Page 1

Management
Software
AT-S100
User’s Guide
For use with the AT-9000/28 and AT-9000/28SP
Managed Layer 2 GE ecoSwitches
Version 1.0.3
613-001138 Rev. A
Page 2

Copyright 2009 Allied Telesis, Inc.
All rights reserved. No part of this publication may be reproduced without prior written permission from Allied Telesis, Inc.
Allied Telesis and the Allied Telesis logo are trademarks of Allied Telesis, Incorporated. All other product names, company names, logos or
other designations mentioned herein are trademarks or registered trademarks of their respective owners.
Allied Telesis, Inc. reserves the right to make changes in specifications and other information contained in this document without prior
written notice. The information provided herein is subject to change without notice. In no event shall Allied Telesis, Inc.be liable for any
incidental, special, indirect, or consequential damages whatsoever, including but not limited to lost profits, arising out of or related to this
manual or the information contained herein, even if Allied Telesis, Inc. has been advised of, known, or should have known, the possibility of
such damages.
Page 3

Contents
Preface ............................................................................................................................................................ 11
Document Conventions .................................................................................................................................... 12
Where to Find Web-based Guides ................................................................................................................... 13
Contacting Allied Telesis .................................................................................................................................. 14
Online Support ........................................................................................................................................... 14
Email and Telephone Support.................................................................................................................... 14
Warranty..................................................................................................................................................... 14
Returning Products .................................................................................................................................... 14
Sales or Corporate Information .................................................................................................................. 14
Management Software Updates................................................................................................................. 14
Chapter 1: Getting Started with the Command Line Interface .................................................................. 15
Introducing the Command Modes .................................................................................................................... 16
Privileged Executive Command Mode ....................................................................................................... 18
Configuration Terminal Mode..................................................................................................................... 19
Interface Configuration Command Mode ................................................................................................... 20
VLAN Configuration Command Mode........................................................................................................ 21
Line Mode Commands ............................................................................................................................... 22
Starting the Command Line Interface............................................................................................................... 23
Formatting Commands ..................................................................................................................................... 24
Command Line Interface Features............................................................................................................. 24
Command Formatting Conventions ........................................................................................................... 24
Specifying an Interface............................................................................................................................... 24
Command Line Syntax Conventions.......................................................................................................... 25
Chapter 2: Configuring the AT-S100 Software ........................................................................................... 27
Setting the Switch............................................................................................................................................. 28
Assigning an IP Address............................................................................................................................ 28
Setting DHCP............................................................................................................................................. 29
Setting a Gateway Address........................................................................................................................ 29
Setting the Network Time........................................................................................................................... 29
Increasing Frame Size (Jumbo Frames).................................................................................................... 31
Saving the Configuration............................................................................................................................ 31
Adding a User Name and Password .......................................................................................................... 31
Displaying and Setting MAC Addresses .................................................................................................... 32
Rebooting the Switch ................................................................................................................................. 35
Resetting Switch to Factory Default Values ............................................................................................... 35
Upgrading or Downgrading Software ......................................................................................................... 35
Uploading an Image File ............................................................................................................................ 37
Displaying and Saving Configuration Files................................................................................................. 38
Copying Configuration Files ....................................................................................................................... 39
Uploading and Downloading Configuration Files ....................................................................................... 39
Creating VLANs ......................................................................................................................................... 40
Setting the Ports ............................................................................................................................................... 43
Displaying Port Ethernet Statistics ............................................................................................................. 43
Setting Port Mirroring ................................................................................................................................. 43
3
Page 4

Contents
Setting Port Speed and Duplex Mode ........................................................................................................ 44
Enabling and Disabling Ports ..................................................................................................................... 45
Setting MDI and MDIX................................................................................................................................ 45
Setting Port Security................................................................................................................................... 46
Creating Static Trunks ................................................................................................................................49
Enabling Backpressure............................................................................................................................... 50
Enabling Flow Control ................................................................................................................................ 50
Preventing Broadcast Storms.....................................................................................................................51
Configuring Protocols........................................................................................................................................53
Setting GVRP ............................................................................................................................................. 53
Enabling IGMP Snooping ........................................................................................................................... 55
Setting the Link Access Control Protocol (LACP)....................................................................................... 56
Setting 802.1x Port Authentication ............................................................................................................. 56
Configuring RADIUS Authentication...........................................................................................................58
Setting Simple Network Management Protocol (SNMP) ............................................................................ 59
Setting the Secure Shell .............................................................................................................................62
Setting STP and RSTP............................................................................................................................... 62
Configuring 802.1p Class of Service .......................................................................................................... 67
Section I: Command Modes .....................................................................................69
Chapter 3: Privileged Executive Mode Commands .................................................................................... 71
CLEAR MAC ADDRESS-TABLE DYNAMIC..................................................................................................... 73
CLEAR MAC ADDRESS-TABLE MULTICAST................................................................................................. 75
CLEAR MAC ADDRESS-TABLE STATIC ........................................................................................................77
CONFIGURE TERMINAL ................................................................................................................................. 79
COPY................................................................................................................................................................ 81
COPY A.B.C.D ..................................................................................................................................................82
COPY DEFAULT.CFG ...................................................................................................................................... 84
CP ..................................................................................................................................................................... 86
DOWNLOAD TFTP ...........................................................................................................................................87
EXIT .................................................................................................................................................................. 88
LOGOUT ........................................................................................................................................................... 89
SHOW INTERFACE ......................................................................................................................................... 90
SHOW MAC ADDRESS-TABLE ....................................................................................................................... 92
SHOW MAC ADDRESS-TABLE AGEING-TIME ..............................................................................................94
SHOW MAC ADDRESS-TABLE DYNAMIC .....................................................................................................96
SHOW MAC ADDRESS-TABLE INTERFACE.................................................................................................. 98
SHOW MAC ADDRESS-TABLE STATIC ....................................................................................................... 100
SHOW MAC ADDRESS-TABLE VLAN........................................................................................................... 102
SHOW RUNNING-CONFIG INTERFACE.......................................................................................................104
SHOW SPANNING-TREE .............................................................................................................................. 106
SHOW STATIC-CHANNEL-GROUP .............................................................................................................. 109
SHOW USER-PRIORITY................................................................................................................................ 110
SYSTEM FACTORY-RESET...........................................................................................................
SYSTEM REBOOT ......................................................................................................................................... 112
UPLOAD TFTP ............................................................................................................................................... 113
............... 111
Chapter 4: Configuration Terminal Mode Commands .............................................................................. 115
CLOCK SUMMER-TIME RECURRING ..........................................................................................................117
CLOCK TIMEZONE ........................................................................................................................................ 119
CRYPTO KEY GENERATE USERKEY .......................................................................................................... 121
DOT1X SYSTEM-AUTH-CTRL....................................................................................................................... 123
ENABLE PASSWORD.................................................................................................................................... 124
ENABLE SECRET .......................................................................................................................................... 125
4
Page 5

AT-S100 Management Software User’s Guide
EXIT................................................................................................................................................................ 126
HELP .............................................................................................................................................................. 127
HOSTNAME ................................................................................................................................................... 128
INTERFACE ................................................................................................................................................... 129
IP IGMP SNOOPING...................................................................................................................................... 131
IP ROUTE....................................................................................................................................................... 132
IP SSH RSA KEYPAIR-NAME ....................................................................................................................... 133
IP SSH VERSION........................................................................................................................................... 134
LINE CONSOLE ............................................................................................................................................. 135
LINE VTY........................................................................................................................................................ 136
MAC ADDRESS-TABLE AGEING-TIME ........................................................................................................ 138
MAC ADDRESS-TABLE STATIC DISCARD.................................................................................................. 139
MAC ADDRESS-TABLE STATIC FORWARD ............................................................................................... 141
MLS QOS ....................................................................................................................................................... 143
NTP AUTHENTICATE.................................................................................................................................... 145
NTP AUTHENTICATION-KEY ....................................................................................................................... 146
NTP SERVER................................................................................................................................................. 148
NTP TRUSTED-KEY ...................................................................................................................................... 150
SHOW LIST.................................................................................................................................................... 151
SHOW RUNNING-CONFIG ........................................................................................................................... 153
SHOW RUNNING-CONFIG COMMUNITY-LIST ........................................................................................... 158
SHOW RUNNING-CONFIG INTERFACE ...................................................................................................... 160
USERNAME ................................................................................................................................................... 162
Chapter 5: Interface Configuration Mode Commands ............................................................................. 163
CHANNEL-GROUP ........................................................................................................................................ 165
DOT1X PORT-CONTROL.............................................................................................................................. 166
EXIT................................................................................................................................................................ 167
FLOW CONTROL BACKPRESSURE ............................................................................................................ 168
FLOW CONTROL RECEIVE .......................................................................................................................... 169
FLOW CONTROL SEND................................................................................................................................ 170
IP ADDRESS.................................................................................................................................................. 171
IP ADDRESS DHCP....................................................................................................................................... 173
LACP SYSTEM-PRIORITY ............................................................................................................................ 174
MDIX............................................................................................................................................................... 175
MIRROR INTERFACE DIRECTION............................................................................................................... 176
MTU................................................................................................................................................................ 178
SHOW RUNNING-CONFIG INTERFACE ...................................................................................................... 179
SHUTDOWN .................................................................................................................................................. 181
SPEED ........................................................................................................................................................... 182
STATIC-CHANNEL-GROUP ...........................................................................................................
STORM-CONTROL........................................................................................................................................ 185
SWITCHPORT ACCESS VLAN ..................................................................................................................... 187
SWITCHPORT MODE TRUNK ...................................................................................................................... 188
SWITCHPORT TRUNK ALLOWED VLAN ..................................................................................................... 190
TRAFFIC-CLASS-TABLE USER-PRIORITY NUM-TRAFFIC-CLASSES ...................................................... 192
USER-PRIORITY ........................................................................................................................................... 193
............... 184
Section II: Advanced Configuration ...................................................................... 195
Chapter 6: 802.1x Access Control Commands ......................................................................................... 197
DOT1X PORT-CONTROL.............................................................................................................................. 198
DOT1X SYSTEM-AUTH-CTRL ...................................................................................................................... 199
LOGIN REMOTELOCAL ................................................................................................................................ 200
RADIUS-SERVER HOST ............................................................................................................................... 201
5
Page 6

Contents
RADIUS-SERVER KEY .................................................................................................................................. 202
SHOW DOT1X ................................................................................................................................................ 203
SHOW DOT1X ALL ........................................................................................................................................ 204
SHOW DOT1X INTERFACE .......................................................................................................................... 207
SHOW DOT1X STATISTICS INTERFACE..................................................................................................... 209
Chapter 7: GVRP Commands ..................................................................................................................... 211
SET GVRP ...................................................................................................................................................... 212
SET GVRP APPLICANT .................................................................................................................................213
SET GVRP DYNAMIC-VLAN-CREATION ...................................................................................................... 214
SET GVRP REGISTRATION ..........................................................................................................................215
SET GVRP TIMER.......................................................................................................................................... 217
Chapter 8: Port Security Commands .........................................................................................................219
SWITCHPORT PORT-SECURITY MAC-ADDRESS ...................................................................................... 220
SWITCHPORT PORT-SECURITY MAXIMUM ............................................................................................... 222
SWITCHPORT PORT-SECURITY MODE......................................................................................................223
SWITCHPORT PORT-SECURITY VIOLATION .............................................................................................225
Chapter 9: Simple Network Management Protocol (SNMP) Commands ................................................227
SNMP-SERVER COMMUNITY.......................................................................................................................228
SNMP-SERVER CONTACT ........................................................................................................................... 230
SNMP-SERVER ENABLE ..............................................................................................................................232
SNMP-SERVER GROUP ............................................................................................................................... 233
SNMP-SERVER HOST...................................................................................................................................235
SNMP-SERVER USER...................................................................................................................................237
SNMP-SERVER USER REMOTE ..................................................................................................................239
SNMP-SERVER VIEW ...................................................................................................................................241
Chapter 10: Spanning Tree Protocol (STP) Commands ...........................................................................243
SHOW SPANNING-TREE .............................................................................................................................. 244
SPANNING-TREE ENABLE FORWARD........................................................................................................ 247
SPANNING-TREE FORWARD-TIME .............................................................................................................249
SPANNING-TREE HELLO-TIME .................................................................................................................... 250
SPANNING-TREE MAX-AGE ......................................................................................................................... 251
SPANNING-TREE MODE............................................................................................................................... 252
SPANNING-TREE PORTFAST BPDU-FILTER DEFAULT ............................................................................253
SPANNING-TREE PORTFAST BPDU-GUARD DEFAULT............................................................................ 254
SPANNING-TREE PRIORITY ........................................................................................................................ 255
Chapter 11: Virtual Local Area Networks (VLAN) Commands ................................................................. 257
SHOW VLAN ALL ........................................................................................................................................... 258
SHOW VLAN BRIEF .......................................................................................................................................260
SHOW VLAN DYNAMIC .................................................................................................................................262
SHOW VLAN STATIC..................................................................................................................................... 263
SWITCHPORT TRUNK ALLOWED VLAN......................................................................................................265
VLAN............................................................................................................................................................... 267
VLAN ACCESS-MAP ...................................................................................................................................... 268
VLAN DATABASE .......................................................................................................................................... 269
Index .............................................................................................................................................................. 271
6
Page 7

Figures
Figure 1: AT-S100 Command Modes ...................................................................................................................................17
Figure 2: Command Line Login Screen ................................................................................................................................23
Figure 3: SHOW MAC ADDRESS-TABLE Command..........................................................................................................93
Figure 4: SHOW MAC ADDRESS-TABLE AGING-TIME.....................................................................................................94
Figure 5: SHOW MAC ADDRESS-TABLE DYNAMIC Command ........................................................................................97
Figure 6: SHOW MAC ADDRESS-TABLE INTERFACE Command ....................................................................................99
Figure 7: SHOW MAC ADDRESS-TABLE STATIC............................................................................................................101
Figure 8: SHOW MAC ADDRESS-TABLE VLAN Command .............................................................................................103
Figure 9: SHOW RUNNING-CONFIG INTERFACE Port Example ....................................................................................104
Figure 10: SHOW RUNNING-CONFIG INTERFACE VLAN Example................................................................................105
Figure 11: SHOW SPANNING-TREE Command, page 1 ..................................................................................................107
Figure 12: SHOW SPANNING-TREE Command, page 2 ..................................................................................................107
Figure 13: SHOW STATIC-CHANNEL-GROUP.................................................................................................................109
Figure 14: SHOW LIST Command .....................................................................................................................................152
Figure 15: SHOW RUNNING-CONFIG Command, page 1................................................................................................154
Figure 16: SHOW RUNNING-CONFIG Command, page 2................................................................................................155
Figure 17: SHOW RUNNING-CONFIG Command, page 3................................................................................................156
Figure 18: SHOW RUNNING-CONFIG Command, page 4................................................................................................157
Figure 19: SHOW RUNNING-CONFIG INTERFACE Port Example ..................................................................................160
Figure 20: SHOW RUNNING-CONFIG INTERFACE VLAN Example................................................................................161
Figure 21: SHOW RUNNING-CONFIG INTERFACE Port Example ..................................................................................179
Figure 22: SHOW RUNNING-CONFIG INTERFACE VLAN Example................................................................................180
Figure 23: SHOW DOT1X Command.................................................................................................................................203
Figure 24: SHOW DOT1X ALL Command .........................................................................................................................204
Figure 25: SHOW DOT1X INTERFACE Command ...........................................................................................................207
Figure 26: SHOW DOT1X INTERFACE Command ...........................................................................................................209
Figure 27: SHOW SPANNING-TREE Command, page 1 ..................................................................................................245
Figure 28: SHOW SPANNING-TREE Command, page 2 ..................................................................................................245
Figure 29: SHOW VLAN ALL..............................................................................................................................................258
Figure 30: SHOW VLAN BRIEF .........................................................................................................................................260
Figure 31: SHOW VLAN DYNAMIC ...................................................................................................................................262
Figure 32: SHOW VLAN STATIC .......................................................................................................................................263
7
Page 8

