Page 1

ZyWALL USG 2000 Support Notes
ZyWALL USG 2000
Unified Security Gateway
Support Notes
Revision 2.10
Dec, 2008
1
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 2

ZyWALL USG 2000 Support Notes
INDEX
The comparison of ZyNOS and ZLD ............................................................................................. 8
1. Deploying VPN .......................................................................................................................... 9
1.1 Extended Intranets .......................................................................................................... 11
1.1.2 Site to Site VPN solutions (ZyWALL 1050 Ù ZyWALL USG 2000): .............. 11
1.2 Extranet Deployment ..................................................................................................... 18
1.2.1 Site to site VPN solutions (ZyWALL USG 2000 to ZyWALL70) ...................... 19
1.2.2 Interoperability – VPN with other vendors ......................................................... 23
1.2.2.1 ZyWALL with FortiGate VPN Tunneling ................................................ 23
1.2.2.2 ZyWALL with NetScreen VPN Tunneling .............................................. 30
1.2.2.3 ZyWALL with SonicWall VPN Tunneling ............................................... 38
1.3 Remote Access VPN ...................................................................................................... 45
1.3.1 IPSec VPN for Remote Access ........................................................................... 45
1.3.1.1 Steps to configure ..................................................................................... 47
1.3.2 SSL VPN Application - Reverse Proxy ............................................................... 52
1.3.2.1 Scenario topology ..................................................................................... 52
1.3.2.2 Configuration flow ................................................................................... 52
1.3.2.3 Configuration procedure .......................................................................... 52
1.3.3 SSL VPN Application – Network Extension ...................................................... 55
1.3.3.1 Scenario topology ..................................................................................... 55
1.3.3.2 Configuration flow ................................................................................... 55
1.3.3.3 Configuration procedure .......................................................................... 56
1.3.4 L2TP over IPSec Application .............................................................................. 62
1.3.4.1 Scenario topology ..................................................................................... 62
1.3.4.2 Configuration flow ................................................................................... 62
1.3.4.3 Configuration Procedure .......................................................................... 62
1.4 Large-scale VPN Deployment ....................................................................................... 73
1.4.1 Fully Meshed Topology ................................................................................... 73
1.4.2 Star Topology ................................................................................................... 74
1.4.3 Star-Mesh Mixed Topology .............................................................................. 83
1.5 Device HA ...................................................................................................................... 99
1.5.1 Device HA ......................................................................................................... 101
1.5.1.1 Configuration procedure ........................................................................ 101
1.5.2 Device High Availability (HA) Active-Passive mode ....................................... 113
1.5.2.1 Scenario Topology ................................................................................. 113
All contents copyright (c) 2008 ZyXEL Communications Corporation.
2
Page 3

ZyWALL USG 2000 Support Notes
1.5.2.2 Configuration Flow ................................................................................ 113
1.5.2.3 Configuration procedure ........................................................................ 114
1.5.2.4 Steps to configure ................................................................................... 115
2. Security Policy Enforcement .................................................................................................. 125
2.1 Managing IM/P2P Applications ................................................................................... 125
2.1.1 Why bother with managing IM/P2P applications? ............................................ 125
2.1.2 What does ZyWALL USG 2000 provide for managing IM/P2P applications? 126
2.1.3 Configuration Example ..................................................................................... 126
2.2 Zone-based Anti-Virus Protection ................................................................................ 134
2.2.1 Applying Zone-Based Anti-Virus to ZyWALL USG 2000 ............................... 134
2.2.2 Enabling Black and White List ......................................................................... 141
2.2.3 Enabling Anti-Virus Statistics Report ............................................................... 142
2.2.4 Dual AV ............................................................................................................. 143
2.3 Configuring ZyWALL USG 2000 as a Wireless Router .............................................. 143
2.3.1 Configuration procedure ................................................................................... 143
2.3.2 MAC filter in WLAN ........................................................................................ 145
2.4 Mobility Internet Access .............................................................................................. 147
2.4.1 Utilize 3G Wireless for Accessing the Internet ................................................. 148
2.4.1.1 Configuration procedure ........................................................................ 149
3. Seamless Incorporation .......................................................................................................... 156
3.1 Transparent Firewall ..................................................................................................... 156
3.1.1 Bridge mode & Router (NAT) mode co-exist ................................................... 156
3.1.2 NAT & Virtual Server........................................................................................ 159
3.2 Zone-based IDP Protection .......................................................................................... 162
3.2.1 Applying Zone-Based IDP to ZyWALL USG 2000 .......................................... 163
3.3 Anti-spam on the ZyWALL USG 2000 ........................................................................ 169
3.3.1 How Anti-Spam works on ZyWALL USG ....................................................... 170
3.3.2 Using DNSBL (DNS-based blacklist) ............................................................... 170
3.3.2.1 Application scenario to apply DNSBL ................................................... 170
3.3.2.1.1 Scenario I: Email server is located in the ISP/ Internet ...................... 170
3.3.2.1.2 Scenario II: Company’s Email server located in the DMZ ................. 173
3.3.3 Using Black/White list (B/W list) ..................................................................... 176
3.3.3.1 Configuration procedure ........................................................................ 176
3.3.3.2 Scenario topology ................................................................................... 177
3.3.3.3 Steps to configure B/W list .................................................................... 177
3.4 Guaranteed Quality of Service ..................................................................................... 180
3.4.1 Priority & Bandwidth management .................................................................. 181
All contents copyright (c) 2008 ZyXEL Communications Corporation.
3
Page 4

ZyWALL USG 2000 Support Notes
F AQ ............................................................................................................................................ 188
A. Device Management FAQ ............................................................................................. 188
A01. How can I connect to ZyWALL USG 2000 to perform administrator’s tasks? 188
A02. Why can’t I login into ZyWALL USG 2000? ................................................... 188
A03. What’s difference between “Admin Service Control” and “User Service
Control” configuration in GUI menu System > WWW? ........................................... 189
A04. Why ZyWALL USG 2000 redirects me to the login page when I am
performing the management tasks in GUI? ............................................................... 190
A05. Why do I lose my configuration setting after ZyWALL USG 2000 restarts? ... 190
A06. How can I do if the system is keeping at booting up stage for a long time? ..... 190
B. Registration FAQ ........................................................................................................... 192
B01. Why do I need to do the Device Registration? .................................................. 192
B02. Why do I need to activate services? .................................................................. 192
B03. Why can’t I active trial service? ........................................................................ 192
B04. Will the UTM service registration information be reset once restore
configuration in ZyWALL USG 2000 back to manufactory default? ........................ 192
C. File Manager FAQ ......................................................................................................... 193
C01. How can ZyWALL USG 2000 manage multiple configuration files? .............. 193
C02. What are the configuration files like startup-config.conf, system-default.conf
and lastgood.conf? ...................................................................................................... 193
C03. Why can’t I update firmware? ........................................................................... 193
C04. What is the Shell Scripts for in GUI menu File manager > Shell Scripts? ........ 194
C05. How to write a shell script? ............................................................................... 194
C06. Why can’t I run shell script successfully? ......................................................... 194
D. Object FAQ.................................................................................................................... 195
D01. Why does ZyWALL USG 2000 use object? ...................................................... 195
D02. What’s the difference between Trunk and the Zone Object? ............................ 196
D03. What is the difference between the default LDAP and the group LDAP? What
is the difference between the default RADIUS and the group RADIUS? ................. 196
E. Interface FAQ ................................................................................................................ 197
E01. How to setup the WAN interface with PPPoE or PPTP? ................................... 197
E02. How to add a virtual interface (IP alias)? .......................................................... 197
E03. Why can’t I get IP address via DHCP relay? ..................................................... 197
E04. Why can’t I get DNS options from ZyWALL’s DHCP server? ......................... 197
E05. Why does the PPP interface dials successfully even its base interface goes
down? ......................................................................................................................... 198
F. Routing and NAT FAQ ................................................................................................... 199
All contents copyright (c) 2008 ZyXEL Communications Corporation.
4
Page 5

ZyWALL USG 2000 Support Notes
F01. How to add a policy route? ................................................................................ 199
F02. How to configure local loopback in ZyWALL USG 2000? ............................... 199
F03. How to configure a NAT? .................................................................................. 203
F04. After I installed a HTTP proxy server and set a http redirect rule, I still can’t
access web. Why? ...................................................................................................... 204
F05. How to limit some application (for example, FTP) bandwidth usage? ............. 204
F06. What’s the routing order of policy route, dynamic route, and static route and
direct connect subnet table? ....................................................................................... 204
F07. Why ZyWALL USG 2000 cannot ping the Internet host, but PC from LAN side
can browse internet WWW? ...................................................................................... 205
F08. Why can’t I ping to the, Internet, after I shutdown the prim ary WAN interface?205
F09. Why the virtual server or port trigger does not work? ....................................... 205
F10. Why port trigger does not work? ....................................................................... 205
F11. How do I use the traffic redirect feature in ZyWALL USG 2000? .................... 206
F12. Why can’t ZyWALL learn the route from RIP and/or OSPF? ........................... 206
G. VPN and Certificate ...................................................................................................... 207
G01. Why can't the VPN connections dial to a remote gateway? .............................. 207
G02. VPN connections are dialed successfully, but the traffic still cannot go through
the IPsec tunnel. ......................................................................................................... 207
G03. Why ZyWALL USG 2000 VPN tunnel had been configured correctly and the
VPN connection status is connected but the traffic still can not reach the remote
VPN subnet? ............................................................................................................... 207
G04. VPN connections are dialed successfully, and the policy route is set. But the
traffic is lost or there is no response from remote site. .............................................. 208
G05. Why don’t the Inbound/Outbound traffic NAT in VPN work? ......................... 208
H. Firewall FAQ ................................................................................................................. 209
H01. Why doesn’t my LAN to WAN or WAN to LAN rule work? ........................... 209
H02. Why does the intra-zone blocking malfunction after I disable the firewall? .... 209
H03. Can I have access control rules to the device in firewall? ................................ 209
I. Application Patrol FAQ................................................................................................... 210
I01. What is Application Patrol? ................................................................................ 210
I02. What applications can the Application Patrol function inspect? ........................ 210
I03. Why does the application patrol fail to drop/reject invalid access for some
applications? ............................................................................................................... 211
I04. What is the difference between “Auto” and “Service Ports” settings in the
Application Patrol configuration page? ..................................................................... 212
I05. What is the difference between BWM (bandwidth management) in Policy Route
5
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 6

ZyWALL USG 2000 Support Notes
and App. Patrol ? ........................................................................................................ 213
I06. Do I have to purchase iCards specifically for using AppPatrol feature? ............ 214
I07. Can I configure different access level based on application for different users? 214
I08. Can I migrate AppPatrol policy and bandwidth management control from
ZLD1.0x to ZLD2.0x? ............................................................................................... 214
J. lDP FAQ ......................................................................................................................... 215
J01. Why doesn’t the IDP work? Why has the signature updating failed? ................ 215
J02. When I use a web browser to configure the IDP, sometimes it will popup
"wait data timeout". .................................................................................................... 215
J03. When I want to configure the packet inspection (signatures), the GUI becomes
very slow. ................................................................................................................... 215
J04. After I select "Auto Update" for IDP, when will it update the signatures? ........ 215
J05. If I want to use IDP service, will it is enough if I just complete the registration
and turn on IDP? ........................................................................................................ 215
J06. What are the major design differences in IDP in ZLD1.0x and latest IDP/ADP
in ZLD2.0x? ............................................................................................................... 215
J07. Does IDP subscription have anything to do with AppPatrol? ............................ 216
J08. How to get a detailed description of an IDP signature? ..................................... 217
J09. After an IDP signature updated, does it require ZyWALL to reboot to make new
signatures take effect? ................................................................................................ 217
K. Content Filtering FAQ ................................................................................................... 218
K01. Why can’t I enable external web filtering service? Why does the external web
filtering service seem not to be working? .................................................................. 218
K02. Why can’t I use MSN after I enabled content filter and allowed trusted
websites only? ............................................................................................................ 218
L. Device HA FAQ ............................................................................................................. 219
L01. What does the “Preempt” mean? ....................................................................... 219
L02. What is the password in Synchronization? ........................................................ 219
L03. What is “Link Monitor” and how to enable it? .................................................. 219
L04. Can Link Monitor of Device HA be used in backup VRRP interfaces? ............ 220
L05. Why do both the VRRP interfaces of master ZW USG 2000 and backup ZW
USG 2000 are activated at the same time? ................................................................. 220
M. User Management FAQ ................................................................................................ 221
M01. What is the difference between user and guest account?.................................. 221
M02. What is the “re-authentication time” and “lease time”? ................................... 221
M03. Why can’t I sign in to the device? .................................................................... 221
M04. Why is the TELNET/SSH/FTP session to the device disconnected? Why is the
All contents copyright (c) 2008 ZyXEL Communications Corporation.
6
Page 7

