Watchguard Firebox X5, Firebox X15, Firebox X50, Firebox X500, Firebox X5000 Reference Manual
...Page 1

WatchGuard
®
Firebox® System
Reference Guide
WatchGuard Firebox System
Page 2

Notice to Users
Information in this guide is subject to change without notice. Companies, names, and data used in examples herein are
fictitious unless otherwise noted. No part of this guide may be reproduced or transmitted in any form or by any means,
electronic or mechanical, for any purpose, without the express written permission of WatchGuard Technologies, Inc.
Copyright, Trademark, and Patent Information
Copyright© 1998 - 2003 WatchGuard Technologies, Inc. All rights reserved.
AppLock, AppLock/Web, Designing peace of mind, Firebox, Firebox 1000, Firebox 2500, Firebox 4500, Firebox II,
Firebox II Plus, Firebox II FastVPN, Firebox III, Firebox SOHO, Firebox SOHO 6, Firebox SOHO 6tc, Firebox
SOHO|tc, Firebox V100, Firebox V80, Firebox V60, Firebox V10, LiveSecurity, LockSolid, RapidStream, RapidCore,
ServerLock, WatchGuard, WatchGuard Technologies, Inc., DVCP technology, Enforcer/MUVPN, FireChip,
HackAdmin, HostWatch, Make Security Your Strength, RapidCare, SchoolMate, ServiceWatch, Smart Security.
Simply Done., Vcontroller, VPNforce, The W-G logo are either registered trademarks or trademarks of WatchGuard
Technologies, Inc. in the United States and/or other courtries.
© Hi/fn, Inc. 1993, including one or more U.S. Patents: 4701745, 5016009, 5126739, and 5146221 and other
patents pending.
Microsoft®, Internet Explorer®, Windows® 95, Windows® 98, Windows NT® and Windows® 2000 are either
registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
Netscape and Netscape Navigator are registered trademarks of Netscape Communications Corporation in the United
States and other countries.
RC2 Symmetric Block Cipher, RC4 Symmetric Stream Cipher, RC5 Symmetric Block Cipher, BSAFE, TIPEM, RSA
Public Key Cryptosystem, MD, MD2, MD4, and MD5 are either trademarks or registered trademarks of RSA Data
Security, Inc. Certain materials herein are Copyright © 1992-1999 RSA Data Security, Inc. All rights reserved.
RealNetworks, RealAudio, and RealVideo are either a registered trademark or trademark of RealNetworks, Inc. in the
United States and/or other countries.
Java and all Jave-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. in the United
States and other countries. All right reserved.
© 1995-1998 Eric Young (eay@cryptsoft). All rights reserved.
© 1998-2000 The OpenSSL Project. All rights reserved. Redistribution and use in source and binary forms, with or
without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgment:
"This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://
www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to endorse or promote products derived from
this software without prior written permission. For written permission, please contact openssl-core@openssl.org.
5. Products derived from this software may not be called "OpenSSL" nor may "OpenSSL" appear in their names without
prior written permission of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following acknowledgment: "This product includes software
developed by the OpenSSL Project for use in the OpenSSL Toolkit (http://www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY EXPRESSED OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL
PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com). This product includes software written by Tim
ii WatchGuard Firebox System
Page 3

Hudson (tjh@cryptsoft.com).
© 1995-1998 Eric Young (eay@cryptsoft.com)
All rights reserved.
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as the following conditions are aheared to. The
following conditions apply to all code found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not just the
SSL code. The SSL documentation included with this distribution is covered by the same copyright terms except that
the holder is Tim Hudson (tjh@cryptsoft.com).
Copyright remains Eric Young's, and as such any Copyright notices in the code are not to be removed. If this package is
used in a product, Eric Young should be given attribution as the author of the parts of the library used. This can be in
the form of a textual message at program startup or in documentation (online or textual) provided with the package.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgement:
"This product includes cryptographic software written by Eric Young (eay@cryptsoft.com)" The word 'cryptographic'
can be left out if the routines from the library being used are not cryptographic related :-).
4. If you include any Windows specific code (or a derivative thereof) from the apps directory (application code) you
must include an acknowledgement: "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
The licence and distribution terms for any publicly available version or derivative of this code cannot be changed. i.e.
this code cannot simply be copied and put under another distribution licence [including the GNU Public Licence.]
The mod_ssl package falls under the Open-Source Software label because it's distributed under a BSD-style license. The
detailed license information follows.
Copyright (c) 1998-2001 Ralf S. Engelschall. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgment:
"This product includes software developed by Ralf S. Engelschall <rse@engelschall.com> for use in the mod_ssl
project (http://www.modssl.org/)."
4. The names "mod_ssl" must not be used to endorse or promote products derived from this software without prior
written permission. For written permission, please contact rse@engelschall.com.
5. Products derived from this software may not be called "mod_ssl" nor may "mod_ssl" appear in their names without
prior written permission of Ralf S. Engelschall.
6. Redistributions of any form whatsoever must retain the following acknowledgment: "This product includes software
developed by Ralf S. Engelschall <rse@engelschall.com> for use in the mod_ssl project (http://www.modssl.org/)."
THIS SOFTWARE IS PROVIDED BY RALF S. ENGELSCHALL ``AS IS'' AND ANY EXPRESSED OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL RALF S.
ENGELSCHALL OR HIS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
Reference Guide iii
Page 4

TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The Apache Software License, Version 1.1
Copyright (c) 2000 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. The end-user documentation included with the redistribution, if any, must include the following acknowledgment:
"This product includes software developed by the Apache Software Foundation (http://www.apache.org/)." Alternately,
this acknowledgment may appear in the software itself, if and wherever such third-party acknowledgments normally
appear.
4. The names "Apache" and "Apache Software Foundation" must not be used to endorse or promote products derived
from this software without prior written permission. For written permission, please contact apache@apache.org.
5. Products derived from this software may not be called "Apache", nor may "Apache" appear in their name, without
prior written permission of the Apache Software Foundation.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE APACHE SOFTWARE FOUNDATION
OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE,
EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on behalf of the Apache Software
Foundation. For more information on the Apache Software Foundation, please see <http://www.apache.org/>.
Portions of this software are based upon public domain software originally written at the National Center for
Supercomputing Applications, University of Illinois, Urbana-Champaign.
All other trademarks or trade names mentioned herein, if any, are the property of their respective owners.
Part No:
WFS Software Number 7.0
iv WatchGuard Firebox System
Page 5

Contents
CHAPTER 1 Internet Protocol Reference ..................... 1
Internet Protocol Header .................................................. 1
Internet Protocol Options ................................................. 6
Transfer Protocols ............................................................ 7
IP header number list ..................................................... 2
UDP ........................................................................... 7
TCP ........................................................................... 8
ICMP .......................................................................... 8
Other protocols ............................................................ 8
Standard Ports and Random Ports .................................... 9
CHAPTER 2 MIME Content Types ............................... 11
CHAPTER 3 Services and Ports ................................... 27
Ports Used by WatchGuard Products ............................... 28
Ports used by Microsoft Products .................................... 29
Well-Known Services List ................................................ 30
CHAPTER 4 Types of Services ..................................... 39
Packet Filter Services ..................................................... 39
Any .......................................................................... 39
AOL ......................................................................... 40
Reference Guide v
Page 6

archie ....................................................................... 40
auth (ident) ................................................................ 41
Citrix ICA (WinFrame) .................................................. 42
Clarent-gateway ..........................................................42
Clarent-command ....................................................... 43
CU-SeeMe .................................................................44
DHCP-Server/Client ..................................................... 44
DNS ......................................................................... 45
Filtered-HTTP ............................................................. 45
Filtered-SMTP ............................................................46
finger ........................................................................ 46
Gopher ..................................................................... 47
HTTPS ...................................................................... 47
IMAP ........................................................................ 47
LDAP ........................................................................ 48
Lotus Notes ...............................................................48
NNTP .......................................................................49
NTP ..........................................................................50
Outgoing Services ....................................................... 50
pcAnywhere ...............................................................50
ping ......................................................................... 51
POP2 and POP3 ......................................................... 51
PPTP ........................................................................52
RADIUS ..................................................................... 52
RIP ...........................................................................53
SMB (Windows Networking) .......................................... 53
SNMP ....................................................................... 55
SNMP-Trap ................................................................ 55
SQL*Net ................................................................... 55
Sybase SQL-Server ...................................................... 56
ssh ........................................................................... 56
syslog ....................................................................... 57
TACACS .................................................................... 58
TACACS+ .................................................................. 58
telnet ........................................................................59
vi WatchGuard Firebox System
Page 7

TFTP ........................................................................ 59
Timbuktu .................................................................. 60
Time ........................................................................ 60
traceroute ................................................................. 60
WAIS ........................................................................ 61
WatchGuard .............................................................. 61
WatchGuard Encrypted Connections .............................. 62
WatchGuard Logging .................................................. 62
WGAgent .................................................................. 62
whois ....................................................................... 63
Proxied Services ............................................................ 63
DCE-RPC .................................................................. 63
FTP .......................................................................... 64
H323 ........................................................................ 65
HTTP ........................................................................ 65
Proxied-HTTP ............................................................. 66
RTSP ........................................................................ 67
SMTP ....................................................................... 67
CHAPTER 5 Common Log Messages .......................... 69
CHAPTER 6 Resources ................................................. 81
Publishers ..................................................................... 81
Books ........................................................................... 82
Non-Fiction ............................................................... 82
Fiction ...................................................................... 83
White Papers & Requests for Comments ......................... 83
Mailing Lists .................................................................. 84
Web Sites ..................................................................... 84
Newsgroups .................................................................. 86
CHAPTER 7 Out-of-Band Initialization Strings ........... 87
PPP Initialization Strings ................................................. 87
Modem Initialization Strings ........................................... 93
CHAPTER 8 Firebox Read-Only System Area ............ 97
Read-Only System Area ................................................. 97
Reference Guide vii
Page 8

Enhanced System Mode .................................................98
Initializing a Firebox using TCP/IP ...................................98
Initializing a Firebox Using a Serial Cable ......................... 99
Booting from the system area ......................................100
Working with a Firebox booted from the read-only system
area
Trou ble sh oo ti ng ........................................................101
................................................................100
Initializing a Firebox Using a Modem .............................102
Initializing using Remote Provisioning ............................102
Managing Flash Disk Memory .......................................104
Making a backup of the current configuration ................. 104
Restoring a backup configuration .................................105
CHAPTER 9 Glossary .................................................. 107
CHAPTER 10 Field Definitions ..................................... 153
System Manager ..........................................................153
Connect to Firebox dialog box ....................................153
Enter Read/Write Passphrase dialog box ........................ 154
Polling dialog box .....................................................154
Syslog Color dialog box .............................................154
Flash Disk Management Tool .......................................155
Enter Encryption Key dialog box ..................................155
Flash Disk Management Tool dialog box ........................155
Log Utility .................................................................... 156
Copy or Merge Logs dialog box ................................... 156
LogViewer ...................................................................157
Find Keyphrase dialog box ..........................................157
Preferences dialog box ...............................................158
Search Fields dialog box .............................................158
Policy Manager ............................................................160
1-to-1 Mapping dialog box .........................................160
Add Address dialog box .............................................160
Add Dynamic NAT dialog box .....................................161
Add Exception dialog box ..........................................161
Add External IP dialog box ......................................... 162
viii WatchGuard Firebox System
Page 9

Add Firebox Group dialog box .................................... 162
Add IP Address dialog box ......................................... 162
Add Member dialog box ............................................ 163
Add Port dialog box .................................................. 163
Add Route dialog box ............................................... 164
Add Service dialog box .............................................. 164
Add Static NAT dialog box ......................................... 164
Advanced DVCP Policy Configuration dialog box ............ 165
Advanced Dynamic NAT dialog box ............................. 165
Advanced Export File Preferences dialog box ................. 166
Advanced Mobile User VPN Policy Configuration dialog
box
................................................................ 166
Aliases dialog box ..................................................... 168
Authentication Servers dialog box ................................ 168
Basic DVCP Server Configuration dialog box .................. 172
Blocked Ports dialog box ........................................... 172
Blocked Sites dialog box ............................................ 173
Blocked Sites Exceptions dialog box ............................ 174
Certificate Authority Configuration ............................... 174
Configure Gateways dialog box ................................... 175
Configure IPSec Tunnels dialog box .............................. 175
Configure Tunnels dialog box ...................................... 176
Configure Tunnel dialog box ....................................... 176
Connect to Firebox dialog box .................................... 177
Default Gateway dialog box ........................................ 177
Default Packet Handling dialog box ............................. 177
DHCP Server dialog box ............................................ 179
DHCP Subnet Properties dialog box ............................. 180
DVCP Client Setup dialog box ..................................... 181
DVCP Client Wizard .................................................. 182
DVCP Server Properties dialog box .............................. 183
DVCP Server Properties dialog box .............................. 184
Dynamic NAT dialog box ........................................... 185
Edit Routing Policy dialog box ..................................... 186
Enter Firebox Access Passphrases dialog box ................. 187
Reference Guide ix
Page 10

Enter Tunnel Name dialog box .....................................187
Filter Authentication dialog box ...................................188
Firebox Flash Disk dialog box ...................................... 189
Firebox Name dialog box ........................................... 190
FTP Proxy dialog box .................................................190
Generate Key dialog box ............................................ 191
High Availability dialog box ......................................... 191
Host Alias dialog box .................................................192
HTTP Proxy dialog box ...............................................192
Incoming dialog box ..................................................200
Incoming SMTP Proxy dialog box .................................201
IPSec Configuration dialog box ....................................204
IPSec Logging dialog box ........................................... 206
Logging and Notification dialog box .............................206
Logging Setup dialog box ..........................................207
Manual Security dialog box ......................................... 208
Mobile User Client - Select New Passphrase dialog box .... 208
Mobile User VPN Wizard ............................................209
Mobile User VPN dialog box .......................................212
NAT Setup dialog box ................................................212
Network Configuration dialog box ................................ 214
New MIME Type dialog box ........................................ 219
New Service dialog box .............................................. 219
Outgoing SMTP Proxy dialog box ................................220
PPTP Logging dialog box ........................................... 222
Remote Gateway dialog box ....................................... 222
Remote User Setup dialog box ....................................223
Select Firebox Time Zone dialog box ............................225
Select Gateway dialog box ..........................................225
Select MIME Type dialog box ......................................225
Services dialog box ...................................................225
Service Properties dialog box ...................................... 226
Set Policy Ordering dialog box .................................... 228
Setup Firebox User dialog box .....................................228
Setup New User dialog box ......................................... 229
x WatchGuard Firebox System
Page 11

Setup Routes dialog box ............................................ 229
Slash Notation dialog box .......................................... 230
SpamScreen dialog box ............................................. 230
WatchGuard Find dialog box ...................................... 231
WatchGuard VPN dialog box ...................................... 231
Firebox Monitors ......................................................... 233
Add Displayed Service dialog box ................................ 233
Remove Site dialog box ............................................. 233
View Properties dialog box ......................................... 233
Historical Reports ........................................................ 234
Add Report Filter dialog box ....................................... 234
Historical Reports dialog box ...................................... 236
Report Properties dialog box ...................................... 237
HostWatch .................................................................. 240
Filter Properties dialog box ......................................... 240
Properties dialog box ................................................ 242
WatchGuard Security Event Processor ........................... 243
Set Log Encryption Key dialog box ............................... 246
Index .................................................................... 247
Reference Guide xi
Page 12

