Dell PowerVault TL4000 User Manual [ko]

Dell™PowerVault™Encryption Key Manager
gkZ H;-


Dell™PowerVault™Encryption Key Manager
gkZ H;-

© 2007, 2010 Dell Inc. All rights reserved.
L %! in VB $8B kv xL /fI v V@OY.
n0Q fD8Ng Dell Inc.G -i BN xB 9&B -BOT ]vKOY. L .-! gkH Dell, DELL Nm W PowerVaultB
Dell Inc.G s%TOY.
b8 s% W s#& gkOB }N GB Li }NG &0; p^Ob 'X 8
gG s% W s#! ; .-!- gkI v V@O
Y. Dell Inc.B ZgG ML FQ s% GB s#! kX n0Q R/G5 .v J@OY.

qw
W2 .................v
% .................vii
-. .................ix
L %! kQ $8 ............ix
L %G 6Z .............ix
L %! gkH T" W kn .......ix
VGgW ................x
|C -{ ...............x
Linux $8 ..............x
Microsoft Windows $8 .........x
BsN vx..............x
UzPn_ R gW ...........xiii
Dell ,t3 ..............xiii
& 1 e WLA O#- 3d ........1-1
DwM. ...............1-2
O#- |. ..............1-3
@kANW%!-
sLj/.!- |.OB O#- ......1-6
O#- 0 $8 .............1-6
& 2 e Encryption Key Manager /fh9 2-1
O#- 3$ [w 3d ..........2-1
Encryption Key Manager 3$ [w ....2-1
sLj/.!- |.OB WLA O#- h9 2-2
Oe~n W RA.~n d8gW .......2-2
Linux VgG DwM. .........2-3
Windows VgG D
0 zeR mAgW ...........2-4
JCEKS 0 zeR ...........2-4
|
O#- 0 W LTO 4 W LTO 5 WLA esL
j ................2-4
0 zeR %LM iw .........2-6
iwk8N )/ 3G Key Manager vx ...2-8
Encryption Key Manager -v 8: ....2-9
eV 98 gL. mAgW ........2-11
@AgL.!- O#-H WLA& x/OB fl
mAgW...............2-11
FIPS(Federal Information Processing Standard)
mAgW ............2-12
140-2
|.OB WLA O#- ...1-5
wM. ........2-3
& 3 e Encryption Key Manager W 0 zeR
3! ................3-1
|
VE v| Key Manager ISO LLv YnNe . . 3-1
Linux! Encryption Key Manager 3! ....3-1
Windows! Encryption Key Manager 3! ...3-3
GUI& gkO) 8: DO, 0 zeR W Nu-
[: ................3-6
|
LTO 4 W LTO 5!- O#-! kQ 0 W 0m
}: ................3-11
0 Wl [: W |. ..........3-16
& 4 e Encryption Key Manager 8: ...4-1
GUI& g
8: |+ ...............4-1
8: b; gW .............4-4
& 5 e Encryption Key Manager |. ...5-1
Key Manager -v C[, uN m' W _v ...5-1
mI` NMdL: ,sLp. ........5-6
CLI mI ...............5-9
& 6 e .&! G0 ...........6-1
Y=G
-v.&! .N ............6-1
CLI ,sLp. W EKM -v # kE .&! p
vk ................6-2
Key Manager -v.&! pvk ......6-3
Encryption Key Manager!- 8mOB @y . . 6-6
^Cv ...............6-10
kO) Encryption Key Manager 8: 4-1
WLA esLj WLm Z? w%L. ....4-1
N 3G Key Manager -v gL!- %LM ?
b- ...............4-2
_d DO!- Encryption Key Manager
8: DOL v$Gv J= .......6-10
esLj _! GP ..........6-10
NW DO! F+Lj GP .......6-10
8: h& GP ...........6-11
esLj
!.@b GP ............6-11
8:v$ GP ...........6-12
DOL': N(null)O v x= ......6-12
DO )b QhB =vO v x= .....6-12
?b-R %LM x= .........6-13
CY#v J:TB ..........6-13
Wq h& GP ........6-11
iii

8: DOG SSL w. x#! CY#v J= 6-14
8: DOG TCP w. x#! CY#v J= 6-14
8: DO!- SSL w. x#& v$X_ T 6-14
8: DO!- TCP w. x#& v$X_ T 6-15
-v C[ GP ...........6-15
?b- GP ............6-15
v$H (g NW DOL Pb |kS ....6-16
|. 0 zeR& Ne
0 zeR& NeR v x= .......6-17
|[ 0 zeR& NeR v x= .....6-17
vxGv JB 6! ..........6-18
& 7 e (g 9Ze ...........7-1
(g 3d...............7-1
(g 8: E3/v ...........7-1
Audit.event.types ...........7-1
Audit.event.outcome ..........7-2
Audit.eventQueue.max .........7-2
Audit.handler.file.directory ........7-3
Audit.handler.file.size .........7-3
Audit.handler.file.name .........7-4
Audit.handler.file.multithreads ......7-4
Audit.handler.file.threadlifespan ......7-4
(g 9Ze |D ............7-5
R v x= .....6-16
Encryption Key Manager!-G (g v! . . 7-5
(g 9Z
(gH L%. .............7-8
& 8 e ^8%LM gk .........8-1
NO A. yC DO ...........A-1
yC C[ pU :)3. .........A-1
Linux C'{ ............A-1
yC 8: DO.............A-1
NO B. Encryption Key Manager 8: nO $
8 DO ...............B-1
Encryption Key Manager -v 8: nO $8 D
O .................B-1
CLI ,sLp. 8: nO $8 DO .....B-11
NO C. ZV /B z.
VGgW ...............D-1
s% ................D-1
kn ................E-1
vN ................X-1
e S: ...........7-6
(FAQ) .......C-1
iv Dell Encryption Key Manager gkZ H;-

W2
1-1. Encryption Key ManagerG W !v b;
DwM. ............1-3
1-2. O#- $% #x W 0 |.! V; v V
B N '! ............1-5
|
1-3. k* O#- 0& gkO) O#- 1-8
|
2-1. LTO 4 GB LTO 5 WLA esLjG O
#- 2b 6[ d; ........2-5
|
2-2. LTO 4 GB LTO 5 WLA esLjG O
#- Pb 6[ d; ........2-6
2-3. _d DO iw " .........2-8
||
2-4. \O -
2-5. 8:; x/OB N 3G -v .....2-10
||
2-6. 0:e!! W<:OB -N Y% 8:G
|
||
N 3G -v...........2-10
3-1. ks '! 1C(Choose Destination
Location) " ...........3-3
v 8: ..........2-9
3-2. b;*8N L JVM v| 3$ .....3-4
3-3. DO 9g C[ " .........3-4
3-4. EKM -v 8:(EKM Server
Configuration) dLv ........3-7
3-5. EKM -v Nu- 8:(EKM Server
Certificate Configuration) dLv ....3-8
3-6. _d DO iw " .........3-9
3-7. 0 Wl [:...........3-18
3-8. b; 2b 0 Wl /f .......3-19
3-9. esLj! Wl v$ ........3-20
3-10. esLj h& ..........3-21
5-1. -v sB ............5-2
5-2. NWN " ............5-2
v

vi Dell Encryption Key Manager gkZ H;-

%
1. L %! gkH Nb T" .......ix
1-1. O#- 0 d` ..........1-8
2-1. Linux!-G VRRA.~n d8gW 2-3
2-2. Windows!-G VRRA.~n d8gW 2-3
6-1. Encryption Key Manager!- 8mH @y 6-6
7-1. Encryption Key Manager!(g DO!
2B (g 9Ze /| ........7-6
7-2. (gH L%.0 (g 9Ze /| 7-8
8-1. ^8%LM 68 bB |
D ......8-3
vii

