Page 1

REFERENCE GUIDE
Cisco Small Business Pro
SPS208G/SPS224G4/SPS2024 Ethernet Switches
Command Line Interface
Page 2

6bZg^XVh=ZVYfjVgiZgh
8^hXdHnhiZbh!>cX#
HVc?dhZ!86
6h^VEVX^[^X=ZVYfjVgiZgh
8^hXdHnhiZbhJH6EiZ#AiY#
H^c\VedgZ
:jgdeZ=ZVYfjVgiZgh
8^hXdHnhiZbh>ciZgcVi^dcVa7K
6bhiZgYVb!I]ZCZi]ZgaVcYh
8^hXd]VhbdgZi]Vc '%%d[[^XZhldgaYl^YZ#6YYgZhhZh!e]dcZcjbWZgh!VcY [VmcjbWZghVgZa^hiZYdci]Z8^hXdLZWh^iZVilll#X^hXd#Xdb$\d$d[[^XZh#
889:!88:CI!8^hXd:dh!8^hXdAjb^c!8^hXdCZmjh!8^hXdHiVY^jbK^h^dc!8^hXdIZaZEgZhZcXZ!8^hXdLZW:m!i]Z8^hXdad\d!98:!VcYLZaXdbZidi]Z=jbVcCZildg`VgZigVYZbVg`h08]Vc\^c\i]ZLVnLZLdg`!
6bZg^XVh=ZVYfjVgiZgh
8^hXdHnhiZbh!>cX#
HVc?dhZ!86
6h^VEVX^[^X=ZVYfjVgiZgh
8^hXdHnhiZbhJH6EiZ#AiY#
H^c\VedgZ
:jgdeZ=ZVYfjVgiZgh
8^hXdHnhiZbh>ciZgcVi^dcVa7K
6bhiZgYVb!I]ZCZi]ZgaVcYh
8^hXd]VhbdgZi]Vc '%%d[[^XZhldgaYl^YZ#6YYgZhhZh!e]dcZcjbWZgh!VcY [VmcjbWZghVgZa^hiZYdci]Z8^hXdLZWh^iZVilll#X^hXd#Xdb$\d$d[[^XZh#
889:!88:CI!8^hXd:dh!8^hXdAjb^c!8^hXdCZmjh!8^hXdHiVY^jbK^h^dc!8^hXdIZaZEgZhZcXZ!8^hXdLZW:m!i]Z8^hXdad\d!98:!VcYLZaXdbZidi]Z=jbVcCZildg`VgZigVYZbVg`h08]Vc\^c\i]ZLVnLZLdg`!
A^kZ!EaVn!VcYAZVgcVcY8^hXdHidgZVgZhZgk^XZbVg`h0VcY6XX ZhhGZ\^higVg!6^gdcZi!6hncXDH!7g^c\^c\i]ZBZZi^c\IdNdj!8ViVanhi!8896!889E!88>:!88>E!88C6!88CE!88HE!88KE!8^hXd!i]Z8^hXd8Zgi^[^ZY
>ciZgcZildg`:meZgiad\d!8^hXd>DH!8^hXdEgZhh!8^hXdHnhiZbh!8^hXdHnhiZbh8Ve^iVa!i]Z8^hXdHnhiZbhad\d!8^hX dJc^in!8daaVWdgVi^dcL^i]djiA^b^iVi^dc!:i]Zg;Vhi!:i]ZgHl^iX]!:kZci8ZciZg!;VhiHiZe!;daadlBZ
7gdlh^c\!;dgbH]VgZ!<^\V9g^kZ!=dbZA^c`!>ciZgcZiFjdi^Zci!>DH!^E]dcZ!^Fj^X`HijYn!>gdcEdgi!i]Z>gdcEdgiad\d!A^\]iHigZVb!A^c`hnh!BZY^VIdcZ!BZZi^c\EaVXZ!BZZi^c\EaVXZ8]^bZHdjcY!B<M!CZildg`Zgh!CZildg`^c\
6XVYZbn!CZildg`GZ\^higVg!E8Cdl!E>M!EdlZgEVcZah!Egd8dccZXi!HXg^eiH]VgZ!HZcYZg7VhZ!HB6GIcZi!HeZXigjb:meZgi!HiVX`L^h Z!I]Z;VhiZhiLVnid>cXgZVhZNdjg>ciZgcZiFjdi^Zci!IgVchEVi]!LZW:m!VcYi]ZLZW:m
ad\dVgZgZ\^hiZgZYigVYZbVg`hd[8^hXdHnhiZbh!>cX#VcY$dg^ihV[[^a^ViZh^ci]ZJc^iZYHiViZhVcYXZgiV^cdi]ZgXdjcig^Zh#
6aadi]ZgigVYZbVg`hbZci^dcZY^ci]^hYdXjbZcidglZWh^iZVgZi]ZegdeZgind[i]Z^ggZheZ Xi^kZdlcZgh#I]ZjhZd[i]ZldgYeVgicZgYdZhcdi^beanVeVg icZgh]^egZaVi^dch]^eWZilZZc8^hXdVcYVcndi]ZgXdbeVcn#%-%.G
6bZg^XVh=ZVYfjVgiZgh
8^hXdHnhiZbh!>cX#
HVc?dhZ!86
6h^VEVX^[^X=ZVYfjVgiZgh
8^hXdHnhiZbhJH6EiZ#AiY#
H^c\VedgZ
:jgdeZ=ZVYfjVgiZgh
8^hXdHnhiZbh>ciZgcVi^dcVa7K
6bhiZgYVb!I]ZCZi]ZgaVcYh
© 2008 Cisco Systems, Inc. All rights reserved. OL-18485-01
Page 3
Chapter 1: Introduction 18
Contents
Overview 18
CLI Command Modes 18
Accessing the Command Line Interface 22
Editing Features 28
Chapter 2: AAA Commands 33
aaa authentication login 33
aaa authentication enable 35
login authentication 36
enable authentication 37
ip http authentication 39
ip https authentication 40
show authentication methods 41
password 43
enable password 44
username 45
show users accounts 46
show privilege 47
Chapter 3: ACL Commands 48
ip access-list 48
permit (ip) 49
deny (IP) 52
mac access-list 56
permit (MAC) 57
deny (MAC) 58
service-policy 60
service-acl 60
show access-lists 61
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 1
Page 4

show interfaces access-lists 62
Chapter 4: ARP Inspection Commands 64
ip arp inspection 64
ip arp inspection vlan 65
ip arp inspection trust 66
ip arp inspection validate 67
ip arp inspection list create 68
ip mac 69
ip arp inspection list assign 70
ip arp inspection logging interval 71
show ip arp inspection 72
Contents
show ip arp inspection list 73
Chapter 5: Address Table Commands 75
bridge address 75
bridge multicast filtering 76
bridge multicast address 77
bridge multicast forbidden address 79
bridge multicast forward-all 80
bridge multicast forbidden forward-all 82
bridge aging time 83
clear bridge 84
port security 85
port security mode 86
port security max 87
show bridge address-table 88
show bridge address-table static 89
show bridge address-table count 91
show bridge multicast address-table 92
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 2
Page 5
show bridge multicast address-table static 94
show bridge multicast filtering 95
show ports security 96
show ports security addresses 98
Chapter 6: Clock Commands 100
clock set 100
clock source 101
clock timezone 102
clock summer-time 103
sntp authentication-key 105
sntp authenticate 106
Contents
sntp port 107
sntp trusted-key 108
sntp client poll timer 109
sntp broadcast client enable 110
sntp anycast client enable 111
sntp client enable 112
sntp client enable (Interface) 113
sntp unicast client enable 114
sntp unicast client poll 115
sntp server 116
show clock 117
show sntp configuration 119
show sntp status 120
Chapter 7: Configuration and Image File Commands 122
copy 122
delete startup-config 125
show running-config 126
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 3
Page 6

show startup-config 127
Chapter 8: DHCP Commands 129
ip dhcp snooping 129
ip dhcp snooping vlan 130
ip dhcp snooping trust 131
ip dhcp information option allowed-untrusted 132
ip dhcp snooping verify 133
ip dhcp snooping database 134
ip dhcp snooping database update-freq 135
ip dhcp snooping binding 136
clear ip dhcp snooping database 137
Contents
show ip dhcp snooping 138
show ip dhcp snooping binding 139
Chapter 9: DHCP Relay Commands 141
ip dhcp relay enable (global) 141
ip dhcp relay enable (interface) 142
ip dhcp relay address 143
show ip dhcp relay 144
Chapter 10: DHCP Option 82 Commands 145
ip dhcp information option 145
show ip dhcp information option 146
Chapter 11: DHCP Auto-configuration 147
ip dhcp autoconfig 147
ip dhcp autoconfig file 148
show ip dhcp autoconfig 149
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 4
Page 7
Chapter 12: Ethernet Configuration Commands 150
interface ethernet 150
interface range ethernet 151
shutdown 152
description 153
speed 154
duplex 155
negotiation 156
port jumbo-frame 157
show system flowcontrol 158
flowcontrol 159
mdix 160
Contents
back-pressure 161
port jumbo-frame 162
sfp speed 163
clear counters 164
set interface active 165
show interfaces configuration 166
show interfaces status 167
show interfaces advertise 169
show interfaces description 170
show interfaces counters 171
show ports jumbo-frame 174
port storm-control broadcast enable 175
port storm-control broadcast rate 176
port storm-control include-multicast 177
port storm-control unknown-unicast fastethernet enable 178
port storm-control unknown-unicast fastethernet rate 179
show ports storm-control 180
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 5
Page 8
Chapter 13: GVRP Commands 182
Contents
gvrp enable (Global) 182
gvrp enable (Interface) 183
garp timer 184
gvrp vlan-creation-forbid 185
gvrp registration-forbid 186
clear gvrp statistics 187
show gvrp configuration 188
show gvrp statistics 189
show gvrp error-statistics 190
Chapter 14: IGMP Snooping Commands 192
ip igmp snooping (global) 192
ip igmp snooping (Interface) 193
ip igmp snooping mrouter 194
ip igmp snooping querier enable 195
ip igmp snooping host-time-out 196
ip igmp snooping mrouter-time-out 197
ip igmp snooping leave-time-out 198
ip igmp snooping multicast-tv 199
ip igmp snooping map cpe vlan 200
show ip igmp snooping mrouter 201
show ip igmp snooping interface 202
show ip igmp snooping groups 203
show ip igmp snooping multicast-tv 205
show ip igmp snooping cpe vlans 206
Chapter 15: IP Address Commands 208
ip address 208
ip address dhcp 209
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 6
Page 9

Contents
renew dhcp 211
ip default-gateway 212
show ip interface 213
arp 214
arp timeout 215
clear arp-cache 216
show arp 217
ip domain-lookup 218
ip domain-name 219
ip name-server 220
ip host 221
clear host 222
clear host dhcp 223
show hosts 224
Chapter 16: IP Source Guard Commands 226
ip source-guard (global) 226
ip source-guard (interface) 227
ip source-guard binding 228
ip source-guard tcam retries-freq 229
show ip source-guard configuration 230
show ip source-guard status 231
show ip source-guard inactive 233
Chapter 17: LACP Commands 235
lacp system-priority 235
lacp port-priority 236
lacp timeout 237
show lacp ethernet 238
show lacp port-channel 240
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 7
Page 10

