Page 1

HP 1920 Gigabit Ethernet Switch Series
User Guide
Part number: 5998-5627
Software version: Release 1102
Document version: 5W100-20140620
Page 2

Legal and notice information
© Copyright 2014 Hewlett-Packard Development Company, L.P.
No part of this documentation may be reproduced or transmitted in any form or by any means without
prior written consent of Hewlett-Packard Development Company, L.P.
The information contained herein is subject to change without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS
MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not be liable for errors contained
herein or for incidental or consequential damages in connection with the furnishing, performance, or
use of this material.
The only warranties for HP products and services are set forth in the express warranty statements
accompanying such products and services. Nothing herein should be construed as constituting an
additional warranty. HP shall not be liable for technical or editorial errors or omissions contained
herein.
Page 3

Contents
Overview ······································································································································································ 1
Configuring the switch in the Web interface ············································································································· 2
Restrictions and guidelines ··············································································································································· 2
Operating system requirements ······························································································································ 2
Web browser requirements ····································································································································· 2
Others ········································································································································································ 5
Overview ············································································································································································ 6
Logging in to the Web interface······································································································································ 6
Logging out of the Web interface ··································································································································· 7
Web interface ··································································································································································· 7
Web user level ·································································································································································· 8
Web-based NM functions ················································································································································ 8
Common items on the Web pages ······························································································································ 16
Configuring the switch at the CLI ······························································································································ 20
Getting started with the CLI ··········································································································································· 20
Setting up the configuration environment ··········································································································· 20
Setting terminal parameters ·································································································································· 21
Logging in to the CLI ············································································································································· 24
CLI commands ································································································································································ 24
initialize ·································································································································································· 25
ipsetup ···································································································································································· 25
ipsetup ipv6 ··························································································································································· 26
password ································································································································································ 26
ping ········································································································································································· 27
ping ipv6 ································································································································································ 27
quit ·········································································································································································· 28
reboot ····································································································································································· 29
summary ································································································································································· 29
upgrade ·································································································································································· 30
upgrade ipv6 ························································································································································· 31
Configuration example for upgrading the system software image at the CLI ························································· 32
Configuration wizard ················································································································································· 34
Basic service setup ················································································································································ 34
Entering the configuration wizard homepage ···································································································· 34
Configuring system parameters ··························································································································· 34
Configuring management IP address ·················································································································· 36
Finishing configuration wizard ···························································································································· 37
Configuring stack ······················································································································································· 39
Overview ········································································································································································· 39
Configuration task list ···················································································································································· 39
Configuring global parameters of a stack ·················································································································· 40
Configuring stack ports ················································································································································· 41
Displaying topology summary of a stack ···················································································································· 42
Displaying device summary of a stack ························································································································ 42
Logging in to a member device from the master ········································································································ 42
Stack configuration example ········································································································································ 43
Configuration guidelines ··············································································································································· 46
i
Page 4

Displaying system and device information ··············································································································· 47
Displaying system information ······································································································································ 47
Displaying basic system information ··················································································································· 47
Displaying the system resource state ··················································································································· 48
Displaying recent system logs ······························································································································ 48
Setting the refresh period ····································································································································· 48
Displaying device information ······································································································································ 48
Configuring basic device settings ····························································································································· 50
Configuring system name ·············································································································································· 50
Configuring idle timeout period ··································································································································· 50
Maintaining devices ··················································································································································· 52
Software upgrade ·························································································································································· 52
Device reboot ································································································································································· 53
Electronic label ······························································································································································· 54
Diagnostic information ·················································································································································· 54
Configuring system time ············································································································································ 56
Overview ········································································································································································· 56
Displaying the current system time ······························································································································· 56
Manually configuring the system time·························································································································· 56
Configuring system time by using NTP ························································································································ 57
System time configuration example ····························································································································· 58
Network requirements ··········································································································································· 58
Configuring the system time ································································································································· 59
Verifying the configuration ··································································································································· 59
Configuration guidelines ··············································································································································· 59
Configuring syslog ····················································································································································· 61
Displaying syslogs ·························································································································································· 61
Setting the log host························································································································································· 62
Setting buffer capacity and refresh interval ················································································································ 63
Managing the configuration······································································································································ 64
Backing up the configuration ········································································································································ 64
Restoring the configuration ··········································································································································· 64
Saving the configuration ··············································································································································· 65
Resetting the configuration ············································································································································ 66
Managing files ··························································································································································· 67
Displaying files ······························································································································································· 67
Downloading a file ························································································································································ 67
Uploading a file ····························································································································································· 68
Removing a file ······························································································································································· 68
Specifying the main boot file ········································································································································ 68
Managing ports ·························································································································································· 69
Setting operation parameters for a port ······················································································································ 69
Displaying port operation parameters ························································································································· 73
Displaying a specified operation parameter for all ports ················································································· 73
Displaying all the operation parameters for a port ··························································································· 74
Port management configuration example ···················································································································· 75
Network requirements ··········································································································································· 75
Configuring the switch ·········································································································································· 75
Configuring port mirroring ········································································································································ 79
Terminology ···································································································································································· 79
ii
Page 5

Mirroring source ···················································································································································· 79
Mirroring destination ············································································································································ 79
Mirroring direction ················································································································································ 79
Mirroring group ····················································································································································· 79
Local port mirroring ······················································································································································· 79
Configuration restrictions and guidelines ···················································································································· 80
Recommended configuration procedures ···················································································································· 80
Configuring a mirroring group ····································································································································· 80
Configuring ports for the mirroring group ··················································································································· 81
Local port mirroring configuration example ················································································································ 83
Network requirements ··········································································································································· 83
Configuration procedure ······································································································································ 83
Managing users ························································································································································· 86
Adding a local user ······················································································································································· 86
Setting the super password ··········································································································································· 87
Switching to the management level ····························································································································· 88
Configuring a loopback test ······································································································································ 89
Configuration guidelines ··············································································································································· 89
Configuration procedure ··············································································································································· 89
Configuring VCT ························································································································································ 91
Overview ········································································································································································· 91
Testing cable status ························································································································································ 91
Configuring the flow interval ····································································································································· 92
Viewing port traffic statistics ········································································································································· 92
Configuring RMON ··················································································································································· 93
Overview ········································································································································································· 93
Working mechanism ············································································································································· 93
RMON groups ······················································································································································· 93
RMON configuration task list ······································································································································· 95
Configuring a statistics entry ································································································································ 97
Configuring a history entry ··································································································································· 98
Configuring an event entry ··································································································································· 99
Configuring an alarm entry ································································································································ 100
Displaying RMON statistics ································································································································ 101
Displaying RMON history sampling information ····························································································· 103
Displaying RMON event logs ···························································································································· 104
RMON configuration example ··································································································································· 105
Configuring energy saving ····································································································································· 109
Configuring energy saving on a port ························································································································ 109
Configuring SNMP ·················································································································································· 111
Overview ······································································································································································· 111
SNMP mechanism ··············································································································································· 111
SNMP protocol versions ····································································································································· 112
Recommended configuration procedure···················································································································· 112
Enabling SNMP agent ········································································································································ 113
Configuring an SNMP view ········································································································································ 115
Creating an SNMP view····································································································································· 115
Adding rules to an SNMP view ························································································································· 116
Configuring an SNMP community ····························································································································· 117
Configuring an SNMP group ······································································································································ 118
iii
Page 6

Configuring an SNMP user ········································································································································· 120
Configuring SNMP trap function ································································································································ 121
Displaying SNMP packet statistics ····························································································································· 123
SNMPv1/v2c configuration example ························································································································ 124
SNMPv3 configuration example ································································································································ 127
Displaying interface statistics ································································································································· 132
Configuring VLANs ················································································································································· 133
Overview ······································································································································································· 133
VLAN fundamentals············································································································································· 133
VLAN types ·························································································································································· 134
Port-based VLAN ················································································································································· 135
Recommended VLAN configuration procedures ······································································································· 137
Recommended configuration procedure for assigning an access port to a VLAN ······································ 137
Recommended configuration procedure for assigning a trunk port to a VLAN ··········································· 137
Recommended configuration procedure for assigning a hybrid port to a VLAN ········································· 138
Creating VLANs ··························································································································································· 139
Configuring the link type of a port ····························································································································· 140
Setting the PVID for a port ··········································································································································· 141
Selecting VLANs ··························································································································································· 142
Modifying a VLAN ······················································································································································· 143
Modifying ports ···························································································································································· 144
VLAN configuration example ······································································································································ 145
Network requirements ········································································································································· 145
Configuring Switch A ·········································································································································· 145
Configuring Switch B ·········································································································································· 149
Configuration guidelines ············································································································································· 149
Configuring VLAN interfaces ································································································································· 150
Overview ······································································································································································· 150
Creating a VLAN interface ·········································································································································· 150
Modifying a VLAN interface ······································································································································· 152
Configuration guidelines ············································································································································· 155
Configuring a voice VLAN ····································································································································· 156
Overview ······································································································································································· 156
OUI addresses ····················································································································································· 156
Voice VLAN assignment modes ························································································································· 156
Security mode and normal mode of voice VLANs ··························································································· 158
Recommended voice VLAN configuration procedure ······························································································ 159
Configuring voice VLAN globally ······························································································································ 160
Configuring voice VLAN on ports ······························································································································ 161
Adding OUI addresses to the OUI list ······················································································································· 162
Voice VLAN configuration examples ························································································································· 163
Configuring voice VLAN on a port in automatic voice VLAN assignment mode ········································· 163
Configuring a voice VLAN on a port in manual voice VLAN assignment mode ········································· 167
Configuration guidelines ············································································································································· 172
Configuring the MAC address table ····················································································································· 173
Overview ······································································································································································· 173
How a MAC address entry is created ·············································································································· 173
Types of MAC address entries ··························································································································· 174
Displaying and configuring MAC address entries ··································································································· 174
Setting the aging time of MAC address entries ········································································································ 175
MAC address table configuration example ·············································································································· 175
Network requirements ········································································································································· 175
iv
Page 7

Creating a static MAC address entry················································································································ 176
Configuring MSTP ··················································································································································· 177
Overview ······································································································································································· 177
Introduction to STP ······················································································································································· 177
STP protocol packets ··········································································································································· 177
Basic concepts in STP ·········································································································································· 178
Calculation process of the STP algorithm ········································································································· 179
Introduction to RSTP ····················································································································································· 184
Introduction to MSTP ···················································································································································· 185
MSTP features ······················································································································································ 185
MSTP basic concepts ·········································································································································· 185
How MSTP works ················································································································································ 189
MSTP implementation on devices ······················································································································ 189
Protocols and standards ····································································································································· 190
Configuration guidelines ············································································································································· 190
Recommended MSTP configuration procedure ········································································································· 190
Configuring an MST region ········································································································································ 191
Configuring MSTP globally ········································································································································· 192
Configuring MSTP on a port ······································································································································· 195
Displaying MSTP information of a port ····················································································································· 197
MSTP configuration example ······································································································································ 199
Network requirements ········································································································································· 199
Configuration procedure ···································································································································· 200
Configuring link aggregation and LACP ··············································································································· 205
Overview ······································································································································································· 205
Basic concepts ····················································································································································· 205
Link aggregation modes ····································································································································· 206
Configuration procedures ··········································································································································· 208
Configuring a static aggregation group ··········································································································· 208
Configuring a dynamic aggregation group ····································································································· 208
Creating a link aggregation group ··················································································································· 208
Displaying aggregate interface information ····································································································· 209
Setting LACP priority ··········································································································································· 211
Displaying LACP-enabled port information ······································································································· 211
Link aggregation and LACP configuration example ································································································· 213
Configuration guidelines ···································································································································· 215
Configuring LLDP ····················································································································································· 217
Overview ······································································································································································· 217
Basic concepts ····················································································································································· 217
LLDP operating modes ········································································································································· 221
Working mechanism ··········································································································································· 221
Protocols and standards ·············································································································································· 222
Recommended LLDP configuration procedure ··········································································································· 222
Enabling LLDP on ports ················································································································································ 223
Setting LLDP parameters on ports ······························································································································· 224
Setting LLDP parameters for a single port ········································································································· 224
Setting LLDP parameters for ports in batch ······································································································· 227
Configuring LLDP globally ··········································································································································· 227
Displaying LLDP information for a port ······················································································································ 229
Displaying global LLDP information ··························································································································· 234
Displaying LLDP information received from LLDP neighbors ···················································································· 236
LLDP configuration example ········································································································································ 236
Network requirements ········································································································································· 236
v
Page 8

Configuring Switch A ·········································································································································· 236
Configuring Switch B ·········································································································································· 239
Verifying the configuration ································································································································· 239
LLDP configuration guidelines ····································································································································· 241
Configuring ARP ······················································································································································ 242
Overview ······································································································································································· 242
ARP message format ··········································································································································· 242
ARP operating mechanism ································································································································· 242
ARP table ······························································································································································ 243
Gratuitous ARP ····················································································································································· 244
Configuring ARP entries ·············································································································································· 244
Displaying ARP entries ········································································································································ 244
Creating a static ARP entry ································································································································ 245
Removing ARP entries ·················································································································································· 245
Configuring gratuitous ARP ········································································································································· 246
Static ARP configuration example ····················································································································· 246
Configuring ARP attack protection ························································································································· 250
Overview ······································································································································································· 250
User validity check ·············································································································································· 250
ARP packet validity check ·································································································································· 250
Configuring ARP detection ·········································································································································· 250
Configuring IGMP snooping ·································································································································· 252
Overview ······································································································································································· 252
Basic IGMP snooping concepts ························································································································· 252
How IGMP snooping works ······························································································································· 254
Protocols and standards ····································································································································· 255
Recommended configuration procedure···················································································································· 255
Enabling IGMP snooping globally ····························································································································· 256
Configuring IGMP snooping in a VLAN ···················································································································· 257
Configuring IGMP snooping port functions ··············································································································· 258
Displaying IGMP snooping multicast forwarding entries ························································································· 259
IGMP snooping configuration example ····················································································································· 260
Network requirements ········································································································································· 260
Configuration procedure ···································································································································· 261
Verifying the configuration ································································································································· 264
Configuring MLD snooping ···································································································································· 266
Overview ······································································································································································· 266
Basic MLD snooping concepts ··························································································································· 266
How MLD snooping works ································································································································· 268
Protocols and standards ····································································································································· 269
Recommended configuration procedure···················································································································· 269
Enabling MLD snooping globally ······················································································································ 270
Configuring MLD snooping in a VLAN ············································································································· 270
Configuring MLD snooping port functions ········································································································ 272
Displaying MLD snooping multicast forwarding entries ·················································································· 273
MLD snooping configuration example ······················································································································· 274
Network requirements ········································································································································· 274
Configuration procedure ···································································································································· 274
Verifying the configuration ································································································································· 277
Configuring IPv4 and IPv6 routing ························································································································ 278
Overview ······································································································································································· 278
Routing table ························································································································································ 278
vi
Page 9

Static route ··························································································································································· 278
Default route ························································································································································· 279
Displaying the IPv4 active route table ······················································································································· 279
Creating an IPv4 static route ······································································································································· 280
Displaying the IPv6 active route table ······················································································································· 281
Creating an IPv6 static route ······································································································································· 281
IPv4 static route configuration example ····················································································································· 283
Network requirements ········································································································································· 283
Configuration considerations ····························································································································· 283
Configuration procedure ···································································································································· 283
Verifying the configuration ································································································································· 286
IPv6 static route configuration example ····················································································································· 287
Network requirements ········································································································································· 287
Configuration considerations ····························································································································· 287
Configuration procedure ···································································································································· 287
Verifying the configuration ································································································································· 290
Configuration guidelines ············································································································································· 291
DHCP overview ······················································································································································· 292
DHCP address allocation ············································································································································ 292
Allocation mechanisms ······································································································································· 292
IP address allocation process ····························································································································· 293
IP address lease extension·································································································································· 293
DHCP message format ················································································································································· 294
DHCP options ······························································································································································· 295
Common DHCP options ······································································································································ 295
Option 82 ···························································································································································· 295
Protocols and standards ·············································································································································· 296
Configuring DHCP relay agent ······························································································································ 297
Overview ······································································································································································· 297
Recommended configuration procedure···················································································································· 298
Enabling DHCP and configuring advanced parameters for the DHCP relay agent ············································· 299
Creating a DHCP server group ·································································································································· 300
Enabling the DHCP relay agent on an interface ······································································································ 301
Configuring and displaying clients' IP-to-MAC bindings ························································································· 302
DHCP relay agent configuration example ················································································································· 303
Configuring DHCP snooping ·································································································································· 306
Overview ······································································································································································· 306
Application of trusted ports ································································································································ 306
DHCP snooping support for Option 82 ············································································································ 308
Recommended configuration procedure···················································································································· 308
Enabling DHCP snooping ··········································································································································· 309
Configuring DHCP snooping functions on an interface ··························································································· 309
Displaying clients' IP-to-MAC bindings ······················································································································ 310
DHCP snooping configuration example ···················································································································· 311
Managing services ·················································································································································· 314
Overview ······································································································································································· 314
Managing services ······················································································································································· 315
Using diagnostic tools ············································································································································· 317
Ping ················································································································································································ 317
Traceroute ····································································································································································· 317
Ping operation ······························································································································································ 318
Traceroute operation ··········································································································································· 319
vii
Page 10

