Page 1

Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
First Published: 2014-03-15
Last Modified: 2017-01-22
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Text Part Number: OL-31641-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH
THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY,
CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version
of the UNIX operating system. All rights reserved. Copyright©1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWAREOF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS.
CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT
LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS
HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network
topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional
and coincidental.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: http://
www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership
relationship between Cisco and any other company. (1110R)
©
2014 Cisco Systems, Inc. All rights reserved.
Page 3

CONTENTS
Preface
CHAPTER 1
CHAPTER 2
CHAPTER 3
Preface xix
Audience xix
Document Conventions xix
Related Documentation for Cisco Nexus 5600 Series NX-OS Software xxi
Documentation Feedback xxii
Obtaining Documentation and Submitting a Service Request xxii
New and Changed Information 1
New and Changed Information 1
Overview 3
System Management Features 3
Configuring Switch Profiles 7
Information About Switch Profiles 8
Switch Profile Configuration Modes 8
Configuration Validation 9
Software Upgrades and Downgrades with Switch Profiles 10
Prerequisites for Switch Profiles 10
Guidelines and Limitations for Switch Profiles 10
Configuring Switch Profiles 12
Adding a Switch to a Switch Profile 13
Adding or Modifying Switch Profile Commands 15
Importing a Switch Profile 17
Importing Configurations in a vPC Topology 19
Verifying Commands in a Switch Profile 19
Isolating a Peer Switch 20
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 iii
Page 4

Contents
Deleting a Switch Profile 20
Deleting a Switch from a Switch Profile 21
Displaying the Switch Profile Buffer 22
Synchronizing Configurations After a Switch Reboot 23
Switch Profile Configuration show Commands 23
Configuration Examples for Switch Profiles 24
Creating a Switch Profile on a Local and Peer Switch Example 24
Verifying the Synchronization Status Example 26
Displaying the Running Configuration 26
Displaying the Switch Profile Synchronization Between Local and Peer Switches 27
Displaying Verify and Commit on Local and Peer Switches 28
Successful and Unsuccessful Synchronization Examples 29
Configuring the Switch Profile Buffer, Moving the Buffer, and Deleting the Buffer 29
CHAPTER 4
CHAPTER 5
Replacing a Cisco Nexus 5000 Series Switch 30
Configuring Module Pre-Provisioning 33
Information About Module Pre-Provisioning 33
Guidelines and Limitations 33
Enabling Module Pre-Provisioning 34
Removing Module Pre-Provisioning 35
Verifying the Pre-Provisioned Configuration 35
Configuration Examples for Pre-Provisioning 36
Using Cisco Fabric Services 37
Information About CFS 37
Cisco Fabric Services over Ethernet 38
Guidelines and Limitations for CFS 38
CFS Distribution 39
CFS Distribution Modes 39
Uncoordinated Distribution 39
Coordinated Distribution 39
Unrestricted Uncoordinated Distributions 40
Verifying the CFS Distribution Status 40
CFS Support for Applications 40
CFS Application Requirements 40
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
iv OL-31641-01
Page 5

Contents
Enabling CFS for an Application 41
Verifying Application Registration Status 41
Locking the Network 41
Verifying CFS Lock Status 42
Committing Changes 42
Discarding Changes 43
Saving the Configuration 43
Clearing a Locked Session 43
CFS Regions 44
About CFS Regions 44
Example Scenario 44
Managing CFS Regions 44
Creating CFS Regions 44
Assigning Applications to CFS Regions 45
Moving an Application to a Different CFS Region 45
Removing an Application from a Region 46
Deleting CFS Regions 46
Configuring CFS over IP 47
Enabling CFS over IPv4 47
Enabling CFS over IPv6 47
Verifying the CFS Over IP Configuration 48
Configuring IP Multicast Addresses for CFS over IP 48
Configuring IPv4 Multicast Address for CFS 48
Configuring IPv6 Multicast Address for CFS 48
Verifying the IP Multicast Address Configuration for CFS over IP 49
Default Settings for CFS 49
Enabling CFS to Distribute Smart Call Home Configurations 50
Enabling CFS to Distribute Device Alias Configurations 50
Enabling CFS to Distribute DPVM Configurations 51
Enabling CFS to Distribute FC Domain Configurations 52
Enabling CFS to Distribute FC Port Security Configurations 53
Enabling CFS to Distribute FC Timer Configurations 53
Enabling CFS to Distribute IVR Configurations 54
Enabling CFS to Distribute NTP Configurations 55
Enabling CFS to Distribute RADIUS Configurations 56
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 v
Page 6

Contents
Enabling CFS to Distribute RSCN Configurations 56
Enabling CFS to Distribute TACACS+ Configurations 57
CHAPTER 6
CHAPTER 7
Configuring PTP 59
Information About PTP 59
PTP Device Types 60
PTP Process 61
Clock Management 62
High Availability for PTP 62
Licensing Requirements for PTP 62
Guidelines and Limitations for PTP 62
Default Settings for PTP 63
Configuring PTP 63
Configuring PTP Globally 63
Configuring PTP on an Interface 65
Verifying the PTP Configuration 66
Feature History for PTP 67
Configuring User Accounts and RBAC 69
Information About User Accounts and RBAC 69
User Roles 69
Predefined SAN Admin User Role 70
Rules 71
SAN Admin Role-Feature Rule Mapping 71
User Role Policies 73
User Account Configuration Restrictions 74
User Password Requirements 75
Guidelines and Limitations for User Accounts 75
Configuring User Accounts 76
Configuring SAN Admin Users 77
Configuring RBAC 78
Creating User Roles and Rules 78
Creating Feature Groups 79
Changing User Role Interface Policies 80
Changing User Role VLAN Policies 80
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
vi OL-31641-01
Page 7
Contents
Changing User Role VSAN Policies 81
Verifying the User Accounts and RBAC Configuration 82
Configuring User Accounts Default Settings for the User Accounts and RBAC 82
CHAPTER 8
CHAPTER 9
Configuring Session Manager 85
Information About Session Manager 85
Guidelines and Limitations for Session Manager 85
Configuring Session Manager 86
Creating a Session 86
Configuring ACLs in a Session 86
Verifying a Session 87
Committing a Session 87
Saving a Session 87
Discarding a Session 87
Configuration Example for Session Manager 88
Verifying the Session Manager Configuration 88
Configuring Online Diagnostics 89
Information About Online Diagnostics 89
Bootup Diagnostics 89
CHAPTER 10
Health Monitoring Diagnostics 90
Expansion Module Diagnostics 91
Configuring Online Diagnostics 92
Verifying the Online Diagnostics Configuration 92
Default Settings for Online Diagnostics 93
Configuring System Message Logging 95
Information About System Message Logging 95
Syslog Servers 96
Licensing Requirements for System Message Logging 96
Guidelines and Limitations for System Message Logging 97
Default Settings for System Message Logging 97
Configuring System Message Logging 97
Configuring System Message Logging to Terminal Sessions 97
Configuring System Message Logging to a File 99
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 vii
Page 8

Contents
Configuring Module and Facility Messages Logging 101
Configuring Logging Timestamps 102
Configuring Syslog Servers 103
Configuring syslog on a UNIX or Linux System 104
Configuring syslog Server Configuration Distribution 105
Displaying and Clearing Log Files 107
Verifying the System Message Logging Configuration 107
Configuring ACL Logging 108
Information About ACL Logging 108
Configuring the ACL Logging Cache 110
Applying ACL Logging to an Interface 110
Configuring VLAN Access Map with Logging 111
Configuring the ACL Log Match Level 112
CHAPTER 11
Configuring Rate Limiter for ACL Logging 112
Clearing ACL Logs 112
Verifying ACL Logging 113
Configuring Smart Call Home 115
Information About Smart Call Home 115
Smart Call Home Overview 116
Smart Call Home Destination Profiles 116
Smart Call Home Alert Groups 117
Smart Call Home Message Levels 118
Call Home Message Formats 119
Guidelines and Limitations for Smart Call Home 124
Prerequisites for Smart Call Home 124
Default Call Home Settings 125
Configuring Smart Call Home 125
Registering for Smart Call Home 125
Configuring Contact Information 126
Creating a Destination Profile 127
Modifying a Destination Profile 128
Associating an Alert Group with a Destination Profile 130
Adding Show Commands to an Alert Group 130
Configuring E-Mail Server Details 131
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
viii OL-31641-01
Page 9

Contents
Configuring Periodic Inventory Notifications 132
Disabling Duplicate Message Throttling 133
Enabling or Disabling Smart Call Home 134
Testing the Smart Call Home Configuration 134
Verifying the Smart Call Home Configuration 135
Sample Syslog Alert Notification in Full-Text Format 136
Sample Syslog Alert Notification in XML Format 136
CHAPTER 12
CHAPTER 13
Configuring Rollback 141
Information About Rollbacks 141
Guidelines and Limitations for Rollback 141
Creating a Checkpoint 142
Implementing a Rollback 143
Verifying the Rollback Configuration 143
Configuring DNS 145
Information About DNS Client 145
Name Servers 145
DNS Operation 146
High Availability 146
Prerequisites for DNS Clients 146
Licensing Requirements for DNS Clients 146
Default Settings for DNS Clients 146
Configuring DNS Clients 147
CHAPTER 14
Configuring SNMP 149
Information About SNMP 149
SNMP Functional Overview 149
SNMP Notifications 150
SNMPv3 150
Security Models and Levels for SNMPv1, v2, and v3 151
User-Based Security Model 152
CLI and SNMP User Synchronization 152
Group-Based SNMP Access 153
Licensing Requirements for SNMP 153
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 ix
Page 10

Contents
Guidelines and Limitations for SNMP 153
Default SNMP Settings 154
Configuring SNMP 154
Configuring SNMP Users 154
Enforcing SNMP Message Encryption 155
Assigning SNMPv3 Users to Multiple Roles 155
Creating SNMP Communities 156
Filtering SNMP Requests 156
Configuring SNMP Notification Receivers 156
Configuring SNMP Notification Receivers with VRFs 158
Filtering SNMP Notifications Based on a VRF 158
Configuring a Source Interface for Sending Out All SNMP Notifications 159
Configuring a Host Receiver for SNMP Notifications 160
CHAPTER 15
Configuring SNMP for Inband Access 160
Enabling SNMP Notifications 161
Configuring Link Notifications 163
Disabling Link Notifications on an Interface 164
Enabling One-Time Authentication for SNMP over TCP 165
Assigning SNMP Switch Contact and Location Information 165
Configuring the Context to Network Entity Mapping 165
Modifying the AAA Synchronization Time 166
Disabling SNMP 167
Verifying the SNMP Configuration 167
Configuring RMON 169
Information About RMON 169
RMON Alarms 169
RMON Events 170
Configuration Guidelines and Limitations for RMON 170
Configuring RMON 171
Configuring RMON Alarms 171
Configuring RMON Events 172
Verifying the RMON Configuration 172
Default RMON Settings 173
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
x OL-31641-01
Page 11

Contents
CHAPTER 16
Configuring SPAN 175
Information About SPAN 176
SPAN Sources 176
Characteristics of Source Ports 176
SPAN Destinations 177
Characteristics of Destination Ports 177
Multiple SPAN Destinations 177
SPAN with ACL 178
SPAN on Drop 178
SPAN-on-Latency Sessions 178
Guidelines and Limitations for SPAN 178
Creating or Deleting a SPAN Session 181
Configuring an Ethernet Destination Port 182
Configuring MTU Truncation for Each SPAN Session 183
Configuring the Rate Limit for SPAN Traffic 183
Configuring Source Ports 184
CHAPTER 17
Configuring Source Port Channels, VSANs, or VLANs 185
Configuring the Description of a SPAN Session 185
Configuring an ACL Filter for a SPAN Session 186
Configuring a SPAN-on-Drop Session 187
Configuring a SPAN-on-Latency Session 188
Activating a SPAN Session 189
Suspending a SPAN Session 190
Troubleshooting SPAN session issues 190
Troubleshooting SPAN session with large number of source ports issues 190
Displaying SPAN Information 191
Configuration Example for a SPAN ACL 192
Configuration Example for SPAN-on-Latency Session 192
Configuring ERSPAN 193
Information About ERSPAN 193
ERSPAN Source Sessions 193
Monitored Traffic 194
ERSPAN Types 194
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 xi
Page 12

Contents
ERSPAN Sources 195
ERSPAN Destinations 195
Truncated ERSPAN 196
ERSPAN with ACL 196
ERSPAN SPAN on Drop 196
ERSPAN SPAN-on-Latency 196
Multiple ERSPAN Sessions 197
High Availability 197
Licensing Requirements for ERSPAN 197
Prerequisites for ERSPAN 197
Guidelines and Limitations for ERSPAN 197
Guidelines and Limitations for ERSPAN Type III 201
Default Settings for ERSPAN 201
Configuring ERSPAN 201
Configuring an ERSPAN Source Session 201
Configuring an ERSPAN Type III Source Session 203
Configuring Truncated ERSPAN 206
Configuring an ERSPAN Destination Session 207
Configuring an ERSPAN SPAN-on-Drop Session 209
Configuring an ERSPAN SPAN-on-Latency Session 210
Shutting Down or Activating an ERSPAN Session 212
Verifying the ERSPAN Configuration 214
Configuration Examples for ERSPAN 215
Configuration Example for an ERSPAN Source Session 215
Configuration Example for an ERSPAN Type III Source Session 215
Configuration Example for an IP Address as the Source for an ERSPAN Session 215
Configuration Example for Truncated ERSPAN 216
Configuration Example for an ERSPAN Destination Session 216
Configuration Example for an ERSPAN ACL 216
Configuration Example for an ERSPAN SPAN-on-Drop Session 216
Configuration Example for ERSPAN SPAN-on-Latency Session 217
Additional References 217
Related Documents 217
CHAPTER 18
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
xii OL-31641-01
Configuring NTP 219
Page 13

Contents
Information About NTP 219
Information About the NTP Server 219
NTP as Time Server 220
Distributing NTP Using CFS 220
Clock Manager 220
High Availability 220
Licensing Requirements 221
Prerequisites for NTP 221
Guidelines and Limitations for NTP 221
Default Settings for NTP 222
Configuring NTP 222
Enabling or Disabling NTP 222
CHAPTER 19
Configuring the Device as an Authoritative NTP Server 223
Configuring an NTP Server and Peer 224
Configuring NTP Authentication 225
Configuring NTP Access Restrictions 226
Configuring the NTP Source IP Address 227
Configuring the NTP Source Interface 228
Configuring NTP Logging 228
Enabling CFS Distribution for NTP 229
Committing NTP Configuration Changes 229
Discarding NTP Configuration Changes 230
Releasing the CFS Session Lock 230
Verifying the NTP Configuration 231
Configuration Examples for NTP 232
Configuring EEM 235
Information About Embedded Event Manager 235
EEM Policies 236
EEM Event Statement 237
EEM Action Statements 238
VSH Script Policies 238
EEM Event Correlation 238
EEM Virtualization Support 239
EEM Licensing Requirements 239
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 xiii
Page 14

Contents
Prerequisites for EEM 239
Guidelines and Limitations for EEM 239
Default Settings for EEM 240
Configuring EEM 240
Defining an Environment Variable 240
Defining a User Policy Using the CLI 241
Event Statement Configuration 242
Action Statement Configuration 244
Defining a Policy Using a VSH Script 245
Registering and Activating a VSH Script Policy 246
Overriding a Policy 246
Configuring the Syslog as an EEM Publisher 247
Defining a User Policy Using the CLI to Trigger a Tcl Script 249
CHAPTER 20
Defining a User Policy Using the CLI to Trigger a Python Script 250
Verifying the EEM Configuration 251
Configuration Examples for EEM 252
Configuring OpenFlow 253
Information About OpenFlow 253
OpenFlow Limitations 254
Supported Interface Types 254
Unsupported Interface Types 254
Supported Interface Modes 254
Supported Match Fields 254
Supported Actions 255
Scale Flow Numbers 255
Pipeline Support 255
Prerequisites for OpenFlow 256
Setting Up an OpenFlow Virtual Service 257
Enabling OpenFlow 257
Configuring the OpenFlow Switch 258
Verifying OpenFlow 259
CHAPTER 21
Configuring NetFlow 261
NetFlow Overview 261
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
xiv OL-31641-01
Page 15

Contents
Flow Record 262
Flow Exporter 262
NetFlow Match Keys 262
Specifying the Match Parameters 263
NetFlow Collect Parameters 264
Specifying the Collect Parameters 264
Sampled NetFlow 265
Guidelines and Limitations for NetFlow 265
How to Configure NetFlow 266
Enabling the NetFlow Feature 267
Creating a Flow Record 267
Creating a Flow Exporter 268
CHAPTER 22
Creating a Flow Monitor 270
Creating a Sampler 271
Applying a Flow Monitor to an Interface 271
Configuring Bridged NetFlow on a VLAN 272
Configuring NetFlow Timeouts 273
Verifying the NetFlow Configuration 274
Monitoring NetFlow 275
Configuration Examples for NetFlow 275
Example: Creating and Applying a Flow 275
Example: Configuring a NetFlow Exporter 275
Soft Reload 277
Information About Soft Reload 277
Soft Reload Debugging 277
Licensing Requirements for Soft Reload 278
Guidelines and Limitations for Soft Reload 278
Default Setting for Soft Reload 279
Configuring Soft Reload 280
Enabling the Switch to Perform a Soft Reload After a Process Crash 280
Performing a Manual Soft Reload 280
Configuration Examples for Soft Reload 281
Verifying the Soft Reload Status 281
Additional References for Soft Reload 281
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 xv
Page 16

Contents
Feature History for Soft Reload 281
CHAPTER 23
Configuring GIR (Cisco NX-OS Release 7.3(0)N1(1)) 283
Information About GIR 283
Maintenance Profile 285
Unplanned Maintenance 286
Maintenance Mode Timer 286
Snapshot 287
Suppress FIB Pending 289
FEX Group GIR Functionality 289
Guidelines and Limitations for GIR 290
Configuring Custom Maintenance Mode and Custom Normal Mode Profile 291
Creating a Snapshot 292
Adding Show Commands to Snapshots 293
Dumping Snapshot Sections 295
Entering Maintenance Mode 295
Returning to Normal Mode 300
Deleting a Maintenance Profile 302
CHAPTER 24
Configuration Examples for GIR 302
Verifying GIR 309
Verifying GIR at Protocol Level 310
Feature History for GIR 312
Configuring GIR (Cisco NX-OS Release 7.1(0)N1(1)) 313
Information About GIR 313
Guidelines and Limitations for GIR 314
Performing the GIR Cycle 314
Configuring the Normal Mode Profile File 315
Creating a Snapshot 316
Entering Maintenance Mode 317
Returning to Normal Mode 317
Configuring the Maintenance Mode Profile File 318
Verifying GIR 319
CHAPTER 25
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
xvi OL-31641-01
Class-based Quality-of-Service MIB 323
Page 17

