Page 1

Dell FluidFS V3 NAS Solutions For PowerVault
NX3500, NX3600, And NX3610
Administrator's Guide
Page 2

Notes, Cautions, and Warnings
NOTE: A NOTE indicates important information that helps you make better use of your computer.
CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you
how to avoid the problem.
WARNING: A WARNING indicates a potential for property damage, personal injury, or death.
Copyright © 2014 Dell Inc. All rights reserved. This product is protected by U.S. and international copyright and
intellectual property laws. Dell™ and the Dell logo are trademarks of Dell Inc. in the United States and/or other
jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies.
2014 - 01
Rev. A02
Page 3

Contents
1 Introduction.............................................................................................................. 11
How PowerVault FluidFS NAS Works ................................................................................................. 11
FluidFS Terminology............................................................................................................................ 11
Key Features Of PowerVault FluidFS Systems.................................................................................... 12
Overview Of PowerVault FluidFS Systems..........................................................................................13
Internal Cache............................................................................................................................... 14
Internal Backup Power Supply...................................................................................................... 14
Internal Storage............................................................................................................................. 14
PowerVault FluidFS Architecture........................................................................................................ 14
Client/LAN Network.......................................................................................................................15
MD System..................................................................................................................................... 16
SAN Network..................................................................................................................................16
Internal Network............................................................................................................................16
Data Caching And Redundancy..........................................................................................................16
File Metadata Protection..................................................................................................................... 16
High Availability And Load Balancing..................................................................................................17
Failure Scenarios............................................................................................................................ 17
Ports Used by the FluidFS System.......................................................................................................18
Required Ports............................................................................................................................... 18
Feature-Specific Ports...................................................................................................................18
Other Information You May Need...................................................................................................... 19
2 Upgrading to FluidFS Version 3...........................................................................21
Supported Upgrade Paths................................................................................................................... 21
FluidFS V2 and FluidFS V3 Feature and Configuration Comparison................................................. 21
Performing Pre-Upgrade Tasks..........................................................................................................24
Upgrading from FluidFS Version 2.0 to 3.0 .......................................................................................25
3 FluidFS Manager User Interface Overview.......................................................29
FluidFS Manager Layout......................................................................................................................29
Navigating Views.................................................................................................................................29
Working With Panes, Menus, And Dialogs......................................................................................... 30
Showing And Hiding Panes...........................................................................................................30
Opening A Pane Menu..................................................................................................................30
Opening A Table Element Menu.................................................................................................. 30
Changing Settings Within A Dialog............................................................................................... 31
Accessing NAS Volume SubTopics.....................................................................................................32
Working With The Event Log.............................................................................................................. 32
Page 4

Viewing The Event Log..................................................................................................................32
Viewing Event Details....................................................................................................................33
Sorting The Event Log...................................................................................................................33
Searching the Event Log............................................................................................................... 33
4 FluidFS 3.0 System Management........................................................................35
Connecting to the FluidFS Cluster .................................................................................................... 35
Connecting to the FluidFS Cluster Using the FluidFS Manager Web Client............................... 35
Connecting to the FluidFS Cluster CLI Using a VGA Console.....................................................35
Connecting to the FluidFS Cluster CLI through SSH Using a Password.....................................36
Connecting to the FluidFS Cluster CLI through SSH without Using a Password....................... 36
Managing Secured Management....................................................................................................... 36
Adding a Secured Management Subnet ...................................................................................... 37
Changing the Netmask for the Secured Management Subnet .................................................. 38
Changing the VLAN ID for the Secured Management Subnet ...................................................38
Changing the VIP for the Secured Management Subnet............................................................ 38
Changing the NAS Controller IP Addresses for the Secured Management Subnet...................39
Deleting the Secured Management Subnet ................................................................................39
Enabling Secured Management ...................................................................................................39
Disabling Secured Management ..................................................................................................40
Managing the FluidFS Cluster Name .................................................................................................40
Viewing the FluidFS Cluster Name............................................................................................... 40
Renaming the FluidFS Cluster...................................................................................................... 40
Managing Licensing ............................................................................................................................41
Viewing License Information ........................................................................................................41
Accepting the End-User License Agreement .............................................................................. 41
Managing the System Time ................................................................................................................41
Viewing the Time Zone................................................................................................................. 41
Setting the Time Zone...................................................................................................................42
Viewing the Time ..........................................................................................................................42
Setting the Time Manually............................................................................................................ 42
Viewing the NTP Servers ..............................................................................................................42
Add or Remove NTP Servers ........................................................................................................43
Enabling NTP ................................................................................................................................ 43
Disabling NTP................................................................................................................................ 43
Managing the FTP Server ...................................................................................................................44
Accessing the FTP Server .............................................................................................................44
Enabling or Disabling the FTP Server........................................................................................... 44
Managing SNMP .................................................................................................................................44
Obtaining SNMP MIBs and Traps .................................................................................................45
Changing the SNMP Read-Only Community ............................................................................. 45
Changing the SNMP Trap System Location or Contact ............................................................. 45
Page 5

Adding or Removing SNMP Trap Recipients ...............................................................................45
Enabling or Disabling SNMP Traps .............................................................................................. 46
Managing the Health Scan Throttling Mode .....................................................................................46
Viewing the Health Scan Throttling Mode .................................................................................. 46
Changing the Health Scan Throttling Mode ............................................................................... 47
Managing the Operation Mode.......................................................................................................... 47
Viewing the Operation Mode .......................................................................................................47
Changing the Operation Mode ....................................................................................................47
Managing Client Connections ...........................................................................................................48
Displaying the Distribution of Clients between NAS Controllers ...............................................48
Viewing Clients Assigned to a NAS Controller ............................................................................48
Assigning a Client to a NAS Controller ........................................................................................48
Unassigning a Client from a NAS Controller ...............................................................................48
Manually Migrating Clients to another NAS Controller .............................................................. 49
Failing Back Clients to Their Assigned NAS Controller ...............................................................49
Rebalancing Client Connections across NAS Controllers ..........................................................49
Shutting Down and Restarting NAS Controllers ...............................................................................50
Shutting Down the FluidFS Cluster ..............................................................................................50
Starting Up the FluidFS Cluster ....................................................................................................50
Rebooting a NAS Controller ........................................................................................................ 50
Managing NAS Appliance and NAS Controller .................................................................................. 51
Enabling or Disabling NAS Appliance and Controller Blinking.................................................... 51
5 FluidFS 3.0 Networking ........................................................................................53
Managing the Default Gateway ......................................................................................................... 53
Viewing the Default Gateway .......................................................................................................53
Changing the Default Gateway.....................................................................................................53
Managing DNS Servers and Suffixes...................................................................................................53
Viewing DNS Servers and Suffixes................................................................................................ 54
Adding DNS Servers and Suffixes..................................................................................................54
Removing DNS Servers and Suffixes............................................................................................ 54
Managing Static Routes...................................................................................................................... 55
Viewing the Static Routes............................................................................................................. 55
Adding a Static Route....................................................................................................................55
Changing the Target Subnet for a Static Route........................................................................... 56
Changing the Gateway for a Static Route....................................................................................56
Deleting a Static Route..................................................................................................................56
Managing the Internal Network..........................................................................................................57
Viewing the Internal Network IP Address..................................................................................... 57
Changing the Internal Network IP Address.................................................................................. 57
Managing the Client Networks........................................................................................................... 57
Viewing the Client Networks........................................................................................................ 58
Page 6

Creating a Client Network............................................................................................................ 58
Changing the Netmask for a Client Network...............................................................................58
Changing the VLAN Tag for a Client Network............................................................................. 59
Changing the Client VIPs for a Client Network............................................................................59
Changing the NAS Controller IP Addresses for a Client Network...............................................59
Deleting a Client Network............................................................................................................ 60
Viewing the Client Network MTU.................................................................................................60
Changing the Client Network MTU..............................................................................................60
Viewing the Client Network Bonding Mode................................................................................ 60
Changing the Client Network Bonding Mode..............................................................................61
Managing SAN Fabrics.........................................................................................................................61
Managing SAN Fabrics/Subnets....................................................................................................62
Viewing the SAN Network Configuration.....................................................................................62
Adding an iSCSI Fabric.................................................................................................................. 62
Modifying an iSCSI Fabric’s Configuration................................................................................... 62
Deleting an iSCSI Fabric................................................................................................................63
Modifying iSCSI Portals................................................................................................................. 63
Viewing Storage Identifiers........................................................................................................... 64
6 FluidFS 3.0 Account Management And Authentication .............................. 65
Account Management and Authentication........................................................................................65
Default Administrative Accounts........................................................................................................ 65
Administrative Account.................................................................................................................66
Support Account........................................................................................................................... 66
Enabling or Disabling the Support Account.................................................................................66
Changing the Support Account Password...................................................................................67
Using the Escalation Account.......................................................................................................67
CLI Account...................................................................................................................................68
Default Local User and Local Group Accounts................................................................................. 68
Managing Administrator Accounts.....................................................................................................68
Viewing Administrators................................................................................................................. 69
Adding an Administrator............................................................................................................... 69
Assigning NAS Volumes to a Volume Administrator....................................................................70
Changing an Administrator’s Permission Level............................................................................70
Changing an Administrator’s Email Address................................................................................ 70
Changing a Local Administrator Password...................................................................................71
Deleting an Administrator..............................................................................................................71
Managing Local Users..........................................................................................................................71
Adding a Local User....................................................................................................................... 71
Changing a Local User’s Group.................................................................................................... 72
Enabling or Disabling a Local User............................................................................................... 72
Changing a Local User Password................................................................................................. 73
Page 7

Deleting a Local User.................................................................................................................... 73
Managing Password Age and Expiration............................................................................................ 73
Changing the Maximum Password Age........................................................................................73
Enabling or Disabling Password Expiration.................................................................................. 74
Managing Local Groups......................................................................................................................74
Viewing Local Groups................................................................................................................... 74
Adding a Local Group....................................................................................................................74
Changing the Users Assigned to a Local Group...........................................................................75
Deleting a Local Group................................................................................................................. 76
Managing Active Directory..................................................................................................................76
Enabling Active Directory Authentication.....................................................................................77
Modifying Active Directory Authentication Settings.................................................................... 78
Disabling Active Directory Authentication................................................................................... 78
Managing LDAP................................................................................................................................... 78
Enabling LDAP Authentication......................................................................................................78
Changing the LDAP Base DN........................................................................................................79
Adding or Removing LDAP Servers.............................................................................................. 80
Enabling or Disabling LDAP on Active Directory Extended Schema.......................................... 80
Enabling or Disabling Authentication for the LDAP Connection................................................80
Enabling or Disabling TLS Encryption for the LDAP Connection................................................81
Disabling LDAP Authentication..................................................................................................... 81
Managing NIS.......................................................................................................................................81
Enabling NIS Authentication.........................................................................................................82
Changing the NIS Domain Name................................................................................................. 82
Changing the Order of Preference for NIS Servers..................................................................... 82
Disabling NIS Authentication........................................................................................................ 83
Managing User Mappings between Windows and UNIX/Linux Users.............................................. 83
User Mapping Policies...................................................................................................................83
User Mapping Policy and NAS Volume Security Style................................................................. 83
Managing the User Mapping Policy..............................................................................................84
Managing User Mapping Rules..................................................................................................... 84
7 FluidFS 3.0 NAS Volumes, Shares, and Exports............................................... 87
Managing the NAS Pool...................................................................................................................... 87
Discovering New or Expanded LUNs............................................................................................87
Viewing Internal Storage Reservations......................................................................................... 87
Viewing the Size of the NAS Pool................................................................................................. 87
Expanding the Size of the NAS Pool.............................................................................................88
Enabling or Disabling the NAS Pool Used Space Alert ............................................................... 88
Enabling or Disabling the NAS Pool Unused Space Alert ...........................................................88
Managing NAS Volumes .................................................................................................................... 89
File Security Styles.........................................................................................................................89
Page 8

Thin and Thick Provisioning for NAS Volumes............................................................................ 90
Choosing a Strategy for NAS Volume Creation...........................................................................90
Example NAS Volume Creation Scenarios................................................................................... 91
NAS Volumes Storage Space Terminology ................................................................................. 92
Configuring NAS Volumes ........................................................................................................... 92
Cloning a NAS Volume..................................................................................................................96
NAS Volume Clone Defaults.........................................................................................................96
NAS Volume Clone Restrictions................................................................................................... 97
Managing NAS Volume Clones.....................................................................................................97
Managing CIFS Shares........................................................................................................................ 98
Configuring CIFS Shares............................................................................................................... 98
Viewing and Disconnecting CIFS Connections.........................................................................100
Using CIFS Home Shares ............................................................................................................101
Changing the Owner of a CIFS Share ........................................................................................102
Managing ACLs or SLPs on a CIFS Share....................................................................................103
Accessing a CIFS Share Using Windows.................................................................................... 104
Accessing a CIFS Share Using UNIX/Linux................................................................................. 105
Managing NFS Exports......................................................................................................................105
Configuring NFS Exports.............................................................................................................105
Setting Permissions for an NFS Export.......................................................................................109
Accessing an NFS Export ........................................................................................................... 109
Managing Quota Rules .....................................................................................................................110
Viewing Quota Rules for a NAS Volume.....................................................................................110
Setting the Default Quota per User ........................................................................................... 110
Setting the Default Quota per Group..........................................................................................111
Adding a Quota Rule for a Specific User ....................................................................................111
Adding a Quota Rule for Each User in a Specific Group............................................................112
Adding a Quota Rule for an Entire Group ..................................................................................112
Changing the Soft Quota or Hard Quota for a User or Group..................................................113
Enabling or Disabling the Soft Quota or Hard Quota for a User or Group .............................. 113
Deleting a User or Group Quota Rule.........................................................................................114
Managing Data Reduction.................................................................................................................114
Enabling Data Reduction at the System Level............................................................................ 115
Enabling Data Reduction on a NAS Volume ..............................................................................115
Changing the Data Reduction Type for a NAS Volume............................................................. 116
Changing the Candidates for Data Reduction for a NAS Volume.............................................116
Disabling Data Reduction on a NAS Volume.............................................................................. 117
8 FluidFS 3.0 Data Protection................................................................................119
Managing the Anti-Virus Service.......................................................................................................119
Excluding Files and Directory Paths from Scans........................................................................120
Supported Anti-Virus Applications............................................................................................. 120
Page 9

Configuring Anti-Virus Scanning................................................................................................120
Viewing Anti-Virus Events .......................................................................................................... 123
Managing Snapshots......................................................................................................................... 123
Creating On-Demand Snapshots............................................................................................... 124
Managing Scheduled Snapshots ................................................................................................124
Modifying and Deleting Snapshots.............................................................................................126
Restoring Data from a Snapshot.................................................................................................127
Managing NDMP............................................................................................................................... 129
Supported DMAs......................................................................................................................... 130
Configuring NDMP .....................................................................................................................130
Specifying NAS Volumes Using the DMA................................................................................... 132
Viewing NDMP Jobs and Events.................................................................................................132
Managing Replication........................................................................................................................133
How Replication Works...............................................................................................................134
Target NAS Volumes................................................................................................................... 136
Managing Replication Partnerships............................................................................................ 136
Replicating NAS Volumes............................................................................................................138
Recovering an Individual NAS Volume....................................................................................... 141
Restoring the NAS Volume Configuration................................................................................. 142
Restoring Local Users .................................................................................................................144
Restoring Local Groups...............................................................................................................145
Using Replication for Disaster Recovery.................................................................................... 146
9 FluidFS 3.0 Monitoring........................................................................................ 153
Viewing the Status of Hardware Components.................................................................................153
Viewing the Status of the Interfaces ..........................................................................................153
Viewing the Status of the Disks...................................................................................................153
Viewing the Status of the Power Supplies..................................................................................154
Viewing the Status of a Backup Power Supply...........................................................................154
Viewing the Status of the Fans....................................................................................................154
Viewing the Status of FluidFS Cluster Services................................................................................ 154
Viewing the Status of Background Processes..................................................................................156
Viewing FluidFS Cluster NAS Pool Trends........................................................................................156
Viewing Storage Usage..................................................................................................................... 156
Viewing FluidFS NAS Pool Storage Usage.................................................................................. 156
Viewing Volume Storage Usage..................................................................................................156
Viewing FluidFS Traffic Statistics.......................................................................................................156
Viewing NAS Controller Load Balancing Statistics...........................................................................157
10 FluidFS 3.0 Maintenance...................................................................................159
Adding and Deleting NAS Appliances in a FluidFS Cluster ............................................................. 159
Adding NAS Appliances to the FluidFS Cluster...........................................................................159
Page 10

Deleting a NAS Appliance from the FluidFS Cluster...................................................................161
Detaching, Attaching, and Replacing a NAS Controller...................................................................161
Detaching a NAS Controller........................................................................................................ 161
Attaching a NAS Controller ........................................................................................................162
Replacing a NAS Controller........................................................................................................ 162
Managing Service Packs....................................................................................................................163
Viewing the Upgrade History .....................................................................................................163
Managing Firmware Updates............................................................................................................164
Reinstalling FluidFS from the Internal Storage Device.................................................................... 164
11 Troubleshooting..................................................................................................167
Viewing the Event Log.......................................................................................................................167
Running Diagnostics......................................................................................................................... 167
Running FluidFS Diagnostics on a FluidFS Cluster .................................................................... 167
Launching the iBMC Virtual KVM......................................................................................................168
Troubleshooting Common Issues....................................................................................................169
Troubleshooting Active Directory Issues................................................................................... 169
Troubleshooting Backup Issues..................................................................................................170
Troubleshooting CIFS Issues....................................................................................................... 171
Troubleshooting NFS Issues........................................................................................................175
Troubleshooting NAS File Access And Permissions Issues........................................................179
Troubleshooting Networking Issues...........................................................................................181
Troubleshooting Replication Issues........................................................................................... 182
Troubleshooting System Issues.................................................................................................. 185
12 Getting Help.........................................................................................................189
Contacting Dell................................................................................................................................. 189
Locating Your System Service Tag................................................................................................... 189
Documentation Feedback................................................................................................................ 189
Page 11
1
Introduction
The Dell Fluid File System (FluidFS) network attached storage (NAS) solution is a highly-available file
storage solution. The solution aggregates multiple NAS controllers into one system and presents them to
UNIX, Linux, and Microsoft Windows clients as one virtual file server.
How PowerVault FluidFS NAS Works
PowerVault FluidFS NAS leverages the PowerVault FluidFS appliances and the Dell PowerVault MD
storage to provide scale‐out file storage to Microsoft Windows, UNIX, and Linux clients. The FluidFS
system supports SMB (CIFS) and NFS clients installed on dedicated servers or on virtual systems deploying
VMware virtualization.
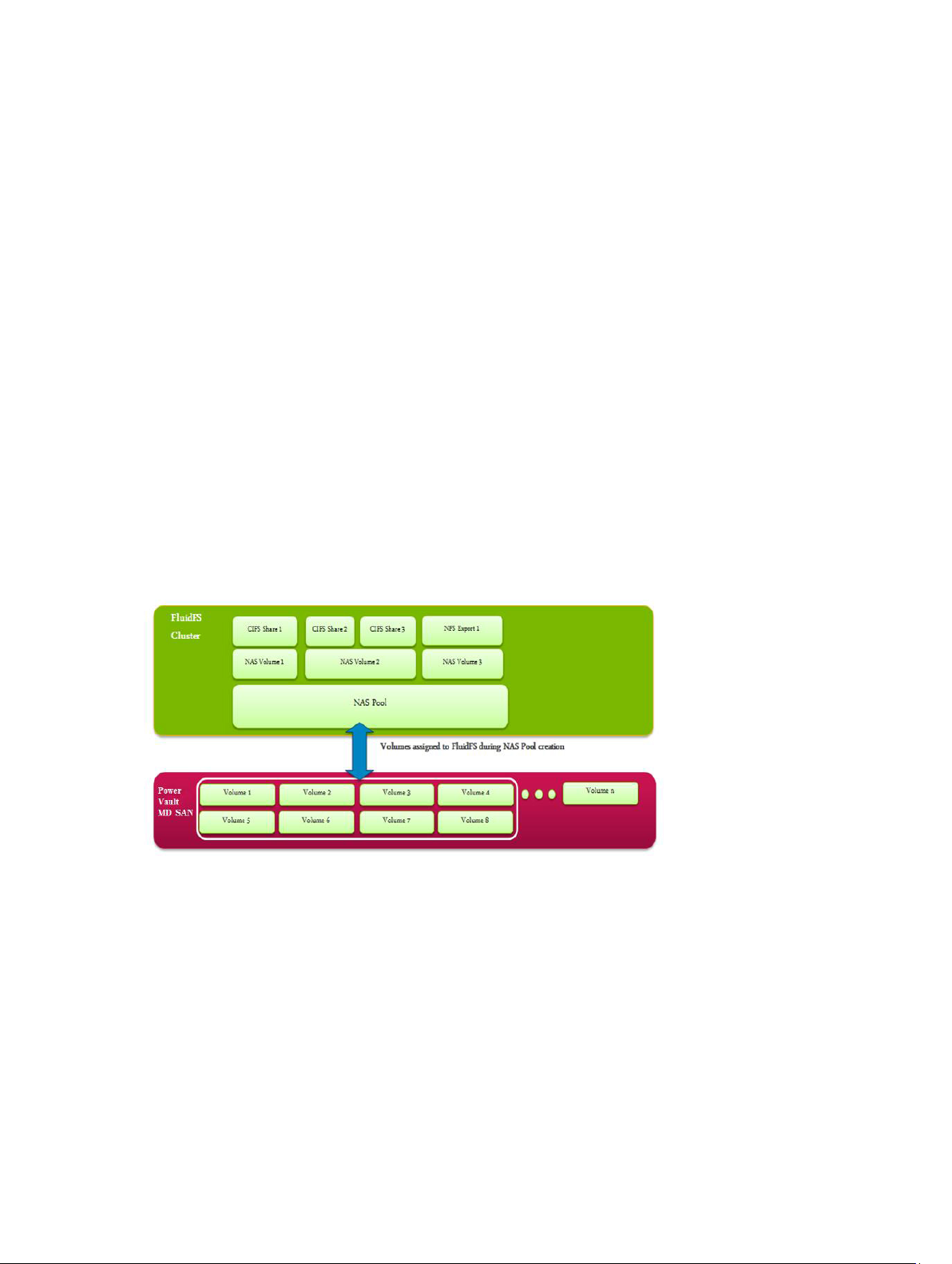
The MD storage systems manage the “NAS pool” of storage capacity. The FluidFS system administrator
can create NAS volumes in the NAS pool, and CIFS shares and/or NFS exports to serve NAS clients
working on different platforms.
To the clients, the FluidFS system appears as a single file server, hosting multiple CIFS shares and NFS
exports, with a single IP address and namespace. Clients connect to the FluidFS system using their
respective operating systems’ NAS protocols:
• UNIX and Linux users access files through the NFS protocol
• Windows users access files through the SMB(CIFS) protocol
The FluidFS system serves data to all clients concurrently, with no performance degradation.
FluidFS Terminology
The following table defines terminology related to FluidFS scale‐out NAS.
11
Page 12