Configuring 802.1X ··············································································································································· 321
802.1X overview ························································································································································· 321
802.1X architecture ············································································································································ 321
Access control methods ······································································································································ 321
Controlled/uncontrolled port and port authorization status ··········································································· 322
Packet formats ······················································································································································ 322
EAP over RADIUS ················································································································································ 323
Initiating 802.1X authentication ························································································································ 324
802.1X authentication procedures ···················································································································· 325
802.1X timers ······················································································································································ 328
Using 802.1X authentication with other features ···························································································· 329
Configuration prerequisites ········································································································································· 331
Recommended configuration procedure···················································································································· 332
Configuring 802.1X globally ····································································································································· 332
Configuring 802.1X on a port ··································································································································· 333
Configuring an 802.1X guest VLAN ················································································································· 335
Configuring an Auth-Fail VLAN ························································································································· 336
802.1X configuration examples ································································································································· 336
MAC-based 802.1X configuration example ···································································································· 336
802.X with ACL assignment configuration example ······················································································· 343
Configuring AAA ···················································································································································· 352
Overview ······································································································································································· 352
AAA application ·················································································································································· 352
Domain-based user management ······················································································································ 353
Configuration prerequisites ········································································································································· 353
Recommended configuration procedure ··········································································································· 353
Configuring an ISP domain ································································································································ 354
Configuring authentication methods for the ISP domain ················································································· 355
Configuring authorization methods for the ISP domain ·················································································· 356
Configuring accounting methods for the ISP domain ······················································································ 357
AAA configuration example ······································································································································· 359
Configuring RADIUS ··············································································································································· 363
Overview ······································································································································································· 363
Client/server model ············································································································································ 363
Security and authentication mechanisms ·········································································································· 364
Basic RADIUS message exchange process ······································································································ 364
RADIUS packet format ········································································································································ 365
Extended RADIUS attributes ······························································································································· 367
Protocols and standards ····································································································································· 368
Configuring a RADIUS scheme ··································································································································· 368
Configuring common parameters ······················································································································ 369
Adding RADIUS servers ······································································································································ 373
RADIUS configuration example ·································································································································· 374
Configuration guidelines ············································································································································· 378
Configuring users ···················································································································································· 380
Configuring a local user ·············································································································································· 380
Configuring a user group ············································································································································ 382
Managing certificates ············································································································································· 384
Overview ······································································································································································· 384
PKI terms ······························································································································································· 384
PKI architecture ···················································································································································· 384
How PKI works ····················································································································································· 385
viii
Page 11

PKI applications ··················································································································································· 386
Recommended configuration procedures ·················································································································· 386
Recommended configuration procedure for manual request ·········································································· 386
Recommended configuration procedure for automatic request ······································································ 388
Creating a PKI entity ···················································································································································· 388
Creating a PKI domain ················································································································································ 390
Generating an RSA key pair······································································································································· 393
Destroying the RSA key pair ······································································································································· 394
Retrieving and displaying a certificate ······················································································································ 394
Requesting a local certificate ······································································································································ 396
Retrieving and displaying a CRL ································································································································ 398
PKI configuration example ·········································································································································· 399
Configuration guidelines ············································································································································· 403
Configuring MAC authentication ··························································································································· 404
Overview ······································································································································································· 404
User account policies ·········································································································································· 404
Authentication methods······································································································································· 404
MAC authentication timers ································································································································· 405
Using MAC authentication with other features ········································································································· 405
VLAN assignment ················································································································································ 405
ACL assignment ··················································································································································· 405
Auth-Fail VLAN ···················································································································································· 405
Configuration prerequisites ········································································································································· 406
Recommended configuration procedure···················································································································· 406
Configuring MAC authentication globally ················································································································ 406
Configuring MAC authentication on a port ····································································································· 408
MAC authentication configuration examples ············································································································ 408
Local MAC authentication configuration example··························································································· 408
ACL assignment configuration example············································································································ 411
Configuring port security ········································································································································ 421
Overview ······································································································································································· 421
Port security features ··········································································································································· 421
Port security modes ············································································································································· 421
Configuration guidelines ············································································································································· 423
Recommended configuration procedure···················································································································· 423
Configuring global settings for port security ············································································································· 424
Configuring basic port security control ······················································································································ 425
Configuring secure MAC addresses ·························································································································· 427
Configuring advanced port security control ·············································································································· 428
Configuring permitted OUIs ········································································································································ 429
Port security configuration examples ························································································································· 430
Basic port security mode configuration example ····························································································· 430
Advanced port security mode configuration example ···················································································· 433
Configuring port isolation ······································································································································· 440
Configuring the isolation group ·································································································································· 440
Port isolation configuration example·························································································································· 441
Configuring authorized IP ······································································································································ 443
Configuration procedure ············································································································································· 443
Authorized IP configuration example ························································································································· 444
Network requirements ········································································································································· 444
Configuration procedure ···································································································································· 444
ix
Page 12

Configuring loopback detection ···························································································································· 447
Recommended configuration procedure···················································································································· 447
Configuring loopback detection globally ·················································································································· 447
Configuring loopback detection on a port ················································································································ 448
Configuring ACLs ···················································································································································· 450
Overview ······································································································································································· 450
ACL categories ···················································································································································· 450
Match order ························································································································································· 450
Implementing time-based ACL rules ··················································································································· 452
IPv4 fragments filtering with ACLs ····················································································································· 452
Configuration guidelines ············································································································································· 452
Recommend ACL configuration procedures ·············································································································· 452
Recommended IPv4 ACL configuration procedure ·························································································· 452
Recommended IPv6 ACL configuration procedure ·························································································· 453
Configuring a time range ··································································································································· 453
Adding an IPv4 ACL ··········································································································································· 454
Configuring a rule for a basic IPv4 ACL ··········································································································· 455
Configuring a rule for an advanced IPv4 ACL ································································································· 456
Configuring a rule for an Ethernet frame header ACL ···················································································· 459
Adding an IPv6 ACL ··········································································································································· 461
Configuring a rule for a basic IPv6 ACL ··········································································································· 462
Configuring a rule for an advanced IPv6 ACL ································································································· 463
Configuring QoS ····················································································································································· 466
Overview ······································································································································································· 466
Networks without QoS guarantee ····················································································································· 466
QoS requirements of new applications ············································································································· 466
Congestion: causes, impacts, and countermeasures ······················································································· 467
End-to-end QoS ···················································································································································· 468
Traffic classification ············································································································································· 468
Packet precedences ············································································································································· 469
Queue scheduling ··············································································································································· 471
Rate limit ······························································································································································· 473
Priority mapping ·················································································································································· 474
Introduction to priority mapping tables ············································································································· 475
Configuration guidelines ············································································································································· 476
Recommended QoS configuration procedures ········································································································· 476
Adding a class ····························································································································································· 478
Configuring classification rules ··································································································································· 479
Adding a traffic behavior ············································································································································ 480
Configuring traffic mirroring and traffic redirecting for a traffic behavior ···························································· 481
Configuring other actions for a traffic behavior ······································································································· 481
Adding a policy ··························································································································································· 483
Configuring classifier-behavior associations for the policy ····················································································· 484
Applying a policy to a port ········································································································································· 484
Configuring queue scheduling on a port ··················································································································· 485
Configuring rate limit on a port ·································································································································· 486
Configuring priority mapping tables ·························································································································· 487
Configuring priority trust mode on a port ················································································································· 488
ACL and QoS configuration example ··················································································································· 489
Network requirements ················································································································································· 489
Configuring Switch ······················································································································································ 489
x
Page 13

Configuring PoE ······················································································································································ 497
Overview ······································································································································································· 497
Configuring PoE ··························································································································································· 498
Configuring PoE ports ········································································································································· 498
Configuring non-standard PD detection ············································································································ 499
Displaying information about PSE and PoE ports ···························································································· 500
PoE configuration example ········································································································································· 501
Support and other resources ·································································································································· 503
Contacting HP ······························································································································································ 503
Subscription service ············································································································································ 503
Related information ······················································································································································ 503
Documents ···························································································································································· 503
Websites ······························································································································································· 503
Conventions ·································································································································································· 504
Index ········································································································································································ 506
xi
Page 14

Overview
The HP 1920 Switch Series can be configured through the command line interface (CLI), Web interface,
and SNMP/MIB. These configuration methods are suitable for different application scenarios.
• The Web interface supports all 1920 Switch Series configurations.
• The CLI provides configuration commands to facilitate your operation. To perform other
configurations not supported by the CLI, use the Web interface.
1
Page 15

Configuring the switch in the Web interface
Restrictions and guidelines
To ensure a successful login, verify that your operating system and Web browser meet the requirements,
and follow the guidelines in this section.
Operating system requirements
• The device supports the following operating systems:
{ Windows XP
{ Windows 2000
{ Windows Server 2003 Enterprise Edition
{ Windows Server 2003 Standard Edition
{ Windows Vista
{ Windows 7
{ Linux
{ MAC OS
• If you are using a Windows operating system, turn off the Windows firewall. The Windows firewall
limits the number of TCP connections. When the limit is reached, you cannot log in to the Web
interface.
Web browser requirements
• HP recommends that you use the following Web browsers:
{ Internet Explorer 6 SP2 or higher
{ Mozilla Firefox 3 or higher
{ Google Chrome 2.0.174.0 or higher
• If you are using a Microsoft Internet Explorer browser, you must enable the security settings (see
"Enabling securing settings in a Mic
controls and plug-ins, Script ActiveX controls marked safe for scripting, and Active scripting.
• If you are using a Mozilla Firefox browser, you must enable JavaScript (see "Enabling JavaScript in a
refox browserEnabling JavaScript in a Firefox browser")
Fi
Enabling securing settings in a Microsoft Internet Explorer browser
1. Launch the Internet Explorer, and select Tools > Internet Options from the main menu.
2. Select the Security tab, and select the content zone where the target Website resides, as shown
in Figure 1.
rosoft Internet Explorer browser"), including Run ActiveX
.
2
Page 16

