Page 1

Camera Browser Interface
TINYON IP 2000 WI / TINYON IP 2000 PIR
en Software manual
Page 2

Page 3

Camera Browser
Interface
Table of contents
Table of Contents | en 3
1
1.1 System requirements 11
1.2 Establishing the connection 11
1.2.1 Password protection in camera 12
1.3 Protected network 12
2
2.1 Live page 13
2.2 Playback 13
2.3 Settings 13
3
3.1 Live page 14
3.1.1 Image selection 14
3.1.2 Digital I/O 15
3.1.3 System Log / Event Log 15
3.1.4 Saving snapshots 16
3.1.5 Recording video sequences 16
3.1.6 Recording status 16
3.1.7 Audio communication 16
3.1.8 Storage, CPU and network status 17
3.1.9 Status icons 18
3.2 Playback 19
3.2.1 Selecting recordings for playback 19
3.2.2 Exporting tracks 19
3.2.3 Searching for tracks 20
3.2.4 Controlling playback 20
4
4.1 Device Access 22
4.1.1 Name 22
4.1.2 Password 22
4.2 Date/Time 23
4.3 Network 24
4.4 Encoder 24
4.5 Audio 25
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Browser connection 11
System overview 13
Operation via the browser 14
Basic Mode 22
Page 4

4 en | Table of Contents
Camera Browser
Interface
4.6 Recording 25
4.7 System Overview 25
5
General settings 26
5.1 Identification 26
5.1.1 Naming 26
5.1.2 ID 26
5.1.3 iSCSI Initiator extension 26
5.2 Password 27
5.2.1 Enter Password 27
5.2.2 Confirm password 27
5.3 Date/Time 28
5.3.1 Date format 28
5.3.2 Device date / Device time 28
5.3.3 Device time zone 28
5.3.4 Daylight saving time 28
5.3.5 Time server IP address 29
5.3.6 Time server type 29
5.4 Display Stamping 30
5.4.1 Camera name stamping 30
5.4.2 Time stamping 30
5.4.3 Display milliseconds 30
5.4.4 Alarm mode stamping 30
5.4.5 Alarm message 31
5.4.6 Transparent stamping 31
5.4.7 Video authentication 31
5.5 GB/T 28181 31
6
Web Interface 32
6.1 Appearance 32
6.1.1 Website language 32
6.1.2 Company logo 32
6.1.3 Device logo 32
6.1.4 Show VCA metadata 32
6.1.5 Show overlay icons 32
6.1.6 Select video player 33
6.1.7 JPEG size, interval and quality 33
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 5

Camera Browser
Interface
Table of Contents | en 5
6.2 LIVE Functions 34
6.2.1 Transmit audio 34
6.2.2 Show alarm inputs 34
6.2.3 Show alarm outputs 34
6.2.4 Show event log 34
6.2.5 Show system log 34
6.2.6 Allow snapshots 34
6.2.7 Allow local recording 35
6.2.8 I-frames-only stream 35
6.2.9 Path for JPEG and video files 35
6.3 Logging 36
6.3.1 Save event log 36
6.3.2 Save system log 36
7
Camera 37
7.1 Installer Menu 37
7.1.1 Base frame rate 37
7.1.2 Camera LED 37
7.1.3 Mirror image 37
7.1.4 Flip image 37
7.1.5 Reboot device 37
7.1.6 Factory defaults 37
7.2 Picture settings – Color 38
7.2.1 White balance 38
7.3 Picture settings – ALC 40
7.3.1 ALC mode 40
7.3.2 ALC level 40
7.3.3 Exposure/frame rate 40
7.4 Picture settings – Enhance 41
7.4.1 Backlight Compensation 41
7.4.2 Intelligent DNR 41
7.5 Encoder Settings 42
7.6 Privacy Masks 43
7.7 Audio 44
7.7.1 Adjust level 44
7.7.2 Recording format 44
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 6

6 en | Table of Contents
Camera Browser
Interface
7.8 Pixel Counter 45
8
Encoder Settings 46
8.1 Introduction to encoder settings 46
8.2 Encoder Profile 47
8.2.1 Pre-defined profiles 47
8.2.2 Changing a profile 47
8.2.3 Profile name 47
8.2.4 Target bit rate 48
8.2.5 Maximum bit rate 48
8.2.6 Encoding interval 48
8.2.7 Standard definition video resolution 48
8.2.8 Expert Settings 48
8.2.9 Default 50
8.3 Encoder Streams 51
8.3.1 H.264 settings 51
8.3.2 JPEG stream 51
8.4 Encoder Regions 53
8.4.1 Selecting regions 53
9
Recording 54
9.1 Introduction to recording 54
9.1.1 WiFi models 54
9.2 Storage Management 55
9.2.1 Device manager 55
9.2.2 Recording media 55
9.2.3 Activating and configuring storage media 56
9.2.4 Formatting storage media 56
9.2.5 Deactivating storage media 57
9.3 Recording Profiles 58
9.3.1 Recording track selection 58
9.3.2 Standard recording 59
9.3.3 Alarm recording 59
9.4 Maximum Retention Time 61
9.5 Recording Scheduler 62
9.5.1 Weekdays 62
9.5.2 Holidays 62
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 7

Camera Browser
Interface
Table of Contents | en 7
9.5.3 Profile names 63
9.5.4 Activate recording 63
9.5.5 Recording status 63
9.6 Recording Status 64
10
Alarm 65
10.1 Alarm Connections 65
10.1.1 Connect on alarm 65
10.1.2 Number of destination IP address 65
10.1.3 Destination IP address 65
10.1.4 Destination password 65
10.1.5 Video transmission 66
10.1.6 Stream 66
10.1.7 Remote port 66
10.1.8 Video output 66
10.1.9 Decoder 67
10.1.10 SSL encryption 67
10.1.11 Auto-connect 67
10.1.12 Audio 67
10.2 Video Content Analyses (VCA) 68
10.3 Audio Alarm 69
10.3.1 Audio alarm 69
10.3.2 Name 69
10.3.3 Signal Ranges 69
10.3.4 Threshold 69
10.3.5 Sensitivity 69
10.4 Alarm E-Mail 70
10.4.1 Send alarm e-mail 70
10.4.2 Mail server IP address 70
10.4.3 SMTP user name 70
10.4.4 SMTP password 70
10.4.5 Format 70
10.4.6 Image size 70
10.4.7 Attach JPEG from camera 71
10.4.8 Destination address 71
10.4.9 Sender name 71
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 8

8 en | Table of Contents
Camera Browser
Interface
10.4.10 Test e-mail 71
10.5 Alarm Task Editor 72
11
Setting up VCA 73
11.1 VCA - Silent VCA 73
11.2 VCA - Profiles 74
11.2.1 Aggregation time [s] 74
11.2.2 Analysis type 74
11.2.3 Motion detector 75
11.2.4 Tamper detection 76
11.3 VCA - Scheduled 80
11.3.1 Weekdays 80
11.3.2 Holidays 80
11.4 VCA - Event triggered 82
11.4.1 Trigger 82
11.4.2 Trigger active 82
11.4.3 Trigger inactive 82
11.4.4 Delay [s] 82
12
Interfaces 83
12.1 Alarm input 83
12.1.1 Name 83
12.2 Alarm output 83
12.2.1 Idle state 83
12.2.2 Operating mode 83
12.2.3 Output follows 83
12.2.4 Output name 84
12.2.5 Trigger output 84
12.2.6 Illuminator 84
13
Network 85
13.1 Network Access 85
13.1.1 Automatic IP assignment 85
13.1.2 IP V4 address 85
13.1.3 IP V6 address 86
13.1.4 DNS server address 86
13.1.5 Video transmission 86
13.1.6 HTTP browser port 86
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 9

Camera Browser
Interface
Table of Contents | en 9
13.1.7 HTTPS browser port 86
13.1.8 RCP+ port 1756 87
13.1.9 Telnet support 87
13.1.10 Interface mode ETH 87
13.1.11 Network MSS [Byte] 87
13.1.12 iSCSI MSS [Byte] 88
13.1.13 Network MTU [Byte] 88
13.2 DynDNS 89
13.2.1 Enable DynDNS 89
13.2.2 Provider 89
13.2.3 Host name 89
13.2.4 User name 89
13.2.5 Password 89
13.2.6 Force registration now 89
13.2.7 Status 90
13.3 Advanced 91
13.3.1 Cloud-based Services 91
13.3.2 RTSP port 91
13.3.3 Authentication (802.1x) 91
13.3.4 TCP metadata input 91
13.4 Network Management 92
13.4.1 SNMP 92
13.4.2 UPnP 92
13.4.3 Quality of Service 93
13.5 WLAN 94
13.6 Multicast 95
13.6.1 Enable 95
13.6.2 Multicast Address 95
13.6.3 Port 96
13.6.4 Streaming 96
13.6.5 Multicast packet TTL 96
13.7 Image Posting 97
13.7.1 JPEG posting 97
13.8 Accounts 98
13.9 IPv4 Filter 99
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 10

10 en | Table of Contents
Camera Browser
Interface
14
Service 100
14.1 Maintenance 100
14.1.1 Update server 100
14.1.2 Firmware 100
14.1.3 Upload History 101
14.1.4 Configuration 101
14.1.5 SSL certificate 101
14.1.6 Maintenance log 102
14.2 System Overview 103
15
Appendices 104
15.1 Copyright notices 104
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 11

Camera Browser
Interface
Browser connection | en 11
1
1.1
Browser connection
A computer with Microsoft Internet Explorer is used to receive
live images, control the unit, and replay stored sequences. The
unit is configured over the network using the browser.
System requirements
– Network access (Intranet or Internet)
– Microsoft Internet Explorer version 9 (32-bit)
– Screen resolution at least 1024 × 768 pixels
– 16- or 32-bit color depth
– JVM installed
The Web browser must be configured to enable Cookies from
the IP address of the unit.
In Windows Vista, deactivate protected mode on the Security
tab under Internet Options.
To play back live video images, an appropriate ActiveX must be
installed on the computer. If necessary, install
Bosch Video Client. This can be downloaded from the following
address:
http://downloadstore.boschsecurity.com/
1.2
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Establishing the connection
The unit must have a valid IP address to operate on your
network and a compatible subnet mask. By default, DHCP is preset at the factory to On and so your DHCP server assigns an IP
address. With no DHCP server the default address is
192.168.0.1
1. Start the Web browser.
2. Enter the IP address of the unit as the URL.
3. During initial installation, confirm any security questions
that appear.
Page 12

12 en | Browser connection
Note:
If you cannot connect, the unit may have reached its maximum
number of connections. Depending on the device and network
configuration, each unit can have up to 50 web browser
connections, or up to 100 connections via Bosch Video Client or
Bosch Video Management System.
Camera Browser
Interface
1.2.1
1.3
Password protection in camera
A unit offers the option of limiting access across various
authorization levels. If the unit is password-protected, a
message to enter the password appears.
1. Enter the user name and the associated password in the
appropriate fields.
2. Click OK. If the password is correct, the desired page is
displayed.
Protected network
If a RADIUS server is used for network access control (802.1x
authentication), the unit must be configured first. To configure
the unit, connect it directly to a computer using a network cable
and configure the two parameters, Identity and Password. Only
after these have been configured can communication with the
unit via the network occur.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 13

