Page 1

Security System Guide
FortiGate-5001SX
CONSOLE
ACC
PWR
A detailed guide to the features and capabilities FortiGate-5001SX Security System. This FortiGate-5001SX Security
System Guide describes FortiGate-5001SX hardware fea tu res , ho w to ins tall the FortiGate-5001SX module in a
FortiGate-5000 series chassis, how to configure the FortiGate-5001SX security system for your network, and
contains troubleshooting information to help you diagnose and fix problems.
The most recent versions of this and all FortiGate-5000 series documents are available from the FortiGate-5000
page of the Fortinet Technical Documentation web site (http://docs.forticare.com).
Visit http://support.fortinet.com to register your FortiGate-5001SX system. By registering you can receive product
USB
updates, technical support, and FortiGuard services.
1 2 3 4 5 6 7 8
STA IPM
FortiGate-5001SX Security System Guide
01-30000-0380-20070201
www.fortinet.com
Page 2

Warnings and cautions
Only trained and qualified personnel should be allowed to install or maintain FortiGate-5000 series
equipment. Read and comply with all warnings, cautions and notices in this document.
CAUTION: Risk of Explosion if Battery is replaced by an Incorrect Type. Dispose of Used Batteries According
!
to the Instructions.
Caution: You should be aware of the following cautions and warnings before installing FortiGate-5000 series
!
hardware
• Turning off all power switches may not turn off all power to the FortiGate-5000 series equipment.
Except where noted, disconnect the FortiGate-5000 series equipment from all power sources,
telecommunications links and networks before installing, or removing FortiGate-5000 series
components, or performing other maintenance tasks. Failure to do this can result in personal injury or
equipment damage. Some circuitry in the Fort iGa te-5000 series equipment may continue to operate
even though all power switches are off.
• An easily accessible disconnect device, such as a circuit breaker, should be incorporated into the data
center wiring that connects power to the FortiGate-5000 series equipment.
• Install FortiGate-5000 series chassis at the lower positions of a rack to avoid making the rack top-heavy
and unstable.
• Do not insert metal objects or tools into open chassis slots.
• Electrostatic discharge (ESD) can damage FortiGate-5000 series equipment. Only perform the
procedures described in this document from an ESD workstation. If no such station is available, you
can provide some ESD protection by wearing an anti-static wrist or ankle strap and attaching it to an
ESD connector or to a metal part of a FortiGate chassis.
• Some FortiGate-5000 series components may overlo ad your supply circuit and imp act your over current
protection and supply wiring. Refer to nameplate ratings to address this concern.
• Make sure all FortiGate-5000 series components have reliable grounding. Fortinet recommends direct
connections to the branch circuit.
• If you install a FortiGate-5000 series component in a closed or multi-unit rack assembly, the operating
ambient temperature of the rack environment may be greater than room ambient. Make sure the
operating ambient temperature does not exceed the manufacturer's maximum rated ambient
temperature.
• Installing FortiGate-5000 series equipment in a rack should be such that the amount of airflow required
for safe operation of the equipment is not compromised.
• This equipment is for installation only in a Restricted Access Location (dedicated equipment room,
service closet or the like), in accordance with the National Electrical Code.
• Per the National Electrical Code, sizing of a Listed circuit breaker or branch circuit fuse and the supply
conductors to the equipment is based on the marked inpu t current rating. A p roduct with a marked input
current rating of 25 A is required to be placed on a 40 A branch circuit. The supply conductors will also
be sized according to the input current rating and also derated for the maximum rated operating
ambient temperature, Tma, of the equipment.
• FortiGate-5000 series equipment shall be installed and connected to an electrical supply source in
accordance with the applicable codes and re gu la tio ns for the location in which it is installed. Particular
attention shall be paid to use of correct wire type and size to comply with the applicable codes and
regulations for the installation / location. Connection of the supply wiring to the terminal block on the
equipment may be accomplished using Listed wire compression lugs, for example, Pressure Terminal
Connector made by Ideal Industries Inc. or equivalent which is suitable for A WG 10. Par ticular attenti on
shall be given to use of the appropriate compre ss ion too l spe cifie d by the compression lug
manufacturer, if one is specified.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201
Page 3

Contents
Contents
Warnings and cautions..................................................................................... 2
FortiGate-5001SX security system................................... 5
Front panel LEDs and connectors................................................................... 6
LEDs ............................................................................................................. 6
Connectors.................................................................................................... 7
Base backplane gigabit interfaces................................................................... 7
Hardware installation......................................................... 9
RAM DIMMs........................................................................................................ 9
Installing SFP transceivers............................................................................. 11
Changing FortiGate-5001SX jumper settings ............................................... 12
Inserting a FortiGate-5001SX module into a chassis................................... 14
Before inserting the FortiGate-5001SX module in a chassis ...................... 15
Insertion procedure ..................................................................................... 15
Removing a FortiGate-5001SX module from a chassis ............................... 17
Troubleshooting .............................................................................................. 19
FortiGate-5001SX does not startup ............................................................ 19
FortiGate-5001SX cannot display chassis information ............................... 21
Quick Configuration Guide ............................................. 23
Registering your Fortinet product ................................................................. 23
Planning the configuration ............................................................................. 23
NAT/Route mode ........................................................................................ 24
Transparent mode....................................................................................... 24
Choosing the configuration tool.................................................................... 25
Web-based manager................................................................................... 25
Command Line Interface (CLI).................................................................... 26
Factory default settings.................................................................................. 26
Configuring NAT/Route mode........................................................................ 27
Using the web-based manager to configure NAT/Route mode................... 27
Using the CLI to configure NAT/Route mode.............................................. 28
Configuring Transparent mode...................................................................... 29
Using the web-based manager to configure Transparent mode................ . 29
Using the CLI to configure Transparent mode ............................................ 30
Upgrading FortiGate-5001SX firmware.......................................................... 31
FortiGate-5001SX base backplane data communication............................. 32
Powering off the FortiGate-5001SX module .................................................. 33
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 3
Page 4

