.
85
Customize Intrusion Detection
The firewall will return to its default settings the next time you run Norton
Personal Firewall.
Customize Intrusion Detection
The default Intrusion Detection settings should provide adequate
protection for most users. You can customize Intrusion Detection by
excluding specific network activity from monitoring, enabling or disabling
AutoBlock, and restricting blocked computers.
Exclude specific network activity from being monitored
In some cases, benign network activity may appear similar to a Norton
Personal Firewall attack signature. If you receive repeated warnings about
possible attacks, and you know that these attacks are being triggered by
Page 86

Guarding against intrusion attempts
86
Customize Intrusion Detection
safe behavior, you can create an exclusion for the attack signature that
matches the benign activity.
w Each exclusion that you create leaves your computer vulnerable to attacks.
Be very selective when excluding attacks. Only exclude behavior that is
always benign.
To exclude attack signatures from being monitored
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Intrusion Detection.
3 In the Intrusion Detection window, click Signatures.
4 In the Signatures list, select the attack signature that you want to
exclude.
5 Click Exclude.
6 When you are done excluding signatures, click OK.
If you have excluded attack signatures that you want to monitor again, you
can include them in the list of active signatures.
To include attack signatures
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Intrusion Detection.
3 In the Intrusion Detection window, click Signatures.
Page 87

4 In the Excluded Signatures list, select the attack signature that you
want to monitor.
5 Click Include.
6 When you are done including signatures, click OK.
Enable or disable AutoBlock
When Norton Personal Firewall detects an attack, it automatically blocks
the connection to ensure that your computer is safe. The program can also
activate AutoBlock, which automatically blocks all incoming
communication from the attacking computer for a set period of time, even if
the incoming communication does not match an attack signature.
AutoBlock stops all inbound communications with the attacking computer
for 30 minutes.
To enable or disable AutoBlock
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Intrusion Detection.
3 In the Intrusion Detection window, check or uncheck Turn on
AutoBlock.
Guarding against intrusion attempts
Customize Intrusion Detection
87
Unblock computers
If a computer that you need to access appears on the list of computers
currently blocked by AutoBlock, unblock it. If you have changed your
protection settings and want to reset your AutoBlock list, you can unblock
all of the computers on the AutoBlock list at once.
To unblock computers currently blocked by AutoBlock
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Intrusion Detection.
3 In the Intrusion Detection window, do one of the following:
2 To unblock one computer, select its IP address, then click
2 To unblock all computers on the AutoBlock list, click Unblock
Unblock.
All.
Page 88

Guarding against intrusion attempts
88
Customize Intrusion Detection
Exclude computers from AutoBlock
If a computer you need to access is repeatedly placed in the AutoBlock list,
you can exclude it from being blocked by AutoBlock.
To exclude specific computers from AutoBlock
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Intrusion Detection.
3 In the Intrusion Detection window, click IP Address.
4 Do one of the following:
2 In the Currently blocked list, select a blocked IP address, then
click Exclude.
2 Click Add, then type the computer’s name, IP address, network
identification, or a range of IP addresses containing the computer
that you want to exclude.
5 When you are done excluding IP addresses, click OK.
Restrict a blocked computer
You can add a blocked computer to your Restricted Zone to permanently
prevent that computer from accessing your computer. Computers added to
the Restricted Zone do not appear on the blocked list because Norton
Personal Firewall automatically rejects any connection attempts by
restricted computers.
To restrict a blocked computer
1 Open Norton Personal Firewall.
2 In the Security Center, double-click Intrusion Detection.
3 In the list of computers that are currently blocked by AutoBlock, select
the computer to add to the Restricted Zone.
4 Click Restrict.
5 When you are done restricting computers, click OK.
Page 89

Protecting your privacy
Every time that you browse the Internet, computers and Web sites collect
information about you. Some of this information comes from forms that you
fill out and choices that you make. Other information comes from your
browser, which automatically provides information about the Web page you
last visited and the type of computer that you’re using.
Malicious users can also collect personal information without your
knowledge. Any time that you send information over the Internet, the data
must pass through a number of computers before it reaches its destination.
During transmission, it’s possible for third parties to intercept this
information.
Computers include some basic security features, but they might not be
enough to protect your personal information. Privacy Control helps protect
your privacy by giving you several levels of control over cookies and other
information that your browser sends to Web sites.
Privacy Control can ensure that users don’t send private information, such
as credit card numbers, over the Internet unless they are encrypted, or you
specifically allow it.
Identify private information to protect
Many Web sites ask for your name, email address, and other personal
information. While it is generally safe to provide this information to large,
reputable sites, malicious sites can use this information to invade your
privacy. It is also possible for people to intercept information sent via the
Web, email, and instant messenger programs.
Page 90