Figure 1 Internet Explorer settings (1)
3. Click Custom Level.
4. In the Security Settings dialog box, enable Run ActiveX controls and plug-ins, Script ActiveX
controls marked safe for scripting, and Active scripting.
3
Page 17
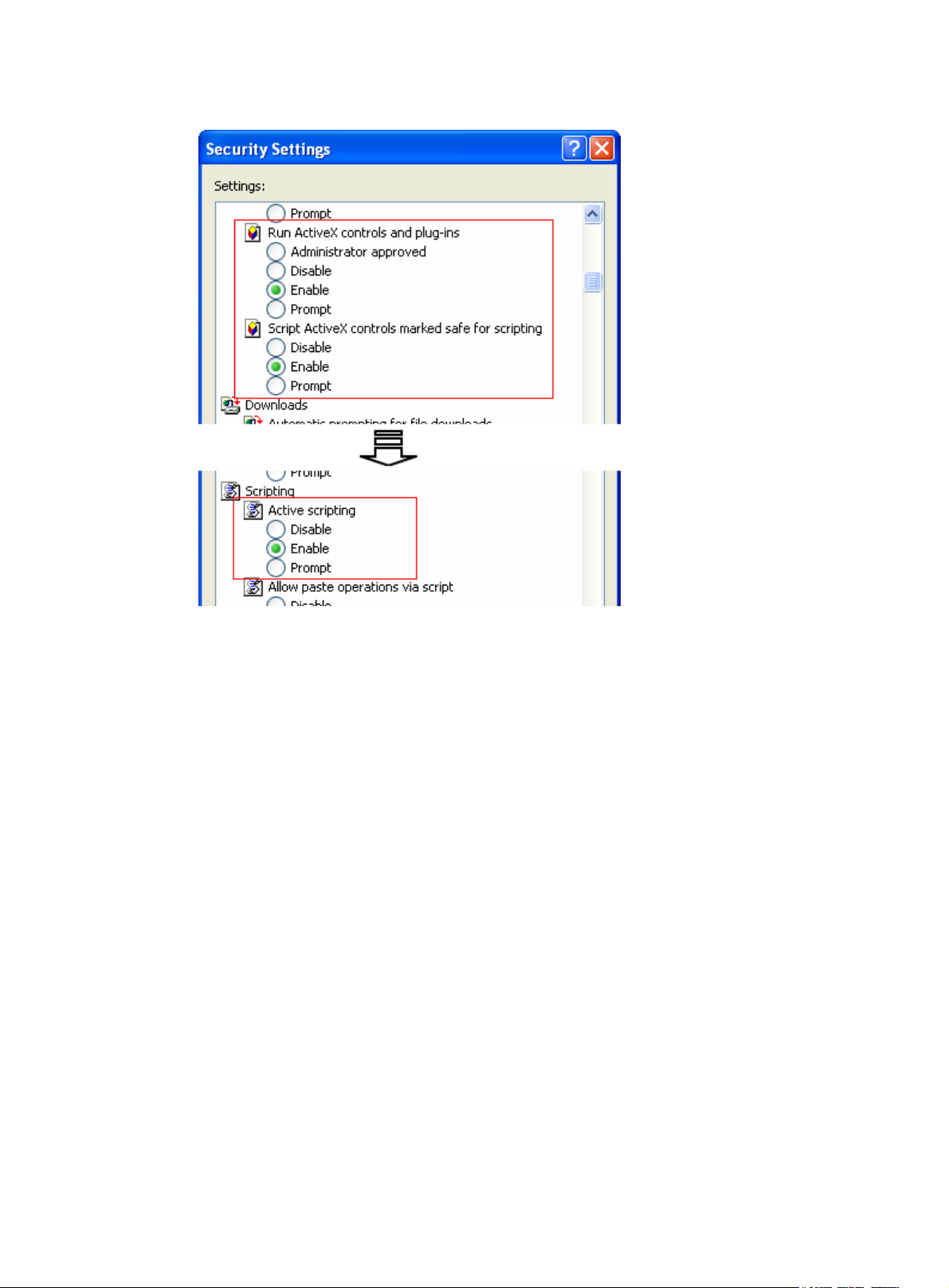
Figure 2 Internet Explorer settings (2)
5. Click OK to save your settings.
Enabling JavaScript in a Firefox browser
1. Launch the Firefox browser, and select Tools > Options.
2. In the Options dialog box, click the Content icon, and select Enable JavaScript.
4
Page 18
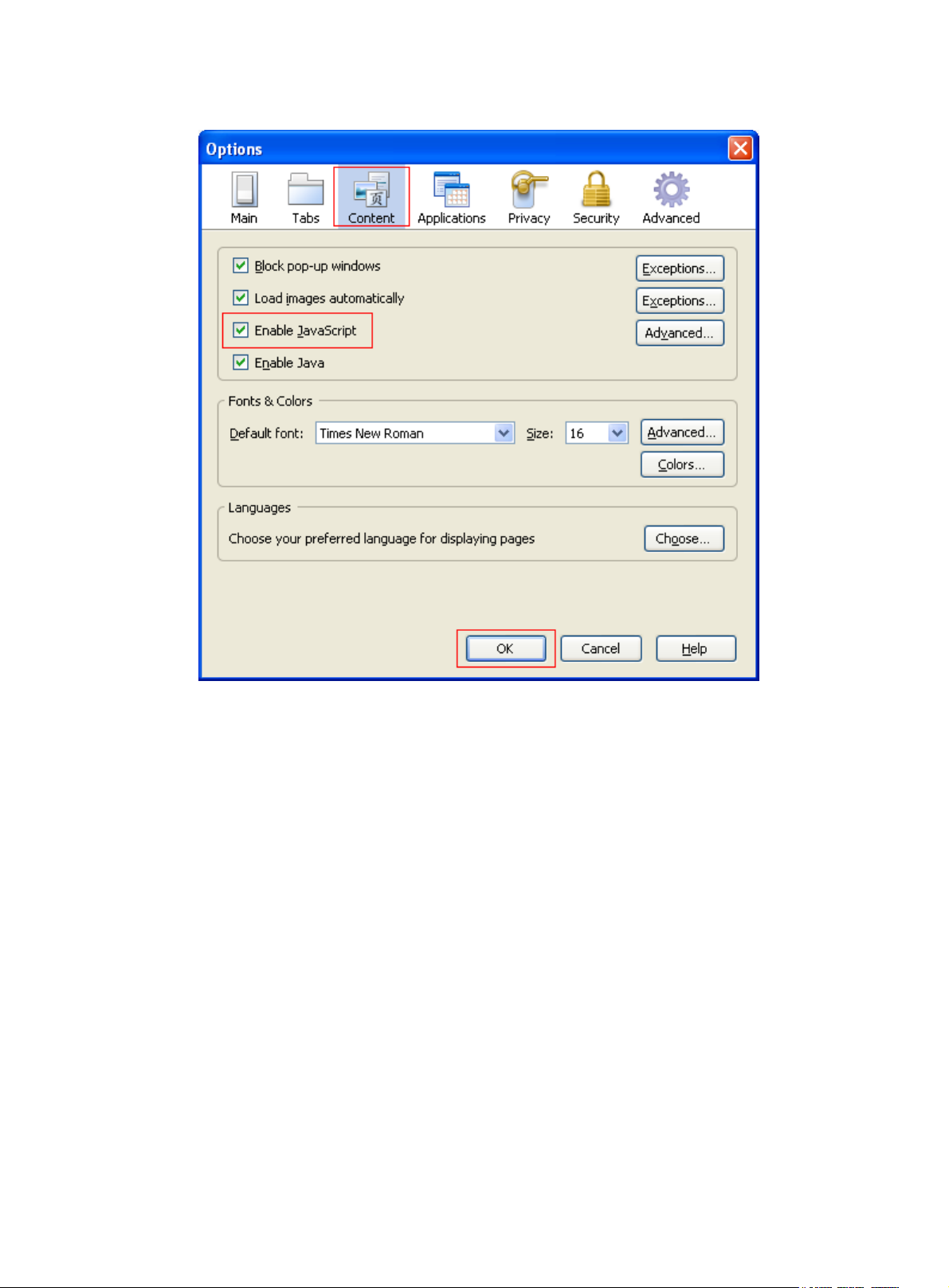
Figure 3 Firefox browser settings
3. Click OK to save your settings.
Others
• The Web interface does not support the Back, Next, and Refresh buttons provided by the browser.
• To ensure correct display of Web page contents after software upgrade or downgrade, clear data
• If you click the verification code displayed on the Web login page, you can get a new verification
• Up to five users can concurrently log in to the device through the Web interface.
• A list can contain a maximum of 20000 entries if displayed in pages.
• The PC where you configure the device is not necessarily a Web-based network management
• After logging in to the Web interface, you can select Device > Users from the navigation tree, create
Using these buttons might result in abnormal display of Web pages.
cached by the browser before you log in.
code.
terminal. A Web-based network management terminal is a PC used to log in to the Web interface
and is required to be reachable to the device.
a new user, and select Wizard or Network > VLAN interface to configure the IP address of the
VLAN interface acting as the management interface. For more information, see the corresponding
configuration guides of these modules.
5
Page 19
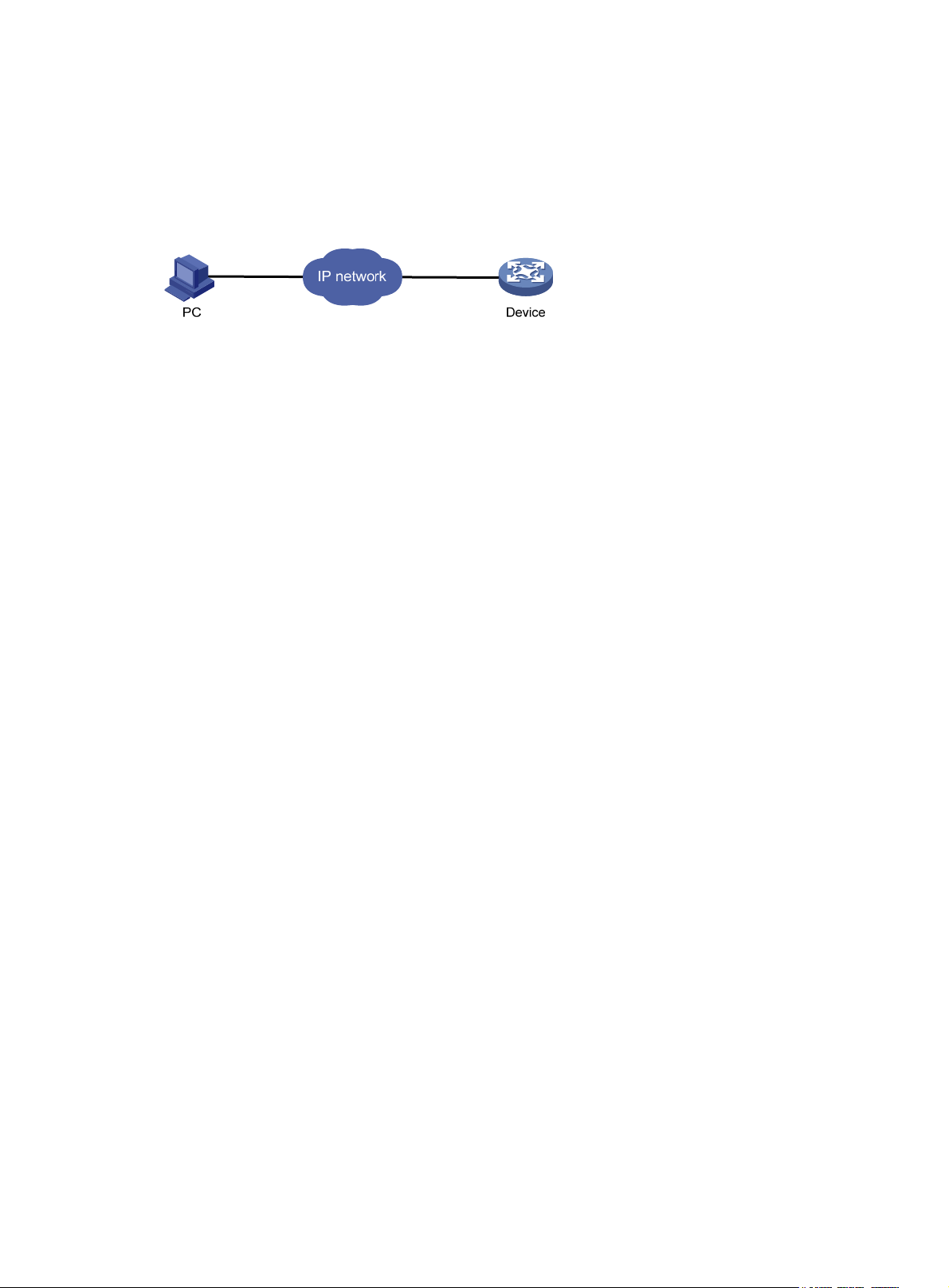
Overview
The device provides web-based configuration interfaces for visual device management and
maintenance.
Figure 4 Web-based network management operating environment
Logging in to the Web interface
You can use the following default settings to log in to the web interface through HTTP:
• Username—admin
• Password—None
• IP address of VLAN-interface 1 on the device—IP address of the device, depending on the status of
the network where the device resides.
{ If the device is not connected to the network, or no DHCP server exists in the subnet where the
device resides, you can get the IP address of the device on the label on the device. IP address
is 169.254.xxx.xxx. If the MAC address is 08004E000102, the IP address would be
169. 2 54 .1.2 .
{ If a DHCP server exists in the subnet where the device resides, the device will dynamically
obtain its IP address through the DHCP server.
You can log in to the device through the console port, and execute the summary command to view the
information about its IP address.
<Sysname> summary
Select menu option: Summary
IP Method: DHCP
IP address: 169.254.1.2
Subnet mask: 255.255.0.0
Default gateway: 0.0.0.0
<Omitted>
Assuming that the IP address of the device is 169.254.1.2, to log in to the Web interface of the device
from a PC:
1. Connect the Ethernet interface of the device to a PC by using a crossover Ethernet cable. By default,
all interfaces belong to VLAN 1.
2. Configure an IP address for the PC and make sure that the PC and device can reach each other.
For example, assign the PC an IP address (for example, 169.254.1.27) within 169.254.0.0/16
(except for the IP address of the device).
3. Open the browser, and input the login information.
a. Type the IP address http:// 169.254.1.2 in the address bar and press Enter.
The login page of the web interface (see Figure 5) appears.
6
Page 20
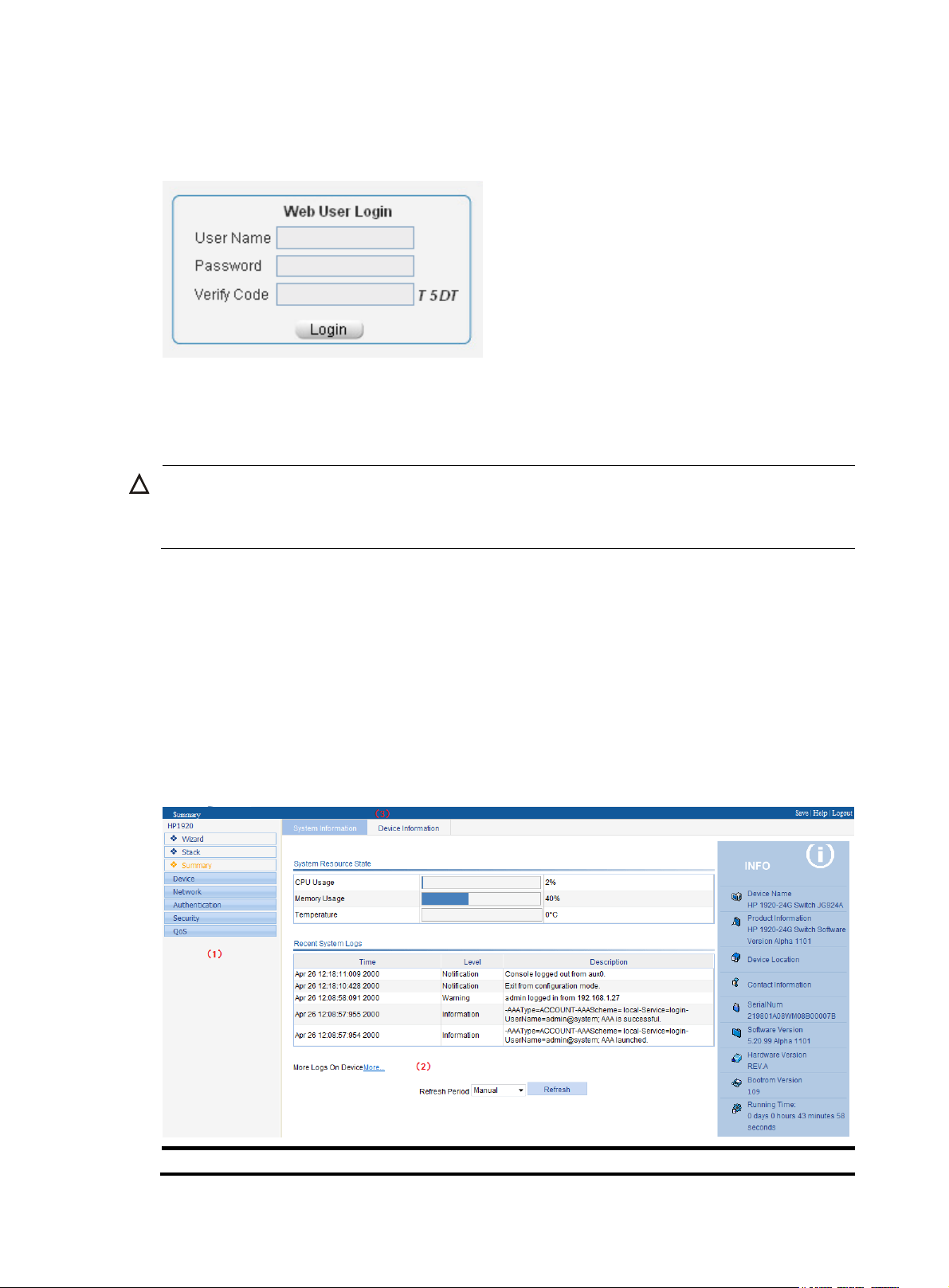
b. Enter the username admin and the verification code, leave the password blank, and click
Login.
Figure 5 Login page of the Web interface
Logging out of the Web interface
CAUTION:
• You cannot log out by directly closing the browser.
• For security purposes, log out of the Web interface after you finish your operations.
1. Save the current configuration.
Because the system does not save the current configuration automatically, HP recommends that
you perform this step to avoid loss of configuration.
2. Click Logout in the upper-right corner of the Web interface.
Web interface
The Web interface includes three parts: navigation tree, title area, and body area, as shown in Figure 6.
Figure 6 Web-based configuration interface
(1) Navigation tree
(2) Body area
7
(3) Title area
Page 21

• Navigation tree—Organizes the Web-based NM functions as a navigation tree, where you can
p
select and configure functions as needed. The result is displayed in the body area.
• Body area—Allows you to configure and display features.
• Title area—On the left, displays the path of the current configuration interface in the navigation
area; on the right, provides the Save button to quickly save the current configuration, the Help button
to display the Web-related help information, and the Logout button to log out of the Web interface.
Web user level
Web user levels, from low to high, are visitor, monitor, configure, and management. A user with a
higher level has all the operating rights of a user with a lower level.
• Visitor—Users of this level can only use the network diagnostic tools ping and Trace Route. They
can neither access the device data nor configure the device.
• Monitor—Users of this level can only access the device data but cannot configure the device.
• Configure—Users of this level can access device data and configure the device, but they cannot
upgrade the host software, add/delete/modify users, or backup/restore configuration files.
• Management—Users of this level can perform any operations to the device.
Web-based NM functions
User level in Table 1 indicates that users of this level or users of a higher level can perform the
corresponding operations.
Table 1 Web-based NM function description
Function menu Descri
Wizard IP Setup Perform quick configuration of the device. Management
Display global settings and port settings of a stack. Configure
Configure global parameters and stack ports. Management
Display the topology summary of a stack. Configure
Display the control panels of stack members. Configure
Display the basic system information, system
resource state, and recent system operation logs.
Display the port information about the device. Monitor
Display and configure the idle timeout period for
logged-in users.
Upload upgrade file from local host, and upgrade
the system software.
Stack
Summary
Devi
ce
Basic
Device
Maintenanc
e
Setup
Topology
Summary
Device
Summary
System
Information
Device
Information
System Name Display and configure the system name. Configure
Web Idle
Timeout
Software
Upgrade
Reboot Reboot the device. Management
tion
User level
Monitor
Configure
Management
8
Page 22

Function menu Description
User level
System Time
Syslog
Configurati
on
Electronic
Label
Diagnostic
Information
System Time Display and configure the system date and time. Configure
Net Time
Loglist
Loghost Display and configure the loghost. Configure
Log Setup
Backup
Restore
Save
Display the electronic label of the device. Monitor
Generate diagnostic information file and view or
save the file to local host.
Display the synchronization status of the system
clock and configure the network time.
Display and refresh system logs. Monitor
Clear system logs. Configure
Display and configure the buffer capacity and
interval for refreshing system logs.
Back up the configuration file to be used at the next
startup from the device to the host of the current
user.
Upload the configuration file to be used at the next
startup from the host of the current user to the
device.
Save the current configuration to the configuration
file to be used at the next startup.
Management
Monitor
Configure
Management
Management
Configure
File
Manageme
nt
Port
Manageme
nt
Port
Mirroring
Users
Initialize Restore the factory default settings. Configure
File
Management
Summary Display port information by features. Monitor
Detail Display feature information by ports. Monitor
Setup
Summary
Add Create a port mirroring group. Configure
Remove Remove a port mirroring group. Configure
Modify Port Configure ports for a mirroring group. Configure
Summary
Super
Password
Create Create an FTP or Telnet user. Management
Manage files on the device, such as displaying the
file list, downloading a file, uploading a file, and
removing a file.
Create, modify, delete, and enable/disable a port,
and clear port statistics.
Display the configuration information about a port
mirroring group.
Display the brief information about FTP and Telnet
users.
Configure a password for a lower-level user to
switch from the current access level to the
management level.
Management
Configure
Monitor
Monitor
Management
Modify Modify FTP or Telnet user information. Management
Remove Remove an FTP or a Telnet user. Management
9
Page 23

Function menu Description
User level
Switch To
Management
Loopback Loopback Perform loopback tests on Ethernet interfaces. Configure
VCT VCT
Flow
Interval
RMON
Energy
Saving
Port Traffic
Statistics
Statistics
History
Alarm Display, create, modify, and clear alarm entries. Configure
Event Display, create, modify, and clear event entries. Configure
Log Display log information about RMON events. Configure
Energy Saving
Setup
Switch the current user level to the management
level.
Check the status of the cables connected to Ethernet
ports.
Display the average rate at which the interface
receives and sends packets within a specified time
interval.
Display, create, modify, and clear RMON
statistics.
Display, create, modify, and clear RMON history
sampling information.
Display and configure the energy saving settings of
an interface.
Display and refresh SNMP configuration and
statistics information.
Configure SNMP. Configure
Visitor
Configure
Monitor
Configure
Configure
Configure
Monitor
SNMP
Interface
Statistics
Community
Group
User
Trap
View
Interface
Statistics
Display SNMP community information. Monitor
Create, modify, and delete an SNMP community. Configure
Display SNMP group information. Monitor
Create, modify, and delete an SNMP group. Configure
Display SNMP user information. Monitor
Create, modify, and delete an SNMP user. Configure
Display the status of the SNMP trap function and
information about target hosts.
Enable or disable the SNMP trap function; create,
modify, and delete a target host.
Display SNMP view information. Monitor
Create, modify, and delete an SNMP view. Configure
Display and clear the statistics information about
an interface.
Monitor
Configure
Configure
10
Page 24

Function menu Description
Select VLAN Select a VLAN range. Monitor
Create Create VLANs. Configure
Port Detail Display the VLAN-related details of a port. Monitor
User level
Net
work
VLAN
VLAN
Interface
Voice VLAN
Detail
Modify VLAN
Modify Port Change the VLAN to which a port belongs. Configure
Remove Remove VLANs. Configure
Summary
Create
Modify
Remove Remove VLAN interfaces. Configure
Summary
Setup Configure the global voice VLAN. Configure
Port Setup Configure a voice VLAN on a port. Configure
OUI Summary
Display the member port information about a
VLAN.
Modify the description and member ports of a
VLAN.
Display information about VLAN interfaces by
address type.
Create VLAN interfaces and configure IP addresses
for them.
Modify the IP addresses and status of VLAN
interfaces.
Display voice VLAN information globally or on a
port.
Display the addresses of the OUIs that can be
identified by voice VLAN.
Monitor
Configure
Monitor
Configure
Configure
Monitor
Monitor
MAC
MSTP
Link
Aggregatio
n
OUI Add
OUI Remove
MAC
Setup Display and configure MAC address aging time. Configure
Region
Global Set global MSTP parameters. Configure
Port Summary Display the MSTP information about ports. Monitor
Port Setup Set MSTP parameters on ports. Configure
Summary
Create Create link aggregation groups. Configure
Modify Modify link aggregation groups. Configure
Remove Remove link aggregation groups. Configure
Add the address of an OUI that can be identified
by voice VLAN.
Remove the address of an OUI that can be
identified by voice VLAN.
Display MAC address information. Monitor
Create and remove MAC addresses. Configure
Display information about MST regions. Monitor
Modify MST regions. Configure
Display information about link aggregation
groups.
Configure
Configure
Monitor
11
Page 25