Chapter 18: Line Commands 242
Contents
line 242
speed 243
exec-timeout 244
show line 245
Chapter 19: Management ACL Commands 247
management access-list 247
management access-class 248
permit (management) 249
deny (management) 251
show management access-list 252
show management access-class 253
Chapter 20: PHY Diagnostics Commands 254
test copper-port tdr 254
show copper-ports tdr 255
show copper-ports cable-length 256
show fiber-ports optical-transceiver 257
Chapter 21: Port Channel Commands 260
interface port-channel 260
interface range port-channel 261
channel-group 262
show interfaces port-channel 263
Chapter 22: Port Monitor Commands 265
port monitor 265
show ports monitor 266
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 8
Page 11

Chapter 23: QoS Commands 268
qos 268
show qos 269
class-map 270
show class-map 271
match 272
policy-map 273
class 274
show policy-map 276
trust 277
set 279
police 280
Contents
qos aggregate-policer 281
show qos aggregate-policer 283
police aggregate 284
wrr-queue bandwidth 285
wrr-queue cos-map 286
priority-queue out num-of-queues 288
traffic-shape 289
rate-limit (Ethernet) 290
show qos interface 291
qos wrr-queue threshold 293
qos map policed-dscp 295
qos map dscp-queue 296
qos map dscp-dp 297
qos trust (Global) 298
qos trust (Interface) 299
qos cos 300
qos dscp-mutation 301
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 9
Page 12

qos map dscp-mutation 302
show qos map 303
Chapter 24: RADIUS Commands 306
Contents
radius-server host 306
radius-server key 308
radius-server retransmit 309
radius-server source-ip 310
radius-server timeout 311
radius-server deadtime 312
show radius-servers 313
Chapter 25: RMON Commands 314
show rmon statistics 314
rmon collection history 317
show rmon collection history 318
show rmon history 319
rmon alarm 323
show rmon alarm-table 325
show rmon alarm 326
rmon event 329
show rmon events 330
show rmon log 331
rmon table-size 333
Chapter 26: SNMP Commands 334
snmp-server community 334
snmp-server view 336
snmp-server group 337
snmp-server user 339
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 10
Page 13

Contents
snmp-server filter 341
snmp-server host 342
snmp-server v3-host 344
snmp-server engineID local 346
snmp-server enable traps 348
snmp-server trap authentication 349
snmp-server contact 350
snmp-server location 351
snmp-server set 352
show snmp 353
show snmp engineID 355
show snmp views 355
show snmp groups 356
show snmp filters 358
show snmp users 359
Chapter 27: RSA and Certificate Commands 361
crypto certificate generate 361
crypto key generate dsa 363
crypto key generate rsa 364
Chapter 28: Spanning Tree Commands 365
spanning-tree 365
spanning-tree mode 366
spanning-tree forward-time 367
spanning-tree hello-time 368
spanning-tree max-age 369
spanning-tree priority 370
spanning-tree disable 371
spanning-tree cost 372
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 11
Page 14

Contents
spanning-tree port-priority 373
spanning-tree portfast 374
spanning-tree link-type 375
spanning-tree pathcost method 376
spanning-tree bpdu 377
spanning-tree guard root 378
clear spanning-tree detected-protocols 379
spanning-tree mst priority 380
spanning-tree mst max-hops 381
spanning-tree mst port-priority 382
spanning-tree mst cost 383
spanning-tree mst configuration 385
instance (mst) 386
name (mst) 387
revision (mst) 388
show (mst) 389
exit (mst) 390
abort (mst) 391
show spanning-tree 392
Chapter 29: SSH Commands 403
ip ssh port 403
ip ssh server 404
ip ssh pubkey-auth 405
crypto key pubkey-chain ssh 406
user-key 407
key-string 408
show ip ssh 410
show crypto key pubkey-chain ssh 411
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 12
Page 15

show crypto key mypubkey 412
crypto certificate request 413
crypto certificate import 415
crypto certificate export 417
show crypto certificate mycertificate 418
Chapter 30: Syslog Commands 420
logging on 420
logging 421
logging console 422
logging buffered 423
logging buffered size 424
Contents
clear logging 425
logging file 426
clear logging file 427
aaa logging 428
file-system logging 429
management logging 430
show logging 431
show logging file 432
show syslog-servers 434
Chapter 31: System Management Commands 436
ping 436
traceroute 438
telnet 441
resume 445
reload 446
hostname 447
service cpu-utilization 448
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 13
Page 16

show cpu utilization 449
show users 450
show sessions 451
show system 452
show version 454
show system tcam utilization 455
Chapter 32: TACACS+ Commands 456
tacacs-server host 456
tacacs-server key 458
tacacs-server timeout 459
tacacs-server source-ip 460
Contents
show tacacs 461
Chapter 33: User Interface Commands 463
login 463
configure 464
exit (configuration) 464
exit(EXEC) 465
end 466
help 467
history 468
history size 469
terminal history 470
terminal history size 471
terminal datadump 472
debug-mode 473
show history 474
do 475
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 14
Page 17
Chapter 34: VLAN Commands 477
switchport protected 477
switchport protected-port 478
switchport protected-port fastethernet 479
vlan database 480
vlan 481
default-vlan vlan 482
interface vlan 483
interface range vlan 484
name 485
switchport mode 486
switchport protected 487
Contents
switchport access vlan 488
switchport access multicast-tv vlan 489
switchport trunk allowed vlan 490
switchport trunk native vlan 491
switchport general allowed vlan 492
switchport general pvid 494
switchport general ingress-filtering disable 495
switchport general acceptable-frame-type tagged-only 496
switchport customer vlan 497
switchport customer multicast-tv vlan 498
switchport forbidden vlan 499
show interfaces protected-ports 500
show protected-ports fastethernet 501
show vlan 502
show vlan multicast-tv 503
show interfaces switchport 504
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 15
Page 18

Chapter 35: Web Server Commands 506
Contents
ip http server 506
ip http port 507
ip http exec-timeout 508
ip https server 509
ip https port 510
ip https exec-timeout 511
ip https certificate 512
show ip http 513
show ip https 514
Chapter 36: 802.1x Commands 516
aaa authentication dot1x 516
dot1x system-auth-control 517
dot1x port-control 518
dot1x re-authentication 519
dot1x timeout re-authperiod 520
dot1x re-authenticate 521
dot1x timeout quiet-period 522
dot1x timeout tx-period 523
dot1x max-req 524
dot1x timeout supp-timeout 525
dot1x timeout server-timeout 527
show dot1x 528
show dot1x users 531
show dot1x statistics 532
Advanced Features 535
dot1x auth-not-req 535
dot1x multiple-hosts 536
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 16
Page 19

dot1x radius-attributes vlan 537
dot1x single-host-violation 538
dot1x bpdu 539
show dot1x bpdu 541
dot1x guest-vlan 542
dot1x guest-vlan enable 543
dot1x mac-authentication 544
show dot1x advanced 545
Appendix A: Alias Names 547
Contents
Alias Name Support 547
Appendix B: Where to Go From Here 548
Product Resources 548
Related Documentation 548
Appendix C: Additional Information 549
Regulatory Compliance and Safety Information 549
Warranty 549
End User License Agreement (EULA) 549
Appendix D: Support Contacts 550
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 17
Page 20

Introduction
Overview
This document describes the Command Line Interface (CLI) used to manage the
Linksys SPS208G, SPS224G4, and SPS2024 switches. Unless noted otherwise,
all of the CLI commands in this document apply to all three switches.
This chapter describes the CLI command modes, how to access the CLI, and the
CLI command editing features.
1
CLI Command Modes
For greater ease of use, the Command Line Interface (CLI) is divided into four
command modes arranged hierarchically by privilege level. The command modes
are (in the order in which they are accessed):
• User EXEC mode (lowest privilege)
• Privileged EXEC mode
• Global Configuration mode
• Interface Configuration mode (highest privilege)
Each command mode has its own unique console prompt and set of CLI
commands. Entering a question mark at the console prompt displays a list of
available commands for the current mode. Specific commands are used to switch
from one mode to another.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 18
Page 21

Introduction
CLI Command Modes
1
User EXEC Mode
This is the initial mode after system login (except for users who are defined as
privileged users; refer to “
tasks that do not change the configuration, such as performing basic tests and
listing system information.
The user-level prompt consists of the Switch host name followed by the angle
bracket >:
Console>
The default host name is Console unless it is changed via the hostname command
in Global Configuration mode.
To access the next higher mode (Privileged EXEC mode), use the enable
command and enter a password when prompted.
Privileged EXEC Mode
”). User EXEC mode is used for
Privileged EXEC Mode
Privileged EXEC mode is password-protected to prevent unauthorized use, as
many of its commands set operating system parameters. The password is not
displayed on the screen and is case-sensitive.
Privileged users start in Privileged EXEC mode. To enter this mode from User
EXEC mode, follow these steps:
STEP 1 At the prompt enter the enable command and press Enter. A password prompt is
displayed.
STEP 2 Enter the password and press Enter. (For security purposes, each character in the
password is replaced by *). The Privileged EXEC mode prompt, consisting of the
Switch host name followed by, is displayed.
Console#
To return from the Privileged EXEC mode to the User EXEC mode, use the disable
command.
The following example illustrates how to access Privileged EXEC mode and then
return to User EXEC mode:
Console> enable
Enter Password: ******
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 19
Page 22

Introduction
CLI Command Modes
1
Console#
Console# disable
Console>
Global Configuration Mode
The Global Configuration mode is used to configure features at the system level,
and not at the interface level.
To access Global Configuration mode from Privileged EXEC mode, enter the
configure command at the Privileged EXEC mode prompt and press Enter. The
Global Configuration mode prompt, consisting of the device host name followed
by (config)#, is displayed:
Console(config)#
Use any of the following commands to return from Global Configuration mode to
the Privileged EXEC mode:
exit
end
Ctrl+Z
The following example shows how to access Global Configuration mode and
return to Privileged EXEC mode:
Console#
Console# configure
Console(config)# exit
Console#
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 20
Page 23
Introduction
CLI Command Modes
1
Interface Configuration Mode
Interface Configuration mode commands perform operations on specific
interfaces. This mode is divided into the following submodes, each with a specific
function:
• Line Interface — Contains commands used to configure the management
connections. These include commands such as line timeout settings, etc.
The line Global Configuration mode command is used to enter the Line
Configuration command mode.
• VLAN Database — Contains commands used to create a VLAN as a whole.
The vlan database Global Configuration mode command is used to enter
the VLAN Database Interface Configuration mode.
• Management Access List — Contains commands used to define
management access-lists. The management access-list Global
Configuration mode command is used to enter the Management Access
List Configuration mode.
• Ethernet — Contains commands used to manage port configuration. The
interface ethernet Global Configuration mode command is used to enter the
Interface Configuration mode.
• Port Channel — Contains commands used to configure port-channels; for
example, assigning ports to a port-channel. Most of these commands are
the same as the commands in the Ethernet interface mode, and are used to
manage the member ports as a single entity. The interface port-channel
Global Configuration mode command is used to enter the Port Channel
Interface Configuration mode.
• SSH Public Key-chain — Contains commands used to manually specify
other device SSH public keys. The crypto key pubkey-chain ssh Global
Configuration mode command is used to enter the SSH Public Key-chain
Configuration mode.
• QoS — Contains commands related to service definitions. The qos Global
Configuration mode command is used to enter the QoS services
configuration mode.
• MAC Access-List — Configures conditions required to allow traffic based
on MAC addresses. The mac access-list Global Configuration mode
command is used to enter the MAC access-list configuration mode.
To return from any Interface Configuration mode to the Global Configuration mode,
use the exit command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 21
Page 24