ZyWALL USG 2000 Support Notes
GUI redirected to login page after I click a button/link? ........................................... 221
M05. What is AAA? ................................................................................................... 222
M06. What are ldap-users and radius-users used for? ............................................... 222
M07. What privileges will be given for ldap-users and radius-users? ....................... 222
N. Centralized Log FAQ .................................................................................................... 224
N01. Why can’t I enable e-mail server in system log settings? ................................. 224
N02. After I have the entire required field filled, why can’t I receive the log mail? . 224
O. Traffic Statistics FAQ .................................................................................................... 225
O01. When I use "Flush Data" in Report, not all the statistic data are cleared. ......... 225
O02. Why isn't the statistic data of "Report" exact? .................................................. 225
O03. Does Report collect the traffic from/to ZyWALL itself? .................................. 225
O04. Why cannot I see the connections from/to ZyWALL itself? ............................. 225
P. Anti-Virus F AQ .............................................................................................................. 226
P01. Is there any file size or amount of concurrent files limitation with ZyWALL
USG 2000 Anti-Virus engine? ................................................................................... 226
P02. Does ZyWALL USG 2000 Anti-Virus support compressed file scanning? ....... 226
P03. What is the maximum concurrent session of ZyWALL USG 2000 Anti-Virus
engine? ....................................................................................................................... 226
P04. How many type of viruses can be recognized by the ZyWALL USG 2000? .... 226
P05. How frequent the AV signature will be updated? .............................................. 226
P06. How to retrieve the virus information in detail? ................................................ 226
P07. I cannot download a file from Internet through ZyWALL USG 2000 because
the Anti-Virus engine considers this file has been infected by the virus; however, I
am very sure this file is not infected because the file is nothing but a plain text file.
How do I resolve this problem? ................................................................................. 226
P08. Does ZyWALL USG 2000 Anti-Virus engine support Passive FTP? ................ 227
P09. What kinds of protocol are currently supported on ZyWALL USG 2000
Anti-Virus engine? ..................................................................................................... 227
P10. If the Anti-Virus engine detects a virus, what action it may take? Can it cure the
file? ............................................................................................................................. 227
All contents copyright (c) 2008 ZyXEL Communications Corporation.
7
Page 8
ZyWALL USG 2000 Support Notes
The comparison of ZyNOS and ZLD
Since ZyXEL USG 2000 adopt ZLD 2.10 as their network operating system. Additionally,
ZLD 2.10 provides many new features and new design in GUI. Hence, the layout in ZyNOS
might not be the same as the one in ZLD 2.10. Accordingly, we provide a comparison table for
your reference.
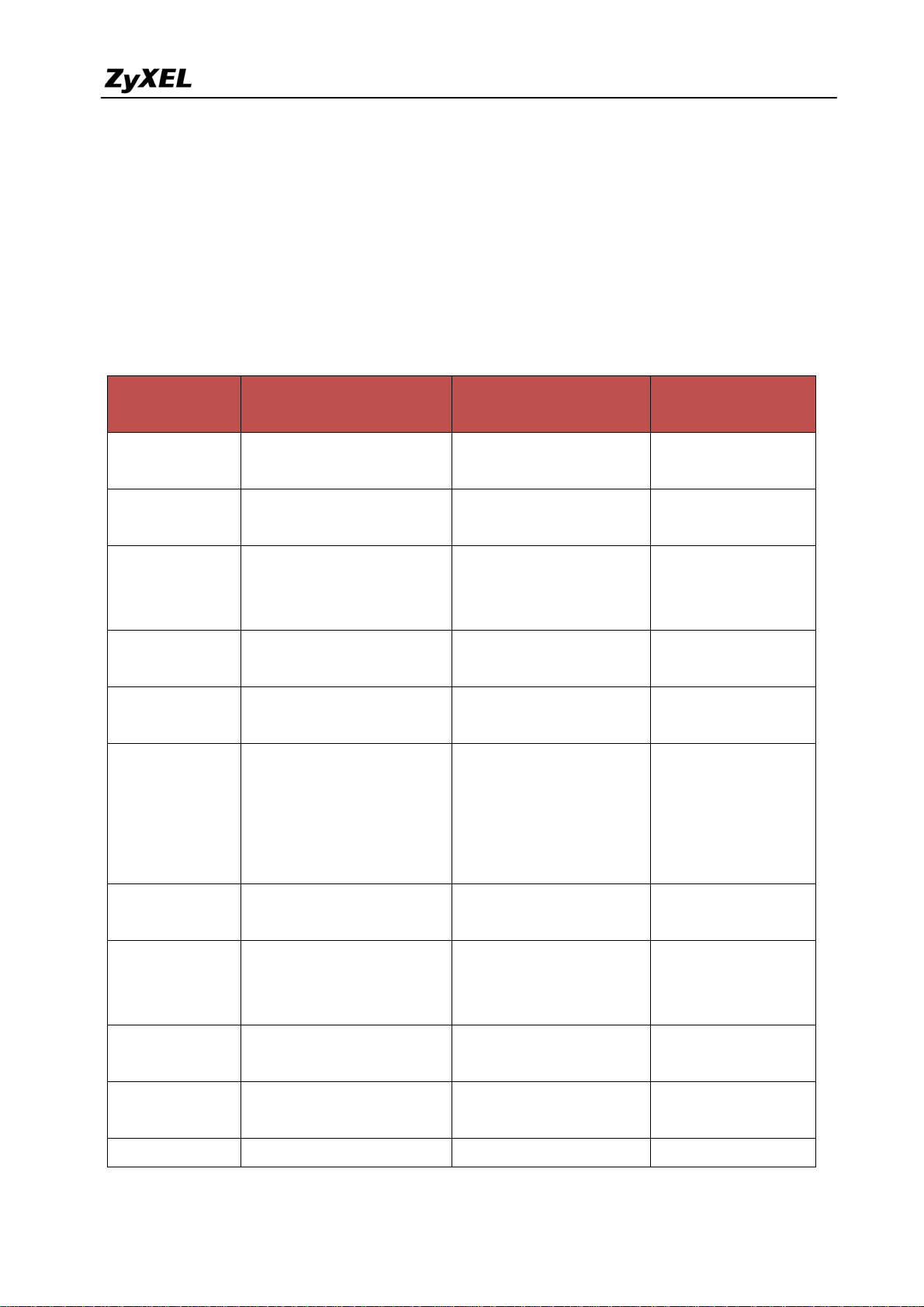
Platform
Feature/Term
NAT
VPN
ZyNOS ZLD Chapter in
Advanced > NAT >
Address Mapping
Advanced > NAT Port
forwarding
Advanced > NAT Port
Trigger
Security> VPN >
Gateway Policy
Security> VPN >
Network Policy
Security> VPN >
Gateway Policy &
Network Policy
Network > Routing >
Policy Route SNAT
Network > Virtual
Server
Network > Routing >
Policy Route Port
Triggering
VPN > IPSec VPN>
VPN Gateway
VPN > IPSec VPN>
VPN Connection
VPN > IPSec VPN>
Concentrator
Support Note
3.1.2 NAT &
Virtual Server
1.1.2 Site to site
VPN solutions
1.1.2 Site to site
VPN solutions
Others
(Hub & Spoke VPN
network)
Advanced > BW MGMT AppPatrol & Network >
Policy Route
Network >
LAN/DMZ/WLAN> IP
alias
Wireless > Wi-Fi Network > Interface >
Wireless > 3G Network > Interface >
Security > Auth Server Object > AAA Server
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Network > Interface >
LAN/DMZ/VLAN/Brid
ge> V irtual Interface
WLAN
Cellular
2.4 Mobility
Internet Access
8
Page 9
ZyWALL USG 2000 Support Notes
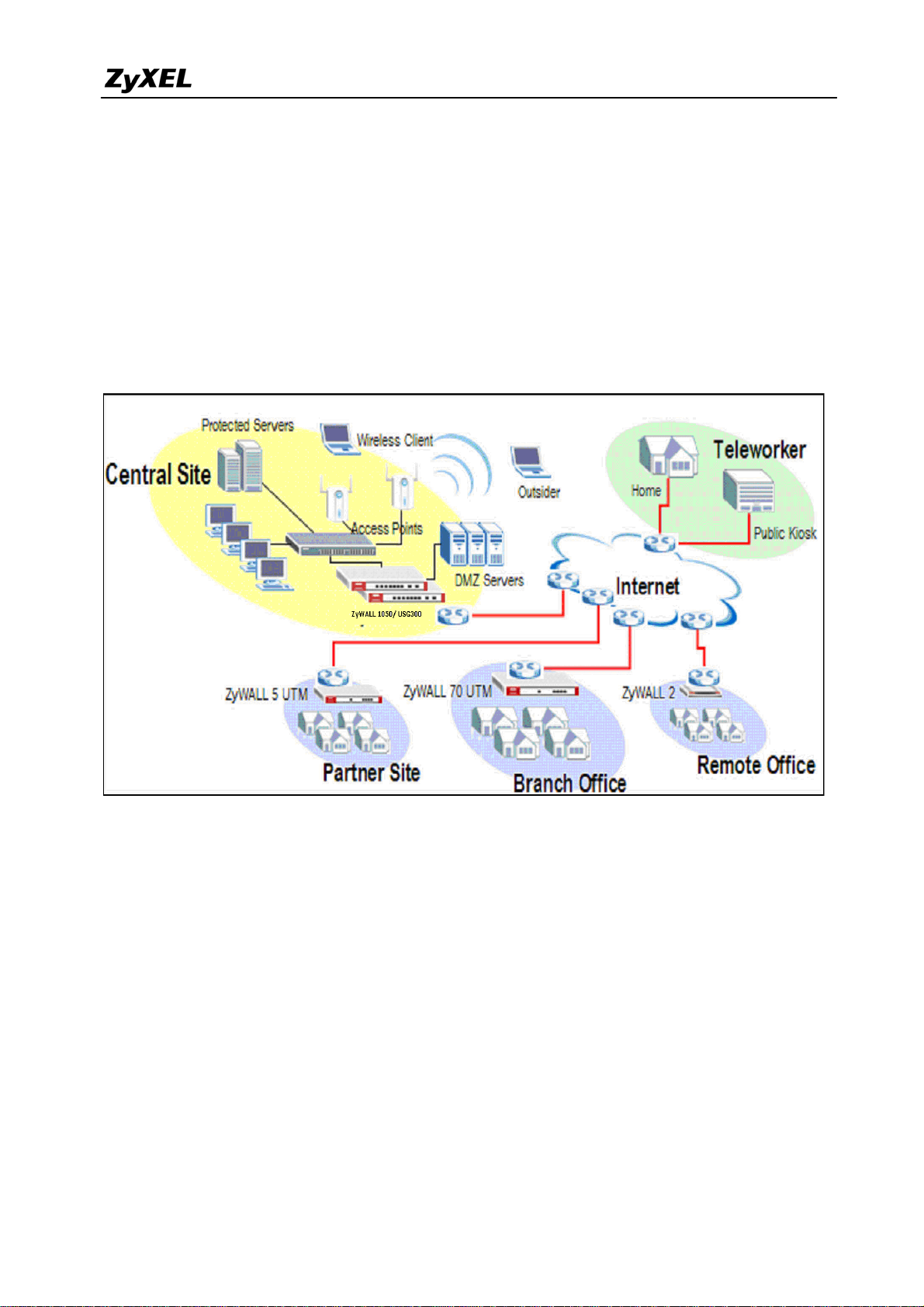
1. Deploying VPN
VPN (Virtual Private Network) allows you to establish a virtual direct connection to remote
locations or for the telecommuters to access the internal network in the office. VPN is a
replacement for the traditional site-to-site lease lines like T1 or ISDN. Through the VPN
applications, it reduces setup cost, works for various types of Internet connection devices
(ISDN modem, ADSL modem and FTTX…) and is easy to troubleshoot.
VPN gives you site-to-site connection flexibility. However, with multiple VPN connections
between sites, it can become more difficult to maintain. Typically, an administrator has to
configure many site-to-site VPN connections to allow a truly global VPN network.
VPN connection management is made easily using the VPN concentrator. The VPN
concentrator routes VPN traffic across multiple remote sites without complex setting, thus
reduces the configuration overhead and the possibility of improper configuration. The VPN
concentrator is also a centralized management tool for administrators because all the traffic
sent between remote sites has to go through the central office first and administrators can set
up different access control rules. These are based on the source address, remote address, user
and schedule to enhance VPN security. To help to reduce network intrusion attacks,
administrators can configure the built-in IDP engine to inspect VPN traffic. For easy
9
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 10
h
N
u
t
B
T
A
u
a
l
r
f
o
g
e
w
o
r
e
y
0
o
N
a
h
y
y
C
o
n
b
u
P
U
o
e
g
a
i
0
o
e
k
y
c
t
t
k
r
a
0
troubles
ooting and
monitorin
, the VPN
concentrat
Z
WALL
r logs and
SG 200
stores syst
Suppor
m informa
Notes
ion and
network
The VP
setting
status for f
concentr
p a globa
rther easy
tor enhanc
VPN net
troublesho
s the VP
ork with
ting and a
routing a
less effort
alysis.
ility and h
but stron
lps networ
er securit
administ
and man
ators in
gement
possibili
For SM
ies.
customer,
ZyXEL pr
vides a tot
l VPN sol
tion from
personal
lient to a 5
0+
people fi
rewall whe
he benefit
e all of th
rom deplo
ll contents c
se devices
ment of Z
pyright (c) 2
ave the V
XEL VPN
08 ZyXEL
N connect
solutions
ommunicati
on ability.
ns Corporati
10
n.
Page 11
ZyWALL USG 2000 Support Notes
‧ Security and Reliability
‧ Improved communications
‧ Increased flexibility
‧ Lower cost
1.1 Extended Intranets
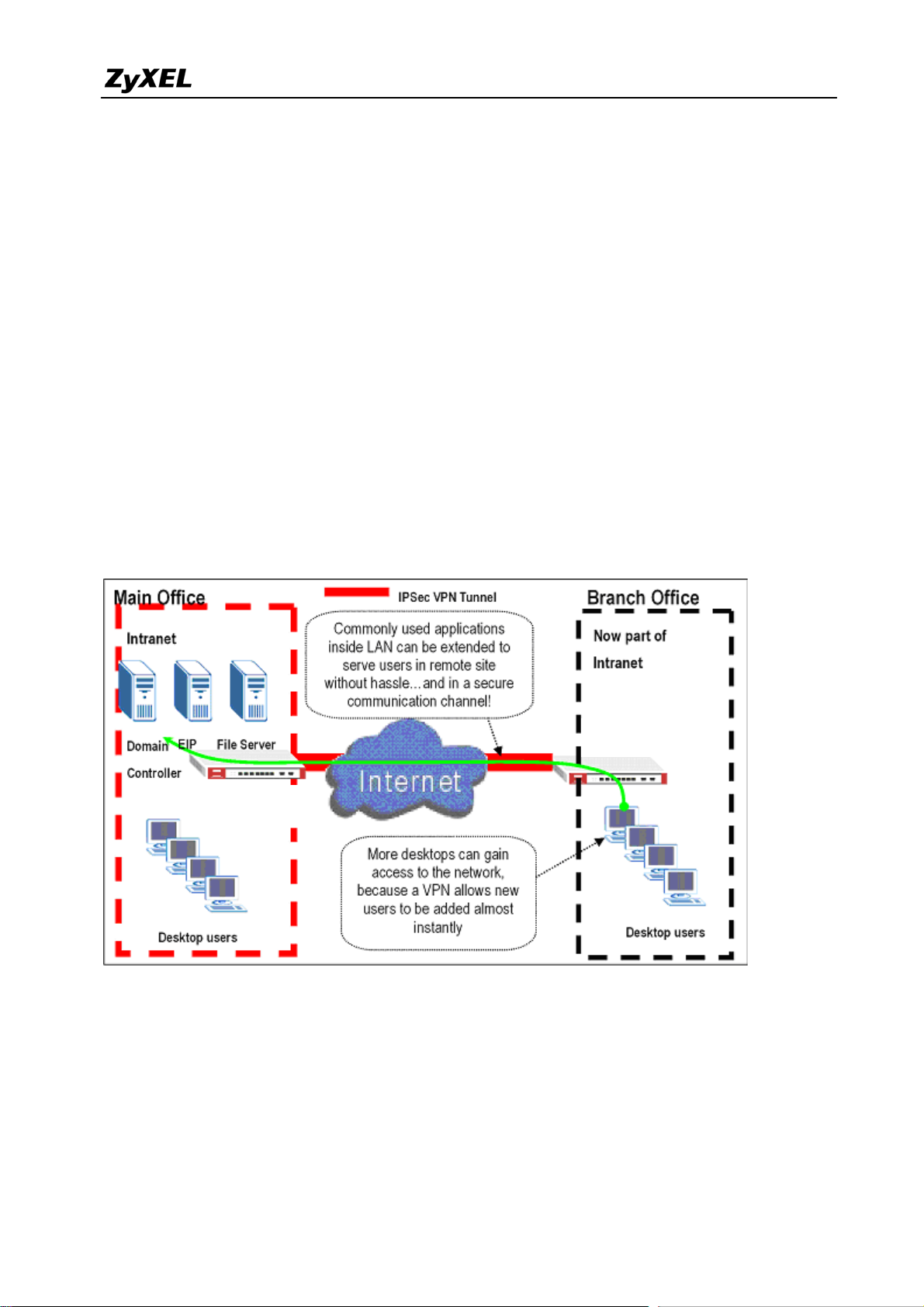
The ZyXEL VPN solutions primarily can be used to extend the intranet and deliver increased
connectivity between operation sites. The branch office subnet will be considered a part of
main office internet. Therefore, user behind branch office also can use the internal network
resources as if he was in the main office. Because of the VPN connection, user will feel like he
is using a local LAN even though he is accessing the network resources via Internet. Use of a
VPN for smaller branch offices, franchise sites and remote workers provides nearly the same
level of connectivity and reliability as a private network. The remote connection cost also can
decrease by leveraging the Internet connections to replace expensive leased lines.
USG 2000
USG2000
1.1.2 Site to Site VPN solutions (ZyWALL 1050 Ù ZyWALL USG 2000):
Site to Site VPN is the basic VPN solution between local and remote gateway. This type of
VPN connection is used to extend and join local networks of both sites into a single intranet.
There are two kinds of connection interface. Static IP and dynamic DNS.
11
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 12
ZyWALL USG 2000 Support Notes
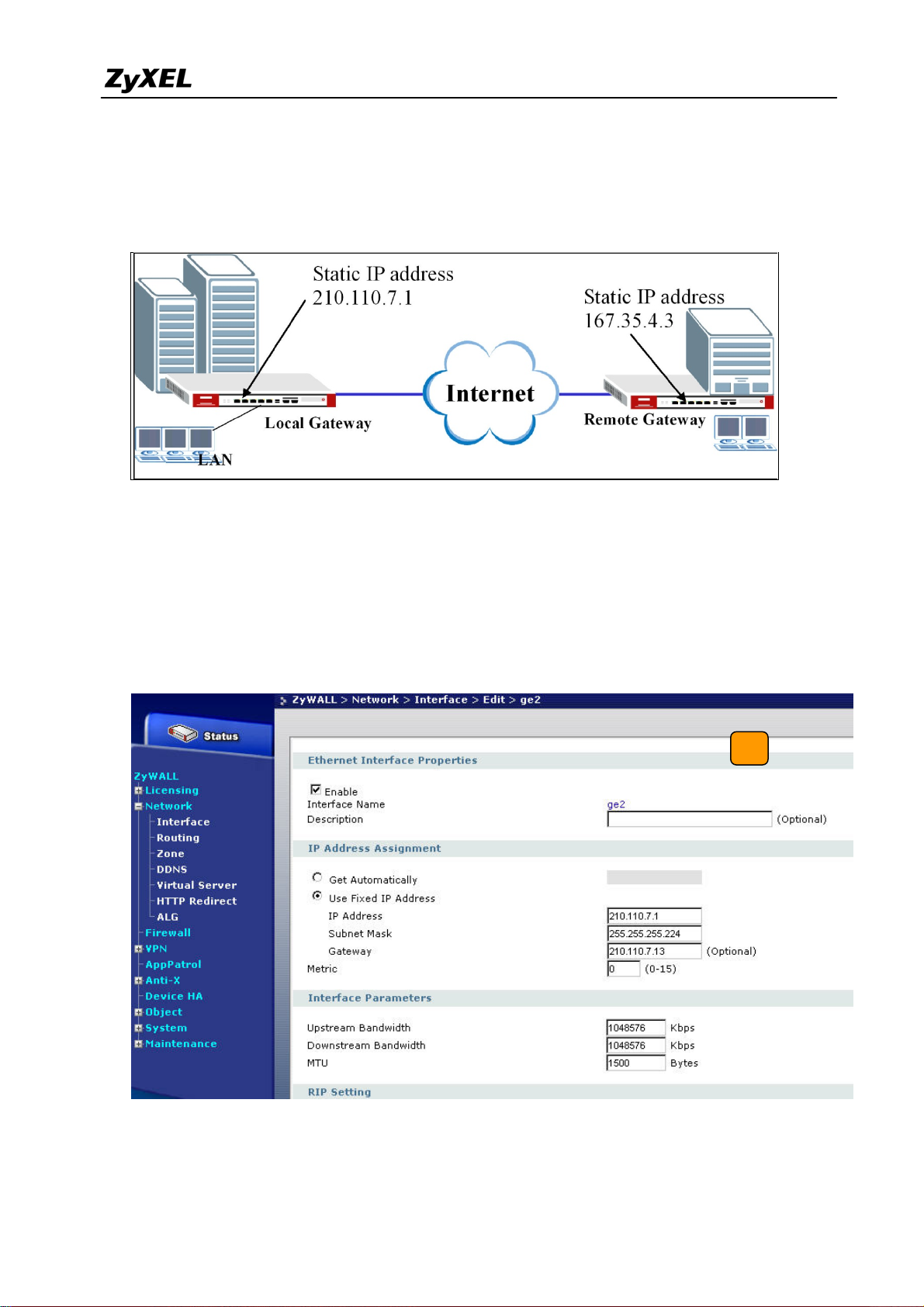
Configure ZyWALL 1050 with Static IP address:
ZyWALL 1050 uses the static IP address for VPN connection. The topology is shown on the
following figure.
User needs to configure the static IP address and then apply to the VPN Gateway
configuration page. The configuration steps are stated below:
1) Login ZyWALL 1050 GUI, setup the ge2 interface for internet connection and manually
assign a static IP. The configuration path in ZyWALL 1050 is Network > Interface >
Ethernet >Edit > ge2
2) Switch to VPN > IPSec VPN > VPN Gateway select interface ge2 as My Address and
12
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 13
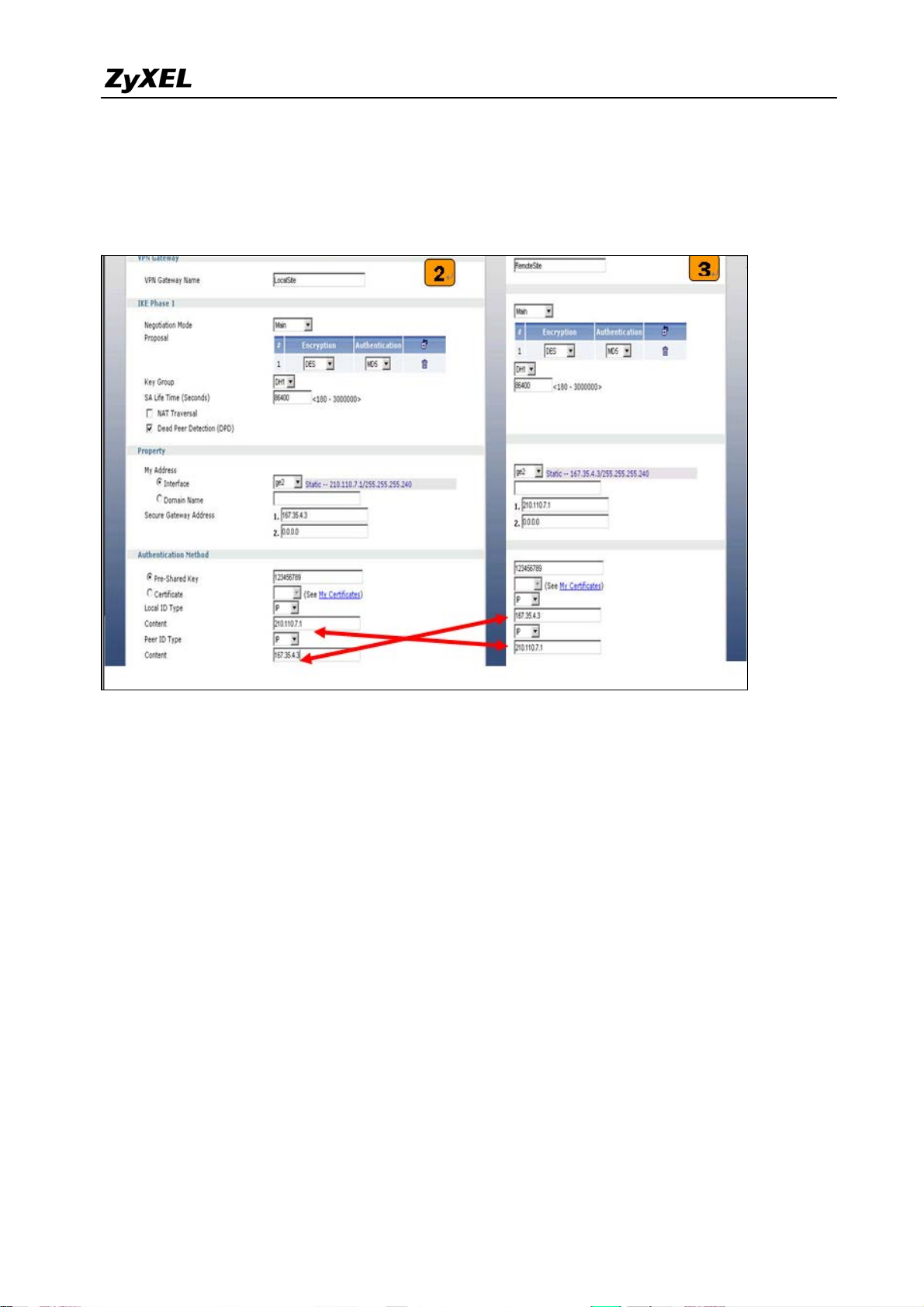
ZyWALL USG 2000 Support Notes
then in Security Gateway Address field set the remote gateway IP to 167.35.4.3. The
Local ID Type and content are IP and 210.110.7.1, Peer ID Type and content are IP and
167.35.4.3.
3) User can refer to the user guide to complete the rest of the settings for VPN tunnel.
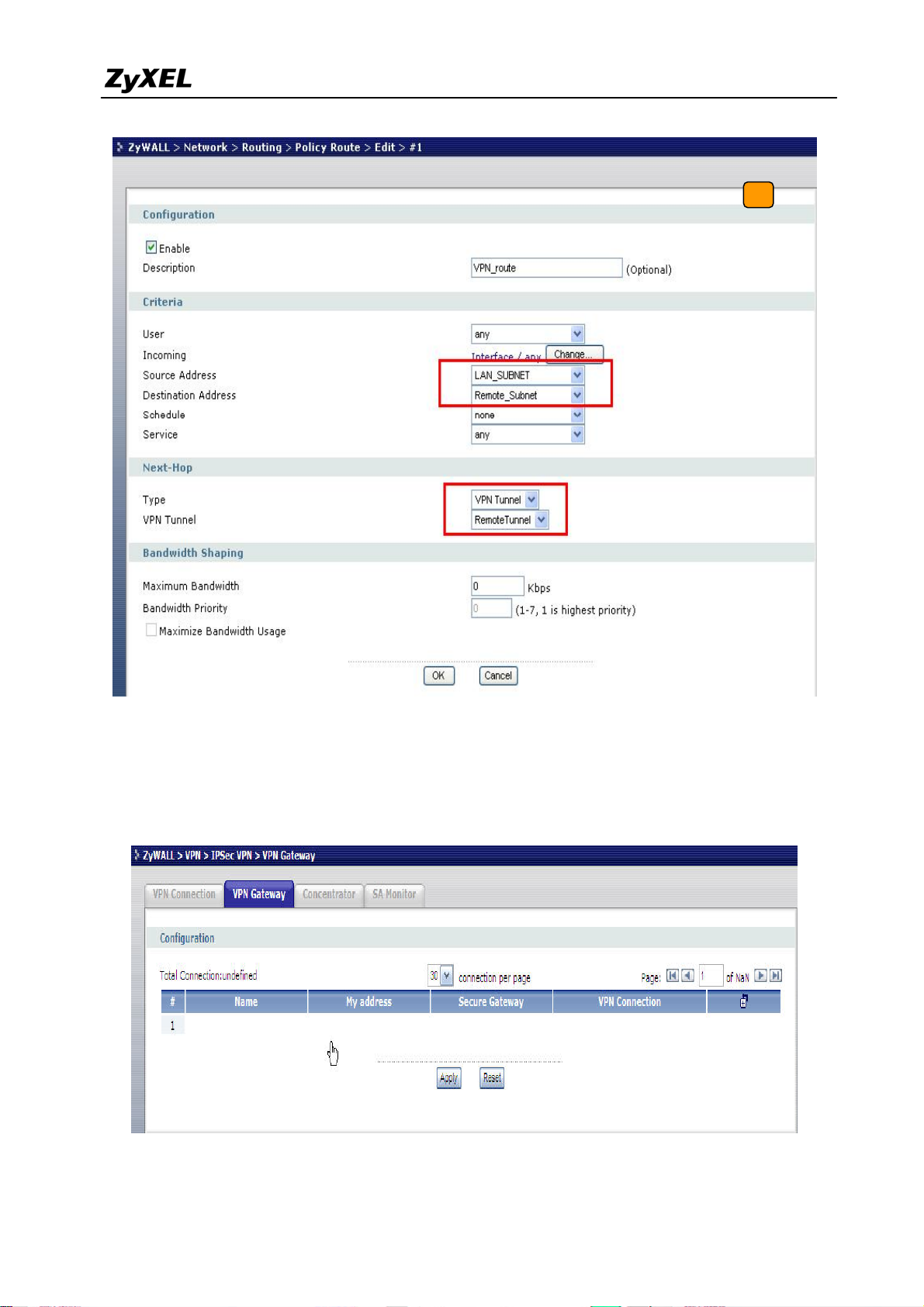
4) The ZyWALL1050 and ZyWALL USG 2000 VPN are route-based VPN. This means the
VPN tunnel can be an interface to route the VPN traffic. Thus, we need to configure a
policy route for VPN traffic from the local subnet to the remote subnet after configuring
the VPN gateway and connection (phase1 and phase2). The purpose of this policy route is
to tell the ZyWALL1050 to send the traffic to VPN tunnel when the traffic flows from the
local subnet to a destination that is in the remote subnet. Switch to ZyWALL 1050 >
Network > Routing > Policy Route and add a new policy route. The source and the
destination addresses are the local and remote subnets. The Next-Hop type is VPN tunnel.
Then choose the corresponding VPN connection rule from the VPN tunnel drop down
menu. Now, the VPN tunnel and routing is configured and user can start to test it.
13
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 14
ZyWALL USG 2000 Support Notes
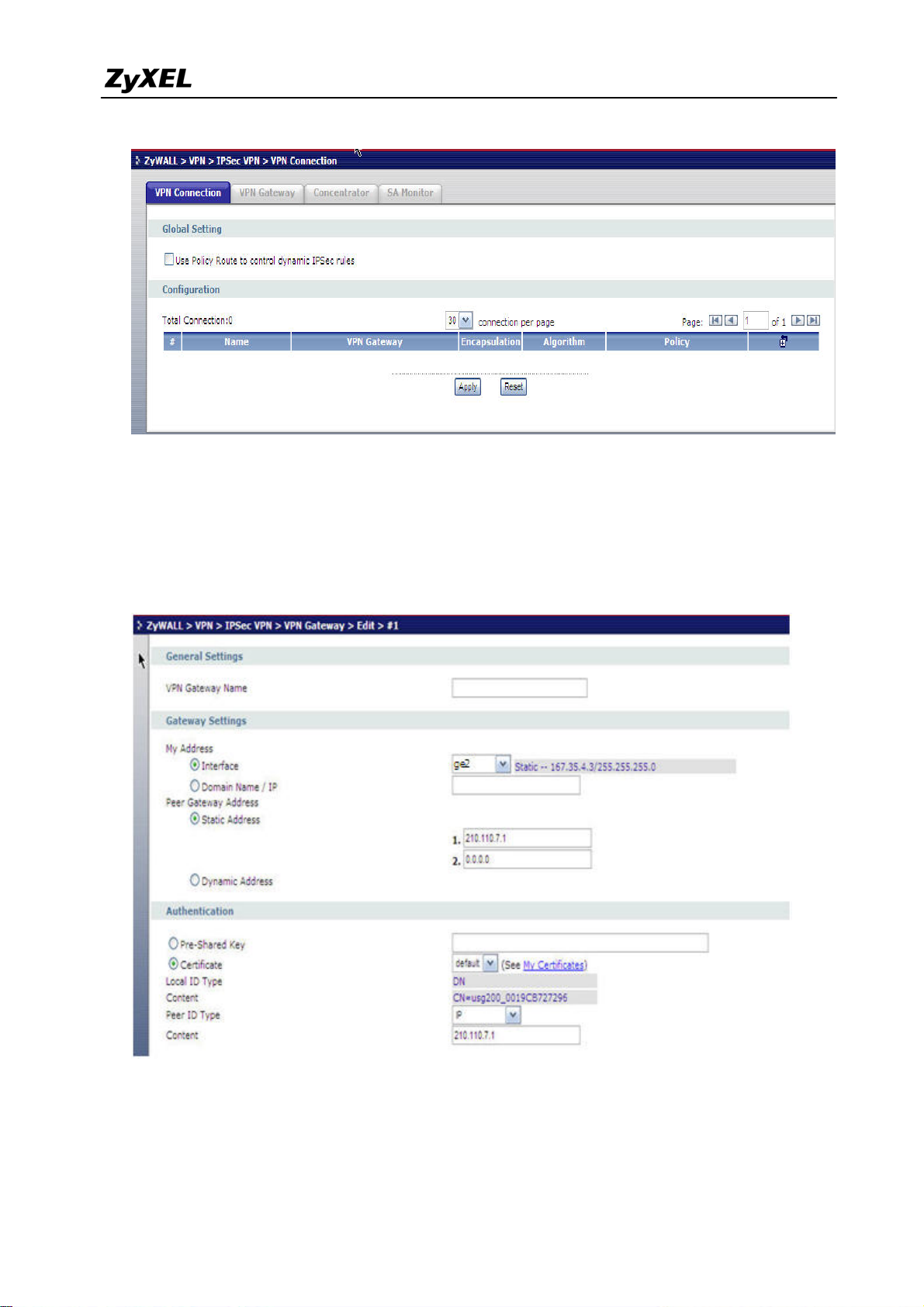
5) Login ZyWALL USG 2000 GUI, setup the ge2 interface for internet connection and
manually assign a static IP. The configuration path in ZyWALL USG 2000 menu is
ZyWALL > VPN > IPSec VPN >VPN Gateway > Add. Select Static site to site VPN and
then create an object if you have not created any wan interface.
14
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 15
ZyWALL USG 2000 Support Notes
6) Switch to VPN > IPSec VPN > VPN Gateway > Edit select interface ge2 as My Address
and then in Security Gateway Address field set the remote gateway IP to 210.110.7.1.
The Local ID Type and content are IP and 167.35.4.3, Peer ID Type and content are IP
and 210.110.7.1.
15
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 16
ZyWALL USG 2000 Support Notes
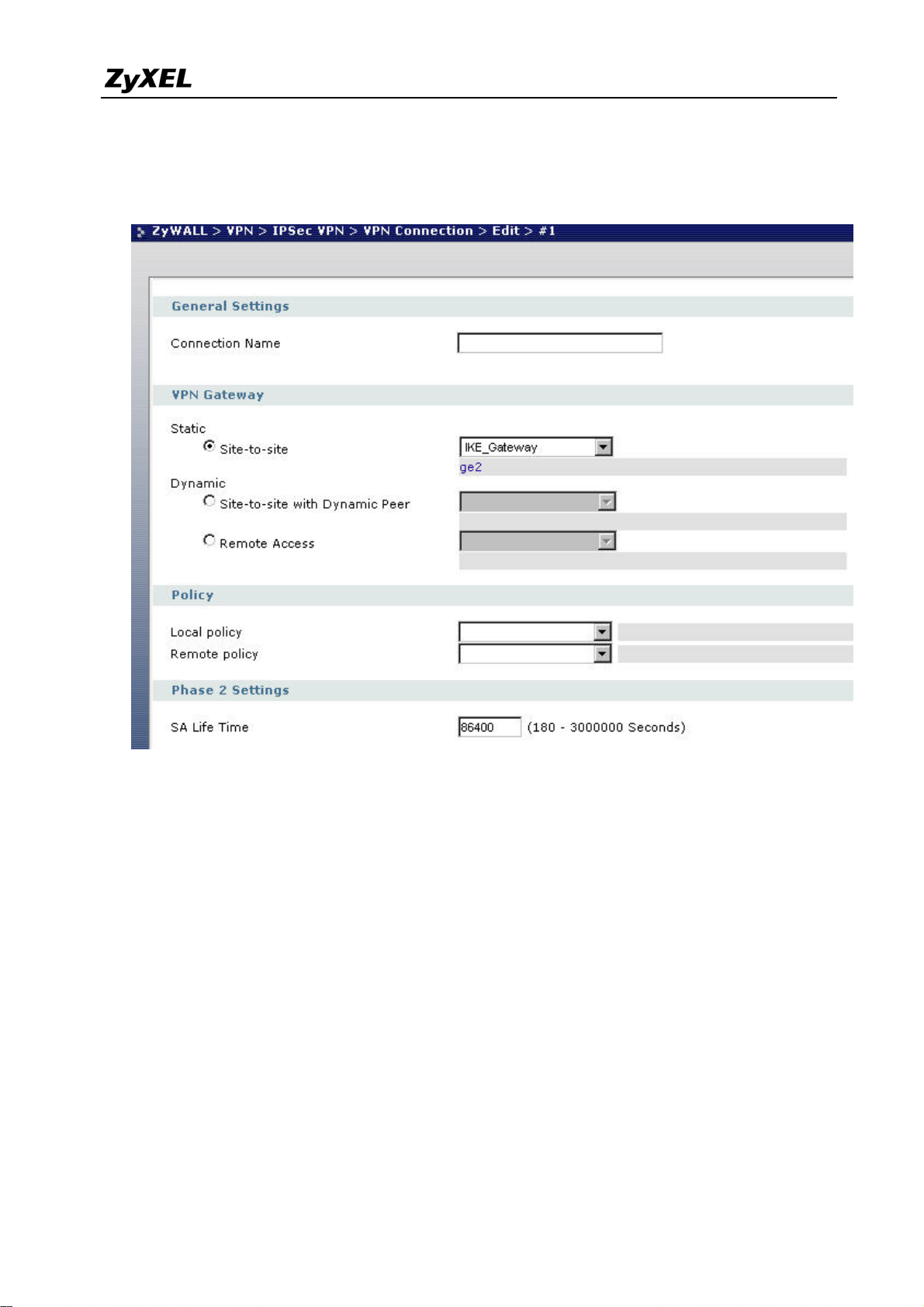
7) Create VPN by selecting ZyWALL > VPN > IPSec VPN > VPN Connection > Edit. As
for more detail, user can refer to the user guide to complete the rest of the settings for VPN
tunnel.
8) The ZyWALL1050 and ZyWALL USG 2000 VPN are route-based VPN. This means the
VPN tunnel can be an interface to route the VPN traffic. Thus, we need to configure a
policy route for VPN traffic from the local subnet to the remote subnet after configuring
the VPN gateway and connection (phase1 and phase2). The purpose of this policy route is
to tell the ZyWALL1050 to send the traffic to VPN tunnel when the traffic flows from the
local subnet to a destination that is in the remote subnet. Switch to ZyWALL 1050 >
Network > Routing > Policy Route and add a new policy route. The source and the
destination addresses are the local and remote subnets. The Next-Hop type is VPN tunnel.
Then choose the corresponding VPN connection rule from the VPN tunnel drop down
menu. Now, the VPN tunnel and routing is configured and user can start to test it.
Tips for application:
1. Make sure the presharekey is the same in both local and remote gateways.
2. Make sure the IKE & IPSec proposal is the same in both local and remote gateways.
16
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 17

