Page 1

Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
First Published: January 29, 2014
Last Modified: May 22, 2014
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Text Part Number: OL-30895-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH
THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY,
CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version
of the UNIX operating system. All rights reserved. Copyright©1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWAREOF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS.
CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT
LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS
HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network
topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional
and coincidental.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: http://
www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership
relationship between Cisco and any other company. (1110R)
©
2014 Cisco Systems, Inc. All rights reserved.
Page 3

CONTENTS
Preface
CHAPTER 1
CHAPTER 2
Preface xix
Audience xix
Document Conventions xix
Related Documentation for Cisco Nexus 5500 Series NX-OS Software xxi
Documentation Feedback xxii
Obtaining Documentation and Submitting a Service Request xxiii
Overview 1
SAN Switching Overview 1
Configuring Fibre Channel Interfaces 5
Configuring Fibre Channel Interfaces 5
Information About Fibre Channel Interfaces 5
Licensing Requirements for Fibre Channel 5
QOS Requirements for Fibre Channel 5
Physical Fibre Channel Interfaces 6
Virtual Fibre Channel Interfaces 6
VF Port 6
VE Ports 7
VNP Ports 8
Interface Modes 8
E Port 9
F Port 9
NP Port 9
TE Port 9
TF Port 10
TNP Port 10
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 iii
Page 4

Contents
SD Port 10
Auto Mode 10
Interface States 10
Administrative States 10
Operational States 11
Reason Codes 11
Buffer-to-Buffer Credits 14
Configuring Fibre Channel Interfaces 15
Configuring a Fibre Channel Interface 15
Configuring a Range of Fibre Channel Interfaces 15
Setting the Interface Administrative State 15
Configuring Interface Modes 16
Configuring Fibre Channel Interfaces 17
Configuring Unified Ports 17
Configuring the Interface Description 18
Configuring Port Speeds 19
Autosensing 19
Configuring SD Port Frame Encapsulation 19
Configuring Receive Data Field Size 20
Understanding Bit Error Thresholds 20
Configuring Buffer-to-Buffer Credits 21
Configuring Global Attributes for Fibre Channel Interfaces 22
Configuring Switch Port Attribute Default Values 22
Information About N Port Identifier Virtualization 23
Enabling N Port Identifier Virtualization 23
Example Port Channel Configurations 24
Verifying Fibre Channel Interfaces 25
Verifying SFP Transmitter Types 25
Verifying Interface Information 25
Verifying BB_Credit Information 26
Default Fibre Channel Interface Settings 27
CHAPTER 3
Configuring Fibre Channel Domain Parameters 29
Information About Domain Parameters 29
Fibre Channel Domains 29
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
iv OL-30895-01
Page 5

Contents
Domain Restarts 30
Restarting a Domain 31
Domain Manager Fast Restart 31
Enabling Domain Manager Fast Restart 31
Switch Priority 32
Configuring Switch Priority 32
About fcdomain Initiation 33
Disabling or Reenabling fcdomains 33
Configuring Fabric Names 33
Incoming RCFs 34
Rejecting Incoming RCFs 34
Autoreconfiguring Merged Fabrics 35
Enabling Autoreconfiguration 35
Domain IDs 36
Domain IDs - Guidelines 36
Configuring Static or Preferred Domain IDs 38
Allowed Domain ID Lists 39
Configuring Allowed Domain ID Lists 39
CFS Distribution of Allowed Domain ID Lists 40
Enabling Distribution 40
Locking the Fabric 40
Committing Changes 41
Discarding Changes 41
Clearing a Fabric Lock 42
Displaying CFS Distribution Status 42
Displaying Pending Changes 42
Displaying Session Status 42
Contiguous Domain ID Assignments 43
Enabling Contiguous Domain ID Assignments 43
FC IDs 43
Persistent FC IDs 44
Enabling the Persistent FC ID Feature 44
Persistent FC ID Configuration Guidelines 45
Configuring Persistent FC IDs 45
Unique Area FC IDs for HBAs 46
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 v
Page 6

Contents
Configuring Unique Area FC IDs for an HBA 46
Persistent FC ID Selective Purging 48
Purging Persistent FC IDs 48
Verifying the fcdomain Configuration 48
Default Settings for Fibre Channel Domains 49
CHAPTER 4
Configuring N Port Virtualization 51
Configuring N Port Virtualization 51
Information About NPV 51
NPV Overview 51
NPV Mode 52
Server Interfaces 52
NP Uplinks 53
FLOGI Operation 53
NPV Traffic Management 54
Automatic Uplink Selection 54
Traffic Maps 54
Disruptive Load Balancing 55
NPV Traffic Management Guidelines 55
NPV Guidelines and Limitations 55
Configuring NPV 56
Enabling NPV 56
Configuring NPV Interfaces 57
Configuring an NP Interface 57
Configuring a Server Interface 58
Configuring NPV Traffic Management 58
Configuring NPV Traffic Maps 58
Enabling Disruptive Load Balancing 59
Verifying NPV 59
Verifying NPV Examples 60
Verifying NPV Traffic Management 61
CHAPTER 5
Configuring FCoE NPV 63
Information About FCoE NPV 63
FCoE NPV Model 65
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
vi OL-30895-01
Page 7

Contents
Mapping Requirements 66
Port Requirements 67
NPV Features 67
vPC Topologies 68
Supported and Unsupported Topologies 69
Guidelines and Limitations 73
FCoE NPV Configuration Limits 73
Default Settings 74
Enabling FCoE and Enabling NPV 75
Enabling FCoE NPV 75
Configuring NPV Ports for FCoE NPV 76
Verifying FCoE NPV Configuration 76
CHAPTER 6
Configuration Examples for FCoE NPV 77
Configuring VSAN Trunking 83
Configuring VSAN Trunking 83
Information About VSAN Trunking 83
VSAN Trunking Mismatches 84
VSAN Trunking Protocol 84
Configuring VSAN Trunking 85
Guidelines and Limitations 85
Enabling or Disabling the VSAN Trunking Protocol 85
Trunk Mode 85
Configuring Trunk Mode 86
Trunk-Allowed VSAN Lists 87
Configuring an Allowed-Active List of VSANs 89
Displaying VSAN Trunking Information 90
Default Settings for VSAN Trunks 90
CHAPTER 7
Configuring SAN Port Channels 93
Configuring SAN Port Channels 93
Information About SAN Port Channels 93
Understanding Port Channels and VSAN Trunking 94
Understanding Load Balancing 95
Configuring SAN Port Channels 97
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 vii
Page 8

Contents
SAN Port Channel Configuration Guidelines 99
F and TF Port Channel Guidelines 99
Creating a SAN Port Channel 100
About Port Channel Modes 100
Configuring Active Mode SAN Port Channel 101
About SAN Port Channel Deletion 102
Deleting SAN Port Channels 102
Interfaces in a SAN Port Channel 102
About Interface Addition to a SAN Port Channel 103
Compatibility Check 103
Suspended and Isolated States 104
Adding an Interface to a SAN Port Channel 104
Forcing an Interface Addition 104
CHAPTER 8
About Interface Deletion from a SAN Port Channel 105
Deleting an Interface from a SAN Port Channel 105
SAN Port Channel Protocol 106
About Channel Group Creation 106
Autocreation Guidelines 108
Enabling and Configuring Autocreation 109
About Manually Configured Channel Groups 109
Converting to Manually Configured Channel Groups 109
Example Port Channel Configurations 109
Verifying SAN Port Channel Configuration 110
Default Settings for SAN Port Channels 111
Configuring and Managing VSANs 113
Configuring and Managing VSANs 113
Information About VSANs 113
VSAN Topologies 113
VSAN Advantages 116
VSANs Versus Zones 116
Guidelines and Limitations for VSANs 117
About VSAN Creation 118
Creating VSANs Statically 118
Port VSAN Membership 119
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
viii OL-30895-01
Page 9

Contents
Assigning Static Port VSAN Membership 120
Displaying VSAN Static Membership 120
Default VSANs 121
Isolated VSANs 121
Displaying Isolated VSAN Membership 122
Operational State of a VSAN 122
Static VSAN Deletion 122
Deleting Static VSANs 123
About Load Balancing 123
Configuring Load Balancing 123
Interop Mode 125
Displaying the Static VSAN Configuration 125
CHAPTER 9
Default Settings for VSANs 125
Configuring and Managing Zones 127
Information About Zones 127
Information About Zoning 127
Zoning Features 127
Zoning Example 129
Zone Implementation 130
Active and Full Zone Sets 130
Configuring a Zone 133
Configuration Examples 133
Zone Sets 134
Activating a Zone Set 135
Default Zone 135
Configuring the Default Zone Access Permission 136
FC Alias Creation 136
Creating FC Aliases 137
Creating FC Aliases Example 137
Creating Zone Sets and Adding Member Zones 138
Zone Enforcement 139
Zone Set Distribution 140
Enabling Full Zone Set Distribution 140
Enabling a One-Time Distribution 140
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 ix
Page 10

Contents
Recovering from Link Isolation 141
Importing and Exporting Zone Sets 142
Zone Set Duplication 142
Copying Zone Sets 143
Renaming Zones, Zone Sets, and Aliases 143
Cloning Zones, Zone Sets, FC Aliases, and Zone Attribute Groups 144
Clearing the Zone Server Database 145
Verifying the Zone Configuration 145
Enhanced Zoning 146
Enhanced Zoning 146
Changing from Basic Zoning to Enhanced Zoning 147
Changing from Enhanced Zoning to Basic Zoning 148
Enabling Enhanced Zoning 148
CHAPTER 10
Modifying the Zone Database 149
Releasing Zone Database Locks 150
Merging the Database 150
Configuring Zone Merge Control Policies 151
Default Zone Policies 152
Configuring System Default Zoning Settings 152
Verifying Enhanced Zone Information 153
Compacting the Zone Database 153
Analyzing the Zone and Zone Set 154
Default Settings for Zones 154
Distributing Device Alias Services 155
Distributing Device Alias Services 155
Information About Device Aliases 155
Device Alias Features 155
Device Alias Requirements 156
Zone Aliases Versus Device Aliases 156
Device Alias Databases 157
Creating Device Aliases 157
Device Alias Modes 158
Device Alias Mode Guidelines and Limitations for Device Alias Services 158
Configuring Device Alias Modes 159
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
x OL-30895-01
Page 11

Contents
Device Alias Distribution 160
Locking the Fabric 160
Committing Changes 160
Discarding Changes 161
Overriding the Fabric Lock 162
Disabling and Enabling Device Alias Distribution 162
Legacy Zone Alias Configuration 163
Importing a Zone Alias 163
Device Alias Database Merge Guidelines 164
Verifying the Device Alias Configuration 164
Default Settings for Device Alias Services 165
CHAPTER 11
Configuring Fibre Channel Routing Services and Protocols 167
Information About Fibre Channel Routing Services and Protocols 167
Information About FSPF 168
FSPF Examples 168
Fault Tolerant Fabric Example 168
Redundant Link Example 169
FSPF Global Configuration 169
SPF Computational Hold Times 170
Link State Records 170
Configuring FSPF on a VSAN 170
Resetting FSPF to the Default Configuration 171
Enabling or Disabling FSPF 171
Clearing FSPF Counters for the VSAN 172
FSPF Interface Configuration 172
FSPF Link Cost 172
Configuring FSPF Link Cost 173
Hello Time Intervals 173
Configuring Hello Time Intervals 173
Dead Time Intervals 174
Configuring Dead Time Intervals 174
Retransmitting Intervals 175
Configuring Retransmitting Intervals 175
About Disabling FSPF for Specific Interfaces 176
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 xi
Page 12

Contents
Disabling FSPF for Specific Interfaces 176
Clearing FSPF Counters for an Interface 176
FSPF Routes 177
Fibre Channel Routes 177
Configuring Fibre Channel Routes 177
In-Order Delivery 178
Reordering Network Frames 179
Reordering SAN Port Channel Frames 180
About Enabling In-Order Delivery 180
Enabling In-Order Delivery 180
Enabling In-Order Delivery for a VSAN 181
Displaying the In-Order Delivery Status 182
Configuring the Drop Latency Time 182
CHAPTER 12
Displaying Latency Information 183
Flow Statistics Configuration 183
Flow Statistics 183
Counting Aggregated Flow Statistics 183
Counting Individual Flow Statistics 184
Clearing FIB Statistics 184
Displaying Flow Statistics 184
Default Settings for FSFP 185
Managing FLOGI, Name Server, FDMI, and RSCN Databases 187
Managing FLOGI, Name Server, FDMI, and RSCN Databases 187
Fabric Login 187
Name Server Proxy 188
About Registering Name Server Proxies 188
Registering Name Server Proxies 188
Rejecting Duplicate pWWNs 188
Rejecting Duplicate pWWNs 189
Name Server Database Entries 189
Displaying Name Server Database Entries 190
FDMI 190
Displaying FDMI 191
RSCN 191
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
xii OL-30895-01
Page 13

Contents
About RSCN Information 191
Displaying RSCN Information 191
Multi-pid Option 192
Configuring the multi-pid Option 192
Suppressing Domain Format SW-RSCNs 192
Clearing RSCN Statistics 193
Configuring the RSCN Timer 193
Verifying the RSCN Timer Configuration 194
RSCN Timer Configuration Distribution 194
Enabling RSCN Timer Configuration Distribution 195
Locking the Fabric 195
Committing RSCN Timer Configuration Changes 196
CHAPTER 13
CHAPTER 14
Discarding the RSCN Timer Configuration Changes 196
Clearing a Locked Session 197
Displaying RSCN Configuration Distribution Information 197
Default Settings for RSCN 197
Discovering SCSI Targets 199
Discovering SCSI Targets 199
Information About SCSI LUN Discovery 199
About Starting SCSI LUN Discovery 199
Starting SCSI LUN Discovery 200
About Initiating Customized Discovery 200
Initiating Customized Discovery 200
Displaying SCSI LUN Information 201
Configuring iSCSI TLV 203
Information about iSCSI TLV 203
iSCSI TLV Configuration 203
Identifying iSCSI Traffic 203
Configuring Type QoS Policies 204
Configuring No-Drop Policy Maps 205
Applying System Service Policies 206
iSCSI TLV and FCoE Configuration 207
Identifying iSCSI and FCoE Traffic 207
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 xiii
Page 14

Contents
Configuring Type QoS Policies 208
Configuring No-Drop Policy Maps 209
Applying System Service Policies 212
CHAPTER 15
Advanced Fibre Channel Features 213
Advanced Fibre Channel Features and Concepts 213
Fibre Channel Timeout Values 213
Timer Configuration Across All VSANs 213
Timer Configuration Per-VSAN 214
fctimer Distribution 215
Enabling or Disabling fctimer Distribution 215
Committing fctimer Changes 216
Discarding fctimer Changes 216
Overriding the Fabric Lock 216
Fabric Database Merge Guidelines 217
Verifying Configured fctimer Values 217
World Wide Names 218
Verifying the WWN Configuration 218
Link Initialization WWN Usage 218
Configuring a Secondary MAC Address 219
CHAPTER 16
FC ID Allocation for HBAs 219
Default Company ID List 220
Verifying the Company ID Configuration 220
Switch Interoperability 221
About Interop Mode 221
Configuring Interop Mode 1 224
Verifying Interoperating Status 225
Default Settings for Advanced Fibre Channel Features 229
Configuring FC-SP and DHCHAP 231
Information About FC-SP and DHCHAP 231
Fabric Authentication 231
Configuring DHCHAP Authentication 232
DHCHAP Compatibility with Fibre Channel Features 233
About Enabling DHCHAP 233
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
xiv OL-30895-01
Page 15

Contents
Enabling DHCHAP 233
DHCHAP Authentication Modes 234
Configuring the DHCHAP Mode 235
DHCHAP Hash Algorithm 236
Configuring the DHCHAP Hash Algorithm 236
DHCHAP Group Settings 237
Configuring the DHCHAP Group Settings 237
DHCHAP Password 237
Configuring DHCHAP Passwords for the Local Switch 238
Password Configuration for Remote Devices 238
Configuring DHCHAP Passwords for Remote Devices 239
DHCHAP Timeout Value 239
CHAPTER 17
Configuring the DHCHAP Timeout Value 239
Configuring DHCHAP AAA Authentication 240
Displaying Protocol Security Information 240
Configuration Examples for Fabric Security 241
Default Settings for Fabric Security 242
Configuring Port Security 245
Configuring Port Security 245
Information About Port Security 245
Port Security Enforcement 246
Auto-Learning 246
Port Security Activation 246
Configuring Port Security 247
Configuring Port Security with Auto-Learning and CFS Distribution 247
Configuring Port Security with Auto-Learning without CFS 248
Configuring Port Security with Manual Database Configuration 248
Enabling Port Security 249
Port Security Activation 249
Activating Port Security 249
Database Activation Rejection 250
Forcing Port Security Activation 250
Database Reactivation 251
Auto-Learning 252
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 xv
Page 16

Contents
About Enabling Auto-Learning 252
Enabling Auto-Learning 252
Disabling Auto-Learning 253
Auto-Learning Device Authorization 253
Authorization Scenario 254
Port Security Manual Configuration 255
WWN Identification Guidelines 255
Adding Authorized Port Pairs 256
Port Security Configuration Distribution 257
Enabling Port Security Distribution 257
Locking the Fabric 258
Committing the Changes 258
Discarding the Changes 258
CHAPTER 18
Activation and Auto-Learning Configuration Distribution 259
Merging the Port Security Database 261
Database Interaction 261
Database Scenarios 263
Copying the Port Security Database 264
Deleting the Port Security Database 264
Clearing the Port Security Database 264
Displaying Port Security Configuration 265
Default Settings for Port Security 265
Configuring Fabric Binding 267
Configuring Fabric Binding 267
Information About Fabric Binding 267
Licensing Requirements for Fabric Binding 267
Port Security Versus Fabric Binding 267
Fabric Binding Enforcement 268
Configuring Fabric Binding 269
Configuring Fabric Binding 269
Enabling Fabric Binding 269
Switch WWN Lists 269
Configuring Switch WWN List 270
Fabric Binding Activation and Deactivation 270
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
xvi OL-30895-01
Page 17