Camera Browser
Interface
System overview | en 13
2
2.1
2.2
2.3
System overview
When a connection is established, the LIVE page is initially
displayed. The application title bar displays three items: LIVE,
PLAYBACK, SETTINGS.
Note:
The PLAYBACK link is only visible if a storage medium has been
configured for recording. (With VRM recording this option is not
active.)
Live page
The LIVE page is used to display the live video stream and
control the unit.
Playback
The PLAYBACK page is used for playing back recorded
sequences.
Settings
The SETTINGS page is used to configure the unit and the
application interface.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 14
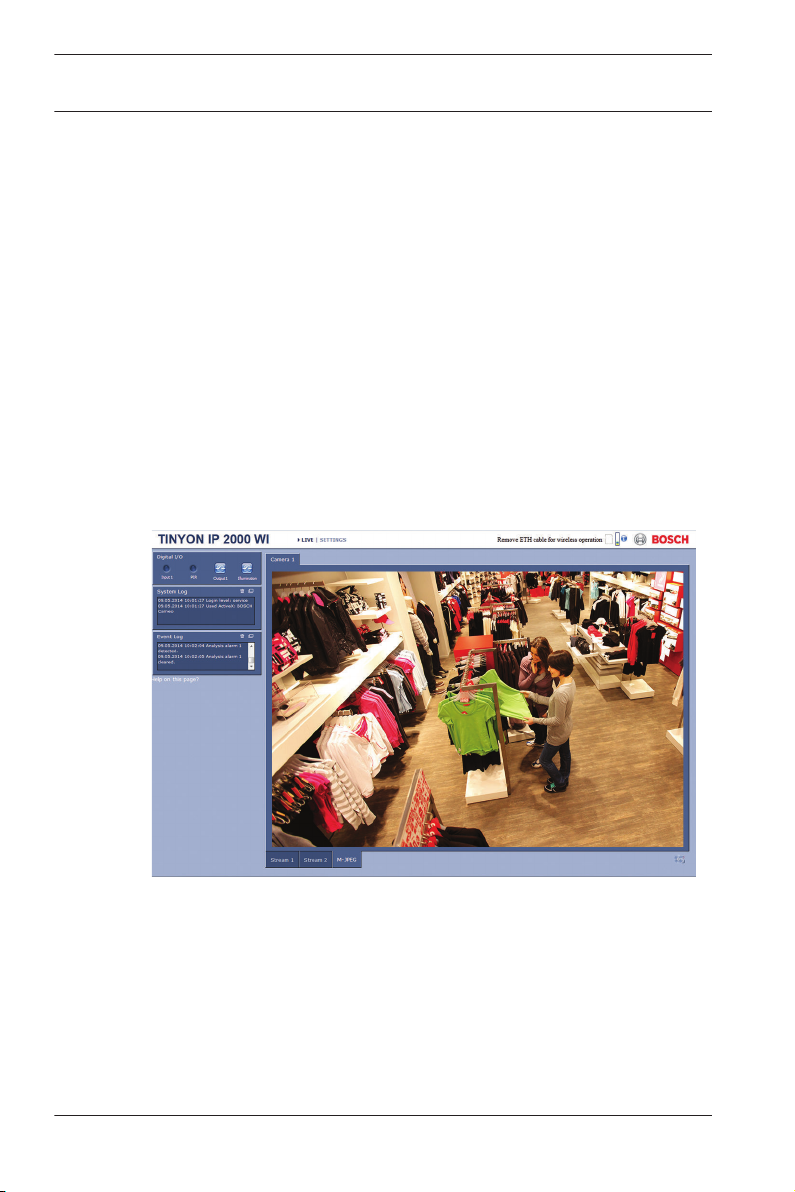
14 en | Operation via the browser
Camera Browser
Interface
3
3.1
3.1.1
Operation via the browser
Live page
After the connection is established, the LIVE page is initially
displayed. It shows the live video image on the right of the
browser window. Depending on the configuration, various text
overlays may be visible on the live video image.
Other information may also be shown next to the live video
image. The items shown depend on the settings on the LIVE
Functions page.
Image selection
Figure 3.1: Live page
Click a tab below the video image to display a camera image
stream.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 15

Camera Browser
Interface
Operation via the browser | en 15
3.1.2
Digital I/O
The alarm input and the PIR alarm indicators are displayed in
the Digital I/O pane next to the image. These alarm symbols
light when an alarm input is detected or when the PIR sensor
detects movement.
The camera alarm Output 1 symbol allows the operation of an
external device (for example, a light or a door opener).
4 To operate the alarm output, click the Output 1 relay
symbol.
The symbol is red when the output is activated.
The PIR detector can also be used to trigger the alarm output.
Refer to Output follows, page 83 to set up this function.
The white LED illuminator is switched on and off using the
illuminator symbol.
4 To operate the illuminator, click the Illumination relay
symbol.
The symbol is red when the illuminator is activated.
The white LED illuminator can also be switched on and off by
various events, including PIR movement detection. Refer to
Output follows, page 83 to set up this function.
3.1.3
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
System Log / Event Log
The System Log field contains information about the operating
status of the camera and the connection.
Events such as the triggering or the end of alarms are shown in
the Event Log field.
1. To view, filter and save these messages to a file, click
in the top right-hand corner.
2. To clear the log, click in the top right-hand corner of
the relevant field.
Page 16
16 en | Operation via the browser
Camera Browser
Interface
3.1.4
3.1.5
Saving snapshots
Individual images from the video sequence that is currently
being shown can be saved in JPEG format on the computer's
hard drive.
4 Click the camera icon
The storage location depends on the configuration of the
camera.
to save a single image.
Recording video sequences
Sections of the video sequence that is currently being shown on
the LIVE page can be saved on the computer's hard drive. The
sequences are recorded at the resolution specified in the
encoder configuration. The storage location depends on the
configuration of the camera.
1. Click the recording icon
– Saving begins immediately. The red dot on the icon
indicates that a recording is in progress.
2. Click the recording icon again to stop recording.
Play back saved video sequences using the Player from
Bosch Security Systems.
to record video sequences.
3.1.6
3.1.7
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Recording status
The hard drive icon below the camera images on the LIVE page
changes during an automatic recording.
The icon lights up and displays a moving graphic to
indicate a running recording. If no recording is taking place, a
static icon is displayed.
Audio communication
Audio can be sent and received via the LIVE page if the unit and
the computer support audio.
Page 17

Camera Browser
Interface
1. Press and hold the F12 key on the keyboard to send an
2. Release the key to stop sending audio.
All connected users receive audio signals sent from the unit but
only the user who first pressed the F12 key can send audio
signals; others must wait for the first user to release the key.
Operation via the browser | en 17
audio signal to the unit.
3.1.8
Storage, CPU and network status
When accessing the unit with a browser, the local storage,
processor and network status icons are shown in the upper
right of the window next to the Bosch logo.
When a local storage card is available, the memory card icon
changes color (green, orange or red) to indicate the local
storage activity. If you hover over this icon with the mouse the
storage activity is shown as a percentage.
If you hover over the middle icon, the CPU load is shown.
If you hover over the right-hand icon, the network load is shown.
This information can help with problem solving or when fine
tuning the unit. For example:
– if the storage activity is too high, change the recording
profile,
– if the CPU load is too big, change the IVA settings,
– if the network load is too big, change the encoder profile to
reduce bitrate.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 18

18 en | Operation via the browser
Camera Browser
Interface
3.1.9
Status icons
Various overlays in the video image provide important status
information. The overlays provide the following information:
Decoding error
The frame might show artifacts due to decoding errors.
Alarm flag
Indicates that an alarm has occurred.
Communication error
A communication error, such as a connection failure to the
storage medium, a protocol violation or a timeout, is indicated
by this icon.
Gap
Indicates a gap in the recorded video.
Watermark valid
The watermark set on the media item is valid. The color of the
check mark changes according to the video authentication
method that has been selected.
Watermark invalid
Indicates that the watermark is not valid.
Motion alarm
Indicates that a motion alarm has occurred.
Storage discovery
Indicates that recorded video is being retrieved.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 19
Camera Browser
Interface
Operation via the browser | en 19
3.2
3.2.1
Playback
Click PLAYBACK in the application title bar to view, search or
export recordings. This link is only visible if a direct iSCSI or
memory card has been configured for recording. (With VRM
recording this option is not active.)
A collapsible panel on the left of the display has four tabs:
– Track list
– Export
– Search
– Search results
Select the recording number to be shown in the Recording
drop-down menu at the top of the window.
Selecting recordings for playback
To see all saved sequences:
1. Click the track list tab .
2. A list of tracks with a number assigned is displayed. Start
time and stop time, recording duration, number of alarms
and recording type are shown for each track.
3. At the bottom of the window, select the maximum number
of tracks to be displayed in the list.
4. Use the arrow buttons at the bottom to browse the list.
5. To view tracks beginning from a particular time, enter the
time code and click Get Tracks.
6. Click a track. The playback for the selected track starts.
3.2.2
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Exporting tracks
1. Select a track in the track list.
2. Click the export tab .
Page 20
20 en | Operation via the browser
3. The start and stop time are filled-in for the selected track. If
required, change the times.
4. Select a target.
5. Select the original or a condensed speed.
Camera Browser
Interface
3.2.3
3.2.4
6. Click the save icon
Note:
The target server address is set on the Network / Accounts
page.
.
Searching for tracks
1. Click the search tab .
2. Click one of the Search mode options to define the search
parameters.
3. To limit the search to a particular time range, enter the
start and stop times.
4. Click Start Search.
5. The results are shown in the search results tab .
6. Click a result to play it back.
7. Click the search tab
again to define a new search.
Controlling playback
The time bar below the video image allows quick orientation.
The time interval associated with the sequence is displayed in
the bar in gray. A green arrow above the bar indicates the
position of the image currently being played back within the
sequence.
The time bar offers various options for navigation in and
between sequences.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 21

Camera Browser
Interface
– Change the time interval displayed by clicking the plus or
– If required, click in the bar at the point in time at which the
– Red bars indicate the points in time where alarms were
To view the current live image, click Now.
Controls
Control playback by means of the buttons below the video
image.
Use the jog dial to quickly scan the
sequences. The time code is displayed above it.
The buttons have the following functions:
Select the playback speed using the speed regulator:
Operation via the browser | en 21
minus icons. The display can span a range from two months
to a few seconds.
playback should begin.
triggered.
Start/Pause playback
Jump to start of active sequence or to previous sequence
Jump to start of the next video sequence in the list
Bookmarks
You can set markers in a sequence and jump to these directly.
These bookmarks are indicated as small yellow arrows above
the time interval. Use the bookmarks as follows:
Jump to the previous bookmark
Set bookmark
Jump to the following bookmark
Bookmarks are only valid while in the Recordings page; they are
not saved with the sequences. All bookmarks are deleted when
you leave the page.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 22

22 en | Basic Mode
Camera Browser
Interface
4
4.1
4.1.1
4.1.2
Basic Mode
Device Access
Name
Assign a unique name to assist in identification. This name
simplifies the management of multiple devices in more extensive
systems.
The name is used for remote identification, for example, in the
event of an alarm. Choose a name that makes it as easy as
possible to identify the location unambiguously.
Password
A password prevents unauthorized access to the device. You can
use different authorization levels to limit access.
Proper password protection is only guaranteed when all higher
authorization levels are also protected with a password.
Therefore, you always have to start from the highest
authorization level when assigning passwords.
You can define and change a password for each authorization
level if you are logged in as service or if the unit is not password
protected.
Enter the password for the appropriate authorization level here.
The maximum password text length is 19 characters and no
special characters are allowed.
The device has three authorization levels: service, user, and live.
– service is the highest authorization level. Entering the
correct password gives access to all the functions and
allows all configuration settings to be changed.
– user is the middle authorization level. At this level you can
operate the device, play back recordings, and also control
camera, for example, but you cannot change the
configuration.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 23