ZyWALL USG 2000 Support Notes
3. Select the correct interface for VPN connection.
4. The Local and Peer ID type and content must the opposite and contain the same.
Make sure the VPN policy route has been configured in ZyWALL1050.
17
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 18
ZyWALL USG 2000 Support Notes
1.2 Extranet Deployment
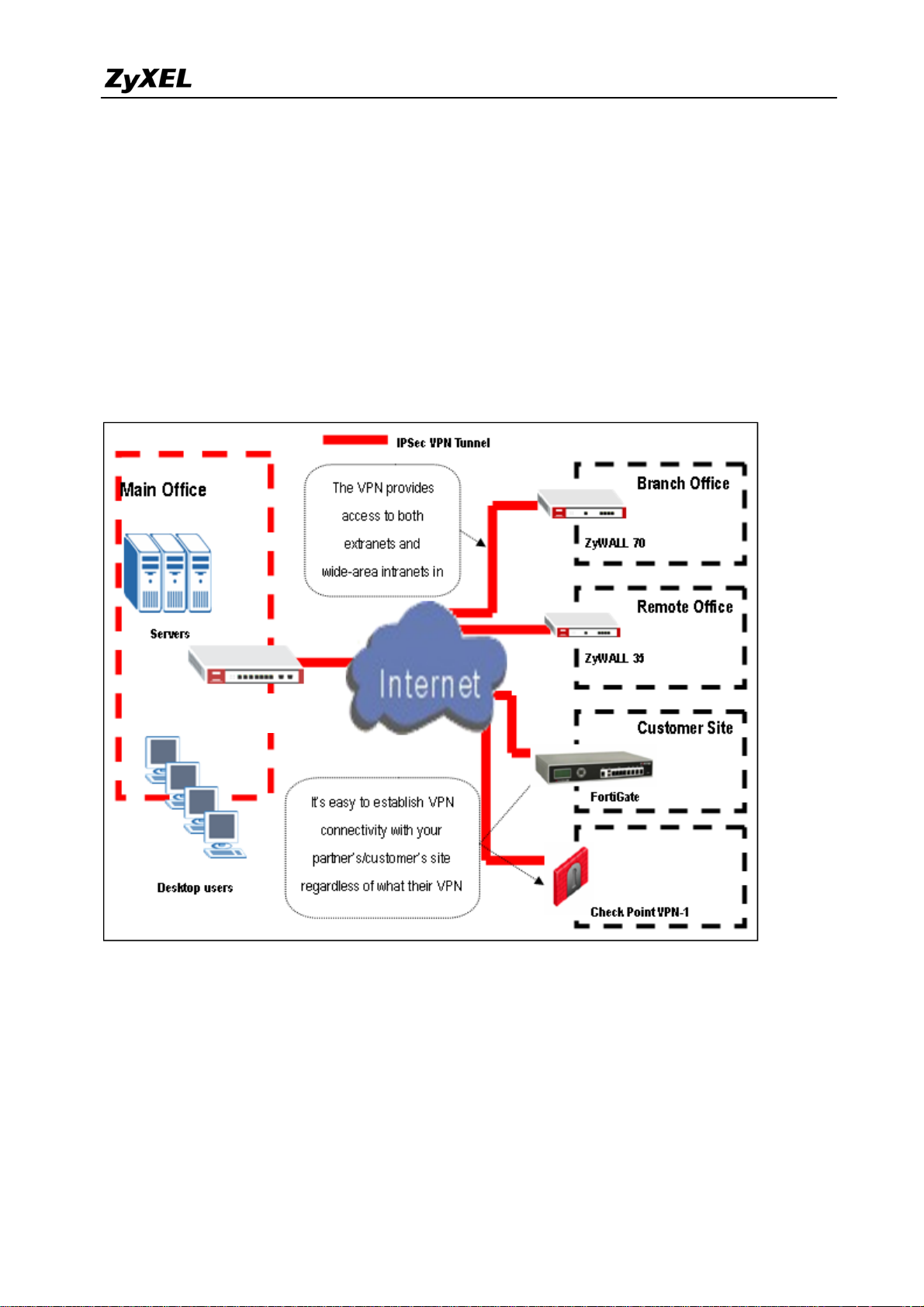
The VPN provides the access to extranets which can provide the security path over internet to
improve the client service, vendor support and company communication. Different flexible
business models have been developed based on the global VPN extranet architecture. For
example, customers can order equipment over the VPN and also suppliers can check the orders
electronically. Another result of its application is that the employees across different branches
can collaborate on project documents and share the different site’s internal resource to
complete the project.
USG 2000
Partner Site
The ZyWALL USG 2000 can be placed as a VPN gateway in the central site. It can
communicate with other ZyXEL’s VPN-capable products as well as VPN products from other
major vendors in the network device industry, e.g. Cisco PIX/IOS VPN products, Check Point
VPN Pro, Juniper NetScreen 100/200 and others…
18
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 19
ZyWALL USG 2000 Support Notes
1.2.1 Site to site VPN solutions (ZyWALL USG 2000 to ZyWALL70)
The exciting ZyWALL35 or 70 in central office gateway can be replaced by ZyWALL USG
2000, and the ZyWALL35 or 70 moved to a remote office. The ZyWALL USG 2000 can
provide higher VPN throughput and deal with multiple VPN tunnels at the same time. To show
how to build tunnel between ZyWALL5/35/70 and ZyWALL USG 2000 we used ZyWALL 70
as an example.
Static IP address
210.110.7.1
Static IP address
167.35.4.3
Internet
CenterOffice Gateway Branch Gateway
LAN: 192.168.1.X
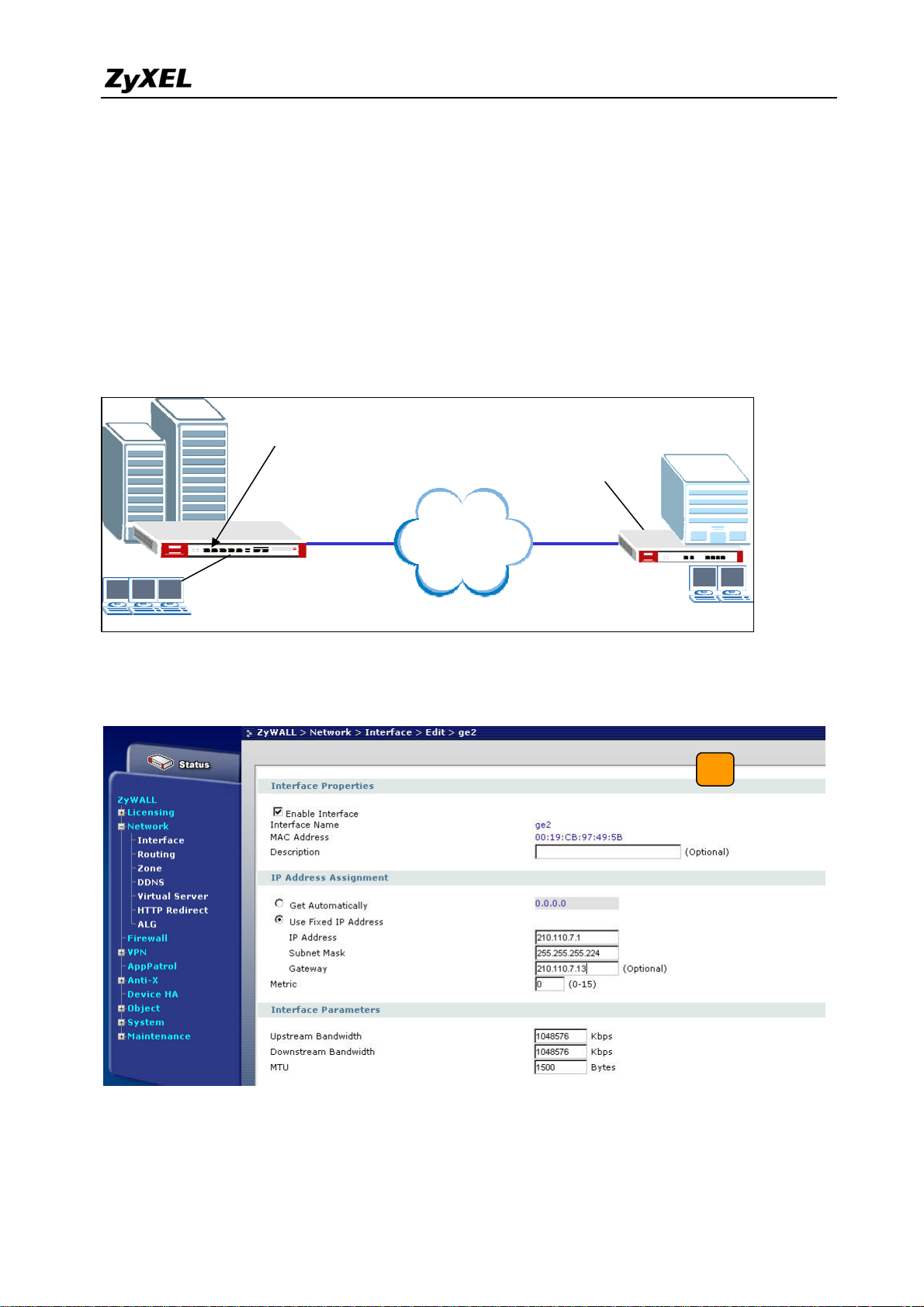
1) Login ZyWALL USG 2000 GUI and setup the ge2 interface for the internet connection
and manually assign a static IP. The configuration path is ZyWALL USG 2000 > Network
> Interface > Edit > ge2
LAN: 192.168.2.X
2) Switch to VPN > IPSec VPN > VPN Gateway, select My Address as interface ge2 and
then in Security Gateway Address field set the remote gateway IP to 167.35.4.3. The
Local ID Type and content are IP and 210.110.7.1, Peer ID Type and content are IP and
19
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 20
ZyWALL USG 2000 Support Notes
167.35.4.3.
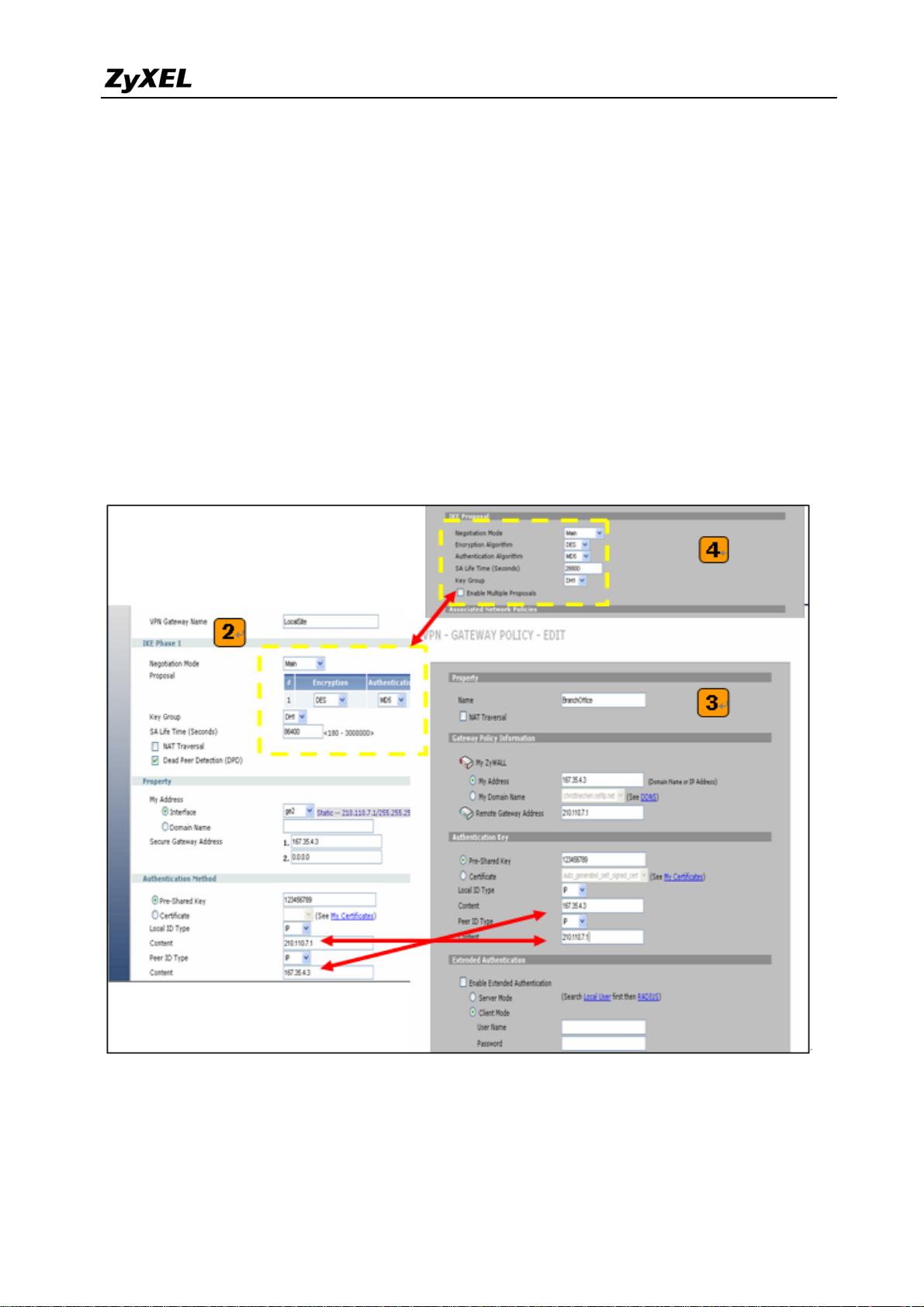
3) Login to ZyWALL70 and go to Security > VPN > Gateway Policy, add a new gateway
policy to connect with central office’s ZyWALL USG 2000. My Address and Remote
Gateway Address are ZyWALL70 and ZyWALL USG 2000 WAN IP addresses. The
Pre-Shared Key configured on both sides must exactly the same Local ID Type &
content and Peer ID Type & content are reverse to the Local ZyWALL USG 2000.
4) The IKE Proposal is very important setting when configuring the VPN tunnel. The
proposal includes Negotiation Mode, Encryption and Authentication Algorithm and….
Make sure the IKE proposal parameters are must the same on both ends.
5) Switch to Network > IPSec VPN > VPN Connection, add a new VPN connection (IPSec
phase2). Setup the Phase2 proposal and local and remote policies. The chosen phase2
proposal chosen must be the same as on the remote site’s ZyWALL70.
20
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 21
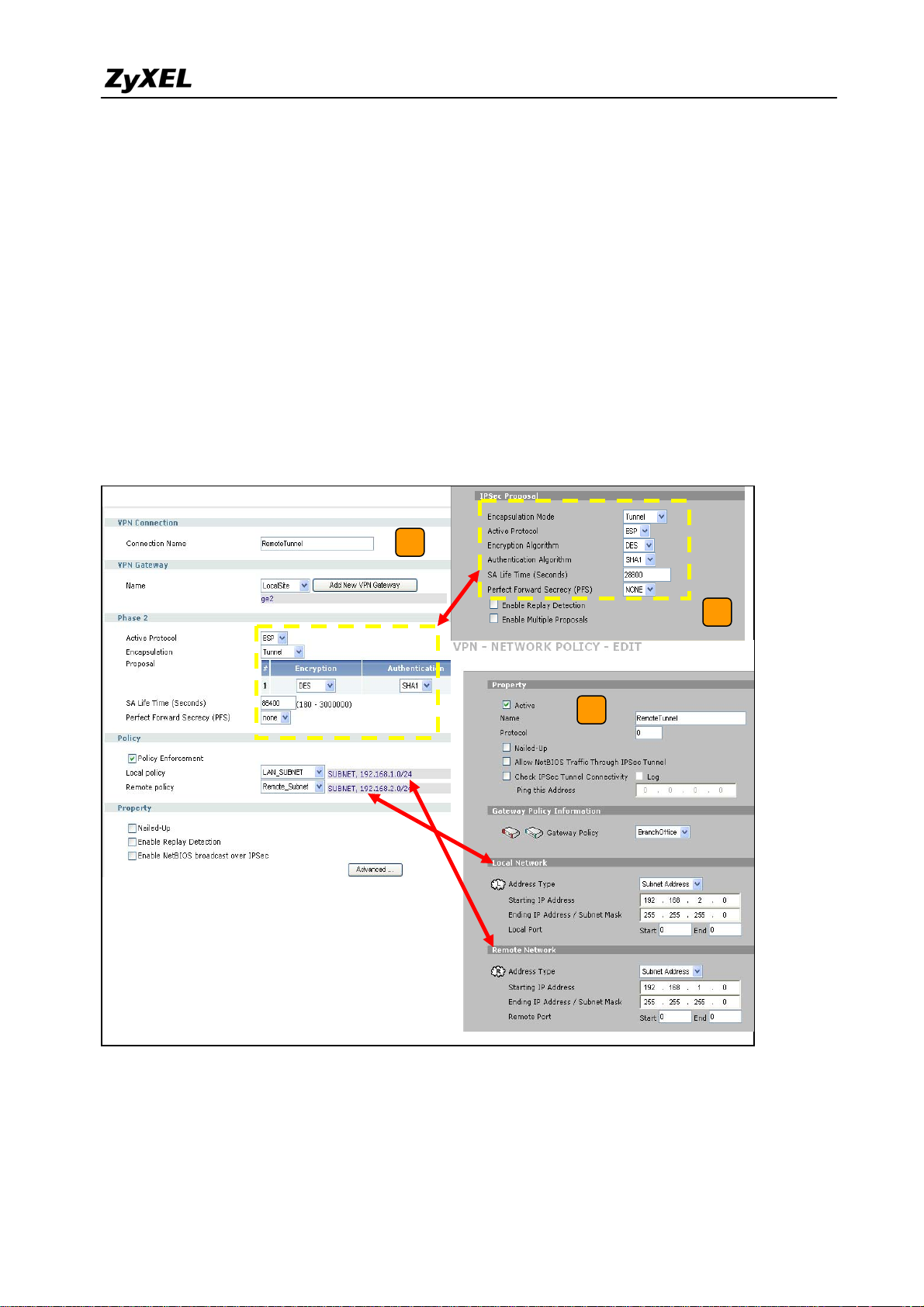
ZyWALL USG 2000 Support Notes
6) In ZyWALL70, VPN is a rule based VPN. This means that whether the traffic is going to
the tunnel or not will depend on the local and remote policies. In this example,
ZyWALL70 local and remote policies are 192.168.2.0 and 192.168.1.0 and the traffic
from 192.168.2.X subnet to 192.168.1.X subnet will go through the VPN tunnel to the
remote site as predefined. The ZyWALL USG 2000 local and remote policies must be
reverse to the ZyWALL70’s settings, otherwise the tunnel will not be built up.
7) Check whether the IPSec proposal on both sites is the same and the configuration is done
on both sites.
5
7
6
8) The ZyWALL USG 2000 VPN is a route-based VPN, this means the VPN tunnel can be an
interface to route the VPN traffic. Thus, we need to configure a policy route for VPN
traffic from the local subnet to the remote subnet after configuring the VPN gateway and
21
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 22
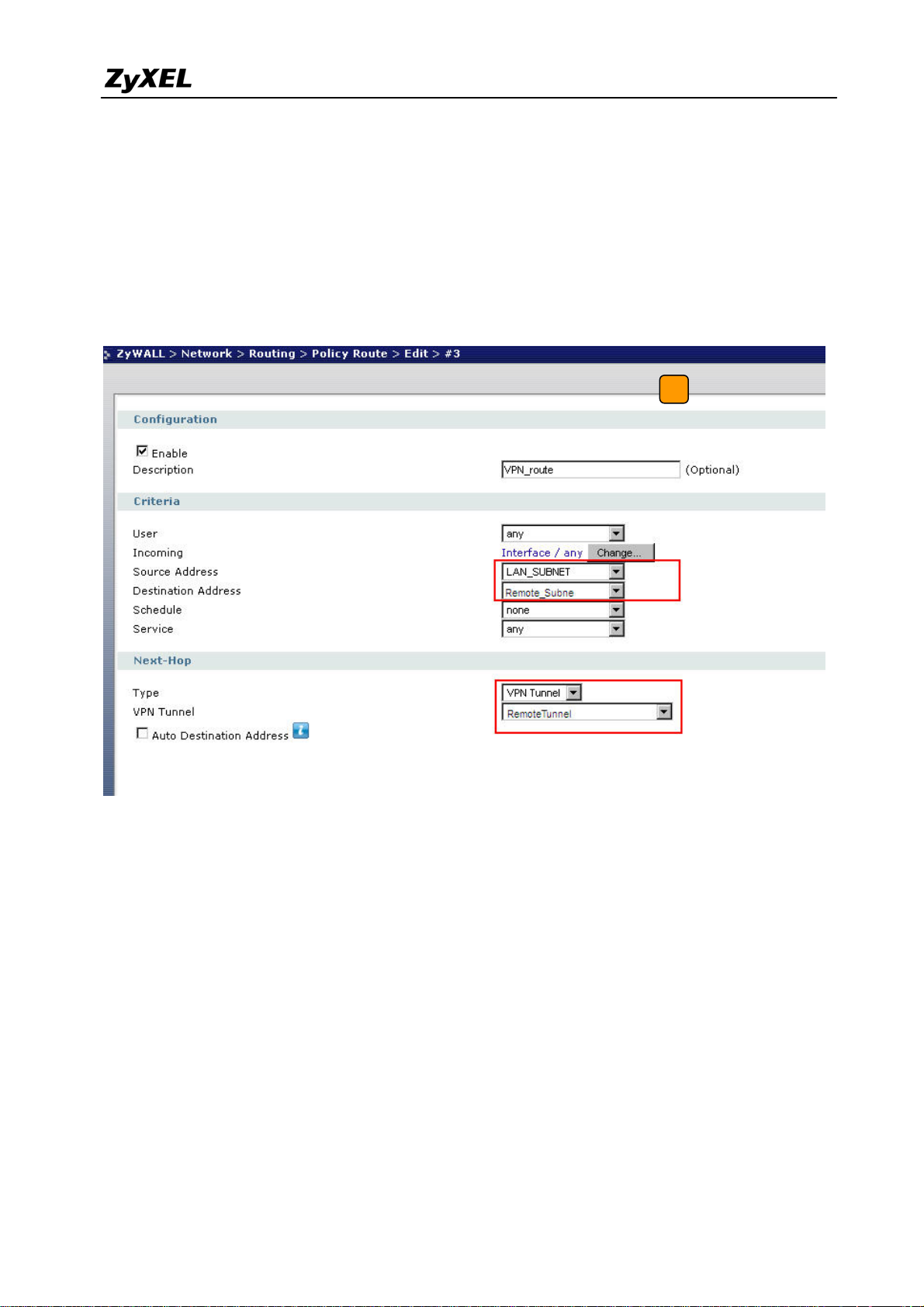
ZyWALL USG 2000 Support Notes
the connection (phase1 and phase2). The purpose for this policy route is to tell the
ZyWALL USG 2000 to send the traffic to the VPN tunnel when the traffic goes from the
local subnet to the destination that is in a remote subnet. Switch to Network> Routing >
Policy > Policy Route and add a new policy route, the source and destination address are
the local and remote subnet and the Next-Hop type is a VPN tunnel. Then choose the
corresponding VPN connection rule from the VPN tunnel drop down menu. Now, the VPN
tunnel and routing is built and user can start to test it.
8
9) After configuring both sides of the VPN, click the “Dial up” icon to test the VPN
connectivity.
10) “VPN tunnel establishment successful,” message appears.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
22
Page 23
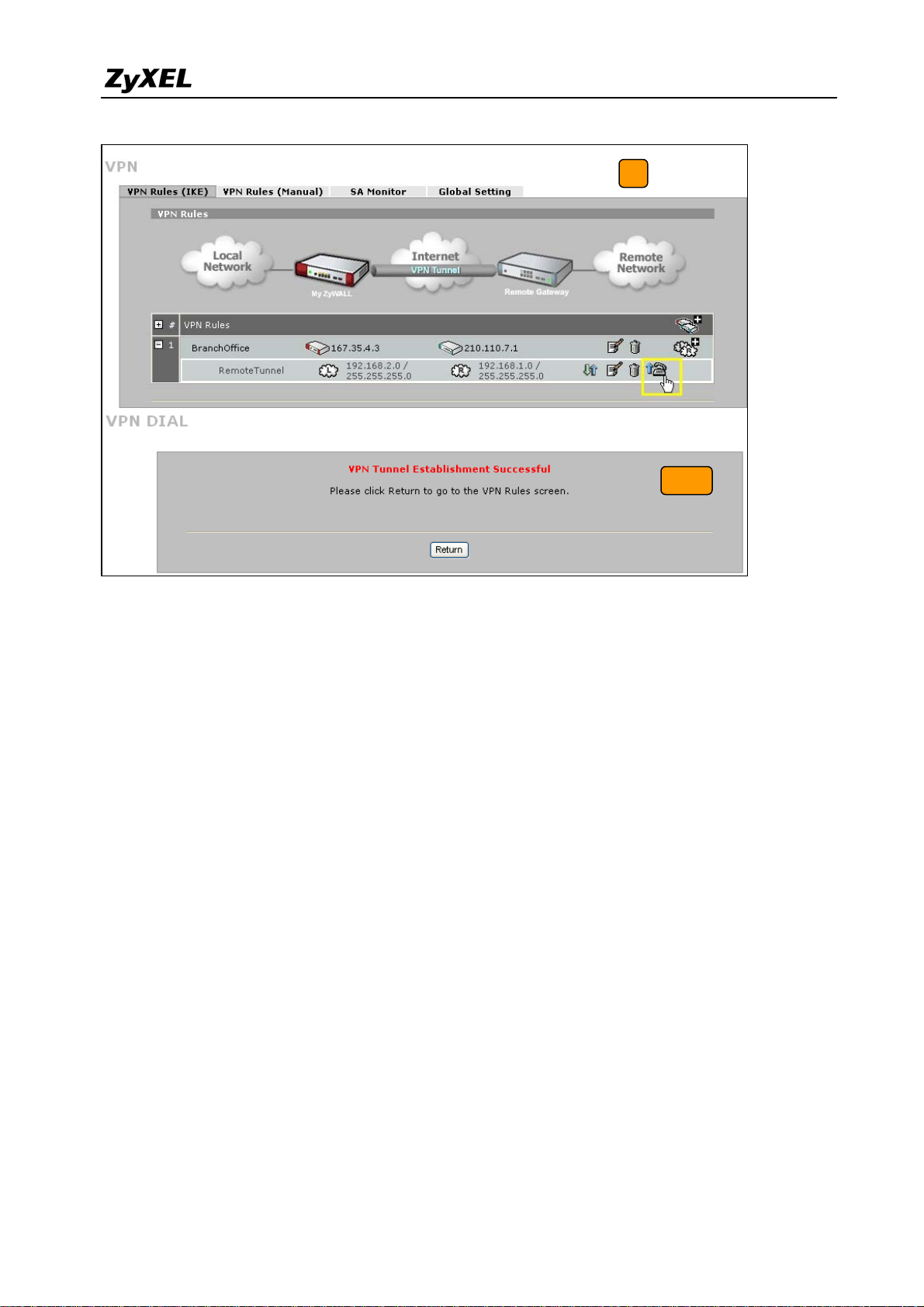
ZyWALL USG 2000 Support Notes
9
10
Tips for application:
1. Make sure the presharekey is the same in both the local and the remote gateways.
2. Make sure the IKE & IPSec proposal is the same in both the local and the remote
gateways.
3. Select the correct interface for the VPN connection.
4. The Local and Peer ID type and content must be the opposite and not of the same content.
5. Make sure the VPN policy route had been setup in ZyWALL USG 2000.
1.2.2 Interoperability – VPN with other vendors
1.2.2.1 ZyWALL with FortiGate VPN Tunneling
This page guides how to setup a VPN connection between the ZyWALL USG 2000 and
FortiGate 200A.
As on the figure shown below, the tunnel between Central and Remote offices ensures the
packet flow between them are secure, because the packets go through the IPSec tunnel are
23
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 24
ZyWALL USG 2000 Support Notes
encrypted. To setup this VPN tunnel, the required settings for ZyWALL and FortiGate are
explained in the following sections.
Static IP address
