Page 1

SpeedTouch™608WL and
SpeedTouch™620 only
SpeedTouch™
(Wireless) Business DSL Router
Hyper-NAT Configuration Guide
Release R5.3.0
Page 2

Page 3

SpeedTouch™
Hyper-NAT Configuration Guide
R5.3.0
Page 4

Copyright
Copyright ©1999-2005 THOMSON. All rights reserved.
Passing on, and copying of this document, use and communication of its contents is not permitted without written authorization
from THOMSON. The content of this document is furnished for informational use only, may be subject to change without notice,
and should not be construed as a commitment by THOMSON. THOMSON assumes no responsibility or liability for any errors or
inaccuracies that may appear in this document.
Thomson Telecom Belgium
Prins Boudewijnlaan, 47
B-2650 Edegem
Belgium
www.speedtouch.com
Trademarks
The following trademarks are used in this document:
SpeedTouch™ is a trademark of THOMSON.
Microsoft®, MS-DOS®, Windows® and Windows NT® are either registered trademarks or trademarks of Microsoft Corpora-
tion in the United States and/or other countries.
UNIX® is a registered trademark of UNIX System Laboratories, Incorporated.
Apple® and Mac OS® are registered trademarks of Apple Computer, Incorporated, registered in the United States and other
countries.
Adobe, the Adobe logo, Acrobat and Acrobat Reader are trademarks or registered trademarks of Adobe Systems, Incorpo-
rated, registered in the United States and/or other countries.
Netscape® and Netscape Navigator® are registered trademarks of Netscape Communications Corporation.
Ethernet™ is a trademark of Xerox Corporation.
UPnP™ is a certification mark of the UPnP™ Implementers Corporation.
Wi-Fi® and the Wi-Fi logo are registered trademarks of the Wi-Fi Alliance. "Wi-Fi CERTIFIED", "Wi-Fi ZONE", "Wi-Fi Alli-
ance", their respective logos and "Wi-Fi Protected Access" are trademarks of the Wi-Fi Alliance.
Other products may be trademarks or registered trademarks of their respective manufacturers.
Document Information
Status: v1.0 (March 2005)
Reference: E-NIT-CTC-20040716-0004
Short Title: Hyper-NAT Configuration Guide ST R5.3.0
Page 5

E-NIT-CTC-20040716-0004 v1.0
3
Contents
About this Hyper-NAT Configuration Guide ............ 5
1 Introduction ................................................................... 7
1.1 The need for address translation ................................................... 8
1.2 What is address translation............................................................ 9
2 NAT, PAT and NAPT ................................................... 11
3 Dynamic versus static address translation............... 13
4 Address translation flavours...................................... 15
4.1 Traditional or outbound address translation ............................... 16
4.1.1 Basic NAT ................................................................................................... 17
4.1.2 Network Address Port Translation (NAPT) ....................................................... 18
4.2 Two-Way NAT............................................................................... 19
4.3 N-N NAT ....................................................................................... 20
4.4 M-N NAT or Multi NAT ................................................................. 21
4.5 Transparent NAT .......................................................................... 22
4.6 Port range shifting ....................................................................... 23
4.7 Translation templates .................................................................. 24
Page 6

E-NIT-CTC-20040716-0004 v1.0
4
5 Application level gateways ........................................25
6 Network address translation configuration on the
SpeedTouch™ ............................................................. 27
6.1 Configure address translation on the GUI ................................... 28
6.1.1 Configuring Hyper-NAT on the Web Pages....................................................... 29
6.1.2 Enable/disable address translation on an interface............................................. 30
6.1.3 Create an address translation mapping ............................................................ 31
6.1.4 Create a template......................................................................................... 34
6.2 Configure address translation on the CLI .................................... 37
6.3 Configure NAT maps .................................................................... 40
6.3.1 Basic NAT ................................................................................................... 41
6.3.2 Two-Way NAT ............................................................................................. 42
6.3.3 N-N NAT ..................................................................................................... 43
6.3.4 Multi NAT ................................................................................................... 44
6.3.5 Transparent NAT.......................................................................................... 46
6.4 Configure NAPT maps.................................................................. 48
6.4.1 Basic NAPT ................................................................................................. 49
6.4.2 NAPT using default server ............................................................................. 50
6.4.3 NAPT using transparent default server ............................................................ 51
6.4.4 NAPT using transparent default server and port range constraint (=IP Passthrough) .
52
6.4.5 NAPT using host function.............................................................................. 53
6.4.6 NAPT using transparent host function............................................................. 54
6.4.7 NAPT using dynamic port range constraint ...................................................... 55
6.5 Configure port shifting maps ....................................................... 56
6.5.1 Inbound port shifting..................................................................................... 57
6.6 Configure templates .................................................................... 58
6.6.1 X+n templates ............................................................................................ 60
Page 7

About this Hyper-NAT Configuration Guide
E-NIT-CTC-20040716-0004 v1.0
5
About this Hyper-NAT Configuration Guide
Used Symbols
Terminology
Generally, the SpeedTouch™608 or SpeedTouch™620 will be referred to as
SpeedTouch™ in this Hyper-NAT Configuration Guide.
Typographical
Conventions
In interactive input and output, typed input is displayed in a bold font and
commands are displayed
like this.
Comments are added in italics.
Example:
Documentation and
software updates
THOMSON continuously develops new solutions, but is also committed to improve
its existing products.
For suggestions regarding this document, please contact
documentation.speedtouch@thomson.net
.
For more information on THOMSON's latest technological innovations, documents
and software releases, visit us at:
www.speedtouch.com
A note provides additional information about a topic.
A tip provides an alternative method or shortcut to perform an action.
!
A caution warns you about potential problems or specific precautions that
need to be taken.
=>language list
CODE LANGUAGE VERSION FILENAME
en* english 4.2.0.1 <system>
Only one language is available
Page 8

About this Hyper-NAT Configuration Guide
E-NIT-CTC-20040716-0004 v1.0
6
Page 9

Introduction
E-NIT-CTC-20040716-0004 v1.0
7
1Introduction
Introduction Internet technology is based on the IP protocol and in order to communicate via IP,
each device participating in the communication must have a unique IP address. This
presents a problem, since the Internet is expanding at an exponential rate. Address
translation is a method for connecting multiple computers to the Internet (or any
other IP network) sharing one public IP address. This allows home users and small
businesses to connect their network to the Internet cheaply and efficiently.
The impetus towards increasing the use of address translation comes from a number
of factors:
A world shortage of IP addresses
Security needs
Ease and flexibility of network administration
Page 10

The need for address translation
E-NIT-CTC-20040716-0004 v1.0
8
1.1 The need for address translation
IP addresses While the number of available addresses seems large, the Internet is growing at such
a pace that it will soon be exhausted. The next generation IP protocol, IP version 6,
allows for more addresses, but it will take years before the existing network
infrastructure will be fully migrated to the new protocol.
Address translation allows a single device, such as the SpeedTouch™, to act as an
agent between the Internet (or public network) and a local (or private) network. This
means that only one, unique IP address is required to represent an entire group of
computers. The outside world is unaware of this division and thinks that only one
computer is connected.
Security Many people view the Internet as a "one-way street"; they forget that while their
computer is connected to the Internet, the Internet is also connected to their
computer. That means that anybody with Internet access can potentially access
resources on their computers (such as files, e-mail, company network etc.). Most
personal computer operating systems are not designed with security in mind, leaving
them wide open to attacks from the Internet.
The security implications can be disastrous. Confidential company information such
as product plans or marketing strategies can be stolen, this can lead to major
financial losses or even cause the company to fold.
Implementing address translation automatically provides firewall-style protection
between your private network and public networks (the Internet or other public
networks). Address translation only allows connections that originate from inside the
private network. Basically, this means that a computer on a public network cannot
connect to your computer unless your computer has initiated the contact. You can
browse the Internet and connect to a site, and even download a file; but somebody
else cannot latch onto your IP address and use it to connect to a port on your
computer.
In specific circumstances (static address translation) devices from public networks
are allowed to initiate connections to computers on the private network. This is only
done when specifically granted by the local network after appropriate configuration.
Administration A real benefit of address translation is apparent in network administration. For
example it is possible to move a Web server or FTP server to another host without
having to worry about broken links. Simply change the inbound mapping at the
Internet Gateway to reflect the new host location. Also changes in the private
network are easily made without any problems, because the only public IP address
either belongs to the Internet Gateway or comes from a pool of global addresses.
!
The device performing address translation should be secure/protected.
Page 11

What is address translation
E-NIT-CTC-20040716-0004 v1.0
9
1.2 What is address translation
Introduction Using address translation, the IP and/or TCP/UDP port identifications can change
while traversing the network.
IP address translation
Figure 1: IP address translation
Quite some private networks use private IP addresses, meaning that these host are
not known (and as such cannot be routed) within the Internet (= public network).
When such a host would enter the Internet, one should assign it an IP identification,
which is allowed to be used in the public network.
This is what will be done. The private network will have an exit point towards the
public network (typically called a gateway) and this exit point will convert the IP
address of the private network towards a valid public IP address. The reverse
procedure is followed when a packet is received back from the public network.
As the address translation is only performed on-demand and due to the fact that not
all private hosts need access to the public network at the same time, a small pool of
available public IP addresses on the WAN interface of the modem will be sufficient,
this means sparing out addresses.
TCP/UDP port
translation
This type of translation will commonly be used in conjunction with IP address
translation. Not only the IP address will be changed but also the port number.
The main advantage of this way of working is that the same public IP address can be
assigned to two different private LAN nodes, yet using a different port numbering
scheme, which in fact boils down to IP address multiplexing.
As several nodes can use the same IP address, a considerable saving is done on the
amount of public IP addresses needed.
Private Public
SpeedTouchTM
Address
Translation
Page 12

What is address translation
E-NIT-CTC-20040716-0004 v1.0
10
Page 13

NAT, PAT and NAPT
E-NIT-CTC-20040716-0004 v1.0
11
2NAT, PAT and NAPT
Introduction Three different categories of address translation exist, namely:
Network Address Translation (NAT): a private IP address X is translated into a
public IP address Y.
Port Address Translation (PAT): a UDP/TCP port number X is translated into a
port number Y.
Network Address and Port Translation (NAPT): both the private IP address and
port number are translated.
NAT If NAT is enabled, then a private IP address is changed into a temporary public IP
address. The NAT translation technique is often used in dial-up or for on-demand
connections in which remote connections go up and down frequently. When the user
is connected, s/he is assigned a single external IP address; once that user
disconnects, the IP address is released and becomes free for use again.
HTTP to 30.0.0.1
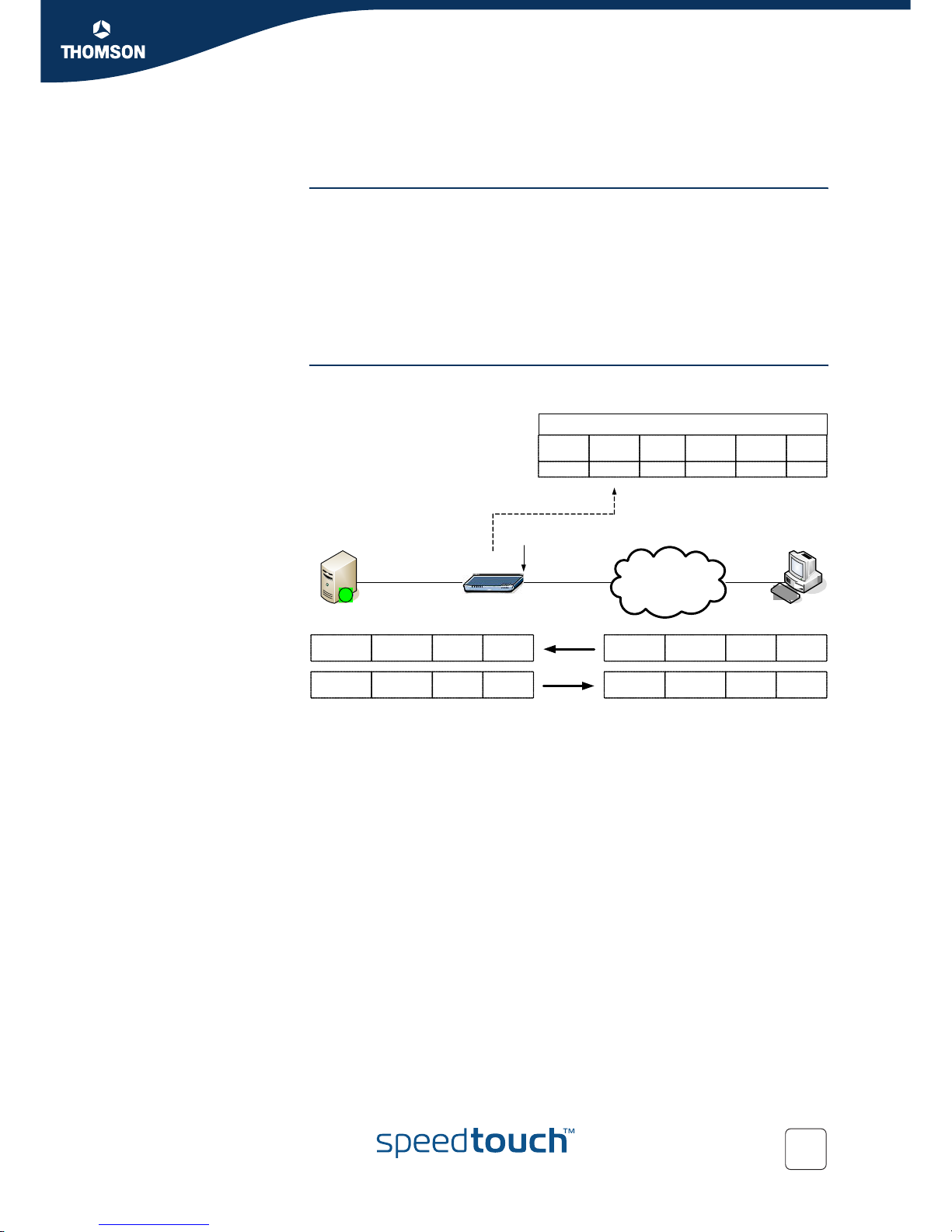
Figure 2: NAT example
As illustrated above, the SpeedTouch™ NAT box has an internally configured
mapping from the private IP address to a public one and vice versa. It is transparent
for NAT whether this table information is persistent or not.
Important to notice is that 30.0.0.1 thinks he receives a message from 20.0.0.1
instead of 192.168.0.1. So NAT hides the original originator.
PAT PAT only changes the port number (TCP or UDP) of the packet. In most cases PAT is
used in combination with NAT. When NAT and PAT are used together, this is called
NAPT.
A common practise is that for outgoing packets the source port number is changed
and for incoming packets it will be the destination port.
PAT is also used when a service is not running on the default internal port. E.g. webs
er vice on port 8080 instead of 80. This will be explained later on in this document.
`
Public
SpeedTouch
TM
192.168.0.1 192.168.0.254
20.0 .0.1 30.0 .0.1
Private Public
192.168.0.1 20.0.0.1
Src : 192.168 .0.1
Dst : 30.0.0.1
Src : 20.0.0.1
Dst : 30.0.0.1
Src : 30. 0.0. 1
Ds t: 20. 0.0. 1
Src : 30.0.0.1
Dst : 192.168 .0.1
Page 14

