Page 1

Acronis Storage 2.0
Administrator’s Guide
April 06, 2017
Page 2

Copyright Statement
Acronis International GmbH, 2002-2016. All rights reserved.
”Acronis” and ”Acronis Secure Zone” are registered trademarks of Acronis International GmbH.
”Acronis Compute with Confidence”, ”Acronis Startup Recovery Manager”, ”Acronis Active Restore”,
”Acronis Instant Restore” and the Acronis logo are trademarks of Acronis International GmbH.
Linux is a registered trademark of Linus Torvalds.
VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the United States and/or other jurisdictions.
Windows and MS-DOS are registered trademarks of Microsoft Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder.
Distribution of this work or derivative work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained
from the copyright holder.
DOCUMENTATION IS PROVIDED ”AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED
WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT
SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
Third party code may be provided with the Software and/or Service. The license terms for such third parties are detailed in the license.txt file located
in the root installation directory. You can always find the latest up-to-date list of the third party code and the associated license terms used with the
Software and/or Service at http://kb.acronis.com/content/7696
Acronis patented technologies
Technologies, used in this product, are covered and protected by one or more U.S. Patent Numbers: 7,047,380; 7,275,139; 7,281,104; 7,318,135;
7,353,355; 7,366,859; 7,475,282; 7,603,533; 7,636,824; 7,650,473; 7,721,138; 7,779,221; 7,831,789; 7,886,120; 7,895,403; 7,934,064; 7,937,612; 7,949,635;
7,953,948; 7,979,690; 8,005,797; 8,051,044; 8,069,320; 8,073,815; 8,074,035; 8,145,607; 8,180,984; 8,225,133; 8,261,035; 8,296,264; 8,312,259; 8,347,137;
8,484,427; 8,645,748; 8,732,121 and patent pending applications.
Page 3

Contents
1. Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
1.1 About Acronis Storage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
1.2 What’s New in Acronis Storage 2.0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
2. Managing Acronis Storage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
2.1 Configuring Node Network Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
2.1.1 Setting Up Network Bonding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
2.1.2 Setting Up VLAN Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
2.2 Creating Acronis Storage Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
2.2.1 Creating the Cluster on the First Node . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
2.2.2 Adding Nodes to Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
2.2.3 Assigning Disk Roles Manually . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
2.3 Releasing Nodes from Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
2.4 Removing Nodes from the Unassigned List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
2.5 Managing Tier Encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
2.6 Managing Acronis Storage Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
2.6.1 Creating User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
2.6.2 Managing User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
2.7 Managing Acronis Storage Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
2.8 Allowing root Access to Cluster Nodes Over SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
2.9 Backing Up and Restoring Management Node . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
2.9.1 Restoring Management Node from Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
2.10 Managing Acronis Storage Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
3. Monitoring Acronis Storage Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
3.1 Monitoring Cluster Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
i
Page 4

3.2 Monitoring Cluster Storage Space . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
3.2.1 Physical Space Chart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
3.2.2 Logical Space Chart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
3.2.2.1 Understanding Logical Space . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
3.2.3 Monitoring Chunk Status and Replication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
3.2.4 Monitoring Cluster Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
3.2.5 Monitoring Cluster I/O Activity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
4. Monitoring Acronis Storage Nodes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
4.1 Node Statuses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
4.2 Monitoring Node Performance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
4.2.1 Monitoring Node Disks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
4.2.1.1 Monitoring the S.M.A.R.T. Status of Node Disks . . . . . . . . . . . . . . . . . . . . . 39
4.3 Monitoring Node Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
5. Exporting Acronis Storage Cluster Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
5.1 Exporting Data via iSCSI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
5.1.1 Creating Acronis Storage iSCSI Targets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
5.1.1.1 Performance Tips . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
5.1.2 Listing, Stopping, and Deleting Acronis Storage iSCSI Targets . . . . . . . . . . . . . . . . . . 43
5.1.3 Configuring Acronis Storage iSCSI Targets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
5.1.3.1 Listing LUNs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
5.1.3.2 Adding LUNs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
5.1.3.3 Configuring LUNs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
5.1.3.4 Deleting LUNs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
5.1.4 Accessing Acronis Storage iSCSI Targets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
5.1.4.1 Accessing Acronis Storage iSCSI Targets from CentOS 6 . . . . . . . . . . . . . . . . 47
5.1.4.2 Accessing Acronis Storage iSCSI Targets from Microsoft Windows Server 2012 R2 47
5.1.4.3 Accessing Acronis Storage iSCSI Targets from VMware ESXi . . . . . . . . . . . . . . 54
5.1.4.4 Accessing Acronis Storage iSCSI Targets from Citrix XenServer 6.2 . . . . . . . . . . 54
5.1.4.5 Accessing Acronis Storage iSCSI Targets from Microsoft Hyper-V . . . . . . . . . . 55
5.1.5 Managing iSCSI Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
5.1.5.1 Creating CHAP Accounts for Acronis Storage iSCSI Targets . . . . . . . . . . . . . . 56
5.1.5.2 Creating Acronis Storage iSCSI Targets Bound to CHAP Accounts . . . . . . . . . . 57
5.1.5.3 Changing CHAP Account Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
5.2 Exporting Data via S3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
ii
Page 5

5.2.1 Object Storage Infrastructure Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
5.2.2 Planning the S3 Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
5.2.3 Sample Object Storage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
5.2.4 Creating the S3 Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
5.2.5 Managing Object Storage Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
5.2.5.1 Adding S3 users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
5.2.5.2 Managing S3 Access Key Pairs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
5.2.6 Managing Object Storage Buckets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
5.2.6.1 Creating Buckets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
5.2.6.2 Managing Bucket Versions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
5.2.6.3 Listing Bucket Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
5.2.6.4 Managing Acronis Notary in Buckets . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
5.2.7 Best Practices for Using S3 in Acronis Storage . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
5.2.7.1 Bucket and Key Naming Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
5.2.7.2 Improving Performance of PUT Operations . . . . . . . . . . . . . . . . . . . . . . . 76
5.2.8 Monitoring S3 Access Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
5.2.9 Releasing Nodes from S3 Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
5.2.10 Supported Amazon S3 Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
5.2.10.1 Supported Amazon S3 REST Operations . . . . . . . . . . . . . . . . . . . . . . . . . 77
5.2.10.2 Supported Amazon Request Headers . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
5.2.10.3 Supported Authentication Scheme . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
5.3 Using Acronis Storage with Acronis Backup Cloud . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
5.3.1 Understanding the Infrastructure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
5.3.2 Configuring Acronis Backup Gateway Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
5.3.3 Releasing Nodes Running Acronis Backup Gateway Services . . . . . . . . . . . . . . . . . . 83
iii
Page 6

CHAPTER 1
Introduction
To support the growing demand for both high performance and high data availability, modern data centers
need a fast, flexible storage solution. Existing solutions, however, are often difficult to manage and maintain,
or not flexible enough (e.g., local RAID arrays), or too expensive (e.g., storage area networks).
Acronis Storage is designed to solve these issues. It can run on commodity hardware, so no significant infras-
tructure investments are needed. It is also is easy to set up and grow on demand.
1.1 About Acronis Storage
Acronis Storage is a software-defined storage solution that allows you to quickly and easily transform low-
cost commodity hardware and network equipment into protected enterprise-grade storage like storage area
networks (SAN) or network-attached storage (NAS).
Acronis Storage is optimized for storing large amounts of data and provides data redundancy (replication and
erasure coding), high availability, self-healing, and storage sharing.
In Acronis Storage, user data is stored on organized clusters of servers in the form of fixed-size chunks. These
chunks are automatically replicated and distributed across available servers in the cluster to ensure high avail-
ability of user data.
Cluster storage space can be exported through access points like iSCSI, S3, or Acronis Backup Gateway.
1.2 What’s New in Acronis Storage 2.0
Acronis Storage 2.0 offers the following new or updated features compared to Acronis Storage 1.0:
1
Page 7

