Page 1

DRAC 5
Dell Remote Access Card 5 Security
Information in this document is subject to change without notice.
© Copyright 2006 Dell Inc. All rights reserved.
Reproduction in any manner whatsoever without the written permission of Dell Inc. is strictly
forbidden.
THIS DOCUMENT IS FOR INFORMATIONAL PURPOSES ONLY. THE CONTENT IS
PROVIDED AS IS, WITHOUT EXPRESS OR IMPLIED WARRANTIES OF ANY KIND.
Dell, the Dell Logo, and OpenMana ge are trademarks of Dell Inc. Other trademarks a nd trade
names may be used in this document to refer to either the entities claiming the m arks and names
or their products. Dell disclaims proprietary interest in the marks a nd names of othe rs.
Page 2

Table of Contents
TERMINOLOGY......................................................................................................................................................................................................4
INTRODUCTION.....................................................................................................................................................................................................6
AUTHENTICATION AND AUTHORIZATION.......................................................................................................................................................7
L
OG IN VIA LOCAL ACCOUNT
RAC Login User Privilege..............................................................................................................................................................................8
RAC Card Configuration Privilege................................................................................................................................................................8
RAC User Configuration Privilege.................................................................................................................................................................8
RAC Log Clear Privilege................................................................................................................................................................................8
RAC Server Reset and Power-on/off Privilege............................................................................................................................................8
RAC Console Redirection Privilege..............................................................................................................................................................8
RAC Virtual Media Privilege..........................................................................................................................................................................8
RAC Test Alert Privilege................................................................................................................................................................................8
RAC Debug Command Privilege..................................................................................................................................................................8
L
OG IN VIA ACTIVE DIRECTORY WITH DELL SCHEMA EXTENSION
L
OG IN VIA ACTIVE DIRECTORY WITHOUT DELL SCHEMA EXTENSION
ENCRYPTION.......................................................................................................................................................................................................12
SSL C
ERTIFICATE MANAGEMENT
S
UPPORTED
S
ECURE SHELL ENCRYPTION
IPMI RMCP+ E
SSL C
NCRYPTION
..................................................................................................................................................................................7
..........................................................................................................................8
..................................................................................................................10
........................................................................................................................................................................12
IPHER SUITES
.......................................................................................................................................................................12
..............................................................................................................................................................................13
................................................................................................................................................................................13
EVENT LOGGING.................................................................................................................................................................................................14
L
OG FORMAT
L
OG EVENTS
ACCESS TO DRAC 5...........................................................................................................................................................................................15
D
ISABLING SERVICES AND CHANGING THE SERVICE PORT NUMBER
S
ECURITY POLICY
IP Blocking....................................................................................................................................................................................................17
Invalid Login Attack Blocking.......................................................................................................................................................................17
SHARED NIC SECURITY....................................................................................................................................................................................19
W
EB BROWSER SECURITY
R
EMOTE
L
OCAL
SSH S
SNMP S
V
IRTUAL MEDIA SECURITY
......................................................................................................................................................................................................14
.......................................................................................................................................................................................................14
....................................................................................................................15
...............................................................................................................................................................................................17
..................................................................................................................................................................................20
CLI S
ECURITY
......................................................................................................................................................................................20
CLI S
ECURITY
..........................................................................................................................................................................................20
ECURITY
...................................................................................................................................................................................................20
ECURITY
................................................................................................................................................................................................21
..................................................................................................................................................................................21
PAGE 2 OF 24
Page 3

