Canon Paper Shredder User Manual

Version 1.4
January, 2013
INTENT OF THIS DOCUMENT:
Canon recognizes the importance of information security and the challenges that your organization faces.
This white paper provides information security facts for Canon imageRUNNER ADVANCE systems. It
provides details on imageRUNNER ADVANCE security technology for networked and stand-alone
environments, as well as an overview of Canon’s device architecture, framework and product tec hn ol og i es
as related to document and information security.
This White Paper is primarily intended for the administrative personnel of a cu stomer charged with
responsibility for the configuration and maintenance of imageRUNNER ADVANCE systems. The
information in this document may be used to more clearly understand the many imageRUNNER ADVANCE
security-related configuration capabilities offered by Canon. The imageRUNNER ADVANCE system offers
a number of standard and optional capabilities that, when used by a customer, can help facilitate effective
management and security of data processed and stored by the system. Ultimately, it is the customer’s
responsibility to select the method(s) most appropriate for securing their information.
Canon does not warrant that use of the information contained within this document will prevent malicious
attacks, or prevent misuse of your imageRUNNER ADVANCE systems.
Products shown with optional accessories/equipment. The features reviewed in this white paper include both standard and optional
solutions for imageRUNNER ADVANCE systems. Specifications and availability subject to change without notice.

y
Table of Contents
1. Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .. . . . . . . . 3
2. Device Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .. . . . . . . . 5
3. Information Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
4. Network Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
5. Security Monitoring & Management. . . . . . . . . . . . . . . . . . . . . 32
6. Logging & Auditing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
7. Canon Solutions & Regulatory Requirements. . . . . . . . . . . . . 35
8. Conclusion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
9. Addendum. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .. . . . . . . . . . . 38
White Paper: Canon imageRUNNER ADVANCE Securit
2

y
Section 1 — Introduction
“If you look at these machines as just copiers or printers, you first wonder if you really need security.
Then you realize conventional office equipment now incorporates significant technology advances and
capabilities that make all documents an integrated part of a corporate network that also involves the
Intranet and Internet. Government agencies, corporations and non-profits are increasingly transitioning
from traditional stand-alone machines to devices that integrate these functions and link them to corporate
networks, raising a whole new era of information management and security issu es.
Our development of features within Canon imageRUNNER ADVANCE systems are designed to help
prevent data loss, help protect against unwanted device infiltration and help keep information from being
compromised.”
—Dennis Amorosano, Sr. Director
Solutions Marketing & Business Support, Canon U.S.A., Inc.
As the marketplace has evolved, the technology associated with office equipment continues to develop at
an ever-increasing pace. Over the last several years alone, traditional office equipment has leapfrogged in
technology, expanding its functional capabilities, while at the same time becoming an integr al part of the
corporate network and the Internet. As a result, a new level of security awareness has become imperative.
Canon’s attention to emerging market trends and details surrounding customer security requirements has
driven the development of features within imageRUNNER ADVANCE systems, which has been designed
to help thwart data loss and the potential threats posed by hackers.
White Paper: Canon imageRUNNER ADVANCE Securit
3

y
Section 1 — Introduction
1.1 — Security Market Overview
In today’s digital world, risks to networks and devices come in more forms and from more directions than
ever before. From identity theft and intellectual property loss to infection by viruses and Trojan horses, IT
administrators today find themselves playing an additional role of security officer to adequately protect
information and assets from threats from the outside as well as within.
Nearly every day destructive threats emerge and undiscovered vulnerabilities are exposed, proving that you
can never be too secure. IT administrators need a holistic security strategy that can be applied at every level
of the organization — from servers, desktops and devices such as MFPs, to the networks that connect them
all.
As if the risks to computers, networks and devices weren’t difficult enough to address, increased
governmental regulations add an additional layer of strict compliance standards that must be met.
Legislation such as Sarbanes-Oxley Act (SOX), Gramm-Leach-Bliley Act (GLB), Health Insurance
Portability and Accountability Act (HIPAA), Family Education Rights Privacy Act (FERPA) and
Homeland Security Presidential Directive (HSPD)-12 all require that IT administrators ensure the security,
privacy, accuracy and reliability of information receives the utmost attention.
1.2 — Imaging & Printing Security Overview
Today’s multifunction devices share many similarities with general purpose PCs. They contain many of the
same components like CPUs, memory and hard disks; and some even use mainstream operating systems
like Windows or Linux. Like any other device on the network, sensitive information may be pa ssed through
these units and stored in the device’s hard disk and memory. Yet at many companies multifunction devices
are not given the same attention concerning information security.
The Canon imageRUNNER ADVANCE Security White Paper has been designed to provide detailed
information on how imageRUNNER ADVANCE systems can address a wide variety of security concerns.
