Avaya ERS 2500, ERS 4500, ERS 5000 Technical Configuration Manual

> Management Access Security for ERS
2500, ERS 4500, and ERS 5000
Technical Configuration Guide
Avaya Data Solutions
Document Date: May 31, 2010
Document Number: NN48500-594
Document Version: 1.0
Ethernet Routing Switch
2500, 4500, 5000
Engineering
1
avaya.com
No
Date
Version
Revised by
Remarks
1
05/19/2010
1.0
PRMGT
Modifications to Software Baseline section
Abstract
This document provides examples on configuring various items related to accessing the ERS
2500, 4500, and 5000 securely for management purposes. This document covers accessing the
switch using telnet, HTTP, SSL, SSH, and SNMP.
Revision Control
Avaya Inc. – External Distribution
2
avaya.com
Table of Contents
Conventions ................................................................................................................................... 4
1. Overview ................................................................................................................................. 5
2. Management IP Address ....................................................................................................... 6
3. Local password protection ................................................................................................... 7
3.1 CLI/WEB Password Protection ........................................................................................ 7
3.2 Password Security ........................................................................................................... 8
3.3 Telnet Password Protection using Local Authentication ............................................... 10
3.4 Telnet Access Configuration Examples using Local Users with Password Security
disabled ..................................................................................................................................... 11
3.4.1 Local Password Configuration - Password Security Disabled ..................................................11
3.4.2 Verify Operations .....................................................................................................................12
3.4.3 Local Password Configuration - Password Security Enabled ...................................................13
4. IP Manager ............................................................................................................................ 14
4.1 IP Manager Configuration Example ............................................................................... 15
5. Telnet Password Protection using RADIUS Authentication ........................................... 16
5.1 Password Fallback ......................................................................................................... 17
5.2 Use Management IP ...................................................................................................... 18
5.3 RADIUS Password Configuration Example ................................................................... 19
5.3.1 Ethernet Routing Switch Configuration ....................................................................................19
5.3.2 IDE RADIUS Configuration ......................................................................................................20
6. TACACS+ .............................................................................................................................. 26
6.1 TACACS+ Configuration Example ................................................................................ 27
6.1.1 Ethernet Routing Switch Configuration ....................................................................................27
6.1.1.1 Ethernet Routing Switch Verify Operations .................................................................................. 27
6.1.2 IDE TACACS+ Configuration ...................................................................................................28
7. SSHv2 ................................................................................................................................... 33
7.1 SSH Configuration Examples ........................................................................................ 34
7.1.1 SSH using Password Authentication ........................................................................................34
7.1.2 Verify Operations .....................................................................................................................37
7.1.3 SSH using Public Key Authentication .......................................................................................38
7.1.4 Verify Operations .....................................................................................................................43
8. WEB Access – Enterprise Device Manager ...................................................................... 44
9. Secure Socket Layer Protocol – SSL................................................................................. 45
10. Simple Network Management Protocol - SNMP ........................................................... 47
10.1 SNMP Basic Operations ................................................................................................ 47
10.2 SNMPv1 Community Strings ......................................................................................... 47
10.3 SNMP MIB View ............................................................................................................ 48
10.4 SNMP Trap Receivers ................................................................................................... 49
10.5 SNMP System Name, Contact, and Location ............................................................... 50
10.6 Disable SNMPv1 and SNMPv2 ..................................................................................... 50
10.7 SNMPv3 ......................................................................................................................... 51
10.8 Enabling Secure SNMP ................................................................................................. 52
Avaya Inc. – External Distribution
3
avaya.com
10.9 SNMP Configuration Examples ..................................................................................... 53
10.9.1 SNMP Community String Configuration Example ................................................................53
10.9.2 Verify Operations .................................................................................................................54
10.9.3 SNMPv3 Configuration Example .........................................................................................56
10.9.4 Verify Operations .................................................................................................................57
10.10 SNMP Trap Notification Control ................................................................................ 59
11. Software Baseline:........................................................................................................... 61
12. Reference Documentation: ............................................................................................. 61
Avaya Inc. – External Distribution
4
avaya.com
Tip – Highlights a configuration or technical tip.
