Page 1

IEEE 802.1
1n Wireless Series
Long-Range USB
User Manual
Adapter
rsion: 2.0
Ve
Date: January 13, 2009
Page 2

FCC Certifications
Federal Communicatio
This equipment has been tested and found to comply with the limits for a Class B digital device,
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection
against harmful interference in a residential installation. This equipment generates, uses and can
radiate radio frequency energy and, if not installed and used in accordance with the instructions,
may cause harmful interference to radio communications. However, there is no guarantee that
interference will not occur in a particular installation. If this equipment does cause harmful
interference to radio or television reception, which can be determined by turning the equipment off
and on, the user is encouraged to try to correct the interference by one of the following measures:
-Reorient or relocate the receiving antenna.
-Increase the separation between the equipment and receiver.
-Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
-Consult the dealer or an experienced radio/TV technician for help.
n Commission Interference Statement
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two
conditions: (1) This device may not cause harmful interference, and (2) this device must accept any
interference received, including interference that may cause undesired operation.
FCC Caution: Any changes or modifications not expressly approved by the party responsible for
compliance could void the user's authority to operate this equipment.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled
environment. This equipment should be installed and operated with minimum distance 20cm
between the radiator & your body.
This transmitter must not be co-located or operating in conjunction with any other antenna or
transmitter.
anuary 13, 2009 / Version: 2.0
J
i
Page 3

CE Mark
Warning
This equipment com
Class B for ITE, the essential protection requirement of Council Directive 89/336/EEC on the
approximation of the laws of the Member States relating to electromagnetic compatibility.
Company has an on-going policy of upgrading its products and it may be possible that information
in this document is not up-to-date. Please check with your local distributors for the latest
information. No part of this document can be copied or reproduced in any form without written
consent from the company.
plies with the requirements relating to electromagnetic compatibility, EN 55022
rademarks:
T
All trade names and trademarks are the properties of their respective companies.
Copyright © 2009, All Rights Reserved.
anuary 13, 2009 / Version: 2.0
J
ii
Page 4

TABLE OF CONTENTS
VERVIEW ..........................................................1
O
PACKING
N
U
I
NTRODUCTI
K
F
EY
INST
SOFTW
MAN
AKING A
M
NFORMA
I
ON TO THE
EATURES
ALLATION GUIDE ........................................2
ARE
TALLATION
INS
AGEMENT GUIDE.........................................5
ASIC NETW
B
TION
.................................................................................................
EEE
I
802.1
1
N WIREL
ESS
USB A
DA
........................................
PTER
................................................................................................................
.................................................................................................
ORK
O
NNECTION
C
..........................................................................
Select a configuration tool .......................................................................................... 5
To connect with Microsoft Zero Configuration tool...................................................... 5
To connect with 802.11n Wireless LAN Utility............................................................ 7
I
NTRODUCTI
ON TO THE
802.1
1
N WIR
ELESS
LA
N
UTILITY
....................................................
Interfaces.................................................................................................................... 8
Link Status Information............................................................................................... 9
Profile ....................................................................................................................... 10
Network .................................................................................................................... 19
Advanced.................................................................................................................. 20
Statistics................................................................................................................... 21
WMM........................................................................................................................ 22
WPS ......................................................................................................................... 24
CCX.......................................................................................................................... 35
Radio On/Off............................................................................................................. 35
AP
MO
DE MANAGEMENT GUIDE FOR
INDOWS
W
2000/XP/V
IST
.........................................
A
Config....................................................................................................................... 38
Security Setting ........................................................................................................ 40
Access Control ......................................................................................................... 41
MAC Table................................................................................................................ 42
Event Log ................................................................................................................. 43
Statistics................................................................................................................... 44
1
1
2
2
5
8
36
anuary 13, 2009 / Version: 2.0
J
ii
i
Page 5
Overview
hank you for purchasing this product. Read this chapter to know about your
T
IEEE 802.11n Wireless USB Adapter.
Unp
Before getting started,
1. IEEE 802.11n Wireless USB Adapter.
2. One Utility/ Manual CD.
acking Information
please verify that your package includes the following items:
Introduction to the IEEE 802.1
The I
EEE 802.11n Wireless USB adapter provides users to launch IEEE 802.11n wireless network
at 150 Mbps in the 2.4GHz (AWUS036NH
band,
11/54 Mbps. You can configure this adapter with ad-hoc mode to connect to other 2.4GHz
(AWUS036NH/AWUS036NEH) or 2.4
with Infrastructure mode to connect to a wireless AP or router for accessing to Internet. Thi s adapter
includes a convenient Utility for scanning available networks and saving preferred networks that
users usually connected with. Security encryption can also be configured by this utility.
which is also compatible with IEEE 802.11b/g and IEEE 802.11a/b/g wireless devices at
GHz&5.2GHz&5.8GHz (A
1n Wireless USB Adapter
/AWUS036NEH) or 2.4GHz&5.2GHz&5.8GHz (AWUS05
WUS051NH) wireless computers or
1NH)
J
anuary 13, 2009 / Version: 2.0
1
Page 6

Key Features
Complies with IEEE 802.11n wireless standards
y
2.4GHz (AWUS036NH / AWUS036NEH)
y
frequency band, MIMO
2.4GHz&5.2GHz&5.8GHz (AWUS051NH) frequency
y
band, MIMO
Complies with USB 2.0
y
y
High speed transfer data rate up to 150 Mbps
Supports auto-installation
y
Supports wireless data encryption with
y
64/128-bit WEP, WPA, WPA2, TKIP, AES
Supports QoS: WMM, WMM-PS
y
Supports multiple BSSID
y
y
Supports driver for Windows 2000, XP 32/64,
Vista 32/64, Windows 7, Linux (2.4.x/2.6.x), and
Mac (10.3.x/10.4.x/10.5.x/10.6.x) Power PC &
PC
Installation Guide
Sof
tware Installation
Note:
y F
or Linux or Mac driver installation guide, please refer to the instruction in
/Driver/Linux/README
or /Dri
ver/Mac/README
he CD-Rom.
in t
y The following driver installation guide uses Windows XP as the presumed operation system.
The procedures and screens in Windows 2000 and Vista are familiar with Windows XP.
1. The system finds the newly installed device automatically . Click Cancel to close this window .
2. In
sert the CD-Rom that came with this product to your CD-Rom drive. The menu window pops
up automatically. Please click the Driver button of this product.
Note: If the CD-Rom fails to auto-run, please click on My Computer > your CD-Rom drive
> (folder of this product) > Driver then double-click the Setup icon to start this menu.
J
anuary 13, 2009 / Version: 2.0
2
Page 7

