Page 1

HP 1:10Gb Ethernet BL-c Switch for c-Class
BladeSystem
Application Guide
Part number: 445881-001
First edition: April 2007
Page 2

Legal notices
© 2007 Hewlett-Packard Development Company, L.P.
The information contained herein is subject to change without notice. The only warranties for HP products and services are set
forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as
constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Microsoft®, Windows®, and Windows NT® are U.S. registered trademarks of Microsoft Corporation.
SunOS™ and Solaris™ are trademarks of Sun Microsystems, Inc. in the U.S. and other countries.
Cisco® is a registered trademark of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries.
2
Page 3

Contents
Contents
Accessing the switch
Introduction........................................................................................................................................... 9
Additional references ........................................................................................................................... 10
Typographical conventions.................................................................................................................... 10
Management Network.......................................................................................................................... 10
Connecting through the console port.................................................................................................. 11
Connecting through Telnet................................................................................................................ 11
Connecting through Secure Shell....................................................................................................... 11
Using the command line interfaces ......................................................................................................... 12
Configuring an IP interface............................................................................................................... 12
Using the Browser-based Interface.......................................................................................................... 13
Using Simple Network Management Protocol .......................................................................................... 14
SNMP v1.0.................................................................................................................................... 14
SNMP v3.0.................................................................................................................................... 14
Default configuration ....................................................................................................................... 14
User configuration........................................................................................................................... 15
View based configurations ............................................................................................................... 16
CLI user equivalent..................................................................................................................... 16
CLI oper equivalent .................................................................................................................... 17
Configuring SNMP trap hosts ........................................................................................................... 17
SNMPv1 trap host...................................................................................................................... 17
SNMPv2 trap host configuration ....................................................................................................... 19
SNMPv3 trap host configuration ....................................................................................................... 19
Secure access to the switch ................................................................................................................... 20
Setting allowable source IP address ranges ........................................................................................ 20
Configuring an IP address range for the management network ........................................................ 21
RADIUS authentication and authorization........................................................................................... 21
How RADIUS authentication works............................................................................................... 21
Configuring RADIUS on the switch (CLI example) ........................................................................... 22
Configuring RADIUS on the switch (BBI example) ........................................................................... 23
RADIUS authentication features.................................................................................................... 24
User accounts for RADIUS users ................................................................................................... 24
RADIUS attributes for user privileges............................................................................................. 25
TACACS+ authentication ...................................................................................................................... 25
How TACACS+ authentication works................................................................................................. 26
TACACS+ authentication features ..................................................................................................... 26
Authorization.................................................................................................................................. 26
Accounting..................................................................................................................................... 27
Configuring TACACS+ authentication on the switch (CLI example) ....................................................... 28
Configuring TACACS+ authentication on the switch (BBI example) ....................................................... 29
Secure Shell and Secure Copy............................................................................................................... 30
Configuring SSH and SCP features (CLI example)........................................................................... 31
Using SSH and SCP client commands........................................................................................... 32
SSH and SCP encryption of management messages ....................................................................... 33
Generating RSA host and server keys for SSH access ..................................................................... 33
SSH/SCP integration with RADIUS and TACACS+ authentication..................................................... 34
3
Page 4

Contents
User access control .............................................................................................................................. 34
Setting up user IDs .......................................................................................................................... 35
Ports and trunking
Introduction......................................................................................................................................... 36
Ports on the switch ............................................................................................................................... 36
Port trunk groups.................................................................................................................................. 37
Statistical load distribution................................................................................................................ 37
Built-in fault tolerance....................................................................................................................... 37
Before you configure trunks ................................................................................................................... 38
Trunk group configuration rules.............................................................................................................. 38
Port trunking example........................................................................................................................... 39
Configuring trunk groups (CLI example) ............................................................................................. 40
Configuring trunk groups (BBI example) ............................................................................................. 41
Configurable Trunk Hash algorithm ........................................................................................................ 43
Link Aggregation Control Protocol.......................................................................................................... 44
Configuring LACP ........................................................................................................................... 45
Port-based Network Access and traffic control
Port-based Network Access control......................................................................................................... 46
Extensible authentication protocol over LAN ....................................................................................... 46
802.1x authentication process.......................................................................................................... 47
EAPoL Message Exchange ............................................................................................................... 47
802.1x port states........................................................................................................................... 48
Supported RADIUS attributes ............................................................................................................ 48
EAPoL configuration guidelines ......................................................................................................... 49
Port-based traffic control ....................................................................................................................... 50
Configuring port-based traffic control................................................................................................. 50
VLANs
Introduction......................................................................................................................................... 51
Overview............................................................................................................................................ 51
VLANs and port VLAN ID numbers......................................................................................................... 51
VLAN numbers ............................................................................................................................... 51
Viewing VLANs ......................................................................................................................... 52
PVID numbers ................................................................................................................................. 52
Viewing and configuring PVIDs......................................................................................................... 52
Port information ......................................................................................................................... 52
Port configuration....................................................................................................................... 52
VLAN tagging ..................................................................................................................................... 53
VLANs and IP interfaces........................................................................................................................ 56
VLAN topologies and design considerations............................................................................................ 56
VLAN configuration rules ................................................................................................................. 57
Multiple VLANS with tagging................................................................................................................. 57
Configuring the example network...................................................................................................... 59
Configuring ports and VLANs on Switch 1 (CLI example) ................................................................ 60
Configuring ports and VLANs on Switch 2 (CLI example) ................................................................ 61
Configuring ports and VLANs on Switch 1 (BBI example) ................................................................ 62
FDB static entries.................................................................................................................................. 65
Trunking support for FDB static entries................................................................................................ 65
Configuring a static FDB entry .......................................................................................................... 65
Spanning Tree Protocol
4
Page 5

Contents
Introduction......................................................................................................................................... 66
Overview............................................................................................................................................ 66
Bridge Protocol Data Units .................................................................................................................... 66
Determining the path for forwarding BPDUs........................................................................................ 67
Bridge priority ........................................................................................................................... 67
Port priority ............................................................................................................................... 67
Port path cost ............................................................................................................................ 67
Spanning Tree Group configuration guidelines ........................................................................................ 67
Default Spanning Tree configuration.................................................................................................. 67
Adding a VLAN to a Spanning Tree Group ........................................................................................ 68
Creating a VLAN ............................................................................................................................ 68
Rules for VLAN tagged ports............................................................................................................. 68
Adding and removing ports from STGs .............................................................................................. 68
Assigning cost to ports and trunk groups ............................................................................................ 69
Multiple Spanning Trees ....................................................................................................................... 69
Why do we need Multiple Spanning Trees? ....................................................................................... 70
VLAN participation in Spanning Tree Groups ..................................................................................... 71
Configuring Multiple Spanning Tree Groups.......................................................................................71
Configuring Switch 1 (CLI example) ............................................................................................. 71
Configuring Switch 2 (CLI example) ............................................................................................. 71
Configuring Switch 1 (BBI example) ............................................................................................. 72
Port Fast Forwarding ............................................................................................................................ 74
Configuring Port Fast Forwarding...................................................................................................... 74
Fast Uplink Convergence ...................................................................................................................... 74
Configuration guidelines .................................................................................................................. 74
Configuring Fast Uplink Convergence................................................................................................ 74
RSTP and MSTP
Introduction......................................................................................................................................... 75
Rapid Spanning Tree Protocol................................................................................................................ 75
Port state changes ........................................................................................................................... 75
Port type and link type..................................................................................................................... 76
Edge port.................................................................................................................................. 76
Link type ................................................................................................................................... 76
RSTP configuration guidelines ........................................................................................................... 76
RSTP configuration example ............................................................................................................. 76
Configuring Rapid Spanning Tree (CLI example) ............................................................................ 76
Configuring Rapid Spanning Tree Protocol (BBI example)................................................................ 77
Multiple Spanning Tree Protocol............................................................................................................. 78
MSTP region................................................................................................................................... 78
Common Internal Spanning Tree ....................................................................................................... 78
MSTP configuration guidelines.......................................................................................................... 79
MSTP configuration example ............................................................................................................ 79
Configuring Multiple Spanning Tree Protocol (CLI example)............................................................. 79
Configuring Multiple Spanning Tree Protocol (BBI example)............................................................. 80
Quality of Service
Introduction......................................................................................................................................... 84
Overview............................................................................................................................................ 84
Using ACL filters .................................................................................................................................. 85
Summary of packet classifiers ........................................................................................................... 85
Summary of ACL actions .................................................................................................................. 87
Understanding ACL precedence........................................................................................................ 87
5
Page 6

Contents
Using ACL Groups ............................................................................................................................... 88
ACL Metering and Re-marking ............................................................................................................... 89
Metering........................................................................................................................................ 89
Re-marking..................................................................................................................................... 89
Viewing ACL statistics........................................................................................................................... 89
ACL configuration examples.................................................................................................................. 90
Configure Access Control Lists (CLI example) ...................................................................................... 90
Configure Access Control Lists and Groups (BBI example 1) ................................................................. 91
Using DSCP values to provide QoS ........................................................................................................ 95
Differentiated Services concepts........................................................................................................ 95
Per Hop Behavior............................................................................................................................ 95
QoS levels ..................................................................................................................................... 96
Using 802.1p priorities to provide QoS.................................................................................................. 96
802.1p configuration (CLI example) .................................................................................................. 98
802.1p configuration (BBI example).................................................................................................. 98
Queuing and scheduling..................................................................................................................... 103
Basic IP routing
IP routing benefits .............................................................................................................................. 104
Routing between IP subnets ................................................................................................................. 104
Example of subnet routing................................................................................................................... 107
Using VLANs to segregate broadcast domains.................................................................................. 108
Dynamic Host Configuration Protocol ................................................................................................... 109
DHCP relay agent ......................................................................................................................... 110
DHCP relay agent configuration...................................................................................................... 110
Routing Information Protocol
Distance vector protocol...................................................................................................................... 112
Stability ............................................................................................................................................ 112
Routing updates................................................................................................................................. 112
RIPv1................................................................................................................................................ 113
RIPv2................................................................................................................................................ 113
RIPv2 in RIPv1 compatibility mode........................................................................................................ 113
RIP Features....................................................................................................................................... 113
Poison ......................................................................................................................................... 113
Triggered updates......................................................................................................................... 113
Multicast...................................................................................................................................... 114
Default......................................................................................................................................... 114
Metric.......................................................................................................................................... 114
Authentication .............................................................................................................................. 114
RIP configuration example................................................................................................................... 115
IGMP Snooping
Introduction....................................................................................................................................... 116
Overview.......................................................................................................................................... 116
IGMPv3....................................................................................................................................... 117
FastLeave..................................................................................................................................... 117
IGMP Filtering .............................................................................................................................. 118
Configuring the range .............................................................................................................. 118
Configuring the action.............................................................................................................. 118
Static multicast router..................................................................................................................... 119
IGMP Snooping configuration example............................................................................................ 119
6
Page 7

Contents
Configuring IGMP Snooping (CLI example) ................................................................................. 119
Configuring IGMP Filtering (CLI example).................................................................................... 120
Configuring a Static Mrouter (CLI example) ................................................................................. 120
Configuring IGMP Snooping (BBI example) ................................................................................. 121
Configuring IGMP Filtering (BBI example) ................................................................................... 123
Configuring a Static Multicast Router (BBI example)...................................................................... 127
OSPF
OSPF overview.................................................................................................................................. 128
Types of OSPF areas ..................................................................................................................... 128
Types of OSPF routing devices........................................................................................................ 129
Neighbors and adjacencies ........................................................................................................... 130
Link-State Database ....................................................................................................................... 130
Shortest Path First Tree................................................................................................................... 130
Internal versus external routing........................................................................................................ 131
OSPF implementation in HP 1:10GbE switch software ............................................................................ 131
Configurable parameters ............................................................................................................... 131
Defining areas.............................................................................................................................. 132
Assigning the area index .......................................................................................................... 132
Using the area ID to assign the OSPF area number ...................................................................... 133
Attaching an area to a network ................................................................................................. 133
Interface cost................................................................................................................................ 133
Electing the designated router and backup .......................................................................................134
Summarizing routes....................................................................................................................... 134
Default routes .................................................................................................................................... 134
Virtual links .................................................................................................................................. 135
Router ID...................................................................................................................................... 135
Authentication .............................................................................................................................. 136
Host routes for load balancing........................................................................................................ 137
OSPF features not supported in this release ...................................................................................... 138
OSPF configuration examples.............................................................................................................. 138
Example 1: Simple OSPF domain (CLI example)................................................................................ 138
Example 1: Simple OSPF domain (BBI example) .......................................................................... 139
Example 2: Virtual links ................................................................................................................. 147
Configuring OSPF for a virtual link on Switch A ........................................................................... 147
Configuring OSPF for a virtual link on Switch B.................................................................................148
Other Virtual Link Options......................................................................................................... 149
Example 3: Summarizing routes...................................................................................................... 149
Verifying OSPF configuration.......................................................................................................... 151
Remote monitoring
Introduction....................................................................................................................................... 152
Overview.......................................................................................................................................... 152
RMON group 1—statistics ............................................................................................................. 152
Configuring RMON Statistics (CLI example)................................................................................. 153
Configuring RMON Statistics (BBI example)................................................................................. 153
RMON group 2—history................................................................................................................ 155
History MIB objects .................................................................................................................. 155
RMON group 3—alarms ............................................................................................................... 157
Alarm MIB objects.................................................................................................................... 157
RMON group 9—events ................................................................................................................ 161
Configuring RMON Events (CLI example).................................................................................... 162
Configuring RMON Events (BBI example).................................................................................... 162
7
Page 8

Contents
High availability
Introduction....................................................................................................................................... 164
Uplink Failure Detection...................................................................................................................... 164
Failure Detection Pair..................................................................................................................... 165
Spanning Tree Protocol with UFD .................................................................................................... 165
Configuration guidelines ................................................................................................................ 166
Monitoring Uplink Failure Detection................................................................................................. 166
Configuring Uplink Failure Detection................................................................................................ 166
Configuring UFD on Switch 1 (CLI example) ................................................................................ 167
Configuring UFD on Switch 2 (CLI example) ................................................................................ 167
Configuring Uplink Failure Detection (BBI example) ...................................................................... 168
VRRP overview................................................................................................................................... 170
VRRP components.......................................................................................................................... 170
Virtual router ........................................................................................................................... 170
Virtual router MAC address....................................................................................................... 170
Owners and renters.................................................................................................................. 170
Master and backup virtual router ............................................................................................... 171
Virtual Interface Router.............................................................................................................. 171
VRRP operation.................................................................................................................................. 171
Selecting the master VRRP router ..................................................................................................... 171
Failover methods................................................................................................................................ 172
Active-Active redundancy............................................................................................................... 172
HP 1:10GbE switch extensions to VRRP ................................................................................................ 173
Tracking VRRP router priority .......................................................................................................... 173
Virtual router deployment considerations............................................................................................... 174
Assigning VRRP virtual router ID ...................................................................................................... 174
Configuring the switch for tracking .................................................................................................. 174
High availability configurations............................................................................................................ 175
Active-Active configuration ............................................................................................................. 175
Task 1: Configure Switch A....................................................................................................... 175
Task 2: Configure Switch B ....................................................................................................... 177
Task 1: Configure Switch A (BBI example)................................................................................... 178
Troubleshooting tools
Introduction....................................................................................................................................... 188
Port Mirroring.................................................................................................................................... 188
Configuring Port Mirroring (CLI example) ......................................................................................... 189
Configuring Port Mirroring (BBI example) ......................................................................................... 190
Other network troubleshooting techniques ............................................................................................. 192
Console and Syslog messages ........................................................................................................ 192
Ping ............................................................................................................................................ 192
Trace route................................................................................................................................... 192
Statistics and state information........................................................................................................ 193
Customer support tools................................................................................................................... 193
Index
8
Page 9

Accessing the switch
Accessing the switch
Introduction
This guide will help you plan, implement, and administer the switch software for the HP 1:10Gb Ethernet
BL-c Switch. Where possible, each section provides feature overviews, usage examples, and configuration
instructions.
• “Accessing the switch” describes how to configure and view information and statistics on the switch
over an IP network. This chapter also discusses different methods to manage the switch for remote
administrators, such as setting specific IP addresses and using Remote Authentication Dial-in User
Service (RADIUS) authentication, Secure Shell (SSH), and Secure Copy (SCP) for secure access to the
switch.
• “Ports and port trunking” describes how to group multiple physical ports together to aggregate the
bandwidth between large-scale network devices.
• “Port-based Network Access and Traffic Control” describes how to authenticate devices attached to
a LAN port that has point-to-point connection characteristics. Port-based Network Access Control
provides security to ports of the HP 1:10GbE switch that connect to servers. Port-based Traffic
Control allows the switch to guard against broadcast storms.
• “VLANs” describes how to configure Virtual Local Area Networks (VLANs) for creating separate
network segments, including how to use VLAN tagging for devices that use multiple VLANs.
• “Spanning Tree Protocol” discusses how spanning trees configure the network so that the switch uses
the most efficient path when multiple paths exist.
• “Rapid Spanning Tree Protocol/Multiple Spanning Tree Protocol” describes extensions to the
Spanning Tree Protocol that provide rapid convergence of spanning trees for fast reconfiguration of
the network.
• “Quality of Service” discusses Quality of Service features, including IP filtering using Access Control
Lists, Differentiated Services, and IEEE 802.1p priority values.
• “Basic IP Routing” describes how to configure the HP 1:10GbE switch for IP routing using IP subnets,
and DHCP Relay.
• “Routing Information Protocol” describes how the HP 1:10GbE switch software implements standard
Routing Information Protocol (RIP) for exchanging TCP/IP route information with other routers.
• “IGMP Snooping” describes how to use IGMP to conserve bandwidth in a multicast-switching
environment.
• “OSPF” describes OSPF concepts, how OSPF is implemented, and examples of how to configure
your switch for OSPF support.
• “Remote Monitoring” describes how to configure the RMON agent on the switch, so the switch can
exchange network monitoring data.
• “High Availability” describes how the HP 1:10GbE switch supports high-availability network
topologies. This release provides Uplink Failure Detection and Virtual Router Redundancy Protocol
(VRRP).
• “Troubleshooting tools” describes Port Mirroring and other troubleshooting techniques.
9
Page 10

Accessing the switch
Additional references
Additional information about installing and configuring the switch is available in the following guides,
which are available at http://www.hp.com/go/bladesystem/documentation
.
• HP 1:10Gb Ethernet BL-c Switch User Guide
• HP 1:10Gb Ethernet BL-c Switch Command Reference
• HP 1:10Gb Ethernet BL-c Switch ISCLI Reference Guide
• HP 1:10Gb Ethernet BL-c Switch Browser-based Interface Reference
• HP 1:10Gb Ethernet BL-c Switch Quick Setup Instructions
Typographical conventions
The following table describes the typographic styles used in this guide:
Table 1 Typographic conventions
Typeface or
symbol
AaBbCc123
AaBbCc123
<AaBbCc123>
[ ]
Meaning Example
This type depicts onscreen computer output and prompts.
This type displays in command examples and shows text
that must be typed in exactly as shown.
This bracketed type displays in command examples as a
parameter placeholder. Replace the indicated text with
the appropriate real name or value when using the
command. Do not type the brackets.
Command items shown inside brackets are optional and
can be used or excluded as the situation demands. Do
not type the brackets.
Management Network
The HP 1:10GbE switch is an integral subsystem within the overall BladeSystem. The BladeSystem chassis
includes an Onboard Administrator as the central element for overall chassis and control.
The HP 1:10GbE switch communicates with the Onboard Administrator through its internal management
port (port 18). The factory default settings permit management and control access to the switch through
the 10/100 Mbps Ethernet port on the Onboard Administrator, or the built-in console port. You also can
use the external Ethernet ports to manage and control the HP 1:10GbE switch.
Main#
Main# sys
To establish a Telnet session, enter:
host# telnet <IP address>
Read your user guide thoroughly.
host# ls [-a]
The HP 1:10GbE switch management network has the following characteristics:
• Port 18—Management port 18 has a fixed configuration, as follows:
○ 100 Mbps
○ Full duplex
○ Flow control: both
○ No auto-negotiation
10
Page 11

Accessing the switch
○ Untagged
○ Port VLAN ID (PVID): 4095
• VLAN 4095—Management VLAN 4095 isolates management traffic within the HP 1:10GbE switch.
VLAN 4095 contains only one member port (port 18). No other ports can be members of
VLAN 4095.
• Interface 256—Management interface 256 is associated with VLAN 4095. No other interfaces can
be associated with VLAN 4095. You can configure the IP address of the management interface
manually or through Dynamic Host Control Protocol (DHCP).
• Gateway 4—This gateway is the default gateway for the management interface.
• STG 128—If the HP 1:10GbE switch is configured to use multiple spanning trees, spanning tree
group 128 (STG 128) contains management VLAN 4095, and no other VLANS are allowed in STG
128. The default status of STG 128 is off.
If the HP 1:10GbE switch is configured to use Rapid Spanning Tree Protocol, STG 1 contains
management VLAN 4095.
To access the HP 1:10GbE switch management interface through the Onboard Administrator:
• Use the Onboard Administrator internal DHCP server, through Enclosure-Based IP Addressing
• Use an external DHCP server. Connect the Onboard administrator and the HP 1:10GbE switch to
the network, and disable Enclosure-Based IP Addressing.
• Assign a static IP interface to the Onboard Administrator and to the HP 1:10GbE switch
management interface (interface 256).
Connecting through the console port
Using a null modem cable, you can directly connect to the switch through the console port. A console
connection is required in order to configure Telnet or other remote access applications. For more
information on establishing console connectivity to the switch, see the HP 1:10Gb Ethernet BL-c Switch
User Guide.
Connecting through Telnet
By default, Telnet is enabled on the switch. Once the IP parameters are configured, you can access the
CLI from any workstation connected to the network using a Telnet connection. Telnet access provides the
same options for a user and an administrator as those available through the console port, minus certain
commands. The switch supports four concurrent Telnet connections.
To establish a Telnet connection with the switch, run the Telnet program on your workstation and issue the
telnet command, followed by the switch IP address:
telnet <switch IP address>
Connecting through Secure Shell
By default, the Secure Shell (SSH) protocol is disabled on the switch. SSH enables you to securely log into
another computer over a network to execute commands remotely. As a secure alternative to using Telnet
to manage switch configuration, SSH ensures that all data sent over the network is encrypted and secure.
For more information, see the “Secure Shell and Secure Copy” section later in this chapter. For additional
information on the CLI, see the HP 1:10Gb Ethernet BL-c Switch Command Reference Guide.
11
Page 12

