Dell PowerVault MD3800i Series, PowerVault MD3820i Series Deployment Manual

Dell PowerVault MD3800i and MD3820i
Series Storage Arrays
Deployment Guide

Notes, cautions, and warnings
NOTE: A NOTE indicates important information that helps you make better use of your computer.
CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you
how to avoid the problem.
WARNING: A WARNING indicates a potential for property damage, personal injury, or death.
Copyright © 2016 Dell Inc. All rights reserved. This product is protected by U.S. and international copyright and
intellectual property laws. Dell™ and the Dell logo are trademarks of Dell Inc. in the United States and/or other
jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies.
2015 - 10
Rev. A01

Contents
1 Introduction...........................................................................................................6
System Requirements............................................................................................................................6
Management Station Requirements............................................................................................... 6
Introduction to Storage Arrays............................................................................................................. 6
Related Documentation........................................................................................................................ 7
2 Hardware Installation...........................................................................................8
Planning The Storage Configuration ...................................................................................................8
Connecting The Storage Array ............................................................................................................ 8
Cabling The Storage Array.................................................................................................................... 9
Redundant And Nonredundant Configurations.............................................................................9
Direct-Attached Configurations..................................................................................................... 9
Network-Attached Configurations............................................................................................... 13
Cabling PowerVault MD1200 Series Expansion Enclosures..............................................................20
Expanding With Previously Configured PowerVault MD1200 Series Expansion Enclosures......21
Expanding With New PowerVault MD1200 Series Expansion Enclosures.................................. 22
3 Installing PowerVault MD Storage Software.................................................24
Modular Disk Configuration Utility..................................................................................................... 25
Graphical Installation (Recommended)..............................................................................................25
Console Installation............................................................................................................................ 26
Silent Installation................................................................................................................................. 26
Silent Installation On Windows Systems...................................................................................... 26
Silent Installation On Linux Systems.............................................................................................26
Enabling Premium Features (Optional)...............................................................................................27
Upgrading MD Storage Software........................................................................................................27
4 Post Installation Tasks.......................................................................................28
Before You Begin................................................................................................................................ 28
iSCSI Configuration Terminology.................................................................................................28
iSCSI Configuration Worksheet.................................................................................................... 29
Configuring iSCSI On Your Storage Array..........................................................................................32
Automatic Configuration Using the Modular Disk Configuration Utility.................................... 33
Post Connection Establishment Steps............................................................................................... 35
Guidelines For Configuring Your Network For iSCSI.........................................................................35
Microsoft Windows Host Setup..........................................................................................................35
Setting Up Microsoft Host Network Using A DHCP server..........................................................35
Setting Up Microsoft Host Network Using Static IP Addressing..................................................35
3

Setting Up Microsoft Host Network Using A DNS server............................................................ 36
Setting Up Microsoft Host Network Using A WINS Server.......................................................... 36
Linux Host Setup................................................................................................................................. 36
Setting Up Linux Host Network Using DHCP...............................................................................36
Setting Up Linux Host Network Using A Static IP Address...........................................................37
5 Uninstalling MD Storage Software.................................................................. 38
Uninstalling MD Storage Software From Windows........................................................................... 38
Uninstalling MD Storage Software From Windows Server GUI Versions....................................38
Uninstalling MD Storage Software From Windows Server Core Versions..................................38
Uninstalling MD Storage Software From Linux..................................................................................38
6 Manual Configuration Of iSCSI........................................................................39
Step 1: Discover the Storage Array (Out-of-band Management Only)............................................ 39
Default Management IPv4 Port Settings...................................................................................... 39
Default Management IPv6 Port Settings...................................................................................... 40
Automatic Storage Array Discovery.............................................................................................. 41
Manual Storage Array Discovery................................................................................................... 41
Setting Up the Array.......................................................................................................................41
Step 2: Configuring The iSCSI Ports On The Storage Array.............................................................. 42
Step 3: Performing Target Discovery From The iSCSI Initiator.........................................................43
Perform Target Discovery From The iSCSI Initiator Using Windows Server GUI Version..........43
Perform Target Discovery From the iSCSI Initiator Using Windows Server Core Version.........43
Perform Target Discovery From the iSCSI Initiator Using Linux................................................. 43
Step 4: Configuring Host Access........................................................................................................44
Understanding CHAP Authentication.................................................................................................44
What is CHAP?...............................................................................................................................44
Target CHAP..................................................................................................................................45
Mutual CHAP................................................................................................................................. 45
CHAP Definitions...........................................................................................................................45
Step 5: Configure CHAP Authentication on the Storage Array (Optional)....................................... 45
Configuring Target CHAP Authentication On The Storage Array...............................................46
Configuring Mutual CHAP Authentication On The Storage Array.............................................. 46
Step 6: Configure CHAP Authentication On The Host Server (Optional).........................................47
Configure CHAP Authentication On The Host Server Using Windows GUI Version..................47
Configure CHAP Authentication On The Host Server Using Windows Server Core Version.....47
Configuring CHAP Authentication Using Linux........................................................................... 48
Configure CHAP Authentication On The Host Server Using SUSE Linux Enterprise Server
GUI.................................................................................................................................................48
Connect To The Target Storage Array From the Host Server Using Windows Server GUI............. 49
Connect To The Target Storage Array From the Host Server Using Windows Server Core
Version.................................................................................................................................................50
4

Connecting The Target Storage Array From The Host Server Using Linux .....................................50
Step 8: Set Up In-Band Management.................................................................................................51
7 Using Internet Storage Naming Service......................................................... 52
8 Load Balancing....................................................................................................53
Load Balance Policy............................................................................................................................ 53
Round Robin With Subset............................................................................................................. 53
Least Queue Depth....................................................................................................................... 53
Least Path Weight..........................................................................................................................53
Changing Load Balance Policies On The Windows Server Operating System...........................54
Increasing Bandwidth With Multiple iSCSI Sessions.................................................................... 54
9 Stopping iSCSI Services In Linux......................................................................55
10 Getting help.......................................................................................................56
Contacting Dell................................................................................................................................... 56
Locating your Dell system Service Tag ............................................................................................. 56
5

1
Introduction
This guide provides information about deploying Dell PowerVault MD3800i and MD3820i storage arrays.
