
ZyWALL OTPv2
Support Notes
Revision 1.00
September, 2010
Written by CSO

ZyXEL – ZyWALL OTPv2 Support Notes
2
Table of Contents
1. Introduction ....................................................................................................................................................... 3
2. Server Installation ............................................................................................................................................. 7
2.1 Pre-requisites .......................................................................................................................................... 7
2.2 Installations walk through ..................................................................................................................... 7
3. OTP Authentication to an OTP-protected Network via SSL VPN over ZyWALL USG ................................. 11
3.1 ZyWALL USG Configurations ................................................................................................................ 12
3.2 SafeWord Server Configurations ......................................................................................................... 15
3.3 Verify OTP via Login from the Remote PC .......................................................................................... 19
4. OTP Authentication to an OTP-protected Network via IPSec VPN Client over the ZyWALL USG ............ 20
4.1 ZyWALL USG Configurations ................................................................................................................ 21
4.2 SafeWord Server Configurations ......................................................................................................... 24
4.3 ZyWALL IPSec VPN Client Configurations .......................................................................................... 28
4.4 Verify OTP via Login from the VPN Client ........................................................................................... 30
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL OTPv2 Support Notes
3
1. Introduction
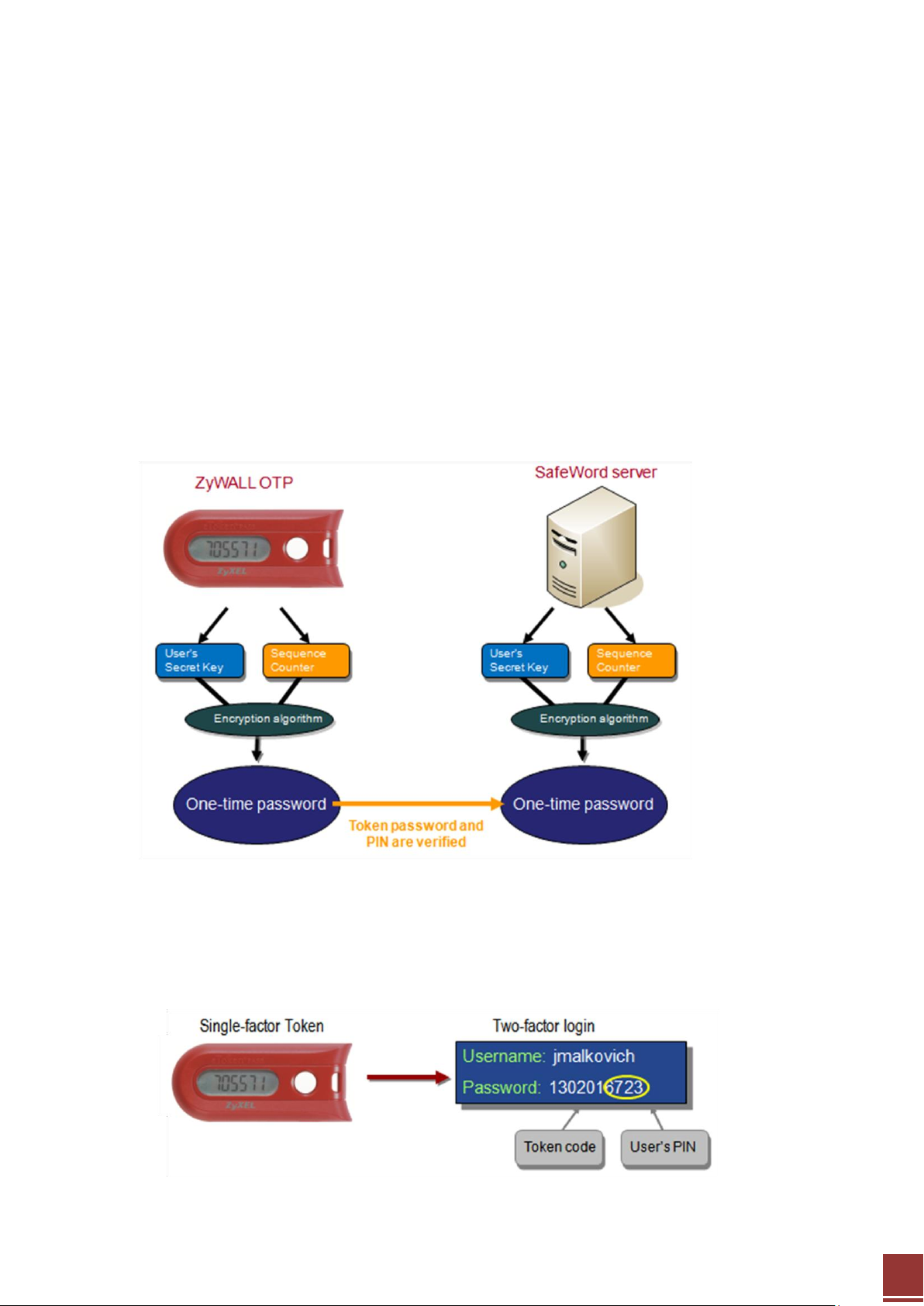
One-Time Password (OTP) Authentication
One-Time Password (OTP) is another optimum security technology that enables a server to authenticate
you based on a password that is unique every time you try to access a protected network.
