Page 1

Cisco IOS XR System Security
Configuration Guide
Cisco IOS XR Software Release 3.5
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Text Part Number: OL-12287-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL
C
C
C
F
L
I
A
b
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
CVP, the Cisco logo, and Welcome to the Human Network are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn is a service mark of
isco Systems, Inc.; and Access Registrar, Aironet, BPX, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, Cisco, the Cisco Certified Internetwork Expert logo,
isco IOS, Cisco
ollow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, iQuick Study,
ightStream, Linksys, MeetingPlace, MGX, Networkers, Networking Academy, Network Registrar, PIX, ProConnect, ScriptShare, SMARTnet, StackWise, The Fastest Way to
ncrease Your Internet Quotient, and TransPath are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
ll other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship
etween Cisco and any other company. (0710R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the
document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
Cisco IOS XR System Security Configuration Guide
© 2007 Cisco Systems, Inc. All rights reserved.
Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step,
Page 3

CONTENTS
Preface xi
Changes to This Document xi
Obtaining Documentation, Obtaining Support, and Security Guidelines xi
Implementing Certification Authority Interoperability on Cisco IOS XR Software SC-1
Contents SC-1
Prerequisites for Implementing Certification Authority SC-2
Restrictions for Implementing Certification Authority SC-2
Information About Implementing Certification Authority SC-2
Supported Standards for Certification Authority Interoperability SC-2
Certification Authorities SC-3
How to Implement CA Interoperability SC-5
Configuring a Router Hostname and IP Domain Name SC-6
Generating an RSA Key Pair SC-7
Declaring a Certification Authority and Configuring a Trusted Point SC-8
Authenticating the CA SC-10
Requesting Your Own Certificates SC-11
Configuring Certificate Enrollment Using Cut-and-Paste SC-12
Configuration Examples for Implementing Certification Authority Interoperability SC-14
Configuring Certification Authority Interoperability: Example SC-14
Where to Go Next SC-16
Additional References SC-16
Related Documents SC-16
Standards SC-16
MIBs SC-17
RFCs SC-17
Technical Assistance SC-17
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software SC-19
Contents SC-20
Prerequisites SC-20
Information About Implementing IKE Security Protocol Configurations for IPSec Networks SC-20
Supported Standards SC-21
Concessions for Not Enabling IKE SC-22
IKE Policies SC-22
Cisco IOS XR System Security Configuration Guide
iii
Page 4

Contents
ISAKMP Identity SC-26
ISAKMP Profile Overview SC-26
Mask Preshared Keys SC-27
Preshared Keys Using a AAA Server SC-27
Internet Key Exchange Mode Configuration SC-28
Banner, Auto-Update, and Browser-Proxy SC-29
Pushing a Configuration URL Through a Mode-Configuration Exchange SC-29
Internet Key Exchange Extended Authentication SC-30
Call Admission Control SC-30
Information About IP Security VPN Monitoring SC-31
Information About IKE for the Cisco IPSec VPN SPA on Cisco IOS XR Software SC-32
IPSec Dead Peer Detection Periodic Message Option SC-32
How to Implement IKE Security Protocol Configurations for IPSec Networks SC-32
Enabling or Disabling IKE SC-33
Configuring IKE Policies SC-34
Defining Group Policy Information for Mode Configuration SC-36
Configuring a Banner SC-40
Configuring Auto-Upgrade SC-40
Configuring a Browser Proxy SC-41
Configuring a Browser-Proxy Map to a Group SC-42
Configuring the Pushing of a Configuration URL Through a Mode-Configuration Exchange SC-43
Manually Configuring RSA Keys SC-44
Configuring ISAKMP Preshared Keys in ISAKMP Keyrings SC-48
Configuring Call Admission Control SC-50
Configuring Crypto Keyrings SC-54
Configuring IP Security VPN Monitoring SC-57
How to Implement IKE for Locally Sourced and Destined Traffic SC-58
Configuring the ISAKMP Profile for Locally Sourced and Destined Traffic SC-58
How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software SC-62
Configuring a Periodic Dead Peer Detection Message SC-63
Configuring the ISAKMP Profile for Service Interfaces SC-64
Configuration Examples for Implementing IKE Security Protocol SC-68
Creating IKE Policies: Example SC-69
Configuring a service-ipsec Interface with a Dynamic Profile: Example SC-69
Configuring Easy VPN with a Local AAA: Example SC-70
Configuring VRF-Aware: Example SC-71
Additional References SC-73
Related Documents SC-73
Standards SC-73
Cisco IOS XR System Security Configuration Guide
iv
Page 5

MIBs SC-74
RFCs SC-74
Technical Assistance SC-74
Implementing Keychain Management on Cisco IOS XR Software SC-75
Contents SC-75
Restrictions for Implementing Keychain Management SC-75
Information About Implementing Keychain Management SC-76
Lifetime of a Key SC-76
How to Implement Keychain Management SC-76
Configuring a Keychain SC-77
Configuring a Tolerance Specification to Accept Keys SC-78
Configuring a Key Identifier for the Keychain SC-79
Configuring the Text for the Key String SC-81
Determining the Valid Keys SC-82
Configuring the Keys to Generate Authentication Digest for the Outbound Application Traffic SC-84
Configuring the Cryptographic Algorithm SC-85
Contents
Configuration Examples for Implementing Keychain Management SC-87
Configuring Keychain Management: Example SC-87
Additional References SC-88
Related Documents SC-88
Standards SC-88
MIBs SC-89
RFCs SC-89
Technical Assistance SC-89
Implementing IPSec Network Security on Cisco IOS XR Software SC-91
Contents SC-92
Prerequisites for Implementing IPSec Network Security SC-92
Restrictions for Implementing IPSec Network Security SC-93
Restrictions for Implementing IPSec Network with a
Cisco IPSec VPN SPA
SC-93
Information About Implementing IPSec Networks SC-94
Crypto Profiles SC-94
Dynamic Crypto Profiles SC-95
Crypto Access Lists SC-95
Transform Sets SC-96
Global Lifetimes for IPSec Security Associations SC-96
Manual IPSec Security Associations SC-97
Cisco IOS XR System Security Configuration Guide
v
Page 6

Contents
Perfect Forward Secrecy SC-97
Checkpointing SC-98
DF Bit Override Functionality with IPSec Tunnels SC-98
IPSec Antireplay Window SC-98
IPSec NAT Transparency SC-99
IPSec Security Association Idle Timers SC-99
Prefragmentation for Cisco IPSec VPN SPAs SC-99
Reverse-Route Injection SC-100
IPSec—SNMP Support SC-101
Information About an IPSec Network with a Cisco IPSec VPN SPA on Cisco IOS XR Software SC-101
Cisco IPSec VPN SPA Overview SC-101
Displaying the SPA Hardware Type SC-101
Information About Security for VPNs with IPSec SC-102
How to Implement General IPSec Configurations for IPSec Networks SC-104
Setting Global Lifetimes for IPSec Security Associations SC-105
Creating Crypto Access Lists SC-106
Defining Transform Sets SC-108
Configuring Crypto Profiles SC-109
Configuring the DF Bit for the Encapsulating Header in IPSec Tunnels SC-114
Configuring the IPSec Antireplay Window: Expanding and Disabling SC-115
Configuring IPSec NAT Transparency SC-118
Configuring IPSec Security Association Idle Timers SC-120
Disabling Prefragmentation for Cisco IPSec VPN SPAs SC-124
Configuring Reverse-Route Injection in a Crypto Profile SC-127
Configuring IPSec Failure History Table Size SC-128
How to Implement IPSec Network Security for Locally Sourced and Destined Traffic SC-129
Applying Crypto Profiles to tunnel-ipsec Interfaces SC-130
Applying Crypto Profiles to Crypto Transport SC-131
How to Implement IPSec Network Security for VPNs SC-132
Configuring IPSec Virtual Interfaces SC-133
Configuring the Default Path Maximum Transmission Unit for the SA SC-139
Configuration Examples for Implementing IPSec Network Security for Locally Sourced Traffic and Destined
Traffic
SC-140
Configuring a Static Profile and Attaching to a Tunnel-ipsec Interface: Example SC-140
Configuring a Dynamic Profile and Attaching to a Tunnel-ipsec Interface: Example SC-141
Configuring a Static Profile and Attaching to Transport: Example SC-142
Configuration Examples for an IPSec Network with a
Cisco IPSec VPN SPA
Configuring IPSec for a VRF-aware Service-ipsec Interface: Example SC-142
Cisco IOS XR System Security Configuration Guide
vi
SC-142
Page 7

Configuring a Service-gre Interface: Example SC-145
Additional References SC-147
Related Documents SC-147
Standards SC-147
MIBs SC-147
RFCs SC-148
Technical Assistance SC-148
Implementing Secure Shell on Cisco IOS XR Software SC-149
Contents SC-149
Prerequisites to Implementing Secure Shell SC-150
Restrictions for Implementing Secure Shell SC-150
Information About Implementing Secure Shell SC-151
SSH Server SC-151
SSH Client SC-151
SFTP Feature Overview SC-151
AAA Feature SC-152
Contents
How to Implement Secure Shell SC-152
Configuring SSH SC-152
Configuring the SSH Client SC-154
Configuration Examples for Implementing Secure Shell SC-156
Configuring Secure Shell: Example SC-156
Additional References SC-156
Related Documents SC-156
Standards SC-157
MIBs SC-157
RFCs SC-157
Technical Assistance SC-158
Implementing Secure Socket Layer on Cisco IOS XR Software SC-159
Contents SC-160
Prerequisites for Implementing Secure Socket Layer SC-160
Information About Implementing Secure Socket Layer SC-160
Purpose of Certification Authorities SC-160
How to Implement Secure Socket Layer SC-161
Configuring Secure Socket Layer SC-161
Configuration Examples for Implementing Secure Socket Layer SC-164
Configuring Secure Socket Layer: Example SC-164
Additional References SC-164
Cisco IOS XR System Security Configuration Guide
vii
Page 8

Contents
Related Documents SC-164
Standards SC-165
MIBs SC-165
RFCs SC-165
Technical Assistance SC-165
Configuring AAA Services on Cisco IOS XR Software SC-167
Contents SC-168
Prerequisites for Configuring AAA Services SC-169
Restrictions for Configuring AAA Services SC-169
Information About Configuring AAA Services SC-169
User, User Groups, and Task Groups SC-170
Cisco IOS XR Software Administrative Model SC-172
Password Types SC-177
Task-Based Authorization SC-178
Task IDs for TACACS+ and RADIUS Authenticated Users SC-179
XML Schema for AAA Services SC-181
About RADIUS SC-182
How to Configure AAA Services SC-183
Configuring Task Groups SC-184
Configuring User Groups SC-186
Configuring Users SC-188
Configuring Router to RADIUS Server Communication SC-190
Configuring RADIUS Dead-Server Detection SC-194
Configuring Per VRF AAA SC-196
Configuring a TACACS+ Server SC-198
Configuring RADIUS Server Groups SC-201
Configuring TACACS+ Server Groups SC-203
Configuring AAA Method Lists SC-204
Applying Method Lists for Applications SC-216
Configuring Login Parameters SC-220
Configuration Examples for Configuring AAA Services SC-221
Configuring AAA Services: Example SC-221
Additional References SC-223
Related Documents SC-223
Standards SC-223
MIBs SC-223
RFCs SC-224
Technical Assistance SC-224
Cisco IOS XR System Security Configuration Guide
viii
Page 9

Configuring Software Authentication Manager on Cisco IOS XR Software SC-225
Implementing Management Plane Protection on Cisco IOS XR Software SC-227
Contents SC-227
Restrictions for Implementing Management Plane Protection SC-228
Information About Implementing Management Plane Protection SC-228
Inband Management Interface SC-228
Control Plane Protection Overview SC-228
Management Plane SC-228
Management Plane Protection Feature SC-229
Benefits of the Management Plane Protection Feature SC-229
How to Configure a Device for Management Plane Protection SC-229
Configuring a Device for Management Plane Protection SC-230
Configuration Examples for Implementing Management Plane Protection SC-232
Configuring Management Plane Protection: Example SC-232
Contents
Additional References SC-233
Related Documents SC-233
Standards SC-233
MIBs SC-233
RFCs SC-234
Technical Assistance SC-234
Index
Cisco IOS XR System Security Configuration Guide
ix
Page 10

Contents
Cisco IOS XR System Security Configuration Guide
x
Page 11

Preface
This guide describes the configuration and examples for system security.
For system security command descriptions, usage guidelines, task IDs, and examples, refer to the
Cisco IOS XR System Security Command Reference.
The preface contains the following sections:
• Changes to This Document, page xi
• Obtaining Documentation, Obtaining Support, and Security Guidelines, page xi
Changes to This Document
Table 1 lists the technical changes made to this document since it was first printed.
Table 1 Changes to This Document
Revision Date Change Summary
OL-12287-01 June 2007 Initial release of this document.
Obtaining Documentation, Obtaining Support, and Security
Guidelines
For information on obtaining documentation, obtaining support, providing documentation feedback,
security guidelines, and also recommended aliases and general Cisco documents, see the monthly
What’s New in Cisco Product Documentation, which also lists all new and revised Cisco technical
documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Cisco IOS XR System Security Configuration Guide
xi
Page 12

Obtaining Documentation, Obtaining Support, and Security Guidelines
Preface
Cisco IOS XR System Security Configuration Guide
xii
Page 13

Implementing Certification Authority
Interoperability on Cisco IOS XR Software
Certification authority (CA) interoperability is provided in support of the IP Security (IPSec), Secure
Socket Layer (SSL), and Secure Shell (SSH) protocols. CA interoperability permits Cisco IOS XR
devices and CAs to communicate so that your Cisco IOS XR device can obtain and use digital
certificates from the CA. Although IPSec can be implemented in your network without the use of a CA,
using a CA provides manageability and scalability for IPSec.
This module describes the tasks that you need to implement CA interoperability on your Cisco IOS XR
network.
Note For a complete description of the public key infrastructure (PKI) commands used in this chapter, refer
to the Public Key Infrastructure Commands on Cisco IOS XR Software module of the Cisco IOS XR
System Security Command Reference. To locate documentation for other commands that appear in this
chapter, use the command reference master index, or search online.
Feature History for Implementing Certification Authority Interoperability on Cisco IOS XR Software
Release Modification
Release 2.0 This feature was introduced on the Cisco CRS-1.
Release 3.0 No modification.
Release 3.2 Support was added for the Cisco XR 12000 Series Router.
Release 3.3.0 No modification.
Release 3.4.0 A procedure was added on how to declare the trustpoint certification
authority (CA) for both the Cisco CRS-1 and
Cisco XR 12000 Series Router.
Release 3.5.0 No modification.
Contents
• Prerequisites for Implementing Certification Authority, page SC-2
• Restrictions for Implementing Certification Authority, page SC-2
• Information About Implementing Certification Authority, page SC-2
• How to Implement CA Interoperability, page SC-5
Cisco IOS XR System Security Configuration Guide
SC-1
Page 14

Implementing Certification Authority Interoperability on Cisco IOS XR Software
Prerequisites for Implementing Certification Authority
• Configuration Examples for Implementing Certification Authority Interoperability, page SC-14
• Additional References, page SC-16
Prerequisites for Implementing Certification Authority
The following prerequisites are required to implement CA interoperability:
• You must be in a user group associated with a task group that includes the proper task IDs for
security commands. For detailed information about user groups and task IDs, see the Configuring
AAA Services on Cisco IOS XR Software module of the Cisco IOS XR System Security
Configuration Guide.
• You must install and activate the Package Installation Envelope (PIE) for the security software.
For detailed information about optional PIE installation, refer to the Cisco IOS XR System
Management Guide.
• You need to have a CA available to your network before you configure this interoperability feature.
The CA must support Cisco Systems PKI protocol, the Simple Certificate Enrollment Protocol
(SCEP) (formerly called certificate enrollment protocol [CEP]).
Restrictions for Implementing Certification Authority
Cisco IOS XR software does not support CA server public keys greater than 2048 bits.
Information About Implementing Certification Authority
To implement CA, you need to understand the following concepts:
• Supported Standards for Certification Authority Interoperability, page SC-2
• Certification Authorities, page SC-3
Supported Standards for Certification Authority Interoperability
Cisco supports the following standards:
• IPSec—IP Security Protocol. IPSec is a framework of open standards that provides data
confidentiality, data integrity, and data authentication between participating peers. IPSec provides
these security services at the IP layer; it uses Internet Key Exchange (IKE) to handle negotiation of
protocols and algorithms based on local policy, and to generate the encryption and authentication
keys to be used by IPSec. IPSec can be used to protect one or more data flows between a pair of
hosts, a pair of security gateways, or a security gateway and a host.
• IKE—A hybrid protocol that implements Oakley and Skeme key exchanges inside the Internet
Security Association Key Management Protocol (ISAKMP) framework. Although IKE can be used
with other protocols, its initial implementation is with the IPSec protocol. IKE provides
authentication of the IPSec peers, negotiates IPSec keys, and negotiates IPSec security associations
(SAs).
• Public-Key Cryptography Standard #7 (PKCS #7)—A standard from RSA Data Security Inc. used
to encrypt and sign certificate enrollment messages.
Cisco IOS XR System Security Configuration Guide
SC-2
Page 15

Implementing Certification Authority Interoperability on Cisco IOS XR Software
• Public-Key Cryptography Standard #10 (PKCS #10)—A standard syntax from RSA Data Security
Inc. for certificate requests.
• RSA keys—RSA is the public key cryptographic system developed by Ron Rivest, Adi Shamir, and
Leonard Adelman. RSA keys come in pairs: one public key and one private key.
• SSL—Secure Socket Layer protocol.
• X.509v3 certificates—Certificate support that allows the IPSec-protected network to scale by
providing the equivalent of a digital ID card to each device. When two devices want to communicate,
they exchange digital certificates to prove their identity (thus removing the need to manually
exchange public keys with each peer or specify a shared key at each peer). These certificates are
obtained from a CA. X.509 is part of the X.500 standard of the ITU.
Certification Authorities
The following sections provide background information about CAs:
• Purpose of CAs, page SC-3
• IPSec Without CAs, page SC-4
Information About Implementing Certification Authority
Purpose of CAs
• IPSec with CAs, page SC-4
• IPSec with Multiple Trustpoint CAs, page SC-4
• How CA Certificates Are Used by IPSec Devices, page SC-5
• CA Registration Authorities, page SC-5
CAs are responsible for managing certificate requests and issuing certificates to participating IPSec
network devices. These services provide centralized key management for the participating devices.
CAs simplify the administration of IPSec network devices. You can use a CA with a network containing
multiple IPSec-compliant devices, such as routers.
Digital signatures, enabled by public key cryptography, provide a means of digitally authenticating
devices and individual users. In public key cryptography, such as the RSA encryption system, each user
has a key pair containing both a public and a private key. The keys act as complements, and anything
encrypted with one of the keys can be decrypted with the other. In simple terms, a signature is formed
when data is encrypted with a user’s private key. The receiver verifies the signature by decrypting the
message with the sender’s public key. The fact that the message could be decrypted using the sender’s
public key indicates that the holder of the private key, the sender, must have created the message. This
process relies on the receiver’s having a copy of the sender’s public key and knowing with a high degree
of certainty that it does belong to the sender and not to someone pretending to be the sender.
Digital certificates provide the link. A digital certificate contains information to identify a user or device,
such as the name, serial number, company, department, or IP address. It also contains a copy of the
entity’s public key. The certificate is itself signed by a CA, a third party that is explicitly trusted by the
receiver to validate identities and to create digital certificates.
To validate the signature of the CA, the receiver must first know the CA’s public key. Normally, this
process is handled out-of-band or through an operation done at installation. For instance, most web
browsers are configured with the public keys of several CAs by default. IKE, an essential component of
IPSec, can use digital signatures to authenticate peer devices for scalability before setting up SAs.
Cisco IOS XR System Security Configuration Guide
SC-3
Page 16

