Page 1

Flex 7500 Wireless Branch Controller
Deployment Guide
Last Updated: August, 2016
Introduction
This document describes how to deploy a Cisco Flex 7500 wireless branch controller. The purpose of
this document is to:
• Explain various network elements of the Cisco FlexConnect solution, along with their
• Provide general deployment guidelines for designing the Cisco FlexConnect wireless branch
Note Prior to release 7.2, FlexConnect was called Hybrid REAP (HREAP). Now it is called
Prerequisites
Requirements
There are no specific requirements for this document.
communication flow.
solution.
FlexConnect.
Components Used
This document is not restricted to specific software and hardware versions.
Cisco Systems, Inc.
www.cisco.com
Page 2

Product Overview
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Product Overview
Figure 1 Cisco Flex 7500
The Cisco Flex 7500 Series Cloud Controller is a highly scalable branch controller for multi-site
wireless deployments. Deployed in the private cloud, the Cisco Flex 7500 series controller extends
wireless services to distributed branch offices with centralized control that lowers total cost of
operations.
The Cisco Flex 7500 series (Figure 1) can manage wireless access points in up to 2000 branch locations
and allows IT managers to configure, manage, and troubleshoot up to 6000 access points (APs) and
64,000 clients from the data center. The Cisco Flex 7500 series controller supports secure guest access,
rogue detection for Payment Card Industry (PCI) compliance, and in-branch (locally switched) Wi-Fi
voice and video.
The following table highlights the scalability differences between the Flex 7500, 8500, WiSM2 and
WLC 5500 controller:
Scalability Flex 7500/8500 WiSM2 WLC 5500
Total Access Points 6,000 1000 500
Total Clients 64,000 15,000 7,000
Max FlexConnect
Groups
Max APs per
FlexConnect Group
Max AP Groups 6000 1000 500
Note Flex 7500 only operates in FlexConnect mode. Additional modes are supported in WiSM2, 5500,
and 8500 series controllers.
Note DTLS license is required for Office Extend AP support.
Flex 7500 Wireless Branch Controller Deployment Guide
2
2000 100 100
100 25 25
Page 3

Product Specifications
Data Sheet
Refer to Cisco Flex 7500 Series Cloud Controller Data Sheet:
http://www.cisco.com/en/US/prod/collateral/wireless/ps6302/ps8322/
ps11635/data_sheet_c78-650053.html
Platform Feature
Figure 2 Flex 7500 Rear View
Product Specifications
Network Interface Ports
Interface Ports Usage
Fast Ethernet Integrated Management Module (IMM)
Port 1: 1G WLC Service Port
Port 2: 1G WLC Redundant Port (RP)
Port 1: 10G WLC Management Interface
Port 2: 10G WLC Backup Management Interface Port (Port
Note • LAG support for 2x10G interfaces allows active-active link operation with fast failover link
redundancy. An additional active 10G link with LAG does not change the controller wireless
throughput.
• 2x10G interfaces.
• 2x10G interfaces support optic cable with SFP product # SFP-10G-SR and SFP-10G-LR.
• Switch side SFP or X2 product should be of the same type SR or LR.
Failure)
Flex 7500 Wireless Branch Controller Deployment Guide
3
Page 4

Flex 7500 Boot Up
System MAC Addresses
Port 1: 10G (Management Interface) System/Base MAC address
Port 2: 10G (Backup Management
Interface)
Port 1: 1G (Service Port) Base MAC address+1
Port 2: 1G (Redundant Port) Base MAC address+3
Serial Console Redirect
The WLC 7500 enables console redirect by default at the baud rate of 9600, simulating Vt100 terminal
with no flow control.
Inventory Information
The following is the WLC 7500 Console:
Base MAC address+5
(Cisco Controller) >show inventory
Burned-in MAC Address............................ E4:1F:13:65:DB:6C
Maximum number of APs supported.................. 2000
NAME: "Chassis" , DESCR: "Cisco Wireless Controller"
PID: AIR-CT7510-K9, VID: V01, SN: KQZZXWL
The Desktop Management Interface (DMI) table contains server hardware and BIOS information. The
WLC 7500 displays BIOS version, PID/VID and Serial Number as part of inventory.
Note Flex 7500 is currently shipped with VID=V02.
Flex 7500 Boot Up
Cisco boot loader options for software maintenance are identical to Cisco's existing controller platforms.
Flex 7500 Wireless Branch Controller Deployment Guide
4
Page 5

Figure 3 Boot-Up Order
Flex 7500 Boot Up
Flex 7500 Wireless Branch Controller Deployment Guide
5
Page 6

Flex 7500 Boot Up
Figure 4 WLC Configuration Wizard
Note The Flex 7500 boot up sequence is equivalent and consistent with existing controller platforms.
Initial boot up requires WLC configuration using the Wizard.
Flex 7500 Wireless Branch Controller Deployment Guide
6
Page 7

Flex 7500 Licensing
AP Base Count Licensing
AP Base Count SKUs
300
500
1000
2000
3000
6000
AP Upgrade Licensing
Flex 7500 Licensing
AP Upgrade SKUs
100
250
500
1000
Except for the base and upgrade counts, the entire licensing procedure that covers ordering, installation,
and viewing is similar to Cisco's existing WLC 5508.
Refer to the WLC 7.3 configuration guide, which covers the entire licensing procedure.
Software Release Support
The Flex 7500 supports WLC code version 7.0.116.x and later only.
Supported Access Points
Access Points 3600, 3500, 2600, 1600, 1550, 1260, 1240, 1140, 1130,1040, 700, and 600 series, Cisco
891 Series Integrated Services Router and Cisco 881 Series Integrated Services Router.
.
Flex 7500 Wireless Branch Controller Deployment Guide
7
Page 8

FlexConnect Architecture
FlexConnect Architecture
Figure 5 Typical Wireless Branch Topology
FlexConnect is a wireless solution for branch office and remote office deployments.
The FlexConnect solution enables the customer to:
• Centralize control and manage traffic of APs from the Data Center.
–
Control traffic is marked by red dashes in Figure 5.
• Distribute the client data traffic at each Branch Office.
–
Data traffic is marked by blue, green, and purple dashes in Figure 5.
–
Each traffic flow is going to its final destination in the most efficient manner.
Advantages of Centralizing Access Point Control Traffic
• Single pane of monitoring and troubleshooting.
• Ease of management.
• Secured and seamless mobile access to Data Center resources.
• Reduction in branch footprint.
• Increase in operational savings.
Flex 7500 Wireless Branch Controller Deployment Guide
8
Page 9

Advantages of Distributing Client Data Traffic
• No operational downtime (survivability) against complete WAN link failures or controller
unavailability.
• Mobility resiliency within branch during WAN link failures.
• Increase in branch scalability. Supports branch size that can scale up to 100 APs and 250,000 square
feet (5000 sq. feet per AP).
The Cisco FlexConnect solution also supports Central Client Data Traffic, but it is limited to Guest data
traffic only. This next table describes the restrictions on WLAN L2 security types only for non-guest
clients whose data traffic is also switched centrally at the Data Center.
Table 1 L2 Security Support for Centrally Switched Non-Guest Users
WLAN L2 Security Type Result
None N/A Allowed
WPA + WPA2 802.1x Allowed
CCKM Allowed
802.1x + CCKM Allowed
PSK Allowed
802.1x WEP Allowed
Static WEP WEP Allowed
WEP + 802.1x WEP Allowed
CKIP - Allowed
FlexConnect Architecture
Note These authentication restrictions do not apply to clients whose data traffic is distributed at the
branch.
Table 2 L3 Security Support for Centrally and Locally Switched Users
WLAN L3 Security Type Result
Web Authentication Internal Allowed
External Allowed
Customized Allowed
Web Pass-Through Internal Allowed
External Allowed
Customized Allowed
Conditional Web
External Allowed
Redirect
Splash Page Web
External Allowed
Redirect
Flex 7500 Wireless Branch Controller Deployment Guide
9
Page 10

FlexConnect Architecture
For more information on Flexconnect external webauth deployment, please refer to Flexconnect External
WebAuth Deployment Guide
For more information on HREAP/FlexConnect AP states and data traffic switching options, refer to
Configuring FlexConnect.
FlexConnect Modes of Operation
FlexConnect Mode Description
Connected A FlexConnect is said to be in Connected Mode
Standalone Standalone mode is specified as the operational
when its CAPWAP control plane back to the
controller is up and operational, meaning the
WAN link is not down.
state the FlexConnect enters when it no longer has
the connectivity back to the controller.
FlexConnect APs in Standalone mode will
continue to function with last known
configuration, even in the event of power failure
and WLC or WAN failure.
For more information on FlexConnect Theory of Operations, refer to the H-Reap/FlexConnect Design
and Deployment Guide.
WAN Requirements
FlexConnect APs are deployed at the Branch site and managed from the Data Center over a WAN link.
The maximum transmission unit (MTU) must be at least 500 bytes.
Deployment
Ty pe
Data 64 Kbps 300 ms 5 25
Data 640 Kbps 300 ms 50 1000
Data 1.44Mbps 1 sec 50 1000
Data + Voice 128 Kbps 100 ms 5 25
Data + Voice 1.44Mbps 100 ms 50 1000
Monitor 64 Kbps 2 sec 5 N/A
Monitor 640 Kbps 2 sec 50 N/A
WAN
Bandwidth
(Min)
WAN RTT
Latency
(Max)
Max APs per
Branch
Max Clients
per Branch
Flex 7500 Wireless Branch Controller Deployment Guide
10
Page 11

Wireless Branch Network Design
Note It is highly recommended that the minimum bandwidth restriction remains 12.8 Kbps per AP
with the round trip latency no greater than 300 ms for data deployments and 100 ms for data +
voice deployments.
For large deployments with scale for max APs per branch = 100 and max clients per branch = 2000.
Key Features
Adaptive wIPS, Context Aware (RFIDs), Rogue Detection, Clients with central 802.1X auth and
CleanAir.
Test Results
For 100 APs, 2000 Clients, 1000 RFIDs, 500 Rogue APs, and 2500 Rogue Clients (Features above
turned on):
Recommended BW = 1.54 Mbps
Recommended RTT latency = 400 ms
Test Results
For 100 APs, 2000 Clients, no rogue, and no RFIDs. (Features above turned off).
Recommended BW = 1.024 Mbps
Recommended Latency = 300 ms
Wireless Branch Network Design
The rest of this document highlights the guidelines and describes the best practices for implementing
secured distributed branch networks. FlexConnect architecture is recommended for wireless branch
networks that meet these design requirements.
Primary Design Requirements
• Branch size that can scale up to 100 APs and 250,000 square feet (5000 sq. feet per AP)
• Central management and troubleshooting
• No operational downtime
• Client-based traffic segmentation
• Seamless and secured wireless connectivity to corporate resources
• PCI compliant
• Support for guests
Flex 7500 Wireless Branch Controller Deployment Guide
11
Page 12

