Dell DL1300 User Manual

Dell DL1300 Appliance
User's Guide

Notes, cautions, and warnings
NOTE: A NOTE indicates important information that helps you make better use of your computer.
CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you
how to avoid the problem.
WARNING: A WARNING indicates a potential for property damage, personal injury, or death.
© 2016 Dell Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual
property laws. Dell and the Dell logo are trademarks of Dell Inc. in the United States and/or other jurisdictions. All other
marks and names mentioned herein may be trademarks of their respective companies.
2016 - 05
Rev. A01

Contents
1 Introducing your Dell DL1300............................................................................8
Dell DL1300 core technologies............................................................................................................8
Live Recovery...................................................................................................................................8
Universal Recovery.......................................................................................................................... 8
True Global Deduplication .............................................................................................................9
Encryption........................................................................................................................................9
Dell DL1300 data protection features.................................................................................................. 9
Dell DL1300 Core............................................................................................................................ 9
Dell DL1300 Smart Agent..............................................................................................................10
Snapshot process.......................................................................................................................... 10
Replication — disaster recovery site or service provider............................................................. 10
Recovery.........................................................................................................................................11
Recovery-as-a-Service ................................................................................................................. 11
Virtualization and cloud................................................................................................................. 11
Dell DL1300 deployment architecture................................................................................................11
Other information you may need....................................................................................................... 13
2 Working with your DL1300...............................................................................14
Accessing the DL1300 Core Console.................................................................................................14
Updating trusted sites in Internet Explorer...................................................................................14
Configuring browsers to remotely access the core console...................................................... 14
Managing licenses .............................................................................................................................. 15
Contacting the license portal server ............................................................................................16
Changing a license key .................................................................................................................16
Changing the AppAssure language manually...............................................................................17
Changing the operating system language during installation..................................................... 17
Managing core settings ......................................................................................................................18
Changing the core display name .................................................................................................18
Changing the nightly job time ..................................................................................................... 18
Modifying the transfer queue settings ......................................................................................... 18
Adjusting the client time-out settings ......................................................................................... 19
Configuring deduplication cache settings ...................................................................................19
Modifying engine settings ............................................................................................................ 19
Modifying deploy settings ............................................................................................................20
Modifying database connection settings .....................................................................................21
Managing Events .................................................................................................................................21
Configuring notification groups .................................................................................................. 22
Configuring an email server..........................................................................................................23
3

Configuring an Email notification template ................................................................................24
Configuring repetition reduction .................................................................................................25
Configuring Event Retention ....................................................................................................... 25
Roadmap for managing a repository .................................................................................................25
Creating a repository ....................................................................................................................26
Viewing repository details.............................................................................................................28
Modifying repository settings ...................................................................................................... 28
Expanding existing repository.......................................................................................................29
Adding a storage location to an existing repository ...................................................................30
Checking a repository ...................................................................................................................31
Deleting a repository .................................................................................................................... 31
Remounting volumes....................................................................................................................32
Recovering a repository................................................................................................................ 32
Managing security .............................................................................................................................. 33
Adding an encryption key ............................................................................................................ 34
Editing an encryption key ............................................................................................................ 34
Changing an encryption key passphrase .................................................................................... 34
Importing an encryption key ........................................................................................................35
Exporting an encryption key ........................................................................................................ 35
Removing an encryption key ....................................................................................................... 35
Managing cloud accounts ................................................................................................................. 35
Adding a cloud account................................................................................................................36
Editing a cloud account................................................................................................................ 37
Configuring cloud account settings............................................................................................. 37
Removing a Cloud account..........................................................................................................38
Monitoring your DL1300.....................................................................................................................38
Rapid Appliance Self Recovery........................................................................................................... 38
Creating the RASR USB key...........................................................................................................38
Executing RASR............................................................................................................................. 39
Recovery and Update Utility...............................................................................................................40
Upgrading your Appliance............................................................................................................40
Repairing your Appliance.............................................................................................................. 41
3 Managing Your Appliance.................................................................................42
Monitoring the status of the Appliance..............................................................................................42
Provisioning storage........................................................................................................................... 42
Provisioning selected storage.......................................................................................................43
Deleting space allocation for a virtual disk........................................................................................ 43
Resolving failed tasks..........................................................................................................................44
4 Protecting workstations and servers..............................................................45
About protecting workstations and servers ...................................................................................... 45
4

Deploying an Agent (Push Install) ......................................................................................................45
Protecting a machine .........................................................................................................................46
Pausing and resuming protection ............................................................................................... 48
Deploying the Agent Software when protecting an agent..........................................................48
Understanding protection schedules ................................................................................................49
Creating custom schedules..........................................................................................................50
Modifying protection schedules ..................................................................................................50
Configuring protected machine settings ...........................................................................................51
Viewing and modifying configuration settings ............................................................................51
Viewing system information for a machine ................................................................................ 52
Viewing license information ........................................................................................................ 53
Modifying transfer settings ...........................................................................................................53
Archiving data......................................................................................................................................55
Creating an archive ...................................................................................................................... 55
Importing an archive .................................................................................................................... 57
Archiving to a cloud...................................................................................................................... 59
Managing SQL attachability ............................................................................................................... 59
Configuring SQL attachability settings ........................................................................................59
Configuring nightly SQL attachability checks and log truncation ............................................. 60
Viewing system diagnostics ............................................................................................................... 61
Viewing machine logs .................................................................................................................. 61
Uploading machine logs............................................................................................................... 61
Canceling operations on a machine ............................................................................................61
Viewing machine status and other details ...................................................................................61
Managing multiple machines ............................................................................................................ 62
Deploying To Multiple Machines ................................................................................................. 63
Monitoring the deployment of multiple machines .....................................................................63
Protecting multiple machines.......................................................................................................63
Monitoring the protection of multiple machines ....................................................................... 65
5 Recovering data..................................................................................................66
Managing recovery ............................................................................................................................ 66
Managing snapshots and recovery points ........................................................................................ 66
Viewing recovery points .............................................................................................................. 66
Viewing a specific recovery point.................................................................................................67
Mounting a recovery point for a Windows machine ..................................................................68
Dismounting select recovery points ........................................................................................... 68
Dismounting all recovery points ..................................................................................................69
Mounting a recovery point for a Linux machine .........................................................................69
Removing recovery points ...........................................................................................................69
Deleting an orphaned recovery point chain................................................................................ 70
Forcing a snapshot .......................................................................................................................70
5