Protecting your privacy
90
Identify private information to protect
Privacy Control lets you create a list of information that you want to remain
private. If someone attempts to send protected information over the
Internet, Norton Personal Firewall warns them about the security risk or
blocks the connection.
Privacy Control and SSL
Some Web sites and email servers use SSL (Secure Sockets Layer)
connections to encrypt connections between your computer and the server.
Privacy Control cannot block private information sent via SSL connections.
However, since the information is encrypted, only the recipient of the email
will be able to read the message.
Add private information
You must add information that you want to protect to the Norton Personal
Firewall Private Information list.
To add private information
1 Start Norton Personal Firewall.
2 Do one of the following:
2 In the Security Center, double-click Privacy Control, then click
2 In the Security Monitor, on the Select a Task menu, click Edit
3 In the Private Information dialog box, click Add.
4 In the Add Private Information dialog box, under Type Of Information
To Protect, select a category.
5 In the Descriptive Name text box, type a description to help you
remember why you are protecting this information.
6 In the Information To Protect text box, type the information that you
want to block from being sent over nonsecure Internet connections.
7 Under Secure this private information in, select the Internet programs
in which Privacy Control should block this information:
2 Web browsers
2 Instant messengers
2 Email programs
8 Click OK.
Private Information.
Private Information.
Page 91

Modify or remove private information
You can modify or remove private information at any time.
To modify or remove private information
1 Start Norton Personal Firewall.
2 In the Security Center, double-click Privacy Control.
3 In the Privacy Control window, click Private Information.
4 Select the private information that you want to change or remove.
5 Select one of the following:
2 Modify
2 Remove
6 Click OK.
Customize Privacy Control
Privacy Control protects four areas:
Private Information Blocks specific strings of text that you do not want sent over
the Internet
Protecting your privacy
Customize Privacy Control
91
Cookie Blocking Stops Web sites from retrieving personal information stored
Browser Privacy Protects information about your browsing habits
Secure
Connections
There are two ways to adjust Privacy Control settings:
1 Set the Privacy Level
Use the slider in the main Privacy Control pane to select pre-set
security levels.
1 Adjust individual Privacy Control settings
Customize your protection by manually adjusting individual settings.
Set the Privacy Level
Norton Personal Firewall offers pre-set security levels that help you set
several Privacy Control options at one time. The Privacy Level slider lets
you select minimal, medium, or high protection.
in cookie files
Prevents users from establishing secure connections to
online stores and other Web sites
Page 92

Protecting your privacy
92
Customize Privacy Control
To set the Privacy Level
1 Start Norton Personal Firewall.
2 Double-click Privacy Control.
3 Move the slider to the Privacy Level that you want. Your options are:
High All personal information is blocked and an alert appears
each time that a cookie is encountered.
Medium
(recommended)
Minimal Confidential information is not blocked. Cookies are not
An alert appears if private information is typed into a
Web form or instant messenger program. Conceals your
browsing from Web sites. Cookies are not blocked.
blocked. Conceals your browsing from Web sites.
4 Click OK.
Adjust individual Privacy Control settings
You can change the settings for Private Information, Cookie Blocking,
Browser Privacy, and Secure Connections if the Privacy Level settings do
not meet your needs. For example, you can choose to block all attempts to
send private information while allowing Web sites to customize their pages
using your browser information.
Change the Private Information setting
Change the Private Information setting to control how Norton Personal
Firewall handles attempts to send information on the Private Information
list over the Internet.
To change the Private Information setting
1 Start Norton Personal Firewall.
2 Double-click Privacy Control.
3 Click Custom Level.
Page 93

4 Select the Private Information setting that you want. Your options are:
High Blocks all private information
Medium Alerts you each time that you attempt to send private
None Does not block private information
5 Click OK.
Change the Cookie Blocking setting
Many Web sites store information they collect in cookies placed on your
hard disk. When you return to a site that has set a cookie on your computer,
the Web server opens and reads the cookie.
Most cookies are harmless. Sites use them to personalize Web pages,
remember choices that you have made on the site, and deliver optimized
pages for your computer. However, sites can also use cookies to track your
Internet usage and browsing habits.
Change the Cookie Blocking setting to control how Norton Personal
Firewall handles sites that attempt to place cookies on your computer.
Protecting your privacy
Customize Privacy Control
information to a nonsecure Web site or through an
instant messenger program
93
To change the Cookie Blocking setting
1 Start Norton Personal Firewall.
2 Double-click Privacy Control.
3 Click Custom Level.
4 Select the Cookie Blocking setting that you want. You have three
options:
High Blocks all cookies
Medium Alerts you each time that a cookie is encountered
None Allows cookies
5 Click OK.
Page 94