The deployment process includes:
• Hardware installation
• Modular Disk Storage Manager (MDSM) software installation
• Initial system configuration
Other information provided includes system requirements, storage array organization, and utilities.
NOTE: For more information on product documentation, see Dell.com/support/manuals.
MDSM enables an administrator to configure and monitor storage arrays for optimum usability. The
version of MDSM included on the PowerVault MD series resource media can be used to manage both the
PowerVault MD3800i and MD3820i series and the earlier storage arrays. MDSM is compatible with both
Microsoft Windows and Linux operating systems.
System Requirements
Before installing and configuring the PowerVault MD3800i and MD3820i series hardware and software,
ensure that the minimum system requirements are met. Also, ensure that the supported operating system
is installed. For more information, see the Dell PowerVault MD34xx/38xx Series Support Matrix at
Dell.com/support/manuals.
Management Station Requirements
A management station uses MDSM to configure and manage storage arrays across the network. For
management station requirements, see Dell PowerVault MD34xx/38xx Series Support Matrix at Dell.com/
powervaultmanuals.
Introduction to Storage Arrays
A storage array includes various hardware components, such as physical disks, RAID controller modules,
fans, and power supplies, gathered into enclosures. The physical disks are accessed through the RAID
controller modules.
One or more host servers attached to the storage array can access the data on the storage array. You can
also establish multiple physical paths between the hosts and the storage array so that loss of any single
path (for example, through failure of a host server port) does not result in loss of access to data on the
storage array.
The storage array is managed by MDSM running on a:
6

• Host server — On a host server system, MDSM and the storage array communicate management
requests and event information using in-band or out-of band-connections.
• Management station — On a management station, MDSM communicates with the storage array either
through an Ethernet connection to the storage array management port or through an Ethernet
connection to a host server. The Ethernet connection passes management information between the
management station and the storage array connectivity.
Using MDSM, you can configure the physical disks in the storage array into logical components called
disk groups or dynamic disk group and then divide the disk groups into virtual disks. Disk groups are
created in the unconfigured capacity of a storage array. Virtual disks are created in the free capacity of a
disk group.
Unconfigured capacity comprises physical disks not already assigned to a disk group. When a virtual disk
is created using unconfigured capacity, a disk group or dynamic disk group is automatically created. If the
only virtual disk in a disk group is deleted, the disk group is also deleted. Free capacity is space in a disk
group that is not assigned to any virtual disk.
Data is written to the physical disks in the storage array using RAID technology. RAID levels define how
data is written to physical disks. Different RAID levels offer different levels of accessibility, redundancy,
and capacity. You can set a specified RAID level for each disk group and virtual disk on your storage array.
For more information about using RAID and managing data in your storage solution, see the Owner’s
Manual at Dell.com/support/manuals.
Related Documentation
NOTE: For all PowerVault documentation, go to Dell.com/support/manuals and enter the system
Service Tag to get your system documentation.
NOTE: For all Dell OpenManage documents, go to Dell.com/openmanagemanuals.
NOTE: For all storage controller documents, go to Dell.com/storagecontrollermanuals.
Your product documentation includes:
• Dell PowerVault MD3800i and MD3820i Storage Arrays Getting Started Guide — Provides an overview
of system features, setting up your system, and technical specifications. This document is also
shipped with your system.
• Dell PowerVault MD3800i and MD3820i Storage Arrays Owner’s Manual — Provides information
about system features and describes how to troubleshoot the system and install or replace system
components.
• Rack Installation Instructions — Describes how to install your system into a rack. This document is
also shipped with your rack solution.
• Dell PowerVault MD Series Storage Arrays Administrator's Guide — Provides information about
configuring and managing the system using the MDSM GUI.
• Dell PowerVault MD34XX/38XX Series Storage Arrays CLI Guide — Provides information about
configuring and managing the system using the MDSM CLI.
• Dell PowerVault MD3800i and MD3820i Storage Arrays Deployment Guide — Provides information
about deploying the storage system in the SAN architecture.
• Dell PowerVault MD34/38 Series Support Matrix — Provides information about the software and
hardware compatibility matrices for the storage array.
7

2
Hardware Installation
Before using this guide, ensure that you review the instructions in the documents:
• Getting Started Guide — The Getting Started Guide shipped with the storage array provides
information to configure the initial setup of the system.
• Owner’s Manual — The Owner’s Manual provides information about important concepts to set up
your storage solution. See the Owner’s Manual at Dell.com/support/manuals.
Planning The Storage Configuration
Consider the following before installing your storage array:
• Evaluate data storage needs and administrative requirements.
• Calculate availability requirements.
• Decide the frequency and level of backups, such as weekly full backups with daily partial backups.
• Consider storage array options, such as password protection and email alert notifications for error
conditions.
• Design the configuration of virtual disks, disk groups, or dynamic disk groups according to a data
organization plan. For example, use one virtual disk for inventory, a second for financial and tax
information, and a third for customer information.
• Decide whether to allow space for hot spares, which automatically replace failed physical disks.
Connecting The Storage Array
The storage array is connected to a host using two hot-swappable RAID controller modules. The RAID
controller modules are identified as RAID controller module 0 and RAID controller module 1.
NOTE: See the Owner’s Manual for a complete description of all the parts on the controller.