Introduction
Accessing the Command Line Interface
Accessing the Command Line Interface
The Command Line Interface (CLI) can be accessed from a terminal or computer
by performing one of the following tasks:
• Running a terminal application, such as HyperTerminal, on a computer that is
directly connected to the Switch’s console port,
—or—
• Running a telnet session from a command prompt on a computer with a
network connection to the Switch.
If access is via a telnet connection, ensure that the following conditions are met
before using CLI commands:
• The Switch has a defined IP address.
1
• Corresponding management access is granted.
• The workstation used to access the Switch is connected to the Switch.
Using HyperTerminal over the Console Interface
NOTE When using HyperTerminal with Microsoft® Windows® 2000, ensure that
Windows® 2000 Service Pack 2 or later is installed on your computer. The arrow
keys will not function properly using HyperTerminal’s VT100 emulation in
Windows® 2000 prior to Service Pack 2. For information on Windows® 2000
service packs, go to www.microsoft.com.
The Switch’s RS-232 serial console port provides a direct connection to a
computer’s serial port using a standard DB-9 null-modem or crossover cable.
Once the computer and Switch are connected, run a terminal application such as
HyperTerminal to access the Command Line Interface.
To access the Command Line Interface using the HyperTerminal application,
perform the following steps:
STEP 1 Click the Start button.
STEP 2 Select All Programs > Accessories > Communications > HyperTerminal.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 22
Page 25

Introduction
Accessing the Command Line Interface
Figure1 Start > All Programs > Accessories > Communications >
HyperTerminal
STEP 3 Enter a name for this connection. Select an icon for the application, then click OK.
Figure 2 HyperTerminal Connection Description Screen
1
STEP 4 Select a port to communicate with the switch. Select COM1 or COM2.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 23
Page 26
Introduction
Accessing the Command Line Interface
Fig ure 3 H yp er Term in al Co nn ec t To Sc re en
1
STEP 5 Set the serial port settings as follows, then click OK.
• Bits per Second: 38400
• Databits: 8
• Parity: one
• Stop bits: 1
• Flow control: None
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 24
Page 27
Introduction
Accessing the Command Line Interface
Figure 4 HyperTerminal Properties Screen
1
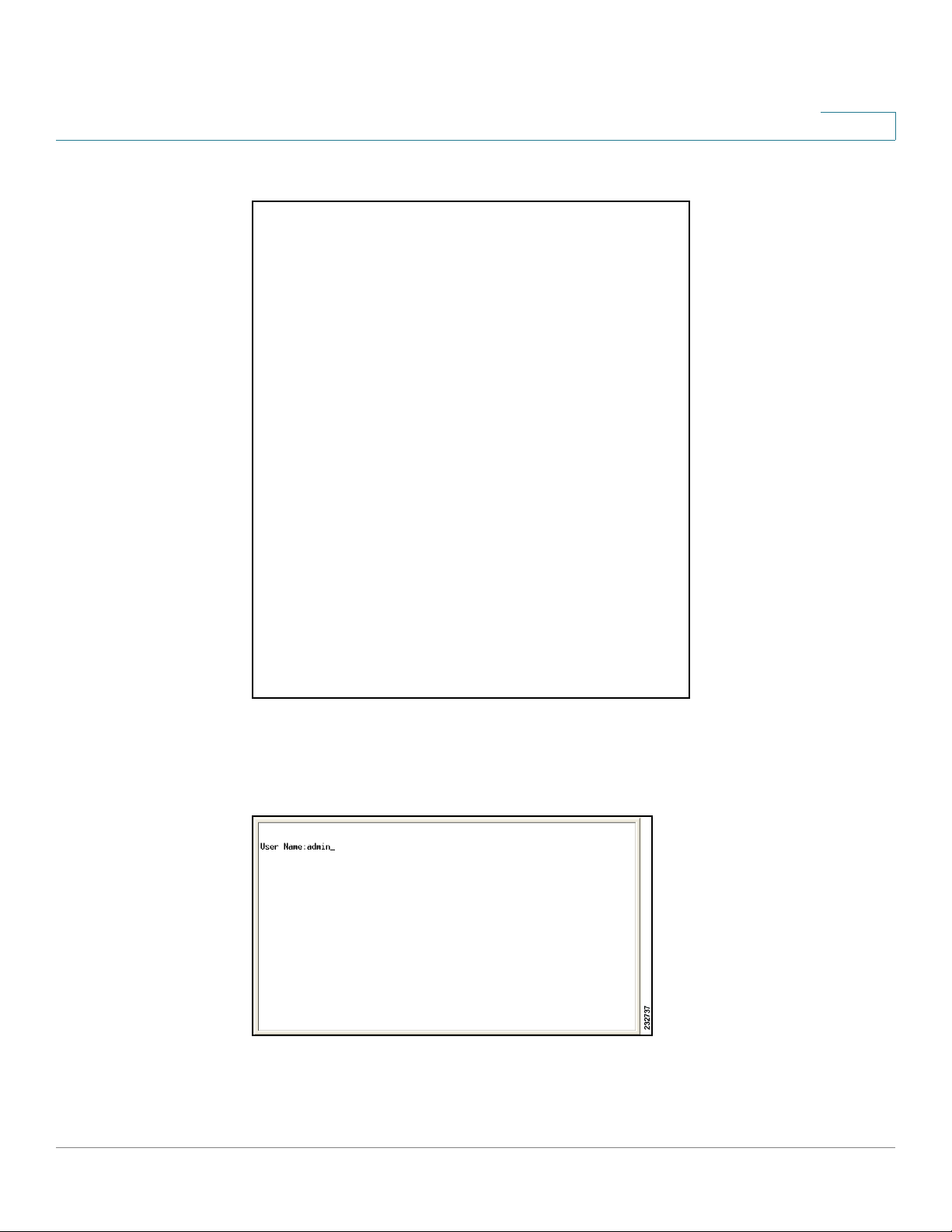
STEP 6 When the
and press Enter.
Figure 5 Command Line User Name Prompt
The console# prompt is displayed. This prompt is where you enter CLI commands.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 25
Command Line Interface
appears, enter admin at the
User Name
prompt
Page 28

Introduction
Accessing the Command Line Interface
Figure 6 Command Line
You can now enter CLI commands to manage the Switch. For detailed information
on CLI commands, refer to the appropriate chapter(s) of this Reference Guide.
1
Using Telnet over an Ethernet Interface
Telnet provides a method of connecting to the Command Line Interface using TCP/
IP over a standard Ethernet connection. A telnet session can be established in
HyperTerminal or from a command prompt.
To establish a telnet session from the command prompt, perform the following
steps:
STEP 1 Click Start, then select All Programs > Accessories > Command Prompt to open a
command prompt.
Figure 7 Start > All Programs > Accessories > Command Prompt
STEP 2 At the prompt, enter telnet 192.168.1.254, then press Enter.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 26
Page 29

Introduction
Accessing the Command Line Interface
Figure 8 Command Prompt
1
STEP 3 The
STEP 4 The console# prompt is displayed. This prompt is where you enter CLI commands.
Command Line Interface
prompt and press Enter.
Figure 9 Command Line User Name Prompt
Figure 10 Command Line
will be displayed. Enter admin at the
User Name
You can now enter CLI commands to manage the Switch. For detailed information
on CLI commands, refer to the appropriate chapter(s) of this Reference Guide.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 27
Page 30
Introduction
Editing Features
Editing Features
Entering Commands
A CLI command is a series of keywords and arguments. Keywords identify a
command, and arguments specify configuration parameters. For example, in the
command show interfaces status ethernet e11,
keywords,
specifies the port.
To enter commands that require parameters, enter the required parameters after
the command keyword. For example, to set a password for the administrator,
enter:
Console(config)# username admin password alansmith
ethernet
show, interfaces
is an argument that specifies the interface type, and
and
status
e1 1
1
are
When working with the CLI, the command options are not displayed. The
command is not selected from a menu, but is manually entered. To see what
commands are available in each mode or within an Interface Configuration, the CLI
does provide a method of displaying the available commands, the command
syntax requirements and in some instances parameters required to complete the
command. The standard command to request help is ?.
There are two instances where help information can be displayed:
• Keyword lookup — The character ? is entered in place of a command. A list
of all valid commands and corresponding help messages are is displayed.
• Partial keyword lookup — If a command is incomplete and or the character
? is entered in place of a parameter, the matched keyword or parameters
for this command are displayed.
To assist in using the CLI, there is an assortment of editing features. The following
features are described:
• Terminal Command Buffer
• Command Completion
• Nomenclature
• Keyboard Shortcuts
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 28
Page 31

Introduction
Editing Features
1
Term inal C o mmand Buffe r
Every time a command is entered in the CLI, it is recorded on an internally
managed Command History buffer. Commands stored in the buffer are maintained
on a First In First Out (FIFO) basis. These commands can be recalled, reviewed,
modified, and reissued. This buffer is not preserved across device resets.
Keyword Description
Up-Arrow key
Ctrl+P
Down-Arrow key Returns to more recent commands in the
By default, the history buffer system is enabled, but it can be disabled at any time.
For more information on enabling or disabling the history buffer, refer to the history
command.
There is a standard default number of commands that are stored in the buffer. The
standard number of 10 commands can be increased to 216. By configuring 0, the
effect is the same as disabling the history buffer system. For more information on
configuring the command history buffer, refer to the history size command.
To display the history buffer, refer to the show history command.
Recalls commands in the history buffer,
beginning with the most recent command.
Repeat the key sequence to recall
successively older commands.
history buffer after recalling commands
with the up-arrow key. Repeating the key
sequence will recall successively more
recent commands.
Negating the Effect of Commands
For many configuration commands, the prefix keyword no can be entered to
cancel the effect of a command or reset the configuration to the default value. This
Reference Guide provides a description of the negation effect for each CLI
command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 29
Page 32

Introduction
Editing Features
1
Command Completion
If the command entered is incomplete, invalid or has missing or invalid parameters,
then the appropriate error message is displayed. This assists in entering the
correct command. By pressing Ta b after an incomplete command is entered, the
system will attempt to identify and complete the command. If the characters
already entered are not enough for the system to identify a single matching
command, press ? to display the available commands matching the characters
already entered.
Nomenclature
Within the CLI, Ethernet ports are denoted as follows:
Switch
SPS208G e1 through e8 g1 through g2
SPS224G4 e1 through e24 g1 through g
PS2024 n/a g1 through g24
S
The ports may be described on an individual basis or within a range. Use format
port number-port number to specify a set of consecutive ports and port number,
port number to indicate a set of non-consecutive ports. For example, g1- 3 stands
for Gigabit Ethernet ports 1, 2, and 3, and g1, 5 stands for Gigabit Ethernet ports 1
and 5.
10/100 Ethernet
ports
Gigabit Ethernet
ports
4
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 30
Page 33