Term Description
Fluid File System (FluidFS) A special purpose, Dell proprietary operating system providing
enterprise class, high‐performance, scalable NAS services using
Dell PowerVault, EqualLogic or Dell Compellent SAN storage
systems.
FluidFS Controller (NAS controller) Dell hardware device capable of running the FluidFS firmware.
FluidFS Appliance (NAS appliance) Enclosure containing two NAS controllers. The controllers in an
appliance are called peers, are hot‐swappable and operate in
active‐active mode.
Backup Power Supply (BPS) A backup power supply that keeps a FluidFS controller running
in the event of power failure and allows it to dump its cache to
a nonvolatile storage device.
FluidFS system (cluster) Multiple NAS controllers appropriately connected and
configured to form a single functional unit.
PowerVault FluidFS Manager WebUI Management user interface used for managing
PowerVault FluidFS systems.
NAS reserve (pool) The SAN storage system LUNs (and their aggregate size)
allocated and provisioned to a FluidFS system.
NAS volume File system (single-rooted directory/folder and file hierarchy),
defined using FluidFS management functions over a portion of
the NAS reserve.
Client Network (Client LAN) The network through which clients access CIFS shares or NFS
exports and also through which the PowerVault FluidFS
Manager is accessed.
Client VIP Virtual IP address(es) that clients use to access CIFS shares and
NFS exports hosted by the FluidFS system.
CIFS share A directory in a NAS volume that is shared on the Client
Network using the SMB (CIFS) protocol.
NFS export A directory in a NAS volume that is shared on the Client
Network using the Network File System (NFS) protocol.
Network Data Management Protocol
(NDMP)
Replication partnership A relation between two FluidFS systems enabling them to
Snapshot A time-specific view of a NAS volume data.
Protocol used for NDMP backup and restore.
replicate NAS volumes between themselves.
Key Features Of PowerVault FluidFS Systems
The following table summarizes key features of PowerVault FluidFS scale‐out NAS.
Feature Description
Shared back‐end infrastructure The MD system SAN and NX36X0 scale‐out NAS leverage the
same virtualized disk pool.
Unified block and file Unified block (SAN) and file(NAS) storage.
High performance NAS Support for a single namespace spanning up to two NAS
appliances (four NAS controllers).
Capacity scaling Ability to scale a single namespace up to 1024 TB capacity.
12
Page 13

Feature Description
Connectivity options 1GbE and 10GbE, copper and optical options for connectivity to
the client network.
Highly available and active‐active
design
Automatic load balancing Automatic balancing of client connections across network ports
Multi‐protocol support Support for CIFS/SMB (on Windows) and NFS (on UNIX and Linux)
Client authentication Control access to files using local and remote client
Quota rules Support for controlling client space usage.
File security style Choice of file security mode for a NAS volume (UNIX or NTFS).
Cache mirroring The write cache is mirrored between NAS controllers, which
Journaling mode In the event of a NAS controller failure, the cache in the remaining
NAS volume thin clones Clone NAS volumes without the need to physically copy the data
Deduplication Policy‐driven post‐process deduplication technology that
Compression LZPS (Level Zero Processing System) compression algorithm that
Metadata protection Metadata is constantly check-summed and stored in multiple
Replication NAS-volume level, snapshot‐based, asynchronous replication to
Snapshots Redirect‐on‐write, user‐accessible snapshots
NDMP backups Snapshot‐based, asynchronous backup (remote NDMP) over
Anti‐virus scanning CIFS anti‐virus scanning by deploying certified third‐party ICAP‐
Monitoring Built‐in performance monitoring and capacity planning.
Redundant, hot‐swappable NAS controllers in each NAS appliance.
Both NAS controllers in a NAS appliance process I/O. BPS allows
maintaining data integrity in the event of a power failure by
keeping a NAS controller online long enough to write the cache
to the internal storage device.
and NAS controllers, as well as back‐end I/O across MD array
LUNs.
protocols with ability to share user data across both protocols.
authentication, including LDAP, Active Directory, and NIS.
ensures a high performance response to client requests and
maintains data integrity in the event of a NAS controller failure.
NAS controller is written to storage and the NAS controller
continues to write directly to storage, which protects against data
loss.
set.
eliminates redundant data at rest.
intelligently shrinks data at rest.
locations for data consistency and protection.
enable disaster recovery.
Ethernet to certified third‐party backup solutions.
enabled anti‐virus solutions.
Overview Of PowerVault FluidFS Systems
PowerVault FluidFS system consists of one or two PowerVault NX36x0 appliances connected and
configured to utilize a PowerVault MD storage array and provide NAS services. PowerVault FluidFS
systems can start with one NX36x0 appliance, and expand with another (identical) appliance as required.
13
Page 14

NOTE: To identify the physical hardware displayed in PowerVault FluidFS Manager, match the
Service Tag shown in FluidFS Manager with the Service Tag printed on a sticker on the front right
side of the NAS appliance.
All NAS appliances in a FluidFS system must use the same controllers — mixing of 1 GbE and 10 GbE
appliances or controllers is not supported. The following appliances are supported:
• NX3500 (legacy) — 1 Gb Ethernet client connectivity with 1GB iSCSI back‐end connectivity to the MD
system(s)
• NX3600 — 1 Gb Ethernet client connectivity with 1GB iSCSI back‐end connectivity to the MD
system(s)
• NX3610 — 10 Gb Ethernet client connectivity with 10GB Ethernet iSCSI back‐end connectivity to the
MD system(s)
NAS appliance numbers start at 1 and NAS controller numbers start at 0. So, NAS Appliance 1 contains
NAS Controllers 0 and 1 and FluidFS Appliance 2 contains NAS Controllers 2 and 3.
Internal Cache
Each NAS controller has an internal cache that provides fast reads and reliable writes.
Internal Backup Power Supply
Each NAS controller is equipped with an internal Backup Power Supply (BPS) that protects data during a
power failure. The BPS units provide continuous power to the NAS controllers for a minimum of 5
minutes and have sufficient battery power to allow the NAS controllers to write all data from the cache to
non‐volatile internal storage before they shut down.
The NAS controllers regularly monitor the BPS battery status for the minimum level of power required for
normal operation. To ensure that the BPS battery status is accurate, the NAS controllers routinely
undergo battery calibration cycles. During a battery calibration cycle, the BPS goes through charge and
discharge cycles; therefore, battery error events during this process are expected. A battery calibration
cycle takes up to seven days to complete. If a NAS controller starts a battery calibration cycle, and the
peer NAS controller BPS has failed, the NAS controllers enter journaling mode, which might impact
performance. Therefore, Dell recommends repairing a failed BPS as soon as possible.
Internal Storage
Each NAS controller has an internal storage device that is used only for the FluidFS images and as a cache
storage offload location in the event of a power failure. The internal hard drive does not provide the NAS
storage capacity.
PowerVault FluidFS Architecture
PowerVault FluidFS scale‐out NAS consists of:
• Hardware:
– FluidFS appliance(s)
– MD system
14
Page 15
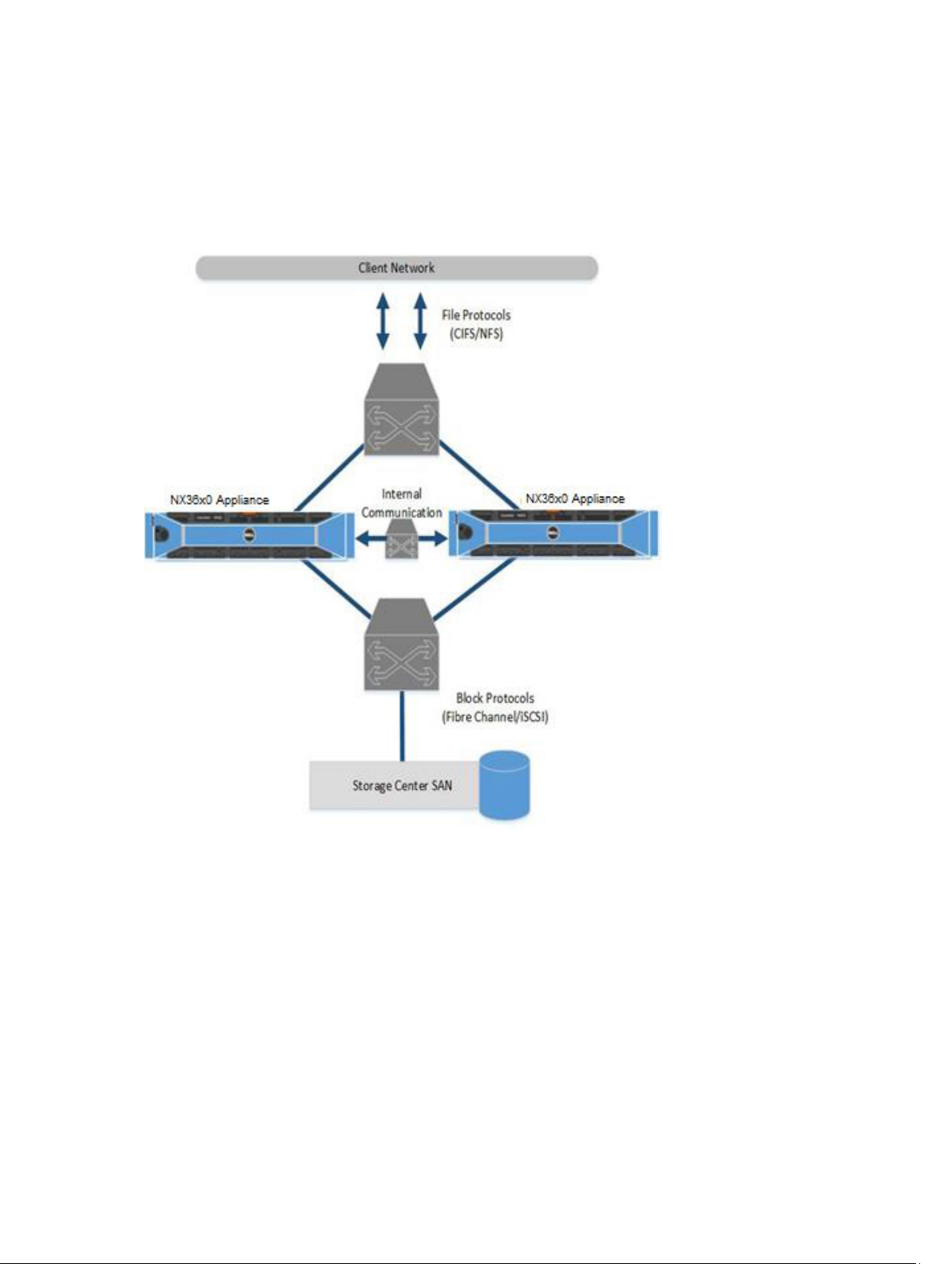
• NAS appliance network interface connections:
– Client/LAN network
– SAN network
– Internal network
The following figure shows an overview of the PowerVault FluidFS architecture:
Figure 1. PowerVault FluidFS Architecture Overview
Client/LAN Network
The client/LAN network is used for client access to the CIFS shares and NFS exports. It is also used by the
storage administrator to manage the FluidFS system. The FluidFS system is assigned one or more virtual
IP addresses (client VIPs) that allow clients to access the FluidFS system as a single entity. The client VIP
also enables load balancing between NAS controllers, and ensures failover in the event of a NAS
controller failure.
If client access to the FluidFS system is not through a router (in other words, the network has a “flat”
topology), define one client VIP. Otherwise, define a client VIP for each client interface port per NAS
controller. If you deploy FluidFS in an LACP environment, please contact Dell Support to get more
information about the optimal number of VIPs for your system.
15
Page 16

MD System
The PowerVault MD array provides the storage capacity for NAS; the NX36x0 cannot be used as a stand‐
alone NAS appliance. The MD array eliminates the need for separate storage capacity for block and file
storage.
SAN Network
The NX36x0 shares a back‐end infrastructure with the MD array. The SAN network connects the NX36x0
to the MD system and carries the block level traffic. The NX36x0 communicates with the MD system
using the iSCSI protocol.
Internal Network
The internal network is used for communication between NAS controllers. Each of the NAS controllers in
the FluidFS system must have access to all other NAS controllers in the FluidFS system to achieve the
following goals:
• Provide connectivity for FluidFS system creation
• Act as a heartbeat mechanism to maintain high availability
• Enable internal data transfer between NAS controller
• Enable cache mirroring between NAS controllers
• Enable balanced client distribution between NAS controllers
Data Caching And Redundancy
New or modified file blocks are first written to a local cache, and then immediately mirrored to the peer
NAS controller (mirroring mode). Data caching provides high performance, while cache mirroring
between peer NAS controllers ensures data redundancy. Cache data is ultimately (and asynchronously)
transferred to permanent storage using optimized data‐placement schemes.
When cache mirroring is not possible, such as during a single NAS controller failure or when the BPS
battery status is low, NAS controllers write directly to storage (journaling mode).
File Metadata Protection
File metadata includes information such as name, owner, permissions, date created, date modified, and a
soft link to the file’s storage location.
The FluidFS system has several built‐in measures to store and protect file metadata:
• Metadata is managed through a separate caching scheme and replicated on two separate volumes.
• Metadata is check-summed to protect file and directory structure.
• All metadata updates are journaled to storage to avoid potential corruption or data loss in the event of
a power failure.
• There is a background process that continuously checks and fixes incorrect checksums.
16
Page 17
High Availability And Load Balancing
To optimize availability and performance, client connections are load balanced across the available NAS
controllers. Both NAS controllers in a NAS appliance operate simultaneously. If one NAS controller fails,
clients are automatically failed over to the remaining controllers. When failover occurs, some CIFS clients
reconnect automatically, while in other cases, a CIFS application might fail, and the user must restart it.
NFS clients experience a temporary pause during failover, but client network traffic resumes
automatically.
Failure Scenarios
The FluidFS system can tolerate a NAS controller failure without impact to data availability and without
data loss. If one NAS controller becomes unavailable (for example, because the NAS controller failed, is
turned off, or is disconnected from the network), the NAS appliance status is degraded. Although the
FluidFS system is still operational and data is available to clients, the administrator cannot perform most
configuration modifications and performance might decrease because data is no longer cached.
The impact to data availability and data integrity following a multiple NAS controller failure depends on
the circumstances of the failure scenario. Dell recommends detaching a failed NAS controller as soon as
possible, so that it can be safely taken offline for service. Data access remains intact as long as one of the
NAS controllers in each NAS appliance in a FluidFS system is functional.
The following table summarizes the impact to data availability and data integrity of various failure
scenarios.
Scenario System Status Data Integrity Comments
Single NAS controller
failure
Available, degraded Unaffected
• Peer NAS controller enters
journaling mode
• Failed NAS controller can be
replaced while keeping the
file system online
Sequential dual‐NAS
controller failure in
single NAS appliance
system
Simultaneous dual‐ NAS
controller failure in
single NAS appliance
system
Sequential dual‐NAS
controller failure in
multiple NAS appliance
system, same NAS
appliance
Simultaneous dual‐NAS
controller failure in
multiple NAS appliance
Unavailable Unaffected Sequential failure assumes that
there is enough time between
NAS controller failures to write all
data from the cache to disk (MD
system or non‐volatile internal
storage)
Unavailable Lose data in cache Data that has not been written to
disk is lost
Unavailable Unaffected Sequential failure assumes that
there is enough time between
NAS controller failures to write all
data from the cache to disk (MD
system or non‐volatile internal
storage)
Unavailable Lose data in cache Data that has not been written to
disk is lost
17
Page 18
Scenario System Status Data Integrity Comments
system, same NAS
appliance
Dual‐NAS controller
failure in multiple NAS
appliance system,
separate NAS appliances
Available, degraded Unaffected
• Peer NAS controller enters
journaling mode
• Failed NAS controller can be
replaced while keeping the
file system online
Ports Used by the FluidFS System
The FluidFS system uses the ports listed in the following table. You might need to adjust your firewall
settings to allow the traffic on these ports. Some ports might not be used, depending on which features
are enabled.
Required Ports
The following table summarizes ports that are required for all FluidFS systems.
Port Protocol Service Name
22 TCP
53 TCP
80 TCP
111 TCP and UDP
427 TCP and UDP
443 TCP
445 TCP and UDP
2049–2049+(domain number ‐ 1)TCP and UDP
SSH
DNS
Internal system use
portmap
SLP
Internal system use
CIFS/SMB
NFS
4000–4000+(domain number ‐ 1)TCP and UDP
4050–4050+(domain number ‐ 1)TCP and UDP
5001–5001+(domain number ‐ 1) TCP and UDP
5051–5051+(domain number ‐ 1) TCP and UDP
44421 TCP
44430–44439 TCP
statd
NLM (lock manager)
mount
quota
FTP
FTP (Passive)
Feature-Specific Ports
The following table summarizes ports that are required, depending on enabled features.
18
Page 19

Port Protocol Service Name
88 TCP and UDP Kerberos
123 UDP NTP
135 TCP AD ‐ RPC
138 UDP NetBIOS
139 TCP NetBIOS
161 UDP SNMP Agent
162 TCP SNMP trap
389 TCP and UDP LDAP
464 TCP and UDP Kerberos v5
543 TCP Kerberos login
544 TCP Kerberos remote shell
636 TCP LDAP over TLS/SSL
711 UDP NIS
714 TCP NIS
749 TCP and UDP Kerberos administration
1344 TCP Anti-virus ‐ ICAP
3268 TCP LDAP global catalog
3269 TCP LDAP global catalog over TLS/SSL
8004 TCP ScanEngine server WebUI (AV host)
9445 TCP Replication trust setup
10000 TCP NDMP
10550‐10551, 10560‐10568 TCP Replication
Other Information You May Need
WARNING: See the safety and regulatory information that shipped with your system. Warranty
information may be included within this document or as a separate document.
• The Getting Started Guide provides an overview of setting up your system and technical
specifications.
• The Owner's Manual provides information about solution features and describes how to troubleshoot
the system and install or replace system components.
• The rack documentation included with your rack solution describes how to install your system into a
rack, if required.
• The System Placemat provides information on how to set up the hardware and install the software on
your NAS solution.
• Any media that ships with your system that provides documentation and tools for configuring and
managing your system, including those pertaining to the operating system, system management
software, system updates, and system components that you purchased with your system.
• For the full name of an abbreviation or acronym used in this document, see the Glossary at dell.com/
support/manuals.
19
Page 20

NOTE: Always check for updates on dell.com/support/manuals and read the updates first because
they often supersede information in other documents.
20
Page 21
2
Upgrading to FluidFS Version 3
Supported Upgrade Paths
To upgrade to FluidFS version 3.0, the FluidFS cluster must be at FluidFS version 2.0.7630 or later. If the
FluidFS cluster is at a pre‐2.0.7630 version, upgrade to version 2.0.7680 prior to upgrading to version 3.0.
The following table summarizes the supported upgrade paths.
Version 2.0 Release Upgrades to Version 3.0.x Supported?
2.0.7680 Yes
2.0.7630 Yes
2.0.7170 No
2.0.6940 No
2.0.6730 No
2.0.6110 No
FluidFS V2 and FluidFS V3 Feature and Configuration Comparison
This section summarizes functionality differences between FluidFS version 2.0 and 3.0. Review the
functionality comparison before upgrading FluidFS to version 3.0.
• Note: The Version 3.0 column in the table below indicates changes that must be made in some cases,
in order to accommodate version 3.0 configuration options.
Feature Version 2.0 Version 3.0
Management interface The NAS ManagerUser Interface has been
updated.
Management
connections
Default management
account
The FluidFS cluster is
managed using a dedicated
Management VIP.
The default administrator
account is named admin.
Version 3.0 does not use a Management VIP—
the FluidFS cluster can be managed using any
client VIP.
During the upgrade, the Management VIP from
version 2.0 is converted to a client VIP.
The default administrator account is named
Administrator.
During the upgrade, the admin account from
version 2.0 is deleted and the CIFS
Administrator account becomes the version
3.0 Administrator account. During the upgrade,
you will be prompted to reset the CIFS
Administrator password if you have not reset it
within the last 24 hours. Make sure to
21
Page 22

