
Datacryptor® Ethernet
User Manual
1270A450-005 June 2008

Datacryptor Ethernet User Manual Preface
Page 2 THALES

Datacryptor Ethernet User Manual Preface
Contents
1 Preface............................................................................................................................................5
Trademark Acknowledgements ............................................................. 5
Revision Status....................................................................................... 5
License Agreement and General Information.............................................. 6
Security Advisory ................................................................................... 9
Contact Information............................................................................. 10
2 About This Document ........................................................................................................ 11
This manual is organized into the following sections: ......................... 12
3 Overview ....................................................................................................................................13
Product Images......................................................................................... 13
Product Features....................................................................................... 15
Element Manager ...................................................................................... 16
4 Background Information ..................................................................................................17
Datacryptor Ethernet Unit ......................................................................... 17
Gigabit Ethernet Technology Overview ..................................................... 17
Ethernet Layer 2 Services ..................................................................... 17
Security Terms..................................................................................... 18
Other Terms ........................................................................................ 18
5 Installation................................................................................................................................19
Hardware Installation................................................................................ 19
Rack-Mounting Instructions ................................................................. 19
Cabling Requirements ......................................................................... 20
To Cable the Datacryptor..................................................................... 21
Power on the Datacryptor .................................................................... 22
Software Installation ................................................................................. 23
Requirements ...................................................................................... 23
Installation Procedure .......................................................................... 24
6 Connecting to Datacryptor Ethernet Units............................................................25
Users ........................................................................................................ 25
IP Parameter Configuration via a Serial Connection .................................. 25
Dial Up Networking.............................................................................. 27
Adding a Unit to Element Manager ........................................................... 28
Direct Invocation of Front Panel Viewer .................................................... 32
Command Line Parameters....................................................................... 32
7 Element Manager Reference ..........................................................................................34
Main Window ............................................................................................ 34
Main Window Pull-down Menus................................................................. 35
File....................................................................................................... 35
Edit ...................................................................................................... 35
View..................................................................................................... 35
Tools.................................................................................................... 36
Help ..................................................................................................... 36
Toolbar Icons............................................................................................ 36
Datacryptor Icons ..................................................................................... 36
Front Panel Viewer .................................................................................... 38
User Key Material ................................................................................. 41
The Front Panel LEDs ........................................................................... 41
The Front Panel Viewer buttons ........................................................... 42
1270A450-005 - June 2008 Page 3

Preface Datacryptor Ethernet User Manual
Configure Dialog ...................................................................................... 43
Key Manager............................................................................................. 46
To commission a unit with the Commission button ................................. 46
Step 1: Installing a new Certificate Authority (CA)................................ 48
Step 2: Installing the authenticating CA: .............................................. 49
Step 3: Setting the unit name:.............................................................. 50
Step 4: Generating a Certificate: .......................................................... 51
Login Dialog ............................................................................................. 53
Change Password Dialog .......................................................................... 53
Logs Window ............................................................................................ 54
Properties Dialog ...................................................................................... 56
The General Tab .................................................................................. 57
The Diagnostics Tab ............................................................................ 59
The IP Management Tab ...................................................................... 61
Configuring SNMP................................................................................ 62
IP Route Config .................................................................................... 70
The Security Tab .................................................................................. 71
The RIP Tab.......................................................................................... 73
The Ethernet Comm Tab for 1 and 10 Gigabit Datacryptors ................ 75
The Ethernet Comm Tab for 100 Mb Datacryptor................................ 77
The Ethernet Encryption Tab................................................................ 79
The Expert Tab .................................................................................... 80
The Ethernet Tunneling Tab ................................................................ 81
The Environment Tab........................................................................... 85
Appendix A: Device Maintenance.....................................................................................86
Appendix B: Loading Datacryptor Unit Software ....................................................88
Appendix C: Product Specifications ................................................................................ 95
Appendix D: Environmental & Regulatory ..................................................................96
Appendix E: SFP and XFP Interfaces................................................................................98
Appendix F: Preventing Electrostatic Discharge.....................................................99
Appendix G: Troubleshooting ......................................................................................... 100
Appendix H: SNMP MIB Support ..................................................................................... 102
Appendix I: Log and SNMP Trap Numbers............................................................... 105
Standard Traps .................................................................................. 105
Log Trap Errors Hardware.................................................................. 106
Log Trap Errors Software ................................................................... 108
Key Errors .......................................................................................... 110
Audit Errors ....................................................................................... 123
Appendix J: Glossary of Terms.......................................................................................132
Page 4 THALES

Datacryptor Ethernet User Manual Preface
1 Preface
Trademark Acknowledgements
Datacryptor is a trademark of Thales e-Security.
Microsoft Windows® XP and Windows® 2003 are registered trademarks of Microsoft
Corporation.
All other logos and product names are trademarks or registered trademarks of their
respective companies.
©2006-2008 Thales e-Security. All rights reserved.