xii WatchGuard Firebox System
Page 13

CHAPTER 1 Internet Protocol Reference
Internet Protocol (IP) specifies the format of packets and the addressing
scheme for sending data over the Internet. By itself, it functions like a
postal system allowing you to address a package and drop it into the
system. There is, however, no direct link between you and the recipient.
In other words, there is no package.
Most networks combine IP with higher-level protocols like Transmission
Control Protocol (TCP). Unlike simple IP, TCP/IP establishes a
connection between two host servers so that they can send messages back
and forth. TCP/IP provides the “packaging.”
Internet Protocol Header
IP is an Internet standard that enables the shipment of datagrams – selfcontained packets of information that include their own address and
delivery instructions. IP prepends a header to each datagram. The IP
header contains a minimum of twelve attributes as well as additional
optional attributes.
Reference Guide 1
Page 14
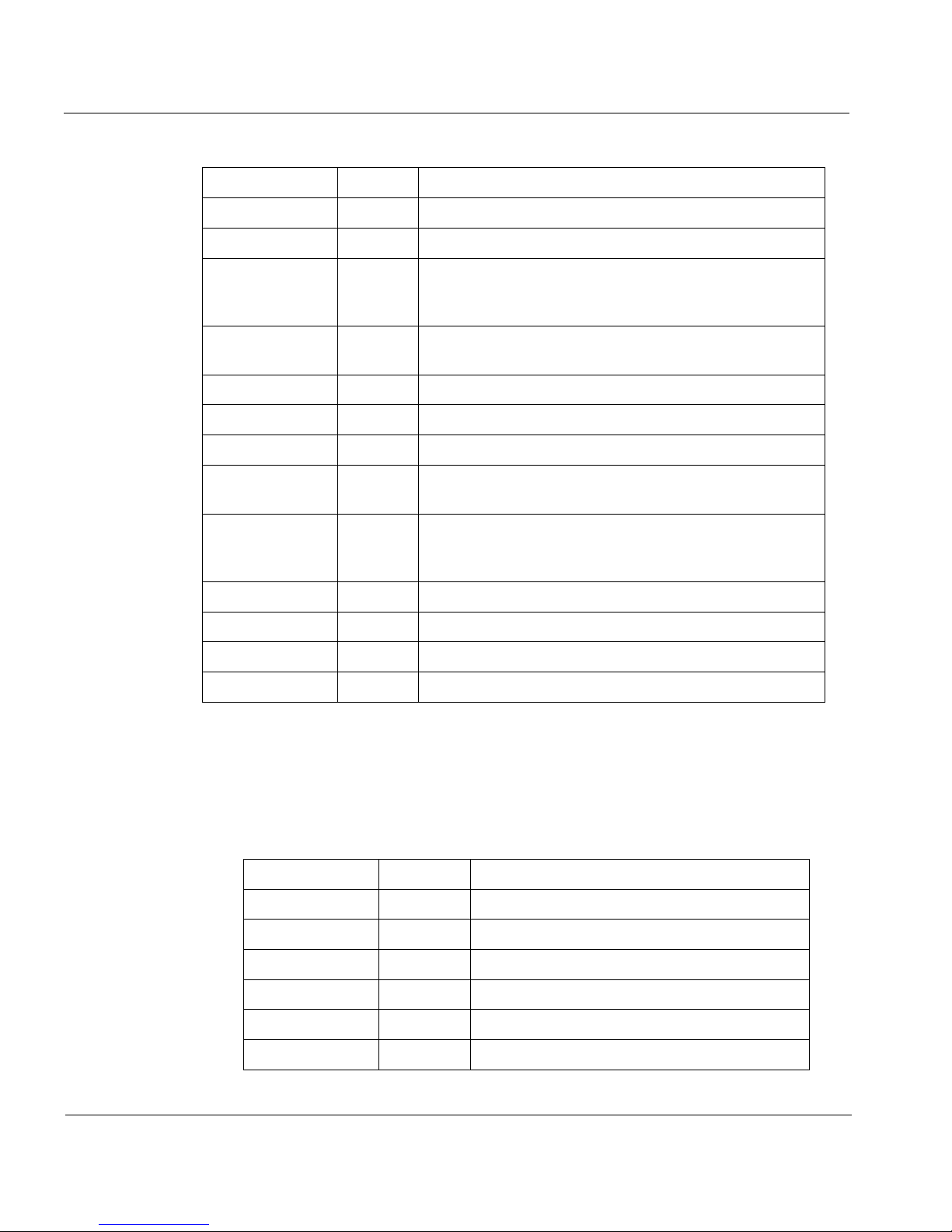
CHAP TER 1: Internet Protocol Reference
Attribute Size Description
Version 4 bits IP format number (Current version = 4)
IHL 4 bits Header length in 32-bit words (Minimum = 5)
TOS 8 bits Type of service sets routing priorities. It is
Tot _Le n 16 bits Total length of packet measured in octets. It is
ID 16 bits Packet ID, used for reassembling fragments.
Flags 3 bits Miscellaneous flags
Frag_Off 13 bits Identifies fragment part for this packet.
TTL 8 bits Time to live. It sets the maximum time the
Protocol 8 bits IP protocol number. Indicates which of TCP,
generally under-utilized because few application
layers can set it.
used in reassembling fragments.
datagram remains alive in the system.
UDP, ICMP, IGMP, or other Transport protocol
is inside.
Check 16 bits Checksum for the IP header
Sour_Addr 32 bits Source IP address
Dest_Addr 32 bits Destination IP address
Options 24 bits IP Options (Present if IHL is 6)
IP header number list
The IP Protocol header contains an 8-bit field that identifies the protocol
for the transport layer for the datagram.
Keyword Number Protocol
ICMP 1 Internet Control Message
IGMP 2 Internet Group Management
GGP 3 Gateway-to-Gateway
IP 4 IP-within-IP (encapsulation)
0 Reserved
ST 5 Stream
2 WatchGuard Firebox System
Page 15
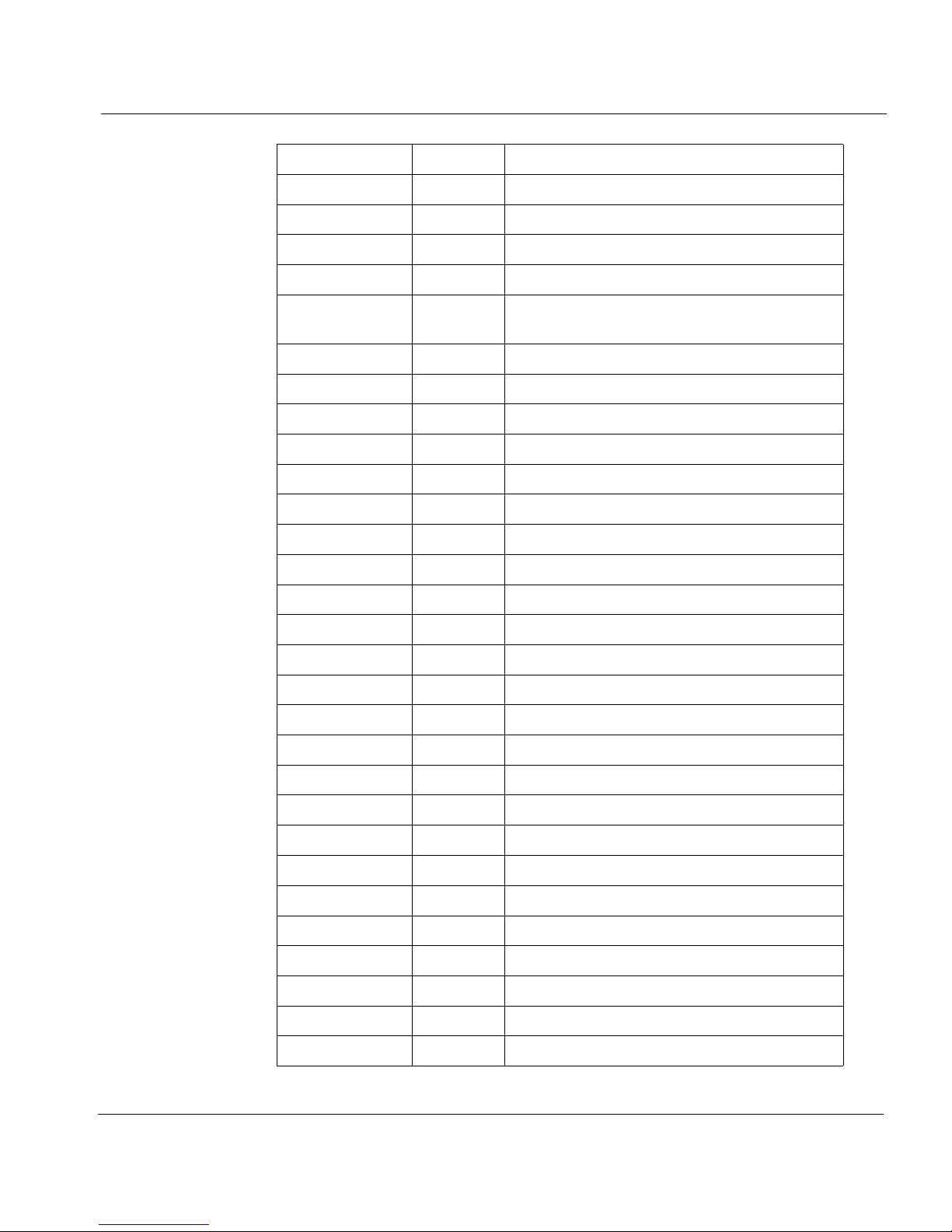
Internet Protocol Header
Keyword Number Protocol
TCP 6 Transmission Control Protocol
UCL 7 UCL
EGP 8 Exterior Gateway Protocol
IGP 9 Any private interior gateway
BBN-RCC-
10 BBN RCC Monitoring
MON
NVP-II 11 Network Voice Protocol
PUP 12 PUP
ARGUS 13 ARGUS
EMCON 14 EMCON
XNET 15 Cross Net Debugger
CHAOS 16 Chaos
UDP 17 User Datagram Protocol
MUX 18 Multiplexing
DCN-MEAS 19 DCN Measurement Subsystems
HMP 20 Host Monitoring
PRM 21 Packet Radio Measurement
XNS-IDP 22 XEROX NS IDP
TRUNK-1 23 Trunk-1
TRUNK-2 24 Trunk-2
LEAF-1 25 Leaf-1
LEAF-2 26 Leaf-2
RDP 27 Reliable Data Protocol
IRTP 28 Internet Reliable Transaction
ISO-TP4 29 ISO Transport Protocol Class 4
NETBLT 30 Bulk Data Transfer Protocol
MFE-NSP 31 MFE Network Services Protocol
MERIT-INP 32 MERIT Internodal Protocol
SEP 33 Sequential Exchange Protocol
3PC 34 Third Party Connect Protocol
Reference Guide 3
Page 16

CHAP TER 1: Internet Protocol Reference
Keyword Number Protocol
IDPR 35 Inter-Domain Policy Routing Protocol
XTP 36 XTP
DDP 37 Datagram Delivery Protocol
IDPR-CMTP 38 IDPR Control Message Transport
TP++ 39 TP++ Transport Protocol
IL 40 IL Transport Protocol
SIP 41 Simple Internet Protocol
SDRP 42 Source Demand Routing Protocol
SIP-SR 43 SIP Source Route
SIP-FRAG 44 SIP Fragment
IDRP 45 Inter-Domain Routing Protocol
RSVP 46 Reservation Protocol
Protocol
GRE 47 General Routing Encapsulation
MHRP 48 Mobile Host Routing Protocol
BNA 49 BNA
ESP 50 Encapsulated Security Payload
AH 51 Authentication Header
I-NLSP 52 Integrated Net Layer Security TUBA
SWIPE 53 IP with Encryption
NHRP 54 NBMA Next Hop Resolution Protocol
55-60 Unassigned
61 Any host internal protocol
CFTP 62 CFTP
63 Any local network
SAT-EXPAK 64 SATNET and Backroom EXPAK
KRYPTOLAN 65 Kryptolan
RVD 66 MIT Remote Virtual Disk Protocol
IPPC 67 Internet Pluribus Packet Core
4 WatchGuard Firebox System
68 Any distributed file system
Page 17
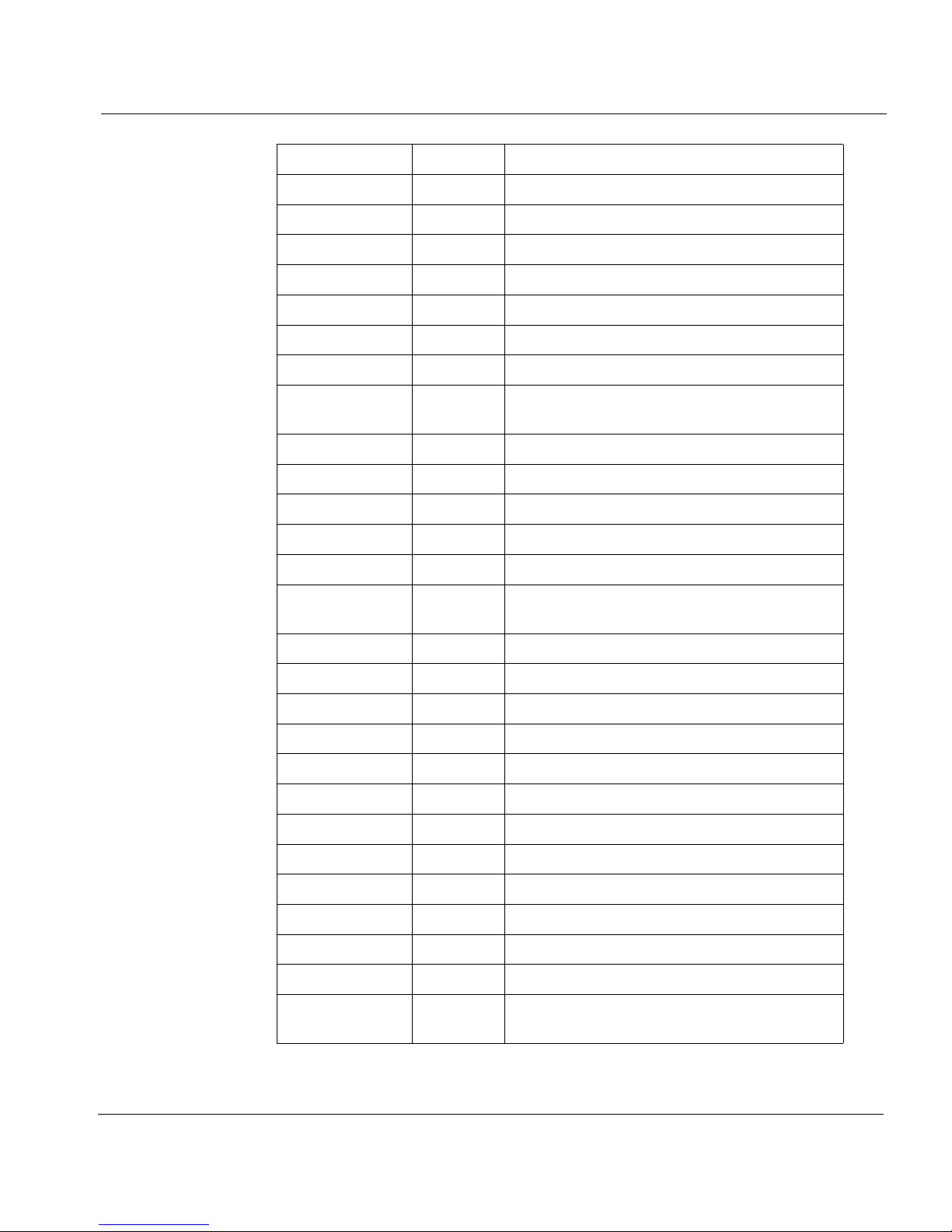
Internet Protocol Header
Keyword Number Protocol
SAT-MON 69 SATNET Monitoring
VISA 70 VISA Protocol
IPCV 71 Internet Packet Core Utility
CPNX 72 Computer Protocol Network Executive
CPHB 73 Computer Protocol Heart Beat
WSN 74 Wang Span Network
PVP 75 Packet Video Protocol
BR-SAT-
76 Backroom SATNET Monitoring
MON
SUN-ND 77 SUN NDPROTOCOL-Temporary
WB-MON 78 WIDEBAND Monitoring
WB-EXPAK 79 WIDEBAND EXPAK
ISO-IP 80 ISO Internet Protocol
VMTP 81 VMTP
SECURE-
82 SECURE-VMTP
VMTP
VINES 83 VINES
TTP 84 TTP
NSFNET-IGP 85 NSFNET-IGP
DGP 86 Dissimilar Gateway Protocol
TCF 87 TCF
IGRP 88 IGRP
OSPFIGP 89 OSPFIGP
SPRITE-RPC 90 Sprite RPC Protocol
LARP 91 Locus Address Resolution Protocol
MTP 92 Multicast Transport Protocol
AX.25 93 AX.25 Frames
IPIP 94 IP-within-IP Encapsulation Protocol
MICP 95 Mobile Internetworking Control
Reference Guide 5
Protocol
Page 18
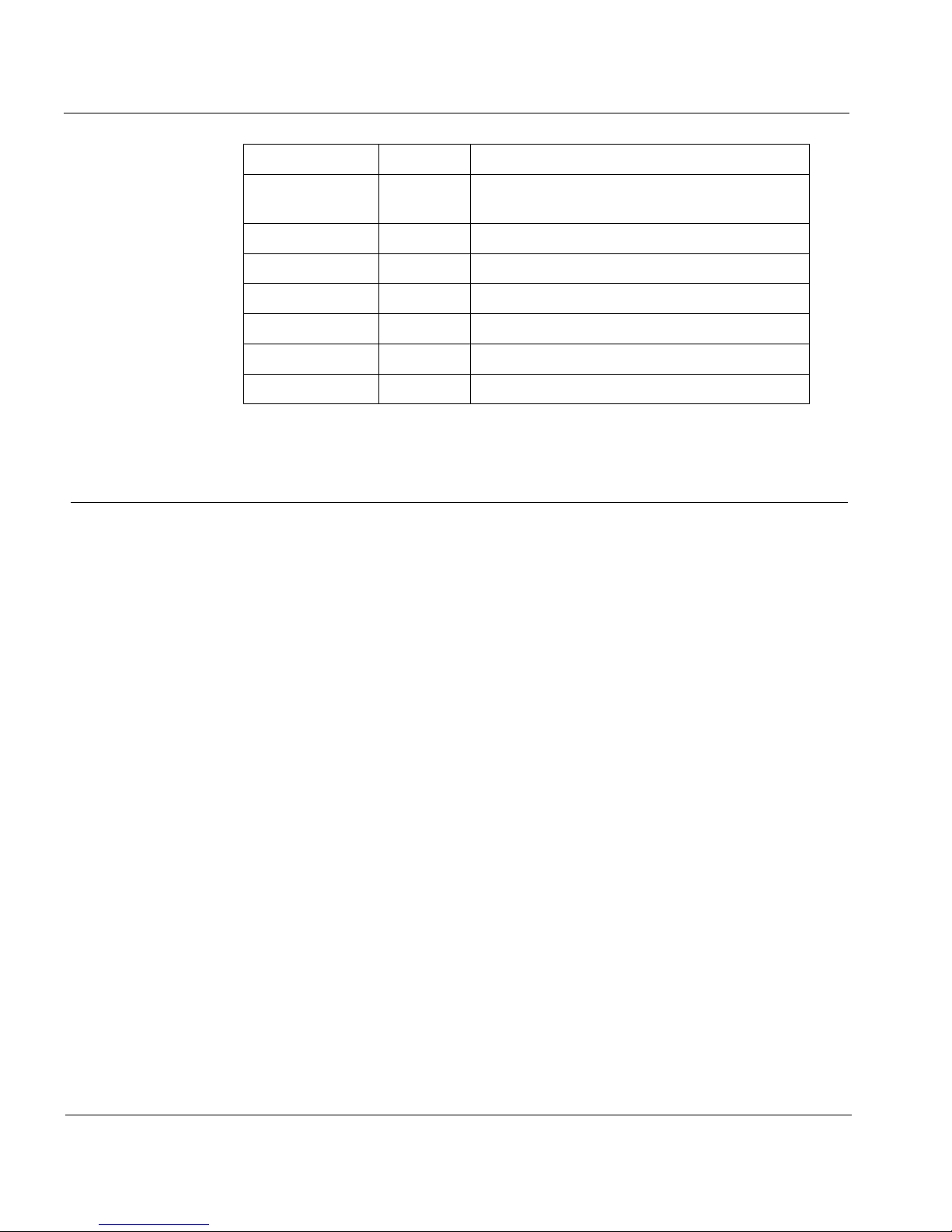
CHAP TER 1: Internet Protocol Reference
Keyword Number Protocol
SCC-SP 96 Semaphore Communications Security
ETHERIP 97 Ethernet-within-IP Encapsulation
ENCAP 98 Encapsulation Header
99 Any private encryption scheme
GMTP 100 GMTP
101-254 Unassigned
255 Reserved
Internet Protocol Options
Internet Protocol options are variable-length additions to the standard IP
header. Unfortunately, enabling IP options can be risky; hackers can use
them to specify a route that helps them gain access to your network.
Because most applications make it very obscure or difficult to use IP
options, they are rarely used.
Protocol
There are several kinds of IP options:
Security
Control routing of IP packets that carry sensitive data. Security
options are rarely supported.
Stream ID (SID)
The stream ID option is rarely supported.
Source Routing
Both the loose source route option and the strict source route
option enable the source of an Internet packet to provide routing
information. Source routing options can be very dangerous,
because a clever attacker might use them to masquerade as
another site. However, loose source routing and the traceroute
facility can also help debug some obscure routing problems.
Record Route
The record route option was originally intended for use in testing
the Internet. Unfortunately, record route can record only ten IP
6 WatchGuard Firebox System
Page 19

