Page 1

Cisco 880 Series Integrated Services Router Software
Configuration Guide
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Text Part Number: OL-22206-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGA RDING THE P RODUCTS IN THIS MA NUAL ARE SUBJECT TO CHANGE W ITH OUT NOT ICE. A LL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILIT Y FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRA NTY FO R THE A CCOMPA NYING PRODUCT A RE SET FORTH IN T HE INFORM ATION P ACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DO CUMENT FILES AND SOFTWARE OF THESE SUPPL IERS ARE PROVI DED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAI M ALL WARRANTIE S, EXPRESSED OR
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICUL AR PURPOSE AN D NONINFRINGE MENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOS T PROFITS OR LOSS OR DAMAGE TO DATA ARISIN G OUT OF THE USE OR INABILI TY TO USE THIS MA NUAL, EVEN I F CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SU CH DAMA GES.
CCDE, CCENT, CCSI, Cisco Eos, Cisco HealthPresence, Cisco IronPort, the Cisco logo, Cisco Lumin, Cisco Nexus, Cisco Nurse Connect, Cisco StackPower,
Cisco
StadiumVision, Cisco TelePresence, Cisco Unified Computing System, Cisco WebEx, DCE, Flip Channels, Flip for Good, Flip Mi no, Flip Video , Flip Video (D esign),
Flipshare (Design), Flip Ultra, and Welcome to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn, Cisco
service marks; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the
Cisco
Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without
Limitation, EtherFast, EtherSwitch, Event Center, Fast Step, Follow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, iQuick Study,
IronPort, the IronPort
PCNow, PIX, PowerPanels, ProConnect, ScriptShare, SenderBase, SMARTnet, Spectrum Expert, StackWise, The Fastest Way to Increase Your Internet Quotient, TransPath,
WebEx, and the WebEx
All other trademarks mentioned in this document or website are the property of th eir respective owners. The use of the word partn er d oes not imply a par tn ers hi p r elati ons hip
between Cisco and any other company. (1005R)
logo, LightStream, Linksys, MediaTone, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, Network Registrar,
logo are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
IMPLIED, INCLUDING, WITHOUT
Store, and Flip Gift Card are
Any Internet Protocol (IP) addresses us ed in this docu ment ar e not i ntend ed to be ac tual address es. A ny exam ples, comman d d isplay output, and fig ures included in the
document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
Cisco 880 Series Integrated Services Router Software Configuration Guide
© 2010-2011 Cisco Systems, Inc. All rights reserved.
Page 3

Preface
This preface describes the objectives, audience, organization, and conventions used in this guide, and
describes related documents that have additional information. It contains the following sections:
• Objective, page xiii
• Audience, page xiii
• Organization, page xiv
• Conventions, page xiv
• Related Documentation, page xv
Objective
Audience
• Searching Cisco Documents, page xv
• Obtaining Documentation and Submitting a Service Request, page xvi
This guide provides an overview and explains how to configure the various features for the Cisco 880
series Integrated Services Routers (ISR). Some information may not apply to your particular router
model.
For warranty, service, and support information, see the “Cisco One-Year Limited Hardware Warranty
Terms” section in Readme First for the Cisco 800 Series Integrated Services Routers that was shipped
with your router.
This guide is intended for Cisco equipment providers who are technically knowledgeable and familiar
with Cisco routers and Cisco
IOS software and features.
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
xiii
Page 4
Organization
This guide is organized into the following parts, chapters, and appendixes.
Chapters
Product Overview Provides a brief description of the router models and
Wireless Device Overview Provides an introduction to the wireless device on
Basic Router Configuration Provides procedures for configuring the basic
Basic Wireless Device Configuration Provides procedures for initial configuration of the
Conventions
Preface
the available software features.
the router and its use in network configurations.
parameters of the router.
wireless device.
These documents use the conventions listed in Table 1 to convey instructions and information.
Table 1 Command Conventions
Convention Description
boldface font Commands and keywords.
italic font Variables for which you supply values.
[ ] Optional keywords or arguments appear in square brackets.
{x | y | z} A choice of required keywords appears in braces separated by vertical bars. You
must select one.
screen font
boldface screen
font
< > Nonprinting characters, for example, passwords, appear in angle brackets in
[ ] Default responses to system prompts appear in square brackets.
Note Means reader take note. Notes contain helpful suggestions or references to additional information and
material.
Examples of information displayed on the screen.
Examples of information you must enter.
contexts where italics are not available.
xiv
Caution This symbol means reader be careful. In this situation, you might do something that could result in
equipment damage or loss of data.
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 5

Preface
Tip Means the following information will help you solve a problem. The tips information might not be
troubleshooting or even an action, but could be useful information, similar to a Timesaver.
Related Documentation
In addition to Cisco 880 Series ISR Software Configuration Guide (this document), it includes the
following documents:
• Readme First for the Cisco 800 Series Integrated Services Routers
• Regulatory Compliance and Safety Information for Cisco 800 Series and SOHO Series Routers
• Declarations of Conformity and Regulatory Information for Cisco Access Products with 802.11n
Radios
• Software Activation on Cisco Integrated Services Routers and Cisco Integrated Service Routers G2
• Cisco IOS Release Notes for Cisco IOS Release 15.1.4 (M)
You might also need to refer to the following documents:
• Cisco System Manager Quick Start Guide
• Cisco IOS Release 12.4 Quality of Service Solutions Configuration Guide
• Cisco IOS Security Configuration Guide, Release 12.4
• Cisco IOS Security Configuration Guide, Release 12.4T
• Cisco IOS Security Command Reference, Release 12.4
• Cisco IOS Security Command Reference, Release 12.4T
• Cisco IOS Command Reference for Cisco Air onet Access Point s and Bridges, versions 12.4(1 0b) JA
and 12.3(8) JEC
• Cisco Aironet 1240AG Access Point Support Documentation
• Cisco 4400 Series Wireless LAN Controllers Support Documentation
• LWAPP Wireless LAN Controllers
• LWAPP Wireless LAN Access Points
• Cisco IOS Release 12.4 Voice Port Configuration Guide
• SCCP Controlled Analog (FXS) Ports with Supplementary Features in Cisco IOS Gateways
• Cisco Software Activation Conceptual Overview
• Cisco Software Activation Tasks and Commands
Searching Cisco Documents
To search an HTML document using a web browser, use the Ctrl+F (Windows) or Cmd+F (Apple)
sequences. In most browsers the option to search whole words only, invoke case sensitivity, or search
forward and backward are also available.
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
xv
Page 6

Preface
To search a PDF document in Adobe Reader, use the basic Find toolbar (Ctrl+F) or the Full Reader
Search window (Shift+Ctrl+F). Use the Find toolbar to find words or phrases within one specific
document. Use the Full Reader Search window to search multiple PDF files simultaneously as well as
change case sensitivity , and ot her options. Adobe Read er comes wit h online help with more information
regarding searching PDF documents.
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional
information, see the monthly What’s
revised Cisco
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What’s New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed
and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free
service and Cisco currently supports RSS version 2.0.
technical documentation, at:
New in Cisco Product Documentation, which also lists all new and
xvi
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 7

Product Overview
This chapter provides an overview of the features available for the Cisco 880 series Integrated Service
Router (ISR), and contains the following sections:
• General Description, page 1-1
• Cisco 880 Series ISR, page 1-1
• Licensing, page 1-3
• 880 SKUs for next generation Cisco 880 Series ISR platforms, page 1-3
• Memory, page 1-5
• LED Overview, page 1-6
• Power Supply, page 1-7
General Description
CHAPTER
1
The Cisco 880 ISR provides Internet, VPN, data, and backup capability to corporate teleworkers and
remote and small offices of fewer than 20 users. These routers are capable of bridging and multiprotocol
routing between LAN and WAN ports, and provide advanced features such as antivirus protection. In
addition, the Cisco
act as a wireless access point.
880W series ISR incorporates an 802.11b/g/n wireless radio that allows the ISR to
Cisco 880 Series ISR
The Cisco 880 series ISRs are a family of fixed-configuration data routers, as described in the following
sections:
• Models of the Cisco 880 Series ISRs, page 1-1
• Common Features, page 1-2
Host router sofware will be runnin gon 1st core and WLAN AP software will be running on 2nd core.
Models of the Cisco 880 Series ISRs
The Cisco 880 series ISRs have data capabilities. Each router has one WA N port. Data backup ports are
also available on most of the routers. The 802.11b/g/n option is available on all models.
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
1-1
Page 8

Cisco 880 Series ISR
Table 1-1 gives the port configurations of the Cisco 880 series data routers.
Table 1-1 Port Configurations of the Cisco 880 Series Data ISRs
Model WAN Port
C886VA-W-E-K9 ADSL2+ UR2
C887VAM-W-E-K9 ADSL2+ Annex M
C887VA-W-A-K9 ADSL2+ Annex A
C887VA-W-E-K9 ADSL2+ Annex A
C881W-A-K9 FE
C881W-E-K9 FE
C881W-P-K9 FE
Common Features
Cisco 880 series ISRs support the following features:
• 4-port 10/100 FE LAN Switch, page 1-2
• 802.11b/g/n Wireless LAN, page 1-2
Chapter 1 Product Overview
• Battery-backed-up Real-Time Clock, page 1-2
• Security Features, page 1-2
4-port 10/100 FE LAN Switch
This switch provides four ports for connecti ng to 10/100BA SE-T FE LANs, access point s, or IP phon es.
A factory installed upgrade is available that gives Power over Ethernet (PoE) on two of the ports to
provide power to access points or phones.
802.11b/g/n Wireless LAN
The Cisco 880W series ISRs have an integrated 802.11b/g/n single radio module for wireless LAN
connectivity. With this module, the router can act as an access point in the local infrastructure.
Battery-backed-up Real-Time Clock
A battery-backed-up real-time clock (RTC) provides the date and time when the system is powered on.
The RTC is used to verify the validity of the Certification Authority stored on the router.
Security Features
The Cisco 880 platforms provide the following security features:
• Intrusion Prevention System (IPS)
• Dynamic Multipoint VPN (DMVPN)
1-2
• IPsec
• Quality of service (QoS)
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 9

