Hikvision DS-2DE2A404IW-DE3, DS-2DE4A204IW-DE, DS-2DE5230W-AE3, DS-2DE5330W-AE, DS-2DE7230IW-AE User Manual
...Page 1

Network PTZ Camera
User Manual
Page 2

User Manual of Network PTZ Camera
i
User Manual
COPYRIGHT © 2018 Hangzhou Hikvision Digital Technology Co., Ltd.
ALL RIGHTS RESERVED.
Any and all information, including, among others, wordings, pictures, graphs are the properties of
Hangzhou Hikvision Digital Technology Co., Ltd. or its subsidiaries (hereinafter referred to be
“Hikvision”). This user manual (hereinafter referred to be “the Manual”) cannot be reproduced,
changed, translated, or distributed, partially or wholly, by any means, without the prior written
permission of Hikvision. Unless otherwise stipulated, Hikvision does not make any warranties,
guarantees or representations, express or implied, regarding to the Manual.
About this Manual
This Manual is applicable to Network PTZ camera.
The Manual includes instructions for using and managing the product. Pictures, charts, images and all
other information hereinafter are for description and explanation only. The information contained in
the Manual is subject to change, without notice, due to firmware updates or other reasons. Please
find the latest version in the company website (http://overseas.hikvision.com/en/).
Please use this user manual under the guidance of professionals.
Trademarks Acknowledgement
and other Hikvision’s trademarks and logos are the properties of Hikvision in various
jurisdictions. Other trademarks and logos mentioned below are the properties of their respective
owners.
Legal Disclaimer
TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, THE PRODUCT DESCRIBED, WITH ITS
HARDWARE, SOFTWARE AND FIRMWARE, IS PROVIDED “AS IS”, WITH ALL FAULTS AND ERRORS, AND
HIKVISION MAKES NO WARRANTIES, EXPRESS OR IMPLIED, INCLUDING WITHOUT LIMITATION,
MERCHANTABILITY, SATISFACTORY QUALITY, FITNESS FOR A PARTICULAR PURPOSE, AND
NON-INFRINGEMENT OF THIRD PARTY. IN NO EVENT WILL HIKVISION, ITS DIRECTORS, OFFICERS,
EMPLOYEES, OR AGENTS BE LIABLE TO YOU FOR ANY SPECIAL, CONSEQUENTIAL, INCIDENTAL, OR
INDIRECT DAMAGES, INCLUDING, AMONG OTHERS, DAMAGES FOR LOSS OF BUSINESS PROFITS,
BUSINESS INTERRUPTION, OR LOSS OF DATA OR DOCUMENTATION, IN CONNECTION WITH THE USE
OF THIS PRODUCT, EVEN IF HIKVISION HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
REGARDING TO THE PRODUCT WITH INTERNET ACCESS, THE USE OF PRODUCT SHALL BE WHOLLY AT
YOUR OWN RISKS. HIKVISION SHALL NOT TAKE ANY RESPONSIBILITES FOR ABNORMAL OPERATION,
PRIVACY LEAKAGE OR OTHER DAMAGES RESULTING FROM CYBER ATTACK, HACKER ATTACK, VIRUS
INSPECTION, OR OTHER INTERNET SECURITY RISKS; HOWEVER, HIKVISION WILL PROVIDE TIMELY
TECHNICAL SUPPORT IF REQUIRED.
SURVEILLANCE LAWS VARY BY JURISDICTION. PLEASE CHECK ALL RELEVANT LAWS IN YOUR
JURISDICTION BEFORE USING THIS PRODUCT IN ORDER TO ENSURE THAT YOUR USE CONFORMS THE
APPLICABLE LAW. HIKVISION SHALL NOT BE LIABLE IN THE EVENT THAT THIS PRODUCT IS USED WITH
ILLEGITIMATE PURPOSES.
© Hikvision
Page 3

User Manual of Network PTZ Camera
ii
IN THE EVENT OF ANY CONFLICTS BETWEEN THIS MANUAL AND THE APPLICABLE LAW, THE LATER
PREVAILS.
0505071080328
© Hikvision
Page 4

User Manual of Network PTZ Camera
iii
Regulatory Information
FCC Information
Please take attention that changes or modification not expressly approved by the party
responsible for compliance could void the user’s authority to operate the equipment.
FCC compliance: This equipment has been tested and found to comply with the limits for a Class
A digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference when the equipment is operated in a
commercial environment. This equipment generates, uses, and can radiate radio frequency
energy and, if not installed and used in accordance with the instruction manual, may cause
harmful interference to radio communications. Operation of this equipment in a residential area
is likely to cause harmful interference in which case the user will be required to correct the
interference at his own expense.
FCC Conditions
This device complies with part 15 of the FCC Rules. Operation is subject to the following two
conditions:
1. This device may not cause harmful interference.
2. This device must accept any interference received, including interference that may cause
undesired operation.
EU Conformity Statement
This product and - if applicable - the supplied accessories too are marked with
"CE" and comply therefore with the applicable harmonized European standards
listed under the Low Voltage Directive 2015/35/EU, the EMC Directive 2014/30/EU,
the RoHS Directive 2011/65/EU.
2012/19/EU (WEEE directive): Products marked with this symbol cannot be
disposed of as unsorted municipal waste in the European Union. For proper
recycling, return this product to your local supplier upon the purchase of
equivalent new equipment, or dispose of it at designated collection points. For
more information see: www.recyclethis.info.
2006/66/EC (battery directive): This product contains a battery that cannot be
disposed of as unsorted municipal waste in the European Union. See the product
documentation for specific battery information. The battery is marked with this
symbol, which may include lettering to indicate cadmium (Cd), lead (Pb), or
mercury (Hg). For proper recycling, return the battery to your supplier or to a designated
collection point. For more information see: www.recyclethis.info.
Industry Canada ICES-003 Compliance
This device meets the CAN ICES-3 (A)/NMB-3(A) standards requirements.
© Hikvision
Page 5
User Manual of Network PTZ Camera
iv
Warnings Follow these safeguards to prevent
serious injury or death.
Cautions Follow these precautions to prevent
potential injury or material damage.
Safety Instruction
These instructions are intended to ensure that the user can use the product correctly to avoid
danger or property loss.
The precaution measure is divided into ‘Warnings’ and ‘Cautions’:
Warnings: Serious injury or death may be caused if any of these warnings are neglected.
Cautions: Injury or equipment damage may be caused if any of these cautions are neglected.
Warnings:
Adopt the power adapter which can meet the safety extra low voltage (SELV) standard. The
power consumption cannot be less than the required value.
Do not connect several devices to one power adapter as an adapter overload may cause
over-heating and can be a fire hazard.
When the product is installed on a wall or ceiling, the device should be firmly fixed.
To reduce the risk of fire or electrical shock, do not expose the indoor used product to rain or
moisture.
This installation should be made by a qualified service person and should conform to all the
local codes.
Install blackouts equipment into the power supply circuit for convenient supply interruption.
If the product does not work properly, contact your dealer or the nearest service center.
Never attempt to disassemble the product yourself. (We shall not assume any responsibility
for problems caused by unauthorized repair or maintenance.)
Cautions:
If the camera fails to synchronize local time with that of the network, you need to set up
camera time manually. Visit the camera (via web browser or client software) and enter
system settings interface for time settings.
Make sure the power supply voltage is correct before using the product.
Do not drop the product or subject it to physical shock. Do not install the product on
vibratory surface or places.
Do not expose it to high electromagnetic radiating environment.
© Hikvision
Page 6

User Manual of Network PTZ Camera
v
Do not aim the lens at the strong light such as sun or incandescent lamp. The strong light can
cause fatal damage to the product.
The sensor may be burned out by a laser beam, so when any laser equipment is being used,
make sure that the surface of the sensor not be exposed to the laser beam.
For working temperature, refer to the specification manual for details.
To avoid heat accumulation, good ventilation is required for a proper operating environment.
While shipping, the product should be packed in its original packing.
Use the provided glove when open up the product cover. Do not touch the product cover
with fingers directly, because the acidic sweat of the fingers may erode the surface coating of
the product cover.
Use a soft and dry cloth when clean inside and outside surfaces of the product cover. Do not
use alkaline detergents.
Improper use or replacement of the battery may result in hazard of explosion. Use the
manufacturer recommended battery type.
© Hikvision
Page 7

User Manual of Network PTZ Camera
vi
Table of Contents
CHAPTER 1 OVERVIEW ................................................................................................................. 1
1.1 SYSTEM REQUIREMENT .................................................................................................................. 1
1.2 FUNCTIONS .................................................................................................................................. 1
CHAPTER 2 NETWORK CONNECTION ............................................................................................ 4
2.1 SETTING THE NETWORK CAMERA OVER THE LAN ................................................................................ 4
2.1.1 Wiring over the LAN ............................................................................................................ 4
2.1.2 Activating the Camera ......................................................................................................... 5
2.1.3 (Optional) Setting Security Question .................................................................................. 10
2.2 SETTING THE NETWORK CAMERA OVER THE WAN ............................................................................ 10
2.2.1 Static IP Connection ........................................................................................................... 10
2.2.2 Dynamic IP Connection ...................................................................................................... 11
CHAPTER 3 ACCESSING TO THE NETWORK SPEED DOME ............................................................ 13
3.1 ACCESSING BY WEB BROWSERS ..................................................................................................... 13
3.2 ACCESSING BY CLIENT SOFTWARE ................................................................................................... 14
CHAPTER 4 BASIC OPERATIONS .................................................................................................. 16
4.1 CONFIGURING LOCAL PARAMETERS ................................................................................................ 16
4.2 LIVE VIEW PAGE ......................................................................................................................... 17
4.3 STARTING LIVE VIEW ................................................................................................................... 18
4.4 OPERATING PTZ CONTROL ........................................................................................................... 20
4.4.1 PTZ Control Panel ............................................................................................................... 21
4.4.2 Auxiliary Functions ............................................................................................................. 22
4.4.3 Setting/Calling a Preset ..................................................................................................... 24
4.4.4 Setting/Calling a Patrol ...................................................................................................... 26
4.4.5 One-touch Patrol ................................................................................................................ 27
4.4.6 Setting/Calling a Pattern ................................................................................................... 28
4.5 PLAYBACK .................................................................................................................................. 29
4.5.1 Play Back Video Files ......................................................................................................... 29
4.5.2 Downloading Video Files ................................................................................................... 31
4.6 PICTURES .................................................................................................................................. 31
CHAPTER 5 SYSTEM CONFIGURATION ......................................................................................... 33
5.1 STORAGE SETTINGS ..................................................................................................................... 33
5.1.1 Configuring Recording Schedule ........................................................................................ 33
5.1.2 Configuring Capture Schedule ........................................................................................... 35
5.1.3 Configuring Net HDD ......................................................................................................... 36
5.2 BASIC EVENT CONFIGURATION ....................................................................................................... 39
5.2.1 Configuring Motion Detection ........................................................................................... 39
5.2.2 Configuring Video Tampering Alarm ................................................................................. 44
5.2.3 Configuring Alarm Input .................................................................................................... 45
5.2.4 Configuring Alarm Output ................................................................................................. 47
© Hikvision
Page 8

User Manual of Network PTZ Camera
vii
5.2.5 Handling Exception ............................................................................................................ 48
5.3 SMART EVENT CONFIGURATION ..................................................................................................... 48
5.3.1 Detecting Audio Exception ................................................................................................. 49
5.3.2 Configuring Face Detection ................................................................................................ 50
5.3.3 Configuring Intrusion Detection ......................................................................................... 50
5.3.4 Configuring Line Crossing Detection .................................................................................. 52
5.3.5 Configuring Region Entrance Detection ............................................................................. 53
5.3.6 Configuring Region Exiting Detection ................................................................................ 54
5.4 PTZ CONFIGURATION .................................................................................................................. 56
5.4.1 Configuring Basic PTZ Parameters ..................................................................................... 56
5.4.2 Configuring PTZ Limits ....................................................................................................... 57
5.4.3 Configuring Initial Position................................................................................................. 58
5.4.4 Configuring Park Actions.................................................................................................... 59
5.4.5 Configuring Privacy Mask .................................................................................................. 60
5.4.6 Configuring Scheduled Tasks .............................................................................................. 61
5.4.7 Clearing PTZ Configurations ............................................................................................... 62
5.4.8 Configuring Smart Tracking ............................................................................................... 63
5.4.9 Prioritize PTZ ...................................................................................................................... 64
CHAPTER 6 CAMERA CONFIGURATION ....................................................................................... 65
6.1 CONFIGURING NETWORK SETTINGS ................................................................................................ 65
6.1.1 Basic Settings ..................................................................................................................... 65
6.1.2 Advanced Settings .............................................................................................................. 69
6.2 CONFIGURING VIDEO AND AUDIO SETTINGS ..................................................................................... 79
6.2.1 Configuring Video Settings ................................................................................................ 79
6.2.2 Configuring Audio Settings ................................................................................................ 81
6.2.3 Configuring ROI Settings .................................................................................................... 82
6.3 CONFIGURING IMAGE SETTINGS ..................................................................................................... 83
6.3.1 Configuring Display Settings .............................................................................................. 84
6.3.2 Configuring OSD Settings ................................................................................................... 89
6.3.3 Configuring Text Overlay Settings ...................................................................................... 91
6.3.4 Configuring Image Parameters Switch............................................................................... 91
6.4 CONFIGURING SYSTEM SETTINGS ................................................................................................... 92
6.4.1 System Settings .................................................................................................................. 92
6.4.2 Maintenance ...................................................................................................................... 97
6.4.3 Security ............................................................................................................................ 100
6.4.4 User Management ........................................................................................................... 102
APPENDIX ...................................................................................................................................... 106
SADP SOFTWARE INTRODUCTION ............................................................................................................ 106
© Hikvision
Page 9

User Manual of Network PTZ Camera
1
Chapter 1 Overview
1.1 System Requirement
System requirement of web browser accessing is as follows:
Operating System: Microsoft Windows XP SP1 and above version/Vista/Win7/Server 2003/Server
2008 32bits
CPU: Intel Pentium IV 3.0 GHz or higher
RAM: 1G or higher
Display: 1024 × 768 resolution or higher
Web Browser: Internet Explorer 8.0 and above version, Apple Safari 5.02 and above version,
Mozilla Firefox 5 and above version and Google Chrome 18 and above versions.
1.2 Functions
The functions vary depending on different camera models.
PTZ Limits
The camera can be programmed to move within the PTZ limits (left/right, up/down).
Scan Modes
The camera provides 5 scan modes: auto scan, tilt scan, frame scan, random scan and panorama
scan.
Presets
A preset is a predefined image position. When the preset is called, the camera will automatically
move to the defined position. The presets can be added, modified, deleted and called.
Label Display
The on-screen label of the preset title, azimuth/elevation, zoom, time and camera name can be
displayed on the monitor. The displays of time and camera name can be programmed.
Auto Flips
In manual tracking mode, when a target object goes directly beneath the camera, the video will
automatically flips 180 degrees in horizontal direction to maintain continuity of tracking. This
function can also be realized by auto mirror image depending on different camera models.
Privacy Mask
This function allows you to block or mask certain area of a scene, for preventing the personal
privacy from recording or live viewing. A masked area will move with pan and tilt functions and
automatically adjust in size as the lens zooms telephoto and wide.
3D Positioning
In the client software, use the left key of mouse to click on the desired position in the video
image and drag a rectangle area in the lower right direction, then the camera system will move
the position to the center and allow the rectangle area to zoom in. Use the left key of mouse to
© Hikvision
Page 10

User Manual of Network PTZ Camera
2
drag a rectangle area in the upper left direction to move the position to the center and allow the
rectangle area to zoom out.
Proportional Pan/Tilt
Proportional pan/tilt automatically reduces or increases the pan and tilt speeds according to the
amount of zoom. At telephoto zoom settings, the pan and tilt speeds will be slower than at wide
zoom settings. This keeps the image from moving too fast on the live view image when there is a
large amount of zoom.
Auto Focus
The auto focus enables the camera to focus automatically to maintain clear video images.
Day/Night Auto Switch
The cameras deliver color images during the day. And as light diminishes at night, the cameras
switch to night mode and deliver black and white images with high quality.
Slow Shutter
In slow shutter mode, the shutter speed will automatically slow down in low illumination
conditions to maintain clear video images by extending the exposure time. The feature can be
enabled or disabled.
Backlight Compensation (BLC)
If you focus on an object against strong backlight, the object will be too dark to be seen clearly.
The BLC (Backlight Compensation) function can compensate light to the object in the front to
make it clear, but this causes the over-exposure of the background where the light is strong.
Wide Dynamic Range (WDR)
The wide dynamic range (WDR) function helps the camera provide clear images even under back
light circumstances. When there are both very bright and very dark areas simultaneously in the
field of view, WDR balances the brightness level of the whole image and provide clear images
with details.
White Balance (WB)
White balance can remove the unrealistic color casts. White balance is the white rendition
function of the camera to adjust the color temperature according to the environment
automatically.
Patrol
A patrol is a memorized series of pre-defined preset function. The scanning speed between two
presets and the dwell time at the preset are programmable.
Pattern
A pattern is a memorized series of pan, tilt, zoom, and preset functions. By default the focus and
iris are in auto status during the pattern is being memorized.
Power Off Memory
The camera supports the power off memory capability with the predefined resume time. It allows
the camera to resume its previous position after power is restored.
Scheduled Task
A time task is a preconfigured action that can be performed automatically at a specific date and
time. The programmable actions include: auto scan, random scan, patrol 1-8 ,pattern 1-4, preset
1-8,frame scan, panorama scan, tilt scan, day, night, reboot, PT adjust, Aux Output, etc.
Park Action
This feature allows the camera to start a predefined action automatically after a period of
© Hikvision
Page 11