3. Select
if you are going to install the driver and wireless utility; or install t he driver only.
4. Select
if you are going to configure your wireless network with this device or with Microsoft
Zero Configuration tool.
Note: This can be changed after installing this software.
anuary 13, 2009 / Version: 2.0
J
3
Page 8

lick the Install button to start installing.
5. C
6. C
lick the Finish button to complete installation.
anuary 13, 2009 / Version: 2.0
J
4
Page 9

Mana
ead this chapter to understand the management interface of the device and
R
how to manage the device.
gement Guide
Making a Basic Network Connection
Select a configuration tool
the following instruction for making a network con nection, we use the Utility we provide to
In
configure your wireless network settings.
Note: You could use either the software we provide or Microsoft Zero Configuration tool to
configure this adapter . To switch between the two configuration tools, please right click on the …..
icon on system tray to select.
To connect w
After speci
ith Microsoft Zero Configuration tool
fying the Microsoft Zero Configuration tool to configure your wireless network, right
click on the
wireless network.
icon on system tray . Select View Available Wireless Networks to specify your
anuary 13, 2009 / Version: 2.0
J
5
Page 10

he tool shows the available wireless networks. Select your demanding network to connect with.
T
To connect to a wireless network with more security settings, please click Change advanced
settings to be compatible with your wireless network security settings.
anuary 13, 2009 / Version: 2.0
J
6
Page 11