NAT, PAT and NAPT
E-NIT-CTC-20040716-0004 v1.0
12
NAPT Network Address & Port Translation (NAPT) is the most popular form of address
translation. It is used almost exclusively by access devices designed to hide small-tomedium sized networks behind a single public IP address. NAPT works by translating
the source IP address and the source port number on the public interface.
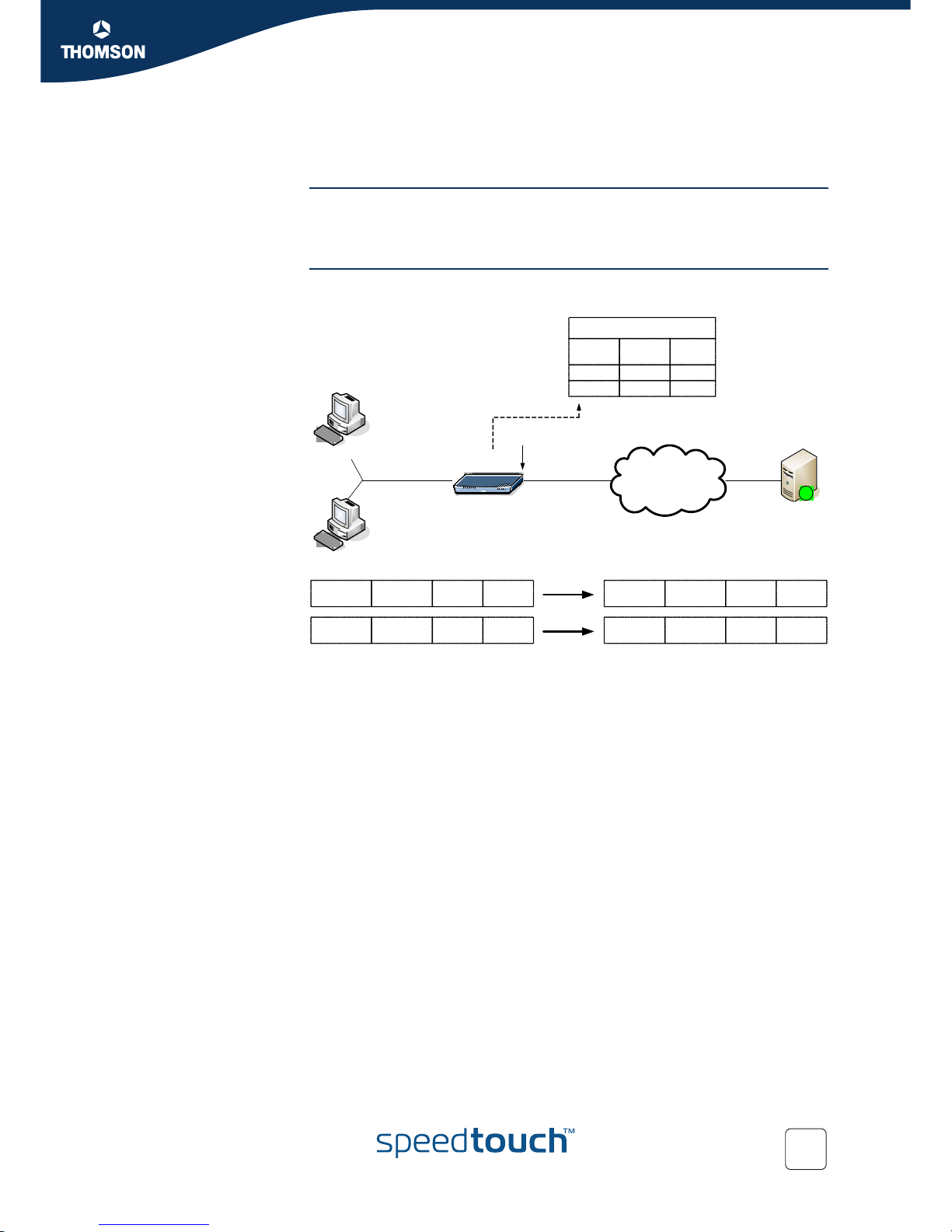
HTTP 30.0.0.1
Figure 3: NAPT example
In case a HTTP session is initiated which has to pass the NAPT enabled box, both the
source IP address and source port number will be translated for outgoing packets.
For incoming connections (belonging to the outgoing connections), the destination IP
address and port number will be changed.
Figure 4: NAPT for multiple hosts (share the same IP address)
Suppose that two hosts want to share one common IP address. For outgoing traffic
there will be no issue: both the IP addresses “192.168.0.1” and “192.168.0.2” are
translated into this same IP address. But, as soon as packets come back (incoming),
the NAPT box has to know to which of the two 192.168.0.x addresses the address
translation needs to be performed.
This is where port translation comes into action: the destination port number in the
incoming packet will be used as input to decide to which of the 192.168.0.x
addresses to translate the address.
` `
Public
192.168.0.1 192.168.0.254
20.0.0.1 30.0.0.1
Private Pub lic
192.168.0.1/600 20.0.0.11/1025
SpeedTouch
TM
NAPT enabled
Src : 192.168 .0.1/600
Dst : 30.0.0.1 /80
Src : 20.0.0. 1/1025
Dst : 30.0.0. 1/80
Src : 30.0.0.1 /80
Dst : 20.0.0.1 /1025
Src : 30.0.0.1 /80
Dst : 192.168 .0.1/600
`
Public
192.168.0.1
30.0.0.1
Private Public
192.168.0.1/734 20.0 .0.1/403
20.0. 0.1/908192.168.0.2/521
`
192.168.0.2
192.168.0.254
20.0.0.1
SpeedTouch
TM
NAPT enabled
Page 15

Dynamic versus static address translation
E-NIT-CTC-20040716-0004 v1.0
13
3 Dynamic versus static address translation
Address translation per
interface
Figure 5: Address translation per interface
Typically several public IP addresses can be assigned to one network device that
gives access to the public network. The routing logic of the network device will
decide to which interface a packet coming from the private network needs to be
send. For each interface to the public network, it’s possible to activate or deactivate
address translation.
In the SpeedTouch™, interfaces can be enabled in three modes:
Disabled: no address translation on the interface.
Enabled: address translation is enabled, but when there is no address
translation map, the packet is dropped.
Transparent: address translation is only performed when there is a address
translation map defined.
This last one has nothing to do with transparent NAT, but with the behaviour of the
interface.
When a packet arrives at the NAT module and a address translation map is found,
the packet will be translated when the interface is in enabled or transparent mode. If
there is no address translation map found, the packet will be dropped in enabled
mode but passed in transparent mode. The NAT module becomes transparent as it
were.
Inbound/outbound
connections
An address translation map is used for mapping one or more private IP
addresses into one or more public IP addresses on a specific interface.
Private Public
SpeedTouch
TM
Network A Network B
Inbound connections
Outbound connections
SpeedTouch
TM
NAT enabled
interface
Page 16

Dynamic versus static address translation
E-NIT-CTC-20040716-0004 v1.0
14
Figure 6: Inbound/outbound connections
All connections, leaving from an interface where NAT is enabled are called outbound
connections.
Connections arriving on the NAT enabled interface are called inbound connections.
Dynamic address
translation
Outgoing connections typically use dynamic address translation. For example a
connection initiated from IP address X in the private network will be translated into
public IP address Y on an enabled public interface. This mapping will be added
dynamically in an internal table of the device and will exist only for the lifetime of
that connection.
This also implies that, when resetting the device, this dynamic – non-persistent –
table entry will be lost. It is necessary to enable address translation on a public
interface to take profit of this dynamic translation.
Static address
translation
Connections initiated from the public network (so called incoming connections) make
use of static address mapping. An incoming initiator packet will need to pass the
static address translation table before being forwarded to the private network. This
information is non-volatile and needs to be configured in advance. Different
configuration flavours exist to configure this static mapping (individual, template,
default) and will be discussed further on in the document.
Applicability of address
translation
Address translation is used in case:
Multiple private hosts access a public network through the same gateway
(single public address on the gateway).
The inside address is not routable on the outside network.
The user wants to prevent the inside address(es) from outside attacks.
The user wants to avoid network renumbering when changing service
provider.
The user wants to make servers accessible from the outside network.
Netwo rk A Netwo rk B
Outbound connections
Inbound connections
SpeedTouch
TM
NAT enabled
interface
Page 17

Address translation flavours
E-NIT-CTC-20040716-0004 v1.0
15
4 Address translation flavours
Introduction Network Address Translation is a method by which IP addresses are mapped from
one address realm to another, providing transparent routing to end hosts.
Several flavours of network address translation transforms can be defined depending
on the relationship between inside IP addresses and outside IP addresses.
Topi c Pag e
4.1 Traditional or outbound address translation 16
4.2 Two-Way NAT 19
4.3 N-N NAT 20
4.4 M-N NAT or Multi NAT 21
4.5 Transparent NAT 22
4.6 Port range shifting 23
4.7 Translation templates 24
Page 18

Traditional or outbound address translation
E-NIT-CTC-20040716-0004 v1.0
16
4.1 Traditional or outbound address translation
Introduction Traditional NAT (sometimes referred to as outbound address translation) is the most
common method of using address translation. Its primary use is to translate private
addresses to legal addresses for use in a public network. When configured for
dynamic operation, hosts within a private network can initiate access to the public
network. On the contrary external nodes on the outside network will not be able to
access the private network.
Two types of traditional NAT exist — basic NAT and NAPT.
Page 19

Basic NAT
E-NIT-CTC-20040716-0004 v1.0
17
4.1.1 Basic NAT
Introduction With Basic NAT, a block of public addresses are set aside for translating addresses of
hosts in a private domain as they originate sessions to the public domain.
Basic NAT involves only address translation, no port mapping is done. This requires
an external IP address for each simultaneous connection.
Basic NAT example
Figure 7: Basic NAT example
Host 192.168.0.1 sends a packet to the Web server 30.0.0.1. As soon as the
packet is processed by the SpeedTouch™ its source IP address is translated into the
outside IP address 20.0.0.1 and forwarded to the Web server.
!
Basic NAT is the least secure translation method. By not defining the
translation to the port level, and accepting return information on any port,
basic NAT can leave private hosts open to port access.
`
Public
192.168.0.1
192.168.0.254
20.0.0.1 30.0.0.1
Src IP
192.168.0.1
Des t IP
30. 0.0.1
Src port
5500
Dest port
80
Src IP
20.0.0.1
Dest IP
30.0.0.1
Src port
5500
Dest port
80
Src IP
30.0.0.1
Des t IP
192.168.0.1
Src port
80
Dest port
5500
Src IP
30.0.0.1
Dest IP
20.0.0.1
Src port
80
Dest port
5500
NAT box Internal Mappings
Inside IP
192.168.0.1
192.168.0.2
Ouside IP
20.0.0.1
20.0.0.2
Des t. IP
30.0.0.1
30.0.0.1
`
192.168.0.2
SpeedTouch
TM
NAT enabl ed
Page 20

