Page 1

User Guide for Cisco Unified
Personal Communicator
for Macintosh, Release 1.1
9/14/2006
Corporate Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 526-4100
Text Part Number: OL-10984-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT
NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT
ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR
THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION
PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO
LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as
part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE
PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED
OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL
DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR
INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES.
Required Notices:
H.263
UB VIDEO INC. IS THE LICENSOR OF THE UB VIDEO H.263 PROFILE 3 CODEC (ANNEXES I, J, K AND T).
H.264
PORTIONS OF THE H.264 CODEC WERE PROVIDED BY VANGUARD SOFTWARE SOLUTIONS INC 1995-2005 ALL RIGHTS RESERVED
THIS PRODUCT IS LICENSED UNDER THE AVC PATENT PORTFOLIO LICENSE FOR THE PERSONAL AND NON-COMMERCIAL USE
OF A CONSUMER TO (i) ENCODE VIDEO IN COMPLIANCE WITH THE AVC STANDARD ("AVC VIDEO") AND/OR (ii) DECODE AVC
VIDEO THAT WAS ENCODED BY A CONSUMER ENGAGED IN A PERSONAL AND NON-COMMERCIAL ACTIVITY AND/OR WAS
OBTAINED FROM A VIDEO PROVIDER LICENSED TO PROVIDE AVC VIDEO. NO LICENSE IS GRANTED OR SHALL BE IMPLIED FOR
ANY OTHER USE. ADDITIONAL INFORMATION MAY BE OBTAINED FROM MPEG LA, L.L.C. SEE HTTP://WWW.MPEGLA.COM
resiprocate, dum - http://www.resiprocate.org
The Vovida Software License v. 1.0
Copyright (c) 2000 Vovida Networks, Inc. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
3. The names "VOCAL", "Vovida Open Communication Application Library", and "Vovida Open Communication Application Library (VOCAL)"
must not be used to endorse or promote products derived from this software without prior written permission. For written permission, please contact
vocal@vovida.org.
4. Products derived from this software may not be called "VOCAL", nor may "VOCAL" appear in their name, without prior written permission.
Page 3

THIS SOFTWARE IS PROVIDED "AS IS" AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NONINFRINGEMENT ARE
DISCLAIMED. IN NO EVENT SHALL VOVIDA NETWORKS, INC. OR ITS CONTRIBUTORS BE LIABLE FOR ANY DAMAGES IN EXCESS
OF $1,000, NOR FOR ANY INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF
THE POSSIBILITY OF SUCH DAMAGE.
ares
Copyright 1998 by the Massachusetts Institute of Technology.
Permission to use, copy, modify, and distribute this software and its documentation for any purpose and without fee is hereby granted, provided that
the above copyright notice appear in all copies and that both that copyright notice and this permission notice appear in supporting documentation,
and that the name of M.I.T. not be used in advertising or publicity pertaining to distribution of the software without specific, written prior permission.
M.I.T. makes no representations about the suitability of this software for any purpose. It is provided "as is" without express or implied warranty.
Neon, G.711
neon is an HTTP and WebDAV client library, with a C language API.
Bindings for other languages may also be available, see the web site for more details.
neon is Copyright (C) 1999-2004 Joe Orton <joe@manyfish.co.uk>
Portions are:
Copyright (C) 1999-2000 Tommi Komulainen <Tommi.Komulainen@iki.fi>
Copyright (C) 1999-2000 Peter Boos <pedib@colorfullife.com>
Copyright (C) 1991, 1995, 1996, 1997 Free Software Foundation, Inc.
Copyright (C) 2004 Aleix Conchillo Flaque <aleix@member.fsf.org>
Copyright (C) 2004-2005, Vladimir Berezniker @ http://public.xdi.org/=vmpn
GNU Lesser General Public License (LGPL)
This library is free software; you can redistribute it and/or modify it under the terms of the GNU Library General Public License as published by
the Free Software Foundation; either version 2 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Library General Public License for more details.
You should have received a copy of the GNU Library General Public License along with this library; if not, write to the Free Software Foundation,
Inc., 59 Temple Place - Suite 330, Boston,MA 02111-1307, USA
iLBC
Full Copyright Statement
Copyright (C) The Internet Society (2004).
This document is subject to the rights, licenses and restrictions contained in BCP 78, and except as set forth therein, the authors retain all their rights.
Page 4

This document and the information contained herein are provided on an"AS IS" basis and THE CONTRIBUTOR, THE ORGANIZATION HE/SHE
REPRESENTS OR IS SPONSORED BY (IF ANY), THE INTERNET SOCIETY AND THE INTERNET ENGINEERING TASK FORCE
DISCLAIM ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF THE
INFORMATION HEREIN WILL NOT INFRINGE ANY RIGHTS OR ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS
FOR A PARTICULAR PURPOSE.
Intellectual Property
The IETF takes no position regarding the validity or scope of any Intellectual Property Rights or other rights that might be claimed to pertain to the
implementation or use of the technology described in this document or the extent to which any license under such rights might or might not be
available; nor does it represent that it has made any independent effort to identify any such rights. Information on the IETF's procedures with respect
to rights in IETF Documents can be found in BCP 78 and BCP 79.
Copies of IPR disclosures made to the IETF Secretariat and any assurances of licenses to be made available, or the result of an attempt made to obtain
a general license or permission for the use of such proprietary rights by implementers or users of this specification can be obtained from the IETF
on-line IPR repository at http://www.ietf.org/ipr.
The IETF invites any interested party to bring to its attention any copyrights, patents or patent applications, or other proprietary rights that may cover
technology that may be required to implement this standard. Please address the information to the IETF at ietf- ipr@ietf.org.
AES
Copyright (C) Mok-Kong Shen 2003. mok-kong.shen@t-online.de
Free license:
This work and all modified versions of it may be freely copied, modified, redistributed and used for all legal civilian purposes without formality albeit
at licensee's own risk and responsibility, subject to the following conditions:
(1) A copy of this copyright notice with the release history list and the site modification history list must be included in any copy of this work or any
modified version of it.
(2) If this work or any modified version of it forms part of a software in object code or binary code, a document for users should accompany the
software stating this fact and include this copyright notice as well as an URL of the licensee where the source code of the package in the version
actually being used in the software can be found.
(3) Any modification (except dropping of the Supplement) should be appropriately documented in the site modification history list below. The last
date of site modification (at the beginning of the package) is to be updated.
(4) In case of non-trivial modifications, i.e. those stemming from efficiency or correctness considerations or from issues of interoperability with other
AES implementations, a copy of the modified package is to be immediately sent to the copyright owner at the address above.
(5) Eventual negative or unfavourable consequences and losses or damages of any form to any persons in connection with the use of this work or its
modified versions do not constitute any liabilities on the part of the copyright owner.
This free license is unlimited in time [1]. Any attempt of non-compliance with the above terms or any occurence of // their practical unsatisfiability
due to whatever reasons, however, automatically terminates the license. Such termination does not affect other licensees who have previously
obtained materials from the person with the terminated license but who continue to comply with the above terms.
Other licenses:
Any usages of the contents of the package that don't qualify for a free license as stated in the above require explicit // specific licenses from the
copyright owner.
[1] Since copyright grants could be revoked after 35 years (see http://www.copyright.gov/title17/92chap2.html#203), it // could be argued that this
license is not timeless for sure On the other hand, the lifespan of AES itself isn't likely to exceed that period. So the issue is not practically relevant
in our context.
DES - (http://www.itl.nist.gov/fipspubs/fip46-2.htm)
Page 5

Cryptographic devices implementing this standard may be covered by U.S. and foreign patents issued to the International Business Machines
Corporation. However, IBM has granted nonexclusive, royalty-free licenses under the patents to make, use and sell apparatus which complies with
the standard. The terms, conditions and scope of the licenses are set out in notices published in the May 13, 1975 and August 31, 1976 issues of the
Official Gazette of the United States Patent and Trademark Office (934 O.G. 452 and 949 O.G. 1717).
MD5
Copyright (C) 1991-2, RSA Data Security, Inc. Created 1991. All rights reserved.
License to copy and use this software is granted provided that it is identified as the "RSA Data Security, Inc. MD5 Message-Digest Algorithm" in all
material mentioning or referencing this software or this function.
License is also granted to make and use derivative works provided that such works are identified as "derived from the RSA Data Security, Inc. MD5
Message-Digest Algorithm" in all material mentioning or referencing the derived work.
RSA Data Security, Inc. makes no representations concerning either the merchantability of this software or the suitability of this software for any
particular purpose. It is provided "as is" without express or implied warranty of any kind.
These notices must be retained in any copies of any part of this documentation and/or software.
SHA1
Copyright (C) The Internet Society (2001). All Rights Reserved.
This document and translations of it may be copied and furnished to others, and derivative works that comment on or otherwise explain it or assist
in its implementation may be prepared, copied, published and distributed, in whole or in part, without restriction of any kind, provided that the above
copyright notice and this paragraph are included on all such copies and derivative works. However, this document itself may not be modified in any
way, such as by removing the copyright notice or references to the Internet Society or other Internet organizations, except as needed for the purpose
of developing Internet standards in which case the procedures for copyrights defined in the Internet Standards process must be followed, or as required
to translate it into languages other than English.
The limited permissions granted above are perpetual and will not be revoked by the Internet Society or its successors or assigns. This document and
the information contained herein is provided on an "AS IS" basis and THE INTERNET SOCIETY AND THE INTERNET ENGINEERING TASK
FORCE DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE
OF THE INFORMATION HEREIN WILL NOT INFRINGE ANY RIGHTS OR ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR
FITNESS FOR A PARTICULAR PURPOSE.
OpenSSL
LICENSE ISSUES
==============
The OpenSSL toolkit stays under a dual license, i.e. both the conditions of the OpenSSL License and the original SSLeay license apply to the toolkit.
See below for the actual license texts. Actually both licenses are BSD-style Open Source licenses. In case of any license issues related to OpenSSL
please contact openssl-core@openssl.org.
OpenSSL License
---------------
/* ====================================================================
* Copyright (c) 1998-2005 The OpenSSL Project. All rights reserved.
*
Page 6

* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the
* distribution.
*
* 3. All advertising materials mentioning features or use of this
* software must display the following acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
*
* 4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to
* endorse or promote products derived from this software without
* prior written permission. For written permission, please contact
* openssl-core@openssl.org.
*
* 5. Products derived from this software may not be called "OpenSSL"
* nor may "OpenSSL" appear in their names without prior written
* permission of the OpenSSL Project.
*
* 6. Redistributions of any form whatsoever must retain the following
* acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit (http://www.openssl.org/)"
*
* THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
* EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
Page 7

* ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
* STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
* OF THE POSSIBILITY OF SUCH DAMAGE.
* ====================================================================
*
* This product includes cryptographic software written by Eric Young
* (eay@cryptsoft.com). This product includes software written by Tim
* Hudson (tjh@cryptsoft.com).
*
*/
Original SSLeay License
-----------------------
/* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
* All rights reserved.
*
* This package is an SSL implementation written
* by Eric Young (eay@cryptsoft.com).
* The implementation was written so as to conform with Netscapes SSL.
*
* This library is free for commercial and non-commercial use as long as
* the following conditions are aheared to. The following conditions
* apply to all code found in this distribution, be it the RC4, RSA,
* lhash, DES, etc., code; not just the SSL code. The SSL documentation
* included with this distribution is covered by the same copyright terms
* except that the holder is Tim Hudson (tjh@cryptsoft.com).
*
* Copyright remains Eric Young's, and as such any Copyright notices in
* the code are not to be removed.
* If this package is used in a product, Eric Young should be given attribution
Page 8

* as the author of the parts of the library used.
* This can be in the form of a textual message at program startup or
* in documentation (online or textual) provided with the package.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* "This product includes cryptographic software written by
* Eric Young (eay@cryptsoft.com)"
* The word 'cryptographic' can be left out if the rouines from the library
* being used are not cryptographic related :-).
* 4. If you include any Windows specific code (or a derivative thereof) from
* the apps directory (application code) you must include an acknowledgement:
* "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
*
* THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* The licence and distribution terms for any publically available version or
Page 9

