Page 1

BCM50e Integrated Router Configuration - Advanced
BCM50e
Business Secure Router
Document Number: N0115789
Document Version: 1.0
Date: August 2006
Page 2

2
Copyright © Nortel 2005–2006
All rights reserved.
The information in this document is subject to change without notice. The statements, configurations, technical data, and
recommendations in this document are believed to be accurate and reliable, but are presented without express or implied
warranty. Users must take full responsibility for their applications of any products specified in this document. The
information in this document is proprietary to Nortel.
Trademarks
Nortel, Nortel (Logo), the Globemark, and This is the way, This is Nortel (Design mark) are trademarks of Nortel.
Microsoft, MS, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation.
All other trademarks and registered trademarks are the property of their respective owners.
N0115789N0115789
Page 3

Contents
Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Before you begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Text conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Related publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Hard-copy technical manuals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
How to get help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
USA and Canada Authorized Distributors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
EMEA (Europe, Middle East, Africa) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
CALA (Caribbean & Latin America) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
APAC (Asia Pacific) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
3
Technical Support - GNTS/GNPS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Presales Support (CSAN) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Technical Support - CTAS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Technical Support - CTAS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Technical Support - GNTS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Chapter 1
Getting to know your BCM50e Integrated Router. . . . . . . . . . . . . . . . . . . . 29
Introducing the BCM50e Integrated Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
Physical features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
4-Port switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Autonegotiating 10/100 Mb/s Ethernet LAN . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Autosensing 10/100 Mb/s Ethernet LAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Autonegotiating 10/100 Mb/s Ethernet WAN . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Time and date . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Reset button . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Nonphysical features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
BCM50e Integrated Router Configuration - Advanced
Page 4

4 Contents
Applications for the BCM50e Integrated Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
IPSec VPN capability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
HTTPS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Brute force password guessing protection . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Content filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Packet filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Universal Plug and Play (UPnP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Call scheduling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
PPPoE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
PPTP Encapsulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Dynamic DNS support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
IP Multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
IP Alias . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Central Network Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Network Address Translation (NAT) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Traffic Redirect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Port Forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
DHCP (Dynamic Host Configuration Protocol) . . . . . . . . . . . . . . . . . . . . . . . . 35
Full network management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Road Runner support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Logging and tracing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Upgrade Business Secure Router Firmware . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Embedded FTP and TFTP Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Secure broadband internet access and VPN . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Chapter 2
Introducing the SMT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Introduction to the SMT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Navigating the SMT interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
N0115789
Initial screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Logging on to the SMT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Page 5

Contents 5
Main menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Changing the system password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
SMT menus at a glance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
SMT menu 1 - general setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Introduction to general setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Configuring general setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Configuring dynamic DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Chapter 3
WAN Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Introduction to WAN setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
WAN setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Chapter 4
LAN setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Introduction to LAN setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Accessing the LAN menus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
LAN port filter setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
TCP/IP and DHCP ethernet setup menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
IP Alias Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Chapter 5
Internet access. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Introduction to internet access setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Ethernet encapsulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Configuring the PPTP client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Configuring the PPPoE client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Basic setup complete . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Chapter 6
Remote Node setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Introduction to Remote Node setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Remote Node setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Remote Node profile setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Ethernet Encapsulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
BCM50e Integrated Router Configuration - Advanced
Page 6

6 Contents
Edit IP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Remote Node filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
Chapter 7
IP Static Route Setup. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
IP Static Route Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Chapter 8
Dial-in User Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Dial-in User Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Chapter 9
Network Address Translation (NAT). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
PPPoE Encapsulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Outgoing Authentication Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Nailed-Up Connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
PPTP Encapsulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Traffic Redirect setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Using NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
NAT setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Configuring a server behind NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
General NAT examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Configuring Trigger Port forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
N0115789
SUA (Single User Account) Versus NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Applying NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Address Mapping Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
SUA Address Mapping Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
User-Defined Address Mapping Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Ordering Your Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Internet access only . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Example 2: Internet access with an inside server . . . . . . . . . . . . . . . . . . . . . . . . 105
Example 3: Multiple public IP addresses with inside servers . . . . . . . . . . . . . . . 106
Page 7

Contents 7
Chapter 10
Introducing the firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Using SMT menus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Activating the firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Chapter 11
Filter configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Introduction to filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Filter Structure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Configuring a Filter Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Configuring a Filter Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Configuring a TCP/IP Filter Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Configuring a Generic Filter Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Example Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Filter Types and NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Firewall Versus Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Applying a Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Applying LAN Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Applying Remote Node Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Chapter 12
SNMP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
SNMP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
SNMP Traps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Chapter 13
System security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
System security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
System password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Configuring external RADIUS server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Chapter 14
System information and diagnosis . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Introduction to System Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
System Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
BCM50e Integrated Router Configuration - Advanced
Page 8

8 Contents
System information and console port speed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Log and trace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Chapter 15
Firmware and configuration file maintenance . . . . . . . . . . . . . . . . . . . . . 159
Filename conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Backup configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Restore configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
Uploading Firmware and Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
System Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Console port speed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Syslog logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
CDR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Packet triggered . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Filter log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
PPP log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
Firewall log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Call-Triggering packet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
WAN DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Backup configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Using the FTP command from the command line . . . . . . . . . . . . . . . . . . . . . . . . 161
Example of FTP commands from the command line . . . . . . . . . . . . . . . . . . . . . . 162
GUI-based FTP clients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
TFTP and FTP over WAN Management Limitations . . . . . . . . . . . . . . . . . . . . . . 162
Backup configuration using TFTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
TFTP command example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
GUI-based TFTP clients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
Restore Using FTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
Restore using FTP session example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Firmware file upload . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Configuration file upload . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
FTP file upload command from the DOS prompt example . . . . . . . . . . . . . . . . . 169
FTP Session Example of Firmware File Upload . . . . . . . . . . . . . . . . . . . . . . . . . 170
TFTP file upload . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
TFTP upload command example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
N0115789
Page 9

Contents 9
Chapter 16
System Maintenance menus 8 to 10 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Command Interpreter mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Command syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Command usage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Call control support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Budget management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Call History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Time and Date setting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Resetting the Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
Chapter 17
Remote Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Remote Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Remote Management Limitations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Chapter 18
Call scheduling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Appendix A
Setting up your computer IP address . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Windows 95/98/Me . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Installing components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Configuring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Verifying Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Windows 2000/NT/XP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Verifying Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Macintosh OS 8/9 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Verifying Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
Macintosh OS X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Verifying settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
Appendix B
BCM50e Integrated Router Configuration - Advanced
Page 10

10 Contents
Triangle Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
The Ideal Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
The Triangle Route Problem . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
The Triangle Route Solutions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
IP aliasing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Appendix C
Importing certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
Import Business Secure Router certificates into Netscape Navigator . . . . . . . . . . . . 207
Importing the Business Secure Router Certificate into Internet Explorer . . . . . . . . . . 208
Enrolling and Importing SSL Client Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Using a certificate when accessing the Business Secure Router example . . . . . . . . 221
Appendix D
PPPoE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
PPPoE in action . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
Benefits of PPPoE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
Traditional dial-up scenario . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
How PPPoE works . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
Business Secure Router as a PPPoE client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
Appendix E
PPTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
What is PPTP? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
PPTP and the Business Secure Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
PPTP protocol overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
Control and PPP connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
Appendix F
Hardware specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Cable pin assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
N0115789
How can we transport PPP frames from a PC to a broadband modem over
Ethernet? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Call connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
PPP data connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Page 11

Contents 11
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Appendix G
IP subnetting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
IP addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
IP classes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
Subnet masks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Subnetting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Example: two subnets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Example: four subnets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Example: eight subnets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Subnetting with Class A and Class B networks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Appendix H
Command Interpreter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Command Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Command usage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Sys commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
Exit Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Ethernet Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
IP commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
IPSec commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Sys firewall commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Bandwidth management commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Certificates commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Appendix I
NetBIOS filter commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Display NetBIOS filter settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
NetBIOS filter configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Example commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 277
Appendix J
BCM50e Integrated Router Configuration - Advanced
Page 12

12 Contents
Enhanced DHCP option commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 278
Enhanced DHCP option commands introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . 278
Nortel BCM50 DHCP server options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
Nortel i2004 IP phone options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
Nortel WLAN handsets 2210 & 2211 phone options . . . . . . . . . . . . . . . . . . . . . . . . . 283
Appendix K
Log descriptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
VPN/IPSec logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 293
VPN responder IPSec log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
Table 81 shows RFC-2408 ISAKMP payload types that the log displays. Refer to the RFC
for detailed information on each type. Log commands . . . . . . . . . . . . . . . . . . . . . . 299
Log command example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
Specifying the Nortel BCM50 IP address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 278
BCM50 DHCP server settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
BCM50 IP sets override setting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 280
VoIP server settings assignment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
VLAN ID assignment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 282
TFTP server IP address assignment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
WLAN IP Telephony Manager IP Address Assignment . . . . . . . . . . . . . . . . . . . . 284
Configuring what you want the Business Secure Router to log . . . . . . . . . . . . . . 302
Displaying logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
Appendix L
Brute force password guessing protection. . . . . . . . . . . . . . . . . . . . . . . . 305
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 307
N0115789
Page 13

Figures
Figure 1 Secure Internet Access and VPN Application . . . . . . . . . . . . . . . . . . . . . 37
Figure 2 Initial screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Figure 3 SMT Login . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Figure 4 Main menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Figure 5 Menu 23.1 System Security: Change Password . . . . . . . . . . . . . . . . . . . 43
Figure 6 SMT overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Figure 7 menu 1: general setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Figure 8 Configure dynamic DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Figure 9 Menu 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Figure 10 Menu 3: LAN setup. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Figure 11 Menu 3.1: LAN port filter setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Figure 12 Menu 3: TCP/IP and DHCP setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Figure 13 Figure 21-4 menu 3.2: TCP/IP and DHCP Ethernet setup . . . . . . . . . . . . 55
Figure 14 Menu 3.2.1: IP Alias setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Figure 15 Menu 4: internet access setup (Ethernet) . . . . . . . . . . . . . . . . . . . . . . . . 62
Figure 16 Internet access setup (PPTP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Figure 17 Internet access setup (PPPoE) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Figure 18 Menu 11 Remote Node Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Figure 19 Menu 11.1: Remote Node profile for Ethernet Encapsulation . . . . . . . . . . 69
Figure 20 Menu 11.1: Remote Node profile for PPPoE Encapsulation . . . . . . . . . . . 71
Figure 21 Menu 11.1: Remote Node Profile for PPTP Encapsulation . . . . . . . . . . . 73
Figure 22 Menu 11.1.2: Remote Node Network Layer Options for Ethernet
Figure 23 Menu 11.1.4: Remote Node filter (Ethernet Encapsulation) . . . . . . . . . . . 78
Figure 24 Menu 11.1.4: Remote Node filter (PPPoE or PPTP Encapsulation) . . . . . 78
Figure 25 Menu 11.1: Remote Node Profile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Figure 26 Menu 11.1.5: Traffic Redirect setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Figure 27 Menu 12: IP Static Route Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Figure 28 Menu 12. 1: Edit IP Static Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
13
Encapsulation 75
BCM50e Integrated Router Configuration - Advanced
Page 14

14 Figures
Figure 29 Menu 14- Dial-in User Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Figure 30 Menu 14.1- Edit Dial-in User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Figure 31 Menu 4: Applying NAT for Internet Access . . . . . . . . . . . . . . . . . . . . . . . . 90
Figure 32 Menu 11.1.2: Applying NAT to the Remote Node . . . . . . . . . . . . . . . . . . . 91
Figure 33 Menu 15: NAT Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Figure 34 Menu 15.1: Address Mapping Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Figure 35 Menu 15.1.255: SUA Address Mapping Rules . . . . . . . . . . . . . . . . . . . . . 94
Figure 36 Menu 15.1.1: First Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Figure 37 Menu 15.1.1.1: Editing or configuring an individual rule in a set . . . . . . . 98
Figure 38 Menu 15.2: NAT Server Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Figure 39 15.2.1: NAT Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Figure 40 Menu 15.2: NAT Server Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Figure 41 Multiple servers behind NAT example . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Figure 42 NAT Example 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Figure 43 Menu 4: Internet access & NAT example . . . . . . . . . . . . . . . . . . . . . . . . 104
Figure 44 NAT Example 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Figure 45 Menu 15.2: Specifying an inside server . . . . . . . . . . . . . . . . . . . . . . . . . 106
Figure 46 NAT example 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Figure 47 Example 3: Menu 11.1.2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Figure 48 Example 3: Menu 15.1.1.1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Figure 49 Example 3: Final Menu 15.1.1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Figure 50 Example 3: Menu 15.2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Figure 51 Menu 15.3: Trigger Port Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Figure 52 Menu 21: Filter and Firewall Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Figure 53 Menu 21.2: Firewall Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Figure 54 Outgoing packet filtering process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Figure 55 Filter rule process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Figure 56 Menu 21: Filter and Firewall Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Figure 57 Menu 21.1: Filter Set Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Figure 58 Menu 21.1.1.1: TCP/IP Filter Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
Figure 59 Executing an IP filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Figure 60 Menu 21.1.1.1: Generic Filter Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Figure 61 Telnet filter Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Figure 62 Example Filter: Menu 21.1.3.1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Figure 63 Example Filter Rules Summary: Menu 21.1.3 . . . . . . . . . . . . . . . . . . . . 132
N0115789
Page 15