The functions of the ports on each controllers are described below:
• 10 gbps iSCSI Host Ports (2) — Allows you to connect host servers to the storage array.
• 12 gpbs SAS Host Ports (2) — Allows you to connect host servers to the storage array.
• 16 gbps Ethernet Management (MGMT) Port (1) — Management port allows for out of band
management of storage array.
• Reserved Ethernet Port (1) — Reserved
• SAS Expansion Ports (2) — Allows you to connect the storage array to optional PowerVault MD1200
series expansion enclosures for additional storage capacity. Only one SAS OUT expansion port can be
used at a time and the recommended expansion port is 0.
8

Each PowerVault MD3800i and MD3820i series storage array can be expanded to a maximum of 120 (or
192, if enabled using Premium Feature activation) slots.
Cabling The Storage Array
The iSCSI interface enables different host-to-controller configurations. The figures in this chapter are
grouped according to the following categories:
• Direct-attached configurations (no Ethernet switches are used)
• Network-attached (SAN) configurations (Ethernet switches are used)
• Mixed configurations that uses all protocols
Redundant And Nonredundant Configurations
Nonredundant configurations are configurations that provide only a single data path from a host to the
storage array. This type of configuration is only recommended for noncritical data storage. Path failure
from a failed or removed cable, or a failed or removed RAID controller module results in loss of host
access to storage on the storage array.
Redundancy is established by installing separate data paths between the host and the storage array. Each
data path is connected to one of the two RAID controller modules installed in the storage array.
Redundancy protects the host from losing access to data in the event of path failure, because both RAID
controller modules can access all the disks in the storage array.
Direct-Attached Configurations
You can connect the Ethernet ports of the host servers directly to the storage array RAID controller
module iSCSI ports.
Single Path Data Configurations
With a single path configuration, a group of heterogeneous hosts can be connected to the storage array
through a single physical Ethernet port. Since there is only one port, there is no redundancy, although
each iSCSI portal supports multiple connections. This configuration is supported for both single
controller and dual controller modes.
The figure below shows a non-redundant cabling configuration to a RAID controller module using a
single path data configuration
9
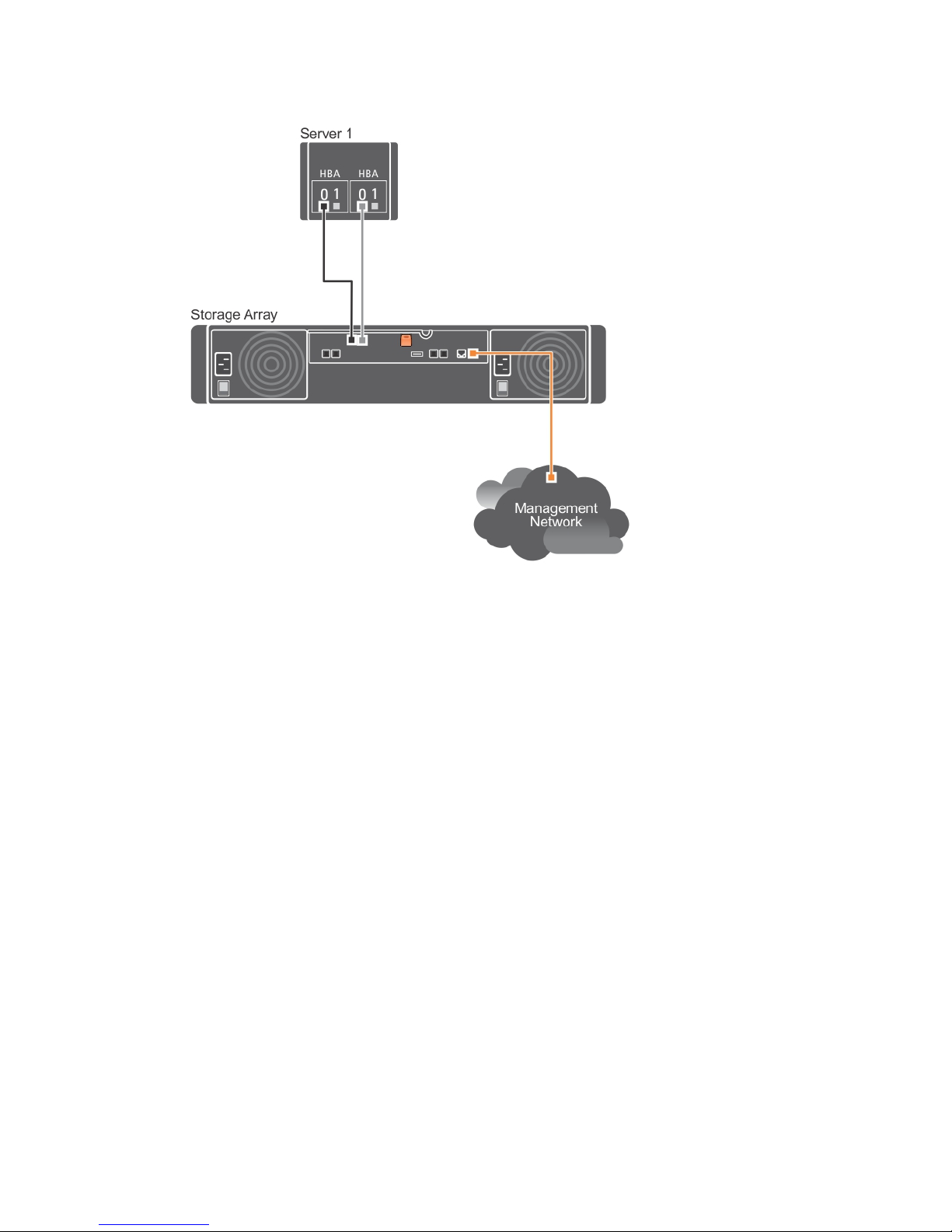
Figure 1. One Host Connected to a Single Controller
The following figure shows four stand-alone hosts supported in a dual controller array configuration with
a single data path.