Two-Factor Authentication
Two-factor authentication is an optimum security methodology, because it requires something you have
(your ZyWALL OTP Token) and something you know (your secure password or PIN). A two-factor system
is far more secure than using just a password, since many skilled hackers can quite easily access
password-only protected computers and networks. The illustration shows the concept of Two-Factor
authentication.
User PIN and Token code
User PIN is what you know and Token code is what you have.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL OTPv2 Support Notes
4
ZyWALL OTP Products Components
ZyWALL OTP, which includes the ZyWALL OTP Token and SafeWord 2008, provides secure verification of
identity to remote Virtual Private Network (VPN) and Local Area Network (LAN) users.
SafeWord product installation always includes:
- SafeWord Core Server
- Management console (AD or SafeWord Management Console)
- Agents or SafeWord RADIUS Server
SafeWord Core Server
The SafeWord Core Server consists of 3 main components:
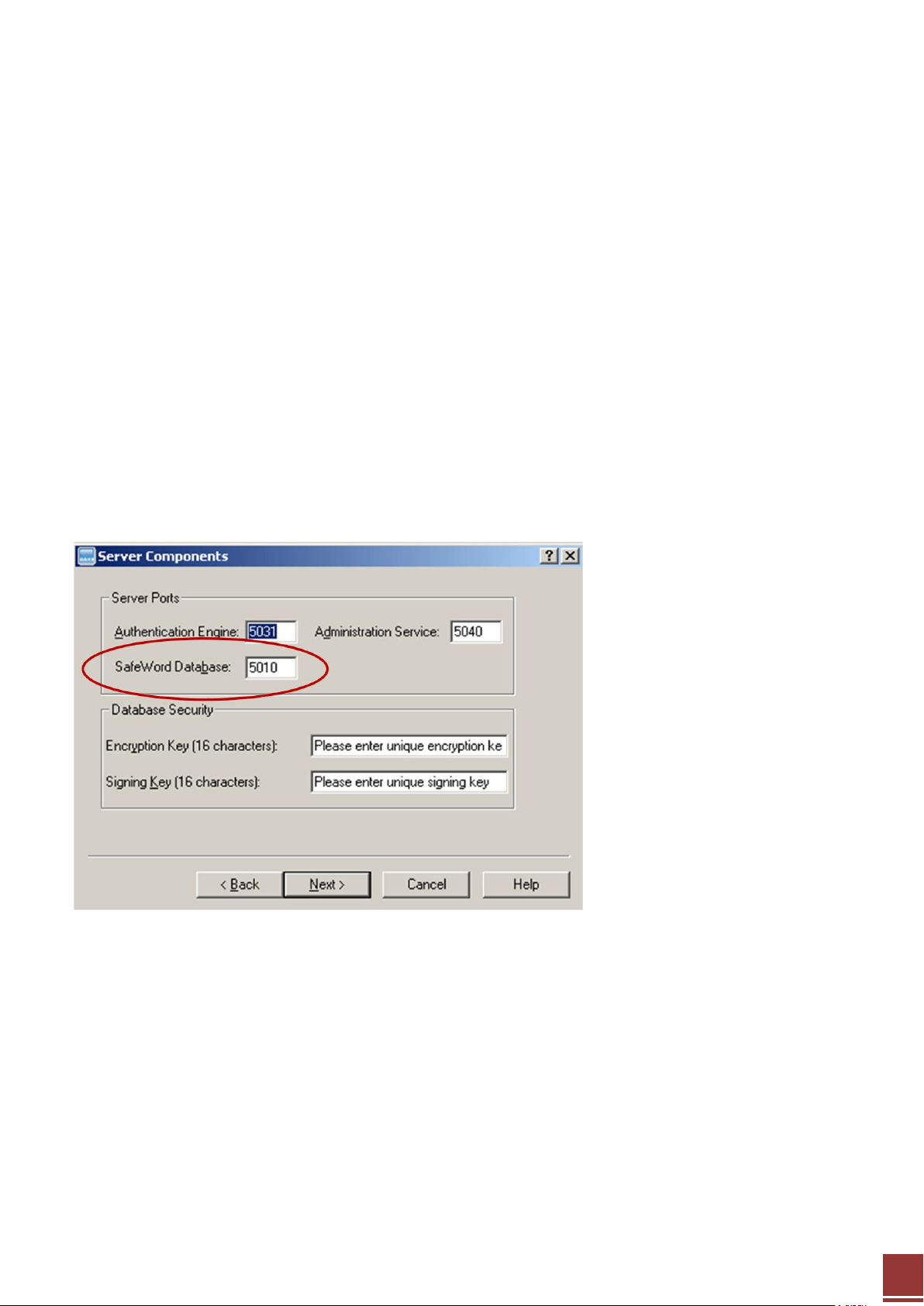
- Database server (MySQL) – installed by default. The SafeWord database serves as the repository for
