Page 1

MAA3182SC, MAB3091SC
INTELLIGENT DISK DRIVES
OEM MANUAL
– SCSI LOGICAL INTERFACE SPECIFICATIONS –
C141-E039-01EN
Page 2
FOR SAFE OPERATION
Handling of This manual
This manual contains important information for using this product. Read thoroughly before
using the product. Use this product only after thoroughly reading and understanding
especially the section “Important Alert Items” in this manual. Keep this manual handy, and
keep it carefully.
FUJITSU makes every effort to prevent users and bystanders from being injured or from
suffering damange to their property. Use the product according to this manual.
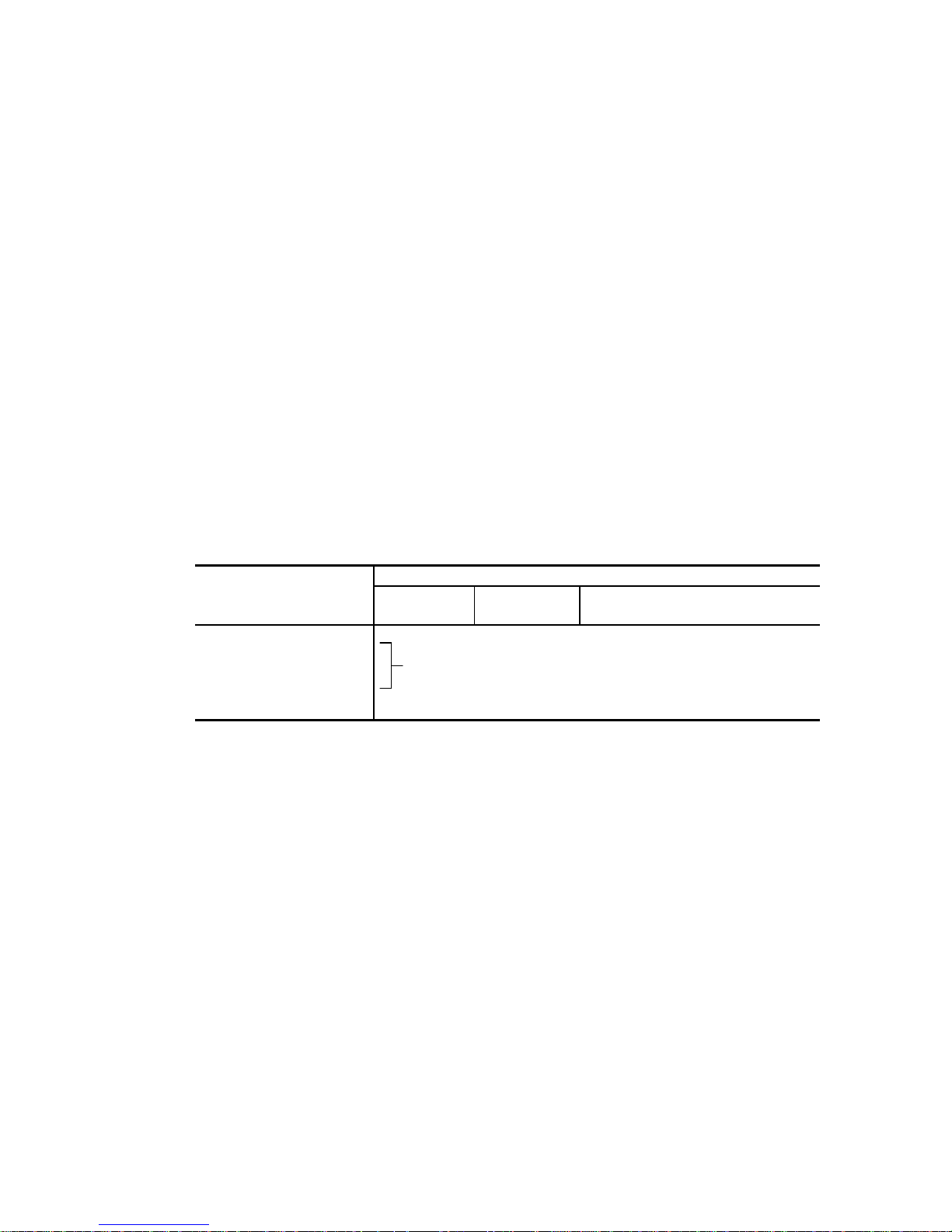
Functional Limitations
There may be certain functional limitations concerning the specifications and functions of the
products covered by this manual depending on the equipment version, especially concerning
the following functions.
Versions in which there functions can be used will be communicated through
“ENGINEERING CHANGE REQUEST/NOTICE”, issued by Fujitsu.
Function Equipment Version Which Supports These Functions
Equipment
Version No.
EPROM
Version No.
Standard INQUIRY Data Product
Revision (ASCII)
READ RAM Command
WRITE RAM
Command
These commands cannot be used in the current version.
(Proceed to the Copyright Page)
C141-E039-01EN i
Page 3
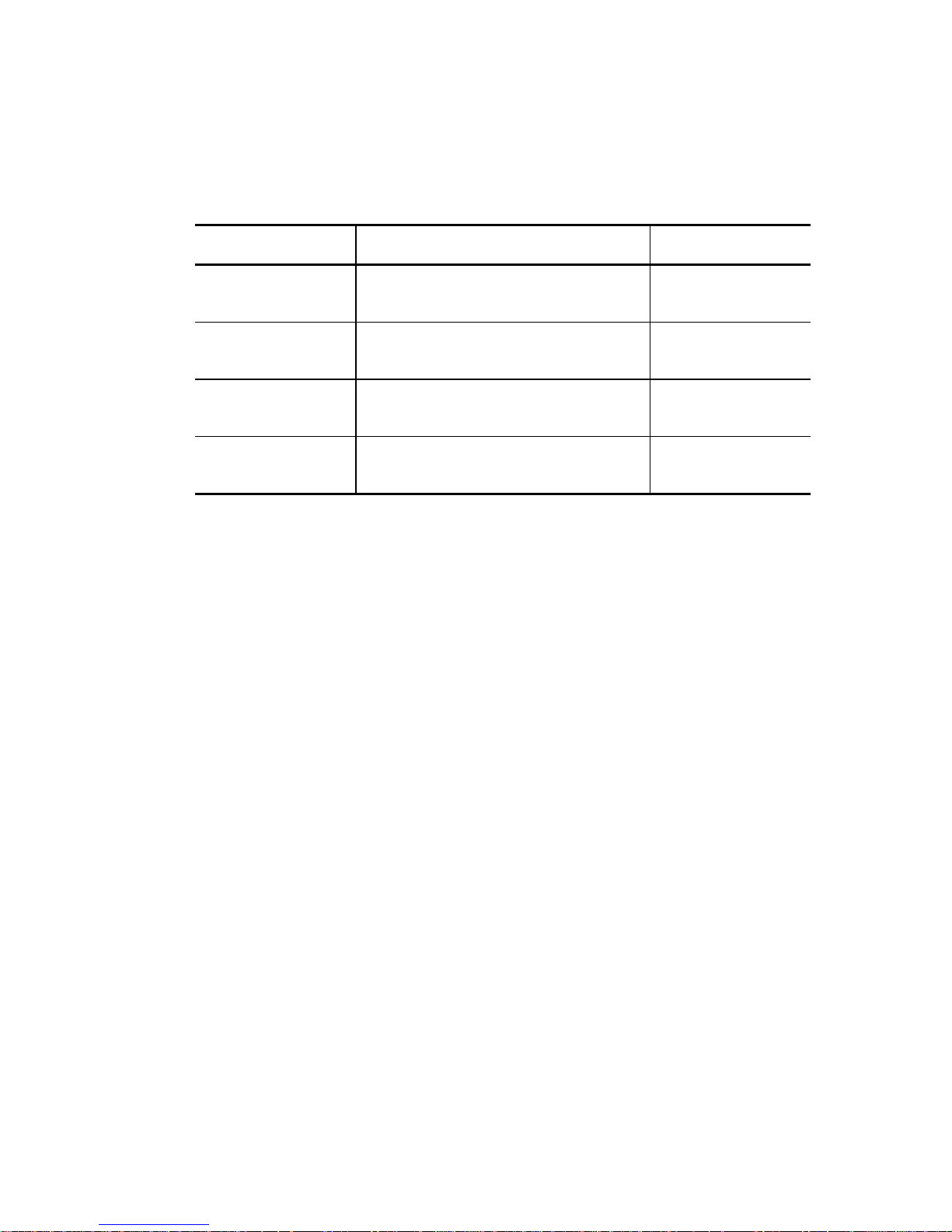
Related Standards
Specifications and functions of products covered by this manual comply with the following
standards.
Standard (Text) No. Name Enacting
ANSI X3. 131-1986 American National Standard for
ANSI X3. 131-1994 American National Standard for
X3T9.2/85-52 Rev
4.B
X3T9.2 855D Rev 12 WORKING DRAFT Information
Information Systems --- Small Computer
System Interface (SCSI)
Information Systems --- Small Computer
System Interface-2 (SCSI-2)
COMMON COMMAND SET (CCS) of
the Small Computer System Interface
(SCSI)
Technology SCSI-3 Parallel Interface
Organization
American National
Standards Institute
(ANSI)
American National
Standards Institute
(ANSI)
American National
Standards Institute
(ANSI)
American National
Standards Institute
(ANSI)
All Rights Reserved, Copyright 1997 Fujitsu, Limited
C141-E039-01ENii
Page 4
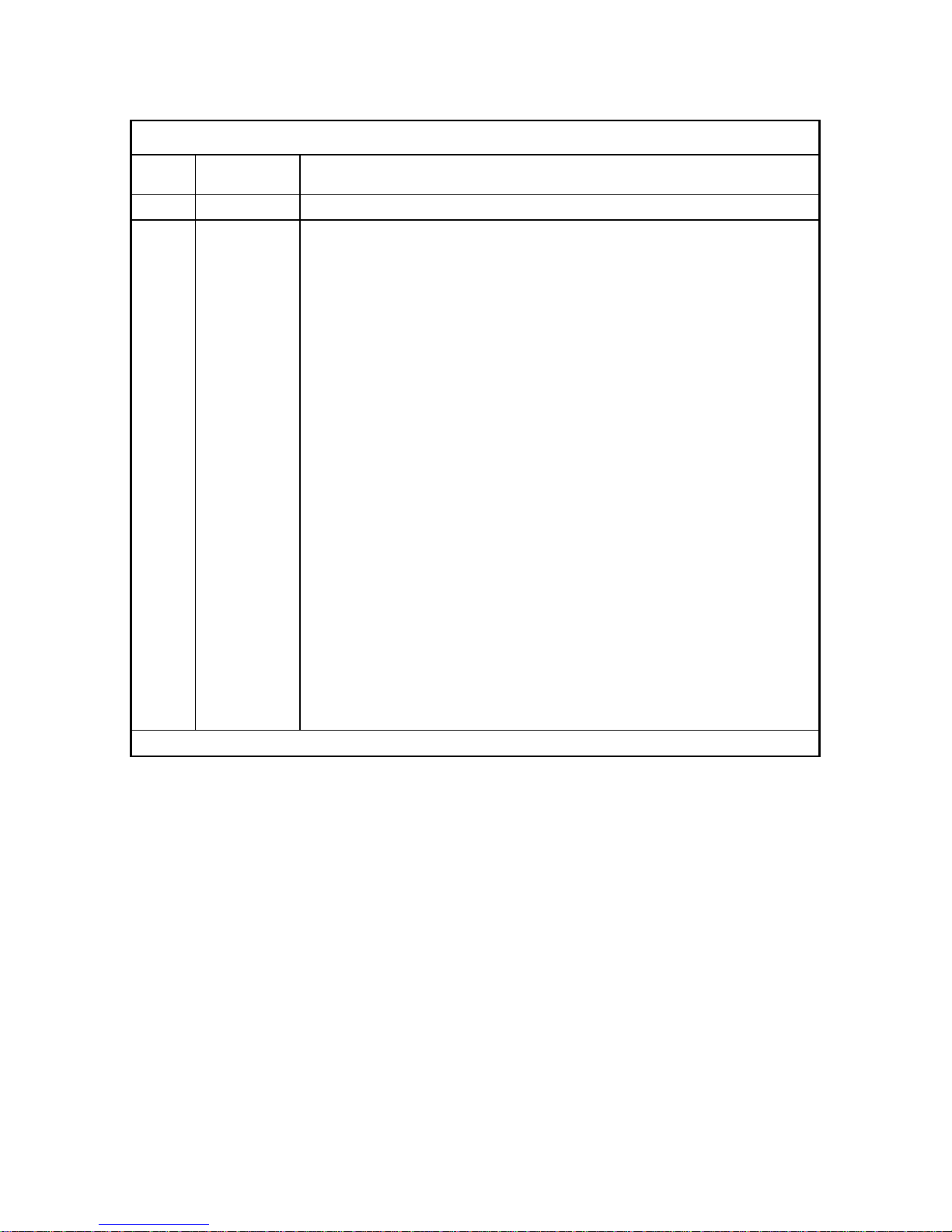
REVISION RECORD
Edition Date
published
01 May.,1997
Revised contents
Specification No.: C141-E039-**EN
The contents of this manual is subject to
change without prior notice.
All Rights Reserved.
Copyright 1997
FUJITSU LIMITED
C141-E039-01EN iii
Page 5

Page 6

This manual explains concerning the MAA3182SC and MAB3091SC series 3.5 inch hard disk
drives with internal SCSI controller.
The purpose of this manual is to provide specifications of each command and detailed
explanations of their functions for use of these magnetic disk drives incorporated into user
systems, and to present the information necessary for creating host system software. This
manual is written for users who have a basic knowledge of hard disk drives and their use in
computer systems.
The composition of manuals related to these disk drives and the range of subjects covered in
this manual are shown in “Manual Organization,” provided on a subsequent page. Please use
these other manuals along with this manual as necessary.
Composition and Contents of This Manual
This manual is composed of the 5 chapters shown below, a glossary and a list of
abbreviations.
Chapter 1 Command Processing
This chapter describes the basic logical specifications related to SCSI command processing in
the MAA3182SC and MAB3091SC series disk drives.
PREFACE
Chapter 2 Data Buffer Management
This chapter describes the data buffer configuration provided in the MAA3182SC and
MAB3091SC series disk drives and concerning data transfer processing functions and cache
operation.
Chapter 3 Command Specifications
This chapter describes detailed specifications of SCSI commands provided by the
MAA3182SC and MAB3091SC series disk drives and how to use them..
Chapter 4 Sense Data and Error Recovery Methods
This chapter describes the configuration and contents of sense data which report to the host
system when an error occurs, etc., key information necessary for error recovery, recommended
procedures for error recovery to be executed through host system software and retry
processing executed internally in the MAA3182SC and MAB3091SC series disk drives for
recovery.
Chapter 5 Disk Media Management
This chapter describes the procedure for initializing the disk media, methods of treating media
defects and data recovery methods for the MAA3182SC and MAB3091SC series disk drives.
C141-E039-01EN v
Page 7

Glossary
The glossary explains technical terms which are necessary to the reader’s understanding when
reading this manual.
List of Abbreviations
This list shows the full spelling of abbreviations used in this manual.
The model name of disk drives covered by this manual differs in its ending suffix (Note 1)
depending on its device type (3 types), the electrical conditions of the SCSI interface used to
connect the disk drive to the host system and its capacity and data format at the time it was
shipped, but in this manual, except in cases where models need to be especially distinguished,
a representative model name (Note 2) is used. In addition, these disk drives are called
Intelligent Disk Drive (IDD), “drive” or “device” in this manual.
Note 1: Model Name
M29 0 X S A
Format When X: 256-byte format (except for M294x and M295x)
Shipped A: 512-byte format (except for M294x and M295x)
B: 1024-byte format (except for M294x and M295x)
SCSI Electrical S: Single-ended, 8-bit SCSI (all series)
Conditions H: Differential, 8-bit SCSI (except for M294x and M295x)
Q: Single-ended, 16-bit SCSI (all series)
R: Differential, 16-bit SCSI (except for M294x and M295x)
C: SCA-1, 16-bit SCSI (M293)
E: SCA-2, 16-bit SCSI (M294x, M295x)
Capacity and 9: 19 heads (M2909) 9: 9 GB (M2949)
Number of 3: 13 heads (M2903) 2: 2 GB (M2932, M2952)
Heads 5: 15 heads (M2915) 4: 5 GB (M2934, M2954)
Device Type 0: Full height, large capacity (M2903, M2909)
1: Full height, high performance (M2915)
3: Full height, large capacity, high performance (M293x)
4: Full height, large capacity, high performance (M2949)
5: 1-inch height, high performance (M2952, M2954)
vi C141-E039-01EN
Page 8

Note 2: Representative Model Names
Representative
Model Name
M2909 M2909SX/SA/SB, M2909HX/HA/HB, M2909QX/QA/QB,
M2903 M2903SX/SA/SB, M2903HX/HA/HB, M2903QX/QA/QB,
M2915 M2915SX/SA/SB, M2915HX/HA/HB, M2915QX/QA/QB,
M2934 M2934SX/SA/SB, M2934HX/HA/HB, M2934QX/QA/QB,
M2932 M2932SX/SA/SB, M2932HX/HA/HB, M2932QX/QA/QB,
M2949 M2949S, M2949Q, M2949E
M2952 M2952S, M2952Q, M2952E
M2954 M2954S, M2954Q, M2954E
Warning Indications
The following warning indications are shown in this manual to prevent the user and other
nearby persons or property from being injured or damaged.
Model Name
M2909RX/RA/RB
M2903RX/RA/RB
M2915RX/RA/RB
M2934RX/RA/RB, M2934CX/CA/CB
M2932RX/RA/RB, M2932CX/CA/CB
Note “Note” indicates the most effective method of use or information that is of value to the
user.
Requesting for User’s Comments
Please use the User’s Comment Form attached to the end of this manual to identify user
comments including error, inaccurate and misleading information of this manual. Contact to
your Fujitsu representative for additional comment forms if required.
C141-E039-01EN vii
Page 9

Page 10
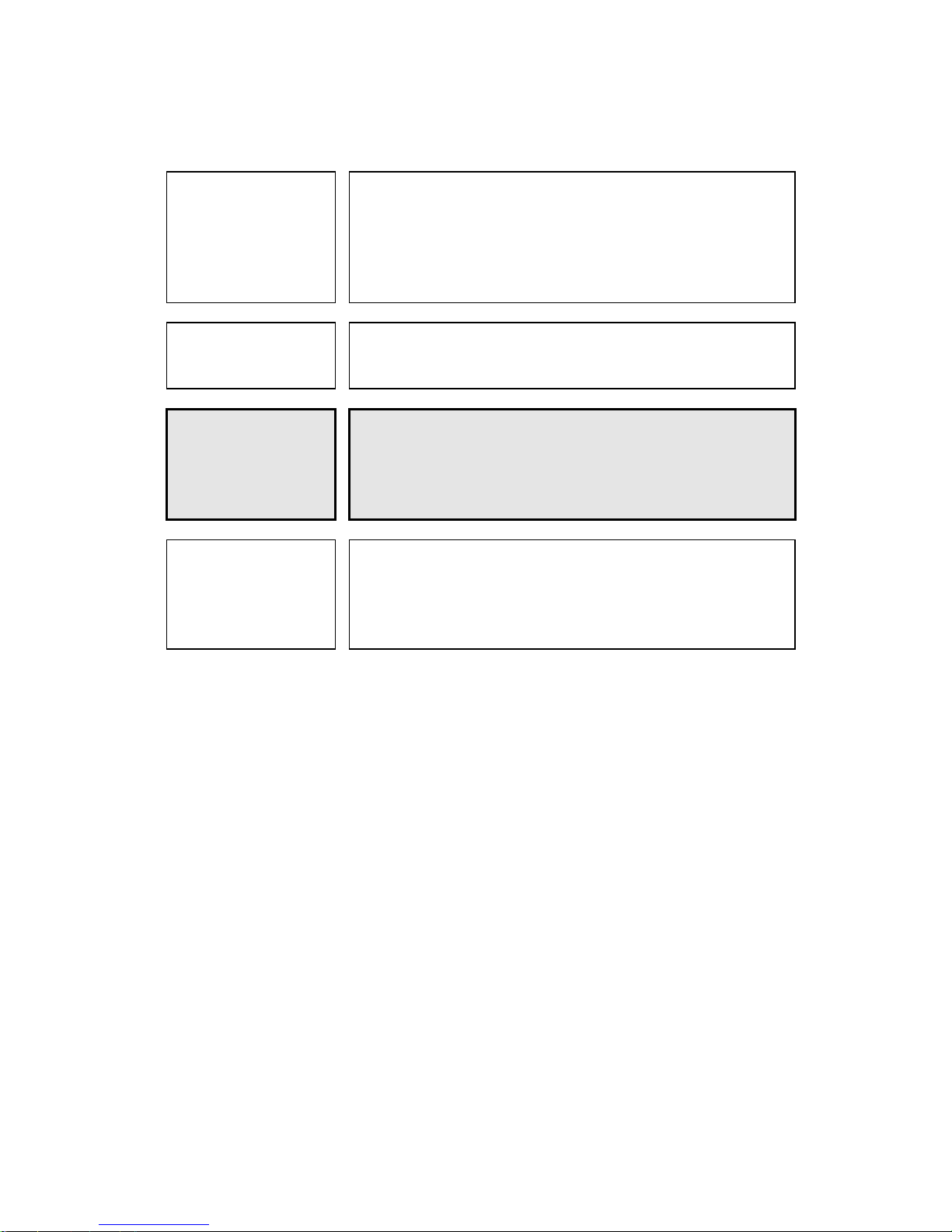
Manual Organization
Product Manual
SCSI Physical
Interface Specifications
SCSI Logical Interface
Specifications
(This Manual)
Maintenance Manual
1. Outline
2. Specifications
3. Data Format
4. Installation Conditions
5. Installation Procedure
6. Diagnosis and Maintenance
1. SCSI Bus
2. SCSI Messages
3. SCSI Bus Error Recovery Processing
1. Command Processing
2. Data Buffer Management
3. Command Specifications
4. Sense Data and Error Recovery Methods
5. Disk Media Management
1. Specifications and Equipment Configuration
2. Maintenance and Diagnosis
3. Troubleshooting
4. Removal and Replacement Procedures
5. Operating Theory
C141-E039-01EN ix
Page 11

Page 12

CONTENTS
page
CHAPTER 1 COMMAND PROCESSING.......................................................... 1-1
1.1 Command Format........................................................................................................... 1-1
1.2 Status Byte ....................................................................................................................... 1-7
1.3 Outline of Command Processing....................................................................................1-10
1.3.1 Single Commands............................................................................................................1-10
1.3.2 Command Link................................................................................................................1-11
1.3.3 Disconnect/Reconnect Procedure..................................................................................... 1-13
1.3.4 Synchronous Mode Data Transfer/Wide Mode Data Transfer..........................................1-17
1.4 Command Queuing Function ......................................................................................... 1-19
1.4.1 Untagged Queuing...........................................................................................................1-19
1.4.2 Tagged Queuing..............................................................................................................1-21
1.5 UNIT ATTENTION Condition...................................................................................... 1-23
1.5.1 Generating the UNIT UNIT ATTENTION Condition.....................................................1-23
1.5.2 Response to the ATTENTION Condition Hold State
and Cancellation Conditions............................................................................................1-25
1.5.3 UNIT ATTENTION Condition Multiple Hold................................................................1-26
1.6 Sense Data Hold State ..................................................................................................... 1-27
1.6.1 Sense Data Hold Conditions............................................................................................1-27
1.6.2 Response to the Sense Data Hold State and Cancellation Conditions...............................1-28
1.7 Command Processing Exceptions................................................................................... 1-29
1.7.1 Overlapping Commands..................................................................................................1-29
1.7.2 Illegal LUN Specification................................................................................................1-30
1.7.3 Reserved Operation Codes...............................................................................................1-30
1.7.4 Command Processing in the Not Ready State..................................................................1-30
1.7.5 Error Recovery Processing...............................................................................................1-32
1.7.6 Reset Processing..............................................................................................................1-34
1.7.7 Fatal Hardware Errors.....................................................................................................1-36
1.8 Data Block Addressing.................................................................................................... 1-37
1.8.1 Definition of Data Space..................................................................................................1-37
1.8.2 Logical Block Addressing................................................................................................1-39
CHAPTER 2 DATA BUFFER MANAGEMENT ............................................... 2-1
2.1 Data Buffer ...................................................................................................................... 2-1
2.1.1 Data Buffer Configuration and Basic Operation...............................................................2-1
2.1.2 Setting the Operating Mode.............................................................................................2-5
C141-E039-01EN xi
Page 13

