Accton Technology ES3552XA, ES3526XA User Manual

Powered by Accton
24/48 10/100 Ports + 2GE
Intelligent Layer 2
Fast Ethernet Switch
Management Guide
www.edge-core.com


Management Guide
Fast Ethernet Switch
Layer 2 Standalone Switch
with 24/48 10/100BASE-TX (RJ-45) Ports,
and 2 Combination Gigabit Ports (RJ-45/SFP)

ES3526XA
ES3552XA
F2.2.6.3 E122006-CS-R02
149100005500H

Contents
Chapter 1: Introduction 1-1
Key Features 1-1
Description of Software Features 1-2
System Defaults 1-5
Chapter 2: Initial Configuration 2-1
Connecting to the Switch 2-1
Configuration Options 2-1
Required Connections 2-2
Remote Connections 2-3
Basic Configuration 2-3
Console Connection 2-3
Setting Passwords 2-4
Setting an IP Address 2-4
Manual Configuration 2-4
Dynamic Configuration 2-5
Enabling SNMP Management Access 2-6
Community Strings (for SNMP version 1 and 2c clients) 2-6
Trap Receivers 2-7
Configuring Access for SNMP Version 3 Clients 2-8
Saving Configuration Settings 2-8
Managing System Files 2-9
Chapter 3: Configuring the Switch 3-1
Using the Web Interface 3-1
Navigating the Web Browser Interface 3-2
Home Page 3-2
Configuration Options 3-3
Panel Display 3-3
Main Menu 3-4
Basic Configuration 3-10
Displaying System Information 3-10
Displaying Switch Hardware/Software Versions 3-11
Displaying Bridge Extension Capabilities 3-13
Setting the Switch’s IP Address 3-14
Manual Configuration 3-15
Using DHCP/BOOTP 3-16
DHCP Relay and Option 82 Information 3-17
Managing Firmware 3-19
Downloading System Software from a Server 3-20
i

Contents
Saving or Restoring Configuration Settings 3-22
Downloading Configuration Settings from a Server 3-23
Console Port Settings 3-24
Telnet Settings 3-26
Configuring Event Logging 3-28
System Log Configuration 3-28
Remote Log Configuration 3-30
Displaying Log Messages 3-31
Sending Simple Mail Transfer Protocol Alerts 3-32
Resetting the System 3-34
Setting the System Clock 3-35
Configuring SNTP 3-35
Configuring NTP 3-36
Setting the Time Zone 3-38
Simple Network Management Protocol 3-38
Enabling the SNMP Agent 3-40
Setting Community Access Strings 3-40
Specifying Trap Managers and Trap Types 3-41
Configuring SNMPv3 Management Access 3-43
Setting a Local Engine ID 3-44
Specifying a Remote Engine ID 3-44
Configuring SNMPv3 Users 3-45
Configuring Remote SNMPv3 Users 3-47
Configuring SNMPv3 Groups 3-49
Setting SNMPv3 Views 3-53
User Authentication 3-54
Configuring User Accounts 3-54
Configuring Local/Remote Logon Authentication 3-56
Configuring HTTPS 3-59
Replacing the Default Secure-site Certificate 3-60
Configuring the Secure Shell 3-61
Generating the Host Key Pair 3-63
Configuring the SSH Server 3-65
Configuring Port Security 3-66
Configuring 802.1X Port Authentication 3-68
Displaying 802.1X Global Settings 3-69
Configuring 802.1X Global Settings 3-70
Configuring Port Settings for 802.1X 3-70
Displaying 802.1X Statistics 3-73
MAC Address Authentication 3-74
Configuring the MAC Authentication Reauthentication Time 3-75
Configuring MAC Authentication for Ports 3-76
Displaying Secure MAC Address Information 3-77
Configuring MAC Address Filters 3-79
Filtering Addresses for Management Access 3-80
ii

Contents
Access Control Lists 3-82
Configuring Access Control Lists 3-82
Setting the ACL Name and Type 3-83
Configuring a Standard IP ACL 3-84
Configuring an Extended IP ACL 3-85
Configuring a MAC ACL 3-87
Binding a Port to an Access Control List 3-88
Port Configuration 3-89
Displaying Connection Status 3-89
Configuring Interface Connections 3-91
Creating Trunk Groups 3-93
Statically Configuring a Trunk 3-94
Enabling LACP on Selected Ports 3-95
Configuring LACP Parameters 3-97
Displaying LACP Port Counters 3-99
Displaying LACP Settings and Status for the Local Side 3-101
Displaying LACP Settings and Status for the Remote Side 3-103
Setting Broadcast Storm Thresholds 3-105
Configuring Port Mirroring 3-106
Configuring Rate Limits 3-107
Rate Limit Granularity 3-107
Rate Limit Configuration 3-108
Showing Port Statistics 3-109
Address Table Settings 3-114
Setting Static Addresses 3-114
Displaying the Address Table 3-115
Changing the Aging Time 3-117
Spanning Tree Algorithm Configuration 3-117
Displaying Global Settings 3-119
Configuring Global Settings 3-123
Displaying Interface Settings 3-127
Configuring Interface Settings 3-130
Configuring Multiple Spanning Trees 3-132
Displaying Interface Settings for MSTP 3-136
Configuring Interface Settings for MSTP 3-137
VLAN Configuration 3-139
IEEE 802.1Q VLANs 3-139
Enabling or Disabling GVRP (Global Setting) 3-142
Displaying Basic VLAN Information 3-142
Displaying Current VLANs 3-143
Creating VLANs 3-145
Adding Static Members to VLANs (VLAN Index) 3-147
Adding Static Members to VLANs (Port Index) 3-148
Configuring VLAN Behavior for Interfaces 3-150
Private VLANs 3-152
iii