Function menu Description
User level
LACP
LLDP
ARP
Manageme
nt
Summary
Setup Set LACP priorities. Configure
Port Setup
Global Setup
Global
Summary
Neighbor
Summary
ARP Table
Gratuitous ARP
Display information about LACP-enabled ports and
their partner ports.
Display the LLDP configuration information, local
information, neighbor information, statistics
information, and status information about a port.
Modify LLDP configuration on a port. Configure
Display global LLDP configuration information. Monitor
Configure global LLDP parameters. Configure
Display global LLDP local information and statistics. Monitor
Display global LLDP neighbor information. Monitor
Display ARP table information. Monitor
Add, modify, and remove ARP entries. Configure
Display the configuration information about
gratuitous ARP.
Configure gratuitous ARP. Configure
Monitor
Monitor
Monitor
ARP
Anti-Attack
IGMP
Snooping
MLD
Snooping
ARP Detection
Basic
Advanced
Basic
Advanced
Summary Display the IPv4 active route table. Monitor
Display ARP detection configuration information. Monitor
Configure ARP detection. Configure
Display global IGMP snooping configuration
information or the IGMP snooping configuration
information in a VLAN, and the IGMP snooping
multicast entry information.
Configure IGMP snooping globally or in a VLAN. Configure
Display the IGMP snooping configuration
information on a port.
Configure IGMP snooping on a port. Configure
Display global MLD snooping configuration
information or the MLD snooping configuration
information in a VLAN, and the MLD snooping
multicast entry information.
Configure MLD snooping globally or in a VLAN. Configure
Display the MLD snooping configuration
information on a port.
Configure MLD snooping on a port. Configure
Monitor
Monitor
Monitor
Monitor
IPv4 Routing
Create Create an IPv4 static route. Configure
Remove Delete the selected IPv4 static routes. Configure
12
Page 26

Function menu Description
Summary Display the IPv6 active route table. Monitor
User level
IPv6 Routing
DHCP
Service Service
Diagnostic
Tools
Create Create an IPv6 static route. Configure
Remove Delete the selected IPv6 static routes. Configure
DHCP Relay
DHCP
Snooping
IPv4 Ping Ping an IPv4 address. Visitor
IPv6 Ping Ping an IPv6 address. Visitor
IPv4
Traceroute
Display information about the DHCP status,
advanced configuration information about the
DHCP relay agent, DHCP server group
configuration, DHCP relay agent interface
configuration, and the DHCP client information.
Enable/disable DHCP, configure advanced DHCP
relay agent settings, configure a DHCP server
group, and enable/disable the DHCP relay agent
on an interface.
Display the status, trusted and untrusted ports and
DHCP client information about DHCP snooping.
Enable/disable DHCP snooping, and configure
DHCP snooping trusted and untrusted ports.
Display the states of services: enabled or disabled. Configure
Enable/disable services, and set related
parameters.
Perform IPv4 trace route operations. Visitor
Monitor
Configure
Monitor
Configure
Management
Auth
entic
ation
IPv6
Traceroute
MAC
Authenticati
on
802.1X 802.1X
Port Security Port Security
AAA
MAC
Authentication
Domain Setup
Authentication
Authorization
Perform IPv6 trace route operations. Visitor
Display MAC authentication configuration
information.
Configure MAC authentication. Configure
Display 802.1X configuration information globally
or on a port.
Configure 802.1X globally or on a port. Configure
Display port security configuration information. Monitor
Configure port security. Configure
Display ISP domain configuration information. Monitor
Add and remove ISP domains. Management
Display the authentication configuration
information about an ISP domain.
Specify authentication methods for an ISP domain. Management
Display the authorization method configuration
information about an ISP domain.
Specify authorization methods for an ISP domain. Management
Monitor
Monitor
Monitor
Monitor
13
Page 27

Function menu Description
User level
RADIUS
Users
Certificate
Manageme
nt
Display the accounting method configuration
Accounting
RADIUS Server Display and configure RADIUS server information. Management
RADIUS Setup Display and configure RADIUS parameters. Management
Local User
User Group
Entity
Domain
Certificate
information about an ISP domain.
Specify accounting methods for an ISP domain. Management
Display configuration information about local
users.
Create, modify, and remove a local user. Management
Display configuration information about user
groups.
Create, modify, and remove a user group. Management
Display information about PKI entities. Monitor
Add, modify, and delete a PKI entity. Configure
Display information about PKI domains. Monitor
Add, modify, and delete a PKI domain. Configure
Display the certificate information about PKI
domains and the contents of a certificate.
Generate a key pair, destroy a key pair, retrieve a
certificate, request a certificate, and delete a
certificate.
Monitor
Monitor
Monitor
Monitor
Configure
Secu
rity
QoS
Port Isolate
Group
Authorized
IP
Loopback
Detection
Time Range
ACL IPv4
CRL
Summary Display port isolation group information. Monitor
Port Setup Configure the ports in an isolation group. Configure
Summary
Setup Configure authorized IP. Management
Loopback
Detection
Summary Display time range configuration information. Monitor
Create Create a time range. Configure
Remove Delete a time range. Configure
Summary Display IPv4 ACL configuration information. Monitor
Create Create an IPv4 ACL. Configure
Basic Setup Configure a rule for a basic IPv4 ACL. Configure
Advanced
Setup
Display the contents of the CRL. Monitor
Receive the CRL of a domain. Configure
Display the configurations of authorized IP, the
associated IPv4 ACL list, and the associated IPv6
ACL list.
Display and configure system loopback detection
parameters and port loopback detection
parameters.
Configure a rule for an advanced IPv4 ACL. Configure
Management
Configure
14
Page 28

Function menu Description
Link Setup Create a rule for a link layer ACL. Configure
Remove Delete an IPv4 ACL or its rules. Configure
Summary Display IPv6 ACL configuration information. Monitor
Create Create an IPv6 ACL. Configure
User level
ACL IPv6
Queue
Line Rate
Classifier
Behavior
Basic Setup Configure a rule for a basic IPv6 ACL. Configure
Advanced
Setup
Remove Delete an IPv6 ACL or its rules. Configure
Summary Display the queue information about a port. Monitor
Setup Configure a queue on a port. Configure
Summary Display line rate configuration information. Monitor
Setup Configure the line rate. Configure
Summary Display classifier configuration information. Monitor
Create Create a class. Configure
Setup Configure the classification rules for a class. Configure
Remove Delete a class or its classification rules. Configure
Summary Display traffic behavior configuration information. Monitor
Create Create a traffic behavior. Configure
Setup Configure actions for a traffic behavior. Configure
Port Setup
Configure a rule for an advanced IPv6 ACL. Configure
Configure traffic mirroring and traffic redirecting
for a traffic behavior
Configure
Remove Delete a traffic behavior. Configure
Summary Display QoS policy configuration information. Monitor
Create Create a QoS policy. Configure
QoS Policy
Port Policy
Priority
Mapping
Port Priority Port Priority
Setup
Remove
Summary Display the QoS policy applied to a port. Monitor
Setup Apply a QoS policy to a port. Configure
Remove Remove the QoS policy from the port. Configure
Priority
Mapping
Configure the classifier-behavior associations for a
QoS policy.
Delete a QoS policy or its classifier-behavior
associations.
Display priority mapping table information. Monitor
Modify the priority mapping entries. Configure
Display port priority and trust mode information. Monitor
Modify port priority and trust mode. Configure
Configure
Configure
15
Page 29

Function menu Description
User level
Display PSE information and PoE interface
information.
PoE PoE
Summary
PSE Setup Configure a PoE interface. Configure
Port Setup Configure a port. Configure
Common items on the Web pages
Buttons and icons
Table 2 Commonly used buttons and icons
Button and icon Function
Applies the configuration on the current page.
Cancels the configuration on the current page.
Refreshes the current page.
Clears all entries in a list or all statistics.
Adds an item.
Monitor
,
Page display function
The Web interface can display contents by pages, as shown in Figure 7. You can set the number of
entries displayed per page, and view the contents on the first, previous, next, and last pages, or go to any
page that you want to check.
Removes the selected items.
Selects all the entries in a list.
Clears selection of all entries in a list.
Buffers but does not apply the configuration of the current step, and enters
the next configuration step.
Buffers but does not apply the configuration of the current step, and returns
to the previous configuration step.
Applies the configurations of all configuration steps.
Enters the modification page of an item so that you can modify the
configurations of the item.
Deletes the item corresponding to this icon.
16
Page 30
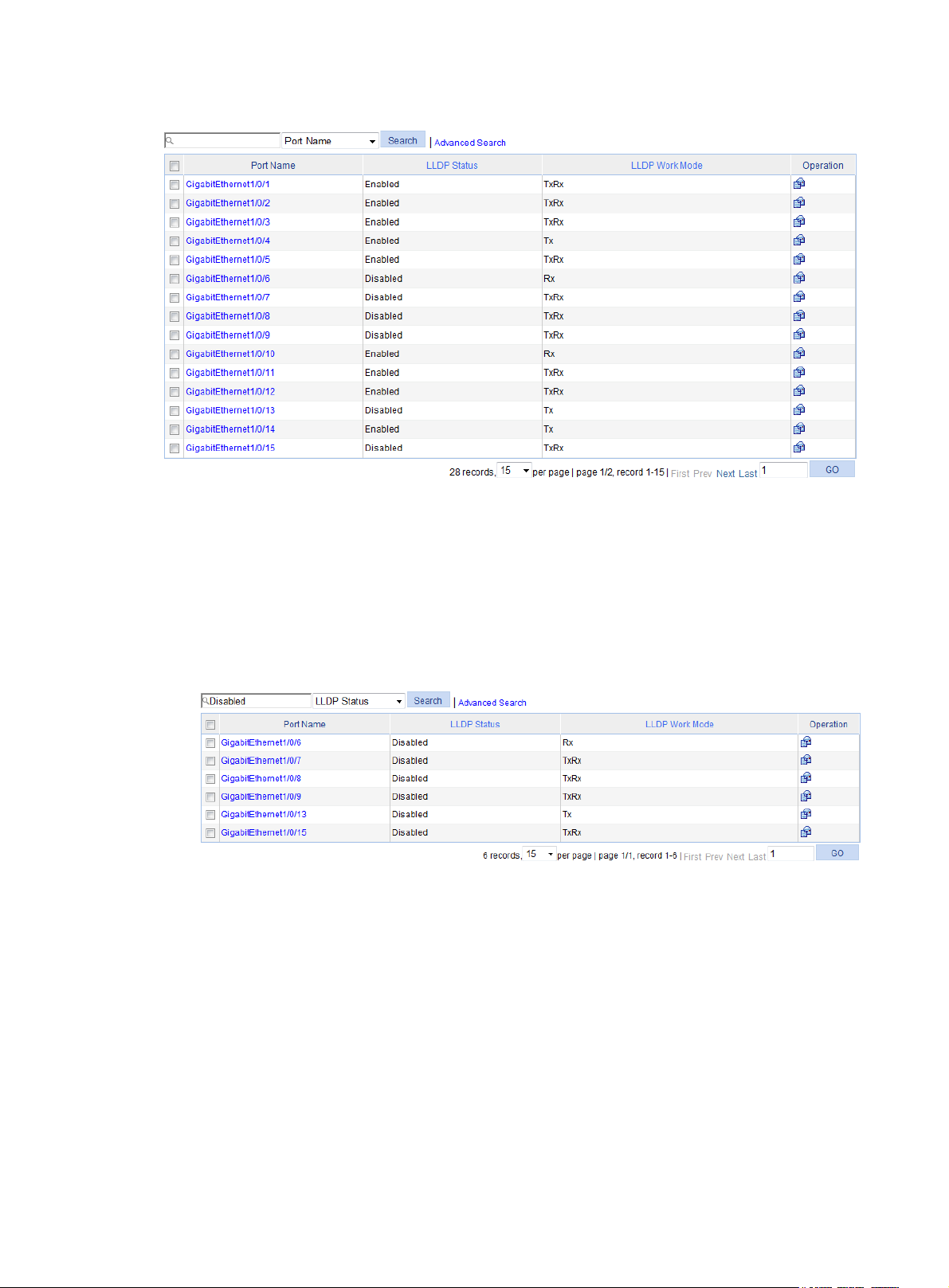
Figure 7 Content display by pages
Search function
The Web interface provides you with the basic and advanced searching functions to display only the
entries that match specific searching criteria.
• Basic search—As shown in Figure 7, t
item from the list and click Search to display the entries that match the criteria. Figure 8 sh
ype the keyword in the text box above the list, select a search
ows an
example of searching for entries with LLDP disabled.
Figure 8 Basic search function example
• Advanced search—As shown in Figure 9, you can click the Advanced Search link to open the
advanced search area. Specify the search criteria, and click Apply to display the entries that match
the criteria.
17
Page 31

Figure 9 Advanced search
Take the LLDP table shown in Figure 7 as an example.
To search for the LLDP entries with LLDP Work Mode TxRx, and LLDP Status Disabled:
1. Click the Advanced Search link, specify the search criteria on the advanced search page as shown
in Figure 10, and c
lick Apply. The LLDP entries with LLDP Work Mode being TxRx are displayed.
Figure 10 Advanced search function example (1)
2. Click the Advanced Search link, specify the search criteria on the advanced search page as shown
in Figure 11, and
click Apply. The LLDP entries with LLDP Work Mode being TxRx and LLDP Status
being Disabled are displayed as shown in Figure 12.
Figure 11 Advanced search function example (
2)
18
Page 32

Sort function
On some list pages, the Web interface provides the sorting function to display the entries in a certain
order.
The Web interface provides you with the sorting functions to display entries in certain orders.
On a list page, you can click the blue heading item of each column to sort the entries based on the
heading item you selected. After your clicking, the heading item is displayed with an arrow beside it as
shown in Figure 13. T
indicates the descending order.
Figure 13 Sort display
Figure 12 Advanced search function example (3)
he upward arrow indicates the ascending order, and the downward arrow
19
Page 33

Configuring the switch at the CLI
The HP 1920 Switch Series can be configured through the CLI, Web interface, and SNMP/MIB, among
which the Web interface supports all 1920 Switch Series configurations. These configuration methods
are suitable for different application scenarios. As a supplementary to the Web interface, the CLI
provides some configuration commands to facilitate your operation, which are described in this chapter.
To perform other configurations not supported by the CLI, use the Web interface.
You will enter user view directly after you log in to the device. Commands in the document are all
performed in user view.
Getting started with the CLI
As a supplementary to the Web interface, the CLI provides some configuration commands to facilitate
your operation. For example, if you forget the IP address of VLAN-interface 1 and cannot log in to the
device through the Web interface, you can connect the console port of the device to a PC, and
reconfigure the IP address of VLAN-interface 1 at the CLI.
This section describes using the CLI to manage the device.
Setting up the configuration environment
To set up the configuration environment, connect a terminal (a PC in this example) to the console port on
the switch with a console cable.
A console cable is an 8-core shielded cable, with a crimped RJ-45 connector at one end for connecting
to the console port of the switch, and a DB-9 female connector at the other end for connecting to the
serial port on the console terminal.
Figure 14 Console cable
A side
Pos.9
A
Pos.1
Use a console cable to connect a terminal device to the switch, as follows:
1. Plug the DB-9 female connector to the serial port of the console terminal or PC.
Main label
8
1
B side
B
2. Connect the RJ-45 connector to the console port of the switch.
CAUTION:
Identify the mark on the console port to make sure that you are connecting to the correct port.
20
Page 34

NOTE:
• The serial port on a PC does not support hot swapping. When you connect a PC to a powered-on switch,
connect the DB-9 connector of the console cable to the PC before connecting the RJ-45 connector to the
switch.
• When you disconnect a PC from a powered-on switch, disconnect the DB-9 connector of the console
cable from the PC after disconnecting the RJ-45 connector from the switch.
Setting terminal parameters
To configure and manage the switch, you must run a terminal emulator program on the console terminal.
The following are the required terminal settings:
• Bits per second—38,400
• Data bits—8
• Parity—None
• Stop bits—1
• Flow control—None
• Emulation—VT100
To set terminal parameters, for example, on a Windows XP HyperTerminal:
1. Select Start > All Programs > Accessories > Communications > HyperTerminal.
The Connection Description dialog box appears.
2. Enter the name of the new connection in the Name field and click OK.
Figure 15 Connection description
3. Select the serial port to be used from the Connect using list, and click OK.
21
Page 35

Figure 16 Setting the serial port used by the HyperTerminal connection
4. Set Bits per second to 38400, Data bits to 8, Parity to None, Stop bits to 1, and Flow control to
None, and click OK.
Figure 17 Setting the serial port parameters
5. Select File > Properties in the HyperTerminal window.
22
Page 36

Figure 18 HyperTerminal window
6. Click the Settings tab, set the emulation to VT100, and click OK in the Switch Properties dialog
box.
Figure 19 Setting terminal emulation in Switch Properties dialog box
23
Page 37