2.2 Look-ahead Cache Mechanism ...................................................................................... 2-7
2.2.1 Caching Operation...........................................................................................................2-7
2.2.2 Caching Parameters .........................................................................................................2-9
2.2.3 Look-ahead Operation, Look-ahead Volume....................................................................2-10
2.3 Write Cache ................................................................ .....................................................2-11
CHAPTER 3 COMMAND SPECIFICATIONS.................................................. 3-1
3.1 Control/Sense Commands................................................................ ............................... 3-1
3.1.1 TEST UNIT READY (00)...............................................................................................3-1
3.1.2 INQUIRY (12) ...............................................................................................................3-2
3.1.3 READ CAPACITY (25) .................................................................................................3-11
3.1.4 CHANGE DEFINITION (40) .......................................................................................3-13
3.1.5 MODE SELECT (15) .....................................................................................................3-17
3.1.6 MODE SELECT EXTENDED (55) ...............................................................................3-57
3.1.7 MODE SENSE (1A) ......................................................................................................3-59
3.1.8 MODE SENSE EXTENDED (5A) .................................................................................3-65
3.1.9 REZERO UNIT (01) ......................................................................................................3-67
3.1.10 START/STOP UNIT (1B) ..............................................................................................3-68
3.1.11 RESERVE (16) ..............................................................................................................3-70
3.1.12 RESERVE EXTENDED (56) (Not Supported)...............................................................3-74
3.1.13 RELEASE (17) ............................................................................................................... 3-75
3.1.14 RELEASE EXTENDED (57) (Not Supported)................................................................3-77
3.1.15 REQUEST SENSE .........................................................................................................3-78
3.2 Data Access Commands..................................................................................................3-80
3.2.1 READ (08) .....................................................................................................................3-80
3.2.2 READ EXTENDED (28) ...............................................................................................3-81
3.2.3 WRITE (0A) ..................................................................................................................3-82
3.2.4 WRITE EXTENDED (2A) .............................................................................................3-84
3.2.5 WRITE AND VERIFY (2E) ..........................................................................................3-85
3.2.6 VERIFY (2F) .................................................................................................................3-86
3.2.7 SEEK (0B) .....................................................................................................................3-87
3.2.8 SEEK EXTENDED (2B) ...............................................................................................3-88
3.2.9 SET LIMITS (33) ...........................................................................................................3-89
3.2.10 SYNCHRONIZE CACHE (35) ......................................................................................3-92
3.3 Format Commands.......................................................................................................... 3-93
3.3.1 FORMAT UNIT (04) .....................................................................................................3-93
3.3.2 REASSIGN BLOCKS (07).............................................................................................3-104
3.3.3 READ DEFECT DATA (37)...........................................................................................3-108
C141-E039-01ENxii
Page 14

3.4 Maintenance, Diagnostic Commands.............................................................................3-113
3.4.1 SEND DIAGNOSTIC (1D).............................................................................................3-113
3.4.2 RECEIVE DIAGNOSTIC RESULTS (1C).....................................................................3-119
3.4.3 WRITE BUFFER (3B)....................................................................................................3-123
3.4.4 READ BUFFER (3C)......................................................................................................3-127
3.4.5 READ LONG (3E) .........................................................................................................3-131
3.4.6 WRITE LONG (3F) .......................................................................................................3-133
CHAPTER 4 SENSE DATA AND ERROR RECOVERY METHODS ........... 4-1
4.1 Sense Data........................................................................................................................4-1
4.1.1 Sense Data Format...........................................................................................................4-1
4.1.2 Sense Data Basic Information..........................................................................................4-3
4.1.3 Sense Data Additional Information.................................................................................. 4-13
4.2 INIT Error Recovery Methods (Recommended) ..........................................................4-13
4.2.1 End Status Analysis and Error Recovery Method.............................................................4-14
4.2.2 Sense Data Analysis and Error Recovery Method............................................................4-16
4.2.3 Error Logging..................................................................................................................4-25
4.3 Disk Drive Error Recovery Processing..........................................................................4-26
4.3.1 Error States and Retry Processing Procedure...................................................................4-26
4.3.2 Automatic Alternate Block Allocation Processing...........................................................4-28
4.3.3 Error Recovery Processing Control..................................................................................4-30
CHAPTER 5 DISK MEDIA MANAGEMENT ................................................... 5-1
5.1 Defect Management......................................................................................................... 5-1
5.2 Disk Media Initialization................................................................................................. 5-4
5.2.1 Initialization during Installation.......................................................................................5-4
5.2.2 Re-initialization...............................................................................................................5-6
5.3 Data Block Verification Method (Recommended) ........................................................ 5-7
5.4 Alternate Block Allocation Processing........................................................................... 5-9
GLOSSARY
ABBREVIATIONS
INDEX
C141-E039-01EN xiii
Page 15

List of Figures and Tables
< Figures >
Fig. 1.1 Basic Format of 6-byte CDB......................................................................................................1-2
Fig. 1.2 Basic Format of 10-byte CDB....................................................................................................1-2
Fig. 1.3 Status Byte.................................................................................................................................1-7
Fig. 1.4 Data Space Configuration...........................................................................................................1-38
Fig. 2.1 Data Buffer Configuration (In the case of 4 cache segments)......................................................2-2
Fig. 2.2 Example of Data Buffer Operation During Read........................................................................2-3
Fig. 2.3 Example of Data Buffer Operation During Write.......................................................................2-4
Fig. 2.4 Reconnection Timing Control Parameters..................................................................................2-5
Fig. 2.5 Cache Control Parameters..........................................................................................................2-9
Fig. 3.1 Standard INQUIRY Data ...........................................................................................................3-1
Fig. 3.2 VPD Information: Identifier List................................................................................................3-8
Fig. 3.3 VPD Information: Device Serial Number...................................................................................3-9
Fig. 3.4 VPD Information: Operation Modes...........................................................................................3-10
Fig. 3.5 READ CAPACITY Data ...........................................................................................................3-12
Fig. 3.6 MODE SELECT Parameter Structure........................................................................................3-19
Fig. 3.7 MODE SELECT Command (Group 0) Parameter Configuration...............................................3-21
Fig. 3.8 MODE SELECT Parameters: Read/Write Error Recovery Parameters.......................................3-26
Fig. 3.9 MODE SELECT Parameters: Disconnect/Reconnect Parameters...............................................3-34
Fig. 3.10 MODE SELECT Parameters: Format Parameters......................................................................3-37
Fig. 3.11 MODE SELECT Parameters: Drive Parameters.........................................................................3-41
Fig. 3.12 MODE SELECT Parameters: Verify Error Recovery Parameters..............................................3-12
Fig. 3.13 MODE SELECT Parameters: Caching Parameters.....................................................................3-13
Fig. 3.14 MODE SELECT Parameters: Control Mode Parameters............................................................3-14
Fig. 3.15 MODE SELECT Parameters: Additional Error Recovery Parameters........................................3-56
Fig. 3.16 MODE SELECT EXTENDED Commands (Group 2) Parameter Configuration........................3-58
Fig. 3.17 MODE SENSE Command (Group 0) Parameter Configuration..................................................3-62
Fig. 3.18 MODE SENSE Command (Group 2) Parameter Configuration..................................................3-66
Fig. 3.19 SET LIMITS Command: Access Enable Range Specification....................................................3-90
Fig. 3.20 FORMAT UNIT Command Parameter List Configuration.........................................................3-96
Fig. 3.21 Defect Descriptor: Byte Distance Format from Index.................................................................3-99
Fig. 3.22 Defect Descriptor: Physical Sector Address Format...................................................................3-100
Fig. 3.23 REASSIGN BLOCKS Command: Defect Data List Configuration............................................3-105
Fig. 3.24 READ DEFECT DATA Command: Defect Data List Configuration.........................................3-109
Fig. 3.25 SEND DIAGNOSTIC Command: Parameter List Configuration...............................................3-116
C141-E039-01ENxiv
Page 16

Fig. 3.26 SEND DIAGNOSTIC Parameters: Page Code List....................................................................3-117
Fig. 3.27 SEND DIAGNOSTIC Parameters: Logical/Physical Address Conversion.................................3-117
Fig. 3.28 RECEIVE DIAGNOSTIC RESULTS Command: Response Data Configuration.......................3-120
Fig. 3.29 RECEIVE DIAGNOSTIC RESULTS Response Data: Page Code List......................................3-121
Fig. 3.30 RECEIVE DIAGNOSTIC RESULTS Response Data:
Logical/Physical Address Conversion.........................................................................................3-121
Fig. 3.31 WRITE BUFFER Command: Buffer Data (Mode = 000, 001)...................................................3-124
Fig. 3.32 READ BUFFER Command: Buffer Data (Mode = 000, 001).....................................................3-128
Fig. 3.33 READ BUFFER Command: Buffer Descriptor..........................................................................3-130
Fig. 4.1 Expansion Sense Data Format....................................................................................................4-2
Fig. 4.2 Sense Key Inherent Information.................................................................................................4-4
Fig. 4.3 End Status Analysis....................................................................................................................4-14
Tables
Table 1.1 Response to the Link Specification Command............................................................................1-12
Table 1.2 Types of Command and Disconnect Processing..........................................................................1-14
Table 1.3 Sense Data in the Not Ready State.............................................................................................1-31
Table 1.4 Outline of SCSI Bus Error Recovery Processing........................................................................1-33
Table 1.5 Outline of Disk drive Error Recovery Processing.......................................................................1-33
Table 1.6 Reset Processing during Write....................................................................................................1-35
Table 3.1 Combinations of Error Recovery Flags.......................................................................................3-30
Table 3.2 MODE SENSE Data Specifications by Type.............................................................................3-61
Table 3.3 FORMAT UNIT Command Defect Processing..........................................................................3-102
Table 3.4 Error Recovery Flags During the Self-diagnosis Test ................................................................3-114
Table 4.1 Sense Key ..................................................................................................................................4-5
Table 4.2 Sense Code/Subsense Code........................................................................................................4-6
Table 4.3 Sense Data Error Classification..................................................................................................4-17
Table 4.4 Error Recovery Processing Procedure.........................................................................................4-21
Table 4.5 Disk Drive Errors and Number of Retries...................................................................................4-31
C141-E039-01EN xv
Page 17

Page 18
CHAPTER 1 COMMAND PROCESSING
1.1 Command Format
1.2 Status Byte
1.3 Outline of Command Processing
1.4 Command Queuing Function
1.5 UNIT ATTENTION Conditions
1.6 Sense Data Maintenance State
1.7 Command Processing Exceptions
1.8 Data Block Addressing
This chapter describes the basic logical specifications of the IDD command processing functions.
Note The IDD operates as the target (TARG) on the SCSI bus. In the explanations in this
chapter, the IDD is mentioned as “TARG”, except in cases where a particularly clear
distinction is necessary.
1.1 Command Format
Input/output operation commands from INIT (initiator) to the IDD are accomplished by the
CDB (Command Descriptor Block). The CDB is information transferred from INIT to TARG
in the COMMAND phase. In a number of commands, the parameters which are necessary for
command execution in the DATA OUT phase may be specified in addition to the CDB
specification. Details concerning these are described in the specifications for each individual
command in Chapter 3.
The CDB used by the IDD has 2 formats, one with a length of 6 bytes and the other with a
length of 10 bytes. The basic format of each respective CDB is shown in Fig. 1.1 and Fig. 1.2.
C141-E039-01EN 1 - 1
Page 19
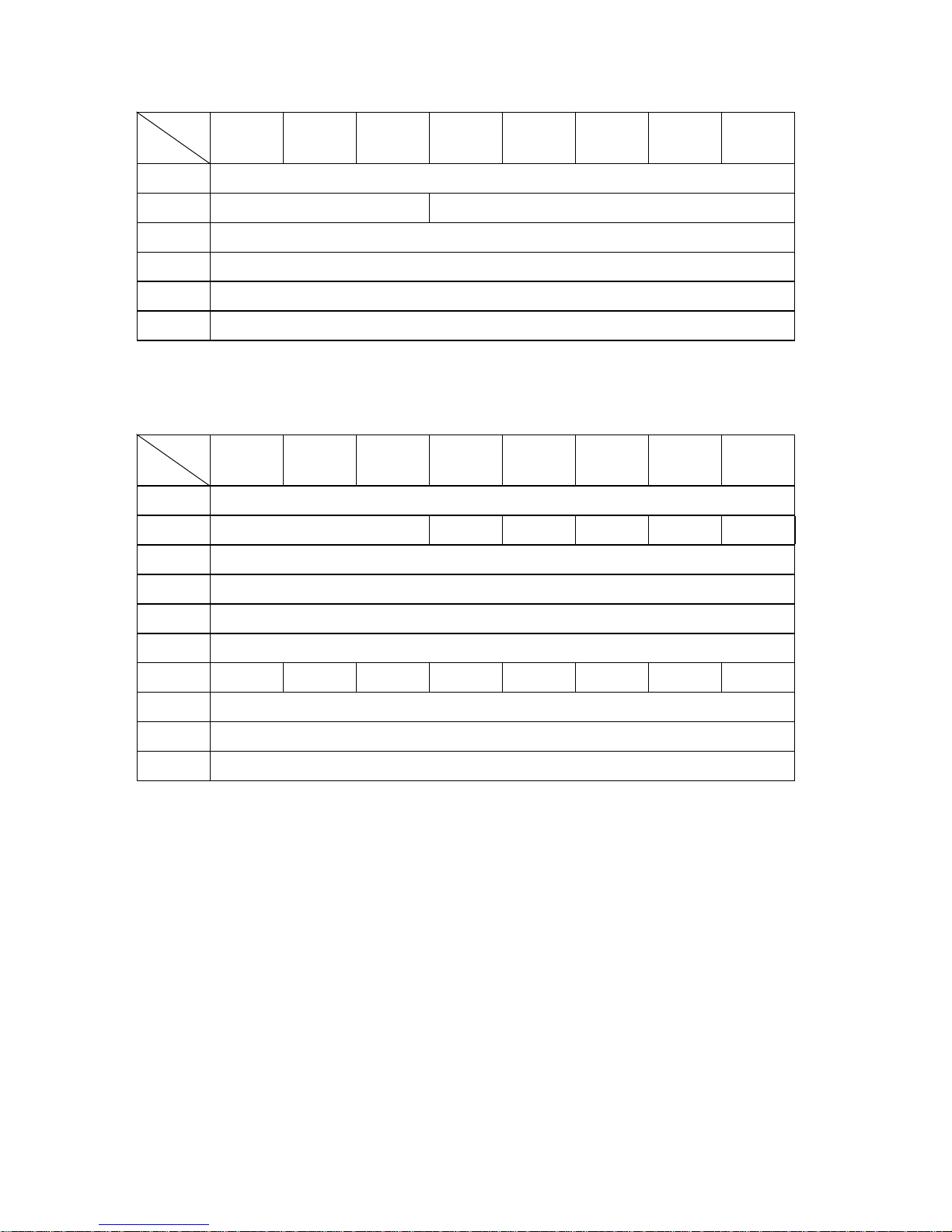
Bit
Byte
7 6 5 4 3 2 1 0
0 Operation Code
1 LUN Logical Block Address (MSB)
2 Logical Block Address
3 Logical Block Address (LSB)
4 Transfer Data Length
5 Control Byte
Fig. 1.1 6 Byte CDB Basic Format
Bit
Byte
7 6 5 4 3 2 1 0
0 Operation Code
1 LUN 0 0 0 0 0
2 Logical Block Address (MSB)
3 Logical Block Address
4 Logical Block Address
5 Logical Block Address (LSB)
6 0 0 0 0 0 0 0 0
7 Transfer Data Length (MSB)
8 Transfer Data Length (LSB)
9 Control Byte
Fig. 1.2 10 Byte CDB Basic Format
The meanings of each of the fields in the CDB are explained below. Depending on the type of
command, the basic format of the CDB, the definitions of fields and their meanings may
differ. Details are described in the specifications for each individual command in Chapter 3.
C141-E039-01EN1 - 2
Page 20
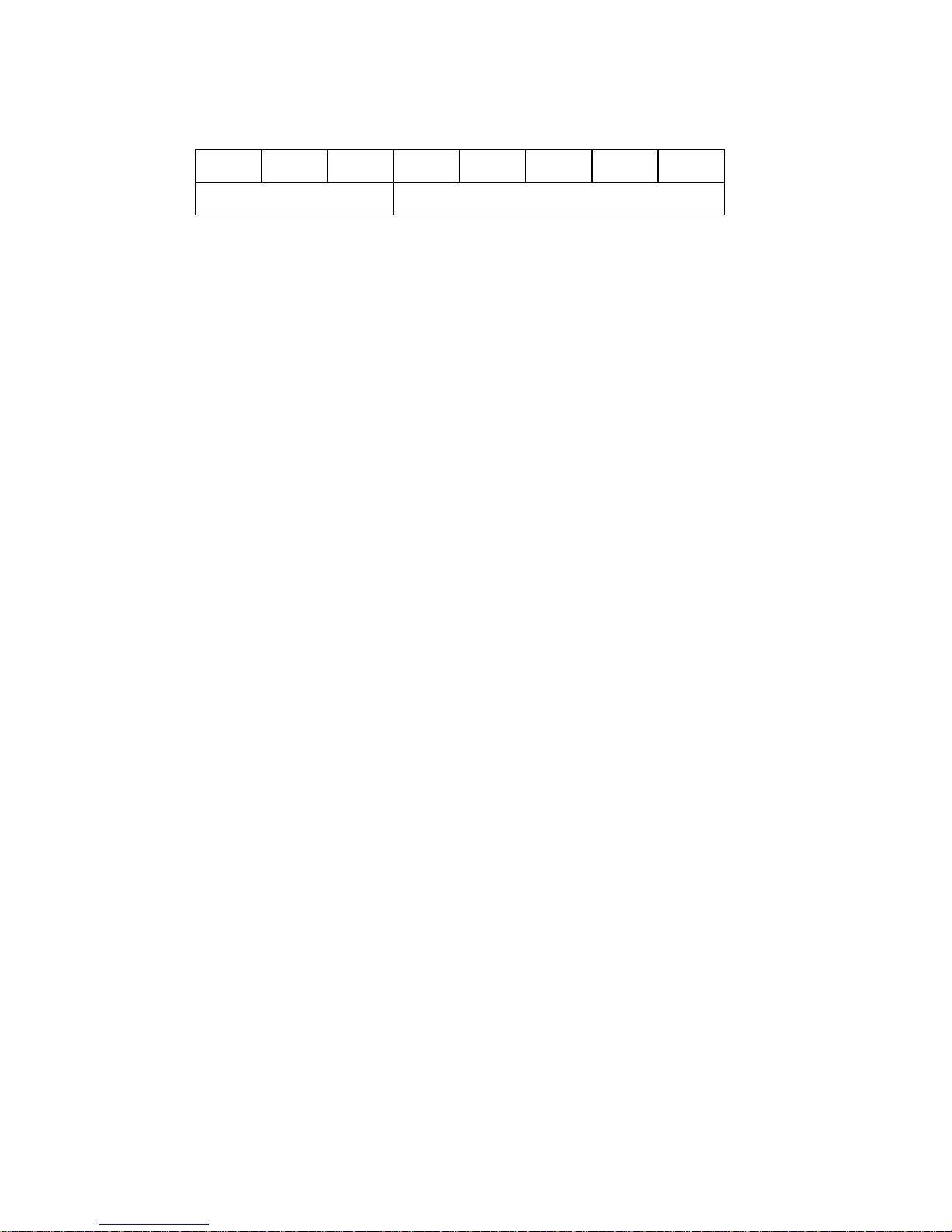
(1) Operation code
Bit 7 6 5 4 3 2 1 0
Group Code Command Code
The top byte of all CDBs shows the format and type of command to be executed.
a. Group Code
The group code specifies the number of bytes and format of the CDB. The groups of
commands shown below are used in the IDD.
• Group 0 (“000”): 6-byte CDB (Shown in Fig. 1.1)
• Group 1 (“001”): 10-byte CDB (Shown in Fig. 1.2)
• Group 2 (“010”): 10-byte CDB (Shown in Fig. 1.2)
• Group 3 (“110”): 10-byte CDB (Shown in Fig. 1.2)
• Group 4 (“111”): Reserved Operation Code (Shown in item 1.7.3.)
b. Command Code
Command code specifies the type of command in each group.
(2) LUN (Logical Unit Number)
This field specifies the address of the logical unit (device) connected under the TARG in cases
where the IDENTIFY message is not used. If the IDENTIFY message is used, the value of the
CDB’s LUN field is disregarded when the LUN is specified.
Note:
It is possible that the definition of this field may be changed in future SCSI standards. It is
recommended that the LUN be specified using the IDENTIFY message, and that a zero be
specified in this CDB field.
(3) Logical Block Address
This field shows the top logical data block address of the data block on the disk media to be
processed by the command. In the group 0 CDB, 21 bit block addressing is possible and in
the group 1, group 2 and group 6 CDBs, 32 bit block addressing is possible. Specifications
for logical data block addressing in the IDD are described in section 1.8.
C141-E039-01EN 1 - 3
Page 21

