Page 1

Cisco Small Business Managed Router Feature Configuration Guide
SRP500 Site to Site IPSec VPNs
Page 2
All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 2 of 9
Introduction
The SRP500 supports the configuration of multiple point to point IPSec VPNs. This guide illustrates how to
create VPN connections between two SRP500 devices, or between an SRP500 and an IOS device.
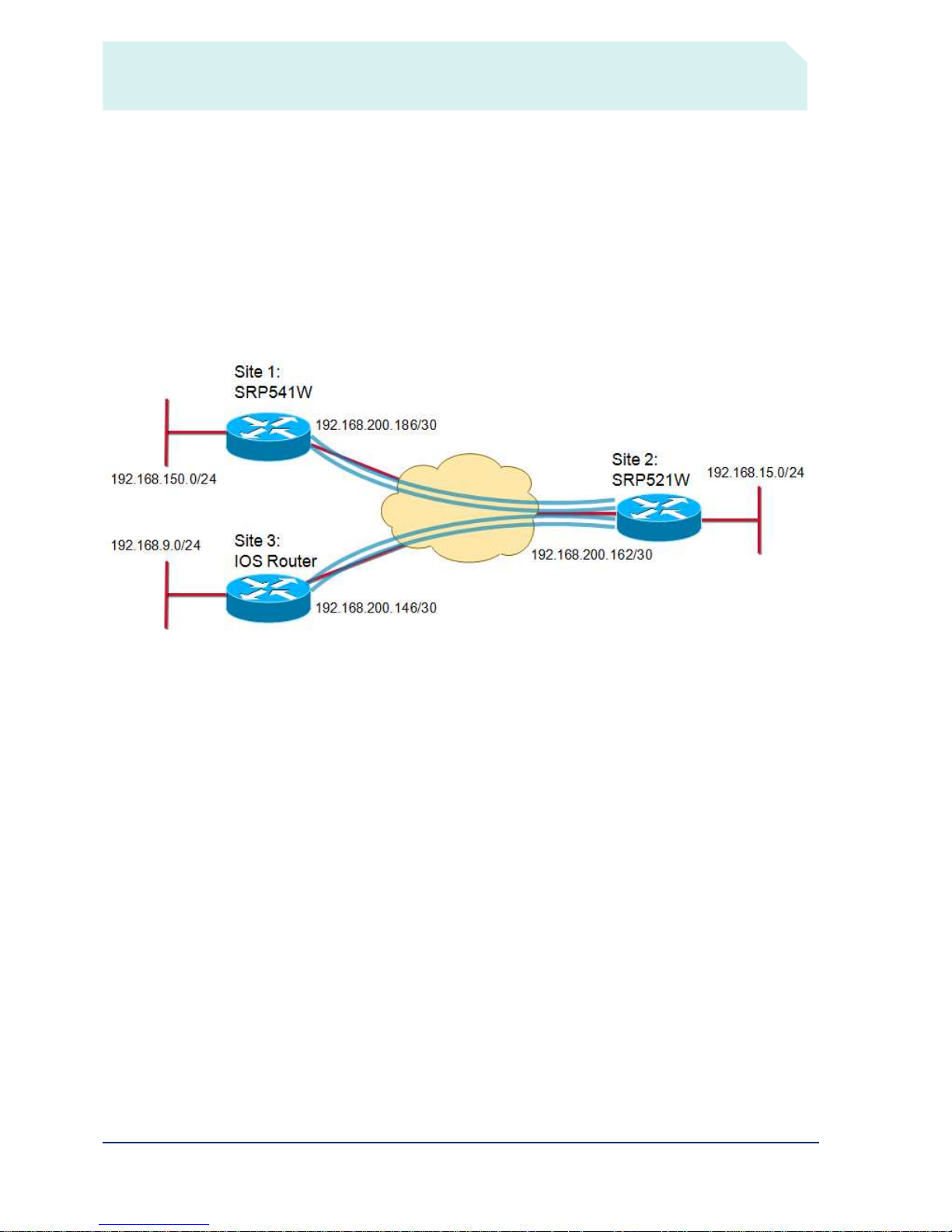
Guide Topology
The following network has been created to demonstrate this configuration. Note that in this case, WAN IP
addresses are statically configured and LAN IP subnets are unique between sites.