Logging in to the CLI
The login process requires a username and password. The default username for first time configuration
is admin, no password is required. Usernames and passwords are case sensitive.
To log in to the CLI:
1. Press Enter. The Username prompt displays:
Login authentication
Username:
2. Enter your username at the Username prompt.
Username:admin
3. Press Enter. The Password prompt appears.
Password:
The login information is verified, and the following CLI menu appears:
<HP 1920 Switch>
If the password is invalid, the following message appears and process restarts.
% Login failed!
CLI commands
This section contains the following commands:
Task Command
Display a list of CLI commands on the device. ?
Reboot the device and run the default configuration. initialize
Configure VLAN-interface 1 to obtain an IPv4 address through
DHCP or manual configuration.
Configure VLAN-interface 1 to obtain an IPv6 address through
the autoconfiguration function or manual configuration.
Modify the login password. password
Log out of the system. quit
Download the Boot ROM image or system software image file
from the TFTP server and specify it as the startup configuration
file.
Reboot the device and run the main configuration file. reboot
View the summary information about the device. summary
Ping a specified destination. ping [ ipv6 ] host
ipsetup { dhcp | ip-address ip-address { mask
| mask-length } [ default-gateway
ip-address ] }
ipsetup ipv6 { auto | address { ipv6-address
prefix-length | ipv6-address/prefix-length }
[ default-gateway ipv6-address ] }
upgrade [ ipv6 ] server-address
source-filename { bootrom | runtime }
Tear down the current connection and quit the system.
24
quit
Page 38

initialize
Syntax
initialize
Parameters
None
Description
Use initialize to delete the configuration file to be used at the next startup and reboot the device with the
default configuration being used during reboot.
Use the command with caution because this command deletes the configuration file to be used at the
next startup and restores the factory default settings.
Examples
# Delete the configuration file to be used at the next startup and reboot the device with the default
configuration being used during reboot.
<Sysname> initialize
The startup configuration file will be deleted and the system will be rebooted.Continue?
[Y/N]:y
Please wait...
ipsetup
Syntax
ipsetup { dhcp | ip-address ip-address { mask | mask-length } [ default-gateway ip-address ] }
Parameters
dhcp: Specifies the interface to obtain an IPv4 address through DHCP.
ip-address ip-address: Specifies an IPv4 address for VLAN-interface 1 in dotted decimal notation.
mask: Subnet mask in dotted decimal notation.
mask-length: Subnet mask length, the number of consecutive ones in the mask, in the range of 0 to 32.
default-gateway ip-address: Specifies the IPv4 address of the default gateway. With this argument and
keyword combination configured, the command not only assigns an IPv4 address to the interface, but
also specifies a default route for the device.
Description
Use ipsetup dhcp to specify VLAN-interface 1 to obtain an IPv4 address through DHCP.
Use ipsetup ip address ip-address { mask | mask-length } to assign an IPv4 address to VLAN-interface 1.
By default, the device automatically obtains its IPv4 address through DHCP; if fails, it uses the assigned
IP address.
Examples
If there is no VLAN-interface 1, either command creates VLAN-interface 1 first, and then specifies its IPv4
address.
# Create VLAN-interface 1 and specify the interface to obtain an IPv4 address through DHCP.
<Sysname> ipsetup dhcp
25
Page 39

# Create VLAN-interface 1 and assign 192.168.1.2 to the interface, and specify 192.168.1.1 as the default
gateway.
<Sysname> ipsetup ip-address 192.168.1.2 24 default-gateway 192.168.1.1
ipsetup ipv6
Syntax
ipsetup ipv6 { auto | address { ipv6-address prefix-length | ipv6-address/prefix-length }
[ default-gateway ipv6-address ] }
Parameters
auto: Enables the stateless address autoconfiguration function. With this function enabled,
VLAN-interface 1 can automatically generate a global unicast address and link local address.
address: Enables manual configuration of a global unicast IPv6 address for VLAN-interface 1.
ipv6-address: Specifies an IPv6 address.
prefix-length: Prefix length in the range of 1 to 128.
default-gateway ipv6-address: Specifies the IPv6 address of the default gateway. With this argument
and keyword combination configured, the command not only assigns an IPv6 address to the interface,
but also specifies a default route for the device.
Description
Use ipsetup ipv6 auto to enable the stateless address autoconfiguration function so a global unicast
address and link local address can be automatically generated.
Use ipsetup ipv6 address { ipv6-address prefix-length | ipv6-address/prefix-length } [ default-gateway
ipv6-address ] to manually assign an IPv6 address to VLAN-interface 1.
Examples
# Create VLAN-interface 1 and enable VLAN-interface 1 to automatically generate a global unicast IPv6
address and link local address.
<Sysname> ipsetup ipv6 auto
# Create VLAN-interface 1 and assign 2001::2 to the interface, with the prefix length 64, and specify
2001::1 as the default gateway.
<Sysname> ipsetup ipv6 address 2001::2 64 default-gateway 2001::1
password
Syntax
password
Parameters
None
Description
Use password to modify the login password of a user.
Examples
# Modify the login password of user admin.
<Sysname> password
26
Page 40

Change password for user: admin
Old password: ***
Enter new password: **
Retype password: **
The password has been successfully changed.
ping
Syntax
ping host
Parameters
host: Destination IPv4 address (in dotted decimal notation) or host name (a string of 1 to 255 characters).
Description
Use ping to ping a specified destination.
To terminate a ping operation, press Ctrl+C.
Examples
# Ping IP address 1.1.2.2.
<Sysname> ping 1.1.2.2
PING 1.1.2.2: 56 data bytes, press CTRL_C to break
Reply from 1.1.2.2: bytes=56 Sequence=1 ttl=254 time=205 ms
Reply from 1.1.2.2: bytes=56 Sequence=2 ttl=254 time=1 ms
Reply from 1.1.2.2: bytes=56 Sequence=3 ttl=254 time=1 ms
Reply from 1.1.2.2: bytes=56 Sequence=4 ttl=254 time=1 ms
Reply from 1.1.2.2: bytes=56 Sequence=5 ttl=254 time=1 ms
--- 1.1.2.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 1/41/205 ms
The output shows that IP address 1.1.2.2 is reachable and the echo replies are all returned from the
destination. The minimum, average, and maximum roundtrip intervals are 1 millisecond, 41 milliseconds,
and 205 milliseconds respectively.
ping ipv6
Syntax
ping ipv6 host
Parameters
host: Destination IPv6 address or host name (a string of 1 to 255 characters).
Description
Use ping ipv6 to ping a specified destination.
To terminate a ping operation, press Ctrl+C.
27
Page 41

Examples
# Ping IPv6 address 2001::4.
<Sysname> ping ipv6 2001::4
PING 2001::4 : 56 data bytes, press CTRL_C to break
Reply from 2001::4
bytes=56 Sequence=1 hop limit=64 time = 15 ms
Reply from 2001::4
bytes=56 Sequence=2 hop limit=64 time = 2 ms
Reply from 2001::4
bytes=56 Sequence=3 hop limit=64 time = 11 ms
Reply from 2001::4
bytes=56 Sequence=4 hop limit=64 time = 2 ms
Reply from 2001::4
bytes=56 Sequence=5 hop limit=64 time = 12 ms
--- 2001::4 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 2/8/15 ms
The output shows that IPv6 address 2001::4 is reachable and the echo replies are all returned from the
destination. The minimum, average, and maximum roundtrip intervals are 2 millisecond, 8 milliseconds,
and 15 milliseconds respectively.
quit
Syntax
quit
Parameters
None
Description
Use quit to log out of the system.
Examples
# Log out of the system.
<Sysname> quit
******************************************************************************
* Copyright (c) 2010-2014 Hewlett-Packard Development Company, L.P. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
User interface aux0 is available.
28
Page 42

reboot
Syntax
reboot
Parameters
None
Description
Use reboot to reboot the device and run the main configuration file.
Use the command with caution because reboot results in service interruption.
If the main configuration file is co rru pted or d oes not exist, the device cannot be rebo oted with the reboot
command. In this case, you can specify a new main configuration file to reboot the device, or you can
power off the device, and then power it on, and the system will automatically use the backup
configuration file at the next startup.
If you reboot the device when file operations are being performed, the system does not execute the
command to ensure security.
Examples
# If the configuration does not change, reboot the device.
<Sysname> reboot
Start to check configuration with next startup configuration file, please
wait.........DONE!
This command will reboot the device. Continue? [Y/N]:y
Now rebooting, please wait...
# If the configuration changes, reboot the device.
<Sysname> reboot
Start to check configuration with next startup configuration file, please
wait.........DONE!
This command will reboot the device. Current configuration will be lost in next startup
if you continue. Continue? [Y/N]:y
Now rebooting, please wait...
summary
Syntax
summary
Parameters
None
Description
Use summary to view the summary of the device, including the IP address of VLAN-interface 1, and
software version information.
Examples
# Display summary information about the device.
<sysname>summary
29
Page 43

Select menu option: Summary
IP Method: Manual
IP address: 192.168.0.233
Subnet mask: 255.255.255.0
Default gateway:
IPv6 Method:
IPv6 link-local address:
IPv6 subnet mask length:
IPv6 global address:
IPv6 subnet mask length:
IPv6 default gateway:
Current boot app is: flash:/hp1920-24G.bin
Next main boot app is: flash:/hp1920-24G.bin
Next backup boot app is: flash:/test.bin
HP Comware Platform Software
Comware Software, Version 5.20.99, ESS 1101
Copyright (c) 2010-2014 Hewlett-Packard Development Company, L.P.
HP 1920-24G Switch uptime is 0 week, 0 day, 1 hour, 25 minutes
HP 1920-24G Switch
128M bytes DRAM
32M bytes Flash Memory
Config Register points to Flash
Hardware Version is VER.A
Bootrom Version is 109
[SubSlot 0] 24GE+4SFP Hardware Version is VER.A
upgrade
Syntax
upgrade server-address source-filename { bootrom | runtime }
Parameters
server-address: IPv4 address or host name (a string of 1 to 20 characters) of a TFTP server.
source-filename: Software package name on the TFTP server.
bootrom: Specifies the Boot ROM image in the software package file as the startup configuration file.
runtime: Specifies the system software image file in the software package file as the startup configuration
file.
Description
Use upgrade server-address source-filename bootrom to upgrade the Boot ROM imag e. If the Boot ROM
image in the downloaded software package file is not applicable, the original Boot ROM image is still
used as the startup configuration file.
30
Page 44

Use upgrade server-address source-filename runtime to upgrade the system software image file. If the
system software image file in the downloaded software package file is not applicable, the original
system software image file is still used as the startup configuration file.
To validate the downloaded software package file, reboot the device.
NOTE:
The HP 1920 Switch Series does not provide an independent Boot ROM image; instead, it integrates the
Boot ROM image with the system software image file together in a software package file with the
extension name of .bin.
Examples
# Download software package file main.bin from the TFTP server and use the Boot ROM image in the
package as the startup configuration file.
<Sysname> upgrade 192.168.20.41 main.bin bootrom
# Download software package file main.bin from the TFTP server and use the system software image file
in the package as the startup configuration file.
<Sysname> upgrade 192.168.20.41 main.bin runtime
upgrade ipv6
Syntax
upgrade ipv6 server-address source-filename { bootrom | runtime }
Parameters
server-address: IPv6 address of a TFTP server.
source-filename: Software package name on the TFTP server.
bootrom: Specifies the Boot ROM image in the software package file as the startup configuration file.
runtime: Specifies the system software image file in the software package file as the startup configuration
file.
Description
Use upgrade ipv6 server-address source-filename bootrom to upgrade the Boot ROM image. If the Boot
ROM image in the downloaded software package file is not applicable, the original Boot ROM image
is still used as the startup configuration file.
Use upgrade ipv6 server-address source-filename runtime to upgrade the system software image file. If
the system software image file in the downloaded software package file is not applicable, the original
system software image file is still used as the startup configuration file.
To validate the downloaded software package file, reboot the device.
NOTE:
The HP 1920 Switch Series does not provide an independent Boot ROM image; instead, it integrates the
Boot ROM image with the system software image file together in a software package file with the
extension name of .bin.
31
Page 45

Examples
# Download software package file main.bin from the TFTP server and use the Boot ROM image in the
package as the startup configuration file.
<Sysname> upgrade ipv6 2001::2 main.bin bootrom
# Download software package file main.bin from the TFTP server and use the system software image file
in the package as the startup configuration file.
<Sysname> upgrade ipv6 2001::2 main.bin runtime
Configuration example for upgrading the system software image at the CLI
Network requirements
As shown in Figure 20, a 1920 switch is connected to the PC through the console cable, and connected
to the gateway through Ethernet 1/0/1. The IP address of the gateway is 192.168.1.1/24, and that of the
TFTP server where the system software image (suppose its name is Switch1920.bin) is located is
192.168.10.1/24. The gateway and the switch can reach each other.
The administrator upgrades the Boot ROM image and the system software image file of the 1920 switch
through the PC and sets the IP address of the switch to 192.168.1.2/24.
Figure 20 Network diagram
Console cable
PC
Configuration procedure
1. Run the TFTP server program on the TFTP server, and specify the path of the file to be loaded.
(Omitted)
2. Configure the switch:
# Configure the IP address of VLAN-interface 1 of the switch as 192.168.1.2/24, and specify the
default gateway as 192.168.1.1.
<Switch> ipsetup ip-address 192.168.1.2 24 default-gateway 192.168.1.1
# Download the software package file Switch1920.bin on the TFTP server to the switch, and
upgrade the system software image in the package.
<Switch> upgrade 192.168.10.1 Switch1920.bin runtime
File will be transferred in binary mode
Downloading file from remote TFTP server, please wait.../
TFTP: 10262144 bytes received in 71 second(s)
File downloaded successfully.
# Download the software package file Switch1920.bin on the TFTP server to the switch, and
upgrade the Boot ROM image.
<Switch> upgrade 192.168.10.1 Switch1920.bin bootrom
The file flash:/Switch1920.bin exists. Overwrite it? [Y/N]:y
Verifying server file...
Switch
IP network
GE1/0/1Console port
Gateway
TFTP server
32
Page 46

Deleting the old file, please wait...
File will be transferred in binary mode
Downloading file from remote TFTP server, please wait.../
TFTP: 10262144 bytes received in 61 second(s)
File downloaded successfully.
BootRom file updating finished!
# Reboot the switch.
<Switch> reboot
After getting the new image file, reboot the switch to validate the upgraded image.
33
Page 47

Configuration wizard
The configuration wizard guides you through configuring the basic service parameters, including the
system name, system location, contact information, and management IP address.
Basic service setup
Entering the configuration wizard homepage
Select Wizard from the navigation tree.
Figure 21 Configuration wizard homepage
Configuring system parameters
1. On the wizard homepage, click Next.
34
Page 48

p
Figure 22 System parameter configuration page
2. Configure the parameters as described in Table 3.
Table 3 Configuration items
Item Descri
Specify the system name.
Sysname
Syslocation
Syscontact
The system name appears at the top of the navigation tree.
You can also set the system name in the System Name page you enter by selecting
Device > Basic. For more information, see "Configuring basic device settings."
Specify the physical location of the system.
You can also set the physical location in the setup page you enter by selecting
Device > SNMP. For more information, see "Configuring SNMP."
Set the contact information for users to get in touch with the device vendor for help.
You can also set the contact information in the setup page you enter by selecting
Device > SNMP. For more information, see "Configuring SNMP."
tion
35
Page 49

p
Configuring management IP address
CAUTION:
Modifying the management IP address used for the current login terminates the connection to the device.
Use the new management IP address to re-log in to the system.
1. On the system parameter configuration page, click Next.
Figure 23 Management IP address configuration page
2. Configure the parameters as described in Table 4.
Table 4 Configuration items
Item Descri
Select a VLAN interface.
Available VLAN interfaces are those configured in the page that you enter by selecting
Select VLAN
Interface
Network > VLAN Interface and selecting the Create tab.
The IP address of a VLAN interface can be used as the management IP address to access
the device. Configure a VLAN interface and its IP address in the page that you enter by
selecting Network > VLAN Interface. For more information, see "Configuring VLAN
interfa
tion
ces."
36
Page 50

Item Description
Enable or disable the VLAN interface.
When errors occurred in the VLAN interface, disable the interface and then enable the
port to bring the port to operate correctly.
Admin status
By default, the VLAN interface is down if no Ethernet ports in the VLAN is up. The VLAN
is in the up state if one or more ports in the VLAN are up.
IMPORTANT:
Disabling or enabling the VLAN interface does not affect the status of the Ethernet ports in
the VLAN. That is, the port status does not change with the VLAN interface status.
DHCP Configure how the VLAN interface obtains an IPv4 address:
BOOTP
• DHCP—Select the option for the VLAN interface to get an IP address
through DHCP.
• BOOTP—Select the option for the VLAN interface to get an IP address
Configure IPv4
address
Manual
through BOOTP.
• Manual—Select this option to manually specify an IPv4 address and
the mask length for the VLAN interface.
IPv4 address
MaskLen
Auto Configure how the VLAN interface obtains an IPv6 link-local address.
Specify an IPv4 address and the mask length for the VLAN interface.
Dotted decimal notation is also allowed for the mask length field.
These two fields are configurable if Manual is selected.
• Auto—Select this option for the device to automatically generate a
link-local address based on the link-local address prefix (FE80::/64)
and the link layer address of the interface.
• Manual—Select this option to manually assign an IPv6 link-local
address to the interface.
Specify an IPv6 link-local address for the VLAN interface.
This field is configurable if you select Manual. The address prefix must be
FE80::/64.
Configure IPv6
link-local address
Manual
IPv6 address
Finishing configuration wizard
After finishing the management IP address configuration, click Next.
The page displays your configurations. Review the configurations and if you want to modify the settings
click Back to go back to the page. Click Finish to confirm your settings and the system performs the
configurations.
37
Page 51