Chapter 1. Introduction
• A web-based user interface that enables access to all Acronis Storage 2.0 features, including management
and monitoring of clusters and nodes, iSCSI targets, S3 object storages, and Acronis Backup Gateways.
• Support for new data redundancy modes by erasure coding to ensure a significant reduction of data
replication overhead.
• Ability to create and manage object storages with support for the Amazon S3 compatible protocol.
• Ability to create and manage iSCSI targets.
• Ability to create and manage Acronis Backup Gateway access points and use Acronis Storage 2.0 to store
backups created with Acronis Backup Cloud.
• Ability to prove authenticity of stored files by means of blockchain notarization. Users can upload files to
object storage repositories and record file fingerprints (in the form of file hashes) in the Acronis Notary
service connected to the Ethereum blockchain.
2
Page 8
CHAPTER 2
Managing Acronis Storage
To start managing Acronis Storage, log in to the management panel as admin (or superadmin) and make sure
that storage nodes are shown on the NODES screen.
The first step to perform, before you can create any clusters, is to create the internal and public networks
required by Acronis Storage. You can do that by configuring the network interfaces of all nodes. Having
created the networks, you can proceed to creating Acronis Storage clusters.
2.1 Configuring Node Network Interfaces
As described in Planning Network in the Acronis Storage 2.0 Installation Guide, Acronis Storage requires one
internal network for node traffic and one public network for exporting the storage space. You need to create
these networks by assigning correct network roles to network interfaces on each node.
Important: To be able to create a cluster, you will need to assign a storage role to a node’s network
interface.
To assign a network role to a network interface, do the following:
1. On the NODES screen, click the node to configure the network interface(s) of.
3
Page 9
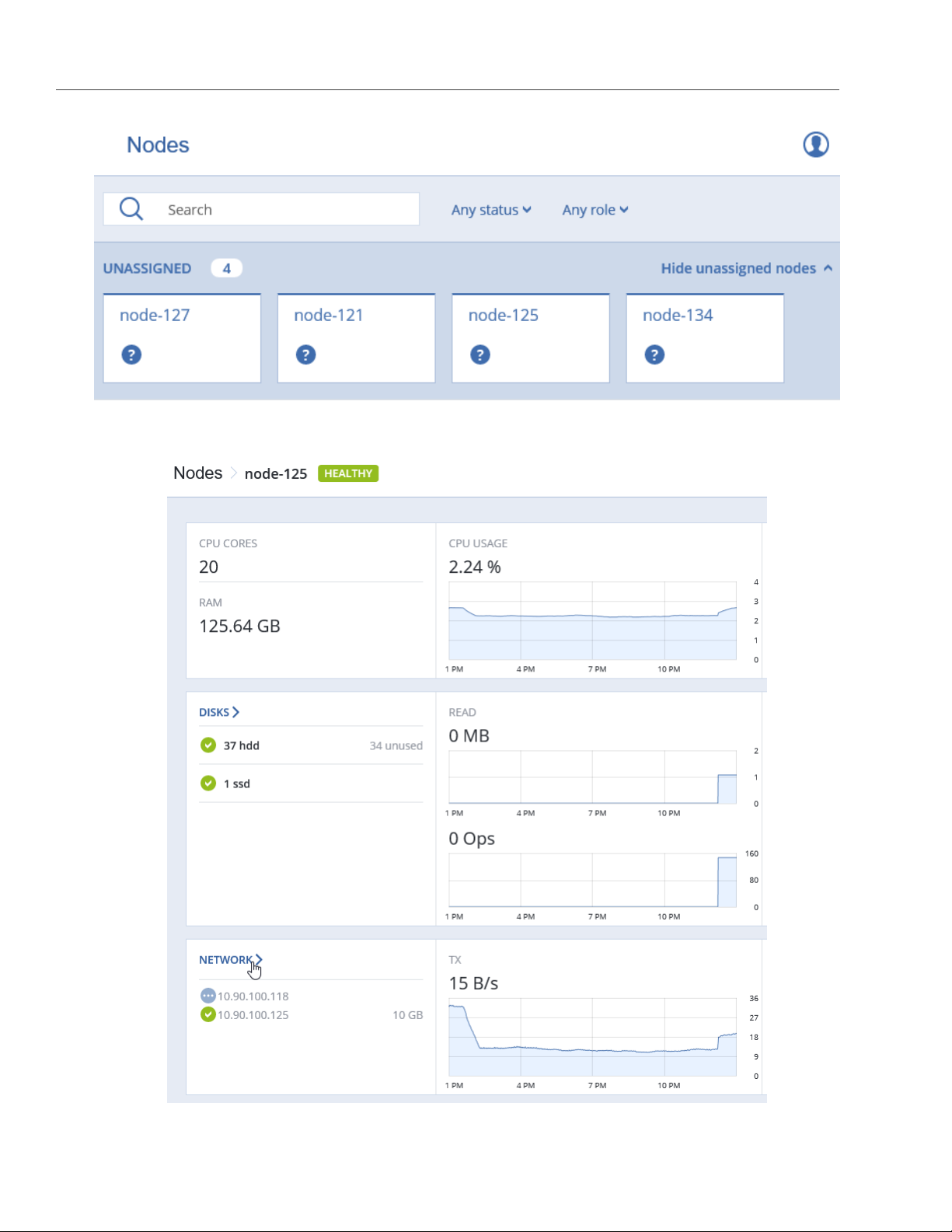
2. On the node overview screen, click NETWORK.
Chapter 2. Managing Acronis Storage
4
Page 10
2.1. Configuring Node Network Interfaces
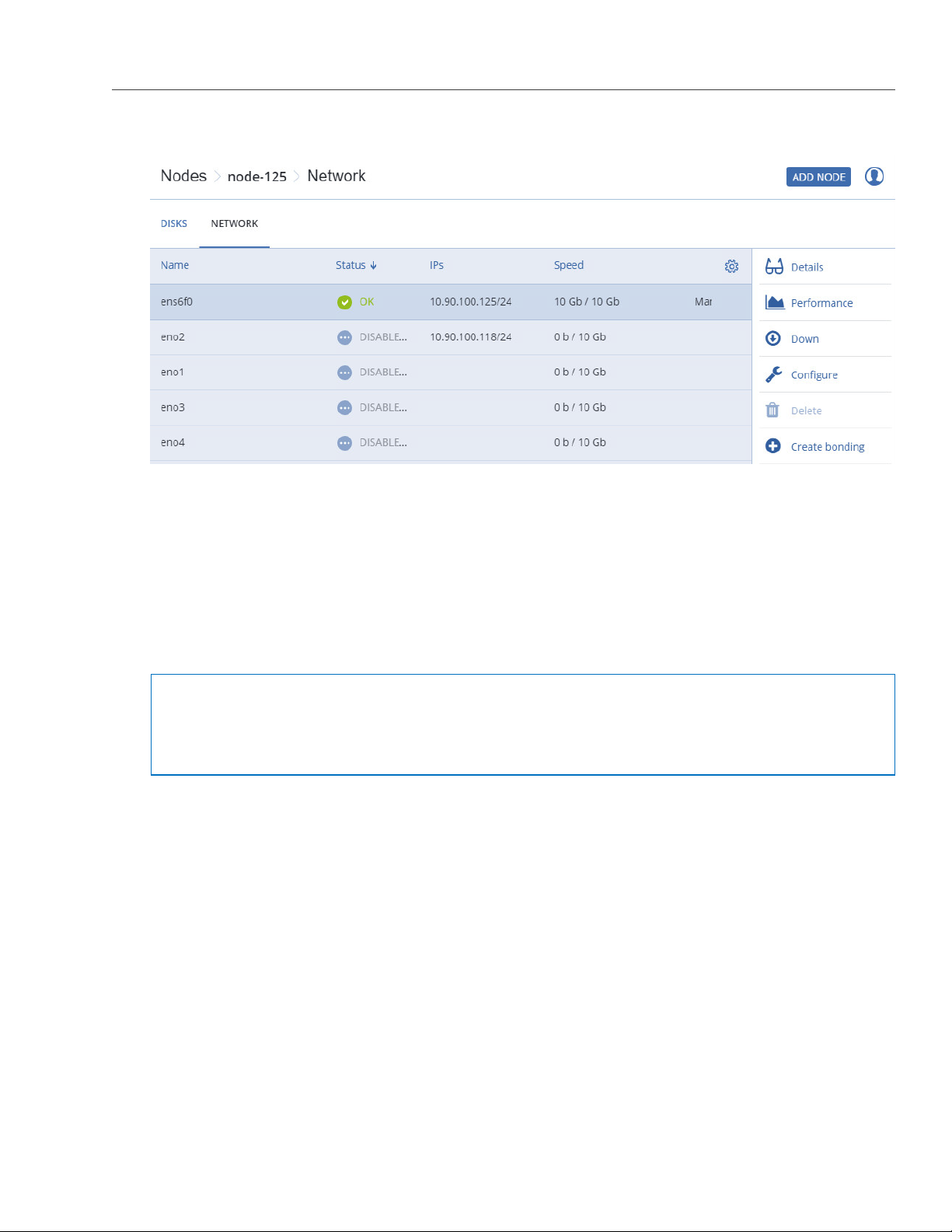
3. Select a network interface and click Configure.
4. On the Configure screen, do one of the following:
• To obtain the IP address, DNS, and routing settings from the DHCP server, select Automatically
(DHCP).
• To obtain just the IP address from the DHCP server, select Automatically (DHCP address only).
• To specify the IP address manually, select Manual and add the IP address.
Warning: Dynamic IP address allocation will cause network issues as soon as the IP addresses of
cluster nodes will change. Configure static IP addresses from the start or as soon as possible.
5
Page 11
Chapter 2. Managing Acronis Storage
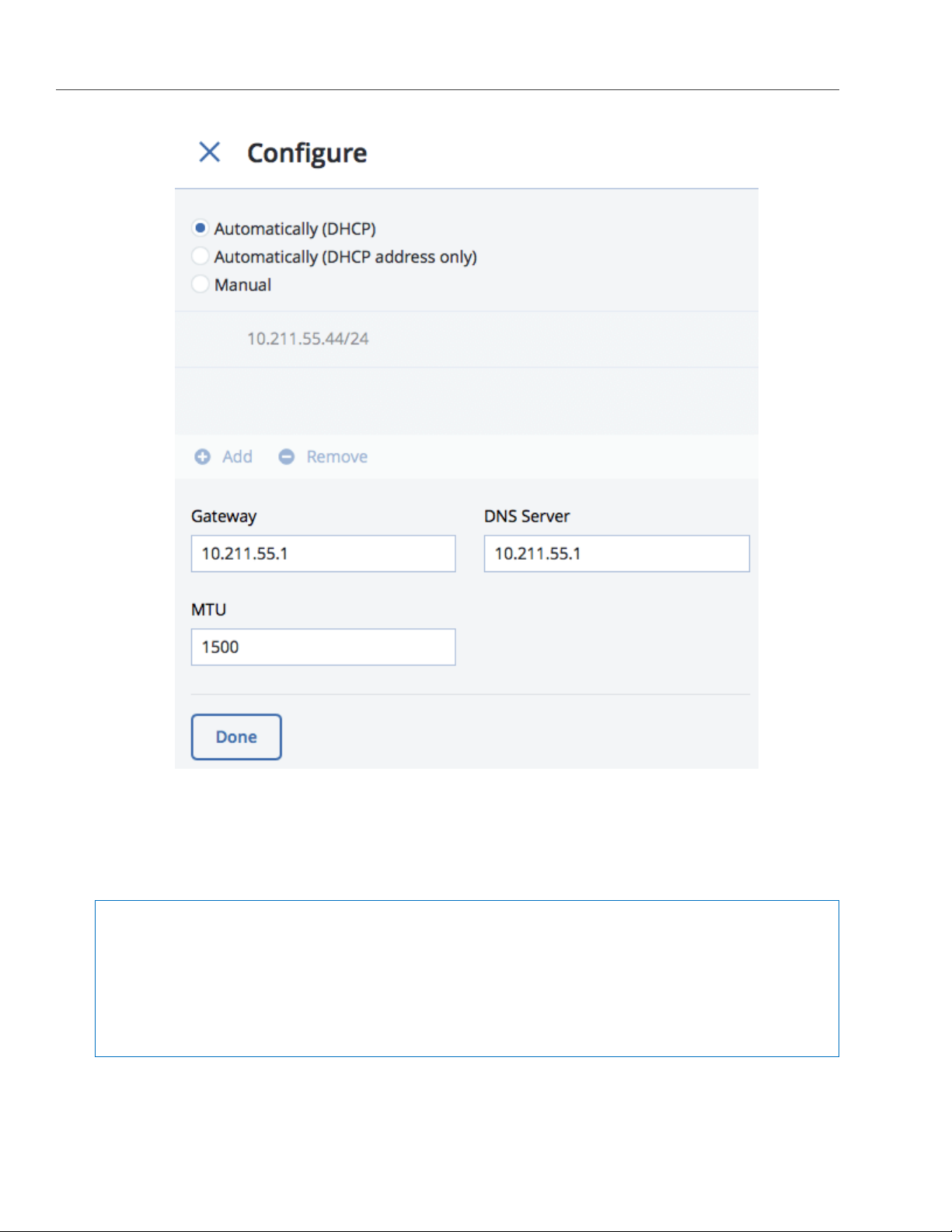
5. If necessary, set up a gateway and a DNS server.
6. If you have set a custom maximum transmission unit (MTU) on the network hardware, set the same value
in the corresponding field.
Warning: Setting a custom MTU in management panel prior to configuring it on the network
hardware will result in network failure on the node and require manual resetting. Setting an MTU
that differs from the one configured on the network hardware may result in network outage or poor
performance.
7. Click Done to return to the list of network interfaces, do not change the selection, and click Choose role.
6
Page 12
2.1. Configuring Node Network Interfaces
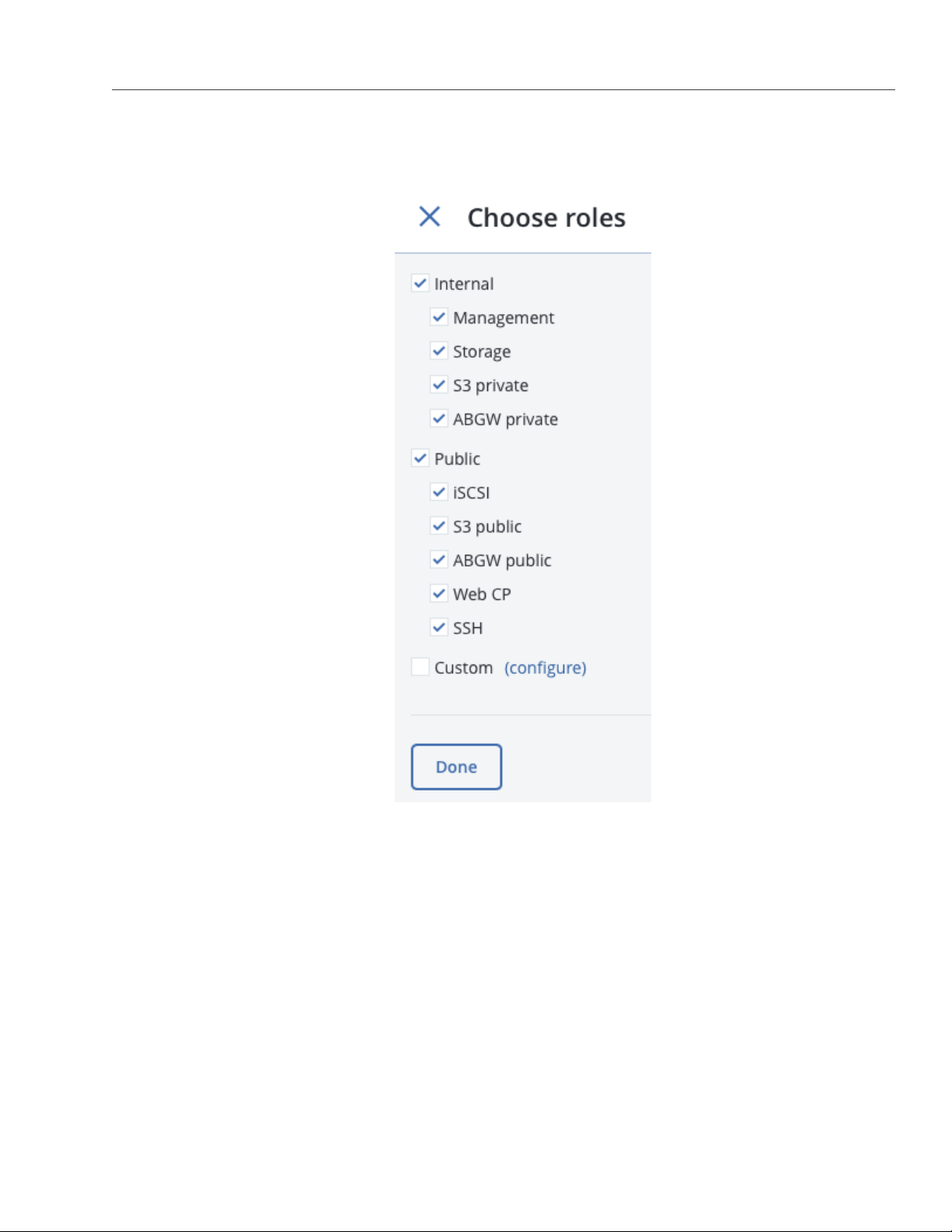
8. On the Choose roles panel, select roles to assign to the network interface (for details, see Network
Interface Roles in the Acronis Storage 2.0 Installation Guide).
9. If you need to open specific ports on a network interface with public roles, do the following:
(a) Click Configure.
7
Page 13
Chapter 2. Managing Acronis Storage
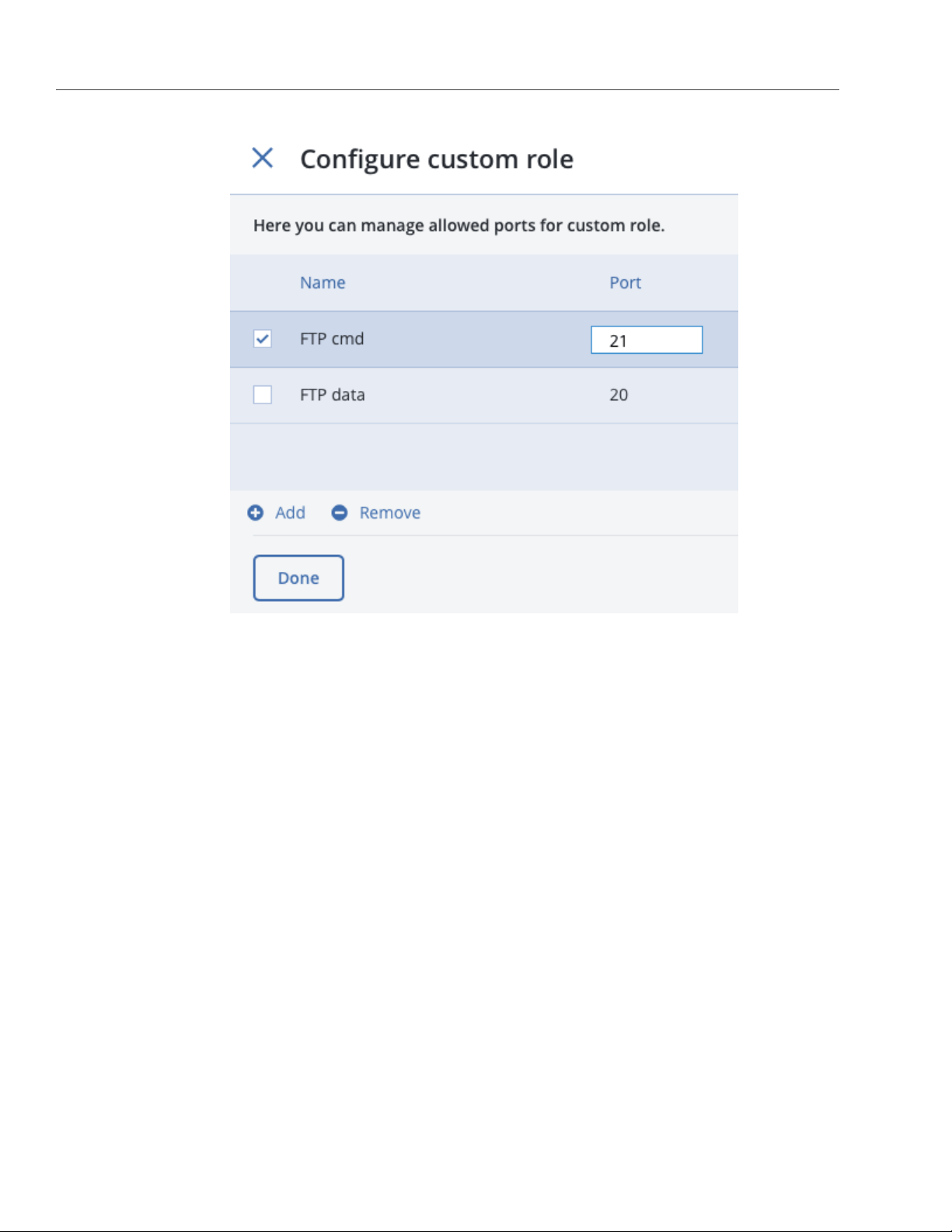
(b) On the Configure custom role panel, create custom roles: click Add and specify role names and
ports. Custom roles can later be assigned to any network interface in a cluster.
To remove a custom role, make sure it is not assigned to any interface, select it, and click Remove.
(c) Click Done to return to the Choose roles panel.
11. Select the required roles and click Done to assign them.
2.1.1 Setting Up Network Bonding
Bonding multiple network interfaces is optional but provides the following benefits:
• High network availability. If one of the interfaces fails, the traffic will be automatically routed through the
working interface(s).
• Higher network performance. For example, two bonded Gigabit interfaces will deliver the throughput of
about 1.7 Gbit/s or up to 200 MB/s. For a storage node, the required number of network interfaces to
bond may depend on the number of disks. For example, an HDD can deliver data at speeds of up to 1
8
Page 14