Camera Browser
Interface
– live is the lowest authorization level. At this level you can
Define and change a separate password for each level. Enter the
password (19 characters maximum; no special characters) for
the selected level.
Re-enter the new password to ensure that there are no typing
mistakes.
Basic Mode | en 23
only view the live video image and switch between the
different live image displays.
4.2
Date/Time
If there are multiple devices operating in the system or network,
it is important to synchronize their internal clocks. For example,
it is only possible to identify and correctly evaluate simultaneous
recordings when all devices are operating on the same time.
Device time, date and time zone are shown.
4 Click Sync to PC to apply the system time from your
computer to the device.
Note:
It is important that the date/time is correct for recording. An
incorrect date/time setting could prevent correct recording.
The unit can receive the time signal from a time server using
various time server protocols and then use it to set the internal
clock. The device polls the time signal automatically once every
minute.
Enter the IP address of a time server.
Select the protocol that is supported by the selected time
server. It is recommended to select the SNTP server protocol.
This protocol provides high accuracy and is required for special
applications and future function extensions.
Select Time server if the server uses the RFC 868 protocol.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 24

24 en | Basic Mode
Camera Browser
Interface
4.3
Network
The settings on these pages are used to integrate the device
into a network. Some changes only take effect after a reboot. In
this case Set changes to Set and Reboot.
1. Make the desired changes.
2. Click Set and Reboot.
The device is rebooted and the changed settings are activated.
If the network has a DHCP server for the dynamic assignment of
IP addresses, select On to automatically accept the DHCPassigned IP address.
For certain applications, the DHCP server must support the
fixed assignment between IP address and MAC address, and
must be appropriately set up so that, once an IP address is
assigned, it is retained each time the system is rebooted.
IP address
Enter the desired IP address for the camera. The IP address
must be valid for the network.
Subnet mask
Enter the appropriate subnet mask for the set IP address.
Gateway address
For the device to establish a connection to a remote location in
a different subnet, enter the IP address of the gateway here.
Otherwise, this field can remain empty (0.0.0.0).
4.4
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Encoder
Select a profile for encoding the video signal on stream 1 (this is
not a selection of the recording profile).
Pre-programmed profiles are available that give priority to
different parameters and they should be selected based on your
operating environment.
When a profile is selected, its details are displayed.
Page 25

Camera Browser
Interface
Basic Mode | en 25
4.5
4.6
4.7
Audio
Switch the camera audio On or Off.
Use the slider to adjust the level for the applicable audio signal.
Recording
Record the images from the camera to a storage medium. For
long-term authoritative images, it is essential to use VRM or an
appropriately sized iSCSI system.
Storage medium
1. Select the required storage medium from the list.
2. Click Start to start recording or Stop to end recording.
System Overview
This page provides general information on the hardware and
firmware system, including version numbers. No items can be
changed on this page but they can be copied for information
purposes when troubleshooting.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 26

26 en | General settings
Camera Browser
Interface
5
5.1
5.1.1
General settings
Identification
Naming
Assign a unique name to assist in identification. This name
simplifies the management of multiple devices in more extensive
systems.
The name is used for remote identification, for example, in the
event of an alarm. Choose a name that makes it as easy as
possible to identify the location unambiguously.
You can use additional lines to enter kanji characters.
1. Click the + sign to add a new line
2. Click the icon next to the new line. A window with a
character map opens.
3. Click the required character. The character is inserted into
the Result field.
4. In the character map, click the << and >> icons to move
between the different pages of the table, or select a page
from the list field.
5. Click the < icon to the right of the Result field to delete the
last character, or click the X icon to delete all characters.
6. Click the OK button to apply the selected characters to the
new line of the name. The window closes.
5.1.2
5.1.3
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
ID
Each device should be assigned a unique identifier that can be
entered here as an additional means of identification.
iSCSI Initiator extension
Add text to an initiator name to make identification easier in
large iSCSI systems. This text is added to the initiator name,
separated from it by a full stop. (You can see the initiator name
in the System Overview page.)
Page 27

Camera Browser
Interface
General settings | en 27
5.2
Password
A password prevents unauthorized access to the device. You can
use different authorization levels to limit access.
Proper password protection is only guaranteed when all higher
authorization levels are also protected with a password.
Therefore, you always have to start from the highest
authorization level when assigning passwords.
You can define and change a password for each authorization
level if you are logged in as service or if the unit is not password
protected.
Enter the password for the appropriate authorization level here.
The maximum password text length is 19 characters and no
special characters are allowed.
The device has three authorization levels: service, user, and live.
– service is the highest authorization level. Entering the
correct password gives access to all the functions and
allows all configuration settings to be changed.
– user is the middle authorization level. At this level you can
operate the device, play back recordings, and also control
camera, for example, but you cannot change the
configuration.
– live is the lowest authorization level. At this level you can
only view the live video image and switch between the
different live image displays.
5.2.1
5.2.2
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Enter Password
Define and change a separate password for each level. Enter the
password (19 characters maximum; no special characters) for
the selected level.
Confirm password
Re-enter the new password to ensure that there are no typing
mistakes.
Page 28

28 en | General settings
Camera Browser
Interface
5.3
5.3.1
5.3.2
Date/Time
Date format
Select the required date format.
Device date / Device time
If there are multiple devices operating in your system or
network, it is important to synchronize their internal clocks. For
example, it is only possible to identify and correctly evaluate
simultaneous recordings when all devices are operating on the
same time.
1. Enter the current date. Since the device time is controlled
by the internal clock, it is not necessary to enter the day of
the week – it is added automatically.
2. Enter the current time or click Sync to PC to apply the
system time from your computer to the device.
Note:
It is important that the date/time is correct for recording. An
incorrect date/time setting could prevent correct recording.
5.3.3
5.3.4
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Device time zone
Select the time zone in which the system is located.
Daylight saving time
The internal clock can switch automatically between normal and
daylight saving time (DST). The unit already contains the data
for DST switch-overs for many years in advance. If the date, time
and zone have been set up correctly, a DST table is
automatically created.
If you decide to create alternative daylight saving time dates by
editing the table, note that values occur in linked pairs (DST
start and end dates).
Page 29

Camera Browser
Interface
First, check the time zone setting. If it is not correct, select the
appropriate time zone and click Set.
1. Click Details to edit the DST table.
2. Select the region or the city which is closest to the
3. Click Generate to fill the table with the preset values from
4. Click one of the entries in the table to make changes. The
5. Click Delete to remove the entry from the table.
6. Choose other values from the list boxes under the table, to
7. If there are empty lines at the bottom of the table, for
8. When finished, click OK to save and activate the table.
General settings | en 29
system's location from the list box below the table.
the unit.
entry is highlighted.
change the selected entry. Changes are immediate.
example after deletions, add new data by marking the row
and selecting values from the list boxes.
5.3.5
Time server IP address
The unit can receive the time signal from a time server using
various time server protocols and then use it to set the internal
clock. The device polls the time signal automatically once every
minute.
Enter the IP address of a time server.
5.3.6
Time server type
Select the protocol that is supported by the selected time
server. It is recommended to select the SNTP server protocol.
This protocol provides high accuracy and is required for special
applications and future function extensions.
Select Time server if the server uses the RFC 868 protocol.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 30

30 en | General settings
Camera Browser
Interface
5.4
5.4.1
5.4.2
5.4.3
Display Stamping
Various overlays or stamps in the video image provide important
supplementary information. These overlays can be enabled
individually and arranged on the image in a clear manner.
Camera name stamping
Select the position of the camera name overlay in the dropdown box. It can be displayed at the Top, at the Bottom, or at a
position of choice using the Custom option, or it can be set to
Off for no overlay information.
If the Custom option is selected, enter values in the X and Y
position fields.
Time stamping
Select the position of the time and date overlay in the dropdown box. It can be displayed at the Top, at the Bottom, or at a
position of choice using the Custom option, or it can be set to
Off for no overlay information.
If the Custom option is selected, enter values in the X and Y
position fields.
Display milliseconds
If necessary, display milliseconds for Time stamping. This
information can be useful for recorded video images; however, it
does increase the processor's computing time. Select Off if
displaying milliseconds is not needed.
5.4.4
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Alarm mode stamping
Select On in the drop-down box for a text message to be
displayed in the event of an alarm. It can be displayed at a
position of choice using the Custom option, or it can be set to
Off for no overlay information.
If the Custom option is selected, enter values in the X and Y
position fields.
Page 31

Camera Browser
Interface
General settings | en 31
5.4.5
5.4.6
5.4.7
5.5
Alarm message
Enter the message to be displayed on the image in the event of
an alarm. The maximum text length is 31 characters.
Transparent stamping
Check this box to make the stamp on the image transparent.
Video authentication
Select a method for verifying the integrity of the video in the
Video authentication drop-down box.
If you select Watermarking all images are marked with an icon.
The icon indicates if the sequence (live or saved) has been
manipulated.
If you want to add a digital signature to the transmitted video
images to ensure their integrity, select one of the cryptographic
algorithms for this signature.
Enter the interval (in seconds) between insertions of the digital
signature.
GB/T 28181
This page allows you to set the parameters for conformance to
the GB/T 28181 national standard “Security and protection
video monitoring network system for information transport,
switch and control”.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 32

32 en | Web Interface
Camera Browser
Interface
6
6.1
6.1.1
6.1.2
6.1.3
Web Interface
Appearance
You can adapt the appearance of the web interface and change
the website language to meet your requirements.
GIF or JPEG images can be used to replace the company and
device logos. The image can be stored on a web server (for
example, http://www.myhostname.com/images/logo.gif).
Ensure that a connection to the web server is always available to
display the image. The image files are not stored on the unit.
To restore the original graphics, delete the entries in the
Company logo and Device logo fields.
Website language
Select the language for the user interface.
Company logo
To replace the company's logo in the top-right part of the
window, enter the path to a suitable image in this field. The
image file must be stored on a web server.
Device logo
To replace the device name in the top-left part of the window,
enter the path to a suitable image in this field. The image file
must be stored on a web server.
6.1.4
6.1.5
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Show VCA metadata
When video analysis is activated, additional information from the
video content analysis (VCA) function is displayed in the live
video image. With the MOTION+ analysis type, for example, the
sensor fields in which motion is recorded are marked with
rectangles.
Show overlay icons
When selected, various status icons are displayed as an overlay
on the video images.
Page 33

Camera Browser
Interface
Web Interface | en 33
6.1.6
6.1.7
Select video player
Select the type of player to be used for live mode viewing.
JPEG size, interval and quality
Select the size, update interval and quality of the M‑JPEG image
displayed on the livepage. The highest quality is 1. When Best
possible is selected for size, the unit determines the quality
based on the network capacity.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 34

34 en | Web Interface
Camera Browser
Interface
6.2
6.2.1
6.2.2
6.2.3
LIVE Functions
You can adapt the LIVE page functions to meet your
requirements. Choose from a variety of different options for
displaying information and controls.
1. Select the check boxes for the functions to be displayed on
the LIVE. The selected elements are checked.
2. Check to see if the desired items are shown.
Transmit audio
When selected, the audio from the camera (if set to On on the
Audio page) is sent to the computer. This setting applies only to
the computer on which the selection is made. Transmitting
audio data requires additional network bandwidth.
Show alarm inputs
The alarm inputs are displayed next to the video image as icons
along with their assigned names. If an alarm is active, the
corresponding icon changes color.
Show alarm outputs
Alarm outputs are shown next to the video image as icons along
with their assigned names. If an output is switched, the icon
changes color.
6.2.4
6.2.5
6.2.6
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Show event log
The event messages are displayed with the date and time in a
field next to the video image.
Show system log
The system messages are displayed with the date and time in a
field next to the video image and provide information about the
establishment and termination of connections, and other
system-level messages.
Allow snapshots
Select the type of player to be used for live mode viewing.
Page 35

