Page 1

MediaPack™ Series
Analog VoIP Media Gateways
MGCP & MEGACO Protocols
User's Manual
MP-1xx & MP-124
Version 6.6
June 2014
Document # LTRT-71405
Page 2

Page 3

User's Manual Contents
Table of Contents
1 Introduction ......................................................................................................... 9
1.1 About the MediaPack Gateway............................................................................... 9
1.2 MediaPack Features ............................................................................................. 10
1.3 Functional Block Diagrams ................................................................................... 11
2 Software Package.............................................................................................. 13
2.1 Installing the Software Package ........................................................................... 13
2.1.1 Installing/Unzipping When Using a Windows™ Operating System ........................13
2.1.2 Unzipping When Using a Linux™/Solaris™ Operating System ..............................13
2.2 Software Directory Contents & Structure .............................................................. 14
3 Getting Started .................................................................................................. 15
3.1 Assigning the MediaPack IP Address ................................................................... 15
3.2 Assigning an IP Address Using HTTP .................................................................. 16
3.3 Assigning an IP Address Using BootP .................................................................. 17
3.4 Restoring Networking Parameters to their Default Values .................................... 18
4 Device Initialization & Configuration Files ...................................................... 19
4.1 Boot Firmware & Operational Firmware ................................................................ 19
4.2 MediaPack Startup ............................................................................................... 19
4.3 Using BootP/DHCP .............................................................................................. 21
4.3.1 BootP/D HCP Ser ver Para meters ............................................................................21
4.3.1.1 Command Line Switches..........................................................................22
4.3.2 Host Name Support .................................................................................................23
4.3.3 Selecti ve BootP .......................................................................................................24
4.3.4 Microsoft™ DHCP/BootP Server .............................................................................24
4.4 Configuration Parameters and Files ..................................................................... 25
4.4.1 Initialization (ini) File ................................................................................................25
4.4.1.1 Parameter Value Structure .......................................................................26
4.4.1.2 Tables of Parameter Value Structure .......................................................27
4.4.1.3 Binary Configuration File Download .........................................................30
4.4.2 Auxiliary Files ...........................................................................................................30
4.4.2.1 Downloading Auxiliary Files via TFTP During the Blade Startup .............30
4.4.2.2 Automatic Update Facility.........................................................................31
4.4.2.3 Downloading the dat File to a Device .......................................................34
4.5 Backup Copies of ini and Auxiliary Files ............................................................... 35
4.6 Upgrading Device Software .................................................................................. 35
5 Automatic Configuration Options .................................................................... 37
5.1 Option A - Local Configuration Server with BootP/TFTP ....................................... 37
5.2 Option B - DHCP-based Configuration Server ...................................................... 38
5.3 Option C - HTTP-based Automatic Updates ......................................................... 39
5.4 Option D - Configuration using DHCP Option 67 .................................................. 40
5.5 Option E - Configuration using FTP or NFS .......................................................... 41
5.6 Option F - TFTP Configuration using DHCP Option 66 ........................................ 41
5.7 Option G - Configuration using AudioCodes EMS ................................................ 41
6 Configuration Using the Web Interface ........................................................... 43
6.1 Limiting the Web Interface to Read-Only Mode .................................................... 43
Version 6.6 3 MediaPack Series
Page 4

6.1.1 Encrypted HTTP Transport (HTTPS - SSL) ............................................................44
6.1.2 Limiting Web Access to a Predefined List of Client IP Addresses ..........................44
6.1.3 Managing Web Server Access Using a RADIUS Server .........................................44
MediaPack Series
6.2 Accessing the Web Interface ................................................................................ 45
6.3 Using Internet Explorer to Access the Web Inter f ace ............................................ 46
6.4 Areas of the GUI ................................................................................................... 47
6.4.1 Toolbar .....................................................................................................................48
6.4.2 Navigation Tree .......................................................................................................49
6.4.2.1 Displaying Navigation Tree in Basic and Full View ..................................49
6.4.2.2 Showing / Hiding the Navigation Pane .....................................................50
6.4.3 Help Infrastructure ...................................................................................................51
6.4.4 Working with Configuration Pages ..........................................................................52
6.4.4.1 Accessing Pages ......................................................................................52
6.4.4.2 Viewing Parameters .................................................................................52
6.4.4.3 Displaying Basic and Advanced Parameters ...........................................53
6.4.4.4 Showing / Hiding Parameter Groups ........................................................54
6.4.4.5 Modifying Parameter Values ....................................................................54
6.4.5 Saving Configuration Changes ................................................................................55
6.4.6 Searching for Configuration Parameters .................................................................55
6.4.7 Creating a Login Welcome Message .......................................................................56
6.4.8 Logging Off the Web Interface .................................................................................57
6.4.9 Getting Help .............................................................................................................58
6.4.10 Using the Home Page ..............................................................................................59
6.4.11 MediaPack Home Page ...........................................................................................60
6.4.12 Viewing the Active Alarms Table .............................................................................61
6.4.13 Viewing Channel Information ...................................................................................62
6.4.14 Viewing Ethernet Port Information ...........................................................................63
6.4.15 Viewing Ethernet Port Information ...........................................................................63
6.4.16 Viewing Trunk Settings ............................................................................................64
6.4.17 Assigning a Name or Brief Description to a Port .....................................................64
6.4.18 Resetting an Analog Channel ..................................................................................65
6.5 Configuration ........................................................................................................ 66
6.5.1 System .....................................................................................................................66
6.5.1.1 Application Settings ..................................................................................66
6.5.1.2 Syslog Settings .........................................................................................68
6.5.1.3 Regional Settings .....................................................................................68
6.5.1.4 TLS Contexts ............................................................................................69
6.5.1.5 Management ............................................................................................75
6.5.2 VoIP .........................................................................................................................88
6.5.2.1 Network ....................................................................................................88
6.5.2.2 IP Interface Table .....................................................................................88
6.5.2.3 Static Route Table ....................................................................................89
6.5.2.4 Network Settings ......................................................................................90
6.5.2.5 QoS Settings ............................................................................................91
6.5.2.6 Security Settings ......................................................................................92
6.5.2.7 Media ......................................................................................................100
6.5.2.8 Quality of Experience .............................................................................115
6.5.2.9 Call Control .............................................................................................116
6.6 Maintenance ....................................................................................................... 122
6.6.1 Maintenance ..........................................................................................................122
6.6.1.1 Maintenance Actions ..............................................................................122
6.6.2 Software Update ....................................................................................................126
6.6.2.1 Load Auxiliary Files ................................................................................126
6.6.2.2 Software Upgrade Key ...........................................................................127
6.6.2.1 Software Upgrade Wizard ......................................................................130
6.6.2.2 Configuration File ...................................................................................136
6.7 Status and Diagnostic Menu ............................................................................... 139
User's Manual 4 Document #: LTRT-71405
Page 5

User's Manual Contents
6.7.1 System Status ........................................................................................................139
6.7.1.1 Message Log ..........................................................................................139
6.7.1.2 Device Information .................................................................................140
6.7.1.3 Ethernet Port Information .......................................................................141
6.7.1.4 Carrier-Grade Alarms .............................................................................141
6.7.2 VoIP Status ............................................................................................................143
6.7.2.1 Active IP Interfaces ................................................................................143
6.7.2.2 Performance Statistics ...........................................................................144
7 Troubleshooting .............................................................................................. 145
7.1 Troubleshooting MediaPack Devices via the RS-232 Port .................................. 145
7.1.1 Viewing the Gateway's Information .......................................................................145
7.1.2 Changing the Networking Parameters ...................................................................146
7.1.3 Determ ining Me dia Pack Initialization Problem s ....................................................146
7.1.4 Reinitializing the MediaPack ..................................................................................147
7.2 LED Indicators .................................................................................................... 149
7.2.1 MediaPack Front View LED Indicators ..................................................................149
7.3 MediaPack Self-Testing ...................................................................................... 150
7.3.1 FXS Line Testing ...................................................................................................150
7.3.2 FXO Line Testing ...................................................................................................151
7.4 Self-Test ............................................................................................................. 152
7.4.1 Operating t he Sys log Ser ve r .................................................................................153
7.4.1.1 Sending the Syslog Messages ...............................................................153
7.4.1.2 Activating the Syslog Client ....................................................................153
7.4.1.3 Setting Syslog Server IP Address, Enabling Syslog, in an ini File
(Example) ..............................................................................................................153
8 List of Abbreviations ....................................................................................... 155
9 Technical Specifications ................................................................................ 159
Version 6.6 5 MediaPack Series
Page 6

MediaPack Series
Reader's Notes
User's Manual 6 Document #: LTRT-71405
Page 7
User's Manual Notices
Notice
This document provides you with information on installation, conf iguration, and operation of
MP-1X8 (8-port), MP-1X4 (4-port), MP-1X2 (2-port) the MP-124 (24-port) Media G ate wa ys.
Information contained in th is document is believed to be accurate and reliab le at the time of
printing. However, due to ongoing product im provements and revisions, AudioC odes cannot
guarantee accuracy of printed material after the Date Published, nor can it accept
responsibility for err ors or omissions. Updates to this document and ot her documents as well
as software files can be viewed by registered customers at
http://www.audiocodes.com/downloads.
© Copyright 2014 AudioCodes Ltd. All rights reserved.
This document is subject to change without notice.
Date Published: June-10-2014
Trademarks
AudioCodes, AC, AudioCoded, Ardito, CTI2, CTI², CTI Squared, HD VoIP, HD VoIP
Sounds Better, InTouc h, IPmedia, Mediant, M ediaPack, NetCoder, Netrak e, Nuera, Open
Solutions Network, OSN, Stretto, TrunkPack, VMAS, VoicePacketizer, VoIPerfect,
VoIPerfectHD, W hat's Inside Matt ers, Your Gateway T o VoIP and 3GX are tradem arks or
registered trademarks of AudioCodes Limited. All other products or trademarks are
property of their r espective owners. Product specif ications are subject to chang e without
notice.
WEEE EU Directive
Pursuant to the W EEE EU Directive, elect ronic and electrical waste m ust not be disposed
of with unsorted waste. Please contact your local recycling authority for disposal of this
product.
Customer Support
Customer technical s upport and s ervices are provided by Au dioCodes or b y an authorized
AudioCodes Service Partner. For more information on how to buy technical support for
AudioCodes products and for contact information, please visit our Web site at
www.audiocodes.com/support
Documentation Feedback
AudioCodes continually strives to produce high quality documentation. If you have any
comments (suggestions or errors) regarding this document, please fill out the
Documentation Feedback form on our Web site at http://www.audiocodes.com/downloads
.
.
Version 6.6 7 MediaPack Series
Page 8

MediaPack Series
Reader's Notes
User's Manual 8 Document #: LTRT-71405
Page 9

User's Manual 1. Introduction
1 Introduction
This document prov ides you with inform ation on i ns tal latio n, c o nf igur at ion , a nd op er ation of
the MP-124 (24-port), MP-1X8 (8-port), MP-1X4 (4-port) and MP-1X2 (2-port) Media
Gateways. As these un its have sim ilar f unctio nalit y (ex cept for the num ber of channels and
some minor features) , they are referred to collecti vely as the MediaPack. Prior knowledge
1.1 About the MediaPack Gateway
of regular telephony and data networking concepts is preferred.
The MediaPack series analog VoIP gateways are cost-effective, cutting e dge technology
products. These st and-alone analog VoI P gateways provide sup erior voice technol ogy for
connecting legacy telephones, fax machines and PBX systems with IP-based telephony
networks, as well as for integration with new IP-based PBX architec ture. These products
are designed and tested to be fully interoperable with leading softswitches and servers.
The MediaPack gatewa ys incorporate up to 24 analog ports f or connection, either directl y
to an enterprise PBX (F XO), to phones, or t o fax (FXS), suppor ting up to 24 simultaneo us
VoIP calls.
Additionally, the MediaPack units are equipped with a 10/100 Base-TX Ethernet port for
connection to the network.
The MediaPack gateways are best suited for small to medium size enterprises, branch
offices or for residential media gateway solutions.
The MediaPack gatewa ys enable users to make free local or international telephone / fax
calls between the d istributed com pany offices, us ing their exis ting telephones / fax. Thes e
calls are routed over the existing network ensuring that voice traffic uses minimum
bandwidth.
The MediaPack gatewa ys are compact devices t hat can be installed as a desk-top unit or
on the wall or in a 19-inch rack.
Version 6.6 9 MediaPack Series
Page 10

MediaPack Series
1.2 MediaPack Features
The followin g provides a high-level overview of some of the many MediaPack supported
features.
Superior, high quality Voice, Data and Fax over IP networks.
Toll quality voice compression.
Vocoder configuration options include:
• G.711 A/u-law PCM, G.726 ADPCM, G.727 ADPCM, G.723.1, G.729 A B,
EG.711, G.722 (in Analog modules)
Enhanced capabilities including MWI, long haul, metering, CID and outdoor protection.
Proven integration with leading PBXs, IP-PBXs, Softswitches and servers.
Spans a range of 2 to 24 FXS/FXO analog ports.
Selectable G.711 or multiple Low Bit Rate (LBR) coders per channel.
T.38 fax with superior performance (handling a round-trip delay of up to nine
seconds).
Echo Canceler, Jitter Buffer, Voice Activity Detection (VAD) and Comfort Noise
Generation (CNG) support.
Comprehensive support for supplementary services.
Web Management for easy configuration and installation.
EMS for comprehensive management operations (FCAPS).
Simple Network Management Protocol (SNMP) and Syslog support.
SMDI support for Voice Mail applications.
Multiplexes RTP streams from several users together to reduce bandwidth overhead.
T.38 fax fallback to PCM (or NSE).
Can be integrated into a VLAN-aware environment.
Capable of automatically updating its firmware version and configuration.
Web access (HTTPS) and Telnet access using SSL / TLS.
User's Manual 10 Document #: LTRT-71405
Page 11
User's Manual 1. Introduction
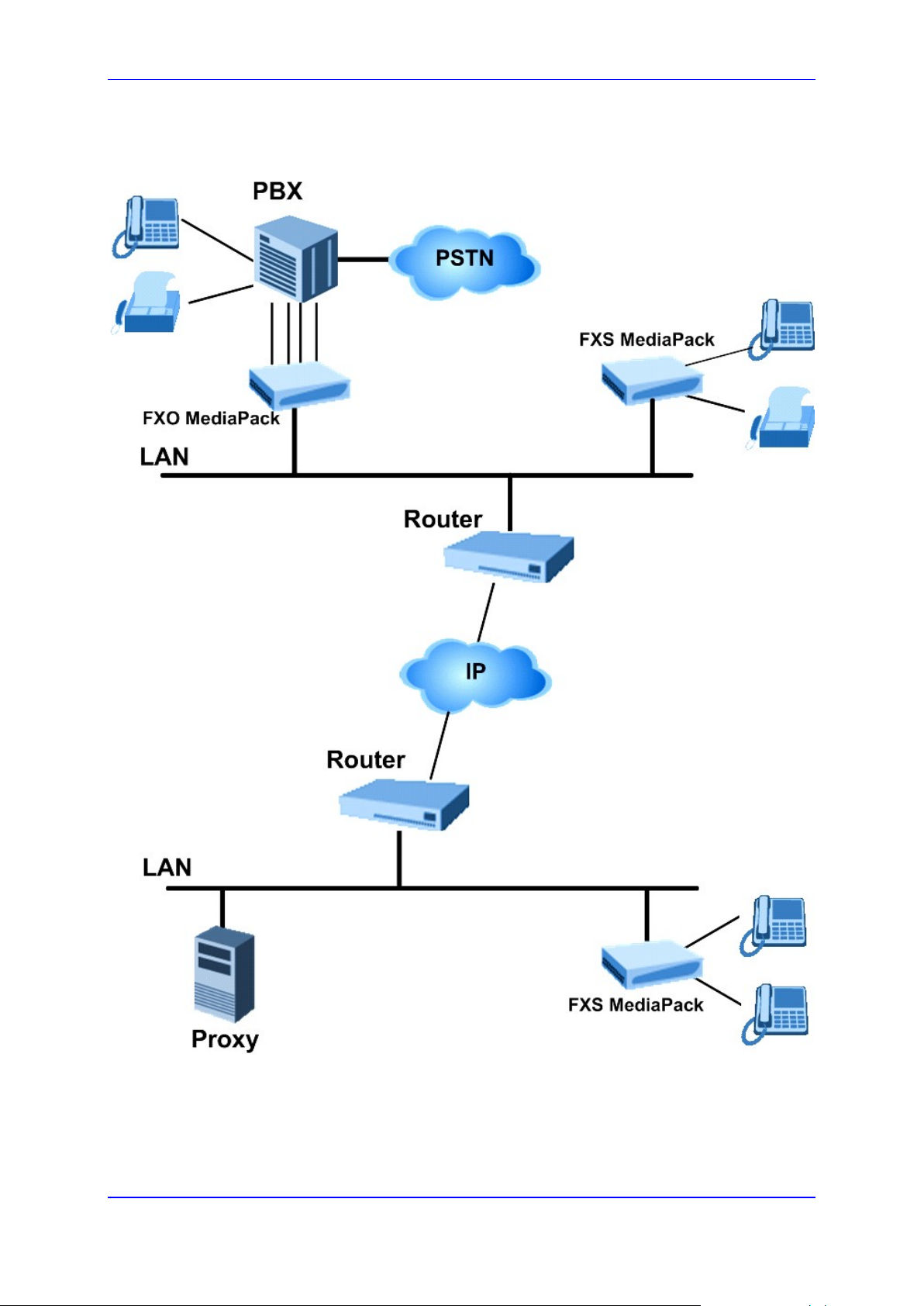
1.3 Functional Block Diagrams
Figure 1: Typical MP-11x Application Diagram
Version 6.6 11 MediaPack Series
Page 12

RS-232
DTYPE-9
RJ-45
10/100
BASE-TX
PHY
CPU
DSPs
PCM
Highway
CODECs SLICs
DTYPE-
50
PCM
Highway
Host Port
PBX
RJ-45
10/100
BASE-TX
PHY
CPU
CODECs
DSPs
DAAs
RJ-11
RS-232
PS2
(debug)
PCM
Highway
Host Port
PBX
RJ-45
10/100
BASE-TX
PHY
CPU
CODECs
DSPs
DAAs
RJ-11
RS-232
PS2
(debug)
RJ-45
10/100
BASE-TX
PHY
CPU
RS-232
PS2
(debug)
DSPs
PBX
CODECs
DAAs
RJ-11
PCM
Highway
CODECs
SLICs
RJ-11
O S u ct o a oc ag a
MediaPack Series
Figure 2: MP-124D Block Diagram
Figure 3: MP-11x FXS Block Diagram
Figure 4: MP-11x FXO+FXS Functional Block Diagram
User's Manual 12 Document #: LTRT-71405
Page 13