User Manual of Network PTZ Camera
3
inactivity.
User Management
The camera allows you to edit users with different levels of permission, in the admin login status.
Multiple users are allowed to access and control the same network camera via network
simultaneously.
3D Digital Noise Reduction
Comparing with the general 2D digital noise reduction, the 3D digital noise reduction function
processes the noise between two frames besides processing the noise in one frame. The noise
will be much less and the video will be clearer.
© Hikvision
Page 12
User Manual of Network PTZ Camera
4
Network Cable
Network Speed Dome
Computer
Chapter 2 Network Connection
You shall acknowledge that the use of the product with Internet access might be under
network security risks. For avoidance of any network attacks and information leakage,
strengthen your own protection. If the product does not work properly, contact with your
dealer or the nearest service center.
To ensure the network security of the network camera, we recommend you to have the
network camera assessed and maintained termly. You can contact us if you need such
service.
Before you start:
If you want to set the network camera via a LAN (Local Area Network), refer to Section 2.1
Setting the Network Camera over the LAN.
If you want to set the network camera via a WAN (Wide Area Network), refer to Section 2.2
Setting the Network Camera over the WAN.
2.1 Setting the Network Camera over the LAN
Purpose:
To view and configure the camera via a LAN, you need to connect the camera in the same subnet
with your computer, and install the SADP or client software to search and change the IP of the
network camera.
For the detailed introduction of SADP, refer to Appendix.
2.1.1 Wiring over the LAN
The following figures show the two ways of cable connection of a network camera and a
computer:
Purpose:
To test the network camera, you can directly connect the network camera to the computer
with a network cable as shown in Figure 2-1.
Refer to the Figure 2-2 to set the network camera over the LAN via a switch or a router.
Figure 2-1 Connecting Directly
© Hikvision
Page 13
User Manual of Network PTZ Camera
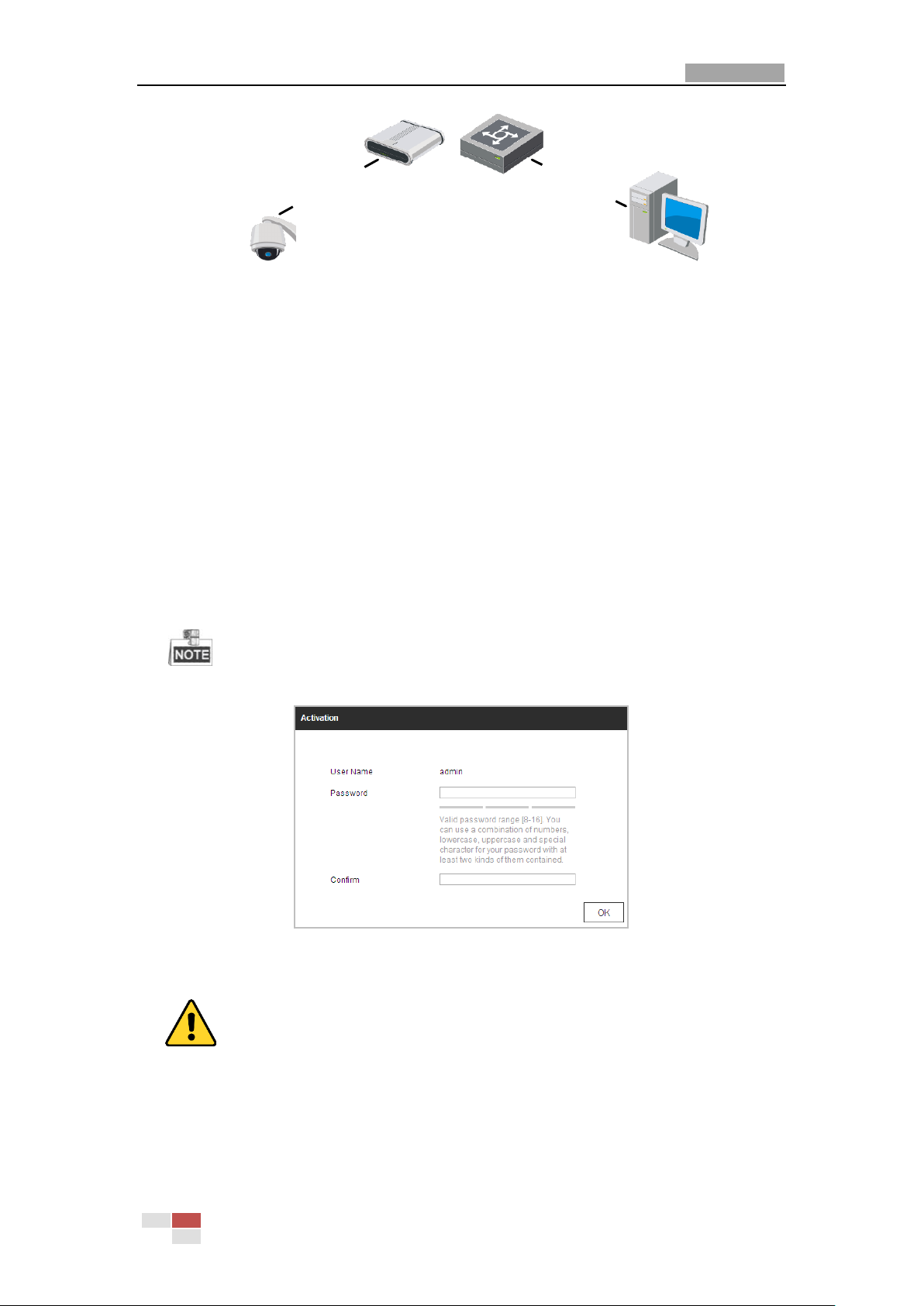
5
Network Cable
Network Cable
or
Network Speed Dome
Computer
Figure 2-2 Connecting via a Switch or a Router
2.1.2 Activating the Camera
Purpose:
You are required to activate the camera first before you can use the camera.
Activation via web browser, activation via SADP, and activation via client software are supported.
Activation via Web Browser
Steps:
1. Power on the camera, and connect the camera to the network.
2. Input the IP address into the address bar of the web browser, and click Enter to enter the
activation interface.
The default IP address of the camera is 192.168.1.64.
Figure 2-3 Activation Interface (Web)
3. Create a password and input the password into the password field.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
© Hikvision
Page 14
User Manual of Network PTZ Camera
6
Select inactive device.
Input and confirm
password.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
4. Confirm the password.
5. Click OK to activate the camera and enter the live view interface.
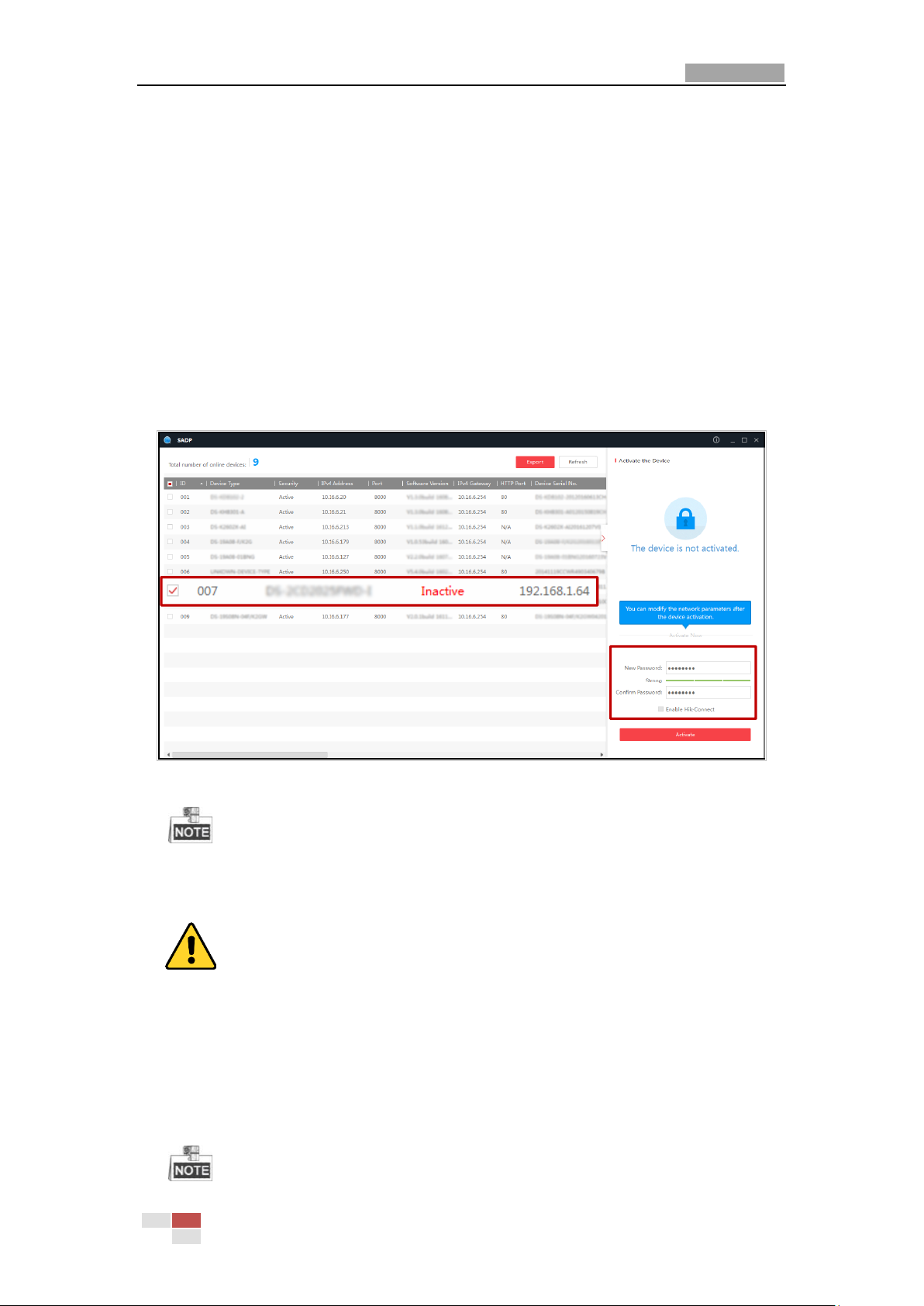
Activation via SADP Software
SADP software is used for detecting the online device, activating the device, and resetting the
password.
Get the SADP software from the supplied disk or the official website, and install the SADP
according to the prompts. Follow the steps to activate the camera.
Steps:
1. Run the SADP software to search the online devices.
2. Check the device status from the device list, and select an inactive device.
Figure 2-4 SADP Interface
The SADP software supports activating the camera in batch. Refer to the user manual of
SADP software for details.
3. Create a password and input the password in the password field, and confirm the password.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
© Hikvision
Page 15
User Manual of Network PTZ Camera
7
You can enable the Hik-Connect service for the device during activation. Hik-Connect
function varies depending on different speed dome models.
4. Click Activate to start activation. You can check whether the activation is completed on the
popup window. If activation failed, make sure that the password meets the requirement and
then try again.
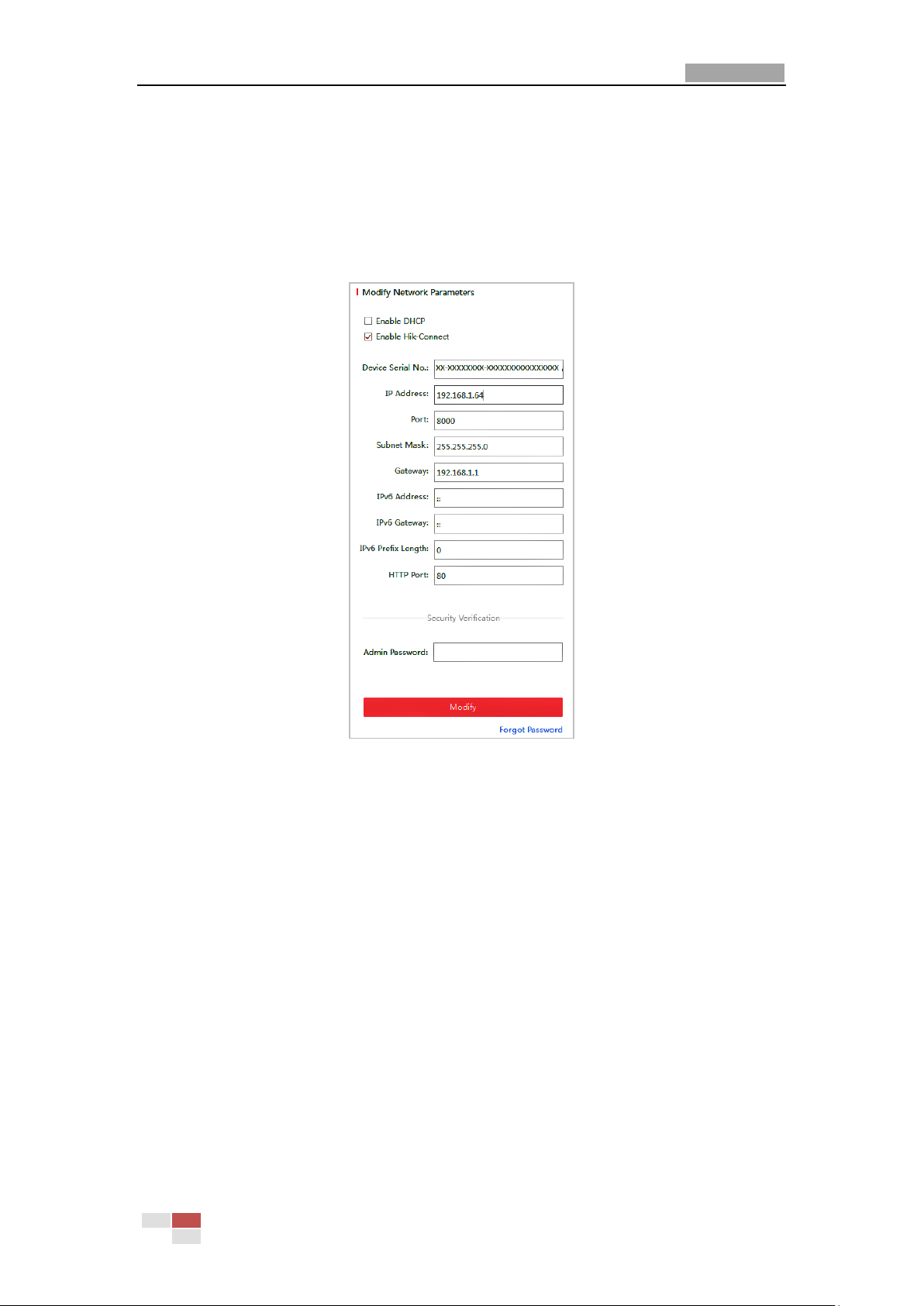
5. Change the device IP address to the same subnet with your computer by either modifying
the IP address manually or checking the Enable DHCP checkbox.
Figure 2-5 Modify the IP Address
6. Input the password and click Modify to activate your IP address modification.
The batch IP address modification is supported by the SADP. Refer to the user manual of
SADP for details.
Activation via Client Software
The client software is versatile video management software for multiple kinds of devices.
Get the client software from the supplied disk or the official website, and install the software
according to the prompts. Follow the steps to activate the camera.
Steps:
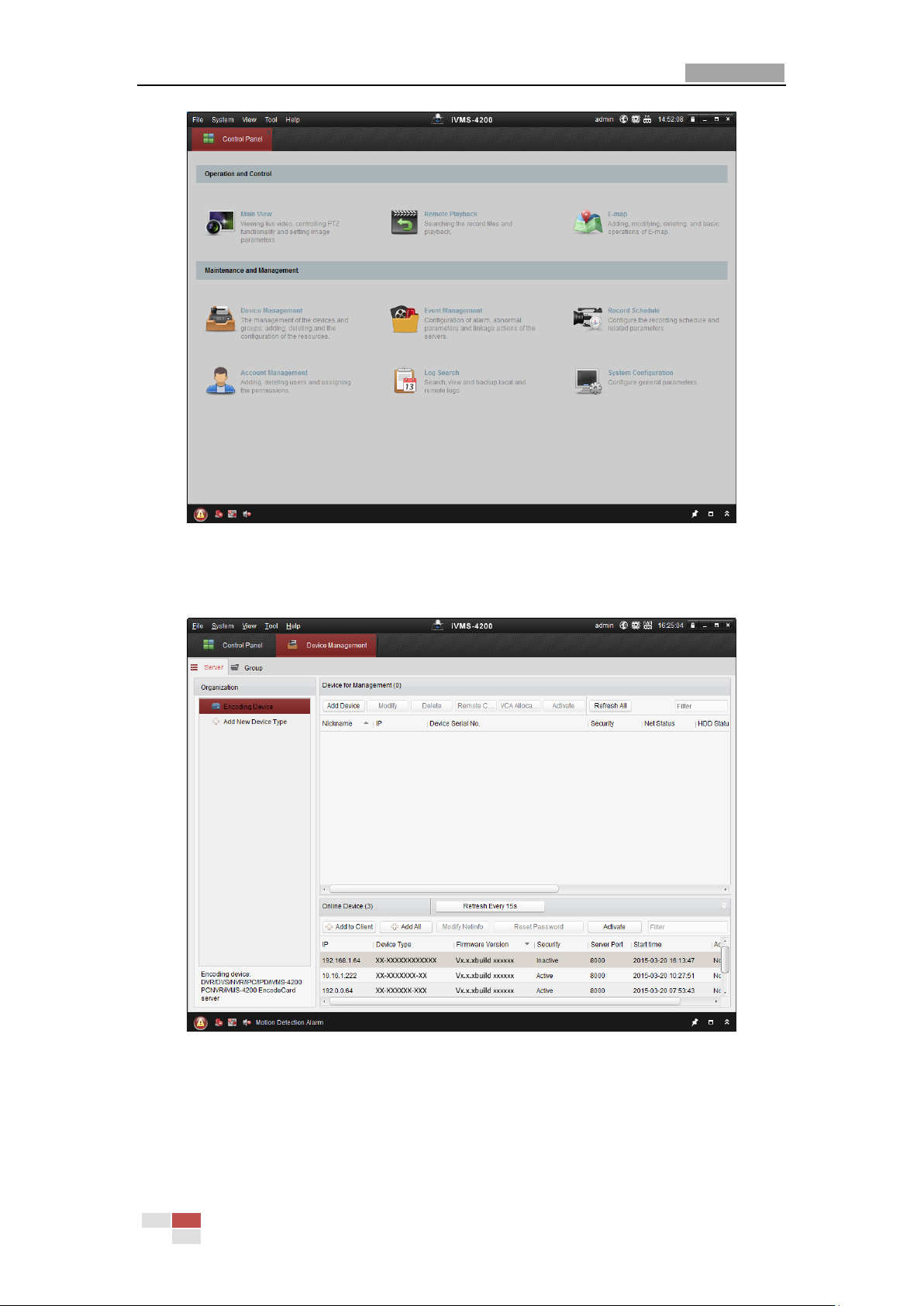
1. Run the client software and the control panel of the software pops up, as shown in Figure
2-6.
© Hikvision
Page 16
User Manual of Network PTZ Camera
8
Figure 2-6 iVMS-4200 Control Panel
2. Click Device Management to enter the Device Management interface, as shown in Figure
2-7.
Figure 2-7 Device Management Interface
3. Check the device status from the device list, and select an inactive device.
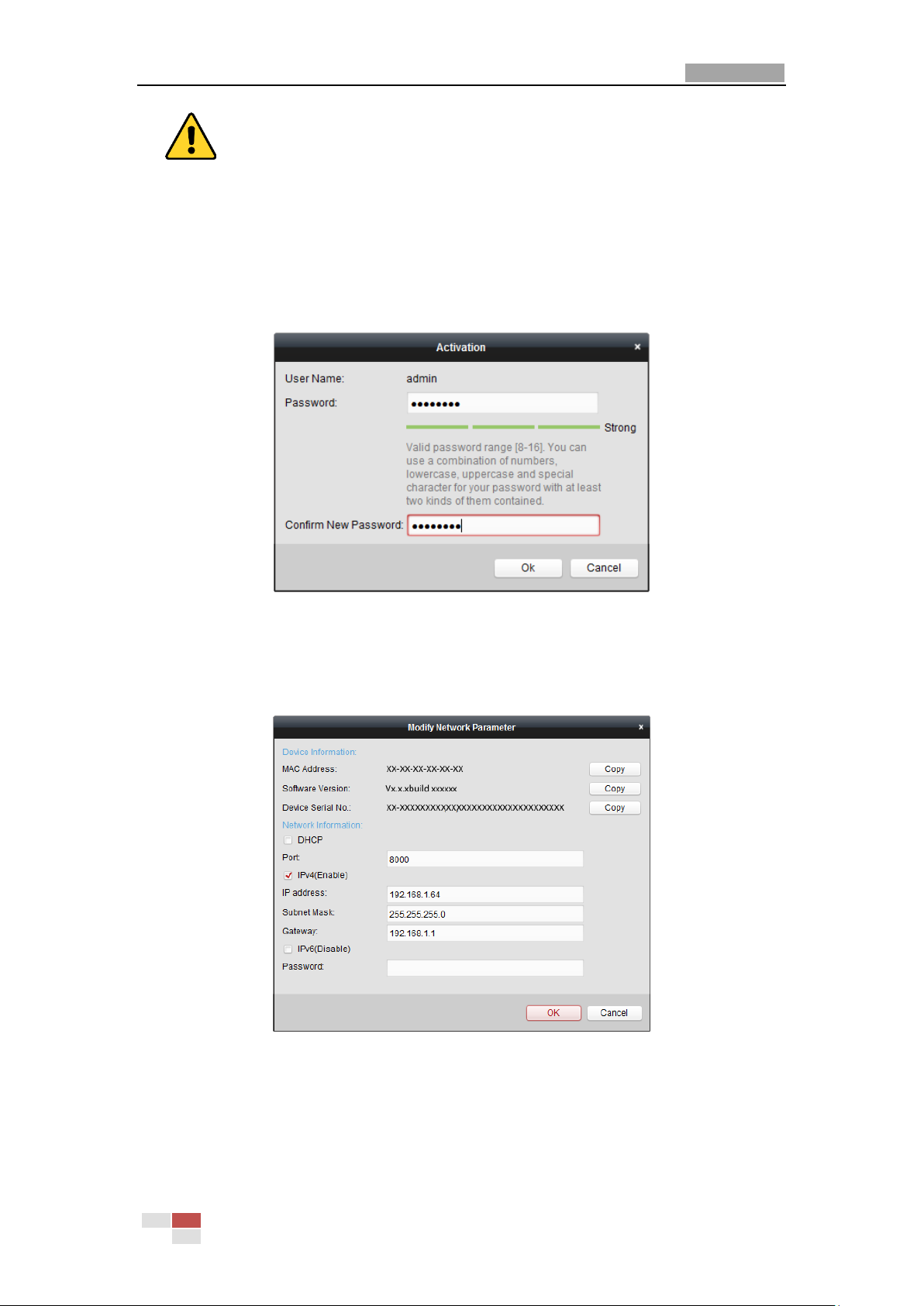
4. Click Activate to pop up the Activation interface.
5. Create a password and input the password in the password field, and confirm the password.
© Hikvision
Page 17
User Manual of Network PTZ Camera
9
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
Figure 2-8 Activation Interface
6. Click OK to start activation.
7. Click Modify Netinfo to pop up the Network Parameter Modification interface, as shown in
Figure 2-9.
Figure 2-9 Modifying the Network Parameters
8. Change the device IP address to the same subnet with your computer by either modifying
the IP address manually or checking the checkbox of Enable DHCP.
9. Input the password to activate your IP address modification.
© Hikvision
Page 18
User Manual of Network PTZ Camera
10
Network
Speed Dome
Network
Cable
Router with Static IP
PC
Network
Cable
Network
Cable
Internet
2.1.3 (Optional) Setting Security Question
Security question is used to reset the admin password when admin user forgets the password.
Admin user can follow the pop-up window to complete security question settings during camera
activation. Or, admin user can go to User Management interface to set up the function.
2.2 Setting the Network Camera over the WAN
Purpose:
This section explains how to connect the network camera to the WAN with a static IP or a
dynamic IP.
2.2.1 Static IP Connection
Before you start:
Apply a static IP from an ISP (Internet Service Provider). With the static IP address, you can
connect the network camera via a router or connect it to the WAN directly.
Connecting the network camera via a router
Steps:
1. Connect the network camera to the router.
2. Assign a LAN IP address, the subnet mask and the gateway. Refer to Section 2.1.2 for detailed
IP address configuration of the camera.
3. Save the static IP in the router.
4. Set port mapping, E.g., 80, 8000 and 554 ports. The steps for port mapping vary depending
on different routers. Call the router manufacturer for assistance with port mapping.
5. Visit the network camera through a web browser or the client software over the internet.
Figure 2-10 Accessing the Camera through Router with Static IP
Connecting the network camera with static IP directly
You can also save the static IP in the camera and directly connect it to the internet without using
a router. Refer to Section 2.1.2 for detailed IP address configuration of the camera.
© Hikvision
Page 19

