ZyXEL ZYWALL USG Reference Manual

Quick Start Guide
ZyWALL / USG (ZLD) Series
Security Firewalls
Version: 4.11
Edition 1, 04/2015
CLI Reference Guide
Default Login Details
LAN Port IP Address
User Name
Password
www.zyxel.com
http://192.168.1.1
admin
1234
Copyright © 2011
Copyright © 2015 ZyXEL Communications Corporation
ZyXEL Communications Corporation
This is a Reference Guide for a series of products intended for people who want to configure ZLDbased ZyWALL / USGs via Command Line Interface (CLI).
Some commands or command options in this guide may not be available in your
product. See your product's User’s Guide for a list of supported features. Every effort
has been made to ensure that the information in this guide is accurate.
Please refer to www.zyxel.com for product specific User Guides and product certifications.
Do not use commands not documented in this guide.
How To Use This Guide
•Read Chapter 1 on page 21 for how to access and use the CLI (Command Line Interface).
•Read Chapter 2 on page 35 to learn about the CLI user and privilege modes.
Related Documentation
• Quick Start Guide
The Quick Start Guide shows how to connect the ZyWALL / USG and access the Web
Configurator wizards. (See the wizard real time help for information on configuring each screen.)
It also contains a connection diagram and package contents list.
• User’s Guide
The User’s Guide explains how to use the Web Configurator to configure the ZyWALL / USG.
It is recommended you use the Web Configurator to configure the ZyWALL / USG.
• Knowledge Base
See Support > Knowledge Base at the ZyXEL website for FAQ s, application examples,
troubleshooting and other technical information on the ZyWALL / USG.

Introduction ........................................................................................................................................19
Command Line Interface .........................................................................................................................21
User and Privilege Modes .......................................................................................................................35
Reference ...........................................................................................................................................39
Object Reference ...................................... ... ... ... .... ... ... ... .... ... .................................................................41
Status ......................................................................................................................................................43
Registration .................................. ................................................................ ...........................................49
AP Management .....................................................................................................................................53
Wireless LAN Profiles ..... ... ... .... ... ... ... .... ... ... ................................................ .... ... ....................................56
Rogue AP ................................................................................................................................................68
Wireless Frame Capture ........................................................................................... .... ... ... ....................72
Dynamic Channel Selection ....................................................................................................................74
Wireless Load Balancing ................................. ... .... ... ... ... .... ................................................ ....................76
Auto-Healing ...........................................................................................................................................79
Interfaces ................................................................................................................................................81
Trunks ...................................................................................................................................................115
Route .................................. ............................................. .... ... ... ............................................................119
Routing Protocol ....................................................................................................................................129
Zones ....................................................................................................................................................133
DDNS ................................. .............................................................. .....................................................137
Virtual Servers .......................................................................................................................................141
HTTP Redirect ......................................................................................................................................145
ALG .................................... .............................................................. .....................................................149
UPnP ..................................... ................................. ................................ ...............................................153
IP/MAC Binding .....................................................................................................................................157
Layer 2 Isolation .... ... .............................................................................................................................160
Secure Policy ........................................................................................................................................163
Web Authentication ............ ... .... ... ... ... .... ... ... .........................................................................................179
RTLS ..................................... ....................................................................... .........................................183
IPSec VPN ................................................................................... .... ... ... ... ... .... .....................................185
SSL VPN ...............................................................................................................................................199
L2TP VPN .............................................................................................................................................203
Bandwidth Management .... ... .... ... ... ... .... ................................................ ... ... .........................................209
Application Patrol ..................................................................................................................................215
Anti-Virus ......................................... ............. ............. ............. ............. ............. .....................................219
IDP Commands .....................................................................................................................................225
Content Filtering ....................................................................................................................................237
Anti-Spam .................................................................. ...... ....... ...... ....... ...... ....... ...... ... ............................247
SSL Inspection ......................................................................................................................................257
Device HA .............................................................................................................................................263
User/Group ................................... ... ... .... ... ... .........................................................................................269
ZyWALL / USG (ZLD) CLI Reference Guide
3

Application Object .................................................................................................................................276
Addresses .............................................................................................................................................279
Services ................................................................................................................................................285
Schedules .............................................................................................................................................289
AAA Server ...........................................................................................................................................291
Authentication Objects ....................................... .... ... ... ... .... ... ...............................................................297
Authentication Server ...... ... ................................................. ... ... ............................................................300
Certificates ............................................................................................................................................303
ISP Accounts ................................... ... .... ... ... .........................................................................................307
SSL Application .....................................................................................................................................309
DHCPv6 Objects ...................................................................................................................................312
System ..................................................................................................................................................315
System Remote Management ...............................................................................................................327
File Manager .........................................................................................................................................339
Logs ......................................................................................................................................................359
Reports and Reboot ..............................................................................................................................365
Session Timeout .................................................... ... ... ... .... ... ... ... .... ... ... ...............................................371
Diagnostics ...........................................................................................................................................373
Packet Flow Explore .............................................................................................................................375
Maintenance Tools .......... ... ... .... ... ... ... .... ... ............................................................................................379
Watchdog Timer ....................................................................................................................................385
ZyWALL / USG (ZLD) CLI Reference Guide4

Table of Contents
Table of Contents
Table of Contents .................................................................................................................................5
Part I: Introduction ..........................................................................................19
Chapter 1
Command Line Interface....................................................................................................................21
1.1 Overview ................................ ... ... .... ... ... ... ... .... ............................................. ... ... .... ..........................21
1.1.1 The Configuration File .............................................................................................................21
1.2 Accessing the CLI .............................................................................................................................21
1.2.1 Console Port ........................... ... ... ... ... .... ... ... ... .... ... .................................................................22
1.2.2 Web Configurator Console ......................................................................................................22
1.2.3 Telnet .................. ... .... ... ... ... .............................................. ... ... ... ... ...........................................25
1.2.4 SSH (Secure SHell) .................................................................................................................25
1.3 How to Find Commands in this Guide ...............................................................................................25
1.4 How Commands Are Explained ........................................................................................................26
1.4.1 Background Information (Optional) ............ ... ... .... ... ... ... .... ... ... ... ... .... ... ....................................26
1.4.2 Command Input Values (Optional) ...........................................................................................26
1.4.3 Command Summary ............... ... ... ... ... .... ................................................ ... .... ..........................26
1.4.4 Command Examples (Optional) ............. ... ... ... .... ... ... ................................................ .... ... .......26
1.4.5 Command Syntax ............................................ .... ... ... ............................................. ... ..............26
1.4.6 Changing the Password ..........................................................................................................27
1.5 CLI Modes ....... ............................................. .... ... ... ... .... ....................................................................27
1.6 Shortcuts and Help ............................................................................................................................28
1.6.1 List of Available Commands ....................................................................................................28
1.6.2 List of Sub-commands or Required User Input .......................................................................28
1.6.3 Entering Partial Commands ....... ... ... ... .... ... ... ... .... ................................................ ... ... ..............29
1.6.4 Entering a ? in a Command .....................................................................................................29
1.6.5 Command History ...................... ... ... ... .... ... ... ... .... ....................................................................29
1.6.6 Navigation .............. .... ... ... ............................................. .... ... ... ... ... .... ... ... ... .... ..........................29
1.6.7 Erase Current Command ................. ... .... ... ..............................................................................29
1.6.8 The no Commands ..................................................................................................................29
1.7 Input Values ................................. .... ... ............................................. ... ... .... ... ... .................................30
1.8 Ethernet Interfaces .... ... .....................................................................................................................33
1.9 Saving Configuration Changes .........................................................................................................33
1.10 Logging Out .....................................................................................................................................34
Chapter 2
User and Privilege Modes..................................................................................................................35
ZyWALL / USG (ZLD) CLI Reference Guide
5