Figures 15
Figure 64 Protocol and Device Filter Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Figure 65 Filtering LAN Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Figure 66 Filtering Remote Node Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Figure 67 Menu 22: SNMP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Figure 68 Menu 23 System security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Figure 69 Menu 23 system security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Figure 70 Menu 23.2 System Security: RADIUS server . . . . . . . . . . . . . . . . . . . . . 142
Figure 71 Menu 24: System Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
Figure 72 Menu 24.1: System Maintenance: Status . . . . . . . . . . . . . . . . . . . . . . . . 147
Figure 73 Menu 24.1 — System Maintenance — Status . . . . . . . . . . . . . . . . . . . . 147
Figure 74 System Information and Console Port Speed . . . . . . . . . . . . . . . . . . . . . 149
Figure 75 Menu 24.2.1: System Maintenance Information . . . . . . . . . . . . . . . . . . 150
Figure 76 Menu 24.2.2: System Maintenance: Change Console Port Speed . . . . 151
Figure 77 Menu 24.3: System Maintenance: Log and Trace . . . . . . . . . . . . . . . . . 151
Figure 78 Menu 24.3.2: System Maintenance: Syslog Logging . . . . . . . . . . . . . . . 152
Figure 79 Call-Triggering packet example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Figure 80 Menu 24.4: System Maintenance: Diagnostic . . . . . . . . . . . . . . . . . . . . 157
Figure 81 WAN & LAN DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Figure 82 Menu 24.5 - System Maintenance - Backup Configuration . . . . . . . . . . 161
Figure 83 FTP Session Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
Figure 84 Telnet into Menu 24.6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Figure 85 Restore using FTP session example . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Figure 86 Telnet Into Menu 24.7.1 Upload System Firmware . . . . . . . . . . . . . . . . 168
Figure 87 Telnet Into Menu 24.7.2 System Maintenance . . . . . . . . . . . . . . . . . . . 168
Figure 88 FTP Session Example of Firmware File Upload . . . . . . . . . . . . . . . . . . . 170
Figure 89 Command mode in Menu 24 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Figure 90 Valid commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Figure 91 Call Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Figure 92 Budget Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
Figure 93 Call History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Figure 94 Menu 24: System Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Figure 95 Menu 24.10 System Maintenance: Time and Date Setting . . . . . . . . . . 180
Figure 96 Menu 24.11 – Remote Management Control . . . . . . . . . . . . . . . . . . . . . 184
Figure 97 Menu 26 Schedule Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Figure 98 Menu 26.1 Schedule Set Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
BCM50e Integrated Router Configuration - Advanced
Page 16

16 Figures
Figure 99 Applying Schedule Sets to a Remote Node (PPPoE) . . . . . . . . . . . . . . . 190
Figure 100 WIndows 95/98/Me: network: configuration . . . . . . . . . . . . . . . . . . . . . . 192
Figure 101 Windows 95/98/Me: TCP/IP properties: IP address . . . . . . . . . . . . . . . . 193
Figure 102 Windows 95/98/Me: TCP/IP Properties: DNS configuration . . . . . . . . . . 194
Figure 103 Windows XP: Start menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Figure 104 Windows XP: Control Panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Figure 105 Windows XP: Control Panel: Network Connections: Properties . . . . . . . 196
Figure 106 Windows XP: Local Area Connection Properties . . . . . . . . . . . . . . . . . . 196
Figure 107 Windows XP: Advanced TCP/IP settings . . . . . . . . . . . . . . . . . . . . . . . . 197
Figure 108 Windows XP: Internet Protocol (TCP/IP) properties . . . . . . . . . . . . . . . . 198
Figure 109 Macintosh OS 8/9: Apple Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Figure 110 Macintosh OS 8/9: TCP/IP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
Figure 111 Macintosh OS X: Apple menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Figure 112 Macintosh OS X: Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Figure 113 Ideal Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Figure 114 Triangle Route Problem . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Figure 115 IP Alias . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
Figure 116 Security Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
Figure 117 Login Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
Figure 118 Certificate General Information before Import . . . . . . . . . . . . . . . . . . . . 209
Figure 119 Certificate Import Wizard 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Figure 120 Certificate Import Wizard 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
Figure 121 Certificate Import Wizard 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212
Figure 122 Root Certificate Store . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212
Figure 123 Certificate General Information after Import . . . . . . . . . . . . . . . . . . . . . . 213
Figure 124 Business Secure Router Trusted CA screen . . . . . . . . . . . . . . . . . . . . . 214
Figure 125 CA certificate example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Figure 126 Personal certificate import wizard 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Figure 127 Personal certificate import wizard 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 217
Figure 128 Personal certificate import wizard 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
Figure 129 Personal certificate import wizard 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 219
Figure 130 Personal certificate import wizard 5 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 220
Figure 131 Personal certificate import wizard 6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 220
Figure 132 Access the Business Secure Router via HTTPS . . . . . . . . . . . . . . . . . . 221
Figure 133 SSL client authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
N0115789
Page 17

Figures 17
Figure 134 Business Secure Router secure login screen . . . . . . . . . . . . . . . . . . . . . 222
Figure 135 Single-PC per Router Hardware Configuration . . . . . . . . . . . . . . . . . . . . 224
Figure 136 Business Secure Router as a PPPoE Client . . . . . . . . . . . . . . . . . . . . . 225
Figure 137 Transport PPP frames over Ethernet . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Figure 138 Business Secure Router as a PPTP client . . . . . . . . . . . . . . . . . . . . . . . 228
Figure 139 PPTP protocol overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
Figure 140 Example message exchange between PC and an ANT . . . . . . . . . . . . . 230
Figure 141 Ethernet cable pin assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Figure 142 NetBIOS Display Filter Settings Command Example . . . . . . . . . . . . . . . 276
Figure 143 Example VPN initiator IPSec log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 294
Figure 144 Example VPN responder IPSec log . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
BCM50e Integrated Router Configuration - Advanced
Page 18

18 Figures
N0115789
Page 19

Tables
Table 1 Feature Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Table 2 Main menu commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Table 3 Main menu summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Table 4 General setup menu fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Table 5 Configure dynamic DNS menu fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Table 6 MAC address cloning in WAN setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Table 7 DHCP Ethernet setup menu fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Table 8 LAN TCP/IP setup menu fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Table 9 IP Alias setup menu field . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Table 10 Menu 4: internet access setup menu fields . . . . . . . . . . . . . . . . . . . . . . . 62
Table 11 New fields in menu 4 (PPTP) Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Table 12 New fields in menu 4 (PPPoE) screen . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Table 13 Fields in menu 11.1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Table 14 Fields in Menu 11.1 (PPPoE Encapsulation Specific) . . . . . . . . . . . . . . . . 72
Table 15 Fields in Menu 11.1 (PPTP Encapsulation) . . . . . . . . . . . . . . . . . . . . . . . 73
Table 16 Remote Node Network Layer Options Menu Fields . . . . . . . . . . . . . . . . . 75
Table 17 Menu 11.1: Remote Node profile (Traffic Redirect Field) . . . . . . . . . . . . . 79
Table 18 Menu 11.1.5: Traffic Redirect setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Table 19 IP Static Route Menu Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Table 20 Menu 14.1- Edit Dial-in User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Table 21 Applying NAT in Menus 4 & 11.1.2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Table 22 SUA Address Mapping Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Table 23 Fields in menu 15.1.1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Table 24 Menu 15.1.1.1: Editing or configuring an individual rule in a set . . . . . . . 98
Table 25 15.2.1: NAT Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Table 26 Menu 15.3: Trigger Port setup description . . . . . . . . . . . . . . . . . . . . . . . 112
Table 27 Abbreviations used in the Filter Rules Summary Menu . . . . . . . . . . . . . 122
Table 28 Rule abbreviations used . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Table 29 TCP/IP Filter Rule Menu fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
19
BCM50e Integrated Router Configuration - Advanced
Page 20

20 Tables
Table 30 Generic Filter Rule Menu fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Table 31 SNMP Configuration Menu Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Table 32 SNMP Traps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Table 33 Menu 23.2 System Security: RADIUS Server . . . . . . . . . . . . . . . . . . . . . 143
Table 34 System Maintenance: Status Menu Fields . . . . . . . . . . . . . . . . . . . . . . . 147
Table 35 Fields in System Maintenance: Information . . . . . . . . . . . . . . . . . . . . . . 150
Table 36 System Maintenance Menu Syslog Parameters . . . . . . . . . . . . . . . . . . . 152
Table 37 System Maintenance menu diagnostic . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Table 38 Filename Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Table 39 General commands for GUI-based FTP clients . . . . . . . . . . . . . . . . . . . 162
Table 40 General commands for GUI-based TFTP clients . . . . . . . . . . . . . . . . . . 164
Table 41 Valid commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Table 42 Budget management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
Table 43 Call History Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Table 44 Time and Date Setting Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Table 45 Menu 24.11 – Remote Management control . . . . . . . . . . . . . . . . . . . . . . 184
Table 46 Menu 26.1 Schedule Set Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
Table 47 General specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Table 49 Allowed IP address range By class . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Table 48 Classes of IP addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Table 50 Natural Masks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Table 51 Alternative Subnet Mask Notation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Table 52 Subnet 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
Table 53 Subnet 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
Table 54 Subnet 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Table 55 Subnet 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Table 58 Eight subnets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Table 56 Subnet 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Table 57 Subnet 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Table 59 Class C subnet planning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Table 60 Class B subnet planning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Table 61 Sys commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
Table 62 Exit Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Table 63 Ether Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Table 64 IP commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
N0115789
Page 21

Tables 21
Table 65 IPSec commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Table 66 Sys firewall commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Table 67 Bandwidth management commands . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Table 68 Certificates commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Table 69 NetBIOS filter default settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Table 70 System error logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
Table 71 System maintenance logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
Table 72 UPnP logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 286
Table 73 Content filtering logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 286
Table 74 Attack logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
Table 75 Access logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289
Table 76 ACL setting notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
Table 77 ICMP notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
Table 78 Sys log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 293
Table 79 Sample IKE key exchange logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 296
Table 80 Sample IPSec logs during packet transmission . . . . . . . . . . . . . . . . . . . 298
Table 81 RFC-2408 ISAKMP payload types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
Table 82 PKI logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
Table 83 Certificate path verification failure reason codes . . . . . . . . . . . . . . . . . . 301
Table 84 Log categories and available settings . . . . . . . . . . . . . . . . . . . . . . . . . . 302
Table 85 Brute force password guessing protection commands . . . . . . . . . . . . . . 305
BCM50e Integrated Router Configuration - Advanced
Page 22

22 Tables
N0115789
Page 23

Preface
Before you begin
This guide is designed to assist you with advanced configuration of your Business
Secure Router for its various applications.
Note: This guide explains how to use the System Management Terminal
(SMT) or the command interpreter interface to configure your Business
Secure Router. See the basic manual for how to use the WebGUI to
configure your Business Secure Router. Not all features can be
configured through all interfaces.
The SMT parts of this manual contain background information solely on features
not configurable by the WebGUI. The WebGUI parts of the basic manual contain
background information on features configurable by the WebGUI and the SMT.
23
Text conventions
This guide uses the following text conventions:
Enter means for you to type one or more characters and press the [ENTER] key.
Select or Choose means for you to use one of the predefined choices.
The SMT menu titles and labels are written in Bold Times New Roman font.
Menu choices are written in Bold Arial font.
BCM50e Integrated Router Configuration - Advanced
Page 24

24 Preface
A single keystroke is written in Arial font and enclosed in square brackets, for
instance, [ENTER] means the Enter key; [ESC] means the escape key and
[SPACE BAR] means the space bar. [UP] and [DOWN] are the up and down
arrow keys.
Mouse action sequences are denoted using a comma. For example, “click the
Apple icon, Control Panels and then Modem” means first click the Apple icon,
then point your mouse pointer to Control Panels and then click Modem.
Related publications
For more information about using the Business Secure Router VPN Switch, refer
to the following publications:
• BCM50e Integrated Router Configuration - Basics (
The basic manual covers how to use the WebGUI to configure your Business
Secure Router.
• WebGUI Online Help
Embedded WebGUI help for descriptions of individual screens and
supplementary information
Hard-copy technical manuals
You can print selected technical manuals and release notes free, directly from the
Internet. Go to www.nortel.com/documentation. Find the product for which you
need documentation. Then locate the specific category and model or version for
your hardware or software product. Use Adobe Reader to open the manuals and
release notes, search for the sections you need, and print them on most standard
printers. Go to Adobe Systems at www.adobe.com to download a free copy of the
Adobe Reader.
How to get help
N0115788)
N0115789
If you do not see an appropriate number in this list, go to www.nortel.com/cs.
Page 25

Preface 25
USA and Canada Authorized Distributors
Technical Support - GNTS/GNPS
Telephone:
1-800-4NORTEL (1-800-466-7835)
If you already have a PIN Code, you can enter Express Routing Code (ERC) 196#. If you
do not yet have a PIN Code, or for general questions and first line support, you can enter
ERC 338#.
Web Site:
www.nortel.com/cs
Presales Support (CSAN)
Telephone:
1-800-4NORTEL (1-800-466-7835)
Use Express Routing Code (ERC) 1063#
EMEA (Europe, Middle East, Africa)
Technical Support - CTAS
Telephone:
*European Free phone 00800 800 89009
European Alternative:
United Kingdom +44 (0)870-907-9009
Africa +27-11-808-4000
Israel 800-945-9779
Calls are not free from all countries in Europe, Middle East, or Africa.
Fax:
44-191-555-7980
E-mail:
emeahelp@nortel.com
BCM50e Integrated Router Configuration - Advanced
Page 26

26 Preface
CALA (Caribbean & Latin America)
Technical Support - CTAS
Telephone:
1-954-858-7777
E-mail:
csrmgmt@nortel.com
APAC (Asia Pacific)
Service Business Centre & Pre-Sales Help Desk:
+61-2-8870-5511 (Sydney)
Technical Support - GNTS
Telephone:
+612 8870 8800
Fax:
+612 8870 5569
E-mail:
asia_support@nortel.com
N0115789
Australia 1-800-NORTEL (1-800-667-835)
China
India 011-5154-2210
Indonesia 0018-036-1004
Japan 0120-332-533
Malaysia 1800-805-380
New Zealand 0800-449-716
Philippines
Singapore 800-616-2004
South Korea 0079-8611-2001
Taiwan
010-6510-7770
1800-1611-0063
0800-810-500
Page 27