Features Addressing Branch Network Design
Figure 6 Wireless Branch Network Design
Overview
Branch customers find it increasingly difficult and expensive to deliver full-featured scalable and secure
network services across geographic locations. In order to support customers, Cisco is addressing these
challenges by introducing the Flex 7500.
The Flex 7500 solution virtualizes the complex security, management, configuration, and
troubleshooting operations within the data center and then transparently extends those services to each
branch. Deployments using Flex 7500 are easier for IT to set up, manage and, most importantly, scale.
Advantages
• Increase scalability with 6000 AP support.
• Increased resiliency using FlexConnect Fault Tolerance.
• Increase segmentation of traffic using FlexConnect (Central and Local Switching).
• Ease of management by replicating store designs using AP groups and FlexConnect groups.
Features Addressing Branch Network Design
The rest of the sections in the guide captures feature usage and recommendations to realize the network
design shown in Figure 6.
Flex 7500 Wireless Branch Controller Deployment Guide
12
Page 13

Ta b l e 3 F e a t u r e s
Primary Features Highlights
AP Groups Provides operational/management
ease when handling multiple branch
sites. Also, gives the flexibility of
replicating configurations for similar
branch sites.
FlexConnect Groups FlexConnect Groups provide the
functionality of Local Backup
Radius, CCKM/OKC fast roaming,
and Local Authentication.
Fault Tolerance Improves the wireless branch
resiliency and provides no
operational downtime.
ELM (Enhanced
Local Mode for
Adaptive wIPS)
Client Limit per
WLAN
AP Pre-image
Download
Auto-convert APs in
FlexConnect
Guest Access Continue existing Cisco’s Guest
Provide Adaptive wIPS functionality
when serving clients without any
impact to client performance.
Limiting total guest clients on branch
network.
Reduces downtime when upgrading
your branch.
Functionality to automatically
convert APs in FlexConnect for your
branch.
Access Architecture with
FlexConnect.
Features Addressing Branch Network Design
Note Flexconnect APs implemented with WIPS mode can increase bandwidth utilization significantly
based on the activity being detected by the APs. If the rules have forensics enabled, the link
utilization can go up by almost 100 Kbps on an average.
Flex 7500 Wireless Branch Controller Deployment Guide
13
Page 14

IPv6 Support Matrix
IPv6 Support Matrix
Features Centrally Switched Locally Switched
IPv6 (Client
Mobility)
IPv6 RA guard Supported Supported Supported Supported
IPv6 DHCP
guard
IPv6 Source
guard
RA throttling/
Rate limit
IPv6 ACL Supported Not Supported Not Supported Not Supported
IPv6 Client
Visibility
IPv6 Neighbor
discovery
caching
IPv6 Bridging Supported Not Supported Supported Supported
5500/
WiSM-2/8500
Supported Not Supported Not Supported Not Supported
Supported Not Supported Not Supported Not Supported
Supported Not Supported Not Supported Not Supported
Supported Not Supported Not Supported Not Supported
Supported Not Supported Not Supported Not Supported
Supported Not Supported Not Supported Not Supported
Flex 7500 5500 /
WiSM-2/8500
Flex 7500
Feature Matrix
Refer to FlexConnect Feature Matrix for a feature matrix for the FlexConnect feature.
AP Groups
After creating WLANs on the controller, you can selectively publish them (using access point groups)
to different access points in order to better manage your wireless network. In a typical deployment, all
users on a WLAN are mapped to a single interface on the controller. Therefore, all users associated with
that WLAN are on the same subnet or VLAN. However, you can choose to distribute the load among
several interfaces or to a group of users based on specific criteria such as individual departments (such
as Marketing, Engineering or Operations) by creating access point groups. Additionally, these access
point groups can be configured in separate VLANs to simplify network administration.
This document uses AP groups to simplify network administration when managing multiple stores
across geographic locations. For operational ease, the document creates one AP-group per store to
satisfy these requirements:
• Centrally Switched SSID Data center across all stores for Local Store Manager administrative
access.
• Locally Switched SSID Store with different WPA2-PSK keys across all stores for hand-held
scanners.
Flex 7500 Wireless Branch Controller Deployment Guide
14
Page 15

Figure 7 Wireless Network Design Reference Using AP Groups
AP Groups
Configurations from WLC
Complete the following steps:
Step 1 On the WLANs > New page, enter Store1 in the Profile Name field, enter store in the SSID field, and
choose 17 from the ID drop-down list.
Note WLAN IDs 1-16 are part of the default group and cannot be deleted. In order to satisfy our
Step 2 Under WLAN > Security, choose PSK from the Auth Key Mgmt drop-down list, choose ASCII from
the PSK Format drop-down list, and click Apply.
requirement of using same SSID store per store with a different WPA2-PSK, you need to use
WLAN ID 17 and beyond because these are not part of the default group and can be limited to
each store.
Flex 7500 Wireless Branch Controller Deployment Guide
15
Page 16

AP Groups
Step 3 Click WLAN > General, verify the Security Policies change, and check the Status box to enable the
WLAN.
Step 4 Repeat steps 1, 2 and 3 for new WLAN profile Store2, with SSID as store and ID as 18.
Flex 7500 Wireless Branch Controller Deployment Guide
16
Page 17

AP Groups
Step 5 Create and enable the WLAN profile with Profile Name DataCenter, SSID DataCenter and ID 1.
Note On creation, WLAN IDs from 1-16 are automatically part of the default-ap-group.
Step 6 Under WLAN, verify the status of WLAN IDs 1, 17 and 18.
Step 7 Click WLAN > Advanced > AP group > Add Group.
Step 8 Add AP Group Name as Store1, same as WLAN profile Store1, and Description as the Location of the
Store. In this example, California is used as the location of the store.
Step 9 Click Add when done.
Step 10 Click Add Group and create the AP Group Name as Store2 and the description as New York.
Step 11 Click Add.
Flex 7500 Wireless Branch Controller Deployment Guide
17
Page 18

AP Groups
Step 12 Verify the group creation by navigating to WLAN > Advanced > AP Groups.
Step 13 Click AP Group Name Store1 to add or edit the WLAN.
Step 14 Click Add New to select the WLAN.
Step 15 Under WLAN, from the WLAN SSID drop-down, choose WLAN ID 17 store(17).
Step 16 Click Add after WLAN ID 17 is selected.
Step 17 Repeat steps (14 -16) for WLAN ID 1 DataCenter(1). This step is optional and needed only if you want
to allow Remote Resource access.
Step 18 Go back to the WLAN > Advanced > AP Groups screen.
Step 19 Click AP Group Name Store2 to add or edit WLAN.
Step 20 Click Add New to select the WLAN.
Step 21 Under WLAN, from WLAN SSID drop-down, choose WLAN ID 18 store(18).
Step 22 Click Add after WLAN ID 18 is selected.
Step 23 Repeat steps 14 -16 for WLAN ID 1 DataCenter(1).
Flex 7500 Wireless Branch Controller Deployment Guide
18
Page 19

AP Groups
Note Adding multiple WLAN profiles with the same SSID under a single AP group is not permitted.
Summary
Note Adding APs to the AP group is not captured in this document, but it is needed for clients to
access network services.
• AP groups simplify network administration.
• Troubleshooting ease with per branch granularity
• Increased flexibility
Flex 7500 Wireless Branch Controller Deployment Guide
19
Page 20
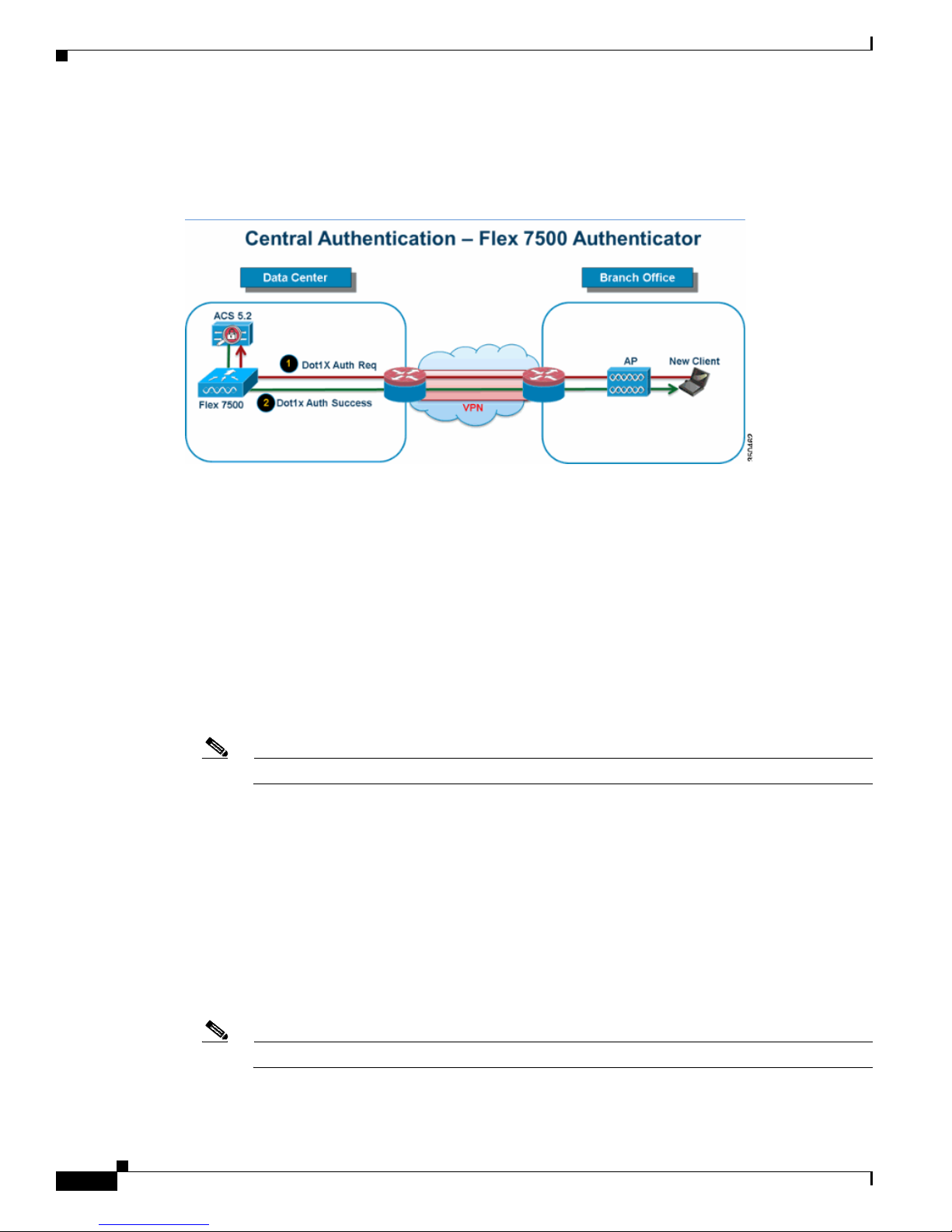
FlexConnect Groups
FlexConnect Groups
Figure 8 Central Dot1X Authentication (Flex 7500 Acting as Authenticator)
In most typical branch deployments, it is easy to foresee that client 802.1X authentication takes place
centrally at the Data Center as shown in Figure 8. Because the above scenario is perfectly valid, it raises
these concerns:
• How can wireless clients perform 802.1X authentication and access Data Center services if Flex
7500 fails?
• How can wireless clients perform 802.1X authentication if WAN link between Branch and Data
Center fails?
• Is there any impact on branch mobility during WAN failures?
• Does the FlexConnect Solution provide no operational branch downtime?
FlexConnect Group is primarily designed and should be created to address these challenges. In addition,
it eases organizing each branch site, because all the FlexConnect access points of each branch site are
part of a single FlexConnect Group.
Note FlexConnect Groups are not analogous to AP Groups.
Primary Objectives of FlexConnect Groups
Backup RADIUS Server Failover
You can configure the controller to allow a FlexConnect access point in standalone mode to perform full
802.1X authentication to a backup RADIUS server. In order to increase the resiliency of the branch,
administrators can configure a primary backup RADIUS server or both a primary and secondary backup
RADIUS server. These servers are used only when the FlexConnect access point is not connected to the
controller.
Note Backup RADIUS accounting is not supported.
Flex 7500 Wireless Branch Controller Deployment Guide
20
Page 21