Table of Contents
2.1 User And Privilege Modes .................................................................................................................35
2.1.1 Debug Commands ........... ... .... .................................................................................................36
Part II: Reference.............................................................................................39
Chapter 3
Object Reference................................................................................................................................41
3.1 Object Reference Commands ...........................................................................................................41
3.1.1 Object Reference Command Example ....................................................................................42
Chapter 4
Status...................................................................................................................................................43
Chapter 5
Registration.........................................................................................................................................49
5.1 myZyXEL.com Overview ........................................ ... .... ... ... ... .... ... ... ... ... ...........................................49
5.1.1 Subscription Services Available on the ZyWALL / USG ..........................................................49
5.2 Registration Commands ............................ ........................................................................................50
5.2.1 Command Examples ....... ... .... ... ... ... ... .... ... ... ...........................................................................51
Chapter 6
AP Management..................................................................................................................................53
6.1 AP Management Overview .... ... ... .... ... ... ... ........................................................................................53
6.2 AP Management Commands .................... ... .....................................................................................53
6.2.1 AP Management Commands Example ...................................................................................55
Chapter 7
Wireless LAN Profiles ........................................................................................................................56
7.1 Wireless LAN Profiles Overview ...................................... ... ... .... ... ....................................................56
7.2 AP Radio Profile Commands ........................................................ ... ... ... .... ... ... ... .... ..........................56
7.2.1 AP Profile Commands Example ......... .... ... ... ... .... ... ... ... .... ................................................ ... ....60
7.3 AP Monitor Profile Commands ..........................................................................................................61
7.4 SSID Profile Commands ..................................... ... ... .... ... ................................................ .................62
7.4.1 SSID Profile Example ............................................. ... ... ...........................................................64
7.5 Security Profile Commands .......................... .... ... ... ... .... ... ... ... .... .......................................................65
7.5.1 Security Profile Example .................... .... ... ... ... .... ... ... ... .... ... ....................................................66
7.6 MAC Filter Profile Commands ................................ ... .... ................................................ ... ... ..............67
7.6.1 MAC Filter Profile Example ....................... ... ... .... ... ... ................................................ .... ... .......67
Chapter 8
Rogue AP.............................................................................................................................................68
8.1 Rogue AP Detection Overview ............................ ... ... .... ... ... ... .... ... ... .................................................68
6
ZyWALL / USG (ZLD) CLI Reference Guide

Table of Contents
8.2 Rogue AP Detection Commands .................................. ... ... ... .... ... ... ... ... .... ... ... ... .... ..........................68
8.2.1 Rogue AP Detection Examples ............................................................................................... 69
8.3 Rogue AP Containment Overview ....................................................................................................70
8.4 Rogue AP Containment Commands .................................................................................................71
8.4.1 Rogue AP Containment Example ............................................................................................71
Chapter 9
Wireless Frame Capture.....................................................................................................................72
9.1 Wireless Frame Capture Overview ...................................................................................................72
9.2 Wireless Frame Capture Commands ............................... ....................................... ..........................72
9.2.1 Wireless Frame Capture Examples ........................ .......................................................... .......73
Chapter 10
Dynamic Channel Selection...............................................................................................................74
10.1 DCS Overview .................................................................................................................................74
10.2 DCS Commands .............................................................................................................................74
10.2.1 DCS Examples ......................................................................................................................75
Chapter 11
Wireless Load Balancing...................................................................................................................76
11.1 Wireless Load Balancing Overview ...................................... .... ... ... .................................................76
11.2 Wireless Load Balancing Commands ......................................... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ....76
11.2.1 Wireless Load Balancing Examples .......................................................................................77
Chapter 12
Auto-Healing .......................................................................................................................................79
12.1 Auto-Healing Overview ...................................................................................................................79
12.2 Auto-Healing Commands ................................................................................................................79
12.2.1 Auto-Healing Examples .........................................................................................................80
Chapter 13
Interfaces.............................................................................................................................................81
13.1 Interface Overview ..........................................................................................................................81
13.1.1 Types of Interfaces ................................................................................................................81
13.1.2 Relationships Between Interfaces .........................................................................................84
13.2 Interface General Commands Summary .................................. ... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... .. ..85
13.2.1 Basic Interface Properties and IP Address Commands .................... ... .................................85
13.2.2 IGMP Proxy Commands ........................................................................................................91
13.2.3 DHCP Setting Commands .....................................................................................................92
13.2.4 Interface Parameter Command Examples ............................................................................96
13.2.5 RIP Commands .....................................................................................................................97
13.2.6 OSPF Commands .................................................................................................................97
13.2.7 Connectivity Check (Ping-check) Commands .......................................................................99
ZyWALL / USG (ZLD) CLI Reference Guide
7

Table of Contents
13.3 Ethernet Interface Specific Commands .........................................................................................100
13.3.1 MAC Address Setting Commands .................................. ..................................................... 100
13.3.2 Port Grouping Commands ...................................................................................................101
13.4 Virtual Interface Specific Commands ............................................................................................102
13.4.1 Virtual Interface Command Examples ................................................................................. 102
13.5 PPPoE/PPTP Specific Commands ...............................................................................................103
13.5.1 PPPoE/PPTP Interface Command Examples .....................................................................104
13.6 Cellular Interface Specific Commands ..........................................................................................105
13.6.1 Cellular Status .....................................................................................................................107
13.6.2 Cellular Interface Command Examples ...................................... .... ... ... ... .... ... ... ... ... .... ........109
13.7 Tunnel Interface Specific Commands ...........................................................................................110
13.7.1 Tunnel Interface Command Examples ................................................................................ 111
13.8 USB Storage Specific Commands ................................................................................................ 111
13.8.1 USB Storage General Commands Example ........................................................................112
13.9 VLAN Interface Specific Commands .................................................... .........................................112
13.9.1 VLAN Interface Command Examples ................................ ..................................................113
13.10 Bridge Specific Commands .........................................................................................................113
13.10.1 Bridge Interface Command Examples ...............................................................................114
Chapter 14
Trunks................................................................................................................................................115
14.1 Trunks Overview ...........................................................................................................................115
14.2 Trunk Scenario Examples .............................................................................................................115
14.3 Trunk Commands Input Values .....................................................................................................116
14.4 Trunk Commands Summary .........................................................................................................116
14.5 Trunk Command Examples ...........................................................................................................1 17
Chapter 15
Route..................................................................................................................................................119
15.1 Policy Route ..................................................................................................................................119
15.2 Policy Route Commands ............................ ....... ... ....... ...... ....... ...... ...... ....... ...... ....... ...... ...............119
15.2.1 Assured Forwarding (AF) PHB for DiffServ .........................................................................124
15.2.2 Policy Route Command Example ........................................................................................125
15.3 IP Static Route ..............................................................................................................................125
15.4 Static Route Commands ...............................................................................................................126
15.4.1 Static Route Commands Examples ..................................................................................... 127
Chapter 16
Routing Protocol...............................................................................................................................129
16.1 Routing Protocol Overview ............................................................................................................129
16.2 Routing Protocol Commands Summary ........................................................................................129
16.2.1 RIP Commands ...................................................................................................................130
16.2.2 General OSPF Commands ..................................................................................................130
8
ZyWALL / USG (ZLD) CLI Reference Guide