Contents
Class-based Quality-of-Service MIB 323
Information About Class-based Quality-of-Service MIB 323
Licensing Requirements for Class-based Quality-of-Service MIB 324
Prerequisite for Class-based Quality-of-Service MIB 324
Guidelines and Limitations for Class-based Quality-of-Service MIB 324
Configuring a QoS Policy 325
Displaying Class-based Quality-of-Service MIB Configuration and Statistics 326
Additional References for Class-based Quality-of-Service MIB 330
Feature History for Class-based Quality-of-Service MIB 331
CHAPTER 26
Performing Software Maintenance Upgrades 333
Performing Software Maintenance Upgrades 333
Prerequisites for SMUs 333
Guidelines and Limitations for SMUs 333
Information About Performing a Software Maintenance Upgrades 334
Overview of SMUs 334
Package Management 335
Impact of Package Activation and Deactivation 335
How to Perform Software Maintenance Upgrades 336
Preparing for Package Installation 336
Downloading the SMU Package File from Cisco.com 337
Copying the Package File to a Local Storage Device or Network Server 338
Adding and Activating Packages 341
Committing the Active Package Set 343
Deactivating and Removing Packages 344
Displaying Installation Log Information 345
Where to Go Next 347
Additional References 348
Feature Information for Performing Software Maintenance Upgrades 348
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 xvii
Page 18

Contents
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
xviii OL-31641-01
Page 19

Preface
The preface contains the following sections:
Audience, page xix
•
Document Conventions, page xix
•
Related Documentation for Cisco Nexus 5600 Series NX-OS Software, page xxi
•
Documentation Feedback, page xxii
•
Obtaining Documentation and Submitting a Service Request, page xxii
•
Audience
This publication is for network administrators who configure and maintain Cisco Nexus devices.
Document Conventions
Note
OL-31641-01 xix
As part of our constant endeavor to remodel our documents to meet our customers' requirements, we have
modified the manner in which we document configuration tasks. As a result of this, you may find a
deviation in the style used to describe these tasks, with the newly included sections of the document
following the new format.
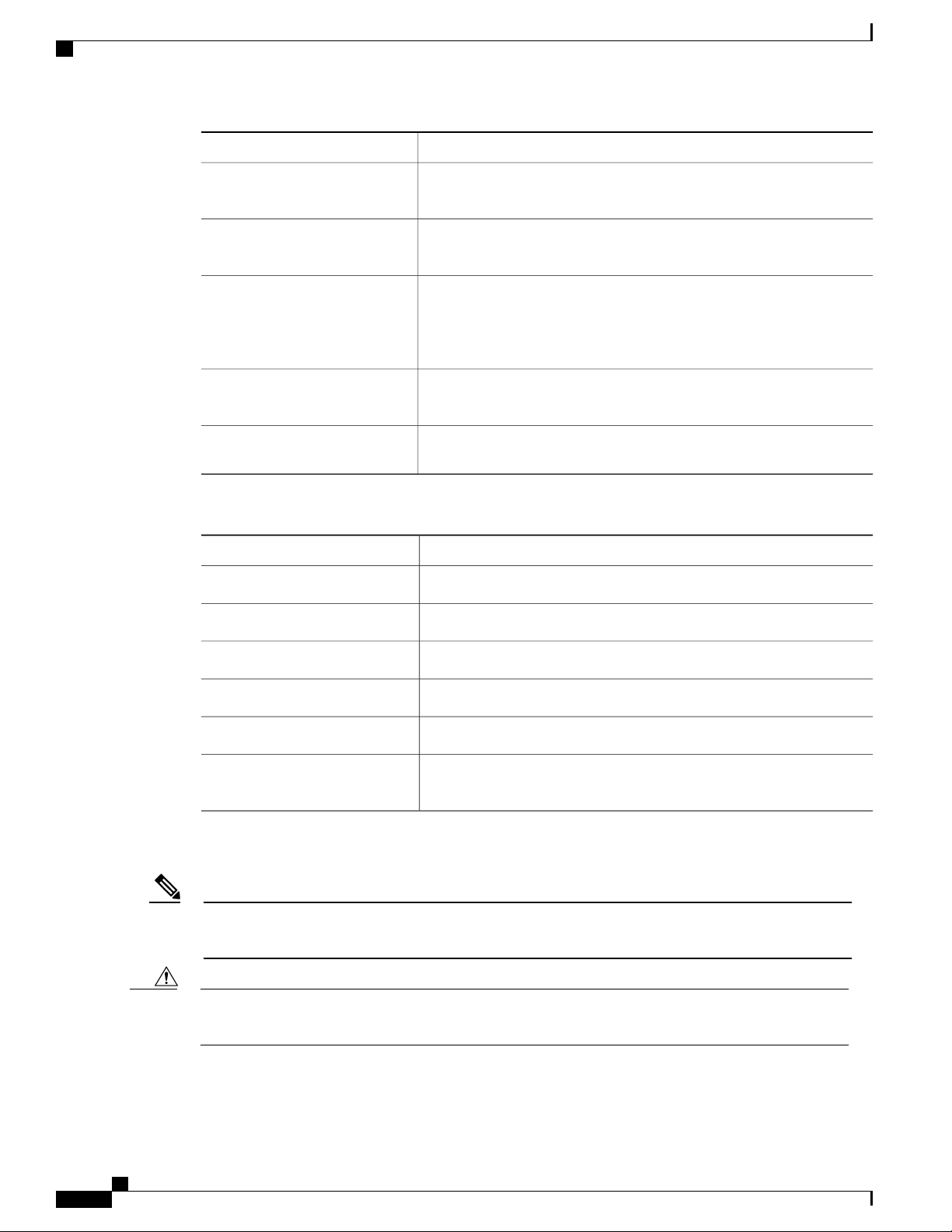
Command descriptions use the following conventions:
DescriptionConvention
bold
Italic
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
Bold text indicates the commands and keywords that you enter literally
as shown.
Italic text indicates arguments for which the user supplies the values.
Square brackets enclose an optional element (keyword or argument).[x]
Page 20
Document Conventions
Preface
DescriptionConvention
[x | y]
Square brackets enclosing keywords or arguments separated by a vertical
bar indicate an optional choice.
{x | y}
Braces enclosing keywords or arguments separated by a vertical bar
indicate a required choice.
[x {y | z}]
Nested set of square brackets or braces indicate optional or required
choices within optional or required elements. Braces and a vertical bar
within square brackets indicate a required choice within an optional
element.
variable
Indicates a variable for which you supply values, in context where italics
cannot be used.
string
A nonquoted set of characters. Do not use quotation marks around the
string or the string will include the quotation marks.
Examples use the following conventions:
DescriptionConvention
Terminal sessions and information the switch displays are in screen font.screen font
Information you must enter is in boldface screen font.boldface screen font
Note
Caution
italic screen font
Arguments for which you supply values are in italic screen font.
Nonprinting characters, such as passwords, are in angle brackets.< >
Default responses to system prompts are in square brackets.[ ]
!, #
An exclamation point (!) or a pound sign (#) at the beginning of a line
of code indicates a comment line.
This document uses the following conventions:
Means reader take note. Notes contain helpful suggestions or references to material not covered in the
manual.
Means reader be careful. In this situation, you might do something that could result in equipment damage
or loss of data.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
xx OL-31641-01
Page 21

Preface
Related Documentation for Cisco Nexus 5600 Series NX-OS Software
Related Documentation for Cisco Nexus 5600 Series NX-OS
Software
The entire Cisco NX-OS 5600 Series documentation set is available at the following URL:
http://www.cisco.com/c/en/us/support/switches/nexus-5000-series-switches/
tsd-products-support-series-home.html
Release Notes
The release notes are available at the following URL:
http://www.cisco.com/c/en/us/support/switches/nexus-5000-series-switches/products-release-notes-list.html
Configuration Guides
These guides are available at the following URL:
http://www.cisco.com/c/en/us/support/switches/nexus-5000-series-switches/
products-installation-and-configuration-guides-list.html
The documents in this category include:
Cisco Nexus 5600 Series NX-OS Adapter-FEX Configuration Guide
•
Cisco Nexus 5600 Series NX-OS FabricPath Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Fibre Channel over Ethernet Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Fundamentals Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Interfaces Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Layer 2 Switching Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Multicast Routing Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Quality of Service Configuration Guide
•
Cisco Nexus 5600 Series NX-OS SAN Switching Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Security Configuration Guide
•
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide
•
Cisco Nexus 5600 Series NX-OS Unicast Routing Configuration Guide
•
Licensing Guide
The License and Copyright Information for Cisco NX-OS Software is available at http://www.cisco.com/en/
US/docs/switches/datacenter/sw/4_0/nx-os/license_agreement/nx-ossw_lisns.html.
Command References
These guides are available at the following URL:
http://www.cisco.com/c/en/us/support/switches/nexus-5000-series-switches/
products-command-reference-list.html
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 xxi
Page 22

Documentation Feedback
The documents in this category include:
Cisco Nexus 5600 Series NX-OS Fabric Extender Command Reference
•
Cisco Nexus 5600 Series NX-OS FabricPath Command Reference
•
Cisco Nexus 5600 Series NX-OS Fibre Channel Command Reference
•
Cisco Nexus 5600 Series NX-OS Fundamentals Command Reference
•
Cisco Nexus 5600 Series NX-OS Interfaces Command Reference
•
Cisco Nexus 5600 Series NX-OS Layer 2 Interfaces Command Reference
•
Cisco Nexus 5600 Series NX-OS Multicast Routing Command Reference
•
Cisco Nexus 5600 Series NX-OS QoS Command Reference
•
Cisco Nexus 5600 Series NX-OS Security Command Reference
•
Cisco Nexus 5600 Series NX-OS System Management Command Reference
•
Cisco Nexus 5600 Series NX-OS TrustSec Command Reference
•
Preface
Cisco Nexus 5600 Series NX-OS Unicast Routing Command Reference
•
Cisco Nexus 5600 Series NX-OS Virtual Port Channel Command Reference
•
Error and System Messages
The Cisco Nexus 5600 Series NX-OS System Message Guide is available at http://www.cisco.com/en/US/docs/
switches/datacenter/nexus5500/sw/system_messages/reference/sl_nxos_book.html.
Troubleshooting Guide
The Cisco Nexus 5600 Series NX-OS Troubleshooting Guide is available at http://www.cisco.com/c/en/us/
support/switches/nexus-5000-series-switches/products-troubleshooting-guides-list.html.
Documentation Feedback
To provide technical feedback on this document, or to report an error or omission, please send your comments
to: .
We appreciate your feedback.
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, using the Cisco Bug Search Tool (BST), submitting a service
request, and gathering additional information, see What's New in Cisco Product Documentation.
To receive new and revised Cisco technical content directly to your desktop, you can subscribe to the What's
New in Cisco Product Documentation RSS feed. RSS feeds are a free service.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
xxii OL-31641-01
Page 23

New and Changed Information
New and Changed Information, page 1
•
New and Changed Information
The following table provides an overview of the significant changes made to this configuration guide. The
table does not provide an exhaustive list of all changes made to this guide or all new features in a particular
release.
CHAPTER 1
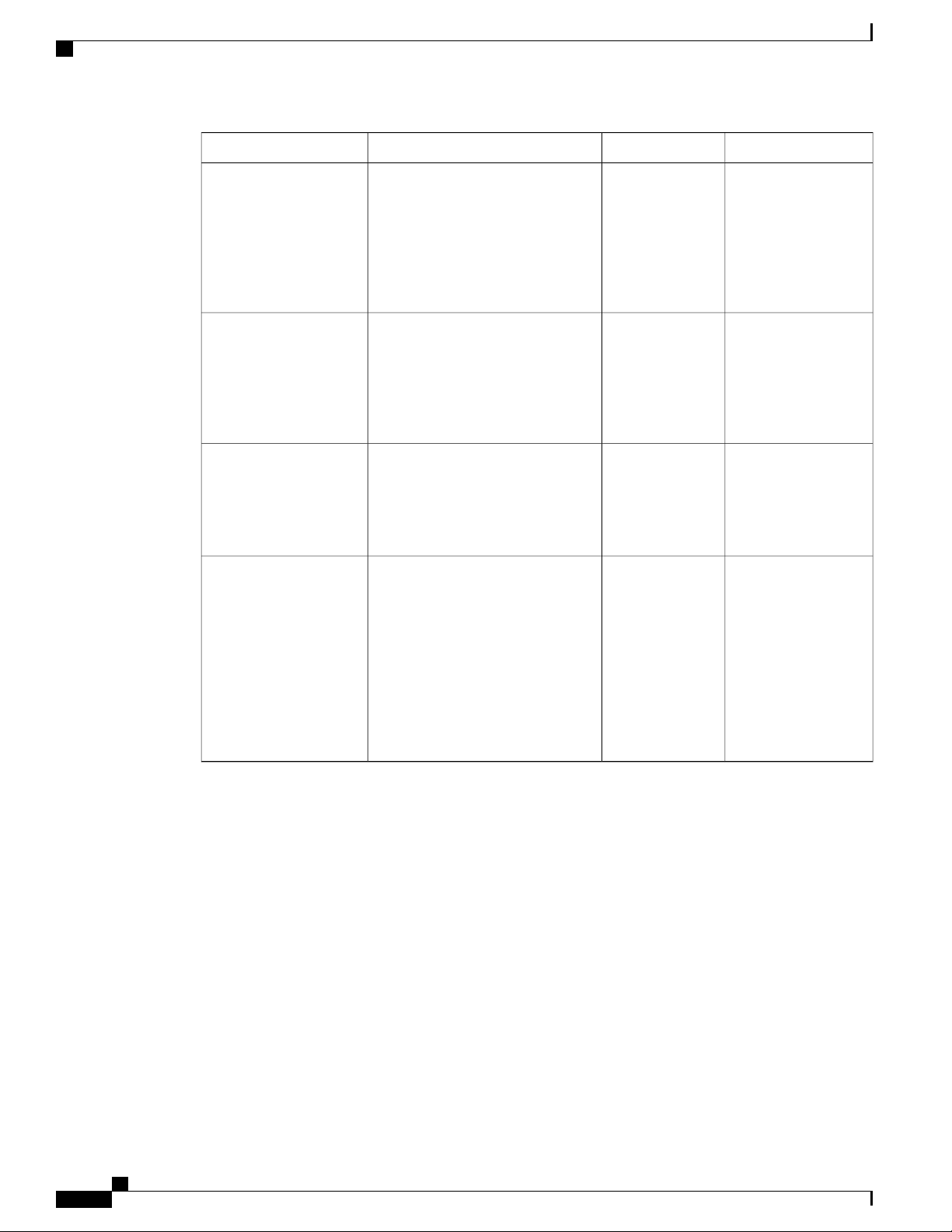
Where DocumentedReleaseDescriptionFeature
Soft Reload
GIR Enhancement
best effort mechanism for the switch
to be gracefully brought up with
minimal impact to production traffic
when a process crash occurs. You
can also use the soft-reload
command to trigger a manual soft
reload of the switch.
7.3(0)N1(1), the default mode for
GIR is “isolate”. Provides support for
Unplanned Maintenance,
Maintenance Mode timer, Supress
FIB Pending, Adding Show
commands to snapshots and dumping
snapshot sections. You can use GIR
to perform maintenance and software
upgrade of the switches and the
connected FEXs. A FEX group is
added to optimize the procedure to
bring up or take down the FEX.
Soft Reload7.3(2)N1(1)The Soft Reload feature provides a
7.3(0)N1(1)Starting with Cisco NX-OS Release
Configuring GIR
(Cisco NX-OS
Release 7.3(0)N1(1))
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 1
Page 24
New and Changed Information
New and Changed Information
Where DocumentedReleaseDescriptionFeature
Class-based
Quality-of-Service MIB
Phase 2
Performing Software
Maintenance Upgrades
Class-based
Quality-of-Service MIB
Isolate and Maintenance
Mode Enhancement
7.3(0)N1(1), the following
cbQoSMIB tables are also supported
by QoS policies:
cbQosClassMapStats,
cbQosMatchStmtStats and
cbQosQueueingStats
(SMU) is a package file that contains
fixes for specific defects. SMUs are
created to respond to immediate
issues and do not include new
features.
Management Protocol (SNMP) MIB
that enables retrieval of class-map
and policy-map configuration and
statistics.
eject a switch and isolate it from the
network so that debugging or an
upgrade can be performed. The
switch is removed from the regular
switching path and put into a
maintenance mode. Once
maintenance on the switch is
complete, you can bring the switch
into full operational mode.
7.3(0)N1(1)Starting with Cisco NX-OS Release
Class-based
Quality-of-Service
MIB
7.2(1)N1(1)A software maintenance upgrade
Performing Software
Maintenance
Upgrades
7.1(1)N1(1)Provides the Simple Network
Class-based
Quality-of-Service
MIB
7.1(0)N1(1)Provides the ability to gracefully
Configuring GIR
(Cisco NX-OS
Release 7.1(0)N1(1))
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
2 OL-31641-01
Page 25