To connect w
W
e provide this Utility for users to connect to a wireless network easily. It provides more
ith 802.11n Wireless LAN Utility
information and configuration for this adapter . As default, the Utility is started automatically upon
starting your computer and connects to a connectab le wireless network with best signal strength
and with no security setting. Right click on the icon in the system ray and select Launch
Config utilities if the Utility does not start. Please refer to the following chapters to get
information regarding to the functions of this Utility.
anuary 13, 2009 / Version: 2.0
J
7
Page 12
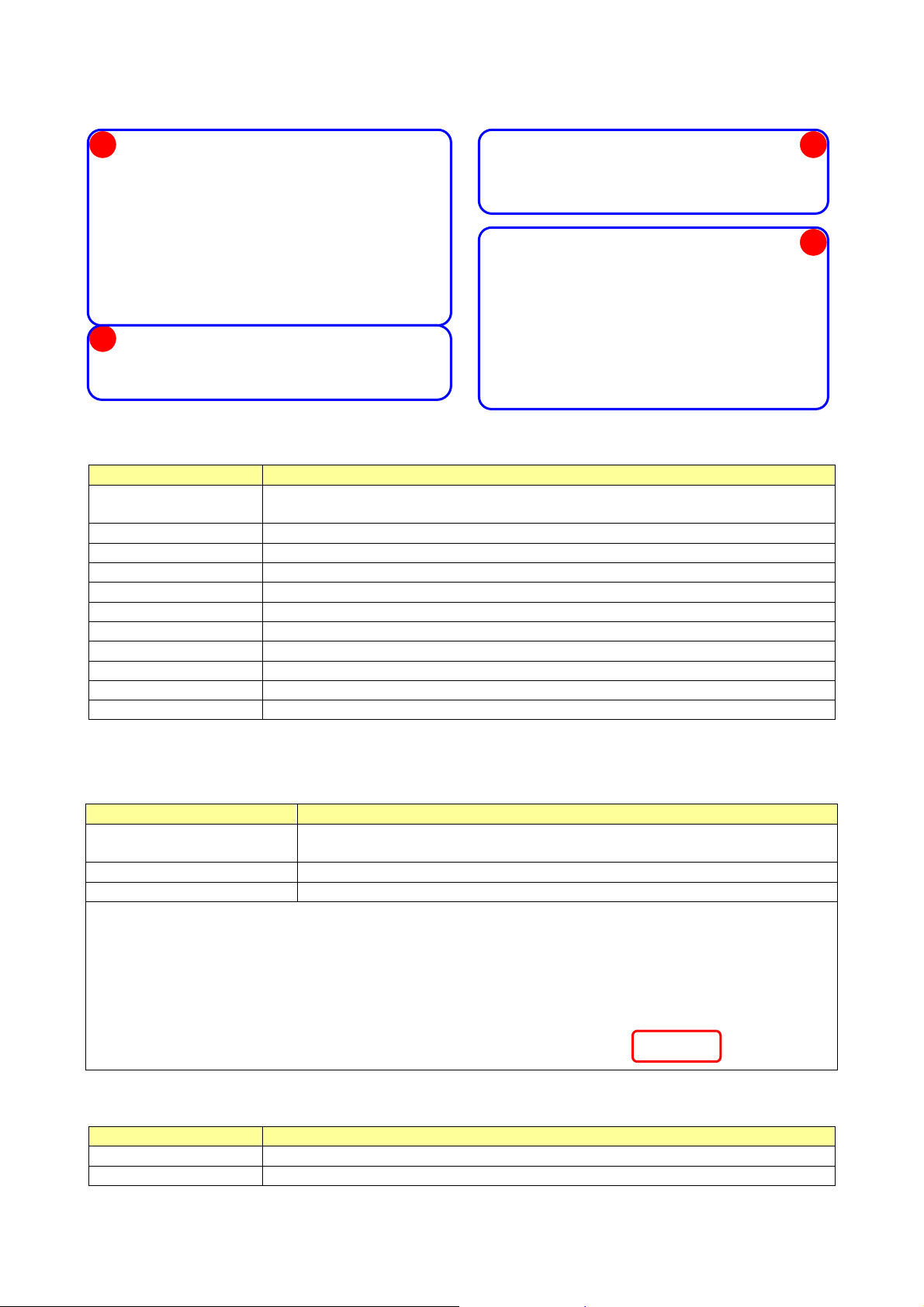
Introduction to the 802.1
1n Wireless LAN Utility
Note: The Uti
lity in Linux and Mac are different from the following.
Interfaces
T
his Utility is basically consisted of three parts:
1
2
3
1. Functi
configuration window.
Note: Click to enable/disable wireless connection status.
2. Configuration Column: Center of the Utility window . Make your cha nges for each function in
this part.
3. Link Status Information: bottom of the utility window. Shows the connection status and
system information.
onal Buttons: on top of the window. You can click each button to access each
anuary 13, 2009 / Version: 2.0
J
8
Page 13
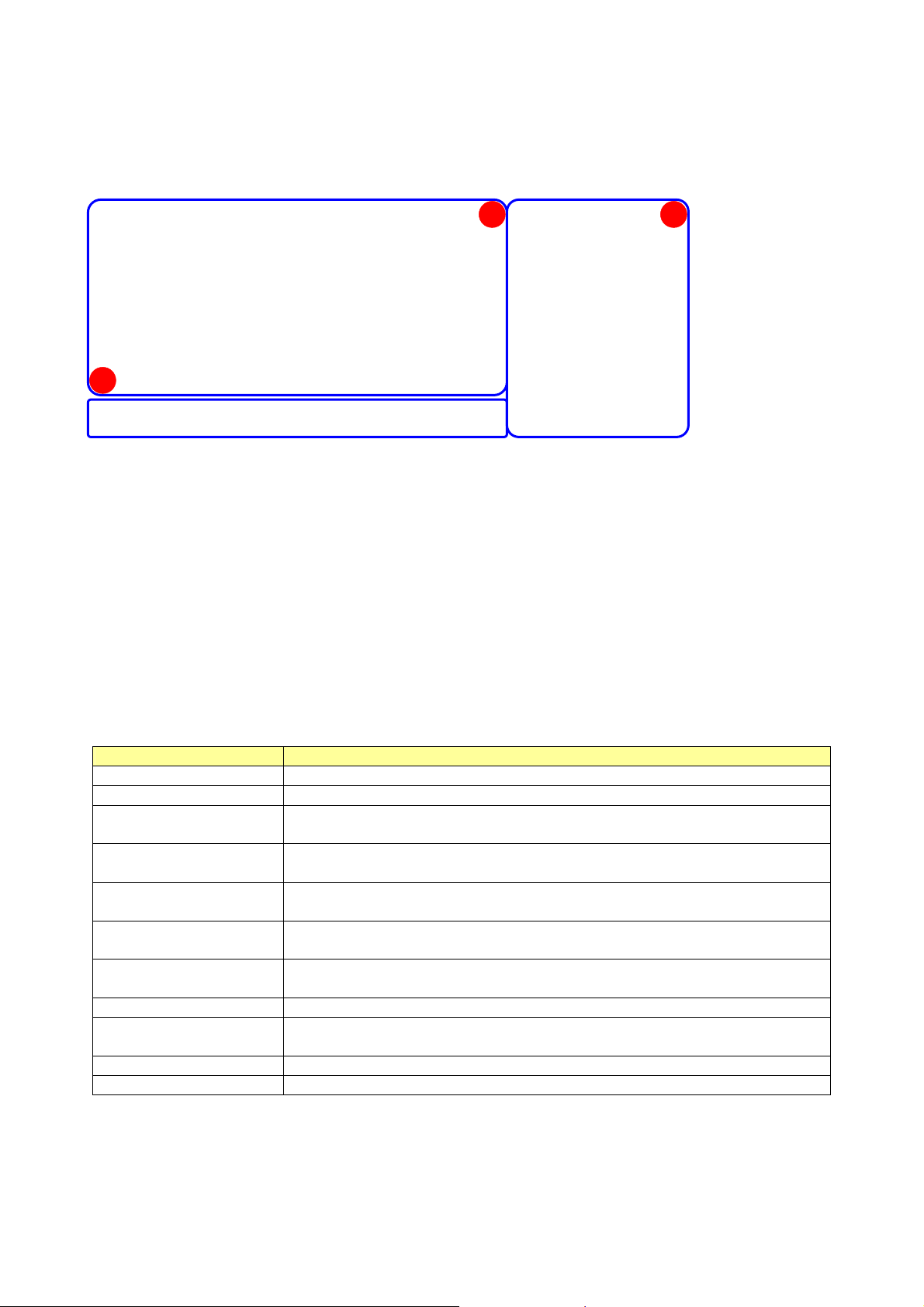
Link Status Information
A
B
A. Network Inf
ormation:
Items Informati
us
Stat
Extr
a Info Display link status in use.
Channel D
Auth
entication Authentication mode in use.
Encryption
Network Type Network
Show the connecting status. Also shows the SSID while connecting to a
valid network.
isplay current channel in use.
Encryption type in use.
type in use.
IP Address IP address of current connection.
Sub M
Default Gateway Defaul
Link Speed Show curre
T
hroughput Display transmit and receive throughput in Mbps.
ask Subnet mask of current connection.
t gateway of current connection.
nt transmit rate and receive r a te.
C
D
on
B. HT:
Display current HT status in use, containing BW, GI, MCS, SNR0, and SNR1 value.
C. Link Quality and Strength Bar:
Items Informati
Link Qu
Sign
al Strength 1 Receive signal strength 1.
ality
Noise Strength Displa
User can c
hoose to display Signal and Noise Strength as percentage or dBm format by mark the
Display connection quality based on signal strength and TX/RX packet
error rate.
y noise signal strength.
dBm checkbox.
D. Stati
stics:
Items Information
Link Speed Show curre
T
hroughput Display transmit and receive throughput in Mbps.
nt transmit rate and receive r a te.
on
anuary 13, 2009 / Version: 2.0
J
9
Page 14
Profile
A
This profile
page allows users to save different wireless settings, which helps users to get access
to wireless networks at home, office or other wireless network environments quickly.
C
B
A. Prof
ile List: The list shows all the profiles you have added before.
B. Buttons: You can cli ck on these buttons to add a new profi le, edit, delete or activ ate an old
profile.
Note: For Vista user, there are extra
and
buttons in this feature.
Click on these buttons to import or export the selected profile.
C. Prof ile Information: While you select a prof ile in the profile list, you can see the prof ile
information shows on here.
Items Information
ile Name The name of the selected profile.
Prof
SSI
D The SSID of the wireless system.
Network Type
entication
Auth
Encryption
Use 80
Tx Powe
2.1x
r
Shows I
selected profile.
Shows the authentication mode in use. There are total 8 modes: Open,
Shared, LEAP, WPA, WPA-PSK, WPA2, WPA2-PSK and WPA-NONE.
Shows the encryption mode in use. There are total 4 modes: None,
WEP, TKIP and AES.
Shows Y e s/No to indicate whether the selected profile use the 802.1 x
feature or not.
Shows the transmit power in use. There are total 7 types: Auto, 100%,
75%, 50%, 25%, 10% and Low.
Channel Shows
Power Save Mode
S Threshold Shows the RTS threshold value in use.
RT
Fra
gment Threshold Shows the fragment threshold in use.
Shows
Awake Mode) and PSM (Power Saving Mode).
nfrastructure / Ad-hoc to indicate the network type of the
the channel in use (1~14) for Ad-Hoc mode.
the power save mode in use. Two selections: CAM (Constantly
anuary 13, 2009 / Version: 2.0
J
10
Page 15