Table of Contents
16.2.3 OSPF Area Commands .......................................................................................................131
16.2.4 Virtual Link Commands ........................................................................................................131
16.2.5 Learned Routing Information Commands ... .........................................................................132
16.2.6 show ip route Command Example .......................................................................................132
Chapter 17
Zones.................................................................................................................................................133
17.1 Zones Overview ............................................................................................................................133
17.2 Zone Commands Summary ..........................................................................................................134
17.2.1 Zone Command Examples ..................................................................................................135
Chapter 18
DDNS..................................................................................................................................................137
18.1 DDNS Overview ............................................................................................................................137
18.2 DDNS Commands Summary ........................................................................................................138
18.3 DDNS Commands Example ..........................................................................................................139
Chapter 19
Virtual Servers ..................................................................................................................................141
19.1 Virtual Server Overview ....... ... ................................................. ... ... ...............................................141
19.1.1 1:1 NAT and Many 1:1 NAT .................................................................................................141
19.2 Virtual Server Commands Summary .................................... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... ... .. ...141
19.2.1 Virtual Server Command Examples .....................................................................................143
19.2.2 Tutorial - How to Allow Public Access to a Server ...............................................................144
Chapter 20
HTTP Redirect...................................................................................................................................145
20.1 HTTP Redirect Overview ..............................................................................................................145
20.1.1 Web Proxy Server .................................... ... ... .... ............................................. ... ... ... ............145
20.2 HTTP Redirect Commands ...........................................................................................................146
20.2.1 HTTP Redirect Command Examples ..................................................................................147
Chapter 21
ALG ....................................................................................................................................................149
21.1 ALG Introduction ...........................................................................................................................149
21.2 ALG Commands ............................................................................................................................150
21.3 ALG Commands Example .............................................................................................................151
Chapter 22
UPnP ..................................................................................................................................................153
22.1 UPnP and NAT-PMP Overview .....................................................................................................153
22.2 UPnP and NAT-PMP Commands ..................................................................................................153
22.3 UPnP & NAT-PMP Commands Example ......................................................................................154
ZyWALL / USG (ZLD) CLI Reference Guide
9

Table of Contents
Chapter 23
IP/MAC Binding.................................................................................................................................157
23.1 IP/MAC Binding Overview .............................................................................................................157
23.2 IP/MAC Binding Commands .........................................................................................................157
23.3 IP/MAC Binding Commands Example ..........................................................................................158
Chapter 24
Layer 2 Isolation ...............................................................................................................................160
24.1 Layer 2 Isolation Overview ............................................................................................................160
24.2 Layer 2 Isolation Commands ........................................................................................................161
24.2.1 Layer 2 Isolation White List Sub-Commands ......................................................................161
24.3 Layer 2 Isolation Commands Example .........................................................................................162
Chapter 25
Secure Policy....................................................................................................................................163
25.1 Secure Policy Overview ................................................................................................................163
25.2 Secure Policy Commands ................................. ....................................... .....................................164
25.2.1 Secure Policy Sub-Commands ................................ .......................... ............................. ..... 167
25.2.2 Secure Policy Command Examples ....................................................................................169
25.3 Session Limit Commands .............................................................................................................171
25.4 ADP Commands Overview ...........................................................................................................173
25.4.1 ADP Command Input Values ................................................................... ............................174
25.4.2 ADP Activation Commands .................................................................................................174
25.4.3 ADP Global Profile Commands ...........................................................................................174
25.4.4 ADP Zone-to-Zone Rule Commands ...................................................................................174
25.4.5 ADP Add/Edit Profile Commands ........................................................................................175
Chapter 26
Web Authentication..........................................................................................................................179
26.1 Web Authentication Overview .......................................................................................................179
26.2 Web Authentication Commands ....................................................................................................179
26.2.1 web-auth policy Sub-commands .........................................................................................180
26.3 SSO Overview ...............................................................................................................................181
26.3.1 SSO Configuration Commands ...........................................................................................181
26.3.2 SSO Show Commands ........................................................................................................182
26.3.3 Command Setup Sequence Example .................................................................................182
Chapter 27
RTLS ..................................................................................................................................................183
27.1 RTLS Overview .............................................................................................................................183
27.1.1 RTLS Configuration Commands ..........................................................................................184
27.1.2 RTLS Configuration Examples ............................................................................................184
10
ZyWALL / USG (ZLD) CLI Reference Guide

Table of Contents
Chapter 28
IPSec VPN..........................................................................................................................................185
28.1 IPSec VPN Overview ....................................................................................................................185
28.2 IPSec VPN Commands Summary ................................................................................................186
28.2.1 IPv4 IKEv1 SA Commands ..................................................................................................187
28.2.2 IPv4 IPSec SA Commands (except Manual Keys) ............... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ..188
28.2.3 IPv4 IPSec SA Commands (for Manual Keys) ....................................................................191
28.2.4 VPN Concentrator Commands ............................................................................................191
28.2.5 VPN Configuration Provisioning Commands ..................... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ..192
28.2.6 SA Monitor Commands .......................................................................................................193
28.2.7 IPv4 IKEv2 SA Commands ..................................................................................................193
28.2.8 IPv6 IKEv2 SA Commands ..................................................................................................195
28.2.9 IPv6 IPSec SA Commands ..................................................................................................196
28.2.10 IPv6 VPN Concentrator Commands ..................................................................................197
Chapter 29
SSL VPN ............................................................................................................................................199
29.1 SSL Access Policy ........................................................................................................................199
29.1.1 SSL Application Objects ......................................................................................................199
29.1.2 SSL Access Policy Limitations .............................................................................................199
29.2 SSL VPN Commands ....................................................................................................................199
29.2.1 SSL VPN Commands ..........................................................................................................200
29.2.2 Setting an SSL VPN Rule Tutorial ........................................................ ...............................201
Chapter 30
L2TP VPN...........................................................................................................................................203
30.1 L2TP VPN Overview ......................................... ... ... ................................................. ... ... ...............203
30.2 IPSec Configuration ......................................................................................................................203
30.2.1 Using the Default L2TP VPN Connection ............................................................................204
30.3 Policy Route ..................................................................................................................................204
30.4 L2TP VPN Commands ......... ... ... .... ... ................................................ ... .... ... ... ... .... ... ... ..................205
30.4.1 L2TP VPN Commands ........................................................................................................205
30.5 L2TP VPN Example ............................................. ... .... ... ... ... .... ... ... ... ... .... ... ... ...............................206
30.5.1 Configuring the Default L2TP VPN Gateway Example ........................................................207
30.5.2 Configuring the Default L2TP VPN Connection Example ....................................................207
30.5.3 Configuring the L2TP VPN Settings Example ................ ... ... ... ... .... ... ..................................207
30.5.4 Configuring the Policy Route for L2TP Example .................................................................208
Chapter 31
Bandwidth Management...................................................................................................................209
31.1 Bandwidth Management Overview ...............................................................................................209
31.1.1 BWM Type ...........................................................................................................................209
31.2 Bandwidth Management Commands ................................................................................ ............209
ZyWALL / USG (ZLD) CLI Reference Guide
11

Table of Contents
31.2.1 Bandwidth Sub-Commands ..................................... ............................................................ 210
31.3 Bandwidth Management Commands Examples ...........................................................................213
Chapter 32
Application Patrol.............................................................................................................................215
32.1 Application Patrol Overview ..........................................................................................................215
32.2 Application Patrol Commands Summary ... .... ...............................................................................215
32.2.1 Application Patrol Commands .............. ... ............................................................................216
Chapter 33
Anti-Virus...........................................................................................................................................219
33.1 Anti-Virus Overview .......................................................................................................................219
33.2 Anti-virus Commands ....................................................................................................................219
33.2.1 General Anti-virus Commands ............................................................................................220
33.2.2 Anti-Virus Profile ..................................................................................................................220
33.2.3 White and Black Lists ..........................................................................................................221
33.2.4 Signature Search Anti-virus Command ...............................................................................222
33.3 Update Anti-virus Signatures ........................................................................................................223
33.3.1 Update Signature Examples ................................................................................................223
33.4 Anti-virus Statistics ........................................................................................................................224
33.4.1 Anti-virus Statistics Example ...............................................................................................224
Chapter 34
IDP Commands .................................................................................................................................225
34.1 Overview .......................................................................................................................................225
34.2 General IDP Commands ...............................................................................................................225
34.2.1 IDP Activation ......................................................................................................................225
34.3 IDP Profile Commands ..................................................................................................................226
34.3.1 Global Profile Commands ....................................................................................................226
34.3.2 Editing/Creating IDP Signature Profiles ......... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ..227
34.3.3 Signature Search .................................................................................................................227
34.4 IDP Custom Signatures .................................................................................................................229
34.4.1 Custom Signature Examples ................................ ... ... .... ... ... ... ... .........................................230
34.5 Update IDP Signatures ........ ... ... .... ................................................ ... ... .........................................233
34.5.1 Update Signature Examples ................................................................................................234
34.6 IDP Statistics .................................................................................................................................234
34.6.1 IDP Statistics Example ........................................................................................................235
Chapter 35
Content Filtering...............................................................................................................................237
35.1 Content Filtering Overview ......................... .................................... ...............................................237
35.2 External Web Filtering Service ....................................... ................................................ ...............237
35.3 Content Filtering Reports ..............................................................................................................237
12
ZyWALL / USG (ZLD) CLI Reference Guide