Note – Highlights important information to the reader.
Warning – Highlights important information about an action that may result in equipment
damage, configuration or data loss.
Bold text indicates emphasis.
Italic text in a Courier New font indicates text the user must enter or select in a menu item, button
or command:
ERS5520-48T# show running-config
Output examples from Avaya devices are displayed in a Lucinda Console font:
ERS5520-48T# show running-config
! Embedded ASCII Configuration Generator Script
! Model = Ethernet Routing Switch 5520-24T-PWR
! Software version = v5.0.0.011
enable
configure terminal
Conventions
This section describes the text, image, and command conventions used in this document.
Symbols:
Text:
Avaya Inc. – External Distribution
5
avaya.com
If SSH is required, the secure version of the software must be installed on the switch.
For each switch model, there is a secure image and standard software image available.
All switches ship with the standard agent image installed.
1. Overview
On an ERS 2500, ERS 4500, or ERS 5000 series switch, there is no access security enabled by
default. This allows a user to access the switch either via the local serial port, HTTP (WEB), or via
Telnet without any user name or password protection. Password protection for Telnet, WEB, or
SSH (user name & password) can be added using local user names and passwords or
authenticating against an external RADIUS or TACACS+ server. In regards to SSH, password
authentication can be enable or disabled in addition to using SSH with public key authentication.
By default, SNMPv1/SNMPv2c is enabled using read and write community strings of public and
private. This can be changed if you wish to use community strings for authentication. Or for
added security, you may wish to disable SNMPv1 and SNMPv2c and only use SNMPv3.
For added security, a source IP manager control list can be added. This list can contain
anywhere from 1 to 50 source IPv4 and/or IPv6 addresses, up to 50 each, that are allowed
access to the switch. This control list in turn can be applied to any access method including
SNMP, SSH, Telnet, and/or WEB.
Avaya Inc. – External Distribution
6
avaya.com
By default all stackable switches will attempt to obtain an IP management address if one
has not been configured. The ERS 4500 and ERS 5000 support both bootp and DHCP,
while the ERS 2500 supports bootp.
Please note that the management VLAN must be created and assigned as a
management VLAN prior to adding an IP address either via the L2 or L3 method. Also, a
brouter port cannot be used as the management IP address.
The Ethernet Routing Switch provides 2 additional means to be able to configure a
management IP Address.
If you connect to the serial console port of a switch with a factory default configuration,
then the switch will automatically start the quickinstall command, which prompts you for
IP address configuration information.
Alternatively you can pre-stage the management IP address plus software and
configuration information if required using the staging function by including a file IP.cfg
in the root directory of a USB drive when you power on the switch.
2. Management IP Address
Before adding any type of remote access, we need to add an IP address to the switch and/or
stack. An IP address can be added in one of two ways. If the switch is strictly used as a Layer 2
switch, then an IP address can be added via the Layer 2 method using the CLI command ip
address <switch|stack> <IP address> netmask <mask> default-gateway <default GW>.
Otherwise, if the switch is configured for Layer 3, it is recommended to add the switch address via
the VLAN interface level.
Layer 2 method assuming the Management VLAN is 200 using a standalone switch
o ERS-Stackable(config)# vlan create 200 name mgmt type port 1
o ERS-Stackable(config)# vlan mgmt 200
o ERS-Stackable(config)# ip address switch 10.1.1.10 netmask 255.255.255.0
default-gateway
Layer 3 method assuming the Management VLAN is 200
o ERS-Stackable(config)# vlan create 200 name mgmt type port 1
o ERS-Stackable(config)# vlan mgmt 200
o ERS-Stackable(config)# interface vlan 200
o ERS-Stackable(config-if)# ip address 10.1.1.10 255.255.255.0
o ERS-Stackable(config-if)# exit
o ERS-Stackable(config)# ip routing
o ERS-Stackable(config)# ip route <destination ip> <destination mask> <next
hop ip> <1-65535>
Avaya Inc. – External Distribution
7
avaya.com
Enabling telnet password protection, either local user/password or against a RADIUS
server, also applies to WEB access.