Contents
Activating Fabric Binding 271
Forcing Fabric Binding Activation 271
Copying Fabric Binding Configurations 272
Clearing the Fabric Binding Statistics 272
Deleting the Fabric Binding Database 272
Verifying the Fabric Binding Configuration 273
Default Settings for Fabric Binding 273
CHAPTER 19
CHAPTER 20
Configuring Fabric Configuration Servers 275
Configuring Fabric Configuration Servers 275
Information About FCS 275
FCS Characteristics 276
FCS Name Specification 277
Displaying FCS Information 277
Default FCS Settings 277
Configuring Port Tracking 279
Configuring Port Tracking 279
Information About Port Tracking 279
Default Settings for Port Tracking 280
Configuring Port Tracking 281
Enabling Port Tracking 281
Configuring Linked Ports 282
Operationally Binding a Tracked Port 282
Tracking Multiple Ports 282
Tracking Multiple Ports 283
Monitoring Ports in a VSAN 283
Monitoring Ports in a VSAN 284
Forcefully Shutting down 284
Forcefully Shutting Down a Tracked Port 285
Displaying Port Tracking Information 285
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 xvii
Page 18

Contents
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
xviii OL-30895-01
Page 19

Preface
The preface contains the following sections:
Audience, page xix
•
Document Conventions, page xix
•
Related Documentation for Cisco Nexus 5500 Series NX-OS Software, page xxi
•
Documentation Feedback, page xxii
•
Obtaining Documentation and Submitting a Service Request, page xxiii
•
Audience
This publication is for network administrators who configure and maintain Cisco Nexus devices and Cisco
Nexus 2000 Series Fabric Extenders.
Document Conventions
Note
OL-30895-01 xix
As part of our constant endeavor to remodel our documents to meet our customers' requirements, we have
modified the manner in which we document configuration tasks. As a result of this, you may find a
deviation in the style used to describe these tasks, with the newly included sections of the document
following the new format.
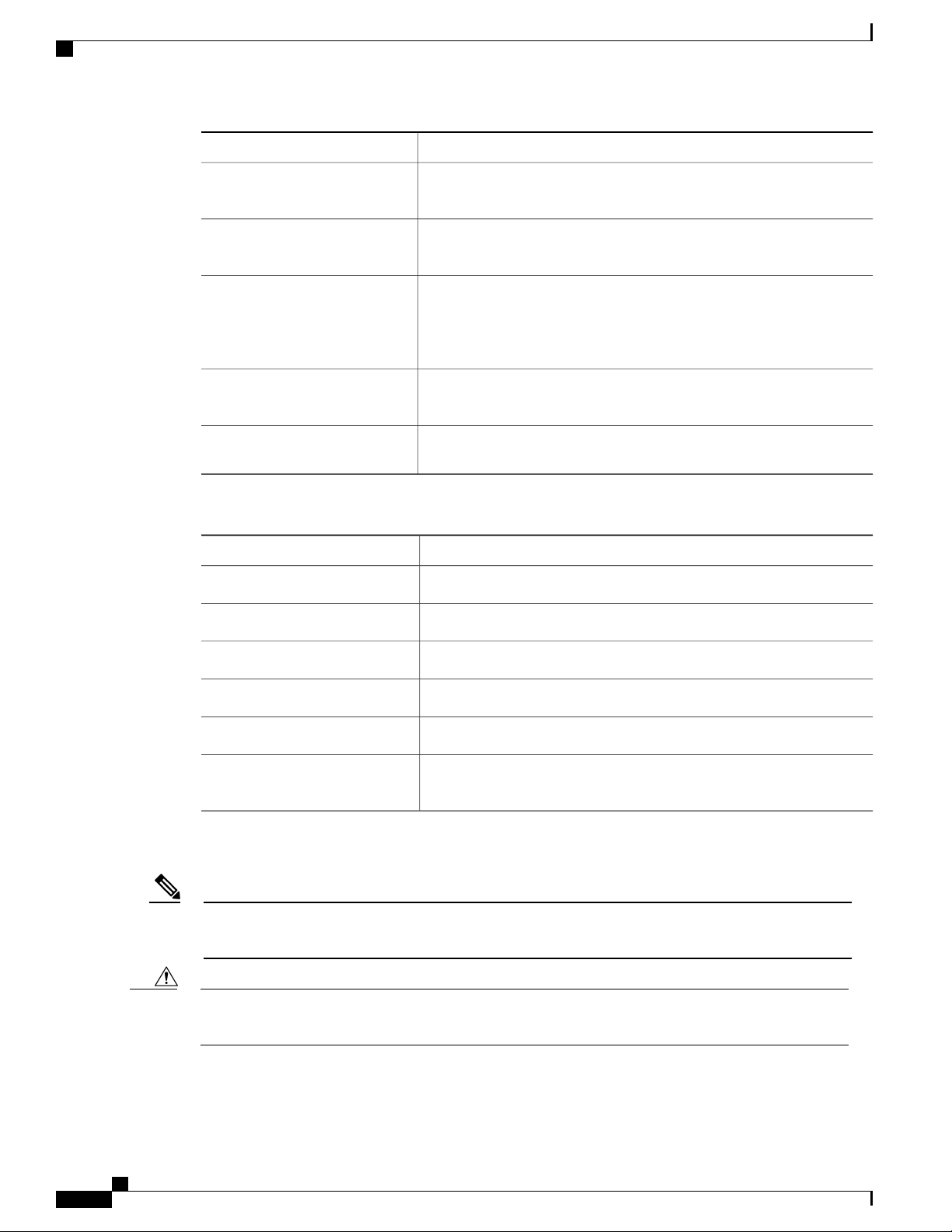
Command descriptions use the following conventions:
DescriptionConvention
bold
Italic
Bold text indicates the commands and keywords that you enter literally
as shown.
Italic text indicates arguments for which the user supplies the values.
Square brackets enclose an optional element (keyword or argument).[x]
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
Page 20
Document Conventions
Preface
DescriptionConvention
[x | y]
Square brackets enclosing keywords or arguments separated by a vertical
bar indicate an optional choice.
{x | y}
Braces enclosing keywords or arguments separated by a vertical bar
indicate a required choice.
[x {y | z}]
Nested set of square brackets or braces indicate optional or required
choices within optional or required elements. Braces and a vertical bar
within square brackets indicate a required choice within an optional
element.
variable
Indicates a variable for which you supply values, in context where italics
cannot be used.
string
A nonquoted set of characters. Do not use quotation marks around the
string or the string will include the quotation marks.
Examples use the following conventions:
DescriptionConvention
Terminal sessions and information the switch displays are in screen font.screen font
Information you must enter is in boldface screen font.boldface screen font
Note
Caution
italic screen font
Arguments for which you supply values are in italic screen font.
Nonprinting characters, such as passwords, are in angle brackets.< >
Default responses to system prompts are in square brackets.[ ]
!, #
An exclamation point (!) or a pound sign (#) at the beginning of a line
of code indicates a comment line.
This document uses the following conventions:
Means reader take note. Notes contain helpful suggestions or references to material not covered in the
manual.
Means reader be careful. In this situation, you might do something that could result in equipment damage
or loss of data.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
xx OL-30895-01
Page 21

Preface
Related Documentation for Cisco Nexus 5500 Series NX-OS Software
Related Documentation for Cisco Nexus 5500 Series NX-OS
Software
The entire Cisco NX-OS 5500 Series documentation set is available at the following URL:
http://www.cisco.com/c/en/us/support/switches/nexus-5000-series-switches/
tsd-products-support-series-home.html
Release Notes
The release notes are available at the following URL:
http://www.cisco.com/en/US/products/ps9670/prod_release_notes_list.html
Configuration Guides
These guides are available at the following URL:
http://www.cisco.com/en/US/products/ps9670/products_installation_and_configuration_guides_list.html
The documents in this category include:
Cisco Nexus 5500 Series NX-OS Adapter-FEX Configuration Guide
•
Cisco Nexus 5500 Series NX-OS FabricPath Configuration Guide
•
Cisco Nexus 5500 Series NX-OS FCoE Configuration Guide
•
Cisco Nexus 5500 Series NX-OS Fundamentals Configuration Guide
•
Cisco Nexus 5500 Series NX-OS Interfaces Configuration Guide
•
Cisco Nexus 5500 Series NX-OS Layer 2 Switching Configuration Guide
•
Cisco Nexus 5500 Series NX-OS Multicast Routing Configuration Guide
•
Cisco Nexus 5500 Series NX-OS Quality of Service Configuration Guide
•
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide
•
Cisco Nexus 5500 Series NX-OS Security Configuration Guide
•
Cisco Nexus 5500 Series NX-OS System Management Configuration Guide
•
Cisco Nexus 5500 Series NX-OS Unicast Routing Configuration Guide
•
Installation and Upgrade Guides
These guides are available at the following URL:
http://www.cisco.com/en/US/products/ps9670/prod_installation_guides_list.html
The document in this category include:
Cisco Nexus 5500 Series NX-OS Software Upgrade and Downgrade Guides
•
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 xxi
Page 22

Documentation Feedback
Licensing Guide
The License and Copyright Information for Cisco NX-OS Software is available at http://www.cisco.com/en/
US/docs/switches/datacenter/sw/4_0/nx-os/license_agreement/nx-ossw_lisns.html.
Command References
These guides are available at the following URL:
http://www.cisco.com/en/US/products/ps9670/prod_command_reference_list.html
The documents in this category include:
Cisco Nexus 5500 Series NX-OS Fabric Extender Command Reference
•
Cisco Nexus 5500 Series NX-OS FabricPath Command Reference
•
Cisco Nexus 5500 Series NX-OS Fundamentals Command Reference
•
Cisco Nexus 5500 Series NX-OS Interfaces Command Reference
•
Cisco Nexus 5500 Series NX-OS Layer 2 Interfaces Command Reference
•
Preface
Cisco Nexus 5500 Series NX-OS Multicast Routing Command Reference
•
Cisco Nexus 5500 Series NX-OS Quality of Service Command Reference
•
Cisco Nexus 5500 Series NX-OS Security Command Reference
•
Cisco Nexus 5500 Series NX-OS System Management Command Reference
•
Cisco Nexus 5500 Series NX-OS TrustSec Command Reference
•
Cisco Nexus 5500 Series NX-OS Unicast Routing Command Reference
•
Cisco Nexus 5500 Series NX-OS Virtual Port Channel Command Reference
•
Technical References
The Cisco Nexus 5500 Series NX-OS MIB Reference is available at http://www.cisco.com/en/US/docs/switches/
datacenter/nexus5500/sw/mib/reference/NX5500_MIBRef.html.
Error and System Messages
The Cisco Nexus 5500 Series NX-OS System Message Guide is available at http://www.cisco.com/en/US/docs/
switches/datacenter/nexus5500/sw/system_messages/reference/sl_nxos_book.html.
Troubleshooting Guide
The Cisco Nexus 5500 Series NX-OS Troubleshooting Guide is available at http://www.cisco.com/en/US/
docs/switches/datacenter/nexus5500/sw/troubleshooting/guide/N5K_Troubleshooting_Guide.html.
Documentation Feedback
To provide technical feedback on this document, or to report an error or omission, please send your comments
to: ciscodfa-docfeedback@cisco.com.
We appreciate your feedback.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
xxii OL-30895-01
Page 23

Preface
Obtaining Documentation and Submitting a Service Request
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, using the Cisco Bug Search Tool (BST), submitting a service
request, and gathering additional information, see What's New in Cisco Product Documentation.
To receive new and revised Cisco technical content directly to your desktop, you can subscribe to the What's
New in Cisco Product Documentation RSS feed. RSS feeds are a free service.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 xxiii
Page 24

Obtaining Documentation and Submitting a Service Request
Preface
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
xxiv OL-30895-01
Page 25

Overview
This chapter contains the following sections:
SAN Switching Overview, page 1
•
SAN Switching Overview
This chapter provides an overview of SAN switching for Cisco NX-OS devices. This chapter includes the
following sections:
Fibre Channel Interfaces
Fibre Channel ports are optional on the Cisco Nexus device.
Each Fibre Channel port can be used as a downlink (connected to a server) or as an uplink (to the data center
SAN fabric).
Domain Parameters
CHAPTER 1
The Fibre Channel domain (fcdomain) feature performs principal switch selection, domain ID distribution,
FC ID allocation, and fabric reconfiguration functions as described in the FC-SW-2 standards. The domains
are configured per VSAN . If you do not configure a domain ID, the local switch uses a random ID.
N Port Virtualization
Cisco NX-OS software supports industry-standard N port identifier virtualization (NPIV), which allows
multiple N port fabric logins concurrently on a single physical Fibre Channel link. HBAs that support NPIV
can help improve SAN security by enabling zoning and port security to be configured independently for each
virtual machine (OS partition) on a host. In addition to being useful for server connections, NPIV is beneficial
for connectivity between core and edge SAN switches.
VSAN Trunking
Trunking, also known as VSAN trunking, enables interconnect ports to transmit and receive frames in more
than one VSAN over the same physical link. Trunking is supported on E ports and F ports.
SAN Port Channels
PortChannels aggregate multiple physical ISLs into one logical link with higher bandwidth and port resiliency
for Fibre Channel traffic. With this feature, up to 16 expansion ports (E-ports) or trunking E-ports (TE-ports)
can be bundled into a PortChannel. ISL ports can reside on any switching module, and they do not need a
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 1
Page 26

SAN Switching Overview
designated master port. If a port or a switching module fails, the PortChannel continues to function properly
without requiring fabric reconfiguration.
Cisco NX-OS software uses a protocol to exchange PortChannel configuration information between adjacent
switches to simplify PortChannel management, including misconfiguration detection and autocreation of
PortChannels among compatible ISLs. In the autoconfigure mode, ISLs with compatible parameters
automatically form channel groups; no manual intervention is required.
PortChannels load balance Fibre Channel traffic using a hash of source FC-ID and destination FC-ID, and
optionally the exchange ID. Load balancing using PortChannels is performed over both Fibre Channel and
FCIP links. Cisco NX-OS software also can be configured to load balance across multiple same-cost FSPF
routes.
Virtual SANs
Virtual SANs (VSANs) partition a single physical SAN into multiple VSANs. VSANs allow the Cisco NX-OS
software to logically divide a large physical fabric into separate, isolated environments to improve Fibre
Channel SAN scalability, availability, manageability, and network security.
Each VSAN is a logically and functionally separate SAN with its own set of Fibre Channel fabric services.
This partitioning of fabric services greatly reduces network instability by containing fabric reconfiguration
and error conditions within an individual VSAN. The strict traffic segregation provided by VSANs can ensure
that the control and data traffic of a specified VSAN are confined within the VSAN's own domain, which
increases SAN security. VSANs can reduce costs by facilitating consolidation of isolated SAN islands into a
common infrastructure without compromising availability.
You can create administrator roles that are limited in scope to certain VSANs. For example, you can set up a
network administrator role to allow configuration of all platform-specific capabilities and other roles to allow
configuration and management only within specific VSANs. This approach improves the manageability of
large SANs and reduces disruptions due to human error by isolating the effect of a user action to a specific
VSAN whose membership can be assigned based on switch ports or the worldwide name (WWN) of attached
devices.
VSANs are supported across Fibre Channel over IP (FCIP) links between SANs, which extends VSANs to
include devices at a remote location. The Cisco SAN switches also implement trunking for VSANs. Trunking
allows Inter-Switch Links (ISLs) to carry traffic for multiple VSANs on the same physical link.
Zoning
Overview
Zoning provides access control for devices within a SAN. The Cisco NX-OS software supports the following
types of zoning:
N port zoning-Defines zone members based on the end-device (host and storage) port.
•
WWN
◦
Fibre Channel identifier (FC-ID)
◦
Fx port zoning-Defines zone members based on the switch port.
•
WWN
◦
WWN plus the interface index, or domain ID plus the interface index
◦
Domain ID and port number (for Brocade interoperability)
•
iSCSI zoning-Defines zone members based on the host zone.
•
iSCSI name
◦
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
2 OL-30895-01
Page 27