C
ONSOLE REDIRECTION SECURITY
.....................................................................................................................................................................22
Authentication and Encryption.....................................................................................................................................................................22
User Session Privacy...................................................................................................................................................................................23
IPMI OUT-OF-B
AND ACCESS SECURITY
..............................................................................................................................................................24
PAGE 3 OF 24
Page 4
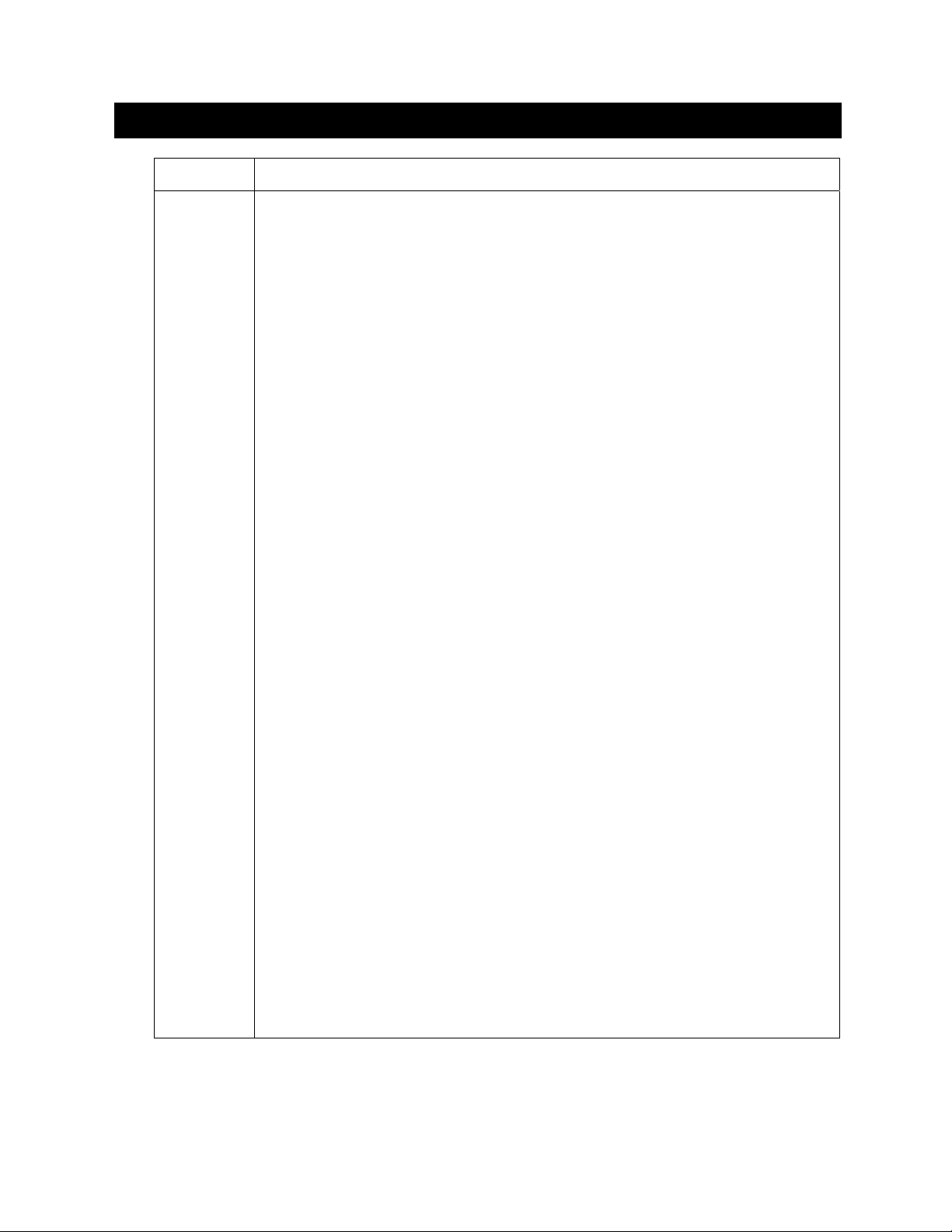
T erminology
Term Definition
CA
CAST 128
CD
CLI
CSR
3 DES
DH
DNS
DRAC 5
DSA
GUI
HTTP
HTTPS
IP
IPMI
KVM
LAN
LDAP
LDAPS
LOM
MAC
MD5
MS
NIC
NVRAM
OS
PET
PKI
RAC
RC4
RMCP
RSA
SEL
Certificate Authorization
CAST Algorithm 128-bit
Compact Disk
Command Line Interface
Certificate Signing Request
Triple Data Encryption Standard
Diffie-Hellman
Domain Name Server
Dell Remote Access Controller
Digital Signature Algorithm
Graphic User Interface
Hypertext Transfer Protocol
Hypertext Transfer Protocol Secure
Internet Protocol
Intelligent Platform Management Interface
Keyboard Video Mouse
Local Area Network
Lightweight Directory Access Protocol
Lightweight Directory Access Protocol Secure
Lay on Mother Board
Media Access Control
Message Digest Algorithm Number 5
Microsoft
Network Interface Card
Non-Volatile Random Access Memory
Operating System
Platform Event Trap
Public Key Infrastructure
Remote Access Controller
ARC Four Algorithm
Remote Management Control Protocol
Rivest Shamir Adleman
System Event Log
PAGE 4 OF 24
Page 5
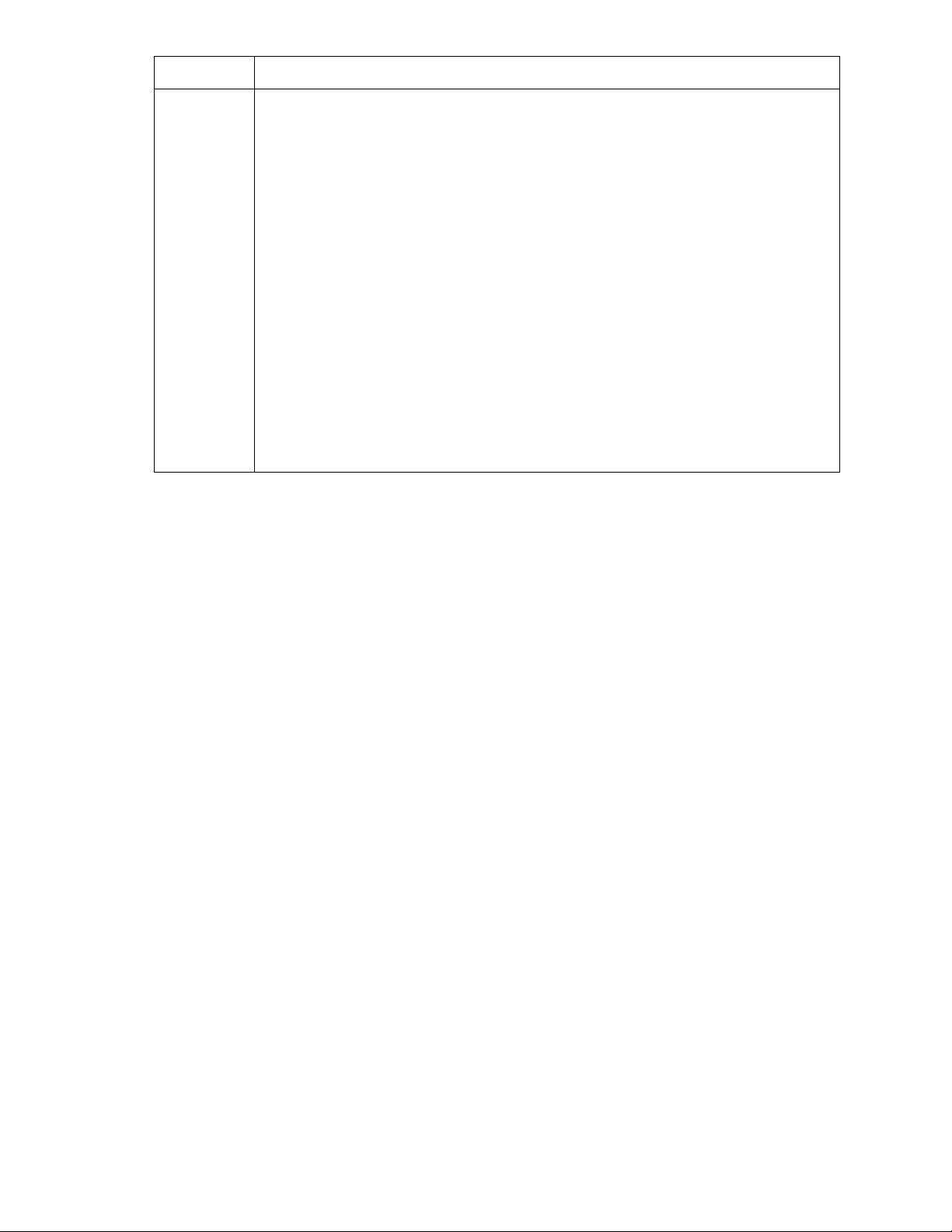
Term Definition
SHA1
SMCLP
SMTP
SNMP
SOL
SSH
SSL
TCP
TCP/IP
TFTP
TLS1.0
UDP
URL
VLAN
VNC
Seane Hash Algorithm
Server Management Command Line Protocol
Simple Mail Transfer Protocol
Simple Network Management Protocol
Serial Over LAN
Secured Shell
Secured Socket Layer
Transmission Control Protocol
Transmission Control Protocol/Internet Protocol
Trivial File Transfer Protocol
Transport Layer Security
User Datagram Protocol
Uniform Resource Locator
Virtual Local Area Network
Virtual Network Computing
PAGE 5 OF 24
Page 6