o add a new profile:
T
1. Click the Add button. The add profile window pops up.
Note: you could also add a new profile quickly by selecting an available network in the
Network function then click the Add to Profile button.
2. There are three tabs o
← Click
on these tabs
n the window:
Setti
ngs for: Profile Name, SSID, Network Type, Tx Power, Preamble,
Power Save Mode, RTS Threshold, and Fragment Threshold.
ngs for: Authentication, Encryption, Preshared K ey, and WEP Key .
Setti
ngs for: EAP Method, Tunnel Authentication, and Session
Setti
Resumption. For different EAP Method, you also have to configure
different require of ID/Password, Client Certificate, or Server
Certificate.
Please follow the steps below to fill in the information gradually.
anuary 13, 2009 / Version: 2.0
J
11
Page 16

3. In
Items Informati
Prof
ile Name Choose a name for this profile, or use default name defined by s ystem.
SSI
D
Network Type
Tx Powe
r
Preamble
Channel C
Power Save Mode
RT
S Threshold
Fra
gment Threshold
section, fill in information for this profile:
on
Fill in the intended SSID name or use the drop list to select from
available APs.
There are two types, infr
astructure and 802.11 Ad-hoc modes. Under
Ad-hoc mode, you could also choose the preamble type; the available
preamble type includes auto and long. In addition to that, the channel
field will be available for setup in Ad-hoc mode.
Transmit power, the amount of power used by a radio transceiver to
send the signal out.
wo selections: Auto, and Long Preamble. This can on ly be set up in
T
Ad –hoc mode.
hannel in use for Ad-Hoc mode.
Choose fro
m CAM (Constantly Awake Mode) or PSM (Power Saving
Mode).
For adjusting the RTS threshold number by sliding the bar or key in the
value directly. The default value is 2347.
Adjust the Fragment threshold number by sliding the bar or key in the
value directly. The default value is 2346.
anuary 13, 2009 / Version: 2.0
J
12
Page 17

4. In
network information:
section, select an encryption type and fill in the corresponding wireless
Items Informati
Auth
entication
For Wi
There are 7 types supported: Open, Shared, LEAP, WPA, WPA-PSK, WPA2,
WPA2-PSK, and WPA- NONE
ndows 2000 User
1
. Pl
ease select a type from the drop down list.
Type
For Vist
a User
There are 7 types supported: Open, Shared, WPA, WP A-PSK, W PA2, WP A2-PSK,
and CCKM. Please select a type from the drop down list.
For Wi
ndows 2000 User
There are 4 types supported: None, WEP, TKIP and AES.
The available encryption selection will differ from the authentication type you
have chosen, the result is shown below:
entication
Auth
Open NONE, W
Shared WEP
LEAP (no selection)
A/WPA2/WPA-PSK
WP
WPA2-PSK/WPA-NONE
Encryption
Type
For Vist
a User
There are 6 types supported: None, WEP, TKIP , AES, TKI P (MFP) and AES (MFP).
The available encryption selection will differ from the authentication type you
have chosen, the result is shown below:
Auth
entication
Open NONE, W
Shared WEP
A/ WPA-PSK/ WPA2-PSK TKIP, AES
WP
A2 TKIP, AES, TKIP(MFP), AES(MFP)
WP
KM WEP, TKIP, AES
CC
on
able Encryption Selection
Avail
TKIP, AES
Avail
able Encryption Selection
EP
EP
1
W
PA-NONE is only available in Ad-hoc mode.
anuary 13, 2009 / Version: 2.0
J
13
Page 18

This checkbox appears while the environment is set to an Open authentication
Use 80
2.1x
Preshared Key
WEP Key
with WEP encryption. Mark the checkbox to mak e the
ailable. The
av
section is also available in WPA and WPA2
section
authentication types.
This is the
shared secret between AP and STA. For WPA-PSK, WPA2-PSK and
WPA-NONE authe ntication mode, this fi eld must be filled with char acters lo nger
than 8 and less than 32 lengths. The following dialog appears if you have input
invalid values.
On
ly available when using WEP encryption algorithm. The key must match AP's
key. Select Hex
1
or
ASCII
2
to setup the key value. The following dialog appears
if you have input invalid values.
1
Hexadecima
2
A
SCII (American Standard Code for Information Interchange) is a code for representing English letters as numbers
from 0-127.
anuary 13, 2009 / Version: 2.0
J
l digits consist of the numbers 0-9 and the letters A-F.
14
Page 19

