Dell SMA 200, SMA 400, SRA 1600, SRA 4600, SMA 500v Administration Manual

Dell™ SonicWALL™
Secure Mobile Access 8.5
Administration Guide
SMA 200/400
SRA 1600/4600
SMA 500v Virtual Appliance
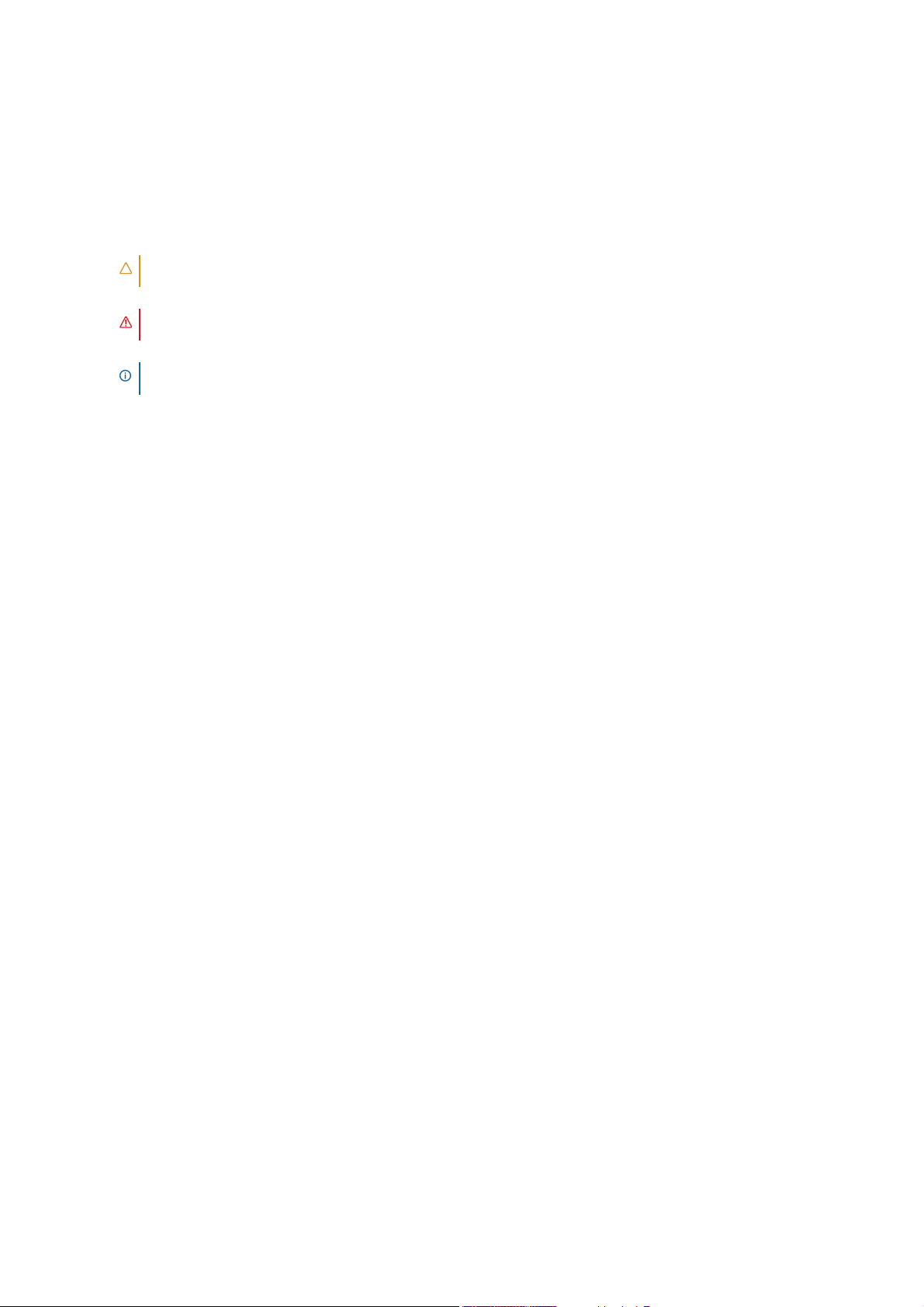
©
2016 Dell Inc.
ALL RIGHTS RESERVED.
This product is protected by U.S. and international copyright and intellectual property laws. Dell™, the Dell logo, and
SonicWALL™ are trademarks of Dell Inc. in the United States and/or other jurisdictions. All other marks and names mentioned
herein may be trademarks of their respective companies.
For more information, go to http://software.dell.com/legal/.
Legend
CAUTION: A CAUTION icon indicates potential damage to hardware or loss of data if instructions are not followed.
WARNING: A WARNING icon indicates a potential for property damage, personal injury, or death.
IMPORTANT NOTE, NOTE, TIP, MOBILE, or VIDEO: An information icon indicates supporting information.
Secure Mobile Access Administration Guide
Updated - August 2016
Software Version - 8.5
232-003313-00 Rev. C

Contents
Part 1. Introduction
About This Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Guide Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13
Secure Mobile Access Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Overview of SMA/SRA Hardware and Components . . . . . . . . . . . . . . . . . . . . . . . . . . .14
Secure Mobile Access Software Components . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
SMA Hardware Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
SRA Hardware Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
SMA 500v Virtual Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
Concepts for Secure Mobile Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Encryption Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
SSL for Virtual Private Networking (VPN) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
SSL Handshake Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
IPv6 Support Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
Portals Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
Domains Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
Application Offloading and HTTP(S) Bookmarks Overview . . . . . . . . . . . . . . . . . . .25
Cross Domain Single Sign-On . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
ActiveSync Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
Network Resources Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
SNMP Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
DNS Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
Network Routes Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
NetExtender Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
Two-Factor Authentication Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .44
One Time Password Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
End Point Control Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48
Secure Virtual Assist Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
Secure Virtual Meeting Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
Web Application Firewall Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
Navigating the Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .74
Browser Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .74
Management Interface Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .75
Navigating the Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .76
Navigation Bar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
Deployment Guidelines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
Support for Numbers of User Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
Resource Type Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Integration with Dell SonicWALL Products . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Typical Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Two-armed Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .82
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
3

Part 2. Configuring Secure Mobile Access
System Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
System > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .84
System > Status Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .84
Registering Your SMA/SRA Appliance with System Status . . . . . . . . . . . . . . . . . . . .86
Configuring Network Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
System > Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
System > Licenses Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
Registering the SMA/SRA Appliance with System > Licenses . . . . . . . . . . . . . . . . . .90
Activating or Upgrading Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
System > Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
System > Time Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
Setting the Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .96
Enabling Network Time Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .96
System > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .97
System > Settings Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .97
Managing Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Managing Firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Managing Language Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
System > Administration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
System > Administration Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Configuring Login Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Configuring HTTP DOS Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Configuring Web Management Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Configuring SNMP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Enabling GMS Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
External FTP/TFTP Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Configuring External FTP/TFTP Server Settings . . . . . . . . . . . . . . . . . . . . . . . . . 110
System > Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
System > Certificates Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Certificate Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Generating a Certificate Signing Request . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Viewing and Editing Certificate Information . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Importing a Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Adding Additional CA Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
System > Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
System > Monitoring Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Setting The Monitoring Period . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Refreshing the Monitors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
System > Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
System > Diagnostics Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Downloading & Generating the Tech Support Report . . . . . . . . . . . . . . . . . . . . . . 117
Performing Diagnostic Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
System > Restart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
System > Restart Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Restarting the SMA/SRA Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
System > About . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
4

Network Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .121
Network > Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Network > Interfaces Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Configuring Network Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Network > DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Network > DNS Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
Configuring Hostname Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Configuring DNS Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Configuring WINS Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Network > Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Network > Routes Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Configuring a Default Route for the SMA/SRA Appliance . . . . . . . . . . . . . . . . . . . 127
Configuring Static Routes for the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Network > Host Resolution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Network > Host Resolution Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Configuring Host Resolution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Network > Network Objects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Network > Network Objects Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Adding Network Objects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Editing Network Objects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Portals Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .134
Portals > Portals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Portals > Portals Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Adding Portals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Configuring General Portal Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Configuring Login Schedules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Configuring the Home Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Configuring Per-Portal Virtual Assist Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Configuring Virtual Meeting Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Configuring Virtual Host Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
Adding a Custom Portal Logo . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
Portals > Application Offloading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Application Offloading Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Configuring an HTTP/HTTPS Application Offloading Portal . . . . . . . . . . . . . . . . . . 151
Configuring with the Offloading Portal Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . 154
General Server Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Load Balancing Server Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
URL-based Aliasing Server Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
Configuring the Security Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Configuring the Miscellaneous Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Modifying the General Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Configuring the Offloading Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Configuring an HTTP/HTTPS Application Offloading Portal . . . . . . . . . . . . . . . . . . 164
Using Offloaded Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Configuring Application Offloading with SharePoint 2013 . . . . . . . . . . . . . . . . . . . 166
Microsoft Outlook Anywhere with Autodiscover Overview . . . . . . . . . . . . . . . . . . 166
Configuring the Outlook Anywhere Portal . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
5