2.1. Configuring Node Network Interfaces
Gbps.
To create a bond, do the following:
1. On the NODES screen, click the node to bond the network interfaces on.
2. On the node overview screen, click NETWORK.
3. In the NETWORK list, check network interfaces to bond, and click Create bonding in the menu to the
right.
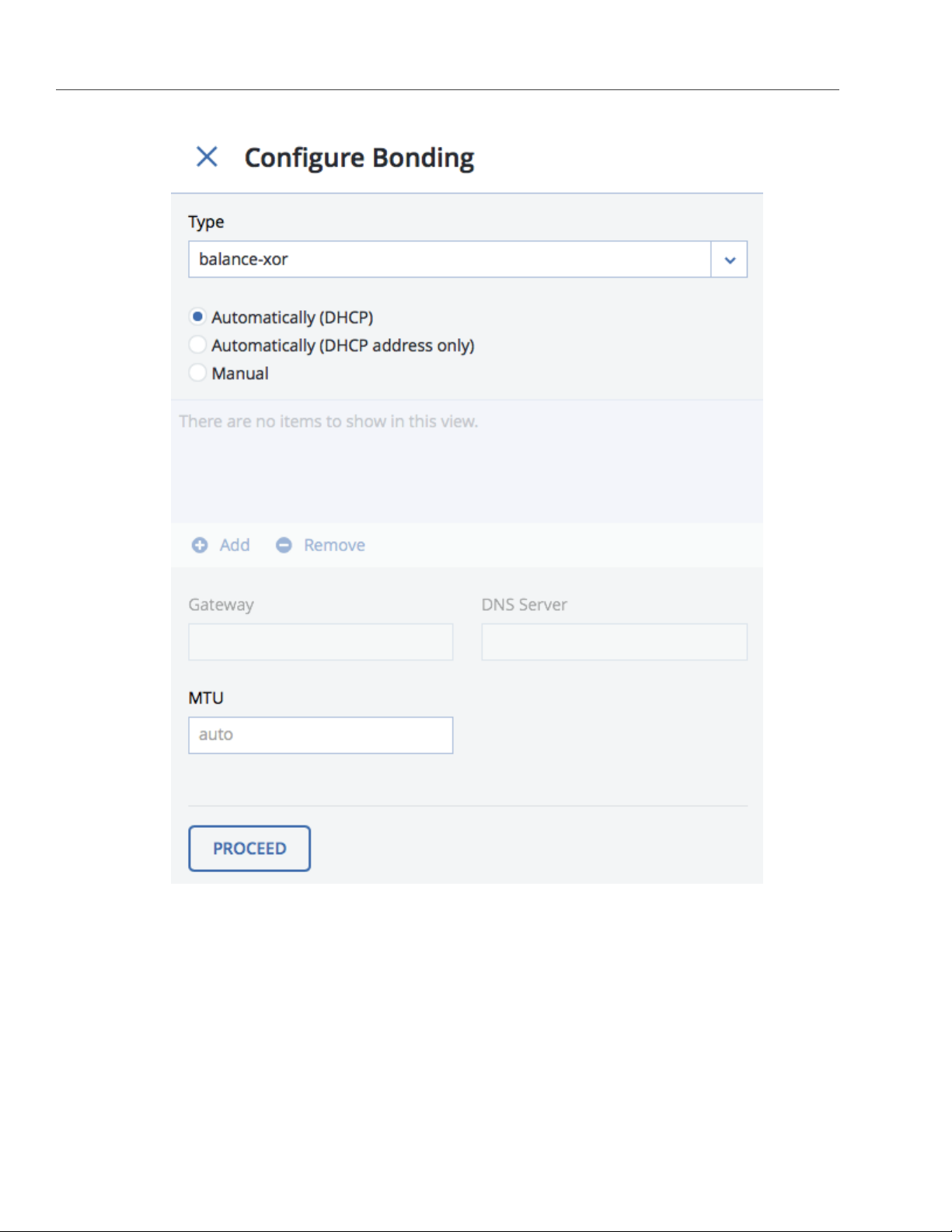
4. On the Configure Bonding panel, select the bonding type from the drop-down list. The balance-xor type
is selected by default and recommended for both fault tolerance and good performance.
9
Page 15
Chapter 2. Managing Acronis Storage
5. Set up network parameters as described in step 4 in Configuring Node Network Interfaces on page 3 and
click PROCEED.
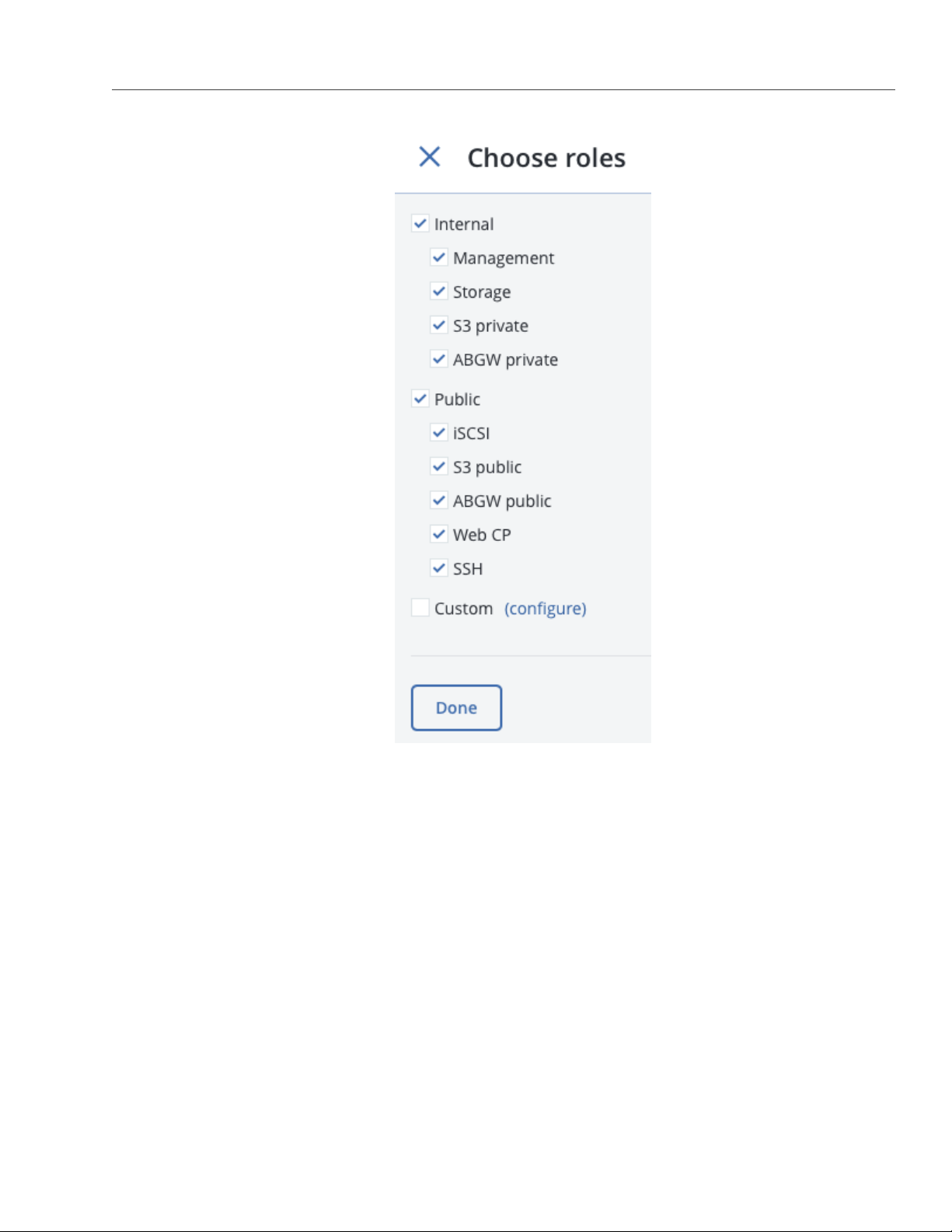
6. On the Choose roles panel, select roles to assign to the bonding network interface (for details, see Net-
work Interface Roles in the Acronis Storage 2.0 Installation Guide).
10
Page 16
2.1. Configuring Node Network Interfaces
7. Click Done.
2.1.2 Setting Up VLAN Interfaces
To set up a VLAN network interface, do the following:
1. On the NODES screen, click the node on which to configure VLAN.
2. On the node overview screen, click NETWORK.
3. Select a network interface and click Create VLAN.
4. On the Configure VLAN panel, specify a number for VLAN, add an IP address, and, if necessary, set up a
gateway and a DNS server.
11
Page 17
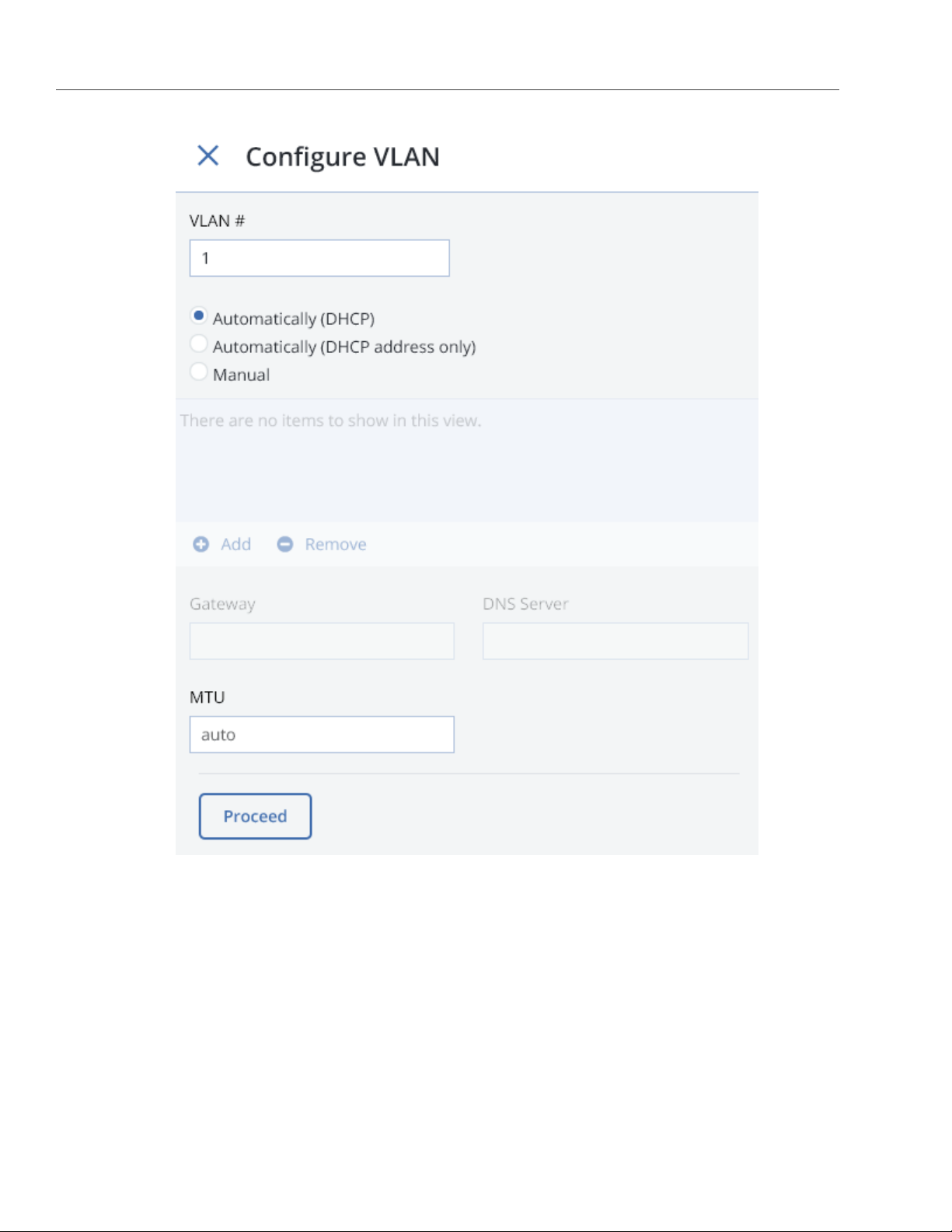
Chapter 2. Managing Acronis Storage
5. Click Proceed to create a VLAN interface.
2.2 Creating Acronis Storage Clusters
To create an Acronis Storage cluster means to create a cluster on one (first) node, then populate it with more
nodes.
12
Page 18
2.2. Creating Acronis Storage Clusters
Important: To be able to create a cluster, you will need to assign a storage role to a node’s network
interface.
2.2.1 Creating the Cluster on the First Node
1. Open the NODES screen and click a node in the UNASSIGNED list.
2. On the node overview screen, click Create cluster.
3. In the Cluster field, type a name for the cluster. The name may only contain Latin letters (a-z, A-Z),
numbers (0-9), underscores (“_”) and dashes (“-”).
13
Page 19
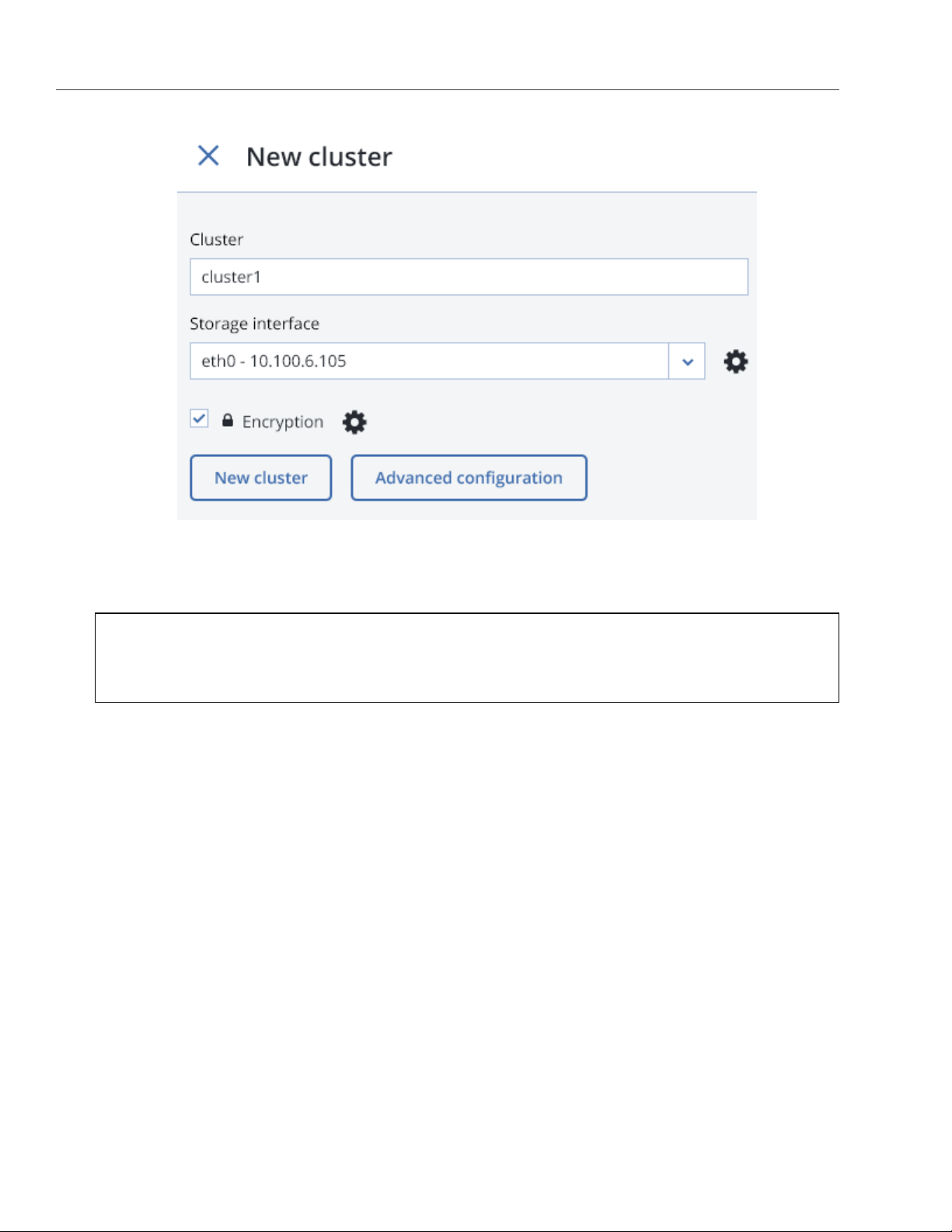
Chapter 2. Managing Acronis Storage
4. Make sure a configured network interface with a storage role is selected from the Storage interface
drop-down list.
Note: If the network was not previously configured, click the cogwheel icon and, on the Network