Restoring data .....................................................................................................................................71
About exporting protected data from Windows machines to virtual machines.........................71
Managing exports.......................................................................................................................... 72
Exporting backup information from your Windows machine to a virtual machine .................. 73
Exporting Windows data using ESXi export .................................................................................73
Exporting Windows data using VMware workstation export ......................................................75
Exporting Windows data using Hyper-V export ..........................................................................78
Exporting Windows data using Oracle VirtualBox export ...........................................................81
Virtual Machine Management.......................................................................................................83
Restoring Volumes from a Recovery Point .................................................................................86
Restoring volumes for a Linux machine using the Command Line ...........................................89
Launching Bare Metal Restore for Windows machines ................................................................... 90
Roadmap for performing a Bare Metal Restore for a Windows machine .................................. 91
Launching a bare metal restore for a Linux machine .......................................................................95
Installing the screen utility............................................................................................................ 97
Creating bootable partitions on a Linux machine........................................................................97
6 Replicating recovery points............................................................................. 98
Replication...........................................................................................................................................98
Roadmap for performing replication ................................................................................................ 99
Replicating to a self-managed core.............................................................................................99
Replicating to a core managed by a third party.........................................................................103
Replicating a new agent .............................................................................................................103
Replicating agent data on a machine ........................................................................................104
Setting replication priority for an agent .................................................................................... 104
Monitoring replication ................................................................................................................105
Managing replication settings ....................................................................................................106
Removing replication .......................................................................................................................106
Removing a protected machine from replication on the source Core.................................... 107
Removing a protected machine on the target Core................................................................. 107
Removing a target Core from replication.................................................................................. 107
Removing a source Core from replication.................................................................................107
Recovering replicated data ..............................................................................................................108
Understanding failover and failback ................................................................................................108
Performing Failover ....................................................................................................................108
Performing Failback ................................................................................................................... 109
7 Reporting............................................................................................................ 111
About reports .................................................................................................................................... 111
About the reports toolbar ................................................................................................................. 111
About compliance reports ................................................................................................................111
About errors reports ......................................................................................................................... 112
6

About the Core Summary Report .................................................................................................... 112
Repositories summary ................................................................................................................ 112
Agents summary ......................................................................................................................... 113
Generating a report for a Core or agent ..........................................................................................113
About the Central Management Console Core reports ................................................................. 114
Generating a report from the Central Management Console ........................................................114
8 Getting help....................................................................................................... 115
Finding documentation and software updates................................................................................ 115
Documentation............................................................................................................................115
Software updates......................................................................................................................... 115
Contacting Dell..................................................................................................................................115
Documentation feedback..................................................................................................................115
7

1
Introducing your Dell DL1300
Your Dell DL1300 combines backup and replication into a unified data protection product. It provides
reliable application data recovery from your backups to protect virtual machines and physical machines.
Your appliance is capable of handling up to terabytes of data with built-in global deduplication,
compression, encryption, and replication to specific private or public cloud infrastructure. Server
applications and data can be recovered in minutes for data retention and compliance purposes.
Your DL1300 supports multi-hypervisor environments on VMware vSphere, Oracle VirtualBox and
Microsoft Hyper-V private and public clouds.
Dell DL1300 core technologies
Your appliance combines the following technologies:
• Live Recovery
• Universal Recovery
• True Global Deduplication
• Encryption
Live Recovery
Live Recovery is instant recovery technology for VMs or servers. It gives you near-continuous access to
data volumes on virtual or physical servers.
DL1300 backup and replication technology records concurrent snapshots of multiple VMs or servers,
providing near instantaneous data and system protection. You can resume the use of the server by
mounting the recovery point without waiting for a full restore to production storage.
Universal Recovery
Universal Recovery provides unlimited machine restoration flexibility. You can restore your backups from
physical systems to VMs, VMs to VMs, VMs to physical systems, or physical systems to physical systems,
and carry out bare metal restores to dissimilar hardware.
Universal Recovery technology also accelerates cross-platform moves among virtual machines. For
example, moving from VMware to Hyper-V or Hyper-V to VMware. It builds in application-level, itemlevel, and object-level recovery (individual files, folders, email, calendar items, databases, and
applications).
8

True Global Deduplication
True Global Deduplication eliminates redundant or duplicate data by performing incremental block-level
backups of the machines.
The typical disk layout of a server consists of the operating system, application, and data. In most
environments, the administrators often use a common version of the server and desktop operating
system across multiple systems for effective deployment and management. When backup is performed at
the block-level across multiple machines, it provides a more granular view of what is in the backup and
what is not, irrespective of the source. This data includes the operating system, the applications, and the
application data across the environment.
Figure 1. Diagram of True Global Deduplication
Encryption
Your DL1300 provides encryption to protect backups and data-at-rest from unauthorized access and use,
ensuring data privacy. The data can be accessed and decrypted using the encryption key. Encryption is
performed inline on snapshot data, at line speeds without impacting performance.
Dell DL1300 data protection features
Dell DL1300 Core
The Core is the central component of the DL1300 deployment architecture. The Core stores and
manages machine backups and provides services for backup, recovery, retention, replication, archival,
and management. The Core is a self-contained network, addressable computer that runs a 64-bit version
of Microsoft Windows Server 2012 R2 Foundation and Standard operating systems. The appliance
performs target-based inline compression, encryption, and data deduplication of the data received from
the agent. The Core then stores the snapshot backups in the repository, which resides on the appliance.
Cores are paired for replication.
The repository resides on internal storage within the Core. The Core is managed by accessing the
following URL from a JavaScript enabled web browser: https://CORENAME:8006/apprecovery/admin.
9

Dell DL1300 Smart Agent
The Smart Agent is installed on the core-protected machine. The Smart Agent tracks the changed blocks
on the disk volume and then snaps an image of the changed blocks at a predefined interval of protection.
The incremental block-level snapshots’ forever approach prevents repeated copying of the same data
from the protected machine to the Core.
After the agent is configured, it uses smart technology to track the changed blocks on the protected disk
volumes. When the snapshot is ready, it is rapidly transferred to the Core using intelligent multi-threaded,
socket-based connections.
Snapshot process
Your DL1300 protection process begins when a base image is transferred from a protected machine to
the Core. In this phase, full copy of the machine is transported across the network under normal
operation, followed by incremental snapshots forever. The DL1300 Agent for Windows uses Microsoft
Volume Shadow copy Service (VSS) to freeze and quiesce application data to disk to capture a filesystem-consistent and an application-consistent backup. When a snapshot is created, the VSS writer on
the target server prevents content from being written to the disk. During the process of halting of writing
content to disk, all disk I/O operations are queued and resume only after the snapshot is complete, while
the operations in progress will be completed and all open files will be closed. The process of creating a
shadow copy does not significantly affect the performance of the production system.
Your DL1300 uses Microsoft VSS because it has built-in support for all Windows internal technologies
such as NTFS, Registry, Active Directory, to flush data to disk before the snapshot. Additionally, other
enterprise applications, such as Microsoft Exchange and SQL, use VSS Writer plug-ins to get notified
when a snapshot is being prepared and when they have to flush their used database pages to disk to
bring the database to a consistent transactional state. The captured data is rapidly transferred and stored
on the Core.
Replication — disaster recovery site or service provider
Replication is the process of copying recovery points from an AppAssure core and transmitting them to
another AppAssure core in a separate location for disaster recovery. The process requires a paired
source-target relationship between two or more cores.
The source core copies the recovery points of selected protected machines, and then asynchronously
and continually transmits the incremental snapshot data to the target core at a remote disaster recovery
site. You can configure outbound replication to a company-owned data center or remote disaster
recovery site (that is, a “self-managed” target core). Or, you can configure outbound replication to a
third-party managed service provider (MSP) or cloud provider that hosts off-site backup and disaster
recovery services. When replicating to a third-party target core, you can use built-in work flows that let
you request connections and receive automatic feedback notifications.
Replication is managed on a per-protected-machine basis. Any machine (or all machines) protected or
replicated on a source core can be configured to replicate to a target core.
Replication is self-optimizing with a unique Read-Match-Write (RMW) algorithm that is tightly coupled
with deduplication. With RMW replication, the source and target replication service matches keys before
transferring data and then replicates only the compressed, encrypted, deduplicated data across the WAN,
resulting in a 10x reduction in bandwidth requirements.
10

