Page 1

Cisco IOS XE Intelligent Services Gateway
Configuration
Release 2
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Guide
Page 2

THE SPECIFICATIONS AND INFORMATION REGA RDING THE P RODUCTS IN TH IS MA NUAL ARE SUBJECT TO CHAN GE W ITHOUT NOT ICE. ALL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILIT Y FOR THEIR APPLICAT ION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED W ARRANTY FO R THE ACCOMPA NYING PRODUCT ARE SET FO RTH IN THE IN FORMAT ION P ACKET TH AT
S
HIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compres
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DO CUMENT FILES AND SOFTWARE OF THESE SUPPL IERS ARE PROVIDED “AS IS” WITH
AL
L FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WA RRANTIES, EXPRESSE D OR IMPLIED, INCLUDING, WITHOUT
LIM
ITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRI NGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
W
ITHOUT LIMITATION, LOST P ROFITS OR LO SS OR DAMAGE TO DATA ARISIN G OUT OF THE USE OR INABILI TY TO USE THIS MA NUAL, EVEN I F CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SU CH DAMA GES.
CCDE, CCENT, CCSI, Cisco Eos, Cisco HealthPresence, Cisco IronPort, the Cisco logo, Cisco Nurse Connect, Cisco Pulse, Cisco SensorBase, Cisco StackPower,
Cis
co StadiumVision, Cisco TelePresence, Cisco Unified Computing System, Cisco WebEx, DCE, Flip Channels, Flip for Goo d, Fl
Flip Video, Flip Video (Design), I nstant Broad band, and Welco me to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn, Cisco Capital,
Cis
co Capital (Design), Cisco:Financed (Stylized), Cisco Store, Flip Gift Card, and One Million Acts of G
AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo,
Cis
co IOS, Cisco Lumin, Cisco Nexus, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation,
Co
ntinuum, EtherFast, EtherSwitch, Event Center, Explorer, Follow Me Browsing, GainMaker, iLYNX, IOS, iPhone, IronPort, the IronPort logo, Laser Link, LightStream,
Linksys, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, PCNow, PIX, PowerKEY, PowerPanels, PowerTV, PowerTV (Design ),
PowerVu, Prisma, ProConnect, ROSA, SenderBase, SMARTnet , Spectr um Expert, StackWise, WebEx, and t he WebEx logo are registered trade marks of Cisco Systems, Inc.
and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the propert
between Cisco and any other company. (0910R)
Any Internet Protocol (IP) addresses u sed in this d ocument are not i
document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
Cisco IOS XE Intelligent Services Gateway Configuration Guide
© 2009 Cisco Systems, Inc. All rights reserved.
sion is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
ip Mino, Flipshare (Design), Flip Ultra,
reen are service marks; and Access Registrar, Aironet, AllTouch,
y of their respective owners. The use of the word partner does not imply a partnershi p relati onshi p
ntended to be actual addresses. Any examples, command display output, and figures included in the
Page 3

About Cisco IOS XE Software Documentation
Last Updated: December 1, 2009
This document describes the objectives, audience, conventions, and organization used in Cisco IOS XE
software documentation. Also included are resources for obtaining technical assistance, additional
documentation, and other information from Cisco. This document is organized into the following
sections:
• Documentation Objectives, page i
• Audience, page i
• Documentation Conventions, page ii
• Documentation Organization, page iii
• Additional Resources and Documentation Feedback, page x
Documentation Objectives
Cisco IOS XE documentation describe the tasks and commands available to configure and maintain
Cisco networking devices.
Audience
The Cisco IOS XE documentation set is intended for users who conf igure and maintain Cisco netw orking
devices (such as routers and switches) but who may not be familiar with the configuration and
maintenance tasks, the relationship among tasks, or the Cisco IOS commands necessary to perform
particular tasks. The Cisco IOS XE documentation set is also intended for those users experienced with
Cisco IOS XE software who need to know about new features, new configuration options, and new
software characteristics in the current Cisco IOS XE release.
i
Page 4
Documentation Conventions
Documentation Conventions
In Cisco IOS XE documentation, the term router may be used to refer to various Cisco products; for
example, routers, access servers, and switches. These and other networking devices that support
Cisco IOS XE software are shown interchangeably in examples and are used only for illustrative
purposes. An example that shows one product does not necessarily mean that other products are not
supported.
This section contains the following topics:
• Typographic Conventions, page ii
• Command Syntax Conventions, page ii
• Software Conventions, page iii
• Reader Alert Conventions, page iii
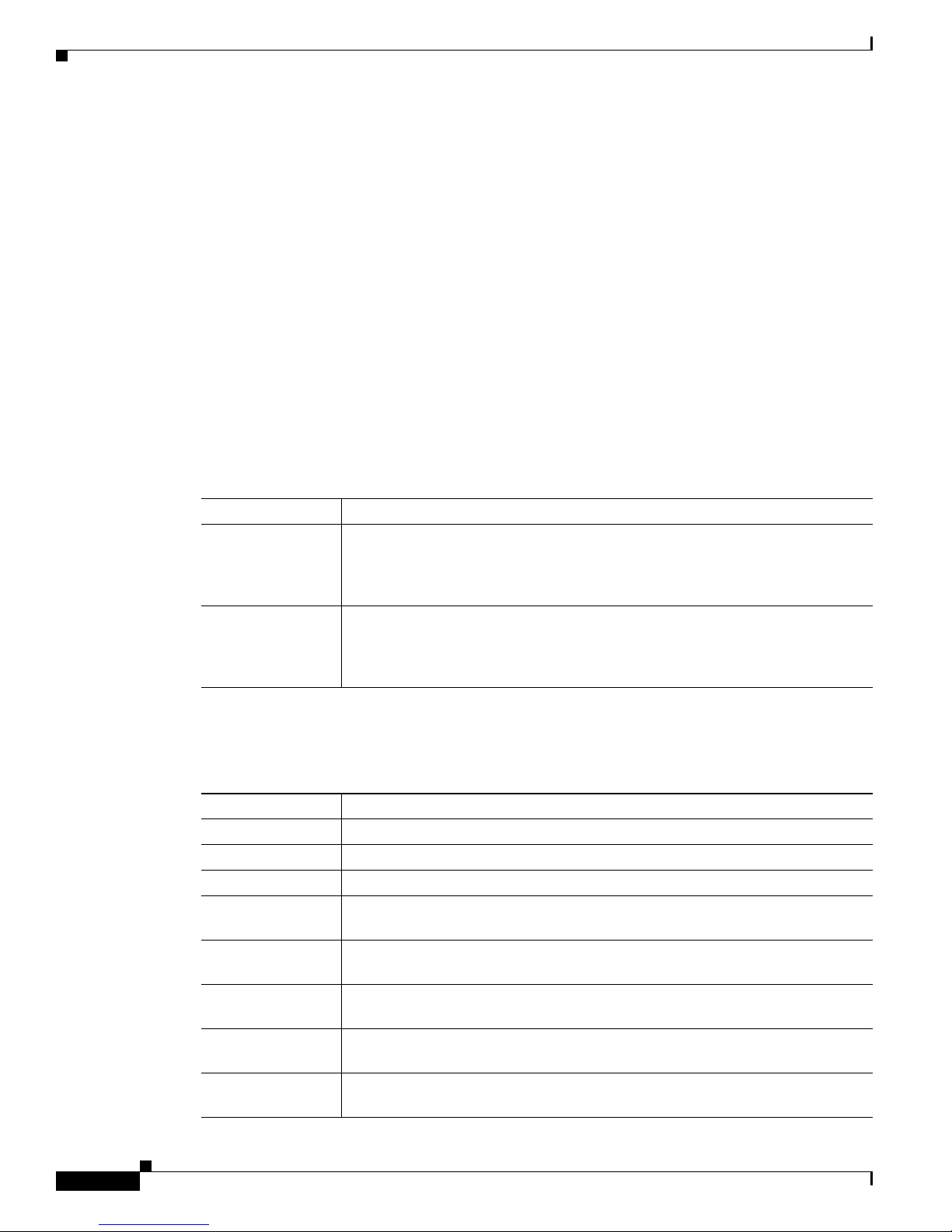
Typographic Conventions
Cisco IOS XE documentation uses the following typographic conventions:
About Cisco IOS XE Software Documentation
Convention Description
^ or Ctrl Both the ^ symbol and Ctrl represent the Control (Ctrl) key on a keyboard. For
example, the key combination ^D or Ctrl-D means that you hold down the
Control key while you press the D key. (Keys are indicated in capital letters but
are not case sensitive.)
string A string is a nonquoted set of characters shown in italics. For example, when
setting a Simple Network Management Protocol (SNMP) community string to
public, do not use quotation marks around the string; otherwise, the string will
include the quotation marks.
Command Syntax Conventions
Cisco IOS XE documentation uses the following command syntax conventions:
Convention Description
bold Bold text indicates commands and keywords that you enter as shown.
italic Italic text indicates arguments for which you supply values.
[x] Square brackets enclose an optional keyword or argument.
... An ellipsis (three consecutive nonbolded periods without spaces) after a syntax
element indicates that the element can be repeated.
| A vertical line, called a pipe, indicates a choice within a set of keywords
or arguments.
[x | y] Square brackets enclosing keywords or arguments separated by a pipe indicate an
optional choice.
{x | y} Braces enclosing keywords or arguments separated by a pipe indicate a
required choice.
[x {y | z}] Braces and a pipe within square brackets indicate a required choice within an
optional element.
ii
Page 5
About Cisco IOS XE Software Documentation
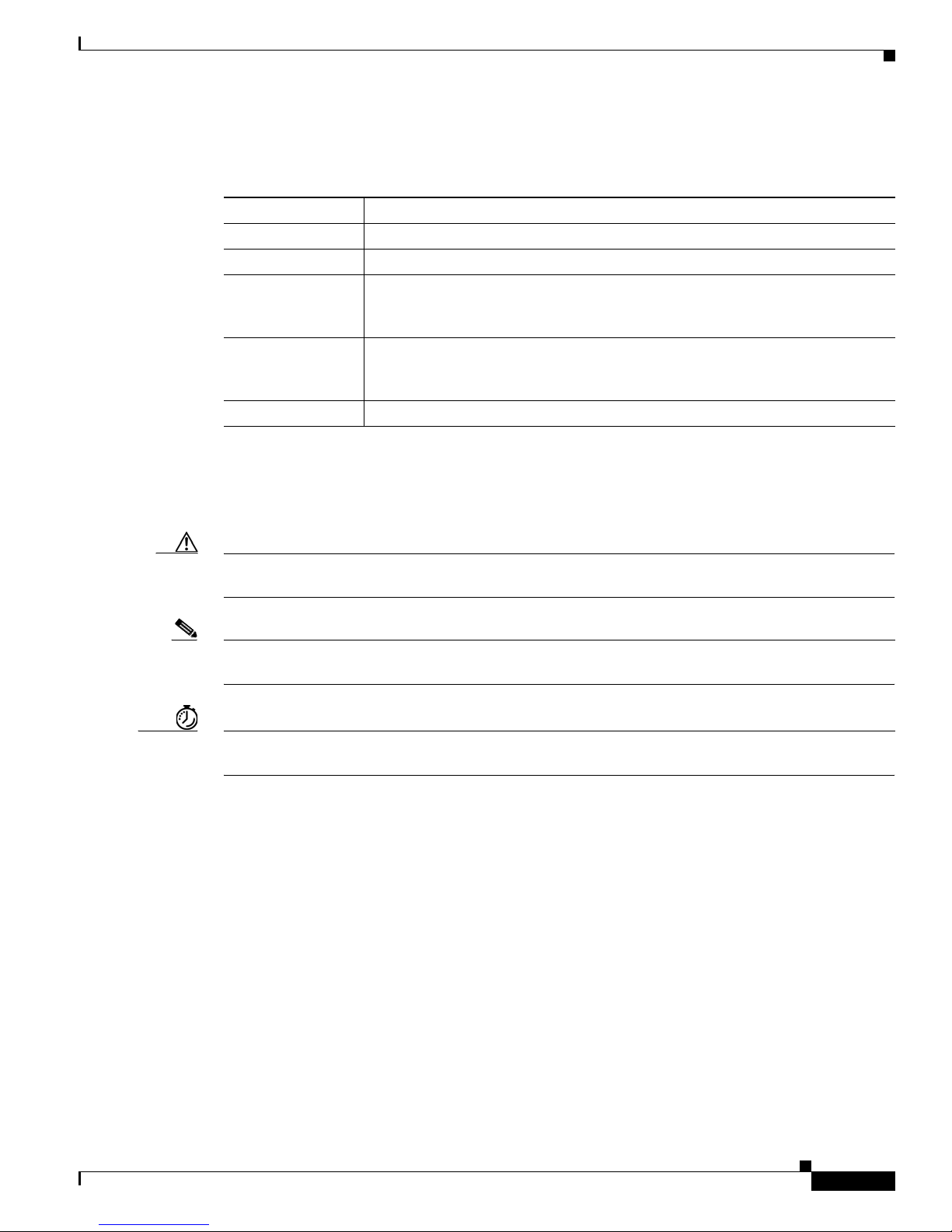
Software Conventions
Cisco IOS XE software uses the following conventions:
Convention Description
Courier font
Bold Courier font
< > Angle brackets enclose text that is not displayed, such as a password. Angle
! An exclamation point at the beginning of a line indicates that the text that follows
[ ] Square brackets enclose default responses to system prompt s.
Reader Alert Conventions
Documentation Organization
Courier font is used for information that is displayed on a PC or terminal screen.
Bold Courier font indicates text that the user must enter.
brackets also are used in contexts in which the italic font style is not supported;
for example, ASCII text.
is a comment, not a line of code. An exclamation point is also displayed by the
Cisco IOS XE software for certain processes.
Cisco IOS XE documentation uses the following conventions for reader alerts:
Caution Means reader be careful. In this situation, you might do something that could result in equipment
damage or loss of data.
Note Means reader take note. Notes contain helpful suggestions or references to material not covered in the
manual.
Timesaver Means the described action saves time. You can save time by performing the action described in the
paragraph.
Documentation Organization
This section describes the Cisco IOS XE documentation set, ho w it i s or gan ized, and ho w to access it on
Cisco.com. Listed are configuration guides, command references, and supplementary references and
resources that comprise the documentation set.
• Cisco IOS XE Documentation Set, page iv
• Cisco IOS XE Documentation on Cisco.com, page iv
• Configuration Guides, Command References, and Supplementary Resources, page v
iii
Page 6

Documentation Organization
Cisco IOS XE Documentation Set
The Cisco IOS XE documentation set consists of the following:
• Release notes and caveats provide information about platform, technology, and feature support for
a release and describe severi ty 1 (catastrophic), seve rity 2 (severe), and se verity 3 (moderat e) defects
in released Cisco IOS XE software. Review release notes before other documents to learn whethe r
updates have been made to a feature.
• Sets of configuration guides and command references organized by technology and published for
each standard Cisco IOS XE release.
–
Configuration guides—Compilations of documents that provide conceptual and task-oriented
descriptions of Cisco IOS XE features.
–
Command references—Alphabe tical compilations of command pages that provide detailed
information about the commands used in the Cisco IOS XE features and the processes that
comprise the related configuration guides. For each technology, there is a single command
reference that covers all Cisco IOS XE releases and that is updated at each standard release.
• Command reference book for debug commands.
• Lists of all the commands in a specific release and all commands that are new, modified, removed,
or replaced in the release.
About Cisco IOS XE Software Documentation
• Reference book for system messages for all Cisco IOS XE releases.
Cisco IOS XE Documentation on Cisco.com
The following sections describe the documentation organization and how to access various document
types.
Use Cisco Feature Navigator to find information about Cisco IOS XE software image support. T o access
Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
New Features List
The New Features List for each release provides a list of all features in the release with hyperlinks to the
feature guides in which they are documented.
Configuration Guides
Configuration guides are provided by technology and release and comprise a set of individual feature
guides relevant to the release and technology.
Command References
Command reference books describe Cisco IOS XE commands that are supported in many different
software releases and on many different platforms. The books are organized by technology. For
information about all Cisco IOS XE commands, use the Command Lookup Tool at
http://tools.cisco.com/Support/CLILookup or the Cisco IOS Master Command List, All Releases, at
http://www.cisco.com/en/US/docs/ios/mcl/allreleasemcl/all_book.html.
Cisco IOS XE Supplementary Documents and Resources
Supplementary documents and resources are listed in Table 2 on page x.
iv
Page 7
About Cisco IOS XE Software Documentation
Documentation Organization
Configuration Guides, Command References, and Supplementary Resources
Ta ble 1 lists, in alphabetical order, Cisco IOS XE software configuration guides and
command references, including brief descriptions of the contents of the documents. The command
references contain commands for both Cisco IOS software and Cisco IOS XE software, for all releases.
The command references support many different software releases and platforms. Your Cisco IOS XE
software release or platform may not support all these technologies.
Table 2 lists documents and resources that supplement the Cisco IOS XE software configuration guides
and command references. These supplementary resources include release notes and caveats; master
command lists; new, modified, removed, and replaced command lists; system messages; and the debug
command reference.
For additional information about configuring and operating specific networking devices, and to access
Cisco IOS documentation, go to the Product/Technologies Support area of Cisco.com at the following
location:
http://www.cisco.com/go/techdocs
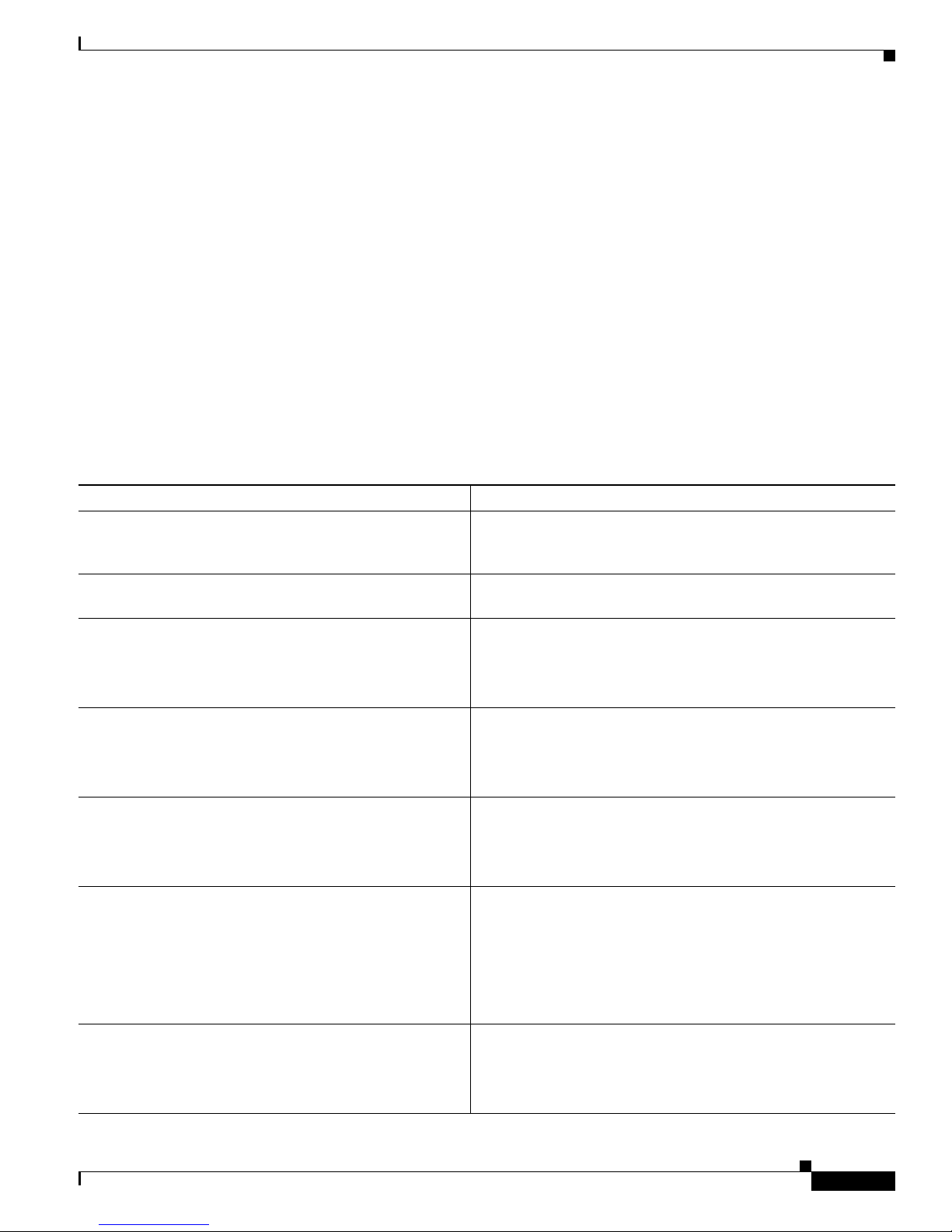
Table 1 Cisco IOS XE Configuration Guides and Command References
Configuration Guide and Command Reference Titles Features/Protocols/Technologies
• Cisco ASR 1000 Series Aggregation Services Routers
SIP and SPA Software Configuration Guide
Configuration and troubleshooting of SPA interface processors
(SIPs) and shared port adapters (SP As) t hat are supported on t he
Cisco ASR 1000 Series Router.
• Cisco ASR 1000 Series Aggregation Services Routers
Software Configuration Guide
• Cisco IOS XE Access Node Control Protocol
Configuration Guide
• Cisco IOS Access Node Control Protocol
Overview of software functionality that is specific to the
Cisco ASR 1000 Series Aggregation Services Routers.
Communication protocol between digital subscriber line access
multiplexers (DSLAMs) and a broadband remote access server
(BRAS).
Command Reference
• Cisco IOS XE Asynchronous Transfer Mode
LAN ATM, multiprotocol over ATM (MPoA), and WAN ATM.
Configuration Guide
• Cisco IOS Asynchronous Transfer Mode
Command Reference
• Cisco IOS XE Broadband Access Aggr egation and DSL
PPP over Ethernet (PPPoE).
Configuration Guide
• Cisco IOS Broadband Access Aggregation and DSL
Command Reference
• Cisco IOS XE Carrier Ethernet Configuration Guide
• Cisco IOS Carrier Ethernet Command Reference
IEEE 802.3ad Link Bundling; Link Aggregation Control
Protocol (LACP) support for Eth ernet and Gigabit Ethernet links
and EtherChannel bundles; LACP support for stateful
switchover (SSO), in service software upgrade (ISSU), Cisco
nonstop forwarding (NSF), and nonstop routing (NSR) on
Gigabit EtherChannel bundles; and IEEE 802.3ad Link
Aggregation MIB.
• Cisco IOS XE Configuration Fundamentals
Configuration Guide
• Cisco IOS Configuration Fundamentals
Autoinstall, Setup, Cisco IOS command- line inter face (CLI),
Cisco IOS file system (IFS), Cisco IOS web browser user
interface (UI), basic file transfer services, and file management.
Command Reference
v
Page 8
About Cisco IOS XE Software Documentation
Documentation Organization
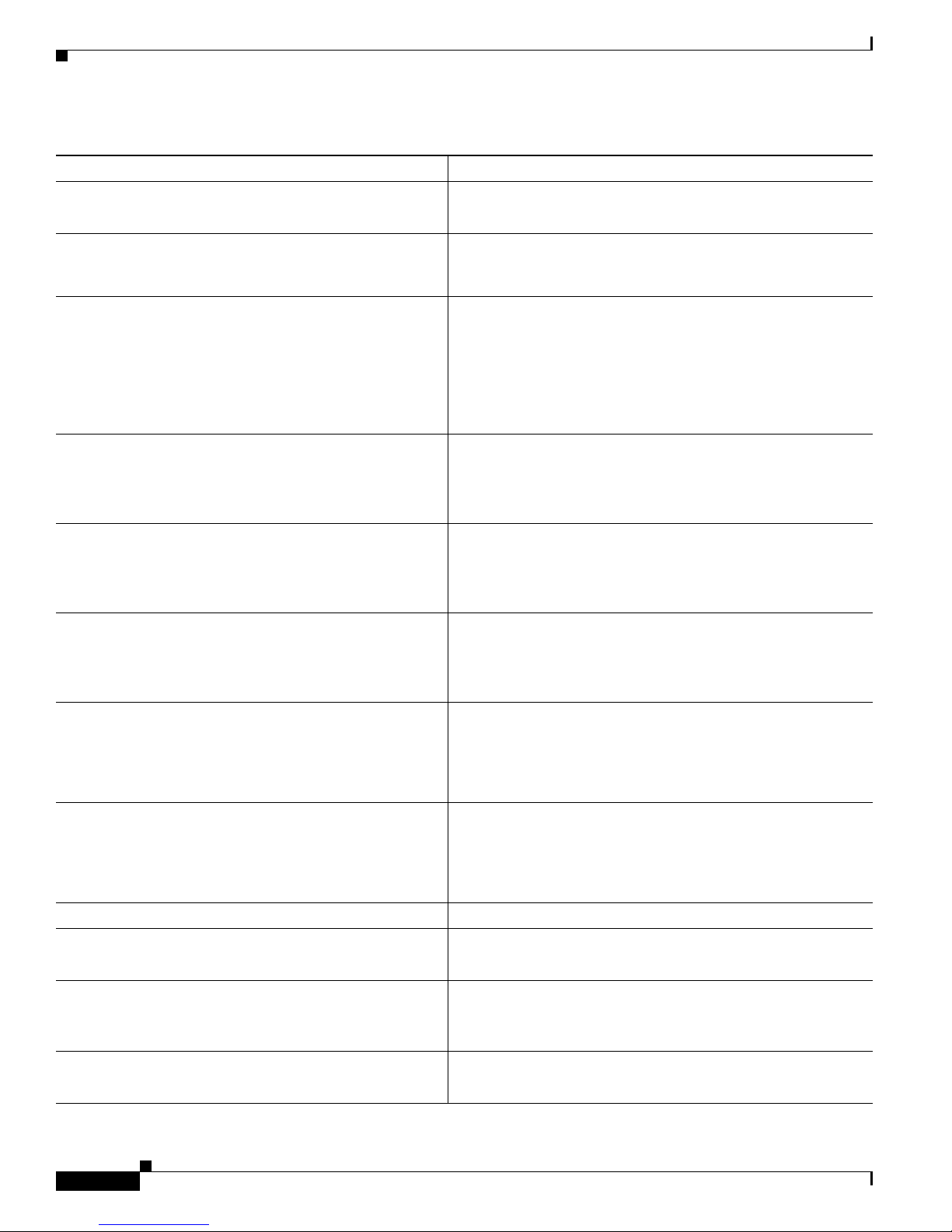
Table 1 Cisco IOS XE Configuration Guides and Command References (continued)
Configuration Guide and Command Reference Titles Features/Protocols/Technologies
• Cisco IOS XE DECnet Configuration Guide
• Cisco IOS DECnet Command Reference
• Cisco IOS XE Dial Technologies Configuration Guide
• Cisco IOS Dial Technologies Command Reference
• Cisco IOS XE High Availability Configuration Guide
• Cisco IOS High Availability Command Reference
• Cisco IOS XE Intelligent Services Gateway
Configuration Guide
• Cisco IOS Intelligent Services Gateway
Command Reference
• Cisco IOS XE Interface and Hardware Component
Configuration Guide
• Cisco IOS Interface and Hardware Component
Command Reference
• Cisco IOS XE IP Addressing Services
Configuration Guide
• Cisco IOS IP Addressing Services
Command Reference
• Cisco IOS XE IP Application Services
Configuration Guide
• Cisco IOS IP Application Services
Command Reference
• Cisco IOS XE IP Multicast Configuration Guide
• Cisco IOS IP Multicast Command Reference
• Cisco IOS XE IP Routing: BFD Configuration Guide Bidirectional forwarding detection (BFD).
• Cisco IOS XE IP Routing: BGP Configuration Guide
• Cisco IOS IP Routing: BGP Command Reference
• Cisco IOS XE IP Routing: EIGRP
Configuration Guide
DECnet protocol.
Asynchronous communications, dial backup, dial er technolog y,
Multilink PPP (MLP), PPP, and virtual private dialup network
(VPDN).
A variety of high availability (HA) features and technologies
that are available for different network segments (from
enterprise access to service provider core) to facilitate creation
of end-to-end highly av ailable networks. Cisco IOS HA features
and technologies can be categorized in three key areas:
system-level resilienc y, network-level resiliency , an d embedded
management for resiliency.
Subscriber identification, service and policy determination,
session creation, session policy enforcement, session life-cycle
management, accounting for access and service usage, and
session state monitoring.
LAN interfaces, logical interfaces, serial interfaces, virtual
interfaces, and interface configuration.
IP addressing, Address Resolution Protocol (ARP), Network
Address Translation (NAT), Domain Name System (DNS),
Dynamic Host Configuration Protocol (DHCP), and Next Hop
Address Resolution Protocol (NHRP).
Enhanced Object Tracking (EOT), Gateway Load Balancing
Protocol (GLBP), Hot Standby Router Protocol (HSRP), IP
Services, TCP, Web Cache Communication Protocol (WCCP),
User Datagram Protocol (UDP), and V irtual Router Redu ndancy
Protocol (VRRP).
Protocol Independent Multicast (PIM) sparse mode (PIM-SM),
bidirectional PIM (bidir-PIM), Source Specific Multicast
(SSM), Multicast Source Discovery Protocol (MSDP), Internet
Group Management Protocol (IGMP), and Multicast VPN
(MVPN).
Border Gateway Protocol (BGP), multi protocol B GP,
multiprotocol BGP extensions for IP multicast.
Enhanced Interior Gateway Routing Protocol (EIGRP).
• Cisco IOS IP Routing: EIGRP Command Reference
• Cisco IOS XE IP Routing: ISIS Configuration Guide
• Cisco IOS IP Routing: ISIS Command Reference
vi
Intermediate System-to-Intermediate System (IS-IS).
Page 9
About Cisco IOS XE Software Documentation
Table 1 Cisco IOS XE Configuration Guides and Command References (continued)
Configuration Guide and Command Reference Titles Features/Protocols/Technologies
• Cisco IOS XE IP Routing: ODR Configuration Guide
• Cisco IOS IP Routing: ODR Command Reference
• Cisco IOS XE IP Routing: OSPF Configuration Guide
• Cisco IOS IP Routing: OSPF Command Reference
• Cisco IOS XE IP Routing: Protocol-Independent
Configuration Guide
• Cisco IOS IP Routing: Protocol-Independent
Command Reference
• Cisco IOS XE IP Routing: RIP Configuration Guide
• Cisco IOS IP Routing: RIP Command Reference
• Cisco IOS XE IP SLAs Configuration Guide
• Cisco IOS IP SLAs Command Reference
• Cisco IOS XE IP Switching Configuration Guide
• Cisco IOS IP Switching Command Reference
• Cisco IOS XE IPv6 Configuration Guide
• Cisco IOS IPv6 Command Reference
• Cisco IOS XE ISO CLNS Configuration Guide
• Cisco IOS ISO CLNS Command Reference
• Cisco IOS XE LAN Switching Configuration Guide
• Cisco IOS LAN Switching Command Reference
• Cisco IOS XE Multiprotocol Label Switching
Configuration Guide
• Cisco IOS Multiprotocol Label Switching
Command Reference
• Cisco IOS XE NetFlow Configuration Guide
• Cisco IOS NetFlow Command Reference
• Cisco IOS XE Network Management
Configuration Guide
• Cisco IOS Network Management Command Reference
• Cisco IOS XE Novell IPX Configuration Guide
On-Demand Routing (ODR).
Open Shortest Path First (OSPF).
IP routing protocol-independent features and commands.
Generic policy-based routing (PBR) features and commands are
included.
Routing Information Protocol (RIP).
Cisco IOS IP Service Level Agreements (IP SLAs).
Cisco Express Forwarding.
For a list of IPv6 features, protocols, and technolog ies, go to the
IPv6 “Start Here” document at the following URL:
http://www.cisco.com/en/US/docs/ios/ios_xe/ipv6/configuratio
n/guide/ip6-roadmap_xe.html
ISO Connectionless Network Service (CLNS).
VLANs and multilayer switching (MLS).
MPLS Label Distribution Protocol (LDP), MPLS Layer 2 VPNs,
MPLS Layer 3 VPNs, MPLS Traffic Engineering (TE), and
MPLS Embedded Management (EM) and MIBs.
Network traffic data analysis, aggregation caches, and export
features.
Basic system management, system monitoring and logging,
Cisco IOS Scripting with Tool Control Language (Tcl),
Cisco networking services (CNS), Embedded Event Manager
(EEM), Embedded Syslog Manager (ESM), HTTP, Remote
Monitoring (RMON), and SNMP.
Novell Internetwork Packet Exchange (IPX) protocol.
Documentation Organization
• Cisco IOS Novell IPX Command Reference
vii
Page 10