Overview
SAN Switching Overview
IP address
◦
LUN zoning-When combined with N port zoning, logical unit number (LUN) zoning helps ensure that
•
LUNs are accessible only by specific hosts, providing a single point of control for managing heterogeneous
storage-subsystem access.
Read-only zones-An attribute can be set to restrict I/O operations in any zone type to SCSI read-only
•
commands. This feature is useful for sharing volumes across servers for backup, data warehousing, and
so on.
Broadcast zones-An attribute can be set for any zone type to restrict broadcast frames to members of
•
the specific zone.
To provide strict network security, zoning is always enforced per frame using access control lists (ACLs) that
are applied at the ingress switch. All zoning polices are enforced in the hardware, and none of them cause
performance degradation. Enhanced zoning session-management capabilities further enhance security by
allowing only one user at a time to modify zones.
Device Alias Services
The software supports Device Alias Services (device alias) on per VSAN and fabric wide. Device alias
distribution allows you to move host bus adapters (HBAs) between VSANs without manually reentering alias
names.
Fibre Channel Routing
Fabric Shortest Path First (FSPF) is the protocol used by Fibre Channel fabrics. FSPF is enabled by default
on all Fibre Channel switches. You do not need to configure any FSPF services except in configurations that
require special consideration. FSPF automatically calculates the best path between any two switches in a
fabric. Specifically, FSPF is used to perform these functions:
Dynamically compute routes throughout a fabric by establishing the shortest and quickest path between
•
any two switches.
Select an alternative path if a failure occurs on a given path. FSPF supports multiple paths and
•
automatically computes an alternative path around a failed link. FSPF provides a preferred route when
two equal paths are available.
SCSI Targets
Small Computer System Interface (SCSI) targets include disks, tapes, and other storage devices. These targets
do not register logical unit numbers (LUNs) with the name server. The SCSI LUN discovery feature is initiated
on demand, through CLI or SNMP. This information is also synchronized with neighboring switches, if those
switches belong to the Cisco Nexus device.
Advanced Fibre Channel Features
You can configure Fibre Channel protocol-related timer values for distributed services, error detection, and
resource allocation.
You must uniquely associate the WWN to a single switch. The principal switch selection and the allocation
of domain IDs rely on the WWN. Cisco Nexus devices support three network address authority (NAA) address
formats.
Fibre Channel standards require that you allocate a unique FC ID to an N port that is attached to an F port in
any switch. To conserve the number of FC IDs used, Cisco Nexus devices use a special allocation scheme.
FC-SP and DHCHAP
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 3
Page 28

SAN Switching Overview
The Fibre Channel Security Protocol (FC-SP) provides switch-to-switch and hosts-to-switch authentication
to overcome security challenges for enterprise-wide fabrics. The Diffie-Hellman Challenge Handshake
Authentication Protocol (DHCHAP) is an FC-SP protocol that provides authentication between Cisco SAN
switches and other devices. DHCHAP consists of the CHAP protocol combined with the Diffie-Hellman
exchange.
With FC-SP, switches, storage devices, and hosts can prove their identity through a reliable and manageable
authentication mechanism. With FC-SP, Fibre Channel traffic can be secured per frame to prevent snooping
and hijacking even over untrusted links. A consistent set of policies and management actions are propagated
through the fabric to provide a uniform level of security across the entire fabric.
Port Security
The port security feature prevents unauthorized access to a switch port by binding specific world-wide names
(WWNs) that have access to one or more given switch ports.
When port security is enabled on a switch port, all devices connecting to that port must be in the port security
database and must be listed in the database as bound to a given port. If both of these criteria are not met, the
port will not achieve an operationally active state and the devices connected to the port will be denied access
to the SAN.
Fabric Binding
Overview
Fabric binding ensures Inter-Switch Links (ISLs) are enabled only between specified switches in the fabric
binding configuration, which prevents unauthorized switches from joining the fabric or disrupting the current
fabric operations. This feature uses the Exchange Fabric Membership Data (EEMD) protocol to ensure that
the list of authorized switches is identical in all of the switches in a fabric.
Fabric Configuration Servers
The Fabric Configuration Server (FCS) provides discovery of topology attributes and maintains a repository
of configuration information of fabric elements. A management application is usually connected to the FCS
on the switch through an N port. Multiple VSANs constitute a fabric, where one instance of the FCS is present
per VSAN.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
4 OL-30895-01
Page 29

Configuring Fibre Channel Interfaces
This chapter contains the following sections:
Configuring Fibre Channel Interfaces, page 5
•
Configuring Fibre Channel Interfaces
Information About Fibre Channel Interfaces
Licensing Requirements for Fibre Channel
On Cisco Nexus devices, Fibre Channel capability is included in the Storage Protocol Services license.
Ensure that you have the correct license installed (N5010SS or N5020SS) before using Fibre Channel interfaces
and capabilities.
CHAPTER 2
Note
You can configure virtual Fibre Channel interfaces without a Storage Protocol Services license, but these
interfaces will not become operational until the license is activated.
QOS Requirements for Fibre Channel
The FCoE QoS must be configured if the following types of interfaces are in use:
Native FC - for FC
•
FCoE - for vFC
•
FC and FCoE - for FC and vFC
•
The FCoE QoS must be added even if Ethernet is not configured on the switch.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 5
Page 30

Information About Fibre Channel Interfaces
The following commands will enable the default QoS configuration which must be configured for native FC
or FCoE or FC and FCoE:
switch(config)# system qos
switch(config-sys-qos)# service-policy type queuing input fcoe-default-in-policy
switch(config-sys-qos)# service-policy type queuing output fcoe-default-out-policy
switch(config-sys-qos)# service-policy type qos input fcoe-default-in-policy
switch(config-sys-qos)# service-policy type network-qos fcoe-default-nq-policy
Physical Fibre Channel Interfaces
Cisco Nexus devices support up to sixteen physical Fibre Channel (FC) uplinks through the use of two, optional
explansion modules. The first module contains eight FC interfaces. The second module includes four Fibre
Channel ports and four Ethernet ports.
Each Fibre Channel port can be used as a downlink (connected to a server) or as an uplink (connected to the
data center SAN network). The Fibre Channel interfaces support the following modes: E, F, NP, TE, TF,
TNP, SD, and Auto.
Virtual Fibre Channel Interfaces
Configuring Fibre Channel Interfaces
VF Port
Fibre Channel over Ethernet (FCoE) encapsulation allows a physical Ethernet cable to simultaneously carry
Fibre Channel and Ethernet traffic. In Cisco Nexus devices, an FCoE-capable physical Ethernet interface can
carry traffic for one virtual Fibre Channel (vFC) interface.
Like any interface in Cisco NX-OS, vFC interfaces are manipulable objects with properties such as configuration
and state. Native Fibre Channel and vFC interfaces are configured using the same CLI commands.
vFC interfaces support only F mode and operate in trunk mode only.
The following capabilities are not supported for virtual Fibre Channel interfaces:
SAN port channels.
•
The SPAN destination cannot be a vFC interface.
•
Buffer-to-buffer credits.
•
Exchange link parameters (ELP), or Fabric Shortest Path First (FSPF) protocol.
•
Configuration of physical attributes (speed, rate, mode, transmitter information, MTU size).
•
Port tracking.
•
vFC interfaces always operate in trunk mode; vFC interfaces do not operate in any other mode. You can
configure allowed VSANs on a vFC by using the switchport trunk allowed vsan command under the vfc
interface (which is similar to FC TF and TE ports). For vFC interfaces that are connected to hosts, port VSAN
is the only VSAN that supports logins (FLOGI). We recommend that you restrict the allowed VSANs for
such vFC interfaces to the port VSAN by using the switchport trunk allowed vsan command in the interface
mode to configure a VF port.
Includes support for 160 vFC interfaces.
The vFC VSAN assignment and the global VLAN-to-VSAN mapping table enables the Cisco Nexus device
to choose the appropriate VLAN for a VF port.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
6 OL-30895-01
Page 31

Configuring Fibre Channel Interfaces
The VF port support over 10G-FEX interfaces feature is supported only in Cisco Nexus Fabric Extender
straight-through topologies where each Fabric Extender is directly connected to a Cisco Nexus device.
VE Ports
A virtual E port (VE port) is a port that emulates an E port over a non-Fibre Channel link. VE port connectivity
between Fibre Channel Forwarders (FCFs) is supported over point-to-point links. These links can be individual
Ethernet interfaces or members of an Ethernet port-channel interface. For each of the FCF connected Ethernet
interfaces you must create and bind an vFC interface to the Ethernet interface. Configure vFC interfaces as
VE ports by using the switchport mode e command in interface mode.
VE ports have the following guidelines:
Auto mode on the vFC is not supported.
•
VE Port trunking is supported over FCoE-enabled VLANs.
•
VE Port interface binding to MAC addresses is not supported.
•
By default the VE Port is enabled for trunk mode.
•
You can configure multiple VSANs on the VE port. You must configure the FCoE VLANs that correspond
to the VE port’s VSANs on the bound Ethernet interface.
Information About Fibre Channel Interfaces
The Spanning Tree Protocol is disabled on the FCoE VLANs on any interface that a vFC interface is
•
bound to, which includes the interfaces that the VE ports are bound to.
The number of VE port pairs that can be supported between a given FCF and a peer FCF depends on the
FCF-MAC advertising capability of the peer FCF:
If a peer FCF advertises the same FCF-MAC address over all its interfaces, the FCF can connect to it
•
over one VE port. In such a topology, we recommended that you use one port-channel interface for
redundancy.
If a peer FCF advertises multiple FCF-MAC addresses, the limits in the table apply.
•
VE Ports in a vPC Topology
VE ports in a vPC topology have the following guidelines:
Dedicated links are required for FCoE VLANs between FCFs connected over a vPC for LAN traffic.
•
FCoE VLANs must not be configured on the inter-switch vPC interfaces.
•
FSPF Parameters
FSPF operates on a per-VSAN basis over a VE port once it is brought up on the VSAN. The default FSPF
cost (metric) of the vFC interface is as per 10-Gbps bandwidth. For VE ports that are bound to Ethernet port
channels, the cost is adjusted based on the number of operational member ports.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 7
Page 32

Information About Fibre Channel Interfaces
VE Port Configuration Limits
Ethernet Interface
Ethernet Port-Channel
Interface
VNP Ports
Connectivity from an FCoE NPV bridge to the FCF is only supported over point-to-point links. These links
can be individual Ethernet interfaces or members of an Ethernet port channel interface. For each FCF connected
Ethernet interfaces, a vFC interface must be created and bound to the Ethernet interface. These vFC interfaces
must be configured as VNP ports. On the VNP port, an FCoE NPV bridge emulates an FCoE-capable host
with multiple enodes, each with a unique enode MAC address. A VNP port interface binding to MAC address
is not supported. By default, the VNP port is enabled in trunk mode. Multiple VSANs can be configured on
the VNP port. The FCoE VLANs that correspond to the VNP port VSANs must be configured on the bound
Ethernet interface.
The spanning-tree protocol (STP) is automatically disabled in the FCoE VLAN on the interfaces that the VNP
port are bound to.
Configuring Fibre Channel Interfaces
PlatformInterface Type
10G Fabric ExtendersCisco Nexus 5500 Series Switch
Not supported16 VE PortsVE Port bound to an
Not supported4 VE PortsVE Port bound to an
Interface Modes
Each physical Fibre Channel interface in a switch may operate in one of several port modes: E mode, TE
mode, F mode, TF mode, TNP mode, and SD mode. A physical Fibre Channel interface can be configured
as an E port, an F port, or an SD port. Interfaces may also be configured in Auto mode; the port type is
determined during interface initialization.
In NPV mode, Fibre Channel interfaces may operate in NP mode, F mode, or SD mode.
Virtual Fibre Channel interfaces can only be configured in F mode.
Interfaces are automatically assigned VSAN 1 by default.
Each interface has an associated administrative configuration and an operational status:
Related Topics
The administrative configuration does not change unless you modify it. This configuration has various
•
attributes that you can configure in administrative mode.
The operational status represents the current status of a specified attribute such as the interface speed.
•
This status cannot be changed and is read-only. Some values may not be valid when the interface is
down (for example, the operational speed).
Configuring and Managing VSANs, on page 113
Configuring N Port Virtualization, on page 51
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
8 OL-30895-01
Page 33

Configuring Fibre Channel Interfaces
E Port
In expansion port (E port) mode, an interface functions as a fabric expansion port. This port may be connected
to another E port to create an Inter-Switch Link (ISL) between two switches. E ports carry frames between
switches for configuration and fabric management. They serve as a conduit between switches for frames
destined to remote N ports. E ports support class 3 and class F service.
An E port connected to another switch may also be configured to form a SAN port channel.
Related Topics
Configuring SAN Port Channels, on page 93
F Port
In fabric port (F port) mode, an interface functions as a fabric port. This port may be connected to a peripheral
device (host or disk) operating as a node port (N port). An F port can be attached to only one N port. F ports
support class 3 service.
Information About Fibre Channel Interfaces
NP Port
TE Port
When the switch is operating in NPV mode, the interfaces that connect the switch to the core network switch
are configured as NP ports. NP ports operate like N ports that function as proxies for multiple physical N
ports.
Related Topics
Configuring N Port Virtualization, on page 51
In trunking E port (TE port) mode, an interface functions as a trunking expansion port. It may be connected
to another TE port to create an extended ISL (EISL) between two switches. TE ports connect to another Cisco
Nexus device or a Cisco MDS 9000 Family switch. They expand the functionality of E ports to support the
following:
VSAN trunking
•
Fibre Channel trace (fctrace) feature
•
In TE port mode, all frames are transmitted in EISL frame format, which contains VSAN information.
Interconnected switches use the VSAN ID to multiplex traffic from one or more VSANs across the same
physical link. This feature is referred to as VSAN trunking in the Cisco Nexus device. TE ports support class
3 and class F service.
Related Topics
Configuring VSAN Trunking, on page 83
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 9
Page 34

Information About Fibre Channel Interfaces
TF Port
When the switch is operating in NPV mode, the interfaces that connect the switch to the core network switch
are configured as NP ports. NP ports operate like N ports that function as proxies for multiple physical N
ports.
In trunking F port (TF port) mode, an interface functions as a trunking expansion port. It may be connected
to another trunked N port (TN port) or trunked NP port (TNP port) to create a link between a core switch and
an NPV switch or an HBA to carry tagged frames. TF ports expand the functionality of F ports to support
VSAN trunking.
In TF port mode, all frames are transmitted in an EISL frame format, which contains VSAN information.
Interconnected switches use the VSAN ID to multiplex traffic from one or more VSANs across the same
physical link. This feature is referred to as VSAN trunking in Cisco Nexus devices. TF ports support class 3
and class F service.
TNP Port
In trunking NP port (TNP port) mode, an interface functions as a trunking expansion port. A TNP Port may
be connected to a trunked F port (TF port) to create a link to a core NPIV switch from an NPV switch.
Configuring Fibre Channel Interfaces
SD Port
In SPAN destination port (SD port) mode, an interface functions as a switched port analyzer (SPAN). The
SPAN feature monitors network traffic that passes though a Fibre Channel interface. This monitoring is done
using a standard Fibre Channel analyzer (or a similar switch probe) that is attached to an SD port. SD ports
do not receive frames, instead they transmit a copy of the source traffic. The SPAN feature is nonintrusive
and does not affect switching of network traffic for any SPAN source ports.
Auto Mode
Interfaces configured in auto mode can operate in one of the following modes: E, F, NP, TE, TF, and TNP
port. The port mode is determined during interface initialization. For example, if the interface is connected
to a node (host or disk), it operates in F port mode. If the interface is attached to a third-party switch, it operates
in E port mode. If the interface is attached to another switch in the Cisco Nexus device or Cisco MDS 9000
Family, it may become operational in TE port mode.
SD ports are not determined during initialization and are administratively configured.
Related Topics
Interface States
The interface state depends on the administrative configuration of the interface and the dynamic state of the
physical link.
Configuring VSAN Trunking, on page 83
Administrative States
The administrative state refers to the administrative configuration of the interface. The table below describes
the administrative states.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
10 OL-30895-01
Page 35

Configuring Fibre Channel Interfaces
Table 1: Administrative States
Information About Fibre Channel Interfaces
DescriptionAdministrative State
Interface is enabled.Up
Operational States
The operational state indicates the current operational state of the interface. The table below describes the
operational states.
Table 2: Operational States
Down
Up
Interface is disabled. If you administratively disable
an interface by shutting down that interface, the
physical link layer state change is ignored.
DescriptionOperational State
Interface is transmitting or receiving traffic as desired.
To be in this state, an interface must be
administratively up, the interface link layer state must
be up, and the interface initialization must be
completed.
Interface cannot transmit or receive (data) traffic.Down
Interface is operational in TE or TF mode.Trunking
Reason Codes
Reason codes are dependent on the operational state of the interface. The following table describes the reason
codes for operational states.
Table 3: Reason Codes for Interface States
Reason CodeOperational StatusAdministrative Configuration
None.UpUp
DownDown
Administratively down. If you
administratively configure an
interface as down, you disable the
interface. No traffic is received or
transmitted.
See the table below.DownUp
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 11
Page 36

Information About Fibre Channel Interfaces
If the administrative state is up and the operational state is down, the reason code differs based on the
nonoperational reason code. The table below describes the reason codes for nonoperational states.
Only some of the reason codes are listed in the table.Note
Table 4: Reason Codes for Nonoperational States
Configuring Fibre Channel Interfaces
Applicable ModesDescriptionReason Code (long version)
Link failure or not connected
SFP not present
Initializing
Reconfigure fabric in progress
Offline
Inactive
AllThe physical layer link is not
operational.
AllThe small form-factor pluggable
(SFP) hardware is not plugged in.
AllThe physical layer link is
operational and the protocol
initialization is in progress.
The fabric is currently being
reconfigured.
The switch software waits for the
specified R_A_TOV time before
retrying initialization.
The interface VSAN is deleted or
is in a suspended state.
To make the interface operational,
assign that port to a configured and
active VSAN.
A hardware failure is detected.Hardware failure
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
12 OL-30895-01
Page 37

Configuring Fibre Channel Interfaces
Information About Fibre Channel Interfaces
Applicable ModesDescriptionReason Code (long version)
Error disabled
Isolation because limit of active
port channels is exceeded.
Error conditions require
administrative attention. Interfaces
may be error-disabled for various
reasons. For example:
Configuration failure.
•
Incompatible buffer-to-buffer
•
credit configuration.
To make the interface operational,
you must first fix the error
conditions causing this state and
then administratively shut down or
enable the interface.
The interface is isolated because
the switch is already configured
with the maximum number of
active SAN port channels.
The port negotiation failed.Isolation due to ESC failure
Only E ports and TE portsThe port negotiation failed.Isolation due to ELP failure
Isolation due to domain overlap
Isolation due to domain ID
assignment failure
Isolation due to the other side of
the link E port isolated
Isolation due to invalid fabric
reconfiguration
disabled
Isolation due to VSAN mismatch
port channel administratively down
The Fibre Channel domains
(fcdomain) overlap.
The assigned domain ID is not
valid.
The E port at the other end of the
link is isolated.
The port is isolated due to fabric
reconfiguration.
The fcdomain feature is disabled.Isolation due to domain manager
The zone merge operation failed.Isolation due to zone merge failure
The VSANs at both ends of an ISL
are different.
Only SAN port channel interfacesThe interfaces belonging to the
SAN port channel are down.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 13
Page 38