Introduction
Editing Features
1
Keyboard Shortcuts
The CLI has a range of keyboard shortcuts to assist in editing the CLI commands.
The following table describes the CLI shortcuts.
Keyboard Key
Up-arrow Recalls commands from the history buffer,
Down-arrow Returns the most recent commands from the
Ctrl+A Moves the cursor to the beginning of the
Ctrl+E Moves the cursor to the end of the command line.
Ctrl+Z / End Returns back to the Privileged EXEC mode from
Backspace Deletes one character left to the cursor position.
Description
beginning with the most recent command. Repeat
the key sequence to recall successively older
commands.
history buffer after recalling commands with the
up arrow key. Repeating the key sequence will
recall successively more recent commands.
command line.
any configuration mode.
CLI Command Conventions
When entering commands there are certain command entry standards that apply
to all commands. The following table describes the command conventions.
Convention
[ ] In a command line, square brackets indicate an
{ } In a command line, curly brackets indicate a
parameter Italic text indicates a parameter.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 31
Description
option entry.
selection of compulsory parameters separated
the | character. One option must be selected. For
example, flowcontrol {auto|on|off} means that for
the flowcontrol command, either auto, on, or off
must be selected.
Page 34

Introduction
Editing Features
1
Convention
press key Names of keys to be pressed are shown in bold.
Ctrl+F4 Keys separated by the + character are to be
Screen Display Fixed-width font indicates CLI prompts, CLI
all When a parameter is required to define a range of
Description
pressed simultaneously on the keyboard
commands entered by the user, and system
messages displayed on the console.
ports or parameters and all is an option, the
default for the command is all when no parameters
are defined. For example, the command interface
range port-channel has the option of either
entering a range of channels, or selecting all.
When the command is entered without a
parameter, it automatically defaults to all.
Copying and Pasting Text
Up to 1000 lines of text (or commands) can be copied and pasted into the device.
NOTE It is the user’s responsibility to ensure that the text copied into the device consists
of legal commands only.
This feature is dependent on the baud rate of the device.
When copying and pasting commands from a configuration file, make sure that the
following conditions exist:
• A device Configuration mode has been accessed.
• The commands contain no encrypted data, like encrypted passwords or
keys. Encrypted data cannot be copied and pasted into the device.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 32
Page 35

AAA Commands
aaa authentication login
The aaa authentication login Global Configuration mode command defines login
authentication. To restore defaults, use the no form of this command.
Syntax
2
aaa authentication login {default |
no aaa authentication login {default |
list-name} method1 [method2...
list-name
}
Parameters
•
default — Uses the listed authentication methods that follow this argument
as the default list of methods when a user logs in.
•
list-name
methods activated when a user logs in. (Range: 1-12 characters)
•
method1 [method2...
Keyword Description
enable Uses the enable password for authentication.
line Uses the line password for authentication.
local Uses the local username database password
— Character string used to name the list of authentication
] — Specify at least one method from the following list:
for authentication.
]
none Uses no authentication.
radius Uses the list of all RADIUS servers for
authentication.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 33
Page 36

AAA Commands
aaa authentication login
NOTE If the authentication method is not defined, console users will be able to log in
2
Keyword Description
tacacs Uses the list of all TACACS+ servers for
authentication.
Default Configuration
The local user database is checked. This has the same effect as the command aaa
authentication login
without any authentication check.
list-name local.
Command Mode
Global Configuration mode
User Guidelines
The default and optional list names created with the aaa authentication login
command are used with the login authentication command.
Create a list by entering the aaa authentication login
for a particular protocol, where
list. The
algorithm tries, in the given sequence.
The additional methods of authentication are used only if the previous method
returns an error, not if it fails. To ensure that the authentication succeeds even if all
methods return an error, specify none as the final method in the command line.
method
argument identifies the list of methods that the authentication
list-name
is any character string used to name this
list-name method
command
Example
The following example configures the authentication login:
Console(config)# aaa authentication login default radius tacacs
enable line local none
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 34
Page 37

AAA Commands
aaa authentication enable
aaa authentication enable
The aaa authentication enable Global Configuration mode command defines
authentication method lists for accessing higher privilege levels. To restore
defaults, use the no form of this command.
Syntax
2
aaa authentication enable {default |
no aaa authentication enable default
list-name} method1 [method2...
Parameters
•
default — Uses the listed authentication methods that follow this argument
as the default list of methods, when using higher privilege levels.
•
list-name
methods activated, when using access higher privilege levels. (Range: 1-12
characters)
•
method1 [method2...
Keyword Description
enable Uses the enable password for authentication.
line Uses the line password for authentication.
none Uses no authentication.
— Character string used to name the list of authentication
] — Specify at least one method from the following list:
]
radius Uses the list of all RADIUS servers for
authentication.
tacacs Uses the list of all TACACS+ servers for
authentication.
Default Configuration
If the default list is not set, only the enable password is checked. This has the
same effect as the command aaa authentication enable default enable.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 35
Page 38

AAA Commands
login authentication
2
On the console, the enable password is used if it exists. If no password is set, the
process still succeeds. This has the same effect as using the command aaa
authentication enable default enable none.
Command Mode
Global Configuration mode
User Guidelines
The default and optional list names created with the aaa authentication enable
command are used with the enable authentication command.
The additional methods of authentication are used only if the previous method
returns an error, not if it fails. To ensure that the authentication succeeds even if all
methods return an error, specify none as the final method in the command line.
All aaa authentication enable
TACACS+ server include the username $enabx$., where x is the requested
privilege level.
Example
The following example sets the enable password for authentication when
accessing higher privilege levels.
Console(config)# aaa authentication enable default enable
login authentication
The login authentication Line Configuration mode command specifies the login
authentication method list for a remote telnet or console. To restore the default
configuration specified by the aaa authentication login command, use the no form
of this command.
default
requests sent by the device to a RADIUS or
Syntax
login authentication {default |
no login authentication
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 36
list-name
}
Page 39

AAA Commands
enable authentication
Parameters
default — Uses the default list created with the aaa authentication login
•
command.
•
list-name —
command.
Uses the indicated list created with the aaa authentication login
Default Configuration
Uses the default set with the command aaa authentication login.
Command Mode
Line Configuration mode
2
User Guidelines
To change (or rename) an authentication method, use the negate command and
create a new rule with the new method name.
Example
The following example specifies the default authentication method for a console.
Console(config)# line console
Console(config-line)# login authentication default
enable authentication
The enable authentication Line Configuration mode command specifies the
authentication method list when accessing a higher privilege level from a remote
Telnet or console. To restore the default configuration specified by the aaa
authentication enable command, use the no form of this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 37
Page 40

AAA Commands
enable authentication
2
Syntax
enable authentication {default |
no enable authentication
list-name
}
Parameters
•
default — Uses the default list created with the aaa authentication enable
command.
•
list-name
enable command.
— Uses the indicated list created with the aaa authentication
Default Configuration
Uses the default set with the aaa authentication enable command.
Command Mode
Line Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example specifies the default authentication method when
accessing a higher privilege level from a console.
Console(config)# line console
Console(config-line)# enable authentication default
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 38
Page 41

AAA Commands
ip http authentication
ip http authentication
The ip http authentication Global Configuration mode command specifies
authentication methods for HTTP server users. To restore the default
configuration, use the no form of this command.
Syntax
2
ip http authentication
no ip http authentication
method1 [method2...
]
Parameters
•
method1 [method2...
Keyword Description
local Uses the local username database for
authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for
authentication.
tacacs Uses the list of all TACACS+ servers for
authentication.
] — Specify at least one method from the following list:
Default Configuration
The local user database is checked. This has the same effect as the command ip
http authentication
local
.
Command Mode
Global Configuration mode
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 39
Page 42

AAA Commands
ip https authentication
User Guidelines
The additional methods of authentication are used only if the previous method
returns an error, not if it fails. To ensure that the authentication succeeds even if all
methods return an error, specify none as the final method in the command line.
Example
The following example configures the HTTP authentication.
Console(config)# ip http authentication radius tacacs local none
ip https authentication
2
The ip https authentication Global Configuration mode command specifies
authentication methods for HTTPS server users. To restore the default
configuration, use the no form of this command.
Syntax
ip https authentication
no ip https authentication
method1 [method2...
]
Parameters
•
method1 [method2...
Keyword Description
local Uses the local username database for
authentication.
none Uses no authentication.
] — Specify at least one method from the following list:
radius Uses the list of all RADIUS servers for
authentication.
tacacs Uses the list of all TACACS+ servers for
authentication.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 40
Page 43

AAA Commands
show authentication methods
2
Default Configuration
The local user database is checked. This has the same effect as the command ip
https authentication
Command Mode
Global Configuration mode
User Guidelines
The additional methods of authentication are used only if the previous method
returns an error, not if it fails. To ensure that the authentication succeeds even if all
methods return an error, specify none as the final method in the command line.
local
.
Example
The following example configures HTTPS authentication.
Console(config)# ip https authentication radius tacacs local
none
show authentication methods
The show authentication methods Privileged EXEC mode command displays
information about the authentication methods.
Syntax
show authentication methods
Default Configuration
This command has no default configuration.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 41
Page 44

AAA Commands
show authentication methods
2
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example displays the authentication configuration.
Console# show authentication methods
Login Authentication Method Lists
--------------------------------Default: Radius, Local, Line
Enable Authentication Method Lists
---------------------------------Default: Radius, Enable
Console_Enable: Enable, None
LineLogin Method ListEnable Method List
----------------------------------------------ConsoleConsole_LoginConsole_Login
TelnetDefaultDefault
SSHDefaultDefault
http: Radius, Local
https: Radius, Local
dot1x: Radius
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 42
Page 45

AAA Commands
password
password
2
The password Line Configuration mode command specifies a password on a line.
To remove the password, use the no form of this command.
Syntax
password
no password
password
[encrypted]
Parameters
password
•
— Password for this level. (Range: 1-159 characters)
• encrypted — Encrypted password to be entered, copied from another
device configuration.
Default Configuration
No password is defined.
Command Mode
Line Configuration mode
User Guidelines
If a password is defined as encrypted, the required password length is 32
characters.
Example
The following example specifies the password called ‘secret’ on a console.
Console(config)# line console
Console(config-line)# password secret
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 43
Page 46

AAA Commands
enable password
enable password
The enable password Global Configuration mode command sets a local
password to control access to user and privilege levels. To remove the password
requirement, use the no form of this command.
Syntax
2
enable password [level
no enable password [level
level] password
level]
encrypted]
Parameters
•
password —
•
level —
(Range: 1-15).
Password for this level. (Range: 1-159 characters)
Level for which the password applies. If not specified the level is 15
• encrypted — Encrypted password entered, copied from another device
configuration.
Default Configuration
No enable password is defined.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets a local level 15 password called ‘secret’ to control
access to user and privilege levels.
Console(config)# enable password secret level 15
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 44
Page 47

AAA Commands
username
username
2
The username Global Configuration mode command creates a user account in the
local database. To remove a user name, use the no form of this command.
Syntax
username
no username
name
name
[password
password
] [evel
level
] [encrypted]
Parameters
name —
•
•
password
characters)
•
level
automatically set to 1.
The name of the user. (Range: 1-20 characters)
— The authentication password for the user. (Range: 1-159
— The user level (Range: 1-15). If a level is not specified, the level is
• encrypted — Encrypted password entered, copied from another device
configuration.
Default Configuration
No user is defined.
Command Mode
Global Configuration mode
User Guidelines
User account can be created without a password.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 45
Page 48