Chapter 1 Product Overview
• Firewall
• URL filtering
Licensing
The Cisco 880 ISR is shipped with licensed software installed. Software features may be upgraded and
the software licenses may be managed through Cisco Licensing Manager. See
Cisco Integrated Services Routers on Cisco.com for details.
When you order a new router, you can specify the soft ware image and feature set. The image and feature
set are installed on your router before you receive it, so you do not need to purchase a software license.
The router stores the software license file on the flash memory.
Selecting Feature Sets
Some feature sets are bundled and offered with a software license that is installed on the hardware
platforms. For a list of features available with a software license on the Cisco
Sheet. See Cisco IOS Software Activation Tasks and Commands on Cisco.com for details about how to
activate and manage the software licenses.
Licensing
Software Activation On
880, see Cisco 880 Data
880 SKUs for next generation Cisco 880 Series ISR platforms
The following lists the SKUs particular for Next generation Cisco 880 Series ISR platforms.
C881W
• 512 MB memory
• 256 MB Flash
• 4-port 10/100 Switch
• 2-port PoE is a factory-configurable option
• 10/100 FE WAN
• 1 port console/aux
• 1 port external USB 2.0
• Real-time clock
• Embedded WLAN antenna on wireless models
C886VA-W
OL-22206-01
• 512 MB memory
Cisco 880 Series Integrated Services Router Software Configuration Guide
1-3
Page 10

880 SKUs for next generation Cisco 880 Series ISR platforms
• 256 MB Flash
• 4-port 10/100 Switch
• 2-port PoE is a factory-configurable option
• 1 port console/aux
• 1 port external USB 2.0
• ADSL2+ Annex B
• ISDN backup WAN
• Real-time clock
• Embedded WLAN antenna on wireless models
C887VAM-W
• 512 MB memory
• 256 MB Flash
• 4-port 10/100 Switch
Chapter 1 Product Overview
C887VA-W
• 2-port PoE is a factory-configurable option
• 1 port console/aux
• 1 port external USB 2.0
• ADSL2+ Annex M
• Real-time clock
• Embedded WLAN antenna on wireless model
• 512 MB memory
• 256 MB Flash
• 4-port 10/100 Switch
• 2 port PoE is a factory-configurable option
• 1 port console/aux
• 1 port external USB 2.0
• ADSL2+ Annex A
• Real-time clock
• Embedded WLAN antenna on wireless model
C881GW
Cisco 880 Series Integrated Services Router Software Configuration Guide
1-4
• 512 MB memory
• 256 MB Flash
OL-22206-01
Page 11

Chapter 1 Product Overview
C887GW
Memory
• 4-port 10/100 Switch
• 2-port PoE is a factory-configurable option
• 10/100 FE WAN
• 3G modem with Dual SIMM card slots
• 1 port console/aux
• 1 port external USB 2.0
• Real-time clock
• Embedded WLAN antenna on wireless models
• 512 MB memory
• 256 MB Flash
• 4-port 10/100 Switch
• 2-port PoE is a facotry-configurable option
Memory
• 1 port console/aux
• 1 port external USB 2.0
• ADSL2+ Annex A
• 3G modem with Dual SIMM card slots
• Real-time clock
• Embedded WLAN antenna on wireless models
Table 1-2 illustrates the on board memory and flash size for the first and second core. The total memory
installed is 512 MB + 256 MB flash, and they are partitioned as shown in the following table.
Table 1-2 Memory Specifications
On Board Memory 1st core 2nd core
512 MB 384 MB 128 MB
Flash size
256 192 64
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
1-5
Page 12
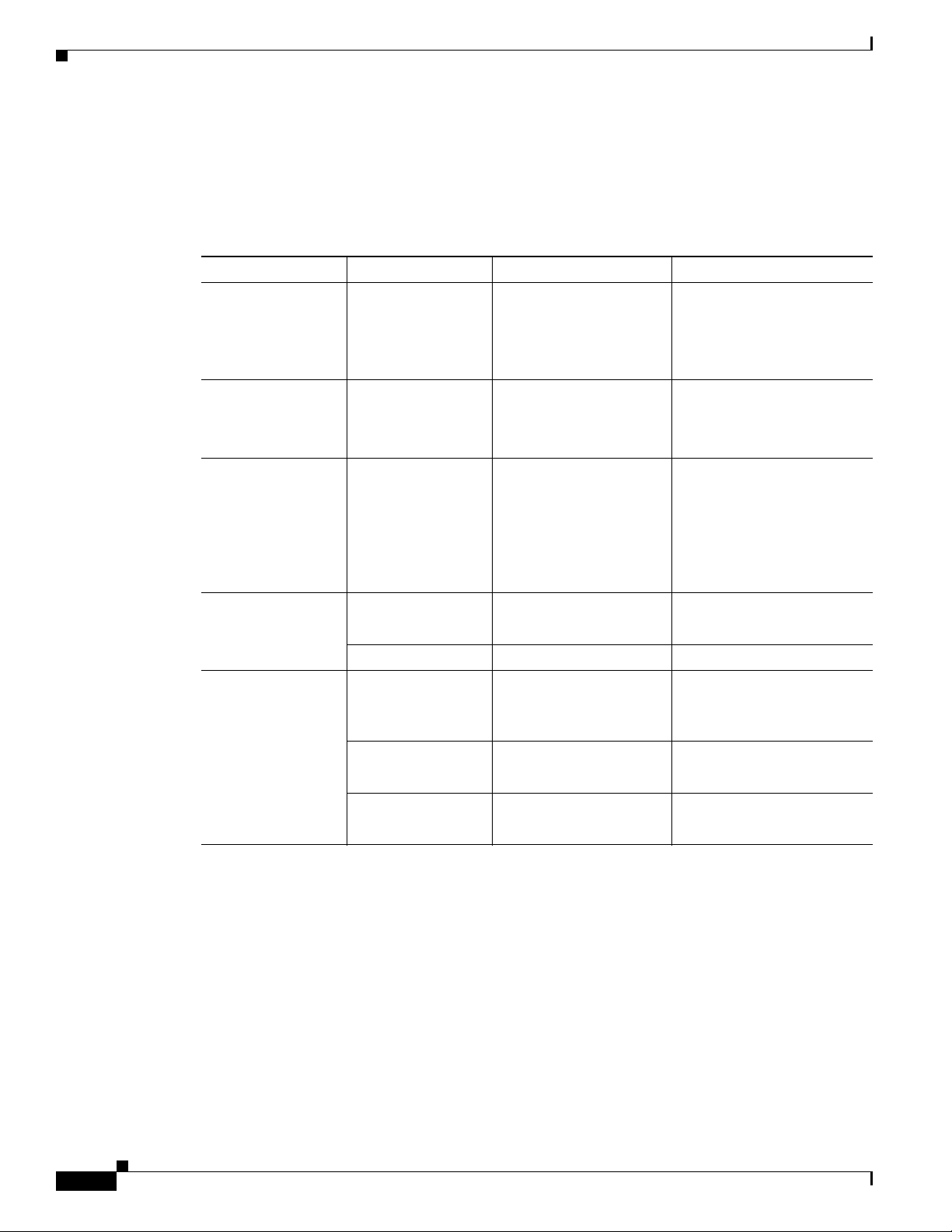
LED Overview
LED Overview
All LEDs are visible on the front of the chassis (bezel side). No LEDs are mounted on the I/O side.
Table 1-3 LED Definition Summary by Interface
LED Color Description Indication
PWR Ok Green Power On OK, Rourter
Ethernet Switch and
FE/GE LAN/WAN
ports
PoE Green/Yellow PoE Status Off= no device powered, PoE
Chapter 1 Product Overview
Off= no power
Operational
Green Ethernet Switch Off= No link
Steady on= normal operation
Blink= boot up phase in
ROM Monitor mode
Steady on= link
Blink= TXD/RXD data
administratively disabled
Steady on green= PD
connected and powered
Steady on yellow= PD denied
power, power delivery fault
xDSL Green CD Steady on= connected
Blink= training
Green Data Blink= TXD/RXD data
ISDN data Green Link Off= no connection
Steady on= BRI S/T
connection established
Green B1 channel data Off= No data
Blin= TXD/RXD data
Green B2 channel data Off= No data
Blink= TXD/RXD data
1-6
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 13
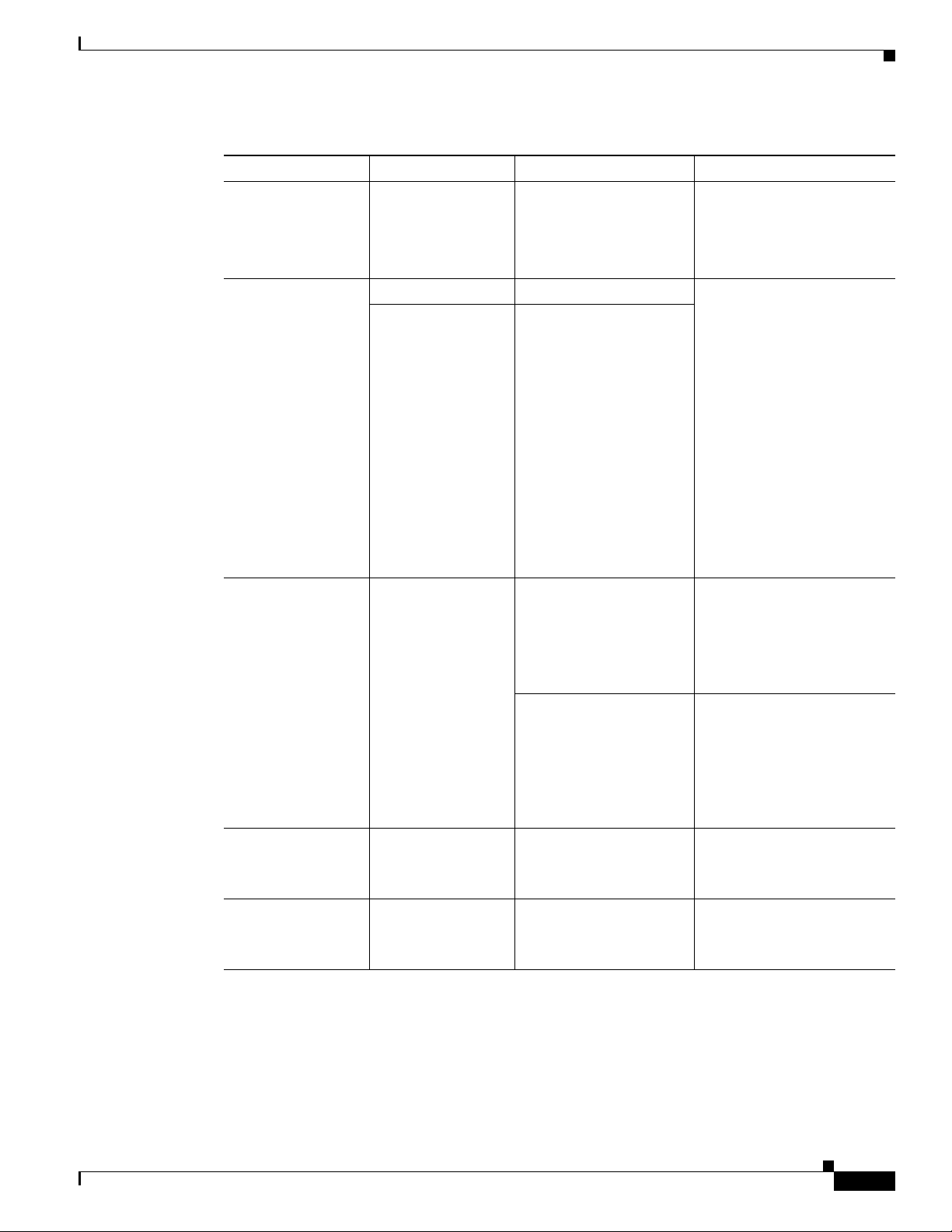
Chapter 1 Product Overview
Table 1-3 LED Definition Summary by Interface (continued)
LED Color Description Indication
PWR Ok Green Power On OK, Rourter
LED Overview
Off= no power
Operational
Steady on= normal operation
Blink= boot up phase in
ROM Monitor mode
Wireless/LAN Green 2.4 GHz Radio Off= Radio is down (no SSID
Green If dual-radio is installed
configured)
Steady on= Radio is up, SSID
configured, beacons being
send, client is associated, no
data traffic being
sent/received
Slow blink= Radio is up
(SSID configured and
sending beacon)
Fast Blink= Radio is up,
client is associated, radio is
sending/receiving data traffic
Green Autonomous Mode Off= Ethernet link down
On= Ethernet link up no
traffic
Blink= Ethernet link up with
data traffic
Unified Mode Off= Ethernet link down
On= Ethernet link up,
connected to controller
OL-22206-01
Blink= AP not
communicating with
controller
VPN_OK Off= no tunnel
Steady on= at least one
tunnel is up
PPP_OK Off=no PPP session
Steady on= at least one PPP
established
Cisco 880 Series Integrated Services Router Software Configuration Guide
1-7
Page 14