User's Manual 2. Software Package
2 Software Package
After installing and powering up the device, you are ready to install the utilities that are
included in the software package. This software package must be installed on the host
PC/machine to be us ed to manage the device. The s oftware package c an be downlo aded
by registered users from the AudioCodes Web site at www.audiocodes.com/support.
To become a registered user, follow the instructions on the Web site.
To get started:
1. To install the software package refer to Installing the Software Pack age on page 13.
2. Check the software package contents (refer to 'Software Directory Contents &
Structure' on page 14.)
2.1 Installing the Software Package
3. Perform 'Getting Started' on page 15.
The software package is available on the AudioCodes' FTP Web site.
Customers using a Windows™ operating system may choose to install the package
via the installation wizard, or choose to unzip the software package from the supplied
zip file (refer to "Installing/Unzipping When Using a Windows™ Operating System"
below).
2.1.1 Installing/Unzipping When Using a Windows™ Operating System
To install the package:
1. Double-click on the setup.exe executable file.
2. Follow on-page instructions.
To unzip when using a Windows™ Operating System:
1. Using a tool like WinZip™, open the zip file.
2. Click the ‘Extract’ button; the ‘Extract’ page opens.
3. Navigate to the directory that you require to be the r oot directory for the installation
and click the ‘Extract’ button; the files are extracted to the location you specified.
2.1.2 Unzipping When Using a Linux™/Solaris™ Operating System
To unzip when using a Linux™/Solaris™ Oper ating System:
1. To open the tar.Z archive, un-compress the tar.Z file.
2. Enter the command: tar -xvf xxxxxx.tar.
Version 6.6 13 MediaPack Series
Page 14
MediaPack Series
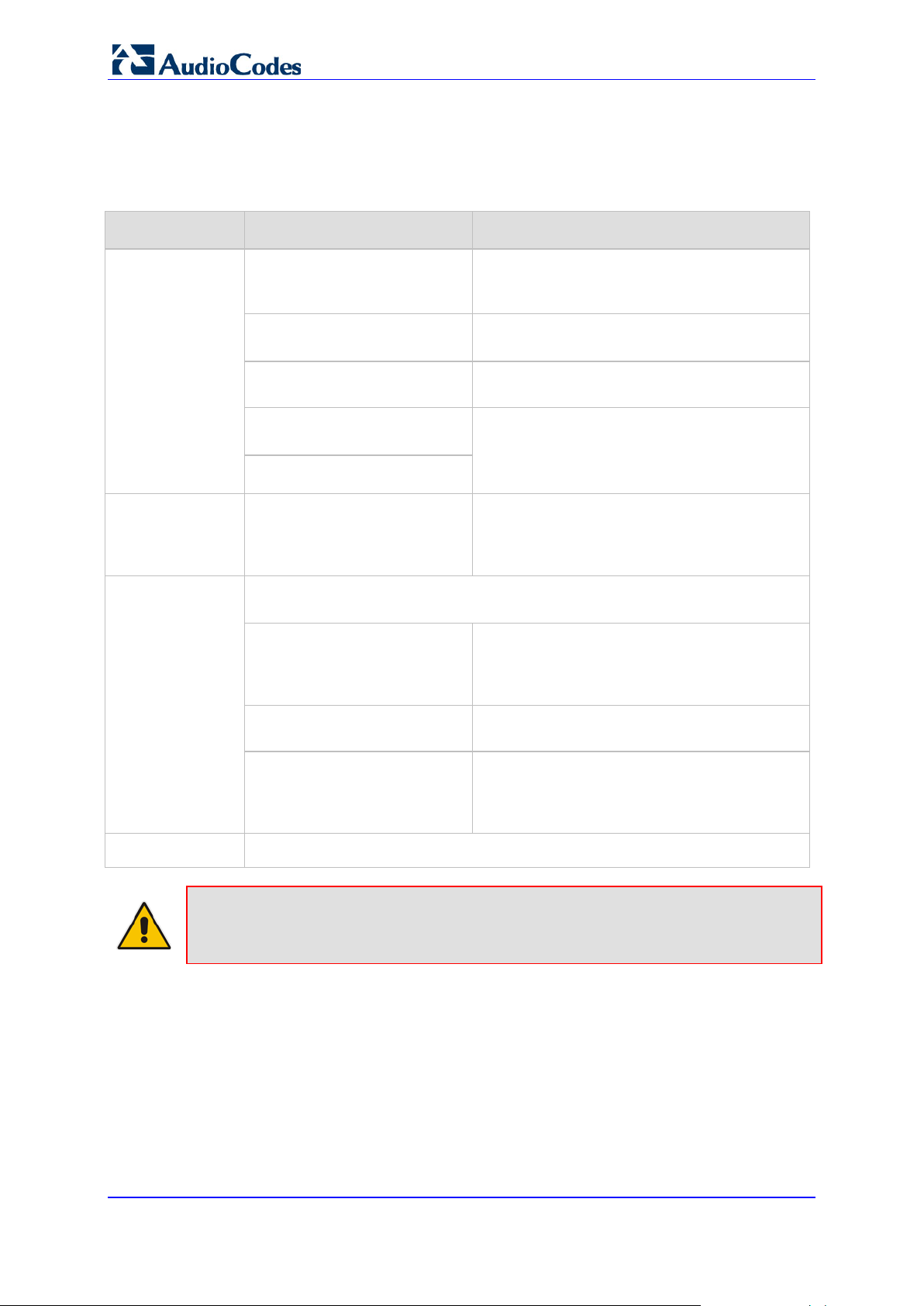
2.2 Software Directory Contents & Structure
Software Package Contents
Contents Directory Description
Auxiliary Files
Firmware
Utilities
.\Auxiliary_Files\MIB_Files
Various MIB files, e.g., SNMP MIB files:
ACL.my, RTP.my, ds1.my, MIB_2.my,
V2_MIB.my.
.\Auxiliary_Files\Sample_Call_
Progress_Files
.\Auxiliary_Files\Sample_CAS
Contains examples of Call Progress Tones
configuration files.
Contains examples of CAS protocol files.
_Protocol_Files
.\Auxiliary_Files\Sample_Ini_Fi
les
.\Firmware
Contains examples of configuration (ini) files.
Users can utilize these sample files as a
baseline for creating customized configuration
files.
Contains cmp files, loaded to the device when
changing the version of the software. When
the device is supplied to customers, it is
already configured with pre -installed firmware.
AudioCodes’ utilities pro vid e you with us er-friendly interfaces that enhance
device usability and smooth your transition to the new VoIP infrastructure.
.\Utilities\DConvert
Contains the TrunkPack Downloadable
Construction Utilit y. Use the utilit y to build Call
Progress Tones, Voice Prompts, and CAS
files.
Documentation
Note: All the demo programs described above are for reference only. Flawless
operation and stability of these applications cannot be guaranteed.
.\Utilities\PSTN_TRACE_UTILI
TY
.\Utilities\WiresharkPlugins
This utility is designed to convert Wireshark log
files containing the PSTN trace to text format.
Contains the plugins for the Wireshark network
diagnostic tool. The plugin registers itself to
handle a dissection of AudioCodes' proprietary
protocol.
All relevant product documentation
User's Manual 14 Document #: LTRT-71405
Page 15
User's Manual 3. Getting Started
3 Getting Started
The MediaPack is supplied with application software alr eady resident in its flash memory
(with factory default parameters). The MediaPack is also supplied with a Web interface.
For detailed inform ation on how to fully configure the gateway refer to Device Ini tialization
& Configuration Files and the Web interface chapter below.
3.1 Assigning the MediaPack IP Address
To assign an IP address to the MediaPack u se o n e of the following methods:
HTTP using a Web browser (see 'Assigning an IP Address Using HTTP' on page 16).
BootP (see 'Assigning an IP Address Using BootP' on page 17).
DHCP (see 'Using BootP/DHCP' on page 21).
Serial communication software (e.g., HyperTerminalTM) connected to the MediaPack
via the RS-232 port.
You can use the Reset button to restore the MediaPack networking parameters to their
factory default values (refer to Restoring Networking Parameters to their Initial State on
page 18).
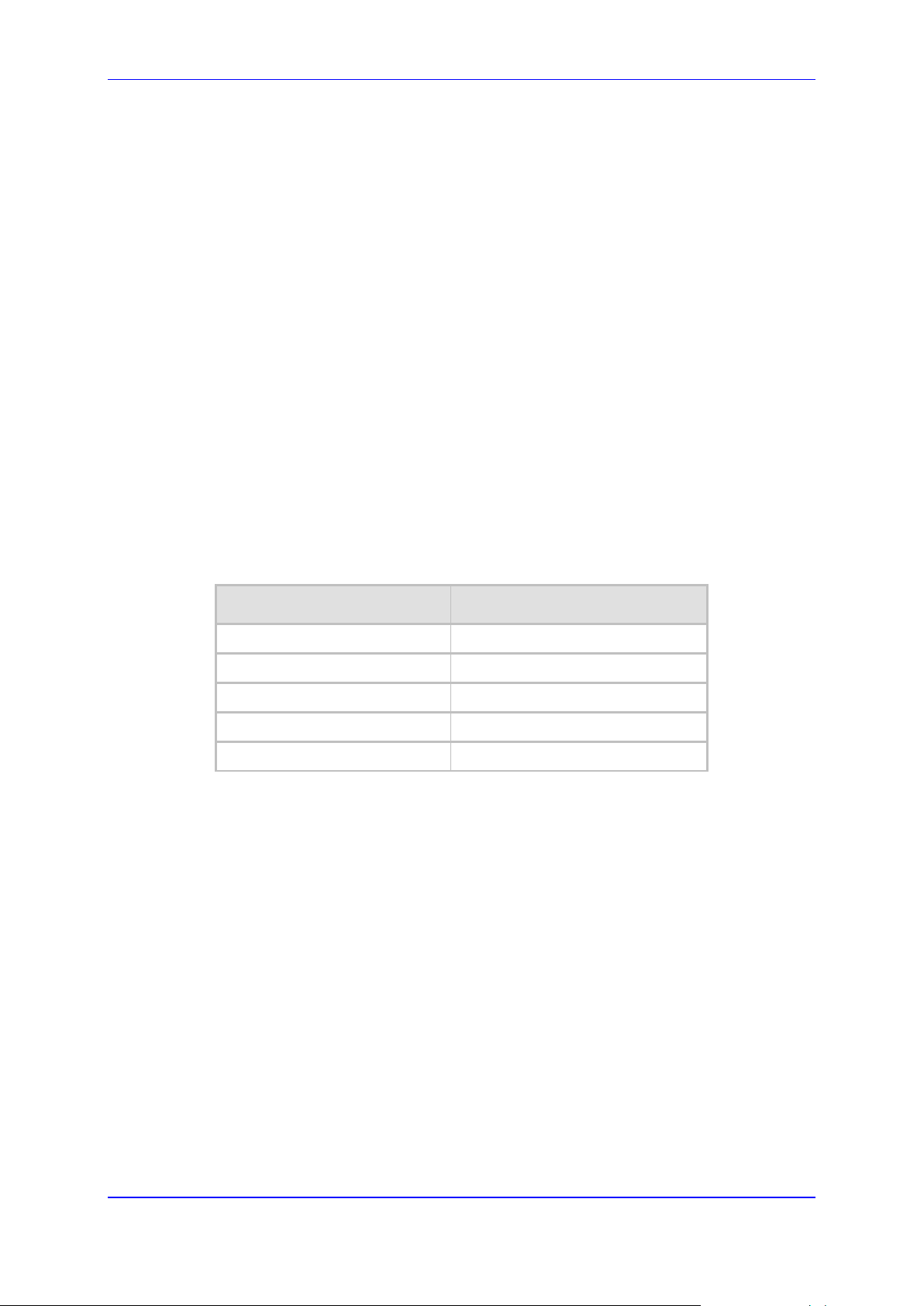
The default device IP Addresses are shown below.
MediaPack Default IP Parameters
FXS/FXO Interfaces Default IP Address
FXS 10.1.10.10
FXO 10.1.10.11
FXS & FXO 10.1.10.10
Default Subnet Mask 255.255.0.0
Default Gateway IP Address 0.0.0.0
Version 6.6 15 MediaPack Series
Page 16

use a
MediaPack Series
3.2 Assigning an IP Address Using HTTP
To assign an IP address using HTTP:
1. Connect your PC to the device. Either connec t the network interfac e on your PC to a
port on a network hub / switch (using an RJ-45 Ethernet c able), or use an Ethernet
cross-over cable to directly connect the network interface on your PC to the RJ-45
jack on the device.
2. Change your PC’s IP addr ess and subnet mask to c orrespond with the device fac tory
default IP address and subnet mask, shown in the table above. For details on
changing the IP address and subnet mask of your PC, refer to Windows™ Online Help
(Start>Help and Support).
3. Access the Web interface (ref er to the Web interface chapter in the Pr od uct R ef erenc e
Manual).
4. Click Reset and click OK in the prompt. The device ap plies the changes and rest arts.
This takes approximately 1 minute to complete. When the device has finished
restarting, the Ready and LAN LEDs on the front view are lit green.
Tip: Record and retain t he IP address and subnet m ask you assign the devic e.
Do the same when defining a new username or password. If the Web interface is
unavailable (for example, if you’ve lost your username and password),
BootP/TFTP conf iguration uti lity to acces s the de vice, “ reflash” the load and r eset the
password.
5. Disconnect your PC from the device or from the hub / switch (depending on the
connection method you used in step 1 above).
6. Reconnect the device and your PC (if necessary) to the LAN.
7. Restore your PC’s IP address & subnet mask to what they originally were. If
necessary, restart your PC and re-access the device via the Web interface with its
new assigned IP address.
User's Manual 16 Document #: LTRT-71405
Page 17

User's Manual 3. Getting Started
3.3 Assigning an IP Address Using BootP
Notes:
• The BootP procedure should be performed using any standard
compatible BootP server.
Tip: You can also use BootP to load the auxiliar y files to the device (refer to
'Using BootP/DHCP' on page 29).
• For Mediant 3000 HA, in order to get the BootP reset request from the
blade, perform a double reset on the system, as described in Private IP
Address and System (Global) IP Address.
To assign an IP address using BootP:
1. Obtain and install a BootP server application on your PC.
2. Add the client configuration for the device.
3. Reset the gateway physical ly causin g it to us e Bo otP. The dev ice chan ges i ts net work
parameters to the values provided by BootP.
Version 6.6 17 MediaPack Series
Page 18

MediaPack Series
3.4 Restoring Networking Parameters to their Default Values
You can use the Reset button to restore the MediaPack networking parameters to their
factory default values (described in Default Device IP Addresses) and to reset the
username and password.
Note that this process also restores the MediaPack parameters to their factory settings,
therefore you must load your previously backed-up ini file, or the default ini file (receiv ed
with the software kit) to set them to their correct values.
To restore parameters to their initial state, take these 6 steps:
1. Back up the ini file. Refer to Backup Copies of ini and Auxiliary Files on page 35.
2. Disconnect the MediaPack from the power and network cables.
3. Reconnect the power cable; the gateway is powered up. After approximately 45
seconds, the Ready LED turns to green and the Control LED blinks for about 3
seconds.
4. While the Control LED is blink ing, use a pa per c lip to pres s shor tly on th e reset b utton
(located next to the Au dioC odes logo on the f ront v iew). The gate way resets a se cond
time and is restored with factory default parameters (username: Admin, password:
Admin - both case-sensitive).
5. Reconnect the network cable.
6. Load your previously backed-up ini file, or the default ini file (received with the
software kit). To load the ini file via the Web interface, refer to 'Software Upgrade
Wizard'.
User's Manual 18 Document #: LTRT-71405
Page 19

User's Manual 4. Device Initialization & Configuration Files
4 Device Initialization & Configuration Files
This section describes the Initialization Procedures and Configuration Options for the
device. It includes:
Startup Process (see below)
Configuration Parameters and Files (refer to Configuration Parameters and Files on
25)
page
4.1 Boot Firmware & Operational Firmware
BootP/DHCP (see Using B ootP /DHCP on page 21)
The MediaPack runs two distinct software programs: Boot firmware and operational
firmware.
Boot firmware - Boot firmware (also known as flash software) resides in the
MediaPack's non-volatile memory. When the MediaPack is reset, Boot software is
initialized and the operational software is loaded into the SDRAM from a TFTP server
or integral non-volatile memory. Boot software is also responsible for obtaining the
MediaPack's IP parameters and ini file name (used to obtain the MediaPack's
configuration parameters) via integral BootP or DHCP clients. The Boot firmware
version can be viewed on the Embedded Web Server’s GUI ('Embedded Web Server'
on page
43). The last step the Boot firmware performs is to jump to invoke in the
operational software.
cmp Operational firmware file - The device is supplied with a cmp file pre-installed on
its flash memory. Therefore, this file is not included on the supplied CD. However, if
you are an AudioCodes registered customer, you can obtain the latest cmp version
files (as well as documentation and other software listed in the table above) from
AudioCodes Web site at www.audiocodes.com/support (customer registration is
performed online at this Web site). If you are not a direct customer of AudioCodes,
please contact the AudioCodes' Distributor and Reseller from whom this product was
purchased.
Note: The ini, MIB and Utility files are shipped with the device in CD format
4.2 MediaPack Startup
The MediaPack's startup process begins when the MediaPack is reset. The startup
process ends when the o perational firm ware is running. T he startup process includes how
the MediaPack obtains its IP parameters, firmware and configuration files.
The MediaPack is reset when one of the following scenarios occurs:
1. The MediaPack is manually reset.
2. acOpenRemoteBoard() is called with RemoteOpenBoardOperationMode set to Full
Configuration Mode (valid for VoPLib API users only).
3. There is a device irregularity.
4. Users perform a reset in the Embedded Web Server GUI or SNMP manager.
5. The flowchart in the figure below illustrates the process that occurs in these scenarios.
Version 6.6 19 MediaPack Series
Page 20
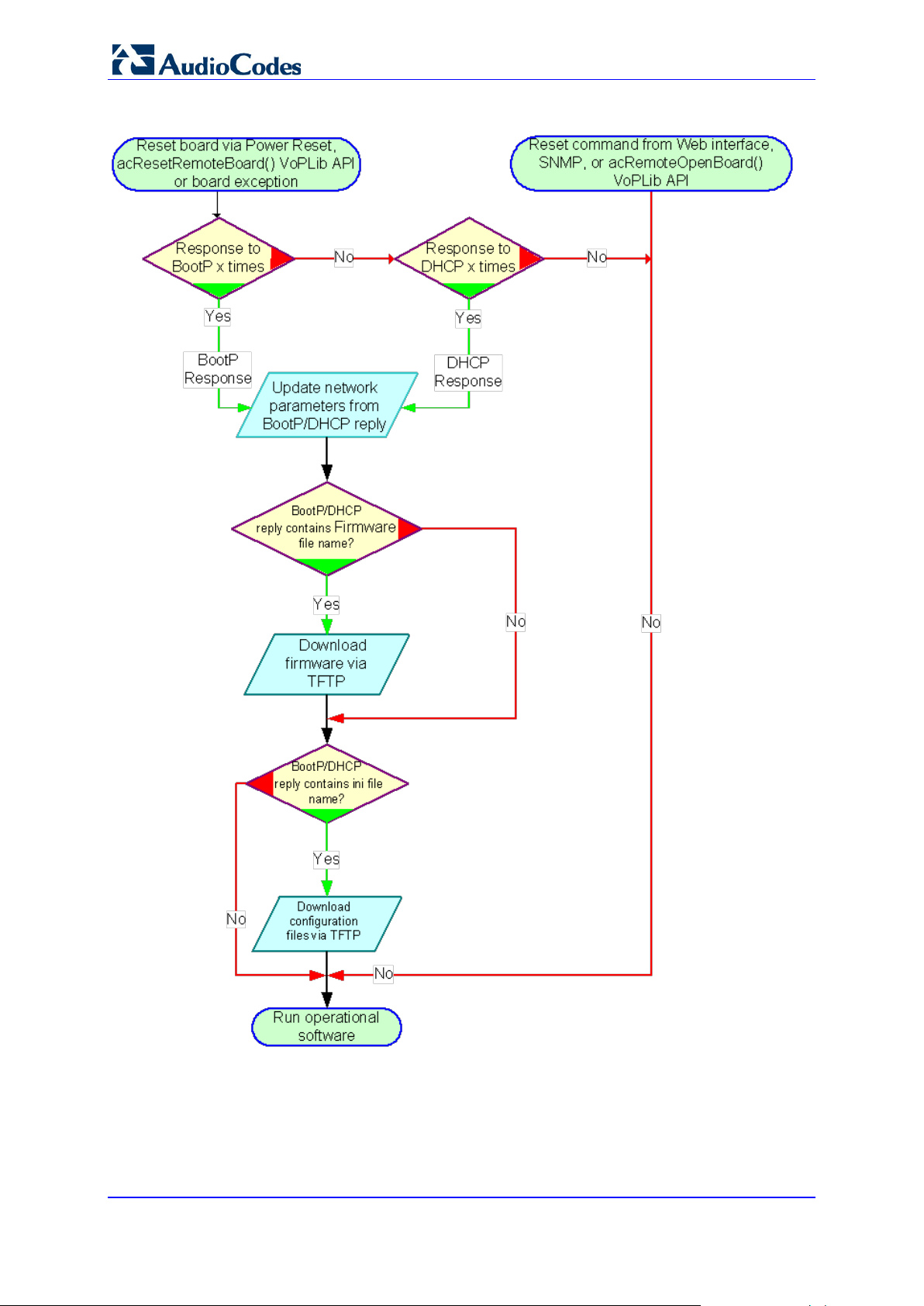
MediaPack Series
Figure 5: MediaPack Startup Process Diagram
User's Manual 20 Document #: LTRT-71405
Page 21
User's Manual 4. Device Initialization & Configuration Files
4.3 Using BootP/DHCP
Notes:
• This sub-section is not applicable to Mediant 3000 HA.
• The BootP/DHCP server should be defined with an ini file name when you
need to modify configuration parameter s or when you're working with a
large Voice Prompt file that is not stored in non-volatile memory and must
be loaded after every reset.
• The default time duration between BootP/DHCP requests is set to 1
second. This can be changed by the BootPDelay ini file parameter. Also,
the default number of requests is 3 and can be changed by the
BootPRetries ini file parameter. Both parameters can also be set using the
Command Line Switches in the BootP reply packet.
• The ini file configuration parameters are stored in non-volatile memory
after the file is loaded. When a parameter is missing from the ini file, a
default value is assigned to this parameter and stored in non-volatile
memory (thereby overriding any previous value set for that parameter).
Refer to Using BootP/DHCP below.
The device uses the Bootstrap Protocol (BootP) and the Dynamic Host Configuration
Protocol (DHCP) to obtain its net working parameters and conf iguration automaticall y after
it is reset. BootP and DHC P are also used to provide the IP addr ess of a TFTP server on
the network, and files (cmp and ini) to be loaded into memory.
Both DHCP and Boot P are network protocols t hat ena ble a de vice to dis cover its ass igned
IP address; DHCP differs from BootP in that it provides a time-limited "lease" to the
assigned address. Both protocols have been extended to enable the configuration of
additional parameters specific to the device.
While BootP is always available, DHCP has to be specifically enabled in the device
configuration, before it can be used.
A BootP/DHCP request is issued after a power reset or after a device exception.
Note: BootP is normally used to initially configure the device. Thereafter, BootP is no
longer required as all parameters can be stored in the gateway’s non-volatile memory
and used when BootP is inaccessible. For example, BootP can be used again to change
the private (local) IP address of the device.
4.3.1 BootP/DHCP Server Parameters
BootP/DHCP can be used to provision the following parameters (included in the
BootP/DHCP reply. Note that some parameters are optional):
IP address, subnet mask - These mandatory parameters are sent to the device every
time a BootP/DHCP process occurs. Note that in High Availability (HA) mode, this IP
address is only private (local) and is not the HA System (global) IP address that must
be configured separately through the Interface Table.
Default gateway IP address - An optional parameter that is sent to the device only if
configured in the BootP/DHCP serv er .
Version 6.6 21 MediaPack Series
Page 22