About Cisco IOS XE Software Documentation
Documentation Organization
Table 1 Cisco IOS XE Configuration Guides and Command References (continued)
Configuration Guide and Command Reference Titles Features/Protocols/Technologies
• Cisco IOS XE Quality of Service Solutions
Configuration Guide
• Cisco IOS Quality of Service Solutions
Command Reference
• Cisco IOS Security Command Reference Access control lists (ACLs); authentication, authorization, and
• Cisco IOS XE Security Configuration Guide: Secure
Connectivity
• Cisco IOS XE Security Configuration Guide: Securing
the Data Plane
• Cisco IOS XE Security Configuration Guide: Securing
User Services
• Cisco IOS XE Service Advertisement Framework
Configuration Guide
Class-based weighted fair queueing (CBWFQ), low latency
queueing (LLQ), Modular Quality of Service (QoS)
Command-Line Interface (CLI) (MQC), Network-Based
Application Recognition (NBAR), priority queueing, Mult ilink
PPP (MLP) for QoS, header compression, Resource Reservation
Protocol (RSVP), weighted fair queueing (WFQ ), and weighted
random early detection (WRED).
accounting (AAA); firewalls; IP security and encryption;
neighbor router authentication; network access security; public
key infrastructure (PKI); RADIUS; and TACACS+.
Internet Key Exchange (IKE) for IPsec VPNs; security for VPNs
with IPsec; VPN availability features (reverse route injection,
IPsec preferred peer, and real-time resolution for the IPsec
tunnel peer); IPsec data plane features; IPsec management plane
features; Public Key Infrastructure (PKI); Dynamic Multipoint
VPN (DMVPN); Easy VPN; and Cisco Group Encrypted
Transport VPN (GET VPN).
Access Control Lists (ACLs); Firewalls: Context-Based Access
Control (CBAC) and Zone-Based Firew all; Cisco IOS Intrusio n
Prevention System (IPS); Flexible Packet Matching; Unicast
Reverse Path Forwarding (uRPF); Threat Information
Distribution Protocol (TIDP) and TMS.
AAA (includes Network Admission Control [NAC]); Security
Server Protocols (RADIUS and TACACS+); Secure Shell
(SSH); Secure Access for Networking Devices (includes
Autosecure and Role-Based CLI access); Lawful Intercept.
Cisco Service Advertisement Framework.
• Cisco IOS Service Advertisement Framework
Command Reference
• Cisco IOS XE VPDN Configuration Guide
• Cisco IOS VPDN Command Reference
• Cisco IOS XE Wide-Area Networking
Configuration Guide
• Cisco IOS Wide-Area Networking
Command Reference
viii
Multihop by Dialed Number Identification Service (DNIS),
timer and retry enhancements for L2TP and Layer 2 Forwarding
(L2F), RADIUS Attribute 82 (tunnel assignment ID),
shell-based authentication of VPDN users, and tunnel
authentication via RADIUS on tunnel terminator.
Frame Relay; L2VPN Pseudowire Redundancy; and
Media-Independent PPP and Multilink PPP.
Page 11

About Cisco IOS XE Software Documentation
Table 1 Cisco IOS XE Configuration Guides and Command References (continued)
Configuration Guide and Command Reference Titles Features/Protocols/Technologies
• Cisco Unified Border Element (Enterprise)
Configuration Guide
• Cisco IOS Voice Command Reference
• Cisco Unified Border Element (SP Edition)
Configuration Guide: Distributed Model
• Cisco Unified Border Element (SP Edition)
Command Reference: Distributed Model
• Cisco Unified Border Element (SP Edition)
Configuration Guide: Unified Model
• Cisco Unified Border Element (SP Edition)
Command Reference: Unified Model
The Cisco Unified Border Element (Enterprise) on the
Cisco ASR 1000 brings a scalable op tion for ente rprise
customers. Running as a process on the Cisco ASR 1000 and
utilizing the high-speed RTP packet processing path, the Cisco
Unified Border Element (Enterprise) is used as an IP-to-IP
gateway by enterprises and commercial cust omers to
interconnect SIP and H.323 voice and video networks. The
Cisco UBE (Enterprise) provides a network-to-network
demarcation interface for signaling interworking, media
interworking, address and port translations, billing, security,
quality of service (QoS), and bandwidth management.
The Cisco Unified Border Element (SP Edit ion) is a sessi on
border controller (SBC) that is VoIP-enabled and deployed at the
edge of networks. For Cisco IOS XE Release 2.3 and earlier
releases, Cisco Unified Border Element (SP Edition) is
supported only in the distributed mode. Operating in the
distributed mode, the SBC is a toolkit of functions that can be
used to deploy and manage VoIP services, such as signaling
interworking, network hiding, security, and quality of service.
The Cisco Unified Border Element (SP Edit ion) is a highly
scalable, carrier-grade session border controller (SBC) that is
designed for service providers and that is generally deployed at
the border of the enterprise or SP networks to enable the easy
deployment and management of VoIP services. Cisco Unified
Border Element (SP Edition) is integrated into Cisco routing
platforms and can use a large number of router functions to
provide a very feature-rich and intelligent SBC application .
Formerly known as Integrated Session Border Controller,
Cisco Unified Border Element (SP Edition) provides a
network-to-network demarcation interface for signaling
interworking, media interworking, address and port translati ons,
billing, security, quality of service, call admission control, and
bandwidth manageme nt.
For Cisco IOS XE Release 2.4 and later releases, Cisco Unified
Border Element (SP Edition) can operate in two modes or
deployment models: unified and distributed. The configuration
guide documents the features in the unified mode.
Documentation Organization
Table 2 lists documents and resources that supplement the Cisco IOS XE software configuration guides
and command references.
ix
Page 12

About Cisco IOS XE Software Documentation
Additional Resources and Documentation Feedback
Table 2 Cisco IOS XE Software Supplementary Documents and Resources
Document Title or Resource Description
Cisco IOS Master Command List, All Releases Alphabetical list of all the commands documented in all
Cisco IOS XE software releases.
Cisco IOS Debug Command Reference Alphabetical list of debug commands including brief
descriptions of use, command syntax, and usage guidelines.
Cisco IOS XE system messages List of Cisco IOS XE system messages and descriptions. System
messages may indicate problems with your system, may be
informational only, or may help diagnose problems with
communications lines, internal hardware, or the system
software.
Release notes and caveats Information about new and changed features, system
requirements, and other useful information about specific
software releases; information about defects in specific
Cisco IOS XE software releases.
MIBs Files used for network monitoring. To locate and download
MIBs for selected platforms, Cisco IOS XE software releases,
and feature sets, use Cisco MIB Locator at the following URL:
http://www.cisco.com/go/mibs
RFCs Standards documents maintained by the Internet Engineering
T ask Force (IETF) that Ci sco IOS XE documentation references
where applicable. The full text of referenced RFCs may be
obtained at the following URL:
http://www.rfc-editor.org/
Additional Resources and Documentation Feedback
What’s New in Cisco Product Documentation is updated monthly and describes all new and revised
Cisco technical documentation. The What’s New in Cisco Product Documentation publication also
provides information about obtaining the following resources:
• Technical documentation
• Cisco product security overview
• Product alerts and field notices
• Technical assistance
Cisco IOS XE software technical documentation includes embedd ed feedback forms where y ou can rate
documents and provide suggestions for improvement. Your feedback helps us improve our
documentation.
x
Page 13

About Cisco IOS XE Software Documentation
CCDE, CCENT, CCSI, Cisco Eos, Cisco HealthPresence, Cisco IronPort, the Cisco logo, Cisco Nurse Connect, Cisco Pulse, Cisco SensorBase,
Cisco StackPower, Cisco StadiumV ision, Cisco TelePresence, Cisco Unified Computing System, Cisco W e bEx, D CE, Flip Chann els, Fli p for Good,
Flip Mino, Flipshare (Design), Flip Ultra, Fli p Video, Flip V i deo (Design), Instant Broadband, and Welcome to the Human Network are trademarks;
Changing the Way We Work, Live, Play, and Learn, Cisco Capit al, C isco Capit al (D esign), Cis co:Finan ced (Styl ized), Cisco Stor e, Flip Gift Card,
and One Million Acts of Green are service marks; and Access Registrar, Aironet, AllTouch, AsyncOS, Bringing the Meeting T o You, Catalyst, CCDA,
CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Lumin, Cisco Nexus,
Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation, Cont inuum, E th erFast,
EtherSwitch, Event Center, Explor er, Follow Me Browsi ng, Gain Mak er, iLYNX, IOS, iPhone, IronPort, the IronPort logo, Laser Link, LightStream,
Linksys, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, PCNow, PIX, PowerKEY, PowerPanels, PowerTV,
PowerTV (Design), PowerVu, Prisma, ProConnect, ROSA, SenderBase, SMARTnet, Spectrum Expert, StackWise, WebEx, and the WebEx logo are
registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0910R)
Any Internet Protocol (IP) addresses an d ph one nu mbers u sed in this document are not intended to be actual addresses and phone numbers. Any
examples, command display output, network topology diagrams, and other fig ures included in the document are sho wn for illust rati v e purp oses only.
Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
© 2009 Cisco Systems, Inc. All rights reserved.
Additional Resources and Documentation Feedback
xi
Page 14

Additional Resources and Documentation Feedback
About Cisco IOS XE Software Documentation
xii
Page 15

Using the Command-Line Interface in
Cisco IOS XE Software
Last Updated: December 1, 2009
This document provides basic information about the command-line interface (CLI) in Cisco IOS XE
software and how you can use some of the CLI features. This document contains the follo wing sections:
• Initially Configuring a Device, page i
• Using the CLI, page ii
• Saving Changes to a Configuration, page xii
• Additional Information, page xii
For more information about using the CLI, see “Part 1: Using the Cisco IOS Command-Line Interface
(CLI)” of the Cisco IOS XE Configuration Fundamentals Configuration Guide.
For information about the software documentation set, see the “About Cisco IOS XE Software
Documentation” document.
Initially Configuring a Device
Initially configuring a device varies by platform. For information about performing an initial
configuration, see the hardware installation documentation that is provided with the orig inal packaging
of the product or go to the Product Support area of Cisco.com at http://www.cisco.com/go/techdocs.
After you have performed the initial configuration and connected the device to your network, you can
configure the device b y using the console port or a remote access method, such as Telnet or Secure Shell
(SSH), to access the CLI or by using the configuration method provided on the device, such as Security
Device Manager.
i
Page 16

Using the CLI
Changing the Default Settings for a Console or AUX Port
There are only two settings that you can change on a console port or an AUX port:
• Change the port speed with the config-register 0x command. Changing the port speed is not
• Change the behavior of the port; for example, by adding a password or changing the timeout value.
Note The AUX port on the Route Processor (RP) installed in a Cisco ASR 1000 series router does not serve
any useful customer purpose and should be accessed only under the advisement of a customer support
representative.
Using the CLI
This section describes the following topics:
• Understanding Command Modes, page ii
• Using the Interactive Help Feature, page v
Using the Command-Line Interface in Cisco IOS XE Software
recommended. The well-known default speed is 9600.
• Understanding Command Syntax, page vi
• Understanding Enable and Enable Secret Passwords, page viii
• Using the Command History Feature, page viii
• Abbreviating Commands, page ix
• Using Aliases for CLI Commands, page ix
• Using the no and default Forms of Commands, page x
• Using the debug Command, page x
• Filtering Output Using Output Modifiers, page xi
• Understanding CLI Error Messages, page xi
Understanding Command Modes
The CLI command mode structure is hierarchical, and each mode supports a se t of specific commands.
This section describes the most common of the many modes that exist.
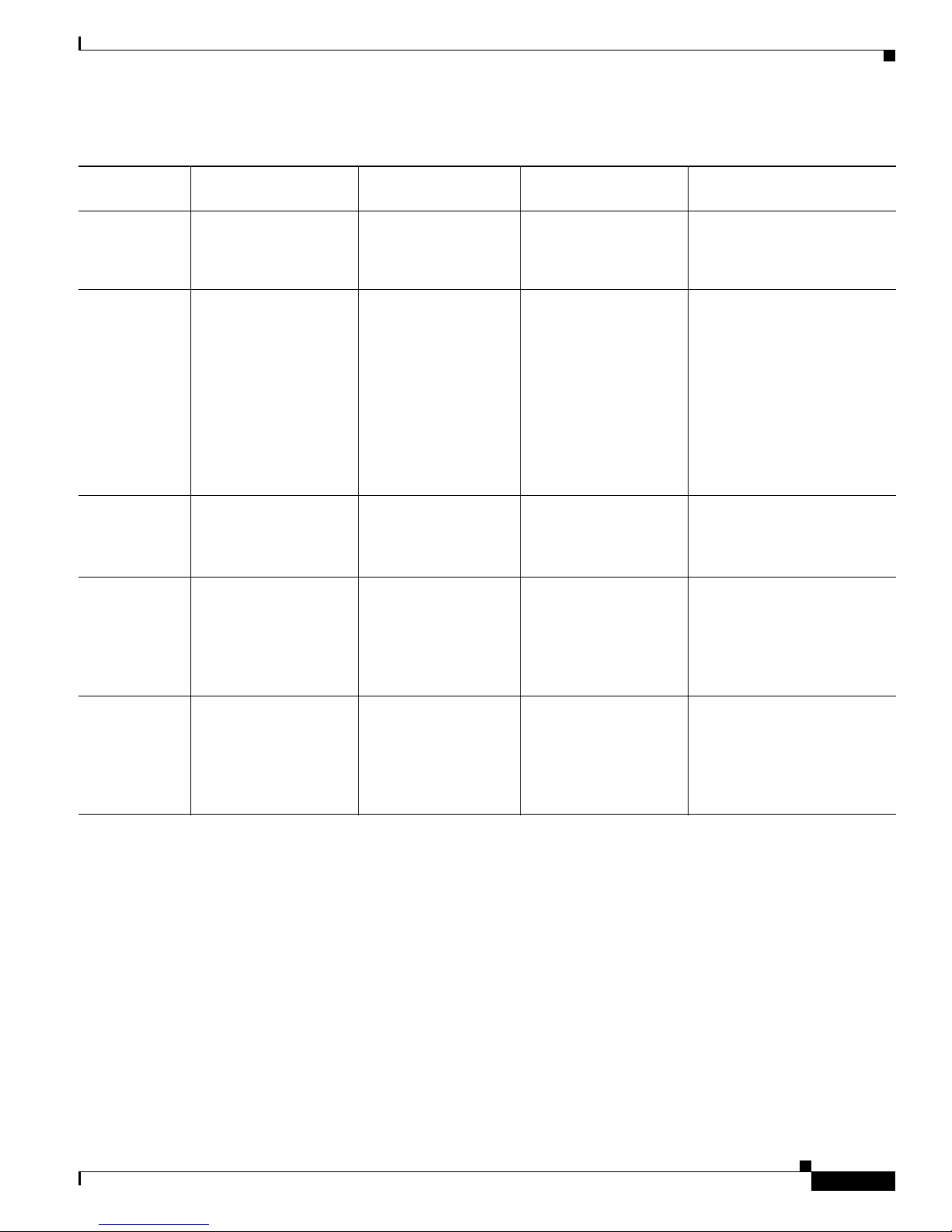
Ta bl e 1 lists common command modes with associated CLI prompts, access and exit methods, and a
brief description of how each mode is used.
ii
Page 17
Using the Command-Line Interface in Cisco IOS XE Software
Table 1 CLI Command Modes
Using the CLI
Command
Access Method Prompt Exit Method Mode Usage
Mode
User EXEC Log in.
Privileged
EXEC
From user EXEC mode,
issue the enable
command.
Global
configuration
From privileged EXEC
mode, issue the
configure terminal
command.
Interface
configuration
From global
configuration mode,
issue the interface
command.
Line
configuration
From global
configuration mode,
issue the line vty or line
console command.
Router>
Router#
Router(config)#
Router(config-if)#
Router(config-line)#
Issue the logout or exit
command.
Issue the disable
command or the exit
command to return to
user EXEC mode.
Issue the exit command
or the end command to
return to privileged
EXEC mode.
Issue the exit command
to return to global
configuration mode or
the end command to
return to privileged
EXEC mode.
Issue the exit command
to return to global
configuration mode or
the end command to
return to privileged
EXEC mode.
• Change terminal settings.
• Perform basic tests.
• Display device status.
• Issue show and debug
commands.
• Copy images to the
device.
• Reload the device.
• Manage device
configuration files.
• Manage device file
systems.
Configure the device.
Configure individual
interfaces.
Configure individual terminal
lines.
iii
Page 18

Using the CLI
Table 1 CLI Command Modes (continued)
Using the Command-Line Interface in Cisco IOS XE Software
Command
Access Method Prompt Exit Method Mode Usage
Mode
ROM monitor From privileged EXEC
mode, issue the reload
command. Press the
Break key during the
first 60 seconds while
the system is booting.
Diagnostic The router boots or
enters diagnostic mode
in the following
scenarios. When a
Cisco IOS XE process
or processes fail, in
most scenarios the
router will reload.
• A user-configured
access policy was
configured using
the transport-map
command, which
directed the user
into diagnostic
mode.
• The router was
accessed using an
RP auxiliary port.
• A break signal
(Ctrl-C,
Ctrl-Shift-6, or the
send break
command) was
entered, and the
router was
configured to enter
diagnostic mode
when the break
signal was received.
rommon # >
The # symbol
represents the line
number and increments
at each prompt.
Router(diag)#
Issue the continue
command.
If a Cisco IOS XE
process failure is the
reason for entering
diagnostic mode, the
failure must be resolved
and the router must be
rebooted to exit
diagnostic mode.
If the router is in
diagnostic mode
because of a
transport-map
configuration, access
the router through
another port or use a
method that is
configured to connect to
the Cisco IOS XE CLI.
If the RP auxiliary port
was used to access the
router, use another port
for access. Accessing
the router through the
auxiliary port is not
useful for customer
purposes.
• Run as the default
operating mode when a
valid image cannot be
loaded.
• Access the fall-back
procedure for loading an
image when the device
lacks a valid image and
cannot be booted.
• Perform password
recovery when a
CTRL-Break sequence is
issued within 60 seconds
of a power-on or reload
event.
• Inspect various states on
the router, including the
Cisco IOS XE state.
• Replace or roll back the
configuration.
• Provide methods of
restarting the
Cisco IOS XE software or
other processes.
• Reboot hardware, such as
the entire router, an RP, an
ESP , a SIP, a SP A, or other
hardware components.
• Transfer files into or off
of the router using remote
access methods such as
FTP, TFTP, and SCP.
iv
Page 19
Using the Command-Line Interface in Cisco IOS XE Software
EXEC commands are not saved when the soft war e reboots. Co mmands that you i ssue in a configuration
mode can be saved to the startup configuration. If you save the running configuration to the startup
configuration, these commands will execute when the software is rebooted. Global configuration mode
is the highest level of configuration mode. From global configuration mode, you can enter a variety of
other configuration modes, including prot ocol-speci fic modes.
ROM monitor mode is a separate mode that is used when the software cannot load properly. If a valid
software image is not found when the software boots or if the configuration file is corrupted at startup,
the software might enter ROM monitor mode. Use the question symbol (?) to view the commands that
you can use while the device is in ROM monitor mode.
rommon 1 > ?
alias set and display aliases command
boot boot up an external process
confreg configuration register utility
cont continue executing a downloaded image
context display the context of a loaded image
cookie display contents of cookie PROM in hex
.
.
.
rommon 2 >
Using the CLI
The following example sho ws ho w the command prompt changes to indicate a different command mode:
Router> enable
Router# configure terminal
Router(config)# interface ethernet 1/1
Router(config-if)# ethernet
Router(config-line)# exit
Router(config)# end
Router#
Note A keyboard alternative to the end command is Ctrl-Z.
Using the Interactive Help Feature
The CLI includes an interactive Help feature. Table 2 describes how to use the Help feature.
Table 2 CLI Interactive Help Commands
Command Purpose
help Provides a brief description of the Help feature in any command mode.
? Lists all commands available for a particular command mode.
partial command? Provides a list of commands that begin with the character string (no
partial command<Tab> Completes a partial command name (no space between the command
command ? Lists the keywords, arguments, or both associated with the command
command keyword ? Lists the arguments that are associated with the keyword (space between
space between the command and the question mark).
and <Tab>).
(space between the command and the question mark).
the keyword and the question mark).
v
Page 20