viii Dell Encryption Key Manager gkZ H;-
-.
L %! kQ $8
L %G 6Z
L %! gkH T" W kn
L H;-!B Dell™Encryption Key ManagerG 3! W [?! JdQ $8M v
CgWL wTGn V@OY. GQ Y=! |Q 3d W |C ANCz! V@OY.
v O#- !I LTO 4 W LTO 5 WLA esLj
v O#- 0
v pvP Nu-
L %: _dQ %LMG 8H Wiw; cgOB :d.v W 8H |.ZMn5
/f!- Encryption Key Manager -vG 3! W /v8v& vxOB gkZ& k
s8N UOY. L %!-B 6Z! :d.v e! W W.v)! kQ G&{N vD
; ._zYm!$UOY.
L %!-BY=Nb T"; gkUOY.
%1.L %! gkH Nb T"
T" gk}
=:< =:<N %CH \n* .ZB mIn, DOL',
C!W L', fN L' W 1CH ^: IGz0
L .Z WkN gkX_ OB C:[ dR& *8
@OY.
m$ [C 9&, gkZ! v$Q X:. W C:[!- %CO
B $8B m$ [
boS< boS<
_ OB /v*; *8@OY.
[Wq] 1C{ Wq; *8@OY.
{Wq} |D W 8. 3m!- Wq; 1CX_ OB qO
; -@OY.
| <N 7kB 1CgW qO!- Wq; 8PUOY.
<0> )#B 0
N %CH \n* .ZB gkZ! &xX
& *8@OY.
CN %CUOY.
ix

VGgW
|C -{
VGgW: ANW%, e!, C:[ GB %LM! UsI !I:L V=; *8@OY.
VGgW!B@&% b#! T2 %CI v Vv8 Ws %CGvB J@OY. Y=:
VGgW! kQ yCTOY.
fm: esLv& gkO) L}w& v`OB fl WLA! U
sI v V@OY.
Z<Q $8BY= -{; |6OJC@.
™
v Dell
$8& &xUOY.
v Dell
Reference!-B SCSI NMdL: ?[; &nOB vxGB SCSI mI W ANd
]; &xUOY.
PowerVault™TL2000
™
PowerVault™TL2000 Tape Library and TL4000 Tape Library SCSI
W
TL4000
WLA sLj/. C[Ob
!-B 3!
Linux $8
Red Hat $8
Y=: Red Hat Linux®C:[z|CH URLTOY.
v http://www.redhat.com
SuSE $8
Y=: SuSE Linux C:[z|CH URLTOY.
v http://www.suse.com
Microsoft Windows $8
Y=: Microsoft®Windows®C:[! kQ $8! W<:R v VB URLTOY.
v http://www.microsoft.com
BsN vx
Y= |C -{; 8Ai http://support.dell.com; f.OJC@.
Dell Encryption Key Manager
$8& &xUOY.
|% C[ H;-
!-B b; 8:3$! kQ
Y= |C -{; 8Ai http://www.dell.com; f.OJC@.
x
Dell Encryption Key Manager gkZ H;-

Library Managed Encryption for Tape i-!-B LTO WLA O#-! kQ
p| gJ& &xUOY.
-. xi

xii Dell Encryption Key Manager gkZ H;-

UzPn_ R gW
Dell ,t3
L9! EVOB m4: 800-WWW-DELL(800-999-3355)N |-OJC@.
V: NM] ,aL 0:- Gn Vv J: fl!B 8E [e, we m<-, ;8- G
B Dell &0 +;NW!- cgZ $8& #; v V@OY.
Dell: )/ !v BsN, |- b] vx W -q: IG; &xUOY.
: 9! W &0! {s Y#g, Q9!-B ON -q:& gkOv xR v5 V@O
Y. 5w, bz vx GB m4 -q: .&N Dell!,tOAi Y=; v`OJC@.
1. http://supportapj.dell.com/support/index.aspx; f.OJC@.
2. dLv G F!! VB Choose A Country/Region eS Yn ^:!- Xg 9
GB v*; .NOJC@.
!
3. dLvG ^J!- Contact Us& ,/OJC@.
4. Jd! {s {}Q -q: GB vx 5)& 1COJC@.
5. gkZ!T m.Q Dell ,t f}; 1COJC@.
L/Q IG
xiii