Portals > Domains . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Portals > Domains Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Viewing the Domains Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Removing a Domain . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Adding or Editing a Domain . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Adding or Editing a Domain with Local User Authentication . . . . . . . . . . . . . . . . . 172
Adding or Editing a Domain with Active Directory Authentication . . . . . . . . . . . . . 174
Adding or Editing a Domain with LDAP Authentication . . . . . . . . . . . . . . . . . . . . 177
Adding or Editing a Domain with RADIUS Authentication . . . . . . . . . . . . . . . . . . . 180
Adding or Editing a Domain with Digital Certificates . . . . . . . . . . . . . . . . . . . . . . 183
Configuring Two-Factor Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Portals > Custom Logos . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Portals > Load Balancing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Portals > Load Balancing Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Configuring a Load Balancing Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Portals > URL Based Aliasing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
URL Based Aliasing overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
Adding a URL Based Aliasing group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
Default Site Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
URL Based Aliasing Group with Application Offloading . . . . . . . . . . . . . . . . . . . . 202
Part 3. Configuring Services & Clients
Services Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .205
Services > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
Services > Bookmarks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Feature comparison between HTML5, JAVA, and ActiveX bookmarks . . . . . . . . . . . 211
SSHv2 feature comparison between HTML5 and JAVA bookmarks . . . . . . . . . . . . . . 212
Adding or Editing a Bookmark . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Services > Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Adding a Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Editing a Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Deleting a Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Device Management Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .228
Device Management > Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
Device Management > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
Register settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
ActiveSync Provision Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Notification Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Device Management > Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Device Management > Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
NetExtender Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .233
NetExtender > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
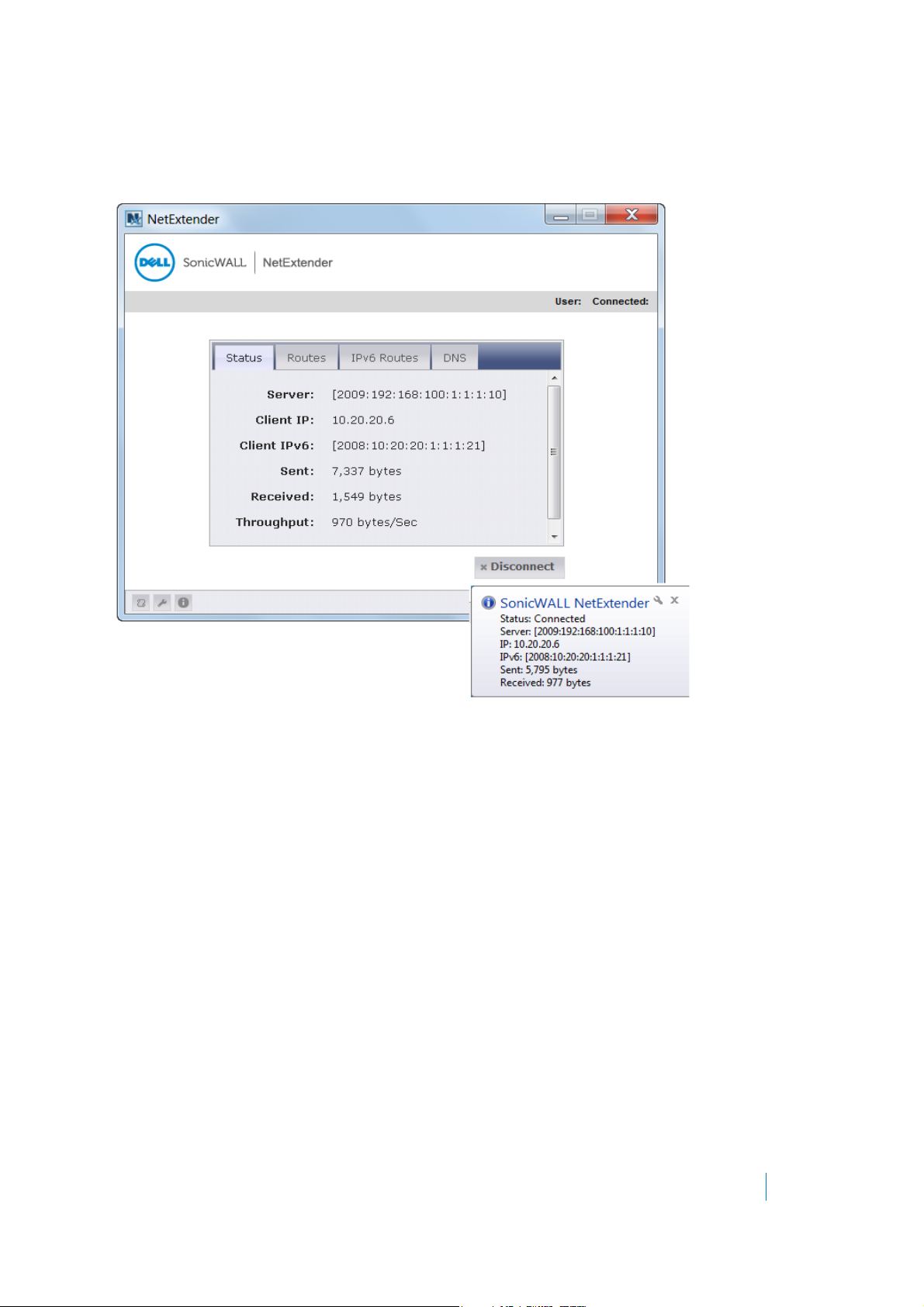
NetExtender > Status Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Viewing NetExtender Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
NetExtender > Client Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
6

NetExtender > Client Settings Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Configuring the Global NetExtender IP Address Range . . . . . . . . . . . . . . . . . . . . 235
Configuring Global NetExtender Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Configuring Internal Proxy Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
Configuring Post-Connection Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
NetExtender > Client Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
NetExtender > Client Routes Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Adding NetExtender Client Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
NetExtender > Advanced Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
NetExtender Traffic Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Post Connection Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
NetExtender > Client Downloads . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
NetExtender > Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
NetExtender User and Group Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Configuring User-Level NetExtender Settings . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Configuring Group-Level NetExtender Settings . . . . . . . . . . . . . . . . . . . . . . . . . 246
End Point Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .249
Configuring End Point Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
End Point Control > Device Profiles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
Users > Local Groups > Edit EPC Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
Users > Local Users > Edit EPC Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
End Point Control > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
End Point Control > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
End Point Control > Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
Secure Virtual Assist Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .259
Secure Virtual Assist > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Secure Virtual Assist > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
General Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Request Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
Notification Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Customer Portal Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Restriction Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Secure Virtual Assist > Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Secure Virtual Assist > Licensing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Secure Virtual Assist > Licensing Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Secure Virtual Meeting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .269
Secure Virtual Meeting > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 269
Secure Virtual Meeting > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
General Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Notification Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271
Secure Virtual Meeting > Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 272
Secure Virtual Meeting > Licensing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 272
Licensing Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 272
Licensing Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
7

Web Application Firewall Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .274
Licensing Web Application Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Configuring Web Application Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 277
Viewing and Updating Web Application Firewall Status . . . . . . . . . . . . . . . . . . . . 277
Configuring Web Application Firewall Settings . . . . . . . . . . . . . . . . . . . . . . . . . . 279
Configuring Web Application Firewall Signature Actions . . . . . . . . . . . . . . . . . . . 286
Determining the Host Entry for Exclusions . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290
Configuring Custom Rules and Application Profiling . . . . . . . . . . . . . . . . . . . . . . 292
Using Web Application Firewall Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . 308
Using Web Application Firewall Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315
Verifying and Troubleshooting Web Application Firewall . . . . . . . . . . . . . . . . . . . . . . 318
Geo IP and Botnet Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .320
Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 320
General Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 321
Botnet Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 321
Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 322
General Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 322
Remediation Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 323
Access Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 324
Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 325
Licensing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 328
High Availability Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .329
High Availability Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 329
Supported Platforms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 330
Configuring High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 330
Physical Connectivity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 330
Preparing for High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 330
Configuring High Availability Settings on a hardware appliance . . . . . . . . . . . . . . 331
Configuring High Availability Settings on a Virtual Appliance . . . . . . . . . . . . . . . . 333
Enabling Interface Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 334
Configuring Network Monitoring Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . 335
Configuring Management Settings for Idle Unit . . . . . . . . . . . . . . . . . . . . . . . . . 335
Synchronizing Firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 336
Synchronizing Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 336
Synchronizing Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 336
Technical FAQ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 336
Part 4. Configuring Users & Logs
Users Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .339
Users > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 339
Access Policies Concepts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 340
Access Policy Hierarchy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 340
Users > Local Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 341
Users > Local Users Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 341
Removing a User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 342
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
8