Accessing the switch
Using the command line interfaces
The command line interface (CLI) can be accessed via local terminal connection or a remote session using
Telnet or SSH. The CLI is the most direct method for collecting switch information and performing switch
configuration.
The HP 1:10GbE switch provides two CLI modes: The menu-based AOS CLI, and the tree-based ISCLI.
You can set the HP 1:10GbE switch to use either CLI mode.
The Main Menu of the AOS CLI, with administrator privileges, is displayed below:
[Main Menu]
info - Information Menu
stats - Statistics Menu
cfg - Configuration Menu
oper - Operations Command Menu
boot - Boot Options Menu
maint - Maintenance Menu
diff - Show pending config changes [global command]
apply - Apply pending config changes [global command]
save - Save updated config to FLASH [global command]
revert - Revert pending or applied changes [global command]
exit - Exit [global command, always available]
For complete information about the AOS CLI, see the HP 1:10Gb Ethernet BL-c Switch Command
Reference.
The ISCLI provides a tree-based command structure, for users familiar with similar products.
An example of a typical ISCLI command is displayed below:
Switch(config)# spanning-tree stp 1 enable
For complete information about the ISCLI, refer to the ISCLI Reference Guide.
Configuring an IP interface
An IP interface address must be set on the switch to provide management access to the switch over an IP
network. By default, the management interface is set up to request its IP address from a Bootstrap Protocol
(BOOTP) server.
If you have a BOOTP server on your network, add the Media Access Control (MAC) address of the switch
to the BOOTP configuration file located on the BOOTP server. The MAC address can be found on a small
white label on the back panel of the switch. The MAC address can also be found in the System
Information menu (see the HP 1:10Gb Ethernet BL-c Switch Command Reference or ISCLI Reference.) If
you are using a DHCP server that also does BOOTP, you do not have to configure the MAC address.
If you do not have a BOOTP server, you must manually configure an IP address.
12
Page 13

Accessing the switch
The following example shows how to manually configure an IP address on the switch:
1. Configure an IP interface for the Telnet connection, using the sample IP address of 205.21.17.3.
2. The pending subnet mask address and broadcast address are automatically calculated.
>> # /cfg/l3/if 1 (Select IP interface 1)
>> IP Interface 1# addr 205.21.17.3 (Assign IP address for the interface)
Current IP address: 0.0.0.0
New pending IP address: 205.21.17.3
Pending new subnet mask: 255.255.255.0
. . . . . . . . . . . .
>> IP Interface 1# ena (Enable IP interface 1)
3. If necessary, configure up to two default gateways.
4. Configuring the default gateways allows the switch to send outbound traffic to the routers.
>> IP Interface 5# ../gw 1 (Select primary default gateway)
>> Default gateway 1# addr 205.21.17.1 (Assign IP address for primary router)
>> Default gateway 1# ena (Enable primary default gateway)
>> Default gateway 1# ../gw 2 (Select secondary default gateway)
>> Default gateway 2# addr 205.21.17.2 (Assign address for secondary router)
>> Default gateway 2# ena (Enable secondary default gateway)
5. Apply, verify, and save the configuration.
>> Default gateway 2# apply (Apply the configuration)
>> Default gateway 2# save (Save the configuration)
>> # /cfg/dump (Verify the configuration)
Using the Browser-based Interface
By default, the Browser-based Interface (BBI) protocol is enabled on the switch. The Browser-based
Interface (BBI) provides access to the common configuration, management and operation features of the
switch through your Web browser. For more information, see the HP 1:10Gb Ethernet BL-c Switch
Browser-based Interface Reference.
The BBI is organized at a high level as follows:
• Configuration—These menus provide access to the configuration elements for the entire switch.
○ System—Configure general switch configuration elements.
○ Switch ports—Configure switch ports and related features.
○ Port-based port mirroring—Configure mirrored ports and monitoring ports.
○ Layer 2—Configure Layer 2 features, including trunk groups, VLANs, and Spanning Tree
Protocol.
○ RMON menu—Configure Remote Monitoring (RMON) functions.
○ Layer 3—Configure all of the IP related information, including IGMP Snooping.
○ QoS—Configure Quality of Service features.
○ Access Control—Configure Access Control Lists and Groups.
○ Uplink Failure Detection—Configure a Failover Pair of Links to Monitor and Links to Disable.
• Statistics—These menus provide access to the switch statistics and state information.
• Dashboard—These menus display settings and operating status of a variety of switch features.
13
Page 14

Accessing the switch
Using Simple Network Management Protocol
The switch software provides SNMP v1.0 and SNMP v3.0 support for access through any network
management software, such as HP-OpenView.
SNMP v1.0
To access the SNMP agent on the switch, the read and write community strings on the SNMP manager
should be configured to match those on the switch. The default read community string on the switch is
public and the default write community string is private.
The read and write community strings on the switch can be changed using the following commands on the
CLI.
>> /cfg/sys/ssnmp/rcomm
-and-
>> /cfg/sys/ssnmp/wcomm
The SNMP manager should be able to reach the management interface or any one of the IP interfaces on
the switch.
For the SNMP manager to receive the traps sent out by the SNMP agent on the switch, the trap host on
the switch should be configured with the following command:
/cfg/sys/ssnmp/snmpv3/taddr
For more details, see “Configuring SNMP trap hosts”.
SNMP v3.0
SNMPv3 is an enhanced version of the Simple Network Management Protocol, approved by the Internet
Engineering Steering Group in March, 2002. SNMP v3.0 contains additional security and authentication
features that provide data origin authentication, data integrity checks, timeliness indicators, and
encryption to protect against threats such as masquerade, modification of information, message stream
modification, and disclosure.
SNMP v3 ensures that the client can use SNMP v3 to query the MIBs, mainly for security.
To access the SNMP v3.0 menu, enter the following command in the CLI:
>> # /cfg/sys/ssnmp/snmpv3
For more information on SNMP MIBs and the commands used to configure SNMP on the switch, see the
HP 1:10Gb Ethernet BL-c Switch Command Reference.
Default configuration
The switch software has two users by default. Both the users adminmd5 and adminsha have access to
all the MIBs supported by the switch.
• username 1—adminmd5/password adminmd5. Authentication used is MD5.
• username 2—adminsha/password adminsha. Authentication used is SHA.
• username 3—v1v2only/password none.
To configure an SNMP user name, enter the following command from the CLI:
>> # /cfg/sys/ssnmp/snmpv3/usm 6
14
Page 15

Accessing the switch
User configuration
Users can be configured to use the authentication/privacy options. The HP 1:10GbE switch supports two
authentication algorithms: MD5 and SHA, as specified in the following command:
/cfg/sys/ssnmp/snmpv3/usm <x>/auth md5|sha
1. To configure a user with name admin, authentication type MD5, authentication password of admin,
and privacy option DES with privacy password of admin, use the following CLI commands:
>> # /cfg/sys/ssnmp/snmpv3/usm 5
>> SNMPv3 usmUser 5 # name "admin" (Configure ‘admin’ user type)
>> SNMPv3 usmUser 5 # auth md5
>> SNMPv3 usmUser 5 # authpw admin
>> SNMPv3 usmUser 5 # priv des
>> SNMPv3 usmUser 5 # privpw admin
2. Configure a user access group, along with the views the group may access. Use the access table to
configure the group’s access level.
>> # /cfg/sys/ssnmp/snmpv3/access 5
>> SNMPv3 vacmAccess 5 # name "admingrp" (Configure an access group)
>> SNMPv3 vacmAccess 5 # level authPriv
>> SNMPv3 vacmAccess 5 # rview "iso"
>> SNMPv3 vacmAccess 5 # wview "iso"
>> SNMPv3 vacmAccess 5 # nview "iso"
Because the read view (rview), write view (wview), and notify view (nview) are all set to “iso,” the
user type has access to all private and public MIBs.
3. Assign the user to the user group. Use the group table to link the user to a particular access group.
>> # /cfg/sys/ssnmp/snmpv3/group 5
>> SNMPv3 vacmSecurityToGroup 5 # uname admin
>> SNMPv3 vacmSecurityToGroup 5 # gname admingrp
If you want to allow user access only to certain MIBs, see the “View based configurations” section.
15
Page 16

Accessing the switch
View based configurations
CLI user equivalent
To configure an SNMP user equivalent to the CLI user, use the following configuration:
/c/sys/ssnmp/snmpv3/usm 4
name "usr" (Configure the user)
/c/sys/ssnmp/snmpv3/access 3
name "usrgrp" (Configure access group 3)
rview "usr"
wview "usr"
nview "usr"
/c/sys/ssnmp/snmpv3/group 4 (Assign user to access group 3)
uname usr
gname usrgrp
/c/sys/ssnmp/snmpv3/view 6 (Create views for user)
name "usr"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.1.2" (Agent statistics)
/c/sys/ssnmp/snmpv3/view 7
name "usr"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.1.3" (Agent information)
/c/sys/ssnmp/snmpv3/view 8
name "usr"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.2.2" (L2 statistics)
/c/sys/ssnmp/snmpv3/view 9
name "usr"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.2.3" (L2 information)
/c/sys/ssnmp/snmpv3/view 10
name "usr"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.3.2" (L3 statistics)
/c/sys/ssnmp/snmpv3/view 11
name "usr"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.3.3" (L3 information)
16
Page 17

Accessing the switch
CLI oper equivalent
To configure an SNMP user equivalent to the CLI oper, use the following configuration:
/c/sys/ssnmp/snmpv3/usm 5
name "oper" (Configure the oper)
/c/sys/ssnmp/snmpv3/access 4
name "opergrp" (Configure access group 4)
rview "oper"
wview "oper"
nview "oper"
/c/sys/ssnmp/snmpv3/group 4 (Assign oper to access group 4)
uname oper
gname opergrp
/c/sys/ssnmp/snmpv3/view 20 (Create views for oper)
name "oper"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.1.2" (Agent statistics)
/c/sys/ssnmp/snmpv3/view 21
name "oper"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.1.3" (Agent information)
/c/sys/ssnmp/snmpv3/view 22
name "oper"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.2.2" (L2 statistics)
/c/sys/ssnmp/snmpv3/view 23
name "oper"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.2.3" (L2 information)
/c/sys/ssnmp/snmpv3/view 24
name "oper"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.3.2" (L3 statistics)
/c/sys/ssnmp/snmpv3/view 25
name "oper"
tree " 1.3.6.1.4.1.11.2.3.7.11.33.1.2.3.3" (L3 information)
Configuring SNMP trap hosts
SNMPv1 trap host
1. Configure a user with no authentication or password.
/c/sys/ssnmp/snmpv3/usm 10 (Configure user named “v1trap”)
name "v1trap"
2. Configure an access group and group table entries for the user. Use the following command to
specify which traps can be received by the user:
/c/sys/ssnmp/snmpv3/access <x>/nview
/c/sys/ssnmp/snmpv3/access 10 (Define access group to view SNMPv1 traps)
name "v1trap"
model snmpv1
nview "iso"
/c/sys/ssnmp/snmpv3/group 10 (Assign user to the access group)
model snmpv1
uname v1trap
gname v1trap
In this example the user will receive the traps sent by the switch.
17
Page 18

Accessing the switch
3. Configure an entry in the notify table.
/c/sys/ssnmp/snmpv3/notify 10 (Assign user to the notify table)
name v1trap
tag v1trap
4. Specify the IP address and other trap parameters in the Target Address( targetAddr) and Target
Parameters (targetParam) tables. Use the following command to specify the user name used with this
targetParam table:
c/sys/ssnmp/snmpv3/tparam <x>/uname
/c/sys/ssnmp/snmpv3/taddr 10 (Define an IP address to send traps)
name v1trap
addr 47.80.23.245
taglist v1trap
pname v1param
/c/sys/ssnmp/snmpv3/tparam 10 (Specify SNMPv1 traps to send)
name v1param
mpmodel snmpv1
uname v1trap
model snmpv1
5. Use the community table to define the community string used in the traps.
/c/sys/ssnmp/snmpv3/comm 10 (Define the community string)
index v1trap
name public
uname v1trap
18
Page 19

Accessing the switch
SNMPv2 trap host configuration
The SNMPv2 trap host configuration is similar to the SNMPv1 trap host configuration. Wherever you
specify the model, specify snmpv2 instead of snmpv1.
c/sys/ssnmp/snmpv3/usm 10 (Configure user named “v2trap”)
name "v2trap"
/c/sys/ssnmp/snmpv3/access 10 (Define access group to view SNMPv2 traps)
name "v2trap"
model snmpv2
nview "iso"
/c/sys/ssnmp/snmpv3/group 10 (Assign user to the access group)
model snmpv2
uname v2trap
gname v2trap
/c/sys/ssnmp/snmpv3/notify 10 (Assign user to the notify table)
name v2trap
tag v2trap
/c/sys/ssnmp/snmpv3/taddr 10 (Define an IP address to send traps)
name v2trap
addr 47.81.25.66
taglist v2trap
pname v2param
/c/sys/ssnmp/snmpv3/tparam 10 (Specify SNMPv2 traps to send)
name v2param
mpmodel snmpv2c
uname v2trap
model snmpv2
/c/sys/ssnmp/snmpv3/comm 10 (Define the community string)
index v2trap
name public
uname v2trap
SNMPv3 trap host configuration
To configure a user for SNMPv3 traps, you can choose to send the traps with both privacy and
authentication, with authentication only, or without privacy or authentication. Use the following commands
to configure the access table:
/c/sys/ssnmp/snmpv3/access <x>/level
/c/sys/ssnmp/snmpv3/tparam <x>
Configure the user in the user table to match the configuration of the access table.
It is not necessary to configure the community table for SNMPv3 traps because the community string is not
used by SNMPv3.
19
Page 20

Accessing the switch
The following example shows how to configure a SNMPv3 user v3trap with authentication only:
/c/sys/ssnmp/snmpv3/usm 11 (Configure user named “v3trap”)
name "v3trap"
auth md5
authpw v3trap
/c/sys/ssnmp/snmpv3/access 11 (Define access group to view SNMPv3 traps)
name "v3trap"
level authNoPriv
nview "iso"
/c/sys/ssnmp/snmpv3/group 11 (Assign user to the access group)
uname v3trap
gname v3trap
/c/sys/ssnmp/snmpv3/notify 11 (Assign user to the notify table)
name v3trap
tag v3trap
/c/sys/ssnmp/snmpv3/taddr 11 (Define an IP address to send traps)
name v3trap
addr 47.81.25.66
taglist v3trap
pname v3param
/c/sys/ssnmp/snmpv3/tparam 11 (Specify SNMPv3 traps to send)
name v3param
uname v3trap
level authNoPriv (Set the authentication level)
For more information on using SNMP, see the HP 1:10Gb Ethernet BL-c Switch Command Reference.
See the HP 1:10Gb Ethernet BL-c Switch User Guide for a complete list of supported MIBs.
Secure access to the switch
Secure switch management is needed for environments that perform significant management functions
across the Internet. The following are some of the functions for secured management:
• Limiting management users to a specific IP address range. See the “Setting allowable source IP
address ranges” section in this chapter.
• Authentication and authorization of remote administrators. See the “RADIUS authentication and
authorization” section or the “TACACS+ authentication” section, both later in this chapter.
• Encryption of management information exchanged between the remote administrator and the switch.
See the “Secure Shell and Secure Copy” section later in this chapter.
Setting allowable source IP address ranges
To limit access to the switch without having to configure filters for each switch port, you can set a source
IP address (or range) that will be allowed to connect to the switch IP interface through Telnet, SSH, SNMP,
or the switch browser-based interface (BBI).
When an IP packet reaches the application switch, the source IP address is checked against the range of
addresses defined by the management network and management mask. If the source IP address of the
host or hosts is within this range, it is allowed to attempt to log in. Any packet addressed to a switch IP
interface with a source IP address outside this range is discarded.
20
Page 21

Accessing the switch
Configuring an IP address range for the management network
Configure the management network IP address and mask from the System Menu in the CLI. For example:
>> Main# /cfg/sys/access/mgmt/add
Enter Management Network Address: 192.192.192.0
Enter Management Network Mask: 255.255.255.128
In this example, the management network is set to 192.192.192.0 and management mask is set to
255.255.255.128. This defines the following range of allowed IP addresses:
192.192.192.1 to 192.192.192.127
The following source IP addresses are granted or not granted access to the switch:
• A host with a source IP address of 192.192.192.21 falls within the defined range and would be
allowed to access the switch.
• A host with a source IP address of 192.192.192.192 falls outside the defined range and is not
granted access. To make this source IP address valid, you would need to shift the host to an IP
address within the valid range specified by the mnet and mmask or modify the mnet to be
192.192.192.128 and the mmask to be 255.255.255.128. This would put the 192.192.192.192
host within the valid range allowed by the mnet and mmask (192.192.192.128-255).
RADIUS authentication and authorization
The switch supports the Remote Authentication Dial-in User Service (RADIUS) method to authenticate and
authorize remote administrators for managing the switch. This method is based on a client/server model.
The Remote Access Server (RAS)—the switch—is a client to the back-end database server. A remote user
(the remote administrator) interacts only with the RAS, not the back-end server and database.
RADIUS authentication consists of the following components:
• A protocol with a frame format that utilizes User Datagram Protocol (UDP) over IP, based on Request
For Comments (RFC) 2138 and 2866
• A centralized server that stores all the user authorization information
• A client, in this case, the switch
The switch, acting as the RADIUS client, communicates to the RADIUS server to authenticate and authorize
a remote administrator using the protocol definitions specified in RFC 2138 and 2866. Transactions
between the client and the RADIUS server are authenticated using a shared key that is not sent over the
network. In addition, the remote administrator passwords are sent encrypted between the RADIUS client
(the switch) and the back-end RADIUS server.
How RADIUS authentication works
RADIUS authentication works as follows:
1. A remote administrator connects to the switch and provides the user name and password.
2. Using Authentication/Authorization protocol, the switch sends the request to the authentication
server.
3. The authentication server checks the request against the user ID database.
4. Using RADIUS protocol, the authentication server instructs the switch to grant or deny administrative
access.
21
Page 22

Accessing the switch
Configuring RADIUS on the switch (CLI example)
To configure RADIUS on the switch, do the following:
1. Turn RADIUS authentication on, and then configure the Primary and Secondary RADIUS servers. For
example:
>> Main# /cfg/sys/radius (Select the RADIUS Server menu)
>> RADIUS Server# on (Turn RADIUS on)
Current status: OFF
New status: ON
>> RADIUS Server# prisrv 10.10.1.1 (Enter primary server IP)
Current primary RADIUS server: 0.0.0.0
New pending primary RADIUS server: 10.10.1.1
>> RADIUS Server# secsrv 10.10.1.2 (Enter secondary server IP)
Current secondary RADIUS server: 0.0.0.0
New pending secondary RADIUS server: 10.10.1.2
2. Configure the primary RADIUS secret and secondary RADIUS secret.
>> RADIUS Server# secret
Enter new RADIUS secret: <1-32 character secret>
>> RADIUS Server# secret2
Enter new RADIUS second secret: <1-32 character secret>
CAUTION: If you configure the RADIUS secret using any method other than a direct console
connection, the secret may be transmitted over the network as clear text.
3. If desired, you may change the default User Datagram Protocol (UDP) port number used to listen to
RADIUS. The well-known port for RADIUS is 1645.
>> RADIUS Server# port
Current RADIUS port: 1645
Enter new RADIUS port [1500-3000]: <UDP port number>
4. Configure the number of retry attempts for contacting the RADIUS server and the timeout period.
>> RADIUS Server# retries
Current RADIUS server retries: 3
Enter new RADIUS server retries [1-3]: <server retries>
>> RADIUS Server# time
Current RADIUS server timeout: 3
Enter new RADIUS server timeout [1-10]: 10 (Enter the timeout period
in seconds)
5. Apply and save the configuration.
>> RADIUS Server# apply
>> RADIUS Server# save
22
Page 23

Accessing the switch
Configuring RADIUS on the switch (BBI example)
1. Configure RADIUS parameters.
a. Click the Configure context button.
b. Open the System folder, and select Radius.
c. Enter the IP address of the primary and secondary RADIUS servers, and enter the RADIUS secret
for each server. Enable the RADIUS server.
CAUTION: If you configure the RADIUS secret using any method other than a direct console
connection, the secret may be transmitted over the network as clear text.
d. Click Submit.
23
Page 24