Figures
8
Page 9

Tab le s
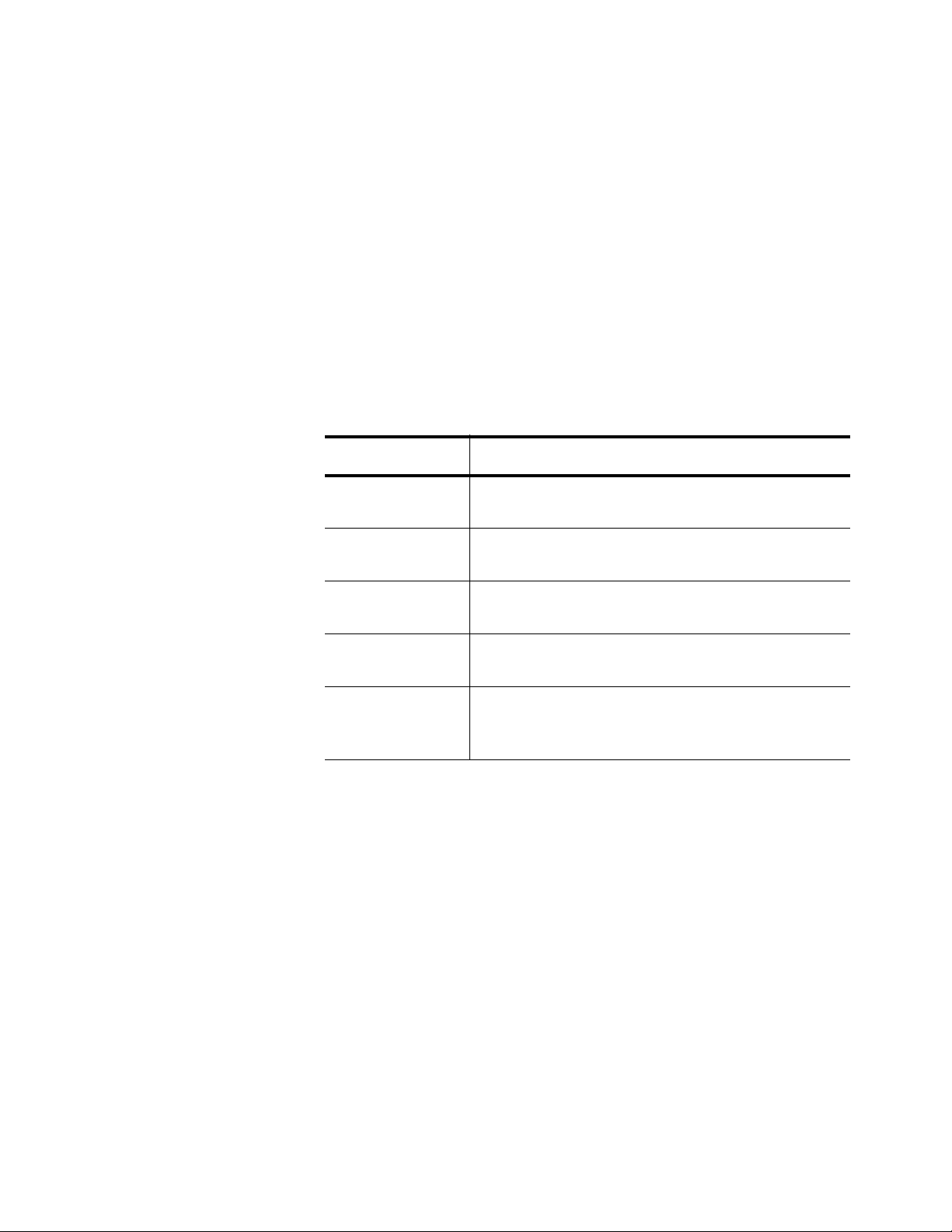
Table 1: Command Modes ..................................................................................................................................................17
Table 2: Examples of Privileged Executive Mode Commands ............................................................................................19
Table 3: Examples of Configuration Terminal Mode Commands ........................................................................................20
Table 4: Examples of Interface Configuration Mode Commands ........................................................................................21
Table 5: Examples of VLAN Mode Commands ...................................................................................................................22
Table 6: Command Line Syntax Conventions .....................................................................................................................25
Table 7: SHOW DOT1X Parameter Description ................................................................................................................205
9
Page 10

Tables
10
Page 11

Preface
The AT-S100 Management Software is the operating system for the
AT-9000/28 and AT-9000/28SP Managed Layer 2 GE ecoSwitches. This
guide describes the commands included in the management software that
you use to control and monitor the operating parameters of both AT-9000
switches.
This Preface contains the following sections:
“Document Conventions” on page 12
“Where to Find Web-based Guides” on page 13
“Contacting Allied Telesis” on page 14
11
Page 12

Preface
Document Conventions
This document uses the following conventions:
Note
Notes provide additional information.
Caution
Cautions inform you that performing or omitting a specific action
may result in equipment damage or loss of data.
Warning
Warnings inform you that performing or omitting a specific action
may result in bodily injury.
12
Page 13

Where to Find Web-based Guides
The installation and user guides for all Allied Telesis products are available
in portable document format (PDF) on our web site at
www.alliedtelesis.com. You can view the documents online or download
them onto a local workstation or server.
For details about the features and functions of the AT-9000/28 and AT9000/28SP switches, see the following installation guide on our web site:
AT-9000 Managed Layer 2 GE ecoSwitch Family Installation Guide
(part number 613-001100)
AT-100 Management Software User’s Guide
13
Page 14

Preface
Contacting Allied Telesis
This section provides Allied Telesis contact information for technical
support as well as sales and corporate information.
Online Support You can request technical support online by accessing the Allied Telesis
Knowledge Base: www.alliedtelesis.com/support/kb.aspx. You can use
the Knowledge Base to submit questions to our technical support staff and
review answers to previously asked questions.
Email and
Telephone
Support
Warranty The AT-9000/28 9000 Series Managed Layer 2 GE ecoSwitch is covered
Returning
Products
Sales or
Corporate
Information
Management
Software Updates
For Technical Support via email or telephone, refer to the Support section
of the Allied Telesis web site: www.alliedtelesis.com.
under a Lifetime Warranty (Two Years Fan & Power Supply). For warranty
information, go to the Allied Telesis web site at www.alliedtelesis.com.
Products for return or repair must first be assigned a return materials
authorization (RMA) number. A product sent to Allied Telesis without an
RMA number will be returned to the sender at the sender’s expense. For
instructions on how to obtain an RMA number, go to the Support section
on our web site at www.alliedtelesis.com/support.rma.aspx.
You can contact Allied Telesis for sales or corporate information through
our web site at www.alliedtelesis.com.
New releases of the management software for our managed products are
available from the following Internet sites:
14
Allied Telesis web site: www.alliedtelesis.com
Allied Telesis FTP server: ftp://ftp.alliedtelesis.com
If the FTP server prompts you to log on, enter “anonymous” as the user
name and your email address as the password.
Page 15

Chapter 1
Getting Started with the Command Line Interface
This chapter describes the command modes of the AT-S100 command
line interface (CLI) and how to access them. This chapter includes the
following sections:
“Introducing the Command Modes” on page 16
“Starting the Command Line Interface” on page 23
“Formatting Commands” on page 24
15
Page 16

Chapter 1: Getting Started with the Command Line Interface
Introducing the Command Modes
This chapter describes the CLI command modes and how to access the
command line interface. There are 5 command modes:
Privileged Executive
Configuration Terminal
VLAN Configuration
Interface Configuration
Line
In the AT-S100 software, the commands are accessed through a
hierarchy of command modes. Each command mode contains a subset of
commands that are available within that mode. See Figure 1 on page 17
for an illustration of the command modes.
When you log on to the CLI interface, the default command mode that you
access depends on your login id. There are two default login ids that are
sent from the factory. The operator login id enables you to display
information about the software configuration. With this login, you access
the View command mode automatically. The manager login id permits full
administrator capabilities. With this login, you access the Privileged
Executive mode by default.
You enter a specific command to navigate from one command mode to
another. For example, to access the Configuration Terminal mode, enter
the CONFIGURE TERMINAL command from the Privileged Executive
mode. Once you enter a new command mode, the AT-S100 prompt
changes to indicate the new mode.
16
Page 17

Privileged
Executive
mode
AT-S100 Management Software User’s Guide
configure
terminal
Command used to
enter the next mode
Configuration
Terminal
mode
Commands used to
enter the next mode
VLAN
database
VLAN
Configuration
mode
Figure 1. AT-S100 Command Modes
See Table 1 for information about the commands used to access the
modes and their respective prompts.
interface
IFNAME
Interface
Configuration
mode
line vty [FIRST]
(LAST)
Line
mode
1221
Command
Mode
Privileged
Executive
Mode
Configuration
Terminal Mode
Prompt Description
Switch#
Switch(config)#
Table 1. Command Modes
This is the default command mode for the manager
login.
Enter the EXIT or LOGOUT commands to exit the
management session.
Use the CONFIGURE command to enter this mode
from the Privileged Executive mode.
To return to the Privileged Executive mode, enter
the EXIT command.
17
Page 18

Chapter 1: Getting Started with the Command Line Interface
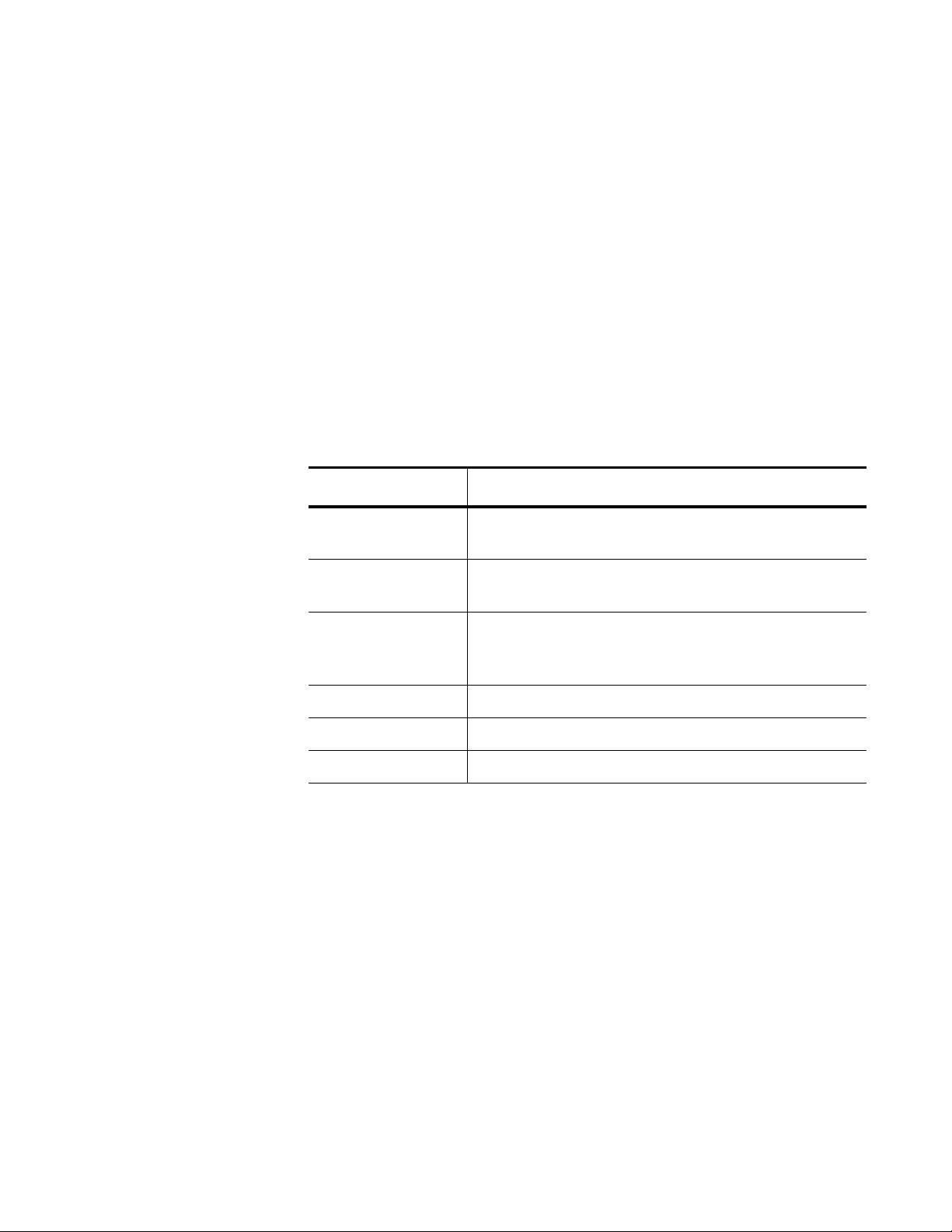
Table 1. Command Modes (Continued)
Command
Mode
Interface
Switch(config-if)#
Prompt Description
Configuration
VLAN
Switch(config-vlan)#
Configuration
Line Switch(config-line)
In addition, there are commands that allow you to move between the
modes. For example, typing the EXIT command when you are in the
Interface Configuration mode returns you to the Configuration Terminal
mode. From the Privilege Executive mode, the LOGOUT command exits
the software.
To access interface 1, enter the following from the
Configuration Terminal mode:
interface ge1
Enter the EXIT command to return to the
Configuration Terminal mode.
From the Configuration Terminal mode, type the
VLAN DATABASE command.
Enter the EXIT command to return to the
Configuration Terminal mode.
From the Configuration Terminal mode, type the
LINE VTY command.
Enter the EXIT command to return to the
Configuration Terminal mode.
Privileged
Executive
Command Mode
If you enter a command that is not accessible from a command mode, the
software displays a “command not found” message. For example, you can
enter the SHOW SNMP command from the Privileged Executive mode,
but you cannot enter this command from the VLAN Configuration mode.
Within the manual, a command mode is listed for each command.
See the following sections for a description of each command mode:
“Privileged Executive Command Mode” on page 18
“Configuration Terminal Mode” on page 19
“Interface Configuration Command Mode” on page 20
“VLAN Configuration Command Mode” on page 21
“Line Mode Commands” on page 22
The Privileged Executive command mode is the default command mode
for the manager login. The commands in this mode permit you to perform
system level commands such as:
rebooting and resetting the system
displaying feature configuration and status
18
Page 19
AT-S100 Management Software User’s Guide
downloading new image files
displaying Ethernet port statistics
The prompt changes to “Switch#” to indicate the Privileged Executive
mode.
To access the Configuration Terminal mode from the Privileged Executive
mode, enter the CONFIGURE TERMINAL command. To return to the
Privileged Executive mode, enter the EXIT command.
See Table 2 for a sample list of commands that can be access from the
Privileged Executive command mode. See Chapter 3, “Privileged
Executive Mode Commands” on page 71 for detailed information about the
commands in this mode.
Table 2. Examples of Privileged Executive Mode Commands
Command Description
Configuration
Terminal Mode
COPY RUN
Saves the current configuration.
START
CONFIGURE
TERMINAL
Changes the mode to the Configuration
Terminal Mode.
COPY Uploads the configuration file to an image or
configuration file.
SHOW
Displays interface configuration and status.
INTERFACE
SYSTEM
FACTORY-
Resets the AT-S100 software to the factory
default settings
RESET
The Configuration Terminal mode allows you to configure advanced
system features such as:
broadcast storm control
GVRP
IGMP Snooping
SNMP
STP and RSTP
To access this mode, you must first access the Privileged Executive mode.
Then type CONFIGURE TERMINAL to access the Configuration Terminal
mode. The prompt changes to “Switch(config)#” to indicate the software
has entered the Configuration Terminal mode. To return to the Privilege
Executive Mode, enter the EXIT command. To exit the management
session, enter the EXIT command again.
19
Page 20