Using the CLI
Using the Command-Line Interface in Cisco IOS XE Software
The following examples show how to use the help commands:
help
Router> help
Help may be requested at any point in a comma nd by entering a question mark '?'. If nothing
matches, the help list wil l be empty and you must backup unti l ent ering a '?' shows the
available options.
Two styles of help are provided:
1. Full help is available wh en you are re ady to enter a c ommand argume nt (e.g. 'show ? ')
and describes each possible argument.
2. Partial help is provided when an abbreviated argum ent is entered and you w ant to know
what arguments match the input (e.g. 'show pr?'.)
?
Router# ?
Exec commands:
access-enable Create a temporary access-List entry
access-profile Apply user-profile to interface
access-template Create a temporary access-List entry
alps ALPS exec commands
archive manage archive files
<snip>
partial command?
Router(config)# zo?
zone zone-pair
partial command<Tab>
Router(config)# we<Tab> webvpn
command ?
Router(config-if)# pppoe ?
enable Enable pppoe
max-sessions Maximum PPPOE sessions
command keyword ?
Router(config-if)# pppoe enable ?
group attach a BBA group
<cr>
Understanding Command Syntax
Command syntax is the format in which a command should be entered in the CLI. Commands include
the name of the command, keywords, and arguments. Keywords are alphanumeric strings that are used
literally. Arguments are placeholders for values that a user must supply. Keywords and arguments may
be required or optional.
Specific conventions convey information about syntax and command elements. Table 3 des cribes these
conventions.
vi
Page 21
Using the Command-Line Interface in Cisco IOS XE Software
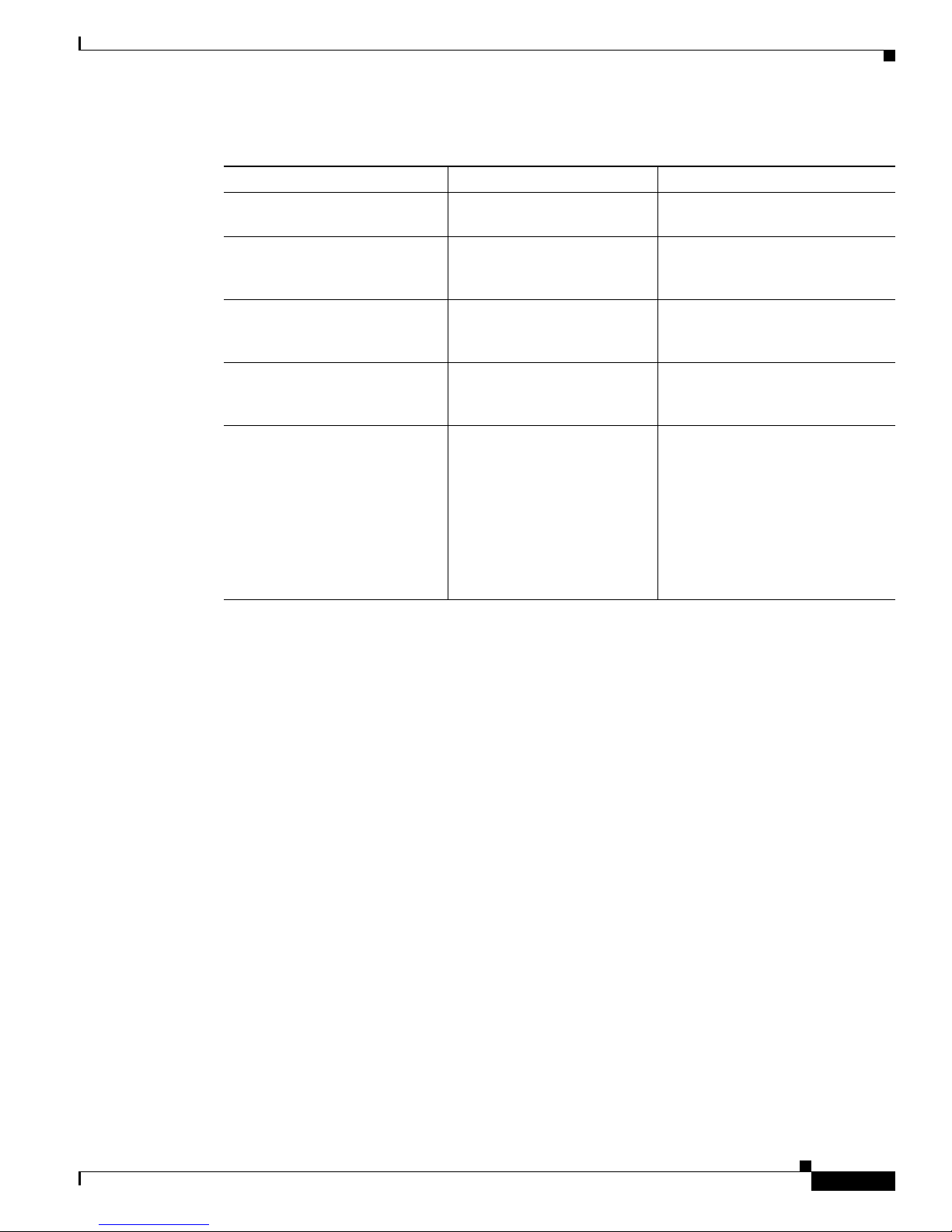
Table 3 CLI Syntax Conventions
Symbol/Text Function Notes
< > (angle brackets) Indicate that the option is an
A.B.C.D. Indicates that you must enter a
WORD (all capital letters) Indicates that you must enter
LINE (all capital letters) Indicates that you must enter
<cr> (carriage return) Indicates the e n d o f t h e l i s t of
argument.
dotted decimal IP address.
one word.
more than one word.
available keywords and
arguments, and also indicates
when keywords and arguments
are optional. When <cr> is the
only option, you have reached
the end of the branch or the end
of the command if the command
has only one branch.
Using the CLI
Sometimes arguments are disp laye d
without angle brackets.
Angle brackets (< >) are not always
used to indicate that an IP address is
an argument.
Angle brackets (< >) are not always
used to indicate that a WORD is an
argument.
Angle brackets (< >) are not always
used to indicate that a LINE is an
argument.
—
The following examples show syntax conventions:
Router(config)# ethernet cfm domain ?
WORD domain name
Router(config)# ethernet cfm domain dname ?
level
Router(config)# ethernet cfm domain dname level ?
<0-7> maintenance level number
Router(config)# ethernet cfm domain dname level 7 ?
<cr>
Router(config)# snmp-server file-transfer access-group 10 ?
protocol protocol options
<cr>
Router(config)# logging host ?
Hostname or A.B.C.D IP address of the syslog server
ipv6 Configure IPv6 syslog server
vii
Page 22
Using the Command-Line Interface in Cisco IOS XE Software
Using the CLI
Understanding Enable and Enable Secret Passwords
Some privileged EXEC commands are used for actions that impact the system, and it is recommended
that you set a password for these commands to pre vent unauthorized use. Two types of passwords, enable
(not encrypted) and enable secret (encrypted), can be set. The following commands set these passwords
and are issued in global configuration mo de:
• enable password
• enable secret password
Using an enable secret password is recommended because it is encrypted and more secure than the
enable password. When you use an enable secret password, text is encrypted (unreadable) before it is
written to the config.text f ile. When you use an enable password, the text is written as entered (readable)
to the config.text file.
Each type of password is case sensitiv e, can contai n from 1 to 25 uppercase and lo wercase alphanumeric
characters, and can start with a number. Spaces are also valid password characters; for example,
“two words” is a valid password. Leading spaces are ignored, but trailing spaces are recognized.
Note Both password commands have numeric keyw ords that are single inte ger v alues. If you choose a numb er
for the first character of your password follo wed by a space, the system will read the number as if it were
the numeric keyword and not as part of your password.
When both passwords are set, the enable secret password takes precedence over the enable password.
To remove a password, use the no form of the commands: no enable password or
no enable secret password.
For more information about password recovery procedures for Cisco products, see
http://www.cisco.com/en/US/products/sw/iosswrel/ps1831/
products_tech_note09186a00801746e6.shtml.
Using the Command History Feature
The command history feature saves the commands that you enter during a session in a comman d history
buffer. The default number of commands saved is 10, b ut the nu mber is configurable within the range of
0 to 256. This command history feature is particularly useful for recalling long or complex commands.
To change the number of commands saved in the history buffer for a terminal session, issue the
terminal history size command:
Router# terminal history size num
A command history buffer is also available in line configuration mode with the same default and
configuration options. To set the command history buffer size for a terminal session in line configuration
mode, issue the history command:
Router(config-line)# history [size num]
viii
Page 23
Using the Command-Line Interface in Cisco IOS XE Software
To recall commands from the history buffer, use the following methods:
• Press Ctrl-P or the Up Arrow key—Recalls commands beginning with the most recent command.
Repeat the key sequence to recall successively older commands.
• Press Ctrl-N or the Down Arrow key—Recalls the most recent commands in the history buf fer aft er
they have been recalled using Ctrl-P or the Up Arrow key. Repeat the key sequence to recall
successively more recent commands.
Note The arrow keys function only on ANSI-compatible terminals such as the VT100.
• Issue the show history command in user EXEC or privileged EXEC mode—Lists the most recent
commands that you entered. The number of commands that are displayed is determined by the
setting of the terminal history size and history commands.
The command history feature is enabled by default. To disable this feature for a terminal session,
issue the terminal no history command in user EXEC or privileged EXEC mode or the no history
command in line configuration mode.
Using the CLI
Abbreviating Commands
Typing a complete command name is not always required for the command to execute. The CLI
recognizes an abbreviated command when the abbreviation contains enough characters to uniquely
identify the command. For example, the show version command can be abbreviated as sh ver. It cannot
be abbreviated as s ver because s could mean show, set, or systat. The sh v abbreviation also is not valid
because the show command has vrrp as a keyword in addition to ve rsion.
Using Aliases for CLI Commands
To save time and the repetition of entering the same command multiple times, you can use a command
alias. An alias can be configured to do anything that can be done at the command line, but an alias cannot
move between modes, type in passwords, or perform any interactive functions.
Ta ble 4 shows the default command aliases.
Table 4 Default Command Aliases
Command Alias Original Command
h help
lo logout
p ping
s show
u or un undebug
w where
ix
Page 24
Using the CLI
To create a command alias, issue the alias command in global configuration mode. The syntax of the
command is alias mode command-alias original-command. Following are some examples:
• Router(config)# alias exec prt partition—privileged EXEC mode
• Router(config)# alias configure sb source-bridge—global configuration mode
• Router(config)# alias interface rl rate-limit—interface configuration mode
To view both default and user-created aliases, issue the show alias command.
For more information about the alias command, see
http://www.cisco.com/en/US/docs/ios/fundamentals/command/reference/cf_book.html.
Using the no and default Forms of Commands
Most configuration commands have a no form that is used to reset a command to its default value or
disable a feature or function. For example, the ip routing command is enabled b y default. To disable this
command, you would issue the no ip routing command. To re-enable IP routing, you would issue the
ip routing command.
Configuration commands may also have a default form, which returns the command settings to their
default values. For commands that are disabled b y def ault, u sing the default form has the same ef fect as
using the no form of the command. For commands that are enabled by default and have default settings,
the default form enables the command and returns the settings to their default values.
The no form is documented in the command pages of command references. The default form is
generally documented in the command pages only when the default form performs a different function
than the plain and no forms of the command. To see what default commands are available on your
system, enter default ? in the appropriate command mode.
Using the Command-Line Interface in Cisco IOS XE Software
Using the debug Command
A debug command produces extensive output that helps you troubleshoot problems in your network.
These commands are available for many features and functions within Cisco IOS XE software. Some
debug commands are debug all, debug aaa accounting, and debug mpls packets. To use debug
commands during a Telnet session with a device, you must first enter the terminal monitor command.
To turn off debugging completely, you must enter the undebug all command.
For more information about debug commands, see the Cisco IOS Debug Command Reference at
http://www.cisco.com/en/US/docs/ios/debug/command/reference/db_book.html.
Caution Debugging is a high priority and high CPU utilization process that can render your dev ice unusable. Use
debug commands only to troubleshoot specific problems. The best times to run debugging are during
periods of low network traffic and when few users are interacting with the network. Debugging during
these periods decreases the likelihood that the debug command processing overhead will af fect network
performance or user access or response times.
x
Page 25

Using the Command-Line Interface in Cisco IOS XE Software
Filtering Output Using Output Modifiers
Many commands produce lengthy output that may use several screens to display. You can use output
modifiers to filter this output to show only the information that you want to see.
The following three output modifiers are available:
• begin regular-expression—Displays the first line in which a match of the regular e xpression is found
and all lines that follow.
• include regular-expression—Displays all lines in which a match of the regular expression is found.
• exclude regular-expression—Displays all lines except those in which a match of the regular
expression is found.
To use one of these output modifiers, type the command followed by the pipe symbol (|), the modifier,
and the regular expression that you want to search for or filter. A regular expression is a case-sensitive
alphanumeric pattern. It can be a single character or number, a phrase, or a more complex string.
The following example illustrates how to filter output of the show interface command to display only
lines that include the expression “protocol.”
Router# show interface | include protocol
Using the CLI
FastEthernet0/0 is up, line protocol is up
Serial4/0 is up, line protocol is up
Serial4/1 is up, line protocol is up
Serial4/2 is administratively down, line protocol is down
Serial4/3 is administratively down, line protocol is down
Understanding CLI Error Messages
You may encounter some error messages while using the CLI. Table 5 shows the common CLI error
messages.
Table 5 Common CLI Error Messages
Error Message Meaning How to Get Help
% Ambiguous command:
“show con”
% Incomplete command. You did not enter all the
% Inv alid input detected at “^”
marker.
You did not enter enough
characters for the command to
be recognized.
keywords or values required
by the command.
You entered the command
incorrectly. The caret (^)
marks the point of the error.
Reenter the command followed by a
space and a question mark (?). The
keywords that you are allowed to
enter for the command appear.
Reenter the command followed by a
space and a question mark (?). The
keywords that you are allowed to
enter for the command appear.
Enter a question mark (?) to display
all the commands that are available in
this command mode. The keywords
that you are allowed to enter for the
command appear.
For more system error messages, see the System Messages for Cisco IOS XE document.
xi
Page 26

Saving Changes to a Configuration
Saving Changes to a Configuration
T o sa ve changes that you made to the confi guration of a de vice, you must i ssue the copy running-conf ig
startup-config command or the copy system:running-config nvram:startup-config comma nd. When
you issue these commands, the configuration changes that you made are saved to the startup
configuration and saved when the software reloads or power to the device is turned off or interrupted.
The following example shows the syntax of the copy running-config startup-config command:
Router# copy running-config startup-config
Destination filename [startup-config]?
You press Enter to accept the startup-config filename (the default), or type a n ew f ilename and then press
Enter to accept that name. The following outpu t is displayed indicating that the conf igurat ion was sa v ed:
Building configuration...
[OK]
Router#
On most platforms, the configuration is sa ved to NVRAM. On platforms with a Class A flash file system,
the configuration is saved to the location specified by the CONFIG_FILE environment variable. The
CONFIG_FILE variable defaults to NVRAM.
Using the Command-Line Interface in Cisco IOS XE Software
Additional Information
• “Part 1: Using the Cisco IOS Command-Line Interface (CLI)” of the Cisco IOS XE Configuration
Fundamentals Configuration Guide
http://www.cisco.com/en/US/docs/ios/ios_xe/fundamentals/configuration/guide/2_xe/cf_xe_book.
html
or
“Using Cisco IOS XE Software” chapter of the Cisco ASR 1000 Series Aggregation Services Routers
Software Configuration Guide
http://www.cisco.com/en/US/docs/routers/asr1000/configuration/guide/chassis/Using_CLI.html
• Cisco Product Support Resources
http://www.cisco.com/go/techdocs
• Support area on Cisco.com (also search for documentation by task or product)
http://www.cisco.com/en/US/support/index.html
• Software Download Center (downloads; tools; licensing, registration, advisory, and general
information) (requires Cisco.com user ID and password)
http://www.cisco.com/kobayashi/sw-center/
• Error Message Decoder, a tool to help you research and resolve error messages for
Cisco IOS XE software
http://www.cisco.com/pcgi-bin/Support/Errordecoder/index.cgi
xii
Page 27

Using the Command-Line Interface in Cisco IOS XE Software
• Command Lookup Tool, a tool to help you find detailed descriptions of Cisco IOS XE commands
(requires Cisco.com user ID and password)
http://tools.cisco.com/Support/CLILookup
• Output Interpreter, a troubleshooting tool that analyzes command output of supported
show commands
https://www.cisco.com/pcgi-bin/Support/OutputInterpreter/home.pl\
CCDE, CCENT, CCSI, Cisco Eos, Cisco HealthPresence, Cisco IronPort, the Cisco logo, Cisco Nurse Connect, Cisco Pulse, Cisco SensorBase,
Cisco StackPower, Cisco StadiumV ision, Cisco TelePresence, Cisco Unified Computing System, Cisco W e bEx, D CE, Flip Chann els, Fli p for Good,
Flip Mino, Flipshare (Design), Flip Ultra, Fli p Video, Flip V i deo (Design), Instant Broadband, and Welcome to the Human Network are trademarks;
Changing the Way We Work, Live, Play, and Learn, Cisco Capit al, C isco Capit al (D esign), Cis co:Finan ced (Styl ized), Cisco Stor e, Flip Gift Card,
and One Million Acts of Green are service marks; and Access Registrar, Aironet, AllTouch, AsyncOS, Bringing the Meeting T o You, Catalyst, CCDA,
CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Lumin, Cisco Nexus,
Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation, Cont inuum, E th erFast,
EtherSwitch, Event Center, Explor er, Follow Me Browsi ng, Gain Mak er, iLYNX, IOS, iPhone, IronPort, the IronPort logo, Laser Link, LightStream,
Linksys, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, PCNow, PIX, PowerKEY, PowerPanels, PowerTV,
PowerTV (Design), PowerVu, Prisma, ProConnect, ROSA, SenderBase, SMARTnet, Spectrum Expert, StackWise, WebEx, and the WebEx logo are
registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0910R)
Any Internet Protocol (IP) addresses an d ph one nu mbers u sed in this document are not intended to be actual addresses and phone numbers. Any
examples, command display output, network topology diagrams, and other fig ures included in the document are sho wn for illust rati v e purp oses only.
Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
© 2009 Cisco Systems, Inc. All rights reserved.
Additional Information
xiii
Page 28

Additional Information
Using the Command-Line Interface in Cisco IOS XE Software
xiv
Page 29

Intelligent Services Gateway Features Roadmap
First Published: March 20, 2006
Last Updated: November 25, 2009
This feature roadmap lists the Cisco IOS XE features documented in the Cisco IOS XE Intelligent
Services Gateway Configuration Guide and maps them to the documents in which they appear. The
roadmap is organized so that you can select your release train and see the features in that release. Find
the feature name you are searching for and click on the URL in the “Where Documented” column to
access the document containing that feature.
Feature and Release Support
Table 1 lists ISG feature support for Cisco IOS XE Release 2. Use Cisco Feature Navigator to find
information about platform support and software image support. Cisco Feature Navigator enables you to
determine which Cisco IOS XE software images support a specific software release, feature set, or platform.
To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not
required.
Note Table 1 lists only the Cisco IOS XE software release that introduced support for a given feature in a
given Cisco IOS XE software release train. Unless noted otherwise, subsequent re leases of t hat
Cisco IOS software release train also support that feature.
Table 1 lists the most recent release of the software train first and the features in alphabetical order
within the release.
Americas Headquarters:
Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA
Page 30
Intelligent Services Gateway Features Roadmap
Table 1 Supported ISG Features in Cisco IOS XE Release 2
Release Feature Name Feature Description Where Documented
Cisco IOS XE
Release 2.5
ISG:Session: Creation:
Interface IP Session: L2
ISG IP interface sessions include all IP traffic received
on a specific physical or virtual interface. IP interface
sessions are provisioned through the CLI; that is, a
Configuring ISG Access
for IP Subscriber
Sessions
session is created when the IP interface session
commands are entered.
Cisco IOS XE
Release 2.5
ISG:Session: Creation:
Interface IP Session: L3
ISG IP interface sessions include all IP traffic received
on a specific physical or virtual interface. IP interface
sessions are provisioned through the CLI; that is, a
Configuring ISG Access
for IP Subscriber
Sessions
session is created when the IP interface session
commands are entered.
Cisco IOS XE
Release 2.5
ISG:Session: Multicast:
Coexistence
This feature introduces the ability to host all the
subscribers and services (data and multicast) on the
same VLAN by enabling multicast and IP sessions to
Configuring ISG Access
for IP Subscriber
Sessions
coexist on the same subinterface.
Cisco IOS XE
Release 2.5
ISG:Session: Static
Session Creation
This feature enables administrator-initiated static IP
sessions.
Configuring ISG Access
for IP Subscriber
Sessions
Cisco IOS XE
Release 2.5
ISG:Instrumentation:
DHCP Lease Query
Support
The DHCP Lease Query transaction is a DHCP
transaction with special message types that enable,
among other things, clients to query DHCP servers
Configuring ISG Access
for IP Subscriber
Sessions
regarding the owner and th e lease-expiration-t ime of an
IP address.
Cisco IOS XE
Release 2.5
ISG:AAA Wireless
Enhancements
This feature enhances ISG RADIUS proxy
functionality to provide additional support for mobile
Configuring ISG as a
RADIUS Proxy
wireless environments. It includes changes to RADIUS
attribute 31 processing.
Cisco IOS XE
Release 2.5
ISG:Authentication:
Radius Proxy WiMax
RADIUS proxy enhancements provide additional
support for WiMax broadband environments.
Configuring ISG as a
RADIUS Proxy
Enhancements
Cisco IOS XE
Release 2.5
Cisco IOS XE
Release 2.5
ISG:Policy Control:
Differentiated Initial
Policy Control
This feature provides minimal or temporary network
access to the subscribers when the RADIUS servers are
down or cannot be accessed because of network issues.
ISG:Accounting: Prepaid ISG prepaid billing support allows ISG to check a
subscriber's available credit to determine whether to
allow the subscriber access to a service and how long
Configuring ISG Control
Policies
Configuring ISG
Support for Prepaid
Billing
the access can last. ISG supports volume-based and
time-based prepaid billing.
Cisco IOS XE
Release 2.2
Cisco IOS XE
Release 2.2
IP Subscriber Session
CLI Updates
ISG:Accounting: Per
Session, Service, and
Flow
Some of the commands that are used to configure ISG
IP subscriber sessions were modifi ed or replaced in this
release.
ISG accounting provides a means to bill for account or
service usage. ISG accounting uses the RADIUS
protocol to facilitate interactio n between ISG and an
Configuring ISG Access
for IP Subscriber
Sessions
Configuring ISG
Accounting
external RADIUS-based AAA or mediation server.
2
Page 31