Contents
For more information ...................................................... 35
Fortinet documentation .................................................................................. 35
Fortinet Tools and Documentation CD........................................................ 35
Fortinet Knowledge Center ........................................................................ 35
Comments on Fortinet technical documentation ........................................ 35
Customer service and technical support...................................................... 35
Register your Fortinet product....................................................................... 35
FortiGate-5001SX Security System Guide
4 01-30000-0380-20070201
Page 5
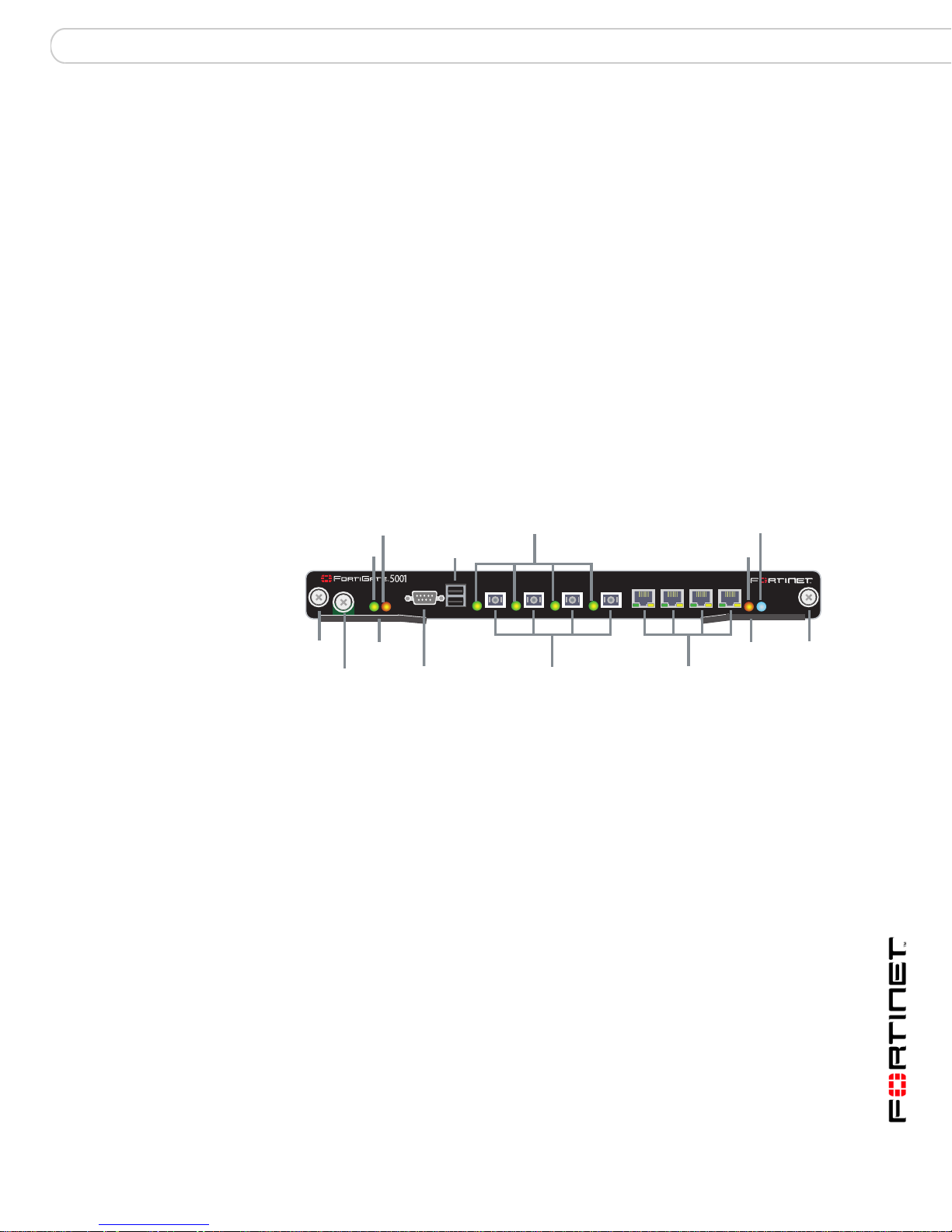
FortiGate-5001SX security system
FortiGate-5001SX security system
The FortiGate-5001SX security system is a high-performance FortiGate security
system with a total of 8 front panel Gigabit ethernet interfaces and two base
backplane interfaces. Use the front panel interfaces for connections to your
networks and the backplane interfaces for communication between
FortiGate-5000 series modules over the FortiGate-5000 chassis backplane.
You can also configure two or more FortiGate-5001SX modules to create a high
availability (HA) cluster using the base backplane interfaces for HA heartbeat
communication through chassis backplane, leaving all eight front panel gigabit
interfaces available for network connections.
The FortiGate-5001SX module also supports high-end FortiGate features
including 802.1Q VLANs, multiple virtual domains, 802.3ad aggregate interfaces,
and FortiGate-5000 chassis monitoring.
Figure 1: FortiGate-5001SX front panel
Module
PositionLink/Traffic
Status
STA IPM
Extraction
Lever
Mounting
Knot
Mounting
Knot
Locking
Screw
Flash Disk
Access
Power
PWR
Extraction
Lever
ACC
CONSOLE
RS-232
Serial
USB
USB
1 2 3 4 5 6 7 8
1 2 3 4
SFP Gigabit fiber
or copper
5 6 7 8
Gigabit Copper
The FortiGate-5001SX module includes the following features:
• A total of eight front panel gigabit interfaces
• Four gigabit interfaces that can accept Small Formfactor Pluggable (SFP)
fiber or copper transceivers (interfaces 1, 2, 3, and 4)
• Four 10/100/1000Base-T gigabit copper network interfaces (i nterfaces 5, 6,
7, and 8)
• Two base backpla ne gigabit interfaces (port9 and port10) for HA heartbeat and
data communications across the FortiGate-5000 chassis backplane.
• DB-9 RS-232 serial console connection
• One USB connector
• Mounting hardware
• LED status indicators
The FortiGate-5001SX module comes supplied with four fiber or four copp er SFP
transceivers. Before you can connect FortiGate-5001SX interfaces 1 to 4, you
must insert the SFP transceivers into the FortiGate-5001SX front panel cage slots
numbered 1 to 4.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 5
Page 6
Front panel LEDs and connectors FortiGate-5001SX security system
The FortiGate-5001SX module ships with two RAM DIMMs installed on the
FortiGate-5001SX circuit board. You should confirm that the RAM DIMMs are
installed correctly before inserting the FortiGate-5001SX module into a chassis.
Front panel LEDs and connectors
From the FortiGate-5001SX font panel you can view the status of the front panel
LEDs to verify that the module is functioning normally. You also connect the
FortiGate-5001SX module to your network through the front panel ethernet
connections. The front panel also includes the RS-232 console port for connecting
to the FortiOS CLI and a USB port. The USB port can be used with a Fortinet USB
key. For information about using the FortiUSB key, see the FortiGa te -5000 Ser ies
Firmware and FortiUSB Guide.
LEDs
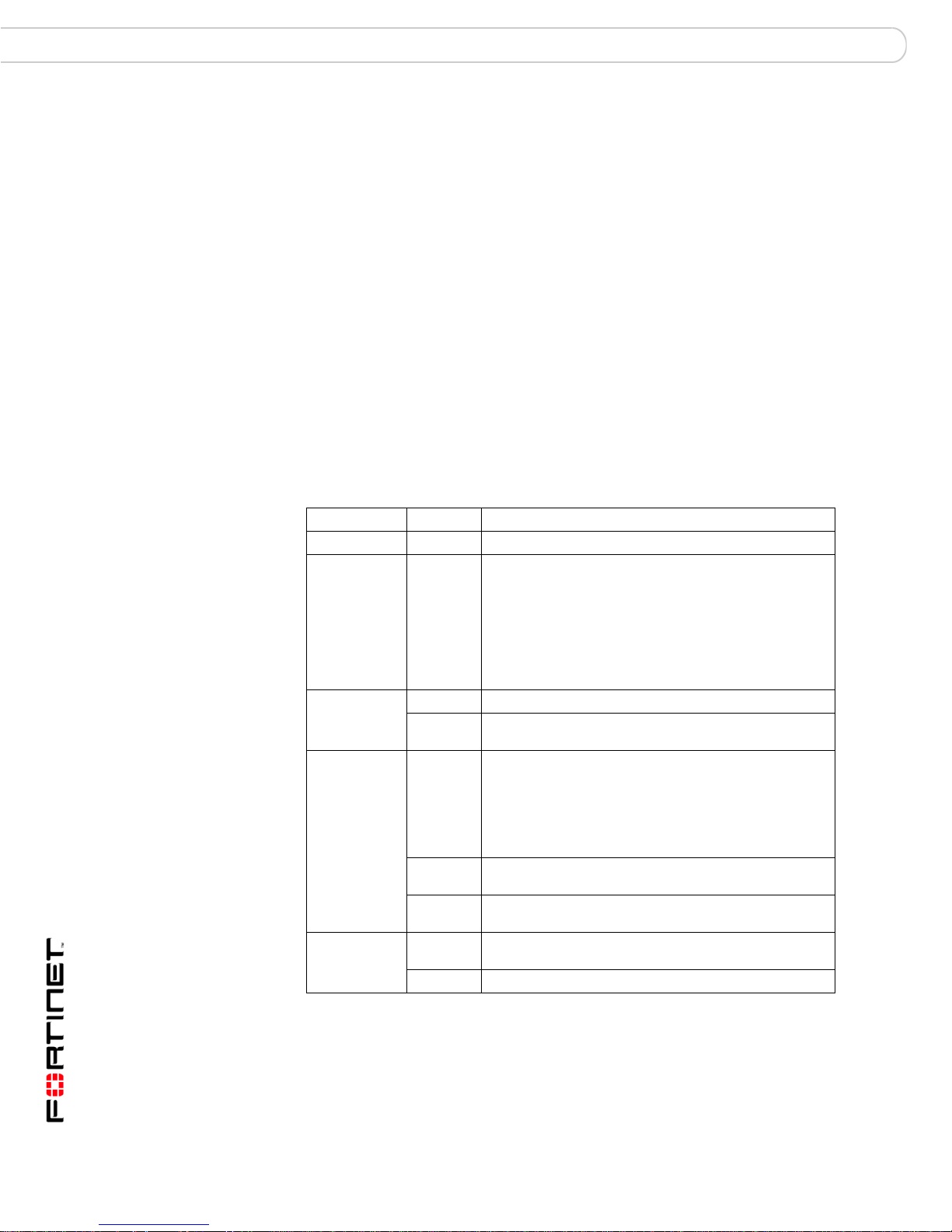
Table 1 lists and describes the FortiGate-5001SX module LEDs.
Table 1: FortiGate-5001SX LEDs
LED State Description
PWR Green The FortiGate-5001SX module is powered on.
ACC Off or
Flashing
red
STA Green Normal operation.
Red The FortiGate-5001SX is starting or a fault condition
IPM Blue The FortiGate-5001SX is ready to be hot-swapped
Flashing
Blue
Off Normal operation. The FortiGate-5001SX module is in
1, 2, 3, 4 Green The correct cable is connected to the gigabit SFP
Flashing Network activity at the gigabit SFP interface.
The ACC LED flashes red when the FortiGate-5001SX
module accesses the FortiOS flash disk. The FortiOS
flash disk stores the current FortiOS firmware build and
configuration files. The system accesses the flash disk
when starting up, during a firmware upgrade, or when
an administrator is using the CLI or GUI to change the
FortiOS configuration. Under normal operating
conditions this LED flashes occasionally, but is mostly
off.
exists.
(removed from the chassis). If the IPM light is blue and
no other LEDs are lit the FortiGate-5001SX module has
lost power, possibly because of a loose or incorrectly
aligned left extraction lever. See “Inserting a
FortiGate-5001SX module into a chassis” on page 14
for more information.
The FortiGate-5001SX is changing from hot swap to
running mode or from running mode to hot swap.
contact with the chassis backplane.
interface.
FortiGate-5001SX Security System Guide
6 01-30000-0380-20070201
Page 7
FortiGate-5001SX security system Base backplane gigabit interfaces
Table 1: FortiGate-5001SX LEDs (Continued)
LED State Description
5, 6,
7, 8
Link
LED
Speed
LED
Green The correct cable is inserted into this interface and the
connected equipment has power.
Flashing Network activity at this interface.
Green The interface is connected at 1000 Mbps.
Amber The interface is connected at 100 Mbps.
Unlit The interface is connected at 10 Mbps.
Connectors
Table 2 lists and describes the FortiGate-5001SX connectors.
Table 2: FortiGate-5001SX connectors
Connector T ype Speed Protocol Description
1, 2, 3, 4 LC
SFP
5, 6, 7, 8 RJ-45 10/100/1000
CONSOLE DB-9 9600 bps RS-232 serial Serial connection to the command line
USB USB FortiUSB key firmware updates and
1000Base-SX Ethernet Four gigabit SFP interfaces that can
Ethernet Copper gigabit connection to
Base-T
accept fiber or copper gigabit
transceivers. These interfaces only
operate at 1000Mbps.
10/100/1000Base-T copper networks.
interface.
configuration backup (FortiOS v3.0).
Base backplane gigabit interfaces
The FortiGate-5001SX port9 and port10 base backplane gigabit interfaces can be
used for HA heartbeat communication between FortiGate-5001SX modules
installed in the same or in different FortiGate-5000 chassis. You can also
configure FortiGate-5001SX modules to use the base backplane interfaces for
data communication between FortiGate modules. To support base backplane
communications your FortiGate-5140 or 5050 chassis must include one or more
FortiSwitch-5003 modules. FortiSwitch-5003 modules are installed in chassis
slots 1 and 2. The FortiGate-5020 chassis supports base backplane
communication with no additions or changes to the chassis.
For information about base backplane communication in FortiGate-5140 and
FortiGate-5050 chassis, see the FortiGate-5000 Base Backplane Communication
Guide. For information about the FortiSwitch-5003 module, see the
FortiSwitch-5003 Guide.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 7
Page 8