Local Authentication
Before the 7.0.98.0 code release, local authentication was supported only when FlexConnect is in
Standalone Mode to ensure client connectivity is not affected during WAN link failure. With the
7.0.116.0 release, this feature is now supported even when FlexConnect access points are in Connected
Mode.
Figure 9 Central Dot1X Authentication (FlexConnect APs Acting as Authenticator)
FlexConnect Groups
As shown in Figure 9, branch clients can continue to perform 802.1X authentication when the
FlexConnect Branch APs lose connectivity with Flex 7500. As long as the RADIUS/ACS server is
reachable from the Branch site, wireless clients will continue to authenticate and access wireless
services. In other words, if the RADIUS/ACS is located inside the Branch, then clients will authenticate
and access wireless services even during a WAN outage.
Note With Local Authentication turned on, the AP will always authenticate the clients locally, even
when it is in connected mode. When Local Authentication is disabled, the controller will
authenticate clients to the Central RADIUS server when the FlexConnect AP is in connected
mode. When the AP is in Standalone mode, the AP will authenticate clients to the Local
RADIUS / Local EAP on AP configured on the FlexConnect Group.
Note This feature can be used in conjunction with the FlexConnect backup RADIUS server feature.
If a FlexConnect Group is configured with both backup RADIUS server and local authentication,
the FlexConnect access point always attempts to authenticate clients using the primary backup
RADIUS server first, followed by the secondary backup RADIUS server (if the primary is not
reachable), and finally the Local EAP Server on FlexConnect access point itself (if the primary
and secondary are not reachable).
Flex 7500 Wireless Branch Controller Deployment Guide
21
Page 22

FlexConnect Groups
Local EAP (Local Authentication Continuation)
Figure 10 Dot1X Authentication (FlexConnect APs Acting as Local-EAP Server)
•
You can configure the controller to allow a FlexConnect AP in standalone or connected mode to
perform LEAP or EAP-FAST authentication for up to 100 statically configured users. The controller
sends the static list of user names and passwords to each FlexConnect access point of that particular
FlexConnect Group when it joins the controller. Each access point in the group authenticates only
its own associated clients.
• This feature is ideal for customers who are migrating from an autonomous access point network to
a lightweight FlexConnect access point network and are not interested in maintaining a large user
database, or adding another hardware device to replace the RADIUS server functionality available
in the autonomous access point.
• As shown in Figure 10, if the RADIUS/ACS server inside the Data Center is not reachable, then
FlexConnect APs automatically acts as a Local-EAP Server to perform Dot1X authentication for
wireless branch clients.
CCKM/OKC Fast Roaming
• FlexConnect Groups are required for CCKM/OKC fast roaming to work with FlexConnect access
points. Fast roaming is achieved by caching a derivative of the master key from a full EAP
authentication so that a simple and secure key exchange can occur when a wireless client roams to
a different access point. This feature prevents the need to perform a full RADIUS EAP
authentication as the client roams from one access point to another. The FlexConnect access points
need to obtain the CCKM/OKC cache information for all the clients that might associate so they can
process it quickly instead of sending it back to the controller. If, for example, you have a controller
with 300 access points and 100 clients that might associate, sending the CCKM/OKC cache for all
100 clients is not practical. If you create a FlexConnect Group comprising a limited number of
access points (for example, you create a group for four access points in a remote office), the clients
roam only among those four access points, and the CCKM/OKC cache is distributed among those
four access points only when the clients associate to one of them.
• This feature along with Backup Radius and Local Authentication (Local-EAP) ensures no
operational downtime for your branch sites.
Note CCKM/OKC fast roaming among FlexConnect and non-FlexConnect access points is not
Flex 7500 Wireless Branch Controller Deployment Guide
22
supported.
Page 23

Figure 11 Wireless Network Design Reference Using FlexConnect Groups
FlexConnect Groups
FlexConnect Group Configuration from WLC
Complete the steps in this section in order to configure FlexConnect groups to support Local
Authentication using LEAP, when FlexConnect is either in Connected or Standalone mode. The
configuration sample in Figure 11 illustrates the objective differences and 1:1 mapping between the AP
Group and FlexConnect group.
Step 1 Click New under Wireless > FlexConnect Groups.
Step 2 Assign Group Name Store 1, similar to the sample configuration as shown in Figure 11.
Step 3 Click Apply when the Group Name is set.
Flex 7500 Wireless Branch Controller Deployment Guide
23
Page 24

FlexConnect Groups
Step 4 Click the Group Name Store 1 that you just created for further configuration.
Step 5 Click Add AP.
Flex 7500 Wireless Branch Controller Deployment Guide
24
Page 25

FlexConnect Groups
Step 6 Check the Enable AP Local Authentication box in order to enable Local Authentication when the AP
is in Standalone Mode.
Note Step 20 shows how to enable Local Authentication for Connected Mode AP.
Step 7 Check the Select APs from current controller box in order to enable the AP Name drop-down menu.
Step 8 Choose the AP from the drop-down that needs to be part of this FlexConnect Group.
Step 9 Click Add after the AP is chosen from the drop-down.
Step 10 Repeat steps 7 and 8 to add all the APs to this FlexConnect group that are also part of AP-Group Store
1. See Figure 11 to understand the 1:1 mapping between the AP-Group and FlexConnect group.
If you have created an AP-Group per Store (Figure 7), then ideally all the APs of that AP-Group should
be part of this FlexConnect Group (Figure 11. Maintaining 1:1 ratio between the AP-Group and
FlexConnect group simplifies network management.
Flex 7500 Wireless Branch Controller Deployment Guide
25
Page 26

FlexConnect Groups
Step 11 Click Local Authentication > Protocols and check the Enable LEAP Authentication box.
Step 12 Click Apply after the check box is set.
Note If you have a backup controller, make sure the FlexConnect groups are identical and AP MAC
address entries are included per FlexConnect group.
Flex 7500 Wireless Branch Controller Deployment Guide
26
Page 27

FlexConnect Groups
Step 13 Under Local Authentication, click Local Users.
Step 14 Set the UserName, Password and Confirm Password fields, then click Add in order to create user entry
in the Local EAP server residing on the AP.
Step 15 Repeat step 13 until your local user name list is exhausted. You cannot configure or add more than 100
users.
Step 16 Click Apply after step 14 is completed and the No of Users count is verified.
Step 17 From the top pane, click WLANs.
Step 18 Click WLAN ID 17. This was created during the AP Group creation. See Figure 7.
Step 19 Under WLAN > Edit for WLAN ID 17, click Advanced.
Step 20 Check the FlexConnect Local Auth box in order to enable Local Authentication in Connected Mode.
Note Local Authentication is supported only for FlexConnect with Local Switching.
Note Always make sure to create the FlexConnect Group before enabling Local Authentication under
WLAN.
Flex 7500 Wireless Branch Controller Deployment Guide
27
Page 28

FlexConnect Groups
NCS and Cisco Prime also provides the FlexConnect Local Auth check box in order to enable Local
Authentication in Connected Mode as shown here:
Flex 7500 Wireless Branch Controller Deployment Guide
28
Page 29

FlexConnect Groups
NCS and Cisco Prime also provides facility to filter and monitor FlexConnect Locally Authenticated
clients as shown here:
Flex 7500 Wireless Branch Controller Deployment Guide
29
Page 30

FlexConnect Groups
Flex 7500 Wireless Branch Controller Deployment Guide
30
Page 31

Verification Using CLI
Client authentication state and switching mode can quickly be verified using this CLI on the WLC:
(Cisco Controller) >show client detail 00:24:d7:2b:7c:0c
Client MAC Address............................... 00:24:d7:2b:7c:0c
Client Username ................................. N/A
AP MAC Address................................... d0:57:4c:08:e6:70
Client State..................................... Associated
H-REAP Data Switching............................ Local
H-REAP Authentication............................ Local
FlexConnect VLAN Override
In the current FlexConnect architecture, there is a strict mapping of WLAN to VLAN, and thus the client
getting associated on a particular WLAN on FlexConnect AP has to abide by a VLAN which is mapped
to it. This method has limitations, because it requires clients to associate with different SSIDs in order
to inherit different VLAN-based policies.
From 7.2 release onwards, AAA override of VLAN on individual WLAN configured for local switching
is supported. In order to have dynamic VLAN assignment, AP would have the interfaces for the VLAN
pre-created based on a configuration using existing WLAN-VLAN Mapping for individual FlexConnect
AP or using ACL-VLAN mapping on a FlexConnect group. The WLC is used to pre-create the
sub-interfaces at the AP.
FlexConnect VLAN Override
Flex 7500 Wireless Branch Controller Deployment Guide
31
Page 32