* derivative of this code cannot be changed. i.e. this code cannot simply be
* copied and put under another distribution licence
* [including the GNU Public Licence.]
*/
Libxml2
Except where otherwise noted in the source code (e.g. the files hash.c, list.c and the trio files, which are covered by a similar licence but with different
Copyright notices) all the files are:
Copyright (C) 1998-2003 Daniel Veillard. All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to
deal in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED
TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT
SHALL THE DANIEL VEILLARD BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of Daniel Veillard shall not be used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization from him.
NTP
This document and the NTPTime program and source code are all Copyright (c) Tom Horsley, 1997-2004. All rights reserved. The right to unlimited
distribution and use of this program is granted to anyone who agrees to keep the copyright notice intact and not alter the program.
Translation: You want changes in the program, make 'em yourself, but don't go distributing the new version with my name on it (or with your name
on it either, since you didn't write most of it :-). If there are changes you would like to see distributed, by all means send 'em in to me, and if I like
'em I'll incorporate them in the next version.
expat
The MIT License
Copyright (c) 1998, 1999, 2000 Thai Open Source Software Center Ltd
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to
deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or
sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED
TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT
SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN
ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE
OR OTHER DEALINGS IN THE SOFTWARE.
Page 10

_______________________________________________________
CCSP, CCVP, the Cisco Square Bridge logo, Follow Me Browsing, and StackWise are trademarks of Cisco Systems, Inc.; Changing the Way We
Work, Live, Play, and Learn, and iQuick Study are service marks of Cisco Systems, Inc.; and Access Registrar, Aironet, BPX, Catalyst, CCDA,
CCDP, CCIE, CCIP, CCNA, CCNP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems
Capital, the Cisco Systems logo, Cisco Unity, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, FormShare, GigaDrive,
GigaStack, HomeLink, Internet Quotient, IOS, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, LightStream, Linksys, MeetingPlace,
MGX, the Networkers logo, Networking Academy, Network Registrar, Packet, PIX, Post-Routing, Pre-Routing, ProConnect, RateMUX,
ScriptShare, SlideCast, SMARTnet, The Fastest Way to Increase Your Internet Quotient, and TransPath are registered trademarks of Cisco Systems,
Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0601R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and
figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and
coincidental.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
© 2006 Cisco Systems, Inc. All rights reserved.
Page 11

CONTENTS
CHAPTER
1 Introducing
Cisco Unified Personal Communicator
About Cisco Unified Personal Communicator 1-1
About Available Features 1-2
Cisco Product Security Overview 1-2
Setting Up Cisco Unified Personal Communicator 1-3
System Requirements 1-3
Installing Cisco Unified Personal Communicator 1-3
Before You Use Cisco Unified Personal Communicator 1-4
Logging In for the First Time 1-5
Setting Essential Preferences 1-5
About Logging In 1-6
Launching and Logging In 1-6
About the Cisco Unified Personal Communicator Console 1-7
Overview of the Console 1-7
Changing the View of the Console and Its Panes 1-9
Working With Items Listed in Panes 1-10
Getting Documentation 1-11
1-1
CHAPTER
OL-10984-01
Uninstalling 1-12
2 Having Conversations 2-1
About Conversations 2-1
Starting Conversations 2-2
Starting Audio Conversations 2-2
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
xi
Page 12

Contents
Responding to Incoming Calls 2-8
Working With Conversations In Progress 2-9
Entering Touch-Tone Responses 2-10
Transferring Calls 2-10
Showing or Hiding the Roster of Participants 2-11
Changing the Audio Volume and Video Transmission 2-11
Putting Conversations on Hold and Retrieving Them 2-12
Ending Conversations 2-13
CHAPTER
CHAPTER
3 Using Video 3-1
About Video Conversations 3-1
Before You Use Video 3-2
Previewing Your Video Image 3-2
Starting Video Conversations 3-3
Adding Video to Conversations 3-3
Responding to Requests to Add Video to Conversations 3-4
Working With Video Conversations In Progress 3-4
Removing Video from a Conversation 3-5
4 Using Web Conferencing 4-1
About Web Conferencing 4-1
Adding Web Conferencing to Conversations 4-2
Adding Participants to Web Conferencing Sessions 4-2
Working With Web Conferencing Sessions In Progress 4-3
Comparison with Cisco Unified MeetingPlace Express Web Meetings 4-4
CHAPTER
xii
5 Hosting Conference Calls 5-1
Creating Conference Calls 5-1
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 13

About Merging Calls 5-1
Merging Calls 5-2
Working With Conference Calls In Progress 5-3
Contents
CHAPTER
CHAPTER
CHAPTER
CHAPTER
6 Sending E-Mail Messages 6-1
7 Managing Contacts 7-1
About the Contact List 7-1
Working With Contacts 7-2
Searching for Contacts 7-3
Accessing Contact Details 7-4
Deleting Contacts from the Contact List 7-5
Working with Groups of Contacts 7-5
8 Working With Recent Communications 8-1
About Recent Communications 8-1
Working With the Recent Communications List and Its Entries 8-2
About Recent Communications Items 8-3
Accessing Voice Mail 8-4
9 About Your Preferences and Status 9-1
OL-10984-01
Viewing Your Current Status 9-1
Specifying Preferences 9-2
Setting Up Voice Mail and Web Conferencing 9-2
Setting Up Automatic Login and Password Entry 9-4
Choosing the Active Phone 9-5
Specifying Your Preferred Contact Method and Contact Information 9-7
Specifying Your Reachability Status 9-9
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
xiii
Page 14

Contents
CHAPTER
G
LOSSARY
10 Troubleshooting 10-1
Installation Problems 10-2
Problems Logging In and Connecting to the Network 10-2
Configuration Problems 10-2
Problems with the Console 10-3
Problems with Reachability 10-3
Problems Making Calls 10-4
Problems With Incoming Calls 10-4
Problems During a Conversation 10-4
Problems with Video 10-6
Problems with Web Conferencing 10-7
Problems in the Recent Communications Pane 10-7
Problems with Search 10-8
Capturing Information About Problems 10-8
Enabling Detailed Logging 10-9
I
NDEX
xiv
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 15

CHA P T ER
Introducing
Cisco Unified Personal Communicator
This introduction includes the following topics:
• About Cisco Unified Personal Communicator, page 1-1
• Setting Up Cisco Unified Personal Communicator, page 1-3
• About Logging In, page 1-6
• About the Cisco Unified Personal Communicator Console, page 1-7
• Getting Documentation, page 1-11
• Uninstalling, page 1-12
About Cisco Unified Personal Communicator
1
OL-10984-01
An integral part of the Cisco Unified Communications family of products,
Cisco Unified Personal Communicator is a desktop computer application that
helps enable more effective communications. By transparently integrating your
most frequently used communications applications and services,
Cisco Unified Personal Communicator streamlines the communication
experience, helping you work smarter and faster. With
Cisco Unified Personal Communicator, you can access voice, video, document
sharing, and presence information—all from a single, rich-media interface.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
1-1
Page 16

About Cisco Unified Personal Communicator
Key Features and Benefits
• View real-time availability of other people who use
Cisco Unified Personal Communicator.
• Click-to-call from the contact list or from a number in any application.
• Use either the integrated soft phone (software that lets you use your computer
as a phone) or an associated Cisco Unified IP Phone.
• Exchange ideas "face-to-face" with a video display on your computer screen.
• Add communication methods during a session; for example, you can add
video or web conferencing.
• Create audio conference calls simply by merging conversation sessions.
• View, playback, sort, and delete voice-mail messages, all from the same client
application.
Related Topics
• About Available Features, page 1-2
• Cisco Product Security Overview, page 1-2
Chapter 1 Introducing Cisco Unified Personal Communicator
About Available Features
The features and functionality that are available to you depend on the components
that your company has enabled. For example, you may or may not have access to
soft-phone or web-conferencing features.
Also, the options you see at any time depend on the current situation and what you
are doing. For example, if you have not selected a contact, the buttons to call a
contact are dimmed.
Some features may available only via your desk phone or only via your soft
phone, such as call transferring or video.
Cisco Product Security Overview
This product contains cryptographic features and is subject to United States and
local country laws governing import, export, transfer and use. Delivery of Cisco
cryptographic products does not imply third-party authority to import, export,
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
1-2
OL-10984-01
Page 17

Chapter 1 Introducing Cisco Unified Personal Communicator
Setting Up Cisco Unified Personal Communicator
distribute or use encryption. Importers, exporters, distributors and users are
responsible for compliance with U.S. and local country laws. By using this
product you agree to comply with applicable laws and regulations. If you are
unable to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found
at: http://www.cisco.com/wwl/export/crypto/tool/stqrg.html. If you require
further assistance please contact us by sending e-mail to export@cisco.com.
Setting Up Cisco Unified Personal Communicator
Complete the following tasks in order:
• System Requirements, page 1-3
• Installing Cisco Unified Personal Communicator, page 1-3
• Before You Use Cisco Unified Personal Communicator, page 1-4
• Logging In for the First Time, page 1-5
• Setting Essential Preferences, page 1-5
• (Optional) Specifying Preferences, page 9-2
System Requirements
Your system administrator should ensure that your equipment meets the system
requirements for using this product.
You must have Administrator privileges to install software on your computer.
Installing Cisco Unified Personal Communicator
If your system administrator has not installed
Cisco Unified Personal Communicator on your computer, install it.
Procedure
Step 1 Make sure your Finder is set to display files as icons.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
1-3
Page 18

Chapter 1 Introducing Cisco Unified Personal Communicator
Setting Up Cisco Unified Personal Communicator
Step 2 Obtain the disk image (CiscoUnifiedPersonalCommunicator-K9.dmg) from your
system administrator.
Step 3 If the disk image does not mount automatically, double-click it.
Step 4 Accept the license agreement.
Step 5 Follow the instructions.
Step 6 (Optional) Move the disk image to the trash.
Step 7 Continue with the instructions in the “Before You Use
Cisco Unified Personal Communicator” section on page 1-4.
Before You Use Cisco Unified Personal Communicator
Before you launch Cisco Unified Personal Communicator, prepare your
equipment:
• Setting Up Your Headset, page 1-4
• Setting Up Your Camera, page 1-4
Setting Up Your Headset
If you will use a headset with your soft phone, follow the instructions that came
with the headset.
After you plug in your headset, you may need to wait a few moments before you
do anything else.
Setting Up Your Camera
The software for supported Apple cameras is included with the Macintosh
operating system software.
Procedure
Step 1 Set up your camera following the instructions that came with it.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
1-4
OL-10984-01
Page 19

