Page 1

Dell DL4300 Appliance
User's Guide
Page 2

Notes, cautions, and warnings
NOTE: A NOTE indicates important information that helps you make better use of your computer.
CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you
how to avoid the problem.
WARNING: A WARNING indicates a potential for property damage, personal injury, or death.
Copyright © 2016 Dell Inc. All rights reserved. This product is protected by U.S. and international copyright and
intellectual property laws. Dell™ and the Dell logo are trademarks of Dell Inc. in the United States and/or other
jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies.
2015 - 12
Rev. A01
Page 3

Contents
1 Introduction to Dell DL4300 Appliance......................................................... 10
Core technologies...............................................................................................................................10
Live Recovery................................................................................................................................. 11
Verified Recovery........................................................................................................................... 11
Universal Recovery.........................................................................................................................11
True Global Deduplication.............................................................................................................11
True Scale architecture........................................................................................................................11
Deployment architecture.................................................................................................................... 12
Smart Agent................................................................................................................................... 14
DL4300 Core................................................................................................................................. 14
Snapshot process.......................................................................................................................... 14
Replication of disaster recovery site or service provider............................................................. 15
Recovery.........................................................................................................................................15
Product features ................................................................................................................................. 15
Repository...................................................................................................................................... 16
True Global Deduplication ........................................................................................................... 16
Encryption...................................................................................................................................... 17
Replication..................................................................................................................................... 18
Recovery-as-a-Service (RaaS).......................................................................................................19
Retention and archiving................................................................................................................ 19
Virtualization and cloud................................................................................................................ 20
Alerts and event management......................................................................................................20
License portal................................................................................................................................ 20
Web console..................................................................................................................................20
Service management APIs.............................................................................................................21
2 Working with the DL4300 Core.......................................................................22
Accessing the DL4300 Core Console................................................................................................22
Updating trusted sites in Internet Explorer...................................................................................22
Configuring browsers to remotely access the Core Console.....................................................22
Roadmap for configuring the Core ...................................................................................................23
Managing licenses ..............................................................................................................................24
Changing a license key ................................................................................................................ 24
Contacting the license portal server ........................................................................................... 24
Changing the AppAssure language manually.................................................................................... 25
Changing the OS language during installation.................................................................................. 25
Managing Core settings .....................................................................................................................26
Changing the Core display name ................................................................................................26
3
Page 4

Adjusting the nightly job time ......................................................................................................26
Modifying the transfer queue settings .........................................................................................26
Adjusting the client time-out settings ......................................................................................... 27
Configuring deduplication cache settings .................................................................................. 27
Modifying engine settings ............................................................................................................28
Modifying database connection settings .................................................................................... 29
About repositories ..............................................................................................................................29
Roadmap for managing a repository ................................................................................................ 30
Creating a repository ................................................................................................................... 30
Viewing repository details.............................................................................................................33
Modifying repository settings .......................................................................................................33
Expanding an existing repository..................................................................................................34
Adding a storage location to an existing repository ................................................................... 34
Checking a repository ..................................................................................................................36
Deleting a repository ....................................................................................................................36
Remounting volumes....................................................................................................................36
Recovering a repository................................................................................................................ 37
Managing security ..............................................................................................................................38
Adding an encryption key ............................................................................................................ 38
Editing an encryption key ............................................................................................................ 39
Changing an encryption key passphrase .................................................................................... 39
Importing an encryption key ....................................................................................................... 39
Exporting an encryption key ........................................................................................................40
Removing an encryption key .......................................................................................................40
Managing cloud accounts .................................................................................................................40
Adding a cloud account................................................................................................................40
Editing a cloud account................................................................................................................42
Configuring cloud account settings.............................................................................................42
Understanding replication ................................................................................................................. 43
About protecting workstations and servers ................................................................................ 43
About replication ..........................................................................................................................43
About seeding .............................................................................................................................. 44
About failover and failback .......................................................................................................... 45
About replication and encrypted recovery points ...................................................................... 45
About retention policies for replication ...................................................................................... 46
Performance considerations for replicated data transfer .......................................................... 46
Roadmap for performing replication .................................................................................................47
Replicating to a self-managed core............................................................................................. 47
Replicating to a core managed by a third party........................................................................... 51
Monitoring replication ..................................................................................................................53
Managing replication settings ......................................................................................................55
Removing replication ......................................................................................................................... 55
4
Page 5

Removing a protected machine from replication on the source Core...................................... 55
Removing a protected machine on the target Core................................................................... 56
Removing a target Core from replication.................................................................................... 56
Removing a source Core from replication...................................................................................56
Recovering replicated data .......................................................................................................... 56
Roadmap for failover and failback .....................................................................................................57
Setting up an environment for failover ........................................................................................57
Performing failover on the target Core ....................................................................................... 57
Performing failback ...................................................................................................................... 58
Managing events ................................................................................................................................ 59
Configuring notification groups .................................................................................................. 59
Configuring an email server and email notification template .................................................... 61
Configuring repetition reduction .................................................................................................62
Configuring event retention ........................................................................................................ 62
Managing recovery .............................................................................................................................62
About system information ................................................................................................................. 63
Viewing system information ........................................................................................................ 63
Downloading installers ...................................................................................................................... 63
About the agent installer ....................................................................................................................63
Downloading and installing the agent installer ...........................................................................63
About the local mount utility .............................................................................................................64
Downloading and installing the local mount utility ....................................................................64
Adding a core to the local mount utility ......................................................................................65
Mounting a recovery point by using the local mount utility ...................................................... 66
Dismounting a recovery point by using the local mount utility .................................................66
About the local mount utility tray menu ..................................................................................... 67
Using Core and agent options......................................................................................................67
Managing retention policies ..............................................................................................................68
Archiving to a cloud............................................................................................................................68
About archiving ..................................................................................................................................68
Creating an archive ...................................................................................................................... 68
Setting a scheduled archive .........................................................................................................69
Pausing or resuming scheduled archive ..................................................................................... 70
Editing a scheduled archive ..........................................................................................................71
Checking an archive .....................................................................................................................72
Importing an archive .................................................................................................................... 72
Managing SQL attachability ............................................................................................................... 73
Configuring SQL attachability settings ........................................................................................ 73
Configuring nightly SQL attachability checks and log truncation ............................................. 74
Managing exchange database mountability checks and log truncation ......................................... 74
Configuring exchange database mountability and log truncation ............................................ 74
Forcing a mountability check .......................................................................................................75
5
Page 6

Forcing checksum checks ............................................................................................................75
Forcing log truncation ..................................................................................................................75
Recovery point status indicators ..................................................................................................76
3 Managing Your Appliance.................................................................................78
Monitoring the status of the Appliance..............................................................................................78
Provisioning storage............................................................................................................................78
Provisioning selected storage.......................................................................................................79
Deleting space allocation for a virtual disk........................................................................................80
Resolving failed tasks..........................................................................................................................80
Upgrading your Appliance..................................................................................................................80
Repairing your Appliance.................................................................................................................... 81
4 Protecting workstations and servers..............................................................82
About protecting workstations and servers ......................................................................................82
Configuring machine settings ........................................................................................................... 82
Viewing and modifying configuration settings ........................................................................... 82
Viewing system information for a machine ................................................................................ 83
Configuring notification groups for system events .................................................................... 83
Editing notification groups for system events .............................................................................85
Customizing retention policy settings .........................................................................................87
Viewing license information ........................................................................................................ 89
Modifying protection schedules ..................................................................................................89
Modifying transfer settings .......................................................................................................... 90
Restarting a service ...................................................................................................................... 92
Viewing machine logs ..................................................................................................................93
Protecting a machine .........................................................................................................................93
Deploying the agent software when protecting an agent.......................................................... 95
Creating custom schedules for volumes .................................................................................... 96
Modifying exchange server settings ............................................................................................96
Modifying SQL server settings ......................................................................................................97
Deploying an agent (push install) ...................................................................................................... 97
Replicating a new agent .................................................................................................................... 98
Managing machines ...........................................................................................................................99
Removing a machine ................................................................................................................... 99
Replicating agent data on a machine ..........................................................................................99
Setting replication priority for an agent .................................................................................... 100
Canceling operations on a machine ......................................................................................... 100
Viewing machine status and other details .................................................................................101
Managing multiple machines .......................................................................................................... 102
Deploying to multiple machines ................................................................................................102
Monitoring the deployment of multiple machines ...................................................................106
6
Page 7

Protecting multiple machines ....................................................................................................106
Monitoring the protection of multiple machines ..................................................................... 108
Managing snapshots and recovery points ...................................................................................... 108
Viewing recovery points ............................................................................................................ 109
Viewing a specific recovery point...............................................................................................109
Mounting a recovery point for a Windows machine .................................................................110
Dismounting select recovery points............................................................................................111
Dismounting all recovery points..................................................................................................111
Mounting a recovery point volume on a Linux machine ...........................................................111
Removing recovery points ..........................................................................................................112
Deleting an orphaned recovery point chain...............................................................................112
Forcing a snapshot ......................................................................................................................113
Pausing and resuming protection ..............................................................................................113
Restoring data ...................................................................................................................................114
Backup..........................................................................................................................................114
About exporting protected data from Windows machines to virtual machines.......................115
Exporting backup information from your Microsoft Windows machine to a virtual
machine .......................................................................................................................................117
Exporting Windows data using ESXi export ............................................................................... 117
Exporting Windows data using VMware workstation export ....................................................119
Exporting Windows data using Hyper-V export ........................................................................ 121
Exporting Microsoft Windows data using Oracle VirtualBox export ........................................124
Virtual Machine Management.....................................................................................................126
Performing a rollback .................................................................................................................130
Performing a rollback for a Linux machine by using the command line.................................. 131
About bare metal restore for Windows machines .......................................................................... 132
Prerequisites for performing a bare metal restore for a Windows machine ............................132
Roadmap for performing a bare metal restore for a Windows machine .......................................133
Creating a bootable CD ISO image............................................................................................ 133
Loading a boot CD...................................................................................................................... 135
Launching a restore from the Core ...........................................................................................136
Mapping volumes ....................................................................................................................... 136
Viewing the recovery progress ...................................................................................................137
Starting the restored target server ............................................................................................. 137
Repairing startup problems.........................................................................................................137
Performing a bare metal restore for a Linux machine ....................................................................138
Installing the screen utility.......................................................................................................... 139
Creating bootable partitions on a Linux machine......................................................................139
Viewing events and alerts ................................................................................................................ 140
5 Protecting server clusters............................................................................... 141
About server cluster protection ....................................................................................................... 141
7
Page 8

Supported applications and cluster types ..................................................................................141
Protecting a cluster ..........................................................................................................................142
Protecting nodes in a cluster ...........................................................................................................143
Process of modifying cluster node settings ....................................................................................144
Roadmap for configuring cluster settings .......................................................................................144
Modifying cluster settings .......................................................................................................... 145
Configuring cluster event notifications .....................................................................................145
Modifying the cluster retention policy ...................................................................................... 146
Modifying cluster protection schedules .................................................................................... 147
Modifying cluster transfer settings .............................................................................................147
Converting a protected cluster node to an agent ..........................................................................148
Viewing server cluster information ................................................................................................. 148
Viewing cluster system information ..........................................................................................148
Viewing summary information .................................................................................................. 149
Working with cluster recovery points ............................................................................................. 149
Managing snapshots for a cluster ....................................................................................................149
Forcing a snapshot for a cluster ................................................................................................ 150
Pausing and resuming cluster snapshots ..................................................................................150
Dismounting local recovery points ................................................................................................. 150
Performing a rollback for clusters and cluster nodes ..................................................................... 151
Performing a rollback for CCR (Exchange) and DAG clusters .................................................. 151
Performing a rollback for SCC (Exchange, SQL) clusters...........................................................151
Replicating cluster data .................................................................................................................... 151
Removing a cluster from protection ................................................................................................151
Removing cluster nodes from protection .......................................................................................152
Removing all nodes in a cluster from protection ......................................................................152
Viewing a cluster or node report .....................................................................................................153
6 Reporting........................................................................................................... 154
About reports ....................................................................................................................................154
About the reports toolbar ................................................................................................................ 154
About compliance reports ...............................................................................................................154
About errors reports .........................................................................................................................155
About the Core Summary Report ....................................................................................................155
Repositories summary ................................................................................................................155
Agents summary .........................................................................................................................156
Generating a report for a Core or agent ......................................................................................... 156
About the Central Management Console Core reports ................................................................. 157
Generating a report from the Central Management Console ........................................................157
7 Completing a full recovery of the DL4300 Appliance............................... 158
Creating a RAID 1 partition for the operating system......................................................................158
8
Page 9

Installing the operating system.........................................................................................................159
Running the recovery and update utility..........................................................................................159
8 Changing the host name manually............................................................... 161
Stopping the Core service.................................................................................................................161
Deleting server certificates................................................................................................................161
Deleting Core server and registry keys.............................................................................................161
Launching the Core with the new host name................................................................................. 162
Changing the display name ............................................................................................................. 162
Updating trusted sites in Internet Explorer...................................................................................... 162
9 Appendix A— scripting.................................................................................... 163
About powershell scripting ..............................................................................................................163
Powershell scripting prerequisites .............................................................................................163
Testing scripts .............................................................................................................................163
Input parameters ..............................................................................................................................164
VolumeNameCollection (namespace Replay.Common.Contracts.Metadata.Storage) ..........168
Pretransferscript.ps1 ...................................................................................................................169
Posttransferscript.ps1 .................................................................................................................169
Preexportscript.ps1 .....................................................................................................................170
Postexportscript.ps1 ....................................................................................................................171
Prenightlyjobscript.ps1 ................................................................................................................171
Postnightlyjobscript.ps1...............................................................................................................173
Sample scripts ...................................................................................................................................175
10 Getting help.....................................................................................................176
Finding documentation and software updates................................................................................176
Contacting Dell..................................................................................................................................176
9
Page 10

1
Introduction to Dell DL4300 Appliance
This chapter provides an introduction and overview of DL4300. It describes the features, functionality,
and architecture, and consists of the following topics:
• Core technologies
• True Scale architecture
• Deployment architecture
• Product features
Your appliance sets a new standard for unified data protection by combining backup, replication, and
recovery in a single solution that is engineered to be the fastest and most reliable backup for protecting
virtual machines (VM), physical machines, and cloud environments.
Your appliance is capable of handling up to petabytes of data with built-in global deduplication,
compression, encryption, and replication to any private or public cloud infrastructure. Server applications
and data can be recovered in minutes for data retention (DR) and compliance.
Your appliance supports multi-hypervisor environments on VMware vSphere and Microsoft Hyper-V
private and public clouds.
Your appliance combines the following technologies:
• Live Recovery
• Verified Recovery
• Universal Recovery
• True Global Deduplication
These technologies are engineered with secure integration for cloud disaster recovery and deliver fast
and reliable recovery. With its scalable object store, your appliance is uniquely capable of handling up to
petabytes of data very rapidly with built-in global deduplication, compression, encryption, and replication
to any private or public cloud infrastructure.
AppAssure addresses the complexity and inefficiency of legacy tools through its core technology and
support of multi-hypervisor environments including those running on VMware vSphere and Microsoft
Hyper-V, which comprise both private and public clouds. AppAssure offers these technological advances
while dramatically reducing IT management and storage costs.
Core technologies
Details about the core technologies of AppAssure are described in the following topics.
10
Page 11

Live Recovery
Live Recovery is instant recovery technology for VMs or servers. It gives you near-continuous access to
data volumes on virtual or physical servers. You can recover an entire volume with near-zero RTO and an
RPO of minutes.
The backup and replication technology records concurrent snapshots of multiple VMs or servers,
providing near instantaneous data and system protection. You can resume the use of the server directly
from the backup file without waiting for a full restore to production storage. Users remain productive and
IT departments reduce recovery windows to meet today's increasingly stringent Recovery Time Objective
(RTO) and Recovery Point Objective (RPO) service-level agreements.
Verified Recovery
Verified Recovery enables you to perform automated recovery testing and verification of backups. It
includes, but is not limited to, file systems:- Microsoft Exchange 2007, 2010, and 2013, and different
versions of Microsoft SQL Server 2005, 2008, 2008 R2, 2012 and 2014. Verified Recovery provides
recoverability of applications and backups in virtual and physical environments. It features a
comprehensive integrity checking algorithm based on 256-bit SHA keys that check the correctness of
each disk block in the backup during archiving, replication, and data seeding operations. This ensures that
data corruption is identified early and prevents corrupted data blocks from being maintained or
transferred during the backup process.
Universal Recovery
Universal Recovery technology gives you unlimited machine restoration flexibility. You can restore your
backups from physical systems to virtual machines, virtual machines to virtual machines, virtual machines
to physical systems, or physical systems to physical systems, and carry out bare metal restores to
dissimilar hardware. For example, P2V, V2V, V2P, P2P, P2C, V2C, C2P, and C2V.
Universal Recovery technology also accelerates cross-platform moves among virtual machines. For
example, moving from VMware to Hyper-V or Hyper-V to VMware. It builds in application-level, itemlevel, and object-level recovery (individual files, folders, e-mail, calendar items, databases, and
applications). With AppAssure, you can recover or export physical to cloud, or virtual to cloud.
True Global Deduplication
Your appliance provides true global deduplication that reduces your physical disk drive capacity
requirements by offering space reduction ratios exceeding 50:1, while still meeting the data storage
requirements. AppAssure True Scale inline block-level compression and deduplication with line speed
performance, along with built-in integrity checking, prevents data corruption from affecting the quality of
the backup and archiving processes.
True Scale architecture
Your appliance is built on AppAssure True Scale architecture. It leverages dynamic, multi-core pipeline
architecture that is optimized to consistently deliver solid performance for your enterprise environments.
True Scale is designed from the ground up to linearly scale and efficiently store and manage big data, and
deliver RTOs and RPOs of minutes without compromising performance. It comprises of a purpose-built
11
Page 12
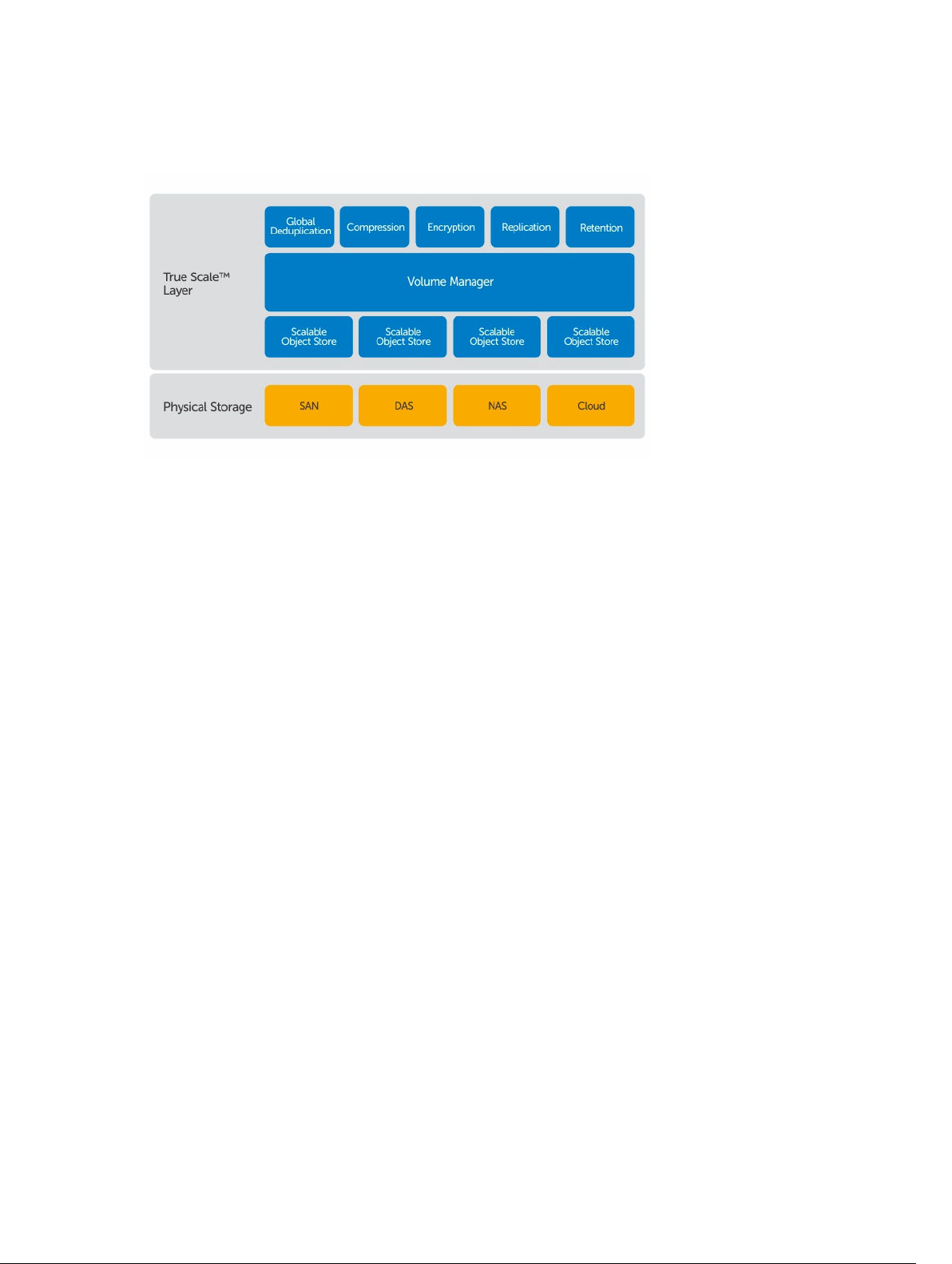
object and a volume manager with integrated global deduplication, compression, encryption, replication,
and retention. The following diagram describes the AppAssure True Scale architecture.
Figure 1. AppAssure True Scale architecture
The AppAssure Volume Manager and Scalable Object Store serve as the foundation of the AppAssure
True Scale architecture. The scalable object store stores block-level snapshots that are captured from
virtual and physical servers. The volume manager manages the numerous object stores by providing a
common repository or just-in-time storage for only what is needed. The Object Store concurrently
supports everything with asynchronous I/O that delivers high throughput with minimal latency and
maximizes system utilization. The repository resides on different storage technologies such as Storage
Area Network (SAN), Direct Attached Storage (DAS), or Network Attached Storage (NAS).
The role of the AppAssure Volume Manager is similar to the role of the volume manager in an operating
system. It takes various storage devices which can be of different sizes and types and combines them into
logical volumes, using striped or sequential allocation policies. The object store saves, retrieves,
maintains, and then replicates objects that are derived from application-aware snapshots. The volume
manager delivers scalable I/O performance in tandem with global data deduplication, encryption, and
retention management.
Deployment architecture
Your appliance is a scalable backup and recovery product that is flexibly deployed within the enterprise or
as a service delivered by a managed service provider. The type of deployment depends on the size and
requirements of the customer. Preparing to deploy your appliance involves planning the network storage
topology, core hardware and disaster recovery infrastructure, and security.
The deployment architecture consists of local and remote components. The remote components may be
optional for those environments that do not require leveraging a disaster recovery site or a managed
service provider for off-site recovery. A basic local deployment consists of a backup server called the
Core and one or more protected machines. The off-site component is enabled using replication that
provides full recovery capabilities in the DR site. The Core uses base images and incremental snapshots to
compile recovery points of protected machines.
Additionally, your appliance is application-aware because it can detect the presence of Microsoft
Exchange and SQL and their respective databases and log files, and then automatically group these
12
Page 13
volumes with dependency for comprehensive protection and effective recovery. This ensures that you
never have incomplete backups when you are performing recoveries. Backups are performed by using
application-aware block-level snapshots. Your appliance can also perform log truncation of the
protected Microsoft Exchange and SQL servers.
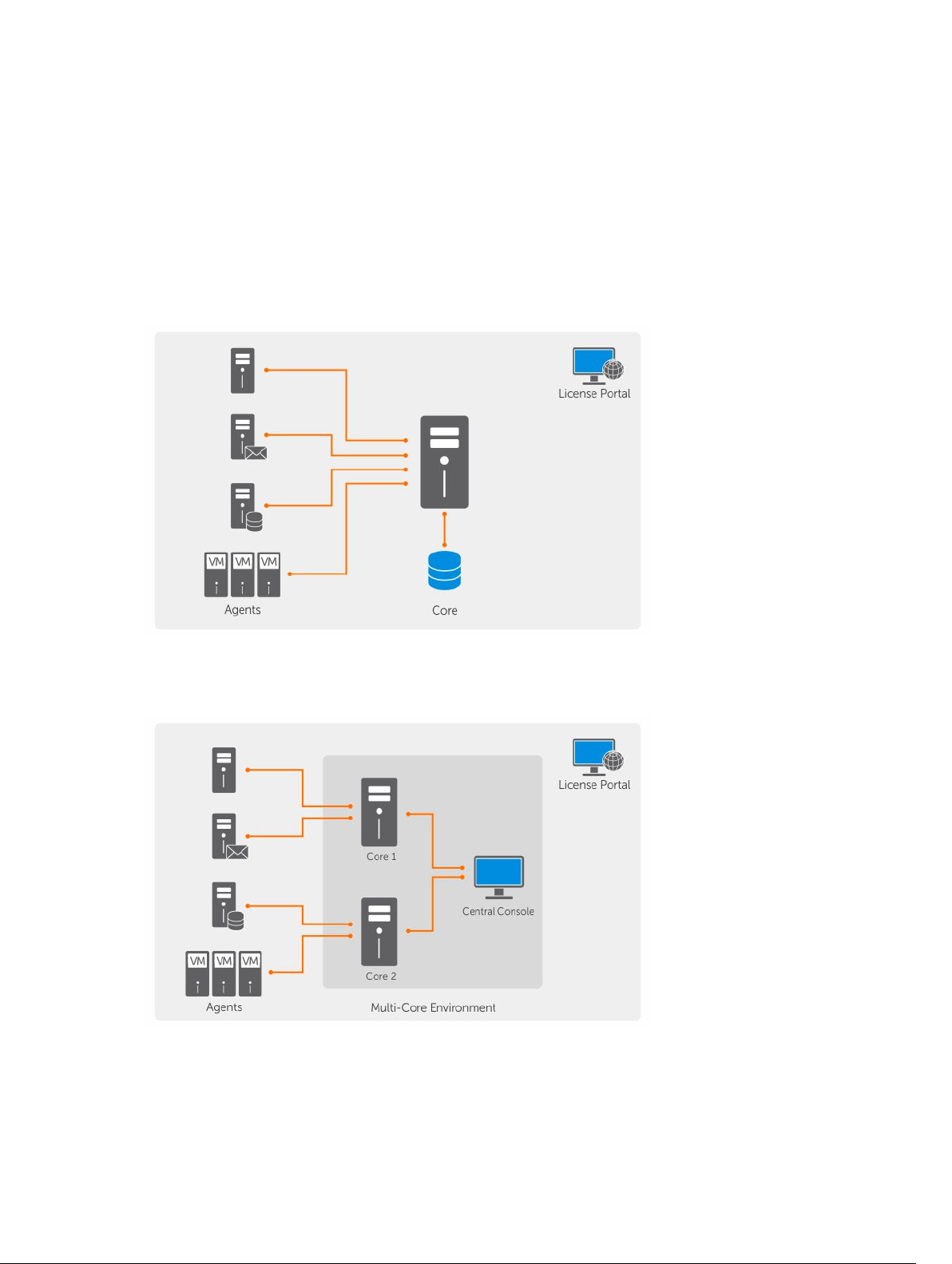
The following diagram depicts a simple deployment. In this diagram, AppAsure agent software is installed
on machines such as a file server, email server, database server, or virtual machines and connect to and
are protected by a single Core, which also consists of the central repository. The License Portal manages
license subscriptions, groups and users for the protected machines and cores in your environment. The
License Portal allows users to log in, activate accounts, download software, and deploy protected
machines and cores per your license for your environment.
Figure 2. Basic deployment architecture
You can also deploy multiple Cores as shown in the following diagram. A central console manages
multiple cores.
Figure 3. Multi—Core deployment architecture
13
Page 14