AAA Commands
show users accounts
Example
The following example configures a user named ‘bob’ with password ‘lee’ and user
level 15 to the system.
Console(config)# username bob password lee level 15
show users accounts
The show users accounts Privileged EXEC mode command displays information
about the users local database.
Syntax
2
show users accounts
Default Configuration
No default configuration for this command.
Command Mode
Privileged EXEC mode
User Guidelines
User account can be created without a password.
Example
The following example displays information about the users local database.
Console# show users accounts
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 46
Page 49

AAA Commands
show privilege
show privilege
2
Username Privilege
-------- --------Bob 15
Robert 15
Smith 15
To display your current level of privilege, use the show privilege command in EXEC
mode.
Syntax
show privilege
Parameters
This command has no arguments or key words
Default Configuration
This command has no default configuration.
Command Mode
EXEC
Example
Console# show privilege
Current privilege level is 15
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 47
Page 50

ACL Commands
ip access-list
The ip access-list Global Configuration mode command enables the IP-Access
Configuration mode and creates Layer 3 ACLs. To delete an ACL, use the no form
of this command.
3
Syntax
ip access-list
no ip access-list access-list-name
Parameters
access-list-name
•
characters) Use “” for empty string.
Default Configuration
The default for all ACLs is deny-all.
Command Mode
Global Configuration mode
access-list-name
— Specifies the name of the ACL. (Range: 0-32
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 48
Page 51

ACL Commands
permit (ip)
permit (ip)
3
Example
The following example shows how to create an IP ACL.
Console(config)# ip access-list ip-acl1
Console(config-ip-al)#
The permit IP-Access List Configuration mode command permits traffic if the
conditions defined in the permit statement match.
Syntax
permit {any |
destination-wildcard
permit-icmp {any | {
wildcard
ip-precedence
permit-igmp {any | {
wildcard
permit-tcp {any | {
destination-wildcard
ip-precedence
permit-udp {any | {
destination-wildcard
ip-precedence
protocol
}} {ny |
}} {ny |
source source-wildcard
icmp-type
]
source source-wildcard
igmp-type
source source-wildcard
] [flags
source source-wildcard
]
Parameters
source
•
indicate IP address 0.0.0.0 and mask 255.255.255.255.
— Specifies the source IP address of the packet. Specify any to
} {any | {
}} [dscp
}} {ny |
list-of-flags
}} {any |
source source-wildcard
dscp-number
} {any |
} [dscp
destination-port
destination-port
| ip-precedence
}} {any | {
icmp-code
dscp-number
]
} [dscp
}} {any | {
}} {any |
} [dscp
}} {any |
}} {any | {
destination destination-
dscp-number
destination destination-
| ip-precedence
source-port
dscp-number
source-port
} [dscp
dscp-number
destination
ip-precedence
| ip-precedence
ip-precedence
} {any |{
} {any | {
destination
| ip-precedence
destination
| ip-precedence
]
]
•
source-wildcard
address. Use 1s in bit positions to be ignored. Specify any to indicate IP
address 0.0.0.0 and mask 255.255.255.255.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 49
— Specifies wildcard to be applied to the source IP
Page 52

ACL Commands
permit (ip)
•
destination
any to indicate IP address 0.0.0.0 and mask 255.255.255.255.
•
destination-wildcard
IP address. Use 1s in bit positions to be ignored. Specify any to indicate IP
address 0.0.0.0 and mask 255.255.255.255.
•
protocol
(Range: 0-255). The following table lists the protocols that can be specified:
— Specifies the destination IP address of the packet. Specify
— Specifies wildcard to be applied to the destination
— Specifies the abbreviated name or number of an IP protocol.
3
IP Protocol Abbreviated
Name
Internet Control Message Protocol icmp 1
Internet Group Management Protocol igmp 2
IP in IP (encapsulation) Protocol ip 4
Transmission Control Protocol tcp 6
Exterior Gateway Protocol egp 8
Interior Gateway Protocol igp 9
User Datagram Protocol udp 17
Host Monitoring Protocol hmp 20
Reliable Data Protocol rdp 27
Inter-Domain Policy Routing Protocol idpr 35
Ipv6 protocol ipv6 41
Routing Header for IPv6 ipv6-route 43
Protocol
Number
Fragment Header for IPv6 ipv6-frag 44
Inter-Domain Routing Protocol idrp 45
Reservation Protocol rsvp 46
General Routing Encapsulation gre 47
Encapsulating Security Payload (50) esp 50
Authentication Header ah 51
ICMP for IPv6 ipv6-icmp 58
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 50
Page 53

ACL Commands
permit (ip)
3
IP Protocol Abbreviated
Name
(any IP protocol) any (25504)
EIGRP routing protocol eigrp 88
Open Shortest Path Protocol ospf 89
IP-within-IP Encapsulation Protocol ipip 94
Protocol Independent Multicast pim 103
Layer Two Tunneling Protocol l2tp 115
ISIS over IPv4 isis 124
• dscp — Indicates matching the
(Range: 0-63)
• ip-precedence — Indicates matching the
packet ip-precedence value. (Range: 0-7)
•
icmp-type
Enter a value or one of the following values: echo-reply, destinationunreachable, source-quench, redirect, alternate-host-address,
echorequest, router-advertisement, router-solicitation, time-exceeded,
parameter-problem, timestamp, timestamp-reply,information-request,
information-reply, address-mask-request,address-mask-reply, traceroute,
datagram-conversion-error,mobile-host-redirect, ipv6-where-are-you, ipv6i-am-here,mobile-registration-request, mobile-registration-reply, domainname-request,domain-name-reply, skip and photuris. (Range: 0-255)
— Specifies an ICMP message type for filtering ICMP packets.
dscp-number
ip-precedence
with the packet dscp value.
Protocol
Number
number with the
•
icmp-code
ICMP packets that are filtered by ICMP message type can also be filtered
by the ICMP message code. (Range: 0-255)
•
igmp-type
number or one of the following values: dvmrp, host-query, host-report, im or
trace. (Range: 0-255)
•
destination-port
65535)
•
source-port
— Specifies an ICMP message code for filtering ICMP packets.
— IGMP packets can be filtered by IGMP message type. Enter a
— Specifies the UDP/TCP destination port. (Range: 0-
— Specifies the UDP/TCP source port. (Range: 0-65535)
• list-of-flags — Specifies a list of TCP flags that can be triggered. If a flag is
set, it is prefixed by “+”. If a flag is not set, it is prefixed by “-”. The possible
values are: +urg, +ack, +psh, +rst, +syn, +fin, -urg, -ack, -psh, -rst, -syn and -
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 51
Page 54

ACL Commands
deny (IP)
3
fin. The flags are concatenated into one string. For example: +fin-ack. To
define more than 1 flag - enter additional flags one after another without a
space (example +syn-ack).
Default Configuration
No IPv4 ACL is defined.
Command Mode
IP-Access List Configuration mode
User Guidelines
deny (IP)
Use the ip access-list Global Configuration mode command to enable the IPAccess List Configuration mode.
Before an Access Control Element (ACE) is added to an ACL, all packets are
permitted. After an ACE is added, an implied deny-any-any condition exists at the
end of the list and those packets that do not match the conditions defined in the
permit statement are denied.
Example
The following example shows how to define a permit statement for an IP ACL.
Console(config)# ip access-list ip-acl1
Console(config-ip-al)# permit rsvp 192.1.1.1 0.0.0.0 any dscp 56
The deny IP-Access List Configuration mode command denies traffic if the
conditions defined in the deny statement match.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 52
Page 55

ACL Commands
deny (IP)
3
Syntax
deny [disable-port] {any |
{
destination destination-wildcard
precedence
deny-icmp [disable-port] {any | {
destination-wildcard
precedence
deny-igmp [disable-port] {any | {
destination-wildcard
deny-tcp [disable-port] {any | {
destination destination-wildcard
{
precedence
eny-udp [disable-port] {any | {
{
destination destination-wildcard
precedence
]
number
number
number
protocol
}} {ny |
]
}} {any |
] [flags
]
icmp-type
igmp-type
source source-wildcard
list-of-flags
source source-wildcard
Parameters
•
disable-port — Specifies that the port is disabled.
} {any | {
}} [dscp
source source-wildcard
source source-wildcard
}} {any |
}} {any |
source source-wildcard
dscp number
} {any |
icmp-code
} [dscp
]
number
destination-port
destination-port
| ip-precedence
}} {any |
}} {any |
}} {ny |
| ip-precedence
}} {any | {
} [dscp
}} {any | {
} [dscp
} [dscp
destination
number
destination
source-port
number
source-port
number
ip-
| ip-
number
} {any |
| ip-
} {any |
| ip-
]
•
source
sent. Specify any to indicate IP address 0.0.0.0 and mask 255.255.255.255.
•
source-wildcard
placing 1’s in bit positions to be ignored. Specify any to indicate IP address
0.0.0.0 and mask 255.255.255.255.
•
destination
being sent. Specify any to indicate IP address 0.0.0.0 and mask
255.255.255.255.
•
destination-wildcard
by placing 1’s in bit positions to be ignored. Specify any to indicate IP
address 0.0.0.0 and mask 255.255.255.255.
— Specifies the IP address or host name from which the packet was
— (Optional for the first type) Specifies wildcard bits by
— Specifies the IP address or host name to which the packet is
— (Optional for the first type) Specifies wildcard bits
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 53
Page 56

ACL Commands
deny (IP)
•
protocol
(Range: 0-255). The following table lists the protocols that can be specified:
— Specifies the abbreviated name or number of an IP protocol.
3
IP Protocol Abbreviated
Name
Internet Control Message Protocol icmp 1
Internet Group Management Protocol igmp 2
IP in IP (encapsulation) Protocol ip 4
Transmission Control Protocol tcp 6
Exterior Gateway Protocol egp 8
Interior Gateway Protocol igp 9
User Datagram Protocol udp 17
Host Monitoring Protocol hmp 20
Reliable Data Protocol rdp 27
Inter-Domain Policy Routing Protocol idpr 35
Ipv6 protocol ipv6 41
Routing Header for IPv6 ipv6-route 43
Protocol
Number
Fragment Header for IPv6 ipv6-frag 44
Inter-Domain Routing Protocol idrp 45
Reservation Protocol rsvp 46
General Routing Encapsulation gre 47
Encapsulating Security Payload (50) esp 50
Authentication Header ah 51
ICMP for IPv6 ipv6-icmp 58
EIGRP routing protocol eigrp 88
Open Shortest Path Protocol ospf 89
IP-within-IP Encapsulation Protocol ipip 94
Protocol Independent Multicast pim 103
Layer Two Tunneling Protocol l2tp 115
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 54
Page 57

ACL Commands
deny (IP)
3
IP Protocol Abbreviated
Name
ISIS over IPv4 isis 124
(any IP protocol) any (25504)
Protocol
Number
• in-port port-num — (Optional) Specifies the input port of the device. In case
of egress classification this port will be the device input port.
• out-port port-num — (Optional) Specifies the output port of the device.
• dscp
• ip-precedence
number
value.
with the packet ip-precedence value.
— Indicates matching the dscp
number
— Indicates matching the ip-precedence
number
with the packet dscp
number
Default Configuration
This command has no default configuration
Command Mode
IP-Access List Configuration mode
User Guidelines
Use the ip access-list Global Configuration mode command to enable the IPAccess List Configuration mode.
Before an Access Control Element (ACE) is added to an ACL, all packets are
permitted. After an ACE is added, an implied deny-any-any condition exists at the
end of the list and those packets that do not match the defined conditions are
denied.
Example
The following example shows how to define a permit statement for an IP ACL.
Console(config)# ip access-list ip-acl1
Console(config-ip-al)# deny rsvp 192.1.1.1 0.0.0.255 any
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 55
Page 58