Protecting your privacy
94
Customize Privacy Control
Enable or disable Browser Privacy
Browser Privacy prevents Web sites from learning the type of browser that
you are using, the Web site that you last visited, and other information
about your browsing habits. Some Web sites that depend on JavaScript may
not work correctly if they cannot identify the type of browser that you are
using.
To enable or disable Browser Privacy
1 Start Norton Personal Firewall.
2 Double-click Privacy Control.
3 Click Custom Level.
4 In the Customize Privacy Settings dialog box, check or uncheck
Enable Browser Privacy.
5 Click OK.
Disable or enable secure Web connections
When you visit a secure Web site, your browser sets up an encrypted
connection with the Web site. By default, Norton Personal Firewall lets any
account use secure connections. If you want to ensure that users are not
sending private information to secure Web sites, you can disable secure
Web connections.
w If you disable secure Web connections, your browser will not encrypt any
information that it sends. You should only disable secure Web connections
if you are protecting your personal data in the Private Information list.
To disable or enable secure Web connections
1 Start Norton Personal Firewall.
2 Double-click Privacy Control.
3 Click Custom Level.
4 In the Customize Privacy Settings dialog box, check or uncheck
Enable Secure Connections (https).
5 Click OK.
Page 95

Blocking Internet advertisements
Many Web sites are using more aggressive techniques to draw attention to
the ads on their pages. Some have begun using larger, more prominent ads,
while others rely on ad windows that appear when you enter or leave the
site. Along with increasing the amount of time that it takes to display Web
pages, some ads contain offensive content, cause software conflicts, or use
HTML tricks to open additional browser windows.
Ad Blocking helps avoid these problems. When Ad Blocking is active,
Norton Personal Firewall transparently removes:
1 Ad banners
1 Pop-up and pop-under ads
1 Macromedia Flash-based ads
How Ad Blocking works
Norton Personal Firewall detects and blocks ads based on two criteria: their
dimensions and their locations.
Blocking by dimensions
Most online advertisers use one or more standard sizes for their ads.
Norton Personal Firewall now includes the ability to block images, Flash
animations, and other HTML elements that have the same dimensions as
these common ad sizes.
Page 96

Blocking Internet advertisements
96
Enable or disable Ad Blocking
Blocking by location
Every file on the Internet has a unique address or URL. When you view a
Web page, your computer connects to a URL and displays the file that is
stored there. If the page points to graphics, audio files, and other
multimedia content, your browser displays the files as part of the page.
When you go to a Web page that includes a banner ad, the instructions used
to display the page might include the following:
<p>Greetings from the Ajax company<img src="http://www.ajax.com/
nifty_images/image7.gif">
Your browser displays the text Greetings from the Ajax company on the
screen. Then it connects to www.ajax.com and requests a file called
/nifty_images/image7.gif. (The suffix .gif indicates that this is a Graphics
Interchange Format file, a common image file format.) The computer at
www.ajax.com sends the file to the browser, which displays the image.
When Ad Blocking is enabled and you connect to a Web site, Norton
Personal Firewall scans Web pages and compares their contents to two
lists:
See “Keeping
current with
LiveUpdate” on
page 53.
1 A default list of ads that Norton Personal Firewall blocks
1 A list that you create as you block specific ads. You can add to and
automatically. Use LiveUpdate to keep the list of blocked ads current.
change this list.
If the page includes files from a blocked domain, Norton Personal Firewall
removes the link and downloads the rest of the page.
Enable or disable Ad Blocking
Norton Personal Firewall searches for the addresses of the ads that are
being blocked as the Web page is downloaded by your browser. If it finds an
address that matches the list of ads to block, it removes the ad so that it
does not appear in your browser. It leaves the rest of the Web page intact so
that you can view the page without the advertisements.
To enable or disable Ad Blocking
1 Open Norton Personal Firewall.
Page 97

2 Double-click Ad Blocking.
Blocking Internet advertisements
Enable or disable Popup Window Blocking
97
3 Check or uncheck Turn on Ad Blocking.
4 Click OK.
Enable or disable Popup Window Blocking
Pop-up and pop-under ads are secondary windows that Web sites open
when you visit or leave the sites. Pop-ups appear on top of the current
window, while pop-unders appear behind the current window.
When Popup Window Blocking is active, Norton Personal Firewall
automatically blocks the programming code Web sites use to open
secondary windows without your knowledge. Sites that open secondary
windows when you click a link or perform other actions are not affected.
To enable or disable Popup Window Blocking
1 Open Norton Personal Firewall.
2 Double-click Ad Blocking.
3 Check or uncheck Turn on Popup Window Blocking.
4 Click OK.
Page 98