Copyright in this document is the property of Thales e-Security. It is not to be
reproduced, modified, adapted, published, translated in any material form (including
storage in any medium by electronic means whether or not transiently or incidentally) in
whole or in part nor disclosed to any third party without the prior written permission of
Thales e-Security neither shall it be used otherwise than for the purpose for which it is
supplied.
Thales e-Security reserves the right to modify or revise all or part of this document
without notice and shall not be responsible for any loss, cost, or damage, including
consequential damage, caused by reliance on these materials.
Revision Status
Revision Changes Release Date
1270A450-001 First Issue March 2006
1270A450-002 Release 1.1 August 2006
1270A450-003 10 Gig Ethernet unit added and Updates
for product release 4.00
1270A450-004 100 Mb Ethernet unit added March 2008
1270A450-005 Unsupported features in the 10Gig
Ethernet unit: Auto-negotiation; Disabling
CTS mode; Fragmentation
November 2007
June 2008
1270A450-005 - June 2008 Page 5

Preface Datacryptor Ethernet User Manual
License Agreement and General Information
THALES e-SECURITY LTD. ("THALES") COMPUTER PROGRAM LICENSE AGREEMENT
YOU SHOULD CAREFULLY READ THE FOLLOWING TERMS AND CONDITIONS OF THIS LICENSE AGREEMENT (the
"AGREEMENT"). FOR PURPOSES OF THIS AGREEMENT, “SOFTWARE” IS DEFINED TO INCLUDE COMPUTER PROGRAMS
INTENDED TO BE RUN ON A WORK STATION, PC, OR SIMILAR MACHINE, AND INCLUDES THE CD-ROM OR OTHER
MEDIA ON WHICH THE SOFTWARE IS CONTAINED. “FIRMWARE” IS DEFINED TO INCLUDE COMPUTER PROGRAMS
WHICH ARE INTENDED TO BE RUN SOLELY ON OR WITHIN A HARDWARE MACHINE (“MACHINE”) PROVIDED BY
THALES, INCLUDING, WITHOUT LIMITATION, FPGA BITSTREAMS. THE SOFTWARE AND FIRMWARE AND THE
ACCOMPANYING USER DOCUMENTATION (THE “DOCUMENTATION”) ARE LICENSED (NOT SOLD) TO YOU BY THALES
DIRECTLY OR THROUGH AUTHORIZED RESELLERS OF THALES. OPENING OR INSTALLING ANY OF THE CONTENTS OF
THIS CD-ROM OR OTHER PROVIDED MEDIA PACKAGE INDICATES YOUR ACCEPTANCE OF THE TERMS AND
CONDITIONS OF THIS LICENSE. IF YOU DO NOT AGREE WITH THE TERMS AND CONDITIONS, PROMPTLY RETURN THE
PACKAGE, THE MACHINE WHICH CONTAINS A COPY OF THE LICENSED FIRMWARE, AND ALL OTHER ENCLOSED ITEMS,
IF ANY, TO THE PLACE WHERE YOU OBTAINED THEM, AND YOU WILL RECEIVE A REFUND.
LICENSE GRANT
A. In consideration of the license fee paid to THALES or to an authorized THALES reseller, THALES hereby grants you,
and you accept a nonexclusive license to use the Software on a single machine (if a “single license” is purchased) or multiple
machines (if an “organizational license” is purchased) owned, leased, or otherwise controlled by you, and to use the
Firmware solely on the Machine sold to you by THALES or its dealers, if any, but only to operate or engage those features
and/or applications for which a charge appears on your order and invoice under the terms stated in this Agreement. If a
software or Firmware enabling key or other similar access device (the “Key”) is provided, you agree to use same solely for
accessing the Software on a single PC or Firmware on a single Machine. Title and ownership of the Software, Firmware,
Documentation and/or Key remain in THALES or its suppliers. If an organizational license is purchased, then you may use
the Software or Firmware on multiple Machines in your organization regardless of quantity, provided all Machines are
located within a single country. A separate single or organizational license will be required in each country.
B. You may not decompile, reverse engineer, modify, or copy the Software, Firmware, or Documentation for any
purpose, except you may copy the Software into machine-readable or printed form for backup purposes in the event the CDROM or other provided media is damaged or destroyed. You may combine the Software with other programs. Any portion
of the Software merged into or used in conjunction with another program will continue to be the property of THALES and is
subject to the terms and conditions of this Agreement.
C. The Software, Firmware, and the Documentation are copyrighted by THALES and/or its suppliers. You agree to
respect and not to remove or conceal from view any copyright or trademark notice appearing on the Software, Firmware, or
Documentation, and to reproduce any such copyright or trademark notice on all copies of the Software, Firmware, and
Documentation or any portion thereof made by you as permitted hereunder and on all portions contained in or merged into
other programs and documentation.