FlexConnect VLAN Override
Summary
Procedure
Step 1 Create a WLAN for 802.1x authentication.
• AAA VLAN override is supported from release 7.2 for WLANs configured for local switching in
central and local authentication mode.
• AAA override should be enabled on WLAN configured for local switching.
• The FlexConnect AP should have VLAN pre-created from WLC for dynamic VLAN assignment.
• If VLANs returned by AAA override are not present on AP client, they will get an IP from the
default VLAN interface of the AP.
Complete these steps:
Step 2 Enable AAA override support for local switching WLAN on the WLC. Navigate to WLAN GUI >
WLAN > WLAN ID > Advance tab.
Flex 7500 Wireless Branch Controller Deployment Guide
32
Page 33

FlexConnect VLAN Override
Step 3 Add the AAA server details on the controller for 802.1x authentication. In order to add the AAA server,
navigate to WLC GUI > Security > AAA > Radius > Authentication > New.
Step 4 The AP is in local mode by default, so covert the mode to FlexConnect mode. Local mode APs can be
converted to FlexConnect mode by going to Wireless > All APs, and click the Individual AP.
Flex 7500 Wireless Branch Controller Deployment Guide
33
Page 34

FlexConnect VLAN Override
Step 5 Add the FlexConnect APs to the FlexConnect group.
Navigate under WLC GUI > Wireless > FlexConnect Groups > Select FlexConnect Group > General
tab > Add AP.
Step 6 The FlexConnect AP should be connected on a trunk port and WLAN mapped VLAN and AAA
overridden VLAN should be allowed on the trunk port.
Flex 7500 Wireless Branch Controller Deployment Guide
34
Page 35

FlexConnect VLAN Override
Note In this configuration, VLAN 109 is used for WLAN VLAN mapping and VLAN 3 is used for
AAA override.
Step 7 Configure WLAN to VLAN Mapping for the FlexConnect AP. Based on this configuration, the AP
would have the interfaces for the VLAN. When the AP receives the VLAN configuration, corresponding
dot11 and Ethernet sub-interfaces are created and added to a bridge-group. Associate a client on this
WLAN and when the client associates, its VLAN (default, based on the WLAN-VLAN mapping) is
assigned.
Navigate to WLAN GUI > Wireless > All APs, click the specific AP > FlexConnect tab, and click
VLAN Mapping.
Step 8 Create a user in the AAA server and configure the user to return VLAN ID in IETF Radius attribute.
Step 9 In order to have dynamic VLAN assignment, the AP would have the interfaces for the dynamic VLAN
pre-created based on the configuration using existing WLAN-VLAN Mapping for the individual
FlexConnect AP or using ACL-VLAN mapping on FlexConnect group.
In order to configure AAA VLAN on the FlexConnect AP, navigate to WLC GUI > Wireless >
FlexConnect Group, click the specific FlexConnect group > VLAN-ACL mapping, and enter VLAN
in the Vlan ID field.
Flex 7500 Wireless Branch Controller Deployment Guide
35
Page 36

FlexConnect VLAN Based Central Switching
Step 10 Associate a client on this WLAN and authenticate using the user name configured in the AAA server in
order to return the AAA VLAN.
Step 11 The client should receive an IP address from the dynamic VLAN returned via the AAA server.
Step 12 In order to verify, click WLC GUI > Monitor > Client, click the specific client MAC address in order
to check the client details.
Limitations
• Cisco Airespace-specific attributes will not be supported and IETF attribute VLAN ID will only be
supported.
• A maximum of 16 VLANs can be configured in per-AP configuration either via WLAN-VLAN
Mapping for individual FlexConnect AP or using ACL-VLAN mapping on the FlexConnect group.
FlexConnect VLAN Based Central Switching
Summary
In controller software releases 7.2, AAA override of VLAN (Dynamic VLAN assignment) for locally
switched WLANs will put wireless clients to the VLAN provided by the AAA server. If the VLAN
provided by the AAA server is not present at the AP, the client is put to a WLAN mapped VLAN on that
AP and traffic will switch locally on that VLAN. Further, prior to release 7.3, traffic for a particular
WLAN from FlexConnect APs can be switched Centrally or Locally depending on the WLAN
configuration.
From release 7.3 onwards, traffic from FlexConnect APs can be switched Centrally or Locally depending
on the presence of a VLAN on a FlexConnect AP.
Traffic flow on WLANs configured for Local Switching when Flex APs are in Connected Mode:
• If the VLAN is returned as one of the AAA attributes and that VLAN is not present in the Flex AP
database, traffic will switch centrally and the client will be assigned this VLAN/Interface returned
from the AAA server provided that the VLAN exists on the WLC.
• If the VLAN is returned as one of the AAA attributes and that VLAN is not present in the Flex AP
database, traffic will switch centrally. If that VLAN is also not present on the WLC, the client will
be assigned a VLAN/Interface mapped to a WLAN on the WLC.
Flex 7500 Wireless Branch Controller Deployment Guide
36
Page 37

Procedure
FlexConnect VLAN Based Central Switching
• If the VLAN is returned as one of the AAA attributes and that VLAN is present in the FlexConnect
AP database, traffic will switch locally.
• If the VLAN is not returned from the AAA server, the client will be assigned a WLAN mapped
VLAN on that FlexConnect AP and traffic will switch locally.
Traffic flow on WLANs configured for Local Switching when Flex APs are in Standalone Mode:
• If the VLAN returned by an AAA server is not present in the Flex AP database, the client will be
put to default VLAN (that is, a WLAN mapped VLAN on Flex AP). When the AP connects back,
this client will be de-authenticated and will switch traffic centrally.
• If the VLAN returned by an AAA server is present in the Flex AP database, the client will be put
into a returned VLAN and traffic will switch locally.
• If the VLAN is not returned from an AAA server, the client will be assigned a WLAN mapped
VLAN on that FlexConnect AP and traffic will switch locally.
Complete these steps:
Step 1 Configure a WLAN for Local Switching and enable AAA override.
Flex 7500 Wireless Branch Controller Deployment Guide
37
Page 38

FlexConnect VLAN Based Central Switching
Step 2 Enable Vlan based Central Switching on the newly created WLAN.
Step 3 Set AP Mode to FlexConnect.
Flex 7500 Wireless Branch Controller Deployment Guide
38
Page 39

FlexConnect VLAN Based Central Switching
Step 4 Make sure that the FlexConnect AP has some sub-interface present in its database, either via
WLAN-VLAN Mapping on a particular Flex AP or via configuring VLAN from a Flex group. In this
example, VLAN 63 is configured in WLAN-VLAN mapping on Flex AP.
Step 5 In this example, VLAN 62 is configured on WLC as one of the dynamic interfaces and is not mapped to
the WLAN on the WLC. The WLAN on the WLC is mapped to Management VLAN (that is, VLAN 61).
Flex 7500 Wireless Branch Controller Deployment Guide
39
Page 40

FlexConnect VLAN Based Central Switching
Step 6 Associate a client to the WLAN configured in Step 1 on this Flex AP and return VLAN 62 from the AAA
server. VLAN 62 is not present on this Flex AP, but it is present on the WLC as a dynamic interface so
traffic will switch centrally and the clie nt wil l be assigne d VLAN 62 on the WLC . In the outp ut captured
here, the client has been assigned VLAN 62 and Data Switching and Authentication are set to Central.
40
Note Observe that although WLAN is configured for Local Switching, the Data Switching field for
this client is Central based on the presence of a VLAN (that is, VLAN 62, which is returned from
the AAA server, is not present in the AP Database).
Step 7 If another user associates to the same AP on this created WLAN and some VLAN is returned from the
AAA server which is not present on the AP as well as the WLC, traffic will switch centrally and the client
will be assigned the WLAN mapped interface on the WLC (that is, VLAN 61 in this example setup),
because the WLAN is mapped to the Management interface which is configured for VLAN 61.
Flex 7500 Wireless Branch Controller Deployment Guide
Page 41

FlexConnect VLAN Based Central Switching
Note Observe that although WLAN is configured for Local Switching, the Data Switching field for
this client is Central based on the presence of a VLAN. That is, VLAN 61, which is returned
from the AAA server, is not present in the AP Database but is also not present in the WLC
database. As a result, the client is assigned a default interface VLAN/Interface which is mapped
to the WLAN. In this example, the WLAN is mapped to a management interface (that is, VLAN
61) and so the client has received an IP address from VLAN 61.
Step 8 If another user associates to it on this created WLAN and VLAN 63 is returned from the AAA server
(which is present on this Flex AP), the client will be assigned VLAN 63 and traffic will switch locally.
Limitations
• VLAN Based Central Switching is only supported on WLANs configured for Central Authentication
and Local Switching.
• The AP sub-interface (that is, VLAN Mapping) should be configured on the FlexConnect AP.
Flex 7500 Wireless Branch Controller Deployment Guide
41
Page 42

FlexConnect ACL
FlexConnect ACL
With the introduction of ACLs on FlexConnect, there is a mechanism to cater to the need of access
control at the FlexConnect AP for protection and integrity of locally switched data traffic from the AP.
FlexConnect ACLs are created on the WLC and should then be configured with the VLAN present on
the FlexConnect AP or FlexConnect group using VLAN-ACL mapping which will be for AAA override
VLANs. These are then pushed to the AP.
Summary
Procedure
Step 1 Create a FlexConnect ACL on the WLC. Navigate to WLC GUI > Security > Access Control List >
• Create FlexConnect ACL on the controller.
• Apply the same on a VLAN present on FlexConnect AP under AP Level VLAN ACL mapping.
• Can be applied on a VLAN present in FlexConnect Group under VLAN-ACL mapping (generally
done for AAA overridden VLANs).
• While applying ACL on VLAN, select the direction to be applied which will be “ingress”, “egress”
or “ingress and egress”.
Complete these steps:
FlexConnect ACLs.
Step 2 Click New.
Step 3 Configure the ACL Name.
Flex 7500 Wireless Branch Controller Deployment Guide
42
Page 43

FlexConnect ACL
Step 4 Click Apply.
Step 5 Create rules for each ACL. In order to create rules, navigate to WLC GUI > Security > Access Control
List > FlexConnect ACLs, and click the above created ACL.
Step 6 Click Add New Rule.
Note Configure the rules as per the requirement. If the permit any rule is not configured at the end,
there is an implicit deny which will block all traffic.
Step 7 Once the FlexConnect ACLs are created, it can be mapped for WLAN-VLAN mapping under individual
FlexConnect AP or can be applied on VLAN-ACL mapping on the FlexConnect group.
Step 8 Map FlexConnect ACL configured above at AP level for individual VLANs under VLAN mappings for
individual FlexConnect AP. Navigate to WLC GUI > Wireless > All AP, click the specific AP >
FlexConnect tab > VLAN Mapping.
Flex 7500 Wireless Branch Controller Deployment Guide
43
Page 44