Smart Agent
Smart Agent tracks the changed blocks on the disk volume and then snaps an image of the changed
blocks at a predefined interval of protection. The incremental forever block-level snapshots approach
prevents repeated copying of the same data from the protected machine to the Core. The Smart Agent is
installed on the machines that is protected by the Core.
The Smart Agent is application-aware and is dormant when not in use, with near zero (0) percent CPU
utilization and less than 20 MB of memory overhead. When the Smart Agent is active, it uses up to 2 to 4
percent processor utilization and less than 150 MB memory, which includes transferring the snapshots to
the Core.
The Smart Agent is application-aware and it detects the type of application that is installed and also the
location of the data. It automatically groups data volumes with dependency, such as databases, and then
logs them together for effective protection and rapid recovery. After the AppAssure Agent software is
configured, it uses smart technology to keep track of changed blocks on the protected disk volumes.
When the snapshot is ready, it is rapidly transferred to the Core using intelligent multi-threaded, socketbased connections. To preserve CPU bandwidth and memory on the protected machines, the smart
agent does not encrypt or deduplicate the data at the source and protected machines are paired with a
Core for protection.
DL4300 Core
The Core is the central component of the deployment architecture. The Core stores and manages all of
the machine backups and provides core services for backup, recovery, and retention; replication, archival,
and management. The Core is a self-contained network-addressable computer that runs a 64-bit version
of Microsoft Windows operating system. Your appliance performs target-based inline compression,
encryption, and deduplication of the data received from the protected machine. The Core then stores the
snapshot backups in repositories such as, Storage Area Network (SAN) or Direct Attached Storage (DAS).
The repository can also reside on internal storage within the Core. The Core is managed by accessing the
following URL from a Web browser: https://CORENAME:8006/apprecovery/admin. Internally, all core
services are accessible through REST APIs. The Core services can be accessed from within the core or
directly over the Internet from any application that can send an HTTP/HTTPS request and receive an
HTTP/HTTPS response. All API operations are performed over SSL and mutually authenticated using X.
509 v3 certificates.
Cores are paired with other cores for replication.
Snapshot process
A snapshot is when a base image is transferred from a protected machine to the Core. This is the only
time a full copy of the machine is transported across the network under normal operation, followed by
incremental snapshots. AppAssure Agent software for Windows uses Microsoft Volume Shadow copy
Service (VSS) to freeze and quiesce application data to disk to capture a file-system-consistent and an
application-consistent backup. When a snapshot is created, the VSS, and the writer on the target server
prevent content from being written to the disk. When the writing of content to disk is halted, all disk I/O
operations are queued and resume only after the snapshot is complete, while the operations already in
flight are completed and all open files are closed. The process of creating a shadow copy does not
significantly impact the performance of the production system.
14
Page 15

AppAssure uses Microsoft VSS because it has built-in support for all Windows internal technologies such
as NTFS, Registry, Active Directory, to flush data to disk before the snapshot. Additionally, other enterprise
applications, such as Microsoft Exchange and SQL, use VSS Writer plug-ins to get notified when a
snapshot is being prepared and when they have to flush their used database pages to disk to bring the
database to a consistent transactional state. It is important to note that VSS is used to quiesce system and
application data to disk; it is not used to create the snapshot. The captured data is immediately
transferred and stored on the Core. Using VSS for backup does not render the application server in
backup mode for an extended period of time because the time taken to create the snapshot is seconds
and not hours. Another benefit of using VSS for backups is that it lets the AppAsssure Agent software to
take a snapshot of large quantities of data at one time because the snapshot works at the volume level.
Replication of disaster recovery site or service provider
The replication process requires a paired source-target relationship between two cores. The source core
copies the recovery points of the protected machines and then asynchronously and continuously
transmits them to a target core at a remote disaster recovery site. The off-site location can be a
company-owned data center (self-managed core) or a third-party managed service provider’s (MSP’s)
location, or cloud environment. When replicating to a MSP, you can use built-in workflows that let you
request connections and receive automatic feedback notifications. For the initial transfer of data, you can
perform data seeding using external media, which is useful for large sets of data or sites with slow links.
In the case of a severe outage, your appliance supports failover and failback in replicated environments.
In case of a comprehensive outage, the target core in the secondary site can recover instances from
replicated protected machines and immediately commence protection on the failed-over machines.
After the primary site is restored, the replicated core can fail-back data from the recovered instances back
to protected machines at the primary site.
Recovery
Recovery can be performed in the local site or the replicated remote site. After the deployment is in
steady state with local protection and optional replication, the Core allows you to perform recovery using
Verified Recovery, Universal Recovery, or Live Recovery.
Product features
You can manage protection and recovery of critical data using the following features and functionality:
• Repository
• True Global Deduplication (Features)
• Encryption
• Replication
• Recovery-as-a-Service (RaaS)
• Retention and archiving
• Virtualization And Cloud
• Alerts and Event Management
• License portal
• Web console
• Service Management APIs
15
Page 16

Repository
The repository uses Deduplication Volume Manager (DVM) to implement a volume manager that provides
support for multiple volumes, each of which could reside on different storage technologies such as
Storage Area Network (SAN), Direct Attached Storage (DAS), Network Attached Storage (NAS), or cloud
storage. Each volume consists of a scalable object store with deduplication. The scalable object store
behaves as a records-based file system, where the unit of storage allocation is a fixed-sized data block
called a record. This architecture allows you to configure block-sized support for compression and
deduplication. Rollup operations are reduced to metadata operations from disk intensive operations
because the rollup no longer moves data but only moves the records.
The DVM can combine a set of object stores into a volume and they can be expanded by creating
additional file systems. The object store files are pre-allocated and can be added on demand as storage
requirements change. It is possible to create up to 255 independent repositories on a single Core and to
further increase the size of a repository by adding new file extents. An extended repository may contain
up to 4,096 extents that span across different storage technologies. The maximum size of a repository is
32 exabytes. Multiple repositories can exist on a single core.
True Global Deduplication
True global deduplication is an effective method of reducing backup storage needs by eliminating
redundant or duplicate data. Deduplication is effective because only one unique instance of the data
across multiple backups is stored in the repository. The redundant data is stored, but not physically; it is
simply replaced with a pointer to the one unique data instance in the repository.
Conventional backup applications have been performing repetitive full backups every week, but your
appliance performs incremental block-level backups of the machine. The incremental-forever approach
in tandem with data deduplication helps to drastically reduce the total quantity of data committed to the
disk.
The typical disk layout of a server consists of the operating system, application, and data. In most
environments, the administrators often use a common flavor of the server and desktop operating system
across multiple systems for effective deployment and management. When backup is performed at the
block level across multiple machines at the same time, it provides a more granular view of what is in the
backup and what is not, irrespective of the source. This data includes the operating system, the
applications, and the application data across the environment.
16
Page 17

Figure 4. Diagram of deduplication
Your appliance performs target-based inline data deduplication, where the snapshot data is transmitted
to the Core before it is deduplicated. Inline data deduplication simply means the data is deduplicated
before it is committed to disk. This is different from at-source or post-process deduplication, where the
data is deduplicated at the source before it is transmitted to the target for storage, and in post-process
the data is sent raw to the target where it is analyzed and deduplicated after the data has been committed
to disk. At-source deduplication consumes precious system resources on the machine whereas the postprocess data deduplication approach needs all the requisite data on disk (a greater initial capacity
overhead) before commencing the deduplication process. On the other hand, inline data deduplication
does not require additional disk capacity and CPU cycles on the source or on the Core for the
deduplication process. Lastly, conventional backup applications perform repetitive full backups every
week, while your appliance performs incremental block-level backups of the machines forever. This
incremental- forever approach in tandem with data deduplication helps to drastically reduce the total
quantity of data committed to the disk with a reduction ratio of as much as 50:1.
Encryption
Your appliance provides integrated encryption to protect backups and data-at-rest from unauthorized
access and use, ensuring data privacy. Only a user with the encryption key can access and decrypt the
data. There is no limit to the number of encryption keys that can be created and stored on a system. DVM
uses AES 256-bit encryption in the Cipher Block Chaining (CBC) mode with 256-bit keys. Encryption is
performed inline on snapshot data, at line speeds without impacting performance. This is because DVM
implementation is multi-threaded and uses hardware acceleration specific to the processor on which it is
deployed.
Encryption is multi-tenant ready. Deduplication has been specifically limited to records that have been
encrypted with the same key; two identical records that have been encrypted with different keys will not
be deduplicated against each other. This design ensures that deduplication cannot be used to leak data
between different encryption domains. This is a benefit for managed service providers, as replicated
backups for multiple tenants (customers) can be stored on a single core without any tenant being able to
see or access other tenant’s data. Each active tenant encryption key creates an encryption domain within
the repository where only the owner of the keys can see, access, or use the data. In a multi-tenant
scenario, data is partitioned and deduplicated within the encryption domains.
17
Page 18
In replication scenarios, your appliance uses SSL 3.0 to secure the connections between the two cores in
a replication topology to prevent eavesdropping and tampering.
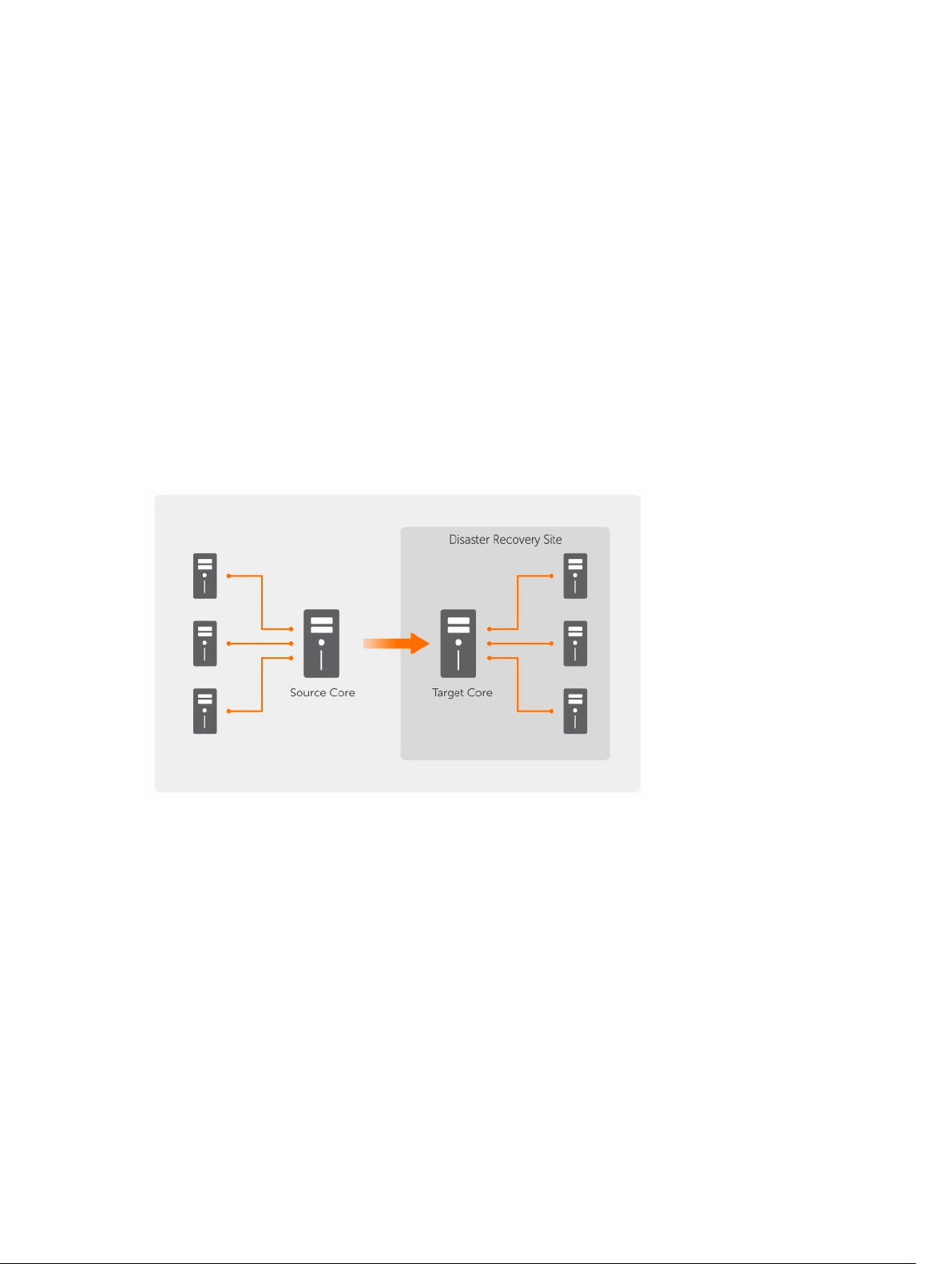
Replication
Replication is the process of copying recovery points from an AppAssure core and transmitting them to
another AppAssure core in a separate location for the purpose of disaster recovery. The process requires
a paired source-target relationship between two or more cores.
The source core copies the recovery points of selected protected machines, and then asynchronously
and continually transmits the incremental snapshot data to the target core at a remote disaster recovery
site. You can configure outbound replication to a company-owned data center or remote disaster
recovery site (that is, a self-managed target core). Or, you can configure outbound replication to a thirdparty managed service provider (MSP) or the cloud that hosts off-site backup and disaster recovery
services. When replicating to a third-party target core, you can use built-in work flows that let you
request connections and receive automatic feedback notifications.
Replication is managed on a per-protected-machine basis. Any machine (or all machines) protected or
replicated on a source core can be configured to replicate to a target core.
Figure 5. Basic replication architecture
Replication is self-optimizing with a unique Read-Match-Write (RMW) algorithm that is tightly coupled
with deduplication. With RMW replication, the source and target replication service matches keys before
transferring data and then replicates only the compressed, encrypted, deduplicated data across the WAN,
resulting in a 10x reduction in bandwidth requirements.
Replication begins with seeding. Seeding is the initial transfer of deduplicated base images and
incremental snapshots of the protected machines. The data can add up to hundreds or thousands of
gigabytes. Initial replication can be seeded to the target core using external media. This is useful for large
sets of data or sites with slow links. The data in the seeding archive is compressed, encrypted and
deduplicated. If the total size of the archive is larger than the space available on the external media, the
archive can span across multiple devices. During the seeding process, the incremental recovery points
18
Page 19

replicate to the target site. After data has been transferred to the target core, the newly replicated
incremental recovery points automatically synchronize.
Recovery-as-a-Service (RaaS)
Managed service providers (MSPs) can fully leverage the appliance as a platform for delivering recovery as
a service (RaaS). RaaS facilitates complete recovery-in-the-cloud by replicating customers' physical and
virtual servers along with their data to the service provider's cloud as virtual machines to support recovery
testing or actual recovery operations. Customers wanting to perform recovery-in-the-cloud can
configure replication on their protected machines on the local cores to an AppAssure service provider. In
the event of a disaster, the MSPs can instantly spin-up virtual machines for the customer.
MSPs can deploy multi-tenant AppAssure RaaS infrastructure that can host multiple and discrete
organizations or business units (the tenants) that ordinarily do not share security or data on a single server
or a group of servers. The data of each tenant is isolated and secure from other tenants and the service
provider.
Retention and archiving
In your appliance, backup and retention policies are flexible and, therefore, easily configurable. The ability
to tailor retention polices to the needs of an organization not only helps to meet compliance
requirements, but does so without compromising on RTO.
Retention policies enforce the periods of time in which backups are stored on short-term (fast and
expensive) media. Sometimes certain business and technical requirements mandate extended retention
of these backups, but use of fast storage is cost prohibitive. Therefore, this requirement creates a need
for long-term (slow and cheap) storage. Businesses often use long-term storage for archiving both
compliance and non-compliance data. The archive feature supports extended retentions for compliance
and non-compliance data, it can also be used for seeding replication data to a target core.
Figure 6. Custom retention policy
In your appliance, retention policies can be customized to specify the length of time a backup recovery
point is maintained. As the age of the recovery points approaches the end of their retention period, the
recovery points age out and are removed from the retention pool. Typically, this process becomes
inefficient and eventually fails as the amount of data and the period of retention start grows rapidly. Your
19
Page 20