token records independent of the management mode. It stores the Token’s serial numbers and Token
(seed) used to generating OTP. The database server listens on port 5010 by default and only the
Administration service and Authentication engines can query it directly.
- Administration server – runs administration services and performs tasks initiated by administrators
or users. Updates the SafeWord database and synchronizes SafeWord database data in configurations
with MMC console and User Center. Also performs replication of changes between peers. It is listening
on port 5040 by default.
- Authentication server (AAA) – runs the authentication engine that verifies that the passcode supplied
with an access request is correct for the token assigned to a specific user. It is listening on port 5031
by default.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL OTPv2 Support Notes
5
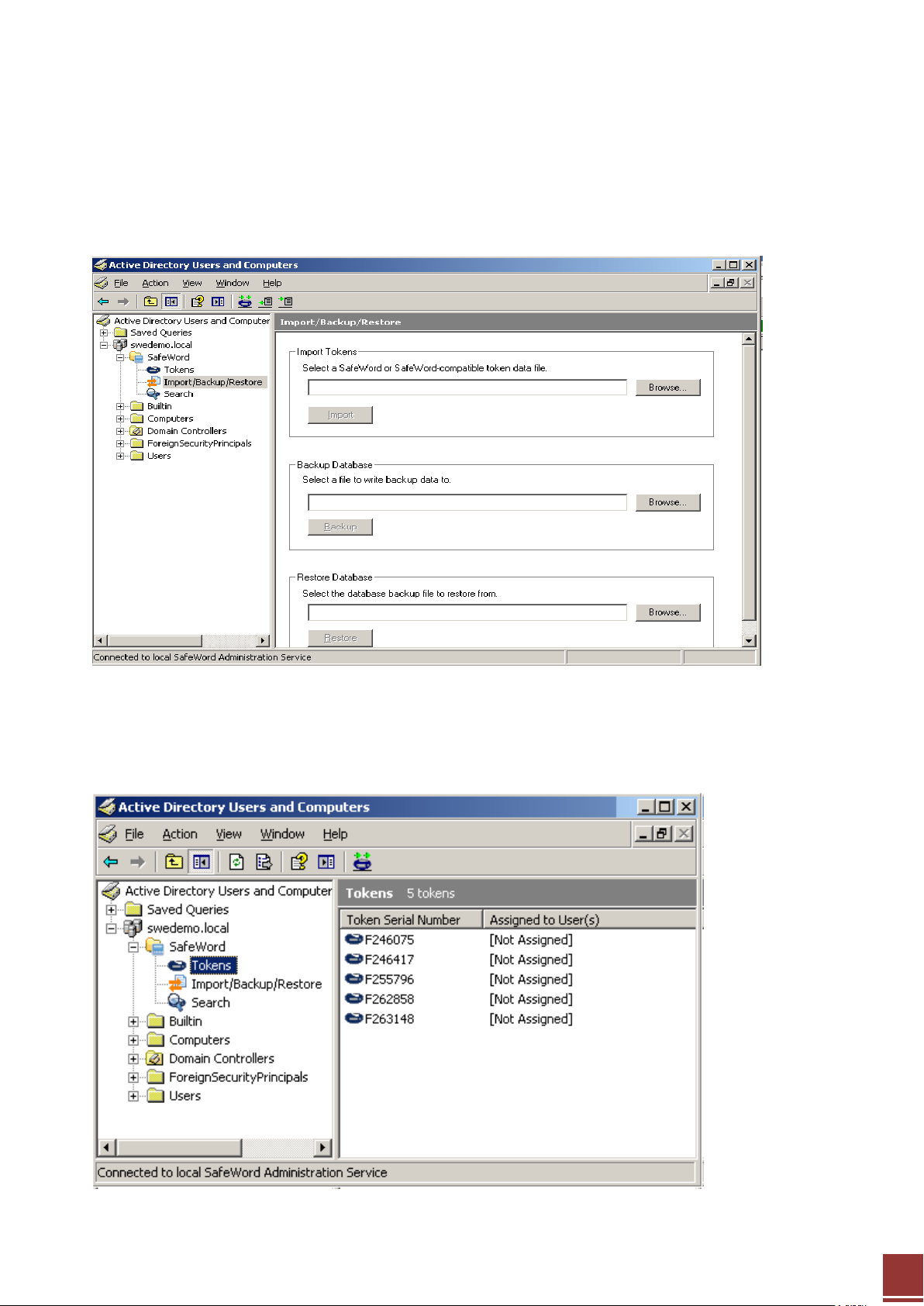
Management Console (AD)
The Management console integrated with Microsoft AD is the interface used to directly update the
database via the SafeWord Administration Service.
You can use this to import Tokens (add tokens serial numbers to SafeWord database) or backup and
restore Token data.
It also lets you view and manage all imported Tokens.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
6
Agents or SafeWord RADIUS Server
The OTP RADIUS authentication server is a standard Microsoft RADIUS component based on Internet
Authentication Service (IAS). The agent contains a configuration file specifying where the SafeWord
server holds the user repository and the Authentication service.
An agent can be installed only if it’s supporting (base) software components exist. Otherwise the agent
will not appear for selection in the installation components window. For example, RADIUS server agent
can be installed only when there is IAS installed.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL OTPv2 Support Notes
7
2. Server Installation
2.1 Pre-requisites
Before starting to install the SafeWord server, user needs to verify:
- Hardware requirements of the system
CPU – Pentium IV or AMD @ 1.8 GHz (min), 2 GHz (recommended)
RAM – 1 GB (min), 4 GB (recommended)
Disk space – 3 to 5 GB (min)
- Software requirements of the system
Server OS – 32 or 64 bit Windows Server 2003 or 2008
Desktop OS – 32 or 64 bit Windows XP (SP2) or Vista
Have a working Active Directory environment if you are installing SafeWord 2008 ESP for
managing users.