Replication begins with seeding: the initial transfer of deduplicated base images and incremental
snapshots of the protected machines, which can add up to hundreds or thousands of gigabytes of data.
Initial replication can be seeded to the target core using external media. This is typically useful for large
sets of data or sites with slow links. The data in the seeding archive is compressed, encrypted and
deduplicated. If the total size of the archive is larger than the space available on the removable media, the
archive can span across multiple devices based on the available space on the media. During the seeding
process, the incremental recovery points replicate to the target site. After the target core consumes the
seeding archive, the newly replicated incremental recovery points automatically synchronize.
Recovery
Recovery can be performed in the local site or the replicated remote site. After the deployment is in
steady state with local protection and optional replication, the DL1300 Core allows you to perform
recovery using Verified Recovery, Universal Recovery, or Live Recovery.
Recovery-as-a-Service
Managed Service Providers (MSPs) can fully leverage DL1300 as a platform for delivering Recovery As A
Service (RaaS). RaaS facilitates complete recovery-in-the-cloud by replicating customers' physical and
virtual servers. The service provider's cloud are used as virtual machines to support recovery testing or
actual recovery operations. Customers wanting to perform recovery-in-the-cloud can configure
replication on their protected machines on the local cores to an AppAssure service provider. In the event
of a disaster, the MSPs can instantly spin-up virtual machines for the customer.
The DL1300 is not multi-tenant. The MSPs can use the DL1300 at multiple sites and create a multi-tenant
environment at their end.
Virtualization and cloud
The DL1300 Core is cloud-ready, which allows you to leverage the compute capacity of the cloud for
recovery and archive.
DL1300 can export any protected or replicated machine to licensed versions of VMware or Hyper-V. With
continuous exports, the virtual machine is incrementally updated after every snapshot. The incremental
updates are fast and provide standby-clones that are ready to be powered up with a click of a button. The
supported virtual machine exports are:
• VMware Workstation or Server on a folder
• Direct export to a Vsphere or VMware ESXi host
• Export to Oracle VirtualBox
• Microsoft Hyper-V Server on Windows Server 2008 (x64)
• Microsoft Hyper-V Server on Windows Server 2008 R2
• Microsoft Hyper-V Server on Windows Server 2012 R2
You can now archive your repository data to the cloud using platforms such as Microsoft Azure, Amazon
S3, Rackspace Cloud Block Storage, or other OpenStack-based cloud services.
Dell DL1300 deployment architecture
Your DL1300 deployment architecture consists of local and remote components. The remote
components may be optional for those environments that do not require leveraging a disaster recovery
11
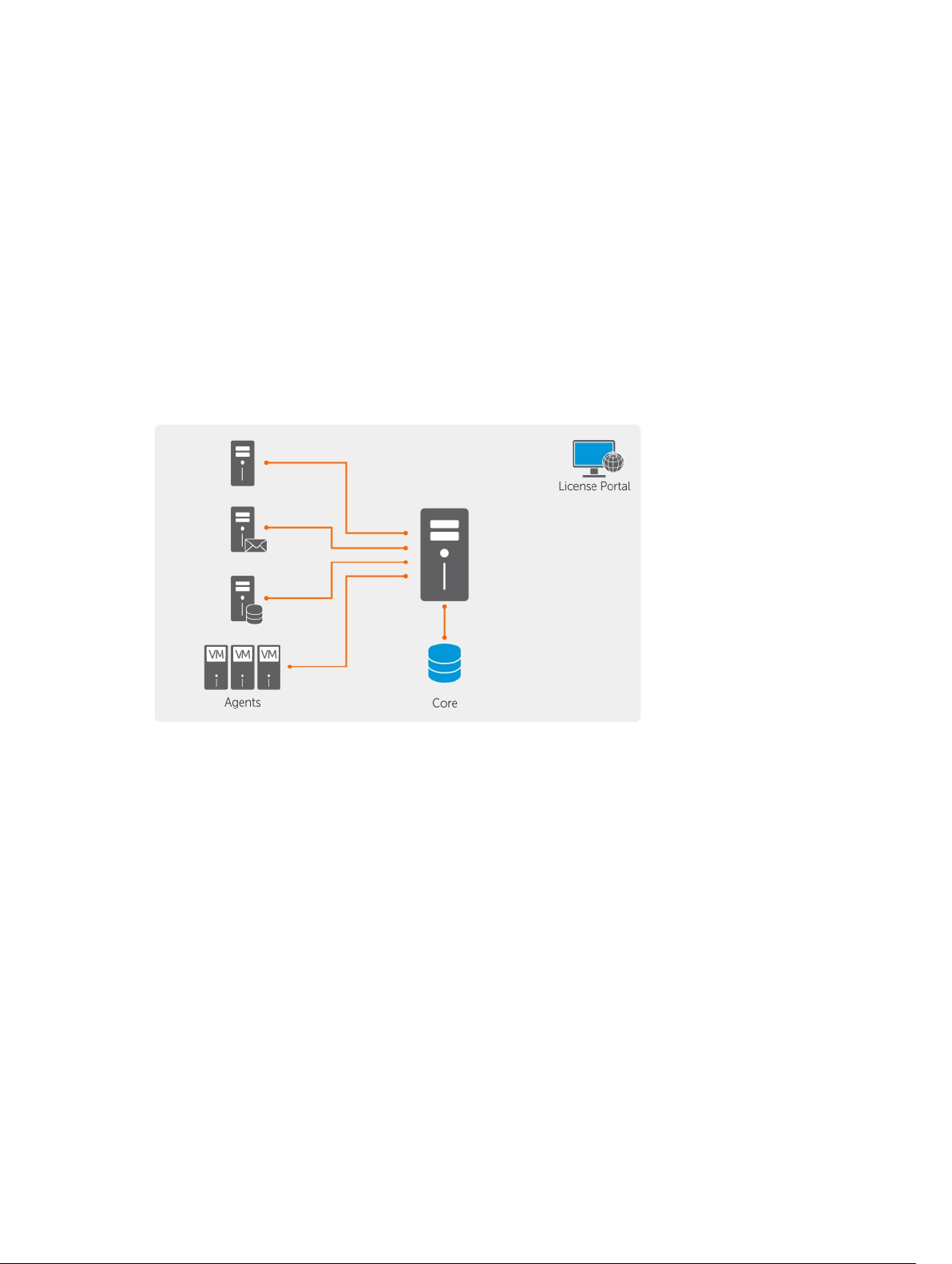
site or a managed service provider for off-site recovery. A basic local deployment consists of a backup
server called the Core and one or more protected machines known as the agents. The off-site
component is enabled using replication that provides full recovery capabilities in the disaster recovery
site. The DL1300 Core uses base images and incremental snapshots to compile recovery points of
protected agents.
Also, DL1300 is application-aware because it can detect the presence of Microsoft Exchange and SQL
and their respective databases and log files. Backups are performed by using application-aware blocklevel snapshots. DL1300 performs log truncation of the protected Microsoft Exchange server.
The following diagram depicts a simple DL1300 deployment. DL1300 Agents are installed on machines
such as a file server, email server, database server, or virtual machines are connected to and protected by
a single DL1300 Core, which consists of the central repository. The Dell software License Portal manages
license subscriptions, groups and users for the agents and cores in your environment. The License Portal
allows users to log in, activate accounts, download software, and deploy agents and cores per your
license for your environment.
Figure 2. Dell DL1300 Deployment Architecture
You can also deploy multiple DL1300 Cores as shown in the following diagram. A central console
manages multiple cores.
12
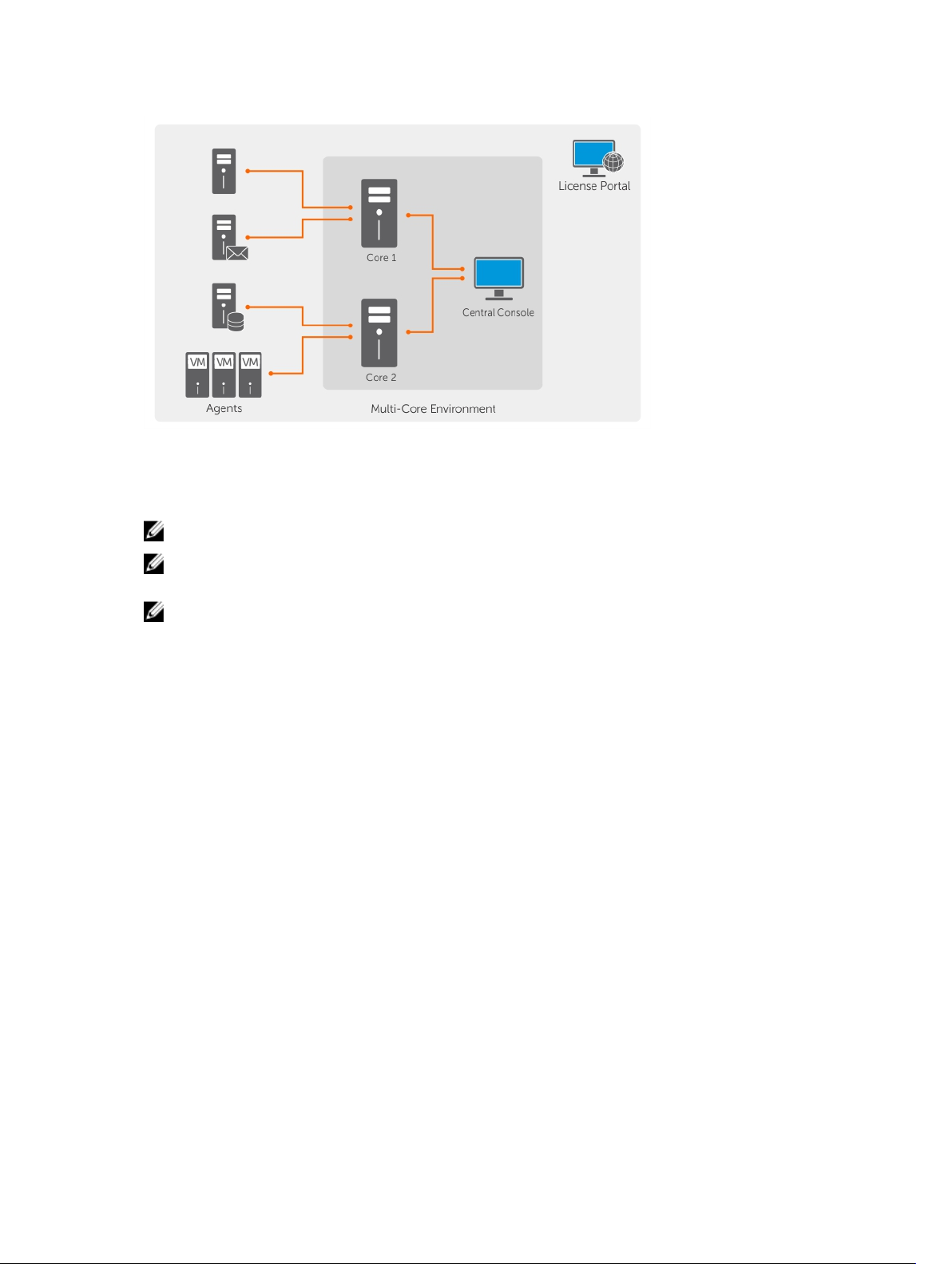
Figure 3. DL1300 Multi—Core Deployment Architecture
Other information you may need
NOTE: For all Dell OpenManage documents, go to Dell.com/openmanagemanuals.
NOTE: Always check for updates on Dell.com/support/home and read the updates first because
they often supersede information in other documents.
NOTE: For any documentation related to Dell OpenManage Server Administrator, see Dell.com/
openmanage/manuals.
Your product documentation includes:
Getting Started
Guide
System Placemat Provides information on how to set up the hardware and install the software on
Owner’s Manual Provides information about system features and describes how to troubleshoot the
Deployment Guide Provides information on hardware deployment and the initial deployment of the
User’s Guide Provides information about configuring and managing the system.
Release Notes Provides product information and additional information on the Dell DL1300
Interoperability
Guide
OpenManage
Server
Administrator
User’s Guide
Provides an overview of setting up your system, and technical specifications. This
document is shipped with your system.
your appliance.
system and install or replace system components.
appliance.
Appliance.
Provides information on supported software and hardware for your appliance as
well as usage considerations, recommendations, and rules.
Provides information about using Dell OpenManage Server Administrator to
manage your system.
13
2
Working with your DL1300
Accessing the DL1300 Core Console
To access the DL1300 Core Console:
1. Update trusted sites in your browser.
2. Configure your browsers to remotely access the DL1300 Core Console. See Configuring Browsers
To Remotely Access The Core Console.
3. Perform one of the following to access the DL1300 Core Console:
• Log on locally to your DL1300 core server, and then double-click the Core Console icon.
• Type one of the following URLs in your web browser:
– https://<yourCoreServerName>:8006/apprecovery/admin/core
– https://<yourCoreServerIPaddress>:8006/apprecovery/admin/core
Updating trusted sites in Internet Explorer
To update the trusted sites in Internet Explorer:
1. Open Internet Explorer.
2. If the File, Edit View, and other menus are not displayed, press <F10>.
3. Click the Tools menu, and select Internet Options.
4. In the Internet Options window, click the Security tab.
5. Click Trusted Sites and then click Sites.
6. In Add this website to the zone, enter https://[Display Name], using the new name you provided for
the Display Name.
7. Click Add.
8. In Add this website to the zone, enter about:blank.
9. Click Add.
10. Click Close and then OK.
Configuring browsers to remotely access the core console
To access the Core Console from a remote machine, you need to modify your browser settings.
NOTE: To modify the browser settings, log in to the system as an administrator.
NOTE: Google Chrome uses Microsoft Internet Explorer settings, change Chrome browser settings
using Internet Explorer.
14