Adding a Local User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 342
Editing User Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 343
Users > Local Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 382
Users > Local Groups Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 383
Deleting a Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 383
Adding a New Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 383
Editing Group Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 384
Group Configuration for LDAP Authentication Domains . . . . . . . . . . . . . . . . . . . . 404
Group Configuration for Active Directory and RADIUS Domains . . . . . . . . . . . . . . . 409
Creating a Citrix Bookmark for a Local Group . . . . . . . . . . . . . . . . . . . . . . . . . . 410
Global Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 413
Edit Global Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 413
Edit Global Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 415
Edit Global Bookmarks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 416
Edit EPC Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 417
Log Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .418
Log > View . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 418
Log > View Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 418
Viewing Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 420
Emailing Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 421
Log > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 421
Log > Settings Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 422
Configuring Log Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 422
Configuring the Mail Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 424
Log > Categories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 424
Log > ViewPoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 425
Log > ViewPoint Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 426
Adding a ViewPoint Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 426
Log > Analyzer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 426
Log > Analyzer Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 426
Adding an Analyzer Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 427
Part 5. Using Virtual Office
Virtual Office Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .429
Virtual Office . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 429
Virtual Office Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 429
Using the Virtual Office . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 430
Dell SonicWALL Secure Mobile Access Connect Agent . . . . . . . . . . . . . . . . . . . . . . . . 431
Supported Operating Systems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 431
Downloading and Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 431
Setting up the SMA Connect Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 432
Part 6. Appendices
Using Online Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .437
Online Help Button . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 437
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
9

Using Context Sensitive Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 437
Configuring the SMA/SRA Appliance with a Third-Party Gateway . . . . . . . . . . . . . . .438
Cisco PIX Configuration for SMA/SRA Appliance Deployment . . . . . . . . . . . . . . . . . . . 438
Before you Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 438
Method One – SMA/SRA Appliance on LAN Interface . . . . . . . . . . . . . . . . . . . . . . 439
Method Two – SMA/SRA Appliance on DMZ Interface . . . . . . . . . . . . . . . . . . . . . . 441
Linksys WRT54GS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 444
WatchGuard Firebox X Edge . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 444
NetGear FVS318 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 446
Netgear Wireless Router MR814 SSL configuration . . . . . . . . . . . . . . . . . . . . . . . . . . 448
Check Point AIR 55 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 448
Setting up an SMA/SRA Appliance with Check Point AIR 55 . . . . . . . . . . . . . . . . . . 449
Static Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 450
ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 450
Use Cases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .451
Importing CA Certificates on Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 451
Importing a goDaddy Certificate on Windows . . . . . . . . . . . . . . . . . . . . . . . . . . 451
Importing a Server Certificate on Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . 454
Creating Unique Access Policies for AD Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . 454
Creating the Active Directory Domain . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 455
Adding a Global Deny All Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 456
Creating Local Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 457
Adding the SSHv2 PERMIT Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 459
Adding the OWA PERMIT Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 460
Verifying the Access Policy Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 462
NetExtender Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .466
Frequently Asked Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .469
Hardware FAQ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 472
Digital Certificates and Certificate Authorities FAQ . . . . . . . . . . . . . . . . . . . . . . . . . 476
NetExtender FAQ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 480
General FAQ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 482
Using the Command Line Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .488
SafeMode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 491
Using SMS Email Formats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .494
Support Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .499
GNU General Public License (GPL) Source Code . . . . . . . . . . . . . . . . . . . . . . . . . . . 499
Limited Hardware Warranty . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 499
End User License Agreement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 500
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .513
About Dell . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .514
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
10

Contacting Dell . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 514
Technical support resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 514
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
11

• About This Guide
• Secure Mobile Access Overview
Part 1
Introduction
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
12

1
About This Guide
This Dell SonicWALL Secure Mobile Access Administration Guide provides network administrators with a high-
level overview of Dell SonicWALL Secure Mobile Access (SMA) technology, including activation, configuration,
and administration of Dell SonicWALL SMA/SRA appliances using the Secure Mobile Access management
interface.
Refer to https://support.software.dell.com for the latest version of this guide as well as other Dell SonicWALL
product and services documentation.
Guide Conventions
The following conventions are used in this guide:
Table 1. Conventions used in this guide
Convention Use
Bold Highlights field, button, and tab names. Also highlights window, dialog box,
and screen names. Also used for file names and text or values you are being
instructed to type into the interface.
Italic Indicates the name of a technical manual, emphasis on certain words in a
sentence, or the first instance of a significant term or concept.
Menu Item > Menu Item Indicates a multiple step management interface menu choice. For example,
System > Status means select the Status page under the System menu.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
13