For the purposes of these configurations, the following devices and firmware versions were used:
Site 1: SRP541W running v1.1.19(004)
Site 2: SRP521W running v1.2.0(023)
Site 3: SR520 running IOS 15.1(1)T
Configuring the SRP500 for IPSec
The following screenshots illustrate how to configure the SRP500 IKE and IPSec policies for connecting to a
remote IOS device. Connecting to a remote SRP500 can follow exactly the same approach, allowing of
course the appropriate address and subnet in that case.
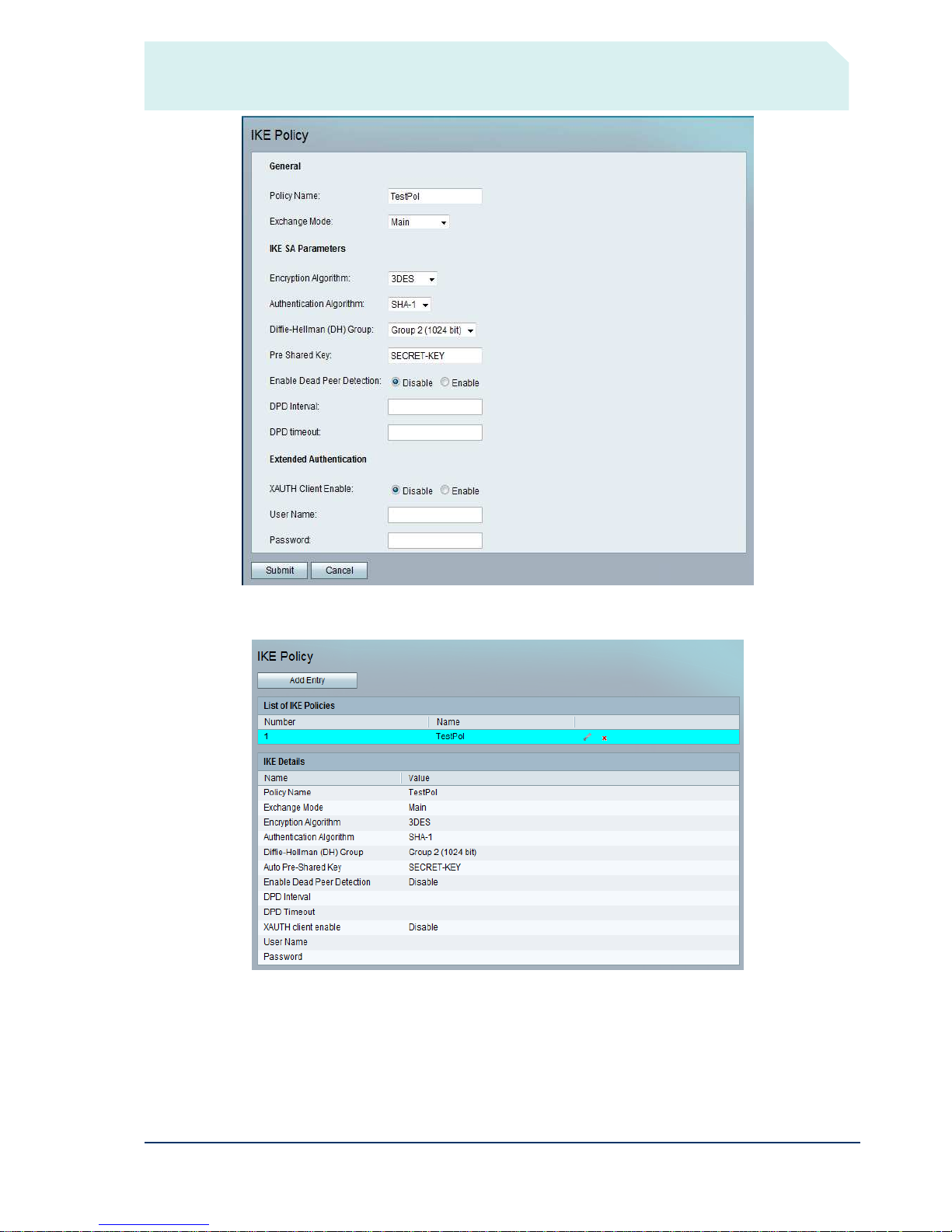
IKE Policy configuration
In this example, the IKE policy is defined to require 3DES encryption with SHA-1 authentication. The
connection is secured with a pre-shared key “SECRET-KEY”. These details will also be used for the IOS
configuration.