appliance solves the big data problem by managing the retention of large amounts of data with complex
retention policies and performing rollup operations for aging data using efficient metadata operations.
Backups can be performed with an interval of a few minutes. As these backups age over days, months,
and years, retention policies manage the aging and deletion of old backups. A simple waterfall method
defines the aging process. The levels within the waterfall are defined in minutes, hours, days, weeks,
months, and years. The retention policy is enforced by the nightly rollup process.
For long-term archiving, your appliance provides the ability to create an archive of the source or target
core on any removable media. The archive is internally optimized and all data in the archive is
compressed, encrypted, and deduplicated. If the total size of the archive is larger than the space available
on the removable media, the archive spans across multiple devices based on the available space on the
media. The archive also can be locked with a passphrase. Recovery from an archive does not require a
new core; any core can ingest the archive and recover data if the administrator has the passphrase and
the encryption keys.
Virtualization and cloud
The Core is cloud-ready, which allows you to leverage the compute capacity of the cloud for recovery.
Your appliance can export any protected or replicated machine to a virtual machine, such as licensed
versions of VMware or Hyper-V. You can perform a one-time virtual export, or you can establish a virtual
standby VM by establishing a continuous virtual export. With continuous exports, the virtual machine is
incrementally updated after every snapshot. The incremental updates are very fast and provide standby
clones that are ready to be powered up with a click of a button. The supported virtual machine export
types are VMware Workstation/Server on a folder; direct export to a vSphere/VMware ESX(i) host; export
to Oracle VirtualBox; and export to Microsoft Hyper-V Server on Windows Server 2008 (x64), 2008 R2,
2012 (x64), and 2012 R2 (including support for Hyper-V generation 2 VMs)
Additionally, you can now archive your repository data to the cloud using Microsoft Azure, Amazon S3,
Rackspace Cloud Block Storage, or other OpenStack-based cloud services.
Alerts and event management
In addition to HTTP REST API, your appliance also includes an extensive set of features for event logging
and notification using e-mail, Syslog, or Windows Event Log. email notifications can be used to alert users
or groups of the health or status of different events in response to an alert. The Syslog and Windows
Event Log methods are used for centralized logging to a repository in multi-operating system
environment. In Windows-only environments, only the Windows Event Log is used.
License portal
The License Portal provides easy-to-use tools for managing license entitlements. You can download,
activate, view, and manage license keys and create a company profile to track your license assets.
Additionally, the portal enables service providers and re-sellers to track and manage their customer
licenses.
Web console
Your appliance features a new web-based central console that manages distributed cores from one
central location. MSPs and enterprise customers with multiple distributed cores can deploy the central
console to get a unified view for central management. The central console provides the ability to
20
Page 21

organize the managed cores in hierarchical organizational units. These organizational units can represent
business units, locations, or customers for MSPs with role-based access. The central console can also run
reports across managed cores.
Service management APIs
Your appliance comes bundled with a service management API and provides programmatic access to all
of the functionality available through the Central Management Console. The service management API is a
REST API. All the API operations are performed over SSL and are mutually authenticated using X.509 v3
certificates. The management service can be accessed from within the environment or directly over the
Internet from any application that can send and receive an HTTPS request and response. This approach
facilitates easy integration with any web application such as relationship management methodology
(RMM) tools or billing systems. Also included is an SDK client for PowerShell scripting.
21
Page 22
2
Working with the DL4300 Core
Accessing the DL4300 Core Console
To access the Core Console:
1. Update trusted sites in your browser. See Updating Trusted Sites In Internet Explorer.
2. Configure your browsers to remotely access the Core Console. See Configuring Browsers To
Remotely Access The Core Console.
3. Perform one of the following to access the Core Console:
• Log on locally to your DL4300 core server, and then double-click the Core Console icon.
• Type one of the following URLs in your web browser:
– https://<yourCoreServerName>:8006/apprecovery/admin/core
– https://<yourCoreServerIPaddress>:8006/apprecovery/admin/core
Updating trusted sites in Internet Explorer
To update trusted sites in Microsoft Internet Explorer:
1. Open Internet Explorer.
2. If the File, Edit View, and other menus are not displayed, press <F10>.
3. Click the Tools menu, and select Internet Options.
4. In the Internet Options window, click the Security tab.
5. Click Trusted Sites and then click Sites.
6. In Add this website to the zone, enter https://[Display Name], using the new name you provided for
the Display Name.
7. Click Add.
8. In Add this website to the zone, enter about:blank.
9. Click Add.
10. Click Close and then OK.
Configuring browsers to remotely access the Core Console
To access the Core Console from a remote machine, you need to modify your browser settings.
NOTE: To modify the browser settings, log in to the system as an administrator.
NOTE: Google Chrome uses Microsoft Internet Explorer settings, change Chrome browser settings
using Internet Explorer.
22
Page 23

NOTE: Ensure that the Internet Explorer Enhanced Security Configuration is turned on when you
access the Core Web Console either locally or remotely. To turn on the Internet Explorer
Enhanced Security Configuration:
1. Open Server Manager.
2. Select Local Server IE Enhanced Security Configuration displayed on the right. Ensure that it is
On.
Configuring browser settings in Internet Explorer and Chrome
To modify browser settings in Internet Explorer and Chrome:
1. Open Internet Explorer.
2. From the Tools menu, select Internet Options, Security tab.
3. Click Trusted Sites and then click Sites.
4. Deselect the option Require server verification (https:) for all sites in the zone, and then add
http://<hostname or IP Address of the Appliance server hosting the AppAssure Core> to Trusted
Sites.
5. Click Close, select Trusted Sites, and then click Custom Level.
6. Scroll to Miscellaneous → Display Mixed Content and select Enable.
7. Scroll to the bottom of the screen to User Authentication → Logon, and then select Automatic
logon with current user name and password.
8. Click OK, and then select the Advanced tab.
9. Scroll to Multimedia and select Play animations in webpages.
10. Scroll to Security, check Enable Integrated Windows Authentication, and then click OK.
Configuring Mozilla Firefox browser settings
NOTE: To modify Mozilla Firefox browser settings in the latest versions of Firefox, disable
protection. Right-click the Site Identify button (located to the left of the URL), go to Options and
click on
To modify Mozilla Firefox browser settings:
1. In the Firefox address bar, type about:config, and then click I’ll be careful, I promise if prompted.
2. Search for the term ntlm.
The search should return at least three results.
3. Double-click network.automatic-ntlm-auth.trusted-uris and enter the following setting as
appropriate for your machine:
• For local machines, enter the host name.
• For remote machines, enter the host name or IP address separated by a comma of the appliance
4. Restart Firefox.
Disable protection for now.
system hosting the AppAssure Core; for example, IPAddress, host name.
Roadmap for configuring the Core
Configuration includes tasks such as creating and configuring the repository for storing backup
snapshots, defining encryption keys for securing protected data, and setting up alerts and notifications.
After you complete the configuration of the Core, you can then protect agents and perform recovery.
23
Page 24

Configuring the Core involves understanding certain concepts and performing the following initial
operations:
• Create a repository
• Configure encryption keys
• Configure event notification
• Configure retention policy
• Configure SQL attachability
NOTE: If you are using this Appliance, it is recommended that you use the Appliance tab to
configure the Core. For more information about configuring the Core after initial installation, see
the Dell DL4300 Appliance Deployment Guide at dell.com/support/home.
Managing licenses
You can manage licenses directly from the Core Console. From the console, you can change the license
key and contact the license server. You can also access the License Portal from the Licensing page in the
Core console.
The Licensing page includes the following information:
• License type
• License status
• License constraints
• Number of machines protected
• Status of last response from the licensing server
• Time of last contact with the licensing server
• Next scheduled attempt of contact with the licensing server
Changing a license key
To change a license key:
1. Navigate to the Core Console.
2. Select Configuration → Licensing.
The Licensing page appears.
3. From the License Details section, click Change License.
The Change License dialog box appears.
4. In the Change License dialog box, enter the new license key and then click Continue.
Contacting the license portal server
The Core Console frequently contacts the portal server to remain current with any changes made in the
license portal. Typically, communication with the portal server occurs automatically at designated
intervals; however, you can initiate communication on demand.
To contact the portal server:
1. Navigate to the Core Console.
2. Click Configuration → Licensing.
3. From the License Server option, click Contact Now.
24
Page 25

Changing the AppAssure language manually
AppAssure allows you to change the language that you had selected while running AppAssure Appliance
Configuration Wizard to any of the supported languages.
To change the AppAssure language to the desired language:
1. Launch the registry Editor using regdit command.
2. Navigate to HKEY_LOCAL_MACHINE → SOFTWARE → AppRecovery → Core → Localization.
3. Open Lcid.
4. Select decimal.
5. Enter the required language value in the Value data box, the supported language values are:
a. English: 1033
b. Brazilian Portuguese: 1046
c. Spanish: 1034
d. French: 1036
e. German: 1031
f. Simplified Chinese: 2052
g. Japanese: 1041
h. Korean: 1042
6. Right-click and restart the services in the given order:
a. Windows Management Instrumentation
b. SRM Web Service
c. AppAssure Core
7. Clear the browser cache.
8. Close the browser and restart the core console from the desktop icon.
Changing the OS language during installation
On a running Windows installation, you can use the control panel to select language packs and configure
additional international settings.
To change OS language:
NOTE: It is recommended that the OS language and the AppAssure language be set to the same
language. otherwise, some messages may be displayed in mixed languages.
NOTE: It is recommended to change the OS language before changing the AppAssure language.
1. On the Start page, type language, and make sure that the search scope is set to Settings.
2. In the Results panel, select Language.
3. In the Change your language preferences pane, select Add a language.
4. Browse or search for the language that you want to install.
For example, select Catalan, and then select Add. Catalan is now added as one of your languages.
5. In the Change your language preferences pane, select Options next to the language that you added.
6. If a language pack is available for your language, select Download and install language pack.
7. When the language pack is installed, the language is displayed as available to use for the Windows
display language.
25
Page 26

8. To make this language your display language, move it to the top of your language list.
9. Log out and log in again to Windows for the change to take effect.
Managing Core settings
The Core settings are used to define various settings for configuration and performance. Most settings
are configured for optimal use, but you can change the following settings as necessary:
• General
• Nightly Jobs
• Transfer Queue
• Client Timeout Settings
• Deduplication Cache Configuration
• Database Connection Settings
Changing the Core display name
NOTE: It is recommended that you select a permanent display name during the initial configuration
of your Appliance. If you change it later, you must perform several steps manually to ensure that the
new host name takes effect and the appliance functions properly. For more information, see
Changing The Host Name Manually.
To change the Core display name:
1. Navigate to the Core Console.
2. Click Configuration → Settings
3. In the General pane, click Change.
The General Settings dialog box appears.
4. In the Display Name text box, enter a new display name for the Core.
This is the name that will display in the Core Console. You can enter up to 64 characters.
5. In the Web Server Port text box, enter a port number for the web server. The default is 8006.
6. In the Service Port, enter a port number for the service. The default is 8006.
7. Click OK.
Adjusting the nightly job time
To adjust the nightly job time:
1. Navigate to the Core Console.
2. Click Configuration → Settings.
3. In the Nightly Jobs area, click Change.
The Nightly Jobs dialog box appears.
4. In the Nightly Jobs Time text box, enter a new time to perform the nightly jobs.
5. Click OK.
Modifying the transfer queue settings
Transfer queue settings are core-level settings that establish the maximum number of concurrent
transfers and the maximum number of retries for transferring data.
26
Page 27

To modify the transfer queue settings:
1. Navigate to the Core Console.
2. Click Configuration → Settings.
3. In the Transfer Queue pane, click Change.
The Transfer Queue dialog box appears.
4. In the Maximum Concurrent Transfers text box, enter a value to update the number of concurrent
transfers.
Set a number from 1 to 60. The smaller the number, the lesser the load is on network and other
system resources. As the capacity that is processed increases, so does the load on the system.
5. In the Maximum Retries text box, enter a value to update the maximum number of retries.
6. Click OK.
Adjusting the client time-out settings
To adjust the client time-out settings:
1. Navigate to the Core Console.
2. Click Configuration → Settings.
3. In the Client Timeout Settings Configuration area, click Change.
The Client Timeout Settings dialog box appears.
4. In the Connection Timeout text box, enter the number of minutes and seconds before a connection
time-out occurs.
5. In the Connection UI Timeout text box, enter the number of minutes and seconds before a
connection UI time out occurs.
6. In the Read/Write Timeout text box, enter the number of minutes and seconds that you want to
lapse before a time-out occurs during a read/write event.
7. In the Read/Write UI Timeout text box, enter the number of minutes and seconds that will to lapse
before a read/write UI time out occurs.
8. Click OK.
Configuring deduplication cache settings
To configure deduplication cache settings:
1. Navigate to the Core Console.
2. Click Configuration → Settings
3. In the Deduplication Cache Configuration area, click Change.
The Deduplication Cache Configuration dialog box appears.
4. In the Primary Cache Location text box, enter an updated value to change the primary cache
location.
5. In the Secondary Cache Location text box, enter an updated value to change the secondary cache
location.
6. In the Metadata Cache Location text box, enter an updated value to change the metadata cache
location.
7. In the Dedupe Cache Size text box, enter a value corresponding to the amount of space you want to
allocate for the deduplication cache.
From the unit size drop-down field, select either GB (gigabytes) or TB (terabytes), to specify the unit
of measurement for the value in the Dedupe Cache Size text box.
27
Page 28

8. Click OK.
NOTE: You must restart the Core service for the changes to take effect.
Modifying engine settings
To modify the engine settings:
1. Navigate to the Core Console.
2. Click Configuration → Settings
3. In the Replay Engine Configuration pane, click Change.
The Replay Engine Configuration dialog box appears.
4. Enter the configuration information described as follows:
Text Box Description
IP address
Preferable Port Enter a port number or accept the default setting (8007 is the default port).
Port in use Represents the port that is in use for the Replay Engine configuration.
Allow port autoassigning
Admin Group Enter a new name for the administration group. The default name is BUILTIN
Minimum Async
I/O Length
Receive Buffer
Size
Send Buffer Size Enter an outbound buffer size or accept the default setting. The default setting
Read Timeout Enter a read timeout value or choose the default setting. The default setting is
Write Timeout Enter a write timeout value or choose the default setting. The default setting is
• To use the preferred IP address from your TCP/IP, click Automatically
Determined
• To manually enter an IP address, click Use a specific address.
The port is used to specify the communication channel for the engine.
Click for allow for automatic TCP port assignment.
\Administrators.
Enter a value or choose the default setting. It describes the minimum
asynchronous input/output length. The default setting is 65536.
Enter an inbound buffer size or accept the default setting. The default setting is
8192.
is 8192.
00:00:30.
00:00:30.
No Delay It is recommended that you leave this check box unchecked as doing
otherwise will impact network efficiency. If you determine that you need to
modify this setting, contact Dell Support for guidance.
5. Click OK.
28
Page 29

Modifying database connection settings
To modify database connection settings:
1. Navigate to the Core Console.
2. Click Configuration → Settings
3. In the Database Connection Settings area, choose one of the following:
• Click Apply Default.
• Click Change.
The Database Connection Settings dialog box appears.
4. Enter the settings for modifying the database connection described as follows:
Text Box Description
Host Name Enter a host name for the database connection.
Port Enter a port number for the database connection.
User Name
(optional)
Password
(optional)
Retain event and
job history for,
days
Max connection
pool size
Min connection
pool size
5. Click Test Connection to verify your settings.
6. Click Save.
Enter a user name for accessing and managing the database connection
settings. It is used to specify the log in credentials for accessing the database
connection.
Enter a password for accessing and managing the database connection
settings.
Enter the number of days to retain the event and job history for the database
connection.
Sets the maximum number of database connections cached to allow dynamic
reuse. Default setting is 100.
Sets the minimum number of database connections cached to allow dynamic
reuse. Default setting is 0.
About repositories
A repository stores the snapshots that are captured from your protected workstations and servers. The
repository can reside on different storage technologies such as Storage Area Network (SAN), Direct
Attached Storage (DAS), or Network Attached Storage (NAS).
When you create a repository, the Core preallocates the storage space required for the data and
metadata in the specified location. You can create up to 255 independent repositories on a single core
that span across different storage technologies. In addition, you can further increase the size of a
repository by adding new file extents or specifications. An extended repository can contain up to 4096
extents that span across different storage technologies.
Key repository concepts and considerations include:
• The repository is based on the AppAssure Scalable Object File System.
29
Page 30
• All data stored within a repository is globally deduplicated.
• The Scalable Object File System can deliver scalable I/O performance in tandem with global data
deduplication, encryption, and retention management.
NOTE: DL4300 repositories are stored on primary storage devices. Archival storage devices such as
Data Domain are not supported due to performance limitations. Similarly, repositories must not be
stored on NAS filers that tier to the cloud as these devices tend to have performance limitations
when used as primary storage.
Roadmap for managing a repository
The roadmap for managing a repository covers tasks such as creating, configuring, and viewing a
repository, and includes the following topics:
• Accessing The Core Console
• Creating A Repository
• Viewing Repository Details
• Modifying Repository Settings
• Adding A Storage Location To An Existing Repository
• Checking A Repository
• Deleting A Repository
• Recovering A Repository
NOTE: It is recommended that you use the Appliance tab to configure repositories.
Before you begin using your appliance, you must set up one or more repositories on the core server. A
repository stores your protected data. More specifically, it stores the snapshots that are captured from the
protected servers in your environment.
When you configure a repository, you can perform various tasks such as specifying where to locate the
data storage on the Core server, how many locations can be added to each repository, the name of the
repository, how many current operations the repositories support.
When you create a repository, the Core preallocates the space required for storing data and metadata in
the specified location. You can create up to 255 independent repositories on a single core. To further
increase the size of a single repository, you can add new storage locations or volumes.
You can add or modify repositories in the Core Console.
Creating a repository
NOTE: If you are using this appliance as a SAN, it is recommended that you use the Appliance tab to
create repositories, see Provisioning selected storage.
Perform the following to manually create a repository:
1. Navigate to the Core Console.
2. Click Configuration → Repositories.
3. Click Add new.
The Add New Repository dialog box appears.
4. Enter the information as described in the following table.
30
Page 31

Text Box Description
Repository Name Enter the display name of the repository. By default, this text box consists of
the word Repository and an index number which sequentially adds a number
to the new repository starting with 1. You can change the name as needed.
You can enter up to 150 characters.
Concurrent
Operations
Comments Optionally, enter a descriptive note about this repository.
5. To define the specific storage location or volume for the repository, click Add Storage Location.
CAUTION: If the AppAssure repository that you are creating in this step is later removed, all
files at the storage location of your repository will be deleted. If you do not define a
dedicated folder to store the repository files, then those files will be stored in the root;
deleting the repository will also delete the entire contents of the root, resulting in
catastrophic data loss.
NOTE: Repositories are stored on primary storage devices. Archival storage devices such as
Data Domain are not supported due to performance limitations. Similarly, repositories must not
be stored on NAS filers that tier to the cloud as these devices tend to have performance
limitations when used as primary storage.
The Add Storage Location dialog box is displayed.
6. Specify how to add the file for the storage location. You can choose to add the file on the local disk
or on CIFS share.
• To specify a local machine, click Add file on local disk, and then enter the information described
as follows:
Define the number of concurrent requests that you want the repository to
support. By default the value is 64.
Text Box Description
Data Path Enter the location for storing the protected data; for example, type X:
\Repository\Data.
When specifying the path, use only alphanumeric characters, the hyphen,
and the period (only to separate host names and domains). The letters a to
z are case-insensitive. Do not use spaces. No other symbols or punctuation
characters are permitted.
Metadata Path Enter the location for storing the protected metadata; for example, type X:
\Repository\Metadata.
When specifying the path, use only alphanumeric characters, the hyphen,
and the period (only to separate host names and domains). The letters a to
z are case-insensitive. Do not use spaces. No other symbols or punctuation
characters are permitted.
• Or, to specify a network share location, click Add file on CIFS share, and then enter the
information described as follows:
Text Box Description
UNC Path Enter the path for the network share location.
31
Page 32

Text Box Description
If this location is at the root, define a dedicated folder name (for example,
Repository). The path must begin with \\. When specifying the path, use
only alphanumeric characters, the hyphen, and the period (only to separate
host names and domains). The letters a to z are case insensitive. Do not use
spaces. No other symbols or punctuation characters are permitted.
User Name Specify a user name for accessing the network share location.
Password Specify a password for accessing the network share location.
7. In the Details pane, click Show/Hide Details and enter the details for the storage location described
as follows:
Text Box Description
Size Set the size or capacity for the storage location. The default is 250 MB. You
can choose from the following:
• MB
• GB
• TB
NOTE: The size that you specify cannot exceed the size of the volume.
NOTE: If the storage location is a New Technology File System (NTFS)
volume using Windows XP or Windows 7, the file size limit is 16 TB.
If the storage location is an NTFS volume using Windows 8 or Windows
Server 2012, the file size limit is 256 TB.
Write Caching
Policy
NOTE: To validate the operating system, Windows Management
Instrumentation (WMI) must be installed on the intended storage location.
The write caching policy controls how the Windows Cache Manager is used in
the repository and helps to tune the repository for optimal performance on
different configurations.
Set the value to one of the following:
• On
• Off
• Sync
If the value is set to On, which is the default, Windows controls the caching.
NOTE: Setting the write caching policy to On could result in faster
performance. If you are using a version of Windows Server prior to Server
2012, the recommended setting is Off.
If set to Off, AppAssure controls the caching.
If set to Sync, Windows controls the caching as well as the synchronous input/
output.
32
Page 33

Text Box Description
Bytes per Sector Specify the number of bytes you want each sector to include. The default
value is 512.
Average Bytes per
Record
8. Click Save.
The Repositories screen is displayed to include the newly added storage location.
9. Repeat step 4 through step 7 to add more storage locations for the repository.
10. Click Create to create the repository.
The Repository information appears in the Configuration tab.
Specify the average number of bytes per record. The default value is 8192.
Viewing repository details
To view repository details:
1. Navigate to the Core Console.
2. Click Configuration → Repositories.
3. Click > next to the Status column of the repository for which you want to view the details.
4. From the expanded view, you can perform the following actions:
• Modify Settings
• Add a Storage Location
• Check a Repository
• Delete a Repository
Details also display for the repository and include the storage locations and statistics. Storage
location details include the metadata path, data path, and size. Statistical information includes:
• Deduplication — Reported as the number of block dedupe hits, block dedupe misses, and block
compression rate.
• Record I/O — Consisting of the rate (MB/s), read rate (MB/s), and write write (MB/s).
• Storage Engine — Include the rate (MB/s) read rate (MB/s), and write write (MB/s).
Modifying repository settings
After you add a repository, you can modify the repository settings such as the description or the
maximum concurrent operations. You can also create a new storage location for the repository.
To modify repository settings:
1. Navigate to the Core Console.
2. Click Configuration → Repositories.
3. Click the Settings icon next to the Compression Ratio column below the Actions button, and then
Settings.
The Repository Settings dialog box appears.
4. Edit the repository information described as follows:
33
Page 34