Camera Browser
Interface
Web Interface | en 35
6.2.7
6.2.8
6.2.9
Allow local recording
Specify whether the icon for saving video sequences locally
should be displayed below the live image. Video sequences can
only be saved locally on your hard disk if this icon is visible.
I-frames-only stream
Select to display an additional tab on the LIVE page where only
I-frames can be viewed. Ensure that I-frame quality is not set to
Auto or no updates will occur.
Path for JPEG and video files
Enter the path for the storage location of individual images and
video sequences saved from the LIVE. If necessary, click
Browse... to find a suitable folder.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 36

36 en | Web Interface
Camera Browser
Interface
6.3
6.3.1
6.3.2
Logging
Save event log
Select this option to save event messages in a text file on the
local computer. This file can be viewed, edited, and printed with
any text editor or standard office software.
File for event log
Enter the path for saving the event log. If necessary, click
Browse... to find a suitable folder.
Save system log
Select this option to save system messages in a text file on the
local computer. This file can be viewed, edited, and printed with
any text editor or standard office software.
File for system log
Enter the path for saving the system log. If necessary, click
Browse... to find a suitable folder.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 37

Camera Browser
Interface
Camera | en 37
7
7.1
7.1.1
7.1.2
7.1.3
7.1.4
7.1.5
Camera
Installer Menu
Base frame rate
Select the base frame rate for the camera.
Note:
Shutter times and frame rates, and the analog output (if
present) are affected by this value.
Camera LED
Disable the Camera LED on the camera to switch it off.
Mirror image
Select On to output a mirror image of the camera picture.
Flip image
Select On to output an upside down camera image.
Reboot device
Click Reboot to restart the camera.
7.1.6
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Factory defaults
Click Defaults to restore the factory defaults for the camera. A
confirmation screen appears. Allow several seconds for the
camera to optimize the picture after a reset.
Page 38

38 en | Camera
Camera Browser
Interface
7.2
7.2.1
Picture settings – Color
Contrast (0...255)
Adjust the contrast with the slider from 0 to 255.
Saturation (0...255)
Adjust the color saturation with the slider from 0 to 255.
Brightness (0...255)
Adjust the brightness with the slider from 0 to 255.
White balance
– Standard auto mode allows the camera to continually
adjust for optimal color reproduction in an outdoor
environment.
– In Manual mode the Red, Green, and Blue gain can be
manually set to a desired position.
Hold
Click Hold to put ATW on hold and save the current color
settings. The mode changes to manual.
R-gain
In Manual white balance mode, adjust the red gain slider to
offset the factory white point alignment (reducing red
introduces more cyan).
G-gain
In Manual white balance mode, adjust the green gain slider to
offset the factory white point alignment (reducing green
introduces more magenta).
B-gain
In Manual white balance mode, adjust the blue gain slider to
offset the factory white point alignment (reducing blue
introduces more yellow).
Note:
It is only necessary to change the white point offset for special
scene conditions.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 39

Camera Browser
Interface
Default
Click Default to set all video values to their factory setting.
Camera | en 39
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 40

40 en | Camera
Camera Browser
Interface
7.3
7.3.1
7.3.2
7.3.3
Picture settings – ALC
ALC mode
Select the mode:
– Fluorescent 50 Hz
– Fluorescent 60 Hz
– Outdoor
ALC level
Adjust the video output level (-15 to 0 to +15).
Select the range within which the ALC will operate. A positive
value is more useful for low-light conditions; a negative value is
more useful for very bright conditions.
Exposure/frame rate
Automatic exposure
Select to let the camera automatically set the optimum shutter
speed. The camera tries to maintain the selected shutter speed
as long as the light level of the scene permits.
4 Select the minimum frame rate for automatic exposure.
(The values available depend on the value set for the Base
frame rate in the Installer Menu.)
Fixed exposure
Select to set a fixed shutter speed.
4 Select the shutter speed for fixed exposure. (The values
available depend on the value set for the ALC mode.)
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 41

Camera Browser
Interface
Camera | en 41
7.4
7.4.1
7.4.2
Picture settings – Enhance
Backlight Compensation
Select Off to switch off backlight compensation.
Select On to capture details in high-contrast and extremely
bright-dark conditions.
Intelligent DNR
Select On to activate intelligent Dynamic Noise Reduction (DNR)
which reduces noise based on motion and light levels.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 42

42 en | Camera
Camera Browser
Interface
7.5
Encoder Settings
The encoder settings allow you to adapt the video data
transmission characteristics for your operating environment
(network structure, bandwidth, data load). The device
simultaneously generates two H.264 video streams and an
M‑JPEG stream for transmission. Select the compression
settings of these streams individually, for example, one setting
for transmissions to the Internet and one for LAN connections.
Refer to Encoder Profile, page 47 for more information on
setting up the encoder profile.
Refer to Encoder Streams, page 51 for more information on
setting up the encoder streams.
Refer to Encoder Regions, page 53 for more information on
setting up the encoder regions.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 43

Camera Browser
Interface
Camera | en 43
7.6
Privacy Masks
Privacy masking is used to block a specific area of a scene from
being viewed. Four privacy mask areas can be defined. The
activated masked areas are filled with the selected pattern in
live view.
1. Select the pattern to be used for all masks.
2. Check the box of the mask you wish to activate.
3. Use the mouse to define the area for each of the masks.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 44

44 en | Camera
Camera Browser
Interface
7.7
7.7.1
7.7.2
Audio
You can set the gain of the audio signals to suit your specific
requirements. The live video image is shown in the window to
help you check the audio source. Your changes are effective
immediately.
If you connect via Web browser, you must activate the audio
transmission on the LIVE Functions page. For other
connections, the transmission depends on the audio settings of
the respective system.
The audio signals are sent in a separate data stream parallel to
the video data, and so increase the network load. The audio
data is encoded according to the selected format and requires
additional bandwidth. If you do not want any audio data to be
transmitted, select Off.
Adjust level
Adjust the audio level with the slider(s). Adjust so that the
indicator does not go into the red zone.
Recording format
Select a format for audio recording. The default value is AAC 48
kbps. You can select AAC 80 kbps, G.711 or L16 depending on
the required audio quality or sampling rate.
AAC audio technology is licensed by Fraunhofer IIS.
(http://www.iis.fraunhofer.de/amm/)
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 45

Camera Browser
Interface
Camera | en 45
7.8
Pixel Counter
The number of horizontal and vertical pixels covered by the
highlighted area is displayed below the picture. With these
values you can check whether the requirements for specific
functions, for example, identification tasks, are fulfilled.
1. Click Freeze to freeze the camera image if the object that
you want to measure is moving.
2. To reposition a zone, place the cursor over the zone, hold
down the mouse button and drag into position.
3. To change the shape of a zone, place the cursor over the
edge of the zone, hold down the mouse button and drag
the edge of the zone to the required position.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 46

46 en | Encoder Settings
Camera Browser
Interface
8
8.1
Encoder Settings
Introduction to encoder settings
The encoder settings determine the characteristics of the four
streams generated by the camera. The types of streams that can
be generated are:
– HD streams
– SD streams
– I-frame only streams for recording
– M-JPEG streams
The bit rates, the encoding interval, and the Group-of-Pictures
(GOP) structure and quality, are defined and stored for eight
different profiles on the Encoder Profile page. The SD
(Standard Definition) resolution is also selected here.
The resolution of the two H.264 streams and the pre-defined
profile to be used for each stream is selected on the Encoder
Streams page. The maximum frame rate and quality of the JPEG
stream is also selected here.
The streams and profiles for recording are selected on the
Recording Profiles page.
The Encoder Regions page allows you to select different quality
levels for various areas of the image. This can help in reducing
the bit rate. For example, important objects can be selected to
provide higher quality encoding than selected background areas.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 47

Camera Browser
Interface
Encoder Settings | en 47
8.2
8.2.1
Encoder Profile
Profiles are rather complex and include a number of parameters
that interact with one another, so it is generally best to use the
pre-defined profiles. Only change a profile if completely familiar
with all the configuration options.
Pre-defined profiles
Eight definable profiles are available. The pre-defined profiles
give priority to different parameters.
– Profile 1
High resolution for high bandwidth connections
– Profile 2
High resolution with lower data rate
– Profile 3
High resolution for low bandwidth connections
– Profile 4
Standard resolution for high bandwidth connections
– Profile 5
Standard resolution with lower data rate
– Profile 6
Standard resolution for low bandwidth connections
– Profile 7
Standard resolution for DSL connections
– Profile 8
Low resolution for mobile phone connections
8.2.2
8.2.3
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Changing a profile
To change a profile, select it by clicking its tab and then change
the parameters within that profile.
If a setting outside the permitted range for a parameter is
entered, the nearest valid value is substituted when the settings
are saved.
Profile name
If required, enter a new name for the profile.
Page 48

48 en | Encoder Settings
Camera Browser
Interface
8.2.4
8.2.5
8.2.6
Target bit rate
To optimize use of the bandwidth in the network, limit the data
rate for the device. The target data rate should be set according
to the desired picture quality for typical scenes with no
excessive motion.
For complex images or frequent changes of image content due
to frequent movements, this limit can temporarily be exceeded
up to the value entered in the Maximum bit rate field.
Maximum bit rate
This maximum data rate is not exceeded under any
circumstances. Depending on the video quality settings for the Iframes and P-frames, this can result in individual images being
skipped.
The value entered here must be at least 10% higher than the
value entered in the Target bit rate field. If the value entered
here is too low, it is automatically adjusted.
Encoding interval
The Encoding interval slider determines the interval at which
images are encoded and transmitted. This can be particularly
advantageous with low bandwidths. The image rate in ips
(images per second) is displayed next to the slider.
8.2.7
8.2.8
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Standard definition video resolution
Select the desired resolution for the standard definition video
image.
Note:
These resolutions are not used by a HD stream.
Expert Settings
If necessary, use the expert settings to adapt the I-frame quality
and the P-frame quality to specific requirements. The setting is
based on the H.264 quantization parameter (QP).
Page 49

Camera Browser
Interface
GOP structure
Select the structure you require for the Group-of-Pictures
(GOP). Depending on whether you place greater priority on
having the lowest possible delay (IP frames only) or using as
little bandwidth possible, you choose IP, IBP or IBBP. (GOP is
not available for megapixel cameras.)
Averaging period
Select the appropriate averaging period as a means of stabilizing
the long term bit rate.
I-frame distance
Use the slider to set the distance between I-frames to Auto or to
between 3 and 60. An entry of 3 means that every third image is
an I-frame.The lower the number, the more I-frames are
generated.
Min. P-frame QP
In the H.264-protocol, the Quantization Parameter (QP)
specifies the degree of compression and thus the image quality
for every frame. The lower the QP value, the higher the encoding
quality. A higher quality produces a higher data load. Typical QP
values are between 18 and 30. Define the lower limit for the
quantization of the P-frames here, and thus the maximum
achievable quality of the P-frames.
Encoder Settings | en 49
I/P-frame delta QP
This parameter sets the ratio of the I-frame QP to the P-frame
QP. For example, you can set a lower value for I-frames by
moving the slide control to a negative value. Thus, the quality of
the I-frames relative to the P-frames is improved. The total data
load will increase, but only by the portion of I-frames.
To obtain the highest quality at the lowest bandwidth, even in
the case of increased movement in the picture, configure the
quality settings as follows:
1. Observe the coverage area during normal movement in the
preview images.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 50

