Watchguard Firebox X5, Firebox X15, Firebox X50, Firebox X500, Firebox X5000 Reference Manual
...
WatchGuard
®
Firebox® System
Reference Guide
WatchGuard Firebox System

Notice to Users
Information in this guide is subject to change without notice. Companies, names, and data used in examples herein are
fictitious unless otherwise noted. No part of this guide may be reproduced or transmitted in any form or by any means,
electronic or mechanical, for any purpose, without the express written permission of WatchGuard Technologies, Inc.
Copyright, Trademark, and Patent Information
Copyright© 1998 - 2003 WatchGuard Technologies, Inc. All rights reserved.
AppLock, AppLock/Web, Designing peace of mind, Firebox, Firebox 1000, Firebox 2500, Firebox 4500, Firebox II,
Firebox II Plus, Firebox II FastVPN, Firebox III, Firebox SOHO, Firebox SOHO 6, Firebox SOHO 6tc, Firebox
SOHO|tc, Firebox V100, Firebox V80, Firebox V60, Firebox V10, LiveSecurity, LockSolid, RapidStream, RapidCore,
ServerLock, WatchGuard, WatchGuard Technologies, Inc., DVCP technology, Enforcer/MUVPN, FireChip,
HackAdmin, HostWatch, Make Security Your Strength, RapidCare, SchoolMate, ServiceWatch, Smart Security.
Simply Done., Vcontroller, VPNforce, The W-G logo are either registered trademarks or trademarks of WatchGuard
Technologies, Inc. in the United States and/or other courtries.
© Hi/fn, Inc. 1993, including one or more U.S. Patents: 4701745, 5016009, 5126739, and 5146221 and other
patents pending.
Microsoft®, Internet Explorer®, Windows® 95, Windows® 98, Windows NT® and Windows® 2000 are either
registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
Netscape and Netscape Navigator are registered trademarks of Netscape Communications Corporation in the United
States and other countries.
RC2 Symmetric Block Cipher, RC4 Symmetric Stream Cipher, RC5 Symmetric Block Cipher, BSAFE, TIPEM, RSA
Public Key Cryptosystem, MD, MD2, MD4, and MD5 are either trademarks or registered trademarks of RSA Data
Security, Inc. Certain materials herein are Copyright © 1992-1999 RSA Data Security, Inc. All rights reserved.
RealNetworks, RealAudio, and RealVideo are either a registered trademark or trademark of RealNetworks, Inc. in the
United States and/or other countries.
Java and all Jave-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. in the United
States and other countries. All right reserved.
© 1995-1998 Eric Young (eay@cryptsoft). All rights reserved.
© 1998-2000 The OpenSSL Project. All rights reserved. Redistribution and use in source and binary forms, with or
without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgment:
"This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://
www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to endorse or promote products derived from
this software without prior written permission. For written permission, please contact openssl-core@openssl.org.
5. Products derived from this software may not be called "OpenSSL" nor may "OpenSSL" appear in their names without
prior written permission of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following acknowledgment: "This product includes software
developed by the OpenSSL Project for use in the OpenSSL Toolkit (http://www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY EXPRESSED OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL
PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com). This product includes software written by Tim
ii WatchGuard Firebox System

Hudson (tjh@cryptsoft.com).
© 1995-1998 Eric Young (eay@cryptsoft.com)
All rights reserved.
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as the following conditions are aheared to. The
following conditions apply to all code found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not just the
SSL code. The SSL documentation included with this distribution is covered by the same copyright terms except that
the holder is Tim Hudson (tjh@cryptsoft.com).
Copyright remains Eric Young's, and as such any Copyright notices in the code are not to be removed. If this package is
used in a product, Eric Young should be given attribution as the author of the parts of the library used. This can be in
the form of a textual message at program startup or in documentation (online or textual) provided with the package.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgement:
"This product includes cryptographic software written by Eric Young (eay@cryptsoft.com)" The word 'cryptographic'
can be left out if the routines from the library being used are not cryptographic related :-).
4. If you include any Windows specific code (or a derivative thereof) from the apps directory (application code) you
must include an acknowledgement: "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
The licence and distribution terms for any publicly available version or derivative of this code cannot be changed. i.e.
this code cannot simply be copied and put under another distribution licence [including the GNU Public Licence.]
The mod_ssl package falls under the Open-Source Software label because it's distributed under a BSD-style license. The
detailed license information follows.
Copyright (c) 1998-2001 Ralf S. Engelschall. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgment:
"This product includes software developed by Ralf S. Engelschall <rse@engelschall.com> for use in the mod_ssl
project (http://www.modssl.org/)."
4. The names "mod_ssl" must not be used to endorse or promote products derived from this software without prior
written permission. For written permission, please contact rse@engelschall.com.
5. Products derived from this software may not be called "mod_ssl" nor may "mod_ssl" appear in their names without
prior written permission of Ralf S. Engelschall.
6. Redistributions of any form whatsoever must retain the following acknowledgment: "This product includes software
developed by Ralf S. Engelschall <rse@engelschall.com> for use in the mod_ssl project (http://www.modssl.org/)."
THIS SOFTWARE IS PROVIDED BY RALF S. ENGELSCHALL ``AS IS'' AND ANY EXPRESSED OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL RALF S.
ENGELSCHALL OR HIS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
Reference Guide iii

TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The Apache Software License, Version 1.1
Copyright (c) 2000 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. The end-user documentation included with the redistribution, if any, must include the following acknowledgment:
"This product includes software developed by the Apache Software Foundation (http://www.apache.org/)." Alternately,
this acknowledgment may appear in the software itself, if and wherever such third-party acknowledgments normally
appear.
4. The names "Apache" and "Apache Software Foundation" must not be used to endorse or promote products derived
from this software without prior written permission. For written permission, please contact apache@apache.org.
5. Products derived from this software may not be called "Apache", nor may "Apache" appear in their name, without
prior written permission of the Apache Software Foundation.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE APACHE SOFTWARE FOUNDATION
OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE,
EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on behalf of the Apache Software
Foundation. For more information on the Apache Software Foundation, please see <http://www.apache.org/>.
Portions of this software are based upon public domain software originally written at the National Center for
Supercomputing Applications, University of Illinois, Urbana-Champaign.
All other trademarks or trade names mentioned herein, if any, are the property of their respective owners.
Part No:
WFS Software Number 7.0
iv WatchGuard Firebox System