NOTE: Ensure that the Internet Explorer Enhanced Security Configuration is turned on when you
access the Core Web Console either locally or remotely. To turn on the Internet Explorer
Enhanced Security Configuration:
1. Open Server Manager.
2. Select Local Server IE Enhanced Security Configuration displayed on the right. Ensure that it is
On.
To modify browser settings in Internet Explorer and Chrome:
1. Open Internet Explorer.
2. From the Tools menu, select Internet Options, Security tab.
3. Click Trusted Sites and then click Sites.
4. Deselect the option Require server verification (https:) for all sites in the zone, and then add
http://<
Sites.
5. Click Close, select Trusted Sites, and then click Custom Level.
6. Scroll to Miscellaneous → Display Mixed Content and select Enable.
7. Scroll to the bottom of the screen to User Authentication → Logon, and then select Automatic
logon with current user name and password.
8. Click OK, and then select the Advanced tab.
9. Scroll to Multimedia and select Play animations in webpages.
10. Scroll to Security, check Enable Integrated Windows Authentication, and then click OK.
hostname or IP Address of the Appliance server hosting the AppAssure Core> to Trusted
To modify Mozilla Firefox browser settings:
1. In the Firefox address bar, type about:config, and then click I’ll be careful, I promise if prompted.
2. Search for the term ntlm.
The search should return at least three results.
3. Double-click network.automatic-ntlm-auth.trusted-uris and enter the following setting as
appropriate for your machine:
• For local machines, enter the host name.
• For remote machines, enter the host name or IP address separated by a comma of the appliance
system hosting the AppAssure Core; for example, IPAddress,host name.
4. Restart Firefox.
Managing licenses
You can manage your DL1300 licenses directly from the Core Console. From the console, you can
change the license key and contact the license server. You can also access the License Portal from the
Licensing page in the Core console or you can access the license portal at https:// licenseportal.com.
The Licensing page includes the following information:
• License type
• License status
• Details of the repository
• Replication master cores (inbound)
15