Information About Implementing Certification Authority
Without digital signatures, a user must manually exchange either public keys or secrets between each
pair of devices that use IPSec to protect communication between them. Without certificates, every new
device added to the network requires a configuration change on every other device with which it
communicates securely. With digital certificates, each device is enrolled with a CA. When two devices
want to communicate, they exchange certificates and digitally sign data to authenticate each other. When
a new device is added to the network, a user simply enrolls that device with a CA, and none of the other
devices needs modification. When the new device attempts an IPSec connection, certificates are
automatically exchanged and the device can be authenticated.
IPSec Without CAs
Without a CA, if you want to enable IPSec services (such as encryption) between two Cisco routers, you
must first ensure that each router has the key of the other router (such as an RSA public key or a shared
key). This requirement means that you must manually perform one of the following operations:
• At each router, enter the RSA public key of the other router.
• At each router, specify a shared key to be used by both routers.
If you have multiple Cisco routers in a mesh topology and want to exchange IPSec traffic passing among
all of those routers, you must first configure shared keys or RSA public keys among all of those routers.
Every time a new router is added to the IPSec network, you must configure keys between the new router
and each of the existing routers.
Implementing Certification Authority Interoperability on Cisco IOS XR Software
Consequently, the more devices there are that require IPSec services, the more involved the key
administration becomes. This approach does not scale well for larger, more complex encrypting
networks.
IPSec with CAs
With a CA, you need not configure keys between all the encrypting routers. Instead, you individually
enroll each participating router with the CA, requesting a certificate for the router. When this enrollment
has been accomplished, each participating router can dynamically authenticate all the other participating
routers.
To add a new IPSec router to the network, you need only configure that new router to request a certificate
from the CA, instead of making multiple key configurations with all the other existing IPSec routers.
IPSec with Multiple Trustpoint CAs
With multiple trustpoint CAs, you no longer have to enroll a router with the CA that issued a certificate
to a peer. Instead, you configure a router with multiple CAs that it trusts. Thus, a router can use a
configured CA (a trusted root) to verify certificates offered by a peer that were not issued by the same
CA defined in the identity of the router.
Configuring multiple CAs allows two or more routers enrolled under different domains (different CAs)
to verify the identity of each other when using IKE to set up IPSec tunnels.
Through SCEP, each router is configured with a CA (the enrollment CA). The CA issues a certificate to
the router that is signed with the private key of the CA. To verify the certificates of peers in the same
domain, the router is also configured with the root certificate of the enrollment CA.
To verify the certificate of a peer from a different domain, the root certificate of the enrollment CA in
the domain of the peer must be configured securely in the router.
Cisco IOS XR System Security Configuration Guide
SC-4
Page 17

Implementing Certification Authority Interoperability on Cisco IOS XR Software
During IKE phase one signature verification, the initiator will send the responder a list of its CA
certificates. The responder should send the certificate issued by one of the CAs in the list. If the
certificate is verified, the router saves the public key contained in the certificate on its public key ring.
With multiple root CAs, Virtual Private Network (VPN) users can establish trust in one domain and
easily and securely distribute it to other domains. Thus, the required private communication channel
between entities authenticated under different domains can occur.
How CA Certificates Are Used by IPSec Devices
When two IPSec routers want to exchange IPSec-protected traffic passing between them, they must first
authenticate each other—otherwise, IPSec protection cannot occur. The authentication is done with IKE.
Without a CA, a router authenticates itself to the remote router using either RSA-encrypted nonces or
preshared keys. Both methods require keys to have been previously configured between the two routers.
With a CA, a router authenticates itself to the remote router by sending a certificate to the remote router
and performing some public key cryptography. Each router must send its own unique certificate that was
issued and validated by the CA. This process works because the certificate of each router encapsulates
the public key of the router, each certificate is authenticated by the CA, and all participating routers
recognize the CA as an authenticating authority. This scheme is called IKE with an RSA signature.
Your router can continue sending its own certificate for multiple IPSec sessions and to multiple IPSec
peers until the certificate expires. When its certificate expires, the router administrator must obtain a new
one from the CA.
How to Implement CA Interoperability
When your router receives a certificate from a peer from another domain (with a different CA), the
certificate revocation list (CRL) downloaded from the CA of the router does not include certificate
information about the peer. Therefore, you should check the CRL published by the configured trustpoint
with the Lightweight Directory Access Protocol (LDAP) URL to ensure that the certificate of the peer
has not been revoked.
To query the CRL published by the configured trustpoint with the LDAP URL, use the query url
command in trustpoint configuration mode.
CA Registration Authorities
Some CAs have a registration authority (RA) as part of their implementation. An RA is essentially a
server that acts as a proxy for the CA so that CA functions can continue when the CA is offline.
How to Implement CA Interoperability
This section contains the following procedures:
• Configuring a Router Hostname and IP Domain Name, page SC-6 (required)
• Generating an RSA Key Pair, page SC-7 (required)
• Declaring a Certification Authority and Configuring a Trusted Point, page SC-8 (required)
• Authenticating the CA, page SC-10 (required)
• Requesting Your Own Certificates, page SC-11 (required)
• Configuring Certificate Enrollment Using Cut-and-Paste, page SC-12
Cisco IOS XR System Security Configuration Guide
SC-5
Page 18

Implementing Certification Authority Interoperability on Cisco IOS XR Software
How to Implement CA Interoperability
Configuring a Router Hostname and IP Domain Name
This task configures a router hostname and IP domain name.
You must configure the hostname and IP domain name of the router if they have not already been
configured. The hostname and IP domain name are required because the router assigns a fully qualified
domain name (FQDN) to the keys and certificates used by IPSec, and the FQDN is based on the
hostname and IP domain name you assign to the router. For example, a certificate named
router20.example.com is based on a router hostname of router20 and a router IP domain name of
example.com.
SUMMARY STEPS
1. configure
2. hostname name
3. domain name domain-name
4. end
or
commit
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
hostname
Example:
RP/0/RP0/CPU0:router(config)# hostname myhost
name
Enables global configuration mode.
Configures the hostname of the router.
Cisco IOS XR System Security Configuration Guide
SC-6
Page 19
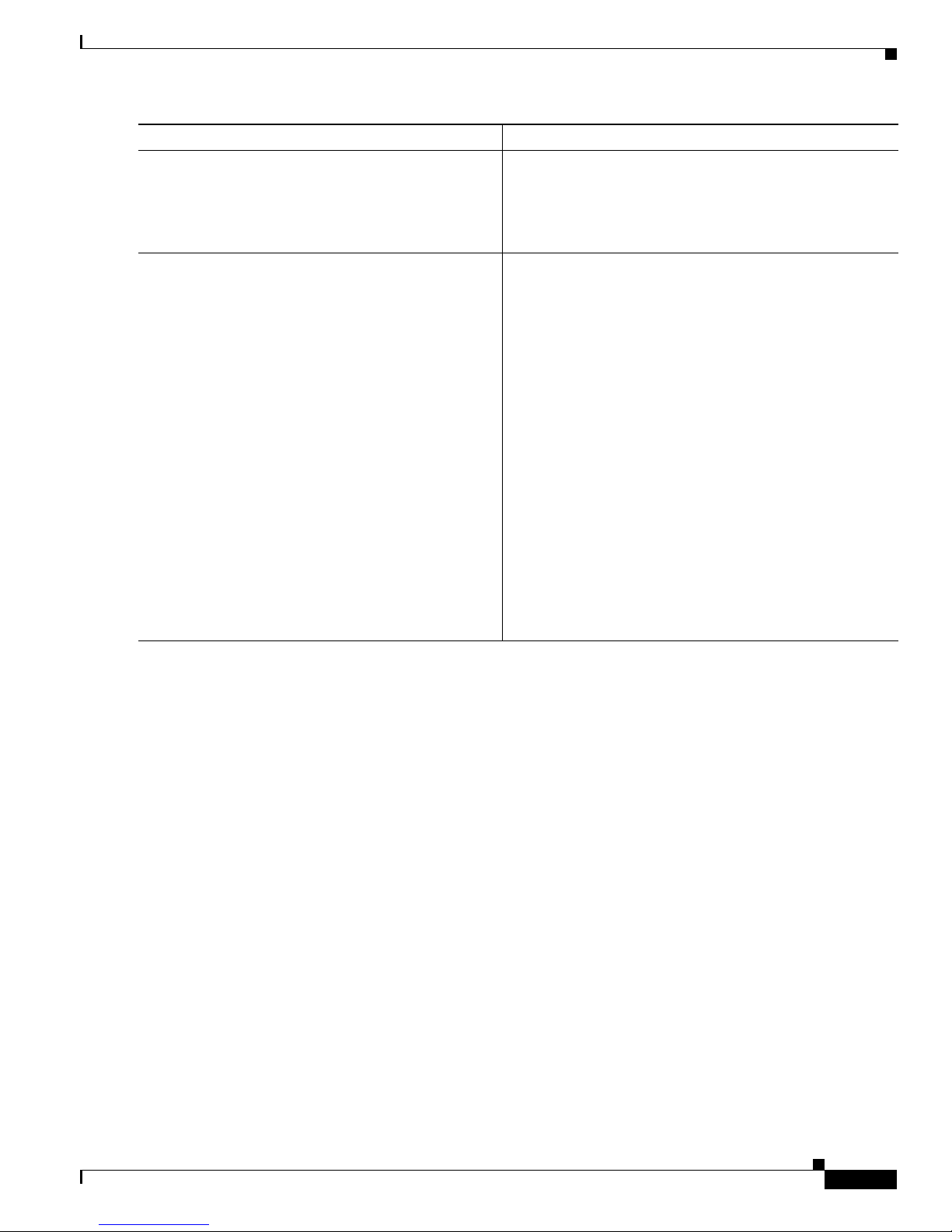
Implementing Certification Authority Interoperability on Cisco IOS XR Software
Command or Action Purpose
Step 3
domain name
domain-name
Example:
RP/0/RP0/CPU0:router(config)# domain name
mydomain.com
Step 4
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
How to Implement CA Interoperability
Configures the IP domain name of the router.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
Generating an RSA Key Pair
This task generates an RSA key pair.
RSA key pairs are used to sign and encrypt IKE key management messages and are required before you
can obtain a certificate for your router.
SUMMARY STEPS
1. crypto key generate rsa [usage keys | general-keys] [keypair-label]
2. crypto key zeroize rsa [keypair-label]
3. show crypto key mypubkey rsa
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Cisco IOS XR System Security Configuration Guide
SC-7
Page 20
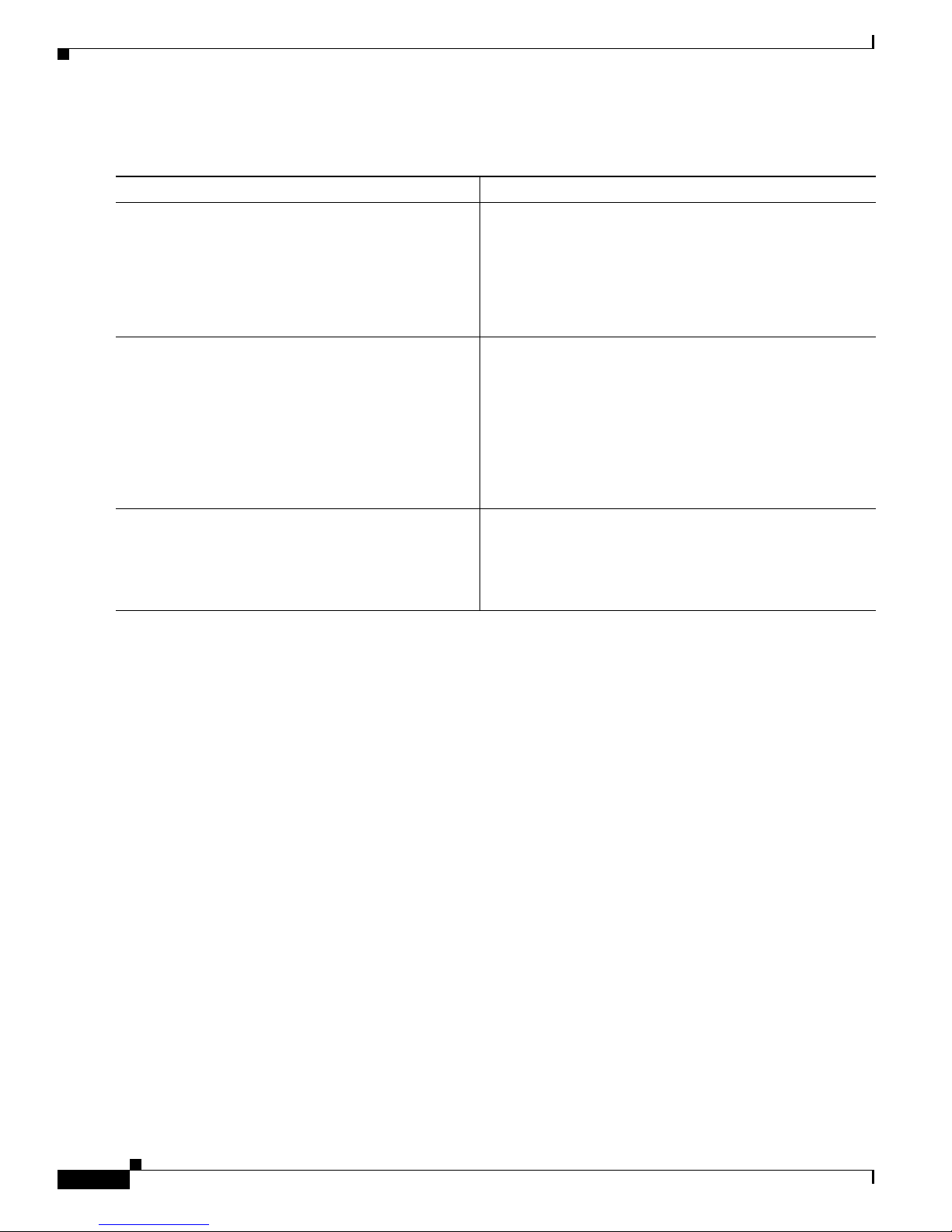
How to Implement CA Interoperability
DETAILED STEPS
Command or Action Purpose
Step 1
crypto key generate rsa [usage keys |
general-keys] [
Example:
RP/0/RP0/CPU0:router# crypto key generate rsa
general-keys
Step 2
crypto key zeroize rsa [
Example:
RP/0/RP0/CPU0:router# crypto key zeroize rsa
key1
Step 3
show crypto key mypubkey rsa
keypair-label
keypair-label
Implementing Certification Authority Interoperability on Cisco IOS XR Software
Generates RSA key pairs.
]
• Use the usage keys keyword to specify special usage
keys; use the general-keys keyword to specify generalpurpose RSA keys.
• The keypair-label argument is the RSA key pair label
that names the RSA key pairs.
]
(Optional) Deletes all RSAs from the router.
• Under certain circumstances, you may want to delete
all RSA keys from you router. For example, if you
believe the RSA keys were compromised in some way
and should no longer be used, you should delete the
keys.
• To remove a specific RSA key pair, use the
keypair-label argument.
(Optional) Displays the RSA public keys for your router.
Example:
RP/0/RP0/CPU0:router# show crypto key mypubkey
rsa
Declaring a Certification Authority and Configuring a Trusted Point
This task declares a CA and configures a trusted point.
SUMMARY STEPS
1. configure
2. crypto ca trustpoint ca-name
3. enrollment url CA-URL
4. query url LDAP-URL
5. enrollment retry period minutes
6. enrollment retry count number
7. rsakeypair keypair-label
8. end
or
commit
Cisco IOS XR System Security Configuration Guide
SC-8
Page 21