Table of Contents
35.4 Content Filter Command Input Values ..........................................................................................238
35.5 General Content Filter Commands ...............................................................................................239
35.6 Content Filter Filtering Profile Commands ........................... .... ... ..................................................241
35.7 Content Filtering Statistics .............................................................................................................243
35.7.1 Content Filtering Statistics Example ....................................................................................243
35.8 Content Filtering Commands Example .........................................................................................243
Chapter 36
Anti-Spam..........................................................................................................................................247
36.1 Anti-Spam Overview ......................................................................................................................247
36.2 Anti-Spam Commands ..................................................................................................................247
36.2.1 Anti-spam Profile Rules .......................................................................................................247
36.2.2 White and Black Lists ..........................................................................................................250
36.2.3 DNSBL Anti-Spam Commands ............................................................................................252
36.3 Anti-Spam Statistics ......................................................................................................................254
36.3.1 Anti-Spam Statistics Example ..............................................................................................255
Chapter 37
SSL Inspection..................................................................................................................................257
37.1 SSL Inspection Overview ..............................................................................................................257
37.2 SSL Inspection Commands Summary ..........................................................................................257
37.2.1 SSL Inspection Exclusion Commands .................................................................................258
37.2.2 SSL Inspection Profile Settings ...........................................................................................258
37.2.3 SSL Inspection Certificate Cache ........................................................................................ 259
37.2.4 SSL Inspection Certificate Update .......................................................................................259
37.2.5 SSL Inspection Statistics .....................................................................................................260
37.2.6 SSL Inspection Command Examples ..................................................................................261
Chapter 38
Device HA..........................................................................................................................................263
38.1 Device HA Overview .....................................................................................................................263
38.1.1 Before You Begin .................................................................................................................264
38.2 General Device HA Commands ........................ ................................................................ ............264
38.3 Active-Passive Mode Device HA ...................................................................................................264
38.4 Active-Passive Mode Device HA Commands ...............................................................................265
38.4.1 Active-Passive Mode Device HA Commands ......................................................................265
38.4.2 Active-Passive Mode Device HA Command Example ........................................................267
Chapter 39
User/Group........................................................................................................................................269
39.1 User Account Overview .................................................................................................................269
39.1.1 User Types ..........................................................................................................................269
39.2 User/Group Commands Summary .......................... ....................................... ...............................270
ZyWALL / USG (ZLD) CLI Reference Guide
13

Table of Contents
39.2.1 User Commands ..................................................................................................................270
39.2.2 User Group Commands .......................................................................................................271
39.2.3 User Setting Commands .....................................................................................................271
39.2.4 MAC Auth Commands .........................................................................................................273
39.2.5 Additional User Commands .................................................................................................274
Chapter 40
Application Object............................................................................................................................276
40.1 Application Object Commands Summary .....................................................................................276
40.1.1 Application Object Commands ............................................................................................276
40.1.2 Application Object Group Commands .................................................................................277
Chapter 41
Addresses .........................................................................................................................................279
41.1 Address Overview .........................................................................................................................279
41.2 Address Commands Summary .....................................................................................................279
41.2.1 Address Object Commands .................................................................................................280
41.2.2 Address Group Commands .................................................................................................282
Chapter 42
Services.............................................................................................................................................285
42.1 Services Overview ........................................................................................................................285
42.2 Services Commands Summary .....................................................................................................285
42.2.1 Service Object Commands ................................ ...................................................... ............285
42.2.2 Service Group Commands ..................................................................................................286
Chapter 43
Schedules..........................................................................................................................................289
43.1 Schedule Overview .......................................................................................................................289
43.2 Schedule Commands Summary ................................................................................................... 289
43.2.1 Schedule Command Examples ...........................................................................................290
Chapter 44
AAA Server........................................................................................................................................291
44.1 AAA Server Overview ...................................................................................................................291
44.2 Authentication Server Command Summary ...................................... ... .... ... ... ... .... ... ... ... ... .... ........291
44.2.1 ad-server Commands ..........................................................................................................291
44.2.2 ldap-server Commands .............. ... ... .... ... ... ... ......................................................................292
44.2.3 radius-server Commands ....................................................................................................293
44.2.4 radius-server Command Example .......................................................................................293
44.2.5 aaa group server ad Commands .........................................................................................293
44.2.6 aaa group server ldap Commands ......................................................................................294
44.2.7 aaa group server radius Commands ...................................................................................295
14
ZyWALL / USG (ZLD) CLI Reference Guide

Table of Contents
44.2.8 aaa group server Command Example .................................................................................296
Chapter 45
Authentication Objects.....................................................................................................................297
45.1 Authentication Objects Overview ..................................................................................................297
45.2 aaa authentication Commands .....................................................................................................297
45.2.1 aaa authentication Command Example ...............................................................................298
45.3 test aaa Command ........................................................................................................................298
45.3.1 Test a User Account Command Example ............................................................................298
Chapter 46
Authentication Server ......................................................................................................................300
46.1 Authentication Server Overview ........................... .................................... .....................................300
46.2 Authentication Server Commands ................................................................................................300
46.2.1 Authentication Server Command Examples ........................................................................301
Chapter 47
Certificates........................................................................................................................................303
47.1 Certificates Overview ....................................................................................................................303
47.2 Certificate Commands ...................................................................................................................303
47.3 Certificates Commands Input Values ... ... ... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ...............303
47.4 Certificates Commands Summary ....................................... .... ... ... ... ... .... ... ... ...............................304
47.5 Certificates Commands Examples ........................................................... ... ... ... .... ... ... ... ... .... ... .....306
Chapter 48
ISP Accounts.....................................................................................................................................307
48.1 ISP Accounts Overview .................................................................................................................307
48.1.1 PPPoE and PPTP Account Commands ..............................................................................307
48.1.2 Cellular Account Commands ...............................................................................................308
Chapter 49
SSL Application................................................................................................................................309
49.1 SSL Application Overview .............................................................................................................309
49.1.1 SSL Application Object Commands ....................................................................................309
49.1.2 SSL Application Command Examples .................................. ...............................................311
Chapter 50
DHCPv6 Objects................................................................................................................................312
50.1 DHCPv6 Object Commands Summary .........................................................................................312
50.1.1 DHCPv6 Object Commands ................................................................................................312
50.1.2 DHCPv6 Object Command Examples .................................................................................313
Chapter 51
System...............................................................................................................................................315
ZyWALL / USG (ZLD) CLI Reference Guide
15

