Avaya 2330, 4134 Configuration

Configuration — Layer 2 Ethernet
Avaya Secure Router 2330/4134
Release 10.3.5
NN47263-501
Issue 04.03
July 2013

©
2013 Avaya Inc.
All Rights Reserved.
Notice
While reasonable efforts have been made to ensure that the
information in this document is complete and accurate at the time of
printing, Avaya assumes no liability for any errors. Avaya reserves the
right to make changes and corrections to the information in this
document without the obligation to notify any person or organization of
such changes.
Documentation disclaimer
“Documentation” means information published by Avaya in varying
mediums which may include product information, operating instructions
and performance specifications that Avaya generally makes available
to users of its products. Documentation does not include marketing
materials. Avaya shall not be responsible for any modifications,
additions, or deletions to the original published version of
documentation unless such modifications, additions, or deletions were
performed by Avaya. End User agrees to indemnify and hold harmless
Avaya, Avaya's agents, servants and employees against all claims,
lawsuits, demands and judgments arising out of, or in connection with,
subsequent modifications, additions or deletions to this documentation,
to the extent made by End User.
Link disclaimer
Avaya is not responsible for the contents or reliability of any linked
websites referenced within this site or documentation provided by
Avaya. Avaya is not responsible for the accuracy of any information,
statement or content provided on these sites and does not necessarily
endorse the products, services, or information described or offered
within them. Avaya does not guarantee that these links will work all the
time and has no control over the availability of the linked pages.
Warranty
Avaya provides a limited warranty on its hardware and Software
(“Product(s)”). Refer to your sales agreement to establish the terms of
the limited warranty. In addition, Avaya’s standard warranty language,
as well as information regarding support for this Product while under
warranty is available to Avaya customers and other parties through the
Avaya Support website:
you acquired the Product(s) from an authorized Avaya reseller outside
of the United States and Canada, the warranty is provided to you by
said Avaya reseller and not by Avaya. “Software” means computer
programs in object code, provided by Avaya or an Avaya Channel
Partner, whether as stand-alone products or pre-installed on hardware
products, and any upgrades, updates, bug fixes, or modified versions.
Licenses
THE SOFTWARE LICENSE TERMS AVAILABLE ON THE AVAYA
WEBSITE,
APPLICABLE TO ANYONE WHO DOWNLOADS, USES AND/OR
INSTALLS AVAYA SOFTWARE, PURCHASED FROM AVAYA INC.,
ANY AVAYA AFFILIATE, OR AN AUTHORIZED AVAYA RESELLER
(AS APPLICABLE) UNDER A COMMERCIAL AGREEMENT WITH
AVAYA OR AN AUTHORIZED AVAYA RESELLER. UNLESS
OTHERWISE AGREED TO BY AVAYA IN WRITING, AVAYA DOES
NOT EXTEND THIS LICENSE IF THE SOFTWARE WAS OBTAINED
FROM ANYONE OTHER THAN AVAYA, AN AVAYA AFFILIATE OR
AN AVAYA AUTHORIZED RESELLER; AVAYA RESERVES THE
RIGHT TO TAKE LEGAL ACTION AGAINST YOU AND ANYONE
ELSE USING OR SELLING THE SOFTWARE WITHOUT A LICENSE.
BY INSTALLING, DOWNLOADING OR USING THE SOFTWARE, OR
AUTHORIZING OTHERS TO DO SO, YOU, ON BEHALF OF
YOURSELF AND THE ENTITY FOR WHOM YOU ARE INSTALLING,
DOWNLOADING OR USING THE SOFTWARE (HEREINAFTER
REFERRED TO INTERCHANGEABLY AS “YOU” AND “END USER”),
AGREE TO THESE TERMS AND CONDITIONS AND CREATE A
BINDING CONTRACT BETWEEN YOU AND AVAYA INC. OR THE
APPLICABLE AVAYA AFFILIATE (“AVAYA”).
HTTP://SUPPORT.AVAYA.COM/LICENSEINFO ARE
http://support.avaya.com. Please note that if
Avaya grants you a license within the scope of the license types
described below, with the exception of Heritage Nortel Software, for
which the scope of the license is detailed below. Where the order
documentation does not expressly identify a license type, the
applicable license will be a Designated System License. The applicable
number of licenses and units of capacity for which the license is granted
will be one (1), unless a different number of licenses or units of capacity
is specified in the documentation or other materials available to you.
“Designated Processor” means a single stand-alone computing device.
“Server” means a Designated Processor that hosts a software
application to be accessed by multiple users.
Copyright
Except where expressly stated otherwise, no use should be made of
materials on this site, the Documentation, Software, or hardware
provided by Avaya. All content on this site, the documentation and the
Product provided by Avaya including the selection, arrangement and
design of the content is owned either by Avaya or its licensors and is
protected by copyright and other intellectual property laws including the
sui generis rights relating to the protection of databases. You may not
modify, copy, reproduce, republish, upload, post, transmit or distribute
in any way any content, in whole or in part, including any code and
software unless expressly authorized by Avaya. Unauthorized
reproduction, transmission, dissemination, storage, and or use without
the express written consent of Avaya can be a criminal, as well as a
civil offense under the applicable law.
Third Party Components
“Third Party Components” mean certain software programs or portions
thereof included in the Software that may contain software (including
open source software) distributed under third party agreements (“Third
Party Components”), which contain terms regarding the rights to use
certain portions of the Software (“Third Party Terms”). Information
regarding distributed Linux OS source code (for those Products that
have distributed Linux OS source code) and identifying the copyright
holders of the Third Party Components and the Third Party Terms that
apply is available in the Documentation or on Avaya’s website at:
support.avaya.com/Copyright. You agree to the Third Party Terms for
any such Third Party Components.
Note to Service Provider
The Product may use Third Party Components that have Third Party
Terms that do not allow hosting and may need to be independently
licensed for such purpose.
Preventing Toll Fraud
“Toll Fraud” is the unauthorized use of your telecommunications
system by an unauthorized party (for example, a person who is not a
corporate employee, agent, subcontractor, or is not working on your
company's behalf). Be aware that there can be a risk of Toll Fraud
associated with your system and that, if Toll Fraud occurs, it can result
in substantial additional charges for your telecommunications services.
Avaya Toll Fraud intervention
If you suspect that you are being victimized by Toll Fraud and you need
technical assistance or support, call Technical Service Center Toll
Fraud Intervention Hotline at +1-800-643-2353 for the United States
and Canada. For additional support telephone numbers, see the Avaya
Support website:
vulnerabilities with Avaya products should be reported to Avaya by
sending mail to: securityalerts@avaya.com.
Trademarks
The trademarks, logos and service marks (“Marks”) displayed in this
site, the Documentation and Product(s) provided by Avaya are the
registered or unregistered Marks of Avaya, its affiliates, or other third
parties. Users are not permitted to use such Marks without prior written
consent from Avaya or such third party which may own the Mark.
Nothing contained in this site, the Documentation and Product(s)
should be construed as granting, by implication, estoppel, or otherwise,
http://support.avaya.com. Suspected security
http://
2 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com

any license or right in and to the Marks without the express written
permission of Avaya or the applicable third party.
Avaya is a registered trademark of Avaya Inc.
All non-Avaya trademarks are the property of their respective owners.
Linux® is the registered trademark of Linus Torvalds in the U.S. and
other countries.
Downloading Documentation
For the most current versions of Documentation, see the Avaya
Support website: http://support.avaya.com.
Contact Avaya Support
See the Avaya Support website: http://support.avaya.com for product
notices and articles, or to report a problem with your Avaya product.
For a list of support telephone numbers and contact addresses, go to
the Avaya Support website: http://support.avaya.com, scroll to the
bottom of the page, and select Contact Avaya Support.
Configuration — Layer 2 Ethernet July 2013 3

4 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com

Contents
Chapter 1: Introduction......................................................................................................
Introduction...............................................................................................................................................
Related Resources....................................................................................................................................
Documentation.................................................................................................................................
Training............................................................................................................................................
Avaya Mentor videos........................................................................................................................
Support.............................................................................................................................................
Chapter 2: New in this release...........................................................................................
Features....................................................................................................................................................
Common and internal spanning tree information.............................................................................
Other changes...........................................................................................................................................
Chapter 3: Secure Router 2330/4134 Ethernet interface fundamentals.........................
Ethernet interface fundamentals...............................................................................................................
FE and FE/PoE Medium Modules....................................................................................................
GbE Medium Module........................................................................................................................
GbE Large Module...........................................................................................................................
Chassis Ethernet ports.....................................................................................................................
Chapter 4: Ethernet Connectivity Fault Management......................................................
Maintenance Domain................................................................................................................................
Maintenance End Point....................................................................................................................
Maintenance Intermediate Point.......................................................................................................
Connectivity Fault Management messages.....................................................................................
Connectivity Fault Management modes....................................................................................................
Connectivity Fault Management errors and statistics...............................................................................
Chapter 5: Layer 2 fundamentals......................................................................................
Layer 2 switching and bridging.................................................................................................................
MAC bridging............................................................................................................................................
VLANs.......................................................................................................................................................
Independent VLAN learning.............................................................................................................
Static multicast MAC filtering............................................................................................................
VLAN classification...........................................................................................................................
VLAN stacking..................................................................................................................................
Multiple IP Helper Addresses on a VLAN.........................................................................................
Spanning Tree Protocol............................................................................................................................
Multiple Spanning Tree Protocol......................................................................................................
MSTP regions...................................................................................................................................
Common Spanning Tree..................................................................................................................
MSTP instance.................................................................................................................................
Rapid transitions...............................................................................................................................
IGMP Snooping.........................................................................................................................................
IGMP proxy......................................................................................................................................
IGMP querier....................................................................................................................................
Query interval...................................................................................................................................
Last member query interval..............................................................................................................
11
11
11
11
11
11
12
13
13
13
13
15
15
15
17
18
18
21
21
22
26
27
28
28
29
29
29
30
31
32
32
33
33
34
34
35
36
37
38
39
40
40
40
41
Configuration — Layer 2 Ethernet July 2013 5