Contents
CHAPTER 1 Internet Protocol Reference ..................... 1
Internet Protocol Header .................................................. 1
Internet Protocol Options ................................................. 6
Transfer Protocols ............................................................ 7
IP header number list ..................................................... 2
UDP ........................................................................... 7
TCP ........................................................................... 8
ICMP .......................................................................... 8
Other protocols ............................................................ 8
Standard Ports and Random Ports .................................... 9
CHAPTER 2 MIME Content Types ............................... 11
CHAPTER 3 Services and Ports ................................... 27
Ports Used by WatchGuard Products ............................... 28
Ports used by Microsoft Products .................................... 29
Well-Known Services List ................................................ 30
CHAPTER 4 Types of Services ..................................... 39
Packet Filter Services ..................................................... 39
Any .......................................................................... 39
AOL ......................................................................... 40
Reference Guide v

archie ....................................................................... 40
auth (ident) ................................................................ 41
Citrix ICA (WinFrame) .................................................. 42
Clarent-gateway ..........................................................42
Clarent-command ....................................................... 43
CU-SeeMe .................................................................44
DHCP-Server/Client ..................................................... 44
DNS ......................................................................... 45
Filtered-HTTP ............................................................. 45
Filtered-SMTP ............................................................46
finger ........................................................................ 46
Gopher ..................................................................... 47
HTTPS ...................................................................... 47
IMAP ........................................................................ 47
LDAP ........................................................................ 48
Lotus Notes ...............................................................48
NNTP .......................................................................49
NTP ..........................................................................50
Outgoing Services ....................................................... 50
pcAnywhere ...............................................................50
ping ......................................................................... 51
POP2 and POP3 ......................................................... 51
PPTP ........................................................................52
RADIUS ..................................................................... 52
RIP ...........................................................................53
SMB (Windows Networking) .......................................... 53
SNMP ....................................................................... 55
SNMP-Trap ................................................................ 55
SQL*Net ................................................................... 55
Sybase SQL-Server ...................................................... 56
ssh ........................................................................... 56
syslog ....................................................................... 57
TACACS .................................................................... 58
TACACS+ .................................................................. 58
telnet ........................................................................59
vi WatchGuard Firebox System

TFTP ........................................................................ 59
Timbuktu .................................................................. 60
Time ........................................................................ 60
traceroute ................................................................. 60
WAIS ........................................................................ 61
WatchGuard .............................................................. 61
WatchGuard Encrypted Connections .............................. 62
WatchGuard Logging .................................................. 62
WGAgent .................................................................. 62
whois ....................................................................... 63
Proxied Services ............................................................ 63
DCE-RPC .................................................................. 63
FTP .......................................................................... 64
H323 ........................................................................ 65
HTTP ........................................................................ 65
Proxied-HTTP ............................................................. 66
RTSP ........................................................................ 67
SMTP ....................................................................... 67
CHAPTER 5 Common Log Messages .......................... 69
CHAPTER 6 Resources ................................................. 81
Publishers ..................................................................... 81
Books ........................................................................... 82
Non-Fiction ............................................................... 82
Fiction ...................................................................... 83
White Papers & Requests for Comments ......................... 83
Mailing Lists .................................................................. 84
Web Sites ..................................................................... 84
Newsgroups .................................................................. 86
CHAPTER 7 Out-of-Band Initialization Strings ........... 87
PPP Initialization Strings ................................................. 87
Modem Initialization Strings ........................................... 93
CHAPTER 8 Firebox Read-Only System Area ............ 97
Read-Only System Area ................................................. 97
Reference Guide vii

Enhanced System Mode .................................................98
Initializing a Firebox using TCP/IP ...................................98
Initializing a Firebox Using a Serial Cable ......................... 99
Booting from the system area ......................................100
Working with a Firebox booted from the read-only system
area
Trou ble sh oo ti ng ........................................................101
................................................................100
Initializing a Firebox Using a Modem .............................102
Initializing using Remote Provisioning ............................102
Managing Flash Disk Memory .......................................104
Making a backup of the current configuration ................. 104
Restoring a backup configuration .................................105
CHAPTER 9 Glossary .................................................. 107
CHAPTER 10 Field Definitions ..................................... 153
System Manager ..........................................................153
Connect to Firebox dialog box ....................................153
Enter Read/Write Passphrase dialog box ........................ 154
Polling dialog box .....................................................154
Syslog Color dialog box .............................................154
Flash Disk Management Tool .......................................155
Enter Encryption Key dialog box ..................................155
Flash Disk Management Tool dialog box ........................155
Log Utility .................................................................... 156
Copy or Merge Logs dialog box ................................... 156
LogViewer ...................................................................157
Find Keyphrase dialog box ..........................................157
Preferences dialog box ...............................................158
Search Fields dialog box .............................................158
Policy Manager ............................................................160
1-to-1 Mapping dialog box .........................................160
Add Address dialog box .............................................160
Add Dynamic NAT dialog box .....................................161
Add Exception dialog box ..........................................161
Add External IP dialog box ......................................... 162
viii WatchGuard Firebox System

Add Firebox Group dialog box .................................... 162
Add IP Address dialog box ......................................... 162
Add Member dialog box ............................................ 163
Add Port dialog box .................................................. 163
Add Route dialog box ............................................... 164
Add Service dialog box .............................................. 164
Add Static NAT dialog box ......................................... 164
Advanced DVCP Policy Configuration dialog box ............ 165
Advanced Dynamic NAT dialog box ............................. 165
Advanced Export File Preferences dialog box ................. 166
Advanced Mobile User VPN Policy Configuration dialog
box
................................................................ 166
Aliases dialog box ..................................................... 168
Authentication Servers dialog box ................................ 168
Basic DVCP Server Configuration dialog box .................. 172
Blocked Ports dialog box ........................................... 172
Blocked Sites dialog box ............................................ 173
Blocked Sites Exceptions dialog box ............................ 174
Certificate Authority Configuration ............................... 174
Configure Gateways dialog box ................................... 175
Configure IPSec Tunnels dialog box .............................. 175
Configure Tunnels dialog box ...................................... 176
Configure Tunnel dialog box ....................................... 176
Connect to Firebox dialog box .................................... 177
Default Gateway dialog box ........................................ 177
Default Packet Handling dialog box ............................. 177
DHCP Server dialog box ............................................ 179
DHCP Subnet Properties dialog box ............................. 180
DVCP Client Setup dialog box ..................................... 181
DVCP Client Wizard .................................................. 182
DVCP Server Properties dialog box .............................. 183
DVCP Server Properties dialog box .............................. 184
Dynamic NAT dialog box ........................................... 185
Edit Routing Policy dialog box ..................................... 186
Enter Firebox Access Passphrases dialog box ................. 187
Reference Guide ix