Introduction
Today, managing distributed servers from a remote location i s a critical require ment.
DRAC 5 enables users to remotely monitor, tro ubleshoot , and repair se rvers even when th e server
is down. DRAC 5 offers a rich set of features like virtual medi a, virtual KVM, and so on, which have
the potential to make the system prone to security risks. DRAC 5 security features mit igate the
security risks that exist while data is being tra nsmitted across the network. Thi s white pape r briefly
describes the security features that DRA C 5 uses to hel p ensure aut henticati on, authorization,
privacy, and data integrity.
PAGE 6 OF 24
Page 7

Authentication and Authorization
Log in via Local Account
The DRAC 5 ships with a default local user accou nt that is pre-co nfigured with an admin istrator
role. This default user name is “root” and the password i s “calvin” for this user.
Dell strongly recommends changing thi s default setti ng during deployment of the DRAC 5.
DRAC 5 supports up to 16 local users. Each user can be enabled or disabled. You can secure the
DRAC 5 by disabling all local user accounts and using only Micro soft
®
Active Directory® users since
Active Directory is considered to have stronger secure policy management.
Local users’ user names and passwords can be changed. DRAC 5 local users’ account policy is as
follows:
Anonymous user is NOT supported
NULL user name is NOT supported
NULL password is NOT supported
Maximum user name length is 16 characters
Maximum user password length is 20 characters
DRAC 5 local user account information is stored on NVRAM and is encrypted via a proprietary
algorithm.
DRAC 5 supports privilege-based access to a DRAC. Every local user or Active Directory user has
a privilege set associated with it. The privilege is per channel per user. The privilege set decides
what kind of rights a user has on the DRAC 5 on each of the access channe ls.
There are three types of access channels on DRAC 5:
IPMI LAN channel
IPMI Serial channel
RAC channel – including RA C web GUI, RAC serial/t elnet /SSH console , RACADM CLI , RAC
SM-CLP, RAC virtual media, RAC cons ole redire ction
IPMI LAN and IPMI serial channel privilege are defined in the IPMI 2.0 specification. (See IPMI
Out-of-band Access Security
for further information.)
PAGE 7 OF 24
Page 8

The DRAC 5 RAC channel has nine privil eges. Each user ca n have any combi nation of the nine
privileges. The nine privileges are as follows:
RAC Login User Privilege
This privilege allows a user to log in to the DRAC 5 card. An ad ministrat or can easily disa ble a user
from a DRAC 5 by removing this privilege. Removing th e login privilege from a user is not the
same as deleting a user. The user will remain in the user database but will not be able to log in
and use this DRAC 5 card. An administrat or can quickly re-en able this user by g ranting the login
privilege without having to totally reconfigure this user.
RAC Card Configuration Privilege
This privilege allows a user to change all DRAC 5 card configurations except fo r the user
configuration, for example, out-of-band NIC confi guration, SNMP trap configuration, SSL certificate
configuration, and so on.
RAC User Configuration Privilege
This privilege allows a user to add or delete a user or chang e existing user privile ges.
RAC Log Clear Privilege
This privilege allows a user to clear the System Event Log (SEL), RA C log, or last crash scree n
log.
RAC Server Reset and Power-on/off Privilege
This privilege allows a user to do any power manageme nt operation (like reset or power-on/off a
system).
RAC Console Redirection Privilege
This privilege allows a user to use the console redirection feat ure.
RAC Virtual Media Privilege
This privilege allows a user to use the virtual media feature.
RAC Test Alert Privilege
This privilege allows a user to submit a request to DRAC 5 to test an S NMP trap alert to a pre configured destination.
RAC Debug Command Privilege
This privilege allows a user to issue any debug command. Most of debug command s are used to
help debug or diagnose a DRAC 5.
Dell strongly recommends assig ning this pri vilege only to adm inistrators or service per sonnel
required to help debug or diagnose the DRAC 5.
Log in via Active Directory With Dell Schema Ext ension
A directory service maintains a common database of all i nformation needed f or controlling users,
computers, printers and so forth on a network. If your compa ny uses the Active Dire ctory service
software, you can configure the softwa re to provide access to t he DRAC 5 allowi ng you to add and
control DRAC 5 user privileges to existing users in the Active Directory software.
PAGE 8 OF 24
Page 9