(4) Transfer Data Length
In this field, the length of data to be transferred between INIT and TARG when the command
is executed is specified by the number of logical data blocks or the number of bytes. In
subsequent descriptions, the former is called the “transfer block count” and the latter is called
the “transfer byte length” or “parameter list length.”
Furthermore, this field may be used with a different meaning, or it may not have any meaning
at all, depending on the type of command. There are also some commands which allocate 3 or
more bytes as the transfer data length field. Detailed specifications of these commands are
described in the individual command specifications in Chapter 3.
a. Transfer Block Count
When the “Transfer Data Length” is specified as the “Transfer Block Count,” this field
specifies the number of logical data blocks to be transferred between INIT and the IDD.
In commands where this field is 1 byte in length, if the field’s specified value is 0, it is
regarded as specifying 256 blocks, and it is possible to specify a block count ranging from
1 to 256 blocks. On the other hand, in commands where this field is 2 bytes in length, if
the field’s specified value is 0, no data transfer is executed. It is possible to specify a
block count ranging from 0 to 65,535 blocks.
b. Transfer Byte Length or Parameter List Length
When this field is specified as the “Transfer Byte Length” or “Parameter List Length,” that
command specifies data length to be transferred between the INIT and the IDD, expressed
as the number of bytes. When 0 is specified in this field, data transfer is not executed,
except in cases where it is expressly stated in the individual command specifications in
Chapter 3.
In commands which send parameters necessary for executing a command from the INIT to
the IDD, this field is called the “Parameter List Length,” and it specifies the total number
of types in the parameter list which the INIT is sending.
On the other hand, in commands for receiving information from the IDD (REQUEST
SENSE, INQUIRY, etc.), this field is called the “Transfer Byte Length,” and specifies the
maximum number of bytes (the which the INIT can receive (the number of bytes of area
secured within the INIT for receiving information). The IDD transfers either the number
of effective bytes of the type of information specified in the command, or the value
specified in the “Transfer Byte Length” field, whichever is the smallest number of bytes,
and only that number, to the INIT.
C141-E039-01EN1 - 4
Page 22
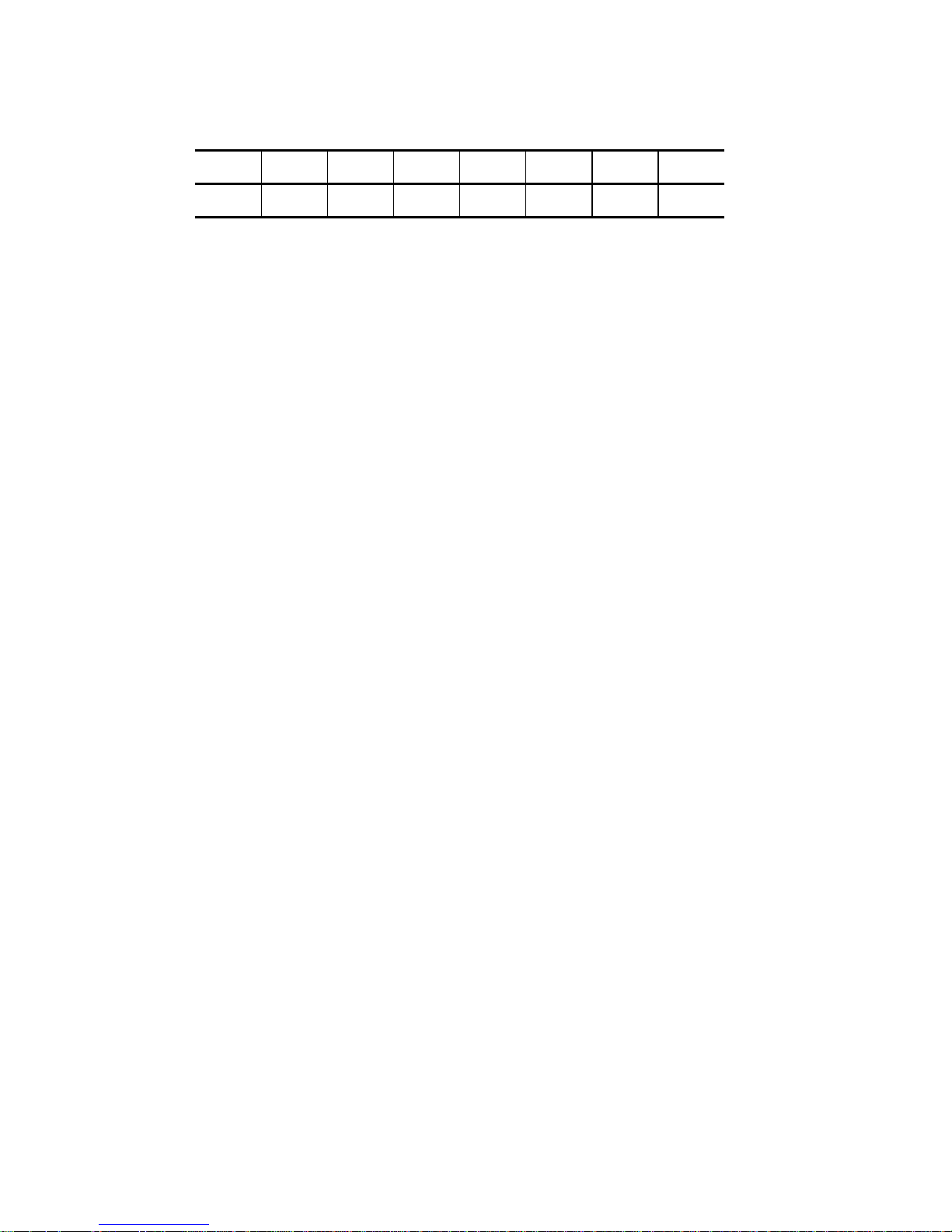
(5) Control Byte
Bit 7 6 5 4 3 2 1 0
0 0 0 0 0 0 Flag Link
a. Link
Command link is specified by this bit is “1.” Details of the operation of the command link
are described in item 1.3.2.
b. Flag
This bit is valid only when “1” is specified in the Link bit. If “0” is specified in the Link
bit, “1” must not be specified in this bit.
This bit specifies the type of message sent from the TARG to the INIT when a command
which is a link specification has been completed normally. The IDD sends the LINKED
COMMAND COMPLETE WITH FLAG message when this bit is “1,” and the LINKED
COMMAND COMPLETE message when this bit is “0,” to the INIT.
Normally, this bit is used to generate an interrupt to software in the INIT when execution
of a specific command in a group of commands linked together in a series has been
completed.
c. Bit 7, 6 (vendor unique)
Except in cases where it is expressly specified in the individual commands, specification
of these bits has no meaning, and the IDD disregards the specified values.
Note
It is possible that bits 7 and 6 of the control byte will be used in future product
specifications as an inherent control field. It is recommended that zeros be specified
in this field.
C141-E039-01EN 1 - 5
Page 23

(6) Handling an Illegal CDB
If there is an error in the contents of a description (specification) in the CDB, or if there is an
error in the specifications in parameters transferred from the INIT, that command ends with a
CHECK CONDITION status. In the case of a command to change the data on the disk media,
when there is an error in the CDB’s specifications, the disk media is not changed by that
command, but when there is an error in the parameters transferred in the DATA OUT phase,
the contents of the disk media in the range specified by the command may be changed. Also,
even in cases where there is an error in the CDB’s specifications in a command accompanying
the DATA OUT phase, the DATA OUT phase is executed after the COMMAND phase is
terminated, but those data are not used. For example, if there is an error in the CDB
specification of a WRITE command, the IDD executes the transfers several bytes of data (the
data length to be transferred is not specified), but those data are not written to the disk media.
Details are described in the individual command specifications in Chapter 3.
If there is an error in the CDB specification in a command which executes disconnect
processing (shown in item 1.3.3), the disconnect processing may be executed after the
COMMAND phase is terminated. In this case, reconnect processing is executed afterward and
the status (CHECK CONDITION) is reported.
Note:
If a CDB with an undefined group code (group 3, 4, 5) is specified, the IDD requests
transfer of 10 bytes in the COMMAND phase and if the group code [group 5] is specified,
it requests transfer of 12 bytes. After that has been received, the status (CHECK
CONDITION) is reported.
C141-E039-01EN1 - 6
Page 24
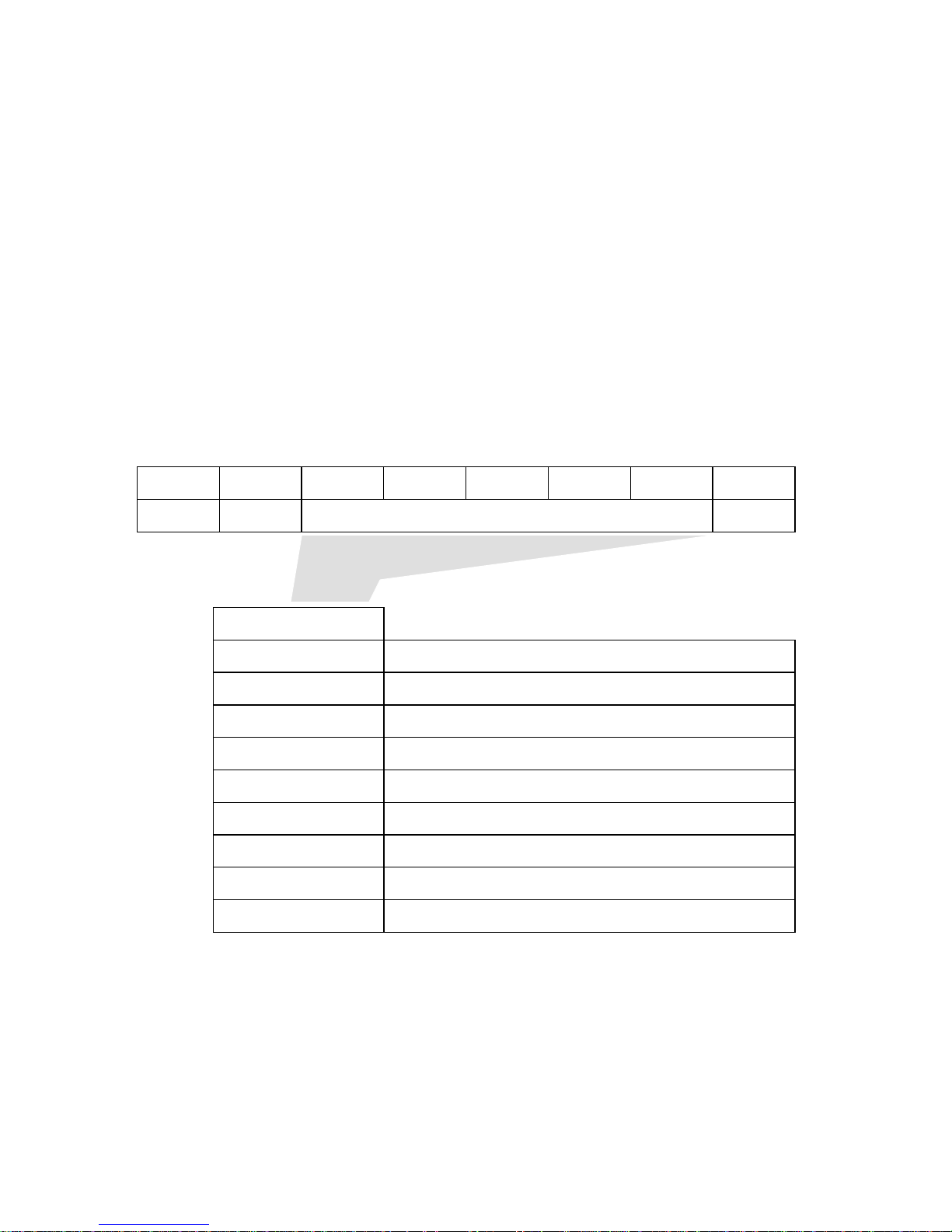
1.2 Status Byte
Fig. 1.3 shows status byte format and the type of status the IDD supports.
The status byte is one byte of information sent from the TARG to the INIT in the STATUS
phase when one command is completed, and notifies the INIT of the results of the command’s
execution. The status byte is also sent even in cases when the TARG is in a state which it
makes it impossible for it to execute the command when it receives a request for an
input/output operation. However, if the command is cleared by switching to the BUS FREE
phase forcibly through an ABORT message, an ABORT TAG message, a CLEAR QUEUE
message, a BUS DEVICE RESET message, a RESET condition or a SCSI bus error state, etc.,
the status byte for that command is not reported.
After the TARG reports the status byte in the STATUS phase, it will always send a
COMMAND COMPLETE message or a LINKED COMMAND COMPLETE (WITH FLAG)
message, and notify the INIT of the validity of the status byte.
Bit 7 6 5 4 3 2 1 0
0 0 Status Byte Code 0
Bit 5 4 3 2 1
0 0 0 0 0 GOOD Status
0 0 0 0 1 CHECK CONDITION Status
0 0 0 1 0 CONDITION MET Status
0 0 1 0 0 BUSY Status
0 1 0 0 0 INTERMEDIATE Status
0 1 0 1 0 INTERMEDIATE CONDITION MET Status
0 1 1 0 0 RESERVATION CONFLICT Status
1 0 0 0 1 COMMAND TERMINATED Status
1 0 1 0 0 QUEUE FULL Status
Figure 1.3 Status Byte
C141-E039-01EN 1 - 7
Page 25

(1) GOOD Status
This status indicates that execution of the command ended normally.
(2) CHECK CONDITION Status
This status is reported in the following cases a) to c). The IDD generates sense data when it
reports this status and displays the detailed cause. The INIT issues a REQUEST SENSE
command when it receives this status and should sample sense data.
a) If the sense key of the sense data indicates RECOVERED ERROR [=1], the last command,
which is the final command, indicates that it ended normally with the error recovery
processing executed by the IDD.
b) If the sense key of the sense data indicates UNIT ATTENTION [=6], it indicates that the
IDD was holding the UNIT ATTENTION condition. Details of the UNIT ATTENTION
condition are described in section 1.5.
c) In cases other than the above, it indicates that command execution is impossible, or that
command execution was terminated abnormally.
(3) CONDITION MET Status
This status indicates that the PRE-FETCH command condition has been met, and is reported
when it is possible to secure the cache memory area necessary for reading all the logical data
blocks specified in the PRE-FETCH command (in the case of “Immed = 1”), or when reading
of all the specified logical data blocks is completed (in the case of “Immed = 0”).
The IDD does not support the PRE-FETCH command. Therefore, reporting of this status is
not reported.
(4) BUSY Status
This status indicates that the IDD is in the busy state or that it cannot receive a new command.
Normally, an INIT that receives this status reissues the original command after waiting an
appropriate period of time.
The IDD reports the BUSY status in the following cases (the command stack function is
explained in section 1.4).
a) If the IDD receives a new command while it is executing a command, is queuing or is
executing its initial self-diagnosis (except a command with an object other than disconnect
processing as shown in item 1.3.3), if the INIT which issued that command does not
satisfy the disconnect enable conditions.
b) If the IDD receives a command with an object other than disconnect processing (as shown
in item 1.3.3) while it is executing a command, is queuing or is executing its initial self-
diagnosis.
c) If the DISCONNECT message for command queuing has been rejected by the INIT.
d) If a command with untagged disconnect processing as its object is received while the
command queue is full.
C141-E039-01EN1 - 8
Page 26

(5) INTERMEDIATE Status
This status indicates that a command which specifies a link (except the final command in a
group of linked commands with “1” as its Link bit) has been completed normally. If a
command which specifies a link is completed abnormally and the CHECK CONDITION
status or RESERVATION CONFLICT status is reported, the command link is broken an the
subsequent linked commands are not executed.
(6) INTERMEDIATE CONDITION MET Status
This status indicates that the PRE-FETCH command intermediate condition has been met, and
is reported when it is possible to secure the cache memory area necessary to read all the logical
data blocks specified in a PRE-FETCH command which specifies a link (in the case of
“Immed = 1”), or when reading of all the specified logical data blocks is completed (in the
case of “Immed = 0”).
The IDD does not support the PRE-FETCH command. Therefore, this status is not reported.
(7) RESERVATION CONFLICT Status
This status indicates that the IDD is reserved by another INIT, and that use is impossible until
the reserved status is canceled. Normally, an INIT which receives this status reissues the
original command after waiting an appropriate period of time.
(8) COMMAND TERMINATED Status
This status is reported when the IDD has completed the input/output operation it was
executing when it received a TERMINATE I/O PROCESS message from the INIT.
(9) QUEUE FULL Status
This status is reported if the IDD cannot register a tagged command it has received in the
command queue because there is no empty space in the command queue.
C141-E039-01EN 1 - 9
Page 27

1.3 Outline of Command Processing
1.3.1 Single Commands
Some processing examples of single commands which are the most basic operations on the
SCSI bus are shown below. Furthermore, if disconnect processing is permitted, it may be
accompanied by disconnect/reconnect processing during the interval until execution is
completed, depending on the type of command, but this operation is omitted in the following
explanation. The disconnect function is described in item 1.3.3.
1) The INIT sets the command’s initial values in the command pointer, data pointer and
status pointer.
2) The INIT selects the TARG in the SELECTION phase after acquiring the right to use the
SCSI bus in the ARBITRATION phase. After the SELECTION phase is ended, the right
to control the SCSI bus is entrusted to the TARG.
3) If the ATTENTION condition exists when the TARG responds to the SELECTION phase,
the TARG executes the MESSAGE OUT phase. Normally, the INIT sends the IDENTIFY
message as the initial message and specifies the device (LUN) that is the object of the
operation.
4) The TARG next executes the COMMAND phase and receives the CDB from the INIT.
The TARG judges the length of the CDB by the group code in the first byte of the CDB
and requests transfer of the necessary number of bytes.
5) The TARG interprets the contents of the command and executes the requested operation.
In the case of commands for which data transfer on the SCSI bus is necessary, the DATA
IN or the DATA OUT phase is executed.
6) When execution of the command is completed, the TARG notifies the INIT of the
execution results by the status byte in the STATUS phase.
7) The TARG notifies the INIT of the COMMAND COMPLETE message in the final
MESSAGE IN phase and enters the BUS FREE phase.
C141-E039-01EN1 - 10
Page 28

1.3.2 Command Link
The command link function is a function which causes the TARG to execute continuous
processing of multiple commands. Some examples of command link processing are shown
below.
1) The INIT sets the command’s initial values in the command pointer, data pointer and
status pointer.
2) Acquiring of the right to use the SCSI bus, selection of the TARG and specification of the
LUN by the IDENTIFY message are the same as in the case of single commands.
3) The TARG receives commands from the INIT in the COMMAND phase, but “1” is
specified in the Link bit of the CDB’s control byte.
4) The TARG analyzes the command and executes the requested processing.
5) If processing of the command is completed normally, the TARG notifies the INIT of the
INTERMEDIATE status in the STATUS phase. At this time, the command link function
becomes effective.
6) The TARG informs the INIT of the LINKED COMMAND COMPLETE or the LINKED
COMMAND COMPLETE WITH FLAG message, depending on the value of the Flag bit
in the CDB’s control byte. When the INIT has received the LINKED COMMAND
COMPLETE (WITH FLAG) message, the command, data and status pointers are updated
to the initial values for the next command in the link.
7) The TARG enters the COMMAND phase immediately after the MESSAGE IN phase and
receives the command it is to execute next. After that, it performs either single command
(Link bit = “0”) processing or command link (Link bit = “1”) processing.
The command link continues until a command with “0” specified in the Link bit of its CDB is
issued or until a command terminates abnormally.
The command link function is made effective only in the case that commands with link
specifications are completed normally. If a command with a link specification is completed in
an error state or in an exception state, the command link function is invalidated. Table 1.1
shows the response of the IDD when commands with a Link specification are terminated.
C141-E039-01EN 1 - 11
Page 29
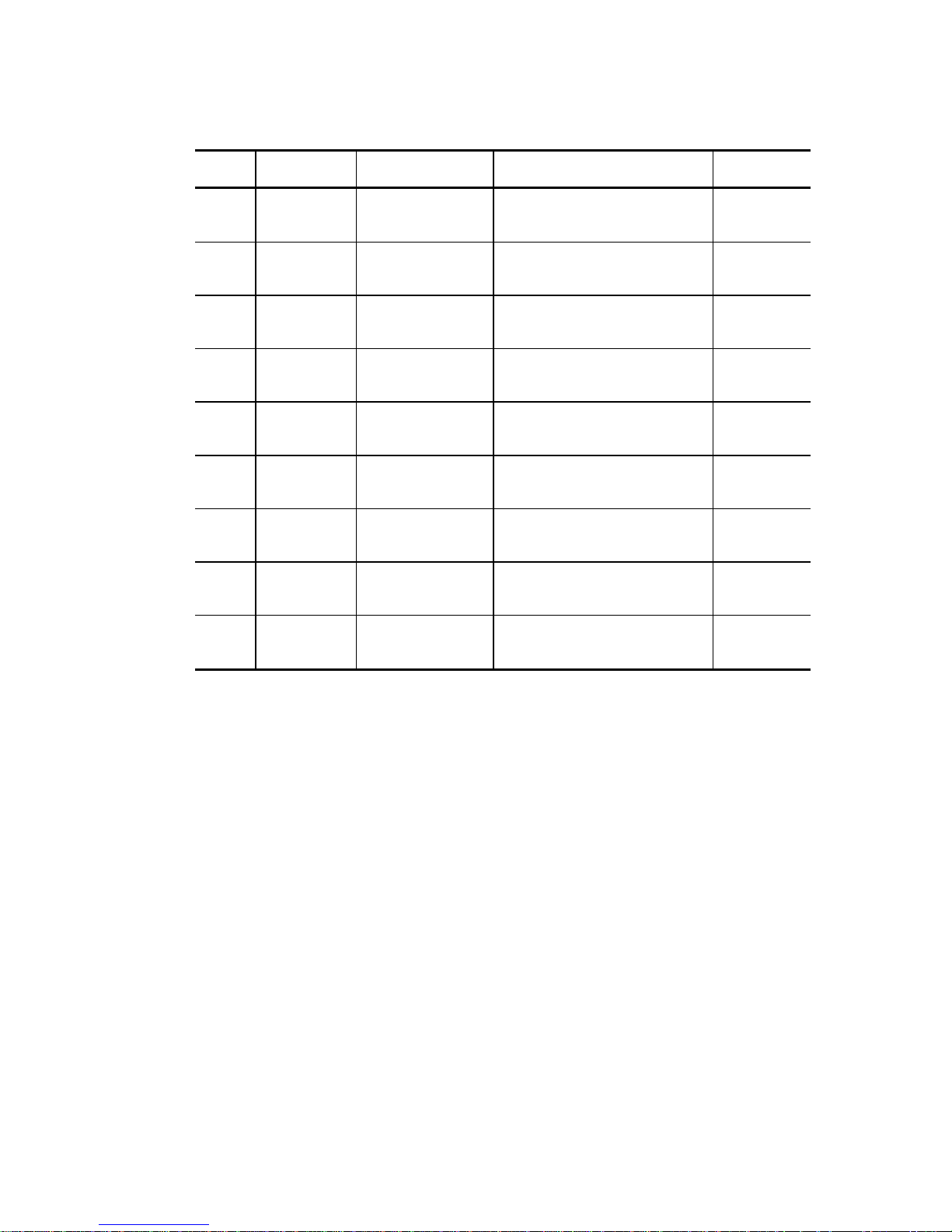
Table 1.1 Responses to Link Specification Commands
Flag End Status Status Message Link Function
0
1
×
0
1
×
×
×
×
Completed
Normally
Completed
Normally
Completed
Abnormally
Conditions Met INTERMEDIATE
Conditions Met INTERMEDIATE
Unable to Start
Receive
Reserved State RESERVATION
Forced
Termination
Queue Full
State
INTERMEDIATE LINKED COMMAND
INTERMEDIATE LINKED COMMAND
CONDITION
CONDITION MET
CONDITION MET
COMMAND
TERMINATED
QUEUE FULL COMMAND COMPLETE Not Effective
Effective
COMPLETE
Effective
COMPLETE WITH FLAG
CHECK
BUSY COMMAND COMPLETE Not Effective
CONFLICT
COMMAND COMPLETE Not Effective
LINKED COMMAND
COMPLETE
LINKED COMMAND
COMPLETE WITH FLAG
COMMAND COMPLETE Not Effective
COMMAND COMPLETE Not Effective
Effective
Effective
Only a single logical unit can operate a series of linked commands. When the IDD receives
the first command, the logical unit specified by the IDENTIFY message or the LUN field of
the CDB becomes the object of operation in a series of linked commands and the values
specified in the LUN field in the 2nd and subsequent CDBs are disregarded.
Note:
An INIT which uses the command link function must make the ATN signal in the
SELECTION phase TRUE and notify the TARG that it is capable of receiving messages
other than the COMMAND COMPLETE message. If “1” has been specified in the Link
bit of the CDB without the ATN being made TRUE by the INIT in the SELECTION
phase, the IDD terminates that command abnormally by sending a CHECK CONDITION
status (ILLEGAL REQUEST [=5] / Invalid field in CDB [=24-00]).
C141-E039-01EN1 - 12
Page 30