Network Address Port Translation (NAPT)
E-NIT-CTC-20040716-0004 v1.0
18
4.1.2 Network Address Port Translation (NAPT)
Introduction NAPT extends the notion of translation one step further by also translating the
transport identifier (For example TCP and UDP port numbers, ICMP query identifiers).
NAPT allows a set of hosts to share one single public address. Note that NAPT can
be combined with Basic NAT so that a pool of public addresses are used in
conjunction with port translation.
NAPT example
Figure 8: NAPT example
Host 192.168.0.1 and 192.168.0.2 both send a packet to the Web server 30.0.0.1.
The SpeedTouch™ translates the inside IP addresses into the outside IP address
20.0.0.1.
For returning packets, the SpeedTouch™ needs to know to which 192.168.0.x
address the translation needs to be performed, that’s why the SpeedTouch™ also
translates the source port numbers.
`
Public
192.168.0.2
192.168.0.254
20.0.0.1 30.0.0.1
Src IP
192.168.0.1
Dest IP
30.0.0.1
Src port
5500
Dest port
80
Src IP
20.0.0.1
Des t IP
30.0.0.1
Src port
2013
Dest port
80
Src IP
192.168.0.2
Dest IP
30.0.0.1
Src port
5500
Dest port
80
Src IP
20.0.0.1
Des t IP
30.0.0.1
Src port
4013
Dest port
80
192.168.0.1
`
NAT box Internal Mappings
Inside IP Insid e Po rt
Outsid e
Port
192.168.0.1 5500 2013
Dest.
Port
80
192.168.0.2 5500 4013 80
Ousid e IP
20.0. 0.1
20.0. 0.1
Des t. IP
30.0.0.1
30.0.0.1
SpeedTouch
TM
NAT enabl ed
Page 21
Two-Way NAT
E-NIT-CTC-20040716-0004 v1.0
19
4.2 Two-Way NAT
Introduction Traditional NAT is designed to handle only outbound transactions; clients on the local
network initiate requests and devices on the Internet send back responses. However,
in some circumstances, we may want to go in the opposite direction. That is, we
may want to have a device on the outside network initiate a transaction with one on
the inside. To permit this, we need a more capable type of NAT. This enhancement
goes by various names, most commonly Bidirectional NAT, Two-Way NAT and
Inbound NAT. All of these convey the concept that this kind of NAT allows both the
type of transaction we saw in the previous topic and also transactions initiated from
the outside network
Two-way NAT example
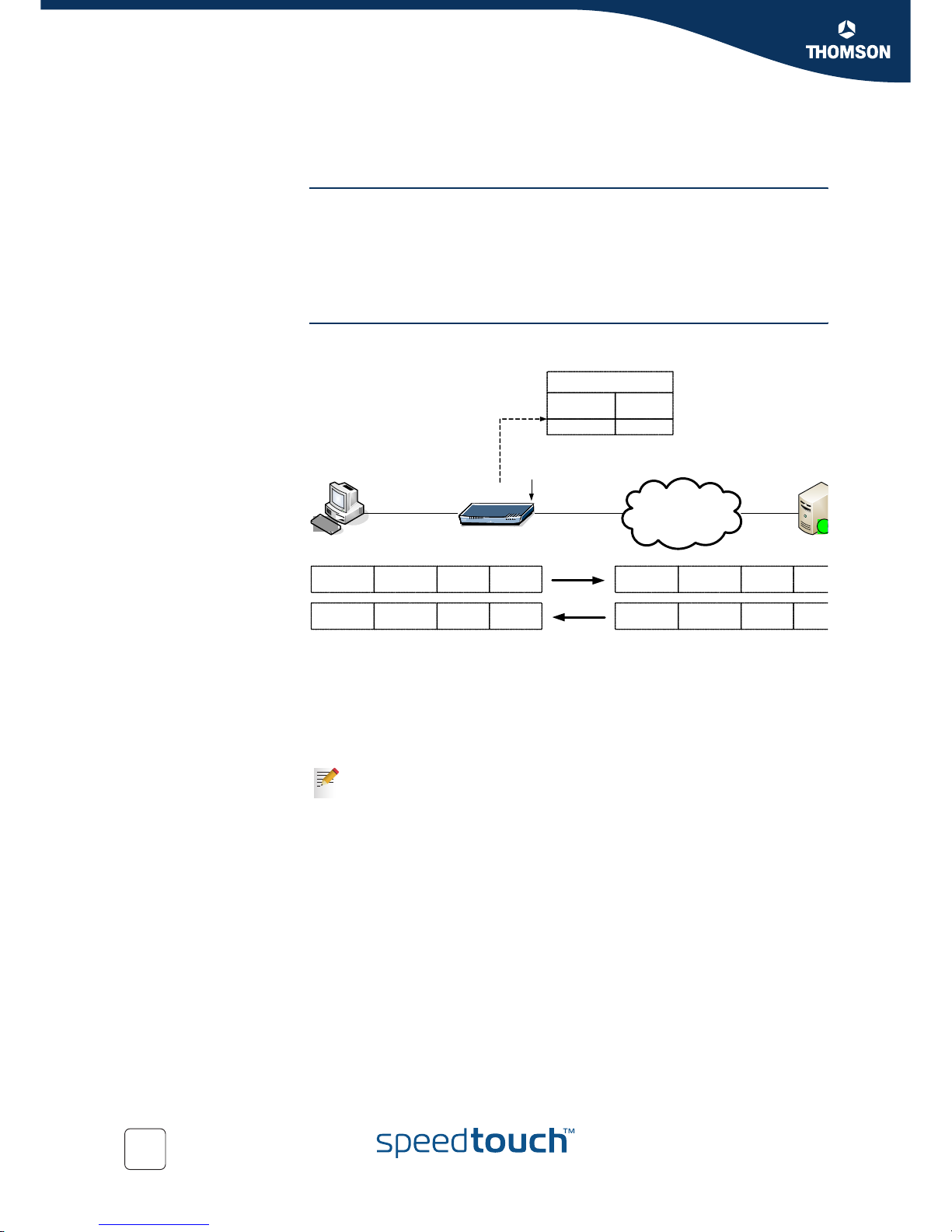
Figure 9: Two-Way NAT example
Host 30.0.0.1 wants to make a connection to the Web server 192.168.0.1 on the
private network.
There’s a static mapping in the SpeedTouch™ which maps the private IP address
192.168.0.1 to 20.0.0.1. Host 30.0.0.1 knows IP address 20.0.0.1 and sends the
packet to the SpeedTouch™. The SpeedTouch™ translates the outside address
20.0.0.1 to the inside address 192.168.0.1 and forwards the packet.
`
Public
192.168.0.1 192.168.0.254
20.0.0.1 30.0.0.1
SpeedTouch
TM
Src IP
30 .0.0. 1
Dest IP
192.168.0.1
Src port
5500
Dest port
80
Src IP
30.0.0.1
Des t IP
20.0.0.1
Src port
5500
Dest port
80
Src IP
192.168.0.1
Dest IP
30.0.0.1
Src port
80
Dest port
5500
Src IP
20.0.0.1
Des t IP
30.0.0.1
Src port
80
Dest port
5500
20.0. 0.1: stati c dest. address
NAT box Internal Mappings
Inside IP Insid e Po rt
Outsid e
Port
192.168.0.1 5500 5500
Dest.
Port
80
Ousid e IP
20.0. 0.1
Des t. IP
30.0.0.1
NAT enabl ed
Page 22

N-N NAT
E-NIT-CTC-20040716-0004 v1.0
20
4.3 N-N NAT
Introduction N-N NAT is the generalization of Two-Way NAT or Basic NAT.
A chosen range of inside hosts (N inside IP addresses) can be mapped to an
equivalent range of outside IP addresses (N outside IP addresses) for inbound and
outbound traffic.
Page 23
M-N NAT or Multi NAT
E-NIT-CTC-20040716-0004 v1.0
21
4.4 M-N NAT or Multi NAT
Introduction A chosen set of inside hosts (M inside IP addresses) can be mapped to a set of
outside IP addresses (N outside IP addresses) for outbound traffic only. This feature
is called Many-to-Few NAT: M-N NAT (with M > N).
Multi NAPT example
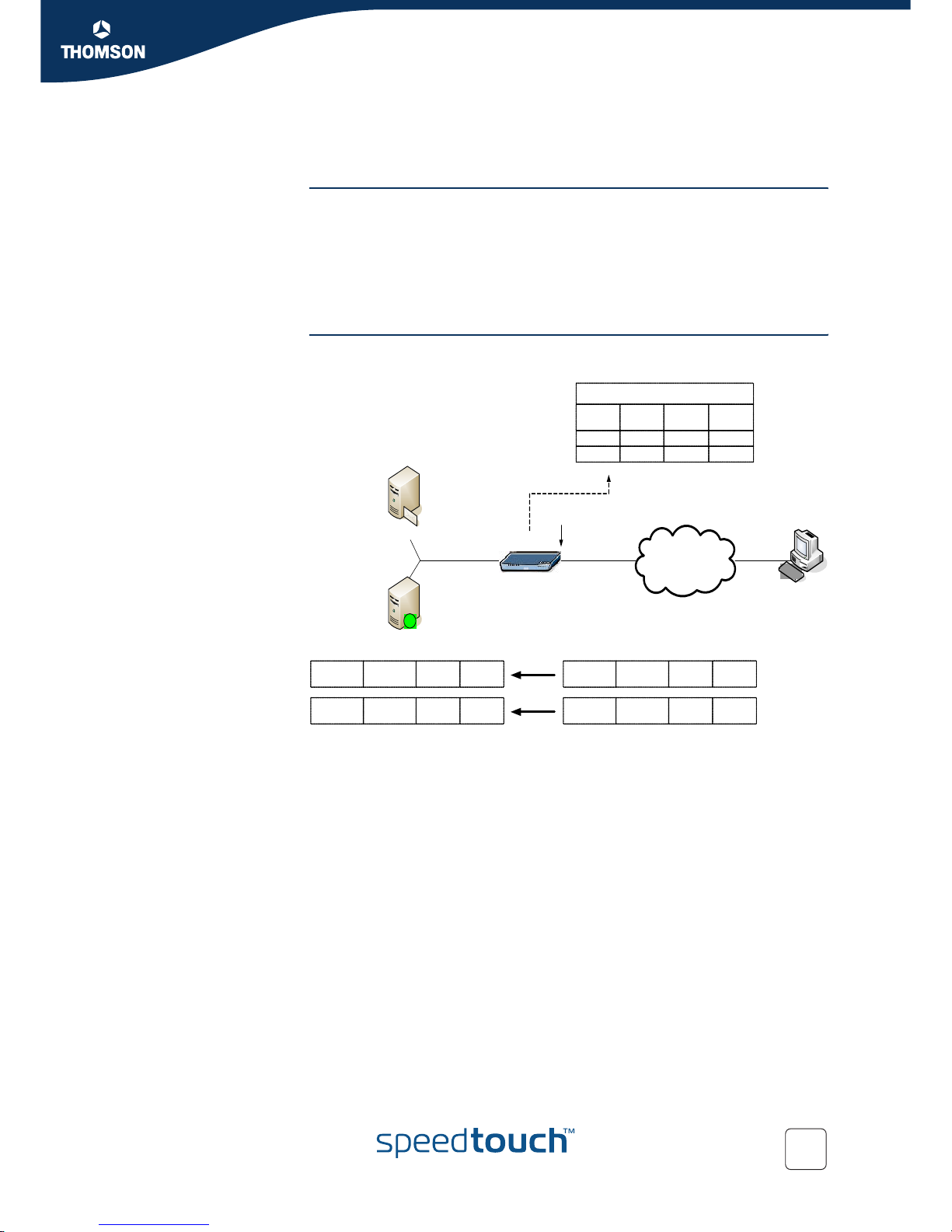
Figure 10: Multi NAT example
A pool of public addresses is used. The first host that wants to make a connection to
the public network gets the first address of the pool. The second host gets the
second address of the pool and so on.
`
Public
192.168.0.2
192.168.0.254
20.0.0.1
30.0.0.1
Src IP
192.168.0.1
Dest IP
30.0.0.1
Src port
5500
Dest port
80
Src IP
20.0.0.1
Des t IP
30.0.0.1
Src port
5500
Dest port
80
Src IP
192.168.0.2
Dest IP
30.0.0.1
Src port
5500
Dest port
80
Src IP
20.0.0.2
Des t IP
30.0.0.1
Src port
5500
Dest port
80
`
192.168.0.1
POOL:
20.0. 0.1-20.0.0 .4
NAT box Internal Mappings
Inside IP
192.168.0.1
192.168.0.2
Ouside IP
20.0.0.1
20.0.0.2
Des t. IP
30.0.0.1
30.0.0.1
SpeedTouch
TM
NAT enabl ed
Page 24
Transparent NAT
E-NIT-CTC-20040716-0004 v1.0
22
4.5 Transparent NAT
Introduction First of all there is a difference between Transparent NAT and Transparent Interface.
For more information on Transparent Interface see “ Address translation per
interface” on page 13
Transparent NAT translates an inside address into the same outside IP address. In
fact, no translation happens and the IP packets passing through the SpeedTouch™
remains untouched.
Transparent NAT
example
Figure 11: Transparent NAT example
Host 20.0.0.1 receives the same address as the outside public IP address. In fact
there is no translation.
The SpeedTouch™ just forwards the packets.
The
The applicability of transparent NAT is explained in section
“6.3.5 Transparent NAT” on page 46
`
Public
20.0.0.1 20.0.0.254
20.0.0.1 30.0.0
SpeedTouch
TM
Src IP
20.0.0.1
Dest IP
30.0.0.1
Src port
5500
Dest port
80
Src IP
20.0.0.1
Dest IP
30.0.0.1
Src port
5500
Dest p
o
80
Src IP
30.0.0.1
Dest IP
20.0.0.1
Src port
80
Dest port
5500
Src IP
30.0.0.1
Dest IP
20.0.0.1
Src port
80
Dest p
o
550
0
NAT box Internal Mappings
Inside IP
20.0.0.1
Ouside IP
20.0.0.1
NAT enabled
Page 25
Port range shifting
E-NIT-CTC-20040716-0004 v1.0
23
4.6 Port range shifting
Introduction For inbound traffic, port shifting allows to shift a UDP/TCP outside port range to a
UDP/TCP inside port range.
Port range shifting is used in case:
Multiple private hosts serving the same service must be accessible from
the outside network.
A well-known port for a service must be hidden from the outside network.
Port range shifting
example
Figure 12: Port range shifting example
In the first entry listed in the address translation table (NAT box Internal Mappings),
the outside port 25 is mapped to inside port 25. So there’s no change.
In the second entry outside port 8080 is mapped to inside port 80. This is to hide the
Web service from the outside network.
`
Public
192.168.0.2
192.168.0.1
20.0.0.1 30.0.0.1
SpeedTouch
TM
Src IP
30.0.0.1
Dest IP
192.168.0.1
Src port
9483
Dest port
25
Src IP
30.0.0.1
Dest IP
20.0.0 .6
Src port
9483
Dest port
25
Src IP
30.0.0.1
Dest IP
192.168.0.2
Src port
5098
Dest port
80
Src IP
30.0.0.1
Dest IP
20.0.0 .6
Src port
5098
Dest port
8080
192.168.0.1
20.0.0.6:
port forw arding address
NAT box Internal Mappings
Inside IP
Inside Port
Outside
Port
192.168.0.1
25
25
192.168.0.2
80
8080
Ouside IP
20.0.0.6
20.0.0.6
PAT enabled
Page 26