10
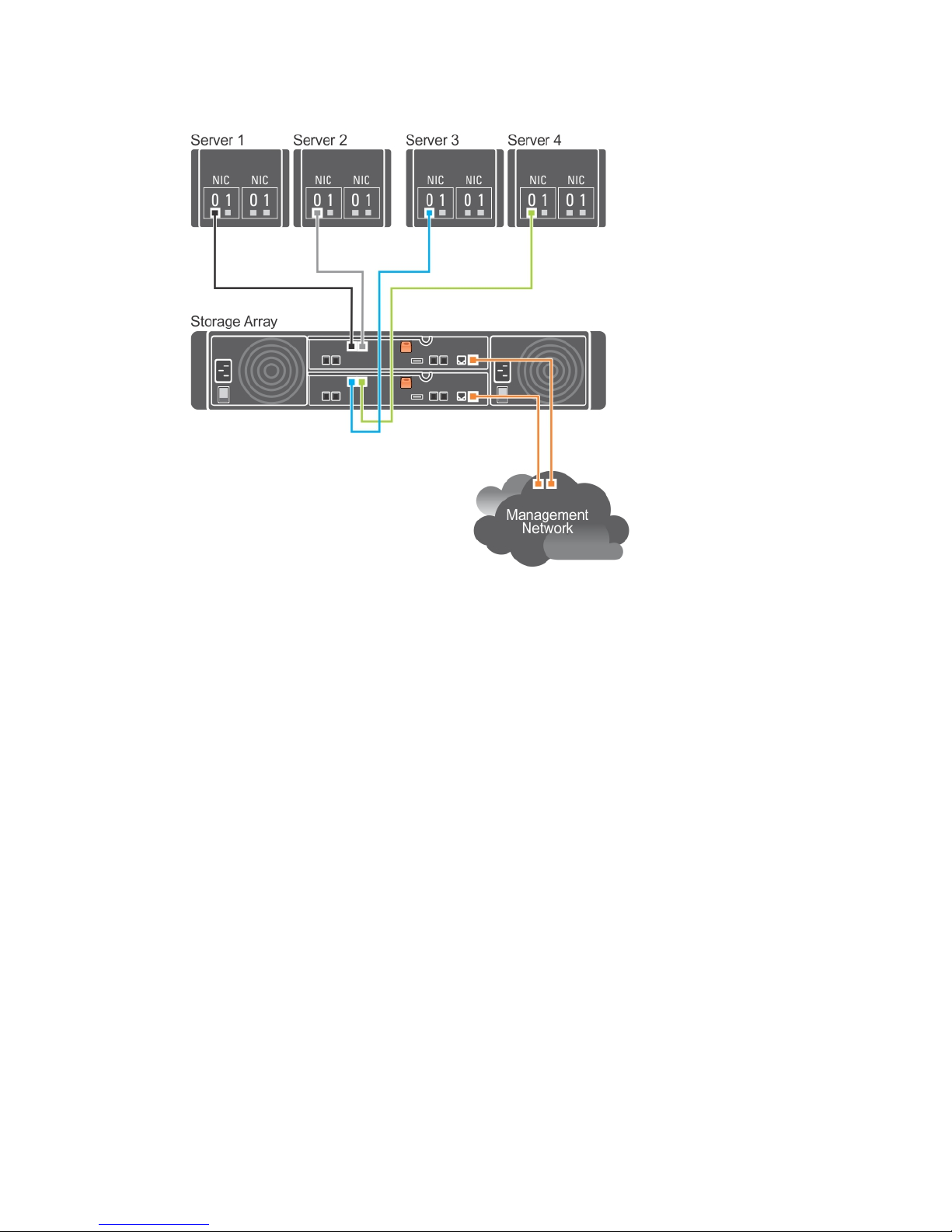
Figure 2. Four Hosts in a Dual-Controller Configuration Using One HBA Each
11
Dual Path Data Configuration
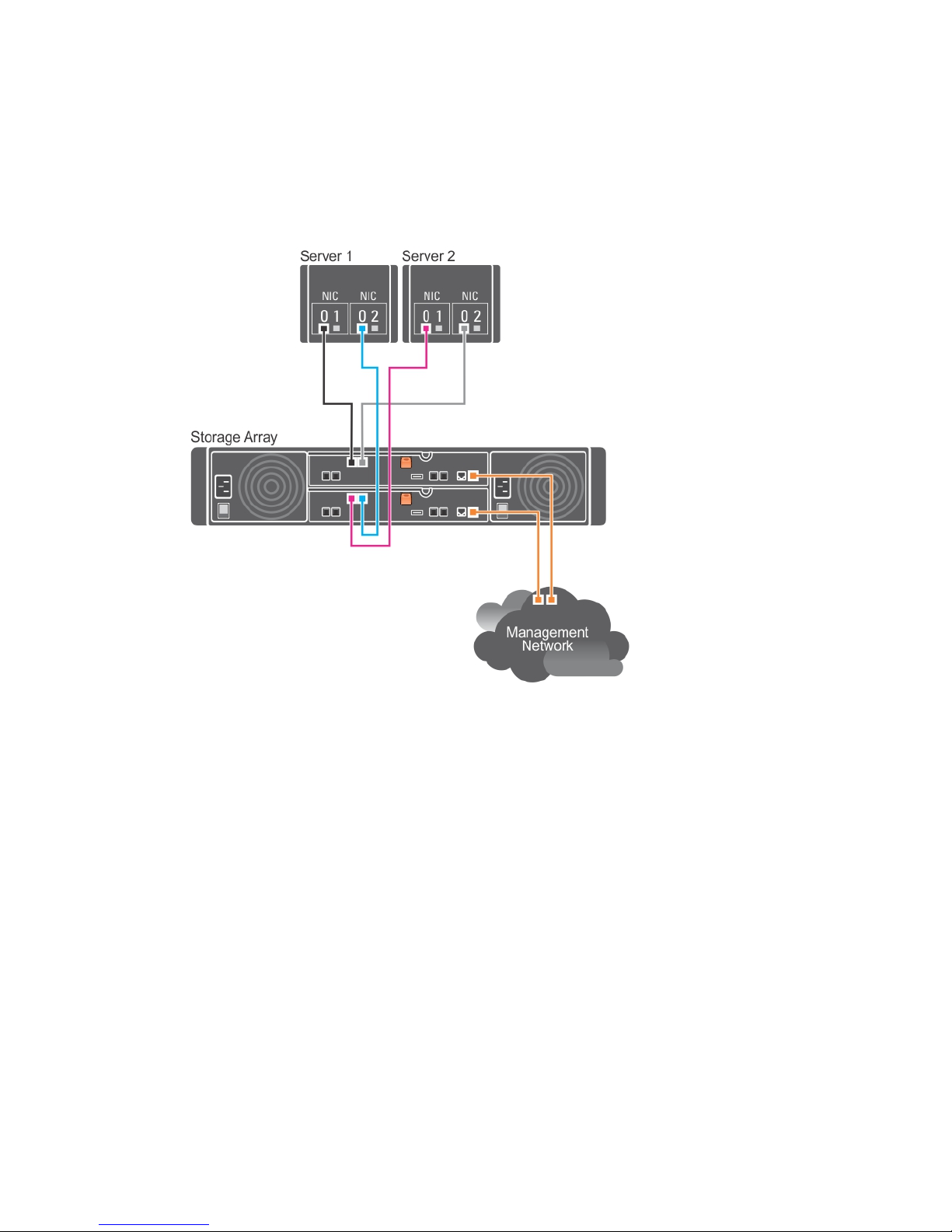
In the following figure, up to two servers are directly attached to the RAID controller modules. If the host
server has a second Ethernet connection to the array, it can be attached to the iSCSI ports on the array's
second controller. This configuration provides improved availability by allowing two separate physical
paths for each host, which ensures full redundancy if one of the paths fail.
Figure 3. Two Hosts Connected to Two Controllers
In the following figure, up to two cluster nodes are directly attached to two RAID controller modules.