Thailand 001-800-611-3007
Preface 27
Service Business Centre &
Pre-Sales Help Desk
+61-2-8870-5511
BCM50e Integrated Router Configuration - Advanced
Page 28

28 Preface
N0115789
Page 29

Chapter 1
Getting to know your BCM50e Integrated Router
This chapter introduces the main features and applications of the Business Secure
Router.
Introducing the BCM50e Integrated Router
The BCM50e Integrated Router is an ideal secure gateway for all data passing
between the Internet and the Local Area Network (LAN).
By integrating Network Address Translation (NAT), firewall and Virtual Private
Network (VPN) capability, the Business Secure Router is a complete security
solution that protects your Intranet and efficiently manages data traffic on your
network.
29
Features
This section lists the key features of the Business Secure Router.
Table 1 Feature Specifications
Feature Specification
Number of static routes 12
Number of NAT sessions 4096
Number of SUA servers 12
Number of address mapping rules 10
Number of configurable VPN rules (gateway policies) 10
Number of configurable IPSec VPN IP policies (network policies) 60
BCM50e Integrated Router Configuration - Advanced
Page 30
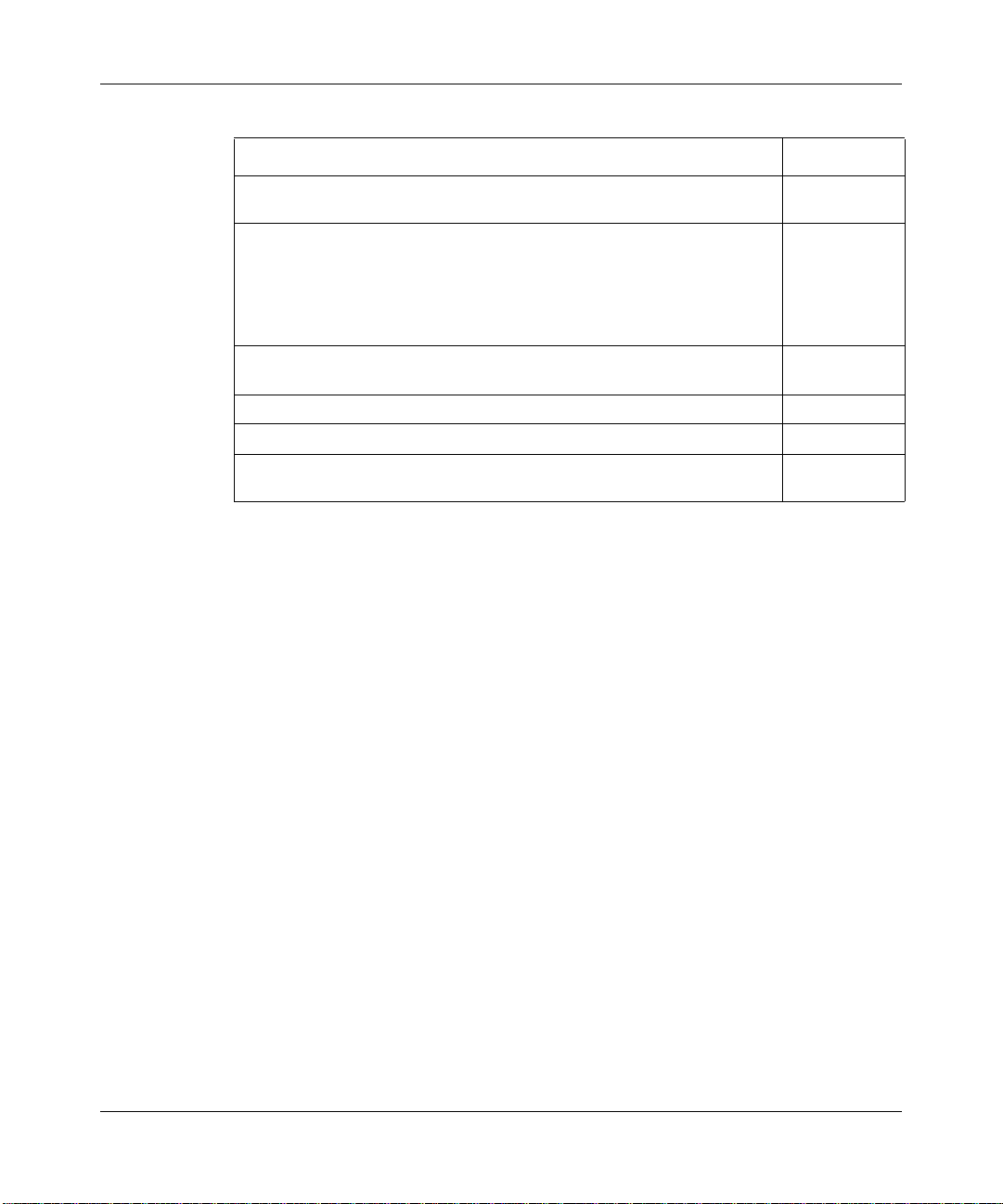
30 Chapter 1 Getting to know your BCM50e Integrated Router
Table 1 Feature Specifications
Feature Specification
Number of concurrent IKE Phase 1 Security Associations:
These correspond to the gateway policies.
Number of concurrent IPSec VPN tunnels (Phase 2 Security
Associations):
These correspond to the network policies and are also monitorable and
manageable. For example, five IKE gateway policies could each use 12
IPSec tunnels for a total of 60 phase 2 IPSec VPN tunnels. This total
includes both branch office tunnels and VPN client termination tunnels.
Number of IP pools can be used to assign IP addresses to remote users
for VPN client termination
Number of configurable split networks for VPN client termination 16
Number of configurable inverse split networks for VPN client termination 16
Number of configurable subnets per split network for VPN client
termination
Physical features
4-Port switch
A combination of switch and router makes your BCM50e Integrated Router a cost
effective and viable network solution. You can connect up to four computers or
phones to the Business Secure Router without the cost of a switch. Use a switch to
add more than four computers or phones to your LAN.
10
60
3
64
N0115789
Autonegotiating 10/100 Mb/s Ethernet LAN
The LAN interfaces automatically detect if they are on a 10 or a 100 Mb/s
Ethernet.
Autosensing 10/100 Mb/s Ethernet LAN
The LAN interfaces automatically adjust to either a crossover or straight through
Ethernet cable.
Page 31

Chapter 1 Getting to know your BCM50e Integrated Router 31
Autonegotiating 10/100 Mb/s Ethernet WAN
The 10/100 Mb/s Ethernet WAN port attaches to the Internet via broadband
modem or router and automatically detects if it is on a 10 or a 100 Mb/s Ethernet.
Time and date
Using the Business Secure Router, you can get the current time and date from an
external server when you turn on your Business Secure Router. You can also set
the time manually.
Reset button
There is a 'Cold Reset Router' button that is accessible from the Element Manager
Administration/Utilities/Reset page.Use this button to restore the factory default
password to PlsChgMe! and the IP address to 192.168.1.1, subnet mask
255.255.255.0, and DHCP server enabled with a pool of 126 IP addresses starting
at 192.168.1.2.
Nonphysical features
IPSec VPN capability
Establish Virtual Private Network (VPN) tunnels to connect home or office
computers to your company network using data encryption and the Internet; thus
providing secure communications without the expense of leased site-to-site lines.
VPN is based on the IPSec standard and is fully interoperable with other
IPSec-based VPN products.
Certificates
The Business Secure Router can use certificates (also called digital IDs) to
authenticate users. Certificates are based on public-private key pairs. Certificates
provide a way to exchange public keys for use in authentication.
BCM50e Integrated Router Configuration - Advanced
Page 32

32 Chapter 1 Getting to know your BCM50e Integrated Router
SSH
The Business Secure Router uses the SSH (Secure Shell) secure communication
protocol to provide secure encrypted communication between two hosts over an
unsecured network.
HTTPS
HyperText Transfer Protocol over Secure Socket Layer, or HTTP over SSL is a
web protocol that encrypts and decrypts web sessions. Use HTTPS for secure
WebGUI access to the Business Secure Router.
Firewall
The Business Secure Router has a stateful inspection firewall with DoS (Denial of
Service) protection. By default, when the firewall is activated, all incoming traffic
from the WAN to the LAN is blocked unless it is initiated from the LAN. The
Business Secure Router firewall supports TCP/UDP inspection, DoS detection
and protection, real time alerts, reports and logs.
N0115789
Brute force password guessing protection
The Business Secure Router has a special protection mechanism to discourage
brute force password guessing attacks on the Business Secure Router’s
management interfaces. You can specify a wait time that must expire before you
can enter a fourth password after entering three incorrect passwords.
Content filtering
The Business Secure Router can block web features such as ActiveX controls,
Java applets, and cookies, as well as disable web proxies. The Business Secure
Router can block specific URLs by using the keyword feature. The administrator
can also define time periods and days during which content filtering is enabled.
Packet filtering
The packet filtering mechanism blocks unwanted traffic from entering or leaving
your network.
Page 33

Chapter 1 Getting to know your BCM50e Integrated Router 33
Universal Plug and Play (UPnP)
Using the standard TCP/IP protocol, the Business Secure Router and other
UPnP-enabled devices can dynamically join a network, obtain an IP address, and
convey its capabilities to other devices on the network.
Call scheduling
Configure call time periods to restrict and allow access for users on remote nodes.
PPPoE
PPPoE facilitates the interaction of a host with an Internet modem to achieve
access to high-speed data networks via a familiar dial-up networking user
interface.
PPTP Encapsulation
Point-to-Point Tunneling Protocol (PPTP) is a network protocol that enables
secure transfer of data from a remote client to a private server, creating a Virtual
Private Network (VPN) using a TCP/IP-based network.
PPTP supports on-demand, multiprotocol, and virtual private networking over
public networks, such as the Internet. The Business Secure Router supports one
PPTP server connection at any given time.
Dynamic DNS support
With Dynamic DNS (Domain Name System) support, you can have a static host
name alias for a dynamic IP address, so the host is more easily accessible from
various locations on the Internet. You must register for this service with a
Dynamic DNS service provider.
IP Multicast
The Business Secure Router can use IP multicast to deliver IP packets to a specific
group of hosts. IGMP (Internet Group Management Protocol) is the protocol used
to support multicast groups. The Business Secure Router supports versions 1 and
2.
BCM50e Integrated Router Configuration - Advanced
Page 34

34 Chapter 1 Getting to know your BCM50e Integrated Router
IP Alias
Using IP Alias, you can partition a physical network into logical networks over
the same Ethernet interface. The Business Secure Router supports three logical
LAN interfaces via its single physical Ethernet LAN interface with the Business
Secure Router itself as the gateway for each LAN network.
Central Network Management
With Central Network Management (CNM), an enterprise or service provider
network administrator can manage your Business Secure Router. The enterprise
or service provider network administrator can configure your Business Secure
Router, perform firmware upgrades, and do troubleshooting for you.
SNMP
SNMP (Simple Network Management Protocol) is a protocol used for exchanging
management information between network devices. SNMP is a member of the
TCP/IP protocol suite. Your Business Secure Router supports SNMP agent
functionality, which means that a manager station can manage and monitor the
Business Secure Router through the network. The Business Secure Router
supports SNMP versions 1 and 2 (SNMPv1 and SNMPv2).
N0115789
Network Address Translation (NAT)
NAT (Network Address Translation — NAT, RFC 1631) translate multiple IP
addresses used within one network to different IP addresses known within another
network.
Traffic Redirect
Traffic Redirect forwards WAN traffic to a backup gateway when the Business
Secure Router cannot connect to the Internet, thus acting as an auxiliary backup
when your regular WAN connection fails.
Page 35

Chapter 1 Getting to know your BCM50e Integrated Router 35
Port Forwarding
Use this feature to forward incoming service requests to a server on your local
network. You can enter a single port number or a range of port numbers to be
forwarded, and the local IP address of the desired server.
DHCP (Dynamic Host Configuration Protocol)
With DHCP (Dynamic Host Configuration Protocol), individual client computers
can obtain the TCP/IP configuration at start-up from a centralized DHCP server.
The Business Secure Router has built in DHCP server capability, enabled by
default, which means it can assign IP addresses, an IP default gateway, and DNS
servers to all systems that support the DHCP client. The Business Secure Router
can also act as a surrogate DHCP server, where it relays IP address assignment
from another DHCP server to the clients.
Full network management
The embedded web configurator is an all platform, web based utility that you can
use to easily manage and configure the Business Secure Router. Most functions of
the Business Secure Router are also software configurable via the SMT (System
Management Terminal) interface. The SMT is a menu driven interface that you
can access over a Telnet connection.
Road Runner support
In addition to standard cable modem services, the Business Secure Router
supports Time Warner’s Road Runner Service.
Logging and tracing
The Business Secure Router supports the following logging and tracing functions
to help with management:
• Built in message logging and packet tracing
• Unix syslog facility support
BCM50e Integrated Router Configuration - Advanced
Page 36

36 Chapter 1 Getting to know your BCM50e Integrated Router
Upgrade Business Secure Router Firmware
The firmware of the Business Secure Router can be upgraded manually via the
WebGUI.
Embedded FTP and TFTP Servers
The Business Secure Router’s embedded FTP and TFTP Servers enable fast
firmware upgrades, as well as configuration file backups and restoration.
Applications for the BCM50e Integrated Router
Secure broadband internet access and VPN
You can connect a cable, DSL, or other modem to the BCM50e Integrated Router
via Ethernet WAN port for broadband Internet access. The Business Secure
Router also provides IP address sharing and a firewall protected local network
with traffic management.
N0115789
VPN is an ideal, cost effective way to connect branch offices and business
partners over the Internet without the need (and expense) of leased lines between
sites. The LAN computers can share the VPN tunnels for secure connections to
remote computers.
Page 37