Power Supply
Power Supply
External 12V Power Supply Adapter
The following power supplies are used accross Next generation Cisco 880 ISR platforms depending on
SKU:
• New grounded 12 V 30 W external desktop adapter for all 86x and 88x models. Connection to the
chassis is with a single barrel connector.
.
On board 12V Power supply
PoE ports powered from 12 VDC on motherboard.
Power over Ethernet (PoE Inline Power Option)
Chapter 1 Product Overview
Inline power is a configurator option. PoE configured boxes are supplied with a 12 VDC 60 W adapter
in lieu of the 30 W.
Images supported
c800-universalk9-mz
This image offers all IOS features supported by c8xx platforms.
c800-universalk9_npe-mz
This image does not support VPN payload and secure voice functionality, and statisfies import
considerations for CIS countries.
Licenses for each image:
For universalk9 image:
Technology Package licenses:
–
Advipservices
–
advsecurityk9
1-8
Feature licenses:
–
ios-ips-update
–
SSL_VPN
For universalk9_npe image:
Technology Package licenses:
–
advipservices_npe
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 15

Chapter 1 Product Overview
–
advsecurity_npe
Feature licenses:
–
ios-ips-ipdate
Minimum software version needed to support AP802
Table 1-4 Software version needed for AP802
Software Minimum version
Router IOS 15.1(4) M
AP IOS (Autonomous mode) TBD
AP IOS (unified mode) J.MR2
WLC J.MR2
WCS J.MR2
Images supported
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
1-9
Page 16

Images supported
Chapter 1 Product Overview
1-10
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 17

Wireless Device Overview
Wireless devices (commonly configured as access points) provide a secure, af fordable, and easy-to-use
wireless LAN solution that combines mobility and flexibility with the enterprise-class features required
by networking professionals. When configured as a access point, the wireless device serves as the
connection point between wireless and wired networks or as the center point of a stand-alone wireless
network. In large installations, wireless users within radio range can roam throughout a facility while
maintaining seamless, uninterrupted access to the network.
With a management system based on Cisco IOS software, wireless devices are Wi-Fi CERTIFIED™,
802.11b-compliant, 802.11g-compliant, and 802.11n-compliant wireless LAN transceivers.
Software Modes
The access point is shipped with an autonomous image and a recovery image on the access point’s flash.
The default mode is autonomous; however , the access p oint can be upgraded to operate in Cisco Unified
Wireless mode.
Each mode is described below:
–
Autonomous mode—supports standalone network configurations, where all configuration
settings are maintained locally on the wireless device. Each autonomous device can load its
starting configuration independently, and still operate in a cohesive fashion on the network.
CHAPTER
2
OL-22206-01
–
Cisco Unified Wireless mode—operates in conjunction with a Cisco Unified Wireless LAN
controller, where all configurat ion information is maintained within the cont roller. In the Cisco
Unified Wireless LAN architecture, wireless devi ces operate in the lightweight mode using
Leightweight Access Point Protocol (LWAPP), (as opposed to autonomous mode). The
lightweight access point, or wireless device, has no configuration until it associates to a
controller. The configuration on the wireless device can be modified by the controller only when
the networking is up and running. The controller manages the wireless device configuration,
firmware, and control transactions such as 802.1x authentication. All wireless traffic is tunneled
through the controller.
See Why Migrate to a Cisco Unified Wireless Network? on Cisco.com for more about this
network architecture design.
Cisco 880 Series Integrated Services Router Software Configuration Guide
2-1
Page 18

Management Options
Management Options
The wireless device runs its own version of Cisco IOS software that is separate from the Cisco IOS
software operating on the router. You can configure and monitor the access point with several different
tools:
• Cisco IOS software CLI
• Simple Network Management Protocol (SN MP)
• Web-browser interface:
http://cisco.com/en/US/docs/wireless/access_point/12.4_10b_JA/configuration/guide/scg12410b-c
hap2-gui.html
Note The web-browser interface is fully compatible with Microsoft Internet Explorer version 6.0 on
Windows 98, 2000, and XP plat forms, and with Netscape version 7.0 on W indow s 98, 2000, XP,
and Solaris platforms.
Chapter 2 Wireless Device Overview
Note A void using t he CLI and the web-browser t ools concurrently t o configure the wireless devi ce. If
you configure the wireless device using the CLI, the web-browser interface may display an
inaccurate interpretation of the configuration. This inappropriate display of information does not
necessarily mean the wireless device is misconfigured .
Use the interface dot11radio global configuration CLI command to place the wireless device into the
radio configuration mode.
2-2
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 19

Chapter 2 Wireless Device Overview
Access point
Access point
135445
Network Configuration Examples
Setup the access point role in any of these common wireless network configurations. The access point
default configuration is as a root unit co nnec te d to a wired LAN or as the central unit in an all-wireless
network. Access points can also be configured as bridges and workgroup bridges. These roles require
specific configurations, as defined in the following examples.
• Root Access Point, page 2-3
• Central Unit in an All-Wireless Network, page 2-4
Root Access Point
An access point connected directly to a wired LAN provides a connection point for wireless users. If
more than one access point is connected to the LAN, users can roam from one area of a facility to another
without losing their connection to the network. As users move out of range of one access point, they
automatically connect to th e networ k (assoc iate) through another access point. The roaming process is
seamless and transparent to the user.
Figure 1 shows access points acting as root units on a wired LAN.
Network Configuration Examples
Figure 1 Access Points as Root Units on a Wired LAN
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
2-3
Page 20

Network Configuration Examples
Access point
135443
Central Unit in an All-Wireless Network
In an all-wireless network, an access point acts as a stand-alone root unit. The access point is not
attached to a wired LAN; it functions as a hub linking all stations together. The access point serves as
the focal point for communications, increasing the communication range of wireless users.
shows an access point in an all-wireless network.
Figure 2 Access Point as Central Unit in All-Wireless Network
Chapter 2 Wireless Device Overview
Figure 2
2-4
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 21

CHAPTER
3
Basic Router Configuration
This chapter provides procedures for configuring the basic parameters of your Cisco router, including
global parameter settings, routing protocols, interfaces, and command-line access. It also describes the
default configuration on startup.
• Interface Ports, page 3-2
• Default Configuration, page 3-2
• Information Needed for Configuration, page 3-4
• Configuring Command-Line Access, page 3-5
• Configuring Global Parameters, page 3-7
• Configuring WAN Interfaces, page 3-7
• Configuring a Fast Ethernet WAN Interface, page 3-8
• Configuring the Fast Ethernet LAN Interfaces, page 3-16
• Configuring the Wireless LAN Interface, page 3-16
• Configuring a Loopback Interface, page 3-17
• Configuring Static Routes, page 3-18
OL-22206-01
• Configuring Dynamic Routes, page 3-20
Note Individual router models may not support every feature described in this guide. Features that are not
supported by a particular router are indicated whenever possible.
This chapter includes configuration examples and verification steps, as available.
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-1
Page 22

Interface Ports
Interface Ports
Table 3-1 lists the interfaces that are supported for each router and their associated port labels on the
equipment.
Table 3-1 Supported Interfaces and Associated Port Labels by Cisco Router
Router Interface Port Label
Cisco 880 Fast Ethernet LAN LAN, FE0–FE3
Cisco 881, 881W, 881G,
881GW
Cisco 886, 886W, 886G,
886GW
Cisco 887, 887W ADSL2oPOTS WAN ADSLoPOTS
Cisco 887V, 887VW,
887VG, 887VGW
Cisco 888, 888W G.SHDSL WA N G.SHDSL
Chapter 3 Basic Router Configuration
Wireless LAN (no label)
Fast Ethernet WAN WAN, FE4
ADSLoverISDN ADSLoPOTS
VDSL2oPOTS WAN VDSLoPOTS
Default Configuration
When you first boot up your Cisco router, some basic configuration has already been performed. All of
the LAN and WAN interfaces have b een created, console and vty ports are configured, and the inside
interface for Network Address Translation (NAT) has been assigned. Use the show
command to view the initial configuration, as shown in the following example for a Cisco 881W.
Router# show running-config
User Access Verification
Password:
Router> en
Password:
Router# show running-config
Building configuration...
Current configuration : 986 bytes
!
version 12.4
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$g4y5$NxDeM.0hON6YA51bcfGvN1
enable password ciscocisco
!
running-config
3-2
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 23