addresses. On the present Internet, typical long-haul
transmissions can involve twenty or thirty hops, rendering the
record route option obsolete.
Time Stamp
The time stamp option helps measure network propagation
delays. This task is done more effectively, however, with higherlevel time protocols or time-stamp messages.
Transfer Protocols
The IP protocol encapsulates information contained in the transport layer.
The transport layer has several protocols that specify how to transmit
data between applications: for example, UDP, TCP, ICMP, and others.
UDP
Transfer Protocols
User Datagram Protocol (UDP) is a connectionless, potentially unreliable
datagram protocol. It trades reliability for speed and low overhead. To
ensure accurate transmission, it requires that the application layer verify
that packets arrive at their destination.
Characteristics of UDP include:
• Often used for services involving the transfer of small amounts of
data where retransmitting a request is not a problem.
• Used for services such as time synchronization in which an
occasionally lost packet will not affect continued operation. Many
systems using UDP resend packets at a constant rate to inform their
peers about interesting events.
• Primarily used on LANs, in particular for Network File System (NFS)
services where its low overhead gives it a substantial performance
advantage. (Network File System is a popular TCP/IP service for
providing shared file systems over a network.) A lack of congestion
control means that using UDP for bulk data transfer over long-haul
connections is not recommended.
• Supports broadcasts.
• Provides abstraction of ports.
Reference Guide 7
Page 20

CHAP TER 1: Internet Protocol Reference
• A connection is described by its source and destination ports and its
source and destination IP addresses. In typical usage, port numbers
below 1024 are reserved for well-known services (destinations), and
the client side is supposed to use ports above 1023 for the source of
the connection. However, this rule has many notable exceptions. In
particular, NFS (port 2049) and Archie (port 1525) use server ports at
numbers above 1024. Some services use the same source and
destination port for server-to-server connections. Common examples
are DNS (53), NTP (123), syslog (514), and RIP (520).
TCP
Transmission Control Protocol (TCP) provides reliable stream-oriented
services. It trades speed and overhead for increased reliability. Like UDP,
TCP provides source and destination ports that are used in a similar
fashion.
TCP uses a rather complicated state machine to manage connections.
There are several attribute bits that control the state of a connection. Three
very important attribute bits of TCP packets are the SYN, ACK, and FIN
bits. The SYN bit is set only on the first packet sent in each direction for a
given connection. The ACK bit is set when the other side is
acknowledging the receipt of data to the peer. The FIN bit is set when
either side chooses to close the connection.
ICMP
The Internet Control Message Protocol (ICMP) is used primarily to
deliver error information about other services. It is otherwise quite similar
in practical operation to UDP. That is, it is connectionless and does not
guarantee that packets are delivered to their destination. One dangerous
ICMP packet is the ICMP redirect packet, which can change routing
information on the machines that receive it.
Other protocols
The vast majority of the traffic on the Internet uses one of the three
protocols mentioned in the previous section. Some other protocols are as
follows:
8 WatchGuard Firebox System
Page 21

Standard Ports and Random Ports
IGMP (Internet Group Multicast Protocol)
A protocol primarily designed for hosts on multiaccess networks
to inform locally attached routers of their group membership
information.
IPIP (IP-within-IP)
An encapsulation protocol used to build virtual networks over the
Internet.
GGP (Gateway-Gateway Protocol)
A routing protocol used between autonomous systems.
GRE
A protocol used for PPTP.
ESP
An encryption protocol used for IPSec.
Standard Ports and Random Ports
UDP and TCP encapsulate information contained within the application
layer. The appropriate application processes are designated by source and
destination port numbers. These port numbers, along with the source and
destination IP addresses, specify a unique connection on the Internet.
For example, it is reasonable to have two telnet sessions from one host to
another. However, since telnet uses a well-known service number of 23,
something must distinguish these two connections. The other port in
these cases will be a port that is typically greater than 1023. This
alternative port designation is dynamically allocated by the operating
system on the client side.
Random ports can cause a great amount of trouble if they happen to
match a well-known service on a port above 1023. If some client machine
assigns a random port of 2049, the connection may mysteriously fail.
Similar problems can occur with the X Window and Archie services.
In practice, most operating systems cycle port numbers between 1024 and
a number somewhere in the range of 2100, depending on how many TCP
connections are currently open and whether a recently closed connection
used a similar port number. This makes the above problem rare.
Reference Guide 9
Page 22

CHAP TER 1: Internet Protocol Reference
10 WatchGuard Firebox System
Page 23

CHAPTER 2 MIME Content Types
A content-type header is used by applications to determine what kind of
data they are receiving, thus allowing them to make decisions about how
it should be handled. It allows clients to correctly identify and display
video clips, images, sound, or non-HTML data. People are probably most
familiar with the MIME content types sent in email.
The WatchGuard Proxied HTTP service uses content-type headers to
determine whether to allow or deny an HTTP transaction. Use Policy
Manager to configure the Proxied HTTP service to allow or deny contenttypes. Content types are also used in SMTP and are configurable in the
SMTP proxy. This chapter contains a list of the more commonly used
MIME content-types.
Wildcards may be used to select all subtypes within a type, thereby
denying all or allowing all of that MIME type. For example, to allow all
content-types that are text (including text/enriched, text/plain, and
others), use the content-type
New, registered MIME content types appear regularly. WatchGuard
recommends frequent checking of an online reference for the most current
list. One source of current MIME types is:
ftp://ftp.isi.edu/in-notes/iana/assignments/media-types
Reference Guide 11
text/*.
Page 24

CHAPTER 2: MIME Content T yp es
In addition, WatchGuard encourages you to email requests for inclusion
of new content types in our master list to:
manual@watchguard.com
Typ e Subtype Reference
text plain [RFC2646, RFC2046]
richtext [RFC2045, RFC2046]
enriched [RFC1896]
tab-separated-values [Paul Lindner]
html [RFC2854]
sgml [RFC1874]
vnd.latex-z [Lubos]
vnd.fmi.flexstor [Hurtta]
uri-list [RFC2483]
vnd.abc [Allen]
rfc822-headers [RFC1892]
vnd.in3d.3dml [Powers]
prs.lines.tag [Lines]
vnd.in3d.spot [Powers]
css [RFC2318]
xml [RFC3023]
x ml - ex t er n a l- pa r s ed -e n t it y [RFC3023]
rtf [Lindner]
directory [RFC2425]
calendar [RFC2445]
vnd.wap.wml [Stark]
vnd.wap.wmlscript [Stark]
vnd.motorola.reflex [Patton]
vnd.fly [Gurney]
vnd.wap.sl [WAP-Forum]
vnd.wap.si [WAP-Forum]
12 WatchGuard Firebox System
Page 25
t140 [RFC2793]
vn d.m s-m edia pa cka ge [Nelson]
vnd.IPTC.NewsML [IPTC]
text vnd.IPTC.NITF [IPTC]
vnd.curl [Hodge]
vnd.DMClientScript [Bradley]
parityfec [RFC3009]
multipart mixed [RFC2045, RFC2046]
alternative [RFC2045, RFC2046]
digest [RFC2045, RFC2046]
parallel [RFC2045, RFC2046]
appledouble [MacMime, Patrick
Faltstrom
header-set [Dave Crocker]
form-data [RFC2388]
related [RFC2387]
report [RFC1892]
voice-message [RFC2421, RFC2423]
signed [RFC1847]
encrypted [RFC1847]
byteranges [RFC2068]
me ssa ge rfc822 [RFC2045, RFC2046]
partial [RFC2045, RFC2046]
external-body [RFC2045, RFC2046]
news [RFC 1036, Henry
Spencer]
http [RFC2616]
delivery-status [RFC1894]
disposition-notification [RFC2298]
s-http [RFC2660]
application octet-stream [RFC2045, RFC2046]
Reference Guide 13
Page 26

CHAPTER 2: MIME Content T yp es
postscript [RFC2045, RFC2046]
oda [RFC2045, RFC2046]
atomicmail [atomicmail, Borenstein]
application andrew-inset [andrew-inset, Borenstein]
slate [slate, terry crowley]
wita [Wang Info Transfer,
dec-dx [Digital Doc Trans, Larry
dca-rft [IBM Doc Content Arch,
activemessage [Ehud Shapiro]
rtf [Paul Lindner]
applefile [MacMime, Patrick
Larry Campbell]
Campbell]
Larry Campbell]
Faltstrom]
mac-binhex40 [MacMime, Patrik
Faltstrom]
news-message-id [RFC1036, Henry
Spencer]
news-transmission [RFC1036, Henry
Spencer]
wordperfect5.1 [Paul Lindner]
pdf [Paul Lindner]
zip [Paul Lindner]
macwriteii [Paul Lindner]
msword [Paul Lindner]
remote-printing [RFC1486, Rose]
mathematica [Van Nostern]
cybercash [Eastlake]
commonground [Glazer]
iges [Parks]
riscos [Smith]
eshop [Katz]
14 WatchGuard Firebox System
Page 27
x400-bp [RFC1494]
sgml [RFC1874]
cals-1840 [RFC1895]
pgp-encrypted [RFC3156]
application pgp-signature [RFC3156]
pgp-keys [RFC3156]
vnd.framemaker [Wexler]
vnd.mif [Wexler]
vnd.ms-excel [Gill]
vnd. ms-pow erpoint [Gill]
vnd.ms-project [Gill]
vnd.ms-works [Gill]
vnd.ms-tnef [Gill]
vnd.svd [Becker]
vnd.music-niff [Butler]
vnd.ms-artgalry [Slawson]
vnd.truedoc [Chase]
vnd.koan [Cole]
vnd.street-stream [Levitt]
vnd.fdf [Zilles]
set- pay ment-initiation [Korver]
set-payment [Korver]
set-registra ti on -i ni tiation [Korver]
set-registration [Korver]
vnd.seemail [Webb]
vnd.businessobjects [Imoucha]
vnd.meri dian -s li ng shot [Wedel]
vnd.xara [Matthewman]
sgml-open-catalog [Grosso]
vnd.rapid [Szekely]
vnd.enliven [Santinelli]
Reference Guide 15
Page 28

CHAPTER 2: MIME Content T yp es
vnd.japannet-registration-wakeup [Fujii]
vnd.japannet-verification-wakeup [Fujii]
v n d . j a p a n n e t - p a y m e n t - w a k e u p [Fujii]
v n d . j a p a n n e t - d i r e c t o r y - s e r v i c e [Fujii]
application vnd.intertrust.digibox [Tomasello]
vnd.intertrust.nncp [Tomasello]
prs.alvestrand.titrax-sheet [Alvestrand]
vnd.noblenet-sealer [Solomon]
vnd.webturbo [Rehem]
vnd.noblenet-web [Solomon]
vnd.noblenet-directory [Solomon]
prs.nprend [Doggett]
hyperstudio [Domino]
vnd.shana.informed.formtemplat
[Selzler]
e
vnd.shana.informed.formdata [Selzler]
vnd.shana.informed.package [Selzler]
vnd.shana.informed.interchange [Selzler]
vnd.$commerce_battelle [Applebaum]
vnd.osa.netdeploy [Klos]
vnd.ibm.MiniPay [Herzberg]
vnd.japannet-jpnstore-wakeup [Yoshitake]
vnd.japannet-setstore-wakeup [Yoshitake]
vnd.japannet-verification [Yoshitake]
vnd.japannet-registration [Yoshitake]
vnd.hp-HPGL [Pentecost]
vnd.hp-PCL [Pentecost]
vnd.hp-PCLXL [Pentecost]
vnd.musician [Adams]
16 WatchGuard Firebox System
vnd.FloGraphIt [Floersch]
vnd. int ercon. for mnet [Gurak]
Page 29

vemmi [RFC2122]
vnd.ms-asf [Fleischman]
vnd.ecdis-update [Buettgenbach]
vnd.powerbuilder6 [Guy]
vnd.powerbuilder6-s [Guy]
application vnd.lotus-wordpro [Wattenberger]
vnd.lotus-approach [Wattenberger]
vnd.lotus-1-2-3 [Wattenberger]
vnd.lotus-organizer [Wattenberger]
vnd.lotus-screencam [Wattenberger]
vnd.lotus-freelance [Wattenberger]
vnd.fujitsu.oasys [Togashi]
vnd.fujitsu.oasys2 [Togashi]
vnd.swiftview-ics [Widener]
vnd.dna [Searcy]
prs.cww [Rungchavalnont]
vnd.wt.stf [Wohler]
vnd.dxr [Duffy]
vnd.mitsubishi.misty-
[Tanaka]
guard.trustweb
vnd.ibm.modcap [Hohensee]
vnd.acucobol [Lubin]
vnd.fujitsu.oasys3 [Okudaira]
marc [RFC2220]
vnd.fujitsu.oasysprs [Ogita]
vnd.fujitsu.oasysgp [Sugimoto]
vnd.visio [Sandal]
vnd.netfpx [Mutz]
vnd.audiograph [Slusanschi]
vnd.epson.salt [Nagatomo]
vnd.3M.Post-it-Notes [O'Brien]
Reference Guide 17
Page 30

CHAPTER 2: MIME Content T yp es
application pkcs7-mime [RFC2311]
pkcs7-signature [RFC2311]
pkcs10 [RFC2311]
vnd.novadigm.EDX [Swenson]
vnd.novadigm.EXT [Swenson]
vnd.novadigm.EDM [Swenson]
vnd.claymore [Simpson]
vnd.comsocaller [Dellutri]
vnd.yellowriver-custom-menu [Yellow]
vnd.ecowin.chart [Olsson]
vnd.ecowin.series [Olsson]
vnd. eco win.filerequest [Olsson]
vnd. eco win.fileupdate [Olsson]
vn d.e cow in. seri es requ est [Olsson]
vn d.e cow in. seri es upda te [Olsson]
EDIFACT [RFC1767]
EDI-X12 [RFC1767]
EDI-Consent [RFC1767]
vnd.wrq-hp3000-labelled [Bartram]
vnd.minisoft-hp3000-save [Bartram]
vnd.ffsns [Holstage]
vnd.hp-hps [Aubrey]
vn d.f uji xer ox.d oc uwor ks [Taguchi]
xml [RFC3023]
x ml - ex t er n a l- pa r s ed -e n t it y [RFC3023]
xml-dtd [RFC3023]
vnd.anser-web-funds-transfer-
[Mori]
initiation
vnd.anser-web-certificate-issue-
[Mori]
initiation
18 WatchGuard Firebox System
vnd.is-xpr [Natarajan]
Page 31

vnd.intu.qbo [Scratchley]
vnd.publishare-delta-tree [Ben-Kiki]
vnd.cybank [Helmee]
batch-SMTP [RFC2442]
vnd.uplanet.alert [Martin]
application vnd.uplanet.cacheop [Martin]
vnd.uplanet.list [Martin]
vnd.uplanet.listcmd [Martin]
vnd.uplanet.channel [Martin]
vnd.uplanet.bearer-choice [Martin]
vnd.uplanet.signal [Martin]
vnd.uplanet.alert-wbxml [Martin]
vnd.uplanet.cacheop-wbxml [Martin]
vnd.uplanet.list-wbxml [Martin]
vnd.uplanet.listcmd-wbxml [Martin]
vnd.uplanet.channel-wbxml [Martin]
vnd.uplanet.bearer-choice-wbxml [Martin]
vnd. ep so n. qu ic ka ni me [Gu]
vnd.commonspace [Chandhok]
vnd.fut-misnet [Pruulmann]
vnd.xfdl [Manning]
vnd.intu.qfx [Scratchley]
vnd.epson.ssf [Hoshina]
vnd.epson.msf [Hoshina]
vnd.powerbuilder7 [Shilts]
vnd.powerbuilder7-s [Shilts]
vnd.lotus-notes [Laramie]
pkixcmp [RFC2510]
vnd.wap.wmlc [Stark]
vnd.wap.wmlscriptc [Stark]
Reference Guide 19
vnd.motorola.flexsuite [Patton]
Page 32