Information About Fibre Channel Interfaces
Configuring Fibre Channel Interfaces
Applicable ModesDescriptionReason Code (long version)
Suspended due to incompatible
speed
Suspended due to incompatible
mode
Suspended due to incompatible
remote switch WWN
Bound physical interface down
STP not forwarding in FCoE
mapped VLAN
The interfaces belonging to the
SAN port channel have
incompatible speeds.
The interfaces belonging to the
SAN port channel have
incompatible modes.
An improper connection is
detected. All interfaces in a SAN
port channel must be connected to
the same pair of switches.
The Ethernet interface bound to a
virtual Fibre Channel interface is
not operational.
The Ethernet interface bound to a
virtual Fibre Channel interface is
not in an STP forwarding state for
the VLAN associated with the
virtual Fibre Channel interface
Only virtual Fibre Channel
interfaces
Only virtual Fibre Channel
interfaces
Buffer-to-Buffer Credits
Buffer-to-buffer credits (BB_credits) are a flow-control mechanism to ensure that Fibre Channel interfaces
do not drop frames. BB_credits are negotiated on a per-hop basis.
In Cisco Nexus devices, the BB_credit mechanism is used on Fibre Channel interfaces but not on virtual Fibre
Channel interfaces. The receive BB_credit determines the receive buffering capability on the receive side
without having to acknowledge the peer. This is important for links with large bandwidth-delays (long links
with large latency) to be able to sustain line-rate traffic with increased latency.
The receive BB_credit value (fcrxbbcredit) may be configured for each Fibre Channel interface. In most cases,
you do not need to modify the default configuration.
For virtual Fibre Channel interfaces, BB_credits are not used. Virtual Fibre Channel interfaces provide flow
control based on capabilities of the underlying physical Ethernet interface.
Note
The receive BB_credit values depend on the port mode. For physical Fibre Channel interfaces, the default
value is 16 for F mode and E mode interfaces. This value can be changed as required. The maximum value
is 240 .
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
14 OL-30895-01
Page 39

Configuring Fibre Channel Interfaces
Configuring Fibre Channel Interfaces
Configuring a Fibre Channel Interface
To configure a Fibre Channel interface, perform this task:
Procedure
Configuring Fibre Channel Interfaces
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface {fc
slot/port}|{vfc vfc-id}
Enters configuration mode.switch# configuration terminal
Selects a Fibre Channel interface and enters interface
configuration mode.
Note
Note
Configuring a Range of Fibre Channel Interfaces
To configure a range of Fibre Channel interfaces, perform this task:
Procedure
Step 1
Step 2
switch(config)# interface { fc slot/port port [ , fc slot/port - port ] | vfc vfc-id - vfc-id
[ , vfc vfc-id - vfc-id ] }
When a Fibre Channel interface is configured, it is
automatically assigned a unique world wide name
(WWN). If the interface’s operational state is up, it is
also assigned a Fibre Channel ID (FC ID).
If this is a QSFP+ GEM, the slot/port syntax is
slot/QSFP-module/port.
PurposeCommand or Action
Enters configuration mode.switch# configuration terminal
Selects the range of Fibre Channel interfaces and
enters interface configuration mode.
Note
If this is a QSFP+ GEM, the slot/port
syntax is slot/QSFP-module/port.
Setting the Interface Administrative State
To gracefully shut down an interface, perform this task:
To enable traffic flow, perform this task:
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 15
Page 40

Configuring Fibre Channel Interfaces
Procedure
Configuring Fibre Channel Interfaces
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface {fc
slot/port}|{vfc vfc-id}
Step 3
switch(config-if)# shutdown
Configuring Interface Modes
Procedure
Step 1
Example:
switch# configure terminal
switch(config)#
Step 2
Step 3
switch(config) # interface vfc vfc-id}
Example:
switch(config) # interface vfc 20
switch(config-if) #
Example:
switch(config-if) # switchport mode E
switch(config-if) #
Enters configuration mode.switch# configuration terminal
Selects a Fibre Channel interface and enters interface
configuration mode.
Note
If this is a QSFP+ GEM, the slot/port syntax
is slot/QSFP-module/port.
Gracefully shuts down the interface and
administratively disables traffic flow (default).
PurposeCommand or Action
Enters global configuration mode.configure terminal
Selects a virtual Fibre Channel interface and
enters interface configuration mode.
Sets the port mode.switch(config-if) # switchport mode {E|NP}
vFC interfaces support modes F, E, or NP.
Note
SD ports cannot be configured
automatically. They must be
administratively configured.
This example shows how to configure VE port 20 and bind it to Ethernet slot 1, port 3:
switch# config t
switch(config) # interface vfc 20
switch(config-if) # bind interface ethernet 1/3
switch(config-if) # switchport mode E
switch(config-if) # exit
switch#
This example shows the running configuration for vFC 20 bound to the Ethernet slot1,port 3 interface.
switch# show running-config
switch(config) # interface vfc20
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
16 OL-30895-01
Page 41

Configuring Fibre Channel Interfaces
switch(config-if) # bind interface Ethernet 1/3
switch(config-if) # switchport mode E
switch(config-if) # no shutdown
This example shows how to configure VNP port 10 and bind it to Ethernet slot 2, port 1:
switch # config t
switch(config) # interface vfc 10
switch(config-if) # bind interface ethernet 2/1
switch(config-if) # switchport mode NP
switch(config-if) # exit
switch#
Configuring Fibre Channel Interfaces
Configuring Unified Ports
Before You Begin
Confirm that you have a supported Cisco Nexus switch. Unified Ports are available on the following Cisco
Nexus switches:
Configuring Fibre Channel Interfaces
Cisco Nexus 5596T
•
Cisco Nexus 5548UP
•
Cisco Nexus 5596UP
•
Cisco Nexus 5548P switch with an installed Cisco N55-M16UP expansion module
•
Cisco Nexus 5672UP
•
Cisco Nexus 56128 with N56-M24UP2Q GEM
•
Cisco Nexus
•
•
•
If you're configuring a unified port as Fibre Channel or FCoE, confirm that you have enabled the feature fcoe
command.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config) # slot slot number
Enters global configuration mode.switch# configure terminal
Identifies the slot on the switch.
Note
If this is a QSFP+ GEM, the slot/port syntax is
slot/QSFP-module/port.
Step 3
switch(config-slot) # port port
number type {ethernet | fc}
Configures a unified port as a native Fibre Channel port
and an Ethernet port.
• type—Specifies the type of port to configure on a
slot in a chassis.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 17
Page 42

Configuring Fibre Channel Interfaces
Configuring Fibre Channel Interfaces
PurposeCommand or Action
• ethernet—Specifies an Ethernet port.
• fc—Specifies a Fibre Channel (FC) port.
Step 4
switch(config-slot) # copy
running-config startup-config
Step 5
Step 6
Step 7
switch(config) # slot slot number
switch(config-slot) # no port port
number type fc
This example shows how to configure a unified port on a Cisco N55-M16UP expansion module:
switch# configure terminal
switch(config)# slot 2
switch(config-slot)# port 1-16 type fc
switch(config-slot)# copy running-config startup-config
switch(config-slot)# poweroff module 2
switch(config-slot)# no poweroff module 2
Configuring the Interface Description
Note
Changing unified ports on an expansion module
(GEM) requires that you power cycle the GEM
card. You do not have to reboot the entire switch
for changes to take effect.
Copies the running configuration to the startup
configuration.
Reboots the switch.switch(config-slot) # reload
Identifies the slot on the switch.
Removes the unified port.
Interface descriptions should help you identify the traffic or use for that interface. The interface description
can be any alphanumeric string.
To configure a description for an interface, perform this task:
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface {fc
slot/port}|{vfc vfc-id}
Enters configuration mode.switch# configuration terminal
Selects a Fibre Channel interface and enters
interface configuration mode.
Note
If this is a QSFP+ GEM, the slot/port
syntax is slot/QSFP-module/port.
Step 3
Step 4
switch(config-if)# switchport description
cisco-HBA2
Configures the description of the interface. The
string can be up to 80 characters long.
Clears the description of the interface.switch(config-if)# no switchport
description
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
18 OL-30895-01
Page 43

Configuring Fibre Channel Interfaces
Configuring Port Speeds
Port speed can be configured on a physical Fibre Channel interface but not on a virtual Fibre Channel interface.
By default, the port speed for an interface is automatically calculated by the switch.
Changing the interface speed is a disruptive operation.Caution
To configure the port speed of the interface, perform this task:
Procedure
Configuring Fibre Channel Interfaces
PurposeCommand or Action
Autosensing
Step 1
Step 2
Step 3
Step 4
switch(config)# interface fc
slot/port
speed 1000
switch(config-if)# no switchport
speed
Enters configuration mode.switch# configuration terminal
Selects the specified interface and enters interface
configuration mode.
Note
You cannot configure the port speed of a virtual Fibre
Channel interface.
Note
If this is a QSFP+ GEM, the slot/port syntax is
slot/QSFP-module/port.
Configures the port speed of the interface to 1000 Mbps.switch(config-if)# switchport
The number indicates the speed in megabits per second
(Mbps). You can set the speed to 1000 (for 1-Gbps interfaces),
2000 (for 2-Gbps interfaces), 4000 (for 4-Gbps interfaces), or
auto (default).
Reverts to the factory default (auto) administrative speed of
the interface.
Configuring SD Port Frame Encapsulation
The switchport encap eisl command only applies to SD port interfaces. This command determines the frame
format for all frames transmitted by the interface in SD port mode. If the encapsulation is set to EISL, all
outgoing frames are transmitted in the EISL frame format, for all SPAN sources.
The switchport encap eisl command is disabled by default. If you enable encapsulation, all outgoing frames
are encapsulated, and you will see a new line (Encapsulation is eisl) in the show interface SD_port_interface
command output.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 19
Page 44

Configuring Fibre Channel Interfaces
Configuring Receive Data Field Size
You can configure the receive data field size for native Fibre Channel interfaces (but not for virtual Fibre
Channel interfaces). If the default data field size is 2112 bytes, the frame length will be 2148 bytes.
To configure the receive data field size, perform this task:
Procedure
Configuring Fibre Channel Interfaces
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface fc
slot/port
Step 3
switch(config-if)# switchport
fcrxbufsize 2000
Understanding Bit Error Thresholds
The bit error rate threshold is used by the switch to detect an increased error rate before performance degradation
seriously affects traffic.
The bit errors can occur for the following reasons:
Faulty or bad cable.
•
Faulty or bad GBIC or SFP.
•
GBIC or SFP is specified to operate at 1 Gbps but is used at 2 Gbps.
•
Enters configuration mode.switch# configuration terminal
Selects a Fibre Channel interface and enters interface
configuration mode.
Note
If this is a QSFP+ GEM, the slot/port syntax is
slot/QSFP-module/port.
Reduces the data field size for the selected interface to
2000 bytes. The default is 2112 bytes and the range is
from 256 to 2112 bytes.
GBIC or SFP is specified to operate at 2 Gbps but is used at 4 Gbps.
•
Short haul cable is used for long haul or long haul cable is used for short haul.
•
Momentary synchronization loss.
•
Loose cable connection at one or both ends.
•
Improper GBIC or SFP connection at one or both ends.
•
A bit error rate threshold is detected when 15 error bursts occur in a 5-minute period. By default, the switch
disables the interface when the threshold is reached.
You can enter the shutdown/no shutdown command sequence to reenable the interface.
You can configure the switch to not disable an interface when the threshold is crossed.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
20 OL-30895-01
Page 45

Configuring Fibre Channel Interfaces
Configuring Fibre Channel Interfaces
Note
The switch generates a syslog message when bit error threshold events are detected, even if the interface
is configured not to be disabled by bit-error threshold events.
To disable the bit error threshold for an interface, perform this task:
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface fc slot/port
Enters configuration mode.switch# configuration terminal
Selects a Fibre Channel interface and enters interface
configuration mode.
Note
If this is a QSFP+ GEM, the slot/port syntax
is slot/QSFP-module/port.
Step 3
Step 4
switch(config-if)# switchport ignore
bit-errors
switch(config-if)# no switchport
ignore bit-errors
Prevents the detection of bit error threshold events
from disabling the interface.
Prevents the detection of bit error threshold events
from enabling the interface.
Configuring Buffer-to-Buffer Credits
Procedure
Step 1
Step 2
Step 3
Step 4
switch(config)# interface fc
slot/port
switch(config-if)# switchport
fcrxbbcredit default
switch(config-if)# switchport
fcrxbbcredit number mode {E
| F | TE}
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Selects a Fibre Channel interface and enters interface
configuration mode.
Note
If this is a QSFP+ GEM, the slot/port syntax is
slot/QSFP-module/port.
Applies the default operational value to the selected interface.
The operational value depends on the port mode.
The default values are assigned based on the port capabilities.
Assigns a buffer-to-buffer credit number to the selected interface
and optionally specifies if the port is operating in E, F, or TE
mode.
Note
If you specify E, F, or TE for the mode, the
buffer-to-buffer credit value is applicable only when
the port is set to that particular mode.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 21
Page 46

Configuring Global Attributes for Fibre Channel Interfaces
Configuring Fibre Channel Interfaces
PurposeCommand or Action
The number range for buffer-to-buffer credits is between 1 and
240.
The default value is 16.
Step 5
switch(config-if)# do show int
fc slot/port
Displays the receive and transmit buffer-to-buffer credit along
with other pertinent interface information for this interface.
Note
The buffer-to-buffer credit values are correct at the time
the registers are read. They are useful to verify situations
when the data traffic is slow.
Note
If this is a QSFP+ GEM, the slot/port syntax is
slot/QSFP-module/port.
Step 6
switch(config-if)# copy
running-config startup-config
(Optional)
Saves the change persistently through reboots and restarts by
copying the running configuration to the startup configuration.
Configuring Global Attributes for Fibre Channel Interfaces
Configuring Switch Port Attribute Default Values
You can configure attribute default values for various switch port attributes. These attributes will be applied
globally to all future switch port configurations, even if you do not individually specify them at that time.
To configure switch port attributes, perform this task:
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# no system default
switchport shutdown san
Enters configuration mode.switch# configuration terminal
Configures the default setting for administrative state of an
interface as Up. (The factory default setting is Down).
This command is applicable only to interfaces for
Tip
which no user configuration exists for the
administrative state.
Step 3
switch(config)# system default
switchport shutdown san
Configures the default setting for administrative state of an
interface as Down. This is the factory default setting.
This command is applicable only to interfaces for
Tip
which no user configuration exists for the
administrative state.
Step 4
switch(config)# system default
switchport trunk mode auto
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
22 OL-30895-01
Configures the default setting for administrative trunk mode
state of an interface as Auto.
Page 47

Configuring Fibre Channel Interfaces
Information About N Port Identifier Virtualization
N port identifier virtualization (NPIV) provides a means to assign multiple FC IDs to a single N port. This
feature allows multiple applications on the N port to use different identifiers and allows access control, zoning,
and port security to be implemented at the application level. The following figure shows an example application
using NPIV.
Figure 1: NPIV Example
Configuring Global Attributes for Fibre Channel Interfaces
PurposeCommand or Action
Note
The default setting is trunk mode
on.
Enabling N Port Identifier Virtualization
You can enable or disable NPIV on the switch.
Before You Begin
You must globally enable NPIV for all VSANs on the switch to allow the NPIV-enabled applications to use
multiple N port identifiers.
All of the N port identifiers are allocated in the same VSAN.Note
Procedure
Step 1
Example:
switch# configure terminal
switch(config)#
PurposeCommand or Action
Enters configuration mode.configure terminal
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 23
Page 48

Example Port Channel Configurations
Configuring Fibre Channel Interfaces
PurposeCommand or Action
Step 2
feature npiv
Example:
switch(config)# feature npiv
Step 3
Example:
switch(config)# no feature npiv
Example Port Channel Configurations
This section shows examples on how to configure an F port channel in shared mode and how to bring up the
link between F ports on the NPIV core switches and NP ports on the NPV switches. Before you configure the
F port channel, ensure that F port trunking, F port channeling, and NPIV are enabled.
This example shows how to create the port channel:
switch(config)# interface port-channel 2
switch(config-if)# switchport mode F
switch(config-if)# switchport dedicated
switch(config-if)# channel mode active
switch(config-if)# exit
This example shows how to configure the port channel member interfaces on the core switch in dedicated
mode:
switch(config)# interface fc1/4-6
switch(config-if)# shut
switch(config-if)# switchport mode F
switch(config-if)# switchport speed 4000
switch(config-if)# switchport rate-mode dedicated
switch(config-if)# switchport trunk mode on
switch(config-if)# channel-group 2
switch(config-if)# no shut
switch(config-if)# exit
Enables NPIV for all VSANs on the
switch.
Disables (default) NPIV on the switch.no feature npiv
This example shows how to create the port channel in dedicated mode on the NPV switch:
switch(config)# interface san-port-channel 2
switch(config-if)# switchport mode NP
switch(config-if)# no shut
switch(config-if)# exit
This example shows how to configure the port channel member interfaces on the NPV switch:
switch(config)# interface fc2/1-2
switch(config-if)# shut
switch(config-if)# switchport mode NP
switch(config-if)# switchport trunk mode on
switch(config-if)# channel-group 2
switch(config-if)# no shut
switch(config-if)# exit
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
24 OL-30895-01
Page 49