Feature Version 2.0 Version 3.0
remember this password because it is required
to manage the FluidFS cluster in version 3.0.
User‐defined
management accounts
Command Line
Interface (CLI) access
and commands
Dell Technical Support
Services remote
troubleshooting
account
FluidFS cluster name
and NetBIOS name
Data reduction
overhead
Anti‐virus scanning You can specify which file
Supported NFS
protocol versions
Supported SMB
protocol versions
Only local administrator
accounts can be created.
Administrator accounts log
into the CLI directly.
The remote troubleshooting
account is named fse (field
service engineer).
The FluidFS cluster name and
NetBIOS name do not have
to match. The NetBIOS name
can begin with a digit.
Version 2.0 does not include
a data
reduction feature.
types to scan.
Version 2.0 supports NFS
protocol version 3.
Version 2.0 supports SMB
protocol version 1.0.
You can create local administrator accounts or
create administrator accounts for remote users
(members of Active Directory, LDAP or NIS
repositories).
During the upgrade, any user‐defined
administrator accounts from version 2.0 are
deleted.
Workaround: Use one of the following
options:
Convert the administrator accounts to local
users before upgrading and convert them back
to administrator accounts after upgrading.
Re‐create administrator accounts after the
upgrade.
Version 3.0 introduces a cli account that must
be used in conjunction with an administrator
account to log into the CLI.
In addition, the command set is significantly
different in version 3.0.
The remote troubleshooting account is named
support. During the upgrade, the fse account
from version 2.0 is deleted. After the upgrade,
the support account is disabled by default.
The FluidFS cluster name is used as the
NetBIOS name.
Before upgrading, the FluidFS cluster name and
NetBIOS name must be changed to match.
Also, the FluidFS cluster name cannot be
longer than 15 characters and cannot begin
with a digit.
Version 3.0 introduces a data reduction
feature. If data reduction is enabled, the system
deducts an additional 100GB per NAS
appliance from the NAS pool for data reduction
processing. This is in addition to the amount of
space that the system deducts from the NAS
pool for internal use.
You cannot specify which files types to scan—
all files smaller than the specified file size
threshold are scanned.
You can specify whether to allow or deny
access to files larger than the file size
threshold.
As in version 2.0, you can specify file types and
directories to exclude from anti‐virus scanning.
Version 3.0 supports NFS protocol version 3
and 4.
Version 3.0 supports SMB protocol version 1.0,
2.0, and 2.1.
22
Page 23

Feature Version 2.0 Version 3.0
CIFS home shares Clients can access CIFS
home shares in two ways:
\\<client_VIP_or_name>
\<path_prefix>\<username>
\\<client_VIP_or_name>
\homes
Both access methods point
to the same folder.
Local user names A period can be used as the
last
character of a local user
name.
Local users and local
groups UID/GID range
Guest account
mapping policy
NDMP client port The NDMP client port must
Replication ports TCP ports 10560–10568 and
Snapshot schedules Snapshot schedules can be
Internal subnet The internal (interconnect)
A unique UID (user ID) or GID
(group ID) can be configured
for
local users and local groups.
By default, unmapped users
are
mapped to the guest
account, which allows a
guest account to access a file
if the CIFS share allows guest
access.
be in
the range 1–65536.
26 are used for replication.
disabled.
subnet
can be changed from a Class
C
subnet during or after
deployment.
Version 3.0 does not include the “homes”
access method. After the upgrade, the “homes”
share will not be present, and clients will need
to use the “username” access method instead.
If you have a policy that mounts the \
\<client_VIP_or_name>\homes share when
client systems start, you must change the
policy to mount the \\<client_VIP_or_name>
\<path_prefix>\<username> share.
A period cannot be used as the last character
of a local user name.
Before upgrading, delete local user names that
have a period as the last character and re‐
create the accounts with a different name.
The UID/GID range for local users and local
groups is 1001 to 100,000. There is no way to
configure or determine the UID/GID of local
users and local groups. This information is
internal to the FluidFS cluster.
During the upgrade, any existing local users
and local
groups from version 2.0 with a UID/GID that is
outside the version 3.0 UID/GID range will
remain unchanged. Local users and local
groups created after the upgrade will use the
version 3.0 UID/GID range.
Unmapped users cannot access any CIFS
share, regardless of whether the CIFS share
allows guest access.
Guest access is enabled automatically after the
upgrade only if there are guest users already
defined for any CIFS shares in version 2.0.
The NDMP client port must be in the range
10000–10100.
Before upgrading, the NDMP client port must
be changed to be in the range 10000–10100.
You must also make the reciprocal change on
the DMA servers.
TCP ports 10550–10551 and 10560–10568 are
used for replication.
Snapshot schedules cannot be disabled.
During the upgrade, disabled snapshot
schedules from version 2.0 are deleted.
The internal subnet must be a Class C subnet.
Before upgrading, the internal subnet must be
changed to a Class C subnet, otherwise the
service pack installation will fail with the
following message:
“Please allocate a new C-class subnet for
FluidFS Internal Network, run the following
23
Page 24

Feature Version 2.0 Version 3.0
command, and then repeat the upgrade:
system
networking subnets add NEWINTER Primary
255.255.255.0 -PrivateIPs x.y.z.1,x.y.z.2
(where x.y.z.* is the new subnet)”.
Note: If you receive this message while
attempting to
upgrade, obtain a Class C subnet that is not
used in your network, run the command to set
the internal subnet (for example: system
networking subnets add NEWINTER Primary
255.255.255.0 –PrivateIPs 172.41.64.1,
172.41.64.2), and retry the service pack
installation.
Port for management
and remote KVM
1GbE to 10GbE client
connectivity upgrade
Only subnet‐level isolation of
management traffic is
supported.
Version 2.0 does not support
upgrading an appliance from
1GbE client connectivity to
10GbE client connectivity.
The following features are available:
Physical isolation of management traffic
Remote KVM that allows you to view and
manage the NAS controller console remotely
over a network
These features are implemented using the
Ethernet port located on the lower right side of
the back panel of a NAS controller.
Version 3.0 introduces support for upgrading
an appliance from 1GbE client connectivity to
10GbE client connectivity. Upgrades must be
performed by a Dell installer or certified
business partner.
Performing Pre-Upgrade Tasks
Complete the following tasks before upgrading.
• The FluidFS cluster must be at FluidFS version 2.0.7630 or later before upgrading to FluidFS version
3.0.
• When upgrading to V3 “admin” user will not be available anymore, and local “Administrator” must be
used instead. Make sure to know its password, Administrator password must be changed up to 24
Hours before the upgrade. To change Administrator password Login to CLI ( Using SSH ) and run the
following command :system authentication local-accounts users change-password Administrator
CAUTION: The password you set will be required to manage the FluidFS cluster after
upgrading to version 3.0. Make sure that you remember this password or record it in a secure
location.
• Change the FluidFS cluster name to match the NetBIOS name, if needed. Also, ensure that the FluidFS
cluster name is no longer than 15 characters and does not begin with a digit.
• Change the internal subnet to a Class C subnet, if needed.
• Convert user‐defined administrator accounts to local users, if needed.
• Change policies that mount the \\<client_VIP_or_name>\homes share to mount the \
\<client_VIP_or_name>\<path_prefix>\<username> share, if needed.
24
Page 25

• Delete local user names that have a period as the last character and re‐create the accounts with a
different name, if needed.
• Change the NDMP client port to be in the range 10000–10100, if needed. You must also make the
reciprocal change on the DMA servers.
• Stop all NDMP backup sessions, if needed. If an NDMP backup session is in progress during the
upgrade, the temporary NDMP snapshot is left in place.
• Open additional ports on your firewall to allow replication between replication partners, if needed.
• Remove parentheses characters from the Comment field for CIFS shares and NFS exports.
• Ensure the NAS volumes do not have the following names (these names are reserved for internal
FluidFS cluster functions):
– .
– ..
– .snapshots
– acl_stream
– cifs
– int_mnt
– unified
– Any name starting with locker_
• Ensure that at least one of the defined DNS servers is accessible using ping and dig (DNS lookup
utility).
• Ensure that the Active Directory domain controller is accessible using ping and that the FluidFS cluster
system time is in sync with the Active Directory time.
• Ensure that the NAS controllers are running, attached, and accessible using ping, SSH, and rsync.
• Although the minimum requirement to upgrade is that at least one NAS controller in each NAS
appliance must be running, Dell recommends ensuring that all NAS controllers are running before
upgrading.
• Ensure that the FluidFS cluster system status shows running.
Upgrading from FluidFS Version 2.0 to 3.0
Use the following procedure to upgrade a Dell PowerVault NX3500/NX3600/NX3610 FluidFS cluster from
FluidFS version 2.0 to 3.0.
25
Page 26
NOTE:
• Perform pre‐upgrade tasks.
• Installing a service pack causes the NAS controllers to reboot during the installation process.
This might cause interruptions in CIFS and NFS client connections. Therefore, Dell recommends
scheduling a maintenance window to perform service pack installations.
• Contact Dell Technical Support Services to obtain the latest FluidFS version 3.0 service pack. Do
not modify the service pack filename.
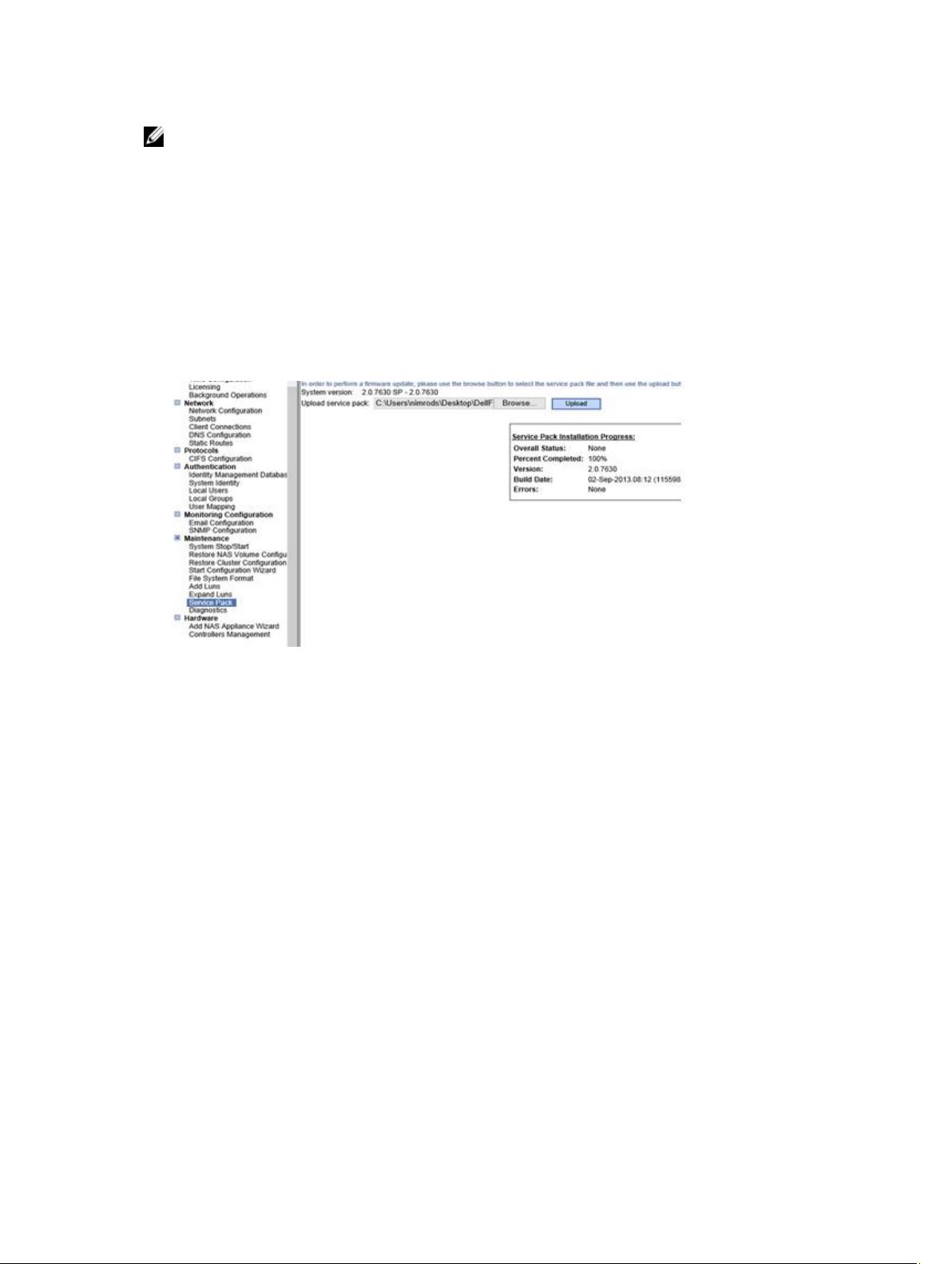
1. Login to the FluidFS v2 Manager application using a browser and go to Cluster Management →
Cluster Management → Maintenance → Service Packs.
2. Browse to the ISO location and click Upload.
The system starts uploading the service pack file.
26
Page 27
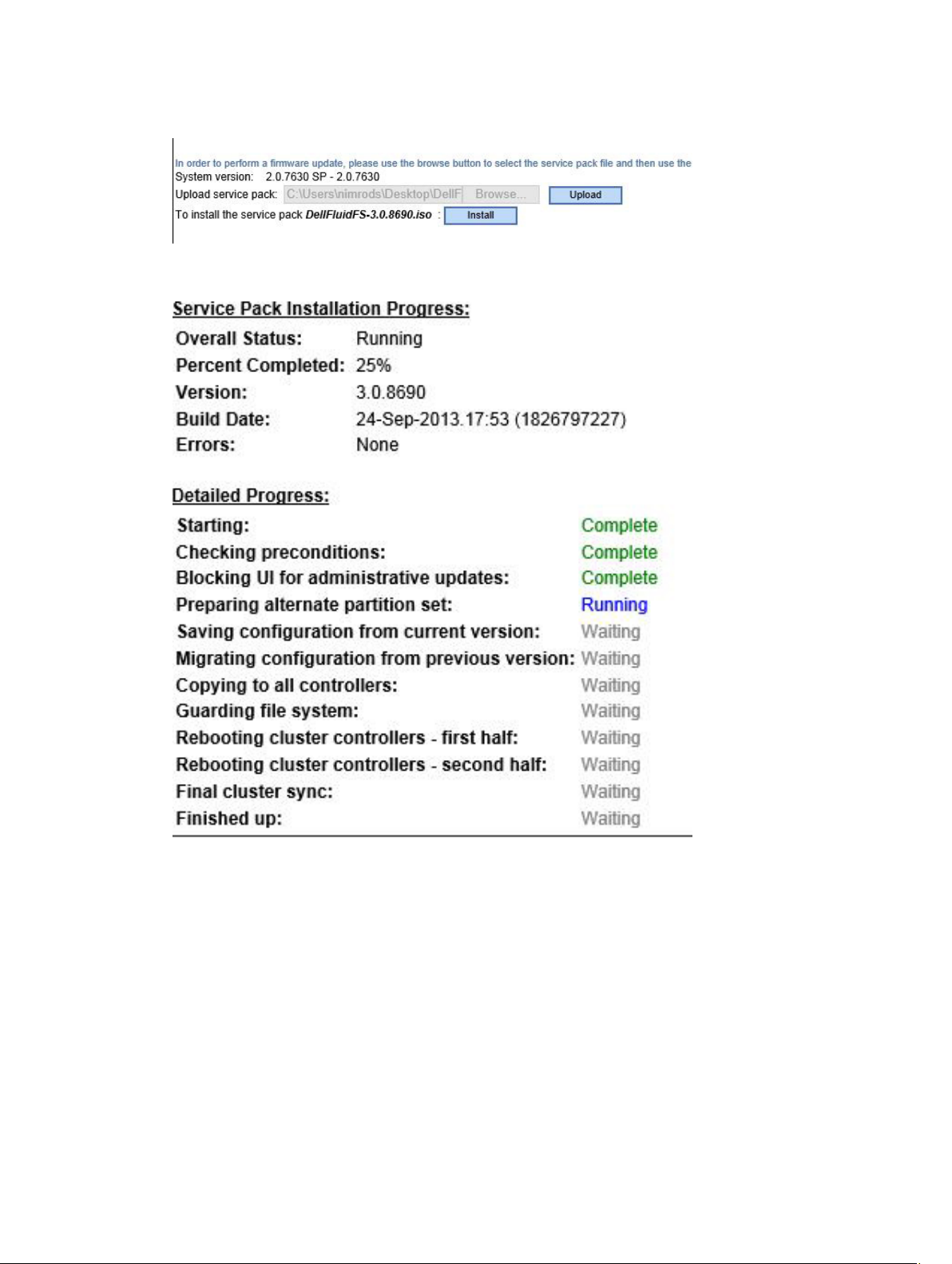
3. When the file is uploaded, click Install.
The upgrade process starts and may take an hour or more. The upgrade’s progress is displayed as
follows:
4. During the upgrade, you will be notified that a node has been rebooted. After receiving this message,
wait 15 minutes more so that the reboot of both nodes and the Final Sync are completed.
5. Login again with the Administrator user (the Admin user is no longer available). The new FluidFS
version 3 Manager UI is displayed.
6. Make sure the system is fully operational and all components are in Optimal status, before you start
working with it.
27
Page 28

28
Page 29
3
FluidFS Manager User Interface Overview
FluidFS Manager Layout
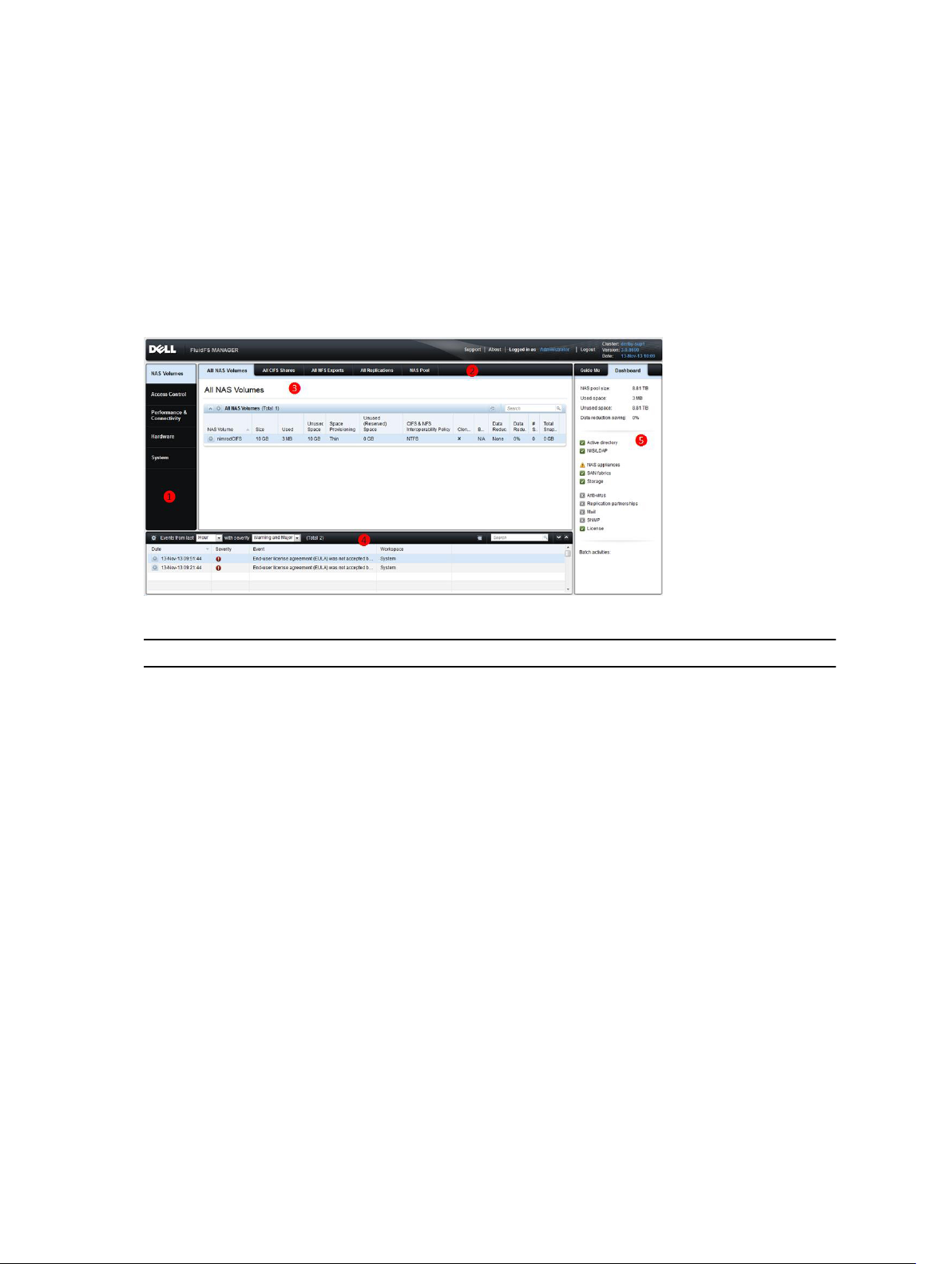
The following image and legend describe the layout of the FluidFS Manager.
Figure 2. FluidFS Manager Web User Interface Layout
FluidFS Manager Sections
❶ Left-hand tabs, used to select a view topic.
❷ Upper tabs, used to select a view subtopic.
❸ Main view area, containing one or more panes. Each pane refers to a different FluidFS
element or configuration setting, which can be viewed/modified/deleted.
❹ The event log, which shows a sortable table of event messages.
❺ The dashboard, which displays various system statistics, statuses and services at a glance.
Navigating Views
A specific FluidFS Manager view is displayed when you select a topic, by clicking the topic tab on the left,
and select a subtopic, by clicking a subtopic tab on top.
For example, to display the System\SNMP view, click the System tab on the left and the SNMP tab on
top.
The FluidFS elements and settings related to the view you selected are displayed in the main view area.
29
Page 30
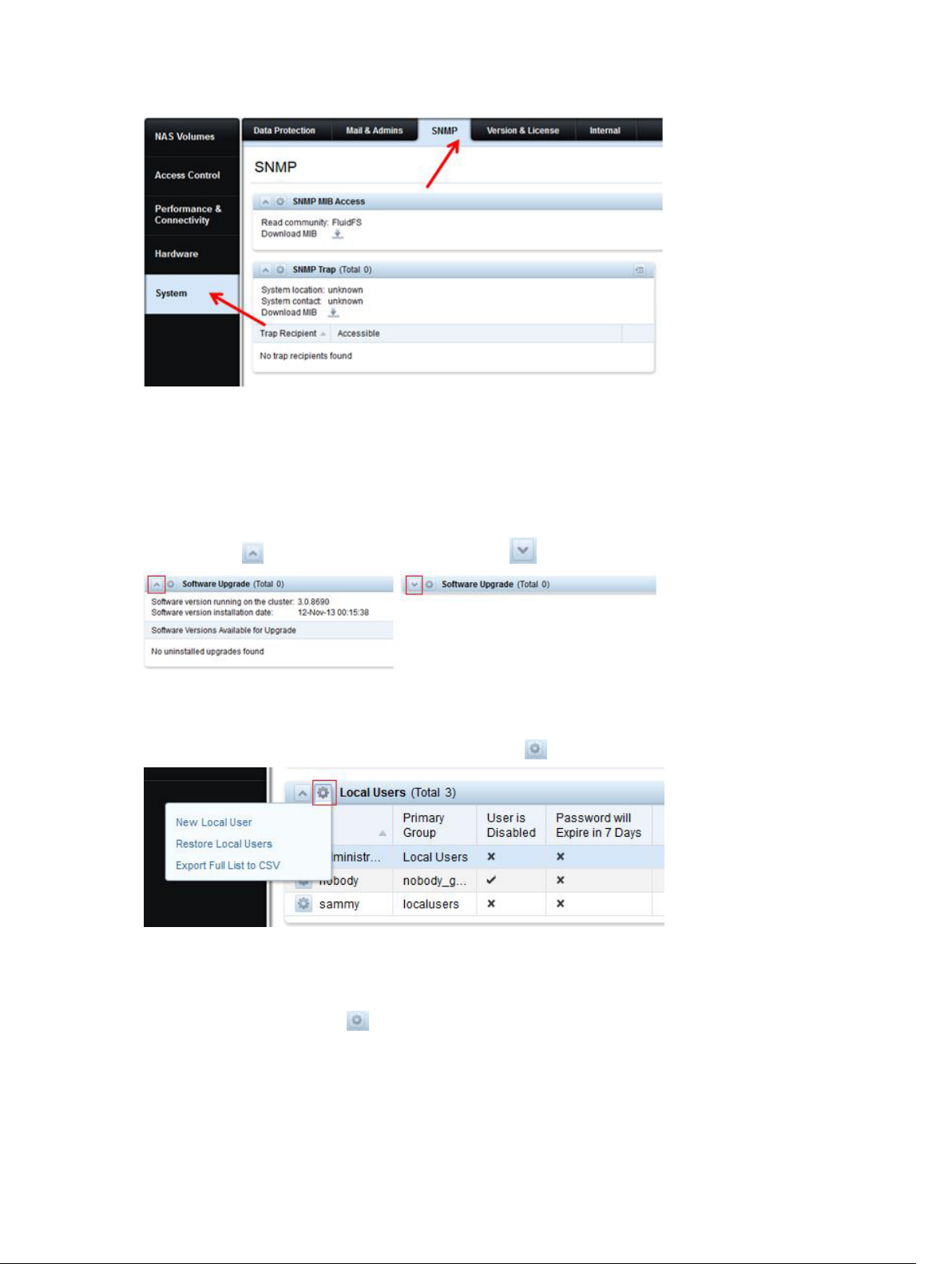
Figure 3. Navigating Views in FluidFS Manager
Working With Panes, Menus, And Dialogs
Showing And Hiding Panes
Panes within the main view area display FluidFS elements and settings. A pane’s contents may be hidden
by clicking the button, and displayed by clicking the button.
Opening A Pane Menu
To modify a setting or add an element to a pane, click the button and select the desired menu option.
Opening A Table Element Menu
Some panes display a table of elements, each of which may be edited independently. To modify or delete
an element in a table, click the button in the row of the element you want to change, then select the
desired menu option.
30
Page 31