Overview
This chapter contains the following sections:
System Management Features, page 3
•
System Management Features
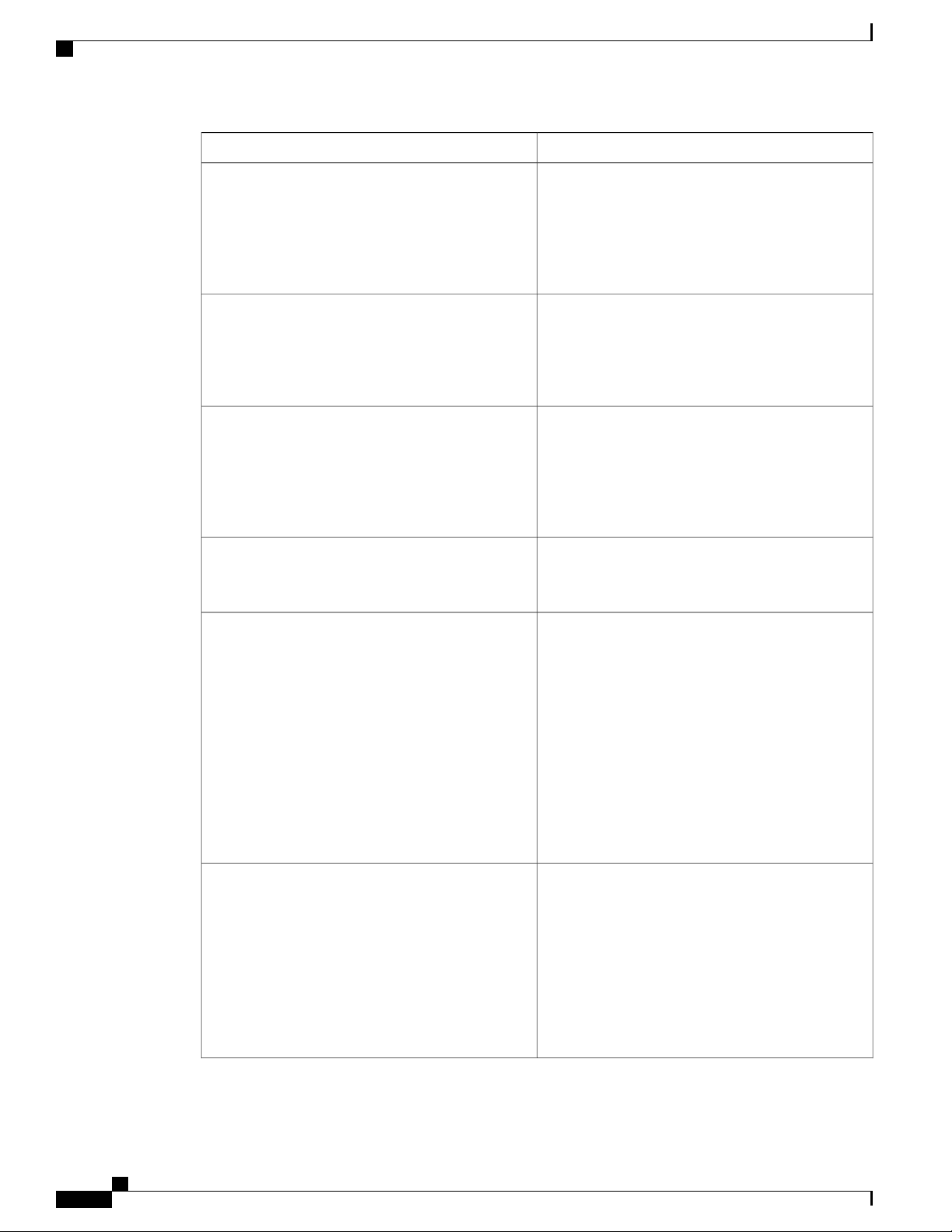
The system management features documented in this guide are described below:
CHAPTER 2
DescriptionFeature
Switch Profiles
Module Pre-Provisioning
Configuration synchronization allows administrators
to make configuration changes on one switch and
have the system automatically synchronize the
configuration to a peer switch. This feature eliminates
misconfigurations and reduces the administrative
overhead.
The configuration synchronization mode
(config-sync) allows users to create switch profiles
to synchronize local and peer switch.
Module pre-provisioning feature allows users to
pre-configure interfaces before inserting or attaching
a module to a Cisco Nexus Series switch. If a module
goes offline, users can also use pre-provisioning to
make changes to the interface configurations for the
offline module. In some vPC topologies,
pre-provisioning is required for the configuration
synchronization feature. Pre-provisioning allows users
to synchronize the configuration for an interface that
is online with one peer but offline with another peer.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 3
Page 26
System Management Features
Overview
DescriptionFeature
Cisco Fabric Services
Precision Time Protocol
User Accounts and RBAC
Session Manager
Online Diagnostics
The Cisco MDS NX-OS software uses the Cisco
Fabric Services (CFS) infrastructure to enable
efficient database distribution and to promote device
flexibility. CFS simplifies SAN provisioning by
automatically distributing configuration information
to all switches in a fabric.
The Precision Time Protocol (PTP) is a time
synchronization protocol for nodes distributed across
a network. Its hardware timestamp feature provides
greater accuracy than other time synchronization
protocols such as Network Time Protocol (NTP).
User accounts and role-based access control (RBAC)
allow you to define the rules for an assigned role.
Roles restrict the authorization that the user has to
access management operations. Each user role can
contain multiple rules and each user can have multiple
roles.
Session Manager allows you to create a configuration
and apply it in batch mode after the configuration is
reviewed and verified for accuracy and completeness.
Cisco Generic Online Diagnostics (GOLD) define a
common framework for diagnostic operations across
Cisco platforms. The online diagnostic framework
specifies the platform-independent fault-detection
architecture for centralized and distributed systems,
including the common diagnostics CLI and the
platform-independent fault-detection procedures for
boot-up and run-time diagnostics.
The platform-specific diagnostics provide
hardware-specific fault-detection tests and allow you
to take appropriate corrective action in response to
diagnostic test results.
System Message Logging
You can use system message logging to control the
destination and to filter the severity level of messages
that system processes generate. You can configure
logging to a terminal session, a log file, and syslog
servers on remote systems.
System message logging is based on RFC 3164. For
more information about the system message format
and the messages that the device generates, see the
Cisco NX-OS System Messages Reference.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
4 OL-31641-01
Page 27
Overview
System Management Features
DescriptionFeature
Smart Call Home
Configuration Rollback
SNMP
Call Home provides an e-mail-based notification of
critical system policies. Cisco NX-OS provides a
range of message formats for optimal compatibility
with pager services, standard e-mail, or XML-based
automated parsing applications. You can use this
feature to page a network support engineer, e-mail a
Network Operations Center, or use Cisco Smart Call
Home services to automatically generate a case with
the Technical Assistance Center.
The configuration rollback feature allows users to
take a snapshot, or user checkpoint, of the Cisco
NX-OS configuration and then reapply that
configuration to a switch at any point without having
to reload the switch. A rollback allows any authorized
administrator to apply this checkpoint configuration
without requiring expert knowledge of the features
configured in the checkpoint.
The Simple Network Management Protocol (SNMP)
is an application-layer protocol that provides a
message format for communication between SNMP
managers and agents. SNMP provides a standardized
framework and a common language used for the
monitoring and management of devices in a network.
RMON
SPAN
RMON is an Internet Engineering Task Force (IETF)
standard monitoring specification that allows various
network agents and console systems to exchange
network monitoring data. Cisco NX-OS supports
RMON alarms, events, and logs to monitor Cisco
NX-OS devices.
The Switched Port Analyzer (SPAN) feature
(sometimes called port mirroring or port monitoring)
selects network traffic for analysis by a network
analyzer. The network analyzer can be a Cisco
SwitchProbe, a Fibre Channel Analyzer, or other
Remote Monitoring (RMON) probes.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 5
Page 28
System Management Features
Overview
DescriptionFeature
ERSPAN
Encapsulated remote switched port analyzer
(ERSPAN) is used to transport mirrored traffic in an
IP network. ERSPAN supports source ports, source
VLANs, and destinations on different switches, which
provide remote monitoring of multiple switches across
your network. ERSPAN uses a generic routing
encapsulation (GRE) tunnel to carry traffic between
switches.
ERSPAN consists of an ERSPAN source session,
routable ERSPAN GRE-encapsulated traffic, and an
ERSPAN destination session. You separately
configure ERSPAN source sessions and destination
sessions on different switches.
To configure an ERSPAN source session on one
switch, you associate a set of source ports or VLANs
with a destination IP address, ERSPAN ID number,
and virtual routing and forwarding (VRF) name. To
configure an ERSPAN destination session on another
switch, you associate the destinations with the source
IP address, the ERSPAN ID number, and a VRF
name.
The ERSPAN source session copies traffic from the
source ports or source VLANs and forwards the traffic
using routable GRE-encapsulated packets to the
ERSPAN destination session. The ERSPAN
destination session switches the traffic to the
destinations.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
6 OL-31641-01
Page 29

CHAPTER 3
Configuring Switch Profiles
This chapter contains the following sections:
Information About Switch Profiles, page 8
•
Switch Profile Configuration Modes, page 8
•
Configuration Validation, page 9
•
Software Upgrades and Downgrades with Switch Profiles, page 10
•
Prerequisites for Switch Profiles, page 10
•
Guidelines and Limitations for Switch Profiles, page 10
•
Configuring Switch Profiles, page 12
•
Adding a Switch to a Switch Profile, page 13
•
Adding or Modifying Switch Profile Commands, page 15
•
Importing a Switch Profile, page 17
•
Importing Configurations in a vPC Topology, page 19
•
Verifying Commands in a Switch Profile, page 19
•
Isolating a Peer Switch, page 20
•
Deleting a Switch Profile, page 20
•
Deleting a Switch from a Switch Profile, page 21
•
Displaying the Switch Profile Buffer, page 22
•
Synchronizing Configurations After a Switch Reboot, page 23
•
Switch Profile Configuration show Commands, page 23
•
Configuration Examples for Switch Profiles, page 24
•
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 7
Page 30

Information About Switch Profiles
Information About Switch Profiles
Several applications require consistent configuration across Cisco Nexus Series switches in the network. For
example, with a Virtual Port Channel (vPC), you must have identical configurations. Mismatched configurations
can cause errors or misconfigurations that can result in service disruptions.
The configuration synchronization (config-sync) feature allows you to configure one switch profile and have
the configuration be automatically synchronized to the peer switch. A switch profile provides the following
benefits:
Allows configurations to be synchronized between switches.
•
Merges configurations when connectivity is established between two switches.
•
Provides control of exactly which configuration gets synchronized.
•
Ensures configuration consistency across peers through merge and mutual-exclusion checks.
•
Provides verify and commit semantics.
•
Supports configuring and synchronizing port profile configurations.
•
Configuring Switch Profiles
Provides an import command to migrate existing vPC configurations to a switch profile.
•
Switch Profile Configuration Modes
The switch profile feature includes the following configuration modes:
Configuration Synchronization Mode
•
Switch Profile Mode
•
Switch Profile Import Mode
•
Configuration Synchronization Mode
The configuration synchronization mode (config-sync) allows you to create switch profiles using the config
sync command on the local switch that you want to use as the master. After you create the profile, you can
enter the config sync command on the peer switch that you want to synchronize.
Switch Profile Mode
The switch profile mode allows you to add supported configuration commands to a switch profile that is later
synchronized with a peer switch. Commands that you enter in the switch profile mode are buffered until you
enter the commit command.
Switch Profile Import Mode
When you upgrade from an earlier release, you have the option to enter the import command to copy supported
running-configuration commands to a switch profile. After entering the import command, the switch profile
mode (config-sync-sp) changes to the switch profile import mode (config-sync-sp-import). The switch profile
import mode allows you to import existing switch configurations from the running configuration and specify
which commands you want to include in the switch profile.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
8 OL-31641-01
Page 31

Configuring Switch Profiles
Because different topologies require different commands that are included in a switch profile, the import
command mode allows you to modify the imported set of commands to suit a specific topology. For example,
a dual homed Fabric Extender (FEX) topology requires that most of the configuration is synchronized. In
other vPC topologies, the configuration that needs to be synchronized might be a much smaller set of commands.
You need to enter the commit command to complete the import process and move the configuration into the
switch profile. Because configuration changes are not supported during the import process, if you added new
commands before entering the commit command, the switch profile remains unsaved and the switch remains
in the switch profile import mode. You can remove the added commands or abort the import. Unsaved
configurations are lost if the process is aborted. You can add new commands to the switch profile after the
import is complete.
Configuration Validation
Two types of configuration validation checks can identify two types of switch profile failures:
Mutual Exclusion Checks
•
Merge Checks
•
Configuration Validation
Mutual Exclusion Checks
To reduce the possibility of overriding configuration settings that are included in a switch profile, mutual
exclusion (mutex) checks the switch profile commands against the commands that exist on the local switch
and the commands on the peer switch. A command that is included in a switch profile cannot be configured
outside of the switch profile or on a peer switch. This requirement reduces the possibility that an existing
command is unintentionally overwritten.
As a part of the commit process, the mutex-check occurs on both switches if the peer switch is reachable;
otherwise, the mutex-check is performed locally. Configuration changes made from the configuration terminal
occur only on the local switch.
If a mutex-check identifies errors, they are reported as mutex failures and they must be manually corrected.
The following exceptions apply to the mutual exclusion policy:
• Interface configuration—Port channel interfaces must be configured fully in either switch profile mode
or global configuration mode.
Note
Several port channel subcommands are not configurable in switch profile mode. These
commands can be configured from global configuration mode even if the port channel
is created and configured in switch profile mode.
For example, the following command can only be configured in global configuration
mode:
switchport private-vlan association trunk primary-vlan secondary-vlan
Shutdown/no shutdown
•
System QoS
•
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 9
Page 32

Configuring Switch Profiles
Software Upgrades and Downgrades with Switch Profiles
Merge Checks
Merge checks are done on the peer switch that is receiving a configuration. The merge checks ensure that the
received configuration does not conflict with the switch profile configuration that already exists on the receiving
switch. The merge check occurs during the merge or commit process. Errors are reported as merge failures
and must be manually corrected.
When one or both switches are reloaded and the configurations are synchronized for the first time, the merge
check verifies that the switch profile configurations are identical on both switches. Differences in the switch
profiles are reported as merge errors and must be manually corrected.
Software Upgrades and Downgrades with Switch Profiles
When you downgrade to an earlier release, you are prompted to remove an existing switch profile that is not
supported on earlier releases.
When you upgrade from an earlier release, you have the option to move some of the running-configuration
commands to a switch profile. The import command allows you to import relevant switch profile commands.
An upgrade can occur if there are buffered configurations (uncommitted); however, the uncommitted
configurations are lost.
When you perform an In Service Software Upgrade (ISSU) on one of the switches included in a switch profile,
a configuration synchronization cannot occur because the peer is unreachable.
Prerequisites for Switch Profiles
Switch profiles have the following prerequisites:
You must enable Cisco Fabric Series over IP (CFSoIP) distribution over mgmt0 on both switches by
•
entering the cfs ipv4 distribute command.
You must configure a switch profile with the same name on both peer switches by entering the config
•
sync and switch-profile commands.
Configure each switch as peer switch by entering the sync-peers destination command
•
Guidelines and Limitations for Switch Profiles
The Switch profile has the following guidelines and limitations:
You can only enable configuration synchronization using the mgmt0 interface.
•
Configuration synchronization is performed using the mgmt 0 interface and cannot be performed using
•
a management SVI.
You must configure synchronized peers with the same switch profile name.
•
Commands that are qualified for a switch profile configuration are allowed to be configured in the
•
configuration switch profile (config-sync-sp) mode.
Supported switch profile commands relate to virtual port channel (vPC) commands. Fiber Channel over
•
Ethernet (FCoE) commands are not supported.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
10 OL-31641-01
Page 33

Configuring Switch Profiles
Guidelines and Limitations for Switch Profiles
One switch profile session can be in progress at a time. Attempts to start another session will fail.
•
Supported command changes made from the configuration terminal mode are blocked when a switch
•
profile session is in progress. You should not make unsupported command changes from the configuration
terminal mode when a switch profile session is in progress.
When you enter the commit command and a peer switch is reachable, the configuration is applied to
•
both peer switches or neither switch. If there is a commit failure, the commands remain in the switch
profile buffer. You can then make necessary corrections and try the commit again.
We recommend that you enable preprovisioning for all Generic Expansion Modules (GEMs) and Cisco
•
Nexus Fabric Extender modules whose interface configurations are synchronized using the configuration
synchronization feature. Follow these guidelines in Cisco Nexus Fabric Extender active/active topologies
where the Fabric Extenders might not be online on one switch and its configuration is changed and
synchronized on the other switch. In this scenario, if you do not enable preprovisioning, a commit fails
and the configuration is rolled back on both switches.
Once a port channel is configured using switch profile mode, it cannot be configured using global
•
configuration (config terminal) mode.
Note
Several port channel subcommands are not configurable in switch profile mode. These
commands can be configured from global configuration mode even if the port channel
is created and configured in switch profile mode.
For example, the following command can only be configured in global configuration
mode:
switchport private-vlan association trunk primary-vlan secondary-vlan
Shutdown and no shutdown can be configured in either global configuration mode or switch profile
•
mode.
If a port channel is created in global configuration mode, channel groups including member interfaces
•
must also be created using global configuration mode.
Port channels that are configured within switch profile mode may have members both inside and outside
•
of a switch profile.
If you want to import a member interface to a switch profile, the port channel including the member
•
interface must also be present within the switch profile.
Guidelines for Synchronizing After Reboot, Connectivity Loss, or Failure
• Synchronizing configurations after vPC peer link failure— If both switches are operational when a peer
link fails, the secondary switch shuts down its vPC ports. In a Fabric Extender A/A topology, the A/A
Fabric Extender disconnects from the secondary switch. If the configuration is changed using a switch
profile on the primary switch, configurations are not accepted on the secondary switch unless the A/A
Fabric Extender is preprovisioned. When using the configuration synchronization feature, we recommend
that you preprovision all A/A Fabric Extenders.
• Synchronizing configurations after mgmt0 interface connectivity loss—When mgmt0 interface
connectivity is lost and configuration changes are required, apply the configuration changes on both
switches using the switch profile. When connectivity to the mgmt0 interface is restored, both switches
synchronize automatically.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 11
Page 34

Configuring Switch Profiles
If a configuration change is made on only one switch, a merge occurs when the mgmt0 interface comes
up and the configuration is applied on the other switch.
Synchronizing configurations when an ISSU is performed on one switch and a configuration change is
•
made on the peer switch—In a vPC topology, configuration changes on the peer switch are not allowed
when an ISSU is performed on the other switch. In topologies without vPCs, configuration changes are
allowed and the switch undergoing an ISSU synchronizes new configurations when the upgrade is
complete.
Configuring Switch Profiles
You can create and configure a switch profile. Enter the switch-profile name command in the configuration
synchronization mode (config-sync).
Before You Begin
You must create the switch profile with the same name on each switch and the switches must configure each
other as a peer. When connectivity is established between switches with the same active switch profile, the
switch profiles are synchronized.
Configuring Switch Profiles
Procedure
Step 1
Step 2
Step 3
Step 4
Step 5
Example:
switch# configure terminal
switch(config)#
cfs ipv4 distribute
Example:
switch(config)# cfs ipv4 distribute
switch(config)#
Example:
switch# config sync
switch(config-sync)#
switch-profile name
Example:
switch(config-sync)# switch-profile abc
switch(config-sync-sp)#
sync-peers destination IP-address
PurposeCommand or Action
Enters global configuration mode.configure terminal
Enables CFS distribution between the peer
switches.
Enters configuration synchronization mode.config sync
Configures the switch profile, names the
switch profile, and enters switch profile
synchronization configuration mode.
Configures the peer switch.
Example:
switch(config-sync-sp)# sync-peers
destination 10.1.1.1
switch(config-sync-sp)#
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
12 OL-31641-01
Page 35