Enter Tunnel Name dialog box .....................................187
Filter Authentication dialog box ...................................188
Firebox Flash Disk dialog box ...................................... 189
Firebox Name dialog box ........................................... 190
FTP Proxy dialog box .................................................190
Generate Key dialog box ............................................ 191
High Availability dialog box ......................................... 191
Host Alias dialog box .................................................192
HTTP Proxy dialog box ...............................................192
Incoming dialog box ..................................................200
Incoming SMTP Proxy dialog box .................................201
IPSec Configuration dialog box ....................................204
IPSec Logging dialog box ........................................... 206
Logging and Notification dialog box .............................206
Logging Setup dialog box ..........................................207
Manual Security dialog box ......................................... 208
Mobile User Client - Select New Passphrase dialog box .... 208
Mobile User VPN Wizard ............................................209
Mobile User VPN dialog box .......................................212
NAT Setup dialog box ................................................212
Network Configuration dialog box ................................ 214
New MIME Type dialog box ........................................ 219
New Service dialog box .............................................. 219
Outgoing SMTP Proxy dialog box ................................220
PPTP Logging dialog box ........................................... 222
Remote Gateway dialog box ....................................... 222
Remote User Setup dialog box ....................................223
Select Firebox Time Zone dialog box ............................225
Select Gateway dialog box ..........................................225
Select MIME Type dialog box ......................................225
Services dialog box ...................................................225
Service Properties dialog box ...................................... 226
Set Policy Ordering dialog box .................................... 228
Setup Firebox User dialog box .....................................228
Setup New User dialog box ......................................... 229
x WatchGuard Firebox System

Setup Routes dialog box ............................................ 229
Slash Notation dialog box .......................................... 230
SpamScreen dialog box ............................................. 230
WatchGuard Find dialog box ...................................... 231
WatchGuard VPN dialog box ...................................... 231
Firebox Monitors ......................................................... 233
Add Displayed Service dialog box ................................ 233
Remove Site dialog box ............................................. 233
View Properties dialog box ......................................... 233
Historical Reports ........................................................ 234
Add Report Filter dialog box ....................................... 234
Historical Reports dialog box ...................................... 236
Report Properties dialog box ...................................... 237
HostWatch .................................................................. 240
Filter Properties dialog box ......................................... 240
Properties dialog box ................................................ 242
WatchGuard Security Event Processor ........................... 243
Set Log Encryption Key dialog box ............................... 246
Index .................................................................... 247
Reference Guide xi