MediaPack Series
TFTP server IP address - An optional parameter that contains the address of the
TFTP server from which the firmware (cmp) and ini files are loaded.
DNS server IP address (primary and secondary) - Optional parameters that contain
the IP addresses of the primary and secondary DNS servers. These parameters are
available only in DHCP and from Boot version 1.92.
Syslog server IP address - An optional parameter that is sent to the device only if
configured in the BootP/DHCP server. This parameter is available only in DHCP.
Firmware file name – An op tional parameter that contains the name of the CMP
firmware file to be loaded to the gateway via TFTP.
ini file name - An optional parameter that contains the name of the ini file to be loaded
to the gateway via TFTP. The ini file name shall be separated from the CMP file name
using a semicolon.
Note: After programming a new cmp software image file, all configuration parameters
and tables are erased. Re-program them by downloading the ini file.
Configuration (ini) file name - The ini file is a proprietary configuration file with an ini
extension, containing configuration parameters and tables. For more information on
this file, refer to 'Configuration Parameters and Files' on page
detects that this optional parameter field is defined in BootP, it initiates a TFTP
process to load the file into the device. The new configuration contained in the ini file
can be stored in the device's integral non-volatile memory. Whenever the device is
reset and no BootP reply is sent to the blade or the ini file name is missing in the
BootP reply, the device uses the previously stored ini file.
4.3.1.1 Command Line Switches
In the BootP/TFTP Server configuration, you can add c ommand line switches in the B oot
File field. Command line s witches are used for various tasks, s uch as to determine if the
firmware should be burn ed on the non-volatile m emory or not. The table below describes
the different command line switches.
To use a command line switch:
1. In the Boot File field, leave the filename defined in the field as it is (e.g., ramxxx.cmp).
2. After "cmp", leave a space and type in the switch you require (refer to the table
below).
Example: ramxxx.cmp -fb to burn flash memory
ramxxx.cmp -fb -em 4 to burn flash memory and for Ethernet Mode 4 (auto-negotiate)
The table below lists and describes the available switches.
25. When the device
User's Manual 22 Document #: LTRT-71405
Page 23

User's Manual 4. Device Initialization & Configuration Files
Command Line Switch Descriptions
Switch Description
-fb Burn ram.cmp in non-volatile memory. Only the cmp file (the compressed firmware file)
can be burned to the device's non-volatile memory.
-em# Use this switch to set Ethernet mode.
0 = 10 Base-T half-duplex
1 = 10 Base-T full-duplex
2 = 100 Base-TX half-duplex
3 = 100 Base-TX full-duplex
4 = auto-negotiate (default)
Auto-negotiate falls back to half-duplex mode when the opposite port is not in auto-
negotiate but the speed (10 Base-T or 100 Base-TX) in this mode is always configured
correctly.
-br BootP retries:
1 = 1 BootP retry, 1 sec
2 = 2 BootP retries, 3 sec
3 = 3 BootP retries, 6 sec
4 = 10 BootP retries, 30 sec
5 = 20 BootP retries, 60 sec
6 = 40 BootP retries, 120 sec
7 = 100 BootP retries, 300 sec
15 = BootP retries indefinitely
Use this switch to set the number of BootP retries that the device sends during start-up.
The device stops issuing BootP requests when either a BootP reply is received or
Number Of Retries is reached. This switch takes effect only from the next device reset.
-bd BootP delays. 1 = 1 sec (default), 2 = 10 sec, 3 = 30 sec, 4 = 60 sec, 5 = 120 sec. This
sets the delay from the device’s reset until the first BootP request is issued by the
device. The switch only takes effect from the next reset of the device.
-bs Selective BootP: The device ignores BootP replies where option 43 does not contain the
name "AUDC". Refer to Selective BootP on page 24.
-be Use -be 1 for the device to send client information back to the DHCP server. See the
“Vendor Specific Information” section below for more information.
4.3.2 Host Name Support
If DHCP is selected, the device requests a device-specif ic Host Name on the D NS server
by defining the Host Name field of the DHCP request. The host name is set to
ACL_nnnnnnn, where nnnnnnn is the serial number of the device (the serial number is
equal to the last 6 digits of the MAC address converted to decimal representation). The
DHCP server usually registers this Host Name on the DNS server. On networks which
support this setting, this feature allows us ers to configure the de vice via the web browse r
by providing the following URL: http://ACL_nnnnnnn (instead of using the device's IP
address).
Version 6.6 23 MediaPack Series
Page 24

MediaPack Series
4.3.3 Selective BootP
The Selective BootP mechanism, allows the integral BootP client to filter out unsolicited
BootP replies. This c an be beneficial for environm ents where m ore than one BootP server
is available and only one BootP server is used to configure AudioCodes devices.
To activate this feature, add the command line switch -bs 1 to the Firmware File Name
field. When activated, the device accepts only BootP replies containing the text AUDC
in the Vendor Specific Information field (option 43).
To de-activate, use -bs 0.
4.3.4 Microsoft™ DHCP/BootP Server
The device can be co nfigured with an y BootP serv er, includ ing the Mic rosoft™ Windows™
DHCP server, to provide the device with an IP address and other initial parameter
configurations.
To configure the Microsof t™ Windows™ DHCP Serv er to c onf igure a n I P addr e s s to Boot P
clients, add a reservation for each BootP client.
For information on ho w to add a reservation, vie w t he "Mana gi ng Client Reservati ons He lp "
topic in the DHCP console.
The reservation builds an association between MAC address (12 digits), provided in the
accompanying devic e docu mentation) a nd the IP address . Windo ws™ Server pr ovides th e
IP address based on the device MAC address in the BootP request frame.
To configure the Microsof t™ Windows™ DHCP server to pr ovide Boot File information to
BootP clients, edit the BootP Table in the DHCP console. The BootP Table should be
enabled from the Action > Properties dialog, select the option "Show the BootP Table
Folder" and press OK. For information on editing the BootP Table, view the "Manage
BOOTP and remote access clients" Help topic in the DHCP console.
The following parameters must be specified:
Loc al IP addres s - The device’s IP address
Subnet mask
Gateway IP address - Default Gateway IP address
BootP File name - Optional (refer to the following Note)
Note: The BootP File field should normally not be used. The field is only used for
software upgrade (refer to Upgrading Device Software on page 35).
User's Manual 24 Document #: LTRT-71405
Page 25

User's Manual 4. Device Initialization & Configuration Files
4.4 Configuration Parameters and Files
The device's configuration is stored in two file groups.
The Initialization file - an initialization (ini) text file containing configuration parameters
of the device.
The Auxiliary files - dat files containing the raw data used for various tasks such as
Call Progress Tones, Voice Prompts, logo image, etc.
These files contain factory-pre-configured parameter defaults when supplied with the
device and are store d i n th e de vice's non-volatile mem ory. T he de vice is s tar te d up in it ially
with this default configuration. Subsequently, these files can be modified and reloaded
using either of the following methods:
BootP/TFTP during the startup process (refer to 'Using BootP/DHCP' on page 21).
Web Interface (refer to Configuration Using the Web Interface on page 43).
Automatic Update facility (refer to Automatic Update Facility on pag e 31).
The modified auxiliar y files are burned into the n on-volatile memory s o that the modified
configuration is utilized with subsequent resets. T he configuration file is al ways stored on
the non-volatile memory. There is no need to repeatedly reload the modified files after
reset.
Notes:
• Users who configure the device with the Web interface do not require ini
files to be downloaded and have no need to utilize a TFTP server.
• SNMP users configure the device via SNMP. Therefore a very small ini file
is required which contains the IP address for the SNMP traps.
4.4.1 Initialization (ini) File
The ini file name must not include hyphens or spaces. Use underscores instead.
The ini file can contain a num ber of par ameters . The ini file st ructure s uppor ts the f ollowing
parameter value constructs:
Parameter = Value (refer to 'Parameter = Value Constructs' on page 163). The lists of
parameters are provided in the ini File Parameters chapter of the Product Reference
Version 6.6 25 MediaPack Series
Manual.
Tables of Parameter Value (refer to 'Table of Parameter Value Constructs' on page
27).
The example below shows a sample of the general structure of the ini file for both the
Parameter = Value and Tables of Parameter Value Constructs.
[Sub Section Name]
Parameter_Name = Parameter_Value
Parameter_Name = Parameter_Value
.
..
; REMARK
[Sub Section Name]
Page 26

MediaPack Series
...
; Tables Format Rules:
[Table_Name]
; Fields declaration
Format Index_Name_1 ... Index_Name_N = Param_Name_1 ...
Param_Name_M
; Table's Lines (repeat for each line)
Table_Name Index_1_val ... Index_N_val = Param_Val_1 ...
Param_Val_M
[\Table_Name]
4.4.1.1 Paramet er Val ue St r uct u re
The following are the rules in the ini File structure for individual ini file parameters
(Parameter = Value):
Lines beginning with a semi-colon ';' (as the first character) are ignored.
A carriage-return/line-feed must be the final character of each line.
The number of spaces before and after "=" is not relevant.
If there is a syntax error in the parameter name, the value is ignored.
Syntax errors in the parameter value field can cause unexpected errors (because
parameters may be set to the incorrect values).
Sub-section names are optional.
String parameters, representing file names, for example,
CallProgressTonesFileName, must be placed between two inverted commas ('…').
The parameter name is NOT case sensitive; the parameter value is usually case
sensitive.
Numeric parameter values should be entered only in decimal format.
The ini file should be ended with one or more empty lines.
The example below shows a sample ini file for the MediaPack.
[MGCP]
EndpointName = 'ACgw'
CallAgentIP = 192.1.10.3
CallAgentPort = 2427
BaseUDPPort = 4000
FlashHookPeriod = 700
[Channel Params]
DJBufferMinDelay = 75
RTPRedundancyDepth = 1
User's Manual 26 Document #: LTRT-71405
Page 27

User's Manual 4. Device Initialization & Configuration Files
file name extension is xxx.ini and NOT erroneously xxx.ini.ini or xxx~.ini.
[Files]
CallProgressTonesFilename = 'CPUSA.dat'
VoicePromptsFilename = 'tpdemo_723.dat'
FXSLOOPCHARACTERISTICSFILENAME = 'coeff.dat'
Note: Before loading an ini file to the device, make sure that the extension of the ini file
saved on your PC is correct: Verify that the checkbox Hide extension for known file
types (My Computer>Tools>Folder Options>View) is unchecked. Then, verify that the ini
The lists of individual ini file parameters are provided in ini File Parameters.
4.4.1.2 Tables of Parameter Value Structure
Tables group the r elated parameters of a given ent ity. Tables are compos ed of rows and
columns. The colum ns represent parameters types, while each row represent s an entity.
The parameters in e ach row are called the line attr ibutes. Rows in tables ma y represent
(for example) a trunk, SS7 Link, list of timers for a given application, etc.
Examples of the struc ture of the tables are provided below. For a list of support ed tables
please refer to the ini File Table Parameters section in the Product Reference Manual.
[ SS7_SIG_INT_ID_TABLE ]
FORMAT SS7_SIG_IF_ID_INDEX = SS7_SIG_IF_ID_VALUE,
SS7_SIG_IF_ID_NAME, SS7_SIG_IF_ID_OWNER_GROUP,
SS7_SIG_IF_ID_LAYER, SS7_SIG_IF_ID_NAI, SS7_SIG_M3UA_SPC;
SS7_SIG_INT_ID_TABLE 1 = 101, AMSTERDAM1, 3, 3, 1, 4;
SS7_SIG_INT_ID_TABLE 5 = 100, BELFAST12, 3, 3, 0, 11;
[ \SS7_SIG_INT_ID_TABLE ]
The table below is shown in document format for description purposes:
Table Structure Example
IF ID
Index
IF ID
Value
SS7_SIG_IF_ID
_NAME
SS7_SIG_IF_ID_
OWNER_GROUP
SS7_SIG_IF_ID
_LAYER
SS7_SIG_IF_
ID_NAI
SS7_SIG_
M3UA_SPC
1 101 AMSTERDAM1 3 3 1 4
5 100 BELFAST12 3 3 0 11
Version 6.6 27 MediaPack Series
Page 28

MediaPack Series
4.4.1.2.1 Table Structure Rules
Tables are composed of four elements:
Table-Title - The Table's string name in square brackets. In the example above, the
Table Title is:
[ SS7_SIG_INT_ID_TABLE ].
Format Line - This line specifies the table's fields by their string names. In the example
above, the format line is: FORMAT SS7_SIG_IF_ID_INDEX =
SS7_SIG_IF_ID_VAL UE, S S7_ SIG_IF_ID_NAME,
SS7_SIG_IF_ID_OWNER_GROUP, SS7_SIG_IF_ID_LAYER, SS7_SIG_IF_ID_NAI,
SS7_SIG_M3UA_SPC
• The first word MUST be "FORMAT" (in capital letters), followed by indices field
names, and after '=' sign, all data fields names should be listed.
• Items must be separated by ',' sign.
• The Format Line must end with ';' sign.
Data Lin e( s) - The actual values for parameters are specified in each Data line. The
values are interpreted according to the format line. The first word must be the table's
string name.
• Items must be separated by a comma (',' sign).
• A Data line must end with a semicolon (';' sign).
• Indices (in both the Format line and the Data lines) must all appear in order, as
determined by the table's specific documentation. The Index field must NOT be
omitted. Each row in a table must be unique. For this reason, each table defines
one or more Index fields. The combination of the Index fields determines the 'linetag'. Each line-tag may appear only once. In the exam ple prov id ed in the tab le
above, Table Structure Example', there is only one index field. This is the
simplest way to mark rows.
• Data fields in the Format line may use a sub-set of all of the configurable fields in
a table only. In this case, all other fields are assigned with the pre-defined default
value for each configured line.
• The order of the Data fields in the Format line is not significant (unlike the Index-
fields). Field values in Data lines are interpreted according to the order specified
in the Format line.
• Specifying '$$' in the Data line causes the pre-defined default value assigned to
the field for the given line.
• The order of Data lines is insignificant.
• Data lines must match the Format line, i.e. must contain exactly the same number
of Indices and Data fields and should be in exactly the same order.
• A line in a table is identified by its table-name and its indices. Each such line may
appear only once in the ini file.
End-of-Table-Mark: Marks the end of a table. Same as Table title, but the string name
is preceded by '\'.
Below is an example of the table structure in an ini file.
; Table: Items Table.
; Fields: Item_Name, Item_Serial_Number, Item_Color, Item_weight.
; NOTE: Item_Color is not specified. It will be given default
value.
[Items_Table]
; Fields declaration
Format Item_Index = Item_Name, Item_Serial_Number, Item_weight;
User's Manual 28 Document #: LTRT-71405
Page 29

User's Manual 4. Device Initialization & Configuration Files
Items_Table 0 = Computer, 678678, 6;
Items_Table 6 = Computer-page, 127979, 9;
Items_Table 2 = Computer-pad, 111111, $$;
[\Items_Table]
4.4.1.2.2 Secret Tables
A table is defined as a secret table if it contains at least one secret data field or if it
depends on such a table. A sec r et data f iel d is a f ield t hat must not be revealed to the user.
An example of a secret field can be f ound in an IPSec application. The IPsec tables are
defined as secret tables be cause the IKE ta ble c ontain s a pre-shared key field, whic h m ust
not be revealed. The SPD table depends on the IKE table. Therefore, the SPD table is
defined as a secret table.
There are two major differences between tables and secret tables:
The secret field itself cannot be viewed via SNMP, Web Server or any other tool.
ini File behavior: These t ables are never uploaded in the ini File (e.g., 'Get IN I-File from
Web'). Instead, ther e is a c omm ented title that states that the secret t able is present at the
blade, and is not to be revealed.
Secret tables are al ways kept in the blad e’s non-vola tile mem ory, and may be ov er-written
by new tables that s hould be provided in a new ini Fi le. If a secret table appears in an ini
File, it replaces the cur rent table r egardless of its cont ent. The wa y to delete a s ecret tabl e
from a blade is, for exam ple, to provide an em pty table of that t ype (with no data lines) as
part of a new ini File. The empty table replaces the previous table in the blade.
4.4.1.2.3 Tables in the Uploaded ini File
Tables are grouped according to the applications they configure.
When uploading the i ni file, the polic y is to include only tab les that belong to ap plications,
which have been configured. (Dynamic tables of other applications are empty, but static
tables are not.) The trigger for upload ing tables is further docum ented in the applications'
specific sectio ns.
4.4.1.2.4 Secret Tables
A table is defined as a secret table if it contains at least one secret data field or if it
depends on such a table. A sec r et data f iel d is a f ield t hat must not be revealed to the user.
An example of a secret field can be f ound in an IPSec application. The IPsec tables are
defined as secret tables be cause the IKE ta ble c ontain s a pre-shared key field, which m ust
not be revealed. The SPD table depends on the IKE table. Therefore, the SPD table is
defined as a secret table.
There are two major differences between tables and secret tables:
The secret field itself cannot be viewed via SNMP, Web Server or any other tool.
ini File behavior: These tables are never uploaded in the ini File (e.g., 'Get INI-File
from Web'). Instead, there is a commented title that states that the secret table is
present at the blade, and is not to be revealed.
Secret tables are al ways kept in the blad e’s non-vola tile mem ory, and may be ov er-written
by new tables that s hould be provided in a new ini Fi le. If a secret table appears in an ini
File, it replaces the cur rent table r egardless of its cont ent. The w ay to delete a sec ret table
from a blade is, for exam ple, to provide an em pty table of that t ype (with no data lines) as
part of a new ini File. The empty table replaces the previous table in the blade.
Version 6.6 29 MediaPack Series
Page 30

