ZyWALL 1050/ZyWALL USG 300 Support Notes
ZyWALL 1050 (ZyWALL USG 300)
Internet Security Appliance
Support Notes
Revision 2.02
September,2007
1
All contents copyright (c) 2007 ZyXEL Communications Corporation.

ZyWALL 1050/ZyWALL USG 300 Support Notes
INDEX
1. Deploying VPN.......................................................................................................................... 8
1.1 Extended Intranets.......................................................................................................... 10
1.1.1 Site to Site VPN (ZyWALL 1050/USG 300 Ù ZyWALL 1050/USG 300): ...... 10
1.1.2 Site to Site VPN solutions (ZyWALL 1050 Ù ZyWALL USG 300):................ 14
1.2 Extranet Deployment ..................................................................................................... 19
1.2.1 Site to site VPN solutions (ZyWALL1050/ZyWALL USG 300 to ZyWALL70)20
1.2.2 Interoperability – VPN with other vendors...................................................... 26
1.2.2.1 ZyWALL with FortiGate VPN Tunneling............................................. 26
1.2.2.2 ZyWALL with NetScreen VPN Tunneling ........................................... 32
1.2.2.3 ZyWALL with SonicWall VPN Tunneling............................................ 41
1.3 Remote Access VPN ...................................................................................................... 50
1.3.1 IPSec VPN for Remote Access ........................................................................... 50
1.3.2 SSL VPN Application - Reverse Proxy............................................................ 59
1.3.3 Using Two-factor Authentication to Provide Stronger Password Security ...... 67
1.3.4 L2TP over IPSec Application........................................................................... 77
1.4 Large-scale VPN Deployment .......................................................................................85
1.4.1 Fully Meshed Topology ................................................................................... 86
1.4.2 Star Topology ................................................................................................... 87
1.4.3 Star-Mesh Mixed Topology.............................................................................. 96
1.5 Access via Central Site................................................................................................. 112
1.5.1 VPN Tunnel to Central Site (ZyWALL 70 to ZyWALL 1050/ZyWALL USG
300) ............................................................................................................................ 112
1.6 Multiple Entry Point (MEP).........................................................................................124
1.6.1 Deploying MEP.............................................................................................. 124
1.7 Device HA together with VPN HA.............................................................................. 163
1.7.1 Device HA...................................................................................................... 164
1.7.2 VPN HA ......................................................................................................... 182
1.8 VoIP over VPN ............................................................................................................ 189
2. Security Policy Enforcement.................................................................................................. 200
2.1 Managing IM/P2P Applications ................................................................................... 200
2.1.1 Why bother with managing IM/P2P applications?.........................................200
2.1.2 What does ZyWALL 1050/ZyWALL USG 300 provide for managing IM/P2P
applications?............................................................................................................... 200
2.1.3 Configuration Example ..................................................................................... 201
2
All contents copyright (c) 2007 ZyXEL Communications Corporation.

ZyWALL 1050/ZyWALL USG 300 Support Notes
2.2 Zone-based Anti-Virus Protection................................................................................ 210
2.2.1 Applying Zone-Based Anti-Virus to ZyWALL 1050/ZyWALL USG 300........ 210
2.2.2 Enabling Black and White List ......................................................................... 216
2.2.3 Enabling Anti-Virus Statistics Report ............................................................... 218
2.3 Managing WLAN......................................................................................................... 219
2.3.1 Why the wireless networks need to be managed?.......................................... 219
2.3.2 What can we do against the wireless insecurity? ........................................... 219
2.4 Employee Internet Management (EIM) ....................................................................... 231
2.4.1 Benefits of deploying Employee Internet Management................................. 231
2.4.2 EIM on ZyWALL 1050/ZyWALL USG 300.....................................................231
3. Seamless Incorporation .......................................................................................................... 241
3.1 Transparent Firewall..................................................................................................... 241
3.1.1 Bridge mode & Router (NAT) mode co-exist ................................................ 241
3.1.2 NAT & Virtual Server .................................................................................... 246
3.2 Zone-based IDP Protection .......................................................................................... 250
3.2.1 Applying Zone-Based IDP to ZyWALL 1050/ZyWALL USG 300 .................. 250
3.3 Networking Partitioning Using VLAN ........................................................................ 260
3.3.1 Creating VLAN virtual interfaces..................................................................... 260
3.3.2 Adding VLAN virtual interfaces to the Zone.................................................... 264
3.3.3 Applying firewall policy to the Zone of VLANs ..............................................266
3.4 Connecting Multiple ISP Links.................................................................................... 270
3.4.1 Multiple PPPoE links ........................................................................................ 270
3.4.2 Multiple fixed WAN links................................................................................. 280
3.5 Guaranteed Quality of Service ..................................................................................... 298
3.5.1 Priority & Bandwidth management ..................................................................298
FAQ ............................................................................................................................................306
A. Device Management FAQ ............................................................................................. 306
A01. How can I connect to ZyWALL 1050/ZyWALL USG 300 to perform
administrator’s tasks?.................................................................................................306
A02. Why can’t I login into ZyWALL 1050/ZyWALL USG 300?............................306
A03. What’s difference between “Admin Service Control” and “User Service
Control” configuration in GUI menu Configuration > System > WWW? ................ 307
A04. Why ZyWALL 1050/ZyWALL USG 300 redirects me to the login page when I
am performing the management tasks in GUI?.......................................................... 307
A05. Why do I lose my configuration setting after ZyWALL 1050/ZyWALL USG
300 restarts? ............................................................................................................... 308
A06. How can I do if the system is keeping at booting up stage for a long time?..... 308
3
All contents copyright (c) 2007 ZyXEL Communications Corporation.

ZyWALL 1050/ZyWALL USG 300 Support Notes
B. Registration FAQ ........................................................................................................... 310
B01. Why do I need to do the Device Registration?..................................................310
B02. Why do I need to activate services? .................................................................. 310
B03. Why can’t I active trial service?........................................................................ 310
B04. Will the UTM service registration information be reset once restore
configuration in ZyWALL 1050/ZyWALL USG 300 back to manufactory default? 310
C. File Manager FAQ ......................................................................................................... 311
C01. How can ZyWALL 1050/ZyWALL USG 300 manage multiple configuration
files? ........................................................................................................................... 311
C02. What are the configuration files like startup-config.conf, system-default.conf
and lastgood.conf?...................................................................................................... 311
C03. Why can’t I update firmware?........................................................................... 311
C04. What is the Shell Scripts for in GUI menu File manager > Shell Scripts?........312
C05. How to write a shell script? ............................................................................... 312
C06. Why can’t I run shell script successfully?......................................................... 312
D. Object FAQ....................................................................................................................313
D01. Why does ZyWALL 1050/ZyWALL USG 300 use objects? ............................ 313
D02. What’s the difference between Trunk and the Zone Object? ............................314
D03. What is the difference between the default LDAP and the group LDAP? What
is the difference between the default RADIUS and the group RADIUS? ................. 314
E. Interface FAQ ................................................................................................................ 315
E01. How to setup the WAN interface with PPPoE or PPTP?................................... 315
E02. How to add a virtual interface (IP alias)? .......................................................... 315
E03. Why can’t I get IP address via DHCP relay?.....................................................315
E04. Why can’t I get DNS options from ZyWALL’s DHCP server? ......................... 315
E05. Why does the PPP interface dials successfully even its base interface goes
down? ......................................................................................................................... 315
E06. What is the port grouping used for in ZyWALL 1050/ZyWALL USG 300? .... 316
E07. What's the maximum VLAN interface supported by ZyWALL 1050/ZyWALL
USG 300 ? .................................................................................................................. 316
F. Routing and NAT FAQ ................................................................................................... 317
F01. How to add a policy route? ................................................................................ 317
F02. How to configure local loopback in ZyWALL 1050/ZyWALL USG 300?...... 317
F03. How to configure a NAT? .................................................................................. 321
F04. After I installed a HTTP proxy server and set a http redirect rule, I still can’t
access web. Why? ......................................................................................................322
F05. How to limit some application (for example, FTP) bandwidth usage? ............. 322
4
All contents copyright (c) 2007 ZyXEL Communications Corporation.

ZyWALL 1050/ZyWALL USG 300 Support Notes
F06. What’s the routing order of policy route, dynamic route, and static route and
direct connect subnet table? ....................................................................................... 322
F07. Why ZyWALL 1050/ZyWALL USG 300 cannot ping the Internet host, but PC
from LAN side can browse internet WWW?............................................................. 323
F08. Why can’t I ping to the, Internet, after I shutdown the primary WAN interface?323
F09. Why the virtual server or port trigger does not work?.......................................323
F10. Why port trigger does not work? ....................................................................... 323
F11. How do I use the traffic redirect feature in ZyWALL 1050/ZyWALL USG 300?324
F12. Why can’t ZyWALL learn the route from RIP and/or OSPF?........................... 324
G. VPN and Certificate ....................................................................................................... 325
G01. Why can't the VPN connections dial to a remote gateway?.............................. 325
G02. VPN connections are dialed successfully, but the traffic still cannot go through
the IPsec tunnel. ......................................................................................................... 325
G03. Why ZyWALL 1050/ZyWALL USG 300 VPN tunnel had been configured
correctly and the VPN connection status is connected but the traffic still can not
reach the remote VPN subnet?................................................................................... 325
G04. VPN connections are dialed successfully, and the policy route is set. But the
traffic is lost or there is no response from remote site. .............................................. 326
G05. Why don’t the Inbound/Outbound traffic NAT in VPN work? ......................... 326
H. Firewall FAQ ................................................................................................................. 327
H01. Why doesn’t my LAN to WAN or WAN to LAN rule work? ........................... 327
H02. Why does the intra-zone blocking malfunction after I disable the firewall? .... 327
H03. Can I have access control rules to the device in firewall? ................................ 327
I. Application Patrol FAQ................................................................................................... 328
I01. What is Application Patrol? ................................................................................ 328
I02. What applications can the Application Patrol function inspect? ........................ 328
I03. Why does the application patrol fail to drop/reject invalid access for some
applications?............................................................................................................... 329
I04. What is the difference between “Auto” and “Service Ports” settings in the
Application Patrol configuration page? ..................................................................... 330
I05. What is the difference between BWM (bandwidth management) in Policy Route
and App. Patrol ? ........................................................................................................ 331
I06. Do I have to purchase iCards specifically for using AppPatrol feature? ............ 332
I07. Can I configure different access level based on application for different users? 332
I08. Can I migrate AppPatrol policy and bandwidth management control from
ZLD1.0x to ZLD2.0x? ...............................................................................................332
J. lDP FAQ ......................................................................................................................... 333
All contents copyright (c) 2007 ZyXEL Communications Corporation.
5

ZyWALL 1050/ZyWALL USG 300 Support Notes
J01. Why doesn’t the IDP work? Why has the signature updating failed? ................ 333
J02. When I use a web browser to configure the IDP, sometimes it will popup
"wait data timeout"..................................................................................................... 333
J03. When I want to configure the packet inspection (signatures), the GUI becomes
very slow. ...................................................................................................................333
J04. After I select "Auto Update" for IDP, when will it update the signatures? ........ 333
J05. If I want to use IDP service, will it is enough if I just complete the registration
and turn on IDP? ........................................................................................................333
J06. What are the major design differences in IDP in ZLD1.0x and latest IDP/ADP
in ZLD2.0x? ............................................................................................................... 333
J07. Does IDP subscription have anything to do with AppPatrol? ............................ 334
J08. How to get a detailed description of an IDP signature? ..................................... 335
J09. After an IDP signature updated, does it require ZyWALL to reboot to make new
signatures take effect? ................................................................................................ 335
K. Content Filtering FAQ................................................................................................... 336
K01. Why can’t I enable external web filtering service? Why does the external web
filtering service seem not to be working? .................................................................. 336
K02. Why can’t I use MSN after I enabled content filter and allowed trusted
websites only? ............................................................................................................ 336
L. Device HA FAQ.............................................................................................................337
L01. What does the “Preempt” mean? ....................................................................... 337
L02. What is the password in Synchronization?........................................................ 337
L03. What is “Link Monitor” and how to enable it?.................................................. 337
L04. Can Link Monitor of Device HA be used in backup VRRP interfaces?............ 338
L05. Why do both the VRRP interfaces of master ZW 1050 and backup ZW 1050
are activated at the same time?................................................................................... 338
M. User Management FAQ ................................................................................................ 339
M. User Management FAQ ................................................................................................ 339
M01. What is the difference between user and guest account?.................................. 339
M02. What is the “re-authentication time” and “lease time”?................................... 339
M03. Why can’t I sign in to the device? .................................................................... 339
M04. Why is the TELNET/SSH/FTP session to the device disconnected? Why is the
GUI redirected to login page after I click a button/link? ........................................... 339
M05. What is AAA?................................................................................................... 340
M06. What are ldap-users and radius-users used for? ...............................................340
M07. What privileges will be given for ldap-users and radius-users? ....................... 340
N. Centralized Log FAQ .................................................................................................... 342
All contents copyright (c) 2007 ZyXEL Communications Corporation.