xiv Dell Encryption Key Manager gkZ H;-

& 1 e WLA O#- 3d
%LMB foB VB qnO: /f!- El _dQ !!& vOB Zx _ O*TO
Y. 8HG _d:L N"GB vG!- L/Q %LM& 8#Om L! kQ W<:&
&nOg %LM b3& .NOB ?C! !k:;/v8vOB bIL !e l
m V@OY. %LM O#-B L/Q 9: d8! kX d; Y v VB 58TOY.
Dell Encryption Key Manager(LDNB Encryption Key ManagerN v*T))B O
#- [w; \x-UOY.
1CG
|
|
LTO 4 W LTO 5 esLjB LTO 4 W LTO 5 %LM +..v! %LM& 2B
fl Xg %LM& O#-R v V@OY. L u
-N NQ :I zO W 3. @vleG _} W |k b8! kQ qk; vbOv
Jm5 zeH%LM! kQ -BQ 8H v\; _!UOY.
WLA esLj O#- VgG: Y=z0: < !vVddRN 8:KOY.
O#- !I
pg LTO 4 W LTO 5 WLA esLjB sLj/. NMdL:& kX gkI
v Vn_ UOY.
WLA esLj! kQ Z<Q $8B 2-2 dLvG :Oe~n W RA.~n d
8gW;; |6OJC@.
O#- 0 |.
O#-B OCG ,SH
0G }:, /v8v, &n W |[: O#-OB WLA esLj! 3!H n5
/f! {s Y(OY. ON @kANW%: 0 |.& v`R v V@OY. L/
Q @kANW%L xB /f GB @kAN
/fG fl, Dell Encryption Key Manager!- JdQ pg 0 |. [w; v
`R v V@OY. 1-3 dLvG :O#- |.;!- L/Q [w;Z<w 3mU
OY.
Q WLA esLj
h~!- )/ >yG 0 gkz|CLV@OY. L/Q
Nn bI: -v!-v`GB O#
W%! >SGv JB O#-! JdQ
O#- $%
O#-& 8vOB % gkGB f}TOY. )b!B 0 1C ^?Or W O#-
<}; &nOB T"L wTKOY. L/Q T"; 3$OB f} W '!B
OB
n5 /f! {s Y(OY. Z<Q $8B 1-3 dLvG :O#- |.;& |6O
JC@.
1-1
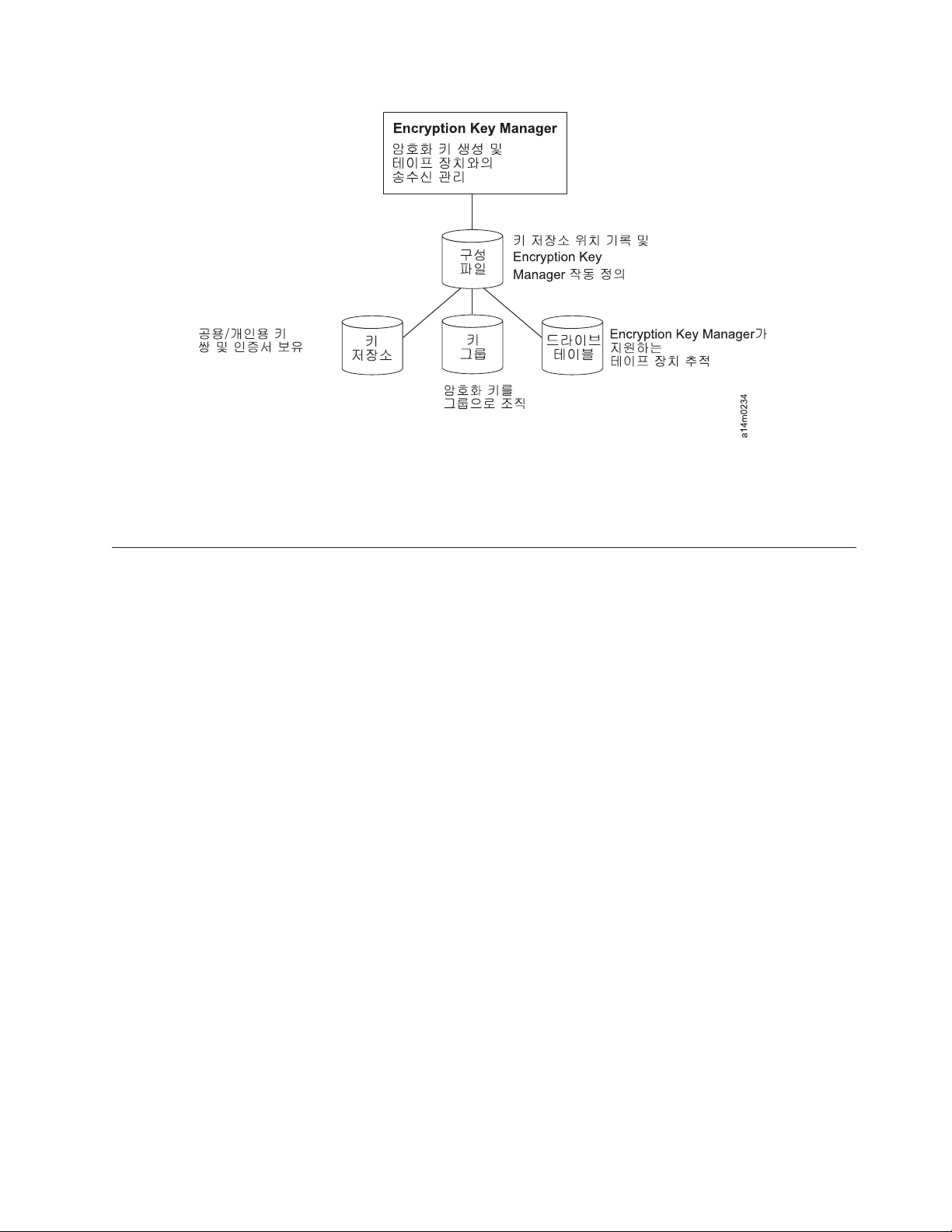
DwM.
Encryption Key ManagerB Java /f! wTGn V8g O# bI;'X Java
Security DwM.& gkUOY. Java Security DwM.! kQ Z<Q $8B |C
-{; |6OJC@. Encryption Key Manager!B Xg ?[; &nOB % gkG
B < !v b; DwM.! V@OY. L DwM.BY=z0@OY.
Java Security 0 zeR
0 zeRB
Java SecurityG dR W JCE(Java Cryptography Extension)G
ONN $GKOY. GQ Java SecurityB Java Runtime EnvironmentGO
NN wTKOY. 0 zeRB Encryption Key Manager!- O#- 6[;
v`Ob 'X gkOB Nu- W 0& 8/Om VE* Xg Wq8N wN
MOB M; ;UOY. gkZG d8& f7C0b 'X YgQ 6[ /:;
OB )/ !v>yG Java 0 zeR! vxKOY. L/Q /:: 2-4
&x
dLvG :0 zeR mAgW;!- Z<w 3mUOY.
0 zeR %LM& 88OB [w: El _dUOY. 0 zeR! W<:Ov J8i
O#-H WLAG O#& X6R v x@OY. F! V&& Z<w Pm 0 zeR %
LM& 8#OB % gkR v VB f}; KdOJC@.
8: DO
8: DO; gkOi 6w d8&87O5O Encryption Key ManagerG ?
[; gkZ $GR v V@OY. L/Q ?[! kQ IG:L.-!- Z
<w 3mUOY. 2-1 dLvG & 2 e :Encryption Key Manager /fh
9;, 4-1 dLvG & 4 e :Encryption Key Manager 8:;!- wJN 3
mOm 6v7!B NO B!
WLA esLj WLm
WLA esLj WLm: Encryption Key Manager!- vxOB WLA e
!& _{R ' gkKOY. WLA esLj WLm: m}R v xB 2x D
OLg Xg '!B 8: DO! v$Gn V@OY. L'!B g
BT /f!IUOY.
KeyGroups.xml DO
L O#N 8#GB DO!B pg O#- 0 WlGL' W " 0 Wlz ,
|H O#- 0 0mL wTKOY.
- 8: IGG|< <.& 3mUOY.
kZ d8!
Dell Encryption Key Manager gkZ H;-
1-2
W2
1-1. Encryption Key Manager
O#- |.
G W !v b; DwM.
Dell Encryption Key ManagerB WLA E<(WLA W +..v |D)! 5 $8&
O#-OE* )b!- P8AB $8& O# X6OB % gkGB O#- 0& }:,
™
8#, ze W /v8vOB fl O#- !I WLA esLj& vxOB Java
R
A.~n ANW%TOY. Encryption Key ManagerB Linux(SLES W RHEL) W
Windows!- [?Og, #MAsLn ; )/ '!! hwH x/Zx8N iWsn
e!- G`O5O 3hGn V@OY. mI` NMdL: ,sLp.B gkZ /f!
BT Encryption Key Manager& gkZ $GOm LG [?; pOM
R v VB m
I <.& &xUOY. Dell Encryption Key Manager GUI(Graphical User Interface)
!-5 9: gkZ $G W pOM5 bI; gkR v V@OY. Encryption Key
ManagerB pg O#- [w! JdQ Nu- W 0& 8/OE* Xg Wq8N w
NMOb 'XO* LsG 0 zeR& gkUOY. Z<Q ;k: 2-4 dLvG :
0
zeR mAgW;; |6OJC@.
& 1 e WLA O#- 3d 1-3