Base backplane gigabit interfaces FortiGate-5001SX security system
FortiGate-5001SX Security System Guide
8 01-30000-0380-20070201
Page 9

Hardware installation RAM DIMMs
Hardware installation
Before use, the FortiGate-5001SX module must be correctly inserted into a
FortiGate-5140, FortiGate-50 50 , or FortiG ate-5020 chassis.
Before inserting the module into a chassis you should make sure RAM DIMMS
are installed and FortiGate-5001SX jumpers are set. SFP transceivers must also
be installed for interfaces 1 to 4 before these interfaces can be connected to
network devices.
This section describes:
• RAM DIMMs
• Installing SFP transceivers
• Changing FortiGate-5001SX jumper settings
• Inserting a FortiGate-5001SX module into a chassis
• Removing a FortiGate-5001SX module from a chassis
• Troubleshooting
RAM DIMMs
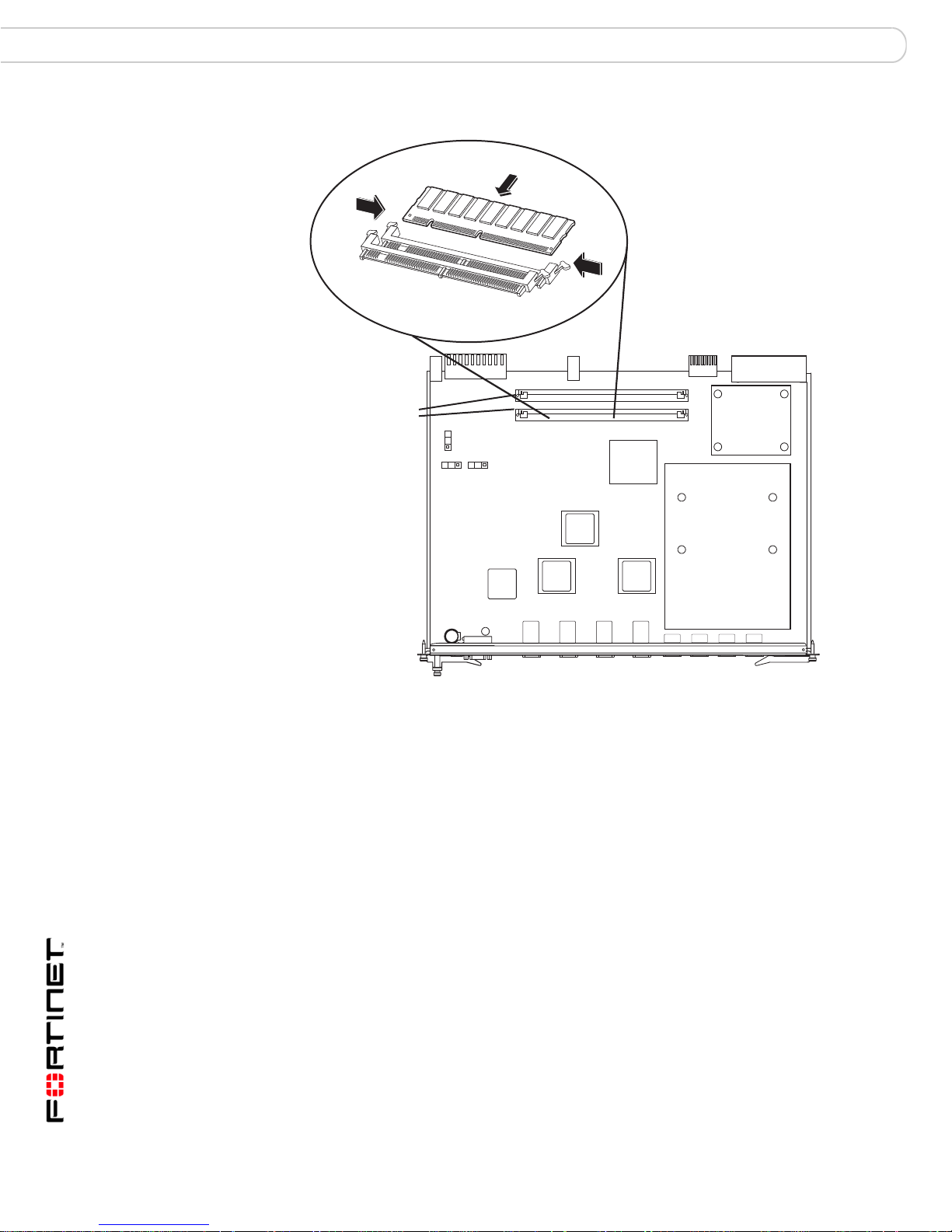
The FortiGate-5001SX module ships with two RAM DIMMs installed on the
FortiGate-5001SX circuit board. You should confirm that the RAM DIMMs are
installed correctly before inserting the FortiGate-5001SX module into a chassis.
To install FortiGate-5001SX RAM DIMMs
To complete this procedure, you need:
• A FortiGate-5001SX module
• Two RAM DIMMs to be installed into the FortiGate-5001SX module RAM
DIMM slots
• An electrostatic discharge (ESD) preventive wrist or ankle strap with
connection cord
Caution: FortiGate-5001SX modules must be protected from static discharge and physical
shock. Only handle or work with FortiGate-5001SX modules at a static-free workstation.
!
Always wear a grounded electrostatic discharge (ESD) preventive wrist or ankle strap when
handling FortiGate-5001SX modules.
1 Attach the ESD wrist or ankle strap to your wrist or ankle and to an ESD socket or
to a bare metal surface on a chassis or frame.
Caution: Handle DIMMs by the edges only. DIMMs are ESD-sensitive components that
!
can be damaged by mishandling.
2 Remove RAM DIMMs from their antistatic packaging.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 9
Page 10
RAM DIMMs Hardware installation
Figure 2: Location of FortiGate-5001SX RAM DIMM slots
RAM DIMM
slots
JP2
JP1
JP3
Front Faceplate
3 Insert each RAM DIMM perpendicular to the RAM DIMM slots. Push the DIMM
firmly into place using the minimum amount of force required. When the DIMM is
properly seated, the socket guide posts click into place.
Do not use excessive force when installing a DIMM.
The RAM slots allow only one alignment of each RAM DIM. If you cannot lock the
locking levers the DIM is not aligned correctly or is in upside-down.
FortiGate-5001SX Security System Guide
10 01-30000-0380-20070201
Page 11