Accessing the switch
2. Apply, verify, and save the configuration.
RADIUS authentication features
The switch supports the following RADIUS authentication features:
• Supports RADIUS client on the switch, based on the protocol definitions in RFC 2138 and
RFC 2866.
• Allows RADIUS secret password up to 32 bytes.
• Supports secondary authentication server so that when the primary authentication server is
unreachable, the switch can send client authentication requests to the secondary authentication
server. Use the /cfg/sys/radius/cur command to show the currently active RADIUS
authentication server.
• Supports user-configurable RADIUS server retry and time-out values:
○ Time-out value = 1-10 seconds
○ Retries = 1-3
• The switch will time out if it does not receive a response from the RADIUS server in one to three
retries. The switch will also automatically retry connecting to the RADIUS server before it declares the
server down.
• Supports user-configurable RADIUS application port. The default is 1645/User Datagram Protocol
(UDP)-based on RFC 2138. Port 1812 is also supported.
• Allows network administrator to define privileges for one or more specific users to access the switch
at the RADIUS user database.
• Allows the administrator to configure RADIUS backdoor and secure backdoor for Telnet, SSH, HTTP,
and HTTPS access.
User accounts for RADIUS users
The user accounts listed in the following table can be defined in the RADIUS server dictionary file.
Table 2 User access levels
User account Description and tasks performed
User User interaction with the switch is completely passive; nothing can be changed on the
switch. Users may display information that has no security or privacy implications, such as
switch statistics and current operational state information.
Operator Operators can only effect temporary changes on the switch. These changes are lost when
the switch is rebooted/reset. Operators have access to the switch management features
used for daily switch operations. Because any changes an operator makes are undone by a
reset of the switch, operators cannot severely impact switch operation, but do have access
to the Maintenance menu. By default, the operator account is disabled and has no
password.
24
Page 25

Accessing the switch
Table 2 User access levels
User account Description and tasks performed
Administrator Administrators are the only ones that can make permanent changes to the switch
configuration—changes that are persistent across a reboot/reset of the switch.
Administrators can access switch functions to configure and troubleshoot problems on the
switch level. Because administrators can also make temporary (operator-level) changes as
well, they must be aware of the interactions between temporary and permanent changes.
RADIUS attributes for user privileges
When the user logs in, the switch authenticates the level of access by sending the RADIUS access request,
that is, the client authentication request, to the RADIUS authentication server.
If the authentication server successfully authenticates the remote user, the switch verifies the privileges of
the remote user and authorizes the appropriate access. The administrator has the option to allow
backdoor access through the console port only, or through the console and Telnet/SSH/HTTP/HTTPS
access. When backdoor access is enabled, access is allowed even if the primary and secondary
authentication servers are reachable. Only when both the primary and secondary authentication servers
are not reachable, the administrator has the option to allow secure backdoor (secbd) access through the
console port only, or through the console and Telnet/SSH/HTTP/HTTPS access. When RADIUS is on, you
can have either backdoor or secure backdoor enabled, but not both at the same time. The default value
for backdoor access through the console port only is enabled. You always can access the switch via the
console port, by using noradius and the administrator password, whether backdoor/secure backdoor
are enabled or not. The default value for backdoor and secure backdoor access through
Telnet/SSH/HTTP/HTTPS is disabled.
All user privileges, other than those assigned to the administrator, must be defined in the RADIUS
dictionary. RADIUS attribute 6, which is built into all RADIUS servers, defines the administrator. The file
name of the dictionary is RADIUS vendor-dependent. The RADIUS attributes shown in the following table
are defined for user privilege levels.
Table 3 Proprietary attributes for RADIUS
User name/access User service type Value
User Vendor-supplied 255
Operator Vendor-supplied 252
TACACS+ authentication
The switch software supports authentication, authorization, and accounting with networks using the Cisco
Systems TACACS+ protocol. The switch functions as the Network Access Server (NAS) by interacting with
the remote client and initiating authentication and authorization sessions with the TACACS+ access
server. The remote user is defined as someone requiring management access to the switch either through
a data or management port.
25
Page 26

Accessing the switch
TACACS+ offers the following advantages over RADIUS:
• TACACS+ uses TCP-based connection-oriented transport; whereas RADIUS is UDP based. TCP offers
a connection-oriented transport, while UDP offers best-effort delivery. RADIUS requires additional
programmable variables such as re-transmit attempts and time-outs to compensate for best-effort
transport, but it lacks the level of built-in support that a TCP transport offers.
• TACACS+ offers full packet encryption whereas RADIUS offers password-only encryption in
authentication requests.
• TACACS+ separates authentication, authorization, and accounting.
How TACACS+ authentication works
TACACS+ works much in the same way as RADIUS authentication.
1. Remote administrator connects to the switch and provides user name and password.
NOTE: The user name and password can have a maximum length of 128 characters. The
password cannot be left blank.
2. Using Authentication/Authorization protocol, the switch sends request to authentication server.
3. Authentication server checks the request against the user ID database.
4. Using TACACS+ protocol, the authentication server instructs the switch to grant or deny
administrative access.
During a session, if additional authorization checking is needed, the switch checks with a TACACS+
server to determine if the user is granted permission to use a particular command.
TACACS+ authentication features
Authentication is the action of determining the identity of a user, and is generally done when the user first
attempts to log in to a device or gain access to its services. Switch software supports ASCII inbound login
to the device. PAP, CHAP and ARAP login methods, TACACS+ change password requests, and one-time
password authentication are not supported.
Authorization
Authorization is the action of determining a user’s privileges on the device, and usually takes place after
authentication.
The default mapping between TACACS+ authorization privilege levels and switch management access
levels is shown in the table below. The privilege levels listed in the following table must be defined on the
TACACS+ server.
Table 4 Default TACACS+ privilege levels
User access level TACACS+ level
user 0
oper 3
admin 6
26
Page 27

Accessing the switch
Alternate mapping between TACACS+ privilege levels and switch management access levels is shown in
the table below. Use the command /cfg/sys/tacacs/cmap ena to use the alternate TACACS+
privilege levels.
Table 5 Alternate TACACS+ privilege levels
User access level TACACS+ level
user 0—1
oper 6—8
admin 14—15
You can customize the mapping between TACACS+ privilege levels and HP 1:10GbE switch
management access levels. Use the command /cfg/sys/tacacs/usermap to manually map each
TACACS+ privilege level (0-15) to a corresponding HP 1:10GbE switch management access level (user,
oper, admin, none).
If the remote user is authenticated by the authentication server, the HP 1:10GbE switch verifies the
privileges of the remote user and authorizes the appropriate access. When both the primary and
secondary authentication servers are not reachable, the administrator has an option to allow backdoor
access via the console only or console and Telnet access. The default value is disabled for Telnet access
and enabled for console access. The administrator also can enable secure backdoor
(/cfg/sys/tacacs/secbd) to allow access if both the primary and secondary TACACS+ servers fail to
respond.
Accounting
Accounting is the action of recording a user’s activities on the device for the purposes of billing and/or
security. It follows the authentication and authorization actions. If the authentication and authorization is
not performed via TACACS+, no TACACS+ accounting messages are sent out.
You can use TACACS+ to record and track software logins, configuration changes, and interactive
commands.
The switch supports the following TACACS+ accounting attributes:
• protocol (console/telnet/ssh/http)
• start_time
• stop_time
• elapsed_time
NOTE: When using the browser-based Interface, the TACACS+ Accounting Stop records are sent
only if the Quit button on the browser is clicked.
27
Page 28

Accessing the switch
Configuring TACACS+ authentication on the switch
(CLI example)
1. Turn TACACS+ authentication on, and then configure the Primary and Secondary TACACS+ servers.
>> Main# /cfg/sys/tacacs (Select the TACACS+ Server menu)
>> TACACS+ Server# on (Turn TACACS+ on)
Current status: OFF
New status: ON
>> TACACS+ Server# prisrv 10.10.1.1 (Enter primary server IP)
Current primary TACACS+ server: 0.0.0.0
New pending primary TACACS+ server: 10.10.1.1
>> TACACS+ Server# secsrv 10.10.1.2 (Enter secondary server IP)
Current secondary TACACS+ server: 0.0.0.0
New pending secondary TACACS+ server: 10.10.1.2
2. Configure the TACACS+ secret and second secret.
>> TACACS+ Server# secret
Enter new TACACS+ secret: <1-32 character secret>
>> TACACS+ Server# secret2
Enter new TACACS+ second secret: <1-32 character secret>
CAUTION: If you configure the TACACS+ secret using any method other than a direct console
connection, the secret may be transmitted over the network as clear text.
3. If desired, you may change the default TCP port number used to listen to TACACS+. The well-known
port for TACACS+ is 49.
>> TACACS+ Server# port
Current TACACS+ port: 49
Enter new TACACS+ port [1-65000]: <TCP port number>
4. Configure the number retry attempts for contacting the TACACS+ server and the timeout period.
>> TACACS+ Server# retries
Current TACACS+ server retries: 3
Enter new TACACS+ server retries [1-3]: 2
>> TACACS+ Server# time
Current TACACS+ server timeout: 5
Enter new TACACS+ server timeout [4-15]: 10 (Enter the timeout period
in minutes)
5. Configure custom privilege-level mapping (optional).
>> TACACS+ Server# usermap 2
Current privilege mapping for remote privilege 2: not set
Enter new local privilege mapping: user
>> TACACS+ Server# usermap 3 user
>> TACACS+ Server# usermap 4 user
>> TACACS+ Server# usermap 5 oper
6. Apply and save the configuration.
28
Page 29

Accessing the switch
Configuring TACACS+ authentication on the switch
(BBI example)
1. Configure TACACS+ authentication for the switch.
a. Click the Configure context button.
b. Open the System folder, and select Tacacs+.
c. Enter the IP address of the primary and secondary TACACS+ servers, and enter the TACACS+
secret. Enable TACACS+.
d. Click Submit.
29
Page 30

Accessing the switch
Configure custom privilege-level mapping (optional). Click Submit to accept each mapping
e.
change.
2. Apply, verify, and save the configuration.
Secure Shell and Secure Copy
Secure Shell (SSH) and Secure Copy (SCP) use secure tunnels to encrypt and secure messages between a
remote administrator and the switch. Telnet does not provide this level of security. The Telnet method of
managing a switch does not provide a secure connection.
SSH is a protocol that enables remote administrators to log securely into the switch over a network to
execute management commands. By default, SSH is disabled (off) on the switch.
SCP is typically used to copy files securely from one machine to another. SCP uses SSH for encryption of
data on the network. On a switch, SCP is used to download and upload the switch configuration via
secure channels. By default, SCP is disabled on the switch.
30
Page 31

Accessing the switch
The switch implementation of SSH is based on version 1.5 and version 2.0, and supports SSH clients from
version 1.0 through version 2.0. Client software can use SSH version 1 or version 2. The following SSH
clients are supported:
• SSH 3.0.1 for Linux (freeware)
• SecureCRT® 4.1.8 (VanDyke Technologies, Inc.)
• OpenSSH_3.9 for Linux (FC 3)
• FedoraCore 3 for SCP commands
• PuTTY Release 0.58 (Simon Tatham) for Windows
Configuring SSH and SCP features (CLI example)
Before you can use SSH commands, use the following commands to turn on SSH and SCP.
Enabling or disabling SSH
To enable the SSH feature, connect to the switch CLI and enter the following commands:
>> # /cfg/sys/sshd/on (Turn SSH on)
Current status: OFF
New status: ON
SSHD# apply (Apply the changes to start generating
RSA host and server keys)
RSA host key generation starts
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
RSA host key generation completes (lasts 212549 ms)
RSA host key is being saved to Flash ROM, please don’t reboot the box
immediately.
RSA server key generation starts
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
RSA server key generation completes (lasts 75503 ms)
RSA server key is being saved to Flash ROM, please don’t reboot the box
immediately.
------------------------------------------------------------------------Apply complete; don’t forget to “save” updated configuration.
NOTE: Secure Shell can be configured using the console port only. SSH menus do not display if
you access the switch using Telnet or the Browser-based Interface.
Enabling or disabling SCP apply and save
Enter the following commands from the switch CLI to enable the SCP putcfg_apply and
putcfg_apply_save commands:
>> # /cfg/sys/sshd/ena (Enable SCP apply and save)
>> # /cfg/sys/sshd/dis (Disable SCP apply and save)
SSHD# apply (Apply the changes)
31
Page 32

Accessing the switch
Configuring the SCP administrator password
To configure the scpadmin (SCP administrator) password, first connect to the switch via the RS-232
management console. For security reasons, the scpadmin password can be configured only when
connected directly to the switch console.
To configure the password, enter the following CLI command. At factory default settings, the current SCP
administrator password is admin.
>> # /cfg/sys/sshd/scpadm
Changing SCP-only Administrator password; validation required. . .
Enter current administrator password: <password>
Enter new SCP-only administrator password: <new password>
Re-enter new SCP-only administrator password: <new password>
IMPORTANT: The SCP-only administrator password must be different from the regular
New SCP-only administrator password accepted.
administrator password.
Using SSH and SCP client commands
The following shows the format for using some client commands. The examples below use
205.178.15.157 as the IP address of a sample switch.
Logging in to the switch
Enter the following command to log in to the switch:
ssh <user>@<switch IP address>
For example:
>> # ssh admin@205.178.15.157
Downloading configuration from the switch using SCP
Enter the following command to download the switch configuration using SCP. You will be prompted for a
password:
scp <user>@<switch IP address>:getcfg <local filename>
For example:
>> # scp scpadmin@205.178.15.157:getcfg ad4.cfg
The switch prompts you for the scpadmin password.
Uploading configuration to the switch using SCP
Enter the following command to upload configuration to the switch. You will be prompted for a password.
scp <local filename> <user>@<switch IP address>:putcfg
For example:
>> # scp ad4.cfg admin@205.178.15.157:putcfg
32
Page 33

Accessing the switch
Applying and saving configuration
Enter the apply and save commands after the command above (scp ad4.cfg
205.178.15.157:putcfg), or use the following commands. You will be prompted for a password.
>> # scp <local_filename> <user>@<switch IP addr>:putcfg_apply
>> # scp <local_filename> <user>@<switch IP addr>:putcfg_apply_save
For example:
>> # scp ad4.cfg admin@205.178.15.157:putcfg_apply
NOTE:
•
• putcfg_apply runs the apply command after the putcfg is done.
• putcfg_apply_save saves the new configuration to the flash after putcfg_apply is done.
• The putcfg_apply and putcfg_apply_save commands are provided because extra apply and
>> # scp ad4.cfg admin@205.178.15.157:putcfg_apply_save
The diff command is automatically executed at the end of putcfg to notify the remote client of the
difference between the new and the current configurations.
save commands are usually required after a putcfg.
SSH and SCP encryption of management messages
The following encryption and authentication methods are supported for SSH and SCP:
• Server Host Authentication—Client RSA authenticates the switch at the beginning of every connection
• Key Exchange—RSA
• Encryption—AES256-CBC, AES192-CBC, 3DES-CBC, 3DES, ARCFOUR
• User Authentication—Local password authentication, RADIUS, TACACS+
Generating RSA host and server keys for SSH access
To support the SSH server feature, two sets of RSA keys (host and server keys) are required. The host key
is 1024 bits and is used to identify the switch. The server key is 768 bits and is used to make it
impossible to decipher a captured session by breaking into the switch at a later time.
When the SSH server is first enabled and applied, the switch automatically generates the RSA host and
server keys and is stored in the flash memory.
To configure RSA host and server keys, first connect to the switch console connection (commands are not
available via Telnet connection), and enter the following commands to generate them manually:
>> # /cfg/sys/sshd/hkeygen (Generates the host key)
>> # /cfg/sys/sshd/skeygen (Generates the server key)
These two commands take effect immediately without the need of an apply command.
When the switch reboots, it will retrieve the host and server keys from the flash memory. If these two keys
are not available in the flash memory and if the SSH server feature is enabled, the switch automatically
generates them during the system reboot. This process may take several minutes to complete.
The switch can also automatically regenerate the RSA server key. To set the interval of RSA server key
autogeneration, use the following command:
>> # /cfg/sys/sshd/intrval <number of hours (0-24)>
33
Page 34

Accessing the switch
A value of 0 denotes that RSA server key autogeneration is disabled. When greater than 0, the switch will
auto generate the RSA server key every specified interval; however, RSA server key generation is skipped
if the switch is busy doing other key or cipher generation when the timer expires.
The switch will perform only one session of key/cipher generation at a time. Thus, an SSH/SCP client will
not be able to log in if the switch is performing key generation at that time, or if another client has logged
in immediately prior. Also, key generation will fail if an SSH/SCP client is logging in at that time.
SSH/SCP integration with RADIUS and TACACS+ authentication
SSH/SCP is integrated with RADIUS and TACACS+ authentication. After the RADIUS or TACACS+ server
is enabled on the switch, all subsequent SSH authentication requests will be redirected to the specified
RADIUS or TACACS+ servers for authentication. The redirection is transparent to the SSH clients.
User access control
The switch allows an administrator to define end user accounts that permit end users to perform limited
actions on the switch. Once end user accounts are configured and enabled, the switch requires
username/password authentication.
For example, an administrator can assign a user who can log into the switch and perform operational
commands (effective only until the next switch reboot).
The administrator defines access levels for each switch user, as shown in the following table.
Table 6 User access levels
User account Description Password
Administrator The Administrator has complete access to all menus, information, and
configuration commands on the switch, including the ability to change both
the user and administrator passwords.
Operator The Operator manages all functions of the switch. The Operator can reset
ports or the entire switch.
User The User has no direct responsibility for switch management.
Users can view all switch status information and statistics but cannot make
any configuration changes to the switch.
admin
oper
user
Passwords can be up to 128 characters in length for TACACS+, Telnet, SSH, console, and BBI access.
When RADIUS authentication is used, the maximum password length is 16 characters.
If RADIUS authentication is used, the user password on the Radius server will override the user password
on the switch. Also note that the password-change command on the switch modifies only the use
switch password and has no effect on the user password on the Radius server. RADIUS authentication
and user password cannot be used concurrently to access the switch.
34
Page 35

Accessing the switch
Setting up user IDs
The administrator can configure up to 10 user accounts.
To configure an end-user account, perform the following steps:
1. Select a user ID to define.
>> # /cfg/sys/access/user/uid 1
2. Define the user name and password.
>> User ID 1 # name jane (Assign name “jane” to user ID 1)
Current user name:
New user name: jane
3. Define the user access level. By default, the end user is assigned to the user access level. To change
the user’s access level, enter the user Class of Service (cos) command, and select one of the
available options.
>> User ID 1 # cos <user|oper|admin>
4. Enable the user ID.
>> # /cfg/sys/access/user/uid <#>/ena
Once an end user account is configured and enabled, the user can login to the switch using the
username/password combination. The level of switch access is determined by the user CoS for the
account. The CoS corresponds to the user access levels described in the User access levels table.
35
Page 36

Ports and trunking
Ports and trunking
Introduction
The first part of this chapter describes the different types of ports used on the switch. This information is
useful in understanding other applications described in this guide, from the context of the embedded
switch/server environment.
For specific information on how to configure ports for speed, auto-negotiation, and duplex modes, see the
port commands in the HP 1:10Gb Ethernet BL-c Switch Command Reference.
The second part of this chapter provides configuration background and examples for trunking multiple
ports together. Trunk groups can provide super-bandwidth, multi-link connections between switches or
other trunk-capable devices. A trunk group is a group of links that act together, combining their
bandwidth to create a single, larger virtual link. The switch provides trunking support for the seven
external ports, one crosslink port, and 16 server ports.
Ports on the switch
The following table describes the Ethernet ports of the switch, including the port name and function.
NOTE: The actual mapping of switch ports to NIC interfaces is dependant on the operating
system software, the type of server blade, and the enclosure type. For more information, see the
HP 1:10Gb Ethernet BL-c Switch User Guide.
Table 7 Ethernet switch port names
Port number Port alias
1 Downlink1
2 Downlink2
3 Downlink3
4 Downlink4
5 Downlink5
6 Downlink6
7 Downlink7
8 Downlink8
9 Downlink9
10 Downlink10
11 Downlink11
12 Downlink12
36
Page 37

Ports and trunking
Table 7 Ethernet switch port names
Port number Port alias
13 Downlink13
14 Downlink14
15 Downlink15
16 Downlink16
17 XConnect1
18 Mgmt
19 Uplink1
20 Uplink2
21 Uplink3
22 Uplink4
23 Uplink5
24 Uplink6
25 Uplink7
Port trunk groups
When using port trunk groups between two switches, you can create an aggregate link operating at up to
five Gigabits per second, depending on how many physical ports are combined. The switch supports up
to 12 trunk groups per switch, each with up to six ports per trunk group.
The trunking software detects broken trunk links (link down or disabled) and redirects traffic to other trunk
members within that trunk group. You can only use trunking if each link has the same configuration for
speed, flow control, and auto-negotiation.
Statistical load distribution
In a configured trunk group containing more than one port, the load distribution is determined by
information embedded within the data frame. For IP traffic, the switch will calculate the trunk port to
use for forwarding traffic by implementing the load distribution algorithm on value equals to modulus of
(XOR of last 3 bits of Source and last 3 bits of Destination IP address). For non-IP traffic, the switch will
calculate the trunk port to use for forwarding traffic by implementing the load distribution algorithm on
value equals to modulus of (XOR of last 3 bits of Source and last 3 bits of Destination MAC address).
Built-in fault tolerance
Since each trunk group is composed of multiple physical links, the trunk group is inherently fault tolerant.
As long as even one physical link between the switches is available, the trunk remains active.
Statistical load distribution is maintained whenever a link in a trunk group is lost or returned to service.
37
Page 38