A single IKE policy may be used for all IPSec tunnels, or a separate one created for each, depending on your
security requirements. Access the VPN > IKE Policy SRP500 page and click Add Entry to define a new
policy.
Page 3
All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 3 of 9
This configuration is summarised as follows once the configuration is submitted.
IPSec Policy Configuration
An IPSec policy must be created for each site to site tunnel. Each SRP500 device may define up to five IPSec
policies.
Page 4

All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 4 of 9
The following screenshots show the configuration required for the site two SRP500 to establish a VPN
tunnel to the IOS device at site 3. Access the VPN > IPSec Policy SRP500 page and click Add Entry to define
a new policy.
For these configurations, it should be sufficient to use the Auto Policy type setting.
Once submitted, the IPSec policy is summarised as follows. Note that in this case, IPSec NAT traversal
(NAT-T) is not required. (NAT Traversal may be configured using the VPN > NAT Traversal page on the
SRP540 products.)
Page 5

All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 5 of 9
IOS Configuration
The following IOS command line configuration is required at site three to establish an IPSec tunnel to site
two.
In this case, interface FastEthernet4 is the WAN interface of the SR520 router to which the IPSec tunnel will
be bound. The first section above (isakmp policy) follows the SRP500 IKE Policy configuration. The
following ipsec transform-set and map sections follow the SRP500 IPSec policy configuration.
Access list 110 specifies that all traffic from the local VLAN addressed for the SRP500 VLAN at site two
should traverse the IPSec tunnel.
Verification
Once both endpoints are configured, the VPN tunnel will automatically establish. The SRP500 Status > VPN
page can be used to verify that the connection has been established. This page may also be used to
manually Disconnect/Connect the tunnel if required.
To monitor the VPN connection process on the IOS device, you may use the debug crypto isakmp and
debug crypto ipsec features. The following capture illustrates the connection process for this example.
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 28800
crypto isakmp key SECRET-KEY address 192.168.200.162
!
!
crypto ipsec transform-set SETNAME esp-3des esp-sha-hmac
!
crypto map CISCO 1 ipsec-isakmp
set peer 192.168.200.162
set transform-set SETNAME
set pfs group2
match address 110
!
interface FastEthernet4
ip address 192.168.200.146
crypto map CISCO
!
interface Vlan1
ip address 192.168.9.1 255.255.255.0
!
access-list 110 permit ip 192.168.9.0 0.0.0.255 192.168.15.0 0.0.0.255
Page 6

All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 6 of 9
####### Site 2 SRP500 Initiates the connection here using the status page
ISAKMP (0): received packet from 192.168.200.162 dport 500 sport 500 Global (N) NEW SA
ISAKMP: Created a peer struct for 192.168.200.162, peer port 500
ISAKMP: New peer created peer = 0x83952688 peer_handle = 0x8000001E
ISAKMP: Locking peer struct 0x83952688, refcount 1 for crypto_isakmp_process_block
ISAKMP: local port 500, remote port 500
ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 83953838
ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
ISAKMP:(0): processing SA payload. message ID = 0
ISAKMP:(0): processing vendor id payload
ISAKMP:(0): vendor ID seems Unity/DPD but major 0 mismatch
ISAKMP:(0): processing vendor id payload
ISAKMP:(0): vendor ID is DPD
ISAKMP:(0):found peer pre-shared key matching 192.168.200.162
ISAKMP:(0): local preshared key found
ISAKMP : Scanning profiles for xauth ...