Canon imageRUNNER ADVANCE systems offer many standard security capabilities, as well as a number
of advanced security options that may be added for a higher level of confidentiality, integrity and
availability of your mission critical information.
1.3 — Key Security Concentration Areas
Canon recognizes the vital need to help prevent data loss, protect against unwanted device use, and mitigate
the risk of information being compromised. As a result, all imageRUNNER ADVANCE systems include
many standard security features to help safeguard information. Canon imageRUNNER ADVANCE
security capabilities fall into five key areas:
Device Security
Information Security
Network Security
Security Monitoring / Management Tools
Logging & Auditing
NOTE: Please refer to Table 9.2 in Addendum for the Security Features Table illustrating Device
compatibility, and where a feature is standard or optional on the device.
Canon dedicates a significant amount of time and resources to continually improve the security capabilities
of its imageRUNNER devices. Numerous robust capabilities are available for administrators to restrict
access to the device’s features and functions at a granular level, while maintaining high availability and
productivity.
White Paper: Canon imageRUNNER ADVANCE Securit
4

y
Section 2 — Device Security
2.1 — imageRUNNER ADVANCE Controller Security
The imageRUNNER ADVANCE series is built upon a new platform that provides powerful enhancements to
security and productivity. The new architecture centers on a new operating system powered by an embedded
version of Linux, which is quickly becoming the most widely adopted platform for sophisticated devices. The
source version used by imageRUNNER ADVA NCE devices has been hardened by removing all unnece ssary
drivers and services so that only the ones essential to its operation are included.
The nature of embedded Linux and the hardening of the operating system drastically reduce the exposure to
exploits as compared to a desktop or server version of a Linux or Windows operating system. Canon strives to
develop products that meet or exceed our customer’s security requirements. Some of the security related activities
include independent testing by security consulting companies of Canon imageRUNNER ADVANCE devices
during various phases of the development process to flush out any potential vulnerability prior to production. Also,
Canon has collaborated with industry initiatives, such as the development of the IEEE 2600.1 CC Certification
standards for hardcopy device and system security.
2.2 – Authentication
Canon imageRUNNER ADVANCE systems include a number of authentication options which administrators can
use to ensure that only approved walk-up and network-based users can access the device and its functions, such as
print, copy and Scan and Send features. Beyond limiting access to only authorized users, authentication also
provides the ability to control usage of color output, and total pr int counts by department or user.
Device-Based Authentication
Department ID Mode
An embedded feature within imageRUNNER ADVANCE systems, the Department ID Management mode
permits administrators to control device access. If Department ID authentication is enabled, end users are
required to enter a password before they are able to access the device. Up to 1,000 Department IDs can be
configured and each can be configured with device function limitations, such as limiting, printing, copying
and access to Advance Boxes, Mail Boxes and facsimile.
Access to Advanced Boxes, Mail Boxes, and Scan and Send (if applicable) can each be turned “On” or
“Off” from the Limit Functions screen located under Department ID Management.
The settings can be made under Settings / Registration > Management Settings > User
Management > Department ID Management
Single Sign On (SSO) and SSO Hybrid (SSO-H) Login
Single Sign On (SSO) is a Multifunctional Embedded Application Platform (MEAP) login service that can
be used stand-alone with user data registered locally on the device or in conjunction with an Active
Directory (AD) network environment. SSO supports the following modes:
Local Device Authentication – with credentials stored in the device
Domain Authentication – in this mode, user authentication can be linked to an Active Directory
environment on the network
Domain Authentication + Local Device Authentication
White Paper: Canon imageRUNNER ADVANCE Securit
5

y
Section 2 — Device Security
When used in Domain Authentication mode, a user must successfully authenticate using valid credentials
on the system’s control panel, Remote UI utility, or web browser when accessed via a network prior to
gaining access to any of the device functions.
SSO ships standard with MEAP capable imageRUNNER ADVANCE systems and can support up to 200
trusted domains plus the users that belong to the same domain as the device. Canon imageRUNNER
ADVANCE systems also ship with SSO-H, which supports direct authentication against an Active
Directory domain using Kerberos or NTLMv2 as the authentication protocol. SSO-H does not require any
additional software to perform the user authentication as it is able to directly communicate with the Active
Directory domain controllers. In Local Device Authentication mode, SSO-H can support up to 5,000
users. For a combined use of Domain Authentication and Local Device Authentication, an LDAP server
can be configured instead of Domain Authentication.