Table of Contents
51.1 System Overview ..........................................................................................................................315
51.2 Customizing the WWW Login Page ..............................................................................................315
51.3 Host Name Commands .................................................................................................................317
51.4 Time and Date ..............................................................................................................................317
51.4.1 Date/Time Commands .................................................... ............................................. ........318
51.5 Console Port Speed .....................................................................................................................318
51.6 DNS Overview ..............................................................................................................................319
51.6.1 Domain Zone Forwarder ......... ............................................. ... ... .... .....................................319
51.6.2 DNS Commands ..................................................................................................................320
51.6.3 DNS Command Examples ...................................................................................................322
51.7 Authentication Server Overview ........................... .................................... .....................................322
51.7.1 Authentication Server Commands .......................................................................................323
51.7.2 Authentication Server Command Examples ........................................................................324
51.8 Language Commands ...................................................................................................................324
51.9 IPv6 Commands ............................................................................................................................325
51.10 ZON Overview .............................................................................................................................325
51.10.1 LLDP ..................................................................................................................................325
51.10.2 ZON Commands ................................................................................................................325
51.10.3 ZON Examples ..................................................................................................................326
Chapter 52
System Remote Management..........................................................................................................327
52.1 Remote Management Overview ....................................................................................................327
52.1.1 Remote Management Limitations ........................................................................................327
52.1.2 System Timeout ...................................................................................................................327
52.2 Common System Command Input Values ....................................................................................328
52.3 HTTP/HTTPS Commands .............................................................................................................328
52.3.1 HTTP/HTTPS Command Examples ....................................................................................330
52.4 SSH ...............................................................................................................................................330
52.4.1 SSH Implementation on the ZyWALL / USG .......................................................................330
52.4.2 Requirements for Using SSH ................................... ... .... ... ... ... ... .........................................330
52.4.3 SSH Commands ..................................................................................................................331
52.4.4 SSH Command Examples ...................................................................................................331
52.5 Telnet ............................................................................................................................................332
52.6 Telnet Commands .........................................................................................................................332
52.6.1 Telnet Commands Examples ...... ....................................................... .................................. 332
52.7 Configuring FTP ...........................................................................................................................333
52.7.1 FTP Commands ..................................................................................................................333
52.7.2 FTP Commands Examples ..................................................................................................333
52.8 SNMP ...........................................................................................................................................334
52.8.1 Supported MIBs ...................................................................................................................334
52.8.2 SNMP Traps ........................................................................................................................334
52.8.3 SNMP Commands ...............................................................................................................335
16
ZyWALL / USG (ZLD) CLI Reference Guide

Table of Contents
52.8.4 SNMP Commands Examples ..............................................................................................336
52.9 ICMP Filter ...................................................................................................................................337
Chapter 53
File Manager......................................................................................................................................339
53.1 File Directories ..............................................................................................................................339
53.2 Configuration Files and Shell Scripts Overview ...................................................................... ... ..339
53.2.1 Comments in Configuration Files or Shell Scripts ...............................................................340
53.2.2 Errors in Configuration Files or Shell Scripts .......................................................................341
53.2.3 ZyWALL / USG Configuration File Details ...........................................................................341
53.2.4 Configuration File Flow at Restart .......................................................................................342
53.3 File Manager Commands Input Values .........................................................................................342
53.4 File Manager Commands Summary .............................................................................................343
53.5 File Manager Dual Firmware Commands ................................... ... ... ... .... ... ... ... .... ........................344
53.6 File Manager Command Examples ......................... ....................................... ...............................345
53.7 FTP File Transfer ..........................................................................................................................345
53.7.1 Command Line FTP File Upload .........................................................................................346
53.7.2 Command Line FTP Configuration File Upload Example ....................................................346
53.7.3 Command Line FTP File Download .....................................................................................346
53.7.4 Command Line FTP Configuration File Download Example ...............................................347
53.8 ZyWALL / USG File Usage at Startup ............................................ ... ... .... .....................................347
53.9 Notification of a Damaged Recovery Image or Firmware .............................................................348
53.10 Restoring the Recovery Image ....................................................................................................349
53.11 Restoring the Firmware ...... ... ... .... ... ... ... ......................................................................................351
53.12 Restoring the Default System Database .....................................................................................353
53.12.1 Using the atkz -u Debug Command ..................................................................................355
Chapter 54
Logs...................................................................................................................................................359
54.1 Log Commands Summary ............................................................................................................359
54.1.1 Log Entries Commands .......................................................................................................360
54.1.2 System Log Commands ......................................................................................................360
54.1.3 Debug Log Commands ........................................................................................................361
54.1.4 E-mail Profile Commands ....................................................................................................363
54.1.5 Console Port Logging Commands .......................................................................................364
Chapter 55
Reports and Reboot..........................................................................................................................365
55.1 Report Commands Summary ........................................................................................................365
55.1.1 Report Commands ..............................................................................................................365
55.1.2 Report Command Examples ...............................................................................................366
55.1.3 Session Commands ............................................................................................................366
55.1.4 Packet Size Statistics Commands ....................................................................................... 366
ZyWALL / USG (ZLD) CLI Reference Guide
17

Table of Contents
55.2 Email Daily Report Commands ............................ .........................................................................367
55.2.1 Email Daily Report Example .......................... .......................................................... ............368
55.3 Reboot ...........................................................................................................................................370
Chapter 56
Session Timeout...............................................................................................................................371
Chapter 57
Diagnostics ......................................................................................................................................373
57.1 Diagnostics ....................................................................................................................................373
57.2 Diagnosis Commands ...................................................................................................................373
57.3 Diagnosis Commands Example ....................................................................................................373
Chapter 58
Packet Flow Explore.........................................................................................................................375
58.1 Packet Flow Explore .....................................................................................................................375
58.2 Packet Flow Explore Commands ...................... ............................................................................375
58.3 Packet Flow Explore Commands Example ...................................................................................376
Chapter 59
Maintenance Tools............................................................................................................................379
59.1 Maintenance Command Examples ...............................................................................................381
59.1.1 Packet Capture Command Example ....... ... ... .... ... ... ... .... ... ... ...............................................382
Chapter 60
Watchdog Timer................................................................................................................................385
60.1 Hardware Watchdog Timer ............................... ... ... .... ... ... ................................................ ............385
60.2 Software Watchdog Timer ................................. ... ... .... ... ... ................................................ ............385
60.3 Application Watchdog ...................................................................................................................386
60.3.1 Application Watchdog Commands Example ........................................................................387
List of Commands (Alphabetical)....................................................................................................389
18
ZyWALL / USG (ZLD) CLI Reference Guide
PART I
Introduction
19