6

ZyWALL 1050/ZyWALL USG 300 Support Notes
N01. Why can’t I enable e-mail server in system log settings? ................................. 342
N02. After I have the entire required field filled, why can’t I receive the log mail? . 342
O. Traffic Statistics FAQ .................................................................................................... 343
O01. When I use "Flush Data" in Report, not all the statistic data are cleared.......... 343
O02. Why isn't the statistic data of "Report" exact? .................................................. 343
O03. Does Report collect the traffic from/to ZyWALL itself? ..................................343
O04. Why cannot I see the connections from/to ZyWALL itself?............................. 343
P. Anti-Virus FAQ .............................................................................................................. 344
P01. Is there any file size or amount of concurrent files limitation with
ZyWALL1050 Anti-Virus engine?............................................................................. 344
P02. Does ZyWALL1050 Anti-Virus support compressed file scanning?................. 344
P03. What is the maximum concurrent session of ZyWALL1050 Anti-Virus engine344
P04. How many type of viruses can be recognized by the ZyWALL 1050/ZyWALL
USG 300? ................................................................................................................... 344
P05. How frequent the AV signature will be updated? ..............................................344
P06. How to retrieve the virus information in detail?................................................ 345
P07. I cannot download a file from Internet through ZyWALL1050 because the
Anti-Virus engine considers this file has been infected by the virus; however, I am
very sure this file is not infected because the file is nothing but a plain text file. How
do I resolve this problem? .......................................................................................... 345
P08. Does ZyWALL1050 Anti-Virus engine support Passive FTP?.......................... 345
P09. What kinds of protocol are currently supported on ZyWALL1050 Anti-Virus
engine? .......................................................................................................................345
P10. If the Anti-Virus engine detects a virus, what action it may take? Can it cure the
file?............................................................................................................................. 345
7
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
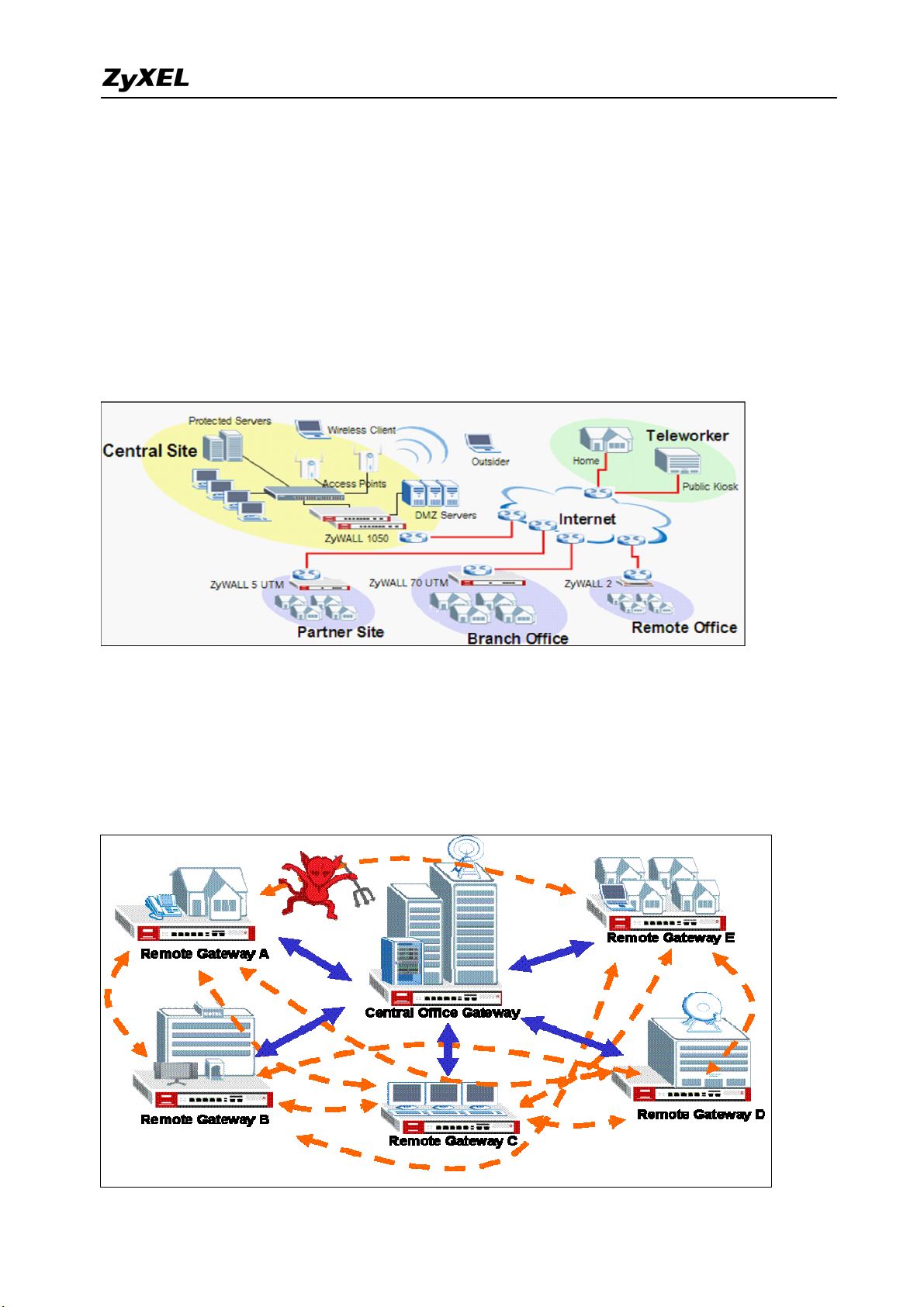
1. Deploying VPN
VPN (Virtual Private Network) allows you to establish a virtual direct connection to remote
locations or for the telecommuters to access the internal network in the office. VPN is a
replacement for the traditional site-to-site lease lines like T1 or ISDN. Through the VPN
applications, it reduces setup cost, works for various types of Internet connection devices
(ISDN modem, ADSL modem and FTTX…) and is easy to troubleshoot.
VPN gives you site-to-site connection flexibility. However, with multiple VPN connections
between sites, it can become more difficult to maintain. Typically, an administrator has to
configure many site-to-site VPN connections to allow a truly global VPN network.
VPN connection management is made easily using the VPN concentrator. The VPN
co
nc
en
tr
at
or
ro
ut
es
V
P
N
8
All contents copyright (c) 2007 ZyXEL Communications Corporation.
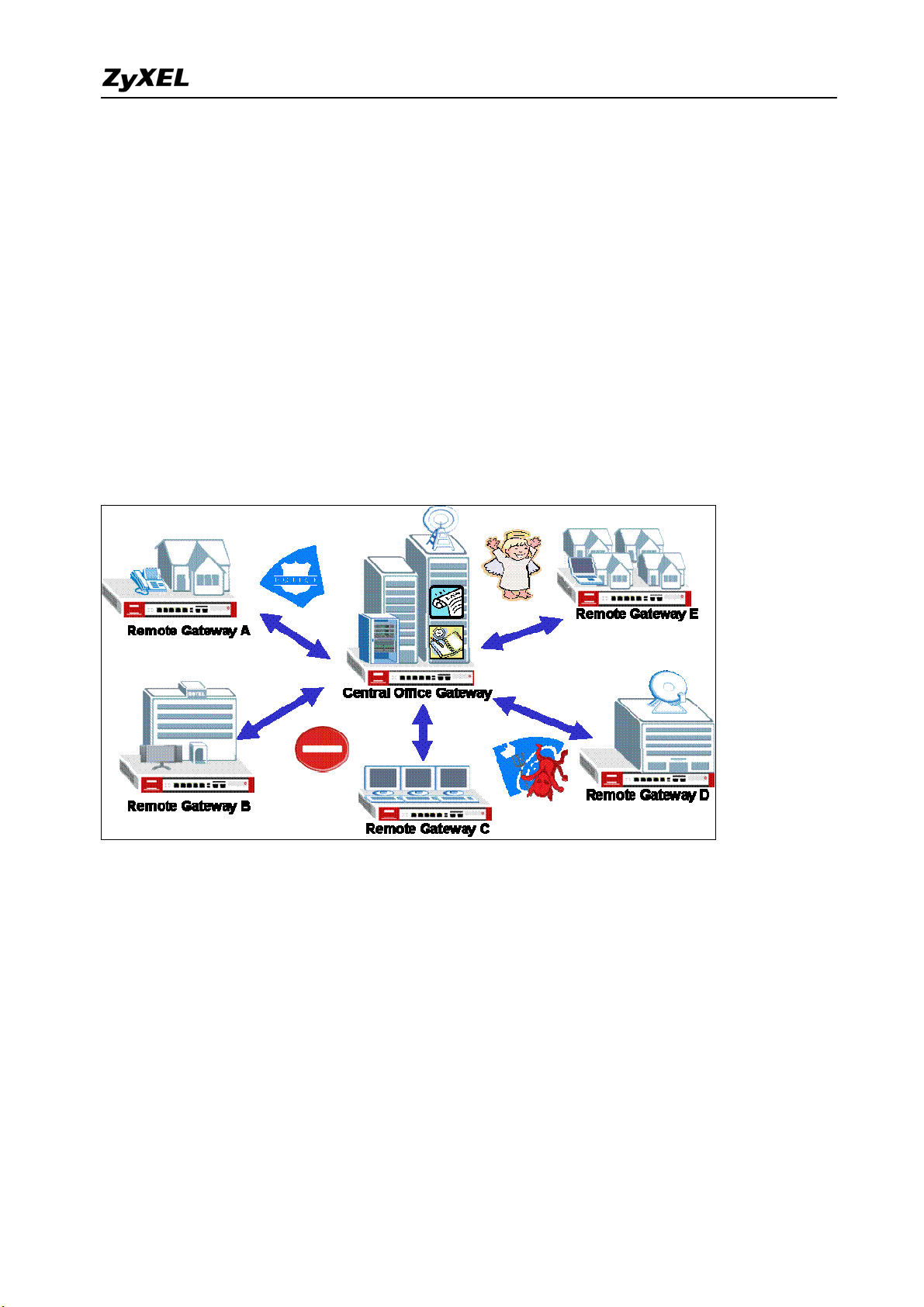
ZyWALL 1050/ZyWALL USG 300 Support Notes
traffic across multiple remote sites without complex setting, thus reduces the configuration
overhead and the possibility of improper configuration. The VPN concentrator is also a
centralized management tool for administrators because all the traffic sent between remote
sites has to go through the central office first and administrators can set up different access
control rules. These are based on the source address, remote address, user and schedule to
enhance VPN security. To help to reduce network intrusion attacks, administrators can
configure the built-in IDP engine to inspect VPN traffic. For easy troubleshooting and
monitoring, the VPN concentrator logs and stores system information and network status for
further easy troubleshooting and analysis.
The VPN concentrator enhances the VPN routing ability and helps network administrators
in setting up a global VPN network with less effort but stronger security and management
possibilities.
For SMB customer, ZyXEL provides a total VPN solution from a personal client to a 500+
people firewall where all of these devices have the VPN connection ability.
The benefit from deployment of ZyXEL VPN solutions
‧ Security and Reliability
‧ Improved communications
‧ Increased flexibility
‧ Lower cost
All contents copyright (c) 2007 ZyXEL Communications Corporation.