5. Specify the
A
802.1x information if you are using the 802.1X certification method.
Users that do not use this function or connecting to an open-wireless network please skip this
part.
B C
A. EAP Meth
F
or Windows 2000 User: There are total 5 modes: PEAP , TLS/Smart Card, T TLS, EAP-F AST , and
od:
MD5-Challenge.
For Vist
a User: There are total 4 modes: PEAP, TLS/Smart Card, EAP-FAST, and LEAP.
Please select an EAP method from the drop down list.
Items Informati
Extensible Authentication Protocol. PEAP transport securely authenticates
PEAP
Protect
data by using tunneling between PEAP clients and an authentication server. PEAP can
authenticate wireless LAN clients using only server-side certificates, thus simplifying
the implementation and administration of a secure wireless LAN.
T ransport Layer Security . Provides for certificate-based and mutual authentication of
the client and the network. It relies on client-side and server-side certificates to
Card
art
perform authentication and can be used to dynamically generate user-based and
session-based WEP keys to secure subsequent communications between the WLA N
TLS/Sm
client and the access point.
Tu
nneled Transport Layer Security. This security method provides for
TTLS
certificate-based, mutual authentication of the client and network through an
encrypted channel. Unlike EAP-TLS, EAP-TTLS requires only server-side certificates.
lexible Authentication via Secure Tunneling. It was developed by Cisco. Instead of
F
using a certificate, mutual authentication is achieved by means of a PAC (Protected
Access Credential) which can be managed dynamically by the authentication server.
EAP-FAST
The PAC can be supplied (distributed one time) to the client either manually or
automatically. Manually, it is delivered to the clien t via disk or a secured network
distribution method. Automatically, it is supplied as an in-band, over the air,
distribution. For tunnel authentication, only support "Generic Token Card"
authentication.
MD5-
Chall
LEAP
enge
Message Digest Challenge. Challenge is an EAP authent ication type that provides
base-level EAP support. It provides for only one-way authentication - there is no
mutual authentication of wireless client and the network.
Li
ght Extensible Authentication Protocol is an EAP authentication type used primarily
by Cisco Aironet WLANs. It encrypts data tr ansmissions using dynamically generated
WEP keys, and supports mutual authentication.
on
anuary 13, 2009 / Version: 2.0
J
15
Page 20

B. Tunn
el Authentication: The tunnel authentication will differ from the E AP method you
have chosen, the result is shown below:
or Windows 2000 User:
F
For Vist
a User:
C. Sessi
EAP Meth
TLS/Smart Card
D5-Challenge (no selection)
M
EAP Meth
TLS/Smart Card
od
P EAP-MSCHAP v2 , EAP- TLS/Smart Card, Generic Token Card
PEA
(no selection)
TLS CHP, MS-CHAP, MS-CHAP-V2, PAP, EAP-MD5
T
E
AP-FAST Generic Token Card
od
P EAP-MSCHAP v2 , EAP- TLS/Smart Card, Generic Token Card
PEA
(no selection)
AST (no selection)
EAP-F
LEAP (no
selection)
on Resumption: Mark to enable this function or unmark it to disable.
Tunn
el Authentication
Tunn
el Authentication
After doing the above settings, please cl ick on the tabs below. There are several tabs on the
window, please fill in the information gradually.
Setti
ngs for: Authentication ID/Password, Tunnel ID/Password and
Password Mode
Setti
ngs for using the Client Certificate function or not.
ngs for using the Server Certificate function or not.
Setti
ng for EAP-FAST method.
Setti
Settings for
system.
← Click
1
.
on these tabs
Single Sign On. Note: This tab only appears in Vista
1
P
assword mode is only available in EAP-FAST method.
anuary 13, 2009 / Version: 2.0
J
16
Page 21

ID \ PASSWORD
Items Information
entication ID / Password The identity, password and domain name for server. Only
Auth
"EAP-FAST" and "LEAP" authentication can be keyed in
domain name. Blank space can be keyed in domain name.
el ID / Password Identity and Password for server.
Tunn
Pa
ssword Mode Select the power save mode.
or Windows 2000 User
F
There are two selections: Soft Token and Static Password.
For Vist
a User
There are four selections: Soft Token, Static Password,
Windows Logon and Prompt User.
Client Certi
ficate
Items Informati
Use Client certific
Use my sm
art card Client certificate for server authentication.
ate Client certificate for server authentication.
on
anuary 13, 2009 / Version: 2.0
J
17
Page 22

Serv
er Certificate
Items Informati
se Certificate chain Mark the checkbox to enable using certification chain.
U
Allow inti
ver name
Ser
EAP Fast
Items Informati
Allow un
provision mode
Use prot
authentication
credential
midate certificates
authenticated
ected
M
ark to allow intimidates certification.
Enter a
During the PAC can be provisioned (distributed one time) to
the client automatically. It only supported "Allow
unauthenticated provision mode" and use "EAP-MSCHAP v2"
authentication to authenticate now . It causes to conti nue with
the establishment of the inner tunnel even though it is made
with an unknown server. Mark to enable unauthenticated
provision mode.
Use protected authentication cre
certificate can be provided to the client manually via disk or a
secured network distribution method. Mark to use protected
authentication credential.
on
n authentication sever root.
on
dential: Using PAC, the
anuary 13, 2009 / Version: 2.0
J
18
Page 23

ork
A
Netw
T
his network lists the available wireless networks. The Utility connects to a wireless network with
best signal strength automatically. You can change the connecting network by clicking on the
network name and click the Connect button. To see detail information of each network, please
double click on each item to pop up the information wind ow.
B
C
A. Sort
ed by: Click each button to sort the listing networks by SSID, channel and Signal
strength.
B. Show dBm: Mark the checkbox to show the
signal and noise strength in dBm, unmark to
show in percentage.
C. Buttons: You can click on these buttons to add a
new profile, edit, delete or activate an old profile.
Items Informati
an To rescan available wireless networks.
Resc
Con
nect To connect to a designated network.
Add to Pr
anuary 13, 2009 / Version: 2.0
J
ofile To add a network to profile after selecting a network.
19
on
Page 24