For the standard image, the default password for the read-only user is user and secure
for the read-write user. For the secure software image, the default password for the
read-only user is userpasswd and securepswd for the read-write user. The default readonly user name is RO while the default read-write user name is RW. Please note, these
user names and passwords are only applicable once you enable local password
security.
3. Local password protection
3.1 CLI/WEB Password Protection
By default, on the ERS 2500, ERS 4500, or ERS 5000 series switch, serial port and telnet/web
access is allowed without any password protection.
The following command displays the various password options available.
ERS-Stackable(config)# cli password ?
read-only Modify read-only password
read-write Modify read-write password
serial Enable/disable serial port password.
stack Modify stack passwords.
switch Modify switch (stand-alone) passwords.
telnet Enable/disable telnet and web password.
The following command displays the various telnet access options. The choices are local user
name & password protection, none, radius, or tacacs.
ERS-Stackable(config)# cli password <switch|stack> telnet ?
local Use local password.
none Disable password.
radius Use RADIUS password authentication.
tacacs Use TACACS+ AAA services
The following command displays the various local serial port access options. The choices are
local user name & password protection, none, radius, or tacacs
ERS-Stackable(config)# cli password serial ?
local Use local password.
none Disable password.
radius Use RADIUS password authentication.
tacacs Use TACACS+ AAA services
To add a user name, enter the following command when password security is disabled – please
see next section regarding Password Security.
ERS-Stackable(config)# username <user name> <password>
Avaya Inc. – External Distribution
8
avaya.com
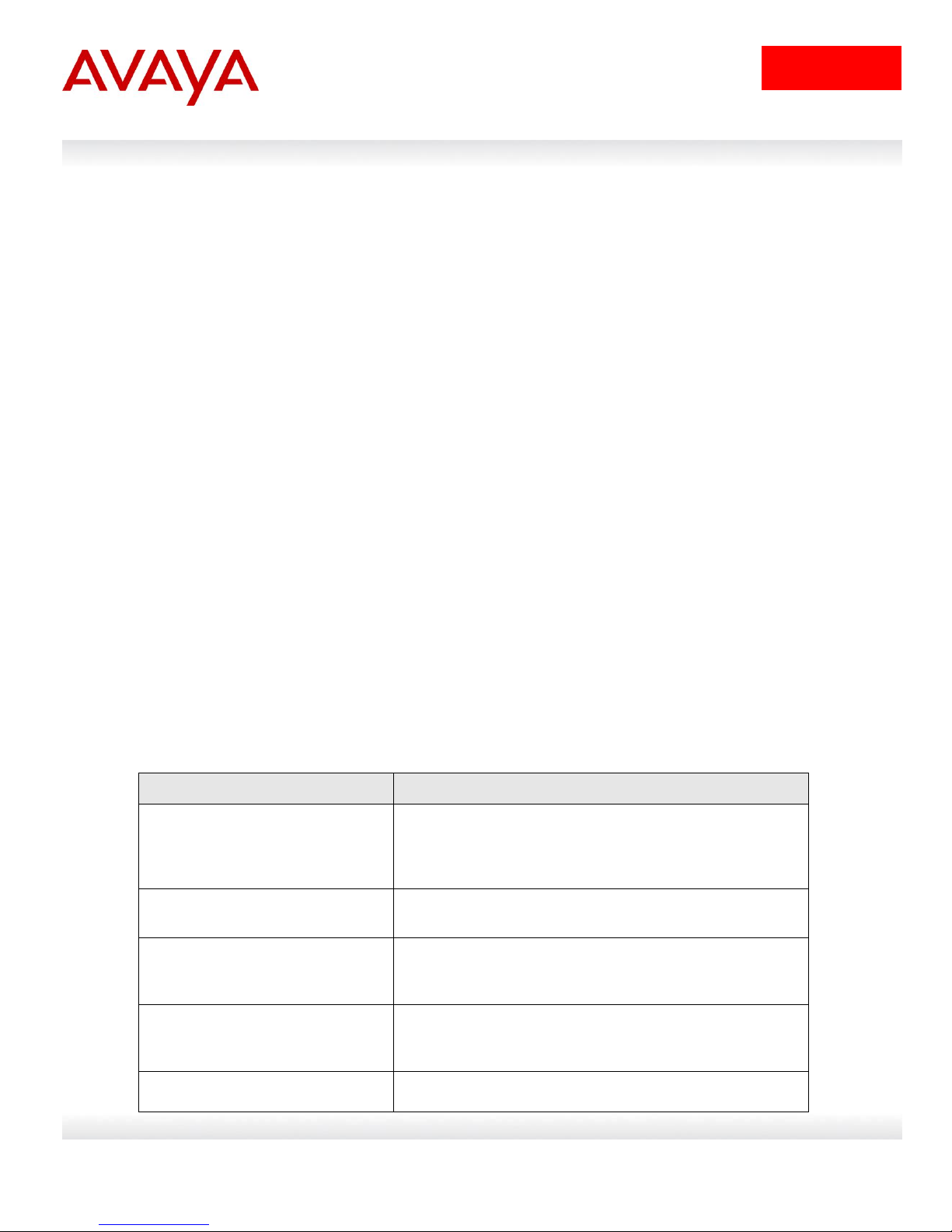
Feature/Requirement
Description
Password composition
The password must contain a minimum of 2 of each of
the following types of characters: lowercase letters,
capital letters, numbers, and special symbols such as
!@#$%^&*().
Password length
The password must consist of between 10 and 15
characters.
Log on attempts
The switch allows only a specified maximum number of
consecutive failed log on attempts. The number of
allowed retries is configurable. The default is three.
Password history
The switch can be configured to store up to 10 previously
used passwords. The passwords stored in the password
history until they pass out of the history table.