Chapter 1 Getting to know your BCM50e Integrated Router 37
Figure 1 Secure Internet Access and VPN Application
BCM50e Integrated Router
BCM50e Integrated Router Configuration - Advanced
Page 38

38 Chapter 1 Getting to know your BCM50e Integrated Router
N0115789
Page 39

Chapter 2
Introducing the SMT
This chapter explains how to access the System Management Terminal and gives
an overview of its menus.
Introduction to the SMT
The Business Secure Router SMT (System Management Terminal) is a
menu-driven interface that you can access over a Telnet connection. This chapter
shows you how to navigate the SMT, and how to configure SMT menus.
Initial screen
When you turn on your Business Secure Router, it performs several internal tests
as well as line initialization.
39
After the tests, the Business Secure Router asks you to press
as shown in Figure 2.
Figure 2 Initial screen
initialize ch =0, ethernet address: 00:A0:C5:22:1A:03
initialize ch =1, ethernet address: 00:A0:C5:22:1A:04
Press ENTER to continue...
Logging on to the SMT
The logon screen appears after you press [ENTER], prompting you to enter the
username, as shown in Figure 3.
[ENTER] to continue,
BCM50e Integrated Router Configuration - Advanced
Page 40

40 Chapter 2 Introducing the SMT
Type the username (nnadmin is the default) and press [ENTER].
The logon screen prompts you to enter the password.
Figure 3 SMT Login
Enter Username : XXXX
Enter Password : XXXX
Type the password (PlsChgMe! is the default) and press [ENTER]. As you type
the password, the screen displays an X for each character you type.
Note that if there is no activity for longer than five minutes after you log on, your
Business Secure Router will automatically log you off and display a blank screen.
If you see a blank screen, press [ENTER] to bring up the logon screen again.
Navigating the SMT interface
N0115789
The SMT is an interface that you use to configure your Business Secure Router.
Table 2 lists several operations you must be familiar with before attempting to
modify the configuration.
Table 2 Main menu commands
Operations Keystrokes Descriptions
Move down to
another menu
Move up to a
previous menu
Move to a
“hidden” menu
[ENTER] To move forward to a submenu, type in the
number of the desired submenu and press
[ENTER].
[ESC] Press the [ESC] key to move back to the
previous menu.
Press [SPACE BAR]
to change No to Yes
then press [ENTER].
Fields beginning with “Edit” lead to hidden
menus and have a default setting of No. Press
[SPACE BAR] to change No to Yes, and then
press [ENTER] to go to a “hidden” menu.
Page 41

Table 2 Main menu commands
Operations Keystrokes Descriptions
Chapter 2 Introducing the SMT 41
Move the
cursor
Entering
information
Required fields <? > All fields with the symbol <?> must be filled in
N/A fields <N/A> Some of the fields in the SMT will show a <N/A>.
Save your
configuration
Exit the SMT Type 99, then press
[ENTER] or [UP] or
[DOWN] arrow keys
Fill in, or press
[SPACE BAR], then
press [ENTER] to
select from choices.
[ENTER] Save your configuration by pressing [ENTER] at
[ENTER].
Within a menu, press [ENTER] to move to the
next field. You can also use the [UP] or [DOWN]
arrow keys to move to the previous or the next
fields, respectively.
When you are at the top of a menu, press the
[UP] arrow key to move to the bottom of a menu.
There are two types of fields. The first requires
you to type in the appropriate information. The
second allows you to cycle through the available
choices by pressing [SPACE BAR].
order be able to save the new configuration.
This symbol refers to an option that is Not
Applicable.
the message “Press ENTER to confirm or ESC to
cancel”. Saving the data on the screen will take
you, in most cases, to the previous menu.
Make sure you save your settings in each screen
that you configure.
Type 99 at the main menu prompt and press
[ENTER] to exit the SMT interface.
Main menu
After you enter the password, the SMT displays the Business Secure Router Main
Menu, as shown in Figure 4. Not all models have all the features shown.
BCM50e Integrated Router Configuration - Advanced
Page 42

42 Chapter 2 Introducing the SMT
Figure 4 Main menu
Business Secure Router Main Menu
Getting Started Advanced Management
1. General Setup
2. WAN Setup
3. LAN Setup
4. Internet Access Setup
Advanced Applications
11. Remote Node Setup
12. Static Routing Setup
14. Dial-in User Setup
15. NAT Setup
Enter Menu Selection Number:
21. Filter and Firewall Setup
22. SNMP Configuration
23. System Security
24. System Maintenance
26. Schedule Setup
99.Exit
Table 3 describes the fields in Figure 4.
Table 3 Main menu summary
No. Menu Title Function
N0115789
1 General Setup Use this menu to set up dynamic DNS and
administrative information.
2 WAN Setup Use this menu to clone a MAC address from a
computer on your LAN and configure the backup WAN
dial-up connection.
3 LAN Setup Use this menu to apply LAN filters, configure LAN
DHCP and TCP/IP settings.
4 Internet Access Setup Configure your Internet Access setup (Internet
address, gateway IP address, and logon) with this
menu.
11 Remote Node Setup Use this menu to configure detailed remote node
settings (your ISP is also a remote node) as well as
apply WAN filters.
12 Static Routing Setup Configure IP static routes in this menu.
14 Dial-in User Setup Use this menu to configure the Dial-in User
information
15 NAT Setup Use this menu to configure Network Address
Translation.
21 Filter and Firewall Setup Configure filters, activate or deactivate the firewall,
and view the firewall log.
Page 43

Table 3 Main menu summary
No. Menu Title Function
22 SNMP Configuration Use this menu to configure SNMP-related parameters.
23 System Security Use this menu to change your password and enable
network user authentication.
24 System Maintenance From displaying system status to uploading firmware,
this menu provides comprehensive system
maintenance.
26 Schedule Setup Use this menu to schedule outgoing calls.
99 Exit Use this menu to exit (necessary for remote
configuration).
Changing the system password
To change the Business Secure Router administrator password:.
1 From the main menu, enter 23 to display Menu 23 – System Security.
Chapter 2 Introducing the SMT 43
2 Enter 1 to display Menu 23.1 – System Security – Change Password.
Figure 5 Menu 23.1 System Security: Change Password
Menu 23.1 – System Security – Change Password
Old Password= ****
New Password= ?
Retype to confirm= ?
Enter here to CONFIRM or ESC to CANCEL:
3 Type your existing system password in the Old Password field, and press
[ENTER].
4 Type your new system password in the New Password field (up to 30
characters), and press [ENTER].
5 Retype your new system password in the Retype to confirm field for
confirmation and press [ENTER].
Note that as you type a password, the screen displays an asterisk * for each
character you type.
BCM50e Integrated Router Configuration - Advanced
Page 44

44 Chapter 2 Introducing the SMT
SMT menus at a glance
Figure 6 SMT overview
N0115789
Page 45

SMT menu 1 - general setup
Introduction to general setup
Menu 1 - general setup contains administrative and system-related information.
Configuring general setup
Enter 1 in the main menu to open Menu 1: general setup.
The Menu 1 - General Setup screen appears, as shown in Figure 7. Fill in the
required fields.
Figure 7 menu 1: general setup
Menu 1 - General Setup
System Name= Business Secure Router
Domain Name= www.nortel.com
First System DNS Server= From ISP
IP Address= N/A
Second System DNS Server= From ISP
IP Address= N/A
Third System DNS Server= From ISP
IP Address= N/A
Edit Dynamic DNS= No
45
Press ENTER to confirm or ESC to cancel:
BCM50e Integrated Router Configuration - Advanced
Page 46

46 Chapter 2 SMT menu 1 - general setup
Table 4 describes the fields in Figure 7.
Table 4 General setup menu fields
Field Description Example
System name Choose a descriptive name for identification purposes.
Nortel recommends you enter your computer name in
this field. This name can be up to 30 alphanumeric
characters long. Spaces, dashes - and underscores _
are accepted.
Domain name Enter the domain name (if you know it) here. If you
leave this field blank, the ISP assigns a domain name
via DHCP. You can go to menu 24.8 and type sys
domain name to see the current domain name used by
your router.
The domain name entered by you is given priority over
the ISP-assigned domain name. If you want to clear
this field just press [SPACE BAR] and then [ENTER].
Business
Secure Router
nortel.com
N0115789
Page 47

Chapter 2 SMT menu 1 - general setup 47
Table 4 General setup menu fields
Field Description Example
First system
DNS server
Second system
DNS server
Third system
DNS server
DNS (Domain Name System) is for mapping a domain
name to its corresponding IP address and vice versa.
The DNS server is extremely important because
without it, you must know the IP address of a machine
before you can access it. The Business Secure Router
uses a system DNS server (in the order you specify
here) to resolve domain names for VPN, DDNS and
the time server.
Press [SPACE BAR] and then [ENTER] to select an
option. Select From ISP if your ISP dynamically
assigns DNS server information (and the Business
Secure Router's WAN IP address). The IP Address
field below displays the (read-only) DNS server IP
address that the ISP assigns. If you chose From ISP,
but the Business Secure Router has a fixed WAN IP
address, From ISP changes to None after you save
your changes. If you select From ISP for the second
or third DNS server, but the ISP does not provide a
second or third IP address, From ISP changes to
None after you save your changes.
Select User-Defined if you have the IP address of a
DNS server. The IP address can be public or a private
address on your local LAN. Enter the DNS server's IP
address in the field to the right.
A User-Defined entry with the IP address set to
0.0.0.0 changes to None after you save your changes.
A duplicate User-Defined entry changes to None after
you save your changes.
Select None if you do not want to configure DNS
servers. If you do not configure a system DNS server,
you must use IP addresses when configuring VPN,
DDNS and the time server.
Select Private DNS if the DNS server has a private IP
address and is located behind a VPN peer. Enter the
DNS server IP address in the field to the right.
With a private DNS server, you must also configure
the first DNS server entry in SMT menu 3.1 to use
DNS Relay.
BCM50e Integrated Router Configuration - Advanced
Page 48

48 Chapter 2 SMT menu 1 - general setup
Table 4 General setup menu fields
Field Description Example
You must also configure a VPN branch office rule
since the Business Secure Router uses a VPN tunnel
when it relays DNS queries to the private DNS server.
One of the rule’s IP policies must include the LAN IP
address of the Business Secure Router as a local IP
address and the IP address of the DNS server as a
remote IP address.
A Private DNS entry with the IP address set to 0.0.0.0
changes to None after you click Apply. A duplicate
Private DNS entry changes to None after you save
your changes.
Edit dynamic
DNS
Press [SPACE BAR] and then [ENTER] to select Yes
or No (default). Select Yes to configure Menu 1.1:
Configure Dynamic DNS, discussed next.
After you complete this menu, press [ENTER] at the
prompt “Press ENTER to Confirm…” to save your
configuration, or press [ESC] at any time to cancel.
Configuring dynamic DNS
No
(default)
N0115789
To configure Dynamic DNS, go to Menu 1: General Setup and press
[SPACE BAR] to select Yes in the Edit Dynamic DNS field. Press [ENTER] to
display Menu 1.1— Configure Dynamic DNS (Figure 8). Not all models have
every field shown.
Page 49

Chapter 2 SMT menu 1 - general setup 49
Figure 8 Configure dynamic DNS
Menu 1.1 - Configure Dynamic DNS
Service Provider= WWW.DynDNS.ORG
Active= No
DDNS Type= DynamicDNS
Host Name 1=
Host Name 2=
Host Name 3=
Username=
Password= ********
Enable Wildcard Option= No
Enable Off Line Option= N/A
IP Address Update Policy:
DDNS Server Auto Detect IP Address= No
Use Specified IP Address= No
Use IP Address= N/A
Press ENTER to confirm or ESC to cancel:
Follow the instructions in Tab le 5 to configure Dynamic DNS parameters.
Table 5 Configure dynamic DNS menu fields
Field Description Example
Service Provider This is the name of your Dynamic DNS service
provider.
Active Press [SPACE BAR] to select Yes and then press
www.dyndns.org
(default)
Yes
[ENTER] to make dynamic DNS active.
DDNS Type Press [SPACE BAR] and then [ENTER] to select
DynamicDNS if you have a dynamic IP address.
DynamicDNS
(default)
Select StaticDNS if you have a static IP address.
Select CustomDNS to have dyns.org provide DNS
service for a domain name that you already have
from a source other than dyndns.org.
Host1-3 Enter your host names in the fields provided. You
me.dyndns.org
can specify up to two host names separated by a
comma in each field.
EMAIL Enter your e-mail address. mail@mailserver
User Enter your username.
Password Enter the password assigned to you.
Enable Wildcard Your Business Secure Router supports DYNDNS
Wildcard. Press [SPACE BAR] and then [ENTER]
to select Yes or No This field is N/A when you
choose DDNS client as your service provider.
BCM50e Integrated Router Configuration - Advanced
Page 50