CHAPTER 2: MIME Content T yp es
application vnd.motorola.flexsuite.gotap [Patton]
ipp [RFC2910]
ocsp-request [RFC2560]
ocsp-response [RFC2560]
vnd.wap.wbxml [Stark]
vnd.motorola.flexsuite.wem [Patton]
vnd.motorola.flexsuite.kmr [Patton]
vnd.motorola.flexsuite.adsi [Patton]
vnd.motorola.flexsuite.fis [Patton]
vnd.motorola.flexsuite.ttc [Patton]
vnd.ufdl [Manning]
vnd.accpac.simply.imp [Leow]
vnd.accpac.simply.aso [Leow]
vnd.vcx [T.Sugimoto]
vnd.previewsystems.box [Smolgovsky]
vnd.mediastation.cdkey [Flurry]
vnd.pg.format [Gandert]
vnd.pg.osasli [Gandert]
vnd.hp-hpid [Gupta]
pkix-cert [RFC2585]
pkix-crl [RFC2585]
vnd.Mobius.TXF [Kabayama]
vnd.Mobius.PLC [Kabayama]
vnd.Mobius.DIS [Kabayama]
vnd.Mobius.DAF [Kabayama]
vnd.Mobius.MSL [Kabayama]
vnd.cups-raster [Sweet]
vnd.cups-postscript [Sweet]
vnd.cups-raw [Sweet]
index [RFC2652]
index.cmd [RFC2652]
20 WatchGuard Firebox System
Page 33

index.response [RFC2652]
index.obj [RFC2652]
index.vnd [RFC2652]
vnd.triscape.mxs [Simonoff]
vnd.powerbuilder75 [Shilts]
application vnd.powerbuilder75-s [Shilts]
vnd.dpgraph [Parker]
http [RFC2616]
sdp [RFC2327]
vnd.eudora.data [Resnick]
v n d . f u j i x e r o x . d o c u w o r k s . b i n d e r [Matsumoto]
vnd.vectorworks [Pharr]
vnd.grafeq [Tupper]
vnd.bmi [Gotoh]
vnd.ericsson.quickcall [Tidwell]
vnd.hzn-3d-c ro ss word [Minnis]
vnd.wap.slc [WAP-Forum]
vnd.wap.sic [WAP-Forum]
vnd.groove-injector [Joseph]
vnd.fujixerox.ddd [Onda]
vnd.groove-account [Joseph]
vnd.groove-identity-message [Joseph]
vnd. gr oo ve -t oo l- me ss ag e [Joseph]
vnd. gr oo ve -t oo l- te mp la te [Joseph]
vnd.groove-vcard [Joseph]
vnd.ctc-posml [Kohlhepp]
vnd.canon-lips [Muto]
vnd.canon-cpdl [Muto]
vnd.trueapp [Hepler]
vnd.s3sms [Tarkkala]
iotp [RFC2935]
Reference Guide 21
Page 34

CHAPTER 2: MIME Content T yp es
vnd.mcd [Gotoh]
application vnd.contact.cmsg [Patz]
vnd.epson.esf [Hoshina]
whoispp-query [RFC2957]
whoispp-response [RFC2958]
vnd.mozilla.xul+xml [McDaniel]
parityfec [RFC3009]
vnd.palm [Peacock]
vnd.fsc.weblaunch [D.Smith]
vnd.tve-trigger [Welsh]
vnd.httphone [Lefevre]
vnd.informix- vi sionar y [Gales]
vnd.msign [Borcherding]
vnd.ms-lrm [Ledoux]
dvcs [RFC3029]
sieve [RFC3028]
vnd.vividence.scriptfile [Risher]
vnd. hhe.le sson-player [Jones]
beep+xml [RFC3080]
font-tdpfr [RFC3073]
vnd.mseq [Le Bodic]
vnd.aether.imp [Moskowitz]
vnd.Mobius.MQY [Devasia]
vnd.Mobius.MBK [Devasia]
v nd . vi d so f t .v i dc o nf e re n ce [Hess]
vnd. ibm .afplined ata [Buis]
v n d . i r e p o s i t o r y . p a c k a g e + x m l [Knowles]
vnd.sss-ntf [Bruno]
vnd.sss-dtf [Bruno]
vnd.sss-cod [Dani]
vnd.pvi.ptid1 [Lamb]
22 WatchGuard Firebox System
Page 35

isup [RFCISUP]
qsig [RFCISUP]
timestamp-query [RFC3161]
timestamp-reply [RFC3161]
v n d . p w g- x h t m l - pr i n t + x m l [Wright]
image jpeg [RFC2045,RFC2046]
gif [RFC2045,RFC2046]
ief [RFC1314]
g3fax [RFC1494]
tiff [RFC2302]
cgm [Francis]
naplps [Ferber]
vnd.dwg [Moline]
vnd.svf [Moline]
vnd.dxf [Moline]
png [Randers-Pehrson]
vnd.fpx [Spencer]
vnd.net-fpx [Spencer]
vnd.xiff [SMartin]
prs.btif [Simon]
vnd.fastbidsheet [Becker]
vnd.wap.wbmp [Stark]
prs.pti [Laun]
vnd.cns.inf2 [McLaughlin]
vnd.mix [Reddy]
vnd. fu ji xe ro x. ed mi cs -r lc [Onda]
v n d . f u j i x e r o x . e d m i c s - m m r [Onda]
vnd.fst [Fuldseth]
audio basic [RFC2045,RFC2046]
32kadpcm [RFC2421,RFC2422]
vnd.qcelp [Lundblade]
Reference Guide 23
Page 36

CHAPTER 2: MIME Content T yp es
audio vnd.nortel.vbk [Parsons]
L16 [RFC2586]
vnd.everad.plj [Cicelsky]
telephone-event [RFC2833]
tone [RFC2833]
vnd.digital-winds [Strazds]
vnd.lucent.voice [Vaudreuil]
vnd.octel.sbc [Vaudreuil]
vnd.rh etor ex.3 2k ad pcm [Vaudreuil]
vnd.vmx.cvsd [Vaudreuil]
vnd.cns.anp1 [McLaughlin]
vnd.cns.inf1 [McLaughlin]
prs.sid [Walleij]
vnd.nuera.ecelp4800 [Fox]
vnd.nuera.ecelp7470 [Fox]
mpeg [RFC3003]
parityfec [RFC3009]
MP4A-LATM [RFC3016]
vnd.nuera.ecelp9600 [Fox]
G.722.1 [RFC3047]
mpa-robust [RFC3119]
vnd.cisco.nse [Kumar]
video mpeg [RFC2045,RFC2046]
quicktime [Paul Lindner]
vnd.vivo [Wolfe]
vnd.motorola.video [McGinty]
vnd.motorola.videop [McGinty]
vnd.fvt [Fuldseth]
pointer [RFC2862]
parityfec [RFC3009]
vnd.mpegurl Recktenwald]
24 WatchGuard Firebox System
Page 37

MP4V-ES [RFC3016]
vnd.nokia.interleaved-multimedia [Kangaslampi]
model * [RFC2077]
iges [Parks]
vrml [RFC2077]
mo de l mesh [RFC2077]
vnd.dwf [Pratt]
vnd.gtw [Ozaki]
vnd.flatland.3dml [Powers]
vnd.vtu [Rabinovitch]
vnd.mts [Rabinovitch]
vnd.gdl [Babits]
vnd.gs-gdl [Babits]
vnd.parasolid.transmit.text [Dearnaley, Juckes]
vnd.parasolid.transmit.binary [Dearnaley, Juckes]
Reference Guide 25
Page 38

CHAPTER 2: MIME Content T yp es
26 WatchGuard Firebox System
Page 39

CHAPTER 3 Services and Ports
Well-known services are a combination of port number and transport
protocol for specific, standard applications. This chapter contains several
tables that list service names, port number, protocol, and description.
Reference Guide 27
Page 40

CHAPTER 3: Services and Ports
Ports Used by WatchGuard Products
The WatchGuard Firebox, Management Station, and WatchGuard
Security Event Processor use several ports during normal functioning.
Port # Protocol Purpose
4100 TCP Authentication applet
4101 TCP WSEP and Management Station
4105 TCP WatchGuard service
4106 TCP WebBlocker
4107 TCP WSEP and Firebox
4103 TCP Retrieve WebBlocker database
4102 TCP Used only in Firebox System (LSS) 3.0x
or earlier for logs
28 WatchGuard Firebox System
Page 41

Ports used by Microsoft Products
Port # Protocol Purpose
137, 138 UDP Browsing
67, 68 UDP DHCP Lease
135 TCP DHCP Manager
Ports used by Microsoft Products
138
139
UDP
TCP
Directory Replication
135 TCP DNS Administration
53 UDP DNS Resolution
139 TCP Event Viewer
139 TCP File Sharing
137, 138
139
UDP
TCP
Logon Sequence
138 UDP NetLogon
137, 138
139
UDP
TCP
Pass Through Validation
139 TCP Performance Monitor
1723
47
137, 138
139
TCP
IP
UDP
TCP
PPTP
Printing
139 TCP Registry Editor
139 TCP Server Manager
137, 138
139
139 TCP User Manager
139 TCP WinNT Diagnostics
137, 138
139
42 TCP WINS Replication
135 TCP WINS Manager
137 TCP WINS Registration
Reference Guide 29
UDP
TCP
UDP
TCP
Tru sts
WinNT Secure Channel
Page 42

CHAPTER 3: Services and Ports
Port # Protocol Purpose
135 TCP Client/Server
Communications
135 TCP Exchange Administrator
143 TCP IMAP
993 TCP IMAP (SSL)
389 TCP LDAP
636 TCP LDAP (SSL)
102 TCP MTA - X.400 over TCP/IP
110 TCP POP3
995 TCP POP3 (SSL)
135 TCP RCP
25 TCP SMTP
137 UDP SMB
138 UDP SMB
139 TCP SMB
445 TCP/UDP SMB
119 TCP NNTP
563 TCP NNTP (SSL)
Well-Known Services List
In addition to the ports used by services described above, WatchGuard
maintains a list of well-known services. Because software developers
regularly add new services, this does not represent a comprehensive list
of all possible services. For more information, see J. Reynolds and J.
Postel, Assigned Numbers, RFC1700, available at these Web sites:
http://www.cis.ohio-state.edu/htbin/rfc/rfc1700.html
http://www.iana.org/assignments/port-numbers
If you would like to recommend additions to this list, please send them to:
manual@watchguard.com.
30 WatchGuard Firebox System
Page 43

Service Name Port # Protocol Description
tcpmux 1 TCP/UDP TCP Port Service Multiplexer
compressnet 2,3 TCP/UDP Management Utility
rje 5 TCP/UDP Remote Job Entry
echo 7 TCP/UDP Echo
discard 9 TCP/UDP Discard
systat 11 TCP/UDP Active Users
daytime 13 TCP/UDP Daytime
qotd 17 TCP/UDP Quote of the Day
msp 18 TCP/UDP Message Send Protocol
chargen 19 TCP/UDP Character Generator
ftp-data 20 TCP/UDP File Transfer [Default Data]
ftp 21 TCP/UDP File Transfer [Control]
Well-Known Services List
ssh 22 TCP/UDP SSH Remote Login Protocol
telnet 23 TCP/UDP Tel ne t
smtp 25 TCP/UDP Simple Mail Transfer
nsw-fe 27 TCP/UDP NSW User system FE
msg-icp 29 TCP/UDP MSG ICP
msg-auth 31 TCP/UDP MSG Authentication
dsp 33 TCP/UDP Display Support Protocol
time 37 TCP/UDP Time
rap 38 TCP/UDP Route Access Protocol
rlp 39 TCP/UDP Resource Location Protocol
graphics 41 TCP/UDP Graphics
nameserver 42 TCP/UDP Host Name Server
nicname 43 TCP/UDP whois
mpm-flags 44 TCP/UDP MPM Flags
mpm 45 TCP/UDP MPM
mpm-snd 46 TCP/UDP MPM Send
ni-ftp 47 TCP/UDP NI FTP
Reference Guide 31
Page 44

CHAPTER 3: Services and Ports
Service Name Port # Protocol Description
auditd 48 TCP/UDP Digital Audit Daemon
tacacs 49 TCP/UDP Login Host Protocol (TACACS)
re-mail-ck 50 TCP/UDP Remote Mail Checking Protocol
la-maint 51 TCP/UDP IMP Logical Address Maintenance
xns-time 52 TCP/UDP XNS Time Protocol
domain 53 TCP/UDP Domain Name Server
xns-ch 54 TCP/UDP XNS Clearinghouse
isi-gl 55 TCP/UDP ISI Graphics Language
xns-auth 56 TCP/UDP XNS Authentication
xns-mail 58 TCP/UDP XNS Mail
ni-mail 61 TCP/UDP NI MAIL
acas 62 TCP/UDP ACA Services
whois++ 63 TCP/UDP whois++
covia 64 TCP/UDP Communications Integrator (CI)
tacacs-ds 65 TCP/UDP TACACS-Database Service
sql*net 66 TCP/UDP Oracle SQL*NET
bootps 67 TCP/UDP Bootstrap Protocol Server
bootpc 68 TCP/UDP Bootstrap Protocol Client
tftp 69 TCP/UDP Trivial File Transfer
gopher 70 TCP/UDP Gopher
netrjs-1 71 TCP/UDP Remote Job Service
netrjs-2 72 TCP/UDP Remote Job Service
netrjs-3 73 TCP/UDP Remote Job Service
netrjs-4 74 TCP/UDP Remote Job Service
deos 76 TCP/UDP Distributed External Object Store
vettcp 78 TCP/UDP vettcp
finger 79 TCP/UDP Finger
www-http 80 TCP/UDP World Wide Web HTTP
hosts2-ns 81 TCP/UDP HOSTS2 Name Server
xfer 82 TCP/UDP XFER utility
32 WatchGuard Firebox System
Page 45

Well-Known Services List
Service Name Port # Protocol Description
mit-ml-dev 83 TCP/UDP MIT ML device
ctf 84 TCP/UDP Common Trace Facility
mit-ml-dev 85 TCP/UDP MIT ML device
mfcobol 86 TCP/UDP Micro Focus Cobol
kerberos 88 TCP/UDP Kerberos
sug-mit-tug 89 TCP/UDP SU/MIT Telnet gateway
dnsix 90 TCP/UDP DNSIX Secure Application Token Map
mit-dov 91 TCP/UDP MIT Dover Spooler
npp 92 TCP/UDP Network Printing Protocol
dcp 93 TCP/UDP Device Control Protocol
objcall 94 TCP/UDP Tivoli Object Dispatcher
supdup 95 TCP/UDP SUPDUP
dixie 96 TCP/UDP DIXIE Protocol Specification
swift-rvf 97 TCP/UDP Swift Remote Virtual File Protocol
tacnews 98 TCP/UDP TAC News
metagram 99 TCP/UDP Metagram Relay
newacct 100 TCP [unauthorized use]
hostname 101 TCP/UDP NIC Host Name Server
iso-tsap 102 TCP/UDP ISO-TSAP
gppitnp 103 TCP/UDP Genesis Point-to-Point Trans Net
acr-nema 104 TCP/UDP ACR-NEMA Digital Imag. Comm. 300
cso 105 TCP/UDP CCSO name server protocol
csnet-ns 105 TCP/UDP Mailbox Name Nameserver
3com-tsmux 106 TCP/UDP 3COM-TSMUX
rtelnet 107 TCP/UDP Remote Telnet Service
snagas 108 TCP/UDP SNA Gateway Access Server
pop2 109 TCP/UDP Post Office Protocol - Version 2
pop3 110 TCP/UDP Post Office Protocol - Version 3
sunrpc 111 TCP/UDP SUN Remote Procedure Call
mcidas 112 TCP/UDP McIDAS Data Transmission Protocol
Reference Guide 33
Page 46

CHAPTER 3: Services and Ports
Service Name Port # Protocol Description
auth(ident) 113 TCP/UDP Authentication Service
audionews 114 TCP/UDP Audio News Multicast
sftp 115 TCP/UDP Simple File Transfer Protocol
ansanotify 116 TCP/UDP ANSA REX Notify
uucp-path 117 TCP/UDP UUCP Path Service
sqlserv 118 TCP/UDP SQL Services
nntp 119 TCP/UDP Network News Transfer Protocol
cfdptkt 120 TCP/UDP CFDPTKT
erpc 121 TCP/UDP Encore Expedited RPC
smakynet 122 TCP/UDP SMAKYNET
ntp 123 TCP/UDP Network Time Protocol
ansatrader 124 TCP/UDP ANSA REX Trader
locus-map 125 TCP/UDP Locus PC-Interface Net Map
unitary 126 TCP/UDP Unisys Unitary Login
locus-con 127 TCP/UDP Locus PC-Interface Conn Server
gss-xlicen 128 TCP/UDP GSS X License Verification
pwdgen 129 TCP/UDP Password Generator Protocol
cisco-fna 130 TCP/UDP cisco FNATIVE
cisco-tna 131 TCP/UDP cisco TNATIVE
cisco-sys 132 TCP/UDP cisco SYSMAINT
statsrv 133 TCP/UDP Statistics Service
ingres-net 134 TCP/UDP INGRES-NET Service
epmap 135 TCP/UDP DCE-RPC Endpoint resolution
profile 136 TCP/UDP PROFILE naming system
netbios-ns 137 TCP/UDP NETBIOS Name Service
netbios-dgm 138 TCP/UDP NETBIOS Datagram Service
netbios-ssn 139 TCP/UDP NETBIOS Session Service
imap 143 TCP/UDP Internet Message Access Protocol
news 144 TCP/UDP NewS
jargon 148 TCP/UDP Jargon
34 WatchGuard Firebox System
Page 47