Implementing Certification Authority Interoperability on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto ca trustpoint
ca-name
Example:
RP/0/RP0/CPU0:router(config)# crypto ca
trustpoint myca
Step 3
enrollment url
CA-URL
Example:
RP/0/RP0/CPU0:router(config-trustp)# enrollment
url
http://ca.domain.com/certsrv/mscep/mscep.dll
Step 4
query url
LDAP-URL
How to Implement CA Interoperability
Enters global configuration mode.
Declares a CA.
• Configures a trusted point with a selected name so that
your router can verify certificates issued to peers.
• Enters trustpoint configuration mode.
Specifies the URL of the CA.
• The URL should include any nonstandard cgi-bin script
location.
(Optional) Specifies the location of the LDAP server if your
CA system supports the LDAP protocol.
Step 5
Step 6
Example:
RP/0/RP0/CPU0:router(config-trustp)# query url
ldap://my-ldap.domain.com
enrollment retry period
minutes
Example:
RP/0/RP0/CPU0:router(config-trustp)# enrollment
retry period 2
enrollment retry count
number
Example:
RP/0/RP0/CPU0:router(config-trustp)# enrollment
retry count 10
(Optional) Specifies a retry period.
• After requesting a certificate, the router waits to receive
a certificate from the CA. If the router does not receive
a certificate within a period of time (the retry period)
the router will send another certificate request.
• Range is from 1 to 60 minutes. Default is 1 minute.
(Optional) Specifies how many times the router continues to
send unsuccessful certificate requests before giving up.
• The range is from 1 to 100.
Cisco IOS XR System Security Configuration Guide
SC-9
Page 22
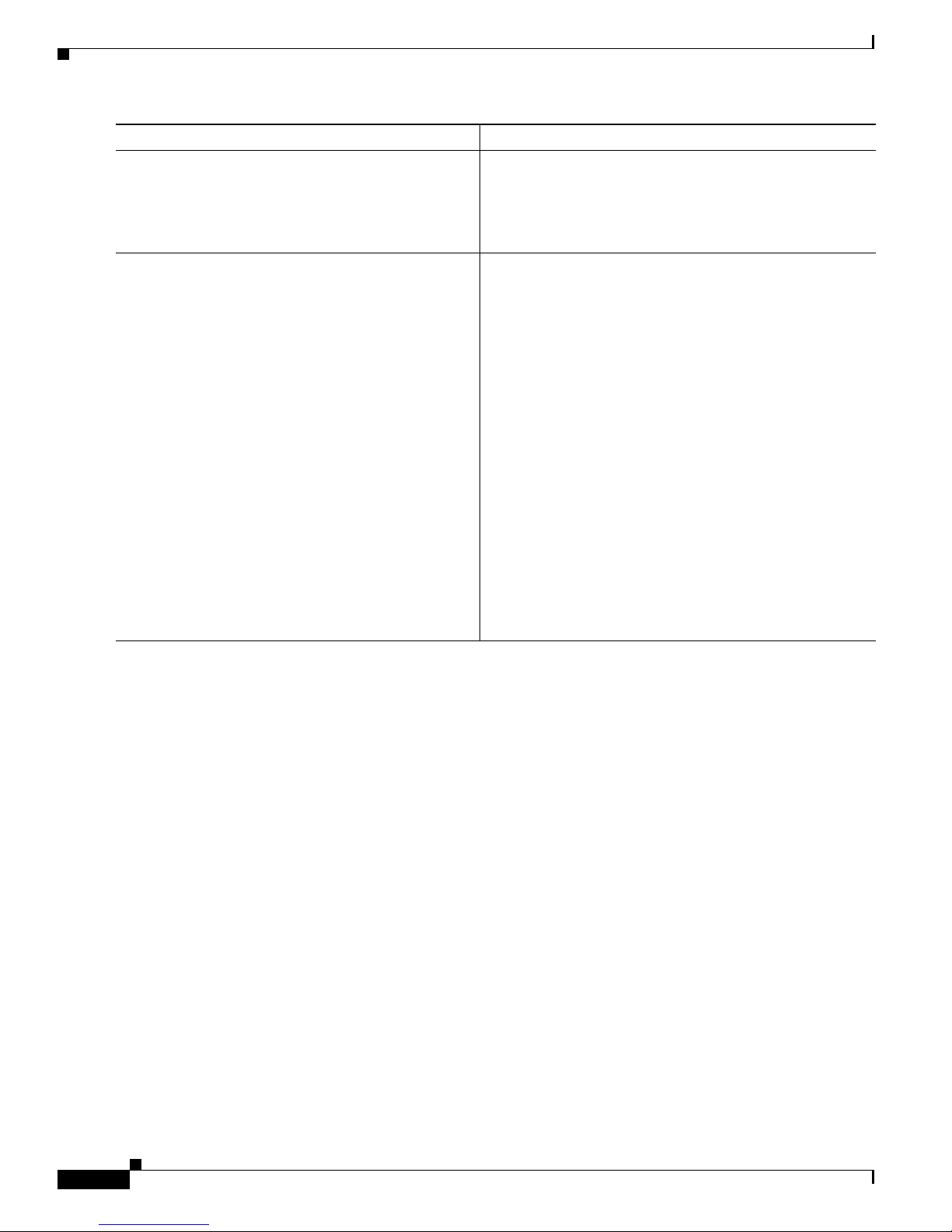
How to Implement CA Interoperability
Command or Action Purpose
Step 7
rsakeypair
keypair-label
Implementing Certification Authority Interoperability on Cisco IOS XR Software
(Optional) Specifies a named RSA key pair generated using
the crypto key generate rsa command for this trustpoint.
Step 8
Example:
RP/0/RP0/CPU0:router(config-trustp)# rsakeypair
mykey
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-trustp)# end
or
RP/0/RP0/CPU0:router(config-trustp)# commit
• Not setting this key pair means that the trustpoint uses
the default RSA key in the current configuration.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Authenticating the CA
This task authenticates the CA to your router.
The router must authenticate the CA by obtaining the self-signed certificate of the CA, which contains
the public key of the CA. Because the certificate of the CA is self-signed (the CA signs its own
certificate), manually authenticate the public key of the CA by contacting the CA administrator to
compare the fingerprint of the CA certificate.
SUMMARY STEPS
1. crypto ca authenticate ca-name
2. show crypto ca certificates
Cisco IOS XR System Security Configuration Guide
SC-10
Page 23
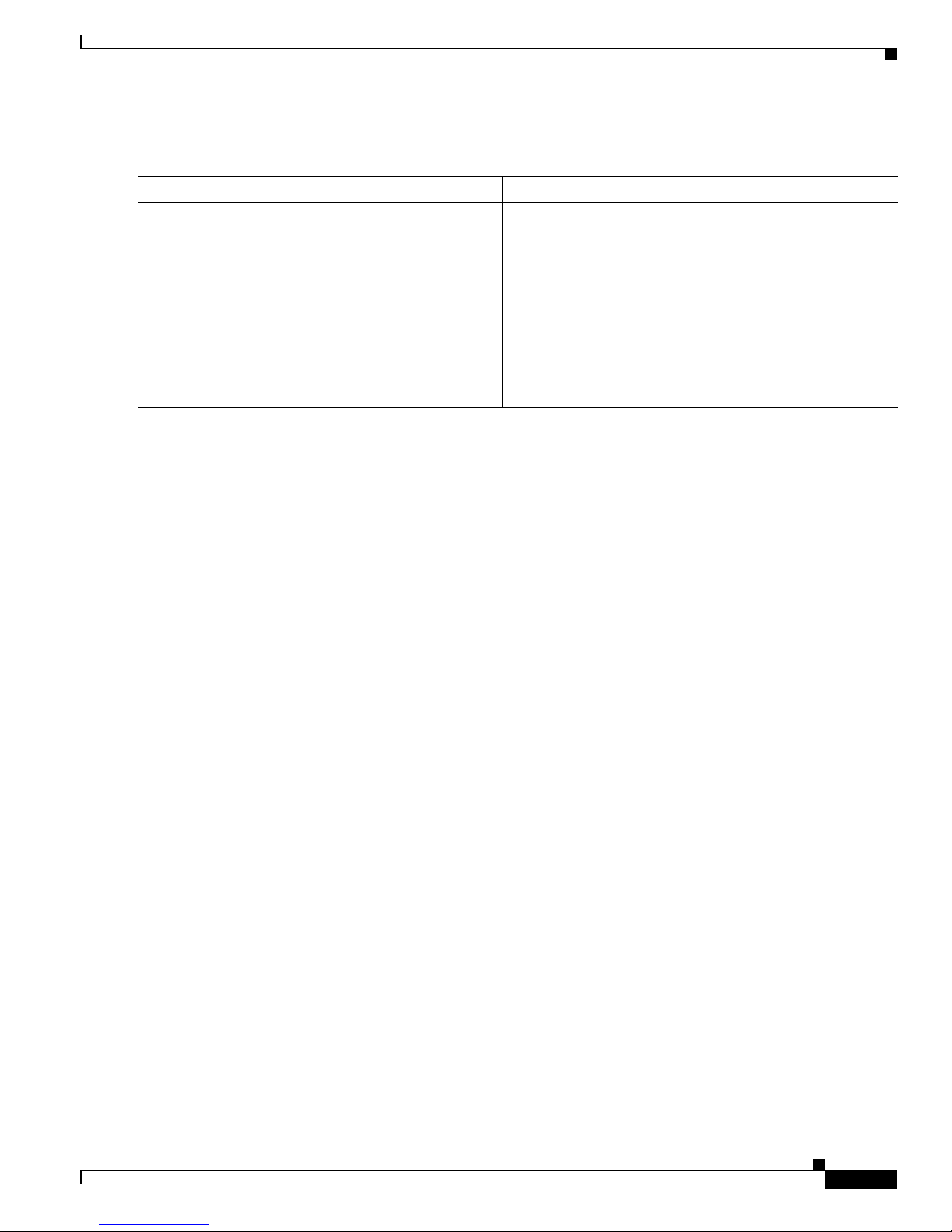
Implementing Certification Authority Interoperability on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
crypto ca authenticate
ca-name
Example:
RP/0/RP0/CPU0:router# crypto ca authenticate
myca
Step 2
show crypto ca certificates
Example:
RP/0/RP0/CPU0:router# show crypto ca
certificates
Requesting Your Own Certificates
How to Implement CA Interoperability
Authenticates the CA to your router by obtaining a CA
certificate, which contains the public key for the CA.
(Optional) Displays information about the CA certificate.
SUMMARY STEPS
This task requests certificates from the CA.
You must obtain a signed certificate from the CA for each of your router’s RSA key pairs. If you
generated general-purpose RSA keys, your router has only one RSA key pair and needs only one
certificate. If you previously generated special usage RSA keys, your router has two RSA key pairs and
needs two certificates.
1. crypto ca enroll ca-name
2. show crypto ca certificates
Cisco IOS XR System Security Configuration Guide
SC-11
Page 24
How to Implement CA Interoperability
DETAILED STEPS
Command or Action Purpose
Step 1
crypto ca enroll
Example:
RP/0/RP0/CPU0:router# crypto ca enroll myca
Step 2
show crypto ca certificates
ca-name
Implementing Certification Authority Interoperability on Cisco IOS XR Software
Requests certificates for all of your RSA key pairs.
• This command causes your router to request as many
certificates as there are RSA key pairs, so you need
only perform this command once, even if you have
special usage RSA key pairs.
• This command requires you to create a challenge
password that is not saved with the configuration. This
password is required if your certificate needs to be
revoked, so you must remember this password.
• A certificate may be issued immediately or the router
sends a certificate request every minute until the
enrollment retry period is reached and a timeout occurs.
If a timeout occurs, contact your system administrator
to get your request approved, and then enter this
command again.
(Optional) Displays information about the CA certificate.
Example:
RP/0/RP0/CPU0:router# show crypto ca
certificates
Configuring Certificate Enrollment Using Cut-and-Paste
This task declares the trustpoint certification authority (CA) that your router should use and configures
that trustpoint CA for manual enrollment by using cut-and-paste.
SUMMARY STEPS
1. configure
2. crypto ca trustpoint ca-name
3. enrollment terminal
4. end
or
commit
5. crypto ca authenticate ca-name
6. crypto ca enroll ca-name
7. crypto ca import ca-name certificate
8. show crypto ca certificates
Cisco IOS XR System Security Configuration Guide
SC-12
Page 25
Implementing Certification Authority Interoperability on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto ca trustpoint
ca-name
How to Implement CA Interoperability
Enters global configuration mode.
Declares the CA that your router should use and
enters trustpoint configuration mode.
Step 3
Step 4
Example:
RP/0/RP0/CPU0:router(config)# crypto ca trustpoint
myca
RP/0/RP0/CPU0:router(config-trustp)#
enrollment terminal
Example:
RP/0/RP0/CPU0:router(config-trustp)# enrollment
terminal
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-trustp)# end
or
RP/0/RP0/CPU0:router(config-trustp)# commit
• Use the ca-name argument to specify the name
of the CA.
Specifies manual cut-and-paste certificate
enrollment.
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
Step 5
crypto ca authenticate
ca-name
Example:
RP/0/RP0/CPU0:router# crypto ca authenticate myca
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Authenticates the CA by obtaining the certificate of
the CA.
• Use the ca-name argument to specify the name
of the CA. Use the same name that you entered
in Step 2.
Cisco IOS XR System Security Configuration Guide
SC-13
Page 26
Configuration Examples for Implementing Certification Authority Interoperability
Command or Action Purpose
Step 6
crypto ca enroll
ca-name
Example:
RP/0/RP0/CPU0:router# crypto ca enroll myca
Step 7
crypto ca import ca-
name
certificate
Example:
RP/0/RP0/CPU0:router# crypto ca import myca
certificate
Step 8
show crypto ca certificates
Implementing Certification Authority Interoperability on Cisco IOS XR Software
Obtains the certificates for your router from the CA.
• Use the ca-name argument to specify the name
of the CA. Use the same name that you entered
in Step 2.
Imports a certificate manually at the terminal.
• Use the ca-name argument to specify the name
of the CA. Use the same name that you entered
in Step 2.
Note You must enter the crypto ca import
command twice if usage keys (signature and
encryption keys) are used. The first time the
command is entered, one of the certificates
is pasted into the router; the second time the
command is entered, the other certificate is
pasted into the router. (It does not matter
which certificate is pasted first.
Displays information about your certificate and the
CA certificate.
Example:
RP/0/RP0/CPU0:router# show crypto ca certificates
Configuration Examples for Implementing Certification
Authority Interoperability
This section provides the following configuration example:
• Configuring Certification Authority Interoperability: Example, page SC-14
Configuring Certification Authority Interoperability: Example
The following example shows how to configure CA interoperability.
Comments are included within the configuration to explain various commands.
configure
hostname myrouter
domain name mydomain.com
end
Uncommitted changes found, commit them? [yes]:yes
crypto key generate rsa mykey
The name for the keys will be:mykey
Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose
Keypair
Choosing a key modulus greater than 512 may take a few minutes.
How many bits in the modulus [1024]:
Generating RSA keys ...
Cisco IOS XR System Security Configuration Guide
SC-14
Page 27

Implementing Certification Authority Interoperability on Cisco IOS XR Software
Configuration Examples for Implementing Certification Authority Interoperability
Done w/ crypto generate keypair
[OK]
show crypto key mypubkey rsa
Key label:mykey
Type :RSA General purpose
Size :1024
Created :17:33:23 UTC Thu Sep 18 2003
Data :
30819F30 0D06092A 864886F7 0D010101 05000381 8D003081 89028181 00CB8D86
BF6707AA FD7E4F08 A1F70080 B9E6016B 8128004C B477817B BCF35106 BC60B06E
07A417FD 7979D262 B35465A6 1D3B70D1 36ACAFBD 7F91D5A0 CFB0EE91 B9D52C69
7CAF89ED F66A6A58 89EEF776 A03916CB 3663FB17 B7DBEBF8 1C54AF7F 293F3004
C15B08A8 C6965F1E 289DD724 BD40AF59 E90E44D5 7D590000 5C4BEA9D B5020301
0001
! The following commands declare a CA and configure a trusted point.
configure
crypto ca trustpoint myca
enrollment url http://xyz-ultra5
enrollment retry count 25
enrollment retry period 2
rsakeypair mykey
end
Uncommitted changes found, commit them? [yes]:yes
! The following command authenticates the CA to your router.
crypto ca authenticate myca
Serial Number :01
Subject Name :
cn=Root coax-u10 Certificate Manager,ou=HFR,o=Cisco Systems,l=San Jose,st=CA,c=US
Issued By :
cn=Root coax-u10 Certificate Manager,ou=HFR,o=Cisco Systems,l=San Jose,st=CA,c=US
Validity Start :07:00:00 UTC Tue Aug 19 2003
Validity End :07:00:00 UTC Wed Aug 19 2020
Fingerprint:58 71 FB 94 55 65 D4 64 38 91 2B 00 61 E9 F8 05
Do you accept this certificate?? [yes/no]:yes
! The following command requests certificates for all of your RSA key pairs.
crypto ca enroll myca
% Start certificate enrollment ...
% Create a challenge password. You will need to verbally provide this
password to the CA Administrator in order to revoke your certificate.
% For security reasons your password will not be saved in the configuration.
% Please make a note of it.
Password:
Re-enter Password:
Fingerprint: 17D8B38D ED2BDF2E DF8ADBF7 A7DBE35A
! The following command displays information about your certificate and the CA
certificate.
show crypto ca certificates
Trustpoint :myca
==========================================================
Cisco IOS XR System Security Configuration Guide
SC-15
Page 28

Where to Go Next
Implementing Certification Authority Interoperability on Cisco IOS XR Software
CA certificate
Serial Number :01
Subject Name :
cn=Root coax-u10 Certificate Manager,ou=HFR,o=Cisco Systems,l=San Jose,st=CA,c=US
Issued By :
cn=Root coax-u10 Certificate Manager,ou=HFR,o=Cisco Systems,l=San Jose,st=CA,c=US
Validity Start :07:00:00 UTC Tue Aug 19 2003
Validity End :07:00:00 UTC Wed Aug 19 2020
Router certificate
Key usage :General Purpose
Status :Available
Serial Number :6E
Subject Name :
unstructuredName=myrouter.mydomain.com,o=Cisco Systems
Issued By :
cn=Root coax-u10 Certificate Manager,ou=HFR,o=Cisco Systems,l=San Jose,st=CA,c=US
Validity Start :21:43:14 UTC Mon Sep 22 2003
Validity End :21:43:14 UTC Mon Sep 29 2003
CRL Distribution Point
ldap://coax-u10.cisco.com/CN=Root coax-u10 Certificate Manager,O=Cisco Systems
Where to Go Next
After you have finished configuring CA interoperability, you should configure IKE, IPSec, and SSL. IKE
configuration is described in the Implementing Internet Key Exchange Security Protocol on
Cisco IOS XR Software module, IPSec in the Implementing IPSec Network Security on Cisco IOS XR
Software module, and SSL in the Implementing Secure Socket Layer on Cisco IOS XR Software module.
These modules are located in Cisco IOS XR System Security Configuration Guide.
Additional References
The following sections provide references related to implementing certification authority
interoperability.
Related Documents
Related Topic Document Title
PKI commands: complete command syntax, command
modes, command history, defaults, usage guidelines,
and examples
Public Key Infrastructure Commands on Cisco IOS XR Software
module in the Cisco IOS XR System Security Command Reference,
Release 3.5
Standards
Standards Title
No new or modified standards are supported by this
feature, and support for existing standards has not been
modified by this feature.
Cisco IOS XR System Security Configuration Guide
SC-16
—
Page 29

Implementing Certification Authority Interoperability on Cisco IOS XR Software
Additional References
MIBs
MIBs MIBs Link
— To locate and download MIBs using Cisco IOS XR software, use the
Cisco MIB Locator found at the following URL and choose a
platform under the Cisco Access Products menu:
http://cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml
RFCs
RFCs Title
No new or modified RFCs are supported by this
feature, and support for existing RFCs has not been
modified by this feature.
—
Technical Assistance
Description Link
The Cisco Technical Support website contains
thousands of pages of searchable technical content,
including links to products, technologies, solutions,
technical tips, and tools. Registered Cisco.com users
can log in from this page to access even more content.
http://www.cisco.com/techsupport
Cisco IOS XR System Security Configuration Guide
SC-17
Page 30

Additional References
Implementing Certification Authority Interoperability on Cisco IOS XR Software
Cisco IOS XR System Security Configuration Guide
SC-18
Page 31

Implementing Internet Key Exchange Security
Protocol on Cisco IOS XR Software
Internet Key Exchange (IKE) is a key management protocol standard that is used in conjunction with the
IP Security (IPSec) standard. IPSec is a feature that provides robust authentication and encryption of IP
packets.
IKE is a hybrid protocol that implements the Oakley key exchange and the Skeme key exchange inside
the Internet Security Association and Key Management Protocol (ISAKMP) framework. (ISAKMP,
Oakley, and Skeme are security protocols implemented by IKE.)
IPSec can be configured without IKE, but IKE enhances IPSec by providing additional features,
flexibility, and ease of configuration for the IPSec standard.
This module describes the tasks that you need to implement IKE on your Cisco IOS XR network.
Note For a complete description of the IKE commands used in this chapter, see the Internet Key Exchange
Security Protocol Commands on Cisco IOS XR Software module of the Cisco IOS XR System Security
Command Reference. To locate documentation of other commands that appear in this chapter, use the
command reference master index, or search online.
Feature History for Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Release Modification
Release 2.0 This feature was introduced on the Cisco CRS-1.
Release 3.0 No modification.
Release 3.2 Support was added for the Cisco XR 12000 Series Router.
Release 3.3.0 No modification.
Release 3.4.0
Release 3.5.0
• Support was added for IKE for the Cisco XR 12000 Series Router
IPSec VPN SPA.
• Support was added to implement IKE for locally sourced and destined
traffic on both the Cisco CRS-1 and Cisco XR 12000 Series Router.
• The IP Security VPN Monitoring feature was added.
• Banner, Auto-Update, and Browser-Proxy features were added to aid
in managing a Cisco Easy VPN remote device.
• Pushing a configuration URL through a mode-configuration exchange
feature was added.
Cisco IOS XR System Security Configuration Guide
SC-19
Page 32

Contents
Contents
• Prerequisites, page SC-20
• Information About Implementing IKE Security Protocol Configurations for IPSec Networks,
• Information About IKE for the Cisco IPSec VPN SPA on Cisco IOS XR Software, page SC-32
• How to Implement IKE Security Protocol Configurations for IPSec Networks, page SC-32
• How to Implement IKE for Locally Sourced and Destined Traffic, page SC-58
• How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software, page SC-62
• Configuration Examples for Implementing IKE Security Protocol, page SC-68
• Additional References, page SC-73
Prerequisites
The following prerequisites are required to implement Internet Key Exchange:
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
page SC-20
• You must be in a user group associated with a task group that includes the proper task IDs for
security commands. For detailed information about user groups and task IDs, see the Configuring
AAA Services on Cisco IOS XR Software module of the Cisco IOS XR System Security
Configuration Guide.
• You must install and activate the package installation envelope (PIE) for the security software.
For detailed information about optional PIE installation, see the Cisco IOS XR System Management
Guide.
Information About Implementing IKE Security Protocol
Configurations for IPSec Networks
To implement IKE, you should understand the following concepts:
• Supported Standards, page SC-21
• Concessions for Not Enabling IKE, page SC-22
• IKE Policies, page SC-22
• ISAKMP Identity, page SC-26
• ISAKMP Profile Overview, page SC-26
• Mask Preshared Keys, page SC-27
• Preshared Keys Using a AAA Server, page SC-27
• Internet Key Exchange Mode Configuration, page SC-28
• Banner, Auto-Update, and Browser-Proxy, page SC-29
• Pushing a Configuration URL Through a Mode-Configuration Exchange, page SC-29
• Internet Key Exchange Extended Authentication, page SC-30
Cisco IOS XR System Security Configuration Guide
SC-20
Page 33