2
Secure Mobile Access Overview
This section provides an overview of the Dell SonicWALL Secure Mobile Access (SMA) technology, concepts, basic
navigational elements and standard deployment guidelines.
To pi cs :
• Overview of SMA/SRA Hardware and Components on page 14
• Concepts for Secure Mobile Access on page 21
• Navigating the Management Interface on page 74
• Deployment Guidelines on page 80
Overview of SMA/SRA Hardware and Components
The SMA and SRA appliances provide organizations with a simple, secure and clientless method of access to
applications and network resources specifically for remote and mobile employees. Organizations can use Secure
Mobile Access connections without the need to have a pre-configured, large-installation host. Users can easily
and securely access email files, intranet sites, applications, and other resources on the corporate Local Area
Network (LAN) from any location by accessing a standard Web browser.
This section contains the following subsections:
• Secure Mobile Access Software Components on page 14
• SMA Hardware Components on page 15
• SRA Hardware Components on page 18
• SMA 500v Virtual Appliance on page 20
Secure Mobile Access Software Components
SMA/SRA appliances provide clientless identity-based secure remote access to the protected internal network.
Using the Virtual Office environment, SMA/SRA appliances can provide users with secure remote access to your
entire private network, or to individual components such as File Shares, Web servers, FTP servers, remote
desktops, or even individual applications hosted on Citrix or Microsoft Terminal Servers.
Although Secure Mobile Access protocols are described as clientless, the typical Secure Mobile Access portal
combines Web, Java, and ActiveX components that are downloaded from the portal transparently, allowing
users to connect to a remote network without needing to manually install and configure a VPN client
application. In addition, Secure Mobile Access enables users to connect from a variety of devices, including
Windows, Macintosh, and Linux PCs. ActiveX components are only supported on Windows platforms.
For administrators, the Secure Mobile Access web-based management interface provides an end-to-end Secure
Mobile Access solution. This interface can configure Secure Mobile Access users, access policies, authentication
methods, user bookmarks for network resources, and system settings.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
14
For clients, web-based Secure Mobile Access customizable user portals enable users to access, update, upload,
Secure Mobile Access 400
| O | O |
!
X2X3X0
X1
Front Panel
Ethernet Ports (X0-X3)
Provide 1000 Mbps (1Gb) Ethernet
connectivity
USB / SSD ports (2)
External USB and SSD hard drive support
Console Port
Access the Command Line Interface (CLI) using a
compatible console cable
Power Button
Press button to turn appliance on
or o
Reset Button
Press and hold for several seconds to
set the appliance into SafeMode
Appliance LEDs
- Power LED: Indicates Power Supply status
- Test LED: Indicates appliance activity
- Solid Yellow: Appliance is starting
- Blinking Yellow: SafeMode
- O: Appliance is powered up and operational
- Alarm LED: Indicates a critical warning or error
and download files and use remote applications installed on desktop machines or hosted on an application
server. The platform also supports secure web-based FTP access, network neighborhood-like interface for file
sharing, Secure Shell versions 1 and 2 (SSHv1) and (SSHv2), Telnet emulation, VNC (Virtual Network Computing)
and RDP (Remote Desktop Protocol) support, Citrix Web access, bookmarks for offloaded portals (external Web
sites), and Web and HTTPS proxy forwarding.
The Secure Mobile Access network extension client, NetExtender, is available through the Secure Mobile Access
Web portal through an ActiveX control on Windows or using Java on MacOS or Linux systems. It is also available
through stand-alone applications for Windows, Linux, and MacOS platforms. The NetExtender standalone
applications are automatically installed on a client system the first time the user clicks the NetExtender link in
the Virtual Office portal. NetExtender enables end users to connect to the remote network without needing to
install and configure complex software, providing a secure means to access any type of data on the remote
network. NetExtender supports IPv6 client connections from Windows systems running Vista or newer, and from
Linux clients.
NOTE: The SSHv2 applet requires SUN JRE 1.6.0_10 or higher and can only connect to a server that
supports SSHv2. The RDP Java applet requires SUN JRE 1.6.0_10 or higher. Telnet, SSHv1 and VNC applets
support MS JVM in Internet Explorer, and run on other browsers with SUN JRE 1.6.0_10 or higher.
SMA Hardware Components
See the following sections for descriptions of the hardware components on SMA appliances:
• SMA 400 Front and Back Panels Overview on page 15
• SMA 200 Front and Back Panels Overview on page 17
SMA 400 Front and Back Panels Overview
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
15
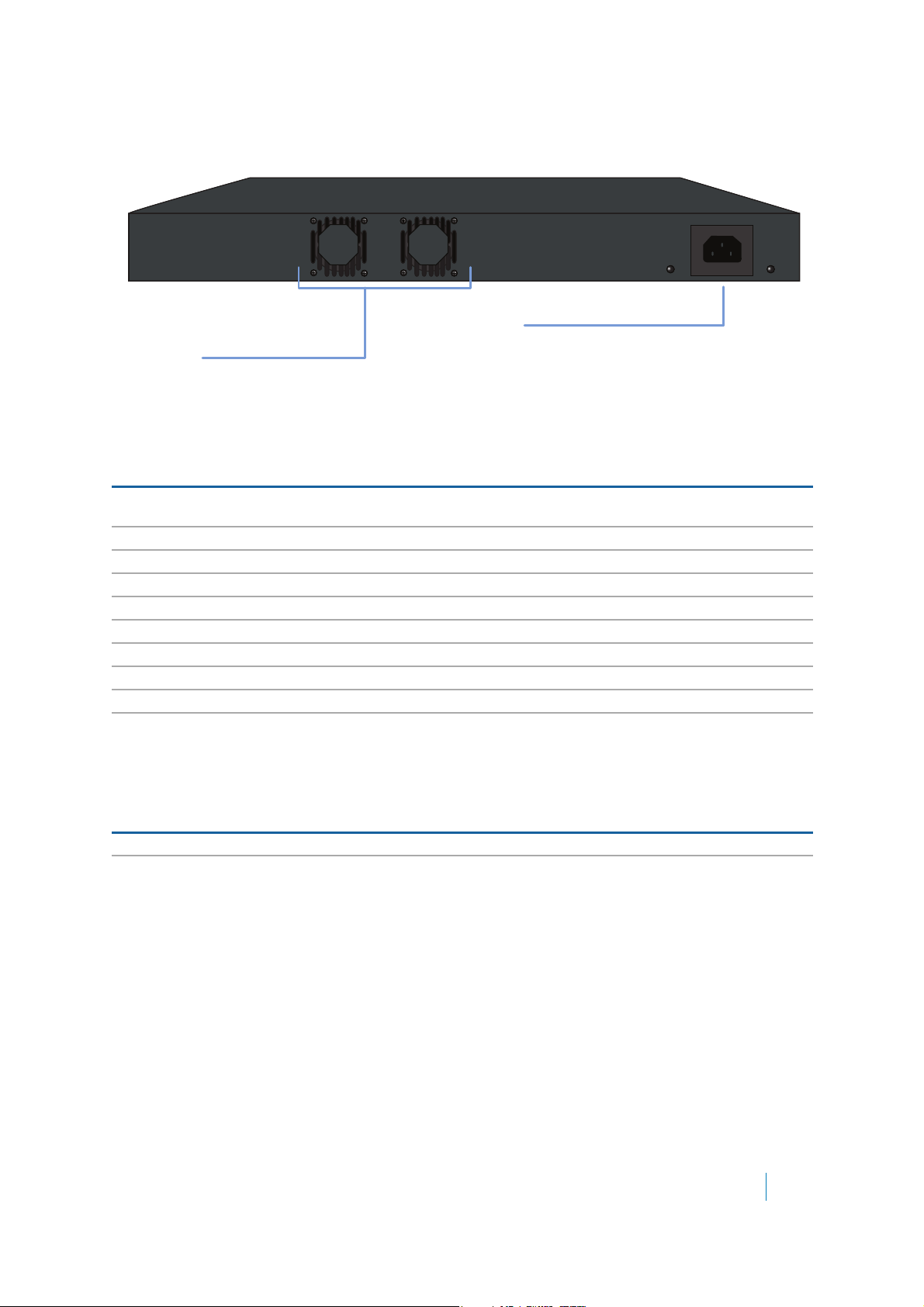
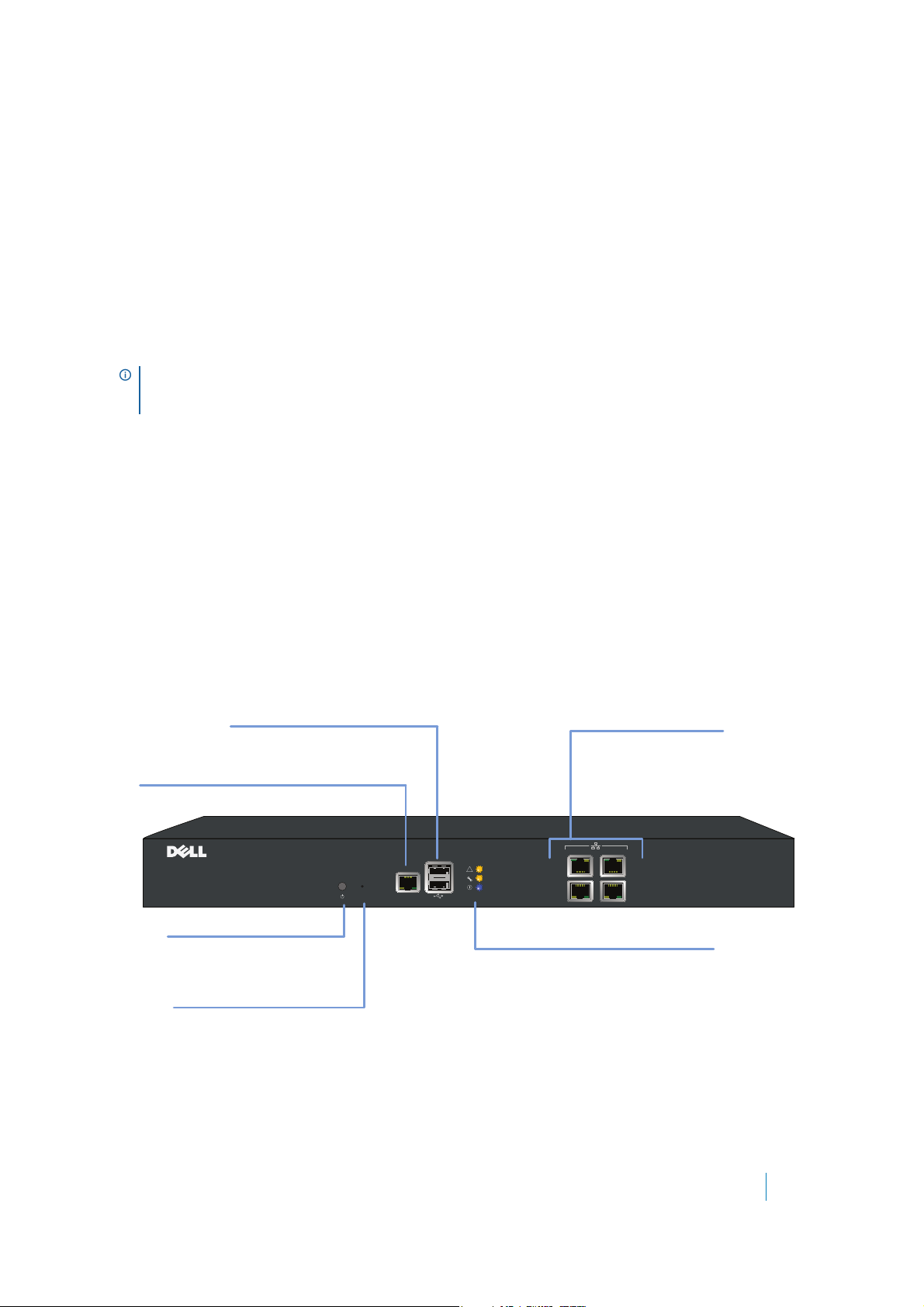
Table 2. SMA 400 Front Panel Features
Rear Panel
Exhaust Fans
Provides optimal cooling for the
Dell SonicWALL SMA appliance
Power Supply Plug
Use the supplied power cord to provide
power to the appliance
Front Panel Feature Description
Console Port RJ-45 port, provides access to console messages with serial connection
(115200 Baud). Provides access to command line interface (for future use).
USB/SSD Ports Provides access to external USB and SSD hard drive support.
Reset Button Provides access to SafeMode.
Power LED Indicates the SMA 400 is powered on.
Test LED Indicates the SMA 400 is in test mode.
Alarm LED Indicates a critical error or failure.
X3 Provides access to the X3 interface and to SMA resources.
X2 Provides access to the X2 interface and to SMA resources.
X1 Provides access to the X1 interface and to SMA resources.
X0 Default management port. Provides connectivity between the SMA 400 and
your gateway.
Table 3. SMA 400 Back Panel Features
Back Panel Feature Description
Exhaust fans Provides optimal cooling for the SMA 400 appliance.
Power supply plug Provides power connection using supplied power cord.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
16
SMA 200 Front and Back Panels Overview
Secure Mobile Access 200
| O | O |
!
X0
X1
Ethernet Ports (X0-X1)
Provide 1000 Mbps (1 Gb)
Ethernet connectivity
USB / SSD ports (2)
External USB and SSD hard drive support
Console Port
Access the Command Line Interface (CLI) using a
compatible console cable
Power Button
Press button to turn appliance on
or o
Reset Button
Press and hold for several seconds to
set the appliance into SafeMode
Appliance LEDs
- Power LED: Indicates Power Supply status
- Test LED: Indicates appliance activity
- Solid Yellow: Appliance is starting
- Blinking Yellow: SafeMode
- O: Appliance is powered up and operational
- Alarm LED: Indicates a critical warning or error
Front Panel
Rear Panel
Exhaust Fans
Provides optimal cooling for the
Dell SonicWALL SMA appliance
Power Supply Plug
Use the supplied power cord to provide
power to the appliance
Table 4. SMA 200 Front Panel Features
Front Panel Feature Description
Console Port RJ-45 port, provides access to console messages with serial connection
USB/SSD Ports Provides access to external USB and SSD hard drive support.
Reset Button Provides access to SafeMode.
Power LED Indicates the SMA 200 is powered on.
Test LED Indicates the SMA 200 is in test mode.
Alarm LED Indicates a critical error or failure.
(115200 Baud). Provides access to command line interface.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
17