Chapter 1 Introducing Cisco Unified Personal Communicator
Step 2 If necessary, set the camera as the default microphone: Choose System
Preferences > Sound, then click Input.
Step 3 Click your camera in the list and adjust volume settings as needed.
Step 4 Relaunch Cisco Unified Personal Communicator if it is running.
Logging In for the First Time
Before You Begin
• Follow the procedures in the “Before You Use
Cisco Unified Personal Communicator” section on page 1-4.
Procedure
Step 1 Obtain the following information from your system administrator:
• Your username and password for Cisco Unified Personal Communicator.
Setting Up Cisco Unified Personal Communicator
• An IP address for the login server.
Step 2 Launch Cisco Unified Personal Communicator.
Step 3 Enter the information that you obtained in Step 1. Username and password are
case-sensitive.
Step 4 After you log in, perform the tasks in the “Setting Essential Preferences” section
on page 1-5.
Setting Essential Preferences
After you log in for the first time, you must perform the following tasks in order
to use Cisco Unified Personal Communicator:
• Choosing the Active Phone, page 9-5
• Setting Up Voice Mail and Web Conferencing, page 9-2
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
1-5
Page 20
About Logging In
Related Topics
• Setting Up Cisco Unified Personal Communicator, page 1-3
About Logging In
You must log in in order to use Cisco Unified Personal Communicator.
You can log in to Cisco Unified Personal Communicator from any computer on
your corporate network (if Cisco Unified Personal Communicator is installed and
connected to the network). Your contact list will be available to you after you log
in.
You should be logged in only once at any time.
Related Topics
• Logging In for the First Time, page 1-5
• Launching and Logging In, page 1-6
• Setting Up Automatic Login and Password Entry, page 9-4
Chapter 1 Introducing Cisco Unified Personal Communicator
Launching and Logging In
To Do This Do This
Launch Cisco
Unified Personal
Communicator
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
1-6
First, perform the tasks in the “Before You Use
Cisco Unified Personal Communicator” section on page 1-4.
Then, follow standard procedures for launching applications.
OL-10984-01
Page 21
Chapter 1 Introducing Cisco Unified Personal Communicator
To Do This Do This
Log in If you are logging in for the first time, see the “Logging In for
the First Time” section on page 1-5.
Otherwise, do the following:
• Respond to the window that appears when you launch
Cisco Unified Personal Communicator.
Note In order to log in remotely, you must first connect to
Note Username and password are case-sensitive.
Set up automatic
login
Related Topics
• About Logging In, page 1-6
See the “Setting Up Automatic Login and Password Entry”
section on page 9-4.
About the Cisco Unified Personal Communicator Console
your corporate network, for example via virtual
private network (VPN).
About the Cisco Unified Personal Communicator
Console
The console is the main hub of the Cisco Unified Personal Communicator
application. Information about the console includes:
• Overview of the Console, page 1-7
• Changing the View of the Console and Its Panes, page 1-9
• Working With Items Listed in Panes, page 1-10
Overview of the Console
Unless otherwise noted, all descriptions and instructions in this documentation
are based on the default configuration described in this section.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
1-7
Page 22
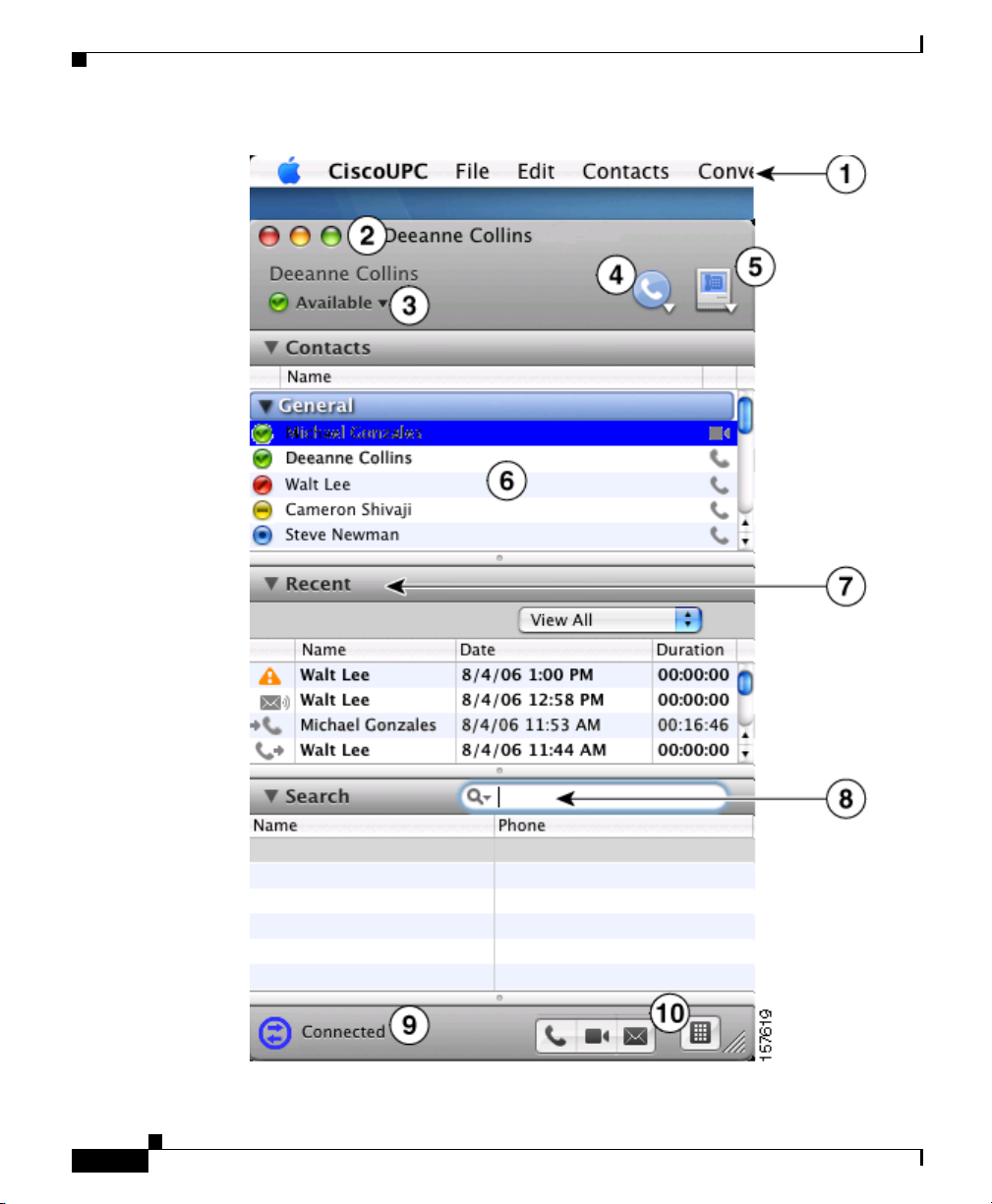
About the Cisco Unified Personal Communicator Console
Chapter 1 Introducing Cisco Unified Personal Communicator
1-8
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 23
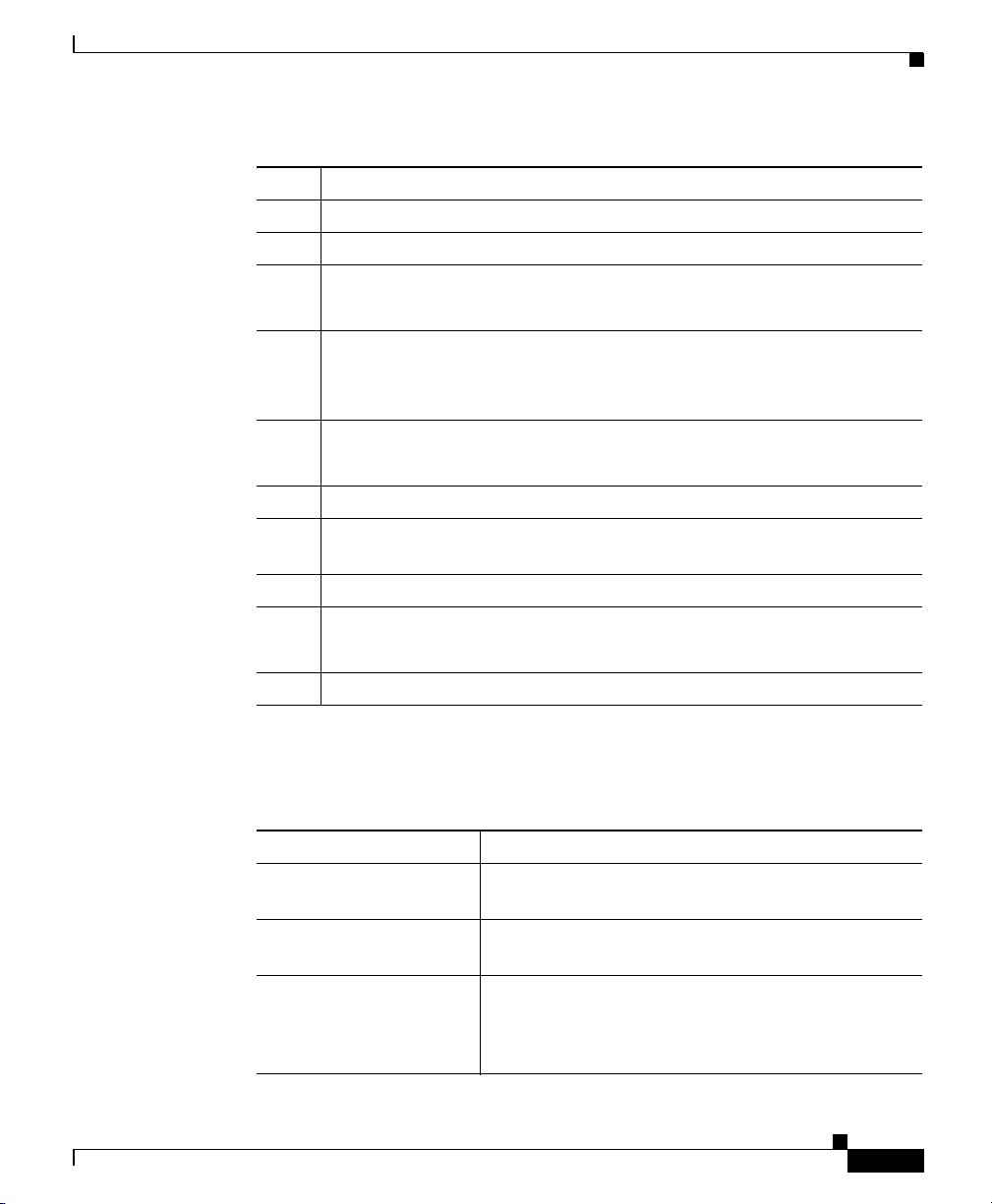
Chapter 1 Introducing Cisco Unified Personal Communicator
Item Description
1
2
3
Menu bar
Title bar with standard operating system buttons.
Pop-up menu to set your current reachability status.
See the “Specifying Your Reachability Status” section on page 9-9.
4
Pop-up menu to choose your preferred contact method.
See the “Specifying Your Preferred Contact Method and Contact
Information” section on page 9-7.
5
Pop-up menu to choose your active phone.
See the “Choosing the Active Phone” section on page 9-5.
6
7
Contacts pane. See Chapter 7, “Managing Contacts.”
Recent Communications pane. See Chapter 8, “Working With Recent
Communications.”
8
9
Search pane. See the “Searching for Contacts” section on page 7-3.
The current status of your connection.
About the Cisco Unified Personal Communicator Console
If needed, see Chapter 10, “Troubleshooting.”
10
Buttons to initiate communications.
Changing the View of the Console and Its Panes
To Do This Do This
Minimize the console Click the standard operating system control at the
top of the window.
Maximize the console Click the Cisco Unified Personal Communicator
icon in the dock.
Expand a pane in the
console
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
• Click the title bar of the pane.
• Choose Window > Toggle [pane] View.
1-9
Page 24
Chapter 1 Introducing Cisco Unified Personal Communicator
About the Cisco Unified Personal Communicator Console
To Do This Do This
Collapse a pane
• Click the title bar of the pane.
• Choose Window > Toggle [pane] View.
Resize a pane Position your mouse on the border between panes so
that you see the up-and-down arrows, then drag.
Resize the columns in a
pane
Position your mouse between column headings and
drag.
Resize the console Drag its bottom right corner.
Working With Items Listed in Panes
Panes list people or communications.
To Do This Do This
See more information about an item Hover your mouse pointer over the
• See and choose options for an item
in any pane
• Perform an action on an item
Select multiple names in the Recent
Communications and Search panes
item.
• Click the item to select it, then
choose an option from the menu
bar.
• Control-click the item and choose
an option from the menu that
appears.
• Shift-click each name to select.
• To select all names in the list,
press Command-A.
1-10
Work with individual Contacts See the “Working With Contacts”
section on page 7-2.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 25

Chapter 1 Introducing Cisco Unified Personal Communicator
To Do This Do This
Work with Recent Communications See the “Working With the Recent
Work with Search results See the “Working With Search
Getting Documentation
The following documentation is available for this product:
Quick Start Guide
http://www.cisco.com/en/US/products/ps6844/products_user_guide_list.html
Online Help
From any menu bar in Cisco Unified Personal Communicator, choose Help >
CiscoUPC Help. In the web conferencing window, click the Help menu.
Getting Documentation
Communications List and Its Entries”
section on page 8-2.
Results” section on page 7-4.
OL-10984-01
Updated Documentation (PDF)
The most current version of this documentation is available as a PDF file at:
http://www.cisco.com/en/US/products/ps6844/products_user_guide_list.html
Other Useful Documentation
Documentation for Cisco Unified MeetingPlace Express:
http://www.cisco.com/application/pdf/en/us/guest/products/ps6533/c1626/ccmig
ration_09186a00806c511e.pdf.
Documentation for your Cisco desk phone:
http://www.cisco.com/en/US/products/hw/phones/ps379/products_user_guide_li
st.html
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
1-11
Page 26
Uninstalling
Uninstalling
Procedure
Step 1 Quit Cisco Unified Personal Communicator.
Step 2 Move the following items to the trash:
This Item In this Folder
The Cisco Unified Personal
Communicator-K9 application
CiscoUPC_Dialer.bundle <Your hard disk>/Library/Address Book
Cisco folder (If it exists)
Cisco folder (If it exists)
com.cisco.UnifiedClient.plist
file (If it exists)
Cisco folder (If it exists)
Cisco Unified Personal
Communicator-K9.crash.log
file (If it exists)
Chapter 1 Introducing Cisco Unified Personal Communicator
<Your hard disk>/Applications/
Plug-Ins/
<Your hard disk>/Users/<your user
name>/Library/Caches/
<Your hard disk>/Users/<your user
name>/Library/Preferences/
<Your hard disk>/Users/<your user
name>/Library/Preferences/
<Your hard disk>/Users/<your user
name>/Library/Logs/
<Your hard disk>/Users/<your user
name>/Library/Logs/CrashReporter/
1-12
Step 3 Empty the trash.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 27