Password update verification
Any password change must be verified by typing the new
3.2 Password Security
Password security, if enabled, enhances password security for the switch or stack read-only
password and read-write passwords. By default, password security is disabled for the standard
software image and enabled for the secure software image. If password security is disabled,
there is no minimum restriction on number of characters required or are there any other
restrictions. If password security is enabled, then there are restrictions put into place where the
password must be between 10 and 15 characters containing at minimum 2 upper, 2 lowercase
characters, 2 numbers, and 2 special characters. Password security is enabled from the CLI
interface only.
To enable password security, enter the following command:
ERS-Stackable(config)# password security
To disable password security, enter the following command
ERS-Stackable(config)# no password security
When Password Security is disabled, upon enabling Password Security, you will be prompted
with the following text. Please note, all previous passwords will be cleared.
ERS-Stackable(config)# password security
% RO Switch password should have between 10 and 15 characters.
% Password should contain a minimum of 2 upper, 2 lowercase letters,
% 2 numbers and 2 special characters like !@#$%^&*().
% Please change the password
Enter RO Switch password: *************
% RW Switch password should have between 10 and 15 characters.
% Password should contain a minimum of 2 upper, 2 lowercase letters,
% 2 numbers and 2 special characters like !@#$%^&*().
% Please change the password
Enter RW Switch password: *************
Avaya Inc. – External Distribution
9
avaya.com
password twice.
Password aging time
Passwords expire after a specified period. The aging time
is configurable. The default is 180 days.
Password display masking
Any time a password is displayed or entered in NNCLI,
each character of the password is displayed as an
asterisk (*).
Password security factory default
By default, password security is enabled on the SSH
software image and disabled on the non-SSH software
image.
Avaya Inc. – External Distribution

10
avaya.com
These settings can be stored for both switch standalone operation and stack mode
operation. It is recommended to make the same setting for both switch standalone and
stack operation otherwise if a unit changes operational mode (e.g. unit removed from a
stack, or a stack of 2 units and 1 unit fails) then a different setting might become active.