Table 4. SMA 200 Front Panel Features (Continued)
Console Port: Provides
serial access to console
messages.
USB Ports:
(for future use)
Reset Button
Power LED
Test LED
Alarm LED
X0: Gigabit Ethernet
Default management port.
Provides connectivity between
the SRA and your gateway.
X1:
Gigabit Ethernet
X2:
Gigabit Ethernet
X3:
Gigabit Ethernet
Exhaust fan
Power plug
Power switch
Front Panel Feature Description
X1 Provides access to the X1 interface and to SMA resources.
X0 Default management port. Provides connectivity between the SMA 200 and
your gateway.
Table 5. SMA 200 Back Panel Features
Back Panel Feature Description
Exhaust fans Provides optimal cooling for the SMA 200 appliance.
Power supply plug Provides power connection using supplied power cord.
SRA Hardware Components
See the following sections for descriptions of the hardware components on SRA appliances:
• SRA 4600 Front and Back Panels Overview on page 18
• SRA 1600 Front and Back Panels Overview on page 19
SRA 4600 Front and Back Panels Overview
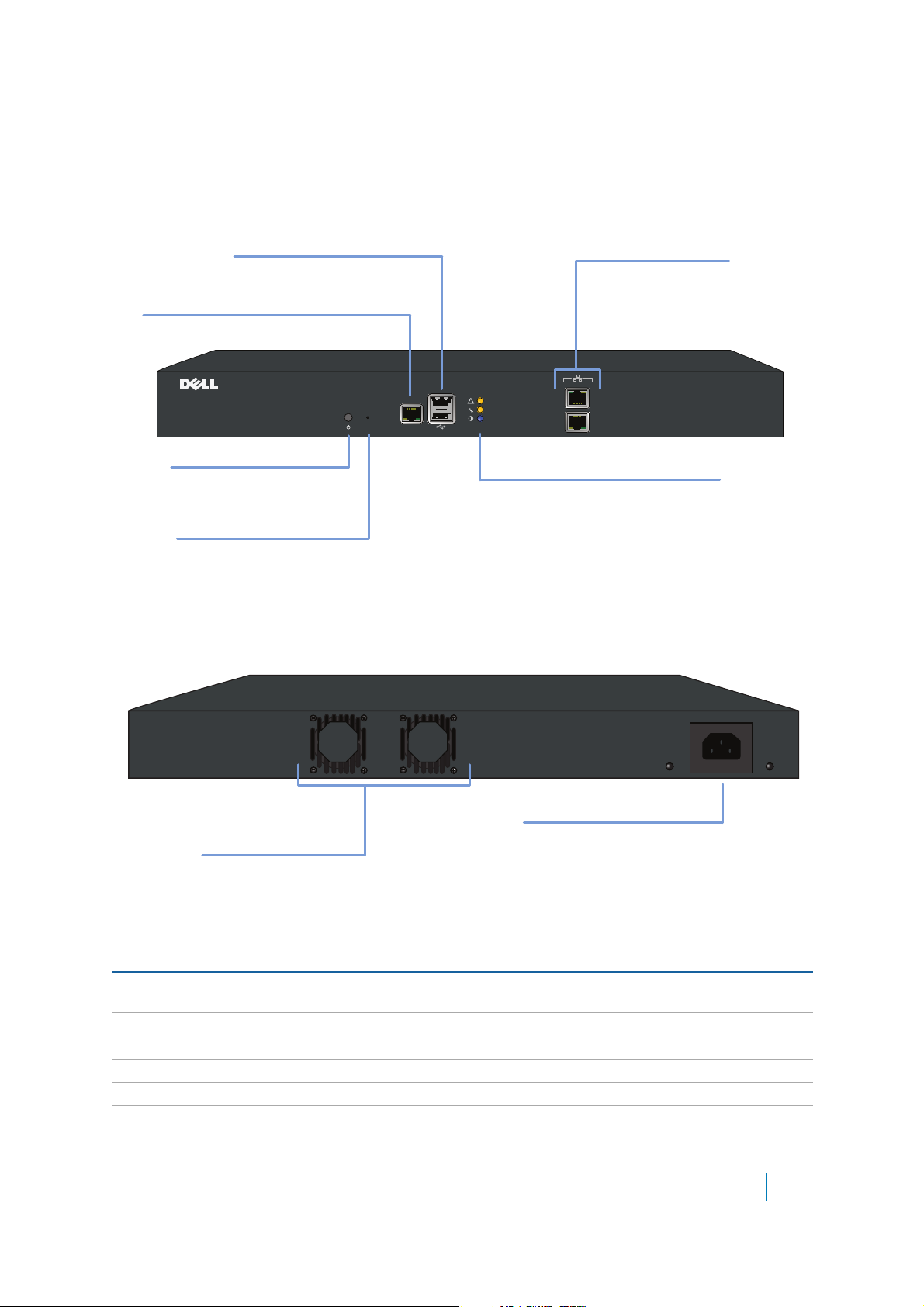
Figure 1. SRA 4600 Front and Back Panels
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
18

Table 6. SRA 4600 Front Panel Features
Console Port: Provides
serial access to console
messages.
USB Ports:
(for future use)
Reset Button
Power LED
Test LED
Alarm LED
X0: Gigabit Ethernet
Default management port.
Provides connectivity between
the SRA and your gateway.
X1:
Gigabit Ethernet
Exhaust fan Power switch
Power plug
Front Panel Feature Description
Console Port RJ-45 port, provides access to console messages with serial connection
(115200 Baud). Provides access to command line interface (for future use).
USB Ports Provides access to USB interface (for future use).
Reset Button Provides access to SafeMode.
Power LED Indicates the SRA 4600 is powered on.
Test LED Indicates the SRA 4600 is in test mode.
Alarm LED Indicates a critical error or failure.
X3 Provides access to the X3 interface and to SRA resources.
X2 Provides access to the X2 interface and to SRA resources.
X1 Provides access to the X1 interface and to SRA resources.
X0 Default management port. Provides connectivity between the SRA 4600 and
your gateway.
Table 7. SRA 4600 Back Panel Features
Back Panel Feature Description
Exhaust fan Provides optimal cooling for the SRA 4600 appliance.
Power plug Provides power connection using supplied power cord.
Power switch Powers the SRA 4600 on and off.
SRA 1600 Front and Back Panels Overview
Figure 2. SRA 1600 Front and Back Panels
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
19