Changing Settings Within A Dialog
When you select a menu option, a dialog box is displayed, which allows you to modify or delete the
element or setting you chose. When you edit a setting and click OK, the dialog closes and the change
takes effect.
31
Page 32

Accessing NAS Volume SubTopics
NAS Volumes have additional configuration subtopics that are not displayed by default. To display NAS
Volume subtopics and their views:
1. Enter the NAS Volumes / All NAS Volumes view.
2. In the All NAS Volumes pane, click in the row of the volume whose subtopic views you want to
display.
3. Click View Details.
The top tabs are replaced by the volume subtopic tabs, and you can access their views by clicking
them.
Working With The Event Log
FluidFS generates events to log normal operations and problems. Events allow you to monitor the FluidFS
cluster, and detect and solve problems.
Events are logged to the Event Log.
Viewing The Event Log
You can view events contained in the Event Log, displayed in the bottom pane of the FluidFS Manager.
32
Page 33

Figure 4. Event Log
Viewing Event Details
View detailed information for an event contained in the Event Log.
In the Events pane on the bottom of the FluidFS Manager interface, click in the row of the event
whose details you want to view. A dialog box displays the event details.
Sorting The Event Log
You can sort events contained in the Event Log by column heading.
In the Events pane on the bottom of the FluidFS Manager interface, click the column headings of the
table to sort the events by the values in that column (for example Date, Event).
Searching the Event Log
Search events contained in the Event Log for a specified string.
1. In the Search field at the top-right of the Events pane, type a search string
2. Press Enter or click the icon.
3. The Events table displays all events containing the search string (the search is case-insensitive).
33
Page 34

34
Page 35

4
FluidFS 3.0 System Management
Connecting to the FluidFS Cluster
As a storage administrator, you can use either the FluidFS Manager web client or command line interface
(CLI) to connect to and manage the FluidFS cluster. The FluidFS cluster is accessed through the client
network.
NOTE: To avoid potential management conflicts, Dell recommends that you do not attempt to log
on to both FluidFS Manager and the CLI at the same time.
Connecting to the FluidFS Cluster Using the FluidFS Manager Web Client
Through a browser, log on to the FluidFS Manager web client to manage the FluidFS cluster.
1. In a browser, enter the FluidFS Manager URL.
The URL for the FluidFS Manager any of the FluidFS VIPs or the DNS name. For example, http://
172.41.2.200/login.
The FluidFS login window is displayed.
2. In the Username field, type the administrator user name.
By default, the administrator username is Administrator.
3. In the Password field, type the administrator password.
By default, the administrator username is Stor@ge!
4. Click Ok.
The FluidFS Manager All NAS Volumes screen is displayed.
Connecting to the FluidFS Cluster CLI Using a VGA Console
Log on to the CLI using a VGA console to manage the FluidFS cluster.
Connect a monitor to one of the NAS controller’s VGA port and connect a keyboard to its USB ports.
1. In the command line, type cli at the login as prompt.
A welcome message is displayed.
2. Type the FluidFS cluster administrator user name at the login as prompt.
The default user name is Administrator.
3. Type the FluidFS cluster administrator password at the password prompt.
The default password is Stor@ge!
You are logged on to the CLI and a Welcome window is displayed, listing the installed FluidFS version
and the available commands in the main menu.
35
Page 36

Connecting to the FluidFS Cluster CLI through SSH Using a Password
Log on to the CLI through SSH to manage the FluidFS cluster.
1. Use either of the following options:
– For Windows — Using an SSH client, connect to a client VIP. From the command line, type cli at
the login as prompt:
– For UNIX/Linux — type the following command from a prompt:
ssh cli@<client_VIP_or_name>
2. Type the FluidFS cluster administrator user name at the login as prompt.
The default user name is Administrator.
3. Type the FluidFS cluster administrator password at the password prompt.
The default password is Stor@ge!
You are logged on to the CLI and a Welcome window is displayed, listing the installed FluidFS version
and the available commands in the main menu.
Connecting to the FluidFS Cluster CLI through SSH without Using a Password
You can use SSH keys to bypass the SSH login prompt to manage the FluidFS cluster.
1. Log on to a UNIX/Linux workstation for which you want to bypass the SSH login prompt.
2. From the command line, type the following command:
ssh-keygen -t rsa
3. Press <Enter> at the Enter file in which to save the key (/home/<user_name>/.ssh/id_rsa)
prompt.
4. Press Enter at the Enter passphrase (empty for no passphrase) prompt and again at the Enter same
passphrase again prompt.
An SSH key is generated at /home/<user_name>/.ssh/id_rsa.pub.
5. Copy the SSH key.
6. Log on to the FluidFS system using the CLI with the administrator username and password.
7. Type the following command:
system administrators edit Administrator -SSHKey “<SSH_key>” in the CLI using a
password.
8. Now you can use the following command to log on to the FluidFS cluster from the workstation
without needing a password:
ssh <FluidFS_administrator_user_name>@<client_VIP_or_name>
9. You can also use the following format to run commands from the workstation without needing a
password:
ssh <FluidFS_administrator_user_name>@<client_VIP_or_name> <CLI_command>
Managing Secured Management
By default, all FluidFS cluster management ports are open on all subnets, along with the other ports
needed for client access (CIFS/NFS), replication, and NDMP. Secured management, when enabled,
exclusively limits all management traffic to one specific subnet. The subnet on which secured
management is enabled also has the necessary ports open for client access, replication, and NDMP
36
Page 37

traffic. Other subnets will not have any of the management ports listening on them, making them
available only for client access, replication, and NDMP traffic. This prevents users on client (data) access
subnets from accessing any FluidFS cluster management functions.
In FluidFS, the ports listed in the following table do not participate in CIFS/NFS communication, but are
exposed on the client network by default. Enabling secured management allows you to expose the
management ports on a management subnet only.
Service Ports
Web Services 80
Secure Web Services 443
FTP 44421
FTP (Passive) 44430–44439
SSH 22
FluidFS Manager communication 35451
Secured management can be enabled only after the system is deployed. To make a subnet secure:
• It must exist prior to enabling the secured management feature
• It can reside on the client network (subnet‐level isolation of management traffic) or the LOM (Lights
Out Management) Ethernet port (physical isolation of management traffic). The LOM Ethernet port is
on the lower right side of the back panel of a NAS controller.
• Log in from this subnet.
Secured management configuration, together with other networking features, is accessed through the
Security Access pane in the System\Internal view.
Adding a Secured Management Subnet
The subnet on which you enable secured management must exist prior to enabling the secured
management feature.
To add a secured management subnet:
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
4. Click New Subnet for FluidFS Management.
The New Subnet for FluidFS Management dialog box is displayed.
5. Click to the right of the VIP1 field.
6. In the IP Address field, type a management IP address and click OK.
7. For each NAS controller:
a) Click to the right of the NAS controller field.
b) In the IP Address field, type an IP address for the NAS controller and click OK.
8. To automatically fill the IP addresses for the NAS Controllers and VIP, click Auto Fill.
37
Page 38

9. (Optional) Configure the remaining FluidFS management subnet attributes as needed.
– To change the netmask of the network, type a netmask in the Netmask field.
– To specify a VLAN ID, type a VLAN ID in the VLAN Id field.
When a VLAN spans multiple switches, the VLAN ID is used to specify to which ports and
interfaces to send broadcast packets.
10. To separate the new subnet from all client subnets, select This subnet should be physically
separated from all client subnets.
11. Click OK.
Changing the Netmask for the Secured Management Subnet
Change the netmask for the secured management subnet.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
4. Click Modify Subnet for FluidFS Management.
The Modify Subnet for FluidFS Management dialog box is displayed.
5. In the Netmask field, type a netmask for the secured management subnet.
6. Click OK.
Changing the VLAN ID for the Secured Management Subnet
Change the VLAN ID for the secured management subnet. When a VLAN spans multiple switches, the
VLAN ID is used to specify to which ports and interfaces to send broadcast packets.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
4. Click Modify Subnet for FluidFS Management.
The Modify Subnet for FluidFS Management dialog box is displayed.
5. In the VLAN Id field, type a VLAN Id for the secured management VLAN Id.
6. Click OK.
Changing the VIP for the Secured Management Subnet
Change the secured management subnet VIP through which the administrator manages the FluidFS
cluster.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
4. Click Modify Subnet for FluidFS Management.
The Modify Subnet for FluidFS Management dialog box is displayed.
5. Click to the right of the VIP1 field.
6. In the IP Address field, type the new VIP address and click OK.
38
Page 39

7. Click OK.
Changing the NAS Controller IP Addresses for the Secured Management Subnet
Change the NAS controller IP addresses for the secured management subnet.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
4. Click Modify Subnet for FluidFS Management.
The Modify Subnet for FluidFS Management dialog box is displayed.
5. Click to the right of the NAS controller you want to change.
6. In the IP Address type an IP address for the NAS controller and click OK.
7. Click OK.
Deleting the Secured Management Subnet
Delete the secured management subnet if you no longer want to exclusively limit management traffic to
one specific subnet.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
4. Click Delete Subnet for FluidFS Management .
The Delete Subnet for FluidFS Management dialog box is displayed.
5. Click OK.
Enabling Secured Management
Enable secured management to exclusively limit management traffic to one specific subnet.
NOTE:
After enabling secured management, if you are connected to FluidFS Manager through the secured
management subnet, your management session is temporarily interrupted while the change takes
effect. During this time the following message is displayed in FluidFS Manager:
Communication with the cluster was interrupted in process of issuing a command that performs
modification to the cluster.
After the change takes effect, your management session will resume automatically. Management
sessions on all other subnets are disconnected.
NOTE: The subnet on which you enable secured management must exist prior to enabling the
secured management feature.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
39
Page 40

4. Click Restrict Access of FluidFS Management.
The Restrict Access of FluidFS Management dialog box appears.
5. Check the box whose text starts with All FluidFS management communication….
6. Click OK.
Disabling Secured Management
Disable secured management to allow management traffic from any subnet.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Security Access pane, click .
4. Click Restrict Access of FluidFS Management.
The Restrict Access of FluidFS Management dialog box appears.
5. Uncheck the box whose text starts with All FluidFS management communication….
6. Click OK.
Managing the FluidFS Cluster Name
The FluidFS cluster name is a unique name used to identify the FluidFS cluster in FluidFS Manager and the
name that clients use to access the FluidFS cluster. This name is also the FluidFS cluster NetBIOS name.
If clients access the FluidFS cluster by name (instead of IP address), you must add an entry in the DNS
server that associates the FluidFS cluster name to the FluidFS cluster client VIPs. If you are using multiple
client VIPs, add all client VIPs to the DNS server and associate them with the same FluidFS cluster name
(known as round‐robin DNS). This enables client load balancing between client VIPs.
Viewing the FluidFS Cluster Name
View the current FluidFS cluster name that is displayed in FluidFS Manager and the name that clients use
to access the FluidFS cluster.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. The FluidFS cluster name is displayed in the Internal Settings pane, in the Cluster name field.
Renaming the FluidFS Cluster
Changing the FluidFS cluster name changes the name that is displayed in FluidFS Manager and the name
that clients use to access the FluidFS cluster. You must also make the reciprocal change on the DNS
server.
1. Click the System tab on the left.
2. Click the Internal tab on top.
3. In the Internal Settings pane, click .
4. Click Modify Cluster Name.
The Modify Cluster Name dialog box appears.
5. In the Cluster Name field, type a new name for the FluidFS cluster.
6. Click OK.
40
Page 41

Managing Licensing
The license determines which NAS features are available in the FluidFS cluster.
Viewing License Information
All FluidFS cluster features are automatically included in the license for PowerVault scale‐out NAS. FluidFS
Manager displays FluidFS cluster license information, but the license cannot be modified.
1. Click the System tab on the left.
2. Click the Version & License tab on top.
The license information is displayed in the License pane.
Accepting the End-User License Agreement
You must accept the end‐user license agreement (EULA) before using the system. Accepting the EULA is
usually completed during deployment.
1. Click the System tab on the left.
2. Click the Version & License tab on top.
3. In the License Agreement pane, click .
4. Click Accept License Agreement.
The License Agreement dialog box appears.
5. Click the box next to I accept the license agreement terms and click OK
Managing the System Time
Setting the system time enables:
• Windows clients to mount the file system
• Scheduled activities, such as snapshot and replication tasks, to occur at the appropriate time
• The correct time to be recorded in the Event Log.
There are two options for setting the system time:
• Manually set the time: Manually set the time for the FluidFS cluster.
• Automatically synchronize the time with an NTP server: Network Time Protocol (NTP) synchronizes
clocks over a network. If the FluidFS cluster is part of a Windows network, the Active Directory server
can serve as the NTP server. If the FluidFS cluster is not part of a Windows network, configure it to
synchronize with a local NTP server (if such a server exists), or with an NTP server on the Internet.
Viewing the Time Zone
View the current time zone for the FluidFS cluster.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. The time zone is displayed in the Time pane.
41
Page 42

Setting the Time Zone
Set the time zone for the FluidFS cluster.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Time pane, click .
4. Click Modify Time Configuration.
The Modify Time Configuration dialog box appears.
5. Click the […] button to the right of the Time Zone field.
The Time Zone Search window opens.
6. Type the name of the city or region that represents the time zone and click the button.
NOTE: If the time zone is not found, try entering another search string.
7. When your time zone is found, click OK.
8. Click OK.
Viewing the Time
The system date and time are displayed in the upper right corner of the FluidFS Management web client
application.
Setting the Time Manually
Manually set the time for the FluidFS cluster if you are not using NTP.
NOTE: NTP must be disabled.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Time pane, click .
4. Click Modify Current Time .
The Modify Current Time dialog box appears.
5. Click the […] button to the right of the Date and time field.
The Choose Date and Time window opens.
6. Click the [-] and [+] buttons to adjust the year, month, day, hour, minute and second values, then
click OK
7. Click OK.
Viewing the NTP Servers
View the current NTP servers for the FluidFS cluster.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. The NTP servers are displayed in the Time pane.
42
Page 43

Add or Remove NTP Servers
Add one or more NTP servers with which to synchronize the FluidFS cluster time. Adding multiple NTP
servers ensures continued time synchronization in the event of an NTP server failure. If the FluidFS cluster
cannot establish contact with the first server, it attempts to connect to the remaining servers in order.
Remove an NTP server if it is no longer available.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Time pane, click .
4. Click Modify Time Configuration.
The Modify Time Configuration dialog box appears.
5. Add or remove NTP servers.
– To add an NTP server, type the host name or IP address of an NTP server in the NTP Servers text
field and click Add.
– To remove NTP server, select an NTP server from the NTP Servers list and click
6. Click OK.
Enabling NTP
Enable NTP to synchronize the FluidFS cluster time with an NTP server.
NOTE: Add one or more NTP servers with which to synchronize the FluidFS cluster time.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Time pane, click .
4. Click Modify Time Configuration.
The Modify Time Configuration dialog box appears.
5. Select the Use NTP server(s) to keep the cluster time synchronized check box.
6. Click OK.
Disabling NTP
Disable NTP if you prefer to manually set the FluidFS cluster time.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Time pane, click .
4. Click Modify Time Configuration.
The Modify Time Configuration dialog box appears.
5. Uncheck the Use NTP server(s) to keep the cluster time synchronized check box.
6. Click OK.
43
Page 44

Managing the FTP Server
The FluidFS cluster includes an FTP server that provides a storage location for the following types of
system files:
• Diagnostic results files
• License file
• SNMP MIBs and traps
• Service pack files
Accessing the FTP Server
The FTP server can be accessed at:
ftp://<FluidFS_administrator_user_name>@<client_VIP_or_name>:44421/
For example:
ftp://Administrator@172.22.69.32:44421/
Upon access, you are prompted for the FluidFS cluster administrator password.
Enabling or Disabling the FTP Server
By default, the FTP server is enabled to allow FluidFS Manager to transfer the FluidFS cluster diagnostics.
The FTP server must be enabled to upload service packs and license files, to access and transfer FluidFS
cluster diagnostic results, and to access SNMP MIBs and traps.
To enable or disable the FTP server:
1. Click the System tab on the left.
2. Click the Internal tab on the top.
3. In the Security Access pane, click .
4. Click Modify FTP Accessibility Policy.
The Modify FTP Accessibility Policy dialog box appears.
5. Enable or disable the FTP server.
– To enable the FTP server, select the Allow FTP Access`check box.
– To disable the FTP server, clear the Allow FTP Access check box.
6. Click OK.
Managing SNMP
Simple Network Management Protocol (SNMP) is one way to monitor the health of the system and
generate alert messages (SNMP traps) for system problems. To use SNMP, the FluidFS cluster‐specific
Management Information Bases (MIBs) and traps must be compiled into a customer‐provided SNMP
management station. The MIBs are databases of information specific to the FluidFS cluster.
44
Page 45