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
• Call Admission Control, page SC-30
• Information About IP Security VPN Monitoring, page SC-31
Supported Standards
Cisco implements the following standards:
• IKE—Internet Key Exchange. A hybrid protocol that implements Oakley and Skeme key exchanges
inside the ISAKMP framework. IKE can be used with other protocols, but its initial implementation
is with the IPSec protocol. IKE provides authentication of the IPSec peers, negotiates IPSec keys,
and negotiates IPSec security associations (SAs).
IKE is implemented following RFC 2409, The Internet Key Exchange.
• IPSec—IP Security Protocol. IPSec is a framework of open standards that provides data
confidentiality, data integrity, and data authentication between participating peers. IPSec provides
these security services at the IP layer; it uses IKE to handle negotiation of protocols and algorithms
based on local policy and to generate the encryption and authentication keys to be used by IPSec.
IPSec is used to protect one or more data flows between a pair of hosts, a pair of security gateways,
or a security gateway and a host.
For more information on IPSec, see the Implementing IPSec Network Security on Cisco IOS XR
Software module of the Cisco IOS XR System Security Configuration Guide.
• ISAKMP—Internet Security Association and Key Management Protocol. A protocol framework
that defines payload formats, the mechanics of implementing a key exchange protocol, and the
negotiation of a security association.
ISAKMP is implemented following the latest version of the Internet Security Association and Key
Management Protocol (ISAKMP) Internet Draft (RFC 2408).
• Oakley—A key exchange protocol that defines how to derive authenticated keying material.
• Skeme—A key exchange protocol that defines how to derive authenticated keying material, with
rapid key refreshment.
The component technologies implemented for use by IKE include the following:
• DES—Data Encryption Standard. An algorithm that is used to encrypt packet data. IKE implements
the 56-bit DES-CBC with Explicit IV standard. Cipher Block Chaining (CBC) requires an
initialization vector (IV) to start encryption. The IV is explicitly given in the IPSec packet.
Cisco IOS XR software also implements Triple DES (168-bit) encryption, depending on the
software versions available for a specific platform. Triple DES (3DES) is a strong form of
encryption that allows sensitive information to be sent over untrusted networks. It enables
customers, particularly in the finance industry, to use network-layer encryption.
• AES—Advanced Encryption Standard. 128-bit, 192-bit, and 256-bit AESs are supported.
Note Cisco IOS XR images that have strong encryption (including, but not limited to, 56-bit data
encryption feature sets) are subject to U.S. government export controls, and have a limited
distribution. Images that are to be installed outside the United States require an export
license. Customer orders might be denied or subject to delay because of U.S. government
regulations. Contact your sales representative or distributor for more information, or send
e-mail to export@cisco.com.
Cisco IOS XR System Security Configuration Guide
SC-21
Page 34

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
• Diffie-Hellman—A public-key cryptography protocol that allows two parties to establish a shared
secret over an unsecure communications channel. Diffie-Hellman is used within IKE to establish
session keys. 768-bit, 1024-bit, and 1536-bit Diffie-Hellman groups are supported.
• MD5 (HMAC variant)—Message Digest 5. A hash algorithm used to authenticate packet data.
HMAC is a variant that provides an additional level of hashing.
• SHA (HMAC variant)—Secure Hash Algorithm. A hash algorithm used to authenticate packet data.
HMAC is a variant that provides an additional level of hashing.
• RSA signatures and RSA encrypted nonces—RSA is the public key cryptographic system developed
by Ron Rivest, Adi Shamir, and Leonard Adelman. RSA signatures provide nonrepudiation, and
RSA encrypted nonces provide repudiation. (Repudiation and nonrepudiation are associated with
traceability.)
IKE interoperates with the X.509v3 certificates standard. It is used with the IKE protocol when
authentication requires public keys. This certificate support allows the protected network to scale by
providing the equivalent of a digital ID card to each device. When two devices want to communicate,
they exchange digital certificates to prove their identity; thus, removing the need to manually exchange
public keys with each peer or to manually specify a shared key at each peer.
Concessions for Not Enabling IKE
IKE is disabled by default in Cisco IOS XR software. If you do not enable IKE, you must make these
concessions at the peers:
• You must manually specify all IPSec security associations in the crypto profiles at all peers. (Crypto
profile configuration is described in the module Implementing IPSec Network Security on
Cisco IOS XR Software.)
• The IPSec security associations of the peers never time out for a given IPSec session.
• During IPSec sessions between the peers, the encryption keys never change.
• Antireplay services are not available between the peers.
• Certification authority (CA) support cannot be used.
IKE Policies
You must create IKE policies at each peer. An IKE policy defines a combination of security parameters
to be used during the IKE negotiation.
Before you create and configure IKE policies you should understand the following concepts:
• IKE Policy Creation, page SC-23
• Definition of Policy Parameters, page SC-23
• IKE Peer Agreement for Matching Policies, page SC-23
• Value Selection for Parameters, page SC-24
• Policy Creation, page SC-25
• Additional Configuration Required for IKE Policies, page SC-25
Cisco IOS XR System Security Configuration Guide
SC-22
Page 35

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
IKE Policy Creation
IKE negotiations must be protected, so each IKE negotiation begins by agreement of both peers on a
common (shared) IKE policy. This policy states which security parameters will be used to protect
subsequent IKE negotiations and mandates how the peers are authenticated.
After the two peers agree on a policy, the security parameters of the policy are identified by a security
association established at each peer, and these security associations apply to all subsequent IKE traffic
during the negotiation.
You can create multiple, prioritized policies at each peer to ensure that at least one policy matches the
policy of a remote peer.
Definition of Policy Parameters
Table 2 lists the five parameters to define in each IKE policy.
Table 2 IKE Policy Parameter Definitions
Parameter Accepted Values Keyword Default Value
Encryption algorithm 56-bit DES-CBC
des
56-bit DES-CBC
168-bit DES
128-bit AES
192-bit AES
256-bit AES
Hash algorithm SHA-1 (HMAC variant)
MD5 (HMAC variant)
Authentication method RSA signatures
RSA encrypted nonces
Preshared keys
Diffie-Hellman group
identifier
768-bit Diffie-Hellman or
1024-bit Diffie-Hellman
1536-bit Diffie-Helman
Lifetime of the security
association
1. For information about this lifetime and how it is used, see the command description for the lifetime command.
1
Any number of seconds — 86400 seconds (1 day)
3des
aes
aes 192
aes 256
sha
md5
rsa-sig
rsa-encr
pre-share
1
2
5
SHA-1
RSA signatures
768-bit Diffie-Hellman
These parameters apply to the IKE negotiations when the IKE security association is established.
IKE Peer Agreement for Matching Policies
When the IKE negotiation begins, IKE looks for an IKE policy that is the same on both peers. The peer
that initiates the negotiation will send all its policies to the remote peer, and the remote peer will try to
find a match. The remote peer looks for a match by comparing its own highest priority policy against the
policies received from the other peer. The remote peer checks each of its policies in order of its priority
(highest priority first) until a match is found.
Cisco IOS XR System Security Configuration Guide
SC-23
Page 36

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
A match is made when both policies from the two peers contain the same encryption, hash,
authentication, and Diffie-Hellman parameter values, and when the remote peer’s policy specifies a
lifetime that is less than or equal to the lifetime in the policy being compared. (If the lifetimes are not
identical, the shorter lifetime—from the remote peer’s policy—is used.)
If no acceptable match is found, IKE refuses negotiation and IPSec is not established.
If a match is found, IKE completes negotiation, and IPSec security associations are created.
Note Depending on which authentication method is specified in a policy, additional configuration might be
required (as described in the “Additional Configuration Required for IKE Policies” section on page 25).
If a peer’s policy does not have the required companion configuration, the peer does not submit the
policy when attempting to find a matching policy with the remote peer.
Value Selection for Parameters
You can select certain values for each parameter, following the IKE standard. But why choose one value
over another?
If you are interoperating with a device that supports only one of the values for a parameter, your choice
is limited to the value supported by the other device. Aside from this, a trade-off between security and
performance often exists, and many of these parameter values represent such a trade-off. You should
evaluate the level of security risks for your network and your tolerance for these risks. Then the
following tips might help you select which value to specify for each parameter:
• The encryption algorithm has five options: 56-bit DES-CBC, 168-bit DES, 128-bit AES, 192-bit
AES, and 256-bit AES.
• The hash algorithm has two options: SHA-1 and MD5.
MD5 has a smaller digest and is considered to be slightly faster than SHA-1. A demonstrated
successful (but extremely difficult) attack has been demonstrated against MD5; however, the HMAC
variant used by IKE prevents this attack.
• The authentication method has three options: RSA signatures, RSA encrypted nonces, and preshared
keys.
–
RSA signatures provide nonrepudiation for the IKE negotiation (you can prove to a third party
after the fact that you did indeed have an IKE negotiation with the remote peer).
RSA signatures allow the use of a CA. Using a CA can dramatically improve the manageability
and scalability of your IPSec network. Additionally, RSA signature-based authentication uses
only two public key operations, whereas RAS encryption uses four public key operations,
making it costlier in terms of overall performance.
You can also exchange the public keys manually, as described in the “Manually Configuring
RSA Keys” section on page 44.
–
RSA encrypted nonces provide repudiation for the IKE negotiation (you cannot prove to a third
party that you had an IKE negotiation with the remote peer).
RSA encrypted nonces require that peers possess each other’s public keys but do not use a
certification authority. Instead, two ways exist for peers to get each other’s public keys:
–
During configuration, you manually configure RSA keys (as described in the “Manually
Configuring RSA Keys” section on page 44).
Cisco IOS XR System Security Configuration Guide
SC-24
Page 37

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
–
If your local peer has previously used RSA signatures with certificates during a successful IKE
negotiation with a remote peer, your local peer already possesses the remote peer’s public key.
(The peers’ public keys are exchanged during the RSA-signatures-based IKE negotiations, if
certificates are used.)
–
Preshared keys are clumsy to use if your secured network is large, and they do not scale well
with a growing network. However, they do not require use of a certification authority, as do RSA
signatures, and might be easier to set up in a small network with fewer than ten nodes. RSA
signatures also can be considered more secure when compared with preshared key
authentication.
• The Diffie-Hellman group identifier has three options: 768-bit, 1024-bit Diffie-Hellman, and
1536-bit Diffie Helman.
The 1024-bit Diffie-Hellman and 1536-bit Diffie Helman options are harder to crack but require
more CPU time to execute.
• The lifetime of the security association can be set to any value.
As a general rule, the shorter the lifetime (up to a point), the more secure your IKE negotiations.
However, with longer lifetimes, future IPSec security associations can be set up more quickly. For
more information about this parameter and how it is used, see the command description for the
lifetime command.
Policy Creation
You can create multiple IKE policies, each with a different combination of parameter values. For each
policy that you create, assign a unique priority (1 through 10,000, with 1 being the highest priority).
You can configure multiple policies on each peer—but at least one of these policies must contain exactly
the same encryption, hash, authentication, and Diffie-Hellman parameter values as one of the policies
on the remote peer. (The lifetime parameter need not necessarily be the same; see details in the “IKE
Peer Agreement for Matching Policies” section on page 23.)
If you do not configure any policies, your router uses the default policy, which is always set to the lowest
priority and contains the default value of each parameter.
Additional Configuration Required for IKE Policies
Depending on the authentication method you specify in your IKE policies, you must perform certain
additional configuration tasks before IKE and IPSec can successfully use the IKE policies.
Each authentication method requires additional companion configuration as follows:
• RSA signatures method. If you specify RSA signatures as the authentication method in a policy, you
may configure the peers to obtain certificates from a CA. (The CA must be properly configured to
issue the certificates.) Configure this certificate support as described in the module “Implementing
Certification Authority Interoperability.”
The certificates are used by each peer to exchange public keys securely. (RSA signatures require that
each peer has the public signature key of the remote peer.) When both peers have valid certificates,
they automatically exchange public keys with each other as part of any IKE negotiation in which
RSA signatures are used.
You may also want to exchange the public keys manually, as described in the “Manually Configuring
RSA Keys” section on page 44.
• RSA encrypted nonces method. If you specify RSA encrypted nonces as the authentication method
in a policy, you must ensure that each peer has the public keys of the other peers.
Cisco IOS XR System Security Configuration Guide
SC-25
Page 38

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
Unlike RSA signatures, the RSA encrypted nonces method cannot use certificates to exchange
public keys. Instead, you ensure that each peer has the others’ public keys by one of the following
methods:
–
Manually configuring RSA keys, as described in the “Manually Configuring RSA Keys” section
on page 44.
–
Ensuring that an IKE exchange using RSA signatures with certificates has already occurred
between the peers. (The peers’ public keys are exchanged during the RSA-signatures-based IKE
negotiations if certificates are used.)
To make this happen, specify two policies: a higher-priority policy with RSA encrypted nonces
and a lower-priority policy with RSA signatures. When IKE negotiations occur, RSA signatures
are used the first time because the peers do not yet have each other’s public keys. Then future
IKE negotiations are able to use RSA encrypted nonces because the public keys will have been
exchanged.
This alternative requires that you have certification authority support configured.
• Preshared keys authentication method. If you specify preshared keys as the authentication method
in a policy, you must configure these preshared keys as described in the “Configuring ISAKMP
Preshared Keys in ISAKMP Keyrings” section on page 48.
If RSA encryption is configured and signature mode is negotiated (and certificates are used for signature
mode), the peer requests both signature and encryption keys. Basically, the router requests as many keys
as the configuration supports. If RSA encryption is not configured, it just requests a signature key.
ISAKMP Identity
You should set the ISAKMP identity for each peer that uses preshared keys in an IKE policy.
When two peers use IKE to establish IPSec security associations, each peer sends its identity to the
remote peer. Each peer sends either its hostname or its IP address, depending on how you have set the
ISAKMP identity of the router.
By default, the ISAKMP identity of a peer is the IP address of the peer. If appropriate, you could change
the identity to be the peer’s hostname instead. As a general rule, set the identities of all peers the same
way—either all peers should use their IP addresses or all peers should use their host names. If some peers
use their host names and some peers use their IP addresses to identify themselves to each other, IKE
negotiations could fail if the identity of a remote peer is not recognized and a domain name server (DNS)
lookup is unable to resolve the identity.
ISAKMP Profile Overview
The ISAKMP profile is an enhancement to Internet Security Association and Key Management Protocol
(ISAKMP) configurations. It enables modularity of ISAKMP configuration for phase 1 negotiations.
This modularity allows mapping different ISAKMP parameters to different IP Security (IPSec) tunnels,
and mapping different IPSec tunnels to different VPN forwarding and routing (VRF) instances.
Currently, many applications and enhancements use the ISAKMP profile, including quality of service
(QoS), router certificate management, and Multiprotocol Label Switching (MPLS) VPN configurations.
An ISAKMP profile is a repository for IKE Phase 1 and IKE Phase 1.5 configuration for a set of peers.
An ISAKMP profile applies parameters to an incoming IPSec connection identified uniquely through its
concept of match identity criteria. These criteria are based on the IKE identity that is presented by
incoming IKE connections and includes IP address, fully qualified domain name (FQDN), and group
(the Virtual Private Network [VPN] remote client grouping). The granularity of the match identity
Cisco IOS XR System Security Configuration Guide
SC-26
Page 39

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
criteria imposes the granularity of applying the specified parameters. The ISAKMP profile applies
parameters specific to each profile, such as trust points, peer identities, and XAUTH authentication,
authorization, and accounting (AAA) list, and so forth.
ISAKMP Profile Considerations
The following considerations are listed on when to use the ISAKMP profile:
• Any router with two or more IPSec connections that requires different phase 1 parameters for
different sites (for example, configuring site-to-site and remote access on the same router).
• Custom Internet Key Exchange (IKE) Phase 1 policies might be needed for different peers. For
example, whether XAUTH is applied to a specific peer, rather than being applied on every
connection.
• IPSec configuration using VRF-aware IPSec, which allows the use of single IP address to connect
to different peers with different IKE Phase 1 parameters.
Mask Preshared Keys
A mask preshared key lets a group of remote users with the same level of authentication share an IKE
preshared key. The preshared key of the remote peer must match the preshared key of the local peer for
IKE authentication to occur.
A mask preshared key is usually distributed through a secure out-of-band channel. In a remote
peer-to-local peer scenario, any remote peer with the IKE preshared key configured can establish IKE
SAs with the local peer.
If you specify a subnet-address value with the crypto keyring command, it is up to you to use a subnet
address, which allows more peers to share the same key. That is, the preshared key is no longer restricted
to use between two users.
Note We do not recommend using 0.0.0.0 as a subnet address, because it encourages group preshared keys,
which allow all peers to have the same group key, thereby reducing the security of your user
authentication.
Mask preshared keys have the following restrictions:
• The SA cannot be established between the IPSec peers until all IPSec peers are configured for the
same preshared key.
• The mask preshared key must be distinctly different for remote users requiring varying levels of
authorization. You must configure a new preshared key for each level of trust and assign the correct
keys to the correct parties. Otherwise, an untrusted party may obtain access to protected data.
Preshared Keys Using a AAA Server
Preshared keys do not scale well when you are trying to deploy a large scale Virtual Private Network
(VPN) without using a CA. When dynamic IP addressing such as DHCP or PPP dialups is used, the
changing IP address can make key lookup difficult or impossible unless a mask preshared key is used.
However, mask preshared keys are not very secure because a large number of users are given the same
secret, thus reducing the security of the secret.
Cisco IOS XR System Security Configuration Guide
SC-27
Page 40

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
Configuring preshared keys using an authentication, authorization, and accounting (AAA) server allows
each user to have his or her own key, which is stored on an external AAA server. This allows for central
management of the user database, linking it to an existing AAA database, in addition to allowing every
user to have a unique, more secure preshared key.
To configure this feature, you must perform the following tasks at each peer:
• Configure AAA.
• Configure a dynamic crypto ISAKMP profile.
• Configure extended authentication (optional)
• Configure ISAKMP policy.
For information on configuring crypto ISAKMP profiles, including enabling an IPSec peer for preshared
keys using an AAA server, see both the “Configuring Crypto Keyrings” section on page 54 and the
“Configuring the ISAKMP Profile for Locally Sourced and Destined Traffic” section on page 58.
Preshared keys using an AAA server have the following restrictions:
• The shared secret can be accessed only in aggressive mode. The ID of the IKE exchange is used as
the username to query AAA if no local key can be found on the Cisco IOS XR router to which the
user is trying to connect. Aggressive mode provides the ID in the first part of the IKE exchange;
main mode does not provide the ID until the latter part of the IKE exchange, which is too late for
key lookup.
• Only the following ID types can be used:
–
IPv4 address (can be different from the one assigned by the Internet service provider [ISP])
–
FQDN (fully qualified domain name)
–
E-mail address
Internet Key Exchange Mode Configuration
IKE mode configuration, as defined by the Internet Engineering Task Force (IETF), allows a gateway to
download an IP address (and other network level configuration) to the client as part of an IKE
negotiation. Using this exchange, the gateway gives IP addresses to the IKE client to be used as an
“inner” IP address encapsulated under IPSec. This method provides a known IP address for the client
that can be matched against IPSec policy.
To implement the Cisco IPSec VPN SPAs between remote access clients that have dynamic IP addresses
and a corporate gateway, you have to dynamically administer scalable IPSec policy on the gateway once
each client is authenticated. With IKE mode configuration, the gateway can set up scalable policy for a
very large set of clients irrespective of the IP addresses of those clients.
The client initiation type of IKE mode configuration is supported. The client initiates the configuration
mode with the gateway. The gateway responds with an IP address that it has allocated for the client.
Mode configuration must be applied to a crypto ISAKMP profile to be enforced.
For instructions on how to apply mode configuration to a crypto ISAKMP profile, see the “Defining
Group Policy Information for Mode Configuration” section on page 36.
Interfaces with crypto ISAKMP profiles, which are configured for IKE mode configuration, may
experience a slightly longer connection setup time. This longer setup time is true even for IKE peers that
refuse to be configured or do not respond to the configuration mode request. In both cases, the gateway
initiates the configuration of the client.
Cisco IOS XR System Security Configuration Guide
SC-28
Page 41

