Page 1

BiPAC 6300NX(L)
Fibre/4G LTE/Cable Gigabit Wireless-N
(VPN) Broadband Router
User Manual
Version Released: 1.02b.rc5.dy2
Last Revised Date: May 30, 2013
Page 2

Table of Contents
Chapter1................................................................................................................................................................1
1.1IntroducingtheBiPAC6300NX(L) ................................................................................................................1
1.2FeaturesoftheBiPAC6300NX(L)................................................................................................................. 3
NetworkProtocolsandFeatures....................................................................................................................3
Firewall ...........................................................................................................................................................4
QualityofServiceControl...............................................................................................................................4
IPTVApplications............................................................................................................................................4
WirelessLAN...................................................................................................................................................4
USBApplicationServer................................................................................................................................... 4
VirtualPrivateNetwork(VPN)(BiPAC6300NXonly) .....................................................................................4
Management ..................................................................................................................................................5
1.3HardwareSpecifications
...............................................................................................................................5
PhysicalInterface
............................................................................................................................................ 5
1.4ApplicationsfortheBiPAC6300NX(L).......................................................................................................... 6
Chapter2................................................................................................................................................................7
2.1ImportantnoteforusingtheBiPAC6300NX(L) ...........................................................................................7
2.2PackageContents .........................................................................................................................................8
2.3TheFrontLEDs..............................................................................................................................................9
2.4TheRearPorts ............................................................................................................................................10
ThedetailinstructioninResetButton.......................................................................................................... 11
2.6Cabling........................................................................................................................................................11
Chapter3..............................................................................................................................................................12
3.1BeforeConfiguration
..................................................................................................................................12
3.1.1Confi
guringaPCinWindows7 ........................................................................................................... 13
3.1.2Confi
guringaPCinWindowsVista......................................................................................................16
3.1.3Confi
guringaPCinWindowsXP ......................................................................................................... 18
3.1.3ConfiguringaPCinWindows2000 ..................................................................................................... 20
3.1.4ConfiguringaPCinWindows98/Me...................................................................................................21
3.1.5ConfiguringaPCinWindowsNT4.0 .................................................................................................... 22
3.2FactoryDefaultSettings .............................................................................................................................23
3.2.1UsernameandPassword..................................................................................................................... 23
3.3LANandWANPortAddresses.................................................................................................................... 24
3.4InformationfromyourISP ......................................................................................................................... 24
Chapter4..............................................................................................................................................................25
4.1EasySign‐On(EZSO) ...................................................................................................................................25
Chapter5
.............................................................................................................................................................. 28
Page 3

5.1Configuring6300NX(L)withyourWebBrowser........................................................................................ 28
5.2Status..........................................................................................................................................................30
5.2.1DeviceInfo ...........................................................................................................................................31
5.2.2SystemLog...........................................................................................................................................33
5.2.3Statistics...............................................................................................................................................33
5.2.4DHCPTable ..........................................................................................................................................37
5.2.5ARPTable.............................................................................................................................................37
5.2.6IPSECStatus(6300NXonly) .................................................................................................................38
5.2.7PPTPStatus(6300NXonly) ..................................................................................................................39
5.2.8DiskStatus ...........................................................................................................................................40
5.2.9L2TPStatus(6300NXonly)....................................................................................................................40
5.3QuickStart..................................................................................................................................................41
5.4Configuration..............................................................................................................................................47
5.4.1InterfaceSetup ....................................................................................................................................48
5.4.1.1Internet .........................................................................................................................................48
5.4.1.2LAN................................................................................................................................................ 57
5.4.1.3Wireless.........................................................................................................................................60
5.4.1.4WirelessMACAddressFilter.........................................................................................................72
5.4.2DualWAN ............................................................................................................................................73
5.4.2.1GeneralSetting .............................................................................................................................73
5.4.2.2OutboundLoadBalance(6300NXonly)........................................................................................ 76
5.4.2.3ProtocolBinding(6300NXonly)....................................................................................................77
5.4.3AdvancedSetup...................................................................................................................................78
5.4.3.1Firewall..........................................................................................................................................78
5.4.3.2Routing..........................................................................................................................................79
5.4.3.3NAT................................................................................................................................................81
5.4.3.4StaticDNS......................................................................................................................................86
5.4.3.5QoS
................................................................................................................................................ 87
5.4.3.6InterfaceGrouping(6300NXLonly) ..............................................................................................88
5.4.3.6IPSECSetting(6300NXonly) .........................................................................................................90
5.4.3.7PPTP(6300NXonly) ...................................................................................................................... 99
5.4.3.8PPTPClient(6300NXonly) ..........................................................................................................101
5.4.3.9L2
TP(6300NXonly).....................................................................................................................112
5.4.3.10Por
tIsolation.............................................................................................................................122
5.4.3.11Tim
eSchedule...........................................................................................................................123
5.4.4AccessManagement..........................................................................................................................124
5.4.4.1SNMP........................................................................................................................................... 124
5.4.4.2UPnP............................................................................................................................................125
5.4.4.3DDNS ...........................................................................................................................................126
5.4.4.4AccessControl.............................................................................................................................128
5.4.4.5Filter ............................................................................................................................................130
5.4.4.6CWMP(TR‐069)...........................................................................................................................134
5.4.4.7ParentalControl
..........................................................................................................................136
5.4.4.8SAMBA&FTPSe
rver................................................................................................................... 137
5.4.5Maint
enance......................................................................................................................................142
5.4.5.1UserManagement
......................................................................................................................142
Page 4

5.4.5.2TimeZone ...................................................................................................................................143
5.4.5.3Firmware..................................................................................................................................... 144
5.4.5.4SystemRestart ............................................................................................................................146
5.4.5.5DiagnosticsTool .......................................................................................................................... 147
Chapter6............................................................................................................................................................148
Problemsstartinguptherouter .............................................................................................................148
ProblemswiththeLANInterface............................................................................................................ 148
Recoveryproceduresfornon‐workingrouters ......................................................................................149
APPENDIX ...........................................................................................................................................................150
Page 5

1
Chapter 1
Introduction the BiPAC 6300NX(L)
1.1 Introducing the BiPAC 6300NX(L)
Thank you for purchasing BiPAC 6300NX(L) Router. The BiPAC 6300NX(L) is a compact and advanced
broadband gateway(router) that offers flexible and multiple internet connection services for home, SOHO and
office users to enjoy high-speed, high-level security internet connection via cellular wireless and/or Ethernet
WAN. With dual-WAN interfaces, the auto failover feature quickly and smoothly backs up the internet
connection to ensure optimal internet connectivity. With an integrated 802.11n wireless access point and 4-point
Gigabit Ethernet LAN ports, the gateway enables faster wireless speed of up to 300Mbps and LAN connection
10 times faster than regular 10/100Mbps Ethernet LAN. The BiPAC 6300NX(L) provides a unique Management
Center, enabling users to monitor 3G/4G LTE signal strength, bandwidth, download speed and many other
more.
3G/4G LTE Mobility and Always-on Connectivity
With 3G/LTE-based Internet connection (requires an additional 3G/4G LTE USB modem), user can access
internet through 3G/4G LTE, whether you are seated at your desk or taking a cross-country trip. The Auto
failover feature ensures maximum connectivity and minimum interruption by quickly and smoothly connecting to
a 3G/4G LTE network in the event that your fibre/cable line fails. The BiPAC 6300NX(L) will then automatically
reconnect to the fibre/cable connection when it is restored, reducing connection costs. These features are
perfect for office situations where a constant and uninterrupted connection is in need.
Maximize Bandwidth (BiPAC 6300NX only)
This device supports superfast fibre connections via dual-WAN connectivity through a Gigabit Ethernet WAN
port and two USB 2.0 ports. Using load balancing, both links can be in use all the time. Moreover, bandwidth can
be manually managed in the form of a percentage and load balancing to maximize bandwidth of outbound
traffic.
Wireless Mobility and Security
With an integrated 802.11n Wireless Access Point, the router delivers up to 3 times the wireless coverage of a
802.11b/g network device, so that wireless access is available everywhere in the house or office. If your network
requires wider coverage, the built-in Wireless Distribution System (WDS) allows you to expand your wireless
network without additional wires or cables. The BiPAC 6300NX(L) also supports the Wi-Fi Protected Setup
(WPS) standard and allows users to establish a secure wireless network just by pressing a button. Multiple
SSIDs allow users to access different networks through a single access point. Network managers can assign
different policies and functions for each SSID, increasing the flexibility and efficiency of the network
infrastructure.
Page 6

2
Secure VPN Connections (BiPAC 6300NX only)
The BiPAC 6300NX supports comprehensive and robust IPSec、PPTP and L2TP VPN (Virtual Private Network)
protocols for business users to establish private encrypted tunnels over the public Internet to secure data
transmission between headquarters and branch offices. With a built-in DES/3DES VPN accelerator, the router
enhances IPSec VPN performance significantly.
3G/4G LTE Management Center
The BiPAC 6300NX(L) Cellular Management Center visually displays its current 3G/4G LTE signal status It also
calculates the total amount of hours or data traffic used per month, allowing you to manage your 3G/4G LTE
monthly subscriptions.
IPv6 supported
Internet Protocol version 6 (IPv6) is a version of the Internet Protocol that is designed to succeed IPv4. IPv6 has
a vastly larger address space than IPv4. The router is already supporting IPv6, you can use it in IPv6
environment no need to change device. The dual-stack protocol implementation in an operating system is a
fundamental IPv4-to-IPv6 transition technology. It implements IPv4 and IPv6 protocol stacks either
independently or in a hybrid form. The hybrid form is commonly implemented in modern operating systems
supporting IPv6.
Easy Sign-On (EZSO)
This special feature makes it easier for you to configure your router so that you can connect to the internet in a
couple of seconds without having to logon to the router GUI for any detail configuration. This configuration
method is usually auto initiated if user is to connect to the internet via 6300NX(L).
Quick Start Wizard
Support a WEB GUI page to install this device quickly. With this wizard, end users can enter the information
easily which they get from their ISP, then surf the Internet immediately.
Firmware Upgradeable
Device can be upgraded to the latest firmware through the WEB based GUI.
Page 7

3
1.2 Features of the BiPAC 6300NX(L)
• Dual-WAN ports for 3G/4G LTE, Gigabit Ethernet WAN (EWAN) for broadband connectivity
• Gigabit WAN and LAN
• Auto failover feature to ensure an always-on connectivity
• Fibre (FTTC/FTTP/FTTH) ready with high WAN throughput
• IPv6 ready (IPv4/IPv6 dual stack)
• Multiple wireless SSIDs with wireless guest access and client isolation
• IEEE
802.11 b/g/n compliant Wireless Access Point with Wi-Fi Protected Setup (WPS)
•
Wi-Fi Protected Access (WPA-PSK/ WPA2-PSK) and Wired Equivalent Privacy (WEP)
•
Secured IPSec VPN with powerful DES/ 3DES/ AES (BiPAC 6300NX only)
• PPTP VPN with Pap/ Chap/ MPPE authentication
(BiPAC 6300NX only)
• L2TP VPN with Pap/Chap authentication
(BiPAC 6300NX only)
• 24 VPN tunnels
(BiPAC 6300NX only)
•
SOHO Firewall Security with DoS Preventing and Packet Filtering
• Load balancing to maximize bandwidth of outband traffic
(BiPAC 6300NX only)
•
Quality of Service Control for traffic prioritization and Bandwidth management
•
Universal Plug and Play (UPnP) Compliance
•
Supports IPTV Application
*2
• Two
USB port for NAS(Samba), and 3G/4G LTE USB modem
• Ease of Use with Quick Installation Wizard and EZSO
• Ideal for SOHO, office and home users
Network Protocols and Features
•
IPv4 or IPv4 / IPv6 Dual Stack
•
NAT, static (v4/v6) routing and RIP-1 / 2
•
Dual WAN failover and failback
• Dual WAN load balance (BiPAC 6300NX only)
•
DHCPv6
•
Universal Plug and Play (UPnP) Compliant
•
Dynamic Domain Name System (DDNS)
•
Virtual Server and DMZ
•
SNTP, DNS relay, IGMP snooping and IGMP proxy
•
MLD snooping and MLD proxy for video service
Page 8

4
Firewall
•
Built-in NAT Firewall
•
Stateful Packet Inspection (SPI)
• DoS attack prevention
• IP&MAC filter, URL Content Filter
• Password protection for system management
• VPN pass-through
Quality of Service Control
•
Supports the DiffServ approach
•
Traffic prioritization and bandwidth management based-on IPv4/IPv6 protocol, port number and address
IPTV Applications*2
•
IGMP Snooping and IGMP Proxy
• MLD Snooping and MLD Proxy
•
Virtual LAN (VLAN)
•
Quality of Service (QoS)
Wireless LAN
•
Compliant with IEEE 802.11 b/ g/ n standards
•
2.4 - 2.484GHz radio band for wireless
•
Up to 300 Mbps wireless operation rate
•
64 / 128 bits WEP supported for encryption
•
WPS (Wi-Fi Protected Setup) for easy setup
•
Wireless Security with WPA-PSK / WPA2-PSK support
• Multiple wireless SSIDs with wireless guest access and client isolation
•
WDS repeater function support
USB Application Server
• 3G/4G LTE dongle support
•
Storage/NAS: Samba server, FTP Server
Virtual Private Network (VPN) (BiPAC 6300NX only)
• 8 IPSec VPN Tunnels
• 8 PPTP VPN Tunnels (Dial-in:4, Dial-out:4)
• 8 L2TP VPN Tunnels (Dial-in:4, Dial-out:4)
Page 9

5
Management
•
Easy Sign-on (EZSO)
• Quick Installation wizard
•
Web-based GUI for remote and local management (IPv4/IPv6)
•
Firmware upgrades and configuration data upload and download via web-based GUI
•
Supports DHCP server / client / relay
• Supports
SNMP v1,v2, v3, MIB-I and MIB-II
•
TR-069*
1
supports remote management
• Auto failover and fallback
1. On request for Telco / ISP projects
2. IPTV application may require subscription to IPTV services from a Telco / ISP.
3. Specifications on this datasheet are subject to change without prior notice.
Page 10

5
1.3 Hardware Specifications
Physical Interface
•
WLAN: 2 detachable antennas
•
USB: 2 USB 2.0 type A port for storage service and 3G/4G LTE dongle
•
Ethernet: 4-port 10 / 100 / 1000Mbps auto-crossover (MDI / MDI-X) Switch
•
EWAN: RJ-45 Gigabit Ethernet port for connecting to ADSL/Cable/VDSL/Fibre modem for Broadband
connectivity.
•
Factory default reset button
• Wireless on/off and
WPS push button
•
Power jack
•
Power switch
Page 11

6
1.4 Applications for the BiPAC 6300NX(L)
BiPAC 6300NX(L) is a all-in-one router, supporting alternative ways (3G, EWAN) to connect to the Internet.
Then users can choose one of the ways to connect to the Internet or ISP.
Broadband router mode
Page 12

6
3G router mode
BiPAC 6300NX(L) embeds two USB ports supporting two 3G/4G LTE connections at the same time, which is
especially useful if one 3G/4G LTE card is running out of cost (the USB port can also support the NAS storage
device).
Page 13