_d Encryption Key Manager #:. -v 8: $8: Dell Encryption Key Manager
ANW%; #:.OB C:[: %LM /GG'h; VR-Ob 'X ECC ^p.&
gkR M; GeUOY. Encryption Key ManagerB O#- 0G }:; d;Om L
|
i 0& LTO 4 W LTO 5 WLA esLj! |^OB bI; v`UOY. &H(O#
-H) 0B
! bOH%LM& 98(O# X6)R v V8Ai @y xL 0& {}Q WLA es
Lj! |[X_ UOY. C:[ ^p.G q. @yN 0! UsGzm +..v! %L
M& 5 ' L 0& gkOB fl, Xg +.
Y.(o, wD! O#& X6R v x@OY.) L/Q %LM @y! _}Ov J5O O
B 8# e!! 6CGn V@OY. W/* Encryption Key Manager& #:.OB C
:[L ECC(Error Correction Code) ^p.& gkOv JB fl, C:[ ^p.! V
B ?H 0!
V@OY. LM 0: %LM /G !I::{v8 _d @kANW%(9: Encryption Key
Manager); #:.OB C:[: ECC ^p.& gkR M; GeUOY.
3. _ Encryption Key Manager! C:[ ^p.! h!UOY. +..v
.v! 2)x %LMB 98R v x@O
UsGm L/Q Us8N %LM /GL _}R v VB !I:: 2F
Encryption Key ManagerB WLA sLj/.MG TCP/IP kE fN& kX |[H
0 5x d; GB 0 }:; bY.B iWsne AN<: *R; UOY. WLA e
sLj!- O#-H%LM& 2B fl Uz Encryption Key Manager! O#- 0
& d;UOY. d;L 5xOi Encryption Key ManagerBY=[w; v`UOY.
Encryption Key ManagerB 0 zeR!- b8G AES 0& !.M 8H |[;'
X 5x C L 0& &NX&Om L 0& gkO) WLA! 5 %LM& O#-O
B WLA esLj! 05N&NUOY.
|
LTO 4 GB LTO 5 esLj!- O#-H WLA& PB fl Encryption Key
ManagerB WLAG 0 ID! wTH
$8! {s 0 zeR!- JdQ 0& !.B
Y= 8H |[;'X &NH WLA esLj! &xUOY.
1CR v VB O#- |. f}: N !v! V@OY. L f}: O#- $% #x
LVB '!M O#- VgG!- 0 |.& v`OB '!, esLjM Encryption
Key ManagerG ,
a f}! {s Y(OY. VsG f}: n5 /f!- a$UO
Y. 0 |. W O#- $% #x: Y= N /fh~ _ O*! V@OY.
1-4
Dell Encryption Key Manager gkZ H;-
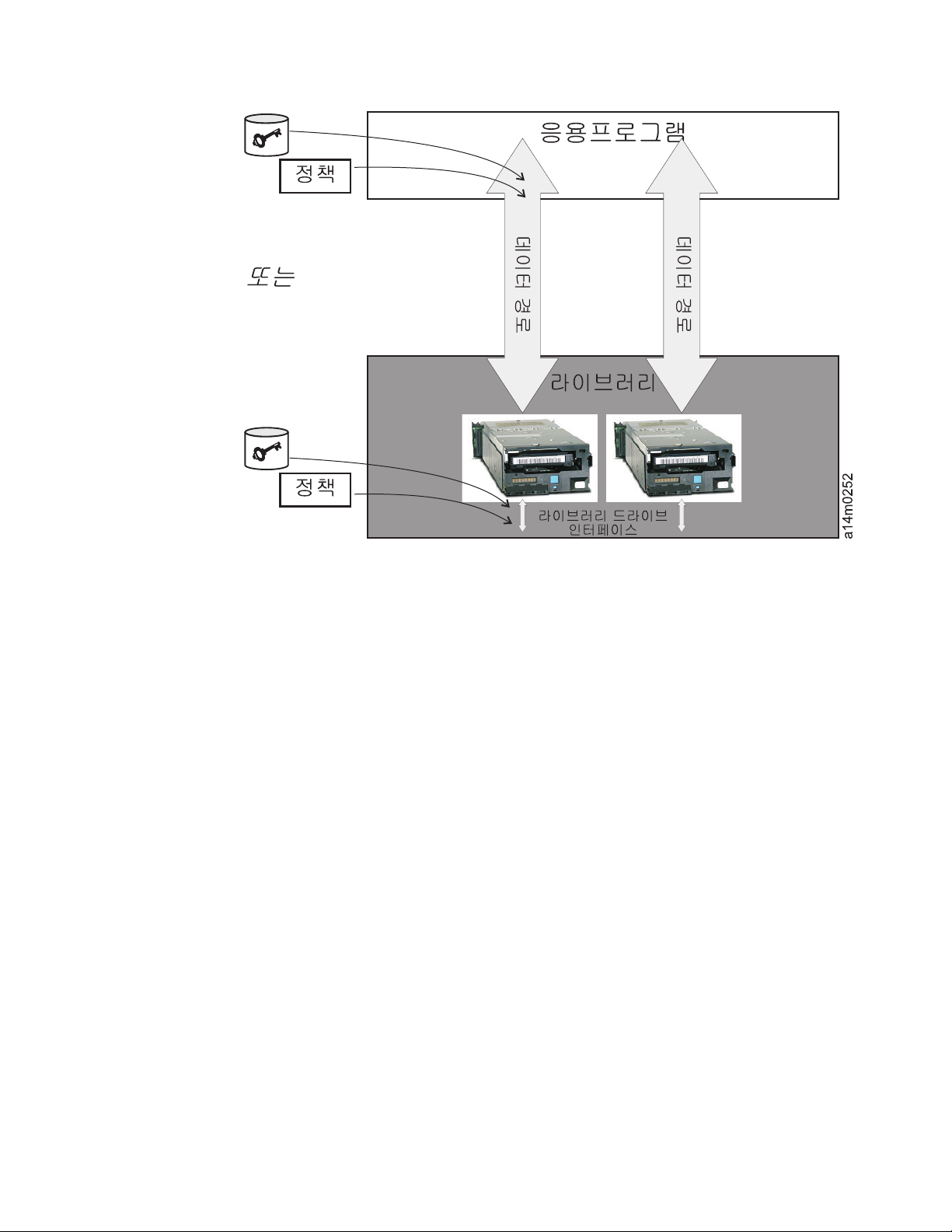
W2
1-2.
O#- $% #x W 0 |.! V; v VB N '!
@kANW% h~
Key ManagerMB 05N @kANW%: WLA :d.v!- %LM |[; C
[UOY. vxGB @kANW%: :@kANW%!- |.OB WLA O#-;&
|6OJC@.
sLj/. h~
WLA :d.vG ]3e!(9: Dell PowerVault TL2000/TL4000 W
&0:LL! XgUOY. dr&xGB WLA sLj/.!B ;N! " WL
A esLj! kQ ;N NMdL:! V@OY.
@kANW%!- |.OB WLA O#-
L f}: n5 /f!- LL O#- $% W 0& }:Om|.R v VB @kA
NW%; G`OB fl! !e{UUOY. O#-& gkR Cb& v$OB $%:
@kANW% NMdL:& kX $GKOY. $% W 0B @kANW% h~z O#
-Q WLA esL
#- !IQ WLA esLj gL!- s# [kQ azLg O#- '.! C:[ W
sLj/. h~; /fRJdB x@OY. @kANW%!- O#- 0& |.OGN
@kANW%; gkO
@kANW%!- |.OB O#- f}; gkX_8 P; v V@OY.
j # %LM fN& kX |^KOY. O#-B @kANW% W O
) 2m O#-H <}:@kANW%!- <}; 4 fDkN
ML6000
Encryption Key ManagerB @kANW%!- |.OB WLA O#-!- gkG
E* d;GB Wq: FUOY.
& 1 e WLA O#- 3d 1-5