Hardware installation Installing SFP transceivers
Installing SFP transceivers
The FortiGate-5001SX module ships with four SFP transceivers that you must
install for normal operation of the FortiGate-5001SX module. The SFP
transceivers are inserted into cage sockets numbered 1 to 4 on the
FortiGate-5001SX front panel. You can install the SFP transceivers be fore or af ter
inserting the FortiGate-5001SX module into a FortiGate chassis.
You can install 1000Base-LX (single-mode fiber) or 1000Base-T (copper cable)
SFP transceivers. The 1000Base-LX transceivers use fiber connectors while the
1000Base-T transceivers use RJ-45 connectors.
You can install the following types of SFP transceivers for connectors 1, 2, 3,
and 4:
• SFP fiber transceivers
• SFP 1000Base-LX, SM module
• SFP 1000Base-SX, MM module (multimode)
• SFP copper transceivers
• SFP 1000Base-T, SERDES version only (SGMII version not supported)
To install SFP transceivers
To complete this procedure, you need:
• A FortiGate-5001SX module
• Four SFP transceivers
• An electrostatic discharge (ESD) preventive wrist or ankle strap with
connection cord
Caution: FortiGate-5001SX modules must be protected from static discharge and physical
shock. Only handle or work with FortiGate-5001SX modules at a static-free workstation.
!
Always wear a grounded electrostatic discharge (ESD) preventive wrist or ankle strap when
handling FortiGate-5001SX modules.
1 Attach the ESD wrist or ankle strap to your wrist or ankle and to an ESD socket or
to a bare metal surface on the chassis or frame.
2 Remove the caps from SFP cage sockets on the FortiGate-5001SX front panel.
Caution: Handling the SFP transceivers by holding the release Latch can damage the
connector. Do not force the SFP transceivers into the cage slots. If the transceiver does not
!
easily slide in and click into place, it may not be aligned correctly. If this happens, remove
the SFP transceiver, realign it and slide it in again.
3 Hold the sides of the SFP transceiver and slide SFP transceiver into the cage
socket until it clicks into place.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 11
Page 12

Changing FortiGate-5001SX jumper settings Hardware installation
Changing FortiGate-5001SX jumper settings
The JP3 jumper on the FortiGate-5001SX module is factory set by Fortinet into
one of two positions (see Figure 3 on page 13):
• For a FortiGate-5140 or FortiGate-5050 chassis, the jumper connects pins 2
and 3
• For a FortiGate-5020 chassis, the jumper connects pins 1 and 2
The jumper must connect pins 2 and 3 if the chassis contains a shelf manager.
Both the FortiGate-5140 and the FortiGate-5050 contain shelf managers, and the
FortiGate-5020 does not.
If the JP3 jumper settings are incorrect, when you insert the FortiGate-5001SX
module into a chassis the module may not start up or may not be able to
communicate with the chassis shelf manager.
Normally, because the jumpers are factory set, you do not have to change them.
However, if you are moving a FortiGate-5001SX from a FortiGate-5140 or
FortiGate-5050 to a FortiGate-5020 or the reverse, you need to move the JP3
jumper.
Also, if a new FortiGate-5001SX module does not function properly, you should
check the JP3 jumper settings.
Table 3: FortiGate-5001SX JP3 jumper settings for each chassis
Chassis Correct JP3
Jumper Setting
FortiGate-5140 pins 2 and 3 Shelf manager cannot find FortiGate-5001SX module.
FortiGate-5050 pins 2 and 3 Shelf manager cannot find FortiGate-5001SX module.
FortiGate-5020 pins 1 and 2 FortiGate-5001SX module will not start up.
Note: If the shelf manager in a FortiGate-5140 or FortiGate-5050 chassis is missing or not
functioning, FortiGate-5001SX modules with JP3 jumper connecting pins 2 and 3 will not
start up. To operate FortiGate-5001SX modules in a FortiGate-5140 or FortiGate-5050
chassis without a shelf manager, set the JP3 jumper to connect pins 1 and 2.
Result of wrong jumper setting
No chassis information available
No chassis information available
To change or verify the JP3 jumper setting
To complete this procedure, you need:
• A FortiGate-5001SX module
• A tool for moving jumpers (optional)
• An electrostatic discharge (ESD) preventive wrist or ankle strap with
connection cord
Caution: FortiGate-5001SX modules must be protected from static discharge and physical
shock. Only handle or work with FortiGate-5001SX modules at a static-free workstation.
!
Always wear a grounded electrostatic discharge (ESD) preventive wrist or ankle strap when
handling FortiGate-5001SX modules.
1 Attach the ESD wrist or ankle strap to your wrist or ankle and to an ESD socket or
to a bare metal surface on a chassis or frame.
FortiGate-5001SX Security System Guide
12 01-30000-0380-20070201
Page 13

Hardware installation Changing FortiGate-5001SX jumper settings
2 If you have installed the FortiGate-5001SX module in a chassis, remove it.
For removal instructions, see “Removing a FortiGate-5001SX module from a
chassis” on page 17.
3 Use Figure 3 to locate the jumper settings on the module circuit board.
4 If required, carefully move the jumper to the correct setting.
5 You can now insert the module into a chassis and verify that it is operating
correctly.
For inserting instructions, see “Inserting a FortiGate-5001SX module into a
chassis” on page 14.
Figure 3: FortiGate-5001SX jumper settings
Pins 2 and 3
Pins 1 and 2
5050 and 5140 chassis
JP3
5020 chassis
JP3
JP2
JP1
JP3
Front Faceplate
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 13
Page 14

Inserting a FortiGate-5001SX module into a chassis Hardware installation
A
Inserting a FortiGate-5001SX module into a chassis
The following procedure describes how to correctly use the FortiGate-5001SX
mounting components shown in Figure 4 to insert a FortiGate-5001SX module
into a FortiGate-5000 series chassis slot.
The FortiGate-5001SX module left extraction lever contacts to a hidden power
switch. The module must be fully installed in a chassis slot and this extraction
lever must be closed and locked for the FortiGate-5001SX module to receive
power and operate normally. If the FortiGate-5001SX module is not receiving
power, the IPM LED glows blue and all other LEDs remain off.
It is important to carefully seat the FortiGate-5001SX module all the way into the
chassis, to not use too much force on the extraction levers, and to make sure that
the extraction levers are properly locked and engaged with the hidden power
switch. Only then will the FortiGate-5001SX module power-on and start up
correctly.
Figure 4: FortiGate-5001SX module mounting components
Closed
lignment Pin
Alignment Pin
Mounting
Knot
Locking
Screw
Left Extraction
Lever
Mounting Knot
Locking
Screw
Left Extraction
Lever
Open
Alignment Pin
Locking
Screw
Mounting Knot
Left Extraction
Power
Switch
Switch
Contact
Lever
FortiGate-5001SX Security System Guide
14 01-30000-0380-20070201
Page 15