Ports and trunking
Before you configure trunks
When you create and enable a trunk, the trunk members (switch ports) take on certain settings necessary
for correct operation of the trunking feature.
Before you configure your trunk, you must consider these settings, along with specific configuration rules,
as follows:
1. Read the configuration rules provided in the “Trunk group configuration rules” section.
2. Determine which switch ports (up to six) are to become trunk members (the specific ports making up
the trunk).
3. Ensure that the chosen switch ports are set to enabled, using the following command: /cfg/port
4. Trunk member ports must have the same VLAN configuration.
5. Consider how the existing spanning tree will react to the new trunk configuration. See the “Spanning
Tree Protocol” chapter for spanning tree group configuration guidelines.
6. Consider how existing VLANs will be affected by the addition of a trunk.
Trunk group configuration rules
The trunking feature operates according to specific configuration rules. When creating trunks, consider
the following rules that determine how a trunk group reacts in any network topology:
• All trunks must originate from one device, and lead to one destination device. For example, you
cannot combine a link from Server 1 and a link from Server 2 into one trunk group.
• Any physical switch port can belong to only one trunk group.
• Trunking from non-HP devices must comply with Cisco® EtherChannel® technology.
• All trunk member ports must be assigned to the same VLAN configuration before the trunk can be
enabled.
• All trunk member ports must be set to full duplex mode.
• All trunk member ports must be configured for the same speed.
• If you change the VLAN settings of any trunk member, you cannot apply the change until you
change the VLAN settings of all trunk members.
• When an active port is configured in a trunk, the port becomes a trunk member when you enable the
trunk using the /cfg/l2/trunk x/ena command. The spanning tree parameters for the port then
change to reflect the new trunk settings.
• All trunk members must be in the same spanning tree group and can belong to only one spanning
tree group. However if all ports are tagged, then all trunk ports can belong to multiple spanning tree
groups.
• When a trunk is enabled, the trunk spanning tree participation setting takes precedence over that of
any trunk member.
• You cannot configure a trunk member as a monitor port in a Port Mirroring configuration.
• A monitor port cannot monitor trunks; however, trunk members can be monitored.
38
Page 39

Ports and trunking
Port trunking example
In this example, the Gigabit uplink ports on each switch are configured into a total of four trunk groups:
two on each switch.
NOTE: The actual mapping of switch ports to NIC interfaces is dependant on the operating
system software, the type of server blade, and the enclosure type. For more information, see the
HP 1:10Gb Ethernet BL-c Switch User Guide.
Figure 1 Port trunk group configuration example
The trunk groups are configured as follows:
Trunk groups 2-5 consist of two Gigabit uplink ports each, configured to act as a single link to the
upstream routers. The trunk groups on each switch are configured so that there is a link to each router for
redundancy.
Prior to configuring each switch in this example, you must connect to the appropriate switch CLI as the
administrator. For details about accessing and using any of the commands described in this example, see
the HP 1:10Gb Ethernet BL-c Switch Command Reference.
39
Page 40

Ports and trunking
Configuring trunk groups (CLI example)
1. On Switch 1, configure trunk groups 5 and 3:
>> # /cfg/l2/trunk 5 (Select trunk group 5)
>> Trunk group 5# add 24 (Add port 24 to trunk group 5)
>> Trunk group 5# add 25 (Add port 25 to trunk group 5)
>> Trunk group 5# ena (Enable trunk group 5)
>> Trunk group 5# apply (Make your changes active)
>> # /cfg/l2/trunk 3 (Select trunk group 3)
>> Trunk group 3# add 22 (Add port 22 to trunk group 3)
>> Trunk group 3# add 23 (Add port 23 to trunk group 3)
>> Trunk group 3# ena (Enable trunk group 3)
>> Trunk group 3# apply (Make your changes active)
>> Trunk group 3# save (Save for restore after reboot)
2. On Switch 2, configure trunk groups 4 and 2:
>> # /cfg/l2/trunk 4 (Select trunk group 4)
>> Trunk group 4# add 24 (Add port 24 to trunk group 4)
>> Trunk group 4# add 25 (Add port 25 to trunk group 4)
>> Trunk group 4# ena (Enable trunk group 4)
>> Trunk group 4# apply (Make your changes active)
>> # /cfg/l2/trunk 2 (Select trunk group 2)
>> Trunk group 2# add 22 (Add port 22 to trunk group 2)
>> Trunk group 2# add 23 (Add port 23 to trunk group 2)
>> Trunk group 2# ena (Enable trunk group 2)
>> Trunk group 2# apply (Make your changes active)
>> Trunk group 2# save (Save for restore after reboot)
NOTE: In this example, two switches are used. Any third-party device supporting link aggregation
should be configured manually. Connection problems might arise when using automatic trunk group
negotiation on the third-party device.
3. Examine the trunking information on each switch, using the following command:
>> /info/l2/trunk (View trunking information)
Information about each port in each configured trunk group is displayed. Make sure that trunk groups
consist of the expected ports and that each port is in the expected state.
40
Page 41

Ports and trunking
Configuring trunk groups (BBI example)
1. Configure trunk groups.
a. Click the Configure context button on the Toolbar.
b. Open the Layer 2 folder, and select Trunk Groups.
c. Click a Trunk Group number to select it.
41
Page 42

Ports and trunking
Enable the Trunk Group. To add ports, select each port in the Ports Available list, and click Add.
d.
e. Click Submit.
2. Apply, verify, and save the configuration.
3. Examine the trunking information on each switch.
a. Click the Dashboard context button on the Toolbar.
42
Page 43

Ports and trunking
Select Trunk Groups.
b.
c. Information about each configured trunk group is displayed. Make sure that trunk groups consist
of the expected ports and that each port is in the expected state.
Configurable Trunk Hash algorithm
This feature allows you to configure the particular parameters for the HP 1:10GbE switch Trunk Hash
algorithm instead of having to utilize the defaults. You can configure new default behavior for Layer 2
traffic and Layer 3 traffic, using the CLI menu cfg/l2/thash. You can select a minimum of one or a
maximum of two parameters to create one of the following configurations:
• Source IP (SIP)
• Destination IP (DIP)
• Source MAC (SMAC)
• Destination MAC (DMAC)
• Source IP (SIP) + Destination IP (DIP)
• Source MAC (SMAC) + Destination MAC (DMAC)
43
Page 44

Ports and trunking
Link Aggregation Control Protocol
Link Aggregation Control Protocol (LACP) is an IEEE 802.3ad standard for grouping several physical
ports into one logical port (known as a dynamic trunk group or Link Aggregation group) with any device
that supports the standard. Refer to the IEEE 802.3ad-2002 for a full description of the standard.
The 802.3ad standard allows standard Ethernet links to form a single Layer 2 link using the Link
Aggregation Control Protocol (LACP). Link aggregation is a method of grouping physical link segments of
the same media type and speed in full duplex, and treating them as if they were part of a single, logical
link segment. If a link in a LACP trunk group fails, traffic is reassigned dynamically to the remaining link(s)
of the dynamic trunk group.
NOTE: Currently, LACP implementation does not support the Churn machine, an option used to
detect if the port is operable within a bounded time period between the actor and the partner. Only
the Market Responder is implemented, and there is no marker protocol generator.
A port’s Link Aggregation Identifier (LAG ID) determines how the port can be aggregated. The Link
Aggregation ID (LAG ID) is constructed mainly from the system ID and the port’s admin key, as follows:
• System ID—The system ID is an integer value based on the switch’s MAC address and the system
priority assigned in the CLI.
• Admin key—A port’s admin key is an integer value (1-65535) that you can configure in the CLI.
Each HP 1:10GbE switch port that participates in the same LACP trunk group must have the same
admin key value. The admin key is local significant, which means the partner switch does not need
to use the same admin key value.
For example, consider two switches, an Actor (the HP 1:10GbE switch) and a Partner (another switch), as
shown in the following table:
Table 8 Actor vs. partner LACP configuration
Actor Switch Partner Switch 1 Partner Switch 2
Port 20 (admin key = 100) Port 1 (admin key = 50)
Port 21 (admin key = 100) Port 2 (admin key = 50)
Port 22 (admin key = 200) Port 3 (admin key = 60)
Port 23 (admin key = 200) Port 4 (admin key = 60)
In the configuration shown in the table above, Actor switch ports 20 and 21 aggregate to form an LACP
trunk group with Partner switch ports 1 and 2. At the same time, Actor switch ports 22 and 23 form a
different LACP trunk group with a different partner.
LACP automatically determines which member links can be aggregated and then aggregates them. It
provides for the controlled addition and removal of physical links for the link aggregation.
44
Page 45

Ports and trunking
Each port in the HP 1:10GbE switch can have one of the following LACP modes.
• off (default)—The user can configure this port in to a regular static trunk group.
• active—The port is capable of forming an LACP trunk. This port sends LACPDU packets to partner
system ports.
• passive—The port is capable of forming an LACP trunk. This port only responds to the LACPDU
packets sent from an LACP active port.
Each active LACP port transmits LACP data units (LACPDUs), while each passive LACP port listens for
LACPDUs. During LACP negotiation, the admin key is exchanged. The LACP trunk group is enabled as
long as the information matches at both ends of the link. If the admin key value changes for a port at
either end of the link, that port’s association with the LACP trunk group is lost.
When the system is initialized, all ports by default are in LACP off mode and are assigned unique admin
keys. To make a group of ports aggregatable, you assign them all the same admin key. You must set the
port’s LACP mode to active to activate LACP negotiation. You can set other port’s LACP mode to passive,
to reduce the amount of LACPDU traffic at the initial trunk-forming stage.
Use the /info/l2/trunk command or the /info/l2/lacp/dump command to check whether the
ports are trunked.
NOTE: If you configure LACP on ports with 802.1x network access control, make sure the ports on
both sides of the connection are properly configured for both LACP and 802.1x.
Configuring LACP
Use the following procedure to configure LACP for port 22 and port 23 to participate in link aggregation.
1. Set the LACP mode on port 20.
>> # /cfg/l2/lacp/port 22 (Select port 22)
>> LACP port 22# mode active (Set port 22 to LACP active mode)
2. Define the admin key on port 22. Only ports with the same admin key can form a LACP trunk group.
>> LACP port 22# adminkey 100 (Set port 22 adminkey to 100)
Current LACP port adminkey: 17
New pending LACP port adminkey: 100
3. Set the LACP mode on port 23.
>> # /cfg/l2/lacp/port 23 (Select port 23)
>> LACP port 21# mode active (Set port 21 to LACP active mode)
4. Define the admin key on port 23.
>> LACP port 23# adminkey 100 (Set port 23 adminkey to 100)
Current LACP port adminkey: 18
New pending LACP port adminkey: 100
5. Apply and verify the configuration.
>> LACP port 23# apply (Make your changes active)
>> LACP port 23# cur (View current trunking configuration)
6. Save your new configuration changes.
>> LACP port 23# save (Save for restore after reboot)
45
Page 46

Port-based Network Access and traffic control
Port-based Network Access and traffic control
Port-based Network Access control
Port-based Network Access control provides a means of authenticating and authorizing devices attached
to a LAN port that has point-to-point connection characteristics. It prevents access to ports that fail
authentication and authorization. This feature provides security to all ports of the HP 1:10GbE switch
(except the management port 18).
The following topics are discussed in this section:
• Extensible Authentication Protocol over LAN
• 802.1x Authentication Process
• 802.1x Port States
• Supported RADIUS Attributes
• Configuration Guidelines
Extensible authentication protocol over LAN
HP 1:10GbE switch software can provide user-level security for its ports using the IEEE 802.1x protocol,
which is a more secure alternative to other methods of port-based network access control. Any device
attached to an 802.1x-enabled port that fails authentication is prevented access to the network and
denied services offered through that port.
The 802.1x standard describes port-based network access control using Extensible Authentication
Protocol over LAN (EAPoL). EAPoL provides a means of authenticating and authorizing devices attached
to a LAN port that has point-to-point connection characteristics and of preventing access to that port in
cases of authentication and authorization failures.
EAPoL is a client-server protocol that has the following components:
• Supplicant or Client—The Supplicant is a device that requests network access and provides the
required credentials (user name and password) to the Authenticator and the Authentication Server.
• Authenticator—The Authenticator enforces authentication and controls access to the network. The
Authenticator grants network access based on the information provided by the Supplicant and the
response from the Authentication Server. The Authenticator acts as an intermediary between the
Supplicant and the Authentication Server: requesting identity information from the client, forwarding
that information (encapsulated in RADIUS packets) to the Authentication Server for validation,
relaying the server’s responses to the client, and authorizing network access based on the results of
the authentication exchange. The HP 1:10GbE switch acts as an Authenticator.
• Authentication Server—The Authentication Server validates the credentials provided by the
Supplicant to determine if the Authenticator should grant access to the network. The Authentication
Server may be co-located with the Authenticator. The switch relies on external RADIUS servers for
authentication.
Upon a successful authentication of the client by the server, the 802.1x-controlled port transitions from
unauthorized to authorized state, and the client is allowed full access to services through the port. When
the client sends an EAP-Logoff message to the authenticator, the port will transition from authorized to
unauthorized state.
46
Page 47
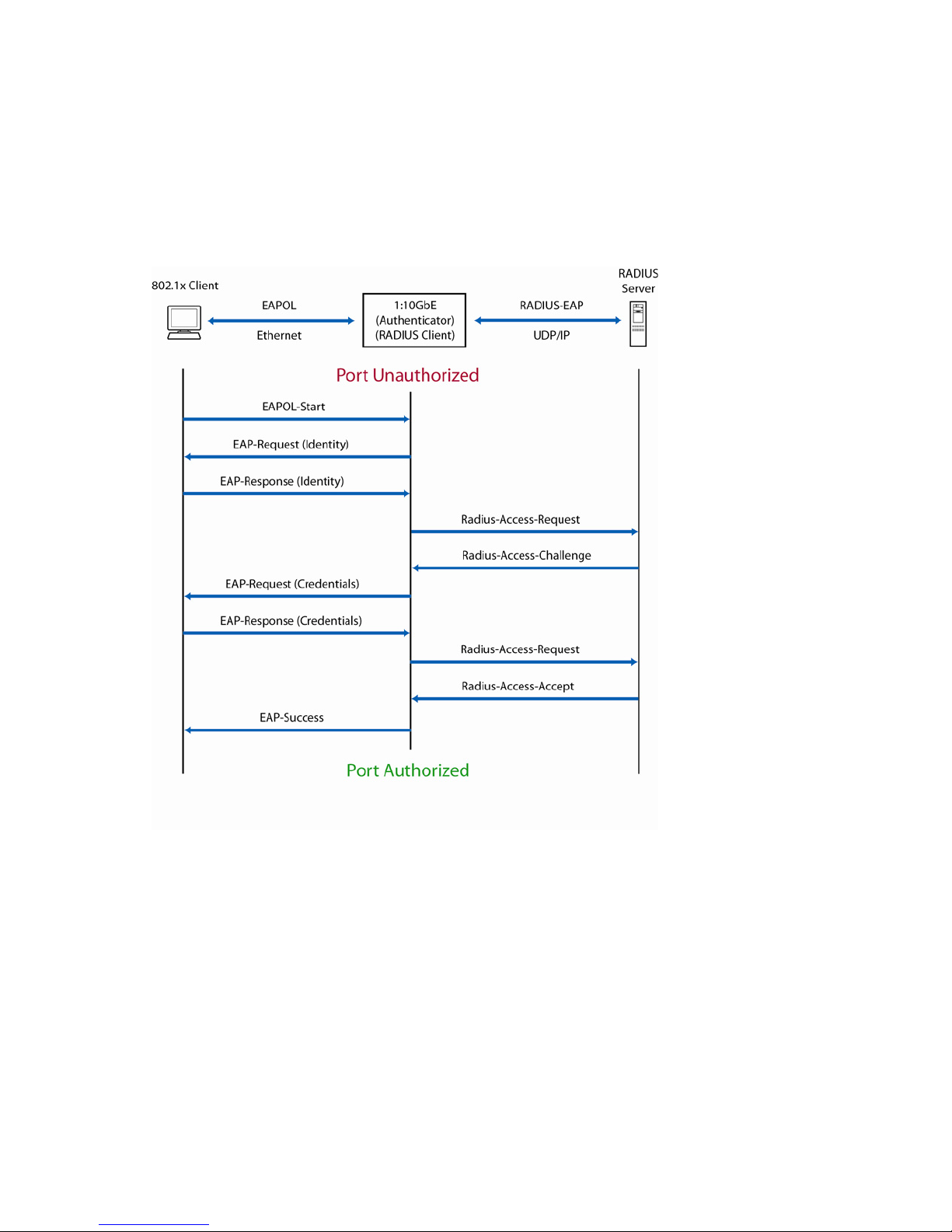
Port-based Network Access and traffic control
802.1x authentication process
The clients and authenticators communicate using Extensible Authentication Protocol (EAP), which was
originally designed to run over PPP, and for which the IEEE 802.1x Standard has defined an
encapsulation method over Ethernet frames, called EAP over LAN (EAPOL).
The following figure shows a typical message exchange initiated by the client.
Figure 2 Using EAPoL to authenticate a port
EAPoL Message Exchange
During authentication, EAPOL messages are exchanged between the client and the switch authenticator,
while RADIUS-EAP messages are exchanged between the switch authenticator and the Radius
authentication server.
Authentication is initiated by one of the following methods:
Switch authenticator sends an EAP-Request/Identity packet to the client.
Client sends an EAPOL-Start frame to the switch authenticator, which responds with an EAP-
Request/Identity frame.
The client confirms its identity by sending an EAP-Response/Identity frame to the switch authenticator,
which forwards the frame encapsulated in a RADIUS packet to the server.
47
Page 48

Port-based Network Access and traffic control
The Radius server chooses an EAP-supported authentication algorithm to verify the client’s identity, and
sends an EAP-Request packet to the client via the switch authenticator. The client then replies to the Radius
server with an EAP-Response containing its credentials.
Upon a successful authentication of the client by the server, the 802.1x-controlled port transitions from
unauthorized to authorized state, and the client is allowed full access to services through the controlled
port. When the client later sends an EAPOL-Logoff message to the switch authenticator, the port transitions
from authorized to unauthorized state.
If a client that does not support 802.1x connects to an 802.1x-controlled port, the switch authenticator
requests the client's identity when it detects a change in the operational state of the port. The client does
not respond to the request, and the port remains in the unauthorized state.
NOTE: When an 802.1x-enabled client connects to a port that is not 802.1x-controlled, the client
initiates the authentication process by sending an EAPOL-Start frame. When no response is
received, the client retransmits the request for a fixed number of times. If no response is received,
the client assumes the port is in authorized state, and begins sending frames, even if the port is
unauthorized.
802.1x port states
The state of the port determines whether the client is granted access to the network, as follows:
• Unauthorized—While in this state, the port discards all ingress and egress traffic except EAP
packets.
• Authorized—When the client is authenticated successfully, the port transitions to the authorized state
allowing all traffic to and from the client to flow normally.
• Force Unauthorized—You can configure this state that denies all access to the port.
• Force Authorized—You can configure this state that allows full access to the port.
Use the 802.1x Global Configuration Menu (/cfg/l2/8021x/global) to configure 802.1x
authentication for all ports in the switch. Use the 802.1x Port Menu (/cfg/l2/8021x/port x) to
configure a single port.
Supported RADIUS attributes
The HP 1:10GbE switch 802.1x Authenticator relies on external RADIUS servers for authentication with
EAP. The following table lists the RADIUS attributes that are supported as part of RADIUS-EAP
authentication based on the guidelines specified in Annex D of the 802.1x standard and RFC 3580.
Table 9 EAP support for RADIUS attributes
# Attribute Attribute Value A-R A-A A-C A-R
1 User-Name The value of the Type-Data field from the
4 NAS-IP-Address IP address of the authenticator used for
5 NAS-Port Port number of the authenticator port to which
supplicant’s EAP-Response/Identity message.
If the Identity is unknown (i.e. Type-Data field
is zero bytes in length), this attribute will have
the same value as the Calling-Station-Id.
RADIUS communication.
the supplicant is attached.
1 0-1 0 0
1 0 0 0
1 0 0 0
48
Page 49

Port-based Network Access and traffic control
Table 9 EAP support for RADIUS attributes
# Attribute Attribute Value A-R A-A A-C A-R
24 State Server-specific value. This is sent unmodified
back to the server in an Access-Request that is
in response to an Access-Challenge.
30 Called-Station-ID The MAC address of the authenticator
encoded as an ASCII string in canonical
format, e.g. 000D5622E3 9F.
31 Calling-Station-ID The MAC address of the supplicant encoded
as an ASCII string in canonical format, e.g.
00034B436206.
79 EAP-Message Encapsulated EAP packets from the supplicant
to the authentication server (Radius) and viceversa. The authenticator relays the decoded
packet to both devices.
80 Message-Authenticator Always present whenever an EAP-Message
attribute is also included. Used to integrityprotect a packet.
87 NAS-Port-ID Name assigned to the authenticator port, e.g.
Server1_Port3
Legend:
RADIUS Packet Types: A-R (Access-Request), A-A (Access-Accept), A-C (Access-Challenge), A-R (Access-Reject)
RADIUS Attribute Support:
0—This attribute MUST NOT be present in a packet.
0+—Zero or more instances of this attribute MAY be present in a packet.
0-1—Zero or one instance of this attribute MAY be present in a packet.
1—Exactly one instance of this attribute MUST be present in a packet.
1+—One or more of these attributes MUST be present.
0-1 0-1 0-1 0
1 0 0 0
1 0 0 0
1+ 1+ 1+ 1+
1 1 1 1
1 0 0 0
EAPoL configuration guidelines
When configuring EAPoL, consider the following guidelines:
• The 802.1x port-based authentication is currently supported only in point-to-point configurations, that
is, with a single supplicant connected to an 802.1x-enabled switch port.
• When 802.1x is enabled, a port has to be in the authorized state before any other Layer 2 feature
can be operationally enabled. For example, the STG state of a port is operationally disabled while
the port is in the unauthorized state.
• The 802.1x supplicant capability is not supported. Therefore, none of its ports can connect
successfully to an 802.1x-enabled port of another device, such as another switch, which acts as an
authenticator, unless access control on the remote port is disabled or is configured in forcedauthorized mode. For example, if a HP 1:10GbE switch is connected to another HP 1:10GbE
switch, and if 802.1x is enabled on both switches, the two connected ports must be configured in
force-authorized mode.
49
Page 50