The Active Directory data is a distributed database of Attributes and Classe s. The Active Di rectory
schema includes the rules that det ermine the type of data that ca n be added or i ncluded in the
database. The user class is one exam ple of a Class that is stored in the dat abase. Some example
user class attributes can include t he user’s first nam e, last name, phone number, and so on.
Companies can extend the Active Directory data base by adding thei r own unique Attribute s and
Classes to solve environment-specific needs. Dell has e xtended the schema to in clude the
necessary changes to support remote manage ment Authentication and Authorization.
To provide the greatest flexibility in a variety of customer environments, Dell provides a group of
properties that can be configured by the user depending on the desired results. Dell has extended
the schema to include Association, Device, and Privilege properti es. The Associatio n property is
used to link together the users or groups with a specific set of p rivileges to one or more RA C
devices. This model provides an Administrator with maximum flexibility over the diff erent
combinations of users, RAC privileges, an d RAC devices o n the network with out adding too mu ch
complexity.
Figure 1: Dell Extended Schema Active Directory Architecture
DRAC 5 authenticates against Active Dire ctory using LDAP sim ple binding and q ueries Active
Directory objects via an SSL channel. All data incl uding use r name and passwo rd for
authentication are sent via an encrypted channel to Active Dire ctory. When a DRA C 5 establis hes
an SSL connection with Active Directory Domain Controller, it verifies the Domain Controll er entity
via SSL server authentication. The root CA SSL certificate (whi ch is used to sign all the Dom ain
Controller= SSL certificates) has been impo rted to the DRAC. DRAC 5 support s up to a 4096-bit
root CA certificate and Domain Controller SSL certificate.
Dell strongly recommend following the M icrosoft PKI best practi ces and using 4096-bit for the root
CA certificate and a 1024-bit for the Domain Controll er certificate.
PAGE 9 OF 24
Page 10

For an Active Directory user to have authority to access a DRAC 5, thi s user object or grou p has to
be added to the Dell Association object. A Dell privilege object with the right privilege setting a lso
needs to be added to the Dell Association object. Finally, a Dell RAC d evice object which
represents a DRAC 5 is added to Dell Associatio n object. The RA C device object name has to be
configured to that DRAC 5.
The basis for searching Active Directory to authenticate and authorize the RAC User will be that
there is a member-memberOf relationship on the Associ ation Object -- it is deriv ed from group.
Every member of a Group has a corresponding Linked Attribut e member called m emberOf that is
part of the User Class. When we authenticate a user wi th LDAP, we can get the membe rOf
Attribute that will contain all of the Groups that this user is a member of. We can then walk
through these groups until we arrive at our dellAsso cationObject class. Note that the user could be
a member of multiple association object classes, so we must take this into account in our query.
When we find the dellAssocationObject Class that this user is a member of, we will then access the
dellProductMembers attribute and walk this in t he reverse order to dete rmine if the RacDevice,
from which we are authenticating, is part of this attri bute. Note that the dellProductM embers can
be groups of RACs and will retain the aforementione d member-memberOf relati onship. So, we wi ll
walk the list using the Member attribute for all of the g roups that are in t he list. If we find the na me
of the RAC Device that we are authenticating in the li st, then we have a uthenticated the u ser and
all we need to do is read the dellPrivilegeObject attributes and return them to the RA C as the
authorization data (Privileges).
Log in via Active Directory Without Dell Schema Extension
NOTE: Requires DRAC 5 version 1.20 firm ware and lat er.
Dell has been using Active Directory to m anage DRA C 5 users and t heir acce ss privileges on
different DRAC 5 cards. The schema-extending solution provides maximum flexibility to the user
but may be intimidating to some customers because the sch ema extension is not rev ersible.
To meet the requirements from those customer s who do not want to ex tend their exist ing Active
Directory schema, Dell now provides a standard schem a solution in additio n to the schema
extension. This solution will provide the same flexibility of the current schema-extending solution –
it will allow granting different users different privileges on different DRAC 5 cards. The difference is
that all the objects used in the standa rd schema solutio n are stand ard Active Dire ctory objects
while the schema-extending solution adds Dell objects to the u sers’ Active Di rectory.
The basic authentication and SSL con nection are the sa me as the Active Dire ctory with the Del l
schema extension solution.
Instead of using the Dell Association object, Dell privilege obj ect, and RAC device obj ect to link a
user, a standard group object has been used a s a role group object. Any user s in that role g roup
have assigned privileges on certain DRAC 5 cards. The privilege of that rol e group has bee n
defined in each individual DRAC 5 configu ration database. Different DRA C 5 cards can giv e the
same role group object different privileges.
PAGE 10 OF 24
Page 11