ISAKMP:(0):Checking ISAKMP transform 0 against priority 1 policy
ISAKMP: life type in seconds
ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x53
ISAKMP: encryption 3DES-CBC
ISAKMP: hash SHA
ISAKMP: auth pre-share
ISAKMP: default group 2
ISAKMP:(0):atts are acceptable. Next payload is 0
ISAKMP:(0):Acceptable atts:actual life: 28800
ISAKMP:(0):Acceptable atts:life: 0
ISAKMP:(0):Fill atts in sa vpi_length:4
ISAKMP:(0):Fill atts in sa life_in_seconds:86355
ISAKMP:(0):Returning Actual lifetime: 28800
ISAKMP:(0)::Started lifetime timer: 28800.
ISAKMP:(0): processing vendor id payload
ISAKMP:(0): vendor ID seems Unity/DPD but major 0 mismatch
ISAKMP:(0): processing vendor id payload
ISAKMP:(0): vendor ID is DPD
ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM1
ISAKMP:(0): sending packet to 192.168.200.162 my_port 500 peer_port 500 (R) MM_SA_SETUP
ISAKMP:(0):Sending an IKE IPv4 Packet.
ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM2
ISAKMP (0): received packet from 192.168.200.162 dport 500 sport 500 Global (R)
MM_SA_SETUP
ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
ISAKMP:(0):Old State = IKE_R_MM2 New State = IKE_R_MM3
ISAKMP:(0): processing KE payload. message ID = 0
ISAKMP:(0): processing NONCE payload. message ID = 0
ISAKMP:(0):found peer pre-shared key matching 192.168.200.162
ISAKMP:(2026):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
ISAKMP:(2026):Old State = IKE_R_MM3 New State = IKE_R_MM3
ISAKMP:(2026): sending packet to 192.168.200.162 my_port 500 peer_port 500 (R)
MM_KEY_EXCH
ISAKMP:(2026):Sending an IKE IPv4 Packet.
ISAKMP:(2026):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
ISAKMP:(2026):Old State = IKE_R_MM3 New State = IKE_R_MM4
ISAKMP (2026): received packet from 192.168.200.162 dport 500 sport 500 Global (R)
MM_KEY_EXCH
ISAKMP:(2026):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
ISAKMP:(2026):Old State = IKE_R_MM4 New State = IKE_R_MM5
Page 7

All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 7 of 9
ISAKMP:(2026): processing ID payload. message ID = 0
ISAKMP (2026): ID payload
next-payload : 8
type : 1
address : 192.168.200.162
protocol : 0
port : 0
length : 12
ISAKMP:(0):: peer matches *none* of the profiles
ISAKMP:(2026): processing HASH payload. message ID = 0
ISAKMP:(2026):SA authentication status:
authenticated
ISAKMP:(2026):SA has been authenticated with 192.168.200.162
ISAKMP: Trying to insert a peer 192.168.200.146/192.168.200.162/500/, and inserted
successfully 83952688.
ISAKMP:(2026):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
ISAKMP:(2026):Old State = IKE_R_MM5 New State = IKE_R_MM5
ISAKMP:(2026):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
ISAKMP (2026): ID payload
next-payload : 8
type : 1
address : 192.168.200.146
protocol : 17
port : 500
length : 12
ISAKMP:(2026):Total payload length: 12
ISAKMP:(2026): sending packet to 192.168.200.162 my_port 500 peer_port 500 (R)
MM_KEY_EXCH
ISAKMP:(2026):Sending an IKE IPv4 Packet.
ISAKMP:(2026):Returning Actual lifetime: 28800
ISAKMP: set new node 1956323662 to QM_IDLE
ISAKMP:(2026):Sending NOTIFY RESPONDER_LIFETIME protocol 1
spi 2227348128, message ID = 1956323662
ISAKMP:(2026): sending packet to 192.168.200.162 my_port 500 peer_port 500 (R)
MM_KEY_EXCH
ISAKMP:(2026):Sending an IKE IPv4 Packet.