Configuration screen, configure a storage role for a network interface.
5. If required, to enable data encryption, check the Encryption box (see Managing Tier Encryption on page 21)
and proceed to create the cluster. Encryption will be enabled for all tiers by default.
To enable encryption for particular tiers, click the cogwheel icon to open the Encryption Configuration
panel, select tiers to encrypt, and click Done.
14
Page 20
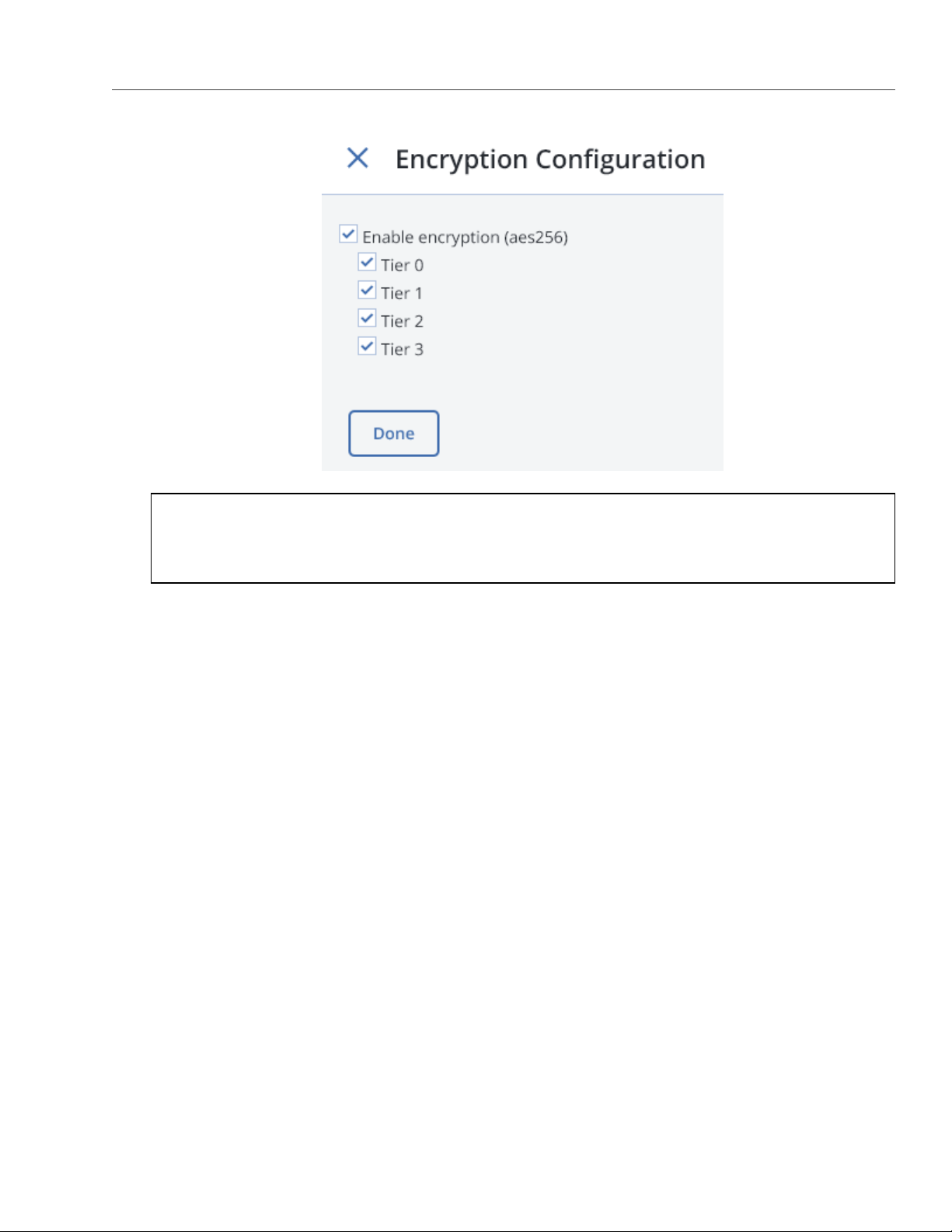
2.2. Creating Acronis Storage Clusters
Note: You can later disable encryption for new chunk services (CS) on the SETTINGS > Advanced
settings panel.
6. Click New cluster to have Acronis Storage assign the roles to disks automatically. Alternatively, click
Advanced configuration to assign the roles to each drive manually (see Assigning Disk Roles Manually on
page 17).
You can monitor cluster creation progress in the HEALTHY list of the NODES screen. The creation might take
some time depending on the number of disks to be configured. Once the automatic configuration is complete,
the cluster is created.
2.2.2 Adding Nodes to Cluster
To add an unassigned node to a cluster, do the following:
1. On the NODES screen, click an unassigned node.
15
Page 21
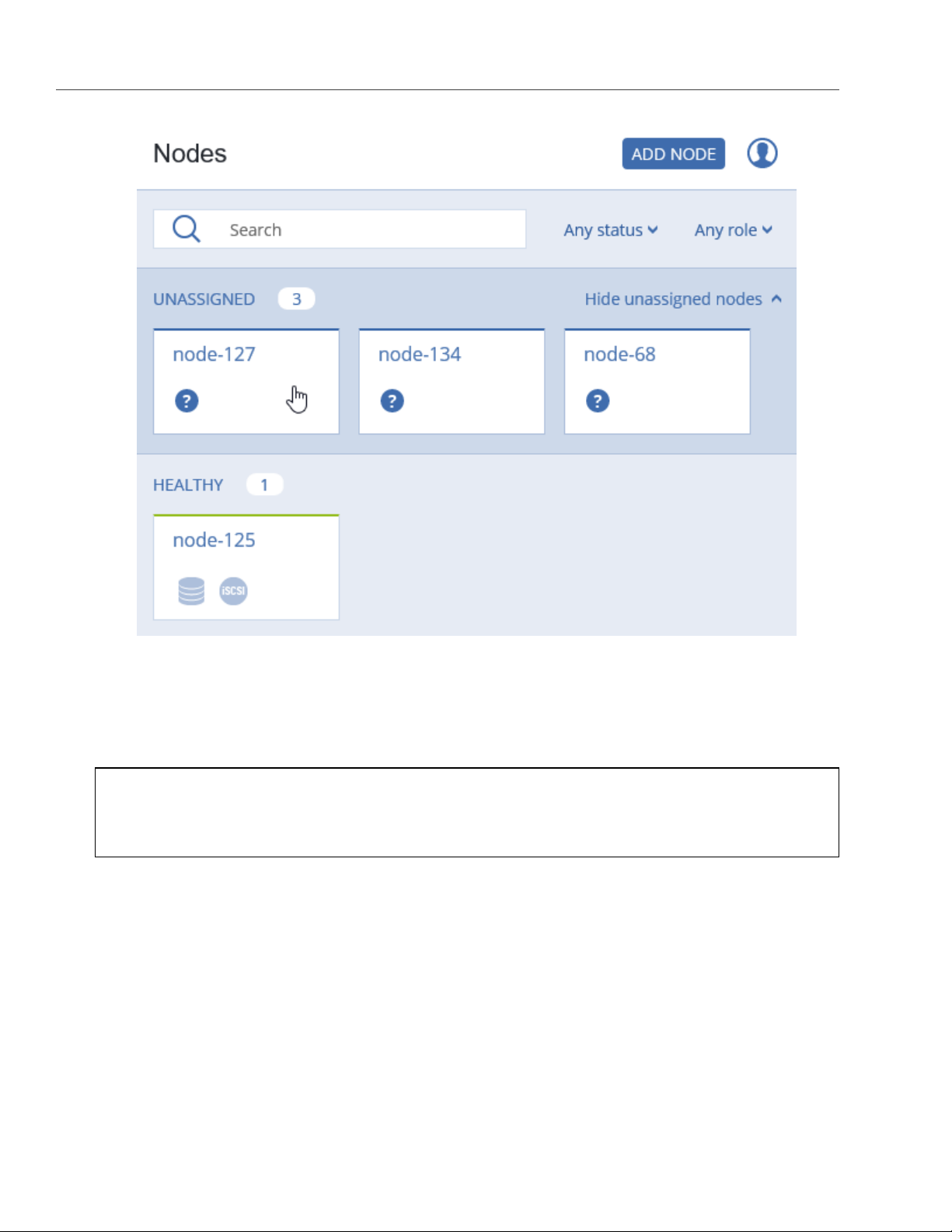
Chapter 2. Managing Acronis Storage
2. On the node overview screen, click Join cluster.
3. Make sure a configured network interface with a storage role is selected from the Storage interface
drop-down list.
Note: If the network was not previously configured, click the cogwheel icon and, on the Network
Configuration screen, configure a storage role for a network interface.
16
Page 22
2.2. Creating Acronis Storage Clusters
5. Click
Join cluster
current cluster. Alternatively, click Advanced configuration to assign the roles to each drive manually
(see Assigning Disk Roles Manually on page 17).
to have Acronis Storage assign the roles to disks automatically and add the node to the
2.2.3 Assigning Disk Roles Manually
If you clicked Advanced configuration while creating a cluster or adding nodes to it, you will be taken to the
list of drives on the node where you can manually assign roles to these drives. Do the following:
1. On the Join cluster or New cluster panel, select a drive or check multiple drives in the list and click
Configure.
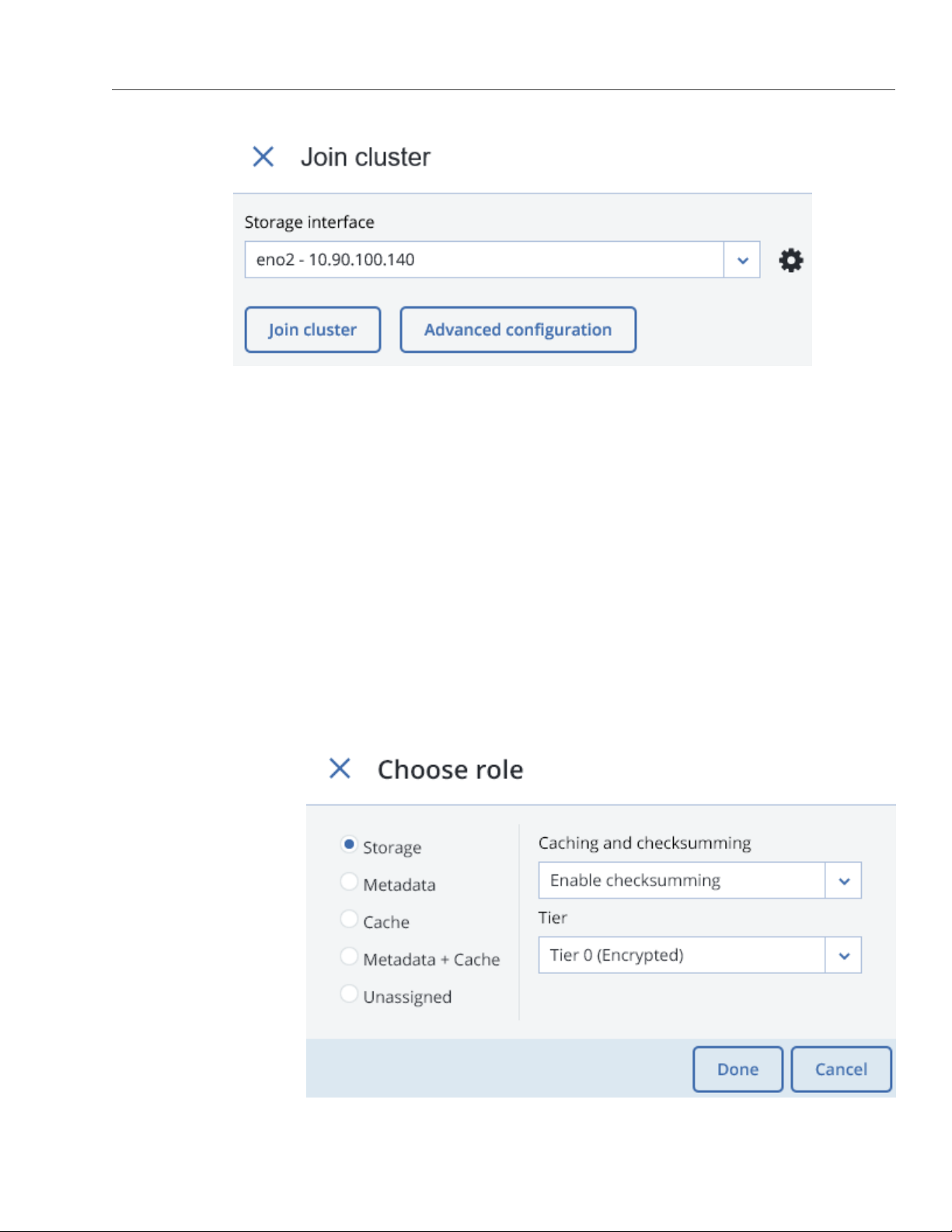
2. On the Choose role screen, select one of the following roles for the disk:
17
Page 23