Figure 24 Configuration complete
38
Page 52

Configuring stack
Overview
The stack management feature allows you to configure and monitor a group of connected devices by
logging in to one device in the stack, as shown in Figure 25.
Figure 25 Stacking devi
To set up a stack for a group of connected devices, you must log in to one device to create the stack. This
device is the master device for the stack. You configure and monitor all member devices on the master
device. The ports that connect the stack member devices are called stack ports.
ces
Configuration task list
Perform the tasks in Table 5 to configure a stack.
Table 5 Stack configuration task list
Task Remarks
Configuring the master device of a stack:
Required.
Configure a private IP address pool for a stack and establish the
Configuring global parameters of a stack
Configuring stack ports
stack, and meantime the device becomes the master device of the
stack.
By default, no IP address pool is configured for a stack and no stack
is established.
Required.
Configure the ports of the master device that connect to member
devices as stack ports.
By default, a port is not a stack port.
39
Page 53
Task Remarks
Configuring member devices of a stack:
Required.
Configuring stack ports
Configure a port of a member device that connects to the master
device or another member device as a stack port.
By default, a port is not a stack port.
Displaying topology summary of a stack
Displaying device summary of a stack
Logging in to a member device from the
master
Optional.
Display information about stack members.
Optional.
Display the control panels of stack members.
IMPORTANT:
Before viewing the control panel of a member device, you must make
sure the username, password, and access right you used to log on to
the master device are the same with those configured on the member
device; otherwise, the control panel of the member device cannot be
displayed.
Optional.
Log in to the Web network management interface of a member
device from the master device.
IMPORTANT:
Before logging in to a member device, you must make sure the
username, password, and access right you used to log on to the
master device are the same with those configured on the member
device. Otherwise, you cannot log in to the member device. You can
configure them by selecting Device and then clicking Users from the
navigation tree.
Configuring global parameters of a stack
Select Stack from the navigation tree to enter the page shown in Figure 26. You can configure global
parameters of a stack in the Global Settings area.
40
Page 54

p
Figure 26 Setting up
Table 6 Configuration items
Item Descri
Configure a private IP address pool for the stack.
The master device of a stack must be configured with a private IP address pool to
make sure it can automatically allocate an available IP address to a member device
Private Net IP
Mask
Build Stack
when the device joints the stack.
When you configure a private IP address pool for a stack, the number of IP addresses
in the address pool needs to be equal to or greater than the number of devices to be
added to the stack. Otherwise, some devices might not be able to join the stack
automatically for lack of private IP addresses.
Enable the device to establish a stack.
After you enable the device to establish a stack, the device becomes the master
device of the stack and automatically adds the devices connected to its stack ports to
the stack.
You can delete a stack only on the master device of the stack. The Global Settings area
on a member device is grayed out.
tion
IMPORTANT:
IMPORTANT:
Configuring stack ports
Select Stack from the navigation tree to enter the page shown in Figure 26. You can configure stack ports
in the Port Settings area.
• Select the box before a port name, and click Enable to configure the port as a stack port.
• Select the box before a port name, and click Disable to configure the port as a non-stack port.
41
Page 55

p
Displaying topology summary of a stack
Select Stack from the navigation tree and click the Topology Summary tab to enter the page shown
in Figure 27.
Figure 27 Topology Summary tab
Table 7 Field description
Fields Descri
Member ID of the device in the stack:
Device ID
Device Role Role of the device in the stack: master or slave.
• Value 0 indicates that the device is the master device of the stack.
• A value other than 0 indicates that the device is a member device and the value
tion
is the member ID of the member device in the stack.
Displaying device summary of a stack
Select Stack from the navigation tree and click the Device Summary tab to enter the page shown in Figure
28. On this page, you can view interfaces on the panel of each stack member by clicking the tab of the
corresponding member device.
Figure 28 Device summary (the master device)
Logging in to a member device from the master
Select Stack from the navigation tree, click the Device Summary tab, and click the tab of a member
device to enter the page shown in Figure 29.
Cl
ick the Configuring the Device hyperlink, you can log in to the Web interface of the member device to
manage and maintain the member device directly.
42
Page 56

Figure 29 Device summary (a member device)
Stack configuration example
Network requirements
As shown in Figure 30, Switch A, Switch B, Switch C, and Switch D are connected to one another.
Create a stack, where Switch A is the master device, and Switch B, Switch C, and Switch D are member
devices. An administrator can log in to Switch B, Switch C, and Switch D through Switch A to perform
remote configurations.
Figure 30 Network diagram
Configuration procedure
1. Configure global parameters for the stack on Switch A:
a. Select Stack from the navigation tree of Switch A, and then perform the subsequent steps on the
Setup tab, as shown in Figure 31.
b. Typ
c. Type 255.255.255.0 in the field of Mask.
d. Select Enable from the Build Stack list.
e. Click Apply.
e 192.168.1.1 in the field of Private Net IP.
43
Page 57
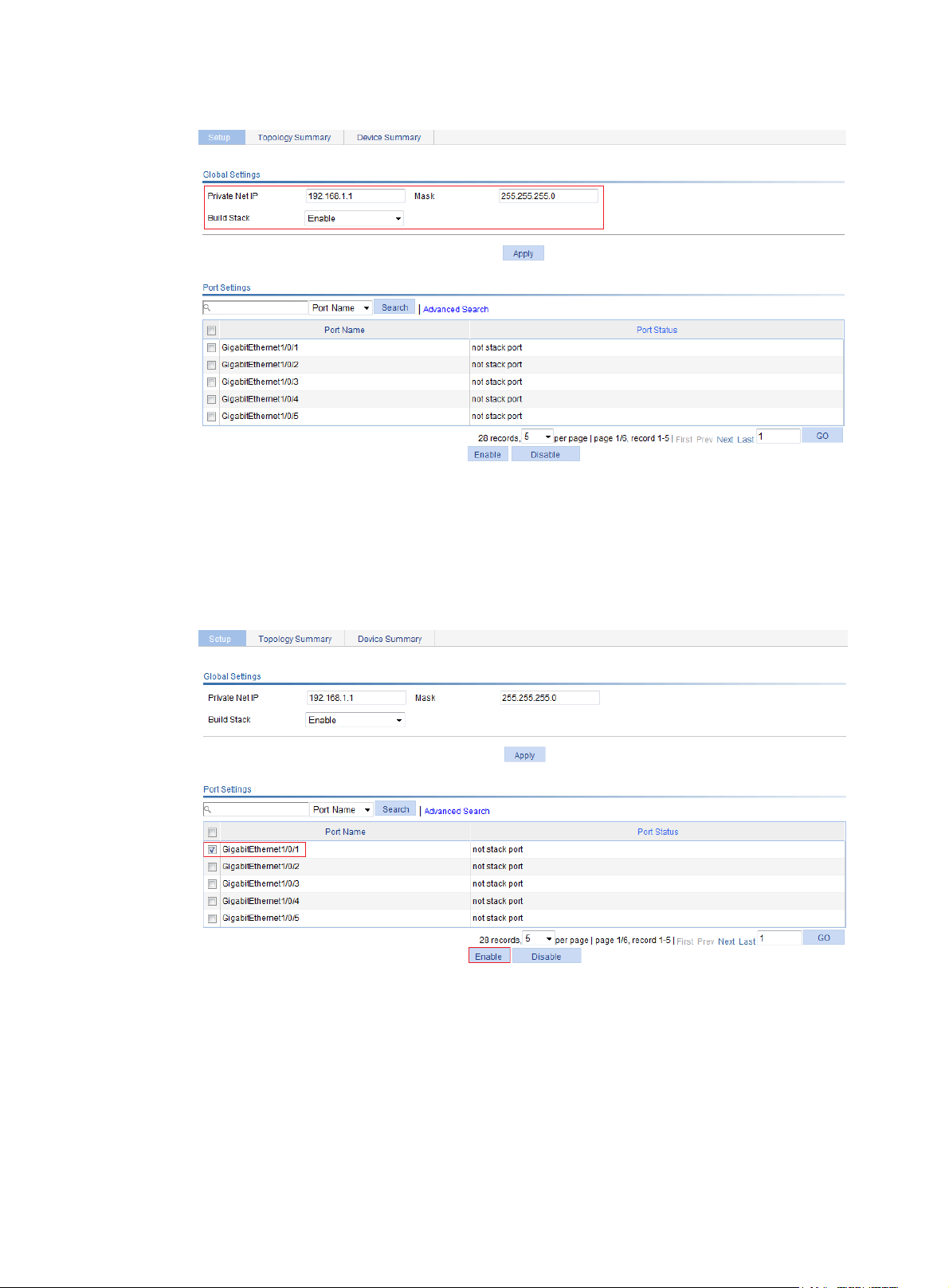
Figure 31 Configuring global parameters for the stack on Switch A
Switch A becomes the master device.
2. Configure a stack port on Switch A:
a. In the Port Settings area on the Setup tab, select GigabitEthernet1/0/1.
b. Click Enable.
Figure 32 Configuring a stack port on Switch A
3. On Switch B, configure GigabitEthernet 1/0/2 (connected to Switch A), GigabitEthernet 1/0/1
(connected to Switch C), and GigabitEthernet 1/0/3 (connected to Switch D) as stack ports:
a. Select Stack from the navigation tree of Switch B.
b. In the Port Settings area on the Setup tab, select GigabitEthernet1/0/1, GigabitEthernet1/0/2,
and GigabitEthernet1/0/3.
c. Click Enable.
44
Page 58

Figure 33 Configuring stack ports on Switch B
Switch B becomes a member device.
4. On Switch C, configure GigabitEthernet 1/0/1 (the port connected to Switch B) as a stack port:
a. Select Stack from the navigation tree of Switch C.
b. In the Port Settings area on the Setup tab, select GigabitEthernet1/0/1.
c. Click Enable.
Figure 34 Configuring a stack port on Switch C
Switch C becomes a member device.
5. On Switch D, configure GigabitEthernet 1/0/1 (the port connected to Switch B) as a stack port:
a. Select Stack from the navigation tree of Switch D.
b. In the Port Settings area on the Setup tab, select GigabitEthernet1/0/1.
c. Click Enable.
Switch D becomes a member device.
45
Page 59

Verifying the configuration
To verify the stack topology on Switch A:
1. Select Stack from the navigation tree of Switch A.
2. Click the Topology Summary tab.
Figure 35 Verifying the configuration
Configuration guidelines
When you configure a stack, follow these guidelines:
• If a device is already configured as the master device of a stack, you cannot modify the private IP
address pool on the device.
• If a device is already configured as a member device of a stack, the Global Settings area on the
member device is not available.
46
Page 60

p
Displaying system and device information
Displaying system information
Select Summary from the navigation tree to enter the System Information page to view the basic system
information, system resource state, and recent system logs.
Figure 36 System information
Displaying basic system information
Table 8 Field description
Item Descri
Product Information Description for the device.
Device Location
Contact Information
SerialNum Serial number of the device.
Software Version Software version of the device.
Hardware Version Hardware version of the device.
Bootrom Version Boot ROM version of the device.
Running Time System up time.
Device location, which you can configure on the page you enter by
selecting Device > SNMP > Setup.
Contact information, which you can configure on the page you enter
by selecting Device > SNMP > Setup.
tion
47
Page 61

p
Displaying the system resource state
The System Resource State area displays the most recent CPU usage, memory usage, and temperature.
Displaying recent system logs
Table 9 Field description
Field Descri
Time Time when the system logs were generated.
Level Severity of the system logs.
Description Description for the system logs.
The System Information page displays up to five the most recent system logs.
To display more system logs, click More to enter the Log List page. You can also enter this page by
selecting Device > Syslog. For more information, see "Configuring syslog."
tion
Setting the refresh period
To set the interval for refreshing system information, select one of the following options from the Refresh
Period list:
• If you select a certain period, the system refreshes system information at the specified interval.
• If you select Manual, the system refreshes system information only when you click the Refresh button.
Displaying device information
Select Summary from the navigation tree, and click the Device Information tab to enter the page that
displays information about the device ports. Hover the cursor over a port and the port details appear,
including the port name, type, speed, utilization, and status, as shown in Figure 37. T
group number is also displayed if the port is added to an aggregation group. For the description about
the port number and its color, see Figure 37.
he aggregation
48
Page 62

Figure 37 Device information
To set the interval for refreshing device information, select one of the following options from the Refresh
Period list:
• If you select a certain period, the system refreshes device information at the specified interval.
• If you select Manual, the system refreshes device information only when you click the Refresh button.
49
Page 63

Configuring basic device settings
The device basic information feature provides the following functions:
• Set the system name of the device. The configured system name is displayed on the top of the
navigation bar.
• Set the idle timeout period for logged-in users. The system logs an idle user off the Web for security
purpose after the configured period.
Configuring system name
1. Select Device > Basic from the navigation tree.
The system name configuration page appears.
Figure 38 Configuring the system name
2. Enter the system name.
3. Click Apply.
Configuring idle timeout period
1. Select Device > Basic from the navigation tree.
2. Click the Web Idle Timeout tab.
The page for configuring idle timeout period appears.
Figure 39 Configuring the idle timeout period
50
Page 64

3. Set the idle timeout period for logged-in users.
4. Click Apply.
51
Page 65
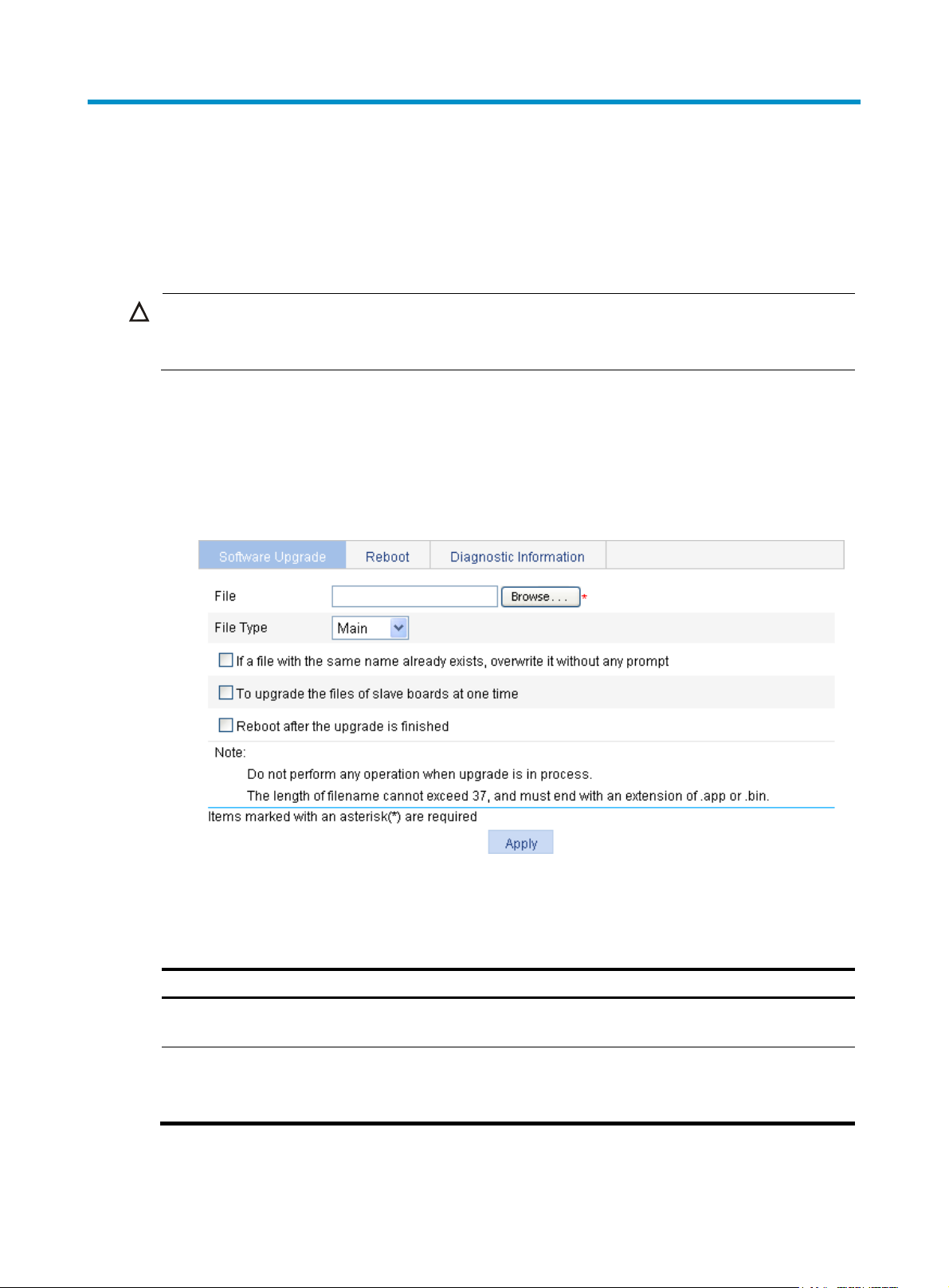
p
Maintaining devices
Software upgrade
CAUTION:
Software upgrade takes some time. Avoid performing any operation on the Web interface during the
upgrading procedure. Otherwise, the upgrade operation may be interrupted.
A boot file, also known as the system software or device software, is an application file used to boot the
device. Software upgrade allows you to obtain a target application file from the local host and set the file
as the boot file to be used at the next reboot. In addition, you can select whether to reboot the device to
bring the upgrade software into effect.
1. Select Device > Device Maintenance from the navigation tree to enter the Software Upgrade tab.
Figure 40 Software upgrade configuration page
2. Configure software upgrade parameters as described in Table 10.
3. Click Apply.
Table 10 Configuration items
Item Descri
File
File Type
Specify the path and filename of the local application file, which must be suffixed
with the .app or .bin extension.
Specify the type of the boot file for the next boot:
• Main—Boots the device.
• Backup—Boots the device when the main boot file is unavailable.
tion
52
Page 66