Port-based Network Access and traffic control
• The 802.1x standard has optional provisions for supporting dynamic virtual LAN assignment via
RADIUS tunneling attributes, for example, Tunnel-Type (=VLAN), Tunnel-Medium-Type (=802), and
Tunnel-Private-Group-ID (=VLAN id). These attributes are not supported and might affect 802.1x
operations. Other unsupported attributes include Service-Type, Session-Timeout, and Termination-
Action.
RADIUS accounting service for 802.1x-authenticated devices or users is not supported.
Configuration changes performed using SNMP and the standard 802.1x MIB take effect immediately.
Port-based traffic control
Port-based traffic control prevents HP 1:10GbE switch ports from being disrupted by LAN storms. A LAN
storm occurs when data packets flood the LAN, which can cause the network to become congested and
slow down. Errors in the protocol-stack implementation or in the network configuration can cause a LAN
storm.
You can enable port-based traffic control separately for each of the following traffic types:
• Broadcast—packets with destination MAC address ff:ff:ff:ff:ff:ff
• Multicast—packets that have MAC addresses with the least significant bit of their first octet set to one
• Destination Lookup Failed (DLF)—packets with unknown destination MAC address, that are treated
like broadcast packets
With Port-based Traffic Control enabled, the port monitors incoming traffic of each type noted above. If
the traffic exceeds a configured threshold, the port blocks traffic that exceeds the threshold until the traffic
flow falls back within the threshold.
The HP 1:10GbE switch supports separate traffic-control thresholds for broadcast, multicast, and DLF
traffic. The traffic threshold is measured in number of frames per second.
NOTE: All ports that belong to a trunk must have the same traffic-control settings.
Configuring port-based traffic control
To configure a port for traffic control, perform the following steps:
1. Configure the traffic-control threshold and enable traffic control.
Main# /cfg/port 2
>> Port 2# brate 150000 (Set broadcast threshold)
>> Port 2# mrate 150000 (Set multicast threshold)
>> Port 2# drate 150000 (Set DLF threshold)
2. To disable a traffic-control threshold, use the following command:
>> Port 2# mrate dis (Disable multicast threshold)
3. Apply and save the configuration.
>> Port 2# apply (Apply the port configurations)
>> Port 2# save (Save the port configurations)
50
Page 51
VLANs
VLANs
Introduction
This chapter describes network design and topology considerations for using Virtual Local Area Networks
(VLANs). VLANs are commonly used to split up groups of network users into manageable broadcast
domains, to create logical segmentation of workgroups, and to enforce security policies among logical
segments.
The following topics are discussed in this chapter:
• VLANs and Port VLAN ID Numbers
• VLAN Tagging
• VLANs and IP Interfaces
• VLAN Topologies and Design Considerations
NOTE: Basic VLANs can be configured during initial switch configuration.
More comprehensive VLAN configuration can be done from the command line interface. See the
HP 1:10Gb Ethernet BL-c Switch Command Reference.
Overview
Setting up VLANs is a way to segment networks to increase network flexibility without changing the
physical network topology. With network segmentation, each switch port connects to a segment that is a
single broadcast domain. When a switch port is configured to be a member of a VLAN, it is added to a
group of ports (workgroup) that belongs to one broadcast domain.
Ports are grouped into broadcast domains by assigning them to the same VLAN. Multicast, broadcast,
and unknown unicast frames are flooded only to ports in the same VLAN.
VLANs and port VLAN ID numbers
VLAN numbers
The HP 1:10GbE switch supports up to 1,000 VLANs per switch. Even though the maximum number of
VLANs supported at any given time is 1,000, each can be identified with any number between 1 and
4095. VLAN 1 is the default VLAN, and all ports are assigned to it. VLAN 4095 is reserved for switch
management, and it cannot be configured.
51
Page 52

VLANs
Viewing VLANs
The VLAN information menu (/info/l2/vlan) displays all configured VLANs and all member ports that
have an active link state, for example:
>> Layer 2# vlan
VLAN Name Status Ports
---- -------------------------------- ------ ---------------------1 Default VLAN ena 1 4-18 19-25
2 VLAN 2 ena 2 3
4095 VLAN 4095 ena 18
PVID numbers
Each port in the switch has a configurable default VLAN number, known as its PVID. This places all ports
on the same VLAN initially, although each port PVID is configurable to any VLAN number between
1 and 4094.
The default configuration settings for switches have all ports set as untagged members of VLAN 1 with all
ports configured as PVID = 1. In the default configuration example shown in the following figure, all
incoming packets are assigned to VLAN 1 by the default port VLAN identifier (PVID =1).
Viewing and configuring PVIDs
You can view PVIDs from the following CLI commands:
Port information
>> /info/port
Port Tag RMON PVID NAME VLAN(s)
---- --- ---- ---- -------------- ------------------------------ 1 n d 1 Downlink1 1
2 n e 1 Downlink2 1
3 n d 1 Downlink3 1
4 n d 1 Downlink4 1
5 n d 1 Downlink5 1
6 n d 1 Downlink6 1
7 n d 1 Downlink7 1
:
:
Port configuration
>> /cfg/port 22/pvid 22
Current port VLAN ID: 1
New pending port VLAN ID: 22
>> Port 22#
Each port on the switch can belong to one or more VLANs, and each VLAN can have any number of
switch ports in its membership. Any port that belongs to multiple VLANs, however, must have VLAN
tagging enabled. See the “VLAN tagging” section in this chapter.
Any untagged frames (those with no VLAN specified) are classified with the PVID of the sending port.
52
Page 53

VLANs
VLAN tagging
The switch supports IEEE 802.1Q VLAN tagging, providing standards-based VLAN support for Ethernet
systems.
Tagging places the VLAN identifier in the frame header, allowing each port to belong to multiple VLANs.
When you configure multiple VLANs on a port, you must also enable tagging on that port.
Since tagging fundamentally changes the format of frames transmitted on a tagged port, you must
carefully plan network designs to prevent tagged frames from being transmitted to devices that do not
support 802.1Q VLAN tags, or devices where tagging is not enabled.
Important terms used with the 802.1Q tagging feature are:
• VLAN identifier (VID)—the 12-bit portion of the VLAN tag in the frame header that identifies an
explicit VLAN.
• Port VLAN identifier (PVID)—a classification mechanism that associates a port with a specific VLAN.
For example, a port with a PVID of 3 (PVID = 3) assigns all untagged frames received on this port to
VLAN 3.
• Tagged frame—a frame that carries VLAN tagging information in the header. The VLAN tagging
information is a 32-bit field (VLAN tag) in the frame header that identifies the frame as belonging to
a specific VLAN. Untagged frames are marked (tagged) with this classification as they leave the
switch through a port that is configured as a tagged port.
• Untagged frame—a frame that does not carry any VLAN tagging information in the frame header.
• Untagged member—a port that has been configured as an untagged member of a specific VLAN.
When an untagged frame exits the switch through an untagged member port, the frame header
remains unchanged. When a tagged frame exits the switch through an untagged member port, the
tag is stripped and the tagged frame is changed to an untagged frame.
• Tagged member—a port that has been configured as a tagged member of a specific VLAN. When
an untagged frame exits the switch through a tagged member port, the frame header is modified to
include the 32-bit tag associated with the PVID. When a tagged frame exits the switch through a
tagged member port, the frame header remains unchanged (original VID remains).
NOTE: If an 802.1Q tagged frame is sent to a port that has VLAN-tagging disabled, then the
frames are forwarded based on their port-VLAN ID (PVID).
53
Page 54
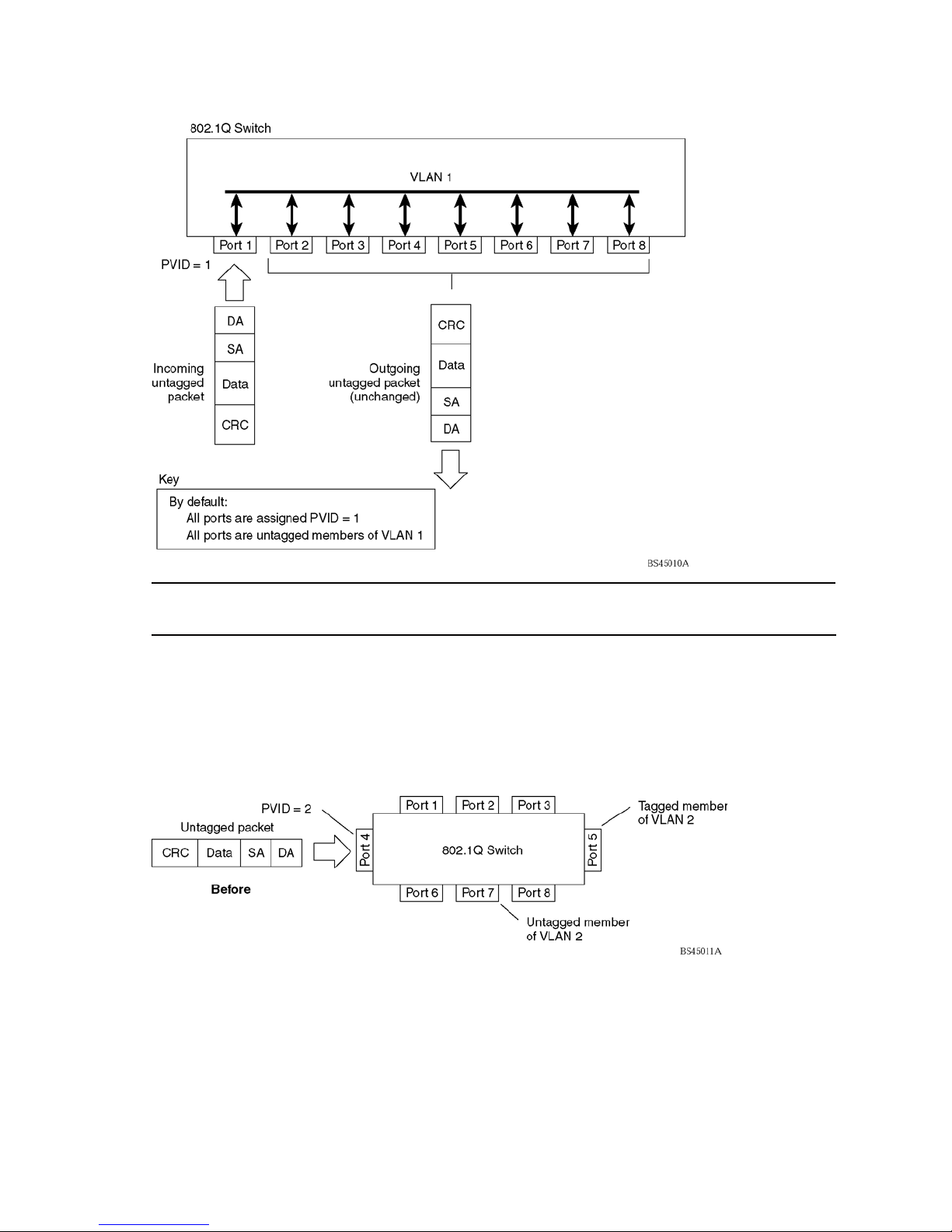
VLANs
Figure 3 Default VLAN settings
NOTE: The port numbers specified in these illustrations may not directly correspond to the physical
port configuration of your switch model.
When you configure VLANs, you configure the switch ports as tagged or untagged members of specific
VLANs. See the following figures.
In the following figure, the untagged incoming packet is assigned directly to VLAN 2 (PVID = 2). Port 5 is
configured as a tagged member of VLAN 2, and port 7 is configured as an untagged member of
VLAN 2.
Figure 4 Port-based VLAN assignment
As shown in the following figure, the untagged packet is marked (tagged) as it leaves the switch through
port 5, which is configured as a tagged member of VLAN 2. The untagged packet remains unchanged as
it leaves the switch through port 7, which is configured as an untagged member of VLAN 2.
54
Page 55

VLANs
Figure 5 802.1Q tagging (after port-based VLAN assignment)
In the following figure, the tagged incoming packet is assigned directly to VLAN 2 because of the tag
assignment in the packet. Port 5 is configured as a tagged member of VLAN 2, and port 7 is configured
as an untagged member of VLAN 2.
Figure 6 802.1Q tag assignment
As shown in the following figure, the tagged packet remains unchanged as it leaves the switch through
port 5, which is configured as a tagged member of VLAN 2. However, the tagged packet is stripped
(untagged) as it leaves the switch through port 7, which is configured as an untagged member of
VLAN 2.
55
Page 56
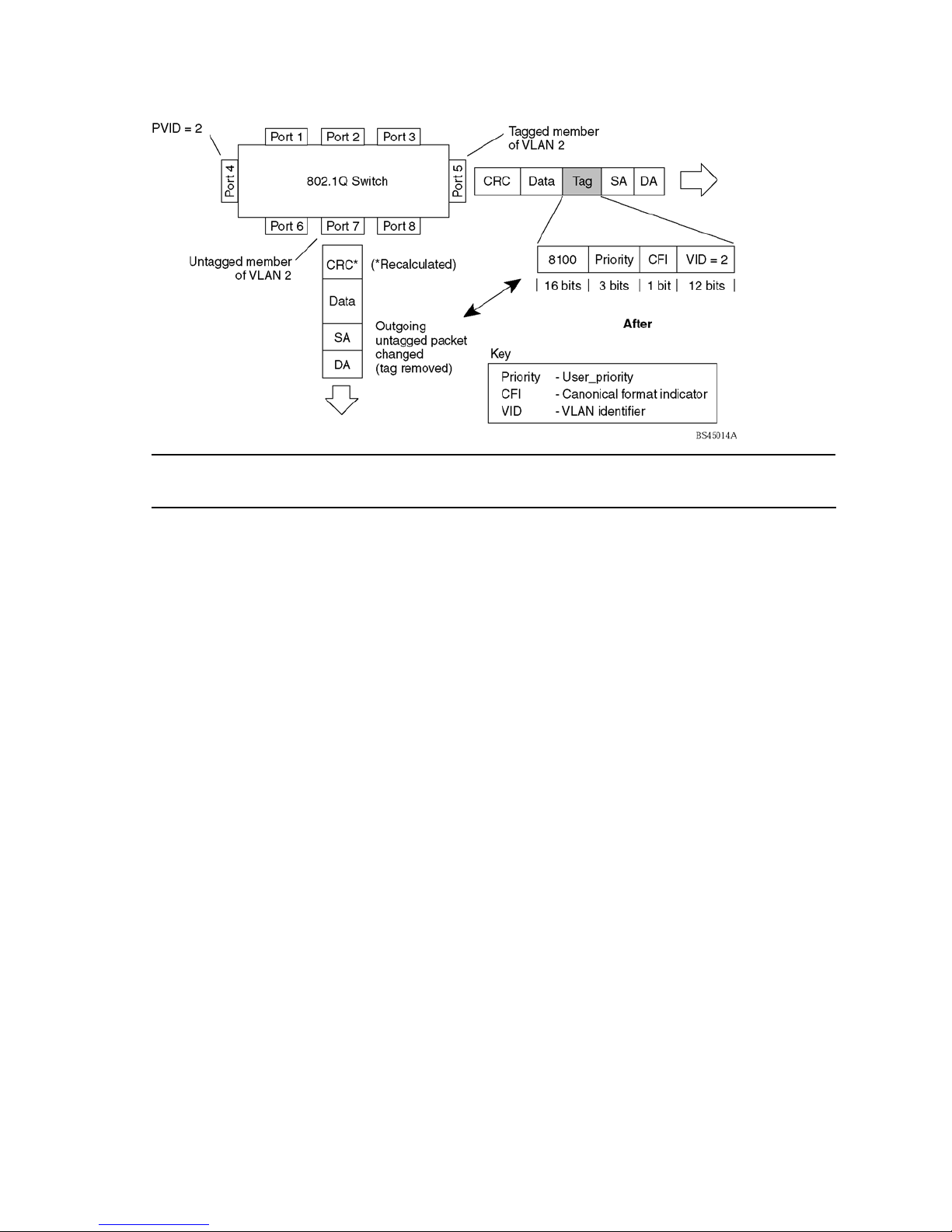
VLANs
Figure 7 802.1Q tagging (after 802.1Q tag assignment)
NOTE: Using the /boot/conf factory command resets all ports to VLAN 1 (except
management port 18) and all other settings to the factory defaults at the next reboot.
VLANs and IP interfaces
Carefully consider how you create VLANs within the switch, so that communication with the switch
remains possible. In order to access the switch for remote configuration, trap messages, and other
management functions, be sure that at least one IP interface on the switch has a VLAN defined.
You can also inadvertently cut off access to management functions if you exclude the ports from the VLAN
membership. For example, if all IP interfaces are left on VLAN 1 (the default), and all ports are configured
for VLAN 2, and then switch management features are effectively cut off.
To remedy this, keep all ports used for remote switch management on the default VLAN and assign an IP
interface to the default VLAN.
For more information on configuring IP interfaces, see the “Configuring an IP interface” section in the
“Accessing the switch” chapter.
VLAN topologies and design considerations
By default, all switch ports are configured to the default VLAN 1. This configuration groups all ports into
the same broadcast domain. The VLAN has an 802.1Q VLAN ID of 1. VLAN tagging is turned off,
because, by default, all ports are members of a single VLAN only.
If configuring Spanning Tree Protocol (/cfg/l2/stp), note that each of spanning tree groups 2-128
may contain only one VLAN. If configuring Multiple Spanning Tree Protocol (/cfg/l2/mrst), each of
the spanning tree groups (1-32 for MSTP) may contain multiple VLANs.
56
Page 57

VLANs
VLAN configuration rules
VLANs operate according to specific configuration rules which must be considered when creating VLANs.
For example:
• HP recommends that all ports involved in trunking and Port Mirroring have the same VLAN
configuration. If a port is on a trunk with a mirroring port, the VLAN configuration cannot be
changed. For more information on port trunking, see the “Port trunking example” section in the “Ports
and trunking” chapter.
• All ports that are involved in Port Mirroring must have memberships in the same VLANs. If a port is
configured for Port Mirroring, the port’s VLAN membership cannot be changed. For more
information on configuring Port Mirroring, see the “Port Mirroring” section in the “Troubleshooting
tools” appendix.
• When you delete a VLAN, untagged ports are moved to the default VLAN (VLAN 1). Tagged ports
that belong only to the deleted VLAN are moved to the default VLAN 1. Tagged ports that belong to
multiple VLANs are removed from the deleted VLAN only.
Multiple VLANS with tagging
The following figure shows only those switch port to server links that must be configured for the example.
While not shown, all other server links remain set at their default settings.
57
Page 58

VLANs
Figure 8 Multiple VLANs with VLAN tagging
The features of this VLAN are described in the following table:
Table 10 Multiple VLANs with tagging
Component Description
Switch 1 Switch 1 is configured for VLANS 1, 2, and 3. Port 1 is tagged to accept traffic from
VLANs 1 and 2. Port 17 is tagged, and accepts traffic from VLANs 1 and 3. Port 19 is
tagged to accept traffic from VLANs 1, 2, and 3. Port 21 is an untagged member of
VLAN 2.
Switch 2 Switch 2 is configured for VLANS 1, 3, and 4. Port 2 is tagged to accept traffic from VLANS
3 and 4. Port 4 is configured only for VLAN 3, so VLAN tagging is off. Port 19 is tagged to
accept traffic from VLANs 1 and 3. Port 21 is an untagged member of VLAN 4.
58
Page 59