Card-Based Authentication
uniFLOW Card Authentication
When combined with the optional uniFLOW Output Manager Suite, imageRUNNER ADVANCE
systems are able to securely authenticate users through contactless cards, chip cards, magnetic
cards and PIN codes. uniFLOW supports HID Prox, MIFARE, Legic, Hitag and Magnetic cards
natively using its own reader, as well as others through custom integrations. Certain models of RF
Ideas Card Readers can also be integrated to support authentication using radio-frequency
identification (RFID) cards.
Advanced Authentication—Proximity Card
Using a MEAP application, imageRUNNER ADVANCE systems can be customized to
automatically perform user authentication with contactless cards typically used in corporate
environments. User data can be stored locally in a secure table to eliminate the need for an
external server, or integrated with an existing authentication server through customization.
Support is provided for cards from HID Prox, HID iClass, Casi-Rusco, MIFARE and AWID.
Additionally, Universal Login Manager can now support over 35 card types with a new MI Card +
reader. Customization can also be performed to provide support for other card types.
Advanced Authentication—Common Access Card (CAC)/Personal Identity Verification
(PIV) Card
Federal agencies—both civilian and military (DoD)—require enhanced user authentication, data
security, and information assurance to help comply with the requirements of the Homeland
Security Presidential Directive 12 (HSPD-12). Employees must verify their identity and security
classifications using secure and reliable forms of identification, such as Common Access Card
(CAC) and Personal Identity Verification (PIV). And with networked multifunction printers
(MFPs) being deployed on a greater scale in these locations, Canon developed Advanced
Authentication CAC/PIV—an easy-to-use, two-factor embedded authentication solution to lock
and unlock Canon devices. This serverless solution ensures that all device functions are locked
down until users insert their government-issued Common Access Card/Personal Identity
Verification into the card reader and enter their PIN. Only those authenticated individuals are
granted access to the device.
Authorized Send Common Access Card (CAC)/Personal Identity Verification (PIV) Card
To fulfill the strict security requirements of government agencies as dictated by Homeland
Security Presidential Directive-12 (HSPD-12), imageRUNNER ADVANCE systems support the
use of Common Access Card (CAC) and/or Personal Ident ity Verification (PIV) card
authentication for the embedded Authorized Send MEAP application. Authorized Send for
CAC/PIV is a server-less application that protects the Scan-to-Email, Scan-to-Netw ork Folder and
Scan-to-Network Fax functions, while allowing general use of walk-up operations like print and
copy.
White Paper: Canon imageRUNNER ADVANCE Securit
6
y
Section 2 — Device Security
Authorized Send for CAC/PIV supports two-factor authentication by prompting users to insert
their card into the device’s card reader and requiring them to enter their PIN. ASEND for
CAC/PIV supports the Online Certificate Status Protocol (OCSP) to check the revocation status of
the user’s card, and then authenticates the user against the Public Key Infrastructure (PKI) and
Active Directory. Once authenticated, users can access the document distribution features of
Authorized Send.
Authorized Send for CAC/PIV supports enhanced e-mail security features such as nonrepudiation, digital signing of e-mail, and encryption of e-mail and file attachments. The
cryptographic engine used by Authorized Send for CAC/PIV is based on the industry leading RSA
BSAFE security software and has undergone the stringent testing and validation requirements of
the FIPS 140 standard.
Control Cards/Card Reader System
Canon imageRUNNER ADVANCE systems offer support for an optional Control Card/Card
Reader system for device access and to manage usage. The Control Card/Card Reader system
option requires the use of intelligent cards that must be inserted in the system before granting
access to functions, which automates the process of Department ID authentication. The optional
Control Card/Card Reader system manages populations of up to 300 departments or users.
2.3 – Access Control
Canon imageRUNNER ADVANCE systems support a number of access control options to help you
manage the use of device settings and functions in addition to specific capabilities of certain functions.
Access control solutions for the imageRUNNER ADVANCE can help Authentication, Authorization, and
Auditing. Canon offers solutions that can lock down the entire device, or simply lock down specific
functions (e.g. Send-to-Email), while leaving other applications availabl e fo r general use. With the power
and flexibility of MEAP, some solutions can be customized to meet your specific requirements.