Maximum response time..................................................................................................................
Fast-leave processing......................................................................................................................
Multicast router ports........................................................................................................................
GVRP........................................................................................................................................................
Link aggregation........................................................................................................................................
LACP................................................................................................................................................
Port mirroring............................................................................................................................................
Selectable range of ports..........................................................................................................................
Chapter 6: Power over Ethernet configuration................................................................
Configuring the PoE port mode.................................................................................................................
Configuring PoE port power......................................................................................................................
Configuring PoE port priority commands..................................................................................................
Configuring PoE device detection.............................................................................................................
Configuring PoE port power limits.............................................................................................................
Viewing PoE information...........................................................................................................................
Chapter 7: Ethernet Connectivity Fault Management configuration..............................
Accessing the CFM tools..........................................................................................................................
Configuring the number of path trace cache entries.................................................................................
Configuring the CFM frame ethertype.......................................................................................................
Enabling CFM event messages................................................................................................................
Creating a Maintenance Domain..............................................................................................................
Configuring a Maintenance Association....................................................................................................
Configuring a Maintenance End Point......................................................................................................
Deleting a Maintenance End Point...................................................................................................
Configuring a remote Maintenance End Point..........................................................................................
Deleting a remote Maintenance End Point...............................................................................................
Configuring a Maintenance Intermediate Point.........................................................................................
Deleting a Maintenance Intermediate Point.....................................................................................
Configuring Continuity Check Messages..................................................................................................
Removing an auto-detected remote Maintenance End Point...................................................................
Issuing CFM loopback tests......................................................................................................................
Verifying the path to a remote MEP.................................................................................................
Verifying the path to a remote MIP...................................................................................................
Issuing CFM linktrace tests.......................................................................................................................
Tracing the path to a remote MEP...................................................................................................
Tracing the path to a remote MIP.....................................................................................................
Example of configuring Ethernet Connectivity Fault Management...........................................................
Displaying Ethernet CFM information.......................................................................................................
Displaying information related to Maintenance Domains.................................................................
Displaying information related to Maintenance Associations...........................................................
Displaying information related to MEPs and MIPs...........................................................................
Displaying information related to continuity checks..........................................................................
Displaying information related to CFM errors...................................................................................
Displaying information related to CFM stats.....................................................................................
Displaying information related to path trace cache entries...............................................................
Displaying CFM global configuration................................................................................................
Clearing Ethernet CFM information...........................................................................................................
41
41
42
42
43
43
43
44
45
45
46
47
48
48
49
51
51
51
52
53
54
55
56
57
58
59
59
60
61
62
62
63
64
65
65
66
67
71
71
72
72
73
73
74
75
75
76
6 Configuration — Layer 2 Ethernet July 2013

Chapter 8: Secure Router 2330/4134 Ethernet interfaces configuration.......................
Configuring Maximum Transmission Unit size..........................................................................................
Configuring jumbo frames.........................................................................................................................
Adding comments to an interface.............................................................................................................
Adding comments at the beginning of a configuration file................................................................
Adding comments at the end of a configuration file.........................................................................
Adding a description to an interface.................................................................................................
Configuring the speed of an interface.......................................................................................................
Chapter 9: Layer 2 configuration.......................................................................................
Prerequisites to Layer 2 configuration......................................................................................................
Layer 2 configuration procedures.............................................................................................................
Chapter 10: Interface mode configuration........................................................................
Configuring trunking on Ethernet interfaces..............................................................................................
Enabling trunking on an Ethernet port..............................................................................................
Specifying VLANs to trunk................................................................................................................
Disabling trunking.............................................................................................................................
Verifying trunks.................................................................................................................................
Example of configuring trunking on a chassis Ethernet interface.....................................................
Configuring trunking on a WAN interface..................................................................................................
Enabling trunking on WAN interfaces...............................................................................................
Adding all VLANs to a trunk link.......................................................................................................
Removing all VLANs from a trunk link..............................................................................................
Adding a specified VLAN to a trunk link...........................................................................................
Removing a specified VLAN from a trunk link..................................................................................
Disabling trunking.............................................................................................................................
Verifying trunks.................................................................................................................................
Example of configuring trunking on a WAN interface.......................................................................
Configuring a hybrid link on an Ethernet interface....................................................................................
Associating VLANs with hybrid links................................................................................................
Disabling a hybrid link......................................................................................................................
Verifying a hybrid link.......................................................................................................................
Example of configuring a hybrid link on a chassis Ethernet interface..............................................
Configuring a hybrid link on a WAN interface...........................................................................................
Enabling a hybrid link on a WAN interface.......................................................................................
Adding all VLANs to a hybrid link.....................................................................................................
Removing all VLANs from a hybrid link............................................................................................
Adding a specified VLAN to a hybrid link.........................................................................................
Removing a specified VLAN from a link...........................................................................................
Disabling a hybrid link......................................................................................................................
Verifying a hybrid link.......................................................................................................................
Example of configuring a hybrid link on a WAN interface................................................................
Configuring an access port on an Ethernet interface................................................................................
Enabling an access link on an Ethernet port....................................................................................
Associating VLANs with access links...............................................................................................
Disabling an access port..................................................................................................................
Verifying an access port...................................................................................................................
Configuring an access port on a WAN interface.......................................................................................
77
77
78
78
79
79
80
81
83
83
83
85
85
85
86
87
88
88
88
89
90
90
90
91
91
91
92
92
93
95
95
95
96
96
97
97
98
98
98
99
99
99
100
100
100
101
101
Configuration — Layer 2 Ethernet July 2013 7

Enabling an access link on a WAN interface....................................................................................
Changing the VLAN on an access port............................................................................................
Disabling an access port..................................................................................................................
Verifying an access port...................................................................................................................
Example of configuring an access port on a WAN interface............................................................
Chapter 11: Link aggregation configuration....................................................................
Configuring LACP.....................................................................................................................................
Configuring static mode....................................................................................................................
Configuring passive mode................................................................................................................
Configuring active mode...................................................................................................................
Changing the channel group.....................................................................................................................
Example of changing the channel group number to reconfigure an interface..................................
Removing LACP configuration..................................................................................................................
Configuring the LACP timeout..................................................................................................................
Configuring LACP system priority.............................................................................................................
Restoring the default LACP system priority......................................................................................
Configuring a LAG interface......................................................................................................................
Prerequisites....................................................................................................................................
Example of configuring a LAG interface...........................................................................................
Verifying the successful configuration of a LAG.......................................................................................
Viewing channel-group information..................................................................................................
Viewing aggregator member information.........................................................................................
Viewing LACP dynamic information.................................................................................................
Viewing LAG interface information...................................................................................................
Example of configuring LACP...................................................................................................................
Configuration on SWITCH_1............................................................................................................
Configuration on SWITCH_2............................................................................................................
Chapter 12: VLAN configuration........................................................................................
Creating a VLAN.......................................................................................................................................
Removing a VLAN.....................................................................................................................................
Verifying VLANs........................................................................................................................................
Shutting down a VLAN interface...............................................................................................................
Configuring multiple IP Helper addresses on a VLAN..............................................................................
Example of creating VLANs and binding each VLAN to an interface.......................................................
Example of creating VLANs.............................................................................................................
Example of binding a bundle access interface to a VLAN................................................................
Example of binding a LAG trunk port to VLANs...............................................................................
Example of binding an Ethernet hybrid port to VLANs.....................................................................
Chapter 13: VLAN classification configuration................................................................
Creating VLAN classification rules............................................................................................................
Configuring an IPv4 subnet-based VLAN classification rule............................................................
Configuring a protocol-based VLAN classification rule....................................................................
Deleting VLAN classification rules............................................................................................................
Verifying VLAN classification rules............................................................................................................
Creating VLAN classification rules on an interface...................................................................................
Creating protocol VLAN classification rules.....................................................................................
Creating IPv4 VLAN classification rules...........................................................................................
101
102
103
103
103
105
105
105
106
106
107
107
108
108
109
109
110
110
110
111
111
111
111
112
112
112
113
115
115
115
116
116
116
117
117
118
119
119
121
121
121
122
123
123
123
124
124
8 Configuration — Layer 2 Ethernet July 2013