VLANs
Table 10 Multiple VLANs with tagging
Component Description
Blade Server #1 This high-use blade server needs to be accessed from all VLANs and IP subnets. The server
has a VLAN-tagging adapter installed with VLAN tagging turned on.
One adapter is attached to one of the switch's 10/100/1000 Mbps ports, that is configured
for VLANs 1 and 2. One adapter is configured for VLANs 3 and 4.
Because of the VLAN tagging capabilities of both the adapter and the switch, the server is
able to communicate on all four VLANs in this network while maintaining broadcast
separation among all four VLANs and subnets.
Blade Server #2 This blade server belongs to VLAN 3. The port that the VLAN is attached to is configured
only for VLAN 3, so VLAN tagging is off.
PC #1 This PC is a member of VLAN 2 and 3. Via VLAN 2, it can communicate with Server 1,
PC 3, and PC 5. Using VLAN 3, it can communicate with Server 1, Server 2, and PC 4.
PC #2 This PC is a member of VLAN 4, and can only communicate with Server 1.
PC #3 This PC is a member of VLAN 1 and VLAN 2. Using VLAN 1, it can communicate with
Server 1 and PC 5. Using VLAN 2, it can communicate with Server 1, PC 1, and PC 5.
PC #4 This PC is a member of VLAN 3, and it can communicate with Server 1, Server 2, and PC 1.
PC #5 This PC is a member of both VLAN 1 and VLAN 2. Using VLAN 1, it can communicate with
Server 1 and PC 3. Using VLAN 2, it can communicate with Server 1, PC 1, and PC 3. The
Layer 2 switch port to which it is connected is configured for both VLAN 1 and VLAN 2 and
has tagging enabled.
NOTE: All PCs connected to a tagged port must have an Ethernet adapter with VLAN-tagging
capability installed.
Configuring the example network
These examples describe how to configure ports and VLANs on Switch 1 and Switch 2.
59
Page 60
VLANs
Configuring ports and VLANs on Switch 1 (CLI example)
To configure ports and VLANs on Switch 1, do the following:
1. On Switch 1, enable VLAN tagging on the necessary ports.
Main# /cfg/port 1
>> Port 1# tag e (Select port 1: connection to server 1)
Current VLAN tag support: disabled
New VLAN tag support: enabled (Enable tagging)
Port 1 changed to tagged.
Main# /cfg/port 17 (Select crosslink link port 17)
>> Port 17# tag e (Enable tagging)
Current VLAN tag support: disabled
New VLAN tag support: enabled
Port 17 changed to tagged.
Main# /cfg/port 19 (Select uplink port 19)
>> Port 19# tag e (Enable tagging)
Current VLAN tag support: disabled
New VLAN tag support: enabled
Port 19 changed to tagged.
>> Port 19# apply (Apply the port configurations)
2. Configure the VLANs and their member ports. Since all ports are by default configured for VLAN 1,
configure only those ports that belong to VLAN 2. Crosslink port 17 must belong to VLANs 1 and 2.
>> /cfg/l2/vlan 2
>> VLAN 2# add 1 (Add port 1 to VLAN 2)
Current ports for VLAN 2: empty
Pending new ports for VLAN 2: 1
>> VLAN 2# add 19 (Add port 19 to VLAN 2)
Current ports for VLAN 2: 1
Pending new ports for VLAN 2: 19
>> VLAN 2# add 21 (Add port 21 to VLAN 2)
Port 21 is an UNTAGGED port and its current PVID is 1.
Confirm changing PVID from 1 to 2 [y/n]: y
Current ports for VLAN 2: 1, 19
Pending new ports for VLAN 2: 21
>> /cfg/l2/vlan 3
>> VLAN 3# add 17 (Add port 17 to VLAN 3)
Current ports for VLAN 3: empty
Pending new ports for VLAN 3: 17
>> VLAN 3# add 19 (Add port 19 to VLAN 3)
Current ports for VLAN 3: 17
Pending new ports for VLAN 3: 19
>> apply (Apply the port configurations)
>> save (Save the port configurations)
60
Page 61
VLANs
Configuring ports and VLANs on Switch 2 (CLI example)
To configure ports and VLANs on Switch 2, do the following:
1. On Switch 2, enable VLAN tagging on the necessary ports. Port 4 (connection to server 2) remains
untagged, so it is not configured below.
Main# /cfg/port 2 (Select port 2: connection to server 1)
>> Port 2# tag e
Current VLAN tag support: disabled
New VLAN tag support: enabled
Port 2 changed to tagged.
Main# /cfg/port 17 (Select crosslink link port 17)
>> Port 17# tag e (Enable tagging)
Current VLAN tag support: disabled
New VLAN tag support: enabled
Port 17 changed to tagged.
Main# /cfg/port 19 (Select uplink port 19)
>> Port 19# tag e (Enable tagging)
Current VLAN tag support: disabled
New VLAN tag support: enabled
Port 19 changed to tagged.
>> Port 19# apply (Apply the port configurations)
2. Configure the VLANs and their member ports. Since all ports are by default configured for VLAN 1,
configure only those ports that belong to other VLANs.
>> /cfg/l2/vlan 3
>> VLAN 3# add 2
Current ports for VLAN 3: empty
Pending new ports for VLAN 3: 2
>> VLAN 3# add 4
Current ports for VLAN 3: 2
Pending new ports for VLAN 3: 17
>> VLAN 3# add 17
Current ports for VLAN 3: 2, 4
Pending new ports for VLAN 3: 17
>> VLAN 3# add 24
Current ports for VLAN 3: 2, 17
Pending new ports for VLAN 3: 24
>> /cfg/l2/vlan 4
>> VLAN 4# add 2
Current ports for VLAN 4: empty
Pending new ports for VLAN 4: 2
>> VLAN 4# add 21
Port 21 is an UNTAGGED port and its current PVID is 1.
Confirm changing PVID from 1 to 4 [y/n]: y
Current ports for VLAN 4: 2, 4
Pending new ports for VLAN 4: 21
>> apply (Apply the port configurations)
>> save (Save the port configurations)
The external Layer 2 switches should also be configured for VLANs and tagging.
61
Page 62

VLANs
Configuring ports and VLANs on Switch 1 (BBI example)
To configure ports and VLANs on Switch 1, do the following:
1. On the switch 1, enable VLAN tagging on the necessary ports.
a. Click the Configure context button on the Toolbar.
b. Open the Switch folder, and select Switch Ports (click the underlined text, not the folder).
c. Click a port number to select it.
62
Page 63

VLANs
Enable the port and enable VLAN tagging.
d.
e. Click Submit.
2. Configure the VLANs and their member ports.
a. Open the Virtual LANs folder, and select Add VLAN.
63
Page 64

VLANs
Enter the VLAN name, VLAN ID number, and enable the VLAN. To add ports, select each port in
b.
the Ports Available list and click Add. Since all ports are configured for VLAN 1 by default,
configure only those ports that belong to VLAN 2. The crosslink port 17 must belong to VLAN 1
and VLAN 2.
c. Click Submit.
The external Layer 2 switches should also be configured for VLANs and tagging.
3. Apply, verify, and save the configuration.
64
Page 65

VLANs
FDB static entries
Static entries in the Forwarding Database (FDB) allow the switch to forward packets without flooding ports
to perform a lookup. A FDB static entry is a MAC address associated with a specific port and VLAN. The
switch supports 128 static entries. Static entries are manually configured, using the following command:
/cfg/l2/fdb/static
FDB static entries are permanent, so the FDB Aging value does not apply to them. Static entries are
manually added to the FDB, and manually deleted from the FDB.
Incoming frames that contain the static entry as the source MAC can use only ports configured for the
static entry.
Trunking support for FDB static entries
A FDB static entry can be added to a port that is a member of a trunk group, as follows:
• Static (manually configured) trunk group
• Dynamic (LACP) trunk group
The trunk group supports the FDB static entry. If the port with the static entry fails, other ports in the trunk
handle the traffic. If the port is removed from the trunk, the static entry is removed from the trunk, but
remains configured on the port.
The FDB information commands (/info/l2/fdb) display trunk support for static FDB entries, if
applicable:
>> Forwarding Database# dump
MAC address VLAN Port Trnk State
----------------- ---- ---- ---- ---- 00:00:2e:9b:db:f8 1 1 TRK
00:00:5e:00:01:f4 1 24 FWD
00:01:81:2e:b5:60 1 24 FWD
00:02:a5:e9:76:30 1 1 TRK
00:03:4b:e2:15:f1 1 24 FWD
Configuring a static FDB entry
Perform the following actions to configure a static FDB entry:
Main# /cfg/l2/fdb/static (Select static FDB menu)
>> Static FDB# add 00:60:af:00:02:30
Enter VLAN number: 2
Enter port (1-25): 2
>> Static FDB# apply (Apply the configuration)
>> Static FDB# save (Save the configuration)
65
Page 66

Spanning Tree Protocol
Spanning Tree Protocol
Introduction
When multiple paths exist on a network, Spanning Tree Protocol (STP) configures the network so that a
switch uses only the most efficient path. The following topics are discussed in this chapter:
• Overview
• Bridge Protocol Data Units (BPDUs)
• Spanning Tree Group (STG) configuration guidelines
• Multiple Spanning Trees
Overview
Spanning Tree Protocol (STP) detects and eliminates logical loops in a bridged or switched network. STP
forces redundant data paths into a standby (blocked) state. When multiple paths exist, STP configures the
network so that a switch uses only the most efficient path. If that path fails, STP automatically sets up
another active path on the network to sustain network operations.
The switch supports IEEE 802.1d Spanning Tree Protocol for STG 1, and Per VLAN Spanning Tree
Protocol (PVST+) for STGs 2-128, by default.
NOTE: The switch also supports IEEE 802.1w Rapid Spanning Tree Protocol and IEEE 802.1s
Multiple Spanning Tree Protocol. For more information, see the “RSTP and MSTP” chapter in this
guide.
Bridge Protocol Data Units
To create a spanning tree, the application switch generates a configuration Bridge Protocol Data Unit
(BPDU), which it then forwards out of its ports. All switches in the Layer 2 network participating in the
spanning tree gather information about other switches in the network through an exchange of BPDUs.
A BPDU is a 64-byte packet that is sent out at a configurable interval, which is typically set for two
seconds. The BPDU is used to establish a path, much like a hello packet in IP routing. BPDUs contain
information about the transmitting bridge and its ports, including bridge and MAC addresses, bridge
priority, port priority, and port path cost. If the ports are tagged, each port sends out a special BPDU
containing the tagged information.
The generic action of a switch on receiving a BPDU is to compare the received BPDU to its own BPDU that
it will transmit. If the received BPDU has a priority value closer to zero than its own BPDU, it will replace
its BPDU with the received BPDU. Then, the application switch adds its own bridge ID number and
increments the path cost of the BPDU. The application switch uses this information to block any redundant
paths.
66
Page 67

Spanning Tree Protocol
Determining the path for forwarding BPDUs
When determining which port to use for forwarding and which port to block, the switch uses information
in the BPDU, including each bridge priority ID. A technique based on the lowest root cost is then
computed to determine the most efficient path for forwarding.
Bridge priority
The bridge priority parameter controls which bridge on the network is the STP root bridge. To make one
switch the root bridge, configure the bridge priority lower than all other switches and bridges on your
network. The lower the value, the higher the bridge priority. The bridge priority is configured using the
following command:
/cfg/l2/stp x/brg/prior
Port priority
The port priority helps determine which bridge port becomes the designated port. In a network topology
that has multiple bridge ports connected to a single segment, the port with the lowest port priority
becomes the designated port for the segment. The port priority is configured using the following
command:
/cfg/l2/stp y/port x/prior
Port path cost
The port path cost assigns lower values to high-bandwidth ports, such as Gigabit Ethernet, to encourage
their use. The objective is to use the fastest links so that the route with the lowest cost is chosen. A value of
0 indicates that port cost is computed dynamically based on link speed. This works when forcing link
speed, so it does not just apply to auto negotiated link speed.
By default, all switch ports have the path cost set to 4, independent of the link speed. To use dynamic
path cost, based on link speed, set the path cost to 0 (zero). For example, if the path cost is set to zero:
• A 100 Mbps link receives a path cost of 19
• A 10 Mbps link receives a path cost of 100
Configure the port path cost using the following command:
/cfg/l2/stp y/port x/cost
Spanning Tree Group configuration guidelines
This section provides important information on configuring Spanning Tree Groups (STGs).
Default Spanning Tree configuration
In the default configuration, a single STG with the ID of 1 includes all ports on the switch. It is called the
default STG. All other STGs (except the default STG) are empty, and VLANs must be added by the user.
You cannot assign ports directly to an STG. Add the ports to a VLAN, and add the VLAN to the STG.
STGs 1-127 are enabled by default and assigned an ID number from 1 to 127. STG 128 is disabled by
default, and contains the management VLAN 4095.
An STG cannot be deleted, only disabled. If you disable the STG while it still contains VLAN members,
Spanning Tree will be off on all ports belonging to that VLAN.
67
Page 68

Spanning Tree Protocol
Adding a VLAN to a Spanning Tree Group
If no VLANs exist beyond the default VLAN 1, see the “Creating a VLAN” section in this chapter for
information on adding ports to VLANs.
Add the VLAN to the STG using the command /cfg/l2/stp <stg number>/add <vlan number>.
Creating a VLAN
When you create a VLAN, then that VLAN automatically belongs to STG 1, the default STG. If you want
the VLAN in another STG, you must move the VLAN by assigning it to another STG.
To move a newly created VLAN to an existing STG:
1. Create the VLAN.
2. Add the VLAN to an existing STG.
When creating a VLAN also consider the following:
• A VLAN cannot belong to more than one STG.
• VLANs that span multiple switches must be mapped within the same Spanning Tree Group (have the
same STG ID) across all the switches.
Rules for VLAN tagged ports
Rules for VLAN tagged ports are listed below:
• If a port is tagged, it can belong to multiple STGs.
• When a tagged port belongs to more than one STG, the egress BPDUs are tagged to distinguish the
BPDUs of one STG from those of another STG.
• An untagged port cannot span multiple STGs.
Adding and removing ports from STGs
Information on adding and removing ports from STGs is as follows:
• By default, all ports belong to VLAN 1 and STG 1.
• Each port is always a member of at least one VLAN. Each VLAN is always a member of at least one
STG. Port membership within VLANs can be changed, and VLAN membership within STGs can be
changed. To move a port from one STG to another, move the VLAN to which the port belongs, or
move the port to a VLAN that belongs to the STG.
• When you remove a port from a VLAN, that port is also removed from the STG to which the VLAN
belongs. However, if that port belongs to another VLAN in the same STG, the port remains in the
STG.
• If you remove an untagged port from a non-default VLAN and STG, it is added to VLAN 1 and
STG 1.
68
Page 69

Spanning Tree Protocol
The relationship between ports, trunk groups, VLANs, and spanning trees is shown in the following table.
Table 11 Ports, trunk groups, and VLANs
Switch element Belongs to
Port Trunk group, or one or more VLANs
Trunk group Only one VLAN
VLAN (non-default) One Spanning Tree Group
Assigning cost to ports and trunk groups
When you configure a trunk group to participate in a Spanning Tree Group, all ports must have the same
Spanning Tree configuration, as follows:
• port priority
• path cost
• link type
• Edge port status
• Port Fast Forward status
Assign lower path costs on each member of a trunk group, to ensure the trunk group remains in the
Forwarding state.
Multiple Spanning Trees
Each switch supports a maximum of 128 Spanning Tree Groups (STGs). Multiple STGs provide multiple
data paths, which can be used for load-balancing and redundancy.
You enable independent links on two switches using multiple STGs by configuring each path with a
different VLAN and then assigning each VLAN to a separate STG. Each STG is independent. Each STG
sends its own Bridge Protocol Data Units (BPDUs), and each STG must be independently configured.
The STG, or bridge group, forms a loop-free topology that includes one or more virtual LANs (VLANs).
The switch supports 128 STGs running simultaneously. The default STG 1 supports IEEE 802.1d Spanning
Tree Protocol, and may contain more than one VLAN. All other STGs support Per VLAN Spanning Tree
(PVST+), and may contain only one VLAN each. The switch can support multiple VLANs in STGs 2-128;
however, you must enable IEEE 802.1s Multiple Spanning Tree Protocol mode. For more information, see
the “RSTP and MSTP” chapter in this guide.
69
Page 70

Spanning Tree Protocol
Why do we need Multiple Spanning Trees?
The following figure shows a simple example of why we need multiple Spanning Trees. This example
assumes that port 24 and 25 are not part of a Trunk Group. Two VLANs (VLAN 1 and VLAN 2) exist
between Switch 1 and Switch 2. If the same Spanning Tree Group is enabled on both switches, the
switches see an apparent loop and block port 25 on Switch 2, which cuts off communication between the
switches for VLAN 2.
Figure 9 Two VLANs on one instance of Spanning Tree Protocol
In the following figure, VLAN 1 and VLAN 2 belong to different Spanning Tree Groups. The two instances
of spanning tree separate the topology without forming a loop, so that both VLANs can forward packets
between the switches without losing connectivity.
Figure 10 Two VLANs on separate instances of Spanning Tree Protocol
70
Page 71

Spanning Tree Protocol
VLAN participation in Spanning Tree Groups
The following table shows which switch ports participate in each Spanning Tree Group. By default, server
ports (ports 1-16) do not participate in Spanning Tree, even though they are members of their respective
VLANs.
Table 12 VLAN participation in Spanning Tree Groups
VLAN 1 VLAN 2
Switch 1 Spanning Tree Group 1
Port 24
Switch 2 Spanning Tree Group 1
Port 24
Spanning Tree Group 2
Port 25
Spanning Tree Group 2
Port 25
Configuring Multiple Spanning Tree Groups
This section explains how to assign each VLAN to its own Spanning Tree Group on the switches 1 and 2.
By default, Spanning Tree Groups 2-127 are empty, and Spanning Tree Group 1 contains all configured
VLANs until individual VLANs are explicitly assigned to other Spanning Tree Groups. Except for the
default Spanning Tree Group 1, which may contain more than one VLAN, Spanning Tree Groups 2-128
may contain only one VLAN each.
NOTE: Each instance of Spanning Tree Group is enabled by default.
Configuring Switch 1 (CLI example)
1. Configure port and VLAN membership on Switch 1 as described in the “Configuring ports and
VLANs on Switch 1 (CLI example)” section, in the “VLANs” chapter of this guide.
2. Add VLAN 2 to Spanning Tree Group 2.
>> /cfg/l2/stp 2 (Select Spanning Tree Group 2)
>> Spanning Tree Group 2# add 2 (Add VLAN 2)
3. VLAN 2 is automatically removed from spanning tree group 1.
4. Apply and save.
>> apply (Apply the port configurations)
>> save (Save the port configurations)
Configuring Switch 2 (CLI example)
1. Configure port and VLAN membership as described in the “Configuring ports and VLANs on Switch
2 (CLI example)” section in the “VLANs” chapter of this guide.
2. Add VLAN 2 to Spanning Tree Group 2.
>> /cfg/l2/stp 2 (Select Spanning Tree Group 2)
>> Spanning Tree Group 2# add 2 (Add VLAN 2)
3. VLAN 2 is automatically removed from Spanning Tree Group 1.
4. Apply and save.
>> apply (Apply the port configurations)
>> save (Save the port configurations)
71
Page 72

Spanning Tree Protocol
Configuring Switch 1 (BBI example)
1. Configure port and VLAN membership on Switch 1 as described in the “Configuring ports and
VLANs on Switch 1 (BBI example)” section, in the “VLANs” chapter of this guide.
2. Add VLAN 2 to Spanning Tree Group 2.
a. Click the Configure context button on the Toolbar.
b. Select Spanning Tree Groups (click the underlined text, not the folder).
c. Select a Spanning Tree Group number.
72
Page 73

Spanning Tree Protocol
Enter the Spanning Tree Group number and set the Switch Spanning Tree State to on. To add a
d.
VLAN to the Spanning Tree Group, select the VLAN in the VLANs Available list, and click Add.
VLAN 2 is automatically removed from Spanning Tree Group 1.
e. Scroll down, and click Submit.
3. Apply, verify, and save the configuration.
73
Page 74

Spanning Tree Protocol
Port Fast Forwarding
Port Fast Forwarding permits a port that participates in Spanning Tree to bypass the Listening and
Learning states and enter directly into the Forwarding state. While in the Forwarding state, the port listens
to the BPDUs to learn if there is a loop and, if dictated by normal STG behavior (following priorities, etc.),
the port transitions into the Blocking state.
This feature permits the switch to interoperate well with Fast Path, a NIC Teaming feature.
Configuring Port Fast Forwarding
Use the following CLI commands to enable Port Fast Forwarding on an external port.
>> # /cfg/l2/stp 1/port 20 (Select port 20)
>> Spanning Tree Port 20# fastfwd ena (Enable Port Fast Forwarding)
>> Spanning Tree Port 20# apply (Make your changes active)
>> Spanning Tree Port 20# save (Save for restore after reboot)
Fast Uplink Convergence
Fast Uplink Convergence enables the switch to quickly recover from the failure of the primary link or trunk
group in a Layer 2 network using Spanning Tree Protocol. Normal recovery can take as long as 60
seconds, while the backup link transitions from Blocking to Listening to Learning and then Forwarding
states. With Fast Uplink Convergence enabled, the switch immediately places the secondary path into
Forwarding state, and sends multicasts of addresses in the forwarding database (FDB) and ARP table over
the secondary link so that upstream switches can learn the new path.
Configuration guidelines
When you enable Fast Uplink Convergence, the switch software automatically makes the following
configuration changes:
• Increases the bridge priority to 65500 so that it does not become the root switch.
• Increases the cost of all of the external ports by 3000, across all VLANs and Spanning Tree Groups.
This ensures that traffic never flows through the switch to get to another switch unless there is no
other path.
When you disable Fast Uplink Convergence, the bridge priorities and path cost are set to their default
values for all STP groups.
Configuring Fast Uplink Convergence
Use the following CLI commands to enable Fast Uplink Convergence on external ports:
>> # /cfg/l2/upfast ena(Enable Fast Uplink convergence)
>> Layer 2# apply(Make your changes active)
>> Layer 2# save(Save for restore after reboot)
74
Page 75