50 Chapter 2 SMT menu 1 - general setup
Table 5 Configure dynamic DNS menu fields
Field Description Example
Offline This field is only available when CustomDNS is
selected in the DDNS Type field. Press
[SPACE BAR] and then [ENTER] to select Yes.
When Yes is selected,
traffic is redirected to a URL that you have
previously specified (see
details).
IP Address
Update Policy:
DDNS Server
Auto Detect IP
Address
Use Specified IP
Address
Use IP Address Enter the static public IP address if you select Yes
You can select Yes in either the DDNS Server
Auto Detect IP Address field (recommended) or
the Use Specified IP Address field, but not both.
With the DDNS Server Auto Detect IP Address
and Use Specified IP Address fields both set to
No, the DDNS server automatically updates the IP
address of the host names with the Business
Secure Router’s WAN IP address.
DDNS does not work with a private IP address.
When both fields are set to No, the Business
Secure Router must have a public WAN IP
address in order for DDNS to work.
Press [SPACE BAR] to select Yes and then press
[ENTER] to have the DDNS server automatically
update the IP address of the host names with the
public IP address that the Business Secure Router
uses or is behind.
You can set this field to Yes whether the IP
address is public or private, static or dynamic.
Press [SPACE BAR] to select Yes and then press
[ENTER] to update the IP address of the host
names to the IP address specified below.
Only select Yes if the Business Secure Router
uses or is behind a static public IP address.
in the Use Specified IP Address field.
After you complete this menu, press [ENTER] at
the prompt “Press ENTER to Confirm…” to save
your configuration, or press [ESC] at any time to
cancel.
http://www.dyndns.org/
www.dyndns.org for
Yes
No
N/A
N0115789
The IP address updates when you reconfigure menu 1 or perform DHCP client
renewal.
Page 51

Chapter 3
WAN Setup
This chapter describes how to configure the WAN using menu 2.
Introduction to WAN setup
This chapter explains how to configure settings for your WAN port.
WAN setup
From the main menu, enter 2 to open menu 2
51
BCM50e Integrated Router Configuration - Advanced
Page 52

52 Chapter 3 WAN Setup
Figure 9 Menu 2
Menu 2 - WAN Setup
MAC Address:
Assigned By= Factory default
IP Address= N/A
Dial-Backup:
Active= No
Port Speed= 115200
AT Command String:
Init= at&fs0=0
Edit Advanced Setup= No
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
Table 6 describes the fields in Figure 9.
N0115789
Table 6 MAC address cloning in WAN setup
Field Description Example
MAC Address
Assigned By Press [SPACE BAR] and then [ENTER] to choose one
of two methods to assign a MAC Address. Choose
Factory Default to select the factory-assigned default
MAC Address. Choose IP address attached on LAN
to use the MAC Address of that workstation whose IP
you give in the following field.
IP Address This field is applicable only if you choose the IP
address attached on LAN method in the Assigned
By field. Enter the IP address of the computer on the
LAN whose MAC you are cloning.
After you complete this menu, press [ENTER] at the
prompt “Press ENTER to Confirm…” to save your
configuration, or press [ESC] at any time to cancel.
IP address
attached on
LAN
192.168.1.35
Page 53

Chapter 4
LAN setup
This chapter describes how to configure the LAN using Menu 3: LAN Setup.
Introduction to LAN setup
This section describes how to configure the Business Secure Router for LAN
connections.
Accessing the LAN menus
From the main menu, enter 3 to open Menu 3 – LAN setup
Figure 10 Menu 3: LAN setup.
53
Menu 3 - LAN Setup
1. LAN Port Filter Setup
2. TCP/IP and DHCP Setup
Enter Menu Selection Number:
LAN port filter setup
With Menu 3, you can specify the filter sets that you wish to apply to the LAN
traffic. You seldom need to filter the LAN traffic, however, the filter sets are
useful to block certain packets, reduce traffic, and prevent security breaches.
BCM50e Integrated Router Configuration - Advanced
Page 54

54 Chapter 4 LAN setup
Figure 11 Menu 3.1: LAN port filter setup
Menu 3.1 – LAN Port Filter Setup
Input Filter Sets:
protocol filters=
device filters=
Output Filter Sets:
protocol filters=
device filters=
Press ENTER to Confirm or ESC to Cancel:
TCP/IP and DHCP ethernet setup menu
From the main menu, enter 3 to open Menu 3 - LAN Setup to configure TCP/IP
(RFC 1155) and DHCP Ethernet setup.
Figure 12 Menu 3: TCP/IP and DHCP setup
Menu 3 - LAN Setup
1. LAN Port Filter Setup
2. TCP/IP and DHCP Setup
Enter Menu Selection Number:
From menu 3, select the submenu option TCP/IP and DHCP Setup and press
N0115789
[ENTER]. The screen now displays
Setup
, as shown in Figure 13.
Menu 3.2: TCP/IP and DHCP Ethernet
Page 55

Figure 13 Figure 21-4 menu 3.2: TCP/IP and DHCP Ethernet setup
Menu 3.2 - TCP/IP and DHCP Ethernet Setup
DHCP= Server TCP/IP Setup:
Client IP Pool:
Starting Address= 192.168.1.2 IP Address= 192.168.1.1
Size of Client IP Pool= 126 IP Subnet Mask= 255.255.255.0
First DNS Server= From ISP RIP Direction= None
IP Address= N/A Version= N/A
Second DNS Server= From ISP Multicast= None
IP Address= N/A Edit IP Alias= No
Third DNS Server= From ISP
IP Address= N/A
DHCP Server Address= N/A
Chapter 4 LAN setup 55
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
Follow the instructions in Tab le 7 to configure the DHCP fields.
Table 7 DHCP Ethernet setup menu fields
Field Description Example
DHCP This field enables and disables the DHCP server.
Configuration:
Client IP Pool
Starting Address
If set to Server, your Business Secure Router will
act as a DHCP server.
If set to None, the DHCP server will be disabled.
This field specifies the first of the contiguous
addresses in the IP address pool.
BCM50e Integrated Router Configuration - Advanced
Server
192.168.1.2
Page 56

56 Chapter 4 LAN setup
Table 7 DHCP Ethernet setup menu fields
Field Description Example
Size of Client IP
Pool
First DNS Server
Second DNS
Server
Third DNS Server
This field specifies the size or count of the IP
address pool.
The Business Secure Router passes a DNS
(Domain Name System) server IP address (in the
order you specify here) to the DHCP clients.
Select From ISP if your ISP dynamically assigns
DNS server information (and the Business Secure
Router's WAN IP address). The IP Address field
below displays the (read-only) DNS server IP
address that the ISP assigns. If you chose From
ISP, but the Business Secure Router has a fixed
WAN IP address, From ISP changes to None after
you save your changes. If you chose From ISP for
the second or third DNS server, but the ISP does
not provide a second or third IP address, From ISP
changes to None after you save your changes.
Select User-Defined if you have the IP address of a
DNS server. Enter the DNS server's IP address in
the IP Address field below. If you chose
User-Defined, but leave the IP address set to
0.0.0.0, User-Defined changes to None after you
save your changes. If you set a second choice to
User-Defined, and enter the same IP address, the
second User-Defined changes to None after you
save your changes.
Select DNS Relay to have the Business Secure
Router act as a DNS proxy. The Business Secure
Router's LAN IP address displays in the IP Address
field below (read-only). The Business Secure Router
tells the DHCP clients on the LAN that the Business
Secure Router itself is the DNS server. When a
computer on the LAN sends a DNS query to the
Business Secure Router, the Business Secure
Router forwards the query to the Business Secure
Router's system DNS server (configured in the
SYSTEM General screen) and relays the response
back to the computer. You can only select DNS
Relay for one of the three servers; if you select DNS
Relay for a second or third DNS server, that choice
changes to None after you save your changes.
Select None if you do not want to configure DNS
servers. If you do not configure a DNS server, you
must know the IP address of a machine in order to
access it.
126
N0115789
Page 57

Chapter 4 LAN setup 57
Use the instructions in Tab le 8 to configure TCP/IP parameters for the LAN port.
Table 8 LAN TCP/IP setup menu fields
Field Description Example
TCP/IP Setup:
IP Address Enter the IP address of your Business Secure
Router in dotted decimal notation.
IP Subnet Mask Your Business Secure Router automatically
calculates the subnet mask based on the IP
address that you assign. Unless you are
implementing subnetting, use the subnet mask
computed by the Business Secure Router.
RIP Direction Press [SPACE BAR] and then [ENTER] to select
the RIP direction. Options are: Both, In Only,
Out Only or None.
Version Press [SPACE BAR] and then [ENTER] to select
the RIP version. Options are:
RIP-1, RIP-2B or RIP-2M.
Multicast IGMP (Internet Group Multicast Protocol) is a
network-layer protocol used to establish
membership in a Multicast group. The Business
Secure Router supports both IGMP version 1
(IGMP-v1) and version 2 (IGMP-v2). Press
[SPACE BAR] and then [ENTER] to enable IP
Multicasting or select None (default) to disable it.
Edit IP Alias The Business Secure Router supports three
logical LAN interfaces via its single physical
Ethernet interface with the Business Secure
Router itself as the gateway for each LAN
network. Press [SPACE BAR] to select Yes and
then press [ENTER] to display menu 3.2.1.
192.168.1.1
(default)
255.255.255.0
Both
(default)
RIP-1
(default)
None
Yes
IP Alias Setup
You must use menu 3.2 to configure the first network. Move the cursor to the Edit
IP Alias field, press [SPACE BAR] to choose Yes and press [ENTER] to
configure the second and third network.
Press [ENTER] to open Menu 3.2.1 - IP Alias Setup, as shown in Figure 14.
BCM50e Integrated Router Configuration - Advanced
Page 58

58 Chapter 4 LAN setup
Figure 14 Menu 3.2.1: IP Alias setup
Menu 3.2.1 - IP Alias Setup
IP Alias 1= No
IP Address= N/A
IP Subnet Mask= N/A
RIP Direction= N/A
Version= N/A
Incoming protocol filters= N/A
Outgoing protocol filters= N/A
IP Alias 2= No
IP Address= N/A
IP Subnet Mask= N/A
RIP Direction= N/A
Version= N/A
Incoming protocol filters= N/A
Outgoing protocol filters= N/A
Enter here to CONFIRM or ESC to CANCEL:
Press Space Bar to Toggle.
Use the instructions in Tab le 9 to configure IP Alias parameters.s
Table 9 IP Alias setup menu field
Field Description Example
IP Alias Choose Ye s to configure the LAN network for
the Business Secure Router.
IP Address Enter the IP address of your Business Secure
Router in dotted decimal notation.
IP Subnet Mask Your Business Secure Router automatically
calculates the subnet mask based on the IP
address that you assign. Unless you are
implementing subnetting, use the subnet mask
computed by the Business Secure Router.
N0115789
Yes
192.168.1.1
255.255.255.0
Page 59

Chapter 4 LAN setup 59
Table 9 IP Alias setup menu field
Field Description Example
RIP Direction Press [SPACE BAR] and then [ENTER] to
select the RIP direction. Options are
Both, In Only, Out Only or None.
Version Press [SPACE BAR] and then [ENTER] to
select the RIP version. Options are
RIP-1, RIP-2B or RIP-2M.
Incoming Protocol
Filters
Outgoing Protocol
Filters
Enter the filter sets you wish to apply to the
incoming traffic between this node and the
Business Secure Router.
Enter the filter sets you wish to apply to the
outgoing traffic between this node and the
Business Secure Router.
None
RIP-1
1
2
BCM50e Integrated Router Configuration - Advanced
Page 60

60 Chapter 4 LAN setup
N0115789
Page 61

Chapter 5
Internet access
This chapter shows you how to configure your Business Secure Router for
Internet access.
Introduction to internet access setup
Use the information from your ISP along with the instructions in this chapter to
set up your Business Secure Router to access the Internet. There are three
different menu 4 screens, depending on whether you chose Ethernet, PPTP or
PPPoE Encapsulation. Contact your ISP to determine which encapsulation type
you should use.
Ethernet encapsulation
61
If you choose Ethernet in menu 4 you will see Figure 15.
BCM50e Integrated Router Configuration - Advanced
Page 62

62 Chapter 5 Internet access
Figure 15 Menu 4: internet access setup (Ethernet)
Menu 4 - Internet Access Setup
ISP's Name= ChangeMe
Encapsulation= Ethernet
Service Type= Standard
My Login= N/A
My Password= N/A
Retype to Confirm= N/A
Login Server IP= N/A
IP Address Assignment= Dynamic
IP Address= N/A
IP Subnet Mask= N/A
Gateway IP Address= N/A
Network Address Translation= SUA Only
Press ENTER to Confirm or ESC to Cancel:
Table 10 describes the fields in Figure 15.
N0115789
Table 10 Menu 4: internet access setup menu fields
Field Description
ISP’s Name Enter the name of your Internet Service Provider, e.g., myISP.
This information is for identification purposes only.
Encapsulation Press [SPACE BAR] and then press [ENTER] to choose
Ethernet. The encapsulation method influences your choices
for the IP Address field.
Service Type Press [SPACE BAR] and then [ENTER] to select Standard,
RR-Toshiba (Road Runner Toshiba authentication method),
RR-Manager (Road Runner Manager authentication method) or
RR-Telstra. Choose a Road Runner flavor if your ISP is Time
Warner's Road Runner; otherwise choose Standard.
DSL users must choose the Standard option only. The My
Login, My Password and Login Server fields are not
applicable in this case.
My Login Enter the logon name given to you by your ISP.
My Password Enter the password associated with the login name above.
Page 63