xii WatchGuard Firebox System

CHAPTER 1 Internet Protocol Reference
Internet Protocol (IP) specifies the format of packets and the addressing
scheme for sending data over the Internet. By itself, it functions like a
postal system allowing you to address a package and drop it into the
system. There is, however, no direct link between you and the recipient.
In other words, there is no package.
Most networks combine IP with higher-level protocols like Transmission
Control Protocol (TCP). Unlike simple IP, TCP/IP establishes a
connection between two host servers so that they can send messages back
and forth. TCP/IP provides the “packaging.”
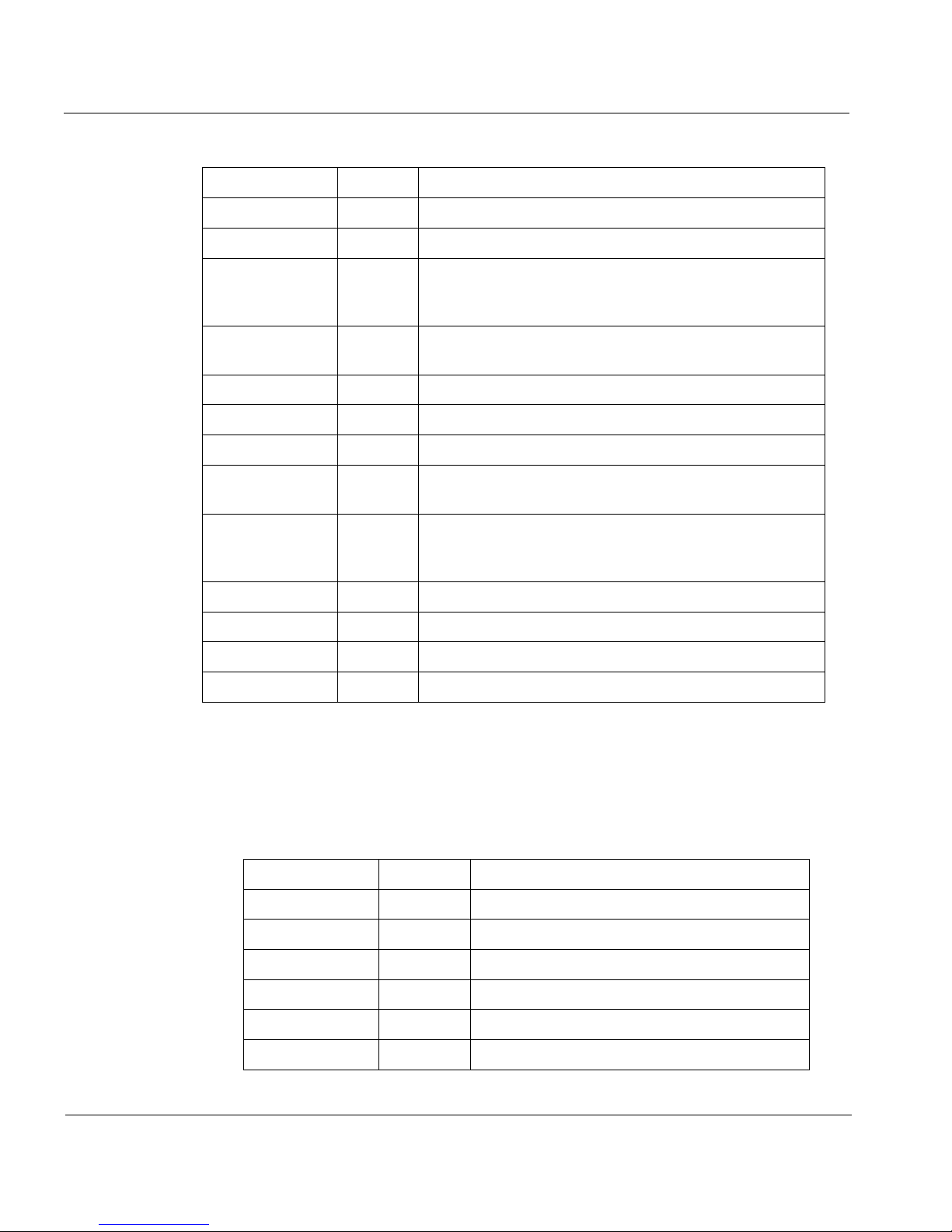
Internet Protocol Header
IP is an Internet standard that enables the shipment of datagrams – selfcontained packets of information that include their own address and
delivery instructions. IP prepends a header to each datagram. The IP
header contains a minimum of twelve attributes as well as additional
optional attributes.
Reference Guide 1
CHAP TER 1: Internet Protocol Reference
Attribute Size Description
Version 4 bits IP format number (Current version = 4)
IHL 4 bits Header length in 32-bit words (Minimum = 5)
TOS 8 bits Type of service sets routing priorities. It is
Tot _Le n 16 bits Total length of packet measured in octets. It is
ID 16 bits Packet ID, used for reassembling fragments.
Flags 3 bits Miscellaneous flags
Frag_Off 13 bits Identifies fragment part for this packet.
TTL 8 bits Time to live. It sets the maximum time the
Protocol 8 bits IP protocol number. Indicates which of TCP,
generally under-utilized because few application
layers can set it.
used in reassembling fragments.
datagram remains alive in the system.
UDP, ICMP, IGMP, or other Transport protocol
is inside.
Check 16 bits Checksum for the IP header
Sour_Addr 32 bits Source IP address
Dest_Addr 32 bits Destination IP address
Options 24 bits IP Options (Present if IHL is 6)
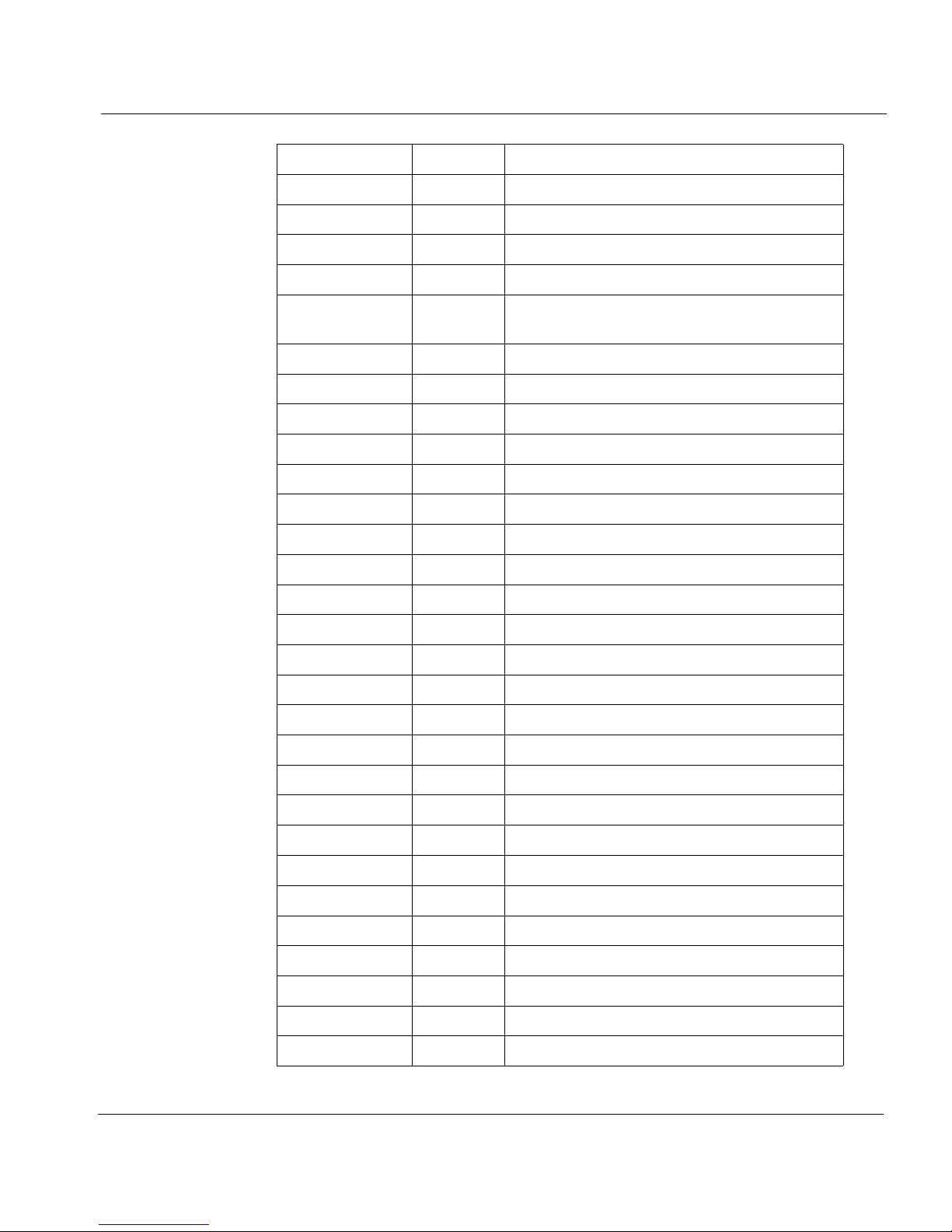
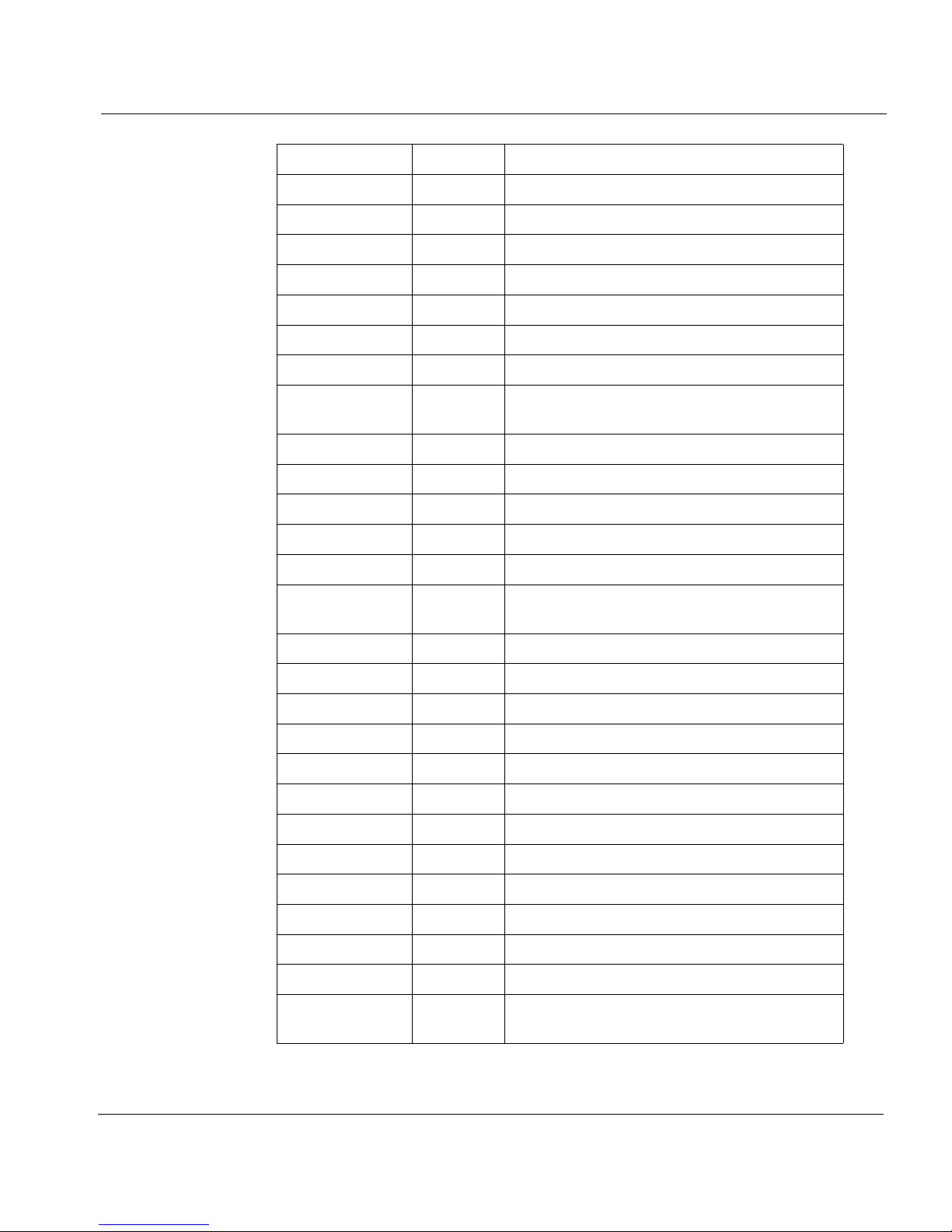
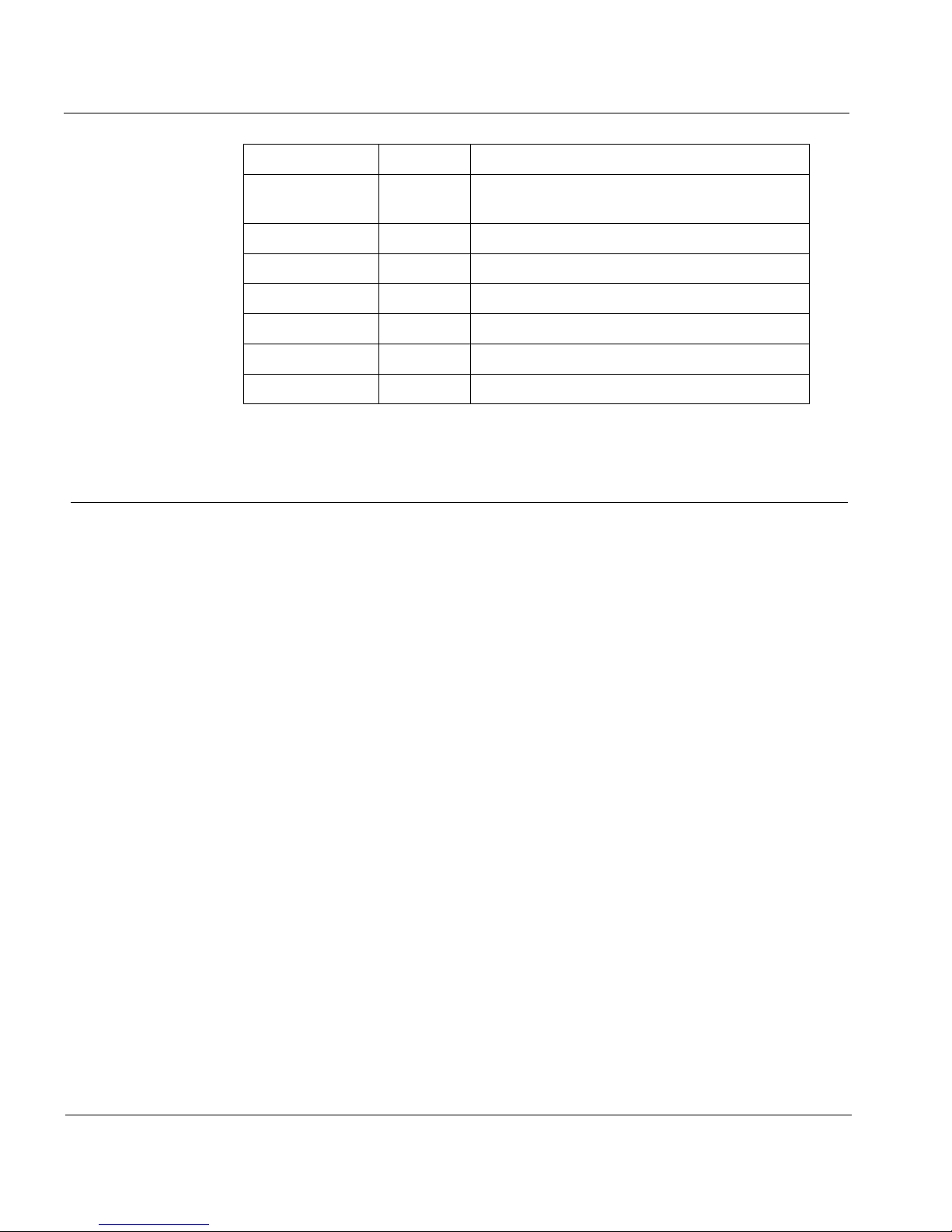
IP header number list
The IP Protocol header contains an 8-bit field that identifies the protocol
for the transport layer for the datagram.
Keyword Number Protocol
ICMP 1 Internet Control Message
IGMP 2 Internet Group Management
GGP 3 Gateway-to-Gateway
IP 4 IP-within-IP (encapsulation)
0 Reserved
ST 5 Stream
2 WatchGuard Firebox System
Internet Protocol Header
Keyword Number Protocol
TCP 6 Transmission Control Protocol
UCL 7 UCL
EGP 8 Exterior Gateway Protocol
IGP 9 Any private interior gateway
BBN-RCC-
10 BBN RCC Monitoring
MON
NVP-II 11 Network Voice Protocol
PUP 12 PUP
ARGUS 13 ARGUS
EMCON 14 EMCON
XNET 15 Cross Net Debugger
CHAOS 16 Chaos
UDP 17 User Datagram Protocol
MUX 18 Multiplexing
DCN-MEAS 19 DCN Measurement Subsystems
HMP 20 Host Monitoring
PRM 21 Packet Radio Measurement
XNS-IDP 22 XEROX NS IDP
TRUNK-1 23 Trunk-1
TRUNK-2 24 Trunk-2
LEAF-1 25 Leaf-1
LEAF-2 26 Leaf-2
RDP 27 Reliable Data Protocol
IRTP 28 Internet Reliable Transaction
ISO-TP4 29 ISO Transport Protocol Class 4
NETBLT 30 Bulk Data Transfer Protocol
MFE-NSP 31 MFE Network Services Protocol
MERIT-INP 32 MERIT Internodal Protocol
SEP 33 Sequential Exchange Protocol
3PC 34 Third Party Connect Protocol
Reference Guide 3