Table 8. SRA 1600 Front Panel Features
Front Panel Feature Description
Console Port RJ-45 port, provides access to console messages with serial connection
(115200 Baud). Provides access to command line interface (for future use).
USB Ports Provides access to USB interface (for future use).
Reset Button Provides access to SafeMode.
Power LED Indicates the SRA 1600 is powered on.
Test LED Indicates the SRA 1600 is in test mode.
Alarm LED Indicates a critical error or failure.
X1 Provides access to the X1 interface and to SRA resources.
X0 Default management port. Provides connectivity between the SRA 1600 and
your gateway.
Table 9. SRA 1600 Back Panel Features
Back Panel Feature Description
Exhaust fan Provides optimal cooling for the SRA 1600 appliance.
Power plug Provides power connection using supplied power cord.
Power switch Powers the SRA 1600 on and off.
SMA 500v Virtual Appliance
The SMA 500v Virtual Appliance (formerly SRA Virtual Appliance) is a virtual machine that runs the Secure
Mobile Access software on a VMware platform. All software components, features, and functionality described
in this guide are supported by the SMA 500v Virtual Appliance, except High Availability and SSL Off-loading.
Deploying Secure Mobile Access as a virtual appliance allows leveraging of shared computing resources to
optimize utilization, easy migration and reduced capital costs. The SMA 500v Virtual Appliance provides the
following benefits:
• Cost savings:
• Multiple virtual machines can run on a single server, reducing hardware costs, power
consumption, and maintenance costs.
• Microsoft Windows Server is not required, eliminating the cost of the Windows license.
• Operational ease:
• In a virtual environment, it is easy to commission new servers or decommission old ones, or to
bring servers up or down.
• Installation is accomplished by importing a file into the virtual environment, with no need to run
an installer.
• Security:
• The SMA 500v Virtual Appliance provides the same hardened operating system that comes with
the SMA/SRA hardware appliances.
The elements of basic VMware structure must be implemented prior to deploying the SMA 500v Virtual
Appliance. For detailed information about deploying the SMA 500v Virtual Appliance, see the Dell SonicWALL
SMA 500v Virtual Appliance Getting Started Guide, available at:
http://www.sonicwall.com/us/support/3893.html
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
20

Concepts for Secure Mobile Access
This section provides an overview of the following key concepts that the administrator should be familiar with
when using the SMA/SRA appliance and Secure Mobile Access web-based management interface:
• Encryption Overview on page 21
• SSL for Virtual Private Networking (VPN) on page 21
• SSL Handshake Procedure on page 22
• IPv6 Support Overview on page 22
• Portals Overview on page 25
• Domains Overview on page 25
• Application Offloading and HTTP(S) Bookmarks Overview on page 25
• Cross Domain Single Sign-On on page 29
• ActiveSync Authentication on page 30
• Network Resources Overview on page 35
• SNMP Overview on page 40
• DNS Overview on page 40
• Network Routes Overview on page 40
• NetExtender Overview on page 40
• Two-Factor Authentication Overview on page 44
• One Time Password Overview on page 46
• End Point Control Overview on page 48
• Secure Virtual Assist Overview on page 49
• Web Application Firewall Overview on page 63
Encryption Overview
Encryption enables users to encode data, making it secure from unauthorized viewers. Encryption provides a
private and secure method of communication over the Internet.
A special type of encryption known as Public Key Encryption (PKE) comprises a public and a private key for
encrypting and decrypting data. With public key encryption, an entity, such as a secure Web site, generates a
public and a private key. A secure Web server sends a public key to a user who accesses the Web site. The public
key allows the user’s Web browser to decrypt data that had been encrypted with the private key. The user’s Web
browser can also transparently encrypt data using the public key and this data can only be decrypted by the
secure Web server’s private key.
Public key encryption allows the user to confirm the identity of the Web site through an SSL certificate. After a
user contacts the SMA/SRA appliance, the appliance sends the user its own encryption information, including an
SSL certificate with a public encryption key.
SSL for Virtual Private Networking (VPN)
A Secure Socket Layer-based Virtual Private Network (SSL VPN) allows applications and private network
resources to be accessed remotely through a secure connection. Using SSL VPN, mobile workers, business
partners, and customers can access files or applications on a company’s intranet or within a private local area
network.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
21

Organizations use Virtual Private Networks (VPNs) to establish secure, end-to-end private network connections
over a public networking infrastructure, allowing them to reduce their communications expenses and to provide
private, secure connections between a user and a site in the organization. By offering Secure Socket Layer (SSL)
VPN, without the expense of special feature licensing, the SMA/SRA appliance provides customers with costeffective alternatives to deploying parallel remote-access infrastructures.
SSL Handshake Procedure
The following procedure is an example of the standard steps required to establish an SSL session between a user
and an SMA/SRA gateway using the Secure Mobile Access web-based management interface:
1 When a user attempts to connect to the SMA/SRA appliance, the user’s Web browser sends information
about the types of encryption supported by the browser to the appliance.
2 The appliance sends the user its own encryption information, including an SSL certificate with a public
encryption key.
3 The Web browser validates the SSL certificate with the Certificate Authority identified by the SSL
certificate.
4 The Web browser generates a pre-master encryption key, encrypts the pre-master key using the public
key included with the SSL certificate and sends the encrypted pre-master key to the SMA/SRA gateway.
5 The SMA/SRA gateway uses the pre-master key to create a master key and sends the new master key to
the user’s Web browser.
6 The browser and the SMA/SRA gateway use the master key and the agreed upon encryption algorithm to
establish an SSL connection. From this point on, the user and the SMA/SRA gateway encrypts and
decrypts data using the same encryption key. This is called symmetric encryption.
7 After the SSL connection is established, the SMA/SRA gateway encrypts and sends the Web browser the
SMA/SRA gateway login page.
8 The user submits their user name, password, and domain name.
9 If the user’s domain name requires authentication through a RADIUS, LDAP, or Active Directory Server,
the SMA/SRA gateway forwards the user’s information to the appropriate server for authentication.
10 After being authenticated, the user can access the Secure Mobile Access portal.
IPv6 Support Overview
Internet Protocol version 6 (IPv6) is a replacement for IPv4 that is becoming more frequently used on networked
devices. IPv6 is a suite of protocols and standards developed by the Internet Engineering Task Force (IETF) that
provides a larger address space than IPv4, additional functionality and security, and resolves IPv4 design issues.
You can use IPv6 without affecting IPv4 communications.
IPv6 supports stateful address configuration that is used with a DHCPv6 server, and stateless address
configuration, where hosts on a link automatically configure themselves with IPv6 addresses for the link, called
link-local addresses.
In IPv6, source and destination addresses are 128 bits (16 bytes) in length. For reference, the 32-bit IPv4
address is represented in dotted-decimal format, divided by periods along 8-bit boundaries. The 128-bit IPv6
address is divided by colons along 16-bit boundaries, where each 16-bit block is represented as a 4-digit
hexadecimal number. This is called colon-hexadecimal.
The IPv6 address, 2008:0AB1:0000:1E2A:0123:0045:EE37:C9B4 can be simplified by removing the leading zeros
within each 16-bit block, as long as each block has at least one digit. When suppressing leading zeros, the
address representation becomes: 2008:AB1:0:1E2A:123:45:EE37:C9B4
When addresses contain contiguous sequences of 16-bit blocks set to zeros, the sequence can be compressed to
::, a double-colon. For example, the link-local address of 2008:0:0:0:B67:89:ABCD:1234 can be compressed to
2008::B67:89:ABCD:1234. The multicast address 2008:0:0:0:0:0:0:2 can be compressed to 2008::2.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
22

The IPv6 prefix is the part of the address that indicates the bits of the subnet prefix. Prefixes for IPv6 subnets,
routes, and address ranges are written as address/prefix-length, or CIDR notation. For example, 2008:AA::/48
and 2007:BB:0:89AB::/64 are IPv6 address prefixes.
Secure Mobile Access supports IPv6 in the following areas:
Services
• FTP Bookmark – Define a FTP bookmark using an IPv6 address.
• Telnet Bookmark – Define a Telnet bookmark using an IPv6 address.
• SSHv1 / SSHv2 Bookmark – Define an SSHv1 or SSHv2 bookmark using an IPv6 address.
• Reverse proxy for HTTP/HTTPS Bookmark – Define an HTTP or HTTPS bookmark using an IPv6 address.
• Citrix Bookmark – Define a Citrix bookmark using an IPv6 address.
• RDP Bookmark - Define an RDP bookmark using an IPv6 address.
• VNC Bookmark - Define a VNC bookmark using an IPv6 address.
NOTE: IPv6 is not supported for File Shares (CIFS).
Settings
•Interface Settings – Define an IPv6 address for the interface. The link-local address is displayed in a
tooltip on Interfaces page.
• Route Settings – Define a static route with IPv6 destination network and gateway.
•Network Object – Define the network object using IPv6. An IPv6 address and IPv6 network can be
attached to this network object.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
23
NetExtender
When a client connects to NetExtender, it can get an IPv6 address from the SMA/SRA appliance if the client
machine supports IPv6 and an IPv6 address pool is configured on the SMA/SRA appliance. NetExtender supports
IPv6 client connections from Windows systems running Vista or newer, and from Linux clients.
Secure Virtual Assist
Users and Technicians can request and provide support when using IPv6 addresses.
Rules
•Policy rule – User or Group Policies. Three IPv6 options in the Apply Policy To drop-down list:
• IPv6 Address
• IPv6 Address Range
• All IPv6 Address
•Login rule – Use IPv6 for address fields:
• Define Login From Defined Addresses using IPv6
• Two IPv6 options in the Source Address drop-down list: IPv6 Address / IPv6 Network
Virtual Hosts
An administrator can assign an IPv6 address to a virtual host, and can use this address to access the virtual host.
Application Offloading
An administrator can assign an IPv6 address to an application server used for application offloading, and can use
this address to access the server.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
24