User Manual of Network PTZ Camera
11
Network
Speed Dome
PC
Network
Cable
Network
Cable
Internet
Figure 2-11 Accessing the Camera with Static IP Directly
2.2.2 Dynamic IP Connection
Before you start:
Apply a dynamic IP from an ISP. With the dynamic IP address, you can connect the network
camera to a modem or a router.
Connecting the network camera via a router
Steps:
1. Connect the network camera to the router.
2. In the camera, assign a LAN IP address, the subnet mask and the gateway. Refer to Section
2.1.2 for detailed LAN configuration.
3. In the router, set the PPPoE user name, password and confirm the password.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
4. Set port mapping. E.g. 80, 8000 and 554 ports. The steps for port mapping vary depending on
different routers. Call the router manufacturer for assistance with port mapping.
5. Apply a domain name from a domain name provider.
6. Configure the DDNS settings in the setting interface of the router.
7. Visit the camera via the applied domain name.
Connecting the network camera via a modem
Purpose:
This camera supports the PPPoE auto dial-up function. The camera gets a public IP address by
ADSL dial-up after the camera is connected to a modem. You need to configure the PPPoE
parameters of the network camera. Refer to Section 6.1.1 Configuring PPPoE Settings for
detailed configuration.
© Hikvision
Page 20

User Manual of Network PTZ Camera
12
The obtained IP address is dynamically assigned via PPPoE, so the IP address always changes after
rebooting the camera. To solve the inconvenience of the dynamic IP, you need to get a domain
name from the DDNS provider (E.g. DynDns.com). Follow the steps below for normal domain
name resolution and private domain name resolution to solve the problem.
Normal Domain Name Resolution
Steps:
1. Apply a domain name from a domain name provider.
2. Configure the DDNS settings in the DDNS Settings interface of the network camera. Refer to
Section 6.1.1 Configuring DDNS Settings for detailed configuration.
3. Visit the camera via the applied domain name.
© Hikvision
Page 21

User Manual of Network PTZ Camera
13
Chapter 3 Accessing to the Network
Speed Dome
3.1 Accessing by Web Browsers
Steps:
1. Open the web browser.
2. In the address field, input the IP address of the network camera, e.g., 192.168.1.64 and press
the Enter key to enter the login interface.
3. Activate the camera for the first time using, refer to the section 2.1.2 Activating the Camera.
4. Select English as the interface language on the top-right of login interface.
5. Input the user name and password and click .
The admin user should configure the device accounts and user/operator permissions properly.
Delete the unnecessary accounts and user/operator permissions.
The device IP address gets locked if the admin user performs 7 failed password attempts (5
attempts for the user/operator).
Figure 3-1 Login Interface
6. Install the plug-in before viewing the live video and operating the camera. Follow the
installation prompts to install the plug-in.
You may have to close the web browser to install the plug-in. Reopen the web browser and
log in again after installing the plug-in.
© Hikvision
Page 22
User Manual of Network PTZ Camera
14
Figure 3-2 Download and Install Plug-in
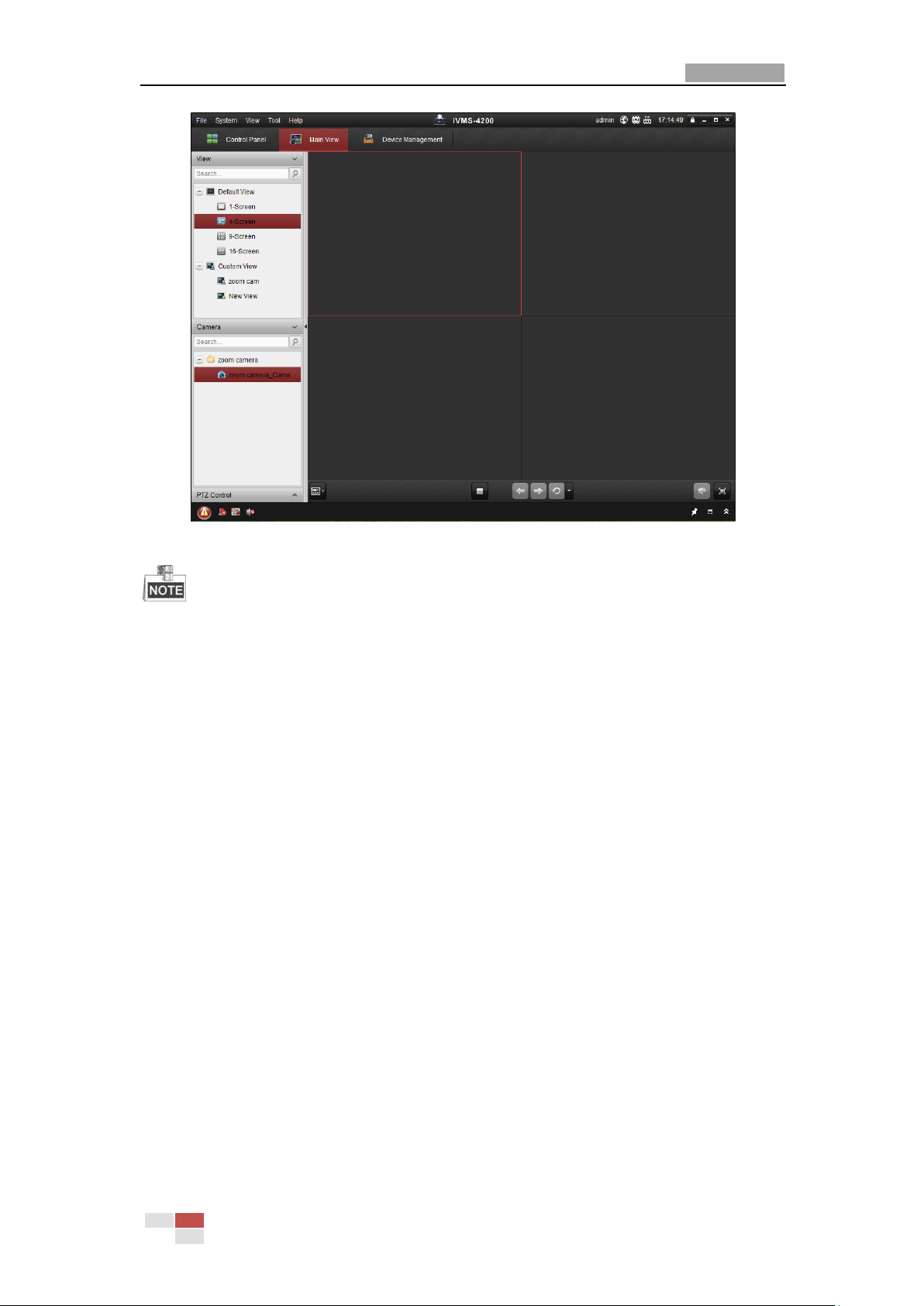
3.2 Accessing by Client Software
The product CD contains the client software. You can view the live video and manage the
camera with the client software.
Follow the installation prompts to install the client software and WinPcap. The configuration
interface and live view interface of client software are shown in Figure 3-3.
Figure 3-3 iVMS-4200 Control Panel
© Hikvision
Page 23
User Manual of Network PTZ Camera
15
Figure 3-4 iVMS-4200 Live View Interface
If you use third party VMS software, contact technical support of our branch for camera
firmware.
For detailed information about client software of our company, refer to the user manual of
the software. This manual mainly introduces accessing to the network camera by web browser.
© Hikvision
Page 24
User Manual of Network PTZ Camera
16
Chapter 4 Basic Operations
In this and the following chapters, operation of the camera by the web browser will be taken as
an example.
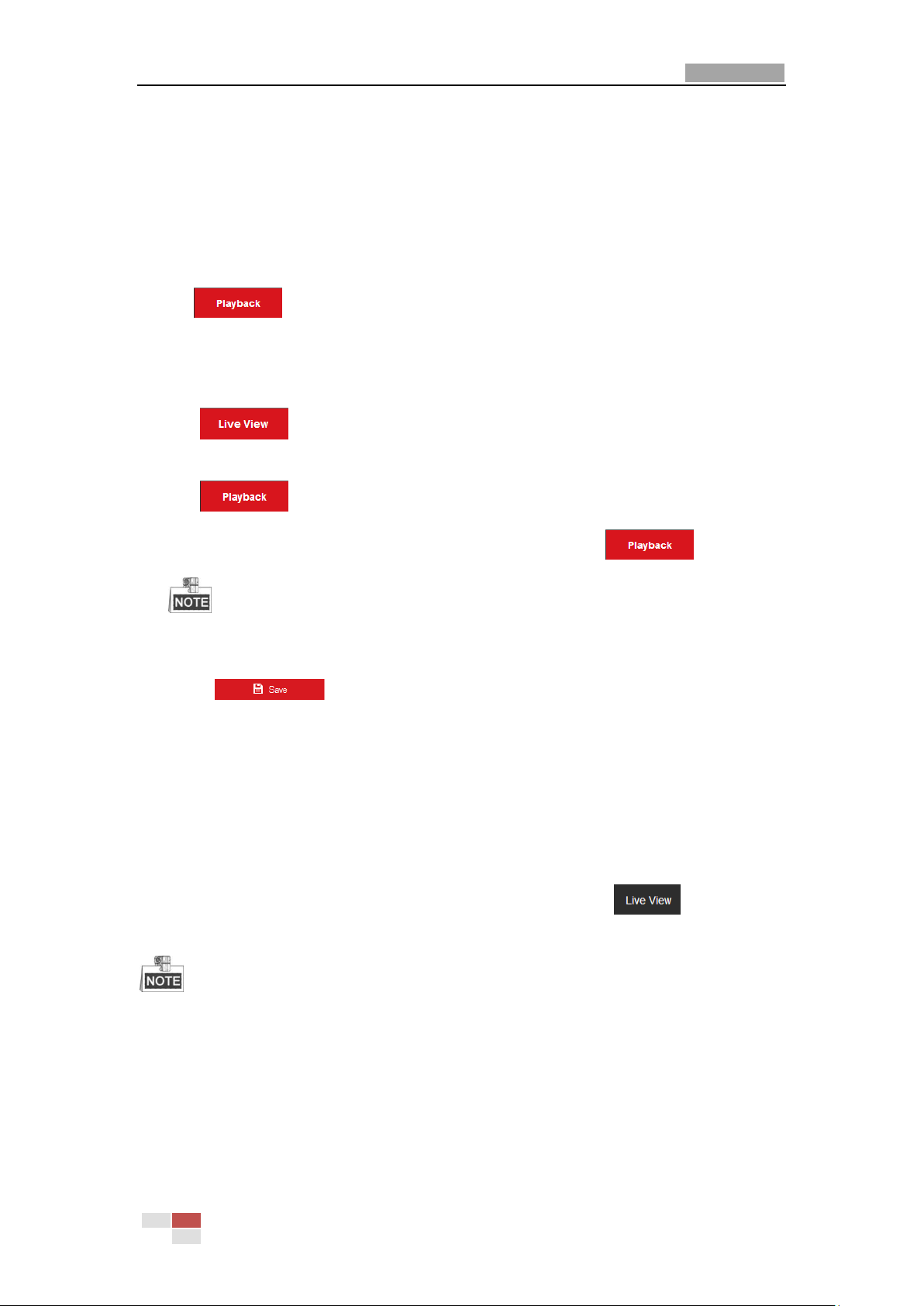
4.1 Configuring Local Parameters
The local configuration refers to the parameters of the live view and other operations using the
web browser.
Steps:
1. Enter the Local Configuration interface:
Configuration > Local
Figure 4-1 Local Configuration Interface
2. Configure the following settings:
Live View Parameters: Set the protocol type, play performance, rules and image format.
Protocol Type: TCP, UDP, MULTICAST and HTTP are selectable.
TCP: Ensures complete delivery of streaming data and better video quality, yet the
real-time transmission will be affected.
UDP: Provides real-time audio and video streams.
MULTICAST: It’s recommended to select the protocol type to MULTICAST when using
the Multicast function.
HTTP: Allows the same quality as of TCP without setting specific ports for streaming
under some network environments.
Play Performance: Set the play performance to Shortest Delay, Balanced, or Fluent.
Rules: You can enable or disable the rules of dynamic analysis for motion here.
© Hikvision
Page 25
User Manual of Network PTZ Camera
17
Image Format: The captured pictures can be saved as different format. JPEG and BMP are
available.
Record File Settings: Set the saving path of the video files.
Record File Size: Select the packed size of manually recorded and downloaded video files.
The size can be set to 256M, 512M or 1G.
Save record files to: Set the saving path for the manually recorded video files.
Save downloaded files to: Set the saving path for the downloaded video files in
interface.
Picture and Clip Settings: Set the saving paths of the captured pictures and clipped video
files.
Save snapshots in live view to: Set the saving path of the manually captured pictures in
interface.
Save snapshots when playback to: Set the saving path of the captured pictures in
interface.
Save clips to: Set the saving path of the clipped video files in interface.
You can click Browse to change the directory for saving video files, clips and pictures.
You can click Open to directly open the video files, clips and pictures.
3. Click to save the settings.
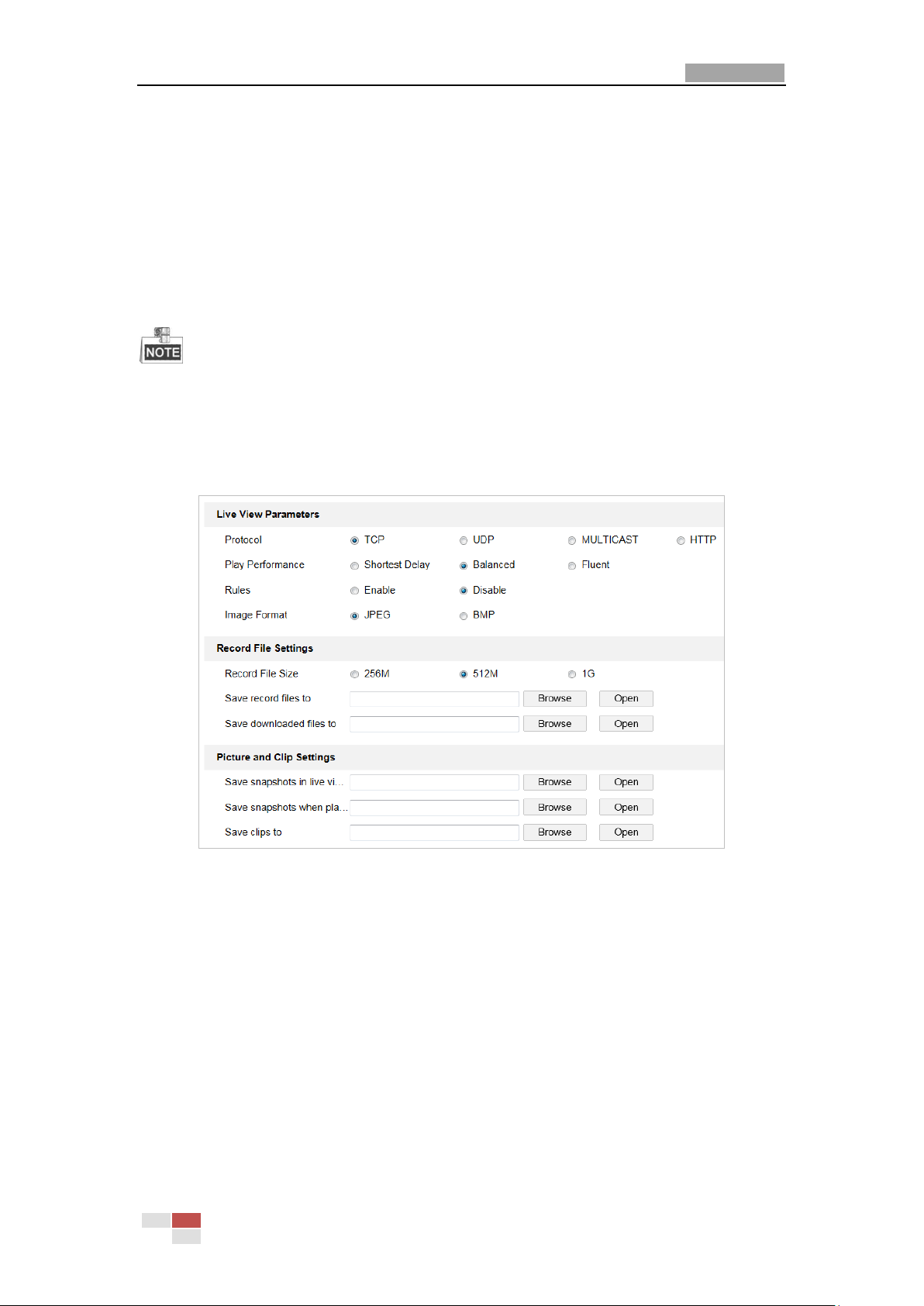
4.2 Live View Page
Purpose:
The live video page allows you to view live video, capture images, realize PTZ control, set/call
presets and configure video parameters.
Log in the network camera to enter the live view page, or you can click on the menu
bar of the main page to enter the live view page.
The functions vary depeding on different camera models. Refer to the actual interface as
standard.
© Hikvision
Page 26