CHAP TER 1: Internet Protocol Reference
Keyword Number Protocol
IDPR 35 Inter-Domain Policy Routing Protocol
XTP 36 XTP
DDP 37 Datagram Delivery Protocol
IDPR-CMTP 38 IDPR Control Message Transport
TP++ 39 TP++ Transport Protocol
IL 40 IL Transport Protocol
SIP 41 Simple Internet Protocol
SDRP 42 Source Demand Routing Protocol
SIP-SR 43 SIP Source Route
SIP-FRAG 44 SIP Fragment
IDRP 45 Inter-Domain Routing Protocol
RSVP 46 Reservation Protocol
Protocol
GRE 47 General Routing Encapsulation
MHRP 48 Mobile Host Routing Protocol
BNA 49 BNA
ESP 50 Encapsulated Security Payload
AH 51 Authentication Header
I-NLSP 52 Integrated Net Layer Security TUBA
SWIPE 53 IP with Encryption
NHRP 54 NBMA Next Hop Resolution Protocol
55-60 Unassigned
61 Any host internal protocol
CFTP 62 CFTP
63 Any local network
SAT-EXPAK 64 SATNET and Backroom EXPAK
KRYPTOLAN 65 Kryptolan
RVD 66 MIT Remote Virtual Disk Protocol
IPPC 67 Internet Pluribus Packet Core
4 WatchGuard Firebox System
68 Any distributed file system
Internet Protocol Header
Keyword Number Protocol
SAT-MON 69 SATNET Monitoring
VISA 70 VISA Protocol
IPCV 71 Internet Packet Core Utility
CPNX 72 Computer Protocol Network Executive
CPHB 73 Computer Protocol Heart Beat
WSN 74 Wang Span Network
PVP 75 Packet Video Protocol
BR-SAT-
76 Backroom SATNET Monitoring
MON
SUN-ND 77 SUN NDPROTOCOL-Temporary
WB-MON 78 WIDEBAND Monitoring
WB-EXPAK 79 WIDEBAND EXPAK
ISO-IP 80 ISO Internet Protocol
VMTP 81 VMTP
SECURE-
82 SECURE-VMTP
VMTP
VINES 83 VINES
TTP 84 TTP
NSFNET-IGP 85 NSFNET-IGP
DGP 86 Dissimilar Gateway Protocol
TCF 87 TCF
IGRP 88 IGRP
OSPFIGP 89 OSPFIGP
SPRITE-RPC 90 Sprite RPC Protocol
LARP 91 Locus Address Resolution Protocol
MTP 92 Multicast Transport Protocol
AX.25 93 AX.25 Frames
IPIP 94 IP-within-IP Encapsulation Protocol
MICP 95 Mobile Internetworking Control
Reference Guide 5
Protocol
CHAP TER 1: Internet Protocol Reference
Keyword Number Protocol
SCC-SP 96 Semaphore Communications Security
ETHERIP 97 Ethernet-within-IP Encapsulation
ENCAP 98 Encapsulation Header
99 Any private encryption scheme
GMTP 100 GMTP
101-254 Unassigned
255 Reserved
Internet Protocol Options
Internet Protocol options are variable-length additions to the standard IP
header. Unfortunately, enabling IP options can be risky; hackers can use
them to specify a route that helps them gain access to your network.
Because most applications make it very obscure or difficult to use IP
options, they are rarely used.
Protocol
There are several kinds of IP options:
Security
Control routing of IP packets that carry sensitive data. Security
options are rarely supported.
Stream ID (SID)
The stream ID option is rarely supported.
Source Routing
Both the loose source route option and the strict source route
option enable the source of an Internet packet to provide routing
information. Source routing options can be very dangerous,
because a clever attacker might use them to masquerade as
another site. However, loose source routing and the traceroute
facility can also help debug some obscure routing problems.
Record Route
The record route option was originally intended for use in testing
the Internet. Unfortunately, record route can record only ten IP
6 WatchGuard Firebox System