Service Name Port # Protocol Description
sql-net 150 TCP/UDP SQL-NET
bftp 152 TCP/UDP Background File Transfer
sgmp 153 TCP/UDP SGMP
sqlsrv 156 TCP/UDP SQL Service
pcmail-srv 158 TCP/UDP PCMail Server
sgmp-traps 160 TCP/UDP SGMP-TRAPS
snmp 161 TCP/UDP SNMP
snmptrap 162 TCP/UDP SNMPTRAP
cmip-man 163 TCP/UDP CMIP/TCP Manager
cmip-agent 164 TCP CMIP/TCP Agent
smip-agent 164 UDP CMIP/TCP Agent
namp 167 TCP/UDP NAMP
rsvd 168 TCP/UDP RSVD
Well-Known Services List
send 169 TCP/UDP SEND
xyplex-mux 173 TCP/UDP Xyplex MUX
xdmcp 177 TCP/UDP X Display Manager Control Protocol
NextStep 178 TCP/UDP NextStep Window Server
bgp 179 TCP/UDP Border Gateway Protocol
unify 181 TCP/UDP Unify
irc 194 TCP/UDP Internet Relay Chat Protocol
at-rtmp 201 TCP/UDP AppleTalk Routing Maintenance
at-nbp 202 TCP/UDP AppleTalk Name Binding
at-3 203 TCP/UDP AppleTalk Unused
at-echo 204 TCP/UDP AppleTalk Echo
at-5 205 TCP/UDP AppleTalk Unused
at-zis 206 TCP/UDP AppleTalk Zone Information
at-7 207 TCP/UDP AppleTalk Unused
at-8 208 TCP/UDP AppleTalk Unused
qmtp 209 TCP/UDP Quick Mail Transfer Protocol
z39.50 210 TCP/UDP ANSI Z39.50 (WAIS)
Reference Guide 35
Page 48

CHAPTER 3: Services and Ports
Service Name Port # Protocol Description
ipx 213 TCP/UDP IPX
imap3 220 TCP/UDP Interactive Mail Access Protocol v3
fln-spx 221 TCP/UDP Berkeley rlogind with SPX auth
rsh-spx 222 TCP/UDP Berkeley rshd with SPX auth
backweb 371 UDP BackWeb
ulistserv 372 TCP/UDP Unix Listserv
netware-ip 396 TCP/UDP Novell Netware over IP
biff 512 UDP Used by mail system to notify users
exec 512 TCP Remote process execution
login 513 TCP/UDP Login Host Protocol
who 513 UDP Maintains databases showing who’s who
cmd 514 TCP Like exec, but automatic
syslog 514 UDP logging facilities
printer 515 TCP/UDP Spooler
talk 517 TCP/UDP Talk protocol
ntalk 518 TCP/UDP another Talk
utime 519 TCP/UDP Unixtime
router 520 UDP RIP local routing process (on site)
timed 525 TCP/UDP Timeserver
tempo 526 TCP/UDP Newdate
courier 530 TCP/UDP Rpc
conference 531 TCP/UDP Chat
netnews 532 TCP/UDP Readnews
netwall 533 TCP/UDP For emergency broadcasts
uucp 540 TCP/UDP Uucpd
uucp-rlogin 541 TCP/UDP Uucp-rlogin Stuart Lynne
klogin 543 TCP/UDP Kerberos (v4/v5)
kshell 544 TCP/UDP krcmd Kerberos (v4/v5)
dhcpv6-client 546 TCP/UDP DHCPv6 Client
dhcpv6-server 547 TCP/UDP DHCPv6 Server
36 WatchGuard Firebox System
Page 49

Well-Known Services List
Service Name Port # Protocol Description
cybercash 551 TCP/UDP Cybercash
remotefs 556 TCP/UDP Rfs server
9pfs 564 TCP/UDP Plan 9 file service
whoami 565 TCP/UDP Whoami
msn 569 TCP Microsoft Network
doom 666 TCP/UDP Doom Id Software
kerberos-adm 749 TCP/UDP Kerberos administration
webster 765 TCP/UDP Network dictionary
phonebook 767 TCP/UDP Phone
socks 1080 TCP/UDP Socks
hermes 1248 TCP/UDP Hermes
lotusnote 1352 TCP/UDP Lotus Notes
netware-csp 1366 TCP/UDP Novell NetWare Comm Service Platform
novell-lu6.2 1416 TCP/UDP Novell LU6.2
netopia 1419
8000
UDP
TCP
Netopia Virtual Office
ms-sql-s 1433 TCP/UDP Microsoft-SQL-Server
ms-sql-m 1434 TCP/UDP Microsoft-SQL-Monitor
winframe 1494 TCP WinFrame
watcom-sql 1498 TCP/UDP Watcom-SQL
ingreslock 1524 TCP/UDP Ingres
groupwise 1677 TCP GroupWise
nfs 2049 TCP/UDP Network File Server
www-dev 2784 TCP/UDP World Wide Web - development
Squid 3128 TCP/UDP Web proxy/caching service -- frequently scanned
for vulnerabilities
ccmail 3264 TCP/UDP Cc:mail/lotus
ICQ 2109
4000
Firstclass 3000
TCP
Used for chat
UDP
TCP FirstClass (ftp channel on 510 TCP)
30004
Reference Guide 37
Page 50

CHAPTER 3: Services and Ports
Service Name Port # Protocol Description
compuserve 4144 TCP CompuServe Online
rfe 5002 TCP/UDP Radio free ethernet
aol 5190 TCP America Online
x11 6000 TCP/UDP X Window System (through 6063)
font-service 7100 TCP/UDP X Font Service
nas 8000 TCP/UDP NCD Network Audio Server
iphone 6670 TCP for connecting to the phone server
iphone 22555 UDP for audio
iphone 25793 TCP for the address server, in 4.x and 5.0
iphone 1490 TCP for the conference engine in 4.x and 5.0
38 WatchGuard Firebox System
Page 51

CHAPTER 4 Types of Services
This chapter describes well-known services, their protocols, and their
ports as well as special considerations for adding the service to a security
policy configuration. Rather than explain every service in detail, this
chapter explains the telnet service thoroughly as an example from which
to extrapolate configuration details for similar services. Services fall into
two broad categories–packet filters and proxies.
Packet Filter Services
Packet filter services examine the source and destination headers of each
packet. Packets are then either allowed or denied passage based on
whether the headers appear to be coming from and going to legitimate
addresses.
Any
The Any service should be used only to allow ALL traffic between any
two specific, trusted IP or network addresses. Configuring the Any
service opens a “hole” through the Firebox, allowing all traffic to flow
unfiltered between specific hosts. WatchGuard strongly recommends that
the Any service be used only for traffic over a VPN.
Reference Guide 39
Page 52

CHAPTER 4: Types of Services
The Any service has different semantics from other services. For example,
if you allow FTP to a specific host, all other FTP sessions are implicitly
denied by that service (unless you have also configured other FTP service
icons). The Any service, however, does not implicitly deny like other
services.
You also cannot use an Any service unless specific IP addresses, network
addresses, host aliases, group names, or user names are used in the From
or To lists – otherwise the Any service is deemed too permissive and will
not function.
Characteristics
•Protocol: Any
•Client Port: Ignore
• Port Number: None
AOL
The America Online proprietary protocol allows access to the AOL
service through a TCP/IP network, instead of the usual dial-up
connection. The AOL client must be specifically configured to use TCP/IP
instead of a modem.
Characteristics
•Protocol: TCP
• Server Port(s): 5190
• Client Port(s): client
archie
archie is a search protocol used to find files on FTP servers. Because there
are a limited number of archie servers, it is safe to provide outgoing archie
service. A current list of archie servers is available via anonymous FTP
from:
ftp://microlib.cc.utexas.edu/microlib/mac/info/archie-servers.txt
External hosts can be spoofed; WatchGuard cannot verify that these
packets were actually sent from the correct location. You can configure
40 WatchGuard Firebox System
Page 53

WatchGuard to add the source IP address to the Blocked Sites List
whenever an incoming archie connection is denied. All of the usual
logging options can be used with archie.
WatchGuard recommends that you use the available WWW interfaces to
archie, such as: http://www.macsch.com/stress/archie.html
Characteristics
•Protocol: UDP
• Server Port(s): 1525
• Client Port(s): greater than 1023
auth (ident)
auth (ident) is a protocol used to map TCP connections back to a user
name. It is used primarily by large public SMTP and FTP servers and
certain security packages. While useful for logging, the information is
seldom reliable, as attackers can make modified servers that return
incorrect information. Incoming auth service responds with “fake”
information to hide internal user information.
Packet Filter Services
When using SMTP with incoming static NAT, you must add auth to the
Services Arena. Configure auth to allow incoming to the Firebox. This
enables outgoing mail messages to flow unrestricted from behind the
Firebox to the numerous SMTP servers on the Internet that use auth to
verify other mail servers’ identities, and allows these servers to return
messages through the Firebox to their senders.
If you are not using incoming sdymtatic NAT, allow incoming auth to the
IP address of your mail server.
WatchGuard recommends that both incoming and outgoing auth services
be allowed, but be aware that such services can collect valid user names
which can be used for hacking purposes.
Characteristics
•Protocol: TCP
• Server Port(s): 113
• Client Port(s): greater than 1023
Reference Guide 41
Page 54

CHAPTER 4: Types of Services
• RFC: 1413
Citrix ICA (WinFrame)
Citrix ICA is a protocol used by Citrix for their applications, including the
Winframe product. Winframe is a server-based application from Citrix
that provides access to Windows from a variety of clients. ICA uses TCP
port 1494 for its WinFrame software.
Adding the Citrix ICA service could compromise network security
because it allows traffic inside the firewall without authentication. In
addition, your Winframe server may be subject to denial of service
attacks. WatchGuard recommends using VPN options to provide
additional security for such a configuration. All of the usual logging
options can be used with WinFrame.
Characteristics
•Protocol: TCP
• Server Port(s): 1494, 1604
• Client Port(s): client
For more information on adding the Citrix ICA service, refer to the
Advanced FAQs in the Knowledge Base. (Go to www.watchguard.com/
support and log in to the LiveSecurity Service.)
Clarent-gateway
Clarent Corporation is an IP telephony technology supplier to
mainstream carriers and service providers. Clarent products enable voiceover-IP for doing voice calls between Clarent gateways across the
Internet. This service supports the Clarent v3.0 product and later.
Clarent products use two sets of ports, one for gateway-to-gateway
communications (UDP ports 4040, 4045, and 5010) and one for gatewayto-command center communications (UDP ports 5001 and 5002). Use the
Clarent-command service icon for the latter.
Enable incoming connections only from specific external gateways to
your gateway or command center.
42 WatchGuard Firebox System
Page 55

Clarent also supports the use of PCAnywhere for management. Refer to
the PCAnywhere implementation notes for further information.
Adding the Clarent-gateway service could compromise network security
because it allows traffic inside the firewall based only on network address
which is not a reliable method of authentication. In addition, your Clarent
server may be subject to denial of service attacks in this configuration.
Where possible, WatchGuard recommends using VPN options to provide
additional security for such a configuration.
Characteristics
•Protocol: UDP
•Client Port: ignore
• Port Number(s): 4040, 4045, 5010
Clarent-command
Packet Filter Services
Clarent Corporation is an IP telephony technology supplier to
mainstream carriers and service providers. Clarent products enable voiceover-IP for doing voice calls between Clarent gateways across the
Internet. This service supports the Clarent v3.0 product and later.
The Clarent products use two sets of ports, one for gateway-to-gateway
communications (UDP ports 4040, 4045, and 5010) and one for gatewayto-command center communications (UDP ports 5001 and 5002). Use the
Clarent-gateway service icon for the former.
Enable incoming connections only from specific external gateways to
your gateway or command center.
Clarent also supports the use of PCAnywhere for management. Refer to
the PCAnywhere implementation notes for further information.
Adding the Clarent-command service could compromise network
security because it allows traffic inside the firewall based only on network
address which is not a reliable method of authentication. In addition, your
Clarent server may be subject to denial of service attacks in this
configuration. Where possible, WatchGuard recommends using VPN
options to provide additional security for such a configuration.
Reference Guide 43
Page 56

CHAPTER 4: Types of Services
Characteristics:
•Protocol: UDP
•Client Port: ignore
• Port Numbers(s): 5001, 5002
CU-SeeMe
CU-SeeMe is a program used to do video conferencing over the Internet.
For CU-SeeMe to work through the Firebox, you must ensure that you are
not on a network using outgoing dynamic NAT, and configure the CUSeeMe service for both incoming and outgoing access.
The nature of the CU-SeeMe protocol dictates that you configure this
service for both incoming and outgoing, regardless of which side is
originating the connection. The CU-SeeMe icon allows the proper
combination of ports to enable use of CU-SeeMe versions 2.X and 3.X.
CU-SeeMe Version 2.X runs on UDP port 7648. Version 3.X, in addition to
UDP port 7648, runs on UDP port 24032 (for H.323 conferences) and TCP
port 7648 (video conference directories).
Characteristics
Because CU-SeeMe has a three-step send/receive/send sequence, its
protocol and port information is grouped in triads.
• Port Protocol, UDP; Source Port, port; Destination Port, 7648
• Port Protocol, TCP; Source Port, client; Destination Port, 7648
• Port Protocol, UDP; Source Port, ignore; Destination Port, 24032
DHCP-Server/Client
Dynamic Host Configuration Protocol (DHCP) provides a means of
dynamically allocating IP addresses to devices on a network.
Characteristics
• Service Name: DHCP-Server or DHCP-Client
•Protocol: UDP
•Client Port: client
• Port Number: Server: 68; Client: 67
44 WatchGuard Firebox System
Page 57

DNS
Domain Name Service (DNS) maps host names to IP addresses. You will
probably not need to add a DNS service icon unless you maintain a public
DNS server behind the Firebox, because outgoing UDP traffic is enabled
by default. The DNS multi-service icon allows UDP DNS traffic, as well as
TCP zone transfers to occur as specified. All of the usual logging options
can be used with DNS.
Characteristics
• Protocol: Multi: TCP (for server-server zone transfers) and UDP (for
client-server lookups)
• Server Port(s): 53
• Client Port(s): ignore
•RFC: 883
Packet Filter Services
Filtered-HTTP
The multi-service rule Filtered-HTTP combines configuration options for
incoming HTTP on port 80 with a rule allowing all outgoing TCP
connections by default. Using Filtered-HTTP will not result in applying
the HTTP proxy rule set to any traffic. To proxy HTTP traffic, use the
Proxied-HTTP service. WatchGuard recommends that incoming HTTP be
allowed only to any public HTTP servers maintained behind the Firebox.
External hosts can be spoofed. WatchGuard cannot verify that these
packets were actually sent from the correct location. Configure
WatchGuard to add the source IP address to the Blocked Sites List
whenever an incoming HTTP connection is denied. All of the usual
logging options can be used with HTTP.
Characteristics
• Protocol: Multi (includes top and http)
•Client Port: ignore
•Port Number: 80
Reference Guide 45
Page 58

CHAPTER 4: Types of Services
Filtered-SMTP
Filtered SMTP allows SMTP traffic (email) without using the SMTP proxy.
One use of Filtered-SMTP eliminates the need for outgoing mail to be
routed through the SMTP proxy twice. With the Filtered SMTP icon
between the trusted network and the mail server on the optional network,
mail is only proxied when it is outbound to the Internet.
Characteristics
•Protocol: TCP
• Server Port(s): 25
• Client Port(s): client
finger
finger is a protocol used to list information about users on a given host.
Although this information is often useful, it can also reveal too much
information that can be abused.
WatchGuard does not recommend putting finger servers on the trusted
interface.
Characteristics
•Protocol: TCP
• Server Port(s): 79
• Client Port(s): greater than 1023
Common Scenario
Description
There is a specially built finger server running on the optional
interface.
Icons in the Services Arena
A finger service icon–Incoming allow from Any to the finger
server on the optional interface.
46 WatchGuard Firebox System
Page 59

Gopher
Gopher is a data-retrieval protocol developed at the University of
Minnesota. As HTML has proliferated and Web browsers improved
Gopher servers replaced by Web servers. It is unlikely that you will ever
need to run a Gopher server.
Characteristics
•Protocol: TCP
• Server Port(s): 70 although servers can and are configured to use other
ports
• Client Port(s): greater than 1023
HTTPS
HTTPS is a secured and encrypted version of the HTTP protocol. The
client and the web server set up an encrypted session over TCP port 443.
Because this session is encrypted on both ends, the proxy cannot examine
packet contents; therefore, this icon enables a packet-filter service, not a
proxy.
Packet Filter Services
The HTTPS service is needed only if you are hosting an HTTPS server, or
if you do not have an Outgoing, Filtered-HTTP, Proxy or Proxied HTTP
icon in your configuration.
Characteristics
•Protocol: TCP
• Server Port(s): 443
• Client Port(s): client
IMAP
Internet Mail Access Protocol (IMAP) is a method of accessing email or
bulletin board messages residing on a remote mail server as if they were
local. Thus e-mail stored on an IMAP server can be accessed from
N
OTE
Reference Guide 47
Page 60