User Manual of Network PTZ Camera
18
Menu Bar
Live View
Parameters
Live View Window
Toolba r
Show or hide PTZ
control panel
PTZ Control
Preset/Patrol/Pattern
Descriptions of the live view page:
Figure 4-2 Live View Page
Menu Bar:
Click each tab to enter Live View, Playback, Picture, and Configuration page respectively.
Click to display the help file of the network camera.
Click to logout the system.
Live View Window:
Display the live video.
Toolbar:
Operations on the live view page, e.g., live view, capture, record, audio on/off, regional exposure,
regional focus, etc.
PTZ Control:
Panning, tilting, focusing and zooming actions of the network. The lighter, wiper, one-touch focus
and lens initialization control.
Preset/patrol/pattern:
Set and call the preset/patrol/pattern for the camera.
Live View Parameters:
Configure the image size, stream type, plug-in type, and two-way audio of the live video.
4.3 Starting Live View
In the live view window as shown in Figure 4-3, click on the toolbar to start the live view of
the network.
© Hikvision
Page 27
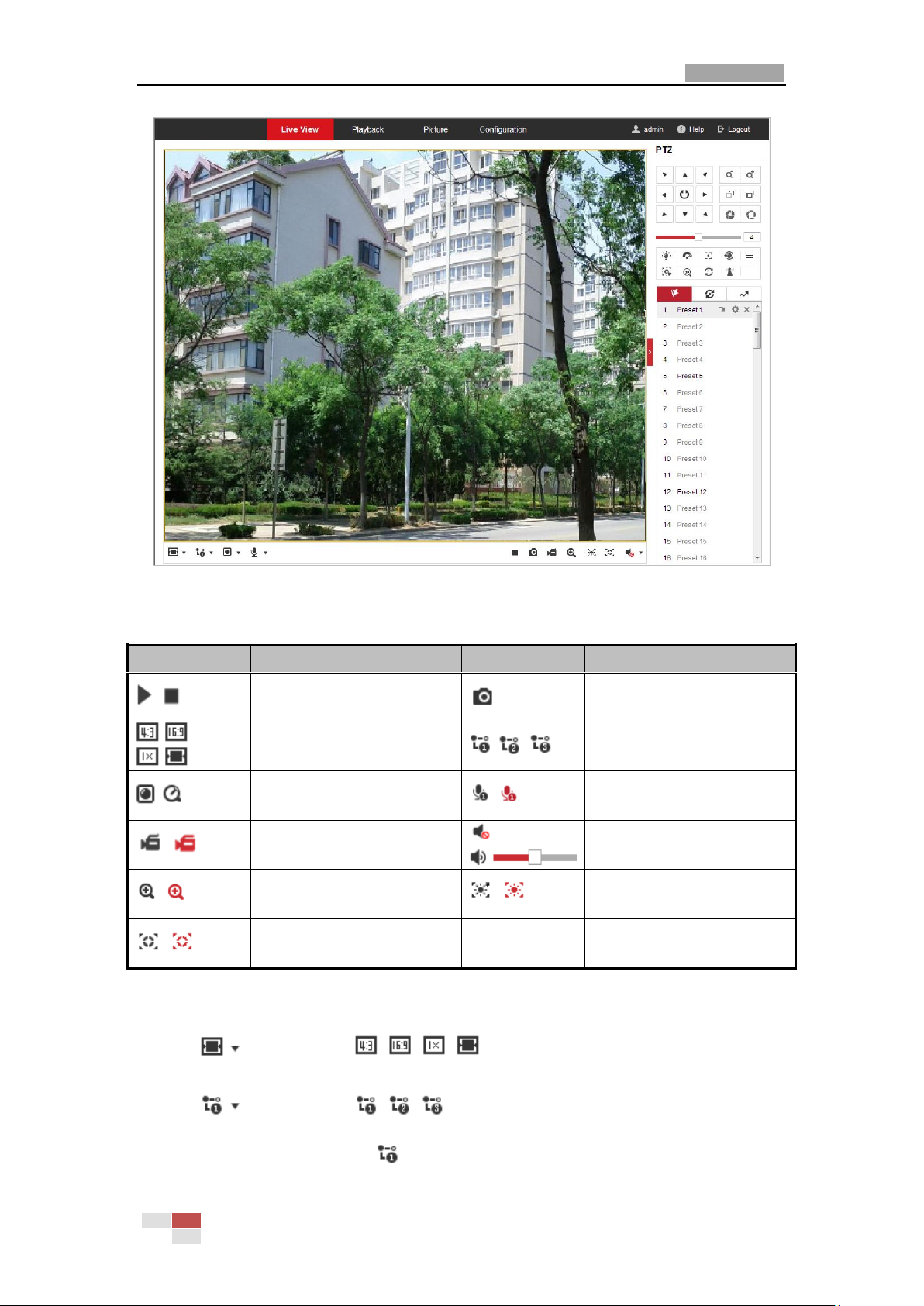
User Manual of Network PTZ Camera
19
Icon
Description
Icon
Description
/
Start/stop Live view.
Manually capture the pictures.
/ /
/
Display in 4:3/16:9/original/
self-adaptive window size.
/ /
Live view with the
main/sub/third stream.
/
Play via webcomponents/
quick time.
/
Start/stop two-way audio.
/
Manual start/stop recording.
/
Mute/audio on and adjust
volume
/
Start/stop digital zoom.
/
Enable/disable regional
exposure
/
Enable/disable regional focus
Figure 4-3 Start Live View
Table 4-1 Descriptions of the Toolbar
Double-click on the live video to switch the current live view into full-screen or return to
normal mode from the full-screen.
Click to select from and display live video in 4:3/16:9/
original/self-adaptive window size.
Click to select from and display live video with the main/ sub/third
stream. The main stream is with a relatively high resolution and needs much bandwidth. The
default setting of stream type is .
© Hikvision
Page 28
User Manual of Network PTZ Camera
20
For some certain camera models, disable the third stream first and then the true WDR function is
valid.
Click to select between and play the live video via player Webcomponents
or Quick Time. The live video is played via webcomponents by default, and other types of
players are supported for the browser, such as MJPEG, and VLC. You are required to download
and install the player to play the live video.
Click and it displays . Click to enable two-way audio and the icon turns
into . Click the icon again to stop two-way audio.
Click to start live view and the icon turns into . Click the icon again to stop live view.
Click to capture the picture.
Click to start recording and the icon turns into . Click the icon again to stop
recording.
Click to enable digital zoom function and the icon turns into . Then drag the mouse
towards low right direction to draw a rectangle on the image as the desired zoom. After
viewing it you can click any place of the picture to get back to normal picture.
Click the on the toolbar to enter the regional exposure operation mode and the icon
turns into . Then drag the mouse to draw a rectangle on the image as the desired
exposure region.
Click the on the toolbar to enter the regional focus operation mode and the icon turns
into . Then drag the mouse to draw a rectangle on the image as the desired focus region.
Click to display the . Drag the slider to adjust the volume.
Before using the two-way audio or recording with audio functions, set the Stream Type to Video
& Audio referring to Section 6.2.1 Configuring Video Settings.
Refer to the following sections for more information:
Configuring remote recording in Section 5.1.1 Configuring Recording Schedule.
Setting the image quality of the live video in Section 6.3 Configuring Image Settings and
Section 6.2.1 Configuring Video Settings.
Setting the OSD text on live video in Section 6.3.2 Configuring OSD Settings.
4.4 Operating PTZ Control
Purpose:
In the live view interface, you can use the PTZ control buttons to control panning, tilting and
zooming.
© Hikvision
Page 29
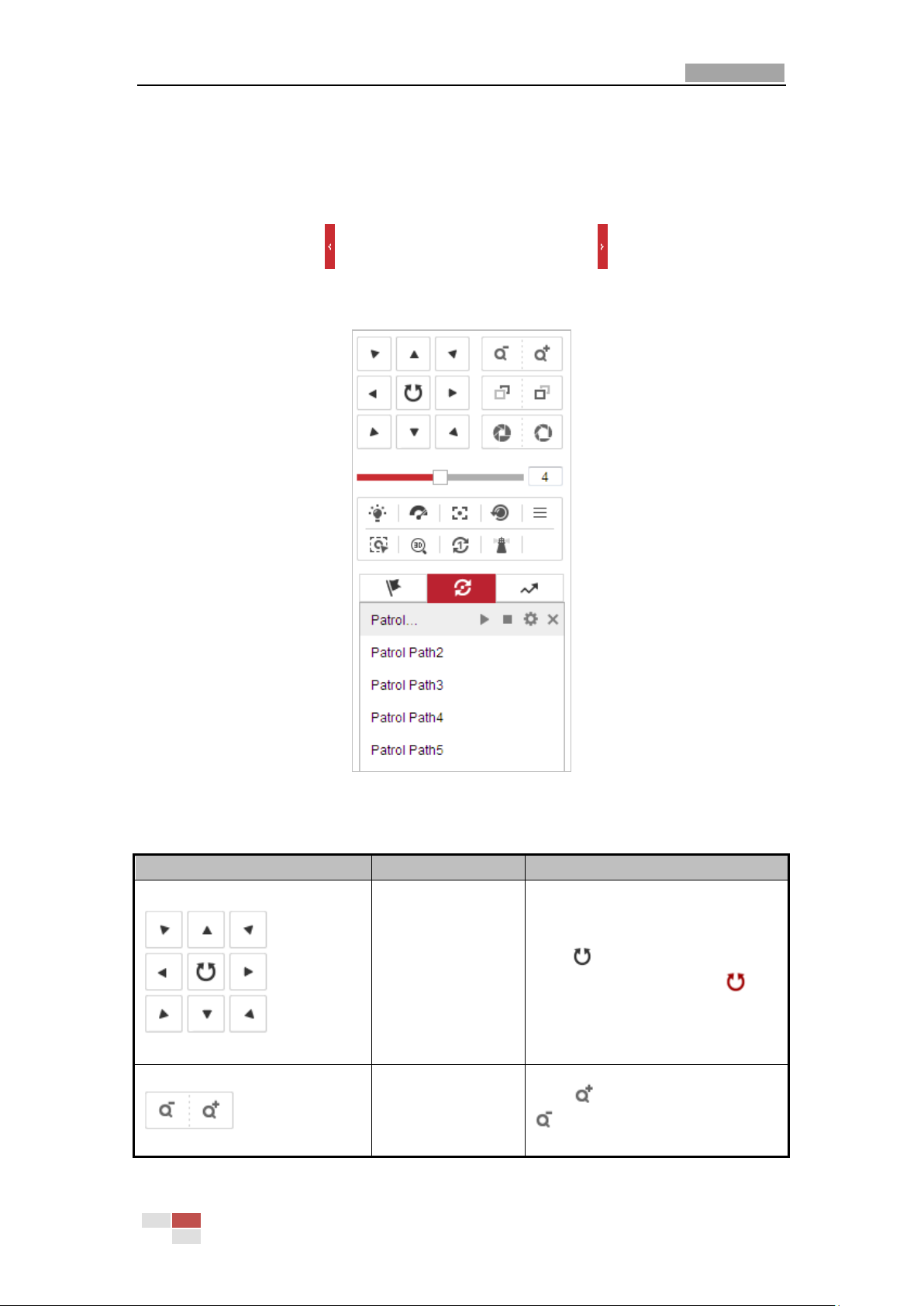
User Manual of Network PTZ Camera
21
Button
Name
Description
PTZ Control Panel
Hold and press the direction button
to pan/tilt the camera.
Click and the camera keeps
panning, the icon turns into .
Click the icon again to stop the
camera.
Zoom out/in
Click , the lens zooms in, click
, and the lens zooms out.
PTZ functions vary depending on different camera models.
4.4.1 PTZ Control Panel
On the live view page, click to show the PTZ control panel or click to hide it.
Click the direction buttons to control the pan/tilt movements.
Click the zoom/iris/focus buttons to realize lens control.
© Hikvision
Figure 4-4 PTZ Control Panel
Table 4-2 Descriptions of PTZ Control Panel
Page 30
User Manual of Network PTZ Camera
22
Button
Name
Description
Focus near/far
Click , the lens focus far and the
items far away gets clear. Click ,
the lens focus near and the items
nearby gets clear.
Iris close/open
When the image is too dark, click
to open the iris. When the
image is too bright, click to
close the iris.
Auxiliary Functions
The auxiliary functions include light,
wiper, auxiliary focus, lens
initialization, manual tracking, 3D
positioning, one-touch patrol, and
one-touch park.
Speed Adjustment
Adjust speed of pan/tilt movements.
Preset
Refer to 4.4.3 for detailed
information of setting preset.
Patrol
Refer to 4.4.4 for detailed
information of setting patrol.
Pattern
Refer to4.4.6 for detailed
information of setting pattern.
Buttons
Description
Start the selected patrol/pattern.
Stop current patrol/pattern.
Set the selected preset/patrol.
Delete the selected preset/patrol/pattern.
Start recording a pattern.
Stop recording the pattern.
Buttons on the Preset/Patrol/Patterns interface:
4.4.2 Auxiliary Functions
The Auxiliary functions panel is shown in Figure 4-5.
© Hikvision
Table 4-3 Descriptions of Buttons
Page 31

User Manual of Network PTZ Camera
23
Figure 4-5 Auxiliary Functions
Light
Click to enable/disable the light supplement of the camera. This function is reserved.
Wiper
Click to move the wiper once.
Auxiliary Focus
The auxiliary focus function is reserved.
Manual Tracking
Before you start:
Enter the Smart Tracking settings interface and enable smart tracking first.
Configuration > PTZ > Smart Tracking
Steps:
1. Click on the toolbar of live view interface.
2. Click a moving object in the live video.
The camera will track the object automatically.
3D Positioning
Steps:
1. Click on the toolbar of live view interface.
2. Operate the 3D positioning function:
Click a position of the live video. The corresponding position will be moved to the center of
the live video.
Hold down the left mouse button and drag the mouse to the lower right on the live video.
The corresponding position will be moved to the center of the live video and zoomed in.
Hold down the left mouse button and drag the mouse to the upper left on the live video.
The corresponding position will be moved to the center of the live video and zoomed out.
One-touch Patrol
Click to call one-touch patrol. For detailed information of setting one-touch patrol,
refer to 4.4.5 One-touch Patrol.
One-touch Park
Click to save the current view as the preset No. 32 and start park at the the current
position.
© Hikvision
Page 32