Hardware installation Inserting a FortiGate-5001SX module into a chassis
Before inserting the FortiGate-5001SX module in a chassis
Before installing the FortiGate-5001SX module in a chassis you should verify that
the RAM DIMMs are installed and the JP3 jumper is set correctly. You can also
install the SFP transceivers before inserting the module.
• “RAM DIMMs” on page 9
• “Installing SFP transceivers” on page 11
• “Changing FortiGate-5001SX jumper settings” on page 12
Insertion procedure
FortiGate-5001SX modules are hot swappable. The procedure for inserting the
FortiGate-5001SX module into a FortiGate-5000 series chassis slot is the same
whether or not the FortiGate-5000 series chassis is powered on or not.
To insert a FortiGate-5001SX module into a FortiGate-5000 series chassis
Caution: Do not carry the FortiGate-5001SX module by holding the extraction levers.
When inserting or removing the FortiGate-5001SX module from a chassis slot, handle the
!
module by the front panel. The extraction levers are designed for positioning and locking
the FortiGate-5001SX module into a slot in a chassis only and should not be used for
handling the module. If the extraction levers become bent or damaged the
FortiGate-5001SX module may not align correctly in the chassis slot and the left extraction
lever may not activate the power switch.
To complete this procedure, you need:
• A FortiGate-5001SX module
• A FortiGate-5000 series chassis with an empty slot
• An electrostatic discharge (ESD) preventive wrist or ankle strap with
connection cord
Caution: FortiGate-5001SX modules must be protected from static discharge and physical
shock. Only handle or work with FortiGate-5001SX modules at a static-free workstation.
!
Always wear a grounded electrostatic discharge (ESD) preventive wrist or ankle strap when
handling FortiGate-5001SX modules.
1 Attach the ESD wrist or ankle strap to your wrist or ankle and to an ESD socket or
to a bare metal surface on the chassis or frame.
2 Fully loosen the left extraction lever locking screw to unlock the left extraction
lever.
Left Extraction Lever
locking screw
Loosen
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 15
Page 16

Inserting a FortiGate-5001SX module into a chassis Hardware installation
A
3 Open the left and right extraction levers to their fully open positions.
Alignment Pin
Left Extraction
Lever
Open Fully Open
Alignment Pin
Left Extraction
Lever
4 Insert the FortiGate-5001SX module into the empty slot in the chassis.
5 Carefully guide the module into the chassis using the rails in the slot.
Insert the module by applying moderate force to the front faceplate (not the
extraction levers) to slide the module into the slot. The module should glide
smoothly into the chassis. If you encounter any resistance while sliding the
module in, the module could be aligned incorrectly. Pull the module back out and
try inserting it again.
6 Slide the module in until the alignment pins are inserted half way into their sockets
in the chassis.
If the chassis is powered on the IPM LED lights up and turns blue.
7 Turn both extraction levers to their fully-closed positions.
The extraction levers should hook into the sides of the chassis slot. Closing the
extraction levers draws the FortiGate-5001SX module into place in the chassis
slot and into contact with the chassis backplane. Th e FortiGate-5001SX front
panel should be in contact with the chassis front panel.
If the chassis is powered on, as the module slides into place the IPM LED starts
flashing blue.
16 01-30000-0380-20070201
lignment Pin Alignment Pin
Left Extraction
Lever
Close
FortiGate-5001SX Security System Guide
Fully Closed
Left Extraction
Lever
Page 17

Hardware installation Removing a FortiGate-5001SX module from a chassis
8 Fully tighten the left extraction lever locking screw to lock the left extraction lever.
.
Mounting
Knot
Tighten
Locking Screw
9 Fully tighten the left and right mounting knots to lock the FortiGate-5001SX
module into position in the chassis slot.
If the chassis is powered on the PWR LED turns green and the STA LED turns
RED. The ACC LED also starts flashing red. After a few minutes, if the module is
operating correctly the front panel LEDs are lit as described in Table 4.
Table 4: FortiGate-5001SX norma l operating LEDs
LED State
PWR Green
ACC Off (Or flashing red when the system accesses the flash disk.)
STA Green
IPM Off
Removing a FortiGate-5001SX module from a chassis
The following procedure describes how to correctly use the FortiGate-5001SX
mounting components shown in Figure 4 on page 14 to remove a
FortiGate-5001SX module from a FortiGate-5000 series chassis slot.
To remove a FortiGate-5001SX module from a FortiGate-5000 series chassis
FortiGate-5001SX modules are hot swappable. The procedure for removing the
FortiGate-5001SX module from a FortiGate-5000 series chassis slot is the same
whether or not the FortiGate-5000 series chassis is powered on or not.
Caution: Do not carry the FortiGate-5001SX module by holding the extraction levers.
When inserting or removing the FortiGate-5001SX module from a chassis slot, handle the
!
module by the front panel. The extraction levers are designed for positioning and locking
the FortiGate-5001SX module into a slot in a chassis only and should not be used for
handling the module. If the extraction levers become bent or damaged the
FortiGate-5001SX module may not align correctly in the chassis slot and the left extraction
lever may not activate the power switch.
To complete this procedure, you need:
• A FortiGate-5000 series chassis with a FortiGate-5001SX module installed
• An electrostatic discharge (ESD) preventive wrist or ankle strap with
connection cord
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 17
Page 18

Removing a FortiGate-5001SX module from a chassis Hardware installation
A
Caution: FortiGate-5001SX modules must be protected from static discharge and physical
shock. Only handle or work with FortiGate-5001SX modules at a static-free workstation.
!
Always wear a grounded electrostatic discharge (ESD) preventive wrist or ankle strap when
handling FortiGate-5001SX modules.
1 Attach the ESD wrist or ankle strap to your wrist or ankle and to an ESD socket or
to a bare metal surface on the chassis or frame.
2 Disconnect all cables from the FortiGate-5001SX module, including all network
cables, the console cable, and any USB cables or keys.
3 Fully loosen the mounting knots on the left and right sides of the
FortiGate-5001SX front panel.
4 Fully loosen the left extraction lever locking screw to unlock the left extraction
lever.
Mounting
Knot
Loosen
Locking Screw
5 Turn both extraction levers to their fully open positions.
Opening the extraction levers slides the module a short distance out of the slot,
disconnecting the module from the chassis backplane.
The IPM LED turns blue. All other LEDs turn off.
lignment Pin Alignment Pin
Left Extraction
Lever
Open Fully Open
Left Extraction
Lever
6 Pull the module about half way out.
All LEDs turn off.
18 01-30000-0380-20070201
FortiGate-5001SX Security System Guide
Page 19

Hardware installation Troubleshooting
7 Turn both extraction levers to their fully-closed positions.
Alignment Pin
Left Extraction
Lever
Close
Alignment Pin
Fully Closed
Left Extraction
Lever
8 Fully tighten the left extraction lever locking screw to lock the left extraction lever.
.
Tighten
Locking Screw
9 Carefully slide the module completely out of the slot.
Troubleshooting
FortiGate-5001SX does not startup
This section describes the following troubleshooting topics:
• FortiGate-5001SX does not startup
• FortiGate-5001SX cannot display chassis information
Positioning of FortiGate-5001SX extraction levers, the presence or absence of a
functioning shelf manager, incorrect jumper settings and firmware problems may
all prevent a FortiGate-5001SX module for starting up cor rectly. This section
describes how to find and fix each of these problems.
All chassis: left extraction lever not contacting power switch
The left extraction lever activates the FortiGate-5001SX module power switch
(Figure 5).
If the left extraction lever is damaged or positioned incorrectly the
FortiGate-5001SX module does not receive power and will not start up. Make sure
the left extraction lever is correctly aligned and fully inserted and make sure the
left extraction lever locking screw is fully tightened. Sometimes you may have to
make small adjustments to the extraction lever to achieve contact with the switch.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 19
Page 20

T roubleshooting Hardware installation
Figure 5: Location of FortiGate-5001SX power switch
Alignment Pin
Locking
Screw
Power
Mounting Knot
Left Extraction
Lever
Switch
Switch
Contact
FortiGate-5020 chassis: incorrect FortiGate-5001SX jumper
settings
If the JP3 jumper on the FortiGate-5001SX circuit board is set to detect a shelf
manager, the FortiGate-5001SX module will not start up when inserted into a
FortiGate-5020 chassis. This occurs because the FortiGate-5020 chassis does
not have a shelf manager.
To fix the problem, remove the FortiGate-5001SX module and check the position
of the JP3 jumper (see Figure 3 on page 13). Make sure the jumper connects pins
1 and 2 (to the right when seen from the front of the module).
FortiGate-5140 or 5050 chassis: shelf manager not installed or
not functioning
If you are operating a FortiGate-5001SX in a FortiGate-51 40 o r 5050 chassis, th e
FortiGate-5001SX module will not start up if the JP3 jumper connects pins 2 and 3
(see Figure 3 on page 13) and a shelf manager is not installed or is not operating
correctly.
If the shelf manager is not installed or not operating correctly, when you insert a
FortiGate-5001SX module, the module attempts to communicate with the shelf
manager. If the FortiGate-5001SX module cannot communicate with the shelf
manager, the module will not startup.
If a shelf manager is installed, make sure it is functioning normally (the S t atus LED
is green and all other LEDs are off). If the shelf manager is not functioning
normally, you can try removing it from the chassis and reinstalling it. If this does
not solve the problem, contact Fortinet Technical Support.
If the shelf manager has been removed from the chassis, you should re-install it. If
you are planning on operating the chassis without a sh elf manager, you can move
the FortiGate-5001SX JP3 jumper between pins 1 and 2. The FortiGate-5001SX
should now start up.
FortiGate-5001SX Security System Guide
20 01-30000-0380-20070201
Page 21