7
Chapter 2
Installing the BiPAC 6300NX(L)
2.1 Important note for using the BiPAC 6300NX(L)
Place the BiPAC 6300NX(L) on a stable surface.
Only use the power adapter that comes with the package. Using a
different voltage rating power adaptor may damage the router.
Attention
Do not use the BiPAC 6300NX(L) in high humidity or high
temperatures.
Do not use the same power source for the BiPAC 6300NX(L) as
other equipment.
Do not open or repair the case yourself. If the BiPAC 6300NX(L) is
too hot, turn off the power immediately and have it repaired at a
qualified service center.
Avoid using this product and all accessories outdoors.
Warning
Page 14
8
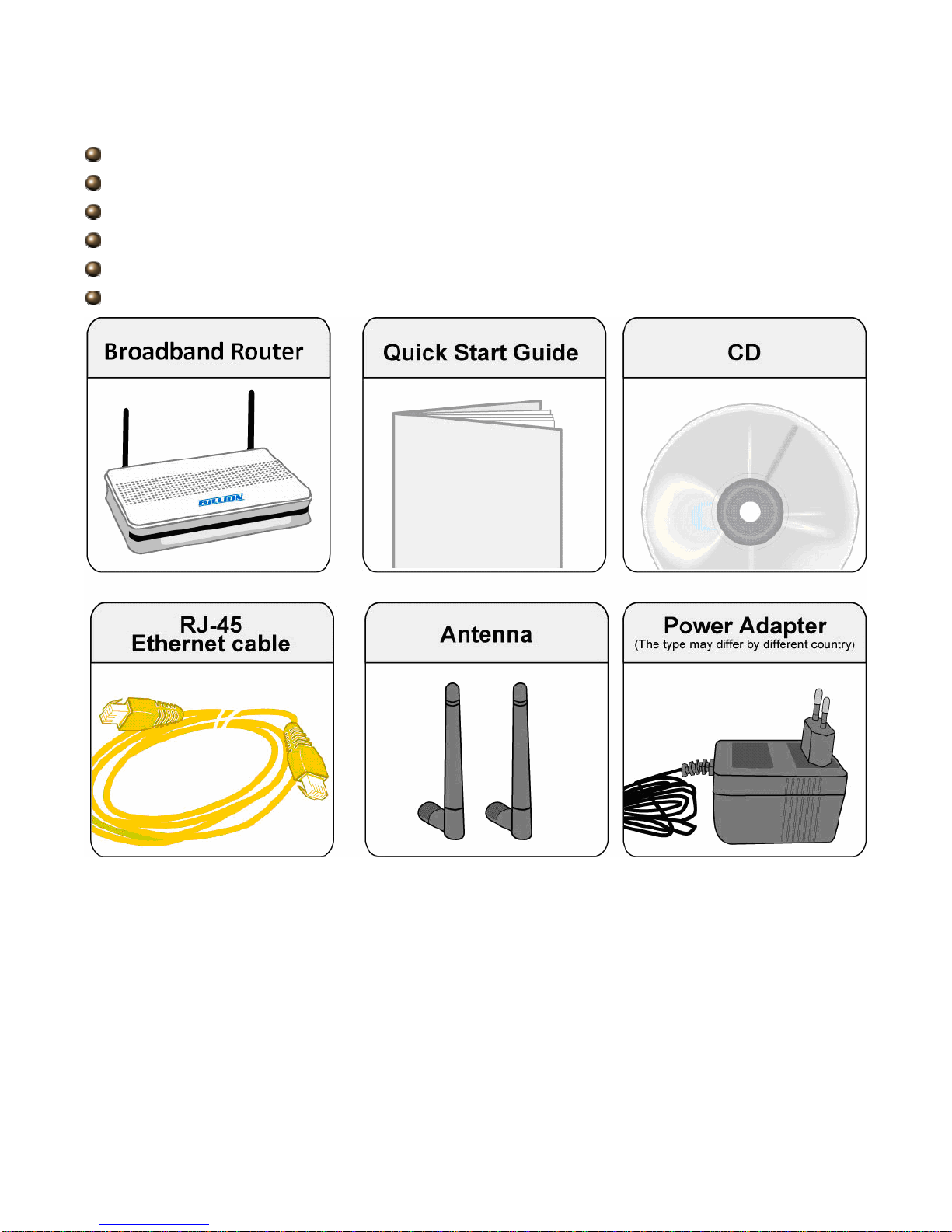
2.2 Package Contents
BiPAC 6300NX(L) Fibre/4G LTE/Cable Gigabit Wireless-N (VPN) Broadband Router
CD containing user manual
Ethernet (CAT-5 LAN) cable
Power adapter
Quick Start Guide
Two 2dBi detachable Antennas
Page 15
9
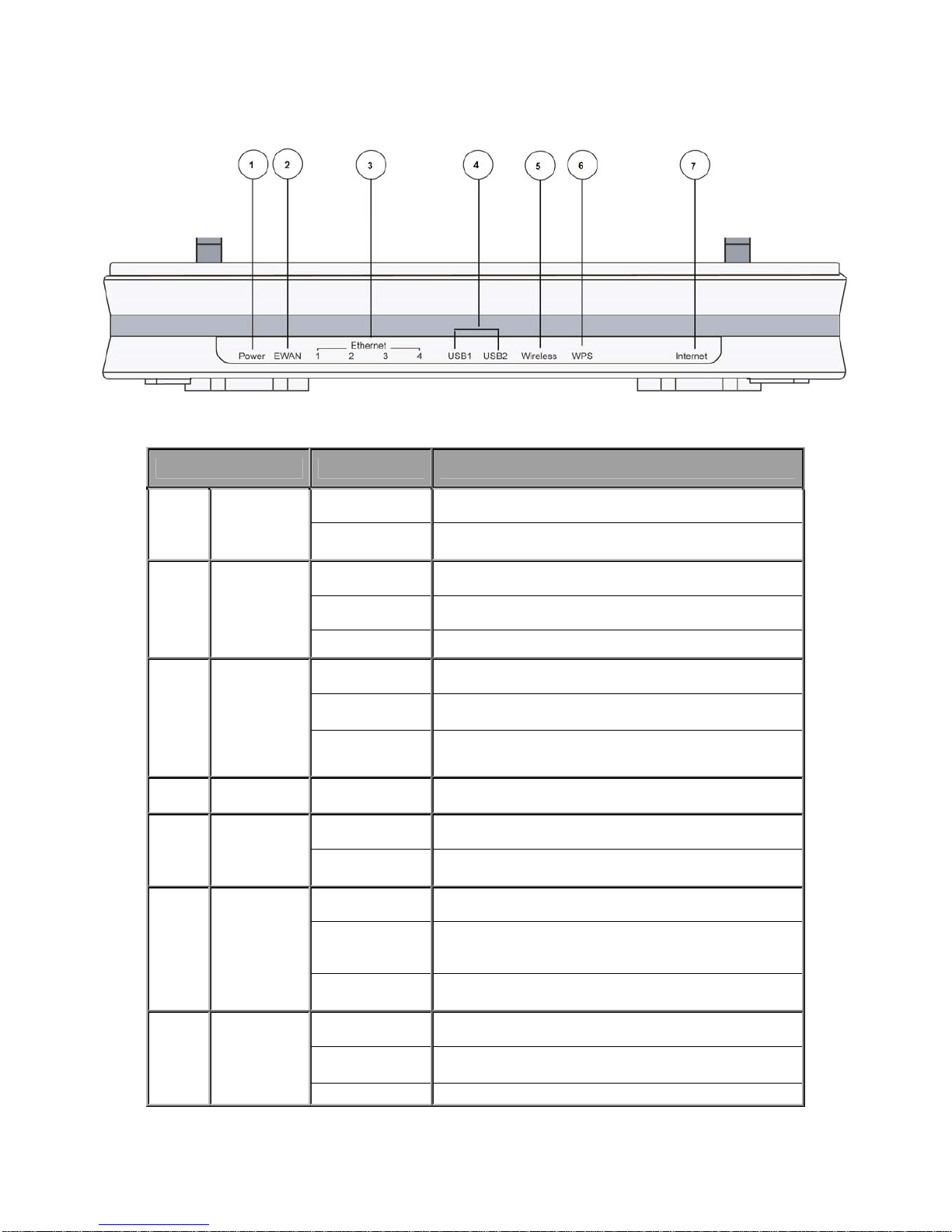
2.3 The Front LEDs
LED Status Meaning
Red
Router powered on
1 Power
Green
System ready
Green Transmission speed hitting 1000Mbps
Orange Transmission speed hitting 10/100Mbps
2 EWAN
Blinking Data being transmitted/received
Green Transmission speed hitting 1000Mbps
Orange Transmission speed hitting 10/100Mbps
3
Ethernet Port
1-4
Blinking Data being transmitted/received
4
USB
Green Connected to a 3G/4G LTE modem or storage device
Green Wireless connection established
5 Wireless
Green blinking Sending/receiving data
Green blinking WPS configuration being in progress
Lit up brightly and
then goes off in 5
seconds
WPS established
6 WPS
Flash for 2 mins
and then goes off
WPS establishment failure
Red Obtaining IP failure
Green Having obtained an IP address successfully
7 Internet
Off Router in bridged mode or WAN connection not present.
Page 16
10
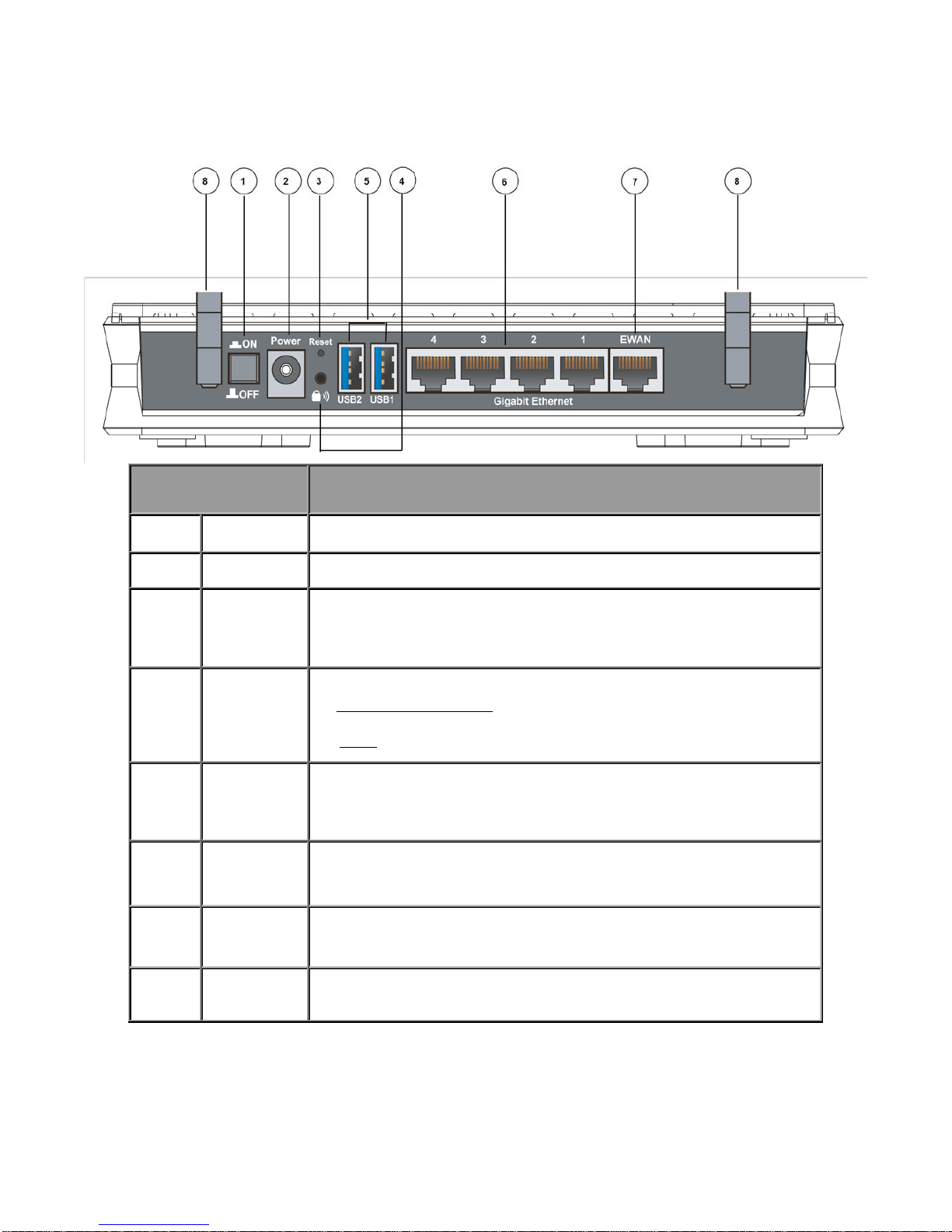
2.4 The Rear Ports
Port Meaning
1 Power Switch
Power ON/OFF switch
2 Power
Connect the supplied power adapter to this jack.
3 RESET
After the device is powered on, press it 6 seconds or above: to restore to factory
default settings (this is used when you can not login to the router, e.g. forgot the
password)
4
WPS
By controlling the pressing time, users can achieve two different effects:
(1) Wireless ON/OFF button:
Press over 6 seconds to switch on wireless function
when wireless is off and press over 6 seconds again to disable wireless function.
(2) WPS:
Press less than 6 seconds to trigger WPS function.
5
USB
Connect the 3G/4G LTE USB modem or storage device to this port.
6
Ethernet
Connect a UTP Ethernet cable (Cat-5 or Cat-5e) to one of the four LAN ports when
connecting to a PC or an office/home network of 10Mbps/ 100Mbps/ 1000Mbps.
7
EWAN
Connect to Cable Modem, Fiber Modem or PON optic lines with your RJ-45 cable.
8
Antenna
Connect the detachable antenna to this port.
Page 17

11
The detail instruction in Reset Button
Recovery procedures for non-working routers (e.g. after a failed firmware upgrade flash):
Power on the router, once the Power LED lit red, please press this reset button using the end of paper clip or
other small pointed object immediately.
The router’s emergency-reflash web interface will then be accessible via http://192.168.1.1
where you can
upload a firmware image to restore the router to a functional state.
Please note that the router will only respond with its web interface at this address (192.168.1.1), and will not
respond to ping request from your PC or other telnet operations.
Note:
Before starting recovery process, please configure the IP address of the PC as 192.168.1.100 and proceed with
the following step-by-step guide.
1. Power the router off.
2. Power on the router, once the Power lights Red, press reset button immediately.
3. Internet flashes Green, router entering recovery procedure and router's IP will reset to Emergency IP address
(Say 192.168.1.1)
4. Open IE and access http://192.168.1.1
to upload the firmware.
5. Internet lit Red, and router starts to write firmware into flash. Please DO NOT power off the router at this step.
6. Internet lit Green when successfully upgrade firmware.
7. Power the router off and then on.
2.6 Cabling
One of the most common causes of problems is bad cabling. Make sure that all connected devices are turned
on. On the front panel of the product is a bank of LEDs. Verify that the LAN Link and LEDs are lit. If they are not,
verify that you are using the proper cables.
Make sure that all other devices (e.g. telephones, fax machines, analogue modems) connected to the same
telephone line as your Billion router have a line filter connected between them and the wall socket (unless you
are using a Central Splitter or Central Filter installed by a qualified and licensed electrician), and that all line
filters are correctly installed in a right way. If the line filter is not correctly installed and connected, it may cause
problems to your connection or may result in frequent disconnections.
Page 18