Having Conversations
This section includes the following topics:
• About Conversations, page 2-1
• Starting Conversations, page 2-2
• Responding to Incoming Calls, page 2-8
• Working With Conversations In Progress, page 2-9
About Conversations
You can have conversations using the following media:
CHA P T ER
2
OL-10984-01
Medium For More Information, See
Audio Starting Audio Conversations, page 2-2
Video Chapter 3, “Using Video”
Web conferencing Chapter 4, “Using Web Conferencing”
You can simultaneously have:
• One active conversation.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-1
Page 28

Starting Conversations
• Multiple conversations on hold.
• Multiple people in one conversation (a conference call.) See Chapter 5,
“Hosting Conference Calls.”
Starting Conversations
You can start audio and audio-and-video conversations.
• Starting Audio Conversations, page 2-2
• Starting Video Conversations, page 3-3
• Redialing the Last Number You Called, page 2-7
Related Topics
• Chapter 5, “Hosting Conference Calls”
• Chapter 4, “Using Web Conferencing”
Chapter 2 Having Conversations
Starting Audio Conversations
Depending on your situation, choose a method:
• Starting Conversations With People Listed in the Console, page 2-3
• Starting Conversations With People Who Are Not on a List, page 2-6
• Redialing the Last Number You Called, page 2-7
• Dialing a Number in Other Applications, page 2-7
Note You can also always make calls using your desk phone.
Related Topics
• Chapter 5, “Hosting Conference Calls”
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-2
OL-10984-01
Page 29
Chapter 2 Having Conversations
Starting Conversations With People Listed in the Console
If the person to call appears on any list in your console, use one of the methods in
this section.
If the person is not listed in your console, see the following topics:
• Searching for Contacts, page 7-3
• Starting Conversations With People Who Are Not on a List, page 2-6.
• Dialing a Number in Other Applications, page 2-7
• Dialing From Your Macintosh Address Book, page 2-8
To Call a Person in
To Dial This Number
For named entries in a list:
• The preferred phone
number of a person, if
the person has specified
one.
• Otherwise, the primary
phone number for the
person, as listed in the
source directory.
For phone number entries in
Recent Communications:
• The phone number of
the original
communication.
This List Do This
Any list in the console
• Double-click a name (except in the Recent
Communications list).
(This method initiates a phone call only if
your preferred contact method is set to
Phone or Video. See the “Specifying Your
Preferred Contact Method and Contact
Information” section on page 9-7.)
• Click a name or entry in the list, then click
the Place a Call button at the bottom of the
console.
• Control-click a name or entry and choose
Place Audio Call.
• Click a name or entry in the list, then choose
Contacts > Place Audio Call.
Starting Conversations
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-3
Page 30
Starting Conversations
To Dial This Number
An alternate number listed
in the Contact Details for the
person.
Related Topics
• Determining Callee Reachability, page 2-4
• Identifying Preferred Contact Methods, page 2-6
To Call a Person in
This List Do This
• Contacts or
Search panes
• Recent
Communications,
if the entry is a
name (not a
phone number).
1. Do one of the following:
–
–
2. If necessary: Click the arrow beside
Additional Details to view additional
contact information for that person.
3. Click the button beside the number to dial.
Chapter 2 Having Conversations
Control-click a name and choose Get
Info.
Click a name, then choose File > Get
Info.
Determining Callee Reachability
You can view the reachability status of people in your Contacts list in order to
determine the best time or method to reach them.
Note You can initiate communication with other people regardless of their reachability
status.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-4
OL-10984-01
Page 31

Chapter 2 Having Conversations
The reachability icon beside the name of a person in the contact list tells you the
availability of the person. Alternately, you can view their Contact Details.
Table 2-1 Reachability Icons
Reachability
Status Symbol Description
Available
Busy
Idle The person is logged in to Cisco Unified Personal
Awa y
Offline The person is not logged in to Cisco Unified Personal
Starting Conversations
The person is logged in to Cisco Unified Personal
Communicator and has recently been using his or her
computer or phone. Or the person has set the status to
Available.
The person is on the phone or has set the status to
Busy.
Communicator. However, the person has not used the
computer for the length of time specified in
Preferences for this status to appear.
The person is logged in to Cisco Unified Personal
Communicator. However, the person has not used his
or her phone or computer for the length of time the
person has specified in Preferences for this status to
appear. Or the person has set the status to Away.
Communicator.
OL-10984-01
Unknown Reachability status is not available, because the
system is unable to determine the status of the person.
Related Topics
• Specifying Your Reachability Status, page 9-9
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-5
Page 32

Starting Conversations
Identifying Preferred Contact Methods
Every person in your corporate directory has a preferred contact method. Each
person can also specify a phone number or e-mail address by which they want to
be contacted.
To identify the preferred contact method of other users, use one of the following
methods:
• Rest your pointer over a name in the console.
• Look at the icon to the right of the name in the Contacts list. Icons are
explained in the following table:
Icon Preferred Contact Method
Chapter 2 Having Conversations
Phone
Video
E-mail
Related Topics
• Specifying Your Preferred Contact Method and Contact Information,
page 9-7
Starting Conversations With People Who Are Not on a List
If people you want to call are not in a list in your console and you cannot find them
via Search (see the “Searching for Contacts” section on page 7-3), you can use the
dial pad to call them.
Procedure
Step 1 Do one of the following:
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-6
OL-10984-01
Page 33

Chapter 2 Having Conversations
• In the console, click the Open Dialer button.
• Choose File > Toggle New Call Dialer.
Step 2 (Optional) If all panes in the console are minimized, maximize one pane to view
the entire dialer.
Step 3 Enter the phone number using one of these methods:
• Enter the number.
• Click the numbers on the dial pad.
• Copy and paste the number into the dial pad.
• In the dial pad, click the arrow, then choose a number from the list of recent
Dial exactly as you would when dialing from your desk phone. For example, you
may need to dial a 9 before you call someone outside your company.
You can enter numbers, letters, and the following characters: - + ( ) . # * " .
Step 4 Press the <Enter> key on your keyboard, or click the telephone button in the dial
pad.
Step 5 (Optional) If you need to press numbers to respond to instructions that you hear,
see the “Entering Touch-Tone Responses” section on page 2-10.
Starting Conversations
calls.
Tip To hide the dial pad, drag its edge toward the console.
Related Topics
• Working With Conversations In Progress, page 2-9
Redialing the Last Number You Called
Choose File > Redial Most Recent Number.
Dialing a Number in Other Applications
You can dial a number that appears as text in other applications, such as an e-mail
message or document.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
2-7
Page 34

Responding to Incoming Calls
Procedure
Step 1 Select the number to dial.
Step 2 From the application menu, choose Services > Dial With CiscoUPC.
Dialing From Your Macintosh Address Book
Procedure
Step 1 Following standard Address Book procedures, click the number.
Step 2 Choose Dial With CiscoUPC.
Chapter 2 Having Conversations
Responding to Incoming Calls
You can always answer calls using your desk phone.
If Cisco Unified Personal Communicator is running on your computer when
someone calls you, a pop-up notification appears at the lower left corner of your
computer screen, with options for you to choose from.
To Do This Do This
Answer a call with
audio only.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-8
• To answer using your soft phone: In the pop-up
notification, click the Answer Call button.
• To answer using your desk phone: Answer your
Cisco Unified IP Phone as you normally would.
OL-10984-01
Page 35

Chapter 2 Having Conversations
To Do This Do This
Answer a call with
audio and video
Send a call to voice
mail
Working With Conversations In Progress
In the pop-up notification, click the Answer With
Video button.
Note If you do not meet the requirements in the
“Before You Use Video” section on page 3-2,
you can see the person who calls you but the
other person cannot see your image.
In the pop-up notification, click the Send to Voicemail
button.
The caller is unaware that you have chosen to divert the
call.
Respond to a new call
when you are already
on a call
• Answer the call.
Any existing call is automatically put on hold.
When you want to retrieve a call, see the “Putting
Conversations on Hold and Retrieving Them”
section on page 2-12.
• Send the call to voice mail.
Answer multiple
simultaneous incoming
calls
• Answer each call individually.
Each call that you answer automatically puts the
previous call on hold.
To retrieve calls on hold, see the “Putting
Conversations on Hold and Retrieving Them”
section on page 2-12.
• Send each call to voice mail.
Working With Conversations In Progress
You can do many things during a conversation:
• Entering Touch-Tone Responses, page 2-10
• Transferring Calls, page 2-10
• Showing or Hiding the Roster of Participants, page 2-11
OL-10984-01
• Changing the Audio Volume and Video Transmission, page 2-11
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-9
Page 36

Working With Conversations In Progress
• Putting Conversations on Hold and Retrieving Them, page 2-12
• Adding Video to Conversations, page 3-3
• Responding to Requests to Add Video to Conversations, page 3-4
• Removing Video from a Conversation, page 3-5
• About Web Conferencing, page 4-1
• Creating Conference Calls, page 5-1
• Ending Conversations, page 2-13
Entering Touch-Tone Responses
During a call on your soft phone, if you hear instructions to choose options or
enter a number such as a password, use this procedure.
Procedure
Step 1 Do one of the following:
Chapter 2 Having Conversations
• Enter the numbers, then skip the rest of this procedure.
• In the active conversation window, click the Open Dialer keypad button.
• Make sure the conversation window is active, then choose Conversation >
Toggle Session Keypad.
Step 2 Enter the number in one of the following ways:
• Enter the number.
• Click the numbers on the dial pad.
Transferring Calls
Use the procedure in the “Merging Calls” section on page 5-2 to create a
conference call that includes yourself, the caller to be transferred, and the person
to whom you want to transfer the call. After all participants are in the
conversation, you can hang up and the others can continue the conversation.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
2-10
OL-10984-01
Page 37

Chapter 2 Having Conversations
Working With Conversations In Progress
Showing or Hiding the Roster of Participants
The roster lists audio and video participants in a conversation. If the participant is
in your directory or contact list, the name appears. Otherwise, the phone number
appears.
Procedure
Step 1 Do one of the following:
• In the active conversation window, click the Show roster of participants
button.
• Make sure the conversation window is active, then choose Conversation >
Toggle Session Roster.
Step 2 To perform actions on an entry in the list, control-click the entry.
Changing the Audio Volume and Video Transmission
When the Active Phone is Desk Phone
See the documentation that came with your phone.
When the Active Phone is Soft Phone
To Do This Do This
Mute your audio so that
participants cannot
hear you
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
• Make sure the conversation window is active, then
choose Conversation > Mute Microphone.
• In the active conversation window: Click the Mute
Audio button.
When you are muted, the mute button is blue.
If you mute a call, then put it on hold, then retrieve the
call from hold, your audio will no longer be muted.
2-11
Page 38

Working With Conversations In Progress
To Do This Do This
Change the
conversation volume
Chapter 2 Having Conversations
In the active conversation window:
• Drag the volume slider
Freeze (pause) the
video image of you that
other participants see
• Make sure the conversation window is active, then
choose Conversation > Pause Video.
• In the active conversation window: Click the
Pause Video button.
Your view of yourself, if visible, does not freeze.
If you pause your video, then put the call on hold, then
retrieve the call from hold, your video will no longer
be paused.
Putting Conversations on Hold and Retrieving Them
To Do This Do This Notes
Put a
conversation on
hold
• In the active conversation
window, click the Hold
button.
• Make sure the conversation
window is active, then
choose Conversation >
Hold Call.
You can be in only one
active conversation at a
time.
Multiple
web-conferencing
windows can remain
active.
2-12
Retrieve a call
that is on hold
• In the held conversation
window, click the Hold
button.
• Make sure the conversation
window is active, then
choose Conversation >
Hold Call.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
When you retrieve a
conversation from hold,
any other active
conversation is
automatically put on
hold.
OL-10984-01
Page 39