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
Banner, Auto-Update, and Browser-Proxy
Table 3 describes the features that provide support for attributes that aid in the management of the
Cisco Easy VPN remote device.
Table 3 Features that Aid in the Management of the Cisco Easy VPN Remote Device
Feature Description
Banner Configures a Cisco Easy VPN server to push a
Auto-Update Configures a Cisco Easy VPN server to provide an
Browser-Proxy Configures a Cisco Easy VPN server so that the
banner to a Cisco Easy VPN remote device.
automated mechanism to make software and
firmware upgrades automatically available to a
Cisco Easy VPN remote device.
Cisco Easy VPN remote device can access
resources on the corporate network. With this
configuration, the user does not have to manually
modify the proxy settings of his or her web
browser when connecting and does not have to
manually revert the proxy settings when
disconnecting.
After a Cisco Easy VPN connection is up, use the crypto ipsec server send-update command in EXEC
mode to send auto-update notifications at anytime.
Pushing a Configuration URL Through a Mode-Configuration Exchange
When remote devices connect to a corporate gateway for creating an IPsec VPN tunnel, some policy and
configuration information must be applied to the remote device when the VPN tunnel is active to allow
the remote device to become a part of the corporate VPN. The URL contains the configuration
information that the remote device must download and apply to the running configuration.
The configuration that is pushed to the remote device is persistent by default. The configuration is
applied when the IPsec tunnel is “up,” but it is not withdrawn when the IPsec tunnel goes “down.”
However, it is possible to write a section of configuration that is transient in nature, in which case, the
configuration of the section is reverted when the tunnel is disconnected.
There are no restrictions on where the configuration distribution server is physically located. However,
we recommended that a secure protocol such as HTTPS (Secure HTTP) be used to retrieve the
configuration. The configuration server is located in the corporate network, so because the transfer
happens through the IPsec tunnel, insecure access protocols (such as HTTP) are used.
Regarding backward compatibility: the remote device asks for the CONFIGURATION-URL and
CONFIGURATION-VERSION attributes. The server sends the configuration url and version attributes
whether they were on the group or user. The standard attribute priority scheme, which was used for all
the attributes, are also used. There is no built-in restriction to push the configuration, but bootstrap
configurations (such as for the IP address) cannot be sent because those configurations are required to
set up the Cisco Easy VPN tunnel, and the CONFIGURATION-URL comes into effect only after the
Cisco Easy VPN tunnel comes up.
Cisco IOS XR System Security Configuration Guide
SC-29
Page 42

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
Internet Key Exchange Extended Authentication
IKE extended authentication (Xauth) is a draft RFC based on the IKE protocol. Xauth allows all
Cisco IOS XR software AAA authentication methods to perform user authentication in a separate phase
after the IKE authentication phase 1 exchange. The AAA configuration list name must match the Xauth
configuration list name for user authentication to occur.
Xauth does not replace IKE. IKE allows for device authentication and Xauth allows for user
authentication, which occurs after IKE device authentication. Xauth occurs after IKE authentication
phase 1 but before IKE IPSec SA negotiation phase 2.
To configure Xauth, perform the following tasks:
• Configure AAA (you must set up an authentication list).
• Configure a static crypto ISAKMP profile.
• Configure ISAKMP policy.
• Configure a dynamic crypto ISAKMP profile (optional).
For information on configuring crypto ISAKMP profiles, see the “Configuring the ISAKMP Profile for
Locally Sourced and Destined Traffic” section on page 58.
Call Admission Control
The Call Admission Control (CAC) for Internet Key Exchange (IKE) feature describes the application
of CAC to the IKE protocol in Cisco IOS XR software. CAC limits the number of simultaneous IKE
security associations (SAs) (that is, calls to CAC) that a router can establish. In addition, there is an
option to limit the maximum number of active IKE SAs allowed in the system and the CPU usage that
is consumed by the IKE process or global CPU. The main function of CAC is to protect the router from
severe resource depletion and to prevent crashes.
IKE Session
You can configure the absolute IKE SA limit by using the crypto isakmp call admission limit
command. The router drops new IKE SA requests when the value has been reached.
Security Association Limit
A security association (SA) is a description of how two or more entities use security services to
communicate securely on behalf of a particular data flow. IKE requires and uses SAs to identify the
parameters of its connections. IKE can negotiate and establish its own SA. An IKE SA is used by IKE
only, and it is bidirectional. An IKE SA cannot limit IPsec.
IKE drops SA requests based on a user-configured SA limit. To configure an IKE SA limit, use the
crypto isakmp call admission limit command. When there is a new SA request from a peer router, IKE
determines if the number of active IKE SAs plus the number of SAs being negotiated meets or exceeds
the configured SA limit. If the number is greater than or equal to the limit, the new SA request is rejected
and a system log is generated. This log contains the source destination IP address of the SA request.
Cisco IOS XR System Security Configuration Guide
SC-30
Page 43

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About Implementing IKE Security Protocol Configurations for IPSec Networks
Information About IP Security VPN Monitoring
The IP Security (IPSec) VPN Monitoring feature provides VPN session monitoring enhancements that
allow you to troubleshoot the Virtual Private Network (VPN) and monitor the end-user interface. Session
monitoring includes the following enhancements:
• Ability to specify an Internet Key Exchange (IKE) peer description in the configuration file.
• Summary listing of crypto session status.
• Ability to clear both IKE and IP Security (IPSec) security associations (SAs) using one
command-line interface (CLI).
• Ability to expend the filtering mechanism by using the options from the show crypto session
command.
To implement IPSec VPN monitoring, you must understand the following concepts:
• Crypto Sessions Background, page SC-31
• Per-IKE Peer Description, page SC-31
• Summary Listing of Crypto Session Status, page SC-31
• IKE and IPSec Security Exchange Clear Command, page SC-32
Crypto Sessions Background
A crypto session is a set of IPSec connections (flows) between two crypto endpoints. If the two crypto
endpoints use IKE as the keying protocol, they are IKE peers to each other. Typically, a crypto session
consists of one IKE security association (for control traffic) and at least two IPSec security associations
(for data traffic—one per each direction). There may be duplicated IKE security associations (SAs) and
IPSec SAs or duplicated IKE SAs or IPSec SAs for the same session in the duration of rekeying or
because of simultaneous setup requests from both sides.
Per-IKE Peer Description
The Per-IKE Peer Description function allows you to enter a description of your choice for an IKE peer.
The unique peer description, which includes up to 80 characters, is used whenever you are referencing
that particular IKE peer. To add the peer description, use the description (ISAKMP peer) command.
The primary application of this description field is for monitoring purposes (for example, when using
show commands or for logging [syslog messages]). The description field is purely informational.
Summary Listing of Crypto Session Status
You can obtain a list of status information for active crypto sessions by using the show crypto session
command. The listing includes the following summary status of the crypto session:
• Interface
• IKE SAs that are associated with the peer by whom the IPSec SAs are created
• IPSec SAs serving the flows of a session
Multiple IKE or IPSec SAs can be established for the same peer (for the same session), in which case
IKE peer descriptions are repeated with different values for the IKE SAs that are associated with the peer
and for the IPSec SAs that are serving the flows of the session.
Cisco IOS XR System Security Configuration Guide
SC-31
Page 44

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Information About IKE for the Cisco IPSec VPN SPA on Cisco IOS XR Software
In addition, you can use the show crypto session command with the detail keyword to obtain more
detailed information about the sessions.
IKE and IPSec Security Exchange Clear Command
The clear crypto session command allows you to clear both IKE and IPSec. To clear a specific crypto
session or a subset of all the sessions (for example, a single tunnel to one remote site), you need to
provide session-specific parameters, such as a local or remote IP address, a local or remote port, a front
door VPN routing and forwarding (FVRF) name, or an inside VRF (IVRF) name. Typically, the remote
IP address is used to specify a single tunnel to be deleted.
If a local IP address is provided as a parameter when you use the clear crypto session command, all the
sessions (and their IKE SAs and IPSec SAs) that share the IP address as a local crypto endpoint (IKE
local address) are cleared. If you do not provide a parameter, all IPSec SAs and IKE SAs that are in the
router are deleted.
Information About IKE for the Cisco IPSec VPN SPA on
Cisco IOS XR Software
To implement IKE for the Cisco IPSec VPN SPAs, you should understand the following concept:
• IPSec Dead Peer Detection Periodic Message Option, page SC-32
IPSec Dead Peer Detection Periodic Message Option
The IPSec Dead Peer Detection (DPD) Periodic Message Option feature allows you to configure your
router to query the liveliness of its Internet Key Exchange (IKE) peer at regular intervals. The benefit of
this approach over the default approach (on-demand dead peer detection) is earlier detection of dead
peers.
DPD, which is defined in RFC 3706, is a mechanism used to detect dead IPSec peers. IPSec is a
peer-to-peer technology. IP connectivity can be lost between the peers due to routing problems, peer
reloading, or some other situation that can result in black holes in which traffic is lost. DPD, based on a
traffic-detection method, is one possible mechanism to remedy this situation.
How to Implement IKE Security Protocol Configurations for
IPSec Networks
To configure the IKE security protocol for IPSec networks, perform the tasks described in the following
sections. The tasks in the first two sections are required; the remaining may be optional, depending on
which parameters are configured.
• Enabling or Disabling IKE, page SC-33 (required)
• Configuring IKE Policies, page SC-34 (required)
• Defining Group Policy Information for Mode Configuration, page SC-36 (required)
• Configuring a Banner, page SC-40 (optional)
• Configuring Auto-Upgrade, page SC-40 (optional)
Cisco IOS XR System Security Configuration Guide
SC-32
Page 45

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
• Configuring a Browser Proxy, page SC-41 (optional)
• Configuring a Browser-Proxy Map to a Group, page SC-42 (optional)
• Configuring the Pushing of a Configuration URL Through a Mode-Configuration Exchange,
page SC-43 (optional)
• Manually Configuring RSA Keys, page SC-44 (optional, depending on IKE parameters)
• Configuring ISAKMP Preshared Keys in ISAKMP Keyrings, page SC-48 (optional, depending on
IKE parameters)
• Configuring Call Admission Control, page SC-50
• Configuring Crypto Keyrings, page SC-54
• Configuring IP Security VPN Monitoring, page SC-57
Enabling or Disabling IKE
This task enables or disables the Internet Key Exchange protocol.
IKE is disabled by default. IKE need not be enabled for individual interfaces, but it is enabled globally
for all interfaces at the router.
How to Implement IKE Security Protocol Configurations for IPSec Networks
SUMMARY STEPS
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp
1. configure
2. crypto isakmp
3. no crypto isakmp
4. end
or
commit
Enters global configuration mode.
Globally enables IKE at the peer router.
Cisco IOS XR System Security Configuration Guide
SC-33
Page 46

How to Implement IKE Security Protocol Configurations for IPSec Networks
Command or Action Purpose
Step 3
no crypto isakmp
Example:
RP/0/RP0/CPU0:router(config)# no crypto isakmp
Step 4
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
(Optional) Disables IKE at the peer router.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
Configuring IKE Policies
This task configures IKE policies.
SUMMARY STEPS
1. configure
2. crypto isakmp policy priority
3. encryption {des | 3des | aes | aes 192 | aes 256}
4. hash {sha | md5}
5. authentication {pre-share | rsa-sig | rsa-encr}
6. group {1 | 2 | 5}
7. lifetime seconds
8. end
or
commit
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
9. show crypto isakmp policy
Cisco IOS XR System Security Configuration Guide
SC-34
Page 47

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp policy
priority
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp
policy 5
Step 3
encryption {des | 3des | aes | aes 192 | aes
256}
Example:
RP/0/RP0/CPU0:router(config-isakmp)# encryption
aes
Step 4
hash {sha | md5}
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Identifies the policy to create.
• Each policy is uniquely identified by the priority
number you assign.
• This command places the router in ISAKMP policy
configuration mode.
Specifies the encryption algorithm.
Specifies the hash algorithm.
Step 5
Step 6
Step 7
Example:
RP/0/RP0/CPU0:router(config-isakmp)# hash md5
authentication {pre-share | rsa-sig | rsa-encr}
Example:
RP/0/RP0/CPU0:router(config-isakmp)#
authentication rsa-sig
group {1 | 2 | 5}
Example:
RP/0/RP0/CPU0:router(config-isakmp)# group 5
lifetime
seconds
Example:
RP/0/RP0/CPU0:router(config-isakmp)# lifetime
50000
Specifies the authentication method.
Specifies the Diffie-Hellman group identifier.
Specifies the lifetime of the security association. The range,
in seconds, is from 60 to 86400.
Cisco IOS XR System Security Configuration Guide
SC-35
Page 48

How to Implement IKE Security Protocol Configurations for IPSec Networks
Command or Action Purpose
Step 8
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isakmp)# end
or
RP/0/RP0/CPU0:router(config-isakmp)# commit
Step 9
show crypto isakmp policy
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
(Optional) Displays all existing IKE policies.
Example:
RP/0/RP0/CPU0:router# show crypto isakmp policy
Defining Group Policy Information for Mode Configuration
Although users can belong to only one group for each connection, they may belong to specific groups
with different policy requirements. Thus, users may decide to connect to the client using a different
group ID by changing their client profile on the VPN device.
This task defines the group policy attributes that are pushed to the client through mode configuration.
SUMMARY STEPS
1. configure
2. crypto isakmp client configuration group group-name
3. key preshared-key
4. acl acl-name
5. backup-server {ip-address | hostname}
6. dns primary-server [secondary-server]
7. domain name
8. firewall are-u-there
9. group-lock
10. include-local-lan
Cisco IOS XR System Security Configuration Guide
SC-36
Page 49

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
11. max-logins number-of-logins
12. max-users number-of-users
13. netmask mask
14. pfs
15. pool name
16. save-password
17. split-dns domain-name
18. wins primary-server [secondary-server]
19. end
or
commit
DETAILED STEPS
Command or Action Purpose
Step 1
configure
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Step 2
Step 3
Step 4
Step 5
Example:
RP/0/RP0/CPU0:router# configure
crypto isakmp client configuration group
group-name
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp
client configuration group cisco
key
preshared-key
Example:
RP/0/RP0/CPU0:router(config-group)# key
samplekey
acl
acl-name
Example:
RP/0/RP0/CPU0:router(config-group)# acl group1
backup-server {ip-address | hostname}
Example:
RP/0/RP0/CPU0:router(config-group)#
backup-server 10.1.1.1
Specifies which group's policy profile is defined and enters
ISAKMP group configuration mode.
• If no specific group matches and a default group is
defined, users are automatically given the default
group's policy.
Specifies the IKE preshared key for group policy attribute
definition.
Note This command must be enabled if the client
identifies itself with a preshared key.
(Optional) Configures split tunneling.
• Use the acl-name argument to specify a group of ACL
rules that represent protected subnets for split tunneling
purposes.
Specifies the backup server.
• Use the ip-address argument to specify the IP address
of the server.
• Use the hostname argument to specify the hostname of
the server.
Cisco IOS XR System Security Configuration Guide
SC-37
Page 50

How to Implement IKE Security Protocol Configurations for IPSec Networks
Command or Action Purpose
dns
Step 6
primary-server [secondary-server
]
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Specifies the primary and secondary Domain Name Service
(DNS) addresses.
Step 7
Step 8
Step 9
Step 10
Step 11
Example:
RP/0/RP0/CPU0:router(config-group)# dns 2.2.2.2
2.3.2.3
domain
name
Example:
RP/0/RP0/CPU0:router(config-group)# domain
cisco.com
firewall are-u-there
Example:
RP/0/RP0/CPU0:router(config-group)# firewall
are-u-there
group-lock
Example:
RP/0/RP0/CPU0:router(config-group)# group-lock
include-local-lan
Example:
RP/0/RP0/CPU0:router(config-group)#
include-local-lan
max-logins
number-of-logins
• Use the primary-server argument to specify the IP
address of the primary DNS.
• (Optional) Use the secondary-server argument to
specify the IP address of the secondary DNS.
Specifies the DNS domain to which a group belongs.
• Use the name argument to specify the default name of
the DNS domain.
Adds the Firewall-Are-U-There attribute to the server group
if your PC is running the Black Ice or Zone Alarm personal
firewalls.
Allows you to enter your extended authentication (Xauth)
username, including the group name, when preshared key
authentication is used with IKE.
Configures the Include-Local-LAN attribute to allow a
nonsplit-tunneling connection to access the local
subnetwork at the same time as the client.
Specifies the maximum number of concurrent logins that
are allowed for a certain user.
Step 12
Step 13
Step 14
SC-38
Example:
RP/0/RP0/CPU0:router(config-group)# max-logins
8
max-users
number-of-users
Example:
RP/0/RP0/CPU0:router(config-group)# max-users
1200
netmask
mask
Example:
RP/0/RP0/CPU0:router(config-group)# netmask
255.255.255.0
pfs
Example:
RP/0/RP0/CPU0:router(config-group)# pfs
Cisco IOS XR System Security Configuration Guide
• Use the number-of-logins argument to specify the
number of logins. The value ranges from 0 to 16 and
384.
Limits the number of connections to a specific server group.
• Use the number-of-users argument to specify the
number of connected users. The value ranges from 0 to
16 and 384.
Sets the IP network mask.
• Use the mask argument to specify the IP network mask.
Configures a server to notify the client of the central-site
policy regarding whether PFS is required for any IP
Security (IPSec) Security Association (SA).
Page 51

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Command or Action Purpose
pool
Step 15
name
How to Implement IKE Security Protocol Configurations for IPSec Networks
Defines the name of an address-pool in which an address is
allocated if required.
Step 16
Step 17
Step 18
Step 19
Example:
RP/0/RP0/CPU0:router(config-group)# pool dog
save-password
Example:
RP/0/RP0/CPU0:router(config-group)#
save-password
split-dns
domain-name
Example:
RP/0/RP0/CPU0:router(config-group)# split-dns
green.com
RP/0/RP0/CPU0:router(config-group)# split-dns
acme.org
wins
primary-server [secondary-server
]
Example:
RP/0/RP0/CPU0:router(config-group)# wins
10.1.1.2 10.1.1.3
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-group)# end
or
RP/0/RP0/CPU0:router(config-group)# commit
• Use the name argument to specify the name of the local
pool address.
Saves your extended authentication (Xauth) password
locally on your PC or Easy VPN client.
Specifies a domain name that must be tunneled or resolved
to the private network.
• Use the domain-name argument to specify the name of
the DNS domain that must be tunneled or resolved to
the private network.
Note If you have to configure more than one domain
name, you have to add a split-dns command line for
each.
Specifies the primary and secondary Windows Internet
Naming Service (WINS) servers.
• Use the primary-server argument to specify the name
of the primary WINS server.
• (Optional) Use the secondary-server argument to
specify the name of the secondary WINS server.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Cisco IOS XR System Security Configuration Guide
SC-39
Page 52