• Replication slave cores (outbound)
• Simultaneous rolluos
• Rollup retention policy
• Encryption keys
• Vartual standby exports
• Mountability checks
• Exchange log truncations
• SQL log truncation
• Minimum snapshot interval
Contacting the license portal server
The Core Console contacts the portal server to update changes made in the license portal.
Communication with the portal server occurs automatically at designated intervals; however, you can
initiate communication on demand.
To contact the portal server:
1. Navigate to the Core Console and then click Configuration → Licensing.
The Licensing page is displayed.
2. From the License Server option, click Contact Now.
Changing a license key
To change a license key:
1. Navigate to the Core Console, select Configuration → Licensing.
The Licensing page is displayed.
2. From the License Details page, click Change License.
The Change License dialog box is displayed.
3. Update the new license key. To update the license key:
• Select the appropriate license key using the Browse tab in the Upload License File box.
To download the appropriate license:
1. Go to www.rapidrecovery.licenseportal.com.
2. From the Software drop-down menu on the upper-left corner of the page, select Appliance.
All the available licenses and related information is displayed.
3. In the Actions column, click the download icon.
The license is downloaded on your system.
• Enter the license key in the Enter License Key field.
4. Click Continue.
The license on your system is updated.
16

Changing the AppAssure language manually
AppAssure allows you to change the language that you had selected while running AppAssure Appliance
Configuration Wizard to any of the supported languages.
To change the AppAssure language to the desired language:
1. Launch the registry Editor using regedit command.
2. Navigate to HKEY_LOCAL_MACHINE → SOFTWARE → AppRecovery → Core → Localization.
3. Open Lcid.
4. Select decimal.
5. Enter the required language value in the Value data box, the supported language values are:
a. English: 1033
b. Brazilian Portuguese: 1046
c. Spanish: 1034
d. French: 1036
e. German: 1031
f. Simplified Chinese: 2052
g. Japanese: 1041
h. Korean: 1042
6. Right-click and restart the services in the given order:
a. Windows Management Instrumentation
b. SRM Web Service
c. AppAssure Core
7. Clear the browser cache.
8. Close the browser and restart the core console from the desktop icon.
Changing the operating system language during installation
On a running Microsoft Windows installation, you can use the control panel to select language packs and
configure additional international settings.
To change operating system (OS) language:
NOTE: It is recommended that the OS language and the AppAssure language be set to the same
language. otherwise, some messages may be displayed in mixed languages.
NOTE: It is recommended to change the OS language before changing the AppAssure language.
1. On the Start page, type language, and make sure that the search scope is set to Settings.
2. In the Results panel, select Language.
3. In the Change your language preferences pane, select Add a language.
4. Browse or search for the language that you want to install.
For example, select Catalan, and then select Add. Catalan is now added as one of your languages.
5. In the Change your language preferences pane, select Options next to the language that you added.
6. If a language pack is available for your language, select Download and install language pack.
7. When the language pack is installed, the language is displayed as available to use for the Windows
display language.
8. To make this language your display language, move it to the top of your language list.
17