Figure 2: Dell Standard Schema Active Directory Architecture
PAGE 11 OF 24
Page 12

Encryption
The SSL security protocol that is built upon public key/private key encry ption technology has b een
universally accepted on the World Wide Web for authenticat ed and encrypte d communication
between clients and servers to prevent eavesdrop ping across the net work. Running abov e TCP/IP
and below higher-level protocols such a s HTTP, SSL allows an SSL -enabled serv er to
authenticate itself to an SSL-enabled client and the clie nt to authenticat e itself to the server. SSL
allows both servers to establish an encry pted conn ection.
SSL Certificate Management
DRAC 5 ships with a default self-signed SSL certificate. DRAC 5 uses 1024 -bit RSA with SHA-1.
Dell strongly recommends replacin g the default certif icate with you r own SSL certifi cate to secure
the DRAC 5 since all DRAC 5 cards ship with the same SSL certifi cate and wit h the same SSL
private key.
The DRAC 5 server SSL certificate is used by the web server, Virtual Media server, and Console
Redirection server.
Administrators can replace the DRAC 5 server SSL certif icate usi ng the following steps:
Generate the CSR and the Private Key from a DRAC 5. 102 4-bit, 2048-bit and 4096 -bit RSA
key are supported.
Dell strongly recommends havi ng CSR CN (com mon name) set to be the same a s your DRAC 5
RAC name to avoid a host name mismatch complai nt during SSL conne ction from browsers.
Large certificate asymmetric key size (RS A key size ) can affect DRA C 5 performance.
Microsoft PKI best practices suggest using 1024-bit to secure your web server application.
Sign the CSR by a trusted CA.
Upload the signed CSR (Certificate) to your DRAC 5.
Supported SSL Cipher Suites
DRAC 5 supports SSL version 3 and TLS version 1. 0. The following a re ciphers su pported on
DRAC 5:
SSL_RSA_WITH_RC4_128_MD5
SSL_RSA_WITH_RC4_128_SHA
SSL_RSA_WITH_3DES_EDE_CBC_SHA
SSL_RSA_WITH_3DES_EDE_CBC_MD5
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
PAGE 12 OF 24
Page 13

Secure Shell Encryption
DRAC 5 supports only SSH-2.0 because SSH-1.0 is not considered secure.
The following are ciphers supported by th e DRAC 5 SSH:
Public key: DSA, RSA
Hash: SHA-1, MD5
Symmetric: 3DES, RC4, Blowfish, CAST-128
IPMI RMCP+ Encryption
DRAC 5 IPMI over LAN and SOL use RMCP+ for Auth entication and Key exchang e. For detail s on
the RMCP+ protocol, see the IPMI 2.0 specification.
DRAC 5 IPMI supports the following encry ption algorithms:
AES-CBC-128 (128-bit AES with CBC)
RC4-128 (128-bit RC4)
PAGE 13 OF 24
Page 14

Event Logging
DRAC 5 has a persistent log which st ores all critical events like user logi n/logout, DRAC 5
configuration changes, and critical operations to a serve r via DRAC 5, and so o n. Administrators
can use this log to audit critical operations on th e DRAC 5.
Log Format
All log entries include:
Time of the event
Application associated with the event
User or initiating process
Remote IP address associated with the event
Detailed description of the event
Log Events
The following are categories of events logged in t he DRAC 5 l og:
All valid and failed login attempts
All logout events
All security policy changes, like channel privilege, IP blocking, and so on
All user account management changes (such as user creation o r deletion, user privi lege
changes, and so on)
All PET alerts or test alerts sent by a DRAC 5
All server power management via a DRAC 5 such as power on, power off, power cycle, and
hard reset to a system
DRAC 5 firmware update
Start /Stop a DRAC 5 Virtual Media session
Start/Stop a DRAC 5 Console Redirection se ssion
PAGE 14 OF 24
Page 15

Access to DRAC 5
Disabling Services and Changing the Service Port Numbe r
There are several out-of-band services running on a DRAC 5 by default. These service s open a
network port that listens for a connection.
Dell strongly recommends disabling all un used services on DRAC 5 card s
.
The following are services which can be enable d or disabled by a dministrators:
SNMP Agent
Telnet (disabled by default)
SSH
Web Server
Console Redirection Service
Virtual Media Service
IPMI LAN interface (disabled by default)
IPMI SOL interface
Ports must be correctly configured to allo w DRAC 5 to work throu gh firewall s. The followi ng table
lists the ports used by DRAC 5.
Port # Protocol Port
Type
DRAC 5
Firmware
Version
Maximum
Encryption
Level
Direction Usage Configurable
22 SSH version 2 TCP 1.0 128-bit In/Out Optional Secure
Shell (SSH) CLI
management
23 Telnet TCP 1.0 None In/Out Optional Telnet CLI
management
25 SMTP TCP 1.0 None In/Out Optional e-mail alert
messages
53 DNS UDP 1.0 None In/Out Dynamic Domain
name server (DNS)
registration of the
host name assigned
within DRAC 5 and
ADS authentication
DNS lookup
PAGE 15 OF 24
Yes
Yes
No
No
Page 16