1.3.3 Disconnect/Reconnect Processing
When processing is performed by the TARG during the command execution process which
does not require operation on the SCSI bus, the TARG temporarily returns the SCSI bus to the
BUS FREE phase by disconnect processing, making it possible for the TARG to execute the
command internally. Through this function, the INIT is enabled to process multiple
commands on the SCSI bus.
(1) Conditions where disconnects are permitted and commands which are the object of
disconnect processing
If all of the conditions shown below for permitting a disconnect are satisfied, the IDD executes
disconnect processing. However, As shown in Table 1.2, disconnect processing may be valid
or invalid, and the disconnect processing execution timing may differ, depending on the type
of command.
Conditions for Permitting a Disconnect
1) The SCSI ID of the INIT is notified in the SELECTION phase.
2) The INIT generates the ATTENTION condition in the selection phase.
3) The INIT notifies the TARG that disconnect processing is permitted by an IDENTIFY
message.
C141-E039-01EN 1 - 13
Page 31

Table 1.2 Types of Command and Disconnect Processing (1 / 2)
Commands which execute disconnect processing. (Note 2)
Commands which are not objects of disconnect processing. (Note 1)
C CHANGE DEFINITION (40) O
F FORMAT UNIT (04) O
I INQUIRY (12) O
L LOG SENSE (4D) O
M MODE SELECT (15) O
MODE SELECT EXTENDED (55) O
MODE SENSE (1A) O
MODE SENSE EXTENDED (5A) O
N
P
R READ (08) O
READ BUFFER (3C) O
READ CAPACITY (25) O
READ DEFECT DATA (37) O
READ EXTENDED (28) O
READ LONG (3E) O
REASSIGN BLOCKS (07) O
RECEIVE DIAGNOSTIC RESULTS (1C) O
RELEASE (17) O
REQUEST SENSE (03) O
RESERVE (16)
REZERO UNIT (01) O
S SEEK (0B) O
SEEK EXTENDED (2B) O
SEND DIAGNOSTIC (1D) O
START/STOP UNIT (1B) O
SYNCHRONIZE CACHE (35) O
T TEST UNIT READY (00) O
V VERIFY (2F) O
W WRITE (0A) O
WRITE AND VERIFY (2E) O
WRITE BUFFER (3B) O
WRITE EXTENDED (2A) O
WRITE LONG (3F) O
WRITE SAME (41) O
(Note 1) Commands which are not objects of disconnect processing: In cases only where
commands are issued without a tag, queuing processing (see section 1.4) and disconnect
processing cannot be performed in the execution sequence.
(Note 2) Commands which execute disconnect processing: Regardless of command queuing, in a
command’s execution process (after the COMMAND phase is completed and during or after the
completion of data transfer), disconnect processing is performed. However, in the case of
commands with a data state (in cases where it is hit in the cache, etc.), or with a number of
processing modes, other than cases where the command is in a queue, disconnect processing
may not be executed depending on the processing content specification of the command.
C141-E039-01EN1 - 14
Page 32

(2) Basic Disconnect Processing Procedure
Disconnect processing is executed basically by the following processing procedure.
1) If the IDD judges that it is possible for it to disconnect from the SCSI bus during execution
of a command, it sends a DISCONNECT message to the INIT and enters the BUS FREE
phase. At this time, if necessary, the IDD sends a message to activate a pointer in the INIT
which precedes sending of the DISCONNECT message. Furthermore, for details
concerning the pointer mechanism, refer to the SCSI pointer description in “SCSI Physical
Interface Specifications” and “Chapter 2 SCSI Messages.”
2) After the IDD enters the BUS FREE phase, it is possible for the INIT to issue other
commands. Also, it is possible for an IDD which has performed disconnect processing to
receive input/output operation requests from each INIT (this is explained in the description
of the command queuing function in section 1.4).
3) The IDD executes the command which performs disconnect processing internally.
4) After that, the IDD executes reconnection processing at the point when it is necessary for
operation on the SCSI bus, reconnecting with the INIT (See item (6) concerning
reconnection processing).
(3) Disconnect Processing Procedure after COMMAND Phase Execution
If commands are queued (see section 1.4), disconnect processing is performed immediately after the
COMMAND phase execution is completed. In this case, the IDD switches from the COMMAND
phase to the MESSAGE IN phase and sends the DISCONNECT message to the INIT.
(4) Disconnect Processing Procedure After Data Transfer Execution
In commands which accompany a data transfer, disconnect processing may be performed
during DATA IN or DATA OUT phase execution or after transfer of the final data is
completed. In this case, caution is necessary when executing the following types of pointer
controls.
a. If disconnecting during a data transfer
In cases where data transfer has begun (DATA IN phase or DATA OUT phase) and it will
take time until transfer of subsequent data can be transferred (Example: When the data
buffer has been emptied by a READ command, or the data buffer has ceased to be empty
due to a WRITE command), disconnect processing is performed during data transfer. In
this case, the IDD sends the SAVE DATA POINTER message before sending the
DISCONNECT message. When the INIT receives the SAVE DATA POINTER message,
it must save the current value of the current data pointer and make it possible to transfer
the subsequent data at reconnection time.
b. If disconnecting after the final data transfer is completed
In the case of a disconnect after transfer of all the data necessary for execution of a
command has been completed normally, (Example: a WRITE command), the IDD sends a
DISCONNECT message after sending the SAVE DATA POINTER message.
After that, the IDD executes reconnection processing and enters the STATUS phase
immediately, reporting the status byte without requesting a data transfer.
C141-E039-01EN 1 - 15
Page 33

Note
In disconnect processing in this case, transfer of all the data accompanying execution of the command
is completely and there is actually no necessity for the SAVE DATA POINTER message.
However, by issuing the SAVE DATA POINTER message, processing time increases due
to the message transfer, but as a result of the pointer restore operation that is executed
internally by the INIT during reconnection processing for the status report, the current data
pointer can reflect the final results of the data transfer.
(5) Disconnect Processing Exceptions
When the previously mentioned disconnect processing is executed, if the ATTENTION condition is
generated for the DISCONNECT message sent by the IDD and the INIT returns the MESSAGE
REJECT message, the IDD executes the command with the connections to the SCSI bus remaining
as is, without executing disconnect processing. Cases of disconnect processing in which a pointer
operation is necessary and the SAVE DATA POINTER message is rejected are the same.
(6) Reconnection Processing Procedure
The reconnection processing procedure is as shown below.
1) The IDD executes the ARBITRATION phase at the point when processing on the SCSI
bus is necessary and acquires the right to control the SCSI bus, then reconnects with the
INIT in the RESELECTION phase.
2) After that, the IDD sends the IDENTIFY message to the INIT and notifies it of the logical
unit number (LUN) necessary for reconnection processing. If a tagged queuing command
is executed, the TARG sends the SIMPLE QUEUE TAG message to inform the INIT of
the tag ID. The INIT fetches the save (Saved) pointer (command, data and status)
corresponding to the LUN specified at this time and restores it to the current pointer.
Note:
1) If there is no response to the INIT within the specified time (default: 250 ms) in the
RESELECTION phase, the IDD performs time out processing, then enters the BUS FREE
phase. In this case, after waiting 200 s or longer, the IDD executes the predetermined
number of retries (re-executing the RESELECTION phase). However, if it still cannot
reconnect with the INIT after that, the IDD clears the command necessary for reconnection
processing and generates sense data indicating ABORTED COMMAND[=B]/Select
/Reselect failure[=45-80].
2) If the NIT rejects the IDENTIFY message, or if the SIMPLE QUEUE TAG message is rejected
when executing a tagged queuing command, the IDD clears the command that was being
executed during reconnection processing and enters the BUS FREE phase. In this case, the IDD
generates sense data indicating ABORTED COMMAND[=B]/Message error[=43-00].
3) After the INIT that accepts the IDENTIFY message normally completes the pointer restore
operation, it should make the ACK signal for the IDENTIFY message FALSE. If the
ATTENTION condition does not exist when the ACK signal becomes FALSE during
sending of the IDENTIFY message, the IDD regards the reconnection processing as having
been normally completed and begins subsequent processing.
C141-E039-01EN1 - 16
Page 34

For further details, refer to CHANGE DEFINITION parameter list (Reselection Retry, Reselection
Time-out Delay) in item 3.1.4 and SCSI Bus (RESELECTION Phase) in Chapter 1 of “SCSI
Physical Interface Specifications” and SCSI Bus Error Recovery Processing in Chapter 3.
1.3.4 Synchronous Mode Data Transfer/Wide Mode Data Transfer
The IDD is equipped with a synchronous mode data transfer function and wide mode data
transfer function for processing high speed data transfers (DATA IN and DATA OUT phases)
on the SCSI bus. Data transfers on the SCSI bus can be executed in any desired combination
of the asynchronous mode or synchronous mode and in 8 bit widths or 16 bit widths (wide
mode), but by using synchronous mode data transfer or wide mode data transfer, command
processing time is shortened and throughput for input/output processing by multiple command
processing using idle time on the SCSI bus can be improved.
Following IDD power on, after generating a RESET condition on the SCSI bus or after one of
the INITs issues a BUS DEVICE RESET message, the IDD’s data transfer mode (default
mode) is the asynchronous mode. In order to use wide mode data transfer, the INIT must
exchange a SYNCHRONOUS DATA TRANSFER REQUEST message with the IDD, and the
parameters necessary for executing synchronous mode transfers must be decided. When
exchange of the WIDE DATA TRANSFER REQUEST message is completed, if the
synchronous mode has been established between the INIT and IDD previously, caution should
be exercised as to whether the asynchronous mode is set.
The INIT which uses wide mode data transfer normally sends the WIDE DATA TRANSFER
REQUEST to the IDD following the IDENTIFY message after the initial SELECTION phase,
and requests that the TARG (IDD) set the SCSI bus width in the wide mode. Also, if
synchronous mode data transfer is used, after settling the SCSI bus width, the INIT exchanges
the SYNCHRONOUS DATA TRANSFER REQUEST message and requests that the TARG
(IDD) set the synchronous data transfer mode.
The data transfer mode set with the INIT once is effective until a RESET condition is
generated or until a BUS DEVICE RESET message is issued by any one of the INITs.
Therefore, in order for the INIT to avoid overhead time for message exchange, it is not
necessary to send the WIDE DATA TRANSFER REQUEST message or the
SYNCHRONOUS DATA TRANSFER REQUEST message to the TARG each time the
SELECTION phase is executed.
When the synchronous mode transfer/wide mode data transfer request through the
specification of the CHANGE DEFINITION command (synchronous mode transfer/wide
mode data transfer request) is permitted, and the IDD is maintaining the default transfer mode
(asynchronous, 8 bit width), if a WIDE DATA TRANSFER REQUEST message is not sent
from the INIT, the IDD enters the MESSAGE IN phase immediately after the COMMAND
phase and sends the WIDE DATA TRANSFER REQUEST message to the INIT, and tests the
16 bit wide mode setting. After establishing the bus width, the IDD sends the
SYNCHRONOUS DATA TRANSFER REQUEST message to the INIT and tests the
synchronous mode transfer parameters (REQ/ACK offset = 15, Transfer period = 100 ns).
The IDD maintains separate data transfer mode settings between itself and each INIT.
Therefore, an INIT which uses asynchronous mode transfer and an INIT which uses
synchronous mode transfer can both coexist on the same SCSI bus. The parameters for
synchronous mode transfers decided by the SYNCHRONOUS DATA TRANSFER REQUEST
message can differ for each INIT and an INIT which uses the 8 bit wide transfer mode can
coexist with an INIT which uses the 16 bit wide transfer mode.
C141-E039-01EN 1 - 17
Page 35

Note:
When the INIT issues the first command after the TARG’s power is switched on, or after a
RESET condition occurs, it can send the WIDE DATA TRANSFER REQUEST message
and the SYNCHRONOUS DATA TRANSFER REQUEST message. However, when the
TARG is set internally on a data transfer mode established previously by a BUS DEVICE
RESET message issued by another INIT, generally, the INIT is not aware of it. In such a
case, if the CHANGE DEFINITION command’s specification (synchronous mode, wide
mode transfer request) permits the synchronous mode/wide mode transfer request, the
TARG (IDD) will send the WIDE DATA TRANSFER REQUEST message and the
SYNCHRONOUS DATA TRANSFER REQUEST message in order to reestablish
synchronous mode/wide mode transfers, so it is necessary for the INIT change its settings
to the required parameters in response to this message.
See “CHANGE DEFINITION” in 3.1.4, SCSI Bus (INFORMATION TRANSFER Phase) in
Chapter 1 and SCSI Messages (SYNCHRONOUS DATA TRANSFER REQUEST, WIDE
DATA TRANSFER REQUEST) in Chapter 2 of “SCSI Physical Interface Specifications” for
further details.
C141-E039-01EN1 - 18
Page 36

1.4 Command Queuing Function
The IDD is equipped with a command queuing function. Through queuing of commands, the
IDD can receive multiple commands in advance and execute them.
There are two methods used in the queuing function, tagged and untagged. In tagged queuing,
it is possible for the IDD to receive multiple commands from each INIT. In untagged queuing,
it is possible for the IDD to receive a single command from the INIT.
Both cueing methods are possible for the IDD, but an INIT can use only one queuing method
or the other at a time. However, if a different INIT selects a different method, the IDD
controls both methods of command queuing.
1.4.1 Untagged Queuing
In untagged queuing, the IDD can receive a command from an INIT while it is executing
processing of a command from another INIT. The IDD can receive one command at a time
from each INIT. It is the role of the INIT to confirm that only one command is issued every
time.
When the IDD receives a new command from an INIT, if it is processing another command
from a different INIT, or if it is currently executing its initial self-diagnosis, that command is
queued in the command queue. In this case, the IDD executes disconnect processing and
command queuing processing is completed.
After the IDD finishes executing the command it is currently processing, if there is a command
in the queue, it fetches that command and executes it. If there are multiple commands in the
queue, they are fetched and executed in the order in which they were received.
When a command is in the queued state, if a RESET condition occurs, and the IDD receives a
BUS DEVICE RESET message from any INIT, it clears all the commands in the queue. At
this time, the IDD generates a unit attention condition for all the INITs.
When an ABORT message is sent from an INIT that has issued a command which is in the
queue, if the correct LUN (0) is specified, only the command issued by that INIT is cleared
and the other commands in the queue are not effected. An ABORT message which does not
specify a LUN, or one which specifies an illegal LUN (1 to 7), does not effect the commands
in the queue.
Untagged queuing exception processing (events and operations executed by the IDD) is shown
below.
• If the TEST UNIT READY, REQUEST SENSE or INQUIRY command is received.
When one of these commands is received, if there is no link instruction in that command, the
IDD executes that command immediately without queuing the command or executing
disconnect processing. At this time, there is no effect on the commands from other INITs
which are currently being executed, or on the commands in the queue.
If these commands contain link instructions, they are queued.
C141-E039-01EN 1 - 19
Page 37

• If disconnect processing is impossible.
If disconnect processing is impossible because the INIT which issued the command does not
meet the conditions for permitting a disconnect (see item 1.3.3), or if the DISCONNECT
message is rejected by the INIT even though it meets the conditions for permitting a
disconnect, when another command is already being executed, or if another command is
already being executed or queuing is currently being executed, or when the initial selfdiagnosis is being executed, except in cases covered in 1), the IDD responds with a BUSY
status without queuing the received command. If this is not the case, the received command is
executed immediately.
• If the IDD is reserved
If the IDD has been reserved by an INIT using the RESERVE command, and receives a TEST
UNIT READY, REQUEST SENSE or INQUIRY command after that, when that command
conflicts with the reserved state, it responds with a RESERVATION CONFLICT status.
Commands after that are queued, and the reserved state is checked when a command is fetched
from the queue. Conflicts with the reserved state are explained in the description of the
RESERVE command (item 3.1.11).
Note
Through the operation of the command queuing function, except for exceptions described on
this page, the IDD does not respond to commands issued by the INIT with a BUSY status.
This function is applied under the multi-initiator environment, and overhead for re-issuing
commands caused by the BUSY status is unnecessary. Normally, the INIT does not have to
be aware of the existence of a queuing function, but it is necessary to exercise caution in the
following items when controlling input/output processing.
1) When a command is queued, the time from the queuing of the command to its actual
execution will vary depending on the commands already in the queue, or on the content of
the processing currently being executed. At times when a command is queued, the time
until that queued command is actually executed will vary depending on the commands
already in the queue ahead of that command, and the contents of processing of that
command when it is executed. Particularly in cases where the FORMAT UNIT command
and START/STOP UNIT command (Immed = 0), and data access commands which
specify large processing block counts, are already queued or being executed, the newly
queued command will be forced to wait a long time until it is executed.
2) In the following cases, a command may not be executed even after it has been queued.
a) When there is an error in the CDB, the IDD responds with a CHECK CONDITION
status at the point when that command is fetched from the queue.
b) If the IDD is in the not ready state at the point when the queued command is fetched,
it responds with a CHECK CONDITION status.
c) If a UNIT ATTENTION condition is generated before the queued command is
fetched, it responds with a CHECK CONDITION status.before the command is
dequeued, a CHECK CONDITION status may be replied.
C141-E039-01EN1 - 20
Page 38

1.4.2 Tagged Queuing
Through the tagged queuing function, the IDD can receive multiple commands from the same
INIT or from different INITs until the command queue is full. The number of commands that
it is possible to receive by the IDD is 128 maximum, without relation to the INIT. When the
IDD receives a new command, if the command queue is full, it responds to the new command
with the QUEUE FULL status.
The IDD manages the command queue, but it is possible for the INIT to add or clear
commands from the queue. When adding a command to the queue, it is possible for the INIT
to specify the order in which commands should be executed or the command that should be
executed next to the IDD.
If the disconnect right is not recognized in the IDENTIFY message of a tagged command, the
IDD responds with a BUSY status.
Through the QUEUE TAG message, the INIT can attach a unique tag (ID) to each command.
The INIT can set that command’s pointer correctly by the tag sent when the IDD reconnects.
One INIT can issue multiple commands to the IDD only when the respective commands have
unique tags.
If an ORDERED QUEUE TAG message is used, the IDD executes the other commands not
included in the ORDERED QUEUE TAG message in the order in which they are received.
All commands received with a SIMPLE QUEUE TAG message before commands are received
with an ORDERED QUEUE TAG message are executed before those commands received
with the ORDERED QUEUE TAG message. All commands with SIMPLE QUEUE TAG
messages received after commands received with the ORDERED QUEUE TAG message are
executed after the commands received with the ORDERED QUEUE TAG message.
Commands received with a HEAD OF QUEUE TAG message are registered at the top of the
execution wait queue and are executed after execution of the current command is completed
by the IDD. Processing of the command currently being executed is not interrupted. When
commands with the HEAD OF QUEUE message are received continuously, the IDD first
executes the command which was received last.
During execution of a tagged command by the IDD, or during queuing, except when the IDD
is in the sense hold state, the same INIT must issue untagged commands.
The IDD handles a series of linked commands as if it were processing a single command and
processes the series of commands by the tag received with the top command. A command
with a HEAD OF QUEUE TAG received before processing of a series of linked commands is
completed is executed by the IDD after all the linked commands in the series have been
executed.
The RESERVE and RELEASE commands should be issued together with an ORDERED
QUEUE TAG. If the HEAD OF QUEUE TAG message is used with these commands,
previously issued commands and reserved states may become redundant.
The TEST UNIT READY and INQUIRY commands do not influence the state of the IDD, so
they can be issued together with a HEAD OF QUEUE TAG message.
C141-E039-01EN 1 - 21
Page 39

The INIT can specify 2 error recovery options by the QErr bit of the control mode parameter
(Page A) of the mode select parameters.
When “0” is specified in the QErr bit, the IDD enters any one of a number of sense hold states,
and when this state is cleared, it continues to execute the commands in the queue. The IDD
queues any commands received from other INITs while it is in the sense hold state, but during
this period, but execution of all the commands in the queue is interrupted. In order for
recovery to occur, all the commands used must be untagged commands. In recovery
processing, all the commands in the queue, or a portion of them, can be removed from the
queue.
If “1” is specified in the QErr bit, if the IDD enters any one of a number of sense hold states,
the queue is cleared after the sense hold state is cleared. When the queue is cleared through
this recovery option, the UNIT ATTENTION condition is held for all the INITs which had
their commands cleared (excluding the INIT that set the sense hold state). The sense code
Commands cleared by another INIT [=2F-00] is set.
Deferred errors are reported for all commands that have already been completed. Therefore,
the queue tag values attached to those commands are not reported.
If a QUEUE TAG message is received by the IDD when tagged commands are prohibited by
the DQue bit of the control mode page, it rejects the message with the MESSAGE REJECT
message processes the accompanying command as an untagged command.
The ABORT, ABORT TAG, BUS DEVICE RESET or CLEAR QUEUE messages are used to
clear some or all of the commands in the queue. See “OEM Manual Interface Specifications”
for details.
If ‘0001’ is specified in the Queue algorithm modifier of the control mode page, the IDD
performs command reordering processing of commands issued with SIMPLE QUEUE TAG
messages. Reordering processing is performed with the objective of reducing total processing
time for command processing.
• Conditions for Reordering:
If a command which is the object of reordering is issued by an INIT that permits reordering
with an accompanying SIMPLE QUEUE TAG.
• Commands which are Objects of Reordering:
READ, READ EXTENDED,
WRITE, WRITE EXTENDED
If an INIT permits command reordering processing, the IDD changes the processing order of
the commands. It is necessary for the INIT to manage concerning the legality of the data, etc.
See 3.1.5, “MODE SELECT” for details of the control mode page.
C141-E039-01EN1 - 22
Page 40

1.5 UNIT ATTENTION Condition
The UNIT ATTENTION condition is a function used to notify the INIT asynchronously of an
event (status change) that has occurred in the TARG or logical unit.
1.5.1 Generation of the UNIT ATTENTION Condition
Events which cause a UNIT ATTENTION condition to be generated are one of the following.
(1) When Power on, RESET or BUS DEVICE RESET occurs
If the IDD’s power is switched on, enters the RESET condition or is reset by a BUS DEVICE
RESET message, this UNIT ATTENTION condition is generated for all the INITs, regardless
of whether the disk drive is in the ready state or not.
(2) Mode parameters changed (If changed by another INIT)
If the following parameters specified in the MODE SELECT or MODE SELECT EXTENDED
commands are changed by any INIT, a UNIT ATTENTION condition is generated for al the
INITs other than the INIT which changed the parameters.
– Parameters related to the data format (block descriptor, Page 3: format parameters, Page 4:
drive parameters, any one)
– Parameters related to the cache segment (Page 8: caching parameter, byte 13)
– Parameters related to command queuing (Page A: Except the RLEC bit of byte 3 of the
control mode parameter)
(3) Commands cleared by another INIT
Commands which are being executed or which are queued are cleared if the following events
occur, and this UNIT ATTENTION condition is generated.
• If the CLEAR QUEUE message is issued by any INIT.
• If tagged queuing is prohibited in a MODE SELECT or MODE SELECT EXTENDED
command (Page A send) from any INIT. (DQue = “1”)
• If the sense hold state of an INIT is canceled when “1” is specified in the QErr bit of
MODE SELECT parameter page A.
However, the IDD does not enter the UNIT ATTENTION condition hold state for an INIT that
issues a CLEAR QUEUE message, an INIT that issues a MODE SELECT or MODE SELECT
EXTENDED command, or an INIT that cancels the sense hold state.
C141-E039-01EN 1 - 23
Page 41