D. You may transfer the Software, Firmware, and this license to another party if the other party agrees to accept the
terms and conditions of this Agreement. If you transfer the Software and/or Firmware, you must at the same time either
transfer all copies whether in printed or machine-readable form, and the Machine, if any, on which the Firmware is licensed
for use, to the same party or destroy any copies not transferred; this includes all modifications and portions of the Software
and/or contained or merged into other programs.
YOU MAY NOT USE, COPY, MODIFY, OR TRANSFER THE SOFTWARE, FIRMWARE, DOCUMENTATION OR KEY, OR ANY COPY,
MODIFICATION OR MERGED PORTION, IN WHOLE OR IN PART, EXCEPT AS EXPRESSLY PROVIDED FOR IN THIS LICENSE.
IF YOU TRANSFER POSSESSION OF ANY COPY, MODIFICATION OR MERGED PORTION OF THE SOFTWARE, FIRMWARE, OR
DOCUMENTATION OR KEY TO ANOTHER PARTY, EXCEPT AS PROVIDED IN THIS SECTION D, YOUR LICENSE IS
AUTOMATICALLY TERMINATED.
TERM
This Agreement is effective upon your acceptance (as set forth above) and shall continue until terminated. You may
terminate this license at any time by destroying the Software, Key, and Documentation along with all copies, modifications
and merged portions in any form, and return the Machine (including Firmware) to THALES or its authorized resellers. It will
also terminate upon conditions set forth elsewhere in this Agreement if you fail to comply with any term or condition of this
Agreement. You agree upon such termination to destroy the Software, Documentation, and Key together with all copies,
modifications and merged portions in any form, and to return the Machine (including Firmware) to THALES or its authorized
resellers.
Page 6 THALES

Datacryptor Ethernet User Manual Preface
LIMITED WARRANTY
The following limited warranty applies only to the Software and/or Firmware licensed hereunder. The hardware Machine is
warranted pursuant to a separate Warranty set forth in the Machine documentation. The Machine documentation is
contained on the CD-ROM, if any.
During the first 90 days after receipt of the Software and/or Firmware by you, as evidenced by a copy of your receipt, invoice
or other proof of purchase (the "Warranty Period"), THALES warrants, for your benefit alone, that the Software and Firmware
when properly installed, will perform substantially in conformance with the Documentation provided by THALES at the time
you obtained the Software and/or Firmware from THALES or its authorized resellers, and that the media on which the
Software and/or Firmware is furnished will be free from defects in materials and workmanship under normal use.
EXCEPT AS SPECIFICALLY PROVIDED ABOVE, THE WARRANTIES PROVIDED HEREIN ARE EXCLUSIVE AND IN LIEU OF ALL OTHER
WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE
SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OF IMPLIED WARRANTIES, SO THE ABOVE EXCLUSION MAY NOT APPLY
TO YOU. WHEREVER SUCH EXCLUSION IS NOT PERMITTED BY LAW, ALL IMPLIED WARRANTIES, INCLUDING THOSE OF
MERCHANTABILITY AND/OR FITNESS FOR A PARTICULAR PURPOSE, SHALL BE LIMITED TO THE WARRANTY PERIOD. THIS
WARRANTY GIVES YOU SPECIFIC LEGAL RIGHTS, AND YOU MAY ALSO HAVE OTHER RIGHTS WHICH MAY VARY FROM
JURISDICTION TO JURISDICTION.
THALES does not warrant that the functions contained in the Software or Firmware will meet your requirements or that their
operation will be uninterrupted or error free.
LIMITATIONS OF REMEDIES
THALES, its authorized resellers’, and/or its suppliers' entire liability and your exclusive remedies under this Agreement are
as follows:
(1) THALES shall use commercially reasonable efforts to correct any defect in the Software or Firmware which is
reported by you during the Warranty Period in writing to THALES, provided such defect can be recreated by THALES
in an unmodified version of the Software or Firmware. However, if THALES is unable to correct such defect within a
reasonable amount of time, you may terminate this Agreement by returning the Software, Machine including
Firmware, Documentation, and Key to the place where you obtained them either for replacement or, if so elected
by THALES, a refund of the amount paid by you for the subject item.
(2) THALES shall replace any media not meeting THALES’ "Limited Warranty" and which is returned to THALES with a
copy of your receipt, invoice or other proof of purchase or, if THALES is unable to deliver replacement media which
is free from defects in materials or workmanship, you may terminate this Agreement by returning the Software,
Firmware, Documentation, and Key to the place where you obtained them for a refund of the amount paid by you
for the subject item.