12
Chapter 3
Basic Installation
The router can be configured with your web browser. A web browser is included as a standard application in the
following operating systems: Windows 98/NT/2000/XP/Vista/Win7, Linux, Mac OS, etc. The product provides
an easy and user-friendly interface for configuration.
3.1 Before Configuration
PCs must have an Ethernet interface installed properly and be connected to the router either directly or through
an external repeater hub, and have TCP/IP installed and configured to obtain an IP address through a DHCP
server or a fixed IP address that must be in the same subnet as the router. The default IP address of the router
is 192.168.1.254 and the subnet mask is 255.255.255.0 (i.e. any attached PC must be in the same subnet, and
have an IP address in the range of 192.168.1.1 to 192.168.1.253). The best and easiest way is to configure the
PC to get an IP address automatically from the router using DHCP. If you encounter any problems accessing the
router’s web interface it may also be advisable to uninstall any kind of software firewall on your PCs, as they
can cause problems accessing the 192.168.1.254 IP address of the router. Users should make their own
decisions on how to best protect their network.
Please follow the steps below for your PC’s network environment installation. First of all, please check your PC’s
network components. The TCP/IP protocol stack and Ethernet network adapter must be installed. If not, please
refer to your Windows-related or other operating system manuals.
Any TCP/IP capable workstation can be used to communicate with or
through the BiPAC 6300NX(L). To configure other types of workstations,
please consult the manufacturer’s documentation.
Page 19
13
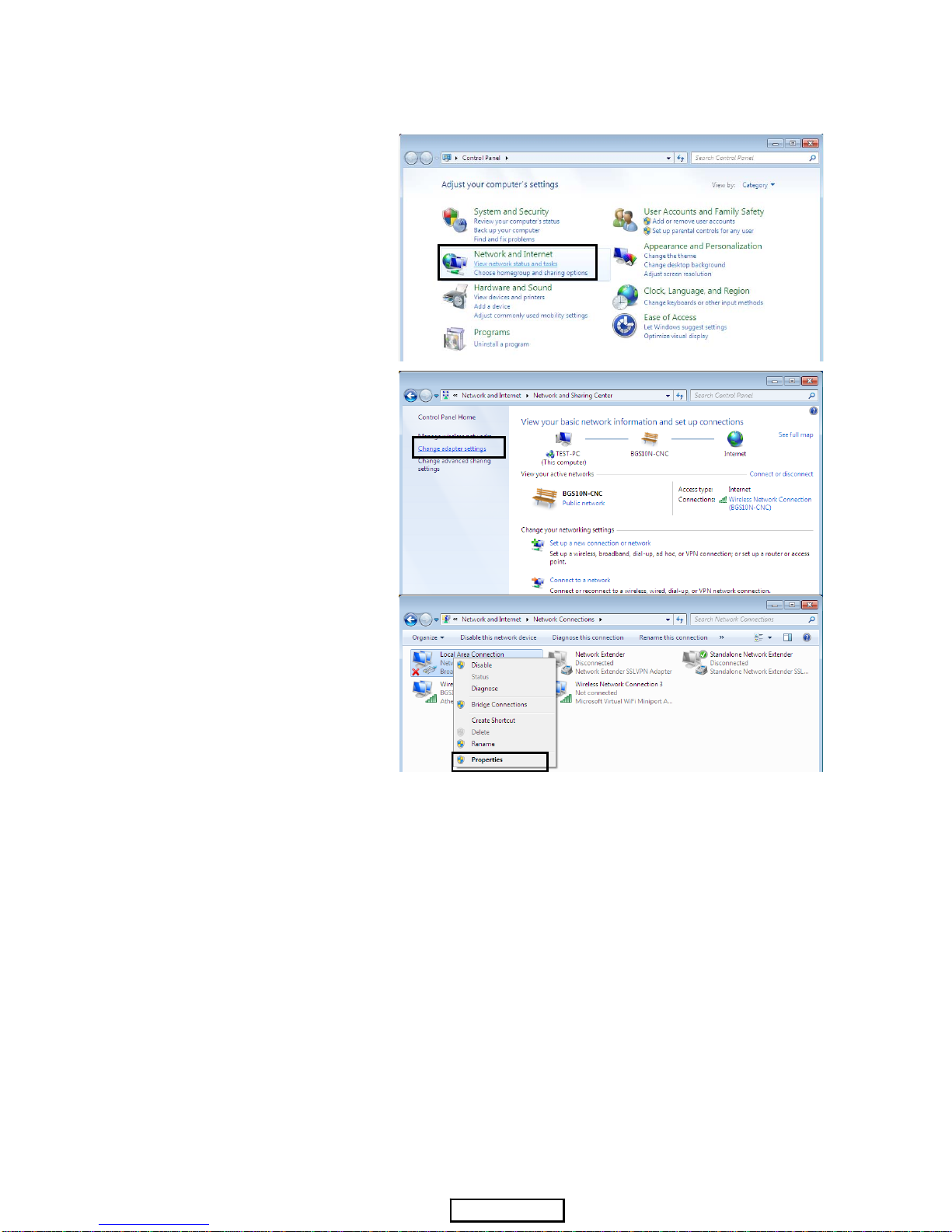
3.1.1 Configuring a PC in Windows 7
1. Go to Start. Click on Control
Panel.
Then click on Network and
Internet.
2. When the Network and
Sharing Center window pops
up, select and click on Change
adapter settings on the left
window panel.
3. Select the Local Area
Connection, and right click the
icon to select Properties.
Page 20
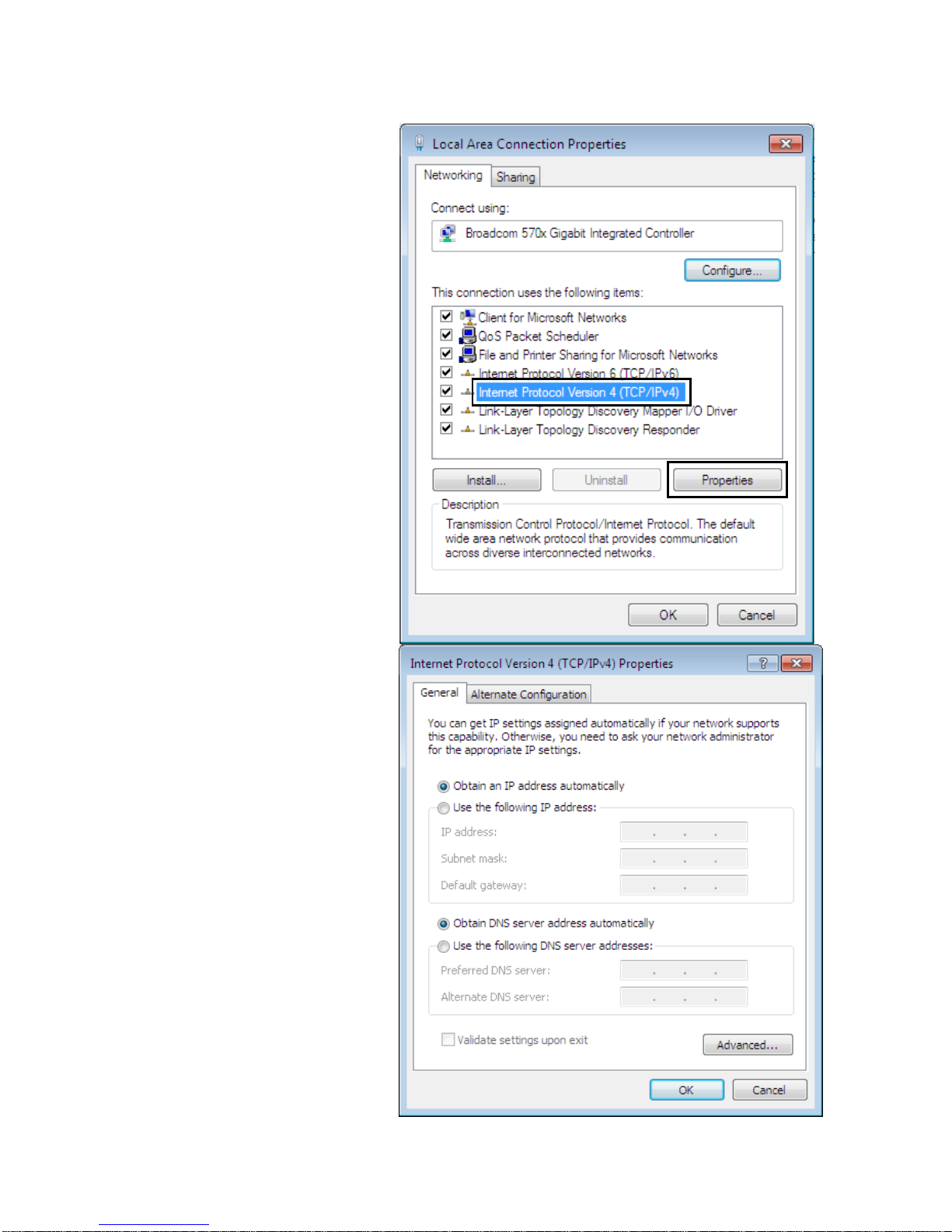
14
IPv4:
1) Select I
nternet Protocol
Version 4 (TCP/IPv4) then
click Properties
2) In the TCP/IPv4 properties
window, select the Obt ain an IP
address automatically and
Obtain DNS Server address
automatically radio buttons.
Then click OK to exit the
setting.
3) Click OK again in the Local Area
Connection Properties
window to apply the new
configuration.
Page 21
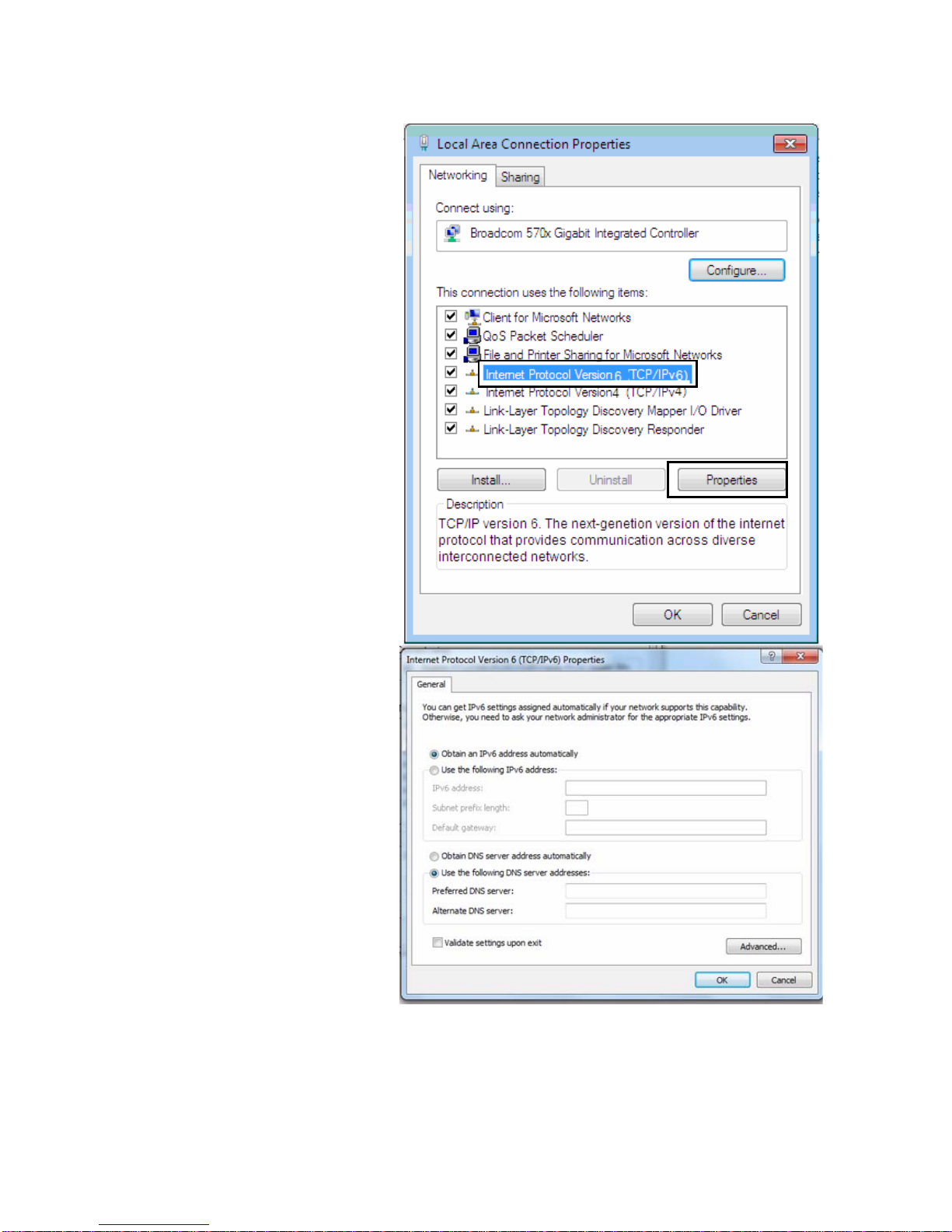
15
IPv6:
4. Select Internet Protocol
Version 6 (TCP/IPv6) then
click Properties
5. In the TCP/IPv6 properties
window, select the Obtain an
IPv6 address automatically
and Obtain DNS Server
address automatically radio
buttons. Then click OK to exit
the setting.
6. Click OK again in the Local
Area Connection Properties
window to apply the new
configuration.
Page 22
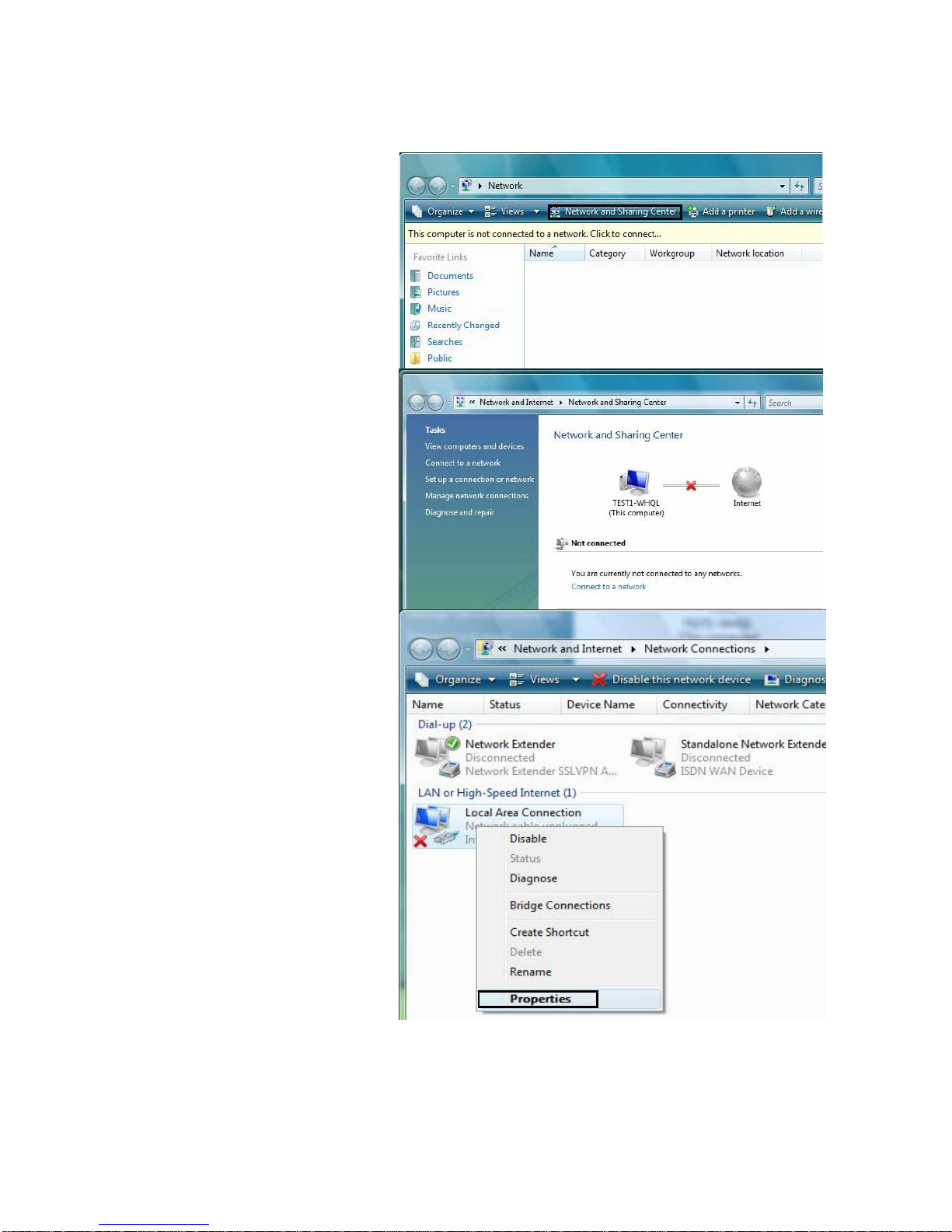
16
3.1.2 Configuring a PC in Windows Vista
1. Go to Start. Click on Network.
1. Then click on Network and
Sharing Center at the top bar.
2. When the Network and
Sharing Center window pops
up, select and click on Manage
network connections on the
left window pane.
3. Select the Local Area
Connection, and right click the
icon to select Properties.
Page 23
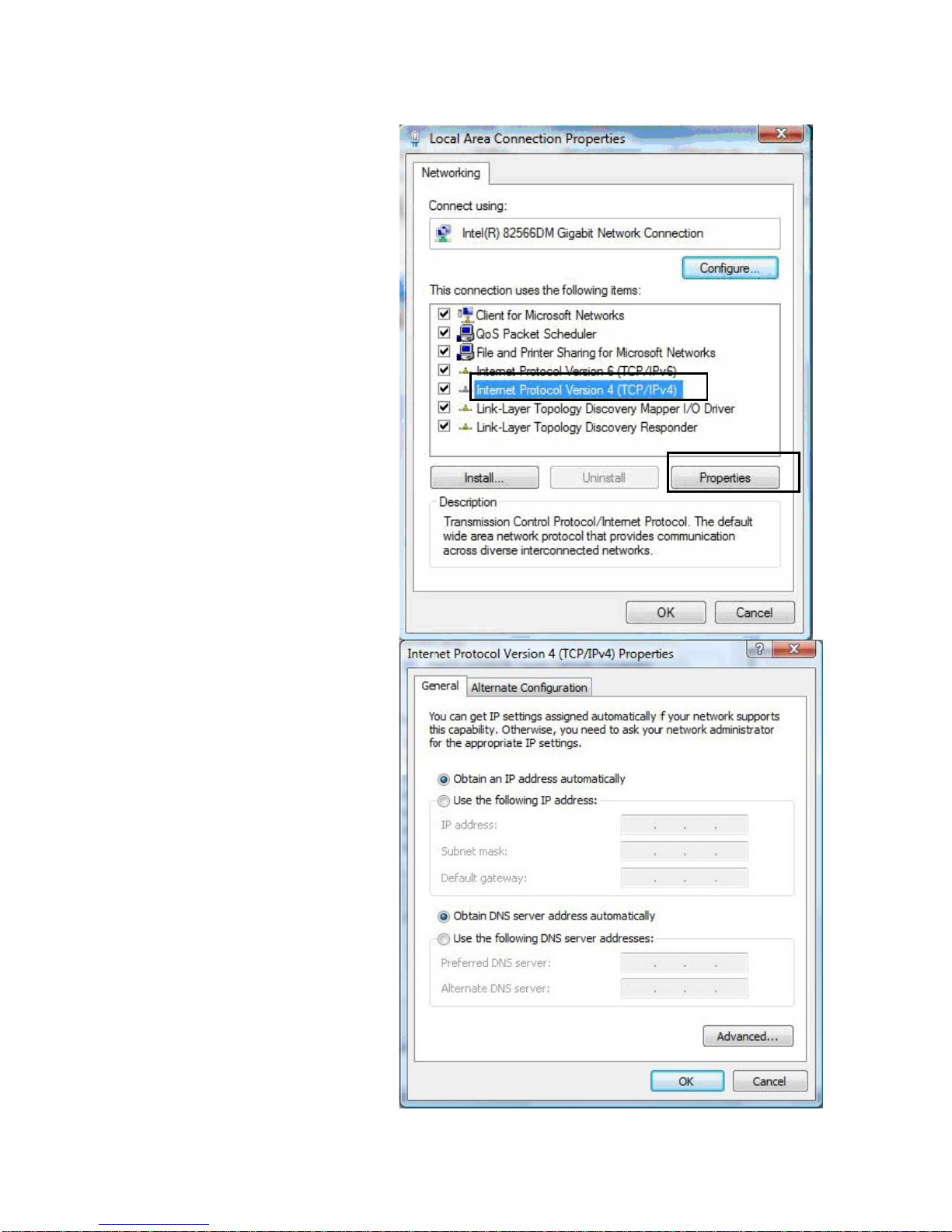
17
IPv4:
4. Select In
ternet Protocol
Version 4 (TCP/IPv4) then click
Properties.
5. In the TCP/IPv4 properties
window, select the Obtain an IP
address automatically and
Obtain DNS Server address
automatically radio buttons.
Then click OK to exit the setting.
6. Click OK again in the Local
Area Connection Properties
window to apply the new
configuration.
Page 24
18
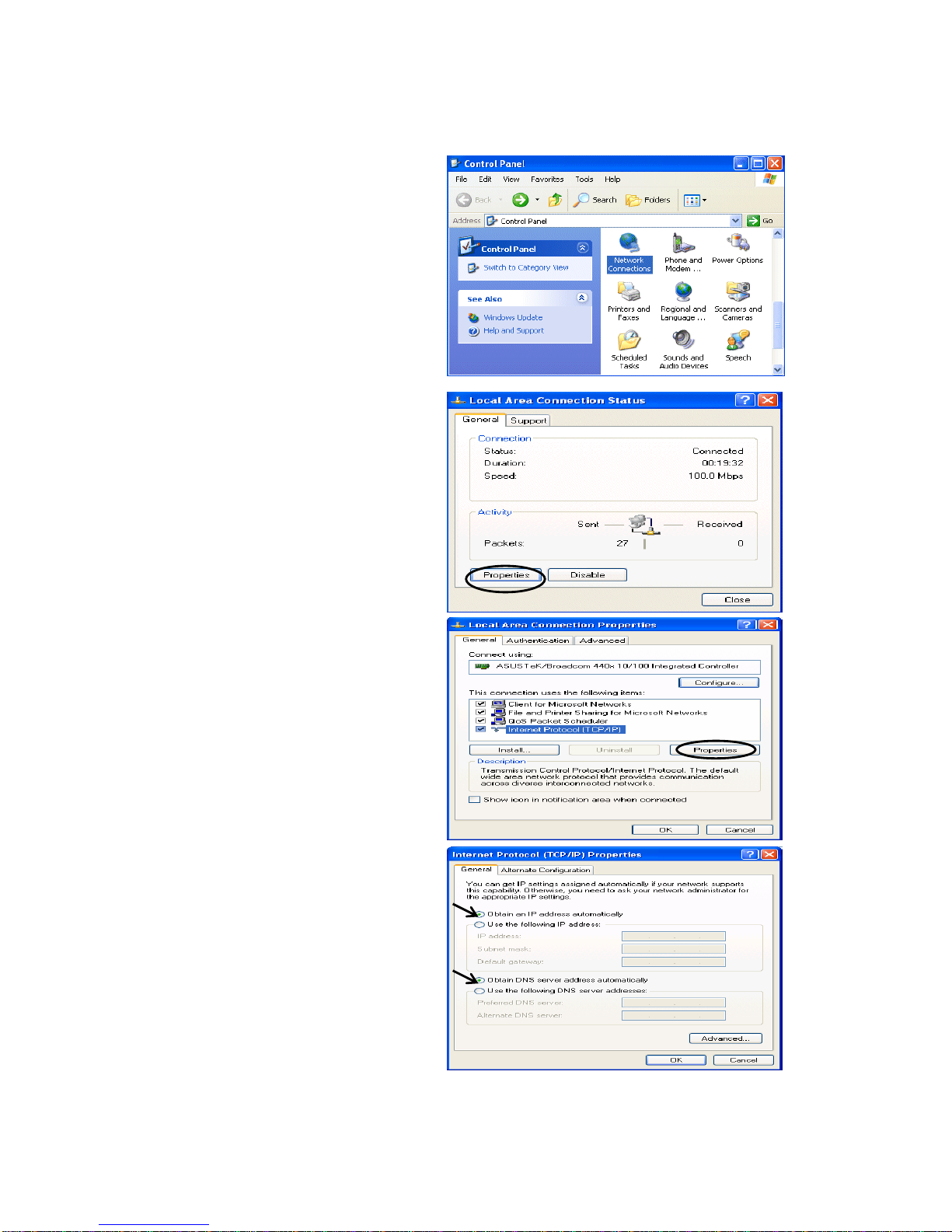
3.1.3 Configuring a PC in Windows XP
IPv4:
7. Go to Start / Control Panel (in Classic
View). In the Control Panel, double-click on
Network Connections
8. Double-click Local Area Connection.
9. In the Local Area Connection Status
window, click Properties.
10. Select Internet Protocol (TCP/IP) and click
Properties.
11. Select the Obtain an IP address
automatically and the Obtain DNS server
address automatically radio buttons.
12. Click OK to finish the configuration.
Page 25
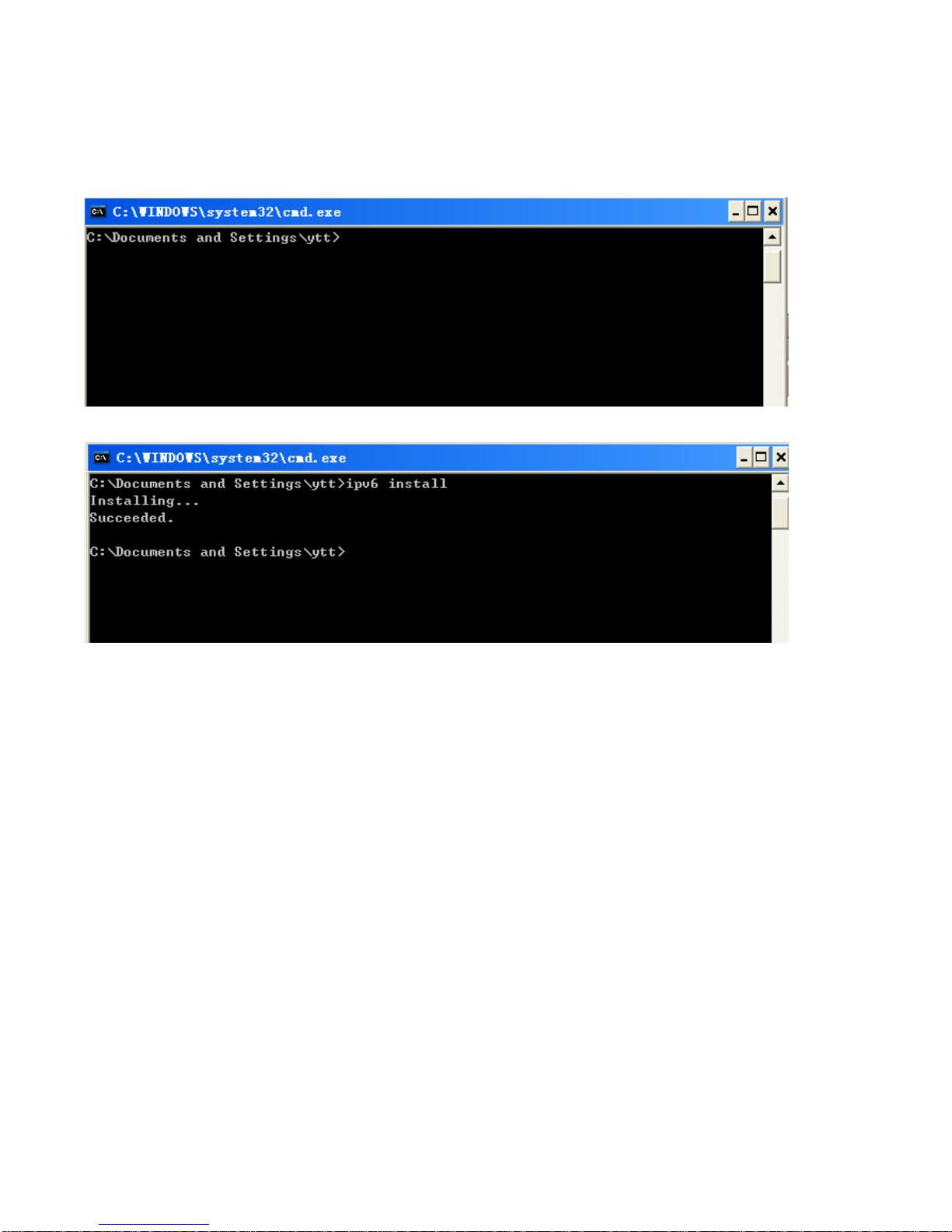
19
IPv6:
IPv6 is supported by Windows XP, but you should install it first.
Act as shown below:
1. On the desktop, Click Start > Run, type cmd, then press Enter key in the keyboard, the following screen
appears.
2. Key in command ipv6 install
Configuration is OK now, you can test whether it works ok.
Page 26
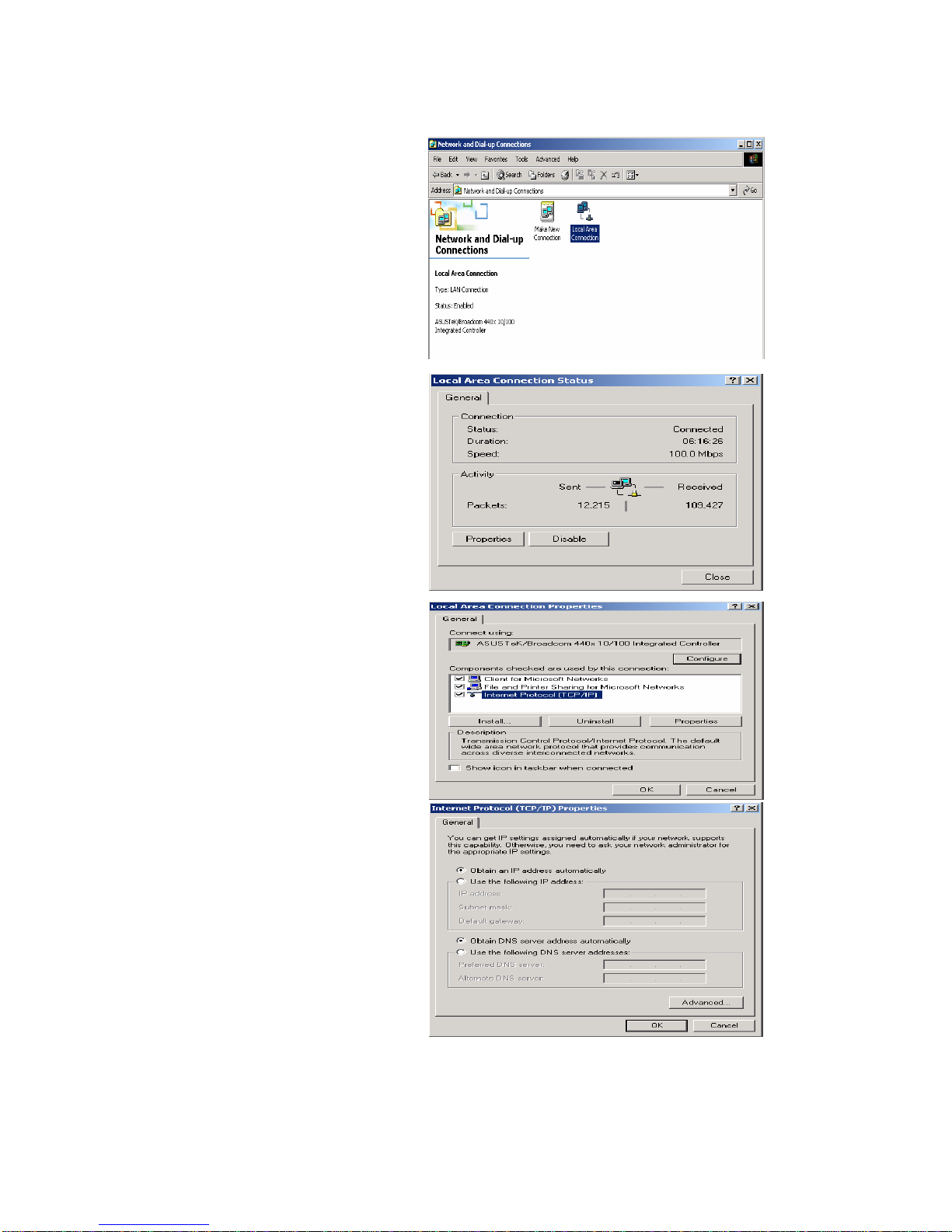
20
3.1.3 Configuring a PC in Windows 2000
1. Go to Start / Settings / Control Panel. In
the Control Panel, double-click on Network
and Dial-up Connections.
2. Double-click Local Area Connection.
3. In the Local Area Connection Status
window click Properties.
4. Select Internet Protocol (TCP/IP) and click
Properties.
5. Select the Obtain an IP address
automatically and the Obtain DNS server
address automatically radio buttons.
6. Click OK to finish the configuration.
Page 27
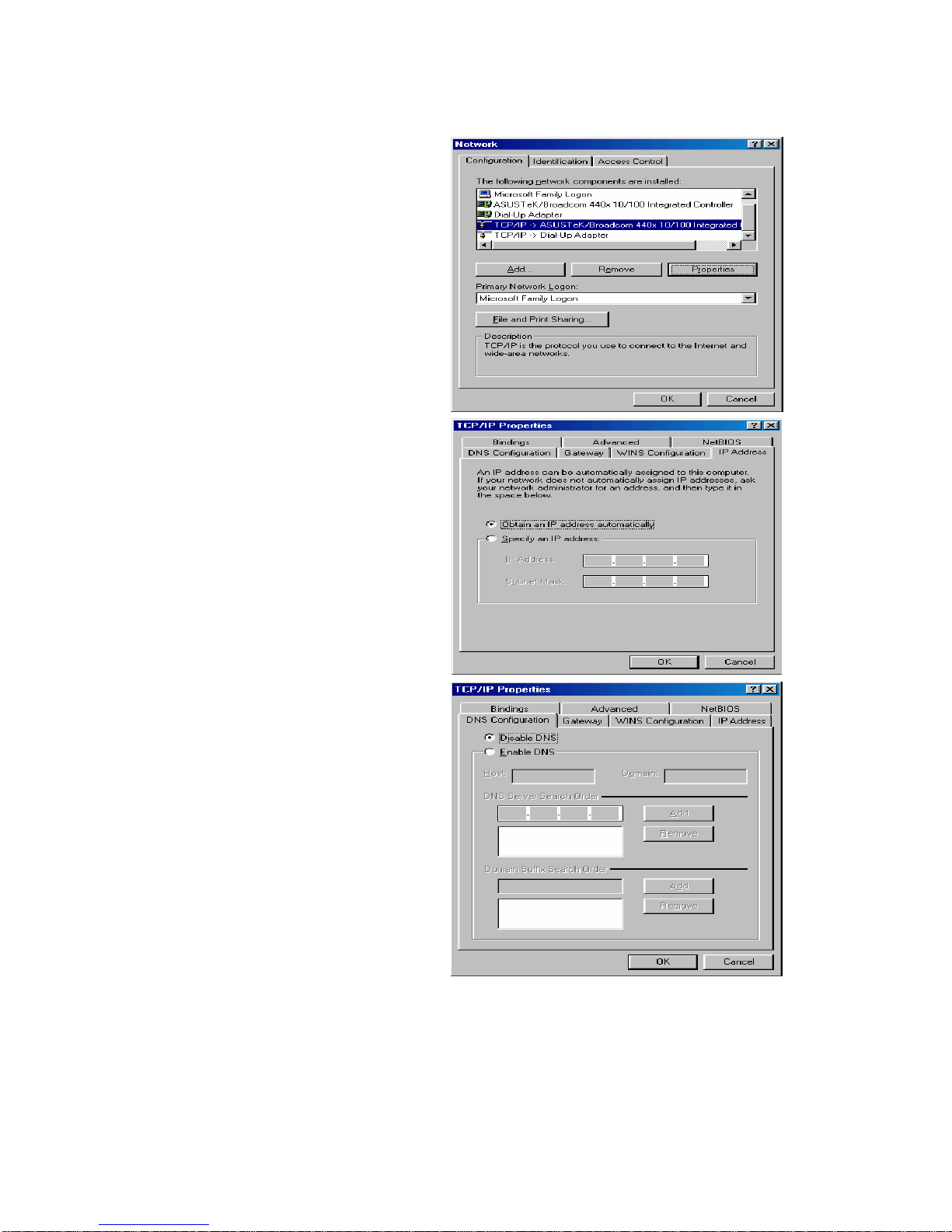
21
3.1.4 Configuring a PC in Windows 98/Me
1. Go to Start / Settings / Control Panel. In
the Control Panel, double-click on Network
and choose the Configuration tab.
2. Select TCP/IP ->NE2000 Compatible, or
the name of your Network Interface Card
(NIC) in your PC.
3. Select the Obtain an IP address
automatically radio button.
4. Then select the DNS Configuration tab.
5. Select the Disable DNS radio button and
click OK to finish the configuration.
Page 28