9

ZyWALL 1050/ZyWALL USG 300 Support Notes
1.1 Extended Intranets
The ZyXEL VPN solutions primarily can be used to extend the intranet and deliver
increased connectivity between operation sites. The branch office subnet will be considered a
part of main office internet. Therefore, user behind branch office also can use the internal
network resources as if he was in the main office. Because of the VPN connection, user will
feel like he is using a local LAN even though he is accessing the network resources via
Internet. Use of a VPN for smaller branch offices, franchise sites and remote workers provides
nearly the same level of connectivity and reliability as a private network. The remote
connection cost also can decrease by leveraging the Internet connections to replace expensive
leased lines.
1.1.1 Site to Site VPN (ZyWALL 1050/USG 300 Ù ZyWALL 1050/USG 300):
Site to Site VPN is the basic VPN solution between local and remote gateway. This type of
VPN connection is used to extend and join local networks of both sites into a single intranet.
There are two kinds of connection interface. Static IP and dynamic DNS.
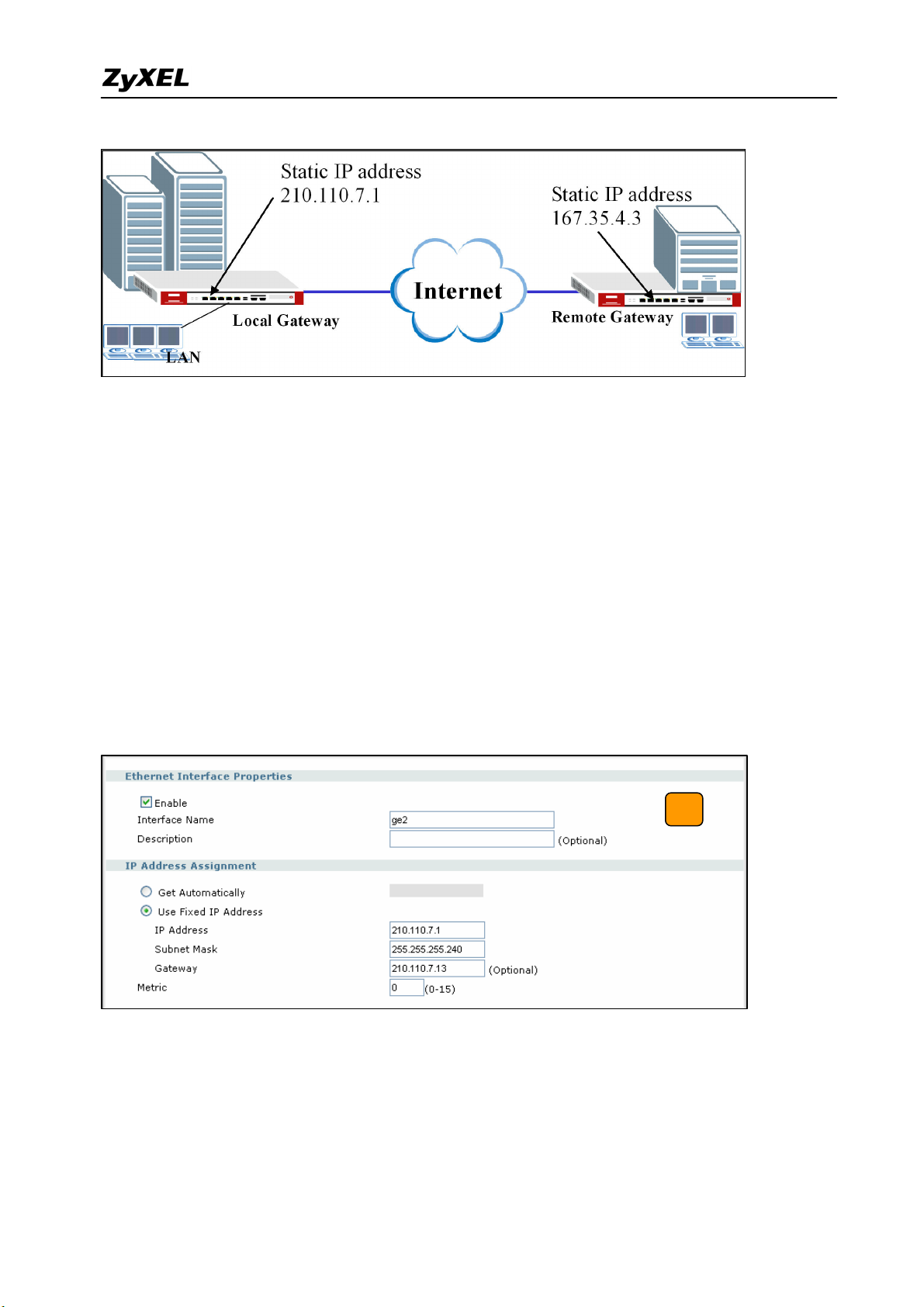
Configure ZyWALL 1050(USG 300) with Static IP address:
ZyWALL 1050(USG 300) uses the static IP address for VPN connection. The topology is
shown on the following figure.
10
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
User needs to configure the static IP address and then apply to the VPN Gateway
configuration page. The configuration steps are stated below:
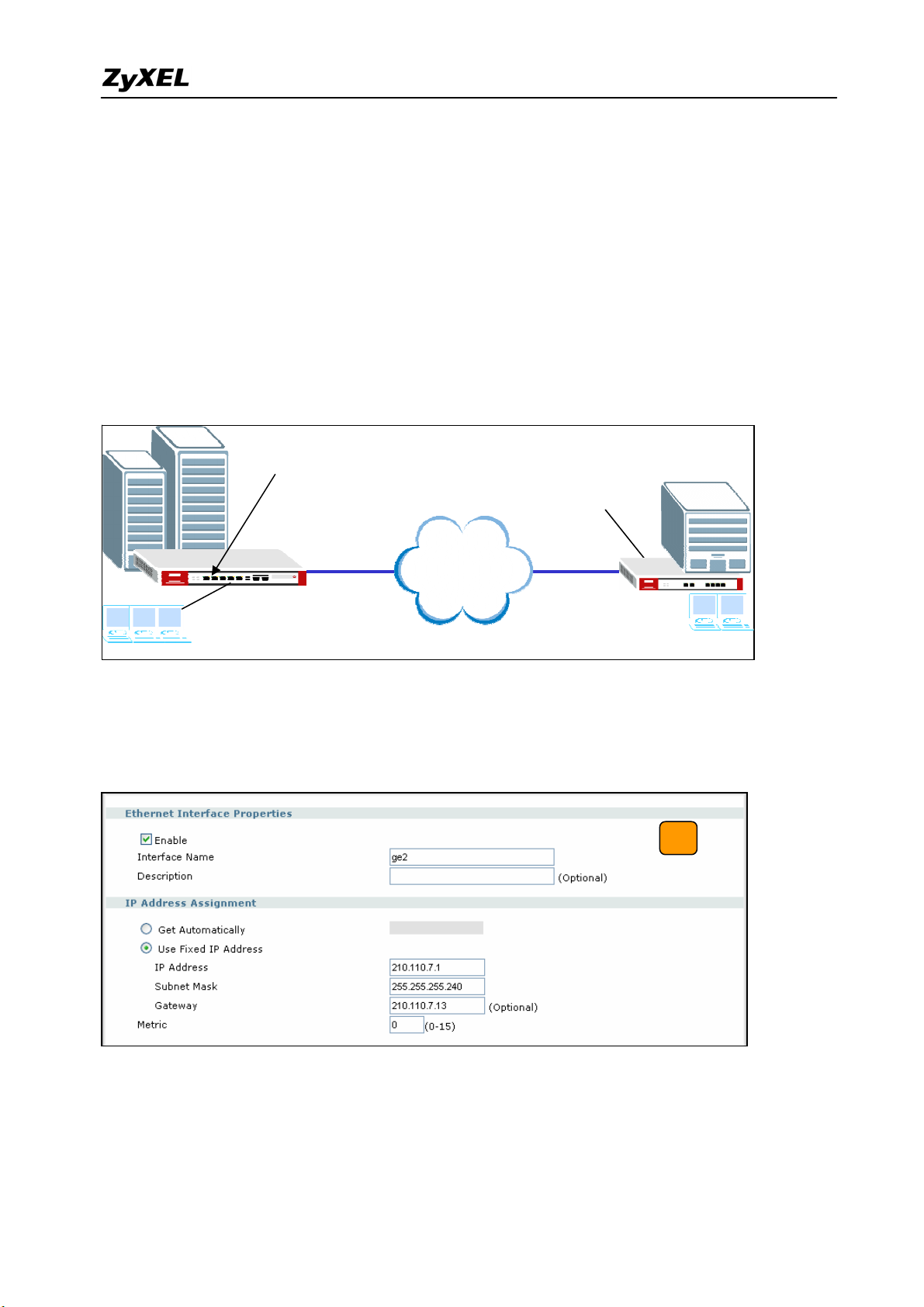
1) Login ZyWALL 1050(USG 300) GUI, setup the ge2 interface for internet connection and