Chapter 2. Managing Acronis Storage
• Storage. Use the disk to store chunks and run a chunk service on the node. From the Caching and
checksumming drop-down list, select one of the following:
•
Use SSD for caching and checksumming (available and recommended only for SSD).
Data caching improves cluster performance by placing the frequently accessed data on an SSD.
Data checksumming generates checksums each time some data in the cluster is modified. When
this data is then read, a new checksum is computed and compared with the old checksum. If the
two are not identical, a read operation is performed again, thus providing better data reliability
and integrity.
•
Enable checksumming (better reliability). Checksumming is available for both SSD and HDD.
•
Disable checksumming (better performance).
With this role, also select a tier from the Tier drop-down list (see Understanding Storage Tiers in
the Acronis Storage 2.0 Installation Guide).
Note: If the disk contains old data that was not placed there by Acronis Storage, the disk will
not be considered suitable for use in Acronis Storage.
• Metadata. Use the disk to store metadata and run a metadata service on the node.
• Cache. Use the disk to store write cache. This role is only for SSDs. To cache a specific storage tier,
select it from the drop-down list. Otherwise, all tiers will be cached.
• Metadata+Cache. A combination of two roles described above.
• Unassigned. Remove the roles from the disk.
Note: System disks are reserved for the operating system. Such disks cannot be configured unless
they are SSDs and have capacity of more than 100 GB. In this case, such disks can be assigned
metadata roles.
3. Click Done.
4. Repeat steps 1 to 3 for every disk you want to be used in the Acronis Storage cluster.
5. Click NEW CLUSTER or JOIN CLUSTER. On the Configuration summary screen, check the number of
disks per each configuration category.
18
Page 24
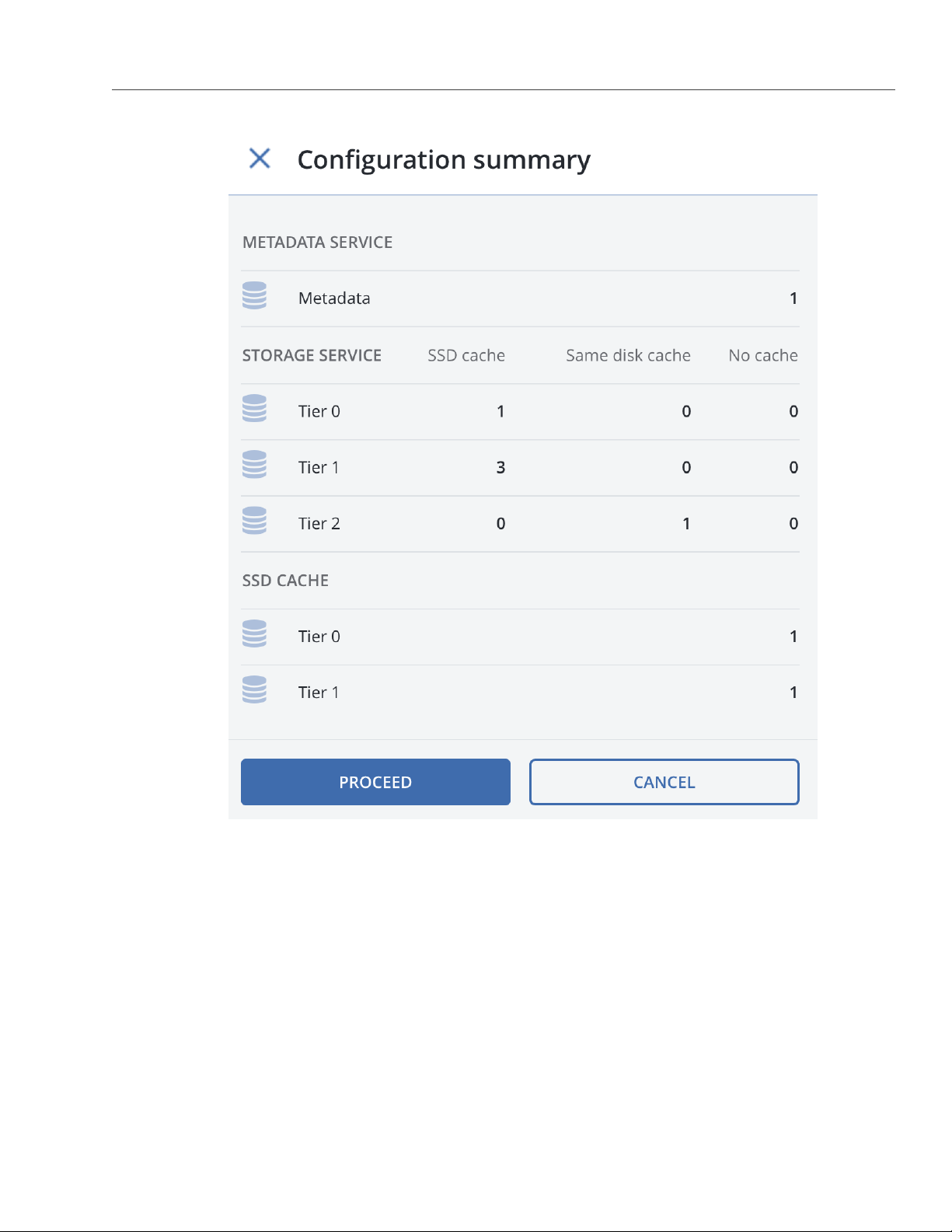
2.3. Releasing Nodes from Cluster
6. Click PROCEED. You can monitor disk configuration progress in the HEALTHY list of the NODES screen.
2.3 Releasing Nodes from Cluster
To release a node means to remove it from the cluster (e.g., for maintenance). As the node may be running
services needed by the cluster, do the following prior to releasing it to avoid cluster degradation:
1. If the node runs one of the five required metadata services, add a metadata role to another node. You
need to make sure that the cluster has at least five metadata services running at any time.
19
Page 25
Chapter 2. Managing Acronis Storage
2. If the node has any access points, make sure that the same access points are configured on other nodes
in the cluster as well.
3. If the node has iSCSI targets, move them to a different node.
4. If the node has an S3 gateway or ABGW, reconfigure DNS for S3 and ABGW access points to remove the
node from DNS records. Next, release the node from S3 and ABGW in the corresponded sections of the
SERVICES screen.
5. Make sure the cluster has enough storage space to accommodate the data from the released node.
Once you initiate the release, the cluster will start replicating data chunks that were stored on the released
node and distributing them among other storage nodes in the cluster. Depending on the amount of data to
replicate, the process may take as much as several hours.
If necessary, you can also release a node forcibly, that is, without replication.
Warning: Releasing nodes forcibly may result in data loss.
To release a node from a cluster, do the following:
1. On the NODES screen, click the node to release.
2. On the node overview screen, click Release.
3. If necessary, in the Release node window, check force to release the node forcibly (highly not recom-
mended).
4. Click Yes. The released node will return to the UNASSIGNED list on the NODES screen.
2.4 Removing Nodes from the Unassigned List
Nodes in the UNASSIGNED list can be completely removed from Acronis Storage.
Do the following: on the NODES screen, select the node in the UNASSIGNED list and click Remove (forget).
Nodes completely removed from Acronis Storage can be re-added to the UNASSIGNED list in two ways:
• By logging in to the node via SSH and running /usr/libexec/vstorage-ui-agent/bin/register-storage-node.sh -m
MN_ADDRESS -t TOKEN in the node’s console (MN_ADDRESS is the management node IP address and TOKEN is the
20
Page 26
2.5. Managing Tier Encryption
token obtained in the management panel).
• By reinstalling Acronis Storage on the node from scratch.
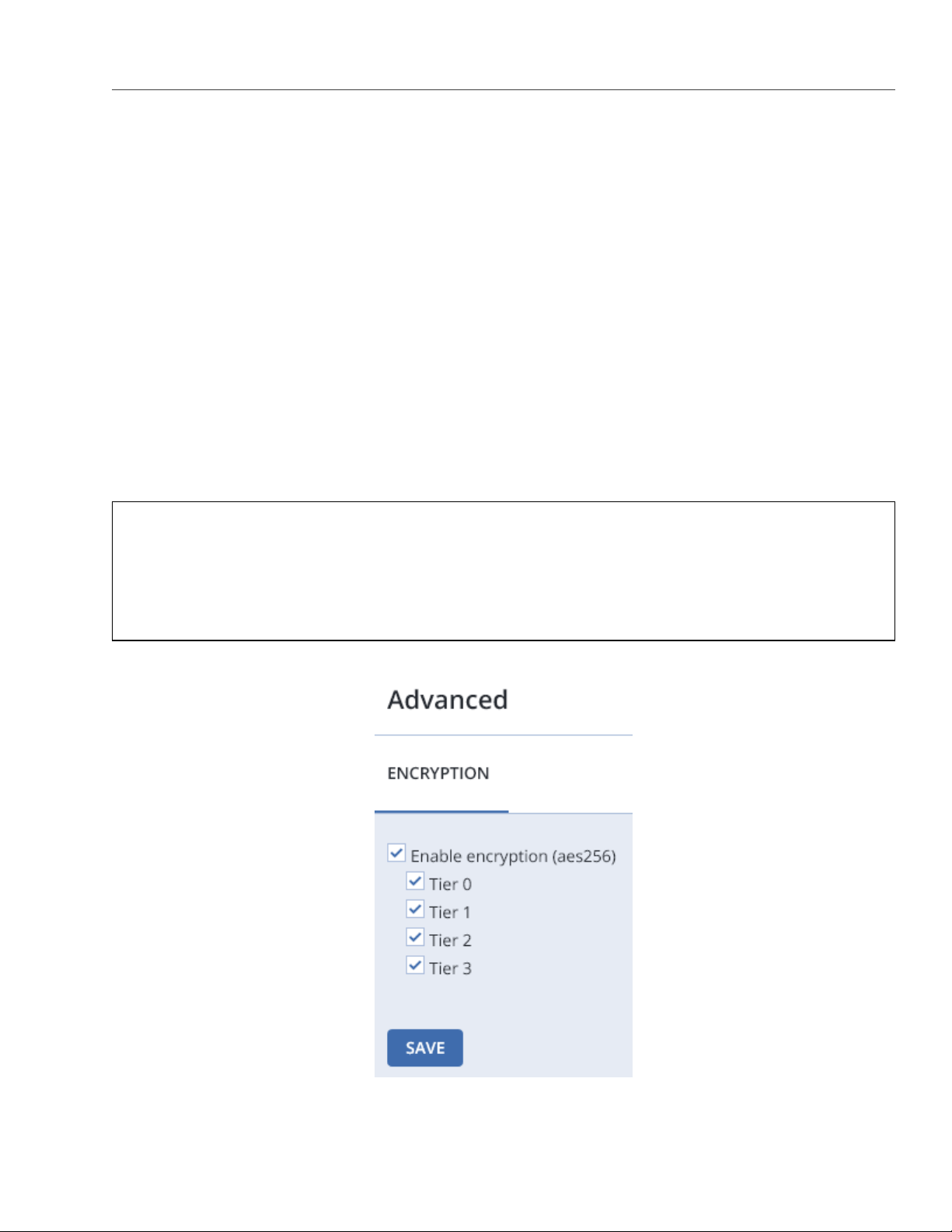
2.5 Managing Tier Encryption
Acronis Storage can encrypt data stored on disks with the AES-256 standard, so if a disk gets lost or stolen the
data will be safe. Acronis Storage stores disk encryption keys in cluster’s metadata (MDS).
Encryption can be enabled or disabled only for the newly created chunk services (CS). Once tier encryption
is enabled, you can decrypt disks (CSs) by manually releasing them from encrypted tiers. Correspondingly,
simply enabling encryption on the disk’s tier will not encrypt it’s CS. To encrypt a disk, you must assign it to an
encrypted tier.
Note:
1. Acronis Storage does not encrypt data transmitted over the internal network.
2. Enabled encryption slightly decreases performance.
21
Page 27
Chapter 2. Managing Acronis Storage
To enable or disable tier encryption, on the SETTINGS > Advanced settings panel, select or deselect tiers and
click SAVE.
2.6 Managing Acronis Storage Users
The web-based user interface of Acronis Storage supports the following user types:
• Observer. Observers can monitor Acronis Storage performance and parameters but cannot change any
settings.
• Administrator. Administrators have complete control over Acronis Storage but cannot manage user
accounts.
• Superadmin. The default unique account. The user name is admin, the password is specified during the
management panel installation on the first node. The superadmin has complete control over Acronis
Storage and can also manage user accounts.
Note: All users can change their own passwords (see Managing User Accounts on page 23).
2.6.1 Creating User Accounts
To create a user account in the web-based user interface, do the following:
1. Log in to the management panel as the superadmin.
2. Open the SETTINGS > Users screen and click ADD USER.
3. On the Add user panel, specify the user name, password, and, if required, a user description in the
corresponding fields.
22
Page 28