Chapter 2 Having Conversations
Related Topics
• Creating Conference Calls, page 5-1
Ending Conversations
Note If you want to end a call on hold, retrieve the call first, then end it. If you end the
call without retrieving the call first, the other person remains on hold after you
hang up.
Use one of the following methods to end a two-person conversation:
• If you are using a desk phone, hang up the receiver.
• Click the (x) button in the conversation window.
• Close the conversation window using the standard operating system controls
in the title bar.
• Make sure the conversation window is active, then choose Conversation >
End Call.
Working With Conversations In Progress
Note If you are in a conference call and you hang up, the other participants in the
conference can continue their conversation.
Closing Conversation Windows
To specify preferences related to closing conversation windows:
Choose CiscoUPC > Preferences, click Profile, then choose options:
• Close conversation window on disconnect
• Warn before closing active conversation window
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
2-13
Page 40

Working With Conversations In Progress
Chapter 2 Having Conversations
2-14
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 41

CHA P T ER
Using Video
Topics about video include:
• Setting Up Your Camera, page 1-4
• About Video Conversations, page 3-1
• Before You Use Video, page 3-2
• Previewing Your Video Image, page 3-2
• Starting Video Conversations, page 3-3
• Adding Video to Conversations, page 3-3
• Responding to Requests to Add Video to Conversations, page 3-4
• Working With Video Conversations In Progress, page 3-4
• Removing Video from a Conversation, page 3-5
3
About Video Conversations
The following information applies to video conversations:
• You can use video during two-party calls, but not during conference calls.
• To view incoming video, you do not need a camera.
• If you use video, people who do not have a video camera may see your image,
even though you cannot see them.
• Caller and callee can each decide whether to use video, or to use audio only.
• Requirements apply. See the “Before You Use Video” section on page 3-2.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
3-1
Page 42

Before You Use Video
You can view video images in conversations with any of the following users:
• People who use Cisco Unified Personal Communicator and are set up to use
video
• People who use Cisco Unified Video Advantage 2.0
• People who use Cisco Unified IP Phone model 7985
Before You Use Video
In order to transmit your video image:
• You must be set up to use video. See the “Setting Up Your Camera” section
on page 1-4.
• Your camera must be plugged in.
• Your active phone must be your soft phone.
• If you are adding video to a call, the active call must not be a conference call.
• You should verify that your video camera is operating correctly. See the
“Previewing Your Video Image” section on page 3-2.
Chapter 3 Using Video
Related Topics
• About Video Conversations, page 3-1
Previewing Your Video Image
To see your video image:
• Choose Window > Show Camera Preview.
If you do not see your image, see the “Problems with Video” section on page 10-6.
Related Topics
• Working With Video Conversations In Progress, page 3-4
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
3-2
OL-10984-01
Page 43

Chapter 3 Using Video
Starting Video Conversations
For general information about video conversations, see the “About Video
Conversations” section on page 3-1.
Procedure
Step 1 Make sure you are ready to use video. See the “Before You Use Video” section on
page 3-2.
Step 2 Perform one of the following procedures:
From Do This
Any list in the console
• Click a name or entry, then:
–
Click the Place a Video Call button at the
bottom of the console.
–
Choose Contacts > Place Video Call.
• Control-click a name and choose Place Video Call.
• Start an audio call using any procedure in the
“Starting Audio Conversations” section on
page 2-2, then add video using the procedure in the
“Adding Video to Conversations” section on
page 3-3.
Starting Video Conversations
Adding Video to Conversations
For general information about video conversations, see the “About Video
Conversations” section on page 3-1.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
3-3
Page 44

Responding to Requests to Add Video to Conversations
Procedure
Step 1 Make sure you are ready to use video. See the “Before You Use Video” section on
page 3-2.
Step 2 In the active conversation window:
• Click the Actions button, then choose Add/Remove Video.
Or make sure the conversation window is active, then choose Conversation >
Add/Remove Video.
Responding to Requests to Add Video to
Conversations
During a conversation, if the other person on the call adds video, buttons will
appear in the conversation window. You can choose whether to add video:
Chapter 3 Using Video
To Do This Click This Button
View the video image of the other person and let the
other person view your image.
View the video image of the other person but not let
the other person view your image.
Not add video to the conversation.
(You might choose this option if you are accessing
the network remotely using a slow connection.)
Accept Two-Way Video
Receive Video Only
Continue with Audio
Only
Working With Video Conversations In Progress
Information about audio conversations in progress applies also to video calls. See
the “Working With Conversations In Progress” section on page 2-9.
By default, your image appears as a picture-in-picture inside the larger window
that shows the image of the other person.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
3-4
OL-10984-01
Page 45

Chapter 3 Using Video
Removing Video from a Conversation
A pulsating video icon in the conversation window indicates that your video
image is being transmitted.
To Do This Do This
Move your own image to a different
corner of the window.
Make your picture-in-picture image
smaller or larger.
View your image in a separate window. Control-click the image and choose
Move your separate image back to the
picture-in-picture window
Click and drag the picture-in-picture to
the location you want it. It will snap to
a corner.
Control-click your image and choose a
size.
Detach Preview.
Click the (x) in the title bar of your
separate image to close the window.
Removing Video from a Conversation
OL-10984-01
If you are in an audio-and-video conversation, you can return the conversation to
audio-only without ending the conversation.
Use one of the following methods:
• Make sure the conversation window is active, then choose Conversation >
Add/Remove Video.
• In the active conversation window, click the Action button and choose
Add/Remove Video.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
3-5
Page 46

Removing Video from a Conversation
Chapter 3 Using Video
3-6
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 47

Using Web Conferencing
Web conferencing topics include:
• About Web Conferencing, page 4-1
• Adding Web Conferencing to Conversations, page 4-2
• Working With Web Conferencing Sessions In Progress, page 4-3
• Comparison with Cisco Unified MeetingPlace Express Web Meetings,
page 4-4
About Web Conferencing
If your company offers web conferencing, you can add it to your conversations.
Web conferencing lets you display documents and applications on your computer
for other participants to see. All participants can draw or write on a transparent
overlay over the content you share, leaving your originals intact.
If you are familiar with Cisco Unified MeetingPlace Express web meetings, see
the “Comparison with Cisco Unified MeetingPlace Express Web Meetings”
section on page 4-4.
CHA P T ER
4
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
4-1
Page 48

Chapter 4 Using Web Conferencing
Adding Web Conferencing to Conversations
Adding Web Conferencing to Conversations
Procedure
Step 1 Make sure you are set up to use web conferencing. See the “Setting Up Voice Mail
and Web Conferencing” section on page 9-2.
Step 2 In the active conversation window, do one of the following:
• Click the Action button, then choose Start/Stop Web Conferencing.
• Make sure the conversation window is active, then choose Conversation >
Start Web Conferencing.
Step 3 A web conferencing window will open on the screen of all conversation
participants who are using Cisco Unified Personal Communicator.
Step 4 If you see a window asking if you can close the window, click Ye s. This closes an
unneeded auxiliary window.
Step 5 If some participants in the conversation are not using
Cisco Unified Personal Communicator, see the “Adding Participants to Web
Conferencing Sessions” section on page 4-2.
Step 6 If additional participants join the conversation and they do not see the web
conference, use the procedure in Step 5 to allow them to join the web conference.
Step 7 For more information about web conferencing, see the table in the “Working With
Web Conferencing Sessions In Progress” section on page 4-3.
Adding Participants to Web Conferencing Sessions
Participants in the conversation who are using Cisco Unified
Personal Communicator join the web conference automatically.
If some participants in the conversation are not using Cisco Unified
Personal Communicator, you must perform the following procedure in order for
those participants to join the web conference.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
4-2
OL-10984-01
Page 49

Chapter 4 Using Web Conferencing
Working With Web Conferencing Sessions In Progress
Procedure
Step 1 In the active conversation window, click the E-mail Invite button.
Step 2 Add the e-mail addresses of the participants who need to join the web conference.
Step 3 Send the e-mail.
Step 4 Recipients must click the link in the e-mail message.
Working With Web Conferencing Sessions In
Progress
To Do This Do This
Get help with web
conferencing
During the conference: From the menu bar at the top
of the web conferencing window, choose Help >
Cisco Unified MeetingPlace Express Help.
Anytime: See the “Getting Documentation” section
on page 1-11.
OL-10984-01
Note The term “share-only web meeting” in that
documentation is equivalent to “web
conferencing” in this document.
Allow additional people
to join the web
conference
Reopen the web
conferencing window of
a session in progress if
you have closed the
browser window.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
See the “Adding Participants to Web Conferencing
Sessions” section on page 4-2.
In the active conversation window, click the Rejoin
Conference button.
4-3
Page 50

Chapter 4 Using Web Conferencing
Comparison with Cisco Unified MeetingPlace Express Web Meetings
To Do This Do This
End a web-conferencing
session
In the active conversation window, click the End
Conference button.
Only the person who added web conferencing can do
this.
Comparison with
Cisco Unified MeetingPlace Express Web Meetings
Note Information in this section is useful only to people who are familiar with
Cisco Unified MeetingPlace Express.
Web conferences that you add to Cisco Unified Personal Communicator
conversations include a subset of the functionality that is available in web
meetings that you initiate from Cisco Unified MeetingPlace Express.
4-4
Web conferences that you add to Cisco Unified Personal Communicator
conversations always have the following characteristics:
• Only sharing and annotating features and connection- and
screen-management functions are available.
• No Cisco Unified MeetingPlace Express password or profile is required to
participate, but you may need a profile in order to add web conferencing.
• People can join these web conferences only via a
Cisco Unified Personal Communicator conversation or a URL from the
conversation. People cannot find or join these web conferences via the
Cisco Unified MeetingPlace Express web pages or service on
Cisco Unified IP Phones.
• All participants in the conference, including the initiator of the web
conference, have Presenter privileges.
• There are no meeting notifications for these conferences.
• Your Cisco Unified MeetingPlace Express profile settings do not apply to
web conferences that you add via Cisco Unified Personal Communicator.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 51

Chapter 4 Using Web Conferencing
• You do not need to schedule these conferences in advance.
• You cannot change the display language of the web conference.
If you require full Cisco Unified MeetingPlace Express conferencing
functionality, and you have a profile in that application, consider starting your
conference from Cisco Unified MeetingPlace Express instead of
Cisco Unified Personal Communicator.
For more information, see the online Help in
Cisco Unified MeetingPlace Express, or the documentation listed for that product
in the “Getting Documentation” section on page 1-11.
Comparison with Cisco Unified MeetingPlace Express Web Meetings
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
4-5
Page 52

Comparison with Cisco Unified MeetingPlace Express Web Meetings
Chapter 4 Using Web Conferencing
4-6
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 53

Hosting Conference Calls
You can create conference calls by merging conversations.
• Creating Conference Calls, page 5-1
• About Merging Calls, page 5-1
• Working With Conference Calls In Progress, page 5-3
Creating Conference Calls
You create conference calls by merging multiple conversations: Call two people
and merge the conversations, then call (or answer a call from) another person and
merge that person into the call, then repeat for each additional person until all
participants are in a single conference call.
CHA P T ER
5
About Merging Calls
You can merge conversations to bring multiple callers into a single conversation.
You can merge the following:
• Two conversations
• A conversation and a conference
• Multiple conversations sequentially into a single conference.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
5-1
Page 54

About Merging Calls
Note • The Merge button is active only when more than one conversation is in
Merging Calls
Step 1 Choose the conversation that you want to keep, and put it on hold. For example,
Chapter 5 Hosting Conference Calls
progress, and only in the conversation window of the active conversation.
• Video conversations become audio-only after merging.
• When you merge a conversation that includes web conferencing, make sure
the conversation with web conferencing is NOT the active conversation when
you merge the conversations.
• If you merge two conversations and subsequently hang up, the other
participants can continue the conference call.
Procedure
if one conversation includes web conferencing or multiple participants, put that
conversation on hold.
5-2
Step 2 Make the other conversation active.
Step 3 Merge the conversations using one of the following methods:
• In the active conversation window, click the Merge button.
• Choose Conversation > Merge.
Step 4 Choose the person with whose conversation you want to merge.
The conversation that was on hold becomes the active conversation; all
participants are in it.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 55

Chapter 5 Hosting Conference Calls
Working With Conference Calls In Progress
Working With Conference Calls In Progress
Information about conversations applies also to conference calls. See the
“Working With Conversations In Progress” section on page 2-9.
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
5-3
Page 56

Working With Conference Calls In Progress
Chapter 5 Hosting Conference Calls
5-4
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 57