Deleting VLAN classification rules from an interface................................................................................
Deleting protocol rules from an interface..........................................................................................
Deleting IPv4 rules from an interface...............................................................................................
Example of configuring VLAN classification rules.....................................................................................
Chapter 14: VLAN stacking configuration........................................................................
Enabling VLAN stacking............................................................................................................................
Disabling VLAN stacking...........................................................................................................................
Verifying VLAN stacking configuration......................................................................................................
Example of configuring VLAN stacking.....................................................................................................
Configuration of the Secure Router 2330/4134 on interface A.........................................................
Configuration of the Secure Router 2330/4134 on interface B.........................................................
Configuration of the Secure Router 2330/4134 on interface C........................................................
Chapter 15: Port mirroring configuration.........................................................................
Enabling port mirroring..............................................................................................................................
Disabling port mirroring.............................................................................................................................
Verifying port mirroring configuration........................................................................................................
Example of configuring port mirroring.......................................................................................................
Chapter 16: MAC entry configuration...............................................................................
Adding static MAC address entries to the MAC address table.................................................................
Deleting a static MAC address entry.........................................................................................................
Verifying static MAC address entries........................................................................................................
Example of configuring static MAC address entries.................................................................................
Configuring MAC address aging time.......................................................................................................
Restoring the default MAC address aging time........................................................................................
Verifying the MAC address aging time......................................................................................................
Example of configuring MAC address aging time.....................................................................................
Chapter 17: Multiple Spanning Tree Protocol configuration..........................................
Configuring the region name and revision number...................................................................................
Resetting the revision number..........................................................................................................
Configuring Common Spanning Tree.......................................................................................................
Configuring bridge priority................................................................................................................
Configuring hop count......................................................................................................................
Configuring link path cost and priority..............................................................................................
Configuring PortFast........................................................................................................................
Configuring PortFast BPDU Guard..................................................................................................
Configuring PortFast BPDU Filter....................................................................................................
Configuring MSTP timers.................................................................................................................
Configuring forward delay................................................................................................................
Configuring maximum age time........................................................................................................
Configuring link types.......................................................................................................................
Configuring an MSTP instance.................................................................................................................
Creating an MSTP instance.............................................................................................................
Associating a VLAN with an instance...............................................................................................
Configuring priority for an instance...................................................................................................
Configuring link path cost and priority for an instance......................................................................
Verifying MSTP operation.........................................................................................................................
Viewing information for MSTP Common Spanning Tree..................................................................
124
124
125
125
127
127
127
128
128
130
130
131
133
133
134
134
134
135
135
135
136
136
136
137
137
138
139
139
140
140
140
141
143
146
148
149
150
152
154
155
157
157
158
159
161
164
164
Configuration — Layer 2 Ethernet July 2013 9

Viewing common and internal spanning tree information.................................................................
Viewing information for MSTP instances..........................................................................................
Viewing bridge information for an instance......................................................................................
Viewing interface information...........................................................................................................
Viewing VLAN information for all instances......................................................................................
Viewing VLAN information for a specified instance..........................................................................
Chapter 18: GVRP configuration.......................................................................................
Enabling GVRP globally............................................................................................................................
Disabling GVRP globally...........................................................................................................................
Enabling GVRP on ports and configuring port registration state..............................................................
Disabling GVRP on an interface...............................................................................................................
Configuring GVRP for dynamic VLAN creation.........................................................................................
Disabling dynamic VLAN creation.............................................................................................................
Configuring GVRP timers..........................................................................................................................
Resetting GVRP timers.............................................................................................................................
Verifying GVRP configuration...................................................................................................................
Clearing GVRP command options............................................................................................................
Example of configuring GVRP..................................................................................................................
Example of configuring SWITCH_1..................................................................................................
164
165
165
165
166
166
167
167
167
168
169
169
170
171
172
172
173
174
174
10 Configuration — Layer 2 Ethernet July 2013
Chapter 1: Introduction
Introduction
This document provides information you need to configure Ethernet interfaces and Layer 2
features.
Related Resources
Documentation
See the Avaya Secure Router 2330/4134 Documentation Roadmap, NN47263-103, for a list
of the documentation for this product.
Training
Ongoing product training is available. For more information or to register, you can access the
Web site at http://avaya-learning.com.
Avaya Mentor videos
Avaya Mentor is an Avaya-run channel on YouTube that includes technical content on how to
install, configure, and troubleshoot Avaya products.
Go to http://www.youtube.com/AvayaMentor and perform one of the following actions:
• Enter a key word or key words in the Search Channel to search for a specific product
or topic.
• Scroll down Playlists, and click the name of a topic to see the available list of videos
posted on the site.
Configuration — Layer 2 Ethernet July 2013 11

Introduction
Support
Visit the Avaya Support website at
documentation, product notices, and knowledge articles. You can also search for release
notes, downloads, and resolutions to issues. Use the online service request system to create
a service request. Chat with live agents to get answers to questions, or request an agent to
connect you to a support team if an issue requires additional expertise.
http://support.avaya.com for the most up-to-date
12 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com
Chapter 2: New in this release
The following sections detail what is new in Avaya Secure Router 2330/4134 Configuration — Layer 2
Ethernet (NN47263-501) for Release 10.3.5.
Features
The following new feature content has been added to Avaya Secure Router 2330/4134
Configuration — Layer 2 Ethernet (NN47263-501) for Release 10.3.5.
Common and internal spanning tree information
The common and internal spanning tree (CIST) is the default spanning tree instance of Multiple
Spanning Tree Protocol (MSTP). Avaya Secure Router 2330/4134 Release 10.3.5 introduces
a command that allows you to view CIST information for a VLAN or a port. For more information,
see Viewing common and internal spanning tree information on page 164.
Other changes
The following section details other changes made to Avaya Secure Router 2330/4134
Configuration — Layer 2 Ethernet, (NN47263-501) for Release 10.3.5.
IGMP Snooping configuration
The chapter IGMP Snooping configuration has been removed. For information on how to
configure IGMP snooping, see Avaya Secure Router 2330/4134 Configuration — IPv4
Multicast Routing, (NN47263-504).
Configuration — Layer 2 Ethernet July 2013 13