22
3.1.5 Configuring a PC in Windows NT4.0
1. Go to Start / Settings / Control Panel. In
the Control Panel, double-click on Network
and choose the Protocols tab.
2. Select TCP/IP Protocol and click
Properties.
3. Select the Obtain an IP address from a
DHCP server radio button and click OK.
Page 29
23
3.2 Factory Default Settings
Before configuring your router, you need to know the following default settings.
Web Interface:
Username: admin
Password: admin
LAN Device IP Settings:
IP Address: 192.168.1.254
Subnet Mask: 255.255.255.0
ISP setting in WAN site:
PPPoE
DHCP server:
DHCP server is enabled.
Start IP Address: 192.168.1.100
IP pool counts: 20
3.2.1 Username and Password
The default username and password are “admin” and “admin” respectively.
Attention
Attention
If you ever forget the password to log in, you may press the RESET button
up to 6 seconds to restore the factory default settings.
Page 30
24
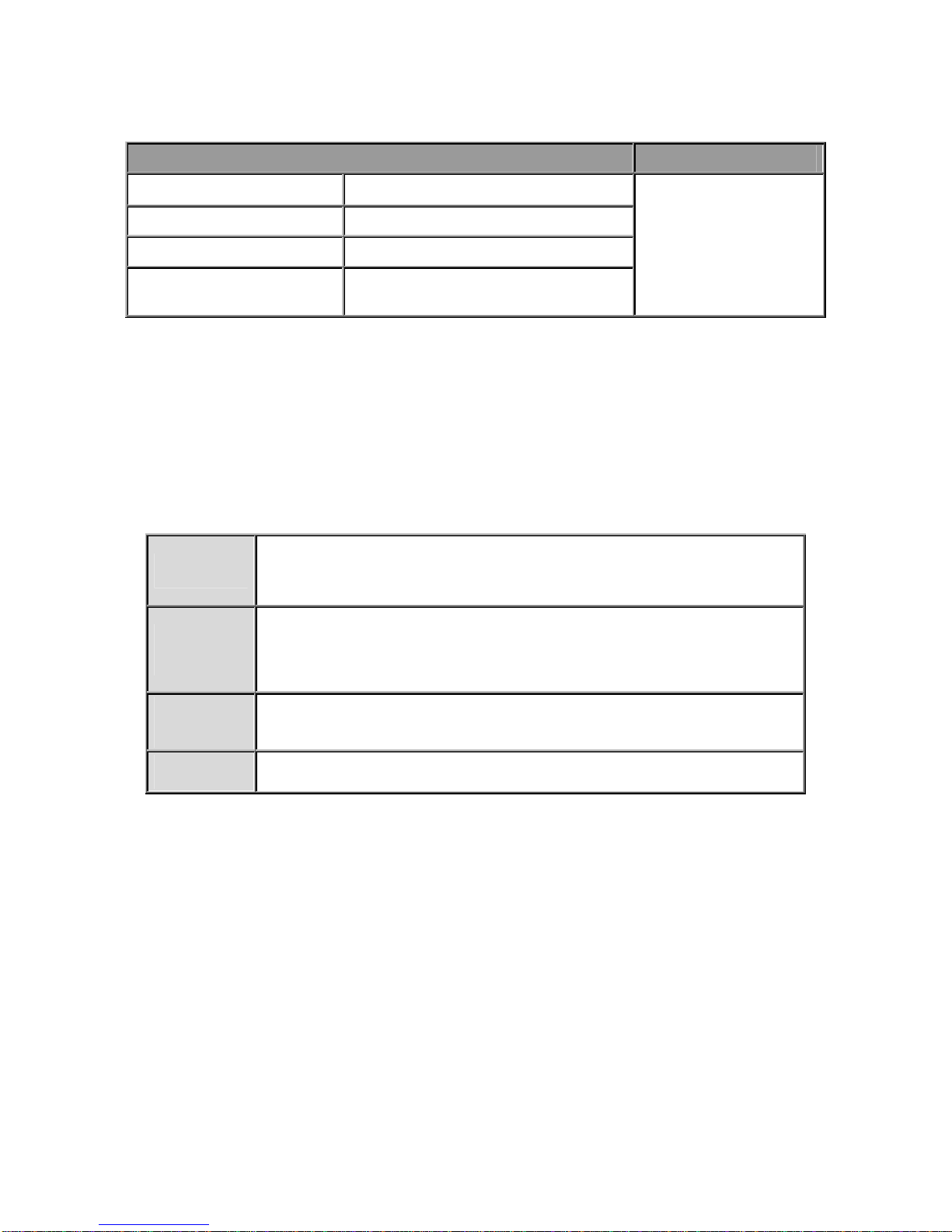
3.3 LAN and WAN Port Addresses
The parameters of LAN and WAN ports are pre-set in the factory. The default values are shown below.
IPv4:
LAN Port WAN Port
IP address
192.168.1.254
Subnet Mask
255.255.255.0
DHCP server function
Enabled
IP addresses for
distribution to PCs
20 IP addresses continuing from
192.168.1.100 through 192.168.1.119
The PPPoE function is
enabled to automatically
get the WAN port
configuration from the
ISP.
3.4 Information from your ISP
Before configuring this device, you have to check with your ISP (Internet Service Provider) what kind of service
is provided such as EWAN ((Dynamic IP address, Static IP address, PPPoE, Bridge Mode).
Gather the information as illustrated in the following table and keep it for reference.
EWAN:
PPPoE
Username, Password, Service Name, and Domain Name System (DNS) IP address
(it can be automatically assigned by your ISP when you connect or be set
manually).
Dynamic IP
Address
Domain Name System (DNS) IP address (it can be automatically assigned by your
ISP when you connect or be set manually).
Static IP
Address
Static IP Address, IP Subnet Mask, Gateway IP Address, and Domain Name
System (DNS) IP address.
Bridge Mode
Pure bridge.
Page 31