Intelligent Services Gateway Features Roadmap
Table 1 Supported ISG Features in Cisco IOS XE Release 2
Release Feature Name Feature Description Where Documented
Cisco IOS XE
Release 2.2
ISG:Accounting:
Postpaid
ISG accounting provides a means to bill for account or
service usage. ISG sends accounting start and stop
Configuring ISG
Accounting
records for sessions and services to an accounting
server for postpaid billing. The accounting server
interprets the records to generate bills.
Cisco IOS XE
Release 2.2
ISG:Accounting: Tariff
Switching
ISG accounting provides a means to bill for account or
service usage. Where bi lling rates cha nge at f ixed tim es
Configuring ISG
Accounting
and sessions are active across the boundary at which the
rates change, ISG will provides accounting data to the
billing server indicating the boundary. Tariff switching
can also be used between accounting methods, such as
switching from prepaid billing to post paid billing.
Cisco IOS XE
Release 2.2
ISG:Authentication:
DHCP Option 82 Line ID
- AAA Authorization
This feature enhances ISG automatic subscriber logon
by providing support for authorization on the basis of
the circuit-Id and remote-Id.
Configuring ISG
Policies for Automatic
Subscriber Logon
Support
Cisco IOS XE
Release 2.2
ISG:Flow Control: Flow
Redirect
The ISG Layer 4 Redirect feature enables service
providers to better control the user experience by
allowing subscriber TCP or UDP packets to be
Redirecting Subscriber
Traffic Using ISG Layer
4 Redirect
redirected to specified servers for appropr iate handling.
ISG Layer 4 redirection can be applied to individual
subscriber sessions or flows.
Cisco IOS XE
Release 2.2
Cisco IOS XE
Release 2.2
ISG:Flow Control: QoS
Control: Dynamic Rate
Limiting
ISG:Instrumentation:
Advanced Conditional
Debugging
ISG can change the allowed bandwidth of a session or
flow by dynamically applying rate-limiting policies.
ISG provides the ability to def ine various conditio ns for
filtering debug output. Conditional debugging
generates very specific and relevant information that
can be used for session, flow, subscriber, and service
Configuring ISG
Network Forwarding
Policies
Troubleshooting ISG
with Session Monitoring
and Distributed
Conditional Debugging
diagnostics.
Cisco IOS XE
Release 2.2
ISG:Instrumentation:
Session and Flow
Monitoring
ISG provides a mechanism for continuously monitor ing
interface and CPU statistics. This feature introduces the
show interface monitor and show processes cpu
monitor commands, which display statistics that are
Troubleshooting ISG
with Session Monitoring
and Distributed
Conditional Debugging
updated at specified intervals.
Cisco IOS XE
Release 2.2
ISG:Network Interface:
IP Routed, VRF-Aware
MPLS
ISG supports several types of forwarding to connect
subscriber sessions to networks. These connections can
be to the Internet, corporate intranets, ISPs, or walled
Configuring ISG
Network Forwarding
Policies
gardens for content delivery. ISG supports both routed
and MPLS-enabled interfaces for network access.
Cisco IOS XE
Release 2.2
ISG:Network Interface:
Tunneled (L2TP)
ISG supports several types of forwarding to connect
subscriber sessions to networks. These connections can
be to Internet, corporate Intranets, ISPs or walled
Configuring ISG
Network Forwarding
Policies
gardens for content delivery. ISG supports tunneled
interfaces to networks.
3
Page 32

Intelligent Services Gateway Features Roadmap
Table 1 Supported ISG Features in Cisco IOS XE Release 2
Release Feature Name Feature Description Where Documented
Cisco IOS XE
Release 2.2
ISG:Policy Control:
Cisco Policy Language
ISG control policies are a structured replacement for
feature-specific configuration commands and allow
Configuring ISG Control
Policies
configurable functionality to be expressed in terms of
an event, a condition, and an action. Control policies
provide an intuitive and extensible framework, with a
consistent set of CLI commands, for specifying system
behavior. The ISG policy language is aligned with the
Cisco Common Classification Policy Language
(C3PL).
Cisco IOS XE
Release 2.2
Cisco IOS XE
Release 2.2
ISG:Policy Control:
DHCP Proxy
ISG:Policy Control:
ISG-SCE Control Bus
This feature enables ISG to dynamically interact with
DHCP and apply policies that influence the IP
addresses that DHCP assigns to subscribers.
This feature enables integration of an ISG device with
an SCE device at the control plane level, allowing the
Configuring ISG Access
for IP Subscriber
Sessions
Configuring ISG
Integration with SCE
two devices to work as one when policies are applied to
a subscriber session.
Cisco IOS XE
Release 2.2
ISG:Policy Control:
Multidimensional
Identity per Session
ISG control policies provide a flexible way to collect
pieces of subscriber identity during session
establishment. Control policies also allow session
Configuring ISG Control
Policies
policy to be applied iteratively as more elements of
identity become available to the system.
Cisco IOS XE
Release 2.2
ISG:Policy Control:
Policy: Domain Based
(Auto-domain, Proxy)
ISG control policies manage the primary services and
rules used to enforce particular contracts. Polices can be
configured to interpret the domain as a request to
Configuring ISG Control
Policies
activate the service associated with that domain name,
allowing users to automatically receive services in
accordance with the domain that they are attempting to
connect.
Cisco IOS XE
Release 2.2
ISG:Policy Control:
Policy: Triggers
ISG control policies can be configured with time-based,
volume-based, and duration-based policy triggers.
Configuring ISG Control
Policies
Time-based triggers use an internal clock, allowing
policies to be applied at specific times. Volume-based
triggers are based on packet count; when the packet
count reaches a specified value, the specified policy is
applied. Duration-based triggers are based on an
internal timer. Upon expiration of the timer, the
specified policy is applied.
Cisco IOS XE
Release 2.2
Cisco IOS XE
Release 2.2
ISG:Policy Control:
Policy Server: CoA
ISG:Policy Control:
Policy Server: CoA
ASCII Command Code
Support
This feature provides ISG support for the RADIUS
Change of Authorization (CoA) extension, which
facilitates dynamic authorization.
This feature enables ISG to receive ASCII command
codes for Account Logon, Account Logoff, Service
Logon, Service Logoff, and Account Status queries and
to perform the required functionality based on the
Enabling ISG to Interact
with External Policy
Servers
Cisco IOS ISG RADIUS
Interface Guide
command code.
4
Page 33

Intelligent Services Gateway Features Roadmap
Table 1 Supported ISG Features in Cisco IOS XE Release 2
Release Feature Name Feature Description Where Documented
Cisco IOS XE
Release 2.2
Cisco IOS XE
Release 2.2
ISG:Policy Control:
Policy Server:
SSG-SESM Protocol
ISG:Policy Control:
Service Profiles
ISG supports Cisco’s proprietary protocol to
communicate with the SESM policy server.
ISG defines a service as a collection of policies that can
be applied to any subscriber session. Services can be
Cisco SSG-to-ISG DSL
Broadband Migration
Guide
Configuring ISG
Subscriber Services
configured on the router or on an external AAA server.
Cisco IOS XE
Release 2.2
ISG:Policy Control:
RADIUS Proxy
Enhancement
The ISG RADIUS proxy feature enables ISG to serve as
a proxy between a client device that uses RADIUS
authentication and a AAA server. ISG RADIUS proxy
Configuring ISG as a
RADIUS Proxy
functionality enables ISG to “sniff” (look at) the
RADIUS packet flows and, upon successful
authentication, transparently create a corresponding
ISG session.
Cisco IOS XE
Release 2.2
ISG:Policy Control: User
Profiles
ISG user profiles specify services and functionality that
should be applied to ISG sessions for the specified
Overview of ISG
subscriber. User profiles are defined on an external
AAA server.
Cisco IOS XE
Release 2.2
ISG:Session: Auth:
PBHK
The ISG Port-Bundle Host Key feature serves as an
in-band signaling mechanism for session identification
Configuring ISG
Port-Bundle Host Key
at external portals. TCP packets from subscribers are
mapped to a local IP address for the ISG gateway and a
range of ports. This mapping allows the portal to
identify the ISG gateway from which the session
originated.
Cisco IOS XE
Release 2.2
ISG:Session: Auth:
Single Sign-On
Single sign-on eliminates the need to authenticate a
session more than once when a subscriber has access to
Overview of ISG
services provided by other devices in the administrative
domain of the access or service provider.
Cisco IOS XE
Release 2.2
ISG:Session:
Authentication
ISG automatic subscriber logon enables another
specified identifier to be used in place of the username
in authorization requests. Enabling the AAA server to
Configuring ISG
Policies for Automatic
Subscriber Logon
authorize subscribers on the basis of a specified
identifier allows subscriber profiles to be downloaded
from the AAA server as soon as packets are received
from subscribers.
Cisco IOS XE
Release 2.2
ISG:Session: Creation:
Interface IP Session: L2
ISG IP interface sessions include all IP traffic received
on a specific physical or virtual interface. IP interface
sessions are provisioned through the CLI; that is, a
Configuring ISG Access
for IP Subscriber
Sessions
session is created when the IP interface session
commands are entered.
Cisco IOS XE
Release 2.2
ISG:Session: Creation:
Interface IP Session: L3
ISG IP interface sessions include all IP traffic received
on a specific physical or virtual interface. IP interface
sessions are provisioned through the CLI; that is, a
Configuring ISG Access
for IP Subscriber
Sessions
session is created when the IP interface session
commands are entered.
5
Page 34

Intelligent Services Gateway Features Roadmap
Table 1 Supported ISG Features in Cisco IOS XE Release 2
Release Feature Name Feature Description Where Documented
Cisco IOS XE
Release 2.2
ISG:Session: Creation:
IP Session: Protocol
Event (DHCP)
Most ISG sessions are created upon detection of a data
flow that cannot be affiliated with an already active
session. An ISG can be configured to create an IP
Configuring ISG Access
for IP Subscriber
Sessions
session upon receipt of the first DHCP DISCOVER
packet received from a subscriber.
Cisco IOS XE
Release 2.2
ISG:Session: Creation:
IP Session: Subnet and
Source IP: L2
The ISG session is the primary component used for
associating services and policies across specific data
flows. An IP subnet session is an ISG session that
Configuring ISG Access
for IP Subscriber
Sessions
includes any IP traffic from a single IP subnet. A
source-IP-based session includes traffic from a single
source IP address.
Cisco IOS XE
Release 2.2
ISG: Session: Creation:
IP Session: Subnet and
Source IP: L3
The ISG session is the primary component used for
associating services and policies across specific data
flows. An IP subnet session is an ISG session that
Configuring ISG Access
for IP Subscriber
Sessions
includes any IP traffic from a single IP subnet. A
source-IP-based session includes traffic from a single
source IP address.
Cisco IOS XE
Release 2.2
ISG:Session: Creation:
P2P Session (PPPoE,
PPPoXoX)
The ISG session is the primary context to which
services and policies are associated across specific data
flows. Point-to-point (P2P) sessions are established
Configuring ISG Access
for PPP Sessions
through a signaling protocol. ISG handles many
variants of P2P encapsulation, such as PPP, PPPoE, and
PPPoA.
Cisco IOS XE
Release 2.2
ISG:Session: Lifecycle:
Idle Timeout
The ISG idle timeout controls how long a connection
can be idle before it is terminated.
Configuring ISG
Policies for
Session Maintenance
Cisco IOS XE
Release 2.2
ISG:Session: Lifecycle:
Packet of Disconnect
(POD)
An ISG can be configured to interact wi th external
policy servers. A policy server can use RADIUS Packet
of Disconnect (POD) to manage the life cycle of any
Configuring ISG
Policies for
Session Maintenance
ISG session. The primary role of the POD message is to
terminate an ISG session.
Cisco IOS XE
Release 2.2
ISG:Session: VRF
Transfer
The ISG session is the primary component used for
associating services and policies with specific data
flows. ISG sessions are associated with virtual routing
Configuring ISG Access
for IP Subscriber
Sessions
and forwarding instances when routing is required for
the network service. ISG VRF transfer provides a
means to dynamically switch an active session between
virtual routing domains.
Cisco IOS XE
Release 2.2
ISG:Session Protection
and Resiliency:
Keepalive—ARP, ICMP
This feature allows IP subscriber session health to be
monitored by configuring keepalive messages using
ARP or ICMP, depending upon the type of connection
Configuring ISG
Policies for
Session Maintenance
to be monitored.
Cisco IOS XE
Release 2.2
Service Gateway
Interface
The SGI implements a web services interface to access
the policy, subscriber, and session management
Service Gateway
Interface
functionality of ISG.
6
Page 35

Intelligent Services Gateway Features Roadmap
CCDE, CCENT, CCSI, CiscoEos, Cisco HealthPresence, Cisco IronPort, the Cisco logo, Cisco Nurse Connect, Cisco Pulse, Cisco SensorBase,
Cisco StackPower, Cisco StadiumVision, Cisco TelePresence, Cisco Unified Computing System, Cisco WebEx, DCE, Flip Channels, Flip for Good,
Flip Mino, Flipshare (Design), Flip Ultra, Fli p Video, Flip V i deo (Design), Instant Broadband, and Welcome to the Human Network are trademarks;
Changing the Way We Work, Live, Play, and Learn, Cisco Capital, Cisco Capital (Design), Cisco:Financed (Stylized), Cisco Store, Flip Gift Card,
and One Million Acts of Green are service marks; and Access Registrar, Aironet, AllTouch, AsyncOS, Bringing the Meeting T o You, Catalyst, CCDA,
CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Lumin, Cisco Nexus,
Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collabor ation Without Limitation, Continuum, EtherFast,
EtherSwitch, Event Center, Explor er, Follow Me Browsi ng, Gain Mak er, iLYNX, IOS, iPhone, IronPort, the IronPort logo, Laser Link, LightStream,
Linksys, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, PCNow, PIX, PowerKEY, PowerPanels, PowerTV,
PowerTV (Design), PowerVu, Prisma, ProConnect, ROSA, SenderBase, SMARTnet, Spectrum Expert, StackWise, WebEx, and the WebEx logo are
registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0910R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and
figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and
coincidental.
© 2006–2009 Cisco Systems, Inc. All rights reserved.
7
Page 36

Intelligent Services Gateway Features Roadmap
8
Page 37

Overview of ISG
First Published: March 20, 2006
Last Updated: March 2, 2009
Intelligent Services Gateway (ISG) is a Cisco IOS and Cisco IOS XE software feature set that provides
a structured framework in which edge devices can deliver flexible and scalable services to subscribers.
This document provides information about what ISG is, the benefits of ISG, and how to begin
implementing it.
Finding Feature Information
For the latest feature information and caveats, see the release notes for your platform and software
release. To find information about the features documented in this module, and to see a list of the releases in
which each feature is supported, see the “Feature Information for th e Overview of ISG” section on page 9.
Use Cisco Feature Navigator to find information about platform support and Cisco IOS XE software
image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on
Cisco.com is not required.
Contents
• Information About ISG, page 1
• Additional References, page 8
• Feature Information for the Overview of ISG, page 9
Information About ISG
This section contains the following concepts:
• What Is ISG?, page 2
• ISG Principles, page 3
Americas Headquarters:
Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA
© 2006–2009 Cisco Systems, Inc. All rights reserved.
Page 38

Information About ISG
What Is ISG?
Overview of ISG
• Benefits of ISG, page 6
• Planning for ISG Implementation, page 6
ISG is a structured framework in which edge access devices can deliver flexible and scalable services to
subscribers. ISG handles the following key aspects of subscriber management:
• Subscriber identification
• Service and policy determination
• Session policy enforcement
• Session life-cycle management
• Accounting for access and service usage
• Session state monitoring
In addition, ISG introduces a dynamic element to the provisioning and activation of services through
control policies and Change of Authorization (CoA) extensions to the RADIUS protocol.
An ISG-enabled device may be deployed at the access edge and service edge of a network and is
applicable to a range of subscriber network environments, such as digital subscriber line (DSL), public
wireless LAN (PWLAN), and mobile wireless. Moreover, ISG has been designed to accommodate a
flexible distribution o f subscriber and service information within a giv en solution. Figure 1 illustrates a
typical DSL deployment for which service profi le data may be stored in an authentication, autho rization,
and accounting (AAA) database and retrieved and cached on demand.
Figure 1 Sample Topology for a DSL Deployment
AAA
server
DSLAM
DSL
Policy
server
Web
portal
ISG
DHCP
server
Walled
garden
Remote
access VPN
Internet
browsing
Internet
135148
It is also possible to define services directly on an ISG. In all cases, service activation may be triggered
as a result of a locally defined control policy, user profile associations, or CoA commands from an
external policy server or portal application.
2
Page 39

Overview of ISG
ISG Principles
Fundamental to the ISG architecture is the provisioning of a common session layer at which the
management of generic subscriber sessi ons is deco upled from t he technol ogy that is used to provide
access to the edge device.
Within this session management layer, common methods are provided for the extraction of subscriber
identity information and the determination and activation of services. These methods are described in
the following sections:
• Subscriber Sessions, page 3
• Subscriber Access, page 4
• Subscriber Identification, page 4
• Subscriber Services, page 4
• Policies, page 5
• Dynamic Policy Updates, page 5
Subscriber Sessions
Information About ISG
An ISG subscriber session is a generic system context that is created for every subscriber who interacts
with the edge device. A subscriber session is created on first interaction so that policies may be applied
as early as possible. Such policies may facilitate the retrieval of subscriber identity information. All
subscriber sessions are assigned a locally unique identifier that may subsequently be used to reference
the session.
The session context is the basis for common handling at the session management layer, but the type of
traffic that is encompassed in a session context may vary. Broadly, session types may be categorized as
Layer 2 or Layer 3, depending on the packet types that are being handled by the session. For instance, a
PPP session is a Layer 2 session in that it includes all packets transferred o ver a link that w as established
using PPP negotiation. An IP session is Layer 3 because it includes all IP packets exchanged with a
subscriber device at a single IP address. Whether a session is Layer 2 or Layer 3 will, to some extent,
determine the type of polices that may be activated for the session.
ISG also provides flexibility in terms of how an IP session is defined for an interface. For example, on
a particular interface, ISG can be provisioned to classify IP sessions on the basis of a single address (an
IP session), a subnet (an IP subnet session), or the interface itself (an IP interface session), wherein all
IP packets transferred over the interface are encompassed by the same session.
In a network deployment, ISG session types should be provisioned to represent individual subscriber
entities. For example, a particular ISG interface may be directly conn ected to a subscriber household in
which several subscriber devices with individual IP addresses are attached to a household LAN. If the
plan is to model each LAN-attached device as a separate subscriber and apply different policies and
services to each, the interface should be provisioned to expect IP sessions. However, if the household
represents a single subscriber account, and common handling is required for all packets exchanged, the
interface should be provisioned as an IP interface or subnet session.
3
Page 40

Information About ISG
Subscriber Access
Under ISG, the provisioning and handling of specific access media and protocols is decoupled as far as
possible from the functionality that is applicable to all session types. This model has the following
benefits:
• A common set of subscriber services may be use d on an ISG at wh ich heteroge neous subscr iber
networks are aggregated.
• A common set of subscriber services may be used for multiple ISGs, even when the access
technology differs.
• For a giv en subscriber , the access method may be altered (th rough prov isioning or roaming ) without
any need to change the service provisioning.
• As new access protocols become available, they can be leveraged by existing edge deployments
without requiring changes to the service content; ne w access protocols pl ug into the ISG fr amew ork.
Subscriber Identification
A subscriber session is created when the first control protocol packet is received from the subscriber
device. The control protocol will vary depending on the session type. If there is no control protocol, the
session is signaled by the first data packet from the subscriber.
At session start, certain identity information is available, although typically not enough to completely
identify the subscriber . Th rough the use of cont rol pol icies, the identit y informat ion a vailable at session
start can be used to drive t he ex traction of furt her identity f rom the subscriber and d etermine ne w policy
for the session. The following example illustrates how ISG might handle subscriber identity:
Overview of ISG
• For an IP session, where session start is signaled by a DHCP protocol ev ent, a TCP redirection policy
Subscriber Services
An ISG service is a collection of policies applicable to a subscriber session. When a service is activ ated
on a session, all policies contained within that service are activated on the session. Likewise, when a
service is deactivated, all policies that are contained within the service are deactivated or removed from
the session.
Services are useful for handling fix ed policy combinatio ns that are applicable to a number of subscribers.
This application reduces duplication of persistent d ata and allo ws a group of poli cies to be acti v ated with
a single action and a single reference.
A service may be defined on the edge device directly, through the command-line interface (CLI), or in
an external repository and downloaded as required. A downloaded service definition is cached on the
device for as long as it is active on one or more sessions.
A service may be activated in one of the following ways:
• As a result of control policy execution
• By receipt of a CoA service-logon command
• By reference in a user profile, where the service is flagged for automatic activation
could be activated. This policy would facilitate the collection of a username and credential at an
external web portal.
4
Page 41

Overview of ISG
Policies
Information About ISG
Services primarily contain traffic policies. There are some restrictions regarding the policies that may
be combined in a given service; for example, a service may not contain two traffic policies that specify
a different nondefault traffic class unless they apply to different traffic directions (inbound versus
outbound).
Where a service contains a network-forwarding policy, it is known as a primary service. Only one
primary service may be active for a given session at any point in time; that is, primary services are
mutually exclusive.
ISG introduces support for two basic policy types:
• Traffic policies
• Control policies
Traffic policies define the handling of data packets and consist of a traffic class, which defines the
packet-based criteria for which the policy is applicable, and one or more traffic actions, which are
functional instances that perform specific operations on a data stream and are often referred to as
features. The traffic actions configured within a traffic policy are invoked for data packets that meet the
criteria defined by the traffic class.
Network-forwarding policies are a specific type of traffic policy, for which the action is a
network-forwarding action, such as to route packets using a specific virtual routing and forwarding
instance (VRF) or to forward packets over a Layer 2 connection. Network-forwarding policies are
“classless” in that it is not possible to refine the criteria for which the forwarding action is applicable.
Control policies define the handling of system e v ents and consist o f one or more contr ol policy rul es and
a decision strategy that governs how the constituent policy rules are evaluated. A control policy rule
consists of a control class (a flexible condition clause), an event for which the condition is evaluated,
and one or more control actions. Control actions are general system functions, such as “authenticate” or
“activate a service.”
Control policies may be activated on various targets, such as interfaces or ATM virtual circuits (VCs),
and typically control the extraction and authentication of subscriber identity and the activation of
services on sessions. Traffic policies may be activated only on sessions and are typically (though not
always) applied through service activation.
Control policies are a structured replacement for feature-specific configuration commands and allow
configurable functionality to be expressed in terms of an event, a condition, and an action. Control
policies represent an intuitive and extensible framework for specifying system behavior. As additional
functionality is added to the system, an administrator just has to learn what new events and actions can
be included in a control policy, not a completely new set of configuration commands.
Dynamic Policy Updates
Traditionally, subscriber policy has been determined at one point only, at session establishment time,
once the principal identity o f a subscrib er has be en authenticated. ISG introduces a dynamic policy
model in which session policy may be altered at any time.
Session policy is evaluated at session start and may be reassessed whenever additional identity or service
selection information is gleaned from the subscriber via the access protocol. In addition, policy may be
updated for a session through the activation of control policies or by means of CoA commands from an
external application. In the latter case, the external application may update policy as a result of
administrator activity, back-end processing, or subscriber activity (such as service selection at a web
portal).
5
Page 42

Information About ISG
Benefits of ISG
Overview of ISG
ISG provides the following benefits:
• A common system for session management across Cisco products and access technologies. New
access protocols, forwarding protocols, and feat ures may be plugged in with minimal impact and
maximum potential for reuse.
• Separation of the concerns of subscriber identification, service application, and subscriber access
and session type.
• Flexible session definitions.
• Flexible session detection.
• Flexible, iterative approach to identification, service activation, and policy activation.
• Different trust levels. Session authorization is not contingent on authentication.
• Control policies. Control policies facilitate distrib uted polic y decisi on-making, reducin g round-trip
latency between the edge devi ce and policy serv er, and allow system event handling to be described
in a consistent and intuitive manner.
• Common policy model and language for control and traffic policy.
• Provision for dynamic policy updates via CoA (through service activation or “policy push”).
• Use of existing Cisco IOS infrastructure to provide session functionality.
• Use of existing Cisco IOS infrastructure to track session state and life cycle.
• Creation of a session context at first instance of subscriber interaction, thereby facilitating the
immediate application of policy to subscriber traffic.
• Flexible distribution of service data.
• Range of accounting options, including prepaid accounting, postpaid accounting, tariff switching
for prepaid and postpaid accounting, interim accounting, event-based accounting, and flow-based
accounting.
• Single sign-on services to an external application.
• Flexible infrastructure in support of “equal-access” deployments, such as service-based Dynamic
Host Configuration Protocol (DHCP) pool and DHCP server determination, dynamic readdressing
through DHCP, and VRF transfer.
• Support for standard external interfaces, such as RADIUS and CoA.
Planning for ISG Implementation
ISG is very flexible and suppor ts a wide v ariety of fun ctionality. Before you begin to configure ISG, you
should plan your system carefully . The fo llowing secti ons describe some of the important aspect s of your
system that you should consider:
• Trust Model, page 7
• Subscriber Access Model, page 7
• Single Sign-On Requirements, page 7
• Network Forwarding, page 7
• Service Packaging, page 8
• Billing Model, page 8
6
Page 43

Overview of ISG
Trust Model
Information About ISG
Trust levels are determined by the security needs of a particular application domain and the inherent
security afforded by the subscriber network. In the following situations, it may not be necessary to
authenticate subscriber identity:
• When security is not considered paramount
• When end-to-end security is provided in-band
• When the subscriber network is intrinsically secure
Whether or not subscribers must be authenticated will influence the choice of access protocol. When
authentication is not required, control policies may be used to determine authori zation and other session
policy on the basis of subscriber identity.
Where authentication is considered necessary, the authenticated identity may be trusted:
• For the duration of the session
• Until a periodic reauthentication is instigated
• Beyond the duration of a session; for example, for the lifetime of a subscription
For complete security, cryptographic methods may be used to secure the session (to the edge) following
authentication, obviating the need for reauthentication. However, there are administrative and
performance overheads associated with this practice.
Subscriber Access Model
The trust model will, to a large extent, determine the choice of access protocol. However, the access
model will also depend on other factors such as the underlying media (for example, ATM versus
Ethernet), type of endpoint (for example, PC, cell phone, PDA), mobility requirements, the system’s
ability to influence the software installed on a subscriber device, and scalability requirements.
Single Sign-On Requirements
Where a subscriber will have access to services provided by other devices in the administrative domain
of the access or service provider, is an additional authentication required, or should the identity of the
subscriber be trusted? It may be necessary for the latte r device to query the access device to collect
additional subscriber identity information and ascertain whether the subscriber has already been
authenticated by the access device. The single sign-on facility is provided through the “session query”
capability of CoA.
Network Forwarding
How should subscribers be given access to network services? Network forwarding options include the
following:
• Layer 2 connections; for example, a Layer 2 Tunneling Protocol (L2TP) tunnel to an L2TP netw ork
server (LNS)
• Layer 3 connections, by associating all session packets with a particular VRF or routing domain
7
Page 44