Field Description
Repository Name Represents the display name of the repository. By default, this text box consists
of the word Repository and an index number, which corresponds to the
number of the repository.
NOTE: You cannot edit the repository name.
Description Optionally, enter a descriptive note about the repository.
Maximum
Concurrent
Operations
Enable
Deduplication
Enable
Compression
5. Click Save.
Define the number of concurrent requests that you want the repository to
support.
To turn off deduplication, clear this check box. To enable deduplication, select
this check box.
NOTE: Changing this setting only applies to backups taken after the
setting has been made. Existing data, or data replicated from another core
or imported from an archive, retains the deduplication values in place at
the time the data was captured from the protected machine.
To turn off compression, clear this check box. To enable compression, select
this check box.
NOTE: This setting applies only to backups taken after the setting has
been changed. Existing data, or data replicated from another core or
imported from an archive, retains the compression values in place at the
time the data was captured from the protected machine.
Expanding an existing repository
If you add another MD1400 DAS to your appliance, you can use the available storage to expand an
existing repository.
To expand an existing repository:
1. After you install the MD1400 DAS, open the Core Console and select the Appliance tab, click Tasks.
2. On the Tasks screen, next to the new storage, click Provision.
3. On the Provisioning Storage screen, select Expand the existing repository, select the repository that
you want to expand.
4. Click Provision.
The Tasks screen displays the Status Description next to the storage device as Provisioned.
Adding a storage location to an existing repository
Adding a storage location lets you define where you want to store the repository or volume.
To add a storage location to an existing repository:
1. Click > next to the Status column of the repository for which you want to add a storage location.
2. Click Add Storage Location.
The Add Storage Location dialog box appears.
34
Page 35

3. Specify how to add the file for the storage location. You can choose to add the file on the local disk
or on a CIFS share.
• To specify a local machine, click Add file on local disk, enter the information as follows:
Text Box Description
Metadata Path Enter the location for storing the protected metadata.
Data Path Enter the location for storing the protected data.
• To specify a network share location, click Add file on CIFS share, enter the information as
follows:
Text Box Description
UNC Path Enter the path for the network share location.
User Name Specify a user name for accessing the network share location.
Password Specify a password for accessing the network share location.
4. In the Details section, click Show/Hide Details and enter the details for the storage location
described as follows:
Text Box Description
Size Set the size or capacity for the storage location. The default size is 250 MB.
You can choose from the following:
• MB
• GB
• TB
Write Caching
Policy
NOTE: The size that you specify cannot exceed the size of the volume.
NOTE: If the storage location is an NTFS volume using Windows XP or
Window 7, the file size limit is 16 TB.
If the storage location is an NTFS volume using Windows 8 or Windows
Server 2012, the file size limit is 256 TB.
NOTE: To validate the operating system, WMI must be installed on the
intended storage location.
The write caching policy controls how the Windows Cache Manager is used in
the repository and helps to tune the repository for optimal performance on
different configurations. Set the value to one of the following:
• On
• Off
• Sync
If set to On, which is the default, Windows controls the caching.
NOTE: Setting the write caching policy to On could result in faster
performance; however the recommended setting is Off.
If set to Off, AppAssure controls the caching.
35
Page 36

Text Box Description
If set to Sync, Windows controls the caching as well as the synchronous input/
output.
Bytes per Sector Specify the number of bytes you want each sector to include. The default
value is 512.
Average Bytes per
Record
5. Click Save.
The Repositories screen is displayed to include the newly added storage location.
6. Repeat Step 4 through Step 7 to add more storage locations for the repository.
7. Click OK.
Specify the average number of bytes per record. The default value is 8192.
Checking a repository
The appliance can perform a diagnostic check of a repository volume when errors occur. Core errors
could be the result of it being improperly shut down, or a hardware failure, among other reasons.
NOTE: This procedure must only be performed for diagnostic purposes.
To check a repository:
1. On the Configuration tab, click Repositories, select > next to the repository that you want to check.
2. In the Actions pane, click Check.
The Check Repository dialog box appears.
3. In the Check Repository dialog box, click Check.
NOTE: If the check fails, restore the repository from an archive.
Deleting a repository
To delete a repository:
1. On the Configuration tab, click Repositories, select > next to the repository that you want to delete.
2. In the Actions pane, click Delete.
3. In the Delete Repository dialog box, click Delete.
CAUTION: When a repository is deleted, the data contained in the repository is discarded and
cannot be recovered.
When you delete a repository, then you must go through the Open Manage System Administrator
and delete the virtual disks that housed the repository. After you delete the virtual disks, you can reprovision the disks and recreate the repository.
Remounting volumes
To remount the volumes:
1. Navigate to the Core Console.
2. Appliance → Tasks.
3. Click Remount Volumes.
36
Page 37

The Volumes remount.
Resolving foreign volumes
If a provisioned MD1400 is powered off or disconnected and then later powered back on, an event
appears on the Core Console reporting that the MD1400 is connected. However, no task appears on the
Appliance tab Tasks screen that permits you to recover it. The Enclosures screen reports the MD1400 as
being in a foreign state and the repositories on the foreign virtual disks as off-line.
To resolve foreign volumes:
1. From the Core Console, select the Appliance tab, and then click Remount Volumes.
The volumes remount.
2. Select the Configuration tab, and then click Repositories.
3. Expand the repository with the red status indicator by clicking > next to Status.
4. To verify the repository integrity, under Actions, click Check.
Recovering a repository
When the appliance fails to import a repository, it reports the failure in the Tasks screen with the task
status indicated by a red circle, and the status description reporting
view the error details from the Tasks screen, expand the task details by clicking > next to the Status
column. Status Details reports that the recovery task status is exception, and the Error Message column
provides additional details about the error condition.
To recover a repository from a failed import state:
1. Navigate to the Core Console.
The Repositories screen displays the failed repository with a red status indicator.
2. Click Configuration → Repositories.
3. Expand the failed repository by clicking > next to Status.
4. From the Actions section, click Check, and then click Yes to confirm that you want to run the check.
The appliance recovers the repository.
Error, Completed — Exception. To
Manually recovering a repository
During disaster recovery, you installed the operating system, downloaded and ran the Recovery Update
, completed AppAssure Appliance Configuration Wizard, and launched AppAssure to finish the
Utility
recovery process. However, incomplete breadcrumbs prevent the Remount Volume process from
mounting volumes.
To recover a repository manually:
1. Launch Computer Management, then select Storage Management → Disk Management.
2. Add a drive letter to the volume labeled DL_REPO_xxxx.
3. Verify the DL_REPO_xxxx volume; note the drive letter, the file path, and ensure that an
AppRecoveryCoreConfigurationBackup file exists.
4. From the AppAssure Core Console, select the Configuration tab, then select Restore.
5. In the Enter Local Directory Path text box, enter the drive letter and file path to the repository, and
then select the option Restore Repositories.
6. Click Restore.
AppAssure restores the repository, but the repository status is red.
7. Expand the repository information, and copy the metadata path.
8. To create the mount point folder, open a PowerShell window, and type the following command:
37
Page 38

md "<metadata path>"
NOTE: Ensure that you remove the \File_x portion of the metadata path, and enclose the
metadata path in quotes.
9. From Computer Management → Storage Management → Disk Management, add the mount path
to the volume.
NOTE: Ensure that you remove the \File_x portion of the metadata path.
10. Remove the drive letter.
11. Add drive letters to all DL_VMRSRV_x volumes.
12. From the AppAssure Core Console → Configuration → Restore screen, click fix path, and then click
Save.
The repository is back online and display a green status.
NOTE: You must repeat Step 9 through Step 12 for each DL_REPO_xxxx volume.
Managing security
The Core can encrypt protected machine snapshot data within the repository. Instead of encrypting the
entire repository, you can specify an encryption key during the protection of a machine in a repository
which lets the keys be reused for different protected machines. Encryption does not affect performance,
as each active encryption key creates an encryption domain, thus letting a single core support
multitenancy by hosting multiple encryption domains. In a multi-tenant environment, data is partitioned
and deduplicated within the encryption domains. Because you manage the encryption keys, loss of the
volume cannot leak the keys. Key security concepts and considerations include:
• Encryption is performed using 256 bit AES in Cipher Block Chaining (CBC) mode that is compliant
with SHA-3.
• Deduplication operates within an encryption domain to ensure privacy.
• Encryption is performed without impact on performance.
• You can add, remove, import, export, modify, and delete encryption keys that are configured on the
Core.
• There is no limit to the number of encryption keys you can create on the Core.
Adding an encryption key
To add an encryption key:
1. Navigate to the Core Console.
2. Click Configuration → Security.
The Encryption Keys page appears.
3. Click Actions, and then click Add Encryption Key.
The Create Encryption Key dialog box displays.
4. In the Create Encryption Key dialog box, enter the details for the key described as follows.
Text Box Description
Name Enter a name for the encryption key.
38
Page 39

Text Box Description
Description Enter a description of the encryption key. It is used to provide more details for
the encryption key.
Passphrase Enter a passphrase. It is used to control access.
Confirm
Passphrase
5. Click OK.
CAUTION: It is recommended that you protect the passphrase. If you lose the passphrase,
you cannot access the data.
Re-enter the passphrase. It is used to confirm the passphrase entry.
Editing an encryption key
To edit an encryption key:
1. Navigate to the Core Console.
2. Click Configuration → Security
The Encryption Keys screen is displayed.
3. Select the encryption key that you want to modify, click Edit.
The Edit Encryption Key dialog box appears.
4. In the Edit Encryption Key dialog box, edit the name or modify the description of the encryption key.
5. Click OK.
Changing an encryption key passphrase
To change an encryption key passphrase:
1. Navigate to the Core Console.
2. Click Configuration → Security.
The Encryption Keys page appears.
3. Select the encryption key you want to modify and click Change Passphrase.
The Change Passphrase dialog box appears.
4. In the Change Passphrase dialog box, enter the new passphrase for the encryption and then re-enter
the passphrase to confirm what you entered.
5. Click OK.
CAUTION: It is recommended that you protect the passphrase. If you lose the passphrase,
you cannot access the data on the system.
Importing an encryption key
To import an encryption key:
1. Navigate to the Core Console.
2. Click Configuration → Security.
3. Select the Actions drop-down menu, and then click Import.
The Import Key dialog box appears.
4. In the Import Key dialog box, click Browse to locate the encryption key that you want to import, and
then click Open.
39
Page 40

5. Click OK.
Exporting an encryption key
To export an encryption key:
1. Navigate to the Core Console.
2. Click Configuration → Security.
3. Click > next to the name of the encryption key that you want to export, and then click Export.
The Export Key dialog box appears.
4. In the Export Key dialog box, click Download Key to save and store the encryption keys in a secure
location.
5. Click OK.
Removing an encryption key
To remove an encryption key:
1. Navigate to Core Console.
2. Click Configuration → Security.
3. Click > next to the name of the encryption key that you want to remove, and then click Remove.
The Remove Key dialog box appears.
4. In the Remove Key dialog box, click OK to remove the encryption key.
NOTE: Removing an encryption key does decrypt the data.
Managing cloud accounts
Your DL Appliance allows you to backup your data by creating a backup archive of recovery points to a
cloud. With your DL Appliance, you can create, edit, and manage your cloud account through a cloud
storage provider. You can archive your data to the cloud using Microsoft Azure, Amazon S3, Rackspace
Cloud Block Storage, or other OpenStack-based cloud services. See the following topics to manage your
cloud accounts:
• Adding A Cloud Account
• Editing a Cloud Account
• Configuring Cloud Account Settings
• Removing a Cloud Account
Adding a cloud account
Before you can export your archived data to a cloud, add the account for your cloud provider in the Core
Console.
To add a cloud account:
1. In the Core Console, click the Tools tab.
2. In the left menu, click Clouds.
3. On the Clouds page, click Add New Account.
The Add New Account dialog box opens.
4. Select a compatible cloud provider from the Cloud Type drop-down list.
40
Page 41

5. Enter the details described in the following table based on the cloud type selected in Step 4.
Table 1. Adding a cloud account
Cloud Type Text Box Description
Microsoft Azure Storage Account Name Enter the name of your
Windows Azure storage
account.
Access Key Enter the access key for your
account.
Display Name Create a display name for this
account in AppAssure; for
example, Windows Azure 1.
Amazon S3 Access Key Enter the access key for your
Amazon cloud account.
Secret Key Enter the secret key for this
account.
Display Name Create a display name for this
account in AppAssure; for
example, Amazon 1.
Powered by OpenStack User Name Enter the user name for you
OpenStack-based cloud
account.
API Key Enter the API key for your
account.
Display Name Create a display name for this
account in AppAssure; for
example, OpenStack 1.
Tenant ID Enter your tenant ID for this
account.
Authentication URL Enter the authentication URL
for this account.
Rackspace Cloud Block Storage User Name Enter the user name for your
Rackspace cloud account.
API Key Enter the API key for this
account.
Display Name Create a display name for this
account in AppAssure; for
example, Rackspace 1.
6. Click Add.
The dialog box closes, and your account is displayed on the Clouds page of the Core Console.
41
Page 42

Editing a cloud account
Perform the following steps to edit a cloud account:
1. In the Core Console, click the Tools tab.
2. In the left menu, click Clouds.
3. Next to the cloud account you want to edit, click the drop-down menu, and then click Edit.
The Edit Account window opens.
4. Edit the details as necessary, and then click Save.
NOTE: You cannot edit the cloud type.
Configuring cloud account settings
The cloud configuration settings let you determine the number of times AppAssure should attempt to
connect to your cloud account, and the amount of time spent on an attempt before it times out.
To configure the connection settings for your cloud account:
1. In the Core Console, click the Configuration tab.
2. In the left menu, click Settings.
3. On the Settings page, scroll down to Cloud Configuration.
4. Click the drop-down menu next to the cloud account you want to configure, and then do one of the
following:
• Click Edit.
The Cloud Configuration dialog box appears.
1. Use the up and down arrows to edit either of the following options:
– Request Timeout: Displayed in minutes and seconds, it determines the amount of time
AppAssure should spend on a single attempt to connect to the cloud account when
there is a delay. Connection attempts will cease after the entered amount of time.
– Retry Count: Determines the number of attempts AppAssure should conduct before
determining that the cloud account cannot be reached.
– Write Buffer Size: Determines the buffer size reserved for writing archived data to the
cloud.
– Read Buffer Size: Determines the block size reserved for reading archived data from the
cloud.
2. Click Next.
• Click Reset. Returns the configuration to the following default settings:
– Request Timeout: 01:30 (minutes and seconds)
– Retry Count: 3 (attempts)
Removing a Cloud account
You can remove a Cloud account to, discontinue your cloud service, or stop using it for a particular Core.
To remove a cloud account:
1. On the Core Console, click the Tools tab.
2. In the left menu, click Clouds.
3. Next to the cloud account you want to edit, click the drop-down menu, and then click Remove.
42
Page 43
4. In the Delete Account window, click Yes to confirm that you want to remove the account.
5. If the cloud account is currently in use, a second window asks you if you still want to remove it. Click
Yes to confirm.
NOTE: Removing an account that is currently in use causes all archive jobs scheduled for this
account to fail.
Understanding replication
About protecting workstations and servers
To protect your data add the workstations and servers you want to protect in the Core Console; for
example, your Exchange server, SQL Server, or your Linux server.
NOTE: In this section, generally the word machine also refers to the AppAssure Agent software
installed on that machine.
In the Core Console, you can identify the machine on which an AppAssure Agent software is installed and
specify which volumes to protect, define schedules for protection, add extra security measures such as
encryption, and more. For more information on how to access the Core Console to protect workstations
and servers, see Protecting A Machine.
NOTE: If the used capacity on your DL Appliance exceeds the capacity for which you have
purchased a license, the snapshot functionality will be disabled. Please contact your Dell Software
Group Account Manager for further assistance.
About replication
Replication is the process of copying recovery points and transmitting them to a secondary location for
disaster recovery. The process requires a paired source-target relationship between two cores. The
source core copies the recovery points of the protected machines and then asynchronously and
continuously transmits them to a target core at a remote disaster recovery site. The off-site location can
be a company-owned data center (self-managed core) or a third-party managed service provider’s
(MSP’s) location or cloud environment. When replicating to an MSP, you can use built-in work flows that
let you request connections and receive automatic feedback notifications. Possible scenarios for
replication include:
• Replication to a Local Location. The target core is located in a local data center or on-site location,
and replication is maintained at all times. In this configuration, the loss of the Core does not prevent a
recovery.
• Replication to an Off-site Location. The target core is at an off-site disaster recovery facility for
recovery in the event of a loss.
• Mutual Replication. Two data centers in two different locations each contain a core and are
protecting agents and serving as the off-site disaster recovery backup for each other. In this scenario,
each core replicates the protected machines to the Core that is located in the other data center.
• Hosted and Cloud Replication. AppAssure MSP partners maintain multiple target cores in a data
center or a public cloud. On each of these cores, the MSP partner lets one or more of their customers
replicate recovery points from a source core on the customer’s site to the MSP’s target core for a fee.
NOTE: In this scenario, customers only have access to their own data.
Possible replication configurations include:
43
Page 44

• Point to Point. Replicates a single protected machine from a single source core to a single target
core.
Figure 7. Basic Replication Architecture Diagram
• Multi-Point to Point. Replicates multiple source cores to a single target core.
Figure 8. Multi-Point Replication Architecture Diagram
About seeding
Replication begins with seeding: the initial transfer of deduplicated base images and incremental
snapshots of the protected machines, which can add up to hundreds or thousands of gigabytes of data.
Initial replication can be seeded to the target core using external media to transfer the initial data to the
target core. This is typically useful for large sets of data or sites with slow links.
44
Page 45

NOTE: While it is possible to seed the base data over a network connection, it is not recommended.
Initial seeding involves potentially very large amounts of data, which could overwhelm a typical
WAN connection. For example, if the seed data measures 10 GB and the WAN link transfers 24
Mbps, the transfer could take more than 40 days to complete.
The data in the seeding archive is compressed, encrypted, and deduplicated. If the total size of the
archive is larger than the space available on the removable media, the archive can span across multiple
devices based on the available space on the media. During the seeding process, the incremental recovery
points are replicated to the target site. After the target core consumes the seeding archive, the newly
replicated incremental recovery points automatically synchronize.
Seeding is a two-part process (also known as copy-consume):
• The first part involves copying, which is the writing of the initial replicated data to a removable media
source. Copying duplicates all of the existing recovery points from the source core to a local
removable storage device such as a USB drive. After copying is complete, you must then transport the
drive from the source core location to the remote target core location.
• The second part is consuming, which occurs when a target core receives the transported drive and
copies the replicated data to the repository. The target core then consumes the recovery points and
uses them to form replicated protected machines.
NOTE: While replication of incremental snapshots can occur between the source and target cores
before seeding is complete, the replicated snapshots transmitted from the source to the target
remains “orphaned” until the initial data is consumed, and they are combined with the replicated
base images.
Because large amounts of data need to be copied to the portable storage device, an eSATA, USB 3.0, or
other high-speed connection to the portable storage device is recommended.
About failover and failback
In the case of a severe outage in which your source core and protected machines fail, your DL Appliance
supports failover and failback in replicated environments. Failover refers to switching to a redundant or
standby target Core upon system failure or abnormal termination of a source core and associated
protected machines. The main goal of failover is to launch a new agent identical to the failed agent that
was protected by the failed source core. The secondary goal is to switch the target core into a new mode
so that the target core protects the failover agent in the same way as the source core protected the initial
agent before the failure. The target core can recover instances from replicated agents and immediately
commence protection on the failed-over machines.
Failback is the process of restoring a protected machine and core back to their original states (before
failure). The primary goal of failback is to restore the protected machine (in most cases, this is a new
machine replacing a failed agent) to a state identical to the latest state of the new, temporary agent.
When restored, it is protected by a restored source core. Replication is also restored, and the target core
acts as a replication target again.
About replication and encrypted recovery points
While the seed drive does not contain backups of the source core registry and certificates, the seed drive
does contain encryption keys from the source core if the recovery points being replicated from source to
target are encrypted. The replicated recovery points remain encrypted after they are transmitted to the
target core. The owners or administrators of the target core need the passphrase to recover the
encrypted data.
45
Page 46

About retention policies for replication
The retention policy on the source core determines the retention policy for the data replicated to the
target core, because the replication task transmits the merged recovery points that result from a rollup or
ad-hoc deletion.
NOTE: The target core is not capable of rollup or of ad-hoc deletion of recovery points. These
actions can only be performed by the source core.
Performance considerations for replicated data transfer
If the bandwidth between the source core and the target core cannot accommodate the transfer of
stored recovery points, replication begins with seeding the target core with base images and recovery
points from the selected servers protected on the source core. The seeding process only has to be
performed once, as it serves as the foundation that is required for regularly scheduled replication.
When preparing for replication, you must consider the following factors:
Change Rate The change rate is the rate at which the amount of protected data is accumulated.
The rate depends on the amount of data that changes on protected volumes and
the protection interval of the volumes. If a set of blocks change on the volume,
reducing the protection interval reduces the change rate.
Bandwidth The bandwidth is the available transfer speed between the source core and the
target core. It is crucial that the bandwidth be greater than the change rate for
replication to keep up with the recovery points created by the snapshots. Due to
the amount of data transmitted from core to core, multiple parallel streams may be
required to perform at wire speeds up to the speed of a 1 GB Ethernet connection.
NOTE: Bandwidth specified by the ISP is the total available bandwidth. The
outgoing bandwidth is shared by all devices on the network. Make sure that
there is enough free bandwidth for replication to accommodate the change
rate.
Number of
protected
machines
Depending on your network configuration, replication can be a time-consuming process.
The following table shows examples of the necessary bandwidth per Gigabyte for a reasonable change
rate
NOTE: For optimum results, adhere to the recommendations listed in the following table.
It is important to consider the number of protected machines per source core and
how many you plan to replicate to the target. AppAssure lets you perform
replication on a per protected server basis, so you can choose to replicate certain
servers. If all protected servers must be replicated, this drastically affects the
change rate, particularly if the bandwidth between the source and target cores is
insufficient for the amount and size of the recovery points being replicated.
46
Page 47