Configuring Fibre Channel Interfaces
Verifying Fibre Channel Interfaces
Verifying SFP Transmitter Types
The SPF transmitter type can be displayed for a physical Fibre Channel interface (but not for a virtual Fibre
Channel).
The small form-factor pluggable (SFP) hardware transmitters are identified by their acronyms when displayed
in the show interface brief command. If the related SFP has a Cisco-assigned extended ID, then the show
interface and show interface brief commands display the ID instead of the transmitter type. The show
interface transceiver command and the show interface fc slot/port transceiver command display both values
for Cisco supported SFPs.
Verifying Interface Information
The show interface command displays interface configurations. If no arguments are provided, this command
displays the information for all the configured interfaces in the switch.
You can also specify arguments (a range of interfaces or multiple, specified interfaces) to display interface
information. You can specify a range of interfaces by entering a command with the following example format:
interface fc2/1 - 4 , fc3/2 - 3
The following example shows how to display all interfaces:
switch# show interface
Verifying Fibre Channel Interfaces
fc3/1 is up
...
fc3/3 is up
...
Ethernet1/3 is up
...
mgmt0 is up
...
vethernet1/1 is up
...
vfc 1 is up
The following example shows how to display multiple specified interfaces:
switch# show interface fc3/1 , fc3/3
fc3/1 is up
...
fc3/3 is up
...
The following example shows how to display a specific interface:
switch# show interface vfc 1
vfc 1 is up
...
The following example shows how to display interface descriptions:
switch# show interface description
------------------------------------------------Interface Description
------------------------------------------------fc3/1 test intest
Ethernet1/1 -vfc 1 -...
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 25
Page 50

Verifying Fibre Channel Interfaces
The following example shows how to display all interfaces in brief:
switch# show interface brief
The following example shows how to display interface counters:
switch# show interface counters
The following example shows how to display transceiver information for a specific interface:
switch# show interface fc3/1 transceiver
The show interface transceiver command is only valid if the SFP is present.Note
The show running-configuration command displays the entire running configuration with information for
all interfaces. The interfaces have multiple entries in the configuration files to ensure that the interface
configuration commands execute in the correct order when the switch reloads. If you display the running
configuration for a specific interface, all the configuration commands for that interface are grouped together.
The following example shows the interface display when showing the running configuration for all interfaces:
switch# show running configuration
...
interface fc3/5
switchport speed 2000
...
interface fc3/5
switchport mode E
...
interface fc3/5
channel-group 11 force
no shutdown
Configuring Fibre Channel Interfaces
The following example shows the interface display when showing the running configuration for a specific
interface:
switch# show running configuration fc3/5
interface fc3/5
switchport speed 2000
switchport mode E
channel-group 11 force
no shutdown
Verifying BB_Credit Information
The following example shows how to display the BB_credit information for all Fibre Channel interfaces:
switch# show interface fc2/1
...
fc2/1 is up
Hardware is Fibre Channel, SFP is short wave laser w/o OFC (SN)
Port WWN is 20:41:00:2a:6a:78:5a:80
Admin port mode is F, trunk mode is on
snmp link state traps are enabled
Port mode is F, FCID is 0x400220
Port vsan is 1
Speed is 8 Gbps
Transmit B2B Credit is 5
Receive B2B Credit is 15
Receive data field Size is 2112
Beacon is turned off
1 minute input rate 0 bits/sec, 0 bytes/sec, 0 frames/sec
1 minute output rate 0 bits/sec, 0 bytes/sec, 0 frames/sec
50797511 frames input, 94079655820 bytes
0 discards, 0 errors
1 CRC, 0 unknown class
0 too long, 0 too short
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
26 OL-30895-01
Page 51

Configuring Fibre Channel Interfaces
53584181 frames output, 94072838324 bytes
0 discards, 0 errors
0 input OLS, 0 LRR, 0 NOS, 0 loop inits
1 output OLS, 1 LRR, 0 NOS, 0 loop inits
last clearing of "show interface" counters never
15 receive B2B credit remaining
5 transmit B2B credit remaining
0 low priority transmit B2B credit remaining
Interface last changed at Mon May 19 20:15:53 2014
Default Fibre Channel Interface Settings
The following table lists the default settings for native Fibre Channel interface parameters.
Table 5: Default Native Fibre Channel Interface Parameters
Default Fibre Channel Interface Settings
DefaultParameters
AutoInterface mode
AutoInterface speed
Shutdown (unless changed during initial setup)Administrative state
On (unless changed during initial setup)Trunk mode
1 to 4093Trunk-allowed VSANs
Default VSAN (1)Interface VSAN
Off (disabled)Beacon mode
DisabledEISL encapsulation
2112 bytesData field size
The following table lists the default settings for virtual Fibre Channel interface parameters.
Table 6: Default Virtual Fibre Channel Interface Parameters
DefaultParameters
F modeInterface mode
n/aInterface speed
Shutdown (unless changed during initial setup)Administrative state
OnTrunk mode
All VSANsTrunk-allowed VSANs
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 27
Page 52

Default Fibre Channel Interface Settings
Configuring Fibre Channel Interfaces
DefaultParameters
Default VSAN (1)Interface VSAN
n/aEISL encapsulation
n/aData field size
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
28 OL-30895-01
Page 53

CHAPTER 3
Configuring Fibre Channel Domain Parameters
This chapter describes how to configure Fibre Channel domain parameters.
This chapter includes the following sections:
Information About Domain Parameters, page 29
•
Information About Domain Parameters
The Fibre Channel domain (fcdomain) feature performs principal switch selection, domain ID distribution,
FC ID allocation, and fabric reconfiguration functions as described in the FC-SW-2 standards. The domains
are configured on a per-VSAN basis. If you do not configure a domain ID, the local switch uses a random
ID.
Caution
Changes to fcdomain parameters should not be performed on a daily basis. These changes should be made
by an administrator or individual who is completely familiar with switch operations.
When you change the configuration, be sure to save the running configuration. The next time you reboot the
switch, the saved configuration is used. If you do not save the configuration, the previously saved startup
configuration is used.
Fibre Channel Domains
The fcdomain has four phases:
• Principal switch selection—This phase guarantees the selection of a unique principal switch across the
fabric.
• Domain ID distribution—This phase guarantees that each switch in the fabric obtains a unique domain
ID.
• FC ID allocation—This phase guarantees a unique FC ID assignment to each device attached to the
corresponding switch in the fabric.
• Fabric reconfiguration—This phase guarantees a resynchronization of all switches in the fabric to ensure
they simultaneously restart a new principal switch selection phase.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 29
Page 54

Fibre Channel Domains
The following figure shows an example fcdomain configuration.
Figure 2: Sample fcdomain Configuration
Configuring Fibre Channel Domain Parameters
Domain Restarts
Fibre Channel domains can be started disruptively or nondisruptively. If you perform a disruptive restart,
reconfigure fabric (RCF) frames are sent to other switches in the fabric and data traffic is disrupted on all the
switches in the VSAN (including remotely segmented ISLs). If you perform a nondisruptive restart, build
fabric (BF) frames are sent to other switches in the fabric and data traffic is disrupted only on the switch.
If you are attempting to resolve a domain ID conflict, you must manually assign domain IDs. A disruptive
restart is required to apply most configuration changes, including manually assigned domain IDs. Nondisruptive
domain restarts are acceptable only when changing a preferred domain ID into a static one (and the actual
domain ID remains the same).
Note
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
30 OL-30895-01
A static domain is specifically configured by the user and may be different from the runtime domain. If
the domain IDs are different, the runtime domain ID changes to take on the static domain ID after the next
restart, either disruptive or nondisruptive.
If a VSAN is in interop mode, you cannot disruptively restart the fcdomain for that VSAN.
Page 55

Configuring Fibre Channel Domain Parameters
You can apply most of the configurations to their corresponding runtime values. Each of the following sections
provide further details on how the fcdomain parameters are applied to the runtime values.
The fcdomain restart command applies your changes to the runtime settings. Use the disruptive option to
apply most of the configurations to their corresponding runtime values, including preferred domain IDs.
Restarting a Domain
You can restart the fabric disruptively or nondisruptively.
Procedure
Fibre Channel Domains
PurposeCommand or Action
Step 1
Example:
switch# configure terminal
switch(config)#
Step 2
Step 3
fcdomain restart vsan vsan-id
Example:
switch (config)# fcdomain restart vsan 100
switch(config)# fcdomain restart disruptive vsan
vsan-id
Example:
switch (config)# fcdomain restart
disruptive vsan 101
Domain Manager Fast Restart
When a principal link fails, the domain manager must select a new principal link. By default, the domain
manager starts a build fabric (BF) phase, followed by a principal switch selection phase. Both of these phases
involve all the switches in the VSAN, and together take at least 15 seconds to complete. To reduce the time
required for the domain manager to select a new principal link, you can enable the domain manager fast restart
feature.
When fast restart is enabled and a backup link is available, the domain manager needs only a few milliseconds
to select a new principal link to replace the one that failed. Also, the reconfiguration required to select the
new principal link only affects the two switches that are directly attached to the failed link, not the entire
VSAN. When a backup link is not available, the domain manager reverts to the default behavior and starts a
BF phase, followed by a principal switch selection phase. The fast restart feature can be used in any
interoperability mode.
Enters global configuration mode.configure terminal
Forces the VSAN to reconfigure without
traffic disruption. The VSAN ID ranges
from 1 to 4093.
Forces the VSAN to reconfigure with data
traffic disruption.
Enabling Domain Manager Fast Restart
You can enable the domain manager fast restart feature.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 31
Page 56

Fibre Channel Domains
Procedure
Configuring Fibre Channel Domain Parameters
PurposeCommand or Action
Step 1
Step 2
Step 3
Switch Priority
By default, the configured priority is 128. The valid range to set the priority is between 1 and 254. Priority 1
has the highest priority. Value 255 is accepted from other switches, but cannot be locally configured.
Any new switch cannot become the principal switch when it joins a stable fabric. During the principal switch
selection phase, the switch with the highest priority becomes the principal switch. If two switches have the
same configured priority, the switch with the lower world-wide name (WWN) becomes the principal switch.
The priority configuration is applied to runtime when the fcdomain is restarted. This configuration is applicable
to both disruptive and nondisruptive restarts.
Example:
switch# configure terminal
switch(config)#
fcdomain optimize fast-restart vsan vsan-id
Example:
switch(config)# fcdomain optimize
fast-restart vsan 1
no fcdomain optimize fast-restart vsan vsan-id
Example:
switch(config)# no fcdomain optimize
fast-restart vsan 1
Enters global configuration mode.configure terminal
Enables domain manager fast restart in the
specified VSAN. The VSAN ID range is from
1 to 4093.
Disables (default) domain manager fast restart
in the specified VSAN. The VSAN ID range
is from 1 to 4093.
Configuring Switch Priority
You can configure the priority for the principal switch.
Procedure
PurposeCommand or Action
Step 1
Example:
switch# configure terminal
switch(config)#
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
32 OL-30895-01
Enters global configuration mode.configure terminal
Page 57

Configuring Fibre Channel Domain Parameters
Fibre Channel Domains
PurposeCommand or Action
Step 2
Step 3
fcdomain priority number vsan vsan-id
Example:
switch(config)# fcdomain priority 12
vsan 1
no fcdomain priority number vsan
vsan-id
Example:
switch(config)# no fcdomain priority
12 vsan 1
About fcdomain Initiation
By default, the fcdomain feature is enabled on each switch. If you disable the fcdomain feature in a switch,
that switch can no longer participate with other switches in the fabric. The fcdomain configuration is applied
to runtime through a disruptive restart.
Disabling or Reenabling fcdomains
To disable or reenable fcdomains in a single VSAN or a range of VSANs, perform this task:
Configures the specified priority for the local switch
in the specified VSAN. The fcdomain priority
ranges from 1 to 254. The VSAN ID ranges from 1
to 4093.
Reverts the priority to the factory default (128) in
the specified VSAN. The fcdomain priority ranges
from 1 to 254. The VSAN ID ranges from 1 to 4093.
Procedure
Step 1
Step 2
Step 3
Configuring Fabric Names
You can set the fabric name value for a disabled fcdomain.
switch(config)# no fcdomain vsan vsan-id
- vsan-id
switch(config)# fcdomain vsan vsan-id
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Disables the fcdomain configuration in the
specified VSAN range.
Enables the fcdomain configuration in the
specified VSAN.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 33
Page 58

Fibre Channel Domains
Procedure
Configuring Fibre Channel Domain Parameters
PurposeCommand or Action
Step 1
Step 2
Step 3
Incoming RCFs
You can configure the rcf-reject option on a per-interface, per-VSAN basis. By default, the rcf-reject option
is disabled (that is, RCF request frames are not automatically rejected).
The rcf-reject option takes effect immediately.
No fcdomain restart is required.
Example:
switch# configure terminal
switch(config)#
fcdomain fabric-name 20:1:ac:16:5e:0:21:01
vsan vsan-id
Example:
switch(config)# fcdomain fabric-name
20:1:ac:16:5e:0:21:01 vsan 1
no fcdomain fabric-name 20:1:ac:16:5e:0:21:01
vsan vsan-id
Example:
switch(config)# no fcdomain fabric-name
20:1:ac:16:5e:0:21:01 vsan 1
Enters global configuration mode.configure terminal
Assigns the configured fabric name value in
the specified VSAN. The VSAN ID ranges
from 1 to 4093.
Changes the fabric name value to the factory
default (20:01:00:05:30:00:28:df) in VSAN
3010. The VSAN ID ranges from 1 to 4093.
You do not need to configure the RCF reject option on virtual Fibre Channel interfaces.Note
Rejecting Incoming RCFs
You can reject incoming RCF request frames.
Procedure
PurposeCommand or Action
Step 1
Example:
switch# configure terminal
switch(config)#
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
34 OL-30895-01
Enters global configuration mode.configure terminal
Page 59

Configuring Fibre Channel Domain Parameters
Fibre Channel Domains
PurposeCommand or Action
Step 2
Step 3
fcdomain rcf-reject vsan vsan-id
Example:
switch(config-if)# fcdomain rcf-reject
vsan 10
no fcdomain rcf-reject vsan vsan-id
Example:
switch(config-if)# no fcdomain
rcf-reject vsan 10
Autoreconfiguring Merged Fabrics
By default, the autoreconfigure option is disabled. When you join two switches belonging to two different
stable fabrics that have overlapping domains, the following situations can occur:
If the autoreconfigure option is enabled on both switches, a disruptive reconfiguration phase is started.
•
If the autoreconfigure option is disabled on either or both switches, the links between the two switches
•
become isolated.
The autoreconfigure option takes immediate effect at runtime. You do not need to restart the fcdomain. If a
domain is currently isolated due to domain overlap, and you later enable the autoreconfigure option on both
switches, the fabric continues to be isolated. If you enabled the autoreconfigure option on both switches before
connecting the fabric, a disruptive reconfiguration (RCF) will occur. A disruptive reconfiguration can affect
data traffic. You can nondisruptively reconfigure the fcdomain by changing the configured domains on the
overlapping links and eliminating the domain overlap.
Enables the RCF filter on the specified interface
in the specified VSAN. The VSAN ID ranges
from 1 to 4093.
Disables (default) the RCF filter on the specified
interface in the specified VSAN. The VSAN ID
ranges from 1 to 4093.
Enabling Autoreconfiguration
You can enable automatic reconfiguration in a specific VSAN (or range of VSANs).
Procedure
PurposeCommand or Action
Step 1
Example:
switch# configure terminal
switch(config)#
Step 2
OL-30895-01 35
fcdomain auto-reconfigure vsan vsan-id
Example:
switch(config)# fcdomain
auto-reconfigure vsan 1
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
Enters global configuration mode.configure terminal
Enables the automatic reconfiguration option in
the specified VSAN. The VSAN ID ranges from
1 to 4093.
Page 60

Domain IDs
Configuring Fibre Channel Domain Parameters
PurposeCommand or Action
Step 3
Domain IDs
Domain IDs uniquely identify a switch in a VSAN. A switch may have different domain IDs in different
VSANs. The domain ID is part of the overall FC ID.
Domain IDs - Guidelines
The configured domain ID can be preferred or static. By default, the configured domain ID is 0 (zero) and
the configured type is preferred.
The 0 (zero) value can be configured only if you use the preferred option.Note
If you do not configure a domain ID, the local switch sends a random ID in its request. We recommend that
you use static domain IDs.
When a subordinate switch requests a domain, the following process takes place (see the figure below):
no fcdomain auto-reconfigure vsan vsan-id
Example:
switch(config)# no fcdomain
auto-reconfigure vsan 1
Disables the automatic reconfiguration option
and reverts it to the factory default in the
specified VSAN. The VSAN ID ranges from 1
to 4093.
The local switch sends a configured domain ID request to the principal switch.
•
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
36 OL-30895-01
Page 61

Configuring Fibre Channel Domain Parameters
The principal switch assigns the requested domain ID if available. Otherwise, it assigns another available
•
domain ID.
Figure 3: Configuration Process Using the Preferred Option
Domain IDs
The operation of a subordinate switch changes based on three factors:
The allowed domain ID lists
•
The configured domain ID
•
The domain ID that the principal switch has assigned to the requesting switch
•
In specific situations, the changes are as follows:
When the received domain ID is not within the allowed list, the requested domain ID becomes the
•
runtime domain ID and all interfaces on that VSAN are isolated.
When the assigned and requested domain IDs are the same, the preferred and static options are not
•
relevant, and the assigned domain ID becomes the runtime domain ID.
When the assigned and requested domain IDs are different, the following cases apply:
•
If the configured type is static, the assigned domain ID is discarded, all local interfaces are isolated,
◦
and the local switch assigns itself the configured domain ID, which becomes the runtime domain
ID.
If the configured type is preferred, the local switch accepts the domain ID assigned by the principal
◦
switch and the assigned domain ID becomes the runtime domain ID.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 37
Page 62