Chapter 3 Basic Router Configuration
no aaa new-model
!
!
!
!
no ip routing
no ip cef
!
!
!
!
!
multilink bundle-name authe
!
!
archive
log config
hidekeys
!
!
!
!
!
interface FastEthernet0
!
interface FastEthernet1
shutdown
!
interface FastEthernet2
shutdown
!
interface FastEthernet3
shutdown
!
interface FastEthernet4
ip address 10.1.1.1 255.255.255.0
no ip route-cache
duplex auto
speed auto
!
interface Vlan1
no ip address
no ip route-cache
shutdown
!
interface wlan-ap0
description Service Module interface to manage the embedded AP
ip unnumbered Vlan1
no cdp enable
arp timeout 0
!
ip route 0.0.0.0 0.0.0.0 10.1.1.1
!
!
no ip http server
no ip http secure-server
!
!
!
!
!
control-plane
!
!
Default Configuration
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-3
Page 24

Information Needed for Configuration
line con 0
no modem enable
line aux 0
line vty 0 4
password cisco
login
transport input telnet ssh
!
scheduler max-task-time 5000
!
webvpn cef
end
Router#
Information Needed for Configuration
You need to gather some or all of the following information, depending on your planned network
scenario, before configuring your network:
Chapter 3 Basic Router Configuration
• If you are setting up an Internet connection, gather the following information:
–
PPP client name that is assigned as your login name
–
PPP authentication type: Challenge Handshake Authentication Protocol (CHAP) or Password
Authentication Protocol (PAP)
–
PPP password to access your Internet service provider (ISP) account
–
DNS server IP address and default gateways
• If you are setting up a connection to a corporate network, you and the network administrator must
generate and share the following information for the WAN interfaces of the routers:
–
PPP authentication type: CHAP or PAP
–
PPP client name to access the router
–
PPP password to access the router
• If you are setting up IP routing:
–
Generate the addressing scheme for your IP network.
–
Determine the IP routing parameter information, including IP address and ATM permanent
virtual circuits (PVCs). These PVC parameters are typically vi rtual path identifier (VPI), virtual
circuit identifier (VCI), and traffic-shaping parameters.
–
Determine the number of PVCs that your service provider has given y ou, along with their V PIs
and VCIs.
–
For each PVC determine the type of AAL5 encapsulation supported. It can be one of the
following:
3-4
AAL5SNAP—This can be either routed RFC 1483 or br idged RFC 1483. For routed RFC 1483 ,
the service provider must provide you with a static IP address. For bridged RFC 148 3, you may
use DHCP to obtain your IP address, or you may obtain a static IP address from your service
provider.
AAL5MUX PPP—With this type of encapsulation, you need to determine the PPP-related
configuration items.
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 25

Chapter 3 Basic Router Configuration
• If you plan to connect over an ADSL or G.SHDSL line:
–
Order the appropriate line from your public telephone service provider.
For ADSL lines—Ensure that the ADSL signaling type is DMT (also known as ANSI T1.413)
or DMT Issue 2.
For G.SHDSL lines—Verify that the G.SHDSL line conforms to the ITU G.991.2 standard and
supports Annex A (North America) or Annex B (Europe ).
After you have collected the appropriate information, you can perform a full configuration on your
router, beginning with the tasks in the
“Configuring Command-Line Access” section on page 3-5.
To obtain or change software licenses:
• See Softwar e Activation on Cisco Integrated Services Routers and Cisco Integrated Service Routers
G2
Configuring Command-Line Access
To configure parameters to control access to the router perform these steps, beginning in global
configuration mode:
Configuring Command-Line Access
Step 1
Step 2
Step 3
SUMMARY STEPS
1. line [aux | console | tty | vty] line-number
2. password password
3. login
4. exec-timeout minutes [seconds]
5. line [aux | console | tty | vty] line-number
6. password password
7. login
8. end
DETAILED STEPS
Command Purpose
line [aux | console | tty | vty] line-number
Enters line configuration mode, and specifies the
type of line.
Example:
Router(config)# line console 0
Router(config-line)#
password password
This example specifies a console terminal for
access.
Specifies a unique password for the console
terminal line.
Example:
Router(config)# password 5dr4Hepw3
Router(config-line)#
login
Enables password checking at terminal session
login.
Example:
Router(config-line)# login
Router(config-line)#
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-5
Page 26

Configuring Command-Line Access
Command Purpose
Step 4
exec-timeout minutes [seconds]
Example:
Router(config-line)# exec-timeout 5 30
Router(config-line)#
Step 5
line [aux | console | tty | vty] line-number
Example:
Router(config-line)# line vty 0 4
Router(config-line)#
Step 6
password password
Example:
Router(config-line)# password aldf2ad1
Router(config-line)#
Step 7
login
Example:
Router(config-line)# login
Router(config-line)#
Step 8
end
Example:
Router(config-line)# end
Router#
Chapter 3 Basic Router Configuration
Sets the interval that the EXEC command
interpreter waits until user input is detected. The
default is 10 minutes. Optionally, add seconds to
the interval value.
This example shows a timeout of 5 minutes and
30
seconds. Entering a timeout of 0 0 specifies
never to time out.
Specifies a virtual terminal for remote console
access.
Specifies a unique password for the virtual
terminal line.
Enables password checking at the virtual terminal
session login.
Exits line configuration mode, and returns to
privileged EXEC mode.
Example
3-6
The following configuration shows the command-line access commands.
You do not need to input the commands marked “default.” These commands appear autom atically in t he
configuration file generated when you use the show running-config command.
!
line con 0
exec-timeout 10 0
password 4youreyesonly
login
transport input none (default)
stopbits 1 (default)
line vty 0 4
password secret
login
!
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 27

Chapter 3 Basic Router Configuration
Configuring Global Parameters
To configure selected global parameters for your router, perform these steps:
SUMMARY STEPS
1. configure terminal
2. hostname name
3. enable secret password
4. no ip domain-lookup
DETAILED STEPS
Command Purpose
Step 1
Step 2
configure terminal
Example:
Router> enable
Router# configure terminal
Router(config)#
hostname name
Configuring Global Parameters
Enters global configuration mode, when using the
console port.
If you are connecting to the router using a remote
terminal, use the following:
telnet router name or address
Login: login id
Password: *********
Router> enable
Specifies the name for the router.
Example:
Router(config)# hostname Router
Router(config)#
Step 3
Step 4
enable secret password
Example:
Router(config)# enable secret cr1ny5ho
Router(config)#
no ip domain-lookup
Example:
Router(config)# no ip domain-lookup
Router(config)#
Configuring WAN Interfaces
Configure the WAN interface for your router using one of the following as appropriate:
• Configuring a Fast Ethernet WAN Interface, page 3-8
• Configuring a VDSL2 WAN Interface, page 3-8
• Configuring ADSL or VDSL on Cisco Multi Mode 886VA and 887VA ISRs, page 3-9
• Configuring ADSL Mode, page 3-10
Specifies an encrypted password to prevent
unauthorized access to the router.
Disables the router from translating unfamiliar
words (typos) into IP addresses.
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-7
Page 28

Configuring WAN Interfaces
Configuring a Fast Ethernet WAN Interface
To configure the Fast Ethernet interface on a Cisco 861 or 881 ISR, perform these steps, beginning in
global configuration mode:
SUMMARY STEPS
1. interface type number
2. ip address ip-address mask
3. no shutdown
4. exit
DETAILED STEPS
Command Purpose
Step 1
Step 2
Step 3
Step 4
interface type number
Example:
Router(config)# interface fastethernet 4
Router(config-if)#
ip address ip-address mask
Example:
Router(config-if)# ip address 192.168.12.2
255.255.255.0
Router(config-if)#
no shutdown
Example:
Router(config-if)# no shutdown
Router(config-if)#
exit
Example:
Router(config-if)# exit
Router(config)#
Chapter 3 Basic Router Configuration
Enters the configuration mode for a Fast
Ethernet WAN interface on the router.
Sets the IP address and subnet mask for the
specified Fast Ethernet interface.
Enables the Ethernet interface, changing its
state from administratively down to
administratively up.
Exits configuration mode for the Fast Ethernet
interface and returns to global configuration
mode.
Configuring a VDSL2 WAN Interface
The VDSL2 WAN interface is used on the Cisco 887V ISR platforms. Note that the VDSL2 WAN
interface uses Ethernet as the Layer 2 transport mechanism. To configure VDSL2 on the Cisco
ISR, perform these steps, beginning in global configuration mode.
SUMMARY STEPS
1. controller vdsl 0
2. interface type number
3. ip address ip-address mask
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-8
887V
OL-22206-01
Page 29

Chapter 3 Basic Router Configuration
4. shutdown
5. no shutdown
6. exit
DETAILED STEPS
Command Purpose
Step 1
controller vdsl 0
Example:
Router# config t
Router(config)# controller vdsl 0
Step 2
interface type number
Example:
Router(config)# interface ethernet 0
Router(config-if)#
Step 3
ip address ip-address mask
Example:
Router(config-if)# ip address 192.168.12.2
255.255.255.0
Router(config-if)#
Step 4
shutdown
Example:
Router(config-if)# no shutdown
Router(config-if)#
Step 5
no shutdown
Example:
Router(config-if)# no shutdown
Router(config-if)#
Step 6
exit
Example:
Router(config-if)# exit
Router(config)#
Configuring WAN Interfaces
Enters controller configuration mode and the
controller number.
Note There is no need to configure any
VDSL2 parameters from CPE side.
Any specific VDSL2 settings should
be set on the DSLAM side.
Enters the configuration mode for Ethernet
Layer 2 transport on the VDSL WAN interface
on the router.
Sets the IP address and subnet mask for the
interface.
Disables the interface, changing its state from
administratively up to administratively down.
Enables the interface, changing its state from
administratively down to administratively up.
Exits configuration mode and returns to glo bal
configuration mode.
Configuring ADSL or VDSL on Cisco Multi Mode 886VA and 887VA ISRs
The Cisco customer premise equipment (CPE) 886VA and 887VA integrated services routers (ISRs)
support asymmetric digital subscriber line (ADSL) 1/2/2+ and very high speed digital subscriber line 2
(VDSL2) transmission modes, also called multi mode. The 886VA supports xDSL over ISDN and the
887VA supports xDSL over a plain old telephone system (POTS).
The default CPE operating mode is auto. Auto mode means that the CPE trains up to the mode configu red
on the digital subscriber line access multiplexer (DSLAM), ADSL1/2/2+ or VDSL2.
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
3-9
Page 30

Configuring WAN Interfaces
The following examples assume the DSLAM is configured in either ADSL2+ mode or VDSL2, and the
CPE is configured in auto mode.
Figure 3-1 shows an ATM WAN or Ethernet WAN network topography.
Figure 3-1 Example Topology
Chapter 3 Basic Router Configuration
Note A DSLAM in Layer 1 mode may be con figured for a uto mode. A DSLAM in L ayer 2 mode must be
configured for ATM mode or packet transfer mode (PTM).
Note Cisco 886VA and 887VA allow a maximum of four permanent virtual circuits (PVCs).
Configuring ADSL Mode
Configuration tasks
Perform the following tasks to configure ADSL mode:
• Configuring ADSL Auto Mode
• Configuring CPE and Peer for ADSL Mode
• ADSL Configuration Example
• Verifying ADSL Configuration
3-10
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 31