Chapter 1: Getting Started with the Command Line Interface
See Table 3 for a sample list of commands that can be accessed from the
Configuration Terminal mode. For more information about the commands
in this mode, see the Chapter 4, “Configuration Terminal Mode
Commands” on page 115.
Table 3. Examples of Configuration Terminal Mode Commands
Command Description
IP-ACCESS-LIST Creates an access list.
LINE CONSOLE Sets the console configuration. Accesses the
HOSTNAME Sets the name of the system.
INTERFACE Accesses the Interface Configuration command
Line mode.
mode (you must also specify an interface).
Interface
Configuration
Command Mode
SNMP-SERVER
ENABLE
USERNAME Sets a system user name and password.
The Interface Configuration command mode allows you to configure
features that pertain to the port and VLAN interfaces such as flow control
and duplex mode. To access this mode, you must first access the
Privileged Executive and Configuration Terminal modes, depending on
your login id.
There are 28 ports on the AT-9000/28 and AT-9000/28SP switches. To
specify a port, precede the port number with “ge.” For example, to access
port 5 enter the following from the Configuration Terminal mode:
interface ge5
The prompt changes to “Switch(config-if)#” to indicate the Interface
Configuration mode.
To specify a VLAN interface, precede the VLAN ID with “vlan.” For
example, to access VLAN 1 (the default VLAN), enter the following from
the Configuration Terminal mode:
Enables an SNMP agent on the switch.
20
interface vlan1
Page 21
AT-S100 Management Software User’s Guide
After you have accessed the Interface Configuration mode, the commands
you enter apply only to the interface specified in the Configuration
Terminal mode. For example, if you enter “interface ge3” in the
Configuration Terminal mode, all of the subsequent commands that you
enter apply to interface 3 only. To perform interface-specific commands on
another interface, do the following:
exit the Interface mode by entering the EXIT command
specify the new interface in the Configuration Terminal mode
re-enter the commands for the new interface
For a sample list of commands that can be accessed from the Interface
Configuration command mode, see Table 4. For more detailed information
about the commands in the Interface Configuration mode, see Chapter 5,
“Interface Configuration Mode Commands” on page 163.
Table 4. Examples of Interface Configuration Mode Commands
Commands Description
VLAN
Configuration
Command Mode
DOT1X MAXREQ
Sets the maximum number of reauthentication
attempts after authentication fails.
FLOWCONTROL ONEnables flow control and configures the flow
control mode for the interface.
IP ADDRESS Sets an IP address for the switch or specifies that
the switch uses a DHCP client to obtain an IP
address.
MAC-ADDRESS Sets the MAC address for a specified interface.
SHUTDOWN Disables an interface.
SPEED Sets the speed and duplex mode for an interface.
The VLAN Configuration command mode allows you to configure
commands that are applied to a specific VLAN interface. For instance, you
can assign an IP address to a VLAN interface in this mode.
To access this mode, you must first access the Privileged Executive, and
Configuration Terminal modes. From the Configuration Terminal
command mode, type the VLAN DATABASE command. The prompt
changes to “Switch(config-vlan)#” to indicate the VLAN Configuration
mode.
21
Page 22

Chapter 1: Getting Started with the Command Line Interface
After you have accessed the VLAN Configuration mode, enter commands
that apply to a specific VLAN. For a sample list of commands that can be
accessed from the VLAN Configuration command mode, see Table 5 on
page 22. For more detailed information about the commands in this mode,
see Chapter 11, “Virtual Local Area Networks (VLAN) Commands” on
page 257.
The default VLAN has a VLAN ID of 1 and it includes all 28 ports. You can
configure up to 25 VLANs, with VLAN IDs of between 2 and 4094.
However, you cannot configure VLAN 1 as it always remains the default
VLAN. In addition, you can display information about VLANs.
Commands Description
Table 5. Examples of VLAN Mode Commands
Line Mode
Commands
SHOW RUNNINGCONFIGURATION
SWITCH VLAN
VLAN Creates a VLAN and enables it.
VLAN NAME Assigns a name to a VLAN.
VLAN STATE Sets the operational state of the VLAN.
The Line mode permits you to determine the length of the console lines
when creating a Telnet connection and enables password checking on the
RADIUS server. Access the Line mode through the Configuration
Terminal mode, with the LINE VTY command. The prompt changes to
“Switch(config-line)#” to indicate the Line mode.
Once you enter the line mode there is one Line mode command, see
“LOGIN REMOTELOCAL” on page 200.
To exit the Line mode and return to the Configuration Terminal mode, use
the EXIT command.
Displays information about VLANs on the
switch.
22
Page 23
Starting the Command Line Interface
To start the command line interface, perform the following procedure:
1. Type the user id and password.
There are two default user ids and passwords. For the system
administrator login, the default user id is “manager” and the default
password is “friend.”
A command line prompt is displayed in Figure 2.
Username:manager
Password:
(none)#
Figure 2. Command Line Login Screen
AT-S100 Management Software User’s Guide
The default switch name is “(none)” and the pound sign (#) prompt
indicates the Privileged Executive mode which is the default mode
accessed by the manager login.
23
Page 24

Chapter 1: Getting Started with the Command Line Interface
Formatting Commands
The AT-S100 software command line interface follows the same
formatting conventions in all of the command modes. There are command
line interface features which apply to the general use of the command line
and command syntax conventions which apply when entering the
commands. See the following sections.
Command Line
Interface
Features
The following features are supported in the command line interface:
Command history - Use the up and down arrow keys.
Context-specific help - Press the question mark key, ?, to display a list
of permitted parameters or all of the available commands for a
particular command mode. There are two formatting options:
– command ? - List the keywords or arguments that
are required by a particular command. A space
between a command and a question mark is required.
– abbreviated command? - Provides a list of
commands that begin with a particular character string.
There is no space between the command and the
question mark.
Keyword abbreviations - Any keyword can be recognized by typing an
unambiguous prefix, for example, type “sh” and the software responds
with “show.”
Tab key - Pressing the Tab key fills in the rest of the keyword
automatically. For example, typing “di” and then pressing the Tab key
enters “disable” on the command line.
Formatting
Conventions
Specifying an
24
Command
Interface
The following formatting conventions are used in this manual:
screen text font - This font illustrates the format of a command and
command examples.
ALL CAPITAL LETTERS- All capital letters indicate a command for
you to enter.
[ ] - Brackets indicate optional parameters.
| - Vertical line separates parameter options for you to choose from.
Both the AT-9000/28 and the AT-9000/28SP switches have 28 ports.
Within the command line interface, specify each interface with “ge” and
the number of the interface. For example, interface 3 is specified as “ge3.”
Page 25
AT-S100 Management Software User’s Guide
Command Line
Syntax
Conventions
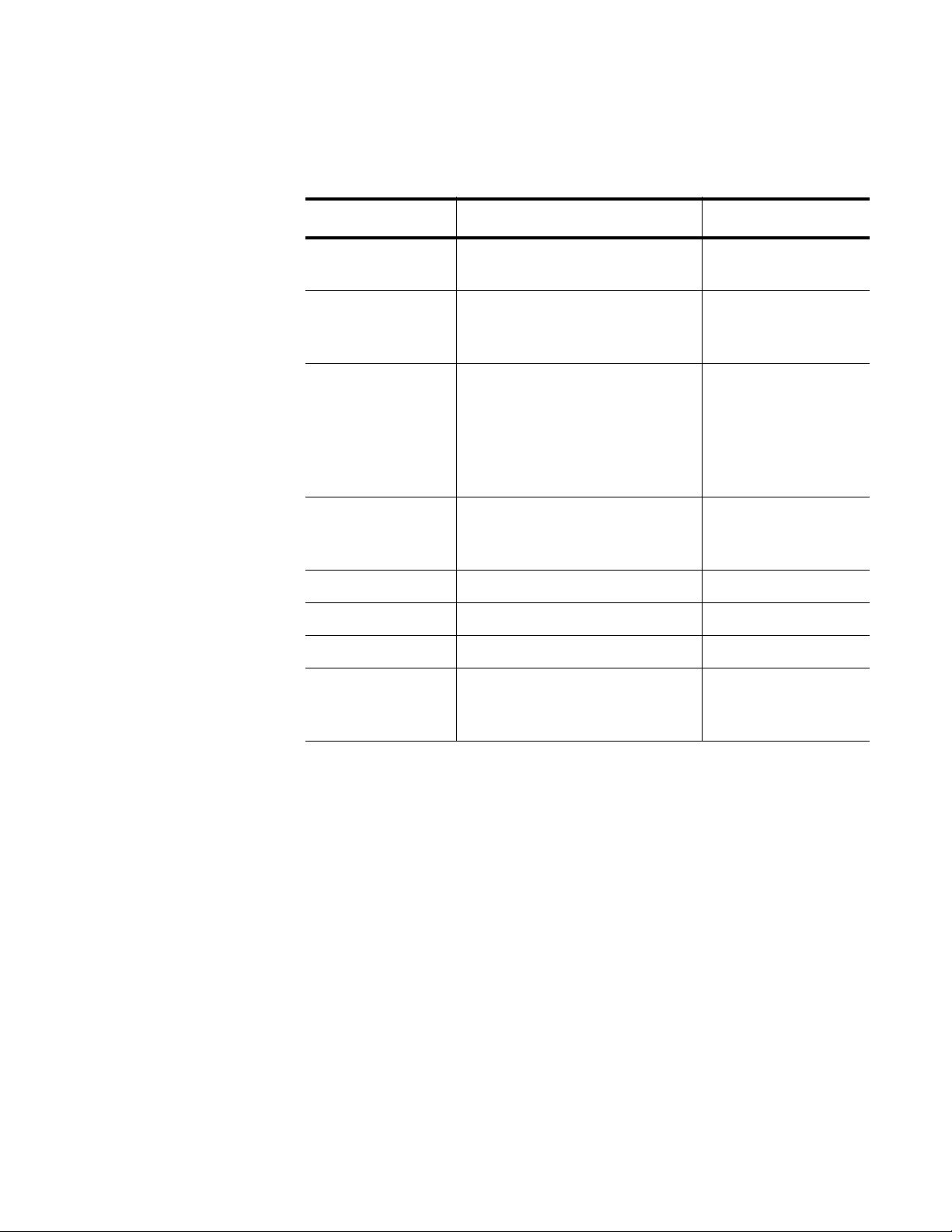
The following table describes the conventions used in the AT-S100
command interface.
Table 6. Command Line Syntax Conventions
Convention Description Example
A.B.C.D/M Indicates an IP address and a
subnet mask.
line Indicates a line of text that
accepts spaces without
quotation marks.
string Indicates a string of
alphanumeric characters,
including special characters
such as spaces. You must
place quotation marks around
a value with spaces.
IFNAME or
IF_NAME
Indicates an interface name.
Specify values ge1 through
ge28.
192.68.1.11/24
Switch 24, San
Jose, Building 4
“Switch 24, San
Jose, Building 4”
ge3
mask Indicates a subnet mask. 255.255.240.0
sec Indicates seconds. 120
min Indicates minutes. 8
VLANID Indicates a VLAN instance
(including name and VLAN
identifier).
vlan3
25
Page 26

Chapter 1: Getting Started with the Command Line Interface
26
Page 27

Chapter 2
Configuring the AT-S100 Software
This chapter provides configuration information about the AT-S100
software.The features are divided into three sections.
This chapter contains the following sections:
“Setting the Switch” on page 28
“Setting the Ports” on page 43
“Configuring Protocols” on page 53
27
Page 28

Chapter 2: Configuring the AT-S100 Software
Setting the Switch
The procedures in this section describe how to perform basic switch
functions such as assigning an IP address, creating a user name and
password, and downloading software. See the following sections:
“Assigning an IP Address” on page 28
“Setting DHCP” on page 29
“Setting a Gateway Address” on page 29
“Setting the Network Time” on page 29
“Increasing Frame Size (Jumbo Frames)” on page 31
“Saving the Configuration” on page 31
“Adding a User Name and Password” on page 31
“Displaying and Setting MAC Addresses” on page 32
“Rebooting the Switch” on page 35
Assigning an IP
Address
“Resetting Switch to Factory Default Values” on page 35
“Upgrading or Downgrading Software” on page 35
“Uploading an Image File” on page 37
“Displaying and Saving Configuration Files” on page 38
“Copying Configuration Files” on page 39
“Uploading and Downloading Configuration Files” on page 39
“Creating VLANs” on page 40
The IP address for the switch enables you to access the switch through
the console port. You must assign an IP address to a VLAN in the
Interface Command Mode. You may assign the IP address to the default
VLAN which is VLAN 1 or to a VLAN that you have created. For
information about how to create a VLAN, see “Creating VLANs” on
page 40.
The syntax of the IP address command is:
ip address xxx.xxx.xxx.xxx/subnet mask
To set the IP address to 192.68.12.8 with a subnet mask of 255.255.255.0
(24 bits) to VLAN 1, enter the following commands:
28
switch# configure terminal
switch(config)# interface vlan1
switch(config-if)# ip address 192.68.12.8/24
Page 29

AT-S100 Management Software User’s Guide
For more information about this command, see “IP ADDRESS” on
page 171.
Setting DHCP The DHCP feature enables the switch to obtain an IP address from the
DHCP server. You must assign the DHCP command to the default VLAN,
VLAN 1, in the Interface mode. The syntax of the DHCP address
command is:
ip address dhcp
The following example sets the DHCP feature on the switch.
switch# configure terminal
switch(config)# interface vlan1
switch(config-if)# ip address dhcp
For more information about this command, see “IP ADDRESS DHCP” on
page 173.
Setting a
Gateway Address
Setting the
Network Time
The gateway address consists of an IP address and a subnet mask that
you assign to an interface on the switch. The local router uses this
information to allow devices that are not on the LAN to communicate with
the switch. The syntax of the gate address command, IP ROUTE, is:
ip route 0.0.0.0/0 interface
To set the gateway address on port 20 to 192.168.1.1 and with a subnet
mask of 24, enter the following commands:
switch# configure terminal
switch(config)# ip route 192.168.1.1/24 ge20
For more information about this command, see “IP ROUTE” on page 132.
The Network Time Protocol (NTP) is used to configure the time on the
switch by setting the IP address of an NTP server and setting a key to
ensure the proper NTP server has access to the switch. In addition, an
NTP server ensures that the time on the switch is set using the Greenwich
Mean Standard.
Note
You must have access to an NTP server to use this feature. Allied
Telesis does not provide an NTP server.
29
Page 30

Chapter 2: Configuring the AT-S100 Software
Setting the NTP Server Address
Setting an NTP server allows the switch to have an official time. The basic
syntax of this command is:
ntp server xxx.xxx.xxx.xxx
To set the IP address of an NTP server to 198.10.1.1, enter the following
commands:
switch# configure terminal
switch(config)# ntp server 198.10.1.1
For more information about this command, see “NTP SERVER” on
page 148.
Turning on NTP Authentication
After you have assigned an NTP server, you can turn on NTP
authentication. The basic syntax of this command is:
ntp authenticate
To turn on NTP authentication, enter the following commands:
switch# configure terminal
switch(config)# ntp authenticate
For more information about this command, see “NTP AUTHENTICATE”
on page 145.
Configuring an NTP Trusted Key
You may want to configure an NTP Trusted key as a security measure to
verify that the NTP server that you have allowed to access your switch is
the one you specified.
The basic syntax of this command is:
ntp trusted-key <1-xx>
To configure an NTP trusted key, enter the following commands:
switch# configure terminal
30
switch(config)# ntp trusted-key
For more information about this command, see “NTP TRUSTED-KEY” on
page 150.
Page 31