20

This chapter describes how to access and use the CLI (Command Line Interface).
1.1 Overview
If you have problems with your Z yWALL / USG, customer support may request that you issue some
of these commands to assist them in troubleshooting.
Use of undocumented commands or misconfiguration can damage the
ZyWALL / USG and possibly render it unusable.
1.1.1 The Configuration File
CHAPTER 1
Command Line Interface
When you configure the ZyWALL / USG using either the CLI (Command Line Interface) or the web
configurator, the settings are saved as a series of commands in a configuration file on the ZyWALL /
USG. You can store more than one configuration file on the ZyWALL / USG. However, only one
configuration file is used at a time.
You can perform the following with a configuration file:
• Back up ZyWALL / USG configuration once the ZyWALL / USG is set up to work in your network.
• Restore ZyWALL / USG configuration.
• Save and edit a configuration file and upload it to multiple ZyW ALL / USGs (of the same model) in
your network to have the same settings.
Note: You may also edit a configuration file using a text editor.
1.2 Accessing the CLI
You can access the CLI using a terminal emulation progr am on a computer connected to the console
port, from the web configurator or access the ZyWALL / USG using Telnet or SSH (Secure SHell).
Note: The ZyWALL / USG might force you to log out of your session if reauthent ic a ti on
time, lease time, or idle timeout is reached. See Chapter 39 on page 269 for more
information about these settings.
ZyWALL / USG (ZLD) CLI Reference Guide 21
Chapter 1 Command Line Interface
1.2.1 Console Port
The default settings for the console port are as follows.
Table 1 Managing the ZyWALL / USG: Console Port
SETTING VALUE
Speed 115200 bps
Data Bits 8
Parity None
Stop Bit 1
Flow Control Off
When you turn on your ZyWALL / USG, it performs several internal tests as well as line
initialization. You can view the initialization information using the console port.
• Garbled text displays if your terminal emulation program’s speed is set lower than the ZyWALL /
USG’s.
• No text displays if the speed is set higher than the ZyWALL / USG’s.
• If changing your terminal emulation program’s speed does n ot get anything to display, restart the
ZyWALL / USG.
• If restarting the ZyWALL / USG does not get anything to display, contact your local customer
support.
Figure 1 Console Port Power-on Display
U-Boot 2011.03 (Development build, svnversion: u-boot:424M, exec:exported) (Build
time: Aug 28 2013 - 14:19:07)
BootModule Version: V1.01 | Aug 28 2013 14:19:07
DRAM: Size = 1024 Mbytes
Press any key to enter debug mode within 3 seconds.
After the initialization, the login screen displays.
Figure 2 Login Screen
Welcome to USG60W
Username:
Enter the user name and password at the prompts.
Note: The default login use rnam e is admin and password is 1234. The username and
password are case-sensitive.
1.2.2 Web Configurator Console
22
Note: Before you can access the CLI through the web configurator, make sure your
computer supports the Java Runtime Environment. You will be prompted to
download and install the Java plug-in if it is not already installed.
ZyWALL / USG (ZLD) CLI Reference Guide
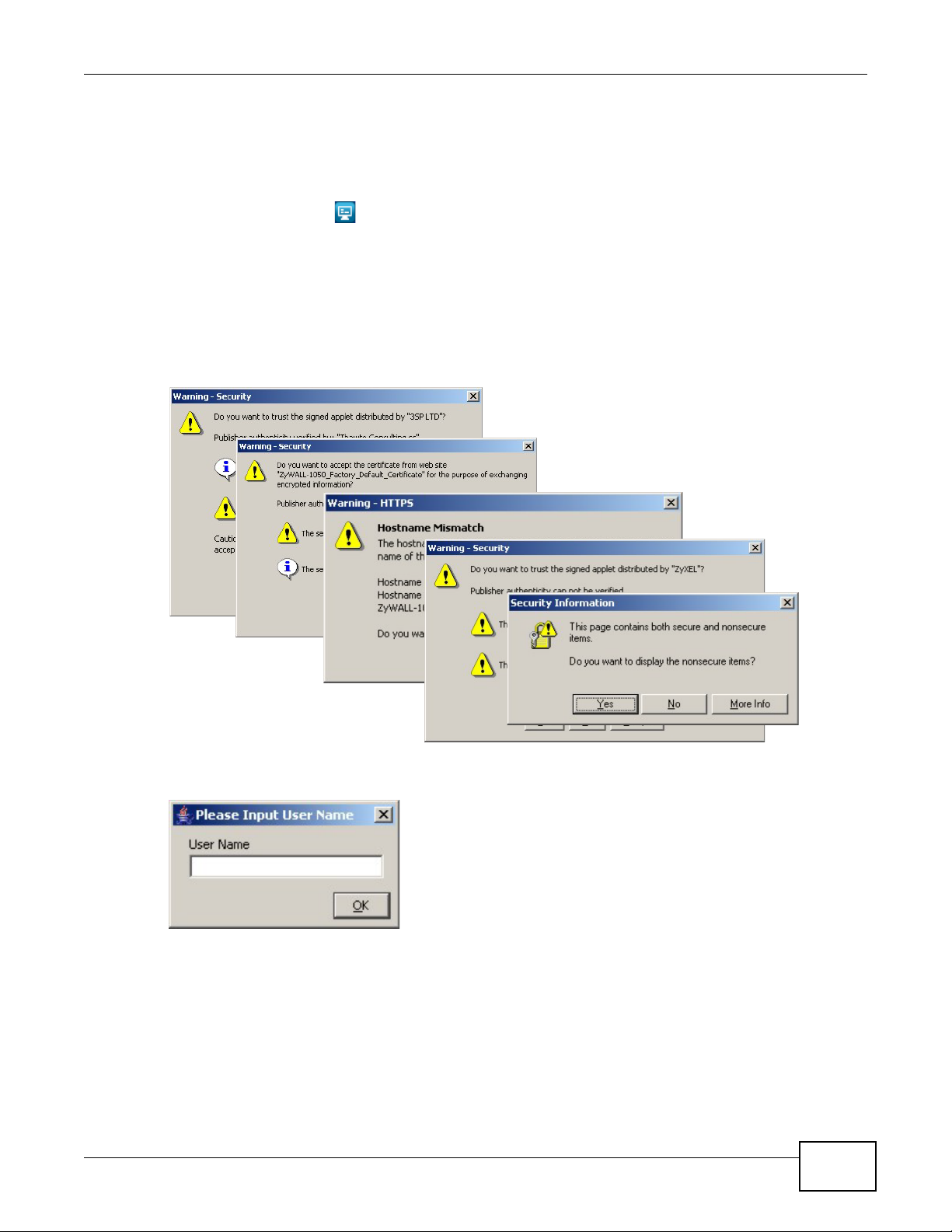
Chapter 1 Command Line Interface
When you access the CLI using the web console, your computer establishes a SSH (Secure SHell)
connection to the ZyWALL / USG. Follow the steps below to access the web console.
1 Log into the web configurator.
2 Click the Console icon in the top-right corner of the web configurator screen.
3 If the Java plug-in is already installed, skip to step 4.
Otherwise, you will be prompted to install the Java plug-in. If the prompt does not display and the
screen remains gray, you have to download the setup program.
4 The web console starts. This might take a few seconds. One or more security screens may display.
Click Yes or Always.
Figure 3 Web Console: Security Warnings
Finally, the User Name screen appears.
Figure 4 Web Console: User Name
5 Enter the user name you want to use to log in to the console. The console begins to connect to the
ZyWALL / USG.
ZyWALL / USG (ZLD) CLI Reference Guide
23
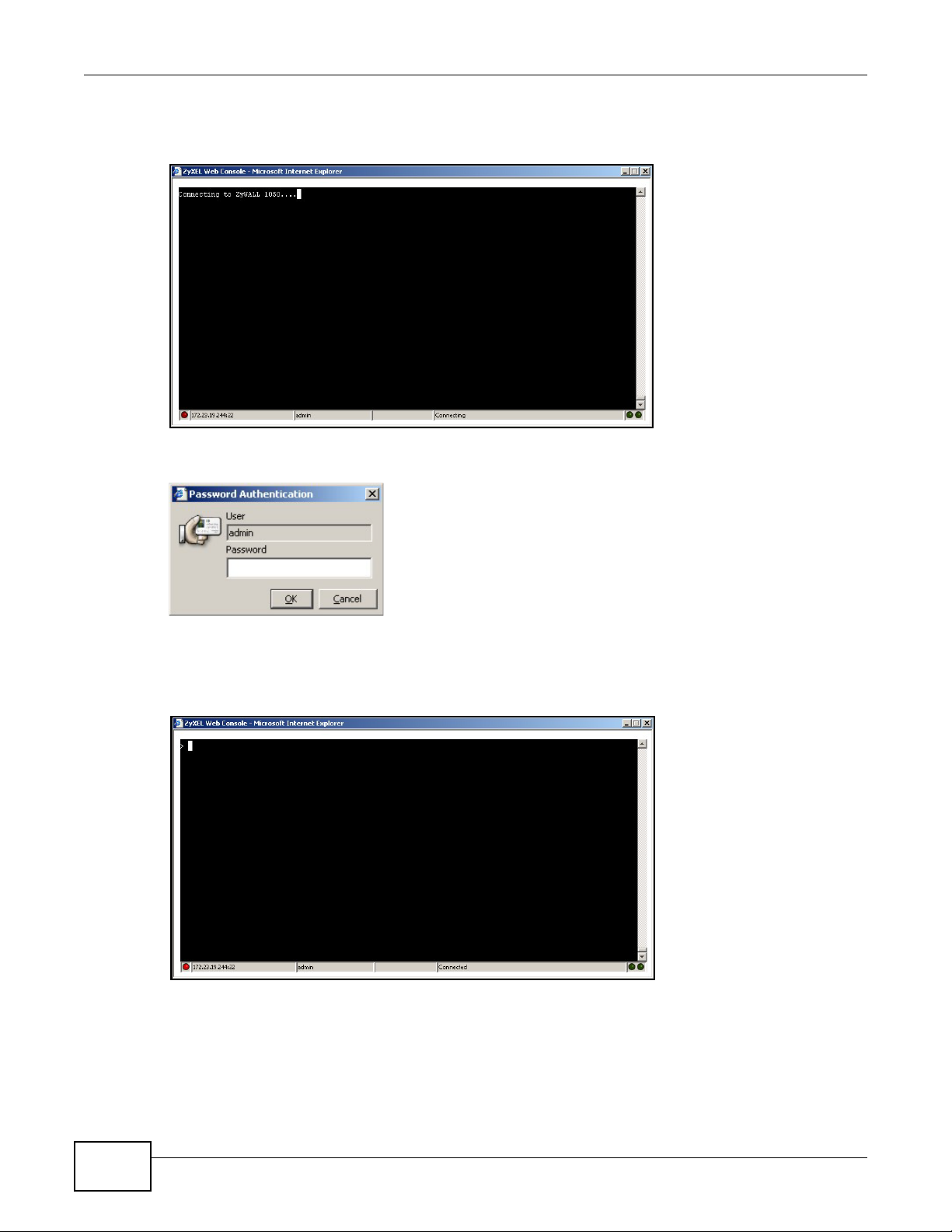
Chapter 1 Command Line Interface
Note: The default login use rnam e is admin. It is case-sensitive.
Figure 5 Web Console: Connecting
Then, the Password screen appears.
Figure 6 Web Console: Password
6 Enter the password for the user name you specified earlier, and click OK. If you enter the password
incorrectly, you get an error message, and you may have to close the console window and open it
again. If you enter the password correctly, the console screen appears.
Figure 7 Web Console
7 To use most commands in this User’s Guide, enter
change to
Router(config)#.
configure terminal. The prompt should
24
ZyWALL / USG (ZLD) CLI Reference Guide
1.2.3 Telnet
Use the following steps to Telnet into your ZyWALL / USG.
1 If your computer is connected to the ZyWALL / USG over the Internet, skip to the next step. Make
sure your computer IP address and the ZyWALL / USG IP address are on the same subnet.
2 In Windows, click Start (usually in the bottom left corner) and Run. Then type telnet and the
ZyWALL / USG’s IP address. For example, enter
IP address).
3 Click OK. A login screen displays. Enter the user name and password at the prompts.
Note: The default login use rnam e is admin and password is 1234. The username and
password are case-sensitive.
1.2.4 SSH (Secure SHell)
You can use an SSH client progr am to access the CLI. The following figure shows an example using
a text-based SSH client program. Refer to the documentation that comes with your SSH program
for information on using it.
Chapter 1 Command Line Interface
telnet 192.168.1.1 (the default management
Note: The default login use rnam e is admin and password is 1234. The username and
password are case-sensitive.
Figure 8 SSH Login Example
C:\>ssh2 admin@192.168.1.1
Host key not found from database.
Key fingerprint:
xolor-takel-fipef-zevit-visom-gydog-vetan-bisol-lysob-cuvun-muxex
You can get a public key's fingerprint by running
% ssh-keygen -F publickey.pub
on the keyfile.
Are you sure you want to continue connecting (yes/no)? yes
Host key saved to C:/Documents and Settings/user/Application Data/SSH/hostkeys/
ey_22_192.168.1.1.pub
host key for 192.168.1.1, accepted by user Tue Aug 09 2005 07:38:28
admin's password:
Authentication successful.
1.3 How to Find Commands in this Guide
You can simply look for the feature chapter to find commands. In addition, you can use the List of
Commands (Alphabetical) at the end of the guide. This section lists the commands in alphabetical
order that they appear in this guide.
If you are looking at the CLI Reference Guide electronically, you might have additional options (for
example, bookmarks or Find...) as well.
ZyWALL / USG (ZLD) CLI Reference Guide
25