O#-& |.OB fl Y=z0: VR v|G @kANW%; gkR v V@OY.
v CommVault Galaxy 7.0 SP1
v Symantec Backup Exec 12
|
@kANW%!- |.OB WLA O#-BY=z0: LTO 4 W LTO 5 WLA
esLj!- vxKOY.
™
v Dell
v Dell
v Dell
PowerVault™TL2000 WLA sLj/.
™
PowerVault™TL4000 WLA sLj/.
™
PowerVault™ML6000 WLA sLj/.
O#- $% W 0 |. f}; KAi WLA iw RA.~n @kANW% .-&
|6OJC@.
sLj/.!- |.OB O#-
Dell™PowerVault™TL2000 WLA sLj/., Dell™PowerVault™TL4000 WL
™
|
|
A sLj/. GB Dell
5 WLA esLj!- L f}; gkUOY. 0 }: W |.B sLj/.!,aH
#:.!- G`GB Java @kANW%N Encryption Key Manager!-v`UOY.
$% &n W 0B sLj/.!- esLjN ,aH NMdL:& kX |^
#-B @kANW%! kX umUOY.
PowerVault™ML6000 WLA sLj/.G LTO 4 W LTO
GGN O
O#- 0 $8
O#- 0B %LM& :)%m(O>G O#-)Om L& X&Ob 'X /0w }:H
+[' q. .Z-TOY. O#- 0B " 0!m/Om 0& 9sR v x5O 3h
H Km.r; gkO) [:KOY. 0!- L/Q fD8N 8:H fL! fvO O
#- Ze& zb u nF@OY. IBM W T10G O#- f} pN%LM& O#-
OB % 256q. AES Km.r; gkUOY. 256q. AESB vg L9 $N!-
N$ W GeOB O#- %X8N < !v -N Y% 0 fL& ckUOY. 256q.
0B AES!- ckQ 0 _ !e fL! iOY
.
Encryption Key Manager!-Bk* Km.r W qk* Km.rz0: N !v
/|G O#- Km.r; gkUOY. k* GB qP 0 O#-!-B O#- W O
# X6! \O 0& gkUOY. 8k k* 0 O#-B 9: gG %LM& ?2{8
N O#-OB fl! gkKOY. 256q. AES 0
Bk* 0TOY. qk* GB x
k/3Nk 0 O#-B Q VG 0& gkUOY. 0 O*& gkO) O#-H%LM
B xk/3Nk 0 VG Y% 0& gkX_8 O#& X6R v V@OY. qk* 0
VL }:Gi xk 0B O#-!, 3Nk 0B O# X6
! gkKOY.
1-6
Dell Encryption Key Manager gkZ H;-

Encryption Key Manager!-Bk* W qk* 0&pN gkUOY. k* O#-
B gkZ GB #:. %LM& !. O#-OB fl!, qk* O#-Bk* 0&
8#OB fl(S5! u@2)! gkKOY.
keytoolz0:/?.<& gkO) Encryption Key Manager! kQ O#- 0&
}:R v V@OY. AES 0& }
:OB %Sz L& WLA esLj! |[OB f
D: O#- |. f}! {s Y(OY. W/* Encryption Key Manager!- O#
- 0& gkOB f}z Y% @kANW%!- gkOB f} gLG wL& LXO
i 5rL I v V@OY.
Dell Encryption Key Manager!-G O#- 0 3.
|
|
sLj/.!- |.OB WLA O#-G fl O#-Gv J: %LMB LTO 4 G
B LTO 5 WLA esLjN |[Gn Encryption Key Manager!- gk !IQ
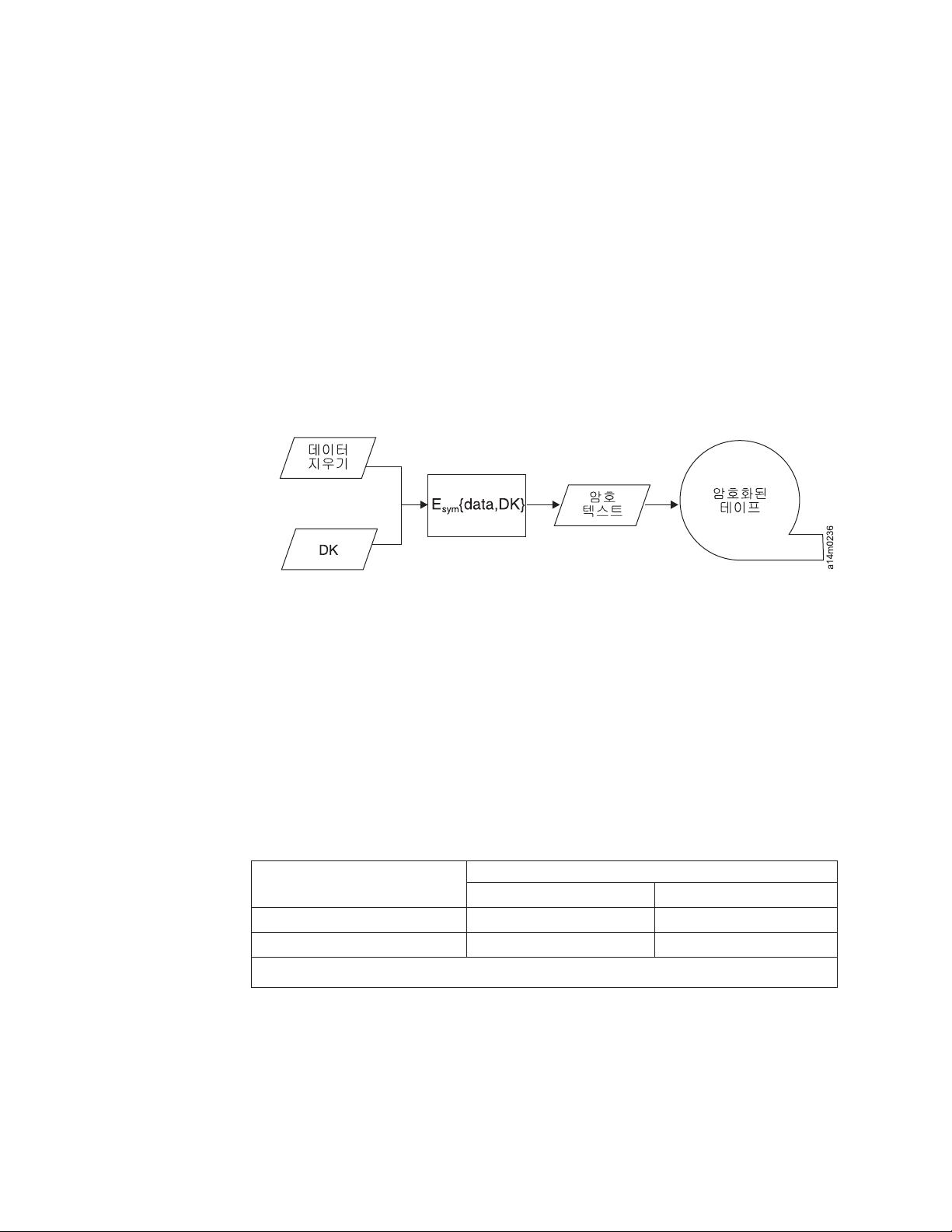
0 zeRG g|! }:H k* %LM0(DK)& gkO) O# X:.N //H D
YC WLA! bOKOY. Encryption Key ManagerB sne Ns
fD8N g|!
}:H DK& 1CUOY. )/ 3G WLA +..v!- g| }:H DK v! N7
Q fl DK& YC gkUOY.DKB Encryption Key Manager!- O#- GB
|
|
|
&NH gD8N LTO 4 GB LTO 5 WLA esLjN |[KOY. LTO 4 W LTO
5 WLA esLjB L/Q DK& &
NX&O) O#- GB O# X6! gkUO
Y. W/* &NX&Gv J: 0B LTO 4 GB LTO 5 WLA +..vG SGG
'!! zeKOY. O#-H <}L bOGi DKB <}!- P: x-kN 0m G
B 0 9Lm! {s W<: !IOm Encryption Key Manager!- gkR v Vn
_ UOY. 1-8
dLvG W2 1-3!- L AN<:& 8)]OY.
Dell Encryption Key Manager!-B LTO O#-& 'Q k* 0& 0 Wl8N 6
wOB bI5 &xUOY. L' O#-OB %LM /|, L %LM! W<:OB g
kZ GBY% _dQ /!! {s 0& Wl-R v V@OY. Z<Q
$8B 3-16
dLvG :0 Wl [: W |.;& |6OJC@.
Y% @kANW%!- O#- 0 3.
|
|
|
@kANW%!- |.OB WLA O#-G fl O#-Gv J: %LMB LTO 4 W
LTO 5 WLA esLjN |[Gn Xg @kANW%!- &xOBk* DK& g
kO) O# X:.N //H D YC WLA! bOKOY.DKB WLA +..vG
SGG '!! zeG
v J@OY. O#-H <}L bOGi DKB 9& in <}!
- P: x-kN @kANW%!- gk !IQ '!, -v %LM#L:! Vn_ U
OY.
@kANW%!- |.OB O#-G fl LTO 4 W LTO 5 WLA esLjB
Yosemite(Dell PowerVault TL2000 W TL4000 WLA sLj/.k), CommVault
Symantec Backup ExecM 0:@kANW%; gkR v V@OY.
W
& 1 e WLA O#- 3d 1-7
|
|
GB O#-& v`OB T10 mI <.& gkOB @kANW%G fl LTO 4 W
LTO 5 WLA esLj& gkR v V@OY. T10 mI <.B @kANW%!- &
xOBk* 256q. AES 0& gkUOY.T10: WLA +..vg m/Q )/ DK
& gkR v V8g O#-H%L
M W O] %LM& 0: WLA +..v! 5 v
V@OY. @kANW%!- WLA +..v& O#-OB fl @kANW%!- G
0Q f}; gkO) DK& 1COE* }:Q D WLA esLjN |[UOY. 0
B qk* xk 0& gkO) &
NGv J8g WLA +..v! zeGv J@OY.
O#-H%LM! WLA! bOGi DKB %LM& P: x-kN @kANW%!
- gk !IQ '!! Vn_ UOY.
@kANW%!- |.OB O#- W sLj/.!- |.OB O#-! |Q WLA
#-! kQAN<:B W2 1-3! *M V@OY.
O
W2
1-3.
k* O#- 0& gkO) O#-
#- W @kANW%!- |.OB O#-
d`
" <}!- gkR v VB O#- 0G vB O#-& |.OB % gkOB f},
|
||
O#- %X W WLA esLj! {s Y(OY. LTO 4 W LTO 5G um O#-
(o, Encryption Key Manager!- sLj/. |. O#- gk)G fl DKG m/
T: Encryption Key Manager!- fPQ vG g| }:H 0& gkR
! >SGn V@OY.
%
1-1.
O#- 0 d`
O#- |. f}
sLj/.!- |.OB O#- \O DK/+..v N/A
@kANW%!- |.OB O#- 9v DK/+..v 9v DK/+..v
DK = k* AES 256q. DK
. LTO 4 W LTO 5 WLA esLj!-G sLj/.!- |.OB O
v VBv
gkGB 0
IBM O#- T10 O#-
1-8 Dell Encryption Key Manager gkZ H;-