Chapter 3 Basic Router Configuration
• Verifying CPE to Peer Connection for ADSL
Configuring ADSL Auto Mode
Perform these steps to configure the DSL controller to auto mode, star ting in gl obal configur ation mode.
Note Configure the DSLAM in ADSL 1/2//2+ mode prior to configuring the router.
SUMMARY STEPS
1. controller vdsl slot
2. operating mode {auto|adsl1|adsl2|adsl2+|vdsl2|ansl}
3. end
DETAILED STEPS
Command Purpose
Step 1
Step 2
controller vdsl slot
Example:
Router (config) #
Controller vdsl 0
operating mode
{auto|adsl1|adsl2|adsl2+|vdsl2|
ansl}
Configuring WAN Interfaces
Enters config mode for the VDSL
controller.
Configures the operating mode. The
default is auto and is recommended.
Example:
Router (config-controller) #
operating mode
auto
Step 3
end
Example:
Router (config-conroller) #
end
Router
When configured in auto, the operating mode does not appear in the show running command.
Configuring CPE and Peer ADSL Mode
When configuring for ADSL, the ATM main interface or ATM sub-interface must be configured with a
PVC and an IP address, perform a no shutdown command on the interface if needed.
Exits the configuration mode and enters
EXEC mode.
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-11
Page 32

Configuring WAN Interfaces
Configuring the ATM CPE SIDE
Perform the following steps to configure the ATM CPE side, starting in global configuration mode.
SUMMARY STEPS
1. interface type number
2. no shutdown
3. interface atm0.1 point-to-point
4. ip address ip-address mask
5. ppvc [name] vpi/vci
6. protocol protocol {protocol-address [virtual-template] | inarp} [[no] broadcast |
disable-check-subnet | [no] enable-check-subnet]
7. end
DETAILED STEPS
Com man d Purpose
Step 1
Step 2
Step 3
Step 4
interface type number
Example:
Router (config) # interface atm0
no shutdown
Example:
Router (config-if) # no
shutdown
Router (config-if) #
interface atm0.1 point-to-point
Example:
Router (config-if) # interface
ATM0.1
point-to-point
Router (config-subif) #
ip address ip-address mask
Chapter 3 Basic Router Configuration
Enters configuration mode for the ATM
WAN interface (ATM0).
Enables the configuration changes to
the ATM interfa ce.
Enables the ATM0.1 point-to-point
interface.
Enters IP address and subnet mask.
3-12
Example:
Router (config-subif)# ip address
30.0.0.1 255.255.255.0
Step 5
pvc [name] vpi/vci
Example:
Router (config-subif) # pvc 13/32
Router (config-if-atm-vc) #
Cisco 880 Series Integrated Services Router Software Configuration Guide
Creates or assigns a name to an ATM
PVC and enters the ATM virtual circuit
configuration mode.
OL-22206-01
Page 33

Chapter 3 Basic Router Configuration
Com mand Purpose
Step 6 protocol protocol {protocol-address
Step 7 end
[virtual-template] | inarp} [[no]
broadcast | disable-check-subnet | [no]
enable-check-subnet]
Example:
Router (config-if-atm-vc) #
protocol ip 30.0.0.2
broadcast
Example:
Router (config-if-atm-vc) #
end
Router #
Configuring WAN Interfaces
Configures a static map for an ATM
PVC.
Exits the configuration mode and enters
EXEC mode.
ADSL Configuration Example
The following example shows a typical ADSL2+ configuration set to auto mode. Outputs in bold are
critical.
Router# show running
Building configuration...
Current configuration : 1250 bytes
!
! Last configuration change at 02:07:09 UTC Tue Mar 16 2010
!
version 15.1
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 10
ip source-route
!
!
!
!
ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO887-V2-K9 sn FHK1313227E
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-13
Page 34

Configuring WAN Interfaces
license boot module c880-data level adviperservices
!
!
vtp domain cisco
vtp mode transparet
!
!
controller VDSL 0
!
vlan 2-4
!
!
!
!
!
interface Ethernet 0
no ip address
shutdown
no fair-queue
!
interface BRI0
no ip address
encapsulation hdlc
shutdown
isdn termintation multidrop
!
interface ATM0
no ip address
no atm ilmi-keepalive
!
interface ATM0.1 point-to-point
ip address 30.0.0.1 255.255.255.0
pvc 15/32
protocol ip 30.0.0.2 broadcast
!
!
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
!
interface Vlan1
no ip address
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
!
!
!
!
!
control-palne
!
!
line con 0
no modem enable
line aux 0
line vty 0 4
Chapter 3 Basic Router Configuration
3-14
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 35

Chapter 3 Basic Router Configuration
login
transport input all
!
exception data-corruption buffer truncate
end
Verifying ADSL Configuration
Verify that the configuration is set properly by using the show controller vdsl 0 command from the
privileged EXEC mode. Outputs in bold are critical.
Router# show controller vdsl 0
Controller VDSL 0 is UP
Daemon Status: Up
XTU-R (DS) XTU-C (US)
chip Vendor ID: ‘BDM’ ‘BDCM’
Chip Vendor Specific: 0x0000 0x6110
Chip Vendor Country: 0xB500 0xB500
Modem Vendor ID: ‘csco’ ‘BDCM’
Modem Vendor Specific: 0x4602 0x6110
Modem Vendor Country: 0xB500 0xB500
Serial Number Near: FHK1313227E 887-V2-K 15.1(20100
Serial Number Far:
Modem Version Nead: 15.1(20100426:193435) [changahn
Modem Version Far: 0x6110
Configuring WAN Interfaces
Modem Status: TC Sync (Showtime!)
DSL Config Mode: AUTO
Trained Mode: G.992.5 (ADSL2+) Annex A
TC Mode: ATM
Selftest Result: 0x00
DELT configuration: disabled
DELT state: not running
Trellis: ON ON
Line Attenuation: 1.0 dB 1.4 dB
Signal Attenuation: 1.0 dB 0.0 dB
Noise Margin: 6.8 dB 13.6 dB
Atteinable Rate: 25036 kbits/s 1253 kbits/s
Actual Power: 13.7 dBm 12.3 dBM
Total FECS: 0 0
Total ES: 0 0
Total SES: 0 0
Total LOSS: 0 0
Total UAS: 0 0
Total LPRS: 0 0
Total LOFS: 0 0
Total LOLS: 0 0
Bit swap: 163 7
Full inits: 32
Failed Full inits: 0
Short inits: 0
Failed short inits: 0
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-15
Page 36

Configuring the Fast Ethernet LAN Interfaces
Firmware Source Filename (version)
-------- ------ -----------------VDSL embedded VDSL_LINUX_DEV_01212008 (1)
Modem FW Version: 100426_1053-4.02L.03.A2pv6C030f.d22j
Modem PHY Version: A2pv6C030f.d22j
DS Channel1 DS Channel0 US Channel1 US channel0
Speed (kbps): 0 24184 0 1047
Previous Speed: 0 24176 0 1047
Total Cells: 0 317070460 0 13723742
User Cells: 0 0 0 0
Reed-solomon EC: 0 0 0 0
CRC Errors: 0 0 0 0
Header Errors: 0 0 0 0
Interleave (ms): 0.00 0.08 0.00 13.56
Actual INP: 0.00 0.00 0.00 1.80
Training Log: Stopped
Training Log Filename: flash:vdsllog.bin
Chapter 3 Basic Router Configuration
Verifying CPE to Peer Connection for ADSL
Ping the peer to confirm that CPE to peer configuration is setup correctly.
Router# ping 30.0.0.2 rep 20
Type escape sequence to abort.
Sending 20, 100-byte ICMP Echos to 30.0.0.2, timeout is 2 seconds:
!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (20/20), round-trip min/avg/max = 20/22/28 ms
Router#
Configuring the Fast Ethernet LAN Interfaces
The Fast Ethernet LAN interfaces on your router are automatically configured as part of the default
VLAN and are not configured with individual addresses. Access is provided through the VLAN. You
may assign the interfaces to other VLANs.
Configuring the Wireless LAN Interface
3-16
The Cisco 880 series wireless routers have an integrated 802.11n module for wireless LAN connectivity.
The router can then act as an access point in the local infrastructure. For more information about
configuring a wireless connection, see
Cisco 880 Series Integrated Services Router Software Configuration Guide
Chapter 4, “Basic Wireless Device Configuration”.
OL-22206-01
Page 37

Chapter 3 Basic Router Configuration
Configuring a Loopback Interface
The loopback interface acts as a placeholder for the static IP address and provides default routing
information.
To configure a loopback interface perform these steps, beginning in global configuration mode:
SUMMARY STEPS
1. interface type number
2. ip address ip-address mask
3. exit
DETAILED STEPS
Command Purpose
Step 1
Step 2
Step 3
interface type number
Example:
Router(config)# interface Loopback 0
Router(config-if)#
ip address ip-address mask
Example:
Router(config-if)# ip address 10.108.1.1
255.255.255.0
Router(config-if)#
exit
Example:
Router(config-if)# exit
Router(config)#
Configuring a Loopback Interface
Enters configuration mode for the loopback
interface.
Sets the IP address and subnet mask for the
loopback interface.
Exits configuration mode for the loopback
interface and returns to global configuration
mode.
Example
OL-22206-01
The loopback interface in this sample configuration is used to support Network Address Translation
(NAT) on the virtua l-temp late inte rface. Th is configur ation exa mple show s the loopback interface
configured on the Fast Ethernet interface with an IP address of 200.200.100.1/24, which acts as a static
IP address. The loopback interface points back to virtual-template1, which has a negotiated IP address.
!
interface loopback 0
ip address 200.200.100.1 255.255.255.0 (static IP address)
ip nat outside
!
interface Virtual-Template1
ip unnumbered loopback0
no ip directed-broadcast
ip nat outside
!
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-17
Page 38