Contents
Displaying Current Private VLANs 3-153
Configuring Private VLANs 3-154
Associating VLANs 3-154
Displaying Private VLAN Interface Information 3-155
Configuring Private VLAN Interfaces 3-156
Class of Service Configuration 3-158
Layer 2 Queue Settings 3-158
Setting the Default Priority for Interfaces 3-158
Mapping CoS Values to Egress Queues 3-160
Selecting the Queue Mode 3-162
Setting the Service Weight for Traffic Classes 3-163
Layer 3/4 Priority Settings 3-164
Mapping Layer 3/4 Priorities to CoS Values 3-164
Selecting IP Precedence/DSCP Priority 3-164
Mapping IP Precedence 3-165
Mapping DSCP Priority 3-166
Mapping IP Port Priority 3-168
Mapping CoS Values to ACLs 3-169
Multicast Filtering 3-170
Layer 2 IGMP (Snooping and Query) 3-171
Configuring IGMP Snooping and Query Parameters 3-171
Enabling IGMP Immediate Leave 3-173
Displaying Interfaces Attached to a Multicast Router 3-174
Specifying Static Interfaces for a Multicast Router 3-175
Displaying Port Members of Multicast Services 3-176
Assigning Ports to Multicast Services 3-177
IGMP Filtering and Throttling 3-178
Enabling IGMP Filtering and Throttling 3-178
Configuring IGMP Filter Profiles 3-179
Configuring IGMP Filtering and Throttling for Interfaces 3-181
Multicast VLAN Registration 3-183
Configuring Global MVR Settings 3-184
Displaying MVR Interface Status 3-185
Displaying Port Members of Multicast Groups 3-186
Configuring MVR Interface Status 3-187
Assigning Static Multicast Groups to Interfaces 3-188
Configuring Domain Name Service 3-189
Configuring General DNS Service Parameters 3-189
Configuring Static DNS Host to Address Entries 3-192
Displaying the DNS Cache 3-193
Switch Clustering 3-194
Cluster Configuration 3-194
Cluster Member Configuration 3-195
Cluster Member Information 3-196
Cluster Candidate Information 3-197
iv

Contents
Chapter 4: Command Line Interface 4-1
Using the Command Line Interface 4-1
Accessing the CLI 4-1
Console Connection 4-1
Telnet Connection 4-1
Entering Commands 4-3
Keywords and Arguments 4-3
Minimum Abbreviation 4-3
Command Completion 4-3
Getting Help on Commands 4-3
Showing Commands 4-4
Partial Keyword Lookup 4-5
Negating the Effect of Commands 4-5
Using Command History 4-5
Understanding Command Modes 4-5
Exec Commands 4-6
Configuration Commands 4-7
Command Line Processing 4-8
Command Groups 4-9
Line Commands 4-11
line 4-11
login 4-12
password 4-13
timeout login response 4-14
exec-timeout 4-14
password-thresh 4-15
silent-time 4-16
databits 4-16
parity 4-17
speed 4-18
stopbits 4-18
disconnect 4-19
show line 4-19
General Commands 4-20
enable 4-20
disable 4-21
configure 4-22
show history 4-22
reload 4-23
end 4-23
exit 4-24
quit 4-24
System Management Commands 4-25
Device Designation Commands 4-25
v

Contents
prompt 4-25
hostname 4-26
User Access Commands 4-26
username 4-27
enable password 4-28
IP Filter Commands 4-29
management 4-29
show management 4-30
Web Server Commands 4-31
ip http port 4-31
ip http server 4-31
ip http secure-server 4-32
ip http secure-port 4-33
Telnet Server Commands 4-34
ip telnet port 4-34
ip telnet server 4-34
Secure Shell Commands 4-35
ip ssh server 4-37
ip ssh timeout 4-38
ip ssh authentication-retries 4-38
ip ssh server-key size 4-39
delete public-key 4-39
ip ssh crypto host-key generate 4-40
ip ssh crypto zeroize 4-40
ip ssh save host-key 4-41
show ip ssh 4-41
show ssh 4-42
show public-key 4-43
Event Logging Commands 4-44
logging on 4-44
logging history 4-45
logging host 4-46
logging facility 4-46
logging trap 4-47
clear logging 4-47
show logging 4-48
show log 4-49
SMTP Alert Commands 4-50
logging sendmail host 4-50
logging sendmail level 4-51
logging sendmail source-email 4-52
logging sendmail destination-email 4-52
logging sendmail 4-53
show logging sendmail 4-53
Time Commands 4-54
vi