Chapter 5 Internet access 63
Table 10 Menu 4: internet access setup menu fields
Field Description
Retype to Confirm Enter the password again to make sure that you have entered it
correctly.
Login Server The Business Secure Router finds the Road Runner Server IP if
IP Address
Assignment
IP Address Enter the (fixed) IP address assigned to you by your ISP (static
IP Subnet Mask Enter the subnet mask associated with your static IP.
Gateway IP Address Enter the gateway IP address associated with your static IP.
Network Address
Translation
this field is left blank. If it does not, then you must enter the
authentication server IP address.
If your ISP did not assign you a fixed IP address, press
[SPACE BAR] and then [ENTER] to select Dynamic, otherwise
select Static and enter the IP address and subnet mask in the
following fields.
IP address Assignment is selected in the previous field).
With the NAT, you can translate an Internet protocol address
used within one network (for example a private IP address used
in a local network) to a different IP address known within
another network (for example a public IP address used on the
Internet).
Choose None to disable NAT.
Choose SUA Only if you have a single public IP address. SUA
(Single User Account) is a subset of NAT that supports two
types of mapping: Many-to-One and Server.
Choose Full Feature if you have multiple public IP addresses.
Full Feature mapping types include: One-to-One,
Many-to-One (SUA/PAT), Many-to-Many Overload, Many-
One-to-One and Server. When you select Full Feature you
must configure at least one address mapping set!
See Chapter 9, “Network Address Translation (NAT),” on page
89 for a more detailed discussion on the Network Address
Translation feature.
Configuring the PPTP client
Note: The Business Secure Router supports only one PPTP server
connection at any given time.
To configure a PPTP client, you must configure the My Login and Password
fields for a PPP connection and the PPTP parameters for a PPTP connection.
BCM50e Integrated Router Configuration - Advanced
Page 64

64 Chapter 5 Internet access
After configuring My Login and Password for PPP connection, press
[SPACE BAR] and then [ENTER] in the Encapsulation field in Menu 4
-Internet Access Setup to choose PPTP as your encapsulation option. This
brings up the screen show in Figure 16.
Figure 16 Internet access setup (PPTP)
Menu 4 - Internet Access Setup
ISP's Name= ChangeMe
Encapsulation= PPTP
Service Type= N/A
My Login= username
My Password= ******
Retype to Confirm= ******
Idle Timeout= 100
IP Address Assignment= Dynamic
IP Address= N/A
IP Subnet Mask= N/A
Gateway IP Address=N/A
Network Address Translation= SUA Only
Press ENTER to Confirm or ESC to Cancel:
Table 11 contains instructions about the new fields when you choose PPTP in the
Encapsulation field in menu 4.
Table 11 New fields in menu 4 (PPTP) Screen
Field Description Example
Encapsulation Press [SPACE BAR] and then press [ENTER] to
choose PPTP. The encapsulation method influences
your choices for the IP Address field.
Idle Timeout This value specifies the time, in seconds, that elapses
before the Business Secure Router automatically
disconnects from the PPTP server.
Configuring the PPPoE client
If you enable PPPoE in menu 4, you will see the screen in figure 24. For more
information about PPPoE, see Appendix E, “PPPoE,” on page 227.
N0115789
PPTP
100
(default)
Page 65

Figure 17 Internet access setup (PPPoE)
Menu 4 - Internet Access Setup
ISP's Name= ChangeMe
Encapsulation= PPPoE
Service Type= N/A
My Login=
My Password= ********
Retype to Confirm= ******
Idle Timeout= 100
IP Address Assignment= Dynamic
IP Address= N/A
IP Subnet Mask= N/A
Gateway IP Address= N/A
Network Address Translation= Full Feature
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
Chapter 5 Internet access 65
Table 12 describes the fields in Figure 17.
Table 12 New fields in menu 4 (PPPoE) screen
Field Description Example
Encapsulation Press [SPACE BAR] and then press [ENTER] to
choose PPPoE. The encapsulation method
influences your choices in the IP Address field.
Idle Timeout This value specifies the time in seconds that
elapses before the Business Secure Router
automatically disconnects from the PPPoE server.
PPPoE
100
(default)
If you need a PPPoE service name to identify and reach the PPPoE server, go to
menu 11 and enter the PPPoE service name provided to you in the Service Name
field.
BCM50e Integrated Router Configuration - Advanced
Page 66

66 Chapter 5 Internet access
Basic setup complete
Well done! You have successfully connected, installed and set up your Business
Secure Router to operate on your network, as well as access the Internet.
Note: When the firewall is activated, the default policy can
communicate to the Internet if the communication originates from the
LAN, and blocks all traffic to the LAN that originates from the Internet.
You can deactivate the firewall in menu 21.2 or via the Business Secure Router
embedded WebGUI. You can also define additional firewall rules or modify
existing ones, but exercise extreme caution in doing so. See the chapters on
firewalls in BCM50e Integrated Router Configuration - Basics (
more information on the firewall.
N0115788) for
N0115789
Page 67

Chapter 6
Remote Node setup
This chapter shows you how to configure a remote node.
Introduction to Remote Node setup
A remote node is required for placing calls to a remote gateway. A remote node
represents both the remote gateway and the network behind it across a WAN
connection. Note that when you use menu 4 to set up Internet access, you are
actually configuring a remote node. The following describes how to configure
Menu 11.1 Remote Node Profile, Menu 11.1.2 - Remote Node Network Layer
Options and Menu 11.1.4 - Remote Node Filter.
Remote Node setup
67
From the main menu, select menu option 11 to open Menu 11 Remote Node
Setup (Figure 18).
Enter 1 to open Menu 11.1 Remote Node Profile and configure the setup for
your regular ISP.
BCM50e Integrated Router Configuration - Advanced
Page 68

68 Chapter 6 Remote Node setup
Figure 18 Menu 11 Remote Node Setup
Menu 11 - Remote Node Setup
1. ChangeMe (ISP, SUA)
2. -GUI (BACKUP_ISP, SUA)
Enter Node # to Edit:
Remote Node profile setup
This section explains how to configure the remote node profile menu.
Ethernet Encapsulation
There are two variations of menu 11.1 depending on whether you choose
Ethernet Encapsulation or PPPoE Encapsulation. You must choose the
Ethernet option when the WAN port is used as a regular Ethernet. The first
menu 11.1 screen you see is for Ethernet encapsulation shown in Figure 19.
N0115789
Page 69

Chapter 6 Remote Node setup 69
Figure 19 Menu 11.1: Remote Node profile for Ethernet Encapsulation
Menu 11.1 - Remote Node Profile
Rem Node Name= ChangeMe Route= IP
Active= Yes
Encapsulation= Ethernet Edit IP= No
Service Type= Standard Session Options:
Service Name= N/A Edit Filter Sets= No
Outgoing:
My Login= N/A
My Password= N/A Edit Traffic Redirect= No
Retype to Confirm= N/A
Server= N/A
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
Table 13 describes the fields in Figure 19.
Table 13 Fields in menu 11.1
Field Description Example
Rem Node Name Enter a descriptive name for the remote node. This field
can be up to eight characters.
Active Press [SPACE BAR] and then [ENTER] to select Yes
(activate remote node) or No (deactivate remote node).
Encapsulation Ethernet is the default encapsulation. Press
[SPACE BAR] and then [ENTER] to change to PPPoE or
PPTP encapsulation.
Service Type Press [SPACE BAR] and then [ENTER] to select from
Standard, RR-Toshiba (Road Runner Toshiba
authentication method) or RR-Manager (Road Runner
Manager authentication method). Choose one of the
Road Runner methods if your ISP is Time Warner's Road
Runner; otherwise choose Standard.
BCM50e Integrated Router Configuration - Advanced
LAoffice
Yes
Ethernet
Standard
Page 70

70 Chapter 6 Remote Node setup
Table 13 Fields in menu 11.1
Field Description Example
Service Name If you are using PPPoE encapsulation, then type the
name of your PPPoE service here. Only valid with
PPPoE encapsulation.
Outgoing
My Login
My Password Enter the password assigned by your ISP when the
Retype to
Confirm
Server IP This field is valid only when Road Runner is selected in
Route This field refers to the protocol that is routed by your
Edit IP This field leads to a “hidden” menu. Press [SPACE BAR]
Session Options
Edit Filter sets
This field is applicable for PPPoE encapsulation only.
Enter the logon name assigned by your ISP when the
Business Secure Router calls this remote node. Some
ISPs append this field to the Service Name field above
(e.g., jim@poellc) to access the PPPoE server.
Business Secure Router calls this remote node. Valid for
PPPoE encapsulation only.
Type your password again to make sure that you have
entered it correctly.
the Service Type field. The Business Secure Router
finds the Road Runner Server IP automatically if this field
is left blank. If it does not, then you must enter the
authentication server IP address here.
Business Secure Router.
to select Yes and press [ENTER] to go to Menu 11.1.2 -
Remote Node Network Layer Options.
This field leads to another “hidden” menu. Use
[SPACE BAR] to select Yes and press [ENTER] to open
menu 11.1.4 to edit the filter sets. See “Remote Node
filter” on page 77 for more details.
After you configure this menu, press [ENTER] at the
message “Press ENTER to Confirm...” to save your
configuration, or press [ESC] at any time to cancel.
poellc
jim
*****
*****
IP
No
(default)
No
(default)
PPPoE Encapsulation
N0115789
The Business Secure Router supports PPPoE (Point-to-Point Protocol over
Ethernet). You can only use PPPoE encapsulation when you are using the
Business Secure Router with a DSL modem as the WAN device. If you change
the Encapsulation to PPPoE, you then see Figure 20. Please see Appendix E,
“PPPoE,” on page 227 for more information about PPPoE.
Page 71

Chapter 6 Remote Node setup 71
Figure 20 Menu 11.1: Remote Node profile for PPPoE Encapsulation
Menu 11.1 - Remote Node Profile
Rem Node Name= ChangeMe Route= IP
Active= Yes
Encapsulation= PPPoE Edit IP= No
Service Type= Standard Telco Option:
Service Name= Allocated Budget(min)= 0
Outgoing: Period(hr)= 0
My Login= Schedules=
My Password= ******** Nailed-Up Connection= No
Retype to Confirm= ********
Authen= CHAP/PAP
Session Options:
Edit Filter Sets= No
Idle Timeout(sec)= 100
Edit Traffic Redirect= No
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
Outgoing Authentication Protocol
Generally speaking, you must employ the strongest authentication protocol
possible. However, some vendors’ implementation includes a specific
authentication protocol in the user profile. It disconnects if the negotiated protocol
is different from that in the user profile, even when the negotiated protocol is
stronger than specified. If you encounter a case where the peer disconnects right
after a successful authentication, make sure that you specify the correct
authentication protocol when connecting to such an implementation.
BCM50e Integrated Router Configuration - Advanced
Page 72

72 Chapter 6 Remote Node setup
Nailed-Up Connection
A nailed-up connection is a dial-up line where the connection is always up,
regardless of traffic demand. The Business Secure Router does two things when
you specify a nailed-up connection. The first is that idle timeout is disabled. The
second is that the Business Secure Router tries to bring up the connection when
turned on and whenever the connection is down. A nailed-up connection can be
very expensive.
Do not specify a nailed-up connection unless your telephone company offers
flat-rate service or you need a constant connection and the cost is of no concern.
Table 14 describes the fields specific to PPPoE encapsulation.
Table 14 Fields in Menu 11.1 (PPPoE Encapsulation Specific)
Field Description Example
Authen This field sets the authentication protocol used for
outgoing calls.
Options for this field are:
CHAP/PAP - Your Business Secure Router accepts either
CHAP or PAP when requested by this remote node.
CHAP - accept CHAP only.
PAP - accept PAP only.
Telco Option
Allocated
Budget
Period(hr) This field is the time period in which the budget is reset.
Schedules You can apply up to four call schedule sets here.
Nailed-Up
Connection
Session
Options
Idle Timeout
The field sets a ceiling for outgoing call time for this remote
node. The default for this field is 0, meaning no budget
control.
For example, if we are allowed to call this remote node for
a maximum of 10 minutes every hour, then the Allocated
Budget is (10 minutes) and the Period(hr) is 1 (hour).
This field specifies if you want to make the connection to
this remote node a nailed-up connection. More details are
given earlier in this section.
Type the length of idle time (when there is no traffic from
the Business Secure Router to the remote node) in
seconds that can elapse before the Business Secure
Router automatically disconnects the PPPoE connection.
This option only applies when the Business Secure Router
initiates the call.
CHAP/PAP
0
(default)
0
(default)
No
(default)
100
seconds
(default)
N0115789
Page 73

Chapter 6 Remote Node setup 73
PPTP Encapsulation
If you change the Encapsulation to PPTP in menu 11.1, then you will see the next
screen. See Appendix F, “PPTP,” on page 231 for information about PPTP.
Figure 21 Menu 11.1: Remote Node Profile for PPTP Encapsulation
Menu 11.1 - Remote Node Profile
Rem Node Name= ChangeMe Route= IP
Active= Yes
Encapsulation= PPTP Edit IP= No
Service Type= Standard Telco Option:
Service Name= N/A Allocated Budget(min)= 0
Outgoing: Period(hr)= 0
My Login= Schedules=
My Password= ******** Nailed-Up Connection= No
Retype to Confirm= ********
Authen= CHAP/PAP
PPTP: Session Options:
My IP Addr= Edit Filter Sets= No
My IP Mask= Idle Timeout(sec)= 100
Server IP Addr=
Connection ID/Name= Edit Traffic Redirect= No
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
Table 15 shows how to configure fields in menu 11.1 not previously discussed.
Table 15 Fields in Menu 11.1 (PPTP Encapsulation)
Field Description Example
Encapsulation Press [SPACE BAR] and then [ENTER] to select
PPTP. You must also go to menu 11.1.2 to check
the IP Address setting after you select the
encapsulation method.
My IP Addr Enter the IP address of the WAN Ethernet port. 10.0.0.140
My IP Mask Enter the subnet mask of the WAN Ethernet port. 255.255.255.0
My Server IP Addr Enter the IP address of the ANT modem. 10.0.0.138
BCM50e Integrated Router Configuration - Advanced
PPTP
Page 74