Configuring Switch Profiles
Adding a Switch to a Switch Profile
PurposeCommand or Action
Step 6
show switch-profile name status
(Optional)
Views the switch profile on the local switch
and the peer switch information.
Exits the switch profile configuration mode
Step 7
Example:
switch(config-sync-sp)# show
switch-profile abc status
switch(config-sync-sp)#
exit
and returns to EXEC mode.
Example:
switch(config-sync-sp)# exit
switch#
Step 8
copy running-config startup-config
(Optional)
Saves the change persistently through reboots
Example:
switch(config)# copy running-config
startup-config
and restarts by copying the running
configuration to the startup configuration.
The following example shows how to configure a switch profile and shows the switch profile status.
switch# configuration terminal
switch(config)# cfs ipv4 distribute
switch(config-sync)# switch-profile abc
switch(config-sync-sp)# sync-peers destination 10.1.1.1
switch(config-sync-sp)# show switch-profile abc status
Start-time: 15801 usecs after Mon Aug 23 06:21:08 2010
End-time: 6480 usecs after Mon Aug 23 06:21:13 2010
Profile-Revision: 1
Session-type: Initial-Exchange
Peer-triggered: Yes
Profile-status: Sync Success
Local information:
---------------Status: Commit Success
Error(s):
Peer information:
---------------IP-address: 10.1.1.1
Sync-status: In Sync.
Status: Commit Success
Error(s):
switch(config-sync-sp)# exit
switch#
Adding a Switch to a Switch Profile
Enter the sync-peers destination destination IP command in switch profile configuration mode to add the
switch to a switch profile.
Follow these guidelines when adding switches:
Switches are identified by their IP address.
•
Destination IPs are the IP addresses of the switches that you want to synchronize.
•
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 13
Page 36

Adding a Switch to a Switch Profile
The committed switch profile is synchronized with the newly added peers (when they are online) if the
•
peer switch is also configured with configuration synchronization.
If you want to import a member interface to a switch profile, the port channel including the member
interface must also be present within the switch profile.
Before You Begin
After creating a switch profile on the local switch, you must add the second switch that will be included in
the synchronization.
Procedure
Configuring Switch Profiles
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
Example:
switch# config sync
switch(config-sync)#
switch-profile name
Example:
switch(config-sync)# switch-profile abc
switch(config-sync-sp)#
sync-peers destination destination IP
Example:
switch(config-sync-sp)# sync-peers
destination 10.1.1.1
switch(config-sync-sp)#
Example:
switch(config-sync-sp)# exit
switch#
show switch-profile peer
Example:
switch# show switch-profile peer
copy running-config startup-config
Example:
switch# copy running-config startup-config
Enters configuration synchronization mode.config sync
Configures switch profile, names the switch
profile, and enters switch profile
synchronization configuration mode.
Adds a switch to the switch profile.
Exits switch profile configuration mode.exit
(Optional)
Displays the switch profile peer
configuration.
(Optional)
Copies the running configuration to the
startup configuration.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
14 OL-31641-01
Page 37

Configuring Switch Profiles
Adding or Modifying Switch Profile Commands
Adding or Modifying Switch Profile Commands
To modify a command in a switch profile, add the modified command to the switch profile and enter the
commit command to apply the command and synchronize the switch profile to the peer switch if it is reachable.
Follow these guidelines when adding or modifying switch profile commands:
Commands that are added or modified are buffered until you enter the commit command.
•
Commands are executed in the same order in which they are buffered. If there is an order-dependency
•
for certain commands, for example, a QoS policy must be defined before being applied, you must
maintain that order; otherwise, the commit might fail. You can use utility commands, such as the show
switch-profile name buffer command, the buffer-delete command, or the buffer-move command, to
change the buffer and correct the order of already entered commands.
Before You Begin
After configuring a switch profile on the local and the peer switch, you must add and commit the supported
commands to the switch profile. The commands are added to the switch profile buffer until you enter the
commit command. The commit command does the following:
Triggers the mutex check and the merge check to verify the synchronization.
•
Creates a checkpoint with a rollback infrastructure.
•
Applies the configuration on the local switch and the peer switch.
•
Executes a rollback on all switches if there is a failure with an application on any of the switches in the
•
switch profile.
Deletes the checkpoint.
•
Procedure
PurposeCommand or Action
Step 1
Step 2
Example:
switch# config sync
switch(config-sync)#
switch-profile name
Enters configuration synchronization mode.config sync
Configures the switch profile, names the
switch profile, and enters switch profile
synchronization configuration mode.
Adds a command to the switch profile.
Step 3
Example:
switch(config-sync)# switch-profile abc
switch(config-sync-sp)#
Command argument
Example:
switch(config-sync-sp)# interface
Port-channel100
switch(config-sync-sp-if)# speed 1000
switch(config-sync-sp-if)# interface
Ethernet1/1
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 15
Page 38

Adding or Modifying Switch Profile Commands
switch(config-sync-sp-if)# speed 1000
switch(config-sync-sp-if)# channel-group
100
Step 4
show switch-profile name buffer
Example:
switch(config-sync-sp)# show
switch-profile abc buffer
switch(config-sync-sp)#
Step 5
verify
Example:
switch(config-sync-sp)# verify
Step 6
commit
Example:
switch(config-sync-sp)# commit
Step 7
show switch-profile name status
Example:
switch(config-sync-sp)# show
switch-profile abc status
switch(config-sync-sp)#
Step 8
Configuring Switch Profiles
PurposeCommand or Action
(Optional)
Displays the configuration commands in the
switch profile buffer.
Verifies the commands in the switch profile
buffer.
Saves the commands in the switch profile
and synchronizes the configuration with the
peer switch.
(Optional)
Displays the status of the switch profile on
the local switch and the status on the peer
switch.
Exits the switch profile configuration mode.exit
Example:
switch(config-sync-sp)# exit
switch#
Step 9
copy running-config startup-config
(Optional)
Copies the running configuration to the
Example:
switch# copy running-config startup-config
startup configuration.
The following example shows how to create a switch profile, configure a peer switch, and add commands to
the switch profile.
switch# configuration terminal
switch(config)# cfs ipv4 distribute
switch(config-sync)# switch-profile abc
switch(config-sync-sp)# sync-peers destination 10.1.1.1
switch(config-sync-sp)# interface port-channel100
switch(config-sync-sp-if)# speed 1000
switch(config-sync-sp-if)# interface Ethernet1/1
switch(config-sync-sp-if)# speed 1000
switch(config-sync-sp-if)# channel-group 100
switch(config-sync-sp)# verify
switch(config-sync-sp)# commit
switch(config-sync-sp)# exit
switch#
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
16 OL-31641-01
Page 39

Configuring Switch Profiles
The following example shows an existing configuration with a defined switch profile. The second example
shows how the switch profile command changed by adding the modified command to the switch profile.
switch# show running-config
switch-profile abc
interface Ethernet1/1
switchport mode trunk
switchport trunk allowed vlan 1-10
switch# config sync
switch(config-sync)# switch-profile abc
switch(config-sync-sp)# interface Ethernet1/1
switch(config-sync-sp-if)# switchport trunk allowed vlan 5-10
switch(config-sync-sp-if)# commit
switch# show running-config
switch-profile abc
interface Ethernet1/1
switchport mode trunk
switchport trunk allowed vlan 5-10
Importing a Switch Profile
Importing a Switch Profile
You can import a switch profile based on the set of commands that you want to import. Using the configuration
terminal mode, you can do the following:
Add selected commands to the switch profile.
•
Add supported commands that were specified for an interface.
•
Add supported system-level commands.
•
Add supported system-level commands excluding the physical interface commands.
•
When you import commands to a switch profile, the switch profile buffer must be empty.
If new commands are added during the import, the switch profile remains unsaved and the switch remains in
the switch profile import mode. You can enter the abort command to stop the import. For additional information
importing a switch profile, see the “Switch Profile Import Mode” section.
Procedure
PurposeCommand or Action
Step 1
Enters configuration synchronization mode.config sync
Example:
switch# config sync
switch(config-sync)#
Step 2
switch-profile name
Configures the switch profile, names the switch
profile, and enters switch profile synchronization
configuration mode.
Identifies the commands that you want to import
and enters switch profile import mode.
Step 3
Example:
switch(config-sync)# switch-profile
abc
switch(config-sync-sp)#
import {interface port/slot | running-config
[exclude interface ethernet]}
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 17
Page 40

Importing a Switch Profile
Example:
switch(config-sync-sp)# import
ethernet 1/2
switch(config-sync-sp-import)#
Configuring Switch Profiles
PurposeCommand or Action
• <CR>—Adds selected commands.
• interface—Adds the supported commands for
a specified interface.
• running-config—Adds supported
system-level commands.
running-config exclude interface
•
ethernet—Adds supported system-level
commands excluding the physical interface
commands.
Step 4
Step 5
Step 6
Step 7
Step 8
commit
Example:
switch(config-sync-sp-import)# commit
abort
Example:
switch(config-sync-sp-import)# abort
Example:
switch(config-sync-sp)# exit
switch#
show switch-profile
Example:
switch# show switch-profile
copy running-config startup-config
Example:
switch# copy running-config
startup-config
Imports the commands and saves the commands to
the switch profile.
(Optional)
Aborts the import process.
Exits switch profile import mode.exit
(Optional)
Displays the switch profile configuration.
(Optional)
Copies the running configuration to the startup
configuration.
The following example shows how to import supported system-level commands excluding the Ethernet
interface commands into the switch profile named sp:
switch(config-vlan)# conf sync
switch(config-sync)# switch-profile sp
Switch-Profile started, Profile ID is 1
switch(config-sync-sp)# show switch-profile buffer
switch-profile : sp
---------------------------------------------------------Seq-no Command
----------------------------------------------------------
switch(config-sync-sp)# import running-config exclude interface ethernet
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
18 OL-31641-01
Page 41

Configuring Switch Profiles
Importing Configurations in a vPC Topology
switch(config-sync-sp-import)#
switch(config-sync-sp-import)# show switch-profile buffer
switch-profile : sp
---------------------------------------------------------Seq-no Command
---------------------------------------------------------3 vlan 100-299
4 vlan 300
4.1 state suspend
5 vlan 301-345
6 interface port-channel100
6.1 spanning-tree port type network
7 interface port-channel105
switch(config-sync-sp-import)#
Importing Configurations in a vPC Topology
You can import configurations in a two-switch vPC topology.
For specific information about the following steps, see the appropriate sections in this chapter.Note
1
Configure the switch profile with the same name on both switches.
2
Import the configurations to both switches independently.
Note
Ensure that the configuration moved to the switch profile on both switches is identical; otherwise, a
merge-check failure might occur.
3
Configure the switches by entering the sync-peer destination command.
4
Verify that the switch profiles are the same by entering the appropriate show commands.
Verifying Commands in a Switch Profile
You can verify the commands that are included in a switch profile by entering the verify command in switch
profile mode.
Procedure
PurposeCommand or Action
Step 1
Example:
switch# config sync
switch(config-sync)#
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 19
Enters configuration synchronization mode.config sync
Page 42

Isolating a Peer Switch
Configuring Switch Profiles
PurposeCommand or Action
Step 2
Step 3
switch-profile name
Example:
switch(config-sync)# switch-profile abc
switch(config-sync-sp)#
verify
Example:
switch(config-sync-sp)# verify
Step 4
Example:
switch(config-sync-sp)# exit
switch#
Step 5
copy running-config startup-config
Example:
switch# copy running-config
startup-config
Isolating a Peer Switch
Configures the switch profile, names the switch
profile, and enters switch profile
synchronization configuration mode.
Verifies the commands in the switch profile
buffer.
Exits the switch profile configuration mode.exit
(Optional)
Copies the running configuration to the startup
configuration.
You can isolate a peer switch in order to make changes to a switch profile. This process can be used when
you want to block a configuration synchronization or when you want to debug configurations.
Isolating a peer switch requires that you remove the switch from the switch profile and then add the peer
switch back to the switch profile.
To temporarily isolate a peer switch, follow these steps:
1
Remove a peer switch from a switch profile.
2
Make changes to the switch profile and commit the changes.
3
Enter debug commands.
4
Undo the changes that were made to the switch profile in Step 2 and commit.
5
Add the peer switch back to the switch profile.
Deleting a Switch Profile
You can delete a switch profile by selecting the all-config or the local-config option:
• all-config—Deletes the switch profile on both peer switches (when both are reachable). If you choose
this option and one of the peers is unreachable, only the local switch profile is deleted. The all-config
option completely deletes the switch profile on both peer switches.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
20 OL-31641-01
Page 43

Configuring Switch Profiles
Procedure
Deleting a Switch from a Switch Profile
• local-config—Deletes the switch profile on the local switch only.
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Example:
switch# config sync
switch(config-sync)#
Example:
switch(config-sync)# no
switch-profile abc local-config
switch(config-sync-sp)#
Example:
switch(config-sync-sp)# exit
switch#
copy running-config startup-config
Example:
switch# copy running-config
startup-config
Enters configuration synchronization mode.config sync
Deletes the switch profile as follows:
• all-config—Deletes the switch profile on the
local and peer switch. If the peer switch is not
reachable, only the local switch profile is
deleted.
• local-config—Deletes the switch profile and
local configuration.
Exits configuration synchronization mode.exit
(Optional)
Copies the running configuration to the startup
configuration.
Deleting a Switch from a Switch Profile
You can delete a switch from a switch profile.
Procedure
PurposeCommand or Action
Step 1
Example:
switch# config sync
switch(config-sync)#
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 21
Enters configuration synchronization mode.config sync
Page 44

Displaying the Switch Profile Buffer
Configuring Switch Profiles
PurposeCommand or Action
Step 2
Step 3
Step 4
Step 5
Step 6
switch-profile name
Example:
switch(config-sync)# switch-profile abc
switch(config-sync-sp)#
no sync-peers destination destination IP
Example:
switch(config-sync-sp)# no sync-peers
destination 10.1.1.1
switch(config-sync-sp)#
Example:
switch(config-sync-sp)# exit
switch#
show switch-profile
Example:
switch# show switch-profile
copy running-config startup-config
Example:
switch# copy running-config
startup-config
Configures the switch profile, names the
switch profile, and enters the switch profile
synchronization configuration mode.
Removes the specified switch from the switch
profile.
Exits the switch profile configuration mode.exit
(Optional)
Displays the switch profile configuration.
(Optional)
Copies the running configuration to the
startup configuration.
Displaying the Switch Profile Buffer
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config-sync) # switch-profile
profile-name
Step 3
switch(config-sync-sp) # show
switch-profileprofile-name buffer
The following example shows how to display the switch profile buffer for a service profile called sp:
switch# configure sync
Enter configuration commands, one per line. End with CNTL/Z.
switch(config-sync)# switch-profile sp
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
22 OL-31641-01
Enters configuration synchronization mode.switch# configure sync
Enters switch profile synchronization configuration
mode for the specified switch profile.
Enters interface switch profile synchronization
configuration mode for the specified interface.
Page 45

Configuring Switch Profiles
Switch-Profile started, Profile ID is 1
switch(config-sync-sp)# show switch-profile sp buffer
---------------------------------------------------------Seq-no Command
---------------------------------------------------------1 vlan 101
1.1 ip igmp snooping querier 10.101.1.1
2 mac address-table static 0000.0000.0001 vlan 101 drop
3 interface Ethernet1/2
3.1 switchport mode trunk
3.2 switchport trunk allowed vlan 101
switch(config-sync-sp)# buffer-move 3 1
switch(config-sync-sp)# show switch-profile sp buffer
---------------------------------------------------------Seq-no Command
---------------------------------------------------------1 interface Ethernet1/2
1.1 switchport mode trunk
1.2 switchport trunk allowed vlan 101
2 vlan 101
2.1 ip igmp snooping querier 10.101.1.1
3 mac address-table static 0000.0000.0001 vlan 101 drop
switch(config-sync-sp)#
Synchronizing Configurations After a Switch Reboot
Synchronizing Configurations After a Switch Reboot
If a Cisco Nexus Series switch reboots while a new configuration is being committed on a peer switch using
a switch profile, complete the following steps to synchronize the peer switches after reload:
Procedure
Step 1
Step 2
Step 3
Reapply configurations that were changed on the peer switch during the reboot.
Enter the commit command.
Verify that the configuration is applied correctly and both peers are back synchronized.
Switch Profile Configuration show Commands
The following show commands display information about the switch profile.
PurposeCommand
show switch-profile name
show switch-profile name buffer
Displays the commands in a switch profile.
Displays the uncommitted commands in a switch profile, the
commands that were moved, and the commands that were
deleted.
show switch-profile name peer IP-address
show switch-profile name session-history
show switch-profile name status
Displays the synchronization status for a peer switch.
Displays the status of the last 20 switch profile sessions.
Displays the configuration synchronization status of a peer
switch.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 23
Page 46

Configuration Examples for Switch Profiles
Configuring Switch Profiles
PurposeCommand
Displays details about the port profile.show running-config expand-port-profile
show running-config exclude-provision
Displays the configurations for offline preprovisioned
interfaces that are hidden.
show running-config switch-profile
Displays the running configuration for the switch profile on
the local switch.
show startup-config switch-profile
Displays the startup configuration for the switch profile on
the local switch.
For detailed information about the fields in the output from these commands, see the system management
command reference for your platform.
Configuration Examples for Switch Profiles
Creating a Switch Profile on a Local and Peer Switch Example
The following example shows how to create a successful switch profile configuration on a local and peer
switch including configuring QoS policies; a vPC peer-link, and a vPC in a switch profile.
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
Enable CFSoIP distribution on the local and the peer switch.
Example:
switch# configuration terminal
switch(config)# cfs ipv4 distribute
Create a switch profile on the local and the peer switch.
Example:
switch(config-sync)# switch-profile abc
switch(config-sync-sp)# sync-peers destination 10.1.1.1
Verify that the switch profiles are the same on the local and the peer switch.
Example:
switch(config-sync-sp)# show switch-profile abc status
Start-time: 15801 usecs after Mon Aug 23 06:21:08 2010
End-time: 6480 usecs after Mon Aug 23 06:21:13 2010
Profile-Revision: 1
Session-type: Initial-Exchange
Peer-triggered: Yes
Profile-status: Sync Success
Local information:
---------------Status: Commit Success
Error(s):
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
24 OL-31641-01
Page 47