addresses. On the present Internet, typical long-haul
transmissions can involve twenty or thirty hops, rendering the
record route option obsolete.
Time Stamp
The time stamp option helps measure network propagation
delays. This task is done more effectively, however, with higherlevel time protocols or time-stamp messages.
Transfer Protocols
The IP protocol encapsulates information contained in the transport layer.
The transport layer has several protocols that specify how to transmit
data between applications: for example, UDP, TCP, ICMP, and others.
UDP
Transfer Protocols
User Datagram Protocol (UDP) is a connectionless, potentially unreliable
datagram protocol. It trades reliability for speed and low overhead. To
ensure accurate transmission, it requires that the application layer verify
that packets arrive at their destination.
Characteristics of UDP include:
• Often used for services involving the transfer of small amounts of
data where retransmitting a request is not a problem.
• Used for services such as time synchronization in which an
occasionally lost packet will not affect continued operation. Many
systems using UDP resend packets at a constant rate to inform their
peers about interesting events.
• Primarily used on LANs, in particular for Network File System (NFS)
services where its low overhead gives it a substantial performance
advantage. (Network File System is a popular TCP/IP service for
providing shared file systems over a network.) A lack of congestion
control means that using UDP for bulk data transfer over long-haul
connections is not recommended.
• Supports broadcasts.
• Provides abstraction of ports.
Reference Guide 7