Configuring Static Routes
Verifying Configuration
To verify that you have properly configured the loopback interface, enter the show interface loopback
command. You should see verification output similar to the following example.
Router# show interface loopback 0
Loopback0 is up, line protocol is up
Hardware is Loopback
Internet address is 200.200.100.1/24
MTU 1514 bytes, BW 8000000 Kbit, DLY 5000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation LOOPBACK, loopback not set
Last input never, output never, output hang never
Last clearing of "show interface" counters never
Queueing strategy: fifo
Output queue 0/0, 0 drops; input queue 0/75, 0 drops
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 packets output, 0 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 output buffer failures, 0 output buffers swapped out
Chapter 3 Basic Router Configuration
Another way to verify the loopback interface is to ping it:
Router# ping 200.200.100.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.200.100.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Configuring Static Routes
Static routes provide fixed routing paths through the network. They are manually configured on the
router. If the networ k topo logy changes, the stati c route must be updated with a new route. Static routes
are private routes unless they are redistributed by a routing protocol.
To configure static routes perform these steps, beginning in global configuration mode:
SUMMARY STEPS
1. ip route prefix mask {ip-address | interface-type interface-nu mber [ip-address]}
2. end
3-18
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 39

Chapter 3 Basic Router Configuration
DETAILED STEPS
Command Purpose
Step 1
ip route prefix mask {ip-address | interface-type
interface-number [ip-address]}
Example:
Router(config)# ip route 192.168.1.0
255.255.0.0 10.10.10.2
Router(config)#
Step 2
end
Example:
Router(config)# end
Router#
Example
Configuring Static Routes
Specifies the static route for the IP packets.
For details about this command and about
additional parameters that can be set, see the
Cisco
IOS IP Routing Protocols Command Reference.
Exits router configuration mode, and enters
privileged EXEC mode.
In the following configuration example, the static route sends out all IP packets with a destination IP
address of 192.168.1.0 and a subnet mask of 255.255.255.0 on the Fast Ethernet interface to another
device with an IP address of 10.10.10.2. Specifically, the packets are sent to the configured PVC.
You do not need to enter the command marked “(default).” This command appears automatically in the
configuration file generated when you use the show running-config command.
!
ip classless (default)
ip route 192.168.1.0 255.255.255.0 10.10.10.2!
Verifying Configuration
To verify that you have properly configured static routing, enter the show ip route command and look
for static routes signified by the “S.”
You should see verification output similar to the following:
Router# show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
OL-22206-01
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
C 10.108.1.0 is directly connected, Loopback0
S* 0.0.0.0/0 is directly connected, FastEthernet0
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-19
Page 40

Configuring Dynamic Routes
Configuring Dynamic Routes
In dynamic routing, the network protocol adjusts the path automatically, based on network traffic or
topology. Changes in dynamic routes are shared with other routers in the network.
The Cisco routers can use IP routing protocols, such as Routing Information Proto col (RIP) or Enhanced
Interior Gateway Routing Protocol (EIG RP), to learn routes dynamically. You can configure either of
these routing protocols on your router.
• Configuring Routing Information Protocol, page 3-20
• Configuring Enhanced Interior Gateway Routing Protocol, page 3-22
Configuring Routing Information Protocol
To configure the RIP routing protocol on the router, perform these steps, beginning in global
configuration mode:
SUMMARY STEPS
1. router rip
Chapter 3 Basic Router Configuration
Step 1
Step 2
Step 3
2. version {1 | 2}
3. network ip-address
4. no auto-summary
5. end
DETAILED STEPS
Command Task
router rip
Enters router configuration mode, and enables RIP
on the router.
Example:
Router> configure terminal
Router(config)# router rip
Router(config-router)#
version {1 | 2}
Example:
Router(config-router)# version 2
Router(config-router)#
network ip-address
Specifies use of RIP version 1 or 2.
Specifies a list of networks on which RIP is to be
applied, using the address of the network of each
Example:
Router(config-router)# network 192.168.1.1
Router(config-router)# network 10.10.7.1
Router(config-router)#
directly connected network.
3-20
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 41

Chapter 3 Basic Router Configuration
Command Task
Step 4
no auto-summary
Example:
Router(config-router)# no auto-summary
Router(config-router)#
Step 5
end
Example:
Router(config-router)# end
Router#
Example
The following configuration example shows RIP version 2 enabled in IP network 10.0.0.0 and
192.168.1.0.
Configuring Dynamic Routes
Disables automatic summarization of subnet routes
into network-level routes. Th is allow s subpref ix
routing information to pass across classful network
boundaries.
Exits router configuration mode, and enters
privileged EXEC mode.
To see this configuration, use the show running-config command from privileged EXEC mode.
!
Router# show running-config
router rip
version 2
network 10.0.0.0
network 192.168.1.0
no auto-summary
!
Verifying Configuration
To verify that you have properly configured RIP, enter the show ip route command and look for RIP
routes signified by “R.” You should see a verification output like the example shown below.
Router# show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
C 10.108.1.0 is directly connected, Loopback0
R 3.0.0.0/8 [120/1] via 2.2.2.1, 00:00:02, Ethernet0/0
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-21
Page 42

Chapter 3 Basic Router Configuration
Configuring Dynamic Routes
Configuring Enhanced Interior Gateway Routing Protocol
To configure Enhanced Interior Gateway Routing Protocol (EIGRP) perform these steps, beginning in
global configuration mode
SUMMARY STEPS
1. router eigrp as-number
2. network ip-address
3. end
:DETAILED STEPS
Command Purpose
Step 1
Step 2
Step 3
router e ig r p as-number
Example:
Router(config)# router eigrp 109
Router(config)#
network ip-address
Example:
Router(config)# network 192.145.1.0
Router(config)# network 10.10.12.115
Router(config)#
end
Example:
Router(config-router)# end
Router#
Enters router configuration mode, and enables
EIGRP on the router. The autonomous-system
number identifies the route to other EIGRP routers
and is used to tag the EIGRP information.
Specifies a list of networks on which EIGRP is to
be applied, using the IP address of the network of
directly connected networks.
Exits router configuration mode, and enters
privileged EXEC mode.
Example
The following configuration example shows the EIGRP routing protocol enabled in IP networks
192.145.1.0 and 10.10.12.115. The EIGRP autonomous system number is 109.
T o see this configurat ion, use the show running-config command, beginning in privileged EXEC mode.
!
router eigrp 109
network 192.145.1.0
!
Verifying Configuration
To verify that you have properly configured IP EIGRP, enter the show ip rou te command, and look for
EIGRP routes indicated by “D.” You should see verification output similar to the following:
Router# show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-22
network 10.10.12.115
OL-22206-01
Page 43

Chapter 3 Basic Router Configuration
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
C 10.108.1.0 is directly connected, Loopback0
D 3.0.0.0/8 [90/409600] via 2.2.2.1, 00:00:02, Ethernet0/0
Configuring Dynamic Routes
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
3-23
Page 44

Configuring Dynamic Routes
Chapter 3 Basic Router Configuration
3-24
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 45

CHAPTER
4
Basic Wireless Device Configuration
This chapter describes how to configure t he autono mous wire less devi ce on the fo llowing
Integrated
• Cisco 880 Series
Note To upgrade the autonomous software to Cisco Unified software on the embedded wireless
The wireless device is embedded and does not have an external console port for connections. To
configure the wireless device, use a console cable to connect a personal computer to the host router’s
console port, and perform these procedures to establish connectivity and conf igure the wireless settings.
• Starting a Wireless Configuration Session, page 4-2
• Configuring Wireless Settings, page 4-4
• Configuring the Access Point in Hot Standby Mode, page 4-9 (Optional)
• Upgrading to Cisco Unified Software, page 4-9
Services Router (ISR)
device, see the “Upgrading to Cisco Unified Software” section on page 4-9 for instructions.
OL-22206-01
• Related Documentation, page 4-12
Cisco 880 Series Integrated Services Router Software Configuration Guide
4-1
Page 46

Chapter 4 Basic Wireless Device Configuration
Starting a Wireless Configuration Session
Starting a Wireless Configuration Session
Note Before you configure the wireless settings in the router’s setup, you must follow these steps to
open a session between the router and the access point.
Enter the following commands in global configuration mode on the router’s Cisco IOS CLI.
SUMMARY STEPS
1. interface wlan-ap0
2. ip address subnet mask
3. no shutdown
4. interface vlan1
5. ip address subnet mask
6. exit
7. exit
8. service-module wlan-ap 0 session
DETAILED STEPSf
Step 1
Step 2
Step 3
Command Purpose
interface wlan-ap0
Defines the router’s console interface to the wireless
device. The interface is used for communication
between the router’s console and the wireless device.
Example:
router(config)# interface wlan-ap0
router(config-if)#
ip address subnet mask
Always use port 0.
The following message appears:
The wlan-ap 0 interface is used for managing
the embedded AP. Please use the service-module
wlan-ap 0 session command to console into the
embedded AP.
Specifies the interface IP address and subnet mask.
Note The IP address can be shared with the IP
Example:
router(config-if)# ip address
10.21.0.20 255.255.255.0
or
router(config-if)# ip unnumbered vlan1
no shutdown
Specifies that the internal interface connection will
remain open.
Example:
router(config-if)# no shutdown
address assigned to the Cisco Integrated
Services Router by using the ip unnumbered
vlan1 command.
4-2
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 47

Chapter 4 Basic Wireless Device Configuration
Command Purpose
Step 4
interface vlan1
Example:
router(config-if)# interface vlan1
Step 5
ip address subnet mask
Example:
router(config-if)# ip address
10.10.0.30 255.255.255.0
Step 6
exit
Example:
router(config-if)# exit
router(config)#
Step 7
exit
Starting a Wireless Configuration Session
Specifies the virtual LAN interface for data
communication on the internal Gigabit Ethernet 0
(GE0) port to other interfaces.
• All the switch ports inherit the default vlan1
interface on the Cisco
880 Series ISR.
Specifies the interface IP address and subnet mask.
Exits the interface configur ation mo de.
Exits the global configuration mode.
Step 8
Tip If you want to create a Cisco IOS software alias for the console to session into the wireless device, enter
Closing the Session
Example:
router(config)# exit
router#
service-module wlan-ap 0 session
Opens the connection between the wireless device and
the router’s console.
Example:
router# service-module wlan-ap0
session
Trying 10.21.0.20, 2002 ... Open
ap>
the alias exec dot11radio service-module wlan-ap 0 session command at the EXEC prompt. After
entering this command, you will automatically skip to the dot11 radio level in the Cisco IOS software.
To close the session between the wireless device and the router’s console, perform the following steps.
Wireless Device
1. Control-Shift-6 x
Router
1. disconnect
OL-22206-01
2. Press Enter
Cisco 880 Series Integrated Services Router Software Configuration Guide
4-3
Page 48