Have IAS Agent installed for RADIUS authentication
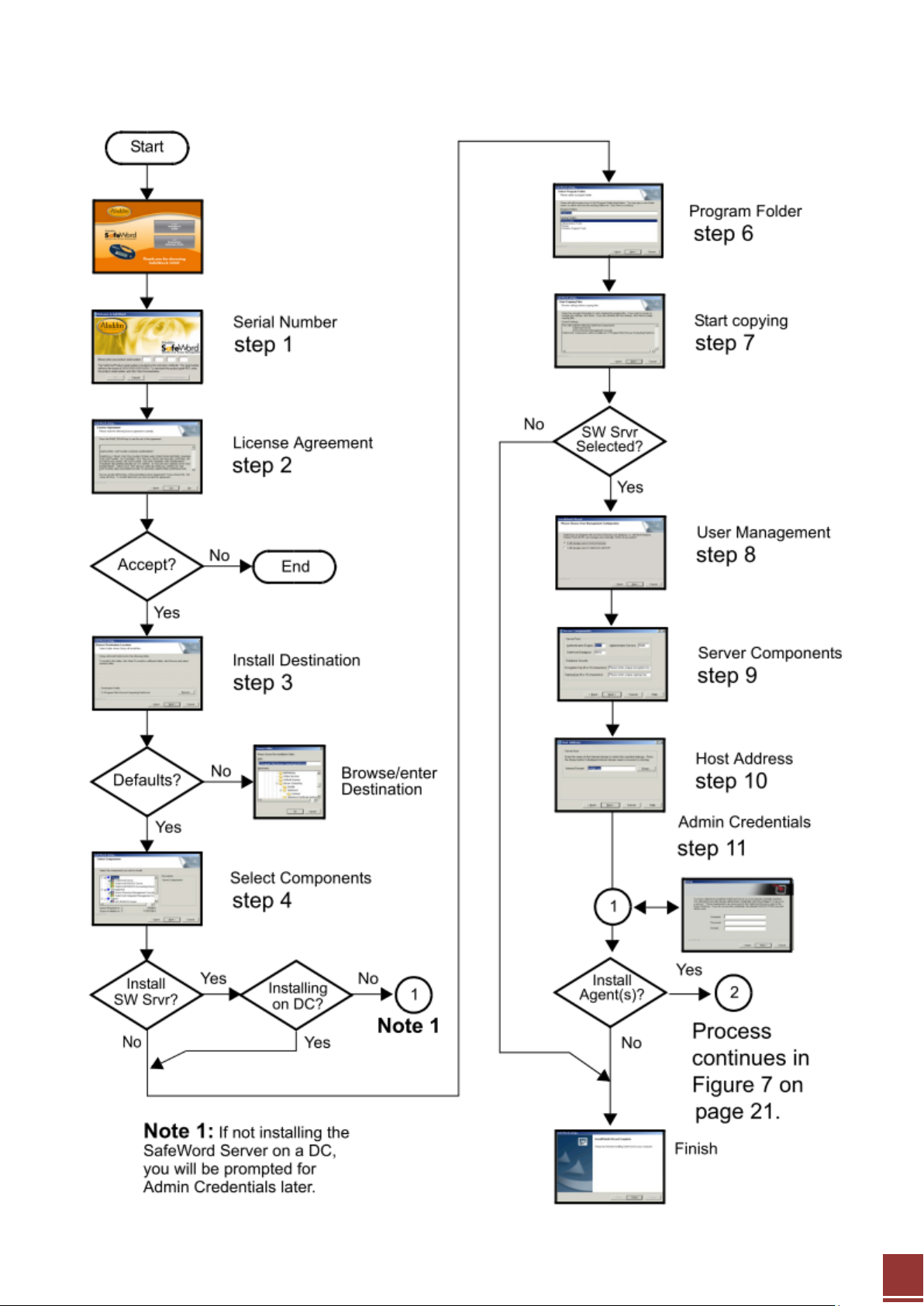
2.2 Installations walk through
We will briefly walk through the system installation process. For the up to date user manuals, users can
check SafeNet’s website. The link is: http://www.aladdin.com/safeword/docs/2008.aspx
Step1. Install SafeWord 2008 server
Below is a flow chart-type snapshot of the installation process, with no Agents selected for installation.
Users can check more detail information in chapter 2 “Installing and Activating SafeWord 2008” of
SafeWord 2008 Administration Guide on the SafeNet website.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL OTPv2 Support Notes
8
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL OTPv2 Support Notes
9
Step2. Activate SafeWord 2008 server
By default, SafeWord 2008 comes with a 30-day evaluation license. If you want to continue using it,
activation is required.
There are two methods of activating SafeWord 2008: using ADUC, or directly from Aladdin’s Website if
not using ADUC. In either case, you must sign in and register on the Aladdin portal at
https://portal.aladdin.com, before you can complete and submit an activation form. After activating, your
information will be verified, and the activation key and token records will be ownloaded automatically for
ADUC, and manually if you are not using ADUC.