Item Description
If a file with the same
name already exists,
overwrite it without any
prompt
Reboot after the upgrade
finished
Device reboot
CAUTION:
• Before rebooting the device, save the configuration. Otherwise, all unsaved configuration will be lost
after device reboot.
• When the device reboots, re-log in to the device.
1. Select Device > Device Maintenance from the navigation tree.
2. Click the Reboot tab.
Figure 41 Device reboot page
Specify whether to overwrite the file with the same name.
If you do not select the option, when a file with the same name exists, a dialog box
appears, telling you that the file already exists and you cannot continue the
upgrade.
Specify whether to reboot the device to make the upgraded software take effect
after the application file is uploaded.
3. Enable or disable the "Check whether the current configuration is saved in the next startup
configuration file" option.
4. Click Reboot. A confirmation dialog box appears.
5. Click OK.
{ If you select Check whether the current configuration is saved in the next startup configuration
file, the system will check the configuration before rebooting the device. If the check succeeds,
the system reboots the device. If the check fails, a dialog box appears, telling you that the
current configuration and the saved configuration are inconsistent, and the device is not
rebooted. In this case, save the current configuration manually before you can reboot the
device.
{ If you do not select the box, the system reboots the device directly.
53
Page 67

Electronic label
Electronic label allows you to view information about the device electronic label, which is also known as
the permanent configuration data or archive information. The information is written into the storage
medium of a device or a card during the debugging and testing processes, and includes card name,
product bar code, MAC address, debugging and testing dates, and manufacture name.
1. Select Device > Device Maintenance from the navigation tree.
2. Click the Electronic Label tab to view the electronic label information.
Figure 42 Electronic label
Diagnostic information
Each functional module has its own running information. Generally, you view the output for each module
one by one. To receive as much information as possible in one operation during daily maintenance or
when system failure occurs, the diagnostic information module allows you to save the running statistics of
multiple functional modules to a file named default.diag, and then you can locate problems faster by
checking this file.
1. Select Device > Device Maintenance from the navigation tree.
2. Click the Diagnostic Information tab.
Figure 43 Diagnostic information
3. Click Create Diagnostic Information File.
The system begins to generate a diagnostic information file.
4. Click Click to Download.
The File Download dialog box appears.
5. Select to open this file or save this file to the local host.
54
Page 68

Figure 44 The diagnostic information file is created
The generation of the diagnostic file takes a period of time. During this process, do not perform any
operation on the Web page.
After the diagnostic file is generated successfully, you can view this file on the page you enter by
selecting Device > File Management, or downloading this file to the local host. For more information, see
"Managing files."
55
Page 69

Configuring system time
Overview
You must configure a correct system time so that the device can operate correctly with other devices. The
system time module allows you to display and set the device system time on the Web interface.
You can set the system time through manual configuration or network time protocol (NTP) automatic
synchronization.
Defined in RFC 1305, the NTP synchronizes timekeeping among distributed time servers and clients. NTP
can keep consistent timekeeping among all clock-dependent devices within the network, and ensure a
high clock precision so that the devices can provide diverse applications based on consistent time.
Displaying the current system time
To view the current system date and time, select Device > System Time from the navigation tree to enter
the System Time page.
Figure 45 System time configuration page
Manually configuring the system time
1. Select Device > System Time from the navigation tree.
The page for configuration the system time appears.
2. Click the System Time Configuration text to open a calendar.
56
Page 70

Figure 46 Calendar page
3. Enter the system date and time in the Time field, or select the date and time in the calendar. To set
the time on the calendar page, select one of the following methods:
{ Click Today. The date setting in the calendar is synchronized to the current local date
configuration, and the time setting does not change.
{ Select the year, month, date, and time, and then click OK.
4. Click Apply on the system time configuration page to save your configuration.
Configuring system time by using NTP
1. Select Device > System Time from the navigation tree.
2. Click the Network Time Protocol tab.
The page for configuring the system time through NTP appears.
Figure 47 NTP configuration page
3. Configure the system time as described in Table 11.
4. Click Apply.
57
Page 71

p
Table 11 Configuration items
Item Descri
Clock status Display the synchronization status of the system clock.
Source Interface Set the source interface for an NTP message.
This configuration makes the source IP address in the NTP messages the
primary IP address of this interface. If the specified source interface is
down, the source IP address is the primary IP address of the egress
interface.
If you do not want the IP address of an interface on the local device to
become the destination address of response messages, specify the
source interface for NTP messages.
Key 1 Set NTP authentication key.
Key 2
Enable the NTP authentication feature for a system running NTP in a
network that requires high security. This feature improves the network
security by means of client-server key authentication, and prohibits a
client from synchronizing with a device that has failed authentication.
You can set two authentication keys, each of which has a key ID and a
key string.
tion
TIP:
• ID—ID of a key.
• Key string—Character string of the MD5 authentication key.
External
Reference
Source
NTP Server
1/Reference
Key ID.
NTP Server
2/Reference
Key ID.
Specify the IP address of an NTP server, and configure the
authentication key ID used for the association with the NTP server. The
device synchronizes its time to the NTP server only if the key provided
by the server is the same as the specified key.
You can configure two NTP servers. The clients choose the optimal
reference source.
IMPORTANT:
The IP address of an NTP server is a unicast address, and cannot be a
broadcast or a multicast address, or the IP address of the local clock
source.
System time configuration example
Network requirements
As shown in Figure 48:
• The local clock of Device A is set as the reference clock.
• Switch B operates in client mode, and uses Device A as the NTP server.
Configure NTP authentication on Device A and Switch B so that Switch B is to be synchronized to Device
A.
58
Page 72

Figure 48 Network diagram
Configuring the system time
1. Configure the local clock as the reference clock, with the stratum of 2. Enable NTP authentication,
set the key ID to 24, and specify the created authentication key aNiceKey as a trusted key. (Details
not shown.)
2. On Switch B, configure Device A as the NTP server:
a. Select Device > System Time from the navigation tree.
b. Click the Network Time Protocol tab.
c. Enter 24 in the ID field, enter aNiceKey in the Key String field for key 1, enter 1.0.1.11 in the
NTP Server 1 field, and enter 24 in the Reference Key ID field.
d. Click Apply.
Figure 49 Configuring Device A as the NTP server of Switch B
Verifying the configuration
After the configuration, verify that Device A and Switch B have the same system time.
Configuration guidelines
When you configure the system time, follow these guidelines:
• A device can act as a server to synchronize the clock of other devices only after its clock has been
synchronized. If the clock of a server has a stratum level higher than or equal to the level of a client's
clock, the client will not synchronize its clock to the server's.
59
Page 73

• The synchronization process takes some time. The clock status might be displayed as
unsynchronized after your configuration. In this case, refresh the page to view the clock status and
system time later on.
• If the system time of the NTP server is ahead of the system time of the device, and the time gap
exceeds the Web idle time specified on the device, all online Web users are logged out because of
timeout after the synchronization finishes.
60
Page 74

Configuring syslog
System logs record network and device information, including running status and configuration changes.
With system logs, administrators can take corresponding actions against network problems and security
problems.
The system sends system logs to the following destinations:
• Console
• Monitor terminal, a terminal that has logged in to the device through the AUX or VTY user interface
• Log buffer
• Log host
• Web interface
• Log file
Displaying syslogs
1. Select Device > Syslog from the navigation tree.
The page for displaying syslogs appears. You can click Reset to clear all system logs saved in the
log buffer on the Web interface. You can click Refresh to manually refresh the page, or you can
set the refresh interval on the Log Setup page to enable the system to automatically refresh the
page periodically. For more information, see "Setting buffer capacity and refresh interval."
Figure 50 Displaying syslogs
2. View system logs.
61
Page 75

p
Table 12 Field description
Field Descri
Time/Date
Source
Displays the time/date when the system log was generated.
Displays the module that generated the system log.
Displays the severity level of the system log. The information is classified into eight
levels by severity:
• Emergency—The system is unusable.
• Alert—Action must be taken immediately.
• Critical—Critical condition.
Level
• Error—Error condition.
• Warning—Warning condition.
• Notification—Normal but significant condition.
• Information—Informational message.
• Debug—Debug-level message.
Digest Displays the brief description of the system log.
Description
Displays the content of the system log.
Setting the log host
tion
1. Select Device > Syslog from the navigation tree.
2. Click the Loghost tab.
The log host configuration page appears.
Figure 51 Setting the log host
3. Configure the log host as described in Table 13.
62
Page 76

p
p
4. Click Apply.
Table 13 Configuration items
Item Descri
IPv4/Domain
Loghost IP/Domain
IPv6
Loghost IP
Specify the IPv4 address or domain name
of the log host.
Set the IPv6 address of the log host.
tion
IMPORTANT:
You can specify up to four log hosts.
Setting buffer capacity and refresh interval
1. Select Device > Syslog from the navigation tree.
2. Click the Log Setup tab.
The syslog configuration page appears.
Figure 52 Syslog configuration page
3. Configure buffer capacity and refresh interval as described in Table 14.
4. Click Apply.
Table 14 Configuration items
Item Descri
Buffer Capacity
Refresh Interval
Set the number of logs that can be stored in the log buffer.
Set the log refresh interval.
You can select manual refresh or automatic refresh:
• Manual—Click Refresh to view the latest log information.
tion
• Automatic—Select to refresh the Web interface every 1 minute, 5 minutes, or 10
minutes.
63
Page 77

Managing the configuration
You can back up, restore, save, or reset the device configuration.
Backing up the configuration
Configuration backup allows you to do the following:
• Open and view the configuration files for the next startup, including the .cfg file and .xml file.
• Back up the configuration files for the next startup to your local host.
IMPORTANT:
HP recommends backing up both the .cfg and .xml files. If you back up only the .cfg file, some
configuration information might not be restored when, for example, the configuration is mistakenly
removed.
To back up the configuration:
1. Select Device > Configuration from the navigation tree.
The Backup page appears.
Figure 53 Backing up the configuration
2. Click the upper Backup button.
The file download dialog box appears.
3. Choose to view the .cfg file or to save the file to your local host.
4. Click the lower Backup button.
The file download dialog box appears.
5. Choose to view the .xml file or to save the file to the local host.
Restoring the configuration
Configuration restoration allows you to do the following:
• Upload a .cfg file from your local host to the device.
• Upload an .xml file from your local host to the device, and delete the .xml configuration file that
was used for the next startup.
The restored configuration takes effect at the next device startup.
64
Page 78

To restore the configuration:
1. Select Device > Configuration from the navigation tree.
2. Click the Restore tab.
Figure 54 Restoring the configuration
3. Click the upper Browse button.
The file upload dialog box appears.
4. Select the .cfg file to be uploaded, and click OK.
5. Click the lower Browse button.
The file upload dialog box appears.
6. Select the .xml file to be uploaded, and click OK.
Saving the configuration
You save the running configuration to both the .cfg configuration file and .xml configuration file that will
be used at the next startup.
Saving the configuration takes some time.
Only one administrator can save the configuration at a moment. If you save the configuration while the
system is saving the configuration as required by another administrator, the system prompts you to try
again later.
You can save the configuration in either of the following modes:
• Fast mode.
To save the configuration in fast mode, click the Save button at the upper right of the auxiliary
area.
65
Page 79

Figure 55 Saving the configuration
• Common mode.
To save the configuration in common mode:
a. Select Device > Configuration from the navigation tree.
b. Click the Save tab.
c. Click Save Current Settings.
Resetting the configuration
Resetting the configuration restores the device's factory defaults, deletes the current configuration files,
and reboots the device.
To reset the configuration:
1. Select Device > Configuration from the navigation tree.
2. Click the Initialize tab.
3. Click Restore Factory-Default Settings.
Figure 56 Resetting the configuration
66
Page 80

Managing files
The device requires a series of files for correct operation, including boot files and configuration files.
These files are saved on the storage media. You can display files on the storage media, download,
upload, or remove a file, or specify the main boot file.
Displaying files
1. Select Device > File Management from the navigation tree.
Figure 57 File management page
2. Select a medium from the Please select disk list.
Two categories of information are displayed:
{ Medium information, including the used space, the free space, and the capacity of the medium.
{ File information, including all files on the medium, the file sizes, and the boot file types (Main or
Backup). The boot file type is only displayed for an application file (.bin or .app file) that will be
used as the main or backup boot file.
Downloading a file
1. Select Device > File Management from the navigation tree to enter the file management page
(see Figure 57).
2. From the Plea
3. Select the file from the list.
Only one file can be downloaded at a time.
se select disk list, select the medium where the file to be downloaded resides.
67
Page 81

4. Click Download File.
The File Download dialog box appears.
5. Open the file or save the file to a path.
Uploading a file
IMPORTANT:
Uploading a file takes some time. HP recommends not performing any operation on the Web interface
during the upload.
1. Select Device > File Management from the navigation tree to enter the file management page
(see Figure 57).
2. In the Upload File area, selec
3. Click Browse to navigate to the file to be uploaded.
4. Click Apply.
t the medium for saving the file from the Please select disk list.
Removing a file
1. Select Device > File Management from the navigation tree to enter the file management page
(see Figure 57).
2. Do one of the follow
{ Click the icon of a file to remove the file.
{ Select a file from the file list and click Remove File.
To remove multiple files, repeat step 2, or select the files from the file list and click Remove File.
ing:
Specifying the main boot file
1. Select Device > File Manage from the navigation tree to enter the file management page
(see Figure 57).
2. From the Plea
main boot file.
se select disk list, select the medium that holds the application file to be used as the
3. Select the application file (.bin or .app file) from the file list.
4. Click Set as Main Boot File.
68
Page 82

Managing ports
You can use the port management feature to set and view the operation parameters of a Layer 2 Ethernet
port and an aggregate interface.
• For a Layer 2 Ethernet port, these operation parameters include its state, speed, duplex mode, link
type, PVID, description, MDI mode, flow control settings, MAC learning limit, and storm
suppression ratios.
• For an aggregate interface, these operation parameters include its state, link type, PVID, description,
and MAC learning limit.
Setting operation parameters for a port
1. Select Device > Port Management from the navigation tree.
2. Click the Setup tab.
69
Page 83

p
Figure 58 The Setup tab
3. Set the operation parameters for the port as described in Table 15.
4. Click Apply.
Table 15 Configuration items
Item Descri
Enable or disable the port.
Port State
Sometimes, after you modify the operation parameters of a port, you must disable and
then enable the port to have the modifications take effect.
tion
70
Page 84

Item Description
Set the transmission speed of the port:
• 10—10 Mbps.
• 100—100 Mbps.
• 1000—1000 Mbps.
• Auto—Autonegotiation.
Speed
• Auto 10—Autonegotiated to 10 Mbps.
• Auto 100—Autonegotiated to 100 Mbps.
• Auto 1000—Autonegotiated to 1000 Mbps.
• Au t o 10 100—Autonegotiated to 10 or 100 Mbps.
• Au t o 10 1000—Autonegotiated to 10 or 1000 Mbps.
• Auto 100 1000—Autonegotiated to 100 or 1000 Mbps.
• Au t o 10 100 1000—Autonegotiated to 10, 100, or 1000 Mbps.
Set the duplex mode of the port:
Duplex
• Auto—Autonegotiation.
• Full—Full duplex.
• Half—Half duplex.
Set the link type of the current port, which can be access, hybrid, or trunk. For more
Link Type
PVID
Description Set the description of the port.
information, see "Configuring VLANs."
o change the link type of a port from trunk to hybrid, or vice versa, you must first set its link
T
type to access.
Set the port VLAN ID (PVID) of the interface. For more information about setting the PVID,
see "Configuring VLANs."
To make
the link must have the same PVID.
sure a link correctly transmits packets, the trunk or hybrid ports at the two ends of
MDI
Set the MDI mode of the port.
You can use two types of Ethernet cables to connect Ethernet devices: crossover cable and
straight-through cable. To accommodate these two types of cables, an Ethernet port can
operate in one of the following three MDI modes: across, normal, and auto.
An Ethernet port is composed of eight pins. By default, each pin has its particular role. For
example, pin 1 and pin 2 are used for transmitting signals, and pin 3 and pin 6 are used
for receiving signals. You can change the pin roles by setting the MDI mode.
• For an Ethernet port in across mode, pin 1 and pin 2 are used for transmitting signals,
and pin 3 and pin 6 are used for receiving signals. The pin roles are not changed.
• For an Ethernet port in auto mode, the pin roles are decided through autonegotiation.
• For an Ethernet port in normal mode, the pin roles are changed. Pin 1 and pin 2 are
used for receiving signals, and pin 3 and pin 6 are used for transmitting signals.
To enable normal communication, you must connect the local transmit pins to the remote
receive pins. Configure the MDI mode depending on the cable types.
When you configure the MID mode, follow these guidelines:
• Typically, use the auto mode. The other two modes are used only when the device
cannot determine the cable type.
• When straight-through cables are used, the local MDI mode must be different from the
remote MDI mode.
• When crossover cables are used, the local MDI mode must be the same as the remote
MDI mode, or the MDI mode of at least one end must be set to auto.
71
Page 85