Contents
sntp client 4-54
sntp server 4-55
sntp poll 4-56
show sntp 4-56
ntp client 4-57
ntp server 4-57
ntp poll 4-58
ntp authenticate 4-59
ntp authentication-key 4-59
show ntp 4-60
clock timezone 4-61
calendar set 4-62
show calendar 4-62
System Status Commands 4-63
show startup-config 4-63
show running-config 4-65
show system 4-67
show users 4-67
show version 4-68
Frame Size Commands 4-69
jumbo frame 4-69
Flash/File Commands 4-70
copy 4-70
delete 4-73
dir 4-73
whichboot 4-74
boot system 4-75
Authentication Commands 4-76
Authentication Sequence 4-76
authentication login 4-76
authentication enable 4-77
RADIUS Client 4-78
radius-server host 4-78
radius-server port 4-79
radius-server key 4-79
radius-server retransmit 4-80
radius-server timeout 4-80
show radius-server 4-81
TACACS+ Client 4-81
tacacs-server host 4-82
tacacs-server port 4-82
tacacs-server key 4-82
show tacacs-server 4-83
Port Security Commands 4-84
port security 4-84
vii

Contents
802.1X Port Authentication 4-85
dot1x system-auth-control 4-86
dot1x default 4-86
dot1x max-req 4-87
dot1x port-control 4-87
dot1x operation-mode 4-88
dot1x re-authenticate 4-88
dot1x re-authentication 4-89
dot1x timeout quiet-period 4-89
dot1x timeout re-authperiod 4-90
dot1x timeout tx-period 4-90
show dot1x 4-90
Network Access 4-94
network-access mode 4-94
network-access max-mac-count 4-95
network-access mac-filter 4-96
network-access port-mac-filter 4-97
network-access dynamic-vlan 4-97
mac-authentication reauth-time 4-98
clear network-access 4-99
show network-access 4-99
show network-access mac-filter 4-100
show network-access mac-address-table 4-100
Access Control List Commands 4-102
IP ACLs 4-103
access-list ip 4-103
permit, deny (Standard ACL) 4-104
permit, deny (Extended ACL) 4-105
show ip access-list 4-107
ip access-group 4-107
show ip access-group 4-108
map access-list ip 4-108
show map access-list ip 4-109
MAC ACLs 4-110
access-list mac 4-110
permit, deny (MAC ACL) 4-111
show mac access-list 4-112
mac access-group 4-112
show mac access-group 4-113
map access-list mac 4-113
show map access-list mac 4-114
ACL Information 4-115
show access-list 4-115
show access-group 4-115
SNMP Commands 4-116
viii

Contents
snmp-server 4-117
show snmp 4-117
snmp-server community 4-118
snmp-server contact 4-119
snmp-server location 4-119
snmp-server host 4-120
snmp-server enable traps 4-122
snmp-server engine-id 4-123
show snmp engine-id 4-124
snmp-server view 4-125
show snmp view 4-126
snmp-server group 4-126
show snmp group 4-127
snmp-server user 4-128
show snmp user 4-130
Interface Commands 4-131
interface 4-131
description 4-132
speed-duplex 4-132
negotiation 4-133
capabilities 4-134
flowcontrol 4-135
shutdown 4-136
switchport broadcast packet-rate 4-137
clear counters 4-137
show interfaces status 4-138
show interfaces counters 4-139
show interfaces switchport 4-140
Mirror Port Commands 4-142
port monitor 4-142
show port monitor 4-143
Rate Limit Commands 4-144
rate-limit 4-144
rate-limit granularity 4-145
show rate-limit 4-145
Link Aggregation Commands 4-146
channel-group 4-147
lacp 4-148
lacp system-priority 4-149
lacp admin-key (Ethernet Interface) 4-150
lacp admin-key (Port Channel) 4-151
lacp port-priority 4-152
show lacp 4-152
Address Table Commands 4-156
mac-address-table static 4-157
ix

Contents
clear mac-address-table dynamic 4-158
show mac-address-table 4-158
mac-address-table aging-time 4-159
show mac-address-table aging-time 4-159
Spanning Tree Commands 4-160
spanning-tree 4-161
spanning-tree mode 4-161
spanning-tree forward-time 4-163
spanning-tree hello-time 4-163
spanning-tree max-age 4-164
spanning-tree priority 4-164
spanning-tree pathcost method 4-165
spanning-tree transmission-limit 4-166
spanning-tree mst-configuration 4-166
mst vlan 4-167
mst priority 4-168
name 4-168
revision 4-169
max-hops 4-169
spanning-tree spanning-disabled 4-170
spanning-tree cost 4-170
spanning-tree port-priority 4-171
spanning-tree edge-port 4-172
spanning-tree portfast 4-173
spanning-tree link-type 4-173
spanning-tree mst cost 4-174
spanning-tree mst port-priority 4-175
spanning-tree protocol-migration 4-176
show spanning-tree 4-176
show spanning-tree mst configuration 4-178
VLAN Commands 4-179
Editing VLAN Groups 4-179
vlan database 4-179
vlan 4-180
Configuring VLAN Interfaces 4-181
interface vlan 4-181
switchport mode 4-182
switchport acceptable-frame-types 4-182
switchport ingress-filtering 4-183
switchport native vlan 4-184
switchport allowed vlan 4-185
switchport forbidden vlan 4-186
Displaying VLAN Information 4-186
show vlan 4-187
Configuring Private VLANs 4-188
x