Hardware installation Troubleshooting
All chassis: Firmware problem
If the FortiGate-5001SX module power switch is connected and the JP3 jumper
and shelf manager are set as required, and the FortiGate-5001SX still does not
start up, the problem could be with FortiOS. Connect to the FortiGate-5001SX
console and try cycling the power to the module. If the BIOS starts up, interrupt
the BIOS startup and install a new firmware image. For details about installing a
new firmware image in this way, see the FortiGate-5000 Series Firmware and
FortiUSB Guide.
If this does not solve the problem, contact Fortinet Technical Support.
FortiGate-5001SX cannot display chassis information
If the FortiGate-5001SX module is installed in a FortiGate-5140 or 5050 ch assis, if
a shelf manager is operating in the chassis, and if the JP3 jumper is set between
pins 2 and 3, the FortiGate-5001SX module should be able to communicate with
the chassis shelf manager.
If the FortiGate-5001SX module can communicate with the shelf manager, the
FortiGate-5001SX web-based manager System > Chassis pages should display
information about the modules installed in the chassis. If any o ne of the conditions
listed above are not met, theFortiGate-5001SX web-based manager system
chassis pages will not display chassis information.
If all of the above conditions are met, the FortiGate-5001SX System > Chassis >
Blades list displays a list of all of the modules installed in the chassis. If any of the
other FortiGate-5001SX modules in the chassis have the JP3 jumper between
pins 1 and 2, these slots will appear empty. Figure 6 shows the blades list for a
FortiGate-5001SX module installed in slot 3 of a FortiGate-5050 cha ssis . Th e
FortiGate-5001SX modules in slots 3 and 4 are called node cards. The FortiGate5003 module in slot 2 is called a switch card.
Figure 6: Example System > Chassis > Blades web-based manager page
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 21
Page 22

T roubleshooting Hardware installation
FortiGate-5001SX Security System Guide
22 01-30000-0380-20070201
Page 23

Quick Configuration Guide Registering your Fortinet product
Quick Configuration Guide
This section is a quick start guide to connecting and configuring a
FortiGate-5001SX security system for your network.
Before using this chapter, your FortiGate-5000 series chassis should be mounted
and connected to your power system. In addition, your FortiGate-5001SX
modules should have SFP transceivers installed, jumper s set (if required), and the
module should be inserted into your FortiGate-5000 series chassis. The modules
should also be powered up and the front panel LEDs should indicate that the
modules are functioning normally.
This chapter includes the following topics:
• Registering your Fortinet product
• Planning the configuration
• Choosing the configuration tool
• Factory default settings
• Configuring NAT/Route mode
• Configuring Transparent mode
• Upgrading FortiGate-5001SX firmware
• FortiGate-5001SX base backplane da ta commu ni cat ion
• Powering off the FortiGate-5001SX module
Registering your Fortinet product
Register your Fortinet product to receive Fortinet customer services such as
product updates and technical support. You must also register your product for
FortiGuard services such as FortiGuard Antivirus and Intrusion Prevention
updates and for FortiGuard Web Filtering and AntiSpam.
Register your product by visiting http://support.fortinet.com and selecting Product
Registration.
To register, enter your contact information and the serial numbers of the Fortinet
products that you or your organization have purchased. You can register multiple
Fortinet products in a single session without re-entering your contact information.
Planning the configuration
Before beginning to configure your FortiGate-5001SX security system, you need
to plan how to integrate the system into your network. Your configuration plan
depends on the operating mode that you select: NAT/Route mode (the default) or
Transparent mode.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 23
Page 24

Planning the configuration Quick Configuration Guide
NAT/Route mode
In NAT/Route mode, the FortiGate-5001SX security system is visible to the
networks that it is connected to. Each interface connected to a network must be
configured with an IP address that is valid for that network. In many
configurations, in NAT/Route mode all of the FortiGate interfaces are on different
networks, and each network is on a separate subnet.
You would typically use NAT/Route mode when the FortiGate-5001SX security
system is deployed as a gateway between private and public networks. In the
default NAT/Route mode configuration, the FortiGate-5001SX security system
functions as a firewall. Firewall policies control communications through the
FortiGate-5001SX security system. No traffic can pass through the
FortiGate-5001SX security system until you add firewall policies.
In NAT/Route mode, firewall policies can operate in NAT mode or in Route mode.
In NAT mode, the FortiGate firewall performs network address translation before
IP packets are sent to the destination network. In Route mode, no translation
takes place.
Figure 7: Example FortiGate-5001SX module operating in NAT/Route mode
controlling traffic between
internal and external
Transparent mode
In Transparent mode, the FortiGate-5001SX security system is invisible to the
network. All of the FortiGate-5001SX interfaces are connected to different
segments of the same network. In T ransparent mode you only have to configure a
management IP address so that you can connect to the FortiGate-5001SX
security system to make configuration changes and so the FortiGate-5001SX
security system can connect to external services such as the FortiGuard
Distribution Network (FDN).
NAT mode policies
networks.
Internal
network
Internet
port2
204.23.1.2
USB
CONSOLE
ACC
PWR
port1
192.168.1.99
Route mode policies
controlling traffic between
Internal networks.
FortiGate-5001SX module
in NAT/Route mode
1 2 3 4 5 6 7 8
port3
10.10.10.1
STA IPM
NAT mode policies
controlling traffic between
internal and external
networks.
Internal
network
FortiGate-5001SX Security System Guide
24 01-30000-0380-20070201
Page 25

Quick Configuration Guide Choosing the configuration tool
Figure 8: Example FortiGate-5001SX module operating in Transparent mode
Internet
Transparent mode policies
controlling traffic between
internal and external
networks.
Internal
network
204.23.1.2
192.168.1.1
port2
USB
CONSOLE
ACC
PWR
port1
Transparent mode policies
controlling traffic between
internal network segments.
Gateway to
public
network
FortiGate-5001SX module
in Transparent mode
1 2 3 4 5 6 7 8
port3
192.168.1.99
Management IP
Transparent mode policies
controlling traffic between
STA IPM
internal and external
Internal
network
networks.
You would typically deploy a FortiGate-5001SX security system in Transparent
mode on a private network behind an existing firewall or behind a router. In the
default Transparent mode configuration, the FortiGate-5001SX security system
functions as a firewall. No traffic can pass through the FortiGate-5001SX security
system until you add firewall policies.
Choosing the configuration tool
You can use either the web-based manager or the Command Line In te rface (CLI)
to configure the FortiGate module.
Web-based manager
The FortiGate-5001SX web-based manager is an easy to use management tool.
Use the web-based manager to configure the FortiGate-5001SX administrator
password, the interface addresses, the default gateway, and the DNS server
addresses.
Requirements:
• An Ethernet connection between the FortiGate-5001SX module and
management computer.
• Internet Explorer 6.0 or higher on the management computer.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 25
Page 26

Factory default settings Quick Configuration Guide
Command Line Interface (CLI)
The CLI is a full-featured management tool. Use it to configure the administrator
password, the interface addresses, the default gateway, and the DNS server
addresses.
Requirements:
• The serial connector that came packaged with your For tiGa te-5001 SX module.
• Terminal emulation application (for example, HyperTerminal for Windows) on
the management computer.
Factory default settings
The FortiGate-5001SX unit ships with a factory defau lt con fig uration. The default
configuration allows you to connect to and use the FortiGate-5001SX web-based
manager to configure the FortiGate-5001SX module onto the network. To
configure the FortiGate-5001SX module onto the network you add an
administrator password, change the network interface IP addresses, add DNS
server IP addresses, and, if required, configure basic routing.
Table 5: FortiGate-5001SX factory default settings
Operation Mode NAT/Route
Administrator Account User Name: admin
Password: (none)
port1 IP/Netmask 192.168.1.99/24
port2 IP/Netmask 192.168.100.99/24
port3 to port8 IP/Netmask 0.0.0.0/0.0.0.0
Default route Gateway: 192.168.100.1
Device: port2
Primary DNS Server: 65.39.139.53
Secondary DNS Server: 65.39.139.53
Note: At any time during the configuration process, if you run into problems, you can reset
the FortiGate-5001SX module to the factory defaults and start over. From the web-based
manager go to System > Status find System Operation at the bottom of the page and
select Reset to Factory Default. From the CLI enter execute factory reset.
FortiGate-5001SX Security System Guide
26 01-30000-0380-20070201
Page 27