210.110.7.1
Static IP address
167.35.4.3
Internet
Central Office Gateway
ZyWALL
LAN: 192.168.1.X
The central office gateway ZyWALL USG 2000’s interface and VPN setting retain the same
setting as in the previous example. If you jumped this section first, please refer to ‘ZyWALL
Branch Gateway
FortiGate 200A
LAN: 192.168.2.X
USG 2000 to ZYWALL70 VPN tunnel setting’ on page 8.
This list below is to briefly show the VPN phase1 and phase2 configuration parameters:
ZyWALL FortiGate
WAN: 210.110.7.1
LAN: 192.168.1.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
WAN: 167.35.4.3
LAN: 192.168.2.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Perfect Forward Secrecy (PFS): None
Authentication: SHA1
1) Configure the ZyWALL USG 2000 ‘s VPN gateway and VPN connection as on the list.
Also, remember to configure the policy route for the VPN traffic routing. Refer to the
24
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 25
ZyWALL USG 2000 Support Notes
previous scenario or user guide to find help on setting the ZyWALL USG 2000 VPN.
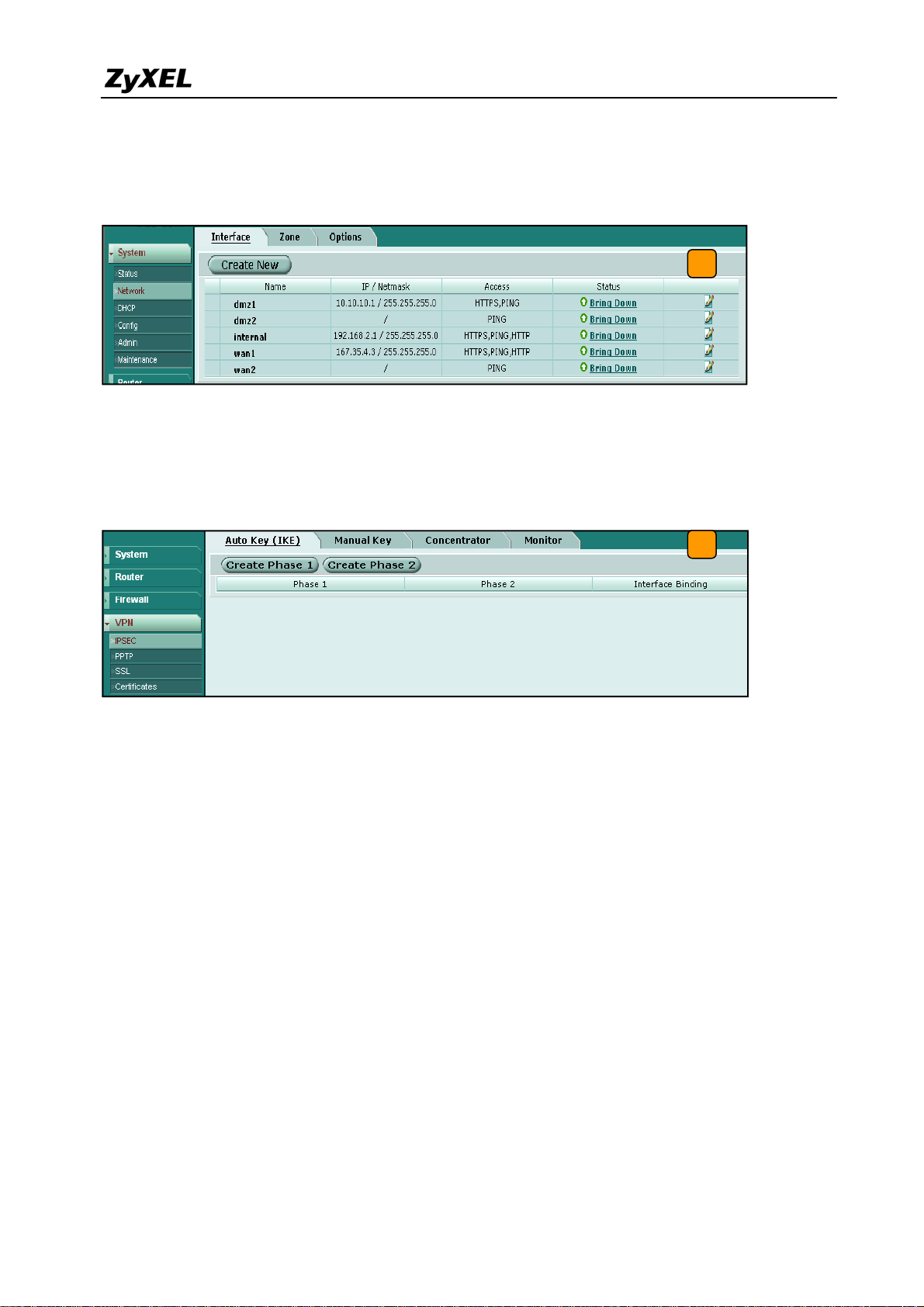
2) Login to the FortiGate GUI and switch to System > Network > Interface and set the wan1
interface to 167.35.4.3 and internal interface to 192.168.2.1/255.255.255.0.
2
Note: About the detail interface settings, refer to FortiGate user guide.
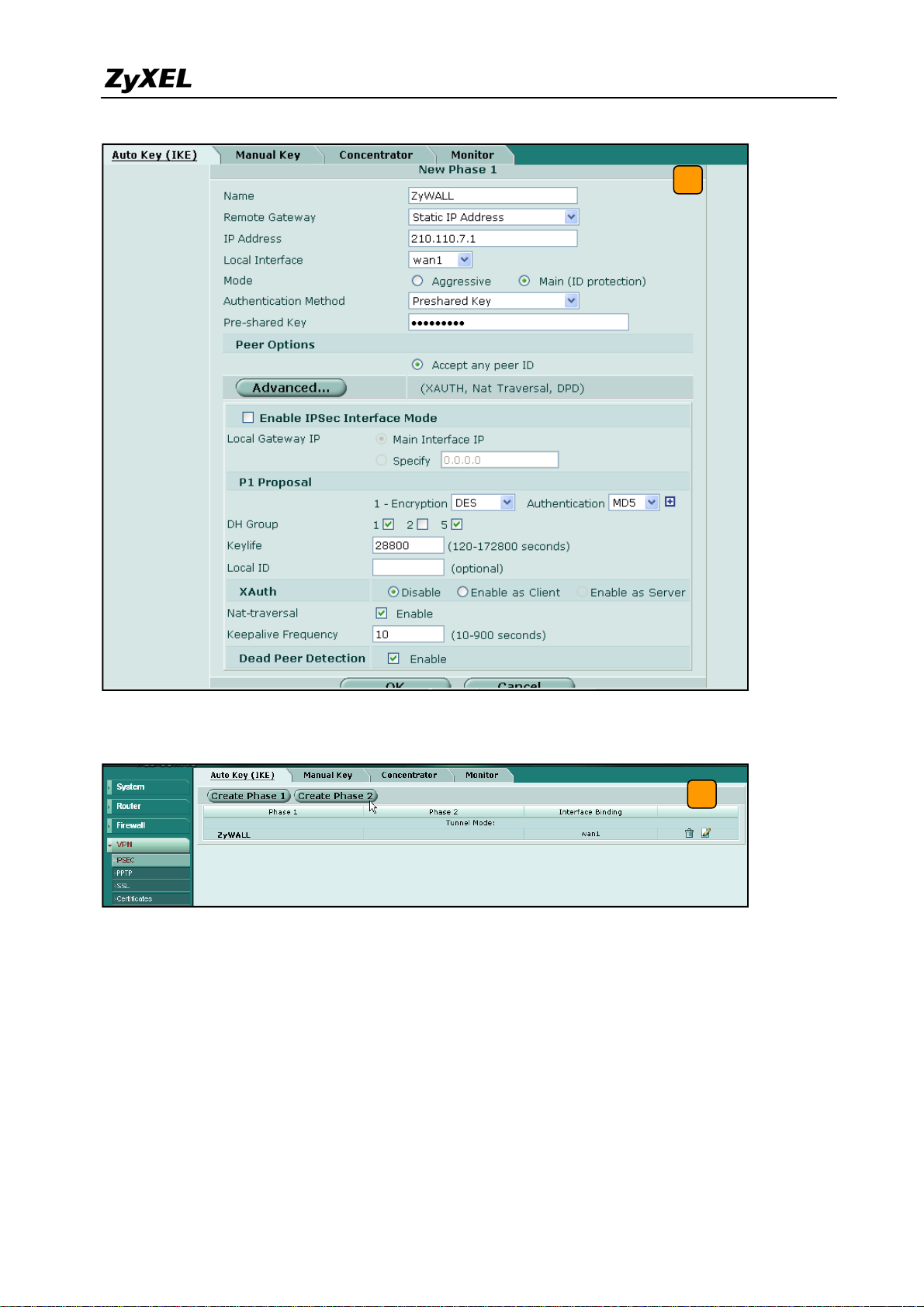
3) Switch to System > VPN > IPSEC and select the Auto Key (IKE) tab and click the Create
Phase 1 button. This will open a new page for VPN phase1 setup.
3
4) Fill-in the VPN phase1 setting according to the table listed. We don’t have to setup the ID
type and content because the FortiGate accepts any peer ID. Make sure both the pre-shares
key and proposal are the same as in the ZyWALL USG 2000.
25
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 26
ZyWALL USG 2000 Support Notes
4
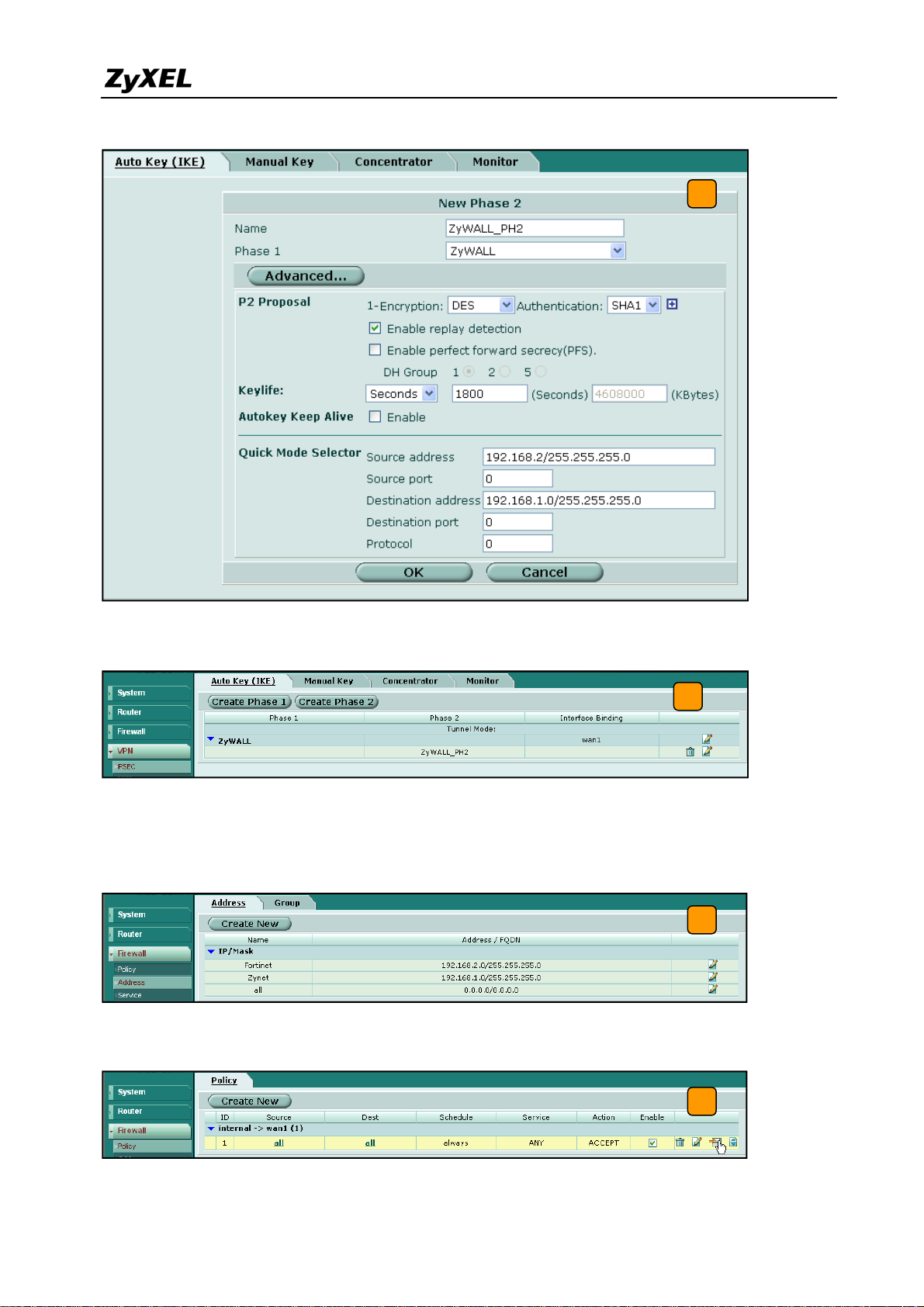
5) Get back to the VPN configuration page again and click the Create Phase 2 button to add
a new Phase2 policy.
5
6) Select the “ZyWALL”(configured in the step 4) policy from the Phase 1 drop down menu
and click the Advanced… button to edit the phase 2 proposal and source and destination
address. Please make sure the phase 2 proposal is the same as in ZyWALL USG 2000
phase 2.
26
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 27
ZyWALL USG 2000 Support Notes
6
7) The VPN tunnel configuration is finished and the VPN IPSec page will show the VPN
phase 1 and phase 2 rules in the Auto Key (IKE) tab.
7
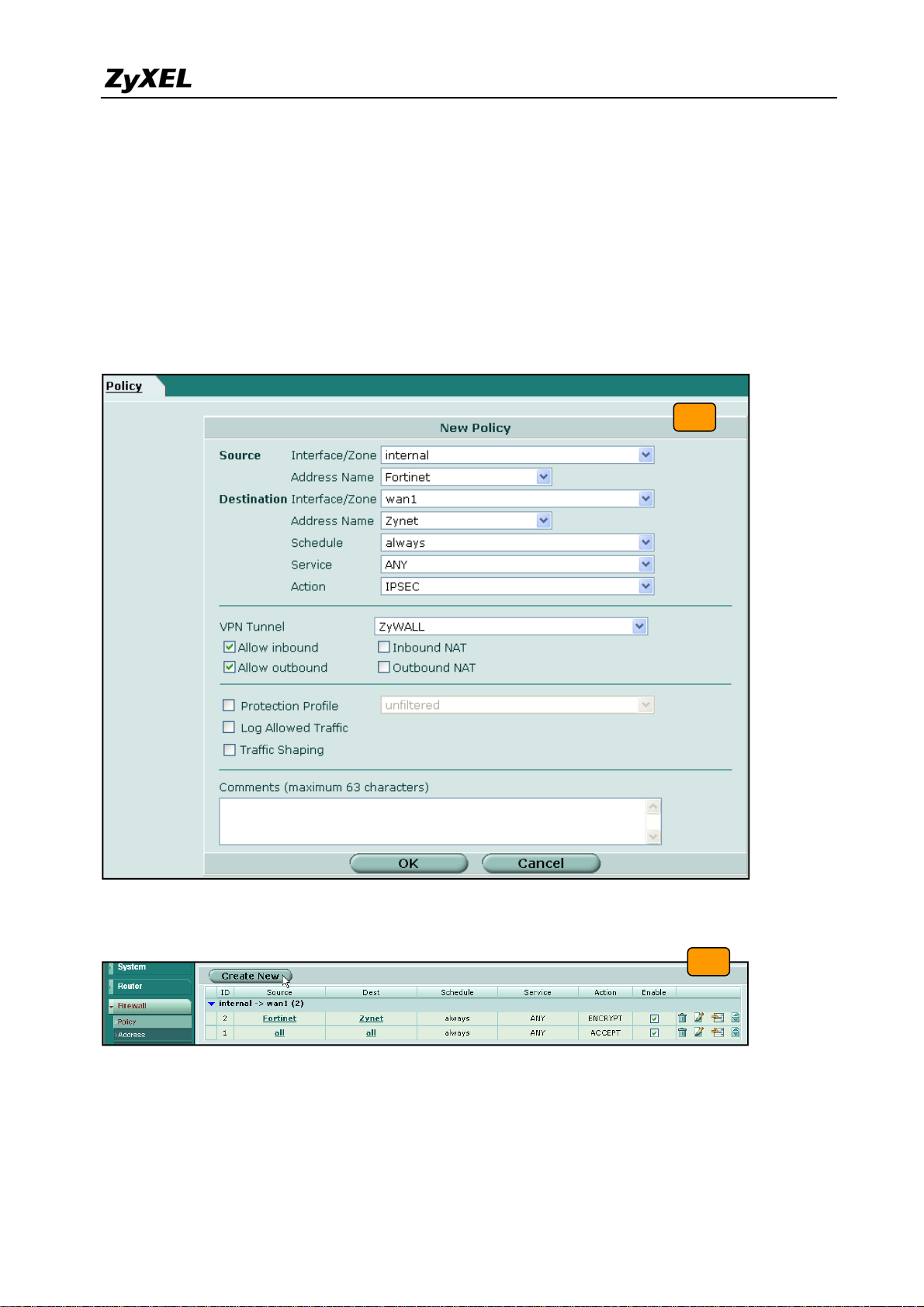
8) We need to setup the firewall rules for IPSec VPN traffic transmitting from ZyWALL to
FortiGate and from FortiGate to ZyWALL. Switch to Firewall > VPN >Address menu and
add two new address object which stand for ZyWALL LAN subnet and FortiGate LAN
subnet. Using the “Create New” button to create a new address object.
8
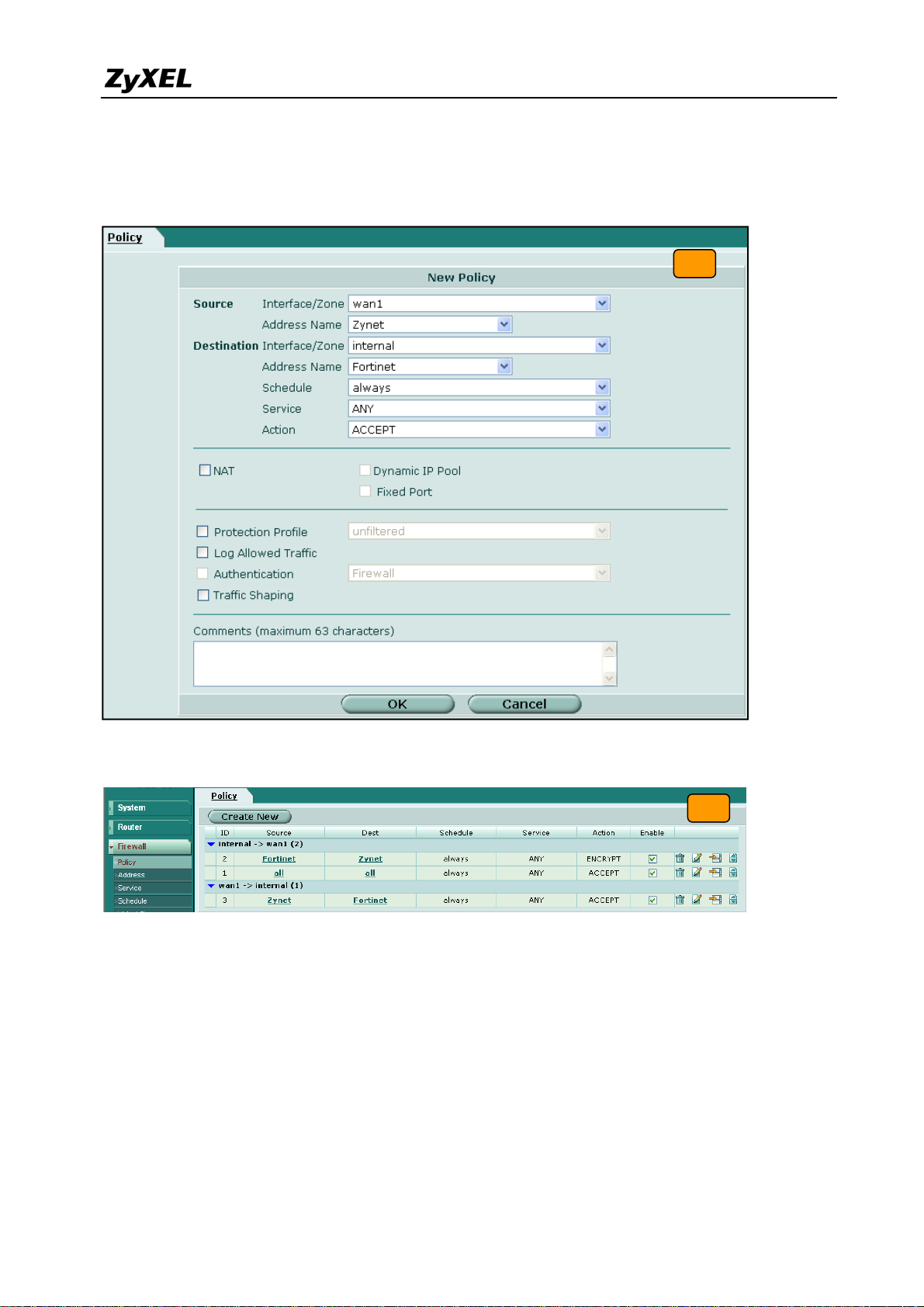
9) Switch to Firewall > Policy and click “Insert Policy Before” icon to add new policy for the
VPN traffic from FortiGate to ZyWALL.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
9
27
Page 28
ZyWALL USG 2000 Support Notes
10) We will setup the FortiGate to ZyWALL policy in the new page. The source interface is
internal and Address name is Fortinet (192.168.2.0/255.255.255.0 address object). The
destination interface is wan1 and Address name is Zynet (192.168.1.0/255.255.255.0
address object). Schedule and service type are “always” and “ANY” to ensure that all
kinds of traffic can pass through the VPN tunnel at any time. There are three kinds of
“Action” available for user to configure, because the traf fic is send from “internal” to
WAN and will be encrypted by IPSec VPN tunnel. Thus, we select “IPSEC” as action and
chose allow inbound and outbound traffic in the ZyWALL tunnel.
10
11) Switch to Firewall > Policy and click “Create New” button to add new policy for the VPN
traffic from ZyWALL to FortiGate.
11
12) We setup the ZyWALL to FortiGate policy in the new page. The source interface is wan1
and Address name is Zynet (192.168.1.0/255.255.255.0 address object). The destination
interface is internal and the Address name is Fortinet (192.168.2.0/255.255.255.0 address
object). Schedule and service type are always and ANY to ensure that all kinds of traffic
28
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 29
ZyWALL USG 2000 Support Notes
can pass through the VPN tunnel at any time. Select “ACCEPT” as an action this time
because the traffic sent from wan to internal must be decrypted first and only then can be
transmitted. Don’t select the IPSec as the Action in this VPN traffic flow direction.
12
13) The overall firewall policy is shown on the following figure. The VPN tunnel between
ZyWALL and FortiGate has been successfully setup.
13
Tips for application:
1. Make sure the Pre-Shared Key is the same in both local and remo te gateways.
2. Make sure both IKE and IPSec proposal are the same in both local and remote gateways.
3. Make sure the VPN policy route has been configured in ZyWALL USG 2000.
4. Make sure the Firewall rule has been configured in FortiGate.
29
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 30
ZyWALL USG 2000 Support Notes
1.2.2.2 ZyWALL with NetScreen VPN Tunneling
This section guides how to setup a VPN connection between the ZyWALL USG 2000 and
NetScreen 5GT.
As on the figure below, the tunnel between Central and Remote offices ensures the packet
flows between them are secure. This is because the packets flowing through the IPSec tunnel
are encrypted. The required settings to setup this VPN tunnel using ZyWALL and NetScreen
are stated in the following section.
Static IP address
210.110.7.1
Static IP address
167.35.4.3
Internet
Central Office Gateway
ZyWALL
LAN: 192.168.1.X
The central office gateway ZyWALL USG 2000’s interface and VPN setting retain the same
settings as in the previous example. If you jumped to this section first, please refer to
‘ZyWALL USG 2000 to ZYWALL70 VPN tunnel setting’ on the page 8.
This list below is to briefly show the VPN phase1 and phase2 configuration parameters:
ZyWALL NetScreen
WAN: 210.110.7.1
LAN: 192.168.1.0/24
Branch Gateway
NetScreen 5GT
LAN: 192.168.2.X
WAN: 167.35.4.3
LAN: 192.168.2.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Authentication :MD5
Key Group :DH1
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Phase 1
Encryption :DES
Key Group :DH1
30
Page 31