Portals Overview
Secure Mobile Access provides a mechanism called Virtual Office that is a web-based portal interface that
provides clients with easy access to internal resources in your organization. Components such as NetExtender,
Secure Virtual Assist, and bookmarks to file shares and other network resources are presented to users through
the Virtual Office portal. For organizations with multiple user types, the SMA/SRA appliance allows for multiple
customized portals, each with its own set of shared resource bookmarks. Portals also allow for individual
domain and security certificates on a per-portal basis. The components in a portal are customized when adding
a portal.
File Shares
File shares provide remote users with a secure Web interface to Microsoft File Shares using the CIFS (Common
Internet File System) or SMB (Server Message Block) protocols. Using a Web interface similar in style to
Microsoft’s familiar Network Neighborhood or My Network Places, File Shares allow users with appropriate
permissions to browse network shares, rename, delete, retrieve, and upload files, and to create bookmarks for
later recall. File shares can be configured to allow restricted server path access.
Custom Portals
SMA/SRA appliances allow you to configure multiple portals, each with their own title, banner, login message,
logo and set of available resources. Each portal also enables you to set individual Virtual Hosts/Domain Names
to create a unique default portal URL. When a user logs into a portal, he or she sees a set of pre-configured
links and bookmarks that are specific to that portal. You can configure whether or not NetExtender is displayed
on a Virtual Office portal, and if you want NetExtender to automatically launch when users log in to the portal.
The administrator configures which elements each portal displays through the Portal Settings window. For
information on configuring portals, refer to Portals > Portals on page 134.
Domains Overview
A domain in the Secure Mobile Access environment is a mechanism that enables authentication of users
attempting to access the network being serviced by the SMA/SRA appliance. Domain types include the Secure
Mobile Access internal LocalDomain, and the external platforms Microsoft Active Directory, LDAP, and RADIUS.
Often, only one domain suffices to provide authentication to your organization, although a larger organization
might require distributed domains to handle multiple nodes or collections of users attempting to access
applications through the portal.
Application Offloading and HTTP(S) Bookmarks Overview
SMA/SRA appliances use HTTP(S) bookmarks and application offloading to provide access to web-based
applications running on servers within the intranet. This includes SharePoint 2007 and the enhanced versions of
commonly-used Web mail interfaces, such as Microsoft OWA Premium and Domino Web Access 8.0.1, 8.5.1, and
8.5.2. SharePoint 2010 is supported with application offloading, but not with HTTP(S) bookmarks. SharePoint
2013 is supported with application offloading. Note that third-party modules that are not proxy friendly might
not be supported by SharePoint.
Both application offloading and HTTP(S) bookmarks use an HTTP(S) reverse proxy. A reverse proxy is a proxy
server that is deployed between a remote user outside an intranet and a target Web server within the intranet.
The reverse proxy intercepts and forwards packets that originate from outside the intranet. An HTTP(S) reverse
proxy specifically intercepts HTTP(S) requests and responses.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
25

Application Offloading provides secure access to both internal and publicly hosted Web applications. An
application offloading host is created as a special-purpose portal with an associated virtual host acting as a
proxy for the backend Web application.
Unlike HTTP(S) bookmarks, access to offloaded applications is not limited to remote users. The administrator
can enforce strong authentication and access policies for specific users or groups. For instance, in an
organization certain guest users might need Two-factor or Client Certificate authentication to access Outlook
Web Access (OWA), but are not allowed to access OWA public folders. If authentication is enabled, multiple
layers of advanced authentication features such as One Time Password, Two-factor Authentication, Client
Certificate Authentication and Single Sign-On can be applied on top of each other for the offloaded host.
The offloaded application portal must be configured as a virtual host with a suitable Secure Mobile Access
domain. It is possible to disable authentication and access policy enforcement for such an offloaded host.
Web transactions can be centrally monitored by viewing the logs. In addition, Web Application Firewall can
protect offloaded application hosts from any unexpected intrusion, such as Cross-site scripting or SQL Injection.
Access to offloaded Web applications happens seamlessly as URLs in the proxied page are not rewritten in the
manner used by HTTP or HTTPS bookmarks.
Benefits of HTTP(S) Bookmarks
By using HTTP(S) bookmarks, users can access the full-featured versions of SharePoint 2007, Microsoft OWA
Premium, and Domino Web Access 8.0.1, 8.5.1, and 8.5.2 Web mail interfaces. These interfaces are easier to
use and provide more enhanced features than their basic counterparts.
Benefits of Application Offloading
An offloaded Web application has the following advantages over configuring the Web application as an HTTP(S)
bookmark in Secure Mobile Access:
• No URL rewriting is necessary, thereby improving throughput significantly.
• The functionality of the original Web application is retained almost completely, while an HTTP(S)
bookmark is a best-effort solution.
• Application offloading extends Secure Mobile Access security features to publicly hosted Web sites.
Application offloading can be used in any of the following scenarios:
• To function as an SSL offloader and add HTTPS support to the offloaded Web application, using SSL
acceleration of the SMA/SRA appliance.
• In conjunction with the Web Application Firewall subscription service to provide the offloaded Web
application continuous protection from malicious Web attacks.
• To add strong or stacked authentication to the offloaded Web application, including Two-factor
authentication, One Time Passwords and Client Certificate authentication.
• To control granular access to the offloaded Web application using global, group or user based access
policies.
• To support Web applications not currently supported by HTTP/HTTPS bookmarks. Application Offloading
does not require URL rewriting, thereby delivering complete application functionality without
compromising throughput.
• To authenticate ActiveSync Application Offloading technology that delivers Web applications using
Virtual Hosting and Reverse Proxy. ActiveSync authentication does not require URL rewriting in order to
deliver the Web applications seamlessly. As an example, the ActiveSync protocol is used by a mobile
phone’s email client to synchronize with an Exchange server, as explained in ActiveSync Authentication
on page 30.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
26

Supported Platforms
Appliance Platforms
Application Offloading and HTTP(S) bookmarks are supported on all the SMA/SRA appliances that support the
Dell SonicWALL Secure Mobile Access 8.5 release:
• SMA 400
• SMA 200
• SRA 4600
• SRA 1600
• SMA 500v Virtual Appliance
HTTP Versions
HTTP(S) bookmarks and application offloading portals support both HTTP/1.0 and HTTP/1.1.
Certain performance optimization features, such as caching, compression, SSL hardware acceleration, HTTP
connection persistence, TCP connection multiplexing and transfer-chunk encoding for proxies are automatically
enabled depending on the usage.
Applications
SharePoint 2010 and SharePoint 2013 are supported with application offloading, but not with HTTP(S)
bookmarks. The following features have been tested and verified as working well on the indicated browsers:
Table 10. Supported SharePoint features
SharePoint Features Browsers
Add Announcement
Delete Announcement
Download Document
Add Document
Delete Document
Add New Item
Delete Item
The following Web applications have been tested and verified to work with HTTP(S) bookmarks and as offloaded
applications:
• Microsoft Outlook Web Access 2013
Microsoft Outlook Web Access 2010
Microsoft Outlook Web Access 2007
NOTE: Outlook Web Access is supported on the SMA 400/200, SRA 4600/1600, and the SMA 500v
Virtual Appliance platforms.
• Windows SharePoint 2013 (supported only using App Offloading)
Windows SharePoint 2007 (supported only using App Offloading)
Windows SharePoint Services 3.0
NOTE: The integrated client features of SharePoint are not supported.
Internet Explorer 9
Firefox 16.0 and later
Chrome 22.0 and later
• Lotus Domino Web Access 8.0.1
Lotus Domino Web Access 8.5.1
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
27
Lotus Domino Web Access 8.5.2
NOTE: Domino Web Access is supported on the SMA 400/200, SRA 4600/1600, and the SMA 500v
Virtual Appliance platforms.
• Novell Groupwise Web Access 7.0
• ActiveSync with Microsoft Exchange 2010
• ActiveSync with Microsoft Exchange 2007
• ActiveSync with Microsoft Exchange 2003
Exchange ActiveSync is supported on the following:
• Apple iPhone
• Apple iPad
• Android 2.3.x (Gingerbread), 4.0.x (ICS) and 4.1 (Jelly Bean) based phones
NOTE: Application Offloading supports authentication for ActiveSync. ActiveSync is a protocol used
by a mobile phone’s email client to synchronize with an Exchange server. The Administrator can
create an offloading portal and set the application server host to the backend Exchange server.
Then, a user can use the new virtual host name in a mobile phone’s email client, and synchronize
with the backend Exchange server through the SMA/SRA appliance.
Authentication Schemes
The following authentication schemes are supported for use with application offloading and HTTP(S)
bookmarks:
•Basic – Collects credentials in the form of a username and password.
• Forms-based authentication – Uses a Web form to collect credentials.
Software Prerequisites
The following end-user requirements must be met in order to access the complete set of application offloading
and HTTP(S) bookmarks features:
• Internet Explorer 9.0 or newer
• Windows 10 and Windows 7
NOTE:
• The maximum number of users supported is limited by the number of applications being accessed
and the volume of application traffic being sent.
• Feature support varies based on your hardware and installation, see the respective sections for
more detailed information about specific application support.
TIP: If you are using the correct Web browser and operating system, and a supported application does not
work, delete the browser session cookies, close and reopen all instances of your browser, clear the
browser cache, and then try again.
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
28