CHA P T ER
6
Sending E-Mail Messages
Use the procedures in the following table to open a blank e-mail message
addressed to the preferred e-mail address of the selected person.
To Send E-Mail From Do This
Any pane in the console
• Double-click a name (except in the Recent
Communications pane).
(This method opens an e-mail message only if
you have specified e-mail as your preferred
contact method.)
• Select a contact (or multiple contacts, except in
the Contacts pane), then click the Send e-mail
button.
• Select a contact (or multiple contacts, except in
the Contacts pane). Then, choose Contacts >
Send E-mail.
OL-10984-01
• Control-click a name and choose Send E-mail.
The roster of a
conversation in progress
A communication details
window
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
Control-click a name and choose Send e-mail.
• Click the Send E-mail button.
• Choose Contacts > Send E-mail.
6-1
Page 58

Chapter 6 Sending E-Mail Messages
6-2
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 59

Managing Contacts
The following topics describe how to manage your contact list:
• About the Contact List, page 7-1
• Working With Contacts, page 7-2
• Working with Groups of Contacts, page 7-5
About the Contact List
You can add up to 100 names to your personal contact list, from the following
sources:
• Other users of Cisco Unified Personal Communicator. These may be all or
some of the people in your corporate directory.
• If you use Cisco IP Phone Messenger on your Cisco Unified IP Phone, your
buddy list from that application.
If you add contacts to either application, they also appear in the other
application.
CHA P T ER
7
OL-10984-01
Only you can see the contacts in your contact list, and you can see your contact
list when you log in from any computer.
Other applications on your computer or on the network cannot access information
from this contact list.
Related Topics
• Working With Contacts, page 7-2
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
7-1
Page 60

Working With Contacts
• Changing the View of the Console and Its Panes, page 1-9
• Identifying Preferred Contact Methods, page 2-6
Working With Contacts
You can perform the following actions related to individual contacts:
To Do This Do This
Add contacts See the “Adding Contacts to Groups”
Search for contacts See the “Searching for Contacts”
Determine the reachability of a contact See the “Determining Callee
Determine the preferred contact
method of a contact
View more information about a contact
in the list
Chapter 7 Managing Contacts
section on page 7-6.
section on page 7-3.
Reachability” section on page 2-4.
See the “Identifying Preferred Contact
Methods” section on page 2-6.
• Hover your mouse pointer over an
entry in any list in the console.
7-2
• Perform one of the actions in the
“Accessing Contact Details”
section on page 7-4.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 61

Chapter 7 Managing Contacts
To Do This Do This
Modify contact information To add a nickname:
Delete contacts See the “Deleting Contacts from the
Searching for Contacts
Working With Contacts
• Click the contact in the contact
list; then choose Contacts > Edit
Nickname.
• Control-click a contact in the list,
then choose Edit Nickname.
To remove a nickname, follow one of
the steps to add a nickname, then:
• Click Clear.
Contact List” section on page 7-5.
OL-10984-01
You can search your corporate directory for a contact that matches your criteria.
Procedure
Step 1 Enter your search criteria in the field in the search pane.
Enter part or all of a full name, first name, last name, nickname, user ID, or phone
number.
Searches are not case-sensitive, and the letters you enter can appear in any
position in the name. For example, if you search for “and”, you find “Anderson”
and “Cassandra”. Username is often the part of the e-mail address that precedes
the “@” sign.
Step 2 Press the <Enter> key.
Step 3 (Optional) To stop the search, click the (x) button.
Step 4 To work with the results you found, see the “Working With Search Results”
section on page 7-4.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
7-3
Page 62

Working With Contacts
Working With Search Results
To Do This Do This
Sort the list of found results Click a column heading in the Search
Change the view of the pane See the “Changing the View of the
Clear the list of Search results Click the (x) button in the Search field
See and use more options for Search
results
Chapter 7 Managing Contacts
pane.
Click again to reverse the sort order.
Console and Its Panes” section on
page 1-9
or delete the text you entered.
See the “Working With Items Listed in
Panes” section on page 1-10
Accessing Contact Details
All information in the Contact Details window except the nickname comes from
the corporate directory. To change a contact’s nickname, see the table in the
“Working With Contacts” section on page 7-2.
From Here Do This
Any pane in the console Contacts and Search panes:
The roster of an active
conversation
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
7-4
• Control-click a name > Get Info.
• Click a name, then choose File > Get Info.
In the Recent Communications pane, contact details
are available only for named entries. Control-click
and choose Get Contact Info.
Control-click a name in the list > Get Info.
OL-10984-01
Page 63

Chapter 7 Managing Contacts
Deleting Contacts from the Contact List
Note If a contact appears more than once in your console, you must delete each instance
separately.
To delete contacts, use any of the following methods:
• Control-click a contact > Delete Contact.
• Click an entry to select it. Then choose Edit > Delete.
Note • To delete a group and all of its contacts, see the “Deleting Groups” section on
page 7-7.
• To delete Recent Communications entries, see the table in the “Working With
the Recent Communications List and Its Entries” section on page 8-2.
• You cannot delete entries in the Search pane. To clear the list, see the
“Working With Search Results” section on page 7-4.
Working with Groups of Contacts
Working with Groups of Contacts
You can create groups to organize your contacts.
To Do This Do This
Create a group
Add contacts to a group See the “Adding Contacts to Groups”
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
• Control-click a group name > New
• Choose Contacts > New Group
section on page 7-6.
Group.
7-5
Page 64

Working with Groups of Contacts
To Do This Do This
Rename a group
You cannot rename the General group.
Hide the contacts in a group Click the group name.
Show the contacts in a group Click the group name.
Delete a group See the “Deleting Groups” section on
Adding Contacts to Groups
The contact that you want to add must already exist in your corporate directory.
You can add a contact to one or more groups.
Chapter 7 Managing Contacts
• Control-click a group name >
Rename Group.
• Choose Contacts > Rename
Group > [choose a group to
rename].
page 7-7.
7-6
Procedure
Step 1 If the group does not yet exist, create it. For instructions, see the table in the
“Working with Groups of Contacts” section on page 7-5.
Step 2 Do one of the following:
To Add a Contact From Do This
The Contacts pane
• Control-click a contact and choose Move Contact
To or Copy Contact To, then choose a group.
• Select a contact and choose Contacts > Add
Contact To > [group name].
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 65

Chapter 7 Managing Contacts
Deleting Groups
Working with Groups of Contacts
To Add a Contact From Do This
The Recent
Communications or
Search panes
The roster Right-click a name and choose Add Contact To, then
When you delete a group, contacts in the group are also deleted. However, if the
contact belongs to multiple groups, only the one instance is deleted.
You cannot delete the General group.
To delete groups, use any of the following methods:
• Control-click a group name > Delete Group.
• Select a contact or contacts. Then choose
Contacts > Add Contact To > [group name].
• Control-click a contact and choose Add Contact
To, then choose a group.
choose the name of group.
OL-10984-01
• Choose Contacts > Delete Group > [choose a group to delete].
Related Topics
• Deleting Contacts from the Contact List, page 7-5
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
7-7
Page 66

Working with Groups of Contacts
Chapter 7 Managing Contacts
7-8
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 67

Working With Recent Communications
Recent Communications topics include:
• About Recent Communications, page 8-1
• Working With the Recent Communications List and Its Entries, page 8-2
• Accessing Voice Mail, page 8-4
About Recent Communications
Your call history appears in the Recent Communications pane, so you can easily
see and return calls and listen to voice mail.
The Recent Communication pane lists all voice-mail messages you have received,
and up to 50 received, initiated, or missed calls.
New voice-mail messages appear in the list within one minute.
Unread communications appear in bold text. Icons for unread communications
may also appear in color.
CHA P T ER
8
OL-10984-01
Calls that you make or receive while using your Cisco Unified IP Phone only
appear in the Recent Communications list if Cisco Unified Personal
Communicator is running. Calls that you make using your desk phone appear only
if you have set the active phone to Desk Phone. Voice mail appears regardless.
If you log on from different computers, only the communications that occur while
you are logged into a particular computer appear in the recent communications list
on that computer.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
8-1
Page 68

Chapter 8 Working With Recent Communications
Working With the Recent Communications List and Its Entries
Working With the Recent Communications List and
Its Entries
To Do This Do This
Identify the
communication type
of an entry
• Show only one
type of
communication
• View all recent
communications
Sort the list Click any column heading to sort by that heading.
The first column in the Recent Communications pane
shows the type of communication. To identify the icons,
see the “About Recent Communications Items” section
on page 8-3.
• From the pop-up menu in the Recent pane, choose
an option.
• Choose Recent > Display and choose an option.
Click again to reverse the sort order.
8-2
View details about an
entry
Mark entries unread
Add an entry to your
Contacts list
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
• Hover your mouse pointer over an entry.
• Choose File > Get Info.
• Control-click an entry in the Recent
Communications list and choose Get Info.
• Control-click an entry and choose Mark Recent
Item Unread.
• Click an entry and choose Recent > Mark Item as
Unread.
• View details about the entry. Then choose Actions >
Mark Unread.
See the “Adding Contacts to Groups” section on
page 7-6.
OL-10984-01
Page 69

Chapter 8 Working With Recent Communications
To Do This Do This
Delete entries To mark an entry for deletion:
Undelete entries
Working With the Recent Communications List and Its Entries
• Control-click an entry and choose Delete Recent
Item.
• Click an entry and choose Recent > Delete item or
Edit > Delete.
• View details about an entry. Then click the Action
menu and choose Delete.
• Select an entry and press the Delete key on your
keyboard.
To permanently delete all entries marked for deletion:
Choose Recent > Purge Deleted Items.
Note When you delete voice mail using your desk
phone, you must separately delete the same voice
mail from Cisco Unified Personal
Communicator.
• Control-click an entry that is marked for deletion
and choose Undelete Recent Item.
• Click an entry and choose Recent > Undelete Item.
• View details about the entry. Then click the Action
menu and choose Undelete.
Work wi t h the
Recent
See the “Working With Items Listed in Panes” section on
page 1-10.
Communications list
Change the view of
the pane
See the “Changing the View of the Console and Its
Panes” section on page 1-9.
About Recent Communications Items
The following information describes the items listed in the Recent
Communications pane.
• Items that are deleted but not yet purged appear in strikethrough text.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
8-3
Page 70

Accessing Voice Mail
Chapter 8 Working With Recent Communications
• Items in bold are unread.
Icon Communication Type
Voice-mail message
Unread instances are in color.
Missed call
Unread instances are in color.
Answered incoming call
Outgoing call
Accessing Voice Mail
You can receive and listen to voice-mail messages in
Cisco Unified Personal Communicator.
To Do This Do This
Set up voice mail
access via Cisco
Unified Personal
Communicator
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
8-4
See the “Setting Up Voice Mail and Web Conferencing”
section on page 9-2.
OL-10984-01
Page 71

Chapter 8 Working With Recent Communications
To Do This Do This
Listen to voice mail
• Rewind to
beginning
• Fast-play
reverse
• Play
• Pause
• Fast-play
forward
• Seek (Rewind to
a specific point
in the message)
• Change
playback
volume
Perform other
actions
Accessing Voice Mail
In the Recent Communications list:
• Double-click a voice-mail entry.
• Control-click a voice-mail entry > Play Voice Mail.
• Click a voice-mail entry in the list, then choose
Recent > Play Voice Mail.
In the window:
• Click the appropriate button, or slide the appropriate
slider. The larger slider is the Seek slider.
See the “Working With the Recent Communications List
and Its Entries” section on page 8-2.
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
8-5
Page 72

Accessing Voice Mail
Chapter 8 Working With Recent Communications
8-6
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 73

About Your Preferences and Status
Preferences and status topics include:
• Viewing Your Current Status, page 9-1
• Specifying Preferences, page 9-2
Viewing Your Current Status
To View This Do This
The status of your connection Look at the bottom of the console.
Your reachability status
Your contact information Choose Contacts > Show My Info.
Your video image See the “Previewing Your Video
CHA P T ER
• Choose Contacts > Show My
Info.
• To have a constant view of your
status: Add yourself to your
contacts list. See the “Adding
Contacts to Groups” section on
page 7-6.
Status icon descriptions are in the
“Determining Callee Reachability”
section on page 2-4.
Image” section on page 3-2.
9
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
9-1
Page 74