After logging into the SafeNet portal, users can click the “SafeWord Activation” link to perform on-line
activation. Please refer to the following manual:
http://www.aladdin.com/pdf/safeword/Safeword-Products-Activation.pdf
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
10
For off-line activation, two files are provided to the customer upon purchase of tokens:
- Server license - a software activation file (
key.html
) that includes an activation key. This key should be
entered in place of the software serial ID.
- An import file containing the serial numbers of the tokens bought by the customer (
Import*.dat
).
Step1. Software activation - The activation file (key.html) is copied to the specific activation folder
(default is C:\Program Files\Secure Computing\SafeWord\SERVERS\AdminServer\activation) and then
the administration server is restarted.
Step2. Once activated, the activation file name is automatically changed to key.activated.html, and the
support expiration date will display a value of the valid expiration date.
Step3. From AD Users & Computers console, use the import option under the SafeWord tree item for
importing the tokens data.
Step3. Assign authenticators to domain users
Before you can assign and use hardware tokens, the token data records downloaded during activation
must be imported by AUDC. After the process is done, there are two ways to assign SafeWord tokens to
Active Directory users. You may use the Token Assignment Wizard, or you can manually enter the token
serial number in the serial number field.
Users can check more detailed information on chapter 3 “Active Directory Management” of SafeWord
2008 Administration Guide on the SafeNet website.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
11
3. OTP Authentication to an OTP-protected Network via SSL VPN over
ZyWALL USG
In the following example, we will employ Two Factor Authentication (ZyXEL OTP pack) to enhance
password security by using SSL VPN application provided by ZyWALL USG.
In order to use this application, you are required to configure your ZyWALL USG and SafeWord according
to the following steps:
1. Install the SafeWord server software on a computer.
(Note: Please refer to the SafeWord installation guide in Chapter 2. For more details, please check the
SafeNet website for the installation documentation)
2. Create the user accounts on the ZyWALL USG and in the SafeWord server.
3. Import each token’s database file into the server.
4. Assign the users to the OTP tokens (on the SafeWord server).
5. Configure the SafeWord as a RADIUS server in the ZyWALL USG Object > AAA Server screens.
6. Give the OTP tokens to (local or remote) the users who will remote login into the ZyWALL USG.
Note: ZyWALL OTP is a stand-alone product, which is not included in the ZyWALL USG package.
Network Topology
In this example, we will have one token and we will create user “OTP” who will log into ZyWALL USG with
OTP.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
12
3.1 ZyWALL USG Configurations
Step1. Create a user account on ZyWALL USG
1) Go to CONFIGURATION > Object > User/Group and click the “Add” button to create a new user
account.
2) Enter the user’s name, description and select the user type “ext-user” on the User configuration page.
3) Click the OK button to finish the configuration on this page.
Step2. Configure the AAA Server
1) Go to CONFIGURATION > Object > AAA Server and then navigate to the RADIUS page.
2) Configure the SafeWord server as:
Enter the IP address of the SafeWord server in the server address.
Enter the authentication port to RADIUS server, like Microsoft IAS; the default value is 1812.
Enter the Shared secret to RADIUS server in Key field.
Select the Group Membership Attribute; the default value is 11.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
13
Step3. Configure the Authentication Method
1) Go to CONFIGURATION > Object > Auth. Method and click the “Edit” button to modify the default
authentication method.
2) In the edit page, click “Add” to add the “group radius” into method list.
Step4. Create the SSL Application(s) according to your needs
1) Go to CONFIGURATION > Object > SSL Application and click the “Add” button to create an SSL VPN
application object.
2) For example, you create a web application to let you can remote access the FTP server via SSL VPN.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
14
Step5. Create the SSL VPN access policy
1) Go to CONFIGURATION > VPN > SSL VPN and click the “Add” button to create an SSL VPN access
policy.
2) Configure the access policy as:
Enter the policy name and description.
Select the User/Group object to apply this policy.
Select the application object to apply this policy.
Select the address object to apply if needed.