FlexConnect ACL
Step 9 FlexConnect ACL can also be applied on VLAN-ACL mapping in the FlexConnect group. VLANs
Limitations
created under VLAN-ACL mapping in FlexConnect group are mainly used for dynamic VLAN override.
• A maximum of 512 FlexConnect ACLs can be configured on WLC.
• Each individual ACL can be configured with 64 rules.
• A maximum of 32 ACLs can be mapped per FlexConnect group or per FlexConnect AP.
• At any given point in time, there is a maximum of 16 VLANs and 32 ACLs on the FlexConnect AP.
Flex 7500 Wireless Branch Controller Deployment Guide
44
Page 45

FlexConnect Split Tunneling
In WLC releases prior to 7.3, if a client connecting on a FlexConnect AP associated with a centrally
switched WLAN needs to send some traffic to a device present in the local site/network, they need to
send traffic over CAPWAP to the WLC and then get the same traffic back to the local site over CAPWAP
or using some off-band connectivity.
From release 7.3 onwards, Split Tunneling introduces a mechanism by which the traffic sent by the
client will be classified based on packet contents using Flex ACL. Matching packets are switched
locally from Flex AP and the rest of the packets are centrally switched over CAPWAP.
The Split Tunneling functionality is an added advantage for OEAP AP setup where clients on a
Corporate SSID can talk to devices on a local network (printers, wired machine on a Remote LAN Port,
or wireless devices on a Personal SSID) directly without consuming WAN bandwidth by sending packets
over CAPWAP. Split tunneling is not supported on OEAP 600 APs. Flex ACL can be created with rules
in order to permit all the devices present at the local site/network. When packets from a wireless client
on the Corporate SSID matches the rules in Flex ACL configured on OEAP AP, that traffic is switched
locally and the rest of the traffic (that is, implicit deny traffic) will switch centrally over CAPWAP.
The Split Tunneling solution assumes that the subnet/VLAN associated with a client in the central site
is not present in the local site (that is, traffic for clients which receive an IP address from the subnet
present on the central site will not be able to switch locally). The Split Tunneling functionality is
designed to switch traffic locally for subnets which belong to the local site in order to avoid WAN
bandwidth consumption. Traffic which matches the Flex ACL rules are switched locally and NAT
operation is performed changing the client’s source IP address to the Flex AP’s BVI interface IP address
which is routable at the local site/network.
FlexConnect Split Tunneling
Summary
• The Split Tunneling functionality is supported on WLANs configured for Central Switching
advertised by Flex APs only.
• The DHCP required should be enabled on WLANs configured for Split Tunneling.
• The Split Tunneling configuration is applied per WLAN configured for central switching on per Flex
AP or for all the Flex APs in a FlexConnect Group.
Procedure
Complete these steps:
Flex 7500 Wireless Branch Controller Deployment Guide
45
Page 46

FlexConnect Split Tunneling
Step 1 Configure a WLAN for Central Switching (that is, Flex Local Switching should not be enabled).
Step 2 Set DHCP Address Assignment to Required.
Step 3 Set AP Mode to FlexConnect.
Flex 7500 Wireless Branch Controller Deployment Guide
46
Page 47

FlexConnect Split Tunneling
Step 4 Configure FlexConnect ACL with a permit rule for traffic which should be switched locally on the
Central Switch WLAN. In this example, the FlexConnect ACL rule is configured so it will alert ICMP
traffic from all the clients which are on the 9.6.61.0 subnet (that is, exist on the Central site) to 9.1.0.150
to be switched locally after the NAT operation is applied on Flex AP. The rest of the traffic will hit an
implicit deny rule and be switched centrally over CAPWAP.
Step 5 This created FlexConnect ACL can be pushed as a Split Tunnel ACL to individual Flex AP or can also
be pushed to all the Flex APs in a Flex Connect group.
Complete these steps in order to push Flex ACL as a Local Split ACL to individual Flex AP:
a. Click Local Split ACLs.
Flex 7500 Wireless Branch Controller Deployment Guide
47
Page 48

FlexConnect Split Tunneling
b. Select WLAN Id on which Split Tunnel feature should be enabled, choose Flex-ACL, and click
Add.
c. Flex-ACL is pushed as Local-Split ACL to the Flex AP.
Flex 7500 Wireless Branch Controller Deployment Guide
48
Page 49

FlexConnect Split Tunneling
Complete these steps in order to push Flex ACL as Local Split ACL to a FlexConnect Group:
a. Select the WLAN Id on which the Split Tunneling feature should be enabled. On the WLAN-ACL
mapping tab, select FlexConnect ACL from the FlexConnect group where particular Flex APs are
added, and click Add.
b. The Flex-ACL is pushed as LocalSplit ACL to Flex APs in that Flex group.
Flex 7500 Wireless Branch Controller Deployment Guide
49
Page 50

Fault Tolerance
Limitations
• Flex ACL rules should not be configured with permit/deny statement with same subnet as source
and destination.
• Traffic on a Centrally Switched WLAN configured for Split Tunneling can be switched locally only
when a wireless client initiates traffic for a host present on the local site. If traffic is initiated by
clients/host on a local site for wireless clients on these configured WLANs, it will not be able to
reach the destination.
• Split Tunneling is not supported for Multicast/Broadcast traffic. Multicast/Broadcast traffic will
switch centrally even if it matches the Flex ACL.
Fault Tolerance
FlexConnect Fault Tolerance allows wireless access and services to branch clients when:
• FlexConnect Branch APs lose connectivity with the primary Flex 7500 controller.
• FlexConnect Branch APs are switching to the secondary Flex 7500 controller.
• FlexConnect Branch APs are re-establishing connection to the primary Flex 7500 controller.
Summary
FlexConnect Fault Tolerance, along with Local EAP as outlined above and PEAP/EAP-TLS
authentication on FlexConnect AP with release 7.5, together provide zero branch downtime during a
network outage. This feature is enabled by default and cannot be disabled. It requires no configuration
on the controller or AP. However, to ensure Fault Tolerance works smoothly and is applicable, this
criteria should be maintained:
• WLAN ordering and configurations have to be identical across the primary and backup Flex 7500
controllers.
• VLAN mapping has to be identical across the primary and backup Flex 7500 controllers.
• Mobility domain name has to be identical across the primary and backup Flex 7500 controllers.
• It is recommended to use Flex 7500 as both the primary and backup controllers.
• FlexConnect will not disconnect clients when the AP is connecting back to the same controller
provided there is no change in configuration on the controller.
• FlexConnect will not disconnect clients when connecting to the backup controller provided there is
no change in configuration and the backup controller is identical to the primary controller.
• FlexConnect will not reset its radios on connecting back to the primary controller provided there is
no change in configuration on the controller.
Limitations
• Supported only for FlexConnect with Central/Local Authentication with Local Switching.
• Centrally authenticated clients require full re-authentication if the client session timer expires
before the FlexConnect AP switches from Standalone to Connected mode.
• Flex 7500 primary and backup controllers must be in the same mobility domain.
Flex 7500 Wireless Branch Controller Deployment Guide
50
Page 51

Client Limit per WLAN
Along with traffic segmentation, the need for restricting the total client accessing the wireless services
arises. For example, limiting total Guest Clients from branch tunneling back to the Data Center.
In order to address this challenge, Cisco is introducing Client Limit per WLAN feature that can restrict
the total clients allowed on a per WLAN basis.
Primary Objective
• Set limits on maximum clients
• Operational ease
Note This is not a form of QoS.
By default, the feature is disabled and does not force the limit.
Client Limit per WLAN
Limitations
This feature does not enforce client limit when the FlexConnect is in Standalone state of operation.
WLC Configuration
Complete these steps:
Step 1 Select the Centrally Switched WLAN ID 1 with SSID DataCenter. This WLAN was created during THE
AP Group creation. See Figure 7.
Step 2 Click the Advanced tab for WLAN ID 1.
Step 3 Set the client limit value for the Maximum Allowed Clients text field.
Step 4 Click Apply after the text field for Maximum Allowed Clients is set.
Flex 7500 Wireless Branch Controller Deployment Guide
51
Page 52

Client Limit per WLAN
Default for Maximum Allowed Clients is set to 0, which implies there is no restriction and the feature is
disabled.
NCS Configuration
In order to enable this feature from the NCS, go to Configure > Controllers > Controller IP > WLANs
> WLAN Configuration > WLAN Configuration Details.
Flex 7500 Wireless Branch Controller Deployment Guide
52
Page 53

Client Limit per WLAN
Configuration through Cisco Prime
In order to enable this feature from the Cisco Prime, go to Configure > Controllers > Controller IP >
WLANs > WLAN Configuration > WLAN Configuration Details.
Flex 7500 Wireless Branch Controller Deployment Guide
53
Page 54

Peer-to-Peer Blocking
Peer-to-Peer Blocking
In controller software releases prior to 7.2, peer-to-peer (P2P) blocking was only supported for central
switching WLANs. Peer-to-peer blocking can be configured on WLAN with any of these three actions:
• Disabled – Disables peer-to-peer blocking and bridged traffic locally within the controller for clients
in the same subnet. This is the default value.
• Drop – Causes the controller to discard packets for clients in the same subnet.
• Forward Up-Stream – Causes the packet to be forwarded on the upstream VLAN. The devices above
the controller decide what action to take regarding the packet.
From release 7.2 onwards, peer-to-peer blocking is supported for clients associated on local switching
WLAN. Per WLAN, peer-to-peer configuration is pushed by the controller to FlexConnect AP.
Summary
• Peer-to-peer Blocking is configured per WLAN
Flex 7500 Wireless Branch Controller Deployment Guide
54
Page 55