Chapter 9 About Your Preferences and Status
Specifying Preferences
Specifying Preferences
• Setting Up Voice Mail and Web Conferencing, page 9-2
• Setting Up Automatic Login and Password Entry, page 9-4
• Choosing the Active Phone, page 9-5
• Specifying Your Preferred Contact Method and Contact Information,
page 9-7
• Specifying Your Reachability Status, page 9-9
Setting Up Voice Mail and Web Conferencing
Use the procedures referenced in this section if:
• You have just logged in to Cisco Unified Personal Communicator for the first
time.
• Your system administrator tells you to set up
Cisco Unified Personal Communicator to use voice mail or web
conferencing.
• Your voice-mail or web-conferencing passwords change and you need to
update the passwords in Cisco Unified Personal Communicator to match.
Procedures
• Setting Up Voice Mail, page 9-2
• Setting Up Web Conferencing, page 9-3
Setting Up Voice Mail
Use this procedure if you want to access voice mail via Cisco Unified Personal
Communicator.
Procedure
Step 1 From your system administrator, obtain the username and password that you must
enter into Cisco Unified Personal Communicator in order to use voice mail.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
9-2
OL-10984-01
Page 75

Chapter 9 About Your Preferences and Status
Step 2 Choose CiscoUPC > Preferences.
Step 3 Click Accounts.
Step 4 Click Account Information.
Step 5 In the list on the left side of the window, click Unity Voicemail.
Step 6 Enter your login information for voice-mail access. If your system administrator
gave you two passwords, use the Cisco Unity Assistant (web) password.
Step 7 Click Save.
Related Topics
• Setting Up Cisco Unified Personal Communicator, page 1-3
• Accessing Voice Mail, page 8-4
Setting Up Web Conferencing
Specifying Preferences
OL-10984-01
Note Anyone can participate in web conferencing. Your system administrator will tell
you if you need to follow this procedure in order to add web conferencing to a
conversation.
Procedure
Step 1 From your system administrator, obtain the username and password that you must
enter into Cisco Unified Personal Communicator in order to use web
conferencing.
Step 2 Choose CiscoUPC > Preferences.
Step 3 Click Accounts.
Step 4 Click Account Information.
Step 5 In the list on the left side of the window, click MeetingPlace Express.
Step 6 Enter your login information for web conferencing.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
9-3
Page 76

Chapter 9 About Your Preferences and Status
Specifying Preferences
Step 7 Click Save.
Related Topics
• Setting Up Cisco Unified Personal Communicator, page 1-3
• Using Web Conferencing, page 4-1
Setting Up Automatic Login and Password Entry
These settings apply only on the computer on which you set them.
Before Logging In
Procedure
Step 1 Launch the application
Step 2 Enter your username and password.
Step 3 Check one or both check boxes:
Step 4 Click Login.
After Logging In
Step 1 Choose CiscoUPC > Preferences, then click Profile
Step 2 Check one or both check boxes:
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
9-4
• Remember password in Keychain
• Automatically log in as: [user name]
You must check both check boxes to log in automatically.
Procedure
• Remember the password for this profile
OL-10984-01
Page 77

Chapter 9 About Your Preferences and Status
• Automatically log in using this profile.
In order to log in automatically, you must also check Remember the
password for this profile.
Related Topics
• Canceling Automatic Log In and Password Entry, page 9-5
Canceling Automatic Log In and Password Entry
You can cancel the settings described in the “Setting Up Automatic Login and
Password Entry” section on page 9-4.
Procedure
Step 1 Choose CiscoUPC > Preferences.
Step 2 Click Profile.
Step 3 In the Log In section, uncheck the appropriate check box or boxes.
Specifying Preferences
Choosing the Active Phone
Cisco Unified Personal Communicator can work with a Cisco Unified IP Phone
such as the one on your desk, or work independently as a soft phone. A soft phone
is a software application that lets you use your computer as a telephone.
You can change the active phone at any time, except during a call.
If your soft phone is the active phone, you can use your desk phone, but calls you
make using your desk phone do not appear in the Recent Communications list.
Procedure
Step 1 To change the active phone, do one of the following:
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
9-5
Page 78

Specifying Preferences
• Choose CiscoUPC > Preferences. Then click Profile and choose a Phone
Mode option.
• From the pop-up menu near the top of the console, choose a phone option.
Note If you want to use video, choose Soft Phone.
Step 2 If you chose Desk Phone, see the “Choosing the Associated Desk Phone” section
on page 9-6.
Choosing the Associated Desk Phone
If your system administrator has enabled this feature, you may be able to associate
Cisco Unified Personal Communicator with one of several desk phones. For
example, you may be able to temporarily use a phone in a conference room as if
it were the phone on your own desk.
By default, the Cisco Unified IP Phone on your desk is the associated desk phone.
Chapter 9 About Your Preferences and Status
9-6
Procedure
Step 1 Using the method described in the User Guide for your Cisco IP Phone, log in to
the phone that you want to associate with Cisco Unified Personal Communicator.
Step 2 Make sure your active phone is Desk Phone.
Step 3 Do one of the following:
• From the Phone Mode drop-down list near the top of the console, choose
Choose Desk Phone.
• Choose CiscoUPC > Preferences. Then click Profile. Then, for the Phone
Mode option, choose Choose Desk Phone.
Step 4 Click a phone in the list to select it. Use the information in the table to help you
identify the phones in the list:
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 79

Chapter 9 About Your Preferences and Status
Column
Number Column Name Description
1
2
3
4
5
Device status The currently associated desk phone is identified by a
Device type Hover your mouse pointer over the icon to identify the
Name To identify a phone for future reference, double-click
Device Name Number printed on the MAC label on the bottom of
Lines Phone numbers (extensions) available via this phone.
Specifying Preferences
green bubble with a check mark.
Tip: To identify a phone, take the phone off the hook;
if a device status in the list changes to blue with a dot
in the center, you have identified the phone.
model of the phone.
the name and enter a name of your choice.
the phone.
Note To choose the phone on your own desk after you have changed it, click
Restore Default.
Step 5 Click OK.
Related Topics
• Choosing the Active Phone, page 9-5
Specifying Your Preferred Contact Method and Contact Information
Your preferred contact method specifies two things:
• The default contact method that Cisco Unified Personal Communicator uses
when you contact people.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
9-7
Page 80

Chapter 9 About Your Preferences and Status
Specifying Preferences
For example, if your preferred contact method is Phone then when you
double-click a contact name, Cisco Unified Personal Communicator will
phone that person. If you choose E-mail, Cisco Unified Personal
Communicator will open a blank e-mail message addressed to the person.
• The contact method and phone number or e-mail address that you want other
people to use to contact you.
To learn how this information is used, see the “Identifying Preferred Contact
Methods” section on page 2-6.
Specifying the Method, Phone Number, and E-mail Address
Procedure
Step 1 Choose CiscoUPC > Preferences.
Step 2 Click Profile.
Step 3 For Preferred Contact, choose an option.
Step 4 For Preferred phone and Preferred e-mail, add the preferred contact number or
address:
a. Click the pop-up menu and choose Add/Remove...
b. Enter the contact information in New, click Add, then click Done.
Step 5 Choose your preferred phone number and e-mail address from the pop-up menus
in Step 4.
By default, the system uses information from your corporate directory.
Specifying Only the Method
Click the Preferred Contact icon near the top of the console and choose an option.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
9-8
OL-10984-01
Page 81

Chapter 9 About Your Preferences and Status
Specifying Your Reachability Status
Your reachability status automatically changes based on when you use your
computer or your phone, unless you choose a reachability status to display. If you
set your status, this setting reverts to Automatic each time you log in to
Cisco Unified Personal Communicator.
Reachability statuses are described in the “Determining Callee Reachability”
section on page 2-4.
Procedure
Step 1 Perform the following:
• Near the top of the console, click the selection that is currently showing.
Step 2 Choose an option:
Option Details
Automatically change status for
activity
If there is no check mark beside the
option, select the option.
Specifying Preferences
Cisco Unified Personal Communicator
will display your status according to
the descriptions in the table in the
“Determining Callee Reachability”
section on page 2-4.
OL-10984-01
To specify the conditions under which
your status shows as Idle or Away, see
the “Specifying When Your
Reachability Status Changes
Automatically” section on page 9-10.
Ava il abl e The option you choose shows until you
Busy
change it or quit Cisco Unified
Personal Communicator.
Away
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
9-9
Page 82

Chapter 9 About Your Preferences and Status
Specifying Preferences
Step 3 (Optional) Specify a custom status message. See the “Specifying Your Custom
Status Message” section on page 9-11.
Specifying When Your Reachability Status Changes Automatically
When your reachability status is set to Automatic, you should specify the
conditions under which you appear to other users of Cisco Unified Personal
Communicator as Available, Busy, Idle, or Away.
These settings apply whenever you are logged in to Cisco Unified Personal
Communicator. They remain until you change them; you do not need to set them
each time you log in.
Procedure
Step 1 Choose CiscoUPC > Preferences.
Step 2 Click Reachability.
9-10
To Do This Do This
Always appear to other users as
Uncheck both check boxes in the window.
Available or Busy
Never appear to other users as Idle Uncheck To Idle when I have not used
the computer for: ___minutes
Never appear to other users as Away Uncheck To Away when I have not used
the computer for: ___minutes
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 83

Chapter 9 About Your Preferences and Status
To Do This Do This
Let your status reflect your activity,
so that other users see your status as
Available, Busy, Idle, or Away.
Related Topics
• Specifying Your Reachability Status, page 9-9
Specifying Preferences
Do all of the following:
• Check both check boxes.
• Specify the number of minutes that
your phone or keyboard remains idle
before your status changes to Idle
and to Away.
The number of minutes that you
specify for Idle must be less than the
number of minutes you specify for
Away.
Specifying Your Custom Status Message
You can enter a custom status message that users see when they do the following:
• Hover their mouse pointer over your name in their contact list or Recent
Communications.
• Look at your contact card (the message appears below your name.)
You can create and store multiple status messages from which to choose:
• Creating Custom Status Messages, page 9-11
• Choosing a Message to Display, page 9-12
• Modifying Custom Status Messages, page 9-12
• Deleting Custom Status Messages, page 9-12
Creating Custom Status Messages
Step 1 Click the Reachability pop-up menu near the top of the console and choose Edit
Status Menu....
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
9-11
Page 84

Specifying Preferences
Step 2 Click the [+] button below the category of message you want to add (Available,
Step 3 Enter your custom status message, then press the <Enter> key.
Step 4 Click Done.
Step 5 (Optional) Choose the message to display.
Chapter 9 About Your Preferences and Status
Busy, or Away).
Choosing a Message to Display
After you have created and saved a custom status message, you can choose it at
any time:
Click the Reachability pop-up menu near the top of the console and choose a
custom status message.
Note If there is a check mark beside Automatically change status for activity,
and your reachability status changes, your message does not change. For
more information about automatic status change, see the “Specifying
Your Reachability Status” section on page 9-9.
9-12
Modifying Custom Status Messages
Step 1 Click the Reachability pop-up menu near the top of the console and choose Edit
Status Menu.
Step 2 Double-click a message to change.
Step 3 Enter your new message.
Step 4 Click Done.
Deleting Custom Status Messages
Step 1 Click the Reachability pop-up menu near the top of the console and choose Edit
Status Menu.
Step 2 Click a message to delete.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 85

Chapter 9 About Your Preferences and Status
Step 3 Click the [-] button below the message.
Step 4 Click Done.
Specifying Preferences
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
9-13
Page 86

Specifying Preferences
Chapter 9 About Your Preferences and Status
9-14
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 87

CHA P T ER
Troubleshooting
The following topics can assist you with troubleshooting.
• Installation Problems, page 10-2
• Problems Logging In and Connecting to the Network, page 10-2
• Configuration Problems, page 10-2
• Problems with the Console, page 10-3
• Problems with Reachability, page 10-3
• Problems Making Calls, page 10-4
• Problems With Incoming Calls, page 10-4
• Problems During a Conversation, page 10-4
• Problems with Video, page 10-6
• Problems with Web Conferencing, page 10-7
• Problems in the Recent Communications Pane, page 10-7
10
OL-10984-01
• Problems with Search, page 10-8
• Capturing Information About Problems, page 10-8
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
10-1
Page 88

Chapter 10 Troubleshooting
Installation Problems
Installation Problems
Problem When I double-click the disk image, I do not see an opportunity to install
the application.
Solution Make sure the Finder is set to display in Icon View. Choose Finder >
Preferences and uncheck the check box to Open new windows in column view.
Problems Logging In and Connecting to the Network
Problem On initial login, I see an error message.
Solution Make sure you have entered your username, password, and login server
information correctly. If you still have problems, contact your system
administrator.
Problem When I try to log in, the Login window reappears.
Solution Respond to the error message that appears near the bottom of the Login
window.
Configuration Problems
Problem When I choose a phone, the active phone reverts to Disabled and I cannot
make or receive calls.
Solution Try the following:
• Choose the other phone option.
• If you are trying to choose your desk phone, make sure you are connected to
the network to which your desk phone is connected.
• Contact your system administrator.
Problem I’m trying to choose a desk phone other than the one on my desk, but the
phone I want is not listed.
Solution Not all phones are set up for extension mobility; contact your system
administrator.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
10-2
OL-10984-01
Page 89