Click the “OK” button to finish the configuration.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
15
3.2 SafeWord Server Configurations
Step1. Create a RADIUS client
1) Take Microsoft IAS as the example.
2) Right click the RADIUS Client folder and click New > RADIUS Client to add a new setting.
Step2. Create a RADIUS client
1) Enter the name for the rule.
2) The Client address is the ZyWALL USG’s WAN IP address.
3) Click the “Next” button for the next step.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
16
4) Enter the Shared secret; the “Key” on ZyWALL USG AAA Server setting.
5) Click the “Finish” button to finish the configuration.
6) The new OTP client has been created.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
17
Step3. Assign the token to User
1) Enable the ADUC (Active Directory Users and Computers).
2) Click the “Users” folder to list all users and groups in RADIUS server.
3) Right click the OTP user, and then click “Properties”. Go to the “SafeWord” tab.
4) Enter the serial number of the assigned token. If needed, enter the PIN code for it. (this one is used as
the Password when login the ZyWALL USG)
5) After the configuration, you can click the “Tokens” link and check the token status.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
18
Step4. Enable the Remote Access
1) To allow the user to log in via SSL VPN, you have to enable the Remote Access Permission for this user.
2) Right click the OTP user, and then click the “Properties”. Go to the “Dial-in” tab and choose “Allow
access”.
Step5. Change the sequence of entering OTP and PIN for authentication
By Safenet default setting the password entry sequence is OTP + PIN. You should change this sequence to
match ZyWALL USG’s behavior (PIN+OTP). Here is the instruction for this.
1) Go to C:\Program files\Aladdin\SafeWord\Servers\Shared\ folder and open the file
(use Notepad for editing).
2) Search for the string: “
3) At the command “
4) Reload the SafeWord server.
# Set this to 'on' to force SoftPin to precede the password
Pin_Before_Password=off
”, change the value to ‘on’.
SCCservers.ini
”
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
19
3.3 Verify OTP via Login from the Remote PC
Step1. Login device
1) Enter the user name, password (PIN code which configured on chapter 3.2 step 3), and One-Time
Password which generated from the token.
2) Click the “SSL VPN” button to submit login information.
3) Once the OTP works correctly, you will see the SSL application that configured to the user to use.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
20
4. OTP Authentication to an OTP-protected Network via IPSec VPN
Client over the ZyWALL USG
In the following example, we will employ 2 Factor Authentication (ZyXEL OTP pack) to enhance password
security by using SSL VPN application provided by ZyWALL USG.
In order to use this application, you are required to configure your ZyWALL USG and SafeWord according
to the following steps:
2. Install the SafeWord server software on a computer.
(Note: Please refer to the SafeWord installation guide in Chapter 2. For more details, please check the
SafeNet website for the installation documentation)
2. Create the user accounts on the ZyWALL USG and in the SafeWord server.
3. Import each token’s database file into the server.
4. Assign the users to the OTP tokens (on the SafeWord server).
5. Configure the SafeWord as a RADIUS server in the ZyWALL USG Object > AAA Server screens.
6. Give the OTP tokens to (local or remote) the users who will remote login into the ZyWALL USG.
Note: ZyWALL OTP is a stand-alone product, which is not included in ZyWALL USG package.
Network Topology
In this example, we will have one token and we will create user “OTP” who will be the authenticator to
establish the IPSec VPN tunnel to ZyWALL USG.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
21
4.1 ZyWALL USG Configurations
Step1. Create a user account on ZyWALL USG
1) Go to CONFIGURATION > Object > User/Group and click the “Add” button to create a new user
account.
2) Enter the user’s name, description and select the user type “ext-user” on the User configuration page.
3) Click the OK button to finish the configuration on this page.
Step2. Configure the AAA Server
1) Go to CONFIGURATION > Object > AAA Server and then navigate to the RADIUS page.
2) Configure the SafeWord server as:
Enter the IP address of the SafeWord server in the server address.
Enter the authentication port of the RADIUS server, like Microsoft IAS; the default value is 1812.
Enter the Shared secret to RADIUS server in Key field.
Select the Group Membership Attribute; the default value is 11.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
22
Step3. Configure the Authentication Method
1) Go to CONFIGURATION > Object > Auth. Method and click the “Edit” button to modify the default
authentication method.