2.6. Managing Acronis Storage Users
4. Choose a user type–Observer or Administrator–and click Done.
2.6.2 Managing User Accounts
The only user management option available to all users except the superadmin is changing the account pass-
word. To do that, on any screen, click the user icon in the top left corner of the management panel and click
Change password.
The superadmin can do the following with user accounts: create and delete, enable and disable (prevent from
logging in), change user type, password, and description. To manage a user account, login as the superadmin,
open the Settings -> Users screen, select a user from the list, and click Configure or Delete depending on
what you need to do.
23
Page 29

Chapter 2. Managing Acronis Storage
2.7 Managing Acronis Storage Updates
You can update your Acronis Storage infrastructure using the web-based user interface.
Important: To check for and download updates, the cluster must be healthy and each node in the
infrastructure must be able to open outgoing Internet connections.
To update Acronis Storage, do the following:
1. Open the SETTINGS > Updates screen and click CHECK FOR UPDATES. The scrupt will run yum update on
each node. If updates are available for a node, said node’s status will change to Update available.
24
Page 30

2.8. Allowing root Access to Cluster Nodes Over SSH
2. To apply all available updates, click UPDATE NOW.
While updates are being applied, some of the Acronis Storage services might be unavailable for a short period
of time.
2.8 Allowing root Access to Cluster Nodes Over SSH
In certain situations, you or the technical support team may need root access to cluster nodes via SSH. To allow
root access to all nodes in the cluster, do the following:
1. Obtain an SSH public key from the technical support team.
2. Open the SETTINGS > SSH screen, click ADD KEY, paste the key, and click Add key.
25
Page 31

Chapter 2. Managing Acronis Storage
To delete the key after root access is no longer required, select the key and click Delete.
2.9 Backing Up and Restoring Management Node
Acronis Storage stores node information, statistics, and configuration in a database on the node with the
management panel. Database backups are created automatically every day.
To back up the database manually, open the SETTINGS > Backup screen and click BACKUP NOW.
26
Page 32

2.9. Backing Up and Restoring Management Node
Once backup is completed, the Last backup date will be refreshed.
2.9.1 Restoring Management Node from Backup
You can restore a management node database from backup on the following nodes:
• the same management node or any node assigned to a cluster,
• a new node outside the cluster. In this case, Acronis Storage will restore the database and install only
the management panel component on the node.
To restore to the same management node or a cluster node, run the following script:
# /usr/libexec/vstorage-ui-backend/bin/restore-management-node.sh \
-x <public_network_interface> -i <internal_network_interface>
where <public_network_interface> and <internal_network_interface> are interfaces with already assigned public and in-
ternal roles. They will be assigned the Web CP and Management roles, respectively.
27
Page 33

Chapter 2. Managing Acronis Storage
Note: You can specify the same network interface in both parameters.
To restore the database to a new node, do the following:
1. Copy the backup file /mnt/vstorage/webcp/backup/backup-<timestamp>.tar from the initial management node to the
same directory on the target node.
2. Run the following script on the target node:
# /usr/libexec/vstorage-ui-backend/bin/restore-management-node.sh \
-x <public_network_interface> -i <internal_network_interface> \
-f <path-to-backup-file>
where <public_network_interface> and <internal_network_interface> are interfaces to be assigned the Web CP and
Management roles, respectively.
2.10 Managing Acronis Storage Licenses
To activate or upgrade a Acronis Storage license, do the following:
1. On the LICENSES screen, click Register key.
2. On the Register license keys panel, enter one or more license keys, one per line, and click Register.
3. Back on the Licenses screen, the expiration date and storage space limit will change according to the
licenses entered.
If you are registering the first and only license key, click Activate. If you have already activated license
28
Page 34

2.10. Managing Acronis Storage Licenses
keys before and want to upgrade, choose one of the following:
• Upgrade, to increase the storage space limit.
• Prolong, to prolong the license.
4. Click Activate to activate or upgrade the license.
29
Page 35

CHAPTER 3
Monitoring Acronis Storage Clusters
From the management panel, you can monitor the performance of both the whole cluster and its parts.
3.1 Monitoring Cluster Status
The overall cluster statistics are available on the cluster OVERVIEW screen. Pay attention to the cluster status
that can be one of the following:
• HEALTHY. All cluster components are active and operate normally.
• UNKNOWN. Not enough information about the cluster state (e.g., because the cluster is inaccessible).
• DEGRADED. Some of the cluster components are inactive or inaccessible. The cluster is trying to heal
itself, data replication is scheduled or in progress.
• FAILURE. The cluster has too many inactive services, automatic replication is disabled. If the cluster
enters this state, troubleshoot the nodes or contact the support team.
3.2 Monitoring Cluster Storage Space
You can monitor cluster storage space on the cluster OVERVIEW screen. Typical statistics may look like this:
30
Page 36

3.2. Monitoring Cluster Storage Space
The two charts that provide information on how storage space is used are PHYSICAL SPACE and LOGICAL
SPACE. They are described in the following sections in more detail.
3.2.1 Physical Space Chart
The PHYSICAL SPACE chart shows the combined space of all disks available to the cluster. The following
statistics are available:
• Used space. The space occupied by all data chunks and their replicas plus the space occupied by any
other data stored on cluster nodes’ disks.
• Free space. The unused space on all cluster nodes’ disks.
• Total space. The total space on all cluster nodes’ disks.
3.2.2 Logical Space Chart
The LOGICAL SPACE chart represents all the space that can be allocated and used by the cluster for storing
user data. This space includes the following:
• Total space. The maximum disk space available as defined by license.
• Used space. The space occupied exclusively by user data. Replicas and erasure coding metadata are not
31
Page 37

Chapter 3. Monitoring Acronis Storage Clusters
taken into account.
• Free space. The difference between the two above.
3.2.2.1 Understanding Logical Space
When monitoring disk space information in the cluster, keep in mind that logical space is the amount of free
disk space that can be used for storing user data in the form of data chunks and all their replicas. Once this
space runs out, no data can be written to the cluster.
To better understand how logical disk space is calculated, consider the following example:
• The cluster has three disks with the storage role. The first disk has 200 GB of space, the second one has
500 GB, and the third one has 1 TB.
• If the redundancy mode is set to three replicas, each data chunk must be stored as three replicas on
three different disks with the storage role.
In this example, the available logical disk space will be 200 GB, that is, equal to the capacity of the smallest disk
with the storage role. The reason is that each replica must be stored on a different disk. So once the space
on the smallest disk (i.e. 200 GB) runs out, no new chunk replicas can be created unless a new disk with the
storage role is added or the redundancy mode is changed to two replicas.
With the two replicas redundancy mode, the available logical disk space would be 700 GB, because the two
smallest disks combined can hold 700 GB of data.
3.2.3 Monitoring Chunk Status and Replication
You can monitor the state of all chunks in the cluster in the CHUNKS section of the cluster OVERVIEW screen.
The table below lists all possible states a chunk can have.
State Description
healthy Percentage of chunks that have enough active replicas. The normal state of chunks.
offline Percentage of chunks all replicas of which are offline. Such chunks are completely inaccessible
for the cluster and cannot be replicated, read from or written to. All requests to an offline chunk
32
are frozen until a CS that stores that chunk’s replica goes online.
Get offline cluster nodes back online as soon as possible to avoid data loss.
Page 38

3.2. Monitoring Cluster Storage Space
State Description
blocked Percentage of chunks which have fewer active replicas than the set minimal amount. Write re-
quests to a blocked chunk are frozen until it has at least the set minimum amount of replicas.
Read requests to blocked chunks are allowed, however, as they still have some active replicas
left. Blocked chunks have higher replication priority than degraded chunks.
Having blocked chunks in the cluster increases the risk of losing data, so postpone any mainte-
nance on working cluster nodes and get offline chunk servers back online as fast as possible.
degraded Percentage of chunks with the number of active replicas lower than normal but equal to or higher
than the set minimum. Such chunks can be read from and written to.
3.2.4 Monitoring Cluster Services
You can monitor two types of services in the SERVICES section on the cluster OVERVIEW screen:
• MDS, metadata services. Ensure that five are running at all times.
• CS, chunk services. With this chart, you can also keep track of all disks with the storage role.
Typical statistics may look like this:
33
Page 39

Chapter 3. Monitoring Acronis Storage Clusters
If some of the services were not in the healthy state for some time, these time periods will be highlighted in
red on the charts.
3.2.5 Monitoring Cluster I/O Activity
You can monitor the history of the cluster I/O activity on the READ and WRITE charts on the cluster OVERVIEW
screen. Typical statistics may look like this:
34
Page 40

3.2. Monitoring Cluster Storage Space
The current cluster I/O activity averaged for the last 10 seconds is shown as:
• the speed of read and write I/O operations, in megabytes per second (MB/s).
• the number of read and write I/O operations per second (IOPS).
35
Page 41

CHAPTER 4
Monitoring Acronis Storage Nodes
Nodes added to the Acronis Storage infrastructure are listed on the NODES screen, grouped by their statuses.
If there are no clusters in Acronis Storage, you will only see a list of the UNASSIGNED nodes. If there are
clusters, you can select one in the drop-down list on the left. The cluster nodes will be listed on the screen
alongside the unassigned nodes.
4.1 Node Statuses
A node can have one of the following statuses:
• HEALTHY. All the storage services on the node are running.
• OFFLINE. The node cannot be reached from the management panel, although it may still be up and its
services may be running.
• FAILED. One or more storage services on the node have failed.
• UNASSIGNED. The node is not assigned to a cluster.
4.2 Monitoring Node Performance
To monitor the performance of a cluster node, open the NODES screen and click the node. On the node
overview screen, you will see performance statistics described below.
36
Page 42

4.2. Monitoring Node Performance
The overall statistics include:
• the number of CPUs and the amount of RAM,
• CPU usage, in percent over time,
• RAM usage, in percent over time.
The DISKS section shows:
• the number of HDD and SSD drives and their statuses,
• node I/O activity over time on the read and write charts.
The NETWORK section shows:
• the list of network interfaces and their statuses,
• the amount of transmitted (TX) and received (RX) traffic over time.
37
Page 43

Chapter 4. Monitoring Acronis Storage Nodes
The SERVICES section shows Acronis Storage services running on the node and their statuses.
The following sections provide more information on disk and network usage.
4.2.1 Monitoring Node Disks
To monitor the usage and status of node disks, click the DISKS link on the node overview screen. You will see
a list of all disks on the node and their status icons.
A disk status icon shows the combined status of S.M.A.R.T. and the service corresponding to the disk role. It
can be one of the following:
• Ok. The disk and service are healthy.
• Failed. The service has failed or S.M.A.R.T. reported an error.
• Releasing. The service is being released. When the process finishes, the disk status will change to Ok.
On this screen, you can:
• monitor the details and performance of each disk,
• manage disk roles,
• have the disk blink its activity LED. Works only for LSI and PERC controllers.
To monitor performance of a particular disk, select it and click Performance. The Drive performance panel
will display the I/O activity of the disk.
To view information about the disk, including its S.M.A.R.T. status, click Details.
To have the disk blink its activity LED, select the disk, and click Blink. To have the disk stop blinking, click
Unblink.
38
Page 44

4.3. Monitoring Node Network
4.2.1.1 Monitoring the S.M.A.R.T. Status of Node Disks
The S.M.A.R.T. status of all disks is monitored by a tool installed along with Acronis Storage. Run every 10
minutes, the tool polls all disks attached to nodes, including journaling SSDs and system disks, and reports the
results to the management node.
Note: For the tool to work, make sure the S.M.A.R.T. functionality is enabled in node’s BIOS.
If a S.M.A.R.T. warning message is shown in the node status, one of that node’s disks is in pre-failure condition
and should be replaced. If you continue using the disk, keep in mind that it may fail or cause performance
issues.
Pre-failure condition means that at least one of these S.M.A.R.T. counters is not zero:
• Reallocated Sector Count
• Reallocated Event Count
• Current Pending Sector Count
• Offline Uncorrectable
4.3 Monitoring Node Network
To monitor the node’s network usage, click NETWORK on the node overview screen.
To display the performance charts of a specific network interface, select it in the list and click Performance.
When monitoring network performance, keep in mind that if the TX DROPS and/or RX DROPS charts are not
empty, the network is experiencing issues and requires attention.
To display the details of a network interface, click Details. The Network details panel shows the interface
state, bandwidth, MTU, MAC address, and all IP addresses.
39
Page 45

CHAPTER 5
Exporting Acronis Storage Cluster Data
Acronis Storage allows you to export storage space as:
• Block storage via iSCSI for virtualization, databases and other needs.
• Object storage for storing unlimited number of files via an Amazon S3 compatible protocol. You can store
data like media files, backups, dropbox-like applications, and Open Xchange files. You can build your own
Amazon S3 compatible object storage services as a part of your cloud offering or for internal needs.
• A back-end for Acronis Backup Cloud backups.
5.1 Exporting Data via iSCSI
Acronis Storage allows you to export cluster disk space to external operating systems in the form of LUN block
devices over iSCSI in a SAN-like manner.
In Acronis Storage, you can create and run multiple iSCSI targets per Acronis Storage cluster node. In turn,
each iSCSI target can have multiple LUNs (virtual disks). At any given moment, each iSCSI target runs on a
single node. If a node fails, iSCSI targets hosted on it are moved to and re-launched on a healthy node.
The figure below shows a typical network configured for exporting Acronis Storage disk space over iSCSI.
40
Page 46

5.1. Exporting Data via iSCSI
In this example there are three hardware nodes working in an Acronis Storage cluster. Two nodes host one
iSCSI target each, while the third hosts two iSCSI targets. Each node has two network connections: one internal
for cluster communication and one external for iSCSI exporting. Each iSCSI target has its own static IP address
assigned from the datacenter network. The iSCSI network must be properly configured to run iSCSI targets.
Each iSCSI target has a unique IP address from the iSCSI subnetwork different from the host IP address. So
make sure you have a range of unused IP addresses for iSCSI targets.
5.1.1 Creating Acronis Storage iSCSI Targets
Note:
1. Each iSCSI target must be assigned at least one unique IP address from DC network’s static pool.
2. The name of each iSCSI target must be unique in the Acronis Storage cluster.
3. Acronis Storage iSCSI targets support persistent reservations to allow iSCSI initiators obtain exclusive
access to the specified target’s LUNs.
41
Page 47

Chapter 5. Exporting Acronis Storage Cluster Data
To create and start a target, do the following:
1. On the SERVICES > iSCSI > Targets screen, click ADD TARGET.
2. On the Add target panel, type a name for the new target in the Name field.
3. In the node drop-down list, select a node on which the target will be located. The node should have an
iSCSI role assigned to one of its network interfaces to appear in the list.
4. If necessary, check the Enable CHAP box and select an iSCSI user in the corresponding drop-down list
(For more information on CHAP users, see Managing iSCSI Users on page 56).
5. Click Add to specify one or more IP addresses for the target.
42
Page 48