User Manual of Network PTZ Camera
24
4.4.3 Setting/Calling a Preset
Purpose:
A preset is a predefined image position. For the defined preset, you can click the calling button to
quickly view the desired image position.
Setting a Preset:
Steps:
1. In the PTZ control panel, select a preset number from the preset list.
Figure 4-6 Setting a Preset
2. Use the PTZ control buttons to move the lens to the desired position.
• Pan the camera to the right or left.
• Tilt the camera up or down.
• Zoom in or out.
• Refocus the lens.
3. Click to finish the setting of the current preset.
4. Edit a preset name by double clicking on the default name such as preset 1. (The pre-defined
presets are named already and not configurable. Refer to the user manual for detailed
function description.)
5. You can click to delete the preset.
You can configure up to 256 presets.
Calling a Preset:
In the PTZ control panel, select a defined preset from the list and click to call the preset.
Figure 4-7 Calling a Preset
For convenient preset selection, refer to the following steps to navigate to the preset you want.
© Hikvision
Page 33

User Manual of Network PTZ Camera
25
Preset
Function
Preset
Function
33
Auto flip
92
Start to set limit stops
34
Back to initial position
93
Set limit stops manually
35
Call patrol 1
94
Remote reboot
36
Call patrol 2
95
Call OSD menu
37
Call patrol 3
96
Stop a scan
38
Call patrol 4
97
Start random scan
39
Day mode (IR cut filter in)
98
Start frame scan
40
Night mode (IR cut filter out)
99
Start auto scan
41
Call pattern 1
100
Start tilt scan
42
Call pattern 2
101
Start panorama scan
43
Call pattern 3
102
Call patrol 5
44
Call pattern 4
103
Call patrol 6
45
One-touch Patrol
104
Call patrol 7
90
Wiper
105
Call patrol 8
Steps:
1. Select any preset from the list.
2. Click the preset number you need on the keyboard.
The following presets are predefined with special commands. You can only call them but not
configure them. For instance, preset 99 is the “Start auto scan”. If you call the preset 99, the
camera starts auto scan function.
Pattern function varies depending on different camera models.
Table 4-4 Special Presets
You may need to use the OSD (On Screen Display) menu when controlling the camera
remotely. To display the OSD menu on the live view screen, you can call the preset number
95.
Figure 4-8 Special Preset
© Hikvision
Page 34

User Manual of Network PTZ Camera
26
Name
Description
Patrol Time
It is the duration staying on one patrol point. The camera moves to
another patrol point after the patrol time.
Patrol Speed
It is the speed of moving from one preset to another.
4.4.4 Setting/Calling a Patrol
Purpose:
A patrol is a memorized series of preset function. It can be configured and called on the patrol
settings interface. There are up to 8 patrols for customizing. A patrol can be configured with 32
presets.
Before you start:
Make sure that the presets you want to add into a patrol have been defined.
Setting a Patrol:
Steps:
1. In the PTZ control panel, click to enter the patrol settings interface.
2. Select a patrol number from the list and click .
3. Click to enter the adding interface of preset, as shown in Figure 4-9.
Figure 4-9 Adding Presets
4. Configure the preset number, patrol time and patrol speed.
5. Click OK to save a preset into the patrol.
6. Repeat the steps from 3 to 5 to add more presets.
7. Click OK to save all the patrol settings.
Calling a Patrol:
In the PTZ control panel, select a defined patrol from the list and click to call the patrol, as
shown in Figure 4-10.
© Hikvision
Page 35

User Manual of Network PTZ Camera
27
4.4.5 One-touch Patrol
Figure 4-10 Calling a Preset
Purpose:
One-touch patrol is an automatically created patrol. The system automatically add preset No.1 to
No.32 to the patrol path 8. You can call the one-touch patrol and the camera moves as the patrol
path 8 automatically.
Steps:
1. Set preset No.1 to No.32. Refer to 4.4.3 Setting/Calling a Preset for detailed information of
setting preset.
2. Call preset No. 45, and the camera moves as patrol path 8.
3. Click to enter the patrol settings interface and start/stop one-touch patrol, edit the
patrol time and the speed.
4. You can click of the PTZ control panel to start one-touch patrol.
Figure 4-11 Patrol Path 8
© Hikvision
Page 36

User Manual of Network PTZ Camera
28
Buttons
Description
Start the selected patrol/pattern.
Stop current patrol/pattern.
Set the selected preset/patrol.
Delete the selected preset/patrol/pattern.
Start recording a pattern.
Stop recording the pattern.
4.4.6 Setting/Calling a Pattern
Purpose:
A pattern is a memorized series of pan, tilt, zoom, and preset functions. It can be called on the
pattern settings interface. There are up to 4 patterns for customizing.
Pattern function varies depending on different camera models.
Setting a Pattern:
Steps:
1. In the PTZ control panel, click to enter the pattern settings interface.
2. Select a pattern number from the list as shown in Figure 4-12.
Figure 4-12 Patterns Settings Interface
3. Click to enable recording the panning, tilting and zooming actions.
4. Use the PTZ control buttons to move the lens to the desired position after the information of
PROGRAM PATTERN REMAINNING MEMORY(%) is displayed on the screen.
Pan the camera to the right or left.
Tilt the camera up or down.
Zoom in or out.
Refocus the lens.
5. Click to save all the pattern settings.
Buttons on the Patterns interface:
© Hikvision
Page 37

User Manual of Network PTZ Camera
29
These 4 patterns can be operated separately and with no priority level.
When configuring and calling the pattern, proportional pan is valid; the limit stops and auto
flip will be invalid; and the 3D positioning operation is not supported.
4.5 Playback
Purpose:
This section explains how to view the video files stored in the network disks or memory cards.
4.5.1 Play Back Video Files
Steps:
1. Click on the menu bar to enter playback interface.
Figure 4-13 Playback Interface
2. Select the date and click .
© Hikvision
Page 38

User Manual of Network PTZ Camera
30
Button
Operation
Button
Operation
Play
Capture a picture
Pause
/
Start/Stop clipping
video files
Stop
/
Audio on and adjust
volume/Mute
Speed down
Download
Speed up
Playback by frame
/
Enable/Disable
digital zoom
Figure 4-14 Search Video
3. Click to play the video files found on this date.
The toolbar on the bottom of Playback interface can be used to control playing process.
Figure 4-15 Playback Toolbar
Table 4-5 Description of the buttons
You can choose the file paths locally for downloaded playback video files and pictures in Local
Configuration interface. Refer to Section 4.1 Configuring Local Parameters for details.
Drag the progress bar with the mouse to locate the exact playback point. You can also input the
time and click to locate the playback point in the Set playback time field. You can also
click to zoom out/in the progress bar.
Figure 4-16 Set Playback Time
© Hikvision
Page 39

User Manual of Network PTZ Camera
31
Figure 4-17 Progress Bar
The different colors of the video on the progress bar stand for the different video types as shown
in Figure 4-18.
Figure 4-18 Video Types
4.5.2 Downloading Video Files
Steps:
1. Click on the playback interface. The pop-up menu is shown in Figure 4-19.
2. Set the start time and end time. Click Search. The corresponding video files are listed on the
left.
Figure 4-19 Video Downloading interface
3. Check the checkbox in front of the video files that you need to download.
4. Click to download the video files.
4.6 Pictures
Purpose:
This section explains how to view the captured picture files stored in the network disks or the
© Hikvision
Page 40

User Manual of Network PTZ Camera
32
memory cards and download the captured pictures.
Steps:
1. Click on the menu bar to enter picture interface.
Figure 4-20 Picture Interface
2. Select the file type of capturing the pictures from the list as timing, alarm, motion, etc.
3. Set the start time and end time. Click Search. The corresponding picture files will be listed.
4. Check the checkbox in front of the files that you need to download.
5. Click to download the files.
© Hikvision
Page 41

User Manual of Network PTZ Camera
33
Chapter 5 System Configuration
5.1 Storage Settings
Before you start:
To configure record settings, make sure that you have the network storage device within the
network or the memory card inserted in your camera.
5.1.1 Configuring Recording Schedule
Purpose:
There are two kinds of recording for the camera: manual recording and scheduled recording. In
this section, you can follow the instructions to configure the scheduled recording. By default, the
record files of scheduled recording are stored in the memory card (if supported) or in the
network disk.
Steps:
1. Enter the Record Schedule settings interface:
Configuration > Storage > Schedule Settings > Record Schedule
Figure 5-1 Recording Schedule Interface
2. Check the checkbox of Enable to enable scheduled recording.
3. To set the advanced settings of the camera, click to enter the advanced settings
interface.
© Hikvision
Page 42

User Manual of Network PTZ Camera
34
Figure 5-2 Record Parameters
Pre-record: The time you set to start recording before the scheduled time or the event.
For example, if an alarm triggers recording at 10:00, and the pre-record time is set as 5
seconds, the camera starts to record at 9:59:55.
The pre-record time can be configured as No Pre-record, 5 s, 10 s, 15 s, 20 s, 25 s, 30 s or
not limited.
The pre-record time changes according to the video bitrate.
Post-record: The time you set to stop recording after the scheduled time or the event.
For example, if an alarm triggered recording ends at 11:00, and the post-record time is
set as 5 seconds, the camera records until 11:00:05.
The Post-record time can be configured as 5 s, 10 s, 30 s, 1 min, 2 min, 5 min or 10 min.
Stream Type: You can select the stream type for recording; Main Stream, Sub-Stream
and Third Stream are selectable. If you select the sub-stream, you can record for a longer
time with the same storage capacity.
The Pre-record and Post-record parameters vary depending on different camera models.
4. Click OK to save the advanced setting.
5. Select a Record Type. The record type can be Continuous, Motion, Alarm, Motion | Alarm,
Motion & Alarm, and Event.
Normal: If you select Continuous, the video will be recorded automatically according to
the time of the schedule.
Record Triggered by Motion Detection: If you select Motion, the video will be recorded
when the motion is detected. Besides configuring the recording schedule, you have to
set the motion detection area and check the checkbox of Trigger Channel in the Linkage
Method of Motion Detection settings interface. For detailed information, refer to
Section Motion Detection.
Record Triggered by Alarm: If you select Alarm, the video will be recorded when the
alarm is triggered via the external alarm input channels. Besides configuring the
recording schedule, you have to set the Alarm Type and check the checkbox of Trigger
Channel in the Linkage Method of Alarm Input settings interface. For detailed
information, refer to Section Alarm Input.
Record Triggered by Motion & Alarm: If you select Motion & Alarm, the video will be
recorded when the motion and alarm are triggered at the same time. Besides
© Hikvision
Page 43

User Manual of Network PTZ Camera
35
configuring the recording schedule, you have to configure the settings on the Motion
Detection and Alarm Input settings interfaces.
Record Triggered by Motion | Alarm: If you select Motion | Alarm, the video will be
recorded when the external alarm is triggered or the motion is detected. Besides
configuring the recording schedule, you have to configure the settings on the Motion
Detection and Alarm Input settings interfaces.
Record Triggered by Event: If you select to record by event, the video will be recorded
when any of the events is triggered.
6. Click to save the settings.
5.1.2 Configuring Capture Schedule
Purpose:
You can configure the scheduled snapshot and event-triggered snapshot. The captured picture
can be stored in the local storage or network storage.
Steps:
1. Enter the Snapshot settings interface:
Configuration > Storage > Storage Settings > Capture
Figure 5-3 Snapshot Settings
2. Click to enter the Capture Schedule interface.
3. Select the timeline of a certain day, and drag the left button of the mouse to set the capture
schedule (the start time and end time of the recording task).
4. After you set the scheduled task, you can click and copy the task to other days
(optional).
5. After setting the capture schedule, you can click a capture segment to display the segment
capture settings interface to edit the segment capture parameters. (optional)
© Hikvision
Page 44

User Manual of Network PTZ Camera
36
Figure 5-4 Segment Snapshot Settings
6. Click to enter the advanced setting interface. You can select the stream type of
the capture.
7. Click to enter the Capture Parameters Interface.
8. Check the Enable Timing Snapshot checkbox to enable continuous snapshot, and configure
the schedule of timing snapshot. Check the Enable Event-triggered Snapshot checkbox to
enable event-triggered snapshot.
9. Select the format, resolution, quality of the snapshot.
10. Set the time interval between two snapshots.
11. Click to save the settings.
Uploading to FTP
Make sure that the FTP server is online.
You can follow below configuration instructions to upload the snapshots to FTP.
Upload continuous snapshots to FTP
Steps:
1) Configure the FTP settings and check Upload Picture checkbox in FTP Settings interface.
Refer to Section 6.1.2 Configuring FTP Settings for more details to configure FTP parameters.
2) Check the Enable Timing Snapshot checkbox.
3) Click Edit to set the snapshot schedule. Refer to Section 5.2.1 Configuring Motion
Detection.
Upload event-triggered snapshots to FTP
Steps:
1) Configure the FTP settings and check Upload Picture checkbox in FTP Settings interface.
Refer to Section 6.1.2 Configuring FTP Settings for more details to configure FTP parameters.
2) Check Upload to FTP checkbox in Motion Detection Settings or Alarm Input interface. Refer
to Section 5.2.1 Configuring Motion Detection.
3) Check the Enable Event-triggered Snapshot checkbox.
5.1.3 Configuring Net HDD
Before you start:
© Hikvision
Page 45

User Manual of Network PTZ Camera
37
The network disk should be available within the network and properly configured to store the
recorded files, log files, etc.
Steps:
Add the network disk
1. Enter the NAS (Network-Attached Storage) settings interface:
Configuration > Storage > Storage Management > Net HDD
Figure 5-5 Select Net HDD Type
2. Enter the IP address and the file path of the network disk.
3. Select the mounting type. NFS and SMB/CIFS are selectable. You can set the user name and
password to guarantee the security if SMB/CIFS is selected.
Refer to the NAS User Manual for creating the file path.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
4. Click to add the network disk.
After having saved successfully, you need to reboot the camera to activate the settings.
Initialize the added network disk.
1. Enter the HDD settings interface (Configuration > Storage > Storage Management > HDD
Management), in which you can view the capacity, free space, status, type and property of
the disk.
© Hikvision
Page 46

User Manual of Network PTZ Camera
38
Figure 5-6 Storage Management Interface
2. If the status of the disk is Uninitialized, check the corresponding checkbox to select the disk
and click Format to start initializing the disk.
3. When the initialization completed, the status of disk will become Normal as shown in Figure
5-7.
Figure 5-7 View Disk Status
Define the Quota for Record and Pictures
1. Input the quota percentage for picture and for record.
2. Click Save and refresh the browser page to activate the settings.
Figure 5-8 Quota Settings
Up to 8 NAS disks can be connected to the camera.
To initialize and use the memory card after insert it to the camera, refer to the steps of NAS
disk initialization
© Hikvision
Page 47

User Manual of Network PTZ Camera
39
5.2 Basic Event Configuration
Purpose:
This section explains how to configure the network camera to respond to alarm events, including
motion detection, video tampering alarm input, alarm output and exception. These events can
trigger the alarm actions, such as Send Email, Notify Surveillance Center, etc.
For example, when motion detection is triggered, the network camera sends a notification to an
e-mail address.
On the event configuration page, click to show the PTZ control panel or click to hide it.
Click the direction buttons to control the pan/tilt movements.
Click the zoom/iris/focus buttons to realize lens control.
The functions vary depending on different camera models.
5.2.1 Configuring Motion Detection
Purpose:
Motion detection is a feature which can trigger alarm actions and actions of recording videos
when the motion occurred in the surveillance scene.
Steps:
1. Enter the motion detection setting interface:
Configuration > Event > Basic Event > Motion Detection
2. Check the checkbox of the Enable Motion Detection to enable this function.
You can check the Enable Motion Detection in PTZ Control checkbox and when the speed
dome is performing PTZ action, motion detection can also trigger alarm.
You can check the Enable Dynamic Analysis for Motion checkbox if you want the detected
object get marked with rectangle in the live view.
3. Select the configuration mode as Normal or Expert and set the corresponding motion
detection parameters.
Normal
© Hikvision
Page 48

User Manual of Network PTZ Camera
40
Figure 5-9 Motion Detection Settings-Normal
Steps:
(1) Click and drag the mouse on the live video image to draw a motion
detection area.
(2) Click to finish drawing.
You can click to clear all of the areas.
(3) Move the slider to set the
sensitivity of the detection.
Expert
© Hikvision
Page 49

User Manual of Network PTZ Camera
41
Figure 5-10 Motion Detection Settings-Expert
Steps:
(1) Set the Schedule Image Settings, there are OFF, Auto-Switch and Scheduled-Switch
selectable. If the schedule image switch mode is enabled, you can configure the
detection rule for the day and night separately.
OFF: Disable the day and night switch.
Auto-Switch: Switch the day and night mode according to the illumination
automatically.
Scheduled-Switch: Switch to the day mode and the night mode according to the
configured time. You need to set the start time and end time.
(2) Select Area from the dropdown list to configure.
(3) Set the values of sensitivity and percentage.
Sensitivity: The greater the value is, the easier the alarm will be triggered.
Percentage: When the size proportion of the moving object exceeds the predefined
value, the alarm will be triggered. The less the value is, the easier the alarm will be
triggered.
4. Set the Arming Schedule for Motion Detection.
(1) Click tab to enter the arming schedule setting interface.
© Hikvision
Page 50

User Manual of Network PTZ Camera
42
Figure 5-11 Arming Schedule
(2) Select the timeline of a certain day, and drag the mouse to set the arming schedule (the
start time and end time of the arming task).
(3) After you set the scheduled task, you can click and copy the task to other days
(optional).
Figure 5-12 Arming Time Schedule
(4) After setting the arming schedule, you can click a segment to display the segment
arming settings interface to edit the segment record parameters (optional).
Figure 5-13 Segment Arming Settings
© Hikvision
Page 51

User Manual of Network PTZ Camera
43
(5) Click to save the settings.
The time of each period cannot be overlapped. Up to 8 periods can be configured for each
day.
5. Set the Alarm Actions for Motion Detection.
Click tab to enter the Linkage Method interface.
You can specify the linkage method when an event occurs. The following contents are about
how to configure the different types of linkage method.
Figure 5-14 Linkage Method
Check the checkbox to select the linkage method. Notify Surveillance Center, Send
Email, Upload to FTP/Memory/NAS, Trigger Alarm Output and Trigger Recording are
selectable.
Notify Surveillance Center
Send an exception or alarm signal to remote management software when an event
occurs.
Send Email
Send an email with alarm information to a user or users when an event occurs.
To send the Email when an event occurs, you need to refer to Section Configuring Email
Settings to set the Email parameters.
Upload to FTP/Memory/NAS
© Hikvision
Page 52