Password-Protected System Settings
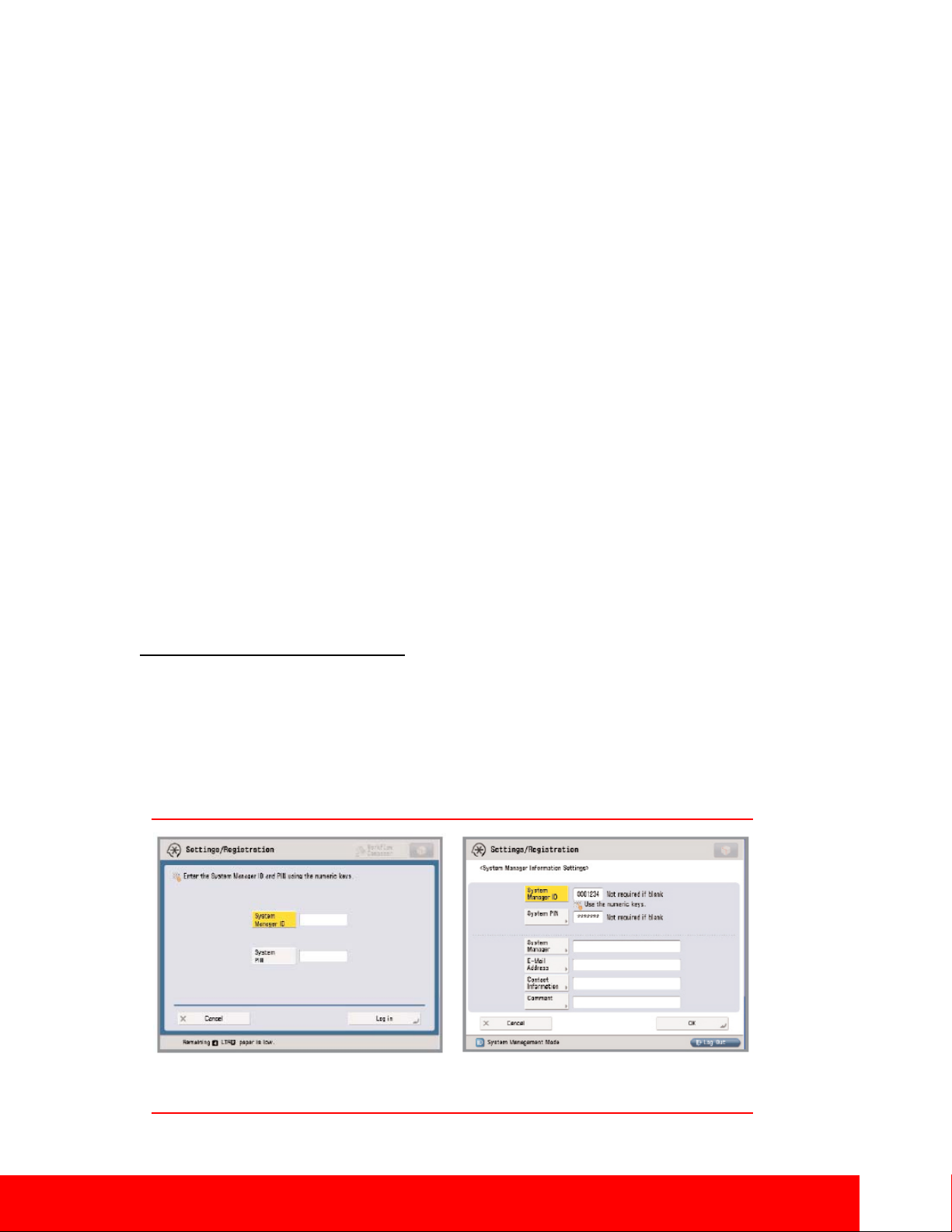
As a standard feature, imageRUNNER ADVANCE systems setup screens support passwor d pr otect i o n t o
restrict device setting changes from the control panel and Remote UI tool. System Administrators can set
network information, system configuration, enable, and disable network and printing protocols among
many other options. Canon highly recommends setting an administrator password at time of installation
since it controls critical device settings.
System Manager Screen
Store ID and Password Screen
7
White Paper: Canon imageRUNNER ADVANCE Securit
y
Section 2 — Device Security
Access Management System
The Access Management System, which is standard on imageRUNNER ADVANCE systems, can be used
to tightly control access to device functionality. Restrictions can be assigned to users and groups, to restrict
entire functions or restrict specific features within a function. Access restrictions are managed in units
called “roles”. Roles contain information that determines which of the various functions of the device may
be used or not.
Roles can be set up based on individual user’s job title or responsibilities or by group, enabling the
administrator to create roles specific to certain departments or workgroups. Since the administrator is not
limited to restricting all or none of a particular function, the roles can be as specific as is required for a
number of business needs. Beyond the Base roles which contain default access restrictions, up to 100 new
Custom roles can be registered for up to 5,000 users. The administrator can also define whether to allow
unregistered users to log in as guests and then specify settings for guest user’s roles.
The following describes the various Base access levels (roles) that are available:
Privileges by Access Level
Predefined Role Access Privileges
Administrator Given privileges to operate all device functions.
Network Manager/Admin Network manager mainly manages the settings related to the network under Settings/Registration.
Device Manager/Admin Device Manager can specify settings related to management settings for paper type and function settings for Send/Receive.