CHAP TER 1: Internet Protocol Reference
• A connection is described by its source and destination ports and its
source and destination IP addresses. In typical usage, port numbers
below 1024 are reserved for well-known services (destinations), and
the client side is supposed to use ports above 1023 for the source of
the connection. However, this rule has many notable exceptions. In
particular, NFS (port 2049) and Archie (port 1525) use server ports at
numbers above 1024. Some services use the same source and
destination port for server-to-server connections. Common examples
are DNS (53), NTP (123), syslog (514), and RIP (520).
TCP
Transmission Control Protocol (TCP) provides reliable stream-oriented
services. It trades speed and overhead for increased reliability. Like UDP,
TCP provides source and destination ports that are used in a similar
fashion.
TCP uses a rather complicated state machine to manage connections.
There are several attribute bits that control the state of a connection. Three
very important attribute bits of TCP packets are the SYN, ACK, and FIN
bits. The SYN bit is set only on the first packet sent in each direction for a
given connection. The ACK bit is set when the other side is
acknowledging the receipt of data to the peer. The FIN bit is set when
either side chooses to close the connection.
ICMP
The Internet Control Message Protocol (ICMP) is used primarily to
deliver error information about other services. It is otherwise quite similar
in practical operation to UDP. That is, it is connectionless and does not
guarantee that packets are delivered to their destination. One dangerous
ICMP packet is the ICMP redirect packet, which can change routing
information on the machines that receive it.
Other protocols
The vast majority of the traffic on the Internet uses one of the three
protocols mentioned in the previous section. Some other protocols are as
follows:
8 WatchGuard Firebox System

Standard Ports and Random Ports
IGMP (Internet Group Multicast Protocol)
A protocol primarily designed for hosts on multiaccess networks
to inform locally attached routers of their group membership
information.
IPIP (IP-within-IP)
An encapsulation protocol used to build virtual networks over the
Internet.
GGP (Gateway-Gateway Protocol)
A routing protocol used between autonomous systems.
GRE
A protocol used for PPTP.
ESP
An encryption protocol used for IPSec.
Standard Ports and Random Ports
UDP and TCP encapsulate information contained within the application
layer. The appropriate application processes are designated by source and
destination port numbers. These port numbers, along with the source and
destination IP addresses, specify a unique connection on the Internet.
For example, it is reasonable to have two telnet sessions from one host to
another. However, since telnet uses a well-known service number of 23,
something must distinguish these two connections. The other port in
these cases will be a port that is typically greater than 1023. This
alternative port designation is dynamically allocated by the operating
system on the client side.
Random ports can cause a great amount of trouble if they happen to
match a well-known service on a port above 1023. If some client machine
assigns a random port of 2049, the connection may mysteriously fail.
Similar problems can occur with the X Window and Archie services.
In practice, most operating systems cycle port numbers between 1024 and
a number somewhere in the range of 2100, depending on how many TCP
connections are currently open and whether a recently closed connection
used a similar port number. This makes the above problem rare.
Reference Guide 9

CHAP TER 1: Internet Protocol Reference
10 WatchGuard Firebox System

CHAPTER 2 MIME Content Types
A content-type header is used by applications to determine what kind of
data they are receiving, thus allowing them to make decisions about how
it should be handled. It allows clients to correctly identify and display
video clips, images, sound, or non-HTML data. People are probably most
familiar with the MIME content types sent in email.
The WatchGuard Proxied HTTP service uses content-type headers to
determine whether to allow or deny an HTTP transaction. Use Policy
Manager to configure the Proxied HTTP service to allow or deny contenttypes. Content types are also used in SMTP and are configurable in the
SMTP proxy. This chapter contains a list of the more commonly used
MIME content-types.
Wildcards may be used to select all subtypes within a type, thereby
denying all or allowing all of that MIME type. For example, to allow all
content-types that are text (including text/enriched, text/plain, and
others), use the content-type
New, registered MIME content types appear regularly. WatchGuard
recommends frequent checking of an online reference for the most current
list. One source of current MIME types is:
ftp://ftp.isi.edu/in-notes/iana/assignments/media-types
Reference Guide 11
text/*.

CHAPTER 2: MIME Content T yp es
In addition, WatchGuard encourages you to email requests for inclusion
of new content types in our master list to:
manual@watchguard.com
Typ e Subtype Reference
text plain [RFC2646, RFC2046]
richtext [RFC2045, RFC2046]
enriched [RFC1896]
tab-separated-values [Paul Lindner]
html [RFC2854]
sgml [RFC1874]
vnd.latex-z [Lubos]
vnd.fmi.flexstor [Hurtta]
uri-list [RFC2483]
vnd.abc [Allen]
rfc822-headers [RFC1892]
vnd.in3d.3dml [Powers]
prs.lines.tag [Lines]
vnd.in3d.spot [Powers]
css [RFC2318]
xml [RFC3023]
x ml - ex t er n a l- pa r s ed -e n t it y [RFC3023]
rtf [Lindner]
directory [RFC2425]
calendar [RFC2445]
vnd.wap.wml [Stark]
vnd.wap.wmlscript [Stark]
vnd.motorola.reflex [Patton]
vnd.fly [Gurney]
vnd.wap.sl [WAP-Forum]
vnd.wap.si [WAP-Forum]
12 WatchGuard Firebox System
t140 [RFC2793]
vn d.m s-m edia pa cka ge [Nelson]
vnd.IPTC.NewsML [IPTC]
text vnd.IPTC.NITF [IPTC]
vnd.curl [Hodge]
vnd.DMClientScript [Bradley]
parityfec [RFC3009]
multipart mixed [RFC2045, RFC2046]
alternative [RFC2045, RFC2046]
digest [RFC2045, RFC2046]
parallel [RFC2045, RFC2046]
appledouble [MacMime, Patrick
Faltstrom
header-set [Dave Crocker]
form-data [RFC2388]
related [RFC2387]
report [RFC1892]
voice-message [RFC2421, RFC2423]
signed [RFC1847]
encrypted [RFC1847]
byteranges [RFC2068]
me ssa ge rfc822 [RFC2045, RFC2046]
partial [RFC2045, RFC2046]
external-body [RFC2045, RFC2046]
news [RFC 1036, Henry
Spencer]
http [RFC2616]
delivery-status [RFC1894]
disposition-notification [RFC2298]
s-http [RFC2660]
application octet-stream [RFC2045, RFC2046]
Reference Guide 13