RSTP and MSTP
RSTP and MSTP
Introduction
Rapid Spanning Tree Protocol (IEEE 802.1w) enhances the Spanning Tree Protocol (IEEE 802.1d) to
provide rapid convergence on Spanning Tree Group 1. Multiple Spanning Tree Protocol (IEEE 802.1s)
extends the Rapid Spanning Tree Protocol to provide both rapid convergence and load balancing in a
VLAN environment.
The following topics are discussed in this chapter:
• Rapid Spanning Tree Protocol (RSTP)
• Multiple Spanning Tree Protocol (MSTP)
Rapid Spanning Tree Protocol
Rapid Spanning Tree Protocol (RSTP) provides rapid convergence of the spanning tree and provides for
fast reconfiguration critical for networks carrying delay-sensitive traffic such as voice and video. RSTP
significantly reduces the time to reconfigure the active topology of the network when changes occur to the
physical topology or its configuration parameters. RSTP reduces the bridged-LAN topology to a single
Spanning Tree.
For more information about Spanning Tree Protocol, see the “Spanning Tree Protocol” chapter in this
guide.
RSTP parameters are configured in Spanning Tree Group 1. STP Groups 2-128 do not apply to RSTP, and
must be cleared. There are new STP parameters to support RSTP, and some values to existing parameters
are different.
RSTP is compatible with devices that run 802.1d Spanning Tree Protocol. If the switch detects 802.1d
BPDUs, it responds with 802.1d-compatible data units. RSTP is not compatible with Per VLAN Spanning
Tree (PVST) protocol.
Port state changes
The port state controls the forwarding and learning processes of Spanning Tree. In RSTP, the port state
has been consolidated to the following: discarding, learning, and forwarding.
Table 13 RSTP vs. STP port states
Port operational status STP port state RSTP port state
Enabled Blocking Discarding
Enabled Listening Discarding
Enabled Learning Learning
Enabled Forwarding Forwarding
Disabled Disabled Discarding
75
Page 76

RSTP and MSTP
Port type and link type
Spanning Tree Configuration includes the following parameters to support RSTP and MSTP:
• Edge port
• Link type
Although these parameters are configured for Spanning Tree Groups 1-128 (/cfg/l2/stp y/port x),
they only take effect when RSTP/MSTP is turned on.
Edge port
A port that connects to a server or stub network is called an edge port. Therefore, ports 1-16 should have
edge enabled. Edge ports can start forwarding as soon as the link is up.
Edge ports do not take part in Spanning Tree, and should not receive BPDUs. If a port with edge enabled
does receive a BPDU, it begins STP processing until it is re-enabled.
Link type
The link type determines how the port behaves in regard to Rapid Spanning Tree. The link type
corresponds to the duplex mode of the port. A full-duplex link is point-to-point (p2p), while a half-duplex
link should be configured as shared. If you select auto as the link type, the port dynamically configures
the link type.
RSTP configuration guidelines
This section provides important information about configuring Rapid Spanning Tree Groups:
• When RSTP is turned on, STP parameters apply only to STP Group 1.
• When RSTP is turned on, all VLANs from STP Groups other than STP Group 1 are moved to STP
Group 1. The other STP Groups (2-128) are turned off.
RSTP configuration example
This section provides steps to configure Rapid Spanning Tree on the switch, using the Command Line
Interface (CLI) or the Browser-based Interface (BBI).
Configuring Rapid Spanning Tree (CLI example)
1. Configure port and VLAN membership on the switch, as described in the “Configuring ports and
VLANs (CLI example)” section in the “VLANs” chapter of this guide.
2. Set the Spanning Tree mode to Rapid Spanning Tree.
>> /cfg/l2/mrst (Select Multiple Spanning Tree menu)
>> Multiple Spanning Tree# mode rstp (Set mode to Rapid Spanning Tree)
>> Multiple Spanning Tree# on (Turn Rapid Spanning Tree on)
3. Apply and save the changes.
>> # apply (Apply the configuration)
>> # save (Save the configuration)
76
Page 77

RSTP and MSTP
Configuring Rapid Spanning Tree Protocol (BBI example)
1. Configure port and VLAN membership on the switch, as described in the “Configuring ports and
VLANs (BBI example)” section in the “VLANs” chapter of this guide.
2. Configure RSTP general parameters.
a. Click the Configure context button on the Toolbar.
b. Open the MSTP/RSTP folder, and select General.
c. Select RSTP mode, and set the MSTP/RSTP state to ON.
d. Click Submit.
77
Page 78

RSTP and MSTP
3. Apply, verify, and save the configuration.
Multiple Spanning Tree Protocol
IEEE 802.1s Multiple Spanning Tree extends the IEEE 802.1w Rapid Spanning Tree Protocol through
multiple Spanning Tree Groups. MSTP maintains up to 32 spanning-tree instances that correspond to STP
Groups 1-32.
In Multiple Spanning Tree Protocol (MSTP), several VLANs can be mapped to each Spanning-Tree
instance. Each Spanning-Tree instance is independent of other instances. MSTP allows frames assigned to
different VLANs to follow separate paths, each path based on an independent Spanning-Tree instance.
This approach provides multiple forwarding paths for data traffic, enabling load balancing, and reducing
the number of Spanning-Tree instances required to support a large number of VLANs.
MSTP region
A group of interconnected bridges that share the same attributes is called an MST region. Each bridge
within the region must share the following attributes:
• Alphanumeric name
• Revision level
• VLAN-to-STG mapping scheme
MSTP provides rapid reconfiguration, scalability, and control due to the support of regions, and multiple
Spanning-Tree instances support within each region.
Common Internal Spanning Tree
The Common Internal Spanning Tree (CIST) provides a common form of Spanning Tree Protocol, with one
Spanning Tree instance that can be used throughout the MSTP region. CIST allows the switch to
interoperate with legacy equipment, including devices that run IEEE 802.1d (STP).
CIST allows the MSTP region to act as a virtual bridge to other bridges outside of the region, and
provides a single Spanning-Tree instance to interact with them.
CIST is the default spanning tree group. When VLANs are removed from STG 1-128, the VLANs
automatically become members of the CIST.
CIST port configuration includes Hello time, Edge port status (enable/disable), and Link Type. These
parameters do not affect Spanning Tree Groups 1-128. They apply only when the CIST is used.
78
Page 79

RSTP and MSTP
MSTP configuration guidelines
This section provides important information about configuring Multiple Spanning Tree Groups:
• When you turn on MSTP, the switch automatically moves VLAN 1 to the Common Internal Spanning
Tree (CIST).
• Region Name and revision level must be configured. Each bridge in the region must have the same
name and revision level.
• The VLAN and STP Group mapping must be the same across all bridges in the region.
• You can move any VLAN to the CIST.
• You can move VLAN 1 into any Spanning Tree Group.
MSTP configuration example
This section provides steps to configure Multiple Spanning Tree Protocol on the switch, using the
Command Line Interface (CLI) or the Browser-based Interface (BBI).
Configuring Multiple Spanning Tree Protocol (CLI example)
1. Configure port and VLAN membership on the switch, as described in the “Configuring ports and
VLANs (CLI example)” section in the “VLANs” chapter of this guide.
2. Set the mode to Multiple Spanning Tree, and configure MSTP region parameters.
>> /cfg/l2/ mrst (Select Multiple Spanning Tree menu)
>> Multiple Spanning Tree# mode mstp (Set mode to
Multiple Spanning Trees)
>> Multiple Spanning Tree# on (Turn Multiple Spanning Trees on)
>> Multiple Spanning Tree# name xxxxxx (Define the Region name)
>> Multiple Spanning Tree: rev xx (Define the Region revision level)
3. Assign VLANs to Spanning Tree Groups.
>> /cfg/l2/stp 2 (Select Spanning Tree Group 2)
>> Spanning Tree Group 2# add 2 (Add VLAN 2)
>> Spanning Tree Group 2# apply (Apply the configurations)
79
Page 80
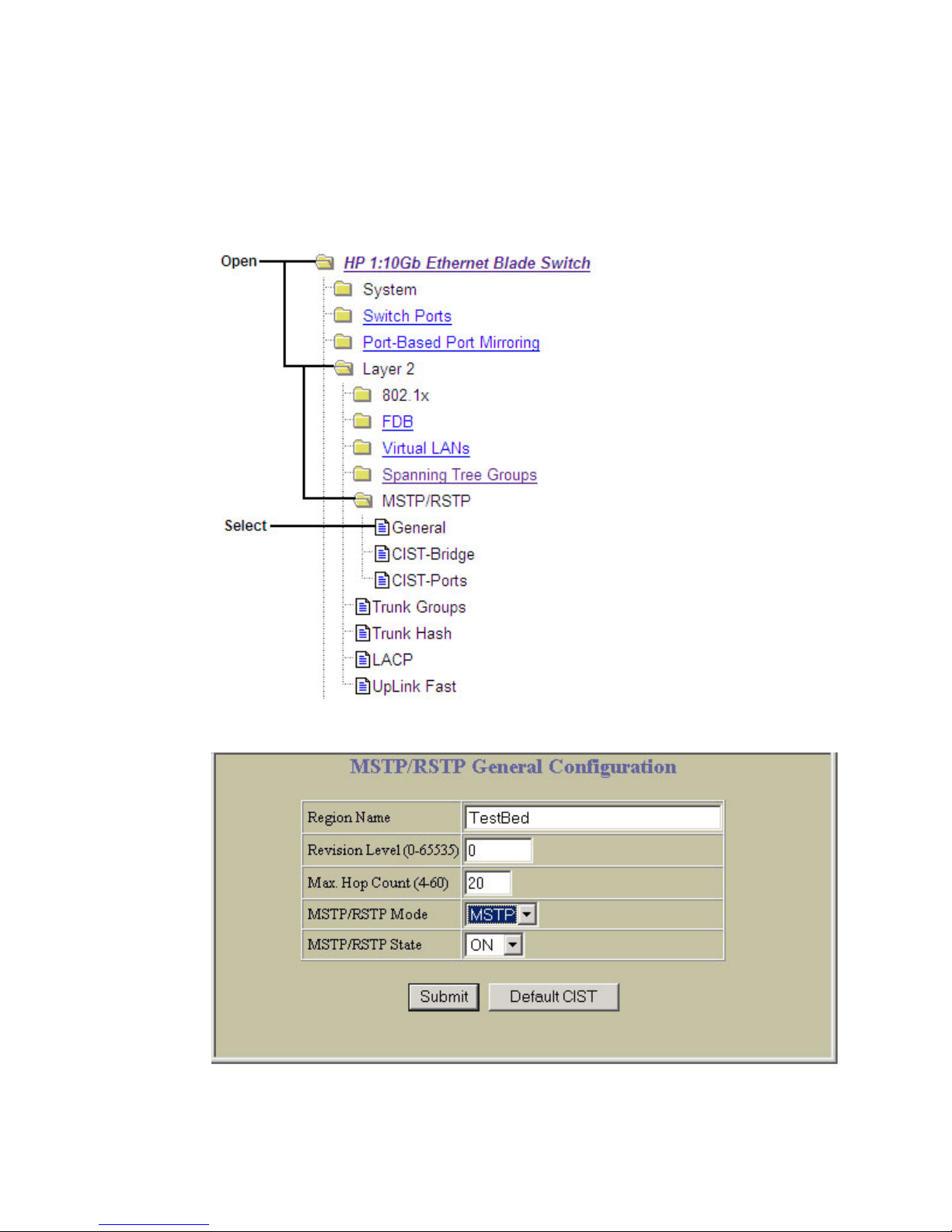
RSTP and MSTP
Configuring Multiple Spanning Tree Protocol (BBI example)
1. Configure port and VLAN membership on the switch, as described in the “Configuring ports and
VLANs (BBI example)” section in the “VLANs” chapter of this guide.
2. Configure MSTP general parameters.
a. Click the Configure context button on the Toolbar.
b. Open the MSTP/RSTP folder, and select General.
c. Enter the region name and revision level. Select MSTP mode, and set the MSTP/RSTP state to
ON.
d. Click Submit.
80
Page 81

RSTP and MSTP
3. Configure Common Internal Spanning Trees (CIST) bridge parameters.
a. Open the MSTP/RSTP folder, and select CIST-Bridge.
b. Enter the Bridge Priority, Maximum Age, and Forward Delay values.
c. Click Submit.
81
Page 82

RSTP and MSTP
4. Configure Common Internal Spanning Tree (CIST) port parameters.
a. Open the MSTP/RSTP folder, and select CIST-Ports.
b. Click a port number to select it.
82
Page 83
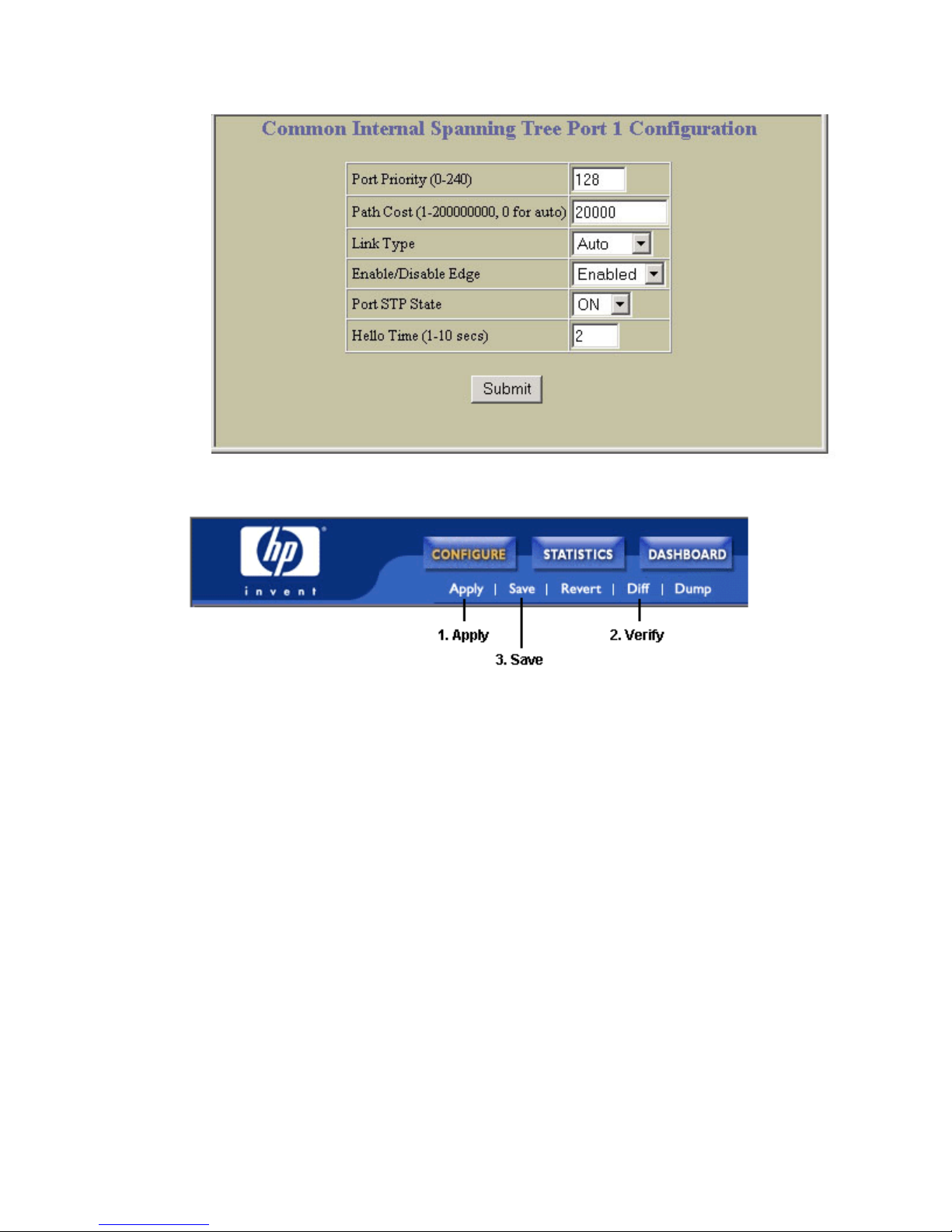
RSTP and MSTP
Enter the Port Priority, Path Cost, and select the Link Type. Set the CIST Port State to ON.
c.
d. Click Submit.
5. Apply, verify, and save the configuration.
83
Page 84
Quality of Service
Quality of Service
Introduction
Quality of Service features allow you to allocate network resources to mission-critical applications at the
expense of applications that are less sensitive to such factors as time delays or network congestion. You
can configure your network to prioritize specific types of traffic, ensuring that each type receives the
appropriate Quality of Service (QoS) level.
The following topics are discussed in this section:
• Quality of Service Overview
• Using ACL Filters
• Using DSCP Values to Provide QoS
• Using 802.1p Priorities to Provide QoS
• Queuing and Scheduling
Overview
QoS helps you allocate guaranteed bandwidth to the critical applications, and limit bandwidth for less
critical applications. Applications such as video and voice must have a certain amount of bandwidth to
work correctly; using QoS, you can provide that bandwidth when necessary. Traffic for applications that
are sensitive to timing out or cannot tolerate delay can be assigned to a high-priority queue.
By assigning QoS levels to traffic flows on your network, you can ensure that network resources are
allocated where they are needed most. QoS features allow you to prioritize network traffic, thereby
providing better service for selected applications.
The following figure shows the basic QoS model used by the HP 1:10GbE switch.
Figure 11 QoS model
Ingress
The switch uses the Differentiated Services (DiffServ) architecture to provide QoS functions. DiffServ
is described in IETF RFCs 2474 and 2475.
With DiffServ, you can establish policies to direct traffic. A policy is a traffic-controlling mechanism
that monitors the characteristics of the traffic, (for example, its source, destination, and protocol) and
performs a controlling action on the traffic when certain characteristics are matched.
Ports
Classify
Packets
ACL
Filter
Meter
Traffic
ACL
Meter
Perform
Actions
Drop/Pass/
Re-Mark
Queue and
Schedule
COS
Queue
Egress
The switch can classify traffic by reading the IEEE 802.1p priority value, or by using filters to match
specific criteria. When network traffic attributes match those specified in a traffic pattern, the policy
instructs the switch to perform specified actions on each packet that passes through it. The packets are
assigned to different Class of Service (COS) queues and scheduled for transmission.
84
Page 85

Quality of Service
The basic HP 1:10GbE switch QoS model works as follows:
• Classify traffic:
○ Read 802.1p Priority
○ Match ACL filter parameters
• Meter traffic:
○ Define bandwidth and burst parameters
○ Select actions to perform on in-profile and out-of-profile traffic
• Perform actions:
○ Drop packets
○ Pass packets
○ Mark DSCP or 802.1p Priority
○ Set COS queue (with or without re-marking)
• Queue and schedule traffic:
○ Place packets in one of two COS queues
○ Schedule transmission based on the COS queue weight
Using ACL filters
Access Control Lists are filters that allow you to classify and segment traffic, so you can provide different
levels of service to different traffic types. Each filter defines the conditions that must match for inclusion in
the filter, and also the actions that are performed when a match is made.
Summary of packet classifiers
The HP 1:10GbE switch allows you to classify packets based on various parameters, such as:
• Ethernet
○ Source MAC address/mask
○ Destination MAC address/mask
○ VLAN number/mask
○ Ethernet type
○ Ethernet Priority, which is the IEEE 802.1p Priority
• IPv4
○ Source IP address/mask
○ Destination IP address/mask
○ Type of Service value
○ IP protocol number: The protocol number or name as shown in the following table:
Table 14 Well-known protocol types
Number Protocol Name
1
2
6
17
icmp
igmp
tcp
udp
85
Page 86

Quality of Service
Table 14 Well-known protocol types
Number Protocol Name
89
112
ospf
vrrp
• TCP/UDP
○ TCP/UDP application source port, as shown in the table titled “Well-Known Application Ports”
○ TCP/UDP application destination port, as shown in the table titled “Well-Known Application
Ports”
○ TCP/UDP flag value, as shown in the table titled “Well-Known TCP Flag Values”
Table 15 Well-known application ports
Number TCP/UDP
Application
20
21
22
23
25
37
ftp-data
ftp
ssh
telnet
smtp
time
Number TCP/UDP
Application
79
80
109
110
111
119
finger
http
pop2
pop3
sunrpc
nntp
Number TCP/UDP
Application
179
194
220
389
443
520
irc
imap3
ldap
https
rip
rtsp
42
43
53
69
70
name
whois
domain
tftp
gopher
123
143
144
161
162
ntp
imap
news
snmp
snmptrap
554
1645;1812
1813
1985
Radius
Radius
Accounting
hsrp
Table 16 Well-known TCP flag values
Flag Value
URG
ACK
PSH
RST
SYN
FIN
0x0020
0x0010
0x0008
0x0004
0x0002
0x0001
86
Page 87