Additional References
Service Packaging
Billing Model
Overview of ISG
How should subscriber policies be organized into services, if at all? Some considerations for service
packaging include the following:
• Are certain policy combinations common to multiple subscribers?
• Are shared policy combinations dependent on a particular forwarding domain?
• Is it necessary for a subscriber to move between service domains?
• Should services be defined on the de vice or in a remote repository? Ext ernally def ined services wi ll
be cached locally for as long as they are activated for one or more sessions.
How should subscribers be billed for service usage? Billing options include the following:
• Billing by usage of time or volume
• Billing at regular intervals (traditional postpaid)
• Billing according to policies provisioned for the session
• Billing according to the time of day (tariff switching)
Additional References
The following sections provide references related to ISG.
Related Documents
Related Topic Document Title
ISG commands Cisco IOS Intelligent Services Gateway Command Reference
Technical Assistance
Description Link
The Cisco Support website provides extensive online
resources, including documentation and tools for
troubleshooting and resolving technical issues with
Cisco products and technologies.
To receive security and technical information about
your products, you can subscribe to various services,
such as the Product Alert Tool (accessed from Field
Notices), the Cisco Technical Services Ne wsletter , and
Really Simple Syndication (RSS) Feeds.
Access to most tools on the Cisco Support website
requires a Cisco.com user ID and password.
http://www.cisco.com/techsupport
8
Page 45

Overview of ISG
Feature Information for the Overview of ISG
Feature Information for the Overview of ISG
Table 1 lists the features in this module and provides links to specific configuration information. For
information about a feature in this technology that is not documented here, see the “Intelligent Services
Gateway Features Roadmap.”
Use Cisco Feature Navigator to find information about platform support and software image support.
Cisco Feature Navigator enables you to determine which Cisco IOS XE software images support a
specific software release, feature set, or platform. To access Cisco Feature Navigator, go to
http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Note Table 1 list only the Cisco IOS XE software release that introduced support for a gi ven feature in a gi ven
Cisco IOS software release train. Unless noted otherwise, subsequent releases of that Cisco IOS XE
software release train also support that feature.
Table 1 Feature Information for the Overview of ISG
Feature Name Releases Feature Configuration Information
ISG:Session: Auth: Single Sign-on Cisco IOS XE
Release 2.2.
Single sign-on eliminates the need to authenticate a session
more than once when a subscriber has access to services
provided by other devices in the administrative domain of
the access or service provider.
The following section provides information about this
feature:
• Planning for ISG Implementation, page 6
CCDE, CCENT, CiscoEos, Cisco HealthPresence, the Cisco logo, CiscoLumin, CiscoNexus, CiscoStadiumVision, CiscoTelePresence,
Cisco WebEx, DCE, and Welcome to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn and Cisco Store are
service marks; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP,
CCVP , Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo,
Cisco Unity, Collaboration Without Limitation, EtherFast, EtherSwitch, Event Center, Fast Step, Follow Me Browsing, FormShare, GigaDrive,
HomeLink, Internet Quotient, IOS, iPhone, iQuick Study, IronPort, the IronPortlogo, LightStream, Linksys, MediaTone, MeetingPlace,
MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, Network Registrar, PCNow, PIX, PowerPanels, ProConnect, ScriptShare,
SenderBase, SMARTnet, Spectru m Expert, St ackWise, The Fastest W ay to Increase Your Internet Quotient, TransPath, W ebEx, and the WebEx logo
are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0812R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and
figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and
coincidental.
© 2006–2009 Cisco Systems, Inc. All rights reserved.
9
Page 46

Feature Information for the Overview of ISG
Overview of ISG
10
Page 47

Configuring ISG Control Policies
First Published: March 20, 2006
Last Updated: November 25, 2009
Intelligent Services Gateway (ISG) is a Cisco IOS XE software feature set that provides a structured
framework in which edge devices can deliver flexible and scalable services to subscribers. ISG control
policies are a means of defining the actions the syst em will take in response to specified conditions and
events. A wide variety of system actions, conditions, and events can be combined using a consistent
policy language, providing a flexible and precise way of configuring ISG. This module provides
information about how to configure ISG control policies.
Finding Feature Information
For the latest feature information and caveats, see the release notes for your platform and software
release. To find information about the features documented in this module, and to see a list of the releases in
which each feature is supported, see the “Feature Information for ISG Control Policies” section on page 21.
Use Cisco Feature Navigator to find information about platform support and Cisco IOS XE software
image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on
Cisco.com is not required.
Contents
• Prerequisites for Configuring ISG Control Policies, page 2
• Restrictions for Configuring ISG Control Policies, page 2
• Information About ISG Control Policies, page 2
• How to Configure an ISG Control Policy, page 4
• Configuration Examples for ISG Control Policies, page 15
• Additional References, page 20
• Feature Information for ISG Control Policies, page 21
Americas Headquarters:
Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA
© 2006–2009 Cisco Systems, Inc. All rights reserved.
Page 48

Prerequisites for Configuring ISG Control Policies
Prerequisites for Configuring ISG Control Policies
For information about release and platform support, see the “Feature Information for ISG Control
Policies” section on page 21.
Authentication, authorization, and accounting (AAA) method lists must be configured prior to defi ning
authentication and authorization actions.
Restrictions for Configuring ISG Control Policies
Control policies are activated for specific contexts, not directly on sessions. Control policies apply to all
sessions hosted on the context.
Only one control policy map may be applied to a given context.
Control policies can be defined only through the router’s command-line interface (CLI).
Not all actions may be associated with all events.
A new control class may not be inserted between existing control classes once a control policy map has
been defined.
Configuring ISG Control Policies
Information About ISG Control Policies
Before you configure ISG control policies, you should understand the following concepts:
• Control Policies, page 2
• Uses of Control Policies, page 3
Control Policies
Control policies define the actions that the system will take in response to specified events and
conditions. For example, a control policy can be configured to au thenticate specif ic subscribers and then
provide them with access to specific services.
A control policy is made of one or more control policy rules. A control policy rule is an association of
a control class and one or more actions. The control class defines the conditions that must be met before
the actions will be executed.
Three steps are involved in defining a control policy:
1. Create one or more control class maps.
A control class map specifies the conditions that must be met for a policy to be activated, and,
optionally , the e v ent that causes the class to be e v aluated. A con trol class map may co ntain multip le
conditions, each of which will ev aluate to either true or false. Match directives can be used to specify
whether all, any, or none of the individual conditions must evaluate true in order for the class to
evaluate true.
2. Create a control policy map.
A control policy map contains one or more control policy rules. A control policy rule associates a
control class map with one or more actions. Actions are numbered and executed sequentially.
2
Page 49

Configuring ISG Control Policies
3. Apply the control policy map.
Note Traffic policies are another type of policy used by ISG. Traffic policies define the handling of data
packets and are configured in service policy maps or service prof iles. For mo re information about t raf fic
policies, see the “Configuring ISG Subscriber Services” module.
Information About ISG Control Policies
A control policy map is activated by applying it to a context. A control policy map can be applied
to one or more of the following types of contexts. In the following list, the context types are listed
in order of precedence. For example, a control policy map that is applied to a PVC takes precedence
over a control policy map that is applied to an interface.
–
Virtual template
–
Subinterface
–
Interface
–
Global
In general, control policy maps that are applied to more specific contexts take precedence over
policy maps applied to more general contexts.
Differentiated Initial Policy Control
Authentication failure for a subscriber may happen for an access-reject (which means a RADIUS server
responded with a Reject) or due to an access request timeout (RADIUS server is unreachable).
Using ISG control policies, and actions configur ed for the 'radius-timeout' and 'access-reject' e vents, the
system can distinguish between the different reasons for an authentication failure. Different events are
thrown by the system (for example, a received authentication reject or an unavailable RADIUS server
event). This allows the control policy to specify differen t actions fo r each type of authentication failure.
For example, if the RADIUS server is down or unreachable, temporary access can be given to
subscribers.
This feature is available only for IP-based sessions for subscriber authentication. This feature does not
support the Point-to-Point Protocol over Ethernet (PPPoE) sessions.
Uses of Control Policies
Use control policies to configure an ISG to perform specific actions in response to specific events and
conditions. For example, control policies could be used for the following purposes:
• To activate a default service when a subscriber session is first detected
• To sequence the gathering of subscriber identity, where a control protocol exists on the access side
• T o determine how the system responds to an idle timeout or to a subscriber who has run out of credit
• T o enable tr ansparent auto logon, which enab les authorization on the basis of an IP address or MAC
address
• To configure the maximum amount of time a session can remain unauthenticated
• To send periodic session state information to other devices
3
Page 50

How to Configure an ISG Control Policy
How to Configure an ISG Control Policy
Perform the following tasks to configure an ISG control policy:
• Configuring a Control Class Map, page 4 (required)
• Configuring a Control Policy Map, page 8 (required)
• Applying the Control Policy Map, page 12 (required)
• Monitoring and Maintaining ISG Control Policies, page 15 (optional)
Configuring a Control Class Map
A control class map contains conditions that must be met for a control policy to be executed. A control
class map can contain one or more conditions. Perform this task to configure a control class map.
SUMMARY STEPS
1. enable
2. configure terminal
3. class-map type control [match-all | match-any | match-none] class-map-name
Configuring ISG Control Policies
4. available {authen-statu s | authenticated-domain | authenticated-username | dnis | media |
mlp-negotiated | nas-port | no-username | protocol | service-name | source-ip-address | timer |
tunnel-name | unauthenticated-domain | unauthenticated-username}
5. greater-than [not] nas-port {[adapter adapter-number] [channel channel-number] [ipaddr
ip-address] [port port-number] [shelf shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type] [vci vci-number] [vlan vlan-id] [vpi vpi-number]}
6. greater-than-or-equal [not] nas-port {[adapter adapter-number] [channel channel-number]
[ipaddr ip-address] [port port-number] [shelf shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type] [vci vci-number] [vlan vlan-id] [vpi vpi-number]}
7. less-than [not] nas-port {[adapter adapter-number] [channel channel-number] [ipaddr
ip-address] [port port-number] [shelf shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type] [vci vci-number] [vlan vlan-id] [vpi vpi-number]}
8. less-than-or-equal [not] nas-port {[adapter adapter-number] [channel channel-number] [ipaddr
ip-address] [port port-number] [shelf shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type] [vci vci-number] [vlan vlan-id] [vpi vpi-number]}
9. match authen-status {authenticated | unauthenticated}
10. match authenticated-domain {domain-n ame | regexp regular-expression}
11. match authenticated-username {username | regexp regular-expression}
12. match dnis {dnis | regexp regular-expression}
13. match media {async | atm | ether | ip | isdn | mpls | serial}
14. match mlp-negotiated {no | yes}
15. match nas-port {adapter adapter-number | channel channel-number | circuit-id name | ipaddr
ip-address | port port-number | remote-id name | shelf shelf-number | slot slot-numbe r |
sub-interface sub-interface-number | type {asy nc | atm | basic-rate | enm | ether | fxo | fxs | none
| primary-rate | synch | vlan | vty} | vci vci-number | vlan vlan-id | vpi vpi-number}
4
Page 51

Configuring ISG Control Policies
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Example:
Router> enable
Step 2
configure terminal
How to Configure an ISG Control Policy
16. match no-username {no | yes}
17. match protocol {atom | ip | pdsn | ppp | vpdn}
18. match service-name {se rvice-name | regexp regular-expression}
19. match source-ip-address ip-address subnet-mask
20. ma tch timer {timer-name | regexp regular-expression}
21. match tunnel-name {tunnel-name | regexp regular-expression}
22. match unauthenticated-domain {domain-name | regexp regular-expression}
23. match unauthenticated-username {username | regexp regular-expression}
24. match vrf {vrf-name | regexp regular-expression}
Enables privileged EXEC mode.
• Enter your password if prompted.
Enters global configuration mode.
Step 3
Step 4
Step 5
Example:
Router# configure terminal
class-map type control [match-all | match-any |
match-none] class-map-name
Example:
Router(config)# class-map type control
match-all class1
available {authen-status | authenticated-domain
| authenticated-username | dnis | media |
mlp-negotiated | nas-port | no-username |
protocol | service-name | source-ip-address |
timer | tunnel-name | unauthenticated-domain |
unauthenticated-username}
Example:
Router(config-control-classmap)# available
nas-port
greater-than [not] nas-port {[adapter
adapter-number] [channel channel-number]
[ipaddr ip-address] [port port-number] [shelf
shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type]
[vci vci-number] [vlan vlan-id] [vpi
vpi-number]}
Creates or modifies a control class map, which defines the
conditions under which the actions of a control policy map
will be executed and enters control class-map configuratio n
mode.
(Optional) Enters control class map mode. Creates a
condition that evaluates true if the specified subscriber
identifier is locally available.
(Optional) Creates a condition that evaluates true if the
subscriber network access server (NAS) port identifier is
greater than the specified value.
Example:
Router(config-control-classmap)# greater-than
nas-port type atm vpi 200 vci 100
5
Page 52

How to Configure an ISG Control Policy
Command or Action Purpose
Step 6
greater-than-or-equal [not] nas-port {[adapter
adapter-number] [channel channel-number]
[ipaddr ip-address] [port port-number] [shelf
shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type]
[vci vci-number] [vlan vlan-id] [vpi
vpi-number]}
Example:
Router(config-control-classmap)#
greater-than-or-equal nas-port vlan 10
Step 7
Step 8
less-than [not] nas-port {[adapter
adapter-number] [channel channel-number]
[ipaddr ip-address] [port port-number] [shelf
shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type]
[vci vci-number] [vlan vlan-id] [vpi
vpi-number]}
Router(config-control-classmap)# less-than
nas-port type atm vpi 200 vci 105
less-than-or-equal [not] nas-port {[adapter
adapter-number] [channel channel-number ]
[ipaddr ip-address] [port port-number] [shelf
shelf-number] [slot slot-number] [sub-interface
sub-interface-number] [type interface-type]
[vci vci-number] [vlan vlan-id] [vpi
vpi-number]}
Configuring ISG Control Policies
(Optional) Creates a condition that evaluates true if the
specified subscriber NAS port identifier is greater than or
equal to the specified value.
(Optional) Creates a condition that evaluates true if the
specified subscriber NAS port identifier is less than the
specified value.
(Optional) Creates a condition that evaluates true if the
specified subscriber NAS port iden tifier is less than or equal
to the specified value.
Step 9
Step 10
Step 11
Example:
Router(config-control-classmap)#
less-than-or-equal nas-port ipaddr 10.10.10.10
match authen-status {authenticated |
unauthenticated}
Example:
Router(config-control-classmap)# match
authen-status authenticated
match authenticated-domain {domain-name |
regexp regular-expression}
Example:
Router(config-control-classmap)# match
authenticated-domain cisco.com
match authenticated-username {username | regexp
regular-expression}
Example:
Router(config-control-classmap)# match
authenticated-username regexp "admin@.*com"
(Optional) Creates a condition that evaluates true if a
subscriber’s authentication status matches the specified
authentication status.
(Optional) Creates a condition that evaluates true if a
subscriber’s authenticated domain matches the specified
domain.
(Optional) Creates a condition that evaluates true if a
subscriber’s authenticated username matches the specified
username.
6
Page 53

Configuring ISG Control Policies
Command or Action Purpose
Step 12
match dnis {dnis | regexp regular-expression}
Example:
Router(config-control-classmap)# match dnis
reg-exp 5551212
Step 13
match media {async | atm | ether | ip | isdn |
mpls | serial}
Example:
Router(config-control-classmap)# match media
atm
Step 14
match mlp-negotiated {no | yes}
Example:
Router(config-control-classmap)# match
mlp-negotiated yes
Step 15
match nas-port {adapter adapter-number |
channel channel-number | circuit-id name |
ipaddr ip-address | port port-number |
remote-id name | shelf shelf-number | slot
slot-number | sub-interface
sub-interface-number | type {async | atm |
basic-rate | enm | ether | fxo | fxs | none |
primary-rate | synch | vlan | vty} | vci
vci-number | vlan vlan-id | vpi vpi-number}
How to Configure an ISG Control Policy
(Optional) Creates a condition that evaluates true if a
subscriber’s Dialed Number Identification Service number
(DNIS number, also referred to as called-party number)
matches the specified DNIS number.
(Optional) Creates a condition that evaluates true if a
subscriber’s access media type matches the specified media
type.
(Optional) Creates a condition that evaluates true or false
depending on whether the subscriber’s session was
established using multilink PPP negotiation.
• If the yes keyword is used, the condition e valuates true
if the subscriber’s session was established using
multilink PPP negotiation.
(Optional) Creates a condition that evaluates true if a
subscriber’s NAS port identifier matches the specified
value.
Step 16
Step 17
Step 18
Example:
Router(config-control-classmap)# match nas-port
type ether slot 3
match no-username {no | yes}
Example:
Router(config-control-classmap)# match
no-username yes
match protocol {atom | ip | pdsn | ppp | vpdn}
Example:
Router(config-control-classmap)# match protocol
ip
match service-name {service-name | regexp
regular-expression}
Example:
Router(config-control-classmap)# match
service-name service1
(Optional) Creates a condition that evaluates true or false
depending on whether or not a subscriber’s username is
available.
• If the yes keyword is used, the condition e valuates true
if the subscriber’s username is not available.
(Optional) Creates a condition that evaluates true if a
subscriber’s access protocol type matches the specified
protocol type.
(Optional) Creates a condition that evaluates true if the
service name associated with a subscriber matches the
specified service name.
7
Page 54

How to Configure an ISG Control Policy
Command or Action Purpose
Step 19
match source-ip-address ip-address subnet-mask
Example:
Router(config-control-classmap)# match
source-ip-address 10.10.10.10 255.255.255.255
Step 20
match timer {timer-name | regexp
regular-expression}
Example:
Router(config-control-classmap)# match timer
TIMERA
Step 21
match tunnel-name {tunnel-name | regexp
regular-expression}
Example:
Router(config-control-classmap)# match
tunnel-name regexp L.*
Step 22
match unauthenticated-domain {domain-name |
regexp regular-expression}
Example:
Router(config-control-classmap)# match
unauthenticated-domain example.com
Step 23
match unauthenticated-username {username |
regexp regular-expression}
Example:
Router(config-control-classmap)# match
unauthenticated-username regexp examplename1
Step 24
match vrf {vrf-name | regexp
regular-expression}
Example:
Router(config-control-classmap)# match vrf
regexp examplename2
Configuring ISG Control Policies
(Optional) Creates a condition that evaluates true if a
subscriber’s source IP address matches the specified IP
address.
(Optional) Creates a condition that evaluates true upon
expiry of a specified policy timer.
(Optional) Creates a condition that evaluates true if a
subscriber’s virtual private dialup network (VPDN) tunnel
name matches the specified tunnel name.
(Optional) Creates a condition that evaluates true if a
subscriber’s unauthenticated domain name matches the
specified domain name.
(Optional) Creates a condition that evaluates true if a
subscriber’s unauthenticated username matches the
specified username.
(Optional) Creates a condition that evaluates true if a
subscriber’s VPN routing and forwarding (VRF) matches
the specified VRF.
Configuring a Control Policy Map
A control policy map contains one o r more cont rol policy rules that associate a control class with one or
more actions. Perform this task to configure a control policy map.
Note The actions that can be configured in a policy rule depend on the type of event that is specified by the
class type control command. For example, if the account-logoff event is specif ied, the on ly act ion that
can be configured in that policy rule is service. The procedure in this section shows all actions that can
be configured in a policy map.
8
Page 55

Configuring ISG Control Policies
Default Method Lists
If you specify the default method list for any of the contr ol policy actions, the def ault list will not appear
in the output of the show running-config command. For example, if you configure the following
command:
Router(config-control-policymap-class-control)# 1 authenticate aaa list default
the following will display in the output for the show running-config command:
1 authenticate
Named method lists will display in the show running-config command output.
SUMMARY STEPS
1. enable
2. configure terminal
3. policy-map type control policy-map-name
4. class type control {control-class-name | always} [event {access-reject | account-logoff |
How to Configure an ISG Control Policy
account-logon | acct-notification | credit-exhausted | dummy-event | quota-depleted |
radius-timeout | service-failed | service-start | service-stop | session-default-service |
session-restart | session-service-found | session-start | timed-policy-expiry}]
5. action-number authenticate aaa list list-name
6. action-number authorize [aaa list list-na me] [password password] [upon network-service-found
{continue | stop}] identifier {authenticated-domain | authenticated-username | auto-detect |
circuit-id [plus remote-id] | dnis | mac-address | nas-port | remote-id [plus circuit-id] |
source-ip-address | tunnel-name | unauthenticated-domain | unauthenticated-username |
vendor-class-id}
7. action-number collect [aaa list list-name] identifier {authen-status | authenticated-domain |
authenticated-username | dnis | mac-address | media | mlp-negotiated | nas-port | no-username
| protocol | service-name | source-ip-address | timer | tunnel-name | unauthenticated-domain |
unauthenticated-username | vrf}
8. action-number if upon network-service-found {continue | stop}
9. action-number proxy accounting aaa list {list-name | default}
10. ac tion-num ber service [disconnect | local | vpdn]
11. ac tion-num ber service-policy type control policy-map-name
12. ac tion-num ber service-policy type service [unapply] [aaa list list-name] {name service-name |
identifier {authenticated-domain | authenticated-username | dnis | nas-port | tunnel-name |
unauthenticated-domain | unauthenticated-username}}
13. ac tion-num ber set name identifier {authen-status | authenticated-domain |
authenticated-username | dnis | mac-address | media | mlp-negotiated | nas-port | no-username
| protocol | service-name | source-ip-address | timer | tunnel-name | unauthenticated-domain |
unauthenticated-username | vrf}
14. ac tion-num ber set-timer name-of-timer minutes
15. ac tion-num ber substitute name matching-pattern pattern-string
16. end
9
Page 56

How to Configure an ISG Control Policy
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Example:
Router> enable
Step 2
configure terminal
Example:
Router# configure terminal
Step 3
policy-map type control policy-map-name
Example:
Router(config)# policy-map type control
MY-POLICY
Step 4
class type control {control-class-name |
always} [event {access-reject | account-logoff
| account-logon | acct-notification |
credit-exhausted | dummy-event | quota-depleted
| radius-timeout | service-failed |
service-start | service-stop |
session-default-service | session-restart |
session-service-found | session-start |
timed-policy-expiry}]
Configuring ISG Control Policies
Enables privileged EXEC mode.
• Enter your password if prompted.
Enters global configuration mode.
Creates or modifies a control policy map, which is used to
define a control policy and enters control policy-map
configuration mode.
Specifies a control class for which actions may be
configured and enters control policy-map class
configuration mode.
• A policy rule for which the control cl ass is always will
always be treated as the lowest priority rule within the
control policy map.
Step 5
Step 6
Example:
Router(config-control-policymap)# class type
control always event session-start
action-number authenticate aaa list list-name
Example:
Router(config-control-policymap-class-control)#
1 authenticate aaa list LIST1
action-number authorize [aaa list list-name]
[password password] [upon network-service-found
{continue | stop}] identifier
{authenticated-domain | authenticated-username
| auto-detect | circuit-id [plus remote-id] |
dnis | mac-address | nas-port | remote-id [plus
circuit-id] | source-ip-address | tunnel-name |
unauthenticated-domain |
unauthenticated-username | vendor-class-id}
Example:
Router(config-control-policymap-class-control)#
1 authorize identifier source-ip-address
(Optional) Initiates an authentication request.
(Optional) Initiates a request for authorization on the basis
of the specified identifier.
10
Page 57

Configuring ISG Control Policies
Command or Action Purpose
Step 7
action-number collect [aaa list list-name]
identifier {authen-status |
authenticated-domain | authenticated-username
| dnis | mac-address | media | mlp-negotiated |
nas-port | no-username | protocol |
service-name | source-ip-address | timer |
tunnel-name | unauthenticated-domain |
unauthenticated-username | vrf}
Example:
Router(config-control-policymap-class-control)#
1 collect identifier authen-status
Step 8
action-number if upon network-service-found
{continue | stop}
Example:
Router(config-control-policymap-class-control)#
2 if upon network-service-found stop
Step 9
action-number proxy accounting aaa list
{list-name | default}
How to Configure an ISG Control Policy
(Optional) Collects the specified subscriber identifier from
the access protocol.
(Optional) Specifies whether the system should continue
processing policy rules once the subscriber’s network
service has been identified.
(Optional) Specifies the list that the request should be
proxied to.
Step 10
Step 11
Step 12
Example:
Router(config-control-policymap-class-control)#
1 proxy accounting aaa list default
action-number service [disconnect | local |
vpdn]
Example:
Router(config-control-policymap-class-control)#
3 service disconnect
action-number service-policy type control
policy-map-name
Example:
Router(config-control-policymap-class-control)#
4 service-policy type control domainBasedAccess
action-number service-policy type service
[unapply] [aaa list list-name] {name
service-name | identifier {authenticated-domain
| authenticated-username | dnis | nas-port |
tunnel-name | unauthenticated-domain |
unauthenticated-username}}
Example:
Router(config-control-policymap-class-control)#
1 service-policy type service aaa list LISTA
name REDIRECT
(Optional) Specifies a network service type for PPP
sessions.
(Optional) Nests the specified control policy map within a
parent control policy map.
(Optional) Activates an ISG service.
• Specifying an identifier instead of a service name will
activate a service that has the same name as the
specified identifier.
11
Page 58