Item Description
Enable or disable flow control on the port.
With flow control enabled at both sides, when traffic congestion occurs on the ingress
Flow Control
Power Save
port, the ingress port sends a Pause frame notifying the egress port to temporarily suspend
the sending of packets. The egress port is expected to stop sending any new packet when
it receives the Pause frame. In this way, flow control helps to avoid dropping of packets.
Flow control works only after it is enabled on both the ingress and egress ports.
Enable or disable auto power-down on a port that is down.
By default, auto power-down is disabled on an Ethernet port that is down.
With auto power-down enabled on an Ethernet port that stays in the down state for a
certain period, the following events occur:
• The device automatically stops supplying power to the port.
• The port enters the power save mode.
When the Ethernet port comes up, the following events occur:
• The device automatically restores power supply to the port.
• The port resumes its normal state.
Set the MAC learning limit on the port:
Max MAC Count
• User Defined—Select this option to set the limit manually.
• No Limited—Select this option to set no limit.
EEE
Broadcast
Suppression
Multicast
Suppression
Enable or disable Energy Efficient Ethernet (EEE) on a link-up port.
With EEE enabled, when a link-up Ethernet port does not receive any packet for a certain
period, it automatically enters low power mode. When a packet arrives later, the device
restores power supply to the port and the port resumes its normal state.
Set broadcast suppression on the port:
• ratio—Sets the maximum percentage of broadcast traffic to the total bandwidth of an
Ethernet port. When you select this option, you must enter a percentage in the box
below.
• pps—Sets the maximum number of broadcast packets that can be forwarded on an
Ethernet port per second. When you select this option, you must enter a number in the
box below.
• kbps—Sets the maximum number of kilobits of broadcast traffic that can be forwarded
on an Ethernet port per second. When you select this option, you must enter a number
in the box below.
Set multicast suppression on the port:
• ratio—Sets the maximum percentage of multicast traffic to the total bandwidth of an
Ethernet port. When you select this option, you must enter a percentage in the box
below.
• pps—Sets the maximum number of multicast packets that can be forwarded on an
Ethernet port per second. When you select this option, you must enter a number in the
box below.
• kbps—Sets the maximum number of kilobits of multicast traffic that can be forwarded
on an Ethernet port per second. When you select this option, you must enter a number
in the box below.
72
Page 86

Item Description
Set unicast suppression on the port:
• ratio—Sets the maximum percentage of unicast traffic to the total bandwidth of an
Ethernet port. When you select this option, you must enter a percentage in the box
below.
Unicast
Suppression
Selected Ports
If you set operation parameters that a port does not support, you are notified of invalid settings and might
fail to set the supported operation parameters for the port or other ports.
• pps—Sets the maximum number of unicast packets that can be forwarded on an
Ethernet port per second. When you select this option, you must enter a number in the
box below.
• kbps—Sets the maximum number of kilobits of unicast traffic that can be forwarded on
an Ethernet port per second. When you select this option, you must enter a number in
the box below.
Interface or interfaces that you have selected from the chassis front panel and the
aggregate interface list below, for which you have set operation parameters.
You can set only the state and MAC learning limit for an aggregate interface.
Displaying port operation parameters
Displaying a specified operation parameter for all ports
1. Select Device > Port Management from the navigation tree.
The Summary page appears by default.
2. Select the option for a parameter you want to view.
The parameter information for all the ports is displayed in the lower part of the page.
73
Page 87

Figure 59 The Summary tab
Displaying all the operation parameters for a port
1. Select Device > Port Management from the navigation tree
2. Click the Detail tab.
3. Select a port whose operation parameters you want to view in the chassis front panel.
The operation parameter settings of the selected port are displayed on the lower part of the page.
Whether the parameter takes effect is displayed in the square brackets.
Figure 60 The Detail tab
74
Page 88
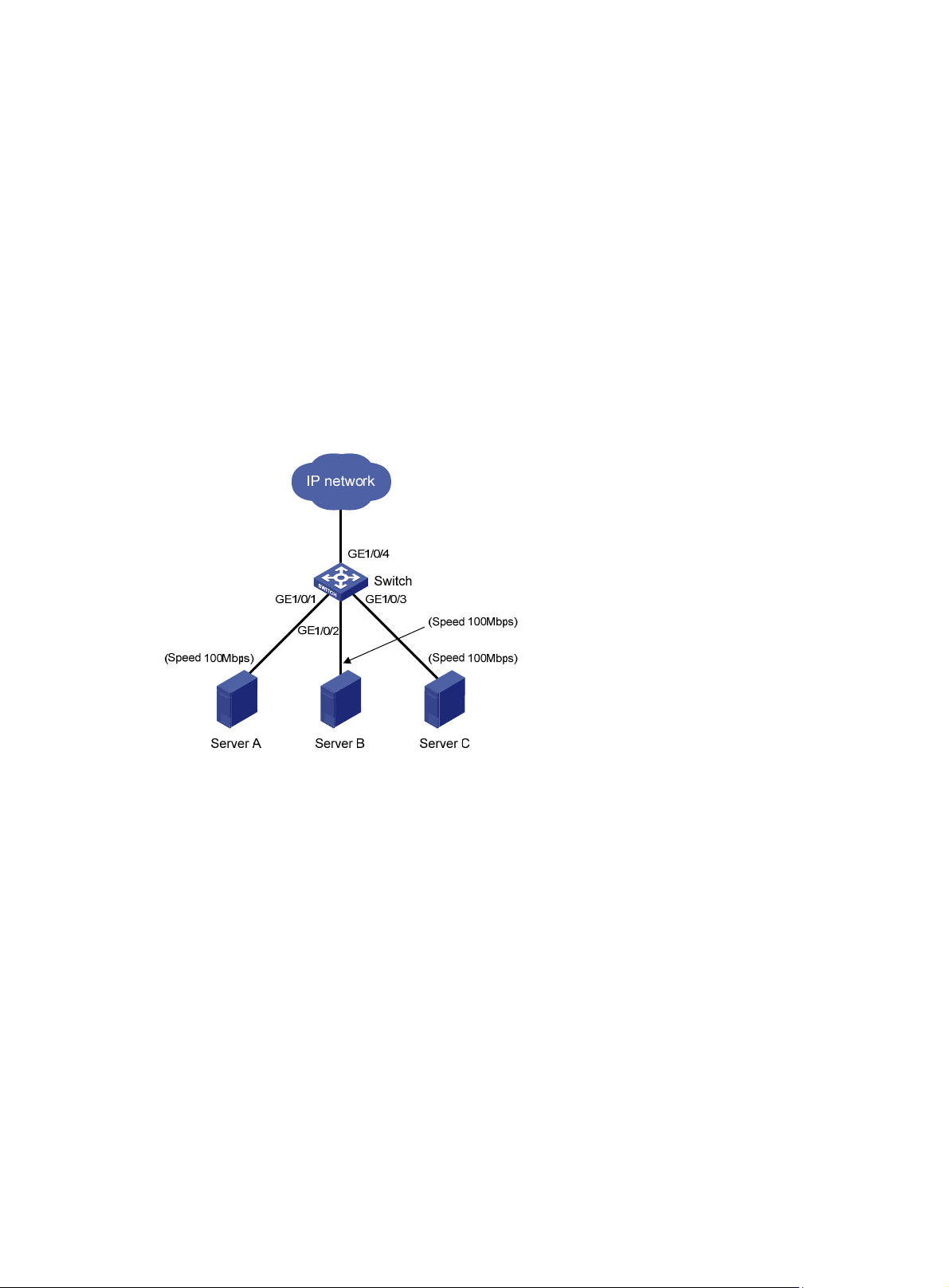
Port management configuration example
Network requirements
As shown in Figure 61:
• Server A, Server B, and Server C are connected to GigabitEthernet 1/0/1, GigabitEthernet 1/0/2,
and GigabitEthernet 1/0/3 of the switch, respectively. The rates of the network adapters of these
servers are all 1000 Mbps.
• The switch connects to the external network through GigabitEthernet 1/0/4 whose speed is 1000
Mbps.
To avoid congestion at the egress port GigabitEthernet 1/0/4, configure the autonegotiation speed
range on GigabitEthernet 1/0/1, GigabitEthernet 1/0/2, and GigabitEthernet 1/0/3 as 100 Mbps.
Figure 61 Network diagram
Configuring the switch
1. As shown in Figure 62, set the speed of GigabitEthernet 1/0/4 to 1000 Mbps:
75
Page 89

Figure 62 Configuring the speed of GigabitEthernet 1/0/4
2. Batch configure the autonegotiation speed range on GigabitEthernet 1/0/1, GigabitEthernet
1/0/2, and GigabitEthernet 1/0/3 as 100 Mbps:
a. On the Setup tab, select Auto 100 from the Speed list.
b. Select 1, 2, and 3 on the chassis front panel.
1, 2, and 3 represent ports GigabitEthernet 1/0/1, GigabitEthernet 1/0/2, and
GigabitEthernet 1/0/3.
c. Click Apply.
76
Page 90

Figure 63 Batch configuring the port speed
3. Display the speed settings of ports:
a. Click the Summary tab.
b. Click the Speed button to display the speed information of all ports on the lower part of the
page, as shown in Figure 64.
77
Page 91

Figure 64 Displaying the speed settings of ports
78
Page 92

Configuring port mirroring
Port mirroring refers to the process of copying the packets passing through a port/VLAN/CPU to the
monitor port connecting to a monitoring device for packet analysis.
Terminology
Mirroring source
The mirroring source can be one or more monitored ports, called source ports. The device where the
ports reside is called a "source device." Packets (called "mirrored packets") passing through them are
copied to a port connecting to a monitoring device for packet analysis.
Mirroring destination
The mirroring destination is the destination port (also known as the monitor port) of mirrored packets and
connects to the data monitoring device. The device where the monitor port resides is called the
"destination device." The monitor port forwards the mirrored packets to its connecting monitoring device.
A monitor port might receive multiple duplicates of a packet in some cases because it can monitor
multiple mirroring sources. For example, assume that Port 1 is monitoring bidirectional traffic on Port 2
and Port 3 on the same device. If a packet travels from Port 2 to Port 3, two duplicates of the packet will
be received on Port 1.
Mirroring direction
The mirroring direction indicates that the inbound, outbound, or bidirectional traffic can be copied on a
mirroring source:
• Inbound—Copies packets received on a mirroring source.
• Outbound—Copies packets sent out of a mirroring source.
• Bidirectional—Copies packets both received and sent on a mirroring source.
Mirroring group
Port mirroring is implemented through mirroring groups, which include local and remote mirroring groups.
Only local mirroring groups are supported.
Local port mirroring
In local port mirroring, the mirroring source and the mirroring destination are on the same device. A
mirroring group that contains the mirroring source and the mirroring destination on the device is called
a "local mirroring group."
79
Page 93

Figure 65 Local port mirroring implementation
As shown in Figure 65, the source port GigabitEthernet 1/0/1 and monitor port GigabitEthernet 1/0/2
reside on the same device. Packets of GigabitEthernet 1/0/1 are copied to GigabitEthernet 1/0/2,
which then forwards the packets to the data monitoring device for analysis.
Configuration restrictions and guidelines
When you configure port mirroring, follow these restrictions and guidelines:
• A local mirroring group can contain multiple source ports, but only one monitor port.
• Do not enable the spanning tree feature on the monitor port.
• Use a monitor port only for port mirroring to make sure the data monitoring device receives and
analyzes only the mirrored traffic rather than a mix of mirrored traffic and other forwarded traffic.
Recommended configuration procedures
Step Remarks
1. Configure a local mirroring
group.
2. Configure source ports for
the mirroring group.
3. Configure the monitor port
for the mirroring group.
Required.
For more information, see "Configuring a mirroring group."
Select the mir
Required.
For more information, see "Configuring ports for the mirroring group."
Selec
t the port type Mirror Port.
Required.
For more information, see "Configuring ports for the mirroring group."
Selec
t the port type Monitor Port.
roring group type local in the Type list.
Configuring a mirroring group
1. From the navigation tree, select Device > Port Mirroring.
80
Page 94

p
2. Click Add to enter the page for adding a mirroring group.
Figure 66 Adding a mirroring group
3. Configure the mirroring group as described in Table 16.
4. Click Apply.
Table 16 Configuration items
Item Descri
Mirroring Group ID
Type
ID of the mirroring group to be added.
Specify the type of the mirroring group to be added as Local, which indicates
adding a local mirroring group.
tion
Configuring ports for the mirroring group
1. From the navigation tree, select Device > Port Mirroring.
2. Click Modify Port to enter the page for configuring ports for a mirroring group.
81
Page 95

p
Figure 67 Modifying ports
3. Configure ports for the mirroring group as described in Table 17.
4. Click Apply.
A progress dialog box appears.
5. After the success notification appears, click Close.
Table 17 Configuration items
Item Descri
Mirroring
Group ID
Port Type
ID of the mirroring group to be configured.
The available groups were added previously.
Select a Local mirroring group ID to configure ports for the local mirroring group.
Configure ports for a local mirroring group:
• Monitor Port—Configures the monitor ports for the local mirroring group.
tion
• Mirror Port—Configures mirroring ports for the local mirroring group.
Set the direction of the traffic monitored by the monitor port of the mirroring group:
Stream
Orientation
• both—Mirrors both received and sent packets on mirroring ports.
• inbound—Mirrors only packets received by mirroring port.
• outbound—Mirrors only packets sent by mirroring ports.
Click the ports to be configured on the chassis front panel. If aggregate interfaces are
Select port(s)
configured on the device, the page displays a list of aggregate interfaces below the chassis
front panel. You can select aggregate interfaces from this list and configure them as
mirroring ports of a port mirroring group.
82
Page 96

Local port mirroring configuration example
Network requirements
As shown in Figure 68, configure local port mirroring on Switch A so the server can monitor the packets
received and sent by the Marketing department and Technical department.
Figure 68 Network diagram
Configuration procedure
Adding a local mirroring group
1. From the navigation tree, select Device > Port Mirroring.
2. Click Add to enter the page for adding mirroring groups as shown in Figure 69.
Figure 69 Adding a loca
l mirroring group
83
Page 97

3. Enter 1 for Mirroring Group ID, and select Local from the Type list.
4. Click Apply.
Configuring GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 as the source ports
1. Click Modify Port.
2. Select 1 – Local from the Mirroring Group ID list.
3. Select Mirror Port from the Port Type list.
4. Select both from the Stream Orientation list.
5. Select 1 (GigabitEthernet 1/0/1) and 2 (GigabitEthernet 1/0/2) on the chassis front panel.
Figure 70 Configuring the source ports
6. Click Apply.
A configuration progress dialog box appears.
7. After the success notification appears, click Close.
Configuring GigabitEthernet 1/0/3 as the monitor port
1. Click Modify Port.
2. Select 1 – Local from the Mirroring Group ID list.
3. Select Monitor Port from the Port Type list.
4. Select 3 (GigabitEthernet 1/0/3) on the chassis front panel.
84
Page 98

Figure 71 Configuring the monitor port
5. Click Apply.
A configuration progress dialog box appears.
6. After the success notification appears, click Close.
85
Page 99

p
Managing users
The user management function allows you to do the following:
• Adding a local user, and specifying the password, access level, and service types for the user.
• Setting the super password for non-management level users to switch to the management level.
• Switching to the management level from a lower level.
Adding a local user
1. Select Device > Users from the navigation tree.
2. Click the Create tab.
Figure 72 Adding a local user
3. Configure a local user as described in Table 18.
4. Click Apply.
Table 18 Configuration items
Item Descri
Username Enter a username for the user.
tion
86
Page 100

Item Description
Select an access level for the user.
Users of different levels can perform different operations. User levels, in order from low
to high, are as follows:
• Visitor—A visitor level user can perform only ping and traceroute operations. They
cannot access the data on the device or configure the device.
Access Level
• Monitor—A monitor level user can perform ping and traceroute operations and
access the data on the device, but they cannot configure the device.
• Configure—A configure level user can perform ping and traceroute operations,
access data on the device, and configure the device, but they cannot upgrade the
software, add/delete/modify users, or back up or restore the configuration file.
• Management—A management level user can perform any operations on the device.
Password
Confirm Password Enter the same password again.
Password
Encryption
Set the password for the user.
Select the password encryption type:
• Reversible—Uses a reversible encryption algorithm. The ciphertext password can be
decrypted to get the plaintext password.
• Irreversible—Uses an irreversible encryption algorithm. The ciphertext password
cannot be decrypted to get the plaintext password.
Service Type
Select the service types for the user to use, including Web, FTP, and Telnet. You must
select at least one service type.
Setting the super password
A management level user can set the password for non-management level users to switch to the
management level. If the password is not set, non-management level users cannot switch to the
management level from a lower level.
To set the super password:
1. Select Device > Users from the navigation tree.
2. Click the Super Password tab.
Figure 73 Setting the super password
3. Configure a super password as described in Table 19.
87
 Loading...
Loading...