Chapter 1 Command Line Interface
1.4 How Commands Are Explained
Each chapter explains the commands for one keyword. The chapters are divided into the following
sections.
1.4.1 Background Information (Optional)
Note: See the User’s Guide for background information about most features.
This section provides background information about features that you cannot configure in the web
configurator. In addition, this section identifies related commands in other chapters.
1.4.2 Command Input Values (Optional)
This section lists common input values for the commands for the feature in one or more tables
1.4.3 Command Summary
This section lists the commands for the feature in one or more tables.
1.4.4 Command Examples (Optional)
This section contains any examples for the commands in this feature.
1.4.5 Command Syntax
The following conventions are used in this User’s Guide.
• A command or keyword in courier new must be entered literally as shown. Do not abbreviate.
• Values that you need to provide are in italics.
• Required fields that have multiple choices are enclosed in curly brackets
• A range of numbers is enclosed in angle brackets <>.
• Optional fields are enclosed in square brackets
•The
For example, look at the following command to create a TCP/UDP service object.
service-object object-name {tcp | udp} {eq <1..65535> | range <1..65535> <1..65535>}
1 Enter service-object exactly as it appears.
2 Enter the name of the object where you see object-name.
| symbol means OR.
{}.
[].
3 Enter
4 Finally, do one of the following.
tcp or udp, depending on the service object you want to create.
•Enter
eq exactly as it appears, followed by a number between 1 and 65535.
26
ZyWALL / USG (ZLD) CLI Reference Guide
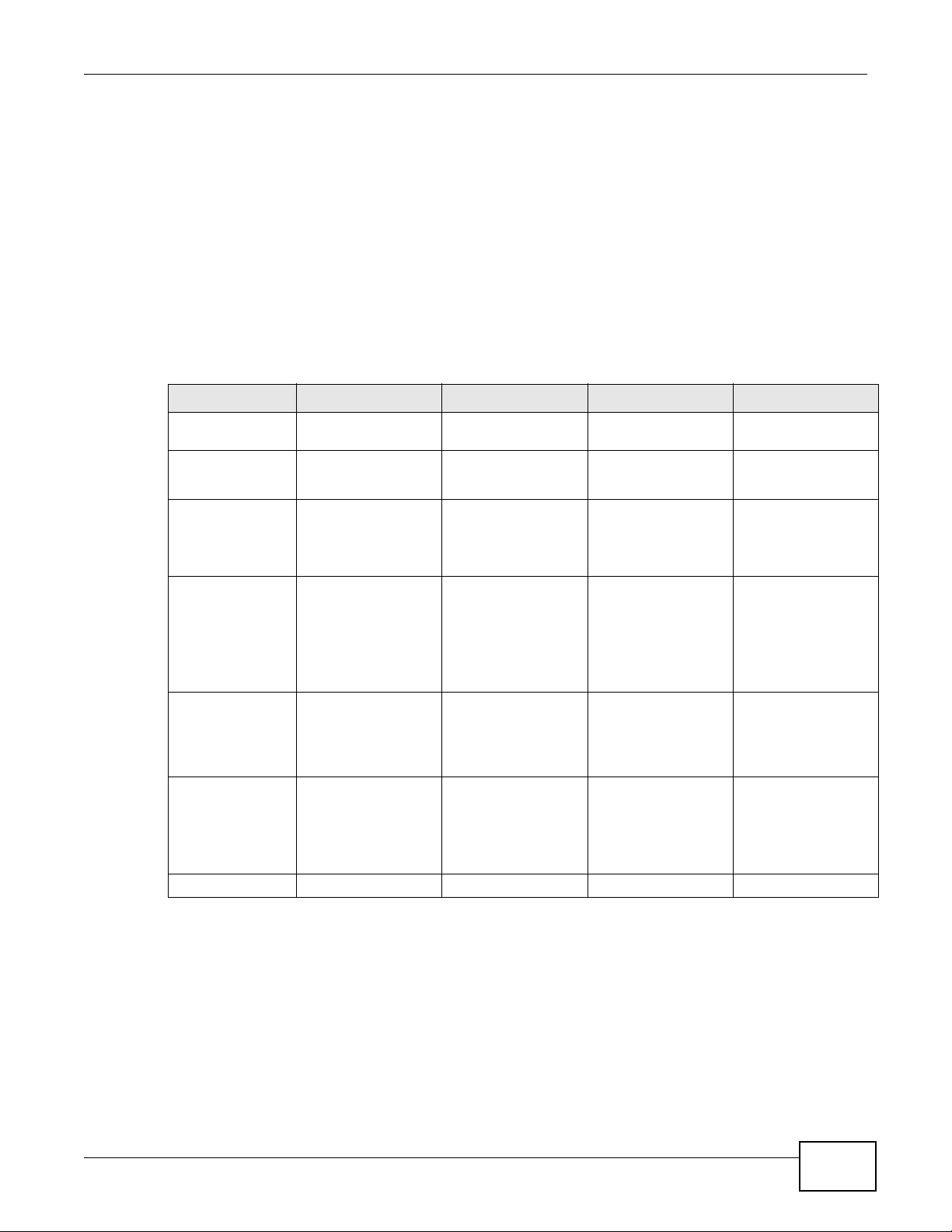
•Enter range exactly as it appears, followed by two numbers between 1 and 65535.
1.4.6 Changing the Password
It is highly recommended that you change the password for accessing the ZyWALL / USG. See
Section 39.2 on page 270 for the appropriate commands.
1.5 CLI Modes
You run CLI commands in one of several modes.
Table 2 CLI Modes
USER PRIVILEGE CONFIGURATION SUB-COMMAND
What Guest users
can do
What User users
can do
What Limited-
Admin users can
do
What Admin
users can do
How you enter it Log in to the ZyWALL
What the prompt
looks like
How you exit it Type exit Type disable Type exit Type exit
Unable to access Unable to access Unable to access Unable to access
• Look at (but not
run) available
commands
• Look at system
information (like
Status screen)
• Run basic
diagnostics
• Look at system
information (like
Status screen)
• Run basic
diagnostics
/ USG
Router> Router# Router(config)# (varies by part)
Chapter 1 Command Line Interface
Unable to access Unable to access Unable to access
• Look at system
information (like
Status screen)
• Run basic
diagnostics
• Look at system
information (like
Status screen)
• Run basic
diagnostics
Type enable in User
mode
Unable to access Unable to access
• Configure simple
features (such as
an address
object)
• Create or remove
complex parts
(such as an
interface)
Type configure
terminal in User or
Privilege mode
• Configure
complex parts
(such as an
interface) in the
ZyWALL / USG
Type the command
used to create the
specific part in
Configuration
mode
Router(zone)#
Router(config-ifge)#
...
See Chapter 39 on page 269 for more information about the user types. User users can only log in,
look at (but not run) the available commands in User mode, and log out. Limited-Admin users
can look at the configuration in the web configurator and CLI, and they can run basic diagnostics in
the CLI. Admin users can configure the ZyWALL / USG in the web configurator or CLI.
At the time of writing, there is not much difference between User and Privilege mode for admin
users. This is reserved for future use.
ZyWALL / USG (ZLD) CLI Reference Guide
27