IN NO EVENT WILL THALES, ITS AUTHORIZED RESELLERS, OR ITS SUPPLIERS BE LIABLE FOR INCIDENTAL, SPECIAL OR
CONSEQUENTIAL DAMAGES OF ANY KIND OR TYPE, INCLUDING, BUT NOT LIMITED TO LOSS OF PROFITS OR REVENUE, LOSS
OF USE OF THE PRODUCT(S) OR ANY ASSOCIATED PRODUCT(S), OR COST OF SUBSTITUTED FACILITIES, PRODUCTS OR
SERVICES WHICH ARISE OUT OF THALES’ PERFORMANCE OR FAILURE TO PERFORM ANY OBLIGATION CONTAINED WITHIN
THIS AGREEMENT OR WITH USE, OR INABILITY TO USE, SOFTWARE AND/OR FIRMWARE, WHETHER THE CLAIM FOR DAMAGES
IS BASED IN CONTRACT, TORT (INCLUDING NEGLIGENCE), STRICT LIABILITY OR OTHERWISE. EXCEPT FOR CLAIMS FOR
PERSONAL INJURY OR FOR DAMAGE TO REAL OR TANGIBLE PROPERTY TO THE EXTENT CAUSED BY THALES’ FAULT OR
NEGLIGENCE, THALES’ MAXIMUM LIABILITY FOR ANY CLAIM FOR DAMAGES RELATING TO THALES’ PERFORMANCE OR NONPERFORMANCE UNDER THIS AGREEMENT SHALL BE LIMITED TO THE LESSER OF (a) YOUR ACTUAL DAMAGES OR (b) THE COST
OF THE PRODUCT GIVING RISE TO THE LIABILITY.
SOME JURISDICTIONS DO NOT ALLOW THE LIMITATION OR EXCLUSION OF LIABILITY FOR INCIDENTAL OR CONSEQUENTIAL
DAMAGES SO THE ABOVE LIMITATION OR EXCLUSION MAY NOT APPLY TO YOU.
PURCHASES BY OR FOR THE FEDERAL GOVERNMENT
The government hereby agrees that this software qualifies as "commercial computer software" as that term is used in the
acquisition regulation applicable to a purchase order or contract. This software may not be acquired by the government in a
contract incorporating clauses prescribed by DFARS Subpart 227.4 (OCT 1988), in which case the government hereby agrees
to return the software unused, in exchange for refund of the full purchase price.
1270A450-005 - June 2008 Page 7

Preface Datacryptor Ethernet User Manual
The government agrees that it shall be bound by the terms and conditions of this license agreement, to the maximum
extent possible under federal law. This license agreement, and the governments assent hereto, supersedes any contrary
terms or conditions in other contract documents (such as any statement of work).
EXPORT AUTHORIZATIONS
You shall assume all responsibility for obtaining any required export authorizations necessary to export any Software and/or
Firmware and Documentation purchased hereunder. You shall not re-export Software and/or Documentation directly or
through others, or the product of such data, to the prescribed countries for which such prohibition exists pursuant to the
U.S. or U.K. export regulations unless properly authorized by the appropriate government.
GENERAL
You may not sublicense, assign or transfer this license, Software, Firmware, Documentation or Key, except as expressly
provided in this Agreement. Any attempt otherwise to sublicense, assign or transfer any of the rights, duties or obligations
hereunder is void.
This Agreement will be governed by the laws of England or the event that the Product was delivered in the United States,
Latin America or Canada, the laws of the State of Virginia.
YOU ACKNOWLEDGE THAT YOU HAVE READ THIS LICENSE AGREEMENT, UNDERSTAND IT AND AGREE TO BE BOUND BY ITS
TERMS AND CONDITIONS. YOU FURTHER AGREE THAT IT IS THE COMPLETE AND EXCLUSIVE STATEMENT OF THE
AGREEMENT BETWEEN YOU AND THALES WHICH SUPERSEDES ANY PRIOR PROPOSAL, REPRESENTATION, OR UNDERSTANDING
(ORAL OR WRITTEN) BETWEEN US RELATING TO THE SOFTWARE OR FIRMWARE.
NOTWITHSTANDING THE ABOVE, IF YOU PREVIOUSLY SIGNED A SEPARATE AGREEMENT HAVING A SOFTWARE LICENSE
PROVISION APPLICABLE TO THIS PROGRAM, WHICH HAS NOT EXPIRED OR BEEN TERMINATED, THE TERMS AND CONDITIONS
OF SUCH SEPARATE AGREEMENT AND THE SOFTWARE LICENSE CONTAINED THEREIN SHALL TAKE PRECEDENCE OVER ALL
CONFLICTING TERMS AND CONDITIONS, IF ANY, CONTAINED IN THIS LICENSE AGREEMENT. OTHERWISE, ANY ADDITIONAL
TERMS AND CONDITIONS SET FORTH IN THIS LICENSE AGREEMENT SHALL SUPPLEMENT AND BE READ IN CONJUNCTION WITH
THE SOFTWARE LICENSE CONTAINED IN ANY SUCH SEPARATE AGREEMENT
.
Hardware Warranty
The period of warranty for this product starts on the date of sale to the original purchaser and ends 365 days
thereafter. Thales e-Security will replace any product that fails within 90 days of the date of sale. For failures which
occur more than 90 days after the date of sale, Thales e-Security will repair the product if returned, postage
prepaid, to our designated repair center.