AT-S100 Management Software User’s Guide
Increasing Frame
Size (Jumbo
Frames)
Saving the
Configuration
The jumbo frame command allows an interface on the switch to accept
large or jumbo frames which are Ethernet frames with greater than 1,500
bytes of payload (MTU). The syntax of the jumbo frame command is:
mtu <64-9216>
To allow jumbo frames to be accepted by port 7, enter the following
commands:
switch# configure terminal
switch(config)# interface ge7
switch(config-if)# mtu 1518
For more information about this command, see “MTU” on page 178.
To save the current configuration of your switch, use the COPY command.
The syntax of this command is:
copy running-config startup-config
In the following example, the running configuration file is copied to the
startup configuration file which is named “startup-config.”
Adding a User
Name and
Password
The software displays:
Building configuration...
[OK]
For more information about this command, see “COPY” on page 81.
To add new users to the switch, you create a user name, determine a
privilege level, and assign a password. These tasks are accomplished with
the USERNAME command. The syntax of this command is:
username WORD privilege <1-15> password LINE <8>
Note
By default, the AT-S100 software provides one USERNAME named
“manager” with “friend” as the default password. A manager login
has permission to perform all of the AT-S100 software commands in
all of the command modes.
privilege Specifies a user privilege level. Enter a value between 1 and
15. Values 1 through 14 provide operator privileges. Value 15
provides an administrator, or manager, privileges.
31
Page 32

Chapter 2: Configuring the AT-S100 Software
LINE Specifies a password for an administrator or manager. Enter
The following commands set the user name to “faye,” the privilege to “15,”
and the password to “friend:”
switch#configure terminal
switch(config)#username faye privilege 15 password
friend
For more information about this command, see “USERNAME” on
page 162.
an alphanumeric value between 1 and 8 characters in length.
Displaying and
Setting MAC
Addresses
A media access control (MAC) address is a unique number assigned to
every network card by the manufacturer. The AT-S100 software keeps
track of the MAC addresses of devices that have passed traffic through
the switch in a MAC address table. There is an 8K limit of MAC addresses
that you can store in the table. As a result, the MAC address table is
flushed automatically in time intervals determined by the ageing time.
In addition, you can enter a MAC address into the table that cannot be
flushed. This type of address is called a static MAC address. You may
want to assign a static MAC address when you have a closed LAN that is
not connected to the Internet.
The following sections explain how to display and set the MAC address
table:
“Displaying the Full MAC Address Table” on page 32
“Displaying the MAC Address Ageing Time” on page 33
“Clearing the MAC Address Table” on page 33
“Setting the Aging Time” on page 33
“Adding a Static MAC Address” on page 34
“Removing a Static MAC Address” on page 34
32
Displaying the Full MAC Address Table
The full MAC address table includes the following information:
All static MAC addresses
All dynamic MAC addresses
MAC addresses assigned to a port
MAC addresses assigned to a VLAN
The syntax of this command is:
show mac address-table
Page 33

AT-S100 Management Software User’s Guide
To display the full MAC address table, enter the following command:
switch#show mac address-table
For more information about this command, including a sample display see
“SHOW MAC ADDRESS-TABLE” on page 92.
Displaying the MAC Address Ageing Time
As stated above, the MAC address aging time indicates the time interval
when the MAC address table is flushed automatically.
The syntax of this command is:
sh mac address-table aging-time
To display the MAC address ageing time for the switch, enter the following
command:
switch#show mac address-table aging-time
For more information about this command, including a sample display, see
“SHOW MAC ADDRESS-TABLE AGEING-TIME” on page 94.
Clearing the MAC Address Table
You can remove the static, multicast, and static MAC addresses from the
MAC address table. The syntax of this command is:
clear mac address-table dynamic|static|multicast
To remove all of the dynamic commands from the MAC address table
enter the following commands:
switch# configure terminal
switch(config)# clear mac address-table dynamic
For more information about this command, see “CLEAR MAC ADDRESSTABLE DYNAMIC” on page 73.
Setting the Aging Time
The MAC address ageing time is set for the switch instead of a port. By
default, the ageing time is set to 300 seconds. The syntax of this command
is:
mac address-table ageing-time (10-1000000)
To set the ageing time to 35 seconds, enter the following commands:
switch# configure terminal
33
Page 34

Chapter 2: Configuring the AT-S100 Software
switch(config)# mac address-table ageing-time 35
For more information about this command, see “MAC ADDRESS-TABLE
AGEING-TIME” on page 138.
Adding a Static MAC Address
To add a static address to the MAC address table, specify the MAC
address, the assigned port number, and the VLAN ID. The syntax of this
command is:
mac address-table static (xxxxxxxxxxxx) forward
interface ge(1-28) vlan(2-4094)
To add a static MAC address, 5679AEB04324, on port 15 and VLAN 2 to
the MAC address table, enter the following commands:
switch# configure terminal
switch(config)# mac address-table static 5679AEB04324
forward interface ge15 vlan2
For more information about this command, see “MAC ADDRESS-TABLE
STATIC FORWARD” on page 141.
Removing a Static MAC Address
To remove a static address from the MAC address table you must specify
the MAC address, the assigned port number, and the VLAN ID. The
syntax of this command is:
mac address-table static (xxxxxxxxxxxx) discard
interface ge(1-28) vlan(2-4094)
To remove static MAC address, 5679AEB04322, from port 15 and VLAN
3, enter the following commands:
switch# configure terminal
switch(config)# mac address-table static 5679AEB04324
forward interface ge15 vlan3
For more information about this command, see “MAC ADDRESS-TABLE
STATIC DISCARD” on page 139.
34
Page 35

AT-S100 Management Software User’s Guide
Rebooting the
Switch
Resetting Switch
to Factory
Default Values
To reboot the switch, enter the following command:
switch# system reboot
When you enter this command the switch temporarily loses power and will
the current session is lost. To start a new session on the switch, log in
again.
For more information about this command, see “SYSTEM REBOOT” on
page 112.
To reset the AT-S100 software to its factory default values, enter the
following command:
switch# system factory-reset
Warning
This command does not save your current configuration. To save
your current configuration, see “COPY DEFAULT.CFG” on page 84.
For more information about this command, see “SYSTEM FACTORYRESET” on page 111.
Upgrading or
Downgrading
Software
To upgrade an AT-9000 switch with the latest version of the AT-S100
software, you need to download the software onto your switch with an
TFTP server. To obtain the latest version of the AT-S100 software, go to
our website, www.alliedtelesis.com and copy it on your PC.
You can use the following procedure to upgrade the AT-S100 software
image file to the latest version or downgrade the software to an earlier
version. However, it is unlikely that you would want to downgrade the
current version of the AT-S100 software to an earlier version.
Note
You do not need to upgrade the bootloader file.
Upgrading or Downgrading the AT-S100 Software with a TFTP
Server
Use the following procedure to upgrade or downgrade the AT-S100
software with a TFTP server.
1. Check the current software version installed on your switch, enter the
SHOW VERSION command.
See below for a sample output of the SHOW VERSION command:
(switch)#show version
Product ID=ATS100
35
Page 36

Chapter 2: Configuring the AT-S100 Software
2. Assign an IP address and subnet mask to the switch with the IP
Application Version=1.0.3
Application BuildTime=12:47:47
Application BuildDate=Nov 21 2008
Serial Number=
Model=AT-9000/28
Ethaddr=
Baudrate=9600
Uptime= 16:01:02 up 1 min, load average:
0.21, 0.08, 0.02
HwRev=B
ADDRESS A.B.C.D/mask command.
The following commands set VLAN 1 with the primary IP address and
mask of 192.0.0.1/8.
switch#configure terminal
switch(config)#interface vlan1
switch(config-if)#ip address 192.0.0.1/8
Caution
Make sure the IP address of the TFTP server is in the same subnet
as the IP address of the switch.
3. Save your configuration by entering the following command:
switch#copy running-config startup-config
4. Use the DOWNLOAD command to download the image file from the
TFTP server onto the switch.
The following command uses a TFTP server, with an IP address of
189.11.1.1, to download the “ATS100_ATI_v103.img” file onto the
switch:
switch#download tftp 189.11.1.1 ATS100_ATI_v103.img
The following is displayed:
36
TFTP IP 189.11.1.1, file name
ATS100_ATI_v103.img
Page 37

AT-S100 Management Software User’s Guide
Erasing 88 Sectors ...
Writing to flash ...
5. If you are downgrading the AT-S100 software to an earlier version, the
following confirmation message is displayed:
Current version of the image is newer. Download
anyway? (y/n)
6. Type “y” to allow the download to proceed.
7. Reboot the switch by entering the following command:
(switch)#system reboot
Uploading an
Image File
The most common reason to upload the image file of the AT-S100
software onto an TFTP server is to make a backup copy of the file. To
upload an image file, use the UPLOAD command. You must have the IP
address of the TFTP server to set this command.
You do not need to know the name of the image file on the switch to
upload it. The filename that you specify in the UPLOAD command
indicates the filename on the TFTP server. As a result, you can name it
anything you’d like as long as the suffix is “.img.”
Uploading an Image File with a TFTP Server
To upload an image file from the switch onto a TFTP server, use the
UPLOAD command. The basic syntax of this command is:
upload tftp xxx.xxx.xxx.xxx filename.img
Note
Create a dummy file on the TFTP server with the same file name as
the file on the switch that you want to upload before you enter the
UPLOAD command. If you do not first create the dummy file, you will
receive an error message. However, the file will upload successfully.
For example, to upload the image file from the switch onto a TFTP server
with an IP address of 192.58.48.10 and a file name of “at100v103.img,”
enter the following command:
switch# upload tftp 192.58.48.10 at100v103.img
The switch displays the following which indicates a successful upload
operation:
TFTP IP 192.58.48.10, file name at100v103.img
37
Page 38

Chapter 2: Configuring the AT-S100 Software
For more information about this command, see “UPLOAD TFTP” on
page 113.
Displaying and
Saving
Configuration
Files
This section describes how to display and save configuration files. These
files have a “.cfg” suffix. See the following sections:
“Displaying the Current Configuration” on page 38
“Saving the Current Configuration” on page 38
Displaying the Current Configuration
There are several ways to display the current configuration of the switch.
You can display the full running configuration of the switch, the running
configuration for a port, and the running configuration for a VLAN ID.
The syntax of this command is:
show running-config interface ge(1-28)| VLANID
To display the full running configuration, enter the following command in
any command mode:
switch# show running-config
In addition, you can display the running configuration for an interface such
as a port or a VLAN. To display the running configuration for port 4, enter
the following command in any command mode:
switch# show running-config interface ge4
To display the status of the current running configuration of a switch for
VLAN 2, enter the following command:
switch#show running-config interface vlan2
For more information about this command including a sample display, see
“SHOW RUNNING-CONFIG” on page 153.
Saving the Current Configuration
The AT-S100 software does not automatically save your changes. As a
result, you want to save your changes to the software frequently. To save
the current configuration to the startup configuration file, enter the
following command:
switch# copy running-config startup-config
For more information about this command, see “COPY” on page 81.
38
Page 39

AT-S100 Management Software User’s Guide
Copying
Configuration
Files
You may want to make a copy of a configuration file in order to have a
backup copy of the file. This section describes how you can make a copy a
configuration file and save it on your switch.
Copying a Configuration File
Use the CP command to make a copy of a configuration file and save it in
the current directory on the switch.
The syntax of CP command is:
cp sourcefile newfile
Note
The CP command does not save your current configuration onto the
switch. To save your current configuration, see the COPY command
described in the previous section.
In the following example, the running configuration file is copied to the
startup configuration file which is named “frank2.cfg:”
switch#cp default.cfg frank2.cfg
Uploading and
Downloading
Configuration
Files
For more information about this command, see “CP” on page 86.
Once you have made a copy of the configuration file on the switch, you
may want to upload it onto a TFTP server to create a backup copy. Or, you
can download a configuration file from a TFTP server onto the switch. See
the following sections for a description of these procedures.
You may want to upload a configuration file from your switch onto a
backup server. Or, you may want to upload a configuration file from your
switch to a TFTP server and then download it to other AT-9000 Series
switches. You must have the IP address of the TFTP server to set this
command.
Caution
Once you have copied a configuration file onto your PC, use the
Wordpad application to open a configuration file in Windows. Do not
use the Notepad application to open the file because it deletes all
line breaks.
Uploading A Configuration File onto a TFTP Server
Use the COPY DEFAULT.CFG command to upload a configuration file
from the switch onto an TFTP server.
39
Page 40

Chapter 2: Configuring the AT-S100 Software
Enter the following command to upload a configuration file called
“frank2.cfg” from the switch onto a TFTP server with an IP address of
192.58.48.1. The file on the TFTP server is called “at100v103.cfg:”
switch# copy frank2.cfg 192.58.48.1 at100v103.cfg
For more information about this command, see “COPY DEFAULT.CFG”
on page 84.
Downloading A Configuration File from an TFTP Server
To download a configuration file from a TFTP sever to the switch, use the
COPY A.B.C.D command. You may want to download a configuration file
from a backup server onto your switch. You must have the IP address of
the TFTP server to set this command.
To download a configuration file from an TFTP Server, do the following:
1. Enter the following command to download a configuration file called
“jenny3.cfg” from a TFTP server with an IP address of 192.58.48.1
onto your switch. The new file is called “at100v103.cfg.”
switch# copy 192.58.48.1 jenny3.cfg at100v103.cfg
The system responds with the following message:
% operation completed.
2. Reboot the switch to make the new configuration file the active
configuration file. Enter:
switch# system reboot
3. Log onto the switch with the username of “manager” and the password
“friend.”
For more information about this command, see “COPY A.B.C.D” on
page 82.
Creating VLANs A VLAN is a group of ports on an Ethernet switch that form a logical
Ethernet segment. The ports of a VLAN form an independent traffic
domain where the traffic generated by the nodes of a VLAN remains within
the VLAN.
With VLANs, you can segment your network through the switch’s AT-S100
Management Software and group nodes with related functions into their
own separate, logical LAN segments. These VLAN groupings can be
based on similar data needs or security requirements. For example, you
could create separate VLANs for the different departments in your
company, such as one for the sales department and another for the
accounting department.
40
Page 41

AT-S100 Management Software User’s Guide
A port-based VLAN is a group of ports on a Gigabit Ethernet Switch that
form a logical Ethernet segment. Each port of a port-based VLAN can
belong to only one VLAN at a time.
You need to specify which ports will be members of the VLAN. In the case
of a tagged VLAN, it is usually a combination of both untagged ports and
tagged ports. You specify which ports are tagged and which are untagged
when you create the VLAN.
An untagged port, whether a member of a port-based VLAN or a tagged
VLAN, can be in only one VLAN at a time. However, a tagged port can be
a member of more than one VLAN. A port can also be an untagged
member of one VLAN and a tagged member of different VLANs
simultaneously.
Creating a VLAN
Use the VLAN command to create a VLAN and enable it. The syntax of
this command is:
vlan <2-4094> name NAME state enable|disable
The following commands create VLAN 4 with a name of “Eng2” and
enables it:
switch# configure terminal
switch(config)# vlan database
switch(config-vlan)# vlan 2 name Eng2 state enable
For more information about this command, see “VLAN” on page 267.
Adding Untagged Ports to a VLAN
To add untagged ports to a VLAN, you must specify a VLAN that you have
created already. Also, you must specify a port in the Interface mode. The
syntax of this command is:
switchport access vlan VLANID <2-4094>
The following commands assign VLAN 2 to port 8:
switch#configure terminal
switch(config)#interface ge8
switch(config-if)#switchport access vlan 2
For more information about this command, see “SWITCHPORT ACCESS
VLAN” on page 187.
41
Page 42