Port # Protocol Port
Type
DRAC 5
Firmware
Version
Maximum
Encryption
Level
Direction Usage Configurable
68 DHCP UDP 1.0 None In/Out DHCP assigned
No
IP address
69 TFTP UDP 1.0 None In/Out Firmware update via
No
Trivial FTP
80 HTTP TCP 1.0 None In/Out Web GUI redirected
Yes
to HTTPS
161 SNMP UDP 1.0 None In/Out SNMP query
No
management
162 SNMP UDP 1.0 None Out SNMP trap event No
443 HTTPS TCP 1.0 128-bit SSL In/Out Web management
Yes
GUI and remote
RACADM CLI utility
623 RMCP/RMCP+ UDP 1.0 128-bit RC4
or AES
636 LDAPS TCP 1.0 128-bit SSL In/Out Optional Active
In/Out IPMI Over LAN and
IPMI SOL
No
No
Directory Services
(ADS) authentication
3269 LDAPS TCP 1.0 128-bit SSL In/Out Optional Active
3668 Proprietary TCP 1.0 None In/Out CD/diskette virtual
3669 Proprietary TCP 1.0 128-bit SSL In/Out CD/diskette virtual
5900 Proprietary TCP 1.0 128-bit SSL In/Out Video redirection Yes
5901 Proprietary TCP 1.0 128-bit SSL In/Out Keyboard/Mouse
Table 1: Port Configuration for DRAC 5
PAGE 16 OF 24
No
Directory Services
(ADS) authentication
Yes
media service
Yes
media service
Yes
redirection
Page 17

Security Policy
To prevent unauthorized access to the remote system, DRAC 5 provides the f ollowing features
which have been described in ”IP Blocking” and “Invalid Logi n Attack Blocking.”
IP address filtering (IPRange) — defines a specifi c range of IP addresses th at can access the
DRAC 5
IP address blocking — limits the n umber of failed login att empts from a specifi c IP address
IP Blocking
This feature is disabled in the DRAC 5 default configuration. Use the RACADM config
subcommand or the Web-based interf ace to enable thi s feature.
Additionally, use this feature in conjunction with the appr opriate sessio n idle timeout values an d a
defined security plan for your network.
IP Filtering (IPRange) and IP address filtering (or IP Range Ch ecking) allo w DRAC 5 to be
accessed only from clients or managemen t workstations wh ose IP addresses are within a userspecific range. All other logins are denied.
IP filtering compares the IP address of an incoming l ogin to the IP address ran ge that is specified
by the following properties:
cfgRacTuneIPRangeEnable Enables the IP range checking feature.
Property Description
cfgRacTuneIPRangeAddr Determines the acceptable IP address bit pattern
cfgRacTuneIPRangeMask Defines the significant bit positions in the IP address. The
Table 2: Properties for RAC Tuning
Invalid Login Attack Blocking
To prevent a repeat attack and a password guess attack to your remote system, the DRAC 5
provides IP address blocking. This feature limits the number of faile d login attempts from a spe cific
IP address.
The IP blocking feature dynamically determines when ex cessive login failures h ave occurred from
a specific IP address and blocks (or prevents) the IP addres s from logging into the DRA C 5 for the
time span configured in the DRAC 5.
positions depending on the 1’s in the subnet mask. This
property is bitwise, and uses the “width with
cfgRacTuneIPRangeMask” property to determine the
upper portion of the allowed IP address. Any IP address
that contains this bit pattern in its upper bits is allowed to
establish a DRAC 5 session. Logins from IP addresses
that are outside this range will fail. The default values in
each property allow an address range from 192.168.1.0
to 192.168.1.255 to establish a DRAC 5 session.
subnet mask should be in the form of a netmask, where
the more significant bits are all 1’s with a single transition
to all zeros in the lower-order bits.
PAGE 17 OF 24
Page 18

As login failures accumulate from a specific IP address, they a re "aged" by an internal co unter.
When the login failures reach the maximum ag e of the internal cou nter window, they are deleted
(or forgiven). When a valid login occu rs from an IP address that is not penali zed (the excessiv e
login failures are being held in cfgRacTune IpBlkPenaltyTime), all previous logi n failures for the IP
address are deleted. The failure history cannot be clea red except by a valid logi n attempt.
When the excessive failures are detected, logi n will be blocked for a pr e-selected time span.
However, this feature can be disabled to allow logi n from the targeted IP add ress.
Dell strongly recommends using the IP blo cking feature and setting the limit on in valid login
attempts to your environment requirements.
PAGE 18 OF 24
Page 19

Shared NIC Security
The DRAC 5 on 9xxx Generation Dell servers has the capability to use the host LOM for DRAC 5
management traffic instead of a dedicated NIC. I n this case, the ho st LOM shares the host traffi c
with DRAC 5 management traffic.
This feature has an advantage for customers who do not want t o maintain a separate network for
management traffic. It can reduce the cabling m ess and netwo rk switch port require ments. The
shared NIC (LOM) contains two sepa rate MAC add resses – one for th e DRAC 5 traf fic and
another for the host system traffic. The MAC layer i s a sub-layer in th e hardware dat a-link laye r.
DRAC 5 maintains its own IP address, whi ch ensures that a client can a ddress DRAC 5
independently of the host system even though the host and man agement traffic sh are the same
port.
The following figure describes the shared NIC architecture in DRA C 5 hardware.
MAC1
DRAC 5
CPU
OPTIONAL CARD
MAC0
Figure 3: Shared NIC Architecture
MII_Share_LOM1
SHARED_NIC_MODE_N
MII_Share_LOM0
MI_Share_LOM0
MII_Dedicated
Switches are
on DRAC 5, not
Planar
Reset_N
UMP
UMP
Dedicated
PHY
LOM 0
ROM0ROM1
LOM 1
DRAC 5 also supports a tagged VLAN. All devi ces in the VLAN appear to be o n the same network
segment which allows having DRAC 5 on a separate n etwork segme nt. Some custo mers may be
PAGE 19 OF 24
Page 20