50 en | Encoder Settings
2. Set the value for Min. P-frame QP to the highest value at
which the image quality still meets your needs.
3. Set the value for I/P-frame delta QP to the lowest possible
value. This is how to save bandwidth and memory in normal
scenes. The image quality is retained even in the case of
increased movement since the bandwidth is then filled up
to the value that is entered under Maximum bit rate.
Background delta QP
Select the appropriate encoding quality level for a background
region defined in Encoder Regions. The lower the QP value, the
higher the encoding quality.
Object delta QP
Select the appropriate encoding quality level for an object
region defined in Encoder Regions. The lower the QP value, the
higher the encoding quality.
Camera Browser
Interface
8.2.9
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Default
Click Default to return the profile to the factory default values.
Page 51

Camera Browser
Interface
Encoder Settings | en 51
8.3
8.3.1
Encoder Streams
H.264 settings
Select H.264 Settings
1. Select a codec algorithm Property for stream 1 from the
drop-down box.
2. Select a codec algorithm Property for stream 2 (the
available choices depend on the algorithm selected for
stream 1).
3. Select the Non-recording profile for each stream from the
eight profiles that have been defined.
– This profile is not used for recording. When a stream is
used for recording, the profile selected on the
Recording Profiles page is used.
Preview >>
Previews of streams 1 and 2 can be shown.
1. Click Preview>> to display a preview of the video for
streams 1 and 2. The current profile is shown above the
preview.
2. Click 1:1 Live View below a preview to open a viewing
window for that stream. Various additional items of
information are shown across the top of the window.
3. Click Preview << to close the preview displays.
Note:
Deactivate the display of the video images if the performance of
the computer is adversely affected by the decoding of the data
stream.
8.3.2
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
JPEG stream
Set the parameters for the M‑JPEG stream.
– Select the Resolution.
– Select the Max. frame rate in images per second (ips).
Page 52

52 en | Encoder Settings
– The Picture quality slider allows adjustment of the M‑JPEG
image quality from Low to High.
Note:
The M-JPEG frame rate can vary depending on system loading.
Camera Browser
Interface
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 53

Camera Browser
Interface
Encoder Settings | en 53
8.4
8.4.1
Encoder Regions
Encoder regions are used to increase or decrease the encoding
quality for selectable areas of the image. They can be used to
give better control of the bitrate by enhancing the encoding
quality of important regions (objects) and decreasing the
encoding quality of less important regions (background).
Selecting regions
1. Select one of the eight available regions from the dropdown box.
2. Use the mouse to define the area for that region by
dragging the center or sides of the shaded window.
3. Select the encoder quality to be used for the defined area.
(Object and background quality levels are defined on the
Expert Settings section of the Encoder Profile page.)
4. If required, select another region and repeat steps 2 and 3.
5. Click Set to apply the region settings.
Preview
Click
the bit rate for the region settings can be previewed.
to open a viewing window where a 1:1 live image and
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 54

54 en | Recording
Camera Browser
Interface
9
9.1
Recording
Introduction to recording
Images can be recorded to an appropriately configured iSCSI
system or, for devices with an SD slot, locally to an SD card.
SD cards are the ideal solution for shorter storage times and
temporary recordings. They can be used for local alarm
recording or to improve the overall reliability of video recording.
For long-term authoritative images use an appropriately sized
iSCSI system.
Two recording tracks are available (Recording 1 and Recording
2). The encoder streams and profiles can be selected for each of
these tracks for both standard and alarm recordings.
Ten recording profiles are available where these recording
tracks can be defined differently. These profiles are then used
for building schedules.
A Video Recording Manager (VRM) can control all recording
when accessing an iSCSI system. The VRM is an external
program for configuring recording tasks for video servers. For
further information, contact your local customer service at
Bosch Security Systems.
9.1.1
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
WiFi models
With WiFi models the recording performance depends on the
wireless transmission efficiency. To avoid degradation for
continuous recording with an iSCSI target storage device, it is
essential to use the Bosch Video Recording Manager or a
DIVAR IP 2000 / DIVAR IP 3000 to manage all recordings without
interruption.
Page 55

Camera Browser
Interface
Recording | en 55
9.2
9.2.1
9.2.2
Storage Management
Device manager
An external Video Recording Manager (VRM) system for the unit
is configured via the Configuration Manager. The Managed by
VRM box is only an indicator; it cannot be changed here.
If the Managed by VRM box is checked, you are not able to
configure any further recording settings on this page.
Recording media
Select a media tab to connect to the available storage media.
iSCSI Media
To use an iSCSI system as the storage medium, a connection to
the desired iSCSI system is required to set the configuration
parameters.
The storage system selected must be available on the network
and completely set up. It must have an IP address and be
divided into logical drives (LUNs).
1. Enter the IP address of the required iSCSI destination in
the iSCSI IP address field.
2. If the iSCSI destination is password protected, enter the
password into the Password field.
3. Click Read.
– The connection to the IP address is established.
The Storage overview field displays the logical drives.
Local Media
An SD card inserted in the camera can be used for local
recording (not available on some cameras).
4 If the SD card is password protected, enter the password
into the Password field.
The Storage overview field displays the local media.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 56

56 en | Recording
Note:
SD card recording performance is highly dependent on the
speed (class) and performance of the SD card. An SD card of
Class 6 or higher is recommended.
Camera Browser
Interface
9.2.3
Activating and configuring storage media
Available media or iSCSI drives must be transferred to the
Managed storage media list, activated, and configured for
storage.
Note:
A iSCSI target storage device can only be associated with one
user. If a target is being used by another user, ensure that the
current user no longer needs the target before decoupling that
user.
1. In the Storage overview section, double-click a storage
medium, an iSCSI LUN or one of the other available drives.
– The medium is added as a target in the Managed
storage media list.
– Newly added media is shown as Not active in the
Status column.
2. Click Set to activate all media in the Managed storage
media list.
– The Status column shows all media as Online.
3. Check the box in the Rec. 1 or Rec. 2 column to specify the
recording tracks to be recorded on the target selected.
9.2.4
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Formatting storage media
All recordings on a storage medium can be deleted at any time.
Check the recordings before deleting and back-up important
sequences on the computer's hard drive.
1. Click a storage medium in the Managed storage media list
to select it.
2. Click Edit below the list.
Page 57

Camera Browser
Interface
3. Click Format in the new window to delete all recordings in
4. Click OK to close the window.
Recording | en 57
the storage medium.
9.2.5
Deactivating storage media
A storage medium in the Managed storage media list can be
deactivated. It is then no longer used for recordings.
1. Click a storage medium in the Managed storage media list
to select it.
2. Click Remove below the list. The storage medium is
deactivated and removed from the list.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 58

58 en | Recording
Camera Browser
Interface
9.3
Recording Profiles
A recording profile contains the characteristics of the tracks that
are used for recording. These characteristics can be defined for
ten different profiles. The profiles can then be assigned to days
or times of day on the Recording Scheduler page.
Each profile is color-coded. The names of the profiles can be
changed on the Recording Scheduler page.
To configure a profile click its tab to open its settings page.
– To copy the currently visible settings to other profiles, click
Copy Settings. A window opens to select the target profiles
for the copied settings.
– If you change a profile’s settings, click Set to save.
– If necessary, click Default to return all settings to their
factory defaults.
Stream profile settings
Select the encoder profile setting that is to be used with stream
1 and 2 when recording. This selection is independent of the
selection for live stream transmission. (The properties of the
encoder profiles are defined on the Encoder Profile page.)
9.3.1
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Recording track selection
Standard and alarm recording can be defined for the two
recording tracks. You must first select the track before setting
up the standard and alarm recording parameters.
1. Click the Recording 1 entry in the list.
2. Set up the standard and alarm recording parameters for
track 1 as described below.
3. Click the Recording 2 entry in the list.
4. Set up the standard and alarm recording parameters for
track 2 as described below.
Page 59

Camera Browser
Interface
Recording includes
Specify whether additional data, such as audio (if available) or
metadata (for example, alarms or VCA data) should also be
recorded. (If audio is available, you can change the global audio
format by clicking the audio format link.)
Note:
Including metadata could make subsequent searches of
recordings easier but it requires additional memory capacity.
Without metadata, it is not possible to include video content
analysis in recordings.
Recording | en 59
9.3.2
9.3.3
Standard recording
Select the mode for standard recordings:
– Continuous: the recording proceeds continuously. If the
maximum recording capacity is reached, older recordings
are overwritten automatically.
– Pre-alarm: recording takes place in the pre-alarm time,
during the alarm and during the post-alarm time only.
– Off: no automatic recording takes place.
Stream
Select the stream to be used for standard recordings:
– Stream 1
– Stream 2
– I-frames only
Alarm recording
Select a period for the Pre-alarm time from the list box.
Select a period for the Post-alarm time from the list box.
Alarm stream
Select the stream to be used for alarm recordings:
– Stream 1
– Stream 2
– I-frames only
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 60

60 en | Recording
Check the encoding interval and bit rates from profile: box and
select an encoder profile to set the associated encoding interval
for alarm recording.
Check the Export to account box to send standard H.264 files
to the target whose address is displayed.
If the target has not yet been defined, click Configure accounts
to jump to the Accounts page where the server information can
be entered.
Alarm triggers
Select the alarm type that is to trigger an alarm recording:
– Alarm input
– Analysis alarm
– Video loss
Select the Virtual alarm sensors that are to trigger a recording,
via RCP+ commands or alarm scripts, for example.
Camera Browser
Interface
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 61

Camera Browser
Interface
Recording | en 61
9.4
Maximum Retention Time
Recordings are overwritten when the retention time entered
here has expired.
4 Enter the required retention time in days for each recording
track.
Make sure that the retention time does not exceed the available
recording capacity.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 62

62 en | Recording
Camera Browser
Interface
9.5
9.5.1
9.5.2
Recording Scheduler
The recording scheduler allows you to link the created recording
profiles to the days and times at which the camera's images are
to be recorded. Schedules can be defined for weekdays and for
holidays.
Weekdays
Assign as many time periods (in 15-minute intervals) as needed
for any day of the week. Move the mouse cursor over the table —
the time is displayed.
1. Click the profile to be assigned in the Time periods box.
2. Click a field in the table and, while holding down the left
mouse button, drag the cursor across all of the fields to be
assigned to the selected profile.
3. Use the right mouse button to deselect any of the intervals.
4. Click Select All to select all of the intervals to be assigned
to the selected profile.
5. Click Clear All to deselect all of the intervals.
6. When finished, click Set to save the settings to the device.
Holidays
Define holidays whose settings will override the settings for the
normal weekly schedule.
1. Click the Holidays tab. Days that have already been defined
are shown in the table.
2. Click Add. A new window opens.
3. Select the desired From date from the calendar.
4. Click in the To box and select a date from the calendar.
5. Click OK to accept the selection which is handled as a
single entry in the table. The window closes.
6. Assign the defined holidays to the recording profile as
described above.
Delete user-defined holidays as follows:
1. Click Delete in the Holidays tab. A new window opens.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 63