How to Implement IKE Security Protocol Configurations for IPSec Networks
Configuring a Banner
This task describes how to configure a banner for a Cisco Easy VPN server.
SUMMARY STEPS
1. configure
2. crypto isakmp client configuration group group-name
3. banner {banner-text}
DETAILED STEPS
Command or Action Purpose
Step 1
Step 2
Step 3
configure
Example:
RP/0/RP0/CPU0:router# configure
crypto isakmp client configuration group group-name
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp client
configuration group cisco
RP/0/RP0/CPU0:router(config-group)#
banner {
banner-text
}
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Enters global configuration mode.
Specifies which group's policy profile is defined and
enters ISAKMP group configuration mode.
• If no specific group matches, you are
automatically given the default group's policy.
• The default group is also used for the other
attributes so they must also be checked and
updated.
Specifies the text of the banner.
Example:
RP/0/RP0/CPU0:router(config-group)# banner
thequickbrowndog
Configuring Auto-Upgrade
This task describes how to configure automatic update parameters for a Cisco Easy VPN remote device.
SUMMARY STEPS
1. configure
2. crypto isakmp client configuration group group-name
3. auto-update client {type-of-system} {url url} {rev review-version}
Cisco IOS XR System Security Configuration Guide
SC-40
Page 53

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp client configuration group group-name
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Specifies which group's policy profile is defined and
enters ISAKMP group configuration mode.
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp client
configuration group cisco
RP/0/RP0/CPU0:router(config-group)#
Step 3
auto-update client {
review-version
type-of-system
}
Example:
RP/0/RP0/CPU0:router(config-group)# auto-update
client Win2000 url
http:www.ourcompanysite.com/newclient rev 3.0.1
Configuring a Browser Proxy
This task describes how to configure browser-proxy parameters for a Cisco Easy VPN remote device.
SUMMARY STEPS
} {url
url
} {rev
• If no specific group matches, you are
automatically given the default group's policy.
• The default group is also used for the other
attributes so they must also be checked and
updated.
Configures automatic update parameters for a
Cisco Easy VPN remote device. The example shows
that the update parameters are set for a Windows
2000 operating system, a URL of
http:www.ourcompanysite.com/newclient, and
version 3.0.1.
For a list of the reserved names that the Cisco Easy
VPN client expects for each type of operating
system, which are used for the type-of-system
argument, see Cisco IOS XR System Security
Command Reference.
1. configure
2. crypto isakmp client configuration browser-proxy {browser-proxy-name}
3. proxy {auto-detect | bypass-local | exception-list semicolon delimited exception list | none |
server}
Cisco IOS XR System Security Configuration Guide
SC-41
Page 54

How to Implement IKE Security Protocol Configurations for IPSec Networks
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp client configuration browser-proxy
browser-proxy-name
{
}
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp client
configuration browser-proxy bproxy
RP/0/RP0/CPU0:router(config-crypto-isakmp-browser-proxy)
#
Step 3
proxy {auto-detect | bypass-local | exception-list
semicolon delimited exception list
| none | server}
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Enters global configuration mode.
Configures browser-proxy parameters for a
Cisco Easy VPN remote device and enters
ISAKMP browser proxy configuration mode.
Configures proxy parameters for a Cisco Easy
VPN remote device.
Example:
RP/0/RP0/CPU0:router(config-crypto-isakmp-browser-proxy)
# proxy auto-detect
Configuring a Browser-Proxy Map to a Group
This task configures a browser-proxy map to a group.
SUMMARY STEPS
1. configure
2. crypto isakmp client configuration group group-name
3. browser-proxy {browser-proxy-map-name}
Cisco IOS XR System Security Configuration Guide
SC-42
Page 55

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp client configuration group
group-name
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Specifies which group's policy profile is defined and
enters ISAKMP group configuration mode.
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp client
configuration group cisco
RP/0/RP0/CPU0:router(config-group)#
• If no specific group matches, you are
automatically given the default group's policy.
• The default group is also used for the other
attributes so they must also be checked and
updated.
Step 3
browser-proxy {
browser-proxy-map-name
}
Specifies browser-proxy parameter settings to a
group.
Example:
RP/0/RP0/CPU0:router(config-group)# browser-proxy
EZVPN
Configuring the Pushing of a Configuration URL Through a Mode-Configuration
Exchange
This task configures a Cisco Easy VPN server to push a configuration URL through a
Mode-Configuration Exchange.
SUMMARY STEPS
1. configure
2. crypto isakmp client configuration group group-name
3. configuration url {url}
4. configuration version {version-number}
Cisco IOS XR System Security Configuration Guide
SC-43
Page 56

How to Implement IKE Security Protocol Configurations for IPSec Networks
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp client configuration group
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Enters global configuration mode.
group-name
Specifies which group's policy profile is defined and
enters ISAKMP group configuration mode.
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp client
configuration group cisco
RP/0/RP0/CPU0:router(config-group)#
Step 3
configuration url {
url
}
Example:
RP/0/RP0/CPU0:router(config-group)# configuration
url http://10.10.8.8/easy.cfg
Step 4
configuration version {
version-number
Example:
RP/0/RP0/CPU0:router(config-group)# configuration
version 10
Manually Configuring RSA Keys
Manually configure RSA keys when you specify RSA encrypted nonces as the authentication method in
an IKE policy and you are not using a CA.
To manually configure RSA keys, perform these tasks at each IPSec peer that uses RSA encrypted
nonces in an IKE policy:
• If no specific group matches, you are
automatically given the default group's policy.
• The default group is also used for the other
attributes so they must also be checked and
updated.
Specifies the URL the remote device must use to get
the configuration from the server.
}
Specifies the version of the configuration.
• The version-number argument is an unsigned
integer in the range of 1 to 10.
• RSA Keys Generation, page SC-44
• Configuring ISAKMP Identity, page SC-44
• Configuring RSA Public Keys of All the Other Peers, page SC-46
RSA Keys Generation
For instructions on how to generate RSA keys, see the “Generating an RSA Key Pair” section on page 7
in the Implementing Certification Authority Interoperability on Cisco IOS XR Software module.
Configuring ISAKMP Identity
This task configures the ISAKMP identity of a peer.
Remember to repeat these tasks at each peer that uses preshared keys in an IKE policy.
Cisco IOS XR System Security Configuration Guide
SC-44
Page 57

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
SUMMARY STEPS
1. configure
2. crypto isakmp identity {address | hostname}
3. host hostname address1 [address2...address8]
4. end
or
commit
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp identity {address | hostname}
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp
identity address
host
Step 3
hostname address1 [address2...address8
]
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
(At the local peer) Specifies the peer’s ISAKMP identity by
IP address or by hostname. See the crypto isakmp identity
command description for guidelines for when to use the IP
address and when to use the hostname.
(At all remote peers) Maps the peer’s hostname to its IP
addresses at all the remote peers.
Step 4
Example:
RP/0/RP0/CPU0:router(config)# host host1
10.0.0.5
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
• This command is used if the local peer’s ISAKMP
identity was specified using a hostname.
• This step might be unnecessary if the hostname or
address is already mapped in a DNS server.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Cisco IOS XR System Security Configuration Guide
SC-45
Page 58

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
How to Implement IKE Security Protocol Configurations for IPSec Networks
Configuring RSA Public Keys of All the Other Peers
This task configures the RSA public keys of all the other peers.
Remember to repeat these tasks at each peer that uses RSA encrypted nonces in an IKE policy.
SUMMARY STEPS
1. configure
2. crypto keyring keyring-name [vrf fvrf-name]
3. rsa-pubkey {address address | name fqdn} [encryption | signature]
4. address ip-address
5. key-string key-string
6. quit
7. end
or
commit
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto keyring
Example:
RP/0/RP0/CPU0:router(config)# crypto keyring
vpnkeyring
RP/0/RP0/CPU0:router(config-keyring)#
8. show crypto key pubkey-chain rsa [name key-name | address key-address]
Enters global configuration mode.
keyring-name
[vrf
fvrf-name
]
Defines a crypto keyring during IKE authentication
• Enters keyring configuration mode.
• Use the keyring-name argument to specify the name of
the crypto keyring.
• (Optional) Use the vrf keyword to specify that the front
door virtual routing and forwarding (FVRF) name is the
keyring that is referenced.
Cisco IOS XR System Security Configuration Guide
SC-46
Page 59

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Command or Action Purpose
Step 3
rsa-pubkey {address
[encryption | signature]
address
| name
fqdn
}
Example:
RP/0/RP0/CPU0:router(config-keyring)#
rsa-pubkey name host.vpn.com
RP/0/RP0/CPU0:router(config-pubkey)
Step 4
address
ip-address
Example:
RP/0/RP0/CPU0:router(config-pubkey)# address
10.5.5.1
Step 5
key-string
key-string
Example:
RP/0/RP0/CPU0:router(config-pubkey)# key-string
005C300D 06092A86 4886F70D 01010105 ...
How to Implement IKE Security Protocol Configurations for IPSec Networks
Defines the Rivest, Shamir, and Adelman (RSA) manual
key to be used for encryption or signature during Internet
Key Exchange (IKE) authentication.
• Use the address keyword to specify the IP address of
the RSA public key of the remote peer. The address
argument is the IP address of the remote RSA public
key of the remote peer that you manually configure.
• Use the name keyword to specify the fully qualified
domain name (FQDN) of the peer.
• Use the encryption keyword to specify that the key is
used for encryption.
• Use the signature keyword to specify that the key is
used for a signature. The signature keyword is the
default.
Specifies the remote peer’s IP address.
• You can use this command if you used a fully qualified
domain name to name the remote peer.
Specifies the remote peer’s RSA public key.
• This is the key previously displayed by the remote
peer’s administrator when the remote router’s RSA
keys were generated.
• To avoid mistakes, you should cut and paste the key
data (instead of attempting to enter in the data).
Step 6
quit
Example:
RP/0/RP0/CPU0:router(config-pubkey)# quit
• Enter a key on each line. You must enter the key-string
command before the key.
• When you have finished specifying the remote peer’s
RSA key, return to global configuration mode by
entering quit at the public key configuration prompt.
Returns to global configuration mode.
Cisco IOS XR System Security Configuration Guide
SC-47
Page 60

How to Implement IKE Security Protocol Configurations for IPSec Networks
Command or Action Purpose
Step 7
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
Step 8
show crypto pubkey-chain rsa [name
address
key-address
]
key-name
Example:
RP/0/RP0/CPU0:router# show crypto pubkey-chain
rsa
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
|
(Optional) Displays a list of all the RSA public keys stored
on your router.
• Use the optional name or address keyword to display
details about a particular RSA public key stored on
your router.
Configuring ISAKMP Preshared Keys in ISAKMP Keyrings
This task configures ISAKMP preshared keys in ISAKMP keyrings.
Prerequisites
To configure ISAKMP preshared keys in ISAKMP keyrings, perform these tasks at each peer that uses
preshared keys in an IKE policy:
• Set the ISAKMP identity of each peer. Each peer’s identity should be set either to its hostname or
by its IP address. By default, a peer’s identity is set to its IP address. Setting ISAKMP identities is
described in the “Configuring ISAKMP Identity” section on page 44.
• Specify the shared keys at each peer. Note that a given preshared key is shared between two peers.
At a given peer you could specify the same key to share with multiple remote peers; however, a more
secure approach is to specify different keys to share between different pairs of peers.
You must specify the support for masked preshared keys.
Remember to repeat these tasks at each peer that uses preshared keys in an IKE policy.
Cisco IOS XR System Security Configuration Guide
SC-48
Page 61

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
SUMMARY STEPS
1. configure
2. crypto keyring keyring-name [vrf fvrf-name]
3. pre-shared-key {address address [mask] | hostname hostname} key key
4. end
or
commit
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto keyring
keyring-name
[vrf
fvrf-name
]
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Defines a crypto keyring during IKE authentication.
Example:
RP/0/RP0/CPU0:router(config)# crypto keyring
vpnkeyring
RP/0/RP0/CPU0:router(config-keyring)#
• Use the keyring-name argument to specify the name of
the crypto keyring.
• (Optional) Use the vrf keyword to specify that the front
door virtual routing and forwarding (FVRF) name is the
keyring that is referenced.
Cisco IOS XR System Security Configuration Guide
SC-49
Page 62

How to Implement IKE Security Protocol Configurations for IPSec Networks
Command or Action Purpose
Step 3
pre-shared-key {address
hostname
hostname
} key
address [mask
key
] |
Example:
RP/0/RP0/CPU0:router(config-keyring)#
pre-shared-key address 10.72.23.11 key vpnkey
RP/0/RP0/CPU0:router(config-keyring)#
pre-shared-key hostname mycisco.com key vpnkey
Step 4
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-keyring)# end
or
RP/0/RP0/CPU0:router(config-keyring)# commit
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Defines a preshared key for IKE authentication.
• Use the address keyword to specify the IP address of
the remote peer or a subnet and mask.
• (Optional) Use the mask argument to match the range of
the address.
• Use the hostname keyword to specify the fully
qualified domain name (FQDN) of the peer.
• (Optional) Use the key keyword to specify the key.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
Configuring Call Admission Control
These tasks are used to configure Call Admission Control (CAC):
• Configuring the IKE Security Association Limit, page SC-50
• Configuring the System Resource Limit, page SC-52
Configuring the IKE Security Association Limit
This task configures the IKE security admission limit.
SUMMARY STEPS
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
1. configure
2. crypto isakmp call admission limit {in-negotiation-sa number | sa number}
Cisco IOS XR System Security Configuration Guide
SC-50
Page 63

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
3. end
or
commit
4. show crypto isakmp call admission statistics
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp call admission limit
{in-negotiation-sa
number
| sa
number
}
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp call
admission limit sa 25
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Specifies the maximum number of IKE SAs that the
router can establish before IKE begins rejecting new
SA requests.
• Use the in-negotiation-sa keyword to specify
the maximum number of in-negotiation
(embryonic) IKE security associations (SAs)
that the router can establish before IKE begins
rejecting new SA requests. The range for the
number argument is from 1 to 100000.
• Use the sa keyword to specify the maximum
number of active IKE SAs that the router can
establish. The range for the number argument is
from 1 to 100000.
Cisco IOS XR System Security Configuration Guide
SC-51
Page 64

How to Implement IKE Security Protocol Configurations for IPSec Networks
Command or Action Purpose
Step 3
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
Step 4
show crypto isakmp call admission statistics
Example:
RP/0/RP0/CPU0:router# show crypto isakmp call
admission statistics
Configuring the System Resource Limit
This task configures the system resource limit.
SUMMARY STEPS
1. configure
2. crypto isakmp call admission limit {cpu {total percent | ike percent}}
3. end
or
commit
4. show crypto isakmp call admission statistics
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Monitors crypto CAC statistics.
Cisco IOS XR System Security Configuration Guide
SC-52
Page 65

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp call admission limit {cpu {total
percent
| ike
percent
}}
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp call
admission limit cpu total 90
Step 3
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Specifies the maximum number of IKE SAs that the
router can establish before IKE begins rejecting new
SA requests.
• Use the cpu keyword to specify the total
resource limit for the CPU usage.
• Use the total keyword to specify the maximum
total CPU usage to accept new calls. The range
for the percent argument is from 1 to 100.
• Use the ike keyword to specify the maximum
IKE CPU usage to accept new calls. The range
for the percent argument is from 1 to 100.
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
Step 4
show crypto isakmp call admission statistics
Example:
RP/0/RP0/CPU0:router# show crypto isakmp call
admission statistics
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Monitors crypto CAC statistics.
Cisco IOS XR System Security Configuration Guide
SC-53
Page 66

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
How to Implement IKE Security Protocol Configurations for IPSec Networks
Configuring Crypto Keyrings
A crypto keyring is a repository of preshared and Rivest, Shamir, and Adelman (RSA) public keys. The
router can have zero or more keyrings. Each keyring optionally allows the specification of a VRF in
which the keys defined in the keyring belong.
This task configures crypto keyrings.
Crypto Keyrings Configuration Guidelines and Restrictions
Follow these guidelines and restrictions when configuring crypto keyrings:
• The VRF associated with a crypto keyring cannot be changed. A different keyring must be
configured with the new VRF value.
• Address overlapping in a keyring is not allowed and must be enforced during configuration.
• A crypto keyring is attached to one or more ISAKMP profiles and cannot be deleted while in use.
SUMMARY STEPS
1. configure
2. crypto keyring keyring-name [vrf fvrf-name]
3. description string
4. local-address ip-address
5. pre-shared-key {address address [mask] | hostname hostname} key key
6. rsa-pubkey {address address | name fqdn} [encryption | signature]
7. key-string key-string
8. quit
9. end
or
commit
Cisco IOS XR System Security Configuration Guide
SC-54
Page 67

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto keyring
keyring-name
[vrf
fvrf-name
]
How to Implement IKE Security Protocol Configurations for IPSec Networks
Enters global configuration mode.
Defines a crypto keyring to be used during IKE
authentication.
Step 3
Step 4
Step 5
Example:
RP/0/RP0/CPU0:router(config)# crypto keyring vpnkey
description
string
Example:
RP/0/RP0/CPU0:router(config-keyring# description
this is a sample keyring
local-address
ip-address
Example:
RP/0/RP0/CPU0:router(config-keyring)# local-address
130.40.1.1
pre-shared-key {address
hostname
} key
key
address [mask
] | hostname
Example:
RP/0/RP0/CPU0:router(config-keyring)# pre-shared-key
address 10.72.23.11 key vpnkey
• Use the keyring-name argument as the name of
the crypto keyring.
• Use the vrf keyword to specify that the front
door virtual routing and forwarding (FVRF)
name is the keyring that is referenced. The
fvrf-name argument must match the FVRF name
that was defined during a (VRF) configuration.
Creates a one-line description for a keyring.
• Use the string argument to specify the character
string that describes the keyring.
Limits the scope of an ISAKMP keyring
configuration to a local termination address or
interface.
• Use the ip-address argument to specify the IP
address to which to bind.
Defines a preshared key to be used for IKE
authentication.
• Use the address keyword to specify the IP
address of the remote peer or a subnet and mask.
The mask argument is optional.
• Use the hostname keyword to specify the fully
qualified domain name (FQDN) of the peer.
• Use the key keyword to specify the secret.
Cisco IOS XR System Security Configuration Guide
SC-55
Page 68

How to Implement IKE Security Protocol Configurations for IPSec Networks
Command or Action Purpose
Step 6
rsa-pubkey {address
| signature]
address
| name
fqdn
Example:
RP/0/RP0/CPU0:router(config-keyring)# rsa-pubkey
name host.vpn.com
RP/0/RP0/CPU0:router(config-keyring)# rsa-pubkey
name host.vpn.com
Step 7
key-string
key-string
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
} [encryption
Defines a Rivest, Shamir, and Adelman (RSA)
public key by address or hostname.
• Use the address keyword to specify the IP
address of the RSA public key of the remote
peer. The address argument is the IP address of
the remote RSA public key of the remote peer
that you manually configure.
• Use the name keyword to specify the FQDN of
the peer.
• (Optional) Use the encryption keyword to
specify that the key is used for encryption.
• (Optional) Use the signature keyword to
specify that the key is used for a signature. The
signature keyword is the default.
Manually specifies the RSA public key of a remote
peer.
Step 8
Step 9
Example:
RP/0/RP0/CPU0:router(config-pubkey)# key-string
005C300D 06092A86 4886F70D 01010105
quit
Example:
RP/0/RP0/CPU0:router(config-pubkey)# quit
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
Returns to global configuration mode.
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
Cisco IOS XR System Security Configuration Guide
SC-56
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Page 69