Domain IDs
Configuring Fibre Channel Domain Parameters
If you change the configured domain ID, the change is only accepted if the new domain ID is included in all
the allowed domain ID lists currently configured in the VSAN. Alternatively, you can also configure
zero-preferred domain ID.
Caution
You must enter the fcdomain restart command if you want to apply the configured domain changes to the
runtime domain.
Note
If you have configured an allow domain ID list, the domain IDs that you add must be in that range for the
VSAN.
Related Topics
Allowed Domain ID Lists, on page 39
Configuring Static or Preferred Domain IDs
You can specify a static or preferred domain ID.
Procedure
Step 1
Example:
switch# configure terminal
switch(config)#
Step 2
Step 3
Step 4
fcdomain domain domain-id static vsan
vsan-id
Example:
switch(config)# fcdomain domain 1
static vsan 3
no fcdomain domain domain-id static
vsan vsan-id
Example:
switch(config)# no fcdomain domain 1
static vsan 3
fcdomain domain domain-id preferred
vsan vsan-id
Example:
switch(config)# fcdomain domain 1
preferred vsan 5
PurposeCommand or Action
Enters global configuration mode.configure terminal
Configures the switch in the specified VSAN to accept
only a specific value and moves the local interfaces
in the specified VSAN to an isolated state if the
requested domain ID is not granted. The domain ID
range is 1 to 239. The VSAN ID range is 1 to 4093.
Resets the configured domain ID to factory defaults
in the specified VSAN. The configured domain ID
becomes 0 preferred.
Configures the switch in the specified VSAN to
request a preferred domain ID 3 and accepts any value
assigned by the principal switch. The domain ID range
is 1 to 239. The VSAN ID range is 1 to 4093.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
38 OL-30895-01
Page 63

Configuring Fibre Channel Domain Parameters
Domain IDs
PurposeCommand or Action
Step 5
no fcdomain domain domain-id
preferred vsan vsan-id
Example:
switch(config)# no fcdomain domain 1
preferred vsan 5
Allowed Domain ID Lists
By default, the valid range for an assigned domain ID list is from 1 to 239. You can specify a list of ranges
to be in the allowed domain ID list and separate each range with a comma. The principal switch assigns domain
IDs that are available in the locally configured allowed domain list.
Use allowed domain ID lists to design your VSANs with nonoverlapping domain IDs. This helps you in the
future if you need to implement IVR without the NAT feature.
If you configure an allowed list on one switch in the fabric, we recommend that you configure the same list
in all other switches in the fabric to ensure consistency or use CFS to distribute the configuration.
Configuring Allowed Domain ID Lists
You can configure the allowed domain ID list.
Resets the configured domain ID to 0 (default) in the
specified VSAN. The configured domain ID becomes
0 preferred.
Procedure
Step 1
Step 2
Step 3
Example:
switch# configure terminal
switch(config)#
fcdomain allowed domain-id range vsan
vsan-id
Example:
switch(config)# fcdomain allowed 3 vsan
10
no fcdomain allowed domain-id range vsan
vsan-id
Example:
switch(config)# no fcdomain allowed 3
vsan 10
PurposeCommand or Action
Enters global configuration mode.configure terminal
Configures the list to allow switches with the
domain ID range in the specified VSAN. The
domain ID range is from 1 to 239. The VSAN
ID range is from 1 to 4093.
Reverts to the factory default of allowing domain
IDs from 1 through 239 in the specified VSAN.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 39
Page 64

Domain IDs
CFS Distribution of Allowed Domain ID Lists
You can enable the distribution of the allowed domain ID list configuration information to all Cisco SAN
switches in the fabric using the Cisco Fabric Services (CFS) infrastructure. This feature allows you to
synchronize the configuration across the fabric from the console of a single switch. Because the same
configuration is distributed to the entire VSAN, you can avoid a possible misconfiguration and the possibility
that two switches in the same VSAN have configured incompatible allowed domains.
Use CFS to distribute the allowed domain ID list to ensure consistency in the allowed domain ID lists on all
switches in the VSAN.
We recommend configuring the allowed domain ID list and committing it on the principal switch.Note
For additional information, refer to Using Cisco Fabric Services in the System Management Configuration
Guide for your device.
Configuring Fibre Channel Domain Parameters
Enabling Distribution
You can enable (or disable) allowed domain ID list configuration distribution.
CFS distribution of allowed domain ID lists is disabled by default. You must enable distribution on all switches
to which you want to distribute the allowed domain ID lists.
Procedure
Step 1
Step 2
Step 3
Example:
switch# configure terminal
switch(config)#
fcdomain distribute
Example:
switch(config)# fcdomain distribute
no fcdomain distribute
Example:
switch(config)# no fcdomain distribute
PurposeCommand or Action
Enters global configuration mode.configure terminal
Enables domain configuration
distribution.
Disables (default) domain configuration
distribution.
Locking the Fabric
The first action that modifies the existing configuration creates the pending configuration and locks the feature
in the fabric. After you lock the fabric, the following conditions apply:
No other user can make any configuration changes to this feature.
•
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
40 OL-30895-01
Page 65

Configuring Fibre Channel Domain Parameters
A pending configuration is created by copying the active configuration. Subsequent modifications are
•
made to the pending configuration and remain there until you commit the changes to the active
configuration (and other switches in the fabric) or discard them.
Committing Changes
You can commit pending domain configuration changes and release the lock.
To apply the pending domain configuration changes to other SAN switches in the VSAN, you must commit
the changes. The pending configuration changes are distributed and, on a successful commit, the configuration
changes are applied to the active configuration in the SAN switches throughout the VSAN and the fabric lock
is released.
Procedure
Domain IDs
PurposeCommand or Action
Step 1
Step 2
Discarding Changes
You can discard pending domain configuration changes and release the lock.
At any time, you can discard the pending changes to the domain configuration and release the fabric lock. If
you discard (abort) the pending changes, the configuration remains unaffected and the lock is released.
Procedure
Step 1
Example:
switch# configure terminal
switch(config)#
fcdomain commit vsan vsan-id
Example:
switch(config)# fcdomain commit vsan 45
Enters global configuration mode.configure terminal
Commits the pending domain
configuration changes.
PurposeCommand or Action
Enters global configuration mode.configure terminal
Example:
switch# configure terminal
switch(config)#
Step 2
fcdomain abort vsan vsan-id
Discards the pending domain
configuration changes.
Example:
switch(config)# fcdomain abort vsan 30
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 41
Page 66

Domain IDs
Clearing a Fabric Lock
If you have performed a domain configuration task and have not released the lock by either committing or
discarding the changes, an administrator can release the lock from any switch in the fabric. If the administrator
performs this task, your pending changes are discarded and the fabric lock is released.
The pending changes are only available in the volatile directory and are discarded if the switch is restarted.
To release a fabric lock, enter the clear fcdomain session vsan command in EXEC mode using a login ID
that has administrative privileges:
switch# clear fcdomain session vsan 10
Displaying CFS Distribution Status
You can display the status of CFS distribution for allowed domain ID lists by using the show fcdomain status
command:
switch# show fcdomain status
CFS distribution is enabled
Configuring Fibre Channel Domain Parameters
Displaying Pending Changes
You can display the pending configuration changes by using the show fcdomain pending command:
switch# show fcdomain pending vsan 10
Pending Configured Allowed Domains
---------------------------------VSAN 10
Assigned or unallowed domain IDs: 1-9,24,100,231-239.
[User] configured allowed domain IDs: 10-230.
You can display the differences between the pending configuration and the current configuration by using
the show fcdomain pending-diff command:
switch# show fcdomain pending-diff vsan 10
Current Configured Allowed Domains
---------------------------------VSAN 10
Assigned or unallowed domain IDs: 24,100.
[User] configured allowed domain IDs: 1-239.
Pending Configured Allowed Domains
---------------------------------VSAN 10
Assigned or unallowed domain IDs: 1-9,24,100,231-239.
[User] configured allowed domain IDs: 10-230.
Displaying Session Status
You can display the status of the distribution session by using the show fcdomain session-status vsan
command:
switch# show fcdomain session-status vsan 1
Last Action: Distribution Enable
Result: Success
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
42 OL-30895-01
Page 67

Configuring Fibre Channel Domain Parameters
Contiguous Domain ID Assignments
By default, the contiguous domain assignment is disabled. When a subordinate switch requests the principal
switch for two or more domains and the domains are not contiguous, the following situations can occur:
If the contiguous domain assignment is enabled in the principal switch, the principal switch locates
•
contiguous domains and assigns them to the subordinate switches. If contiguous domains are not available,
the switch software rejects this request.
If the contiguous domain assignment is disabled in the principal switch, the principal switch assigns the
•
available domains to the subordinate switch.
Enabling Contiguous Domain ID Assignments
You can enable contiguous domains in a specific VSAN (or a range of VSANs).
Procedure
FC IDs
FC IDs
Step 1
Step 2
Step 3
Example:
switch# configure terminal
switch(config)#
fcdomain contiguous-allocation vsan vsan-id
- vsan-id
Example:
switch(config)# fcdomain
contiguous-allocation vsan 22-30
no fcdomain contiguous-allocation vsan
vsan-id
Example:
switch(config)# no fcdomain
contiguous-allocation vsan 7
PurposeCommand or Action
Enters global configuration mode.configure terminal
Enables the contiguous allocation option in the
specified VSAN range.
Note
The contiguous-allocation option takes
immediate effect at runtime. You do not
need to restart the fcdomain.
Disables the contiguous allocation option and
reverts it to the factory default in the specified
VSAN.
When an N port logs into a SAN switch, it is assigned an FC ID. By default, the persistent FC ID feature is
enabled. If this feature is disabled, the following situations can occur:
An N port logs into a SAN switch. The WWN of the requesting N port and the assigned FC ID are
•
retained and stored in a volatile cache. The contents of this volatile cache are not saved across reboots.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 43
Page 68

FC IDs
•
•
•
Persistent FC IDs
When persistent FC IDs are enabled, the following occurs:
•
•
Configuring Fibre Channel Domain Parameters
The switch is designed to preserve the binding FC ID to the WWN on a best-effort basis. For example,
if one N port disconnects from the switch and its FC ID is requested by another device, this request is
granted and the WWN with the initial FC ID association is released.
The volatile cache stores up to 4000 entries of WWN to FC ID binding. If this cache is full, a new (more
recent) entry overwrites the oldest entry in the cache. In this case, the corresponding WWN to FC ID
association for the oldest entry is lost.
N ports receive the same FC IDs if disconnected and reconnected to any port within the same switch (as
long as it belongs to the same VSAN).
The current FC IDs in use in the fcdomain are saved across reboots.
The fcdomain automatically populates the database with dynamic entries that the switch has learned
about after a device (host or disk) is plugged into a port interface.
Note
If you connect to the switch from an AIX or HP-UX host, be sure to enable the persistent FC ID feature
in the VSAN that connects these hosts.
Note
When persistent FC IDs are enabled, FC IDs cannot be changed after a reboot. FC IDs are enabled by
default, but can be disabled for each VSAN.
A persistent FC ID assigned to an F port can be moved across interfaces and can continue to maintain the
same persistent FC ID.
Enabling the Persistent FC ID Feature
You can enable the persistent FC ID feature.
Procedure
Step 1
Example:
switch# configure terminal
switch(config)#
Step 2
fcdomain fcid persistent vsan vsan-id
Example:
switch(config)# fcdomain fcid persistent
vsan 78
PurposeCommand or Action
Enters global configuration mode.configure terminal
Activates (default) persistency of FC IDs
in the specified VSAN.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
44 OL-30895-01
Page 69

Configuring Fibre Channel Domain Parameters
FC IDs
PurposeCommand or Action
Step 3
no fcdomain fcid persistent vsan vsan-id
Example:
switch(config)# no fcdomain fcid persistent
vsan 33
Persistent FC ID Configuration Guidelines
When the persistent FC ID feature is enabled, you can enter the persistent FC ID submode and add static or
dynamic entries in the FC ID database. By default, all added entries are static. Persistent FC IDs are configured
on a per-VSAN basis.
When manually configuring a persistent FC ID, follow these requirements:
Ensure that the persistent FC ID feature is enabled in the required VSAN.
•
Ensure that the required VSAN is an active VSAN. Persistent FC IDs can only be configured on active
•
VSANs.
Verify that the domain part of the FC ID is the same as the runtime domain ID in the required VSAN.
•
If the software detects a domain mismatch, the command is rejected.
Verify that the port field of the FC ID is 0 (zero) when configuring an area.
•
Disables the FC ID persistency feature in
the specified VSAN.
Configuring Persistent FC IDs
You can configure persistent FC IDs.
Procedure
Step 1
Example:
switch# configure terminal
switch(config)#
Step 2
Example:
switch(config)# fcdomain fcid database
Step 3
vsan vsan-id wwn 33:e8:00:05:30:00:16:df
fcid fcid
Example:
switch(config-fcid-db)# vsan 26 wwn
33:e8:00:05:30:00:16:df fcid 4
PurposeCommand or Action
Enters global configuration mode.configure terminal
Enters FC ID database configuration submode.fcdomain fcid database
Configures a device WWN
(33:e8:00:05:30:00:16:df) with the FC ID 0x070128
in the specified VSAN.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 45
Page 70

FC IDs
PurposeCommand or Action
Note
Configuring Fibre Channel Domain Parameters
To avoid assigning a duplicate FC ID, use
the show fcdomain address-allocation
vsan command to display the FC IDs in
use.
Step 4
vsan vsan-id wwn 11:22:11:22:33:44:33:44
fcid fcid dynamic
Example:
switch(config-fcid-db)# vsan 13 wwn
11:22:11:22:33:44:33:44 fcid 6 dynamic
Step 5
vsan vsan-id wwn 11:22:11:22:33:44:33:44
fcid fcid area
Example:
switch(config-fcid-db)# vsan 88 wwn
11:22:11:22:33:44:33:44 fcid 4 area
Unique Area FC IDs for HBAs
Note
Read this section only if the Host Bus Adapter (HBA) port and the storage port are connected to the same
switch.
Some HBA ports require a different area ID than for the storage ports when they are both connected to the
same switch. For example, if the storage port FC ID is 0x6f7704, the area for this port is 77. In this case, the
HBA port’s area can be anything other than 77. The HBA port’s FC ID must be manually configured to be
different from the storage port’s FC ID.
Cisco SAN switches facilitate this requirement with the FC ID persistence feature. You can use this feature
to preassign an FC ID with a different area to either the storage port or the HBA port.
Configures a device WWN
(11:22:11:22:33:44:33:44) with the FC ID
0x070123 in the specified VSAN in dynamic mode.
Configures a device WWN
(11:22:11:22:33:44:33:44) with the FC IDs
0x070100 through 0x701FF in the specified VSAN.
Note
To secure the entire area for this fcdomain,
assign 00 as the last two characters of the
FC ID.
Configuring Unique Area FC IDs for an HBA
You can configure a different area ID for the HBA port.
The following task uses an example configuration with a switch domain of 111(6f hex). The server connects
to the switch over FCoE. The HBA port connects to interface vfc20 and the storage port connects to interface
fc2/3 on the same switch.
Procedure
Step 1
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
46 OL-30895-01
Obtain the port WWN (Port Name field) ID of the HBA using the show flogi database command.
switch# show flogi database
Page 71

Configuring Fibre Channel Domain Parameters
-----------------------------------------------------------------
INTERFACE VSAN FCID PORT NAME NODE NAME
------------------------------------------------------------------
vfc20 3 0x6f7703 50:05:08:b2:00:71:c8:c2 50:05:08:b2:00:71:c8:c0
fc2/3 3 0x6f7704 50:06:0e:80:03:29:61:0f 50:06:0e:80:03:29:61:0f
Note
Both FC IDs in this setup have the same area 77
assignment.
Step 2
Step 3
Shut down the HBA interface in the SAN switch.
switch# configure terminal
switch(config)# interface vfc 20
switch(config-if)# shutdown
switch(config-if)# end
Verify that the FC ID feature is enabled using the show fcdomain vsan command.
switch# show fcdomain vsan 1
...
Local switch configuration information:
State: Enabled
FCID persistence: Disabled
If this feature is disabled, continue to the next step to enable the persistent FC ID.
If this feature is already enabled, skip to the following step.
FC IDs
Step 4
Step 5
Step 6
Step 7
Enable the persistent FC ID feature in the SAN switch.
switch# configure terminal
switch(config)# fcdomain fcid persistent vsan 1
switch(config)# end
Assign a new FC ID with a different area allocation. In this example, replace 77 with ee.
switch# configure terminal
switch(config)# fcdomain fcid database
switch(config-fcid-db)# vsan 3 wwn 50:05:08:b2:00:71:c8:c2
fcid 0x6fee00 area
Enable the HBA interface in the SAN switch.
switch# configure terminal
switch(config)# interface vfc 20
switch(config-if)# no shutdown
switch(config-if)# end
Verify the pWWN ID of the HBA by using the show flogi database command.
switch# show flogi database
------------------------------------------------------------------
INTERFACE VSAN FCID PORT NAME NODE NAME
------------------------------------------------------------------
vfc20 3 0x6fee00 50:05:08:b2:00:71:c8:c2 50:05:08:b2:00:71:c8:c0
fc2/3 3 0x6f7704 50:06:0e:80:03:29:61:0f 50:06:0e:80:03:29:61:0f
Note
Both FC IDs now have different area
assignments.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 47
Page 72