9. Log out and log in again to Windows for the change to take effect.
Managing core settings
The Core settings are used to define various configuration and performance settings. Most settings are
configured for optimal use but you can change the following settings as necessary:
• General
• Nightly Jobs
• Transfer Queue
• Client Timeout Settings
• Deduplication Cache Configuration
• Database Connection Settings
Changing the core display name
NOTE: It is recommended that you select a permanent display name during the initial configuration
of your Appliance. If you change it later, you must perform several steps manually to ensure that the
new host name takes effect and the appliance functions properly.
To change the Core display name:
1. Navigate to the Core Console, click Configuration → Settings.
2. In the General section, click Change.
The Display Name dialog box appears.
3. In the Display Name text box, enter a new display name for the Core.
4. Click OK.
Changing the nightly job time
The Nightly Job option schedules jobs such as rollup, attachability, and truncation for agents protected
by the Core.
To adjust the nightly job time:
1. Navigate to the Core Console and select Configuration → Settings.
2. In the Nightly Jobs section, click Change.
The Nightly Jobs dialog box appears.
3. In the Nightly Jobs Time text box, enter a new start time.
4. Click OK.
Modifying the transfer queue settings
Transfer queue settings are core-level settings that establish the maximum number of concurrent
transfers and retries for transferring data.
To modify the transfer queue settings:
1. Navigate to the Core Console, click Configuration → Settings.
2. In the Transfer Queue section, click Change.
The Transfer Queue dialog box appears.
3. In the Maximum Concurrent Transfers text box, enter a value to update the number of concurrent
transfers.
18

Set a number from 1 to 60. The smaller the number, the lesser the load is on network and other
system resources. As the capacity that is processed increases, so does the load on the system.
4. In the Maximum Retries text box, enter a value to update the maximum number of retries.
5. Click OK.
Adjusting the client time-out settings
Client Timeout Settings specifies the number of seconds or minutes the server waits before it times out
when connecting to a client.
To adjust the client time-out settings:
1. Navigate to the Core Console, and click Configuration → Settings.
2. In the Client Timeout Settings Configuration section, click Change.
The Client Timeout Settings dialog box appears.
3. In the Connection Timeout text box, enter the number of minutes and seconds before a connection
time-out occurs.
4. In the Read/Write Timeout text box, enter the number of minutes and seconds that you want to
lapse before a time-out occurs during a read/write event.
5. Click OK.
Configuring deduplication cache settings
Global deduplication reduces the amount of disk storage space required for your backed up data. The
Deduplication Volume Manager (DVM) combines a set of storage locations into a single repository. The
deduplication cache holds references to unique blocks. By default, the deduplication cache is 1.5 GB. If
the amount of redundant information isso large that the deduplication cache is full, your repository can
no longer take full advantage of further deduplication across your repository for newly added data. You
can then increase the size of the deduplication cache by changing the deduplication cache configuration
in the Core Console.
To configure deduplication cache settings:
1. Navigate to the Core Console, click Configuration → Settings.
2. In the Deduplication Cache Configuration section, click Change.
The Deduplication Cache Configuration dialog box appears.
3. In the Primary Cache Location text box, enter the updated primary cache location.
4. In the Secondary Cache Location text box, enter the updated secondary cache location.
5. In the Metadata Cache Location text box, enter the updated metadata cache location.
6. Click OK.
NOTE: You must restart the Core service for the changes to take effect.
Modifying engine settings
To modify engine settings:
1. Navigate to the Core Console, click Configuration → Settings.
2. In the Replay Engine Configuration section, click Change.
The Replay Engine Configuration dialog box appears.
3. In the Replay Engine Configuration dialog box, specify the IP address. Select one of the following:
19

• To use the preferred IP address from your TCP/IP, click Automatically Determined.
• To manually enter an IP address, click Use a specific IP Address.
4. Enter the configuration information described as follows:
Text Box Description
Preferable Port Enter a port number or accept the default setting (8007 is the default port).
The port is used to specify the communication channel for the engine.
Admin Group Enter a new name for the administration group. The default name is BUILTIN
\Administrators.
Minimum Async
I/O Length
Receive Buffer
Size
Send Buffer Size Enter an outbound buffer size or accept the default setting. The default setting
Read Timeout Enter a read timeout value or choose the default setting. The default setting is
Write Timeout Enter a write timeout value or choose the default setting. The default setting is
5. Select No Delay.
6. Click OK.
Enter a value or choose the default setting. It describes the minimum
asynchronous input/output length. The default setting is 65536.
Enter an inbound buffer size or accept the default setting. The default setting is
8192.
is 8192.
00:00:30.
00:00:30.
Modifying deploy settings
To modify deploy settings:
1. Navigate to the Core Console and click the Configuration tab, and then Settings.
2. In the Deploy Settings pane, click Change.
The Deploy Settings dialog box displays.
3. In the Agent Installer Name text box, enter the name of the agent executable file. The default is
Agentweb. exe.
4. In the Core Address text box, enter the address for the core.
5. In the Failed Receive Timeout text box, enter the number of minutes to wait without activity to
timeout.
6. In the Max Parallel Installs text box, enter a number for the maximum installations that can be
installed in parallel.
7. Select either or both of the following optional settings:
• Automatic reboot after install
• Protect After Deploy
8. Click OK.
20

Modifying database connection settings
To modify database connection settings:
1. Navigate to the Core Console, click Configuration → Settings.
2. In the Database Connection Settings section, perform one of the following:
• To restore the default configuration, click Restore Default.
• To modify the database connection settings, click Change.
On clicking change, the Database Connection Settings dialog box appears.
3. Enter the settings for modifying the database connection described as follows:
Text Box Description
Host Name Enter a host name for the database connection.
Port Enter a port number for the database connection.
User Name
(optional)
Password
(optional)
Retain event and
job history for,
days
4. Click Test Connection to verify your settings.
5. Click Save.
Enter a user name for accessing and managing the database connection
settings. It is used to specify the log in credentials for accessing the database
connection.
Enter a password for accessing and managing the database connection
settings.
Enter the number of days to retain the event and job history for the database
connection.
Managing Events
The Core includes predefined sets of events, which can be used to notify administrators of critical issues
on the Core or the backup jobs.
From the Events tab, you can manage notification groups, e-mail SMTP settings, Server Settings, Enabled
Trace Logs, Cloud Configuration, repetition reduction, and event retention.
The Notification Groups option allows you to manage notification groups, from which you can:
• Specify an event for which you want to generate an alert for the following:
– Clusters
– Attachability
– Jobs
– Licensing
– Log Truncation
– Archive
– Core Service
– Export
– Protection
21

– Replication
– Rollback
• Specify the type of alert (error, warning, and informational).
• Specify to whom and where the alerts are sent. Options include:
– Email Address
– Windows Events Logs
– Syslog Server
• Specify a time threshold for repetition.
• Specify the retention period for all events.
Configuring notification groups
To configure notification groups:
1. From the Core Console, select Configuration → Events.
2. Click Add Group.
The Add Notification Group dialog box opens and displays two panels:
• Enable Alerts
• Notification Options
Enabling alerts
Enabling Alerts allows you to define the set of system events that you want to log, create reports, and set
alerts.
NOTE: To create alerts for all events, select All Alerts.
• To create alerts specific to errors, warnings, informational messages, or a combination, select one of
the following:
– red triangle icon (Error)
– yellow triangle icon (Warning)
– blue circle (Information)
– curved arrow (Restores default)
• To create alerts for specific events click the > symbol next to the relevant group and select the check
box to enable the alert.
Configuring notification options
1. In the Notification Options panel, specify how to handle the notification process.
The notification options are:
Text Box Description
Notify by e-mail Designate the recipients of the email notification. You can enter separate
multiple e-mail addresses as well as blind and carbon copies as shown below:
• To:
• CC:
• BCC:
22