Camera Browser
Interface
2. Click the date to be deleted.
3. Click OK. The selection is removed from the table and the
4. Repeat for any other dates to be deleted.
Recording | en 63
window is closed.
9.5.3
9.5.4
9.5.5
Profile names
Change the names of the recording profiles listed in the Time
periods box.
1. Click a profile.
2. Click Rename.
3. Enter the new name and click Rename again.
Activate recording
After completing configuration, activate the recording schedule
and start scheduled recording. Once activated, the Recording
Profiles and the Recording Scheduler are deactivated and the
configuration cannot be modified. Stop scheduled recording to
modify the configuration.
1. Click Start to activate the recording schedule.
2. Click Stop to deactivate the recording schedule. Recordings
that are currently running are interrupted and the
configuration can be modified.
Recording status
The graphic indicates the recording activity. An animated
graphic is displayed when recording is taking place.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 64

64 en | Recording
Camera Browser
Interface
9.6
Recording Status
Details of the recording status are displayed here for
information. These settings cannot be changed.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 65

Camera Browser
Interface
Alarm | en 65
10
10.1
10.1.1
10.1.2
10.1.3
Alarm
Alarm Connections
In the event of an alarm, the unit can automatically connect to a
pre-defined IP address. The unit can contact up to ten IP
addresses in the order listed until a connection is made.
Connect on alarm
Select On so that the unit automatically connects to a predefined IP address in the event of an alarm.
Select Follows input 1 so that the unit maintains the connection
for as long as an alarm exists on alarm input 1.
Number of destination IP address
Specify the numbers of the IP addresses to be contacted in the
event of an alarm. The unit contacts the remote locations one
after the other in the numbered sequence until a connection is
made.
Destination IP address
For each number, enter the corresponding IP address for the
desired remote station.
10.1.4
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Destination password
If the remote station is password protected, enter the password
here.
Only ten passwords can be defined here. Define a general
password if more than ten connections are required, for
example, when connections are initiated by a controlling system
such as Bosch Video Client or Bosch Video Management System.
The unit connects to all remote stations protected by the same
general password. To define a general password:
1. Select 10 in the Number of destination IP address list box.
2. Enter 0.0.0.0 in the Destination IP address field.
3. Enter the password in the Destination password field.
Page 66

66 en | Alarm
4. Set the user password of all the remote stations to be
Setting destination 10 to the IP-address 0.0.0.0 overrides its
function as the tenth address to try.
Camera Browser
Interface
accessed using this password.
10.1.5
10.1.6
10.1.7
10.1.8
Video transmission
If the unit is operated behind a firewall, select TCP (HTTP port)
as the transfer protocol. For use in a local network, select UDP.
To enable multicast operation, select UDP for the Video
transmission parameter here and on the Network Access page.
Note:
In the event of an alarm, a larger network bandwidth is
sometimes required for additional video streams (if multicast
operation is not possible).
Stream
Select a stream to be transmitted.
Remote port
Select an appropriate browser port depending on the network
configuration.
The ports for HTTPS connections are only available if SSL
encryption is set to On.
Video output
If a hardware receiver is used, select the analog video output to
which the signal should be switched. If the destination device is
unknown, select First available. This places the image on the
first video output with no signal.
The connected monitor only displays images when an alarm is
triggered.
Note:
Refer to the destination unit documentation for more
information on image display options and available video
outputs.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 67

Camera Browser
Interface
Alarm | en 67
10.1.9
10.1.10
10.1.11
Decoder
If a split image is set for the selected video output, select a
decoder to display the alarm image. The decoder selected
determines the position in the split image.
SSL encryption
SSL encryption protects data used for establishing a
connection, such as the password. By selecting On, only
encrypted ports are available for the Remote port parameter.
SSL encryption must be activated and configured on both sides
of a connection.
The appropriate certificates must also have been uploaded.
(Certificates can be uploaded on the Maintenance page.)
Configure and activate encryption for media data (such as video,
metadata or audio when available) on the Encryption page
(encryption is only available if the appropriate license is
installed).
Auto-connect
Select On to automatically re-establish a connection to one of
the previously specified IP addresses after each reboot,
connection breakdown, or network failure.
10.1.12
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Audio
Select On to transmit the audio stream with an alarm
connection.
Page 68

68 en | Alarm
Camera Browser
Interface
10.2
Video Content Analyses (VCA)
The camera has integrated Video Content Analyses (VCA) which
detects and analyzes changes in the picture using image
processing algorithms. Such changes can be due to movements
in the camera's field of view. Detection of movement can be
used to trigger an alarm and to transmit metadata.
Various VCA configurations can be selected and adapted to your
application, as required.
Refer to Setting up VCA, page 73 for more information on
setting up video content analyses.
Note:
If there is not enough computing power, priority is given to live
images and recordings. This can lead to impairment of the VCA
system. Observe the processor load and optimize the encoder
settings or the VCA settings if necessary, or turn off VCA
completely.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 69

Camera Browser
Interface
Alarm | en 69
10.3
10.3.1
10.3.2
10.3.3
10.3.4
Audio Alarm
Alarms can be generated based on audio signals. Configure
signal strengths and frequency ranges so that false alarms, for
example, machine noise or background noise, are avoided.
Set up normal audio transmission before configuring the audio
alarm.
Audio alarm
Select On for the device to generate audio alarms.
Name
The name makes it easier to identify the alarm in extensive video
monitoring systems, for example with the Bosch Video Client
and the Bosch Video Management System. Enter a unique and
clear name here.
Signal Ranges
Exclude particular signal ranges in order to avoid false alarms.
For this reason the total signal is divided into 13 tonal ranges
(mel scale). Check or uncheck the boxes below the graphic to
include or exclude individual ranges.
Threshold
Set up the threshold on the basis of the signal visible in the
graphic Set the threshold using the slide control or,
alternatively, move the white line directly in the graphic using
the mouse.
10.3.5
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Sensitivity
Use this setting to adapt the sensitivity to the sound
environment and effectively suppress individual signal peaks. A
high value represents a high level of sensitivity.
Page 70

70 en | Alarm
Camera Browser
Interface
10.4
10.4.1
10.4.2
10.4.3
10.4.4
10.4.5
Alarm E-Mail
Alarm states can be documented by e-mail. The camera
automatically sends an e‑mail to a user-defined e‑mail address.
This makes it possible to notify a recipient who does not have a
video receiver.
Send alarm e-mail
Select On for the device to automatically send an alarm e‑mail in
the event of an alarm.
Mail server IP address
Enter the IP address of a mail server that operates on the SMTP
standard (Simple Mail Transfer Protocol). Outgoing e‑mails are
sent to the mail server via the address entered. Otherwise, leave
the box blank (0.0.0.0).
SMTP user name
Enter a registered user name for the chosen mail server.
SMTP password
Enter the required password for the registered user name.
Format
Select the data format of the alarm message.
– Standard (with JPEG): e‑mail with JPEG image file
attachment.
– SMS: e‑mail in SMS format to an e‑mail‑to‑SMS gateway
without an image attachment.
When a mobile phone is used as the receiver, make sure to
activate the e‑mail or SMS function, depending on the format, so
that these messages can be received. Obtain information on
operating your mobile phone from your mobile phone provider.
10.4.6
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Image size
Select the size of the JPEG images that are to be sent from the
camera.
Page 71

Camera Browser
Interface
Alarm | en 71
10.4.7
10.4.8
10.4.9
10.4.10
Attach JPEG from camera
Check the box to specify that JPEG images are sent from the
camera.
Destination address
Enter the e‑mail address for alarm e‑mails here. The maximum
address length is 49 characters.
Sender name
Enter a unique name for the e‑mail sender, for example, the
location of the device. This makes it easier to identify the origin
of the e‑mail.
Test e-mail
Click Send Now to test the e‑mail function. An alarm e-mail is
immediately created and sent.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 72

72 en | Alarm
Camera Browser
Interface
10.5
Alarm Task Editor
Editing scripts on this page overwrites all settings and entries
on the other alarm pages. This procedure cannot be reversed.
To edit this page, you should have programming knowledge and
be familiar with the information in the Alarm Task Script
Language document and the English language.
As an alternative to the alarm settings on the various alarm
pages, enter the desired alarm functions in script form here.
This will overwrite all settings and entries on the other alarm
pages.
1. Click Examples under the Alarm Task Editor field to see
some script examples. A new window opens.
2. Enter new scripts in the Alarm Task Editor field or change
existing scripts in line with your requirements.
3. When finished, click Set to transmit the scripts to the
device. If the transfer was successful, the message Script
successfully parsed. is displayed over the text field. If it
was not successful, an error message is displayed with
further information.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 73

Camera Browser
Interface
Setting up VCA | en 73
11
11.1
Setting up VCA
Several VCA configurations are available.
– Off
– Silent VCA
– Profile #1
– Profile #2
– Scheduled
– Event triggered
VCA - Silent VCA
In this configuration, metadata is created to facilitate searches
of recordings, however, no alarm is triggered.
4 In the VCA configuration drop-down list, select Silent VCA.
No parameters can be changed for this selection.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 74

74 en | Setting up VCA
Camera Browser
Interface
11.2
11.2.1
VCA - Profiles
Two profiles can be set up with different VCA configurations
1. In the VCA configuration drop-down list, select profile 1 or
2 and enter the required settings.
2. If necessary, click Default to return all settings to default
values.
To rename a profile:
1. To rename the file, click the icon to the right of the list field
and enter the new profile name in the field.
2. Click the icon again. The new profile name is saved.
The current alarm status is displayed for information purposes.
Aggregation time [s]
Set an aggregation time of between 0 and 20 seconds. The
aggregation time always starts when an alarm event occurs. It
extends the alarm event by the value set. This prevents alarm
events that occur in quick succession from triggering several
alarms and successive events in a rapid sequence. No further
alarm is triggered during the aggregation time.
The post-alarm time set for alarm recordings only starts once
the aggregation time has expired.
11.2.2
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Analysis type
Select the required analysis algorithm. Motion+ offers a motion
detector and essential recognition of tampering.
Metadata is always created for a video content analysis, unless
this is explicitly excluded. Depending on the analysis type
selected and the relevant configuration, additional information
overlays the video image in the preview window next to the
parameter settings. With the Motion+ analysis type, for example,
the sensor fields in which motion is recorded are marked with
rectangles.
Page 75

Camera Browser
Interface
Note:
For suitable devices, additional analysis algorithms with
comprehensive functions, such as IVMD and IVA, are also
available. Refer to the IVA documentation for more information
on using these.
Setting up VCA | en 75
11.2.3
Motion detector
Motion detection is available for the Motion+ analysis type. For
the detector to function, the following conditions must be met:
– Analysis must be activated.
– At least one sensor field must be activated.
– The individual parameters must be configured to suit the
operating environment and the desired responses.
– The sensitivity must be set to a value greater than zero.
Note:
Reflections of light (from glass surfaces, etc.), lights switching
on and off, or changes in the light level caused by cloud
movement on a sunny day can trigger unintended responses
from the motion detector and generate false alarms. Run a
series of tests at different times of the day and night to ensure
that the video sensor is operating as intended. For indoor
surveillance, ensure constant lighting of the areas during the day
and at night.
Sensitivity
Sensitivity is available for the Motion+ analysis type. The basic
sensitivity of the motion detector can be adjusted for the
environmental conditions to which the camera is subject. The
sensor reacts to variations in the brightness of the video image.
The darker the observation area, the higher the value that must
be selected.
Minimum object size
Specify the number of sensor fields that a moving object must
cover to generate an alarm. This setting prevents objects that
are too small from triggering an alarm. A minimum value of 4 is
recommended. This value corresponds to four sensor fields.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 76