Thales e-Security requires a Return Authorization Number (RAN) prior to the return of any equipment under the
provisions of this warranty. Please contact your authorized reseller or the nearest Thales e-Security product
support center for details.
General Requirements
This equipment should be installed by a qualified Service engineer. Incorrect connection will invalidate warranty
and may cause a hazard.
Should any malfunction be suspected in the unit, return the apparatus to your supplier for service and/or repair to
ensure continued compliance. The Datacryptor Ethernet unit contains no user serviceable parts.
The unit should be installed in an environment compatible with the maximum operating temperature of the unit.
Installation of the unit in a rack should not reduce airflow so as to compromise safe operation of the unit.
Particular attention should be made to make sure that the side ventilation holes on the Datacryptor Ethernet are
not obstructed which could reduce the airflow through the unit. Please refer to the Installation chapter, in the
section titled "
When installed in a rack make sure that the unit is securely installed using all the appropriate mechanical fixings so
that it will not cause a hazardous condition.
Airflow" for further information on providing appropriate air flow.
Page 8 THALES

Datacryptor Ethernet User Manual Preface
Security Advisory
This unit is being shipped with a Universal Certificate Authority that is to be used for
demonstration purposes only. USE OF THE DEVICE, AS INITIALLY CONFIGURED, IN AN
OPERATIONAL ENVIRONMENT IS NOT RECOMMENDED. THALES e-SECURITY EXPRESSLY
DISCLAIMS ANY AND ALL LIABILITY FOR DAMAGES, INCLUDING BUT NOT LIMITED TO
CONSEQUENTIAL DAMAGES, RESULTING FROM USE OF THE UNIVERSAL CERTIFICATE OR ANY
OTHER CERTIFICATE SUPPLIED BY THALES e-SECURITY. Prior to use in an operational
environment, please change the certificate authority, following the procedure(s) described in the
Key Manager section.
1270A450-005 - June 2008 Page 9
Preface Datacryptor Ethernet User Manual
Contact Information
SALES OFFICES
Americas
Europe, Middle East, Africa
THALES e-Security, INC
2200 North Commerce Parkway
Suite 200
Weston, Florida 33326
U.S.A.
Tel: +1 954 888 6200
Fax: +1 954 888 6211
Toll free within USA:
+1 888 744 4976
e-mail:
sales@thalesesec.com
THALES e-Security (ASIA) LTD
199 Des Voeux Road, Central
asia.sales@thales-esecurity.com
THALES e-Security LTD
Meadow View House
Long Crendon
Aylesbury
Buckinghamshire HP18 9EQ
England
Tel: +44 (0)1844 201800
Fax: +44 (0)1844 208550
e-mail:
emea.sales@thales-esecurity.com
Asia Pacific
Units 2205-06, 22/F
Vicwood Plaza
Hong Kong
Tel: +852 2815 8633
Fax: +852 2815 8141
e-mail:
PRODUCT SUPPORT CENTERS
Americas
Tel: +1 954 888 6277
Toll free within USA:
+1 800 521 6261
Fax: +1 954 888 6233
e-mail:
support@thalesesec.com
Asia Pacific
Tel: +852 2815 8633
Fax: +852 2815 8141
e-mail:
aisa.support@thales-esecurity.com
Page 10 THALES
Europe, Middle East, Africa
Tel: +44 (0) 1844 202566
Fax: +44 (0) 1844 208356
e-mail:
emea.support@thales-esecurity.com
Datacryptor Ethernet User Manual About This Document
2 About This Document
Viewing this document in Adobe Acrobat PDF Viewer
It is recommended that this PDF document is viewed at 100% size with text smoothing adjusted
to suit your monitor. The viewing size is easily adjusted by the use of the Zoom toolbar; you
may set 100% size, or simply click the Actual Size icon:
Viewing at 100% will provide the best appearance of the images in this document.
To change the appearance of the text, select: Edit > Preferences > Page Display. Change the
Smooth Text option and click OK. Use this option to compare the appearance of the text with
and without text smoothing, and then select the setting that provides the most comfortable
reading experience.
Introduction to this Manual
There are three models in the Datacryptor Ethernet range: 100 Mb Ethernet, 1 Gig Ethernet, and
10 Gig Ethernet. Predominantly, the information in this manual applies equally to all models
and as such, the device is referred to simply as the ‘Datacryptor Ethernet’. Where there are
differences, the unit being described is referred to either as the 100 Mb Ethernet, 1 Gig
Ethernet, or 10 Gig Ethernet, as appropriate. The differences between the two models are
mainly in the speed of operation and the physical size of the casing.
This manual describes how to install the Thales Datacryptor Ethernet unit and the Element
Manager software. It also describes how to use the Element Manager software to configure and
manage the Thales Datacryptor Ethernet device.
This document is intended for use by network technicians, managers and security
administrators who are familiar with setting up and maintaining network equipment. Some
knowledge of network security issues and encryption technologies is assumed.