Translation templates
E-NIT-CTC-20040716-0004 v1.0
24
4.7 Translation templates
Introduction Life is easy and nice in case the interface on the public network has a permanently
assigned IP address. However, what to do with public interfaces which have a
dynamically assigned IP address. For example in the case of PPPoA, 50.0.0.1 can
change to 50.0.0.x the next time the dial-up connection is established.
In order to still be able to configure incoming connections for these types of
interfaces, the concept of templates is available.
A template assigns a wildcard (0.0.0.x) to the IP address of the public interface.
When a PPP session is established, the wildcard is replaced by the effectively
dynamically assigned IP address of the PPP interface.
Translation template
example
Figure 13: Template example
The first entry listed in the address translation table (NAT box Internal Mappings) is
the template we created and is persistently stored. The second one is a temporary
entry which was added to the PPP setup, it is an “instance” of the template. This
instance is now a fully functional static address mapping entry with a lifetime equal
to the lifetime of the PPP connection.
`
Public
192.168.0.1
192.168.0.254
50.0.0.12 50.0.0.
2
SpeedTouch
TM
Src IP
50.0.0.200
Dest IP
192.168.0.1
Src port
80
Dest port
5500
Src IP
50.0.0.200
Dest IP
50.0.0.12
Src port
80
Dest
20
1
0.0.0.1: wildcard
NAT box Internal Mappings
Inside IP Ins ide Port
Outside
Port
192.168.0.1 5500 2013
192.168.0.1 5500 2013
Ouside IP
0.0.0.1
50.0.0.12
Des t. IP
50.0.0.200
50.0.0.200
NAT enabled
Page 27
Application level gateways
E-NIT-CTC-20040716-0004 v1.0
25
5 Application level gateways
Introduction Some of the advanced protocols or applications have more complicated requirements
than other traditional ones and lead to significant problems when deployed in concert
with NAT implementations.
The main structural issues that lead to NAT-unfriendly situations are:
Bundled session
applications
Some advanced applications use several connections for a single call. They exchange
IP address and port parameters within control sessions to establish the subsequent
data sessions. Address translation engines cannot know the inter-dependency of the
bundled sessions and would treat each session as to be unrelated to another one.
As examples,
H.323 uses two Transmission Control Protocol (TCP) connections and
several User Datagram Protocol (UDP) sessions for a single call.
A SIP call may use a TCP control connection or several UDP sessions for
data transfer.
In the FTP protocol, the control messages and the data transfer use
entirely separate TCP connections.
During an RTSP session, an RTSP client may open and close several
sessions to the server to issue RTSP requests.
Use of ephemeral
(dynamic and greater
than 1024) ports in the
connection call setup
process
As examples,
H.323 protocol: the H.245 and the RTP connections use ephemeral ports.
SIP protocol: the RTP connection use momentary ports.
Included IP address and
port information within
the packet payload
Address translation doesn’t typically decode and process payload fields so those
applications would fail because of address translation.
As examples,
H.323 & SIP protocols have addressing information for the data
connections buried in the control packets payload.
Internet Locater Service (ILS): the ILS logins, carried in the packet
payload, conclude the source IP address of the caller.
FTP: the FTP layer 3 connection addressing is embedded within the
payload of a control packet (‘PORT’, ‘PASV’ messages).
Internet Relay Chat (IRC) service: Commands carried over the IRC-DCC
(Direct Client To Client Protocol) connection include the IP address and
the TCP port where the Acceptor client should connect to the Initiator
client
For the buildup of a RTSP session, the setup message includes the
expected UDP port for the client and the server.
RealAudio clients set up an outgoing TCP control connection to initiate
conversation with a real-audio server. Audio session parameters, including
the port number on which the incoming audio traffic will be received by
the clients, are embedded in the TCP control session as byte stream.
The IPv6-to-IPv4 protocol defines a mechanism for interconnecting IPv6
sites over an IPv4 network and its implicit tunnel setup requires that IP
addressing information is carried in the IPv6 packet payload.
Page 28

Application level gateways
E-NIT-CTC-20040716-0004 v1.0
26
Specific session
information required to
de-multiplex incoming
traffic
The following protocols can be given as examples:
IPSec: The “SPI” field available in the ESP protocol is used to identify a
session.
PPTP: In GREv1 frames, the “CallID” field is used as a de-multiplexing
identifier.
6to4 protocol: The “InterfaceID” field, contained in the IPv6 header of a
packet, is used to identify each session.
For those applications, address translation is assisted by Custom Application Level
Gateways (ALGs) that execute the specific processing required to provide a
transparent routing solution to end hosts; the ALGs determine what kind of packet is
being processed and if needed examine and adjust packet’s payload fields.
The following ALGs are embedded in the SpeedTouch™ routers; they are bound on
the mentioned default ports:
For some applications working in a UPnP infrastructure, you can also rely on the
UPnP NAT traversal capability of the SpeedTouch™ to support them across address
translation.
UPnP NAT Traversal is a set of capabilities that allows applications to
discover they are behind an address translation device,
learn the outside IP address,
and automatically configure appropriate static NAT mapping on the address
translation device so that incoming packets be properly routed back to the
application.
If the host’s IP address and port are included in packet payloads, the applications
also update them directly with the proper outside IP address & port. Currently,
applications running on Windows platform (XP, 98, 98SE, ME) support UPnP NAT
traversal.
To enable UPnP feature on the SpeedTouch™, use the following CLI command:
:connection bindlist
Application Proto Portrange Flags
JABBER tcp 15222
JABBER tcp 5222
FTP tcp 21
IRC tcp 6660
H323 tcp 1720
ILS tcp 1002
ILS tcp 389
RTSP tcp 554
RAUDIO(PNA) tcp 7070
CU/SeeMe udp 7648
SIP udp 5060
IKE udp 500
ESP esp 0
PPTP tcp 1723
IP6TO4 6to4 0
:system config upnp=enabled
:system config
upnp discovery: enabled
mdap discovery: enabled
drst support: enabled
digest authentication: enabled
Page 29

Network address translation configuration on the SpeedTouch™
E-NIT-CTC-20040716-0004 v1.0
27
6 Network address translation configuration on
the SpeedTouch™
Overview This chapter covers the following topics:
Network setup The following network setup will be used for all scenarios in this chapter.
Figure 14: network setup
Topi c Pag e
6.1 Configure address translation on the GUI 28
6.3 Configure NAT maps 40
6.4 Configure NAPT maps 48
6.5 Configure port shifting maps 56
6.6 Configure templates 58
`
192.168.0.1/24
SpeedTouch
TM
Internet
192.168.0.254/24
20.0.0.1/8
PPPoA
192.168.0.2/24
`
30.0.0.1/8
Page 30

Configure address translation on the GUI
E-NIT-CTC-20040716-0004 v1.0
28
6.1 Configure address translation on the GUI
Introduction This covers following topics:
Configuring Hyper-NAT on the Web Pages
Enable/disable address translation on an interface
Create an address translation mapping
Create a template
Page 31