Power User Given privileges to operate all device functions, except managing the device itself.
General User Given privileges to operate all device functions, except managing the device itself and specifying/registering address book.
Limited User Restricted from device management, all send functions and only allowed 2-sided printing and copy ing.
Guest Restricted from device management, all send functions and only allowed 2-sided printing and copying.
The following functions and features can be restricted:
Device Function Values Description
Print Allowed, Not Allowed Allows or prohibits using applications related to the Print function.
Copy Allowed, Not Allowed Allows or prohibits using applications related to the Copy function.
Send/Store on Network
E-mail TX Allowed, Not Allowed Allows or prohibits sending via E-mail TX.
I-Fax TX Allowed, Not Allowed Allows or prohibits sending via I-Fax TX.
Fax TX Allows or prohibits sending via Fax TX.
FTP TX Allowed, Not Allowed Allows or prohibits sending via FTP TX.
NetWare (IPX) TX Allowed, Not Allowed Allows or prohibits sending via NetWare (IPX) TX.
Windows (SMB) TX Allowed, Not Allowed Allows or prohibits sending via Windows (SMB) TX.
WebDAV TX Allowed, Not Allowed Allows or prohibits sending via WebDAV TX.
Inbox TX Allowed, Not Allowed Sets restrictions for saving scanned documents to user inboxes.
Specify Address
Domain/Send to Addresses
Received from Cell Phone
Use Address Book/Register
Storage Location for Network
Send to New Addresses/Send
to Addresses Received from
Cell Phone
Add Device Signature to
Sending Files
Sending Files Format Allowed, Not Allowed Allows or prohibits sending file f ormats that a device signature cannot be added to.
Save Functions
(Mailbox/Hold/Memory Media)
Web Access Allowed, Not Allowed Allows or prohibits using applications related to the Web Access function.
Utility Allowed, Not Allowed Allows or prohibits using applications related to Utilities.
Others Allowed, Not Allowed Allows or prohibits using other applications.
MEAP Applications Allowed, Not Allowed Allows or prohibits the use of MEAP applications.
* Requires SSO-H to be enabled.
Allowed, Not Allowed
No Restrictions, Not
Allowed, Read Only
Allowed, Not Allowed
Added, Not Added Allows or prohibits adding of a device signature when sending PDF files.
Allowed, Not Allowed Allows or prohibits saving functions.
Sets restrictions for externally sending scanned documents, user inbox documents,
and saving documents to file servers or network storage.
For imageRUNNER ADVANCE devices, these restrictions also apply to addresses received
from cell phones.
For imageRUNNER ADVANCE devices, these restrictions also apply to registering,
editing, and deleting network storage.
For imageRUNNER ADVANCE devices, these restrictions also apply to addresses
received from cell phones.
White Paper: Canon imageRUNNER ADVANCE Securit
8

y
Section 2 — Device Security
When the Access Management System has been enabled, users must log in to the device using SSO user
authentication. Access Management System supports authentication through local device authentication as
well as Active Directory using SSO-H*, which includes support for Kerberos Authentication. Once a user
logs into the device with their user name and password, the device can determine which roles are assigned
to that particular user. Restrictions are applie d based on the assigned roles. If an entire function is
restricted, it will appear grayed out to the user after authentication.
Function Level Authentication
Canon imageRUNNER ADVANCE systems offer the ability to limit the use of specific functions by
authorized users by requiring authentication to use sensitive functions with Function Level Authentication.
Function Level Authentication is a part of Access Management System and works with SSO-H for
authentication. It enables administrators to choose precisely which functions are permitted by walk-up and
network users without entering credentials versus the ones that require a user to login. For example,
administrators may choose to allow all users to make black-and-white copies while prompting users to
login if they choose to output color or use the Scan and Send function.
Scan and Send Security
On devices that have Scan and Send enabled, certain information such as fax numbers and e-mail addresses
may be considered confidential and sensitive. For these devices, there are additional security features to
prevent confidential information from being accessed.
Address Book Password
Administrative and individual passwords can be set for Address Book Management functions. A
system administrator can define the specific Address Book data that can be viewe d by users,
effectively masking private details. This password may be set separately so individuals other than
the System Manager can administer the Address Book.
By setting a password for an Address Book, the ability to Store, Edit, or Erase individual and
group e-mail addresses in the Address Book is restricted. Therefore, only individuals with the
correct password for an Address Book will be able to make modifications.
This same password is also used for the Address Book Import/Export function through the Remote
UI utility.
* Requires imageWARE Enterprise Management Console and the Access Management System Plug-In when authenticating through
Active Directory.