Since each cluster node has redundant paths, loss of a single path still allows access to the storage array
through the alternate path.
12
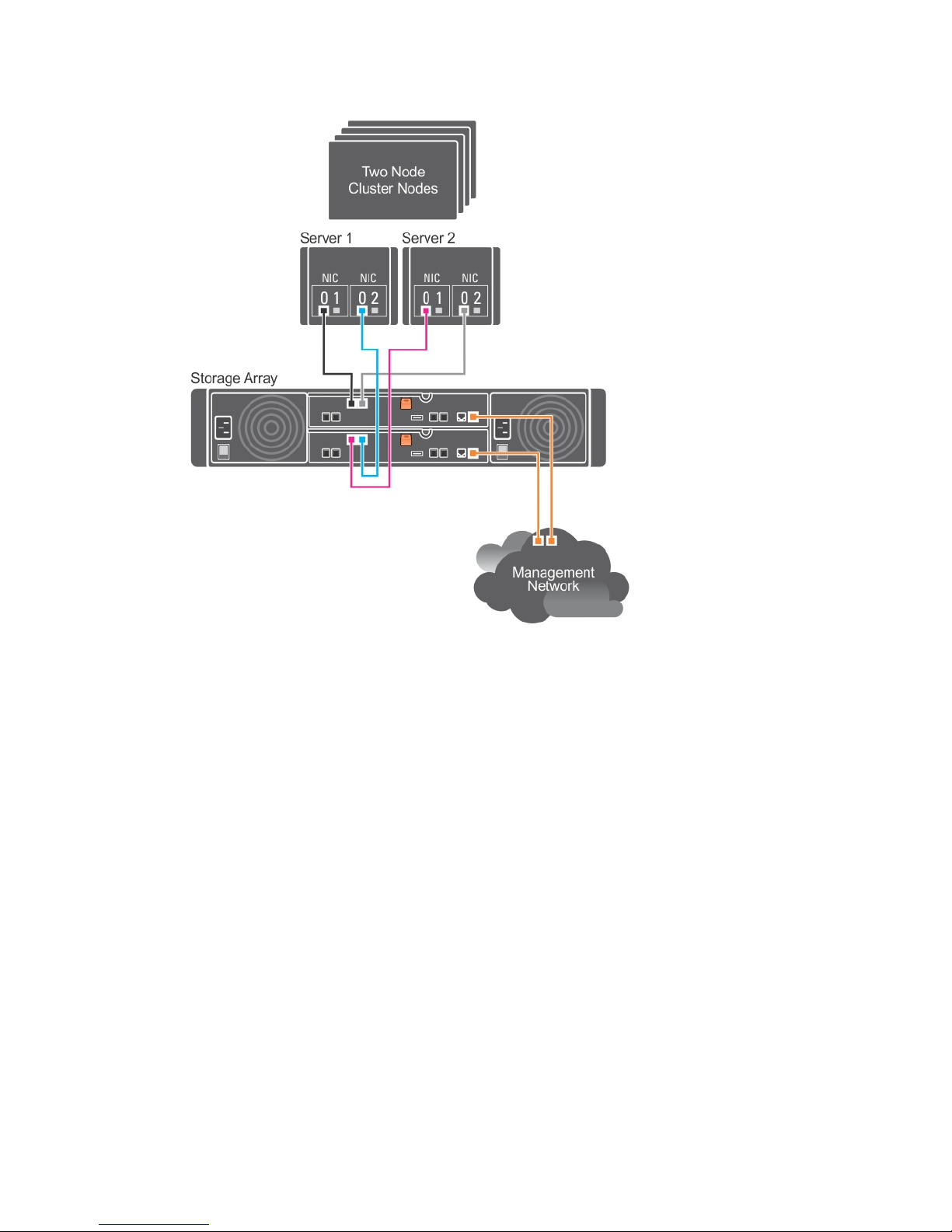
Figure 4. Two Hosts Connected in a Dual-Controller Configuration
Network-Attached Configurations
You can also cable the host servers to the RAID controller module iSCSI ports through industry-standard
10G Ethernet switches. An iSCSI configuration that uses Ethernet switches is frequently referred to as an
IP SAN. By using an IP SAN, the PowerVault MD3800i and MD3820i series storage array can support up to
64 hosts simultaneously. This configuration supports either single or dual path data configurations and
either single or dual RAID controller modules.