manually assign a static IP. The configuration path in ZyWALL 1050(USG 300) menu is
Configuration > Network > Interface > Edit > ge2
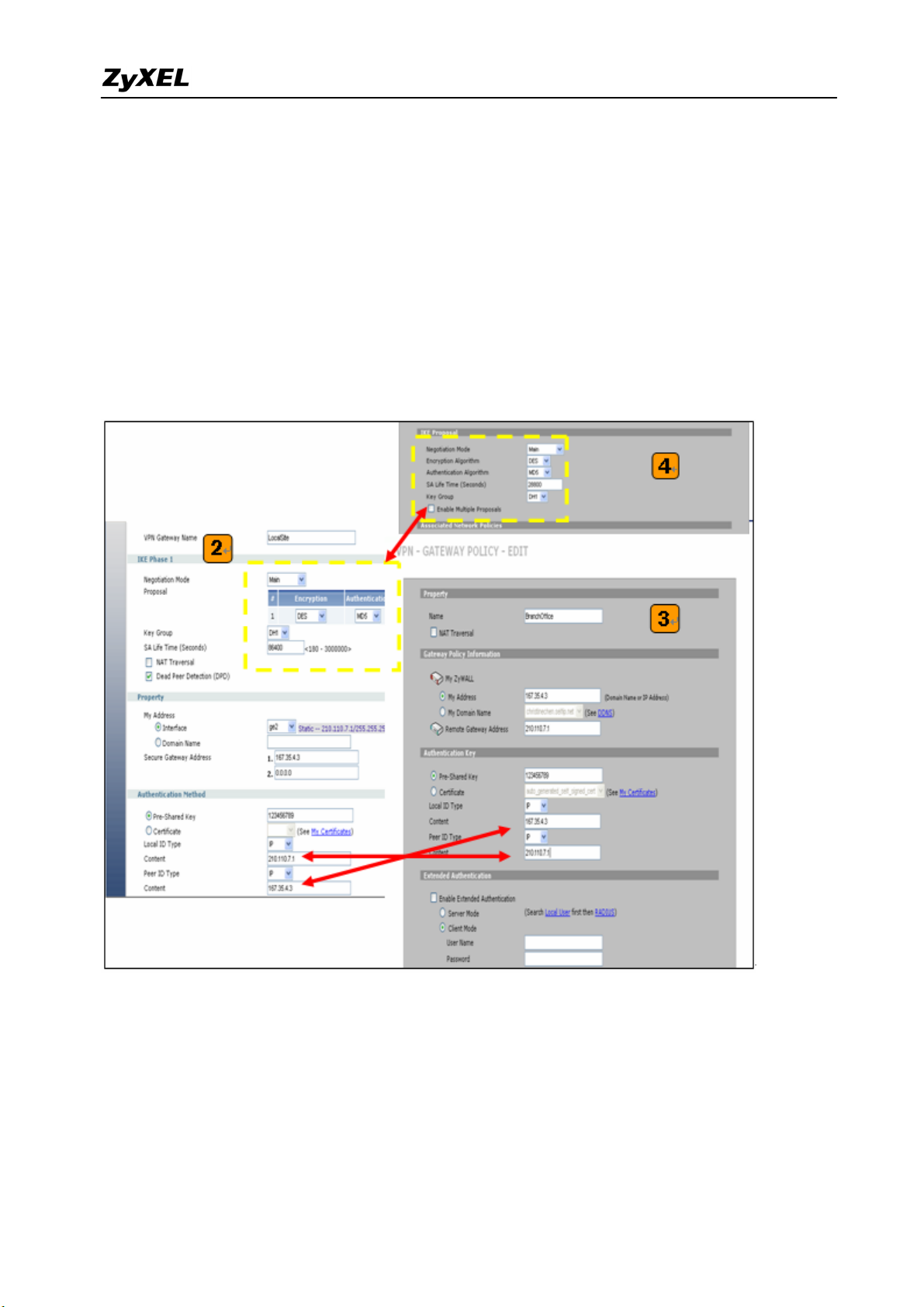
2) Switch to Configuration > Network > IPSec VPN > VPN Gateway select interface ge2
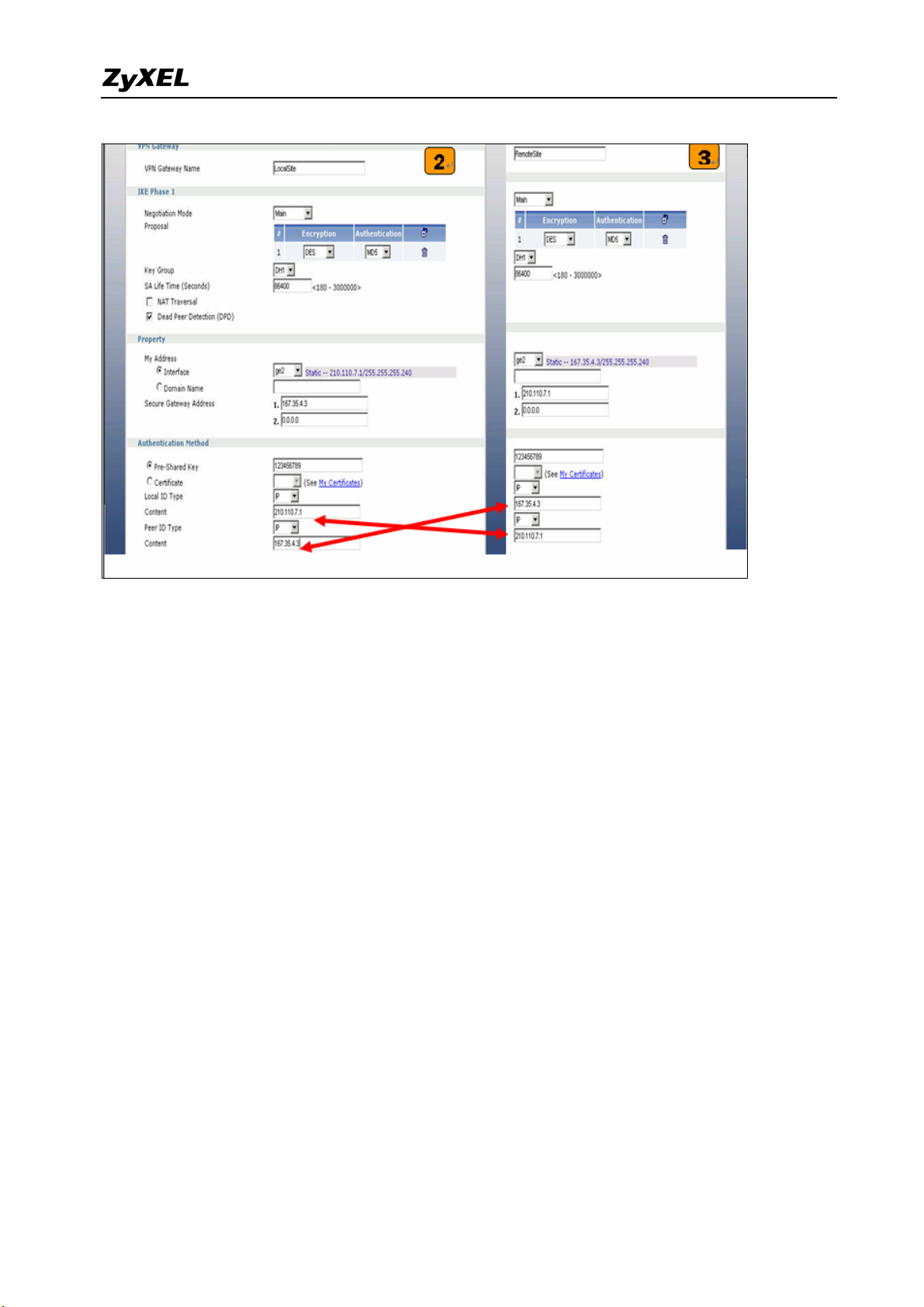
as My Address and then in Security Gateway Address field set the remote gateway IP to
167.35.4.3. The Local ID Type and content are IP and 210.110.7.1, Peer ID Type and
content are IP and 167.35.4.3.
3) Repeat the step1 & 2 to configure the Remote ZyWALL 1050(USG 300). The Local ID
Type & content and Peer ID Type & content are reverse to the Local ZyWALL 1050(USG
300).
11
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
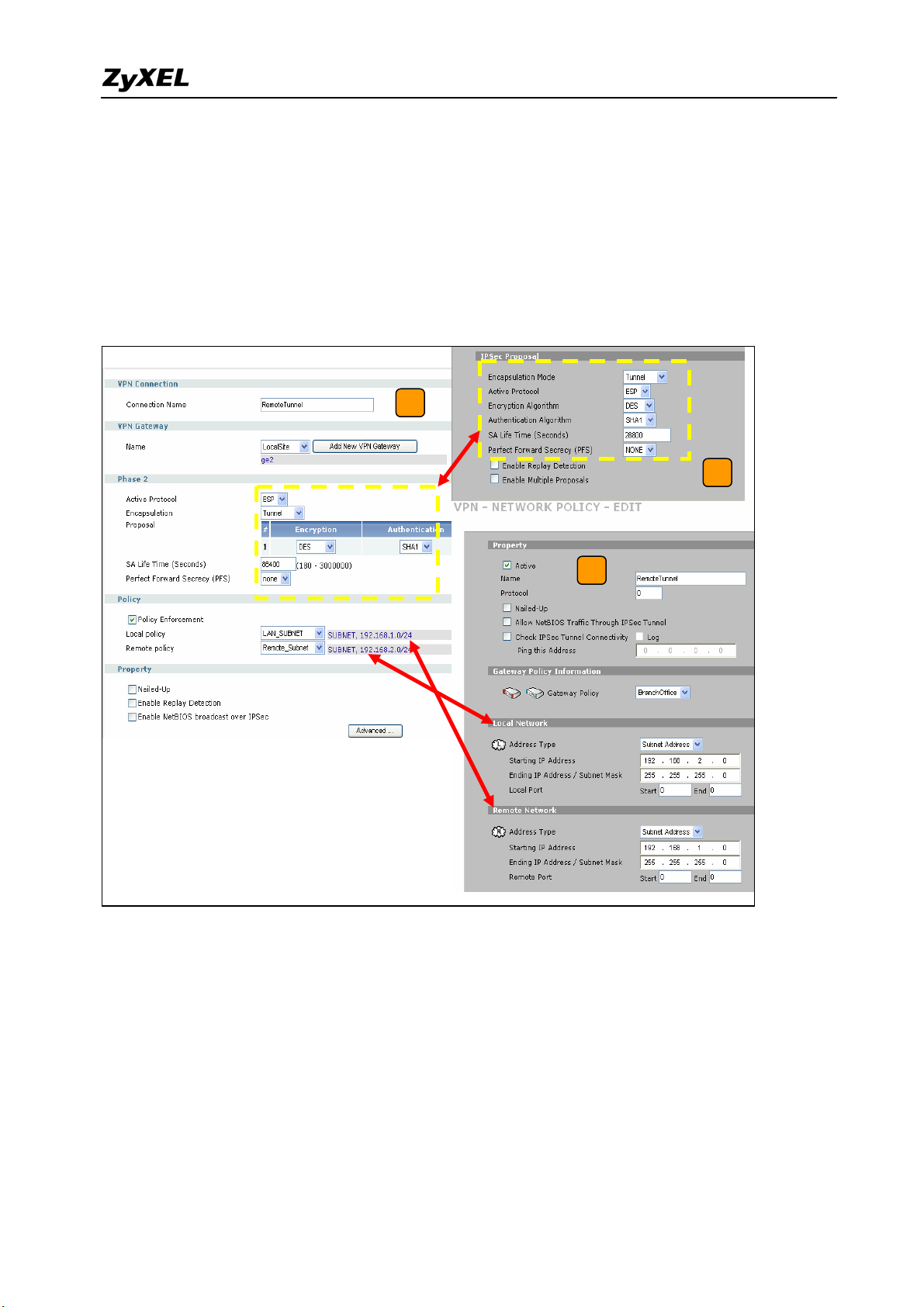
4) User can refer to the user guide to complete the rest of the settings for VPN tunnel.
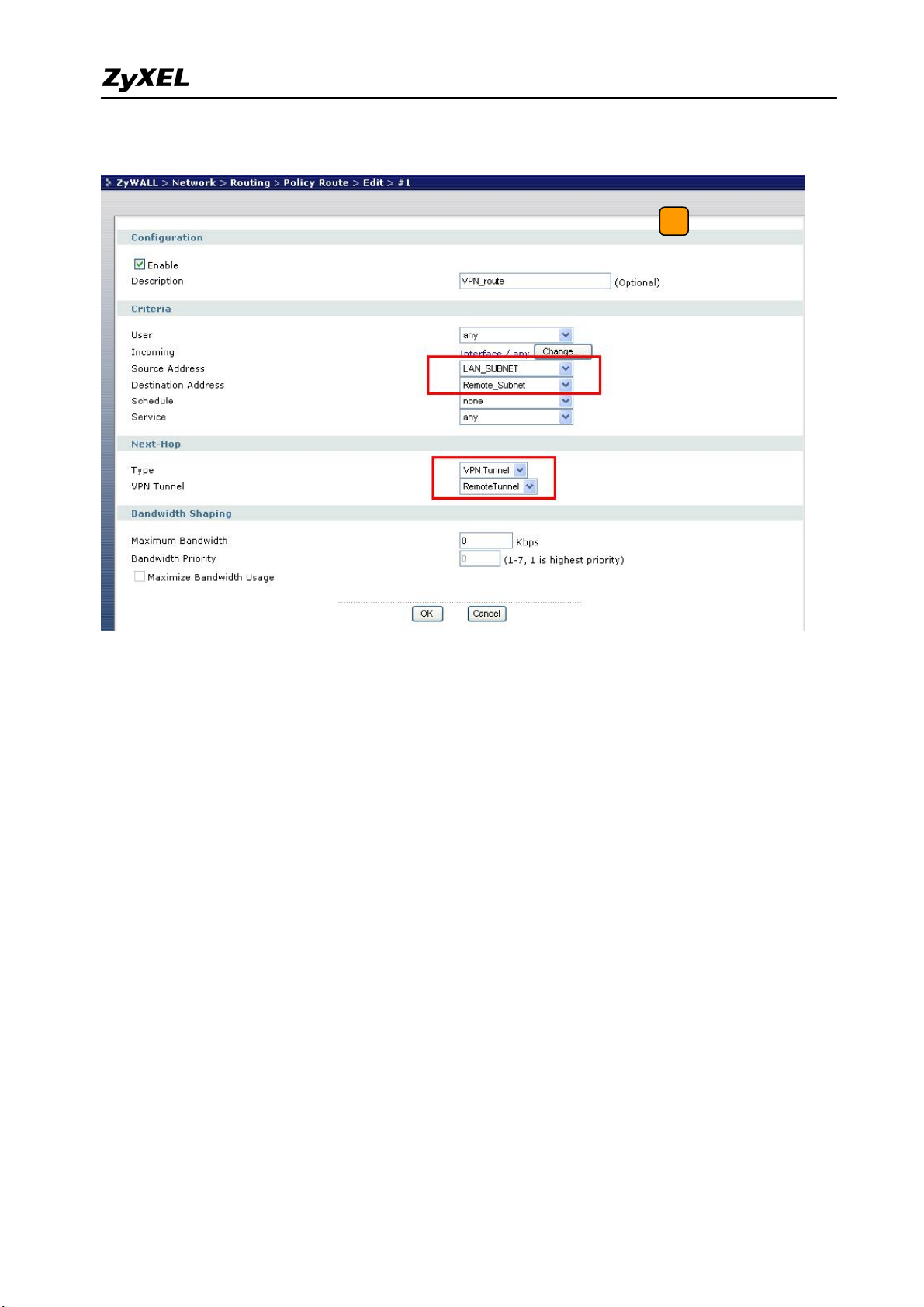
5) The ZyWALL1050 VPN is a route-based VPN. This means the VPN tunnel can be an
interface to route the VPN traffic. Thus, we need to configure a policy route for VPN
traffic from the local subnet to the remote subnet after configuring the VPN gateway and
connection (phase1 and phase2). The purpose of this policy route is to tell the
ZyWALL1050 to send the traffic to VPN tunnel when the traffic flows from the local
subnet to a destination that is in the remote subnet. Switch to ZyWALL > Configuration >
Policy > Route > Policy Route and add a new policy route. The source and the destination
addresses are the local and remote subnets. The Next-Hop type is VPN tunnel. Then
choose the corresponding VPN connection rule from the VPN tunnel drop down menu.