Maximum change rate for wan connection types
Table 2. Maximum change rate for wan connection types
Broadband Bandwidth Max Change Rate
DSL 768 Kbps and up 330 MB per hour
Cable 1 Mbps and up 429 MB per hour
T1 1.5 Mbps and up 644 MB per hour
Fiber 20 Mbps and up 838 GB per hour
If a link fails during data transfer, replication resumes from the previous failure point of the transfer after
link functionality is restored.
Roadmap for performing replication
To replicate data using AppAssure, you must configure the source and target cores for replication. After
you configure replication, you can then replicate data of the protected machine, monitor and manage
replication, and perform recovery.
Performing replication in AppAssure involves performing the following operations:
• Configure self-managed replication. For more information on replicating to a self-managed target
core, see Replicating To A Self-Managed Core.
• Configure third-party replication. Fore more information on replicating to a third-party target core,
see Replicating To A Core Managed By A Third Party
• Replicate a new protected machine attached to the source core. For more information on replicating
a protected machine, see Replicating A New Protected Machine.
• Replicate an existing protected machine. For more information on configuring an agent for
replication, see Replicating Agent Data On A Machine.
• Set replication priority for an agent. For more information on prioritizing the replication of agents, see
Setting Replication Priority For An Agent .
• Monitor replication as needed. For more information on monitoring replication, see Monitoring
Replication.
• Manage replication settings as needed. For more information on managing replication settings, see
Managing Replication Settings
• Recover replicated data in the event of disaster or data loss. For more information on recovering
replicated data, see Recovering Replicated Data
Replicating to a self-managed core
A self-managed core is a core to which you have access, often because it is managed by your company
at an off-site location. Replication can be completed entirely on the source core, unless you choose to
seed your data. Seeding requires that you consume the seed drive on the target core after you configure
replication on the source core.
NOTE: This configuration applies to replication to an off-site location and to mutual replication. The
Core must be installed on all source and target machines. If you are configuring your system for
multi-point to point replication, you must perform this task on all source cores and the one target
core.
47
Page 48

Configuring the source core to replicate to a self-managed target core
To configure the source core to replicate to a self-managed target core:
1. In the Core, click the Replication tab.
2. Click Add Target Core.
The Replication wizard appears.
3. Select I have my own Target Core, and then enter the information as described in the following
table.
Text Box Description
Host Name Enter the host name or IP address of the Core machine to which you are
replicating.
Port Enter the port number on which the AppAssure Core communicates with the
machine. The default port number is 8006.
User Name Enter the user name for accessing the machine. For example, Administrator.
Password Enter the password for accessing the machine.
If the Core you want to add has been paired with this source core previously, perform the following:
a. Select Use an existing target core.
b. Select the target core from the drop-down list.
c. Click Next.
d. Skip to step 7.
4. Click Next.
5. On the Details page, enter a name for this replication configuration; for example, SourceCore1. If
you are re-initiating or repairing a previous replication configuration, select My Core has been
migrated and I would like to repair replication
6. Click Next.
7. On the Agents page, select the agents you want to replicate, and then use the drop-down lists in the
Repository column to select a repository for each agent.
8. If you plan to perform the seeding process for the transfer of the base data, complete the following
steps:
NOTE: Because large amounts of data need to be copied to the portable storage device, an
eSATA, USB 3.0, or other high-speed connection to the portable storage device is
recommended.
a. On the Agents page, select Use a seed drive to perform initial transfer. If you currently have one
or more machines replicating to a target core, you can include these protected machines on the
seed drive by selecting With already replicated.
b. Click Next.
c. On the Seed Drive Location page, use the Location type drop-down list to select one of the
following:
• Local: In the Location text box, enter where you want to save the seed drive; for example, D:
\work\archive.
• Network: In the Location text box, enter where you want to save the seed drive, and then
enter your credentials for the network share in the User name and Password text boxes.
• Cloud: In the Account text box, select the account. To select a cloud account, you must first
have added it in the Core Console. For more information, see Adding A Cloud Account. Select
48
Page 49

the Container associated with your account. Select the Folder Name to which the archived
data is to be saved.
d. Click Next. ntainer
9. In the Seed Drive Option dialog box, enter the information described as follows:
Text Box Description
Maximum Size Large archives of data can be divided into multiple segments. Select the
maximum size of the segment you want to reserve for creating the seed drive
by doing one of the following:
• Select Entire Target to reserve all available space in the path provided on
the Seed Drive Location page for future use (for example, if the location is
D:\work\archive, all of the available space on the D: drive is reserved if
required for copying the seed drive, but is not reserved immediately after
starting the copying process).
• Select the blank text box, enter an amount, and then select a unit of
measurement from the drop-down list to customize the maximum space
you want to reserve.
Customer ID
(optional)
Recycle action In the event that the path already contains a seed drive, select one of the
Comment Enter a comment or description of the archive.
Add all Agents to
Seed Drive
Build RP chains
(fix orphans)
Optionally, enter the customer ID that was assigned to you by the service
provider.
following options:
• Do not reuse — Does not overwrite or clear any existing data from the
location. If the location is not empty, the seed drive write fails.
• Replace this core — Overwrites any pre-existing data pertaining to this
core but leave the data for other cores intact.
• Erase completely — Clears all data from the directory before writing the
seed drive.
Select the agents you want to replicate using the seed drive.
Select this option to replicate the entire recovery point chain to the seed drive.
This option is selected by default.
Typical seeding in AppAssure replicates only the latest recovery point to the
seed drive, which reduces the amount of time and space required for creating
the seed drive. Opting to build recovery point (RP) chains to the seed drive
requires enough space on the seed drive to store the latest recovery points
from the specified agent or agents, and may take additional time to complete
the task.
Use compatible
format
10. On the Agents page, select the agents you want to replicate to the target core using the seed drive.
11. Click Finish.
12. If you created a seed drive, send it to your target core.
Select this option to create the seed drive in a format that is compatible with
both new and older versions of the AppAssure Core.
49
Page 50

The pairing of the source core to the target core is complete. Replication begins, but produces
orphaned recovery points on the target core until the seed drive is consumed and provides the
necessary base images.
Consuming the seed drive on a target core
This procedure is only necessary if you created a seed drive while Configuring Replication For A SelfManaged Core.
To consume the seed drive on a target core:
1. If the seed drive was saved to a portable storage device such as a USB drive, connect the drive to the
target core.
2. From the Core Console on the target core, select the Replication tab.
3. Under Incoming Replication, select the correct source core by using the drop-down menu, and
then click
The Consume window appears.
4. For Location type, select one of the following options from the drop-down list:
• Local
• Network
• Cloud
5. Enter the following information as needed:
Consume.
Text Box Description
Location Enter a path to where the seed drive is located, such as a USB drive or a
network share (for example, D:\).
User name Enter the user name for the shared drive or folder. User name is required only
for a network path.
Password Enter the password for the shared drive or folder. Password is required only for
a network path.
Account Select an account from the drop-down list. To select a cloud account, you
must first have added it in the Core Console.
Container Select a container associated with your account from the drop-down menu.
Folder Name Enter the name of the folder in which the archived data is saved; for example, -
Archive-[DATE CREATED]- [TIME CREATED]
6. Click Check File.
After the Core checks the file, it automatically populates the Date Range with the dates of the oldest
and newest recovery points contained in the seed drive. It also imports any comments entered in
Configuring Replication For A Self-Managed Core.
7. Under Agent Names on the Consume window, select the machines for which you want to consume
data, and then click Consume.
NOTE: To monitor the data consumption progress, select the Events tab.
Abandoning an outstanding seed drive
If you create a seed drive with the intent to consume it on the target core but choose not to send it to the
remote location, a link for the outstanding seed drive remains on the source core Replication tab. You
may want to abandon the outstanding seed drive in favor of different or more current seed data.
50
Page 51

NOTE: This procedure removes the link to the outstanding seed drive from the Core Console on the
source core. It does not remove the drive from the storage location on which it is saved.
To abandon an outstanding seed drive:
1. From the Core Console on the source core, select the Replication tab.
2. Click Outstanding Seed Drive (#).
The Outstanding seed drives section appears. It includes the name of the remote target core, the
data and time at which the seed drive was created, and the data range of the recovery points
included on the seed drive.
3. Click the drop-down menu for the drive that you want to abandon, then select Abandon.
The Outstanding Seed Drive window appears.
4. Click Yes to confirm the action.
The seed drive is removed. If there are no more seed drives that exist on the source core, then the
next time that you open the Replication tab, the Outstanding Seed Drive (#) link and Outstanding
seed drives section do not appear.
Replicating to a core managed by a third party
A third-party core is a target core that it managed and maintained by an MSP. Replicating to a core
managed by a third party does not require you to have access to the target core. After a customer
configures replication on the source core or cores, the MSP completes the configuration on the target
core.
NOTE: This configuration applies to hosted and cloud replication. The AppAssure Core must be
installed on all source core machines.
Configuring replication to a target core managed by a third party
NOTE: This configuration applies to hosted and cloud replication. If you are configuring AppAssure
for multipoint to point replication, you must perform this task on all source cores.
To configure replication for a core managed by a third party:
1. Navigate to the Core Console, and click the Replication tab.
2. In the Actions drop-down menu, click Add Remote Core.
3. In the Select Replication Type dialog box, select the option, I have a subscription to a third-party
providing off-site backup and disaster recovery services, and wish to replicate my backups to that
service, and then enter the information described as follows:
Text Box Description
Host Name Enter the host name, IP address, or FQDN for the remote core machine.
Port Enter the port number that was given to you by your third-party service
provider.
The default port number is 8006.
4. Click Continue.
5. In the Add Remote Core dialog box, do the following:
a. Select the protected machines to replicate.
b. Select a repository for each protected machine.
c. Enter your subscription email address and customer ID that was assigned to you by the service
provider.
51
Page 52

6. If you plan to perform the seeding process for the transfer of base data, select Use a seed drive to
perform initial transfer.
7. Click Submit Request.
NOTE: If you select Use a seed drive to perform initial transfer, the Copy to Seed Drive dialog
box displays.
8. In the Copy to Seed Drive dialog box, enter the information for the seed drive as described in the
following table.
Text Box Description
Location Enter the path to the drive on which you want to save the initial data, such as a
local USB drive.
User name Enter the user name for connecting to the drive.
NOTE: This is required if the seed drive is located on a network share.
Password Enter the password for connecting to the drive.
NOTE: This is required if the seed drive is located on a network share.
Maximum size Select one of the following options:
• The entire target.
• A portion of the drive’s available space.
To designate a portion of the drive:
a. Enter the desired amount of space in the text box.
b. Select the measurement.
Recycle action In the event the path already contains a seed drive, select one of the following
options:
• Do not reuse — Does not overwrite or clear any existing data from the
location. If the location is not empty, the seed drive write fails.
• Replace this core — Overwrites any pre-existing data pertaining to this
core but leave the data for other cores intact.
• Erase completely — Clears all data from the directory before writing the
seed drive.
Comment Enter a comment or description of the archive.
Agents Select the agents you want to replicate using the seed drive.
NOTE: Because large amounts of data need to be copied to the portable storage device, an
eSATA, USB 3.0, or other high-speed connection to the portable storage device is
recommended.
9. Click Start to write the seed drive to the path that you provided.
10. Send the see drive as directed by the third-party service provider.
52
Page 53

Reviewing a replication request
A replication request is sent from the source core to the third-party target core. As the third party, you
can review the request, and then approve it to begin replication for your customer, or you can deny it to
prevent replication from occurring.
To review a replication request on a third-party target core:
1. Open the Core Console on the target core and select the Replication tab.
2. Click Pending Requests (#).
The Pending Replication Requests section appears.
3. Next to the request that you want to review, select Review from the drop-down menu.
The Review Replication Request window appears.
NOTE: The request completed by the customer determines the information that appears in the
Source Core Identity section.
4. On the Review Replication Request window, do one of the following:
• To reject the request, click Deny.
• To approve the request:
1. – Select Replace an existing replicated Core, and then select a core from the drop-down
list.
– Select Create a new source Core. Verify the Core Name, customer Email Address, and
Customer ID, editing the information as necessary..
2. Under Agents, select the machines to which the approval applies, and then use select the
appropriate repository for each machine by using the drop-down list.
3. Optionally, enter any notes that you want to display in the Comment box.
4. Click Send Response.
Replication is accepted.
Ignoring a replication request
As a third-party service provider of a target core, you have the option of ignoring a request for replication
sent from a customer. This option could be used if a customer sent a request by mistake or if you want to
reject a request without first reviewing it.
To ignore a replication request:
1. From the Core Console on the target core, select the Replication tab.
2. On the Replication tab, click Pending Requests (#).
The Pending Replication Requests section appears.
3. Next to the request that you want to ignore, select Ignore by using the drop-down menu.
The target core sends a notification to the source core that the request was ignored.
Monitoring replication
When replication is set up, you can monitor the status of replication tasks for the source and target cores.
You can refresh status information, view replication details, and more.
53
Page 54

To monitor replication:
1. In the Core Console, click the Replication tab.
2. On this tab, you can view information about and monitor the status of replication tasks described as
follows:
Table 3. Monitoring replication
Section Description Available Actions
Pending Replication Requests Lists your customer ID, email
address, and host name when a
replication request is submitted
to a third-party service provider.
It is listed here until the MSP
accepts the request.
Outstanding Seed Drives Lists seed drives that have been
written but not yet consumed
by the target core. It includes
the remote core name, date on
which it was created, and the
date range.
Outgoing Replication Lists all target cores to which
the source core is replicating. It
includes the remote core name,
the state of existence, the
number of protected machines
being replicated, and the
progress of a replication
transmission.
In the drop-down menu, click
Ignore to ignore or reject the
request.
In the drop-down menu, click
Abandon to abandon or cancel
the seed process.
On a source core, in the dropdown menu, you can select the
following options:
• Details — Lists the ID, URI,
display name, state,
customer ID, email address,
and comments for the
replicated core.
• Change Settings — Lists the
display name and lets you
edit the host and port for
the target core.
• Add Agents — Lets you
select a host from a dropdown list, select protected
machines for replication,
and create a seed drive for
the new protected
machine's initial transfer.
Incoming Replication Lists all source machines from
which the target receives
replicated data. It includes the
remote core name, state,
machines, and progress.
On a target core, in the dropdown menu, you can select the
following options:
• Details — Lists the ID, host
name, customer ID, email
address, and comments for
the replicated core.
• Consume — Consumes the
initial data from the seed
drive and saves it to the
local repository.
3. Click the Refresh button to update the sections of this tab with the latest information.
54
Page 55

Managing replication settings
You can adjust a number of settings for how replication executes on the source and target cores.
To manage replication settings:
1. In the Core Console, click the Replication tab.
2. In the Actions drop-down menu, click Settings.
3. In the Replication Settings window, edit the replication settings described as follows:
Option Description
Cache lifetime Specify the amount of time between each target-core status request
performed by the source core.
Volume image
session timeout
Max. concurrent
replication jobs
Max. parallel
streams
4. Click Save.
Specify the amount of time the source core spends attempting to transfer a
volume image to the target core.
Specify the number of protected machines permitted to replicate to the target
core at one time.
Specify the number of network connections permitted to be used by a single
protected machine to replicate that machine’s data at one time.
Removing replication
You can discontinue replication and remove protected machines from replication in several ways. The
options include:
• Removing An Agent From Replication On The Source Core
• Removing An Agent On The Target Core
• Removing A Target Core From Replication
• Removing A Source Core From Replication
NOTE: Removing a source core results in the removal of all replicated machines that are protected
by that core.
Removing a protected machine from replication on the source Core
To remove a protected machine from replication on the source core:
1. From the source core, open the Core Console, and click the Replication tab.
2. Expand the Outgoing Replication section.
3. In the drop-down menu for the protected machine that you want to remove from replication, click
Delete.
4. In the Outgoing Replication dialog box, click Yes to confirm deletion.
55
Page 56

Removing a protected machine on the target Core
To remove a protected machine on the target core:
1. On the target core, open the Core Console, and click the Replication tab.
2. Expand the Incoming Replication section.
3. In the drop-down menu for the protected machine that you want to remove from replication, click
Delete, and then select one of the following options.
Option Description
Relationship Only Removes the protected machine from replication but retains the replicated
recovery points.
With Recovery
Point
Removes the protected machine from replication and deletes all replicated
recovery points received from that machine.
Removing a target Core from replication
To remove a target core from replication:
1. On the source core, open the Core Console, and click to the Replication tab.
2. Under Outgoing Replication, click the drop-down menu next to the remote core that you want to
delete, and click Delete.
3. In the Outgoing Replication dialog box, click Yes to confirm deletion.
Removing a source Core from replication
NOTE: Removing a source core results in the removal of all replicated agents protected by that
core.
To remove a source core from replication:
1. On the target core, open the Core Console, and click the Replication tab.
2. Under Incoming Replication, in the drop-down menu, click Delete, and then select one of the
following options.
Option Description
Relationship Only Removes the source core from replication but retains the replicated recovery
points.
With Recovery
Points
3. In the Incoming Replication dialog box, click Yes to confirm deletion.
Removes the source core from replication and deletes all replicated recovery
points received from that machine.
Recovering replicated data
Day-to-day replication functionality is maintained on the source core, while only the target core is
capable of completing the functions necessary for disaster recovery.
For disaster recovery, the target core can use the replicated recovery points to recover the protected
agents and core.
You can perform the following recovery options from the target core:
56
Page 57

• Mount recovery points.
• Roll back to recovery points.
• Perform a virtual machine (VM) export.
• Perform a bare metal restore (BMR).
• Perform Failback (in the event you have a Failover/Failback replication environment set up).
Roadmap for failover and failback
When you encounter a disaster situation in which your source core and associated protected machine
have failed, you can enable failover in AppAssure to switch protection to your identical failover (target)
core and launch a new (replicated) agent identical to the failed agent. After your source core and agents
have been repaired, you can then perform failback to restore the data from the failed-over core and
agent back to the source core and agent. In AppAssure, failover and failback involve the following
procedures.
• Setting up your environment for failover.
• Perform failover for the target core and associated agent.
• Restore a source core by performing failback.
Setting up an environment for failover
Setting up your environment for failover requires that you have a source and target Core and associated
agent set up for replication. Complete the steps in this procedure to set up replication for failover.
To set up an environment for failover:
1. Install a Core for the source and install a Core for the target.
2. Install an AppAssure Agent to be protected by the source core.
3. Create one repository on the source core and one repository on the target core.
For more information, see Creating A Repository.
4. Add the agent for protection under the source core.
For more information, see Protecting A Machine.
5. Set up replication from the source to target core and replicate the protected agent with all recovery
points.
Follow the steps in the Replicating To A Self-Managed Core to add the target core to which to
replicate.
Performing failover on the target Core
When you encounter a disaster situation in which your source core and associated protected machines
have failed, you can enable failover to switch protection to your identical failover (target) core. The target
core becomes the only core protecting the data in your environment, and you then launch a new agent
to temporarily replace the failed agent.
To perform failover on the target core:
1. Navigate to the Core Console on the target core, and click the Replication tab.
2. Under Incoming Replication, select the source core, and then expand the details under the
individual agent.
3. On the Actions menu for that core, click Failover.
The status in this table for this machine changes to Failover.
57
Page 58

4. Click the Machines tab, and then select the machine that has the associated AppAssure agent with
recovery points.
5. Export the backup recovery point information on that agent to a virtual machine.
6. Shut down the machine that has the AppAssure agent.
7. Start the virtual machine that now includes the exported backup information.
You need to wait for the device driver software to be installed.
8. Reboot the virtual machine and wait for the agent service to start.
9. Go back to the Core Console for the target core and verify that the new agent is displayed on the
Machines tab under Protected Machines and on the Replication tab under Incoming Replication.
10. Force multiple snapshots, and verify they complete correctly.
For more information, see Forcing A Snapshot.
11. You can now proceed with performing failback.
For more information, see Performing Failback.
Performing failback
After you repair or replace the failed original source core and protected machines, you need to move the
data from your failed-over machines to restore the source machines.
To perform failback:
1. Navigate to the Core Console on the target core, and click the Replication tab.
2. Under Incoming Replication, select the failover agent and expand the details.
3. On the Actions menu, click Failback.
The Failback Warnings dialog box opens to describe the steps you need to follow before you click
the Start Failback button.
4. Click Cancel.
5. If the failed-over machine is running Microsoft SQL Server or Microsoft Exchange Server, stop those
services.
6. In the Core Console for the target core, click the Tools tab.
7. Create an archive of the failed-over agent and output it to disk or a network share location.
8. After you create the archive, navigate to the Core Console on the newly repaired source core, and
click the
9. Import the archive you just created in Step 7.
10. Go back to the Core Console on the target core, and click the Replication tab.
11. Under Incoming Replication, select the failover agent and expand the details.
12. On the Actions menu, click Failback.
13. In the Failback Warnings dialog box, click Start Failback.
14. Shut down the machine that contains the exported agent that was created during failover.
15. Perform a bare metal restore (BMR) for the source core and agent.
Tools tab.
NOTE: When you launch the restore, you must use the recovery points that were imported
from the target core to the agent on the virtual machine.
16. Wait for the BMR reboot and for the agent service to restart, and then view and record the network
connection details of the machine.
17. Navigate to the Core Console on the source core, and, on the Machines tab, modify the machine
protection settings to add the new network connection details.
18. Navigate to the Core Console on the target core, and delete the agent from the Replication tab.
58
Page 59

19. In the Core Console of the source core, set up replication again between the source and target by
clicking the Replication tab, and then adding the target core for replication.
Managing events
Managing core events assists with the monitoring of the health and usage of the Core. The core includes
predefined sets of events, which can be used to notify administrators of critical issues on the Core or the
backup jobs.
From the Events tab, you can manage notification groups, e-mail SMTP settings, repetition reduction,
and event retention. The Notification Groups option allows you to manage notification groups, from
which you can:
• Specify an event for which you want to generate an alert for the following:
– Clusters
– Attachability
– Jobs
– Licensing
– Log Truncation
– Archive
– Core Service
– Export
– Protection
– Replication
– Rollback
– SMTP Server Settings
– Enabled Trace logs
– Cloud Configuration
• Specify the type of alert (error, warning, and informational).
• Specify to whom and where the alerts are sent. Options include:
– Email Address
– Windows Events Logs
– Syslog Server
• Specify a time threshold for repetition.
• Specify the retention period for all events.
Configuring notification groups
To configure notification groups:
1. From the Core, select the Configuration tab.
2. From the Manage option, click Events.
3. Click Add Group.
The Add Notification Group dialog box opens and displays three panels:
• General
• Enable Events
59
Page 60