MediaPack Series
4.4.1.3 Binary Configuration File Download
The ini file contains sens itive inform ation require d for appropr iate func tioning of the de vice.
The ini file is uplo ade d to th e de vic e or d o wnlo ade d f r om the gateway using T FTP or HTTP
protocols. These protocols are unsecured (and thus vulnerable to a potential hacker).
Conversely, if the ini file is encoded, the ini file would be significantly less vulnerable to
4.4.1.3.1 Encoding Mechanism
outside harm.
The ini file to be loaded and retrieved is available with or without encoding. When an
encoded ini file is downloaded to the device, it is retrieved as encoded f rom the device.
When a decoded file is downloaded to the device, it is retrieved as decoded from the
device.
In order to create an encod ed in i f ile, t he user must first create an ini file an d the n app l y th e
DConvert utility to it in order to encode it.
In order to decode an encoded ini file retr ieved from the device, the us er must retrieve an
encoded ini file from the device using the Web server (refer to "Downloading Auxiliary
Files" below) and then use the DConvert utility in order to decode it.
(Refer to the Utilities chap ter in the Product Refer ence Manual for detailed ins tructions on
ini file encoding and decoding.)
Downloading the in i f i le w it h or wit hout encoding ma y be per f ormed by utilizing ei ther TFTP
or HTTP.
4.4.2 Auxiliary F iles
The auxiliary files are *.dat files cont aining raw data used for a certain task such as Cal l
Progress Tones, Voice Prompts, logo image, etc. The *.dat files are created using the
DConvert utility (refer to the Utilities chapter in the Product Reference Manual), which
converts auxiliary source files into dat files. Some sample auxiliary source files are
available in the software pac kage under: .\Auxiliary_Files\.dat files. These *.dat files are
downloaded to the device using TFTP (see below) or HTTP via the Software Upgrade
Wizard (refer to Upgrading Device Software on page 35.) This section describes the
various types of auxiliary files.
Note: The auxiliary source files use the same ini file extension type as the ini
configuration file, however, the functionality is different. Whenever the term, "ini file" is
used, it refers to the configuration file and NOT to the auxiliary files.
4.4.2.1 Downloading Auxiliary Files via TFTP During the Blade Startup
Each auxiliary file has a corresponding ini file parameter in the form of
[AuxiliaryFileType]FileName. This parameter takes the name of the auxiliary file to be
downloaded to the device. I f the ini file does no t conta in a par am eter f or a specif ic auxiliar y
file type, the device uses the last auxiliary file that was stored on the non-vo l a tile memory.
The following list contains t he ini file param eters f or the diff erent types of aux iliary files t hat
can be downloaded to the device:
CoderTblFileName – The name (and path) of the file containing the coder table . This
file should be constructed using the “TrunkPack Conversion Utility” supplied as part of
the software package on the CD accompanying the device.
User's Manual 30 Document #: LTRT-71405
Page 31

User's Manual 4. Device Initialization & Configuration Files
VoicePromptsFileName - The name (and path) of the file containing the voice
prompts. This file should be constructed using the “TrunkPack Conversion Utility”
supplied as part of the software package on the CD accompanying the MediaPack.
The Voice Prompt buffer size in the blade is 1 Mbyte.
The Voice Prompt buffer size is also controlled by the software upgrade key. For more
information contact an AudioCodes representative.
CallProgressTonesFilename - The name (and path) of the file containing the Call
Progress and User-Defined Tones definition.
PrerecordedTonesFileName - The name (and path) of the file containing the
Prerecorded Tones. This file should be constructed using the "TrunkPack Conversion
Utility" supplied as part of the software package on the CD accompanying the device.
DialPlanFileName - The name (and path) of the file containing dial-plan configuration
for CAS protocols. This file should be constructed using the "TrunkPack Conversion
Utility" supplied as part of the software package on the CD accompanying the device.
FXSLoopCharacteristicsFileName - The name (and path) of the file providing the FXS
line characteristic parameters.
SaveConfiguration - (default = 1 = enabled) This parameter replaces the following
parameters: BlastCallProgressSetupFile, BlastVoicePromptsFile. When enabled, all
configuration and downloadable files are stored in non-volatile memory.
4.4.2.2 Automatic Update Facility
The device is capable of automatically downloading updates to the ini file, auxiliary files
and firmware image. An y standard W eb server, FTP server or NF S server m ay be used to
host these files.
The Automatic Update processing is performed:
Upon device start-up (after the device is operational)
At a configurable time of day, e.g., 18:00 (disabled by default)
At fixed intervals, e.g., every 60 minutes (disabled by default)
If Secure Startup is enabled (refer to Secure Startup), upon start-up but before the
device is operational.
The Automatic Update process is entirel y controlled by conf iguration param eters in the ini
file. During the Automatic Update process, the device contacts the external server and
requests the latest version of a given set of URLs. An additional benefit of using HTTP
(Web) servers is that c onfig uration i ni fi les wo uld be do wnloade d o nly if the y were modified
since the last update.
The following is an example of an ini file activating the Automatic Update Facility.
# DNS is required for specifying domain names in URLs
DnsPriServerIP = 10.1.1.11
# Load extra configuration ini file using HTTP
INIFILEURL = 'http://webserver.corp.com/AudioCodes/inifile.ini'
# Load call progress tones using HTTPS
CPTFILEURL = 'https://10.31.2.17/usa_tones.dat'
# Load voice prompts, using user "root" and password "wheel"
VPFILEURL = 'ftps://root:wheel@ftpserver.corp.com/vp.dat'
# Update every day at 03:00 AM
AutoUpdatePredefinedTime = '03:00'
Version 6.6 31 MediaPack Series
Page 32

MediaPack Series
Notes on Configuration URLs:
Additional URLs may be specified, as described in the System ini File Parameters in
the Product Reference Manual.
Updates to non-ini files are performed only once. To update a previously-loaded
binary file, you must update the ini file containing the URL for the file.
To provide differential configuration for each of the devices in a network, add the string
"<MAC>" to the URL. This mnemonic is replaced with the hardware (MAC) address of
the device.
To update the firmware image using the Automatic Update facility, use the
CMPFILEURL parameter to point to the image file. As a precaution (in order to protect
the device from an accidental update), you must also set AUTOUPDATECMPFILE to
1.
URLs may be as long as 255 characters.
Note: For the follo wing parameter s, the URLs are reset to their def ault value on
successful Autoupdate. S ubsequent Autoupdat es without re-initializin g the parameters
are not supported.
• CptFileUrl
• PrtFileUrl
• FXSCoeffFileUrl
• FXOCoeffFileUrl
• CasFileUrl
• DialPlanFileUrl
• TLSPkeyFileUrl
• TLSCertFileUrl
• TLSRootFileUrl
• WebLogoFileUrl
• V5PortConfigurationFileURL
To utilize Automatic Updates for deploying the device with minimum manual
configuration:
1. Set up a Web server (in this example it is http://www.corp.com/) where all the
configuration files are to be stored.
2. On each device, pre-configure the following setting: (DHCP/DNS are assumed)
INIFILEURL = 'http://www.corp.com/master_configuration.ini'
User's Manual 32 Document #: LTRT-71405
Page 33

User's Manual 4. Device Initialization & Configuration Files
3. Create a file named master_configuration.ini, with the following text:
# Common configuration for all devices
# -----------------------------------CptFileURL = 'http://www.corp.com/call_progress.dat'
# Check for updates every 60 minutes
AutoUpdateFrequency = 60
# Additional configuration per device
# ----------------------------------# Each device will load a file named after its MAC address,
# e.g. config_00908F033512.ini
IniFileTemplateURL = 'http://www.corp.com/config_<MAC>.ini'
# Reset the device after configuration has been updated.
# The device will reset after all files were processed.
RESETNOW = 1
4. You can modify the mast er_configuration.i ni file (or an y of the conf ig_<MAC>.ini f iles)
at any time. The dev ice queries for the latest vers ion every 60 minutes, and applies
the new settings immediately.
5. For additional securit y, usage of HTTPS an d FTPS protocols is recommended. The
device supports HTTPS (RFC 2818) and FTPS using the AUTH TLS method (RFC
4217) for the Automatic Update facility.
6. To download configuration files from an NFS server, the file system parameters
should be defined in the configuration ini file. The following is an example of a
configuration ini file for downloading files from NFS servers using NFS version 2:
# Define NFS servers for Automatic Update
[ NFSServers ]
FORMAT NFSServers_Index = NFSServers_HostOrIP,
NFSServers_RootPath, NFSServers_NfsVersion;
NFSServers 1 = 10.31.2.10, /usr/share, 2 ;
NFSServers 2 = 192.168.100.7, /d/shared, 2 ;
[ \NFSServers ]
CptFileUrl =
'file://10.31.2.10/usr/share/public/usa_tones.dat'
VpFileUrl =
'file://192.168.100.7/d/shared/audiocodes/voiceprompt.dat'
If you implement the Automatic Update mechanism, the device must not be configured
using the Web interf ace. If you configure p arameters in th e W eb interface and sa ve (burn)
the new settings to t he device's flash m emory, the IniFileURL paramet er (defining the URL
to the ini file for Autom atic Updates) is automatically set to 0 (i.e., A utomatic Updates is
disabled).
The Web interface provides a safeguard for the Automatic Update mechanism. If the
IniFileURL parameter is defined with a URL value (i.e., Automatic Updates is enabled),
then by default, the ' Burn To FLA SH' fie ld under th e Reset Co nfigurat ion group in the W eb
interface's 'Maintenanc e Ac tions' pa ge is autom atic ally s et to "No". T heref ore, this preve nts
an unintended burn-to-flash when resetting the device.
However, if configuration settings in the Web Interface were burnt to flash, you can reinstate the Automatic Upda te mec hanism, b y loading to the de vice, the ini f ile that inclu des
the correct IniFileURL parameter setting, using the Web interface or BootP.
Version 6.6 33 MediaPack Series
Page 34

MediaPack Series
4.4.2.3 Downloading the dat File to a Device
The purpose of the coeff.dat configuration file is to provide the best termination and
transmission quality adaptation for different line types. The file consists of a set of
parameters for the signal processor of the loop interface devices. This parameter set
provides control of the following AC and DC interface parameters:
DC (V / I curve and max current)
AC impedance matching
Transmit gain
Rec ei ve gain
Hybrid balance
Frequency response in transmit and receive direction
Hook thresholds (FXS only)
Ringing generation and detection parameters
Metering parameters
This means, for ex am ple, t hat c ha ng ing impedance matching or h ybrid ba lanc e requ ir es no
hardware modifications , so that a single device can meet user -specific requirements . The
digital nature of the filters and gain stages also ensures high reliability, no drifts (over
temperature or time) and simple variations between different line types.
The .dat configurat io n f ile is produc ed b y Aud ioC odes f or eac h market after comprehens ive
performance analysis an d t es ting and c an be modified on request. The c urr ent f ile suppor ts
US line type of 600 ohm AC im pedanc e (and f or FXS, 40 V RM S rin ging volt age f or REN =
2).
The following list describ es which coeff.dat file is to be used with which MP device. T he
files are located in the Analog_Coefficients_Files folder:
For MP-11x and MP-124RevD FXS coefficients file types:
MP11x-02-1-FXS_16KHZ.dat - supports generation of 16 KHz metering tone and
complies with USA standard.
MP11x-02-2-FXS_16KHZ.dat - supports generation of 16 KHz metering tone and
complies with TBR21 standard (Pan European).
MP11x-02-1-FXS_12KHZ.dat - supports generation of 12 KHz metering tone and
complies with USA standard.
MP11x-02-2-FXS_12KHZ.dat - supports generation of 12 KHz metering tone and
complies with TBR21 standard (Pan European).
In a situation wher e the selec tion of the m etering t ype (16Khz or 12 KHz) is not impor tant,
use MP11x-02-1-FXS_16KHZ.dat.
The dat conf iguration fil e is produc ed by AudioC odes for each mark et after com prehensive
performance analysis and testing, and can be modified on request. The current file
supports US line type of 600 ohm AC impedanc e and 40 V RMS rin ging voltage f or REN =
2.
In future software releases, it is to be expanded to consist of different sets of line
parameters, which can be selected in the ini file, for each port.
To support differ ent types of c ountries and m arkets, it is necessar y to support lo ading of a
new Coefficients.ini file. This file consists of AC a nd DC line par ameters f or the peripheral
devices.
User's Manual 34 Document #: LTRT-71405
Page 35

User's Manual 4. Device Initialization & Configuration Files
To send the Coeff.dat file to the device:
Use either the Web interf ace GUI's Auxiliary Files. Refer to Software Upgrad e Wizard in
the product's User's Manual.
or
The BootP/TFTP Server to send to the device the ini f ile (which sim ultaneously downloads
the Call Progress T one ini file, provided that the device's CallProgressTonesFilename ini
file parameter is defined, a nd provided that both ini f iles are located in the sam e directory.
(Refer to 'BootP/TFTP Server').
4.5 Backup Copies of ini and Auxiliary Files
Be s ure to separate ly store a cop y of the ini f ile and all auxi liary files, as well as a note of
the software version for use should a device require replacement.
4.6 Upgrading Device Software
To upgrade the device's software (firm ware), load the upgraded firm ware cmp file into t he
device (and optionally burn it into integral non-volatile memory) using:
1. Web interface - For a complete description of this option refer to Software Upgrade
Wizard.
2. BootP/TFTP Server - Use t he -fb Boot P command line s witch. The device do wnloads
the specified firmware name via TFTP and also “burns” the firmware on the nonvolatile memory.
Note: Upgrading the device's firmware requires reloading the ini file and re-burning
the configuration files. A Software Upgrade Key may be required (refer to 'Software
Upgrade Wizard').
Version 6.6 35 MediaPack Series
Page 36

MediaPack Series
Reader's Notes
User's Manual 36 Document #: LTRT-71405
Page 37

User's Manual 5. Automatic Configuration Options
5 Automatic Configuration Options
Large-scale deployment of MP-1xx devices calls for automated installation and setup
capabilities. In some cases, the devices are shipped to the end-customer directly from
manufacturing, while in oth er cases the y pass through a stagin g warehouse. Con figuration
may therefore take place at the staging warehouse or at the final customer premises.
The devices may sometimes be pre-configured during the manufacturing process by
AudioCodes (commonly known as "private labeling"). A two-stage configuration process
will be employed, such that the initial configuration includes just the bare minim um, and
final configuration is achieved when the device is deployed in a live network.
The following details the available options for fast automatic configuration.
5.1 Option A - Local Configuration Server with BootP/TFTP
This is the most straightforward alternative:
A computer running BootP and TFTP software is placed in a staging warehouse.
A standard device configuration *.ini file is prepared and placed in the TFTP directory.
BootP is configured with the MAC address of each device.
Each device should be connected to the network and powered-up.
The BootP reply would contain the *.cmp and *.ini file names in the "bootfile" field. The
device will retrieve these files and store them in flash.
If auxiliary files ar e re quire d (coef fic ients, ca ll progr ess tones etc.) th e y may be s pecified in
the *.ini file and downloaded from the same TFTP server.
When the LEDs turn green, the device may be disconnected and shipped to the end
customer.
Local IP addressing at the customer site would normally be provided by DHCP.
This alternative requires the configuration to take place at a staging warehouse.
Version 6.6 37 MediaPack Series
Page 38

MediaPack Series
5.2 Option B - DHCP-based Configuration Server
This alternative is similar to Option A, except that DHCP is used instead of BootP. The
DHCP server may be specially configured to automatically provide AudioCodes devices
with a temporary IP address, so that individual MAC addresses are not required.
Below is a sample configur ation file for Linux DHCP s erver (dhcpd.conf). The devices will
be allocated temporary IP addresses in the range 10.31.4.53 to 10.31.4.75.
TFTP is assumed to be on the same machine as the DHCP server (the "next-server"
directive may be used otherwise).
ddns-update-style ad-hoc;
default-lease-time 60;
max-lease-time 60;
class "audiocodes" {
match if(substring(hardware, 1, 3) = 00:90:8f);
}
subnet 10.31.0.0 netmask 255.255.0.0 {
pool {
allow members of "audiocodes";
range 10.31.4.53 10.31.4.75;
filename "MP118_SIP_5.00A.001.cmp -fb;mp118.ini";
option routers 10.31.0.1;
option subnet-mask 255.255.0.0;
}
}
This alternative requires configuration to take place at a staging warehouse.
User's Manual 38 Document #: LTRT-71405
Page 39

User's Manual 5. Automatic Conf ig ur ati on Optio ns
5.3 Option C - HTTP-based Automatic Updates
An HTTP (or HTT PS) server can usual ly be placed in the c ustomer's core network, where
configuration and software updates will be available for download.
For example, assume the core network HTTP server is https://www.corp.com.
A master configuration *.ini file should be placed on the HTTP server, e.g.
https://www.corp.com/audiocodes/master.ini . This *.ini file could point to additional *.ini
files, auxiliary files (voice prompts, call progress tones, coefficients etc.) and software
upgrades (CMP files), all on the HTTP server or other HTTP servers in the core network.
The major advantage of this method is that the HTTP configuration can be checked
periodically, when the device is deployed at the end customer site; HTTP(S) is not
sensitive to NAT devices , allowing configuration to take place as needed, without on-site
intervention.
For additional security, the URL may contain a different port and a username+password.
The MP-1xx devices should only be configured with the URL of the initial *. ini file. There
are several ways of doing this:
Using Options A or B above - via TFTP at a staging warehouse. The INI file parameter
controlling the configuration URL is IniFileURL.
Private labeling at AudioCodes.
Using DHCP option 67 (see method D below).
Manually on-site, using the RS-232 port or web interface.
When the device is deplo yed at the e nd-custom er s ite, local DHC P provides IP address ing
and DNS server inf ormation. The MP-1xx can then c ontact the HTTP server at the cor e
network and complete its configuration.
The URL can be a simple file name, or contain the device MAC address or IP addres s,
e.g.:
http://corp.com/config-<MAC>.ini turns into http://corp.com/config-00908f030012.ini
http://corp.com/<IP>/config.ini turns into http://corp.com/192.168.0.7/config.ini
Software upgrades m ay be performed using the parameter CmpFileURL. Inclusion of this
parameter in the m aster INI file will c ause the MP-1x x to downloa d and store the specified
software image.
Refer to the user documentation for additional examples of Automatic Updates.
This alternative does not require additional servers at the customer premises.
This alternative is NAT-safe.
Version 6.6 39 MediaPack Series
Page 40