76 en | Setting up VCA
Debounce time 1 s
The debounce time prevents very brief alarm events from
triggering individual alarms. If the Debounce time 1 s option is
activated, an alarm event must last at least 1 second to trigger
an alarm.
Selecting the area
Select the areas of the image to be monitored by the motion
detector. The video image is subdivided into square sensor
fields. Activate or deactivate each of these fields individually. To
exclude particular regions of the camera's field of view from
monitoring due to continuous movement (by a tree in the wind,
for example), the relevant fields can be deactivated.
1. Click Select Area to configure the sensor fields. A new
window opens.
2. If necessary, click Clear All first to clear the current
selection (fields marked red).
3. Left-click the fields to be activated. Activated fields are
marked red.
4. If necessary, click Select All to select the entire video-
frame for monitoring.
5. Right-click any fields to deactivate.
6. Click OK to save the configuration.
7. Click the close button (X) in the window title bar to close
the window without saving the changes.
Camera Browser
Interface
11.2.4
Tamper detection
Detect tampering of cameras and video cables by means of
various options. Run a series of tests at different times of the
day and night to ensure that the video sensor is operating as
intended.
Sensitivity and Trigger delay [s] can only be changed if
Reference check is selected.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 77

Camera Browser
Interface
Sensitivity
The basic sensitivity of the tamper detection can be adjusted for
the environmental conditions to which the camera is subject.
The algorithm reacts to the differences between the reference
image and the current video image. The darker the observation
area, the higher the value that must be selected.
Trigger delay [s]
Set delayed alarm triggering here. The alarm is only triggered
after a set time interval in seconds has elapsed and then only if
the triggering condition still exists. If the original condition has
been restored before this time interval elapses, the alarm is not
triggered. This avoids false alarms triggered by short-term
changes, for example, cleaning activities in the direct field of
vision of the camera.
Global change (slider)
Set how large the global change in the video image must be for
an alarm to be triggered. This setting is independent of the
sensor fields selected under Select Area. Set a high value if
fewer sensor fields need to change to trigger an alarm. With a
low value, it is necessary for changes to occur simultaneously in
a large number of sensor fields to trigger an alarm. This option
allows detection, independently of motion alarms, manipulation
of the orientation or location of a camera resulting from turning
the camera mount bracket, for example.
Setting up VCA | en 77
Global change
Activate this function if the global change, as set with the Global
change slide control, should trigger an alarm.
Scene too bright
Activate this function if tampering associated with exposure to
extreme light (for instance, shining a flashlight directly on the
objective) should trigger an alarm. The average brightness of the
scene provides a basis for recognition.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 78

en | Setting up VCA
78
Camera Browser
Interface
Scene too dark
Activate this function if tampering associated with covering the
objective (for instance, by spraying paint on it) should trigger an
alarm. The average brightness of the scene provides a basis for
recognition.
Scene too noisy
Activate this function if tampering associated with EMC
interference (noisy scene as the result of a strong interference
signal in the vicinity of the video lines) should trigger an alarm.
Reference check
Save a reference image that can be continuously compared with
the current video image. If the current video image in the
marked areas differs from the reference image, an alarm is
triggered. This detects tampering that would otherwise not be
detected, for example, if the camera is turned.
1. Click Reference to save the currently visible video- image
as a reference.
2. Click Select Area and select the areas in the reference
image that are to be monitored.
3. Check the box Reference check to activate the on-going
check. The stored reference image is displayed in black and
white below the current video image, and the selected
areas are marked in yellow.
4. Select the Disappearing edges or Appearing edges option
to specify the reference check once again.
Disappearing edges
The area selected in the reference image should contain a
prominent structure. If this structure is concealed or moved, the
reference check triggers an alarm. If the selected area is too
homogenous, so that concealing and moving the structure would
not trigger an alarm, then an alarm is triggered immediately to
indicate the inadequate reference image.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 79

Camera Browser
Interface
Appearing edges
Select this option if the selected area of the reference image
includes a largely homogenous surface. If structures appear in
this area, then an alarm is triggered.
Selecting the area
Select the image areas in the reference image that are to be
monitored. The video image is subdivided into square fields.
Activate or deactivate each of these fields individually.
Select only those areas for reference monitoring in which no
movement takes place and that are always evenly lit, as false
alarms could otherwise be triggered.
1. Click Select Area to configure the sensor fields. A new
2. If necessary, click Clear All first to clear the current
3. Left-click the fields to be activated. Activated fields are
4. If necessary, click Select All to select the entire video-
5. Right-click any fields to deactivate.
6. Click OK to save the configuration.
7. Click the close button (X) in the window title bar to close
Setting up VCA | en 79
window opens.
selection (fields marked yellow).
marked yellow.
frame for monitoring.
the window without saving the changes.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 80

80 en | Setting up VCA
Camera Browser
Interface
11.3
11.3.1
VCA - Scheduled
A scheduled configuration allows you to link a VCA profile with
the days and times at which the video content analysis is to be
active.
4 In the VCA configuration drop-down list, select Scheduled.
Schedules can be defined for weekdays and for holidays.
The current alarm status is displayed for information purposes.
Weekdays
Link any number of 15-minute intervals with the VCA profiles for
each day of the week. Moving the mouse cursor over the table
displays the time below it. This aids orientation.
1. Click the profile to link in the Time periods field.
2. Click in a field in the table, hold down the mouse button
and drag the cursor over all the periods to be assigned to
the selected profile.
3. Use the right mouse button to deselect any of the intervals.
4. Click Select All to link all time intervals to the selected
profile.
5. Click Clear All to deselect all of the intervals.
6. When finished, click Set to save the settings in the device.
11.3.2
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Holidays
Define holidays on which a profile should be active that are
different to the standard weekly schedule.
1. Click the Holidays tab. Any days that have already been
selected are shown in the table.
2. Click Add. A new window opens.
3. Select the desired date from the calendar. Select several
consecutive calendar days by holding down the mouse
button. These will later be displayed as a single entry in the
table.
4. Click OK to accept the selection. The window closes.
5. Assign the individual holidays to the VCA profiles, as
described above.
Page 81

Camera Browser
Interface
Deleting Holidays
Delete defined holidays at any time:
1. Click Delete. A new window opens.
2. Click the date to delete.
3. Click OK. The item is deleted from the table and the
4. The process must be repeated for deleting additional days.
Setting up VCA | en 81
window closes.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 82

82 en | Setting up VCA
Camera Browser
Interface
11.4
11.4.1
11.4.2
11.4.3
VCA - Event triggered
This configuration allows you to stipulate that the video content
analysis is only to be activated when triggered by an event.
4 In the VCA configuration drop-down list, select Event
triggered.
As long as no trigger is activated, the Silent VCA configuration
in which metadata is created is active; this metadata facilitates
searches of recordings, but does not trigger an alarm.
The current alarm status is displayed for information purposes.
Trigger
Select a physical alarm or a virtual alarm as a trigger. A virtual
alarm is created using software, with RCP+ commands or alarm
scripts, for example.
Trigger active
Select the VCA configuration here that is to be enabled via an
active trigger. A green check mark to the right of the list field
indicates that the trigger is active.
Trigger inactive
Select the VCA configuration here that is to be activated if the
trigger is not active. A green check mark to the right of the list
field indicates that the trigger is inactive.
11.4.4
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Delay [s]
Select the delay period for the reaction of the video content
analysis to trigger signals. The alarm is only triggered after a set
time interval in seconds has elapsed and then only if the
triggering condition still exists. If the original condition has been
restored before this time interval elapses, the alarm is not
triggered. A delay period may be useful in avoiding false alarms
or frequent triggering. During the delay period, the Silent VCA
configuration is always enabled.
Page 83

Camera Browser
Interface
Interfaces | en 83
12
12.1
12.1.1
12.2
12.2.1
Interfaces
Alarm input
Configure the alarm triggers for the unit.
Select N.C. (Normally Closed) if the alarm is to be triggered by
opening the contact.
Select N.O. (Normally Open) if the alarm is to be triggered by
closing the contact.
Name
Enter a name for the alarm input. This is then displayed below
the icon for the alarm input on the LIVE page (if configured).
Alarm output
Configure the switching behavior of the output.
Select different events that automatically activate an output. For
example, turn on a floodlight by triggering a motion alarm and
then turn the light off again when the alarm has stopped.
Idle state
Select Open for the output to operate as a normally open
contact, or select Closed if the output is to operate as a
normally closed contact.
12.2.2
12.2.3
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Operating mode
Select the way the output works.
For example, if you want an activated alarm to stay on after the
alarm ends, select Bistable. If you wish an activated alarm to
stay on for ten seconds for example, select 10 s.
Output follows
Select the event that triggers the output.
Page 84

84 en | Interfaces
Camera Browser
Interface
12.2.4
12.2.5
12.2.6
Output name
The relay can be assigned a name here. The name is shown on
the button next to Trigger output. The LIVE page can also be
configured to display the name next to the relay icon.
Trigger output
Click the button to switch the alarm output manually (for
example, for testing purposes or to operate a door opener).
Illuminator
The white LED illuminator in the camera operates in the same
way as alarm output 1. Click the Illumination button to switch
the light on and off.
Adjust the intensity of the illuminator with the slider.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 85

Camera Browser
Interface
Network | en 85
13
13.1
13.1.1
Network
The settings on these pages are used to integrate the device
into a network. Some changes only take effect after a reboot. In
this case Set changes to Set and Reboot.
1. Make the desired changes.
2. Click Set and Reboot.
The device is rebooted and the changed settings are activated.
Network Access
If the IP address, subnet mask, or gateway address is changed,
then the device is only available under the new addresses after
the reboot.
Automatic IP assignment
If the network has a DHCP server for the dynamic assignment of
IP addresses, select On to automatically accept the DHCPassigned IP address.
For certain applications, the DHCP server must support the
fixed assignment between IP address and MAC address, and
must be appropriately set up so that, once an IP address is
assigned, it is retained each time the system is rebooted.
13.1.2
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
IP V4 address
IP address
Enter the desired IP address for the camera. The IP address
must be valid for the network.
Subnet mask
Enter the appropriate subnet mask for the set IP address.
Gateway address
For the device to establish a connection to a remote location in
a different subnet, enter the IP address of the gateway here.
Otherwise, this field can remain empty (0.0.0.0).
Page 86

86 en | Network
Camera Browser
Interface
13.1.3
13.1.4
13.1.5
IP V6 address
IP address
Enter the desired IP address for the camera. The IP address
must be valid for the network.
Prefix length
Enter the appropriate prefix length for the set IP address.
Gateway address
For the device to establish a connection to a remote location in
a different subnet, enter the IP address of the gateway here.
Otherwise, this field can remain empty (0.0.0.0).
DNS server address
The device is easier to access if it is listed on a DNS server. For
example, to establish an Internet connection to the camera, it is
sufficient to enter the name given to the device on the DNS
server as a URL in the browser. Enter the DNS server's IP
address. Servers are supported for secure and dynamic DNS.
Video transmission
If the device is used behind a firewall, TCP (Port 80) should be
selected as the transmission protocol. For use in a local
network, choose UDP.
Multicast operation is only possible with the UDP protocol. The
TCP protocol does not support multicast connections.
13.1.6
13.1.7
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
HTTP browser port
Select a different HTTP browser port from the list if required.
The default HTTP port is 80. To limit connection to HTTPS,
deactivate the HTTP port. To do this, activate the Off option.
HTTPS browser port
To limit browser access to encrypted connections, choose an
HTTPS port from the list. The standard HTTPS port is 443.
Select the Off option to deactivate HTTPS ports and limit
connections to unencrypted ports.
Page 87