74 Chapter 6 Remote Node setup
Table 15 Fields in Menu 11.1 (PPTP Encapsulation)
Field Description Example
Edit IP
Connection ID/
Name
Schedules You can apply up to four call schedule sets here.
Nailed-Up
Connections
Enter the connection ID or connection name in the
ANT. It must follow the “c:id” and “n:name” format.
This field is optional and depends on the
requirements of your DSL modem.
Press [SPACE BAR] and then [ENTER] to select
Yes if you want to make the connection to this
remote node a nailed-up connection.
N:My ISP
No
Move the cursor to the Edit IP field in menu 11.1, then press [SPACE BAR] to
select Yes. Press [ENTER]
to open Menu 11.1.2 - Network Layer Options.
N0115789
Page 75

Chapter 6 Remote Node setup 75
Figure 22 Menu 11.1.2: Remote Node Network Layer Options for Ethernet
Encapsulation
Menu 11.1.2 - Remote Node Network Layer Options
IP Address Assignment= Dynamic
IP Address= N/A
IP Subnet Mask= N/A
Gateway IP Addr= N/A
Network Address Translation= SUA Only
Metric= N/A
Private= N/A
RIP Direction= None
Version= N/A
Multicast= None
Enter here to CONFIRM or ESC to CANCEL:
Press Space Bar to Toggle.
This menu displays the My WAN Addr field for PPPoE and PPTP
encapsulations and Gateway IP Addr field for Ethernet encapsulation.
Table 16 describes the fields in Figure 22.
Table 16 Remote Node Network Layer Options Menu Fields
Field Description Example
IP Address
Assignment
(Rem) IP
Address
(Rem) IP
Subnet Mask
If your ISP did not assign you an explicit IP address, press
[SPACE BAR] and then [ENTER] to select Dynamic;
otherwise select Static and enter the IP address & subnet
mask in the following fields.
If you have a Static IP Assignment, enter the IP address
assigned to you by your ISP.
If you have a Static IP Assignment, enter the subnet mask
assigned to you.
BCM50e Integrated Router Configuration - Advanced
Dynamic
(default)
Page 76

76 Chapter 6 Remote Node setup
Table 16 Remote Node Network Layer Options Menu Fields
Field Description Example
Gateway IP
Addr
My WAN Addr This field is applicable to PPPoE and PPTP
Network
Address
Translation
Metric Enter a number from 1 to 15 to set this route’s priority
Private This field is valid only for PPTP/PPPoE encapsulation.
RIP Direction Press [SPACE BAR] and then [ENTER] to select the RIP
This field is applicable to Ethernet encapsulation only.
Enter the gateway IP address assigned to you if you are
using a static IP address.
encapsulations only. Some implementations, especially
the UNIX derivatives, require the WAN link to have a
separate IP network number from the LAN and each end
must have a unique address within the WAN network
number. If this is the case, enter the IP address assigned
to the WAN port of your Business Secure Router.
Note that this is the address assigned to your local
Business Secure Router, not the remote router.
With Network Address Translation (NAT), the device can
translate an Internet protocol address used within one
network (for example a private IP address used in a local
network) to a different IP address known within another
network (for example a public IP address used on the
Internet).
Choose None to disable NAT.
Choose SUA Only if you have a single public IP address.
SUA (Single User Account) is a subset of NAT that
supports two types of mapping: Many-to-One and Server.
Choose Full Feature if you have multiple public IP
addresses. Full Feature mapping types include:
One-to-One, Many-to-One (SUA/PAT), Many-to-Many
Overload, Many- One-to-One and Server. When you
select Full Feature you must configure at least one
address mapping set!
See Chapter 9, “Network Address Translation (NAT) for a
full discussion on this feature.
among the Business Secure Router routes. The smaller
the number, the higher priority the route has.
This parameter determines if the Business Secure Router
includes the route to this remote node in its RIP
broadcasts. If set to Yes, this route is kept private and not
included in RIP broadcast. If No, the route to this remote
node is propagated to other hosts through RIP broadcasts.
direction from Both/ None/In Only/Out Only. The default
for RIP on the WAN side is None. Nortel recommends that
you do not change this setting.
SUA Only
(default)
1
No
None
(default)
N0115789
Page 77

Chapter 6 Remote Node setup 77
Table 16 Remote Node Network Layer Options Menu Fields
Field Description Example
Version Press [SPACE BAR] and then [ENTER] to select the RIP
Multicast IGMP (Internet Group Multicast Protocol) is a
Remote Node filter
Move the cursor to the field Edit Filter Sets in menu 11.1, and then press
[SPACE BAR] to set the value to Yes. Press [ENTER] to open
Remote Node Filter.
Use menu 11.1.4 to specify the filter sets to apply to the incoming and outgoing
traffic between this remote node and the Business Secure Router to prevent
certain packets from triggering calls. You can specify up to 4 filter sets separated
by commas, for example, 1, 5, 9, 12, in each filter field. Note that spaces are
accepted in this field. For more information about defining the filters, refer to
Chapter 11, “Filter configuration,” on page 117. For PPPoE or PPTP
encapsulation, you have the additional option of specifying remote node call filter
sets.
version from RIP-1/RIP-2B/RIP-2M or None.
network-layer protocol used to establish membership in a
Multicast group. The Business Secure Router supports
both IGMP version 1 (IGMP-v1) and version 2 (IGMP-v2).
Press [SPACE BAR] to enable IP Multicasting or select
None to disable it.
After you complete filling in Menu 11.1.2 Remote Node
Network Layer Options, press [ENTER] at the message
“Press ENTER to Confirm...” to save your configuration
and return to menu 11.1, or press [ESC] at any time to
cancel.
Menu 11.1.4-
N/A
None
(default)
BCM50e Integrated Router Configuration - Advanced
Page 78

78 Chapter 6 Remote Node setup
Figure 23 Menu 11.1.4: Remote Node filter (Ethernet Encapsulation)
Menu 11.1.4 - Remote Node Filter
Input Filter Sets:
protocol filters=
device filters=
Output Filter Sets:
protocol filters=
device filters=
Enter here to CONFIRM or ESC to CANCEL:
Figure 24 Menu 11.1.4: Remote Node filter (PPPoE or PPTP Encapsulation)
Menu 11.1.4 - Remote Node Filter
Input Filter Sets:
protocol filters=
Device filters=
Output Filter Sets:
protocol filters=
device filters=
Call Filter Sets:
protocol filters=
Device filters=
N0115789
Enter here to CONFIRM or ESC to CANCEL:
To configure the parameters for traffic redirect, enter 11 from the main menu to
display Menu 11.1—Remote Node Profile as shown in Figure 25.
Page 79

Chapter 6 Remote Node setup 79
Figure 25 Menu 11.1: Remote Node Profile
Menu 11.1 - Remote Node Profile
Rem Node Name= ChangeMe Route= IP
Active= Yes
Encapsulation= Ethernet Edit IP= No
Service Type= Standard Session Options:
Service Name= N/A Edit Filter Sets= No
Outgoing:
My Login= N/A
My Password= N/A Edit Traffic Redirect= No
Retype to Confirm= N/A
Server= N/A
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
To configure traffic redirect properties, press [SPACE BAR] to select Yes in the
Edit Traffic Redirect field and then press [ENTER].
Table 17 Menu 11.1: Remote Node profile (Traffic Redirect Field)
Field Description Example
Edit
Traffic
Redirect
Press [SPACE BAR] to select Yes or No.
Select No (default) if you do not want to configure this feature.
Select Yes and press [ENTER] to configure Menu 11.1.5 —
Traffi c Redirect Setup.
Press [ENTER] at the message “Press ENTER to Confirm...” to
save your configuration, or press [ESC] at any time to cancel.
BCM50e Integrated Router Configuration - Advanced
Yes
Page 80

80 Chapter 6 Remote Node setup
Traffic Redirect setup
Configure parameters that determine when the Business Secure Router forwards
WAN traffic to the backup gateway using Menu 11.1.5 — Traffic Redirect
Setup.
Figure 26 Menu 11.1.5: Traffic Redirect setup
Menu 11.1.5 - Traffic Redirect Setup
Active= Yes
Configuration:
Backup Gateway IP Address= 0.0.0.0
Metric= 15
Check WAN IP Address= 0.0.0.0
Fail Tolerance= 3
Period (sec)= 5
Timeout (sec)= 3
N0115789
Press ENTER to Confirm or ESC to Cancel:
Table 18 describes the fields in Figure 26.
Table 18 Menu 11.1.5: Traffic Redirect setup
Field Description Example
Active Press [SPACE BAR] and select Yes (to enable) or No (to
Configuration:
Backup
Gateway IP
Address
Metric Enter a number from 1 to 15 to set this route’s priority
disable) traffic redirect setup. The default is No.
Enter the IP address of your backup gateway in dotted
decimal notation.
The Business Secure Router automatically forwards traffic
to this IP address if the Business Secure Router Internet
connection terminates.
among the Business Secure Router routes. The smaller
the number, the higher priority the route has.
Yes
0.0.0.0
15
(default)
Page 81

Chapter 6 Remote Node setup 81
Table 18 Menu 11.1.5: Traffic Redirect setup
Field Description Example
Check WAN IP
Address
Fail Tolerance Enter the number of times your Business Secure Router
Period (sec) Enter the time interval (in seconds) between WAN
Timeout (sec) Enter the number of seconds the Business Secure Router
Enter the IP address of a reliable nearby computer (for
example, your ISP’s DNS server address) to test your
Business Secure Router’s WAN accessibility.
The Business Secure Router uses the default gateway IP
address if you do not enter an IP address here.
If you are using PPTP or PPPoE Encapsulation, enter
0.0.0.0 to configure the Business Secure Router to check
the PVC (Permanent Virtual Circuit) or PPTP tunnel.
can attempt and fail to connect to the Internet before traffic
is forwarded to the backup gateway. A good number is 2 to
5 seconds.
connection checks. A good number is 5 to 60 seconds.
waits for a ping response from the IP Address in the Check
WAN IP Address field before it times out. The number in
this field should be less than the number in the Period
field. A good number is 3 to 50 seconds.
The WAN connection is considered “down” after the
Business Secure Router times out the number of times
specified in the Fail Toleran ce field.
After you complete this menu, press [ENTER] at the
prompt “Press [ENTER] to confirm or [ESC] to cancel” to
save your configuration or press [ESC] to cancel and go
back to the previous screen.
0.0.0.0
3
5
3
BCM50e Integrated Router Configuration - Advanced
Page 82

82 Chapter 6 Remote Node setup
N0115789
Page 83

Chapter 7
IP Static Route Setup
This chapter shows you how to configure static routes with your Business Secure
Router.
IP Static Route Setup
Enter 12 from the main menu. Select one of the IP static routes as shown in
Figure 27 to configure IP static routes in menu 12. 1.
Note: The “Reserved” static route entry is for the default WAN route.
You cannot modify or delete a static default route.
Figure 27 Menu 12: IP Static Route Setup
83
Menu 12 - IP Static Route Setup
1. Reserved
2. ________
3. ________
4. ________
5. ________
6. ________
7. ________
8. ________
9. ________
10. ________
11. ________
BCM50e Integrated Router Configuration - Advanced
Page 84

84 Chapter 7 IP Static Route Setup
12. ________
Enter selection number:
Now, enter the index number of the static route that you want to configure.
Figure 28 Menu 12. 1: Edit IP Static Route
Menu 12.1 - Edit IP Static Route
Route #: 2
Route Name= ?
Active= No
Destination IP Address= ?
IP Subnet Mask= ?
Gateway IP Address= ?
Metric= 2
Private= No
Press ENTER to CONFIRM or ESC to CANCEL:
N0115789
Table 19 describes the IP Static Route Menu fields.
Table 19 IP Static Route Menu Fields
Field Description
Route # This is the index number of the static route that you chose in menu 12.
Route Name Enter a descriptive name for this route. This is for identification
Active This field allows you to activate or deactivate this static route.
Destination IP
Address
IP Subnet Mask Enter the IP subnet mask for this destination.
Gateway IP
Address
purposes only.
This parameter specifies the IP network address of the final
destination. Routing is always based on network number. If you need to
specify a route to a single host, use a subnet mask of 255.255.255.255
in the subnet mask field to force the network number to be identical to
the host ID.
Enter the IP address of the gateway. The gateway is an immediate
neighbor of your Business Secure Router that forwards the packet to
the destination. On the LAN, the gateway must be a router on the same
segment as your Business Secure Router; over the WAN, the gateway
must be the IP address of one of the remote nodes.
Page 85

Chapter 7 IP Static Route Setup 85
Table 19 IP Static Route Menu Fields
Field Description
Metric Enter a number from 1 to 15 to set the priority for the route among the
Business Secure Router routes. The smaller the number, the higher
priority the route has.
Private This parameter determines if the Business Secure Router includes the
route to this remote node in its RIP broadcasts. If set to Yes, this route
is kept private and not included in RIP broadcast. If No, the route to this
remote node is propagated to other hosts through RIP broadcasts.
After you complete filling in this menu, press [ENTER] at the message
“Press ENTER to Confirm…” to save your configuration, or press [ESC]
to cancel.
BCM50e Integrated Router Configuration - Advanced
Page 86

86 Chapter 7 IP Static Route Setup
N0115789
Page 87

Chapter 8
Dial-in User Setup
This chapter shows you how to create user accounts on the Business Secure
Router.
Dial-in User Setup
By storing user profiles locally, your Business Secure Router can authenticate
users without interacting with a network RADIUS server.
Follow the steps below to set up user profiles on your Business Secure Router.
From the main menu, enter 14 to display Menu 14 - Dial-in User Setup.
Figure 29 Menu 14- Dial-in User Setup
87
Menu 14 - Dial-in User Setup
1. ________ 9. ________ 17. ________ 25. ________
2. ________ 10. ________ 18. ________ 26. ________
3. ________ 11. ________ 19. ________ 27. ________
4. ________ 12. ________ 20. ________ 28. ________
5. ________ 13. ________ 21. ________ 29. ________
6. ________ 14. ________ 22. ________ 30. ________
7. ________ 15. ________ 23. ________ 31. ________
8. ________ 16. ________ 24. ________ 32. ________
Enter Menu Selection Number:
Type a number and press [ENTER] to edit the user profile.
BCM50e Integrated Router Configuration - Advanced
Page 88