Configuring Switch Profiles
Step 4
Creating a Switch Profile on a Local and Peer Switch Example
PurposeCommand or Action
Peer information:
---------------IP-address: 10.1.1.1
Sync-status: In Sync.
Status: Commit Success
Error(s):
Add the configuration commands to the switch profile on the local switch. The commands
will be applied to the peer switch when the commands are committed.
Example:
switch(config-sync-sp)# class-map type qos c1
switch(config-sync-sp-cmap-qos)# match cos 2
switch(config-sync-sp-cmap-qos)# class-map type qos c2
switch(config-sync-sp-cmap-qos)# match cos 5
switch(config-sync-sp-cmap-qos)# policy-map type qos p1
switch(config-sync-sp-pmap-qos)# class c1
switch(config-sync-sp-pmap-c-qos)# set qos-group 2
switch(config-sync-sp-pmap-c-qos)# class c2
switch(config-sync-sp-pmap-c-qos)# set qos-group 3
switch(config-sync-sp-pmap-c-qos)# system qos
switch(config-sync-sp-sys-qos)# service-policy type qos input p1
switch(config-sync-sp-sys-qos)# vlan 1-50
switch(config-sync-sp-vlan)# interface port-channel 100
switch(config-sync-sp-if)# vpc peer-link
switch(config-sync-sp-if)# switchport mode trunk
switch(config-sync-sp-if)# interface port-channel 10
switch(config-sync-sp-if)# vpc 1
switch(config-sync-sp-if)# switchport mode trunk
switch(config-sync-sp-if)# switchport trunk allowed vlan 1, 10-50
Step 5
Step 6
View the buffered commands.
Example:
switch(config-sync-sp-if)# show switch-profile switch-profile buffer
---------------------------------------------------------Seq-no Command
---------------------------------------------------------1 class-map type qos match-all c1
1.1 match cos 2
2 class-map type qos match-all c2
2.1 match cos 5
3 policy-map type qos p1
3.1 class c1
3.1.1 set qos-group 2
3.2 class c2
3.2.1 set qos-group 3
4 system qos
4.1 service-policy type qos input p1
5 vlan 2-50
6 interface port-channel100
6.1 vpc peer-link
6.2 switchport mode trunk
7 interface port-channel10
7.1 vpc 1
7.2 switchport mode trunk
7.3 switchport trunk allowed vlan 1, 10-50
Verify the commands in the switch profile.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 25
Page 48

Verifying the Synchronization Status Example
Example:
switch(config-sync-sp-if)# verify
Verification Successful
Step 7
Apply the commands to the switch profile and to synchronize the configurations between
the local and the peer switch.
Example:
switch(config-sync-sp)# commit
Commit Successful
switch(config-sync)#
Verifying the Synchronization Status Example
Configuring Switch Profiles
PurposeCommand or Action
The following example shows how to verify the synchronization status between the local and the peer switch:
switch(config-sync)# show switch-profile switch-profile status
Start-time: 804935 usecs after Mon Aug 23 06:41:10 2010
End-time: 956631 usecs after Mon Aug 23 06:41:20 2010
Profile-Revision: 2
Session-type: Commit
Peer-triggered: No
Profile-status: Sync Success
Local information:
---------------Status: Commit Success
Error(s):
Peer information:
---------------IP-address: 10.1.1.1
Sync-status: In Sync.
Status: Commit Success
Error(s):
switch(config-sync)#
Displaying the Running Configuration
The following example shows how to display the running configuration of the switch profile on the local
switch:
switch# configure sync
switch(config-sync)# show running-config switch-profile
switch-profile sp
sync-peers destination 10.1.1.1
class-map type qos match-all c1
match cos 2
class-map type qos match-all c2
match cos 5
policy-map type qos p1
class c1
set qos-group 2
class c2
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
26 OL-31641-01
Page 49

Configuring Switch Profiles
Displaying the Switch Profile Synchronization Between Local and Peer Switches
set qos-group 3
system qos
service-policy type qos input p1
vlan 2-50
interface port-channel10
switchport mode trunk
vpc 1
switchport trunk allowed vlan 1,10-50
interface port-channel100
switchport mode trunk
vpc peer-link
switch(config-sync)#
Displaying the Switch Profile Synchronization Between Local and Peer
Switches
This example shows how to display the synchronization status for two peer switches:
switch1# show switch-profile sp status
Start-time: 491815 usecs after Thu Aug 12 11:54:51 2010
End-time: 449475 usecs after Thu Aug 12 11:54:58 2010
Profile-Revision: 1
Session-type: Initial-Exchange
Peer-triggered: No
Profile-status: Sync Success
Local information:
---------------Status: Commit Success
Error(s):
Peer information:
---------------IP-address: 10.193.194.52
Sync-status: In Sync.
Status: Commit Success
Error(s):
switch1#
switch2# show switch-profile sp status
Start-time: 503194 usecs after Thu Aug 12 11:54:51 2010
End-time: 532989 usecs after Thu Aug 12 11:54:58 2010
Profile-Revision: 1
Session-type: Initial-Exchange
Peer-triggered: Yes
Profile-status: Sync Success
Local information:
---------------Status: Commit Success
Error(s):
Peer information:
---------------IP-address: 10.193.194.51
Sync-status: In Sync.
Status: Commit Success
Error(s):
switch2#
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 27
Page 50

Displaying Verify and Commit on Local and Peer Switches
Displaying Verify and Commit on Local and Peer Switches
This example shows how to configure a successful verify and commit of the local and peer switch:
switch1# configure sync
Enter configuration commands, one per line. End with CNTL/Z.
switch1(config-sync)# switch-profile sp
Switch-Profile started, Profile ID is 1
switch1(config-sync-sp)# interface ethernet1/1
switch1(config-sync-sp-if)# description foo
switch1(config-sync-sp-if)# verify
Verification Successful
switch1(config-sync-sp)# commit
Commit Successful
switch1(config-sync)# show running-config switch-profile
switch-profile sp
sync-peers destination 10.193.194.52
interface Ethernet1/1
description foo
switch1(config-sync)# show switch-profile sp status
Start-time: 171513 usecs after Wed Aug 11 17:51:28 2010
End-time: 676451 usecs after Wed Aug 11 17:51:43 2010
Profile-Revision: 3
Session-type: Commit
Peer-triggered: No
Profile-status: Sync Success
Local information:
---------------Status: Commit Success
Error(s):
Peer information:
---------------IP-address: 10.193.194.52
Sync-status: In Sync.
Status: Commit Success
Error(s):
switch1(config-sync)#
Configuring Switch Profiles
switch2# show running-config switch-profile
switch-profile sp
sync-peers destination 10.193.194.51
interface Ethernet1/1
description foo
switch2# show switch-profile sp status
Start-time: 265716 usecs after Wed Aug 11 16:51:28 2010
End-time: 734702 usecs after Wed Aug 11 16:51:43 2010
Profile-Revision: 3
Session-type: Commit
Peer-triggered: Yes
Profile-status: Sync Success
Local information:
---------------Status: Commit Success
Error(s):
Peer information:
---------------IP-address: 10.193.194.51
Sync-status: In Sync.
Status: Commit Success
Error(s):
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
28 OL-31641-01
Page 51

Configuring Switch Profiles
Successful and Unsuccessful Synchronization Examples
switch2#
Successful and Unsuccessful Synchronization Examples
The following example shows a successful synchronization of the switch profile on the peer switch:
switch# show switch-profile abc peer
switch# show switch-profile sp peer 10.193.194.52
Peer-sync-status : In Sync.
Peer-status : Commit Success
Peer-error(s) :
switch1#
The following example shows an unsuccessful synchronization of a switch profile on the peer switch, with a
peer not reachable status:
switch# show switch-profile sp peer 10.193.194.52
Peer-sync-status : Not yet merged. pending-merge:1 received_merge:0
Peer-status : Peer not reachable
Peer-error(s) :
switch#
Configuring the Switch Profile Buffer, Moving the Buffer, and Deleting the Buffer
This example shows how to configure the switch profile buffer, the buffer-move configuration, and the
buffer-delete configuration:
switch# configure sync
Enter configuration commands, one per line. End with CNTL/Z.
switch(config-sync)# switch-profile sp
Switch-Profile started, Profile ID is 1
switch(config-sync-sp)# vlan 101
switch(config-sync-sp-vlan)# ip igmp snooping querier 10.101.1.1
switch(config-sync-sp-vlan)# exit
switch(config-sync-sp)# mac address-table static 0000.0000.0001 vlan 101 drop
switch(config-sync-sp)# interface ethernet1/2
switch(config-sync-sp-if)# switchport mode trunk
switch(config-sync-sp-if)# switchport trunk allowed vlan 101
switch(config-sync-sp-if)# exit
switch(config-sync-sp)# show switch-profile sp buffer
---------------------------------------------------------Seq-no Command
---------------------------------------------------------1 vlan 101
1.1 ip igmp snooping querier 10.101.1.1
2 mac address-table static 0000.0000.0001 vlan 101 drop
3 interface Ethernet1/2
3.1 switchport mode trunk
3.2 switchport trunk allowed vlan 101
switch(config-sync-sp)# buffer-move 3 1
switch(config-sync-sp)# show switch-profile sp buffer
---------------------------------------------------------Seq-no Command
---------------------------------------------------------1 interface Ethernet1/2
1.1 switchport mode trunk
1.2 switchport trunk allowed vlan 101
2 vlan 101
2.1 ip igmp snooping querier 10.101.1.1
3 mac address-table static 0000.0000.0001 vlan 101 drop
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 29
Page 52

Replacing a Cisco Nexus 5000 Series Switch
switch(config-sync-sp)# buffer-delete 1
switch(config-sync-sp)# show switch-profile sp buffer
---------------------------------------------------------Seq-no Command
---------------------------------------------------------2 vlan 101
2.1 ip igmp snooping querier 10.101.1.1
3 mac address-table static 0000.0000.0001 vlan 101 drop
switch(config-sync-sp)# buffer-delete all
switch(config-sync-sp)# show switch-profile sp buffer
switch(config-sync-sp)#
Replacing a Cisco Nexus 5000 Series Switch
When a Cisco Nexus 5000 Series switch has been replaced, perform the following configuration steps on the
replacement switch to synchronize it with the existing Cisco Nexus 5000 Series switch. The procedure can
be done in a hybrid Fabric Extender A/A topology and Fabric Extender Straight-Through topology.
1
Do not connect any peer-link, vPC, A/A or Straight-Through topology fabric ports to the replacement
switch.
Configuring Switch Profiles
2
Boot the replacement switch. The switch comes up with no configuration.
3
Enable pre-provisioning on all Fabric Extender A/A and ST modules.
4
Configure the replacement switch:
If the running-configuration was saved offline, follow steps 5-9 to apply the configuration.
If the running-configuration was not saved offline, you can obtain it from the peer switch if the configuration
synchronization feature is enabled. (See Steps 1 and 2 from "Creating a Switch Profile on a Local and
Peer Switch" then begin with step 10 below).
If neither condition is met, manually add the configuration and then begin with step 10 below.
5
Edit the configuration file to remove the sync-peer command if using the configuration synchronization
feature.
6
Configure the mgmt port IP address and download the configuration file.
7
Copy the saved configuration file to the running configuration.
8
Verify the configuration is correct by entering the show running-config command and the show provision
failed-config slot command.
9
If switch-profile configuration changes were made on the peer switch while the replacement switch was
out-of-service, apply those configurations in the switch-profile and then enter the commit command.
10
Shutdown all Fabric Extender ST topology ports that are included in a vPC topology.
11
Connect the Fabric Extender ST topology fabric ports.
12
Wait for Fabric Extender ST topology switches to come online.
13
Ensure the vPC role priority of the existing switch is better than the replacement switch.
14
Connect the peer-link ports to the peer switch.
15
Connect the Fabric Extender A/A topology fabric ports.
16
Connect the switch vPC ports.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
30 OL-31641-01
Page 53

Configuring Switch Profiles
17
18
19
20
Replacing a Cisco Nexus 5000 Series Switch
Enter the no shutdown command on all Fabric Extender ST vPC ports.
Verify that all vPC switches and the Fabric Extenders on the replacement switch come online and that
there is no disruption in traffic.
If you are using the configuration synchronization feature, add the sync-peer configuration to the
switch-profile if this wasn’t enabled in Step 4.
If you are using the configuration synchronization feature, enter the show switch-profile name status
command to ensure both switches are synchronized.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 31
Page 54

Replacing a Cisco Nexus 5000 Series Switch
Configuring Switch Profiles
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
32 OL-31641-01
Page 55

CHAPTER 4
Configuring Module Pre-Provisioning
This chapter contains the following sections:
Information About Module Pre-Provisioning, page 33
•
Guidelines and Limitations, page 33
•
Enabling Module Pre-Provisioning, page 34
•
Removing Module Pre-Provisioning, page 35
•
Verifying the Pre-Provisioned Configuration, page 35
•
Configuration Examples for Pre-Provisioning, page 36
•
Information About Module Pre-Provisioning
The pre-provisioning feature allows you to preconfigure interfaces before inserting or attaching a module. If
a module goes offline, you can also use pre-provisioning to make changes to the interface configurations for
the offline module. When a pre-provisioned module comes online, the pre-provisioning configurations are
applied. If any configurations were not applied, a syslog is generated. The syslog lists the configurations that
were not accepted.
In some Virtual Port Channel (vPC) topologies, pre-provisioning is required for the configuration
synchronization feature. Pre-provisioning allows you to synchronize the configuration for an interface that is
online with one peer but offline with another peer.
Note
For a list of supported hardware, see the Table 2 Hardware Supported by Cisco NX-OS Release 7.x
Software in the Cisco Nexus 5600 Series Release Notes.
Guidelines and Limitations
Pre-provisioning has the following configuration guidelines and limitations:
When a module comes online, commands that are not applied are listed in the syslog.
•
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 33
Page 56

Enabling Module Pre-Provisioning
If a slot is pre-provisioned for module A and if you insert module B into the slot, module B does not
•
come online.
There is no MIB support for pre-provisioned interfaces.
•
Cisco DCNM is not supported.
•
Enabling Module Pre-Provisioning
You can enable pre-provisioning on a module that is offline. Enter the provision model model command in
module pre-provision mode.
After enabling pre-provisioning, you can configure the interfaces as though they are online.Note
Procedure
Configuring Module Pre-Provisioning
Step 1
Step 2
Step 3
Step 4
Step 5
Example:
switch# config t
switch(config)#
slot slot
Example:
switch(config)# slot 101
switch(config-slot)#
provision model model
Example:
switch(config-slot)# provision model
N2K-C2248T
switch(config-slot)#
Example:
switch(config-slot)# exit
switch#
copy running-config startup-config
Example:
switch# copy running-config startup-config
PurposeCommand or Action
Enters global configuration mode.configuration terminal
Selects the slot to pre-provision and enters
slot configuration mode.
Selects the module that you want to
pre-provision.
Exits slot configuration mode.exit
(Optional)
Copies the running configuration to the
startup configuration.
This example shows how to select slot 101 and the N2K-C2232P module to pre-provision.
switch# configure terminal
switch(config)# slot 101
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
34 OL-31641-01
Page 57

Configuring Module Pre-Provisioning
switch(config-slot)# provision model N2K-C2232P
switch(config-slot)# exit
Removing Module Pre-Provisioning
You can remove a module that has been pre-provisioned.
Procedure
Removing Module Pre-Provisioning
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
Example:
switch# config t
switch(config)#
slot slot
Example:
switch(config)# slot 101
switch(config-slot)#
no provision model model
Example:
switch(config-slot)# no provision model
N2K-C2248T
switch(config-slot)#
Example:
switch(config-slot)# exit
switch#
copy running-config startup-config
Example:
switch# copy running-config startup-config
Enters global configuration mode.configuration terminal
Selects the slot to pre-provision and enters
slot configuration mode.
Removes pre-provisioning from the
module.
Exits slot configuration mode.exit
(Optional)
Copies the running configuration to the
startup configuration.
This example shows how to remove a preprovisioned module from a chassis slot:
switch(config)# slot 2
switch(config-slot)# no provision model N5K-M1404
switch(config-slot)#
Verifying the Pre-Provisioned Configuration
To display the pre-provisioned configuration, perform one of the following tasks:
PurposeCommand
Displays module information.show module
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 35
Page 58

Configuration Examples for Pre-Provisioning
Configuring Module Pre-Provisioning
PurposeCommand
Displays switch profile information.show switch-profile
show running-config
exclude-provision
show provision failed-config
Displays the running configuration without the pre-provisioned
interfaces or modules that are offline.
Displays the pre-provisioned commands that were not applied to the
configuration when the interface or module came online.
This command also displays a history of failed commands.
show running-config
Displays the running configuration including the pre-provisioned
configuration.
show startup-config
Displays the startup configuration including the pre-provisioned
configuration.
Configuration Examples for Pre-Provisioning
The following example shows how to enable pre-provisioning on slot 110 on the Cisco Nexus 2232P Fabric
Extender and how to pre-provision interface configuration commands on the Ethernet 110/1/1 interface.
switch# configure terminal
switch(config)# slot 110
switch(config-slot)# provision model N2K-C2232P
switch(config-slot)# exit
switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
switch(config)# interface Ethernet110/1/1
switch(config-if)# description module is preprovisioned
switch(config-if)# show running-config interface Ethernet110/1/1
Time: Wed Aug 25 21:29:44 2010
version 5.0(2)N1(1)
interface Ethernet110/1/1
description module is preprovisioned
The following example shows the list of pre-provisioned commands that were not applied when the module
came online.
switch(config-if-range)# show provision failed-config 101
The following config was not applied for slot 33
================================================
interface Ethernet101/1/1
service-policy input test
interface Ethernet101/1/2
service-policy input test
interface Ethernet101/1/3
service-policy input test
This example shows how to remove all pre-provisioned modules from a slot:
switch(config)# slot 2
switch(config-slot)# no provision model
switch(config-slot)#
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
36 OL-31641-01
Page 59

Using Cisco Fabric Services
This chapter contains the following sections:
Information About CFS, page 37
•
Guidelines and Limitations for CFS, page 38
•
CFS Distribution, page 39
•
CFS Support for Applications, page 40
•
CFS Regions, page 44
•
Configuring CFS over IP, page 47
•
Default Settings for CFS, page 49
•
Information About CFS
CHAPTER 5
Some features in the Cisco Nexus Series switch require configuration synchronization with other switches in
the network to function correctly. Synchronization through manual configuration at each switch in the network
can be a tedious and error-prone process.
Cisco Fabric Services (CFS) provides a common infrastructure for automatic configuration synchronization
in the network. It provides the transport function and a set of common services to the features. CFS has the
ability to discover CFS-capable switches in the network and to discover feature capabilities in all CFS-capable
switches.
Cisco Nexus Series switches support CFS message distribution over IPv4 networks.
CFS provides the following features:
Peer-to-peer protocol with no client-server relationship at the CFS layer.
•
CFS message distribution over IPv4 and IPv6 networks.
•
Three modes of distribution.
•
Coordinated distributions: Only one distribution is allowed in the network at any given time.
◦
Uncoordinated distributions: Multiple parallel distributions are allowed in the network except when
◦
a coordinated distribution is in progress.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 37
Page 60