Configuring Hyper-NAT on the Web Pages
E-NIT-CTC-20040716-0004 v1.0
29
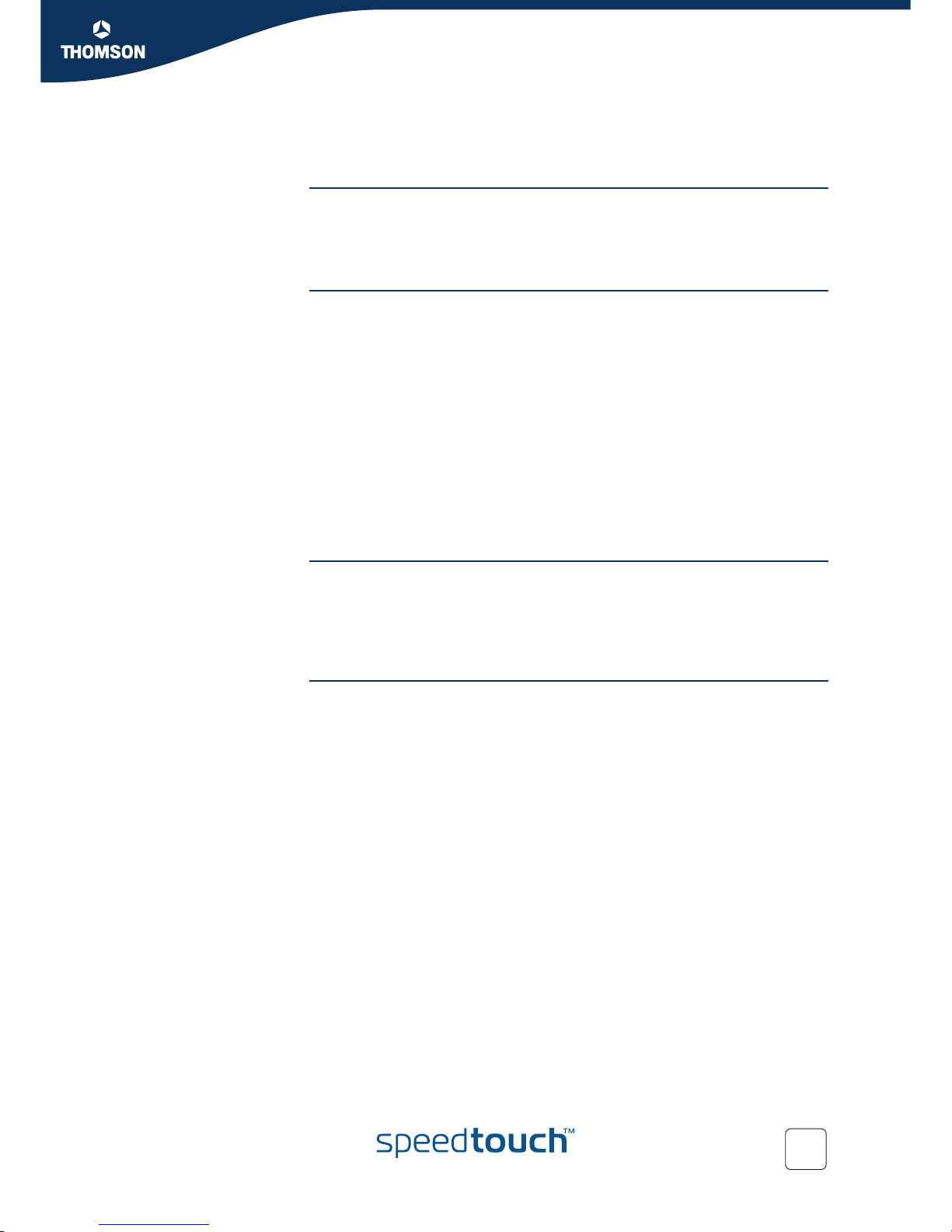
6.1.1 Configuring Hyper-NAT on the Web Pages
Step by step
configuration
Proceed as follows:
1 Open a web browser and browse to the SpeedTouch™ web pages at http://
speedtouch or http://192.168.1.254.
2 Switch to Expert mode
3 Browse to IP router > NAT
Page 32
Enable/disable address translation on an interface
E-NIT-CTC-20040716-0004 v1.0
30
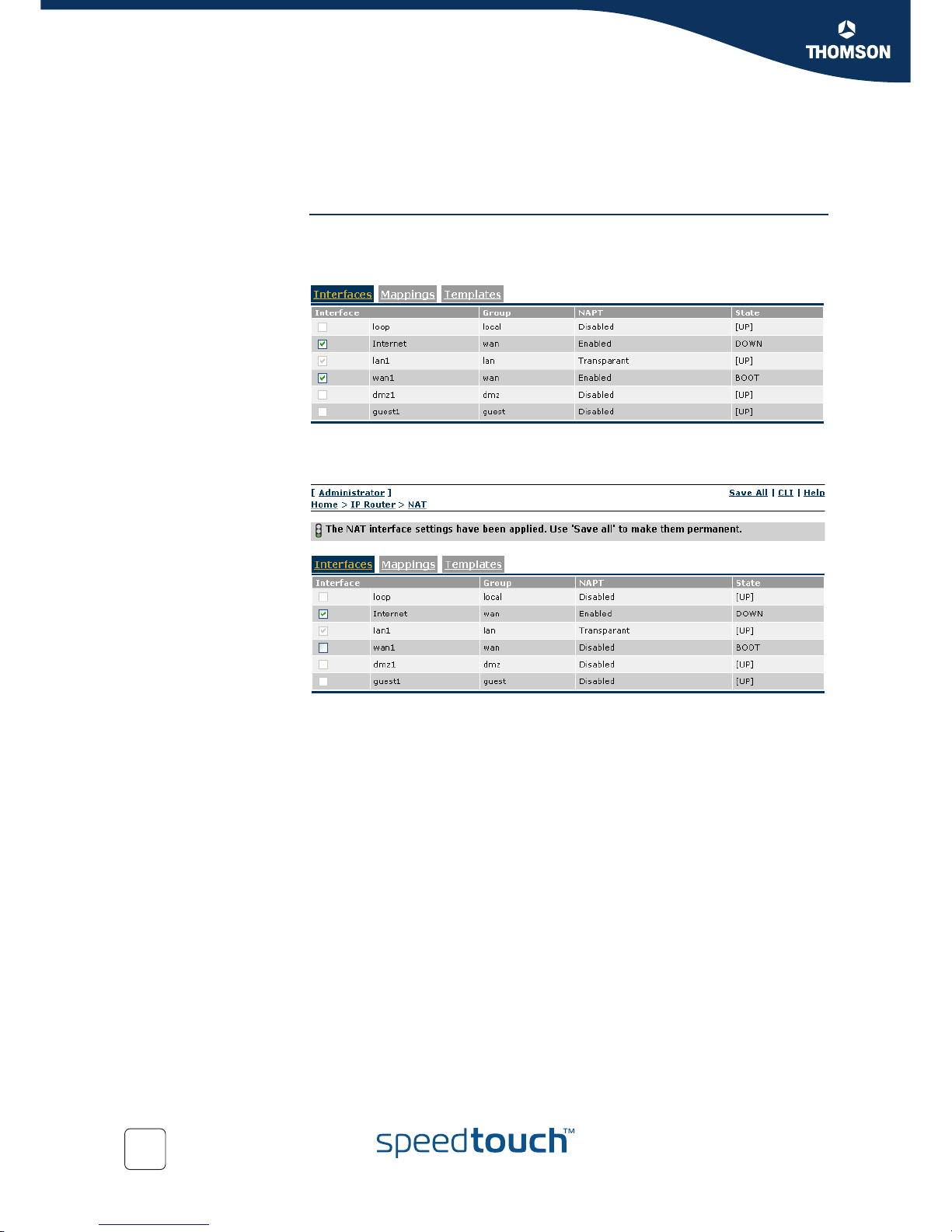
6.1.2 Enable/disable address translation on an
interface
Step by step
configuration
Proceed as follows:
1 Select the Interfaces Menu
2 Select the Interface that has to be enabled/disabled.
3 use Save All to make the settings permanent.
Page 33
Create an address translation mapping
E-NIT-CTC-20040716-0004 v1.0
31
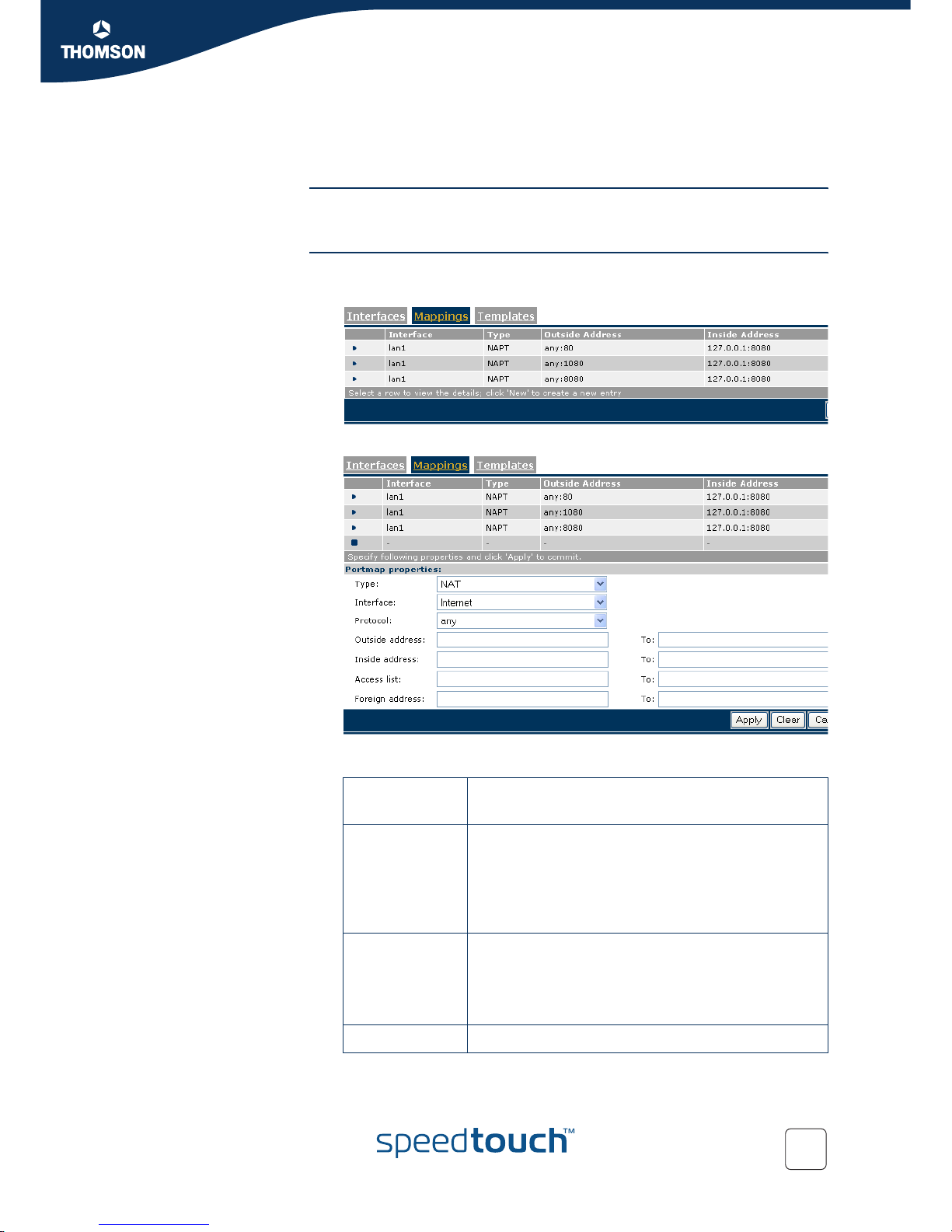
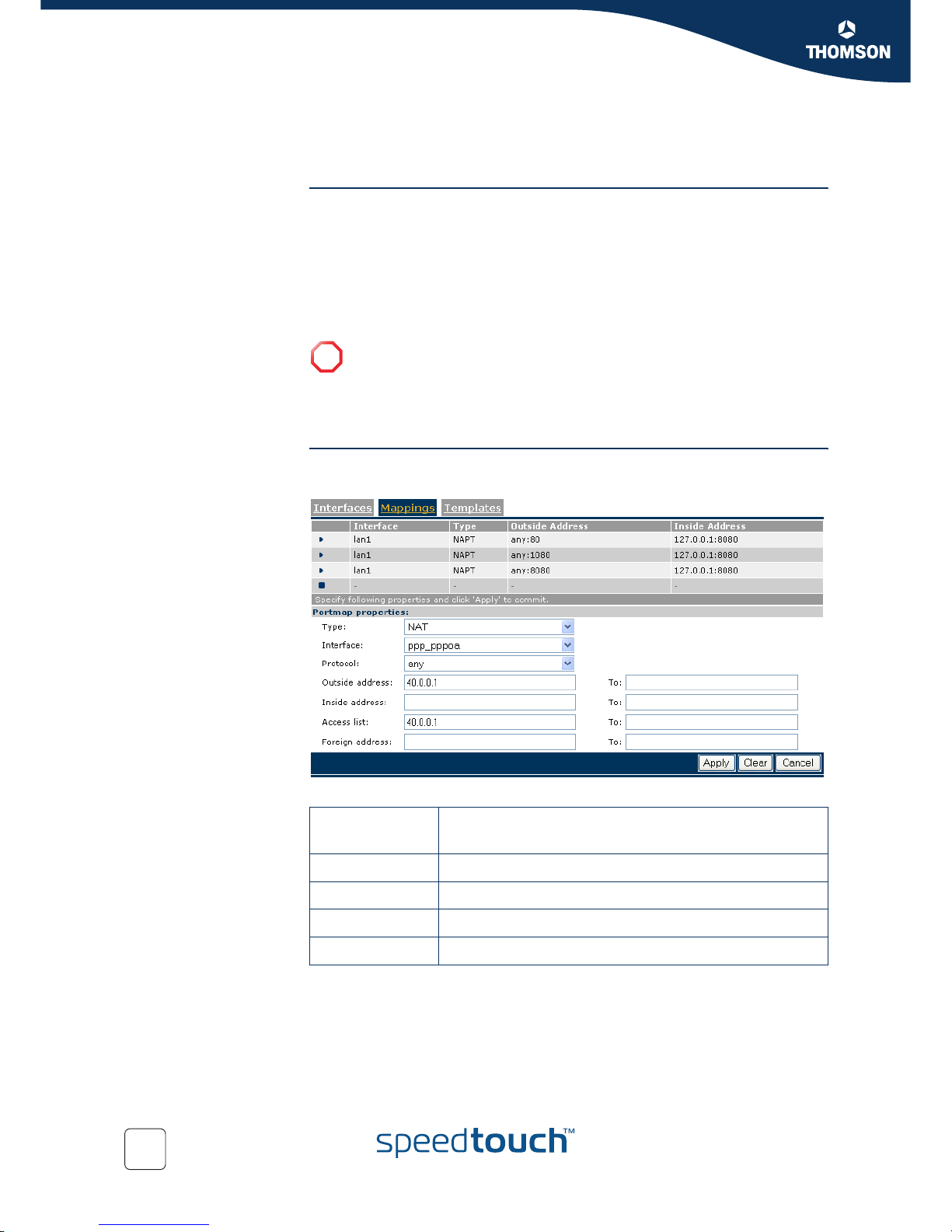
6.1.3 Create an address translation mapping
Introduction An address translation map is used for mapping one or more private IP addresses into
one or more public IP address on a specific interface.
Create a NAT map Proceed as follows:
1 Select the Mappings menu and click New to create a new map
2 Select NAT from the Type list.
3 Select or fill in all required information:
Portmap
properties
Description
Interface The name of the IP interface that needs to be address
translated.
Note: The interface must previously have been NAT
enabled, see “6.1.2 Enable/disable address translation
on an interface” on page 30.
Any interface means all interfaces.
Protocol The IP protocol on which address translation has to be
applied.
Advantage: To link specific traffic (protocol dependent)
to a chosen private host. Any protocol means all
protocols.
Outside address The outside (typically public) IP address(es).
Page 34
Create an address translation mapping
E-NIT-CTC-20040716-0004 v1.0
32
4 Click Apply.
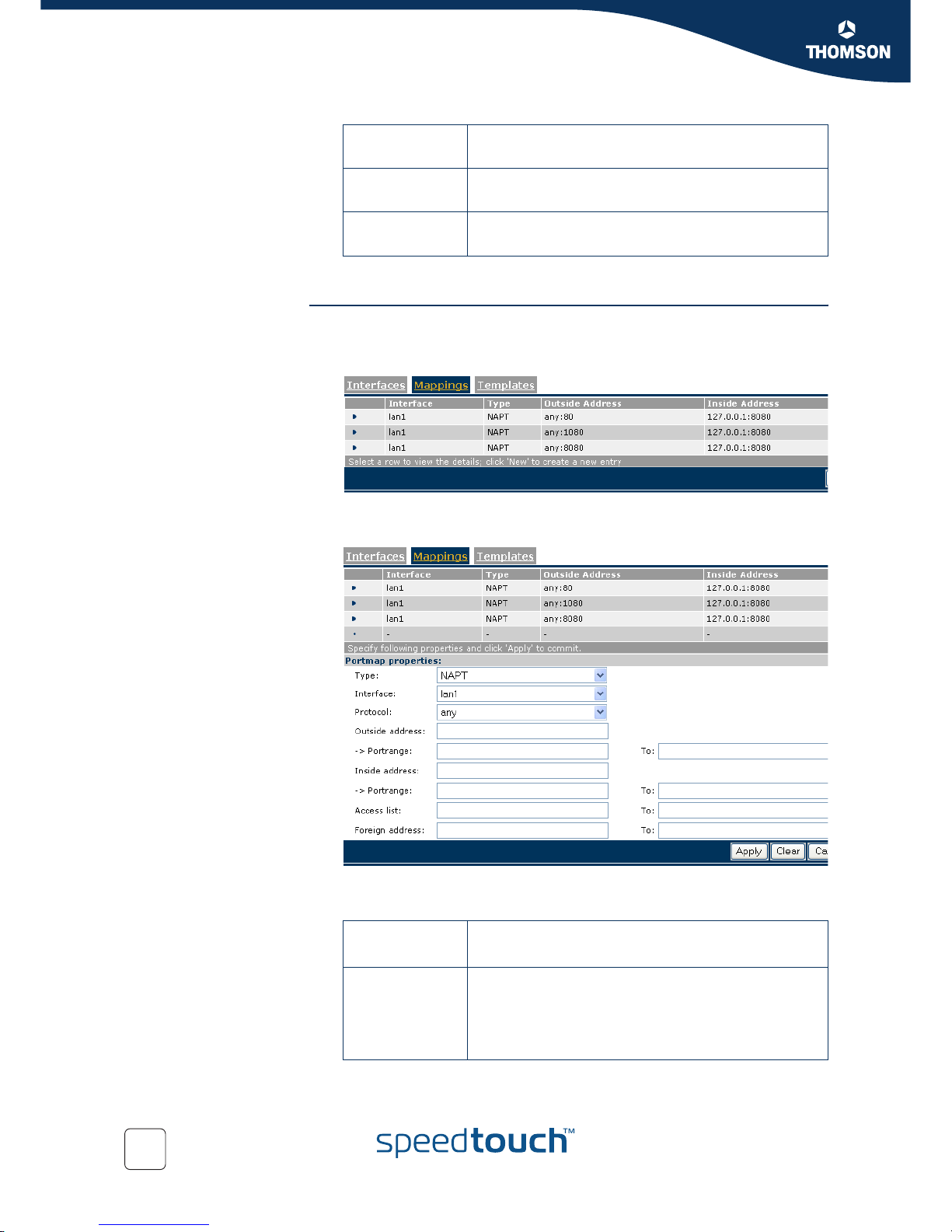
Create a NAPT map Proceed as follows:
1 Select the Mappings menu and click New to create a new map
2 Select NAPT from the Type list.
3 Select or fill in all required information:
Inside address The inside (typically private) IP address(es) to enable
inbound sessions.
Access list You can use the access list to define the address (es)
that are allowed to use the outbound connections.
Foreign address The foreign address is used to define the address (es)
that are allowed to use the inbound connections.
Portmap
properties
Description
Interface The name of the IP interface that needs to be address
translated.
Note: The interface must previously have been enabled
for address translation, see “6.1.2 Enable/disable
address translation on an interface” on page 30.
Page 35