(4) RPL (rotational position locking) Status Change
If one of the events below related to disk rotational synchronization occurs, the UNIT
ATTENTION condition is generated for all INITs.
• Spindle synchronized
When rotational synchronization, started by the specification in the MODE SELECT or
MODE SELECT EXTENDED command (Page 4: Drive parameter), is completed.
• Spindle not synchronized
When rotational synchronization was attempted by the specification in the MODE SELECT or
MODE SELECT EXTENDED command (Page 4: Drive parameter), failed to synchronize the
spindle, or if synchronization which had been completed already deviated for some reason.
C141-E039-01EN1 - 24
Page 42

1.5.2 Response to the UNIT ATTENTION Condition Hold State and Cancellation Conditions
A UNIT ATTENTION condition generated by the IDD by the occurrence of the previously
mentioned events is held individually for each INIT and it is held until it is cleared by the INIT
it is held for issuing the commands specified below.
When the IDD is holding a UNIT ATTENTION condition, if the IDD receives a command
from the INIT that the UNIT ATTENTION condition is held for, it performs one of the
following operations depending on the type of command issued.
(1) Commands other than the INQUIRY and REQUEST SENSE Commands
The IDD reports a CHECK CONDITION status for the command that is issued. The UNIT
ATTENTION condition for that INIT is then cleared by the CHECK CONDITION status
report. The sense key of the sense data generated at this time is UNIT ATTENTION [=6] and
the sense codes shown below indicate the event that generated the UNIT ATTENTION
condition.
• Power-on, RESET, or BUS DEVICE RESET occurred [=29-00]
• Mode parameters changed [=2A-01]
• Log parameters changed [=2A-02]
• Commands cleared by another INIT [=2F-00]
• Threshold condition met [=5B-01]
• Log counter at maximum [=5B-02]
• Spindle synchronized [=5C-01]
• Spindle not synchronized [=5C-02]
However, if the IDD responds with a BUSY status or QUEUE FULL status due to its not
being able to receive the command that was issued, the UNIT ATTENTION condition is not
cleared.
The above CHECK CONDITION status response that is the cause of the UNIT ATTENTION
condition hold can be prohibited by the specification of the CHANGE DEFINITION
command. When the CHECK CONDITION status response is prohibited, the IDD executes
the commands it receives normally, except in the case of a RESERVATION CONFLICT
status, BUSY status or QUEUE FULL status. In this case, the UNIT ATTENTION condition
for the INIT that issued that command is cleared.
See 3.1.4 “CHANGE DEFINITION” concerning setting details.
(2) INQUIRY Command
The INQUIRY command is executed normally, but the UNIT ATTENTION condition is not
cleared.
C141-E039-01EN 1 - 25
Page 43

(3) REQUEST SENSE Command
One or the other of the following operations is performed depending on whether or not the
IDD is in the sense data hold state (shown in item 1.6).
a. In the case of a Sense Data Hold State
The IDD executes the REQUEST SENSE command normally and sends the sense data
which are being held to the INIT. In this case, the UNIT ATTENTION condition is not
cleared.
b. In the case of a State other than a Sense Data Hold State
The IDD executes the REQUEST SENSE command normally and sends the sense data
which indicate the UNIT ATTENTION condition and are being held to the INIT. At this
time, the UNIT ATTENTION condition for that INIT is cleared.
1.5.3 UNIT ATTENTION Condition Multiple Hold
If any UNIT ATTENTION condition is generated and a new UNIT ATTENTION condition is
generated for a different reason before the INIT for which the first UNIT ATTENTION
condition was held clears it, those UNIT ATTENTION conditions are held together, and the
IDD reports these multiple UNIT ATTENTION conditions in sequence. For example, a
“Mode parameters changed,” “Spindle Synchronized” or “Spindle not Synchronized” or other
UNIT ATTENTION condition may be reported after the “Power on, RESET or BUS DEVICE
RESET occurred” UNIT ATTENTION condition is reported.
C141-E039-01EN1 - 26
Page 44

1.6 Sense Data Hold State
1.6.1 Sense Data Hold Condition
The IDD generates sense data if any of the following conditions occurs and enters the sense
data hold state until the conditions for cancellation, described in item 1.6.2, are established.
The sense data which are generated, are held for each individual INIT that issued the
applicable command. The sense data hold state is also maintained individually for each INIT
which is their object.
1) If the IDD reports a CHECK CONDITION status, sense data are generated for the
command that was terminated by the CHECK CONDITION status.
2) If a fatal error occurs on the SCSI bus and the IDD forcibly enters the BUS FREE phase,
sense data are generated for the command that was being executed on the SCSI bus.
However, if the LUN cannot be specified by the point when the error occurs, the IDD does
not generate sense data.
3) Since it is impossible for reconnection processing to be executed without a response from
the INIT in the RESELECTION phase, if the IDD clears the command that is necessary for
reconnection processing, sense data are generated for that command.
Notes:
1. In the case of 3) on the previous page, the IDD does not clearly inform the INIT of the
occurrence of an error, but terminates the command abnormally and enters the sense
data hold state. If a long period of time passes with no response from the IDD, the
INIT that issued the command should issue a REQUEST SENSE command and
confirm the content of the error.
2. If the INIT which is the object of holding of sense data cannot be specified because
the INIT’s SCSI ID was not notified in the SELECTION phase, the INIT enters an
unspecified special sense data hold state. In this case, the IDD regards this as the
INIT that is the object of holding of the sense data starting a new SELECTION phase
in which the INIT’s SCSI ID is not notified.
C141-E039-01EN 1 - 27
Page 45

1.6.2 Response to the Sense Data Hold State and Cancellation Conditions state
The response of the IDD when it receives a new command while it is in the sense data hold
state, and conditions for canceling the sense data hold state are shown below.
1) If issued for the logical unit in the sense data hold state by the INIT which is the object of
sense data holding.
– In the case of an untagged command
REQUEST SENSE Command: The sense data held by the IDD are transferred to the INIT
and the sense hold state is canceled.
Other Commands: The sense data hold state is canceled and the command is
executed normally.
– In the case of a tagged command
The BUSY status is reported without the sense data hold state being canceled.
2) If issued for the logical unit in the sense data hold state from an INIT which is not the
object of sense data holding.
The BUSY status is reported without the sense data hold state being canceled.
3) In the following cases, the sense data hold state is canceled and the sense data being held
are lost.
– If the RESET condition occurs on the SCSI bus.
– If a BUS DEVICE RESET message is issued by any INIT.
– If an ABORT message is issued by an INIT for which sense data held for the logical unit
in the sense data hold state.
C141-E039-01EN1 - 28
Page 46

1.7 Command Processing Exceptions
1.7.1 Overlapping Commands
If the following state occurs, the IDD recognizes that overlapping commands have been
generated and the command is terminated abnormally.
1) If the IDD is executing an untagged command, or an untagged command is in the queue,
and the initiator that issued that command issues either an untagged command or a tagged
command before execution of the previous command is completed.
2) If the IDD is executing a tagged command, or a tagged command is in the queue, and the
initiator that issued that command issues another tagged command with the same tag
specified as the previous command before execution of that command is completed.
Normally, execution of a command is completed at the point when the TARG notifies the
INIT of the COMMAND COMPLETE message. Execution of a command can also be
terminated by the RESET condition, a BUS DEVICE RESET message, CLEAR QUEUE
message, ABORT message or ABORT TAG message.
The IDD abnormally terminates all the commands (commands being executed or in the queue)
received from an INIT which is overlapping commands and the command that generated the
overlap condition by the procedure described below.
1) If the command received form the INIT is being executed, the IDD halts execution of the
command. If the command is still in the queue and execution has not been started, the
IDD clears that command.
2) The IDD reports a CHECK CONDITION status for a command that generates an overlap.
At this time, the sense data generated by the IDD indicates ABORTED COMMAND
[=B]/Overlapped commands attempted [=4e-00], or Tagged Overlapped [=4D-nn] (nn: tag
No.).
Note
1) In order for the INIT to halt processing of a command during a disconnect, it is
permitted to send an ABORT TAG message, ABORT message, CLEAR QUEUE
message or BUS DEVICE RESET message, specifying the logical unit (see item
1.7.6).
2) Specification of overlapping commands applies without dependence upon the type of
command that is issued second. For example, even if the command issued second is
the INQUIRY or REQUEST SENSE command, the IDD reports the CHECK
CONDITION status and terminates both the first command and the second command
abnormally.
C141-E039-01EN 1 - 29
Page 47

1.7.2 Illegal LUN Specification
The only logical unit number (LUN) supported by the IDD is LUN = 0. If a LUN other than
this (1 to 7) is specified, the IDD performs one of the following operations, depending on the
type of command issued at that time.
1) The INQUIRY command is executed normally even if the LUN specification is illegal.
However, byte 0 of the “Standard INQUIRY Data” (“Qualifier” field and “Device Type
Code” field) transferred to the INIT for that command indicates X ‘7F.’
2) The REQUEST SENSE command is executed normally even if the LUN specification is
illegal. However, the sense data transferred to the INIT for that command indicates that
the LUN specification is illegal (ILLEGAL REQUEST [=5]/Logical unit not supported
[=25-00]).
3) If an illegal LUN is specified for a command other than the INQUIRY command or
REQUEST SENSE command, that command is terminated abnormally by a CHECK
CONDITION status. The sense data generated at this time indicate that the LUN
specification is illegal (ILLEGAL REQUEST [=5] /Logical unit not supported [=25-00]).
1.7.3 Reserved Operation Code
Group 7 command operation codes (X ‘EO’ to X ‘FF’) are reserved by Fujitsu. When any
command is issued which includes these operation codes, the IDD always must respond with a
CHECK CONDITION status (ILLEGAL REQUEST [=5] / Invalid command operation code
[=20-00]. The INIT must not issue commands which contain these operation codes.
1.7.4 Command Processing in the Not Ready State
After the IDD’s power is switched on, the initial self-diagnosis is completed normally and the
spindle motor reaches the normal rotational speed, “system information,” which includes such
information as MODE SELECT parameters and disk media defect information is read from the
system space on the disk drive and each type of control information is initialized. When this
operation is completed, the IDD is in a state where it can be used (ready state). Furthermore,
the not ready state is defined as the IDD being in either of the following states.
Not Ready State:
• When the spindle motor has not reached the normal rotational speed.
• When ready of system information is not completed, or reading failed.
Also, if initialization of the disk media (formatting) has not been completed normally, it will
be impossible to access data on the disk media.
Processing of and response to commands received by the IDD when it is in the not ready state
or in the initialization incomplete state are described below. Furthermore, starting control of
the spindle motor when the power is switched on can be selected from either or two methods,
through the setting terminal (motor start mode) on the IDD, with rotation started at the same
time as when the power is switched on or through the START/STOP UNIT command.
C141-E039-01EN1 - 30
Page 48

(1) General Response when in the Not Ready State
The IDD reports a CHECK CONDITION status for a command, except in cases where the
command is one of the commands in item (2). The sense data generated at this time depends
on the state of the IDD, as shown in Table 1.3.
Table 1.3 Sense Data when in the Not Ready State
IDD State Sense Key Sense Code
Spindle motor not
rotating at normal speed.
Reading system
information but not
NOT READY
NOT READY
Logical unit not ready
[=2]
Logical unit not ready
[=2]
completed.
Reading system
information failed.
HARDWARE ERROR
[=4]
Logical unit failed selfconfiguration
(2) Commands that can be Executed even in the Not Ready State
If the IDD receives any of the following commands, it executes those commands even if it is
in the Not Ready state.
• START/STOP UNIT Command
• RESERVE Command
• RELEASE Command
• WRITE BUFFER Command
• READ BUFFER Command
[=04-00]
[=04-00]
[=4C-nn]
• INQUIRY Command: The INQUIRY command is executed normally and the standard
INQUIRY data and byte 0 of the VPD information transferred to the INIT (“Qualifier” field
and “device type code” field) indicate X ‘00.’ However, the values for several fields may
differ depending on whether or not reading of system information is completed. See the
description of the INQUIRY command (item 3.1.2) for details.
• REQUEST SENSE Command: The REQUEST SENSE command is executed normally
and if the sense data hold state exists, the sense data being held at that time are transferred to
the INIT. If the sense data hold state does not exist, sense data appropriate to the IDD’s state
at that time are transferred to the INIT (See Table 1.3).
• REZERO UNIT: If the disk drive’s spindle motor has reached the normal rotational speed,
this command is executed even if reading of system information failed. If the spindle motor
has not reached the normal rotating speed, or if reading of system information is still in
progress, a CHECK CONDITION status is reported as in item (1).
C141-E039-01EN 1 - 31
Page 49

(3) Operation if Formatting is Not Completed Normally
If, while the FORMAT UNIT command is not being executed following a change in data
format related parameters by the MODE SELECT command, the FORMAT UNIT command
is terminated abnormally for any reason (Example: power cut off or RESET condition), the
data on the disk media cannot be accessed normally. In this case, the IDD reports a CHECK
CONDITION status for the command accessing the disk media.
The sense data generated at this time indicate a MEDIUM ERROR [=3] / Medium format
corrupted [=31-00] in the case of the former and MEDIUM ERROR [=3] / FORMAT
command failed [=31-01]. In either case, the IDD is restored to the ready state by
reinitializing the disk media using the FORMAT UNIT command.
1.7.5 Error Recovery Processing
If an error is detected on the SCSI bus or internally in the IDD which can be retried, the IDD
attempts recovery processing of the detected error during command execution.
The INIT can specify detailed parameters related to error recovery processing and whether or
not there is a report for errors which were successfully recovered from using the MODE
SELECT or MODE SELECT EXTENDED command. It can also save those parameters in
accordance with INIT specifications in the system space on the disk media, and can change
them temporarily without saving them. After the power is switched on, or after a reset
(RESET condition or BUS DEVICE RESET message), the saved parameters are read and the
error recovery processing procedures is initialized.
See 3.1.5 “MODE SELECT” and 3.1.6 “MODE SELECT EXTENDED” for details of the
MODE SELECT or MODE SELECT EXTENDED command. See 4.3 “Disk Drive Error
Recovery Processing” and Chapter 3, “SCSI Bus Error Recovery Processing” of “SCSI
Physical Interface Specifications” for details of error recovery processing.
An outline of error recovery processing executed by the IDD is shown below.
C141-E039-01EN1 - 32
Page 50

(1) Recovery Processing for Errors on the SCSI Bus
The IDD does not perform recovery processing for error detected on the SCSI bus. When
error recovery is impossible, or when a major error related to SCSI bus protocols is detected,
the IDD may transfer the SCSI bus forcibly to the BUS FREE phase and clear the command
that is currently being executed.
Table 1.4 Outline of SCSI Bus Error Recovery Processing
Item Type of Error Error Recovery Processing
1 MESSAGE OUT phase parity error “Check Condition” Status
2 COMMAND phase parity error “Check Condition” Status
3 DATA OUT phase parity error “Check Condition” Status
4 Received INITIATOR DETECTED ERROR message. “Check Condition” Status
5 Received MESSAGE PARITY ERROR message. “Check Condition” Status
6 RESELECTION phase time-out Re-execute RESELECTION phase.
(2) Recovery Procedures for Disk Drive Errors
The IDD executes error recovery listed in Table 1.5 for an error detected during access to data
on the disk. Note that the recovery increases command processing time because of rotation
delay for repositioning to the data block on the disk or initialization of the positioning control
system.
The INIT can use the MODE SELECT parameter Page 1 (read/write error recovery parameter),
Page 7 (verify error recovery parameter), and Page 21 (additional error recovery parameter) to
control the retry count. However, use the default value specified by the IDD in general
operation.
Table 1.5 Outline of Disk Drive Error Recovery Processing
Item Type of Error Error Recovery Processing
1 Seek Error Rezero (Return to Zero Cylinder), with positioning control
system readjustment repositioning in the data block.
2 Uncorrectable Data Error Reread
3 Correctable Data Error Correct according to ECC.
Note
The execution start timing of this automatic readjustment operation generally cannot be
predicted by the INIT. The automatic readjustment operation is performed there are no
commands being executed or in the queue, but execution of commands issued
immediately after the IDD starts the readjustment operation, are forced to wait until the
readjustment operation is completed.
C141-E039-01EN 1 - 33
Page 51

1.7.6 Reset Processing
The means which the INIT can use to reset the SCSI bus are shown below.
• RESET Condition
• BUS DEVICE RESET Message
• CLEAR QUEUE Message
• ABORT Message
• ABORT TAG Message
The RESET condition resets all the SCSI devices connected on the same SCSI bus. The IDD
is initialized to the same state as when its power is switched on by the RESET condition, with
the currently executed command as well as all the commands in the queue cleared.
The BUS DEVICE RESET message resets a specific SCSI device (TARG), selected by the
INIT, only and can initialize that TARG to the same state as when its power is switched on,
but in a multi-initiator environment, caution concerning clearing of commands issued by other
INITs is necessary.
The CLEAR QUEUE message causes the IDD to clear the currently executed command and
all the commands in the queue. The previously set environment and conditions, such as
MODE SELECT parameters, are not changed.
An INIT which wants to clear only specific commands it has issued itself must use an ABORT
message or an ABORT TAG message. In this case, the INIT generates an ATTENTION
condition at the desired point in time if that command is currently being executed on the SCSI
bus, then sends the ABORT message to the TARG. Also, if there is a disconnect in effect,
after the INIT selects the TARG, an ABORT message, in the case of an untagged command, or
an ABORT TAG message, in the case of a tagged command, is sent following an IDENTIFY
message which specifies the object logical unit, or the INIT waits until a reconnection request
occurs, then sends an ABORT message or ABORT TAG message. In the case of an ABORT
message, only the commands issued previously in the logical unit specified at that time by the
INIT that issues the ABORT message (currently being executed or in the queue) are cleared
and there is no influence on the other commands.
When an ABORT TAG message is received, only the command issued to the logical unit
specified at that time by the INIT which issued the ABORT TAG message is cleared, and there
is no influence on the other commands. No status byte or COMMAND COMPLETE message
is reported concerning commands cleared in this processing.
In particular, in the case of clearing of a write operation command for writing to the disk
media which is currently being executed, the IDD cuts off processing of that command as
shown in Table 1.6. The case of halting an overlapping command that is currently being
executed (see item 1.7.1) is the same. The INIT must determine the complete completion state
and if necessary, must execute data recovery processing.
C141-E039-01EN1 - 34
Page 52

Table 1.6 Reset Processing During Write
Type of Command Processing to Halt Command Execution
WRITE
WRITE EXTENDED
WRITE AND VERIFY
SEND DIAGNOSTIC (Write/Read Test)
WRITE LONG
WRITE SAME
Data blocks which are currently being written are
processed normally, including the ECC portion, and
execution of the command is terminated at the point
when that processing is completed. Not all the data
transferred from the INIT to the IDD will necessarily be
written to the disk media. If the ATN signal is asserted
immediately after data transfer in the Data Out phase (to
the first ACK signal) and the ABORT message is sent,
the data are not written to the disk media.
FORMAT UNIT At the point when processing of the data block that is
currently being written (initialized) is completed,
execution of the command is halted. Since the
formatting results cannot be guaranteed for the entire
disk surface, it is necessary for the INIT to reissue the
command.
REASSIGN BLOCKS At the point when processing of alternate blocks which
are currently being assigned is completed, execution of
the command is halted. Not all the alternate blocks
specified for reassignment processing by the INIT will
necessarily have been processed.
MODE SELECT
MODE SELECT EXTENDED
LOG SENSE (Parameter save
specification)
If a parameter save operation has already started, that
command is executed until it is completed. However,
since the INIT cannot judge whether the parameters
have been saved or not, it is necessary for the INIT to
confirm the status by the MODE SENSE command or
the LOG SENSE command, or reissue the command.
SYNCHRONIZE CACHE Data blocks which are currently being written are
processed normally, including the ECC portion and the
command is halted at the point when that processing is
completed. Not all the data which is the write object
will necessarily be written to the disk media.
C141-E039-01EN 1 - 35
Page 53

1.7.7 Fatal Hardware Errors
(1) Self-diagnostic Errors
If a fatal error is detected in the hardware in the initial self-diagnosis, in off-line self diagnosis
or in on-line self-diagnosis (SEND DIAGNOSTIC command), rotation of the spindle motor
will be halted.
When in this state, the IDD reports the CHECK CONDITION status for all input/output
operation requests except the REQUEST SENSE command. The sense data reported at this
time indicate HARDWARE ERROR [=4] / Diagnostic failure in component “nn” [=40-nn]. It
is necessary for the INIT either to generate a RESET condition or send a BUS DEVICE
RESET message and attempt to recover from the error state. For recommended procedures for
error recovery methods, see the explanation in 4.2 “INIT’s Error Recovery Methods
(Recommended).” Furthermore, see 6.1.1 “Self-diagnostic Function” in “OEM Manual
Product Specifications/Installation Procedures.”
(2) Unrecoverable Hardware Errors
Limited to cases in which a fatal error occurs in the hardware during execution of a command,
and termination processing such as a CHECK CONDITION status report cannot be executed,
the IDD may halt rotation of the spindle motor.
After this state occurs, the IDD reports the CHECK CONDITION status for all input/output
operation requests except the REQUEST SENSE command. The sense data reported at this
time indicate HARDWARE ERROR [=4] / Internal target failure [=44-nn]. If this state is
reported continuously for input/output operation requests, it is necessary for the INIT to
generate a RESET condition or send a BUS DEVICE RESET message and attempt to recover
from the error state. For recommended procedures for error recovery methods by the INIT, see
the explanation in 4.2 “INIT’s Error Recovery Methods (Recommended).”
C141-E039-01EN1 - 36
Page 54

1.8 Data Block Addressing
1.8.1 Definition of Data Space
The IDD manages the data storage area on the disk drive in the following 2 types of data
space.
• User Space: User Data Storage Area
• System Space: IDD Exclusive Area
Of these 2 areas the user can clearly access the user space. The data format and defect
management methods in this space are the same and it is possible to access this space by
logical data block addressing described in item 1.8.2. System space is accessed by the IDD
internally when the power is switched on or during processing of specific commands, but it
cannot be accessed directly by the user.
Fig. 1.4 shows the data space configuration on the disk drive. The number of cylinders
allocated to user space can be specified by the user (MODE SELECT or MODE SELECT
EXTENDED command).
A spare sector area (alternate area) for use as alternates for defective sectors is secured in user
space. The user can allocate the number of sectors in the final track of each cylinder and the
number of cylinders in the user space (alternate use cylinders) as alternate area (by the MODE
SELECT or MODE SELECT EXTENDED command).
Alternate data blocks are allocated in defect sector units for defective sectors on the disk media
through internal IDD defect management. Through this defect management, the INIT can
access all the logical data blocks in the user space as if they were error free.
For details concerning the data format on the disk media (cylinder configuration, track format
and sector format) and details concerning defect management techniques and alternate block
allocation techniques, Chapter 3 “Data Format” in the “Product Manual.” For an outline of
defect management techniques, see “Disk Media Management Techniques” in Chapter 5 of
this manual.
C141-E039-01EN 1 - 37
Page 55

Sector 0 1 2 3
Cylinder -22
Cylinder -9
Track 0
Track 1
Cylinder 0
Cylinder 1
Cylinder p-q
Cylinder p-q+1
System cylinder x = 14
System cylinder 1
Primary cylinder = 0
Primary cylinder = 1
Primary cylinder = p-q
Alternate cylinder =1
System space
Spare sectors for each cylinder
User space
Lasy cylinder
For
alternate
cylinders
Alternate cylinder = qCylinder p
M2909, M2903 : 3138
M2915 : 3011
M2932, M2934 : 3421
Figure 1.4 Data Space Configuration
C141-E039-01EN1 - 38
Page 56