Now, the VPN tunnel and routing is configured and user can start to test it.
12
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
The CLI commands for application:
Local Gateway:
[0] isakmp policy rename RemoteSite LocalSite
[1] isakmp policy LocalSite
[2] mode main
[3] transform-set des-md5
[4] lifetime 86400
[5] no natt
[6] dpd
[7] local-ip interface ge2
[8] peer-ip 167.35.4.3 0.0.0.0
[9] authentication pre-share
[10] keystring 123456789
[11] local-id type ip 210.110.7.1
[12] peer-id type ip 167.35.4.3
[13] peer-id type ip 167.35.4.3
[14] xauth type server default deactivate
[15] group1
[16] exit
Remote Gateway:
[0] isakmp policy RemoteSite
[1] mode main
[2] transform-set des-md5
[3] lifetime 86400
All contents copyright (c) 2007 ZyXEL Communications Corporation.
13

ZyWALL 1050/ZyWALL USG 300 Support Notes
[4] no natt
[5] dpd
[6] local-ip interface ge2
[7] peer-ip 210.110.7.1 0.0.0.0
[8] authentication pre-share
[9] keystring 123456789
[10] local-id type ip 167.35.4.3
[11] peer-id type ip 210.110.7.1
[12] peer-id type ip 210.110.7.1
[13] xauth type server default deactivate
[14] group1
[15] exit
Policy Route for VPN traffic:
[0] policy 1
[1] no deactivate
[2] no description
[3] no user
[4] interface ge1
[5] source LAN_SUBNET
[6] destination Remote_Subnet
[7] no schedule
[8] service any
[9] no snat
[10] next-hop tunnel RemoteTunnel
[11] no bandwidth
[12] exit
Tips for application:
1. Make sure the presharekey is the same in both local and remote gateways.
2. Make sure the IKE & IPSec proposal is the same in both local and remote gateways.
3. Select the correct interface for VPN connection.
4. The Local and Peer ID type and content must the opposite and contain the same.
5. Make sure the VPN policy route has been configured in ZyWALL1050.
1.1.2 Site to Site VPN solutions (ZyWALL 1050 Ù ZyWALL USG 300):
Site to Site VPN is the basic VPN solution between local and remote gateway. This type of
VPN connection is used to extend and join local networks of both sites into a single intranet.
There are two kinds of connection interface. Static IP and dynamic DNS.
Configure ZyWALL 1050 with Static IP address:
14
All contents copyright (c) 2007 ZyXEL Communications Corporation.

ZyWALL 1050/ZyWALL USG 300 Support Notes
ZyWALL 1050 uses the static IP address for VPN connection. The topology is shown on the
following figure.
User needs to configure the static IP address and then apply to the VPN Gateway
configuration page. The configuration steps are stated below:
6) Login ZyWALL 1050 GUI, setup the ge2 interface for internet connection and manually
assign a static IP. The configuration path in ZyWALL 1050 and ZyWALL USG 300 menu
are Network > Interface > Ethernet >Edit > ge2
7) Switch to VPN > IPSec VPN > VPN Gateway select interface ge2 as My Address and
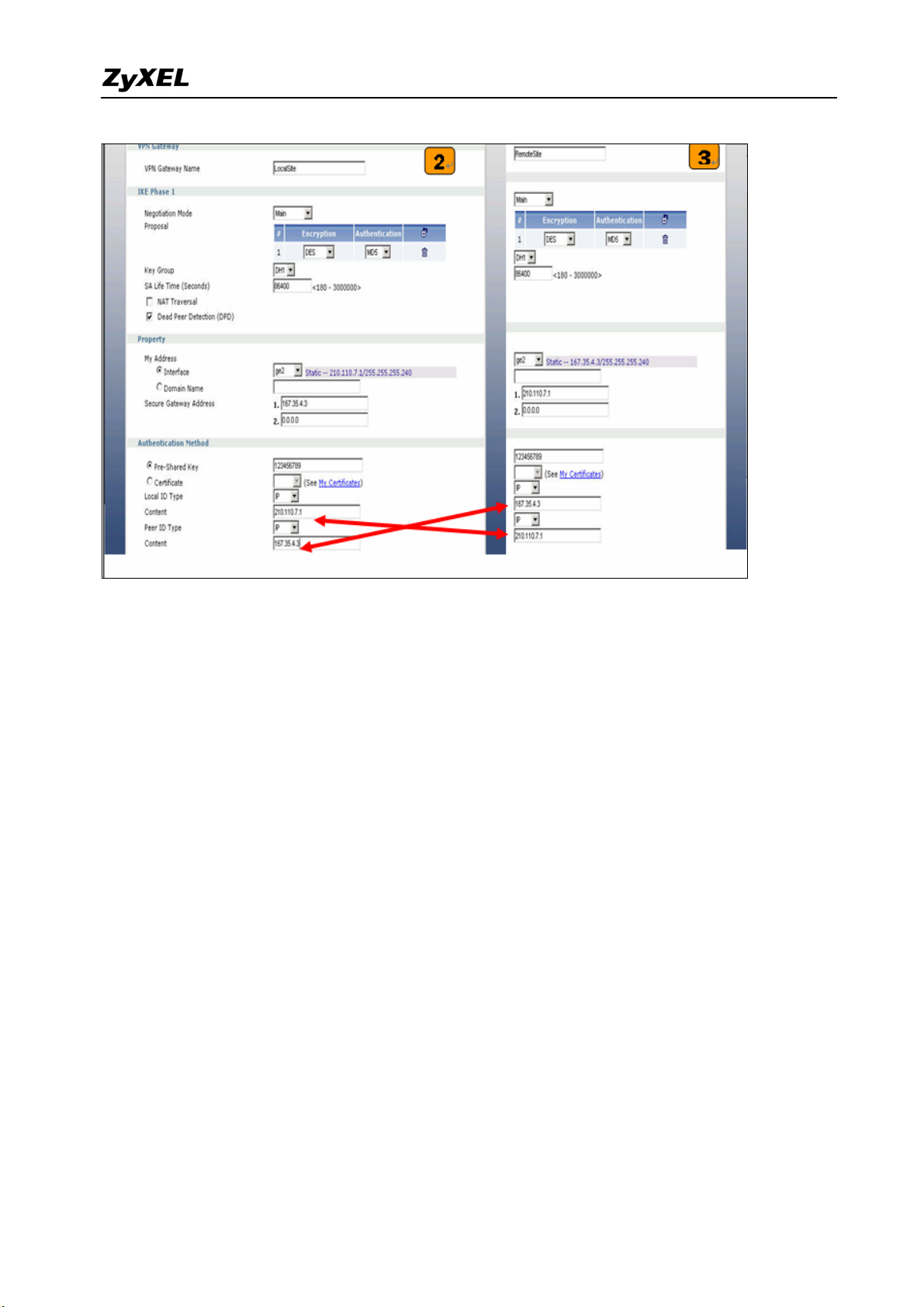
then in Security Gateway Address field set the remote gateway IP to 167.35.4.3. The
Local ID Type and content are IP and 210.110.7.1, Peer ID Type and content are IP and
167.35.4.3.
8) Repeat the step1 & 2 to configure the Remote ZyWALL USG 300. The Local ID Type &
content and Peer ID Type & content are reverse to the Local ZyWALL 1050.
15
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
9) User can refer to the user guide to complete the rest of the settings for VPN tunnel.
10) The ZyWALL1050 and ZyWALL USG 300 VPN are route-based VPN. This means the
VPN tunnel can be an interface to route the VPN traffic. Thus, we need to configure a
policy route for VPN traffic from the local subnet to the remote subnet after configuring
the VPN gateway and connection (phase1 and phase2). The purpose of this policy route is
to tell the ZyWALL1050 to send the traffic to VPN tunnel when the traffic flows from the
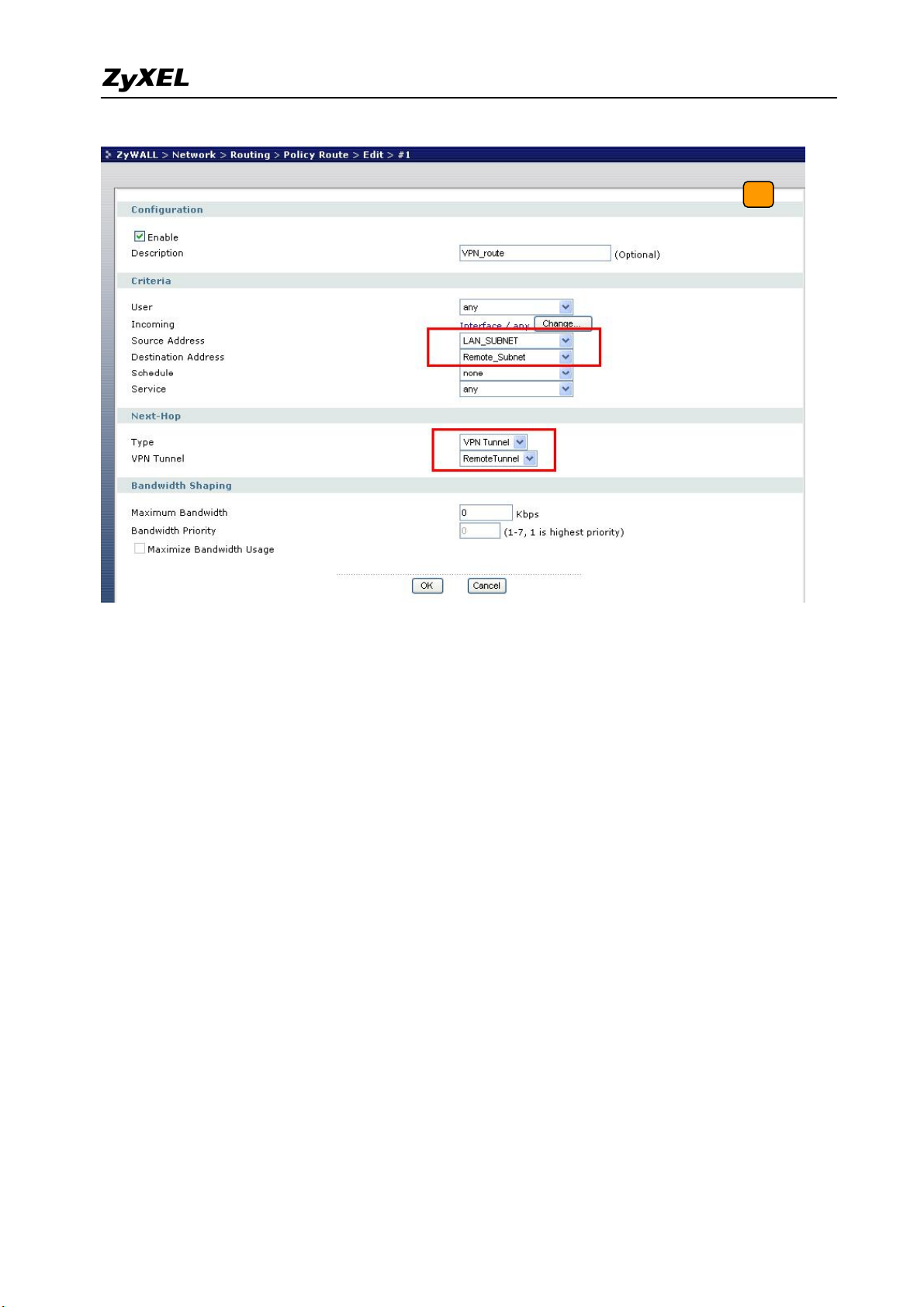
local subnet to a destination that is in the remote subnet. Switch to ZyWALL 1050 >
Network > Routing > Policy Route and add a new policy route. The source and the
destination addresses are the local and remote subnets. The Next-Hop type is VPN tunnel.