How to Configure an ISG Control Policy
Command or Action Purpose
Step 13
action-number set name identifier
{authen-status | authenticated-domain |
authenticated-username | dnis | mac-address |
media | mlp-negotiated | nas-port | no-username
| protocol | service-name | source-ip-address |
timer | tunnel-name | unauthenticated-domain |
unauthenticated-username | vrf}
Example:
Router(config-control-policymap-class-control)#
1 set APJ identifier authen-status
Step 14
action-number set-timer name-of-timer minutes
Example:
Router(config-control-policymap-class-control)#
1 set-timer TIMERA 5
Step 15
action-number substitute name matching-pattern
pattern-string
Configuring ISG Control Policies
(Optional) Sets a variable name.
(Optional) Starts a named policy timer.
• Expiration of the timer generates the event
timed-policy-expiry.
(Optional) Substitutes a matching pattern in variable
content by a rewrite pattern.
Example:
Router(config-control-policymap-class-control)#
1 substitute TPK SUBA SUBB
Step 16
end
(Optional) Ends the current configuration session and
returns to privileged EXEC mode.
Example:
Router(config-control-policymap-class-control)#
end
Applying the Control Policy Map
A control policy map must be activ ated b y applying it to a conte xt. Perform one or more of the follo wing
tasks to apply a control policy to a context:
• Applying a Control Policy Map Globally on the Router, page 12
• Applying an ISG Control Policy Map to an Interface or Subinterface, page 13
• Applying an ISG Control Policy Map to a Virtual Template, page 14
Applying a Control Policy Map Globally on the Router
Perform this task to apply a control policy globally.
SUMMARY STEPS
1. enable
2. configure terminal
3. service-policy type control policy-map-name
12
Page 59

Configuring ISG Control Policies
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Example:
Router> enable
Step 2
configure terminal
Example:
Router# configure terminal
Step 3
service-policy type control policy-map-name
Example:
Router(config)# service-policy type control
policy1
How to Configure an ISG Control Policy
Enables privileged EXEC mode.
• Enter your password if prompted.
Enters global configuration mode.
Applies a control policy.
Applying an ISG Control Policy Map to an Interface or Subinterface
Perform this task to apply an ISG control policy to an interface or subinterface.
SUMMARY STEPS
1. enable
2. configure terminal
3. interface type number [.subinterface number]
4. service-policy type control policy-map-name
DETAILED STEPS
Command or Action Purpose
Step 1
Step 2
enable
Example:
Router> enable
configure terminal
Example:
Router# configure terminal
Enables privileged EXEC mode.
• Enter your password if prompted.
Enters global configuration mode.
13
Page 60

How to Configure an ISG Control Policy
Command or Action Purpose
Step 3
interface type number[.subinterface-number]
Specifies an interface and enters interface configuration
mode.
Example:
Router(config)# interface gigabitethernet
0/0/1.1
Step 4
service-policy type control policy-map-name
Applies a control policy.
Example:
Router(config-if)# service-policy type control
policy1
Applying an ISG Control Policy Map to a Virtual Template
Perform this task to apply an ISG control policy map to a virtual template.
SUMMARY STEPS
Configuring ISG Control Policies
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Example:
Router> enable
Step 2
configure terminal
Example:
Router# configure terminal
Step 3
interface virtual-template number
Example:
Router(config)# interface virtual-template0
Step 4
service-policy type control policy-map-name
1. enable
2. configure terminal
3. interface virtual-template number
4. service-policy type control policy-map-name
Enables privileged EXEC mode.
• Enter your password if prompted.
Enters global configuration mode.
Creates a virtual template interface and enters interface
configuration mode.
Applies a control policy.
Example:
Router(config-if)# service-policy type control
policy1
14
Page 61

Configuring ISG Control Policies
Monitoring and Maintaining ISG Control Policies
Optionally, you can perform this task to monitor and maintain ISG control policy operation. Steps can
be performed in any order.
SUMMARY STEPS
1. enable
2. show class-map type control
3. show policy-map type control
4. clear class-map control
5. clear policy-map control
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Enables privileged EXEC mode.
Configuration Examples for ISG Control Policies
Step 2
Step 3
Step 4
Step 5
Example:
Router> enable
show class-map type control
Example:
Router# show class-map type control
show policy-map type control
Example:
Router# show policy-map type control
clear class-map control
Example:
Router# clear class-map control
clear policy-map control
Example:
Router# clear policy-map control
• Enter your password if prompted.
Displays information about ISG control class maps.
• The display includes statistics on the number of times a
particular class has been eval uated and what the results
were.
Displays information about ISG control policy maps.
• The display includes statistics on the number of times
each policy rule within the policy map has been
executed.
Clears the control class map counters.
Clears the control policy map counters.
Configuration Examples for ISG Control Policies
This section contains the following examples of ISG control policies:
• Control Policy for Layer 2 Access and Service Provisioning: Example, page 16
• Verifying a Control Policy: Examples, page 16
• Control Policy for Restricting Access on the Basis of Interface and Access Media: Example, page 19
• Control Policies for Automatic Subscriber Login: Example, page 20
15
Page 62

Configuring ISG Control Policies
Configuration Examples for ISG Control Policies
Control Policy for Layer 2 Access and Service Provisioning: Example
The following example shows how to configure a control policy that produces the following results:
• VPDN forwarding is applied to anyone dialing in from “example1.com”.
• Access to locally terminated Layer 3 network resources is provided to anyone dialing in from
“example2.com”.
• Anyone else is barred.
username user1@example1.com password 0 lab
username user2@example2.com password 0 lab
username user3@example3.com password 0 lab
!
class-map type control match-all MY-FORWARDING-USERS
match unauthenticated-domain example1.com
!
class-map type control match-all MY-LOCAL-USERS
match unauthenticated-domain example2.com
!
policy-map type control MY-POLICY
class type control MY-FORWARDING-USERS event session-start
1 service local
!
class type control MY-LOCAL-USERS event session-start
1 service local
!
class type control always event session-start
2 service disconnect
!
!
policy-map type control ppp-users
class type control always event session-start
1 collect identifier unauthenticated-domain
2 service-policy type control MY-POLICY
!
Verifying a Control Policy: Examples
The following examp les show sample output generated from the configuration in the Control Policy for
Layer 2 Access and Service Provisioning: Example:
Router# show users
Line User Host(s) Idle Location
* 0 con 0 idle 00:00:00
Interface User Mode Idle Peer Address
Vi1.1 user1@xyz.com PPPoE - 10.1.126.14
Vi1.2 user2@abc.com PPPoE - 10.1.126.15
Router# show subscriber session
Current Subscriber Information: Total sessions 2
Uniq ID Interface State Service Identifier Up-time
2022 Vi1.1 authen Local Term user1@xyz.com 00:08:41
2023 Vi1.2 authen Local Term user2@abc.com 00:08:40
MCP_BBA_8#show subscriber session
MCP_BBA_8#show subscriber session uid 2022 detailed
16
Page 63

Configuring ISG Control Policies
Unique Session ID: 2022
Identifier: user1@xyz.com
SIP subscriber access type(s): PPPoE/PPP
Current SIP options: Req Fwding/Req Fwded
Session Up-time: 00:08:57, Last Changed: 00:08:57
Interface: Virtual-Access1.1
Policy information:
Context 2C655DF0: Handle A2070D8D
AAA_id 00007DE8: Flow_handle 0
Authentication status: authen
Downloaded User profile, excluding services:
service-type 2 [Framed]
Framed-Protocol 1 [PPP]
timeout 720 (0x2D0)
ssg-account-info ''QU;10000;D;20000''
Downloaded User profile, including services:
service-type 2 [Framed]
Framed-Protocol 1 [PPP]
timeout 720 (0x2D0)
ssg-account-info ''QU;10000;D;20000''
Config history for session (recent to oldest):
Access-type: PPP Client: SM
Policy event: Process Config Connecting
Profile name: apply-config-only, 3 references
service-type 2 [Framed]
Framed-Protocol 1 [PPP]
timeout 720 (0x2D0)
ssg-account-info ''QU;10000;D;20000''
Rules, actions and conditions executed:
subscriber rule-map ppp-users
condition always event session-start
1 collect identifier unauthenticated-domain
2 service-policy type control MY-POLICY
subscriber condition-map match-all MY-FORWARDING-USERS
match identifier unauthenticated-domain xyz.com [TRUE]
subscriber rule-map MY-POLICY
condition MY-FORWARDING-USERS event session-start
1 service local
subscriber rule-map ppp-users
condition always event session-start
2 service-policy type control MY-POLICY
Configuration Examples for ISG Control Policies
Session inbound features:
Feature: Policing
Upstream Params:
Average rate = 10000, Normal burst = 1875, Excess burst = 3750
Config level = Per-user
Session outbound features:
Feature: Policing
Dnstream Params:
Average rate = 20000, Normal burst = 3750, Excess burst = 7500
Config level = Per-user
Non-datapath features:
Feature: Session Timeout
Timeout value is 720 seconds
Time remaining is 00:02:56
Configuration sources associated with this session:
Interface: Virtual-Template1, Active Time = 00:09:03
Router# show subscriber session uid 2023 detailed
17
Page 64

Configuration Examples for ISG Control Policies
Unique Session ID: 2023
Identifier: user2@abc.com
SIP subscriber access type(s): PPPoE/PPP
Current SIP options: Req Fwding/Req Fwded
Session Up-time: 00:09:17, Last Changed: 00:09:17
Interface: Virtual-Access1.2
Policy information:
Context 2C656120: Handle F4070D8E
AAA_id 00007DE9: Flow_handle 0
Authentication status: authen
Downloaded User profile, excluding services:
service-type 2 [Framed]
Framed-Protocol 1 [PPP]
timeout 720 (0x2D0)
ssg-account-info ''QU;10000;D;20000''
Downloaded User profile, including services:
service-type 2 [Framed]
Framed-Protocol 1 [PPP]
timeout 720 (0x2D0)
ssg-account-info ''QU;10000;D;20000''
Config history for session (recent to oldest):
Access-type: PPP Client: SM
Policy event: Process Config Connecting
Profile name: apply-config-only, 3 references
service-type 2 [Framed]
Framed-Protocol 1 [PPP]
timeout 720 (0x2D0)
ssg-account-info ''QU;10000;D;20000''
Rules, actions and conditions executed:
subscriber rule-map ppp-users
condition always event session-start
1 collect identifier unauthenticated-domain
2 service-policy type control MY-POLICY
subscriber condition-map match-all MY-FORWARDING-USERS
match identifier unauthenticated-domain xyz.com [FALSE]
subscriber rule-map MY-POLICY
condition MY-FORWARDING-USERS event session-start
subscriber condition-map match-all MY-LOCAL-USERS
match identifier unauthenticated-domain abc.com [TRUE]
subscriber rule-map MY-POLICY
condition MY-LOCAL-USERS event session-start
1 service local
subscriber rule-map ppp-users
condition always event session-start
2 service-policy type control MY-POLICY
Configuring ISG Control Policies
Session inbound features:
Feature: Policing
Upstream Params:
Average rate = 10000, Normal burst = 1875, Excess burst = 3750
Config level = Per-user
Session outbound features:
Feature: Policing
Dnstream Params:
Average rate = 20000, Normal burst = 3750, Excess burst = 7500
Config level = Per-user
Non-datapath features:
Feature: Session Timeout
Timeout value is 720 seconds
18
Page 65

Configuring ISG Control Policies
Configuration Examples for ISG Control Policies
Time remaining is 00:02:40
Configuration sources associated with this session:
Interface: Virtual-Template1, Active Time = 00:09:19
Control Policy for Restricting Access on the Basis of Interface and
Access Media: Example
This example shows how to configure a contr ol policy to allow access only to users who enter the router
from a particular interface and access type. In this case, only PPPoE users will be allowed; everyone else
is barred.
The first condition class map “MATCHING-USERS” evaluates true only if all of the lines within it also
evaluate true; however, within “MATCHING-USERS” is a nested class map (second condition),
“NOT-ATM”. This nested class map represents a subcondition that must also evaluate to true. Note that
the class map “NOT-ATM” specifies “match-none”. This means that “NO T-ATM” evaluates to true only
if every condition line within it evaluates to false.
The third condition specifies matching on the NAS port associated wi th this su bscriber. Specifically,
only subscribers that arrive on a Gigabit Ethernet interface and on slot 3 will evaluate to true.
! Configure the control class maps.
class-map type control match-all MATCHING-USERS
class type control NOT-ATM
match media ether
match nas-port type ether slot 3
!
class-map type control match-none NOT-ATM
match media atm
!
If the conditions in the class map “MATCHING-USERS” evaluate to true, the fi rst action to be ex ecuted
is to authenticate the user. If authentication is successful, the service named “service1” will be
downloaded and applied. Finally, a Layer 3 service is provided.
If “MA TCHING-USERS” is not ev aluated as true, the “always” class will apply, which results in barring
anyone who does not match “MATCHING-USERS”.
! Configure the control policy map.
policy-map type control my-pppoe-rule
class type control MATCHING-USERS event session-start
1 authenticate aaa list XYZ
2 service-policy type service service1
3 service local
!
class type control always
1 service disconnect
!
! Apply the control policy to an interface.
interface gigabitethernet3/0/0
service-policy type control my-pppoe-rule
Finally, the policy is associated with an interface.
19
Page 66

Additional References
Control Policies for Automatic Subscriber Login: Example
In the following example, if the client is from the a subnet, automatic subscriber login is applied and an
authorization request is sent to the list TALLIST with the subscriber’s sou rce IP address as the username.
If the authorization request is successful, any automatic acti vation services specif ied in the returned user
profile are activated for the session and the execution of rules within the control policy stops. If the
authorization is not successful, the rule execu tion proceeds, and the subscriber is redirected to the polic y
server to log in. If the subscriber does not log in within five minutes, the session is disconnected.
interface GigabitEthernet0/0/0
service-policy type control RULEA
aaa authentication login TALLIST group radius
aaa authentication login LOCAL local
access-list 100 permit ip any any
class-map type traffic match-any all-traffic
match access-group input 100
match access-group output 100
policy-map type service redirectprofile
class type traffic all-traffic
redirect to ip 10.0.0.148 port 8080
Configuring ISG Control Policies
class-map type control match-all CONDA
match source-ip-address 209.165.201.1 255.255.255.0
!
class-map type control match-all CONDF
match timer TIMERB
match authen-status unauthenticated
policy-map type control RULEA
class type control CONDA event session-start
1 authorize aaa list TAL_LIST password cisco identifier source-ip-address
2 apply aaa list LOCAL service redirectprofile
3 set-timer TIMERB 5 minutes
class type control CONDF event timed-policy-expiry
1 service disconnect
Additional References
The following sections provide references related to ISG control policies.
Related Documents
Related Topic Document Title
ISG commands Cisco IOS Intelligent Services Gateway Command Reference
Traffic Policies The “Configuring ISG Subscriber Services” module.
20
Page 67

Configuring ISG Control Policies
MIBs
MIB MIBs Link
No new or modified MIBs are supported by this
feature.
T o locate and do wnload MIBs for selected platforms, Cisco IOS XE
releases, and feature sets, use Cisco M IB Locator found at the
following URL:
http://www.cisco.com/go/mibs
Technical Assistance
Description Link
The Cisco Support website provides extensive online
resources, including documentation and tools for
troubleshooting and resolving technical issues with
Cisco products and technologies.
To receive security and technical information about
your products, you can subscribe to various services,
such as the Product Alert Tool (accessed from Field
Notices), the Cisco Technical Services Ne wsletter , and
Really Simple Syndication (RSS) Feeds.
http://www.cisco.com/techsupport
Feature Information for ISG Control Policies
Access to most tools on the Cisco Support website
requires a Cisco.com user ID and password.
Feature Information for ISG Control Policies
Table 1 lists the features in this module and provides links to specific configuration information. For
information about a feature in this technology that is not documented here, see the “Intelligent Services
Gateway Features Roadmap.”
Use Cisco Feature Navigator to find information about platform support and software image support.
Cisco Feature Navigator enables you to determine which Cisco IOS XE software images support a
specific software release, feature set, or platform. To access Cisco Feature Navigator, go to
http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Note Table 1 lists only the Cisco IOS XE s oftware release that introduced support for a given feature in a
given Cisco IOS XE software release train. Unless noted othe rwise, su bsequent releases of that
Cisco IOS XE software release train also support that feature.
21
Page 68

Feature Information for ISG Control Policies
Table 1 Feature Information for ISG Control Policies
Feature Name Releases Feature Configuration Information
ISG: Policy Control: Policy: Domain Based
(Autodomain, Proxy)
Cisco IOS XE
Release 2.2
ISG control policies manage the primary services and rules
used to enforce particular contracts. These policies include
programmable interfaces to dynamic triggers and
conditional logic to be applied to flows within a session, or
other characteristics of a session, upon meeting the policy
criteria. Policies can be configured to interpret the domain
as a request to activate the service associated with that
domain name, allowing users to automatically receive
services in accordance with the domain to which they are
attempting to connect.
The following sections provide mo re information about this
feature:
• Information About ISG Control Policies, page 2
• How to Configure an ISG Control Policy, page 4
ISG: Policy Control: Policy: Triggers Cisco IOS XE
Release 2.2
ISG control policies can be configured with time-based,
volume-based, and duration-based policy triggers.
Time-based triggers use an inte rnal clock, allowing policies
to be applied at specific times. Volume-based triggers are
based on packet count; when the packet count reaches a
specified value, the specified policy is applied.
Duration-based triggers are based on an internal timer.
Upon expiration of the timer , the specif ied policy is applied.
Configuring ISG Control Policies
ISG: Policy Control: Multidimension al Identity
per Session
Cisco IOS XE
Release 2.2
The following sections provide mo re information about this
feature:
• Information About ISG Control Policies, page 2
• How to Configure an ISG Control Policy, page 4
ISG control policies provide a flexible way to collect pieces
of subscriber identity information during session
establishment. Control policies also allow session polic y to
be applied iteratively as more elements of identity
information become available to the system.
The following sections provide mo re information about this
feature:
• Information About ISG Control Policies, page 2
• How to Configure an ISG Control Policy, page 4
22
Page 69

Configuring ISG Control Policies
Feature Information for ISG Control Policies
Table 1 Feature Information for ISG Control Policies (continued)
Feature Name Releases Feature Configuration Information
ISG: Policy Control: Cisco Policy Language Cisco IOS XE
Release 2.2
ISG control policies are a structured replacement for
feature-specific configuration commands and allow
configurable functionality to be expressed in terms of an
event, a condition, and an action. Control policies provide
an intuitive and extensi ble frame w ork, wit h a consistent set
of CLI commands, for specifying system behavior.
The following sections provide mo re information about this
feature:
• Information About ISG Control Policies, page 2
• How to Configure an ISG Control Policy, page 4
ISG: Policy Control: Differentiated Initial
Policy Control
Cisco IOS XE
Release 2.5.0
This features provides the ability to distinguish RADIUS
authentication rejects from RADIUS server unavailability.
It allows minimal or temporary network access to the
subscribers when the RADIUS servers are down or cannot
be accessed because of network problems or when an
authentication reject is received for a subscriber.
In Cisco IOS Release 12.2(33)XNE, support was added for
the Cisco 10000 Series Routers.
The following sections provides more information about
this feature:
• Information About ISG Control Policies, page 2
• How to Configure an ISG Control Policy, page 4
The following command was introduced or modified:
class type control.
CCDE, CCENT, CCSI, CiscoEos, Cisco HealthPresence, Cisco IronPort, the Cisco logo, Cisco Nurse Connect, Cisco Pulse, Cisco SensorBase,
Cisco StackPower, Cisco StadiumVision, Cisco TelePresence, Cisco Unified Computing System, Cisco WebEx, DCE, Flip Channels, Flip for Good,
Flip Mino, Flipshare (Design), Flip Ultra, Fli p Video, Flip V i deo (Design), Instant Broadband, and Welcome to the Human Network are trademarks;
Changing the Way We Work, Live, Play, and Learn, Cisco Capital, Cisco Capital (Design), Cisco:Financed (Stylized), Cisco Store, Flip Gift Card,
and One Million Acts of Green are service marks; and Access Registrar, Aironet, AllTouch, AsyncOS, Bringing the Meeting T o You, Catalyst, CCDA,
CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Lumin, Cisco Nexus,
Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collabor ation Without Limitation, Continuum, EtherFast,
EtherSwitch, Event Center, Explor er, Follow Me Browsi ng, Gain Mak er, iLYNX, IOS, iPhone, IronPort, the IronPort logo, Laser Link, LightStream,
Linksys, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, PCNow, PIX, PowerKEY, PowerPanels, PowerTV,
PowerTV (Design), PowerVu, Prisma, ProConnect, ROSA, SenderBase, SMARTnet, Spectrum Expert, StackWise, WebEx, and the WebEx logo are
registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0910R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and
figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and
coincidental.
© 2006–2009 Cisco Systems, Inc. All rights reserved.
23
Page 70

Feature Information for ISG Control Policies
Configuring ISG Control Policies
24
Page 71

Configuring ISG Access for PPP Sessions
First Published: March 20, 2006
Last Updated: March 2, 2009
Intelligent Services Gateway (ISG) is a Cisco IOS and Cisco IOS XE software feature set that provides
a structured framework in which edge devices can deliver flexible and scalable services to subscribers.
This document provides information about how to configure ISG access for PPP subscribers.
Finding Feature Information
For the latest feature information and caveats, see the release notes for your platform and software
release. To find information about the features documented in this module, and to see a list of the releases in
which each feature is supported, see the “Feature Information for ISG Access for PPP Sessions” section on
page 13.
Use Cisco Feature Navigator to find information about platform support and Cisco IOS XE software
image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on
Cisco.com is not required.
Contents
• Prerequisites for ISG Access for PPP Sessions, page 2
• Restrictions for ISG Access for PPP Sessions, page 2
• Information About Configuring ISG Access for PPP Sessions, page 2
• How to Configure ISG Access for PPP Sessions Using Control Policies, page 4
• Configuration Examples for ISG Access for PPP Sessions, page 9
• Additional References, page 12
• Feature Information for ISG Access for PPP Sessions, page 13
Americas Headquarters:
Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA
© 2009 Cisco Systems, Inc. All rights reserved.
Page 72

Prerequisites for ISG Access for PPP Sessions
Prerequisites for ISG Access for PPP Sessions
For information about release and platform support, see the “Feature Information for ISG Access for PPP
Sessions” section on page 13.
The specific access protocol that is being used must be provisioned on the interface.
If local PPP authentication is required, the ppp authentication command must be configured on the
interface or virtual template.
The tasks and examples in this document assume that you know how to configure and use ISG control
policies. See the module “Configuring ISG Control Policies” for information about how configure
control policies.
Restrictions for ISG Access for PPP Sessions
In Cisco IOS XE, SSO and ISSU are not supported for the following features on ISG PPP sessions:
• Port-Bundle Host Key
Configuring ISG Access for PPP Sessions
• Layer 4 Redirect
• Traffic C l ass
• Accounting
Information About Configuring ISG Access for PPP Sessions
Before you configure access for PPP sessions, you should understand the following concepts:
• Overview of ISG Access for PPP Sessions, page 2
• ISG Subscriber IP Address Management for PPP Sessions, page 3
• VRF Transfer for PPP Sessions, page 3
• Default Policy for ISG Access for PPP Sessions, page 3
Overview of ISG Access for PPP Sessions
Layer 2 sessions are established by means of control protocols that operate between the peer entities and
the ISG device. Typically, Layer 2 sessions are encapsulated to isolate them from other session s on the
same physical media.
Although the system provides defa ult handling f or Layer 2 session s, you may w ant to conf igur e policies
to forward or locally terminate the prot ocol or to locally authenticate su bscribers on the b asis of identity
data that is collected from the access protocol. ISG control policies can be configured to extract identity
and credentials of peer entities from access protocols. This mechanism allows services to be pro visioned
for Layer 2 sessions on the basis of any identity pertaining to the session, whether explicitly provided
via the protocol or native to the underlying media or access port.
ISG supports the following Layer 2 access protocols:
• PPP
• PPP over Ethernet (PPPoE)
2
Page 73

Configuring ISG Access for PPP Sessions
Information About Configuring ISG Access for PPP Sessions
• Layer 2 Tunnel Protocol (L2TP)
ISG Subscriber IP Address Management for PPP Sessions
ISG subscriber IP address management applies to IP sessions or Layer 2 (PPP) sessions that are
terminated locally.
For a subscriber to be routable within a given IP service domain, the subscriber must present a
domain-specific IP address to the network. If a subscriber transfers between IP service domains (which
includes any private domain managed by the access provider), the IP address presented to the network
must change to reflect the ne w domai n. For locally terminated PPP session s, ISG suppor ts the follo wi ng
methods of IP address assignment:
• IP address in a user profile
• IP subnet in a user profile
• Named address pool in a user profile
• Local address pools
• Standard methods of IP address management for PPP (see the Cisco IOS XE Dial Technologies
Configuration Guide for information about IP address management support for PPP sessions)
When a locally terminated PPP session is transferred from one VRF to another VRF, the peer IP address
is renegotiated using IPCP.
VRF Transfer for PPP Sessions
VRF transfer enables an ISG subscriber session to move from one VRF to another following selection
of a new primary service. Once a PPP session comes up with the IP address from the network access
point (NAP), the subscriber can access a web portal and choose a service provider. On VRF transfers in
PPP sessions, ISG must reassign the IP address from the new domain to the PPP session. In PPP sessions,
the IP address is reassigned by IPCP renegotiation.
Without PPP renegotiation, VRF transfer is not supported for PPP sessions.
Default Policy for ISG Access for PPP Sessions
ISG provides default handling of Layer 2 sessions in the absence of a configured control policy. If the
vpdn enable command is configured and a domain name is specified in the username (e.g.,
user@domain) or a Dialed Number Identification Service (DNIS) number has been provided, the system
will perform authorization on the basis of this information. If virtual private dial-up network (VPDN)
tunnel information is found, the session will be forwarded for handling at an L2TP network server
(LNS). If authentication is required by the remote LNS, the ppp authentication command must be
configured at the PPP interface or virtual template. If the vpdn authen-before-forward command is
configured, the system will attempt to authenticate the PPP session locally before for warding it on to the
LNS.
If tunnel information is not found for the domain name or DNIS or the vpdn enable command is not
configured, Stack Group Bidding Protocol (SGBP) a uthorization will be attempted (if SGBP is
configured). If no authorization information is located using SGBP, the PPP session will be terminated
3
Page 74