ZyWALL USG 2000 Support Notes
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Encapsulation: Tunnel
Active Protocol: ESP
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Phase2
Encryption: DES
1) Configure the ZyWALL USG 2000 ‘s VPN gateway and VPN connection as on the list.
Also, remember to configure the policy route for the VPN traffic routing. Refer to the
pervious scenario or user guide to find help on setting the ZyWALL USG 2000 VPN.
2) Using a web browser, login NetScreen by entering the LAN IP address of the NetScreen in
the URL field. The default username and password is netscreen/netscreen.
3) Switch to menu Network > Interfaces and configure the WAN/LAN IP addresses to
WAN: 167.35.4.3 / LAN: 192.168.2.0/24. The trust interface is for LAN, the untrust
interface is for WAN.
3
Note: Regarding the detail interface settings, please refer to NetScreen user guide to get the
detail info.
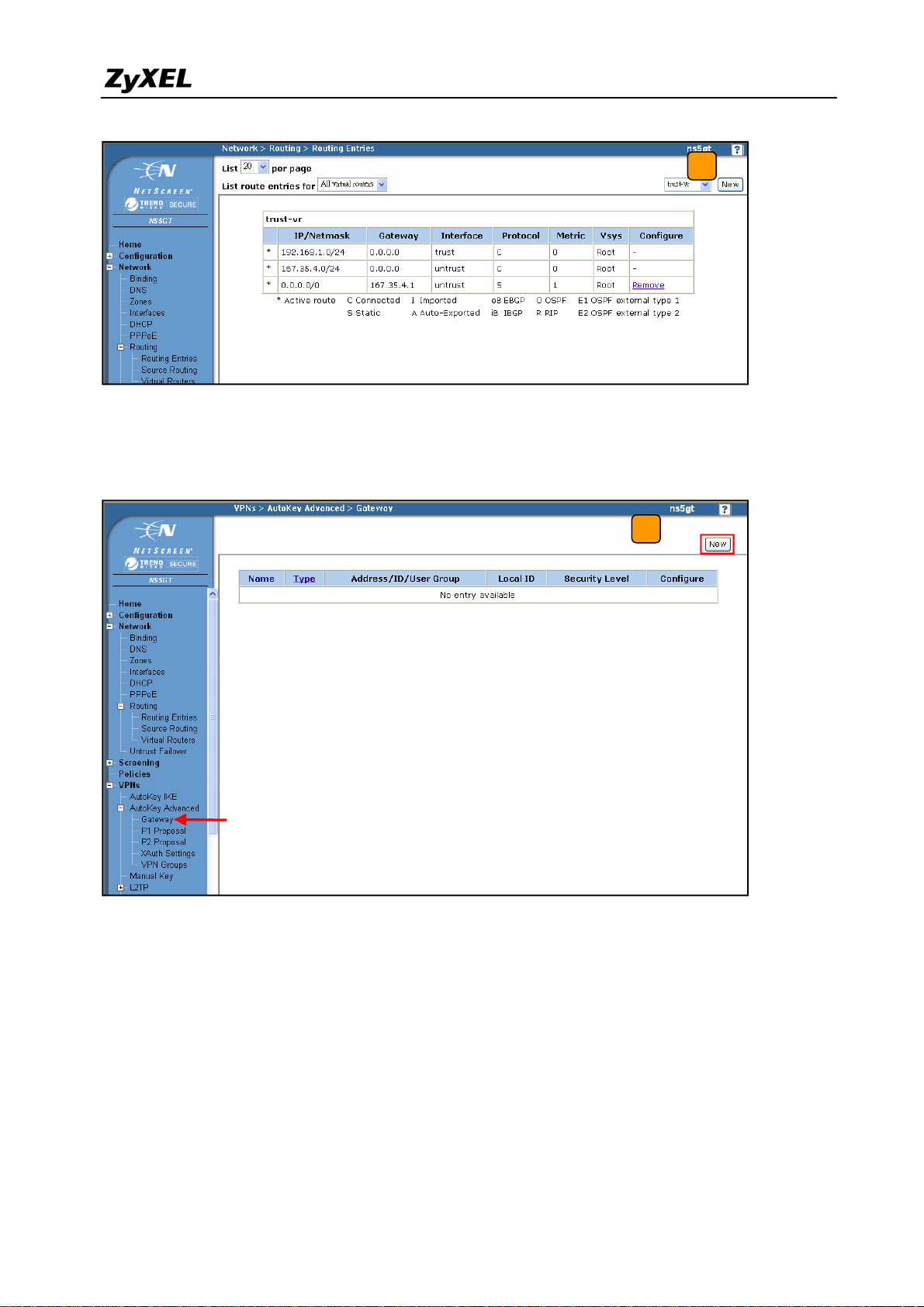
4) NetScreen won’t setup a route for the traffic to the external network. We have to manually
add a route for it. After configuring a static IP address in untrust interface, switch to
Network -> Routing -> Routing Entries to edit a default Gateway IP address. In this
example, the Gateway IP address is 167.35.4.1.
31
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 32
ZyWALL USG 2000 Support Notes
4
5) To edit the IPSec rule, first set the gateway policy and then edit the IKE policy. Switch to
VPNs > AutoKey Advanced > Gateway, and then press the New button.
5
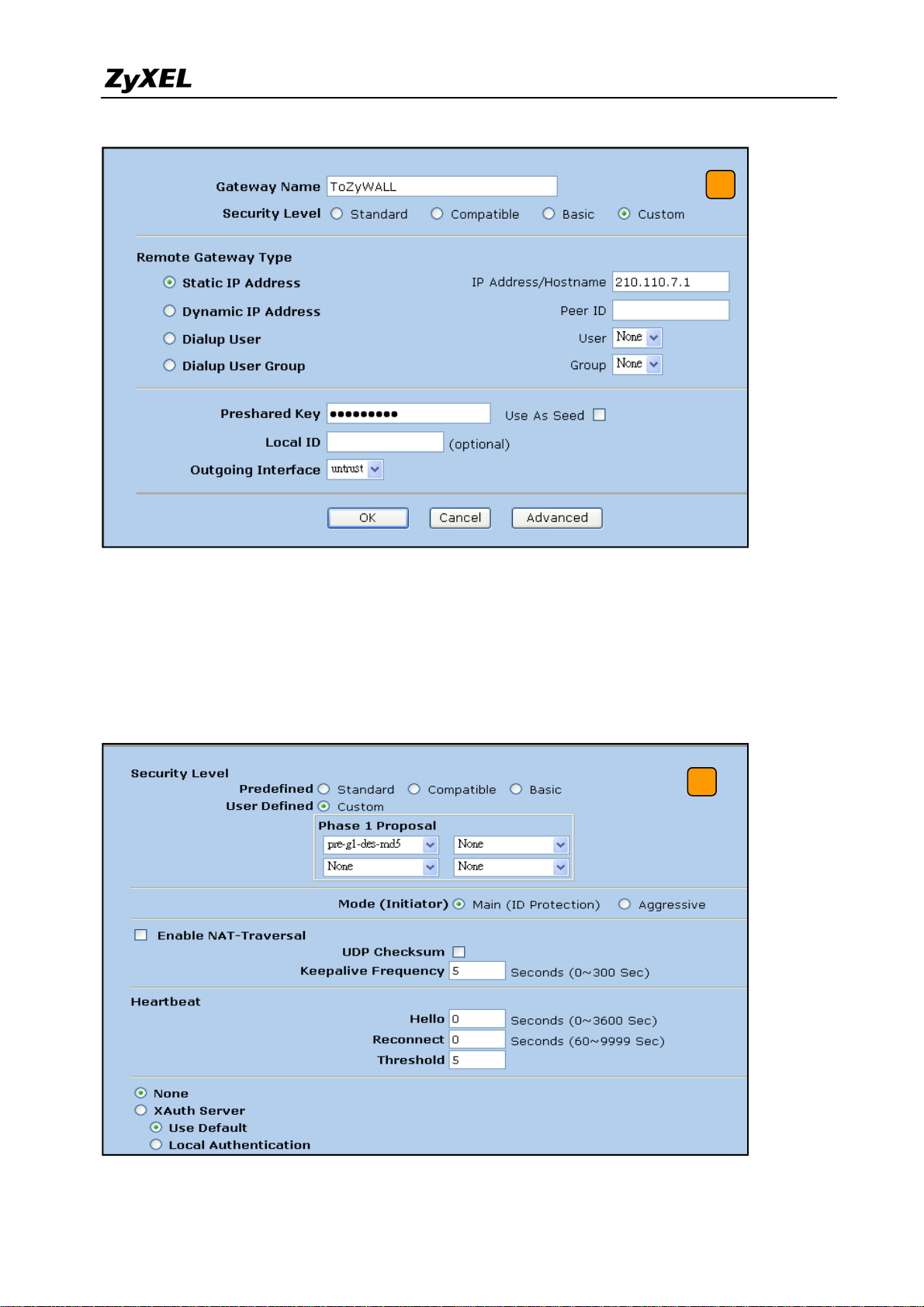
6) Choose a name for the policy, for example “ToZyWALL”. Remote Gateway IP Addr is
the ZyWALL's WAN IP address. In this example, we select Static IP Address option
and enter IP 210.110.7.1 in the text box. Enter the key string 123456789 in Preshared
Key text box, and then press Advanced button to edit the advanced settings.
32
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 33
ZyWALL USG 2000 Support Notes
6
7) On Security Level settings, we can set up phase 1 proposal. In this example, we select
User Defined, and choose pre-g1-des-md5 rule. The pre-g1-des-md5 means Pre-Share
Key, group1, DES for Encryption Algorithm and MD5 for Authentication Algorithm.
Select Main (ID Protection) option for Mode (Initiator). Then, press Return button, and
press OK button on next page to save your settings.
7
33
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 34