3.3 Telnet Password Protection using Local
Authentication
To enable local telnet authentication on a standalone switch, enter the following command:
ERS-Stackable(config)# cli password telnet local
or
ERS-Stackable(config)# cli password switch telnet local
To enable local telnet authentication on a switch stack, enter the following command:
ERS-Stackable(config)# cli password stack telnet local
To verify the configuration, enter the following command:
ERS-Stackable(config)# show cli password type
Console Switch Password Type: None
Console Stack Password Type: None
Telnet/WEB Switch Password Type: Local Password
Telnet/WEB Stack Password Type: None
You have the choice of using the default user names and passwords to access the switch, using
the default passwords and changing the user names, and/or changing the default user names
and passwords. The default user names are RO and RW for the read-only and read-write users
respectively. For the standard image the default password for RO is user and secure for RW. For
the secure software image, the default password for RO is userpasswd and securepasswd for
RW.
To change the default switch or stack CLI passwords, enter the following commands:
ERS-Stackable(config)# cli password <switch|stack> read-only <RO password>
ERS-Stackable(config)# cli password <switch|stack> read-write <RW password>
To view the configuration, enter the following command:
ERS-Stackable# show cli password
Switch
Access Login Username / Password
------ --------- -----------------------------------RW RW RW / ***************
RO RO RO / ***************
Stack
Access Login Username / Password
------ --------- -----------------------------------RW RW RW / ***************
RO RO RO / ***************
Avaya Inc. – External Distribution

11
avaya.com
ERS-STACKABLE: Step 1 – Enable Password Security
ERS-Stackable(config)# no password security
ERS-STACKABLE: Step 2 – Add new user names and passwords
ERS-Stackable(config)# username user1 rwaccess stack rw
ERS-Stackable(config)# username user1 rwaccess switch rw
ERS-Stackable(config)# username user2 roaccess stack ro
ERS-Stackable(config)# username user2 roaccess switch ro
ERS-STACKABLE: Step 3 – Enable telnet local authentication
ERS-Stackable(config)# cli password stack telnet local
ERS-Stackable(config)# cli password switch telnet local
The default user names can be changed using the following CLI command:
ERS-Stackable(config)# username <user_name> <user_password> <switch|stack>
<ro|rw>.
3.4 Telnet Access Configuration Examples using Local
Users with Password Security disabled
3.4.1 Local Password Configuration - Password Security Disabled
For this configuration example, we will configure the following assuming we are using an
ERS5000 stack
Change the default read-write user name from RW to user1
Change the default read-only user name from RO to user2
Disable Password Security
o This applies to secure version as Password Security is enabled by default on
SSH switch server
For user1, use the password rwaccess
For user2, use the password roaccess
Avaya Inc. – External Distribution

12
avaya.com
Step 1 – Verify user names
ERS-Stackable(config)# show cli password
Result:
Switch
Access Login Username / Password
------ --------- -----------------------------------RW RW user1 / ***************
RO RO user2 / ***************
Stack
Access Login Username / Password
------ --------- -----------------------------------RW RW user1 / ***************
RO RO user2 / ***************
Step 2 – Verify that the cli password type is set for local
ERS-Stackable(config)# show cli password type
Result:
Console Switch Password Type: None
Console Stack Password Type: None
Telnet/WEB Switch Password Type: Local Password
Telnet/WEB Stack Password Type: Local Password
If you enable password security at this point, it will prompt you with the following:
ERS-Stackable(config)# password security
% RO Switch password should have between 10 and 15 characters.
% Password should contain a minimum of 2 upper, 2 lowercase letters,
% 2 numbers and 2 special characters like !@#$%^&*().
% Please change the password
Enter RO Switch password: **********
Confirm RO Switch password: **********
Enter RO Switch password: **********
Confirm RO Switch password: **********
3.4.2 Verify Operations
Avaya Inc. – External Distribution

13
avaya.com
ERS-STACKABLE: Step 1 – Add new user names and passwords
ERS-Stackable(config)# username admin stack rw
Enter password: ********* (AdminUser@#1234)
Confirm password: *********
ERS-Stackable(config)# username tech stack ro
Enter password: ********* (TechUser@#1234)
Confirm password: *********
ERS-STACKABLE: Step 2 – Enable telnet local authentication
ERS-Stackable(config)# cli password stack telnet local
ERS-Stackable(config)# cli password switch telnet local
3.4.3 Local Password Configuration - Password Security Enabled
For this configuration example, we will configure the following
Change the default read-write user name from RW to admin
Change the default read-only user name from RO to tech
Assuming Password Security is enabled by default
o This applies to secure version as Password Security is enabled by default on
SSH switch server
o With Password Security enabled, the password should contain a minimum of 2
upper, 2 lowercase letters, 2 numbers and 2 special characters like !@#$%^&*().