Cisco Fabric Services over Ethernet
Unrestricted uncoordinated distributions: Multiple parallel distributions are allowed in the network
◦
in the presence of an existing coordinated distribution. Unrestricted uncoordinated distributions
are allowed to run in parallel with all other types of distributions.
The following features are supported for CFS distribution over IP:
One scope of distribution over an IP network:
•
Physical scope: The distribution spans the entire IP network.
◦
Cisco Fabric Services over Ethernet
The Cisco Fabric Services over Ethernet (CFSoE) is a reliable state transport mechanism that you can use to
synchronize the actions of the vPC peer devices. CFSoE carries messages and packets for many features linked
with vPC, such as STP and IGMP. Information is carried in CFS/CFSoE protocol data units (PDUs).
When you enable the vPC feature, the device automatically enables CFSoE, and you do not have to configure
anything. CFSoE distributions for vPCs do not need the capabilities to distribute over IP or the CFS regions.
You do not need to configure anything for the CFSoE feature to work correctly on vPCs.
You can use the show mac address-table command to display the MAC addresses that CFSoE synchronizes
for the vPC peer link.
Using Cisco Fabric Services
Note
Do not enter the no cfs eth distribute or the no cfs distribute command. CFSoE must be enabled for
vPC functionality. If you do enter either of these commands when vPC is enabled, the system displays an
error message.
When you enter the show cfs application command, the output displays "Physical-eth," which shows the
applications that are using CFSoE.
Guidelines and Limitations for CFS
CFS has the following configuration guidelines and limitations:
If the virtual port channel (vPC) feature is enabled for your device, do not disable CFSoE.
•
CFSoE must be enabled for the vPC feature to work.Note
All CFSoIP-enabled devices with similar multicast addresses form one CFSoIP fabric.
•
Make sure that CFS is enabled for the applications that you want to configure.
•
Anytime you lock a fabric, your username is remembered across restarts and switchovers.
•
Anytime you lock a fabric, configuration changes attempted by anyone else are rejected.
•
While a fabric is locked, the application holds a working copy of configuration changes in a pending
•
database or temporary storage area, not in the running configuration.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
38 OL-31641-01
Page 61

Using Cisco Fabric Services
Configuration changes that have not been committed yet (still saved as a working copy) are not in the
•
running configuration and do not display in the output of show commands.
If you start a CFS session that requires a fabric lock but forget to end the session, an administrator can
•
clear the session.
An empty commit is allowed if configuration changes are not previously made. In this case, the commit
•
command results in a session that acquires locks and distributes the current database.
You can use the commit command only on the specific device where the fabric lock was acquired.
•
CFSoIP and CFSoE are not supported for use together.
•
CFS regions can be applied only to CFSoIP applications.
•
CFS Distribution
The CFS distribution functionality is independent of the lower layer transport. Cisco Nexus Series switches
support CFS distribution over IP. Features that use CFS are unaware of the lower layer transport.
CFS Distribution
CFS Distribution Modes
CFS supports three distribution modes to accommodate different feature requirements:
Uncoordinated Distribution
•
Coordinated Distribution
•
Unrestricted Uncoordinated Distributions
•
Only one mode is allowed at any given time.
Uncoordinated Distribution
Uncoordinated distributions are used to distribute information that is not expected to conflict with information
from a peer. Parallel uncoordinated distributions are allowed for a feature.
Coordinated Distribution
Coordinated distributions allow only one feature distribution at a given time. CFS uses locks to enforce this
feature. A coordinated distribution is not allowed to start if locks are taken for the feature anywhere in the
network. A coordinated distribution consists of three stages:
A network lock is acquired.
•
The configuration is distributed and committed.
•
The network lock is released.
•
Coordinated distribution has two variants:
• CFS driven —The stages are executed by CFS in response to a feature request without intervention from
the feature.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 39
Page 62

Verifying the CFS Distribution Status
• Feature driven—The stages are under the complete control of the feature.
Coordinated distributions are used to distribute information that can be manipulated and distributed from
multiple switches, for example, the port security configuration.
Unrestricted Uncoordinated Distributions
Unrestricted uncoordinated distributions allow multiple parallel distributions in the network in the presence
of an existing coordinated distribution. Unrestricted uncoordinated distributions are allowed to run in parallel
with all other types of distributions.
Verifying the CFS Distribution Status
The show cfs status command displays the status of CFS distribution on the switch:
switch# show cfs status
Distribution : Enabled
Distribution over IP : Enabled - mode IPv4
IPv4 multicast address : 239.255.70.83
IPv6 multicast address : ff15::efff:4653
Distribution over Ethernet : Enabled
Using Cisco Fabric Services
CFS Support for Applications
CFS Application Requirements
All switches in the network must be CFS capable. Switches that are not CFS capable do not receive distributions,
which results in part of the network not receiving the intended distribution. CFS has the following requirements:
• Implicit CFS usage—The first time that you issue a CFS task for a CFS-enabled application, the
configuration modification process begins and the application locks the network.
• Pending database—The pending database is a temporary buffer to hold uncommitted information. The
uncommitted changes are not applied immediately to ensure that the database is synchronized with the
database in the other switches in the network. When you commit the changes, the pending database
overwrites the configuration database (also known as the active database or the effective database).
• CFS distribution enabled or disabled on a per-application basis—The default (enable or disable) for the
CFS distribution state differs between applications. If CFS distribution is disabled for an application,
that application does not distribute any configuration and does not accept a distribution from other
switches in the network.
• Explicit CFS commit—Most applications require an explicit commit operation to copy the changes in
the temporary buffer to the application database, to distribute the new database to the network, and to
release the network lock. The changes in the temporary buffer are not applied if you do not perform the
commit operation.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
40 OL-31641-01
Page 63

Using Cisco Fabric Services
Enabling CFS for an Application
All CFS-based applications provide an option to enable or disable the distribution capabilities.
Applications have the distribution enabled by default.
The application configuration is not distributed by CFS unless distribution is explicitly enabled for that
application.
Verifying Application Registration Status
The show cfs application command displays the applications that are currently registered with CFS. The first
column displays the application name. The second column indicates whether the application is enabled or
disabled for distribution (enabled or disabled). The last column indicates the scope of distribution for the
application (logical, physical, or both).
Enabling CFS for an Application
Note
The show cfs application command only displays applications registered with CFS. Conditional services
that use CFS do not appear in the output unless these services are running.
switch# show cfs application
---------------------------------------------Application Enabled Scope
---------------------------------------------ntp No Physical-all
fscm Yes Physical-fc
rscn No Logical
fctimer No Physical-fc
syslogd No Physical-all
callhome No Physical-all
fcdomain Yes Logical
device-alias Yes Physical-fc
Total number of entries = 8
The show cfs application name command displays the details for a particular application. It displays the
enabled/disabled state, timeout as registered with CFS, merge capability (if it has registered with CFS for
merge support), and the distribution scope.
switch# show cfs application name fscm
Enabled : Yes
Timeout : 100s
Merge Capable : No
Scope : Physical-fc
Locking the Network
When you configure (first-time configuration) a feature (application) that uses the CFS infrastructure, that
feature starts a CFS session and locks the network. When a network is locked, the switch software allows
configuration changes to this feature only from the switch that holds the lock. If you make configuration
changes to the feature from another switch, the switch issues a message to inform the user about the locked
status. The configuration changes are held in a pending database by that application.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 41
Page 64

Committing Changes
If you start a CFS session that requires a network lock but forget to end the session, an administrator can clear
the session. If you lock a network at any time, your username is remembered across restarts and switchovers.
If another user (on the same machine) tries to perform configuration tasks, that user’s attempts are rejected.
Verifying CFS Lock Status
The show cfs lock command displays all the locks that are currently acquired by any application. For each
application the command displays the application name and scope of the lock taken. If the application lock
is taken in the physical scope, then this command displays the switch WWN, IP address, user name, and user
type of the lock holder. If the application is taken in the logical scope, then this command displays the VSAN
in which the lock is taken, the domain, IP address, user name, and user type of the lock holder.
switch# show cfs lock
Application: ntp
Scope : Physical
-------------------------------------------------------------------Switch WWN IP Address User Name User Type
-------------------------------------------------------------------20:00:00:05:30:00:6b:9e 10.76.100.167 admin CLI/SNMP v3
Total number of entries = 1
Application: port-security
Scope : Logical
-----------------------------------------------------------
VSAN Domain IP Address User Name User Type
----------------------------------------------------------1 238 10.76.100.167 admin CLI/SNMP v3
2 211 10.76.100.167 admin CLI/SNMP v3
Total number of entries = 2
Using Cisco Fabric Services
The show cfs lock name command displays the lock details for the specified application.
switch# show cfs lock name ntp
Scope : Physical
-------------------------------------------------------------------Switch WWN IP Address User Name User Type
-------------------------------------------------------------------20:00:00:05:30:00:6b:9e 10.76.100.167 admin CLI/SNMP v3
Total number of entries = 1
Committing Changes
A commit operation saves the pending database for all application peers and releases the lock for all switches.
The commit function does not start a session; only a lock function starts a session. However, an empty commit
is allowed if configuration changes are not previously made. In this case, a commit operation results in a
session that acquires locks and distributes the current database.
When you commit configuration changes to a feature using the CFS infrastructure, you receive a notification
about one of the following responses:
• One or more external switches report a successful status—The application applies the changes locally
and releases the network lock.
• None of the external switches report a successful state—The application considers this state a failure
and does not apply the changes to any switch in the network. The network lock is not released.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
42 OL-31641-01
Page 65

Using Cisco Fabric Services
You can commit changes for a specified feature by entering the commit command for that feature.
Discarding Changes
If you discard configuration changes, the application flushes the pending database and releases locks in the
network. Both the abort and commit functions are supported only from the switch from which the network
lock is acquired.
You can discard changes for a specified feature by using the abort command for that feature.
Saving the Configuration
Configuration changes that have not been applied yet (still in the pending database) are not shown in the
running configuration. The configuration changes in the pending database overwrite the configuration in the
effective database when you commit the changes.
Discarding Changes
If you do not commit the changes, they are not saved to the running configuration.Caution
Clearing a Locked Session
You can clear a lock held by an application from any device in the fabric.
When you clear a lock in the fabric, any pending configurations in any device in the fabric are discarded.Caution
Before You Begin
You must have administrator permissions to release a lock.
Procedure
Step 1
Step 2
switch# show application-name status
switch# clear application-name session
PurposeCommand or Action
(Optional)
Shows the current application state.
Clears the application configuration session and
releases the lock on the fabric. All pending changes
are discarded.
Step 3
switch# show ntp status
Distribution : Enabled
Last operational state: Fabric Locked
switch# clear ntp session
OL-31641-01 43
switch# show application-name status
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
(Optional)
Shows the current application state.
Page 66

CFS Regions
switch# show ntp status
Distribution : Enabled
Last operational state: No session
CFS Regions
About CFS Regions
A CFS region is a user-defined subset of switches for a given feature or application in its physical distribution
scope. When a network spans a vast geography, you might need to localize or restrict the distribution of certain
profiles among a set of switches based on their physical proximity. CFS regions allow you to create multiple
islands of distribution within the network for a given CFS feature or application. CFS regions are designed
to restrict the distribution of a feature’s configuration to a specific set or grouping of switches in a network.
Using Cisco Fabric Services
Note
You can only configure a CFS region based on physical switches. You cannot configure a CFS region in
a VSAN.
Example Scenario
The Smart Call Home application triggers alerts to network administrators when a situation arises or something
abnormal occurs. When the network covers many geographies, and there are multiple network administrators
who are each responsible for a subset of switches in the network, the Smart Call Home application sends alerts
to all network administrators regardless of their location. For the Smart Call Home application to send message
alerts selectively to network administrators, the physical scope of the application has to be fine tuned or
narrowed down. You can achieve this scenario by implementing CFS regions.
CFS regions are identified by numbers ranging from 0 through 200. Region 0 is reserved as the default region
and contains every switch in the network. You can configure regions from 1 through 200. The default region
maintains backward compatibility.
If the feature is moved, that is, assigned to a new region, its scope is restricted to that region; it ignores all
other regions for distribution or merging purposes. The assignment of the region to a feature has precedence
in distribution over its initial physical scope.
You can configure a CFS region to distribute configurations for multiple features. However, on a given switch,
you can configure only one CFS region at a time to distribute the configuration for a given feature. Once you
assign a feature to a CFS region, its configuration cannot be distributed within another CFS region.
Managing CFS Regions
Creating CFS Regions
You can create a CFS region.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
44 OL-31641-01
Page 67

Using Cisco Fabric Services
Procedure
Managing CFS Regions
PurposeCommand or Action
Step 1
Step 2
switch(config)# cfs region region-id
Assigning Applications to CFS Regions
You can assign an application on a switch to a region.
Procedure
Step 1
Step 2
Step 3
switch(config)# cfs region region-id
application
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Creates a region.
Adds application(s) to the region.switch(config-cfs-region)#
Note
You can add any number of applications on the
switch to a region. If you try adding an
application to the same region more than once,
you see the "Application already present in the
same region" error message.
Enters global configuration mode.switch# configure terminal
Creates a region.
The following example shows how to assign applications to a region:
switch# configure terminal
switch(config)# cfs region 1
switch(config-cfs-region)# ntp
switch(config-cfs-region)# callhome
Moving an Application to a Different CFS Region
You can move an application from one region to another region.
Procedure
Step 1
Step 2
Step 3
switch(config)# cfs region region-id
switch(config-cfs-region)#
application
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enters CFS region configuration submode.
Indicates application(s) to be moved from one region into
another.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 45
Page 68

Managing CFS Regions
The following example shows how to move an application into Region 2 that was originally assigned to
Region 1:
switch# configure terminal
switch(config)# cfs region 2
switch(config-cfs-region)# ntp
Removing an Application from a Region
Removing an application from a region is the same as moving the application back to the default region
(Region 0), which brings the entire network into the scope of distribution for the application.
PurposeCommand or Action
Note
Using Cisco Fabric Services
If you try moving an application to the same
region more than once, you see the "Application
already present in the same region" error
message.
Procedure
Step 1
Step 2
Step 3
Deleting CFS Regions
Deleting a region nullifies the region definition. All the applications bound by the region are released back
to the default region.
Procedure
Step 1
Step 2
switch(config)# cfs region region-id
switch(config-cfs-region)# no application
switch(config)# no cfs region region-id
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enters CFS region configuration submode.
Removes application(s) that belong to the
region.
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Deletes the region.
Note
You see the, "All the applications in the
region will be moved to the default region"
warning.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
46 OL-31641-01
Page 69

Using Cisco Fabric Services
Configuring CFS over IP
Enabling CFS over IPv4
You can enable or disable CFS over IPv4.
CFS cannot distribute over both IPv4 and IPv6 from the same switch.Note
Procedure
Configuring CFS over IP
PurposeCommand or Action
Step 1
Step 2
Step 3
Enabling CFS over IPv6
You can enable or disable CFS over IPv6.
CFS cannot distribute over both IPv4 and IPv6 from the same switch.Note
Procedure
Step 1
switch(config)# cfs ipv4 distribute
switch(config)# no cfs ipv4 distribute
Enters global configuration mode.switch# configure terminal
Globally enables CFS over IPv4 for all
applications on the switch.
(Optional)
Disables (default) CFS over IPv4 on the switch.
PurposeCommand or Action
Enters configuration mode.switch# configure
Step 2
Step 3
OL-31641-01 47
switch(config)# cfs ipv6 distribute
switch(config)# no cfs ipv6 distribute
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
Globally enables CFS over IPv6 for all
applications on the switch.
(Optional)
Disables (default) CFS over IPv6 on the switch.
Page 70

Verifying the CFS Over IP Configuration
Verifying the CFS Over IP Configuration
The following example show how to verify the CFS over IP configuration:
switch# show cfs status
Distribution : Enabled
Distribution over IP : Enabled - mode IPv4
IPv4 multicast address : 239.255.70.83
IPv6 multicast address : ff15::efff:4653
Configuring IP Multicast Addresses for CFS over IP
All CFS over IP enabled switches with similar multicast addresses form one CFS over IP network. CFS
protocol-specific distributions, such as the keepalive mechanism for detecting network topology changes, use
the IP multicast address to send and receive information.
CFS distributions for application data use directed unicast.Note
Using Cisco Fabric Services
Configuring IPv4 Multicast Address for CFS
You can configure a CFS over IP multicast address value for IPv4. The default IPv4 multicast address is
239.255.70.83.
Procedure
Step 1
Step 2
Step 3
switch(config)# cfs ipv4
mcast-address ipv4-address
switch(config)# no cfs ipv4
mcast-address ipv4-address
Configuring IPv6 Multicast Address for CFS
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Configures the IPv4 multicast address for CFS distribution
over IPv4. The ranges of valid IPv4 addresses are
239.255.0.0 through 239.255.255.255 and 239.192/16
through 239.251/16.
(Optional)
Reverts to the default IPv4 multicast address for CFS
distribution over IPv4. The default IPv4 multicast address
for CFS is 239.255.70.83.
You can configure a CFS over IP multicast address value for IPv6. The default IPv6 multicast address is
ff13:7743:4653.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
48 OL-31641-01
Page 71

Using Cisco Fabric Services
Procedure
Verifying the IP Multicast Address Configuration for CFS over IP
PurposeCommand or Action
Step 1
Step 2
switch(config)# cfs ipv6
mcast-address ipv4-address
Enters configuration mode.switch# configure
Configures the IPv6 multicast address for CFS distribution
over IPv6. The range of valid IPv6 addresses is ff15::/16
(ff15::0000:0000 through ff15::ffff:ffff) and ff18::/16
(ff18::0000:0000 through ff18::ffff:ffff).
Step 3
switch(config)# no cfs ipv6
mcast-address ipv4-address
(Optional)
Reverts to the default IPv6 multicast address for CFS
distribution over IPv6. The default IPv6 multicast address
for CFS over IP is ff15::efff:4653.
Verifying the IP Multicast Address Configuration for CFS over IP
The following example shows how to verify the IP multicast address configuration for CFS over IP:
switch# show cfs status
Fabric distribution Enabled
IP distribution Enabled mode ipv4
IPv4 multicast address : 10.1.10.100
IPv6 multicast address : ff13::e244:4754
Default Settings for CFS
The following table lists the default settings for CFS configurations.
Table 1: Default CFS Parameters
DefaultParameters
EnabledCFS distribution on the switch
Implicitly enabled with the first configuration changeDatabase changes
Differs based on applicationApplication distribution
Explicit configuration is requiredCommit
DisabledCFS over IP
239.255.70.83IPv4 multicast address
ff15::efff:4653IPv6 multicast address
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 49
Page 72