Supported Application Deployment Considerations
Be aware of these installation and general feature caveats when using application offloading and HTTP(S)
bookmarks with the following software applications:
• SharePoint
• SharePoint 2013 and SharePoint 2010 are supported with application offloading, but not with
HTTP(S) bookmarks.
• Outlook Anywhere
• SMA/SRAs with Application Offloading.
• Outlook Anywhere uses Microsoft’s MS-RPCH proprietary protocol that could conflict with normal
HTTP(S) protocol.
Application Offloading is only supported on SharePoint 2013 and with any application using HTTP/HTTPS. Secure
Mobile Access has limited support for applications using Web services and no support for non-HTTP protocols
wrapped within HTTP.
The application should not contain hard-coded self-referencing URLs. If these are present, the Application
Offloading proxy must rewrite the URLs. Because Web site development does not usually conform to HTML
standards, the proxy can only do a best-effort translation when rewriting these URLs. Specifying hard-coded,
self-referencing URLs is not recommended when developing a Web site because content developers must modify
the Web pages whenever the hosting server is moved to a different IP or hostname.
For example, if the backend application has a hard-coded IP address and scheme within URLs as follows,
Application Offloading must rewrite the URL.
<a href="http://1.1.1.1/doAction.cgi?test=foo">
This can be done by enabling the Enable URL Rewriting for self-referenced URLs setting for the Application
Offloading Portal, but all the URLs might not be rewritten, depending on how the Web application has been
developed. (This limitation is usually the same for other vendors employing reverse proxy mode.)
Cross Domain Single Sign-On
External Website Bookmarks can be created for application offloading portals to achieve a single point of access
for users. This allows users to automatically log in to application offloading portals after logging into the main
portal.
To use Cross Domain Single Sign-on (SSO):
1 Create two or more portals with the same shared domain (from Virtual Host Domain name) and that need
authentication. One portal should be a regular portal. These portals are also in the same SMA/SRA
appliance’s domain so that a user can log in to both of them with the same credentials. Adding Portals on
page 135 explains how to create a portal.
2 Log in to the portal and create a bookmark, as explained in Adding or Editing User Bookmarks on page
354.
3 Set the service to External Web Site, as explained in External Web Site on page 366.
4Enable Automatically log in for the bookmark that enables Cross Domain SSO for this bookmark.
5 Specify a Host that is a portal with the same shared domain name.
6 Save the bookmark and launch it. The new portal is logged in automatically without any credential.
The shared domain names do not need to be identical; a sub-domain also works. For example, one portal is a
regular portal whose virtual host domain name is “www.example.com” and its shared domain name is
“.example.com.” The other portal’s virtual host domain name is “intranet.eng.example.com” and the shared
domain name is “.eng.example.com.” If a bookmark to xyz.eng.example.com is created in the
www.example.com portal, Cross Domain SSO works because “.eng.example.com” is a sub-domain of
“.example.com.”
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
29
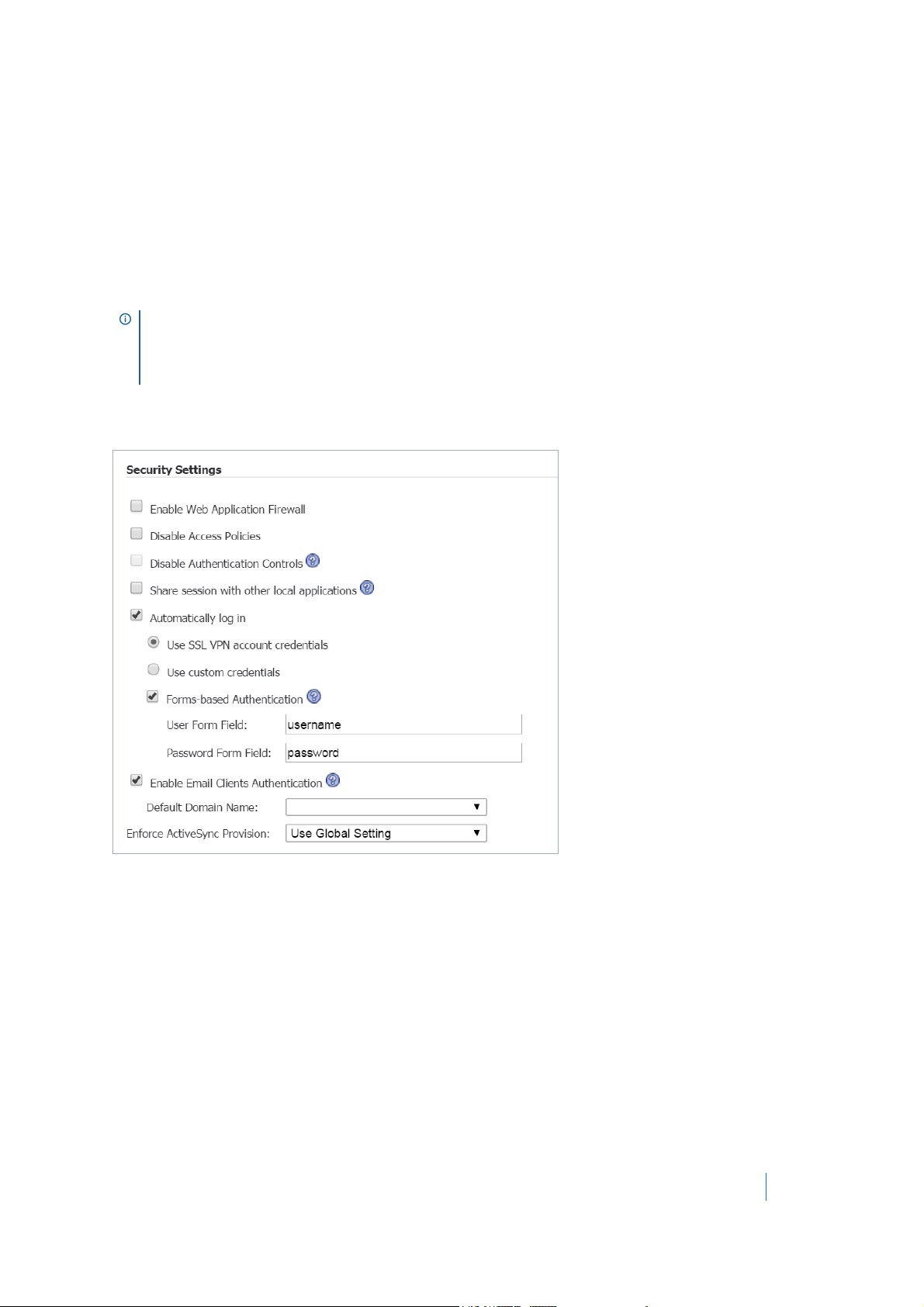
ActiveSync Authentication
Application Offloading now supports authentication for ActiveSync. Application Offloading technology delivers
Web applications using Virtual Hosting and Reverse Proxy. Users still need to authenticate with the SMA/SRA
appliance before accessing the backend Web application. However, the proxy avoids URL rewriting in order to
deliver the Web applications seamlessly.
ActiveSync is a protocol used by a mobile phone’s email client to synchronize with an Exchange server. The
Administrator can create an offloading portal and set the application server host to the backend Exchange
server. Then, a user can use the new virtual host name in a mobile phone’s email client, and synchronize with
the backend Exchange server through the SMA/SRA appliance.
NOTE: On iPhones/iPads running versions earlier than iOS 6.1.2, initial account synchronization might fail
if a calendar contains a recurring invite.
NOTE: To provide better protection for the Exchange Server, anonymous ActiveSync access will not be
supported in the future.
ActiveSync is managed through the Portals > Offload Web Application > Offloading > Security Settings
page:
To configure ActiveSync authentication, clear Disable Authentication Controls to display the authentication
fields. Select Enable ActiveSync authentication and then type the default domain name. The default domain
name cannot be used when the domain name is set in the email client’s setting.
ActiveSync Log Entries
The Log > View page is updated when a Web application is offloaded. Most mobile systems (iPhone, Android,
and so on) support ActiveSync. These log entries identify when the client began to use ActiveSync through the
Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
30
 Loading...
Loading...