Contents
private-vlan 4-189
private vlan association 4-190
switchport mode private-vlan 4-191
switchport private-vlan host-association 4-191
switchport private-vlan isolated 4-192
switchport private-vlan mapping 4-193
show vlan private-vlan 4-193
GVRP and Bridge Extension Commands 4-194
bridge-ext gvrp 4-194
show bridge-ext 4-195
switchport gvrp 4-195
show gvrp configuration 4-196
garp timer 4-196
show garp timer 4-197
Priority Commands 4-198
Priority Commands (Layer 2) 4-198
queue mode 4-199
switchport priority default 4-199
queue bandwidth 4-200
queue cos-map 4-201
show queue mode 4-202
show queue bandwidth 4-202
show queue cos-map 4-203
Priority Commands (Layer 3 and 4) 4-204
map ip port (Global Configuration) 4-204
map ip port (Interface Configuration) 4-205
map ip precedence (Global Configuration) 4-205
map ip precedence (Interface Configuration) 4-206
map ip dscp (Global Configuration) 4-207
map ip dscp (Interface Configuration) 4-207
show map ip port 4-208
show map ip precedence 4-209
show map ip dscp 4-210
Multicast Filtering Commands 4-211
IGMP Snooping Commands 4-212
ip igmp snooping 4-212
ip igmp snooping vlan static 4-212
ip igmp snooping version 4-213
ip igmp snooping immediate-leave 4-213
show ip igmp snooping 4-214
show mac-address-table multicast 4-215
IGMP Query Commands (Layer 2) 4-216
ip igmp snooping querier 4-216
ip igmp snooping query-count 4-216
ip igmp snooping query-interval 4-217
xi

Contents
ip igmp snooping query-max-response-time 4-218
ip igmp snooping router-port-expire-time 4-218
Static Multicast Routing Commands 4-219
ip igmp snooping vlan mrouter 4-219
show ip igmp snooping mrouter 4-220
IGMP Filtering and Throttling Commands 4-221
ip igmp filter (Global Configuration) 4-221
ip igmp profile 4-222
permit, deny 4-223
range 4-223
ip igmp filter (Interface Configuration) 4-224
ip igmp max-groups 4-224
ip igmp max-groups action 4-225
show ip igmp filter 4-226
show ip igmp profile 4-226
show ip igmp throttle interface 4-227
Multicast VLAN Registration Commands 4-227
mvr (Global Configuration) 4-228
mvr (Interface Configuration) 4-229
show mvr 4-230
Domain Name Service Commands 4-233
ip host 4-233
clear host 4-234
ip domain-name 4-234
ip domain-list 4-235
ip name-server 4-236
ip domain-lookup 4-237
show hosts 4-238
show dns 4-239
show dns cache 4-239
clear dns cache 4-240
DHCP Commands 4-241
ip dhcp relay information option 4-241
ip dhcp relay information policy 4-242
ip dhcp relay server 4-242
show ip dhcp-relay 4-243
IP Interface Commands 4-244
ip address 4-244
ip default-gateway 4-245
ip dhcp restart 4-246
show ip interface 4-246
show ip redirects 4-247
ping 4-247
Switch Cluster Commands 4-249
cluster 4-249
xii

Contents
cluster commander 4-250
cluster ip-pool 4-250
cluster member 4-251
rcommand 4-252
show cluster 4-252
show cluster members 4-253
show cluster candidates 4-253
Appendix A: Software Specifications A-1
Software Features A-1
Management Features A-2
Standards A-2
Management Information Bases A-3
Appendix B: Troubleshooting B-1
Problems Accessing the Management Interface B-1
Using System Logs B-2
Glossary
Index
xiii

Contents
xiv

Tables
Table 1-1 Key Features 1-1
Table 1-2 System Defaults 1-5
Table 3-1 Configuration Options 3-3
Table 3-2 Main Menu 3-4
Table 3-3 Logging Levels 3-29
Table 3-6 HTTPS System Support 3-59
Table 3-7 802.1X Statistics 3-73
Table 3-8 LACP Port Counters 3-99
Table 3-9 LACP Internal Configuration Information 3-101
Table 3-10 LACP Neighbor Configuration Information 3-103
Table 3-11 Port Statistics 3-110
Table 3-12 Egress Queue Priority Mapping 3-160
Table 3-13 CoS Priority Levels 3-160
Table 3-14 Mapping IP Precedence 3-165
Table 3-15 Mapping DSCP Priority Values 3-166
Table 3-16 Egress Queue Priority Mapping 3-169
Table 4-1 Command Modes 4-6
Table 4-2 Configuration Modes 4-7
Table 4-3 Command Line Processing 4-8
Table 4-4 Command Groups 4-9
Table 4-5 Line Commands 4-11
Table 4-6 General Commands 4-20
Table 4-7 System Management Commands 4-25
Table 4-8 Device Designation Commands 4-25
Table 4-9 User Access Commands 4-26
Table 4-10 Default Login Settings 4-27
Table 4-11 IP Filter Commands 4-29
Table 4-12 Web Server Commands 4-31
Table 4-13 HTTPS System Support 4-32
Table 4-14 Telnet Server Commands 4-34
Table 4-15 SSH Commands 4-35
Table 4-16 show ssh - display description 4-42
Table 4-17 Event Logging Commands 4-44
Table 4-18 Logging Levels 4-45
Table 4-19 show logging flash/ram - display description 4-48
Table 4-20 show logging trap - display description 4-49
Table 4-21 SMTP Alert Commands 4-50
Table 4-22 Time Commands 4-54
Table 4-23 System Status Commands 4-63
Table 4-24 Frame Size Commands 4-69
Table 4-25 Flash/File Commands 4-70
Table 4-26 File Directory Information 4-74
xv