Procedure
Step 1 Enable peer-to-peer blocking action as Drop on WLAN configured for FlexConnect Local Switching.
AP Pre-Image Download
• Per WLAN, peer-to-peer blocking configuration is pushed by WLC to FlexConnect APs.
• Peer-to-peer blocking action configured as drop or upstream-forward on WLAN is treated as
peer-to-peer blocking enabled on FlexConnect AP.
Complete these steps:
Step 2 Once the P2P Blocking action is configured as Drop or Forward-Upstream on WLAN configured for
local switching, it is pushed from the WLC to the FlexConnect AP. The FlexConnect APs will store this
information in the reap config file in flash. With this, even when FlexConnect AP is in standalone mode,
it can apply the P2P configuration on the corresponding sub-interfaces.
Limitations
• In FlexConnect, solution P2P blocking configuration cannot be applied only to a particular
FlexConnect AP or sub-set of APs. It is applied to all FlexConnect APs that broadcast the SSID.
• Unified solution for central switching clients supports P2P upstream-forward. However, this will not
be supported in the FlexConnect solution. This is treated as P2P drop and client packets are dropped
instead of forwarded to the next network node.
• Unified solution for central switching clients supports P2P blocking for clients associated to
different APs. However, this solution targets only clients connected to the same AP. FlexConnect
ACLs can be used as a workaround for this limitation.
AP Pre-Image Download
This feature allows the AP to download code while it is operational. The AP pre-image download is
extremely useful in reducing the network downtime during software maintenance or upgrades.
Flex 7500 Wireless Branch Controller Deployment Guide
55
Page 56

AP Pre-Image Download
Summary
Procedure
Step 1 Upgrade the image on the primary and backup controllers.
• Ease of software management
• Schedule per store upgrades: NCS or Cisco Prime is needed to accomplish this.
• Reduces downtime
Complete these steps:
Navigate under WLC GUI > Commands > Download File to start the download.
Step 2 Save the configurations on the controllers, but do not reboot the controller.
Step 3 Issue the AP pre-image download command from the primary controller.
a. Navigate to WLC GUI > Wireless > Access Points > All APs and choose the access point to start
pre-image download.
b. Once the access point is chosen, click the Advanced tab.
c. Click Download Primary to initiate pre-image download.
Flex 7500 Wireless Branch Controller Deployment Guide
56
Page 57

FlexConnect Smart AP Image Upgrade
Step 4 Reboot the controllers after all the AP images are downloaded.
The APs now fall back to Standalone mode until the controllers are rebooting.
Note In Standalone mode, Fault Tolerance will keep Clients associated.
Once the controller is back, the APs automatically reboot with the pre-downloaded image. After
rebooting, the APs re-join the primary controller and resume client's services.
Limitations
• Works only with CAPWAP APs.
FlexConnect Smart AP Image Upgrade
The pre-image download feature reduces the downtime duration to a certain extent, but still all the
FlexConnect APs have to pre-download the respective AP images over the WAN link with higher latency.
Flex 7500 Wireless Branch Controller Deployment Guide
57
Page 58

FlexConnect Smart AP Image Upgrade
Efficient AP Image Upgrade will reduce the downtime for each FlexConnect AP. The basic idea is only
one AP of each AP model will download the image from the controller and will act as Master/Server,
and the rest of the APs of the same model will work as Slave/Client and will pre-download the AP image
from the master. The distribution of AP image from the server to the client will be on a local network
and will not experience the latency of the WAN link. As a result, the process will be faster.
Summary
Procedure
Step 1 Upgrade the image on the controller.
Flex 7500 Wireless Branch Controller Deployment Guide
58
• Master and Slave APs are selected for each AP Model per FlexConnect Group
• Master downloads image from WLC
• Slave downloads image from Master AP
• Reduces downtime and saves WAN bandwidth
Complete these steps:
Navigate to WLC GUI > Commands > Download File in order to begin the download.
Page 59

FlexConnect Smart AP Image Upgrade
Step 2 Save the configurations on the controllers, but do not reboot the controller.
Step 3 Add the FlexConnect APs to FlexConnect group.
Navigate to WLC GUI > Wireless > FlexConnect Groups, select FlexConnect Group > General tab
> Add AP.
Step 4 Click the FlexConnect AP Upgrade check box in order to achieve efficient AP image upgrade.
Navigate to WLC GUI > Wireless > FlexConnect Groups, select FlexConnect Group > Image
Upgrade tab.
Flex 7500 Wireless Branch Controller Deployment Guide
59
Page 60

FlexConnect Smart AP Image Upgrade
Step 5 The Master AP can be selected manually or automatically:
a. In order to manually select the Master AP, navigate to WLC GUI > Wireless > FlexConnect
Groups, select FlexConnect Group > Image Upgrade tab > FlexConnect Master APs, and select
AP from the drop-down list, and click Add Master.
Note Only one AP per model can be configured as Master AP. If Master AP is configured manually,
the Manual field will be updated as yes.
b. In order to automatically select Master AP, navigate to WLC GUI > Wireless > FlexConnect
Groups, select FlexConnect Group > Image Upgrade tab, and click FlexConnect Upgrade.
Flex 7500 Wireless Branch Controller Deployment Guide
60
Page 61

FlexConnect Smart AP Image Upgrade
Note If Master AP is selected automatically, the Manual field will be updated as no.
Step 6 In order to start efficient AP image upgrade for all the APs under a specific FlexConnect group, click
FlexConnect Upgrade.
Navigate to WLC GUI > Wireless > FlexConnect Groups, select FlexConnect group > Image
Upgrade tab and click FlexConnect Upgrade.
Note Slave Maximum Retry Count is the number of attempts (44 by default) in which the slave AP
will make in order to download an image from the Master AP, after which it will fall back to
download the image from the WLC. It will make 20 attempts against WLC in order to download
a new image after which the administrator has to re-initiate the download process.
Step 7 Once FlexConnect Upgrade is initiated, only the Master AP will download the image from the WLC.
Under All AP page, Upgrade Role will be updated as Master/Central which means Master AP has
downloaded the image from the WLC which is at the central location. The Slave AP will download the
image from the Master AP which is at the local site and is the reason under All AP page Upgrade Role
will be updated as Slave/Local.
In order to verify this, navigate to WLC GUI > Wireless.
Flex 7500 Wireless Branch Controller Deployment Guide
61
Page 62

Auto Convert APs in FlexConnect Mode
Step 8 Reboot the controllers after all the AP images are downloaded. The APs now fall back to Standalone
mode until the controllers are rebooting.
Note In Standalone mode, Fault Tolerance will keep Clients associated.
Once the controller is back, the APs automatically reboot with the pre-downloaded image. After
rebooting, the APs re-join the primary controller and resume the client's services.
Limitations
• Master AP selection is per FlexConnect group and per AP model in each group.
• Only 3 slave APs of same model can upgrade simultaneously from their master AP and rest of the
• In the instance that the Slave AP fails to download the image from the Master AP for some reason,
slave APs will use the random back-off timer to retry for the Master AP in order to download the
AP image.
it will go to the WLC in order to fetch the new image.
• This works only with CAPWAP APs.
• Smart AP image upgrade does not work when the Master AP is connected over CAPWAPv6.
Auto Convert APs in FlexConnect Mode
The Flex 7500 provides these two options to convert the AP mode to FlexConnect:
• Manual mode
• Auto convert mode
Manual Mode
This mode is available on all the platforms and allows the change to take place only on per AP basis.
1. Navigate to WLC GUI > Wireless > All APs and choose the AP.
2. Select FlexConnect as the AP Mode, then click Apply.
3. Changing the AP mode causes the AP to reboot.
Flex 7500 Wireless Branch Controller Deployment Guide
62
Page 63

Auto Convert APs in FlexConnect Mode
This option is also available on all the current WLC platforms.
Auto Convert Mode
This mode is available only for the Flex 7500 Controller and is supported only using CLI. This mode
triggers the change on all the connected APs. It is recommended that Flex 7500 is deployed in a different
mobility domain than existing WLC campus controllers before you enable this CLI:
• This feature is also supported on the 8510, 5520 and 8540 controllers.
(Cisco Controller) >config ap autoconvert ?
disable............Disables auto conversion of unsupported mode APs to supported modes
when AP joins
flexconnect........Converts unsupported mode APs to flexconnect mode when AP joins
monitor............Converts unsupported mode APs to monitor mode when AP joins
(Cisco Controller) >
Step 1 The Auto-conversion feature is disabled by default, which can be verified by using this show command:
(Cisco Controller) >show ap autoconvert
AP Autoconvert .................................. Disabled
Non-supported AP modes = Local Mode, Sniffer, Rogue Detector and Bridge.
Flex 7500 Wireless Branch Controller Deployment Guide
63
Page 64

FlexConnect WGB/uWGB Support for Local Switching WLANs
This option is currently available only via CLIs.
These CLIs are available only on the WLC 7500.
Step 2 Performing config ap autoconvert flexconnect CLI converts all the APs in the network with
non-supported AP mode to FlexConnect mode. Any APs that are already in FlexConnect or Monitor
Mode are not affected.
(Cisco Controller) >config ap autoconvert flexconnect
(Cisco Controller) >show ap autoconvert
AP Autoconvert .................................. FlexConnect
(Cisco Controller) >
Step 3 Performing config ap autoconvert monitor CLI converts all the APs in the network with non-supported
AP mode to Monitor mode. Any APs that are already in FlexConnect or Monitor mode are not affected.
(Cisco Controller >config ap autoconvert monitor
(Cisco Controller) >show ap autoconvert
AP Autoconvert ................................. Monitor
There is no option to perform both config ap autoconvert flexconnect and config ap autoconvert
monitor at the same time.
FlexConnect WGB/uWGB Support for Local Switching WLANs
From release 7.3 onwards, WGB/uWGB and wired/wireless clients behind WGBs are supported and will
work as normal clients on WLANs configured for local switching.
After association, WGB sends the IAPP messages for each of its wired/wireless clients, and Flex AP will
behave as follows:
• When Flex AP is in connected mode, it forwards all the IAPP messages to the controller and the
controller will process the IAPP messages the same as Local mode AP. Traffic for wired/wireless
clients will be switched locally from Flex APs.
• When AP is in standalone mode, it processes the IAPP messages, wired/wireless clients on the WGB
must be able to register and de-register. Upon transition to connected mode, Flex AP will send the
information of wired clients back to the controller. WGB will send registration messages three times
when Flex AP transitions from Standalone to Connected mode.
Wired/Wireless clients will inherit WGB’s configuration, which means no separate configuration like
AAA authentication, AAA override, and FlexConnect ACL is required for clients behind WGB.
Flex 7500 Wireless Branch Controller Deployment Guide
64
Page 65

Summary
FlexConnect WGB/uWGB Support for Local Switching WLANs
• No special configuration is required on WLC in order to support WGB on Flex AP.
• Fault Tolerance is supported for WGB and clients behind WGB.
• WGB is supported on an IOS AP: 1240, 1130, 1140, 1260, 1600, 1250, 2600, and 3600.
Procedure
Step 1 No special configuration is needed in order to enable WGB/uWGB support on FlexConnect APs for
Complete these steps:
WLANs configured for local switching as WGB. Also, clients behind WGB are treated as normal clients
on local switching configured WLANs by Flex APs. Enable FlexConnect Local Switching on a WLAN.
Flex 7500 Wireless Branch Controller Deployment Guide
65
Page 66