• Notification Options
4. In the General panel, enter basic information for the notification group described as follows:
Text Box Description
Name Enter a name for event notification group, used to identify the event
notification group.
Description Enter a description for the event notification group, used to describe the
purpose of the event notification group.
5. In the Enable Events panel, select the conditions for which event logs (alerts) to create and report.
You can elect to create alerts for:
• All Events
• Appliance Events
• Boot CD
• Security
• DatabaseRetention
• LocalMount
• Clusters
• Notification
• Power Shell Scripting
• Push Install
• Nightly Jobs
• Attachability
• Jobs
• Licensing
• Log Truncation
• Archive
• Core Service
• Export
• Protection
• Replication
• Repository
• Rollback
• Rollup
6. In the Notification Options panel, specify how to handle the notification process.
The notification options are:
Text Box Description
Notify by e-mail Designate the recipients of the email notification. You can choose to specify
separate multiple email addresses as well as blind and carbon copies. You can
choose:
• To:
• CC:
60
Page 61

Text Box Description
• BCC:
Notify by
Windows Event
Log
Notify by sys logd Select this option if you want alerts to be reported through sys logd. Specify
7. Click OK.
Select this option if you want alerts to be reported through the Windows Event
Log. It is used to specify whether the notification of alerts must be reported
through the Windows Event Log.
the details for the sys logd in the following text boxes:
• Hostname:
• Port:1
Configuring an email server and email notification template
If you want to receive email notifications about events, configure an email server and an email
notification template.
NOTE: You must also configure notification group settings, including enabling the Notify by email
option, before email alert messages will be sent. For more information on specifying events to
receive email alerts, see 'Configuring Notification Groups For System Events' in
Appliance User’s Guide.
To configure an email server and email notification template:
1. From the Core, select the Configuration tab.
2. From the Manage option, click Events.
3. In the Email SMTP Settings pane, click Change.
The Edit Email Notification Configuration dialog box appears.
4. Select Enable Email Notifications, and then enter details for the email server described as follows:
Dell DL4300
Text Box Description
SMTP Server Enter the name of the email server to be used by the email notification
template. The naming convention includes the host name, domain, and suffix;
for example, smtp.gmail.com.
Port Enter a port number. It is used to identify the port for the email server; for
example, the port 587 for Gmail.
The default is 25.
Timeout (seconds) To specify how long to try a connection before timing out, enter an integer
value. It is used to establish the time in seconds when trying to connect to the
email server before a time-out occurs.
The default is 30 seconds.
TLS Select this option if the mail server uses a secure connection such as Transport
Layer Security (TLS) or Secure Sockets Layer (SSL).
Username Enter a user name for the email server.
61
Page 62

Text Box Description
Password Enter a password for accessing the email server.
From Enter a return email address. It is used to specify the return email address for
the email notification template; for example, noreply@localhost.com.
Email Subject Enter a subject for the email template. It is used to define the subject of the
email notification template; for example, <hostname> - <level> <name>.
Email Enter information for the body of the template that describes the event, when
it occurred, and the severity.
5. Click Send Test Email and review the results.
6. After you are satisfied with the results of the tests, click OK.
Configuring repetition reduction
To configure repetition reduction:
1. From the Core, click the Configuration tab.
2. From the Manage option, click Events.
3. From the Repetition Reduction area, click Change.
The Repetition Reduction dialog box appears.
4. Select Enable Repetition Reduction.
5. In the Store events for X minutes text box, enter the number of minutes to store the events for
repetition reduction.
6. Click OK.
Configuring event retention
To configure event retention:
1. From the Core, click the Configuration tab.
2. From the Manage option, click Events.
3. Under Database Connection Settings, click change.
The Database Connection Settings dialog box appears.
4. In the Retain event and job history for text box, enter the number of days that you want to retain
information about events.
For example, you could select 30 days (default).
5. Click Save.
Managing recovery
The Core can instantly restore data or recover machines to physical or virtual machines from the
recovery points. The recovery points contain agent volume snapshots captured at the block level. These
snapshots and are application aware, meaning all open transactions and rolling transaction logs are
completed and caches are flushed to disk before creating the snapshot. Using application-aware
snapshots in tandem with Verified Recovery, enables the Core to perform several types of recoveries,
including:
• Recovery of files and folders
62
Page 63

• Recovery of data volumes, using Live Recovery
• Recovery of data volumes for Microsoft Exchange Server and Microsoft SQL Server, using Live
Recovery
• Bare metal restore, using Universal Recovery
• Bare metal restore to dissimilar hardware, using Universal Recovery
• Ad-hoc and continuous export to virtual machines
About system information
AppAssure lets you view information about the Core that includes system information, local and mounted
volumes, and AppAssure engine connections.
If you want to dismount individual or all recovery points that are mounted locally on a core, you can
accomplish this from the Mount option on the Tools tab.
Viewing system information
To view system information:
1. Navigate to the Core, and then select the Tools tab.
2. From the Tools option, click System Info.
Downloading installers
You can download installers from the Core. From the Tools tab, you can choose to download the Agent
Installer or the Local Mount Utility.
NOTE: For access to the Agent Installer, see Downloading And Installing The Agent Installer. For
more information about deploying the Agent Installer, see the Dell DL4300 Appliance Deployment
Guide available at Dell.com/support/home. For access to the Local Mount Utility Installer, see
About The Local Mount Utility and for more information about the Local Mount Utility, see
Downloading And Installing The Local Mount Utility.
About the agent installer
The Agent installer is used to install the AppAssure Agent application on machines that are intended to be
protected by the Core. If you determine that you have a machine that requires the Agent Installer, you
can download the web installer from the Tools tab in the Core.
NOTE: The downloading of the Core is performed from the License Portal. To download the Core
installer, visit https://licenseportal.com.
Downloading and installing the agent installer
You can download and deploy the Agent Installer on any machine that is protected by the Core.
To download and install the agent installer:
1. Download the Agent installer file from the License Portal or from the Core.
For example: Agent-X64-5.3.x.xxxxx.exe
2. Click Save File.
63
Page 64

For more information about installing the agents, see the Dell DL4300 Appliance Deployment Guide
available at Dell.com/support/home.
About the local mount utility
The Local Mount Utility (LMU) is a downloadable application that lets you mount a recovery point on a
remote Core from any machine. The light-weight utility includes the aavdisk and aavstor drivers, but
it does not run as a service. When you install the utility, by default, it is installed in the directory C:
\Program Files\AppRecovery\Local Mount Utility and a shortcut is displayed on the machine’s desktop.
While the utility was designed for remote access to cores, you also can install the LMU on the Core.
When it runs on a core, the application recognizes and displays all mounts from that core, including
mounts performed through the Core Console. Likewise, mounts performed on the LMU are also
displayed in the console.
Downloading and installing the local mount utility
To download and install the Local Mount Utility:
1. From the machine on which you want to install the LMU, access the Core Console by entering the
console URL into your browser and logging on with your user name and password.
2. From the Core Console, click the Tools tab.
3. From the Tools tab, click Downloads.
4. Under Local Mount Utility, click the Download web installer link.
5. From the Opening LocalMountUtility-Web.exe window, click Save File.
The file saves to the local Downloads folder. In some browsers, the folder automatically opens.
6. From the Downloads folder, right-click on the LocalMountUtility-Web executable and click Open.
Depending on your machine’s configuration, the User Account Control window may be displayed.
7. If the User Account Control window is displayed, click Yes to let the program make changes to the
machine.
The AppAssure Local Mount Utility Installation wizard launches.
8. On the AppAssure Local Mount Utility Installation wizard Welcome screen, click Next to continue
to the License Agreement page.
9. On the License Agreement page, select I accept the terms in the license agreement, and then click
Next to continue to the Prerequisites page.
10. On the Prerequisites page, install any necessary prerequisites and click Next to continue to the
Installation Options page.
11. On the Installation Options page, complete the following tasks:
a. Choose a destination folder for the LMU by clicking the Change button.
NOTE: The default destination folder is C:\Program Files\AppRecovery\LocalMountUtility.
b. Select whether or not to Allow Local Mount Utility to automatically send diagnostic and usage
information to AppAssure Software, Inc.
c. Click Next to continue to the Progress page and download the application. The application
downloads to the destination folder, with progress displayed in the progress bar. When finished,
the wizard automatically advances to the
12. Click Finish to close the wizard.
64
Completed page.
Page 65

Adding a core to the local mount utility
To mount a recovery point, you must add the Core to the LMU. There is no limit as to how many cores
you can add.
To add a core to the Local Mount Utility:
1. From the machine on which the LMU is installed, launch LMU by double-clicking the desktop icon.
2. If the User Account Control window displays, click Yes to let the program to make changes to the
machine.
3. In the upper-left corner of the AppAssure Local Mount Utility window, click Add core.
4. In the Add Core window, enter the requested credentials described as follows:
Text Box Description
Host name The name of the Core from which you want to mount recovery points.
NOTE: If installing the LMU on a core, LMU automatically adds the
localhost machine.
Port The port number used to communicate with the Core.
The default port number is 8006.
Use my Windows
user credentials
Use specific
credentials
User name The user name used to access the Core machine.
Password The password used to access the Core machine.
5. Click Connect.
6. If adding multiple cores, repeat Step 3 through Step 5 as necessary.
Select this option if the credentials you use to access the Core are the same as
your Windows credentials.
Select this option if the credentials you use to access the Core are different
from your Windows credentials.
NOTE: This option is only available if you choose to use specific
credentials.
NOTE: This option is only available if you choose to use specific
credentials.
Exploring a mounted recovery point by using the local mount utility
NOTE: This procedure is not necessary if you are exploring a recovery point immediately after
mounting it, as the folder containing the recovery point automatically opens upon completion of
the mounting procedure.
To explore a mounted recovery point using the Local Mount Utility:
1. From the machine on which by LMU is installed, launch LMU by double-clicking the desktop icon.
2. From the main Local Mount Recovery screen, click Active mounts.
The Active Mounts window opens and displays all mounted recovery points.
3. Click Explore beside the recovery point from which you want to recover to open the folder of
deduplicated volumes.
65
Page 66

Mounting a recovery point by using the local mount utility
Before mounting a recovery point, the LMU must connect to the Core on which the recovery point is
stored. As described in Adding A Core To The Local Mount Utility, the number of cores that can be added
to the LMU is unlimited; however, the application can connect to only one core at a time. For example, if
you mount a recovery point of an agent protected by one core and then mount a recovery point of an
agent protected by a different core, the LMU automatically disconnects from the first core to establish a
connection with the second core.
To mount a recovery point by using the Local Mount Utility:
1. From the machine on which the LMU is installed, launch LMU by double-clicking the desktop icon.
2. From the main AppAssure Local Mount Utility window, expand the desired core in the navigation
tree to reveal the protected agents.
3. From the navigation tree, select the desired agent.
The recovery points display in the main frame.
4. Expand the recovery point that you want to mount to reveal individual disk volumes or databases.
5. Right-click the recovery point that you want to mount and select one of the following options:
• Mount
• Mount writable
• Mount with previous writes
• Advanced mount
6. From the Advanced Mount window, complete the options described as follows:
Text Box Description
Mount point path To select a path for the recovery points other than the default mount point
path, click the Browse button.
Mount type Select one of the following options:
• Mount read-only
• Mount writable
• Mount read-only with previous writes
7. Click Mount.
The LMU automatically opens the folder containing the mounted recovery point.
NOTE: Selecting a recovery point that is already mounted causes the Mounting dialog box to
prompt you to dismount the recovery point.
Dismounting a recovery point by using the local mount utility
To dismount a recovery point using the Local Mount Utility:
1. From the machine on which the LMU is installed, launch LMU by double-clicking the desktop icon.
2. From the main Local Mount Recovery screen, click Active mounts.
The Active Mounts window opens and displays all mounted recovery points.
3. Select one of the options described in the table below to dismount recovery points.
66
Page 67

Option Description
Dismount Dismounts only the adjacent recovery point.
a. Click Dismount beside the chosen recovery point.
b. Close the window.
Dismount all Dismounts all mounted recovery points.
a. Click Dismount all.
b. In the Dismount All window, click Yes to confirm.
c. Close the window.
About the local mount utility tray menu
The LMU tray menu is located in your desktop taskbar. Right-click the icon to reveal the following
options:
Browse Recovery
Points
Active Mounts Opens the Active Mounts screen.
Options Opens the Options screen, where you can change the Default Mount Point
About Opens the splash screen of licensing information.
Exit Closes the application.
NOTE: Using the X in the upper corner of the main screen minimizes the application to the tray.
Opens the LMU main screen.
Directory, Default Core Credentials, and Language for the LMU user interface.
Using Core and agent options
By right-clicking the Core or agent in the main LMU screen, you can use certain options. They include:
• Localhost Options
• Remote Core Options
• Agent Options
Accessing localhost options
To access Localhost options, right-click the Core or agent and then click Reconnect to Core.
Information from the Core is updated and refreshed; for example, recently added agents.
Accessing remote core options
To access remote core options, right-click the Core or agent and then select one of the remote core
options described as follows:
Option Description
Reconnect to core Refreshes and updates information from the Core, such as recently added agents.
Remove core Deletes the Core from the Local Mount Utility.
67
Page 68

Option Description
Edit core Opens the Edit Core window, where you can change the host name, port, and
credentials.
Accessing agent options
To access agent options, right-click the Core or agent and then click Refresh recovery points. The list of
recovery points for the selected agent updates.
Managing retention policies
Periodic backup snapshots of all the protected servers accumulate on the Core over time. The retention
policies are used to retain backup snapshots for longer periods of time and to help with management of
these backup snapshots. The retention policy is enforced by a nightly rollup process that helps in aging
and deleting old backups. For information about configuring retention policies, see Customizing
Retention Policy Settings.
Archiving to a cloud
You can archive your data to a cloud by uploading it to a variety of cloud providers directly from the Core
Console. Compatible clouds include Windows Azure, Amazon, Rackspace, and any OpenStack-based
provider.
To export an archive to a cloud:
• Add your cloud account to the Core Console. For more information see, Adding A Cloud Account.
• Archive your data and export it to your cloud account.
• Retrieve archived data by importing it from the cloud location.
About archiving
Retention policies enforce the periods for which backups are stored on short-term (fast and expensive)
media. Sometimes certain business and technical requirements mandate extended retention of these
backups, but use of fast storage is cost prohibitive. Therefore, this requirement creates a need for longterm (slow and cheap) storage. Businesses often use long-term storage for archiving both compliance
and noncompliance data. The archive feature in AppAssure is used to support the extended retention for
compliance and noncompliance data. It is also used to seed replication data to a remote replica core.
Creating an archive
To create an archive
1. In the Core Console, click the Configuration tab.
2. From the Manage option, click Archive.
The Create Archive dialog box appears.
3. In the Create Archive dialog box, enter the details for the archive described as follows:
68
Page 69

Text Box Description
Date range To specify the date range, select the to and from dates.
Archive password Enter a password for the archive, which is used to establish log in credentials
to secure the archive.
Confirm Re-enter the password to secure the archive, which is used to provide
validation of the information that you entered in the Archive Password text
box.
Output Location Enter the location for the output, used to define the location path where you
want the archive to reside. This can be a local disk or a network share. For
example, d:\work\archive or \\servername\sharename for network paths.
NOTE: If the output location is a network share, enter a user name and
password for connecting to the share.
User name Enter a user name, which is used to establish logon credentials for the network
share.
Password Enter a password for the network path, which is used to establish logon
credentials for the network share.
Maximum Size Enter how much space to use for the archive. You can select from:
• Entire Target
• Specific amount in MB or GB
Recycle action Select the appropriate recycle action.
Comment Enter any additional information that is necessary to capture for the archive.
4. Click Archive.
Setting a scheduled archive
The Scheduled Archive feature lets you set a time when an archive of a selected machine will be
automatically created and saved to the specified location. This accommodates situations where you
would want frequent archives of a machine to be saved, without the inconvenience of needing to create
the archives manually. Complete the steps in the following procedure to schedule automatic archiving.
To set a scheduled archive:
1. In the Core Console, click the Tools tab.
2. From the Archive option, click Scheduled.
3. On the Scheduled Archive page, click Add.
The Add Archive Wizard dialog box appears.
4. On the Location page of the Add Archive Wizard, select one of the following options from the
Location Type drop-down list:
• Local: Output location – Enter the location for the output. It defines the location path where you
want the archive to reside.
• Network
– Output location: Enter the location for the output. It defines the location path where you want
the archive to reside.
69
Page 70

– User Name: Enter a user name. It establishes logon credentials for the network share.
– Password: Enter a password for the network path. It establishes logon credentials for the
network share.
• Cloud
– Account : Select an account from the drop-down list. To select a cloud account, you must
first have added it in the Core Console.
– Container: Select a container associated with your account from the drop-down menu.
– Folder Name: Enter a name for the folder in which the archived data is to be saved. The
default name is AppAssure-5-Archive-[DATE CREATED]-[TIME CREATED]
5. Click Next.
6. On the Machines page of the wizard, select which protected machines contain the recovery points
you want to archive.
7. Click Next
8. On the Options page, select one of the following Recycle Actions from the drop-down list:
• Replace this Core: Overwrites any existing archived data pertaining to this core but leaves the
data for other cores intact.
• Erase completely: Clears all archived data from the directory before writing the new archive.
• Incremental: Lets you add recovery points to an existing archive. It compares recovery points to
avoid duplicating data that already exists in the archive.
9. On the Schedule page, select one of the following Send data frequency options:
• Daily: At time – Select the hour of the day you want to create a daily archive.
• Weekly
– At day of week: Select a day of the week on which to automatically create the archive.
– At time: Select the hour of the day you want to create a daily archive.
• Monthly
– At day of months: Select the day of the month on which to automatically create the archive.
– At time: Select the hour of the day you want to create a daily archive.
10. To pause archiving for resuming at a later time, select Initial pause archiving.
You may want to pause the scheduled archive if you need time to prepare the target location before
archiving resumes. If you do not select this option, archiving begins at the scheduled time.
11. Click Finish.
Pausing or resuming scheduled archive
If you opted to initially pause archiving when you performed the Setting a Scheduled Archive procedure,
you would want to resume the scheduled archive at a later time.
To pause or resume scheduled archive:
1. Navigate to the Core Console, and then click the Tools tab.
2. From the Archive option, click Scheduled.
3. On the Scheduled Archive page, do one of the following:
• Select the preferred archive, and then click one of the following actions as appropriate:
– Pause
– Resume
• Next to the preferred archive, click the drop-down menu, and then click one of the following
actions as appropriate:
70
Page 71

– Pause
– Resume
The status of the archive displays in the Schedule column.
Editing a scheduled archive
1. In the Core Console, click the Tools tab.
2. From the Archive option, click Scheduled.
3. On the Scheduled Archive page, click the drop-down menu next to the archive you want to change,
and then click
The Add Archive Wizard dialog box appears.
4. On the Location page of the Add Archive Wizard, select one of the following options from the
Location Type drop-down list:
• Local: Output location – Enter the location for the output. It defines the location path where you
want the archive to reside.
• Network
– Output location: Enter the location for the output. It defines the location path where you want
the archive to reside.
– User Name: Enter a user name. It establishes logon credentials for the network share.
– Password: Enter a password for the network path. It establishes logon credentials for the
network share.
• Cloud
Edit.
– Account : Select an account from the drop-down list. To select a cloud account, you must
first have added it in the Core Console.
– Container: Select a container associated with your account from the drop-down menu.
– Folder Name: Enter a name for the folder in which the archived data is to be saved. The
default name is AppAssure-5-Archive-[DATE CREATED]-[TIME CREATED]
5. Click Next.
6. On the Machines page of the wizard, select which protected machines contain the recovery points
you want to archive.
7. Click Next
8. On the Schedule page, select one of the following Send data frequency options:
• Daily: At time – Select the hour of the day you want to create a daily archive.
• Weekly
– At day of week: Select a day of the week on which to automatically create the archive.
– At time: Select the hour of the day you want to create a daily archive.
• Monthly
– At day of months: Select the day of the month on which to automatically create the archive.
– At time: Select the hour of the day you want to create a daily archive.
9. To pause archiving for resuming at a later time, select Initial pause archiving.
You may want to pause the scheduled archive if you need time to prepare the target location before
archiving resumes. If you do not select this option, archiving begins at the scheduled time.
10. Click Finish.
71
Page 72

Checking an archive
You can scan an archive for structural integrity by performing an archive check. This check verifies the
presence of all necessary files within the archive. To perform an archive check, complete the steps in the
following procedure:
1. In the Core Console, click the Tools tab.
2. From the Archive option, click Check Archive.
The Check Archive dialog box appears.
3. Select one of the following options from the drop-down list:
• Local: Output location – Enter the location for the output. It defines the location path where you
want the archive to reside.
• Network
– Output location: Enter the location for the output. It defines the location path where you want
the archive to reside.
– User Name: Enter a user name. It establishes logon credentials for the network share.
– Password: Enter a password for the network path. It establishes logon credentials for the
network share.
• Cloud
– Account : Select an account from the drop-down list. To select a cloud account, you must
first have added it in the Core Console.
– Container: Select a container associated with your account from the drop-down menu.
– Folder Name: Enter a name for the folder in which the archived data is to be saved. The
default name is AppAssure-5-Archive-[DATE CREATED]-[TIME CREATED]
4. To also perform a structure integrity check, select Structure integrity.
5. Click Check FIle.
Importing an archive
To import an archive:
1. In the Core Console, select the Configuration tab.
2. From the Manage option, click Archive, and then click Import.
The Import Archive dialog box appears.
3. In the Import Archive dialog box, enter the details for importing the archive described as follows:
Text Box Description
Input Location Select the location for importing the archive.
User name To establish access to secure the archive, enter the logon credentials.
Password Enter a password for accessing the archive.
4. Click Check File to validate the existence of the archive to import.
The Restore dialog box appears.
5. In the Restore dialog box, verify the name of the source core.
6. Select the agents to import from the archive.
7. Select the repository.
8. Click Restore to import the archive.
72
Page 73