1.8.2 Logical Block Addressing
The IDD uses logical data block addressing which is not dependent on the disk drive’s
physical structure as the method of data access on the disk medium. The IDD adds
correspondence between each physical sector and each logical data clock address during
formatting. Access to the data on the disk medium is performed in logical data block units
and the INIT specifies the logical data block address that is its object during access.
In logical data block addressing, specifying of a data block address is a function which
specifies 2 continuous binary numbers for each drive. Furthermore, the INIT can know the
logical data block address range in the user space where specification is possible using the
READ CAPACITY command.
(1) User Space Logical Block Addresses
The top data block in the user space is made logical data block address “0,” then continuous
logical data block addresses are allocated to each data block until the final data block in the
user space.
The IDD makes cylinder 0, track 0 sector 0 the top logical data block, and allocates
subsequent logical data blocks in the order described below to addresses in ascending order.
1) Within the same track, logical data blocks are allocated to sector numbers in ascending
order.
2) Within the same cylinder, excluding the final track, succeeding logical data blocks are
allocated to the sectors in each track according to 1) in the ascending order of track
numbers.
3) On the final track inside the same cylinder, succeeding logical data blocks are allocated to
sectors except for spare sectors according to 1).
4) After all the allocation in 1) to 3) is completed within the same cylinder, succeeding
logical data blocks are allocated to the next cylinder beginning with track 0, according to
1) to 3), and so on to each cylinder number in ascending order until the final cylinder
(cylinder p-q in Fig. 1.4) in the user space, with the exception of alternate cylinders.
(2) Alternate Area
The alternate area in user space (spare sectors within each cylinder and alternate cylinders) are
excluded from the abovementioned logical data block addresses. Access to allocated sectors
as alternate blocks within the alternate area is performed automatically by the IDD’s defect
management (sector slip processing and alternate block processing), so it is not particularly
necessary for the user to access the alternate area. Also, data blocks in the alternate area
cannot be clearly specified and accessed directly.
C141-E039-01EN 1 - 39
Page 57

Page 58

CHAPTER 2 DATA BUFFER MANAGEMENT
2.1 Data Buffer
2.2 Read-Ahead Cache Mechanism
2.3 Write Cache
In this chapter, the configuration of the data buffer with which the IDD is equipped, its operation and
the operation of the cache feature are described.
2.1 Data Buffer
2.1.1 Data Buffer Configuration and Basic Operation
The IDD is equipped with a 496 Kbyte data buffer, which makes it possible to efficiently
execute data transfer operations between INIT (initiator) and a disk drive.
The data buffer, with a capacity of 512 KB, can be divided into a maximum of 16 cache
segments. Dividing of the data buffer is controlled by the MODE SELECT parameter (cache
segment parameter: Page code = 8).
Each data buffer is a 2-port configuration FIFO (First-In First-Out) ring buffer, with one port
allocated for transfers with the disk media and the other port for data transfers with the SCSI
bus. Mutual ports operate asynchronously and since it is possible to efficiently absorb
variations in data transfer speed between the ports, the INIT can perform data transfer
operations with the IDD while being virtually unaware of differences between the SCSI bus
data transfer rate and the disk drive data transfer rate.
Even if the data transfer capacity of the SCSI bus (INIT) is lower than the disk drive's data
transfer rate, the data buffer can perform data transfers to the system under optimum
conditions without using sector interleave. Also, if the data transfer capacity of the SCSI bus
(INIT) is higher than the disk drive's data transfer rate, it is possible to minimize the
occupancy time on the SCSI bus by accumulating an appropriate amount of data in the data
buffer.
Only one cache segment of the divided data buffer is used by one command and the data in the
other cache segments are held. The cache segment to be used is determine by the LRU
algorithm.
Fig. 2.1 shows the data buffer image.
C141-E039-01EN 2 - 1
Page 59

INIT
Data Buffer (512 KB FIFO)
Write→
←Read
Figure 2.1 Data Buffer Configuration (In the case of 4 cache segments)
The basic functions and operations of the data buffer in a read operation and a write operation
are shown below.
(1) Read Operation
After data read from the disk media are temporarily stored in the data buffer, they are
transferred to the SCSI bus with the timing specified in the MODE SELECT parameter. The
basic read operation procedure is as shown below.
1) When the IDD receives a command, normally, it disconnects from the SCSI bus through
disconnect processing and locates the data block specified in the command where it is
stored on the disk media.
Buffer 1
Buffer 0
Valid Data
(If data buffer 0 is selected)
Buffer 3
Buffer 2
Write→
←
Read
Disk Media
2) When the target data block has been located, the IDD reads the data form the disk media to
the data buffer. At this time, if a recoverable error is detected, the IDD performs error
recovery processing according to the specification in the MODE SELECT parameter or
corrects the data in the data buffer.
3) When the IDD has read the amount of data specified by the buffer full ratio in the MODE
SELECT parameter (see item 2.1.2) to the data buffer, it performs reconnection processing
with the SCSI bus and begins transferring data to the INIT (SCSI bus) from the data buffer
while continuing to read subsequent data blocks to the data buffer.
4) If the data transfer capacity of the INIT (SCSI bus) is high and the data buffer becomes
empty before completing transfer of the number of data blocks specified by the command,
the IDD performs disconnect processing at that point. Thereafter, reconnection, data
transfer and disconnection (the operations in 3) and 4) above) are repeated until all the data
blocks specified in the command have been transferred.
5) If the number of blocks specified in the command to be transferred is larger than the
capacity of a cache segment and if the data transfer rate of the INIT is lower than the data
transfer rate of the disk drive, the empty space in the data buffer disappears from step 3)
and the IDD may soon not be able to read data from the disk media (data overrun). In this
case, the IDD relocates the block that caused the data overrun after waiting one disk
revolution, and continues the reading process.
6) When transfer of all the specified data is completed, the IDD reports the status and
terminates the command.
C141-E039-01EN2 - 2
Page 60

Note:
in the Buffer
In order to avoid frequent repetition of the disconnect/reconnect processing after data
transfer starts on the SCSI bus, and escape the occurrence of data overruns, it is
necessary to set the buffer full ratio (see item 2.1.2) of the MODE SELECT parameter
so the difference in the data transfer rates between the INIT (SCSI bus) and the disk
drive is maintained in a good balance.
Fig. 2.2 shows an example of the data buffer operating state during a read operation. Details
are explained in item 2.1.2.
Sector
Disk
Amount of Data
Buffer Full Ratio
SCSI Bus
Data Storage Completion Wait
Figure 2.2 Example of Data Buffer Operation during Read
(2) Write Operation
After data transferred from the INIT are stored temporarily in the data buffer, they are written
to the disk media. The basic write operation procedure is as shown below.
1) When the IDD receives a command and disconnects, it immediately reconnects and enters
the DATA OUT phase and stores data transferred from the INIT to the data buffer (data
pre-fetch). At this time, the IDD locates the position of the data block on the disk media
specified by the command in parallel.
When storing of all the data specified in the command in the data buffer is completed, or if the
empty space in the data buffer is all filled during data storage due to the volume of the specified
data, the IDD performs disconnect processing and disconnects from the SCSI bus.
2) When locating of the target data block on the disk media is completed, the IDD writes the
data in the data buffer to the disk media. If the target data block location operation is
completed during the data pre-fetch processing in 1), writing of data to the disk media is
performed in parallel with the data pre-fetch to the data buffer.
DATA IN
Reconnection
3) If the data transfer rate of the INIT (SCSI bus) is lower than the data transfer rate of the
disk drive, since the data pre-fetch of data that are to be written to that data block is not
completed, it may not be possible to write the data continuously to the disk (data
underrun). In this case, the IDD waits one disk revolution while continuing to pre-fetch
data from the INIT, then repositions the block that caused the data underrun and continues
the writing of data to the disk.
C141-E039-01EN 2 - 3
Page 61

4) After disconnect processing, if all the blocks of data specified in the command have not
SCSI
Sector
yet been transferred by the INIT, as writing of data to the disk media progresses, at the
point when the empty space in the data buffer reaches the amount specified in the buffer
empty ratio in the MODE SELECT parameter, the IDD performs reconnection processing
and begins transferring the succeeding data (data pre-fetch).
Writing of data to the disk media is performed in parallel and data transfer with the INIT
continues until the empty space in the data buffer is full or until transfer of all the data
specified in the command is completed. From then on, disconnection, reconnection and
data transfer are repeated until transfer of all the blocks of data specified in the command
is completed.
5) When writing of all the specified data is completed, the IDD reports the status and
terminates the command.
Notes:
1. If the amount of transfer data specified in a command is smaller than the capacity of
the cache segment, all the data necessary for execution of the command are prefetched in a batch in the processing in 1) above, so the value specified in the buffer
empty ratio has not meaning.
2. If the amount of data processed with a single command exceeds the capacity of one
cache segment, in order to avoid frequent repetition of disconnect and reconnect
processing during command execution, and in order to escape the occurrence of data
underrun, it is necessary to set the buffer empty ratio (see item 2.1.2) of the MODE
SELECT parameter so the difference in the data transfer rates between the INIT (SCSI
bus) and the disk drive is maintained in a good balance.
Fig. 2.3 shows an example of the data buffer operating state during a write operation.
Details are explained in item 2.1.2.
Disk
Amount of Data in the Buffer
Bus
COMMAND
DATA OUT
ReconnectionDisconnection
STATUS
Figure 2.3 Example of Data Buffer Operation during Write
C141-E039-01EN2 - 4
Page 62

2.1.2 Setting the Operation Mode
~~~
~
(1) MODE SELECT Parameter
In order to make it possible to control from the INIT the reconnection processing start timing
for executing data transfers with the SCSI bus in read and write operations, the IDD is
provided with the MODE SELECT parameter (Disconnect/Reconnect Parameter: Page code =
2) shown in Fig. 2.4. The user can set the optimum operating state in the system environment
as necessary. The IDD holds the MODE SELECT parameter individually for each INIT's
SCSI ID, so the specified parameter values can differ for each INIT. See item 3.1.5 for details
of the MODE SELECT command.
[Disconnect/Reconnect Parameter (Page code = 2)]
Bit
Byte
0 0 0 0 0 0 0 1 0
1 X‘0E’ (Page Length)
2 Buffer Full Ratio
3 Buffer Empty Ratio
4
15
7 6 5 4 3 2 1 0
Default Value: X‘20’ (=Half the character segment capacity)
Variable Range: X‘00’ to X‘FF’
Default Value: X‘20’ (=Half the character segment capacity)
Variable Range: X‘00’ to X‘FF’
~
a. Buffer Full Ratio
(Other parameters)
Figure 2.4 Parameters for Controlling Reconnection Timing
This parameter specifies the timing for the IDD to start reconnection to perform data
transfer to the INIT in a READ or READ EXTENDED command.
The value specified in this parameter (n) shows the amount of data read to the IDD's data
buffer from the disk media as a proportion [n/256] of the total capacity of the data buffer
until reconnection processing with the SCSI bus is started. The IDD's default cache
segment capacity is 127 Kbytes. Therefore, if the specified value (n) is 128, for example,
it means that a data volume of 63.5 Kbytes was specified (Note)
If it is possible to transfer the amount of data specified in this parameter to the INIT from
the data buffer, reconnection processing is executed and transfer of data to the INIT
begins. However, if the total amount of transfer data specified in the command does not
fill the capacity of the cache segment, the IDD executes reconnection processing and
begins transferring data to the INIT when it becomes possible to transfer the amount of
data blocks from the data buffer which is equivalent to the proportion of the total volume
of transfer data blocks specified in the command that is specified by this parameter.
C141-E039-01EN 2 - 5
Page 63

For example, if a read operation of 16 blocks with a logical data block length of 512 bytes
(8 Kbytes) is requested, when the value specified in this parameter is 32, reconnection
processing is performed when it becomes possible to transfer 2 blocks of data [16 x
(32/256)], from the data buffer.
b. Buffer Empty Ratio
This parameter specifies the timing for the IDD to start reconnection when it is requested
by the INIT to transfer data in the WRITE, WRITE EXTENDED or WRITE AND
VERIFY command. In a write operation, after the IDD receives a command, the IDD
begins transferring data (data pre-fetch) while locating the position of the target data
blocks on the disk media in parallel. Therefore, if the total number of bytes of data
specified in the command is less than the capacity of a cache segment, all the data are prefetched in a batch, so the specification in this parameter is not applied.
The value specified in this parameter (n) indicates a proportion of the total data buffer
capacity of the IDD when the buffer is empty [n/256]. For example, if the specified value
(n) is 128 and the number of cache segments is 4 (this is the default value), the size of the
empty space in the buffer is specified as 63.5 Kbytes. (Note)
While the IDD is writing data to the disk media, it is using the data pre-fetched to the data
buffer in order and when the empty space in the data buffer reaches the amount specified
in this parameter, it executes reconnection processing, requesting transfer of the
succeeding data. However, if the number of data blocks remaining to be transferred
according to the command being executed does not reach the amount of data specified in
this parameter, the IDD executes reconnection processing at the point when the number of
data blocks remaining in the data buffer's empty space reaches the specified number of
data blocks and requests transfer of the succeeding data.
Note:
If the value specified for the "buffer full ratio" or the "buffer empty ratio" is not within
double the integral boundary of the logical data block length, the IDD rounds up the
specified value which is the nearest data block boundary. Also, if zero is specified in any
of these parameters, the IDD treats that parameter as though 1 logical data block has been
specified.
C141-E039-01EN2 - 6
Page 64

2.2 Look-Ahead Cache Feature
In order to use the data buffer more effectively and improve the disk drive's effective access
speed, the IDD is equipped with a simple cache feature called a "Look-Ahead Cache Feature."
The Look-Ahead cache feature is an effective, simple cache function for an INIT which reads
data block groups on the disk media sequentially using multiple commands.
2.2.1 Caching Operation
When the IDD is executing a READ command or a READ EXTENDED command, it reads
the requested data from the disk media and transfers it to the INIT while at the same time
reading (looking ahead at) data blocks which are subsequent to the final logical data block
specified in that command to the data buffer. Then, when a READ command or READ
EXTENDED command issued later specifies any of those Look-Ahead data blocks, the IDD
transfers those data directly to the INIT from the data buffer without accessing the disk media.
In this way, when continuous logical data block groups are read sequentially by multiple
commands, mechanical access operations can be eliminated and effective access time greatly
reduced.
An INIT can prohibit the operation of this Look-Ahead cache feature by setting the caching
parameter described in item 2.2.2.
(1) Caching Object Commands
Commands which execute caching operations are the commands shown below:
• READ
• READ EXTENDED
If all the data block groups which are objects of the processing specified in these commands,
or a portion of the data blocks, including the top logical data block specified in these
commands are relevant data (See item (2)) for caching in the data buffer (if they hit), when the
IDD receives a command and performs disconnect processing, it immediately reconnects and
sends the data on the data buffer which can be transferred to the INIT. The caching operation
can be disabled by the FUA bit of the READ EXTENDED command. If "1" is specified in the
FUA bit, the IDD reads data from the disk media.
On the other hand, if the top logical data block specified in a command is not relevant data for
caching in the data buffer (if they miss), reading of data is performed from the disk media
using the oldest cache segment (selected by time stamp).
(2) Data which are Objects of Caching
Data which exist in the data buffer and which are objects of caching in item (1) (data which are
not accessed from the disk media but are transferred to the INIT from the data buffer) are as
described below.
a) Data read by a READ or a READ EXTENDED command and which have been read to the
data buffer by Look-Ahead are data which are objects of caching. Depending on the
timing for halting Look-Ahead, it is possible that data read by the READ command will be
overwritten by Look-Ahead.
C141-E039-01EN 2 - 7
Page 65

b) Data which have been hit by the READ or READ EXTENDED command and transferred
to the INIT once are also objects of caching as long as they are not invalidated.
c) Data transferred from the INIT and written to the disk media by the WRITE, WRITE
EXTENDED, WRITE AND VERIFY or other data writing command are not objects of
caching.
3) Disabling Caching Data
Various data which are objects of caching in the data buffer are disabled in the following
cases.
a) If any of the following commands is issued for the same data block as data which are the
object of caching, that data block ceases to be an object of caching.
WRITE
•
WRITE EXTENDED
•
WRITE AND VERIFY
•
b) If any of the following commands is issued, all the data which are objects of caching are
disabled.
FORMAT UNIT
•
MODE SELECT
•
MODE SELECT EXTENDED
•
READ DEFECT DATA
•
READ LONG
•
REASSIGN BLOCKS
•
RECEIVE DIAGNOSTIC RESULTS
•
SEND DIAGNOSTIC
•
START/STOP UNIT
•
WRITE BUFFER
•
WRITE LONG
•
WRITE SAME
•
c) If the data buffer where data which are objects of caching are stored is used by any of the
following commands, the data existing in that data buffer which are objects of caching are
disabled.
READ
•
READ EXTENDED
•
PRE-FETCH
•
VERIFY
•
WRITE
•
WRITE EXTENDED
•
WRITE AND VERIFY
•
d) If any of the following events occurs, all the data which are objects of caching are
disabled.
If a RESET condition occurs on the SCSI bus.
•
If a BUS DEVICE RESET message is issued by any INIT.
•
If automatic alternate processing is executed.
•
C141-E039-01EN2 - 8
Page 66

2.2.2 Caching Parameters
The IDD supports the MODE SELECT parameters (caching parameters: page code = 8) shown
in Fig. 2.5 for controlling the cache feature. See item 3.1.5 concerning details of the MODE
SELECT parameters.
[Caching Parameters (Page Code = 8)]
Bit
Byte
0 0 0 0 0 1 0 0 0
1
2 IC (ABPF) (CAP) DISC SIZE WCE MS RCD
Default 1 0 0 1 0 0 0 0
Variable 0 0 0 0 0 1 0 1
3 X‘00’ (Reserved)
4-5 Prefetch-suppressed block count
Default X‘FFFF’
Variable X‘0000’
6-7 Minimum prefetch
Default X‘0000’
Variable X‘FFFF’
8-9 Maximum prefetch
Default X‘00xx’
Variable X‘0000’
10-11
Default X‘FFFF’
Variable X‘0000’
12 FSW (Reserved)
Default 1 0 0 0 0 0 0 0
Variable 0 0 0 0 0 0 0 0
13
Default X‘04’
Variable X‘1F’
14-15 X‘0000’ (cache segment size)
16 X‘00’ (Reserved)
17-19 X‘000000’ (Reserved)
7 6 5 4 3 2 1 0
X‘0A’ or X‘12’ (Page Length)
(1 cache
segment
Maximum prefetch limit block count
Cache segment count
Remark:
The variable column indicates whether the parameter can be changed or not (if "1", the
parameter can be changed).
Figure 2.5 Cache Control Parameters
C141-E039-01EN 2 - 9
Page 67

2.2.3 Look-Ahead Operation, Look-Ahead Volume
1) Excluding the conditions in 3) and 4) for the amount of data specified as the minimum prefetch volume, data are read for look-ahead irrespective of track boundaries or cylinder
boundaries. Commands which are already in the queue or commands which are newly
received while a look-ahead operation is in progress, are executed after the look-ahead
operation is completed. However, if the new command is a READ or READ EXTENDED
command, and it is a command in which the first specified logical data block is a
sequential access data block, the command is executed without the look-ahead operation
being halted. When a newly received command is a command which is not the object of
caching, that command is executed immediately in parallel with a look-ahead operation.
Also, in the case of a command which disables all data which are objects of caching (see
item 2.2.1 (3)), the look-ahead operation is halted and that command is executed
immediately.
2) When commands exist in the queue, the look-ahead operation is halted at the point when
reading of the specified amount of data at the minimum pre-fetch volume is completed,
then execution of the new command starts. When there are no commands that need to be
newly executed, the data look-ahead operation is continued, even after the volume of data
specified as the minimum amount of pre-fetch data have been read, until one of the
following conditions, 1), 3) or 4), occurs.
• When "1" is specified in the DISC bit, if look-ahead of data equal in volume to a cache
segment is completed.
• When "0" is specified in the DISC bit, if look-ahead of all the data is completed up to
the track boundary or the cylinder boundary.
3) During a data look-ahead operation, when any error occurs, the data look-ahead operation
is terminated at that point (retry is not executed).
4) When a RESET condition occurs on the SCSI bus, or when any INIT issues a BUS
DEVICE RESET message, the look-ahead operation is terminated at that point and all the
look-ahead data stored in the data buffer are invalidated.
5) During a look-ahead operation, if "sector slip processing" is applied, or defective sectors
exist in the same cylinder to which "alternate processing" is applicable, the look-ahead
operation is continued without interruption.
C141-E039-01EN2 - 10
Page 68

2.3 Write Cache
The IDD is equipped with a Write cache function in order to reduce the INIT's command
processing time. If that operation is permitted by the MODE SELECT command (caching
parameters: Page code = 8, WCE bit), at the point when the IDD completes the transfer of all
data specified in the WRITE or WRITE EXTENDED command, it reports the GOOD
statement and terminates the command.
Note:
If the Write cache function is permitted, data transferred form the INIT by a WRITE or
WRITE EXTENDED command are written to the disk media after the GOOD status is
reported, so when an unrecoverable write error is detected in that write operation, sense
data are generated. When those sense data are being held, the IDD ordinarily responds to
the command that is executed next by a "CHECK" status (deferred error), notifying the
INIT that sense data are being held. However, ordinarily, it is troublesome for the INIT to
retry when there is an unrecoverable error in a Write cache operation, so adequate caution
should be exercised when using this function.
C141-E039-01EN 2 - 11
Page 69

Page 70

CHAPTER 3 COMMAND SPECIFICATIONS
3.1 Control/Sense Commands
3.2 Data Access Commands
3.3 Format Commands
3.4 Maintenance, Diagnostic Commands
This chapter describes detailed specifications of the SCSI commands which the IDD is equipped with
and how to use them.
3.1 Control/Sense Commands
3.1.1 TEST UNIT READY (00)
Bit
Byte
0 X‘00’
1 LUN 0 0 0 0 0
2 0 0 0 0 0 0 0 0
3 0 0 0 0 0 0 0 0
4 0 0 0 0 0 0 0 0
5 0 0 0 0 0 0 Flag Link
This command checks the status of the disk drive. This command is executed immediately
without queueing in a system which issues only commands with no tags or links.
If the IDD is in the ready state and it is possible for it to be used by the INIT (initiator) which
issues this command, a GOOD status is reported for this command.
If the IDD is not in the ready state, it reports a CHECK CONDITION status for this command.
The sense data generated at this time indicate the IDD's state at this time.
7 6 5 4 3 2 1 0
C141-E039-01EN 3 - 1
Page 71

3.1.2 INQUIRY (12)
Bit
Byte
7 6 5 4 3 2 1 0
0 X‘12’
1 LUN 0 0 0 0 EVPD
2 Page Code
3 0 0 0 0 0 0 0 0
4 Transfer Byte Length
5 0 0 0 0 0 0 Flag Link
This command transfers the information showing the IDD's characteristics (INQUIRY Data) to
the INIT. This command is executed immediately without queueing in a system which issues
only commands with no tags or links.
This command is executed normally even in cases where the UNIT ATTENTION condition is
held, and the UNIT ATTENTION condition is not cleared. This command is also executed
normally when the disk drive is not in the ready state or even when an illegal logical unit
number (LUN) is specified.
A CHECK CONDITION status is reported for this command and it is terminated abnormally
only in the case that one of the following conditions is detected.
• There is an error in the specifications other than the LUN field of the CDB.
• It is impossible to send INQUIRY data because of an IDD hardware error.
• An unrecoverable error was detected on the SCSI bus.
• An error detected during command execution was recovered in the IDD's error recovery
processing (Retry), but the mode which reports "RECOVERED ERROR" is specified in
the MODE SELECT parameter.
• Applicability to overlapping command exception conditions (See item 1.7.1.)
The functions which can be specified in this command's CDB and the contents of information
transferred to the INIT from the IDD differ depending on the specifications in the CHANGE
DEFINITION command. Furthermore, see item 3.1.4, "CHANGE DEFINITION Command"
concerning the CHANGE DEFINITION Command.
C141-E039-01EN3 - 2
Page 72

If bytes 1 and 0, the "EVPD (enable vital product data)" bits, and byte 2, the "Page code" field
in the CDB are enabled only in the case that transfer of the SCSI-2 mode's INQUIRY data is
specified. In the case of the SCSI-1/CCS Mode, zero must be set in these bits and in this field.
If the specification in the "EVPD" bits is "0," the IDD transfers the standard INQUIRY data,
mentioned later, to the INIT. On the other hand, if "1" is specified in the "EVPD" bits,
information called VPD (vital product data) is transferred to the INIT.
Byte 2 of the CDB, the "Page code" field specifies the type of VPD information that should be
transferred to the INIT if the "EVPD" bits are "1." If the "EVPD" bits are "0," zero must be
specified in this field.
Byte 4 of the CDB, the "Transfer Byte Length" field, shows the number of bytes of standard
INQUIRY data or VPD information that the INIT can receive by this command. The IDD
transfers data with the byte length specified in the "Transfer Byte Length" field, or the byte
length in the standard INQUIRY data or VPD information which it is holding, whichever has
the smallest number of bytes, to the INIT. When zero is specified in the "Transfer Byte
Length" field, this command is normally terminated without anything being transferred.
C141-E039-01EN 3 - 3
Page 73

(1) Standard INQUIRY Data
~
~
~~~
~~~
~~~~~~~~~~~
Fig. 3.1 shows the format and contents of the standard INQUIRY data transferred to the INIT
by this command if "0" is specified in the "EVPD" bit.
Bit
Byte
0 Device Type Code
1 RMB Device Type Qualifier
2 ISO Version ECMA Version ANSI Version
3 AENC TrmIOP Response Data Format
4 X‘3B’ (Additional Data Length)
5 0 0 0 0 0 0 0 0
6 0 0 0 0 0 0 0 0
7 0 0 0 0 0 0 0 0
8
9
~
15
16
17
7 6 5 4 3 2 1 0
Qualifier
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 1
0 0 0 0 0 0 1 0
0 0 0 0 0 0 0 1
0 0 0 0 1 0
(Reserved) ACKB
0 0 0 0 0 0 0 0/1
RelAdr WBus32 WBus16 Sync Linked TTD CmdQue SftRe
0 0 0/1 1 1 0 1 0
FUJITSU
~
(vendor ID: ASCII)
(Product ID: ASCII)
(0, 0, 0, 0, 0) or (1, 1, 1, 1, 1)
Addr32 Addr16
REQB
~
31
32
33
34
35
36
37 Device Serial No. (ASCII)
Microcode Version No. (ASCII)
(Product Revision: ASCII)
(*1)
(*2)
(*1)
(*2)
(*1)
(*2)
(*1)
(*2)
~
47
48 X‘00’
63 X‘00’
*1 If set to transfer SCSI-1/CCS Mode INQUIRY data by the CHANGE DEFINITION command.
*2 If set to transfer SCSI-2 Mode INQUIRY data by the CHANGE DEFINITION command.
~
Figure 3.1 Standard INQUIRY Data
C141-E039-01EN3 - 4
Page 74