New in this release
14 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com
Chapter 3: Secure Router 2330/4134
Ethernet interface fundamentals
Ethernet interface fundamentals
Avaya Secure Router 2330/4134 supports the following Ethernet interface modules:
• 24-port FE Medium Module
• 24-port FE/PoE Medium Module
• 10-port GbE Medium Module
• 44-port GbE Large Module
For detailed information about the interface modules that the Secure Router 2330/4134
supports, see Avaya Secure Router 2330/4134 Installation — Hardware Components
(NN47263-301).
FE and FE/PoE Medium Modules
The 24-port Fast Ethernet (FE) and Fast Ethernet/Power over Ethernet (FE/PoE) Medium
Modules each provide 24 Ethernet ports that support 10 Mbps and 100 Mbps operation over
unshielded twisted pair (UTP) wiring. The module is non-blocking. The 24-port FE and FE/PoE
Medium Modules provide both Layer 2 switching and Layer 3 routing functionality.
The 24-port PoE Medium Module supports only Alternative (or mode) A as defined in IEEE
802.3af. Power is fed over pins 1,2 and 3,6.
Important:
You must install the Secure Router 2330/4134 PoE power supply to take advantage of the
PoE capabilities.
Power over Ethernet
You can install up to two PoE power supply modules in the Secure Router 2330/4134. Each
PoE power supply can provide 400 watts. There is a total allocation of 384 watts for each PoE
card to support all 24 ports (with maximum power limit for each port is 16 watts). This section
Configuration — Layer 2 Ethernet July 2013 15
Secure Router 2330/4134 Ethernet interface fundamentals
describes the PoE power distribution scenarios available on the Secure Router 2330/4134, as
well as the commands you use to configure PoE.
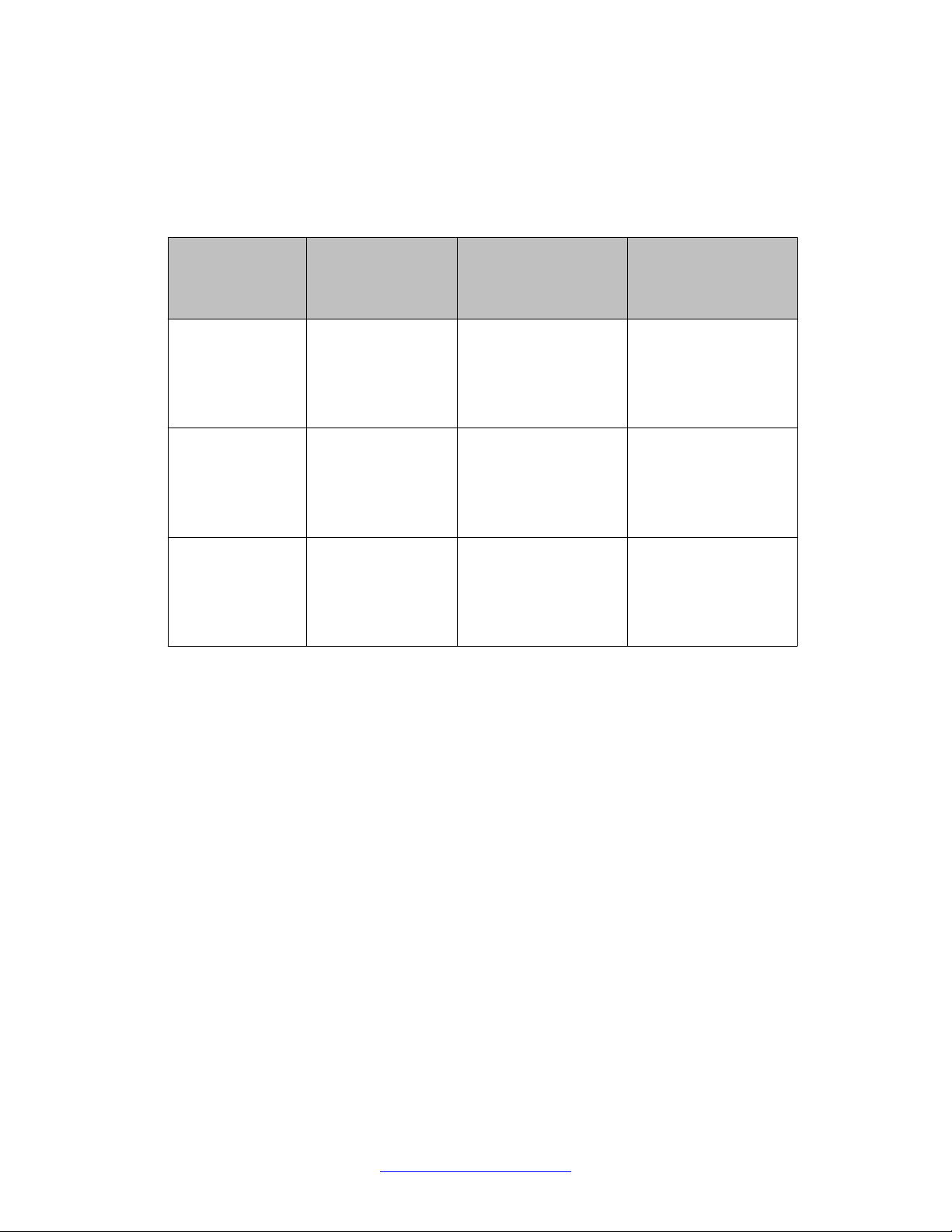
The following table describes power distribution for PoE interface modules.
Table 1: PoE power distribution
Number of
installed PoE
interface
modules
One PoE interface
module (any slot)
One PoE power
supply module
installed
410 W allocated for
the slot
Two PoE power
supply modules
installed
410 W allocated for the
slot
Port state
All ports are shut down
(no power state) until
you configure the poe
portpower or poe
portmode command
Two PoE interface
modules (any
slots)
Each slot receives
200 W
Each slot receives 410WAll ports are shut down
(no power state) until
you configure the poe
portpower or poe
portmode command
Three PoE
interface modules
(any slots)
Slot 5 and 6 each
receive 200 W.
There is no power
for slot 7.
Slot 5 receives 410 W.
Slots 6 and 7 receive
200 W each.
All ports are shut down
(no power state) until
you configure the poe
portpower or poe
portmode command
The number of powered devices that the Secure Router 2330/4134 supports is based on
available power, the number of cards present in the chassis, and the actual power consumption
of the powered devices connected to the PoE module.
The power available with one PoE power supply module installed is 400 watts. The power
available with two PoE power supply modules installed is 800 watts.
If you use a redundant PoE power supply module setup (that is, you have two PoE power
supply modules installed), the Secure Router 2330/4134 provides a failover feature that
ensures that the Secure Router 2330/4134 keeps running, even in situations where you must
remove one power supply module. The second PoE power supply module can provide enough
power for the system to operate without fail (a function of the PoE power provisioning on the
Secure Router 2330/4134).
The following table shows the number of powered devices supported based on the number of
interface modules installed in the Secure Router 2330/4134.
16 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com
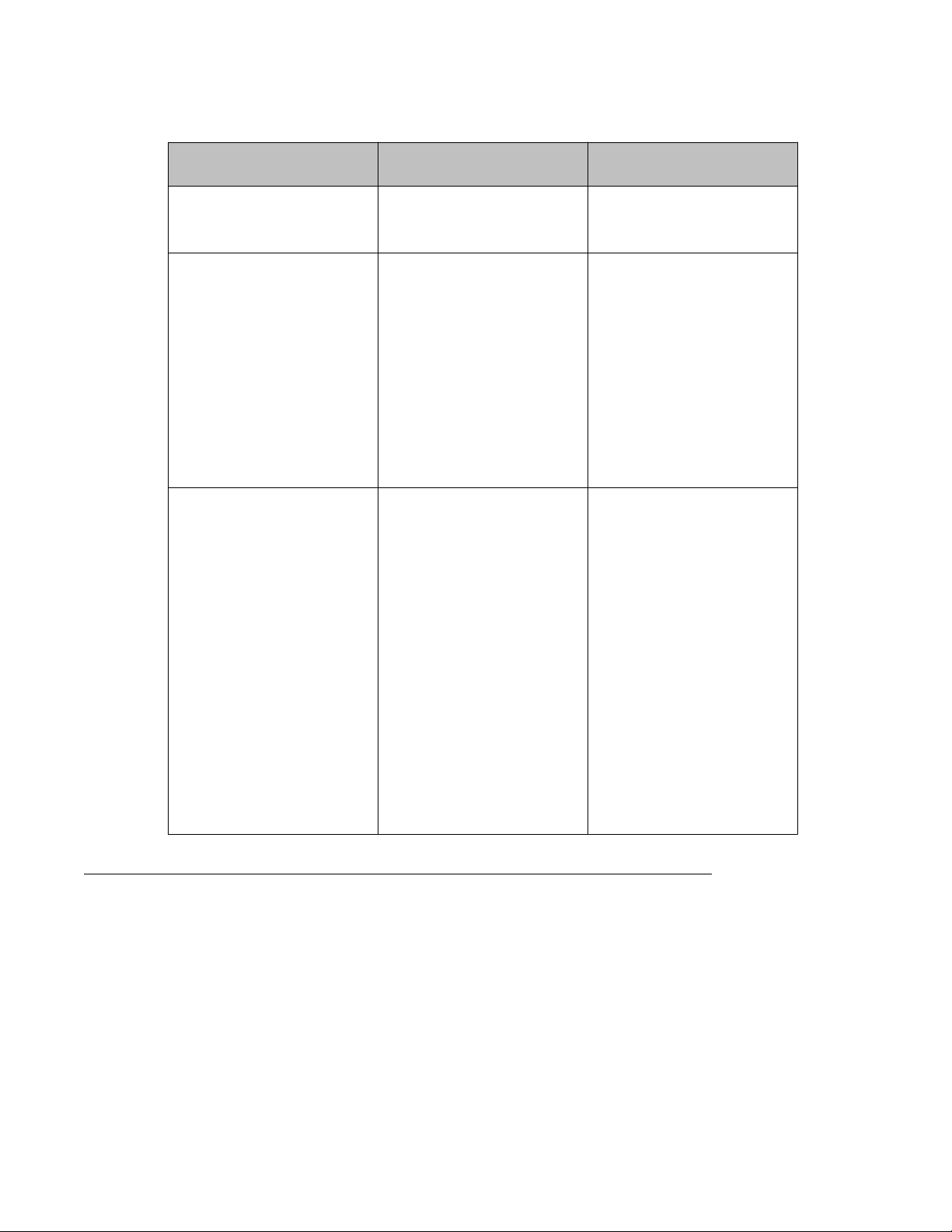
Table 2: Number of ports and PDs supported
Ethernet interface fundamentals
Number of installed PoE
interface modules
1 24 ports are supported
2 24 ports are supported on
3 24 ports are supported on
One PoE power supply
module installed
irrespective of the class of
powered devices.
each interface module with
the combination of class 1
and class 2 powered
devices.
For any other combinations
of powered devices, the
number of ports supported is
based on the actual power
consumption of the powered
devices connected to the
modules.
each interface module in slot
5 and slot 6 with the
combination of class 1 and
class 2 powered devices.
For any other combination of
powered devices, the
number of ports supported is
based on the actual power
consumption of the powered
devices connected to the
modules.
Two PoE power supply
modules installed
24 ports are supported
irrespective of the class of
powered devices.
24 ports are supported on
each interface module
irrespective of the class of
powered devices.
24 ports are supported on the
interface module in slot 5
irrespective of the powered
device class, and 24 ports
are supported on each
interface module in slot 6 and
slot 7 with the combination of
class 1 and class 2 powered
devices (that is, support for a
total of 72 ports).
For any other combination of
powered devices, the
number of ports supported is
based on the actual power
consumption of the powered
devices connected to the
interface module in slot 6 and
slot 7.
GbE Medium Module
The 10-port 10/100/1000 Ethernet Advanced Layer 2/Layer 3 Medium Module provides ten
autonegotiating 10/100/1000 Mbps copper Ethernet ports and two Small form-factor Pluggable
(SFP) Gigabit Ethernet (GbE) ports (full duplex). Up to ten ports can be in use at one time. The
module is non-blocking. The 10-port GbE Medium Module provides both Layer 2 switching and
Layer 3 routing functionality.
To use a GbE Medium Module, you must insert the SFP before you configure modular
Ethernet. The Secure Router 2330/4134 performs a system check for an installed SFP. If no
Configuration — Layer 2 Ethernet July 2013 17