This document assumes that its readers have an understanding of the following:
• Basic principles of network security issues
• Basic principles of encryption technologies and terminology
• Basic principles of Ethernet technology
• Basic principles of TCP/IP networking, including IP addressing, switching and routing
• Personal computer (PC) operation, common PC terminology, and use of terminal
emulation software.
The following conventions are used in the body text of this document:
Bold font: Indicates a command to be issued or selected by the user.
• Courier font: Indicates information input or output to/from the Control PC.
• Italic font: Indicates the name of dialog, parameter, object, etc.
1270A450-005 - June 2008 Page 11
About This Document Datacryptor Ethernet User Manual
This manual is organized into the following sections:
Overview provides general information on the hardware and software.
Background Information provides a brief introduction to the device and Ethernet Layer 2
technology and terminology.
Installation describes how to install the Datacryptor Ethernet hardware and Element Manager
Software.
Connecting to Datacryptor Ethernet Units describes the main methods that can be used to
connect the PC to the Datacryptor Ethernet unit.
Element Manager Reference provides an overview of the functions provided by the Element
Manager, followed by a detailed description of each in turn.
Appendix A: Device Maintenance describes the periodic maintenance required on your Thales
Datacryptor Ethernet unit.
Appendix B: Loading Datacryptor Unit Software describes how to load software into your
Thales Datacryptor Ethernet unit. Your Datacryptor will be supplied pre-loaded with software, so
you will only require the information in this appendix if a re-load or upgrade is needed.
Appendix C: Product Specifications gives the system specifications.
Appendix D: Environment and Regulatory Information describes the operating conditions
and regulatory certifications.
Appendix E: SFP and XFP Interfaces describes the possible transceiver options.
Appendix F: Preventing Electrostatic Discharge describes how to minimize the risk of ESD.
Appendix G: Troubleshooting describes how to diagnose and repair common problems.
Appendix H: SNMP MIB Support describes the SNMP MIBs supported by the device and the
location of them.
Appendix I: Log and SNMP Trap Numbers provides a list of all the log and trap numbers
together with descriptions of their purpose.
Appendix J: Glossary defines terms used in this document.
Page 12 THALES
Datacryptor Ethernet User Manual Overview
3 Overview
The Thales Datacryptor Ethernet is a high speed, high bandwidth, integrated security appliance.
The three models provide different transfer speeds; the 100 Mb Ethernet provides 100 Mbps,
while the 1 Gig and 10 Gig Ethernet units offer encryption at Gigabit Ethernet Layer 2 transfer
rates.
The Datacryptor Ethernet units come in different case styles; the 100 Mb Ethernet and the 1 Gig
Ethernet models are housed in a single unit height 19-inch rack case for transmission speeds
up to 100 Mbps and 1000 Mbps respectively, while the 10 Gig Ethernet model uses a double
height unit for 10,000 Mbps transmission speeds. The 100 Mb Ethernet unit may have its rack
mounting brackets removed so that it can be used as a desktop unit.
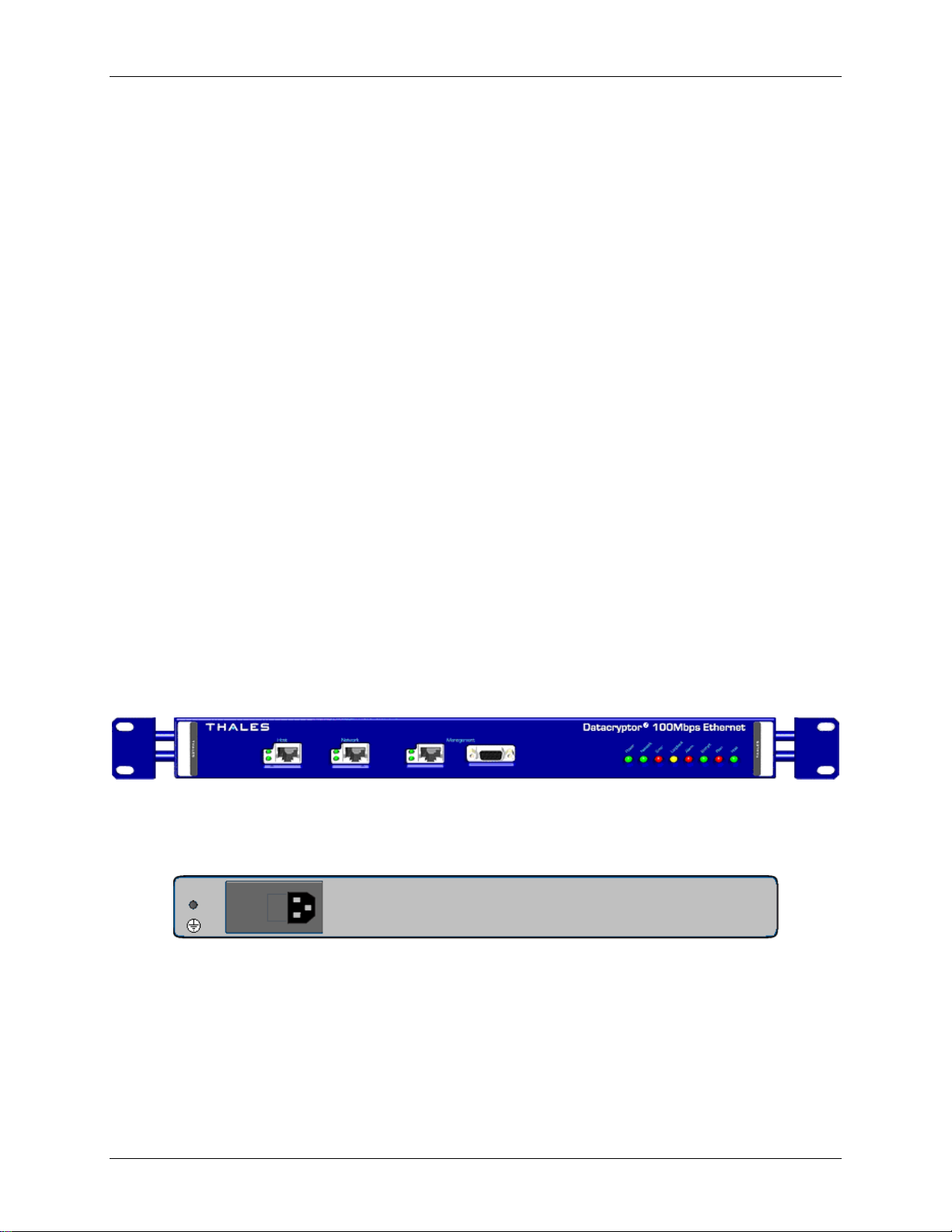