User Manual of Network PTZ Camera
44
Capture the image when an alarm is triggered and upload the picture to a FTP server.
You need a FTP server and set FTP parameters first. Refer to Section Configuring FTP
Settings for setting FTP parameters.
Trigger Alarm Output
Trigger one or more external alarm outputs when an event occurs.
To trigger an alarm output when an event occurs, refer to Section 5.2.4 Configuring
Alarm Output to set the alarm output parameters.
Trigger Recording
Record a video when an event occurs.
You have to set the recording schedule to realize this function. Refer to Section 5.1.1
Configuring Recording Schedule for settings the recording schedule.
5.2.2 Configuring Video Tampering Alarm
Purpose:
You can configure the camera to trigger the alarm actions when the lens is covered.
Steps:
1. Enter the Video Tampering settings interface :
Configuration > Event > Basic Event > Video Tampering
© Hikvision
Page 53

User Manual of Network PTZ Camera
45
Figure 5-15 Tampering Alarm
2. Check Enable checkbox to enable the tampering detection.
3. Click tab to enter the arming schedule setting interface. The arming
schedule configuration is the same as the setting of the arming schedule for motion detection.
Refer to Section 5.2.1 Configuring Motion Detection.
4. Click tab to select the linkage method taken for tampering, notify
surveillance center, send email and trigger alarm output are selectable. Refer to Section 5.2.1
Configuring Motion Detection.
5. Click to save the settings.
5.2.3 Configuring Alarm Input
Steps:
1. Enter the Alarm Input settings interface:
Configuration > Event > Basic Event > Alarm Input
2. Choose the Alarm Input No. and the Alarm Type. The alarm type can be NO (Normally Open)
and NC (Normally Closed).
3. Edit the name in to set a name for the
alarm input (optional).
© Hikvision
Page 54

User Manual of Network PTZ Camera
46
Figure 5-16 Alarm Input Settings
4. Click tab to enter the arming schedule setting interface. The arming
schedule configuration is the same as the setting of the arming schedule for motion detection.
Refer to Section 5.2.1 Configuring Motion Detection.
5. Click tab to select the linkage method taken for alarm input, including
Notify Surveillance Center, Send Email, Upload to FTP/Memory Card/NAS, Trigger Alarm
Output and Trigger Recording. Refer to Section 5.2.1 Configuring Motion Detection.
6. You can also choose the PTZ linking for the alarm input. Check the relative checkbox and
select the No. to enable Preset Calling, Patrol Calling or Pattern Calling.
7. You can copy your settings to other alarm inputs.
8. Click to save the settings.
Figure 5-17 Linkage Method
© Hikvision
Page 55

User Manual of Network PTZ Camera
47
5.2.4 Configuring Alarm Output
Steps:
1. Enter the Alarm Output settings interface:
Configuration> Event > Basic Event > Alarm Output
2. Select one alarm output channel in the Alarm Output dropdown list.
3. Set a name in for the alarm output
(optional).
4. The Delay time can be set to 5sec, 10sec, 30sec, 1min, 2min, 5min, 10min or Manual. The
delay time refers to the time duration that the alarm output remains in effect after alarm
occurs.
5. Click tab to enter the arming schedule setting interface. The time
schedule configuration is the same as the settings of the arming schedule for motion
detection. Refer to Section 5.2.1 Configuring Motion Detection.
Figure 5-18 Alarm Output Settings
6. You can copy the settings to other alarm outputs.
7. Click to save the settings.
© Hikvision
Page 56

User Manual of Network PTZ Camera
48
5.2.5 Handling Exception
The exception type can be HDD full, HDD error, network disconnected, IP address conflicted and
illegal login to the cameras.
Steps:
1. Enter the Exception settings interface:
Configuration > Event > Basic Event > Exception
2. Check the checkbox to set the actions taken for the Exception alarm. Refer to Section 5.2.1
Configuring Motion Detection.
Figure 5-19 Exception Settings
3. Click to save the settings.
5.3 Smart Event Configuration
The functions vary depending on different camera models.
© Hikvision
Page 57

User Manual of Network PTZ Camera
49
5.3.1 Detecting Audio Exception
Purpose:
When you enable this function and audio exception occurs, the alarm actions will be triggered.
Steps:
1. Enter the video audio exception detection interface:
Configuration > Event > Smart Event > Audio Exception Detection
Figure 5-20 Audio Exception Detection
2. Check the checkbox of Audio Loss Detection to enable the audio input exception detection.
3. Check the checkbox of Sudden Increase of Sound Intensity Detection checkbox to enable
the sudden rise detection.
Sensitivity: Range [1-100], the smaller the value the more severe the sound change will
trigger the detection.
Sound Intensity Threshold: Range [1-100], it can filter the sound in the environment, the
louder the environment sound, the higher the value should be. You can adjust it according
to the actual environment.
4. Check the checkbox of Sudden Decrease of Sound Intensity Detection checkbox to enable
the sudden drop detection.
Sensitivity: Range [1-100], the smaller the value the more severe the sound change will
trigger the detection.
5. Click tab to enter the arming schedule setting interface. The time
schedule configuration is the same as the settings of the arming schedule for motion
© Hikvision
Page 58

User Manual of Network PTZ Camera
50
detection. Refer to Section 5.2.1 Configuring Motion Detection.
6. Click tab to select the linkage method taken for the audio input exception,
Notify Surveillance Center, Send Email, Trigger Alarm Output and Trigger Recording are
selectable. Refer to Section 5.2.1 Configuring Motion Detection.
7. Click to save the settings.
5.3.2 Configuring Face Detection
Purpose:
After the face detection is enabled, a face appears in the surveillance area, it will be detected and
certain actions may be triggered by the detection.
Steps:
1. Check the Enable Face Detection checkbox.
2. (Optional) You can check the Enable Dynamic Analysis for Face Detection checkbox if you
want the detected face get marked with rectangle in the live view.
Figure 5-21 Configuring Face Detection
3. Configure the sensitivity for face detection.
Sensitivity: Range [1-5]. The value of the sensitivity defines the size of the object which can
trigger the alarm, when the sensitivity is high, a very small object can trigger the alarm.
4. Click tab to enter the arming schedule setting interface. The time
schedule configuration is the same as the settings of the arming schedule for motion
detection. Refer to Section 5.2.1 Configuring Motion Detection.
5. Click tab to select the linkage method taken for the video loss alarm, Notify
surveillance center, send email, upload to FTP, trigger channel, smart tracking and trigger
alarm output are selectable. Refer to Section 5.2.1 Configuring Motion Detection.
6. Click to save the settings.
5.3.3 Configuring Intrusion Detection
Intrusion detection can set an area in the surveillance scene and once the area is entered, a set
of alarm action is triggered.
Steps:
1. Enter the intrusion detection interface:
Configuration > Events > Smart Event >Intrusion Detection
© Hikvision
Page 59

User Manual of Network PTZ Camera
51
2. Check the Enable checkbox.
Figure 5-22 Configuring Intrusion Area
3. The event triggered and park action related PTZ movement will be locked for 180 seconds
after you enter the intrusion detection interface. Optionally, you can click the
button to manually activate the movement, or lock the movement
when the button turns to by clicking it.
4. Draw area.
1) Select the Region No.in dropdown list.
2) Click to draw a rectangle on the image as a defense region.
3) Click on the image to specify a corner of the rectangle, and right-click the mouse after
four corners are configured.
5. Configure the parameters for each defense region separately.
Threshold: Range [0-10s], the threshold for the time of the object loitering in the region. If
you set the value as 0, alarm is triggered immediately after the object entering the region.
Sensitivity: Range [1-100]. The value of the sensitivity defines the size of the object which
can trigger the alarm, when the sensitivity is high, a very small object can trigger the
alarm.
6. Click tab to enter the arming schedule setting interface. The time
© Hikvision
Page 60

User Manual of Network PTZ Camera
52
schedule configuration is the same as the settings of the arming schedule for motion
detection. Refer to Section 5.2.1 Configuring Motion Detection.
7. Click tab to select the linkage method taken for intrusion detection, Notify
Surveillance Center, Send Email, Upload to FTP/Memory Card/NAS, Trigger Alarm Output and
Trigger Recording are selectable. Refer to Section 5.2.1 Configuring Motion Detection.
8. Click to save the settings.
5.3.4 Configuring Line Crossing Detection
The virtual plane detection can be adopted for the intrusion detection. Once the virtual plane is
detected being traversed according to the configured direction, a set of alarm action is triggered.
Steps:
1. Enter the Line Crossing Detection interface:
Configuration >Event > Smart Event > Line Crossing Detection
2. Check the Enable checkbox to enable the line crossing detection function.
3. Select the Line in dropdown list to configure.
4. The event triggered and park action related PTZ movement will be locked for 180 seconds
after you enter the line crossing detection interface. Optionally, you can click the
button to manually activate the movement, or lock the movement
when the button turns to by clicking it.
Figure 5-23 Configuring Line
© Hikvision
Page 61

User Manual of Network PTZ Camera
53
5. Draw area.
1) Click to draw a line on the image.
2) Click the line to switch to the editing mode.
Drag an end to the desired place to adjust the length and angle of the line. And drag the
line to adjust the location.
6. Configure the parameters for each defense region separately.
Direction: Select the detection direction in the dropdown list, there are A<->B, A->B and
B->A selectable.
Sensitivity: Range [1-100]. The value of the sensitivity defines the size of the object which
can trigger the alarm, when the sensitivity is high, a very small object can trigger the
alarm.
7. Click tab to enter the arming schedule setting interface. The time
schedule configuration is the same as the settings of the arming schedule for motion
detection. Refer to Section 5.2.1 Configuring Motion Detection.
8. Click tab to select the linkage method taken for the line crossing detection,
Notify Surveillance Center, Send Email, Upload to FTP/Memory Card/NAS, Trigger Alarm
Output and Trigger Recording are selectable. Refer to Section 5.2.1 Configuring Motion
Detection.
9. Click to save the settings.
5.3.5 Configuring Region Entrance Detection
Purpose:
Region entrance detection function detects people, vehicle or other objects which enter a
pre-defined virtual region from the outside place, and some certain actions can be taken when
the alarm is triggered.
Steps:
1. Enter the Region Entrance Detection settings interface:
Configuration> Event > Smart Event> Region Entrance Detection
2. Check the checkbox of Enable to enable the Region Entrance Detection function.
© Hikvision
Page 62
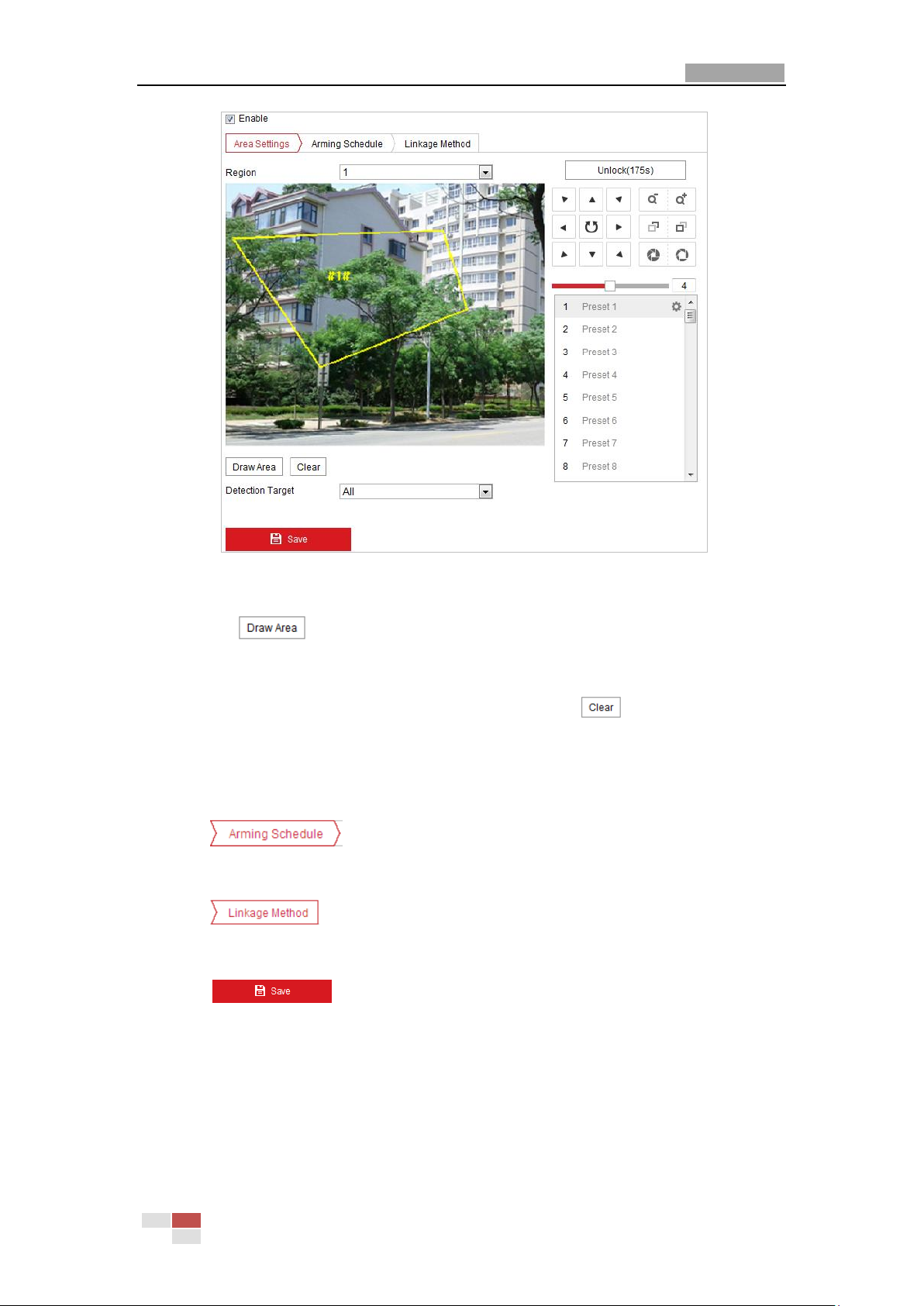
User Manual of Network PTZ Camera
54
Figure 5-24 Configuring Region Entrance Detection
3. Select the region from the dropdown list for detection settings.
4. Click the button to start the region drawing.
5. Click on the live video to specify the four vertexes of the detection region, and right click to
complete drawing.
Repeat the step to configure other regions. You can click the button to clear all
pre-defined regions.
6. Set the detection target for the region entrance detection. You can select human, vehicle, or
all (human &vehicle) as the detection target from the dropdown list. If Human is selected,
only human beings will be identified as detection objects and as well as Vehicle.
7. Click tab to enter the arming schedule setting interface. The time
schedule configuration is the same as the settings of the arming schedule for motion
detection. Refer to Section 5.2.1 Configuring Motion Detection.
8. Click tab to select the linkage method taken for the video loss alarm,
Notify surveillance center, send email, upload to FTP, trigger channel, smart tracking and
trigger alarm output are selectable. Refer to Section 5.2.1 Configuring Motion Detection.
9. Click to save the settings.
5.3.6 Configuring Region Exiting Detection
Purpose:
Region exiting detection function detects people, vehicle or other objects which exit from a
pre-defined virtual region, and some certain actions can be taken when the alarm is triggered.
© Hikvision
Page 63

User Manual of Network PTZ Camera
55
Steps:
1. Enter the Region Exiting Detection settings interface:
Configuration> Event > Smart Event> Region Exiting Detection
2. Check the checkbox of Enable to enable the Region Exiting Detection function.
Figure 5-25 Configuring Region Exiting Detection
3. Select the region from the dropdown list for detection settings.
4. Click the button to start the region drawing.
5. Click on the live video to specify the four vertexes of the detection region, and right click to
complete drawing.
Repeat the step to configure other regions. Up to 4 regions can be set. You can click the
button to clear all pre-defined regions.
6. Set the detection target for the region entrance detection. You can select human, vehicle, or
all (human &vehicle) as the detection target from the dropdown list. If Human is selected,
only human beings will be identified as detection objects and as well as Vehicle.
7. Click tab to enter the arming schedule setting interface. The time
schedule configuration is the same as the settings of the arming schedule for motion
detection. Refer to Section 5.2.1 Configuring Motion Detection.
8. Click tab to select the linkage method taken for the video loss alarm,
Notify surveillance center, send email, upload to FTP, trigger channel, smart tracking and
trigger alarm output are selectable. Refer to Section 5.2.1 Configuring Motion Detection.
9. Click button to save the settings.
© Hikvision
Page 64

User Manual of Network PTZ Camera
56
5.4 PTZ Configuration
On the event configuration page, click to show the PTZ control panel or click to hide it.
Click the direction buttons to control the pan/tilt movements.
Click the zoom/iris/focus buttons to realize lens control.
The functions vary depending on different camera models.
5.4.1 Configuring Basic PTZ Parameters
You can configure the basic PTZ parameters, including proportional pan, preset freezing, preset
speed, etc.
1. Enter the Basic Settings interface:
Configuration > PTZ > Basic Settings
Figure 5-26 Basic Settings
2. Configure the following settings:
Basic Parameters: Set the basic parameters of PTZ.
Proportional Pan: If you enable this function, the pan/tilt speeds change according to
the amount of zoom. When there is a large amount of zoom, the pan/tilt speed will be
slower for keeping the image from moving too fast on the live view image.
Preset Freezing: This function enables the live view to switch directly from one scene
© Hikvision
Page 65

User Manual of Network PTZ Camera
57
defined by a preset to another, without showing the middle areas between these two, to
ensure the surveillance efficiency. It can also reduce the use of bandwidth in a digital
network system.
Preset freezing function is invalid when you calling a pattern.
Preset Speed: You can set the speed of a defined preset from 1 to 8.
Manual Control Speed: The manual control speed can be set as Compatible, Pedestrian,
Non-motor Vehicle, Motor Vehicle or Auto.
Compatible: The control speed is same as the Keyboard Control Speed.
Pedestrian: Choose the Pedestrian when you monitor the pedestrians.
Non-motor Vehicle: Choose the Non-motor Vehicle when you monitor the non-motor
vehicles.
Motor Vehicle: Choose the Motor Vehicle when you monitor the motor vehicles.
Auto: You are recommended to set it as Auto when the application scene of the speed
dome is complicated.
Keyboard Control Speed: Define the speed of PTZ control by a keyboard as Low, Medium
or High.
Auto Scan Speed: The scan speed can be set from level 1 to 40.
Max. Tilt-angle: Set the tilt-angle of the speed dome from the dropdown list.
Zooming Speed: The zoom speed is adjustable from level 1 to 3.
PTZ OSD: Set the on-screen display duration of the PTZ status.
Zoom Status: Set the OSD duration of zooming status as 2 seconds, 5 seconds, 10
seconds, NC (Normally Closed), or NO (Normally Open).
PT Status: Set the azimuth angle display duration while panning and tilting as 2 seconds,
5 seconds, 10 seconds, NC (Normally Closed), or NO (Normally Open).
Preset Status: Set the preset name display duration while calling the preset as 2 seconds,
5 seconds, 10 seconds, NC (Normally Closed), or NO (Normally Open).
Power-off Memory: The speed dome can resume its previous PTZ status or actions after it
restarted from a power-off. You can set the time point of which the dome resumes its PTZ
status. You can set it to resume the status of 30 seconds, 60 seconds, 300 seconds or 600
seconds before power-off.
3. Click to save the settings.
5.4.2 Configuring PTZ Limits
Purpose:
The speed dome can be programmed to move within the configurable PTZ limits (left/right,
up/down).
For some certain camera models, disable PTZ limit and then the pan angle reaches 330°.
© Hikvision
Page 66