ZyWALL USG 2000 Support Notes
8) After applying the previous settings, the new IKE rule is shown on the page.
8
9) To edit the IPSec rule, switch to VPNs > AutoKey IKE, and then press the New button to
edit your IPSec rules.
9
10) Give a name for the VPN, for example “ToZyWALL IPSec”. In Remote Gateway, choose
the Predefined option and select the ToZyWALL rule. Then, press Advanced button to
edit the advanced settings.
10
34
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 35

ZyWALL USG 2000 Support Notes
11) In Security Level settings, choose the option User Defined and choose nopfs-esp-des-sha
rule on Phase 2 Proposal. The nopfs-esp-des-sha means no PFS, ESP Protocol,
Encryption Algorithm to DES and Authentication Algorithm to SHA1. Check the VPN
Monitor check box so that you can monitor your VPN tunnels. Then, press Return button
and OK button on next page to save the settings.
11
12) After applying the settings, the VPN IKE page will show the new IPSec rule.
12
13) Switch to Policies to set up policy rules for VPN traffic. In the field From choose Trust
and in the field To choose Untrust (it means from LAN to WAN). Then press the New
button to edit the policy rules.
35
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 36

ZyWALL USG 2000 Support Notes
13
14) Assign a name to this policy, for example “VPN”. In Source Address, set the Local LAN
IP addresses. In this example, we select New Address option. Type 192.168.2.0 /
255.255.255.0 in the text box. Set the remote IP addresses as Destination Address. In this
example, we select New Address option, and type 192.168.1.0 / 255.255.255.0 in the text
box. In drop down menu Action select the option Tunnel and then select the
ToZyWALLIPSec VPN rule. Check Modify matching bidirectional VPN policy check
box, so that you can create/modify the VPN policy for the opposite direction. Then, press
OK button to save your settings.
14
36
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 37

ZyWALL USG 2000 Support Notes
15) After applying the settings, the new policy rules will be displayed in the Policies page.
15
16) Move the added policy rules to the top, so that the VPN policies will be checked first.
16
17) Ping the remote host and switch to VPNs > Monitor Status to check the VPN link status. If
the Link status is Up, it means the VPN tunnel between ZyWALL and NetScreen has been
successfully built.
37
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 38

ZyWALL USG 2000 Support Notes
1.2.2.3 ZyWALL with SonicWall VPN Tunneling
17
This section guides how to setup a VPN connection between the ZyWALL USG 2000 and
SonicWall TZ170.
As on the figure below, the tunnel between Central and Remote offices ensures the packet
flows between them are secure. This is because the packets flowing through the IPSec tunnel
are encrypted. The required settings to setup this VPN tunnel using ZyWALL and SonicWall
are stated in the following sections.
Static IP address
210.110.7.1
Static IP address
167.35.4.3
Internet
Central Office Gateway
ZyWALL
LAN: 192.168.1.X
Branch Gateway
SonicWall TZ170
LAN: 192.168.2.X
The central office gateway ZyWALL USG 2000’s interface and VPN setting retain the same
settings as in the previous example. If you jumped to this section first, please refer to
‘ZyWALL USG 2000 to ZYWALL70 VPN tunnel setting’ on the page 8.
This list below is to briefly show the VPN phase1 and phase2 configuration parameters:
38
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 39
ZyWALL USG 2000 Support Notes
ZyWALL SonicWall
WAN: 210.110.7.1
LAN: 192.168.1.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Perfect Forward Secrecy (PFS): None
WAN: 167.35.4.3
LAN: 192.168.2.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
1) Configure the ZyWALL USG 2000 ‘s VPN gateway and VPN connection as on the list.
Also, remember to configure the policy route for the VPN traffic routing. Refer to the
previous scenario or user guide to find help on setting the ZyWALL USG 2000 VPN.
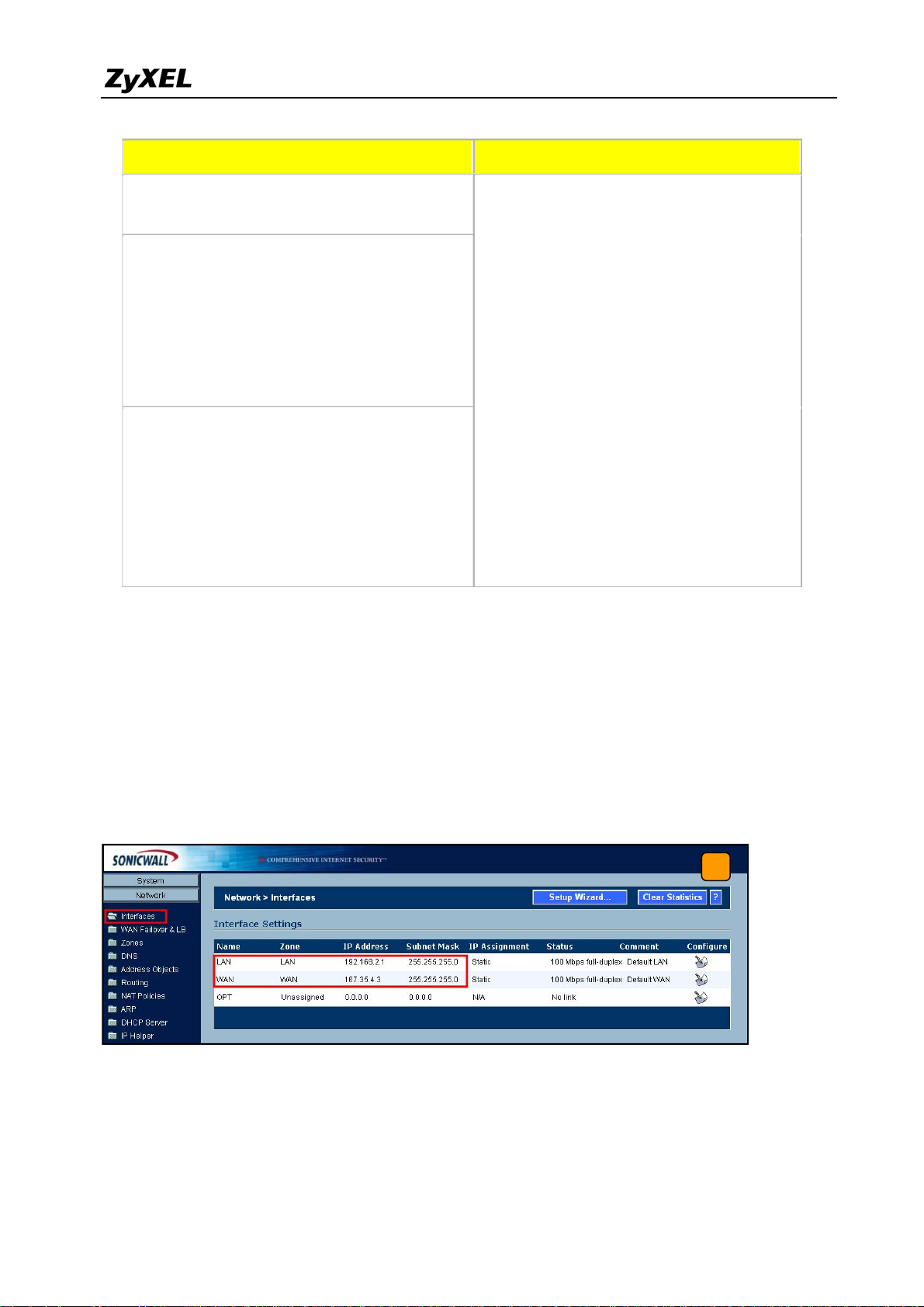
2) Using a web browser, login SonicWall by entering the LAN IP address of SonicWall in the
URL field. The default username and password is admin/password.
3) Switch to menu Network > Interfaces and configure the WAN/LAN IP address to WAN:
167.35.4.3 LAN: 192.168.2.1/24.
3
39
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 40

ZyWALL USG 2000 Support Notes
4) Switch to VPN > Settings, check Enable VPN check box and press Add button. This will
bring the VPN settings.
Note: The VPN Policy Wizard is an alternative way to set up the VPN rules.
4
5) Click the tab General, to bring the Security Policy settings and assign a name to this
policy. In this example, we use ToZyWALL. IPSec Primary Gateway Name or
Address is the ZyWALL's WAN IP Address (IP address of the remote gateway). In this
example, we use 210.110.7.1 in IPSec Primary Gateway Name or Address text box.
Then, enter the key string 123456789 in the text box Shared Secret.
5
40
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 41
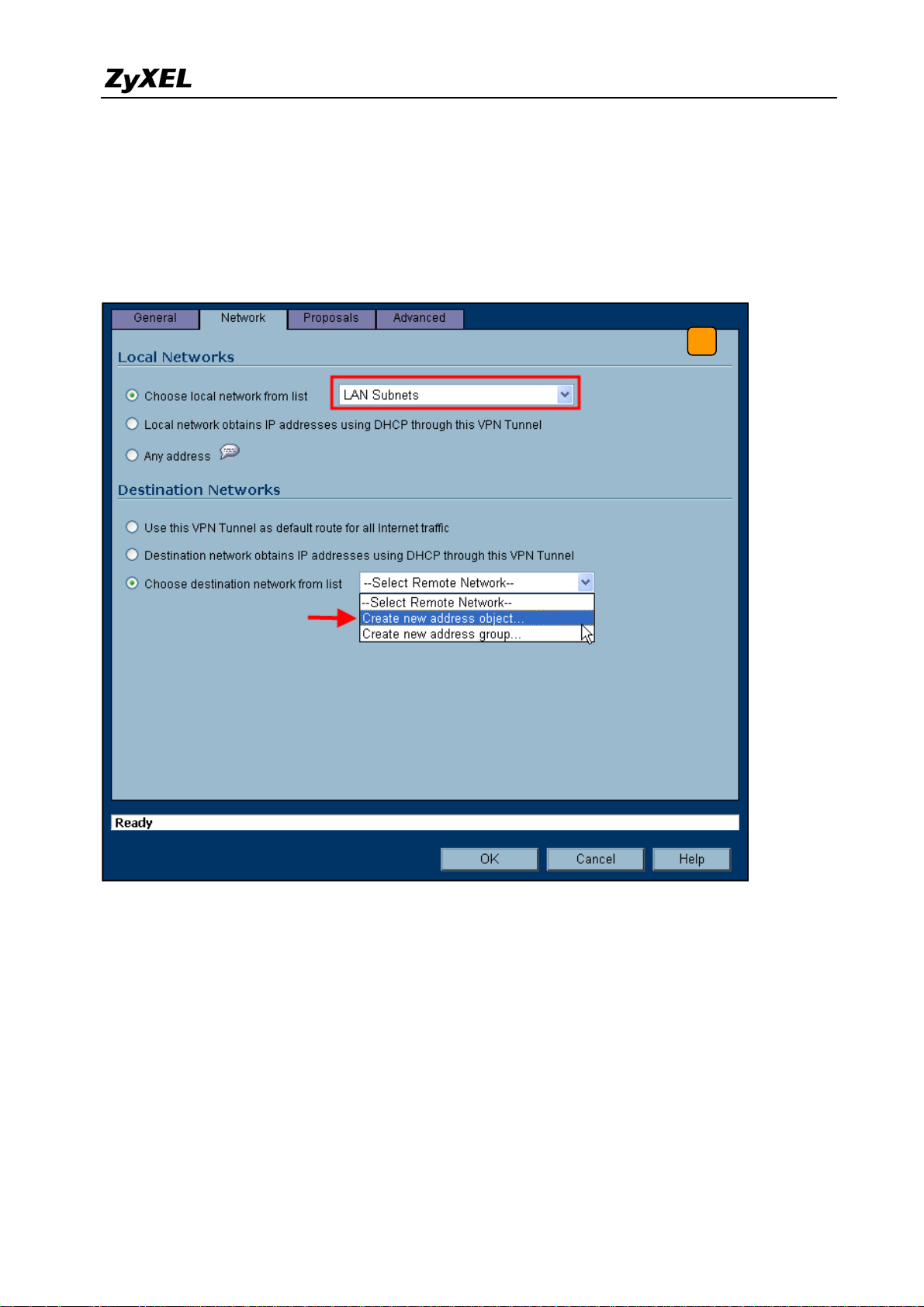
ZyWALL USG 2000 Support Notes
6) Switch to Network tab to configure the local and remote networks for VPN tunnel. We
choose the predefined “LAN Subnets” object from the local network drop down list. There
is no predefined address object for remote subnet. Therefore, we have to create a new
address object in the remote network drop down list. Then a new address object window
will pop-up.
6
All contents copyright (c) 2008 ZyXEL Communications Corporation.
41
Page 42

ZyWALL USG 2000 Support Notes
7) The name for this object can be for example “Remote_Subnet”. The Network IP Address
and the Subnet Mask are the remote site LAN subnet. In this example, enter 192.168.1.0
in Network text box and then type 255.255.255.0 in Subnet Mask text box. Then press
OK. Now after the address object successfully configured, the new address object
“Remote_Subnet” can be selected from the destination network drop down list.
7
8) Switch to Proposals tab. In IKE (Phase1) proposal settings, select Main mode, set DH
Group to Group1, Encryption to DES and Authentication to MD5. In IPSec (Phase2)
proposal settings, select ESP Protocol, Encryption to DES and Authentication to SHA1.
Then press the OK button.
8
42
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 43

ZyWALL USG 2000 Support Notes
9) Switch to Advanced tab. In the setting VPN policy bound to select Interface WAN.
Then press the OK button.
9
10) The VPN status page will show a new VPN rule. Make sure the rule has been enabled.
10
All contents copyright (c) 2008 ZyXEL Communications Corporation.
43
Page 44
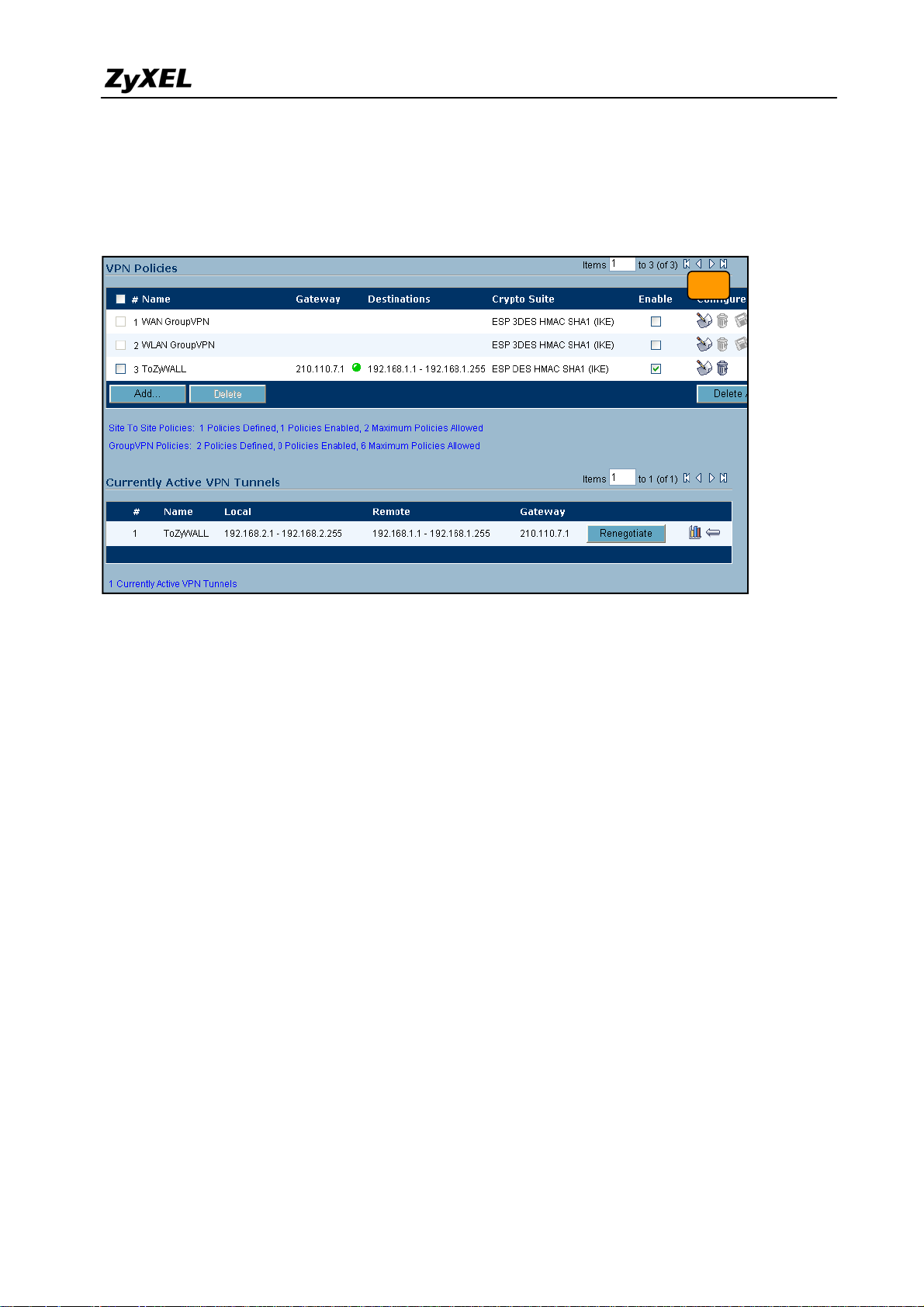
ZyWALL USG 2000 Support Notes
11) Ping the remote host to dial up the tunnel. We can check the connected VPN status in the
VPN status page. The VPN tunnel should appear in the Currently Active VPN Tunnels
page. It should show that the tunnel had been successfully built-up.
11
44
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 45