CHAPTER 2: MIME Content T yp es
postscript [RFC2045, RFC2046]
oda [RFC2045, RFC2046]
atomicmail [atomicmail, Borenstein]
application andrew-inset [andrew-inset, Borenstein]
slate [slate, terry crowley]
wita [Wang Info Transfer,
dec-dx [Digital Doc Trans, Larry
dca-rft [IBM Doc Content Arch,
activemessage [Ehud Shapiro]
rtf [Paul Lindner]
applefile [MacMime, Patrick
Larry Campbell]
Campbell]
Larry Campbell]
Faltstrom]
mac-binhex40 [MacMime, Patrik
Faltstrom]
news-message-id [RFC1036, Henry
Spencer]
news-transmission [RFC1036, Henry
Spencer]
wordperfect5.1 [Paul Lindner]
pdf [Paul Lindner]
zip [Paul Lindner]
macwriteii [Paul Lindner]
msword [Paul Lindner]
remote-printing [RFC1486, Rose]
mathematica [Van Nostern]
cybercash [Eastlake]
commonground [Glazer]
iges [Parks]
riscos [Smith]
eshop [Katz]
14 WatchGuard Firebox System
x400-bp [RFC1494]
sgml [RFC1874]
cals-1840 [RFC1895]
pgp-encrypted [RFC3156]
application pgp-signature [RFC3156]
pgp-keys [RFC3156]
vnd.framemaker [Wexler]
vnd.mif [Wexler]
vnd.ms-excel [Gill]
vnd. ms-pow erpoint [Gill]
vnd.ms-project [Gill]
vnd.ms-works [Gill]
vnd.ms-tnef [Gill]
vnd.svd [Becker]
vnd.music-niff [Butler]
vnd.ms-artgalry [Slawson]
vnd.truedoc [Chase]
vnd.koan [Cole]
vnd.street-stream [Levitt]
vnd.fdf [Zilles]
set- pay ment-initiation [Korver]
set-payment [Korver]
set-registra ti on -i ni tiation [Korver]
set-registration [Korver]
vnd.seemail [Webb]
vnd.businessobjects [Imoucha]
vnd.meri dian -s li ng shot [Wedel]
vnd.xara [Matthewman]
sgml-open-catalog [Grosso]
vnd.rapid [Szekely]
vnd.enliven [Santinelli]
Reference Guide 15

CHAPTER 2: MIME Content T yp es
vnd.japannet-registration-wakeup [Fujii]
vnd.japannet-verification-wakeup [Fujii]
v n d . j a p a n n e t - p a y m e n t - w a k e u p [Fujii]
v n d . j a p a n n e t - d i r e c t o r y - s e r v i c e [Fujii]
application vnd.intertrust.digibox [Tomasello]
vnd.intertrust.nncp [Tomasello]
prs.alvestrand.titrax-sheet [Alvestrand]
vnd.noblenet-sealer [Solomon]
vnd.webturbo [Rehem]
vnd.noblenet-web [Solomon]
vnd.noblenet-directory [Solomon]
prs.nprend [Doggett]
hyperstudio [Domino]
vnd.shana.informed.formtemplat
[Selzler]
e
vnd.shana.informed.formdata [Selzler]
vnd.shana.informed.package [Selzler]
vnd.shana.informed.interchange [Selzler]
vnd.$commerce_battelle [Applebaum]
vnd.osa.netdeploy [Klos]
vnd.ibm.MiniPay [Herzberg]
vnd.japannet-jpnstore-wakeup [Yoshitake]
vnd.japannet-setstore-wakeup [Yoshitake]
vnd.japannet-verification [Yoshitake]
vnd.japannet-registration [Yoshitake]
vnd.hp-HPGL [Pentecost]
vnd.hp-PCL [Pentecost]
vnd.hp-PCLXL [Pentecost]
vnd.musician [Adams]
16 WatchGuard Firebox System
vnd.FloGraphIt [Floersch]
vnd. int ercon. for mnet [Gurak]

vemmi [RFC2122]
vnd.ms-asf [Fleischman]
vnd.ecdis-update [Buettgenbach]
vnd.powerbuilder6 [Guy]
vnd.powerbuilder6-s [Guy]
application vnd.lotus-wordpro [Wattenberger]
vnd.lotus-approach [Wattenberger]
vnd.lotus-1-2-3 [Wattenberger]
vnd.lotus-organizer [Wattenberger]
vnd.lotus-screencam [Wattenberger]
vnd.lotus-freelance [Wattenberger]
vnd.fujitsu.oasys [Togashi]
vnd.fujitsu.oasys2 [Togashi]
vnd.swiftview-ics [Widener]
vnd.dna [Searcy]
prs.cww [Rungchavalnont]
vnd.wt.stf [Wohler]
vnd.dxr [Duffy]
vnd.mitsubishi.misty-
[Tanaka]
guard.trustweb
vnd.ibm.modcap [Hohensee]
vnd.acucobol [Lubin]
vnd.fujitsu.oasys3 [Okudaira]
marc [RFC2220]
vnd.fujitsu.oasysprs [Ogita]
vnd.fujitsu.oasysgp [Sugimoto]
vnd.visio [Sandal]
vnd.netfpx [Mutz]
vnd.audiograph [Slusanschi]
vnd.epson.salt [Nagatomo]
vnd.3M.Post-it-Notes [O'Brien]
Reference Guide 17

CHAPTER 2: MIME Content T yp es
application pkcs7-mime [RFC2311]
pkcs7-signature [RFC2311]
pkcs10 [RFC2311]
vnd.novadigm.EDX [Swenson]
vnd.novadigm.EXT [Swenson]
vnd.novadigm.EDM [Swenson]
vnd.claymore [Simpson]
vnd.comsocaller [Dellutri]
vnd.yellowriver-custom-menu [Yellow]
vnd.ecowin.chart [Olsson]
vnd.ecowin.series [Olsson]
vnd. eco win.filerequest [Olsson]
vnd. eco win.fileupdate [Olsson]
vn d.e cow in. seri es requ est [Olsson]
vn d.e cow in. seri es upda te [Olsson]
EDIFACT [RFC1767]
EDI-X12 [RFC1767]
EDI-Consent [RFC1767]
vnd.wrq-hp3000-labelled [Bartram]
vnd.minisoft-hp3000-save [Bartram]
vnd.ffsns [Holstage]
vnd.hp-hps [Aubrey]
vn d.f uji xer ox.d oc uwor ks [Taguchi]
xml [RFC3023]
x ml - ex t er n a l- pa r s ed -e n t it y [RFC3023]
xml-dtd [RFC3023]
vnd.anser-web-funds-transfer-
[Mori]
initiation
vnd.anser-web-certificate-issue-
[Mori]
initiation
18 WatchGuard Firebox System
vnd.is-xpr [Natarajan]
 Loading...
Loading...