The 100 Mb Ethernet units have standard RJ45 sockets on the front panel for Host and Network
connections, while the 1 Gig and 10 Gig Ethernet units have two Small Form Factor sockets on
the front panel; these accept a range of transmit/receive interfaces. The 1 Gig Ethernet unit
uses SFP type sockets, and the 10 Gig Ethernet unit uses the XFP type sockets.
The host port is connected to the private network and receives the data for encryption.
Encrypted data is then passed through the network port for secure transmission over the public
network.
The Datacryptor Ethernet is designed to operate as a Layer 2 (Data Link) encryptor. The
advantage of this is it makes the unit fully transparent to higher protocols.
The units are housed in a tamper evident chassis with interlock switches that will cause the key
material to be erased if the lid is removed.
Product Images
Figure 3-1: Thales Datacryptor 100 Mb Ethernet Front Panel
Figure 3-2: Datacryptor 100 Mb Ethernet Rear Panel
1270A450-005 - June 2008 Page 13

Overview Datacryptor Ethernet User Manual
Figure 3-3: Thales Datacryptor 1 Gig Ethernet Front Panel
Figure 3-4: Datacryptor 1 Gig Ethernet Rear Panel
Note: See
information on the LED indicators.
Figure 3-5: Thales Datacryptor 10 Gig Ethernet Front Panel
Figure 3-6: Datacryptor 10 Gig Ethernet Rear Panel
The Front Panel LEDs in the Element Manager Reference section for full
Page 14 THALES

Datacryptor Ethernet User Manual Overview
Product Features
Installation
• Mount in any standard 19” rack
or on a tabletop
Interfaces
• The 100 Mb Ethernet has two
RJ45 sockets for connecting to
the Host and Network circuits
• The 1 Gig Ethernet and 10 Gig
Ethernet units have two SFP or
XFP sockets which accept a range
of transceiver modules for the
encrypting and decrypting of
network traffic
• Device management access
through a 10/100 Ethernet port
or an RS-232 craft port
Security features
• Designed to FIPS 140-2 Level 3
Hardware-based encryption
processing
• Very low latency
Maximum Data Transfer Rate
• 200 Mbps full duplex (100 Mb
Ethernet unit), 2 Gbps full duplex
(1 Gig Ethernet unit), or 20 Gbps
full duplex (10 Gig Ethernet unit)
Network Interfaces
• 10/100BaseT: User selectable
between 10 Mbps and 100 Mbps
Key management
• Diffie-Hellman key exchange
(groups 1, 2, and 5)
Encryption
• Advanced Encryption Standard
(AES):
FIPS 197 (256 bit keys)
Management integrity
• HMAC-SHA-1-96 (FIPS PUB 180-1):
RFC 2104, 2404
• HMAC-MD5-96 : RFC 2104, 2403,
1321
Device management
• Element Manager
• Secure download of software
updates
• X.509v1 and X509 v3 digital
certificate support
Power
• 100 Mb Ethernet Unit:
Single fixed AC (universal) or
DC (-48 V) power supply:
15W (51 BTU/hr)
• 1 Gig Ethernet and 10 Gig Ethernet:
Redundant hot swappable AC
(universal) or DC (-48 V) power
supplies:
1 Gig: 120 W (410 BTU/hr)
10 Gig: 140 (480 BTU/hr)
• 1 Gig Ethernet: 1000 Mbps full
duplex
• 10 Gig Ethernet: 10,000 Mbps
full duplex
• Auto negotiation (does not apply
to the 10 Gig Ethernet)
1270A450-005 - June 2008 Page 15

Overview Datacryptor Ethernet User Manual
Element Manager
The Element Manager application provides a secure way to configure, manage, and upgrade the
Datacryptor Ethernet. The program runs under various versions of Microsoft Windows operating
systems. Please see the
environment required.