Then choose the corresponding VPN connection rule from the VPN tunnel drop down
menu. Now, the VPN tunnel and routing is configured and user can start to test it.
16
All contents copyright (c) 2007 ZyXEL Communications Corporation.

ZyWALL 1050/ZyWALL USG 300 Support Notes
The CLI commands for application:
Local Gateway:
[0] isakmp policy rename RemoteSite LocalSite
[1] isakmp policy LocalSite
[2] mode main
[3] transform-set des-md5
[4] lifetime 86400
[5] no natt
[6] dpd
[7] local-ip interface ge2
[8] peer-ip 167.35.4.3 0.0.0.0
[9] authentication pre-share
[10] keystring 123456789
[11] local-id type ip 210.110.7.1
[12] peer-id type ip 167.35.4.3
[13] peer-id type ip 167.35.4.3
[14] xauth type server default deactivate
[15] group1
[16] exit
Remote Gateway:
[0] isakmp policy RemoteSite
[1] mode main
[2] transform-set des-md5
[3] lifetime 86400
All contents copyright (c) 2007 ZyXEL Communications Corporation.
17

ZyWALL 1050/ZyWALL USG 300 Support Notes
[4] no natt
[5] dpd
[6] local-ip interface ge2
[7] peer-ip 210.110.7.1 0.0.0.0
[8] authentication pre-share
[9] keystring 123456789
[10] local-id type ip 167.35.4.3
[11] peer-id type ip 210.110.7.1
[12] peer-id type ip 210.110.7.1
[13] xauth type server default deactivate
[14] group1
[15] exit
Policy Route for VPN traffic:
[0] policy 1
[1] no deactivate
[2] no description
[3] no user
[4] interface ge1
[5] source LAN_SUBNET
[6] destination Remote_Subnet
[7] no schedule
[8] service any
[9] no snat
[10] next-hop tunnel RemoteTunnel
[11] no bandwidth
[12] exit
Tips for application:
6. Make sure the presharekey is the same in both local and remote gateways.
7. Make sure the IKE & IPSec proposal is the same in both local and remote gateways.
8. Select the correct interface for VPN connection.
9. The Local and Peer ID type and content must the opposite and contain the same.
Make sure the VPN policy route has been configured in ZyWALL1050.
All contents copyright (c) 2007 ZyXEL Communications Corporation.
18
ZyWALL 1050/ZyWALL USG 300 Support Notes
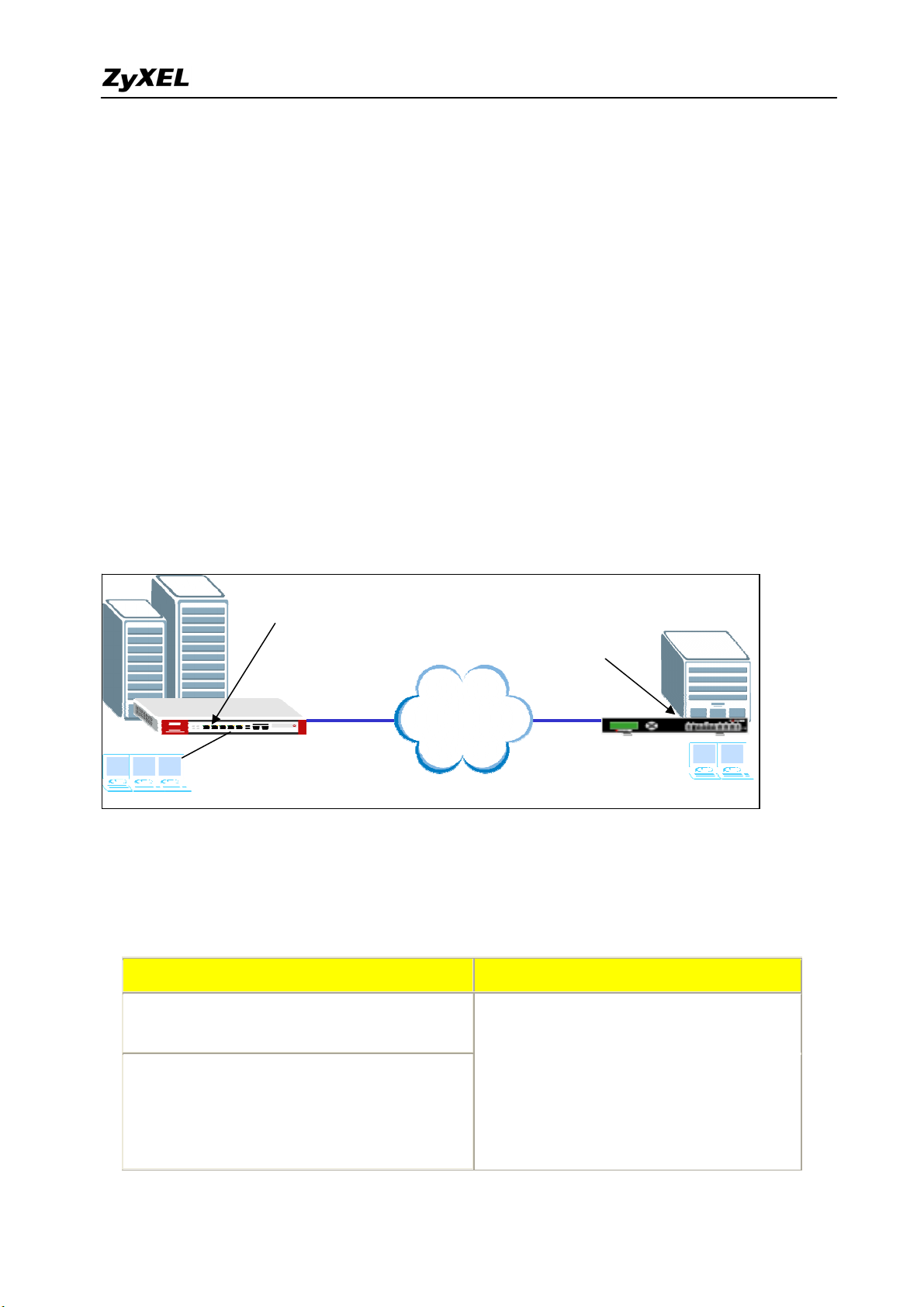
1.2 Extranet Deployment
The VPN provides the access to extranets which can provide the security path over internet
to improve the client service, vendor support and company communication. Different flexible
business models have been developed based on the global VPN extranet architecture. For
example, customers can order equipment over the VPN and also suppliers can check the orders
electronically. Another result of its application is that the employees across different branches
can collaborate on project documents and share the different site’s internal resource to
complete the project.
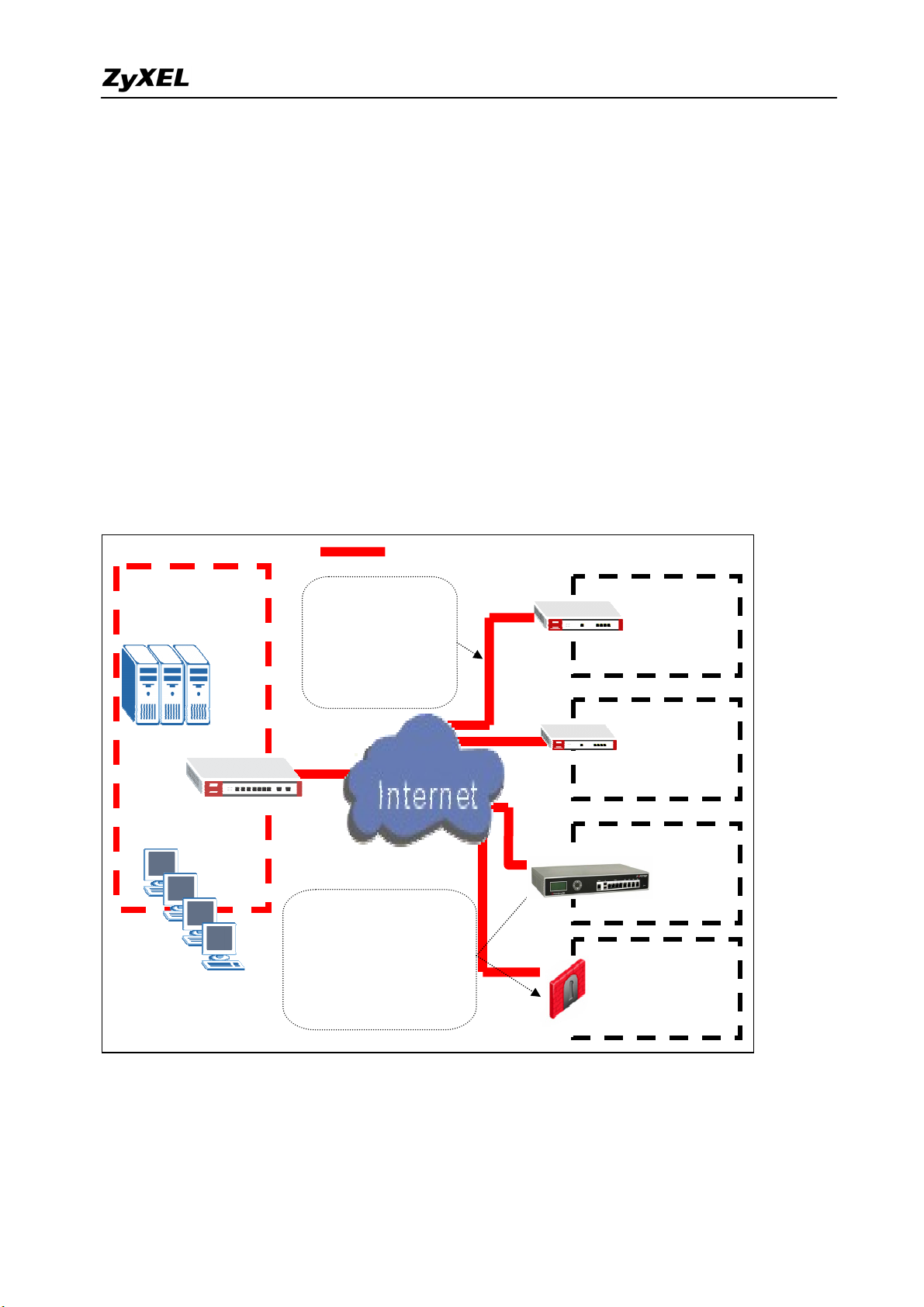
Main Office
Servers
Desktop users
ZyWALL 1050
IPSec VPN Tunnel
The VPN provides
access to both
extranets and
wide-area intranets in
It’s easy to establish VPN
connectivity with your
partner’s/customer’s site
regardless of what their VPN
Branch Office
ZyWALL 70
Remote Office
ZyWALL 35
Customer Site
Partner Site
FortiGate
Check Point VPN-1
The ZyWALL 1050 can be placed as a VPN gateway in the central site. It can communicate
with other ZyXEL’s VPN-capable products as well as VPN products from other major vendors
in the network device industry, e.g. Cisco PIX/IOS VPN products, Check Point VPN Pro,
19
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
Juniper NetScreen series and others…
1.2.1 Site to site VPN solutions (ZyWALL1050/ZyWALL USG 300 to ZyWALL70)
The exciting ZyWALL35 or 70 in central office gateway can be replaced by ZyWALL 1050,
and the ZyWALL35 or 70 moved to a remote office. The ZyWALL 1050 can provide higher
VPN throughput and deal with multiple VPN tunnels at the same time. To show how to build
tunnel between ZyWALL5/35/70 and ZyWALL 1050 we used ZyWALL 70 as an example.
Static IP address
210.110.7.1
Static IP address
167.35.4.3
Internet
CenterOffice Gateway Branch Gateway
LAN: 192.168.1.X
1) Login ZyWALL 1050 GUI and setup the ge2 interface for the internet connection and
manually assign a static IP. The configuration path is ZyWALL 1050 > Configuration >
Network > Interface > Edit > ge2
LAN: 192.168.2.X
2) Switch to Configuration > Network > IPSec VPN > VPN Gateway, select My Address
as interface ge2 and then in Security Gateway Address field set the remote gateway IP to
167.35.4.3. The Local ID Type and content are IP and 210.110.7.1, Peer ID Type and
content are IP and 167.35.4.3.