FlexConnect WGB/uWGB Support for Local Switching WLANs
66
Step 2 Set AP Mode to FlexConnect.
Flex 7500 Wireless Branch Controller Deployment Guide
Page 67

FlexConnect WGB/uWGB Support for Local Switching WLANs
Step 3 Associate WGB with wired clients behind this configured WLAN.
Step 4 In order to check the details for WGB, go to Monitor > Clients, and select WGB from the list of clients.
Step 5 In order to check the details of the wired/wireless clients behind WGB, go to Monitor > Clients, and
select the client.
Flex 7500 Wireless Branch Controller Deployment Guide
67
Page 68

Support for an Increased Number of Radius Servers
Limitations
• Wired clients behind WGB will always be on the same VLAN as WGN itself. Multiple VLAN
support for clients behind WGB is not supported on Flex AP for WLANs configured for Local
Switching.
• A maximum of 20 clients (wired/wireless) are supported behind WGB when associated to Flex AP
on WLAN configured for local switching. This number is the same as what we have today for WGB
support on Local mode AP.
• Web Auth is not supported for clients behind WGB associated on WLANs configured for local
switching.
Support for an Increased Number of Radius Servers
Prior to release 7.4, the configuration of RADIUS servers at the FlexConnect group was done from a
global list of RADIUS servers on the controller. The maximum number of RADIUS servers, which can
be configured in this global list, is 17. With an increasing number of branch offices, it is a requirement
to be able to configure a RADIUS server per branch site. In release 7.4 onwards, it will be possible to
configure Primary and Backup RADIUS servers per FlexConnect group which may or may not be part
of the global list of 17 RADIUS authentication servers configured on the controller.
Summary
Procedure
An AP specific configuration for the RADIUS servers will also be supported. The AP specific
configuration will have greater priority than the FlexConnect group configuration.
The existing configuration command at the FlexConnect Group, which needs the index of the RADIUS
server in the global RADIUS server list on the controller, will be deprecated and replaced with a
configuration command, which configures a RADIUS server at the Flexconnect Group using the IP
address of the server and shared secret.
• Support for configuration of Primary and Backup RADIUS servers per FlexConnect group, which
may or may not be present in the global list of RADIUS authentication servers.
• The maximum number of unique RADIUS servers that can be added on a WLC is the number of
FlexConnect groups that can be configured on a given platform times two. An example is one
primary and one secondary RADIUS server per FlexConnect group.
• Software upgrade from a previous release to release 7.4 will not cause any RADIUS configuration
loss.
• The deletion of the primary RADIUS server is allowed without having to deleting the secondary
RADIUS server. This is consistent with the present FlexConnect group configuration for the
RADIUS server.
Step 1 Mode of configuration prior to release 7.4.
A maximum of 17 RADIUS servers can be configured under the AAA Authentication configuration.
Flex 7500 Wireless Branch Controller Deployment Guide
68
Page 69

Support for an Increased Number of Radius Servers
Step 2 Primary and Secondary RADIUS servers can be associated with a FlexConnect Group using a drop-down
list comprising of RADIUS servers configured on the AAA Authentication page.
Step 3 Mode of configuration at FlexConnect Group in release 7.4.
Primary and Secondary RADIUS servers can be configured under the FlexConnect Group using an IP
address, port number and Shared Secret.
Flex 7500 Wireless Branch Controller Deployment Guide
69
Page 70

Enhanced Local Mode (ELM)
Limitations
• Software downgrade from release 7.4 to a previous release will retain the configuration but with
some limitations.
• Configuring a primary/secondary RADIUS server when a previous one is configured will cause the
older entry to be replaced by the new one.
Enhanced Local Mode (ELM)
ELM is supported on the FlexConnect solution. Refer to the best practices guide on ELM for more
information.
Guest Access Support in Flex 7500
Figure 12 Guest Access Support in Flex 7500
Flex 7500 will allow and continue to support creation of EoIP tunnel to your guest anchor controller in
DMZ. For best practices on the wireless guest access solution, refer to the Guest Deployment Guide.
Flex 7500 Wireless Branch Controller Deployment Guide
70
Page 71

Managing WLC 7500 with NCS
The management of the WLC 7500 from NCS is identical to Cisco's existing WLCs.
Managing WLC 7500 with NCS
For more information on managing WLC and discovering templates, refer to the Cisco Wireless Control
System Configuration Guide, Release 7.0.172.0.
Managing WLC 7500 with Cisco Prime
The management of the WLC 7500 from Cisco Prime is identical to Cisco's existing WLCs.
Flex 7500 Wireless Branch Controller Deployment Guide
71
Page 72

Support for PEAP and EAP-TLS Authentication
Support for PEAP and EAP-TLS Authentication
FlexConnect AP can be configured as a RADIUS server for LEAP and EAP-FAST client authentication.
In standalone mode and also when local authentication feature is enabled on the WLANs, FlexConnect
AP will do dot1x authentication on the AP itself using the local radius. With controller release 7.5, PEAP
and EAP-TLS EAP methods are also supported.
EAP-TLS
Certificate Generation for EAP-TLS
The following steps are needed on the WLC and the client in order to authenticate the client to the
FlexConnect AP using EAP-TLS authentication.
On WLC:
1. Generate device certificate for the WLC.
2. Get device certificate signed by CA server.
3. Generate CA certificate from the CA server.
4. Import device and CA certificate into the WLC in .pem format.
On Client:
1. Generate client certificate.
2. Get client certificate signed by CA server.
3. Generate CA certificate from the CA server.
Flex 7500 Wireless Branch Controller Deployment Guide
72
Page 73

Support for PEAP and EAP-TLS Authentication
4. Install client and CA certificate on the client.
Detailed steps on how to accomplish the above steps are listed in Document-100590
(http://www.cisco.com/en/US/products/ps6366/products_configuration_example09186a008093f1b9.sh
tml)
Figure 13 Document 100590
Configuration of EAP-TLS on FlexConnect AP
1. Create WLAN for Local Switching and Local Authentication.
In the example below, two WLANs have been created, one for EAP-TLS and the other for PEAP
authentication.
Figure 14 WLAN Configuration for PEAP and EAP-TLS
2.
Enable FlexConnect Local Switching and FlexConnect Local Auth
Flex 7500 Wireless Branch Controller Deployment Guide
73
Page 74

Support for PEAP and EAP-TLS Authentication
Figure 15 WLANs for Local Switching and Local Authentication
3.
Enable AP Local Authentication.
Enable the Enable AP Local Authentication check box on the FlexConnect groups edit page.
Radius Servers on the FlexConnect group must be ‘Unconfigured’. If any RADIUS servers are
configured on the FlexConnect group, the AP tries to authenticate the wireless clients using the
RADIUS servers first. AP Local Authentication is attempted only if no RADIUS servers are found,
either because the RADIUS servers timed out or no RADIUS servers were configured.
Figure 16 FlexConnect Group Configuration for AP Local Authentication
Selecting EAP methods will now have two more options, PEAP and EAP-TLS under the
4.
FlexConnect group with the existing LEAP and EAP-FAST options.
a. Current controller release supports downloading of EAP device and root (CA) certificates to the
controller and the same is stored in PEM format on the flash.
Flex 7500 Wireless Branch Controller Deployment Guide
74
Page 75

Figure 17 Downloading Vendor Device Certificate
Figure 18 Downloading Vendor CA Certificate
Support for PEAP and EAP-TLS Authentication
With release 7.5, these certificates will be used for authenticating clients using EAP-TLS. Both
b.
the device and root certificates will be downloaded to all the FlexConnect APs in the
FlexConnect group if the EAP-TLS method is enabled, and the same is used at the AP to
authenticate the clients.
c. When a new AP joins the group, certificates will be pushed to the AP along with other
configurations. The user has to download the EAP device and Root certificates to controller
prior to enabling EAP-TLS on the FlexConnect group.
d. Upon receiving a certificate message from the controller, the AP will import these certificates,
store them in memory and use them for authenticating clients.
e. EAP TLS Certificate Download option is provided to push any updated certificates to the AP.
Flex 7500 Wireless Branch Controller Deployment Guide
75
Page 76

Support for PEAP and EAP-TLS Authentication
Figure 19 Enabling PEAP and EAP TLS on AP Local Authentication under FlexConnect Group
Certificate Files on AP
Four files are downloaded to the AP, when EAP-TLS is enabled.
• eapdev.pem.ca – This is the CA (root) certificate.
• eapdev.pem.crt –This is the public certificate of the device.
• eapdev.pem.prv –This is the RSA private key of the device.
• eapdevpwd – This is the password file to protect the private key.
Figure 20 Files Stored in the Flash on AP
Client Configuration
Configure the wireless profile for EAP-TLS by selecting EAP Type EAP-TLS and specifying the
Trusted Root certificate Authorities and the client certificate.
Flex 7500 Wireless Branch Controller Deployment Guide
76
Page 77

Figure 21 Wireless Profile for EAP-TLS
Support for PEAP and EAP-TLS Authentication
Figure 22 Validate Server Identity
Once the client is connected, Server Based Authentication will reflect EAP-TLS.
Flex 7500 Wireless Branch Controller Deployment Guide
77
Page 78

Support for PEAP and EAP-TLS Authentication
Figure 23 Client Authentication using EAP-TLS
Client Certificates
The Trusted Root and Client Certificates can be viewed as follows (These are the certificates as
generated earlier)
Flex 7500 Wireless Branch Controller Deployment Guide
78
Page 79

Figure 24 Certificates on Client
Support for PEAP and EAP-TLS Authentication
Flex 7500 Wireless Branch Controller Deployment Guide
79
Page 80

Support for PEAP and EAP-TLS Authentication
Figure 25 Trusted Root (CA) Certificate on Client
Flex 7500 Wireless Branch Controller Deployment Guide
80
Page 81

Figure 26 Trusted Client Certificate
Support for PEAP and EAP-TLS Authentication
Show Commands
The EAP type of the client will be reflected on the WLC and can be seen in the output of show client
detail
Flex 7500 Wireless Branch Controller Deployment Guide
81
Page 82