Advanced
This page provides advanced configurations to this adapter . Please refer to the following chart for
definitions of each item.
Items Informati
Wireless mode Select wireless mode. 2
Enable TX
Enable TCP Window
Burst Select to enable connecting to a TX Burst supported device.
Size Mark the checkbox to enable TCP window size, which help
on
.4G/5.2G&5.8G is supported.
enhance throughput.
Fast
Roaming at __ dBm Mark the checkbox to enable fast roaming. Specify the
transmit power for fast roaming.
Show Authentication Status
Dialog
Mark the checkbox to show “Authentication Status Dialog”
while connecting to an AP with authentication.
Authentication Status Dialog displays the process about
802.1 x authentications.
Select You
Code
r Country Region
Eight countries to choose. Channel list:
1 ~ 11 channels (North America)
1 ~ 13 channels (General Europe)
1 ~ 14 channels (Japan)
IEEE802.11a
4 Channels (Japan)
19 Channels (Europe)
13 Channels (USA)
Enable CCX (Cisco
Compatible
extensions)
urn on CCKM Mark to enable CCKM.
T
Enable Radio
Measurements Mark to enable channel measurement every 0~2000
Select to enable CCX. This function can only be applied
when connecting to a Cisco compatible device.
milliseconds.
Non-Serving Channel
Mark to revise the channel measurement.
Measurements limit
Note: F
or Vista user, click on the CCX button to do more configuration. Please refer to CCX
more information.
J
anuary 13, 2009 / Version: 2.0
for
20
Page 25

Statistics
Statistics pa
ge displays the detail counter information based on 802.11 MIB counters. This page
translates the MIB counters into a format easier for user to understand.
Items Informati
Frames Tr
Frames
ansmitted Successfully Frames successfully sent.
Retransmitted
Successfully retransmitted frames numbers.
on
Successfully
Frames Fail To Rec
eive ACK After
Frames failed transmit after hitting retry limit.
All Retries
RT
S Frames Successfully Receive
Successfully receive CTS after sending RTS frame.
CTS
RTS Fr
Reset
ames Fail To Receive CTS Failed to receive CTS after sending RTS.
Counter Reset counters to zero.
Items Informati
F
rames Received Successfully Frames received successfully.
on
Frames Received With CRC Error Frames received with CRC error.
mes Dropped Due To Out-of-Resource Frames dropped due to resource issue.
Fra
Duplic
Reset
anuary 13, 2009 / Version: 2.0
J
ate Frames Received Duplicate received frames.
Counter Reset counters to zero.
21
Page 26

WMM
T
his page allows users to activate the WMM function for this device. Please note that this function
only works while connecting to a WMM compatible device.
Items Informati
WMM Enable
WMM - Power
Enable Wi-Fi Multi-Media.
Save Enable Enable WMM Power Save. Please enable WMM before
on
configuring this function.
Direct Lin
k Setup Enable Enable DLS (Direct Link Setup). Please enable WMM before
configuring this function.
MAC Address Fi
Timeout Value Ti
ll in the blanks of Direct Link with MAC Address of STA.
me of automatically disconnect after some seconds. The
value is integer. The integer must be between 0~65535. It
represents that it always connects if the value is zero.
Default value of Timeout Value is 60 seconds.
Ap
ply / Tear Down After fill in the "MAC Address" and "Timeou t Value", click
"Apply" button to save your configuration. The result will
appear in the following "DLS Status" blanks. To remove
the configuration, please select the configuration in the
blanks and then click "Tear Down" button.
anuary 13, 2009 / Version: 2.0
J
22
Page 27

Steps to
enable Direct Link Setup function:
1. Click the "Direct Link Setup Enable" checkbox.
2. Change to "Network" function. Add an AP that supports DLS features to the Profile.
3. Fill in the blanks of Direct Link wi th MAC Address of STA. The STA must conform to these two
conditions:
y Con
nect with an AP that supports DLS features.
y Ensure that DLS is enabled
4. Fill in the Timeout Value and then click
ter configuring the DLS successfully, the MAC address and Timeout Value are displayed in
5. Af
.
the "DLS Status".
6. If y
DLS Status
ou want to disconnect Direct Link Setup , select the list in “DLS Status” and then click on the
tton.
bu
anuary 13, 2009 / Version: 2.0
J
23
Page 28

WPS
T
he primary goal of Wi-Fi Protected Setup (Wi-Fi Simple Configuration) is to simplify the security
setup and management of Wi-Fi networks. This adapter supports the configuration setup usin g
PIN configuration method or PBC configur ation method through a n internal or external Registrar.
1
2
13
14
15
16
17
Items Informati
1. WPS AP Li
st Display the inf ormation of surrounding APs with WPS IE from last scan
result. List information includes SSID, BSSID, Channel, ID (Device
Password ID), and Security-Enabled.
e
2. WPS Profil
List
Display all of credentials got from the Registrar. List information includes
SID, MAC Address, Authentication and Encryption Type. If STA Enrollee,
S
credentials are created as soon as each WPS success. If STA Registrar,
Utility creates a new credential with WPA2-PSK/AES/64Hex-Key and
doesn't change until next switching to STA Registrar.
3. Resc
4. Informati
an Click to rescan the wireless networks.
on Display the information about WPS IE on the selected network. List
information includes Authentication Type, Encryption Type, Config
Methods, Device Password ID, Selected R egistrar, State, Version, AP Setup
Locked, UUID-E and RF Bands.
5. Pin Code 8-digit num
method. Each Network card has only one PIN Code of Enrollee. Click on the
enew button to renew the PIN code.
R
6. Con
7. Det
8. Con
9. Rot
10. Disconnec
fig Mode Enrollee or an external Registrar.
ail Information about Security and Key in the credential.
nect Command to connect to the selected network inside credentials.
ate Command to connect to the next network inside credentials.
t Stop WPS action and disconnect this active link. And then select th e last
profile at the Profile Page of Utility if exists. If there is an empty profile
page, the driver will select any non-security AP.
11. Export Pr
12. Delet
ofile Click the "Export Profile" button will export the WPS profile.
e Delete an existing credential. And then select the next cre dential if exist. If
there is an empty credential, the driver will select any non-security AP.
13. PIN Start to
14. PBC Start to
15. WPS
ociate IE
ass
16. WPS pr
obe IE Send the probe request with WPS IE during WPS setup. It is optional for
Send the association request with WPS IE d uring WPS setup. It is optional
for STA.
add to Registrar using PIN configuration method.
add to AP using PBC configuration method.
STA.
17. Aut
18. Progr
19. Stat
o Select the AP automatically.
ess Bar Display rate of progress from Start to Connected status.
us Bar Display currently WPS Status.
18
19
on
bers. It is required to enter PIN Code into Registrar using PIN
3
4
5
6
7
8
9
10
11
12
anuary 13, 2009 / Version: 2.0
J
24
Page 29