Text Box Description
Notify by
Windows Event
Log
Notify by sys logd Select this option if you want alerts to be reported through sys logd. Enter the
Notify by Toast
alerts
2. Click OK.
The following message is displayed: The Group name cannot be changed after the creation of the
Notification Group. are you sure you want to use this name?.
• To save the group name, click Yes.
• To change the group name, click No. Return to the Notification Options window, update the
group name and other notification group settings, and save your work.
Select this option if you want notification of alerts to be reported through the
Windows Event Log.
details for the sys logd in the following text boxes:
• Hostname:
• Port:1
Select this option if you want the alert to appear as a pop-up in the lower-right
corner of your screen.
Configuring an email server
NOTE: You must configure notification group settings, including enabling the Notify by email
option, before sending out email alert messages.
To configure an email server and email notification template:
1. From the Core Console, click Configuration → Events.
2. In the Email Settings pane, click SMPT server.
The SMTP Server Settings dialog box appears.
3. Enter details for the email server as follows:
Text Box Description
SMTP Server Enter the name of the email server to be used by the email notification
template. The naming convention includes the host name, domain, and suffix;
for example, smtp.gmail.com.
From Enter a return email address. It is used to specify the return email address for
the email notification template; for example, noreply@localhost.com.
Username Enter a user name for the email server.
Password Enter a password for accessing the email server.
Port Enter a port number. It is used to identify the port for the email server; for
example, the port 587 for Gmail.
The default is 25.
23
Text Box Description
Timeout (seconds) To specify how long to try a connection before timing out, enter an integer
value. It is used to establish the time in seconds when trying to connect to the
email server before a time-out occurs.
The default is 30 seconds.
TLS Select this option if the mail server uses a secure connection such as Transport
Layer Security (TLS) or Secure Sockets Layer (SSL).
4. Click Send Test Email perform the following:
a. In the Send Test Email dialog box, enter a destination email address for the test message and click
Send.
b. If the test message fails, exit the error dialog box and the Send Test Email dialog box, and revise
your email server configuration settings. Repeat step 4.
c. Click OK to confirm.
d. Verify the test email message was sent.
e. Return to the SMTP Server Settings dialog box, click Save to close the dialog box and save your
settings.
Configuring an Email notification template
To receive email notifications about events you must configure an email server and an email notification
template.
NOTE: To receive email alert messages, configure notification group settings and enable the Notify
by email option.
To configure an email server and email notification template:
1. From the Core Console, click Configuration → Events.
2. In the Email Settings pane, click Change.
The Edit Email Notification Configuration dialog box appears.
3. Select Enable email notifications, and then enter details for the email server as follows:
Text Box Description
Email Subject Enter a subject for the email template. It is used to define the subject of the
email notification template; for example, <hostname> - <level> <name>.
Email Enter information for the body of the template that describes the event, when
it occurred, and the severity.
4. Click Send Test Email perform the following:.
a. In the Send Test Email dialog box, enter a destination email address for the test message and click
Send.
b. If the test message fails, exit the error dialog box and the Send Test Email dialog box, click OK to
save the current email template settings, and modify your email server settings, see Configuring
An Email Server And Email Notification Template. Ensure you reenter the password for that email
account. Save the settings and then return to step 4.
c. Click OK to confirm.
d. Verify the test email message was sent.
e. Return to the Edit Email Notification Configuration dialog box, click OK to close the dialog box
and save your settings.
24

Configuring repetition reduction
To configure repetition reduction:
1. From the Core Console, click Configuration → Events.
2. From the Repetition Reduction section, click Change.
The Enable Repetition Reduction dialog box appears.
3. Select Enable Repetition Reduction.
4. In the Store events for text box, enter the number of minutes to store the events for repetition
reduction.
5. Click OK.
Configuring Event Retention
To configure event retention:
1. From the Core Console, click Configuration → Settings.
2. Under Database Connection Settings, click change.
The Database Connection Settings dialog box appears.
3. In the Retain event and job history for text box, enter the number of days that you want to retain
information about events.
For example, you could select 30 days(default).
4. Click Save.
Roadmap for managing a repository
The roadmap for managing a repository covers tasks such as creating, configuring, and viewing a
repository, and includes the following topics:
• Creating A Repository
• Viewing Repository Details
• Modifying Repository Settings
• Expanding existing repository
• Adding A Storage Location To An Existing Repository
• Checking A Repository
• Deleting A Repository
• Recovering A Repository
NOTE: It is recommended that you use the Appliance tab to create– or expand repository.
Before you begin using your appliance, you must set up the repository on the core server. A repository
stores your protected data. More specifically, it stores the snapshots that are captured from the protected
servers in your environment.
By configuring repository, you can perform various tasks such as specifying where to locate the data
storage on the Core server, how many locations can be added to each repository, the name of the
repository, how many current operations the repositories support.
25

When you create a repository, the Core preallocates the space required for storing data and metadata in
the specified location. To further increase the size of a repository, you can add new storage locations or
volumes.
NOTE: The DL1300 Appliance allows you to create only one repository.
All the DL1300 versions support in-box upgrades. The initial repository size available after provisioning
storage in your appliance corresponds to the version of your system. For example: After provisioning the
DL1300 3 TB+2VM appliance, the repository size available is 3 TB. The unused storage space in your
system can be used to expand the existing repositories by upgrading your license. To expand the
repository, see Expanding existing repository.
Table 1. Repository size
Version Initial Repository size in TB
(default)
2 TB 2 8
3 TB+2VM 3 8
4 TB+2VM 4 8
NOTE: The DL1300 4 TB + 2 VM system allows you to expand the repository to 18 TB by purchasing
the appropriate license and connecting the MD 1400 external enclosure.
Expandable repository size in TB
Creating a repository
To create a repository:
1. Navigate to the Core Console.
2. Click Configuration → Repositories.
3. Click Add new.
The Add New Repository dialog box appears.
4. Enter the information as described in the following table.
Text Box Description
Repository Name Enter the display name of the repository. By default, this text box consists of
the word Repository and an index number which sequentially adds a number
to the new repository starting with 1. You can change the name as needed.
You can enter up to 150 characters.
Concurrent
Operations
Comments Optionally, enter a descriptive note about this repository.
5. To define the specific storage location or volume for the repository, click Add Storage Location.
CAUTION: If the AppAssure repository that you are creating in this step is later removed, all
files at the storage location of your repository will be deleted. If you do not define a
dedicated folder to store the repository files, then those files will be stored in the root;
deleting the repository will also delete the entire contents of the root, resulting in
catastrophic data loss.
26
Define the number of concurrent requests that you want the repository to
support. By default the value is 64.