ZyWALL USG 2000 Support Notes
1.3 Remote Access VPN
Remote Access VPN provides a cost-effective alternative to standard dial-in remote access to a
company network. The users can connect to the network via the Internet, eliminating the
expensive long-distance or the toll-free dial-in costs.
The most common scenario for application might look like this: An employee is on the road
(i.e. teleworker). He can gain full network access simply by connecting to the Internet. During
the data transmission between remote and host, this connection should also provide
confidentiality (Data transferring in VPN tunnel with encryption).
Another genius application is a “Mobile office”: Teleworker or home & SOHO employee can
work at airport, cyber café, hot spots, hotel or home. The office building scope can be
eliminated and a global office can start to fully utilize the global resources.
ZyWALL USG 2000 incorporates IPSec, SSL VPN and L2TP over IPSec into a single box.
The customers can choose the most appropriate application for the remote access application.
1.3.1 IPSec VPN for Remote Access
In this scenario, we assume the ZyWALL USG 2000 admin configured the VPN settings in a
way to allow teleworker access internal network resource through remote access VPN. Since it
is unknown what IP address will the remote teleworker’s PC/notebook connect from, 0.0.0.0 is
used as for ZyWALL USG 2000’s remote gateway setting it represents “any IPs”. On the other
end, the teleworker use ZyWALL VPN client on their notebooks to establish IPSec VPN with
the main office.
45
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 46

ZyWALL USG 2000 Support Notes
So we are going to complete the following tasks.
z In ZyWALL USG 2000 create object ‘address’ for both local and remote networks
z In ZyWALL USG 2000 configure a VPN gateway and the VPN connection setting
z In ZyWALL VPN client configure the corresponding VPN setting in ZyWALL VPN
client
ZyWALL USG 2000 ZyWALL VPN Client
My address: ge2(10.59.1.45)
Secure gateway address: 0.0.0.0
Local: 192.168.2.0/24
Remote: 0.0.0.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Secure gateway address: 10.59.1.45
My address: Any
Local: Any
Remote: 192.168.2.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Encryption :DES
Authentication :MD5
Key Group :DH1
46
Page 47

ZyWALL USG 2000 Support Notes
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Encapsulation: Tunnel
Active Protocol: ESP
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Phase2
Encryption: DES
1.3.1.1 Steps to configure
Below is step by step configuration:
1) Login ZyWALL USG 2000 GUI and go to Object > Address to create an address object
(local subnet) for remote access.
2) Create another address object for the remote host. The IP Addr ess of the host should be
0.0.0.0, which means that remote user dials in dynamically.
3) Go to VPN > IPSec VPN > VPN Gateway to create gateway for remote a VPN client.
Because this kind of VPN is initialed from remote user, the Secure Gateway should be set as
47
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 48
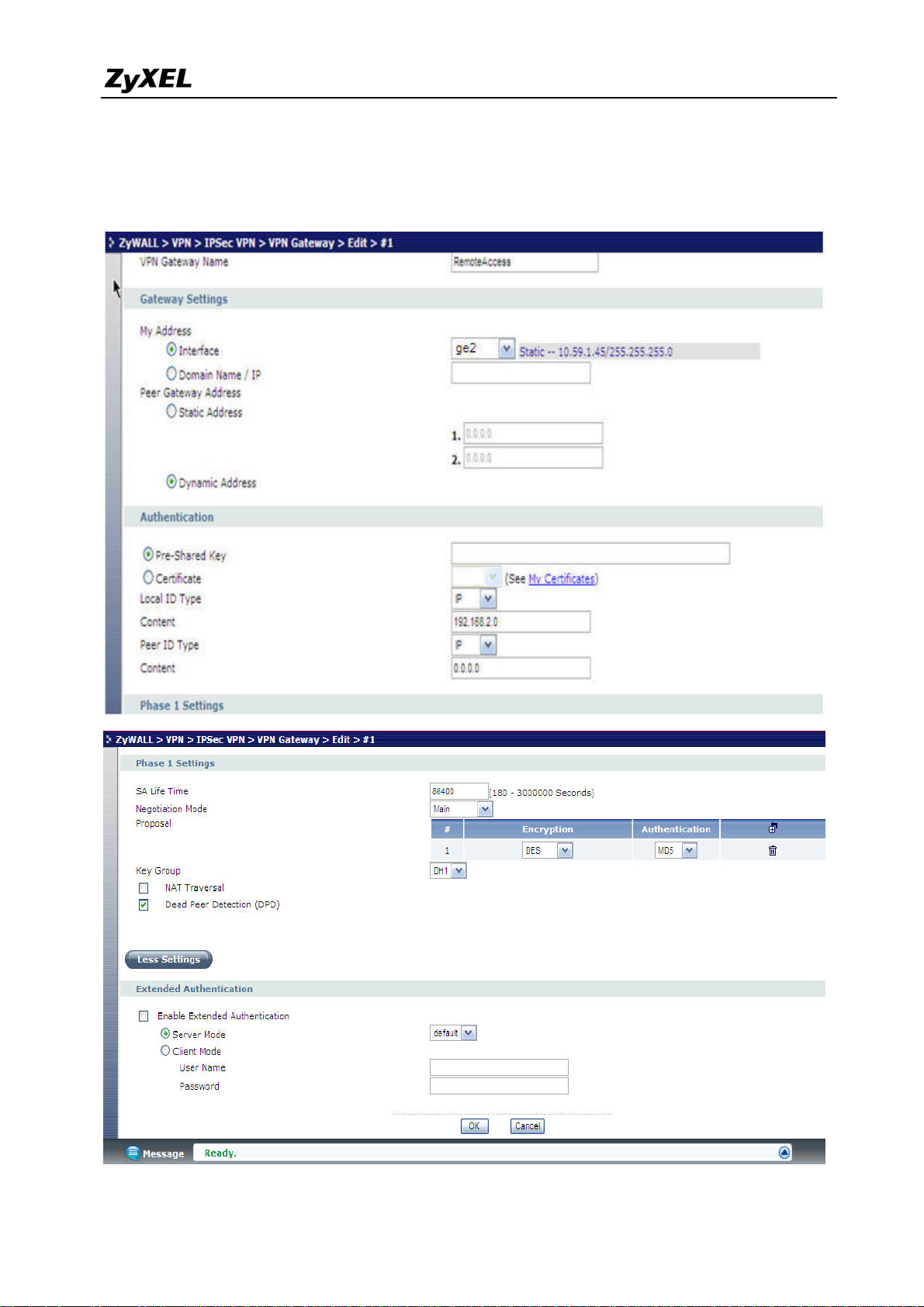
ZyWALL USG 2000 Support Notes
dynamic, 0.0.0.0. Also, the VPN peers should keep consistence with each other for other
parameters, such as Pre-Shared Key, ID Type, Encryption and Authentication proposal and so
on.
48
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 49

ZyWALL USG 2000 Support Notes
4) To create a VPN rule, go to VPN > IPSec VPN > VPN Connection. Check the “Use
Policy Route to control dynamic IPSec rules.” as defined in step 1 and step 2. Remote
policy should be a dynamic host address. We put VPN Gateway as dynamic as was defined in
step 3.
5) Go to remote host to configure ZyXEL VPN Client. We create a Net Connection set remote
access subnet to 192.168.2.x.
In My Identity, select local ID type as Any.
49
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 50

ZyWALL USG 2000 Support Notes
Note: Do not forget to enter Pre-Shared Key by clicking the button Pre-Shared Key.
The last step is to go to Security Policy to configure parameters for Phase1 and Phase 2. After
saving the configuration, the VPN connection should be initialed from the host site.
50
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 51

ZyWALL USG 2000 Support Notes
Tips for application:
1. Make sure both pre-shared key settings are the same in local and remote gateway.
2. Make sure both IKE proposal settings are the same in local and remote gateway.
3. Select the correct interface for the VPN connection.
4. The Local and Peer ID type and content must the opposite and not of the same content.
5. The Local Policy of ZyWALL USG 2000 should be ‘dynamic single host with the value
0.0.0.0’. The VPN tunnel should be initialed from the remote host site.
51
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 52

ZyWALL USG 2000 Support Notes
1.3.2 SSL VPN Application - Reverse Proxy
In order to provide a proper access for remote users, a web server is considered to implement
behind ZyWALL USG 2000. So, remote users can access the internal resource anywhere via a
secure path.
1.3.2.1 Scenario topology
USG2000
The default LAN subnet is combined to ge1 and default IP is 192.168.1.1. Please connect to
lan1 and ZyWALL USG 2000 will dispatch an IP for your PC then we can start to setup the
basic interface and routing setting.
1.3.2.2 Configuration flow
¾ Network setup
¾ Test
1.3.2.3 Configuration procedure
1) Connect your NB at ZyWALL USG 2000’s ge1 port. Get the IP address by DHCP and login
to ZyWALL USG 2000 by http://192.168.1.1. Configure the ZyWALL USG 2000’s ge1 and
ge2 interface with proper IP address.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
52
Page 53

ZyWALL USG 2000 Support Notes
2) Go to menu ZyWA LL> V PN > SSL VPN, create one access privilege rule by clicking the
Add icon.
Then continue to create user or group object. Here we create one user by click the “Add”
button.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
53
Page 54

ZyWALL USG 2000 Support Notes
Then, continue to create one application object. Here we create one for reverse proxy rule
using web application by click the “Add” button.
Login and check if WAN user can access to the ZyWALL GUI by HTTP.
Step 1. Initial a browser and try to connect to http://10.1.1.1
Step 2. Enter the ID/password, check the “log into SSL VPN” and click Login button.
Step 3. Click the Yes buttons until you see the following page, which is the ZW_http link
available in the application list.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
54
Page 55

ZyWALL USG 2000 Support Notes
)
1.3.3 SSL VPN Application – Network Extension
The network extension application enables the user to use specific client tools to access the
server. Unlike reverse proxy applications, the user won’t be limited to the access to the
available application list only. They can access any destination which is allowed and is
pre-defined in “SSL VPN network” list.
1.3.3.1 Scenario topology
WAN(wan1
LAN1
USG 2000
1.3.3.2 Configuration flow
¾ Network setup
All contents copyright (c) 2008 ZyXEL Communications Corporation.
55
Page 56

ZyWALL USG 2000 Support Notes
¾ Test
1.3.3.3 Configuration procedure
Network setup
The default ge1 subnet is combined to ge1 and default IP address is 192.168.1.1. Please
connect your NB to ge1 port and ZyWALL USG 2000 will dispatch an IP address. Then we
can start to setup the basic interface setting.
Step 1. Connect your NB at ZyWALL USG 2000’s LAN (lan1). Get the IP address by
DHCP and login to ZyWALL USG 2000 by http://192.168.1.1. Configure the
ZyWALL USG 2000’s LAN and WA N inte rface with proper IP address in
ZyWALL> Network > Interface.
Step 2. Create address Object for remote IP assignment. Switch to menu Object > Address
and click Add icon to add new user.
Configure a network range from 8.1.1.33 to 8.1.1.50 for remote IP assignment.
56
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 57

ZyWALL USG 2000 Support Notes
Step 3. Create address Object for VPN network which allows remote users to access to.
Switch to menu Object > Address and click Add icon to add new address.
Configure a network subnet 192.168.1.0/24.
Step 4. Modify the SSL rule we created for LAB1 by clicking the modify icon.
57
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 58

ZyWALL USG 2000 Support Notes
Step 5. Keep other settings but choose object we just created for network extension settings
as follows. Click OK button.
Test: Login and check if WAN user can access to the ZyNOS ZyWALL GUI by HTTP
Step 1. Config your NB with IP address 10.1.1.33 and connect it to ZyWALL USG 2000’s
WAN site (ge2). Initial a browser and try to connect to https://10.1.1.1
Step 2. Enter the ID/password, check the “log into SSL VPN” and click Login button.
58
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 59

ZyWALL USG 2000 Support Notes
Step 3. Click Yes buttons until you see the following page. You can find a small window is
processing about the security extender rule (for network extension).
59
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 60

ZyWALL USG 2000 Support Notes
Step 4. After a while, the window will show you the information about network extension.
Step 5. Please check the IP address assigned and routing info on the remote PC/NB.
You will see one PPP interface as below by typing ‘ipconfig’ on command prompt.
60
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 61

ZyWALL USG 2000 Support Notes
You will see the routing information accordingly as below by typing ‘route print’.
Step 6. Still try to connect the ZW_http link. You should be able to access the ZyWALL
login page then.
Step 7. Try to ftp the device and see if you can access the ZyNOS ZyWALL by FTP tool. If
so, that means you have successfully established the network extension and aren’t
limited just by the available application list.
61
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 62

ZyWALL USG 2000 Support Notes
1.3.4 L2TP over IPSec Application
1.3.4.1 Scenario topology
USG 2000
1.3.4.2 Configuration flow
¾ Create object
¾ Configure the default L2TP rule in IPSec VPN Gateway
¾ Configure the default L2TP rule in IPSec VPN Connection
¾ Configure the L2TP rule
¾ Configure Policy Route for L2TP
¾ Remote PC/NB L2TP Setup on WinXP or Win2K
1.3.4.3 Configuration Procedure
Create Object
Step 1. Switch to menu Object > Address, create two object for further VPN connection
setting.
L2TP_IFACE, HOST, 10.1.1.1
L2TP_HOST, HOST, 0.0.0.0
L2TP_Pool, Range, 192.168.2.1 ~ 192.168.2.10
Step 2. Switch to menu Object > User/Group, create one object for L2TP application.
L2TP_user/1234, Local user
All contents copyright (c) 2008 ZyXEL Communications Corporation.
62
Page 63

ZyWALL USG 2000 Support Notes
Configure the default L2TP rule in IPSec VPN Gateway
Step 1. Go to menu VPN > IPSec VPN > VPN Gateway, click the Default_L2TP_VPN_GW
entry’s Edit icon.
Step 2. Ensure the My Address is configured with Interface ge2 with WAN IP address,
10.1.1.1. And the pre-shared key is 12345678. Click the OK button.
Step 3. Enable the rule by clicking the enable icon.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
63
Page 64

ZyWALL USG 2000 Support Notes
Configure the default L2TP rule in IPSec VPN Connection
Step1. Switch to menu VPN > IPSec VPN > VPN Connection, click the
Default_L2TP_VPN_GW entry’s Edit icon.
Step 2. Especially configure the policy enforcement as below. Click OK button.
Step 3. Enable the rule by clicking the enable icon.
64
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 65

ZyWALL USG 2000 Support Notes
Configure the L2TP rule
Step 1. Go to menu VPN > L2TP VPN, configure it as follows.
Configure Policy Route for L2TP
Step 1. Go to menu Network > Routing > Policy Route, configure it as follows.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
65
Page 66

ZyWALL USG 2000 Support Notes
Remote PC/NB L2TP Setup on WinXP or Win2K
Note: Please ensure your computer is using Windows XP and Windows 2000 for the follow
settings.
Before you configure the client, issue one of the following commands from the Windows
command prompt to make sure the computer is running the Microsoft IPSec service. Make sure
you include the quotes.
• For Windows XP, use net start "ipsec services".
• For Windows 2000, use net start "ipsec policy agent".
In Windows XP do the following to establish an L2TP VPN connection.
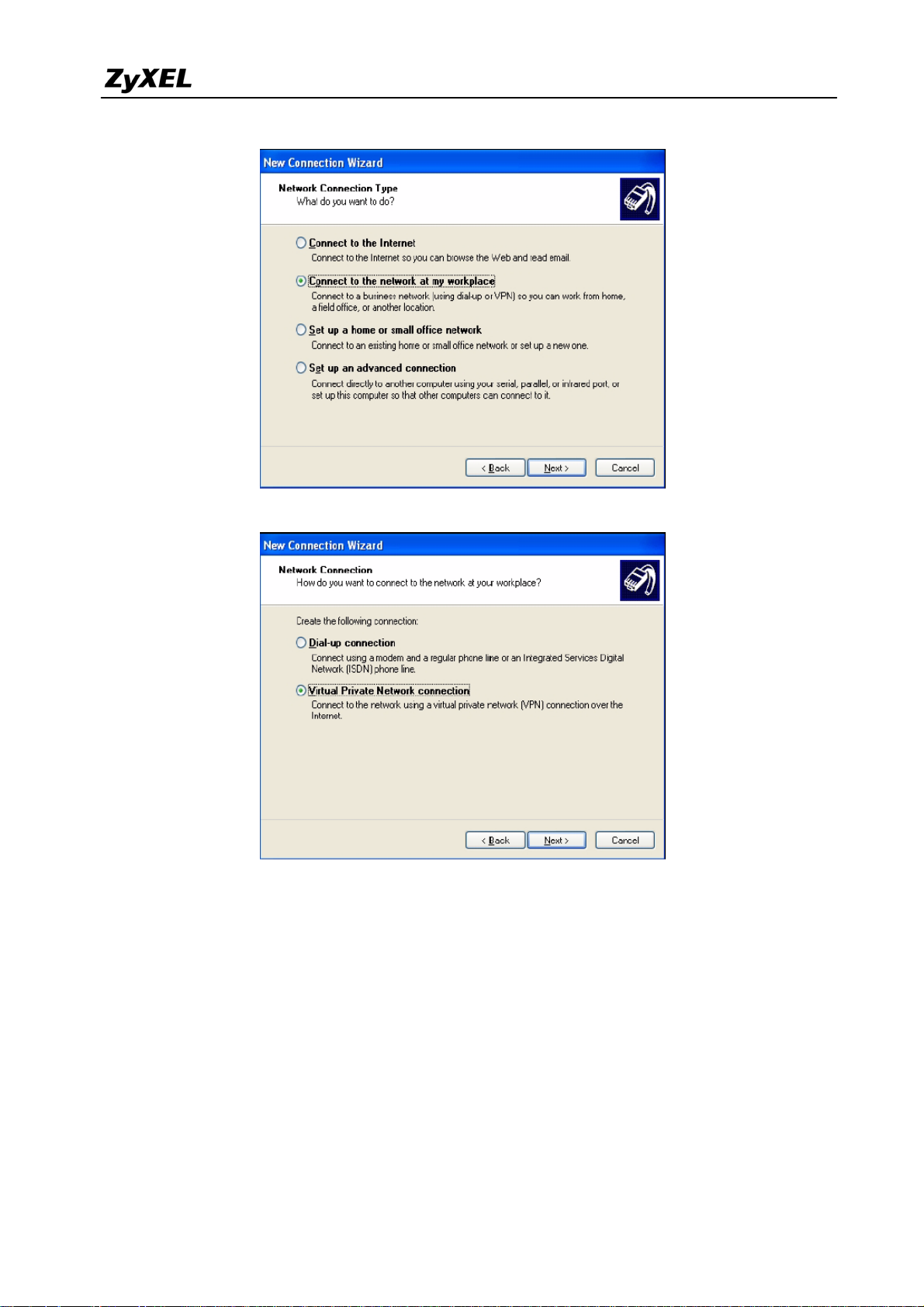
Step 1 Click Start > Control Panel > Network Connections > New Connection Wizard.
Step 2 Click Next in the Welcome screen.
Step 3 Select Connect to the network at my workplace and click Next.
66
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 67
ZyWALL USG 2000 Support Notes
Step 4 Select Virtual Private Network connection and click Next.
Step 5 Type L2TP to ZyWALL as the Company Name.
Step 6 Select Do not dial the initial connection and click Next.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
67
Page 68

ZyWALL USG 2000 Support Notes
Step 7 Enter the domain name or WAN IP address configured as the My Address in the
VPN gateway configuration that the ZyWALL is using for L2TP VPN (10.1.1.1 in
this example). Click Next.
Step 8 Click Finish.
68
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 69

ZyWALL USG 2000 Support Notes
Step 9 The Connect L2TP to ZyWALL screen appears. Click Properties > Security.
Step 10 Click Security, select Advanced (custom settings), and click Settings.
Step 11 Select Optional encryption allowed (connect even if no encryption) and the Allow
these protocols radio button. Select Unencrypted password (PAP) and clear all of
the other check boxes. Click OK.
69
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 70

ZyWALL USG 2000 Support Notes
Step 12 Click IPSec Settings.
Step 13 Select the Use pre-shared key for authentication check box and enter the pre-shared
key used in the VPN gateway configuration that the ZyWALL is using for L2TP VPN.
Click OK.
70
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 71

ZyWALL USG 2000 Support Notes
Step 14 Click Networking. Select L2TP IPSec VPN as the Type of VPN. Click OK.
Step 15 Enter the user name and password of your ZyWALL account. Click Connect.
Step 16 A window appears while the user name and password are verified.
Step 17 A ZyWALL-L2TP icon displays in your system tray. Double-click it to open a status
screen.
Step 18 Click Details to see the address that you received is from the L2TP range you
specified on the ZyWALL (192.168.10.10-192.168.10.20).
Step 19 Access the HTTP server behind the ZyWALL USG 2000 to make sure your access
works.
71
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 72