User Manual of Network PTZ Camera
58
Steps:
1. Enter the Limit configuration interface:
Configuration > PTZ > Limit
Figure 5-27 Configure the PTZ Limit
2. Click the Enable Limit checkbox and choose the limit type as manual stops or scan stops.
Manual Stops:
When manual limit stops are set, you can operate the PTZ control panel manually only in the
limited surveillance area.
Scan Stops:
When scan limit stops are set, the random scan, frame scan, auto scan, tilt scan, panorama
scan is performed only in the limited surveillance area.
Manual Stops of Limit Type is prior to Scan Stops. When you set these two limit types at the
same time, Manual Stops is valid and Scan Stops is invalid.
3. Click the PTZ control buttons to find the left/right/up/down limit stops; you can also call the
defined presets and set them as the limits of the speed dome.
4. Click Set to save the limits or click Clear to clear the limits.
5. Click to save the settings.
5.4.3 Configuring Initial Position
Purpose:
The initial position is the origin of PTZ coordinates. It can be the factory default initial position.
You can also customize the initial position according to your own demand.
© Hikvision
Page 67

User Manual of Network PTZ Camera
59
Customize an Initial Position:
Steps:
1. Enter the Initial Position configuration interface:
Configuration > PTZ > Initial Position
Figure 5-28 PTZ Configuration
2. Click the PTZ control buttons to find a position as the initial position of the speed dome; you
can also call a defined preset and set it as the initial position of the speed dome.
3. Click Set to save the position.
Call/delete an Initial Position:
You can click to call the initial position. You can click to delete the initial position and
restore the factory default initial position.
5.4.4 Configuring Park Actions
Purpose:
This feature allows the camera to start a predefined park action (scan, preset, pattern and etc.)
automatically after a period of inactivity (park time).
Scheduled Tasks function is prior to Park Action function. When these two functions are set
at the same time, only the Scheduled Tasks function takes effect.
Park function varies depending on different camera models.
Steps:
1. Enter the Park Action settings interface:
© Hikvision
Page 68

User Manual of Network PTZ Camera
60
Configuration > PTZ > Park Action
Figure 5-29 Set the Park Action
2. Check the Enable Park Action checkbox.
3. Set the Park Time as the inactivity time of the camera before it starts the park actions.
4. Choose Action Type the from the dropdown list.
5. If you select Patrol, Pattern, or Preset as Action Type, you need to select Action Type ID from
the dropdown list.
6. Click to save the settings.
5.4.5 Configuring Privacy Mask
Purpose:
Privacy mask enables you to cover certain areas on the live video to prevent certain spots in the
surveillance area from being live viewed and recorded.
Steps:
1. Enter the Privacy Mask settings interface:
Configuration > PTZ > Privacy Mask
Figure 5-30 Draw the Privacy Mask
© Hikvision
Page 69

User Manual of Network PTZ Camera
61
2. Click the PTZ control buttons to find the area you want to set the privacy mask.
3. Click ; drag the mouse in the live video window to draw the area.
4. You can drag the corners of the red rectangle area to draw a polygon mask.
5. Click to finish drawing or click to clear all of the areas you set without
saving them.
6. Click to save the privacy mask, and it will be listed in the Privacy Mask List area; set
the value of Active Zoom Ratio on your demand, and then the mask will only appear when
the zoom ratio is greater than the predefined value.
Figure 5-31 Privacy Mask List
7. Check the checkbox of Enable Privacy Mask to enable this function.
5.4.6 Configuring Scheduled Tasks
Purpose:
You can configure the network speed dome to perform a certain action automatically in a
user-defined time period.
Steps:
1. Enter the Scheduled Task settings interface:
Configuration> PTZ > Scheduled Tasks
Figure 5-32 Configure Scheduled Tasks
© Hikvision
Page 70

User Manual of Network PTZ Camera
62
2. Check the Enable Scheduled Task checkbox.
3. Set the Park Time. You can set the park time (a period of inactivity) before the speed dome
starts the scheduled tasks.
4. Select the task type from the dropdown list.
5. Select the timeline of a certain day, and drag the mouse to set the recording schedule (the
start time and end time of the recording task).
6. After you set the scheduled task, you can click and copy the task to other days
(optional).
Figure 5-33 Edit the Schedule and Task Type
7. Click to save the settings.
5.4.7 Clearing PTZ Configurations
Purpose:
You can clear PTZ configurations in this interface, including all presets, patrols, privacy masks, PTZ
limits, scheduled tasks and park actions.
Steps:
1. Enter the Clearing Configuration interface:
Configuration > PTZ > Clear Config
2. Check the checkbox of the items you want to clear.
© Hikvision
Page 71

User Manual of Network PTZ Camera
63
Figure 5-34 Clear Config
3. Click to clear the settings.
5.4.8 Configuring Smart Tracking
Purpose:
The speed dome tracks the moving objects automatically after you configure this function.
Steps:
1. Enter the Smart Tracking settings interface:
Configuration > PTZ > Smart Tracking
Figure 5-35 Configure Smart Tracking
2. Check the Enable Smart Tracking check box to enable smart tracking function.
3. Click the PTZ buttons to select an object.
4. Click to set the current zoom ratio as the tracking zoom ratio.
© Hikvision
Page 72

User Manual of Network PTZ Camera
64
5. Set the tracking duration. The speed dome stops tracking when the duration time is up. The
duration ranges from 0 to 300 seconds.
Setting the duration to 0 means that there’ no duration when speed dome tracks.
This function varies depending on different camera models.
6. Click to clear the settings.
5.4.9 Prioritize PTZ
Steps:
1. Enter the Prioritize PTZ interface:
Configuration > PTZ > Prioritize PTZ.
Figure 5-36 Position Settings
2. Select Network or RS-485 from the dropdown list
3. Set the delay time (Range 2-200s).
4. Click to save the settings.
© Hikvision
Page 73

User Manual of Network PTZ Camera
65
Chapter 6 Camera Configuration
6.1 Configuring Network Settings
The functions vary depending on different camera models.
6.1.1 Basic Settings
Configuring TCP/IP Settings
Purpose:
TCP/IP settings must be properly configured before you operate the camera over network. IPv4
and IPv6 are both supported.
Steps:
1. Enter TCP/IP settings interface:
Configuration > Network > Basic Settings > TCP/IP
Figure 6-1 TCP/IP Settings
2. Configure the NIC settings, including the IPv4(IPv6) Address, IPv4(IPv6) Subnet Mask and
IPv4(IPv6) Default Gateway.
© Hikvision
Page 74

User Manual of Network PTZ Camera
66
3. Click to save the above settings.
You can click Test to make sure that the IP address is valid.
If the DHCP server is available, you can check to automatically obtain an IP
address and other network settings from that server.
The valid value range of Maximum Transmission Unit (MTU) is 1280 to 1500.
The Multicast sends a stream to the multicast group address and allows multiple clients to
acquire the stream at the same time by requesting a copy from the multicast group address.
Before utilizing this function, you have to enable the Multicast function of your router and
configure the gateway of the network camera.
If the DNS server settings are required for some applications (e.g., sending email), you
should properly configure the Preferred DNS Server and Alternate DNS server.
Figure 6-2 DNS Server Settings
The router must support the route advertisement function if you select Route
Advertisement as the IPv6 mode.
Configuring DDNS Settings
Purpose:
If your camera is set to use PPPoE as its default network connection, you can use the Dynamic
DNS (DDNS) for network access.
Before you start:
Registration on the DDNS server is required before configuring the DDNS settings of the camera.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The password
should be something of your own choosing (using a minimum of 8 characters, including
upper case letters, lower case letters, numbers and special characters) in order to increase
the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of the
installer and/or end-user.
Steps:
1. Enter the DDNS settings interface:
Configuration > Network > Basic Settings > DDNS
2. Check the Enable DDNS checkbox to enable this feature.
© Hikvision
Page 75

User Manual of Network PTZ Camera
67
3. Select DDNS Type. Two DDNS types are selectable: DynDNS and NO-IP.
DynDNS:
Steps:
(1) Enter Server Address of DynDNS (e.g. members.dyndns.org).
(2) In the Domain text field, enter the domain name obtained from the DynDNS website.
(3) Enter the Port of DynDNS server.
(4) Enter the User Name and Password registered on the DynDNS website.
(5) Click to save the settings.
Figure 6-3 DynDNS Settings
NO-IP:
Steps:
(1) Enter Server Address of NO-IP.
(2) In the Domain text field, enter the domain name obtained from the NO-IP website.
(3) Enter the Port of NO-IP server.
(4) Enter the User Name and Password registered on the NO-IP website.
(5) Click to save the settings.
Configuring PPPoE Settings
Purpose:
If you have no router but only a modem, you can use Point-to-Point Protocol over Ethernet
(PPPoE) function.
Steps:
1. Enter the PPPoE settings interface:
Configuration > Network > Basic Settings > PPPoE
Figure 6-4 PPPoE Settings
© Hikvision
Page 76

User Manual of Network PTZ Camera
68
2. Check the Enable PPPoE checkbox to enable this feature.
3. Enter User Name, Password, and Confirm password for PPPoE access.
The User Name and Password should be assigned by your ISP.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
4. Click to save and exit the interface.
Configuring Port Settings
Purpose:
If there is a router and you want to access the camera through Wide Area Network (WAN), you
need to forward the 3 ports for the camera.
Steps:
1. Enter the Port settings interface:
Configuration > Network > Basic Settings > Port
Figure 6-5 Port Settings
2. Set the HTTP port, RTSP port and port of the camera.
HTTP Port: The default port number is 80.
RTSP Port: The default port number is 554.
HTTPS Port: The default port number is 443.
Server Port: The default port number is 8000.
3. Click to save the settings.
Configuring NAT (Network Address Translation) Settings
Purpose:
Universal Plug and Play (UPnP™) is a networking architecture that provides compatibility among
networking equipment, software and other hardware devices. The UPnP protocol allows devices
© Hikvision
Page 77

User Manual of Network PTZ Camera
69
to connect seamlessly and to simplify the implementation of networks in the house and
corporate environments.
With the function enabled, you don’t need to configure the port mapping for each port, and the
camera is connected to the Wide Area Network via the router.
Steps:
1. Enter the UPnP™ settings interface.
Configuration >Network > Basic Settings > NAT
2. Check the checkbox to enable the UPnP™ function.
You can edit the Friendly Name of the camera. This name can be detected by corresponding
device, such as a router.
3. Set the port mapping mode:
To port mapping with the default port numbers:
Choose
To port mapping with the customized port numbers:
Choose
And you can customize the value of the port number by yourself.
Figure 6-6 Port Mapping Mode
4. Click to save the settings.
6.1.2 Advanced Settings
Configuring SNMP Settings
Purpose:
You can use SNMP to get camera status and parameters related information.
Before you start:
Before setting the SNMP, use the SNMP software and manage to receive the camera information
via SNMP port. By setting the Trap Address, the camera can send the alarm event and exception
messages to the surveillance center.
The SNMP version you select should be the same as that of the SNMP software.
© Hikvision
Page 78

User Manual of Network PTZ Camera
70
Steps:
1. Enter the SNMP settings interface:
Configuration > Network > Advanced Settings > SNMP
Figure 6-7 SNMP Settings
2. Check the corresponding version checkbox (Enable SNMP v1, Enable SNMP v2c, Enable
SNMP v3) to enable the feature.
3. Configure the SNMP settings.
The configuration of the SNMP software should be the same as the settings you configure
here.
4. Click to save and finish the settings.
Configuring FTP Settings
Purpose:
You can set a FTP server and configure the following parameters for uploading captured pictures.
© Hikvision
Page 79

User Manual of Network PTZ Camera
71
Steps:
1. Enter the FTP settings interface:
Configuration > Network > Advanced Settings > FTP
Figure 6-8 FTP Settings
2. Configure the FTP settings, including server address, port, user name, password, directory,
and upload type.
The server address supports both the domain name and IP address formats.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
Setting the directory in FTP server for saving files:
In the Directory Structure field, you can select the root directory, parent directory and
child directory.
Root directory: The files will be saved in the root of FTP server.
Parent directory: The files will be saved in a folder in FTP server. The name of folder can
be defined as shown in Figure 6-9.
Figure 6-9 Parent Directory
© Hikvision
Page 80

User Manual of Network PTZ Camera
72
Child directory: It is a sub-folder which can be created in the parent directory. The files
will be saved in a sub-folder in FTP server. The name of folder can be defined as shown
in Figure 6-10.
Figure 6-10 Child Directory
Upload type: To enable uploading the captured picture to the FTP server.
3. Click to save the settings.
4. You can click Test to confirm the configuration.
If you want to upload the captured pictures to FTP server, you also have to enable the
continuous snapshot or event-triggered snapshot in Snapshot interface.
Configuring Email Settings
Purpose:
The system can be configured to send an Email notification to all designated receivers if an alarm
event is detected, e.g., motion detection event, video loss, video-tampering, etc.
Before you start:
Configure the DNS Server settings under Configuration> Network > Basic Settings > TCP/IP
before using the Email function.
Steps:
1. Enter the Email settings interface:
Configuration> Network > Advanced Settings > Email
Figure 6-11 Email Settings
2. Configure the following settings:
© Hikvision
Page 81

User Manual of Network PTZ Camera
73
Sender: The name of the email sender.
Sender’s Address: The email address of the sender.
SMTP Server: The SMTP Server IP address or host name (e.g., smtp.263xmail.com).
SMTP Port: The SMTP port. The default TCP/IP port for SMTP is 25.
E-mail encryption: None, SSL, and TLS are selectable. When you select SSL or TLS and disable
STARTTLS, e-mails will be sent after encrypted by SSL or TLS. The SMTP port should be set as
465 for this encryption method. When you select SSL or TLS and enable STARTTLS, emails will
be sent after encrypted by STARTTLS, and the SMTP port should be set as 25.
STARTTLS protocol must be supported by the email server for e-mail encryption with
STARTTLS. When it is not supported by the email server and the checkbox of Enable STARTTLS
is checked, the email will not be encrypted.
Attached Image: Check the checkbox of Attached Image if you want to send emails with
attached alarm images.
Interval: The interval refers to the time between two actions of sending attached pictures.
Authentication (optional): If your email server requires authentication, check this checkbox to
use authentication to log in to this server and enter the login user name and password.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The
password should be something of your own choosing (using a minimum of 8 characters,
including upper case letters, lower case letters, numbers and special characters) in order
to increase the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of
the installer and/or end-user.
Receiver: Select the receiver to which the email is sent. Up to 2 receivers can be configured.
Receiver: The name of the user to be notified.
Receiver’s Address: The email address of user to be notified. (Optional: click Test to make sure
that the email server can send email out.)
3. Click to save the settings.
Configuring Platform Settings
Purpose:
Platform access provides you an option to manage the devices via platform.
This function varies depending on different speed dome models.
Steps:
1. Enter the Platform settings interface:
Configuration> Network > Advanced Settings > Platform Access
© Hikvision
Page 82

User Manual of Network PTZ Camera
74
Figure 6-12 Platform Access
2. Check the Enable checkbox to enable the platform access function of the device.
3. Select the Platform Access Mode.
If you select Platform Access Mode as Hik-Connect,
1) Click and read "Terms of Service" and "Privacy Policy" in pop-up window.
2) Create a verification code or change the verification code for the camera.
The verification code is required when you add the camera to Hik-Connect app.
For more information about the Hik-Connect app, refer to Hik-Connect Mobile Client
User Manual.
4. You can use the default server address. Or you can check the Custom checkbox on the right
and input a desired server address.
5. Click to save the settings.
Hik-Connect is an application for mobile devices. With the App, you can view live image of the
camera, receive alarm notification and so on.
Configuring HTTPS Settings
Purpose:
HTTPS is consisted by SSL&HTTP. It is used for encryption transmission, identity authentication
network protocol which enhances the security of WEB accessing.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The password
should be something of your own choosing (using a minimum of 8 characters, including
upper case letters, lower case letters, numbers and special characters) in order to increase
the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of the
installer and/or end-user.
© Hikvision
Page 83

User Manual of Network PTZ Camera
75
Steps:
1. Enter the HTTPS settings interface.
Configuration > Network > Advanced Settings > HTTPS
2. Create the self-signed certificate or authorized certificate.
Figure 6-13 Create Certificate
OPTION 1: Create the self-signed certificate
1) Select Create Self-signed Certificate.
2) Click Create to create the following dialog box.
Figure 6-14 Create Self-signed Certificate
3) Enter the country, host name/IP, validity and other information.
4) Click OK to save the settings.
OPTION 2: Start the installation when signed certificate is available.
1) Select Signed certificate is available, Start the installation directly.
2) Click Browse to upload the available certificate.
3) Click Install button to install the certificate.
4) Click OK to save the settings.
OPTION 3: Create certificate request first and continue the installation.
1) Select Create certificate request first and continue the installation.
2) Click Create to create the certificate request, and fulfill the required information.
3) Download the certificate request and submit it to the trusted certificate authority for
signature.
4) After receiving the signed valid certificate, import the certificate to the device.
5) Click OK to save the settings.
© Hikvision
Page 84

User Manual of Network PTZ Camera
76
3. There will be the certificate information after you successfully create and install the
certificate.
Figure 6-15 Installed Certificate Property
The default port number of HTTPS is 443. The port value ranges from 1 to 65535.
When the port number is the default number 443, the format of the URL is https://IP address,
eg., https://192.168.1.64.
When the port number is not the default number 443, the format of the URL is https://IP
address:port number, eg., https://192.168.1.64:81.
Configuring QoS Settings
Purpose:
QoS (Quality of Service) can help solve the network delay and network congestion by configuring
the priority of data sending.
Steps:
1. Enter the QoS settings interface:
Configuration >Advanced Configuration > Network > QoS
Figure 6-16 QoS Settings
2. Configure the QoS settings, including video / audio DSCP, event / alarm DSCP and
Management DSCP.
The valid DSCP value ranges from 0 to 63. The DSCP value is bigger, the priority is higher.
3. Click to save the settings.
Make sure that you enable the QoS function of your network device (such as a router).
It will ask for a reboot for the settings to take effect.
© Hikvision
Page 85