25
Chapter 4
Easy Sign-On (EZSO)
4.1 Easy Sign-On (EZSO)
This EZSO feature makes it easier for you to configure your router so that you can connect to the internet in a
couple of seconds without having to logon to the router's GUI for any detail configuration. This configuration
method is usually auto initiated if user is to connect to the internet via 6300NX(L).
When user try to access any internet access via 6300NX(L) (usually the first users of the router ), router would
take you to the EZSO configuration page without logon to the router's GUI.
EWAN
Step 1: Choose the EWAN connection mode. Press Continue to move on.
Step 2: Enter the PPPoE account provided by your ISP. Press NEXT to continue.
Step 3: Configure your wireless network. Press NEXT to continue.
Page 32

26
Step 4: EZSO finished. (The default configuration is base on IPv4/IPv6)
3G
Step 1: Choose the 3G_1 (BiPAC 6300NX(L) supports two 3G connections, and choose one to configure.)
Press Continue to move on.
Step 2: Type the 3G account information. Press NEXT to continue.
Step 3: Configure your wireless network. Press NEXT to continue.
Step 4: Wait while the device is being configured.
Page 33

27
Step 4: EZSO finished.
Page 34

28
Chapter 5
Configuration
5.1 Configuring 6300NX(L) with your Web Browser
Open your web browser, enter the IP address of your router, which by default is 192.168.1.254, and click “OK”,
a user name and password window prompt will appear. The default username and password are “admin” and
“admin”.
Congratulation! You are now successfully logged on to the BiPAC 6300NX(L)!
Page 35

29
At the configuration homepage, the left navigation pane where bookmarks are provided links you directly to the
desired setup page, including:
Status(Device Info, System Log, Statistics, DHCP Table, ARP Table, IPSec Status (6300NX only), PPTP
Status (6300NX only), Disk Status, L2TP Status (6300NX only))
Quick Start (Wizard Setup)
Configuration (Interface Setup, Dual WAN, Advanced Setup, Access Management, Maintenance)
Language
Please see the relevant sections of this manual for detailed instructions on how to configure your Billion router.
Page 36

30
5.2 Status
In this section,you can check the router working status, including Device Info, System Log, Statistics, DHCP
Table, ARP Table, IPSEC Status (6300NX only), PPTP Status (6300NX only), Disk Status, and L2TP Status
(6300NX only).
Page 37

31
5.2.1 Device Info
Page 38

32
Device Information
Model Name: Show model name of the router
Firmware Version: This is the Firmware version
MAC Address: This is the MAC Address
LAN
IPv4:
IP Address: LAN port IPv4 address.
Sub Net Mask: LAN port IP subnet mask.
DHCP Server: LAN port DHCP role - Enabled, Relay or disabled
IPv6:
IP Address: LAN port IPv6 address.
Prefix Length: The prefix length
DHCP Server: The DHCP status.
WAN
Interface: The now used connection method, EWAN, 3G_1 and 3G_2.
Connection Type: The protocol selected.
PPPoE connection Time: The time totaled since it has been successfully connected.
IPv4:
Status: the connection status, Not connected or Connected.
IP Address: WAN port IP address.
Subnet Mask: WAN port IP subnet mask.
Default Gateway: The IP address of the default gateway.
DNS Server: WAN port DHCP role - Enabled, Relay or disabled
IPv6:
Status: the IPv6 connection status.
IP Address: WAN port IPv6 address.
Prefix Length: The prefix length..
Default Gateway: The IP address of the default gateway.
DNS Server: DNS information.
Page 39

33
5.2.2 System Log
In system log, users can check the operations to the router and track the glitches to the router when occurred.
5.2.3 Statistics
Ethernet
Interface:
This field displays the type of port
Transmit Frames: This field displays the number of frames transmitted until the latest second.
Transmit Multicast Frames: This field displays the number of multicast frames transmitted until the latest
second.
Transmit Total Bytes: This field displays the number of bytes transmitted until the latest second.
Transmit Collision: This is the number of collisions on this port.
Transmit Error Frames: This field displays the number of error packets on this port.
Receive Frames: This field displays the number of frames received until the latest second.
Receive Multicast Frames: This field displays the number of multicast frames received until the latest second.
Page 40

34
Receive Total Bytes: This field displays the number of bytes received until the latest second.
Receive CRC Errors: This field displays the number of error packets on this port.
Receive Under-size Frames: This field displays the number of under-size frames received until the latest
second.
REFRESH: Press this button to refresh the statistics.
Wireless
Transmit Frames: This field displays the number of frames transmitted until the latest second.
Transmit Error Frames: This field displays the number of error frames transmitted until the latest second.
Transmit Drop Frames: This field displays the number of drop frames transmitted until the latest second.
Receive Frame: This field displays the number of frames received until the latest second.
Receive Error Frames: This field displays the number of error frames received until the latest second.
Receive Drop Frames: This field displays the number of drop frames received until the latest second.
REFRESH: Press this button to refresh the statistics.
Page 41

35
EWAN
Transmit Frames: This field displays the total number of frames transmitted until the latest second.
Transmit Multicast Frames: This field displays the total number of multicast frames transmitted till the latest
second.
Transmit Total Bytes: This field displays the total number of bytes transmitted until the latest second.
Transmit Collision: This is the number of collisions on this port.
Transmit Error Frames: This field displays the number of error packets on this port.
Receive Frames: This field displays the number of frames received until the latest second.
Receive Multicast Frames: This field displays the number of multicast frames received until the latest second.
Receive Total Bytes: This field displays the number of bytes received until the latest second.
Receive CRC Errors: This field displays the number of error packets on this port.
Receive Under-size Frames: This field displays the number of under-size frames received until the latest
second.
REFRESH: Press this button to refresh the statistics.
Page 42

36
3G_1
Take 3G_1 as an example to describe the 3G/4G LTE connection transmission information.
Transmit Frames of Current Connection: This field displays the total number of 3G/4G LTE frames
transmitted until the latest second for the current connection.
Transmit Bytes of Current Connection: This field shows the total bytes transmitted till the latest second for
the current connection for the current connection.
Transmit Total Frames: The field displays the total number of frames transmitted till the latest second since
system is up..
Transmit Total Bytes: This field displays the total number of bytes transmitted until the latest second since
system is up.
Receive Frames of Current Connection: This field displays the number of frames received until the latest
second for the current connection.
Receive Bytes of Current Connection: This field shows the total bytes received till the latest second for the
current connection..
Receive Total Frames: This field displays the total number of frames received until the latest second since
system is up.
Receive Total Bytes: This field displays the total frames received till the latest second since system is up.
REFRESH: Press this button to refresh the statistics.
Page 43