MediaPack Series
5.4 Option D - Confi guration using DHCP Option 6 7
This option is suitable for deployments where DHC P server configuratio n is feasible at the
end customer site. Most DH CP servers allow conf igur ing ind ividu al DHCP o ption values for
different devices on the network; the DHCP conf iguration should be modified so that the
MP-1xx device will rec eive a conf iguration URL in option 6 7, along wit h IP addre ssing and
DNS server information.
The DHCP response will be proces sed by the MP-1x x upon startu p, and conseq uently the
HTTP server specified b y the configuration URL will be contacted in ord er to complete the
configuration.
The following is a sample Linux DHCP configuration file (dhcpd.conf) illustrating the
required format of option 67.
ddns-update-style ad-hoc;
default-lease-time 3600;
max-lease-time 3600;
class "audiocodes" {
match if(substring(hardware, 1, 3) = 00:90:8f);
}
subnet 10.31.0.0 netmask 255.255.0.0 {
pool {
allow members of "audiocodes";
range 10.31.4.53 10.31.4.75;
option routers 10.31.0.1;
option subnet-mask 255.255.0.0;
option domain-name-servers 10.1.0.11;
option bootfile-name
"INI=http://www.corp.com/master.ini";
option dhcp-parameter-request-list 1,3,6,51,67;
}
}
This alternative does not require additional servers at the customer premises.
This alternative is NAT-safe.
User's Manual 40 Document #: LTRT-71405
Page 41

User's Manual 5. Automatic Configuration Options
5.5 Option E - Confi gura ti on usin g FTP or NFS
Some networks block access to HTTP(S). The Automatic Update facilit y provides limited
support for FTP/FTPS connectivity, however it should be noted that periodic polling for
updates is not possible (since these protocols do not support conditional fetching, i.e.
update the file only if it is changed on the server).
The difference between thi s option and optio ns C and D is simply the protoco l in the URL ftp instead of http.
NFS v2/v3 is support ed as well, see the user documentation for additional configuration
required to enable NFS.
Note that FTP is NAT-safe, while NFS is not.
5.6 Option F - TFTP Configuration using DHCP Option 66
This option is suitable f or cases where the end custo mer network contains a provision ing
TFTP server for all network equipment, without the possibility of distinction between
AudioCodes and non-AudioCodes devices.
Upon startup, the MP-1xx will look for option 66 in the DHCP response. If option 66
contains a valid IP addres s, a TFTP download will b e attempted for a file nam ed after the
device MAC address, e.g. "00908f0130aa.ini".
The configuration file loa ded in this method is a one-tim e action; the download will not be
repeated until the de vice is manuall y restored t o factory d efaults (pr essing t he reset bu tton
for 10 seconds while the Ethernet cable is not connected).
This alternative requires a configuration server at the customer premises.
TFTP access into the core network is not NAT-safe.
5.7 Option G - Conf igura ti on usi ng Aud i oCo des EM S
AudioCodes EMS server functions as a core-network provisioning server. The MP-1xx
should be configured with the IP addres s of the EMS server as the S NMP Manager, using
one of the options detailed above.
As soon as a registered device contacts the EMS server via SNMP, the EMS server
handles all required configuration automatically, upgrading software as needed.
This alternative does not require additional servers at the customer premises. This
alternative is NAT-safe.
Version 6.6 41 MediaPack Series
Page 42

MediaPack Series
Reader's Notes
User's Manual 42 Document #: LTRT-71405
Page 43

User's Manual 6. Configuration Using the Web Interface
6 Configuration Using the Web Interface
The device contains a Web interface to be used for configuration and for run-time
monitoring. The W eb interface enables users equipped w ith any standard W eb-browsing
application such as Micros oft™ Internet Explorer™ (Version 6.0 and higher ) or Firefox™
(Versions 5 through 9.0) to:
Provision devices (refer to Configuration on page 66).
Verify configuration changes in the Status pages (refer to 'Status and Diagnostic
Menu' on page
page 47.
Load the CMP file (refer to Software Upgrade Wizard).
Load the ini, CAS, Voice Prompt, CPT, Prerecorded Tones, Dial Plan, Coder Table,
and AMD Sensitivity Files (refer to Load Auxiliary Files on page
Note: A lthough the Web Interface's recommended resolutions are 1024 x 768 and
1280 x 1024 pixels, AudioCodes supports other advanced resolutions.
139) or Toolbar (refer to Getting Acquainted with the Web Interface on
126).
6.1 Limiting the Web Interface to Read-Only Mode
Initially, the Web interface displays the default parameters that are pre-installed in the
device. These param eters can be modified using the W eb interface, either by modifying
parameters on the various pages or by loading a text configuration ini file to the device.
Administrators can lim it the Web interf ace to read-onl y mode by changing the value of the
DisableWebConfig ini file parameter. The read-only mode feature can be used as a
security measure. This security level provides protection against unauthorized access
(such as Internet hacker attacks), particularly important to users without a firewall.
To limit the Web Server to read-only mode:
Set the ini file parameter DisableWebConfig to 1 (Default = 0, i.e. read-write mode)
and send the modified ini file to the device. All Web pages are presented in read-only
mode. The ability to modify configuration data is disabled. In addition, users do NOT
have access to any "File Loading", "Regional Settings","Web User Accounts",
"Maintenance Actions" and "Conf ig urat ion F ile" pa ges .
Notes:
• 'Read Only' policy can also be employed by setting DisableWebConfig to
0, setting the secondary account to User_Monitor access level and
distributing the Main and Secondary accounts' user name password pairs
according to the organization's security policy.
• When DisableWebConfig is set to 1, all users are demoted to ‘Read Only’
privileges regardless of their access level.
Version 6.6 43 MediaPack Series
Page 44

MediaPack Series
6.1.1 Encrypted HTTP Transport (HTTPS - SSL)
Data transport between the Web server and the Web client may be conducted over a
secured SSL link that encrypts the HTTP layer. The Web server may be configured to
accept communicat ions onl y on a sec ured l ink (HTT PS) or both o n a sec ured l ink (HTTPS)
and a non-secured link (HTTP). For further details refer to the Security chapter in the
Product Reference Manual.
6.1.2 Limiting Web Access to a Predef ined List of Client IP A ddresses
When client IP address es are known in advance, adminis trators can define a list of up to
10 client IP addresses that ar e to be accepted by the Web server. An y client that does not
bear an IP address in the pre-defined list is unable to connect to the Web server. For
further details refer to the Security chapter in the Product Reference Manual.
6.1.3 Managing Web Serv er Access Us ing a RADIUS Server
Users are given the option to manage the web server's password-username pairs via a
RADIUS server. For furthe r details refer to the Securit y chapter in the Product Ref erence
Manual.
User's Manual 44 Document #: LTRT-71405
Page 45

User's Manual 6. Configuration Using the Web Interface
6.2 Accessing the Web Interface
To access the Web interface:
1. Open any standard Web-browser applic ation, such as Microsof t™ Internet Explorer™
(Ver. 6.0 and higher) or Firefox™ (Versions 5 through 9.0).
Note: The browser must be Java-script enabled. If java-script is disabled, a message
box with notification of this is displayed.
2. Specify the IP address of the device in the browser's URL field (e.g., http:// 10. 1.22 9.17
or https://10.1.229.17 for an SSL secure link). The browser's Password page appears.
The default user-name and password are both "Admin" (case-sensitive).
Figure 6: Enter Network Password Screen
Version 6.6 45 MediaPack Series
Page 46

MediaPack Series
6.3 Using Internet Explorer to Access the Web Interface
Internet Explorer's security settings may block access to the Gateway's Web browser if
they're configured incorrectly. If this happens, the following message appears:
Unauthorized
Correct authorizatio n is r equired for this ar ea. E ither your bro wser does not perf orm
authorization or your authorization has failed. RomPager server.
To troubleshoot blocked access to Internet Explorer:
1. Delete all cookies from the Tem porar y Internet files f older. If this does no t clear u p the
problem, the security settings may need to be altered. (Continue to Step 2).
2. In Internet Explorer, from the Tools menu, select Internet Options. The Internet
Options dialog box appears.
3. Select the Security tab, and then, at the b ottom of the dialog box , click Custom Level.
The Security Settings dialog box appears.
4. Scroll down until the Logon options ar e displ a yed a nd change the setting to Prompt for
user name and Password. Click OK.
5. Select the Advanced tab.
6. Scroll down until the HTTP 1.1 S ettings are displayed and verif y that the Use HTTP
1.1 option is checked.
7. Restart the browser. This fixes any issues related to domain use logon policy.
User's Manual 46 Document #: LTRT-71405
Page 47

User's Manual 6. Configuration Using the Web Interface
configuration parameters (see
like structure of elements (configuration menus,
6.4 Areas of the GUI
The areas of the W eb interface's GUI are sho wn in the figure below and described in the
subsequent table.
Figure 7: Areas of the Web GUI
Description of the Web GUI Areas
Item # Description
1
Displays AudioCodes (corporate) logo image.
2 Displays the product name.
3 Toolbar, providing frequentl y required comm and buttons. For more informat ion, see
Toolbar on page 48
4 Displays the username of the Web user that is currently logged in.
5 Navigation bar, providing the following tabs for accessing various functionalities in
the Navigation tree:
Configuration, Maintena nce, and Status & Diagnostics tabs : Access the configuratio n
menus (see Working with Configuration Pages on page 52)
Search tab: Enables a search engine for searching
Searching for Configuration Parameters on page 55)
6 Navigation tree, displaying a tree-
Scenario steps, or search engine) pertaining to the selected tab on the Navigation
bar.
7 Work pane, displaying the configuration page of the selected menu in the Navig ation
tree. This is where configuration is done. For more information, (see Working with
Configuration Pages on page 52).
Version 6.6 47 MediaPack Series
Page 48

6.4.1 Toolbar
The toolbar provides command buttons for quick-and-eas y access to frequently required
commands. The toolbar buttons are described in the table below:
MediaPack Series
Description of Toolbar Buttons
Icon Butto
n
Name
Submit
Burn
-- Device
Actions
Description
Applies parameter settings to the device (refer to Saving Configuration
Changes on page
55).
Note: This icon is grayed out when not applicable to the currently opened
page.
Saves parameter settings to flash memory (refer to Saving Configuration
Changes on page
55).
Opens a drop-down menu list with frequently needed commands:
Load Configuration File: Opens the 'Configuration File' page for loading
an ini file (refer to 'Restoring and Backing Up the device Configuration').
Save Configuration File: Opens the 'Configuration File' page for saving
the ini file to a PC (refer to 'Restoring and Backing Up the device
Configuration').
Reset: Opens the 'Maintenance Actions' page for resetting the device
(refer to Maintenance on page 122).
Restore Defaults: Opens the 'Configuration File' page for restoring the
parameters default values (refer to Restoring Networking Parameters to
their Default Values on page 18).
Software Upgrade Wizard: Opens the 'Software Upgrade Wizard' page
for upgrading the device's software (refer to Software Upgrade Wizard).
Switch Over: Opens the “High Availability Maintenance” page for
switching between Active and Redundant Boards (refer to High
Availability Maintenance).
Reset Redundant: Opens the "High Availability Maintenance" page for
resetting the Redundant Board (refer to High Availability Maintenance).
Home
Help
Log off
Opens the Home page (refer to Using the Home Page).
Opens the Online Help topic of the currently opened configuration page in
the Work pane (refer to Getting Help on page
58).
Logs off a session with the Web interface (refer to Logging Off the Web
Interface on page
57).
Note: If you modify parameters that only take effect after a device reset, af ter
you click the Subm it butto n, the to olbar d ispla ys the word " Reset " (in r ed col or). T his
is a reminder for you to later save ('burn') your settings to flash mem ory and reset
the device.
User's Manual 48 Document #: LTRT-71405
Page 49

User's Manual 6. Configuration Using the Web Interface
6.4.2 Navigation Tree
The Navigation tree, loc ated in the Navig ation pane, displa ys the menus (per taining to the
tab selected on the Navigation bar) used for accessing the configuration pages. The
Navigation tree displays a tree-like structure of menus. You can easily drill-down to the
required page item level to open its corresponding page in the Work pane.
The terminology used throughout this manual for referr ing to the hierarchical structure of
the tree is as follows:
Menu: first level (highest level)
Submenu: second level - contained within a menu.
Page item: last level (lowest level in a menu) - contained within a menu or submenu.
Figure 8: Terminology for Navigation Tree Levels
To view menus in the Navigation tree:
On the Navigation bar, select the required tab (Configuration, Maintenance, or Status
& Diagnostics).
To navigate to a page:
1. Navigate to the required page item, by performing the following:
• Drilling-down using the plus signs to expand the menus and submenus
• Drilling-up using the minus signs to collapse the menus and submenus
2. Select the required page item; the page opens in the Work pane.
6.4.2.1 Displaying Navigation Tree in Basic and Full View
You can view an expanded or reduced Navigation tree display regarding the number of
listed menus and submenus. This is relevant when using the configuration tabs
(Configuration, Maintenance and Status & Diagnostics) on the Navigation bar.
The Navigation tree menu can be displayed in one of two views:
• Basic - Displays only commonly used menus
• Full - Displays all the menus pertaining to a configuration tab
The advantage of the Basic view is that it prevents "cluttering" the Navigation tree with
menus that may not be required. Therefore, a Basic view allows you to easily locate
required menus.
Version 6.6 49 MediaPack Series
Page 50

MediaPack Series
To toggle between Full and Basic view:
Select the Basic optio n (located below the N avigatio n bar) to d isplay a r educed m enu tree;
select the Full option to display all the menus. By default, the Basic option is selected.
Figure 9: Navigation Tree in Basic and Full View
Note: W hen in Scenar io m ode (refer to W ork ing with Sc enarios), the Nav igation
tree is displayed in 'Full' view (i.e., all menus are displayed in the Navigation tree).
6.4.2.2 Showing / Hiding the Navigation Pane
The Navigation pane can be hi dden to provide more space for elem ents displayed in the
Work pane. This is especially useful when the Work pane displays a page with a table
that's wider than the W ork pane and to view the all the colum ns, you need to use scroll
bars. The arrow button located just below the Naviga tion bar is used to hide an d show the
Navigation pane.
To hide the Navigation pan e: click the left-pointing arrow ; the pane is hi dden and the
button is replaced by the right-pointing arrow button.
To show the Navigation p ane: click the right-pointing arrow ; the pane is displa yed and
the button is replaced by the left-pointing arrow button.
User's Manual 50 Document #: LTRT-71405
Page 51

User's Manual 6. Configuration Using the Web Interface
Figure 10: Showing and Hiding Navigation Pane
6.4.3 Help Infrastructure
Almost every page contains a Help Pop-up function which describes the parameter's
description.
To get the Help for a specific page, just click on the Help icon:
You can find this icon on the top frame of the Web interface. After click ing this button, a
new box will appear and contain the Help of that page.
For example, in the Voice Settings page, when clicking on the Help button, the Voice
Settings specific Help appears as shown below.
Figure 11: Voice Settings - Help Screen
Clicking the plus sign opens the description and while clicking the minus sign closes it.
When finished, click on the in the right-hand-side of the help box to close it.
Version 6.6 51 MediaPack Series
Page 52

MediaPack Series
6.4.4 Working with Configuration Pages
The configuration pages contain the parameters for configuring the device. The
configuration pages are displayed in the Work pane, which is located to the right of the
Navigation pane.
6.4.4.1 Accessing Pages
The configuration pages ar e accessed b y clicking the required pag e item in the Navigat ion
tree.
To open a configuration page in the Work pane:
1. On the Navigation bar, click the required ta b (Configuration, Mainte nance, and Status
& Diagnostics); the menu options of the selected tab appear in the Navigation tree.
2. In the Navigation tree, drill-down to the required page item; the page opens in the
Work pane.
You can also access previously opened pages, by clicking your Web browser's Back button
until you have reached the r equired page. T his is useful if you want to view pag es in which
you have performed configurations in the current Web session.
Notes:
• You can also access certain pages from the Device Actions button located
on the toolbar (refer to Getting Acquainted with the Web Interface on page
47).
• To view all the menus in the Navigation tree, ensure that the Navigation
tree is in 'Full' view (refer to Getting Acquainted with the Web Interface on
page 47).
• To get Online Help for the currently opened page, refer to Getting Help on
page 58.
• Certain pages may not be accessible or may only be read-only if your Web
user account's access level is low (refer to Web User Accounts on page
75). If a page is read-only, 'Read-Only Mode' is displayed at the bottom of
the page.
6.4.4.2 Viewing Parameters
For convenience, some pages allow you to view a reduced or expanded display of
parameters. A reduced d isplay allows you to easily identif y required parameters, enab ling
you to quickly configure your device.
The Web Interface provides you with two methods for handling the display of page
parameters:
Dis pl a y of "Basic" and "Ad v anc ed " parameters
Display of parameter groups
Note: Certai n pages may only be rea d-only if your Web user account's access
level is low (refer to Configuring the Web User Accounts). If a page is read-only,
'Read-Only Mode' is displayed at the bottom of the page.
User's Manual 52 Document #: LTRT-71405
Page 53

User's Manual 6. Configuration Using the Web Interface
6.4.4.3 Displaying Basic and Advanced Parameters
Some pages provide you with a n Advanced Parameter List / Basic Param eter List toggle
button that allows you to show or hide advanced param eters (in addition to displaying the
basic parameters). T his button is located on the top-right corner of the page and has two
states:
Advanced Parameter List button with down-pointing arrow: click this button to display
all parameters.
Basic Parameter List button with up-pointing arrow: click this button to show only
common (basic) parameters.
The figure below shows an example of a page displa ying basic parameter s only, and then
showing advanced parameters as well, using the Advanced Parameter List button.
Figure 12: Displaying Basic and advanced Parameters
For ease of identification, the basic parameters are displayed with a darker blue color
background than the advanced parameters.
Notes:
• When the Navigation tree is in 'Full' mode, configuration pages display all
Version 6.6 53 MediaPack Series
their parameters (i.e., the 'Advanced Parameter List' view is displayed).
• If a screen contains only basic parameters, the Basic Parameter List
button will not be shown.
Page 54

6.4.4.4
6.4.4.4 Showing / Hiding Parameter Groups
Some pages provide groups of parameters, which can be hidden or shown. To toggle
6.4.4.4
between hiding and showing a group, simply click the group name button that appears
above each group. The button appears with a down-pointing or up-pointing arrow,
indicating that it can be collapsed or expanded when clicked, respectively.
MediaPack Series
6.4.4.4
Figure 13: Expanding and Collap sing Parameter Groups
6.4.4.5 Modifying Parameter Values
When you enter param eter values on a configuratio n page, the Ed it symbol appears t o
the right of these value fields. This feature is especially useful when modifying many
parameters in a conf igur at i on p age in th at i t h elps to remind you of the parameters that you
have currently modified (before applying the changes, i.e., clicking the Submit button).
Figure 14: Modifying Parameter Values
User's Manual 54 Document #: LTRT-71405
Page 55