Address Book Password Screen
Address Book Access Code Enable/Disable Screen
9
White Paper: Canon imageRUNNER ADVANCE Securit

y
Section 2 — Device Security
Access Code for Address Book
End-users will also have the capacity to place an access number code on addresses in the Address
Book. When registering an address, users can then enter an Access Number to restrict the display
of that entry in the Address Book. This function limits the display and use of an address in the
Address Book to those users who have the correct code. The Access Number can be turned on or
off, depending on the level of security the end-user find s necessary.
Settings / Registration > Register Destinations > Register New Destinations, from here the user
can register an new e-mail address, fax number, I-Fax, file or group address and set an access code
for that specific address entry in the address book.
Destination Restriction Funct ion
Data transmission to a new destination through the Scan and Send and Fax function can be
restricted, prohibiting transmissions to locations other than the destinations registered or permitted
by the System Manager.
In addition to restricting all new destinations, administrators can also restrict the addition of new
addresses for specific destination types that are available to users when sending documents with
Scan and Send and Fax. Permissions can be set to enable or disable the entry of new addresses for
the following:
Entries in the Address Book
LDAP Servers
User Inboxes
One-touch Buttons
Favorites Buttons
The User’s E-mail Address (Send to Myself, if Using SSO Login)
Print Driver Security Features
Print Job Accounting
A standard feature in Canon’s printer drivers, print job accounting requires users to enter an
administrator-defined password prior to printing, thereby restricting device access to those
authorized to print. Printing restrictions can be set using Department ID credentials or through the
Access Management System.
Custom Driver Configuration Tool
Administrators can create custom driver profiles for users to limit access to print features and
specify default settings, thereby protecting the device against unauthorized use, enforcing internal
policies and better controlling output costs. Security conscious settings that can be defined and
enforced include duplex output, secure print, B&W only on color devices, watermarks and custom
print profiles, as well as hiding any desired functions. For easier deployment, the customized
drivers can be distributed to desktops across the organization through the Printer Driver
Management Plug-in for imageWARE Enterprise Management Console (iWEMC).
White Paper: Canon imageRUNNER ADVANCE Securit
10

y
Section 2 — Device Security
USB Block
USB Block allows the System Administrator to help protect the imageRUNNER ADVANCE systems
against unauthorized access through the built-in USB interface. Access to the device’s USB interface for
desktop access and the device’s host mode for other USB devices can each be permitted or disabled.
Go to Settings / Registration > Preferences > External Interface > USB Settings.
imageRUNNER ADVANCE models and select imageRUNNER models have the ability to restrict USB usage for
memory, but allow USB usage for peripherals such as keyboards and card readers. Canon’s USB feature provides
the capability to view and print from the devices only for non-executable files, such as .pdf, .jpg, .tiff, and .png.
Executable files cannot be performed on the device, and this prevents viruses from spreading if being accessed.
2.4 – Third Party MEAP Application and Development
Canon actively collaborates with leading third-party software companies to develop custom solutions for
imageRUNNER ADVANCE systems, known as MEAP applications. Each MEAP enabled device includes
a number of safeguards to help ensure the security and integrity of information stored on the device.
Access to the Software Development Kit for MEAP is tightly restricted and controlled through licensing.
Once an application has been developed, it is thoroughly reviewed by Canon to ensure that it meets strict
guidelines for operability and security. Following the review, the application is digitally signed with a
special encrypted signature to protect the integrity of the application. If the application is modified in any
way, the signature code will not match and the application will not be permitted to run on the device. These
safety measures make it virtually impossible for an altered or rogue MEAP application to be executed on an
imageRUNNER ADVANCE system.
White Paper: Canon imageRUNNER ADVANCE Securit
11
y
Section 3 — Information Security
Protecting your organization’s confidential information is a mission that Canon takes seriously. From your
documents, faxes and e-mails to the underlying data on the internal hard disk drive and in memory, Canon
has built in many controls to help ensure that your information does not become compromised.