Secure Router 2330/4134 Ethernet interface fundamentals
SFP is detected, the system defaults to copper only. If an SFP is detected, the system defaults
to fiber only.
GbE Large Module
The 44-port 10/100/1000 Large Module provides 44 Ethernet ports that each support
10/100/1000 Mbps operation over unshielded twisted pair (UTP) wiring, as well as two SFP
optical ports. Up to 44 ports can be in use at one time.
The 44-port GbE Large Module provides both Layer 2 switching and Layer 3 routing
functionality. The total available bandwidth at all of the ports (44 Gbps) is four times the
available routing bandwidth.
There are three groups on the module: one group has 12 ports, and two groups have 16 ports
each. For Layer 2 switching within each group, packets can be switched at full bandwidth.
However, for Layer 2 switching between groups and for all packets that are routed (Layer 3),
all external ports must share a limited number of links on the module. There are three links
available within the group of 12 ports, and there are four links available within each group of
16 ports. There is, therefore, a 12:3 (4:1) or 16:4 (4:1) contention for the internal links.
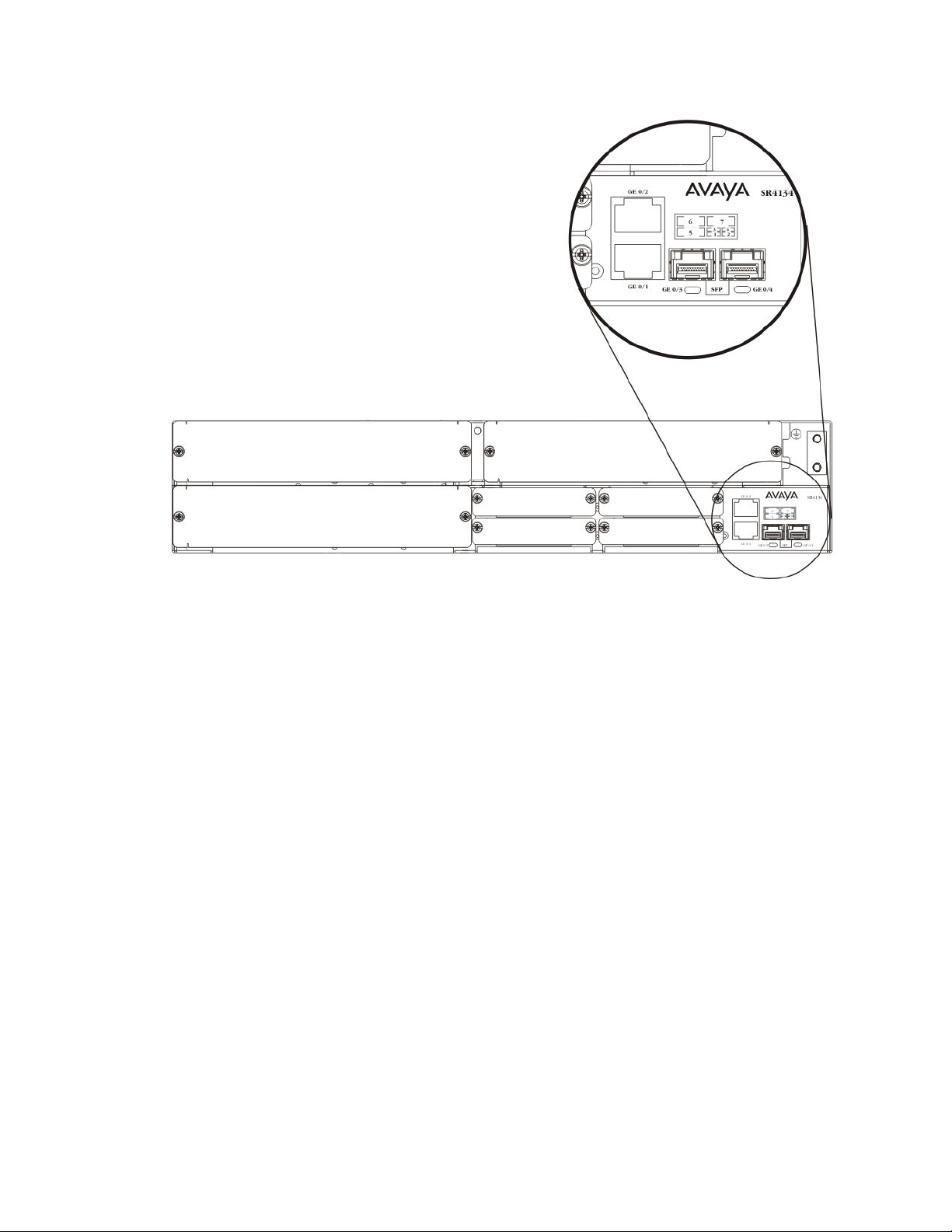
Chassis Ethernet ports
In addition to the module Ethernet ports available for the Secure Router 2330/4134, the router
has four chassis Ethernet ports on the front panel:
• GE 0/1 and GE 0/2 ports — 10/100/1000 Base-T ports
• GE 0/3 and GE 0/4 — SFP ports
The following figure shows the location of the chassis Ethernet ports.
18 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com
Ethernet interface fundamentals
Figure 1: Secure Router 2330/4134 chassis Ethernet ports
All Ethernet ports on the Secure Router 2330/4134 (chassis and interface module Ethernet
ports) support MDI and MDI-X.
Ethernet interfaces on the Secure Router 2330/4134 are routed interfaces, by default. To
configure them as Layer 2 interfaces, you use the switchport command.
Configuration — Layer 2 Ethernet July 2013 19

Secure Router 2330/4134 Ethernet interface fundamentals
20 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com