User Manual of Network PTZ Camera
77
Network
Speed Dome
PC
Network Switch
Internet
PC
RADIUS Server
Authenticator
Authentication
Server
Configuring 802.1X Settings
Purpose:
The camera supports IEEE 802.1X standard.
IEEE 802.1X is a port-based network access control. It enhances the security level of the LAN.
When devices connect to this network with IEEE 802.1X standard, the authentication is needed. If
the authentication fails, the devices don’t connect to the network.
The protected LAN with 802.1X standard is shown in Figure 6-17.
Figure 6-17 Protected LAN
Before connecting the Network Camera to the protected LAN, apply a digital certificate
from a Certificate Authority.
The network camera requests access to the protected LAN via the authenticator (a
switch).
The switch forwards the identity and password to the authentication server (RADIUS
server).
The switch forwards the certificate of authentication server to the network camera.
If all the information is validated, the switch allows the network access to the protected
network.
For your privacy and to better protect your system against security risks, we strongly
recommend the use of strong passwords for all functions and network devices. The password
should be something of your own choosing (using a minimum of 8 characters, including
upper case letters, lower case letters, numbers and special characters) in order to increase
the security of your product.
Proper configuration of all passwords and other security settings is the responsibility of the
installer and/or end-user.
Steps:
1. Connect the network camera to your PC directly with a network cable.
2. Enter the 802.1X settings interface:
Configuration > Network > Advanced Settings > 802.1X
© Hikvision
Page 86

User Manual of Network PTZ Camera
78
Figure 6-18 802.1X Settings
3. Check the Enable IEEE 802.1X checkbox to enable it.
4. Configure the 802.1X settings, including user name and password.
The EAP-MD5 version must be identical with that of the router or the switch.
5. Click to finish the settings.
The camera reboots when you save the settings.
6. After the configuration, connect the camera to the protected network.
Integration Protocol
Purpose:
If you need to access to the camera through the third party platform, you can enable
Hikvision-CGI function. And if you need to access to the device through ONVIF protocol, you can
configure ONVIF user in this interface. Refer to ONVIF standard for detailed configuration rules.
Steps:
1. Enter the Integration Protocol configuration interface.
Configuration > Network > Advanced Settings > Integration Protocol
© Hikvision
Page 87

User Manual of Network PTZ Camera
79
Figure 6-19 Integration Protocol Settings
2. Check the Enable Hikvision-CGI checkbox and then select the authentication from the
dropdown list. Then you can access to the camera through the third party platform.
3. Check the Enable ONVIF checkbox to enable the function.
4. Click Add to add a new ONVIF user. Set the user name and password, and confirm the
password. You can set the user as media user, operator, and administrator.
5. Click Modify to modify the information of the added ONVIF user.
6. Click Delete to delete the selected ONVIF user.
7. Click to save the settings
6.2 Configuring Video and Audio Settings
6.2.1 Configuring Video Settings
Steps:
1. Enter the Video settings interface:
Configuration > Video/Audio > Video
© Hikvision
Page 88

User Manual of Network PTZ Camera
80
Figure 6-20 Configure Video Settings
2. Select the Stream Type of the camera to main stream (normal), sub-stream or third stream.
The main stream is usually for recording and live viewing with good bandwidth, and the
sub-stream can be used for live viewing when the bandwidth is limited. Refer to the Section
4.1 Configuring Local Parameters for switching the main stream and sub-stream for live
viewing.
3. You can customize the following parameters for the selected stream.
The parameters vary depending on different camera models.
Video Type:
Select the stream type to video stream, or video & audio composite stream. The audio signal
will be recorded only when the Video Type is Video & Audio.
Resolution:
Select the resolution of the video output.
Bitrate Type:
Select the bitrate type to constant or variable.
Video Quality:
When bitrate type is selected as Variable, 6 levels of video quality are selectable.
Frame Rate:
The frame rate is to describe the frequency at which the video stream is updated and it is
measured by frames per second (fps). A higher frame rate is advantageous when there is
movement in the video stream, as it maintains image quality throughout.
Max. Bitrate:
Set the Max. bitrate. The higher value corresponds to the higher video quality, but the higher
bandwidth is required.
Video Encoding:
Select Video Encoding from the dropdown list for different stream type.
H.264+/H.265+:
© Hikvision
Page 89

User Manual of Network PTZ Camera
81
Set it as ON or OFF.
H.264+: If you set the main stream as the stream type, and H.264 as the video encoding, you
can see H.264+ available. H.264+ is an improved compression coding technology based on
H.264. By enabling H.264+, users can estimate the HDD consumption by its maximum average
bitrate. Compared to H.264, H.264+ reduces storage by up to 50% with the same maximum
bitrate in most scenes.
H.265+: If you set the main stream as the stream type, and H.265 as the video encoding, you
can see H.265+ available. H.265+ is an improved compression coding technology based on
H.265. By enabling H.265+, users can estimate the HDD consumption by its maximum average
bitrate. Compared to H.265, H.265+ reduces storage by up to 50% with the same maximum
bitrate in most scenes.
You need to reboot the camera if you want to turn on or turn off the H.264+/H.265+. If you
switch from H.264+ to H.265+ directly, and vice versa, a reboot is not required by the system.
Profile:
Basic Profile, Main Profile and High Profile are selectable.
I Frame Interval:
Set the I-Frame interval from 1 to 400.
SVC:
Scalable Video Coding is an extension of the H.264/AVC standard. Select OFF/ON to
disable/enable the SVC function. Select Auto, and the device will automatically extract frames
from the original video when the network bandwidth is insufficient.
Smoothing:
It refers to the smoothness of the stream. The higher value of the smoothing, the better
fluency of the stream, though, the video quality may not be so satisfied. The lower value of
the smoothing, the higher quality of the stream, though it may appear not fluent.
4. Click to save the settings.
6.2.2 Configuring Audio Settings
Steps:
1. Enter the Audio settings interface
Configuration > Video/Audio > Audio
Figure 6-21 Audio Settings
2. Configure the following settings.
Audio Encoding: G.722.1, G.711ulaw, G.711alaw, MP2L2, G.726 and PCM are selectable.
© Hikvision
Page 90

User Manual of Network PTZ Camera
82
Audio Input: When an intercom is connected to the camera, you need to set this option to
LineIn. When a microphone is connected to the camera, you need to set this option to MicIn.
Audio Stream Bitrate: When the Audio Encoding is selected as MP2L2, you can configure the
Audio Stream Bitrate in the dropdown list. The greater the value is, the better the audio
quality will be.
Sampling Rate: When the Audio Encoding is selected as MP2L2, you can configure the
Sampling Rate in the dropdown list. The greater the value is, the better the audio quality will
be.
Input Volume: Slid the bar to turn up/down the volume. The value ranges from 0 to 100.
Environmental Noise Filter: Select ON or OFF in the dropdown list to enable or disable the
function. It’s recommended to enable the function when sampling rate is lower than 32 kHz.
3. Click to save the settings.
6.2.3 Configuring ROI Settings
Purpose:
ROI (Region of Interest) encoding is used to enhance the quality of images which are specified in
advance. There are two different ROI methods: Fixed Region and Dynamic Region. When Fixed
Region is enabled, image quality of ROI area will be enhanced and image quality of other areas
will be reduced. When Dynamic Region is enabled, image quality of tracking target will be
enhanced.
ROI function varies depending on different camera models.
Enter the ROI settings interface:
Configuration >Video/Audio > ROI
Figure 6-22 Region of Interest (1)
© Hikvision
Page 91

User Manual of Network PTZ Camera
83
Figure 6-23 Region of Interest (2)
ROI for Fixed Region
Steps:
1. Check Enable checkbox to enable the Fixed Region function.
2. Select a stream type. You can set the ROI function for main stream, sub-stream or third
stream.
3. Click and then drag the mouse to draw a red frame in the live view image. You
can click to clear it.
The number of areas supported in ROI function varies depending different camera models
4. Select the Region No. from the dropdown list.
5. Adjust the ROI level from 1 to 6. The higher the value, the better image quality in the red
frame.
6. Enter a Region Name.
ROI for Dynamic Region
1. Check Enable Face Tracking checkbox to enable face tracking, and the captured face picture
is set as region of interest. Adjust the ROI level from 1 to 6.
2. Check Enable Target Tracking checkbox to enable target tracking, and the target is set as
region of interest. Adjust the ROI level from 1 to 6.
3. Click to save the settings.
6.3 Configuring Image Settings
© Hikvision
Page 92

User Manual of Network PTZ Camera
84
On the event configuration page, click to show the PTZ control panel or click to hide it.
Click the direction buttons to control the pan/tilt movements.
Click the zoom/iris/focus buttons to realize lens control.
The functions vary depending on different camera models.
6.3.1 Configuring Display Settings
Purpose:
Configure the image adjustment, exposure settings, day/night switch, backlight settings, white
balance, image enhancement, video adjustment, and other parameters in display settings.
The parameters in Display Settings interface vary depending on different camera models.
You can double click the live view to enter full screen mode and double click it again to exit.
Steps:
1. Enter the Display settings interface:
Configuration > Image> Display Settings
2. You can select the Scene in the dropdown list with different predefined image parameters.
3. Set the image parameters of the speed dome.
Figure 6-24 Display Settings
Image Adjustment
Brightness
This feature is used to adjust brightness of the image. The value ranges from 0 to 100.
Contrast
This feature enhances the difference in color and light between parts of an image. The value
ranges from 0 to 100.
Saturation
This feature is used to adjust color saturation of the image. The value ranges from 0 to 100.
Sharpness
© Hikvision
Page 93

User Manual of Network PTZ Camera
85
Sharpness function enhances the detail of the image by sharpening the edges in the image. The
value ranges from 0 to 100.
Exposure Settings
Exposure Mode
The Exposure Mode can be set to Auto, Iris Priority, Shutter Priority, and Manual.
Auto:
The iris, shutter and gain values will be adjusted automatically according to the brightness
of the environment.
Iris Priority:
The value of iris needs to be adjusted manually. The shutter and gain values will be
adjusted automatically according to the brightness of the environment.
Figure 6-25 Manual Iris
Shutter Priority:
The value of shutter needs to be adjusted manually. The iris and gain values will be
adjusted automatically according to the brightness of the environment.
Figure 6-26 Manual Shutter
Manual:
In Manual mode, you can adjust the values of Gain, Shutter, Iris manually.
Figure 6-27 Manual Mode
© Hikvision
Page 94

User Manual of Network PTZ Camera
86
Limit Gain
This feature is used to adjust gain of the image. The value ranges from 0 to 100.
Slow Shutter
This function can be used in underexposure condition. It lengthens the shutter time to
ensure full exposure.
Slow Shutter Level
When slow shutter is set as ON, you can select the slow shutter level from the
dropdown list. The slow shutter lever can be set to Slow Shutter*2, *3, *4, *6, *8.
Figure 6-28 Slow Shutter
Focus Settings
Focus Mode
The Focus Mode can be set to Auto, Manual, and Semi-auto.
Auto:
The speed dome focuses automatically at any time according to objects in the scene.
Semi-auto:
The speed dome focuses automatically only once after panning, tilting and zooming.
Manual:
In Manual mode, you need to use on the control panel to focus manually.
Min. Focus Distance
This function is used to limit the minimum focus distance. The value can be set to 10cm, 50cm,
1.0m, 1.5m, 3m, 6m, 10m and 20m.
The minimum focus value varies depending on different camera models.
Day/Night Switch
Day/Night Switch
The Day/Night Switch mode can be set to Auto, Day, Night and Scheduled-Switch.
This function varies depending on the models of speed dome.
Auto:
In Auto mode, the day mode and night mode can switch automatically according to the
light condition of environment.
Figure 6-29 Auto Mode Sensitivity
© Hikvision
Page 95

User Manual of Network PTZ Camera
87
Day:
In Day mode, the speed dome displays color image. It is used for normal lighting conditions.
Night:
In Night mode, the image is black and white. Night mode can increase the sensitivity in low
light conditions.
Scheduled-Switch:
In Schedule mode, you can set the time schedule for day mode as shown in Figure 6-30.
The rest time out of the schedule is for night mode.
Figure 6-30 Day Night Schedule
Backlight Settings
BLC (Back Light Compensation)
If there’s a bright backlight, the subject in front of the backlight appears silhouetted or dark.
Enabling BLC (back light compensation) function can correct the exposure of the subject. But the
backlight environment is washed out to white.
WDR (Wide Dynamic Range)
The wide dynamic range (WDR) function helps the camera provide clear images even under back
light circumstances. When there are both very bright and very dark areas simultaneously in the
field of view, WDR balances the brightness level of the whole image and provide clear images
with details.
You can enable or disable the WDR function as shown in Figure 6-31. The wide dynamic level
ranges from 0 to 100.
Figure 6-31 WDR
HLC
HLC (High Light Compensation) makes the camera identify and suppress the strong light sources
that usually flare across a scene. This makes it possible to see the detail of the image that would
normally be hidden.
White Balance
The White Balance mode can be set to Auto, MWB, Outdoor, Indoor, Fluorescent Lamp, Sodium
Lamp and Auto-Tracking.
Auto:
In Auto mode, the camera retains color balance automatically according to the current color
temperature.
© Hikvision
Page 96

User Manual of Network PTZ Camera
88
Manual White Balance:
In MWB mode, you can adjust the color temperature manually to meet your own demand as
shown in Figure 6-32.
Figure 6-32 Manual White Balance
Outdoor
You can select this mode when the speed dome is installed in outdoor environment.
Indoor
You can select this mode when the speed dome is installed in indoor environment.
Fluorescent Lamp
You can select this mode when there are fluorescent lamps installed near the speed dome.
Sodium Lamp
You can select this mode when there are sodium lamps installed near the speed dome.
Auto-Tracking
In Auto-Tracking mode, white balance is continuously being adjusted in real-time according to
the color temperature of the scene illumination.
Image Enhancement
3D Digital Noise Reduction
You can set Digital Noise Reduction function to Normal and adjust the Noise Reduction Level as
shown in Figure 6-33. The level ranges from 0 to 100.
Figure 6-33 3D Digital Noise Reduction
If you are a professional technician, you can set it to Expert Mode then adjust Space DNR Level
and Time DNR Level. The level ranges from 0 to 100.
Figure 6-34 Expert Mode
Defog Mode
You can set the Defog Mode to ON or OFF as you need.
© Hikvision
Page 97

User Manual of Network PTZ Camera
89
Figure 6-35 Defog Mode
EIS (Electronic Image Stabilization)
You can set theEIS to ON or OFF as you need.
Figure 6-36 Electronic Image Stabilization
Video Adjustment
The functions vary depending on different camera models.
Mirror
If you turn the MIRROR function on, the image will be flipped. It is like the image in the mirror.
The flip direction can be set to OFF or CENTER.
Video Standard
You can set the Video Standard to 50 Hz (PAL) or 60 Hz (NTSC) according to the video system in
your country.
Capture Mode
You can disable this function or select the capture mode from the list.
Other
The functions vary depending on different camera models.
Lens Initialization
The lens operates the movements for initialization when you enable Lens Initialization.
Zoom Limit
You can set Zoom Limit value to limit the maximum value of zooming. The value can be selected
from the list.
6.3.2 Configuring OSD Settings
Purpose:
The camera supports following on screen displays:
Time: Supports for time display.
Camera Name: Identifies the name of camera.
You can customize the on screen display of time.
Steps:
1. Enter the OSD settings interface:
© Hikvision
Page 98

User Manual of Network PTZ Camera
90
Configuration > Image > OSD Settings
Figure 6-37 OSD Settings
2. Check the corresponding checkbox to select the display of camera name, date or week if
required.
3. Edit the camera name in the text field of Camera Name.
4. Select from the dropdown list to set the time format, date format, display mode, OSD size and
Font color.
5. You can use the mouse to drag the text frame IPdome in the live view window to adjust the
OSD position.
Figure 6-38 Adjust OSD Location
6. Click to activate above settings.
© Hikvision
Page 99

User Manual of Network PTZ Camera
91
6.3.3 Configuring Text Overlay Settings
Purpose:
You can customize the text overlay.
Steps:
1. Enter the Text Overlay settings interface:
Configuration > Image > OSD Settings
2. Check the checkbox in front of textbox to enable the on-screen display.
3. Input the characters in the textbox.
4. Use the mouse to drag the red text frame Text in the live view window to adjust the text
overlay position.
5. Click to save the settings.
6.3.4 Configuring Image Parameters Switch
This function varies depending on different camera models
Purpose:
You can configure Link to Preset or Scheduled-Switch in this interface. Link to Preset: Set the
time period and linked scene for the preset and check the corresponding checkbox to go to the
linked scene in the configured time period. Scheduled-Switch: Set the time period and linked
scene and it will go to the linked scene in the configured time period when you check the
corresponding checkbox.
Steps:
1. Enter the Image Parameters Switch interface:
Configuration > Image > Image Parameters Switch
2. Check the checkbox of Link to Preset or Scheduled-Switch to enable the function. (Only one
function can be enabled in the same time.)
3. When you enable the function of Link to Preset, select one preset from the dropdown list,
check the corresponding checkbox, set the time period and the linked scene for the selected
preset. (Up to 4 periods can be configured for one preset.)
Figure 6-39 Link to Preset
© Hikvision
Page 100

User Manual of Network PTZ Camera
92
Figure 6-40 Linked Scene
4. When you enable the function of Scheduled-Switch, check the corresponding checkbox, set
the time period and the linked scene.
Figure 6-41 Schedule-Switch
5. Click to save the settings.
The two functions are not enabled by default.
6.4 Configuring System Settings
6.4.1 System Settings
Viewing Basic Information
Enter the Device Information interface:
Configuration > System > System Settings > Basic Information
In the Basic Information interface, you can edit the Device Name and Device No.
Other information of the camera, such as Model, Serial No., Firmware Version, Encoding Version,
Web Version, Plugin Version, Number of Channels, Number of HDDs, Number of Alarm Input,
Number of Alarm Output, and Firmware Version Property are displayed. The information cannot
be changed in this menu. It is the reference for maintenance or modification in future.
© Hikvision
 Loading...
Loading...