User's Manual 6. Configuration Using the Web Interface
Once you appl y your parameter changes by click ing the Submit button, the Edit symbols
disappear.
If you enter an invalid parameter value and then click Submit, a message box appears
notifying you of the invalid value. In addition, the parameter value reverts back to its
previous value and is highlighted in red, as shown in the figure below:
Figure 15: Value Reverts to Previous Valid Value
6.4.5 Saving Configuration Changes
To apply configuration changes to the device's volatile memory (RAM), click the Submit
button, which is located on the page in which you are working. Modifications to
parameters with on-the-fly capabilities are immediately applied to the device; other
parameters are applied only after a device reset.
However, parameter s saved to the volat ile memor y revert to their previous settings after a
hardware or soft ware reset (or if the device is po wered down). Therefore, to en sure that
parameter changes (wheth er on-the-f ly or not) are ret ained, you ne ed to save ('b urn') them
to the device's non-volat ile memory (i.e., flas h). To save parameter c hanges to flash, refer
to Saving Configuration.
Note: Param eters precede d by the lig htning sign are not changeab le on-the-
fly and require a device reset.
6.4.6 Searching for Configuration Parameters
The Web interface provides a search engine that allows you to search any ini file
parameter that is configurable by the Web interface (i.e., has a corresponding Web
parameter). You can searc h for a specific parameter (e.g., " EnableIPSec") or a sub-string
of that parameter (e.g., "se c "). I f you search for a sub-string, all parameters that contain the
searched sub-string in their names are listed.
To search for ini file parameters configurable in the Web interface:
1. On the Navigation bar, click the Search tab; the Search engine appears in the
Navigation pane.
2. In the 'Search' field, enter the param eter name or sub-string of the parameter nam e
that you want to search. If you have performed a previous search for such a
parameter, instead of entering the requ ired string, you can use the 'Search History'
drop-down list to select the string (saved from a previous search).
3. Click Search; a list of located parameters based on your search appears in the
Navigation pane. Each searched result displays the following:
• Link (in green) to its location (page) in the Web interface
• Brief description of the parameter
Version 6.6 55 MediaPack Series
Page 56

MediaPack Series
4. In the s earched list, click the required param eter (link in green) to open the page in
which the parameter appears; the relevant page opens in the Work pane and the
searched parameter is highlighted for easy identification, as shown in the figure below:
Note: If the s earched p aram eter is not loca ted, the "No Matc hes F ound For This
String" message is displayed.
Figure 16: Searched Result Screen
6.4.7 Creating a Login Welcome Message
You can create a Welcome message box (alert message) that appears after each
successful login to the device's Web interface. The WelcomeMessage ini file parameter
table allows you to create the W elcome message. Up to 20 lines of character strings c an
be defined for the m ess age. If this parameter is not co nfigured, no W elcome m essage box
is displayed after login.
An example of a Welcome message is shown in the figure below:
Figure 17: User-Defined Web Welcome Message after Login
ini File Parameter for Welcome Login Message
Parameter Description
WelcomeMessage
Defines the Welcome message that appears after a successful login to
the Web interface.
The format for this ini file parameter table is as follows:
[WelcomeMessage]
FORMAT WelcomeMessage_Index = WelcomeMessage_Text;
WelcomeMessage 1 = "..." ;
WelcomeMessage 2 = "..." ;
WelcomeMessage 3 = "..." ;
User's Manual 56 Document #: LTRT-71405
Page 57

User's Manual 6. Configuration Using the Web Interface
[\WelcomeMessage]
ini File Parameter for Welcome Login Message
Parameter Description
For Example:
[WelcomeMessage ]
FORMAT WelcomeMessage_Index = WelcomeMessage_Text;
WelcomeMessage 1 = "**********************************" ;
WelcomeMessage 2 = "********* This is a Welcome message ***" ;
WelcomeMessage 3 = "**********************************" ;
[\WelcomeMessage]
Note: Each index represents a line of text in the Welcome message box.
Up to 20 indices can be defined.
6.4.8 Logging Off the Web Interface
You can log off the Web interface and re-access it with a different user account. For
detailed information on the Web User Accounts, refer to User Accounts.
To log off the Web Interface:
1. On the toolbar, click the Log Off button; th e 'Log Off' confirm ation message box
appears:
Figure 18: Log Off Confirmation Box
2. Click OK; the Web session is logged of f. The "W eb page for the ses sion is logged of f"
message box appears, with a "Log In" button.
3. To log on again, simply click any page item in the navigation tree, and then in the
'Enter Network Password' dialog box, enter your user name and password.
Version 6.6 57 MediaPack Series
Page 58

6.4.9 Getting Help
The Web interface provides you with context-sensitive Online Help. The Online Help
provides you with brief descriptions of most of the param eters you'll need to successfully
configure the device. T he O nline He lp pr o v ides d es c riptio ns of parameters pertaining to th e
currently opened page.
To view the Help topic for a currently opened page:
1. Using the Navigation tree, open the required page for which you want Help.
2. On the toolbar, click the Help button; the Help topic pertaining to the opened
page appears, as shown below:
MediaPack Series
Figure 19: Help Topic for Current Page
3. To view a description of a param eter, click the plus s ign to expand the parameter.
To collapse the description, click the minus sign.
4. To close the Help topic, click the clos e button located on the top-right cor ner of
the Help topic window or click the HELP button.
Note: Instead of click ing the Help button for each page you open, you can open
it once for a page, and then simply leave it open. Each time you open a different
page, the Help topic pertaining to that page is automatically displayed.
User's Manual 58 Document #: LTRT-71405
Page 59

User's Manual 6. Configuration Using the Web Interface
6.4.10 Using the Home Page
The Home icon, locat ed on the toolbar, op ens the 'Home' page. T his page provides you
with a graphical display of the device's front panel. This page allows you to monitor the
functioning of the device by its c olor-coded icons. The 'Hom e' page also displays general
information in the 'G ener al Inform ation' pane suc h as the device's IP address and firm ware
version.
To access the Home page, take this step:
On the toolbar, click the Home icon; the 'Home' page is displayed:
Note: The following 'Home' pages are applicable to MediaPack.
Figure 20: MP-11x Home Page
Figure 21: MP-124 Home Page
Version 6.6 59 MediaPack Series
Page 60

MediaPack Series
MediaPack Home Page Descriptions
Item# / Label Description
Alarms
Channel /
Ports
Uplink (MP-
11x)
LAN (MP-124
Fail
Ready
Power
Displays the highest alarm severity raised (if any) by the device:
Green = no alarms.
Orange = alarms have been raised and are listed in the 'Active Alarms' table.
To view the list of alarms in the 'Active Alarms' table, click the Alarms area (refer to
Viewing the Active Alarms Table on page
61).
Displays the status of the ports (channels):
(red): line not connected (only applicable to FXO devices)
(grey): channel inactive
(blue): handset is off-hook
(green): active RTP stream
You can also view the channel's port settings (refer to Viewing Channel
Information), reset the port (ref er to Resetting an Analo g Cha nne l on page 65), and
assign a name to the port (refer to Assigning a Name or Brief Description to a Port).
If clicked, the 'Ethernet Port Information' page opens, displaying Ethernet port
configuration settings (refer to Viewing Ethernet Port Information).
Currently not supported.
Currently not supported.
Always lit green, indicating power rece iv ed b y the devic e.
6.4.11 MediaPack Home Page
To navigate to the Alarm Table, click on the alarms chassis. The Active Alarms screen
appears as shown below:
Figure 22: 8410 Alarms Table
User's Manual 60 Document #: LTRT-71405
Page 61

User's Manual 6. Configuration Using the Web Interface
6.4.12 Viewing the A ctive A larms Table
The 'Home' page allows you to view a list of currently active alarms. These alarms are
displayed in the 'Active Alarms' page. In addition, the color of the 'Alarms' area in the
'Home' page indicates the highest alarm severity currently listed in the 'Active Alarms'
page.
To view the list of alarms:
On the 'Home' page, click the Alarm s area, next to the Fan Tra y unit (labeled as item #2 in
the figures in Using the 'Home' page above); the 'Active Alarms' page appears:
Figure 23: Viewing Active Al arm s
For each alarm, the following is displayed:
Severity: severity level of the alarm:
• Critical: alarm displayed in red
• Major: alarm displayed in orange
• Minor: alarm displayed in yellow
Source: unit from which the alarm was raised
Description: brief explanation of the alarm
Date: date and time that the alarm was generated
6.4.12.1.1 View ing Alarm History
The Alarms History page displays a list of alarms that have been raised and traps that have
been cleared.
To view the list of history alarms:
Open the Alarms Histor y page (Status & Diag nostics tab > S ystem Status m enu > CarrierGrade Alarms > Alarms History).
Figure 24: Viewing Alarm History
For each alarm, the following information is provided:
Severity: severity level of the alarm:
• Critical (red)
• Major (range)
• Minor (y ellow)
• Cleared (green)
Source: unit from which the alarm was raised
Description: brief explanation of the alarm
Date: date and time that the alarm was generated
You can view the next 20 alarms (if exist), by clicking the Go to page button.
Version 6.6 61 MediaPack Series
Page 62

MediaPack Series
To delete all the alarms in the table:
1. Click the Delete History Table button; a confirmation message box appears.
2. Click OK to confirm.
6.4.13 Viewing Channel Information
To view Trunks and Channels Status:
1. To view the Trunks and Channel Stat us screen, click on the Status & Diagnostics
link on the Navigation Bar.
2. From the navigation tree on th e lef t, cl ick on the T runks & Channels Status l ink. T he
Trunks & Channels Status screen is displayed.
Figure 25: Trunks and Channels Status
The color-coding for the trunk's status is described in the table above. For color-coding
of the trunk's channels, refer to the table below:
Color-Coding for Status Trunk's Channels
Indicator Color Label Description
Light blue Inactive Configured, but currently no call
Green Active Call in progress (RTP traffic)
Purple SS7 Configured for SS7 (Currently not
supported)
Grey Non Voice Not configured
Blue ISDN Si gna ling or
Configured as a D-channel
V5 Signaling (TP-
8410)
Yellow CAS Blocked --
3. To view the configuration settings of the tru nk and / or to modify the trunk's settings, in
the 'Trunks & Channels Status' screen, click the Trunk icon, and then from the
shortcut menu, choose Port Settings; The 'Trunk Settings' screen appears. (For
detailed information on configuring the trunk in this screen, refer to Trunk Settings.)
4. To view information of a specific trunk's channel, in the 'Trunks & Channels Status'
screen, click the required Channel icon.
User's Manual 62 Document #: LTRT-71405
Page 63

User's Manual 6. Configuration Using the Web Interface
6.4.14 Viewing Ethernet Port Information
To view Ethernet port settings via the Home page:
1. Click on the 'Home' page icon.
2. Click the Ethernet port for which you want to view port settings; the 'Ethernet Port
Information' page opens:
Figure 26: Ethernet Port Information
6.4.15 Viewing Ethernet Port Information
To view Ethernet port information via th e Home page:
1. Click on the 'Home' page icon.
2. Click on the 'Uplink' light to view the port information.
Figure 27: MediaPack Home Page
3. The Ethernet port information appears.
Figure 28: Ethernet Port Information
Version 6.6 63 MediaPack Series
Page 64

MediaPack Series
6.4.16 Viewing Trunk Settings
The Home page allows you to view the settings of a selec ted port in the 'Trunk Settings'
page. Accessing this page from the Hom e page prov id es an alt er nat iv e to acc es s ing it f r om
the Advanced Configuration menu (Trunk Settings).
To view Port Settings:
1. On the Home page, click a required trunk port LED o n the blade (l abeled as ite ms #3
and #5 in the figure in Accessing the Home Page); a shortcut menu appears.
2. From the shortcut menu, choose Port Settings; the 'Trunk Settings' page opens.
6.4.17 Ass igning a N ame or Br ief D esc riptio n to a Po rt
The 'Home' page allows you to ass ign an arb itrar y nam e or a br ief des cription to eac h port.
This description appears as a tooltip when you move your mouse over the port.
To add a port description:
1. Click the required port icon; a shortcut menu appears.
Figure 29: MP-124 - Update Port Information
Figure 30: MP-11x - Update Port Information
2. From the shortcut menu, choose Update Port Info; a text box appears.
Figure 31: MP-124 - Apply Port Info
Figure 32: MP-11x - Apply Port Info
Type a brief description for the port, and then click Apply Port Info.
User's Manual 64 Document #: LTRT-71405
Page 65

User's Manual 6. Configuration Using the Web Interface
6.4.18 Resetting an Analog Channel
Note: The following sub-section on Resetting an Analog Channel is only
applicable to MediaPack .
The 'Home' page al lows you to inactivate (r eset) an FXO or FXS ana log channel. This is
sometimes usef ul in scenar ios, f or exam ple, when th e devic e (FX O) is c onnected to a PBX
and the communication bet ween the two can't be disconnected (e.g., when using reverse
polarity).
To reset a channel:
Click the required FX S or FXO port icon , and then from the shortcut menu, cho ose Reset
Channel; the channel is changed to inactive (i.e., LED is displayed in grey).
Figure 33: MP-11x - Reset Channel
Version 6.6 65 MediaPack Series
Page 66

MediaPack Series
6.5 Configuration
Configuration menu options are described below.
6.5.1 System
System sub-menu options are described below.
6.5.1.1 Application Settings
Application Settings inc lude the following features: NT P, Da yli ght S avin g Time, STUN, NFS
and DHCP Settings.
In this option, the following can be configured:
NTP Server
Da y Light Sa ving T ime
STUN Settings
NFS Servers Settings
Enable the DHCP client
To configure the Application Settin g s:
1. Open the Application Settings page (Configuration tab > System menu >
Application Settings).
Figure 34: Application Settings
2. To configure this page, refer to the System Parameters sub-section in the Product
Reference Manual.
3. After configuring/modif ying the param eter f ields, click the Subm it button. The c hanges
are entered into the system and the page is refreshed.
User's Manual 66 Document #: LTRT-71405
Page 67

User's Manual 6. Configuration Using the Web Interface
To configure the NFS Settings:
Network File System (NFS) enables the device to access a remote server's shared files
and directories and to hand le them as if they're locate d locall y. The device can use NF S to
load cmp, ini, and auxiliary files through the Automatic Update mechanism (refer to the
Product Reference Manual).
You can configure up to 16 different NFS file systems. As a file system, the NFS is
independent of m achine types, operati ng systems and net work architectur es. Note that an
NFS file server can share multiple file systems. There must be a separate row for each
remote file system shared by the NFS file server that needs to be accessed by the device.
To add remote NFS file systems:
1. Open the Application Setti ngs page (Configuration t ab > System menu > App lication
Settings).
Under the 'NFS Settings' group, click the NFS Table button; the NFS Table page
appears.
2. Click the Add button; the Add Record dialog box appears:
Figure 35: Add Record Dialog Box - NFS
3. Configure the NFS parameters according to the table below.
4. Click the Submit button; the rem ote NF S file s ystem is imm ediatel y applied, which c an
be verified by the appearance of the 'NFS mount was successful' message in the
Syslog server.
5. To save the changes to flash memory, see Saving Configuration on page 125.
Notes:
• To avoid terminating current calls, a row must not be deleted or modified
while the device is currently accessing files on that remote NFS file
system.
• The combination of 'Host Or IP' and 'Root Path' must be unique for each
row in the table. For example, the table must include only one row with a
Host/IP of 192.168.1.1 and Root Pat h of /audi o.
• The NFS table can also be configured using the table ini file parameter
NFSServers (refer to the 'NFS Parameters' in the Product Reference
Manual).
Version 6.6 67 MediaPack Series
Page 68

MediaPack Series
6.5.1.2 Syslog Settings
The procedure below describes how to configure Syslog.
To configure Syslog:
1. Open the Syslog Settings page (Configuration tab > System menu > Syslog Settings).
Figure 36: Syslog Settings
2. Enable the Syslog feature by setting the 'Enable Syslog' to Enable.
3. Define the Syslog server using the 'Syslog Server IP Address' and 'Syslog Server Port'
parameters.
4. Configure the debug level using the 'Debug Level' parameter.
5. Under the 'Activity Types to Report ...' group, select the activities to report.
6. Click Submit to apply your changes.
6.5.1.3 Regional Settings
The Regional Settings page allows setting the system date and time.
To access the Regional Settings page:
Open the Regional Settings page (Configuration tab > System menu > Regional
Settings).
To set the date and time:
1. Enter the date and/or tim e using the YYYY, MM, and DD field for Year, Month and
Day and HH, MM, and SS fields for Hour, Minutes and Seconds.
2. Click Submit. The date and time is set on the device, accordingly.
Figure 37: Regional Settings
Note: When the NTP feature is enabled (the NTP server is defined in the
Application Settings page), t he date an d t ime are in Read Onl y mode as th e y ar e set
by the NTP server.
User's Manual 68 Document #: LTRT-71405
Page 69

User's Manual 6. Configuration Using the Web Interface
6.5.1.4 TLS Contexts
This page allows managing the securit y certificates loaded on the device. The device is
shipped with a working cer tificate configur ation. Use this pa ge only as needed. For further
information, refer to the Security chapter in the Product Reference Manual.
The Certificates page allow s you to co nfigure X.509 cer tificates, which are used for secure
management of the device, secure SIP transactions, and other security applications.
Note: The device is s hipped with an active T LS setup. Thus, c onfigure cer tificates only
if required.
6.5.1.4.1 Replacing the Device's Certificate
The device is supplied with a working TLS configurat ion consisting of a unique s elf-signed
server certificate. If an or ga nization al Pub lic Ke y Infras tructur e (PKI) is used, you m ay wish
to replace this certificate with one provided by your security administrator.
To replace the device's certificate:
1. Your network administrator s hould allocate a unique DNS name f or the device (e.g.,
dns_name.corp.customer.com). This DNS name is used to access the device and
therefore, must be listed in the server certificate.
2. If the device is operating in HTTPS mode, then set the 'Secured Web Connection
(HTTPS)' parameter (HTTPSOnly) to HTTP and HTTPS. This ensures that you have a
method for acces sing the device in case the new ce rtificate does not work. Restor e
the previous setting after testing the configuration.
3. Open the Certificates page (Configuration tab > System menu > Certificates).
4. Under the Certificate Signing Request group, do the following:
a. In the 'Subject Name [CN]' field, enter the DNS name.
b. Fill in the rest of the request fields according to your security provider's
instructions.
Version 6.6 69 MediaPack Series
Page 70

c. Click the Create CSR button; a textual certificate signing request is displayed in
the area below the button:
MediaPack Series
Figure 6-38: Certificate Signing Request Group
5. Cop y the text and send it t o your securit y provider. The securit y provider, also k nown
as Certification Authority or CA, signs this request and then sends you a server
certificate for the device.
6. Save the certificate to a file (e.g., cert.txt). Ensure that the file is a plain-text file
containing the"‘BEGIN CER TIF ICATE" hea der, as sho wn in the exam ple of a Ba se64Encoded X.509 Certificate below:
-----BEGIN CERTIFICATE-----
MIIDkzCCAnugAwIBAgIEAgAAADANBgkqhkiG9w0BAQQFADA/MQswCQYDVQQGEw
JGUjETMBEGA1UEChMKQ2VydGlwb3N0ZTEbMBkGA1UEAxMSQ2VydGlwb3N0ZSBT
ZXJ2ZXVyMB4XDTk4MDYyNDA4MDAwMFoXDTE4MDYyNDA4MDAwMFowPzELMAkGA1
UEBhMCRlIxEzARBgNVBAoTCkNlcnRpcG9zdGUxGzAZBgNVBAMTEkNlcnRpcG9z
dGUgU2VydmV1cjCCASEwDQYJKoZIhvcNAQEBBQADggEOADCCAQkCggEAPqd4Mz
iR4spWldGRx8bQrhZkonWnNm`+Yhb7+4Q67ecf1janH7GcN/SXsfx7jJpreWUL
f7v7Cvpr4R7qIJcmdHIntmf7JPM5n6cDBv17uSW63er7NkVnMFHwK1QaGFLMyb
FkzaeGrvFm4k3lRefiXDmuOe+FhJgHYezYHf44LvPRPwhSrzi9+Aq3o8pWDguJ
uZDIUP1F1jMa+LPwvREXfFcUW+w==
-----END CERTIFICATE-----
7. Scroll down to the Upload certificates files from your computer group, click the
Browse button c orresponding to the 'Send Dev ice Certificate...' field, na vigate to the
cert.txt file, and then click Send File.
8. After the certificate successfully loads to the device, save the configuration with a
device reset; the Web interface uses the provided certificate.
9. Open the Certificates page again and verify that under the Certificate information
group (at the top of the page), the 'Private key' read-only field displays "OK";
otherwise, consult your security administrator:
Figure 6-39: Private key "OK" in Certificate Information Group
User's Manual 70 Document #: LTRT-71405
Page 71