Chapter 4: Ethernet Connectivity Fault
Management
Avaya Secure Router 2330/4134 supports the 802.1ag protocol, which provides operation, administration,
maintenance (OAM) functionality for Ethernet. Specifically, IEEE 802.1ag Connectivity Fault Management
(CFM) provides OAM tools for the service layer, which allows you to monitor and troubleshoot an end-toend Ethernet service instance. Ethernet CFM enables the service provider to know if an Ethernet Virtual
Circuit (EVC) fails, and if so, provides the tools to rapidly isolate the failure.
The end-to-end service can be provider edge (PE) to PE device or customer edge (CE) to CE device. The
customer VLAN tag defines a service instance. Based on the customer VLAN, the customer receives
service as defined in their customer agreement. When you initiate CFM frames from the Secure Router
2330/4134, the frames are tagged with the C-VLAN only. CFM is not supported on an interface that uses
stacked VLANs.
Ethernet CFM is the standard for Layer 2 ping, Layer 2 traceroute, and the end-to-end connectivity check
of the Ethernet network.
Avaya supports Ethernet CFM on chassis Gigabit Ethernet (GbE) ports only.
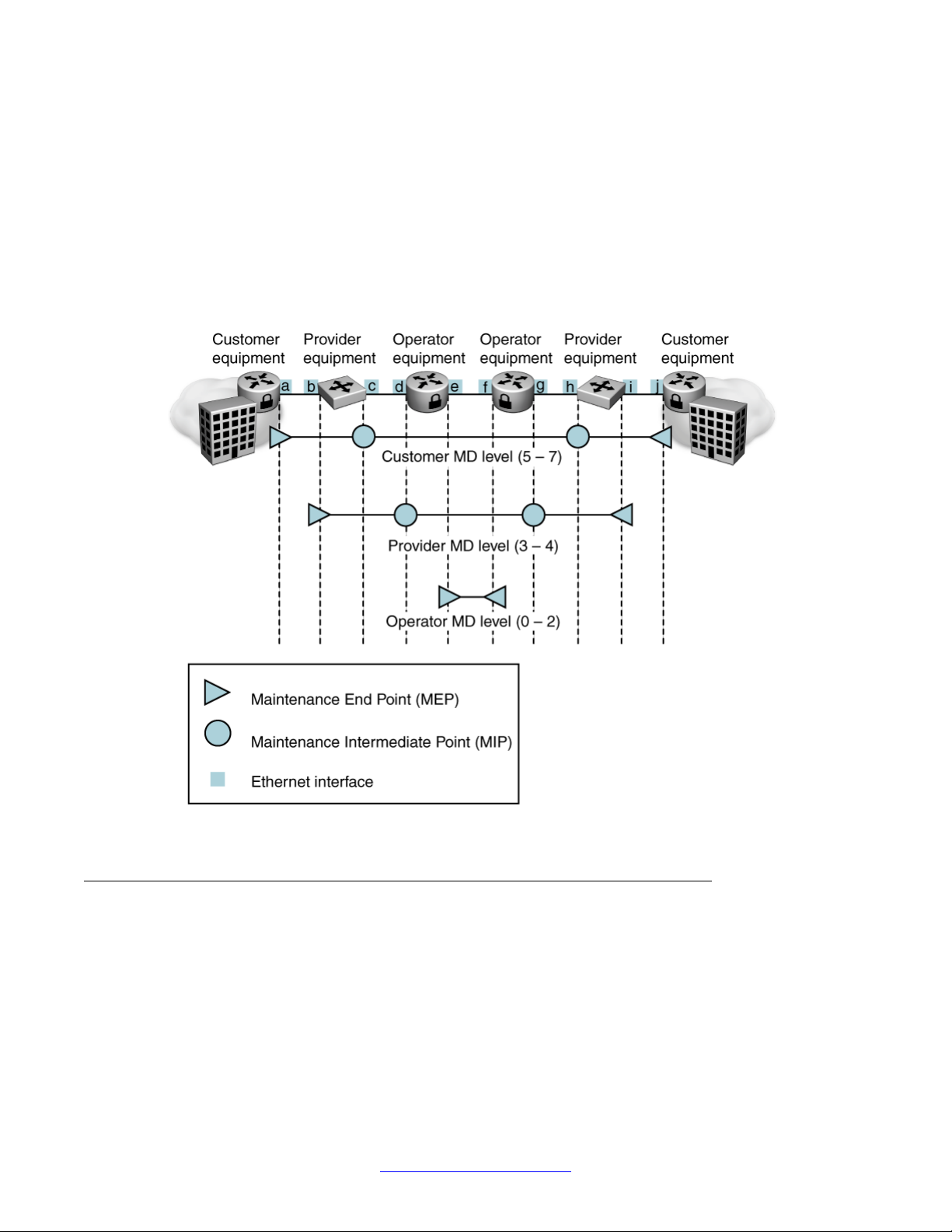
The 802.1ag feature divides or separates a network into administrative domains called Maintenance
Domains (MD). Each MD includes the following attributes:
• Maintenance Associations (MA)
• Maintenance End Points (MEP)
• Maintenance Intermediate Points (MIP)
Maintenance Domain
A Maintenance Domain (MD) is the part of a network that is controlled by a single administrator.
For example, a customer can engage the services of a service provider, who, in turn, can
engage the services of several operators. In this scenario, there can be one MD associated
with the customer, one MD associated with the service provider, and one MD associated with
each of the operators.
The Secure Router 2330/4134 supports up to 64 MDs.
You assign one of the following eight levels to the MD:
• 0–2 (operator levels)
• 3–4 (provider levels)
• 5–7 (customer levels)
Configuration — Layer 2 Ethernet July 2013 21
Ethernet Connectivity Fault Management
The levels separate MDs from each other and provide different areas of functionality to different
devices using the network. An MD is characterized by a level and an MD name (optional).
A single MD can contain several MAs. Each MA is defined by a set of Maintenance Points
(MP). An MP is a demarcation point on an interface that participates in CFM within an MD.
There are two types of MP:
• Maintenance End Point (MEP)
• Maintenance Intermediate Point (MIP)
The following figure shows the MD level assignments.
Figure 2: Maintenance Domain levels
Maintenance End Point
MEPs are points at the edge of the MD. They define a boundary and confine connectivity fault
management messages within this boundary.
22 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com
Maintenance Domain
An MEP acts based on the relationship between the level assigned to the connectivity fault
management frame received and the level assigned to the MEP. The possible MEP actions
are the following:
• Drop frames that have a lower level
• Transparently forward all connectivity fault management frames that have a higher level
• For connectivity fault management frames that have the same level as the MEP, the MEP
does one of the following (based on the type of MEP):
- A Down MEP is one residing in a bridge that transmits connectivity fault management
messages towards, and receives them from, the direction of the physical medium.
For example, see
at point a in the Figure is a Down MEP. A Down MEP does the following:
• processes frames received from the wire side
• drops frames received from the relay side
- An Up MEP is one residing in a bridge that transmits connectivity fault management
messages towards, and receives them from, the direction of the bridge relay entity.
For example, see
at point b in the Figure is an Up MEP. An Up MEP does the following:
Figure 2: Maintenance Domain levels on page 22. The interface
Figure 2: Maintenance Domain levels on page 22. The interface
A MEP provides the following functions:
• fault detection
• fault verification
• fault isolation
• path discovery
• fault notification
Fault detection
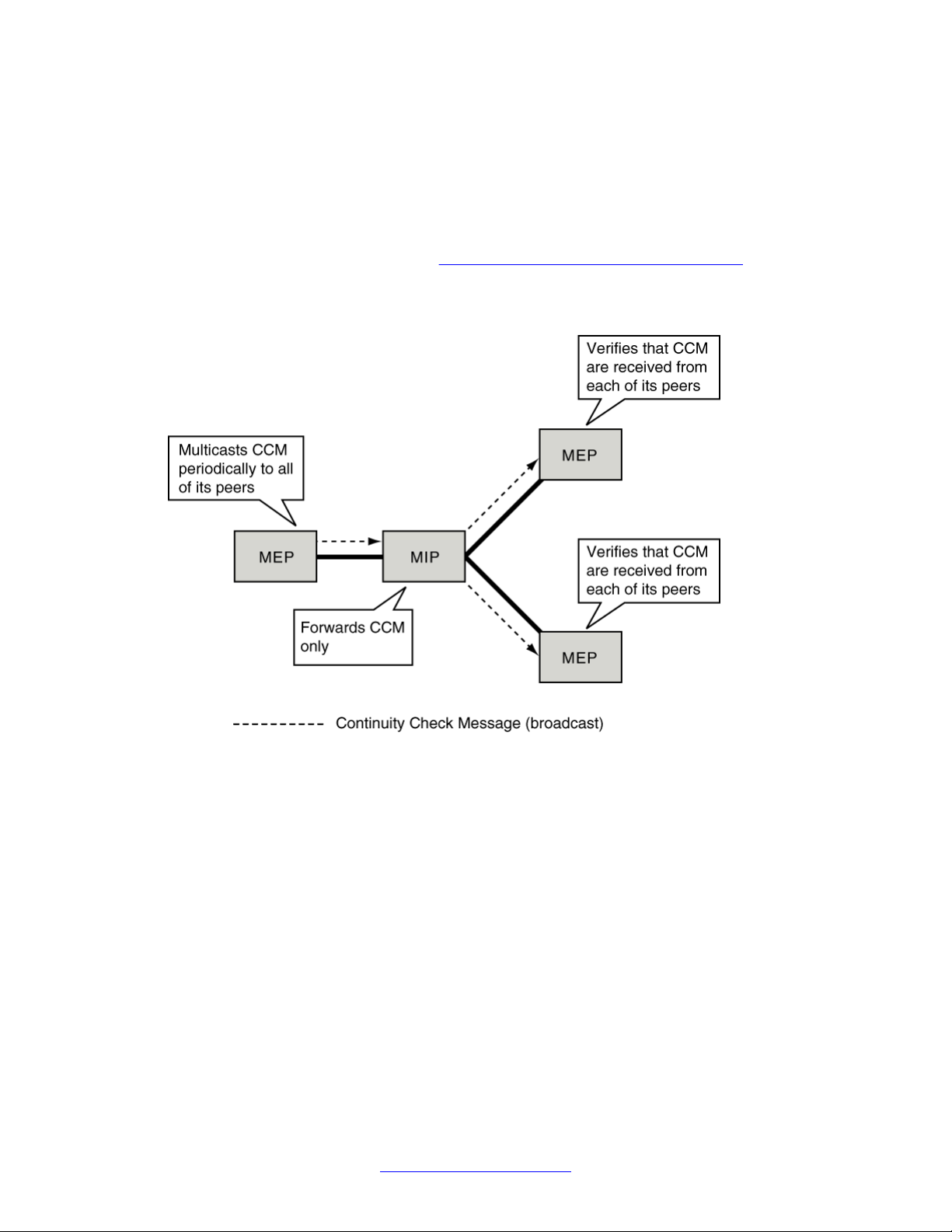
Fault detection is achieved through the use of Continuity Check Messages (CCM). Failure to
receive three consecutive CCM indicates a fault.
Each MEP periodically transmits multicast CCM. A CCM traverses all the bridges until it
reaches an MEP with the same (or, in an error situation, lower) MD level as the sending
MEP.
• drops frames received from the wire side
• processes frames received from the relay side
Important:
Secure Router 2330/4134 Release 10.1 supports Down MEPs only.
Each MEP maintains a list of its peers and expects to receive CCM from each of its peers
periodically. Each MEP maintains a list of “validity” or “lifetime” timers. There is one timer for
each peer (remote) MEP. All MEPs in a singe MA share one CCM transmit period (that is, you
configure the CCM timer only once for each MA). The IEEE 802.1ag standard defines the
Configuration — Layer 2 Ethernet July 2013 23
Ethernet Connectivity Fault Management
"validity" or "lifetime" timer value as 3.5 times greater than the CCM transmit period of a MEP.
Receiving MEPs declare connectivity failures after missing three consecutive CCM from a
peer.
Additionally, transmitting MEPs encode the transmit period in the CCM interval field of the
CCM, which enables the receiving MEP to identify configuration errors and raise an appropriate
alarm. The transmission period is configurable for each MA. Use the cc-interval command to
define the transmission period (see
The following figure shows an MEP sending multicast CCM. Note that all MEPs transmit CCM,
not only the MEP for which the CCM path is shown.
Configuring Continuity Check Messages on page 61).
Figure 3: An MEP transmitting CCM
Fault verification and isolation
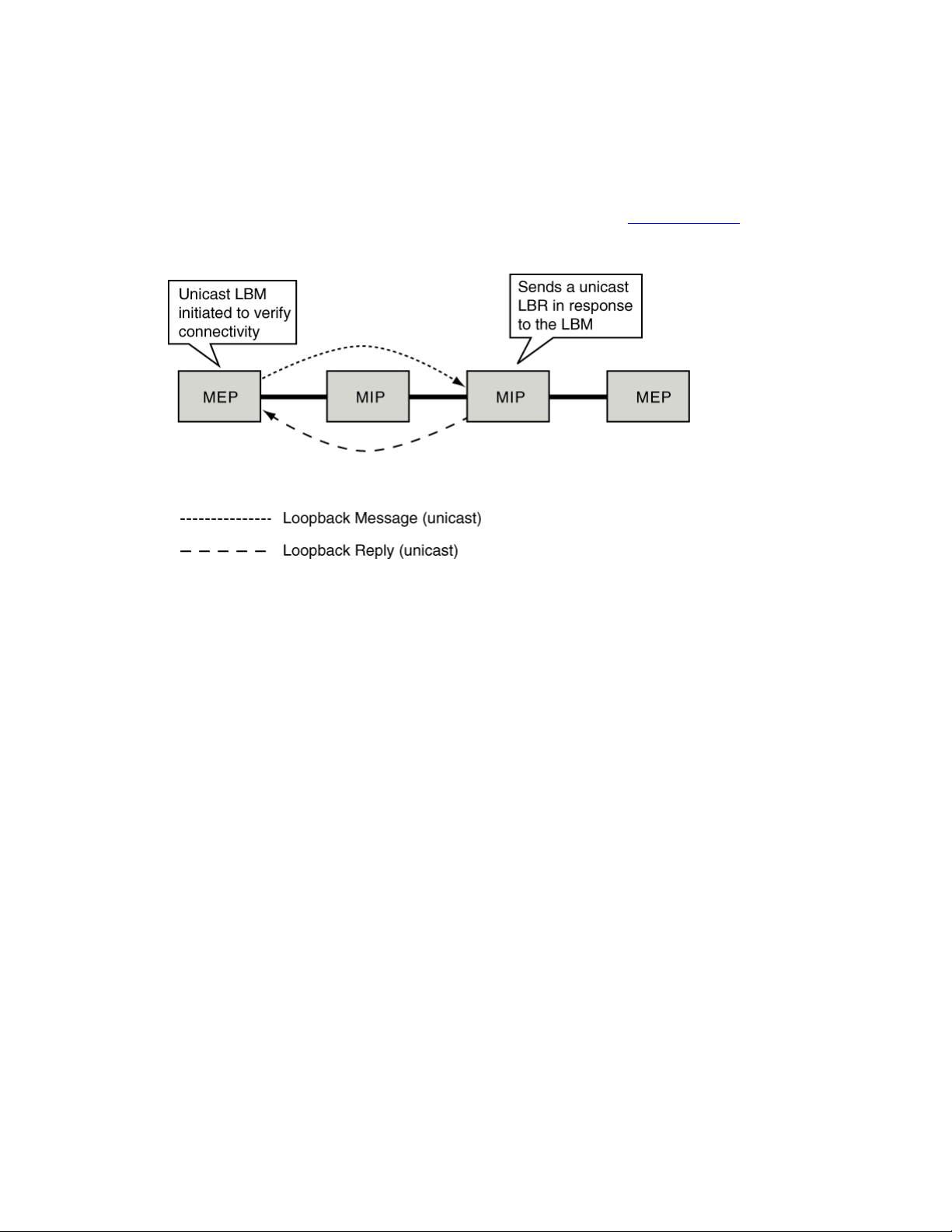
You can use Loopback Messages (LBM) for fault verification and fault isolation. The LBM is a
unicast message you can trigger with a command. LBM can be addressed to either an MEP
or an MIP, but only an MEP can initiate the LBM. You can address a destination MEP with
either its MAC address or its MEP ID, however you can address an MIP only by its MAC
address.
Addressing with the MEP ID is only possible if the MAC address of the remote MEP has
previously been learned. If you use the MEP ID as the address, and the MAC address of the
remote MEP is unavailable, the command fails. You must repeat the command using the MAC
address of the remote MEP.
24 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com
Maintenance Domain
The destination MP responds with a Loopback Reply (LBR). When you issue the command to
send an LBM, the command becomes unavailable until the LBR is received or a timeout
occurs.
You use LBM to discover if the target MP is reachable. LBM does not provide hop-by-hop
discovery of a path. For hop-by-hop discovery of a path, see
The following figure shows the LBM and LBR.
Path discovery on page 25.
Figure 4: Loopback message and reply
Path discovery
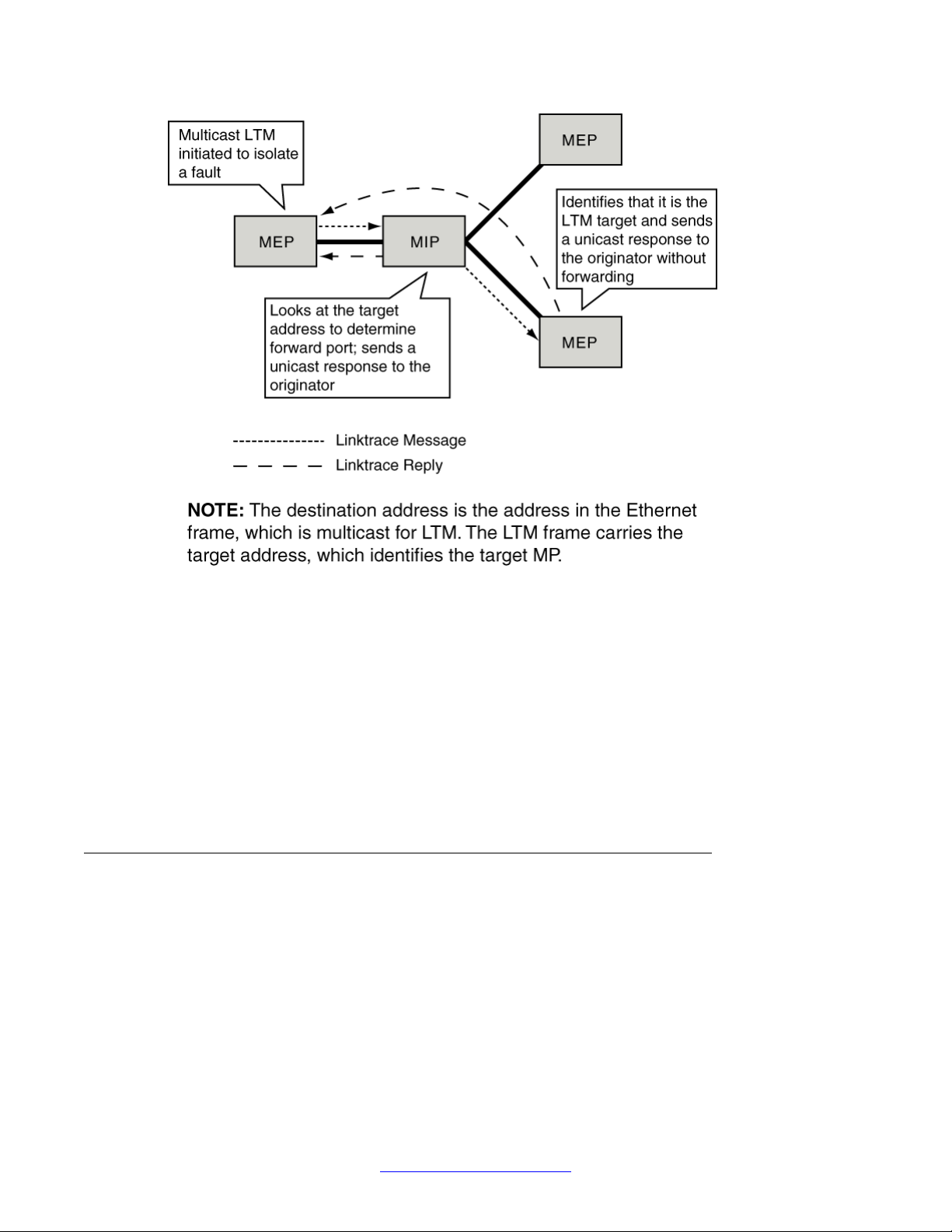
You use Linktrace Messages (LTM) for path discovery. An LTM is a multicast message that
an MEP generates. An LTM frame contains the MAC address of the target MP. The LTM is
intercepted by all MPs that are at the same level as the MEP initiating the LTM to the destination
MP (an LTM can be addressed to either an MEP or an MIP). Each MP that intercepts the LTM
looks at the target address. If the MP determines that it is not the target, the MP performs the
following three actions:
• decrements the “Time To Live” (TTL) field in the LTM frame
• sends a Linktrace Reply (LTR)
• forwards the original LTM to the destination
The LTR is a unicast message addressed to the originating MEP. The LTR is sent only after
a random time delay in the range of 0 to 1 second (as defined in the IEEE 802.1ag protocol).
The LTM is forwarded until it reaches its destination or the TTL value is decremented to 0.
The following figure shows the LTM and LTR.
Configuration — Layer 2 Ethernet July 2013 25
Ethernet Connectivity Fault Management
Figure 5: Linktrace message and reply
You initiate the LTM with a command. When you issue the LTM command, the CLI gives the
session ID for that test and exits. The LTRs are appended to this session in the Linktrace cache
based on the transaction ID. Use the show cfm linktrace-cache <session-id>
command to view results.
Fault notification
The Secure Router 2330/4134 provides fault notification through CLI event messages and
error logs.
Maintenance Intermediate Point
MIPs are internal to an MD (that is, MIPs are never at the boundary of an MD). MIPs respond
to connectivity fault management frames only when triggered by linktrace and loopback
messages. MIPs are associated with an MD, and not with any specific MA. An MIP can
participate in connectivity fault management of one service instance, or an MIP can participate
in CFM of many service instances that have the same MD level as the MIP.
MIPs do not initiate any connectivity fault management messages. MIPs passively receive
connectivity fault management messages, process the messages received, and respond to
the originating MEP. By responding to received connectivity fault management messages,
26 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com