5.1. Exporting Data via iSCSI
6. Click Done to create the target.
The ISCSI target will be automatically started after creation and the initiators will be able to access the target
via the specified IP address.
5.1.1.1 Performance Tips
• Spread iSCSI targets evenly across nodes in the cluster. For example, ten nodes with one iSCSI target per
each will perform better than a single node with ten iSCSI targets on it.
• Fewer LUNs per more iSCSI targets will perform better than more LUNs per fewer iSCSI targets.
5.1.2 Listing, Stopping, and Deleting Acronis Storage iSCSI Targets
On the iSCSI targets screen, you can list and manage all iSCSI targets and their LUNs, and display detailed
information about specific iSCSI targets registered on a node.
To stop or delete an iSCSI target, select it on the iSCSI targets screen and click Stop or Delete, respectively.
Doing so will disconnect the iSCSI initiator from the target. However, breaking the connection in such a way
may result in I/O errors on the iSCSI initiator’s side.
5.1.3 Configuring Acronis Storage iSCSI Targets
To configure an iSCSI target, do the following:
1. On the SERVICES > iSCSI > Targets screen, select the necessary target and click Configure.
2. On the Configure target screen, specify the necessary parameters.
43
Page 49

Chapter 5. Exporting Acronis Storage Cluster Data
3. Click Done.
5.1.3.1 Listing LUNs
In Acronis Storage, each iSCSI target can have multiple LUNs (virtual disks or volumes). You can list the LUNs
of a target and iSCSI initiators that are currently connected.
To list the LUNs, open the SERVICES > iSCSI > Targets screen, select a target and click a link in the LUNs
column.
To list the initiators that are currently connected to iSCSI targets, open the INITIATORS tab on the same screen.
44
Page 50

5.1. Exporting Data via iSCSI
5.1.3.2 Adding LUNs
To add a LUN to an iSCSI target, do the following:
1. On the SERVICES > iSCSI > Targets screen, select the necessary target and click a link in the LUNs column.
2. To add a new LUN to the list, click ADD LUN.
45
Page 51

Chapter 5. Exporting Acronis Storage Cluster Data
3. On the Add LUN screen, select the LUN’s number from the drop-down list.
4. In the LUN Size field, specify the size of the LUN in GB; select a tier from the drop-down list to the right.
For more information on tiers, see Understanding Storage Tiers in the Acronis Storage 2.0 Installation
Guide.
5. From the Failure domain drop-down list, choose a placement policy for replicas. For more details, see
Understanding Failure Domains in the Acronis Storage 2.0 Installation Guide.
6. Choose a data redundancy mode. For more details, see Understanding Data Redundancy in the Acronis
Storage 2.0 Installation Guide.
7. Click Done.
5.1.3.3 Configuring LUNs
To configure a LUN of an iSCSI target, do the following:
1. On the SERVICES > iSCSI > Targets screen, stop the target to which the LUN belongs.
2. Click a link in the target’s LUNs column.
3. On the Configure LUN screen, specify the LUN size in the corresponding field.
4. Click Done.
5.1.3.4 Deleting LUNs
To delete a LUN, do the following:
1. On the SERVICES > iSCSI > Targets screen, select the necessary target and click a link in the LUNs column.
2. Select the necessary LUN in the list and click Delete.
5.1.4 Accessing Acronis Storage iSCSI Targets
This section describes ways to attach Acronis Storage iSCSI targets to a number of operating systems and
third-party virtualization solutions.
46
Page 52

5.1. Exporting Data via iSCSI
5.1.4.1 Accessing Acronis Storage iSCSI Targets from CentOS 6
1. Make sure that the iscsi-initiator-utils package is installed.
2. Discover the required target by its IP address. For example:
# iscsiadm --mode discovery --type sendtargets --portal 192.168.10.100
3. Restart the iscsid service to rescan for newly added drives:
# service iscsi restart
To check that the new drive has appeared in the system, use fdisk, parted or similar tools.
For more information, see the Red Hat Enterprise Linux Storage Administration Guide.
5.1.4.2 Accessing Acronis Storage iSCSI Targets from Microsoft Windows Server 2012 R2
1. In the Server Manager Dashboard, click the Tools menu in the toolbar and select iSCSI Initiator.
2. In the iSCSI Initiator Properties, switch to the Discovery tab and click Discover Portal....
47
Page 53

Chapter 5. Exporting Acronis Storage Cluster Data
3. In the Discover Target Portal window, enter the portal IP address and click OK.
The newly added portal will appear in the Target portals section.
4. On the iSCSI Initiator Properties > Targets tab, select the new target in the Discovered targets section
48
Page 54

5.1. Exporting Data via iSCSI
and click Connect.
5. In the Connect to Target window, click OK.
49
Page 55

Chapter 5. Exporting Acronis Storage Cluster Data
6. Target’s Inactive status will change to Connected.
7. The newly attached disk will appear in Server Manager Dashboard > Computer Management > Stor-
age > Disk Management.
50
Page 56

5.1. Exporting Data via iSCSI
8. Right-click the disk information section and select Online.
The disk status will change to Online.
9. Right-click the disk information section and select Initialize Disk.
51
Page 57

10. In the Initialize Disk window, click OK.
Chapter 5. Exporting Acronis Storage Cluster Data
11. Right-click the disk space section, select New Simple Volume..., and follow the wizard’s instruction to
format the new disk to NTFS.
52
Page 58

5.1. Exporting Data via iSCSI
12. The disk state will change to Healthy.
The new disk will appear in Windows Explorer.
53
Page 59

Chapter 5. Exporting Acronis Storage Cluster Data
5.1.4.3 Accessing Acronis Storage iSCSI Targets from VMware ESXi
1. In the vSphere Client, switch to the Configuration tab, and click Storage Adapters in the Hardware
section.
2. If no software iSCSI adapters have been added, do so by right-clicking in the Storage Adapters section
and selecting Add Software iSCSI Adapter....
3. Open the software iSCSI adapter’s properties, switch to the Static Discovery tab and click Add....
4. In the Add Static Target Server window, enter the target’s IP address and name.
5. Close the software iSCSI adapter’s properties window and rescan the adapter as prompted.
6. The newly added iSCSI target will appear in the Details section of the software iSCSI adapter you have
configured.
For more information, see the VMware vSphere Storage Guide.
5.1.4.4 Accessing Acronis Storage iSCSI Targets from Citrix XenServer 6.2
1. In XenCenter, switch to the Storage tab and click New SR....
2. In the New Storage Repository window:
(a) In the Type section, select the Software iSCSI option,
(b) In the Name section, provide a name or leave the default,
54
Page 60

5.1. Exporting Data via iSCSI
(c) In the Location section, enter target’s IP address in the Target Host field, click Discover IQNs and
select the desired target, then click Discover LUNs and select the desired LUN.
3. Click Finish to format the disk.
The new storage repository will appear in XenCenter.
For more information, see XenCenter documentation.
5.1.4.5 Accessing Acronis Storage iSCSI Targets from Microsoft Hyper-V
Note: Names of the targets to be mounted must not contain underscore characters.
1. Make sure that Microsoft iSCSI Initiator Service, MSiSCSI, is running.
2. Discover a new target portal. For example, for the portal 192.168.10.100, run:
PS C:\Users\Administrator>new-iscsitargetportal \
-targetportaladdress 192.168.10.100
Initiator Instance Name :
Initiator Portal Address :
IsDataDigest : False
IsHeaderDigest : False
TargetPortalAddress : 192.168.10.100
TargetPortalPortNumber : 3260
.. _PSComputerName ::
PSComputerName :
3. Connect to the desired target. For example, for the target iqn.2014-03.com.vstorage:test1
PS C:\Users\Administrator> connect-iscsitarget
cmdlet Connect-IscsiTarget at command pipeline position 1
Supply values for the following parameters:
NodeAddress: iqn.2014-04.com.vstorage:test1
AuthenticationType : NONE
InitiatorInstanceName : ROOT\ISCSIPRT\0000_0
InitiatorNodeAddress : iqn.1991-05.com.microsoft:win-l2dj7g36n7e...
55
Page 61

Chapter 5. Exporting Acronis Storage Cluster Data
InitiatorPortalAddress : 0.0.0.0
InitiatorSideIdentifier : 400001370000
IsConnected : True
IsDataDigest : False
IsDiscovered : True
IsHeaderDigest : False
IsPersistent : False
NumberOfConnections : 1
SessionIdentifier : ffffe00000b5e020-4000013700000005
TargetNodeAddress : iqn.2014-04.com.vstorage:test1
TargetSideIdentifier : 0001
.. _PSComputerName ::
PSComputerName :
4. To check that the disk has been connected, run
PS C:\Users\Administrator> get-disk
Number Friendly Name OperationalStatus Total Size
------ ------------- ----------------- ----------
1 IET VIRTUAL-DISK SCSI Disk Device Offline 100 GB RAW
...
You can now initialise the newly mounted disk for use in Microsoft Hyper-V.
For more information, see iSCSI Cmdlets in Windows PowerShell at http://technet.microsoft.com/en-
us/library/hh826099.aspx.
5.1.5 Managing iSCSI Users
5.1.5.1 Creating CHAP Accounts for Acronis Storage iSCSI Targets
To create a CHAP account, do the following:
1. On the SERVICES > iSCSI Users screen, click Add user.
2. Specify login, password, and, if necessary, a description for the account. The password should be 12 to
16 characters long for Windows clients to be able to establish connections.
56
Page 62

5.1. Exporting Data via iSCSI
3. Click Done.
The newly created CHAP user account will be listed on the iSCSI Users screen.
5.1.5.2 Creating Acronis Storage iSCSI Targets Bound to CHAP Accounts
To create an Acronis Storage iSCSI target bound to a CHAP account, do the following:
1. On the SERVICES > iSCSI > Targets screen, select an iSCSI target and click Configure.
2. On the Configure target screen, check Enable CHAP and/or Enable mutual CHAP and select users in the
corresponding drop-down lists. If you enable CHAP, the target will authenticate the initiator. If you enable
mutual CHAP, the initiator will authenticate the target. These options can be enabled in any combination.
57
Page 63

Chapter 5. Exporting Acronis Storage Cluster Data
3. Click Done.
5.1.5.3 Changing CHAP Account Passwords
To change the password of a CHAP account, do the following:
1. On the SERVICES > iSCSI Users screen, select a user and click Configure.
2. In the Password section on the Configure user screen, click change.
58
Page 64

5.2. Exporting Data via S3
3. Type a new password in the corresponding field and click Done. The password should be 12 to 16 char-
acters long for Windows clients to be able to establish connection.
The new password will become active after target reboot.
5.2 Exporting Data via S3
Acronis Storage allows you to export cluster disk space to customers in the form of an S3-like object-based
storage.
Acronis Storage is implemented as an Amazon S3-like API, which is one of the most common object storage
APIs. End users can work with Acronis Storage as they work with Amazon S3. You can use the usual applications
for S3 and continue working with it after the data migration from Amazon S3 to Acronis Storage.
Object storage is a storage architecture that enables managing data as objects (like in a key-value storage) as
opposed to files on file systems or blocks in a block storage. Except for the data, each object has metadata
59
Page 65

Chapter 5. Exporting Acronis Storage Cluster Data
that describes it as well as a unique identifier that allows finding the object in the storage. Object storage
is optimized for storing billions of objects, in particular for application storage, static web content hosting,
online storage services, big data, and backups. All of these uses are enabled by object storage thanks to a
combination of very high scalability and data availability and consistency.
Compared to other types of storage, the key difference of object storage is that parts of an object cannot be
modified, so if the object changes a new version of it is spawned instead. This approach is extremely important
for maintaining data availability and consistency. First of all, changing an object as a whole eliminates the issue
of conflicts. That is, the object with the latest timestamp is considered to be the current version and that is it.
As a result, objects are always consistent, i.e. their state is relevant and appropriate.
Another feature of object storage is eventual consistency. Eventual consistency does not guarantee that reads
are to return the new state after the write has been completed. Readers can observe the old state for an unde-
fined period of time until the write is propagated to all the replicas (copies). This is very important for storage
availability as geographically distant data centers may not be able to perform data update synchronously (e.g.,
due to network issues) and the update itself may also be slow as awaiting acknowledges from all the data repli-
cas over long distances can take hundreds of milliseconds. So eventual consistency helps hide communication
latencies on writes at the cost of the probable old state observed by readers. However, many use cases can
easily tolerate it.
5.2.1 Object Storage Infrastructure Overview
The infrastructure of the object storage consists of the following entities: object servers (OS), name servers
(NS), and the S3 gateways (GW).
These entities run as services on the Acronis Storage nodes. Each service should be deployed on multiple
Acronis Storage nodes for high availability.
60
Page 66

5.2. Exporting Data via S3
• An object server stores actual object data received from S3 gateway, packed into special containers to
achieve high performance. The containers are redundant, you can specify the redundancy mode while
configuring object storage.
• A name server stores information about objects (metadata) received from the S3 gateway. Metadata
includes object name, size, ACL, location, owner, and such.
• S3 gateway is a data proxy between object servers and users. It receives and handles Amazon S3 protocol
requests and uses nginx web server for external connections. S3 gateway handles S3 user authentication
and ACL checks. It has no data of its own (i.e. is stateless).
5.2.2 Planning the S3 Cluster
Before creating an S3 cluster, do the following:
61
Page 67

Chapter 5. Exporting Acronis Storage Cluster Data
1. Define which nodes of the Acronis Storage cluster will run the S3 storage access point services. It is
recommended to have all nodes available in Acronis Storage run these services.
2. Configure the network so that the following is achieved:
• All components of the S3 cluster communicate with each other via the S3 private network. All nodes
of an S3 cluster must be connected to the S3 private network. Acronis Storage internal network can
be used for this purpose.
• The nodes running S3 gateways must have access to the public network.
• The public network for the S3 gateways must be balanced by an external DNS load balancer.
For more details on network configuration, refer to Planning Network in the Acronis Storage 2.0 Installa-
tion Guide.
3. All components of the S3 cluster should run on multiple nodes for high-availability. Name server and
object server components in the S3 cluster are automatically balanced and migrated between S3 nodes.
S3 gateways are not automatically migrated; their high availability is based on DNS records. You should
maintain the DNS records manually when adding or removing the S3 gateways.
5.2.3 Sample Object Storage
This section shows a sample object storage deployed on top of an Acronis Storage cluster of five nodes that
run various services. The final setup is shown on the figure below.
62
Page 68

5.2. Exporting Data via S3
63
Page 69

Chapter 5. Exporting Acronis Storage Cluster Data
5.2.4 Creating the S3 Cluster
To set up object storage services on a cluster node, do the following:
1. Make sure that S3 private network is configured on each node that will run object storage services.
2. On the SERVICES > Nodes screen, check the box of each cluster node where object storage services will
run.
3. Click Create S3 cluster.
4. Make sure a network interface with an S3 (private) role is selected in the drop-down list. The corre-
sponding interfaces with S3 public roles will be selected automatically.
Note: If necessary, click the cogwheel icon and, on the Network Configuration screen, configure
S3 roles.
64
Page 70