Chapter 2: Configuring the AT-S100 Software
Adding Tagged Ports to a VLAN
To add tagged ports to a VLAN, you must specify a VLAN that you have
created already. You must specify a port in the Interface mode. The syntax
of this command is:
switchport trunk allowed vlan add|remove VLANID
The following commands add VLAN 6, to the member set of port 12:
switch#configure terminal
switch(config)#interface ge12
switch(config-if)#switchport mode trunk
switch(config-if)#switchport trunk allowed vlan add 6
For more information about this command, see “SWITCHPORT TRUNK
ALLOWED VLAN” on page 190.
42
Page 43

Setting the Ports
AT-S100 Management Software User’s Guide
See the following sections:
“Displaying Port Ethernet Statistics” on page 43
“Setting Port Mirroring” on page 43
“Setting Port Speed and Duplex Mode” on page 44
“Enabling and Disabling Ports” on page 45
“Setting MDI and MDIX” on page 45
“Setting Port Security” on page 46
“Creating Static Trunks” on page 49
“Enabling Backpressure” on page 50
“Enabling Flow Control” on page 50
“Preventing Broadcast Storms” on page 51
Displaying Port
Ethernet
Statistics
Setting Port
Mirroring
You may want to display the status of a port as well as configuration
information about a port on the switch. The syntax of this command is:
show interface ge(1-28)
To display the port ethernet statistics for port 17, enter the following
command:
switch# show interface ge17
See “SHOW INTERFACE” on page 90 for a sample display of this
command.
The port mirror feature allows for the unobtrusive monitoring of ingress or
egress traffic on one or more ports on a switch, without impacting network
performance or speed. It copies the traffic from a specified port to another
port where the traffic can be monitored with a network analyzer.
The port whose traffic is mirrored is called the source port. The port where
the traffic is copied to is referred to as the destination port. The syntax of
this command is:
mirror interface ge<1-28> direction
both|receive|transmit
To set port mirroring with port 5 as the source port and port 7 as the
destination port, enter the following commands:
switch# configure terminal
43
Page 44

Chapter 2: Configuring the AT-S100 Software
switch(config)# interface ge5
switch(config-if)# mirror ge7 direction receive
For more information about this command, see “MIRROR INTERFACE
DIRECTION” on page 176.
Setting Port
Speed and Duplex
Mode
A twisted pair port can operate in either half- or full-duplex mode. (Fullduplex mode is the only mode available when a port is operating at 1000
Mbps.) The twisted pair ports are IEEE 802.3u-compliant and AutoNegotiate the duplex mode setting.
You can disable Auto-Negotiation on one or all of the switch ports so that
you can set the duplex mode manually through the AT-S100 Management
Software.
Note
In order for a switch port to successfully Auto-Negotiate its duplex
mode with a 10 or 100 Mbps end node, the end node should also be
configured for Auto-Negotiation. Otherwise, a duplex mode
mismatch can occur. A switch port using Auto-Negotiation defaults
to half-duplex if it detects that the end node is not using AutoNegotiation. This results in a mismatch if the end node is operating
at a fixed duplex mode of full-duplex.
To avoid this problem when connecting an end node with a fixed
duplex mode of full-duplex to a switch port, use the AT-S100
Management Software to disable Auto-Negotiation on the local port
and set the port speed and duplex mode manually.
44
You can set both the port speed and the duplex mode for each port on the
switch. The syntax of this command is:
speed 10000mfull|1000mfull|100mfull|100mhalf|100fx|
10mfull|10mhalf|auto
To set port 28 to 100FX in full-duplex mode, enter the following
commands:
switch# configure terminal
switch(config)# interface ge28
switch(config-if)# speed 100fx
For more information about this command, see “SPEED” on page 182.
Page 45

AT-S100 Management Software User’s Guide
Enabling and
Disabling Ports
To enable or disable a port on the switch, use the SHUTDOWN command.
The syntax of this command is:
shutdown|no shutdown
To enable port 12, enter the following commands:
switch# configure terminal
switch(config)# interface ge12
switch(config-if)# shutdown
To disable port 19, enter the following commands:
switch# configure terminal
switch(config)# interface ge19
switch(config-if)# no shutdown
For more information about this command, see “SHUTDOWN” on
page 181.
Setting MDI and
MDIX
The twisted pair ports on the switch feature auto-MDI and MDIX. This
feature, available when a port’s speed and duplex mode are set through
Auto-Negotiation, configures a switch port to MDI or MDIX automatically,
depending on the wiring configuration of the port on the end node. This
feature allows you to connect any network device to a port on the switch
using a straight-through twisted pair cable.
If Auto-Negotiation is disabled on a port and the speed and duplex mode
are set manually, the auto-MDI/MDI-X feature is also disabled and the
port’s wiring configuration defaults to the MDI-X setting. This setting can
be configured with the AT-S100 Management Software.
The syntax of this command is:
mdix mdi|mdix
To set a port to MDI, enter the following commands:
switch# configure terminal
switch(config)# interface ge12
switch(config-if)# mdix mdi
45
Page 46

Chapter 2: Configuring the AT-S100 Software
To set a port to MDIX, enter the following commands:
switch# configure terminal
switch(config)# interface ge12
switch(config-if)# mdix mdix
For more information about this command, see “MDIX” on page 175.
Setting Port
Security
The Port Security feature is based on assigning and limiting MAC
addresses learned by a port. You can use the MAC-Address-based Port
Security feature to enhance the security of your network by controlling
which end nodes can forward frames through the switch, thereby
preventing unauthorized individuals from accessing your network. This
features uses a MAC address to determine whether the switch should
forward a frame or discard it. The source address is the MAC address of
the end node that sent the frame.
There are three levels of port security:
Limited Mode
Locked Mode
Secured Mode
You set port security on a per port basis. Only one security level can be
active on a port at a time.
Limited Mode
The Limited security mode allows you to specify the maximum number of
dynamic MAC addresses a port can learn. The port forwards only packets
of learned source MAC addresses and discards ingress frames with
unknown source MAC addresses.
46
When the Limited security mode is initially activated on a port, all dynamic
MAC addresses learned by the port are deleted from the MAC address
table. The port then begins to learn new addresses, up to the maximum
allowed. After the port has learned its maximum number of addresses, it
does not learn any new addresses, even when end nodes are inactive.
A dynamic MAC address learned on a port operating in the Limited
security mode never times out from the MAC address table, even when
the corresponding end node is inactive.
Static MAC addresses are retained by the port and are not included in the
count of maximum dynamic addresses. You can continue to add static
MAC addresses to a port operating with this security level, even after the
port has already learned its maximum number of dynamic MAC
addresses.
Page 47

AT-S100 Management Software User’s Guide
Locked Mode
A port set to the Locked mode security level immediately stops learning
new dynamic MAC addresses and forwards frames using the dynamic
MAC addresses it has already learned and any static MAC addresses
assigned to it. Ingress frames with an unknown MAC address are
discarded. Dynamic MAC addresses already learned by a port prior to the
activation of this security level never time out from the MAC address table,
even when the corresponding end nodes are inactive.
You can continue to add new static MAC addresses to a port operating
under this security level.
Secured Mode
The Secured Mode security level uses only static MAC addresses
assigned to a port to forward frames. Consequently, only those end nodes
whose MAC addresses are entered as static addresses are able to
forward frames through a port. Dynamic MAC addresses already learned
on a port are discarded from the MAC table and no new dynamic
addresses are added. Any ingress frames having a source MAC address
not entered as a static address on a port are discarded.
After activating this security level, you must enter the static MAC
addresses of the end nodes that are to forward frames through the port.
MAC Address Maximum
In addition, you can set the maximum number of MAC addresses that can
be learned by a port as well as specific secure MAC addresses that can be
learned by a port.
Once the limit of MAC addresses is reached for the port specified, the
action taken by the software is determined by the setting of the
SWITCHPORT PORT-SECURITY VIOLATION command. There are 3
possible responses to a violation:
Protect
Restrict
Shutdown
Setting the Maximum Number of MAC Addresses
To limit the number of MAC addresses that can be learned by a port, use
the SWITCHPORT PORT-SECURITY MAXIMUM command.
The syntax of this command is:
switchport port-security maximum <1-320>
47
Page 48

Chapter 2: Configuring the AT-S100 Software
To set the maximum number of MAC addresses to 140 on port 8, enter the
following commands:
switch# configure terminal
switch(config)# interface ge8
switch(config-if)#switchport port-security maximum 140
For more information about this command, see “” on page 189.
Assigning Secure MAC Addresses
Assigning the predefined MAC addresses that can be learn on a port,
allows you to limit the devices that can access the port.
The syntax of this command is:
switchport port-security mac address xxxx.xxxx.xxxx
vlan <2-4094>
To add a secure predefined mac address of 00A0.0490.10E0 to port 21
which is assigned to VLAN 3, enter the following commands:
switch# configure terminal
switch(config)# interface ge21
switch(config-if)#switchport port-security mac address
00A0.0490.10E0 vlan 3
For more information about this command, see “” on page 189.
Setting the Port Security Mode
The Port Security Mode determines how a port responds to an undefined
MAC address. The syntax of this command is:
switchport port-security mode limited|locked|secured
To set the port security mode to limited on port 17, enter the following
commands:
switch# configure terminal
48
switch(config)# interface ge17
switch(config-if)#switchport port-security mode
limited
For more information about this command, see “SWITCHPORT PORTSECURITY MODE” on page 223.
Page 49

AT-S100 Management Software User’s Guide
Setting Port Security Violation
The Port Security Violation Feature determines how the AT-S100 software
reacts when the number of port secure MAC addresses reaches the
maximum value set in the SWITCHPORT PORT-SECURITY MAXIMUM
command (see “Setting the Maximum Number of MAC Addresses” on
page 47.)
The syntax of SWITCHPORT PORT-SECURITY VIOLATION command
is:
switchport port-security violation
protect|restrict|shutdown
To set the port security violation mode on port 20 to restrict, enter the
following commands:
switch# configure terminal
switch(config)# interface ge20
Creating Static
Trunks
switch(config-if)#switchport port-security violation
restrict
For more information about this command, see “SWITCHPORT PORTSECURITY VIOLATION” on page 225.
A static port trunk is a group of two to eight ports that function as a single
virtual link between the switch and another device. Traffic is distributed
across the ports to improve performance and enhance reliability by
reducing the reliance on a single physical link.
To configure a static port trunk, you designate the ports of the trunk and
the management software groups them together automatically. You can
also control how traffic is distributed over the trunk ports.
The syntax of the static trunk command is:
static-channel-group<1-8>
For example, to assign port 8 to static port trunk 2, enter the following
commands:
switch# configure terminal
switch(config)# interface ge8
switch(config-if)# static-channel-group2
49
Page 50

Chapter 2: Configuring the AT-S100 Software
To display the static port trunk assigned to port 12, enter the following
commands:
switch# configure terminal
switch(config)# interface ge12
switch(config-if)# show static-channel-group9
For more information about this command, see “STATIC-CHANNELGROUP” on page 184.
Enabling
Backpressure
To maintain the orderly movement of data between the end nodes, an
Ethernet switch may periodically need to signal an end node to stop
sending data. This can occur under several circumstances. For example, if
two end nodes are operating at different speeds, the switch, while
transferring data between the end nodes, might need to instruct the faster
end node to stop transmitting data to allow the slower end node to catch
up. An example of this would be when a server operating at 100 Mbps is
sending data to a workstation operating at only 10 Mbps.
How a switch signals an end node to stop transmitting data differs
depending on the speed and duplex mode of the end node and switch
port. A twisted pair port operating at 100 Mbps and half-duplex mode
stops an end node from transmitting data by forcing a collision. A collision
on an Ethernet network occurs when two end nodes attempt to transmit
data using the same data link at the same time. A collision causes end
nodes to stop sending data. To stop a 100 Mbps, half-duplex end node
from transmitting data, the switch forces a collision on the data link, which
stops the end node. When the switch is ready to receive data again, the
switch stops forcing collisions. This is referred to as back pressure.
The syntax of this command is:
flowcontrol backpressure on|off
Enabling Flow
50
Control
To active the backpressure feature on port 3, enter the following
commands:
switch# configure terminal
switch(config)# interface ge3
switch(config-if)# flowcontrol backpressure on
For more information about this command, see “FLOW CONTROL
BACKPRESSURE” on page 168.
Flow control enables connected Ethernet ports (or interfaces) to control
traffic rates during congestion by allowing congested nodes to pause link
operation at the other end. If one port experiences congestion and cannot
Page 51

AT-S100 Management Software User’s Guide
receive any more traffic, it notifies another port to stop sending traffic until
the condition clears. When the local device detects congestion at its end, it
notifies the remote device by sending a pause frame. After the remote
device receives a pause frame, the remote device stops sending data
packets. Flow control prevents the loss of data packets during the
congestion period.
The flow control command determines whether flow control is set to
transmit or receive on a port. Flow control is set on a per port basis. The
basic command syntax is:
flowcontrol send|receive on|off
To set the flow control to transmit on port 7, enter the following commands:
switch# configure terminal
switch(config)# interface ge7
switch(config-if)# flowcontrol send on
Preventing
Broadcast Storms
For more information about this command, see “FLOW CONTROL SEND”
on page 170.
To set the flow control to receive on port 8, enter the following commands:
switch# configure terminal
switch(config)# interface ge8
switch(config-if)# flowcontrol receive on
For more information about this command, see “FLOW CONTROL
RECEIVE” on page 169.
Flooding techniques are used to block the forwarding of unnecessary
flooded traffic. A packet storm occurs when a large number of broadcast
packets are received on an interface. Forwarding these packets can cause
the network to slow down or timeout.
Use the STORM-CONTROL command to specify the rising threshold level
for broadcasting, multicast, or destination-lookup-failure traffic. The storm
control action occurs when traffic reaches the level specified with the
LEVEL parameter. By default, storm control is disabled.
To prevent broadcast storms, enter the following commands:
switch# configure terminal
switch(config)# interface ge2
51
Page 52

Chapter 2: Configuring the AT-S100 Software
switch(config-if)#storm-control broadcast level (0.0-
100.0)
To prevent multicast storms, enter the following commands:
switch# configure terminal
switch(config)# interface ge2
switch(config-if)# storm-control multicast level (0.0-
100.0)
To configure for destination-lookup-failure traffic, enter the following
commands:
switch# configure terminal
switch(config)# interface ge2
switch(config-if)# storm-control dlf level (0.0-100.0)
For more information about this command, see “STORM-CONTROL” on
page 185.
52
Page 53

Configuring Protocols
This section describes how to set the protocols that are supported by the
AT-S100 Management Software. See the following sections:
“Setting GVRP” on page 53
“Enabling IGMP Snooping” on page 55
“Setting the Link Access Control Protocol (LACP)” on page 56
“Setting 802.1x Port Authentication” on page 56
“Configuring RADIUS Authentication” on page 58
“Setting Simple Network Management Protocol (SNMP)” on page 59
“Setting the Secure Shell” on page 62
“Setting STP and RSTP” on page 62
“Configuring 802.1p Class of Service” on page 67
AT-S100 Management Software User’s Guide
Setting GVRP The GARP VLAN Registration Protocol (GVRP) allows network devices to
share VLAN information. The main purpose of GVRP is to allow switches
to automatically discover some of the VLAN information that would
otherwise need to be manually configured in each switch. This is helpful in
networks where VLANs span more than one switch. Without GVRP, you
must manually configure your switches to ensure that the various parts of
a VLAN can communicate across the different switches. GVRP, which is
an application of the Generic Attribute Registration Protocol (GARP), does
this for you automatically.
The AT-S100 Management Software uses GVRP protocol data units
(PDUs) to share VLAN information among GVRP-active devices. The
PDUs contain the VID numbers of the VLANs on the switch. A PDU
contains the VIDs of all the VLANs on the switch, not just the VID of which
the transmitting port is a member.
When a switch receives a GVRP PDU on a port, it examines the PDU to
determine the VIDs of the VLANs on the device that sent it.
Enabling or Disabling GVRP
By default, the GVRP feature is disabled. The syntax of the command is:
set gvrp enable|disable
To enable the GVRP feature, enter the following commands:
switch# configure terminal
switch(config)# set gvrp enable
53
Page 54