MIPs help you to discover the hop-by-hop path between MEPs, which allows you to isolate
connection failures to smaller segments of the network and to discover the location of faults
along the paths.
You can create, enable, and disable MIPs independently of MEPs.
An MIP acts based on the relationship between the level assigned to the connectivity fault
management frame received and the level assigned to the MIP. The possible MIP actions are
the following:
• transparently forwards all connectivity fault management frames that have a higher or
lower MD level than the MIP
• processes frames that have the same MD level as the MIP
Connectivity Fault Management messages
CFM uses standard Ethernet frames distinguished by EtherType or (for multicast messages)
by MAC address. All connectivity fault management messages are confined to an MD. Secure
Router 2330/4134 supports the following connectivity fault management messages:
Maintenance Domain
• CCM—multicast heartbeat messages that MEPs periodically initiate. CCM provide the
following services:
- allow MEPs to discover other MEPs within an MA of a domain
- allow MIPs to discover MEPs
You configure CCM for an MA within a domain, or you configure CCM for a VLAN.
• Loopback messages—unicast frames transmitted by an MEP. Loopback messages are
similar to an Internet Control Message Protocol (ICMP) ping message. You initiate a
loopback message to verify connectivity to a particular MP, which indicates if a destination
is reachable.
• Linktrace messages—multicast frames transmitted by an MEP. CFM linktrace messages
are similar to User Datagram Protocol (UDP) linktrace messages. The administrator
initiates a linktrace message to track the path (hop-by-hop) to a destination MEP.
Configuration — Layer 2 Ethernet July 2013 27