Tables
Table 4-27 Authentication Commands 4-76
Table 4-28 Authentication Sequence 4-76
Table 4-29 RADIUS Client Commands 4-78
Table 4-30 TACACS Commands 4-81
Table 4-31 Port Security Commands 4-84
Table 4-32 802.1X Port Authentication 4-85
Table 4-33 Network Access 4-94
Table 4-35 IP ACLs 4-103
Table 4-34 Access Control Lists 4-103
Table 4-36 Egress Queue Priority Mapping 4-109
Table 4-37 MAC ACLs 4-110
Table 4-38 Egress Queue Priority Mapping 4-114
Table 4-39 ACL Information 4-115
Table 4-40 SNMP Commands 4-116
Table 4-41 show snmp engine-id - display description 4-124
Table 4-42 show snmp view - display description 4-126
Table 4-43 show snmp group - display description 4-128
Table 4-44 show snmp user - display description 4-130
Table 4-45 Interface Commands 4-131
Table 4-46 Interfaces Switchport Statistics 4-141
Table 4-47 Mirror Port Commands 4-142
Table 4-48 Rate Limit Commands 4-144
Table 4-49 Link Aggregation Commands 4-146
Table 4-50 show lacp counters - display description 4-153
Table 4-51 show lacp internal - display description 4-154
Table 4-52 show lacp neighbors - display description 4-155
Table 4-54 Address Table Commands 4-156
Table 4-53 show lacp sysid - display description 4-156
Table 4-55 Spanning Tree Commands 4-160
Table 4-56 VLANs 4-179
Table 4-57 Editing VLAN Groups 4-179
Table 4-58 Configuring VLAN Interfaces 4-181
Table 4-59 Show VLAN Commands 4-186
Table 4-60 Private VLAN Commands 4-188
Table 4-61 GVRP and Bridge Extension Commands 4-194
Table 4-62 Priority Commands 4-198
Table 4-63 Priority Commands (Layer 2) 4-198
Table 4-64 Default CoS Priority Levels 4-201
Table 4-65 Priority Commands (Layer 3 and 4) 4-204
Table 4-66 Mapping IP Precedence Values 4-206
Table 4-67 IP DSCP to CoS Vales 4-208
Table 4-68 Multicast Filtering Commands 4-211
Table 4-69 IGMP Snooping Commands 4-212
Table 4-70 IGMP Query Commands (Layer 2) 4-216
Table 4-71 Static Multicast Routing Commands 4-219
xvi

Tables
Table 4-72 IGMP Filtering and Throttling Commands 4-221
Table 4-73 Multicast VLAN Registration Commands 4-228
Table 4-74 show mvr - display description 4-231
Table 4-76 show mvr members - display description 4-232
Table 4-75 show mvr interface - display description 4-232
Table 4-77 DNS Commands 4-233
Table 4-78 show dns cache - display description 4-239
Table 4-79 DHCP Commands 4-241
Table 4-80 IP Interface Commands 4-244
Table 4-81 Switch Cluster Commands 4-249
Table B-1 Troubleshooting Chart B-1
xvii

Tables
xviii

Figures
Figure 3-1 Home Page 3-2
Figure 3-2 Panel Display 3-3
Figure 3-3 System Information 3-10
Figure 3-4 Displaying Switch Information 3-12
Figure 3-5 Bridge Extension Configuration 3-13
Figure 3-6 Manual IP Configuration 3-15
Figure 3-7 IP Configuration using DHCP 3-16
Figure 3-8 DHCP Relay Option 82 Configuration 3-18
Figure 3-9 Operation Code Image File Transfer 3-20
Figure 3-10 Select Start-Up Operation File 3-20
Figure 3-11 Deleting Files 3-21
Figure 3-12 Copy Configuration Settings 3-23
Figure 3-13 Setting the Startup Configuration Settings 3-23
Figure 3-14 Console Port Settings 3-25
Figure 3-15 Enabling Telnet 3-27
Figure 3-16 System Logs 3-29
Figure 3-17 Remote Logs 3-30
Figure 3-18 Displaying Logs 3-31
Figure 3-19 Enabling and Configuring SMTP Alerts 3-33
Figure 3-20 Resetting the System 3-34
Figure 3-21 SNTP Configuration 3-35
Figure 3-22 NTP Client Configuration 3-37
Figure 3-23 Setting the System Clock 3-38
Figure 3-24 Enabling the SNMP Agent 3-40
Figure 3-25 Configuring SNMP Community Strings 3-41
Figure 3-26 Configuring SNMP Trap Managers 3-43
Figure 3-27 Setting the SNMPv3 Engine ID 3-44
Figure 3-28 Setting an Engine ID 3-45
Figure 3-29 Configuring SNMPv3 Users 3-46
Figure 3-30 Configuring Remote SNMPv3 Users 3-48
Figure 3-31 Configuring SNMPv3 Groups 3-52
Figure 3-32 Configuring SNMPv3 Views 3-53
Figure 3-33 Access Levels 3-55
Figure 3-34 Authentication Settings 3-58
Figure 3-35 HTTPS Settings 3-60
Figure 3-36 SSH Host-Key Settings 3-64
Figure 3-37 SSH Server Settings 3-65
Figure 3-38 Configuring Port Security 3-67
Figure 3-39 802.1X Global Information 3-69
Figure 3-40 802.1X Configuration 3-70
Figure 3-41 802.1X Port Configuration 3-71
Figure 3-42 Displaying 802.1X Port Statistics 3-74
xix