Support for PEAP and EAP-TLS Authentication
Figure 27 EAP Type for Client Authenticated using EAP-TLS
EAP-PEAP
User Creation
PEAP (EAP-MSCHAPv2 and EAP-GTC) EAP Type is supported with release 7.5 and Users need to be
added on the WLC as shown below. A maximum of 100 users can be added per FlexConnect group.
Figure 28 User Addition for Local Authentication
Flex 7500 Wireless Branch Controller Deployment Guide
82
Page 83

Client Configuration
Selecting EAP Type EAP-MSCHAPv2 or GTC can configure the wireless profile for EAP-PEAP.
Figure 29 Wireless Profile for EAP-PEAP (EAP-MSCHAPv2)
Support for PEAP and EAP-TLS Authentication
Users created on the controller need to be configured on the client.
Flex 7500 Wireless Branch Controller Deployment Guide
83
Page 84

Support for PEAP and EAP-TLS Authentication
Figure 30 User Name and Password for PEAP
Flex 7500 Wireless Branch Controller Deployment Guide
84
Page 85

Support for PEAP and EAP-TLS Authentication
Figure 31 Cisco Aironet Desktop Utility Profile Management
Once the client is connected, Server Based Authentication will reflect PEAP(EAP-MSCHAPv2)
Figure 32 Client Authentication using PEAP(EAP-MSCHAPv2)
Once the client is authenticated, the EAP Type can be seen under the Client Detail page.
Flex 7500 Wireless Branch Controller Deployment Guide
85
Page 86

Support for PEAP and EAP-TLS Authentication
Figure 33 Web GUI Client Details
Show Commands
The EAP type of the client will be reflected on the WLC and can be seen in the output of show client
detail
Figure 34 EAP Type of Client Authenticated using PEAP
CLI Support for PEAP and EAP-TLS on FlexConnect APs
Two new CLIs have been added to configure PEAP and EAP-TLS from the controller.
config flexconnect group <groupName> radius ap peap <enable | disable>
config flexconnect group <groupName> radius ap eap-tls <enable | disable>
Flex 7500 Wireless Branch Controller Deployment Guide
86
Page 87

WLAN-VLAN mapping at FlexConnect Group Level
A CLI for certificate download has been added as well.
config flexconnect group <groupName> radius ap eap-cert download
Configurations at the AP can be seen from the console.
Figure 35 CLI Commands on AP Console
The following commands can be used to troubleshoot this feature:
debug eap all
debug aaa authentication
debug dot11 aaa authenticator all
debug aaa api
debug aaa subsys
debug dot11 aaa dispatcher
debug aaa protocol local
debug radius
debug aaa dead-criteria transaction
Guidelines
• FlexConnect AP should be in standalone mode or configured for Local authentication.
• Certificates must be present on the AP for EAP-TLS to work.
WLAN-VLAN mapping at FlexConnect Group Level
Prior to release 7.5, WLAN to VLAN mapping was done on a per AP basis.
With increasing number of APs in a deployment, there is a need to provide the capability of adding
WLAN to VLAN maps from the FlexConnect group. This will be supported in release 7.5.
Flex 7500 Wireless Branch Controller Deployment Guide
87
Page 88

WLAN-VLAN mapping at FlexConnect Group Level
This will push the WLAN to VLAN mapping to all the APs present in the FlexConnect group. The
FlexConnect level configuration will have a higher precedence compared to the WLAN-VLAN mapping
configured on the WLAN.
WLAN-VLAN Mapping Inheritance
• WLAN level WLAN-VLAN mapping has the lowest precedence.
• Higher precedence mapping will override the mapping of lower precedence
• AP level WLAN-VLAN mapping has the highest precedence
• On deletion of a higher precedence mapping, the next highest precedence mapping will take effect.
The following figure depicts the order of precedence as it refers to WLAN-VLAN mapping at the
WLAN, FlexConnect group and at the AP.
Figure 36 Flow of Inheritance
GUI Configuration
1. Create WLAN for Local Switching
Flex 7500 Wireless Branch Controller Deployment Guide
88
Page 89

Figure 37 WLAN for Local Switching
Figure 38 FlexConnect Local Switching
WLAN-VLAN mapping at FlexConnect Group Level
The WLAN is mapped to the management VLAN 56.
Flex 7500 Wireless Branch Controller Deployment Guide
89
Page 90

WLAN-VLAN mapping at FlexConnect Group Level
Figure 39 WLAN Mapped to VLAN 56 Management Interface
Figure 40 WLAN Mapped to VLAN 56 as Per WLAN-Specific Mapping
When a client connects to this WLAN, it will get an IP in VLAN 56.
Flex 7500 Wireless Branch Controller Deployment Guide
90
Page 91

WLAN-VLAN mapping at FlexConnect Group Level
Figure 41 Client in VLAN 56
2. Create WLAN-VLAN mapping under FlexConnect Groups. This capability is the new feature in
release 7.5.
Figure 42 WLAN Mapped to VLAN 57 under FlexConnect Group
WLAN-VLAN mappings can be viewed per AP from the VLAN Mappings page
Flex 7500 Wireless Branch Controller Deployment Guide
91
Page 92

WLAN-VLAN mapping at FlexConnect Group Level
Figure 43 VLAN Mappings at AP
In this example, the WLAN is mapped to VLAN 57 on the FlexConnect Group, since the Group-specific
mappings take precedence over WLAN-specific mappings.
Figure 44 WLAN 1 Mapped to VLAN 57 as Per Group-Specific Configuration Inheritance
The client is assigned an IP address in VLAN 57.
Flex 7500 Wireless Branch Controller Deployment Guide
92
Page 93

WLAN-VLAN mapping at FlexConnect Group Level
Figure 45 Client in VLAN 57
To create a WLAN-VLAN mapping at the AP, select Make AP Specific under VLAN Mappings.
3.
Once this is done, the WLAN is mapped to VLAN 58 since AP-specific mappings take precedence over
Group-specific and WLAN-specific mappings.
Figure 46 WLAN Mapped to VLAN 58 as Per AP-Specific Mapping Inheritance
The client is assigned an IP address in VLAN 58.
Flex 7500 Wireless Branch Controller Deployment Guide
93
Page 94

WLAN-VLAN mapping at FlexConnect Group Level
Figure 47 Client in VLAN 58
CLI Configuration
The following CLIs have been added as part of this feature:
• config flexconnect group <group> wlan-vlan wlan <wlan-id> add vlan <vlan-id>
• config flexconnect group <group> wlan-vlan wlan <wlan-id> delete
• config ap flexconnect vlan remove wlan <wlan_id> <ap_name>
Figure 48 WLAN-VLAN Configuration at FlexConnect Group from CLI
The command show flexconnect group detail can be used to see the WLAN-VLAN mapping for the
FlexConnect group
Flex 7500 Wireless Branch Controller Deployment Guide
94
Page 95

Figure 49 show flexconnect group detail Output
WLAN-VLAN mapping at FlexConnect Group Level
The command show ap config general <AP name> can be used to view the WLAN-VLAN mappings
per AP.
Figure 50 show ap config general Output
The following commands can be used to troubleshoot this feature:
On WLC:
• debug flexconnect wlan-vlan <enable | disable>
On AP:
• debug capwap flexconnect wlan-vlan
Flex 7500 Wireless Branch Controller Deployment Guide
95
Page 96

Client ACL Support
Guidelines
• The WLAN should be locally switched.
• The configuration will be pushed to the AP only if the WLAN is broadcasted on that AP.
Client ACL Support
Prior to release 7.5, we support FlexConnect ACLs on the VLAN. We also support AAA override of
VLANs. If a client gets an AAA override of VLAN, it is placed on the overridden VLAN and the ACL
on the VLAN applies for the client. If an ACL is received from the AAA for locally switched clients, we
ignore the same. With release 7.5, we address this limitation and provide support for client based ACLs
for locally switched WLANs.
Client ACL Overview
a. This feature allows application of Per-Client ACL for locally switching WLANs.
b. Client ACL is returned from the AAA server on successful Client L2 Authentication/Web Auth
as part of Airespace Radius Attributes.
c. The controller will be used to pre-create the ACLs at the AP. When the AP receives the ACL
configuration, it will create the corresponding IOS ACL. Once, AAA server provides the ACL,
the client structure will be updated with this information.
d. There will be configuration per FlexConnect group as well as per AP. A maximum of 16 ACLs
can be created for a FlexConnect group and a maximum of 16 ACLs can be configured per-AP.
e. In order to support fast roaming (CCKM/PMK) for the AAA overridden clients, the controller
will maintain these ACL in the cache and push them to all APs which are part of the
FlexConnect group.
f. In the case of central authentication, when the controller receives the ACL from the AAA server,
it will send the ACL name to the AP for the client. For locally authenticated clients, the ACL
will be sent from the AP to the controller as part of CCKM/PMK cache, which will then be
distributed to all APs belonging to the FlexConnect-group.
g. Maximum of 16 Client ACLs per FlexConnect group, maximum of 16 Client ACLs per-AP
h. Total of 96 ACLs can be configured on the AP (32 VLAN-ACL, 16 WLAN-ACL, 16 Split
tunnel, 16 FlexConnect Client ACL, 16 AP Client ACL), each ACL with 64 rules.
i. The ACL will be applied on the dot11 side for the client in question. This ACL will be applied
in addition to the VLAN ACL, which is applied on the VLAN of the Ethernet interface of the
AP.
j. Client ACL applied in addition to VLAN-ACL, both can exist simultaneously and are applied
serially.
Flex 7500 Wireless Branch Controller Deployment Guide
96
Page 97

Steps to Configure Client ACL
1. Create a Local Switching WLAN, which is either centrally switched or locally switched.
Figure 51 Create Local Switching WLAN
2.
Turn on AAA override for the WLAN
Enable AAA override
Client ACL Support
3. Create a FlexConnect ACL
FlexConnect ACL can be configured from the Security page as well as from the Wireless page.
Flex 7500 Wireless Branch Controller Deployment Guide
97
Page 98

Client ACL Support
Figure 52 Configure FlexConnect ACL
Figure 53 Configure FlexConnect ACL
4. Assign the FlexConnect ACL to the FlexConnect group or to the AP
Flex 7500 Wireless Branch Controller Deployment Guide
98
Page 99

Figure 54 ACL Mapping on FlexConnect Group
Figure 55 ACL Mapping on AP
Client ACL Support
Configure the Airespace attribute on the Radius/Cisco ACS server/ISE.
5.
Flex 7500 Wireless Branch Controller Deployment Guide
99
Page 100

Client ACL Support
Figure 56 Aire-Acl-Name on Cisco ACS Server
Figure 57 Airespace ACL Name on ISE
Authenticate the client.
6.
Flex 7500 Wireless Branch Controller Deployment Guide
100
 Loading...
Loading...