The following figure shows up to 64 stand-alone servers attached (using multiple sessions) to a single
RAID controller module through a network. Hosts that have a second Ethernet connection to the
network allow two separate physical paths for each host, which ensures full redundancy if one of the
paths fails. It is recommended you use two switches for more redundancy. However, single switch
configuration is also supported.
13
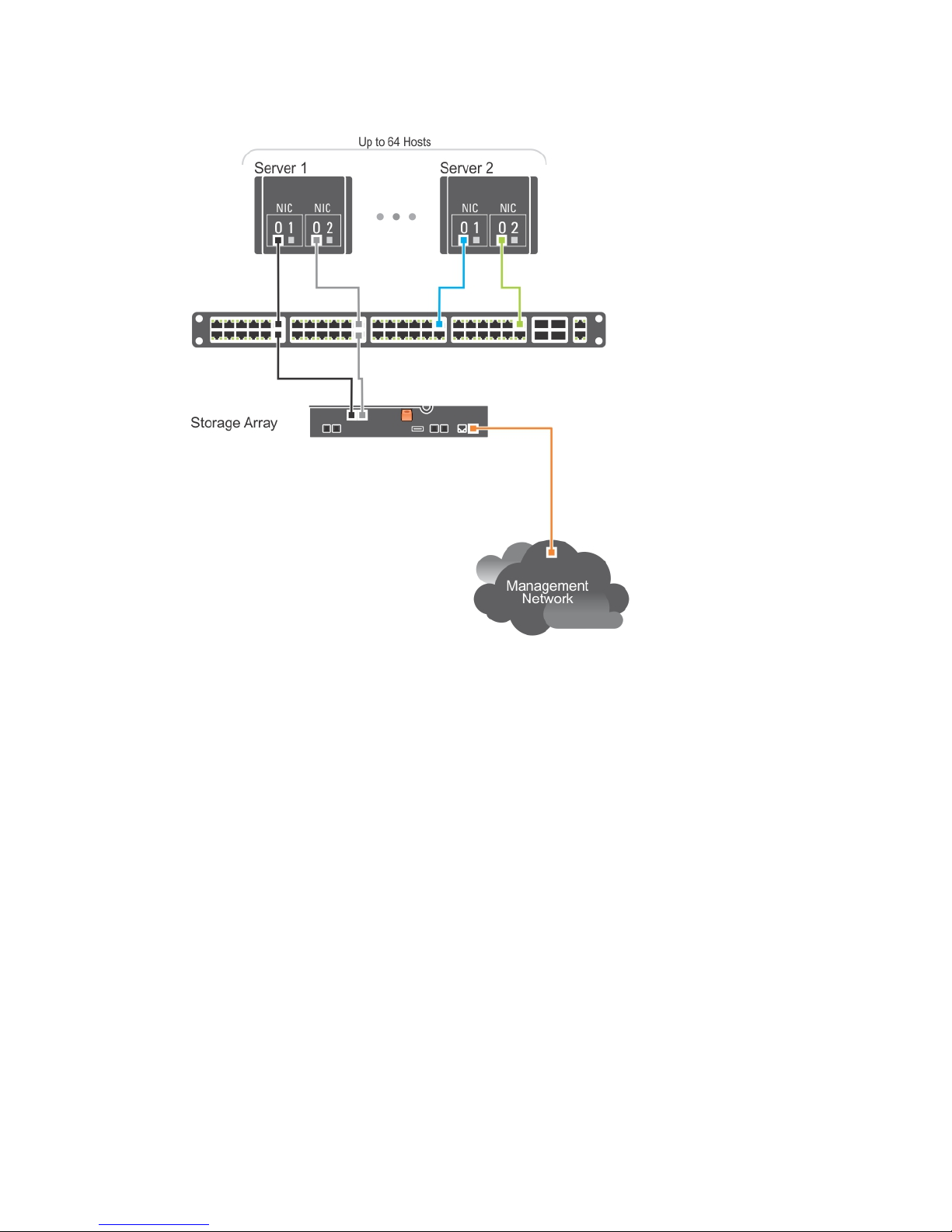
Figure 5. 64 Servers Connected to a Single RAID Controller
The following figure shows how the same number of hosts can be similarly attached to a dual RAID
controller module configuration.