Figures
Figure 3-43 Network Access Configuration 3-76
Figure 3-44 Network Access Port Configuration 3-77
Figure 3-45 Network Access MAC Address Information 3-78
Figure 3-46 Network Access MAC Filter Configuration 3-79
Figure 3-47 Creating a Web IP Filter List 3-81
Figure 3-48 Selecting ACL Type 3-83
Figure 3-49 ACL Configuration - Standard IP 3-84
Figure 3-50 ACL Configuration - Extended IP 3-86
Figure 3-51 ACL Configuration - MAC 3-87
Figure 3-52 Binding a Port to an ACL 3-88
Figure 3-53 Displaying Port/Trunk Information 3-90
Figure 3-54 Port/Trunk Configuration 3-92
Figure 3-55 Configuring Port Trunks 3-94
Figure 3-56 LACP Configuration 3-96
Figure 3-57 LACP - Aggregation Port 3-98
Figure 3-58 LACP - Port Counters Information 3-100
Figure 3-59 LACP - Port Internal Information 3-102
Figure 3-60 LACP - Port Neighbors Information 3-103
Figure 3-61 Port Broadcast Control 3-105
Figure 3-62 Mirror Port Configuration 3-107
Figure 3-63 Rate Limit Granularity Configuration 3-108
Figure 3-64 Output Rate Limit Port Configuration 3-109
Figure 3-65 Port Statistics 3-113
Figure 3-66 Static Addresses 3-115
Figure 3-67 Dynamic Addresses 3-116
Figure 3-68 Address Aging 3-117
Figure 3-69 STA Information 3-121
Figure 3-70 STA Global Configuration 3-126
Figure 3-71 STA Port Information 3-129
Figure 3-72 STA Port Configuration 3-132
Figure 3-73 MSTP VLAN Configuration 3-134
Figure 3-74 MSTP Port Information 3-136
Figure 3-75 MSTP Port Configuration 3-138
Figure 3-76 GLobally Enabling GVRP 3-142
Figure 3-77 VLAN Basic Information 3-142
Figure 3-78 VLAN Current Table 3-144
Figure 3-79 VLAN Static List - Creating VLANs 3-146
Figure 3-80 VLAN Static Table - Adding Static Members 3-148
Figure 3-81 VLAN Static Membership by Port 3-149
Figure 3-82 VLAN Port Configuration 3-151
Figure 3-83 Private VLAN Information 3-153
Figure 3-84 Private VLAN Configuration 3-154
Figure 3-85 Private VLAN Association 3-155
Figure 3-86 Private VLAN Port Information 3-156
Figure 3-87 Private VLAN Port Configuration 3-157
xx

Figures
Figure 3-88 Port Priority Configuration 3-159
Figure 3-89 Traffic Classes 3-161
Figure 3-90 Queue Mode 3-162
Figure 3-91 Configuring Queue Scheduling 3-163
Figure 3-92 IP Precedence/DSCP Priority Status 3-164
Figure 3-93 Mapping IP Precedence Priority Values 3-165
Figure 3-94 Mapping IP DSCP Priority Values 3-167
Figure 3-95 IP Port Priority Status 3-168
Figure 3-96 IP Port Priority 3-168
Figure 3-97 ACL CoS Priority 3-170
Figure 3-98 IGMP Configuration 3-172
Figure 3-99 IGMP Immediate Leave 3-173
Figure 3-100 Displaying Multicast Router Port Information 3-174
Figure 3-101 Static Multicast Router Port Configuration 3-175
Figure 3-102 IP Multicast Registration Table 3-176
Figure 3-103 IGMP Member Port Table 3-177
Figure 3-104 Enabling IGMP Filtering and Throttling 3-179
Figure 3-105 IGMP Profile Configuration 3-180
Figure 3-106 IGMP Filter and Throttling Port Configuration 3-182
Figure 3-107 MVR Global Configuration 3-184
Figure 3-108 MVR Port Information 3-185
Figure 3-109 MVR Group IP Information 3-186
Figure 3-110 MVR Port Configuration 3-188
Figure 3-111 MVR Group Member Configuration 3-189
Figure 3-112 DNS General Configuration 3-191
Figure 3-113 DNS Static Host Table 3-192
Figure 3-114 DNS Cache 3-193
Figure 3-115 Cluster Configuration 3-195
Figure 3-116 Cluster Member Configuration 3-196
Figure 3-117 Cluster Member Information 3-196
Figure 3-118 Cluster Candidate Information 3-197
xxi