& 2 e Encryption Key Manager /fh9
L =G!-B gkZ d8! B5O Encryption Key Manager& 8:OB %5r
L GB $8& &xUOY. O#- |+; 3$OB f}; h9OAi9: dR& m
AX_ UOY.
O#- 3$ [w 3d
WLA esLjG O#- bI; gkOAiUz /$ RA.~n W Oe~n d8
gW; 87X_ UOY. L/Q d8gW; 87OB %5rL G5O Y= !K q
OL &xKOY.
Encryption Key Manager 3$ [w
WLA& O#-OAiUz O#-Q WLA esLjM kER v V5O Encryption
Key Manager& 8: W G`X_ UOY. WLA esLj& 3! OB ?H!B
Encryption Key Manager& G`R Jd! xv8 O#-& v`OAi L& G`X
_ UOY.
v Encryption Key Manager -vN gkR C:[ C'{; a$OJC@.
JdQ fl -v n5 <&& wW9LeOJC@. 2-2 dLvG :Oe~n W R
v
A.~n d8gW;; |6OJC@.
v Java UR(Unrestricted) $% DO; 3!OJC@. 2-2 dLvG :Oe~n W RA
.~n d8gW;; |6OJC@.
v Encryption Key Manager JAR; wW9LeOJC@. 3-1 dLv
|
Manager ISO LLv YnNe;& |6OJC@.
v 0, Nu- W 0 Wl;[:OJC@.
3-6 dLvG :GUI& gkO) 8: DO, 0 zeR W Nu- [:;
3-16 dLvG :0 Wl [: W |.;
v _! 8: IG; 0kOv JB fl 3-6 dLv
0 zeR W Nu- [:;G}w& {zYi L \hB JdOv J@OY.
– JdQ fl 0 W Nu-& !.@JC@. 3-14 dLvG :Keytool -importseckey
& gkO) %LM0!.@b;& |6OJC@.
– 8: nO $8 DO; $GOJC@. 4-1
Manager 8:;; |6OJC@.
– Encryption Key Manager! WLA esLj& $GOE*
drive.acceptUnknownDrives 8: nO $8 *; 3$OJC@. esLj&m
G :GUI& gkO) 8: DO,
dLvG & 4 e :Encryption Key
G :VE v| Key
2-1

C{8N $GOAi 5-10 dLvG :adddrive;& |6OE* 4-1 dLvG :W
LA esLj WLm Z? w%L.;& |6OJC@.
– Encryption Key Manager -v& C[OJC@. 5-1 dLvG :Key Manager
-v C[, uN m' W _v;& |6OJC@.
– mI` NMdL: ,sLp.
& C[OJC@. 5-6 dLvG :mI` NMdL:
,sLp.;& |6OJC@.
sLj/.!- |.OB WLA O#- h9
O#-& v`OAi Y=L JdUOY.
|
v O#- !I LTO 4 W LTO 5 WLA esLj
v 0 zeR
v Dell Encryption Key Manager
sLj/.!- |.OB WLA O#- [w
|
1. LTO 4 W LTO 5 WLA esLj& 3!Om ,aOJC@.
v sLj/. _~n(JdQ fl TL2000, TL4000, ML6000)& w%L.OJC
@. http://supportapj.dell.com/support/index.aspx; f.OJC@.
™
– Dell
PowerVault™TL2000 WLA sLj/. VR Jv _~n v|: 5.xx
TOY.
™
– Dell
PowerVault™TL4000 WLA sLj/. VR Jv _~n v|: 5.xx
TOY.
™
– Dell
PowerVault™ML6000 WLA sLj/. VR Jv _~n v|:
415G.xxxTOY.
v JdQ fl WLA esLj _~n& w%L.OJC@. VR Jv _~n v
|: 77B5TOY.
|
2. sLj/.!- |.OB WLA O#-& 'X LTO 4 W LTO 5 WLA esL
j W WLA sLj/.& 3$
8 |6).
v Encryption Key Manager -v IP VR& _!UOY.
3. sLj/. x\ ANW% bI; gkO) Encryption Key Manager fN W O
#- 8:; .NOJC@(Z<Q ;k: Dell WLA sLj/. $8 |6).
Oe~n W RA.~n d8gW
V: Y=G " C'{!-B JRE(Java Runtime Environment)G IBM v|8
Encryption Key Manager& vxUOY.
Dell Encryption Key Manager gkZ H;-
2-2
OJC@(Z<Q ;k: Dell WLA sLj/. $
Linux VgG DwM.
n5 <&
v RHEL 4
v RHEL 5
v SLES 9
v SLES 10
|
v SLES 11
Encryption Key Manager(Linux!- G` _)
%
2-1. Linux
C'{
|
64q. AMD/Opteron/EM64T
32q. Intel
!-G VRRA.~n d8gW
IBM Software
Developer Kit Zx % gL.
®
#/
Java 6.0 SR5 http://support.dell.com
WLA sLj/.
|
|
|
Dell PowerVault TL2000 WLA sLj/., TL4000 WLA sLj/. W ML6000
WLA s Lj/.G _~n 9'L VENv .NOJC@. _~n& w%L.OAi
http://support.dell.com; f.OJC@.
WLA esLj
|
|
LTO 4 W LTO 5 WLA esLjG _~n 9'L VENv .NOJC@. _~n
& w%L.OAi http://support.dell.com; f.OJC@.
Windows VgG DwM.
n5 <&
|
Windows Server 2003, 2008 W 2008 R2
Dell Encryption Key Manager
Encryption Key ManagerG VR Jv v|: te /%! 2007b 9y 14O(20070914)
LDN 2.1 v|Lg, Y= IBM Runtime Environment _ O*TOY.
%
2-2. Windows
n5 <& IBM Runtime Environment
Windows 2003
!-G VRRA.~n d8gW
v AMD64/EM64T 86G Windows! kQ IBM®64q. Runtime Environment,
Java 2 Technology Edition, v| 5.0 SR5
v Windows! kQ IBM 32q. Runtime Environment, Java 2 Technology
Edition, v| 5.0 SR5
& 2 e Encryption Key Manager /fh9 2-3