Managing SQL attachability
The SQL attachability configuration enables the Core to attach SQL database and log files in a snapshot
of a SQL server using a local instance of Microsoft SQL Server. The attachability test lets the Core check
for the consistency of the SQL databases and ensures that all data files (MDF and LDF files) are available in
the backup snapshot. Attachability checks can be run on demand for specific recovery points or as part of
a nightly job.
Attachability requires a local instance of Microsoft SQL Server on the AppAssure Core machine. This
instance must be a fully licensed version of SQL Server procured from Microsoft or through a licensed
reseller. Microsoft does not allow the use of passive SQL licenses.
Attachability supports SQL Server 2005, 2008, 2008 R2, 2012 and 2014. The account used to perform the
test must be granted the sysadmin role on the SQL Server instance.
The SQL Server on-disk storage format is the same in both 64–bit and 32–bit environments and
attachability works across both versions. A database that is detached from a server instance that is
running in one environment can be attached on a server instance that runs in another environment.
CAUTION: The version of SQL Server on the Core must be equal to or newer than the SQL Server
version on all the agents with SQL Server installed.
Configuring SQL attachability settings
Prior to running attachability checks on protected SQL databases, select a local instance of SQL Server on
the Core machine that will be used to perform the checks against the agent machine.
NOTE: Attachability requires a local instance of Microsoft SQL Server on the AppAssure Core
machine. This instance must be a fully licensed version of SQL Server procured from Microsoft or
through a licensed reseller. Microsoft does not allow the use of passive SQL licenses.
To configure SQL attachability settings:
1. Navigate to the Core Console. click the tab.
2. Click Configuration → Settings.
3. In the Nightly Jobs pane, click change.
The Nightly Job dialog box appears.
4. Select Attachability Check Job and then click Settings.
5. Use the drop-down menus to select the instance of SQL Server installed on the Core from the
following options:
You can choose from:
• SQL Server 2005
• SQL Server 2008
• SQL Server 2008 R2
• SQL Server 2012
• SQL Server 2014
6. Select the credential type.
You can choose from:
• Windows
73
Page 74

• SQL
7. Specify the credentials with administrative privileges for the Windows or SQL Server instances,
described as follows:
Text Box Description
Username Enter a user name for logon permissions to the SQL server.
Password Enter a password for SQL attachability. It is used to control logon activity.
8. Click Test Connection.
NOTE: If you entered the credentials incorrectly, a message is displayed to alert you that the
credentials test failed. Correct the credential information and run the connection test again.
9. Click Save.
Attachability checks are now available to be run on the protected SQL Server databases.
10. In the Nightly Jobs window, click OK.
Attachability checks are now schedule to occur with the nightly jobs.
Configuring nightly SQL attachability checks and log truncation
To configure nightly SQL attachability checks and log truncation:
1. In the left navigation area of the Core, select the machine for which you want to have nightly
attachability checks and log truncation, and click
2. Navigate to the Core Console.
3. Click Configuration → Settings.
4. In the Nightly Jobs section, click Change.
5. Select or clear the following SQL Server settings based on the needs of your organization:
• Attachability Check Job
• Log Truncation Job (simple recovery model only)
6. Click OK.
The attachability and log truncation settings take effect for the protected SQL Server.
SQL Server Settings.
Managing exchange database mountability checks and log truncation
When using AppAssure to back up Microsoft Exchange Servers, mountability checks can be performed on
all Exchange databases after every snapshot. This corruption detection feature alerts administrators of
potential failures and ensures that all data on the Exchange servers is recovered successfully in the event
of a failure.
NOTE: The mountability checks and log truncation features only apply to Microsoft Exchange 2007,
2010, and 2013. Additionally, the AppAssure Agent service account must be assigned the
Organizational Administrator role in Exchange.
Configuring exchange database mountability and log truncation
You can view, enable, or disable Exchange database server settings, including automatic mountability
check, nightly checksum check, or nightly log truncation.
74
Page 75

To configure Exchange database mountability and log truncation:
1. In the left navigation area of the Core Console, select the machine for which you want to configure
mountability checks and log truncation.
The Summary tab for the selected machine is displayed.
2. Click Exchange Server Settings.
The Exchange Server Settings dialog box displays.
3. Select or clear the following Exchange Server settings based on the needs of your organization:
• Enable automatic mountability check
• Enable nightly checksum check
• Enable nightly log truncation
4. Click OK.
The mountability and log truncation settings take effect for the protected Exchange server.
NOTE: For information on forcing log truncation, see Forcing Log Truncation .
Forcing a mountability check
To force a mountability check:
1. In the left navigation area of the Core Console, select the machine for which you want to force the
mountability check, and then click the Recovery Points tab.
2. Click > next to a recovery point in the list to expand the view.
3. Click Force Mountability Check.
A message prompts you to force a mountability check.
4. Click Yes.
NOTE: For instructions on how to view the status of the attachability checks, see Viewing
Events And Alerts.
The system performs the mountability check.
Forcing checksum checks
To force a checksum check:
1. In the left navigation area of the Core Console, select the machine for which you want to force the
checksum check, and then click the Recovery Points tab.
2. Click > next to a recovery point in the list to expand the view.
3. Click Force Checksum Check.
The Force Attachability Check window prompts you to indicate if you want to force a checksum
check.
4. Click Yes.
The system performs the checksum check.
NOTE: For information on how to view the status of the attachability checks, see Viewing
Events And Alerts.
Forcing log truncation
NOTE: This option is only available for Exchange or SQL machines.
75
Page 76

To force log truncation:
1. Navigate to the Core Console and then click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine you want to truncate the log.
• Or, in the navigation pane, select the machine you want to truncate the log.
3. In the Actions drop-down menu for that machine, click Force Log Truncation.
4. Confirm whether to proceed with forcing log truncation.
Recovery point status indicators
After a recovery point is created on a protected SQL or Exchange server, the application is displayed a
corresponding color status indicator in the Recovery Points table. The color that is displayed is based on
the check settings for the protected machine and the success or failure of those checks, as described in
the following tables.
NOTE: For more information on viewing Recovery Points, see Viewing Recovery Points.
The following table lists the status indicators that display for SQL databases.
Recovery Status Point Colors for SQL Databases
Status Color Description
White Indicates that one of the following conditions exist:
• An SQL database did not exist.
• Attachability checks were not enabled.
• Attachability checks have not yet been run.
Yellow Indicates that the SQL database was offline and a check was not possible.
Red Indicates that the attachability check failed.
Green Indicates that the attachability check passed.
The following table lists the status indicators that display for Exchange databases.
Recovery Status Point Colors for Exchange Databases
Term heading Description heading
White Indicates that one of the following conditions exist:
• An Exchange database did not exist.
• Mountability checks were not enabled.
NOTE: This can apply to certain volumes within a recovery point.
Yellow Indicates that the Exchange database mountability checks are enabled, but the
checks have not yet run.
Red Indicates that either the mountability or checksum checks failed on at least one
database.
76
Page 77

Term heading Description heading
Green Indicates that the mountability check passed or that the checksum check passed.
NOTE: Recovery points that do not have an Exchange or SQL database associated with it is
displayed with a white status indicator. In situations where both an Exchange and SQL database
exists for the recovery point, the most severe status indicator is displayed for the recovery point.
77
Page 78

3
Managing Your Appliance
The Core Console includes an Appliance tab, which you can use to provision space, monitor the health
of the appliance, and access management tools.
Monitoring the status of the Appliance
You can monitor the status of the Appliance subsystems by using the Appliance tab Overall Status page.
The Overall Status page displays a status light next to each subsystem, along with a status description
indicating the health of the subsystem.
The Overall Status page also provides links to tools that drill down into the details of each subsystem,
which can be helpful for troubleshooting warnings or errors. The System Administrator link, available for
the Appliance Hardware and Storage Hardware subsystems, prompts you to log on to the System
Administrator application used for managing hardware. For more information about the System
Administrator application, see the OpenManage Server Administrator User’s Guide on dell.com/support/
home. The Provisioning Status link, available for the Storage Provisioning subsystem, opens the Tasks
screen which displays the provisioning status of that subsystem. If storage is available for provisioning, a
link to Provision under Actions displays next to the provision task.
Provisioning storage
The appliance configures available DL4300 internal storage and any attached external storage enclosures
for:
• AppAssure Repositories
NOTE: If fibre channel HBA is configured then the process of creating the repositories is manual.
AppAssure will not create a repository automatically in the root directory. For more information,
see the Dell DL4300 Appliance Deployment Guide.
• Virtual Standby of Protected Machines
NOTE: MD1400s with 1 TB, 2 TB, 4 TB or 6 TB (for high capacity) drives connected to the H830
controller are supported. Up to four MD 1400s are supported.
NOTE: The DL4300 high-capacity configuration supports either H830 PERC SAS adapter or two
Fibre Channel HBAs. For more information on configuring fibre channel HBAs, see the DL4xxx —
Fibre Channel Implementation
Before you begin provisioning storage on the disk, determine how much storage you want for standby
virtual machines. You can allocate any percentage of the available capacity to host standby virtual
machines. For example, if you are using Storage Resource Management (SRM), you can allocate up to
100 percent capacity on any device being provisioned to host virtual machines. Using AppAssure's Live
Recovery feature, you can use these virtual machines to quickly replace any failed server that the
appliance protects.
78
whitepaper located at dell.com/support/home.
Page 79

Based on a medium-sized environment that does not need standby virtual machines, you can use all of
the storage to back up a significant number of agents. However, if you need more resources for standby
virtual machines and back up a smaller number of agent machines, you can allocate more resources for
larger VMs.
When you select the Appliance tab, the AppAssure Appliance software locates the available storage space
for all supported controllers in the system and validates that the hardware meets the requirements.
To complete disk provisioning for all available storage:
1. In the Appliance tab, click Tasks → Provisioning.
The Provisioning screen displays estimated capacity for provisioning. This capacity is used to create
a new AppAssure Repository.
CAUTION: Before proceeding ensure Step 2 through Step 4 is followed in this procedure.
2. Open the Provisioning Storage window by clicking Provision in the Action column next to the
storage that you want to provision.
3. In the Optional Storage Reserve section, select the box next to Allocate a portion of the storage
being provisioned for Standby Virtual Machines or other purposes and indicate a percentage of
storage to allocate. Otherwise, the percentage of storage indicated in the Optional Storage Reserve
section will be taken from all of the attached disks.
4. Click Provision.
Provisioning selected storage
To provision selected storage:
1. In the Appliance tab, click Tasks → Provisioning.
The Provisioning screen displays estimated capacity for provisioning. This capacity is used to create
a new AppAssure Repository.
2. To provision only a portion of the available space, click Provision under Action next to the storage
space that you want to provision.
• To create new repository, select Create a new repository, and provide a name for the repository.
By default, Repository 1 appears as the repository name. You can opt to overwrite the name.
• To add capacity to an existing repository, select Expand the existing repository, and then select
the repository from the Existing Repositories list.
NOTE: To add capacity, it is recommended that you expand an existing repository instead of
adding a repository. Separate repositories do not utilize capacity as efficiently because
deduplication cannot occur across separate repositories.
3. Under Optional Storage Reserve, select Allocate a portion of the storage being provisioned for
Standby Virtual Machines or other purposes, and then specify the percentage of storage to allocate
for the VMs.
79
Page 80

4. Click Provision.
The disk provisioning begins and the status of the AppAssure repository creation is displayed in the
Status area of the Tasks screen. The State displays Provisioned.
5. To view the details after disk provisioning completes, click > next to the status light.
The Tasks page expands and displays status, repository, and virtual disk details (if allocated).
Deleting space allocation for a virtual disk
Before you begin this procedure, determine which virtual disk you want to delete. From the Core
Console, select the Appliance tab, click Tasks, and then expand the repository that contains the virtual
disks to see the virtual disk details.
To delete a space allocation for a virtual disk:
1. From the OpenManage Server Administrator application, expand Storage.
2. Expand the controller that houses the virtual disk, then select Virtual Disks.
3. Select the virtual disk that you want to remove, and then select Delete from the Tasks drop-down
menu.
4. After confirming the deletion, the space appears on the Core Console Appliance tab Tasks screen as
available for provisioning.
Resolving failed tasks
AppAssure reports failed verify, provision, and recovery tasks with an event on the Core Console Home
page, and also on the Appliance tab Tasks screen.
To understand how to resolve a failed task, select the Appliance tab and then click Tasks. Expand the
failed task by clicking > next to Status, and review the error message and recommended action.
Upgrading your Appliance
To upgrade your appliance:
1. Download the Recovery and Update Utility from dell.com/support to the DL4300 Backup to Disk
appliance.
2. Copy the utility to the appliance desktop and extract the files.
3. Double-click the launchRUU icon.
4. When prompted, click Yes to acknowledge that you are not running any of the listed processes.
5. When the Recovery and Update Utility screen appears, click Start.
6. When prompted to reboot, click OK.
The updated versions of the Windows Server Roles and Features, ASP .NET MVC3, LSI Provider, DL
Applications, OpenManage Server Administrator and AppAssure Core Software are installed as part of
the Recovery and Update Utility. In addition to these, the Recovery and Update Utility also updates
the RASR content.
NOTE: As part of the AppAssure Core Software upgrade process, the Recovery and Upgrade
Utility notifies you of the currently installed AppAssure version and prompts you to confirm that
you want to upgrade the Core software to the version that is bundled in the utility. AppAssure
Core software downgrades are not supported.
7. If prompted, reboot your system.
8. After all services and applications are installed, click Proceed.
80
Page 81

The Core Console launches.
Repairing your Appliance
To repair your appliance:
1. Download the Recovery and Update Utility from dell.com/support to your Appliance.
2. Copy the utility to the appliance desktop and extract the files.
3. Double-click the launchRUU icon.
4. When prompted, click Yes to acknowledge that you are not running any of the listed processes.
5. When the Recovery and Update Utility screen displays, click Start.
6. When prompted to reboot, click OK.
The updated versions of the Windows Server Roles and Features, ASP .NET MVC3, LSI Provider, DL
Applications, OpenManage Server Administrator and AppAssure Core Software are installed as part of
the Recovery and Update Utility.
7. If the bundled version in the utility is the same as the installed version, the Recovery and Update
Utility prompts you to confirm that you want to run a repair installation. This step can be skipped if a
repair install of the AppAssure Core is not needed.
8. If the bundled version in the utility is higher than the installed version, then the Recovery and Update
Utility prompts you to confirm that you want to upgrade the AppAssure Core software.
NOTE: AppAssure Core software downgrades are not supported.
9. If prompted, reboot your system.
10. After all services and applications are installed, click Proceed.
AppAssure Appliance Configuration Wizard will be launched if the system needs to be configured
again after repair, otherwise Core Console will be launched.
81
Page 82

4
Protecting workstations and servers
About protecting workstations and servers
To protect your data add the workstations and servers you want to protect in the Core Console; for
example, your Exchange server, SQL Server, or your Linux server.
NOTE: In this section, generally the word machine also refers to the AppAssure Agent software
installed on that machine.
In the Core Console, you can identify the machine on which an AppAssure Agent software is installed and
specify which volumes to protect, define schedules for protection, add extra security measures such as
encryption, and more. For more information on how to access the Core Console to protect workstations
and servers, see Protecting A Machine.
NOTE: If the used capacity on your DL Appliance exceeds the capacity for which you have
purchased a license, the snapshot functionality will be disabled. Please contact your Dell Software
Group Account Manager for further assistance.
Configuring machine settings
After you add protection for machines in AppAssure, you can modify basic machine configuration
settings (such as name and host name), protection settings (changing the protection schedule for
volumes on the machine, adding or removing volumes, or pausing protection), and more.
Viewing and modifying configuration settings
To view and modify configuration settings:
1. After you have added a protected machine, perform one of the following:
• From the Core Console, click the Machines tab and then click the hyperlink for the machine that
you want to modify.
• From the Navigation pane, select the machine that you want to modify.
2. Click the Configuration tab.
The Settings page displays.
3. Click Edit to modify the machine settings as described in the following table.
Text Box Description
Display Name Enter a display name for the machine.
A name for this machine to be displayed in the Core Console. By default, this is
the host name of the machine. You can change the display name to something
more user-friendly if needed.
82
Page 83

Text Box Description
Host Name Enter a host name for the machine.
Port Enter a port number for the machine.
The Core uses the port to communicate with this machine.
Repository Select a repository for the recovery points. Displays the repository on the Core
in which to store the data from this machine.
NOTE: This setting can only be changed if there are no recovery points or
the previous repository is missing.
Encryption Key Edit the encryption key if necessary. Specifies whether encryption is applied to
the data for every volume on the machine that is stored in the repository.
Viewing system information for a machine
The Core Console displays all the machines that are being protected by including a list of the machines
as well as each machine’s status.
To view system information for a machine:
1. In the Core Console, under Protected Machines, select the machine for which you want to view
detailed system information.
2. Click the Tools tab for that machine.
The information about the machine displays in the System Information page. The details that display
include the following:
• Host Name
• OS Version
• OS Architecture
• Memory (Physical)
• Display Name
• Fully Qualified Domain Name
• Virtual Machine Type (if applicable)
Detailed information about the volumes contained on this machine includes:
• Name
• Device ID
• File System
• Capacity (including Raw, Formatted, and Used)
• Processors
• Type of processors
• Network adapters
• IP addresses associated with this machine
Configuring notification groups for system events
In AppAssure, you can configure how system events are reported for your machine by creating
notification groups which can include system alerts, errors, and so on.
83
Page 84

To configure notification groups for system events:
1. In the Core Console, click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine that you want to modify.
• In the navigation pane, select the machine that you want to modify.
The Summary tab appears.
3. Click the Configuration tab, and then click Events.
The Notification Groups page appears.
4. Click Use custom alert settings and then click Apply.
The Custom Notification Groups screen appears.
5. Click Add Group to add new notification groups for sending a list of system events.
The Add Notification Group dialog box displays.
NOTE: To use the default alert settings, select the Use Core alert settings option.
6. Add the notification options as described in the following table.
Text Box Description
Name Enter a name for the notification group.
Description Enter a description for the notification group.
Enable Events Select which events to share with this notification group. You can select All or
select a subset of events to include:
• BootCd
• LocalMount
• Metadata
• Clusters
• Notification
• PowerShellScripting
• PushInstall
• Attachability
• Jobs
• Licensing
• LogTruncation
• Archive
• CoreService
• Export
• Protection
• Replication
• Rollback
• Rollup
84
You can also choose to select by type:
• Info
Page 85

Text Box Description
• Warning
• Error
NOTE: When you choose to select by type, by default, the appropriate
events are automatically enabled. For example, if you choose Warning, the
Attachability, Jobs, Licensing, Archive, CoreService, Export, Protection,
Replication, and Rollback events are enabled.
Notification
Options
7. Click OK to save your changes.
8. To edit an existing notification group, click Edit next to the notification group that you want to edit.
The Edit Notification Group dialog box opens where you can edit the settings.
Select the method to specify how to handle notifications. You can choose
from the following options:
• Notify by Email — Specify to which email addresses to send the events in
the To, CC, and BCC text boxes.
NOTE: To receive mail, SMTP must be previously configured.
• Notify by Windows Event log — The Windows Event log controls the
notification.
• Notify by syslogd — Specify to which host name and port to send the
events.
– Host — Enter the host name for the server.
– Port — Enter a port number for communicating with the server.
Editing notification groups for system events
To edit notification groups for system events:
1. Navigate to the Core Console and then click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine that you want to modify
• Or, in the navigation pane, select the machine that you want to modify.
The Summary tab appears.
3. Click the Configuration tab, and then click Events.
4. Click Use custom alert settings and then click Apply.
The Custom Notification Groups screen appears.
5. Click the Edit icon under the Action column.
The Edit Notification Group dialog box appears.
6. Edit the notification options as described in the following table.
Text Box Description
Name Represents the name of the notification group.
NOTE: You cannot edit the name of the notification group.
85
Page 86

Text Box Description
Description Enter a description for the notification group.
Enable Events Select which events to share with the notification group. You can select All or
select a subset of events to include:
• BootCd
• LocalMount
• Metadata
• Clusters
• Notification
• PowerShellScripting
• PushInstall
• Attachability
• Jobs
• Licensing
• LogTruncation
• Archive
• CoreService
• Export
• Protection
• Replication
• Rollback
• Rollup
Notification
Options
You can also choose to select by type:
• Info
• Warning
• Error
NOTE: When you choose to select by type, by default, the appropriate
events are automatically enabled. For example, if you choose Warning, the
Attachability, Jobs, Licensing, Archive, CoreService, Export, Protection,
Replication, and Rollback events are enabled.
Select the method to specify how to handle notifications. You can choose
from the following options:
• Notify by Email — Specify the e-mail addresses to which to send the
events in the To, CC, and BCC text boxes.
NOTE: To receive e-mail, SMTP must be previously configured.
• Notify by Windows Event log — The Windows Event log controls the
notification.
• Notify by syslogd — You must specify the host name and port to which to
send the events.
– Host — Enter the host name for the server.
86
Page 87

Text Box Description
– Port — Enter a port number for communicating with the server.
7. Click OK.
Customizing retention policy settings
The retention policy for a machine specifies how long the recovery points for an agent machine are
stored in the repository. Retention policies are used to retain backup snapshots for longer periods of time
and to help manage these backup snapshots. A rollup process enforces the retention policy, and helps
with aging and deleting old backups. This task is also a step in
Settings.
To customize retention policy settings:
1. In the Core Console, click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine that you want to modify.
• In the navigation pane, select the machine that you want to modify.
The Summary tab appears.
3. Click the Configuration tab, and then click Retention Policy.
NOTE: To use the default retention policy configured for the Core, ensure that you select the
Use Core default retention policy option.
The Retention Policy screen appears.
4. To set the customized policies, click Use custom retention policy.
The Custom Retention Policy screen appears.
5. Select Enable Rollup, and specify the time intervals for retaining the backup data as needed. The
retention policy options are described as follows:
Process Of Modifying Cluster Node
Text Box Description
Keep all Recovery
Points for n
[retention time
period]
...and then keep
one Recovery
Point per hour for
n [retention time
period]
Specifies the retention period for the recovery points.
Enter a number that represents the retention period and then select the time
period. The default is 3.
You can choose from:
• Days
• Weeks
• Months
• Years
Provides a more refined level of retention. It is used as a building block with
the primary setting to further define how long recovery points are maintained.
Enter a number that represents the retention period and then select the time
period. The default is 2.
You can choose from:
• Days
87
Page 88