Verifying the fcdomain Configuration
Persistent FC ID Selective Purging
Persistent FC IDs can be purged selectively. Static entries and FC IDs currently in use cannot be deleted. The
table below identifies the FC ID entries that are deleted or retained when persistent FC IDs are purged.
Table 7: Purged FC IDs
Configuring Fibre Channel Domain Parameters
ActionPersistent Usage StatePersistent FC ID state
Not deletedIn useStatic
Not deletedNot in useStatic
Not deletedIn useDynamic
DeletedNot in useDynamic
Purging Persistent FC IDs
You can purge persistent FC IDs.
Procedure
Step 1
Step 2
purge fcdomain fcid vsan vsan-id
Example:
switch# purge fcdomain fcid vsan 667
purge fcdomain fcid vsan vsan-id - vsan-id
Example:
switch# purge fcdomain fcid vsan 50-100
Verifying the fcdomain Configuration
Note
If the fcdomain feature is disabled, the runtime fabric name in the display is the same as the configured
fabric name.
PurposeCommand or Action
Purges all dynamic and unused FC IDs in
the specified VSAN.
Purges dynamic and unused FC IDs in the
specified VSAN range.
This example shows how to display information about fcdomain configurations:
switch# show fcdomain vsan 2
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
48 OL-30895-01
Page 73

Configuring Fibre Channel Domain Parameters
Use the show fcdomain domain-list command to display the list of domain IDs of all switches belonging to
a specified VSAN. This list provides the WWN of the switches owning each domain ID. The next example
uses the following values:
A switch with WWN of 20:01:00:05:30:00:47:df is the principal switch and has domain 200.
•
A switch with WWN of 20:01:00:0d:ec:08:60:c1 is the local switch (the one where you typed the CLI
•
command to show the domain-list) and has domain 99.
The IVR manager obtained virtual domain 97 using 20:01:00:05:30:00:47:df as the WWN for a virtual
•
switch.
switch# show fcdomain domain-list vsan 76
Number of domains: 3
Domain ID WWN
--------- ----------------------0xc8(200) 20:01:00:05:30:00:47:df [Principal]
0x63(99) 20:01:00:0d:ec:08:60:c1 [Local]
0x61(97) 50:00:53:0f:ff:f0:10:06 [Virtual (IVR)]
Use the show fcdomain allowed vsan command to display the list of allowed domain IDs configured on this
switch..
switch# show fcdomain allowed vsan 1
Assigned or unallowed domain IDs: 1-96,100,111-239.
[Interoperability Mode 1] allowed domain IDs: 97-127.
[User] configured allowed domain IDs: 50-110.
Ensure that the requested domain ID passes the switch software checks, if interop 1 mode is required in this
switch.
The following example shows how to display all existing, persistent FC IDs for a specified VSAN. You can
also specify the unused option to view only persistent FC IDs that are still not in use.
switch# show fcdomain fcid persistent vsan 1000
The following example shows how to display frame and other fcdomain statistics for a specified VSAN or
SAN port channel:
switch# show fcdomain statistics vsan 1
VSAN Statistics
Number of Principal Switch Selections: 5
Number of times Local Switch was Principal: 0
Number of 'Build Fabric's: 3
Number of 'Fabric Reconfigurations': 0
The following example shows how to display FC ID allocation statistics including a list of assigned and free
FC IDs:
switch# show fcdomain address-allocation vsan 1
The following example shows how to display the valid address allocation cache. The cache is used by the
principal switch to reassign the FC IDs for a device (disk or host) that exited and reentered the fabric. In the
cache content, VSAN refers to the VSAN that contains the device, WWN refers to the device that owned the
FC IDs, and mask refers to a single or entire area of FC IDs.
switch# show fcdomain address-allocation cache
Default Settings for Fibre Channel Domains
Default Settings for Fibre Channel Domains
The following table lists the default settings for all fcdomain parameters.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 49
Page 74

Default Settings for Fibre Channel Domains
Table 8: Default fcdomain Parameters
Configuring Fibre Channel Domain Parameters
DefaultParameters
Enabledfcdomain feature
0 (zero)Configured domain ID
PreferredConfigured domain
Disabledauto-reconfigure option
Disabledcontiguous-allocation option
128Priority
1 to 239Allowed list
20:01:00:05:30:00:28:dfFabric name
Disabledrcf-reject
EnabledPersistent FC ID
DisabledAllowed domain ID list configuration distribution
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
50 OL-30895-01
Page 75

Configuring N Port Virtualization
This chapter contains the following sections:
Configuring N Port Virtualization, page 51
•
Configuring N Port Virtualization
Information About NPV
NPV Overview
By default, Cisco Nexus devices switches operate in fabric mode. In this mode, the switch provides standard
Fibre Channel switching capability and features.
In fabric mode, each switch that joins a SAN is assigned a domain ID. Each SAN (or VSAN) supports a
maximum of 239 domain IDs, so the SAN has a limit of 239 switches. In a SAN topology with a large number
of edge switches, the SAN may need to grow beyond this limit. NPV alleviates the domain ID limit by sharing
the domain ID of the core switch among multiple edge switches.
In NPV mode, the edge switch relays all traffic from server-side ports to the core switch. The core switch
provides F port functionality (such as login and port security) and all the Fibre Channel switching capabilities.
The edge switch appears as a Fibre Channel host to the core switch and as a regular Fibre Channel switch to
its connected devices.
CHAPTER 4
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 51
Page 76

Information About NPV
NPV Mode
Configuring N Port Virtualization
The following figure shows an interface-level view of an NPV configuration.
Figure 4: NPV Interface Configuration
In NPV mode, the edge switch relays all traffic to the core switch, which provides the Fibre Channel switching
capabilities. The edge switch shares the domain ID of the core switch.
To convert a switch into NPV mode, you set the NPV feature to enabled. This configuration command
automatically triggers a switch reboot. You cannot configure NPV mode on a per-interface basis. NPV mode
applies to the entire switch.
In NPV mode, a subset of fabric mode CLI commands and functionality is supported. For example, commands
related to fabric login and name server registration are not required on the edge switch, because these functions
are provided in the core switch. To display the fabric login and name server registration databases, you must
enter the show flogi database and show fcns database commands on the core switch.
Server Interfaces
Server interfaces are F ports on the edge switch that connect to the servers. A server interface may support
multiple end devices by enabling the N port identifier virtualization (NPIV) feature. NPIV provides a means
to assign multiple FC IDs to a single N port, which allows the server to assign unique FC IDs to different
applications.
Note
To use NPIV, enable the NPIV feature and reinitialize the server interfaces that will support multiple
devices.
As the NPIV box has multiple FLOGIs from the NPV box, the disable-feature command is rejected.Note
Server interfaces are automatically distributed among the NP uplinks to the core switch. All of the end devices
connected to a server interface are mapped to the same NP uplink.
In Cisco Nexus devices, server interfaces can be physical or virtual Fibre Channel interfaces.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
52 OL-30895-01
Page 77

Configuring N Port Virtualization
Related Topics
Configuring N Port Virtualization, on page 51
NP Uplinks
All interfaces from the edge switch to the core switch are configured as proxy N ports (NP ports).
An NP uplink is a connection from an NP port on the edge switch to an F port on the core switch. When an
NP uplink is established, the edge switch sends a fabric login message (FLOGI) to the core switch, and then
(if the FLOGI is successful) it registers itself with the name server on the core switch. Subsequent FLOGIs
from end devices connected to this NP uplink are converted to fabric discovery messages (FDISCs).
In the switch CLI configuration commands and output displays, NP uplinks are called External Interfaces.Note
In Cisco Nexus devices, NP uplink interfaces must be native Fibre Channel interfaces.
Related Topics
Fabric Login, on page 187
Information About NPV
FLOGI Operation
When an NP port becomes operational, the switch first logs itself in to the core switch by sending a FLOGI
request (using the port WWN of the NP port).
After completing the FLOGI request, the switch registers itself with the fabric name server on the core switch
(using the symbolic port name of the NP port and the IP address of the edge switch).
The following table identifies port and node names in the edge switch used in NPV mode.
Table 9: Edge Switch FLOGI Parameters
symbolic port name
Derived FromParameter
The fWWN of the NP port on the edge switch.pWWN
The VSAN-based sWWN of the edge switch.nWWN
The edge switch name and NP port interface string.
Note
If no switch name is available, the output
will read "switch." For example, switch: fc
1/5.
The IP address of the edge switch.IP address
The edge switch name.symbolic node name
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 53
Page 78

Information About NPV
Configuring N Port Virtualization
Note
The buffer-to-buffer state change number (BB-SCN) of internal FLOGIs on an NP port is always set to
zero. The BB_SCN is supported by the F port on the edge switch.
We do not recommend using fWWN-based zoning on the edge switch for the following reasons:
Zoning is not enforced at the edge switch (rather, it is enforced on the core switch).
•
Multiple devices attached to an edge switch log in through the same F port on the core, so they cannot
•
be separated into different zones.
The same device might log in using different fWWNs on the core switch (depending on the NPV link
•
it uses) and may need to be zoned using different fWWNs.
Related Topics
Information About Zones, on page 127
NPV Traffic Management
Automatic Uplink Selection
NPV supports automatic selection of NP uplinks. When a server interface is brought up, the NP uplink interface
with the minimum load is selected from the available NP uplinks in the same VSAN as the server interface.
When a new NP uplink interface becomes operational, the existing load is not redistributed automatically to
include the newly available uplink. Server interfaces that become operational after the NP uplink can select
the new NP uplink.
Traffic Maps
Note
In Release 4.0(1a)N2(1) and later software releases, NPV supports traffic maps. A traffic map allows you to
specify the NP uplinks that a server interface can use to connect to the core switches.
When an NPV traffic map is configured for a server interface, the server interface must select only from
the NP uplinks in its traffic map. If none of the specified NP uplinks are operational, the server remains
in a non-operational state.
The NPV traffic map feature provides the following benefits:
Facilitates traffic engineering by allowing configuration of a fixed set of NP uplinks for a specific server
•
interface (or range of server interfaces).
Ensures correct operation of the persistent FC ID feature, because a server interface will always connect
•
to the same NP uplink (or one of a specified set of NP uplinks) after an interface reinitialization or switch
reboot.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
54 OL-30895-01
Page 79

Configuring N Port Virtualization
Disruptive Load Balancing
In Release 4.0(0)N1(2a) and later software releases, NPV supports disruptive load balancing. When disruptive
load balancing is enabled, NPV redistributes the server interfaces across all available NP uplinks when a new
NP uplink becomes operational. To move a server interface from one NP uplink to another NP uplink, NPV
forces reinitialization of the server interface so that the server performs a new login to the core switch.
Only server interfaces that are moved to a different uplink are reinitialized. A system message is generated
for each server interface that is moved.
Redistributing a server interface causes traffic disruption to the attached end devices.Note
To avoid disruption of server traffic, you should enable this feature only after adding a new NP uplink, and
then disable it again after the server interfaces have been redistributed.
If disruptive load balancing is not enabled, you can manually reinitialize some or all of the server interfaces
to distribute server traffic to new NP uplink interfaces.
NPV Guidelines and Limitations
NPV Traffic Management Guidelines
When deploying NPV traffic management, follow these guidelines:
Use NPV traffic management only when automatic traffic engineering does not meet your network
•
requirements.
You do not need to configure traffic maps for all server interfaces. By default, NPV will use automatic
•
traffic management.
Server interfaces configured to use a set of NP uplink interfaces cannot use any other available NP uplink
•
interfaces, even if none of the configured interfaces are available.
When disruptive load balancing is enabled, a server interface may be moved from one NP uplink to
•
another NP uplink. Moving between NP uplink interfaces requires NPV to relogin to the core switch,
causing traffic disruption.
To link a set of servers to a specific core switch, associate the server interfaces with a set of NP uplink
•
interfaces that all connect to that core switch.
Configure Persistent FC IDs on the core switch and use the Traffic Map feature to direct server interface
•
traffic onto NP uplinks that all connect to the associated core switch.
NPV Guidelines and Limitations
When configuring NPV, note the following guidelines and limitations:
In-order data delivery is not required in NPV mode because the exchange between two end devices
•
always takes the same uplink from the edge switch to the core. Upstream of the edge switch, core switches
will enforce in-order delivery if configured.
You can configure zoning for end devices that are connected to edge switches using all available member
•
types on the core switch. For fWWN, sWWN, domain, or port-based zoning, use the fWWN, sWWN,
domain, or port of the core switch in the configuration commands.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 55
Page 80

Configuring NPV
Configuring N Port Virtualization
Port tracking is not supported in NPV mode.
•
Port security is supported on the core switch for devices logged in through the NPV switch. Port security
•
is enabled on the core switch on a per-interface basis. To enable port security on the core switch for
devices that log in through an NPV switch, you must adhere to the following requirements:
The internal FLOGI must be in the port security database; in this way, the port on the core switch
◦
will allow communications and links.
All the end device pWWNs must also be in the port security database.
◦
Edge switches can connect to multiple core switches. In other words, different NP ports can be connected
•
to different core switches.
NPV uses a load-balancing algorithm to automatically assign end devices in a VSAN to one of the NP
•
uplinks (in the same VSAN) upon initial login. If there are multiple NP uplinks in the same VSAN, you
cannot assign an end device to a specific NP uplink.
If a server interface goes down and then returns to service, the interface is not guaranteed to be assigned
•
to the same NP uplink.
Configuring NPV
The server interface is only operational when its assigned NP uplink is operational.
•
Servers can be connected to the switch when in NPV mode.
•
When initiators and targets are assigned to the same border port (NP or NP-PO), then Cisco Nexus 5000
•
Series switches in NPIV mode do not support hairpinning.
Fibre Channel switching is not performed in the edge switch; all traffic is switched in the core switch.
•
NPV supports NPIV-capable servers. This capability is called nested NPIV.
•
Connecting two Cisco NPV switches together is not supported.
•
Only F, NP, and SD ports are supported in NPV mode.
•
For an NPV switch which is configured for trunking on any interface, or for a regular switch where the
•
f port-channel-trunk command is issued to enable the Trunking F Port Channels feature, follow these
configuration guidelines for reserved VSANs and isolated VSAN:
If the trunk mode is enabled for any of the interfaces, or if the NP port channel is up, the reserved
•
VSANs range from 3840 to 4078, which are not available for user configuration.
The Exchange Virtual Fabric Protocol (EVFP) isolated VSAN is 4079, and it is not available for
•
user configuration.
Enabling NPV
When you enable NPV, the system configuration is erased and the switch reboots.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
56 OL-30895-01
Page 81

Configuring N Port Virtualization
Configuring NPV
Note
We recommend that you save your current configuration either in boot flash memory or to a TFTP server
before you enable NPV.
To enable NPV, perform this task:
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# npv enable
Enters configuration mode.switch# configure terminal
Enables NPV mode. The switch reboots, and it comes back up
in NPV mode.
Note
When the switch is reloaded in the NPV mode, only
the following configurations are saved:
switchname
•
management ip configuration and vrf
•
boot variable
•
username / password details
•
ntp configuration
•
callhome configuration
•
Step 3
enable
Configuring NPV Interfaces
After you enable NPV, you should configure the NP uplink interfaces and the server interfaces.
Configuring an NP Interface
After you enable NPV, you should configure the NP uplink interfaces and the server interfaces. To configure
an NP uplink interface, perform this task:
To configure a server interface, perform this task:
snmp-server details
•
feature fcoe
•
Disables NPV mode, which results in a reload of the switch.switch(config-npv)# no npv
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 57
Page 82

Configuring NPV
Configuring N Port Virtualization
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Configuring a Server Interface
To configure a server interface, perform this task:
Procedure
Step 1
Step 2
switch(config)# interface fc slot/port
switch(config)# interface fc slot/port
Enters global configuration mode.switch# configure terminal
Selects an interface that will be connected to the
core NPV switch.
Note
If this is a QSFP+ GEM, the slot/port
syntax is slot/QSFP-module/port.
Configures the interface as an NP port.switch(config-if)# switchport mode NP
Brings up the interface.switch(config-if)# no shutdown
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Selects an interface that will be connected to the
core NPV switch.
Note
If this is a QSFP+ GEM, the slot/port
syntax is slot/QSFP-module/port.
Step 3
Step 4
Configures the interface as an F port.switch(config-if)# switchport mode F
Brings up the interface.switch(config-if)# no shutdown
Configuring NPV Traffic Management
Configuring NPV Traffic Maps
An NPV traffic map associates one or more NP uplink interfaces with a server interface. The switch associates
the server interface with one of these NP uplinks.
Note
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
58 OL-30895-01
If a server interface is already mapped to an NP uplink, you should include this mapping in the traffic
map configuration.
Page 83

Configuring N Port Virtualization
To configure a traffic map, perform this task:
Procedure
Verifying NPV
PurposeCommand or Action
Step 1
Step 2
switch(config)# npv traffic-map
server-interface {fc slot/port | vfc vfc-id}
external-interface fc slot/port
Step 3
switch(config)# no npv traffic-map
server-interface {fc slot/port | vfc vfc-id}
external-interface fc slot/port
Enabling Disruptive Load Balancing
If you configure additional NP uplinks, you can enable the disruptive load-balancing feature to distribute the
server traffic load evenly among all the NP uplinks.
To enable disruptive load balancing, perform this task:
Procedure
Enters global configuration mode.switch# configure terminal
Configures a mapping between a server interface (or
range of server interfaces) and an NP uplink interface
(or range of NP uplink interfaces).
Note
If this is a QSFP+ GEM, the slot/port syntax
is slot/QSFP-module/port.
Removes the mapping between the specified server
interfaces and NP uplink interfaces.
Note
If this is a QSFP+ GEM, the slot/port syntax
is slot/QSFP-module/port.
Verifying NPV
Step 1
Step 2
switch(config)# npv auto-load-balance
disruptive
Step 3
switch (config)# no npv auto-load-balance
disruptive
To display information about NPV, perform the following task:
PurposeCommand or Action
Enters configuration mode on the NPV.switch# configure terminal
Enables disruptive load balancing on the
switch.
Disables disruptive load balancing on the
switch.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 59
Page 84