ISAKMP:(2026):purging node 1956323662
ISAKMP: Sending phase 1 responder lifetime 28800
ISAKMP:(2026):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
ISAKMP:(2026):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
ISAKMP:(2026):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
ISAKMP:(2026):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
ISAKMP (2026): received packet from 192.168.200.162 dport 500 sport 500 Global (R)
QM_IDLE
ISAKMP: set new node 1985749619 to QM_IDLE
ISAKMP:(2026): processing HASH payload. message ID = 1985749619
ISAKMP:(2026): processing SA payload. message ID = 1985749619
ISAKMP:(2026):Checking IPSec proposal 0
ISAKMP: transform 0, ESP_3DES
ISAKMP: attributes in transform:
ISAKMP: group is 2
ISAKMP: encaps is 1 (Tunnel)
ISAKMP: SA life type in seconds
ISAKMP: SA life duration (basic) of 7800
ISAKMP: authenticator is HMAC-SHA
ISAKMP:(2026):atts are acceptable.
IPSEC(validate_proposal_request): proposal part #1
IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 192.168.200.146, remote= 192.168.200.162,
local_proxy= 192.168.9.0/255.255.255.0/0/0 (type=4),
remote_proxy= 192.168.15.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= NONE (Tunnel),
lifedur= 0s and 0kb,
Page 8

All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 8 of 9
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
Crypto mapdb : proxy_match
src addr : 192.168.9.0
dst addr : 192.168.15.0
protocol : 0
src port : 0
dst port : 0
ISAKMP:(2026): processing NONCE payload. message ID = 1985749619
ISAKMP:(2026): processing KE payload. message ID = 1985749619
ISAKMP:(2026): processing ID payload. message ID = 1985749619
ISAKMP:(2026): processing ID payload. message ID = 1985749619
ISAKMP:(2026):QM Responder gets spi
ISAKMP:(2026):Node 1985749619, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
ISAKMP:(2026):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
ISAKMP:(2026): Creating IPSec SAs
inbound SA from 192.168.200.162 to 192.168.200.146 (f/i) 0/ 0
(proxy 192.168.15.0 to 192.168.9.0)
has spi 0xBDE1EBFF and conn_id 0
lifetime of 7800 seconds
outbound SA from 192.168.200.146 to 192.168.200.162 (f/i) 0/0
(proxy 192.168.9.0 to 192.168.15.0)
has spi 0xFD490D63 and conn_id 0
lifetime of 7800 seconds
ISAKMP:(2026): sending packet to 192.168.200.162 my_port 500 peer_port 500 (R) QM_IDLE
ISAKMP:(2026):Sending an IKE IPv4 Packet.
ISAKMP:(2026):Node 1985749619, Input = IKE_MESG_INTERNAL, IKE_GOT_SPI
ISAKMP:(2026):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_R_QM2
IPSEC(key_engine): got a queue event with 1 KMI message(s)
Crypto mapdb : proxy_match
src addr : 192.168.9.0
dst addr : 192.168.15.0
protocol : 0
src port : 0
dst port : 0
IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer
192.168.200.162
IPSEC(policy_db_add_ident): src 192.168.9.0, dest 192.168.15.0, dest_port 0
IPSEC(create_sa): sa created,
(sa) sa_dest= 192.168.200.146, sa_proto= 50,
sa_spi= 0xBDE1EBFF(3185699839),
sa_trans= esp-3des esp-sha-hmac , sa_conn_id= 353
sa_lifetime(k/sec)= (4519827/3600)
IPSEC(create_sa): sa created,
(sa) sa_dest= 192.168.200.162, sa_proto= 50,
sa_spi= 0xFD490D63(4249423203),
sa_trans= esp-3des esp-sha-hmac , sa_conn_id= 354
sa_lifetime(k/sec)= (4519827/3600)
ISAKMP (2026): received packet from 192.168.200.162 dport 500 sport 500 Global (R)
QM_IDLE
ISAKMP:(2026):deleting node 1985749619 error FALSE reason "QM done (await)"
ISAKMP:(2026):Node 1985749619, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
ISAKMP:(2026):Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
IPSEC(key_engine): got a queue event with 1 KMI message(s)
IPSEC(key_engine_enable_outbound): rec'd enable notify from ISAKMP
IPSEC(key_engine_enable_outbound): enable SA with spi 4249423203/50
IPSEC(update_current_outbound_sa): updated peer 192.168.200.162 current outbound sa to
SPI FD490D63
ISAKMP:(2025):purging node -1226010635
ISAKMP:(2025):purging node -605868871
####### Site 2 SRP500 Disconnects the tunnel here using the status page
ISAKMP (2026): received packet from 192.168.200.162 dport 500 sport 500 Global (R)
QM_IDLE
ISAKMP: set new node -528070160 to QM_IDLE
ISAKMP:(2026): processing HASH payload. message ID = -528070160
ISAKMP:(2026): processing DELETE payload. message ID = -528070160
Page 9

All contents are Copyright © 1992-2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Page 9 of 9
ISAKMP:(2026):peer does not do paranoid keepalives.