Create an address translation mapping
E-NIT-CTC-20040716-0004 v1.0
33
4 Click Apply.
Protocol The IP protocol on which address translation has to be
applied.
Advantage: To link specific traffic (protocol dependent)
to a chosen private host. Any protocol means all
protocols.
Outside address
-> Portrange
The outside (typically public) IP address(es) (range).
The outside port number or range.
Inside address
-> Portrange
The inside (typically private) IP address(es) (range) to
enable inbound sessions.
The inside port number or range.
Access list You can use the access list to define the address (es)
that are allowed to use the outbound connections.
Foreign address The foreign address is used to define the address (es)
that are allowed to use the inbound connections.
Page 36

Create a template
E-NIT-CTC-20040716-0004 v1.0
34
6.1.4 Create a template
Create a NAT template Proceed as follows:
1 Select the Te mp la te s menu and click New to create a new template
2 Select NAT from the Type list.
3 Select or fill in all required information:
Portmap
properties
Description
Interface The name of the IP interface that needs to be address
translated.
Note: The interface must previously have been enabled
for address translation, see “6.1.2 Enable/disable
address translation on an interface” on page 30.
Group The IP interface group scope for this template.
Protocol The IP protocol on which address translation has to be
applied.
Advantage: To link specific traffic (protocol dependent)
to a chosen private host. Any protocol means all
protocols.
Outside address The outside (typically public) IP address(es) (range).
Page 37
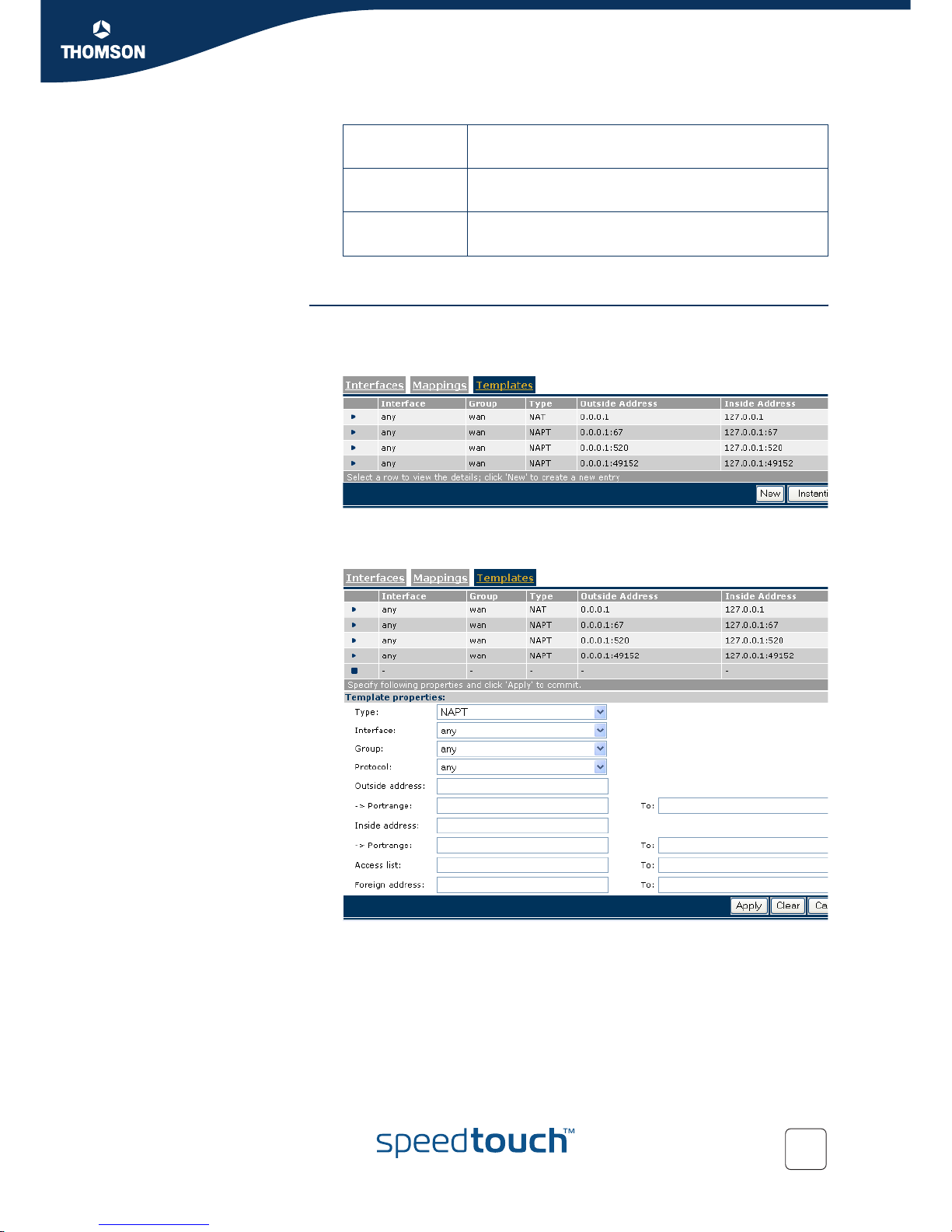
Create a template
E-NIT-CTC-20040716-0004 v1.0
35
4 Click Apply.
Create a NAPT
template
Proceed as follows:
1 Select the Te mp la te s menu and click New to create a new template
2 Select NAPT from the Type list.
Inside address The inside (typically private) IP address(es) (range) to
enable inbound sessions.
Access list You can use the access list to define the address(es)
that are allowed to use the outbound connections.
Foreign address The foreign address is used to define the address(es)
that are allowed to use the inbound connections.
Page 38

Create a template
E-NIT-CTC-20040716-0004 v1.0
36
3 Select or fill in all required information:
4 Click Apply.
Portmap
properties
Description
Interface The name of the interface that needs to be address
translated.
Note: The interface must previously have been enabled for
address translation, see “6.1.2 Enable/disable address
translation on an interface” on page 30.
Group The IP interface group scope for this template.
Protocol The IP protocol on which address translation has to be
applied.
Advantage: To link specific traffic (protocol dependent) to a
chosen private host. Any protocol means all protocols.
Outside address
-> Portrange
The outside (typically public) IP address(es) (range).
The outside port number or range.
Inside address
-> Portrange
The inside (typically private) IP address(es) (range).
The inside port number or range.
Access list You can use the access list to define the address (es) that
are allowed to use the outbound connections.
Foreign address The foreign address is used to define the address (es) that
are allowed to use the inbound connections.
Page 39

Configure address translation on the CLI
E-NIT-CTC-20040716-0004 v1.0
37
6.2 Configure address translation on the CLI
Introduction This covers following topics:
Configuring Hyper-NAT on the CLI
How to enable/disable address translation on an interface
How to create an address translation mapping
How to create a template
Configuring Hyper-NAT
on the CLI
With the CLI command :nat help, you can see all nat commands.
:iflist shows all the interfaces and there state.
How to enable/disable
address translation on
an interface
With the command :nat ifconfig, it is possible to modify the address
translation state of an interface.
nat help
Following commands are available :
ifconfig : Modify address translation on an IP interface.
iflist : Display all interfaces.
mapadd : Add an address mapping to a nat enabled interface.
mapdelete : Delete an address mapping from a nat enabled interfa
ce.
maplist : Display address mappings.
tmpladd : Add an address mapping template.
tmpldelete : Delete an address mapping template.
tmpllist : Display address mapping templates.
tmplinst : Instantiate address mapping templates for a given dy
namic
address.
config : Display/Modify global NAT configuration.
flush : Flush current NAT configuration.
{Administrator}=>
=>:nat iflist
Interface NAT
loop disabled
Internet enabled
lan1 transparent
wan1 enabled
dmz1 disabled
guest1 disabled
ppp_pppoa disabled
=>:nat ifconfig intf=ppp_pppoa translation=enabled
Page 40

Configure address translation on the CLI
E-NIT-CTC-20040716-0004 v1.0
38
How to create an
address translation
mapping
The command :nat mapadd, is used for adding address translation mappings.
How to create a
template
The command :nat tmpladd, is used for adding templates.
=>:nat mapadd
intf = ppp_pppoa
[type] = nat
[outside_addr] =
[inside_addr] =
[access_list] =
[foreign_addr] =
[protocol] =
[outside_port] =
[inside_port] =
Portmap
properties
Description
Interface The name of the IP interface that needs to be address
translated.
Note: The interface must previously have been enabled for
address translation, see “6.1.2 Enable/disable address
translation on an interface” on page 30.
Type The type of the template, NAT of NAPT.
Outside address The outside (typically public) IP address(es) (range).
Inside address The inside (typically private) IP address(es) (range).
Access list You can use the access list to define the address (es) that are
allowed to use the outbound connections.
Foreign address The foreign address is used to define the address (es) that
are allowed to use the inbound connections.
Protocol The IP protocol on which address translation has to be
applied.
Advantage: To link specific traffic (protocol dependent) to a
chosen private host. Any protocol means all protocols.
Outside port The outside port number or range.
Inside port The inside port number or range.
=>:nat tmpladd
[intf] = ppp_pppoa
[group] =
[timeout] =
[type] =
[outside_addr] = 0.0.0.1
[inside_addr] =
[access_list] =
[foreign_addr] =
[protocol] =
[outside_port] =
[inside_port] =
Page 41

Configure address translation on the CLI
E-NIT-CTC-20040716-0004 v1.0
39
Portmap
properties
Description
Interface The name of the IP interface that needs to be address
translated.
Note: The interface must previously have been enabled for
address translation, see “6.1.2 Enable/disable address
translation on an interface” on page 30.
Group The IP interface group scope for this template.
Timeout The lifetime for the template.
Type The type of the template, NAT of NAPT.
Outside address The outside (typically public) IP address(es) (range).
Inside address The inside (typically private) IP address(es) (range).
Access list You can use the access list to define the address (es) that are
allowed to use the outbound connections.
Foreign address The foreign address is used to define the address (es) that
are allowed to use the inbound connections.
Protocol The IP protocol on which address translation has to be
applied.
Advantage: To link specific traffic (protocol dependent) to a
chosen private host. Any protocol means all protocols.
Outside port The outside port number or range.
Inside port The inside port number or range.
Page 42

Configure NAT maps
E-NIT-CTC-20040716-0004 v1.0
40
6.3 Configure NAT maps
Introduction This section explains the configuration of the different NAT maps.
General remarks Depending on the NAT flavour some configuration information is mandatory other
not.
In this chapter we put the mandatory information in emphasis.
The following information is always mandatory:
Interface
Outside address
Not mandatory information is:
Protocol
When selecting a protocol, then the map will only have affect for that protocol.
Access list
You can use the access list to define the address (es) that are allowed to use
the outbound connections.
Foreign address
Foreign address is to define the address (es) that are allowed to use the inbound
connections.
Topi c Pag e
6.3.1 Basic NAT 41
6.3.2 Two-Way NAT 42
6.3.3 N-N NAT 43
6.3.4 Multi NAT 44
6.3.5 Transparent NAT 46
W
If you leave protocol, access list or foreign address empty. This means that
every protocol (for protocol field) or every IP address (es) (access list,
foreign address) is valid.
Page 43

Basic NAT
E-NIT-CTC-20040716-0004 v1.0
41
6.3.1 Basic NAT
Introduction Prerequisites:
Outbound: An inside host address (source address) is translated into an outside
address.
Inbound: No traffic can be initiated.
GUI Create a new NAT map and fill in the required information.
The NAT map will be mapped when an inside host (within the access list) connects
to an outside host.
Only one inside host can use the NAT map at the same time.
CLI
Portmap
property
Value
Interface ppp_pppoa
Protocol any
Outside address 20.0.0.1 (the public IP you have)
Access list Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=nat outside_addr=20.0.0.1
Page 44

Two-Way NAT
E-NIT-CTC-20040716-0004 v1.0
42
6.3.2 Two-Way NAT
Introduction Prerequiresites:
Outbound: An inside host address (source address) is translated into an outside
address.
Inbound: An outside address (destination address) is translated into an inside
host address.
GUI Create a new NAT map and fill in the required information.
Traffic can be initiated from the inside address 192.168.1.64 or from any outside
address.
CLI
Traffic can initiated inbound and outbound.
Specifying an inside address is allowing inbound connections.
Portmap
properties
Value
Interface ppp_pppoa
Protocol any
Outside address 20.0.0.1 (the public IP you have)
Inside address 192.168.1.64 (Define the IP address, to use for inbound
connections)
Access list Define IP address (es) or leave empty.
Foreign address Define IP address (es) or leave empty.
This is in fact the same as N to N NAT with N equals to one.
=>:nat mapadd intf=ppp_pppoa type=nat outside_addr=20.0.0.1 inside_addr
192.168.1.64
Page 45