Figures
xxii
Chapter 1: Introduction
This switch provides a broad range of features for Layer 2 switching. It includes a
management agent that allows you to configure the features listed in this manual.
The default configuration can be used for most of the features provided by this
switch. However, there are many options that you should configure to maximize the
switch’s performance for your particular network environment.
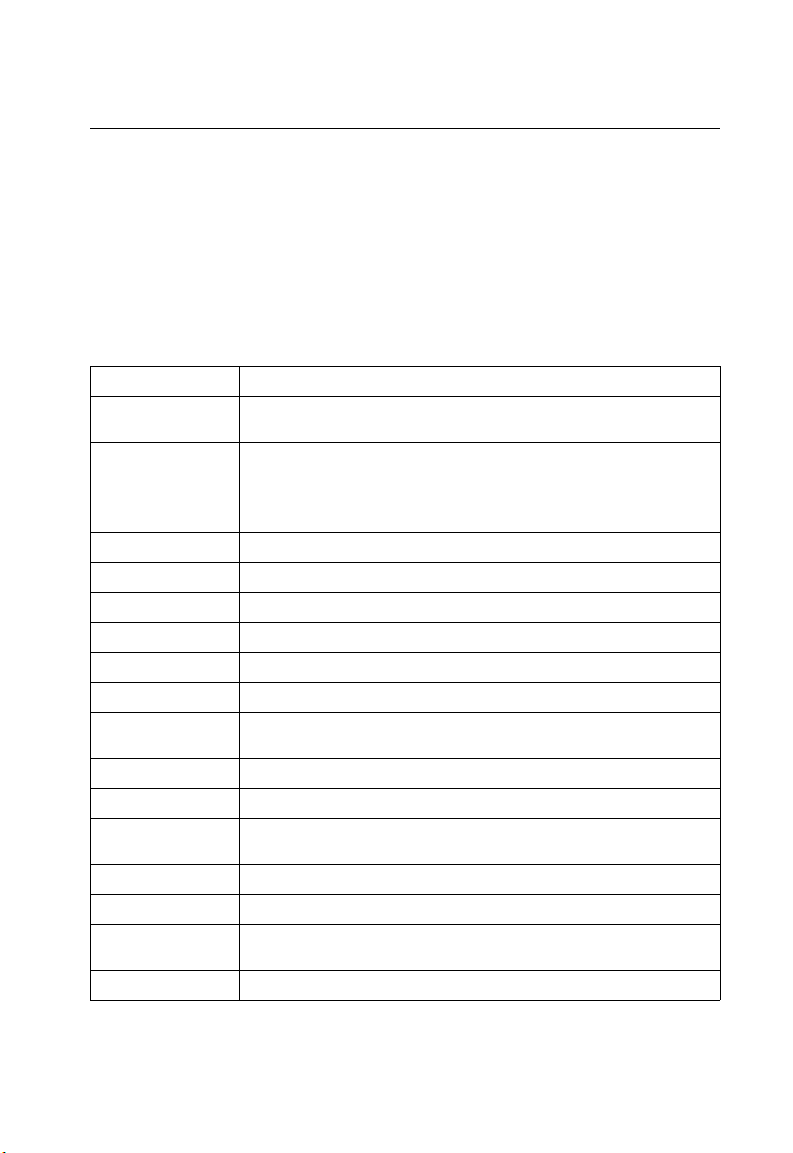
Key Features
Table 1-1 Key Features
Feature Description
Configuration Backup
and Restore
Authentication Console, Telnet, web – User name / password, RADIUS, TACACS+
Access Control Lists Supports up to 88 IP or MAC ACLs
DHCP Client Supported
Port Configuration Speed, duplex mode and flow control
Rate Limiting Input and output rate limiting per port
Port Mirroring One port mirrored to a single analysis port
Port Trunking Supports up to 4 trunks using either static or dynamic trunking (LACP)
Broadcast Storm
Control
Static Address Up to 8K MAC addresses in the forwarding table
IEEE 802.1D Bridge Supports dynamic data switching and addresses learning
Store-and-Forward
Switching
Spanning Tree Protocol Supports standard STP and Rapid Spanning Tree Protocol (RSTP)
Virtual LANs Up to 255 using IEEE 802.1Q, port-based, or private VLANs
Traffic Prioritization Default port priority, traffic class map, queue scheduling, IP Precedence or
Multicast Filtering Supports IGMP snooping and query
Backup to TFTP server
Web – HTTPS; Telnet – SSH
SNMP – Community strings
Port – IEEE 802.1X, MAC address filtering
Supported
Supported to ensure wire-speed switching while eliminating bad frames
Differentiated Services Code Point (DSCP), and TCP/UDP Port
1-1

Introduction
1
Description of Software Features
The switch provides a wide range of advanced performance enhancing features.
Flow control eliminates the loss of packets due to bottlenecks caused by port
saturation. Broadcast storm suppression prevents broadcast traffic storms from
engulfing the network. Port-based and protocol-based VLANs, plus support for
automatic GVRP VLAN registration provide traffic security and efficient use of
network bandwidth. CoS priority queueing ensures the minimum delay for moving
real-time multimedia data across the network. While multicast filtering provides
support for real-time network applications. Some of the management features are
briefly described below.
Configuration Backup and Restore – You can save the current configuration
settings to a file on a TFTP server, and later download this file to restore the switch
configuration settings.
Authentication – This switch authenticates management access via the console
port, Telnet or web browser. User names and passwords can be configured locally or
can be verified via a remote authentication server (i.e., RADIUS or TACACS+).
Port-based authentication is also supported via the IEEE 802.1X protocol. This
protocol uses the Extensible Authentication Protocol over LANs (EAPOL) to request
user credentials from the 802.1X client, and then verifies the client’s right to access
the network via an authentication server.
Other authentication options include HTTPS for secure management access via the
web, SSH for secure management access over a Telnet-equivalent connection, IP
address filtering for SNMP/web/Telnet management access, and MAC address
filtering for port access.
Access Control Lists – ACLs provide packet filtering for IP frames (based on
address, protocol, TCP/UDP port number or TCP control code) or any frames
(based on MAC address or Ethernet type). ACLs can be used to improve
performance by blocking unnecessary network traffic or to implement security
controls by restricting access to specific network resources or protocols.
Port Configuration – You can manually configure the speed, duplex mode, and
flow control used on specific ports, or use auto-negotiation to detect the connection
settings used by the attached device. Use the full-duplex mode on ports whenever
possible to double the throughput of switch connections. Flow control should also be
enabled to control network traffic during periods of congestion and prevent the loss
of packets when port buffer thresholds are exceeded. The switch supports flow
control based on the IEEE 802.3x standard.
Rate Limiting – This feature controls the maximum rate for traffic transmitted or
received on an interface. Rate limiting is configured on interfaces at the edge of a
network to limit traffic into or out of the network. Traffic that falls within the rate limit is
transmitted, while packets that exceed the acceptable amount of traffic are dropped.
1-2