For admin, use the password AdminUser@#1234
For tech, use the password TechUser@#1234
Avaya Inc. – External Distribution
14
avaya.com
4. IP Manager
The IP Manager feature allows you to limit access to the management features on the switch by
defining the IP addresses that are allowed access to the switch. You can define up to 50 IPv4 and
50 IPv6 addresses with masks that are allowed to access the switch. If IP Manager is enabled, no
other IP addresses are allowed. Access to Telnet, SNMP, SSH, and Web-based management
can be configured.
ERS-Stackable(config)# ipmgr ?
snmp Enable IP Manager control over SNMP traffic.
source-ip Set source IP address from which connections are allowed
ssh Enable IP Manager control over SSH sessions.
telnet Enable IP Manager control over TELNET sessions.
web Enable IP Manager control over WEB connections.
ERS-Stackable(config)# ipmgr source-ip ?
<1-50> Select which address/mask pair
<51-100> Select which ipv6 address/prefix
Avaya Inc. – External Distribution
15
avaya.com
ERS-STACKABLE: Step 1 – Add the IP address to the IP manager list and enable telnet
ERS-Stackable(config)# ipmgr telnet
ERS-Stackable(config)# ipmgr source-ip 1 192.168.20.100 mask 255.255.255.255
ERS-Stackable(config)# ipmgr source-ip 2 192.168.30.0 mask 255.255.255.0
Step 1 – Verify IP Manager configuration
ERS-Stackable# show ipmgr
Result:
TELNET Access: Enabled
SNMP Access: Disabled
WEB Access: Disabled
SSH Access: Disabled
TELNET IP List Access Control: Enabled
SNMP IP List Access Control: Enabled
WEB IP List Access Control: Enabled
SSH IP List Access Control: Enabled
Allowed Source IP Address Allowed Source Mask
------------------------- -------------------
1 192.168.20.100 255.255.255.255
2 192.168.30.0 255.255.255.0
3 255.255.255.255 255.255.255.255
Step 2 – You can also view the user log using the following command
ERS-Stackable# show audit log telnet
Result:
dx Pri(/Timestamp/Host) Stat Source(Unit) Uptime Command
----------------------------------------------------------------|
74 <30>42:16:44:41 ERS-Stackable :S telnet(192.168.20.100): 42 days, 16:44:41:
configure terminal
75 <30>42:16:44:50 ERS-Stackable :S telnet(192.168.20.100): 42 days, 16:44:50:
vlan create 89 type port
77 <30>42:16:45:33 ERS-Stackable :S telnet(192.168.20.100): 42 days, 16:45:33:
exit
78 <30>42:16:45:38 ERS-Stackable :S telnet(192.168.20.100): 42 days, 16:45:38:
exit
4.1 IP Manager Configuration Example
Assuming we wish to restrict Telnet/WEB access to users with IPv4 addresses from unicast IP
address 192.168.20.100/32 and subnet 192.168.30.0/24, enter the following commands.