Text Box Description
• Weeks
• Months
• Years
...and then keep
one Recovery
Point per day for n
[retention time
period]
...and then keep
one Recovery
Point per week for
n [retention time
period]
...and then keep
one Recovery
Point per month
for n [retention
time period]
Provides a more refined level of retention. It is used as a building block to
further define how long recovery points are maintained.
Enter a number that represents the retention period and then select the time
period. The default is 4.
You can choose from:
• Days
• Weeks
• Months
• Years
Provides a more refined level of retention. It is used as a building block to
further define how long recovery points are maintained.
Enter a number that represents the retention period and then select the time
period. The default is 3.
You can choose from:
• Weeks
• Months
• Years
Provides a more refined level of retention. It is used as a building block to
further define how long recovery points are maintained.
Enter a number that represents the retention period and then select the time
period. The default is 2.
You can choose from:
• Months
• Years
...and then keep
one Recovery
Point per year for
n [retention time
period]
The Newest Recovery Point text box is displayed the most recent recovery point. The retention
policy settings determine the oldest recovery point.
The following is an example of how the retention period is calculated.
Keep all recovery points for 3 days.
88
Enter a number that represents the retention period and then select the time
period.
Page 89

...and then keep one recovery point per hour for 3 days
...and then keep one recovery point per day for 4 days
...and then keep one recovery point per week for 3 weeks
...and then keep one recovery point per month for 2 months
...and then keep one recovery point per month for 1 year
Newest Recovery Point is set to the current day, month, and year.
In this example, the oldest recovery point can be one year, four months, and six days old.
6. Click Apply to save your changes.
7. To perform a rollup based on the current retention policy for the machine, select Force Rollup, or let
the retention policy you defined to be applied during the nightly rollup.
Viewing license information
You can view current license status information for the AppAssure Agent software installed on a machine.
To view license information:
1. In the Core Console, click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine that you want to view.
• In the navigation pane, select the machine that you want to view.
3. Click the Configuration tab, and then click Licensing.
The Status screen displays the details about the product licensing.
Modifying protection schedules
In AppAssure, you can modify the protection schedules for specific volumes on a machine.
To modify protection schedules:
1. In the Core Console, click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine that you want to modify.
• In the navigation pane, select the machine that you want to modify.
3. Do one of the following:
• In the Volumes table on the Summary tab for the machine, click the hyperlink for the protection
schedule for the volume that you want to customize.
• Click the Configuration tab, and then click Protection Settings. In the list of volumes, click the
Edit icon next to the volume you want to customize.
The Protection Schedule dialog box appears.
4. In the Protection Schedule dialog box, edit the following schedule options as needed for protecting
your data. The following table describes the options.
89
Page 90

Option Description
Interval Weekday — To protect data on a specific time interval (for example, every 15
minutes), select the Interval, and then:
• To customize when to protect data during peak times, you can select a
Start Time, End Time, and an Interval from the drop-down menus.
• To protect data during off-peak times, select the Protection interval
during off-peak times check box, and then select an interval for protection
from the drop-down menu.
Weekends — To protect data during weekends, select the Protection interval
during weekends check box, and then select an interval from the drop-down
menu.
NOTE: If the SQL or Exchange databases and logs are on different
volumes, the volumes must belong to one protection group.
Daily To protect data on a daily basis, select the Daily option, and then and in the
Protection Time drop-down menu, select a time to start protecting data.
No Protection To remove protection from this volume, select the No Protection option.
If you want to apply these custom settings to all the volumes on this machine, select Apply to All
Volumes.
5. When you have made all necessary changes, click OK.
Modifying transfer settings
You can modify the settings to manage the data transfer processes for a protected machine. The transfer
settings described in this section are agent-level settings. To affect transfer at the core level, see
Modifying The Transfer Queue Settings.
CAUTION: Changing transfer setting could have dramatic effects on your environment. Before
modifying transfer settings values, refer to the Transfer Performance Tuning Guide in the Dell
AppAssure knowledge base https://support.software.dell.com/appassure/kb.
There are three types of transfers:
Snapshots
VM Export A type of transfer that creates a virtual machine with all of the backup information
Rollback A process that restores backup information on a protected machine.
Data transfer involves the transmission of a volume of data along a network from Agent machines to the
Core. In the case of replication, transfer also occurs from the originating or source Core to the target
Core.
Data transfer can be optimized for your system through certain performance option settings. These
settings control data bandwidth usage during the process of backing up agent machines, performing VM
export, or performing a rollback. Some factors that affect data transfer performance are:
• Number of concurrent agent data transfers
• Number of concurrent data streams
The transfer that backs up the data on your protected machine.
and parameters as specified by the schedule defined for protecting the machine.
90
Page 91

• Amount of data change on disk
• Available network bandwidth
• Repository disk subsystem performance
• Amount of memory available for data buffering
You can adjust the performance options to best support your business needs and fine-tune the
performance based on your environment.
To modify transfer settings:
1. In the Core Console, do one of the following:
• Click the Machines tab, and then click the hyperlink for the machine that you want to modify.
• In the navigation pane, click the machine that you want to modify.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine that you want to modify.
• In the navigation pane, select the machine that you want to modify.
3. Click the Configuration tab, and then click Transfer Settings.
The current transfer settings appear.
4. On the Transfer Settings page, click Change.
The Transfer Settings dialog box appears.
5. Enter the Transfer Settings options for the machine as described in the following table.
Text Box Description
Priority Sets the transfer priority between protected machines. Enables you to assign
priority by comparison with other protected machines. Select a number from 1
to 10, with 1 being the highest priority. The default setting establishes a priority
of 5.
NOTE: Priority is applied to transfers that are in the queue.
Maximum
Concurrent
Streams
Maximum
Concurrent Writes
Maximum Retries Sets the maximum number of retries for each protected machine, if some of
Maximum
Segment Size
Sets the maximum number of TCP links that are sent to the Core to be
processed in parallel per agent.
NOTE: Dell recommends setting this value to 8. If you experience
dropped packets, try increasing this setting.
Sets the maximum number of simultaneous disk write actions per agent
connection.
NOTE: Dell recommends setting this value to the same value that you
select for Maximum Concurrent Streams. If you experience packet loss,
set this value slightly lower. For example, if Maximum Current Streams is
set at 8, set this option to 7.
the operations fail to complete.
Specifies the largest amount of data, in bytes, that a computer can receive in a
single TCP segment. The default setting is 4194304.
91
Page 92

Text Box Description
CAUTION: Do not change this option from the default setting.
Maximum Transfer
Queue Depth
Outstanding
Reads per Stream
Excluded Writers Select a writer if you want to exclude it. Since the writers that appear in the list
Specifies the number of commands that can be sent concurrently. You can
adjust this option to a higher number if your system as a high number of
concurrent input/output operations.
Specifies how many queued read operations will be stored on the back end.
This setting helps to control the queuing of agents.
NOTE: Dell recommends setting this value to 24.
are specific to the machine that you are configuring, you may not see all the
writers listed. Some writers you may see include:
• ASR Writer
• BITS Writer
• COM+ REGDB Writer
• Performance Counters Writer
• Registry Writer
• Shadow Copy Optimization Writer
• SQLServerWriter
• System Writer
• Task Scheduler Writer
• VSS Metadata Store Writer
• WMI Writer
Transfer Data
Server Port
Transfer Timeout Specifies in minutes and seconds the amount of time to allow a packet to be
Snapshot Timeout Specifies in minutes and seconds the maximum time to wait to take a
Network Read
Timeout
Network Write
Timeout
6. Click OK.
Sets the port for transfers. The default setting is 8009.
static without transfer.
snapshot.
Specifies in minutes and seconds the maximum time to wait for a read
connection. If the network read is not performed in that time, the operation is
repeated.
Specifies the maximum time in seconds to wait for a write connection. If the
network write is not performed in that time, the operation is repeated.
Restarting a service
To restart a service:
1. In the Core Console, click the Machines tab.
2. From the Machines tab, perform one of the following:
92
Page 93

• Click the hyperlink for the machine that you want to restart.
• In the Navigation pane, select the machine that you want to restart.
3. Click the Tools tab, and then click Diagnostics.
4. Select the Restart Service option, and then click the Restart Service button.
Viewing machine logs
If you encounter any errors or issues with the machine, view the logs to troubleshoot.
To view machine logs:
1. In the Core Console, click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine containing the logs that you want to view.
• In the Navigation pane, select the machine containing the logs that you want to view.
3. Click the Tools tab, and then click Diagnostics.
4. Click the View Log link.
Protecting a machine
This topic describes how to start protecting the data on a machine that you specify.
NOTE: The machine must have the Agent software installed in order to be protected. You can
choose to install the Agent software prior to this procedure, or you can deploy the software to the
agent as you define protection in the
software during the process of protecting a machine, see Deploying The Agent Software When
Protecting An Agent.
Connection dialog box. For specific steps to install the agent
When you add protection, you must specify the name or IP address of the machine to protect and the
volumes on that machine to protect as well as define the protection schedule for each volume.
To protect multiple machines at the same time, see Protecting Multiple Machines.
To protect a machine:
1. If you did not do so after installing the Agent software, reboot the machine on which the Agent
software is installed.
2. From the Core Console on the core machine, do one of the following:
• From the Home tab under Protected machines, click Protect Machine.
• Select the Machines tab, and in the Actions drop-down menu, click Protect Machine.
The Connect dialog box appears.
3. In the Connect dialog box, enter the information about the machine to which you want to connect
as described in the following table.
Text Box Description
Host The host name or IP address of the machine that you want to protect.
Port The port number on which the Core communicates with the agent on the
machine. The default port number is 8006.
Username The user name used to connect to this machine; for example, administrator.
93
Page 94

Text Box Description
Password The password used to connect to this machine.
4. Click Connect to connect to this machine.
NOTE: If the Agent software is not yet installed on the machine that you designated, follow the
procedure Deploying The Agent Software When Protecting An Agent. Restart the agent
machine after deploying the Agent software, and then resume with the next step.
5. In the Protect dialog box, edit the settings as needed as described in the following table.
Field Description
Display Name The host name or IP address you specified in the Connect dialog box appears
in this text field. Optionally, enter a new name for the machine to be displayed
in the Core Console.
NOTE: You can also change the display name later by accessing the
Configuration tab for an existing machine.
Repository Select the repository on the Core in which to store the data from this machine.
Encryption Key Specify whether encryption is applied to the data for every volume on this
machine to be stored in the repository.
NOTE: The encryption settings for a repository are defined under the
Configuration tab in the Core Console.
Initially Pause
Protection
Volume Groups Under Volume Groups, you can define which volumes that you want to
6. Click Protect.
After you add a machine for protection, AppAssure automatically begins taking
a base snapshot of data. You can select this check box to pause protection
initially. You then must force a snapshot manually when you are ready to start
protecting your data. For more information about manually forcing a snapshot,
see Forcing A Snapshot.
protect and establish a protection schedule.
To set a default protection schedule of every 60 minutes for all volumes on the
machine, click Apply Default.
You can also select any volume on the machine and define protection
parameters for it individually.
Initial settings apply a default protection schedule of every 60 minutes. To
modify the schedule for any volume, click Edit for that volume. You can then
further define the interval between snapshots (including defining a separate
schedule for weekends) or specify a daily time to begin a snapshot.
For more information on editing the protection schedule for a selected
volume, see Creating Custom Schedules For Volumes.
94
Page 95

The first time protection is added for a machine, a base image (which is a snapshot of all the data in
the protected volumes) immediately begins to transfer to the repository on the Core, unless you
specified to initially pause protection.
CAUTION: If you protected a Linux machine, you must not unmount a protected volume
manually. In the event you need to do this, you must execute the following command before
unmounting the volume: bsctl -d [path_to_volume]. In this command, [path_to_volume]
does not refer to the mount point of the volume but instead refers to the file descriptor of
the volume; it must be in a form similar to this example: /dev/sda1.
Deploying the agent software when protecting an agent
You can download and deploy agents during the process of adding an agent for protection.
NOTE: This procedure is not required if you have already installed the Agent software on a machine
that you want to protect.
To deploy agents during the process of adding an agent for protection:
1. From the Protect Machine → Connect dialog box, after entering the appropriate connection
settings, click Connect.
The Deploy Agent dialog box is displayed.
2. Click Yes to deploy the Agent software remotely to the machine.
The Deploy Agent dialog box is displayed.
3. Enter logon and protection settings as follows:
• Host name — Specifies the host name or IP address of the machine that you want to protect.
• Port — Specifies the port number on which the Core communications with the Agent on the
machine. The default value is 8006.
• User name — Specifies the user name used to connect to this machine; for example,
administrator.
• Password — Specifies the password used to connect to this machine.
• Display name — Specifies a name for the machine which appears on the Core Console. The
display name could be the same value as the host name.
• Protect machine after install — Selecting this option enables AppAssure to take a base snapshot
of the data after you add the machine for protection. This option is selected by default. If you
deselect this option, then you must force a snapshot manually when you are ready to start data
protection. For more information about manually forcing a snapshot, see topic 'Forcing A
Snapshot' in Dell DL4300 Appliance User’s Guide.
• Repository — Select the repository in which to store data from this agent.
NOTE: You can store data from multiple agents in a single repository.
• Encryption Key — Specifies whether encryption should be applied to the data for every volume
on this machine to be stored in the repository.
NOTE: You define encryption settings for a repository under the Configuration tab in the
Core Console.
4. Click Deploy.
The Deploy Agent dialog box closes. There may be a delay before you see the selected agent appear
in the list of protected machines.
95
Page 96

Creating custom schedules for volumes
To create custom schedules for volumes:
1. In the Protect Machine dialog box (for information about accessing this dialog box, see Protecting A
Machine, under Volume Groups, select a volume for protection, and then click Edit.
The Protection Schedule dialog box appears.
2. In the Protection Schedule dialog box, select one of the following schedule options for protecting
your data described as follows:
Text Box Description
Interval You can choose from:
• Weekday — To protect data on a specific interval, select Interval, and then:
– To customize when to protect data during peak times, you can specify
a Start Time, End Time, and an Interval from the drop-down menus.
– To protect data during off-peak times, select Protection interval during
off-peak times, and then select an interval for protection from the Time
drop-down menu.
• Weekends — To protect data during weekends as well, select Protection
interval during weekends, and then select an Interval from the drop-down
menu.
Daily To protect data on a daily basis, select the Daily protection option, and then,
in the Time drop-down menu, select a time to start protecting data.
No Protection To remove protection from this volume, select the No Protection option.
If you want to apply these custom settings to all the volumes on this machine, select Apply to All
Volumes.
3. When you have made all necessary changes, click OK.
4. Repeat step 2 and step 3 for any additional volumes that you want to customize.
5. In the Protect Machine dialog box, click Protect.
Modifying exchange server settings
If you are protecting data from a Microsoft Exchange server, you must configure additional settings in the
Core Console.
To modify Exchange server settings:
1. After you add the Exchange Server machine for protection, select the machine in the Core Console’s
Navigation pane.
The Summary tab appears for the machine.
2. From the Summary tab, click the Exchange Server Settings link.
The Exchange Server Settings dialog box appears.
3. In the Exchange Server Settings dialog box, you can select or clear the following settings:
• Enable automatic mountability check.
• Enable nightly checksum check. You can further customize this setting by selecting the following:
– Automatically truncate Exchange logs after successful checksum check
96
Page 97

– Truncate log before checksum check completes
4. You can also modify the logon credentials for your Exchange Server. To do so, scroll down to the
Exchange Server Information section and then click Change Credentials.
The Set Exchange Credentials dialog box appears.
5. Enter the new credentials and then click OK.
Modifying SQL server settings
If you are protecting data from Microsoft SQL Server, there are additional settings that you need to
configure in the Core Console.
To modify SQL server settings:
1. After you have added the SQL Server machine for protection, select the machine in the Core
Console’s Navigation pane.
The Summary tab appears for the machine.
2. From the Summary tab, click the SQL Server settings link.
The SQL Server Settings dialog box appears.
3. In the SQL Server Settings dialog box, edit the following settings, as needed:
• Enable nightly attachability check
• Truncate log after successful attachability check (simple recovery model only)
4. You can also modify the logon credentials for SQL Server. To do so, scroll down to the SQL Server
Information table and then click Change Credentials.
The Set SQL Server Credentials dialog box appears.
5. Enter the new credentials, and then click OK.
Deploying an agent (push install)
AppAssure requires microsoft.net for the agent installation. Microsoft.net must be installed on any client
machine prior to installing the agent either manually or by a push installation process.
AppAssure lets you deploy the AppAssure Agent Installer to individual Windows machines for protection.
Complete the steps in the following procedure to push the installer to an agent. To deploy agents to
multiple machines at the same time, see Deploying To Multiple Machines.
NOTE: Agents must be configured with a security policy that makes remote installation possible.
To deploy an agent:
1. From the Core Console, click the Machines tab.
2. In the Actions drop-down menu, click Deploy Agent.
The Deploy Agent dialog box appears.
3. In the Deploy Agent dialog box, enter the logon settings as described in the following table.
Text Box Description
Machine Enter the host name or IP address of the machine that you want to deploy.
Username Enter the user name to connect to this machine (for example, administrator).
Password Enter the password to connect to this machine.
97
Page 98

Text Box Description
Automatic reboot
after install
4. Click Verify to validate the credentials you entered.
The Deploy Agent dialog box displays a message indicating that validation is being performed.
5. Click Abort if you want to cancel the verification process.
After the verification process completes, a message indicating that verification has been completed
appears.
6. Click Deploy.
A message indicating that the deployment has started appears. You can view the progress in the
Events tab.
7. Click Show details to view more information about the status of the agent deployment.
8. Click OK.
Select to specify whether the Core starts upon the completion of the
deployment and installation of the AppAssure Agent Installer.
Replicating a new agent
When you add an AppAssure Agent for protection on a source core, AppAssure gives you the option to
replicate the new agent to an existing target core.
To replicate a new agent:
1. Navigate to the Core Console, and then click the Machines tab.
2. In the Actions drop-down menu, click Protect Machine.
3. In the Protect Machine dialog box, enter the information as described in the following table.
Text Box Description
Host Enter the host name or IP address of the machine that you want to protect.
Port Enter the port number the AppAssure Core uses to communicate with the
agent on the machine.
Username Enter the username used to connect to this machine. For example,
Administrator.
Password Enter the password used to connect to this machine.
4. Click Connect to connect to this machine.
5. Click Show Advanced Options, and edit the following settings as needed.
Text Box Description
Display Name Enter a name for the machine to be displayed in the Core Console.
Repository Select the repository on the AppAssure Core where the data from this machine
is stored.
Encryption Key Specify whether encryption is applied to the data for every volume on this
machine stored in the repository.
NOTE: The encryption settings for a repository are defined under the
Configuration tab in the Core Console.
98
Page 99

Text Box Description
Remote Core Specify the target core to which you want to replicate the agent.
Remote
Repository
Pause Select this check box if you want to pause replication; for example, to pause it
Schedule Select one of the following options:
Initially pause
protection
6. Click Protect.
The name of the desired repository on the target core in which to store the
replicated data from this machine.
until after AppAssure takes a base image of the new agent.
• Protect all volumes with default schedule
• Protect specific volumes with custom schedule
NOTE: The default schedule is every 15 minutes.
Select this check box if you want to pause protection; for example, to prevent
AppAssure from taking the base image until after peak usage hours.
Managing machines
This section describes a variety of tasks you can perform in managing your machines, such as removing a
machine from your AppAssure environment, setting up replication, forcing log truncation, canceling
operations, and more.
Removing a machine
1. Navigate to the Core Console and then click the Machines tab.
2. From the Machines tab, perform one of the following:
• Click the hyperlink for the machine that you want to remove.
• Or, in the navigation pane, select the machine that you want to remove.
3. In the Actions drop-down menu, click Remove Machines, and then select one of the option
described in the following table.
Option Description
Relationship Only Removes the source core from replication but retains the replicated recovery
points.
With Recovery
Points
Removes the source core from replication and deletes all replicated recovery
points received from that machine.
Replicating agent data on a machine
Replication is the relationship between the target and source cores in the same site, or across two sites
with slow link on a per agent basis. When replication is set up between two cores, the source core
asynchronously transmits the incremental snapshot data of select agents to the target or source core.
99
Page 100

Outbound replication can be configured to a Managed Service Provider providing off-site backup and
disaster recovery service or to a self-managed core. To replicate agent data on a machine:
1. From the Core Console, click the Machines tab.
2. Select the machine that you want to replicate.
3. In the Actions drop-down menu, click Replication, and then complete one of the following options:
• If you are setting up replication, click Enable.
• If you already have an existing Replication set up, click Copy.
The Enable Replications dialog box appears.
4. In the Host text box, enter a host name.
5. Under Agents, select the machine that has the agent and data that you want to replicate.
6. If needed, select the check box Use a seed drive to perform initial transfer.
7. Click Add.
8. To pause or resume the replication, click Replication in the Actions drop-down menu, and then click
Pause or Resume as needed.
Setting replication priority for an agent
To set replication priority for an agent:
1. From the Core Console, select the protected machine for which you want to set replication priority,
and click the Configuration tab.
2. Click Select Transfer Settings, and then use the Priority drop-down list to select one of the
following options:
• Default
• Highest
• Lowest
• 1
• 2
• 3
• 4
NOTE: The default priority is 5. If one agent is given the priority 1, and another agent is given the
priority Highest, the agent with the Highest priority replicates before the agent with the 1
priority.
3. Click OK.
Canceling operations on a machine
You can cancel currently executing operations for a machine. You can specify to cancel just a current
snapshot or to cancel all current operations, which includes exports, replications, and so on.
To cancel operations on a machine:
1. From the Core Console, click the Machines tab.
2. Select the machine for which you want to cancel operations.
3. In the Actions drop-down menu, click Cancel, and then select one of the options described as
follows:
100
 Loading...
Loading...