ACL Commands
mac access-list
mac access-list
The mac access-list Global Configuration mode command enables the MACAccess List Configuration mode and creates Layer 2 ACLs. To delete an ACL, use
the no form of this command.
Syntax
3
mac access-list
no mac access-list
name
name
Parameters
•
name —
empty string.
Specifies the name of the ACL. (Range: 0-32 characters) Use “” for
Default Configuration
The default for all ACLs is deny all.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example shows how to create a MAC ACL.
Console(config)# mac access-list macl-acl1
Console(config-mac-al)#
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 56
Page 59

ACL Commands
permit (MAC)
permit (MAC)
3
The permit MAC-Access List Configuration mode command defines permit
conditions of an MAC ACL.
Syntax
permit {any | {host
[lan
vlan-id
] [cos
Parameters
source
•
•
source-wildcard
address. Use 1s in bit positions to be ignored.
•
destination
being sent.
•
destination-wildcard —
destination MAC address. Use 1s in bit positions to be ignored.
•
vlan-id
•
cos
•
cos-wildcard —
•
eth-type
(hex))
— Specifies the source MAC address of the packet.
— Specifies the ID of the packet vlan. (Range: 0-4094)
— Specifies the Class of Service (CoS) for the packet. (Range: 0-7)
— Specifies the Ethernet type of the packet .(Range: 05dd-ffff
source source-wildcard
cos cos-wildcard
— Specifies wildcard bits to be applied to the source MAC
— Specifies the MAC address of the host to which the packet is
Specifies wildcard bits to be applied to the CoS.
] thtype
Specifies wildcard bits to be applied to the
} any | {
eth-type
destination destination-wildcard
] [inner-vlan
vlan-id
]
}}
•
inner-vlan vlan-id
— Specifies the inner VLAN ID of a double tagged packet
Default Configuration
No MAC ACL is defined.
Command Mode
MAC-Access List Configuration mode
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 57
Page 60

ACL Commands
deny (MAC)
3
User Guidelines
Before an Access Control Element (ACE) is added to an ACL, all packets are
permitted. After an ACE is added, an implied deny-any-any condition exists at the
end of the list and those packets that do not match the conditions defined in the
permit statement are denied.
If the VLAN ID is specified, the policy map cannot be connected to the VLAN
interface.
Example
The following example shows how to create a MAC ACL with permit rules.
Console(config)# mac access-list macl-acl1
Console(config-mac-al)# permit 6:6:6:6:6:6 0:0:0:0:0:0 ny vlan 6
deny (MAC)
The deny MAC-Access List Configuration mode command denies traffic if the
conditions defined in the deny statement match.
Syntax
deny [disable-port] {any | {
wildcard
[cos
}}[vlan
cos cos-wildcard
vlan-id
source source-wildcard
]
] [ethtype
eth-type
} {any | {
]
destination destination-
Parameters
•
disable-port — Indicates that the port is disabled if the statement is deny.
•
source
was sent.
•
source-wildcard —
placing 1’s in bit positions to be ignored.
— Specifies the MAC address of the host from which the packet
(Optional for the first type) Specifies wildcard bits by
•
destination
being sent.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 58
— Specifies the MAC address of the host to which the packet is
Page 61

ACL Commands
deny (MAC)
•
destination-wildcard —
by placing 1’s in bit positions to be ignored.
•
vlan-id
•
cos
•
cos-wildcard —
•
eth-type
— Specifies the ID of the packet vlan.
— Specifies the packet’s Class of Service (CoS).
Specifies wildcard bits to be applied to the CoS.
— Specifies the packet’s Ethernet type.
(Optional for the first type) Specifies wildcard bits
Default Configuration
This command has no default configuration.
Command Mode
3
MAC-Access List Configuration mode
User Guidelines
MAC BPDU packets cannot be denied.
This command defines an Access Control Element (ACE). An ACE can only be
removed by deleting the ACL, using the no mac access-list Global Configuration
mode command. Alternatively, the Web-based interface canbe used to delete
ACEs from an ACL.
Before an Access Control Element (ACE) is added to an ACL, all packets are
permitted. After an ACE is added, an implied deny-any-any condition exists at the
end of the list and those packets that do not match the conditions defined in the
permit statement are denied.
If the VLAN ID is specified, the policy map cannot be connected to the VLAN
interface.
Example
The following example shows how to create a MAC ACL with deny rules on a
device.
Console(config)# mac access-list macl1
Console (config-mac-acl)# deny 00:00:00:00:10:00 any
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 59
Page 62
ACL Commands
service-policy
service-policy
3
Apply a policy map to the input of a particular interface. Use no form in order to
detach policy map from interface.
The command is available in Advanced mode only.
Syntax
service-policy input policy-map-name
no service-policy input
Parameters
service-acl
•
input — Use input policy-map-name to apply the specified policy-map to
the input interface.
• policy-map-name — Up to 32 characters.
Default Configuration
This command has no default configuration.
Command Mode
Interface configuration (Ethernet, VLAN, Port-Channel)
User Guidelines
Only one policy map per interface per direction is supported.
To control access to an interface, use the service-acl command in interface
configuration mode. To remove the access control, use the no form of this
command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 60
Page 63

ACL Commands
show access-lists
3
Syntax
service-acl input acl-name1
no service-acl input
Parameters
acl-name — Specifies an ACL to apply to the interface. Please see the usage
guidelines.
Default Configuration
No ACL is assigned.
Command Mode
Interface configuration (Ethernet, Port-Channel).
Usage Guidelines
•
• An ACL can’t be added to a port that is already bounded to an ACL, without
show access-lists
The show access-lists Privileged EXEC mode command displays access control
lists (ACLs) defined on the device.
Syntax
Two ACLs of the same type can’t be added to a port.
first removing the current ACL and binding the two ACLs together.
show access-lists [
name
]
Parameters
name
•
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 61
— The name of the ACL.
Page 64

ACL Commands
show interfaces access-lists
3
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example displays access lists defined on a device.
Console# show access-lists
IP access list ACL1
permit ip host 172.30.40.1 any
permit rsvp host 172.30.8.8 any
show interfaces access-lists
The show interfaces access-lists Privileged EXEC mode command displays
access lists applied on interfaces.
Syntax
show interfaces access-lists [ethernet interface | port-channel port-channelnumber]
Parameters
•
interface —
•
port-channel-number —
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 62
Valid Ethernet port.
Valid port-channel number.
Page 65

ACL Commands
show interfaces access-lists
3
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example displays ACLs applied to the interfaces of a device:
Console# show interfaces access-lists
Interface Input
--------- ----e1 ACL1
e2 ACL3
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 63
Page 66

ARP Inspection Commands
ip arp inspection
The ip arp inspection Global Configuration mode command globally enables ARP
inspection. To disable ARP inspection, use the no form of this command.
Syntax
4
ip arp inspection
no ip arp inspection
Default Configuration
The default configuration is set to disabled.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example globally enables ARP inspection.
Console(config)# ip arp inspection
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 64
Page 67
ARP Inspection Commands
ip arp inspection vlan
ip arp inspection vlan
The ip arp inspection vlan Global Configuration mode command enables ARP
inspection based on DHCP snooping database on a VLAN. To disable ARP
inspection on a VLAN, use the no form of this command.
Syntax
4
ip arp inspection
no ip arp inspection
vlan-id
vlan-id
Parameters
•
vlan-id
— Specifies a VLAN ID.
Default Configuration
The default configuration is set to disabled.
Command Mode
Global Configuration mode
User Guidelines
This command enables ARP inspection on a VLAN based on the DHCP snooping
database. The ip arp inspection list assign Global Configuration mode command
enables static ARP inspection.
Example
The following example enables ARP inspection on a VLAN based on the DHCP
snooping database.
Console(config)# ip arp inspection vlan
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 65
Page 68

ARP Inspection Commands
ip arp inspection trust
ip arp inspection trust
The ip arp inspection trust Interface Configuration (Ethernet, Port-channel) mode
command configures an interface trust state that determines if incoming Address
Resolution Protocol (ARP) packets are inspected. To return to the default
configuration, use the no form of this command.
Syntax
ip arp inspection trust
no ip arp inspection trust
Default Configuration
4
The interface is untrusted.
Command Mode
Interface Configuration (Ethernet, Port-channel) mode.
User Guidelines
The switch does not check ARP packets, which are received on the trusted
interface; it simply forwards the packets.
For untrusted interfaces, the switch intercepts all ARP requests and responses. It
verifies that the intercepted packets have valid IP-to-MAC address bindings
before updating the local cache and before forwarding the packet to the
appropriate destination. The switch drops invalid packets and logs them in the log
buffer according to the logging configuration specified with the ip arp inspection
log-buffer vlan Global Configuration mode command.
Example
The following example configures an interface trust state that determines if
incoming Address Resolution Protocol (ARP) packets are inspected.
Console(config)# interface ethernet 1
Console(config-if)# ip arp inspection trust
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 66
Page 69

ARP Inspection Commands
ip arp inspection validate
ip arp inspection validate
The ip arp inspection validate Global Configuration mode command performs
specific checks for dynamic Address Resolution Protocol (ARP) inspection. Use
the no form of this command to return to the default settings.
Syntax
ip arp inspection validate
no ip arp inspection validate
Default Configuration
4
The default configuration is set to disabled.
Command Mode
Global Configuration mode.
User Guidelines
The following are performed:
• Source MAC: Compare the source MAC address in the Ethernet header
against the sender MAC address in the ARP body. This check is performed
on both ARP requests and responses.
• Destination MAC: Compare the destination MAC address in the Ethernet
header against the target MAC address in ARP body. This check is
performed for ARP responses.
• IP addresses: Compare the ARP body for invalid and unexpected IP
addresses. Addresses include 0.0.0.0, 255.255.255.255, and all IP Multicast
addresses.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 67
Page 70

ARP Inspection Commands
ip arp inspection list create
Example
The following example perform specific checks for dynamic Address Resolution
Protocol (ARP) inspection.
Console(config)# ip arp inspection validate
ip arp inspection list create
The ip arp inspection list create Global Configuration mode command creates a
static ARP binding list and to enter the ARP list configuration mode. To delete the
list, use the no form of this command.
4
Syntax
ip arp inspection list create
no ip arp inspection list create
name
Parameters
•
name
— Specifies the list name. (Range: 1-32 characters)
Default Configuration
No static ARP binding list exists.
Command Mode
Global Configuration mode
User Guidelines
name
This command enables static ARP inspection on a VLAN.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 68
Page 71

ARP Inspection Commands
ip mac
Example
The following example creates a static ARP binding list and to enter the ARP list
configuration mode.
Console(config)# ip arp inspection list create
ip mac
The ip mac ARP-list Configuration mode command displays static ARP binding. To
delete a binding, use the no form of this command.
Syntax
4
ip
ip-address
no ip
ip-address
mac
mac-address
mac
mac-address
Parameters
ip-address —
•
•
mac-address —
address.
Specifies the IP address to be entered to the list.
Specifies the MAC address associated with the IP
Default Configuration
No binding is defined.
Command Mode
ARP-list Configuration mode
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 69
Page 72