%
2-2. Windows
n5 <& IBM Runtime Environment
|
|
Windows 2008 W
2008 R2
!-G VRRA.~n d8gW(hS
AMD64/EM64T 86G Windows! kQ IBM 64q. Runtime Environment,
Java 2 Technology Edition, v| 6.0 SR5
)
WLA sLj/.
|
|
|
|
|
|
0 zeR mAgW
JCEKS 0 zeR
Dell™PowerVault™TL2000 WLA sLj/., Dell™PowerVault™TL4000 WL
™
A sLj/. W Dell
PowerVault™ML6000 WLA sLj/.G _~n 9'L
VENv .NOJC@. _~n& w%L.OAi http://support.dell.com; f.OJ
C@.
WLA esLj
LTO 4 W LTO 5 WLA esLjG _~n 9'L VENv .NOJC@. _~n
& w%L.OAi http://support.dell.com; f.OJC@.
0 zeR %LM& 88OB [w: El _dUOY. 0 zeR! W<:Ov J8i
O#-H WLAG O#& X6R v x@OY. F! V&& Z<w Pm 0 zeR %
LM& 8#OB % gkR v VB f}; KdOJC@.
EKM!-B JCEKS 0 zeR /|; vxUOY.
JCEKS(Unix System Services DO b]) B EKM; G`OB pg C'{!- v
xGB DO b] 0 zeRTOY. {s- sk{8N iw W 98 C L 0 zeR
;k; 9gOm eV 98 C N EKM N:O:& ?b-OB [wL kLUOY.
JCEKSB 8
H;'X 0 zeR ;k! kQ O# b] 8#& &xOg sk{8N
g#Q :I; &xUOY. FTPM 0: DO 9g f}; gkR v5 V@OY.
|
O#- 0 W LTO 4 W LTO 5 WLA esLj
Dell Encryption Key Manager W pg vxGB WLA esLjB %LM& O#
-R ' k* 256q. AES 0& gkUOY. L V&!-B L/Q 0 W Nu-M
|CO) KF_ OB $8& 3mUOY.
|
LTO WLA +..vG LTO 4 GB LTO 5 WLA esLj!- O#- [w; v
`OB fl Encryption Key Manager!
-B 256q. AES k* %LM08 gkU
OY.
Dell Encryption Key Manager gkZ H;-
2-4
|
LTO 4 GB LTO 5! 0& d;Oi Encryption Key Manager!-B WLA es
Lj! v$H 0m; gkU OY. W L A e s L j ! v$H 0 m L x8i
symmetricKeySet 8: nO $8! v$H 0 0m |', 0 0mqO GB 0 Wl
G 0mL gkKOY. WLA esLj! kQ /$ 0mL N7O
i 0& UnOT g
kOb 'X wJN Y% #<<!- 0m; 1CUOY.
1CH 0m: L. 0 zeR! NeH k* %LM0(DK)M,|KOY. Encryption
Key Manager!-B WLA esLj! O# X6R v VBY% 0& gkO) &
|
NH L DK& LTO 4 GB LTO 5 WLA esLj! |[
O) %LM& O#-U
OY.DKB O] X:. |D8N TCP/IP& kX |[Gv J@OY. 1CH 0m:
%LM0ID(DKi)sm OB #<<N //Gm LB O#-H%LM& gkO) W
LA! bOKOY. L fD; gkOi Encryption Key Manager!-B DKi& gk