Configuring Wireless Settings
Configuring Wireless Settings
Note If you are configuring the wireless device for the first time, you must start a configuration session
between the access point and the router before you attempt to configure the basic wireless settings. See
the “Starting a Wireless Configuration Session” section on page 4-2.
Configure the wireless device with the tool that matches the software on the device.
• Cisco IOS Command Line Interface, page 4-5—Autonomous software
• Cisco Express Setup, page 4-4—Unified Software
Note If you are running the wireless device in Autonomous mode and would like to upgrade to
Unified mode, see the
upgrade instructions.
After upgrading to Cisco Unified Wireless software, use the web browser interface to
configure the device:
http://cisco.com/en/US/docs/wireless/access_point/12.4_10b_JA/configuration/guide/scg1
2410b-chap2-gui.html
“Upgrading to Cisco Unified Software” section on page 4-9 for
Chapter 4 Basic Wireless Device Configuration
Cisco Express Setup
To configure the Unified wireless device use the web-browser tool:
Step 1 Establish a console connection to the wireless device and get the Bridge-Group Virtual Interface (BVI)
IP address by entering the show interface bvi1 Cisco IOS command.
Step 2 Open a browser window, and enter the BVI IP address in the browser-window address line. Press Enter.
An Enter Network Password window appears.
Step 3 Enter your username. Cisco is the default user name.
Step 4 Enter the wireless device password. Cisco is the default password. The Summary Status page appears.
For details about using the web-browser configuration page, see:
http://cisco.com/en/US/docs/wireless/access_point/12.4_10b_JA/configuration/guide/scg12410b-chap
4-first.html#wp1103336
4-4
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 49

Chapter 4 Basic Wireless Device Configuration
Cisco IOS Command Line Interface
To configure the Autonomous wireless device, use the Cisco IOS CLI tool and perform these tasks:
• Configuring the Radio, page 4-5
• Configuring Wireless Security Settings, page 4-5
• Configuring Wireless Quality of Service, page 4-8 (Optional)
Configuring the Radio
Configure the radio parameters on the wireless device to transmit signals in autonomous or
Cisco
Unified mode. For specific configuration procedures, see Chapter 9, “Configuring Radio
Settings”.
Configuring Wireless Security Settings
• Configuring Authentication, page 4-5
• Configuring WEP and Cipher Suites, page 4-6
Configuring Wireless Settings
• Configuring Wireless VLANs, page 4-6
Configuring Authentication
Authentication types are tied to the Service Set Identifiers (SSIDs) that are configured for the access
point. To serve different types of client devices with the same access point, configure multiple SSIDs.
Before a wireless client device can communicate on your network through the access point, the client
device must authenticate to the access point by using open or shared-key authentication. For maximum
security, client devices should also authenticate to your network using MAC address or Extensible
Authentication Protocol (EAP) authentication. Both auth entication types rely on an authentication server
on your network.
To select an authentication type, see Authentication Types for Wireless Devices at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/SecurityAuthenticationTypes
.html.
To set up a maximum security environment, see RADIUS and TACACS+ Servers in a Wireless
Environment at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/SecurityRadiusTacacs_1.htm
l.
Configuring Access Point as Local Authenticator
To provide local authentication service or backup authentication service for a WAN link failure or a
server failure, you can configure an access point to act as a local authentication server. The access point
can authenticate up to 50 wireless client devices using Lightweight Extensible Authentication Protocol
(LEAP), Extensible Authentication Protocol-Flexible Authentication via Secure Tunneling
(EAP-FAST), or MAC-based authentication. The access point performs up to 5 authentications per
second.
You configure the local a uthenticator access point manually with client usernames and passwords
because it does not synchronize its database with RADIUS servers. You can specify a VLAN and a list
of SSIDs that a client is allowed to use.
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
4-5
Page 50

Configuring Wireless Settings
For details about setting up the wireless device in this role, see Using the Access Point as a Local
Authenticator at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/SecurityLocalAuthent.html
Configuring WEP and Cipher Suites
Wired Equivalent Privacy (WEP) encryption scrambles the data transmitted between wireless devices to
keep the communication private. Wireless devices and their wireless client devices use the same WEP
key to encrypt and decrypt data. WEP keys encrypt both unicast and multicast messages. Unicast
messages are addressed to one device on the network. Multicast messages are addressed to multiple
devices on the network.
Cipher suites are sets of encryption and integrity algorithms designed to protect radio communication
on your wireless LAN. You must use a cipher suite to enable Wi-Fi Protected Access (WPA) or Cisco
Centralized Key Management (CCKM ).
Cipher suites that contain Temporal Key Integrity Protocol (TKIP) provide the greatest security for your
wireless LAN. Cipher suites that contain only WEP are the least secure.
For encryption procedures, see Configuring WEP and Cipher Suites at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/SecurityCipherSuitesWEP.ht
ml
Chapter 4 Basic Wireless Device Configuration
Configuring Wireless VLANs
If you use VLANs on your wireless LAN and assign SSIDs to VLANs, you can create multiple SSIDs
by using any of the four security settings defined in the
can be thought of as a broadcast domain that exists within a defined set of switches. A VLAN consists
of a number of end systems, either hosts or network equipment (such as bridges and routers), that are
connected by a single bridging domain. The bridging domain is support ed on various pieces of network
equipment such as LAN switches that operate bridging protocols between them with a separate g roup of
protocols for each VLAN.
For more information about wireless VLAN architecture, see Configuring Wireless VLANs at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/wireless_vlans.html
Note If you do not use VLANs on your wireless LAN, the security options that you can assign to
Assigning SSIDs
You can configure up to 16 SSIDs on a wireless device in the role of an access point, and you can
configure a unique set of parameters for each SSID. For example, you might use one SSID to allow
guests limited access to the network and another SSID to allow authorized users access to secure data.
For more about creating multiple SSIDs, see Service Set Identifiers document at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/ServiceSetID.html.
“Security T ypes” section on page 4-7. A VLAN
SSIDs are limited because the encryption settings and authentication types are linked on the
Express Security page.
4-6
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 51

Chapter 4 Basic Wireless Device Configuration
Configuring Wireless Settings
Read Without VLANs, encryption settings (WEP and ciphers) apply to an interface, such as the
2.4-GHz radio, and you cannot use more than one encryption setting on an interface. For
example, when you create an SSID with static WEP with VLANs disabled, you cannot create
additional SSIDs with WPA authentication because the SSIDs use different encrypt ion set tings.
If you find that the security setting for an SSID conflicts with the settings for another SSID, you
can delete one or more SSIDs to eliminate the conflict.
Security Types
Table 4-1 describes the four security types that you can assign to an SSID.
Table 4-1 Types of SSID Security
Security Type Description Security Features Enabled
No security This is the least secure option. You should use this option
None.
only for SSIDs in a public space and you should assign it to
a VLAN that restricts access to your network.
Static WEP key This option is more secure than no security. However, static
WEP keys are vulnerable to attack. If you configure this
setting, you should consider limiting association to the
Mandatory WEP. Client devices cannot
associate using this SSID without a WEP
key that matches the wireless de vice key.
wireless device based on MAC address, see Cipher Suites
and WEP at:
http://www.cisco.com/en/US/docs/routers/access/wireless/
software/guide/SecurityCipherSuitesWEP.html.
Or
If your network does not have a RADIUS server, consider
using an access point as a local authentication server.
See Using the Access Point as a Local Authenticator for
instructions:
http://www.cisco.com/en/US/docs/routers/access/wireless/
software/guide/SecurityLocalAuthent.html.
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
4-7
Page 52

Chapter 4 Basic Wireless Device Configuration
Configuring Wireless Settings
Table 4-1 Types of SSID Security (continued)
Security Type Description Security Features Enabled
EAP1
authentication
This option enables 802.1X authentication (such as LEAP2,
PEAP3, EAP-TLS4, EAP-F AST5, EAP-TTLS6, EAP-GTC7,
EAP-SIM8, and other 802.1X/EAP-based products)
Mandatory 802.1X authentication. Client
devices that associate using this SSID must
perform 802.1X authenticati on.
This setting uses mandatory encryption, WEP, open
authentication plus EAP, network EAP authentication, no
key management, and RADIUS server authentication port
1645.
You are required to enter the IP address and shared sec ret
for an authentication server on your network (server
authentication port 1645). Because 802.1X authentication
provides dynamic encryption keys, you do not need to enter
a WEP key.
9
WPA
This option permits wireless access to users who are
authenticated against a database. Access is through the
services of an authentication server . Users’ IP traf fic is then
encrypted with stronger algorithms than those used in WEP.
This setting uses encryption ciphers, TKIP10, open
authentication plus EAP, network EAP authentication, key
management WPA mandatory, and RADIUS server
authentication port 1645.
As with EAP authentication, yo u mu st en te r th e IP ad d ress
and shared secret for an authentication server on your
network (server authentication port 1645).
1. EAP = Extensible Authentication Protocol.
2. LEAP = Lightweight Extensible Authentication Protocol.
3. PEAP = Protected Extensible Authentication Protocol.
4. EAP-TLS = Extensible Authentication Protocol—Transport Layer Security.
5. EAP-FAST = Extensible Authentication Protocol—Flexible Authentication via Secure Tunneling.
6. EAP-TTLS = Extensible Authentication Protocol—Tunneled Transport Layer Security.
7. EAP-GTC = Extensible Authentication Protocol—Generic Token Card.
8. EAP-SIM = Extensible Authentication Protocol—Subscriber Identity Module.
9. WPA = Wi-Fi Protected Access.
10. TKIP = Temporal Key Integrity Protocol.
If radio clients are configured to
authenticate using EAP-FAST, open
authentication with EAP should also be
configured. If you do not configure open
authentication with EAP, the following
warning message appears:
SSID CONFIG WARNING: [SSID]: If radio
clients are using EAP-FAST, AUTH OPEN
with EAP should also be configured.
Mandatory WPA authentication. Client
devices that associate using this SSID must
be WPA capable.
If radio clients are configured to
authenticate using EAP-FAST, open
authentication with EAP should also be
configured. If you don’t configure open
authentication with EAP, the following
warning message appears:
SSID CONFIG WARNING: [SSID]: If radio
clients are using EAP-FAST, AUTH OPEN
with EAP should also be configured.
Configuring Wireless Quality of Service
Configuring quality of service (QoS) can provide preferential treatment to certain traffic at the expense
of other traffic. Without QoS, the device offers best-effort service to each packet, regardless of the
packet contents or size. It sends the packets without any assurance of reliability, delay bounds, or
throughput. To configure quality of service (QoS) for your wireless device, see Quality of Service in a
Wireless Environment at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/QualityOfService.html.
Cisco 880 Series Integrated Services Router Software Configuration Guide
4-8
OL-22206-01
Page 53