Camera Browser
Interface
The camera uses the TLS 1.0 protocol. Ensure that the browser
has been configured to support this protocol. Also ensure that
Java application support is activated (in the Java Plug-in Control
Panel of the Windows Control Panel).
To limit connections to SSL encryption, set the Off option in the
HTTP browser port, the RCP+ port, and Telnet support. This
deactivates all unencrypted connections allowing connections
on the HTTPS port only.
Configure and activate encryption for media data (video, audio,
metadata) on the Encryption page.
Network | en 87
13.1.8
13.1.9
13.1.10
13.1.11
RCP+ port 1756
Activating RCP+ port 1756 allows unencrypted connections on
this port. To allow only encrypted connections, set the Off
option to deactivate the port.
Telnet support
Activating Telenet support allows unencrypted connections on
this port. To allow only encrypted connections, set the Off
option to deactivate telnet support, making telnet connections
impossible.
Interface mode ETH
If necessary, select the Ethernet link type for interface ETH.
Depending on the device connected, it may be necessary to
select a special operation type.
Network MSS [Byte]
Set the maximum segment size for the IP packet's user data
here. This gives the option to adjust the size of the data packets
to the network environment and to optimize data transmission.
In UDP mode, comply with the MTU value set below.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 88

88 en | Network
Camera Browser
Interface
13.1.12
13.1.13
iSCSI MSS [Byte]
Specify a higher MSS value for a connection to the iSCSI system
than for the other data traffic via the network. The potential
value depends on the network structure. A higher value is only
useful if the iSCSI system is located in the same subnet as the
camera.
Network MTU [Byte]
Specify a maximum value in bytes for the package size
(including IP header) to optimize data transmission.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 89

Camera Browser
Interface
Network | en 89
13.2
13.2.1
13.2.2
13.2.3
13.2.4
DynDNS
Enable DynDNS
A dynamic Domain Name Service (DNS) allows you to select the
unit via the Internet using a host name, without having to know
the current IP address of the unit. You can enable this service
here. To do this, you must have an account with one of the
dynamic DNS providers and you must register the required host
name for the unit on that site.
Note:
For information about the service, registration process and
available host names refer to the provider.
Provider
Select your dynamic DNS Provider from the drop-down list.
Host name
Enter the host name registered for the unit.
User name
Enter the user name you registered.
13.2.5
13.2.6
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Password
Enter the password you registered.
Force registration now
Force the registration by transferring the IP address to the
DynDNS server. Entries that change frequently are not provided
in the Domain Name System. It is a good idea to force the
registration when setting up the device for the first time. Only
use this function when necessary and no more than once a day,
to avoid the possibility of being blocked by the service provider.
To transfer the IP address of the device, click the Register
button.
Page 90

90 en | Network
Camera Browser
Interface
13.2.7
Status
The status of the DynDNS function is displayed here for
information purposes; these settings cannot be changed.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 91

Camera Browser
Interface
Network | en 91
13.3
13.3.1
13.3.2
13.3.3
Advanced
Cloud-based Services
The operation mode determines how the camera communicates
with Bosch Cloud-based Security and Services. For more
information about these services and their availability, visit:
http://cloud.boschsecurity.com
– Select Auto to allow the camera to poll the server a few
times; if no contact is made, it stops polling.
– Select On to constantly poll the server.
– Select Off to block polling.
RTSP port
If necessary, select a different port for the exchange of the RTSP
data from the list. The standard RTSP port is 554. Select Off to
deactivate the RTSP function.
Authentication (802.1x)
To configure Radius server authentication, connect the unit
directly to a computer using a network cable. If a Radius server
controls access rights over the network, select On to activate
authentication to communicate with the unit.
1. Enter the user name that the Radius server uses for the unit
in the Identity field.
2. Enter the Password that the Radius server expects from
the unit.
13.3.4
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
TCP metadata input
The device can receive data from an external TCP sender, for
example an ATM or POS device, and store it as metadata. Select
the port for TCP communication. Select Off to deactivate the
function. Enter a valid Sender IP address.
Page 92

92 en | Network
Camera Browser
Interface
13.4
13.4.1
Network Management
SNMP
The camera supports the SNMP V1 (Simple Network
Management Protocol) for managing and monitoring network
components, and can send SNMP messages (traps) to IP
addresses. It supports SNMP MIB II in the unified code.
If On is selected for the SNMP parameter and a SNMP host
address is not entered, the device does not send the traps
automatically and will only reply to SNMP requests. If one or
two SNMP host addresses are entered, SNMP traps are sent
automatically. Select Off to deactivate the SNMP function.
SNMP host addresses
To send SNMP traps automatically, enter the IP address of one
or two target devices here.
SNMP traps
To choose which traps are sent:
1. Click Select. A dialog box appears.
2. Click the check boxes of the appropriate traps.
3. Click Set to close the window and send all of the checked
traps.
13.4.2
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
UPnP
Select On to activate UPnP communication. Select Off to
deactivate it.
When the Universal Plug-and-Play (UPnP) function is activated,
the unit responds to requests from the network and is
automatically registered on the requesting computers as a new
network device. This function should not be used in large
installations due to the large number of registration
notifications.
Page 93

Camera Browser
Interface
Note:
To use the UPnP function on a Windows computer, both the
Universal Plug-and-Play Device Host and the SSDP Discovery
Service must be activated.
Network | en 93
13.4.3
Quality of Service
The priority of the different data channels can be set by defining
the DiffServ Code Point (DSCP). Enter a number between 0 and
252 as a multiple of four. For alarm video you can set a higher
priority than for regular video and you can define a Post Alarm
Time over which this priority is maintained.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 94

94 en | Network
Camera Browser
Interface
13.5
WLAN
To manually set up a wireless connection:
1. Connect the camera to the network using an Ethernet
cable.
2. Select Auto from the drop down box to activate the
wireless LAN connection.
3. Select your region in the Region code drop down box.
4. If you know the service set identifier enter it in the SSID
box.
5. If you do not know the service set identifier, click Scan to
see a list of available services and then click a service.
6. If you know the encryption key, enter it in the PSK box.
7. Instead of entering the encryption key, you can click the
Connect by PIN button.
A dialog box opens where you can enter a PIN code (this is
usually found on a label at the rear of the router or access
point).
8. Click Set and then remove the Ethernet cable as the
camera reboots to activate the wireless connection.
To test the connection, click the Check Connection button.
Note:
To enhance network security, only WPA-PSK (TKIP) and WPA2PSK (AES) encryption is supported.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 95

Camera Browser
Interface
Network | en 95
13.6
Multicast
The camera can enable multiple receivers to receive the video
signal simultaneously. The stream is either duplicated and then
distributed to multiple receivers (Multi-unicast), or it is sent as a
single stream to the network, where it is simultaneously
distributed to multiple receivers in a defined group (Multicast).
Multicast operation requires a multicast-enabled network that
uses UDP and the Internet Group Management protocol
(IGMP V2). The network must support group IP addresses.
Other group management protocols are not supported. The TCP
protocol does not support multicast connections.
A special IP address from 225.0.0.0 to 239.255.255.255 (class D
address) must be configured for multicast operation in a
multicast-enabled network. The multicast address can be the
same for multiple streams, however, it is necessary to use a
different port in each case.
The settings must be made individually for each stream. Enter a
dedicated multicast address and port for each stream. Switch
between the streams by clicking the appropriate tabs.
13.6.1
13.6.2
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Enable
Enable simultaneous data reception on receivers that need to
activate the multicast function. To do this, check the box and
enter the multicast address.
Multicast Address
Enter a valid multicast address to be operated in multicast mode
(duplication of the data stream in the network).
Page 96

96 en | Network
With a 0.0.0.0 setting, the encoder for the stream operates in
multi-unicast mode (copying of data stream in device). The
camera supports multi-unicast connections for up to five
simultaneously connected receivers.
Duplication of data places a heavy demand on the CPU and can
lead to impairment of the image quality under certain
circumstances.
Camera Browser
Interface
13.6.3
13.6.4
13.6.5
Port
Enter the port address for the stream here.
Streaming
Click the checkbox to activate multicast streaming mode. An
activated stream is marked with a check. (Streaming is typically
not required for standard multicast operation.)
Multicast packet TTL
A value can be entered to specify how long the multicast data
packets are active on the network. If multicast is to be run via a
router, the value must be greater than 1.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 97

Camera Browser
Interface
Network | en 97
13.7
13.7.1
Image Posting
A target account must first be defined to use JPEG posting and
for the export of recordings.
JPEG posting
Save individual JPEG images on an FTP server at specific
intervals.
Image size
Select the size of the JPEG images that are to be sent from the
camera. JPEG resolution corresponds to the highest setting
from the two data streams.
File name
Select how file names are created for the individual images that
are transmitted.
– Overwrite: The same file name is always used and any
existing file will be overwritten by the current file.
– Increment: A number from 000 to 255 is added to the file
name and automatically incremented by 1. When it reaches
255, it starts again from 000.
– Date/time suffix: The date and time are automatically
added to the file name. When setting this parameter,
ensure that the date and time of the device are always set
correctly. For eample, the file snap011005_114530.jpg was
stored on October 1, 2005 at 11.45 and 30 seconds.
Posting interval
Enter the interval in seconds at which the images are sent to an
FTP server. Enter zero for no images to be sent.
Target
Select the target account for JPEG posting.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 98

98 en | Network
Camera Browser
Interface
13.8
Accounts
Four separate accounts can be defined for posting and
recording export.
Type
Select either FTP or Dropbox for the account type.
Before using a Dropbox account ensure that the time settings of
the device have been correctly synchronized.
Account name
Enter an account name to be shown as the target name.
FTP server IP address
For an FTP server, enter the IP address.
FTP server login
Enter your login name for the account server.
FTP server password
Enter the password that gives access to the account server.
Click Check to confirm that it is correct.
Path on FTP server
Enter an exact path to post the images on the account server.
Click Browse... to browse to the required path.
Maximum bit rate
Enter the maximum bit rate in kbps that will be allowed when
communicating with the account.
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Page 99

Camera Browser
Interface
Network | en 99
13.9
IPv4 Filter
To restrict the range of IP addresses within which you can
actively connect to the device, fill-in an IP address and mask.
Two ranges can be defined.
4 Click Set and confirm to restrict access.
If either of these ranges are set, no IP V6 addresses are allowed
to actively connect to the device.
The device itself may initiate a connection (for example, to send
an alarm) outside the defined ranges if it is configured to do so.
Bosch Security Systems 2015.01 | v1.59x | AM18-Q0676
Page 100

100 en | Service
Camera Browser
Interface
14
14.1
Service
Maintenance
Notice!
Before starting a firmware update, make sure to select the
correct upload file.
Do not interrupt the firmware installation. Even changing to
another page or closing the browser window leads to
interruption.
Uploading the wrong files or interrupting the upload can result
in the device no longer being addressable, requiring it to be
replaced.
The camera functions and parameters can be updated by
uploading new firmware. To do this, the latest firmware package
is transferred to the device via the network. The firmware is
installed there automatically. Thus, a camera can be serviced
and updated remotely without requiring a technician to make
changes to the device on site. The latest firmware can be
obtained from your customer service center or from the
Bosch Security Systems download area.
14.1.1
14.1.2
2015.01 | v1.59x | AM18-Q0676 Bosch Security Systems
Update server
The address of the Bosch update server appears in the address
box.
1. Click Check to make a connection to this server.
2. Select the appropriate version for your camera to download
the firmware from the server.
Firmware
To update the firmware:
1. First, store the firmware file on your hard disk.
2. Enter the full path for the firmware file in the field or click
Browse... to locate and select the file.
 Loading...
Loading...