reluctant to use the shared NIC feature because they want to sepa rate regular host traffic from
management traffic; if so, they can use VLANs to segment the traffic.
Web Browser Security
The browser connects to our web server via the HTTPS po rt. All the data stre ams are encry pted
using 128-bit SSL to provide privacy and integrity. Any connection to the HTTP port will be
redirected to HTTPS. Administrators can upload their o wn SSL certificate via a n SSL CSR
generation process to secure the web serv er. The default HTTP and HTTPS port s can be
changed. DRAC 5 ensures that user access is restricted by user privileges.
Remote CLI Security
The Remote RACADM utility is a CLI tool that can be used to configure and manage a DRAC 5.
This scriptable utility can be installed on a management station. The RACADM install ed on a
management station is ref erred to a s Remote RA CADM. The Remote RA CADM commu nicates
with DRAC 5 through its network interface, and it uses an HTTPS cha nnel to commu nicate with
DRAC 5. A user must successfully pass its user authentication and mu st have suffici ent privileges
to be able to execute the desired command. Since Re mote RACADM uses an HTTP S channel, all
the command data and return data are encrypte d by SSL. The encryption ciphers suppo rted are
the same as the web GUI interface.
Local CLI Security
The Local RACADM utility is a CLI tool that can be used to configure and manage a DRA C 5 from
the host server. This scriptable utility can only be installed on the managed syst em. The RACADM
installed on a local managed system is called Local RA CADM. Local RACA DM communicate s with
DRAC 5 through its in-band IPMI host interface. Since it is insta lled on the local mana ged system,
users are required to log in to the operating system to run this utility. The Local RACADM utility
requires that a user must have a full administrator privilege or be a root user to use t his utility. On a
Microsoft Windows
Local RACADM utility. If the user does not have administrator privil ege, an error message is
displayed indicating that they do not have privileges to run this utility. On a Linux-based syst em, a
user must log in as root on the system to have a right to run the local RACADM utility.
®
system, a user must have the administrator p rivilege on the system to run the
A user who can run Local RACADM is guarante ed to have admini strator privileg e to the syst em.
The administrator privilege level indicate s that the user has f ull rights to man age DRAC 5 including
configuration, power management, firmware upd ate, debug, and so on.
SSH Security
The SSH service is enabled by default on DRAC 5. RA CADM CLI can be run in SSH. SSH service
can be disabled via DRAC 5 configuration setting. DRAC 5 only suppo rts SSH version 2.
DRAC 5 supports DSA and the RSA host key algorithm. A unique 1024-bit DSA and 1024-bit RSA
host key is generated during a DRAC 5 first time power on.
DRAC 5 SSH:
Supports SHA-1 and MD5 hash algorithms
Supports the diffie-hellman-group1-sha1 key exchange algorithm
Supports DSA and RSA public key (asymmetric encryption) algorit hms
Supports 3DES-CBC, blowfish-cbc, cast128-cbc, and rc4 -cbc symmetric encryption
PAGE 20 OF 24
Page 21

Only supports password user authentication
Provides a default authentication timeout of 2 minutes
Provides six authentication attempts as a default
SNMP Security
An SNMP agent runs on a DRAC 5 by default. The DRAC 5 S NMP agent is used by Dell
OpenManage™ IT Assistant or other management frameworks to discover the DRAC 5 out-ofband service point, for example, a web GUI URL. DRAC 5 only supports SNMP ve rsion 1. Since
SNMP version 1 does not encrypt data and does not have a strong authentication p rotocol, there
could be security concerns about the data l eaking from DRAC 5 (for ex ample, service tag of a
system or IP address of DRAC 5, and so on).
Dell strongly recommends using o ne of the followi ng options to secure your DRA C 5 card from
these concerns:
If the DRAC 5 SNMP agent is not being used in your enviro nment, administ rators can disab le
the DRAC 5 SNMP service.
Change the DRAC 5 SNMP community name to secure thei r SNMP service. The default
DRAC 5 SNMP community name is “public.”
Limit inbound SNMP access by only accepting specific client traffic by configuring the DRAC 5
allowed client IP address range.
Virtual Media Security
Virtual media is a powerful remote access feature that allows a remote user to u se a remote
CD/floppy/image on the client side through the network. Administ rators can u se this feature for
various administrative tasks such as remote operating system installation, remote diagnostics,
remote driver/application software in stallation, and so on.
A security authentication protocol is being used i n the virtual media conne ction when a u ser logs
into a DRAC 5 web server via HTTPS with virtual media p rivilege and select s the virtual medi a tab.
A request for a connection request command is sent to the DRA C 5 firmware. The DRAC 5
firmware responds by sending a set of virtual media configuration informatio n along with an
authentication key via the HTTPS (SSL encrypted) cha nnel. The authen tication key is randomly
generated and is 32 bytes long. To prevent replay attacks, the authentication key is a one-time key
and has its own limited lifetime. If a user selects an en crypted connection, the virtual media client
software starts a connection via an SSL ch annel and sends t he authenticati on key to the virtual
media server for authentication. If the key passes the virt ual media se rver authentication, a vi rtual
media session will be established. Otherwise, a fail authentication message will be sent back to the
client and the connection will be dropped. All virtual media dat a is encrypted vi a a 128-bit RC4 key
and key exchanges via SSL, if an encrypted connection is sel ected. To ke ep virtual media
operation going and still have session idle timeout secu rity, DRAC 5 l ocks the web sessio n when a
virtual media operation is running and the web session i s timed out. A user need s to reauthenticate to unlock the web session aft er sessi on timeout. The virtual me dia operation wil l not
be interrupted during the lock-out period.
PAGE 21 OF 24
Page 22