Blocking Internet advertisements
98
Enable or disable Flash blocking
Enable or disable Flash blocking
When Ad Blocking is active, Norton Personal Firewall automatically blocks
all Flash animations that have the same dimensions as common ads.
Norton Personal Firewall can also block all Flash content. This is useful if
you have a slow connection or are not interested in viewing Flash
animations.
You can choose to have Norton Personal Firewall block all Flash animations
or only block them on certain Web sites.
To enable or disable Flash blocking
1 Open Norton Personal Firewall.
2 In the Security Center, click Options > Internet Security.
3 On the Web Content tab, click the Global Settings tab.
4 In the list of Web sites, do one of the following:
2 To change Flash settings for all sites, click (Defaults).
2 To change Flash settings for a site in the list, click the site’s
name.
2 To change Flash settings for a site not in the list, click Add Site,
then in the New Site/Domain dialog box, type the site’s address.
5 In the Flash animation section, select one of the following:
2 Block
2 Permit
6 Click OK.
w Some Web sites use Flash to create navigation toolbars. Blocking Flash may
make these sites unusable.
Use the Ad Trashcan
As you use the Internet, you may find ads that are not included on the
default Norton Personal Firewall Ad Blocking list. You can use the Ad
Trashcan to add these to your personal list of blocked ads.
To use the Ad Trashcan
1 Open your Web browser and view the page containing the
advertisement that you want to block.
2 Open Norton Personal Firewall.
Page 99

Blocking Internet advertisements
Use text strings to identify ads to block or permit
3 In the Security Center, double-click Ad Blocking.
4 In the Ad Blocking window, ensure that Enable Ad Blocking is
checked.
5 Click Open the Ad Trashcan.
The Ad Trashcan window appears.
6 With the windows arranged so that you can see both the
advertisement and the Ad Trashcan window, do one of the following:
2 If you are using Microsoft Internet Explorer, drag the unwanted
ad from the Web site to the Ad Blocking dialog box.
2 If you are using Netscape, right-click the advertisement, then
click Copy Image Location. In the Ad Trashcan, click Paste.
The address for the advertisement appears in the Ad Details line
of the Ad Trashcan dialog box.
7 Select one of the following:
2 Add: Block this address.
2 Modify: Change the entry before adding it to the Ad Blocking list.
For example, if the advertisement address is
http://www.advertise.org/annoying/ads/numberone.gif, you
could change it to http://www.advertise.org/annoying/ads/ to
block everything in the ads directory.
8 Click OK.
99
Use text strings to identify ads to block or permit
You can control whether Norton Personal Firewall displays specific ads by
creating a list of text strings that identify individual ad banners. Ad
Blocking strings are sections of HTML addresses. If any part of a file’s
address matches the text string, Norton Personal Firewall automatically
blocks the file.
Norton Personal Firewall provides a predefined (Defaults) Ad Blocking list
that is used to determine which images should be blocked when displaying
Web pages.
When Ad Blocking is enabled, all Web pages are scanned for the HTML
strings specified in the (Defaults) list. Norton Personal Firewall looks for
the blocked strings within HTML tags that are used to present advertising.
The HTML structures that contain matching strings are removed from the
page by Norton Personal Firewall before the page appears in the Web
browser.
Page 100

Blocking Internet advertisements
100
Use text strings to identify ads to block or permit
Make sure that what you place in the (Defaults) block list isn't too general.
For example, www by itself is not a good string to block because almost
every URL includes www. A string like www.slowads is more effective
because it only blocks graphics from the slowads domains without affecting
other sites.
How to identify Ad Blocking strings
The way that you define Ad Blocking strings affects how restrictive or
unrestrictive Norton Personal Firewall is when filtering data.
For example, if you add the string ajax.com to the (Defaults) block list, you
block everything in the ajax.com domain. If you are more specific and add
the string nifty_images/image7.gif to the site-specific block list maintained
for www.ajax.com, you block only that particular image.
Blocking all images on a particular site may make that site unusable. A
good compromise is to block only the directories that contain ads. For
example, if www.ajax.com stores its ads in /nifty_images/ and its
navigational images in /useful_images/, you could block www.ajax.com/
nifty_images/ without seriously impeding your ability to use the site.
You can also create permit strings that allow Web sites to display images
that match the string. This allows you to override the blocking effect of any
string in the (Defaults) block list for individual sites. Permit rules take
precedence over Block rules on any site.
Add an Ad Blocking string
You can add strings to the Ad Blocking list for all sites or for individual
sites.
To add an Ad Blocking string
1 Open Norton Personal Firewall.
2 At the top of the Security Center window, click Options > Internet
Security.
3 On the Web Content tab, on the Ad Blocking tab, do one of the
following:
2 To block a string on all Web sites, click (Defaults).
2 To block a string on a Web site in the list, select the site’s name.
2 To block a string on a Web site not in the list, click Add Site, then
in the New Site/Domain dialog box, type the site’s address.
 Loading...
Loading...