20
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
3) Login to ZyWALL70 and go to Security > VPN > Gateway Policy, add a new gateway
policy to connect with central office’s ZyWALL 1050. My Address and Remote Gateway
Address are ZyWALL70 and ZyWALL 1050 WAN IP addresses. The Pre-Shared Key
configured on both sides must exactly the same Local ID Type & content and Peer ID
Type & content are reverse to the Local ZyWALL 1050.
4) The IKE Proposal is very important setting when configuring the VPN tunnel. The
proposal includes Negotiation Mode, Encryption and Authentication Algorithm and….
Make sure the IKE proposal parameters are must the same on both ends.
5) Switch to Configuration > Network > IPSec VPN > VPN Connection, add a new VPN
connection (IPSec phase2). Setup the Phase2 proposal and local and remote policies. The
chosen phase2 proposal chosen must be the same as on the remote site’s ZyWALL70.
6) In ZyWALL70, VPN is a rule based VPN. This means that whether the traffic is going to
the tunnel or not will depend on the local and remote policies. In this example,
21
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
ZyWALL70 local and remote policies are 192.168.2.0 and 192.168.1.0 and the traffic
from 192.168.2.X subnet to 192.168.1.X subnet will go through the VPN tunnel to the
remote site as predefined. The ZyWALL1050 local and remote policies must be reverse to
the ZyWALL70’s settings, otherwise the tunnel will not be built up.
7) Check whether the IPSec proposal on both sites is the same and the configuration is done
on both sites.
5
7
6
8) The ZyWALL1050 VPN is a route-based VPN, this means the VPN tunnel can be an
interface to route the VPN traffic. Thus, we need to configure a policy route for VPN
traffic from the local subnet to the remote subnet after configuring the VPN gateway and
the connection (phase1 and phase2). The purpose for this policy route is to tell the
ZyWALL1050 to send the traffic to the VPN tunnel when the traffic goes from the local
subnet to the destination that is in a remote subnet. Switch to Configuration > Policy >
Route > Policy Route and add a new policy route, the source and destination address are
the local and remote subnet and the Next-Hop type is a VPN tunnel. Then choose the
corresponding VPN connection rule from the VPN tunnel drop down menu. Now, the VPN
All contents copyright (c) 2007 ZyXEL Communications Corporation.
22
ZyWALL 1050/ZyWALL USG 300 Support Notes
tunnel and routing is built and user can start to test it.
8
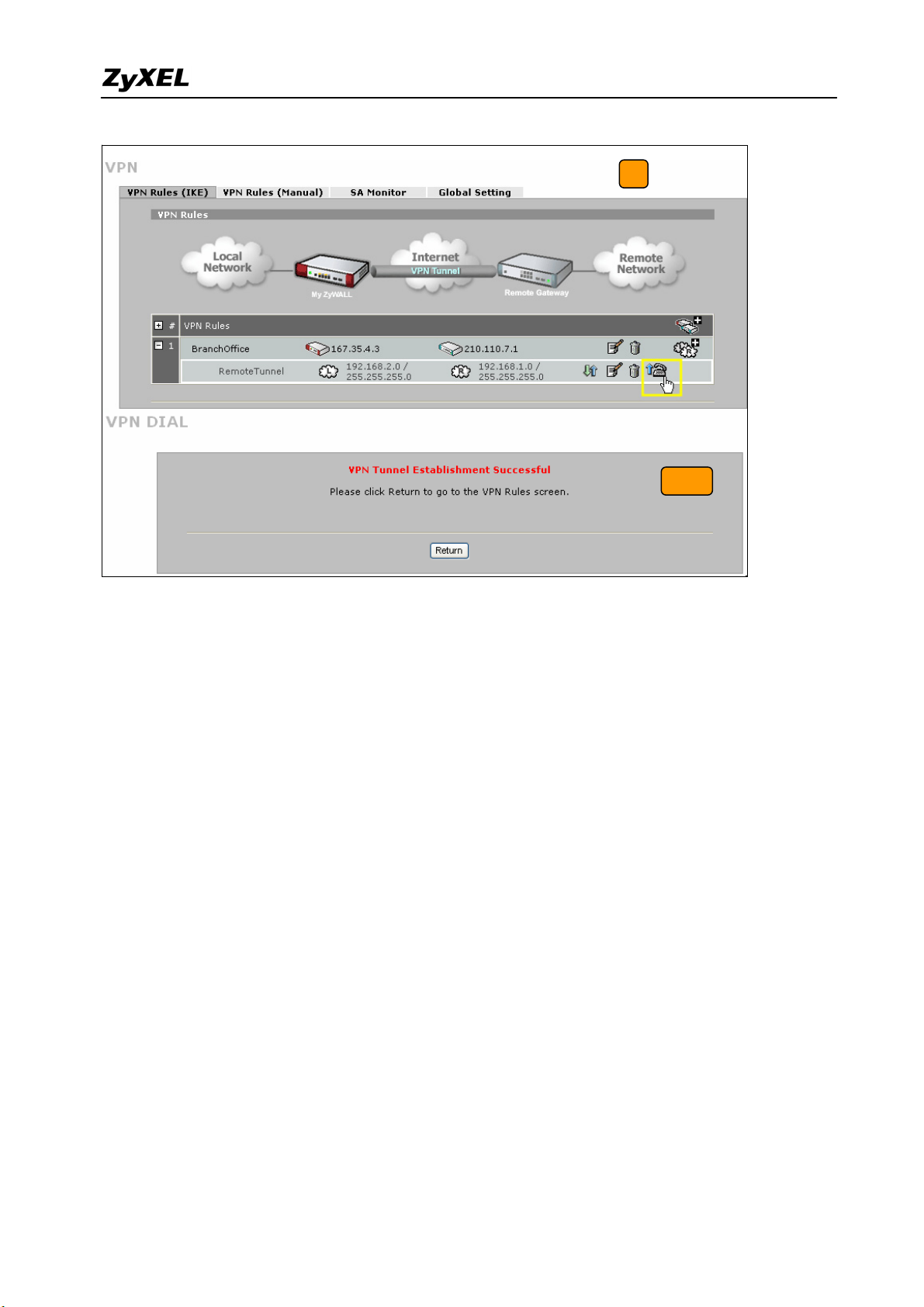
9) After configuring both sides of the VPN, click the Dial up VPN tunnel icon to test the
VPN connectivity.
10) “VPN tunnel establishment successful,” message appears.
23
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
9
10
The CLI command for application:
ZyWALL 1050 VPN Gateway:
[0] isakmp policy LocalSite
[1] mode main
[2] transform-set des-md5
[3] lifetime 86400
[4] no natt
[5] dpd
[6] local-ip interface ge2
[7] peer-ip 167.35.4.3 0.0.0.0
[8] authentication pre-share
[9] keystring 123456789
[10] local-id type ip 210.110.7.1
[11] peer-id type ip 167.35.4.3
[12] peer-id type ip 167.35.4.3
[13] xauth type server default deactivate
[14] group1
[15] exit
ZyWALL 1050 VPN Connection:
[0] crypto map RemoteTunnel
[1] ipsec-isakmp LocalSite
[2] encapsulation tunnel
[3] transform-set esp-des-sha
[4] set security-association lifetime seconds 86400
All contents copyright (c) 2007 ZyXEL Communications Corporation.
24

ZyWALL 1050/ZyWALL USG 300 Support Notes
[5] set pfs none
[6] policy-enforcement
[7] local-policy LAN_SUBNET
[8] remote-policy Remote_Subnet
[9] no nail-up
[10] no replay-detection
[11] no netbios-broadcast
[12] no out-snat activate
[13] no in-snat activate
[14] no in-dnat activate
[15] exit
Policy Route for VPN traffic:
[0] policy 1
[1] no deactivate
[2] no description
[3] no user
[4] interface ge1
[5] source LAN_SUBNET
[6] destination Remote_Subnet
[7] no schedule
[8] service any
[9] no snat
[10] next-hop tunnel RemoteTunnel
[11] no bandwidth
[12] exit
Tips for application:
1. Make sure the presharekey is the same in both the local and the remote gateways.
2. Make sure the IKE & IPSec proposal is the same in both the local and the remote
gateways.
3. Select the correct interface for the VPN connection.
4. The Local and Peer ID type and content must be the opposite and not of the same content.
5. Make sure the VPN policy route had been setup in ZyWALL 1050.
25
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
1.2.2 Interoperability – VPN with other vendors
1.2.2.1 ZyWALL with FortiGate VPN Tunneling
This page guides how to setup a VPN connection between the ZyWALL 1050/ZyWALL
USG 300 and FortiGate 200A.
As on the figure shown below, the tunnel between Central and Remote offices ensures the
packet flow between them are secure, because the packets go through the IPSec tunnel are
encrypted. To setup this VPN tunnel, the required settings for ZyWALL and FortiGate are
explained in the following sections.
Static IP address
210.110.7.1
Static IP address
167.35.4.3
Internet
Central Office Gateway
ZyWALL
LAN: 192.168.1.X
The central office gateway ZyWALL 1050’s interface and VPN setting retain the same setting
as in the previous example. If you jumped this section first, please refer to ‘ZyWALL 1050 to
ZYWALL70 VPN tunnel setting’ on page 8.
This list below is to briefly show the VPN phase1 and phase2 configuration parameters:
ZyWALL FortiGate
Branch Gateway
FortiGate 200A
LAN: 192.168.2.X
WAN: 210.110.7.1
LAN: 192.168.1.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
All contents copyright (c) 2007 ZyXEL Communications Corporation.
WAN: 167.35.4.3
LAN: 192.168.2.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
26
ZyWALL 1050/ZyWALL USG 300 Support Notes
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Perfect Forward Secrecy (PFS): None
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
1) Configure the ZyWALL1050 ‘s VPN gateway and VPN connection as on the list. Also,
remember to configure the policy route for the VPN traffic routing. Refer to the previous
scenario or user guide to find help on setting the ZyWALL1050 VPN.
2) Login to the FortiGate GUI and switch to System > Network > Interface and set the wan1
interface to 167.35.4.3 and internal interface to 192.168.2.1/255.255.255.0.
2
Note: About the detail interface settings, refer to FortiGate user guide.
3) Switch to System > VPN > IPSEC and select the Auto Key (IKE) tab and click the Create
Phase 1 button. This will open a new page for VPN phase1 setup.