14
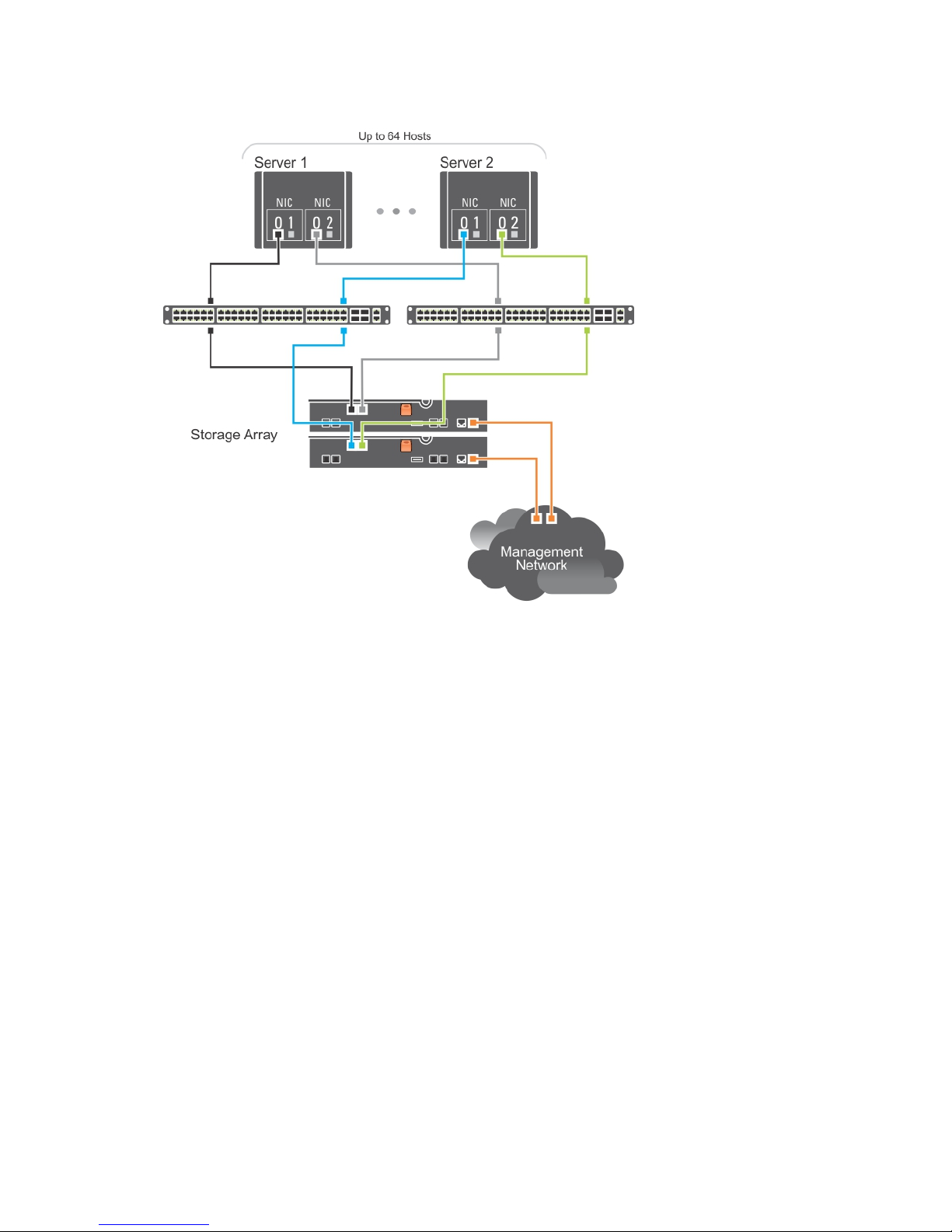
Figure 6. 64 Servers Connected to Two RAID Controllers
The following figure shows up to 64 stand-alone servers attached (using multiple sessions) to a single
RAID controller module through a network using a 10G aggregation scheme. The NICs on the servers are
0 G NICs and the uplink ports are 10G. Hosts that have a second Ethernet connection to the network
allow two separate physical paths for each host, which ensures full redundancy if one of the paths fails. It