Managed System
Web Server
Authentication Key Authentication Key
Virtual Media
Server
Figure 4: Virtual Media Architecture
SSL Channel
Connection Request
VM Info with Authentication Key
SSL if VM encryption enabled
Open session request
(authentication key)
Session established
Management Station
Client
Virtual Media
Client
Console Redirection Security
Authentication and Encryption
DRAC 5 can continuously redirect the managed system’s video, keyboa rd and mouse (KVM) to
the management station. It is a very powerful feature, is very easy to use, and do es not require any
software installation on the managed sy stem. A user can a ccess this feature t o remotely manage
the system as if they were sitting in front of the syst em.
A security authentication and encryption protocol h as been impleme nted in console redirection to
prevent a hostile, rogue client from breaking into the co nsole redirect path with out authenticating
though the web server. 128-bit SSL encryption secure s the keyboa rd keystrokes duri ng the remote
console redirection and therefore does not allow u nauthorized “snooping” of the network traffic.
The following sequence of security protocol operation s is performed duri ng the establishment of a
console redirection session:
1)
A user logs into the main web GUI then clicks the “Open Consoles” ta b.
2)
The Web GUI sends a pre-authentication request to the DRAC 5 web server via the HTTPS
channel (SSL encrypted).
3)
The DRAC 5 web server returns a set of secret data (including an encryption key) via the SSL
channel. The console redirection authentication key (32 bytes long) is dynamically generated
to prevent replay attack.
4)
The Console redirection client sends a login command with an authentication key to a console
redirection server keyboard/mouse port for authentication via SSL chan nel.
5)
If authentication is successful, a console redirection session and two console redirection pipes
(one for keyboard/mouse and one for video) are established. The keyboard/mouse pipe is
always SSL encrypted. The video pipe encryption is optional. (Users can choose to encrypt or
not to encrypt the video pipe before they start their console redi rection sessi on).
PAGE 22 OF 24
Page 23

Managed Node
Web Server
SSL Channel
Connection Request
CR Info with Authentication Key
Management Station
Client
Authentication
Key
Open session request
(Authentication Key)
Session established
Console
Redirection
Server
Keyboard/Mouse pipe
If video encryption enabled
Figure 5: Console Redirection Architecture
User Session Privacy
User session privacy is a security concern in the console redirection feature in DRAC 5.
DRAC 5 supports the following techniques to mai ntain user se ssion privacy a nd prevent user
sessions from being hijacked:
• The default maximum number of console redirection sessions is limited to two.
Administrators can configure the maximum numbe r of console redirection se ssions to one
to avoid another remote user taking control of you r console redirecti on session.
SSL Channel
SSL Channel
Video pipe
SSL Channel
Authentication
Key
Console
Redirection
Client
Dell strongly recommends setting the m aximum num ber of console redi rection se ssions to one
if additional simultaneous remote access is not required.
• Remote users can use the Blank Local Video feature to prevent a local user from vie wing
the remote session.
Dell strongly recommends using the Bla nk Local Video feature if lo cal access is not required
during remote console redirection.
NOTE: Requires DRAC 5 version 1.20 firm ware or later.
• Local users can use the Local RACADM CLI utility to disable console redirection when
they log into the server and want to keep a session private. Users can re-e nable console
redirection after the remote session is ove r.
Dell strongly recommends disa bling con sole redirecti on during local RACA DM usage if
simultaneous remote access is not required.
• In addition to DRAC 5 console redirection, users can use Remote Desktop on the
Windows operating system and VNC Console redirection on a Linux-based ope rating
system to perform post-operating system consol e redirection. For add itional informati on,
refer to the Remote Desktop documentation.
PAGE 23 OF 24
Page 24

IPMI Out-of-Band Access Security
DRAC 5 implements IPMI version 2.0 which dramatically imp roved security over IPMI version 1.5.
IPMI out-of-band including IPMI over LAN and SOL can be di sabled if the se features are not used
in your environment.
Dell strongly recommends disabli ng the IPMI over LA N and SOL featur es if they are not requi red.
IPMI version 2.0 uses RMCP+ for authentication an d encryption key e xchange. The new
algorithms provide a more robust key ex change proce ss for establi shing sessions and
authenticating users.
The IPMI message includes SOL payload carrie d over RMCP+ whi ch can be encrypt ed. This
option enables confidential remote configuration of pa rameters such as passwords a nd transfer of
sensitive payload data over SOL. Please see IPMI RMCP+ encrypti on section
for all supported
encryption algorithms.
IPMI authorization and access to a system can be restri cted throug h connection l evel, channel
level privilege and user level privilege. Each channel, li ke IPMI LAN, can be limite d to operate at
one of three different privilege levels: user, operator o r administrator. Similarly, ea ch user can be
created with any of these privileges for each cha nnel. For example, wh en a particular channel is
limited to operator level, only operator level ope rations ca n be performe d on that chan nel. Refer to
the IPMI version 2.0 specification for more details.
PAGE 24 OF 24
 Loading...
Loading...