Configuring ISG Access for PPP Sessions
How to Configure ISG Access for PPP Sessions Using Control Policies
locally. Local termination means that the PPP session will be established between the peer and the ISG
device, and the IP payload will be routed. In the latter case, authentication will occur only if the ppp
authentication command is configured on the PPP interface or virtual template.
If an ISG control policy is defined for the session-start event, that policy will override the default
handling.
How to Configure ISG Access for PPP Sessions Using Control
Policies
To configure ISG Layer 2 access, perform the following steps:
1. Decide how you want Layer 2 session handling to be influenced by subscriber identity. Do you want
to forward the protocol or terminate it locally? Do you want to authenticate subscribers locally?
2. Configure control policies to provide Layer 2 session handling. See the module “Configuring ISG
Control Policies” for information about how configure control policies. See the “Configuration
Examples for ISG Access for PPP Sessions” section on page 9 for an example of a control policy
for Layer 2 access.
3. Enable ISG VRF transfer for PPP sessions.
4. Verify and troubleshoot the configuration as needed.
This section contains the following tasks:
• Enabling ISG VRF Transfer for PPP Sessions, page 4
• Troubleshooting ISG Access for PPP Sessions, page 7
Enabling ISG VRF Transfer for PPP Sessions
VRF transfer enables an ISG subscriber session to move from one VRF to another following selection
of a new primary service. This procedure contains the following sections:
• Prerequisites, page 4
• Specifying a VRF in a Service Policy Map, page 5
• Verifying VRF Transfer for PPP Sessions
Prerequisites
This procedure assumes that you have configured support for PPP sessions by configuring a virtual
template and method of IP address allocation. Note that the original VRF, loopback interface, and IP
address pool must be specified in a virtual template rather than in a user profile in ord er for VRF transfer
to work. For information about how to configure virtual templates and support for PPP sessions, see the
Cisco IOS XE Dial Technologies Configuration Guide.
4
Page 75

Configuring ISG Access for PPP Sessions
Specifying a VRF in a Service Policy Map
VRF transfer occurs when a new primary service is activated for a session, causing the session to transfer
from one VRF to another. Services can be configured in service profiles on an external AAA server or
they can be configured on the ISG device in service policy maps. Perform this task to configure a VRF
in a service policy map on the ISG device.
SUMMARY STEPS
1. enable
2. configure terminal
3. policy-map type service policy-map-name
4. ip vrf forwarding name-of-vrf
5. sg-service-type primary
6. sg-service-group service-group-name
DETAILED STEPS
How to Configure ISG Access for PPP Sessions Using Control Policies
Step 1
Step 2
Step 3
Step 4
Command or Action Purpose
enable
Enables privileged EXEC mode.
• Enter your password if prompted.
Example:
Router> enable
configure terminal
Enters global configuration mode.
Example:
Router# configure terminal
policy-map type service policy-map-name
Creates or modifies a service policy map, which is used to
define an ISG service, and enters service policy-map
Example:
Router(config)# policy-map type service
service1
ip vrf forwarding name-of-vrf
configuration mode.
Associates the service with a VRF.
Example:
Router(config-service-policymap)# ip vrf
forwarding blue
5
Page 76

How to Configure ISG Access for PPP Sessions Using Control Policies
Command or Action Purpose
Step 5
sg-service-type primary
Example:
Router(config-service-policymap)#
sg-service-type primary
Step 6
sg-service-group service-group-name
Example:
Router(config-service-policymap)#
sg-service-group group1
Verifying VRF Transfer for PPP Sessions
Perform this task to verify VRF transfer for PPP sessions. All of the show steps are optional and may be
performed in any order.
Configuring ISG Access for PPP Sessions
Defines the service as a primary service.
• A primary service is a service that contains a
network-forwarding policy. A primary service must be
defined as a primary service by using the
sg-service-type primary command. Any service that is
not a primary service is defined as a secondary service
by defau lt .
(Optional) Associates an ISG service with a service group.
• A service group is a grouping of services that may be
active simultaneously for a given session. Typically, a
service group includes one primary s ervice and o ne or
more secondary services.
SUMMARY STEPS
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Example:
Router> enable
Step 2
show subscriber session all
Example:
Router# show subscriber session all
1. enable
2. show subscriber session all
3. show idmgr {service key session-handle session-handle service-key service | session key
{domainip-vrf ip-address ip-address vrf-id vrf-id | ip-address ip-address | mac-address
mac-address | nativeip-vrf ip-address ip-address vrf-id vrf-id | portbundle ip ip-address bundle
bundle-number | session-handle session-handle}}
4. show ip route [vrf vrf-name]
Enables privileged EXEC mode.
• Enter your password if prompted.
Displays information pertaining to the service chosen b y the
subscriber.
6
Page 77

Configuring ISG Access for PPP Sessions
Command or Action Purpose
Step 3
show idmgr {service key session-handle
session-handle service-key service | session
key {domainip-vrf ip-address ip-address vrf-id
vrf-id | ip-address ip-address | mac-address
mac-address | nativeip-vrf ip-address
ip-address vrf-id vrf-id | portbundle ip
ip-address bundle bundle-number |
session-handle session-handle}}
Example:
Router# show idmgr session key ip-address
10.0.0.1
Step 4
show ip route [vrf vrf-name]
Example:
Router# show ip route
How to Configure ISG Access for PPP Sessions Using Control Policies
Displays information related to ISG session and service
identity.
Displays the current state of the routing table.
Troubleshooting ISG Access for PPP Sessions
The commands in this task can be used to monitor and troubleshoot Layer 2 sessions. All of these
commands are optional and do not need to be entered in a particular order.
SUMMARY STEPS
1. enable
2. show subscriber session detailed
3. debug condition
4. debug subscriber packet [event | full | detail]
5. debug subscriber error
6. debug subscriber event
7. debug subscriber fsm
8. debug ppp {packet | negotiation | error | authentication | subscriber switch}
DETAILED STEPS
Command or Action Purpose
Step 1
Step 2
enable
Example:
Router> enable
show subscriber session detailed
Enables privileged EXEC mode.
• Enter your password if prompted.
Displays information about ISG subscriber sessions.
Example:
Router# show subscriber session detailed
7
Page 78

How to Configure ISG Access for PPP Sessions Using Control Policies
Command or Action Purpose
Step 3
debug condition condition
Example:
Router# debug condition username user5@isp.com
Step 4
debug subscriber packet [event | full | detail]
Example:
Router# debug subscriber packet event
Step 5
debug subscriber error
Example:
Router# debug subscriber error
Step 6
debug subscriber event
Configuring ISG Access for PPP Sessions
Filters debug output on the basis of the specified condition.
Note See the module “Troubleshooting ISG with Session
Monitoring and Distributed Conditional
Debugging” for information about conditional
debugging.
Displays diagnostic information about packets during
Subscriber Service Switch (SSS) call setup.
Displays diagnostic information about errors that can occur
during SSS call setup.
Displays diagnostic information about SSS call setup
events.
Step 7
Step 8
Example:
Router# debug subscriber event
debug subscriber fsm
Example:
Router# debug subscriber fsm
debug ppp {packet | negotiation | error |
authentication | subscriber switch}
Example:
Router# debug ppp packet
Displays diagnostic information about the SSS call setup
state.
Displays information on traffic and exchanges in an
internetwork that is imple menting the PP P.
8
Page 79

Configuring ISG Access for PPP Sessions
Example
In the following example, the output of the debug subscriber packet detail command is filtered on the
basis of the username “cpe6_1@isp.com”:
Router# debug condition username cpe6_1@isp.com
Condition 1 set
Router# show debug
Condition 1: username cpe6_1@isp.com (0 flags triggered)
Router# debug subscriber packet detail
SSS packet detail debugging is on
Router# show debug
SSS:
SSS packet detail debugging is on
Condition 1: username cpe6_1@isp.com (0 flags triggered)
Configuration Examples for ISG Access for PPP Sessions
Router#
Configuration Examples for ISG Access for PPP Sessions
This section contains the following examples:
• Configuring ISG Access for PPP Sessions: Example, page 9
• VRF Transfer for PPP Sessions Using IPCP Renegotiation: Example, page 11
Configuring ISG Access for PPP Sessions: Example
The following example shows the configuration of an ISG policy that provides services to PPP
subscribers. This example configures ISG to perform the following actions:
• PPP local termination
ISG will provide local termination by activating the service “ispa” for subscribers matching the
domain “ispa”. The system will authenticate the subscriber using method-list “list1”. For local
termination services, the global VRF is applied by default unless another VRF is specified in the
service profile, on the interface, or in the virtual template.
• PPP authentication before forwarding
ISG will locally authenticate subscribers matching domain “isp b” before forw arding the session s to
an LNS. (Sessions are forwarded to an LNS because service policy map “ispb” specifies a VPDN
group). The system will authenticate the subscribers using method-list “list2”.
• PPP forwarding without local authentication
ISG will forward sessions to an LNS without local authentication for subscribers matching domain
“ispc”.
• PPP domain exclusion
9
Page 80

Configuration Examples for ISG Access for PPP Sessions
ISG will deny service to and disconnect the session for subscribers matching domain “ispd”.
• PPP domain-based service activation
For subscribers matching all other domains, ISG will activate a service that has the same name as
the specified domain.
Configure control class maps, which define the conditions that must be met before a control policy rule
will be executed.
class-map type control match-all PPP_SESSION
match protocol ppp
class-map type control match-all NAS_PORT_CONDITION
class type control match identifier name PPP_SESSION
less-than identifier nas-port type atm vpi 200 vci 100
class-map type control match-all ISPA
match unauthenticated-domain ispa
class-map type control match-all ISPB
match unauthenticated-domain ispb
class-map type control match-all ISPC
match unauthenticated-domain ispc
class-map type control match-all ISPD
match unauthenticated-domain ispd
Define the top-level control policy map.
policy-map type control L2_ACCESS
Configuring ISG Access for PPP Sessions
Define a control policy rule that activates a forwarding service on the basis of the ATM VPI/VCI on
which the call came in.
class type control NAS_PORT_CONDITION event session-start
1 service-policy type service xconnect
Define a control policy rule that collects the domain name from the protocol. The domain name is
available from a structured user name (e.g., user@domain).
class type control PPP_SESSION event session-start
1 collect identifier unauthenticated-domain
2 service-policy type control DOMAIN_BASED_ACCESS
Define the nested control policy.
policy-map type control DOMAIN_BASED_ACCESS
Define a control policy rule that provides local termination by activating the service “ispa”.
class type control ISPA event session-start
1 authenticate aaa list list1
2 service-policy type service ispa
Define a control policy rule that configures the system to authenticate the subscriber locally before
activating service “ispb”. The service “ispb” specifies forwarding the session to an LNS.
class type control ISPB event session-start
1 authenticate aaa list list2
2 service-policy type service ispb
Define a control policy rule that activates service “ispc”, which specifies forwarding.
class type control ISPC event session-start
10
Page 81

Configuring ISG Access for PPP Sessions
1 service-policy type service ispc
Define a control policy rule that results in session disconnection for subscribers that match service
“ispd”.
class type control ISPD event session-start
service disconnect
Define a control policy rule that defines the default for all other domains, which is to activate a service
having the same name as the specified domain.
class type control always event session-start
service-policy type service identifier unauthenticated-domain
Configure the service policy maps.
policy-map type service xconnect
service vpdn group 1
policy-map type service ispa
service local
ip vrf forwarding red
policy-map type service ispb
service vpdn group 2
policy-map type service ispc
service vpdn group 3
Apply the control policy map globally.
service-policy type control L2_ACCESS
Configuration Examples for ISG Access for PPP Sessions
VRF Transfer for PPP Sessions Using IPCP Renegotiation: Example
The following example shows a configuration that uses PPPoE to establish a session, and the RADIUS
service profile that is created to associate the VRF. In this example, when a PPP session initially comes
up, it belongs to the default rout ing table, and the IP address i s assigned from the def ault IP ad dress pool
“DEF-POOL”. When the subscriber selects the “ISP-RED” service, ISG downloads the “ISP- RED”
service profile and applies it to the session. The PPP session is then transferred to VRF “RED”. IPCP
renegotiation occurs between the client d evice and the ISG device, and the subscriber is assigned a new
IP address from the pool “POOL-RED”.
ip vrf RED
rd 1:1
interface Loopback0
ip address 10.0.0.1 255.255.255.0
interface Loopback1
ip address 20.0.0.1 255.255.255.0
ip vrf forwarding RED
!
interface GigabitEthernet0/0/0
pppoe enable
interface Virtual-Template1
ip unnumbered Loopback0
service-policy control RULE2
peer default ip address pool DEF-POOL
ppp authentication chap
11
Page 82

Additional References
ip local pool DEF-POOL 172.16.5.1 172.16.5.250
ip local pool POOL-RED 172.20.5.1 172.20.5.250
Service profile for ISP RED
Cisco-AVpair = ip:vrf-id=RED
Cisco-AVpair = "ip:ip-unnumbered=loopback 1"
Cisco-AVpair = ip:addr-pool=POOL-RED
Cisco-AVpair = subscriber:sg-service-type=primary
Cisco-AVpair = subscriber:sg-service-group=RED-GROUP
Cisco-SSG-Service-Info = IPPPOE-RED
Cisco-SSG-Service-Info = R10.1.1.0;255.255.255.0
Framed-Protocol = PPP
Service-Type = Framed
Additional References
The following sections provide references related to ISG access for PPP sessions.
Configuring ISG Access for PPP Sessions
Related Documents
Related Topic Document Title
ISG commands Cisco IOS Intelligent Services Gateway Command Reference
AAA configuration tasks The “Authentication, Authorization, and Accounting (AAA)”
section in the Cisco IOS XE Security Configuration Guide
AAA commands Cisco IOS Security Command Reference
PPP configuration tasks The “PPP Configuration” section of the Ci sco IOS XE Dial Services
Configuration Guide
PPP commands Cisco IOS Dial Services Command Reference
12
Page 83

Configuring ISG Access for PPP Sessions
Feature Information for ISG Access for PPP Sessions
Technical Assistance
Description Link
The Cisco Support website provides extensive online
resources, including documentation and tools for
troubleshooting and resolving technical issues with
Cisco products and technologies.
To receive security and technical information about
your products, you can subscribe to various services,
such as the Product Alert Tool (accessed from Field
Notices), the Cisco Technical Services Ne wsletter , and
Really Simple Syndication (RSS) Feeds.
Access to most tools on the Cisco Support website
requires a Cisco.com user ID and password.
http://www.cisco.com/public/support/tac/home.shtml
Feature Information for ISG Access for PPP Sessions
Table 1 lists the features in this module and provides links to specific configuration information. For
information about a feature in this technology that is not documented here, see the “Intelligent Services
Gateway Features Roadmap.”
Use Cisco Feature Navigator to find information about platform support and software image support.
Cisco Feature Navigator enables you to determine which Cisco IOS XE software images support a
specific software release, feature set, or platform. To access Cisco Feature Navigator, go to
http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Note Table 1 lists only the Cisco IOS XE s oftware release that introduced support for a given feature in a
given Cisco IOS XE software release train. Unless noted othe rwise, su bsequent releases of that
Cisco IOS XE software release train also support that feature.
Table 1 Feature Information for ISG Layer 2 Access
Feature Name Releases Feature Configuration Information
ISG:Session: Creation: P2P Session (PPPoE,
PPPoXoX)
Cisco IOS XE
Release 2.2
The ISG session is the primary context to which services
and policies are associated across specific data flows.
Point-to-point (P2P) sessions are established through a
signaling protocol. ISG handles many variants of P2P
encapsulation, such as PPP, PPPoE and PPPoA.
The following sections provide information about this
feature:
• Information About Configuring ISG Access for PPP
Sessions, page 2
• How to Configure ISG Access for PPP Sessions
Using Control Policies, page 4
13
Page 84

Feature Information for ISG Access for PPP Sessions
CCDE, CCENT, CiscoEos, Cisco HealthPresence, the Cisco logo, Cisco Lumin, Cisco Nexus, Cisco StadiumVision, Cisco TelePresence,
Cisco WebEx, DCE, and Welcome to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn and Cisco Store are
service marks; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP,
CCVP , Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo,
Cisco Unity, Collaboration Without Limitation, EtherFast, EtherSwitch, Event Center, Fast Step, Follow Me Browsing, FormShare, GigaDrive,
HomeLink, Internet Quotient, IOS, iPhone, iQuick Study, IronPort, the IronPort logo, LightStream, Link sys , Medi aTone, MeetingPlace,
MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, Network Registrar, PCNow, PIX, PowerPanels, ProConnect, ScriptShare,
SenderBase, SMARTnet, Spectru m Expert, St ackWise, The Fastest W ay to Increase Your Internet Quotient, TransPath, W ebEx, and th e WebEx logo
are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0812R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and
figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and
coincidental.
© 2006–2009 Cisco Systems, Inc. All rights reserved.
Configuring ISG Access for PPP Sessions
14
Page 85

Configuring ISG Access for IP Subscriber
Sessions
First Published: December 5, 2006
Last Updated: November 25, 2009
Intelligent Services Gateway (ISG) is a Cisco IOS XE software feature set that provides a structured
framework in which edge de v ices can deli v er fle xible and scalable services to subscribers. ISG supports
IP sessions for subscribers who connect to ISG from routed, Layer 2 or Layer 3 access networks. This
module describes how to configure ISG to bring up IP subscriber sessions, manage subscriber IP
addressing, and configure dynamic Virtual Private Network (VPN) selection.
Note This document assumes that Network Address Translation is pe rformed on a Layer 3 g ate way other than
the ISG.
Finding Feature Information
For the latest feature information and caveats, see the release notes for your platform and software
release. To find information about the features documented in this module, and to see a list of the releases in
which each feature is supported, see the “Feature Information for ISG Access for IP Subscriber Sessions”
section on page 40.
Use Cisco Feature Navigator to find information about platform support and Cisco IOS XE software
image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on
Cisco.com is not required.
Contents
• Prerequisites for ISG Access for IP Subscriber Sessions, page 2
• Restrictions for ISG Access for IP Subscriber Sessions, page 2
• Information About ISG Access for IP Subscriber Sessions, page 3
• How to Configure ISG for IP Subscriber Sessions, page 13
Americas Headquarters:
Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA
© 2009 Cisco Systems, Inc. All rights reserved.
Page 86

Configuring ISG Access for IP Subscriber Sessions
Prerequisites for ISG Access for IP Subscriber Sessions
• Configuration Examples for ISG Access for IP Subscriber Sessions, page 34
• Additional References, page 38
• Feature Information for ISG Access for IP Subscriber Sessions, page 40
Prerequisites for ISG Access for IP Subscriber Sessions
For information about release and platfor m requiremen ts, s ee the “Feature Information for ISG Access for
IP Subscriber Sessions” section on page 40.
• Dynamic Host Configuration Protocol (DHCP) server must support the DHCP lease protocol.
Restrictions for ISG Access for IP Subscriber Sessions
Overlapping IP Address Restrictions
Overlapping IP addresses in the same virtual routing and forwarding (VRF) instance are not supported.
Overlapping IP subscribers in different VRFs are not supported on the same interface for static IP
subscriber sessions and routed IP subscriber sessions. Overlappin g IP subscrib er s in different VRFs are
supported on the same interface for Layer 2 connecte d Dynamic H ost Configuration Proto col (DHCP)
subscriber sessions.
IP Subnet Session Restrictions
IP subnet sessions are not supported on an interface configured with the ip subscriber l2-connected
command. IP subnet sessions are supported only when the ip subscriber routed command is conf igured
on the interface.
ISG DHCP Restrictions
ISG cannot relay DHCP requests when a Layer 3 DHCP relay agent is between the ISG device and
subscriber devices.
Dynamic VPN Selection Restrictions
Dynamic VPN selection is not supported for IP subnet sessions and subscribers coming in on nonglob al
VRF interfaces.
Dynamic VPN selection is not supported for subscribers with a static VPN configuration on the access
interface.
Dynamic VPN selection with address reassignment is not supported for routed IP subscriber sessions
that are initiated by DHCP . IP addresses of routed IP subscribers must be routable in the access network.
Because Internet service provider (ISP) or VRF-owned priv ate addresses could o verlap or be unroutabl e
in the network between subscribers and the ISG device, it is not possible to assi gn IP addresses to tho se
subscribers.
General IP Session Restrictions
Packet of Disconnect (PoD) is not supported for IP subscriber sessions.
IP subscriber sessions are not supported on ambiguous IEEE 802.1QinQ (QinQ) or IEEE 802.1Q
(Dot1Q) subinterfaces.
2
Page 87

Configuring ISG Access for IP Subscriber Sessions
IP subscriber sessions are not supported on interfaces that receive multiprotocol label swit ching (MPLS)
packets.
Modular quality of service (QoS) command-line interface (CLI) based (MQC) shaping and queueing is
supported in the egress direction in the default class for IP subscriber sessions.
ISG IP subscriber functionality is not supported on the following types of access interfaces:
• Gigabit EtherChannel (Port Channel)
• Generic routing encapsulation (GRE)
• PPP (virtual-template)
• Layer 2 Tunnel Protocol (L2TP)
ISG IP interface sessions are not supported.
Interface statistics are not generated for ISG multiservice interfaces.
Stateful switchover (SSO) and In Service Software Upgrade (ISSU) are not supported for ISG IP
subscriber sessions or traffic class sessions. Upon switchover, an IP session must be re-created or
restarted (for DHCP sessions) when the session becomes active again.
SSO and ISSU are not supported for any features on IP subscriber sessions or traffic class sessions.
Information About ISG Access for IP Subscriber Sessions
Information About ISG Access for IP Subscriber Sessions
Before you configure ISG access for subscriber sessions, you should understand the following concepts:
• Types of IP Subscriber Sessions, page 3
• IP Subscriber Connectivity, page 5
• IP Subscriber Session Initiation, page 6
• IP Subscriber Addressing, page 6
• IP Subscriber Identity, page 8
• VPN Connectivity and Services for IP Subscribers, page 10
• IP Session Termination, page 12
• IP Session Recovery for DHCP-Initiated IP Sessions, page 13
• Default Services for IP Subscriber Sessions, page 13
Types of IP Subscriber Sessions
ISG supports the following types of IP subscriber sessions on Cisco IOS XE software:
• IP Sessions, page 4
• IP Interface Sessions, page 4
• IP Subnet Sessions, page 4
3
Page 88

Information About ISG Access for IP Subscriber Sessions
IP Sessions
An IP session includes all the traffic that is associated with a single subscriber IP address. If the IP
address is not unique to the system, other distinguishing characteristics such as a VRF or MAC address
form part of the identity of the session. ISG can be configured to create IP sessions upon receipt of DHCP
packets, packets with unclassified IP or MAC addresses, or RADIUS packets. See the “IP Subscriber
Session Initiation” section on page 6 for more information.
IP sessions may be hosted for a connected subscriber de vice (one routing hop from the ISG) or one that
is more than one hop from the gateway.
IP Interface Sessions
An IP interface session includes all IP traffic received on a specific physical or virtual interface. IP
interface sessions are provisioned through the CLI; that is, a session is created when the IP interface
session commands are entered, and the session is continuous, even when the interface is shut down. By
default, IP interface sessions come up in the state “unauthenticated” with full network access.
IP interface sessions might be used in situations in which a subscriber i s represented by an interface (with
the exception of PPP) and communicates using more than one IP address. For example, a subscriber
using routed bridge encapsulation (RBE) access might have a dedicated ATM virtual circuit (VC) to
home customer premises equipment (CPE) that is hosting a number of PCs.
Configuring ISG Access for IP Subscriber Sessions
IP Subnet Sessions
An IP subnet session represents all the traff ic that is associated with a single IP subnet. IP subnet sessions
are used to apply uniform edge processing to packets associated with a particular IP subnet. When an IP
subnet session is configured, ISG treats the subnet as a single subscriber, which means that ISG features
and functionality are applied to the subnet traffic as an aggregate.
IP subnet sessions are supported for routed IP subscriber traffic.
IP subnet sessions are created the same way as IP sessions, except that when a subscriber is authorized
or authenticated and the Framed-IP-Netmask attribute is present in the user or service profile, ISG
converts the source-IP-based session into a subnet session with the subnet value in the
Framed-IP-Netmask attribute.
Note Where an ingress interface ma ps to a single subnet, the subnet might be accommoda ted with an IP
interface session. However, if the ISG is more than one hop away from a subscriber, and there is the
possibility that multiple subnets are accessible through the same interface, IP subnet sessions may be
defined to distinguish the traffic and apply appropriate edge functionality to each subnet.
Coexistence of Multicast and IP sessions
The ISG Session Multicast Coexistence feature introduces the ability to host all the subscribers and
services (data and multicast) on the same VLAN by enabling multicast and IP sessions to coe xist on th e
same subinterface for Cisco ASR 10000 Series Aggregation Routers. ISG IP sessions are supported on
nonaccess-type subinterfaces. In the case of an existing session or even when no session exists, this
support helps the multicast traffic to pass through the interfaces configured for the IP sessions in both
upstream and downstream directions without creating a session.
4
Page 89