ISAKMP:(2026):deleting node -528070160 error FALSE reason "Informational (in) state 1"
IPSEC(key_engine): got a queue event with 1 KMI message(s)
IPSEC(key_engine_delete_sas): rec'd delete notify from ISAKMP
IPSEC(key_engine_delete_sas): delete SA with spi 0xFD490D63 proto 50 for 192.168.200.162
IPSEC(delete_sa): deleting SA,
(sa) sa_dest= 192.168.200.146, sa_proto= 50,
sa_spi= 0xBDE1EBFF(3185699839),
sa_trans= esp-3des esp-sha-hmac , sa_conn_id= 353
sa_lifetime(k/sec)= (4519827/3600),
(identity) local= 192.168.200.146, remote= 192.168.200.162,
local_proxy= 192.168.9.0/255.255.255.0/0/0 (type=4),
remote_proxy= 192.168.15.0/255.255.255.0/0/0 (type=4)
IPSEC(update_current_outbound_sa): updated peer 192.168.200.162 current outbound sa to
SPI 0
IPSEC(delete_sa): deleting SA,
(sa) sa_dest= 192.168.200.162, sa_proto= 50,
sa_spi= 0xFD490D63(4249423203),
sa_trans= esp-3des esp-sha-hmac , sa_conn_id= 354
sa_lifetime(k/sec)= (4519827/3600),
(identity) local= 192.168.200.146, remote= 192.168.200.162,
local_proxy= 192.168.9.0/255.255.255.0/0/0 (type=4),
remote_proxy= 192.168.15.0/255.255.255.0/0/0 (type=4)
ISAKMP (2026): received packet from 192.168.200.162 dport 500 sport 500 Global (R)
QM_IDLE
ISAKMP: set new node -1973569393 to QM_IDLE
ISAKMP:(2026): processing HASH payload. message ID = -1973569393
ISAKMP:(2026): processing DELETE payload. message ID = -1973569393
ISAKMP:(2026):peer does not do paranoid keepalives.
ISAKMP:(2026):deleting SA reason "No reason" state (R) QM_IDLE (peer
192.168.200.162)
ISAKMP:(2026):deleting node -1973569393 error FALSE reason "Informational (in) state 1"
ISAKMP: set new node 261530541 to QM_IDLE
ISAKMP:(2026): sending packet to 192.168.200.162 my_port 500 peer_port 500 (R) QM_IDLE
ISAKMP:(2026):Sending an IKE IPv4 Packet.
ISAKMP:(2026):purging node 261530541
ISAKMP:(2026):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
ISAKMP:(2026):Old State = IKE_P1_COMPLETE New State = IKE_DEST_SA
ISAKMP:(2026):deleting SA reason "No reason" state (R) QM_IDLE (peer
192.168.200.162)
ISAKMP:(0):Can't decrement IKE Call Admission Control stat incoming_active since it's
already 0.
ISAKMP: Unlocking peer struct 0x83952688 for isadb_mark_sa_deleted(), count 0
ISAKMP: Deleting peer node by peer_reap for 192.168.200.162: 83952688
ISAKMP:(2026):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
ISAKMP:(2026):Old State = IKE_DEST_SA New State = IKE_DEST_SA
IPSEC(key_engine): got a queue event with 1 KMI message(s)
ISAKMP:(2025):purging SA., sa=8391F804, delme=8391F804
 Loading...
Loading...