2) In the edit page, click “Add” to add the “group radius” into method list.
Step4. Configure the IPSec VPN Gateway policy
1) Go to CONFIGURATION > VPN > IPSec VPN and then navigate to the VPN Gateway page.
2) Enter the values for VPN phase-1 configuration.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
23
3) Enable the Extended Authentication and choose “Server Mode” for it.
Step5. Configure the IPSec VPN Connection policy
1) Go to CONFIGURATION > VPN > IPSec VPN and then navigate to the VPN Connection page.
2) Enter the values for VPN phase-2 configuration.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
24
4.2 SafeWord Server Configurations
Step1. Create a RADIUS client
1) Take Microsoft IAS as the example.
2) Right click the RADIUS Client folder and click New > RADIUS Client to add a new setting.
Step2. Create a RADIUS client
1) Enter the name for the rule.
2) The Client address is the ZyWALL USG’s WAN IP address.
3) Click the “Next” button for the next step.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
25
4) Enter the Shared secret; the “Key” on ZyWALL USG AAA Server setting.
5) Click the “Finish” button to finish the configuration.
6) The new OTP client has been created.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
26
Step3. Assign the token to User
1) Enable the ADUC console (Active Directory Users and Computers).
2) Click the “Users” folder to list all users and groups in the RADIUS server.
3) Right click the OTP user, and then click “Properties”. Go to “SafeWord” tab.
4) Enter the serial number of the assigned token. If needed, enter the PIN code for it (this one is used as
the Password when login the ZyWALL USG).
5) After the configuration, you can click the “Tokens” link and check the token status.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
27
Step4. Enable the Remote Access
1) To allow the user to log in via SSL VPN, you have to enable the Remote Access Permission for this user.
2) Right click the OTP user, and then click “Properties”. Go to the “Dial-in” tab and choose “Allow access”.
Step5. Change the sequence of entering OTP and PIN for authentication
By Safenet default setting the password entry sequence is OTP + PIN. You should change this sequence to
match ZyWALL USG’s behavior (PIN+OTP). Here is the instruction for this.
1) Go to C:\Program files\Aladdin\SafeWord\Servers\Shared\ folder and open the file
(use Notepad for editing).
2) Search for the string: “
3) At the command “
4) Reload the SafeWord server.
# Set this to 'on' to force SoftPin to precede the password
Pin_Before_Password=off
”, change the value to ‘on’.
SCCservers.ini
”
All contents copyright (c) 2010 ZyXEL Communications Corporation.

28
4.3 ZyWALL IPSec VPN Client Configurations
Step1. Configure the IPSec VPN Phase1 policy
1) Enter the values for VPN phase-1 configuration.
ZyXEL – ZyWALL OTPv2 Support Notes
2) Click the “Advanced Setting” button and click the X-Auth Popup feature.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
29
Step2. Configure the IPSec VPN Phase2 policy
1) Enter the values for VPN phase-2 configuration.
2) Click the “Save & Apply” button to finish the configuration and save it.
3) You can trigger the IPSec VPN tunnel by clicking the “Open Tunnel” button.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
30
4.4 Verify OTP via Login from the VPN Client
Step1. Trigger the IPSec VPN tunnel
1) Click the “Open Tunnel” button on IPSec VPN client (The VPN tunnel must be triggered from Client
side because it is a dynamic tunnel).
2) When doing the Phase-1 authentication, the authentication window will pop-up for the X-Auth login.
3) Enter the user name in the “Login” field and PIN code + password in the “Password” field.
Step2. Trigger the IPSec VPN tunnel
1) There are only 10 seconds to enter the authentication information into X-Auth window. If you use
more time to finish it, the tunnel will fail to establish. You can see the message on VPN Console as in
the picture below.
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL OTPv2 Support Notes
31
2) If the VPN tunnel is established successfully, you can see the message on VPN Console as below
picture.
Step3. Check the VPN tunnel status
You can see the VPN connection status is Connected on CONFIGURATION > VPN > IPSec VPN > VPN
Connection page. Also can check the IPSec VPN SA on MONITOR > VPN Monitor > IPSec page.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
 Loading...
Loading...