The fol
lowing description divides into four parts:
A. WPS Information on AP
B. Example of Adding to Registrar Using PIN Method
C. Example of Adding to Registrar Using PIN Method
D. Example of Configuring a Network/AP Using PIN or PBC Method
anuary 13, 2009 / Version: 2.0
J
25
Page 30

A. WPS Inf
ormation on AP: On Network AP list, double click on the AP then you can see the
information appears below.
Items Informati
entication Type There are three authentication modes supported by this utility. They are
Auth
on
open, Shared, WPA-PSK and WPA system.
Encryption
Type For open and shared authentication mode, the selection of encryption
type are None and WEP. For WPA, WPA2, WPA-PSK and WPA2-PSK
authentication mode, the encryption type supports both TKIP and AES.
Config Methods Correspond to the methods the AP supports as an Enrollee for adding
external Registrars. (a bitwise OR of values)
vice Password ID Indicates the method or identifies the specific password that the selected
De
Registrar intends to use. APs in PBC mode must indicate 0x0004 within
two-minute Walk Time.
Select
ed Registrar Indicates if the user has recently activated a Registra r to add an Enrollee.
The values are "TRUE" and "FALSE".
Stat
e The current configuration state on AP. The values are "Unconfigured"
and "Configured".
on WPS specified version.
Versi
AP Set
UUI
up Locked Indicates if the AP has entered a setup locked state.
D-E The universally unique identifier (UUID) element generated by the
Enrollee. This is a 16 byte value.
ands Indicates all the RF bands available on the AP. A dual-band AP must
RF B
provide
it. The v
alues are "2.4GHz/5.8GHz" and "5GHz".
anuary 13, 2009 / Version: 2.0
J
26
Page 31

B. Example of Addin
g to Registrar Using PIN Method
The user obtains a device password (PIN Code) from the STA and enters the password into the
Registrar. Both the Enrollee and the Registrar use PIN Config method for the configur ation setup.
Please follow the step below.
1. Select "Enrollee" from the Config Mode drop-down list.
2. Click "Rescan" to update available WPS APs.
3. Select
an AP (SSID/BSSID) that STA will join to .
anuary 13, 2009 / Version: 2.0
J
27
Page 32

4. Cl
ick "PIN" to enter the PIN.
5. Enter the PIN Code of the STA into the Registrar when prompted by the Registrar.
Note:
y Allow of a
n exchange between Step 4 and Step 5.
y If you use Microsoft Window Connection Now as an External Registrar, you must start
PIN connection at STA first. After that, search out your WPS Device name and MAC
address at Microsoft Registrar. Add a new device and enter PIN Code of STA at Microsoft
Registrar when prompted.
6. The result should appear as the image below.
anuary 13, 2009 / Version: 2.0
J
28
Page 33

7. C
onfigure one or more credentials. Then connect successfully.
8. C
C. Example of Addin
lick "Detail." You can see the figure below.
g to the Registrar Using the PBC Method
The PBC method requires the user to press a PBC button on both the Enrollee and the Registrar
within a two-minute interval called the Walk Time. If there is only one Registrar in PBC mode, the
PBC mode selected is obtained from ID 0x0004, and is found after a complete scan. The Enrollee
can then immediately begin running the Registration Protocol.
If the Enrollee discovers more than one Registrar in PBC mode, it MUST abort its connection
attempt at this scan and continue searching until the two-minute timeout.
Note: Before you press PBC on STA and candidate AP. Make sure all APs aren't PBC mode or APs
using PBC mode have left their Walk Time. The user can configure WPS profiles with either PIN
method or PBC method.
Please follow the steps below.
anuary 13, 2009 / Version: 2.0
J
29
Page 34

1. Select
"Enrollee" from the Config Mode drop-down list.
2. Cl
ick PBC to start the PBC connection.
3. Push the PBC on AP.
Note: Allow time for an exchange between Step 2 and Step 3.
anuary 13, 2009 / Version: 2.0
J
30
Page 35

4. The progres
s bar as shown in the figure below indicates that scanning progress.
5. When o
ne AP is found, join it.
anuary 13, 2009 / Version: 2.0
J
31
Page 36

6. C
heck WPS Information on the available WPS APs.
7. Confi
gure and receive one or more credential(s).Then connect successfully. The result will be
displayed as it is in the figure below.
anuary 13, 2009 / Version: 2.0
J
32
Page 37

D. Example of Con
figuring a Network/AP Using PIN or PBC Method
1. Select "Registrar" from the Config Mode drop-down list.
2. Enter
the details of the credential and change configurations (SSID, Authentication,
Encryption and Key) manually if needed.
3. If
the PIN configuration is setup, enter the PIN sent from the Enrollee.
4. Start PIN or PBC. The following procedures are as similar as section PIN Enrollee Setup or
PBC Enrollee Setup.
anuary 13, 2009 / Version: 2.0
J
33
Page 38

5. If your AP
Enrollee has been configured before the WPS process, the credential you set in
advance will be updated to the AP itself. Otherwise, after a successful registration, the AP
Enrollee will be re-configured with the new parameters, and the STA Registrar will connect to
the AP Enrollee with these new parameters.
anuary 13, 2009 / Version: 2.0
J
34
Page 39

CCX
T
his page is available for Vista user only. It provides CCX configurations to this adapter. Please
refer to the following chart for definitions of each item.
Items Informati
Enable CCX (Cisco
extensions)
urn on CCKM Mark to enable CCKM.
T
Enable Radio
Non-Ser
Measurements limit
Network EAP Enabl
Enable RF Roaming Enable RF r
Enable CAC (Toler
CAC There are four selections: ADDTS (Directly send TS), DEL TS,
Dia
ving Channel
gnosis Select a profile which the user wants to diagnose, and then
Compatible
Measurements Mark to enable channel measurement every 0~2000
ance) Enable the call admission control
Select to enable CCX. This function can only be applied
when connecting to a Cisco compatible device.
milliseconds.
Mark to revise the channel measurement.
and RESET. Select an item from the drop down list and then
click on the
click on the Diagnose button to perform the
test.
on
e the NetwrokEAP authentication algorithm.
oaming function
button.
Radio On/Off
C
lick on the button to enable/disable wireless connection status.
Connected:
Disconnected:
anuary 13, 2009 / Version: 2.0
J
35
Page 40