Quality of Service
• Packet Format
○ Ethernet format (eth2, SNAP, LLC)
○ Ethernet tagging format
• Egress port packets
Note that the egress port ACL will not match a broadcast, multicast, unknown unicast, or Layer 3
packet. The egress port ACL will not match packets if the destination port is a trunk member.
Summary of ACL actions
Actions determine how the traffic is treated. The HP 1:10GbE switch QoS actions include the following:
• Pass or Drop
• Re-mark a new DiffServ Code Point (DSCP)
• Re-mark the 802.1p field
• Set the COS queue
Understanding ACL precedence
Each ACL has a unique precedence level, based on its number. When an incoming packet matches the
highest precedence ACL, the ACL’s configured action takes place. The other assigned ACLs also are
considered, in order of precedence.
ACLs are divided into Precedence Groups, as shown in the following table.
Precedence Group ACLs Precedence Level
Precedence Group 1 ACL 1 – ACL 128 Low
Precedence Group 2 ACL 129 – ACL 256
Precedence Group 3 ACL 257 – ACL 384
Precedence Group 4 ACL 385 – ACL 512
Precedence Group 5 ACL 513 – ACL 640
Precedence Group 6 ACL 641 – ACL 768
Precedence Group 7 ACL 769 – ACL 896 High
NOTE: Precedence Groups are not related to ACL Groups.
Each Precedence Group has its own precedence level, such that Precedence Group 2 has a higher
precedence level than Precedence Group 1. Within each Precedence Group, higher-numbered ACLs
receive higher precedence, so that the lowest-numbered ACL has the lowest precedence level, and the
highest-numbered ACL has the highest precedence level. However, the other ACLs within the Precedence
Group have an unspecified precedence level, as follows:
ACL 1 = lowest precedence level within Precedence Group 1
ACL 2 = unspecified precedence level within Precedence Group 1
ACL 3 = unspecified precedence level within Precedence Group 1
...
ACL 126 = unspecified precedence level within Precedence Group 1
ACL 127 = unspecified precedence level within Precedence Group 1
ACL 128 = highest precedence level within Precedence Group 1
87
Page 88
Quality of Service
Using ACL Groups
Access Control Lists (ACLs) allow you to classify packets according to a particular content in the packet
header, such as the source address, destination address, source port number, destination port number,
and others. Packet classifiers identify flows for more processing.
You can define a traffic profile by compiling a number of ACLs into an ACL Group, and assigning the
ACL Group to a port.
ACL Groups are assigned and enabled on a per-port basis. Each ACL can be used by itself or in
combination with other ACLs or ACL Groups on a given switch port.
ACLs can be grouped in the following manner:
• Access Control Lists
Access Control Lists (ACLs) allow you to classify packets according to a particular content in the
packet header, such as the source address, destination address, source port number, destination port
number, and others. Packet classifiers identify flows for more processing.
The HP 1:10GbE switch supports up to 896 ACLs. Each ACL defines one filter rule. Each filter rule is
a collection of matching criteria, and can include an action (permit or deny the packet). For
example:
ACL 400:
VLAN = 1
SIP = 10.10.10.1 (255.255.255.0)
Action = permit
• Access Control Groups
An Access Control Group (ACL Group) is a collection of ACLs. For example:
ACL Group 1
ACL 382:
VLAN = 1
SIP = 10.10.10.1 (255.255.255.0)
Action = permit
ACL 383:
VLAN = 2
SIP = 10.10.10.2 (255.255.255.0)
Action = deny
ACL 509:
PRI = 7
DIP = 10.10.10.3 (255.255.0.0)
Action = permit
In the example above, each ACL defines a filter rule. ACL 383 has a higher precedence than
ACL 382, based on its number.
Use ACL Groups to create a traffic profile by gathering ACLs into an ACL Group, and assigning the
ACL Group to a port. The HP 1:10GbE switch supports up to 896 ACL Groups.
88
Page 89

Quality of Service
ACL Metering and Re-marking
You can define a profile for the aggregate traffic flowing through the HP 1:10GbE switch, by configuring
a QoS meter (if desired), and assigning ACL Groups to ports. When you add ACL Groups to a port,
make sure they are ordered correctly in terms of precedence.
For example, consider two ACL Groups, ACL Group 1 and ACL Group 2. Each contains three levels of
precedence. If you add ACL Group 1 to a port, then add ACL Group 2 to the port, the port’s ACL filters
contain a total of six precedence levels. ACL Group 1 has precedence over ACL Group 2.
Each port supports up to seven precedence levels.
Actions taken by an ACL are called In-Profile actions. You can configure additional In-Profile and Out-of-
Profile actions on a port. Data traffic can be metered, and re-marked to ensure that the traffic flow
provides certain levels of service in terms of bandwidth for different types of network traffic.
Metering
QoS metering provides different levels of service to data streams through user-configurable parameters. A
meter is used to measure the traffic stream against a traffic profile, which you create. Thus, creating
meters yields In-Profile and Out-of-Profile traffic for each ACL, as follows:
• In-Profile—If there is no meter configured or if the packet conforms to the meter, the packet is
classified as In-Profile.
• Out-of-Profile—If a meter is configured and the packet does not conform to the meter (exceeds the
committed rate or maximum burst rate of the meter), the packet is classified as Out-of-Profile.
Using meters, you set a Committed Rate in Kb/s (1024 bits per second in each Kb/s). All traffic within
this Committed Rate is In-Profile. Additionally, you set a Maximum Burst Size that specifies an allowed
data burst larger than the Committed Rate for a brief period. These parameters define the In-Profile traffic.
Meters keep the sorted packets within certain parameters. You can configure a meter on an ACL, and
perform actions on metered traffic, such as packet re-marking.
Re-marking
Re-marking allows for the treatment of packets to be reset based on new network specifications or desired
levels of service. You can configure the ACL to re-mark a packet as follows:
• Change the DSCP value of a packet, used to specify the service level traffic should receive.
• Change the 802.1p priority of a packet.
Viewing ACL statistics
ACL statistics display how many packets hit (matched) each ACL. Up to 64 statistic counters can be
displayed for each ACL Precedence Group. Use ACL statistics to check filter performance, and debug the
ACL filters.
You must enable statistics (cfg/acl/acl x/stats ena) for each ACL that you want to monitor.
89
Page 90

Quality of Service
ACL configuration examples
Configure Access Control Lists (CLI example)
The following configuration examples illustrate how to use Access Control Lists (ACLs) to block traffic.
These basic configurations illustrate common principles of ACL filtering.
NOTE: Each ACL filters traffic that ingresses on the port to which the ACL is added. The egrport
classifier filters traffic that ingresses the port to which the ACL is added, and then egresses the port
specified by egrport. In most common configurations, egrport is not used.
• Example 1 Use this configuration to block traffic to a specific host.
>> Main# /cfg/acl/acl 255 (Define ACL 255)
>> ACL 255# ipv4/dip 100.10.1.116 255.255.255.255
>> Filtering IPv4# ..
>> ACL 255# action deny
>> ACL 255# /cfg/port 20/aclqos (Add ACL to port 20)
>> Port 20 ACL# add acl 255
>> Port 20 ACL# apply
>> Port 20 ACL# save
In this example, all traffic that ingresses on port 20 is denied if it is destined for the host at IP
address 100.10.1.116.
• Example 2 Use this configuration to block traffic from a network destined for a specific host
address.
>> Main# /cfg/acl/acl 256 (Define ACL 256)
>> ACL 256# ipv4/sip 100.10.1.0 255.255.255.0
>> ACL 256# ipv4/dip 200.20.1.116 255.255.255.255
>> Filtering IPv4# ..
>> ACL 256# action deny
>> ACL 256# /cfg/port 20/aclqos (Add ACL to port 20)
>> Port 20 ACL# add acl 256
>> Port 20 ACL# apply
>> Port 20 ACL# save
In this example, all traffic that ingresses on port 20 with source IP from the class 100.10.1.0/24
and destination IP 200.20.1.116 is denied.
90
Page 91

Quality of Service
• Example 3 Use this configuration to block traffic from a source that is destined for a specific egress
port.
>> Main# /cfg/acl/acl 1 (Define ACL 1)
>> ACL 1# ethernet/smac 002100000000 ffffffffffff
>> Filtering Ethernet# ..
>> ACL 1# action deny
>> ACL 1# stats e
>> ACL 1# egrport 24
>> ACL 1# action deny
>> ACL 1# stats e
>> ACL 1# /cfg/port 23/aclqos
>> Port 23 ACL# add acl 1 (Add ACL 1 to port 23)
>> Port 23 ACL# apply
>> Port 23 ACL# save
In this example, all traffic (Layer 2 known unicast) that ingresses on port 23 from source MAC
00:21:00:00:00:00 and is destined for port 24 is denied.
Configure Access Control Lists and Groups (BBI example 1)
1. Configure Access Control Lists (ACLs).
a. Click the Configure context button on the Toolbar.
b. Open the Access Control Lists folder, and select Add ACL.
91
Page 92
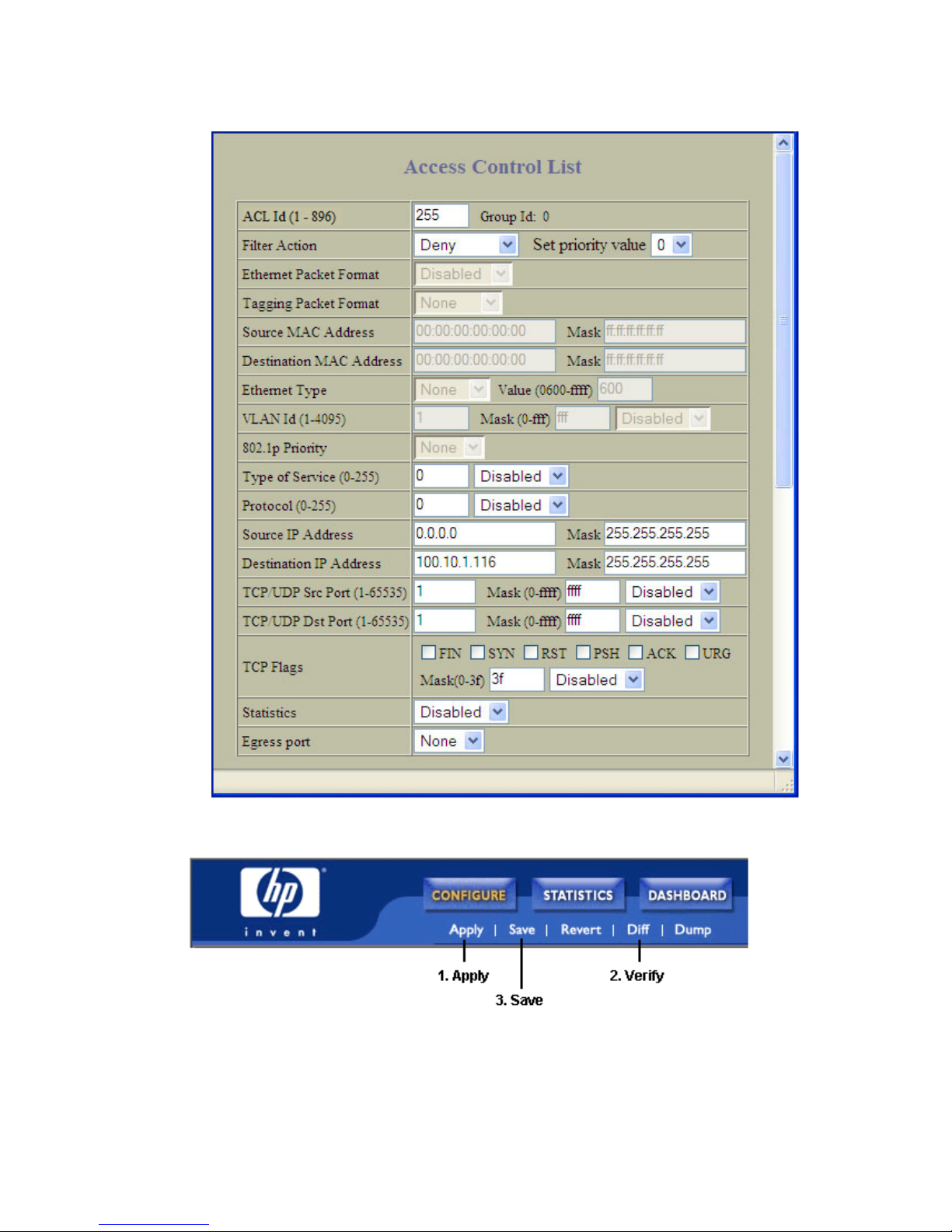
Quality of Service
Configure the ACL parameters. Set the Filter Action to Deny, the Ethernet Type to IPv4, and the
c.
Destination IP Address to 100.10.1.116.
d. Click Submit.
2. Apply, verify, and save the configuration.
92
Page 93

Quality of Service
3. Add ACL 1 to port 1.
a. Click the Configure context button on the Toolbar.
b. Select Switch Ports (click the underlined text, not the folder).
c. Select a port.
93
Page 94

Quality of Service
Add the ACL to the port.
d.
e. Click Submit.
4. Apply, verify, and save the configuration.
94
Page 95

Quality of Service
Using DSCP values to provide QoS
The six most significant bits in the TOS byte of the IP header are defined as DiffServ Code Points (DSCP).
Packets are marked with a certain value depending on the type of treatment the packet must receive in the
network device. DSCP is a measure of the Quality of Service (QoS) level of the packet.
Differentiated Services concepts
To differentiate between traffic flows, packets can be classified by their DSCP value. The Differentiated
Services (DS) field in the IP header is an octet, and the first six bits, called the DS Code Point (DSCP), can
provide QoS functions. Each packet carries its own QoS state in the DSCP. There are 64 possible DSCP
values (0-63).
Figure 12 Layer 3 IPv4 packet
The switch can perform the following actions to the DSCP:
• Read the DSCP value of ingress packets
• Re-mark the DSCP value to a new value
• Map the DSCP value to an 802.1p priority
Once the DSCP value is marked, the switch can use it to direct traffic prioritization.
Per Hop Behavior
The DSCP value determines the Per Hop Behavior (PHB) of each packet. The PHB is the forwarding
treatment given to packets at each hop. QoS policies are built by applying a set of rules to packets,
based on the DSCP value, as they hop through the network.
The HP 1:10GbE switch default settings are based on the following standard PHBs, as defined in the IEEE
standards:
• Expedited Forwarding (EF)—This PHB has the highest egress priority and lowest drop precedence
level. EF traffic is forwarded ahead of all other traffic. EF PHB is described in RFC 2598.
• Assured Forwarding (AF)—This PHB contains four service levels, each with a different drop
precedence, as shown below. Routers use drop precedence to determine which packets to discard
last when the network becomes congested. AF PHB is described in RFC 2597.
Table 17 Assured forwarding drop-down precedence
Drop Precedence Class 1 Class 2 Class 3 Class 4
Low AF11 (DSCP 10) AF21 (DSCP 18) AF31 (DSCP 26) AF41 (DSCP 34)
Medium AF12 (DSCP 12) AF22 (DSCP 20) AF32 (DSCP 28) AF42 (DSCP 36)
High AF13 (DSCP 14) AF23 (DSCP 22) AF33 (DSCP 30) AF43 (DSCP 38)
95
Page 96

Quality of Service
• Class Selector (CS)—This PHB has eight priority classes, with CS7 representing the highest priority,
and CS0 representing the lowest priority, as shown below. CS PHB is described in RFC 2474.
Table 18 Class selector priority classes
Priority Class Selector DSCP
Highest CS7 56
CS6 48
CS5 40
CS4 32
CS3 24
CS2 16
CS1 8
Lowest CS0 0
QoS levels
The following table shows the default service levels provided by the switch, listed from highest to lowest
importance:
Table 19 Default QoS service levels
Service Level Default PHB 802.1p Priority
Critical CS7 7
Network Control CS6 6
Premium EF, CS5 5
Platinum AF41, AF42, AF43, CS4 4
Gold AF31, AF32, AF33, CS3 3
Silver AF21, AF22, AF23, CS2 2
Bronze AF11, AF12, AF13, CS1 1
Using 802.1p priorities to provide QoS
The HP 1:10GbE switch software provides Quality of Service functions based on the priority bits in a
packet’s VLAN header. (The priority bits are defined by the 802.1p standard within the IEEE 802.1q
VLAN header.) The 802.1p bits, if present in the packet, specify the priority given to packets during
forwarding. Packets with a numerically higher (non-zero) priority are given forwarding preference over
packets with lower priority.
Packets with a priority mapped to a higher Class of Service (COS) and COS queue (COSq) weight are
given forwarding preference over packets with priority mapped to a lower COS and COSq weight. The
scheduling scheme is Weight Round Robin (WRR), with user-configurable weight from 0 to 15 for a
COSq. The switch can be configured with either two or eight output Class of Service queues (COSq).
96
Page 97
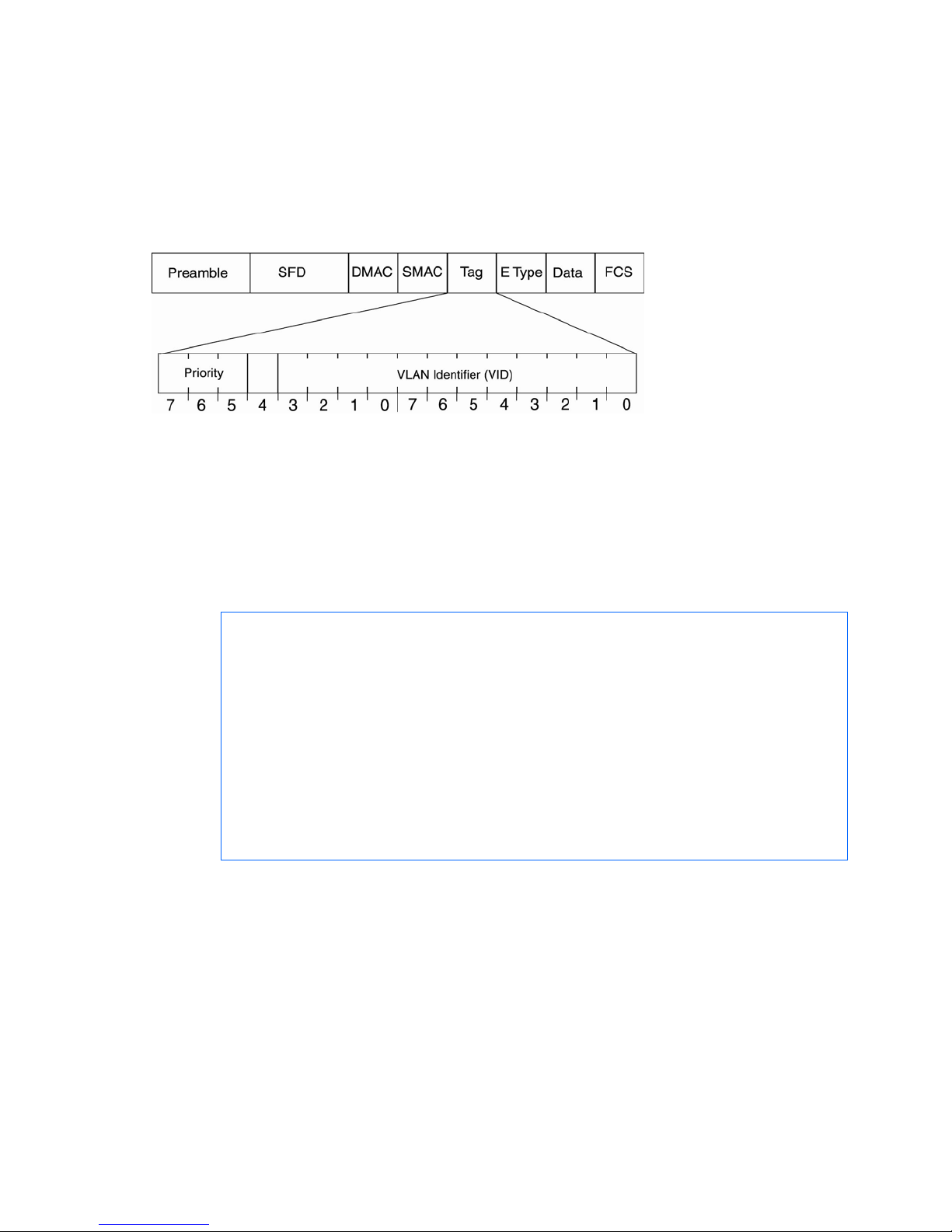
Quality of Service
The IEEE 802.1p standard uses eight levels of priority (0-7). Priority 7 is assigned to highest priority
network traffic, such as OSPF or RIP routing table updates, priorities 5-6 are assigned to delay-sensitive
applications such as voice and video, and lower priorities are assigned to standard applications. A value
of 0 (zero) indicates a best effort traffic prioritization, and this is the default when traffic priority has not
been configured on your network. The switch can filter packets based on the 802.1p values, and it can
assign or overwrite the 802.1p value in the packet.
Figure 13 Layer 2 802.1q/802.1p VLAN tagged packet
Ingress packets receive a priority value, as follows:
• Tagged packets—the switch reads the 802.1p priority in the VLAN tag.
• Untagged packets—the switch tags the packet and assigns an 802.1p priority, based on the port’s
default priority (/cfg/port x/8021ppri).
Egress packets are placed in a COS queue based on the priority value, and scheduled for transmission
based on the scheduling weight of the COS queue.
Use the /cfg/qos/8021p/cur command to display the mapping between 802.1p values, Class of
Service queues (COSq), and COSq scheduling weights.
>> 802.1p# cur
Current priority to COS queue configuration:
Number of COSq: 2
Priority COSq Weight
-------- ---- ----- 0 0 1
1 0 1
2 0 1
3 0 1
4 1 2
5 1 2
6 1 2
7 1 2
97
Page 98
Quality of Service
802.1p configuration (CLI example)
1. Configure a port’s default 802.1 priority.
>> Main# cfg/port 20 (Select port)
>> Port 20# 8021ppri (Set port’s default 802.1p priority)
Current 802.1p priority: 0
Enter new 802.1p priority [0-7]: 1
>> Port 20# apply
2. Map the 802.1p priority value to a COS queue and set the COS queue scheduling weight.
>> Main# cfg/qos/8021p (Select 802.1p menu)
>> 802.1p# priq (Set COS queue assignments)
Enter priority [0-7]: 1
Current COS queue (for priority 1): 0
Enter new COS queue (for priority 1) [0-1]: 1
>> 802.1p# qweight (Set COS queue weights)
Enter COS queue [0-1]: 1
Current weight (for COS queue 1): 0
Enter new weight (for COS queue 1) [0-15]: 1
>> 802.1p# apply
802.1p configuration (BBI example)
1. Configure a port’s default 802.1p priority.
a. Click the Configure context button on the Toolbar.
b. Select Switch Ports (click the underlined text, not the folder).
98
Page 99
Quality of Service
Select a port.
c.
99
Page 100

Quality of Service
Set the 802.1p priority value.
d.
e. Click Submit.
100
 Loading...
Loading...