CHAPTER 4: Types of Services
multiple sites (such as home, work, or laptop) without the need to transfer
messages and files back and forth.
Characteristics
•Protocol: TCP
• Server Port(s): 143
• Client Port(s): client
LDAP
Lightweight Directory Access Protocol (LDAP) is an open-standard
protocol for accessing online directory services. The protocol runs over
Internet transport protocols, such as TCP, and can be used to access standalone directory servers or X.500 directories.
Characteristics
•Protocol: TCP
• Server Port(s): 389
• Client Port(s): client
Lotus Notes
Lotus Notes is an integrated client/server platform for conferencing,
databases, e-mail, and publishing and accessing compound documents.
Adding an icon for this service enables the proprietary Lotus Notes
protocol. Because the protocol supports encapsulation and tunneling, as
well as access to internal data, WatchGuard does not recommend adding
the Lotus Notes service for addresses outside of the trusted network.
Characteristics
•Protocol: TCP
• Server Port(s): 1352
• Client Port(s): client
48 WatchGuard Firebox System
Page 61

NNTP
Network News Transfer Protocol (NNTP) is used to transmit Usenet news
articles.
The best way to use NNTP is to set internal hosts to internal news servers,
and external hosts to news feeds. In most cases NNTP has to be enabled in
both directions. If you are running a public newsfeed, you must allow
NNTP connections from all external hosts. External hosts can be spoofed;
WatchGuard cannot verify that these packets were actually sent from the
correct location.
Configure WatchGuard to add the source IP address to the Blocked Sites
List whenever an incoming NNTP connection is denied. All of the usual
logging options can be used with NNTP.
Characteristics
•Protocol: TCP
Packet Filter Services
• Server Port(s): 119
• Client Port(s): greater than 1023
•RFC: 977
Common Scenarios
Scenario 1
Description
There exists a “public” NNTP server on the optional network.
Icons in the Services Arena
An NNTP icon–Incoming Allow From Any To the server.
Scenario 2
Description
There exists a “public” NNTP server on the Trusted network.
Icons in the Services Arena
The configuration will be the same as for Scenario 1.
Reference Guide 49
Page 62

CHAPTER 4: Types of Services
NTP
Network Time Protocol (NTP) is a protocol built on TCP/IP that ensures
accurate local timekeeping by synchronizing computer clocks with other
clocks located on the Internet. NTP is capable of synchronizing times
within milliseconds over extended time periods.
Characteristics
•Protocol: UDP, TCP
• Server Port(s): 123
• Client Port(s): client
Outgoing Services
Outgoing TCP connections can be allowed or denied. This service icon
serves as a default setting for all outgoing TCP connections, and is
overridden by other service settings. Outgoing connections will not work
unless Proxied-HTTP, Filtered-HTTP, Outgoing, or Proxy icons are
present in the Services Arena. This icon will not enable outgoing FTP
which will function only with an FTP service.
pcAnywhere
pcAnywhere is an application used to remotely access Windows
computers. To enable this protocol, add the PCAnywhere service, and
then allow incoming access from the hosts on the Internet that need to
gain access to internal pcAnywhere servers, and to the internal
pcAnywhere servers.
pcAnywhere is not a particularly secure service and may compromise
network security, because it allows traffic inside the firewall without
authentication. In addition, your pcAnywhere server may be subject to
denial of service attacks. WatchGuard recommends using VPN options to
provide additional security.
Characteristics
• Protocol: Multi: UDP and TCP
• Server Port(s):
-22/UDP
50 WatchGuard Firebox System
Page 63

- 5632/UDP
- 5631/TCP
- 65301/TCP
• Client Port: ignore (all cases)
ping
ping can be used to determine whether a host can be reached and is
operable and on the network). To intercept DOS-based or Windows-based
traceroute packets, configure the ping service.
Like traceroute, it is generally a bad idea to allow ping into a network;
however, outgoing ping is useful for troubleshooting.
Characteristics
•Protocol: ICMP
• Server Port(s): Not Applicable
Packet Filter Services
• Client Port(s): Not Applicable
POP2 and POP3
POP2 and POP3 (Post Office Protocol) are mail transport protocols,
generally used to retrieve individual users’ mailboxes from a POP server.
Characteristics
•Protocol: TCP
• Server Port(s): 109 (POP2), and 110 (POP3)
• Client Port(s): greater than 1023
Common Scenarios
Scenario 1
Description
A POP server on the Trusted interface, generally running on the
same machine as the SMTP server.
Reference Guide 51
Page 64

CHAPTER 4: Types of Services
Icons in the Services Arena
No icons are needed for this scenario as the connections will never
reach the Firebox.
Scenario 2
Description
A POP server on the Optional interface, generally running on the
same machine as the SMTP server.
Icons needed in the Services Arena
Either a Proxy icon or an Outgoing icon allowing all outgoing
TCP connections. In the absence of one of these, a POP icon
allowing outgoing connections to the server.
PPTP
PPTP is a VPN tunnelling protocol with encryption. It uses one TCP port
(for negotiation and authentication of a VPN connection) and one IP
protocol (for data transfer) to connect the two peers in a VPN. Configure
the PPTP service to allow incoming access from Internet hosts to an
internal network PPTP server. PPTP cannot access hosts’ static NAT
because incoming NAT cannot forward IP protocols. Because this service
enables a tunnel to the PPTP server and does not perform any security
checks at the firewall, use of this service should be limited. In addition,
older versions of PPTP were less secure and were prone to password
sniffing and denial of service attacks.
Characteristics
•Protocol: TCP, IP
• Server Port(s): 1723 (TCP); 47 (IP)
• Client Port(s): client
RADIUS
The Remote Authentication Dial-In User Service (RADIUS) provides
remote users with secure access to corporate networks. RADIUS is a
client-server system that stores authentication information for users,
remote access servers, and VPN gateways in a central user database that
is available to all servers. Authentication for the entire network happens
52 WatchGuard Firebox System
Page 65

from one location. RADIUS prevents hackers from intercepting and
responding to authentication requests by transmitting an authentication
key that identifies it to the RADIUS client.
Characteristics
•Protocol: UDP
• Server Port(s): 1645
• Client Port(s): client
RIP
RIP is a routing protocol that predates IP, making it one of the oldest
protocols on the Internet. It is used to automatically build routing tables
for local routers. Because it is directionless, it is quite similar to DNS in
configuration. You should enable RIP only if your Internet service
provider requires that you run a routing daemon.
Packet Filter Services
Incorrect or deceptive routing information can wreak havoc with local
networks, could cause service denial problems, and possibly completely
compromise the local network. Enable this service only after careful
consideration.
Characteristics
•Protocol: UDP
• Server Port(s): 520
• Client Port(s): greater than 1023
SMB (Windows Networking)
Server Message Block (SMB) is used by Windows to share files,
computers, printers, and other network resources.
If you set up replication, you may see repeated attempts to use the port
mapper service on port 135. This will eventually fail, and fall back to
using port 42. Refer to the RFC for DCE, and the DCE-RPC proxy sections
for more details.
Reference Guide 53
Page 66

CHAPTER 4: Types of Services
Allowing SMB through the Firebox is extremely insecure, and is strongly
discouraged unless used through a VPN connection. These configuration
settings are to be used only if there is no other alternative, and service
icon settings should be as specific as possible.
Characteristics
• Protocol: SMB (over TCP and UDP)
• Server Port(s): 137 (UDP), 138 (UDP), 139 (TCP), 42 (TCP for WINS
replication), 445 (TCP and UDP)
• Client Port(s): 136 (UDP), 137 (UDP), 139 (TCP)
• RFC: No RFC, but see:
http://www.microsoft.com
N
OTE
Common Scenarios
Scenario 1
Description
Clients on the trusted interface need to talk to a Windows NT
server on the optional network. Although not required, WINS
servers should be installed on both trusted and optional networks;
configure the clients on the optional network to use the optional
WINS server as a primary and the trusted WINS server as a
secondary.
Configure the clients on the trusted interface to use the trusted
WINS server as a primary and the optional WINS server as a
secondary. If you choose to use two WINS servers, it would be
beneficial to allow WINS replication across the Firebox as well as
adding the browser service to the WINS servers.
Icons in the Services Arena
SMB is a multi-service icon. You may, however, need to add these
icons to your services arena:
- One UDP icon for port 137. Set client port to “port” to enable
NetBIOS lookups.
54 WatchGuard Firebox System
Page 67

- One UDP icon for port 138. Set client port to “port” to enable the
- One TCP icon for port 139. Set client port to “client.” This sets up
SNMP
Simple Network Management Protocol (SNMP) can be used to collect
information about and configure remote computers. This has proven to be
dangerous. A great many Internet attacks have used SNMP.
Characteristics
• Protocols: UDP, TCP
• Server Port(s): 161 (trap servers use 162)
• Client Port(s): greater than 1023
Packet Filter Services
NetBIOS datagram service to transfer information between
hosts.
a NetBIOS TCP channel for passing information between hosts.
Because SNMP could cause quite unpredictable changes in a network if
enabled, carefully consider alternatives and log everything.
SNMP-Trap
Simple Network Management Protocol (SNMP) traps are notification
messages that an SNMP agent (for example, a router) sends to a network
management station. These messages generally report an important event
that should be logged or otherwise investigated.
Characteristics
•Protocols: UDP
• Server Port(s): 162
• Client Port(s): greater than 1023
SQL*Net
Oracle uses one port for its sql*net software. By default, this port is either
1526/tcp or port 1521/tcp, but it is user-configurable by editing the
tnsnames.ora file. To allow sql*net through the Firebox, set up a service
icon for the port that your sql*net server is using, with a protocol of tcp,
Reference Guide 55
Page 68

CHAPTER 4: Types of Services
and a client port of ignore. Then set up incoming access from the allowed
external hosts to the sql*net server.
Characteristics
•Protocols: TCP
• Server Port(s): 1521, 1526
• Client Port(s): ignore
Sybase SQL-Server
Sybase uses one port for the Sybase Central and SQL Advantage software.
There is no factory default port. Rather, the administrator configures the
port during the installation process using the Sybase Network
Connections dialog box. For WinSock TCP/IP, the port number is
specified as the number following the host name. For example, specify
MyHost,10000 as your connection information to set the Sybase SQL-
Server port to 10000.
The Sybase SQL-Server service is set to server port 10000. Verify that your
Sybase SQL-Server is configured for port 10000. If it is not, either
reconfigure the SQL-Server to port 10000 or create a new service with the
server port to the number that matches the SQL-Server installation. In that
case make sure to set the protocol to TCP and the client port to ignore, as
shown under Characteristics below.
With both the WatchGuard SQL-Server and a custom built service,
configure the rest of the service the same way: list the external clients that
should be allowed to connect to the Sybase server as Incoming From, and
the Sybase server address as Incoming To.
Characteristics
•Protocols: TCP
• Server Port(s): 10000
• Client Port(s): ignore
ssh
Secure Shell (ssh) is a free program which allows remote login, command
execution, and file transfer to another computer over a network. It
56 WatchGuard Firebox System
Page 69

provides strong authentication and secure (encrypted) communications.
WatchGuard recommends the use of ssh instead of more vulnerable
protocols like telnet, rssh, and rlogin.
If you use ssh, you should also use its strong authentication mechanisms.
Strong encryption mechanisms are available for U.S. customers, Canadian
customers, and customers who have been approved for use of strong
encryption by WatchGuard and/or the U.S. Government. If you would
like to use strong encryption (128 bit, 3DES) or IPSec, please contact
WatchGuard Technical Support.
UNIX versions are available from ftp.cs.hut.fi (see ftp://ftp.cs.hut.fi/
pub/ssh), and information on versions for Windows can be found at
DataFellows (http://www.datafellows.com).
Characteristics
•Protocol: TCP
• Server Port(s): 22
Packet Filter Services
• Client Port(s): less than 1024
• RFC: No number yet, but see:
http://www.cs.hut.fi/ssh/
Common Scenario
Description
There are one or more ssh servers on the trusted network.
Icons in the Services Arena
An ssh icon – Allowing Incoming To the desired trusted servers,
and Allowing Outgoing From Any To Any.
syslog
syslog is a service used to log operating system events on UNIX hosts.
The most common reason to enable syslog data on a firewall is to collect
data from a host outside the firewall.
Because the syslog port is blocked by default, to allow one log host to
collect logs from multiple Fireboxes:
• Remove port 514 from the Blocked Ports list
Reference Guide 57
Page 70

CHAPTER 4: Types of Services
• Add the WatchGuard Logging icon to the Services Arena
Attacks often focus on flooding syslog with log entries so that attacks are
either lost in the noise or the disk fills up and attack attempts are not
recorded. Generally, syslog traffic should not pass through the Firebox.
Characteristics
•Protocol: UDP
• Server Port(s): 514
TACACS
TACACS user authentication is a server that uses existing user accounts
to authenticate users into a dial-up modem pool, eliminating the need to
maintain duplicate accounts on a UNIX system. TACACS does not
support TACACS+ or RADIUS.
N
OTE
Characteristics
•Protocol: UDP
• Server Port(s): 49
• Client Port(s): greater than 1023
TACACS+
TACACS+ user authentication is a server that uses existing user accounts
to authenticate users into a dial-up modem pool, eliminating the need to
maintain duplicate accounts on a UNIX system. TACAS+ supports
RADIUS.
Characteristics
•Protocol: TCP
• Server Port(s): 49
• Client Port(s): greater than 1023
58 WatchGuard Firebox System
Page 71

telnet
The telnet service is used to log in to a remote computer, and is similar to
using dial-up access except that the connection is made over a network.
Characteristics
•Protocol: TCP
• Server Port(s): 23
• Client Port(s): greater than 1023
•RFC: 854
Common Scenario
Description
Telnet access is not allowed in to any machines on the trusted
network, but access is allowed out to external and/or optional
machines.
Packet Filter Services
TFTP
Icons in the Services Arena
The Proxied-HTTP, Filtered-HTTP, Proxy, or Outgoing icon in the
Services Arena automatically set to Allow Outgoing but Deny
Incoming connections (the default WatchGuard stance). For a
different stance (for example, to allow selected Incoming, or to
restrict Outgoing), add the telnet services and configure as
needed.
Trivial File Transfer Protocol (TFTP) is a simple file transfer protocol
similar to FTP that is usually used to download boot code to diskless
workstations. It supports timeout and retransmission techniques.
Use of this protocol is not recommended because it can allow
unauthorized remote access to system or user files without asking for a
password. WatchGuard recommends TFTP be used only for accessing
limited subdirectory trees that cannot result in root access. TFTP should
be restricted by using a TCP wrapper and filtering packets coming in on
port 111.
Reference Guide 59
Page 72

CHAPTER 4: Types of Services
Characteristics
•Protocols: UDP
• Server Port(s): 69
• Client Port(s): generally greater than 1023
Timbuktu
Timbuktu Pro is remote control and file transfer software used to gain
access to Windows computers. The protocol uses TCP port 1417 and UDP
port 407. Add the Timbuktu service and allow incoming access from the
hosts on the Internet that need to gain access to internal Timbuktu
servers, and to the internal Timbuktu servers.
Timbuktu is not a particularly secure service and may compromise
network security. It allows traffic inside the firewall without
authentication. In addition, the Timbuktu server may be subject to denial
of service attacks. WatchGuard recommends using VPN options to
provide additional security.
Characteristics
• Protocols: UDP, TCP
• Server Port(s): UDP 407, TCP 1417
• Client Port(s): ignore (both cases)
Time
The Time service is similar to NTP and used to synchronize clocks
between hosts on a network. Time is generally less accurate and less
efficient than NTP over a WAN. WatchGuard recommends using NTP.
Characteristics
•Protocols: UDP
• Server Port(s): 37
traceroute
traceroute is an application that can be used to build maps of networks. It
is very helpful for network debugging, analyzing routes, and determining
60 WatchGuard Firebox System
Page 73

a site’s Internet service provider. The WatchGuard traceroute service is
for filtering UNIX-based UDP-style traceroute only. For DOS-based or
Windows-based traceroute packet filtering, use the ping service instead
(see “ping” on page 51).
traceroute uses ICMP and UDP packets to build pathways across
networks using the UDP TTL field to return packets from every router
and machine between a source and a destination. Letting traceroute into a
network may enable an outsider to create a map of your private network.
However, outbound traceroute can be useful for troubleshooting.
Characteristics
• Protocols: UDP, ICMP
• Server Port(s): Not Applicable
• Client Port(s): generally greater than 32768
WAIS
Packet Filter Services
Wide Area Information Services (WAIS) is a protocol used to search for
documents over the Internet originally developed at Thinking Machines
Incorporated. Although WAIS servers are becoming rare, some WWW
sites use WAIS to scan searchable indices, so it might be a good idea to
enable outgoing WAIS.
WAIS is based on the ANSI Z39.50 search protocol, and the terms Z39.50
and WAIS are often used interchangeably.
Characteristics
•Protocol: TCP
• Server Port(s): 210 although servers can be (and often are) configured
on other ports, much like HTTP servers
• Client Port(s): greater than 1023
WatchGuard
The basic WatchGuard service allows configuration and monitoring
connections to be made to the Firebox. WatchGuard recommends
allowing this service only to the Management Station. The service is
typically set up on the trusted interface.
Reference Guide 61
Page 74