37
5.2.4 DHCP Table
DHCP table displays the devices connected to the router with clare information.
#: The index identifying the connected devices.
HostName: Show the hostname of the PC.
IP: The IP allocated to the device.
MAC Address: The MAC of the connected device.
Expire Time: The total remaining interval since the IP assignment to the PC.
5.2.5 ARP T able
This section displays the router’s ARP (Address Resolution Protocol) results, which shows the mapping of
Internet (IP) addresses to Ethernet (MAC) addresses.
ARP table
#: The index marking ARP resolution results.
IP Address: Show the IP Address that the MAC address maps to.
MAC Address: Show the MAC address that is corresponded to the IP address it is mapped to.
Page 44

38
5.2.6 IPSEC Status (6300NX only)
#: The IPSec entry index number.
Connection Name: User-defined IPSEC VPN connection name.
Remote Gateway: The IP of the remote gateway.
Local Address: The IP and netmask of local access range.
Remote address: The IP and netmask of remote access range.
Connected: Show the connecting status.
Action: Connection or Drop the connection.
Page 45

39
5.2.7 PPTP Status (6300NX only)
PPTP Client
User: Four users(sessions) for client sessions. Here shows the using user.
Connection Name: Show user-defined PPTP VPN connection name.
Active: Show if the tunnel is active for connection.
Connection Type: Remote Access or LAN to LAN.
Server IP: Show the IP of VPN Server.
Peer Network IP: Display the remote network and subnet mask in LAN to LAN PPTP connection.
NetmasK: Show the netmask of peer network.
Connected: Show the connecting status.
PPTP Server
User: Four users(sessions) for server sessions. Here shows the using user.
Connection Name: Show user-defined PPTP VPN connection name.
Active: Show if the tunnel is active for connection.
Connection Type: Remote Access or LAN to LAN.
Assigned IP: Show the IP assigned to the client.
Peer Network IP: Display the remote network and subnet mask in LAN to LAN PPTP connection.
NetmasK: Show the netmask of peer network.
Connected: Show the connecting status.
Refresh: Click this button to refresh the connection status.
Page 46

40
5.2.8 Disk Status
Partition: Display the NAS partition.
Disk Space(KB): Display the total storage space of the NAS in KB unit.
Free Space(KB): Display the available space in KB unit.
5.2.9 L2TP Status(6300NX only)
Name: Display the user-defined L2TP connection name.
Type: The VPN mode: dialin or dialout.
Connect: The connecting status.
Active: Show if the L2TP tunnel is active for connection.
Username: The user assigned to client (dialout use) or the user set for client to connect in (dialin use).
Page 47

41
5.3 Quick Start
For detailed instructions on configuring WAN settings, see the Interface Setup section of this manual.
The Quick Start Wizard is a useful and easy utility to help setup the device to quickly connect to your ISP
(Internet Service Provider) with only a few steps required. It will guide you step by step to configure the
password, time zone, and WAN settings of your device. The Quick Start Wizard is a helpful guide for first time
users to the device.
Click NEXT to enter step 1.
Step1. Set new password of the “admin” account. The password was used to manage the web access. The
default is “admin”. Once changed, please remember carefully. Click NEXT to continue.
Step2: Choose your time zone. Click NEXT to continue.
Page 48

42
Step3: Set your wireless connection. Click NEXT to continue.
Page 49

43
Step4: Set your Internet connection
WAN Transfer Modes: EWAN or 3G.
EWAN
1) .Select EWAN. Refer to your ISP to choose the appropriate connection protocol. Click NEXT to continue.
1) Enter the PPPoE account information provided to you by your ISP. Click NEXT to continue.
2).The Setup Wizard has completed. Click on BACK to modify changes or mistakes. Click NEXT to save the
current settings.
3). Quick Start Completed!
Switch to Status > Devic Info to view the status.
Page 50

44
If configuration is completed, users can change to Status > Device Info for information.
Page 51

45
3G
1) Select 3G_1 (for example).
2). Type relevant 3G parameters from your ISP.
3). Click Next to save changes.
4). Quick Start completed!.
Page 52

46
Switch to Status > Device Info to view the status.
Page 53

47
5.4 Configuration
Click this item to access the following sub-items that configure the router: Interface Setup, Dual WAN,
Advanced Setup, Access Management, and Maintenance.
First, let us take a look at the Interface Setup. There are four items contained in this section, namely, Internet,
LAN, Wireless and Wireless MAC Filter.
Each is described in the following scenario.
Page 54

48
5.4.1 Interface Setup
5.4.1.1 Internet
EWAN
BiPAC 6300NXL
Page 55

49
BiPAC 6300NX
Page 56

50
Multi Service (6300NXL only)
Service Num: The index to mark the EWAN interface of different ISP type, ranging from 0-7.
Service Summary: The diagram for view of service information.
Status: Select whether to enable the service.
IPv4/IPv6
IP version: choose IPv4, IPv4/IPv6, IPv6 based on users’ environment.
Here we take IPv4/IPv6 for example, when you just choose IPv4 or IPv6, you can just get information from the
following listed parameters.
ISP Connection Type:
ISP: Select the encapsulation type your ISP uses.
Dynamic IP: Select this option if your ISP provides you an IP address automatically. This option is
typically used for Cable services. Please enter the Dynamic IP information accordingly.
Static IP: Select this option to set static IP information. You will need to enter in the Connection type, IP
address, subnet mask, and gateway address, provided to you by your ISP. Each IP address entered in
the fields must be in the appropriate IP form, which is four IP octets separated by a dot (xx.xx.xx.xx). The
Router will not accept the IP address if it is not in this format.
PPPoE: Select this option if your ISP requires you to use a PPPoE connection.
Bridge: Select this mode if you want to use this device as an OSI layer 2 device like switch.
802.1q Options
802.1q: Select whether to activate 802.1q feature. When activated, please enter the the VLAN ID.
VLAN ID: It is a parameter to specify the VLAN which the frame belongs. Enter the VLAN ID identification,
tagged: 0-4094.
PPPoE
Username: Enter the user name exactly as your ISP assigned.
Password: Enter the password associated with the user name above.
Bridge Interface for PPPoE: When “Activated”, the device will gain WAN IP from your ISP with the PPPoE
account. But if your PC is connected to the router working as a DHCP client, in this mode, the device acts as a
NAT router; while if you dial up with the account within your PC, the device will then work as a bridge forwarding
the PPPoE information to the PPPoE server and send the response to your PC, thus your PC gets a WAN IP
Page 57

51
working in the internet.
Connection Setting
Connection:
Always On: Click on Always On to establish a PPPoE session during start up and to automatically
re-establish the PPPoE session when disconnected by the ISP.
Connect Manually: Select Connect Manually when you don't want the connection up all the time.
TCP MSS Option: Enter the TCP Maximum Segment Size (MSS).
IP Options
Default Route: Select Yes to use this interface as default route interface.
IPv4 options:
Get IP Address: Choose Static or Dynamic
Static IP Address: If Static is selected in the above field, please enter the specific IP address you get from ISP
and the following IP subnet mask and gateway address.
IP Subnet Mask: The default is 0.0.0.0. User can change it to other such as 255.255.255.0.Type the subnet
mask assigned to you by your ISP (if given).
Gateway: Enter the specific gateway IP address you get from ISP.
NAT: Select Enable if you use this router to hold a group of PCs to get access to the internet.
Dynamic Route:
RIP Version: (Routing Information protocol) Select this option to specify the RIP version, including RIP-1,
RIP-2.
RIP Direction: Select this option to specify the RIP direction.
None is for disabling the RIP function.
Both means the router will periodically send routing information and accept routing information then
incorporate into routing table.
IN only means the router will only accept but will not send RIP packet.
OUT only means the router will only send but will not accept RIP packet.
TCP MTU Option:
Maximum Transmission Unit, the maximum is 1500.
IGMP Proxy: IGMP (Internet Group Multicast Protocol) is a network-layer protocol used to establish
membership in a Multicast group. Choose whether enable IGMP proxy.
IPv6 options (only when choose IPv4/IPv6 or just IPv6 in IP version field above):
IPv6 Address: Type the WAN IPv6 address from your ISP.
Obtain IPv6 DNS: Choose if you want to obtain DNS automatically.
Primary/Secondary: if you choose Disable in the Obtain IPv6 DNS field, please type the exactly primary and
secondary DNS.
MLD Proxy: MLD (Multicast Listener Discovery Protocol) is to IPv6 just as IGMP to IPv4. It is a Multicast
Management protocol for IPv6 multicast packets.
MAC Spoofing
MAC spoofing: This option is required by some service providers specifying some specific MAC allowed to join
in network. You must fill in the MAC address specified by your service provider when this information is required.
Page 58

52
When router’s Internet configuration is finished successfully, you can go to status to get the connection
information.
BiPAC 6300NXL
Page 59

53
BiPAC 6300NX
Page 60

54
3G
The BiPAC 6300NX(L) supports two 3G connections, featuring 3G_1 and 3G_2.
Status: Choose Activated to enable the 3G connection.
Usage Allowance: Enable when you want to control 3G usage. Click this link to enter 3G Usage Allowance
to
configure.
Mode: There are 5 options of phone service standards: GSM_ONLY, UTMS_ONLY, GPRS_FIRST,
UMTS_FIRST, and AUTOMATIC. If you are uncertain what services are available to you, then please select
Automatic.
TEL No.: The dial string to make a GPRS / 3G user internetworking call. It may provide by your mobile service
provider.
APN: An APN is similar to a URL on the WWW, it is what the unit makes a GPRS / UMTS call. The service
provider is able to attach anything to an APN to create a data connection, requirements for APNs varies
between different service providers. Most service providers have an internet portal which they use to connect to
a DHCP Server, thus giving you access to the internet i.e. some 3G operators use the APN ‘internet’ for their
portal. The default value is “internet”.
Username/Password: Enter the username and password provided by your service provider. The username
and password are case sensitive.
PIN: PIN stands for Personal Identification Number. A PIN code is a numeric value used in certain systems as a
password to gain access, and authenticate. In mobile phones a PIN code locks the SIM card until you enter the
correct code. If you enter the PIN code incorrectly into the phone 3 times in a row, then the SIM card will be
blocked and you will require a PUK code from your network/service provider.
Connection: Default set to Always on to keep an always-on 3G connection.
Keep Alive: Select Yes to keep the 3G/4G LTE connection always on.
Default Route: Select Yes to use this interface as default route interface.
NAT: Select this option to Disabled/Enable the NAT (Network Address Translation) function. Enable NAT to
grant devices in LAN access to internet through the 3G gateway sharing a single internet IP.
Page 61

55
3G Usage Allowance
Click Usage Allowance to go to the Usage Allowance configuration page.
In order to query online time or volume used, you can set the following options.
Mode: Two methods are provided, that is, Volume-based and Time-based.
Volume-based: If choosing Volume-based, you can view the volume you have used.
Only Download: Only make statistics of Download Traffic.
Only Upload: Only make statistics of Upload Traffic.
Download and Upload: Make statistics of both Download and Upload Traffic.
Page 62

56
Time-based: If choosing Time-based, you can view the online hours you have used.
You can also assign the billing period.
Over usage allowance action: If the online time or traffic you have used exceeds the usage allowance you set.
The system will do the followings operations.
Save the statistics to ROM: Choose the time interval for saving statistics. You can choose to save for Every
one hour or Disable the function.
Page 63

57
5.4.1.2 LAN
A Local Area Network (LAN) is a shared communication system to which many computers are attached and is
limited to the immediate area, usually the same building or floor of a building.
IPv6
The IPv6 address composes of two parts, thus, the prefix and the interface ID.
There are two ways to dynamically configure IPv6 address on hosts. One is statefull configuration, for example
using DHCPv6 (which resembles its counterpart DHCP in IPv4.) In the stateful autoconfiguration model, hosts
obtain interface addresses and/or configuration information and parameters from a DHCPv6 server. The Server
maintains a database that keeps track of which addresses have been assigned to which hosts.
The second way is stateless configuration. Stateless auto-configuration requires no manual configuration of
hosts, minimal (if any) configuration of routers, and no additional servers. The stateless mechanism allows a
host to generate its own addresses using a combination of locally available information (MAC address) and
information (prefix) advertised by routers. Routers advertise prefixes that identify the subnet(s) associated with
a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address
is formed by combining the two. When using stateless configuration, you needn’t configure anything on the
client.
Page 64

58
IPv4 Parameters
IP Address: Enter the IP address of Router in dotted decimal notation, for example, 192.168.1.254 (factory
default).
IP Subnet Mask: The default is 255.255.255.0. User can change it to other such as 255.255.255.128.
Alias IP Address: This is for local networks virtual IP interface. Specify an IP address on this virtual interface.
Alias IP Subnet Mask: Specify a subnet mask on this virtual interface.
IGMP Snooping: Select Activated to enable IGMP Snooping function, Without IGMP snooping, multicast
traffic is treated in the same manner as broadcast traffic - that is, it is forwarded to all ports. With IGMP snooping,
multicast traffic of a group is only forwarded to ports that have members of that group.
Dynamic Route: Select the RIP version from RIP1 or RIP2B.
DHCPv4 Server
DHCP (Dynamic Host Configuration Protocol) allows individual clients to obtain TCP/IP configuration at start-up
from a server.
DHCPv4 Server: If set to Enabled, your BiPAC 6300NX(L) can assign IP addresses, default gateway and DNS
servers to the DHCP client.
If set to Disabled, the DHCP server will be disabled.
If set to Relay, the BiPAC 6300NX(L) acts as a surrogate DHCP server and relays DHCP requests and
responses between the remote server and the clients. Enter the IP address of the actual, remote DHCP
server in the Remote DHCP Server field in this case.
When DHCP is used, the following items need to be set.
Start IP: This field specifies the first of the contiguous addresses in the IP address pool.
IP Pool Count: This field specifies the count of the IP address pool.
Lease Time: The current lease time of client.
DNS Relay Select Automatically obtained or Manually set (if selected. Please set the exactly information). If you
set Static IP in the ISP Connection Type
field, then select Manually here and set the specific DNS information.
Primary DNS Server: Enter the IP addresses of the DNS servers. The DNS servers are passed to the DHCP
clients along with the IP address and the subnet mask.
Secondary DNS Server: Enter the IP addresses of the DNS servers. The DNS servers are passed to the
DHCP clients along with the IP address and the subnet mask.
Fixed Host
In this field, users can map the specific IP (must in the DHCP IP pool) for some specific MAC, and this
information can be listed in the following table.
Page 65

59
IP Address: Enter the specific IP. For example: 192.168.1.110.
MAC Address: Enter the responding MAC. For example: 00:0A:F7:45:6D:ED
When added, you can see the ones listed as showed below:
IPv6 parameters
Interface Address / Prefix Length: enter the static LAN IPv6 address, we suggest leave the field empty
because when setted wrong, it will result in LAN devices not being able to access other IPv6 device through
internet. Router will take the same WAN’s prefix to LAN side if the field is empty.
MLD Snooping: Similar to IGMP Snooping, but applicable for IPv6.
DHCPv6 Server
DHCPv6 Server: Check whether to enable DHCPv6 server.
DHCPv6 Server Type: Select Stateless or Stateful. When DHCPv6 is enabled, this parameter is available.
Stateless: If selected, the PCs in LAN are configured through RA mode, thus, the PCs in LAN are
configured through RA mode, to obtain the prefix message and generate an address using a
combination of locally available information (MAC address) and information (prefix) advertised by
routers, but they can obtain such information like DNS from DHCPv6 Server.
Stateful: If selected, the PCs in LAN will be configured like in IPv4 mode, thus obtain addresses and
DNS information from DHCPv6 server.
Start interface ID: enter the start interface ID. The IPv6 address composed of two parts, thus, the prefix and the
interface ID. Interface is like the Host ID compared to IPv4.
End interface ID: enter the end interface ID.
Leased Time (hour): the leased time, similar to leased time in DHCPv4, is a time limit assigned to clients, when
expires, the assigned ID will be recycled and reassigned.
Issue Router Advertisement: Check whether to enable issue Router Advertisement feature. It is to send
Router Advertisement messages periodically. Router will multicast the v6 Prefix information (similar to v4
network number 192.168.1.0) to all LAN devices if the field is enabled. We suggest enabling this field.
Page 66