AP
mode management guide for Windows 2000/XP/Vista
If
you wish to share the Internet access with the wireless stations in your environment, you can
configure this wireless adapter as a software access point (Soft AP). In this mode, this wireless
adapter becomes the wireless access point that provides local area network and Internet access
for your wireless stations.
To use this adapter as an access point, please right click the icon on system tray and
select Switch to AP mode. Please refer to the following introduction and information about this
AP-mode utility.
Note: In windows X
sure that hotfix Q815485 (require XP SP1 installed) has been installed in your system before you
can start using WPA features. You can check the installation of hotfix in add/remove software
page under control panel.
P, it provides WPA support at hotfix Q815485. However; you have to make
anuary 13, 2009 / Version: 2.0
J
36
Page 41

Software Access Point (Soft AP) Application
anuary 13, 2009 / Version: 2.0
J
37
Page 42

Config
his page provides overall configuration to this adapter. Please find the following items for
T
identification to each field.
1
7
2
8
3
9
10
11
12
4
5
6
13 15 14
1. SSI
D: AP name of user type. User also can select [Use Mac Address] to display it.
2. Wireless Mode: Select wireless mode. Only 2.4G is supported.
anuary 13, 2009 / Version: 2.0
J
38
Page 43

3. Cou
ntry Region Code: eight countries to choose. Country channel list:
Classification Range
0: FCC (Canada) CH1 ~ CH11
1: ETSI CH1 ~ CH13
2: SPAIN CH10 ~ CH11
3: FRANCE CH10 ~ CH13
4: MKK CH14 ~ CH14
5: MKKI (TELEC) CH1 ~ CH14
6: ISRAEL CH3 ~ CH9
7: ISRAEL CH5 ~ CH13
Note: Country Region code is not support for Vista.
4. Beacon (ms): The time between two beacons. System default is 100 ms.
5. TX Power: Manually force the AP transmits power. System default is 100%.
6. Idle Time: Manually force the Idle Time using selected value. Default is 300.
7. Channel: Manually force the AP using the channel. System default is channel 1.
8. Use Mac Address: Use MAC address of used wireless card to be AP name. System default is
APX (X is last number of Mac Address).
9. Security Setting: Authentication mode and encryption algorithm use d within the AP . S ystem
default is no authentication and encryption.
10. No forwarding among wir eless clients: If there is no beacon among the wireless clients,
they can’t share information with each other.
11. Hide SSID: Prevent this AP from recognized in wireless network. This is disabled as default.
12. Allow BW40 MHz: Allow BW40 MHz capability.
13. Default: Use system default value.
14. Cancel: Cancel the above changes.
15. Apply: Apply the above changes.
anuary 13, 2009 / Version: 2.0
J
39
Page 44

Securit
y Setting
This page
below:
pops up after clicking the Security Setting button. Please follow the instructions
1 2
3
4
5
1. Auth
2. Encryption Type: Select an encryption type from the drop list.
3. WPA Pre-shared Key: A shared string between AP and STA. For WPA-PSK
4. Group Rekey Interval: Only valid when using WPA-PSK encryption algorithm.
5. WEP Key: Only valid when using WEP encryption algorithm. The key must match
entication Type: Select to be open, shared, WPA-PSK, WPA2-PSK, or WPA
PSK/WPA2-PSK system.
authentication mode, this field must be filled wi th character longer than 8 and less
than 32 lengths.
The key will change compliance with seconds or beacon that user set.
the key on AP. There are several formats to enter the keys.
a. Hexadecimal (40bits): 10 Hex characters.
b. Hexadecimal (128bits): 32Hex characters.
c. ASCII (40bits): 5 ASCII characters.
d. ASCII (128bits): 13 ASCII characters.
anuary 13, 2009 / Version: 2.0
J
40
Page 45

Access Co
Thi
s function filters users to use this device by designating MAC address. Please refer to the
following chart for introduction.
ntrol
1
2 3
4
5
6
1. Access P
the MAC addresses that you designated are allowed to access the AP or not.
2. MAC Address: Add allowed (or denied) MAC addresses to the MAC address list.
3. Access List: Display all Mac Addresses that you designated.
4. Delete: Delete Mac addresses that you selected.
5. Remove All: Remove all Mac address in [Access List].
6. Apply: Apply changes.
olicy: Choose a method to process access control from the drop list to determine
anuary 13, 2009 / Version: 2.0
J
41
Page 46

MAC Table
his page displays the station detail information of current connection.
T
Items Informati
MAC Address The sta
AID R
Power Saving
Mode
Stat
us The connection status.
aise value by current connection.
C
heck if the connected station supports power
saving.
on
tion MAC address of current connection.
anuary 13, 2009 / Version: 2.0
J
42
Page 47

Event Log
ecord Soft AP all event time and message.
R
Items Informati
Even
t Time (yy/mm/dd-hh:mm:ss) Record event time.
Message All event messages.
on
anuary 13, 2009 / Version: 2.0
J
43
Page 48

Statistics
atistics page displays the detail counter information based on 802.11 MIB counters.
St
1
2
3
ansmit Statistics
1. Tr
Items Informati
Frames Tr
rames Fail To Receive ACK After
F
ansmitted Successfully Frames that successfully sent.
All Retries
RTS Frames Successfully
CTS
RTS Fr
ames Fail To Receive CTS Counts of CTS that fail to be received
Receive
on
Frames that failed to transmit after
hitting retry limit.
Counts of CTS that successfully
received after sending RTS frame.
after sending RTS frame.
Frames Retrans
Successfully
2. Rec
eive Statistics
Items Informati
F
rames Received Successfully Frames received successfully.
Frames Received Wit
Fra
mes Dropped Due To
Out-of-Resource
Duplic
ate Frames Received Duplicate received frames.
mitted
Successfully retransmitted frames
numbers.
on
h CRC Error Frames received with CRC error.
Frames dropped due to resource
issue.
3. Res
anuary 13, 2009 / Version: 2.0
J
et Counters: Reset counters to zero.
44
 Loading...
Loading...