Chapter 1 Command Line Interface
1.6 Shortcuts and Help
1.6.1 List of Available Commands
A list of valid commands can be found by typing ? or [TAB] at the command prompt. To view a list of
available commands within a command group, enter <command> ? or <command> [TAB].
Figure 9 Help: Available Commands Example 1
Router> ?
<cr>
apply
atse
clear
configure
------------------[Snip]-------------------shutdown
telnet
test
traceroute
write
Router>
Figure 10 Help: Available Command Example 2
Router> show ?
<wlan ap interface>
aaa
access-page
account
ad-server
address-object
------------------[Snip]-------------------wlan
workspace
zone
Router> show
1.6.2 List of Sub-commands or Required User Input
To view detailed help information for a command, enter <command> <sub command> ?.
Figure 11 Help: Sub-command Information Example
Router(config)# ip telnet server ?
;
<cr>
port
rule
|
Router(config)# ip telnet server
28
Figure 12 Help: Required User Input Example
Router(config)# ip telnet server port ?
<1..65535>
Router(config)# ip telnet server port
ZyWALL / USG (ZLD) CLI Reference Guide

1.6.3 Entering Partial Commands
The CLI does not accept partial or incomplete commands. You may enter a unique part of a
command and press
[TAB] to have the ZyWALL / USG automatically display the full command.
Chapter 1 Command Line Interface
For example, if you enter
displays.
If you enter a partial command that is not unique and press
of commands that start with the partial command.
Figure 13 Non-Unique Partial Command Example
Router# c [TAB]
clear configure copy
Router# co [TAB]
configure copy
config and press [TAB] , the full command of configure automatically
1.6.4 Entering a ? in a Command
Typing a ? (question mark) usually displays help information. However, some commands allow you
to input a ?, for example as part of a string. Press [CTRL+V] on your keyboard to enter a ? without
the ZyWALL / USG treating it as a help query.
1.6.5 Command History
The ZyWALL / USG keeps a list of commands you hav e entered for the current CLI session. You can
use any commands in the history again by pressing the up () or down () arrow key to scroll
through the previously used commands and press
[TAB], the ZyWALL / USG displays a list
[ENTER].
1.6.6 Navigation
Press [CTRL]+A to move the cursor to the beginning of the line. Press [CTRL]+E to move the cursor to
the end of the line.
1.6.7 Erase Current Command
Press [CTRL]+U to erase whatever you have currently typed at the prompt (before pressing [ENTER]).
1.6.8 The no Commands
When entering the no commands described in this document, you may not need to type the whole
command. For example, with th e “[no] mss <536..1452>” command, you use “m ss 536” to specify
the MSS value. But to disable the MSS setting, you only need to type “no mss” instead of “no mss
536”.
ZyWALL / USG (ZLD) CLI Reference Guide
29
Chapter 1 Command Line Interface
1.7 Input Values
You can use the ? or [TAB] to get more information about the next input value that is required for a
command. In some cases, the next input value is a string whose length and allowable characters
may not be displayed in the screen. For example, in the following example, the next input value is a
string called
Router# configure terminal
Router(config)# interface ge1
Router(config-if-ge)# description
<description>
When you use the example above, note that ZyWALL / USG USG 200 and below models use a name
such as wan1, wan2, opt, lan1, ext-wlan, or dmz.
<description>.
The following table provides more information about input values like
<description>.
Table 3 Input-Value Formats for Strings in CLI Commands
TAG # VALUES LEGAL VALUES
* 1*
all -- ALL
authentication key Used in IPSec SA
32-40
16-20
Used in MD5 authentication keys for RIP/OSPF and text authentication key for RIP
0-16 alphanumeric or _Used in text authentication keys for OSPF
0-8 alphanumeric or _-
certificate name 1-31 alphanumeric or ;`~!@#$%^&()_+[\]{}',.=-
community string 0-63 alphanumeric or .-
connection_id 1+ alphanumeric or -_:
contact 1-61 alphanumeric, spaces, or '()+,/:=?;!*#@$_%-.
country code 0 or 2 alphanumeric
custom signature file
name
description Used in keyword criteria for log entries
distinguished name 1-511 alphanumeric, spaces, or .@=,_-
0-30 alphanumeric or _-.
1-64 alphanumeric, spaces, or '()+,/:=?;!*#@$_%-.
Used in other commands
1-61 alphanumeric, spaces, or '()+,/:=?;!*#@$_%-
“0x” or “0X” + 32-40 hexadecimal values
alphanumeric or ;|`~!@#$%^&*()_+\\{}':,./<>=-
first character: alphanumeric or -
first character: letter
30
ZyWALL / USG (ZLD) CLI Reference Guide
 Loading...
Loading...