Verifying NPV
Configuring N Port Virtualization
Procedure
PurposeCommand or Action
Step 1
Verifying NPV Examples
To display a list of devices on a server interface and their assigned NP uplinks, enter the show npv flogi-table
command on the Cisco Nexus device:
switch# show npv flogi-table
-------------------------------------------------------------------------------SERVER EXTERNAL
INTERFACE VSAN FCID PORT NAME NODE NAME INTERFACE
--------------------------------------------------------------------------------vfc3/1 1 0xee0008 10:00:00:00:c9:60:e4:9a 20:00:00:00:c9:60:e4:9a fc2/1
vfc3/1 1 0xee0009 20:00:00:00:0a:00:00:01 20:00:00:00:c9:60:e4:9a fc2/2
vfc3/1 1 0xee000a 20:00:00:00:0a:00:00:02 20:00:00:00:c9:60:e4:9a fc2/3
vfc3/1 1 0xee000b 33:33:33:33:33:33:33:33 20:00:00:00:c9:60:e4:9a fc2/4
Total number of flogi = 4
For each server interface, the External Interface value displays the assigned NP uplink.Note
To display the status of the server interfaces and the NP uplink interfaces, enter the show npv status command:
switch# show npv status
npiv is enabled
External Interfaces:
====================
Interface: fc2/1, VSAN: 1, FCID: 0x1c0000, State: Up
Interface: fc2/2, VSAN: 1, FCID: 0x040000, State: Up
Interface: fc2/3, VSAN: 1, FCID: 0x260000, State: Up
Interface: fc2/4, VSAN: 1, FCID: 0x1a0000, State: Up
Number of External Interfaces: 4
Server Interfaces:
==================
Interface: vfc3/1, VSAN: 1, NPIV: No, State: Up
Number of Server Interfaces: 1
Displays the NPV configuration.switch# show npv flogi-table [all]
Note
To view fcns database entries for NPV edge switches, you must enter the show fcns database command
on the core switch.
To view all the NPV edge switches, enter the show fcns database command on the core switch:
core-switch# show fcns database
For additional details (such as IP addresses, switch names, interface names) about the NPV edge switches
that you see in the show fcns database output, enter the show fcns database detail command on the core
switch:
core-switch# show fcns database detail
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
60 OL-30895-01
Page 85

Configuring N Port Virtualization
Verifying NPV Traffic Management
To display the NPV traffic map, enter the show npv traffic-map command.
switch# show npv traffic-map
NPV Traffic Map Information:
---------------------------------------Server-If External-If(s)
---------------------------------------fc1/3 fc1/10,fc1/11
fc1/5 fc1/1,fc1/2
----------------------------------------
To display the NPV internal traffic details, enter the show npv internal info traffic-map command.
To display the disruptive load-balancing status, enter the show npv status command:
switch# show npv status
npiv is enabled
disruptive load balancing is enabled
External Interfaces:
====================
Interface: fc2/1, VSAN: 2, FCID: 0x1c0000, State: Up
...
Verifying NPV
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 61
Page 86

Verifying NPV
Configuring N Port Virtualization
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
62 OL-30895-01
Page 87

Configuring FCoE NPV
This chapter contains the following sections:
Information About FCoE NPV, page 63
•
FCoE NPV Model, page 65
•
Mapping Requirements, page 66
•
Port Requirements, page 67
•
NPV Features, page 67
•
vPC Topologies, page 68
•
Supported and Unsupported Topologies, page 69
•
Guidelines and Limitations, page 73
•
FCoE NPV Configuration Limits, page 73
•
Default Settings, page 74
•
CHAPTER 5
Enabling FCoE and Enabling NPV, page 75
•
Enabling FCoE NPV, page 75
•
Configuring NPV Ports for FCoE NPV, page 76
•
Verifying FCoE NPV Configuration, page 76
•
Configuration Examples for FCoE NPV, page 77
•
Information About FCoE NPV
FCoE NPV is supported on the Cisco Nexus devices. The FCoE NPV feature is an enhanced form of FIP
snooping that provides a secure method to connect FCoE-capable hosts to an FCoE-capable FCoE forwarder
(FCF) switch. The FCoE NPV feature provides the following benefits:
FCoE NPV does not have the management and troubleshooting issues that are inherent to managing
•
hosts remotely at the FCF.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 63
Page 88

Information About FCoE NPV
•
•
You can enable FCoE NPV by choosing one of the following methods:
• Enable FCoE and then enable NPV—This method requires that you enable FCoE first using the
• Enable FCoE NPV—When you enable FCoE NPV using the feature fcoe-npv command, the mode
Configuring FCoE NPV
FCoE NPV implements FIP snooping as an extension to the NPV function while retaining the
traffic-engineering, vsan-management, administration and trouble-shooting aspects of NPV.
FCoE NPV and NPV together allow communication through FC and FCoE ports at the same time. This
provides a smooth transition when moving from FC to FCoE topologies.
feature fcoe command and then you enable NPV by using the feature npv command. When FCoE is
enabled, the default mode of operation is FC switching and when you enable NPV, the mode changes
to NPV mode. Switching to NPV mode automatically performs a write erase and reloads the system.
After the reload, the system comes up in NPV mode. To exit NPV mode and return to FC switching
mode, enter the no feature npv command. Exiting NPV mode also triggers a write erase and a switch
reload. This method requires the Storage Protocols Services Package (FC_FEATURES_PKG) license
.
changes to NPV. When you use this method, a write erase and reload does not occur. This method
requires a separate license package (FCOE_NPV_PKG). This license is also included in the Storage
Protocol Services License.
ReloadWrite EraseLicenseMethod
Enable FCoE and then
Enable NPV
Services Package
YesYesStorage Protocols
(FC_FEATURES_PKG)
NoNo(FCOE_NPV_PKG)Enable FCoE NPV
Interoperability with FCoE-Capable Switches
The Cisco Nexus device interoperates with the following FCoE-capable switches:
Cisco MDS 9000 Series Multilayer switches enabled to perform FCF functions (EthNPV and VE)
•
Cisco Nexus 7000 Series switches enabled to perform FCF functions (EthNPV and VE)
•
Cisco Nexus 4000 Series switches enabled for FIP Snooping
•
For detailed information about switch interoperability, see the Cisco Data Center Interoperability Support
Matrix.
Licensing
The following table shows the licensing requirements for FCoE NPV:
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
64 OL-30895-01
Page 89

Configuring FCoE NPV
FCoE NPV Model
License RequirementProduct
NX-OS
FCoE NPV Model
The following figure shows the FCoE NPV bridge connecting hosts and FCFs. From a control plane perspective,
FCoE NPV performs proxy functions towards the FCF and the hosts in order to load balance logins from the
FCoE NPV requires a separate license
(FCOE_NPV_PKG). The FCoE NPV license is also
included in the Storage Protocol Services License.
FCoE and NPV require the Storage Protocols Services
Package (FC_FEATURES_PKG).
For detailed information about features that require
licensing and Cisco NX-OS license installation, see
the Cisco NX-OS Licensing Guide.
For information about troubleshooting licensing
issues, see the Troubleshooting Guide for your device.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 65
Page 90

Mapping Requirements
hosts evenly across the available FCF uplink ports. An FCoE NPV bridge is VSAN-aware and capable of
assigning VSANs to the hosts.
Figure 5: FCoE NPV Model
Configuring FCoE NPV
Mapping Requirements
VSANs and VLAN-VSAN Mapping
VSANs from the hosts must be created and for each VSAN, a dedicated VLAN must also be created and
mapped. The mapped VLAN is used to carry FIP and FCoE traffic for the corresponding VSAN. The
VLAN-VSAN mapping must be configured consistently in the entire fabric. The Cisco Nexus device supports
32 VSANs.
FC Mapping
The FC-MAP value associated with a SAN fabric must be configured on the FCoE NPV bridge which helps
the FCoE NPV bridge isolate misconnections to FCFs in other fabrics.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
66 OL-30895-01
Page 91

Configuring FCoE NPV
Port Requirements
VF Ports
For each host directly connected over Ethernet interfaces on the FCoE NPV bridge, a virtual Fibre Channel
(vFC) interface must be created and bound to the Ethernet interface. By default, the vFC interface is configured
in the F mode (VF port).
The VF port must be configured with the following parameters:
A VF port must be bound to a VLAN trunk Ethernet interface or a port-channel interface. The FCoE
•
VLAN must not be configured as the native VLAN on the Ethernet interface.
A port VSAN must be configured for the VF port.
•
The administrative state must be up.
•
VNP Ports
Connectivity from an FCoE NPV bridge to the FCF is only supported over point-to-point links. These links
can be individual Ethernet interfaces or members of an Ethernet port channel interface. For each FCF connected
Ethernet interfaces, a vFC interface must be created and bound to the Ethernet interface. These vFC interfaces
must be configured as VNP ports. On the VNP port, an FCoE NPV bridge emulates an FCoE-capable host
with multiple enodes, each with a unique enode MAC address. A VNP port interface binding to MAC address
is not supported. By default, the VNP port is enabled in trunk mode. Multiple VSANs can be configured on
the VNP port. The FCoE VLANs that correspond to the VNP port VSANs must be configured on the bound
Ethernet interface.
Port Requirements
Note
The spanning-tree protocol (STP) is automatically disabled in the FCoE VLAN on the interfaces that the
VNP port are bound to.
NPV Features
The following NPV features apply for the FCoE NPV feature:
Automatic Traffic Mapping
•
Static Traffic Mapping
•
Disruptive Load Balancing
•
FCoE Forwarding in the FCoE NPV Bridge
•
FCoE frames received over VNP ports are forwarded only if the L2_DA matches one of the FCoE MAC
•
addresses assigned to hosts on the VF ports otherwise they’re discarded.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 67
Page 92

vPC Topologies
vPC Topologies
When VNP ports are configured vPC topologies between an FCoE NPV bridge and an FCF, the following
limitations apply:
vPC spanning multiple FCFs in the same SAN fabric is not supported.
•
For LAN traffic, dedicated links must be used for FCoE VLANs between the FCoE NPV bridge and
•
the FCF connected over a vPC.
FCoE VLANs must not be configured on the inter-switch vPC interfaces.
•
VF port binding to a vPC member port is not supported for an inter-switch vPC.
•
Figure 6: VNP Ports in an Inter-Switch vPC Topology
Configuring FCoE NPV
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
68 OL-30895-01
Page 93

Configuring FCoE NPV
Supported and Unsupported Topologies
FCoE NPV supports the following topologies:
Figure 7: Cisco Nexus Device As An FCoE NPV Device Connected to a Cisco Nexus Device Over A Non- vPC Port Channel
Supported and Unsupported Topologies
Figure 8: Cisco Nexus Device As An FCoE NPV Device Connected Over a vPC To Another Cisco Nexus Device
Figure 9: Cisco Nexus Device With A 10GB Fabric Extender As An FCoE NPV Device Connected to a Cisco Nexus Device
Over A Non- vPC Port Channel
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 69
Page 94

Supported and Unsupported Topologies
Configuring FCoE NPV
Figure 10: Cisco Nexus Device With A 10GB Fabric Extender as an FCoE NPV Device Connected Over a vPC to Another
Cisco Nexus Device
Figure 11: Cisco Nexus Device As An FCoE NPV Bridge Connecting to a FIP Snooping Bridge
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
70 OL-30895-01
Page 95

Configuring FCoE NPV
Supported and Unsupported Topologies
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 71
Page 96

Supported and Unsupported Topologies
Unsupported Topologies
FCoE NPV does not support the following topologies:
Figure 12: 10GB Fabric Extender Connecting To The Same FCoE NPV Bridge Over Multiple VF Ports
Configuring FCoE NPV
Figure 13: Cisco Nexus Device As An FCoE NPV Bridge Connecting To A FIP Snooping Bridge Or Another FCoE NPV Bridge
Figure 14: VF Port Trunk To Hosts In FCoE NPV Mode
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
72 OL-30895-01
Page 97

Configuring FCoE NPV
Guidelines and Limitations
Figure 15: Cisco Nexus Device As An FCoE NPV Bridge Connecting to an FCoE NPV Bridge
Guidelines and Limitations
The FCoE NPV feature has the following guidelines and limitations:
When FCoE NPV mode is configured on a switch, the FCoE feature cannot be enabled. A warning is
•
displayed to reload the system first in order to enable FCoE.
You can not perform an in-service software downgrade (ISSD) to Cisco NX-OS Release 5.0(3)N1(1)
•
or an earlier release if FCoE NPV is enabled and if VNP ports are configured.
A warning is displayed if an ISSD is performed to Cisco NX-OS Release 5.0(3)N1(1) or an earlier
•
release when FCoE NPV is enabled but VNP ports are not configured.
Before performing an ISSU on an FCoE NPV bridge, use the disable-fka command to disable the timeout
•
value check (FKA check) on the core switch.
FCoE NPV Configuration Limits
The following table lists the FCoE configuration limits over Ethernet, Ethernet port channel, and virtual
Ethernet interfaces.
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 73
Page 98

Default Settings
Configuring FCoE NPV
Table 10: VNP Port Configuration Limits
Cisco Nexus 5500 PlatformInterface Type
interface
channel interface
(vEth) interface
The configuration limits guidelines are as follows:
The number of VF port and VN port interfaces that can be supported between a given FCF and an FCoE
•
NPV bridge also depends on the FCF to MAC advertising capability of the FCF:
If an FCF advertises the same FCF-MAC address over all of its interfaces, then the FCoE NPV
◦
bridge can connect to it over one VNP Port. In this scenario, we recommend that one port channel
interface be used for redundancy.
If an FCF advertises multiple FCF-MAC addresses, then the limits in the previous table apply. For
◦
additional information, see the best practices recommendations for the FCF switch.
The total number of supported VSANs is 31 (excluding the EVFP VSAN).
•
Cisco Nexus 2000 Series (10G
interfaces)
Not Supported16 VNP portsVNP port bound to Ethernet
Not Supported16 VNP portsVNP port bound to Ethernet port
Not SupportedNot SupportedVNP port bound to virtual Ethernet
The total number of supported FCIDs is 2048.
•
Default Settings
The following table lists the default settings for FCoE NPV parameters.
Table 11: Default FCoE NPV Parameters
DefaultParameters
DisabledFCoE NPV
DisabledFCoE
DisabledNPV
DisabledVNP port
DisabledFIP Keep Alive (FKA)
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
74 OL-30895-01
Page 99

Configuring FCoE NPV
Enabling FCoE and Enabling NPV
You can enable FCoE first and then enable NPV. This method requires the full Storage Services License. A
write erase reload occurs when this method is used. This method allows both FCoE and FC upstream and host
NPV connections. You must also configure class-fcoe in all QoS policy types.
1
Enable FCoE.
switch# configure terminal
switch(config)# feature fcoe
FC license checked out successfully
fc_plugin extracted successfully
FC plugin loaded successfully
FCoE manager enabled successfully
FC enabled on all modules successfully
Warning: Ensure class-fcoe is included in qos policy-maps of all types
2
Enable NPV.
switch# configure terminal
switch(config)# feature npv
Enabling FCoE and Enabling NPV
Enabling FCoE NPV
You can enable FCoE NPV using the feature fcoe-npv command. We recommend this method in topologies
that include all FCoE connections. A write erase reload does not occur when you use this method and a storage
service license is not required. Enabling FCoE NPV using the feature fcoe-npv command requires an installed
FCOE_NPV_PKG license.
Before You Begin
FCoE NPV has the following prerequisites:
Ensure that the correct licenses are installed.
•
For the Cisco Nexus 5500 Platform switches, ensure that the FCF supports multiple FC ports and multiple
•
logins (FLOGI) on a single physical VF port.
Configure the VNP ports.
•
Procedure
Step 1
Step 2
Step 3
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables FCoE NPV.feature fcoe-npv
Exits configuration mode.exit
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
OL-30895-01 75
Page 100

Configuring NPV Ports for FCoE NPV
Configuring FCoE NPV
PurposeCommand or Action
Step 4
switch(config)# copy running-config
startup-config
This example shows how to enable FCoE NPV using the feature fcoe-npv command.
switch# configure terminal
switch(config)# feature fcoe-npv
FCoE NPV license checked out successfully
fc_plugin extracted successfully
FC plugin loaded successfully
FCoE manager enabled successfully
FCoE NPV enabled on all modules successfully
This example shows how to enable FCoE NPV using the feature fcoe and feature npv commands.
switch# configure terminal
switch(config)# feature fcoe
switch(config)# feature npv
Configuring NPV Ports for FCoE NPV
You can configure NVP port for FCoE NPV.
1
Create a vFC port.
switch# config t
switch(config)# interface vfc 20
switch(config-if)#
2
Bind the vFC to an Ethernet port.
switch(config-if)# bind interface ethernet 1/20
switch(config-if)#
3
Set the port mode to NP.
switch(config-if)# switchport mode NP
switch(config-if)#
4
Bring up the port:
switch(config-if)# interface vfc 20no shutdown
switch(config-if)#
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
Verifying FCoE NPV Configuration
To display FCoE NPV configuration information, perform one of the following tasks:
PurposeCommand
Displays information about the FCoE database.show fcoe database
Cisco Nexus 5500 Series NX-OS SAN Switching Configuration Guide, Release 7.x
76 OL-30895-01
 Loading...
Loading...