5.2. Exporting Data via S3
5. Click Proceed.
6. In Tier, select the storage tier that will be used for the object storage. For information about storage
tiers, consult Understanding Storage Tiers in the Acronis Storage 2.0 Installation Guide.
7. In Failure domain, choose a placement policy for replicas. For more details, see Understanding Failure
Domains in the Acronis Storage 2.0 Installation Guide.
8. In Data redundancy, select the redundancy mode that the object storage will use. For more details, see
Understanding Data Redundancy in the Acronis Storage 2.0 Installation Guide.
65
Page 71

Chapter 5. Exporting Acronis Storage Cluster Data
Note: You can later change the redundancy mode on the S3 > Settings panel.
9. Click Proceed.
10. Specify the external DNS name for the S3 endpoint that will be used by the end users to access the object
storage. For example, mys3storage.example.com. Click Proceed.
Important: Configure your DNS server according to the example suggested in the management
panel.
11. From the drop-down list, select an S3 endpoint protocol: HTTP, HTTPS or both.
66
Page 72

5.2. Exporting Data via S3
Note: It is recommended to use only HTTPS for production deployments.
If you have selected HTTPS, do one of the following:
• Check Generate self-signed certificate to get a self-signed certificate for HTTPS evaluation.
• Acquire an SSL certificate and key from a third party and upload them.
12. If required, click Configure Acronis Notary and specify Notary DNS name and Notary user key. For
more information on Acronis Notary, see Managing Acronis Notary in Buckets.
13. Click Done to create an S3 cluster.
After the cluster is created, on the S3 Overview screen, you can view cluster status, hostname, used disk
capacity, the number of users, I/O activity, and the state of S3 services.
To start using the S3 storage, you will also need to create at least one S3 user.
67
Page 73

Chapter 5. Exporting Acronis Storage Cluster Data
5.2.5 Managing Object Storage Users
The concept of S3 user is one of the base concepts of object storage along with those of object and bucket
(container for storing objects). The Amazon S3 protocol uses a permission model based on access control
lists (ACLs) where each bucket and each object is assigned an ACL that lists all users with access to the given
resource and the type of this access (read, write, read ACL, write ACL). The list of users includes the entity
owner assigned to every object and bucket at creation. The entity owner has extra rights compared to other
users. For example, the bucket owner is the only one who can delete that bucket.
User model and access policies implemented in Acronis Storage comply with the Amazon S3 user model and
access policies.
User management scenarios in Acronis Storage are largely based on the Amazon Web Services user manage-
ment and include the following operations: create, query, and delete users as well as generate and revoke
user access key pairs.
5.2.5.1 Adding S3 users
To add an S3 user, do the following:
1. On the SERVICES > S3 Users screen, click Add user.
2. Specify a valid email address as login and an optional description for the user, and click Done.
68
Page 74

5.2. Exporting Data via S3
5.2.5.2 Managing S3 Access Key Pairs
Each S3 user has one or two key pairs (access key and secret key) for accessing the S3 cloud. You can think
of the access key as login and the secret key as password. (For more information about S3 key pairs, refer to
http://docs.aws.amazon.com/AWSSimpleQueueService/latest/SQSGettingStartedGuide/AWSCredentials.html.)
The access keys are generated and stored locally in the Acronis Storage cluster on S3 name servers. Each
user can have up to two key pairs. It is recommended to periodically revoke old and generate new access key
pairs.
To view, add, or revoke the S3 access key pairs for an S3 user, do the following:
1. Select a user in the list and click Keys.
69
Page 75

Chapter 5. Exporting Acronis Storage Cluster Data
2. The existing keys will be shown on the Keys panel.
• To revoke a key, click Revoke.
• To add a new key, click Generate access key.
Note: To access a bucket, a user will need the following information: the management panel IP address,
the DNS name of the S3 cluster specified during configuration, the S3 access key ID, and the S3 secret
access key.
5.2.6 Managing Object Storage Buckets
All objects in Amazon S3-like storage are stored in containers called buckets. Buckets are addressed by names
that are unique in the given object storage, so an S3 user of that object storage cannot create a bucket that
has the same name as a different bucket in the same object storage. Buckets are used to:
• group and isolate objects from those in other buckets,
• provide ACL management mechanisms for objects in them,
70
Page 76

5.2. Exporting Data via S3
• set per-bucket access policies, for example, versioning in the bucket.
In the current version of Acronis Storage, you can enable and disable Acronis Notary for object storage buckets
and monitor the space used by them on the SERVICES > S3 > Buckets screen. You cannot create and manage
object storage buckets from Acronis Storage. However, you can list, create and manage buckets via the S3 API
or by using a third-party S3 browser like CyberDuck or DragonDisk (see the following sections).
5.2.6.1 Creating Buckets
To create a new S3 bucket with CyberDuck, do the following:
1. Click Open Connection.
2. Specify the following parameters:
• The external DNS name for the S3 endpoint that you specified when creating the S3 cluster.
• The Access Key ID and the Secret Access Key of an object storage user.
By default, the connection is established over HTTPS. To use CyberDuck over HTTP, you must install a
special S3 profile from https://trac.cyberduck.io/wiki/help/en/howto/s3.
3. Once the connection is established, click File > New Folder.
71
Page 77

Chapter 5. Exporting Acronis Storage Cluster Data
4. Specify a name for the new bucket, and then click Create.
Note: It is recommended to use bucket names that comply with DNS naming conventions. For
more information on bucket naming, see Bucket and Key Naming Policies on page 75.
The new bucket will appear in CyberDuck and you can manage it and upload files into it.
5.2.6.2 Managing Bucket Versions
Versioning is a way of keeping multiple variants of an object in the same bucket. You can use versioning to
preserve, retrieve, and restore every version of every object stored in your S3 bucket. With versioning, you
can easily recover from both unintended user actions and application failures. For more information about
bucket versioning, refer to http://docs.aws.amazon.com/AmazonS3/latest/dev/Versioning.html.
Bucket versioning is turned off by default. You can turn it on from a third-party S3 browser by selecting a
checkbox in the bucket property. For example:
72
Page 78

5.2. Exporting Data via S3
5.2.6.3 Listing Bucket Contents
You can list bucket contents with a web browser. To do this, visit the URL that consists of the external DNS
name for the S3 endpoint that you specified when creating the S3 cluster and the bucket name. For example,
mys3storage.example.com/mybucket.
73
Page 79

Chapter 5. Exporting Acronis Storage Cluster Data
Note: You can also copy the link to bucket contents by right-clicking it in CyberDuck, and then selecting
Copy URL.
5.2.6.4 Managing Acronis Notary in Buckets
Acronis Storage offers integration with the Acronis Notary service to leverage blockchain notarization and
ensure the immutability of data saved in object storage clusters. To use Acronis Notary in user buckets, you
need to set it up in the S3 cluster and enable it for said buckets.
Setting Up Acronis Notary
To set up Acronis Notary, do the following:
1. Get the DNS name and the user key for the notary service from your Acronis sales contact.
2. On the SERVICES > S3 screen, click Notary settings.
74
Page 80

5.2. Exporting Data via S3
3. On the Notary Settings screen, specify the DNS name and user key in the respective fields and click
Done.
Enabling and Disabling Acronis Notary
To enable or disable blockchain notarization for a bucket, select a bucket on the SERVICES > S3 > Buckets
screen and click Enable Notary or Disable Notary, respectively.
Notarization is disabled for new buckets by default.
Note: Once you enable notarization for a bucket, certificates are created automatically only for the
newly uploaded files. The previously uploaded files are left unnotarized. Once a file was notarized, it will
remain notarized even if you disable notarization later.
5.2.7 Best Practices for Using S3 in Acronis Storage
This section offers recommendations on how to best use the S3 feature of Acronis Storage.
5.2.7.1 Bucket and Key Naming Policies
It is recommended to use bucket names that comply with DNS naming conventions:
75
Page 81

Chapter 5. Exporting Acronis Storage Cluster Data
• can be from 3 to 63 characters long,
• must start and end with a lowercase letter or number,
• can contain lowercase letters, numbers, periods (.), hyphens (-), and underscores (_),
• can be a series of valid name parts (described previously) separated by periods.
An object key can be a string of any UTF-8 encoded characters up to 1024 bytes long.
5.2.7.2 Improving Performance of PUT Operations
Object storage supports uploading of objects as large as 5 GB in size with a single PUT request, or 5 TB in
size with multipart upload. Upload performance can be improved, however, by splitting large objects into
pieces and uploading them concurrently with multipart upload API. This approach will divide the load between
multiple OS services.
It is recommended to use multipart uploads for objects larger than 5 MB.
5.2.8 Monitoring S3 Access Points
The S3 monitoring screen enables you to inspect the availability of each S3 component as well as the perfor-
mance of NS and OS services (which are highly available).
If you see that some of the NS or OS services are offline, it means that the S3 access point doesn’t function
properly, and you should contact support consult the CLI guide for low-level troubleshooting. S3 gateways are
not highly available, but DNS load balancing should be enough to avoid downtime if the gateway fails.
The performance charts represent the number of operations that the OS/NS services are performing.
5.2.9 Releasing Nodes from S3 Clusters
Before releasing a node, make sure that the cluster has enough nodes running the Name Server, Object Server,
and S3 Gateway services left.
Warning: When the last node in the S3 cluster is removed, the cluster is destroyed, and all the data is
deleted.
76
Page 82

5.2. Exporting Data via S3
To release a node from an S3 cluster, do the following:
1. On the SERVICES > S3 Nodes screen, check the box of the node to release.
2. Click Release.
5.2.10 Supported Amazon S3 Features
5.2.10.1 Supported Amazon S3 REST Operations
The following Amazon S3 REST operations are currently supported by the Acronis Storage implementation of
the Amazon S3 protocol:
Service operations:
• GET Service
Bucket operations:
• DELETE Bucket
• GET Bucket (List Objects)
• GET Bucket acl
• GET Bucket location
• GET Bucket Object versions
• GET Bucket versioning
• HEAD Bucket
• List Multipart Uploads
• PUT Bucket
• PUT Bucket acl
• PUT Bucket versioning
Object operations:
• DELETE Object
• DELETE Multiple Objects
77
Page 83

• GET Object
• GET Object ACL
• HEAD Object
• POST Object
• PUT Object
• PUT Object - Copy
• PUT Object acl
• Initiate Multipart Upload
• Upload Part
• Complete Multipart Upload
• Abort Multipart Upload
Chapter 5. Exporting Acronis Storage Cluster Data
• List Parts
Note: For a complete list of Amazon S3 REST operations, see Amazon S3 REST API documentation.
5.2.10.2 Supported Amazon Request Headers
The following Amazon S3 REST request headers are currently supported by the Acronis Storage implementa-
tion of the Amazon S3 protocol:
• x-amz-acl
• x-amz-delete-marker
• x-amz-grant-full-control
• x-amz-grant-read-acp
• x-amz-grant-read
• x-amz-grant-write
• x-amz-grant-write-acp
78
Page 84

5.3. Using Acronis Storage with Acronis Backup Cloud
• x-amz-meta-**
• x-amz-version-id
• x-amz-copy-source
• x-amz-metadata-directive
• x-amz-copy-source-version-id
5.2.10.3 Supported Authentication Scheme
The following authentication scheme is supported by the Acronis Storage implementation of the Amazon S3
protocol:
• Signature Version 2.
• Signature Version 4.
5.3 Using Acronis Storage with Acronis Backup Cloud
The Acronis Backup Gateway storage access point is intended for service providers who use Acronis Backup
Cloud and want to organize a storage on their premises to store their clients’ backed-up data.
The Acronis Backup Gateway enables a service provider to easily configure the Acronis Storage cluster for the
proprietary data format used by Acronis.
When configuring the Acronis Backup Gateway, you must provide the credentials of your administrator account
in Acronis Backup Cloud.
5.3.1 Understanding the Infrastructure
The Acronis Backup Gateway storage access point runs as services on the Acronis Storage nodes. It should be
deployed on multiple Acronis Storage nodes for high availability.
79
Page 85

Chapter 5. Exporting Acronis Storage Cluster Data
5.3.2 Configuring Acronis Backup Gateway Clusters
To set up an Acronis Backup Gateway cluster on top of an Acronis Storage cluster, do the following:
1. Make sure that the Acronis Backup Gateway network is configured on each node that will run the gateway
service.
2. On the SERVICES > Acronis Backup Nodes screen, select a check box next to each cluster node where
the gateway services will run.
80
Page 86

5.3. Using Acronis Storage with Acronis Backup Cloud
3. Click Create Gateway.
4. For each node, select the network interface to which the Acronis Backup Gateway network role is as-
signed. The gateway service will listen on the IP address assigned to this interface.
5. Click Proceed.
6. In Tier, select the storage tier that will be used for the object storage. For information about storage
tiers, consult Understanding Storage Tiers in the Acronis Storage 2.0 Installation Guide.
7. In Failure domain, choose a placement policy for replicas. For more details, see Understanding Failure
Domains in the Acronis Storage 2.0 Installation Guide.
81
Page 87

Chapter 5. Exporting Acronis Storage Cluster Data
8. In Data redundancy, select an erasure coding mode. For more details, see Understanding Data Re-
dundancy in the Acronis Storage 2.0 Installation Guide.
82
Note:
(a) Redundancy by replication is not supported for Acronis Backup Gateway.
(b) You can later change the erasure coding mode on the Acronis Backup Gateway > Parameters
panel.
Page 88

5.3. Using Acronis Storage with Acronis Backup Cloud
9. Click Proceed.
10. Specify the external DNS name for this gateway, e.g, backupgateway.example.com. Make sure that the
required port is open for both incoming and outgoing requests on each node running the gateway service.
Backup agents will use this address and port to upload the backed-up data.
Important:
1. Configure your DNS server according to the example suggested in the management panel.
2. Each time you add or remove a node to or from the Acronis Backup Gateway cluster, adjust
the DNS settings accordingly.
11. Click Proceed.
12. In Account Server Name, specify the Acronis Backup Cloud management server address, which matches
the account management console address (https://cloud.acronis.com/).
13. In Acronis Account, specify the credentials of your Acronis Backup Cloud administrator account.
14. Click Done.
5.3.3 Releasing Nodes Running Acronis Backup Gateway Services
Before releasing a node, make sure that the cluster has enough nodes running the Acronis Backup Gateway
service left.
Warning: If the last node running the Acronis Backup Gateway is removed, the Acronis Backup Cloud
customers will not be able to use this cluster as a backup storage backend.
To release a node running an Acronis Backup Gateway service from a cluster, do the following:
1. On the SERVICES > Acronis Backup Gateway Nodes screen, select the checkbox next to the necessary
node.
2. Click Release.
83
 Loading...
Loading...