N-N NAT
E-NIT-CTC-20040716-0004 v1.0
43
6.3.3 N-N NAT
Introduction Prerequisites:
Outbound: A set of inside host addresses (source addresses) are translated into
a set of outside addresses.
Inbound: A set of outside addresses (source addresses) are translated into a set
of inside host addresses.
GUI Create a new NAT map and fill in the fields.
The NAT map will be mapped when an inside/outside host connects to an outside/
inside host. There can only be as many connections as specified in the range. In this
example there can be 2 connections.
CLI
Traffic can be initiated inbound and outbound.
N-N NAT is an extension of Two-Way NAT to multiple hosts.
The number of addresses in inside address range and outside address ranges
must be equal.
Portmap
properties
Value
Interface ppp_pppoa
Protocol any
Outside address 20.0.0.1 to 20.0.0.2 (the public IP addresses you have)
Inside address 192.168.1.64 to 192.168.1.65
Access list Define IP address (es) or leave empty.
Foreign address Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=nat outside_addr=20.0.0.[1-2]
inside_addr=192.168.1.[64-65]
Page 46

Multi NAT
E-NIT-CTC-20040716-0004 v1.0
44
6.3.4 Multi NAT
Introduction Prerequisites:
Outbound: A set of inside host addresses (source addresses) are translated into
a set of outside addresses.
Inbound: No traffic can be initiated.
GUI Create a new NAT map and fill in the fields.
When an inside host (within the access list) connects to an outside host, the
SpeedTouch™ selects an available outside address (not used for another connection
yet) to allow outbound traffic.
When all outside addresses are in use, no other connection is allowed to use the NAT
map.
CLI
Traffic can only be initiated by an inside host.
Portmap
properties
Value
Interface ppp_pppoa
Protocol any
Outside address 20.0.0.1 to 20.0.0.2 (the public IP you have)
Access list Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=nat outside_addr=20.0.0.[1-2]
Page 47

Multi NAT
E-NIT-CTC-20040716-0004 v1.0
45
template instantiation
The entry with outside address 20.0.0.[1..2]:
The created NAT map.
The entry with outside address 20.0.0.1:
Inside host 192.168.1.64 makes a connection to an outside host (e.g.
30.0.0.1)
The SpeedTouch™ uses the first available address 20.0.0.1 to make an
outbound connection.
The entry with outside address 20.0.0.2:
Inside host 192.168.1.65 makes a connection to an outside host (e.g.
30.0.0.1)
The SpeedTouch™ uses the second available address 20.0.0.2 to make an
outbound connection.
From that moment the association between internal and external IP address
is made, also inbound connections can be made.
Page 48
Transparent NAT
E-NIT-CTC-20040716-0004 v1.0
46
6.3.5 Transparent NAT
Introduction A Transparent NAT map is considered as transparent if inside and outside address
are equal. No translation is performed on packet headers. A transparent map is used
in order to avoid issues with NAT unfriendly applications.
There are different transparent maps:
Transparent Basic NAT
Transparent Two-Way NAT
Transparent N-N NAT
Transparent Basic NAT Create a new NAT map and fill in the fields.
Transparent Basic NAT is only for outbound sessions. In this case the access list and
the outside address will be the same. For example 40.0.0.1.
Transparent Basic NAT is applicable for protocols with the host address in the
payload. NAT would translate the host address, but not the payload, by which the
packet becomes invalid.
!
For every transparent natmap it is necessary to add:
an interface route on the SpeedTouch™ to the LAN device (inside
address).
a proxy ARP on the SpeedTouch™, to reach the default gateway (BAS)
from the LAN device.
Portmap
properties
Value
Interface ppp_pppoa
Protocol any
Outside address 40.0.0.1 (the public IP you have)
Access list 40.0.0.1
Page 49

Transparent NAT
E-NIT-CTC-20040716-0004 v1.0
47
Transparent Two-Way
NAT
Transparent NAT is more used for inbound sessions for example to send packets to a
private server with his private IP address. This to avoid re-configuration. You can do
the same with N-N NAT.
Another applicability for transparent NAT is IP-passthrough, see “6.4.4 NAPT using
transparent default server and port range constraint (=IP Passthrough)” on page 52.
Transparent N-N NAT This is the same like Two-Way NAT for multiple host. The number of addresses in
inside address range and outside address ranges must be equal.
Page 50

Configure NAPT maps
E-NIT-CTC-20040716-0004 v1.0
48
6.4 Configure NAPT maps
Introduction This section explains the configuration of the different NAT maps.
Topi c Pag e
Basic NAPT 49
6.4.2 NAPT using default server 50
6.4.3 NAPT using transparent default server 51
6.4.5 NAPT using host function 53
6.4.6 NAPT using transparent host function 54
6.4.7 NAPT using dynamic port range constraint 55
Page 51
Basic NAPT
E-NIT-CTC-20040716-0004 v1.0
49
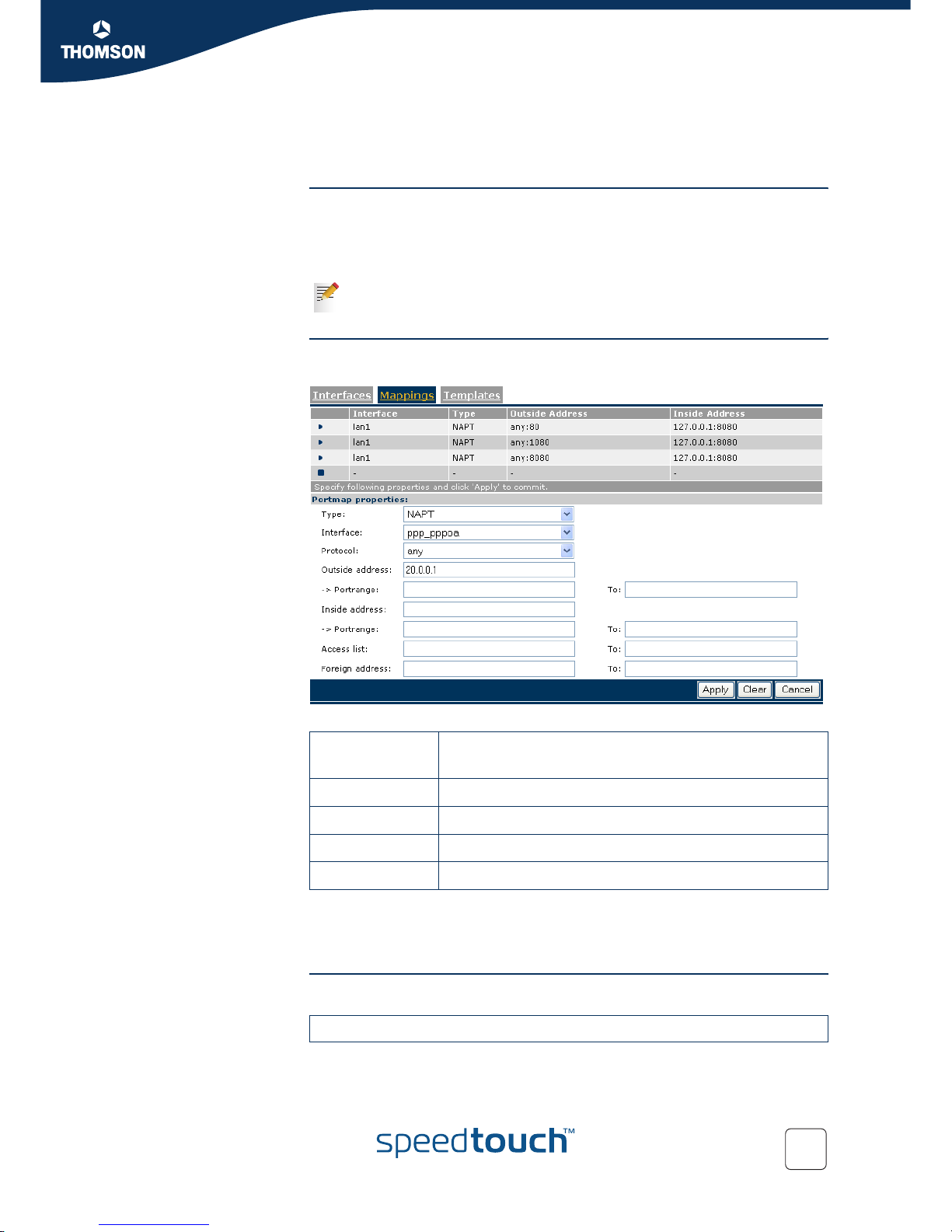
6.4.1 Basic NAPT
Introduction Prerequisites:
Outbound: Inside host addresses (source addresses) are translated into the
outside address, using port translation to differentiate traffic.
Inbound: No traffic can be initiated.
GUI Create a new NAT map and fill in the fields.
The NAPT map is mapped when an inside host (within the access list) connects to an
outside host.
Now all the host can use the NAPT map at the same time.
CLI
Traffic can only be initiated by an inside host.
Portmap
properties
Value
Interface ppp_pppoa
Protocol any
Outside address 20.0.0.1 (the public IP you have)
Access list Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=napt outside_addr=20.0.0.1
Page 52
NAPT using default server
E-NIT-CTC-20040716-0004 v1.0
50
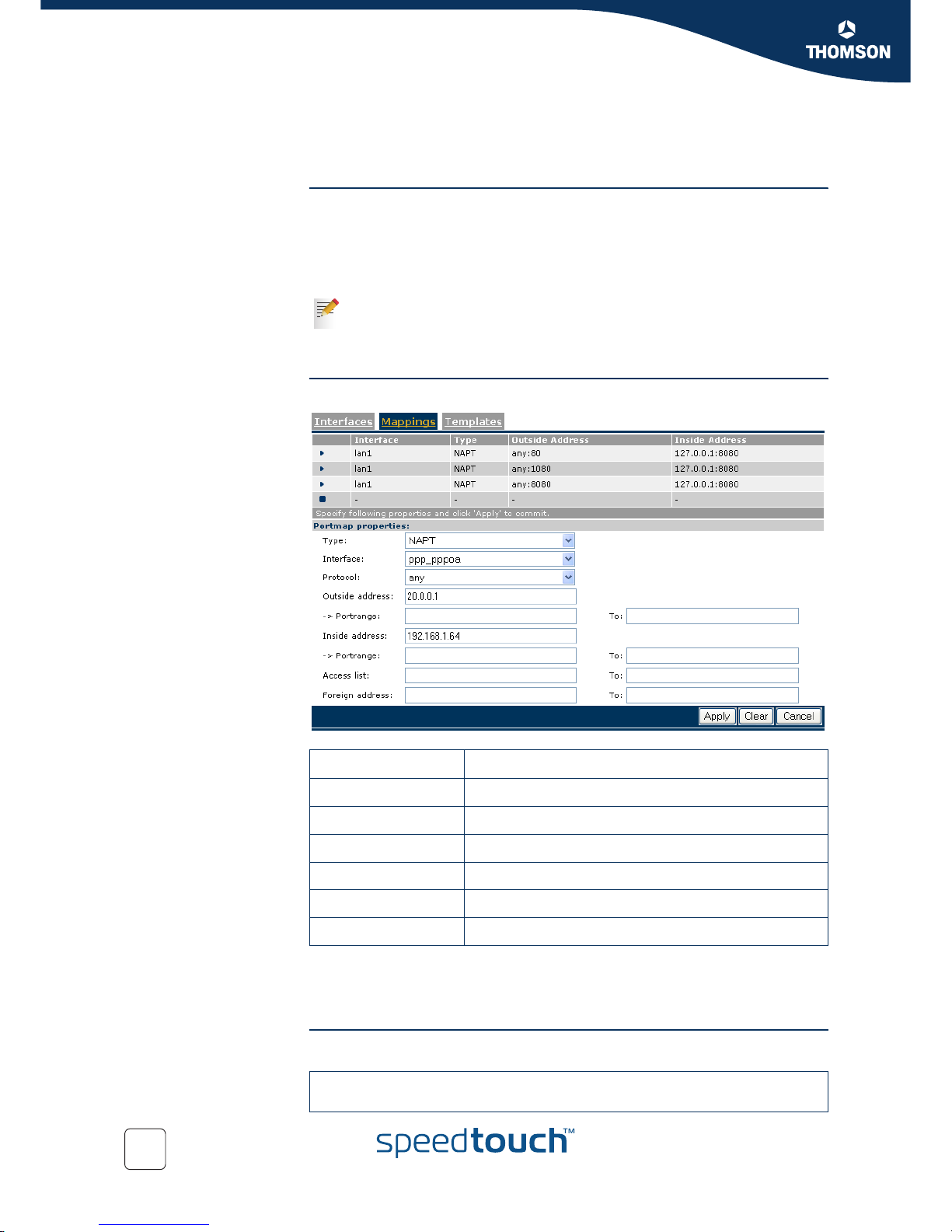
6.4.2 NAPT using default server
Introduction Prerequisites:
Outbound: Inside host addresses (source addresses) are translated into the
outside address, using port translation to differentiate traffic.
Inbound: The outside address (destination address) is translated into the inside
host address (default server).
GUI Create a new NAPT map and fill in the fields.
All inbound packets received on public interface 20.0.0.1, for which no NAT context
exist, will be forwarded to the default server 192.168.1.64. Outbound packets can
be send from any part within the private network.
CLI
If there are many servers runner on the same computer and you don't feel
like creating a long list of static translations, nat defserver is your answer, it
forwards all unsolicited traffic to a single computer. Traffic can be initiated
inbound and outbound.
Portmap properties Value
Interface ppp_pppoa
Protocol any
Outside address 20.0.0.1
Inside address 20.0.0.1 (address of the default server)
Access list Define IP address (es) or leave empty.
Foreign address Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=napt outside_addr=20.0.0.1
inside_addr 192.168.1.64
Page 53