60
5.4.1.3 Wireless
This section
introduces the wireless LAN and some basic configurations. Wireless LANs can be as complex as
a number of computers with wireless LAN cards communicating through access points which bridge network
traffic to the wired LAN.
Page 67

61
Access Point Settings
Access Point: Default setting is set to Activated. If you want to close the wireless interface, select
Deactivated.
Wireless Mode: The default setting is 802.11b+g+n (Mixed mode). If you do not know or have both 11g and
11b devices in your network, then keep the default in mixed mode. From the drop-down manual, you can select
802.11g if you have only 11g card. If you have only 11b card, then select 802.11b and if you only have 802.11n
then select 802.11n.
Channel: The range of radio frequencies used by IEEE 802.11b/g/n wireless devices is called a channel. There
are Regulation Domains and Channel ID in this field. The Channel ID will be different based on Regulation
Domains. Select a channel from the drop-down list box.
Beacon interval: The Beacon Interval value indicates the frequency interval of the beacon. Enter a value
between 20 and 1000. A beacon is a packet broadcast by the Router to synchronize the wireless network.
RTS/CTS Threshold: The RTS (Request To Send) threshold (number of bytes) for enabling RTS/CTS
handshake. Data with its frame size larger than this value will perform the RTS/CTS handshake. Enter a value
between 1500 and 2347.
Fragmentation Threshold: The threshold (number of bytes) for the fragmentation boundary for directed
messages. It is the maximum data fragment size that can be sent. Enter a value between 256 and 2346, even
number only.
DTIM: This value, between 1 and 255, indicates the interval of the Delivery Traffic Indication Message (DTIM).
TX Power: The transmission power of the antennas, ranging from 1-100, the higher the more powerful of the
transmission performance.
11n Settings
Channel Bandwidth: Select either 20 MHz or 20/40 MHz for the channel bandwidth. The wider the Channel
bandwidth the better the performance will be.
Guard Interval: Select either 400nsec or 800nsec for the guard interval. The guard interval is here to ensure
that data transmission do not interfere with each other. It also prevents propagation delays, echoing and
reflections. The shorter the Guard Interval, the better the performance will be. We recommend users to select
Auto.
MCS: There are options 0~15 and AUTO to select for the Modulation and Coding Scheme. We recommend
users selecting AUTO.
SSID Settings
SSID Num: User can determine how many SSIDs to be used. Default is 1, maximum is 4.
SSID Index: Select how many SSIDs you want to lay out. A total of 4 is in list. By default 4 SSIDs are in use.
SSID: The SSID is the unique name of a wireless access point (AP) to be distinguished from another. For
security propose, change the default wlan-ap to a unique ID name to the AP which is already built-in to the
router’s wireless interface. Make sure your wireless clients have exactly the SSID as the device, in order to get
connected to your network.
Broadcast SSID: Select Yes to make the SSID visible so a station can obtain the SSID through passive
scanning. Select No to hide the SSID in so a station cannot obtain the SSID through passive scanning.
SSID Activated: Select the time period during which the SSID is active. Default is always which means the
SSID will be active all the time without time control. See 5.4.3.11 Time Schedule
to set the timeslot to flexibly
control when the SSID functions.
Page 68

62
WPS Settings
WPS (Wi-Fi Protected Setup) feature is a standard protocol created by Wi-Fi Alliance. This feature greatly
simplifies the steps needed to create a Wi-Fi networks for a residential or an office setting. WPS supports 2
types of configuration methods which are commonly known among consumers: PIN Method & PBC Method.
WPS State: Display whether the WPS is configured or unconfigured.
WPS Mode: Select the mode which to start WPS, choose between PIN Code and PBC (Push Button).
Selecting Pin Code mode will require you to know the enrollee PIN code.
To future understand the two modes of configuration; please refer to the following Wi-Fi Protected Setup.
Wi-Fi Protected Setup
PIN Method: Configure AP as Registrar
1. Jot down the client’s Pin (eg. 04640776).
2. Enter the Enrollee(Client) PIN code and then press Start WPS.
Page 69

63
3. Launch the wireless client’s WPS utility (eg. Ralink Utility). Set the Config Mode as Enrollee, press the WPS
button on the top bar, select the AP (eg. Billion_AP) from the WPS AP List column. Then press the PIN button
located on the middle left of the page to run the scan.
Page 70

64
4. The client’s SSID and security setting will now be configured to match the SSID and security setting of the
registrar (router).
Page 71

65
PIN Method: Configure AP as Enrollee
1. Jot down the WPS PIN (eg. 03454435).Press Start WPS.
Page 72

66
2. Launch the wireless client’s WPS utility (eg. Ralink Utility). Set the Config Mode as Registrar. Enter the PIN
number in the PIN Code column then choose the correct AP (eg. Billion_AP) from the WPS AP List before
pressing the PIN button to run the scan.
Page 73

67
3. The router’s (AP’s) SSID and security setting will now be configured to match the SSID and security setting of
the registrar (client).
4. Now to make sure that the setup is correctly done, cross check to see if the SSID and the security setting of
the registrar setting match with the parameters found on both Wireless Configuration and Wireless Security
Configuration page.
Page 74

68
PBC Method:
1. Press the PBC radio button, Then Start WPS.
2. Launch the wireless client’s WPS Utility (eg. Ralink Utility). Set the Config Mode as Enrollee. Then press the
WPS button and choose the correct AP (eg. Billion_AP) from the WPS AP List section before pressing the PBC
button to run the scan.
Page 75

69
3. When the PBC button is pushed, a wireless communication will be established between your router and the
PC. The client’s SSID and security setting will now be configured to match the SSID and security setting of the
router.
Page 76

70
Security Settings
Security Type: You can disable or enable wireless security for protecting wireless network. The default type of
wireless security is OPEN and to allow all wireless stations to communicate with the access points without any
data encryption.
To prevent unauthorized wireless stations from accessing data transmitted over the network, the router offers
secure data encryption, known as WEP and WPA.
There are five alternatives to select from: WEP 64-bit, WEP 128-bit, WPA-PSK, WPA2-PSK, Mixed
WPA/WPA2-PSK. If you require high security for transmissions, please select WPA-PSK, WPA2-PSK or
WPA/WPA2-PSK.
WEP
WEP Authentication Method: WEP authentication method, there are two methods of authentication used,
Open System authentication (OPENWEB) and Share Key authentication (SHAREDWEB). We suggest you
select OPENWEB.
Key 1 to Key 4: Enter the key to encrypt wireless data. To allow encrypted data transmission, the WEP
Encryption Key values on all wireless stations must be the same as the router. There are four keys for your
selection. The input format is in HEX style, 5 and 13 HEX codes are required for 64-bitWEP and 128-bitWEP
respectively.
If you chose WEP 64-bit, then enter any 5 ASCII characters or 10 hexadecimal characters ("0-9", "A-F").
If you chose WEP 128-bit, then enter 13 ASCII characters or 26 hexadecimal characters ("0-9", "A-F").
You must configure all four keys, but only one key can be activated at any one time. The default key is key 1.
Note: When you enable WPS function, this WEP function will be invalid. And if you select one of WEP-64Bits/
WEP-128Bits, the following prompt box will appear to notice you.
Page 77

71
WPA-PSK & WPA2-PSK
WPA Algorithms: TKIP (Temporal Key Integrity Protocol) or AES (Advanced Encryption System) utilizes a
stronger encryption method and incorporates Message Integrity Code (MIC) to provide protection against
hackers.
Pre-Shared key: The key for network authentication. The input format should be 8-63 ASKII characters or 64
hexadecimal characters
Key Renewal Interval: The time interval for changing the security key automatically between wireless client
and AP.
WDS Settings
WDS (Wireless distributed system) is a wireless access point mode that enables wireless link and
communication with other access point. It is easy to be installed, just define the peer’s MAC of the connected
AP.
WDS Mode: select Activated to enable WDS feature and Deactivated to disable this feature.
MAC Address: Enter the AP MAC addresses (in XX:XX:XX:XX:XX:XX format) of the peer connected AP.
Page 78

72
5.4.1.4 Wireless MAC Address Filter
The MAC filter screen a
llows you to configure the router to give exclusive access to up to 8 devices (Allow
Association) or exclude up to 8 devices from accessing the router (Deny Association). Every Ethernet device
has a unique MAC (Media Access Control) address. The MAC address is assigned at the factory and consists of
six pairs of hexadecimal characters, for example, 00:AA:BB:00:00:02. You need to know the MAC address of
the devices to configure this screen.
SSID Index: Select the targeted SSID you want the MAC filter rules to apply to.
Active: Select Activated to enable MAC address filtering.
Action: Define the filter action for the list of MAC addresses in the MAC address filter table.
Select Deny to block access to the AP, MAC addresses not listed will be allowed to access the router. Select
Allow to permit access to the router, MAC addresses not listed will be denied access to the router.
MAC Address: Enter the MAC addresses (in XX:XX:XX:XX:XX:XX format) of the wireless station that are
allowed or denied access to the specified in these address fields.
Page 79

73
5.4.2 Dual WAN
Dual WAN is specially designed to offer users Failover/Fallback or Load Balance feature.
Auto Failover/Failback is to ensure an always-on internet connection. Users can set a WAN1 (main WAN) and
WAN 2 (backup WAN), and when WAN1 fails, it will switch to WAN2, and when WAN1 restores, it will switch to
WAN1 again.
Load balance (only for BiPAC 6300NX) provides optimal bandwidth sharing for multiple PCs on your network, or
allows maximum reliability with network redundancy. Load balance supported by BiPAC 6300NX balance
network bandwidth for network traffic through two WAN connections, ideal for small-to-medium business that
requires increased bandwidth, network scalability, and resilience for mission-critical network and internet
applications.
5.4.2.1 General Setting
Select Failover to enable the failover/failback feature or Load Balance to make the router work in load balance
mode.
Failover
WAN Port Service Detection Policy
WAN1: Select “EWAN”, “3G_1” or “3G_2” for WAN1 (The main WAN).
WAN2: Select the “3G_1” or “3G_2” for WAN2 as backup port if you select “EWAN” as WAN1.
Connectivity Decision: Set how many times of probing failure to switch to backup port.
Probe Cycle: Set the time duration for the Probe Cycle to determine when the router will switch to the backup
connection (backup port) once the main connection (main port) fails. For example, when set to 30 seconds, the
probe will be conducted every 30 seconds.
Page 80

74
Note:
1) The time set is for each probe cycle, but the decision to change to the backup port is determined by Probe
Cycle multiplied by connection Decision amount (e.g. From the image above it will be 30 seconds multiplied
by 3 consecutive fails, the router will determine failover to WAN2 (backup port)).
2).The failback setting follow the same decision policy as the failover. For example, according to settings above
in the screenshot, the connection probe will be carried out every 30 seconds, and 3 consecutive times of probe
success is found, the router will determine failback to WAN1 (main WAN).
Probe WAN 1: Choose the probe policy, to probe gateway or host (users decide themselves)
Gateway: It will send ping packets to gateway of Wan1 interface and wait for response from it in every
“Probe Cycle” to check the connectivity of the gateway of WAN1 interface.
Host: It will send ping packets to specific host and wait for response in every “Probe Cycle”. The host
must be an IP address.
Load Balance (6300NX only)
WAN Port Service Detection Policy
WAN1: Select “EWAN”, “3G_1” or “3G_2” for WAN1 (The main WAN).
WAN2: Select the “3G_1” or “3G_2” for WAN2 as backup port if you select “EWAN” as WAN1.
Connectivity Decision: Set how many times of probing failure to switch to the other WAN port service.
Probe Cycle: Set the time duration for the Probe Cycle to determine when the router will switch to the other
WAN port connection once the WAN connection in use fails. For example, when set to 30 seconds, the probe
will be conducted every 30 seconds.
Note:
The time set is for each probe cycle, but the decision to change to the another WAN port is determined by Probe
Cycle multiplied by connection Decision amount (e.g. From the image above it will be 30 seconds multiplied
by 3 consecutive fails of WAN1, the router will determine to share load to WAN2. Port WAN1 and WAN2 share
the same operation mechanism.)
Page 81

75
Probe WAN 1/2: Choose the probe policy, to probe gateway or host (users decide themselves)
Gateway: It will send ping packets to gateway of Wan1 interface and wait for response from it in every
“Probe Cycle” to check the connectivity of the gateway of WAN1 interface.
Host: It will send ping packets to specific host and wait for response in every “Probe Cycle”. The host
must be an IP address
Page 82

76
5.4.2.2 Outbound Load Balance (6300NX only)
The connect
ions are distributed over WAN1 and WAN2 so that it can utilize bandwidth of both WAN ports. With
Outbound load balance, traffic may be routed to a faster link when one of the WAN is slower or congested so
that user gains better throughput and less delay.
User can distribute outbound traffic based on Session Mechanism or IP Hash Mechanism.
Based on Session Mechanism
Balance by Session (Round Robin): Balance session traffic based on a round robin method.
Balance by Session weight: Balance session traffic based on a weight ratio. Enter the desired ratio in the
fields provided.
Balance by Traffic weight: Balance traffic based on a traffic weight ratio. Enter the desired ratio into the fields
provided.
Based on IP Hash Mechanism
Balance by weight: Use an IP hash to balance traffic based on a ratio. Enter the desired ratio into the fields
provided.
Page 83

77
5.4.2.3 Protocol Binding (6300NX only)
Protocol Binding lets you direct spe
cific traffic to go out from a specific WAN port. Policies determine how
specific types of internet traffic are routed, for example, traffic from a particular IP(es) granted access to only
one WAN port rather than using both of the WAN ports as with load balancing.
Rule Index: The index marking the rule. Maximum entries can be 16.
Active: Select whether to enable the rule.
Bind Interface: To determine the WAN interface the to-be-set rule will apply to and what type of traffic is to be
bound to forward to the which WAN interface.
Source IP Address: Enter the source IP address featuring the traffic origin.
Subnet mask: Enter the subnet mask of the source network.
Port Number: Enter the port number.
Destination IP Address: Enter the destination IP address featuring the traffic destination.
Subnet mask: Enter the subnet of the designation network.
Port Number: Enter the port number which defines the application.
DSCP: The DSCP value. Value Range:0~64, 64 means Don't care
Protocol: Select the protocol traffic is using (TCP, UDP, ICMP).
Press SET to submit the settings.
For example:
Set a rule to realize that web traffic from 192.168.1.105 is to be routed to WAN 1.
Page 84

78
5.4.3 Advanced Setup
5.4.3.1 Firewall
Your router includes a firewall for helping to prevent attacks from hackers. In addition to this, when using NAT
(Network Address Translation) the router acts as a “natural” Internet firewall, since all PCs on your LAN use
private IP addresses that cannot be directly accessed from the Internet.
Firewall: To automatically detect and block Denial of Service (DoS) attacks, such as Ping of Death, SYN Flood,
Port Scan and Land Attack.
Enabled: It activates your firewall function.
Disabled: It disables the firewall function.
SPI: If you enabled SPI, all traffics initiated from WAN would be blocked, including DMZ, Virtual Server, and ACL
WAN side.
Enabled: It activates your SPI function.
Disabled: It disables the SPI function.
Page 85

79
5.4.3.2 Routing
This is st
atic route feature. You are equipped with the capability to control the routing of all the traffic across your
network. With each routing rule created, user can specifically assign the destination where the traffic will be
routed to.
#: Item number
Destination IP Address: IP address of the destination network
Subnet Mask: The subnet mask of destination network.
Gateway IP Address: IP address of the gateway or existing interface that this route uses.
Metric: It represents the cost of transmission for routing purposes. The number need not be precise, but it must
be between 1 and 15.
Interface: Media/channel selected to append the route.
Edit: Edit the route; this icon is not shown for system default route.
Drop: Drop the route; this icon is not shown for system default route.
Page 86