ARP Inspection Commands
ip arp inspection list assign
Example
The following example displays static ARP binding.
Console(config)# ip arp inspection list servers
Console(config-ARP-list)# ip 172.16.1.1 mac 0060.704C.7321
Console(config-ARP-list)# ip 172.16.1.2 mac 0060.704C.7322
ip arp inspection list assign
The ip arp inspection list assign Global Configuration mode command assigns
static ARP binding lists to a VLAN. To delete the assignment, use the no form of this
command.
4
Syntax
ip arp inspection list assign
no ip arp inspection list assign
vlan-id name
vlan
Parameters
•
vlan-id —
•
name —
Specifies the VLAN ID.
Specifies the list name.
Default Configuration
No static ARP binding list assignment exists.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 70
Page 73

ARP Inspection Commands
ip arp inspection logging interval
Example
The following example assigns static ARP binding lists to a VLAN.
Console(config)# ip arp inspection list assign
ip arp inspection logging interval
The ip arp inspection logging interval Global Configuration mode command
configures the minimal interval between successive ARP SYSLOG messages. To
return to the default configuration, use the no form of this command.
Syntax
4
ip arp inspection logging interval {
no ip arp inspection logging interval
seconds
Parameters
seconds —
•
SYSLOG messages. A 0 value means that a system message is
immediately generated. (Range: 0-86400)
• infinite
Specifies the minimal interval between successive ARP
—
Specifies SYSLOG messages are not generated.
Default Configuration
The default value is 5 seconds.
Command Mode
Global Configuration mode
| infinite}
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 71
Page 74

ARP Inspection Commands
show ip arp inspection
Example
The following example configures the minimal interval between successive ARP
SYSLOG messages.
Console(config)# ip arp inspection logging interval
show ip arp inspection
The show ip arp inspection EXEC mode command displays the ARP inspection
configuration.
Syntax
4
show ip arp inspection [ethernet
interface
| port-channel
Parameters
•
interface —
•
port-channel-number —
Specifies an Ethernet port.
Specifies a port-channel number.
Default Configuration
This command has no default configuration.
Command Mode
EXEC
User Guidelines
There are no user guidelines for this command.
port-channel-number
]
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 72
Page 75

ARP Inspection Commands
show ip arp inspection list
Example
The following example displays the ARP inspection configuration.
Console# show ip arp inspection
IP ARP inspection is enabled.
IP ARP inspection is configured on following VLANs: 2, 7-18
Verification of packet header is enabled
Syslog messages interval: 5 seconds
InterfaceTrusted
---------------e1yes
e2no
4
show ip arp inspection list
The show ip arp inspection list Privileged EXEC mode command displays the
static ARP binding list.
Syntax
show ip arp inspection list
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 73
Page 76

ARP Inspection Commands
show ip arp inspection list
Example
The following example displays the static ARP binding list.
Console# show ip arp inspection list
List name: servers
Assigned to VLANs: 1,2
IP ARP
---------- --------------
172.16.1.1 0060.704C.7321
172.16.1.2 0060.704C.7322
4
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 74
Page 77

Address Table Commands
bridge address
The bridge address Interface Configuration (VLAN) mode command adds a MAClayer station source address to the bridge table. To delete the MAC address, use
the no form of this command.
5
Syntax
bridge address mac-address {ethernet interface | port-channel
port-channel-number} [permanent | delete-on-reset | delete-on-
timeout | secure]
no bridge address [mac-address]
Parameters
•
mac-address
•
interface—
•
port-channel-number
• permanent — The address can only be deleted by the no bridge address
command.
• delete-on-reset — The address is deleted after reset.
• delete-on-timeout — The address is deleted after “age out” time has
expired.
— A valid MAC address.
A valid Ethernet port.
— A valid port-channel number.
• secure — The address is deleted after the port changes mode to unlock
learning (no port security command). This parameter is only available when
the port is in the learning locked mode.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 75
Page 78

Address Table Commands
bridge multicast filtering
Default Configuration
No static addresses are defined. The default mode for an added address is
permanent.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Using the no form of the command without specifying a MAC address deletes all
static MAC addresses belonging to this VLAN).
5
Example
The following example adds a permanent static MAC-layer station source address
3aa2.64b3.a245 on port 1 to the bridge table.
Console(config)# interface vlan 2
Console(config-if)# bridge address 3aa2.64b3.a245 ethernet e16
permanent
bridge multicast filtering
The bridge multicast filtering Global Configuration mode command enables
filtering Multicast addresses. To disable filtering Multicast addresses, use the no
form of this command.
Syntax
bridge multicast filtering
no bridge multicast filtering
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 76
Page 79

Address Table Commands
bridge multicast address
Default Configuration
Filtering Multicast addresses is disabled. All Multicast addresses are flooded to all
ports.
Command Mode
Global Configuration mode
User Guidelines
If Multicast devices exist on the VLAN, do not change the unregistered Multicast
addresses state to drop on the switch ports.
If Multicast devices exist on the VLAN and IGMP-snooping is not enabled, the
bridge multicast forward-all command should be used to enable forwarding all
Multicast packets to the Multicast switches.
5
Example
In the following example, bridge Multicast filtering is enabled.
Console(config)# bridge multicast filtering
bridge multicast address
The bridge multicast address Interface Configuration (VLAN) mode command
registers a MAC-layer Multicast address in the bridge table and statically adds
ports to the group. To unregister the MAC address, use the no form of this
command.
Syntax
bridge multicast address {
bridge multicast address {
remove] {ethernet
mac-multicast-address | ip-multicast-address
mac-multicast-address | ip-multicast-address
interface-list
| port-channel
port-channel-number-list
}
} [add |
}
no bridge multicast address {
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 77
mac-multicast-address | ip-multicast-address
}
Page 80

Address Table Commands
bridge multicast address
Parameters
add — Adds ports to the group. If no option is specified, this is the default
•
option.
• remove — Removes ports from the group.
•
mac-multicast-address —
•
ip- multicast-address —
•
interface-list
no spaces; a hyphen is used to designate a range of ports.
•
port-channel-number-list
comma and no spaces; a hyphen is used to designate a range of portchannels.
— Separate nonconsecutive Ethernet ports with a comma and
A valid MAC Multicast address.
A valid IP Multicast address.
— Separate nonconsecutive port-channels with a
5
Default Configuration
No Multicast addresses are defined.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
If the command is executed without add or remove, the command only registers
the group in the bridge database. Static Multicast addresses can only be defined
on static VLANs.
Example
The following example registers the MAC address:
Console(config)# interface vlan 8
Console(config-if)# bridge multicast address 01:00:5e:02:02:03
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 78
Page 81
Address Table Commands
bridge multicast forbidden address
The following example registers the MAC address and adds ports statically.
Console(config)# interface vlan 8
Console(config-if)# bridge multicast address 01:00:5e:02:02:03
add ethernet e1, e2
bridge multicast forbidden address
The bridge multicast forbidden address Interface Configuration (VLAN) mode
command forbids adding a specific Multicast address to specific ports. Use the no
form of this command to restore the default configuration.
Syntax
5
bridge multicast forbidden address {
address
number-list
no bridge multicast forbidden address {
address
} [add | remove] {ethernet
}
}
mac-multicast-address | ip-multicast-
interface-list
mac-multicast-address | ip-multicast-
Parameters
•
add — Adds ports to the group. If no option is specified, this is the default
option.
• remove — Removes ports from the group.
•
mac-multicast-address —
•
ip- multicast-address —
•
interface-list
no spaces; a hyphen is used to designate a range of ports.
•
port-channel-number-list
comma and no spaces; a hyphen is used to designate a range of portchannels.
— Separate nonconsecutive Ethernet ports with a comma and
A valid MAC Multicast address.
A valid IP Multicast address.
— Separate nonconsecutive port-channels with a
| port-channel
port-channel-
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 79
Page 82

Address Table Commands
bridge multicast forward-all
Default Configuration
No forbidden addresses are defined.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Before defining forbidden ports, the Multicast group should be registered.
Example
5
In this example, MAC address 0100.5e02.0203 is forbidden on port e9 within
VLAN 8.
Console(config)# interface vlan 8
Console(config-if)# bridge multicast address 01:00:5e:02:02:03
Console(config-if)# bridge multicast forbidden address
01:00:5e:02:02:03 add ethernet e9
bridge multicast forward-all
The bridge multicast forward-all Interface Configuration (VLAN) mode command
enables forwarding all Multicast packets on a port. Use the no form of this
command to restore the default configuration.
Syntax
bridge multicast forward-all {add | remove} {ethernet
port-channel-number-list
interface-list
}
| port-channel
no bridge multicast forward-all
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 80
Page 83

Address Table Commands
bridge multicast forward-all
Parameters
Default Configuration
This setting is disabled
add — Force forwarding all Multicast packets.
•
• remove — Do not force forwarding all Multicast packets.
•
interface-list
no spaces; a hyphen is used to designate a range of ports.
•
port-channel-number-list
comma and no spaces; a hyphen is used to designate a range of portchannels.
— Separate nonconsecutive Ethernet ports with a comma and
— Separate nonconsecutive port-channels with a
5
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
In this example, all Multicast packets on port e8 are forwarded.
Console(config)# interface vlan 2
Console(config-if)# bridge multicast forward-all add ethernet e8
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 81
Page 84

Address Table Commands
bridge multicast forbidden forward-all
bridge multicast forbidden forward-all
The bridge multicast forbidden forward-all Interface Configuration (VLAN) mode
command forbids a port to be a forward-all-Multicast port. Use the no form of this
command to restore the default configuration.
Syntax
5
bridge multicast forbidden forward-all {add | remove} {ethernet
port-channel
no bridge multicast forbidden forward-all
port-channel-number-list
}
Parameters
add — Forbids forwarding all Multicast packets.
•
• remove — Does not forbid forwarding all Multicast packets.
•
interface-list
and no spaces; a hyphen is used to designate a range of ports.
•
port-channel-number-list
a comma and no spaces; a hyphen is used to designate a range of portchannels.
— Separates nonconsecutive Ethernet ports with a comma
— Separates nonconsecutive port-channels with
Default Configuration
This setting is disabled
interface-list
|
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
IGMP snooping dynamically discovers Multicast device ports. When a Multicast
device port is discovered, all the Multicast packets are forwarded to it
unconditionally.
This command prevents a port from becoming a Multicast device port.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 82
Page 85

Address Table Commands
bridge aging time
Example
In this example, forwarding all Multicast packets to e1 with VLAN 2 is forbidden.
Console(config)# interface vlan 2
Console(config-if)# bridge multicast forbidden forward-all add
ethernet e1
bridge aging time
The bridge aging-time Global Configuration mode command sets the address
table aging time. To restore the default configuration, use the no form of this
command.
5
Syntax
bridge aging-time
no bridge aging-time
seconds
Parameters
•
seconds
— Time in seconds. (Range: 10-630 seconds)
Default Configuration
The default setting is 300 seconds.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 83
Page 86

Address Table Commands
clear bridge
Example
In the following example, the bridge aging time is set to 250 seconds.
Console(config)# bridge aging-time 250
clear bridge
The clear bridge Privileged EXEC mode command removes any learned entries
from the forwarding database.
Syntax
5
clear bridge
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
In the following example, the bridge tables are cleared.
Console# clear bridge
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 84
Page 87