a. Qualifier Field
(0,0,0): The specified logical unit shows the type of input/output device shown in the
"Device Type Code" field. Even if this code is reported, it does not mean that that
logical unit is in the ready state.
(0,0,1): The specified logical unit shows the type of input/output device shown in the
"Device Type Code" field, but it shows that an actual input/output device is not
connected to that logical unit. The IDD does not report this code.
(0,1,1): Shows that the specified logical unit is not supported. When this code is reported,
it X '1F' is shown in the "Device Type Code" field.
b. Device Type Code
(0,0,0,0,0): Direct Access Device
(1,1,1,1,1): Undefined Device
When LUN=0 is specified, the IDD reports "(0,0,0,0,0) : Direct Access Device" as the
device type code. At this time, the "Qualifier" field is "(0,0,0)." Therefore, byte 0
indicates X '00.' On the other hand, when a LUN other than "0" is specified, the IDD
reports "(1,1,1,1,1) : Undefined Device" as the device type code. At this time, the
"Qualifier" field is "(0,1,1)." Therefore, byte 0 indicates X '7F.'
c. RMB Bit
When this bit is "1," it indicates that the memory media has a variable configuration. The
IDD is a fixed disk device, so this bit is always reported as "0."
d. Device Type Qualifier
A zero is always reported for this field.
e. SCSI Standard Version
Byte 2 displays the code which shows the level of the SCSI standard the IDD is applicable
for. Depending on the specification in the CHANGE DEFINITION command, the IDD
reports either (0,0,1) or (0,1,0)as the applicable level of the ANSI standard. Furthermore,
"ANSI Version" code definitions are as follows.
Code Definition
0 0 0 Devices applicable to ANSI X3. 131-1986.
0 0 1 Devices complying with the ANSI X3.131-1986 standard.
0 1 0 Device to which standard ANSI X3T9.2/86-109 (SCSI-2) was applied.
C141-E039-01EN 3 - 5
Page 75

f. Response Data Format Field
This field displays the code which shows the INQUIRY data format. The definition of the
code is as shown below. The IDD reports either (0,0,0,1) or (0,0,1,0), depending on the
specification in the CHANGE DEFINITION command.
"Response Data Format"
3 2 1 0 Standard INQUIRY Data Format
Bit
0 0 0 0 Format specified in ANSI X3.131-1986 (SCSI-1).
0 0 0 1 Format specified in ANSI X3T9.2/85-52 (CCS).
0 0 1 0 Format specified in ANSI X3T9.2/86-109 (SCSI-2).
g. Additional Data Length
This field shows the length of the INQUIRY data (byte length) after byte 5. This value
shows the length in the INQUIRY Data held by the IDD without relation to the
specification in the transfer byte length field in the CDB, and is always X‘3B’ (total data
length = 64 bytes).
h. Supported Functions
The bit positions shown below are valid only when the CHANGE DEFINITION command
is set so that the SCSI-2 Mode INQUIRY data are transferred, and the functions which the
IDD supports are shown in the bit correspondence. When "1" is displayed, it indicates that
that function is supported and when "0" is displayed, it indicates that that function is not
supported. When the CHANGE DEFINITION command is not set so that SCSI-2 Mode
INQUIRY data are transferred, "0" is displayed in all these bit positions.
(a) Byte 3
AENC (asynchronous event notification capability):
This feature notifies the asynchronous condition. [0]
TrmIOP (terminate I/O process):
The TERMINATE I/O PROCESS message. [0]
(b) Byte 6
ACKBREQB (ACKB/REQB):
Use the ACKB and REQB signals with the B cable or the Q cable. [0]
Addr32 (Wide SCSI Address 32):
32 bit SCSI Addressing [0]
Addr16 (Wide SCSI Address 32):
16 bit SCSI Addressing [0/1]
C141-E039-01EN3 - 6
Page 76

(c) Byte 7
RelAdr (relative addressing):
Relative logic block addressing [0]
WBus32 (32-bit wide data transfer) :
Data transfer on a 4-byte bus [0]
WBus16 (16-bit wide data transfer) :
Data transfer on a 2-byte bus [0/1]
Sync (synchronous data transfer):
Data transfer in the synchronous mode [1]
Linked (linked command):
Command link function [1]
TTD (target transfer disable):
TARGET TRANSFER DISABLE Message [0]
Cmd/Que (command queuing):
Tagged command queuing feature [1]
SftRe (soft reset):
"soft" RESET condition [0]
i. Vendor ID Field
This field indicates the name of the product's supplier in left-justified ASCII code, and
always displays FUJITSU. The unused right end is space for the ASCII code.
j. Product ID Field
The product's model name is displayed in left-justified ASCII code in this field. The
model name display is one of the following.
k. Product Revision Field
The IDD's microcode version number is displayed in ASCII code in this field.
l. Device Serial Number Field
The value following byte 4 of the device serial number in the VPD information is
indicated in this field. Higher order digits which do not contain valid numbers are filled
with ASCII code spaces (X '20'). After byte 48, all the positions contain "00."
C141-E039-01EN 3 - 7
Page 77

(2) VPD Information
When "1" is specified in the "EVPD" bits of the CDB, the VPD information described below
is transferred to the INIT by this command. The INIT specifies the type of VPD information
required in the "Page code" field of the CDB. The type of VPD information supported by the
IDD and its page code number are as shown below.
Page Code Page (Hex) Function
00 Page code list of supported VPD information
80 Device Serial Number
C0 Operation Mode
Furthermore, if page codes other than those shown above (VPD information that is not
supported by the IDD) are specified in the CDB, that command is terminated with a CHECK
CONDITION status (ILLEGAL REQUEST [=5] / Invalid field in CBD [=24-00].
The format and contents of each type of VPD information are shown below.
a. Page Code List
This VPD information reports the page code list of VPD information supported by the IDD.
The format of this VPD information is shown in Fig. 3.2.
Bit
Byte
7 6 5 4 3 2 1 0
0 Qualifier Device Type Code
1 X‘00’ (Page Code)
2 X‘00’
3 X‘03’ (Page Length)
4 X‘00’ (Page Code List)
5 X‘80’ (Device Serial No. )
6 X‘C0’ (Operation Mode)
Figure 3.2 VPD Information: VPD Identifier List
The values displayed in the "Qualifier" and "Device Type Code" fields in byte 0 are the
same as those in the previously mentioned standard INQUIRY data. The "Page code" field
in byte 1 indicates the page code (X '00') of this VPD information itself. Also, the "Page
length" field in byte 3 indicates the length (byte length) after byte 4. This value has no
relationship to the specification in the "Transfer Byte Length" in the CDB, but indicates
the length of this VPD information and is always X '03' (Total data length = 7 bytes).
Byte 4 and subsequent bytes list all the VPD information page codes supported by the
IDD, with the VPD page code indicated in ascending order in each byte.
C141-E039-01EN3 - 8
Page 78