Chapter 2: Configuring the AT-S100 Software
To disable the GVRP feature, enter the following commands:
switch# configure terminal
switch(config)# set gvrp disable
For more information about this command, see “SET GVRP” on page 212.
Setting the GVRP Applicant State
By setting the GVRP applicant state, you permit a port to process GVRP
information and transmit PDUs. The GVRP APPLICANT command sets
the GID applicant state on a port to active or normal. The syntax of this
command is:
set gvrp applicant state active|normal ge<1-28>
To set the GID applicant on port 5 to an active state enter the following
commands:
switch#configure terminal
switch(config)#set gvrp applicant state active ge5
For more information about this command, see “SET GVRP APPLICANT”
on page 213.
Enabling Dynamic VLANs
To enable dynamic VLANs to be created on the switch, use the GVRP
DYNAMIC-VLAN-CREATION command. The syntax of this command is:
set gvrp dynamic-vlan-creation
The following commands allow GVRP VLANs to be created dynamically:
switch#configure terminal
switch(config)#set gvrp dynamic-vlan-creation
For more information about this command, see“SET GVRP DYNAMICVLAN-CREATION” on page 214
Setting GVRP Registration
You can allow manual creation of VLANs (fixed), deregister all existing
VLANs with the exception of VLAN 1 (forbidden), and allow dynamic
VLAN creation on a per port basis (normal).
54
The syntax of this command is:
set gvrp registration fixed|forbidden|normal ge<1-28>
Page 55

AT-S100 Management Software User’s Guide
The following commands set GVRP registration to fixed on port 12:
switch#configure terminal
switch(config)#set gvrp registration fixed ge12
For more information about this command, see “SET GVRP
REGISTRATION” on page 215.
Setting Join and Leave Timers
To set the GARP timers to join or leave a group, use the SET GVRP
TIMER command. The syntax of this command is:
set gvrp timer join|leave|leaveall <1-65535> ge<1-28>
The following commands set the leave timer to 0.5 seconds for all GVRP
applications on port 9:
switch#configure terminal
Enabling IGMP
Snooping
switch(config)#set gvrp timer leave 50 seconds ge9
For more information about this command, see “SET GVRP TIMER” on
page 217.
IPv4 routers use IGMP to create lists of nodes that are members of
multicast groups. (A multicast group is a group of end nodes that want to
receive multicast packets from a multicast application.) The router creates
a multicast membership list by periodically sending out queries to the local
area networks connected to its ports. The syntax of this command is:
no|ip igmp snooping
To enable IGMP, enter the following commands:
switch# config t
switch(config)# ip igmp snooping
To disable IGMP, enter the following commands:
switch# config t
switch(config)# no ip igmp snooping
55
Page 56

Chapter 2: Configuring the AT-S100 Software
Setting the Link
Access Control
Protocol (LACP)
LACP (Link Aggregation Control Protocol) port trunks perform the same
function as static trunks. They increase the bandwidth between network
devices by distributing the traffic load over multiple physical links. The
advantage of an LACP trunk over a static port trunk is its flexibility. While
implementations of static trunking tend to be vendor specific, the
implementation of LACP in the AT-S100 Management Software is
compliant with the IEEE 802.3ad standard, making it interoperable with
equipment from other vendors that also comply with the standard.
Therefore, you can create an LACP trunk between an Allied Telesis
device and network devices from other manufacturers.
Another advantage is that ports in an LACP trunk can function in a
standby mode. This adds redundancy and resiliency to the trunk. If a link
in a static trunk goes down, the overall bandwidth of the trunk is reduced
until the link is reestablished or another port is added to the trunk. In
contrast, an LACP trunk can automatically activate ports in a standby
mode when an active link fails so that the maximum possible bandwidth of
the trunk is maintained.
The syntax of this command is:
channel-group (1-10) mode active|passive
Setting 802.1x
Port
Authentication
To configure LACP on port 12 and channel group 1, enter the following
commands:
switch# config t
switch(config)# interf ge12
switch(config-if)# channel-group 1 mode active
To disable LACP on port 7 and channel group 2, enter the following
commands:
switch# config t
switch(config)# interf ge7
switch(config-if)# no channel-group 2 mode passive
The AT-S100 Management Software has several different methods for
protecting your network and its resources from unauthorized access. One
method is 802.1x port-based network access control which uses the
RADIUS protocol to control who can send traffic through and receive
traffic from a switch port. The switch does not allow an end node to send
or receive traffic through a port until the user of the node has been
authenticated by a RADIUS server.
56
The benefit of this type of network security is that you can prevent
unauthorized individuals from connecting a computer to a switch port or
Page 57

AT-S100 Management Software User’s Guide
using an unattended workstation to access your network resources. Only
those users designated as valid network users on the RADIUS server are
permitted to use the switch to access the network.
The switch implements the server side of the IEEE 802.1x Port-based and
MAC-based Network Access Control. This feature allows only authorized
users, or their network devices, access to network resources by
establishing criteria for each interface on the switch.
Displaying 802.1x Port Authentication Status
Displaying the status of the 802.1x Port Authentication feature on the
switch provides the following information:
802.1x Port Authentication status (enabled or disabled)
RADIUS server IP address
RADIUS client IP address
Next RADIUS message ID
The syntax of this command is:
show dot1x
To display the status of the 802.1x Port Authentication feature, enter the
following command:
switch#show dot1x
For more information about this command including a display, see “SHOW
DOT1X” on page 203.
Setting 802.1x Port Authentication
To set 802.1x Port Authentication with a RADIUS server host of
192.168.1.30 and a shared secret key between the RADIUS server and a
client of “Encrypt112,” enter the following commands:
switch# configure terminal
switch(config)# dot1x system-auth-ctrl
switch(config)# interface ge12
switch(config-if)# dot1x port-control auto
switch(config-if)# exit
switch(config)# radius-server host 192.168.1.30
switch(config)# radius-server key Encrypt112
57
Page 58

Chapter 2: Configuring the AT-S100 Software
For more information about the 802.1x commands, see Chapter 6, “802.1x
Access Control Commands” on page 197.
Configuring
RADIUS
Authentication
For those networks managed by just one or two network managers, you
might not need any additional accounts. In the case of larger networks that
are managed by several network managers, you may want to give each
manager his or her own management login account for a switch rather
than have them share an account.
This is where authentication protocols such as RADIUS can be useful.
RADIUS is an acronym for Remote Authentication Dial In User Services.
You can use RADIUS to transfer the task of validating management
access from the switch to an authentication protocol server, enabling you
to create your own manager accounts.
With RADIUS you can create a series of username and password
combinations that define who can manage the switch.
There are three basic functions an authentication protocol provides:
Authentication
Authorization
Accounting
When a network manager logs in to a switch to manage the device, the
switch passes the username and password entered by the manager to the
authentication protocol server. The server checks to see if the username
and password are valid. This is referred to as authentication.
58
If the combination is valid, the authentication protocol server notifies the
switch and the switch completes the login process, allowing the manager
to manage the switch.
If the username and password are invalid, the authentication protocol
server notifies the switch and the switch cancels the login.
Authorization defines what a manager can do after logging in to a switch.
The final function of an authentication protocol is keeping track of user
activity on network devices, referred to as accounting. The AT-S100
Management Software does not support RADIUS accounting as part of
manager accounts.
Note
This manual does not explain how to configure a RADIUS server.
For instructions, refer to the documentation included with the
RADIUS server software.
Page 59

AT-S100 Management Software User’s Guide
Setting RADIUS Authentication
To set RADIUS authentication with a RADIUS-server host of
192.168.1.30, a shared secret key of “Encrypt112,” and RADIUS
password checking turned on, enter the following commands:
switch# configure terminal
switch(config)# radius-server host 192.168.1.30 authport 1812
switch(config)# radius-server key Encrypt112
switch(config)# line console 0
switch(config-line)# login remotelocal
For more information about the 802.1x commands, see Chapter 6, “802.1x
Access Control Commands” on page 197.
Setting Simple
Network
Management
Protocol (SNMP)
You can manage a switch by viewing and changing the management
information base (MIB) objects on the device with the Simple Network
Management Program (SNMP). The AT-S100 Management Software
supports SNMPv1 and SNMPv2c protocols.
To manage a switch using an SNMP application program, you must do the
following:
Activate SNMP management on the switch. The default setting for
SNMP management is disabled.
Load the Allied Telesis MIBs for the switch onto your management
workstation containing the SNMP application program. The MIBs are
available from the Allied Telesis web site at www.alliedtelesis.com.
To manage a switch using SNMP, you need to know the IP address of the
switch or of the master switch of an enhanced stack and at least one of the
switch’s community strings.
Enabling and Disabling SNMP
You enable and disable the SNMP protocol on the switch. The syntax of
this command is:
no|snmp-server enable
To enable the SNMP protocol, enter the following commands:
switch# configure terminal
switch(config)# snmp-server enable
59
Page 60

Chapter 2: Configuring the AT-S100 Software
To disable the SNMP protocol, enter the following commands:
switch# configure terminal
switch(config)# no snmp-server enable
For more information about this command, see “SNMP-SERVER
ENABLE” on page 232.
Creating an SNMP Contact Name
The SNMP contact name is a person who is to be contacted in case of
questions about your SNMP implementation, an email address, or an IP
address for the SNMP system. The syntax of this command is:
snmp-server contact “John Smith”
To create an SNMP contact name of John Smith, enter the following
commands:
switch# configure terminal
switch(config)# snmp-server contact “John Smith”
For more information about this command, see “SNMP-SERVER
CONTACT” on page 230.
Creating SNMP Communities
SNMP Communities have several attributes, including a name and an
access mode. A community name must have a name of one to eight
alphanumeric characters. Spaces are allowed.
The access mode attribute defines the permissions of a community string.
There are two access modes: Read and Read/Write. A community string
with an access mode of Read can only be used to view (but not change
the MIB objects on a switch). A community string with a Read/Write
access can be used to both view the MIB objects and change them.
The AT-S100 Management Software provides two default community
strings: public and private. The public string has an access mode of just
Read and the private string has an access mode of Read/Write. If you
activate SNMP management on the switch, delete or disable the private
community string, which is a standard community string in the industry, or
change its status from open to closed to prevent unauthorized changes to
the switch.
60
The syntax of this command is:
snmp-server community <community name> <ro|rw|view>
Page 61

AT-S100 Management Software User’s Guide
To create an SNMP community called public with an access level of Read
only, enter the following commands:
switch# configure terminal
switch(config)# snmp-server community public ro
For more information about this command, see “SNMP-SERVER
COMMUNITY” on page 228.
Adding Management and Trap Receiver Addresses
A trap is a signal sent to one or more management workstations by the
switch to indicate the occurrence of a particular operating event on the
device. There are numerous operating events that can trigger a trap. For
instance, resetting the switch or the failure of a cooling fan are two
examples of occurrences that cause a switch to send a trap to the
management workstations. You can use traps to monitor activities on the
switch.
Trap receivers are the devices, typically management workstations or
servers, that you want to receive the traps sent by the switch. You specify
the trap receivers by their IP addresses. You assign the IP addresses to
the community strings.
Each community string can have up to eight trap IP addresses.
It does not matter which community strings you assign your trap receivers.
When the switch sends a trap, it looks at all the community strings and
sends the trap to all trap receivers on all community strings. This is true
even for community strings that have a access mode of only Read.
If you are not interested in receiving traps, then you do not need to enter
the IP addresses of trap receivers.
To add a management and trap receiver IP address, enter the following
commands:
switch# config t
switch(config)# snmp-server host <ip address> version
1|2c <community name> traps
snmp-server host 192.168.1.2 version 1 public
snmp-server host 192.168.1.2 version 1 trap
For more information about all of the SNMP commands, see Chapter 9,
“Simple Network Management Protocol (SNMP) Commands” on page
227.
61
Page 62

Chapter 2: Configuring the AT-S100 Software
Setting the Secure
Shell
Secure management is increasingly important in modern networks, as the
ability to easily and effectively manage switches and the requirement for
security are two universal requirements. Switches are often remotely
managed using remote sessions via the Telnet protocol. This method,
however, has a serious security problem—it is only protected by plaintext
usernames and passwords which are vulnerable to wiretapping and
password guessing.
The Secure Shell (SSH) protocol provides encrypted and strongly
authenticated remote login sessions, similar to the Telnet and rlogin
protocols, between a host running a Secure Shell server and a machine
with a Secure Shell client.
The syntax of this command is:
crypto key generate userkey USERNAME rsa <768-32768>
To generate a 2048-bit RSA user key for SSH version 2 connections for a
user named “mel,” enter the following commands:
switch#configure terminal
switch(config)#crypto key generate userkey mel rsa
2048
Setting STP and
RSTP
For more information about this command, see “CRYPTO KEY
GENERATE USERKEY” on page 121.
The performance of a Ethernet network can be negatively impacted by the
formation of a data loop in the network topology. A data loop exists when
two or more nodes on a network can transmit data to each other over
more than one data path. The problem that data loops pose is that data
packets can become caught in repeating cycles, referred to as broadcast
storms, that needlessly consume network bandwidth and can significantly
reduce network performance.
STP and RSTP prevent data loops from forming by ensuring that only one
path exists between the end nodes in your network. Where multiple paths
exist, these protocols place the extra paths in a standby or blocking mode,
leaving only one main active path.
STP and RSTP can also activate a redundant path if the main path goes
down. So not only do these protocols guard against multiple links between
segments and the risk of broadcast storms, but they can also maintain
network connectivity by activating a backup redundant path in case a main
link fails.
Where the two protocols differ is in the time each takes to complete the
process referred to as convergence. When a change is made to the
network topology, such as the addition of a new bridge, a spanning tree
protocol must determine whether there are redundant paths that must be
62
Page 63

AT-S100 Management Software User’s Guide
blocked to prevent data loops, or activated to maintain communications
between the various network segments. This is the process of
convergence.
With STP, convergence can take up to a minute to complete in a large
network. This can result in the loss of communication between various
parts of the network during the convergence process, and the subsequent
lost of data packets.
RSTP is much faster. It can complete a convergence in seconds, and so
greatly diminish the possible impact the process can have on your
network.
Only one spanning tree protocol can be active on the switch at a time. The
default is RSTP.
Setting the Spanning Tree Mode
As mentioned above, the default setting for the spanning tree mode is
RSTP. To change the current spanning tree mode setting, use the
SPANNING-TREE MODE command. The syntax of this command is:
spanning-tree mode stp|rstp
To set the spanning tree mode to STP, enter the following commands:
switch# configure terminal
switch(config)# spanning-tree mode stp
For more information about this command, see “SPANNING-TREE
MODE” on page 252.
Displaying Spanning Tree Settings
The spanning tree display includes the following information:
Bridge setting
Root Path Cost
Root Port
Bridge Priority
Forward Delay time
Hello time
Maximum Age
Root ID
63
Page 64

Chapter 2: Configuring the AT-S100 Software
The syntax of this command is:
show spanning-tree
To display the current spanning tree settings for the STP mode, enter the
following commands:
switch# configure terminal
switch(config)# spanning-tree mode stp
switch(config)# show spanning-tree
For more information about this command including a display, see “SHOW
SPANNING-TREE” on page 244.
Enabling or Disabling the Spanning Tree Mode
To enable or disable the spanning tree mode on the switch, use the
SPANNING-TREE ENABLE FORWARD command. The syntax of this
command is:
spanning-tree stp|rstp enable forward
To enable STP, enter the following commands:
switch# configure terminal
switch(config)# spanning-tree stp enable forward
To disable the RSTP on the switch, enter the following commands:
switch# configure terminal
switch(config)# no spanning-tree rstp enable forward
For more information about this command, see “SPANNING-TREE
ENABLE FORWARD” on page 247.
Setting Spanning-Tree Priority
Use the SPANNING-TREE PRIORITY command to specify the interface
priority for the switch. A lower priority value indicates a greater likelihood
of becoming a root. The default value is 32,768.
The syntax of this command is:
64
spanning-tree priority (0-61440)
Page 65