88 Chapter 8 Dial-in User Setup
Figure 30 Menu 14.1- Edit Dial-in User
Menu 14.1 - Edit Dial-in User
User Name= test
Active= Yes
Password= ********
Press ENTER to Confirm or ESC to Cancel:
Leave name field blank to delete profile
Table 20 describes the fields in Figure 30.
Table 20 Menu 14.1- Edit Dial-in User
Field Description
User Name Enter a username up to 31 alphanumeric characters long for this
Active Press [SPACE BAR] to select Yes and press [ENTER] to enable the
Password Enter a password up to 31 characters long for this user profile.
user profile.
This field is case sensitive.
user profile.
After you complete this menu, press [ENTER] at the prompt “Press
ENTER to confirm or ESC to cancel” to save your configuration or
press [ESC] to cancel and go back to the previous screen.
N0115789
Page 89

Chapter 9
Network Address Translation (NAT)
This chapter discusses how to configure NAT on the Business Secure Router.
Using NAT
Note: You must create a firewall rule in addition to setting up SUA/
NAT, to allow traffic from the WAN to be forwarded through the
Business Secure Router.
SUA (Single User Account) Versus NAT
SUA (Single User Account) is an implementation of a subset of NAT that
supports two types of mapping, Many-to-One and Server. For a detailed
description of NAT set for SUA, see“Address Mapping Sets” on page 92. The
Business Secure Router also supports Full Feature NAT to map multiple global
IP addresses to multiple private LAN IP addresses of clients or servers using
mapping types.
89
Note: Choose SUA Only if you have just one public WAN IP address
for your Business Secure Router.
Choose Full Feature if you have multiple public WAN IP addresses for
your Business Secure Router.
Applying NAT
You apply NAT via menus 4 or 11.1.2 (Figure 32 on page 91). Figure 31 shows
you how to apply NAT for Internet access in menu 4. Enter 4 from the main menu
to go to Menu 4 - Internet Access Setup.
BCM50e Integrated Router Configuration - Advanced
Page 90

90 Chapter 9 Network Address Translation (NAT)
Figure 31 Menu 4: Applying NAT for Internet Access
Menu 4 - Internet Access Setup
ISP's Name= ChangeMe
Encapsulation= Ethernet
Service Type= Standard
My Login= N/A
My Password= N/A
Retype to Confirm= N/A
Login Server= N/A
IP Address Assignment= Dynamic
IP Address= N/A
IP Subnet Mask= N/A
Gateway IP Address= N/A
Network Address Translation= SUA Only
Press ENTER to Confirm or ESC to Cancel:
Press ENTER to Confirm or ESC to Cancel:
N0115789
Figure 32 shows how you apply NAT to the remote node in menu 11.1.
Enter 11 from the main menu.
Move the cursor to the Edit IP field, press [SPACE BAR] to select Yes and then
press [ENTER] to bring up Menu 11.1.2 - Remote Node Network Layer
Options.
Page 91

Chapter 9 Network Address Translation (NAT) 91
Figure 32 Menu 11.1.2: Applying NAT to the Remote Node
Menu 11.1.2 - Remote Node Network Layer Options
IP Address Assignment= Dynamic
IP Address= N/A
IP Subnet Mask= N/A
Gateway IP Addr= N/A
Network Address Translation= Full Feature
Metric= N/A
Private= N/A
RIP Direction= None
Version= N/A
Multicast= None
Enter here to CONFIRM or ESC to CANCEL:
Table 21 describes the fields in Figure 32.
Table 21 Applying NAT in Menus 4 & 11.1.2
Field Description Options
Network
Address
Translation
When you select this option the SMT uses Address
Mapping Set 1 (menu 15.1 - “Address Mapping Sets” on
page 92 for further discussion). Choose Full Feature if you
have multiple public WAN IP addresses for your Business
Secure Router.
When you select Full Feature you must configure at least
one address mapping set!
NAT is disabled when you select this option. None
When you select this option the SMT uses Address
Mapping Set 255 (menu 15.1 - “Address Mapping Sets” on
page 92). Choose SUA Only if you have just one public
WAN IP address for your Business Secure Router.
Full Feature
SUA Only
BCM50e Integrated Router Configuration - Advanced
Page 92

92 Chapter 9 Network Address Translation (NAT)
NAT setup
Use the address mapping sets menus and submenus to create the mapping table
used to assign global addresses to computers on the LAN. You can see two NAT
address mapping sets in menu 15.1. You can only configure Set 1. Set 255 is used
for SUA. When you select Full Feature in menu 4 or 11.1.2, the SMT uses Set 1.
When you select SUA Only, the SMT uses the pre-configured Set 255 (read
only).
The server set is a list of LAN servers mapped to external ports. To use this set, a
server rule must be set up inside the NAT address mapping set. To configure
NAT, enter 15 from the main menu to bring up the screen shown in Figure 33.
Figure 33 Menu 15: NAT Setup
Menu 15 — NAT Setup
1. Address Mapping Sets
2. Port Forwarding Setup
3. Trigger Port Setup
Address Mapping Sets
N0115789
Enter Menu Selection Number:
Note: Configure LAN IP addresses in NAT menus 15.1 and 15.2.
Enter 1 to bring up Menu 15.1—Address Mapping Sets.
Page 93

Chapter 9 Network Address Translation (NAT) 93
Figure 34 Menu 15.1: Address Mapping Sets
Menu 15.1 — Address Mapping Sets
1. NAT_SET
255. SUA (read only)
Enter Menu Selection Number:
SUA Address Mapping Set
Enter 255 to display the screen shown in Figure 35 (see “SUA (Single User
Account) Versus NAT” on page 89). The fields in this menu cannot be changed.
BCM50e Integrated Router Configuration - Advanced
Page 94

94 Chapter 9 Network Address Translation (NAT)
Figure 35 Menu 15.1.255: SUA Address Mapping Rules
Menu 15.1.255 - Address Mapping Rules
Set Name= SUA
Idx Local Start IP Local End IP Global Start IP Global End IP Type
--- --------------- --------------- --------------- --------------- ------
1. 0.0.0.0 255.255.255.255 0.0.0.0 M-1
2. 0.0.0.0 Server
3.
4.
5.
6.
7.
8.
9.
10.
Press ENTER to Confirm or ESC to Cancel:
Table 22 explains the fields in Figure 35.
Note: Menu 15.1.255 is read-only.
Table 22 SUA Address Mapping Rules
Field Description Example
Set Name This is the name of the set you selected in menu
15.1 or enter the name of a new set you want to
create.
Idx This is the index or rule number. 1
Local Start IP Local Start IP is the starting local IP address (ILA). 0.0.0.0
N0115789
SUA
Page 95

Chapter 9 Network Address Translation (NAT) 95
Table 22 SUA Address Mapping Rules
Field Description Example
Local End IP Local End IP is the ending local IP address (ILA). If
the rule is for all local IPs, then the start IP is 0.0.0.0
and the end IP is 255.255.255.255.
Global Start IP This is the starting global IP address (IGA). If you
have a dynamic IP, enter 0.0.0.0 as the Global Start
IP.
Global End IP This is the ending global IP address (IGA).
Type These are the mapping types discussed above. With
Server, you can specify multiple servers of different
types behind NAT to this machine. Examples is
found in the section “General NAT examples” on
page 103.
After you configure a rule in this menu, press
[ENTER] at the message “Press ENTER to
Confirm…” to save your configuration, or press
[ESC] to cancel.
255.255.255.255
0.0.0.0
Server
User-Defined Address Mapping Sets
Go to menu 15.1. Enter 1 to bring up the menu shown in figure below. Look at the
differences from the previous menu. Note the extra Action and Select Rule fields
means you can configure rules in this screen. Note also that the [?] in the Set
Name field means that this is a required field and you must enter a name for the
set.
Note: The entire set is deleted if you leave the Set Name field blank and
press [ENTER] at the bottom of the screen.
BCM50e Integrated Router Configuration - Advanced
Page 96

96 Chapter 9 Network Address Translation (NAT)
Figure 36 Menu 15.1.1: First Set
Menu 15.1.1 - Address Mapping Rules
Set Name= NAT_SET
Idx Local Start IP Local End IP Global Start IP Global End IP Type
--- --------------- --------------- --------------- --------------- ------
1.
2
3.
4.
5.
6.
7.
8.
9.
10.
Action= Edit Select Rule=
Press ENTER to Confirm or ESC to Cancel:
Note: The Type, Local and Global Start/End IPs are configured in
menu 15.1.1.1 (described later) and the values are displayed on the
screen shown in Figure 37.
Ordering Your Rules
Ordering your rules is important because the Business Secure Router applies the
rules in the order that you specify. When a rule matches the current packet, the
Business Secure Router takes the corresponding action and the remaining rules
are ignored. If there are any empty rules before your new configured rule, your
configured rule is pushed up by that number of empty rules. For example, if you
N0115789
Page 97

Chapter 9 Network Address Translation (NAT) 97
have already configured rules 1 to 6 in your current set and now you configure
rule number 9. In the set summary screen, the new rule will be rule 7, not 9.
If you delete rule 4, rules 5 to 7 will be pushed up by 1 rule, so as old rule 5
becomes rule 4, old rule 6 becomes rule 5 and old rule 7 becomes rule 6.
Table 23 Fields in menu 15.1.1
Field Description Example
Set Name Enter a name for this set of rules. This is a required field. If
this field is left blank, the entire set is deleted.
Action The default is Edit. Edit means you want to edit a selected
rule (see following field). Insert Before means to insert a rule
before the rule selected. The rules after the selected rule are
then moved down by one rule. Delete means to delete the
selected rule and all the rules after the selected one advance
one rule. None disables the Select Rule item.
Select Rule When you choose Edit, Insert Before or Delete in the
previous field, the cursor jumps to this field so you can select
the rule to apply the action in question.
NAT_SET
Edit
1
Note: You must press [ENTER] at the bottom of the screen to save the
whole set. You must do this again if you make any changes to the set –
including deleting a rule. No changes to the set take place until this
action is taken.
Selecting Edit in the Action field and then selecting a rule brings up the menu
shown in Figure 37, Menu 15.1.1.1
- Address Mapping Rule in which you can
edit an individual rule and configure the Type, Local and Global Start/End IPs.
Note: An IP End address must be numerically greater than its
corresponding IP Start address.
BCM50e Integrated Router Configuration - Advanced
Page 98

98 Chapter 9 Network Address Translation (NAT)
Figure 37 Menu 15.1.1.1: Editing or configuring an individual rule in a set
Menu 15.1.1.1 Address Mapping Rule
Type= One-to-One
Local IP:
Start=
End = N/A
Global IP:
Start=
End = N/A
Press ENTER to Confirm or ESC to Cancel:
N0115789
Table 24 describes the fields in Figure 37.
Table 24 Menu 15.1.1.1: Editing or configuring an individual rule in a set
Field Description Example
Type Press [SPACE BAR] and then [ENTER] to select from a total
of five types. If you choose Server, you can specify multiple
servers of different types behind NAT to this computer. See
“Example 3: Multiple public IP addresses with inside servers”
on page 106 for an example.
Local IP
Star t
End Enter the ending local IP address (ILA). If the rule is for all
Only local IP fields are N/A for server; Global IP fields must be
set for Server.
Enter the starting local IP address (ILA). 0.0.0.0
local IPs, then put the Start IP as 0.0.0.0 and the End IP as
255.255.255.255. This field is N/A for One-to-One and Server
types.
One-to-On
e
N/A
Page 99

Chapter 9 Network Address Translation (NAT) 99
Table 24 Menu 15.1.1.1: Editing or configuring an individual rule in a set
Field Description Example
Global IP
Star t
End Enter the ending global IP address (IGA). This field is N/A for
Enter the starting global IP address (IGA). If you have a
dynamic IP, enter 0.0.0.0 as the Global IP Start. Note that
Global IP Start can be set to 0.0.0.0 only if the types are
Many-to-One or Server.
One-to-One, Many-to-One and Server types.
After you finish configuring a rule in this menu, press [ENTER]
at the message “Press ENTER to Confirm…” to save your
configuration, or press [ESC] to cancel.
0.0.0.0
N/A
Configuring a server behind NAT
Note: If you do not assign a Default Server IP address, the Business Secure Router
discards all packets received for ports that are not specified here or in the remote
management setup.
Follow these steps to configure a server behind NAT:
1 Enter 15 in the main menu to go to Menu 15 - NAT Setup.
2 Enter 2 to go to Menu 15.2 - NAT Server Setup.
BCM50e Integrated Router Configuration - Advanced
Page 100

100 Chapter 9 Network Address Translation (NAT)
Figure 38 Menu 15.2: NAT Server Sets
Menu 15.2 - NAT Server Setup
Default Server: 0.0.0.0
Rule Act. Start Port End Port IP Address
----------------------------------------------------- 001 No 0 0 0.0.0.0
002 No 0 0 0.0.0.0
003 No 0 0 0.0.0.0
004 No 0 0 0.0.0.0
005 No 0 0 0.0.0.0
006 No 0 0 0.0.0.0
007 No 0 0 0.0.0.0
008 No 0 0 0.0.0.0
009 No 0 0 0.0.0.0
010 No 0 0 0.0.0.0
Select Command= None Select Rule= N/A
Press ENTER to Confirm or ESC to Cancel:
3 Select Edit Rule in the Select Command field; type the index number of the
NAT server you want to configure in the Select Rule field and press
[ENTER] to open Menu 15.2.1 - NAT Server Configuration (see the next
figure).
N0115789
 Loading...
Loading...