b. Device Serial No.
~~~
~
This VPD information reports the device serial number of the IDD. The format of this
VPD information is shown in Fig. 3.3.
Bit
Byte
0 Qualifier Device Type Code
1 X‘80’ (Page Code)
2 X‘00’
3 X‘0C’ (Page Length)
4
5
7 6 5 4 3 2 1 0
Device Serial No. (ASCII)
~
15
Figure 3.3 VPD Information: Device Serial No.
The values displayed in the "Qualifier" and "Device Type Code" fields in byte 0 are the
same as those in the previously mentioned standard INQUIRY data. The "Page code" field
in byte 1 indicates the page code (X '80') of this VPD information itself. Also, the "Page
length" field in byte 3 indicates the length (byte length) after byte 4. This value has no
relationship to the specification in the "Transfer Byte Length" in the CDB, but indicates
the length of this VPD information and is always X '0C' (Total data length = 16 bytes).
~
Bytes 4 to 15 indicate the IDD's device serial number in right-justified decimal (ASCII
code).
C141-E039-01EN 3 - 9
Page 79

c. Operation Mode
This VPD information reports the IDD's current operation mode. The format of this VPD
information is shown in Fig. 3.4.
Bit
Byte
7 6 5 4 3 2 1 0
0 Qualifier Device Type Code
1 X‘C0’ (Page Code)
2 X‘00’
3 X‘04’ (Page Length)
4 0 0 0 WDTR UNTAIN SDTR RSRTY 0
5 0 0 0 0 0 0 RTD
6 X‘xx’ (Spindle Motor Start Delay Timing)
7 X‘00’ (Reserved)
Figure 3.4 VPD Information: Operation Mode
The values displayed in the "Qualifier" and "Device Type Code" fields in byte 0 are the
same as those in the previously mentioned standard INQUIRY data. The "Page code" field
in byte 1 indicates the page code (X 'C0') of this VPD information itself. Also, the "Page
length" field in byte 3 indicates the length (byte length) after byte 4. This value has no
relationship to the specification in the "Transfer Byte Length" in the CDB, but indicates
the length of this VPD information and is always X '04' (Total data length = 8 bytes).
Byte 4 and subsequent bytes list all the VPD information page modes currently set in the
IDD. This operation mode setting is performed by the CHANGE DEFINITION
COMMAND, described in item 3.1.4, and item 3.1.4 shows concerning a detailed
definition of each bit.
C141-E039-01EN3 - 10
Page 80

3.1.3 READ CAPACITY (25)
Bit
Byte
7 6 5 4 3 2 1 0
0 X‘25’
1 LUN 0 0 0 0 0
2 Logical Block Address (MSB)
3 Logical Block Address
4 Logical Block Address
5 Logical Block Address (LSB)
6 0 0 0 0 0 0 0 0
7 0 0 0 0 0 0 0 0
8 0 0 0 0 0 0 0 PM1
9 0 0 0 0 0 0 Flag Link
This command transfers information related to the disk drive's capacity and the data block size
to the INIT.
When bit 0 "PMI (partial medium indicator)" of CDB byte 8 is "0," the logical block address
and block length (byte length) of the final data block which is accessible in the disk drive (user
space) are transferred to the INIT. At this time, the "Logical Block address" field in the CDB
must specify zero.
When the "PMI" bit is "1," the logical block address and block length (byte length) of data
blocks which satisfy either of the following conditions is transferred to the INIT.
• The data block on the cylinder where the specified block exists, which is just before the
block where the first alternate sector processing (not including defective block sector slip
processing) is implemented. However, when alternate sector processing is being
implemented in the specified block, the data block specified in the CDB.
• When no alternate sector processed data block exists in the cylinder where the specified
block exists, the final data block in that cylinder.
C141-E039-01EN 3 - 11
Page 81

By using this command with the "PMI" bit specified as "1", the INIT can search for usable
data space continuously without being interrupted by data transfers for alternate sector
processing or switching of cylinders.
The format of the data transferred to the INIT by this command is shown in Fig. 3.5.
Bit
Byte
7 6 5 4 3 2 1 0
0 Logical Block Address (MSB)
1 Logical Block Address
2 Logical Block Address
3 Logical Block Address (LSB)
4 Block Length (MSB)
5 Block Length
6 Block Length
7 Block Length (LSB)
Figure 3.5 READ CAPACITY Data
C141-E039-01EN3 - 12
Page 82

3.1.4 CHANGE DEFINITION (40)
Bit
Byte
7 6 5 4 3 2 1 0
0 X‘40’
1 LUN 0 0 0 0 0
2 0 0 0 0 0 0 0 Save
3 0 SCSI Level
4 0 0 0 0 0 0 0 0
5 0 0 0 0 0 0 0 0
6 0 0 0 0 0 0 0 0
7 0 0 0 0 0 0 0 0
8 Parameter List Length
9 0 0 0 0 0 0 Flag Link
This command changes the IDD's SCSI level and the operation mode.
The INIT can know the SCSI level and operation mode that the IDD is currently using by the
INQUIRY command (Standard Inquiry Data and VPD Information - Operation Mode Page:
Page code X 'C0').
If the "Save" bit of CDB byte 2 specifies "1," the IDD saves the SCSI level and operation
mode specified in this command in the Boot-ROM (Flash ROM) when the command is
executed.
If this bit specifies "0," the changes are not saved.
This command specifies a different SCSI level in the "SCSI level" field in SCB byte 3. The
SCSI level is indicated by 1 byte of code as shown in the following table. If a code other than
the following codes is specified, the command is terminated by a CHECK CONDITION status
(ILLEGAL REQUEST [=5] / Invalid field in CDB [=24-00] and the SCSI level and operation
mode are not changed.
Operation Code (HEX) SCSI Level
X'00' Not Change
X'01' SCSI-1 (Same as CCS)
X'02' CCS (Same as SCSI-1)
*1 X'03' SCSI-2
*1 Set at shipping time.
C141-E039-01EN 3 - 13
Page 83

If zero is specified in the "SCSI Level" field, the IDD operates at the current SCSI level
Header
Parameter
without changing the SCSI level. However, if the correct operation mode parameter
(described later) is transferred at the same time, the IDD changes its operation mode.
The total byte length of the operation mode parameter transferred by the INIT with this
command is specified in the "Parameter List Length" field in CDB byte 8.
If zero is specified in the "Parameter List Length" field, the command is terminated normally
with only the SCSI level being changed.
When changing the operation mode, the "parameter list length" field must always be specified
by the length (=8) defined by the operation parameter, described later. If a value other than the
defined length in the "parameter byte length" field is specified, this command is terminated
with a CHECK CONDITION status (ILLEGAL REQUEST [=5] / Invalid field in CDB) and
the SCSI level and operation mode are not changed.
If the IDD's operation mode is changed by this command, a UNIT ATTENTION condition
(UNIT ATTENTION [=6] / INQUIRY Data has changed [=3F-00] is generated for all the
INITs except the INIT that issued this command.
The format for the operation mode parameter transferred by this command from the INIT to
the IDD is shown below. If the operation mode parameter is transferred in a format other than
that shown below, this command is terminated with a CHECK CONDITION status (ILLEGAL
REQUEST [=5] / Invalid field in parameter list) [=26-00] and the SCSI level and operation
mode are not changed.
Bit
Byte
7 6 5 4 3 2 1 0
0 X‘00’
1 X‘00’
2 X‘00’
3 X‘04’ (Parameter Length)
4 0 0 0 WDTR
UNTAIN
SDTR RSRTY 0
5 0 0 0 0 0 0 RTD
6 Spindle Motor Start Delay Time
7 X‘00’ (Reserved)
The operation mode parameter is configured from a 4-byte parameter list following a 4-byte
header.
List
C141-E039-01EN3 - 14
Page 84

(1) Header
a) Bytes 0 to 2
X '00' must be specified in this field.
b) Parameter Length
The parameter list length in byte 4 and subsequent bytes which follows the header must be
specified in this field. The parameter list length supported by the IDD is X '04' and the
INIT must not specify a value other than X '04' in this field. If a value other than X '04' is
specified, this command is terminated with a CHECK CONDITION status (ILLEGAL
REQUEST [=5] / Invalid field in parameter list) [=26-00] and the operation mode are not
changed.
(2) Parameter List
a) WDTR (wide data transfer request: Effective for devices which support 16 bit SCSI
only.)
This specifies whether or not a wide mode data transfer request from the IDD is permitted.
"1" (Permitted): After the power is switched on, after a RESET condition occurs or when
the first command is received following reception of a BUS DEVICE
RESET message, if a WIDE DATA TRANSFER REQUEST (WDTR)
message is not sent by the INIT, the IDD sends the WDTR message and
attempts to establish wide mode data transfer.
"0"* (Prohibited):If it is necessary to establish wide mode data transfer, the IDD does not
send the WDTR message. However, if the INIT sends the WDTR
message, the IDD responds normally.
* Set at shipping time
b) UNTATN (Unit Attention Report Mode)
This specifies the response method to commands received from the INIT when the IDD is
holding a UNIT ATTENTION condition:
"1"* (Report): The IDD reports a CHECK CONDITION status (Standard SCSI
specification) in response to commands other than INQUIRY and
REQUEST SENSE.
"0" (No Report): The IDD terminates all commands that are received normally. (A
CHECK CONDITION status which causes a UNIT ATTENTION
condition is not reported.)
* Set at shipping time
C141-E039-01EN 3 - 15
Page 85

c) SDTR (synchronous data transfer request)
Specifies whether or not it is permitted for the TARG to request a synchronous mode data
transfer.
"1" (Permitted) : After the power is switched on, after a RESET condition occurs or when
the first command is received following reception of a BUS DEVICE
RESET message, if a synchronous data transfer request (SDTR) message
is not sent by the INIT, the IDD sends the SDTR message and attempts
to establish synchronous mode data transfer.
"0"* (Prohibited):Even if it is necessary to establish synchronous mode data transfer, no
SDTR message is sent from the IDD. However, if a SDTR message is
sent from the INIT, the IDD responds normally.
* Set at shipping time
d) RSRTY (reselection retry)
This specifies the number of retries in the RESELECTION phase.
"1" *: Unlimited
"0": 10 times
* Set at shipping time
e) RTD (reselection time-out delay)
This specifies the reselection time-out delay time.
Bit 1 Bit 0 Reselection Time-out Delay
0 0 250 [ms]
0 1 3 [ms]
1 0 Reserved
1 1 Reserved
g) Spindle Motor Start Delay Time
This specifies the length of time after power on until the motor starts.
The IDD's motor starts [(value specified in this parameter) x (IDD's SCSI ID x 0.1)]
seconds after the power is switched on. If X '00' is specified in this parameter, the motor
starts immediately after the power is switched on, no matter what SCSI ID is set in the
IDD. Also, the IDD starts the motor immediately no matter what value is specified in this
parameter.
This parameter is enabled only when set in the "Auto Motor Start Mode" with a setting
terminal.
C141-E039-01EN3 - 16
Page 86

3.1.5 MODE SELECT (15)
Bit
Byte
7 6 5 4 3 2 1 0
0 X‘15’
1 LUN PF 0 0 0 SP
2 0 0 0 0 0 0 0 0
3 0 0 0 0 0 0 0 0
4 Parameter List Length
5 0 0 0 0 0 0 Flag Link
This command performs setting and changing of each type of parameter related to disk drive
physical attributes, data format, timing of SCSI bus disconnect/reconnect processing and error
recovery procedures, etc. The INIT can know the types of parameters, the current settings of
each parameter and the types of parameters which can be changed, and the ranges for such
changes, etc. by using the MODE SENSE or MODE SENSE EXTENDED command.
The data (MODE SELECT parameters) transferred from the INIT to the IDD by this
command, are configured from a "Header," "Block Descriptor" and one or more "Page
Descriptors" which describe each parameter, each of which will be explained later.
When the "PF (page format)" bit in CDB byte 1 is "1," it indicates that the MODE SELECT
parameters transferred from the INIT by this command are in the "Page Descriptor" format.
The IDD disregards the value specified in this bit and regards the MODE SELECT parameters
transferred from the INIT as being in the "Page Descriptor" format, executing this command.
The "SP (save pages)" bit in CDB byte 1 specifies whether or not to save the MODE SELECT
parameters specified in this command on the disk. It is possible for the IDD to save all the
MODE SELECT parameters described in the "Page Descriptor" (except for those on page C),
but this bit's specification is valid only for parameters other than "Format parameters (Page 3)"
and "Drive parameters (Page 4: excluding byte 17)."
If "1" is specified in the "SP" bit, the parameters transferred from the INIT are saved to the
disk when this command is executed, except for "Format parameters (page 3)" and "Drive
parameters (Page 4: excluding byte 17)." When the "SP" bit is "0," these parameters are not
saved to the disk. On the other hand, as for "Format parameters (Page 3)" and "Drive
parameters (Page 4: excluding byte 17)," regardless of the specification of the "SP" bit when
this command is executed, these parameters are always saved to the disk when the FORMAT
UNIT command is executed.
The "Parameter length" field of the CDB specifies the total byte length of the MODE SELECT
parameters transferred from the INIT by this command. If zero is specified in the "Parameter
length" field, this command is terminated normally without data transfer being executed with
the INIT. The MODE SELECT parameters have specifically defined formats and lengths, as
explained by the descriptions of each page descriptor in this item, and the INIT must always
specify (transfer) those formats and lengths.
C141-E039-01EN 3 - 17
Page 87

If a "Header," "Block Descriptor" or any "Page Descriptor" cannot be transferred with all the
defined length because the total defined length of the MODE SELECT parameters actually
transferred from the INIT do not match the value specified in the "Parameter List Length"
field, or if the total of the MODE SELECT parameter's defined length transferred from the
INIT exceeds the value specified in the "Parameter list length" field, this command is
terminated with a CHECK CONDITION status (ILLEGAL REQUEST [=5] / Invalid field in
CDB) [=24-00], and all the MODE SELECT parameters transferred in the command are
disabled.
Three types of values exist in the MODE SELECT parameters, "Current," "Save" and
"Default" values. "Current" values are parameters which actually control the IDD's operation,
and the parameters specified by this command are converted to "Current" values. "Save"
values are parameter values specified by this command which are preserved on the disk. And
"Default" values are values which the IDD uses as "Current" values during the time until
reading of "Save" values is completed after the IDD's power is switched on, or when no
"Save" values exist and no MODE SELECT command is being issued.
The IDD has a common set of "Current", "Save" and "Default" values of all the MODE
SELECT parameters for all the INITs.
When the IDD's power is switched on, when a RESET condition occurs or when the IDD
receives a BUS DEVICE RESET message, the "Current" MODE SELECT parameter values
are changed to the "Save" parameter values, if they exist, and are changed to the "Default"
parameter values if the "Save" values do not exist.
When any of the parameters related to the data format on the disk media (Block Descriptor,
Format parameters: Page 3, and Drive parameters: Page 4), parameters related to the segment
buffer (Caching parameters: Page 8, byte 13) and parameters related to command queuing
(Control mode parameters: Page A, byte 3, D Que) is changed by this command, a UNIT
ATTENTION condition (Mode parameters changed [=2A-01] is generated for all the INITs
other than the INIT that issued this command.
When the RESERVE command is issued which specifies the Third Party Reserve function, the
"Current" values of MODE SELECT parameters of the INIT that issued the RESERVE
command are copied to "Current" values for a third party device specified by the RESERVE
command. Details of this function are described in 3.1.11, "RESERVE (16)."
The relation between the three types of parameters, "Current," "Save" and "Default," is shown
in the following diagram.
C141-E039-01EN3 - 18
Page 88

Remark
Save values
Current values
Power-on
RESET condition
MODE
SELECT
[Common to all INITs]
Page:
1, 2, 7, 8, A, C, 1C, 21
[Common to
all INITs]
Block descriptor
Page: 3, 4
Power-on
RESET condition
BUS DEVICE RESET message
Default values
[Common to all INITs]
Page:
1, 2, 7, 8, A, C, 1C, 21
BUS DEVICE RESET
message
MODE SELECT (SP=1)
MODE SELECT
EXTENDED
FORMAT UNIT
Power-on
When the drive is shipped from the
factory, there are no parameter page
"Save" values except for Page 3 (Format
Parameters) and Page 4 (Drive
Parameters). "Save" values for the
parameter pages specified in the MODE
SELECT command are generated for the
first time when that command is executed
with "1" specified in the "SP" bit.
[Common to all INITs]
Page:
1, 2, 7, 8, A, 1C, 21
[Common to all INITs]
Block descriptor
Page: 3, 4
Figure 3.6 MODE SELECT Parameter Structure
The MODE SELECT parameters include parameters which can be changed by the INIT as
desired, parameters which the INIT cannot change, which whose values are determined by the
IDD unilaterally and parameters which can be changed by the INIT within certain appropriate
limits. The IDD also contains parameter fields which are applicable for rounding processing
("rounding up" or "rounding down") of parameter values specified by the INIT to values
which the IDD can use in actual operation.
When changing of parameters other than "variable parameters" is requested by the INIT in the
MODE SELECT parameters which it transfers in this command, or when changes which are
outside the permissible range are requested, even though they are "variable parameters," this
command is terminated with a CHECK CONDITION status (ILLEGAL REQUEST [=5] /
Invalid field in parameter list) [=26-00] and all the parameters specified by the INIT are
disabled. Furthermore, parameter fields exist which ignore the values specified by the INIT,
even if the parameters are "variable parameters." Details are explained in the description of
each page descriptor in this item.
C141-E039-01EN 3 - 19
Page 89

If the IDD performs rounding processing ("rounding up" or "rounding down") of parameter
values specified by the INIT, in some cases a "CHECK CONDITION" status (RECOVERED
ERROR [=1] / Rounded parameter [37-00] is reported, and in some cases it is not reported.
Whether or not a "CHECK CONDITION" status is reported is determined by the type of
"rounding up" or "rounding down" and the conditions.
If the INIT would like to confirm that the IDD is implementing rounding processing, it issues
a MODE SENSE or MODE SENSE EXTENDED command after issuing this command and
reads the values for the "Current" parameters, then compares them with the parameter values
sent in the MODE SELECT command.
Parameter fields which are the object of rounding processing are explained in the descriptions
of each page descriptor in this item.
Fig. 3.7 shows the data configuration of the parameter list transferred by the INIT in this
command. The parameter list is configured from header 4 bytes in length followed by a block
descriptor with a length of 8 bytes. This is followed by one or more page descriptors, or,
when there is no block descriptor the 4-byte header is followed by one or more page
descriptors. The INIT may transfer a header only, or the header and block descriptor only
without the page descriptor added.
C141-E039-01EN3 - 20
Page 90

Header
~
Page
~
~
Bit
Byte
0 X‘00’
1 X‘00’ (Media Type)
2
3 X‘00’ or X‘08’ (Product Descriptor Length)
Block Descriptor
Bit
Byte
0 Data Block Count (MSB)
1 Data Block Count
2 Data Block Count
3 Data Block Count (LSB)
4 X‘00’
5 Data Block Length (MSB)
7 6 5 4 3 2 1 0
×
7 6 5 4 3 2 1 0
0 0
×
0 0 0 0
6 Data Block Length
7 Data Block Length (LSB)
Page Descriptor
Header
Bit
Byte
0 0 0 Page Code
1 Page Length
2
~
n
Figure 3.7 MODE SELECT Command (Group 0) Parameter Configuration
7 6 5 4 3 2 1 0
~
Parameter Field
~
C141-E039-01EN 3 - 21
Page 91

a. Header
• Media Type
X '00' (default type) must be specified in this field.
• Byte 2
Byte 7 and byte 4 of this field have meaning only in the header transferred to the INIT
by the MODE SENSE and MODE SENSE EXTENDED commands. The values
specified in these bits are disregarded in the MODE SELECT and MODE SELECT
EXTENDED commands. "0" must always be specified by the INIT in the other bit
positions.
• Block Descriptor Length
This field indicates the length (block count) of the "Block descriptor" which follows
the header (not including the length of the "Page descriptor"). It is possible to define
only 1 "Block descriptor" to the IDD, and either X '00' or X '08' must be specified in
this field. When X '00' is specified in this field, it indicates that the "Block
descriptor" is not included in the parameter list transferred from the INIT and the
"Page descriptor" follows immediately after the "Header."
b. Block Descriptor
The logical attributes of the data format on the disk media are described in the 8 byte long
"Block descriptor."
Note:
The parameters in the "Block descriptor" are intimately related in the Format
parameters (Page 3) and the Drive parameters (Page 4). If the parameters in the
"Block descriptor" are changed, the INIT should also specify the appropriate values in
the Format parameters (Page 3) and Drive parameters (Page 4) to correct them.
If only the "Block descriptor" in this command is changed, the IDD changes the
values in the "Sector count/track," Data byte length/physical sector," "Track skew
factor" and "Cylinder skew factor," as well as the "Cylinder count" value in the drive
parameters (Page 4) in accordance with the contents specified in the "Block
descriptor," and uses the "Current" values as is for the other parameters.
C141-E039-01EN3 - 22
Page 92

• Data Block Count
This field specifies the total number of logical data blocks (the block length is
specified in "Data block length) allocated in the "User Space" on the disk media. The
maximum logical block address is a value with 1 subtracted from the value in this
field.
The "Data block count" has an intimate relationship with the specifications on Pages 3
and 4.
If only the "Block descriptor" in this command is changed, the "Cylinder count" on
Page 4 is set to a realizable cylinder count which takes into account the "Alternate
track count/drive" and "Alternate sector count/zone" components in Page 3 resulting
from the value specified here (no rounding processing report is made). If this cylinder
count exceeds the maximum cylinder count that can be use din the User Space, the
"Data block count" is rounded to the maximum value that is realizable. (there is a
rounding processing report in this case).
If zero is specified for the "Data block count," or when the block descriptor is not
specified, the total number of blocks that it is possible to use after the "Alternate track
count/drive" and "Alternate sector count/zone" components in Page 3 are subtracted
from the "Cylinder count" on Page 4 is set in the "Data block count" (rounding
processing is not reported).
• Data Block Length
This field specifies the byte length of a logical data block on the disk media.
The logical data block length and physical data block length are the same in the IDD.
The data block length can be specified at 512 to 528 bytes (2-byte boundary).
If less than 512 bytes is specified in this field, the IDD performs rounding processing
(there is a rounding processing report), setting the data block length at 512 bytes. If
more than 528 bytes is specified, rounding processing is performed (there is a
rounding processing report), setting the data block length at 528 bytes. If an odd
number is specified within this range, rounding processing is performed which adds
+1 to the specified value (there is a rounding processing report).
If zero is specified in this field, the value specified in bytes 12 and 13 (Data byte
length/sector) of Page 3 (Format Parameter) is set. At that time, if Page 3 is not
specified at the same time, the current value in Page 3 is used.
If the value set in this field differs from the value specified in bytes 12 and 13 (Data
byte length/sector) of Page 3 (Format Parameter), the data block length in the block
descriptor is set.
C141-E039-01EN 3 - 23
Page 93

c. Page Descriptor
The "Page descriptor" is configured from a 2-byte page header followed by a parameter
field and each parameter function attribute is classified in a unit called a "Page." The
individual "Page descriptors" in the MODE SELECT and MODE SELECT EXTENDED
commands may be specified independently by the INIT and multiple "Page descriptors"
may be specified continuously in the desired sequence.
• Page Code
This field specifies a code (Page No.) that indicates the type of "Page descriptor."
• Page Length
This field indicates the length of the parameter field (number of bytes) after byte 2,
excluding the page header, of the "Page descriptor" and is a fixed value for each page
code. The INIT must specify the same value as the page length reported by the IDD
in the MODE SENSE or MODE SENSE EXTENDED command, except in cases it is
described in each of the page descriptor descriptions in this item.
d. MODE SELECT Parameters of the IDD
The parameter list configuration and its length that can be transferred to the IDD by the
INIT in the MODE SENSE or MODE SENSE EXTENDED command are as shown
below. If a "Page descriptor" that is not supported by the IDD is specified, the command
is terminated with a CHECK CONDITION status (ILLEGAL REQUEST [=5] / Invalid
field in parameter list) [=26-00], and all the MODE SELECT parameters transferred in the
command are disabled.
Parameter Byte Length
Header 4
Block Descriptor 8 or 0
Page Descriptor Page 1: Read/Write Error Recovery Parameter 12
Page 2 Disconnect/Reconnect Parameter 16
Page 3: Format Parameter 24
Page 4: Drive Parameter 24
Page 7: Verify Error Recovery Parameter 12
Page 8: Caching Parameter 20
Page A: Control Mode Parameter 8
Page C Notch Parameter 24
Page
1C:
Page 21: Additional Error Recovery Parameter 4
Information Execution Control 12
C141-E039-01EN3 - 24
Page 94

Notes:
1. The MODE SELECT parameter is ordinarily different in its configuration depending
on the input/output device and the type of controller. It is also possible that current
definitions may be expanded in accordance with the expansion of the functions of the
IDD in the future. In order to assure independence of software from the individual
specifications of input/output devices, before the INIT issues this command, it should
follow the procedure of using the MODE SENSE and MODE SENSE EXTENDED
command to determine the types of parameters the TARG is actually equipped with
and the attributes of those parameters, such as whether or not they can be changed.
2. After changing anything in the "Block descriptor," "Format parameters (Page 3)" or
"Drive parameters (Page 4)," with the MODE SELECT or MODE SELECT
EXTENDED command, it is impossible to execute a command to access the data on
the disk media until execution of the FORMAT UNIT command is completed, and a
CHECK CONDITION status (MEDIUM ERROR [=3] / Medium format corrupted
[=31-00] is reported for all such commands.
The configuration and functions of the "Page descriptors" supported by the IDD are described
below.
Note:
In the diagram that shows the configuration of each individual "Page Descriptor," the
default column shows that parameter's "default" value and the "variable" column shows
whether or not it is possible to vary that parameter ("1" indicates that it can be varied).
The INIT can know those values and attributes by using the MODE SENSE or MODE
SENSE EXTENDED command.
C141-E039-01EN 3 - 25
Page 95

(1) Read/Write Error Recovery Parameters (Page Code = 1)
Fig. 3.8 shows the format of the page descriptor of this MODE SELECT parameter.
Bit
Byte
7 6 5 4 3 2 1 0
0 0 0 0 0 0 0 0 1
1 X‘0A’ or X‘06’ (Page Length)
2 AWRE ARRE TB RC ERR PER DTE DCR
Default 0 0 1 0 1 0 0 0
Variable 1 1 1 1 1 1 1 1
3 Number of retries during READ
Default X‘20’
Variable X‘FF’
4 Correctable Bit Length
Default X‘59’
Variable X‘00’
5 X‘00’ (Head Offset Count)
6 X‘00’ (Data Strobe Offset Count)
7 X‘00’ (Reserved)
(Note)
(=32
times)
(=89
bits)
8 Number of retries during WRITE
Default X‘00’
Variable X‘FF’
9 X‘00’ (Reserved)
10-11 X‘0000’ (Recovery Time Limit)
Figure 3.8 MODE SELECT Parameters: Read/Write Error Recovery Parameters
Note
If transfer of this page descriptor is requested by the MODE SENSE or MODE
SENSE EXTENDED command, the IDD reports X '0A' as the page length (byte 1).
However, if either X '0A' or X '06' is specified for the page length in the MODE
SELECT or MODE SELECT EXTENDED command, the IDD treats it as though the
correct page length was specified. If X '06' is specified for the page length, the value
specified in the "Number of retries during READ" field is used as is in the "Number
of retries during WRITE" field and the value specified in the "Number of retries
during READ" field is also used as is in the "Number of retries during VERIFY"
field. The X '06' page length is included in consideration of compatibility with
previous models, but as much as possible, it is recommended that the INIT use the X
'0A' page length.
(=0
times)
C141-E039-01EN3 - 26
Page 96

Error recovery parameters defined in this page descriptor are applicable for the following
commands, except in cases where it is specifically pointed out.
• READ • WRITE
• READ EXTENDED • WRITE AND VERIFY (Write operation)
• READ LONG • WRITE EXTENDED
• SEND DIAGNOSTIC (Write/read test) • WRITE LONG
a. AWRE (automatic write reallocation enabled)
"1" : An "automatic alternate block allocation processing" operation is specified during
execution of a write operation.
"0" : An "automatic alternate block allocation processing" operation is prohibited during
execution of a write operation.
The IDD does not support automatic alternate processing during a write operation. the IDD
disregards the specification of this bit and operates according to the default value, (=0).
b. ARRE (automatic read reallocation enable)
"1" : An "automatic alternate block allocation processing" operation is specified during
execution of a read operation.
"0" : An "automatic alternate block allocation processing" operation is prohibited during
execution of a read operation.
Automatic alternate block allocation processing is explained in item 4.3.2.
c. TB (transfer block)
"1" : Data blocks which contain errors that are impossible to correct are transferred to the
INIT during a read operation.
"0" : Data blocks which contain errors that are impossible to correct are not transferred to
the INIT during a read operation.
d. RC (Read Continuous)
This bit specifies continuous transfer of all the data requested by a command
unaccompanied by a delay for executing error recovery processing.
The IDD disregards the specification in this bit and operates according to the default value,
(=0).
C141-E039-01EN 3 - 27
Page 97

e. EER (enable early recovery)
"1" : When a correctable data check has been detected, data correction according to the
ECC is applied immediately without executing retry (rereading) up to the number of
times specified in the "Number of retries during READ" parameter.
"0" : When a correctable data check has been detected, retry (rereading) is executed up to
the number of times specified in the "Number of retries during READ" parameter,
then data correction according to the ECC is applied if possible.
The IDD disregards this bit and operates according to the default value, (=1).
f. PER (post error)
"1" : When several errors (errors related to the disk drive), which were recovered from
normally through the IDD's error recovery processing, have been detected, a
CHECK CONDITION status is reported when execution of that command is
completed. In the sense data generated at this time, the sense key indicates
"RECOVERED ERROR [=1]" and the content of the final error to be corrected
successfully is reported.
"0" : Even when several errors (errors related to the disk drive), which were recovered
from normally through the IDD's error recovery processing, have been detected, that
command is completed with a GOOD status and the contents of the recovered errors
are not reported.
g. DTE (disable transfer on error)
"1" : Even when several errors on the disk drive, which were recovered from normally
through the IDD's error recovery processing, have been detected, execution of that
command terminates at that point.
"0" : When several errors on the disk drive, which were recovered from normally through
the IDD's error recovery processing, have been detected, execution of that command
is continued.
The IDD disregards this bit and operates according to the default value, (=0).
h. DCR (disable correction)
"1" : Even when a correctable data check has been detected, data correction according to
the ECC is prohibited. However, On-the-fly correction processing is not prohibited.
"0" : When a correctable data check has been detected, data correction according to the
ECC is applied.
The IDD disregards this bit and operates according to the default value (=0).
C141-E039-01EN3 - 28
Page 98

i. Number of Retries during READ
This parameter specifies the number of retries that should be executed for "Data Check"
type errors detected in read operations on the disk media. The number of retries specified
in this parameter is the maximum number of times reading is retried for each individual
portion of data in each logical data block. If the IDD cannot perform correction of the data
On-the-fly for each portion of data in the data block, it retries the reading of those portions.
The reread retry is executed the number of times specified by the drive parameter
internally by the IDD before this retry is executed, so actually the retry is executed the
number specified here plus the number of internal retries.
The value specified in this parameter is applicable to the READ/READ EXTENDED
commands and the read test in the SEND DIAGNOSTIC command.
When the page length in Page 1 is specified as X '06,' the value specified in this field is
copied to the "Number of retries during WRITE" on this page and "Number of retries
during VERIFY" on Page 7.
j. Correctable Bit Length
This parameter indicates the burst error length (bit length) which it is possible to apply
data correction according to the ECC to. It is impossible to change this parameter from the
INIT. The IDD disregards the value specified in this parameter and operates according to
the "Default" value.
k. Number of Retries during WRITE
This field specifies the maximum number of times writing of data to the disk media is
retried in the case that there has been an interruption in a write operation such as an
impact. the number of retries specified in this field is applied to each logical block unit.
When zero is specified in this field, retrying of writing to the disk is prohibited.
The value specified in this field is applicable to the WRITE command, WRITE
EXTENDED command, write operations in the WRITE AND VERIFY command and
write tests in the SEND DIAGNOSTIC command. When the page length in Page 1 is
specified as X '06,' the value specified in this field is not transferred from the INIT, but in
this case, the value specified in the "Number of retries during READ," on the same Page,
is also applied to this field by the IDD.
C141-E039-01EN 3 - 29
Page 99

l. Recovery Time Limit
This parameter specifies the maximum time that can be used by the TARG for error
recovery processing, as a 1 (s constant. The value specified in this parameter is the
maximum permissible time for error recovery processing for each individual logical data
block. When both this parameter and the "Number of retries" parameter are specified, the
parameter which specifies the shortest time must be given priority in application.
The IDD does not support this parameter. The IDD disregards the value specified in this
parameter.
Table 3.1 Combination of Error Recovery Flags (1/3)
EER PER DTE DCR Error Recovery Procedure
0 0 0 0 1. Rereading is tried repeatedly up to the number of times specified in the "Read
Retry Count", "Write Retry Count" or "Verify Retry Count" parameter. If
possible, data correction is executed afterward according to the ECC.
2. When error recovery has succeeded, processing of the command is continued
3. The contents of recovered errors are not reported.
4. If unrecoverable errors have been detected, execution of that command is
terminated at that point.
5. Transfer of data in blocks which include unrecoverable errors to the INIT is
done in accordance with the specification in the TB bit (Read system
command).
0 0 0 1 1. Rereading is tried repeatedly up to the number of times specified in the "Read
Retry Count", "Write Retry Count" or "Verify Retry Count" parameter. Data
correction is not executed according to the ECC.
2. When error recovery has succeeded, processing of the command is continued.
3. The contents of recovered errors are not reported.
4. If unrecoverable errors have been detected, execution of that command is
terminated at that point.
5. Transfer of data in blocks which include unrecoverable errors to the INIT is
done in accordance with the specification in the TB bit (Read system
command).
0 0 1 0
0 0 1 1
0 1 0 0 1. Rereading is tried repeatedly up to the number of times specified in the "Read
Retry Count", "Write Retry Count" or "Verify Retry Count" parameter. If
possible, data correction is executed afterward according to the ECC.
2. When error recovery has succeeded, processing of the command is continued.
3. If unrecoverable errors have been detected, execution of that command is
terminated at that point.
4. Transfer of data in blocks which include unrecoverable errors to the INIT is
done in accordance with the specification in the TB bit (Read system
command).
5. When recovery from all detected errors has been successful, a CHECK
CONDITION status (RECOVERED ERROR [=1] is reported after all
processing of the command is completed and the sense data indicate the
content of the last error that was successfully recovered from and the address
of the data block where that error occurred.
(Setting prohibited) (See *1 at the end of this table.)
(Setting prohibited) (See *1 at the end of this table.)
C141-E039-01EN3 - 30
Page 100

Table 3.1 Combinations of Error Recovery Flags (2 of 4)
EER PER DTE DCR Error Recovery Procedure
0 1 0 1 1. Rereading is tried repeatedly up to the number of times specified in the "Read
Retry Count", "Write Retry Count" or "Verify Retry Count" parameter. Data
correction is not executed according to the ECC.
2. When error recovery has succeeded, processing of the command is continued.
3. If unrecoverable errors have been detected, execution of that command is
terminated at that point.
4. Transfer of data in blocks which include unrecoverable errors to the INIT is
done in accordance with the specification in the TB bit (Read system
command).
5. When recovery from all detected errors has been successful, a CHECK
CONDITION status (RECOVERED ERROR [=1] is reported after all
processing of the command is completed and the sense data indicate the
content of the last error that was successfully recovered from and the address
of the data block where that error occurred.
0 1 1 0 1. Rereading is tried repeatedly up to the number of times specified in the "Read
Retry Count", "Write Retry Count" or "Verify Retry Count" parameter. If
possible, data correction is executed afterward according to the ECC.
2. When error recovery has succeeded, or even when recovery is impossible,
execution of the command is terminated with a CHECK CONDITION status
at the point when error recovery processing is completed, and the sense data
indicate the data block address where that error occurred.
3. Transfer to the INIT of data in blocks with recovered errors is done, but
transfer to the INIT of data blocks in which the errors were unrecoverable is
done in accordance with the specification in the TB bit (Read system
command).
0 1 1 1 1. Rereading is tried repeatedly up to the number of times specified in the "Read
Retry Count", "Write Retry Count" or "Verify Retry Count" parameter. Data
correction is not executed according to the ECC.
2. When error recovery has succeeded, or even when recovery is impossible,
execution of the command is terminated with a CHECK CONDITION status
at the point when error recovery processing is completed, and the sense data
indicate the data block address where that error occurred.
3. Transfer to the INIT of data in blocks with recovered errors is done, but
transfer to the INIT of data blocks in which the errors were unrecoverable is
done in accordance with the specification in the TB bit (Read system
command).
C141-E039-01EN 3 - 31
 Loading...
Loading...