Obtaining SNMP MIBs and Traps
The SNMP MIBs and traps for the FluidFS cluster are available for download from the FluidFS cluster FTP
server.
NOTE: The FTP server must be enabled.
Download the SNMP MIBs and traps from:
ftp://<FluidFS_administrator_user_name>@<client_VIP_or_name>:44421/mibs/
Changing the SNMP Read-Only Community
Change the read‐only community for devices reading SNMP variables from the FluidFS cluster. By default,
the read‐only community is
1. Click the System tab on the left.
2. Click the SNMP tab on the top.
3. In the SNMP MIB Access pane, click .
4. Click Modify Settings.
The Modify MIB SNMP Access Settings dialog box appears.
5. Type the new community name in the Read community field.
6. Click OK.
FluidFS.
Changing the SNMP Trap System Location or Contact
Change the system location or contact person for FluidFS cluster‐generated SNMP traps. By default, the
SNMP trap system location and contact person are
1. Click the System tab on the left.
2. Click the SNMP tab on the top.
3. In the SNMP Trap pane, click .
4. Click Modify Settings.
The Modify MIB SNMP Trap Settings dialog box appears.
5. To change the SNMP trap system location, type a new location in the System location field.
6. To change the SNMP trap system contact, type a new contact in the System contact field.
7. Click OK.
unknown.
Adding or Removing SNMP Trap Recipients
Add or remove hosts that receive the FluidFS cluster‐generated SNMP traps.
1. Click the System tab on the left.
2. Click the SNMP tab on the top.
3. In the SNMP Trap Access pane, click .
4. Click Modify Settings.
The Modify MIB SNMP Trap Settings dialog box appears.
45
Page 46

5. Add or remove SNMP trap recipients.
– To add an SNMP trap recipient, type a host name or IP address in the Trap Recipients text field
and click Add.
– To remove an SNMP trap recipient, select an SNMP trap recipient and click the button.
6. Click OK.
Enabling or Disabling SNMP Traps
Enable or disable SNMP traps by category (NAS Volumes, Hardware, Access Control, Performance &
Connectivity, or System). For enabled SNMP traps, specify the severity of events for which to send SNMP
traps.
1. Click the System tab on the left.
2. Click the SNMP tab on the top.
3. In the SNMP Trap Filter pane, click .
4. Click Modify.
The Modify SNMP Trap Filter Settings dialog box appears.
5. Enable or disable SNMP traps.
– To enable SNMP traps, check the events for which to send SNMP traps (NAS Volumes, Hardware,
Access Control, Performance & Connectivity, or System) and select the severity (Major or All) of
events to be sent.
– To disable SNMP traps, uncheck the events that you don’t want to be sent.
6. Click OK.
Managing the Health Scan Throttling Mode
Health scan throttling has three modes:
• Normal(Default mode): Health scan is running and scanning the file system to identify potential errors.
• Maintenance: Health scan is running in high priority and scanning the file system to identify potential
errors.
• Off: Health scan is off and does not run.
NOTE: Dell recommends keeping the health scan throttling mode set to Normal unless directed
otherwise by Dell Technical Support Services.
Viewing the Health Scan Throttling Mode
View the current health scan throttling mode.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
The health scan throttling mode is displayed in the Background Processes pane.
46
Page 47

Changing the Health Scan Throttling Mode
Change the health scan throttling mode. Dell recommends keeping the health scan throttling mode set
to Normal unless specifically directed otherwise by Dell Technical Support Services.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
3. In the Background Processes pane, click .
4. Click Modify Health Scan Settings.
The Modify Health Scan Settings dialog box appears.
5. Select the mode you want (Normal mode, Maintenance mode, or Off).
6. Click OK.
Managing the Operation Mode
The FluidFS cluster has three operation modes:
• Normal: System serves clients using CIFS and NFS protocols and operates in mirroring mode.
• Write‐Through Mode: System serves clients using CIFS and NFS protocols, but is forced to operate in
journaling mode. This might have an impact on write performance. This mode of operation is
recommended when, for example, you have repeated electric power failures.
• No Service: System does not serve clients using CIFS or NFS protocols and allows limited
management capabilities. This mode must be enabled before replacing a NAS appliance.
Viewing the Operation Mode
View the current operation mode.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
The operation mode is displayed in the Internal Settings pane, in the Operation Mode field.
Changing the Operation Mode
Changing the operation mode might affect the accessibility and performance of CIFS shares and NFS
exports.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
3. In the Internal Settings pane, click .
4. Click Modify Operation Mode.
The Modify Operation Mode dialog box appears.
5. Select a new operation mode (Normal, Write‐Through on, or No service).
6. You must select the check box next to I acknowledge that changing system operation mode may
have impact on the system accessibility and/or performance
7. Click OK.
.
47
Page 48

Managing Client Connections
Displaying the Distribution of Clients between NAS Controllers
Display the current distribution of clients between NAS controllers.
1. Click the Performance & Connectivity tab on the left.
2. Click the Load Balancing tab on the top.
In the Current Activity pane, the client/router IPs and the NAS Controllers they are connected to are
displayed.
Viewing Clients Assigned to a NAS Controller
View clients that are currently assigned to a particular NAS controller.
1. Click the Performance & Connectivity tab on the left.
2. Click the Load Balancing tab on the top.
In the Current Activity pane you can see all clients and the controllers and corresponding interfaces
to which they are connected (in the NAS Controller column).
Assigning a Client to a NAS Controller
You can permanently assign one or more clients to a particular NAS controller. However, for effective
load balancing, Dell does not recommend manually assigning clients to NAS controllers.
Assigning a client to a NAS controller disconnects the client’s connection. Clients automatically
reconnect to the assigned NAS controller.
1. Click the Performance & Connectivity tab on the left.
2. Click the Load Balancing tab on the top.
3. In the Current Activity pane, click in the row of the client that you want to assign to the NAS
controller.
4. Click Pin Client to NAS Controller.
The Pin Client to NAS Controller dialog box appears.
5. Select the Pin this client to NAS controller check box.
6. Select the NAS controller to which to assign the client.
7. Select the client interface on the NAS controller to which to assign the client.
8. Click OK.
Unassigning a Client from a NAS Controller
You can permanently unassign one or more clients from a particular NAS controller so the client is
subject to the regular FluidFS cluster load balancing.
1. Click the Performance & Connectivity tab on the left.
2. Click the Load Balancing tab on the top.
3. In the Current Activity pane, click in the row of the client that you want to unassign from a NAS
controller..
48
Page 49

4. Click Pin Client to NAS Controller.
The Pin Client to NAS Controller dialog box appears.
5. Ensure that the Pin Client to NAS Controller check box is unchecked.
6. Click OK.
Manually Migrating Clients to another NAS Controller
You can manually migrate clients between NAS controllers if, for example, there is an imbalance in
network load on the NAS controllers. Migrating a client to another NAS controller disconnects the client’s
connection. Clients will then automatically reconnect to the NAS controller to which they were migrated.
1. Click the Performance & Connectivity tab on the left.
2. Click the Load Balancing tab on the top.
3. In the Current Activity pane, click in the row of the client you want to migrate.
4. Click Move to another controller.
The Move Client to NAS Controller dialog box appears.
5. From the Move this client to drop‐down menu, select the NAS controller to which to migrate the
client.
6. Click OK.
Failing Back Clients to Their Assigned NAS Controller
You must fail back client connections to their original NAS controller when a NAS controller that was
down becomes available.
Failing back client connections disconnects only the client connections that failed over due to the
original NAS controller failure. Those clients automatically reconnect to the assigned NAS controller.
1. Click the Performance & Connectivity tab on the left.
2. Click the Load Balancing tab on the top.
3. In the Current Activity pane, click .
4. Click Balance Clients.
The Balance Clients Across NAS Controllers dialog box appears.
5. Click Failback clients.
6. Click OK.
Rebalancing Client Connections across NAS Controllers
Rebalancing client connections evenly distributes connections across all the available NAS controllers.
Rebalance client connections in the following scenarios:
• After FluidFS cluster hardware changes (for example, adding a NAS appliance)
• When a NAS controller that was down, becomes available
Rebalancing client connections disconnects all client connections. Clients automatically reconnect to the
FluidFS cluster.
1. Click the Performance & Connectivity tab on the left.
2. Click the Load Balancing tab on the top.
3. In the Current Activity pane, click .
49
Page 50

4. Click Balance Clients.
The Balance Clients Across NAS Controllers dialog box appears.
5. Click Rebalance clients.
6. Click OK.
Shutting Down and Restarting NAS Controllers
In some cases, you must temporarily shut down a FluidFS cluster or reboot a NAS controller.
Shutting Down the FluidFS Cluster
In some cases, you might need to temporarily shut down all NAS controllers in a FluidFS cluster. For
example, you might need to do this if you are moving the NAS hardware to a different location. When a
FluidFS cluster is shut down, NAS volume data is no longer available to clients and clients are
disconnected.
NOTE: Dell recommends scheduling a maintenance window and informing clients that the
resources hosted by the FluidFS cluster is unavailable.
1. Change the FluidFS cluster operation mode to No Service.
For more information on changing the FluidFS cluster operation mode, see Changing the Operation
Mode
2. To shut down the NAS controllers, press and release the recessed power button at the back of each
NAS controller.
NOTE: Do not press and hold the power button down for several seconds. Pressing and holding
the power button down for several seconds does not shut down the NAS controllers.
Starting Up the FluidFS Cluster
Start up a FluidFS cluster to resume operation after shutting down all NAS controllers in a FluidFS cluster.
NOTE: Before turning on the system, ensure that all cables are connected, and all components are
connected to a power source.
1. If previously shutdown, turn the MD system(s) back on before starting the FluidFS cluster.
2. Press and release the recessed power button at the back of each NAS controller to turn on the NAS
controllers.
3. Change the FluidFS cluster operation mode to Normal.
For more information on changing the FluidFS cluster operation mode, see Changing the Operation
Mode
Rebooting a NAS Controller
Only one NAS controller can be rebooted in a NAS appliance at a time. Rebooting a NAS controller
disconnects client connections while clients are being transferred to other NAS controllers. Clients
automatically reconnect to the FluidFS cluster.
1. Click the Hardware tab on the left.
2. Click the NAS Appliances tab on the top.
3. In the Overview pane, click in the row of the NAS appliance you want to reboot.
50
Page 51

4. Click Reboot.
The Reboot NAS Controller dialog box appears.
5. Click OK.
Managing NAS Appliance and NAS Controller
You can configure the system identification button on the NAS appliances or controllers to blink, in order
to easily locate that particular NAS appliance or controller within a rack. The system identification button
for a NAS appliance is located on the front panel and is labeled. The system identification button for a
NAS controller is located on the back panel.
Enabling or Disabling NAS Appliance and Controller Blinking
When NAS appliance blinking is enabled, the system identification button blinks so you can easily locate
the NAS appliance within a rack.
1. Click the Hardware tab on the left.
2. Click the NAS Appliances tab on the top.
3. In the Overview pane, click in the row of the NAS appliance you want to enable or disable.
4. Click Blink.
The Blink NAS Appliance dialog box appears.
5. To enable or disable NAS appliance blinking, choose one of the following options:
– Turn off blinking for the NAS appliance and its NAS controllers
– Turn on blinking for the NAS appliance and both its NAS controllers
– Turn on blinking for the NAS appliance and its NAS controller in slot 1
– Turn on blinking for the NAS appliance and its NAS controller in slot 2
6. Click OK.
51
Page 52

52
Page 53

5
FluidFS 3.0 Networking
Managing the Default Gateway
The default gateway enables client access across subnets. Only one default gateway can be defined. If
client access does not go through a router (i.e. this is a flat network), a default gateway does not need to
be defined.
Viewing the Default Gateway
View the current default gateway.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
The default gateway is displayed in the Routing pane.
Changing the Default Gateway
Change the default gateway if the default gateway changes for the network.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Routing pane, click .
4. Click Modify Default Gateway.
The Modify Default Gateway dialog box appears.
5. In the Default Gateway field, type a new default gateway IP address.
6. Click The OK dialog box appears.
Managing DNS Servers and Suffixes
Domain Name Service (DNS) is a networking service that enables users to locate computers by providing
name‐to‐IP address and IP address‐to‐name resolution services. You can configure one or more external
DNS servers (external to the FluidFS cluster but within the site) to be used for name resolution. A DNS
suffix specifies a DNS domain name without the host part of the name (for example, west.example.com
rather than computer1.west.example.com).
If clients access the FluidFS cluster by name, you must add an entry in the DNS server that associates the
FluidFS cluster name to the FluidFS cluster client VIPs. If you are using multiple client VIPs, add all client
VIPs to the DNS server and associate them with the same FluidFS cluster name (known as round‐robin
DNS). This enables client load balancing between client VIPs. In addition, you must configure DNS if you
are using Active Directory, and the DNS servers must be the same DNS servers that your Active Directory
domain controllers use.
53
Page 54

Viewing DNS Servers and Suffixes
View the current DNS servers providing name resolution services for the FluidFS cluster and the
associated DNS suffixes.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
The DNS servers and suffixes are displayed in the DNS pane.
Adding DNS Servers and Suffixes
Add one or more DNS servers to provide name resolution services for the FluidFS cluster and add
associated DNS suffixes. Adding multiple DNS servers and suffixes ensures continuous name resolution
services in the event of a DNS server failure. If the FluidFS cluster cannot establish contact with the
preferred server, it will attempt to connect to the remaining servers in order.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the DNS pane, click .
4. Click Modify.
The Modify DNS Settings dialog box appears.
5. To add a DNS server, type the IP address of a DNS server in the DNS Servers text field and click Add.
6. DNS servers are listed in descending order of preference.
– To increase the precedence for a DNS server, select a DNS server and click .
– To decrease the precedence for a DNS server, select a DNS server and click .
7. To add a DNS suffix, type the DNS suffix in the DNS Suffixes text field and click Add.
8. DNS suffixes are listed in descending order of preference.
– To increase the precedence for a DNS suffix, select a DNS suffix and click .
– To decrease the precedence for a DNS suffix, select a DNS suffix and click .
9. Click OK.
Removing DNS Servers and Suffixes
Remove a DNS server or DNS suffix if it is no longer available or used.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the DNS pane, click .
4. Click Modify.
The Modify DNS Settings dialog box appears.
5. To remove a DNS server, select a DNS server in the DNS Servers list and click .
6. To remove a DNS suffix, select a DNS suffix in the DNS Suffixes list and click .
54
Page 55

7. Click OK.
Managing Static Routes
To minimize hops between routers, static routes are recommended in routed networks when there are
multiple direct paths from the FluidFS cluster to various routers. Static routes allow you to configure the
exact paths in which the system communicates with various clients on a routed network.
Consider the network shown in the following figure. There can be only one default gateway for the
system. Assume that router X is designated as the default gateway. Packets that are sent to clients in
subnet Y would be routed to router X, which would then be sent back (through the switch) to router Y.
These packets travel through router X needlessly, reducing the throughput to all subnets in the network.
The solution is to define, in addition to a default gateway, a specific gateway for certain subnets by
configuring static routes. To do this, you must describe each subnet in your network and identify the
most suitable gateway to access that subnet.
Static routes do not have to be designated for the entire network—a default gateway is most suitable
when performance is not an issue. You can select when and where to use static routes to best meet
performance needs.
Viewing the Static Routes
View the current static route.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
The static routes are displayed in the Routing pane.
Adding a Static Route
When adding a static route, specify the subnet properties and the gateway through which to access this
subnet.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Routing pane, click .
55
Page 56

4. Click Add Static Route.
The New Static Route dialog box appears.
5. In the Target network subnet ID field, type a network IP address.
For example, 10.10.5.0
6. In the Target subnet netmask field, type a netmask.
For example, 255.255.255.0
7. In the Gateway field, type the gateway IP address through which to access the subnet.
For example, 10.10.5.1
8. Click OK.
Changing the Target Subnet for a Static Route
Change the subnet properties of a static route.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Routing pane, for the static route that you want modify click .
4. Click Modify static route.
The Modify Static Route dialog box is displayed.
5. In the Target network subnet ID field, type a network IP address.
For example, 10.10.5.0
6. In the Target subnet netmask field, type a netmask.
For example, 255.255.255.0
7. In the Gateway field, type the gateway IP address through which to access the subnet.
8. Click OK.
Changing the Gateway for a Static Route
Change the gateway through which to access the subnet for a static route.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Routing pane, for the static route that you want modify click .
4. Click Modify static route.
The Modify Static Route dialog box appears.
5. In the Gateway field, type the gateway IP address through which to access the subnet.
For example, 10.10.5.1
6. Click OK.
Deleting a Static Route
Delete a static route to send traffic for a subnet through the default gateway instead of a specific
gateway.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
56
Page 57

3. In the Routing pane, select the static route that you want modify and click .
4. Click Delete static route.
The Delete Static Route dialog box appears.
5. Click OK.
Managing the Internal Network
The internal network defines the private subnet dedicated to the FluidFS cluster for internal
communication. This range is not routed or accessible by other machines on the network.
Viewing the Internal Network IP Address
View the current internal network IP address. While it is not displayed in FluidFS Manager, the netmask is a
Class C netmask (255.255.255.0).
1. Click the System tab on the left.
2. Click the Internal tab on the top.
The internal network IP address is displayed in the Internal Settings pane.
Changing the Internal Network IP Address
You can change the internal network IP address. However, the netmask cannot be changed from a Class
C netmask (255.255.255.0). The internal subnet must not conflict with other subnets on the network. If
sharing internal switches with other FluidFS clusters, make sure that the internal subnet does not conflict
with the internal subnet used for the other FluidFS clusters.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
3. In the Internal Settings pane, click .
4. Click Modify Internal Network.
The Modify Internal Network dialog box appears.
5. In the Internal network IP address field, type a network IP address.
For example, 10.255.69.0
6. In the Internal network mask field, type a network mask IP address.
For example, 255.255.255.0
7. Click OK.
Managing the Client Networks
The client networks define the client VIP(s) through which clients access CIFS shares and NFS exports. If
client access to the FluidFS cluster is not through a router (in other words, this is a flat network), Dell
recommends defining one client VIP. If clients access the FluidFS cluster through a router, define a client
VIP for each client interface port per NAS controller.
57
Page 58

Viewing the Client Networks
View the current client networks.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
The client networks are displayed in the Subnets pane.
Creating a Client Network
Create a client network on which clients access CIFS shares and NFS exports.
NOTE: A client network must have at least one client VIP.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Subnets pane, click .
4. Click New Client Subnet.
The New Client Subnet dialog box appears.
5. Add an IP address for each NAS controller.
a) To edit one of the NAS Controller IP values (NAS Controller 0 or NAS Controller 1), select the
relevant row in the IP address list and click to edit.
The Edit NAS Controller dialog box appears.
b) In the IP Address field, type an IP address for the NAS controller and click OK.
c) Repeat steps (a) and (b) for each NAS controller.
6. Add client VIPs through which the clients access CIFS shares and NFS exports.
a) To edit one of the VIP values (VIP1, VIP2, VIP3, or VIP4), select the relevant row in the IP address
list and click to edit.
The Edit VIP dialog box appears.
b) In the IP Address field, type an IP address and click OK.
c) Repeat steps (a) and (b) for each VIP you want to edit.
7. To automatically fill the IP addresses for the NAS Controllers and VIP, click Auto Fill.
8. In the Netmask field, type a netmask for the client network.
9. (Optional) Configure the VLAN ID value if needed. Type a VLAN ID in the VLAN ID field.
NOTE: When a VLAN spans multiple switches, the VLAN tag is used to specify to which ports
and interfaces to send broadcast packets.
10. Click OK.
Changing the Netmask for a Client Network
Change the netmask for a client network.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Subnets pane, in the row of the subnet you want to change, click .
58
Page 59

4. Click Modify.
The Modify Client Subnet dialog box appears.
5. In the Netmask field, type a netmask for the client network.
6. Click OK.
Changing the VLAN Tag for a Client Network
Change the netmask for a client network.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Subnets pane, in the row of the subnet you want to change, click .
4. Click Modify.
The Modify Client Subnet dialog box appears.
5. In the VLAN Id field, type a VLAN Id for the client network.
6. Click OK.
Changing the Client VIPs for a Client Network
Change the client VIPs through which clients access CIFS shares and NFS exports.
NOTE: A client network must have at least one client VIP.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Subnets pane, in the row of the subnet you want to change, click .
4. Click Modify.
The Modify Client Subnet dialog box appears.
5. To edit a client VIP through which the clients access CIFS shares and NFS exports:
a) To edit one of the VIP values (VIP1, VIP2, VIP3, or VIP4), select the relevant row in the IP address
list and click to edit.
The Edit VIP dialog box appears.
b) In the IP Address field, type an IP address and click OK.
c) Repeat steps (a) and (b) for each VIP you want to edit.
6. To remove a client VIP, change the IP address value to an empty string.
7. Click OK.
Changing the NAS Controller IP Addresses for a Client Network
Change the NAS controller IP addresses for a client network.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Subnets pane, in the row of the subnet you want to change, click .
4. Click Modify.
The Modify Client Subnet dialog box appears.
59
Page 60

5. To edit one of the NAS Controller IP values (NAS Controller 0 or NAS Controller 1):
a) Select the relevant row in the IP address list and click to edit.
The Edit NAS Controller dialog box appears.
b) In the IP Address field, type an IP address for the NAS controller and click OK.
c) Repeat steps (a) and (b) for each NAS controller.
6. Click OK.
Deleting a Client Network
Delete a client network if clients no longer need to access CIFS shares and NFS exports on that network.
You cannot delete the Primary subnet.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Subnets pane, in the row of the subnet you want to delete, click .
4. Click Delete.
The Delete Client Subnets dialog box appears.
5. Click OK.
Viewing the Client Network MTU
View the current Maximum Transmission Unit (MTU) of the client network.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
The MTU is displayed in the Client interface field.
Changing the Client Network MTU
Change the Maximum Transmission Unit (MTU) of the client network to match your environment.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Client interface pane, click .
4. Click Modify Settings.
The Modify Client Interface Settings dialog box appears.
5. In the MTU field, type a new MTU.
If your network hardware supports jumbo frames, enter 9000, otherwise enter 1500.
6. Click OK.
Viewing the Client Network Bonding Mode
View the current bonding mode (Adaptive Load Balancing or Link Aggregation Control Protocol) of the
client network interface.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
The bonding mode is displayed in the Client interface pane, under the MTU field.
60
Page 61