ZyWALL USG 2000 Support Notes
72
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 73

ZyWALL USG 2000 Support Notes
V
1.4 Large-scale VPN Deployment
With the business growing, network administrator will face the more and more complicated
VPN topology and applications. ZyWALL USG2000 supports various types of VPN topology
that can meet the needs of the organizations of any size.
ZyWALL USG2000 VPN Topology supports fully meshed topology that can be deployed
when the total number of remote site is small. Star topology is recommended when the total
number of remote sites is high, Even more flexible design, Star and Mesh mixed topology
(cascading topology) can be applied for a global distributed environment.
1.4.1 Fully Meshed Topology
All models in ZyWALL series
can support Fully-meshed VPN
topology, including: ZyWALL 2
Plus/5/35/70/1050/USG2000
Madrid
London
In a fully-meshed VPN topology, an
user can access to resources within
remote VPN sites provided that a
PN tunnel was already established
Oslo
In this topology, each site
plays the same role – handles
incoming encrypted traffic or
Hannover Paris
encrypts outgoing traffic
designated to a remote site
1) In order to achieve the VPN connectivity of all sites in the fully meshed VPN topology, all
the sites must be directly connected with VPN tunnels to all the remote sites. The network
administrator has to pay huge establishment and maintenance effort with the new remote
site joining. This VPN topology is suitable for only a few sites connected with VPN.
2) For example, to complete the above topology, administrator needs to repeat the same steps
at least five times and totally needs to establish 10 VPN tunnels. The tunnels list follows:
Tunnel 1: London ÅVPN ÆMadrid
73
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 74

ZyWALL USG 2000 Support Notes
A
Tunnel 2: London ÅVPN ÆParis
Tunnel 3: London ÅVPN ÆHannover
Tunnel 4: London ÅVPN ÆOslo
Tunnel 5: Madrid ÅVPN Æ Paris
Tunnel 6: Madrid ÅVPN Æ Hannover
Tunnel 7: Madrid ÅVPN Æ Oslo
Tunnel 8: Paris ÅVPN Æ Hannover
Tunnel 9: Paris ÅVPN Æ Oslo
Tunnel 10: Hannover ÅVPN Æ Oslo
3) For help on building up the 10 tunnels, please refer to the section ZyWALL USG2000 to
ZyWALL USG2000 VPN tunnel configuration steps . We will introduce the configuration
steps for a VPN concentrator that will greatly help to reduce the total number of tunnels.
1.4.2 Star Topology
In a Star VPN topology, any user in a
spoke site (in here it’s Madrid) can
access to resources within another
spoke site (London) via the central
site – Amsterdam
Madrid
In a Star VPN topology, ZyWALL
1050 acts as a central site (enabling
Hub & Spoke VPN) and spoke sites
can be any model of ZyWALL series
Paris
London
Central site
Amsterdam
n user in a spoke site (in
here it’s Oslo) can access
resources within central
site – Amsterdam
Oslo
Hannover
74
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 75

ZyWALL USG 2000 Support Notes
The ZyWALL USG2000 supports Star topology via the VPN concentrator feature. The
VPN concentrator can help to reduce the VPN tunnel numbers and allows centralized VPN
tunnel management.
The topology used for our VPN concentrator guide.
This topology is designed to simulate a global VPN network deployment. The company has
a global headquarters in Taiwan and other offices around the world.
This company decided to build up a VPN concentrator to let all the offices’ internal network to
be shared and interconnected based on a security link.
We will separate each group as a member of each office and build up the VPN tunnel with
headquarter and then to route the VPN traffic across the HQ to the destination office’s internal
network.
The VPN configuration parameter
Remote Office HQ
WAN: 10.59.1.11
~
All contents copyright (c) 2008 ZyXEL Communications Corporation.
WAN: 10.59.1.10
LAN: 192.168.100.0/24
75
Page 76

ZyWALL USG 2000 Support Notes
WAN: 10.59.1.17
LAN: 192.168.101.0/24
~
LAN: 192.168.119.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Negotiation Mode : Main
Pre-share key: 123456789
Authentication :MD5
Encapsulation: Tunnel
Active Protocol: ESP
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Phase 1
Encryption :DES
Key Group :DH1
Phase2
Encryption: DES
Setup VPN tunnel between each remote office and HQ
We used the Netherland site (NL) as an example to show how to setup tunnel between NL and
HQ. Please refer the above VPN parameter table to setup the VPN gateway and connection as
I don’t list the detail configuration steps here,.
Configure the NL site address object for each remote office subnet
All contents copyright (c) 2008 ZyXEL Communications Corporation.
76
Page 77

ZyWALL USG 2000 Support Notes
Setup NL site address group that includes all the remote office subnets; the address object
group is used as a policy route destination criterion.
The screenshot below is the NL site VPN Gateway status page.
NL site VPN Connection status page
77
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 78

ZyWALL USG 2000 Support Notes
NL site policy route for VPN traffic, this policy route is used to indicate that the ZyWALL
1050 sends the packets to the VPN tunnel.
HQ VPN concentrator configuration steps:
Here are step by step instructions on how to setup the VPN concentrator in HQ to route all
the remote sites’ VPN traffic.
The amount of tunnels needed to be configured in HQ ZyWALL1050 is the amount of the
remote sites.
This means that if we want HQ to route 5 remote sites VPN traffic, we need to configure 5
VPN tunnels from remote office to HQ.
For the HQ VPN tunnel setting, please refer to the table below.
Remote Office HQ
WAN: 10.59.1.11 WAN: 10.59.1.10
All contents copyright (c) 2008 ZyXEL Communications Corporation.
78
Page 79

ZyWALL USG 2000 Support Notes
~
WAN: 10.59.1.17
LAN: 192.168.101.0/24
~
LAN: 192.168.119.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
LAN: 192.168.100.0/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Perfect Forward Secrecy (PFS): None
Setup the remote offices’ subnets address objects for the further VPN configuring.
Setup the HQ VPN Gateway for all the remote sites
79
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 80

ZyWALL USG 2000 Support Notes
Setup the HQ VPN connection for all the remote sites
The next step is the most important one. We need to build up a VPN concentrator and join all
the remote sites’ VPN traffic to it.
Switch to ZyWALL USG2000 > Configuration > Network > IPSec VPN > Concentrator and
then click the add icon to add a new concentrator.
On the concentrator edit page, click the add icon to add VPN connection to this concentrator.
The VPN traffic can be routed by HQ once the VPN connection has been added to the
80
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 81
ZyWALL USG 2000 Support Notes
concentrator. If this tunnel is already included in the concentrator, user doesn’t need to add any
policy route to the VPN tunnel.
Now after the VPN concentrator setup, all the remote VPN tunnels have been linked to the HQ
concentrator and remote sites can reach other remote sites via HQ.
The VPN concentrator is designed to route the remote sites’ VPN traffic. However, user still
needs to setup the policy route for local subnet VPN traffic. For example, if we setup the VPN
concentrator only for HQ and remote sites A & B, then the A subnet can connect to B subnet
but HQ subnet can’t connect to neither A nor B subnet.
Thus, this depends on how customers want to deploy their Global VPN network.
We can add the following policy route to allow the HQ subnet to connect with all the
concentrator’s remote subnets.
81
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 82

ZyWALL USG 2000 Support Notes
82
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 83

ZyWALL USG 2000 Support Notes
ondo
sterda
Singapore
A
1.4.3 Star-Mesh Mixed Topology
Taipei
An user in a spoke site
(in here it’s T a ipei) can
access the resources
on regional central
site – Singapore
Frankfurt
In a Star-Mesh mixed VPN topology,
any user in a spoke site (in here it’s
Frankfurt) can access the resources
on another spoke site (London) via the
EU central site – Amsterdam
Backbone tunnel
EU Central site
Am
m
sia Central site
Backup tunnel
Tokyo
n
L
If an user in London site needs to access resources
outside the EU sites, i.e. Tokyo site, the traffic will be
routed to the Asia central site (Singapore) then again
routed to the final destination – Tokyo spoke site
In a Star-mesh mixed VPN topology, ZyWALL USG2000 acts as a regional central site
(enabling Hub & Spoke VPN) and spoke sites can be any model of ZyWALL series. The
Star – Mesh Mixed Topology is well suited for an enterprise having a regional operation
center acting as a regional hub and spoke VPN network in the area. The connection between
each regional operation center will be backbone VPN tunnel. To ensure the communication
continuity, we can use VPN HA (secondary security gateway) to configure a backup VPN
tunnel in case the primary VPN connection failure.
We use the below presented network topology to explain how to configure Star-Mesh
Mixed Topology between all the ZyWALL series devices. The ZyWALL USG2000 act as a
Regional Center devices whereas ZyWALL 2 Plus, 5, 35 and 70 are the regional remote sites’
devices which are building VPN tunnel back to the Regional Center and provide connection
with the other area remote nodes via the VPN tunnel between the two Regional Centers.
83
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 84
ZyWALL USG 2000 Support Notes
Asia Region VPN Concentrator
Europe Region VPN Concentrator
ZyWALL5
ZyWALL35
WAN:179.25.106.124
LAN:192.168.12.1/24
Regional Center
ZyWALL USG2000
WAN1:179.25.3.24
WAN2:179.25.133.4
WAN:179.25.13.2
LAN:192.168.11.1/24
Primary VPN
Secondary VPN
Configuration Steps for Asia Region VPN Concentrator
ZyWALL5 and ZyWALL35 interface and VPN setting
ZyWALL70
Regional Center
ZyWALL USG2000
ZyWALL 2 Plus
WAN:220.123.65.117
LAN:192.168.21.1/24
WAN:220.123.97.7
LAN:192.168.22.1/24
WAN1:220.123.113.8
WAN2:220.123.119.9
Please configure the ZyWALL5 WAN and LAN interface as the topology diagram shown
above. We can check the status page to confirm the correctness. Please refer to ZyWALL5
user guide for detail interface setting steps.
The VPN configuration parameters in Asia Region
Regional Remote Sites Regional Center
ZyWALL5 WAN: 179.25.106.124
WAN: 179.25.3.24
Local Policy: 192.168.0.0/16
Local Policy: 192.168.12.0/24
84
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 85

ZyWALL USG 2000 Support Notes
Remote Policy: 192.168.0.0/16
Remote Policy: 192.168.12.0/16
ZyWALL35 WAN: 179.25.13.2
Local Policy: 192.168.11.0/24
Remote Policy: 192.168.0.0/16
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Local Policy: 192.168.0.0/16
Remote Policy: 192.168.11.0/16
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
The next step is to configure the VPN tunnel setting. Following the ZyWALL5 VPN design
logic, we have to define the local and remote policies to force the traffic going through the
VPN tunnel to the remote site. For example, the traffic from ZyWALL5 will be sent to all the
remote sites’ devices like ZyWALL35 (LAN subnet: 192.168.11.x), local center’s ZyWALL
USG2000 (LAN subnet: 192.168.21.x), remote center’s ZyWALL USG2000 (LAN subnet:
192.168.20.x), ZyWALL 2 Plus (LAN subnet: 192.168.21.x) and ZyWALL70 (LAN subnet:
192.168.22.x) by building one VPN tunnel with local center ZyWALL USG2000. Thus a
separate VPN tunnel to each remote site is not needed. We will use a class B subnet
(192.168.0.0/255.255.0.0) as remote policy in order to include all ranges of the remote policies
requirements.
The Local Policy is the local subnet 192.168.12.0/24 and Remote Policy is 192.168.0.0/16
for the tunnel between ZyWALL5 and local center ZyWALL USG2000. Please switch to
menu Security > VPN > Global Setting and activate the “VPN rules skip applying to the
overlap range of local and remote IP addresses” option because the local and remote policies
are in the overlap range in this application. If this feature is not activated, you will fail to
access device because of triggering VPN tunnels.
85
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 86

t
L
A
N
e
t
a
o
a
l
’
e
p
n
0
e
N
V
P
r
y
C
o
fo
n
t
A
U
o
V
k
n
t
W
r
w
0
o
l
e
t
t
o
n
d
p
Z
WALL
SG 200
Suppor
Notes
Based
the VPN
the VPN
USG200
only afte
VPN set
on the VP
status pag
setting. Th
0 didn’t se
r both sites
ing steps.
configur
will brief
e VPN can
up the corr
’ VPN setu
tion param
ist the VP
t be dialed
sponding
is done.
ter table t
tunnel in
up for testi
PN tunnel
lease refer
finish the
rmation li
g because
until now.
o the Zy
PN tunne
e followin
the remote
The test an
ALL5 user
configura
g screen sh
ZyWALL
d debug ca
guide for
ion and
t after
start
etail
There
ZyWAL
are similar
35 WAN
configurati
nd LAN i
ll contents c
on steps fo
terface are
pyright (c) 2
the ZyW
set as follo
08 ZyXEL
LL35 inte
.
ommunicati
face and th
ns Corporati
VPN setu
n.
. The
86
Page 87

e
P
A
s
o
0
r
g
g
y
C
p
h
c
U
o
h
n
Z
0
o
r
U
t
c
n
Z
WALL
SG 200
Suppor
Notes
Pleas
remote I
The V
make sure
addresses
PN tunnel
to activate
” option be
tatus page
the “VPN
fore startin
after confi
ules skip a
to setup t
ured the lo
plying to t
e VPN tu
al center
e overlap
nel.
yWALL
ange of lo
SG2000 tu
al and
nel.
87
ll contents c
pyright (c) 2
08 ZyXEL
ommunicati
ns Corporati
n.
Page 88

ZyWALL USG 2000 Support Notes
As soon as we finish the configuration of ZyWALL5 and ZyWALL35, we can move to
ZyWALL USG2000’s configuration.
Asia Regional Center ZyWALL USG2000 interface and VPN concentrator setting
The VPN configuration parameter for Asia and Europe regional Center ZyWALL
USG2000
Asia Regional Center ZyAWLL USG2000 Europe Regional Center ZyAWLL USG2000
WAN1:179.25.3.24
WAN2:179.25.133.4
LAN:192.168.10.1/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
WAN1:220.123.113.8
WAN2:220.123.119.9
LAN:192.168.20.1/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Perfect Forward Secrecy (PFS): None
Authentication: SHA1
Please refer to the application topology to setup the ZyWALL USG2000 interface first. We
can move to next steps only after setting up the interface. We use ge1 as LAN interface and IP
88
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 89

ZyWALL USG 2000 Support Notes
address is 192.168.10.1/255.255.255.0. The ge2 and ge3 are WAN1 and WAN2 interfaces and
IP address are 179.25.3.24/255.255.0.0 and 179.25.133.4/255.255.0.0.
We have to pre-configure some address objects for the later VPN configuration
requirements. The needed address objects list is as follows:
The address object AsiaRegion (192.168.10.0 – 192.168.15.0) and EuropeRegion
(192.168.20.0 – 192.168.25.0) are used for the two regional center VPN concentrators
employed. When Asia region site like ZyWALL5 (192.168.12.0) tries to access the other
region’s remote site like ZyWALL70 (192.168.22.0) it will match these two addresses’ object
ranges and ZyWALL USG2000 can do next processing.
This ZyWALL USG2000 is the local center of Asia region. We need to setup the VPN
tunnel between local sites ZyWALL5 and ZyWALL35 and Europe region center ZyWALL
USG2000.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
89
Page 90

ZyWALL USG 2000 Support Notes
Follow the VPN parameter tables to setup the three VPN gateways (IKE / IPSec Phase1).
For detail steps please refer to the ZyWALL USG2000 user guide. We have to configure a
secondary security gateway for the VPN gateway between both of the regional centers’
ZyWALL USG2000s. The VPN connection can fail over to secondary gateway in case the
parameter gateway fails.
After configuration, there will be three VPN gateways listed in the VPN Gateway status
page.
90
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 91

ZyWALL USG 2000 Support Notes
The next step is to create the VPN connection (IPSec / IPSec Phase2). Make sure the
parameters are configured correctly, otherwise the VPN will fail to dial. Below is the VPN
connection global page.
Now, we have already successfully added three VPN connection rules and we can start to
edit our regional VPN concentrator. Switch to Concentrator sub menu and click the Add icon
to add a new concentrator.
Give a name to this concentrator and then click add icon to make the existing VPN
connection become a member of this concentrator.
91
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 92
ZyWALL USG 2000 Support Notes
The remote regional center ZyWALL USG2000 VPN connection is also treated as a
member of this concentrator and the packets will be sent to the remote center first and then
following the remote concentrator setting will be routed to the destination sites where the
traffic destination is the site allocated under remote VPN concentrator.
We had finished all settings of the Asia Region VPN concentrator. Now you can test the
local VPN concentrator link. Later on, we can test the connection of both concentrators. This
will be after we setup the Europe Region VPN concentrator.
Configuration Steps for Europe Region VPN Concentrator
ZyWALL 2 Plus and ZyWALL70 interface and VPN setting
ZyWALL 2 Plus WAN and LAN interface setting
The VPN configuration parameters in Europe Region
Regional Remote Sites Regional Center
ZyWALL 2 Plus WAN: 220.123.65.117
Local Policy: 192.168.21.0/24
Remote Policy: 192.168.0.0/16
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Remote Policy: 192.168.21.0/16
WAN: 220.123.113.8
Local Policy: 192.168.0.0/16
92
Page 93

ZyWALL USG 2000 Support Notes
ZyWALL70 WAN: 220.123.97.7
Local Policy: 192.168.22.0/24
Local Policy: 192.168.0.0/16
Remote Policy: 192.168.0.0/16
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Remote Policy: 192.168.22.0/16
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
Remember to activate “VPN rules skip applying to the overlap range of local and remote IP
addresses” option before configuring the VPN tunnel.
Follow the VPN parameter table to configure the VPN tunnel.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
93
Page 94

ZyWALL USG 2000 Support Notes
ZyWALL70 WAN and LAN interface setting.
Remember to activate “VPN rules skip applying to the overlap range of local and remote IP
addresses” option before configuring the VPN tunnel.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
94
Page 95

ZyWALL USG 2000 Support Notes
Follow the VPN parameter table to configure the VPN tunnel.
After we finish the configuration of ZyWALL 2 Plus and ZyWALL70, we can move to
ZyWALL USG2000’s configuration.
Europe Regional Center ZyWALL USG2000 interface and VPN concentrator setting
The VPN configuration parameter for Asia and Europe regional Center ZyWALL
USG2000
Asia Regional Center ZyAWLL USG2000 Europe Regional Center ZyAWLL USG2000
WAN1:179.25.3.24
WAN2:179.25.133.4
LAN:192.168.10.1/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
WAN1:220.123.113.8
WAN2:220.123.119.9
LAN:192.168.20.1/24
Phase 1
Negotiation Mode : Main
Pre-share key: 123456789
Encryption :DES
Authentication :MD5
Key Group :DH1
Phase2
Encapsulation: Tunnel
Active Protocol: ESP
Encryption: DES
Authentication: SHA1
Perfect Forward Secrecy (PFS): None
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Perfect Forward Secrecy (PFS): None
Encryption: DES
Authentication: SHA1
95
Page 96

ZyWALL USG 2000 Support Notes
Please refer to the application topology to setup the ZyWALL USG2000 interface first.
Then we can move to setting the VPN.
We have to pre-configure some address objects for the later VPN configuration
requirements. The needed address objects list is as follows.
This ZyWALL USG2000 is the local center of Europe region. We need to setup the VPN
tunnel between local sites ZyWALL 2 Plus and ZyWALL70 and Asia region center ZyWALL
USG2000. Follow the VPN parameter tables to setup the three VPN gateways (IKE / IPSec
Phase1). We have to configure a secondary security gateway for the VPN gateway between
both regional centers’ ZyWALL USG2000s.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
96
Page 97

ZyWALL USG 2000 Support Notes
After configuration, there will be three VPN gateways listed in the VPN Gateway status
page.
The next step is to create the VPN connection (IPSec / IPSec Phase2). Make sure the
parameters are correctly configured; otherwise the VPN will fail to dial. Below is the VPN
connection global page.
All contents copyright (c) 2008 ZyXEL Communications Corporation.
97
Page 98

ZyWALL USG 2000 Support Notes
Now, we already successfully added the three VPN connection rules and we can start to edit
our regional VPN concentrator. Switch to the Concentrator sub menu and click the Ad d icon to
add a new concentrator.
Assign a name to this concentrator and then click the add icon to make the existing VPN
become the member of this concentrator.
The remote regional center ZyWALL USG2000 VPN connection is also treated as a
member of this concentrator and the packets will be sent to the remote center first and then
All contents copyright (c) 2008 ZyXEL Communications Corporation.
98
Page 99

ZyWALL USG 2000 Support Notes
g
following the remote concentrator setting will be routed to the destination sites where the
traffic destination is the site allocated under remote VPN concentrator.
We have finished all the Star-Mesh Mixed VPN topology setting. Now you can test the local
VPN concentrator link. Also, you can try the connection between both concentrators’ site.
1.5 Device HA
In the Global or multi-site Enterprise network deployment, reliability is another major concern
while planning a VPN deployment.
ZyWALL USG 2000 provides advanced features to support the following scenarios to
achieve high availability of the VPN infrastructure.
Main Office
Resilience of WAN connectivity – VPN HA
supports redundant gateway so that the
network path of VPN can always be available
ZyWALL USG 2000 (Master)
ZyWALL USG 2000
Mitigate the impact of Single Point of Failure –
device HA greatly reduces the device downtime
and
uarantees the non-stop operation
Remote Site 1
ZyWALL 2 Plus
ZyWALL 35
Remote Site 2
The benefits for the customer are:
‧ Dealing with the impact of unreliable WAN connectivity
‧ Mitigates the impact of Single Point of Failure
99
All contents copyright (c) 2008 ZyXEL Communications Corporation.
Page 100

ZyWALL USG 2000 Support Notes
Below is the Application topology. The L3 switch is configured to three VLANs to simulate
the internet environment, and the traffic can be routed between each VLAN.
100
All contents copyright (c) 2008 ZyXEL Communications Corporation.
 Loading...
Loading...