is recommended you use two switches for more redundancy. However, single switch configuration is
also supported.
15
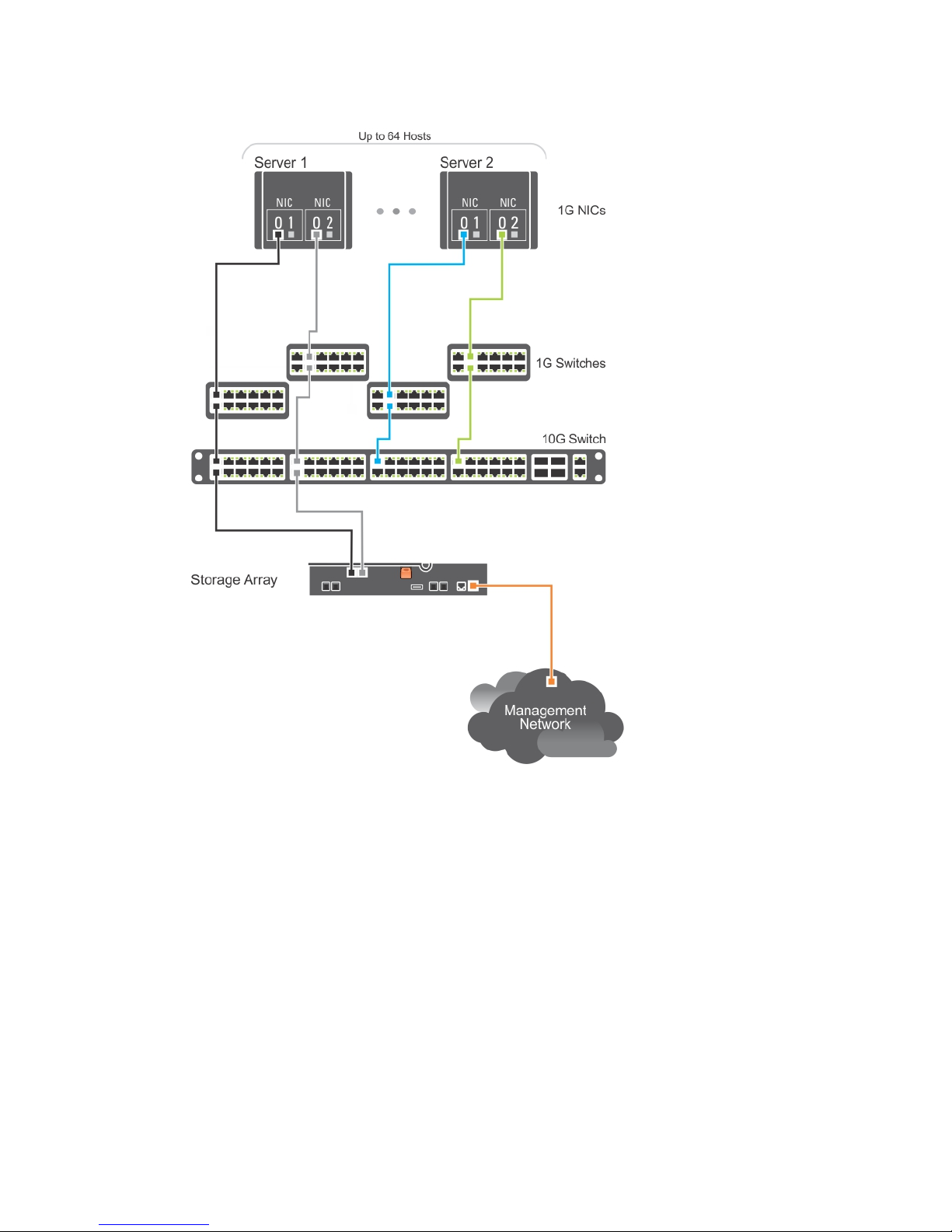
Figure 7. 64 Servers Connected to a Single RAID Controller
The following figure shows how the same number of hosts can be similarly attached to a dual RAID
controller module configuration. Hardware redundancy is achieved in this configuration, in case of any
switch failure.
16
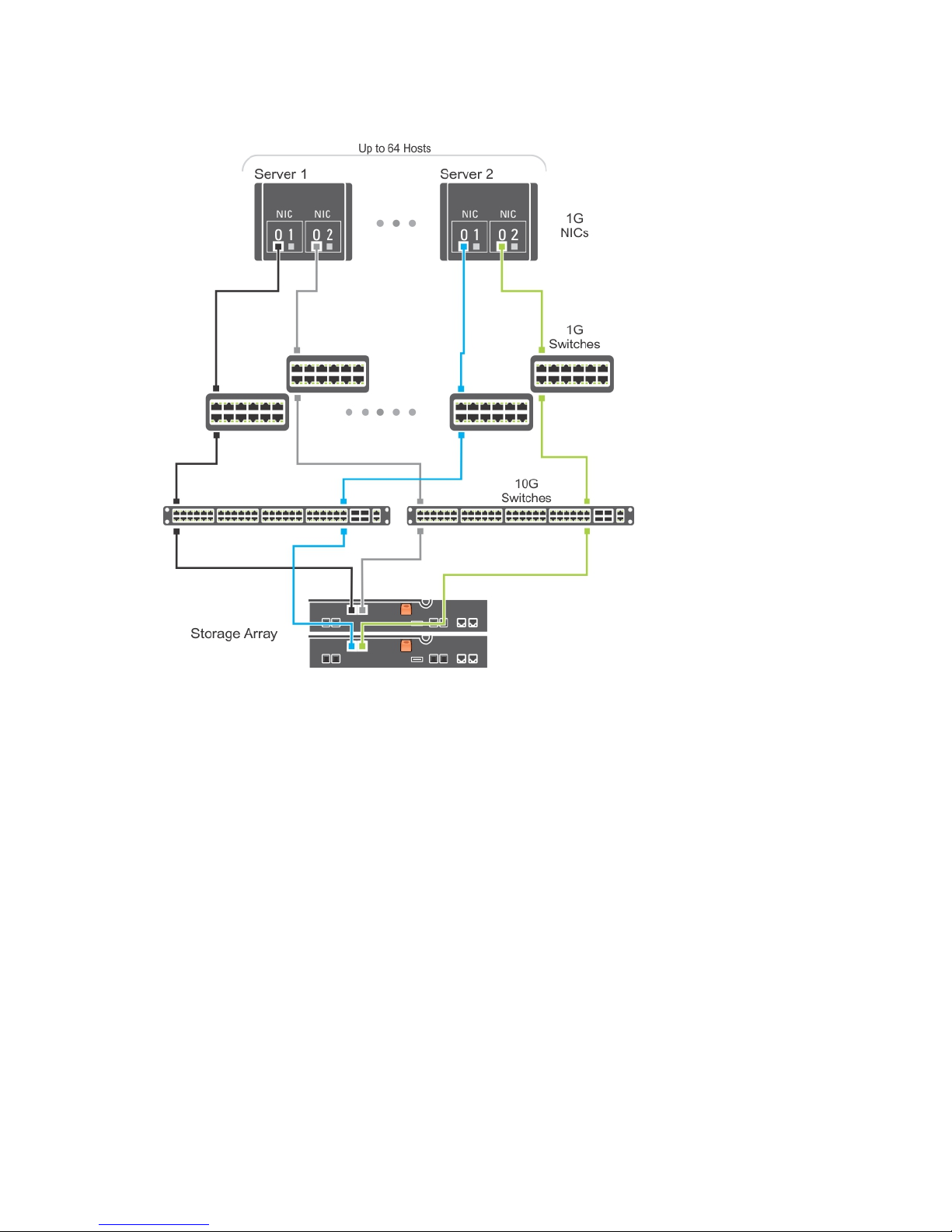
Figure 8. 64 Servers Connected to Two RAID Controllers
17
 Loading...
Loading...