Changing the Client Network Bonding Mode
Change the bonding mode (Adaptive Load Balancing or Link Aggregation Control Protocol) of the client
network interface to match your environment.
• If using ALB, use one client VIP per client port in the FluidFS cluster.
• If using LACP, use one client VIP per NAS controller in the FluidFS cluster.
1. Click the Performance & Connectivity tab on the left.
2. Click the Client Network & Time tab on the top.
3. In the Client Interface pane, click .
4. Click Modify Settings.
The Modify Client Interface Settings dialog box appears.
5. Click the radio button next to the desired option:
– Without link aggregation
– With link aggregation (IEEE 802.1ax), also known as dynamic 802.3ad or LACP
6. Click OK.
Managing SAN Fabrics
SAN subnets or "fabrics" are the network connections between NAS controllers and PowerVault MD
controllers. In PowerVault systems, the SAN network consists of multiple subnets called SAN, SANb,
SANc, etc.
The number of SAN fabrics depends on the number of SAN ports available on the PowerVault NAS
controllers, and MD controller ports assigned to FluidFS/NAS. The general recommendation is to assign 2
ports on each MD controller to NAS traffic, so the number of SAN subnets are also 2.
The following table summarizes the type and number of physical ports on each type of FluidFS controller:
PowerVault FluidFS Controller
NX3500 1GbE eth30, eth31
NX3600 1GbE eth30, eth31, eth32, eth33
NX3610 10GbE eth30, eth31
As a rule:
• Each NAS Controller should have a SAN NIC and an IP address assigned to each subnet: eth30 on
SAN, eth31 on SANb, and so on.
• Each MD controller should have a port and an iSCSI Portal address assigned to each subnet.
The following table summarizes the typical configuration of a system with 2 NAS controllers and 2 MD
controllers:
Subnet/Fabric
SAN eth30:<IP> eth30: <IP> port0, <Portal IP>
SANb eth31:<IP> eth31:<IP> port1, <Portal IP>
The netmask and MTU on all subnets must be identical on all FluidFS and MD controller ports.
NAS Controller0 NAS Controller1 MD Array
SAN ports Type SAN ports
61
Page 62

Managing SAN Fabrics/Subnets
In the FluidFS Manager, the SAN Fabrics view allows you to manage the various subnets and addresses on
the PowerVault FluidFS system to ensure they match the configuration of the MD array(s).
Viewing the SAN Network Configuration
To view the SAN network configuration:
1. Click the Hardware tab on the left.
2. Click the SAN Fabrics tab on the top.
The currently configured SAN Fabrics are displayed in the Overview pane.
In addition, each SAN fabric (named SAN, SANb, SANc…) has its own pane, named Fabric SAN, Fabric
SANb, and so on. In that pane, you can see that status of each fabric and its connections to FluidFS and
MS controllers.
Adding an iSCSI Fabric
To add an iSCSI fabric:
1. Click the Hardware tab on the left.
2. Click the SAN Fabrics tab on the top.
3. In the Overview pane, click .
4. Click New iSCSI Fabric.
The New iSCSI Fabric dialog box appears.
5. In the Network interface dropdown, select the network interface to be used by the SAN fabric.
6. In the Netmask field, type the netmask IP address.
7. In the VLAN Id field, type the VLAN ID for the iSCSI subnet.
8. In the NAS Controller table, for each NAS controller:
a) Click in the row of the NAS controller. The Edit NAS Controller dialog box appears
b) Enter an IP address to be used by the SAN fabric.
c) Click OK.
d) Repeat steps (a) to (c) for each controller.
9. Click OK.
The new SAN fabric appears in the Overview pane.
Modifying an iSCSI Fabric’s Configuration
To modify the configuration of an iSCSI fabric:
1. Click the Hardware tab on the left.
2. Click the SAN Fabrics tab on the top.
3. In the Overview pane, for the SAN fabric (named Fabric SAN, Fabric SANb, and so on) that you want
to modify, click .
4. Click Modify.
The Modify iSCSI Fabric dialog box appears.
62
Page 63

5. In the Network interface dropdown, select the network interface to be used by the SAN fabric.
6. In the Netmask field, type the netmask IP address.
7. In the VLAN Id field, type the VLAN ID for the iSCSI subnet.
8. In the NAS Controller table, for each NAS controller:
a) Click in the row of the NAS controller. The Edit NAS Controller dialog box appears
b) Enter an IP address to be used by the SAN fabric.
c) Click OK.
d) Repeat steps (a) to (c) for each controller.
9. Click OK.
Deleting an iSCSI Fabric
To delete an iSCSI fabric:
1. Click the Hardware tab on the left.
2. Click the SAN Fabrics tab on the top.
3. In the Overview pane, for the SAN fabric (named Fabric SAN, Fabric SANb, and so on) that you want
to delete, click .
4. Click Delete.
The Delete iSCSI Fabric dialog box appears.
5. Click OK.
Modifying iSCSI Portals
To modify the iSCSI portals configuration:
1. Click the Hardware tab on the left.
2. Click the SAN Fabrics tab on the top.
3. In the iSCSI Portals Overview pane click .
4. Click Modify iSCSI Portals.
The Modify iSCSI Portals dialog box appears.
5. If the target requires CHAP authentication, select the Target requires CHAP authentication
checkbox, and enter the user name and password details of an authorized user.
6. To add an iSCSI IP address:
a) Click the Add button under the IP address table. The New IP Address for iSCSI Storage dialog box
appears.
b) Enter the new IP address.
c) Enter a description for the new IP address.
d) Click OK.
7. To delete an iSCSI IP address:
a) Select the iSCSI IP address in the table.
b) Click .
8. Click OK.
63
Page 64

Viewing Storage Identifiers
To view the NAS controller storage identifiers:
1. Click the Hardware tab on the left.
2. Click the SAN Fabrics tab on the top.
The NAS controller storage identifiers are displayed in the Storage Identifier of Type: iSCSI pane.
NOTE: All predefined storage identifiers are displayed, regardless of the number of controllers
found in the system.
64
Page 65

6
FluidFS 3.0 Account Management And Authentication
Account Management and Authentication
There are two types of access to the FluidFS cluster:
• Administrator‐level access for FluidFS cluster management
• Client‐level access to CIFS shares and NFS exports
Administrator accounts control administrator‐level access. Users and groups control client‐level access to
CIFS shares and NFS exports.
The FluidFS cluster supports administrator‐level and client‐level authentication for both local and remote
users and groups:
• Local users and groups: The FluidFS cluster manages and authenticates users and groups. Local
management is useful when you have only a limited number of users and groups. In addition,
authentication does not depend on external servers.
• Remote users and groups: Manage and authenticate users and groups using the following external
database types. Remote management is useful when you have many users and groups, but depends
on the availability of the external database.
– Active Directory: Configure the FluidFS cluster to access an Active Directory database to
authenticate Windows users.
NOTE: Active Directory can also be used as an LDAP database for UNIX/Linux users.
– NIS or LDAP: Configure the FluidFS cluster to access a NIS or LDAP database to authenticate
UNIX/Linux users.
NOTE: Local and remote users can be managed simultaneously.
NOTE: If you configure Active Directory and either NIS or LDAP, you can set up mappings
between the Windows users in Active Directory and the UNIX/Linux users in LDAP or NIS to
allow one set of credentials to be used for both types of data access.
Default Administrative Accounts
The FluidFS cluster has the following built‐in administrative accounts, each of which serves a particular
purpose.
65
Page 66

Login Name
Administrator FluidFS cluster
support FluidFS cluster
enableescalat
ionaccess
escalation FluidFS cluster
cli Gateway to
Purpose SSH
management
(not a UNIX/
Linux user)
troubleshooting
(regular UNIX/
Linux user)
Enable
escalation
account
troubleshooting
when unable to
log in with
support account
command line
interface access
SSH
Access
Enabled by
Default
Yes Yes Yes Yes Stor@ge!
No Yes No Yes None (must
No No Yes Yes N@sst0r3
No Yes No Yes N@sst0r3
Yes (can
bypass
password
using SSH
key)
Access
Allowed
Yes (can
bypass
password
using SSH key)
VGA
Console
Access
Enabled by
Default
N/A N/A N/A
VGA
Console
Access
Allowed
Default
Password
be set by
Administrator)
(cannot be
changed)
(cannot be
changed)
Administrative Account
The Administrator account is used for FluidFS cluster management using the FluidFS Manager Client and
CLI. This account cannot be removed or renamed. This account has write permission on all CIFS shares
by default.
Support Account
If Dell Technical Support Services needs to perform remote troubleshooting, you can make your system
accessible to them using the support account.
CAUTION: Dell strongly recommends that you do not attempt to use the support account.
Operations performed as the support user are for advanced remote troubleshooting to resolve
critical system issues only. Misuse of this account can damage the FluidFS cluster and/or its data.
NOTE: If Dell personnel must access the support account for remote troubleshooting, Dell
recommends that you change the password to a new, strong password after the troubleshooting
session is concluded.
Enabling or Disabling the Support Account
Enable the support account if Dell Technical Support Services needs to perform remote troubleshooting.
When troubleshooting is complete, disable the support account.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
66
Page 67

3. In the Security Access pane, click .
4. Click Modify Remote Support Policy.
The Modify Remote Support Policy dialog box appears.
5. Enable or disable the support account.
– To enable the support account, select the Allow Remote Support check box.
– To disable the support account, clear the Allow Remote Support check box.
6. Click OK.
Changing the Support Account Password
Dell recommends that you change the support account password to a new, strong password after each
troubleshooting session is concluded.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
3. In the Security Access pane, click .
4. Click Change Support User Password.
The Change Support User Passworddialog box appears.
5. In the New Password field, type a password.
The password must be at least seven characters long and contain three of the following elements: a
lowercase character, an uppercase character, a digit, or a special character (such as +, ?, or ∗).
6. In the Repeat Password field, re‐type the password.
7. Click OK.
Using the Escalation Account
If Dell Technical Support Services needs to perform remote troubleshooting, but an administrator is
unable to access the FluidFS Manager Client or CLI to enable the support account, you can use the
escalation account instead. The escalation account is enabled using the enableescalationaccess
account, which requires VGA console access.
CAUTION: Dell strongly recommends that you do not attempt to use the escalation account.
Operations performed as the escalation user are for advanced remote troubleshooting to resolve
critical system issues only. Misuse of this account can damage the FluidFS cluster and/or its data.
NOTE: Connect a monitor to the NAS controller’s VGA port and connect a keyboard to one of the
NAS controller’s USB ports.
1. From the command line, at the login as prompt, enter enableescalationaccess.
2. at the Password prompt, enter N@sst0r3
3. Respond to the prompt to specify the number of minutes to keep the escalation account enabled.
4. Type Yes to the prompt confirming that you want to enable the escalation account.
You are returned to a login prompt and the escalation account is enabled.
5. Type escalation at the login as prompt.
6. Type N@sst0r3 at the Password prompt.
67
Page 68

CLI Account
The CLI account is used with an administrator account to access the command-line interface of the
FluidFS cluster.
Default Local User and Local Group Accounts
The FluidFS cluster has the following built‐in local user and local group accounts, each of which serves a
particular purpose.
Account Type Account Name Purpose
Local User Administrator Account used for FluidFS cluster management
Local User nobody Account used as the owner of everything for guest
accounts
Local Group Administrators
Local Group nobody_group Accommodates the nobody account
Local Group Local Users Accommodates local user accounts
Local Group Users BUILTIN domain group fully compatible with the Windows
Local Group Backup Operators BUILTIN domain group fully compatible with the Windows
• Accommodates the Administrator account, and all
other users (local and remote) designated as
administrators
• BUILTIN domain group fully compatible with the
Windows Administrators group
Users group
Backup Operators group
Managing Administrator Accounts
You can both create local administrators and give remote users (AD/LDAP/NIS) administrator permissions.
System alerts are sent to the email address specified for the administrator.
When creating an administrator, you specify an administrator permission level. The permission level
defines the set of actions that are allowed by the administrator. Permission levels are predefined in the
system as follows:
• NAS Volume Administrator: The following table summarizes which settings a volume administrator
can change for the NAS volume(s) to which they are assigned. They can also view, but not change,
settings for other NAS volumes and the rest of the FluidFS cluster configuration.
• NAS Cluster Administrator: The administrator can manage any aspect of the FluidFS cluster.
NAS Volume Setting Volume Administrator Allowed to
NAS volume folder to which the NAS volume is assigned Yes
Access time granularity Yes
Permissions interoperability Yes
Report zero disk usage Yes
68
Change Setting?
Page 69

NAS Volume Setting Volume Administrator Allowed to
Data reduction Yes
NAS volume space settings and alert thresholds Yes
CIFS shares and NFS exports Yes
Snapshots and snapshot schedules Yes
Restore NAS volume from snapshot Yes
Restore NAS volume configuration Yes
Quotas Yes
NAS volume clones No
Replication No
Change Setting?
Viewing Administrators
View the current list of administrator accounts.
1. Click the System tab on the left.
2. Click the Mail & Admins tab on the top.
The administrators are displayed in the Administrator Users pane.
Adding an Administrator
Add an administrator account to manage the FluidFS cluster using the FluidFS Manager Client and CLI.
You can only define other administrators with permission levels that are hierarchically lower than your
own.
NOTE: Before you can create a local administrator, create a local user that becomes an
administrator.
1. Click the System tab on the left.
2. Click the Mail & Admins tab on the top.
3. In the Administrator Users pane, click .
4. Click New Administrator User.
The New NAS Administrator dialog box appears.
5. Select a local or remote user to become an administrator.
a) Click the […] button to the right of the NAS administrator username field.
The User Browser dialog box appears.
b) From the Domain name drop‐down menu, select the domain to which the user is assigned.
c) In the Starts with field, type either the full name of the user or the beginning of the user name.
d) Click Display.
e) Select a user from the search results and click OK.
6. In the Email address field, type the user’s email address.
7. Select the permission level of the administrator:
– NAS Cluster Administrator: The administrator can manage any aspect of the FluidFS cluster.
– NAS Volume Administrator: The administrator can only view the FluidFS cluster configuration
and manage the NAS volume(s) to which they are assigned.
69
Page 70

8. Click OK.
Assigning NAS Volumes to a Volume Administrator
By default, new volume administrators can manage all NAS volumes. After a volume administrator is
created, you can change the NAS volumes that can be managed by the volume administrator.
1. Click the System tab on the left.
2. Click the Mail & Admins tab on the top.
3. In the Administrator Users pane, click in the row of the administrator you want to modify.
4. Click Modify.
The Modify Administrator User dialog box appears.
5. In the Email address, enter the e-mail address for the selected administrator user.
6. Under Choose the NAS administration level, select NAS volume administrator.
7. Click the button.
The NAS Volume Browser dialog box appears.
a) Select the NAS Volumes to assign to the volume administrator.
b) Click OK.
The NAS Volume Browser dialog closes.
c) Click Add. The volume is added to the administrator’s volume list.
d) Repeat steps (a) to (c) for each volume you want to add.
8. Click OK.
Changing an Administrator’s Permission Level
Change the permission level of an administrator account.
1. Click the System tab on the left.
2. Click the Mail & Admins tab on the top.
3. In the Administrator Users pane, click in the row of the administrator you want to modify.
4. Click Modify.
The Modify Administrator User dialog box appears.
5. Select the permission level of the administrator:
– NAS Cluster Administrator: The administrator can manage any aspect of the FluidFS cluster.
– NAS Volume Administrator: The administrator can only view the FluidFS cluster configuration
and manage the NAS volume(s) to which they are assigned.
6. Click OK.
Changing an Administrator’s Email Address
Change the permission level of an administrator account.
1. Click the System tab on the left.
2. Click the Mail & Admins tab on the top.
3. In the Administrator Users pane, click in the row of the administrator you want to modify.
4. Click Modify.
The Modify Administrator User dialog box appears.
70
Page 71

5. In the Email Address field, type the new email address for the administrator.
6. Click OK.
Changing a Local Administrator Password
You can change the password only for a local administrator account. The password for remote
administrators is maintained in the external database.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Users pane, click in the row of the user whose password you want to change.
4. Click Change Password.
The Change Password for Local User dialog box appears.
5. In the New password field, type a password for the administrator.
The password must be at least seven characters long and contain three of the following elements: a
lowercase character, an uppercase character, a digit, or a special character (such as +, ?, or ∗).
6. In the Repeat new password field, re‐type the password for the administrator.
7. Click OK.
Deleting an Administrator
Delete an administrator account when it is no longer used for FluidFS cluster management. The built‐in
Administrator account cannot be deleted.
1. Click the System tab on the left.
2. Click the Mail & Admins tab on the top.
3. In the Administrator Users pane, click in the row of the administrator you want to modify.
4. Click Delete.
The Delete dialog box appears.
5. Click OK.
Managing Local Users
You can create local users that can access CIFS shares and NFS exports, or that will become a FluidFS
cluster administrator. You might want to create local users in the following cases:
• You do not have remote users (AD/LDAP/NIS)
• Both CIFS/NFS will be used, but you have a remote user repository (AD/LDAP/NIS) relevant for only
one protocol and a small number of users using the other protocol
When prompted to authenticate to access a CIFS share, local users must use the following format for the
user name:
<client_VIP_or_name>\<local_user_name>
Adding a Local User
Add a local user account.
71
Page 72

NOTE: The group to which the local user is assigned must exist.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Users pane, click .
4. Click New Local User.
The New Local User dialog box appears.
5. In the User name field, type a name for the local user.
The user name may contain only the following characters: letters, numbers, underscores, hyphens,
spaces, and periods. Also, a period cannot be used as the last character.
6. Click the […] button to the right of the Primary Local Group field.
The Groups Browser dialog box appears.
7. Select the group to which the local user is assigned and click OK.
8. In the Password field, type a password for the local user.
The password must be at least seven characters long and contain three of the following elements: a
lowercase character, an uppercase character, a digit, or a special character (such as +, ?, or ∗).
9. In the Repeat Password field, re‐type the password for the local user.
10. (Optional) Add secondary groups for this user.
a) Click the […] button under the Secondary Groups list.
The Groups Browser dialog box appears.
b) Select a secondary group you want to add and click OK.
c) Click Add.
d) Repeat steps (a) to (c) for each secondary group you want to add.
11. Click OK.
Changing a Local User’s Group
Change the primary local group to which a local user is assigned.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Users pane, click in the row of the user you want to change.
4. Click Modify.
The Modify Local User dialog box appears.
5. Click the […] button to the right of the Groups field.
The Groups Browser dialog box appears.
6. Select the group to which the local user is assigned and click OK.
7. Click OK.
Enabling or Disabling a Local User
Disabling a local user prevents the local user from accessing CIFS shares and NFS exports.
1. In the Local Users pane, click in the row of the user you want to change.
2. Click Modify.
The Modify Local User dialog box appears.
72
Page 73

3. Enable or disable the local user.
– To enable the local user, clear the Disable access from this local user check box.
– To disable the local user, select the Disable access from this local user check box.
4. Click OK.
Changing a Local User Password
Change the password for a local user account.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Users pane, click in the row of the user you want to change.
4. Click Change Password.
The Change Password for Local User dialog box appears.
5. In the New Password field, type a new password for the local user.
The password must be at least seven characters long and contain three of the following elements: a
lowercase character, an uppercase character, a digit, or a special character (such as +, ?, or ∗).
6. In the Repeat new password field, re‐type the password for the local user.
7. Click OK.
Deleting a Local User
Delete a local user account when the user no longer needs to access CIFS shares and NFS exports, or
manage the FluidFS cluster (in the case of an administrator based on a local user).
NOTE: If the local user has an associated administrator account, you must delete the administrator
account before deleting the local user account.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Users pane, click in the row of the user you want to change.
4. Click Delete.
The Delete Local User dialog box appears.
5. Click OK.
Managing Password Age and Expiration
Changing the Maximum Password Age
You can change the number of days after which local users and local administrators will be forced to
change their password. The password expiration settings for remote users are maintained in the external
database and are not affected by this setting.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
3. In the Security Access pane, click .
4. Click Modify Password Expiration Policy.
The Modify Password Expiration Policy dialog box appears.
73
Page 74

5. Click Edit Password Expiration.
The Edit Password Expiration dialog box appears.
6. In the within [ ] days field, type the number of days after which the password will expire.
7. Click OK.
Enabling or Disabling Password Expiration
When password expiration is enabled, local users and local administrators are forced to change their
password after the specified number of days. The password expiration settings for remote users are
maintained in the external database and are not affected by this setting.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
3. In the Security Access pane, click .
4. Click Modify Password Expiration Policy.
The Modify Password Expiration Policy dialog box appears.
5. Enable or disable local user and administrator password expiration.
– To enable local user and administrator password expiration, select the Password for local users
and administrator users will expire check box.
– To disable local user and administrator password expiration, clear the Password for local users
and administrator users will expire check box.
6. If password expiration is enabled, in the within [ ] days field, type the number of days after which the
password expires.
7. Click OK.
Managing Local Groups
Create local groups to apply quota rules to multiple users. You can assign local users, remote users, and
remote users groups to one or more local groups. The primary group to which a user belongs determines
the quota for the user.
Viewing Local Groups
View the current local groups.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
The local groups are displayed in the Local Groups pane.
Adding a Local Group
Add a local group containing local users, remote users, or remote users groups.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Groups pane, click .
4. Click New Local Group.
The New Local Group dialog box appears.
74
Page 75