Address Table Commands
port security
port security
The port security Interface Configuration mode command locks the port to block
unknown traffic and prevent the port from learning new addresses. To restore
defaults, use the no form of this command.
Syntax
5
port security [forward | discard | discard-shutdown] [trap
no port security
seconds
]
Parameters
•
forward — Forwards packets with unlearned source addresses, but does
not learn the address.
• discard — Discards packets with unlearned source addresses. This is the
default if no option is indicated.
• discard-shutdown — Discards packets with unlearned source addresses.
The port is also shut down.
•
seconds
seconds between consecutive traps. (Range: 1-1000000)
— Sends SNMP traps and defines the minimum amount of time in
• max — Maximum number of addresses that can be learned on the interface.
(Range: 1-128)
Default Configuration
This setting is disabled.
Command Mode
Interface Configuration (Ethernet, port-channel) mode
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 85
Page 88

Address Table Commands
port security mode
Example
In this example, port e1 forwards all packets without learning addresses of
packets from unknown sources and sends traps every 100 seconds if a packet
with an unknown source address is received.
Console(config)# interface ethernet e1
Console(config-if)# port security forward trap 100
port security mode
The port security mode Interface Configuration mode command configures the
port security mode. To restore defaults, use the no form of this command.
5
Syntax
port security mode {lock | mac-addresses}
no port security mode
Parameters
lock — Saves the current dynamic MAC addresses associated with the
•
port and disables learning, relearning and aging.
• mac-addresses — Deletes the current dynamic MAC addresses
associated with the port and learns up to the maximum number addresses
allowed on the port. Relearning and aging are enabled.
Default Configuration
This setting is disabled.
Command Mode
Interface Configuration (Ethernet, port-channel) mode
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 86
Page 89

Address Table Commands
port security max
User Guidelines
There are no user guidelines for this command.
Example
In this example, port security mode is set to dynamic for Ethernet interface e7.
Console(config)# interface ethernet e7
Console(config-if)# port security mode mac-addresses
port security max
5
The port security max Interface Configuration mode command configures the
maximum addresses that can be learned on the port while the port is in port
security max-addresses mode. Use the no form of this command to return to
default.
Syntax
port security max
no port security max
max-addr
Parameters
max-addr
•
port. The range is 1-128.
— Maximum number of addresses that can be learned on the
Default Configuration
The default configuration is 128.
Command Mode
Interface Configuration (Ethernet, port-channel) mode
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 87
Page 90

Address Table Commands
show bridge address-table
User Guidelines
There are no user guidelines for this command.
Example
In this example the port security max interface configuration command configures
the maximum addresses that can be learned on the port while the port is in port
security max-addresses mode.
Console(config)# interface ethernet e7
Console(config-if)# port security max max addr
show bridge address-table
5
The show bridge address-table Privileged EXEC mode command displays all
entries in the bridge-forwarding database.
Syntax
show bridge address-table [vlan
channel-number
| address
mac-address
vlan
] [ethernet
interface
]
| port-channel
port-
Parameters
vlan —
•
•
interface —
•
port-channel-number —
•
mac-address —
Specifies a valid VLAN, such as VLAN 1.
A valid Ethernet port.
A valid port-channel number.
A valid MAC address.
Default Configuration
This command has no default configuration.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 88
Page 91

Address Table Commands
show bridge address-table static
Command Mode
Privileged EXEC mode
User Guidelines
Internal usage VLANs (VLANs that are automatically allocated on ports with a
defined Layer 3 interface) are presented in the VLAN column by a port number
and not by a VLAN ID.
“Special” MAC addresses that were not statically defined or dynamically learned
are displayed in the MAC address table. This includes, for example, MAC
addresses defined in ACLs.
Example
5
In this example, all classes of entries in the bridge-forwarding database are
displayed
Console# show bridge address-table
Aging time is 300 secs
interface mac address Port Type
------------------------- ---- ------1 00:60:70:4C:73:FF e8 dynamic
1 00:60:70:8C:73:FF e8 dynamic
200 00:10:0D:48:37:FF e9 static
show bridge address-table static
The show bridge address-table static Privileged EXEC mode command displays
statically created entries in the bridge-forwarding database.
Syntax
show bridge address-table static [vlan vlan] [ethernet interface
| port-channel port-channel-number]
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 89
Page 92

Address Table Commands
show bridge address-table static
Parameters
5
vlan —
•
•
interface —
•
port-channel-number —
Specifies a valid VLAN, such as VLAN 1.
A valid Ethernet port.
A valid port-channel number.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
In this example, all static entries in the bridge-forwarding database are displayed.
Console# show bridge address-table static
Aging time is 300 sec
vlan mac address port type
---- -------------------- ----------------1 00:60:70:4C:73:FF e8 Permanent
1 00:60.70.8C.73:FF e8 delete-on-timeout
200 00:10:0D:48:37:FF e9 delete-on-reset
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 90
Page 93

Address Table Commands
show bridge address-table count
show bridge address-table count
The show bridge address-table count Privileged EXEC mode command displays
the number of addresses present in the Forwarding Database.
Syntax
5
show bridge address-table count [vlan
channel
port-channel-number
]
vlan
] [Ethernet
Parameters
vlan —
•
•
interface —
•
port-channel-number —
Specifies a valid VLAN, such as VLAN 1.
A valid Ethernet port.
A valid port-channel number.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
interface-number
| port-
User Guidelines
There are no user guidelines for this command.
Example
In this example, the number of addresses present in all VLANs are displayed.
Console# show bridge address-table count
Capacity: 8192
Free: 8083
Used: 109
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 91
Page 94

Address Table Commands
show bridge multicast address-table
Secure addresses: 2
Static addresses: 1
Dynamic addresses: 97
Internal addresses: 9
show bridge multicast address-table
The show bridge multicast address-table Privileged EXEC mode command
displays Multicast MAC address or IP Address Table information.
Syntax
show bridge multicast address-table [vlan vlan-id] [address macmulticast-address | ip-multicast-address] [format ip | format
mac
5
Parameters
vlan-id —
•
•
mac-multicast-address —
•
ip-multicast-address
Indicates the VLAN ID. This has to be a valid VLAN ID value.
A valid MAC Multicast address.
— A valid IP Multicast address.
• format ip / mac — Multicast address format. Can be ip or ac. If the format is
unspecified, the default is mac.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 92
Page 95

Address Table Commands
show bridge multicast address-table
User Guidelines
A MAC address can be displayed in IP format only if it is in the range of
0100.5e00.0000-0100.5e7f.ffff.
Example
In this example, Multicast MAC address and IP Address Table information are
displayed.
Console# show bridge multicast address-table
Vlan MAC Address Type Ports
---- -------------- ------- --------1 01:00:5e:02:02:03 static e1, e13
19 01:00:5e:02:02:08 static e1-e8
19 00:00:5e:02:02:08 dynamic e9-e11
5
Forbidden ports for multicast addresses:
Vlan MAC Address Ports
---- -------------- ----1 01:00:5e:02:02:03 e16
19 01:00:5e:02:02:08 e16
Console# show bridge multicast address-table format ip
Vlan IP/MAC Address Type Ports
---- ----------------- ------- --------1 224-239.130|2.2.3 static e1, e13
19 224-239.130|2.2.8 static e1-e8
19 224-239.130|2.2.8 dynamic e9-e11
Forbidden ports for multicast addresses:
Vlan IP/MAC Address Ports
---- -------------- ----1 224-239.130|2.2.3 e16
19 224-239.130|2.2.8 e16
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 93
Page 96

Address Table Commands
show bridge multicast address-table static
NOTE A Multicast MAC address maps to multiple IP addresses as shown above.
show bridge multicast address-table static
The show bridge multicast address-table static Privileged EXEC mode command
displays the statically configured Multicast addresses.
Syntax
5
show bridge multicast address-table static [vlan
address
[source
|
ip-multicast-address
ip-address
]
]
Parameters
vlan-id
•
•
mac-multicast-address
•
ip-multicast-address
•
ip-address
— Indicates the VLAN ID. This has to be a valid VLAN ID value.
— A valid MAC Multicast address.
— A valid IP Multicast address.
— Source IP address.
Default Configuration
This command has no default configuration.
Command Mode
vlan-id
] [address
mac-multicast-
Privileged EXEC mode
User Guidelines
A MAC address can be displayed in IP format only if it is in the range
0100.5e00.0000 through 0100.5e7f.ffff.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 94
Page 97

Address Table Commands
show bridge multicast filtering
Example
Console# show bridge multicast address-table static
MAC-GROUP Table
Vlan MAC Address Type Ports
---- -------------- ------- ----------1 0100.9923.8787 static e1, e2
Forbidden ports for Multicast addresses:
Vlan MAC Address Ports
---- -------------- -----
5
show bridge multicast filtering
The show bridge multicast filtering Privileged EXEC mode command displays the
Multicast filtering configuration.
Syntax
show bridge multicast filtering
Parameters
•
vlan-id
Default Configuration
This command has no default configuration.
Command Mode
— Indicates the VLAN ID. This has to be a valid VLAN ID value.
vlan-id
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 95
Page 98

Address Table Commands
show ports security
Example
In this example, the Multicast configuration for VLAN 1 is displayed.
Console# show bridge multicast filtering 1
Filtering: Enabled
VLAN: 1
Port Static Status
---- --------- --------e1 Filter
e2 Filter
e3 Filter
5
show ports security
The show ports security Privileged EXEC mode command displays the port-lock
status.
Syntax
show ports security [ethernet
Parameters
interface —
•
•
port-channel-number —
Default Configuration
This command has no default configuration.
interface
A valid Ethernet port.
A valid port-channel number.
| port-channel
port-channel-number
]
Command Mode
Privileged EXEC mode
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 96
Page 99

Address Table Commands
show ports security
User Guidelines
There are no user guidelines for this command.
Example
In this example, all classes of entries in the port-lock status are displayed:
Console# show ports security
Port Status Learning Action Maximum Trap Frequency
---- ------ -------- ------ ------- ---- --------e1 Locked Dynamic Discard 3 Enable100
e2 Unlocked Dynamic - 28-e3 Locked Disabled Discard, 8 Disable-
5
Shutdown
The following table describes the fields shown above.
Field Description
Port The port number
Status The values are: Locked, Unlocked
Learning The learning mode
Action Action on violation
Maximum The maximum number of addresses that can
be associated on this port in the Static
Learning mode or in the Dynamic Learning
mode.
Traps Sends traps in case of a violation.
Frequency The minimum time interval between
consecutive traps.
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 97
Page 100

Address Table Commands
show ports security addresses
show ports security addresses
The show ports security addresses Privileged EXEC mode command displays the
current dynamic addresses in locked ports.
Syntax
5
show ports security addresses [ethernet
number
]
interface
Parameters
interface
•
•
port-channel-number
— A valid Ethernet port.
— A valid port-channel number
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
| port-channel
port-channel-
There are no user guidelines for this command.
Example
This example displays dynamic addresses in all currently locked ports.
Console# show ports security addresses
Port Status Learning Current Maximum
---- -------- -------- ------- ------e1 Disabled Lock - 1
e2 Disabled Lock - 1
e3 Enabled Max-addresses 0 1
SPS208G/SPS224G4/SPS2024 Command Line Interface Reference Guide 98
 Loading...
Loading...