User's Manual 6. Configuration Using the Web Interface
10. If the device was or iginally operating in HTTPS m ode and you disabled it in Ste p 2,
then return it to HTTPS by settin g the 'Secured W eb Connection (HTTPS)' par ameter
to HTTPS Only, and then reset the device with a flash burn.
Notes:
• The certificate replacement process can be repeated when necessary
(e.g., the new certificate expires).
• It is possible to use the IP address of the device (e.g., 10.3.3.1) instead of
a qualified DNS name in the Subject Name. This is not recommended
since the IP address is subject to change and may not uniquely identify the
device.
• The device certificate can also be loaded via the Automatic Update Facility
by using the HTTPSCertFileName ini file parameter.
Version 6.6 71 MediaPack Series
Page 72

MediaPack Series
6.5.1.4.2 Loading a Private Key
The device is shipped with a self -generated random private k ey, which cann ot be extr acte d
from the device. However, some security administrators require that the private key be
generated externally at a secure facility and then loaded to the device through
configuration. Since private keys are sensitive security parameters, take precautions to
load them over a physically-secure connection such as a back-to-back Ethernet cable
connected directly to the managing computer.
To replace the device's private key:
1. Your security administrator should provide you with a private key in either textual PEM
(PKCS #7) or PFX (PKCS #12) format. The file may be encrypted with a short passphrase, which should be provided by your security administrator.
2. If the device is operating in HTTPS mode, then set the 'Secured Web Connection
(HTTPS)' field (HTTPSOnly) to HTTP and HTTPS. This ensures that you have a
method for acces sing the d ev ice in c as e th e ne w c onf i gur ation does not work. Re s tore
the previous setting after testing the configuration.
3. O pen the Certificates page (Configuration tab > System m enu > Certificates) and
scroll down to the Upload certificate files from your computer group.
Figure 6-40: Upload Certificate Files from your Computer Group
4. Fill in the 'Private key pass-phrase' field, if required.
5. Clic k t he Browse button co rrespondi ng to the ' Send P rivate Ke y' field, n avigate t o the
key file, and then click Send File.
6. If the sec urity adm inistr ator has provid ed you with a d evice c ertific ate file, l oad it usin g
the 'Send Device Certificate' field.
7. After the files successfully load to the device, save the configuration with a device
reset; the Web interface uses the new configuration.
8. O pen the Certificates page again, and verify that under the Certificate information
group (at the top of the page) the 'Private key' read-only field displays "OK"; other wis e ,
consult your security administrator.
9. If the device was originally opera ting in HTTPS mode and you disabled it in Step 2,
then enable it by setting the 'Secured Web Connection (HTTPS)' field to HTTPS Only.
User's Manual 72 Document #: LTRT-71405
Page 73

User's Manual 6. Configuration Using the Web Interface
6.5.1.4.3 Mutual TLS Authentication
By default, servers usi ng TLS pro vide one-way authentication. T he client is certain that t he
identity of the server is authentic. When an organizational PKI is used, two-way
authentication may be desired - both c l ien t an d s erv er shoul d be aut henticated using X.50 9
certificates. This is achieved by installing a client certificate on the managing PC and
loading the root CA' s certifi cate to th e device' s Trus ted Root C ertificate Store. T he Tr usted
Root Certificate file may contain more than one CA certificate combined, using a text
editor.
Since X.509 certific ates have an expiration date an d ti me, the device must be configured to
use NTP to obtain the current date and time. Without the correct date and time, client
certificates cannot work.
To enable mutual TLS authentication for HTTPS:
1. Set the 'Secured Web Connection (HTTPS)' field to HTTPS Only to ensure you have
a method for accessing the device in case the client certificate does not work. Restore
the previous setting after testing the configuration.
2. Open the Certificates page (see 'Replacing the Device's Certificate' on page 69).
3. In the Upload certificate files from your computer group, click the Browse button
corresponding to the ' Send T rusted Root Certific ate Store ... ' field, navigate to the f ile,
and then click Send File.
4. When the operation is complete, set the 'Requires Client Certificates for HTTPS
connection' field to Enable (see 'Configuring Web Security Settings' on page 86).
5. Save the configuration with a device reset.
When a user connects to the secured Web interface of the device:
If the user has a client certificate from a CA that is listed in the Trusted Root Certificate
file, the connection is accepted and the user is prompted for the system password.
If both the CA certificate and the client certificate appear in the Trusted Root
Certificate file, the user is not prompted for a password (thus, providing a single-signon experience - the authentication is performed using the X.509 digital signature).
If the user does not have a client certificate from a listed CA or does not have a client
certificate, the connection is rejected.
Notes:
• The process of installing a client certificate on your PC is beyond the
scope of this document. For more information, refer to your operating
system documentation, and/or consult your security administrator.
Version 6.6 73 MediaPack Series
• The root certificate can also be loaded via the Automatic Update facility,
using the HTTPSRootFileName ini file parameter.
• You can enable the device to check whether a peer's certificate has been
revoked by an Online Certificate Status Protocol (OCSP) server.
Page 74

MediaPack Series
6.5.1.4.4 TLS Server Certificate Expiry Check
The device can per iodical ly check the va lidat ion dat e of the instal led TLS server cer tificate .
This periodic check interval is user-defined. In addition, within a user-defined number of
days before the installed TLS server certificate expires, the device can be configured to
send the SNMP trap, acCertificateExpiryNotifiaction to notify of the impending certificate
expiration.
To configure TLS certificate expiry checks and notification:
1. Open the Certificates page.
2. In the 'TLS Expiry Check Start' f ield, enter the number of days before the insta ll ed T LS
server certificate is to expire at which the device must send a trap to notify of this.
Figure 41: TLS Expiry Settings
3. In the 'TLS Expiry Check Period' field, enter the periodical interval (in days) for
checking the TLS server certificate expiry date. By default, the device checks the
certificate every 7 days.
4. Click the Submit TLS Expiry Settings button.
User's Manual 74 Document #: LTRT-71405
Page 75

User's Manual 6. Configuration Using the Web Interface
6.5.1.5 Management
Management - Contains a drop-down list with the following options:
Web User Accounts - Refer to Web User Accounts on page 75
Web Security Settings - Refer to Web Security Settings on page 82
Telnet/SSH Settings - Refer to Telnet/SSH Settings on page 83
Web & Telnet Access List - Refer to Web & Telnet Access List on page 83
Auth ent ic ati on Set tings - Refer to
SNMP - Refer to SNMP on page 85
• SNMP Community Settings - Refer to SNMP Community Settings on page 85
• SNMP Trap Destinations - Refer to SNMP Trap Destinations on page 86
• SNMP Trusted Managers - Refer to SNMP Trusted Managers on page 87
6.5.1.5.1 Web User Account Configuration
• SNMP V3 Users - Refer to SNMP V3 Users on page 87
You can create up to 10 Web user accounts for the device. Up to five Web users can
simultaneously be logged in to the device's Web interface. Web user accounts prevent
unauthorized access to the Web interf ace, enabling login acces s only to users wi th correct
credentials (i.e., username and password). Each Web user account is composed of the
following attributes:
Username and password: Credentials that enable authorized login access to the Web
interface.
Access level (user type): Access privileges specifying what the user can view in the
Web interface and its read/write privileges. The table below describes the different
types of Web user account access levels:
Access Levels of Web User Accounts
User Access
Level
Numeric
Representation*
Privileges
Read / write privileges for all pages. Can create all user
Master 220
types, including additional Master users and Security
Administrators. It can delete all users except the last
Security Administrator.
Read / write privileges for all pages. It can create all user
Security
Administrator
200
types and is the only one that can create the first Master
user.
Note: There must be at least one Security Administrator.
Administrator 100
Monitor 50
Read / write privileges for all pages except securityrelated pages, which are read-only.
No access to security-related and file-lo adi ng pag es ;
read-only access to other pages.
No access to any page.
No Access 0
Note: This access level is not applicable when using
advanced Web user account configuration in the Web
Users table.
* The numeric representation of the access level is used only to define accounts in a RADIUS
server (the access level ranges from 1 to 255).
Version 6.6 75 MediaPack Series
Page 76

MediaPack Series
By default, the device is pre-configured with the following two Web user accounts:
Pre-configured Web User Accounts
User Access Level Username
(Case-Sensitive)
Password
(Case-Sensitive)
Security Administrator Admin Admin
Monitor User User
After you log in to the Web interface, the username is displayed on the toolbar.
If the Web session is idle (i.e., no actions are performed) for more than five minutes, the
Web session expires and you ar e once again requested to login with your username and
password. Users can be banned for a period of time upon a user-defined number of
unsuccessful login attempts. Login information (such as how many login attempts were
made and the last successful login time) can be presented to the user.
To prevent user access after a specific number of failed logins:
1. From the 'Deny Access On Fail Count' drop-down list, select the number of failed
logins after which the us er is prevented access to the devic e for a user-defined tim e
(see next step).
2. In the 'Deny Authentication T imer' field, enter the int erval (in seconds) that the user
needs to wait before a ne w login attem pt f rom the same IP addres s can be don e after
reaching the number of failed login attempts (defined in the previous step).
Notes:
• For security reasons, it's recommended that you change the default
username and password.
• The Security Administrator user can change all attributes of all Web
user accounts. Web users with access levels other than Security
Administrator can change only their password and username.
• To restore the two Web user accounts to default settings (usernames
and passwords), set the ini file parameter ResetWebPassword to 1.
• To log in to the Web interface with a different Web user, click the Log off
button and then login with a different username and password.
• You can set the entire Web interface to read-only (regardless of Web
user access levels), by using the ini file parameter DisableWebConfig
(refer to the 'Web and Telnet Parameters' in the Product Reference
Manual).
• You can define additional Web user accounts using a RADIUS server
(refer to the 'Configuring RADIUS Settings' in the Product Reference
Manual).
User's Manual 76 Document #: LTRT-71405
Page 77

User's Manual 6. Configuration Using the Web Interface
6.5.1.5.1.1 Basic User Accounts Configuration
This section describ es basic Web user account configuration. This is relevant only if the
two default, pre-configured Web user accounts - Security Administrator ("Admin") and
Monitor ("User") - are sufficient for your management scheme.
For the Security Administr ator, you can change only the username and pas sword; not its
access level. For th e Monitor user, you can change username and password as well as
access level (Administrator, Monitor, or No Access).
Notes:
• The access level of the Security Administrator cannot be modified.
• The access level of the second user account can be modified only by the
Security Administrator.
• The username and password can be a string of up to 19 characters. When
you log in to the Web interface, the username and password string values
are case-sensitive, according to your configuration.
• Up to two users can be logged in to the Web interface at the same time,
and they can be of the same user.
To configure the two pre-configured Web user accounts:
1. Open the Web User Accou nts page ( Configuration ta b > System menu > Web User
Accounts). If you are logged in as Security Administrator, bot h Web user ac counts
are displayed (as sho wn below). If you are logged i n with the second user account,
only the details of this user account are displayed.
Figure 42: Web User Accounts Scree n - Security Administrator Level
2. To change the username of an account:
a. In the 'User Name' field, enter the new user name.
b. Click Change User Name; if you are currently logged in to the Web interface with
this account, the 'Web Login' dialog box appears.
c. Log in with your new user name.
Version 6.6 77 MediaPack Series
Page 78

3. To change the password of an account:
a. In the 'Current Password' field, enter the current password.
b. In the 'New Password' and 'Confirm New Password' fields, enter the new
password.
c. Click Change Password; if you are currently logged in to the Web interface with
this account, the 'Web Login' dialog box appears.
d. Log in with your new password.
4. To change the access level of the optional, second account:
a. Under the Account Data for User: User group, from the 'Access Level' drop-down
list, select a new access level user.
b. Click Change Access Level; the new access level is applied immediately.
MediaPack Series
6.5.1.5.1.2 Advanced User Accounts Configuration
This section descr ibes advanced Web user account c onfiguration. This is relevant if you
need the following management scheme:
Enhanced security settings per Web user (e.g., limit session duration)
More than two Web user accounts (up to 10 Web user accounts)
Master users
This advanced W eb user configuration is done in the W eb Users table, which is initially
accessed from the Web User Accounts page (see procedure below). Once this table is
accessed, subsequent ac cess immediatel y opens the W eb Users table instead of the W eb
User Accounts page.
Notes:
• Only the Security Administrator user can initially access the Web Users
table.
• Only Security Administrator and Master users can add, edit, or delete
users.
• Admin users have read-only privileges in the Web Users table. Monitor
users have no access to this page.
• If you delete a user who is currently in an active Web session, the user is
immediately logged off by the device.
• All users can change their own passwords. This is done in the WEB
Security Settings page (see Web Security Settings on page 82).
• To remove the Web Users table and revert to the Web User Accounts
page with the pre-configured, default Web user accounts, set the
ResetWebPassword ini file parameter to 1. This also deletes all other Web
users.
• Once the Web Users table is accessed, Monitor users and Admin users
can only change their passwords in the Web Security Settings page
(see Web Security Settings on page 82). The new password must have at
least four different characters than the previous password. (The Security
Administrator users and Master users can change their passwords in the
Web Users table and in the Web Security Settings page.)
User's Manual 78 Document #: LTRT-71405
Page 79

User's Manual 6. Configuration Using the Web Interface
To add Web user accounts with advanced settings:
1. Open the Web Users Table page:
• Upon initial access:
a. Open the Web User Accounts page (Configuration tab > System menu >
Web User Accounts).
b. Under the Web Users Table group, click the Create Table button.
• Subsequent access: Configuration tab > System menu > Web User Accounts.
The Web Users table appears, listing the two default, pre-configured Web use
accounts - Security Administrator ("Admin") and Monitor ("User"):
Figure 43: Web Users Table Page
2. Click the Add button; the following dialog box is displayed:
Figure 44: Web Users Table - Add Record Dialog Box
3. Add a user as required. For a description of the parameters, see the table below.
4. Click Submit.
Web User Parameters Description
Parameter Description
Web: Username
Version 6.6 79 MediaPack Series
Defines the Web user's username.
The valid value is a string of up to 40 alphanumeric characters,
including the period ".", underscore "_", and hyphen "-" signs.
Page 80

This state is automatically set for users
set by the 'Deny Access on Fail Count' parameter (see
eout configured by
efined
number of days, set by the 'User Inactivity Timer' (see
can only log in to the Web interface if their status is
changed (to New or Valid) by a System Administrator or
MediaPack Series
Parameter Description
Web: Password
Web: Status
Defines the Web user's password.
The valid value is a string of 8 to 40 ASCII characters, which must
include the following:
At least eight characters
At least two letters that are upper case (e.g., "AA")
At least two letters that are lower case (e.g., "aa")
At least two numbers
At least two signs (e.g., the dollar "$" sign)
No spaces in the string
At least four characters different to the previous password
Defines the status of the Web user.
New = (Default) User is required to change its password on the
next login. When the user logs in to the Web interface, the user is
immediately prompted to change the current password.
Valid = User can log in to the Web interface as normal.
Failed Access =
that exceed a user-def ined num ber of failed login at tempts ,
'Configuring Web Sec urity Sett ings' on p age ). Thes e users
can log in only after a user-defined tim
the 'Block Duration' param eter (see below) or if their status
is changed (to New or Valid) b y a System Administrator or
Master.
Old Account = This state is automatically set for user s that
have not accessed the Web interface for a user-d
'Configuring Web Sec urity Sett ings' on p age ). Thes e users
Master.
Notes:
The Old Account status is applicable only to Admin and Monitor
users; System Administrator and Master users can be inactive
indefinitely.
For security, it is recommended to set the status of a newly added
user to New in order to enforce password change.
Web: Password Age
Defines the duration (in days) of the validity of the password. When
this duration elapses, the user is prompted to change the password;
otherwise, access to the Web interface is blocked.
The valid value is 0 to 10000, where 0 means that the password is
Web: Session Limit
always valid. The default is 90.
Defines the maximum number of Web interface sessions allowed for
the user. In other words, this allows the same user account to log in to
the device from different sources (i.e., IP addresses).
The valid value is 0 to 5. The default is 2.
Note: Up to 5 users can be logged in to the Web interface at any
given.
User's Manual 80 Document #: LTRT-71405
Page 81

User's Manual 6. Configuration Using the Web Interface
Parameter Description
Web: Session Timeout
Web: Block Duration
Web: User Level
Defines the duration (in minutes) of Web inactivity of a logged-in user,
after which the user is automatically logged off the Web interface.
The valid value is 0 to 100000. The default is according to the settings
of the 'Session Timeout' global parameter (see Web Security Settings
on page
82).
Defines the duration (in seconds) for which the user is blocked when
the user exceeds a user-defined number of failed login attempts. This
is configured by the 'Deny Access On Fail Count' parameter (see Web
Security Settings on page
82).
The valid value is 0 to 100000, where 0 means that the user can do
as many login failures without getting blocked. The default is
according to the settings of the 'Deny Authentication Timer' parameter
((see Web Security Settings on page 82).
Note: The 'Deny Authentication Timer' parameter relates to failed
Web logins from specific IP addresses.
Defines the user's access level.
Monitor = (Default) Read-only user. This user can only view Web
pages and access to security-related pages is denied.
Admin = Read/write privileges for all pages, except security-related
pages including the Web Users table where this user has only
read-only privileges.
SecAdmin = Read/write privileges for all pages. This user is the
Security Administrator.
Master-User = Read/write privileges for all pages. This user also
functions as a security administrator.
Notes:
At least one Security Administrator must exist. The last remaining
Security Administrator cannot be deleted.
The first Master user can be added only by a Se curi ty
Administrator user.
Additional Master users can be added, edited and deleted only by
Master users.
If only one Master user exists, it can be deleted only by itself.
Master users can add, edit, and delete Security Administrators (but
cannot delete the last Security Administrator).
Only Security Administrator and Master users can add, edit, and
delete Admin and Monitor users.
Version 6.6 81 MediaPack Series
Page 82

MediaPack Series
6.5.1.5.1.3 Web Security Settings
The Web Security Settings page is used to define a secure Web acc ess communication
method. For a description of these parameters, see 'Web and Telnet Param eters' in the
Product Reference Manual
To define Web access security:
1. Open the WEB Security Settings page (Configuration tab > System menu >
Management > WEB Security Settings).
Figure 45: Web Security Settings
2. Configure the parameters as required.
3. Click Submit to apply your changes.
4. To save the changes to flash memory, see Saving Configuration on page 125.
6.5.1.5.1.4 Web Login Authentication using Smart Cards
You can enable Web login authentication using certificates from a third-party, Common
Access Card (CAC) with user identification. When a user attem pts to access the device
through the Web browser (HTTPS), the device retrieves the Web user’s login username
(and other inform at ion, if r equire d) f rom the CAC. The user attempting to access the de v ice
is only required to provide the login password. Typicall y, a TLS connection is establis hed
between the CAC and t he dev ice’s W eb inter fac e, and a R ADIUS s erver is im plem ented to
authenticate the p assword with the username. T herefore, this feature implements a t wofactor authenticatio n - what the user has (i.e., the ph ysical card) and what the user k nows
(i.e., the login password).
This feature is enabled using the EnableMgmtTwoFactorAuthentication parameter.
Note: For s pecific integration re quirements for implementing a third-party smart
card for Web login authentication, contact your AudioCodes representative.
To log in to the Web interface using CAC:
1. Insert the Common Access Card into the card reader.
2. Access the device using the following URL: https://<host name or IP address>; the
device prompts for a username and password.
3. Enter the password only. As som e browsers require that the usernam e be provided,
User's Manual 82 Document #: LTRT-71405
it’s recommended to enter the username with an arbitrary value.
Page 83