Ethernet Routing Switch Verify Operations
Avaya Inc. – External Distribution
16
avaya.com
5. Telnet Password Protection using
RADIUS Authentication
Users who access the Avaya switch or stack through Telnet, serial, or SSHv2 (password
authentication), can be authenticated against a RADIUS server. The ERS 5000, ERS 4500, and
ERS 2500 each support two different user access levels which are read-only and read-write with
support for up to two RADIUS servers. RADIUS attribute type 6, Service-Type, is used to
determine the access level. The following displays the complete list of RADIUS attribute values
for the RADIUS Service-Type attribute where value 6 (Administrative) is used for read-write
access and value 7 (NAS Prompt) is used for read-only access
Sub-registry: Values for RADIUS Attribute 6, Service-Type
Reference: [RFC2865][RFC3575]
Registration Procedures: IETF Consensus
Registry:
Value Description Reference
----- ------------------------------- ---------
1 Login
2 Framed
3 Callback Login
4 Callback Framed
5 Outbound
6 Administrative
7 NAS Prompt
8 Authenticate Only
9 Callback NAS Prompt
10 Call Check
11 Callback Administrative
12 Voice [Chiba]
13 Fax [Chiba]
14 Modem Relay [Chiba]
15 IAPP-Register [IEEE 802.11f][Kerry]
16 IAPP-AP-Check [IEEE 802.11f][Kerry]
17 Authorize Only [RFC3576]
18 Framed-Management [RFC5607]
To add a RADIUS server, enter the following command to view the various configurable options:
ERS-Stackable(config)# radius-server ?
host RADIUS primary host
key RADIUS shared secret
password RADIUS password fallback
port RADIUS UDP port
secondary-host RADIUS secondary host
timeout RADIUS time-out period
Avaya Inc. – External Distribution
17
avaya.com
For the ERS 4500, starting in release 5.4, ERS 5000 in release 6.2, or for the ERS
2500, starting in release 4.3, if using the use-radius setting when configuring the radius
reachability parameter, the switch will periodically send RADIUS requests using a user
name of avaya with a blank password. Hence, your RADIUS server must support blank
passwords. This is not the case with Avaya‟s Ignition Server which does not allow blank
passwords. If using Ignition Server, use the default setting of use-icmp.
Please note the radius reachability parameter is not available in the latest release
(6.1.2) of the ERS5000 series and will be added in release 6.2. By default, the switch
will periodically send RADIUS requests using a user name of nortel with a blank
password to determine RADIUS server reachability. Again, Avaya‟s Ignition Server does
not allow blank passwords, thus, RADIUS requests from an ERS5000 will be rejected.
To view the various RADIUS settings, enter the following command:
ERS-Stackable(config)# radius ?
Configure RADIUS settings
accounting Configure RADIUS accounting settings
dynamic-server RADIUS Dynamic Authorization Client settings
reachability Configure RADIUS server reachability settings
use-management-ip Enable Radius use-management-ip flag.
Up to two RADIUS servers can be configured. Staring in release 5.4 for the ERS4500 and 4.3 for
the ERS2500, the radius reachability setting allows either ICMP packets or dummy RADIUS
requests to determine if the primary RADIUS server is reachable. By default, ICMP is enabled. If
you wish to use dummy RADIUS requests, the switch will generate a regular RADIUS requests
periodically with the username avaya and a blank password. Hence, it is recommended that you
setup an account with the user name avaya and a blank password on your RADIUS server to
avoid invalid RADIUS user login messages. The following command is used to configure the
reachability setting:
ERS-Stackable(config)# radius reachability ?
use-icmp Enable RADIUS server reachability using ICMP
use-radius Enable RADIUS server reachability using RADIUS requests
5.1 Password Fallback
The RADIUS password fallback feature allows the user to log on to the switch or stack by using
the local password if the RADIUS server is unavailable or unreachable for authentication.
RADIUS password fallback is disabled by default.
To enable RADIUS password fallback, please enter the following command
ERS-Stackable(config)# radius-server password fallback
Avaya Inc. – External Distribution
18
avaya.com
5.2 Use Management IP
By default, if Layer 3 is enabled, the switch will use the outgoing interface IP address when
attempting access to the RADIUS server. If you have multiple outgoing interfaces that can reach
the RADIUS server, normally you will have to configure your RADIUS server with each of
interface IP addresses used on the switch. However, the radius use-management-ip command
can be issued to tell the switch to use the switch management IP address for all RADIUS
requests independent of the out-going interface.
To enable RADIUS Management IP, please enter the following command
ERS-Stackable(config)# radius use-management-ip
Avaya Inc. – External Distribution
 Loading...
Loading...