Quick Configuration Guide Configuring NAT/Route mode
Configuring NAT/Route mode
Use Table 6 to gather the information you need to customize NAT/Route mode
settings for the FortiGate-5001SX security system. You can use one table for
each module to configure.
Table 6: FortiGate-5001SX module NAT/Route mode settings
Admin Administrator Password:
port1
port2
port3
port4
port5
port6
port7
port8
Default Route
DNS Servers
IP: _____._____._____._____
Netmask: _____._____._____._____
IP: _____._____._____._____
Netmask: _____._____._____._____
IP: _____._____._____._____
Netmask: _____._____._____._____
IP: _____._____._____._____
Netmask: _____._____._____._____
IP: _____._____._____._____
Netmask: _____._____._____._____
IP: _____._____._____._____
Netmask: _____._____._____._____
IP: _____._____._____._____
Netmask: _____._____._____._____
IP: _____._____._____._____
Netmask: _____._____._____._____
Device (Name of the Interface
connected to the external
network):
Default Gateway IP address: _____._____._____._____
The default route consists of the name of the interface connected
to an external network (usually the Internet) and the defaul t
gateway IP address. The default route directs all non-local traffic to
this interface and to the external network.
Primary DNS Server: _____._____._____._____
Secondary DNS Server: _____._____._____._____
Using the web-based manager to configure NAT/Route mode
1 Connect port1 of the FortiGate-5001SX module to the same hub or switch as the
computer you will use to configure the FortiGate module.
Note: If you cannot connect to port1, see “Using the CLI to configure NAT/Route mode” on
page 28.
2 Configure the management computer to be on the same subnet as the port1
interface of the FortiGate-5001SX module. To do this, change the IP address of
the management computer to 192.168.1.2 and the netmask to 255.255 .255.0.
3 To access the FortiGate web-based manager, start Internet Explorer and browse
to https://192.168.1.99 (remember to include the “s” in https://).
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 27
Page 28

Configuring NAT/Route mode Quick Configuration Guide
4 Type admin in the Name field and select Login.
To change the admin administrator password
1 Go to System > Admin > Administrators.
2 Select Change Password for the admin administrator and enter a new password.
To configure interfaces
1 Go to System > Network > Interface.
2 Select the edit icon for each interface to configure.
3 Set the addressing mode for the interface. (See the online help for information.)
• For manual addressing, enter the IP address and netmask for the interface that
you added to Table 6 on page 27.
• For DHCP addressing, select DHCP and any required settings.
• For PPPoE addressing, select PPPoE and enter the username and password
and any other required settings.
To configure the Primary and Secondary DNS server IP addresses
1 Go to System > Network > Options.
2 Enter the Primary and Secondary DNS IP addre sses that you added to Table 6 on
page 27 as required and select Apply.
To configure the Default Gateway
1 Go to Router > Static and select Edit icon for the static route.
2 Select the Device that you recorded above.
3 Set Gateway to the Default Gateway IP address that you added to Table 6 on
page 27.
4 Select OK.
Using the CLI to configure NAT/Route mode
1 Use the serial cable supplied with your FortiGate-5001SX module to connect the
FortiGate Console port to the management computer serial port.
2 Start a terminal emulation program (HyperTerminal) on the management
computer. Use these settings:
Baud Rate (bps) 9600, Data bits 8, Parity None, Stop bits 1, and Flow Control
None.
3 At the Login: prompt, type admin and press Enter twice (no password required).
4 Change the administrator password.
config system admin
edit admin
set password <password>
end
FortiGate-5001SX Security System Guide
28 01-30000-0380-20070201
Page 29

Quick Configuration Guide Configuring Transparent mode
5 Configure the port1 internal interface to the setting that you added to Table 6 on
page 27.
config system interface
edit port1
set ip <intf_ip>/<netmask_ip>
end
6 Repeat to configure each interface as required, for example, to configure the port2
interface to the setting that you added to Table 6 on page 27.
config system interface
edit port2
...
7 Configure the primary and secondary DNS server IP addresses to the settings
that you added to Table 6 on page 27.
config system dns
set primary <dns-server_ip>
set secondary <dns-server_ip>
end
8 Configure the default gateway to the setting that you added to Table 6 on page 27.
config router static
edit 1
set device <interface_name>
set gateway <gateway_ip>
end
Configuring Transparent mode
Use Table 7 to gather the information you need to customize Transparent mode
settings.
Table 7: Transparent mode settings
Admin Administrator Password:
IP: _____._____._____._____
Management IP
Default Route
DNS Servers
Using the web-based manager to configure Transparent mode
1 Connect port1 of the FortiGate-5001SX module to the same hub or switch as the
computer you will use to configure the FortiGate module.
Note: If you cannot connect to port1, see “Using the CLI to configure Transparent mode” on
page 30.
Netmask: _____._____._____._____
The management IP address and netmask must be valid for the
network where you will manage the FortiGate-5001SX unit.
Default Gateway IP address: _____._____._____._____
In Transparent mode the default route requires the default gateway IP
address. The default route directs all non-local traffic to the external
network.
Primary DNS Server: _____._____._____._____
Secondary DNS Server: _____._____._____._____
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 29
Page 30

Configuring Transparent mode Quick Configuration Guide
2 Configure the management computer to be on the same subnet as the port1
interface of the FortiGate-5001SX module. To do this, change the IP address of
the management computer to 192.168.1.2 and the netmask to 255.255.255.0.
3 To access the FortiGate web-based manager, start Internet Explorer and browse
to https://192.168.1.99 (remember to include the “s” in https://).
4 Type admin in the Name field and select Login.
To switch from NAT/Route mode to transparent mode
1 Go to System > Status and select the Change link beside Operation Mode: NAT.
2 Set Operation Mode to Transparent.
3 Set the Management IP/Netmask to the settings that you added to Table 7 on
page 29.
4 Set the default Gateway to the setting that you added to Table 7 on page 29.
To change the admin administrator password
1 Go to System > Admin > Administrators.
2 Select Change Password for the admin administrator and enter the p assword that
you added to Table 7 on page 29.
To change the management interface
1 Go to System > Config > Operation.
2 Enter the Management IP address and netmask hat you added to Table 7 on
page 29 and select Apply.
To configure the Primary and Secondary DNS server IP addresses
1 Go to System > Network > Options.
2 Enter the Primary and Secondary DNS IP addre sses that you added to Table 7 on
page 29 as required and select Apply.
Using the CLI to configure Transparent mode
1 Use the serial cable supplied with your FortiGate-5001SX module to connect the
FortiGate Console port to the management computer serial port.
2 Start a terminal emulation program (HyperTerminal) on the management
computer. Use these settings:
Baud Rate (bps) 9600, Data bits 8, Parity None, Stop bits 1, and Flow Control
None.
3 At the Login: prompt, type admin and press Enter twice (no password required).
4 Change from NAT/Route mode to Transparent mode. Config ure the Ma nag eme nt
IP address and default gateway to the settings that you added to Table 7 on
page 29.
config system settings
set opmode transparent
set manageip <mng_ip>/<netmask>
set gateway <gateway_ip>
end
FortiGate-5001SX Security System Guide
30 01-30000-0380-20070201
Page 31

Quick Configuration Guide Upgrading FortiGate-5001SX firmware
5 Configure the primary and secondary DNS server IP addresses to the settings
that you added to Table 7 on page 29.
config system dns
set primary <dns-server_ip>
set secondary <dns-server_ip>
end
Upgrading FortiGate-5001SX firmware
Fortinet periodically updates the FortiGate-5001SX FortiOS firmware to include
enhancements and address issues. After you have registered your
FortiGate-5001SX security system (see “Registering your Fortinet product” on
page 23) you can download FortiGate-5001SX firmware from the support web site
http://support.fortinet.com.
Only FortiGate-5001SX administrators (whose access profiles contain system
read and write privileges) and the FortiGate- 50 0 1SX adm i n us er can ch an g e the
FortiGate-5001SX firmware.
For complete details about upgrading and downgrading FortiGa te-5001SX
firmware using the web-based manager or CLI; and using the FortiUSB key, see
the FortiGate-5000 Series Firmware and FortiUSB Guide.
To upgrade the firmware using the web-based manager
1 Copy the firmware image file to your management computer.
2 Log into the web-based manager as the admin administrator.
3 Go to System > Status.
4 Under System Information > Firmware Version, select Update.
5 Type the p ath and filename of the fir mware image file, or select Bro wse and locate
the file.
6 Select OK.
The FortiGate-5001SX module uploads the firmware image file, upgrades to the
new firmware version, restarts, and displays the FortiGate login. This process
takes a few minutes.
7 Log into the web-based manager.
8 Go to System > Status and check the Firmware Version to confirm the firmware
upgrade is successfully installed.
9 Update the FortiGate-5001SX antivirus and attack definitions. See the
FortiGate-5001SX online help for details.
To upgrade the firmware using the CLI
To use the following procedure, you must have a TFTP server the
FortiGate-5001SX module can connect to.
1 Make sure the TFTP server is running.
2 Copy the new firmware image file to the root directory of the TFTP server.
3 Log into the CLI.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 31
Page 32