Enabling CFS to Distribute Smart Call Home Configurations
The CISCO-CFS-MIB contains SNMP configuration information for any CFS-related functions. See the MIB
reference for your platform.
Enabling CFS to Distribute Smart Call Home Configurations
You can enable CFS to distribute Call Home configurations to all Cisco NX-OS devices in the network. The
entire Call Home configuration is distributed except the device priority and the sysContact names.
Procedure
PurposeCommand or Action
Using Cisco Fabric Services
Step 1
Step 2
Step 3
switch(config-callhome)# distribute
Enters global configuration mode.switch# configure terminal
Enters Call Home configuration mode.switch(config)# callhome
Enables CFS to distribute Smart Call Home
configuration updates.
Step 4
switch(config-callhome)# show
application-name status
(Optional)
For the specified application, displays the CFS
distribution status.
Step 5
switch(config-callhome)# copy
running-config startup-config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
switch# configure terminal
switch(config)# callhome
switch(config-callhome)# distribute
switch(config-callhome)# show callhome status
Distribution : Enabled
switch(config-callhome)# copy running-config startup-config
Enabling CFS to Distribute Device Alias Configurations
You can enable CFS to distribute device alias configurations in order to consistently administer and maintain
the device alias database across all Cisco NX-OS devices in the fabric.
Before You Begin
Make sure that you are in the storage VDC. To change to the storage VDC, use the switchto vdc fcoe command.
Procedure
PurposeCommand or Action
Step 1
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
50 OL-31641-01
Enters global configuration mode.switch# configure terminal
Page 73

Using Cisco Fabric Services
Enabling CFS to Distribute DPVM Configurations
PurposeCommand or Action
Step 2
switch(config)# device-alias distribute
Enables CFS to distribute device alias configuration
updates.
Step 3
switch(config)# show cfs application
(Optional)
Displays the CFS distribution status.
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
This example shows how to enable CFS to distribute device alias configurations:
switch(config)# device-alias distribute
switch(config)# show cfs application
---------------------------------------------Application Enabled Scope
---------------------------------------------device-alias Yes Physical-fc
switch(config)# copy running-config startup-config
[########################################] 100%
Enabling CFS to Distribute DPVM Configurations
You can enable CFS to distribute dynamic port VSAN membership (DPVM) configurations in order to
consistently administer and maintain the DPVM database across all Cisco NX-OS devices in the fabric.
Before You Begin
Make sure that you are in the storage VDC. To change to the storage VDC, use the switchto vdc fcoe command.
Make sure that you enable the DPVM feature. To do so, use the feature dpvm command.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# dpvm distribute
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute DPVM configuration
updates.
Step 3
switch(config)# show application-name
status
(Optional)
For the specified application, displays the CFS
distribution status.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 51
Page 74

Enabling CFS to Distribute FC Domain Configurations
Using Cisco Fabric Services
PurposeCommand or Action
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
This example shows how to enable CFS to distribute DPVM configurations:
switch(config)# dpvm distribute
switch(config)# show dpvm status
Distribution is enabled.
switch(config)# copy running-config startup-config
[########################################] 100%
Enabling CFS to Distribute FC Domain Configurations
You can enable CFS to distribute Fibre Channel (FC) domain configurations in order to synchronize the
configuration across the fabric from the console of a single Cisco NX-OS device and to ensure consistency
in the allowed domain ID lists on all devices in the VSAN.
Before You Begin
Make sure that you are in the storage VDC. To change to the storage VDC, use the switchto vdc fcoe command.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# fcdomain distribute
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute FC domain configuration
updates.
Step 3
switch(config)# show application-name
status
(Optional)
For the specified application, displays the CFS
distribution status.
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
This example shows how to enable CFS to distribute FC domain configurations:
switch(config)# fcdomain distribute
switch(config)# show fcdomain status
fcdomain distribution is enabled
switch(config)# copy running-config startup-config
[########################################] 100%
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
52 OL-31641-01
Page 75

Using Cisco Fabric Services
Enabling CFS to Distribute FC Port Security Configurations
Enabling CFS to Distribute FC Port Security Configurations
You can enable CFS to distribute Fibre Channel (FC) port security configurations in order to provide a single
point of configuration for the entire fabric in the VSAN and to enforce the port security policies throughout
the fabric.
Before You Begin
Make sure that you are in the storage VDC. To change to the storage VDC, use the switchto vdc fcoe command.
Make sure that you enable the FC port security feature. To do so, use the feature fc-port-security command.
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config)# fc-port-security
distribute
switch(config)# show cfs application
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute FC port security
configuration updates.
(Optional)
Displays the CFS distribution status.
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
This example shows how to enable CFS to distribute FC port security configurations:
switch(config)# fc-port-security distribute
switch(config)# show cfs application
---------------------------------------------Application Enabled Scope
---------------------------------------------fc-port-securi Yes Logical
switch(config)# copy running-config startup-config
[########################################] 100%
Enabling CFS to Distribute FC Timer Configurations
You can enable CFS to distribute Fibre Channel (FC) timer configurations for all Cisco NX-OS devices in
the fabric.
Before You Begin
Make sure that you are in the storage VDC. To change to the storage VDC, use the switchto vdc fcoe command.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 53
Page 76

Enabling CFS to Distribute IVR Configurations
Procedure
Using Cisco Fabric Services
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config)# fctimer distribute
switch(config)# show application-name
status
Step 4
switch(config)# copy running-config
startup config
This example shows how to enable CFS to distribute FC timer configurations:
switch(config)# fctimer distribute
switch(config)# show fctimer status
Distribution : Enabled
switch(config)# copy running-config startup-config
[########################################] 100%
Enabling CFS to Distribute IVR Configurations
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute FC timer configuration
updates.
(Optional)
For the specified application, displays the CFS
distribution status.
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
You can enable CFS to distribute inter-VSAN routing (IVR) configurations in order to enable efficient IVR
configuration management and to provide a single point of configuration for the entire fabric in the VSAN.
Before You Begin
Make sure that you are in the storage VDC. To change to the storage VDC, use the switchto vdc fcoe command.
Make sure that you install the Advanced SAN Services license.
Make sure that you enable the IVR feature. To do so, use the feature ivr command.
Procedure
PurposeCommand or Action
Step 1
Step 2
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute IVR configuration updates.switch(config)# ivr distribute
Note
You must enable IVR distribution on all
IVR-enabled switches in the fabric.
Step 3
switch(config)# show cfs application
(Optional)
Displays the CFS distribution status.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
54 OL-31641-01
Page 77

Using Cisco Fabric Services
Enabling CFS to Distribute NTP Configurations
PurposeCommand or Action
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
This example shows how to enable CFS to distribute IVR configurations:
switch(config)# ivr distribute
switch(config)# show cfs application
---------------------------------------------Application Enabled Scope
---------------------------------------------ivr Yes Physical-fc
switch(config)# copy running-config startup-config
[########################################] 100%
Enabling CFS to Distribute NTP Configurations
You can enable CFS to distribute NTP configurations to all Cisco NX-OS devices in the network.
Before You Begin
Make sure that you enable the NTP feature (using the feature ntp command).
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config)# show application-name
status
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute NTP configuration updates.switch(config)# ntp distribute
(Optional)
For the specified application, displays the CFS
distribution status.
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
switch# configure terminal
switch(config)# ntp distribute
switch(config)# show ntp status
Distribution : Enabled
switch(config)# copy running-config startup-config
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 55
Page 78

Enabling CFS to Distribute RADIUS Configurations
Enabling CFS to Distribute RADIUS Configurations
You can enable CFS to distribute RADIUS configurations to all Cisco NX-OS devices in the network.
Procedure
PurposeCommand or Action
Using Cisco Fabric Services
Step 1
Step 2
switch(config)# radius distribute
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute RADIUS configuration
updates.
Step 3
switch(config)# show application-name
status
(Optional)
For the specified application, displays the CFS
distribution status.
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
switch# configure terminal
switch(config)# radius distribute
switch(config)# show radius status
Distribution : Enabled
switch(config)# copy running-config startup-config
Enabling CFS to Distribute RSCN Configurations
You can enable CFS to distribute registered state change notification (RSCN) configurations to all Cisco
NX-OS devices in the fabric.
Before You Begin
Make sure that you are in the storage VDC. To change to the storage VDC, use the switchto vdc fcoe command.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# rscn distribute
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute RSCN configuration
updates.
Step 3
switch(config)# show cfs application
(Optional)
Displays the CFS distribution status.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
56 OL-31641-01
Page 79

Using Cisco Fabric Services
Enabling CFS to Distribute TACACS+ Configurations
PurposeCommand or Action
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
This example shows how to enable CFS to distribute RSCN configurations:
switch(config)# rscn distribute
switch(config)# show cfs application
---------------------------------------------Application Enabled Scope
---------------------------------------------rscn Yes Logical
switch(config)# copy running-config startup-config
[########################################] 100%
Enabling CFS to Distribute TACACS+ Configurations
You can enable CFS to distribute TACACS+ configurations to all Cisco NX-OS devices in the network.
Before You Begin
Make sure that you enable the TACACS+ feature (using the feature tacacs+ command).
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# tacacs+ distribute
Enters global configuration mode.switch# configure terminal
Enables CFS to distribute TACACS+ configuration
updates.
Step 3
switch(config)# show application-name
status
(Optional)
For the specified application, displays the CFS
distribution status.
Step 4
switch(config)# copy running-config
startup config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
switch# configure terminal
switch(config)# tacacs+ distribute
switch(config)# show tacacs+ status
Distribution : Enabled
switch(config)# copy running-config startup-config
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 57
Page 80

Enabling CFS to Distribute TACACS+ Configurations
Using Cisco Fabric Services
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
58 OL-31641-01
Page 81

Configuring PTP
This chapter contains the following sections:
Information About PTP, page 59
•
PTP Device Types, page 60
•
PTP Process, page 61
•
Clock Management, page 62
•
High Availability for PTP, page 62
•
Licensing Requirements for PTP, page 62
•
Guidelines and Limitations for PTP, page 62
•
Default Settings for PTP, page 63
•
Configuring PTP, page 63
•
CHAPTER 6
Information About PTP
PTP is a time synchronization protocol for nodes distributed across a network. Its hardware timestamp feature
provides greater accuracy than other time synchronization protocols such as the Network Time Protocol (NTP).
A PTP system can consist of a combination of PTP and non-PTP devices. PTP devices include ordinary clocks,
boundary clocks, and transparent clocks. Non-PTP devices include ordinary network switches, routers, and
other infrastructure devices.
PTP is a distributed protocol that specifies how real-time PTP clocks in the system synchronize with each
other. These clocks are organized into a master-slave synchronization hierarchy with the grandmaster clock,
which is the clock at the top of the hierarchy, determining the reference time for the entire system.
Synchronization is achieved by exchanging PTP timing messages, with the members using the timing
information to adjust their clocks to the time of their master in the hierarchy. PTP operates within a logical
scope called a PTP domain.
Starting from Cisco NXOS Release 6.0(2)A8(3), PTP supports configuring multiple PTP clocking domains,
PTP grandmaster capability, PTP cost on interfaces for slave and passive election, and clock identity.
All the switches in a multi-domain environment, belong to one domain. The switches that are the part of
boundary clock, must have multi-domain feature enabled on them. Each domain has user configurable
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 59
Page 82

PTP Device Types
Configuring PTP
parameters such as domain priority, clock class threshold and clock accuracy threshold. The clocks in each
domain remain synchronized with the master clock in that domain. If the GPS in a domain fails, the master
clock in the domain synchronizes time and data sets associated with the announce messages from the master
clock in the domain where the GPS is active. If the master clock from the highest priority domain does not
meet the clock quality attributes, a clock in the subsequent domain that match the criteria is selected. The Best
Master Clock Algorithm (BMCA) is used to select the master clock if none of the domains has the desired
clock quality attributes. If all the domains have equal priority and the threshold values less than master clock
attributes or if the threshold values are greater than the master clock attributes, BMCA is used to select the
master clock.
Grandmaster capability feature controls the switch’s ability of propagating its clock to other devices that it is
connected to. When the switch receives announce messages on an interface, it checks the clock class threshold
and clock accuracy threshold values. If the values of these parameters are within the predefined limits, then
the switch acts as per PTP standards specified in IEEE 1588v2. If the switch does not receive announce
messages from external sources or if the parameters of the announce messages received are not within the
predefined limits, the port state will be changed to listening mode. On a switch with no slave ports, the state
of all the PTP enabled ports is rendered as listening and on a switch with one slave port, the BMCA is used
to determine states on all PTP enabled ports. Convergence time prevents timing loops at the PTP level when
grandmaster capability is disabled on a switch. If the slave port is not selected on the switch, all the ports on
the switch will be in listening state for a minimum interval specified in the convergence time. The convergence
time range is from 3 to 2600 seconds and the default value is 3 seconds.
The interface cost applies to each PTP enabled port if the switch has more than one path to grandmaster clock.
The port with the least cost value is elected as slave and the rest of the ports will remain as passive ports.
The clock identity is a unique 8-octet array presented in the form of a character array based on the switch
MAC address. The clock identity is determined from MAC according to the IEEE1588v2-2008 specifications.
The clock ID is a combination of bytes in a VLAN MAC address as defined in IEEE1588v2.
PTP Device Types
The following clocks are common PTP devices:
Ordinary clock
Communicates with the network based on a single physical port, similar to an end host. An ordinary
clock can function as a grandmaster clock.
Boundary clock
Typically has several physical ports, with each port behaving like a port of an ordinary clock. However,
each port shares the local clock, and the clock data sets are common to all ports. Each port decides its
individual state, either master (synchronizing other ports connected to it) or slave (synchronizing to a
downstream port), based on the best clock available to it through all of the other ports on the boundary
clock. Messages that are related to synchronization and establishing the master-slave hierarchy terminate
in the protocol engine of a boundary clock and are not forwarded.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
60 OL-31641-01
Page 83

Configuring PTP
PTP Process
Transparent clock
Forwards all PTP messages like an ordinary switch or router but measures the residence time of a packet
in the switch (the time that the packet takes to traverse the transparent clock) and in some cases the link
delay of the ingress port for the packet. The ports have no state because the transparent clock does not
need to synchronize to the grandmaster clock.
There are two kinds of transparent clocks:
End-to-end transparent clock
Measures the residence time of a PTP message and accumulates the times in the correction field
of the PTP message or an associated follow-up message.
Peer-to-peer transparent clock
Measures the residence time of a PTP message and computes the link delay between each port
and a similarly equipped port on another node that shares the link. For a packet, this incoming
link delay is added to the residence time in the correction field of the PTP message or an associated
follow-up message.
Note
PTP operates only in boundary clock mode. We recommend that you deploy a Grand Master Clock (10
MHz) upstream. The servers contain clocks that require synchronization and are connected to the switch.
End-to-end transparent clock and peer-to-peer transparent clock modes are not supported.
PTP Process
The PTP process consists of two phases: establishing the master-slave hierarchy and synchronizing the clocks.
Within a PTP domain, each port of an ordinary or boundary clock follows this process to determine its state:
After the master-slave hierarchy has been established, the clocks are synchronized as follows:
Examines the contents of all received announce messages (issued by ports in the master state)
•
Compares the data sets of the foreign master (in the announce message) and the local clock for priority,
•
clock class, accuracy, and so on
Determines its own state as either master or slave
•
The master sends a synchronization message to the slave and notes the time it was sent.
•
The slave receives the synchronization message and notes the time that it was received. For every
•
synchronization message, there is a follow-up message. The number of sync messages should be equal
to the number of follow-up messages.
The slave sends a delay-request message to the master and notes the time it was sent.
•
The master receives the delay-request message and notes the time it was received.
•
The master sends a delay-response message to the slave. The number of delay request messages should
•
be equal to the number of delay response messages.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 61
Page 84

Clock Management
The slave uses these timestamps to adjust its clock to the time of its master.
•
Clock Management
By default, Cisco NX-OS uses NTP to update the system clock. However, if the clock protocol property is
configured to PTP, PTP is allowed to update the system clock.
If PTP is enabled, NTP does not update the system time.
High Availability for PTP
Stateful restarts are supported for PTP. After a reboot or a supervisor switchover, the running configuration
is applied.
Licensing Requirements for PTP
Configuring PTP
PTP requires no license. Any feature not included in a license package is bundled with the Cisco NX-OS
system images and is provided at no extra charge to you. For a complete explanation of the Cisco NX-OS
licensing scheme, see the Cisco NX-OS Licensing Guide.
Guidelines and Limitations for PTP
PTP operates only in boundary clock mode. End-to-end transparent clock and peer-to-peer transparent
•
clock modes are not supported.
PTP supports transport over User Datagram Protocol (UDP). Transport over Ethernet is not supported.
•
PTP supports only multicast communication. Negotiated unicast communication is not supported.
•
PTP is limited to a single domain per network.
•
All management messages are forwarded on ports on which PTP is enabled. Handling management
•
messages is not supported.
PTP is only configurable on switch ports. Configuring PTP on FEX ports is not supported.
•
PTP-capable ports do not identify PTP packets and do not time-stamp or redirect those packets unless
•
you enable PTP on those ports.
PTP is only supported on physical Ethernet-based ports.
•
In VPC environments, PTP must be individually configured on each member port.
•
PTP over FabricPath is not supported.
•
In case of a nondisruptive ISSU from a release earlier than Cisco NX-OS release 7.1(1)N1(1) to the
•
latest release, perform reload before enabling the PTP feature.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
62 OL-31641-01
Page 85

Configuring PTP
Default Settings for PTP
The following table lists the default settings for PTP parameters.
Table 2: Default PTP Parameters
Default Settings for PTP
DefaultParameters
DisabledPTP
2PTP version
0. PTP multi domain is disabled by default.PTP domain
255PTP priority 1 value when advertising the clock
255PTP priority 2 value when advertising the clock
Configuring PTP
Configuring PTP Globally
You can enable or disable PTP globally on a device. You can also configure various PTP clock parameters
to help determine which clock in the network has the highest priority to be selected as the grandmaster.
Procedure
Step 1
1 log secondPTP announce interval
3 announce intervalsPTP announce timeout
0 log secondsPTP minimum delay request interval
1PTP VLAN
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Step 2
ptp
Step 3
ip-address [vrf vrf]
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 63
Enables or disables PTP on the device.switch(config) # [no] feature
Note
Configures the source IP address for all PTP packets.switch(config) # [no] ptp source
The ip-address can be in IPv4 or IPv6 format.
Enabling PTP on the switch does not enable PTP on
each interface.
Page 86