3.1 – Document Security
Secure Printing
Secured Print / Encrypted Secured Print*
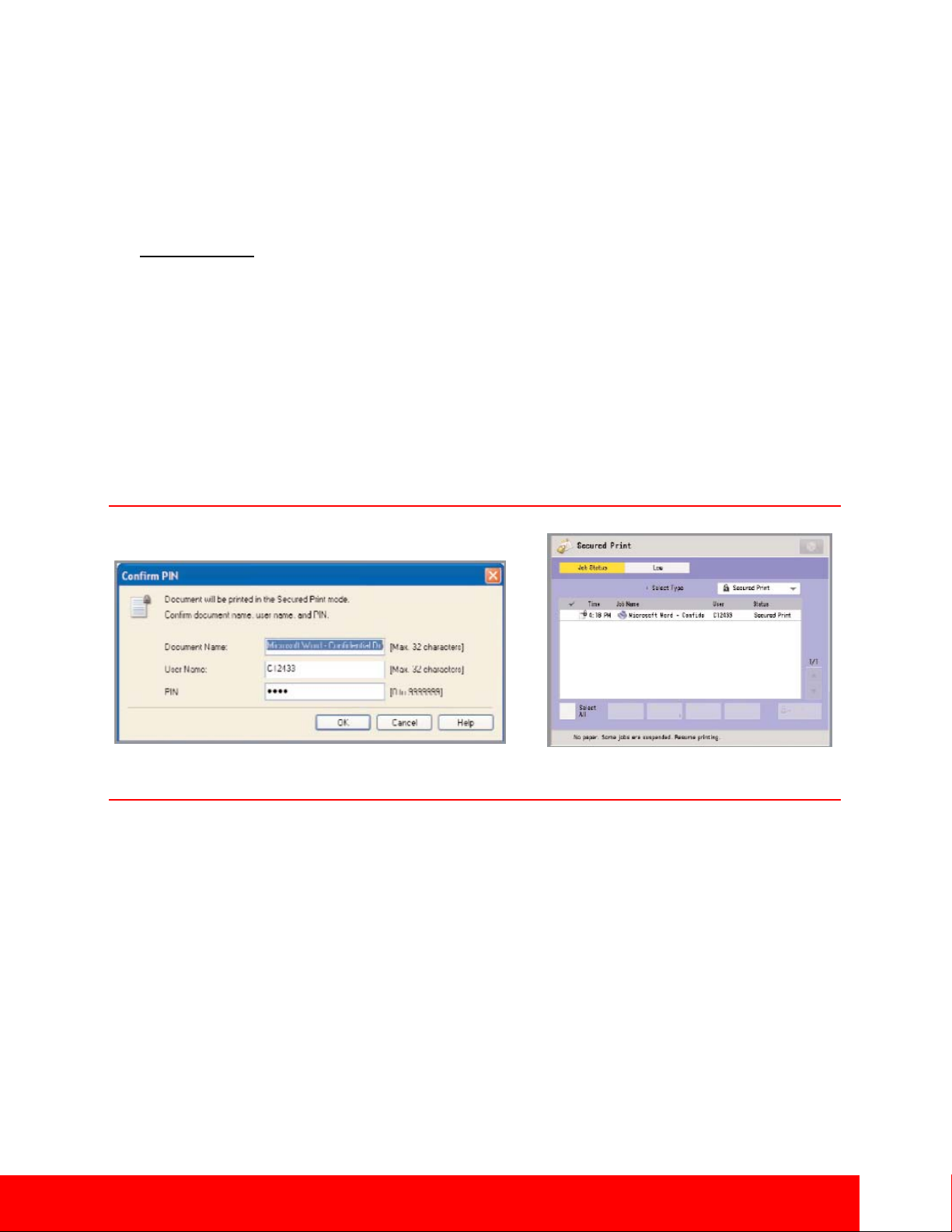
Encrypted Secured Print and Secured Print are print functions that hold a job in queue until the user enters
the appropriate password at the device. This ensures that the user is in close proximity before the document
is printed and minimizes unattended documents left at the device. The imageRUNNER ADVANCE system
requires the user to set a password in the print driver window when sending a print job from a connected
PC. The same password is also required for releasing the job at the device. When using the optional
Encrypted Secured Print software, security is further enhanced by using AES 256-Bit Encryption to protect
the print job data while in transit across the network. On systems equipped with the optional Encrypted
Secured Print, administrators can use the print job restriction feature to permit only encrypted print jobs at
the designated device.
* Requires the Encrypted Secured Print option.