|
O) LTO 4 GB LTO 5 WLA&
P; ' %LM O#& X6OB % JdQ CY
% DK& D0R v V@OY.
5-9 dLvG :CLI mI;G adddrive W moddrive V&!-B WLA esLj!
kQ 0m; v$OB f}; 8)]OY. symmetricKeySet 8: nO $8!- 0 !
|
|
.@b, 0 ;8;b W b;0m v$! |Q $8B 3-11
5!- O#-! kQ 0 W 0m }:;; |6OJC@. 3-16 dLvG :0 Wl [:
dLvG :LTO 4 W LTO
W |.;!-B 0 Wl; $GOm L& 0 zeRG 0m8N $lB f}; 8)]
OY.
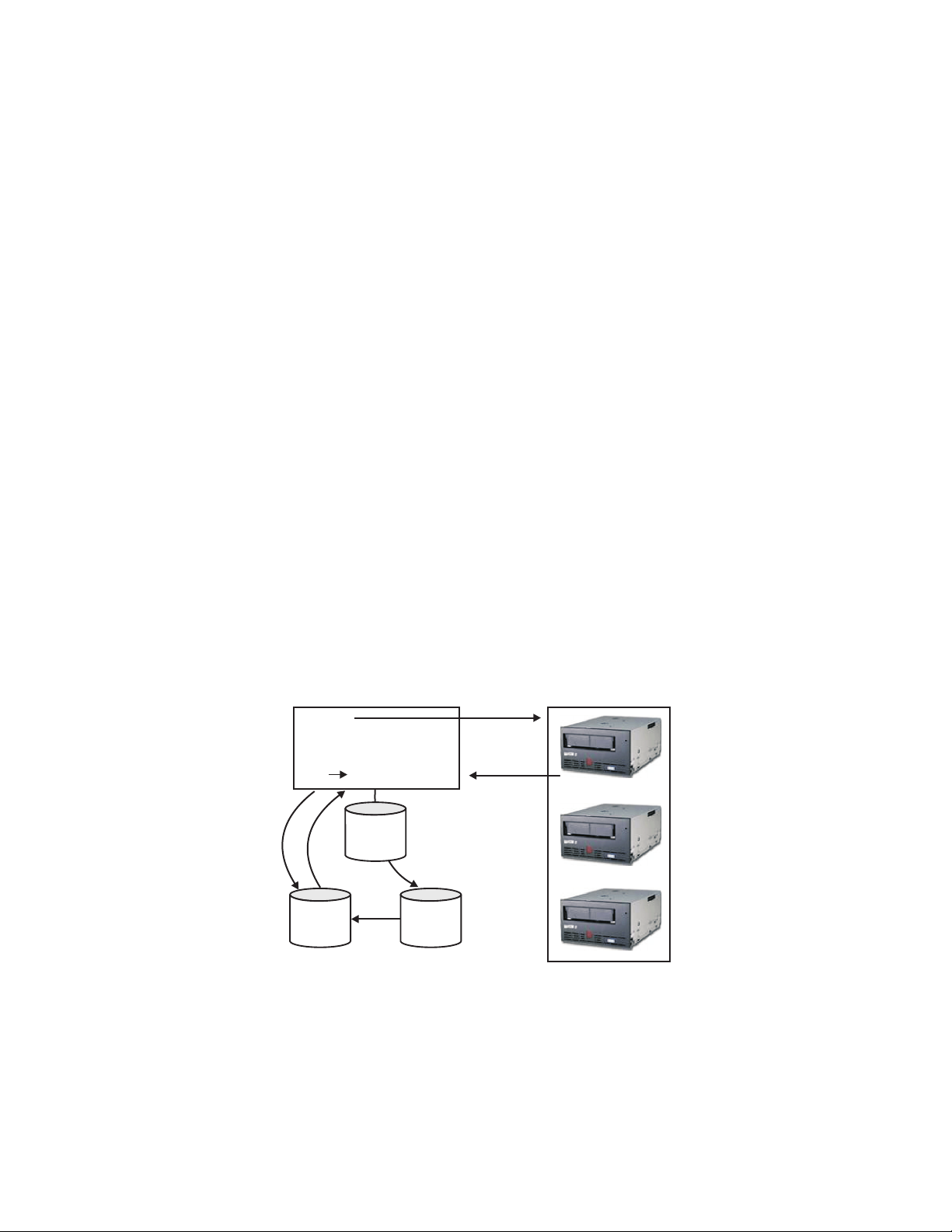
W2 2-1!-B O#-H 2b 6[!- 0& 3.OB f}; 8)]
5
DK, DKi
6
7
OY.
Key Manager
alias
3
DK
1
Config
File
4
Key
store
W2
|
2-1. LTO 4
GB
LTO 5
WLA esLjG O#- 2b 6[ d;
1. WLA esLj!- WLA& O#-OB 0& d;UOY.
2. Encryption Key ManagerB esLj WLmG WLA e!& .NUOY.
2
Drive
Table
& 2 e Encryption Key Manager /fh9 2-5
3. d;!- 0m; v$Ov Jm esLj WLm! v$H 0mL x8i Encryption
Key ManagerB keyAliasList! VB 0 Wl GB 0m <.!- 0m; 1CU
OY.
4. Encryption Key ManagerB L! k@OB DK& 0 zeR!- !.IOY.
5. Encryption Key ManagerB 0m; DKiN //Om esLj! O# X6R v
VB 0&
gkO) DK& &NUOY.
6. Encryption Key ManagerB DK W DKi& WLA esLj! |[UOY.
7. WLA esLj! DK& &NX&Om O#-H%LM W DKi& WLA! 9
OY.
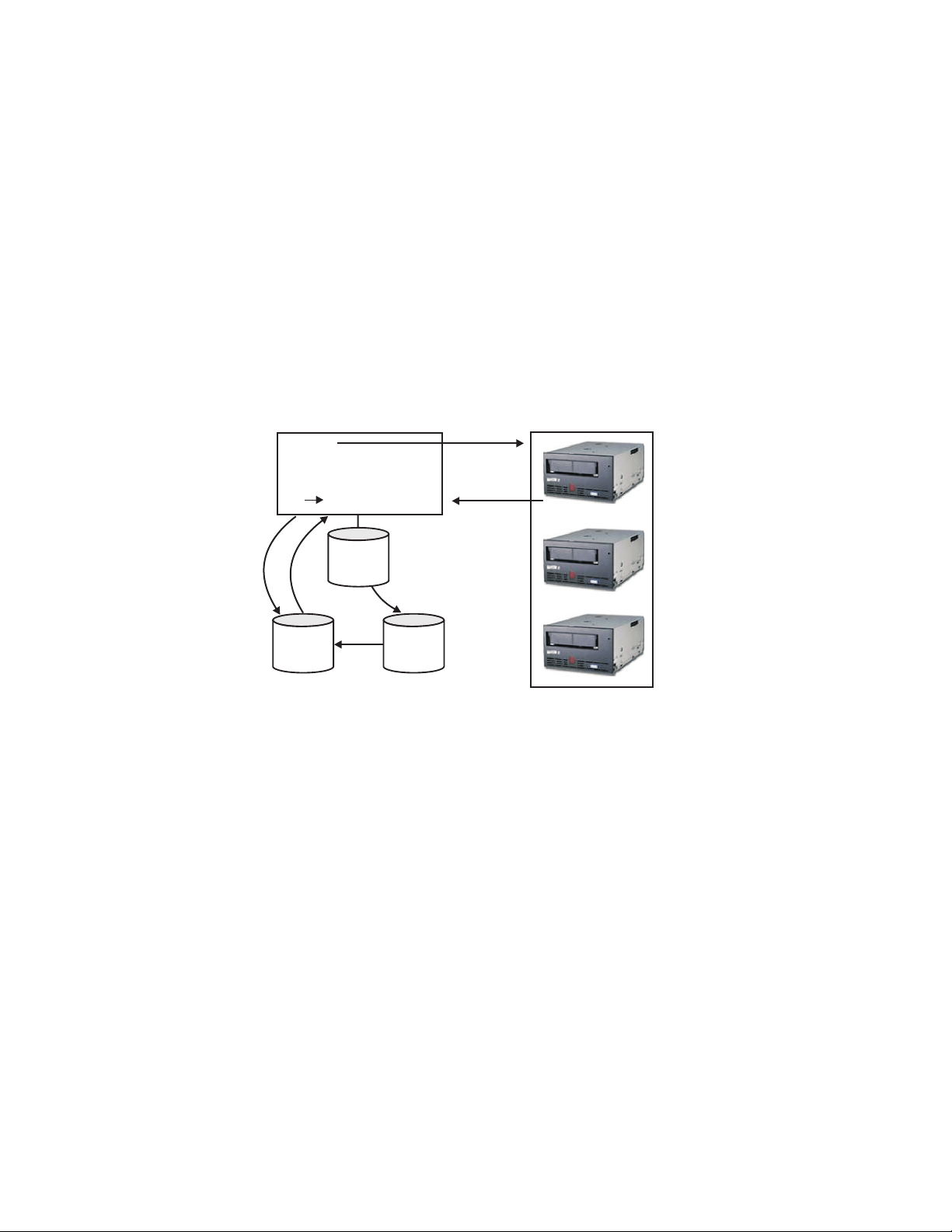
W2 2-2!-B O#-H Pb 6[!- 0& 3.OB f}; 8)]OY.
4
DK
Key Manager
3
DKi Alias
5
6
1
Config
File
2
Key
store
W2
|
2-2. LTO 4
GB
LTO 5
WLA esLjG O#- Pb 6[ d;
1. WLA esLjB Pb d;
[UOY.
2. Encryption Key ManagerB esLj WLmG WLA e!& .NUOY.
3. Encryption Key ManagerB DKi& 0m8N //Om L! k@OB DK& 0
zeR!- !.IOY.
Drive
Table
; vEOg Encryption Key Manager! DKi& |
4. Encryption Key ManagerB esLj! O# X6R v VB 0& gkO) DK
& &NUOY.
5. Encryption Key ManagerB &NH DK& WL
6. WLA esLj! DK& &NX&Om L& gkO) %LM O#& X6UOY.
0 zeR %LM iw
V: 0 zeR! VB 0G _dQ /! '.! O#-Gv J:e!!- L %LM&
iwOB ML _dUOY. W!_8 JdQ fl L& 98O) Xg WLA es
2-6 Dell Encryption Key Manager gkZ H;-
A esLj! |[UOY.
 Loading...
Loading...