NOTE: Repositories are stored on primary storage devices. Archival storage devices such as
Data Domain are not supported due to performance limitations. Similarly, repositories must not
be stored on NAS filers that tier to the cloud as these devices tend to have performance
limitations when used as primary storage.
The Add Storage Location dialog box is displayed.
6. To specify your system's disk space as the new storage location to be added, enter the following
information:
•
Text Box Description
Data Path Enter the location for storing the protected data; for example, type X:
\Repository\Data.
When specifying the path, use only alphanumeric characters, the hyphen,
and the period (only to separate host names and domains). The letters a to
z are case-insensitive. Do not use spaces. No other symbols or punctuation
characters are permitted.
Metadata Path Enter the location for storing the protected metadata; for example, type X:
\Repository\Metadata.
When specifying the path, use only alphanumeric characters, the hyphen,
and the period (only to separate host names and domains). The letters a to
z are case-insensitive. Do not use spaces. No other symbols or punctuation
characters are permitted.
7. In the Details pane, click Show/Hide Details and enter the details for the storage location described
as follows:
Text Box Description
Size Set the size or capacity for the storage location. The default is 250 MB. You
can choose from the following:
• MB
• GB
• TB
NOTE: The size that you specify cannot exceed the size of the volume.
NOTE: If the storage location is a New Technology File System (NTFS)
volume using Windows XP or Windows 7, the file size limit is 16 TB.
If the storage location is an NTFS volume using Windows 8 or Windows
Server 2012, the file size limit is 256 TB.
NOTE: To validate the operating system, Windows Management
Instrumentation (WMI) must be installed on the intended storage location.
Write Caching
Policy
The write caching policy controls how the Windows Cache Manager is used in
the repository and helps to tune the repository for optimal performance on
different configurations.
Set the value to one of the following:
• On
27

Text Box Description
• Off
• Sync
If the value is set to On, which is the default, Windows controls the caching.
NOTE: Setting the write caching policy to On could result in faster
performance. If you are using a version of Windows Server prior to Server
2012, the recommended setting is Off.
If set to Off, AppAssure controls the caching.
If set to Sync, Windows controls the caching as well as the synchronous input/
output.
Bytes per Sector Specify the number of bytes you want each sector to include. The default
value is 512.
Average Bytes per
Record
8. Click Save.
The Repositories screen is displayed to include the newly added storage location.
9. Repeat step 4 through step 7 to add more storage locations for the repository.
10. Click Create to create the repository.
The Repository information appears in the Configuration tab.
Specify the average number of bytes per record. The default value is 8192.
Viewing repository details
To view repository details:
1. Navigate to the Core Console.
2. Click Configuration → Repositories.
3. Click Settings icon next to the repository for which you want to view the details.
4. From the expanded view, you can perform the following actions:
• Add a Storage Location
• Check a Repository
• Modify Settings
• Delete a Repository
Details also display for the repository and include the storage locations and statistics. Storage
location details include the metadata path, data path, and size. Statistical information includes:
• Deduplication — Reported as the number of block dedupe hits, block dedupe misses, and block
compression rate.
• Record I/O — Consisting of the rate (MB/s), read rate (MB/s), and write write (MB/s).
• Storage Engine — Include the rate (MB/s) read rate (MB/s), and write write (MB/s).
Modifying repository settings
After you add a repository, you can modify the repository settings such as the description or the
maximum concurrent operations. You can also create a new storage location for the repository.
28
To modify repository settings:
1. Navigate to the Core Console.
2. Click Configuration → Repositories.
3. Click the Settings icon next to the Compression Ratio column below the Actions button, and then
Settings.
The Repository Settings dialog box appears.
4. Edit the repository information described as follows:
Field Description
Repository Name Represents the display name of the repository. By default, this text box consists
of the word Repository and an index number, which corresponds to the
number of the repository.
NOTE: You cannot edit the repository name.
Description Optionally, enter a descriptive note about the repository.
Maximum
Concurrent
Operations
Enable
Deduplication
Enable
Compression
5. Click Save.
Define the number of concurrent requests that you want the repository to
support.
To turn off deduplication, clear this check box. To enable deduplication, select
this check box.
NOTE: Changing this setting only applies to backups taken after the
setting has been made. Existing data, or data replicated from another core
or imported from an archive, retains the deduplication values in place at
the time the data was captured from the protected machine.
To turn off compression, clear this check box. To enable compression, select
this check box.
NOTE: This setting applies only to backups taken after the setting has
been changed. Existing data, or data replicated from another core or
imported from an archive, retains the compression values in place at the
time the data was captured from the protected machine.
Expanding existing repository
You can use the unused storage in your appliance to expand an existing repository. The type of license
purchased restricts the storage space that can be used from the unused storage to expand an existing
repository.
Only the DL1300 4 TB+2VM appliance allows you to expand repository size by 10 TB by connecting the
MD1400 external enclosure.
NOTE: You can expand the existing repository in the increments of 1 TB or 2 TB by upgrading your
license. To upgrade your license, see Changing a license key section.
29

To expand the repository using the unused storage and the attached external enclosure:
1. Install the MD1400 or upgrade the trial license. Open the Core Console and select the Appliance tab,
click Tasks → Provisioning.
2. On the Provisioning screen, click Provision next to the external storage controller.
Perform this step only when you attach an external enclosure.
3. On the Provisioning screen, click Expand in the Action column next to appropriate provisioning task.
The Expand Repository dialog box is displayed.
4. In the Expand Repository dialog box, select the repository that you want to expand, and then click
Expand.
The new repository location is added to the existing repository.
Adding a storage location to an existing repository
Adding a storage location lets you define where you want to store the repository or volume.
To add a storage location to an existing repository:
1. Click > next to the Status column of the repository for which you want to add a storage location.
2. Click Add Storage Location.
The Add Storage Location dialog box appears.
3. To add your system's disk space as the new storage location, enter the information as follows:
Text Box Description
Metadata Path Enter the location for storing the protected metadata.
Data Path Enter the location for storing the protected data.
4. In the Details section, click Show/Hide Details and enter the details for the storage location
described as follows:
Text Box Description
Size Set the size or capacity for the storage location. The default size is 250 MB.
You can choose from the following:
• MB
• GB
• TB
NOTE: The size that you specify cannot exceed the size of the volume.
NOTE: If the storage location is an NTFS volume using Windows XP or
Window 7, the file size limit is 16 TB.
If the storage location is an NTFS volume using Windows 8 or Windows
Server 2012, the file size limit is 256 TB.
NOTE: To validate the operating system, WMI must be installed on the
intended storage location.
Write Caching
Policy
The write caching policy controls how the Windows Cache Manager is used in
the repository and helps to tune the repository for optimal performance on
different configurations. Set the value to one of the following:
30
 Loading...
Loading...