Chapter 10 Troubleshooting
Problems with the Console
Problem The console is too big; it does not fit on my screen.
Solution The minimum recommended screen resolution is 1024x768.
Choose Apple menu > System Preferences and click Displays.
For more information, see the Help for your operating system.
Problem The menu item, button, or other option that I want to use is dimmed.
Solution Possible solutions include:
• You may need to click a contact or communication, then click the button.
• The option may not be available for the contact or communication that you
have currently selected.
• The option may not apply in the current situation. For example, “Mark
Unread” is not available if you have selected an item that is already marked
Unread.
• See also Problems Making Calls, page 10-4.
Problems with the Console
Problem Columns in the console are too narrow to display all of the information.
Solution Possible solutions include:
• Hover your mouse pointer over an item in a list to view more information.
• Resize the columns. See the “Changing the View of the Console and Its
Panes” section on page 1-9.
• Make the entire console larger. See the “Changing the View of the Console
and Its Panes” section on page 1-9.
Problems with Reachability
Problem Reachability indicators are not appearing correctly.
Solution Make sure your firewall settings are correct. Contact your system
administrator. If necessary, see the online help or documentation for your
operating system.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
10-3
Page 90

Problems Making Calls
Problems Making Calls
Problem I want to start an audio or video call or send an e-mail, but the button and
menu item are dimmed.
Solution Possible solutions include:
• You must first click the name of a contact or communication in the console.
• The contact card for the contact you have selected does not have the required
information. For example, phone number or e-mail address is missing.
• If you have further questions, contact your system administrator.
Problems With Incoming Calls
Problem A notification did not appear on my screen when someone called.
Solution Notifications only operate when Cisco Unified Personal Communicator
is running. Make sure you launch the application each time you turn on your
computer.
Chapter 10 Troubleshooting
Problems During a Conversation
See also:
• Problems with Video, page 10-6
• Problems with Web Conferencing, page 10-7
Problem I am using my soft phone on a call and I hear no sound. However, the
conversation window indicates that I am connected.
Solution Try the following:
• Look at the conversation window and make sure that the volume is not too
low and that the conversation is not on hold.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
10-4
OL-10984-01
Page 91

Chapter 10 Troubleshooting
Problem Other participants cannot hear me.
Solution Try the following:
Problems During a Conversation
• Make sure your computer is not muted or set to very low volume. To test this,
see if you can hear other sounds that your computer normally makes, such as
beeps when you press an incorrect key, or sounds that signal that a message
has arrived.
• Verify that the sound output device (for example, headset) you are using is
selected and not muted. Choose System Preferences > Sound, then click
Output and examine the selections. If you make changes, you may need to
restart the computer.
• If you are connecting via virtual private network (VPN): In the VPN
application window, click the Options menu. The Stateful Firewall option
should NOT have a check mark beside it. If it does, select Stateful Firewall
to remove the check mark.
• Make sure any Mute button on your headset is not on.
• Look at the conversation window and make sure that your audio is not muted.
• Verify that the sound input device (for example, headset or camera) you are
using is selected and not muted. Choose System Preferences > Sound, then
click Input and examine the selections. If you make changes, you may need
to restart the computer.
OL-10984-01
Problem The buttons and controls in my conversation window are dimmed.
Solution The call may be on hold. See the “Putting Conversations on Hold and
Retrieving Them” section on page 2-12.
Problem I am trying to merge two calls but the Merge button is dimmed.
Solution Note the following:
• You cannot merge two conference calls. At least one call must have only one
participant besides yourself. To merge multiple participants into a single call,
see the “Creating Conference Calls” section on page 5-1.
• Make sure one of the calls is not on hold. If a conversation is on hold, the
merge button is dimmed.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
10-5
Page 92

Problems with Video
Problems with Video
Problem The options to start a video conversation, add video to my conversation,
answer a call with video, or “View local video” are dimmed.
Solution You can use video only if your soft phone is the active phone. See the
“Choosing the Active Phone” section on page 9-5. You will need to end any
current conversation and start a new one with the soft phone.
Problem The computer does not properly recognize the camera, or I cannot see my
own video image.
Solution Try the following:
• Make sure you meet the criteria in the “Before You Use Video” section on
page 3-2.
• Unplug the camera and plug it in again.
• Plug the camera into a different USB port.
• Quit Cisco Unified Personal Communicator if it is running, then relaunch it.
Chapter 10 Troubleshooting
10-6
Problem I added video to a conversation, but the video image of the other person
does not appear.
Solution The other person may not have a video camera, or may have declined to
add video to the conversation.
Problem Video is slow or of poor quality, or does not appear.
Solution Try the following:
• If you are running on battery power, plug in the AC adaptor.
• Click the Help menu and make sure there is no check mark beside Enable
Detailed Logging. For more information, see “Enabling Detailed Logging”
section on page 10-9.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 93

Chapter 10 Troubleshooting
Problems with Web Conferencing
Problem I cannot add web conferencing. Or, when I click the button to start a web
conference, I see an error message.
Solution Possible solutions include:
• You may not have correctly specified your
Cisco Unified MeetingPlace Express account information. See the “Setting
Up Voice Mail and Web Conferencing” section on page 9-2. If you do not
know your username and password, contact your system administrator.
• You may need to have a profile (account) in
Cisco Unified MeetingPlace Express. Contact your system administrator.
Problem I have lost connection to the web conference.
Solution Click the Rejoin Conference button in the conversation window.
Problem Some participants in the conversation do not see the web conferencing
window.
Solution Possible solutions include:
• Participants who are not using Cisco Unified Personal Communicator do not
automatically see the web conferencing window. Follow the instructions in
the “Adding Participants to Web Conferencing Sessions” section on page 4-2.
Problems with Web Conferencing
• The Cisco Unified MeetingPlace Express system may not have enough
available resources to accommodate all participants. Contact your system
administrator.
Problems in the Recent Communications Pane
Problem Recent Communications does not list calls that I know occurred.
Solution Calls that you make and receive using your desk phone while
Cisco Unified Personal Communicator is not running do not appear in Recent
Communications.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
10-7
Page 94

Problems with Search
Problem A person in my company has called me, but the Recent Communications
pane shows the phone number of the person, not the name.
Solution The person may have called from a number that the system does not
recognize (for example, a home phone), or the corporate directory may be out of
date.
Problems with Search
Problem Search seems to find incorrect results.
Solution The system searches several different attributes, and depending on how
the administrator has configured them, can include results that you might not
expect.
Capturing Information About Problems
If you experience problems, your system administrator may request log files. Use
the following procedure to collect these files.
Chapter 10 Troubleshooting
10-8
Note If you see the message The application Cisco Unified Personal
Communicator-K9 quit unexpectedly, click Close. Do not send a report to
Apple.
Note If you experience a problem follow these instructions immediately, before you
relaunch the application.
Step 1 Collect the following files:
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 95

Chapter 10 Troubleshooting
File In This Folder
UnifiedClientLog.txt
Cisco Unified Personal
Communicator-K9.crash.log
Step 2 Collect information about your computer:
a. Choose Apple menu > About This Mac.
b. Click More Info.
c. Choose File > Save As and save the file in any available file format.
Step 3 Send the following to your system administrator:
Capturing Information About Problems
<Your hard disk>/Users/<your user
name>/Library/Logs/Cisco/
<Your hard disk>/Users/<your user
name>/Library/Logs/CrashReporter/
or
<Your hard
disk>/Library/Logs/CrashReporter/
(There may not be a file in either
place.)
• All files you collected or saved in this procedure.
• A description of what you were doing when the problem occurred
• Any error messages you received
Related Topics
• Enabling Detailed Logging, page 10-9
Enabling Detailed Logging
If you are experiencing problems using Cisco Unified Personal Communicator
and your administrator tells you to do so, enable detailed logging: Choose Help >
Enable Detailed Logging.
Use the same procedure to turn off detailed logging.
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
10-9
Page 96

Capturing Information About Problems
Your setting remains until you change it, even after you restart. Detailed logging
may impair performance, so you should turn it off as soon as you no longer need
it.
Chapter 10 Troubleshooting
10-10
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
Page 97

C
GLOSSARY
collaboration
console
contact card
conversation
window
D
desk phone
dial pad
See web conference.
The main window in Cisco Unified Personal Communicator. It includes
Contacts, Recent Communications, and Search panes, as well as status
information, buttons, menus, and other control options.
Contact Details window.
A window that displays during a conversation.
A Cisco Unified IP Phone on your company network. Generally, the phone on
your desk.
A small window that functions as a telephone keypad.
There are two dial pads that look similar: one that you use to dial a phone
number, and one that you access from an active conversation window and use to
respond to instructions to enter information such as a numbered choice or a
password.
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
GL-1
Page 98

P
Glossary
preferred contact
method
presence
profile
R
reachability
Allows you to specify the medium through which you want to contact others and
be contacted by others, such as phone or e-mail.
See reachability.
Information about you that is stored in the
Cisco Unified Personal Communicator system, such as which preferences you
have set.
In the context of web conferencing, profile refers to your user account for
Cisco Unified MeetingPlace Express.
The availability status of a Cisco Unified Personal Communicator user, such as
Available, Busy, or Away. This status displays to other users of
Cisco Unified Personal Communicator, who can use it to determine the best
time and method to contact people.
The system can determine your reachability by detecting when you are using
your computer or phone, or you can set your reachability status.
S
soft phone
W
web conference
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
GL-2
Software that functions as a telephone. Cisco Unified Personal Communicator
includes a soft phone.
A Cisco Unified Personal Communicator feature that lets you display
documents and applications on your computer to conversation participants.
OL-10984-01
Page 99

INDEX
A
active phone 1-5, 9-5, 10-6
choosing 1-9
troubleshooting 10-2
Address Book
Macintosh
2-8
answering calls 2-8
troubleshooting 10-4
applications
sharing
4-1
audio
troubleshooting
10-4
audio quality
troubleshooting
10-4
automatic (reachability) 9-9
availability. See Reachability.
available (reachability)
2-5
away (reachability) 2-5
B
busy (reachability) 2-5
buttons
identifying
1-9
troubleshooting 10-3
C
call history 8-1
calls
See also conversations
answering
troubleshooting 10-4
transferring 2-10
Cisco IP Phone Messenger 7-1
Cisco Unified IP Phone 1-2, 7-1, 8-1
See also desk phone
model 7985
Cisco Unified MeetingPlace Express 4-4
See also web conferencing.
Cisco Unified Personal Communicator,
Cisco Unified Video Advantage 3-2
Cisco Unity Connection 9-3
Click-to-call. See conversations, starting.
collaboration. See Web Conferencing.
communication details
conference calls 1-2, 2-13
creating 5-1
about
2-8
3-2
1-1
8-2
OL-10984-01
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
IN-1
Page 100

Index
topics 5-1
configuring 1-5
connecting
troubleshooting
10-2
connections
multiple
1-6
connection status 1-9, 9-1
console 1-7, GL-1
columns 1-10
maximizing 1-9
minimizing 1-9
resizing 1-10
troubleshooting 10-3
contact card GL-1
contact details
modifying
7-3
viewing 7-2, 7-4
contact list 1-6
about 7-1
topics 7-1
contacts
adding to groups
7-6
deleting 7-5
groups 7-5
collapsing 7-6
creating 7-5
deleting 7-7
renaming 7-6
showing 7-6
nickname 7-4
searching for 7-3, 7-4
sorting search results 7-4
topics 7-1
working with 7-2
conversation
active
5-2
identifying participants 2-11
conversations
about
2-1
ending 2-13
multiple 2-9, 5-1
merging 5-2
options during 2-9
starting 2-2, 2-6
troubleshooting 10-3, 10-4
starting video 3-3
topics 2-1
troubleshooting 10-4
conversation window 2-13, GL-1
CrashReporter 10-8
D
deleting
contacts
recent communications 8-3
See also Undeleting recent communications
desk phone
7-3
1-2, 1-11, 2-2, 2-8, 2-11, 2-13, 3-2, 9-5, 9-6,
10-2, 10-7, GL-1
IN-2
User Guide for Cisco Unified Personal Communicator for Macintosh, Release 1.1
OL-10984-01
 Loading...
Loading...