FortiGate-5001SX base backplane data communication Quick Configuration Guide
4 Make sure the FortiGate module can connect to the TFTP server.
You can use the following command to ping the computer running the TFTP
server. For example, if the IP address of the TFTP server is 192.168.1.168:
execute ping 192.168.1.168
5 Enter the following command to copy the firmware image from the TFTP server to
the FortiGate-5001SX module:
execute restore image <name_str> <tftp_ipv4>
Where <name_str> is the name of the firmware image file and <tftp_ipv4> is
the IP address of the TFTP server . For examp le, if the firmware image file nam e is
image.out and the IP address of the TFTP server is 192.168.1.168, enter:
execute restore image image.out 192.168.1.168
The FortiGate-5001SX module responds with the message:
This operation will replace the current firmware version!
Do you want to continue? (y/n)
6 Type y.
The FortiGate-5001SX module uploads the firmware image file, upgrades to the
new firmware version, and restarts. This process takes a few minutes.
7 Reconnect to the CLI.
8 To confirm the firmware image is successfully installed, enter:
get system status
9 Update antivirus and attack definitions. You can use the command
execute update-now
FortiGate-5001SX base backplane data communication
You can configure the FortiGate-5001SX modules for data communications using
the two FortiGate-5140, FortiGate-5050, or FortiGate-5020 chassis base
backplane interfaces.
Note: Different FortiGate-5000 series modules may use different names for the base
backplane interfaces. For example, on the FortiGate-5001SX and FortiGate-5001FA2
modules the base backplane interfaces are called port9 and port10. On the
FortiGate-5005FA2 module the base backplane interfaces are called base1 and base2.
By default the base backplane interfaces are used for HA heartbeat
communication. However, using the information in this section, you can configure
the FortiGate-5001SX to also use the base backplane interfaces for data
communication. Once the base backplane interfaces are configured for data
communication you can operate and configure them in the same way as any
FortiGate-5001SX interface.
Note: VLAN communication over the backplane is only available for FortiGate-5005FA2
modules installed in a FortiGate-5020 chassis. The FortiSwitch-5003 does not support
VLAN-tagged packets so VLAN communication is not available over the FortiGate-5050
and FortiGate-5140 chassis backplanes.
Although not recommended, you can use base backplane interfaces for data
communication and HA heartbeat communication at the same time.
FortiGate-5001SX Security System Guide
32 01-30000-0380-20070201
Page 33

Quick Configuration Guide Powering off the FortiGate-5001SX module
In a FortiGate-5140 or FortiGate-5050 chassis, FortiGate-5001SX base
backplane communication requires one or two FortiSwitch-5003 modules.
A FortiSwitch-5003 module installed in chassis slot 1 provides communication on
the port9 interface. A FortiSwitch-5003 module installed in chassis slot 2 provides
communication on the port10 interface. The FortiGate-5020 chassis supports
base backplane data communication for both interfaces with no additions or
changes to the chassis.
For details and configuration examples of FortiGate- 50 0 1SX ba se back pl an e
communication using the FortiSwitch-5003 module, see the FortiGate-5000 Base
Backplane Communication Guide.
To enable base backplane data communication from the FortiGate-5001SX
web-based manager
From the FortiGate-5001SX web-based manager use the following steps to
enable base backplane data communication.
1 Go to System > Network > Interface.
2 Select Show backplane interfaces.
The port9 and port10 backplane interfaces now appear in the Interface list.
To enable base backplane data communication from the FortiGate-5001SX
CLI
From the FortiGate-5001SX module CLI you can use the following steps to enable
base backplane data communication.
1 Enter the following command to show the backplane interfaces:
config system global
set show-backplane-intf enable
end
The port9 and port10 backplane interfaces now appear in all Interface lists.
Powering off the FortiGate-5001SX module
To avoid potential hardware problems, always shut down the FortiGate-5001SX
operating system properly before removing the FortiGate-5001SX module from a
chassis slot or before powering down the chassis.
To power off a FortiGate-5001SX module
1 Shut down the FortiGate-5001SX operating system:
• From the web-based manager, go to System > Status > System Operation,
select Shutdown and then select Go.
• From the CLI enter execute shutdown
2 Remove the FortiGate-5001SX module from the chassis slot.
Note: Once a shutdown operation is completed, the only way to restart the
FortiGate-5001SX module is to remove and reinsert it.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 33
Page 34

Powering off the FortiGate-5001SX module Quick Configuration Guide
FortiGate-5001SX Security System Guide
34 01-30000-0380-20070201
Page 35

For more information Fortinet documentation
For more information
Support for your Fortinet product is availab le as onlin e he lp fr om within the
web-based manager, from the Tools and Documentation CD included with the
product, on the Fortinet Technical Documentation web site, fro m the Fortinet
Knowledge Center web site, as well as from Fortinet Technical Support.
Fortinet documentation
The most up-to-date publications and previous releases of Fortinet product
documentation are available from the Fortinet Technical Documentation web site
at http://docs.forticare.com. FortiGate-5000 series documentation is located in its
own section of the site at http://docs.forticare.com/fgt5k.html.
Fortinet Tools and Documentation CD
All Fortinet documentation is available from th e Fortinet Tool s and Docu ment ation
CD shipped with your Fortinet product. The documents on this CD are current for
your product at shipping time. For the latest versions of all Fortinet documentation
see the Fortinet Technical Documentation web site at http://docs.forticare.com.
Fortinet Knowledge Center
Additional Fortinet technical documentation is available from the Fortinet
Knowledge Center. The knowledge center contains troubleshooting and how-to
articles, FAQs, technical notes, and more. Visit the Fortinet Knowledge Center at
http://kc.forticare.com.
Comments on Fortinet technical documentation
Please send information about any errors or omissions in this document, or any
Fortinet technical documentation, to techdoc@fortinet.com.
Customer service and technical support
Fortinet Technical Support provides services designed to make sure that your
Fortinet systems install quickly, configure easily, and operate reliably in your
network.
Please visit the Fortinet Technical Support web site at http://support.fortinet.com
to learn about the technical support services that Fortinet provides.
Register your Fortinet product
Register your Fortinet product to receive Fortinet customer services such as
product updates and technical support. You must also register your product for
FortiGuard services such as FortiGuard Antivirus and Intrusion Prevention
updates and for FortiGuard Web Filtering and AntiSpam.
Register your product by visiting http://support.fortinet.com and selecting Product
Registration.
To register, enter your contact information and the serial numbers of the Fortinet
products that you or your organization have purchased. You can register multiple
Fortinet products in a single session without re-entering your contact information.
FortiGate-5001SX Security System Guide
01-30000-0380-20070201 35
Page 36

© Copyright 2007 Fortinet, Inc. All rights reserved. No part of this publication
including text, examples, diagrams or illustrations may be reproduced,
transmitted, or translated in any form or by any means, electronic, mechanical,
manual, optical or otherwise, for any purpose, without prior written permission of
Fortinet, Inc.
Trademarks
Dynamic Threat Prevention System (DTPS), APSecure, FortiASIC, FortiBIOS,
FortiBridge, FortiClient, FortiGate, FortiGate Unified Threat Management System,
FortiGuard, FortiGuard-Antispam, FortiGuard-Antivirus, FortiGuard-Intrusion,
FortiGuard-Web, FortiLog, FortiAnalyzer, FortiManager, Fortinet, FortiOS,
FortiPartner, FortiProtect, FortiReporter, FortiResponse, FortiShield, FortiVoIP,
and FortiWiFi are trademarks of Fortinet, Inc. in the United States and/or other
countries. The names of actual comp anies and products mentio ned herein may be
the trademarks of their respective owners.
Regulatory compliance
FCC Class A Part 15 CSA/CUS
www.fortinet.com
FortiGate-5001SX Security System Guide
01-30000-0380-20070201
 Loading...
Loading...