CHAPTER 4: Types of Services
Characteristics
•Protocol: TCP
• Server Port(s): 4105
• Client Port(s): client
WatchGuard Encrypted Connections
WatchGuard uses one of three levels of encrypted connections to allow
remote configuration and monitoring on ports 4101, 4102, and 4103. The
levels are low, medium, and strong encryption. The level you have
depends on your purchase agreement with WatchGuard. This service
allows or denies connections, and without it, you will not be able to access
a Firebox remotely. If you would like to use strong encryption (128 bit,
TripleDES) or IPSec, please contact WatchGuard Technical Support.
WatchGuard Logging
The WatchGuard Logging service is necessary only if a second Firebox
needs access to a log host on the trusted interface of a Firebox. If there is
only one Firebox, this icon is unnecessary.
Characteristics
•Protocol: TCP
• Server Port(s): 4107
WGAgent
WatchGuard Agent is a service that is primarily used for the management
of software and security policies. It uses one TCP port allowing
WatchGuard Agents to communicate with each other using an SSL
secured connection. For this service to work properly, add the HTTPS
service as well.
Characteristics
•Protocol: TCP
• Server Port(s): 4114
• Client Port(s): client
62 WatchGuard Firebox System
Page 75

whois
The whois protocol gives information about who administers Internet
sites and networks. It is often useful for finding administrative contacts at
other sites.
Because very few sites run whois servers, the only service necessary to
access these sites is an Outgoing or a Proxy icon. In the absence of these,
use a whois icon allowing outgoing connections to the required whois
servers, the most common one being
Characteristics
•Protocol: TCP
• Server Port(s): 43
• Client Port(s): greater than 1023
Proxied Services
rs.internic.net.
Proxied Services
This section describes the services proxied by the WatchGuard Firebox
System, including a separate description of the transparent proxies,
HTTP, SMTP, and FTP. The proxied service opens packets of its particular
type, strips out any embedded forbidden data types, and reassembles the
packets with the proxy’s own origin and destination headers.
Configuring and activating proxies is done the same way you add packet
filtering services.
DCE-RPC
The Distributed Computing Environment (DCE) Remote Procedure Call
(RPC) service allows connections bound for a trusted machine's port 135.
Initial calls typically result in a response from the trusted machine that
redirects the client to a new port for the actual service the client wants.
This service allows the initial port mapper requests used by remote
Windows Name Service (WINS) administration, remote Exchange
administration, Outlook, and other software that relies on DCE RPC. Be
aware that the standard SMB or NetBios ports may also need to be
allowed so that the above software will work properly.
Reference Guide 63
Page 76

CHAPTER 4: Types of Services
DCE-RPE allows
the configured addresses and ports as appropriate)—it does not filter any
of the packets for harmful content.
Characteristics
• Service Name: DCE-RPC
•Protocol: DCE-RPC
•Client Port: client
• Port Number: 135
FTP
FTP is File Transfer Protocol, one of the most common ways to move files
over the Internet.
N
OTE
all
DCE RPC traffic through the firewall (to and from
Characteristics
•Protocol: TCP
• Server Port(s): 20 (command channel), 21 (data channel)
• Client Port(s): greater than 1023
•RFC: 414
Common Scenarios
Scenario 1
Description
There is a “public” FTP server on the optional network.
Icons in the Services Arena
An FTP icon must be present for FTP to work. Incoming
connections must be Allowed To the FTP server. Outgoing
connections are usually Allowed From Any to To Any.
Scenario 2
Description
There is a “public” FTP server on the Trusted network.
64 WatchGuard Firebox System
Page 77

Icons in the Services Arena
Configuration is the same as for Scenario 1.
H323
The H323 service enables applications based on the H.323 protocol to be
used through the Firebox. Popular products that use this protocol include:
• Microsoft NetMeeting
• Intel Internet VideoPhone
This service does not do any filtering for harmful content. It does not
support QoS or rsvp protocol, nor does it support any type of NAT.
Considerations
For incoming connections:
• Any external host must be able to route to the internal host directly.
Use the ping utility if necessary to ensure that the connection is valid.
Proxied Services
• Dynamic NAT must be turned off for the incoming H323 connection
to work properly.
There are no equivalent special considerations for outgoing H323
connections.
Characteristics
• Service Name: H323
• Protocol: Multi (control, data, LDAP)
•Client Port: client
• Port Numbers: 1720 (control), 1503 (data), 389 (LDAP)
HTTP
HTTP is the Hypertext Transfer Protocol used by the World Wide Web to
move information around the Internet.
The WatchGuard service called HTTP Proxy is not to be confused with an
HTTP caching proxy. An HTTP caching proxy is a separate machine, and
it performs caching of Web data. If you use an external caching proxy,
N
OTE
Reference Guide 65
Page 78

CHAPTER 4: Types of Services
you must explicitly enable (by adding service icons) any outgoing services
you intend to use. If you do not, outgoing TCP connections won’t work
properly.
Characteristics
•Protocol: TCP
• Server Port(s): 80 (although servers can be run on any port, a common
alternative is 8080, and Secure Socket Layer (SSL) connections are
generally served on port 443)
• Client Port(s): greater than 1023
• RFC: 1945
Common Scenarios
Scenario 1
Description
“Public” HTTP server on the optional network.
Icons in the Services Arena
An HTTP icon, with Incoming From Any to the HTTP server.
Scenario 2
Description
“Public” HTTP server on the trusted network.
Icons in the Services Arena
Even with dynamic NAT, the HTTP server must have a “public”
address. Configuration is exactly the same as in Scenario 1.
Proxied-HTTP
Proxied-HTTP combines configuration options for HTTP on port 80 with
a rule allowing all outgoing TCP connections by default. Using the
Proxied-HTTP rule ensures that all outgoing HTTP traffic, regardless of
port, will be proxied according to the HTTP proxy rules.
WatchGuard recommends that you allow incoming HTTP only to any
public HTTP servers maintained behind the Firebox. External hosts can be
66 WatchGuard Firebox System
Page 79

spoofed, as WatchGuard cannot verify that these packets were actually
sent from the correct location.
Configure WatchGuard to add the source IP address to the Blocked Sites
List whenever an incoming HTTP connection is denied. Adjusting the
settings and MIME types is the same as for the HTTP Proxy.
RTSP
The Real-Time Streaming Protocol (RTSP) establishes and controls either
a single or several time-synchronized streams of continuous media such
as audio and video. It is the protocol used by RealNetworks G2 and Apple
QuickTime real time streaming media players.
Characteristics
•Protocol: RTSP
• Server Port: 554
Proxied Services
SMTP
•Client Port: any
• RFC: 2326
N
OTE
In addition to these TCP ports, there are some UDP ports that both the
client and the server use. The ports are determined dynamically but the
mostly commonly used ports on the client side are 6970 and 6971.
Simple Mail Transfer Protocol (SMTP) is the Internet standard protocol
for transmitting and receiving email. Generally SMTP servers are (by
nature) “public” servers.
When using incoming static NAT with SMTP, auth must be added (see
“auth (ident)” on page 41) to the Services Arena. Configure auth to allow
incoming auth to the Firebox. This enables outgoing mail messages to
flow unrestricted from behind the Firebox to the numerous SMTP servers
on the Internet that use auth to verify other mail servers’ identities and
allows these servers to return messages through the Firebox to the
senders.
Reference Guide 67
Page 80

CHAPTER 4: Types of Services
Logging incoming SMTP is recommended, but may produce copious log
output. If you do not want to use the SMTP proxy, create a new service
using the Services dialog box with the TCP protocol and port 25.
Characteristics
•Protocol: TCP
• Server Port(s): 25
• Client Port(s): greater than 1023
•RFC: 821
Common Scenarios
Scenario 1
Description
There is an SMTP server on the optional interface.
Icons in the Services Arena
A SMTP service icon – The Incoming tab should Allow To the
SMTP server from Any. The Outgoing tab should Allow To Any
from Any.
Scenario 2
Description
There is an SMTP server on the trusted interface.
Icons in the Services Arena
This scenario is configured exactly as in Scenario 1.
68 WatchGuard Firebox System
Page 81

CHAPTER 5 Common Log Messages
This chapter provides explanations for many of the log messages most
commonly generated by the Firebox. For more information on log
messages, refer to the In-Depth FAQs in the WatchGuard Knowledge
Base. Go to the following Web site and log into the LiveSecurity Service:
http://www.watchguard.com/support
Log messages in this chapter are arranged alphabetically.
xxx.xxx.xxx.xxx's mac address changed to XX:XX:XX:XX:XX:XX
Reports that the ARP table was changed or updated to reflect the
MAC address of a particular IP address. This occurs most
frequently in the case of High Availability where the active
Firebox has failed over and the standby Firebox assumes its IP
address.
authentication[] Time limit exceeded
Indicates that a user’s authentication timed out. Because some
authentication methods are time-sensitive, the Firebox allows you
to configure a timeout value when waiting for user input. The
defaults vary depending on the authentication method being
used.
chat-ttyS0[x]: Failed
The Firebox failed to communicate with the modem. This is not a
problem if you do not have a modem and are not using out-of-
Reference Guide 69
Page 82

CHAPTER 5: Common Log Messages
band management. The Firebox always attempts to communicate
with a PCMCIA modem and will report this error if none is found.
controld: ERROR: Receiving another configuration file from
firebox 10.1.16.2.
Indicates that the current configuration file is corrupted or
incomplete. The Event Processor will close the connection.
deny in eth0 tcp www.xxx.yyy.zzz www.xxx.yyy.zzz 25 1200 80
psh ack
A psh ack is an acknowledgement of a push. Push is a type of TCP
message that tells the receiving process to push the data directly
to the receiving application instead of caching it locally for
transmit. This message appears either because the source is a
blocked site or port, a spoofed source address, or an Any service
with logging enabled.
deny in eth0 tcp www.xxx.yyy.zzz www.xxx.yyy.zzz 2981 80 rst
(blocked site)
TCP connections are controlled through a series of packets
exchanged by the two computers involved in the connection. Old,
stale TCP connections are reset with an RST packet. RST packets
have a sequence number that must be valid according to certain
TCP rules. For example, Denial of Service (DoS) attacks can be
launched against some hosts by spoofing TCP RST packets
against connections that conflict with current connections. Bare
TCP RST packets can also be sent as a type of OS fingerprinting to
determine the target's operating system.
dns-proxy[xx] dns_setup_connect_udp: Unable to create UDP
socket for port: Invalid argument
The DNS proxy has only 256 file descriptors available for its use,
which limits the number of DNS connections in a NAT
environment. Every UDP request that uses dynamic NAT uses a
file descriptor for the duration of the UDP timeout. Every TCP
session that uses dynamic, static, or 1-to-1 NAT uses a file
descriptor for the duration of the session.
The file descriptor limit is rarely a problem, but an occasional site
may notice slow name resolution and many instances of the above
log message
You can work around this problem in two ways (the first method
is the most secure):
70 WatchGuard Firebox System
Page 83

- Avoid using dynamic NAT between your clients and your DNS
server.
- Disable the outgoing portion of the DNS proxied service and
replace it with a filtered DNS service.
firewalld[xxx] cs_server() failed (keys didn't match)
The cs_server is the process that listens for management
connections to the Firebox. There are two conditions under which
the error shown above occurs:
- Incorrectly entered passphrase
- Attempt to make two concurrent read-write connections to the
Firebox
firewalld[xxx]: cs_server() failed (response incomplete)
Firebox System Manager was unable to successfully complete a
connection to the Firebox. There are several potential causes of
this error; a common one is a very high traffic load at the time of
connection.
firewalld[] deny in eth0 68 54 24 29 www.xxx.yyy.zzz
www.xxx.yyy.zzz unknown ? (ip options)
IP options are obsolete IP parameters now used primarily for OS
fingerprinting and other types of IP stack-based probes. Most
routers strip IP options. By default, the Firebox denies them. This
feature can be modified using the Default Packet Handling dialog
box in Policy Manager.
firewalld[]: File synchronization completed
Indicates that the Management Station successfully completed the
transfer of a configuration file to the Firebox.
firewalld[] Pid xxx, died from signal 6.
A Pid is a process ID. In the Linux kernel, any new application is
assigned a process ID. In any case where a Pid dies, it is important
to determine what process was associated with the Pid number.
For instance, the Pid in a real log message may be 106. Earlier logs
could show that the HTTP Proxy was the process assigned Pid
106. In that case, this message would indicate that the HTTPproxy process aborted abnormally.
Reference Guide 71
Page 84

CHAPTER 5: Common Log Messages
firewalld [xxx] proxy accept() failed (Connection reset by
peer)
Indicates that a Web browser reset or failed to complete a
connection. This occurs if the user clicks the Stop or Reload
buttons during load.
firewalld[]: Putting file wg.cfg (from x.x.x.x)
Indicates that the Management Station at x.x.x.x sent a new
configuration file to the Firebox.
firewalld[]: Restarted by x.x.x.x
Indicates that the Firebox was issued a restart command by a
Management Station at IP address x.x.x.x.
ftp-proxy []: Proxy bind() failed (Address already in use)
On rare occasions, the FTP Proxy attempts to bind to a port used
by a static process on the Firebox such as 4105 or 4110. When this
happens, the bind fails.
ftp-proxy[]: [x.x.x.x:11323 x.x.x.x:21] proxy connect
failed (Connection timed out)
Indicates that the proxy was unable to connect to a FTP server.
The Proxy Connect Timeout defines the amount of time (in
seconds) that the proxies will wait before giving up trying to
forward a connection to an unreachable or non-responsive host.
After a connection is established, the standard proxy timeout
values apply. The default value for Proxy Connect Timeout is 10
seconds. If you experience trouble reaching sites through the
proxy that normally require more than 10 seconds before a
connection can be acknowledged (such as systems over slow links
in distant parts of the world, or heavily loaded servers), you can
try raising this value by adding (or editing) the following
property in the configuration file:
services.<service name>.proxies.ftp.connect_timeout:
<value>
Because this property is per proxy service, it may be different for
each FTP proxy icon configured.
fwcheck[x] fwcheck in low memory mode
Indicates that fwcheck is active because the Firebox passed its
predefined low memory threshold.
72 WatchGuard Firebox System
Page 85

fwcheck[] Killing process http-proxy (pid x)
Fwcheck is the process responsible for low memory scavenging
on the Firebox. If Firebox memory is overloaded for some reason,
fwcheck kills other processes until memory usage returns to a
safer state.
http-proxy[] [x.x.x.x:1091 x.x.x.x:80] Request denied: No
URI found
This message indicates a connection to a Web server was not
compliant with RFC 2068. The problem is not with the code of the
Web page but with the server itself. Web servers create headers
when sending packets to clients. These headers contain
information about the page, including information the HTTP
Proxy requires to process the traffic. Part of this is a URI (Uniform
Resource Identifier). According to RFC 2068:
Uniform Resource Identifiers, (URIs) have been known by many
names: WWW addresses, Universal Document Identifiers,
Universal Resource Identifiers, and finally the combination of
Uniform Resource Locators (URL) and Names (URN). As far as
HTTP is concerned, Uniform Resource Identifiers are simply
formatted strings which identify–via name, location, or any other
characteristic–a resource.
RFC 2068 defines the syntax for a URI. ''URI not found'' means
either the URI was not defined or it was defined incorrectly. By
default, HTTP Proxy blocks pages with non-compliant URIs.
Solutions for this problem include:
- Contacting the Web server admin to request an update to make
their server RFC 2068—compliant
- Creating a Filtered-HTTP service for that site
http-proxy[] [x.x.x.x:1091 x.x.x.x:80] removing bogus HTTP
header '? HTTP\1.0'
Most browsers are lax about requiring precise HTTP header
syntax. If the Firebox HTTP Proxy encounters HTTP headers
either with incorrect syntax or not defined per RFC 2068, it strips
them during transfer. The rest of the document still transfers.
http-proxy[] can't read proxy info file
The proxy info file is a file on the Firebox describing the map
between HTTP Proxy services and their internal ports. It is created
by firewalld at the start of the boot sequence. Difficulty reading
Reference Guide 73
Page 86

CHAPTER 5: Common Log Messages
this file indicates that firewalld is taking a long time to create it. A
possible cause is that the configuration file is corrupted.
http-proxy[]: no proxy services configured -- exiting
Indicates that no services defined on the Firebox make use of the
HTTP Proxy. The HTTP Proxy process starts, determines there are
no rules for the process, and then exits.
http-proxy[] proxy connect timeout
Indicates that the HTTP proxy sent a SYN to either an internal or
external HTTP server, but did not receive a SYN-ACK response
within the period of time specified in the Firebox configuration
file. The cause may be a downed HTTP server. The Proxy Connect
Timeout defines the amount of time (in seconds) that proxies wait
before they stop trying to forward a connection to an unreachable
or non-responsive host. After a connection is established, the
standard proxy timeout values apply. You may try raising this
value by adding (or editing) the following property in the
configuration file:
default.proxies.http.timeout: 600
http-proxy[] [x.x.x.x:1620 x.x.x.x:80] server was
unexpectedly closed
Indicates that the server closed the connection before the data
transfer was complete. This can be caused by busy Web servers or
bad network connectivity.
http-proxy[668] [x.x.x.xx:4584 x.x.x.x:80\] Response
denied: Content type required
One feature of the HTTP Proxy is MIME type content checking.
Web servers should send this information, but some do not. The
message above tells you that the HTTP Proxy denied the page
because it lacks a content type.
Some custom applications transfer data using pseudo-HTTP
transfers to enable them to work through most types of HTTP
proxies. If this message appears when a Web page is not being
accessed, it may be because data transfers are being attempted
using HTTP on ports other than 80. The Proxied-HTTP service (as
distinct from the HTTP proxy) proxies any outgoing port, not just
80.
74 WatchGuard Firebox System
Page 87

http-proxy[205]: [x.x.x.x:8921 x.x.x.x:80] Error while
sending/receiving: Invalid transfer-encoding type
"Identity"
HTTP has a provision for defining the encoding type used in the
page data transfer. The default is called "Identity," which means
that no encoding or transformations are performed on the page
data. The RFC for HTTP 1.1 says the following about identity:
identity: The default (identity) encoding; the use of no
transformation whatsoever. This content-coding is used only in
the Accept-Encoding header, and SHOULD NOT be used in the
Content-Encoding header.
The HTTP Proxy strictly enforces the "should not" provision of the
RFC. It denies the content-encoding type as invalid. Connections
to the offending server should be made through a packet filtered
port 80 service.
init[1]: Pid xx: exit 0 (could also be 1)
This message appears when a process that finished whatever it
was doing is now exiting normally. The xx indicates the Process
ID number.
ipseccfg[] Error, cfg entry (networking.ipsec.
remote_gw.195.sharedkey) must contain a shared key.
Indicates that the ipseccfg was unable to parse a shared key hash
from the configuration file, possibly due to a corrupted
configuration file. Try reconfiguring your VPN tunnel options
and/or Mobile User IPSec options.
ipseccfg[] Ipsec inbound policy (12) maps to a nonexistent
tunnel (xxxxxxxxx)
Indicates that the ipseccfg was unable to determine the correct
routing, possibly due to a corrupted configuration file. Try
reconfiguring your VPN tunnel options and/or Mobile User IPSec
options.
ipseccfg[] No inbound policies configured, aborting ipseccfg
This indicates that your Firebox has the IPSec component, but no
tunnels configured. It is harmless if you are not using IPSec VPN.
If you are using IPSec VPN when this message appears, your
configuration file might be corrupted. Try reconfiguring your
VPN tunnel options and/or your mobile user IPSec tunnel
options.
Reference Guide 75
Page 88