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Configuring IP Security VPN Monitoring
The following sections describe how to configure IP Security (IPSec) VPN monitoring:
• Adding the Description of an IKE Peer, page SC-57 (optional)
• Clearing a Crypto Session, page SC-58 (optional)
Adding the Description of an IKE Peer
This task allows you to add the description of an IKE peer to an IPSec VPN session.
SUMMARY STEPS
1. configure
2. crypto isakmp peer {address ip-address | hostname hostname} [description line | vrf fvrf-name]
3. description line-of-description
4. end
or
commit
5. show crypto isakmp peers [ip-address | vrf vrf-name]
How to Implement IKE Security Protocol Configurations for IPSec Networks
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp peer {address
hostname
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp peer
address 40.40.40.2
RP/0/RP0/CPU0:router(config-isakmp-peer)
Step 3
description
Example:
RP/0/RP0/CPU0:router(config-isakmp-peer)#
description citeA
} [description
line-of-description
line
ip-address
| vrf
fvrf-name
| hostname
]
Enters global configuration mode.
Enables an IPSec peer for IKE querying of
authentication, authorization, and accounting
(AAA) for tunnel attributes in aggressive mode and
enters ISAKMP peer configuration mode.
Adds a description for an IKE peer.
Cisco IOS XR System Security Configuration Guide
SC-57
Page 70

How to Implement IKE for Locally Sourced and Destined Traffic
Command or Action Purpose
Step 4
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isakmp-peer)# end
or
RP/0/RP0/CPU0:router(config-isakmp-peer)# commit
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Step 5
show crypto isakmp peers [
Example:
RP/0/RP0/CPU0:router# show crypto isakmp peers
ip-address
| vrf
vrf-name
]
Displays peer descriptions.
Clearing a Crypto Session
Use the clear crypto session command in EXEC mode to delete the crypto sessions (IP Security [IPSec]
and Internet Key Exchange [IKE] security associations [SAs]) for users and groups.
How to Implement IKE for Locally Sourced and Destined Traffic
This section contains the following procedure:
• Configuring the ISAKMP Profile for Locally Sourced and Destined Traffic, page SC-58
Configuring the ISAKMP Profile for Locally Sourced and Destined Traffic
An ISAKMP profile is a repository of commands for a set of peers.
This task configures the ISAKMP profile for locally sourced and destined traffic.
Cisco IOS XR System Security Configuration Guide
SC-58
Page 71

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
SUMMARY STEPS
1. configure
2. crypto isakmp profile [local] profile-name
3. description string
4. keepalive disable
5. self-identity {address | fqdn | user-fqdn user-fqdn}
6. keyring keyring-name
7. match identity {group group-name | address address [mask] vrf [fvrf] | host hostname | host
domain domain-name | user username | user domain domain-name}
8. set interface tunnel-ipsec intf-index
9. set ipsec-profile profile-name
10. end
or
commit
How to Implement IKE for Locally Sourced and Destined Traffic
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
crypto isakmp profile [local]
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp profile
local vpnprofile
RP/0/RP0/CPU0:router(config-isa-prof)#
Step 3
description
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# description
this is a sample profile
Step 4
keepalive disable
string
profile-name
Enters global configuration mode.
Defines an ISAKMP profile and audits IPSec user
sessions.
• (Optional) Use the local keyword to specify that
the profile is used for locally sourced or
terminated traffic.
Note The local keyword is specific only to the
Cisco IPSec VPN SPA.
• Use the profile-name argument to specify the
name of the user profile.
Creates a description for a keyring.
• Use the string argument to specify the character
string that describes the keyring.
Lets the gateway send DPD messages to the
Cisco IOS XR peer.
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# keepalive
disable
• Use the disable keyword to disable the
keepalive global declarations.
Cisco IOS XR System Security Configuration Guide
SC-59
Page 72

How to Implement IKE for Locally Sourced and Destined Traffic
Command or Action Purpose
Step 5
self-identity {address | fqdn | user-fqdn
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
user-fqdn
}
Defines the identity that the local IKE uses to
identify itself to the remote peer.
Step 6
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# self-identity
user-fqdn user@vpn.com
keyring
keyring-name
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# keyring
vpnkeyring
• Use the address keyword to specify the IP
address of the local endpoint.
• Use the fqdn keyword to specify the fully
qualified domain name (FQDN) of the host.
• Use the user-fqdn keyword to specify that the
user FQDN was sent to the remote endpoint.
Configures a keyring with an ISAKMP profile.
• Use the keyring-name argument to specify the
keyring name, which must match the keyring
name that was defined in the global
configuration.
Cisco IOS XR System Security Configuration Guide
SC-60
Page 73

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Command or Action Purpose
Step 7
match identity {group
[
mask
] vrf [
domain-name
domain-name
fvrf
| user
}
group-name
] | host
username
| address
hostname
| host domain
| user domain
address
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# match
identity group vpngroup
RP/0/RP0/CPU0:router(config-isa-prof-match)#
How to Implement IKE for Locally Sourced and Destined Traffic
Matches the identity from a peer in an ISAKMP
profile.
• Use the group keyword to specify a Unity group
that matches identification (ID) type
ID_KEY_ID. If RSA signatures are used, the
group-name argument matches the
organizational unit (OU) field of the
distinguished name (DN).
• Use the address keyword to match the address
argument with the ID type ID_IPV4_ADDR.
• Use the mask argument to specify a range of
addresses.
• Use the vrf keyword to specify the front door
VPN routing and forwarding (VRF) of the peer.
• Use the fvrf argument to match the address in
the front door virtual router forwarding (FVRF)
Virtual Private Network (VPN) space.
• Use the host keyword to specify an identity that
matches the type ID_FQDN, whose fully
qualified domain name (FQDN) ends with the
domain name.
Step 8
set interface tunnel-ipsec
intf-index
Example:
RP/0/RP0/CPU0:router(config-isa-prof-match)# set
interface tunnel-ipsec 50
• Use the host domain keyword to specify an
identity that matches type ID_FQDN. The
domain name is the same as the domain-name
argument.
• Use the user keyword to specify an identity that
matches the FQDN.
• Use the user domain keyword to specify an
identity that matches the type
ID_USER_FQDN. When the user domain
keyword is present, all users having identities of
the type ID_USER_FQDN and ending with
domain-name are matched.
Predefines the interface instance when IKE
negotiates for IPSec service associations (SAs) for
the traffic that is locally sourced or terminated and
the local endpoint is the IKE responder.
• Use the intf-index argument to set the range
from 0 to 4294967295.
Cisco IOS XR System Security Configuration Guide
SC-61
Page 74

How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software
Command or Action Purpose
Step 9
Step 10
set ipsec-profile
Example:
RP/0/RP0/CPU0:router(config-isa-prof-match)# set
ipsec-profile myprofile
end
profile-name
or
commit
Example:
RP/0/RP0/CPU0:router(config-isa-prof-match)# end
or
RP/0/RP0/CPU0:router(config-isa-prof-match)# commit
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Predefines the IPSec profile instance when IKE
negotiates for IPSec service associations (SAs) for
the traffic that is locally sourced or terminated and
the local endpoint is the IKE responder.
• Use the profile-name argument to set the name
of the IPSec profile.
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
How to Implement IKE for Cisco IPSec VPN SPAs on
Cisco IOS XR Software
This section contains the following procedures:
• Configuring a Periodic Dead Peer Detection Message, page SC-63
• Configuring the ISAKMP Profile for Service Interfaces, page SC-64
Cisco IOS XR System Security Configuration Guide
SC-62
Page 75

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software
Configuring a Periodic Dead Peer Detection Message
This task configures a periodic dead peer detection (DPD) message.
SUMMARY STEPS
1. configure
2. crypto isakmp keepalive seconds retry-seconds [periodic | on-demand]
3. end
or
commit
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Enters global configuration mode.
Example:
RP/0/RP0/CPU0:router# configure
Cisco IOS XR System Security Configuration Guide
SC-63
Page 76

How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software
Command or Action Purpose
Step 2
crypto isakmp keepalive
[periodic | on-demand]
seconds retry-seconds
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp
keepalive 20 20 on-demand
Step 3
end
or
commit
Example:
RP/0/RP0/CPU0:router(config)# end
or
RP/0/RP0/CPU0:router(config)# commit
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Uses the IKE security association (SA) feature to
provide a mechanism to detect loss of connectivity
between two IP Security (IPSec) peers.
• Use the seconds argument to specify the number
of seconds between keepalive messages. The
range is from 10 to 3600.
• Use the retry-seconds argument to specify the
number of seconds between retries if keepalive
fails. The range is from 2 to 60.
• (Optional) Use the periodic keyword to specify
the keepalive messages that are sent at regular
intervals for DPD messages.
• (Optional) Use the on-demand keyword to
specify the DPD retries that are sent on demand.
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Configuring the ISAKMP Profile for Service Interfaces
This task configures the ISAKMP profile for service interfaces.
SUMMARY STEPS
1. configure
2. crypto isakmp profile [local] profile-name
Cisco IOS XR System Security Configuration Guide
SC-64
Page 77

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
3. description string
4. keepalive disable
5. self-identity {address | fqdn | user-fqdn user-fqdn}
6. keyring keyring-name
7. match identity {group group-name | address address [mask] vrf [fvrf] | host hostname | host
domain domain-name | user username | user domain domain-name}
8. set interface {service-ipsec | service-gre} intf-index
9. end
or
commit
DETAILED STEPS
Command or Action Purpose
Step 1
configure
How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software
Enters global configuration mode.
Step 2
Step 3
Step 4
Example:
RP/0/RP0/CPU0:router# configure
crypto isakmp profile [local]
profile-name
Example:
RP/0/RP0/CPU0:router(config)# crypto isakmp profile
vpnprofile
RP/0/RP0/CPU0:router(config-isa-prof)#
description
string
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# description
this is a sample profile
keepalive disable
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# keepalive
disable
Defines an ISAKMP profile and audits IPSec user
sessions.
• (Optional) Use the local keyword to specify that
the profile is used for locally sourced or
terminated traffic.
Note The local keyword is specific only to the
Cisco IPSec VPN SPA.
• Use the profile-name argument to specify the
name of the user profile.
Creates a description for a keyring.
• Use the string argument to specify the character
string that describes the keyring.
Lets the gateway send DPD messages to the
Cisco IOS XR peer.
• Use the disable keyword to disable the
keepalive global declarations.
Cisco IOS XR System Security Configuration Guide
SC-65
Page 78

How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software
Command or Action Purpose
Step 5
self-identity {address | fqdn | user-fqdn
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
user-fqdn
}
Defines the identity that the local IKE uses to
identify itself to the remote peer.
Step 6
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# self-identity
user-fqdn user@vpn.com
keyring
keyring-name
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# keyring
vpnkeyring
• Use the address keyword to specify the IP
address of the local endpoint.
• Use the fqdn keyword to specify the fully
qualified domain name (FQDN) of the host.
• Use the user-fqdn keyword to specify that the
user FQDN was sent to the remote endpoint.
Configures a keyring with an ISAKMP profile.
• Use the keyring-name argument to specify the
keyring name, which must match the keyring
name that was defined in the global
configuration.
Cisco IOS XR System Security Configuration Guide
SC-66
Page 79

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Command or Action Purpose
Step 7
match identity {group
[
mask
] vrf [
domain-name
domain-name
fvrf
| user
}
group-name
] | host
username
| address
hostname
| host domain
| user domain
address
Example:
RP/0/RP0/CPU0:router(config-isa-prof)# match
identity group vpngroup
RP/0/RP0/CPU0:router(config-isa-prof-match)#
How to Implement IKE for Cisco IPSec VPN SPAs on Cisco IOS XR Software
Matches the identity from a peer in an ISAKMP
profile.
• Use the group keyword to specify a Unity group
that matches identification (ID) type
ID_KEY_ID. If RSA signatures are used, the
group-name argument matches the
organizational unit (OU) field of the
distinguished name (DN).
• Use the address keyword to match the address
argument with the ID type ID_IPV4_ADDR.
• Use the mask argument to specify a range of
addresses.
• Use the vrf keyword to specify the front door
VPN routing and forwarding (VRF) of the peer.
• Use the fvrf argument to match the address in
the front door virtual router forwarding (FVRF)
Virtual Private Network (VPN) space.
• Use the host keyword to specify an identity that
matches the type ID_FQDN, whose fully
qualified domain name (FQDN) ends with the
domain name.
• Use the host domain keyword to specify an
identity that matches type ID_FQDN. The
domain name is the same as the domain-name
argument.
• Use the user keyword to specify an identity that
matches the FQDN.
• Use the user domain keyword to specify an
identity that matches the type
ID_USER_FQDN. When the user domain
keyword is present, all users having identities of
the type ID_USER_FQDN and ending with
domain-name are matched.
Cisco IOS XR System Security Configuration Guide
SC-67
Page 80

Configuration Examples for Implementing IKE Security Protocol
Command or Action Purpose
Step 8
set interface {service-ipsec | service-gre}
intf-index
Example:
RP/0/RP0/CPU0:router(config-isa-prof-match)# set
interface service-ipsec 50
or
RP/0/RP0/CPU0:router(config-isa-prof-match)# set
interface service-gre 1000
Step 9
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isa-prof-match)# end
or
RP/0/RP0/CPU0:router(config-isa-prof-match)# commit
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Predefines the virtual interface when IKE negotiates
for IPSec SAs and the local endpoint is the IKE
responder.
• Use the service-ipsec keyword to specify the
IPSec service interfaces.
• Use the service-gre keyword to specify the
GRE service interfaces.
• Use the intf-index argument to set the range
from 1 to 65535.
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Configuration Examples for Implementing IKE Security Protocol
This section provides the following configuration examples:
• Creating IKE Policies: Example, page SC-69
• Configuring a service-ipsec Interface with a Dynamic Profile: Example, page SC-69
• Configuring Easy VPN with a Local AAA: Example, page SC-70
• Configuring VRF-Aware: Example, page SC-71
Cisco IOS XR System Security Configuration Guide
SC-68
Page 81

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Creating IKE Policies: Example
This example shows how to create two IKE policies with policy 15 as the highest priority, policy 20 as
the next priority, and the existing default priority as the lowest priority.
crypto isakmp policy 15
encryption 3des
hash md5
authentication rsa-sig
group 2
lifetime 5000
crypto isakmp policy 20
authentication pre-share
lifetime 10000
In the example, the encryption des of policy 15 would not appear in the written configuration because
this is the default value for the encryption algorithm parameter.
If the show crypto isakmp policy command is issued with this configuration, the output is as follows:
Protection suite priority 15
encryption algorithm:DES - Data Encryption Standard (56 bit keys)
hash algorithm:Message Digest 5
authentication method:Rivest-Shamir-Adelman Signature
Diffie-Hellman group:#2 (1024 bit)
lifetime:5000 seconds, no volume limit
Protection suite priority 20
encryption algorithm:DES - Data Encryption Standard (56 bit keys)
hash algorithm:Secure Hash Standard
authentication method:preshared Key
Diffie-Hellman group:#1 (768 bit)
lifetime:10000 seconds, no volume limit
Default protection suite
encryption algorithm:DES - Data Encryption Standard (56 bit keys)
hash algorithm:Secure Hash Standard
authentication method:Rivest-Shamir-Adelman Signature
Diffie-Hellman group:#1 (768 bit)
lifetime:86400 seconds, no volume limit
Configuration Examples for Implementing IKE Security Protocol
Note Although the output shows “no volume limit” for the lifetimes, you can configure only a time lifetime
(such as 86,400 seconds); volume-limit lifetimes are not configurable.
Configuring a service-ipsec Interface with a Dynamic Profile: Example
The following shows how to configure a service-ipsec interface with a dynamic profile:
ipv4 access-list acl1
10 permit ipv4 any any
!
interface service-ipsec1
ipv4 address 44.44.44.44 255.255.255.0
profile ipsec-profile1
tunnel source 100.0.0.1
service-location preferred-active 0/4/0
!
crypto isakmp
crypto isakmp policy 10
authentication pre-share
Cisco IOS XR System Security Configuration Guide
SC-69
Page 82

Configuration Examples for Implementing IKE Security Protocol
group 5
encryption 3des
lifetime 86400
!
crypto keyring ring1 vrf default
pre-shared-key address 40.0.0.1 255.255.255.255 key key1
!
crypto isakmp profile ike-profile1
keyring ring1
match identity address 40.0.0.0/16 vrf default
set interface service-ipsec1
!
!
crypto isakmp keepalive 60 5
crypto ipsec transform-set tsfm1 esp-3des esp-md5-hmac
!
crypto ipsec profile ipsec-profile1
set type dynamic
match acl1 transform-set tsfm1
!
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Configuring Easy VPN with a Local AAA: Example
The following example shows how to configure Easy VPN with a local AAA:
aaa authorization network author-net-local local
aaa authentication login authen-net-local local
aaa authentication login author-net-local local
local pool
ipv4 pool-1 20.20.20.4 20.20.20.255
!
ipv4 access-list acl-3
10 permit ipv4 any any
!
interface Loopback30
ipv4 address 10.20.100.1 255.255.255.255
interface Loopback31
ipv4 address 2.1.0.5 255.255.255.255
!
interface Loopback33
ipv4 address 10.20.100.3 255.255.255.255
interface MgmtEth0/0/CPU0/0
ipv4 address 3.1.73.1 255.255.0.0
!
interface GigabitEthernet0/1/0/0.1
ipv4 address 10.0.83.2 255.255.255.0
dot1q vlan 83
!
interface GigabitEthernet0/1/0/0.2
ipv4 address 10.0.81.4 255.255.255.0
dot1q vlan 81
!
interface GigabitEthernet0/1/0/1
ipv4 address 2.0.0.1 255.0.0.0
negotiation auto
!
interface service-ipsec3
ipv4 address 30.3.3.3 255.255.0.0
profile ipsec-prof-ezvpn
tunnel source 10.20.100.3
Cisco IOS XR System Security Configuration Guide
SC-70
Page 83

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
service-location preferred-active 0/2/0
!
crypto isakmp client configuration group group-a
key group-a-key
pool pool-1
!
crypto isakmp
crypto isakmp policy 30
authentication pre-share
group 2
encryption aes
lifetime 180
!
crypto isakmp profile isakmp-prof3
client authentication list authen-net-local
match identity group group-a
set interface service-ipsec3
!
isakmp authorization list author-net-local
!
crypto ipsec transform-set tsfm3
transform esp-3des esp-sha-hmac
!
crypto ipsec profile ipsec-prof-ezvpn
set type dynamic
match acl-3 transform-set tsfm3
!
Configuration Examples for Implementing IKE Security Protocol
Configuring VRF-Aware: Example
The following example shows how to configure VRF-aware:
ipv4 access-list acl-2_5-1
10 permit ipv4 any any
ipv4 access-list acl-2_5-4
10 permit ipv4 host 2.6.1.3 host 1.7.1.3
vrf IVRF1
!
vrf IVRF2
!
vrf IVRF3
!
vrf FVRF
!
interface GigabitEthernet0/1/0/0.1
vrf FVRF
ipv4 address 10.0.83.2 255.255.255.0
!
interface GigabitEthernet0/1/0/1.1
vrf IVRF1
ipv4 address 2.6.0.1 255.255.0.0
dot1q vlan 61
!
interface GigabitEthernet0/1/0/1.2
vrf IVRF2
ipv4 address 2.6.1.1 255.255.0.0
dot1q vlan 62
!
interface GigabitEthernet0/1/0/1.3
vrf IVRF3
ipv4 address 2.6.0.1 255.255.0.0
Cisco IOS XR System Security Configuration Guide
SC-71
Page 84