5. In the Local group name field, type a name for the group.
6. To add local users to the group:
a) Click the […] button under the Local users in this group list.
The User Browser dialog box appears.
b) In the Search field, type either the full name of the user or the beginning of the user name and
click the button.
c) Select the user you want to add and click OK.
d) Click Add under the Local users in this group list.
e) Repeat steps (a) to (d) for every user you want to add.
7. To add domain users to the group:
a) Click the […] button under the Domain users in this group list.
The User Browser dialog box appears.
b) From the Domain drop‐down menu, select the domain to which the user is assigned.
c) In the Search field, type either the full name of the user or the beginning of the user name and
click the button.
d) Select the user you want to add and click OK.
e) Click Add under the Domain users in this group list.
f) Repeat steps (a) to (e) for every user you want to add.
8. To add domain groups to the group:
a) Click the […] button under the Domain groups in this group list.
The Group Browser dialog box appears.
b) From the Domain drop‐down menu, select the group’s domain.
c) In the Search field, type either the full name of the group or the beginning of the group name and
click the button.
d) Select the group you want to add and click OK.
e) Click Add under the Domain users in this group list.
f) Repeat steps (a) to (e) for every group you want to add.
9. Click OK.
Changing the Users Assigned to a Local Group
Modify which local users, remote users, or remote users groups are assigned to a local group.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Groups pane, click in the row of the group you want to delete.
4. Click Modify.
The Modify Local Group dialog box appears.
75
Page 76

5. To add local users to the group:
a) Click the […] button under the Local users in this group list.
The User Browser dialog box appears.
b) In the Search field, type either the full name of the user or the beginning of the user name and
click the
c) Select the user you want to add and click OK.
d) Click Add under the Local users in this group list.
e) Repeat steps (a) to (d) for every user you want to add.
6. To add domain users to the group:
a) Click the […] button under the Domain users in this group list.
The User Browser dialog box appears.
b) From the Domain drop‐down menu, select the domain to which the user is assigned.
c) In the Search field, type either the full name of the user or the beginning of the user name and
click the button.
d) Select the user you want to add and click OK.
e) Click Add under the Domain users in this group list.
f) Repeat steps (a) to (e) for every user you want to add.
7. To add domain groups to the group:
a) Click the […] button under the Domain groups in this group list.
The Group Browser dialog box appears.
b) From the Domain drop‐down menu, select the group’s domain.
c) In the Search field, type either the full name of the group or the beginning of the group name and
click the button.
d) Select the group you want to add and click OK.
e) Click Add under the Domain users in this group list.
f) Repeat steps (a) to (e) for every group you want to add.
8. Click OK.
button.
Deleting a Local Group
Delete a local group if it is no longer used.
NOTE: Before a local group can be deleted, you must remove its members.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Local Groups pane, click in the row of the group you want to delete.
4. Click Delete.
The Delete Local Group dialog box appears.
5. Click OK.
Managing Active Directory
In environments that use Active Directory (AD), you can configure the FluidFS cluster to join the Active
Directory domain and authenticate Windows clients using Active Directory for access to CIFS shares. The
FluidFS cluster supports mixed mode and native mode Active Directory configurations.
76
Page 77

Enabling Active Directory Authentication
Join the FluidFS cluster to an Active Directory domain to allow it to communicate with the directory
service.
By default, the FluidFS cluster uses the domain controller returned by Active Directory. Alternatively, you
can designate a domain controller if you want to ensure that the FluidFS cluster uses a specific domain
controller. Adding multiple domain controllers ensures continued authentication of users in the event of
a domain controller failure. If the FluidFS cluster cannot establish contact with the preferred server, it will
attempt to connect to the remaining servers in order.
• An Active Directory service must be deployed in your environment.
• The FluidFS cluster must have network connectivity to the directory service.
• You must be familiar with the Active Directory configuration.
• The FluidFS cluster requires credentials from an Active Directory account for the join operation. The
join operation is the only action for which these credentials are required, and they are not stored or
cached by the FluidFS cluster.
Use one of the following options for the account used to join the FluidFS cluster to the domain:
– Use a Domain Admin account. This is the preferred method.
– Use an account that has the "join a computer to the domain" privilege, as well as having full
control over all computer objects in the domain.
– If both of the above options are unavailable, the minimum requirements for an account are:
* An Organizational Unit (OU) admin that has the "join a computer to the domain" privilege, as
well as having full control over objects within that OU, including computer objects.
* Before joining the FluidFS cluster to the domain, a computer object must be created by the OU
admin for the FluidFS cluster; in the OU privileges to administer are provided. The FluidFS
cluster computer object name, and the NetBIOS name used when joining it, must match.
When creating the FluidFS cluster computer object, in the User or Group field under
permissions to join it to the domain, select the OU admin account. Then, the FluidFS cluster
can be joined using the OU admin credentials.
• FluidFS clusters need read access for the tokenGroups attribute for all users. The default
configuration of Active Directory for all domain computers is to allow read access to the
tokenGroups attribute. If the permission is not given, Active Directory domain users that are in nested
groups or OUs encounter Access Denied errors, and users that are not in nested OUs or groups are
permitted access.
• The Active Directory server and the FluidFS cluster must use a common time server.
• You must configure the FluidFS cluster to use DNS. The DNS servers you specify must be the same as
those your Active Directory domain controllers use.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Active Directory for CIFS and NFS users Authentication pane, click .
4. Click Join.
The Join Active Directory dialog box appears.
5. In the Active Directory domain name field, type a domain to which to join the FluidFS cluster.
6. (Optional) To add preferred controllers for the join operation and users authentication:
a) Select the Consider these controllers as preferred check box.
b) Type a domain controller host name or IP address in the controllers text field and click Add.
c) Repeat step (b) for each controller you want to add.
77
Page 78

7. Click OK.
Modifying Active Directory Authentication Settings
You cannot directly modify the settings for Active Directory authentication. You must remove the FluidFS
cluster from the Active Directory domain and then re‐join it to the Active Directory domain.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Active Directory for CIFS and NFS users Authentication pane, click .
4. Click Modify.
The Modify Active Directory dialog box appears.
5. Click OK.
6. Follow the instructions in Enabling Active Directory Authentication.
Disabling Active Directory Authentication
Remove the FluidFS cluster from an Active Directory domain if you no longer need the FluidFS cluster to
communicate with the directory service.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the Active Directory for CIFS and NFS users pane, click .
4. Click Leave.
The Leave Active Directory dialog box appears.
5. Click OK.
6. Follow the instructions in Enabling Active Directory Authentication to re-join the Active Directory.
Managing LDAP
In environments that use Lightweight Directory Access Protocol (LDAP), you can configure the FluidFS
cluster to authenticate UNIX/Linux clients using LDAP for access to NFS exports. The LDAP database can
be provided by either an LDAP server or Active Directory.
The FluidFS clusters support the following LDAP configurations:
• Anonymous LDAP: The connection from the FluidFS cluster to the LDAP server(s) is not
authenticated. The data is sent in plain text.
• Authenticated LDAP: The connection from the FluidFS cluster to the LDAP server(s) is authenticated
using a user name and password. The data is sent in plain text.
• LDAP over TLS/SSL: The connection from the FluidFS cluster to the LDAP server(s) is authenticated
and encrypted. To validate the certificate used by the LDAP service, you must export the SSL
certificate from the LDAP service and upload it to the FluidFS cluster.
Enabling LDAP Authentication
Configure the FluidFS cluster to communicate with the LDAP directory service.
78
Page 79

Adding multiple LDAP servers ensures continued authentication of users in the event of an LDAP server
failure. If the FluidFS cluster cannot establish contact with the preferred server, it will attempt to connect
to the remaining servers in order.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select LDAP.
The LDAP settings fields are displayed.
6. In the Base DN field, type an LDAP base distinguished name to represent where in the directory to
begin searching for users.
It is usually in the format:
dc=domain, dc=com.
7. In the LDAP Servers text field, type the host name or IP address of an LDAP server and click Add.
Repeat this step for any additional LDAP servers.
8. (Optional) Configure the remaining LDAP attributes as needed.
– To indicate that Active Directory provides the LDAP database, select the Use LDAP on Active
Directory Extended Schema check box.
– To authenticate the connection from the FluidFS cluster to the LDAP server, select theUse Non‐
nonymous LDAP bind check box. Then, type the LDAP bind distinguished name used to
authenticate the connection in the Bind DN field and type the LDAP bind password in the Bind
Password field.
– To encrypt the connection from the FluidFS cluster to the LDAP server using TLS, select the Use
TLS over LDAP check box.
– To validate the certificate used by the LDAP service, select the Install LDAP Certificate check box.
Then, click Upload Certificate and select the LDAP SSL certificate to upload to the FluidFS cluster.
9. Click OK.
Changing the LDAP Base DN
The LDAP base distinguished name represents where in the directory to begin searching for users.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select LDAP.
The LDAP settings fields are displayed.
6. In the Based DN field, type an LDAP base distinguished name.
It is usually in the format:
dc=domain, dc=com
7. Click OK.
79
Page 80

Adding or Removing LDAP Servers
There must be at least one LDAP server.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select LDAP.
The LDAP settings fields are displayed.
6. Add or remove LDAP servers.
– To add an LDAP server, type the host name or IP address of an LDAP server in the LDAP Servers
text field and click Add.
– To remove an LDAP server, select an LDAP server and click .
7. Click OK.
Enabling or Disabling LDAP on Active Directory Extended Schema
Enable the extended schema option if Active Directory provides the LDAP database.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Enable or disable LDAP on Active Directory extended schema.
– To indicate that Active Directory provides the LDAP database, select the Use LDAP on Active
Directory Extended Schema check box.
– To indicate that an LDAP server provides the LDAP database, clear the Use LDAP on Active
Directory Extended Schema check box.
6. Click OK.
Enabling or Disabling Authentication for the LDAP Connection
Enable authentication for the connection from the FluidFS cluster to the LDAP server if the LDAP server
requires authentication.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select LDAP.
The LDAP settings fields are displayed.
80
Page 81

6. Enable or disable authentication for the LDAP connection.
– To enable authentication for the LDAP connection, select the Use Non‐Anonymous LDAP bind
check box. Then, type the LDAP bind distinguished name used to authenticate the connection in
the Bind DN field and type the LDAP bind password in the Bind Password field.
– To disable authentication for the LDAP connection, clear the Use Non‐Anonymous LDAP bind
check box.
7. Click OK.
Enabling or Disabling TLS Encryption for the LDAP Connection
Enable TLS encryption for the connection from the FluidFS cluster to the LDAP server to avoid sending
data in plain text. To validate the certificate used by the LDAP service, you must export the LDAP SSL
certificate and upload it to the FluidFS cluster.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select LDAP.
The LDAP settings fields are displayed.
6. Enable or disable TLS encryption for the LDAP connection.
– To enable TLS encryption for the LDAP connection, select the Use LDAP over TLS check box.
– To disable TLS encryption for the LDAP connection, clear the Use LDAP over TLS check box.
7. If TLS encryption is enabled, enable or disable LDAP certificate validation.
– To enable LDAP certificate validation, select the Install LDAP Certificate check box. Then, click
Upload Certificate and select the LDAP SSL certificate to upload to the FluidFS cluster.
– To disable LDAP certificate validation, clear the Install LDAP Certificate check box.
8. Click OK.
Disabling LDAP Authentication
Disable LDAP authentication if you no longer need the FluidFS cluster to communicate with the directory
service.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select None.
6. Click OK.
Managing NIS
In environments that use Network Information Service (NIS), you can configure the FluidFS cluster to
authenticate clients using NIS for access to NFS exports.
81
Page 82

Enabling NIS Authentication
Configure the FluidFS cluster to communicate with the NIS directory service.
Adding multiple NIS servers ensures continued authentication of users in the event of a NIS server failure.
If the FluidFS cluster cannot establish contact with the preferred server, it will attempt to connect to the
remaining servers in order.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select NIS.
The NIS settings fields are displayed.
6. In the Domain Name field, type a NIS domain name.
7. In the NIS Servers text field, type the host name or IP address of a NIS server and click Add.
Repeat this step for any additional NIS servers.
8. NIS servers are listed in descending order of preference.
– To increase the precedence for a NIS server, select a NIS server and click .
– To decrease the precedence for a NIS server, select a NIS server and click .
9. Click OK.
Changing the NIS Domain Name
The NIS domain name specifies which domain to query in the NIS directory service.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. In the NIS Domain Name field, type a NIS domain name.
6. Click OK.
Changing the Order of Preference for NIS Servers
Change the order of preference for a NIS server. If the FluidFS cluster cannot establish contact with the
preferred server, it will attempt to connect to the remaining servers in order.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
82
Page 83

5. NIS servers are listed in descending order of preference.
– To increase the precedence for a NIS server, select a NIS server and click .
– To decrease the precedence for a NIS server, select a NIS server and click .
6. Click OK.
Disabling NIS Authentication
Disable NIS authentication if you no longer need the FluidFS cluster to communicate with the directory
service.
1. Click the Access Control tab on the left.
2. Click the User Repositories tab on the top.
3. In the NIS or LDAP repository for NFS users pane, click .
4. Click Modify Settings.
The Modify NIS/LDAP Settings dialog box appears.
5. Select None.
6. Click OK.
Managing User Mappings between Windows and UNIX/ Linux Users
You can define mappings between Windows users in Active Directory and UNIX/Linux users in LDAP or
NIS. This ensures that a Windows user inherits the UNIX/Linux user permissions, and a UNIX/Linux user
inherits the Windows user permissions, depending on the direction of the mapping and the NAS volume
security style.
User Mapping Policies
The user mapping policies include:
• Automatic mapping: Automatically map all Windows users in Active Directory to the identical UNIX/
Linux users in LDAP or NIS, and map all UNIX/Linux users to the identical Windows users. Automatic
mapping is disabled by default.
• Mapping rules: Define mappings between specific Windows users in Active Directory and the
corresponding UNIX/Linux users in LDAP or NIS. These specific mapping rules take precedence over
automatic mapping. You can select the direction of the mapping — the mapping can go in one
direction or both:
– Mapping is allowed in one direction:
* Windows users to a UNIX/Linux user
* UNIX/Linux user to a Windows user
– Mapping is allowed in both directions between Windows and UNIX/Linux users.
•
User Mapping Policy and NAS Volume Security Style
User mapping permissions depend on the file security style for the NAS volume:
83
Page 84

• NTFS security style: Permissions are controlled by Windows and NTFS. The UNIX/ Linux user adheres
to the permissions of the corresponding Windows user, regardless of the UNIX/Linux permission
settings.
• UNIX security style: Permissions are based on the UNIX/Linux permissions. The Windows user adheres
to the permissions of the corresponding UNIX/Linux user.
• Mixed security style: Both UNIX/Linux and Windows permissions are used. Each user can override the
other userʹ permission settings; therefore, be careful when using the Mixed security style.
Managing the User Mapping Policy
Configure the FluidFS cluster mapping policy to automatically map all users or to only allow mappings
between specific users.
Mapping Windows and UNIX/Linux Users Automatically
Automatically map all Windows users in Active Directory to the identical UNIX/Linux users in LDAP or NIS,
and map all UNIX/Linux users to the identical Windows users. Mapping rules override automatic mapping.
1. Click the Access Control tab on the left.
2. Click the User Mapping tab on the top.
3. In the Mapping Policy pane, click .
4. Click Modify Policy.
The Modify User Mapping Policy dialog box appears.
5. Select Automatically map CIFS and NFS users with the same name.
6. Click OK.
Mapping Windows and UNIX/Linux Users by Mapping Rules Only
Only allow mappings between specific Windows users in Active Directory and the identical UNIX/Linux
users in LDAP or NIS.
1. Click the Access Control tab on the left.
2. Click the User Mapping tab on the top.
3. In the Mapping Policy pane, click .
4. Click Modify Policy.
The Modify User Mapping Policy dialog box appears.
5. Select Map based on the mapping rules only.
6. Click OK.
Managing User Mapping Rules
Manage mapping rules between specific users. Mapping rules override automatic mapping.
Creating a User Mapping Rule
Create a mapping rule between a specific Windows user in Active Directory and the identical UNIX/Linux
user in LDAP or NIS. Mapping rules override automatic mapping.
1. Click the Access Control tab on the left.
2. Click the User Mapping tab on the top.
3. In the Mapping Rules pane, click .
4. Click New.
The New User Mapping Rule dialog box appears.
84
Page 85

5. Click the […] button to the right of the CIFS User (Active Directory) field.
The User Browser dialog box appears.
a) From the Domain drop‐down menu, select the domain to which the user is assigned.
b) In the Starts with field, type either the full name of the user or the beginning of the user name
and click the button.
c) Select the user you want to add and click OK.
6. Click the […] button to the right of the NFS User (NIS/LDAP) field.
The User Browser dialog box appears.
a) From the Domain drop‐down menu, select the domain to which the user is assigned.
b) In the Starts with field, type either the full name of the user or the beginning of the user name
and click the button.
c) Select the user you want to add and click OK.
7. Select the direction of the user mapping:
– The two users have identical file access permissions (using any protocol)
– The NFS user can access any file accessible by the CIFS user
– The CIFS user can access any file accessible by the NFS user
8. Click OK.
Deleting a User Mapping Rule
Delete a mapping rule between a specific Windows user in Active Directory and the identical UNIX/Linux
user in LDAP or NIS.
1. Click the Access Control tab on the left.
2. Click the User Mapping tab on the top.
3. In the Mapping Rules pane, for the mapping rule that you want to delete, click .
4. Click Delete.
The Delete User Mapping Rule dialog box appears.
5. Click OK.
85
Page 86

86
Page 87

7
FluidFS 3.0 NAS Volumes, Shares, and Exports
Managing the NAS Pool
The amount of raw space allocated to the FluidFS cluster (NAS pool) is determined by the MD Array LUNs
assigned to the NAS controllers. The maximum size of the PowerVault FluidFS NAS pool is 1 PB.
The usable size of the NAS pool depends on how much space the system deducts from the NAS pool for
internal use. On average, the system deducts approximately 400 GB per NAS appliance for internal use.
The exact amount of internal space varies by configuration, but it is roughly calculated as follows per
FluidFS cluster:
(256GB ∗ number of NAS appliances) + (4GB ∗ number of MD LUNs/volumes) + 20GB + 0.5% of the
total NAS pool + (100GB * number of NAS appliances, if data reduction is enabled)
Discovering New or Expanded LUNs
You can automatically discover newly created or expanded LUNs on the connected MD Storage arrays.
1. Click the Hardware tab on the left.
2. Click the Storage tab on the top.
3. In the Storage pane, click and select Discover New or Expanded LUNs.
The Discover New or Expanded LUNs dialog prompts you that the LUN discovery occurs in the
background, and you must refresh the browser page to see the view the new LUNs.
4. Select the I noted that Discover LUNs is performed in background ... check box and click OK.
Viewing Internal Storage Reservations
View information about the space that the system deducts from the NAS pool for internal use.
1. Click the System tab on the left.
2. Click the Internal tab on the top.
The internal storage reservations are displayed in the Internal Storage Reservations pane.
Viewing the Size of the NAS Pool
View the current configured size of the NAS pool.
1. Click the Hardware tab on the left.
2. Click the Storage tab on the top.
The NAS pool size is displayed in the Overview pane, in the Space allocated to the NAS pool field.
87
Page 88

Expanding the Size of the NAS Pool
You can increase the size of the NAS pool as your NAS storage space requirements increase, without
affecting the services to the clients. However, you cannot decrease the size of the NAS pool.
The maximum size of the NAS pool is 1 PB.
NOTE: The MD Array(s) must have enough capacity to allocate more storage space to the FluidFS
cluster.
1. Click the Hardware tab on the left.
2. Click the Storage tab on the top.
3. In the Overview pane, click .
4. Click Expand NAS Pool.
The Expand NAS Pool dialog box appears. The Additional allocation to the NAS pool value is
displayed.
5. Click OK.
The progress of the expand NAS pool process is displayed in the Expand NAS Pool dialog box. If you
close the dialog box, the process will continue to run in the background.
Enabling or Disabling the NAS Pool Used Space Alert
You can enable an alert that is triggered when a specified percentage of the NAS pool space has been
used.
1. Click the NAS Volumes ab on the left.
2. Click the NAS Pool tab on the top.
3. In the NAS Pool pane, click .
4. Click Modify Space Threshold.
The Modify NAS Pool Space Threshold dialog box appears.
5. Enable or disable the NAS pool used space alert.
– To enable the NAS pool used space alert, select the Alert when used space is over check box.
– To disable the NAS pool used space alert, clear the Alert when used space is over check box.
6. If the NAS pool used space alert is enabled, in the Alert when used space is over size field, type a
number (from 0 to 100) to specify the percentage of used NAS pool space that triggers an alert.
7. Click OK.
Enabling or Disabling the NAS Pool Unused Space Alert
You can enable an alert that is triggered when the remaining unused NAS pool space is below a specified
size.
1. Click the NAS Volumes tab on the left.
2. Click the NAS Pool tab on the top.
3. In the NAS Pool pane, click .
4. Click Modify Space Threshold.
The Modify NAS Pool Space Threshold dialog box appears.
88
Page 89

5. Enable or disable the NAS pool unused space alert.
– To enable the NAS pool unused space alert, select the Alert when unused space is over check
box.
– To disable the NAS pool unused space alert, clear the Alert when unused space is over check
box.
6. If the NAS pool unused space alert is enabled, in the Alert when unused space is below size field,
type a size in megabytes (MB), gigabytes (GB), or terabytes (TB) to specify the unused NAS pool space
that triggers an alert.
7. Click OK.
Managing NAS Volumes
A NAS volume is a portion of the NAS pool in which you create CIFS shares and NFS exports to make
storage space available to clients. NAS volumes have specific management policies controlling their
space allocation, data protection, security style, and so on.
You can either create one large NAS volume consuming the entire NAS Pool or divide the NAS pool into
multiple NAS volumes. In either case you can create, resize, or delete these NAS volumes.
NAS volume availability depends on the availability of the MD Array(s). If the MD Array is offline, NAS
volume data is not available for the FluidFS cluster. Correct the MD Array problem to resume NAS volume
availability.
Several NAS features are configured on a per NAS volume basis:
• Quota rules
• Security styles
• Data reduction
• Snapshots
• NDMP backup
• Replication
File Security Styles
The Windows and UNIX/Linux operating systems use different mechanisms for resource access control.
Therefore, you assign each NAS volume a file security style (NTFS, UNIX, or Mixed) that controls the type
of access controls (permission and ownership) for the files and directories that clients create in the NAS
volume.
A NAS volume supports the following security styles:
• UNIX: Controls file access using UNIX permissions. A client can change permissions only by using the
chmod and chown commands on the NFS mount point.
• NTFS: Controls file access by Windows permissions. A client can change the permission and
ownership using the Windows File Properties → Security tab.
• Mixed: Supports both NTFS and UNIX security styles. If you choose this option, the security of a file or
directory is the last one set. Permissions and access rights from one method to another are
automatically translated. For example, if a Windows administrator sets up file access permissions on a
file through a CIFS Share, a Linux user can access the file through NFS and change all the file
permissions. This option is not recommended in production environments, except where there is a
need for scratch space and when you are not concerned about file access security and simply need
some NAS volume space to store files temporarily.
Both NTFS and UNIX security styles allow multi‐protocol file access. The security style simply determines
the method of storing/managing the file access permissions information within the NAS volume.
89
Page 90