80
ADD Route
Destination IP Address: This is the destination subnet IP address.
Destination Subnet Mask: The subnet mask of destination network.
Gateway IP Address/Interface:This is the gateway IP address or existing interface to which packets are to be
forwarded.
Metric:It represents the cost of transmission for routing purposes. The number need not be precise, but it must
be between 1 and 15.
Page 87

81
5.4.3.3 NAT
The NA
T (Network Address Translation) feature transforms a private IP into a public IP, allowing multiple users
to access the internet through a single IP account, sharing the single IP address. NAT break the originally
envisioned model of IP end-to-end connectivity across the internet so NAT can cause problems where IPSec/
PPTP encryption is applied or some application layer protocols such as SIP phones are located behind a NAT.
And NAT makes it difficult for systems behind a NAT to accept incoming communications.
In this session, there are “VPN Passthrough”, “SIP ALG”, “DMZ” and “Virtual Server” provided to solve these
nasty problems.
NAT Status: Enabled by default.
VPN Passthrough: VPN pass-through is a feature of routers which allows VPN client on a private network to
establish outbound VPNs unhindered.
SIP ALG: Enable the SIP ALG when SIP phone needs ALG to pass through the NAT. Disable the SIP ALG when
SIP phone includes NAT-Traversal algorithm.
Interface: Select to set DMZ/Virtual Server for “EWAN”, “3G_1” or “3G_2”.
Click
or to move on to set the DMZ or Virtual Server parameters, which are represented in
the following scenario.
Page 88

82
DMZ
The DMZ Host is a local computer exposed to the Internet. When setting a particular internal IP address as the
DMZ Host, all incoming packets will be checked by the Firewall and NAT algorithms then passed to the DMZ
host, when a packet received does not use a port number used by any other Virtual Server entries.
DMZ for: Indicate the related WAN interface which allows outside network to connect in and communicate.
Note: Here you can see the Sing IP Account/EWAN. It is the interface set in the previous NAT page.
DMZ:
Disabled: It disables the DMZ function.
Enabled: It activates your DMZ function.
DMZ Host IP Address: Give a static IP address to the DMZ Host when Enabled radio button is checked. Be
aware that this IP will be exposed to the WAN/Internet.
Select the SAVE button to apply your changes.
Page 89

83
Virtual Server
In TCP/IP networks a port is a 16-bit number used to identify which application program (usually a server)
incoming connections should be delivered to. Some ports have numbers that are pre-assigned to them by the
IANA (the Internet Assigned Numbers Authority), and these are referred to as “well-known ports”. Servers follow
the well-known port assignments so clients can locate them.
If you wish to run a server on your network that can be accessed from the WAN (i.e. from other machines on the
Internet that are outside your local network), or any application that can accept incoming connections (e.g.
Peer-to-peer/P2P software such as instant messaging applications and P2P file-sharing applications) and are
using NAT (Network Address Translation), then you will usually need to configure your router to forward these
incoming connection attempts using specific ports to the PC on your network running the application. You will
also need to use port forwarding if you want to host an online game server.
The reason for this is that when using NAT, your publicly accessible IP address will be used by and point to your
router, which then needs to deliver all traffic to the private IP addresses used by your PCs. Please see the WAN
configuration section of this manual for more information on NAT.
The device can be configured as a virtual server so that remote users accessing services such as Web or FTP
services via the public (WAN) IP address can be automatically redirected to local servers in the LAN network.
Depending on the requested service (TCP/UDP port number), the device redirects the external service request
to the appropriate server within the LAN network.
Virtual Server for: Indicate the related WAN interface which allows outside network to connect in and
communicate.
Protocol: Choose the application protocol.
Start Port Number: Enter a port number as the starting number of the range which you want to give access to
internal server.
End Port Number: Enter a port number as the end number of the range which you want to give access to
internal server..
Local IP Address: Enter your server IP address in this field.
Page 90

84
Examples of well-known and registered port numbers are shown below. For further information, please see
IANA’s website at http://www.iana.org/assignments/port-numbers
Well-known and Registered Ports
Port Number Protocol Description
21 TCP FTP Control
22 TCP & UDP SSH Remote Login Protocol
23 TCP Telnet
25 TCP SMTP (Simple Mail Transfer Protocol)
53 TCP & UDP DNS (Domain Name Server)
69 UDP TFTP (Trivial File Transfer Protocol)
80 TCP World Wide Web HTTP
110 TCP POP3 (Post Office Protocol Version 3)
443 TCP & UDP HTTPS
1503 TCP T.120
1720 TCP H.323
7070 UDP RealAudio
If you have a FTP server in your LAN network, and want to be accessing through WAN, you can have it set as
virtual server.
Page 91

85
Some tips for using DMZ and Virtual Server:
Using port forwarding does have security implications, as outside users will
be able to connect to PCs on your network. For this reason you are advised to
use specific Virtual Server entries just for the ports your application requires,
instead of using DMZ. As doing so will result in all connections from the WAN
attempt to access to your public IP of the DMZ PC specified
.
If you have disabled the NAT option in the WAN-ISP section, the Virtual Server
function will hence be invalid.
If the DHCP server option is enabled, you have to be very careful in assigning
the IP addresses of the virtual servers in order to avoid conflicts. The easiest
way of configuring Virtual Servers is to manually assign static IP address to
each virtual server PC, with an address that does not fall into the range of IP
addresses that are to be issued by the DHCP server. You can configure the
virtual server IP address manually, but it must still be in the same subnet as
the router.
Attention
Page 92

86
5.4.3.4 Static DNS
The Domain Name Syst
em (DNS) is a hierarchical naming system built on a distributed database for computers,
services, or any resource connected to the Internet or a private network associates various information with
domain names assigned to each of the participating entities. Most importantly, it translates domain names
meaningful to humans into the numerical identifiers associated with networking equipment for the purpose of
locating and addressing these devices worldwide.
An often-used analogy to explain the Domain Name System is that it serves as the phone book for the Internet
by translating human-friendly computer hostnames into IP addresses. For example, the domain name
www.example.com can be translated into the addresses 192.0.32.10 (IPv4).
Static DNS is a concept relative to Dynamic DNS, in static DNS system, the IP mapped is static without change.
IP Address: The IP address you are going to give a specific domain name.
Domain Name: The friendly domain name for the IP address.
Press SAVE button to apply your settings.
Page 93

87
5.4.3.5 QoS
QoS help
s you control the upload traffic of each application from LAN(Ethernet and/or Wireless) to WAN
(Internet).
It facilitates you the features to control the quality of throughput for each application. This is useful when there
on certain types of data you want giver higher priority to, such as voice data packets given higher priority than
web data packets.
QoS can be toggled Activated and Deactivated. QoS must be activated before you can edit the following
options. When you are done making changes, click on SAVE to save your changes.
Click on Rule&Action Summary to view the list of QoS rules that have been added.
Rule
You can set 16 different QoS rules. Each QoS rule has its detail setting conditions like: Physical Ports, IP, Port,
Protocol, etc, you can modify the value to any new one you wish. Please notice that only when the packet fulfill
every detail setting conditions here, then this packet will be remarked as the priority queue of each rule. The
non-selected setting part will be treated as “don’t care” and the system will not handle this setting part.
Rule Index: Select 16 different rules, each rule’s detail can be set and saved.
Active: Select whether to activate the rule.
Destination IPv4/IPv6: Set the IPv4/IPv6 address that you want to filter on destination side.
Mask/Prefix: Specify the Mask for IPv4 or prefix for IPv6.
Port Range: Set the port range value that you want to filter on destination side.
Source IPv4/IPv6: Set the IP address value that you want to filter on source side in IPv4 or IPv6.
Mask/Prefix: Specify the Mask for IPv4 or prefix for IPv6.
Port Range: Set the port range value that you want to filter on source side.
Protocol ID: Set the protocol ID type of packets that you want to filter (TCP, UDP, ICMP, IGMP).
Priority: Select to prioritize the traffic which the rule categorizes. High and Low.
Page 94

88
5.4.3.6 Interface Grouping (6300NXL
only)
Interface grouping is a function to group interfaces, known as VLAN. A Virtual LAN, commonly known as a VLAN,
is a group of hosts with the common set of requirements that communicate as if they were attached to the same
broadcast domain, regardless of the physical location. A VLAN has the same attributes as a physical LAN, but it
allows for end stations to be grouped together even if they are not located on the same network switch.Similarly
,
they may also have been split into two different groups, even if they are on the same switch.
Each group will perform as an independent network. To support this feature, you must create mapping groups
with appropriate LAN and WAN interfaces using the SAVE button.
Active: Select Yes to enable Interface Grouping feature.
Group Index: The index number indicating the current goup ranging from 0 to 15.
EWAN Service: The available EWAN interface. Move to 5.4.1 Interface Setup
to add other EWAN interface.
Ethernet: The available Ethernet ports.
WLan: The available wireless ports.
Group Summary: Press PortBinding Summary to check the current group information.
For example, you can create two EWAN services, Service0(PPPoE) and Service1(Bridge).
Page 95

89
You are going to group the ports and services into two working group, as shown below.
Group Index Group Port
0 ewan0_0,e3,e4,w2,w3,w4
1 ewan0_1,e1,e2,w1
Click PortBinding Summary to show the configuration results.
Page 96

90
5.4.3.6 IPSEC Setting (6300NX only)
A V
irtual Private Network (VPN) is a private network that interconnects remote (and often geographically
separate) networks through primarily public communication infrastructures such as the Internet. VPNs provide
security through tunneling protocols and security procedures such as encryption. For example, a VPN could be
used to securely connect the branch offices of an organization to a head office network through the public
Internet.
Internet Protocol Security (IPSec) is a protocol suite for securing Internet Protocol (IP) communications by
authenticating and encrypting each IP packet of a communication session. IPsec also includes protocols for
establish
ing mutual authentication between agents at the beginning of the session and negotiation of
cryptographic keys to be used during the session.
IPSec is an
end-to-end security scheme operating in the Internet Layer of the Internet Protocol Suite. It can be
used in protecting data flows between a pair of s
ecurity gateways (network-to-network), or between a security
gateway and a host (network-to-host).
A total of 8 IPSec tunnels can be added.
Page 97

91
Click Add New Connection to create IPSec connections.
VPN Connection Setting
Active: Select Yes to activate the tunnel.
Connection Name: A given name for the connection (e.g. “connection to office”).
Interface: Select the set used interface for the IPSec connection, when you select EWAN interface, the IPSec
tunnel would transmit data via this interface to connect to the remote peer.
Remote Gateway IP: The WAN IP address of the remote VPN gateway that is to be connected, establishing a
VPN tunnel.
Local Access Range: Set the IP address or subnet of the local network.
Single IP: The IP address of the local host, for establishing an IPSec connection between a security
gateway and a host (network-to-host).
Subnet: The subnet of the local network, for establishing an IPSec tunnel between
a pair of security
gateways (network-to-network)
Remote Access Range: Set the IP address or subnet of the remote network.
Single IP: The IP address of the local host, for establishing an IPSec connection between a security
gateway and a host (network-to-host). If the remote peer is a host, select Single Address.
Subnet: The subnet of the local network, for establishing an IPSec tunnel between a pair of security
gateways (network-to-network), If the remote peer is a network, select Subnet.
IKE Mode: IKE, Internet Key Exchange, is the mechanism to negotiate and exchange parameters and keys
between IPSec peers to establish security associations(SA). Select Main or Aggressive mode.
Pre-Shared Key: This is for the Internet Key Exchange (IKE) protocol, a string from 4 to 128 characters. Both
sides should use the same key. IKE is used to establish a shared security policy and authenticated keys for
services (such as IPSec) that require a key. Before any IPSec traffic can be passed, each router must be able
to verify the identity of its peer. This can be done by manually entering the pre-shared key into both sides
(router or hosts).
Local ID Type and Remote ID Type: When the mode of IKE is aggressive, Local and Remote peers can be
identified by other IDs.
IDContent: Enter IDContent the name you want to identify when the Local and Remote Type are Domain
Name; Enter IDContent IP address you want to identify when the Local and Remote Type are IP addresses
Page 98

92
(IPv4 and IPv6 supported).
Encryption Algorithm: Select the encryption algorithm from the drop-down menu. There are several options:
DES and AES (128, 192 and 256). 3DES and AES are more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption method.
AES: Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as encryption
method.
Authentication Algorithm: Authentication establishes the integrity of the datagram and ensures it is not
tampered with in transmission. There are 3 options: Message Digest 5 (MD5) and Secure Hash Algorithm
(SHA1, SHA256). SHA1 is more resistant to brute-force attacks than MD5. However, it is slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
SHA1: A one-way hashing algorithm that produces a 160−bit hash.
Diffle-Hellman Group: It is a public-key cryptography protocol that allows two parties to establish a shared
secret over an unsecured communication channel (i.e. over the Internet). MODP stands for Modular
Exponentiation Groups.
IPSec Proposal: Select the IPSec security method. There are two methods of verifying the authentication
information, AH(Authentication Header) and ESP(Encapsulating Security Payload). Use ESP for greater
security so that data will be encrypted and the data origin be authenticated but using AH data origin will only be
authenticated but not encrypted.
Authentication Algorithm: Authentication establishes the integrity of the datagram and ensures it is not
tampered with in transmission. There are 3 options: Message Digest 5 (MD5) and Secure Hash Algorithm
(SHA1, SHA256). SHA1 is more resistant to brute-force attacks than MD5. However, it is slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
SHA1: A one-way hashing algorithm that produces a 160−bit hash.
Encryption Algorithm: Select the encryption algorithm from the drop-down menu. There are several options:
DES and AES (128, 192 and 256). 3DES and AES are more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption method.
AES: Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as encryption
method.
SA Lifetime: Specify the number of minutes that a Security Association (SA) will stay active before new
encryption and authentication key will be exchanged. There are two kinds of SAs, IKE and IPSec. IKE
negotiates and establishes SA on behalf of IPSec, an IKE SA is used by IKE.
Phase 1 (IKE): To issue an initial connection request for a new VPN tunnel. The range can be from 5 to
15,000 minutes, and the default is 480 minutes.
Phase 2 (IPSec): To negotiate and establish secure authentication. The range can be from 5 to 15,000
minutes, and the default is 60 minutes. A short SA time increases security by forcing the two parties to
update the keys. However, every time the VPN tunnel re-negotiates, access through the tunnel will be
temporarily disconnected.
PING for Keep Alive:
None: The default setting is None. To this mode, it will not detect the remote IPSec peer has been lost
or not. It only follows the policy of Disconnection time after no traffic, which the remote IPSec will be
disconnected after the time you set in this function.
PING: This mode will detect the remote IPSec peer has lost or not by pinging specify IP address.
DPD: Dead
peer detection (DPD) is a keeping alive mechanism that enables the router to be detected
lively when the connection between the router and a remote IPSec peer has lost. Please be noted, it
must be enabled on the both sites.
PING to the IP: It is able to IP Ping the remote PC with the specified IP address and alert when the connection
fails. Once alter message is received, Router will drop this tunnel connection. Reestablish of this connection is
Page 99

93
required. Default setting is 0.0.0.0 which disables the function
Interval: This sets the time interval between Pings to the IP function to monitor the connection status. Default
interval setting is 10 seconds. Time interval can be set from 0 to 3600 second, 0 second disables the function.
Ping to the IP Interval (sec) Ping to the IP Action
0.0.0.0 0 No
0.0.0.0 2000 No
xxx.xxx.xxx.xxx (A valid IP Address) 0 No
xxx.xxx.xxx.xxx(A valid IP Address) 2000
Yes, activate it in every 2000 second.
Disconnection Time after no traffic: It is the NO Response time clock. When no traffic stage time is beyond
the Disconnection time set, Router will automatically halt the tunnel connection and re-establish it base on the
Reconnection Time set. 180 seconds is minimum time interval for this function.
Reconnection Time: It is the reconnecting time interval after NO TRAFFIC is initiated. 3 minutes is minimum
time interval for this function.
Click SAVE to submit the settings.
Page 100

94
Examples:
1. LAN-to-LAN connection
Two BiPAC 6300NXs want to setup a secure IPSec VPN tunnel
Note: The IPSec Settings shall be consistent between the two routers.
 Loading...
Loading...