3
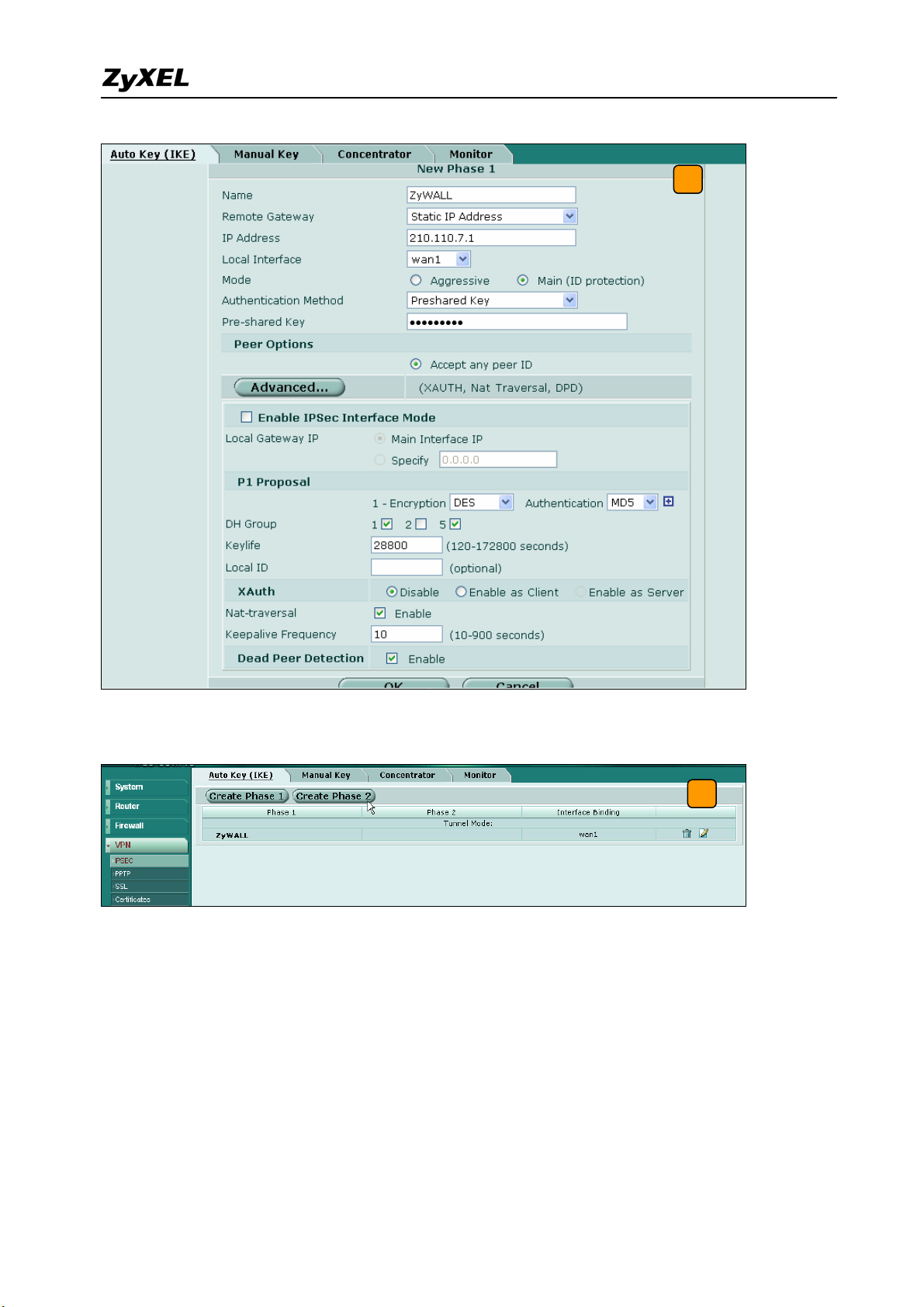
4) Fill-in the VPN phase1 setting according to the table listed. We don’t have to setup the ID
type and content because the FortiGate accepts any peer ID. Make sure both the pre-shares
key and proposal are the same as in the ZyWALL1050.
27
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
4
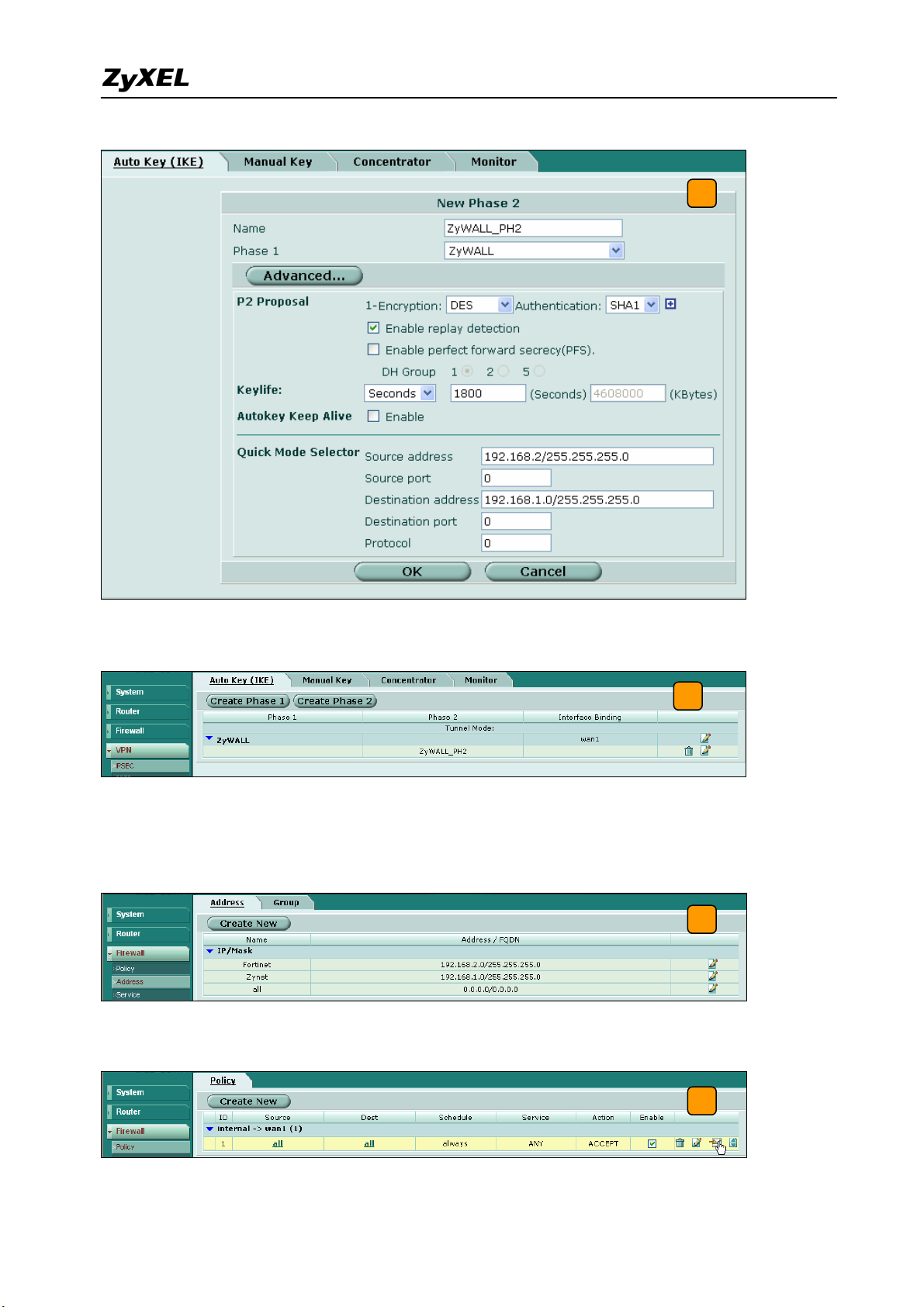
5) Get back to the VPN configuration page again and click the Create Phase 2 button to add
a new Phase2 policy.
5
6) Select the “ZyWALL”(configured in the step 4) policy from the Phase 1 drop down menu
and click the Advanced… button to edit the phase 2 proposal and source and destination
address. Please make sure the phase 2 proposal is the same as in ZyWALL 1050 phase 2.
28
All contents copyright (c) 2007 ZyXEL Communications Corporation.
ZyWALL 1050/ZyWALL USG 300 Support Notes
6
7) The VPN tunnel configuration is finished and the VPN IPSec page will show the VPN
phase 1 and phase 2 rules in the Auto Key (IKE) tab.
7
8) We need to setup the firewall rules for IPSec VPN traffic transmitting from ZyWALL to
FortiGate and from FortiGate to ZyWALL. Switch to Firewall > VPN >Address menu and
add two new address objects which stand for ZyWALL LAN subnet and FortiGate LAN
subnet. Using the “Create New” button to create a new address object.
8
9) Switch to Firewall > Policy and click “Insert Policy Before” icon to add new policy for the
VPN traffic from FortiGate to ZyWALL.
All contents copyright (c) 2007 ZyXEL Communications Corporation.
9
29
ZyWALL 1050/ZyWALL USG 300 Support Notes
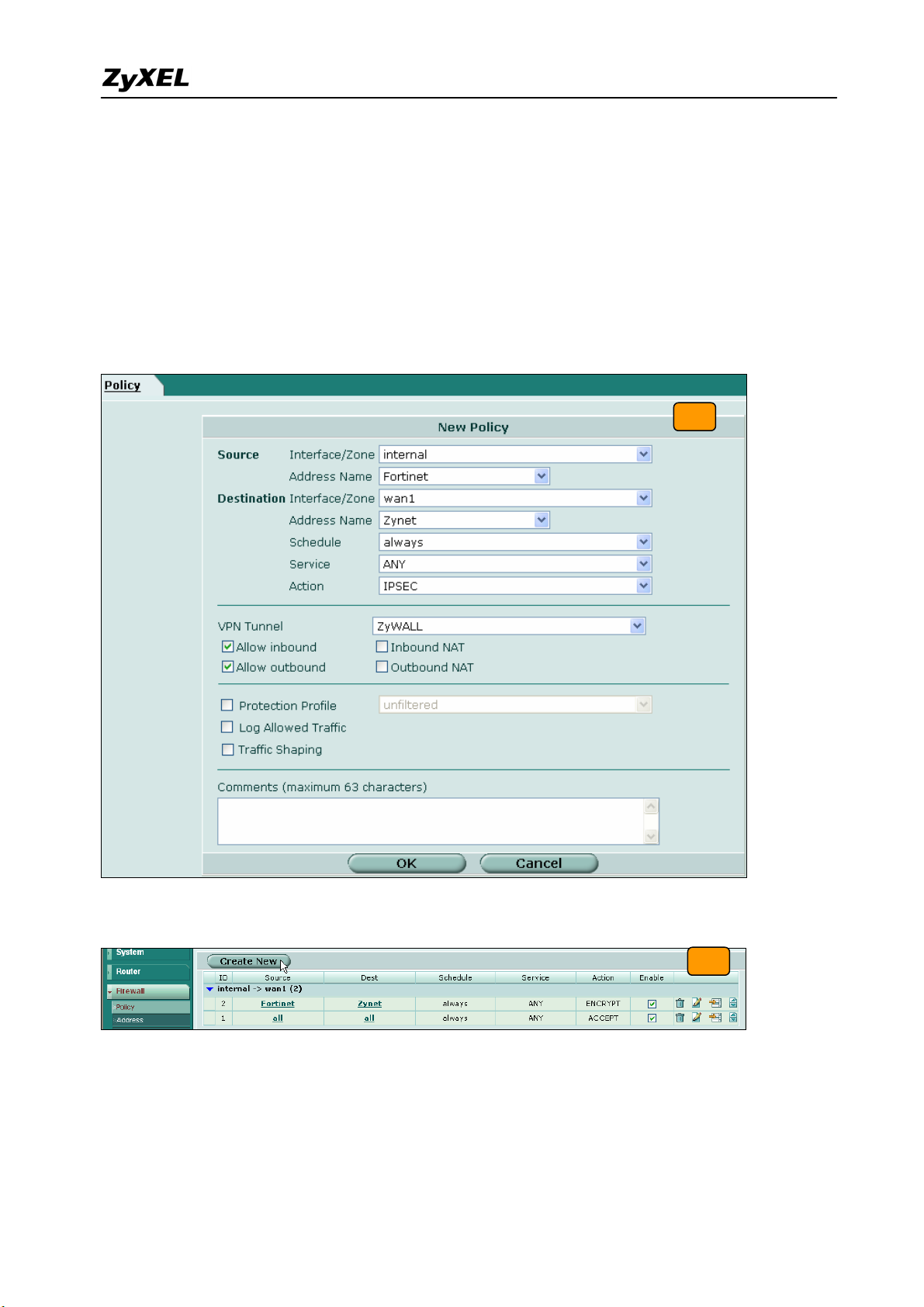
10) We will setup the FortiGate to ZyWALL policy in the new page. The source interface is
internal and Address name is Fortinet (192.168.2.0/255.255.255.0 address object). The
destination interface is wan1 and Address name is Zynet (192.168.1.0/255.255.255.0
address object). Schedule and service type are “always” and “ANY” to ensure that all
kinds of traffic can pass through the VPN tunnel at any time. There are three kinds of
“Action” available for user to configure, because the traffic is send from “internal” to
WAN and will be encrypted by IPSec VPN tunnel. Thus, we select “IPSEC” as action and
chose allow inbound and outbound traffic in the ZyWALL tunnel.
10
11) Switch to Firewall > Policy and click “Create New” button to add new policy for the VPN
traffic from ZyWALL to FortiGate.
11
12) We setup the ZyWALL to FortiGate policy in the new page. The source interface is wan1
and Address name is Zynet (192.168.1.0/255.255.255.0 address object). The destination
interface is internal and the Address name is Fortinet (192.168.2.0/255.255.255.0 address
object). Schedule and service type are always and ANY to ensure that all kinds of traffic
can pass through the VPN tunnel at any time. Select “ACCEPT” as an action this time
30
All contents copyright (c) 2007 ZyXEL Communications Corporation.
 Loading...
Loading...