AT-S100 Management Software User’s Guide
The following commands set the spanning-tree priority on the switch to
8,192:
switch#configure terminal
switch(config)#spanning-tree priority 8192
For more information about this command, see “SPANNING-TREE
PRIORITY” on page 255.
Setting the Max Age
The max-age is the maximum time, in seconds, which a message is
considered valid (if a bridge is the root bridge). This setting prevents the
frames from looping indefinitely. This value is used by all instances.
The syntax of this command is:
spanning-tree max-age (6-40)
The following commands set the max-age time for the bridge to 30
seconds:
switch#configure terminal
switch(config)#spanning-tree max-age 30
For more information about this command, see “SPANNING-TREE MAXAGE” on page 251
Setting the Forward Time
Use the SPANNING-TREE FORWARD-TIME command to set the time,
after which each interface changes to the learning and forwarding states (if
this bridge is the root bridge). This value is measured in seconds and it is
used by all instances. The syntax of this command is:
spanning-tree forward-time (4-30)
The following commands set the forward delay time to 10 seconds:
switch#configure terminal
switch(config)#spanning-tree forward-time 10
For more information about this command, see “SPANNING-TREE
FORWARD-TIME” on page 249.
Setting the Hello Time
The hello-time is the time, in seconds, after which all the bridges in a
bridged LAN exchange Bridge Protocol Data Units (BPDUs). For this to
65
Page 66

Chapter 2: Configuring the AT-S100 Software
occur, the current bridge must be the root bridge. A very low value of this
command leads to excessive traffic on the network, while a higher value
delays the detection of topology change. This value is used by all
instances.
The syntax of this command is:
spanning-tree hello-time (1-10)
The following commands set the hello delay time to 5 seconds:
switch#configure terminal
switch(config)#spanning-tree hello-time 5
For more information about this command, see “SPANNING-TREE
HELLO-TIME” on page 250.
Setting the BPDU Filter
The Spanning Tree Protocol sends BPDUs from all interfaces. Enabling
the BPDU filter ensures that portfast-enabled interfaces do not transmit or
receive any BPDUs. Use the SPANNING-TREE BPDU-FILTER DEFAULT
command to globally enable the BPDU filter on a bridge.
The syntax of this command is:
spanning-tree portfast bpdu-filter default
The following commands enable the BPDU filter on a bridge:
switch#configure terminal
switch(config)#spanning-tree portfast bpdu-filter
default
For more information about this command, see “SPANNING-TREE
PORTFAST BPDU-FILTER DEFAULT” on page 253.
Setting the BPDU Guard
When the BPDU guard feature is set for a bridge, all portfast-enabled
interfaces of the bridge that have the BPDU guard set to default shut down
the interface on receiving a BPDU. In this case, the BPDU is not
processed. You can bring the interface up manually by using the NO
SHUTDOWN command. See “SHUTDOWN” on page 181.
Use the SPANNING-TREE BPDU-GUARD DEFAULT command to enable
the BPDU (Bridge Protocol Data Unit) guard feature on a bridge. This
command indicates the bridge level BPDU-Guard configuration takes
effect.
66
Page 67

AT-S100 Management Software User’s Guide
The syntax of this command is:
spanning-tree portfast bpdu-guard default
The following commands enable the BPDU Guard feature on a bridge:
switch#configure terminal
switch(config)#spanning-tree portfast bpdu-guard
For more information about this command, see “SPANNING-TREE
PORTFAST BPDU-GUARD DEFAULT” on page 254.
Configuring
802.1p Class of
Service
When a port on an Ethernet switch becomes oversubscribed—its egress
queues contain more packets than the port can handle in a timely
manner—the port may be forced to delay the transmission of some
packets, resulting in the delay of packets reaching their destinations. A
port may be forced to delay transmission of packets while it handles other
traffic. Some packets destined to be forwarded to an oversubscribed port
from other switch ports may be discarded.
Although minor delays are often of no consequence to a network or its
performance, there are applications, referred to as delay or time sensitive
applications, that can be impacted by packet delays. Voice transmission
and video conferencing are two examples. A delay in the transmission of
packets carrying their data could impact the quality of the audio or video.
This is where CoS can be of value. What it does is it permits a switch to
give higher priority to some packets over other packets.
There are two principal types of traffic found on the ports of a Gigabit
Ethernet switch, one being untagged packets and the other tagged
packets. As explained in “Tagged VLAN Overview” on page 257, one of
the principal differences between them is that tagged packets contain
VLAN information.
CoS applies mainly to tagged packets because, in addition to carrying
VLAN information, these packets can also contain a priority level
specifying how important (delay sensitive) a packet is in comparison to
other packets. It is this number that the switch refers to when determining
a packet’s priority level.
The 802.1p Class of Service (CoS) feature is configured on a per port
basis. The following examples show how to set this feature.
To assign a CoS ingress value to port 18 with a user-priority of 4, use the
following commands:
switch# configure terminal
67
Page 68

Chapter 2: Configuring the AT-S100 Software
switch(config)# interface ge18
switch(config-if)# user-priority 4
For more information about this command, see “USER-PRIORITY” on
page 193.
To assign a weight of 10 to queue 3, use the following commands:
switch# configure terminal
switch(config)# mls qos 0 0 0 0 0 0 10 0 0 0 0 0 0 0 0 0
For more information about this command, see “MLS QOS” on page 143.
To set CoS mapping on port 12 with a user priority of 7 and a traffic class
of 8, enter the following commands:
Note
Repeat the MLS QOS command for each queue.
switch# configure terminal
switch(config)# interface ge12
switch(config-if)# traffic-class-table user-priority 7
num-traffic-classes 8
For more information about this command, see “TRAFFIC-CLASS-TABLE
USER-PRIORITY NUM-TRAFFIC-CLASSES” on page 192.
68
Page 69

Section I
Command Modes
The chapters in this section provide information and procedures for basic
switch setup using the AT-S100 Management Software. The following
chapters are provided:
Chapter 3, “Privileged Executive Mode Commands” on page 71
Chapter 4, “Configuration Terminal Mode Commands” on page 115
Chapter 5, “Interface Configuration Mode Commands” on page 163
Section I: Command Modes 69
Page 70

70 Section I: Command Modes
Page 71

Chapter 3
Privileged Executive Mode Commands
This chapter describes the commands in the Privileged Executive mode
which are used to perform general switch functions such as copying
configuration file and displaying interface and MAC address table
information. This chapter contains the following commands:
“CLEAR MAC ADDRESS-TABLE DYNAMIC” on page 73
“CLEAR MAC ADDRESS-TABLE MULTICAST” on page 75
“CLEAR MAC ADDRESS-TABLE STATIC” on page 77
“CONFIGURE TERMINAL” on page 79
“COPY” on page 81
“COPY A.B.C.D” on page 82
“COPY DEFAULT.CFG” on page 84
“CP” on page 86
“DOWNLOAD TFTP” on page 87
“EXIT” on page 88
“LOGOUT” on page 89
“SHOW INTERFACE” on page 90
“SHOW MAC ADDRESS-TABLE” on page 92
“SHOW MAC ADDRESS-TABLE AGEING-TIME” on page 94
“SHOW MAC ADDRESS-TABLE DYNAMIC” on page 96
“SHOW MAC ADDRESS-TABLE INTERFACE” on page 98
“SHOW MAC ADDRESS-TABLE STATIC” on page 100
“SHOW MAC ADDRESS-TABLE VLAN Command” on page 103
“SHOW RUNNING-CONFIG INTERFACE” on page 104
“SHOW SPANNING-TREE” on page 106
“SHOW STATIC-CHANNEL-GROUP” on page 109
“SHOW USER-PRIORITY” on page 110
“SYSTEM FACTORY-RESET” on page 111
“SYSTEM REBOOT” on page 112
“UPLOAD TFTP” on page 113
Section I: Command Modes 71
Page 72

Chapter 3: Privileged Executive Mode Commands
Note
For VLAN-specific commands, see Chapter 11, “Virtual Local Area
Networks (VLAN) Commands” on page 257.
72 Section I: Command Modes
Page 73

CLEAR MAC ADDRESS-TABLE DYNAMIC
Syntax
clear mac address-table dynamic|address HHHH.HHHH.HHHH
|interface ge<1-28>|vlan VID
Parameters
address Specifies a MAC address in the following format:
HHHH.HHHH.HHHH
interface Specifies the name of an interface. There are 28 ports on
the 9000/28 and 9000/28SP switches. To specify a port,
precede the port number with “ge.”
VID Specifies the VLAN ID. Use a value between 1 and 4094.
AT-S100 Management Software User’s Guide
Description
Use the CLEAR MAC ADDRESS-TABLE DYNAMIC command to remove
a dynamic MAC address from the switch. You can remove all of the
dynamic MAC addresses, specific MAC addresses, or all MAC addresses
assigned to an VLAN.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Examples
To remove dynamic MAC address 0030.846e.bac7 from the MAC address
table, use the following command:
switch#clear mac address-table dynamic address
0030.846e.bac7
To remove all dynamic MAC addresses from the MAC address table, enter
the following command:
switch#clear mac address-table dynamic
Section I: Command Modes 73
Page 74

Chapter 3: Privileged Executive Mode Commands
Related Commands
“CLEAR MAC ADDRESS-TABLE MULTICAST” on page 75
“CLEAR MAC ADDRESS-TABLE STATIC” on page 77
74 Section I: Command Modes
Page 75

CLEAR MAC ADDRESS-TABLE MULTICAST
Syntax
clear mac address-table multicast|address MACADDR
|interface ge<1-28>|vlan VID
Parameters
address Specifies a multicast MAC address in the following
format:
HHHH.HHHH.HHHH
interface Specifies the name of an interface. There are 28 ports on
the 9000/28 and 9000/28SP switches. To specify a port,
precede the port number with “ge.”
VID Specifies the VLAN ID. Use a value between 1 and 4094.
AT-S100 Management Software User’s Guide
Description
Use the CLEAR MAC ADDRESS-TABLE MULTICAST command to
remove a multicast MAC address from the switch. You can remove all of
the multicast MAC addresses, specific multicast MAC addresses, or all
multicast MAC addresses assigned to an VLAN.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Examples
To remove multicast MAC address 0100.5100.0001 from the MAC
address table, enter the following command:
switch#clear mac address-table multicast address
0100.5100.0001
To remove all multicast MAC addresses from the MAC address table,
enter the following command:
switch#clear mac address-table multicast
Section I: Command Modes 75
Page 76

Chapter 3: Privileged Executive Mode Commands
Related Commands
“CLEAR MAC ADDRESS-TABLE DYNAMIC” on page 73
“CLEAR MAC ADDRESS-TABLE STATIC” on page 77
76 Section I: Command Modes
Page 77

CLEAR MAC ADDRESS-TABLE STATIC
Syntax
clear mac address-table static|address HHHH.HHHH.HHHH
|interface ge<1-28>|vlan VID
Parameters
address Specifies a MAC address in the following format:
HHHH.HHHH.HHHH
interface Specifies the name of an interface. There are 28 ports on
the 9000/28 and 9000/28SP switches. To specify a port,
precede the port number with “ge.”
VID Specifies the VLAN ID. Use a value between 1 and 4094.
AT-S100 Management Software User’s Guide
Description
Use the CLEAR MAC ADDRESS-TABLE STATIC command remove static
MAC addresses from the switch. You can remove all of the static MAC
addresses, specific MAC addresses, or all MAC addresses assigned to an
VLAN.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Examples
To remove static MAC address 0000.cd28.0752 from the MAC address
table, enter the following command:
switch#clear mac address-table static address
0000.cd28.0752
To remove all static MAC addresses from the MAC address table, enter
the following command:
switch#clear mac address-table static
Section I: Command Modes 77
Page 78

Chapter 3: Privileged Executive Mode Commands
Related Commands
“CLEAR MAC ADDRESS-TABLE DYNAMIC” on page 73
“CLEAR MAC ADDRESS-TABLE MULTICAST” on page 75
78 Section I: Command Modes
Page 79

CONFIGURE TERMINAL
Syntax
configure terminal
Parameters
none
Description
Use this command to enter the Configuration Terminal command mode.
After you enter this command, the command prompt changes to
“(config)#” to indicate the new mode.
To exit the Configure Terminal command mode, enter EXIT or CTRL Z.
For a description of the Configuration Terminal mode, see “Configuration
Terminal Mode” on page 19. For information about the commands in the
Configuration Terminal mode, see Chapter 4, “Configuration Terminal
Mode Commands” on page 115.
AT-S100 Management Software User’s Guide
Note
It is not necessary to enter the full command. You can abbreviate
this command to “config t.”
Command Mode
Privileged Executive mode
Examples
To enter the Configure Terminal command mode, enter the following
command:
switch#configure terminal
The prompt changes to:
Switch(config)#
Section I: Command Modes 79
Page 80

Chapter 3: Privileged Executive Mode Commands
To use the abbreviated form of the CONFIGURE TERMINAL command
mode, enter the following command:
switch#config t
The prompt changes to:
Switch(config)#
Related Commands
none
80 Section I: Command Modes
Page 81

COPY
AT-S100 Management Software User’s Guide
Syntax
copy running-config startup-config
Parameters
running-config Indicates the running configuration file.
startup-config Indicates the start-up configuration file.
Description
Use the COPY command to save your current configuration to the start-up
configuration file, called “startup-config,” on the switch.
Command Mode
Privileged Executive mode
Examples
In the following example, the running configuration file is copied to the
startup configuration file which is named “startup-config:”
switch#copy running-config startup-config
The software displays the following:
Building configuration...
[OK]
Enter the abbreviated form of the COPY command to save the current
configuration on the switch to the start-up configuration file called “startupconfig:”
switch# copy run start
The software displays the following:
Building configuration...
[OK]
Related Commands
“CP” on page 86
Section I: Command Modes 81
Page 82

Chapter 3: Privileged Executive Mode Commands
COPY A.B.C.D
Syntax
copy A.B.C.D SCRFILENAME DESTFILENAME
Parameters
A.B.C.D Indicates an IP address in the following format:
SRCFILENAME Indicates the name of the source configuration file.
DESTFILENAME Indicates the name of the destination configuration
Description
xxx.xxx.xxx.xxx
This file name must end with the “.cfg” suffix.
file. This file name must end with the “.cfg” suffix.
Use the COPY A.B.C.D command to download a configuration file from
the switch onto an TFTP server. For example, you may want to download
a configuration file from a backup server onto your switch. You must have
the IP address of the TFTP server to set this command.
Command Mode
Privileged Executive mode
Examples
Enter the following command to download a configuration file called
“jenny3.cfg” from a TFTP server with an IP address of 192.58.48.1 onto
your switch. The name of the new configuration file on the switch is
“at100v103.cfg:”
switch# copy 192.58.48.1 jenny.cfg at100v103.cfg
Enter the following command to download a configuration file called
“test.cfg” from a TFTP server with an IP address of 192.58.48.5 onto your
switch. The name of the new configuration file on the switch is
“master100v103.cfg:”
switch# copy 192.58.48.5 test.cfg master100v103.cfg
Related Commands
“COPY” on page 81
82 Section I: Command Modes
Page 83

“COPY DEFAULT.CFG” on page 84
“CP” on page 86
“DOWNLOAD TFTP” on page 87
“UPLOAD TFTP” on page 113
AT-S100 Management Software User’s Guide
Section I: Command Modes 83
Page 84