Secured Print Screen from the Printer Driver
uniFLOW Secure Print
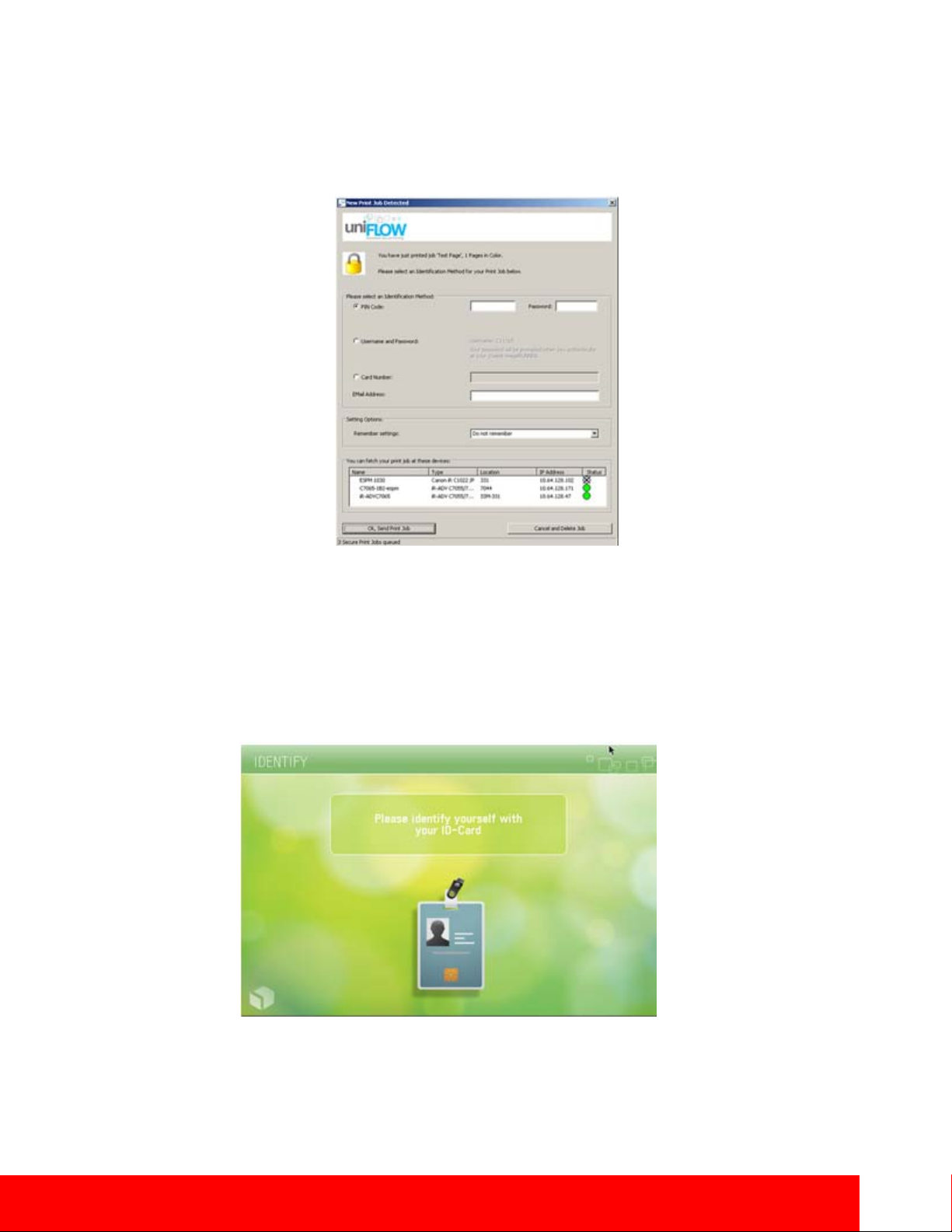
Exclusive to Canon is the uniFLOW Output Manager Suite, which is optional modular software designed
to reduce costs, improve productivity and enhance security. From a security perspective, uniFLOW Output
Manager Suite provides secure printing capabilities by holding jobs at the server until released by the user
at any desired imageRUNNER ADVANCE system. From their desktop, users print documents by choosing
the uniFLOW server as the printer. At the chosen device, users can be authenticated using a wide variety of
supported methods. Users can then access the uniFLOW MEAP client application from the device’s control
panel and release their job from their queue of pending documents.
uniFLOW Serverless Secure Print
uniFLOW Serverless Secure Print (SSP) is a secure print release solution that requires no server.
It also extends a secured print option to Canon Compact MFPs (CMFP), complementing mixed fleet and
MPS business for larger customers. Based on uniFLOW server technology, SSP enables secure printing on
compact Canon MFPs while also including aspects of uniFLOW’s signature follow-me printing and
Print Job Status Screen
White Paper: Canon imageRUNNER ADVANCE Securit
12
y
Section 3 — Information Security
authentication. Serverless Secure Print works by holding the user’s print job on their PC. The users can
then walk to a Canon device in the SSP network, authenticat e, and release jobs held in their SSP queue.
Universal Login Manager
ULM (Universal Login Manager) is a Server-less login application for imageRUNNER ADVANCE
devices, which provides an easy and convenient solution for user authentication. Ideal for small to medium
size businesses, ULM’s simple user authentication includes card log-in, PIN code, or user name and
password, using local or Active Directory (AD), with minimal IT requirements. Utilizing AMS (Access
Management System), found on all imageRUNNER ADVANCE devices, ULM allows comprehensive
control of access on a per-user basis. In addition, ULM delivers simplified tracking, allowing organizations
to obtain a simple overview of user or device usage activity.
White Paper: Canon imageRUNNER ADVANCE Securit
13
 Loading...
Loading...