Configuration Examples for Implementing IKE Security Protocol
dot1q vlan 63
!
interface GigabitEthernet0/1/0/0.11
vrf FVRF
ipv4 address 10.0.91.1 255.255.255.0
dot1q vlan 91
!
interface GigabitEthernet0/1/0/0.12
vrf FVRF
ipv4 address 10.0.92.1 255.255.255.0
dot1q vlan 92
!
interface GigabitEthernet0/1/0/0.13
vrf FVRF
ipv4 address 10.0.93.1 255.255.255.0
dot1q vlan 93
interface service-ipsec15
vrf IVRF1
ipv4 address 115.115.115.115 255.255.0.0
service-location preferred-active 0/2/0
profile ipsec-prof15 tunnel vrf FVRF
tunnel source 10.20.100.15
interface service-ipsec16
vrf IVRF2
ipv4 address 116.116.116.116 255.255.0.0
service-location preferred-active 0/2/0
profile ipsec-prof16 tunnel vrf FVRF
tunnel source 10.20.100.16
tunnel destination 10.0.85.2
router static
address-family ipv4 unicast
1.7.0.3/32 service-ipsec15
1.7.0.4/32 service-ipsec15 vrf FVRF
address-family ipv4 unicast
10.0.0.0/16 10.0.83.1
crypto isakmp
crypto isakmp policy 60
authentication pre-share
hash sha
group 5
encryption aes
lifetime 86400
!
crypto keyring kr11 vrf FVRF
pre-shared-key address 10.0.91.2 255.255.255.255 key key-vrf
pre-shared-key address 10.0.92.2 255.255.255.255 key key-vrf
pre-shared-key address 10.0.93.2 255.255.255.255 key key-vrf
!
crypto keyring kr12 vrf FVRF
local-address 10.20.100.16
pre-shared-key address 0.0.0.0 0.0.0.0 key key16
!
crypto isakmp profile isakmp-prof6
keyring kr11
match identity address 10.0.91.2/32 vrf FVRF
set interface service-ipsec15
match identity address 10.0.92.2/32 vrf FVRF
set interface service-ipsec15
match identity address 10.0.93.2/32 vrf FVRF
set interface service-ipsec15
!
!
Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Cisco IOS XR System Security Configuration Guide
SC-72
Page 85

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
crypto isakmp profile isakmp-prof7
keyring kr12
match identity address 10.0.85.2/32 vrf FVRF
set interface service-ipsec16
!
!
crypto ipsec transform-set tsfm5
transform ah-sha-hmac esp-aes
crypto ipsec transform-set tsfm15
transform esp-3des esp-md5-hmac
crypto ipsec transform-set tsfm16
transform esp-aes esp-sha-hmac
crypto ipsec profile ipsec-prof15
set type dynamic
match acl-2_5-1 transform-set tsfm15
!
crypto ipsec profile ipsec-prof16
match acl-2_5-4 transform-set tsfm16
!
Additional References
Additional References
The following sections provide references related to implementing the IKE security protocol.
Related Documents
Related Topic Document Title
IKE security protocol commands: complete
command syntax, command modes, command
history, defaults, usage guidelines, and examples
IPSec conceptual information and configuration
tasks
Standards
Standards Title
No new or modified standards are supported by this
feature, and support for existing standards has not been
modified by this feature.
Internet Key Exchange Security Protocol Commands on Cisco IOS XR
Software module in the Cisco IOS XR System Security Command
Reference, Release 3.5
Implementing IPSec Network Security on Cisco IOS XR Software module
in the Cisco IOS XR System Security Configuration Guide, Release 3.5
—
Cisco IOS XR System Security Configuration Guide
SC-73
Page 86

Implementing Internet Key Exchange Security Protocol on Cisco IOS XR Software
Additional References
MIBs
MIBs MIBs Link
— To locate and download MIBs using Cisco IOS XR software, use the
Cisco MIB Locator found at the following URL and choose a
platform under the Cisco Access Products menu:
http://cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml
RFCs
RFCs Title
RFC 2409 The Internet Key Exchange
RFC 2408 Internet Security Association and Key Management Protocol
(ISAKMP) Internet Draft
Technical Assistance
Description Link
The Cisco Technical Support website contains
thousands of pages of searchable technical content,
including links to products, technologies, solutions,
technical tips, and tools. Registered Cisco.com users
can log in from this page to access even more content.
http://www.cisco.com/techsupport
Cisco IOS XR System Security Configuration Guide
SC-74
Page 87

Contents
Implementing Keychain Management on
Cisco IOS XR Software
Keychain management is a common method of authentication to configure shared secrets on all the
entities, which exchange secrets such as keys before establishing trust with each other. Routing protocols
and network management applications on Cisco IOS XR software often use authentication to enhance
security while communicating with peers.
Feature History for Implementing Keychain Management on Cisco IOS XR Software
Release Modification
Release 3.3.0 This feature was introduced on Cisco CRS-1 and Cisco XR 12000 Series Router.
Release 3.4.0
Release 3.5.0 Support for hitless key rollover for Open Shortest Path First (OSPF) and
• Support for the MAC authentication algorithm was added.
• Support for hitless key rollover and key acceptance tolerance were added.
Intermediate System-to-Intermediate System (IS-IS) was added.
• Restrictions for Implementing Keychain Management, page SC-75
• Information About Implementing Keychain Management, page SC-76
• How to Implement Keychain Management, page SC-76
• Configuration Examples for Implementing Keychain Management, page SC-87
• Additional References, page SC-88
Restrictions for Implementing Keychain Management
You must be aware that changing the system clock impacts the validity of the keys in the existing
configuration.
Cisco IOS XR System Security Configuration Guide
SC-75
Page 88

Implementing Keychain Management on Cisco IOS XR Software
Information About Implementing Keychain Management
Information About Implementing Keychain Management
The keychain by itself has no relevance; therefore, it must be used by an application that needs to
communicate by using the keys (for authentication) with its peers. The keychain provides a secure
mechanism to handle the keys and rollover based on the lifetime. Border Gateway Protocol (BGP), Open
Shortest Path First (OSPF), and Intermediate System-to-Intermediate System (IS-IS) use the keychain
to implement a hitless key rollover for authentication. For information about BGP, OSPF, and IS-IS
keychain configurations, see Cisco IOS XR Routing Configuration Guide.
BGP uses TCP authentication, which enables the authentication option and sends the Message
Authentication Code (MAC) based on the cryptographic algorithm configured for the keychain.
To implement keychain management, you must understand the following concepts:
• Lifetime of a Key, page SC-76
Lifetime of a Key
If you are using keys as the security method, you must specify the lifetime for the keys and change the
keys on a regular basis when they expire. To maintain stability, each party must be able to store and use
more than one key for an application at the same time. A keychain is a sequence of keys that are
collectively managed for authenticating the same peer, peer group, or both.
Keychain management groups a sequence of keys together under a keychain and associates each key in
the keychain with a lifetime.
Note Any key that is configured without a lifetime is considered invalid; therefore, the key is rejected during
configuration.
The lifetime of a key is defined by the following options:
• Start-time—Specifies the absolute time.
• End-time—Specifies the absolute time that is relative to the start-time or infinite time.
Each key definition within the keychain must specify a time interval for which that key is activated; for
example, lifetime. Then, during a given key's lifetime, routing update packets are sent with this activated
key. Keys cannot be used during time periods for which they are not activated. Therefore, we recommend
that for a given keychain, key activation times overlap to avoid any period of time for which no key is
activated. If a time period occurs during which no key is activated, neighbor authentication cannot occur;
therefore, routing updates can fail.
Multiple keychains can be specified.
How to Implement Keychain Management
This section contains the following procedures:
• Configuring a Keychain, page SC-77 (required)
• Configuring a Tolerance Specification to Accept Keys, page SC-78 (required)
• Configuring a Key Identifier for the Keychain, page SC-79 (required)
• Configuring the Text for the Key String, page SC-81 (required)
Cisco IOS XR System Security Configuration Guide
SC-76
Page 89

Implementing Keychain Management on Cisco IOS XR Software
• Determining the Valid Keys, page SC-82 (optional)
• Configuring the Keys to Generate Authentication Digest for the Outbound Application Traffic,
page SC-84 (required)
• Configuring the Cryptographic Algorithm, page SC-85 (required)
Configuring a Keychain
This task configures a name for the keychain.
You can create or modify the name of the keychain.
SUMMARY STEPS
1. configure
2. key chain key-chain-name
3. end
or
commit
4. show key chain key-chain-name
How to Implement Keychain Management
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
key chain
Example:
RP/0/RP0/CPU0:router(config)# key chain
isis-keys
RP/0/RP0/CPU0:router(config-isis-keys)#
key-chain-name
Enters global configuration mode.
Creates a name for the keychain.
Note Configuring only the keychain name without any
key identifiers is considered a nonoperation. When
you exit the configuration, the router does not
prompt you to commit changes until you have
configured the key identifier and at least one of the
global configuration mode attributes or
keychain-key configuration mode attributes (for
example, lifetime or key string).
Cisco IOS XR System Security Configuration Guide
SC-77
Page 90

How to Implement Keychain Management
Command or Action Purpose
Step 3
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# end
or
RP/0/RP0/CPU0:router(config-isis-keys)# commit
Step 4
show key chain
key-chain-name
Example:
RP/0/RP0/CPU0:router# show key chain isis-keys
Implementing Keychain Management on Cisco IOS XR Software
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
(Optional) Displays the name of the keychain.
Note The key-chain-name argument is optional. If you do
not specify a name for the key-chain-name
argument, all the keychains are displayed.
What to Do Next
After completing keychain configuration, see the Configuring a Tolerance Specification to Accept Keys
section.
Configuring a Tolerance Specification to Accept Keys
This task configures the tolerance specification to accept keys for a keychain to facilitate a hitless key
rollover for applications, such as routing and management protocols.
SUMMARY STEPS
1. configure
2. key chain key-chain-name
3. accept-tolerance [value | infinite]
4. end
or
commit
Cisco IOS XR System Security Configuration Guide
SC-78
Page 91

Implementing Keychain Management on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
key chain
key-chain-name
Example:
RP/0/RP0/CPU0:router(config)# key chain isis-keys
Step 3
accept-tolerance [
value
| infinite]
How to Implement Keychain Management
Enters global configuration mode.
Creates a name for the keychain.
Configures a tolerance value to accept keys for the
keychain.
Step 4
Example:
RP/0/RP0/CPU0:router(config-isis-keys)#
accept-tolerance infinite
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# end
or
RP/0/RP0/CPU0:router(config-isis-keys)# commit
• Use the value argument to set the tolerance
range in seconds. The range is from 1 to
8640000.
• Use the infinite keyword to specify that the
tolerance specification is infinite.
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Configuring a Key Identifier for the Keychain
This task configures a key identifier for the keychain.
You can create or modify the key for the keychain.
Cisco IOS XR System Security Configuration Guide
SC-79
Page 92

How to Implement Keychain Management
SUMMARY STEPS
1. configure
2. key chain key-chain-name
3. key key-id
4. end
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
key chain
key-chain-name
Implementing Keychain Management on Cisco IOS XR Software
or
commit
Enters global configuration mode.
Creates a name for the keychain.
Step 3
Step 4
Example:
RP/0/RP0/CPU0:router(config)# key chain
isis-keys
key
key-id
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# key 8
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isis-keys-0x8)# end
or
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
commit
Creates a key for the keychain. The key ID number is
translated from decimal to hexadecimal to create the
command mode subprompt.
• Use the key-id argument as a 48-bit integer.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
Cisco IOS XR System Security Configuration Guide
SC-80
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Page 93

Implementing Keychain Management on Cisco IOS XR Software
What to Do Next
After configuring a key identifier for the keychain, see the Configuring the Text for the Key String
section.
Configuring the Text for the Key String
This task configures the text for the key string.
SUMMARY STEPS
1. configure
2. key chain key-chain-name
3. key key-id
4. key-string [clear | password] key-string-text
5. end
How to Implement Keychain Management
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
key chain
Example:
RP/0/RP0/CPU0:router(config)# key chain
isis-keys
key
Step 3
key-id
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# key 8
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
or
commit
key-chain-name
Enters global configuration mode.
Creates a name for the keychain.
Creates a key for the keychain.
Cisco IOS XR System Security Configuration Guide
SC-81
Page 94

How to Implement Keychain Management
Command or Action Purpose
Step 4
key-string [clear | password]
Example:
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
key-string password 8
Step 5
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isis-keys-0x8)# end
or
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
commit
key-string-text
Implementing Keychain Management on Cisco IOS XR Software
Specifies the text string for the key.
• Use the clear keyword to specify the key string in clear
text form; use the password keyword to specify the key
in encrypted form.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
What to Do Next
After configuring the text for the key string, see the Configuring the Keys to Generate Authentication
Digest for the Outbound Application Traffic section.
Determining the Valid Keys
This task determines the valid keys for local applications to authenticate the remote peers.
SUMMARY STEPS
1. configure
2. key chain key-chain-name
3. key key-id
4. accept-lifetime start-time [duration durationvalue | infinite | end-time]
5. end
or
commit
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Cisco IOS XR System Security Configuration Guide
SC-82
Page 95

Implementing Keychain Management on Cisco IOS XR Software
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
key chain
key-chain-name
Example:
RP/0/RP0/CPU0:router(config)# key chain
isis-keys
key
Step 3
key-id
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# key 8
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
Step 4
accept-lifetime
durationvalue
start-time
| infinite |
[duration
end-time
How to Implement Keychain Management
Enters global configuration mode.
Creates a a name for the keychain.
Creates a key for the keychain.
(Optional) Specifies the validity of the key lifetime in terms
]
of clock time.
Step 5
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# key 8
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
accept-lifetime 1:00:00 october 24 2005
infinite
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isis-keys-0x8)# end
or
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
commit
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Cisco IOS XR System Security Configuration Guide
SC-83
Page 96

Implementing Keychain Management on Cisco IOS XR Software
How to Implement Keychain Management
Configuring the Keys to Generate Authentication Digest for the Outbound
Application Traffic
This task configures the keys to generate authentication digest for the outbound application traffic.
SUMMARY STEPS
1. configure
2. key chain key-chain-name
3. key key-id
4. send-lifetime start-time [duration durationvalue | infinite | end-time]
5. end
or
commit
DETAILED STEPS
Step 1
Step 2
Step 3
Command or Action Purpose
configure
Enters global configuration mode.
Example:
RP/0/RP0/CPU0:router# configure
key chain
key-chain-name
Creates a name for the keychain.
Example:
RP/0/RP0/CPU0:router(config)# key chain
isis-keys
key
key-id
Creates a key for the keychain.
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# key 8
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
Cisco IOS XR System Security Configuration Guide
SC-84
Page 97

Implementing Keychain Management on Cisco IOS XR Software
Command or Action Purpose
Step 4
send-lifetime
durationvalue
start-time
| infinite |
[duration
end-time
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# key 8
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
send-lifetime 1:00:00 october 24 2005 infinite
Step 5
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isis-keys-0x8)# end
or
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
commit
How to Implement Keychain Management
(Optional) Specifies the set time period during which an
]
authentication key on a keychain is valid to be sent. You can
specify the validity of the key lifetime in terms of clock
time.
In addition, you can specify a start-time value and one of the
following values:
• duration keyword (seconds)
• infinite keyword
• end-time argument
If you intend to set lifetimes on keys, Network Time
Protocol (NTP) or some other time synchronization method
is recommended.
Saves configuration changes.
• When you issue the end command, the system prompts
you to commit changes:
Uncommitted changes found, commit them before
exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to the
running configuration file, exits the configuration
session, and returns the router to EXEC mode.
Configuring the Cryptographic Algorithm
This task allows the keychain configuration to accept the choice of the cryptographic algorithm.
SUMMARY STEPS
1. configure
2. key chain key-chain-name
3. key key-id
–
Entering no exits the configuration session and
returns the router to EXEC mode without
committing the configuration changes.
–
Entering cancel leaves the router in the current
configuration session without exiting or
committing the configuration changes.
• Use the commit command to save the configuration
changes to the running configuration file and remain
within the configuration session.
Cisco IOS XR System Security Configuration Guide
SC-85
Page 98

How to Implement Keychain Management
4. cryptographic-algorithm [HMAC-MD5 | HMAC-SHA1-12 | HMAC-SHA1-20 | MD5 | SHA-1]
5. end
DETAILED STEPS
Command or Action Purpose
Step 1
configure
Example:
RP/0/RP0/CPU0:router# configure
Step 2
key chain
key-chain-name
Example:
RP/0/RP0/CPU0:router(config)# key chain isis-keys
RP/0/RP0/CPU0:router(config-isis-keys)#
key
Step 3
key-id
Implementing Keychain Management on Cisco IOS XR Software
or
commit
Enters global configuration mode.
Creates a name for the keychain.
Creates a key for the keychain.
Example:
RP/0/RP0/CPU0:router(config-isis-keys)# key 8
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
Cisco IOS XR System Security Configuration Guide
SC-86
Page 99

Implementing Keychain Management on Cisco IOS XR Software
Command or Action Purpose
Step 4
Step 5
cryptographic-algorithm [HMAC-MD5 | HMAC-SHA1-12 |
HMAC-SHA1-20 | MD5 | SHA-1]
Example:
RP/0/RP0/CPU0:router(config-isis-keys-0x8)#
cryptographic-algorithm MD5
end
or
commit
Example:
RP/0/RP0/CPU0:router(config-isis-keys-0x8)# end
or
RP/0/RP0/CPU0:router(config-isis-keys-0x8)# commit
Configuration Examples for Implementing Keychain Management
Specifies the choice of the cryptographic algorithm.
You can choose from the following list of
algorithms:
• HMAC-MD5
• HMAC-SHA1-12
• HMAC-SHA1-20
• MD5
• SHA-1
Saves configuration changes.
• When you issue the end command, the system
prompts you to commit changes:
Uncommitted changes found, commit them
before exiting(yes/no/cancel)?
[cancel]:
–
Entering yes saves configuration changes to
the running configuration file, exits the
configuration session, and returns the
router to EXEC mode.
–
Entering no exits the configuration session
and returns the router to EXEC mode
without committing the configuration
changes.
–
Entering cancel leaves the router in the
current configuration session without
exiting or committing the configuration
changes.
• Use the commit command to save the
configuration changes to the running
configuration file and remain within the
configuration session.
Configuration Examples for Implementing Keychain
Management
This section provides the following configuration example:
• Configuring Keychain Management: Example, page SC-87
Configuring Keychain Management: Example
The following example shows how to configure keychain management:
configure
key chain isis-keys
Cisco IOS XR System Security Configuration Guide
SC-87
Page 100

Additional References
Implementing Keychain Management on Cisco IOS XR Software
accept-tolerance infinite
key 8
key-string mykey91abcd
cryptographic-algorithm MD5
send-lifetime 1:00:00 june 29 2006 infinite
accept-lifetime 1:00:00 june 29 2006 infinite
end
Uncommitted changes found, commit them? [yes]: yes
show key chain isis-keys
Key-chain: isis-keys/ -
accept-tolerance -- infinite
Key 8 -- text "1104000E120B520005282820"
cryptographic-algorithm -- MD5
Send lifetime: 01:00:00, 29 Jun 2006 - Always valid [Valid now]
Accept lifetime: 01:00:00, 29 Jun 2006 - Always valid [Valid now]
Additional References
The following sections provide references related to implementing keychain management.
Related Documents
Related Topic Document Title
Keychain management commands: complete
command syntax, command modes, command
history, defaults, usage guidelines, and examples
Standards
Standards Title
No new or modified standards are supported by this
feature, and support for existing standards has not been
modified by this feature.
Keychain Management Commands on Cisco IOS XR Software module in
Cisco IOS XR System Security Command Reference, Release 3.5
—
Cisco IOS XR System Security Configuration Guide
SC-88
 Loading...
Loading...