Chapter 4 Basic Wireless Device Configuration
Configuring the Access Point in Hot Standby Mode
Configuring the Access Point in Hot Standby Mode
In hot standby mode, an access point is designated as a backup for another access point. The standby
access point is placed near the access point that it monitors and is configured exactly like the monitored
access point. The standby access point associates with the monitored access point as a client and sends
Internet Access Point Protocol (IAPP) queries to the monitored access point through the Ethernet and
radio ports. If the monitored access point fails to respond, the standby access point comes online and
takes the monitored access point’s place in the network.
Except for the IP address, the standby access point’s settings should be identical to the settings on the
monitored access point. If the monitored access point goes off line and the standby access point takes its
place in the network, matching settings ensure that client devices can switch easily to the standby access
point. For more information, see Hot Standby Access Points at:
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/RolesHotStandby.html.
Upgrading to Cisco Unified Software
To run the access point in Cisco Unified mode, upgrade the software by performing the following
procedures:
• Preparing for the Upgrade, page 4-9
• Performing the Upgrade, page 4-10
• Downgrading the Software on the Access Point, page 4-11
• Recovering Software on the Access Point, page 4-12
Software Prerequisites
• Cisco 880 Series ISRs with embedded access points are eligible to upgrade from autonomous
software to Cisco Unified software, if the router is running the advipservices feature set and
Cisco
IOS 15.1.(4 )M softw are.
• To use the embedded access point in a Cisco Unified Architecture, the Cisco Wireless LAN
Configuration (WLC) must be running version 15.1.(4)M.
Preparing for the Upgrade
Perform the tasks in the following sections to prepare for the upgrade:
• Secure an IP Address on the Access Point, page 4-10
• Confirm that the Mode Setting is Enabled, page 4-10
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
4-9
Page 54

Upgrading to Cisco Unified Software
Secure an IP Address on the Access Point
Secure an IP address on the access point so it that can communicate with the WLC and download the
Unified image upon boot up. The host router provides the access point DHCP server functionality
through the DHCP pool. Then the access point communicates with the WLC and setup option 43 for the
controller IP address in the DHCP pool configuration. The following is a sample configuration:
ip dhcp pool embedded-ap-pool
network 60.0.0.0 255.255.255.0
dns-server 171.70.168.183
default-router 60.0.0.1
option 43 hex f104.0a0a.0a0f (single WLC IP address(10.10.10.15) in hex format)
int vlan1
ip address 60.0.0.1 255.255.255.0
For more information about the WLC discovery process, see Cisco Wireless LAN Configuration Guide
at:
http://www.cisco.com/en/US/docs/wireless/controller/4.0/configuration/guide/ccfig40.html
Confirm that the Mode Setting is Enabled
Chapter 4 Basic Wireless Device Configuration
To confirm that the mode setting is enabled, perform the following steps.
Step 1 Ping the WLC from the router to confirm IP connectivity.
Step 2 Enter the service-module wlan-ap 0 session command to establish a session into the access point.
Step 3 Confirm that the access point is running an autonomous boot image.
Step 4 Enter the show boot command on the access point to confirm that the mode setting is enabled. The
following is sample output for the command:
# show boot
BOOT path-list: flash:ap802-k9w7-mx.124/ap802-k9w7-mx.124
Config file: flash:/config.txt
Private Config file: flash:/private-config
Enable Break: no
Manual Boot: yes
HELPER path-list: no
NVRAM/Config file
buffer size: 32768
Mode Button: on
Radio Core TFTP:
ap#
Performing the Upgrade
To upgrade the autonomous software to Cisco Unified software, follow these steps:
4-10
Step 1 To change the access point boot image to a Cisco Unified upgrade image (also known as a recovery
image), issue the service-module wlan-ap 0 bootimage unified command, in global configuration
mode.
Router# conf terminal
Router(config)# service-module wlan-ap 0 bootimage unified
Router(config)# end
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 55

Chapter 4 Basic Wireless Device Configuration
Upgrading to Cisco Unified Software
Note If the service-module wlan-ap 0 bootimage unified command does not work successfully,
check whether the software license is still eligible.
T o identify the access point’ s boot image path, use the show boot command in privileged EXEC
mode on the access point console:
autonomous-AP# show boot
BOOT path-list: flash:/ap802-rcvk9w8-mx/ap802-rcvk9w8-mx
Step 2 To perform a graceful shutdown and reboot of the access point to complete the upgrade process, issue
the service-module wlan-ap 0 reload command in global configuration mode. Establish a session into
the access point and monitor the upgrade process.
See “Cisco Express Setup” section on page 4-4 for details about using the GUI co nfiguration page to set
up the wireless device settings.
Troubleshooting an Upgrade or Reverting the AP to Autonomous Mode
Q.
My access point failed to upgrade from autonomous software to Cisco Unified software, and it
appears to be stuck in the recovery mode. What is my next step?
A.
If the access point fails to upgrade from autonomous to Unified software, perform the following
actions:
–
Check to ensure the autonomous access point does not have the static IP address configured on
the BVI interface before you boot the recovery image.
–
Issue a ping between the router/access point and the WLC to confirm communication.
–
Check the access point and WLC clock (time and date) are set correctly.
Q.
My access point is attempting to boot, but it keeps failing. Why?
My access point is stuck in the recovery image and will not upgrade to the Unified software. Why?
A.
The access point may attempt to boot and fail or may become stuck in the recovery mode and fail
to upgrade to the Unified software. If either occurs use the service-module wlan-ap0 reset
bootloader command to return the access point to the bootloader for manual image recovery.
Upgrading AP bootloader
For AP802, the bootloader is available as part of host router image. To upgrade the bootloader, follow
these commands:
Router# service-module wlan-ap 0 upgrade bootloader
Router# service-module wlan-ap 0 reset
Downgrading the Software on the Access Point
To reset the access point BOOT back to the last autonomous image, use the service-module wlan-ap0
bootimage autonomous command in global configuration mode. To reload the access point with the
autonomous software image, use the service-module wlan-ap 0 reload command.
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
4-11
Page 56

Related Documentation
Recovering Software on the Access Point
T o recover the image on the access point, use the service-module wlan-ap0 res et bootloader command
in global configuration mode. This command returns the access point to the bootloader for manual image
recovery.
Caution Use this command with caution. It does not provide an orderly shutdown and consequently
may impact file operations that are in progress. Use this command only to recover from a
shutdown or a failed state.
Related Documentation
Refer to the following documentation for additional autonomous and unified configuration procedures:
• Autonomous Cisco Documentation—Table 4-2
• Cisco Unified Documentation—Table 4-3
Chapter 4 Basic Wireless Device Configuration
Table 4-2 Autonomous Cisco Documentation
Network Design Links
Wireless Overview Chapter 2, “Wireless Device Overview”
Security Links
Authentication Types for Wireless Devices This document describes the authentication types that are configured on the
access point.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/Se
curityAuthenticationTypes.html
RADIUS and TACACS+ Servers in a
Wireless Environment
Using the Access Point as a Local
Authenticator
Cipher Suites and WEP This document describes how to configure the cipher suites required fo r using
This document describes how to enable and configure the RADIUS and
TACACS+ and provides detailed accounting information and flexible
administrative control over authentication and authorization processes.
RADIUS and TACACS+ are facilitated through AAA1 and can be enabled
only through AAA commands.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/Se
curityRadiusTacacs_1.html
This document describes how to use a wireless device in the role of an access
point as a local authenticator, serving as a standalone authenticator for a small
wireless LAN, or providing backup authentication service. As a local
authenticator, the access point performs LEAP, EAP-FAST, and MAC-based
authentication for up to 50 client devices.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/Se
curityLocalAuthent.html
WPA and CCKM2; WEP; and WEP features including AES3, MIC4, TKIP,
and broadcast key rotation.
4-12
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/Se
curityCipherSuitesWEP.html
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
Page 57

Chapter 4 Basic Wireless Device Configuration
Related Documentatio n
Table 4-2 Autonomous Cisco Documentation (continued)
Network Design Links
Hot Standby Access Points This document describes how to configure your wireless device as a hot
standby unit.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/R
olesHotStandby.html
Configuring Wireless VLANs This document describes how to configure an access point to operate with the
VLANs set up on a wired LAN.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/wi
reless_vlans.html
Service Set Identifiers In the role of an access point, a wireless device can support up to 16 SSIDs.
This document describes how to configure and manage SSIDs on the wireless
device.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/Se
rviceSetID.html
Administering Links
Quality of Service This document describes how to configure QoS on your Cisco wireless
interface. With this feature, you can provide preferential treatment to certain
traffic at the expense of other traffic. Without QoS, the device offers
best-effort service to each packet, regardless of the packet contents or size. It
sends the packets without any assuranc e of reliabil ity, delay bounds, or
throughput.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/Q
ualityOfService.html
Regulatory Domains and Channels This document lists the radio channels supported by Cisco access products in
the regulatory domains of the world.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/R
adioChannelFrequencies.html
System Message Logging This document describes how to configure system message logging on your
wireless device.
http://www.cisco.com/en/US/docs/routers/access/wireless/software/guide/Sy
sMsgLogging.html
1. AAA = Authentication, Authorization, and Accounting.
2. CCKM = Cisco Centralized Key Management.
3. AES = Advanced Encryption Standard.
4. MIC = Message Integrity Check.
Table 4-3 Cisco Unified Documentation
Network Design Links
Why Migrate to the Cisco Unified Wireless
Network?
http://www.cisco.com/en/US/prod/collateral/wireless/ps5679/ps6548/prod_
white_paper0900aecd804f19e3_ps6305_Products_White_Paper.html
LWAPP1 Wireless LAN Controllers http://www.cisco.com/en/US/products/ps6366/index.html
OL-22206-01
Cisco 880 Series Integrated Services Router Software Configuration Guide
4-13
Page 58

Chapter 4 Basic Wireless Device Configuration
Related Documentation
Table 4-3 Cisco Unified Documentation (continued)
Network Design Links
LWAPP Wireless LAN Access Points http://www.cisco.com/en/US/prod/collateral/wireless/ps5678/ps6306/prod_
white_paper0900aecd802c18ee_ps6366_Products_White_Paper.html
Cisco IOS Command Reference for Cisco
Aironet Access Points and Bridge s, versio ns
http://www.cisco.com/en/US/docs/wireless/access_point/12.4_10b_JA/com
mand/reference/cr2410b.html
12.4(10b) JA and 12.3(8) JEC
Cisco Aironet 1240AG Access Point Support
Documentation
Cisco 4400 Series Wireless LAN Controllers
Support Documentation
1. LWAPP = Lightweight Access Point Protocol.
http://www.cisco.com/en/US/docs/wireless/access_point/1240/quick/guide/a
p1240qs.html
http://www.cisco.com/en/US/products/ps6366/tsd_products_support_series_
home.html
4-14
Cisco 880 Series Integrated Services Router Software Configuration Guide
OL-22206-01
 Loading...
Loading...