Description of Software Features
Port Mirroring – The switch can unobtrusively mirror traffic from any port to a
monitor port. You can then attach a protocol analyzer or RMON probe to this port to
perform traffic analysis and verify connection integrity.
Port Trunking – Ports can be combined into an aggregate connection. Trunks can
be manually set up or dynamically configured using IEEE 802.3ad Link Aggregation
Control Protocol (LACP). The additional ports dramatically increase the throughput
across any connection, and provide redundancy by taking over the load if a port in
the trunk should fail. The switch supports up to four trunks.
Broadcast Storm Control – Broadcast suppression prevents broadcast traffic from
overwhelming the network. When enabled on a port, the level of broadcast traffic
passing through the port is restricted. If broadcast traffic rises above a pre-defined
threshold, it will be throttled until the level falls back beneath the threshold.
Static Addresses – A static address can be assigned to a specific interface on this
switch. Static addresses are bound to the assigned interface and will not be moved.
When a static address is seen on another interface, the address will be ignored and
will not be written to the address table. Static addresses can be used to provide
network security by restricting access for a known host to a specific port.
IEEE 802.1D Bridge – The switch supports IEEE 802.1D transparent bridging. The
address table facilitates data switching by learning addresses, and then filtering or
forwarding traffic based on this information. The address table supports up to 8K
addresses.
Store-and-Forward Switching – The switch copies each frame into its memory
before forwarding them to another port. This ensures that all frames are a standard
Ethernet size and have been verified for accuracy with the cyclic redundancy check
(CRC). This prevents bad frames from entering the network and wasting bandwidth.
To avoid dropping frames on congested ports, the switch provides 8 MB for frame
buffering. This buffer can queue packets awaiting transmission on congested
networks.
Spanning Tree Algorithm – The switch supports these spanning tree protocols:
Spanning Tree Protocol (STP, IEEE 802.1D) – This protocol provides loop detection
and recovery by allowing two or more redundant connections to be created between
a pair of LAN segments. When there are multiple physical paths between segments,
this protocol will choose a single path and disable all others to ensure that only one
route exists between any two stations on the network. This prevents the creation of
network loops. However, if the chosen path should fail for any reason, an alternate
path will be activated to maintain the connection.
Rapid Spanning Tree Protocol (RSTP, IEEE 802.1w) – This protocol reduces the
convergence time for network topology changes to 3 to 5 seconds, compared to 30
seconds or more for the older IEEE 802.1D STP standard. It is intended as a
complete replacement for STP, but can still interoperate with switches running the
older standard by automatically reconfiguring ports to STP-compliant mode if they
detect STP protocol messages from attached devices.
1
1-3

Introduction
1
Virtual LANs – The switch supports up to 255 VLANs. A Virtual LAN is a collection
of network nodes that share the same collision domain regardless of their physical
location or connection point in the network. The switch supports tagged VLANs
based on the IEEE 802.1Q standard. Members of VLAN groups can be dynamically
learned via GVRP, or ports can be manually assigned to a specific set of VLANs.
This allows the switch to restrict traffic to the VLAN groups to which a user has been
assigned. By segmenting your network into VLANs, you can:
• Eliminate broadcast storms which severely degrade performance in a flat network.
• Simplify network management for node changes/moves by remotely configuring
VLAN membership for any port, rather than having to manually change the network
connection.
• Provide data security by restricting all traffic to the originating VLAN.
• Use private VLANs to restrict traffic to pass only between data ports and the uplink
ports, thereby isolating adjacent ports within the same VLAN, and allowing you to
limit the total number of VLANs that need to be configured.
Traffic Prioritization – This switch prioritizes each packet based on the required
level of service, using four priority queues with strict or Weighted Round Robin
Queuing. It uses IEEE 802.1p and 802.1Q tags to prioritize incoming traffic based on
input from the end-station application. These functions can
independent priorities for delay-sensitive data and best-effort data.
This switch also supports several common methods of prioritizing layer 3/4 traffic to
meet application requirements. Traffic can be prioritized based on the priority bits in
the IP frame’s Type of Service (ToS) octet or the number of the TCP/UDP port.
When these services are enabled, the priorities are mapped to a Class of Service
value by the switch, and the traffic then sent to the corresponding output queue.
Multicast Filtering – Specific multicast traffic can be assigned to its own VLAN to
ensure that it does not interfere with normal network traffic and to guarantee
real-time delivery by setting the required priority level for the designated VLAN. The
switch uses IGMP Snooping and Query to manage multicast group registration.
be used to provide
1-4
 Loading...
Loading...