Configuring PTP Globally
Configuring PTP
PurposeCommand or Action
Step 4
Step 5
Step 6
Step 7
Step 8
switch(config) # [no] ptp
domain number
switch(config) # [no] ptp
priority1 value
switch(config) # [no] ptp
priority2 value
switch(config) # show ptp brief
switch(config) # show ptp clock
(Optional)
Configures the domain number to use for this clock. PTP
domains allow you to use multiple independent PTP clocking
subdomains on a single network.
The range for the number is from 0 to 128.
(Optional)
Configures the priority1 value to use when advertising this
clock. This value overrides the default criteria (clock quality,
clock class, and so on) for the best master clock selection.
Lower values take precedence.
The range for the value is from 0 to 255.
(Optional)
Configures the priority2 value to use when advertising this
clock. This value is used to decide between two devices that
are otherwise equally matched in the default criteria. For
example, you can use the priority2 value to give a specific
switch priority over other identical switches.
The range for the value is from 0 to 255.
(Optional)
Displays the PTP status.
(Optional)
Displays the properties of the local clock.
Step 9
switch(config)# copy
running-config startup-config
(Optional)
Saves the change persistently through reboots and restarts by
copying the running configuration to the startup configuration.
The following example shows how to configure PTP globally on the device, specify the source IP address for
PTP communications, and configure a preference level for the clock:
switch# configure terminal
switch(config)# feature ptp
switch(config)# ptp source 10.10.10.1
switch(config)# ptp priority1 1
switch(config)# ptp priority2 1
switch(config)# show ptp brief
PTP port status
-----------------------
Port State
------- --------------
switch(config)# show ptp clock
PTP Device Type: Boundary clock
Clock Identity : 0:22:55:ff:ff:79:a4:c1
Clock Domain: 0
Number of PTP ports: 0
Priority1 : 1
Priority2 : 1
Clock Quality:
Class : 248
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
64 OL-31641-01
Page 87

Configuring PTP
Accuracy : 254
Offset (log variance) : 65535
Offset From Master : 0
Mean Path Delay : 0
Steps removed : 0
Local clock time:Sun Jul 3 14:13:24 2011
switch(config)#
Configuring PTP on an Interface
After you globally enable PTP, it is not enabled on all supported interfaces by default. You must enable PTP
interfaces individually.
Before You Begin
Make sure that you have globally enabled PTP on the switch and configured the source IP address for PTP
communication.
Procedure
Configuring PTP on an Interface
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
switch(config) # interface ethernet
slot/port
switch(config-if) # [no] ptp
announce {interval log seconds |
timeout count}
switch(config-if) # [no] ptp delay
request minimum interval log
seconds
switch(config-if) # [no] ptp sync
interval log seconds
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Specifies the interface on which you are enabling PTP
and enters interface configuration mode.
Enables or disables PTP on an interface.switch(config-if) # [no] feature ptp
(Optional)
Configures the interval between PTP announce messages
on an interface or the number of PTP intervals before a
timeout occurs on an interface.
The range for the PTP announcement interval is from 0
to 4 seconds, and the range for the interval timeout is
from 2 to 10.
(Optional)
Configures the minimum interval allowed between PTP
delay-request messages when the port is in the master
state.
The range is from log(-6) to log(1) seconds. Where,
log(-2) = 2 frames per second.
(Optional)
Configures the interval between PTP synchronization
messages on an interface.
Step 7
switch(config-if) # [no] ptp vlan
vlan-id
(Optional)
Specifies the VLAN for the interface where PTP is being
enabled. You can only enable PTP on one VLAN on an
interface.
The range is from 1 to 4094.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 65
Page 88

Verifying the PTP Configuration
Configuring PTP
PurposeCommand or Action
Step 8
switch(config-if) # show ptp brief
(Optional)
Displays the PTP status.
Step 9
Step 10
switch(config-if) # show ptp port
interface interface slot/port
switch(config-if)# copy
running-config startup-config
(Optional)
Displays the status of the PTP port.
(Optional)
Saves the change persistently through reboots and restarts
by copying the running configuration to the startup
configuration.
This example shows how to configure PTP on an interface and configure the intervals for the announce,
delay-request, and synchronization messages:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# ptp
switch(config-if)# ptp announce interval 3
switch(config-if)# ptp announce timeout 2
switch(config-if)# ptp delay-request minimum interval 4
switch(config-if)# ptp sync interval -1
switch(config-if)# show ptp brief
PTP port status
-----------------------
Port State
------- --------------
Eth2/1 Master
switch(config-if)# show ptp port interface ethernet 1/1
PTP Port Dataset: Eth1/1
Port identity: clock identity: f4:4e:05:ff:fe:84:7e:7c
Port identity: port number: 0
PTP version: 2
Port state: Slave
VLAN info: 1
Delay request interval(log mean): 0
Announce receipt time out: 3
Peer mean path delay: 0
Announce interval(log mean): 1
Sync interval(log mean): 1
Delay Mechanism: End to End
Cost: 255
Domain: 5
switch(config-if)#
Verifying the PTP Configuration
Use one of the following commands to verify the configuration:
Table 3: PTP Show Commands
PurposeCommand
Displays the PTP status.show ptp brief
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
66 OL-31641-01
Page 89

Configuring PTP
Feature History for PTP
PurposeCommand
show ptp clock
show ptp clock foreign-masters-record
show ptp port interface ethernet slot/port
show ptp domain data
show ptp interface domain
Displays the properties of the local clock, including
the clock identity.
Displays the state of foreign masters known to the
PTP process. For each foreign master, the output
displays the clock identity, basic clock properties,
and whether the clock is being used as a grandmaster.
Displays the last few PTP corrections.show ptp corrections
Displays the properties of the PTP parent.show ptp parent
Displays the status of the PTP port on the switch.
Displays multiple domain data, domain priority, clock
threshold and information about grandmaster
capabilities.
Displays information about the interface to domain
association.
Displays PTP port to cost association.show ptp cost
Feature History for PTP
This table lists the release history for this feature.
InformationReleaseFeature Name
7.1(1)N1(1)PTP
PTP is a time synchronization
protocol for nodes distributed
across a network. Its hardware
timestamp feature provides greater
accuracy than other time
synchronization protocols such as
the Network Time Protocol (NTP).
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 67
Page 90

Feature History for PTP
Configuring PTP
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
68 OL-31641-01
Page 91

CHAPTER 7
Configuring User Accounts and RBAC
This chapter contains the following sections:
Information About User Accounts and RBAC, page 69
•
Guidelines and Limitations for User Accounts, page 75
•
Configuring User Accounts, page 76
•
Configuring RBAC, page 78
•
Verifying the User Accounts and RBAC Configuration, page 82
•
Configuring User Accounts Default Settings for the User Accounts and RBAC, page 82
•
Information About User Accounts and RBAC
Cisco Nexus Series switches use role-based access control (RBAC) to define the amount of access that each
user has when the user logs into the switch.
With RBAC, you define one or more user roles and then specify which management operations each user role
is allowed to perform. When you create a user account for the switch, you associate that account with a user
role, which then determines what the individual user is allowed to do on the switch.
User Roles
User roles contain rules that define the operations allowed for the user who is assigned the role. Each user
role can contain multiple rules and each user can have multiple roles. For example, if role1 allows access only
to configuration operations, and role2 allows access only to debug operations, users who belong to both role1
and role2 can access configuration and debug operations. You can also limit access to specific VSANs,
VLANs, and interfaces.
The switch provides the following default user roles:
network-admin (superuser)
Complete read and write access to the entire switch.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 69
Page 92

User Roles
Configuring User Accounts and RBAC
network-operator
Complete read access to the switch.
Note
If you belong to multiple roles, you can execute a combination of all the commands permitted by these
roles. Access to a command takes priority over being denied access to a command. For example, suppose
a user has RoleA, which denied access to the configuration commands. However, the user also has RoleB,
which has access to the configuration commands. In this case, the user has access to the configuration
commands.
Note
Only network-admin user can perform a Checkpoint or Rollback in the RBAC roles. Though other users
have these commands as a permit rule in their role, the user access is denied when you try to execute these
commands.
Predefined SAN Admin User Role
The SAN admin user role is a noneditable, predefined user role that is designed to provide separation between
LAN and SAN administrative tasks. Users that have been assigned the SAN admin user role have read-only
access to all Ethernet configuration tasks. Write access for Ethernet features is not granted to SAN admin
users unless it is assigned to them through another user role.
The following capabilities are permitted to SAN admin users:
Interface configuration
•
Attribute configuration for Fibre Channel Unified Ports, except creation and deletion
•
VSAN configuration, including database and membership
•
Mapping of preconfigured VLANs for FCoE to VSANs
•
Zoning configuration
•
Configuration of SNMP-related parameters, except SNMP community and SNMP users
•
Read-only access to all other configurations
•
Configuration and management of SAN features such as the following:
•
FC-SP
◦
FC-PORT-SECURITY
◦
FCoE
◦
FCoE-NPV
◦
FPORT-CHANNEL-TRUNK
◦
PORT-TRACK
◦
FABRIC-BINDING
◦
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
70 OL-31641-01
Page 93

Configuring User Accounts and RBAC
Configuration and management for the following of EXEC mode commands:
•
DEBUG
◦
FCDOMAIN
◦
FCPING
◦
SAN-PORT-CHANNEL
◦
SHOW
◦
ZONE
◦
ZONESET
◦
Rules
Rules
Note
The SAN Admin role permits configuration on all interface types, not just Fibre Channel interfaces. The
predefined SAN Admin user role was designed to allow access to all interfaces—including Ethernet
interfaces—so it would not interfere with SNMP operations.
The rule is the basic element of a role. A rule defines what operations the role allows the user to perform. You
can apply rules for the following parameters:
Command
A command or group of commands defined in a regular expression.
Feature
Commands that apply to a function provided by the Cisco Nexus device. Enter the show role feature
command to display the feature names available for this parameter.
Feature group
Default or user-defined group of features. Enter the show role feature-group command to display the
default feature groups available for this parameter.
These parameters create a hierarchical relationship. The most basic control parameter is the command. The
next control parameter is the feature, which represents all commands associated with the feature. The last
control parameter is the feature group. The feature group combines related features and allows you to easily
manage the rules.
You can configure up to 256 rules for each role. The user-specified rule number determines the order in which
the rules are applied. Rules are applied in descending order. For example, if a role has three rules, rule 3 is
applied before rule 2, which is applied before rule 1.
SAN Admin Role-Feature Rule Mapping
The SAN admin role is not editable. The following role-features are part of preconfigured role. The
preconfigured role comes complete read access and the following rules:
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 71
Page 94

Rules
Configuring User Accounts and RBAC
Table 4: Role-Feature Rules for SAN Admin User Role
PermissionsFeature
copy
fabric-binding
fcdomain
fcfe
fcmgmt
fcns
fcoe
fcsp
Read and write permissions for copy-related
commands
Read and write permissions for fabric binding-related
commands
Read and write permissions for Fibre Channel
domain-related commands
Read and write permissions for Fibre Channel
FE-related commands
Read and write permissions for Fibre Channel
management-related commands
Read and write permissions for Fibre Channel-related
service FCNS commands
Read and write permissions for Fibre Channel over
Ethernet-related commands
Read and write permissions for Fibre Channel
Security Protocol (FCSP)-related commands
fdmi
fspf
interface
port-track
port-security
rdl
rmon
Read and write permissions for Fabric Device
Management Interface (FDMI)-related commands
Read and write permissions for Fabric Shortest Path
First (FSPF)-related commands
Read and write permissions for interface-related
commands, which includes all interfaces, not just
Fibre Channel interfaces.
Read and write permissions for port track-related
commands
Read and write permissions for port security-related
commands
Read and write permissions for Remote Domain
Loopback (RDL)-related commands
Read and write permissions for RMON-related
commands
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
72 OL-31641-01
Page 95

Configuring User Accounts and RBAC
User Role Policies
PermissionsFeature
rscn
snmp
snmpTargetAddrEntry
snmpTargetParamsEntry
span
trapRegEntry
trunk
vsan
Read and write permissions for Registered State
Change Notification (RSCN)-related commands
Read and write permissions for SNMP-related
commands
Read and write permissions for SNMP trap
target-related commands
Read and write permissions for SNMP trap target
parameter-related commands
Read and write permissions for SPAN-related
commands
Read and write permissions for SNMP trap
registry-related commands
Read and write permissions for Fibre Channel port
channel trunk-related commands
Read and write permissions for VSAN-related
commands
vsanIfvsan
wwnm
User Role Policies
You can define user role policies to limit the switch resources that the user can access, or to limit access to
interfaces, VLANs, and VSANs.
User role policies are constrained by the rules defined for the role. For example, if you define an interface
policy to permit access to specific interfaces, the user does not have access to the interfaces unless you configure
a command rule for the role to permit the interface command.
If a command rule permits access to specific resources (interfaces, VLANs, or VSANs), the user is permitted
to access these resources, even if the user is not listed in the user role policies associated with that user.
Read and write permissions for FCoE VLAN-VSAN
mapping command-related commands
Read and write permissions for World Wide Name
(WWN)-related commands
Read and write permissions for zoning commandszone
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 73
Page 96

User Account Configuration Restrictions
User Account Configuration Restrictions
The following words are reserved and cannot be used to configure users:
adm
•
bin
•
daemon
•
ftp
•
ftpuser
•
games
•
gdm
•
gopher
•
halt
•
Configuring User Accounts and RBAC
Caution
lp
•
mail
•
mailnull
•
man
•
mtsuser
•
news
•
nobody
•
san-admin
•
shutdown
•
sync
•
sys
•
uucp
•
xfs
•
The Cisco Nexus 5000 and 6000 Series switch does not support all numeric usernames, even if those
usernames were created in TACACS+ or RADIUS. If an all numeric username exists on an AAA server
and is entered during login, the switch rejects the login request.
Usernames must begin with an alphanumeric character and can contain only these special characters: ( +
= . _ \ -). The # and ! symbols are not supported. If the username contains characters that are not allowed,
the specified user is unable to log in. Effective from Cisco NX-OS release 7.3(0)N1(1), usernames starting
with _(underscore) are supported.
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
74 OL-31641-01
Page 97

Configuring User Accounts and RBAC
User Password Requirements
Cisco Nexus device passwords are case sensitive and can contain alphanumeric characters only. Special
characters, such as the dollar sign ($) or the percent sign (%), are not allowed.
User Password Requirements
Note
Starting from Cisco NX-OS Release 7.2(0)N1(1), special characters, such as the dollar sign ($) or the
percent sign (%), can be used in Cisco Nexus device passwords.
If a password is trivial (such as a short, easy-to-decipher password), the Cisco Nexus device rejects the
password. Be sure to configure a strong password for each user account. A strong password has the following
characteristics:
At least eight characters long
•
Does not contain many consecutive characters (such as "abcd")
•
Does not contain many repeating characters (such as "aaabbb")
•
Does not contain dictionary words
•
Does not contain proper names
•
Contains both uppercase and lowercase characters
•
Contains numbers
•
The following are examples of strong passwords:
If2CoM18
•
2009AsdfLkj30
•
Cb1955S21
•
For security reasons, user passwords do not display in the configuration files.Note
Guidelines and Limitations for User Accounts
User accounts have the following guidelines and limitations when configuring user accounts and RBAC:
Up to 256 rules can be added to a user role.
•
A maximum of 64 user roles can be assigned to a user account.
•
You can assign a user role to more that one user account.
•
Predefined roles such as network-admin, network-operator, and san-admin are not editable.
•
Add, delete, and editing of rules is not supported for the SAN admin user role.
•
The interface, VLAN, and/or VSAN scope cannot be changed for the SAN admin user role.
•
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 75
Page 98

Configuring User Accounts
A user account must have at least one user role.Note
Configuring User Accounts
Changes to user account attributes do not take effect until the user logs in and creates a new session.Note
Procedure
Configuring User Accounts and RBAC
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
switch(config)# show role
switch(config) # username user-id
[password password] [expire date]
[role role-name]
switch# show user-account
switch# copy running-config
startup-config
Enters global configuration mode.switch# configure terminal
(Optional)
Displays the user roles available. You can configure other
user roles, if necessary.
Configures a user account.
The user-id is a case-sensitive, alphanumeric character
string with a maximum of 28 characters.
The default password is undefined.
Note
If you do not specify a password, the user might
not be able to log into the switch.
The expire date option format is YYYY-MM-DD. The
default is no expiry date.
Exists global configuration mode.switch(config) # exit
(Optional)
Displays the role configuration.
(Optional)
Copies the running configuration to the startup
configuration.
The following example shows how to configure a user account:
switch# configure terminal
switch(config)# username NewUser password 4Ty18Rnt
switch(config)# exit
switch# show user-account
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
76 OL-31641-01
Page 99

Configuring User Accounts and RBAC
Configuring SAN Admin Users
Procedure
Configuring SAN Admin Users
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config) # username user-id role
san-admin password password
switch(config) # show user-account
Enters global configuration mode.switch# configure terminal
Configures SAN admin user role access for the
specified user.
(Optional)
Displays the role configuration.
Step 4
switch(config) # show snmp-user
(Optional)
Displays the SNMP user configuration.
Step 5
switch(config)# copy running-config
startup-config
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to
the startup configuration.
The following example shows how to configure a SAN admin user and display the user account and SNMP
user configuration:
switch# configure terminal
switch(config)# username user1 role san-admin password xyz123
switch(config)# show user-account
user:admin
this user account has no expiry date
roles:network-admin
user:user1
this user account has no expiry date
roles:san-admin
switch(config) # show snmp user
________________________________________________________________________
SNMP USERS
________________________________________________________________________
User Auth Priv(enforce) Groups
____ ____ _____________ ______
admin md5 des(no) network-admin
user1 md5 des(no) san-admin
________________________________________________________________________
NOTIFICATION TARGET USES (configured for sending V3 Inform)
________________________________________________________________________
User Auth Priv
____ ____ ____
switch(config) #
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
OL-31641-01 77
Page 100

Configuring RBAC
Configuring RBAC
Creating User Roles and Rules
The rule number that you specify determines the order in which the rules are applied. Rules are applied in
descending order. For example, if a role has three rules, rule 3 is applied before rule 2, which is applied before
rule 1.
Procedure
Configuring User Accounts and RBAC
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
switch(config) # role name role-name
switch(config-role) # rule number
{deny | permit} command
command-string
switch(config-role)# rule number
{deny | permit} {read | read-write}
switch(config-role)# rule number
{deny | permit} {read | read-write}
feature feature-name
switch(config-role)# rule number
{deny | permit} {read | read-write}
feature-group group-name
Enters global configuration mode.switch# configure terminal
Specifies a user role and enters role configuration mode.
The role-name argument is a case-sensitive,
alphanumeric character string with a maximum of 16
characters.
Configures a command rule.
The command-string can contain spaces and regular
expressions. For example, interface ethernet * includes
all Ethernet interfaces.
Repeat this command for as many rules as needed.
Configures a read-only or read-and-write rule for all
operations.
Configures a read-only or read-and-write rule for a
feature.
Use the show role feature command to display a list of
features.
Repeat this command for as many rules as needed.
Configures a read-only or read-and-write rule for a
feature group.
Use the show role feature-group command to display
a list of feature groups.
Repeat this command for as many rules as needed.
Step 7
Step 8
Cisco Nexus 5600 Series NX-OS System Management Configuration Guide, Release 7.x
78 OL-31641-01
switch(config-role)# description text
(Optional)
Configures the role description. You can include spaces
in the description.
Exits role configuration mode.switch(config-role)# end
 Loading...
Loading...