If you need to access the same set of files from both Windows and UNIX/Linux, the best way to
implement multi‐protocol access is by setting up individual user mapping rules or by enabling automatic
user mapping. Ownership and access permissions are automatically translated based on user mapping
settings and file access credentials.
Modifying the file security style of a NAS volume affects only files and directories created after the
modification.
Thin and Thick Provisioning for NAS Volumes
Although PowerVault NAS pool is thickly provisioned to the FluidFS system, NAS volumes can be thin‐
provisioned. With thin‐provisioning (the default), storage space is consumed on the MD Arrays(s) only
when data is physically written to the NAS volume, not when the NAS volume is initially created. Thin‐
provisioning allows NAS volumes to account for future increases in usage. However, because it is possible
for the storage space allocated by the NAS volumes to exceed the storage space allocated to the NAS
pool, ensure that you monitor available capacity on the MD array(s) to ensure that the FluidFS system
always has sufficient free space available. You can also specify a portion of the NAS volume (Reserved
Space) that is dedicated to the NAS volume (no other volumes can take the space). The total Reserved
Space of all NAS volumes cannot exceed the available capacity of the NAS pool.
If a file is deleted from a thin‐provisioned NAS volume, the free space as seen in FluidFS Manager
increases. The freed up capacity is also visible and available to clients in the CIFS shares or NFS exports.
However, the MD array does not report any capacity freed up in the NAS pool.
Thick provisioning allows you to allocate storage space on the MD array(s) statically to a NAS volume (no
other volumes can take the space). Thick provisioning is appropriate if your environment requires
guaranteed space for a NAS volume.
Choosing a Strategy for NAS Volume Creation
Choosing to define multiple NAS volumes enables you to apply different management policies, such as
data reduction, data protection, security style, and quotas, based on your storage needs.
Consider the following factors to help choose the right strategy based on your environment’s
requirements:
• General requirements NAS volumes can be easily created, resized (increased or decreased) based
on the system capacity, or deleted.
– NAS volumes can be easily created, resized (increased or decreased) based on the system
capacity, or deleted.
– A single NAS volume can contain NFS exports, CIFS shares, or a combination of NFS exports and
CIFS shares.
– The minimum size of a NAS volume is 20 MB (or if the NAS volume has already been used, the
minimum size is the stored data).
• Business requirements: A company or application requirement for separation or for using a single
NAS volume must be considered. NAS volumes can be used to allocate storage for departments on
demand, using the threshold mechanism to notify administrators when they approach the end of their
allocated free space.
• Data reduction: Each NAS volume can have a dedicated data reduction policy to best suit the type of
data it stores.
• Snapshots: Each NAS volume can have a dedicated snapshot scheduling policy to best protect the
type of data it stores.
• Security style: In multiple protocol environments, it might be beneficial to separate the data and
define NAS volumes with UNIX security style for UNIX/Linux‐ased clients, and NTFS for Windows‐ased
clients. This enables the administrator to match the security style with business requirements and
90
Page 91

various data access patterns. The security style can also be set to Mixed which supports both POSIX
security and Windows ACLs on the same NAS volume.
• Quotas: Different quota policies can be applied to different NAS volumes, allowing the administrator
to focus on managing quotas when it is appropriate.
Example NAS Volume Creation Scenarios
The following scenarios provide examples of how NAS volumes can be created to meet the needs of an
example organization with the following conditions:
1. The average read/write mix is 80/20 and the average hourly change rate for existing data is less than
1%.
2. The departments and NAS volume requirements are as described in the following table:
Department Securit
y Style
Post Production NFS Hourly No Weekly 20 20/80 1%
Administration
and Finance
Broadcast Mixed No No Weekly 10 90/10 None
Press CIFS Daily No No 5 10/90 5%
Marketing CIFS Daily Yes No 5 50/50 None
CIFS No No Weekly 10 50/50 None
SnapshotsReplicationNDMP
Backup
Number
of
CIFS/NF
S
Clients
Read/
Write Mix
Hourly
Change % of
Existing Data
Scenario 1
Create NAS volumes based on departments. The administrator logically breaks up storage and
management into functional groups. In this scenario, the departmental requirements are quite different
and support the design to logically create NAS volumes along department lines.
• Advantages:
– It is logically easy to manage the NAS volumes.
– The NAS volumes are created to match the exact needs of the department.
• Disadvantage: The NAS volumes become difficult to manage if the number of departments in the
organization increases.
Scenario 2
We recommend grouping departments that have similar security requirements into NAS volumes. The
administrator creates three NAS volumes: one for NFS, one for CIFS, and another for mixed.
• Advantage: The NAS volumes work separately between Windows and Linux.
• Disadvantage: Unwanted services may be provided to certain departments. For example, if the CIFS
volume is backed up weekly for the administration and finance departments, the press and marketing
departments also get backups even though they do not require it.
Scenario 3
NAS volumes can be created based on the feature (snapshots, replication, NDMP backup, and so on).
• Advantage: The NAS volumes are created to match the exact needs for each feature.
91
Page 92

• Disadvantage: User mapping is required. A user needs to choose one security style, either NTFS or
UNIX, and based on the security style chosen the correct mapping for other users is set.
NAS Volumes Storage Space Terminology
FluidFS Manager displays storage space details for individual NAS volumes and for all NAS volumes
collectively. The following table defines terminology used in FluidFS Manager related to NAS volume
storage space.
Term Description
Size
Used Space
Reserved Space
Unreserved Space
Available Space
Overcommitted
Space
Snapshot Space
Data Reduction
Saving
Maximum size of a NAS volume defined by the storage administrator.
Storage space occupied by writes to the NAS volume (user data and snapshots).
A portion of a thin‐provisioned NAS volume that is dedicated to the NAS volume (no
other volumes can take the space). The amount of reserved space is specified by the
storage administrator. Reserved space is used before unreserved space.
A portion of a thin‐provisioned NAS volume that is not reserved (other volumes can
take the space). The amount of unreserved space for a NAS volume is: (NAS volume
size) – (NAS volume reserved space).
Storage space that is physically currently available for the NAS volume. The amount
of available space for a NAS volume is: (unused NAS volume reserved space) + (NAS
volume unreserved space, provided that there is free space in the NAS pool).
A portion of a thin‐provisioned NAS volume that is not available and not in use by
the NAS volume. The amount of overcommitted space for a NAS volume is: (sum of
all the NAS volume space) - (NAS Pool: Used Space) - (NAS Pool: Unused (unreserved Space).
With thin‐provisioning, storage space is consumed only when data is physically
written to the NAS volume, not when the NAS volume is initially allocated. This
means more storage space can be allocated to the NAS volumes than has been
allocated in the NAS pool itself.
Storage space occupied by snapshots of a NAS volume.
Storage space reclaimed as a result of data reduction processing.
Configuring NAS Volumes
Manage NAS volumes and NAS volume alerts.
Adding a NAS Volume
Add a NAS volume to allocate storage that can be shared on the network. When a NAS volume is added,
default values are applied for some settings. To change the defaults, you must modify the NAS volume.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
The NAS volumes are displayed in the All NAS Volumes pane.
92
Page 93

Adding a NAS Volume
Add a NAS volume to allocate storage that can be shared on the network. When a NAS volume is added,
default values are applied for some settings. To change the defaults, you must modify the NAS volume.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click .
4. Click New NAS Volume.
The New NAS Volume dialog box appears.
5. In the NAS volume name field, type a name for the NAS volume.
6. In the Size field, type a size for the NAS volume in megabytes (MB), gigabytes (GB), or terabytes (TB).
NOTE: A NAS volume must have a minimum size of 20MB.
7. Click OK.
Renaming a NAS Volume
Rename a NAS volume.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, for the NAS volume that you want to rename, click .
4. Click Rename.
The Rename NAS Volume dialog box appears.
5. In the New name field, type a new name for the NAS volume.
6. Click OK.
Changing Access Time Granularity for a NAS Volume
Change the access time granularity settings of a NAS volume to change the interval at which file‐access
time stamps are updated.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click View Details.
The Space view is displayed for the selected volume.
5. In the NAS Volume Advanced Settings pane, click .
6. Click Modify File Access Time Granularity.
The Modify File Access Time Granularity for NAS Volume dialog is displayed.
7. Select one of the available options:
– Never
– Once (every 5 minutes/an hour/a day)
– Always
8. Click OK.
93
Page 94

Changing Permissions Interoperability for a NAS Volume
Change the permissions interoperability settings of a NAS volume to change the file access security style
for the NAS volume.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click Modify Interoperability Policy.
The Modify CIFS & NFS Interoperability Policy dialog box appears.
5. Select the file access security style for the NAS volume (Unix, NTFS , or Mixed).
6. Click OK.
Enabling or Disabling Zero Disk Usage Reporting for a NAS Volume
When zero disk usage reporting is enabled for a NAS volume, the DU (Disk Usage) command reports 0
when the actual allocated size of a file is unknown (as compatible with VMWare thin provisioning).
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click View Details.
The volume’s Space view is displayed.
5. In the NAS Volume Advanced Settings pane, click .
6. Click Modify DU Compatibility.
The Modify DU Compatibility for NAS Volume dialog box appears.
7. Select one of the following reporting options:
– The size of the file as the allocated size
– Zero (0) as the allocated size (VMWare thin provisioning compatible)
8. Click OK.
Changing the Space Settings of a NAS Volume
Change the space settings of a NAS volume, including provisioning, size, and reserved space.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click Modify NAS Volume Space.
The Modify NAS Volume Space dialog box appears.
5. In the Size section, type a new size for the NAS volume and select the size unit (megabytes [MB],
gigabytes [GB], or terabytes [TB]).
6. In the Space Provisioning section, select the space provisioning type (Thick or Thin).
NOTE: The new size must be larger than the space used by the NAS volume.
94
Page 95

7. For Thin NAS Volumes: in the Reserved Space field, type the size of the storage that is statically
allocated to the NAS volume and select the units as megabytes (MB), gigabytes (GB), or terabytes
(TB).
NOTE: The reserved space must be smaller than the configured size of the NAS volume.
8. Click OK.
Enabling or Disabling a NAS Volume Used Space Alert
You can enable an alert that is triggered when a specified percentage of the NAS volume space has been
used.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click Modify NAS Volume Space.
The Modify NAS Volume Space dialog box appears.
5. Enable or disable a NAS volume used space alert:
– To enable a NAS volume used space alert, select the Alert when used space is over check box.
– To disable a NAS volume used space alert, clear the Alert when used space is over check box.
6. If a NAS volume used space alert is enabled, in the Over X % of NAS Volume Size field, type a number
(from 0 to 100) to specify the percentage of used NAS volume space that triggers an alert.
7. Click OK.
Enabling or Disabling a NAS Volume Unused Space Alert
You can enable an alert that is triggered when the remaining unused NAS volume space is below a
specified size. If a client application requires a certain amount of storage space, you might want to enable
an unused space alert to ensure that the application always has the required storage space.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click Modify NAS Volume Space.
The Modify NAS Volume Space dialog box appears.
5. Enable or disable a NAS volume used space alert:
– To enable a NAS volume used space alert, select the Alert when used space is below check box.
– To disable a NAS volume used space alert, clear the Alert when used space is below check box.
6. If a NAS volume used space alert is enabled, in the Below X % of NAS Volume Size field, type a
number (from 0 to 100) to specify the percentage of used NAS volume space that triggers an alert.
7. Click OK.
Enabling or Disabling a NAS Volume Snapshot Space Consumption Threshold Alert
You can enable an alert that is triggered when a specified percentage of the NAS volume space has been
used for snapshots.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click Modify NAS Volume Space.
The Modify NAS Volume Space dialog box appears.
95
Page 96

5. Enable or disable a NAS volume snapshot space consumption threshold alert.
– To enable a NAS volume snapshot space consumption threshold alert, select the Alert when
snapshot space is over check box.
– To disable a NAS volume snapshot space consumption threshold alert, clear the Alert when
snapshot space is over check box.
6. If a NAS volume snapshot space consumption threshold alert is enabled, in the Over X % of NAS
Volume Size
space that triggers an alert.
7. Click OK.
field, type a number (from 0 to 100) to specify the percentage of used NAS volume
Deleting a NAS Volume
After deleting a NAS volume, the storage space used by the deleted NAS volume is reclaimed by the NAS
pool. Deleting a NAS volume deletes all the files and directories as well as its properties, that is, CIFS
shares and NFS exports, snapshots definitions, and so on. Once deleted, the NAS volume cannot be
restored unless it is redefined and restored from an external backup.
• Before a NAS volume can be deleted, you must remove its CIFS shares, NFS exports, replications,
quota rules, NAS volume clones, and any other reference to the NAS volume.
• Ensure that the NAS volume is not mounted and warn affected clients that the data will be deleted.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume you want to modify.
4. Click Delete.
The Delete NAS Volume dialog box appears.
5. Click OK.
Cloning a NAS Volume
Cloning a NAS volume creates a writable copy of the NAS volume. This is useful to test against non‐
production data sets in a test environment without impacting the production file system environment.
Most operations that can be performed on NAS volumes can also be performed on clone NAS volumes,
such as resizing, deleting, and configuring CIFS shares, NFS exports, snapshots, replication, NDMP, and so
on.
The cloned NAS volume is created from a snapshot (base snapshot) from the original NAS volume (base
volume). No space is consumed by the clone NAS volume until data stored on it is modified.
NAS Volume Clone Defaults
The clone NAS volume will have the following default values:
• Has the same size as its base volume, is thin‐rovisioned, and its reserve space is 0 (and therefore it
consumes no space)
• Quota usage is copied from the base snapshot of the base volume
• Quota rules have the default definitions (like a new NAS volume)
• Has the same permissions on folders including the root directory as the base volume
• Has the same security style and access time granularity definitions as the base volume
• There are no CIFS shares, NFS exports, or snapshot schedules defined
96
Page 97

NAS Volume Clone Restrictions
The following restrictions apply to cloned NAS volumes:
• You cannot create a clone NAS volume of a clone NAS volume (nested clones) unless a clone NAS
volume is replicated to another FluidFS cluster and then cloned.
• You cannot delete a base volume until all of its clone NAS volumes have been deleted.
• A snapshot cannot be deleted as long as there are clone NAS volumes based on it.
• Restoring to an older snapshot fails if it would result in a base snapshot being deleted.
• You can replicate a clone NAS volume only after the base volume is replicated. If the base snapshot in
the base volume is removed, and a clone NAS volume exists on the replication target FluidFS cluster,
replication between NAS volumes will stop. To resume replication, the cloned NAS volume on the
target FluidFS cluster must be deleted.
• You cannot create a clone NAS volume from a replication source NAS volume or NDMP snapshot.
However, you can create a clone NAS volume of a replication target NAS volume.
• Prior to creating a clone NAS volume, data reduction and the snapshot space consumption threshold
alert must be disabled on the base volume (previously deduplicated data is allowed).
• Data reduction cannot be enabled on a clone NAS volume.
• Once a NAS volume is cloned, data reduction cannot be re‐enabled until all clone NAS volumes have
been deleted.
• A clone NAS volume contains user and group recovery information, but not the NAS volume
configuration.
• Clone NAS volumes count towards the total number of NAS volumes in the FluidFS cluster.
Managing NAS Volume Clones
View, create, and delete NAS volume clones.
Viewing NAS Volume Clones
View the current NAS volume clones.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume whose NAS volume clones you want
to view.
4. Click View Details.
5. Click the Snapshots tab on the top.
The cloned volumes are displayed in the Cloned NAS Volumes pane.
Creating a NAS Volume Clone
Cloning a NAS volume creates a writable copy of the NAS volume.
• There must be an existing snapshot from which the clone NAS volume will be created.
• Data reduction must be disabled on the base volume.
97
Page 98

• The snapshot space consumption threshold alert must be disabled on the base volume.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume whose NAS volume clones you want
to view.
4. Click View Details.
5. Click the Snapshots tab on the top.
6. In the Snapshots pane, click in the row of the snapshot on which you want to base the clone.
7. Click Clone NAS Volume.
The Clone NAS Volume dialog box appears.
8. In the Cloned NAS volume name field, type a name for the NAS volume clone.
9. Click OK.
Deleting a NAS Volume Clone
Delete a NAS volume clone if it is no longer used.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
In the All NAS Volumes pane, click in the row of the volume whose NAS volume clones you want
3.
to view.
4. Click View Details.
5. Click the Snapshots tab on the top.
6. In the Snapshotspane, click in the row of the snapshot on which you want to base the clone.
7. Click Delete.
The Deletedialog box appears.
8. Click OK.
A message appears, warning you that all data on the clone will be lost.
9. Click the Ignore the above warning checkbox.
10. Click OK.
Managing CIFS Shares
Common Internet File System (CIFS) shares provide an effective way of sharing files across a Windows
network with authorized clients. The FluidFS cluster supports the SMB protocol versions 1.0, 2.0, and 2.1.
When you first create a CIFS share, access is limited as follows:
• The Administrator account has full access.
• If you are using Active Directory, the AD domain administrator has full access.
To assign other users full access to a CIFS share, you must log in to the CIFS share, using one of the
above mentioned administrator accounts, and set access permissions and ownership of the CIFS share.
Configuring CIFS Shares
View, add, modify, and delete CIFS shares.
98
Page 99

Viewing All CIFS Shares on the FluidFS Cluster
View all current CIFS shares for the FluidFS cluster.
1. Click the NAS Volumes tab on the left.
2. Click the All CIFS Shares tab on the top.
The CIFS shares are displayed in the All CIFS Shares pane.
Viewing CIFS Shares on a NAS Volume
View the current CIFS shares for a NAS volume.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume whose CIFS shares you want to view.
4. Click View Details.
5. Click the CIFS Shares tab on the top.
The details of the volume’s CIFS shares are displayed.
Adding a CIFS Share
Create a CIFS share to share a directory in a NAS volume using the CIFS protocol. When a CIFS share is
added, default values are applied for some settings. To change the defaults, you must modify the CIFS
share.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume whose CIFS shares you want to view.
4. Click View Details.
5. Click the CIFS Shares tab on the top.
6. In the CIFS Shares pane, click .
7. Click New CIFS Shares.
The New CIFS Shares dialog box appears.
8. In the CIFS Share name field, type a name for the new CIFS share.
9. Click the […] button to the right of the Folder field.
The Browse Folders dialog box appears.
10. In the folder tree, click [+] to expand subfolders.
11. Select a folder from the tree or type a folder in the edit box under the folder tree. (To share the root
of the NAS volume, type /).
12. Click OK.
13. If the folder you entered doesn’t exist and you want to create it, check the Create the folder if it
does not exist
14. Click OK.
checkbox.
Enabling or Disabling Accessed-Based Share Enumeration for a CIFS Share
Create a CIFS share to share a directory in a NAS volume using the CIFS protocol. When a CIFS share is
added, default values are applied for some settings. To change the defaults, you must modify the CIFS
share.
When SLP access‐based share enumeration is enabled, if a given user or group does not have share level
permissions for a particular CIFS share, the CIFS share, and its folders and files, will not be visible to that
99
Page 100

user or group. When SLP access‐based share enumeration is disabled, the CIFS share, and its folders and
files, will be visible to users and groups regardless of whether they have permissions for the CIFS share.
To enable or disable accessed-based share enumeration for a CIFS share:
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume whose CIFS shares you want to view.
4. Click View Details.
5. Click the CIFS Shares tab on the top.
6.
In the CIFS Shares pane, click .
7. Click Modify.
The Modify CIFS Shares dialog box appears.
8. To enable or disable access‐based share enumeration, select or clear the Access Based Enumeration
check box.
9. Click OK.
Deleting a CIFS Share
If you delete a CIFS share, the data in the shared directory is no longer shared but it is not removed.
1. Click the NAS Volumes tab on the left.
2. Click the All NAS Volumes tab on the top.
3. In the All NAS Volumes pane, click in the row of the volume whose CIFS shares you want to view.
4. Click View Details.
5. Click the CIFS Shares tab on the top.
6. In the CIFS Shares pane, click .
7. Click Delete.
The Delete CIFS Shares dialog box appears.
8. Click OK.
Viewing and Disconnecting CIFS Connections
You can view active CIFS client connections and disconnect individual CIFS connections.
Displaying Active CIFS Connections
Display the current CIFS connections.
1. Click the Performance & Connectivity tab on the left.
2. Click the CIFS and NDMP Sessions tab on the top.
The active CIFS connections are displayed in the CIFS Session pane.
Disconnecting a CIFS Connection
Disconnect a particular CIFS connection.
1. Click the Performance & Connectivity tab on the left.
2. Click the CIFS & NDMP Sessions tab on the top.
3. In the CIFS Sessions pane, click in the row of the session you want to disconnect.
100
 Loading...
Loading...