NAPT using transparent default server
E-NIT-CTC-20040716-0004 v1.0
51
6.4.3 NAPT using transparent default server
Introduction In configuration “6.4.1 Basic NAPT” on page 49 the inside address and outside
address might be exactly the same (strictly same address). In this case, transparent
address translation applies for inbound traffic. No translation is to be made.
The description of the NAPT map is ‘NAPT using transparent default server’.
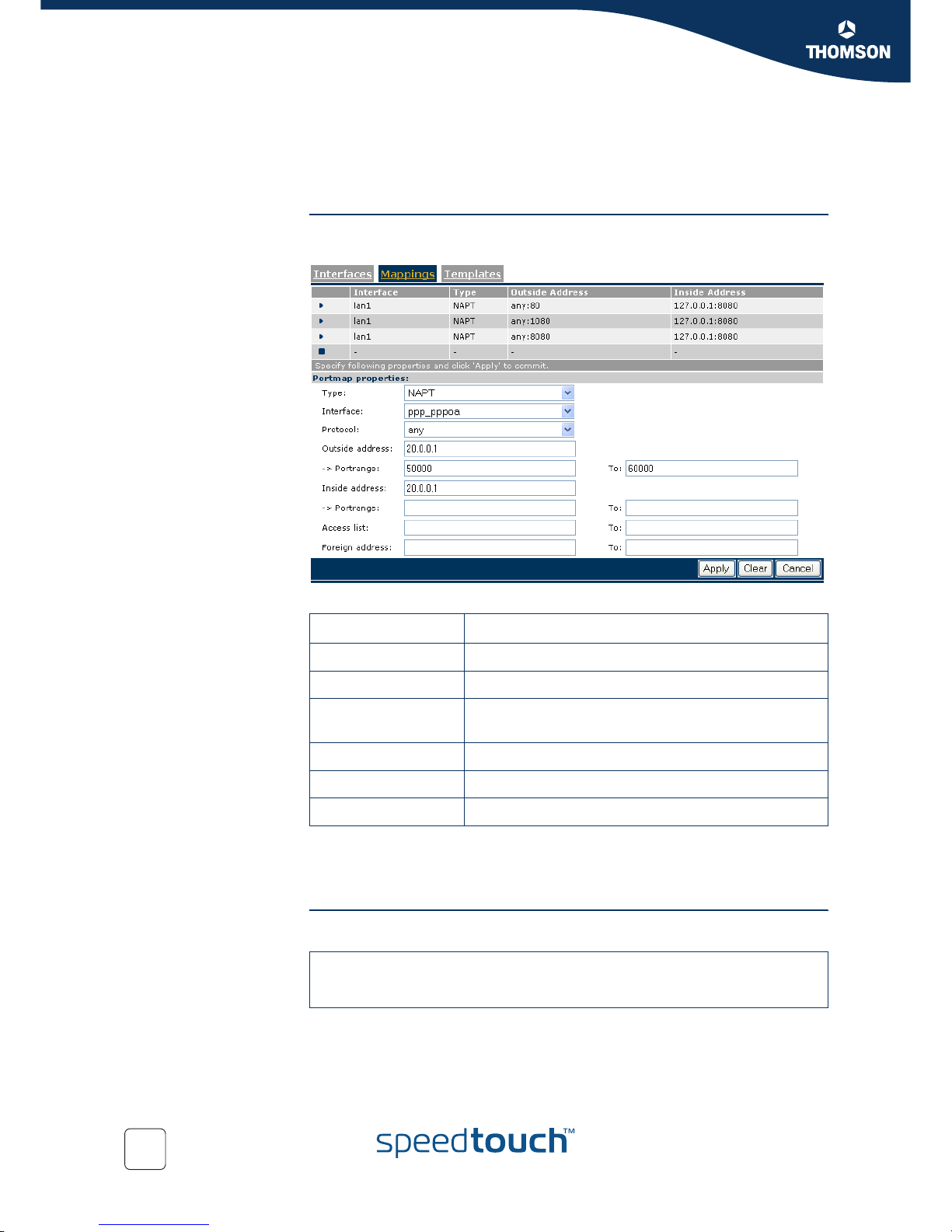
!
This is not the most optimal NAPT configuration because there can be port
overlaps.
So a better scenario is the following one.
Page 54
NAPT using transparent default server and port range constraint (=IP
Passthrough)
E-NIT-CTC-20040716-0004 v1.0
52
6.4.4 NAPT using transparent default server and
port range constraint (=IP Passthrough)
GUI Create a new NAPT map and fill in the fields.
If you pass an IP address coming from a DHCP server in the WAN site, to a host in
the private network, then you need a transparant NAT map to make this one
available.
CLI
Portmap properties Value
Interface pppoa
Protocol any
Outside address
-> Portrange
20.0.0.1
50000 to 60000
Inside address 20.0.0.1 (address of the default server)
Access list Define IP address (es) or leave empty.
Foreign address Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=napt outside_addr=20.0.0.1
inside_addr 192.168.1.64
outside_port=50000-60000
Page 55

NAPT using host function
E-NIT-CTC-20040716-0004 v1.0
53
6.4.5 NAPT using host function
Introduction In configuration “6.4.1 Basic NAPT” on page 49 the inside address might be an IP
address of the SpeedTouch™ itself. The description of the NAPT map is ‘NAPT using
host function’.
Traffic can be initiated inbound and outbound, all inbound traffic is sent to
the SpeedTouch™ itself.
Page 56

NAPT using transparent host function
E-NIT-CTC-20040716-0004 v1.0
54
6.4.6 NAPT using transparent host function
Introduction In configuration “6.4.1 Basic NAPT” on page 49 the inside address and outside
address might be an IP address of the SpeedTouch™ itself. The description of the
NAPT map is ‘NAPT using transparent host function’.
Traffic can be initiated inbound and outbound, all inbound traffic is sent to
the SpeedTouch™ itself.
Page 57
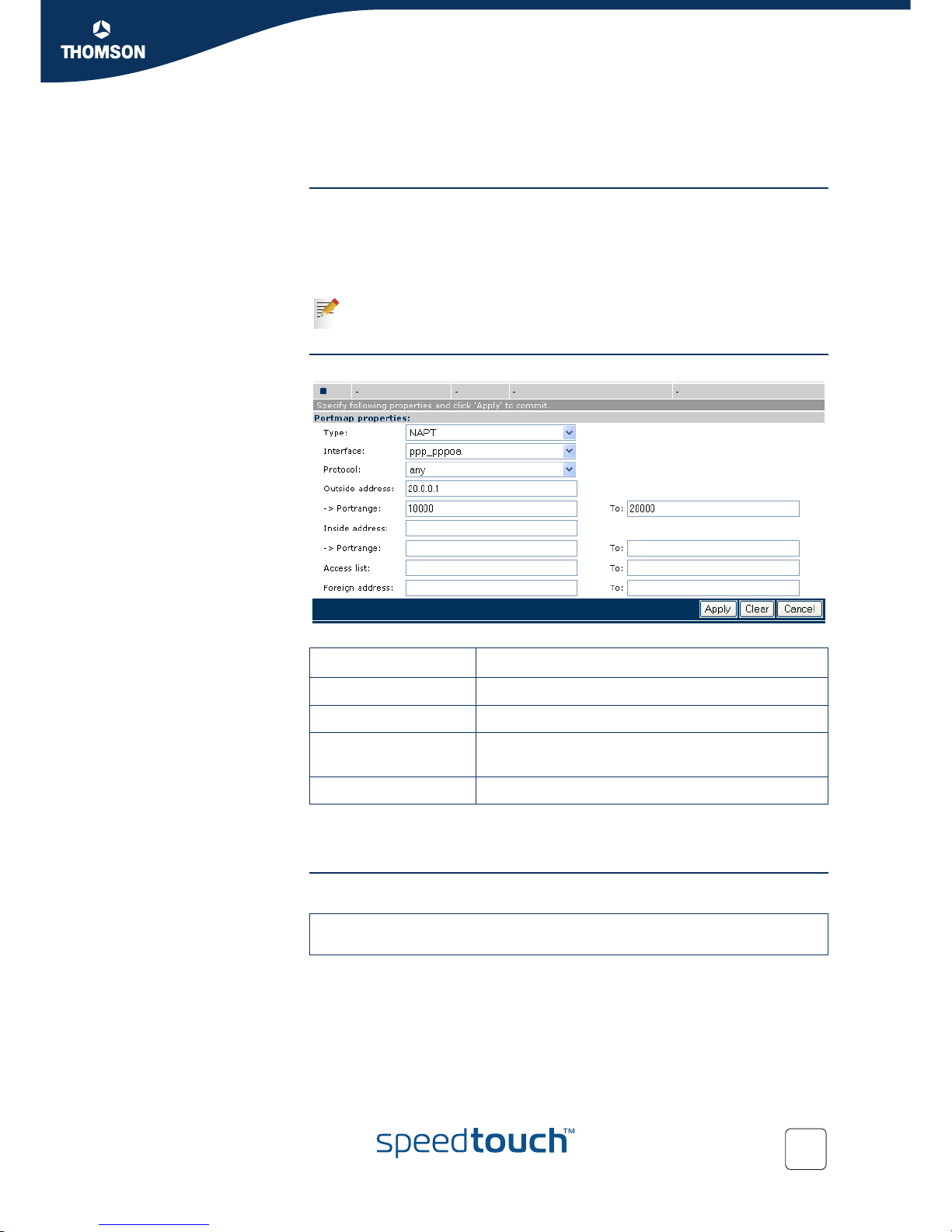
NAPT using dynamic port range constraint
E-NIT-CTC-20040716-0004 v1.0
55
6.4.7 NAPT using dynamic port range constraint
Introduction Prerequisistes:
Outbound: Inside host addresses (source addresses) are translated into the
outside address, using port translation to differentiate traffic.
The dynamic port range use for translation is restricted to a chosen port range.
Inbound: No traffic can be initiated.
GUI Create a new NAPT map and fill in the fields.
The NAPT map will be mapped when an inside host connects to an outside host.
Port translation will always be between port 10000 and 20000.
CLI
Traffic can only be initiated by an inside host.
Portmap properties Value
Interface pppoa
Protocol any
Outside address
-> Portrange
20.0.0.1
10000 to 20000
Access list Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=napt outside_addr=20.0.0.1
outside_port=10000-20000
Page 58

Configure port shifting maps
E-NIT-CTC-20040716-0004 v1.0
56
6.5 Configure port shifting maps
Page 59

Inbound port shifting
E-NIT-CTC-20040716-0004 v1.0
57
6.5.1 Inbound port shifting
Introduction This is an extension of Two-Way NAT where ports of inbound traffic are statically
translated from outside port range to inside port range. Port ranges must have the
same size.
GUI Create a new NAT map and fill in the fields.
An inbound connection to 20.0.0.1 on port 8080, will be forwarded to inside
address 192.168.1.64 on port 80
An inbound connection to 20.0.0.1 on port 8081, will be forwarded to inside
address 192.168.1.64 on port 81.
CLI
Portmap properties Value
Interface pppoa
Protocol tcp (then address translation will only be applied on
TCP packets)
Outside address
-> Portrange
20.0.0.1
8080 to 8081 (your own choice)
Inside address
-> Portrange
192.168.1.64
80 to 81 (your own choice)
Access list Define IP address (es) or leave empty.
Foreign address Define IP address (es) or leave empty.
=>:nat mapadd intf=ppp_pppoa type=napt outside_addr=20.0.0.1
inside_addr=192.168.1.64 outside_port=8080-8081 inside_port=80-81
Page 60

Configure templates
E-NIT-CTC-20040716-0004 v1.0
58
6.6 Configure templates
Introduction Templates are used when the public interfaces gets dynamically assigned IP address.
A template assigns a wildcard (0.0.0.x) to the IP address of the public interface.
Network setup
GUI
Create a NAT template and fill in the fields.
When a PPP connection is established, the wildcard is replaced by the dynamically
assigned IP address of the PPP interface. Select the Mappings menu.
This is the automatically created NAT map, based on the template. The wildcard is
replaced by the dynamically assigned IP address 101.101.101.47. Any inside
address can use this mapping.
`
192.168.0.1
SpeedTouch
TM
Public network
101.101.101.x
192.168.0.254
Wildcard: 0.0.0.1
PPPoA
192.168.0.2
Page 61

Configure templates
E-NIT-CTC-20040716-0004 v1.0
59
CLI
=>:nat tmpladd intf=any group=any type=nat outside_addr=0.0.0.1
Page 62

X+n templates
E-NIT-CTC-20040716-0004 v1.0
60
6.6.1 X+n templates
Introduction This is the same then a normal template but with a whole range of mappings.
GUI Create a NAT template and fill in the fields.
CLI
=>:nat tmpladd intf=any group=any type=nat outside_addr=0.0.0.[3-5]
inside_addr=192.168.1.[64-66]
Page 63

X+n templates
E-NIT-CTC-20040716-0004 v1.0
61
Page 64

X+n templates
E-NIT-CTC-20040716-0004 v1.0
62
Page 65

Page 66
Need more help?
Additional help is available online at www.speedtouch.com
© THOMSON 2005. All rights reserved. E-NIT-CT
C-20040716-0004 v1.0 .
 Loading...
Loading...