Chapter 3: Privileged Executive Mode Commands
COPY DEFAULT.CFG
Syntax
copy default.cfg A.B.C.D FILENAME
Parameters
default.cfg Indicates the name of the source configuration file.
A.B.C.D Indicates an IP address in the following format:
FILENAME Indicates the name of the destination configuration
Description
This file name must end with the “.cfg” suffix.
xxx.xxx.xxx.xxx
file. This file name must end with the “.cfg” suffix.
Use the COPY DEFAULT.CFG command to upload a configuration file
from the switch onto an TFTP server. You may want to upload a
configuration file from your switch onto a backup server. Or, you may want
to upload a configuration file from your switch to a TFTP server and then
download it to other AT-9000 Series switches with the COPY A.B.C.D
command. In addition, you must have the IP address of the TFTP server
to set this command.
Command Mode
Privileged Executive mode
Examples
Enter the following command to upload a file called “may.cfg” from the
switch onto a TFTP server with an IP address of 192.58.48.1. The new
filename is “at100v103.cfg.”
switch# copy may.cfg 192.58.48.1 at100v103.cfg
Enter the following command to upload a text file called “june.cfg” from the
switch onto a TFTP server with an IP address of 192.58.48.5. The new file
name is “s100v103.cfg.”
switch# copy june.cfg 192.58.48.5 s100v103.cfg
Related Commands
“COPY” on page 81
84 Section I: Command Modes
Page 85

“COPY A.B.C.D” on page 82
“CP” on page 86
AT-S100 Management Software User’s Guide
Section I: Command Modes 85
Page 86

Chapter 3: Privileged Executive Mode Commands
CP
Syntax
cp source-file new-file
Parameters
source-file Indicates the source configuration file.
new-file Indicates the new file which becomes a copy of the
Description
Use the CP command to make a copy of a configuration file and save it in
the current directory on the switch.
source file.
Command Mode
Privileged Executive mode
Examples
In the following example, the running configuration file is copied to the
startup configuration file which is named “frank2.cfg:”
switch#copy default.cfg frank2.cfg
You can confirm the file has been copied into the current directory with the
LS command. See the following example of the output of the LS
command:
default.cfg
frank2.cfg
ssh_host_key
ssh_host_key.pub
ssh_host_rsa_key
Related Commands
“COPY” on page 81
“COPY A.B.C.D” on page 82
“COPY DEFAULT.CFG” on page 84
86 Section I: Command Modes
Page 87

DOWNLOAD TFTP
Syntax
download tftp A.B.C.D FILENAME
Parameters
A.B.C.D Indicates the IP address of an TFTP server. Specify
FILENAME Specifies the filename of an image (.img) file.
Description
Use this command to download an image file from an TFTP server onto
the switch. For example, you may want to use this command to download
the latest version of the AT-S100 software onto your switch. You must
have the IP address of the TFTP server to set this command.
AT-S100 Management Software User’s Guide
the IP address in the following format:
xxx.xxx.xxx.xxx
Command Mode
Privileged Executive mode
Example
The following command uses a TFTP server, with an IP address of
189.11.1.1, to download the file called “ATS100_v103.img” onto the
switch:
switch#download tftp 189.11.1.1 ATS100_v103.img
Related Commands
“COPY” on page 81
“COPY DEFAULT.CFG” on page 84
“UPLOAD TFTP” on page 113
Section I: Command Modes 87
Page 88

Chapter 3: Privileged Executive Mode Commands
EXIT
Syntax
exit
Parameters
none
Description
Use the EXIT command to quit the Configuration Terminal mode and enter
the Privileged Executive mode. After you enter this command, the prompt
changes to “Switchname#” to indicate the Privileged Executive mode.
Command Mode
Configuration Terminal mode
Example
Enter the following commands to exit the Configuration Terminal mode
and return the software to the Privileged Executive mode:
switch#configure terminal
switch(config)#exit
The software displays the following prompt:
switch#
Related Commands
none
88 Section I: Command Modes
Page 89

LOGOUT
AT-S100 Management Software User’s Guide
Syntax
logout
Parameters
none
Description
Use the LOGOUT command to quit the Privileged Executive mode and log
out of the software.
Command Mode
Privileged Executive mode
Example
The following is an example of the LOGOUT command:
switch#logout
Related Commands
none
Section I: Command Modes 89
Page 90

Chapter 3: Privileged Executive Mode Commands
SHOW INTERFACE
Syntax
show interface IFNAME ge<1-28>
Parameters
IFNAME Specifies the name of an interface. There are 28 ports on
Description
Use the SHOW INTERFACE command to display the configuration and
status of an interface. If you do not specify an interface, this command
displays the status of all the interfaces.
the AT-9000/28 and AT-9000/28SP switches. To specify
a port, precede the port number with “ge.”
Command Mode
Privileged Executive mode
Example
The following is an example of the SHOW INTERFACE command on port
1 and the sample output:
switch#show interface ge1
Interface ge1
Hardware is Ethernet, address is 0004.2104.0801 (bia
004.2104.0801)
index 2001 metric 1 mtu 1500 duplex-full arp ageing
timeout 0
speed unknown mdix mdi
<UP,BROADCAST,MULTICAST>
VRF Binding: Not bound
input packets 013884, bytes 01642232, multicast
packets 07691 broadcast packets 06185
64-byte packets 05968, 65-127 packets 05346, 128-255
packets 01293
245-511 packets 01366, 512-1023 packets 03, >1024 packets
00
dropped 00, jabber 00 CRC error 03 undersize frames 00
oversize frames 00, fragments 00 collisions 00
output packets 092, bytes 05898, multicast packets 092
broadcast packets 00
90 Section I: Command Modes
Page 91

AT-S100 Management Software User’s Guide
Related Commands
“SHOW MAC ADDRESS-TABLE INTERFACE” on page 98
Section I: Command Modes 91
Page 92

Chapter 3: Privileged Executive Mode Commands
SHOW MAC ADDRESS-TABLE
Syntax
show mac address-table
Parameters
none
Description
Use the SHOW MAC ADDRESS-TABLE command to display the status of
the static and dynamic MAC addresses assigned to the switch.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Example
The following command displays the settings of the MAC address table:
switch#show mac address-table
92 Section I: Command Modes
Page 93

AT-S100 Management Software User’s Guide
See Figure 3 for an example display.
(switch3)# show mac address-table
Mac Address Table
--------------------------------------------------------------Vlan MAC Address Type Ports Forward
---- ----------- ---- ----- ------1 0100.5e7f.fffa STATIC ge1 1
1 0000.cd14.6448 DYNAMIC ge1 1
1 0000.f4d8.3534 DYNAMIC ge1 1
1 0004.5a5e.6fd3 DYNAMIC ge1 1
1 0006.5ba3.67d6 DYNAMIC ge1 1
5 0006.5bb2.6589 DYNAMIC ge8 1
5 0006.5bdd.6c69 DYNAMIC ge8 1
5 0008.749c.101a DYNAMIC ge8 1
5 0008.74a2.04c2 DYNAMIC ge8 1
5 0008.74cb.5fc6 DYNAMIC ge8 1
5 0008.74d3.f02c DYNAMIC ge8 1
10 0008.74dd.87f7 DYNAMIC ge12 1
10 0008.74df.29d8 DYNAMIC ge12 1
(switch3)#
Figure 3. SHOW MAC ADDRESS-TABLE Command
The fields in Figure 3 are defined in the following list:
vlan. This field indicates the VLAN ID.
MAC Address. This field indicates the MAC address in the format:
HHH.HHH.HHH.
Type. This field indicates a static or dynamic MAC address.
Ports. This field indicates the name of the port.
Forward. This field indicates if data is forwarded to a MAC address or
not. A value of 1 indicates data is forwarded to a MAC address. A
value of 0 indicates that data is discarded and is not forwarded to a
MAC address.
Related Commands
“SHOW MAC ADDRESS-TABLE AGING-TIME” on page 94
“SHOW MAC ADDRESS-TABLE DYNAMIC” on page 96
“SHOW MAC ADDRESS-TABLE INTERFACE” on page 98
“SHOW MAC ADDRESS-TABLE STATIC” on page 100
“SHOW MAC ADDRESS-TABLE VLAN” on page 102
Section I: Command Modes 93
Page 94

Chapter 3: Privileged Executive Mode Commands
SHOW MAC ADDRESS-TABLE AGEING-TIME
Syntax
show mac address-table ageing-time
Parameters
none
Description
Use the SHOW MAC ADDRESS-TABLE AGEING-TIME command to
display the aging time of MAC addresses assigned to the switch. By
default, this value is set to 300 seconds (5 minutes).
The switch uses the aging timer to delete inactive dynamic MAC
addresses from the MAC address table. When the switch detects that no
packets have been sent to or received from a particular MAC address in
the table after the period specified by the aging time, the switch deletes
the address. Deleting aged-out MAC addresses prevents the table from
becoming full of addresses of inactive nodes.
When the aging timer is set to 0, it disables the timer. No dynamic MAC
addresses are aged out and the table stops learning new addresses after
reaching its maximum capacity.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Example
The following command displays the MAC address aging-time:
switch#show mac address-table ageing-time
See Figure 4 for an example display.
(switch3)# show mac address-table aging-time
Aging-time 300
(switch3)#
Figure 4. SHOW MAC ADDRESS-TABLE AGING-TIME
94 Section I: Command Modes
Page 95

AT-S100 Management Software User’s Guide
Related Commands
“SHOW MAC ADDRESS-TABLE” on page 92
“SHOW MAC ADDRESS-TABLE DYNAMIC” on page 96
“SHOW MAC ADDRESS-TABLE INTERFACE” on page 98
“SHOW MAC ADDRESS-TABLE STATIC” on page 100
“SHOW MAC ADDRESS-TABLE VLAN” on page 102
Section I: Command Modes 95
Page 96

Chapter 3: Privileged Executive Mode Commands
SHOW MAC ADDRESS-TABLE DYNAMIC
Syntax
show mac address-table dynamic |
begin|exclude|include|redirect
Parameters
dynamic Indicates the dynamic MAC addresses.
| Specifies output variables. Choose from the
following options:
begin Indicates to begin with a line that
matches.
exclude Specifies to exclude lines that match.
include Specifies to include lines that match.
redirect Indicates to redirect the output.
Description
Use the SHOW MAC ADDRESS-TABLE DYNAMIC command to display
the status of the static and dynamic MAC addresses assigned to the
switch.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Example
The following command displays the dynamic MAC addresses:
switch#show mac address-table dynamic
96 Section I: Command Modes
Page 97

AT-S100 Management Software User’s Guide
See Figure 6 for a sample display.
(switch3)# show mac address-table dynamic
Mac Address Table
--------------------------------------------------------------Vlan MAC Address Type Ports Forward
---- ----------- ---- ----- ------1 0000.cd14.6448 DYNAMIC ge3 1
1 0000.f4d8.3534 DYNAMIC ge3 1
1 0004.5a5e.6fd3 DYNAMIC ge3 1
1 0006.5ba3.67d6 DYNAMIC ge3 1
1 0006.5bb2.6589 DYNAMIC ge3 1
1 0006.5bdd.6c69 DYNAMIC ge3 1
1 0008.749c.101a DYNAMIC ge3 1
1 0008.74a2.04c2 DYNAMIC ge3 1
1 0008.74cb.5fc6 DYNAMIC ge3 1
1 0008.74d3.f02c DYNAMIC ge3 1
1 0008.74dd.87f7 DYNAMIC ge3 1
(switch3)#
Figure 5. SHOW MAC ADDRESS-TABLE DYNAMIC Command
The fields in Figure 6 are defined in the following list:
vlan. This field indicates the VLAN ID.
MAC Address. This field indicates the MAC address in the format:
HHH.HHH.HHH.
Type. This field indicates a static or dynamic MAC address.
Ports. This field indicates the name of the port.
Forward. This field indicates if data is forwarded to a MAC address or
not. A value of 1 indicates data is forwarded to a MAC address. A
value of 0 indicates that data is discarded and is not forwarded to a
MAC address.
Related Commands
“SHOW MAC ADDRESS-TABLE” on page 92
“SHOW MAC ADDRESS-TABLE AGEING-TIME” on page 94
“SHOW MAC ADDRESS-TABLE INTERFACE” on page 98
“SHOW MAC ADDRESS-TABLE STATIC” on page 100
“SHOW MAC ADDRESS-TABLE VLAN” on page 102
Section I: Command Modes 97
Page 98

Chapter 3: Privileged Executive Mode Commands
SHOW MAC ADDRESS-TABLE INTERFACE
Syntax
show mac address-table interface ge<1-28>
Parameters
interface Specifies the name of an interface. There are 28 ports on
the 9000/28 and 9000/28SP switches. To specify a port,
precede the port number with “ge.”
Description
Use the SHOW MAC ADDRESS-TABLE INTERFACE command to
display the status of the static and dynamic MAC addresses assigned to a
port.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Example
The following command displays the settings of the MAC address table on
port 3:
switch#show mac address-table interface ge3
98 Section I: Command Modes
Page 99

AT-S100 Management Software User’s Guide
See Figure 6 for an example display.
(switch3)# show mac address-table interface ge3
Mac Address Table
--------------------------------------------------------------Vlan MAC Address Type Ports Forward
---- ----------- ---- ----- ------1 0100.5e7f.fffa STATIC ge3 1
1 0000.cd14.6448 DYNAMIC ge3 1
1 0000.f4d8.3534 DYNAMIC ge3 1
1 0004.5a5e.6fd3 DYNAMIC ge3 1
1 0006.5ba3.67d6 DYNAMIC ge3 1
1 0006.5bb2.6589 DYNAMIC ge3 1
1 0006.5bdd.6c69 DYNAMIC ge3 1
1 0008.749c.101a DYNAMIC ge3 1
1 0008.74a2.04c2 DYNAMIC ge3 1
1 0008.74cb.5fc6 DYNAMIC ge3 1
1 0008.74d3.f02c DYNAMIC ge3 1
1 0008.74dd.87f7 DYNAMIC ge3 1
(switch3)#
Figure 6. SHOW MAC ADDRESS-TABLE INTERFACE Command
The fields in Figure 6 are defined in the following list:
vlan. This field indicates the VLAN ID.
MAC Address. This field indicates the MAC address in the format:
HHH.HHH.HHH.
Type. This field indicates a static or dynamic MAC address.
Ports. This field indicates the name of the port.
Forward. This field indicates if data is forwarded to a MAC address or
not. A value of 1 indicates data is forwarded to a MAC address. A
value of 0 indicates that data is discarded and is not forwarded to a
MAC address.
Related Commands
“SHOW MAC ADDRESS-TABLE” on page 92
“SHOW MAC ADDRESS-TABLE AGEING-TIME” on page 94
“SHOW MAC ADDRESS-TABLE DYNAMIC” on page 96
“SHOW MAC ADDRESS-TABLE STATIC” on page 100
“SHOW MAC ADDRESS-TABLE VLAN” on page 102
Section I: Command Modes 99
Page 100

Chapter 3: Privileged Executive Mode Commands
SHOW MAC ADDRESS-TABLE STATIC
Syntax
show mac address-table static |
(begin|exclude|include|redirect) > WORD
Parameters
static Indicates the static MAC addresses.
| Specifies output variables. Choose from the following
options:
begin Indicates to begin with a line that
exclude Specifies to exclude lines that match.
matches.
include Specifies to include lines that match.
redirect Indicates to redirect the output.
> Redirects the output of the command to a file name.
Description
Use the SHOW MAC ADDRESS-TABLE STATIC command to display the
status of the static MAC addresses assigned to the switch.
For procedures to configure and display the MAC addresses, see
“Displaying and Setting MAC Addresses” on page 32.
Command Mode
Privileged Executive mode
Example
The following command displays the settings of the static MAC addresses:
switch#show mac address-table static
100 Section I: Command Modes
 Loading...
Loading...