CHAPTER 5: Common Log Messages
ipseccfg[] No remote gateway associated with xxx
Indicates that the ipseccfg was unable to parse a preconfigured
remote gateway from the configuration file, possibly due to a
corrupted configuration file. Try reconfiguring your VPN tunnel
options and/or Mobile User IPSec options.
ipseccfg[]: No Remote Gateways configured, aborting ipseccfg
Indicates there are no IPSec tunnels configured on the Firebox.
ipseccfg[] Unable to verify inbound remote user policy(12),
aborting ipsec config
If this error appears, your configuration file might be corrupted.
Try reconfiguring your VPN tunnel options and/or your mobile
user IPSec tunnel options.
ipseccfg[] Will proxyarp for x.x.x.x on ethx
ipseccfg is the process responsible for managing IPSec tunnels.
This message indicates that the ipseccfg determined that it needs
to proxy-ARP for this IP address. This usually occurs for Mobile
User VPN IP addresses.
kernel: eth2: Setting full-duplex based on MII#31 link
partner capability of 45e1
Indicates that the Firebox determined it can set the Ethernet
interface to full-duplex. Earlier Fireboxes had software-type link
negotiation. Later transceivers did this automatically in hardware.
This message should be seen only on older Fireboxes.
kernel GRE: short packet: 30984\\12)
A GRE packet was corrupted on its way to the Firebox. In other
words, the length in the packet was changed and reported an
incorrect number of bytes.
kernel MASQ failed tcp/udp checksum from 205.181.115.231
Usually indicates packet corruption. A checksum is a count of the
number of bits in a transmission unit. This number is included
with the unit so that the receiver can check to see whether the
specified number of bits arrived. If the counts match, the receiver
assumes that it received a complete transmission.
kernel Memory use at 90 percent, low memory condition in
effect
Indicates that fwcheck will activate because the Firebox passed its
predefined low memory threshold.
76 WatchGuard Firebox System
Page 89

kernel Problem: block on freelist at xxxxxxxxx isn't free
If you see this log message, contact WatchGuard Technical
Support immediately. A small number of Fireboxes experienced a
manufacturing problem with their power supply, which causes
this symptom.
kernel: Temporarily blocking host x.x.x.x
Indicates that an IP address was dynamically added to the
blocked site list.
Pid(x) exited status 1
Indicates that a process on the Firebox exited normally.
RBCAST: Error sending data on [some interface]: Network is
unreachable
The Firebox has a rebroadcaster service designed to take UDPdirected broadcast packets from one interface and put them on the
other interfaces. This service is infrequently used. It is enabled
when certain PPTP and MUVPN options are activated.
RBCAST only rebroadcasts directed broadcasts originating on a
primary interface IP address. In other words, secondary networks
will not be the source of an RBCAST. In addition, it will not
rebroadcast to remote interfaces such as PPTP and IPSec
addresses.
RBCAST errors most commonly indicate that your configuration
does not support its use. RBCAST is automatically enabled on
UDP ports 137 and 138 when VPN options are turned on. In
almost all cases, it is safe to ignore these messages.
If you want to obtain more information on this process, open your
configuration file with a text editor. Immediately after the line
that says:
options.proxies.rbcast.ports: 137 138 (might be
additional port numbers)
Insert this line:
options.proxies.rbcast.verbose: ON
If you do not want to see RBCAST messages, use the text editor to
remove the line that says:
options.proxies.rbcast.ports: 137 138
Save this file with the text editor. Open it with Policy Manager,
and save it to the Firebox.
Reference Guide 77
Page 90

CHAPTER 5: Common Log Messages
rbcast[] Error sending data on optional--will not use
anymore: Network is unreachable
The RBCAST service is unable to send broadcasts on the optional
interface. Possible causes include:
- Nothing connected to the interface
- Improper or no rule regarding the traffic
The RBCAST service sends directed broadcasts on UDP ports to
other networks. An Outgoing service rule must be associated with
it.
received an unencrypted packet when crypto active
This message can be safely ignored. It indicates that an
unencrypted packet, (normally a connection notification that has
no data and no bearing on the actual connection), has been
received.
Request blocked by WebBlocker (proxy access blocked)
This generally indicates that some browser on the network is
trying to connect to an http proxy server. WebBlocker interprets
this as an attempt to bypass its protections and denies the attempt.
smtp-proxy[]: [x.x.x.x:35105 x.x.x.x:25] Bad command:
XXXXXX"
The client attempted a non-standard SMTP command not
recognized by the SMTP Proxy.
smtp-proxy[630]: [x.x.x.x:11323 x.x.x.x:25] proxy connect
failed (Connection timed out)
Indicates that the proxy was unable to connect to a mail server.
The Proxy Connect Timeout defines the amount of time (in
seconds) that the proxies will wait before giving up trying to
forward a connection to an unreachable or non-responsive host.
After a connection is established, the standard proxy timeout
values apply. The default value for Proxy Connect Timeout is 10
seconds. If you have trouble reaching sites through the proxy that
normally require more than 10 seconds before a connection can be
acknowledged (such as systems over slow links in distant parts of
the world, or heavily loaded servers), you can try raising this
value by adding (or editing) the following property in the
configuration file:
78 WatchGuard Firebox System
Page 91

- For SMTP:
default.proxies.smtp.connect_timeout: <value>
Note that this property is global to all SMTP services, unlike the
FTP version described previously.
smtp-proxy[589]: [x.x.x.x:1098 x.x.x.x:25] proxy connect
failed (Operation now in progress)
This message indicates a Proxy Backlog. The Proxy Backlog
defines the number of connection requests held by the Firebox
until a proxy can be started to handle the connection. The default
Proxy Backlog value is 20. To raise (or lower) this value, add (or
edit) the following property in the configuration file:
options.proxies.backlog: <value>
smtp-proxy[703] [x.x.x.x:1327 x.x.x.x:25] removing ESMTP
keyword "AUTH"
This message indicates that a client attempted to send an
unsupported ESMTP command through the SMTP Proxy.
Tried to restart iked 3 times within 5 seconds of each
other--something's wrong!
Iked is the Firebox process responsible for negotiating IPSec
tunnels. This message usually occurs when IPSec mobile users are
in the configuration file with no associated network routing
policies. You can edit the configuration file with a text editor and
remove references to IPSec mobile users. If this error appears in
your logs, iked will not run and no IPSec tunnels will start.
tunneld[]: parse_ranges: some addresses may not be in
channel stack (stack is full)
This message indicates that you have a network range with more
than 50 IP addresses used for PPTP tunnels. The Firebox is limited
to 50 PPTP tunnels. Only the first 50 IP addresses are added to the
stack of available addresses.
webblocker[]: received new WebBlocker database from server
x.x.x.x (nnnn bytes, generated on day-month-year-time)
Indicates that the Webblocker process successfully retrieved the
WebBlocker database from the management station.
Reference Guide 79
Page 92

CHAPTER 5: Common Log Messages
80 WatchGuard Firebox System
Page 93

CHAPTER 6 Resources
You can draw upon many resources to support your efforts to improve
network security. This chapter lists several sources of information
commonly used by WatchGuard engineers, developers, and Technical
Support teams to learn more about network security in general and the
WatchGuard product line in particular. These include:
•Publishers
• Books
• White Papers and Requests for Comments
•Mailing Lists
• Web Sites
•Newsgroups
Publishers
Several publishers emphasize network security in their offerings.
Addison-Wesley & Benjamin Cummings
Publishes a Computer Science series that includes several titles
about networking and network security.
http://www.awl.com/
Reference Guide 81
Page 94

CHAPTER 6: Resources
Books
Non-Fiction
Amoroso, Edward and Bellovin, Steven. Intranet and Internet Firewall
Strategies. Indianapolis: Que Corporation, 1996. ISBN 1562764225
Chapman, Brent, and Zwicky, Elizabeth D. Building Internet Firewalls.
Sebastopol: O'Reilly & Associates, 1994. ISBN 1-56592-124-0.
Cheswick and Bellovin. Firewalls and Internet Security: Repelling the Wily
Hacker. Reading, MA: Addison Wesley Longman, Inc., 1994. ISBN 0-20163357-4.
O'Reilly
Publishes many books on network security.
http://www.ora.com/
Curry, David A. UNIX System Security: A Guide for Users and System
Administrators. Reading, MA: Addison Wesley Longman, Inc., 1992.
Denning, Dorothy E. Information Warfare and Security. Addison-Wesley,
1999. ISBN 0201433036.
Farley, Stearns, and Mark Farley Hsu, Tom Stearns, and Jeffrey Hsu, LAN
Times Guide to Security and Data Integrity. Berkeley: Osborne McGraw-Hill,
1996. ISBN 0-07-882166-5.
Garfinkel and Spafford, Simson Garfinkel and Gene Spafford. Practical
Unix and Internet Security. Sebastopol: O'Reilly & Associates, 1994. ISBN
1565921488.
Goncalves, Marcus, Firewalls Complete. New York: McGraw-Hill, 1998.
ISBN 0-07-024645-9.
McClure, Stewart; Scambray, Joel; and Kurtz, George. Hacking Exposed.
Second Edition. McGraw-Hill Publishing, January 2000. ISBN 0072127481.
Power, Richard. Tangled Web: Tales of Digital Crime from the Shadows of
Cyberspace. Que; September 2000. ISBN 078973443x.
82 WatchGuard Firebox System
Page 95

Fiction
White Papers & Requests for Comments
Schneier, Bruce. Applied Cryptography. Second Edition. New York: John
Wiley & Sons, Inc., 1996. ISBN 0-471-11709-9.
Schwartau, Winn. Cybershock: Surviving Hacker, Phreakers, Identity Theives,
Internet Terrorists and Weapons of Mass Disruption. New York: Thunder’s
Mouth Press, 2000. ISBN 1-56025-246-4.
Sheldon, Tom (Editor); Cox, Phil. Windows 2000 Security Handbook.
McGraw-Hill Publishing, November 2000. ISBN 0072124334.
Stevens, W. Richard. TCP/IP Illustrated. Reading MA: Addison Wesley
Longman, Inc., 1994. ISBN 0201633469. (Note: This is a 3-volume set.)
Stoll, Cliff. Cuckoo’s Egg. Pocket Books, 1995. ISBN 0671726889.
Vacca, John, Intranet Security. Rockland, MA: Charles River Media, Inc.,
1997. ISBN 1-886801-56-8.
Stephenson, Neal. Cryptonomicon. New York, NY: HarperCollins
Publishers, 1999. ISBN 0060512806.
White Papers & Requests for Comments
Reynolds, J. and J. Postel, Assigned Numbers. Available at this Web site:
http://www.cis.ohio-state.edu/htbin/rfc/rfc1700.html
Request for Comments Editor
http://www.rfc-editor.org
Internet Request for Comments (RFC)
http://www.cis.ohio-state.edu/hypertext/information/rfc.html
Reference Guide 83
Page 96

CHAPTER 6: Resources
Mailing Lists
Web Sites
wg-users@watchguard.com
WatchGuard sponsors a listserv for our customers. For more
information, see the Technical Support chapter in the User Guide.
firewall-wizards@nfr.net
WatchGuard Frequently Asked Questions
http://www.watchguard.com (Click Support, Log into
LiveSecurityService, click Knowledge Base, click In-Depth FAQs)
Attrition
http://www.attrition.org/
Bugtraq
http://www.securityfocus.com
Center for Education and Research in Information Assurance and
Security
http://www.cerias.purdue.edu/
Complete Intranet Firewalls Resource Page
http://www.intrack.com/intranet/firewall.shtml
CSI Firewall Product Search Center
http://www.gocsi.com/firewall.htm
Explanation of Firewall Logs
http://www.robertgraham.com/pubs/firewall-seen.html
Firewall.com
http://www.firewall.com
Firewall and Proxy Server How To
http://metalab.unc.edu/mdw/HOWTO/Firewall-HOWTO.html
FishNet Security Information
http://www.kcfishnet.com/secinfo/types.html
84 WatchGuard Firebox System
Page 97

Web Sites
Gene Spafford’s Homepage
http://www.cerias.purdue.edu/homes/spaf/
Honeynet Project
http://project.honeynet.org
Information Security Magazine
http://www.infosecuritymag.com
Internet Firewalls - Frequently Asked Questions
http://www.interhack.net/pubs/fwfaq
Internet Firewalls — Resources
http://www.cerias.purdue.edu/coast/firewalls
The Java Security Web Site
http://www.rstcorp.com/javasecurity/
National Institute of Standards and Technology, Computer Security
Resource Center
http://www-08.nist.gov
Note: Yes, the dash after “www” is correct.
Microsoft Security
http://www.microsoft.com/security/
National Institute of Standards and Technology, Computer Security
Division
http://csrc.nist.gov/
Network Computing: Technology Solution Center
http://www.networkcomputing.com
The RealPlayer Website
http://service.real.com/firewall
UNIX Security
http://www.itworld.com/nl/unix_sec
Vicomsoft Network Definitions Webpage
http://www.vicomsoft.com/knowledge/reference/
ks.reference.html
Reference Guide 85
Page 98

CHAPTER 6: Resources
Newsgroups
Dictionaries of Computer Terminology
http://www.webopedia.com/
http://www.whatis.com/
http://info.astrian.net/jargon/
comp.security.firewalls
Use your newsreader or electronic messaging application to
subscribe to the comp.security.firewalls Usenet newsgroup.
Deja.com
Deja.com provides a Web-based alternative to news reader
services. In addition to comp.security.firewalls, it includes several
discussion groups and the occasional room discussing network
security issues. It can be found at: http://www.deja.com/
86 WatchGuard Firebox System
Page 99

CHAPTER 7 Out-of-Band Initialization
Strings
This chapter provides a reference list of PPP and modem initialization
strings used to configure out-of-band (OOB) management.
The PPP client for Linux is called Pppd.
PPP Initialization Strings
These are the strings and syntaxes available for use when configuring a
Firebox for out-of-band management in Policy Manager:
asyncmap <map>
Set the async character map to <map>. This map describes which
control characters cannot be successfully received over the serial
line. Pppd will ask the peer to send these characters as a 2-byte
escape sequence. The argument is a 32-bit hex number with each
bit representing a character to escape. Bit 0 (00000001) represents
the character 0x00; bit 31 (80000000) represents the character 0x1f
or ^_. If multiple asyncmap options are given, the values are
ORed together. If no asyncmap option is given, no async character
map will be negotiated for the receive direction; the peer should
then escape all control characters. To escape transmitted
characters, use the escape option.
Reference Guide 87
Page 100

CHAP TER 7: Out-o f-Band Initia li zation St ring s
escape xx,yy,..
Specifies that certain characters should be escaped on
transmission (regardless of whether the peer requests them to be
escaped with its async control character map). The characters to
be escaped are specified as a list of hex numbers separated by
commas.
Almost any character can be specified for the escape option,
unlike the asyncmap option which allows only control characters
to be specified. The characters that may not be escaped are those
with hex values 0x20 — 0x3f or 0x5e.
mpfto <period>
Specifies how long the PPP session should wait for a valid
management session to begin. If no valid session starts, then PPP
will disconnect after this timeout period. The default is 90
seconds.
mru n
Set the Maximum Receive Unit (MRU) value to n. Pppd will ask
the peer to send packets of no more than n bytes. The minimum
MRU value is 128. The default MRU value is 1,500. A value of 296
is recommended for slow links (40 bytes for TCP/IP header + 256
bytes of data).
mtu n
Set the Maximum Transmit Unit (MTU) value to n. Unless the
peer requests a smaller value via MRU negotiation, pppd will
request that the kernel networking code send data packets of no
more than n bytes through the PPP network interface.
passive
Enables the “passive” option in the LCP. With this option, pppd
will attempt to initiate a connection; if no reply is received from
the peer, pppd will then wait passively for a valid LCP packet
from the peer, instead of exiting, as it would without this option.
bsdcomp nr,nt
Request that the peer compress packets that it sends, using the
BSD-Compress scheme, with a maximum code size of nr bits, and
agree to compress packets sent to the peer with a maximum code
size of nt bits. If nt is not specified, it defaults to the value given
for nr. Values in the range 9 to 15 can be used for nr and nt; larger
88 WatchGuard Firebox System
 Loading...
Loading...