Configuring ISG Access for IP Subscriber Sessions
IP Subscriber Connectivity
IP subscribers connect to ISG through either Layer 2 connected access networks or routed access
networks. The following sections describe these types of IP subscriber connectivity:
• Layer 2 Connected Access Networks
• Routed Access Networks
Layer 2 Connected Access Networks
Layer 2 connected subscribers are either directly attached to the physical interfaces of an ISG or
connected to an ISG through a Layer 2 access network, such as a bridged or a switched netw ork. Layer 3
forwarding is either absent or not used to direct subscriber traffic in the Layer 2 access network. IP
addresses of the subscribers may or may not be on the same subnet as the Layer 2 connected physi cal
interfaces. Figure 1 shows an example of a Layer 2 connected access network.
Figure 1 Layer 2 Connected Access Network
Information About ISG Access for IP Subscriber Sessions
IP subscriber
IP subscriber
Routed Access Networks
Routed subscriber traffic is routed through a Layer 3 access network with at least one transit router
before reaching the ISG. IP addresses of the subscribers are at least routable in the Layer 3 access
network. Layer 3 access networks contain a single routing domain and therefore do not support
overlapping IP addresses. Figure 2 shows an example of a routed access network.
Bridged/switched
access network
Core network
ISG
230024
5
Page 90

Information About ISG Access for IP Subscriber Sessions
Figure 2 Routed Access Network
Configuring ISG Access for IP Subscriber Sessions
access network
IP subscriber
IP subscriber
IP Subscriber Session Initiation
ISG can be configured to allow one or more of the following events to signal the start of an IP session
or IP subnet session on an interface:
• DHCP DISCOVER packet
If the following conditions are met, receipt of a DHCP DISCOVER packet will trigger the creation
of an IP session:
–
The ISG serves as a DHCP relay or server for new IP address assignments.
–
Subscribers are configured for DHCP.
–
The DHCP DISCOVER packet is the first DHCP request received from the subscriber.
• Unclassified source IP address
Routed
Core network
ISG
230025
For routed IP subscribers, a new IP session is triggered by the appearance of an IP packet with an
unclassified source IP address (which means that an IP session does not yet e xist for that IP addr ess).
• Unclassified source MAC address
For Layer 2 connected IP subscribers, a new I P session is triggered by the appearance of an IP packet
with an unclassified source MAC address (which means that an IP session does not yet e xist for that
MAC address).
• RADIUS Access-Request packet
For routed or Layer 2 connected access, a new IP session is triggered by the appearance of a
RADIUS Access-Request packet when ISG is serving as a RADIUS proxy.
IP Subscriber Addressing
The following sections provide information about how ISG handles IP addressing for IP subscribers:
• Methods of ISG Subscriber IP Address Assignment
• Public and Private IP Addresses
• Overlapping IP Addresses
• ISG Subscriber IP Address Assignment Using DHCP
6
Page 91

Configuring ISG Access for IP Subscriber Sessions
Methods of ISG Subscriber IP Address Assignment
IP subscribers either have IP addresses configured statically or obtain IP addresses dynamically throug h
some network protocol that has the ability to assign IP addresses. For a subscriber to be routable within
a given IP service domain, the subscriber must pr esent a domain-specif ic IP address to the network. If a
subscriber transfers between IP service domains (which include any private domain managed by the
access provider), the IP address presented to the network must change to reflect th e new domain.
The following sections describe the methods of IP address assignment that ISG supports for each type
of Layer 3 session:
• IP Interface Sessions
• IP Sessions
• IP Subnet Sessions
IP Interface Sessions
For IP interface sessions, ISG is not inv olv ed in (or aw are of) the assignment of subscriber IP addresses.
IP Sessions
Information About ISG Access for IP Subscriber Sessions
IP Subnet Sessions
For IP sessions, ISG supports the following methods of IP address assignment:
• Static IP addresses
If a subscriber’s static IP address is configured correctly for the service domain, ISG does not have
to be involved in the assignment of an IP address for the subscriber.
• DHCP
If DHCP is being used to assign IP addresses, and the IP address that is assigned by DHCP is correct
for the service domain, ISG does not have to be involved in the assignment of an IP address for the
subscriber.
If the IP address that is assigned by DHCP is not correct for the service domain, or if the domain
changes because of a VRF transfer, ISG can be configured to influence the DHCP IP address
assignment.
The following conditions must be met in order for ISG to influence DHCP IP address assignment:
–
The subscriber must be Layer 2 connected.
–
The ISG device must be in the path of DHCP requests by serving as a DHCP server or relay.
–
Subscribers must not have statically configured IP addresses.
For deployments that support it, DHCP is the recommended method of IP address assignment.
For IP subnet sessions, the IP subnet is specified in the user profile.
Public and Private IP Addresses
No matter how an IP subscriber is assigned an IP address, the IP address falls in either the public or the
private IP address category. If an IP subs criber is assigned with a private IP address and the subscriber
has to reach the Internet, a Layer 3 gateway, such as ISG or a firewall, between the subscriber and the
Internet must perform network address translation (NAT) for the subscriber’s private IP address.
7
Page 92

Information About ISG Access for IP Subscriber Sessions
When the access network is a Layer 2 connected network, a subscriber IP address can be either native or
foreign to an access interface. A native subscriber IP address is one that belongs to the subnet
provisioned on the access interface. A foreign subscriber IP address is one that does not belong to the
subnet provisioned on the access interface. A foreign subscriber IP address could result when a retail
ISP assigns an IP address to the IP subscriber from its own IP address allotment, which is different from
the wholesale ISPs, or when an IP subscriber with a static IP address that is native in the home access
network roams to a foreign access network. To support IP subscribers with foreign IP addresses, ISG
must be able to respond to Address Resolution Protocol (ARP) requests that originate from foreign IP
addresses with a MAC address of the ISG itself. Because the access network is Layer 2 connecte d, ISG
maintains an adjacency to every subscriber.
When the access network is a routed network, a subscriber IP address must be routable in the access
network; otherwise, subscriber traffic will never be able to reach ISG. ISG may not have an adjacency
for each subscriber in this case, but rather an adjacency of the next hop toward a subscriber. The next
hop is determined by the routing process on ISG.
Overlapping IP Addresses
When an access network is deployed without VPN capability, the IP address space in the access network
is shared among all IP subscribers. When the IP addresses are assigned dynamically, care must be taken
to ensure that these addresses do not overlap. In cases where overlapping IP addresses are assigned to IP
subscribers intentionally , th e access network should use a Laye r 2 separation mechanism to dif feren tiate
the IP address spaces. For example, the access network may put each IP address space in a different
VLAN.
In cases in which the access network serves both local IP subscribers and roaming users, the static pri vate
IP address of a roaming subscriber may overlap the native private IP address of another subscriber. For
example, a public wireless hot spot that generally assigns dynamic IP addresses might want to provide
access to occasional roaming users with statically configured IP addresses. To support this special
overlapping condition, all IP subscribers must be in a Layer 2 connected access network in which
overlapping MAC addresses do not exist. In this case, IP subscribers can be distinguished using MAC
addresses.
Configuring ISG Access for IP Subscriber Sessions
ISG Subscriber IP Address Assignment Using DHCP
When ISG is in the path of DHCP requests (as either a DHCP server or a DHCP relay), ISG can influence
the IP address pool and DHCP server that are used to assign subscriber IP addresses. To enable ISG to
influence the IP addresses assigned to subscri bers, a ssoci ate a DHCP a ddress pool class with an address
domain. The DHCP address pool class must also be configured in a service policy map, service profile,
or user profile that is associated with a subscriber. Whe n a DHCP request is received from a subscriber,
DHCP uses the address pool class that is associated with the subscriber to determine which DHCP
address pool should be used to service the request. As a result, on a per-request basis, an IP address is
provided by the local DHCP server or relayed to a remote DHCP server that is defined in the selected
pool.
IP Subscriber Identity
IP subscriber identity is closely related to IP session initiat ion because ISG must uniquely iden tify an IP
subscriber at the moment that it creates the IP session. However, the need to identify an IP subscriber
goes beyond the session initiation phase. The following sections describe how ISG uniquely identifies
IP subscribers:
8
Page 93

Configuring ISG Access for IP Subscriber Sessions
• Routed IP Subscriber Identity
• MAC Address as Secondary Identity
• DHCP Lease Query Support
• Layer 2 Connected IP Subscriber Identity
Routed IP Subscriber Identity
If the access network is a routed network, subscriber IP addresses can be used to uniquely identify IP
subscribers because by definition subscriber IP addresses are at least routable in the access network.
When using a subscriber IP address as the identifier, ISG assumes that the subscriber IP address is
unique. If the access network is deployed with Layer 3 load balancing, redundancy, or asymmetric
routing, ISG also assumes that IP tr affic from the same IP subscriber may arrive at different access
interfaces. To support this type of deployment, ISG assumes a single IP address space for all the access
interfaces connecting to the same access network.
If there is a requirement to support several IP address spaces over a single physical access network, the
access network must use some Layer 2 encapsulation to create a separate logical access network for each
IP address space. In this case, ISG can still have a single IP address space for all the logical access
interfaces that connect to a logical access network.
When subscriber IP addresses are private IP addresses, the access network must be able to route such
subscriber traffic. If the subscriber traffic is destined to the Internet, NAT must be performed.
Information About ISG Access for IP Subscriber Sessions
For routed IP subscribers, the subscriber IP address serves as the key for an IP session. ISG associates
IP traffic with an IP session as follows:
• In the upstream direction, the source IP address of an IP packet is used to identify the IP session.
The source IP address is the subscriber IP address.
• In the downstream direction, the destination IP address of an IP packet is used to identify the IP
session. The destination IP address is the subs criber IP address.
If the IP subscriber is a VPN user, the subscriber IP address must be routable in both the global routing
table and the VPN routing table on the ISG.
In the case of an IP subnet subscriber, a subscriber IP address is defined as an IP prefix address instead
of a /32 IP host address. This IP prefix covers a range of IP addresses used by end users but represents
a single logical IP subscriber from the ISG point of view . In th is deployment, all end users share the same
connectivity and services provided by the ISG.
T o normalize the classificati on of IP subscribers that have dif ferent network masks, ISG uses the netw ork
mask in conjunction with the subscriber IP address for routed IP subscribers.
MAC Address as Secondary Identity
You must configure the collect identif i er mac-addr ess command at the start of a session. This instructs
the ISG devices to store the MAC address as part of the session identifiers. For routed IP subscriber
sessions, the MAC address is collected from the DHCP server using the DHCP Lease Query Protocol.
For information about conf iguri ng the com mand, see the “Con fig uring ISG Control Poli cies” module in
the Cisco IOS ISG Configuration Guide.
9
Page 94

Information About ISG Access for IP Subscriber Sessions
DHCP Lease Query Support
The DHCP Lease Query message is a DHCP message type transmitted from a DHCP relay agent to a
DHCP server. A DHCP Lease Query aware relay agent sends the location of an IP endpoint to the DHCP
Lease Query message.
The DHCP Lease Query transaction is a DHCP transaction with special message types that enable clients
to query DHCP servers regarding the owner and the lease expiration time of an IP address. For
information about configuring DHCP server for Lease Query, see the “Configuring a DHCP Server IP
Address” section on page 28.
Layer 2 Connected IP Subscriber Identity
A Layer 2 connected access network is capabl e of providing IP connectivity to IP subscrib ers with
foreign and overlapping IP addresses, in addition to IP subscribers with native IP addresses. Because
subscriber IP addresses might not be unique in such an access network, ISG uses the subscriber MAC
address to identify Layer 2 connected IP subscribers, regardless of what kind of IP address a subscriber
has.
Traffic that comes from IP subscribers with private or overlapping IP addresses and that is destined to
the Internet is subject to NAT.
Configuring ISG Access for IP Subscriber Sessions
For Layer 2 connected IP subscribers, both the subscriber MAC address (unique within a VLAN) and
the IP address serve as the keys for the IP session, but they are used in different directions:
• In the upstream direction, the VLAN ID and source MA C address of an IP packet are used to identify
the IP session.
• In the downstream direction, both the destination IP address and the VLAN ID of an IP packet are
used to identify the IP subscriber context.
VPN Connectivity and Services for IP Subscribers
The following sections provide informatio n about VPN connectivity and services for ISG IP subscribers:
• Subscriber VPN Membership
• VPN Addressing
• VPN IP Subscriber Identity
• Service Model for VRF Transfers
• Benefits of Dynamic VPN Selection
Subscriber VPN Membership
Depending on deployment requirements, an IP subscriber may or may not have VPN service. If an IP
subscriber does have VPN service, the subscriber may belong to only one VPN domain at any time. An
IP subscriber is associated with a VPN domain in one of the following ways:
• Static VPN assignment—The VPN IP subscriber belongs to a static VPN domain. Whenever the IP
subscriber connects to ISG, the IP subscriber is placed in the preassigned VPN domain.
• Dynamic VPN selection—The VPN IP subscriber can choose and switch among different VPN
domains through dynamic service logon. Whenever a new VPN domain is selected, VPN services
of the current VPN domain must be removed before VPN services of the new VPN domain can be
applied to the IP subscriber.
10
Page 95

Configuring ISG Access for IP Subscriber Sessions
Dynamic VPN selection can be initiated through automatic service logon, where the VRF is
downloaded and applied to the subscriber session at session start, or through subscriber service
selection at a web portal, in which case the subscriber is transferred to the VRF that corresponds to
the selected service.
VPN Addressing
When a subscriber session is transferred from one VPN domain to another, it is effectively entering a
new addressing domain that may or may not overlap the subscriber’s previous domain. The subscriber’s
network-facing address must be altered accordin gly so that packets can be corre ctly routed back from
within the service domain.
A VRF transfer is necessary when a subscriber’s identity and subscribed services cannot be determined
without interaction with a web portal. A local routing context is required, at least initially, so that IP
packets may be routed to and from the portal server. Following portal-based service selection, the
subscriber would typically have to be transferred into the VRF associated with the selected service
domain. Following a VRF transfer, the subscriber must also receive an address that is routable in this
new domain.
If ISG is adjacent to the subscriber device and serves as a DHCP relay or server, DHCP can be used to
assign domain-specific addresses to subscribers.
In order for VRF transfers to be supported, it is strongly recommended that DHCP be configured with
short initial leases, this is because existing subscriber addresses can only be altered once the current
lease has expired. Subscribers will not have access to the selected domain before the next DHCP renew
request is received. Using short initial lease times minimizes the interval between a VRF change and a
DHCP renewal. If long lease times are used, an out-of-band method of initiating IP address change
should be implemented.
Information About ISG Access for IP Subscriber Sessions
When DHCP can be used to assign a new address at the subscriber device, subnet-based VRF selection
can be used to bring about the transfer. Subnet-based VRF selection (also known as VRF autoclassify)
is a feature that selects the VRF at the ingress port on the basis of the source IP subnet address.
Service providers and orga nizations have allocated pub lic IP address blocks that are not overlapping by
nature. Therefore, when they are assigned public IP addresses, VPN IP subscribers have no overlapping
IP addresses. When VPN IP subscribers of different VPN domains have private IP addresses assigned,
they are likely to have overlapping addresses in the access network.
An access network is a single IP address space when there is no Layer 2 encapsulatio n separ a ting VP N
IP subscribers of different VPN domains. Therefore, ISG must be able to handle overlapping IP
addresses when deploying VPN IP subscribers. IP connectivi ty for VPN IP subscribers with ov erlapping
IP addresses is possible only when they are connected to ISG through a Layer 2 connected access
network.
VPN IP Subscriber Identity
ISG identifies VPN IP subscribers in the same way that it identifies non-VPN IP subscribers. Upstream
IP traffic is defined as the subscriber IP traffic traveling from the access network to the VPN (overlaid
on top of the service provider core network). Downstream IP traffic is defined as the subscriber IP traffic
traveling from the VPN to the access network.
11
Page 96

Information About ISG Access for IP Subscriber Sessions
Service Model for VRF Transfers
A primary service is a service that contains a network-forwarding policy (such as a VRF) in its service
definition. Only one primary service at a time can be activated for a session. A secondary service is any
service that does not contain a network-forwarding policy.
When a subscriber for whom a primary service has already been activated tries to select another primary
service, ISG will deactivate all current services (including the current primary service) and activate the
new primary service, and hence switch the VRF.
When a subscriber for whom a primary service has already been activated tries to select a secondary
service, the action taken by ISG depends on whether the secondary service is part of a service group. A
service group is a grouping of services that may be simulta neously active for a given session. Typically,
a service group includes one primary service and one or more secondary services. Table 1 describes the
action that ISG will take when a subscriber selects a secondary service.
Table 1 ISG Activation Policy for Secondary Services
Primary Service Characteristics Secondary Service Characteristics Resulting Behavior at ISG
Primary service with no service
group attribute
Primary service with service
group attribute
Configuring ISG Access for IP Subscriber Sessions
Secondary service with service
group
Secondary service with no service
group
Secondary service with different
service group
Secondary service with same
service group
Secondary service with no service
group
Do not bring up the secondary
service.
Bring up the secondary
service.
Do not bring up the secondary
service.
Bring up the secondary
service.
Bring up the secondary
service.
Benefits of Dynamic VPN Selection
The need for switching of a subscriber session be tween rout ing and forwarding domains (al so called
network services) occurs frequently in markets where so-called equal access networking must be
supported. Equal access networking is often mandated by regulatory rules stating that an access provider
should allow service providers equal access to a retail subscriber network. ISG dynamic VPN selection
facilitates equal access networking by allowing subscribers to transfer between network services.
IP Session Termination
An IP session may be terminated in one of the following ways:
• DHCP Lease Expiry or DHCP Release from client
If DHCP is used to detect a new session, its departure may also be signaled by a DHCP event.
• Application stop
An application command that is used to terminate a session. The application stop command is
typically used to terminate a session when a subscriber initiates an account logoff from a web portal.
An application stop may also result from the actions of an administrator, such as action taken in
response to rogue behavior from a subscriber.
12
Page 97

Configuring ISG Access for IP Subscriber Sessions
• Idle timeout and session timeout
Idle timeouts and session timeouts can be used to detect or impose termination of an IP session.
• Control policy
A control policy containing the “service disconnect” action can be used to terminate a session.
IP Session Recovery for DHCP-Initiated IP Sessions
When an IP session is terminated (for example, by account logoff or session timeout) or lost (for
example, by router reload), the client may continue to hold an unexpired DHCP lease. When this
happens, ISG performs a session restart to prevent the client’s IP connection from being stuck until the
DHCP lease expires. A control policy can be configured to define the actions that ISG will take when
the session restart event occurs. If a policy is not defined, a default policy will take effect. The default
policy causes ISG to disconnect the session after 60 seconds following a session restart and is the
equivalent of the following configuration:
policy-map type control GLOBAL
class type control always event session-restart
1 service disconnect delay 60
How to Configure ISG for IP Subscriber Sessions
This default policy appears in the output for the show subscriber policy rules command as follows:
Rule: internal-rule-session-restart
Class-map: always event session-restart
Action: 1 service disconnect delay 60
Executed: 0
Default Services for IP Subscriber Sessions
Newly created IP sessions may require a default service to allow subsequent subscriber packets to be
processed appropriately; for example, to permit or force TCP packets to a captive portal where
menu-driven authentication and service selection can be performed. A default service policy map or
service profile may be configured for IP sessions to redirect traffic, enable port-bundle host-key
functionality for session identification, or enable transparent autologon. A default service would also
likely include a network service, which allows subscribers to access a web portal for authentication and
service selection.
How to Configure ISG for IP Subscriber Sessions
Perform the following tasks to configure ISG Layer 3 access:
• Creating ISG Sessions for IP Subscribers, page 13 (required)
• Assigning ISG Subscriber IP Addresses Using DHCP, page 24 (required)
• Configuring ISG Dynamic VPN Selection, page 29 (required)
Creating ISG Sessions for IP Subscribers
An ISG device creates IP sessions for IP traffic on subscriber -side interfaces. The following tasks enable
IP sessions and indicate how sessions will be identified:
13
Page 98

How to Configure ISG for IP Subscriber Sessions
• Creating IP Subscriber Sessions for Routed ISG Subscrib ers, page 14 (required)
• Creating IP Subscriber Sessions for Layer 2 Connected ISG Subscribers, page 15 (required)
• Creating ISG IP Interface Sessions, page 17 (required)
• Creating an ISG Static Session, page 18 (required)
• Creating ISG IP Subnet Sessions, page 19 (required)
• Configuring IP Session Recovery for DHCP-Initiated IP Sessions, page 20 (required)
• Verifying ISG IP Subscriber Sessions, page 22 (optional)
• Clearing ISG IP Subscriber Sessions, page 23 (optional)
• Troubleshooting Tips, page 24 (optional)
Creating IP Subscriber Sessions for Routed ISG Subscribers
Routed IP subscribers are subscribers that are routed through a Layer 3 access network with at least one
transit router before reaching the ISG. Perform this task to conf igure ISG to create IP sessions for routed
IP subscribers.
Configuring ISG Access for IP Subscriber Sessions
SUMMARY STEPS
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Example:
Router> enable
Step 2
configure terminal
Example:
Router# configure terminal
Step 3
interface type number
1. enable
2. configure terminal
3. interface type number
4. ip subscriber routed
5. initiator {dhcp [class-aware] | radius-proxy | unclassified ip-address}
6. end
Enables privileged EXEC mode.
• Enter your password if prompted.
Enters global configuration mode.
Specifies an interface and enters interface configuration
mode.
Example:
Router(config)# interface gigabitethernet 0/0/0
Step 4
ip subscriber routed
Example:
Router(config-if)# ip subscriber routed
14
Specifies the type of IP subscriber to be hosted on the
interface, and enters ISG IP subscriber configuration mode.
Page 99

Configuring ISG Access for IP Subscriber Sessions
Command or Action Purpose
Step 5
initiator {dhcp [class-aware] | radius-proxy |
unclassified ip-address}
Example:
Router(config-subscriber)# initiator dhcp
Step 6
end
How to Configure ISG for IP Subscriber Sessions
Configures ISG to create an IP subscriber session upon
receipt of the specified packet type.
• dhcp—ISG will initiate an IP session upon receipt of a
DHCP DISCOVER packet. The class-aware keyword
allows ISG to influence the IP address assigned by
DHCP by providing DHCP with a class name.
• radius-proxy—ISG will initiate an IP session upon
receipt of a RADIUS Access-Request packet.
• unclassified ip-address—ISG will initiate an IP
session upon receipt of the first IP packet with an
unclassified IP source address.
• This command can be entered more than once to
specify more than one method of IP session initiation.
Note If the ISG device serves as either a DHCP relay or
DHCP server in the assignment of client IP
addresses, ISG must be configured to initiate IP
sessions upon receipt of DHCP DISCOVER
packets. In other words, the initiator dhcp
command must be configured instead of the
initiator unclassified ip or initiator unclassified
mac command.
(Optional) Returns to privileged EXEC mode.
Example:
Router(config-subscriber)# end
Creating IP Subscriber Sessions for Layer 2 Connected ISG Subscribers
Layer 2 connected subscribers are either directly attached to the physical interfaces of an ISG or
connected to an ISG through a Layer 2 access network, such as a bridged network or a switched network.
Perform this task to configure ISG to create IP sessions for Layer 2 connected IP subscribers.
SUMMARY STEPS
1. enable
2. configure terminal
3. interface type number
4. ip subscriber l2-connected
5. initiator {dhcp [class-aware] | radius-proxy | unclassified mac-address}
6. end
15
Page 100

How to Configure ISG for IP Subscriber Sessions
DETAILED STEPS
Command or Action Purpose
Step 1
enable
Example:
Router> enable
Step 2
configure terminal
Example:
Router# configure terminal
Step 3
interface type number
Example:
Router(config)# interface gigabitethernet 0/0/0
Step 4
ip subscriber l2-connected
Example:
Router(config-if)# ip subscriber l2-connected
Step 5
initiator {dhcp [class-aware] | radius-proxy |
unclassified mac-address}
Example:
Router(config-subscriber)# initiator
unclassified mac-address
Configuring ISG Access for IP Subscriber Sessions
Enables privileged EXEC mode.
• Enter your password if prompted.
Enters global configuration mode.
Specifies an interface and enters interface configuration
mode.
Specifies the type of IP subscriber to be hosted on the
interface, and enters ISG IP subscriber configuration mode.
Note It is recommended that IP sessions for Layer 2
connected subscribers be configured using the ip
subscriber l2-connected command. However, the
ip subscriber routed command could also be used
if subscriber IP addresses are routable in the access
domain.
Configures ISG to create an IP subscriber session upon
receipt of the specified packet type.
• dhcp—ISG initiates an IP session upon receipt of a
DHCP DISCOVER packet. The class-aware keyword
allows ISG to influence the IP address assigned by
DHCP by providing DHCP with a class name.
16
• radius-proxy—ISG initiates an IP session upon recei pt
of a RADIUS packet.
• unclassified mac-address—ISG will initiate an IP
session upon receipt of the first IP packet with an
unclassified MAC source address.
• This command can be entered more than once to
specify more than one method of IP session initiation.
Note If the ISG device serves as either a DHCP relay or
DHCP server in the assignment of client IP
addresses, ISG must be configured to initiate IP
sessions upon receipt of DHCP DISCOVER
packets. In other words, the initiator dhcp
command must be configured instead of the
initiator unclassified ip or initiator unclassified
mac command.
 Loading...
Loading...