User's Manual 6. Configuration Using the Web Interface
6.5.1.5.2 Telnet/SSH Settings
To enable Telnet:
1. Open the Telnet/SSH Settings page (Configuration tab > System menu >
Management > Telnet/SSH Settings).
Figure 46: Telnet/SSH Settings
2. To configure this page, refer to the Secure Telnet sub-section in the Product
Reference Manual.
3. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
6.5.1.5.2.1 Web & Telnet Access List
To configure the Web & Telnet Access List:
1. Open the Web & Telnet Access List page (Configuration tab > System menu >
Management > Web & Telnet Access List).
Figure 47: Web & Telnet Access List
2. To add a new authorized IP addr ess, in the Add a n ew Authori zed IP Address field at
the bottom portion of the page, enter the required IP address and click Add New Entry.
Version 6.6 83 MediaPack Series
Page 84

MediaPack Series
3. To delete an authorized IP address, in the upper portion of the page, click a
checkmark into the checkbox of the required IP address row (checkmarks in more
than one row is permissible) and click Delete Selected Addresses.
Notes:
• When all authorized IP addresses are deleted, this security feature
becomes disabled (all IP addresses are allowed to connect).
• When adding the first authorized IP address, you should add your own
terminal's IP address, in order to be able to connect to the Web interface. If
entered incorrectly, reset the device to restore configuration from nonvolatile memory and regain web access.
6.5.1.5.3 Authentication Sett ings
To configure the Authentication Settings:
1. Open the RADIUS Settings pag e ( Configuration tab > System menu > Management
> Authentication Settings).
Figure 48: Authenticati o n Settings
2. To configure this page, refer to the Authent ication Settings sub-section in the Product
Reference Manual.
3. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
User's Manual 84 Document #: LTRT-71405
Page 85

User's Manual 6. Configuration Using the Web Interface
6.5.1.5.4 SNMP
The device provides an embedded SNMP Agent that allows it to be managed by
AudioCodes Element Management System (EMS) or a third-part y SNMP Manager (e.g.,
element management system). The SNMP Agent supports standard Management
Information Base (MIBs) and proprietary MIBs, enabling a deeper probe into the
interworking of the device. The SNMP Agent can also send unsolicited events (SNMP
traps) towards the S NMP Manager. All supported MIB files are supplied to cus tomers as
part of the release.
AudioCodes EMS is an advanced solution for standards-based management that covers all
areas vital for the efficient operation, administration, management and provisioning
(OAM&P) of the device. The standards-compliant EMS uses distributed SNMP-based
management sof tware, optimized to suppor t day-to-day Network Operati on Center (NOC)
activities, offering a feature-rich management framework. It supports fault management,
configuration and security.
The following provides configuration relating to SNMP management.
6.5.1.5.4.1 SNMP Community String
A SNMP Communit y String is a basic form of SNMP security. It desc ribes the association
between an SNMP ser ver a nd cl ients T his s trin g is lik e a pas s word that controls the client' s
access to the server.
To configure the SNMP Community String:
1. Open the SNMP Community String page (Configuration tab > System menu >
Management > SNMP > SNMP Community String).
Figure 49: SNMP Community Settings
Version 6.6 85 MediaPack Series
Page 86

MediaPack Series
2. T o add a Community Strin g, enter a name in the Co mmunity String fie ld in the "Read
Only" or "Read/W r ite" sect ion, ( de pen di ng o n th e ne ed ed Ac c ess Le ve l) an d then click
the Submit button, to apply the settings.
Note: Up to five "Read Only" or "Read/Write" Community Strings are permitted.
3. To delete a Community String, select t h e De lete c h eck-box of the Communit y Stri ng to
be deleted and then click the Submit button, to apply the settings.
4. To configure this page, ref er to the SNM P Interf ace Detai ls sub-section in the Pr oduct
Reference Manual.
5. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
6.5.1.5.4.2 SNMP Trap Destinations
To configure the SNMP Trap Destinations:
1. Open the SNMP Trap Destinations page (Configuration tab > System menu >
Management > SNMP > SNMP Trap Destinations).
Figure 50: SNMP Trap Destinations
2. To configure this page, refer to the M ultiple SNMP Trap Destinations sub-sect ion in
the Product Reference Manual.
3. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
User's Manual 86 Document #: LTRT-71405
Page 87

User's Manual 6. Configuration Using the Web Interface
6.5.1.5.4.3 SNMP Trusted Managers
To configure the SNMP Trusted Managers:
1. Open the SNMP Trusted Managers page (Configuration tab > System menu >
Management > SNMP > SNMP Trusted Managers).
Figure 51: SNMP Trusted Managers
2. To configure this page, refer to the SNMP parameters sub-section in the Product
Reference Manual.
3. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
6.5.1.5.4.4 SNMP V3 Users
To configure the SNMP V3 Users:
1. Open the SNMP v3 Users page (Configuration tab > System menu > Management
> SNMP > SNMP V3 Users).
2. Click Add; the following dialog box appears:
3. To configure this page, refer to the SNMPv3 USM U sers sub-section in the Product
Reference Manual.
4. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
Figure 52: SNMP V3 Users
Version 6.6 87 MediaPack Series
Page 88

6.5.2 VoIP
VoIP menu options are described below.
6.5.2.1 Network
MediaPack Series
This section describes the network-related configuration.
To configure the IP Settings:
1. Open the IP Settings page (Configuration tab > VoIP menu > Network >
IP Interface Table).
2. Follow the guidelines in the Product Reference Manual when configuring/modifying
the IP Settings, in the IP Settings page.
3. After configuring/modifying the parameter fields, click DONE. This will validate your
configuration.
4. For configuration guidelines, refer to the MGCP/MEGACO Product Reference Manual.
6.5.2.2 IP Interface Table
To configure the IP Interface table:
1. Open the SIP Interface Table page (Configuration tab > VoIP menu > Network >
IP Interface Table).
2. Click the Add button; the following dialog box appears:
Figure 53: IP Interface Table
3. Click Submit to apply your settings.
User's Manual 88 Document #: LTRT-71405
Page 89

User's Manual 6. Configuration Using the Web Interface
6.5.2.2.1 Changing VLAN Mode and ‘Native’ VLAN ID
The Interface Table web page allows the user to change the VLAN Mode (enable or
disable VLANs), as well as to change the value of the ‘Native’ VLAN ID.
When configuring more than one network interface, VLANS must be enabled.
In order to change one of thes e param et ers, ope n the Netw ork Settings ->I P Sett ings pa ge.
The VLAN Mode and ‘Native’ VLAN ID parameters are displayed below the Interface
Table.
Note that any change of these parameter values will only be applied after burning the
configuration and booting from Flash (not using a BOOTP/DHCP server).
Refer to the Interface Table Configuration Summary and Guidelines section in the
MGCP/MEGACO Product Reference Manual, to ensure a successful configuration.
6.5.2.3 Static Route Table
The IP Routing Table page allows you to define up to 30 static IP routing rules for the
device. These rules can be associated with a network interface (defined in the Multiple
Interface table) and therefore, the routing dec ision is bas ed on the sour ce subnet/VL AN. If
not associated with an IP interface, the static IP rule is based on destination IP addres s.
Traffic destined to the subnet specified in the routing rule is re-directed to the defined
gateway, reachable through the specified interface. Before sending an IP packet, the
device searches this table for an entry that matches the requested destination
host/network. If such an en tr y is found, t he de vice se nds the pac ket to t he indicat ed rou ter.
If no explicit entry is found, the packet is sent to the default gateway.
To configure static route:
1. Open the IP Routing Table page (Configuration tab > VoIP menu > Network >
Static Routing Table).
2. Click the Add button; the following dialog box appears:
Figure 54: Static Route Table
3. Click Submit to apply your settings.
Notes:
• You can delete only inactive routing rules.
• The IP Routing table can also be configured using the table ini file
parameter, StaticRouteTable.
Version 6.6 89 MediaPack Series
Page 90

You can also configure this feature using the ini file parameter
MediaPack Series
6.5.2.4 Network Settings
You can configure the device's handling of ICMP Redirect messages. These messages
can either be rejected (ignored) or permitted.
Note:
DisableICMPRedirects (see 'Routing Parameters' in the Product Reference Manual.
To configure the handling of ICMP Redirect messages:
1. Open the Network Settings page (Configuration tab > VoIP menu > Network >
Network Settings).
Figure 55: Network Settings
2. Click Submit to apply your changes.
User's Manual 90 Document #: LTRT-71405
Page 91

User's Manual 6. Configuration Using the Web Interface
6.5.2.5 QoS Settings
This page allows the user t o configur e values f or the p riority fie ld of the VLAN tag , and th e
DiffServ field of the I P He a der . Ref er to Q o S Parameters in the Product R eference Manual,
for more information.
In order to access this page, set the configuration mode on the Navigation Pane to Full.
To configure the QoS Settings:
1. Open the QoS Settings page (Configuration tab > VoIP menu > Network >
QoS Settings).
Figure 56: QoS Settings
2. To configure this page, refer to the Infrastructure ini File Parameters sub-sec tion in the
Product Reference Manual.
3. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
Version 6.6 91 MediaPack Series
Page 92

MediaPack Series
6.5.2.6 Security Settings
Security Settings - Contains a drop-down list with the follo wing opt ions :
F ir e wa ll Settings - Refer to Firewall Sett in gs on pag e 93
802.1x Settings – Refer to 802.1x Settings on page 96.
General Security Settings - Refer to General Security Settings on page 97
IPSec Proposal Table - Refer to IP Security Proposal Table on page 98
IPSec Association Table - Refer to IP Security Associations Table on page 99
Note: For more information, rel ated to these pag es, refer to the Sec urity chapter in
the Product Reference Manual.
User's Manual 92 Document #: LTRT-71405
Page 93

User's Manual 6. Configuration Using the Web Interface
6.5.2.6.1 Firewall Settings
The following describes Firewall settings.
Note: Refer to the Internal Fire wall sub-sect ion of the Security chapter f or more
information regarding Firewall Settings.
The device provides an internal firewall that enables you to configure network traffic
filtering rules (access list). You can add up to 25 firewall rules. The ac cess list offers the
following firewall possibilities:
Block traffic from known malicious sources
Allow traffic only from known "friendly" sources, and block all other traffic
Mix allowed and blocked network sources
Limit traffic to a user-defined rate (blocking the excess)
Limit traffic to specific protocols, and specific port ranges on the device
For each packet rec eived on the net work inter fac e, the table is sc anned f rom top to bot tom
until the first matching rule is f ound. This rule can either perm it (allow) or deny (block) the
packet. Once a rule in the table is located, subsequent rules further down the table are
ignored. If the end of the table is reached without a match, the packet is accepted.
Notes:
• This firewall applies to a very low-level network layer and overrides all
other security-relate d confi gur ati on. Thus , if you have conf igured hi gherlevel security features (e.g., on the Application level), you must also
configure firewall rules to permit this necessary traffic. For example, if you
have configured IP addresses to access the Web and Telnet interfaces in
the Web Access List (see Web & Telnet Access List on page 83), you must
configure a firewall rule that permits traffic from these IP addresses.
• Only Security Administrator users or Master users can configure firewall
rules.
• Setting the 'Prefix Length' field to 0 means that the rule applies to all
packets, regardless of the defined IP address in the 'Source IP' field.
Therefore, it is highly recommended to set this parameter to a value other
than 0.
• It is recommended to add a rule at the end of your table that blocks all
traffic and to add firewall rules above it that allow required traffic (with
bandwidth limitations). To block all traffic, use the following firewall rule:
• Source IP: 0.0.0.0
• Prefix Length: 0 (i.e., rule matches all IP addresses)
• Start Port - End Port: 0-65535
• Protocol: An y
• Action Upon Match: Block
• You can also configure the firewall settings using the table ini file
parameter, AccessList (see 'Security Parameters' in the Product Reference
Manual).
Version 6.6 93 MediaPack Series
Page 94

MediaPack Series
To add firewall rules:
1. Open the Firewall Settings page (Configuration tab > VoIP menu > Security >
Firewall Settings).
2. Click the Add button; the following dialog box appears:
Figure 57: Firewall Settings
3. Configure the firewall parameters, as required.
4. Click Submit to add the new firewall rule to the table.
5. Reset the device to activate the rules.
The table below provides an example of configured firewall rules:
Parameter
Source IP
Prefix Length
Start Port and End Port
Protocol
Use Specific Interface
Interface Name
Byte Rate
Burst Bytes
1 2 3 4 5
12.194.231.76
16
0-65535
Any
Enable
WAN
0
0
Firewall Rule Examples
Value per Rule
12.194.230.7
16
0-65535
Any
Enable
WAN
0
0
0.0.0.0
0
0-65535
icmp
Disable
None
40000
50000
192.0.0.0
8
0-65535
Any
Enable
Voice-Lan
40000
50000
0.0.0.0
0
0-65535
Any
Disable
None
0
0
Action Upon Match
The firewall rules in the above configuration example do the following:
User's Manual 94 Document #: LTRT-71405
Allow
Allow
Allow
Allow
Block
Page 95

User's Manual 6. Configuration Using the Web Interface
Rules 1 and 2: Typical firewall rules that allow packets ONLY from specified IP
addresses (e.g., proxy servers). Note that the prefix length is configured.
Rule 3: A more "advanced" firewall rule - bandwidth rule for ICMP, which allows a
maximum bandwidth of 40,000 bytes/sec with an additional allowance of 50,000 bytes.
If, for example, the actual traffic rate is 45,000 bytes/sec, then this allowance would be
consumed within 10 seconds, after which all traffic exceeding the allocated 40,000
bytes/sec is dropped. If the actual traffic rate then slowed to 30,000 bytes/sec, the
allowance would be replenished within 5 seconds.
Rule 4: Allows traffic from the LAN voice interface and limits bandwidth.
Rule 5: Blocks all other traffic.
Version 6.6 95 MediaPack Series
Page 96

MediaPack Series
6.5.2.6.2 802.1x Settings
The 802.1x Settings page is used t o configure IE EE 802.1X Ether net security. T he device
can function as an IEEE 802.1X supplicant. IEEE 802.1X is a standard for port-level
security on secure Ethernet switches; when a device is connected to a secure port, no
traffic is allowed until the identity of the device is authenticated.
A typical 802.1X dep loyment cons ists of an Auth enticator (secure LAN switch), an Access
Server (e.g. RADIU S), and one or m ore supplica nts. T he Authenticator bl ocks all traf fic on
the secure port by default and communicates with the supplicant via EAP-over-LAN
frames. The supplicant pr ovides crede ntials which are tr ansmitted to the Ac cess Server. If
the Access Server deter m ines that the cr edenti als are valid, it ins truct s the Auth entic ator to
authorize traffic on the secure port.
The device supports the following Extensible Authentication Protocol (EAP) variants:
MD5-Challenge (EAP-MD5): Authentication is done with a user-def ined 80 2.1X
username and password.
Protected EAP (PEAPv0 with EAP-MSCHAPv2): Authentication is done with a user-
defined 802.1X username and password, however, the protocol is MSCHAPv2 over
an encrypted TLS tunnel.
EAP-TLS: The device's certificate is used to establish a mutually-authenticated TLS
session with the Access Server. This requires prior configuration of the server
certificate and root CA. The user-defined 802.1X username is used to identify the
device, however, the 802.1X password is ignored.
To configure the 802.1x parameters:
1. Open the 802.1x Settings page (Configuration tab > VoIP menu > Security > 802.1x
Settings).
Figure 58: 802.1x Settings
2. Configure the parameters as required, and then click Submit.
User's Manual 96 Document #: LTRT-71405
Page 97

User's Manual 6. Configuration Using the Web Interface
6.5.2.6.3 General Security Settings
To configure the General Security Settings:
1. Open the General Security Settings page (Configuration tab > VoIP menu >
Security > General Security Settings).
Figure 59: General Security Settings
2. Use the *.ini files as a referenc e when configuring/m odifying the fields in the G eneral
Security Settings page.
3. After configuring/modifying the parameter fields, click Submit. The changes are
entered into the system and the page is refreshed.
Version 6.6 97 MediaPack Series
Page 98

MediaPack Series
6.5.2.6.4 IP Sec Proposal Table
Note: IP Security Proposal Settings availability is in accordance with the
device's Software Upgrade Key.
To configure the IP Security Proposal Table:
1. Open the IP Security Proposal Table page (Configuration tab > VoIP menu >
Security > IPSec Proposal Table).
2. Click the Add button; the following dialog box appears:
Figure 60: IP Security Proposals Table - Add Record Dialog Box
3. Use the appropriate tables in the Product Reference Manual as a reference when
configuring/modifying the parameter fields in the page.
4. After configuring/modifying the parameter fields, click Submit. The changes are
entered into the system and the page is refreshed.
5. To commit the changes to non-volatile (flash) memory, click Reset on the Toolbar. The
Reset page appears. If you are modifying m ultiple pages, perform the reset after you
are finished modifying all of the pages you intended and NOT after each page.
6. Select the Burn option and click Reset.
User's Manual 98 Document #: LTRT-71405
Page 99

User's Manual 6. Configuration Using the Web Interface
6.5.2.6.5 IP Sec Associations Table
Notes:
• IP Security Associations Settin gs availab il ity is in accordance with the
device's Software Upgrade Key.
• Refer to the IPSec ini file parameters in the ini file parameters section of
the Product Reference Manual.
• Refer to the IP Security sub-section in the Security chapter of the Product
Reference Manual.
To configure the IP Security Associations table:
1. Open the IP Security Associations Table page (Configuration tab > VoIP menu >
Security > IPSec Association Table).
2. Click the Add button; the following dialog box appears:
Figure 61: IP Security Associations Table
3. Configure the parameters, as required. In the above figure, a single I PSec/IKE peer
(10.3.2.73) is configured. Pre-shared key authentication is selected with the preshared key set to 123456789. In ad dition, a lifetime of 28800 seconds is set f or IKE
and a lifetime of 36 00 seconds is set for IPSec. For a descriptio n of the parameters ,
refer to the Product Reference Manual.
4. Click Submit.
5. To save the changes to flash memory, see Saving Configuration on page 125.
Version 6.6 99 MediaPack Series
Page 100

6.5.2.7 Media
Media - Contains a drop-down list with the following options:
Voice Settings - Refer to 'Voice Settings' on page 100
Fax/Modem/CID Settings - Refer to Fax/Modem/CID Settings on page 101
RTP/RTCP Settings - Refer to RTP Settings on page 102
IPMedia Settings - Refer to IPMedia Settings on page 103
General Media Settings - Refer to General Media Settings on page 104
Media Realm Configuration - Refer to Media Realm Configuration on page 106
Med ia Secur i t y - Refer to Media Security on pag e 113
6.5.2.7.1 Voice Settings
To configure the Voice Settings:
1. Open the Voice Settings page (Configuration tab > VoIP menu > Media > Voice
Settings).
MediaPack Series
Figure 62: Voice Settings
2. Use the appropriate tables in the Product Reference Manual as a reference when
configuring/modifying the Media Settings parameter fields in the Media Settings page.
3. After configuring/modif ying the par ameter fields, click the Submit butto n. The changes
are entered into the system and the page is refreshed.
User's Manual 100 Document #: LTRT-71405
 Loading...
Loading...