Ethernet Connectivity Fault Management
Connectivity Fault Management modes
The Secure Router 2330/4134 supports the following CFM modes:
• Routed mode, in which Secure Router 2330/4134 sends and receives untagged CFM
frames.
• Switched mode, which is, more specifically, one of the following:
- Access mode – Secure Router 2330/4134 can receive both VLAN tagged and
untagged CFM frames, but can send only untagged CFM frames.
- Hybrid mode – Secure Router 2330/4134 can receive both VLAN tagged and
untagged CFM frames. There are two options for sending CFM frames:
• Egress tagged – sends VLAN tagged CFM frames
• Egress untagged – sends untagged CFM frames
- Trunk mode – Secure Router 2330/4134 can receive and send only VLAN tagged
CFM frames.
Connectivity Fault Management errors and statistics
The heartbeat mechanism of CFM (using periodic CCM) makes it possible to detect a number
of errors and accumulate data for statistical purposes.
Inconsistent configuration of the devices in an MD or an MA, or inconsistent configuration of
the MEPs, remote MEPs, and so on in different nodes of the network can result in configuration
errors. The Secure Router 2330/4134 stores configuration errors in a database.
You use the show commands to view the information stored in the databases.
The databases contain data for each MEP in the Secure Router 2330/4134.
28 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com

Chapter 5: Layer 2 fundamentals
Ethernet is one of the most widely deployed Layer 2 Local Area Network (LAN) transport technologies
today. A LAN is a data communications network connecting terminals, computers, and printers within a
building or other geographically limited area. Advantages of Ethernet include:
• Ability to scale in bandwidth and speed — Ethernet switches support high port densities and
forwarding rates in the millions of packets per second
• Support of Class of Service (CoS) that allows up to eight classes of service to be defined
• Ease of deploying multipoint communications
The Avaya Secure Router 2330/4134 Ethernet Layer 2 features support VLAN MAC bridging of traffic
within the LAN, and between LAN to WAN for traffic in and out of the carrier network. The Secure Router
2330/4134 platform uses both the hardware network processor and software forwarding logic for Ethernet
Layer 2 switching. The network processor handles LAN switching. Software forwarding works with the
network processor to achieve LAN to WAN (and WAN to LAN) data switching. The Secure Router
2330/4134 also supports termination of Layer 3 traffic on a VLAN to achieve routing using the Layer 3
engine.
Layer 2 switching and bridging
Local Area Network (LAN) is a data communications network connecting terminals, computers
and printers within a building or other geographically limited areas. These devices could be
connected through wired cables or wireless links. Ethernet and Token Ring are examples of
standard LAN technologies. LAN switching involves examining physical network addresses
that uniquely identify a device in the network.
LAN bridging offers an extension of the LAN by supporting the connection of multiple LAN
segments. MAC addresses of the datagram that flow through bridges are examined to build a
table of known destinations. If the destination of a datagram is on the same segment as the
source of the datagram, the bridge drops the datagram because forwarding is not required.
However, if the destination is on another segment, the bridge transmits the datagram on that
segment only. If the bridge does not know the destination segment, it transmits the datagram
on all segments except the source segment (a technique known as flooding).
MAC bridging
MAC Bridging allows multiple LANs to be connected together. Transparent bridging involves
the creation of MAC address tables, and limits the Ethernet collision domain by filtering data
Configuration — Layer 2 Ethernet July 2013 29

Layer 2 fundamentals
sent between LAN segments. This reduces network congestion and allows networks to be
partitioned for administrative purposes.
VLANs
A Virtual LAN (VLAN) is a switched network that is logically segmented on an organizational
basis, by functions, project teams, or applications rather than on a physical or geographical
basis. VLAN segments the physical local-area network (LAN) infrastructure into different
subnets so that packets are switched only between ports within the same VLAN. Devices on
a VLAN are configured so that they can communicate as if they were attached to the same
physical wire, when in fact they are located on a number of different LAN segments. With VLAN
partitioning, traffic stays within the appropriate groups, minimizing wasteful broadcasts.
A VLAN is made up of a group of ports that define a logical broadcast domain. These ports
can belong to a single device, or they can be spread across multiple devices. In a VLAN-aware
device, every frame received on a port is classified as belonging to one and only one VLAN.
Whenever a broadcast, multicast, or unknown destination frame must be flooded by a VLANaware device, the frame is sent out only through all the other active ports that are members of
this VLAN.
The default device configuration groups all ports into the port-based default VLAN 1. This VLAN
cannot be deleted from the system.
The Secure Router 2330/4134 supports port-based and protocol-based VLANs.
A port-based VLAN is a VLAN whose ports are explicitly configured as members. In port-based
VLANs, all ports are always static members. When creating a port-based VLAN, you assign a
VLAN identification number (VID) and specify which ports belong to the VLAN. The VID is used
to coordinate VLANs across multiple devices.
Protocol-based VLANs are an effective way to segment your network into broadcast domains
according to the network protocols in use. Traffic generated by any network protocol can be
automatically confined to its own VLAN.
VLAN tagging is a MAC option. A VLAN-tagged frame is a basic MAC data frame that has had
a 4-byte VLAN header inserted between the SA and Length/Type fields. The VLAN header
consists of the following fields:
• A reserved 2-byte type value, indicating that the frame is a VLAN frame
• Tag Protocol Identifier (TPID) - defined value of 8100 in hex. When a frame has the
EtherType equal to 8100, this frame carries the tag IEEE 802.1Q/802.1P.
• TCI - Tag Control Information field including user priority, Canonical format indicator and
VLAN ID.
VLAN tagging can be enabled or disabled on each interface.
The Secure Router 2330/4134 uses IEEE 802.1Q tagging of frames and coordinates VLANs
across multiple devices. The following figure shows the additional 4-octet (tag) header that is
inserted into a frame after the source address and before the frame type. The tag contains the
VLAN ID associated with the frame.
30 Configuration — Layer 2 Ethernet July 2013
Comments? infodev@avaya.com
 Loading...
Loading...