The PC can connect to a Datacryptor Ethernet unit to manage it using the IP protocol over a
standard 10/100 Ethernet connection. The PC can also connect to a Datacryptor Ethernet unit
using PPP protocols via a serial connection. Once the PC is connected to the Datacryptor
Ethernet unit, a communications session can be established; and all the functions provided by
the Element Manager are available.
Software Requirements for a more detailed description of the
Page 16 THALES

Datacryptor Ethernet User Manual Background Information
4 Background Information
Datacryptor Ethernet Unit
The Thales Datacryptor Ethernet units are high performance, integrated security appliances that
provide encryption at high line speeds. The 1 Gig and 10 Gig Ethernet units operate at optical
line speeds and have the added advantage that they can, over limited distances, use copper
media. The device’s high-speed processing capabilities eliminate bottlenecks while providing
data encryption and integrity.
It is ideal for bandwidth intensive, latency sensitive applications that demand security and
speed, such as site-to-site VPNs, and the transfer of imaging over the network. It provides
secure transport over private or public networks.
Figure 4-1. An Example of a Site to Site Ethernet Layer 2 connection
A site-to-site VPN application is shown above. The Thales Datacryptor Ethernet is deployed on
either side of the connection, securing the data transmitted across the untrusted public
network. Data is sent from a web server through to the host network. It is then encrypted by the
Datacryptor Ethernet for secure transfer over the public network, where a second Datacryptor
Ethernet decrypts the data at its destination.
Gigabit Ethernet Technology Overview
The Gigabit Ethernet technology used by the 1 Gig and 10 Gig Ethernet units is the latest
specification in the IEEE 802.3 Ethernet standard series. This standard allows the transmission
of data at one or ten Gigabit per second transmission speeds (1 Gbps or 10 Gbps). However the
speed is usually designated as 1,000 Mbps or 10,000 Mbps, as appropriate, to comply with the
standard method of showing Ethernet network speeds.
Ethernet Layer 2 Services
Ethernet Layer 2 security services include:
Encryption - The Advanced Encryption Standard (AES) algorithm is a symmetric block cipher
capable of using cryptographic keys of 128, 192, and 256 bits to encrypt and decrypt data in
blocks of 128 bits. The Datacryptor uses 256 bit keys.
1270A450-005 - June 2008 Page 17

Background Information Datacryptor Ethernet User Manual
Authenticate Management Data - The Datacryptor Ethernet uses the HMAC keyed hash variant
of the SHA-1(Secure Hash Algorithm) to authenticate management data using SNMP v3.
Security Terms
Diffie-Hellman – Diffie-Hellman is a method for key exchange that allows two autonomous
systems to exchange a secret key over an untrusted network without prior secrets. DiffieHellman groups define the strength supplied to the Diffie-Hellman calculation for the later
creation of keys by the peers. Three of the five available groups are generated from modulo
function (MODP) calculations and the leveraging of very large prime numbers.
Peer – A peer is a Datacryptor that acts as a tunnel endpoint. A peer encrypts or decrypts data,
adding or stripping away headers, respectively.
Other Terms
Layer2 -The Datacryptor Ethernet is designed to work as a Layer two encryptor.
The addressing scheme is physical i.e. the addresses are MAC (Media Access Control) addresses
hard coded into a device at the time of manufacture. It is generally a 48-bit address which is
usually displayed in hexadecimal format as six two digit parts 01-0B-3B-18-00-CA.
It should be noted that when the unit is operating in the Tunneling mode the peer unit MAC
address must be obtained and entered in the box provided on the relevant property tab.
Frame Checksum (FCS) - FCS is an error detection system based on the numerical value of the
number of set bits in the Frame (packet). This value is transmitted alongside the message, and
the receiving device then applies the same criteria and compares the two values.
Auto-negotiation - Auto-negotiation was devised to address the need for multi-speed devices
on a network to operate at the optimum settings. It achieves this by taking control of the
connection medium and detecting the various mode options available in the device on the other
end, while also advertising its own capabilities. Thus it enables the connection to configure the
highest performance mode of interoperation.
Note: The Datacryptor 1 Gig Ethernet only supports I000 Mbps full duplex, and the
10 Gig Ethernet unit only supports I0,000 Mbps full duplex. The 100 Mb
Ethernet unit can be set to run at speeds of I0 Mbps and I00 Mbps.
The 10 Gig Ethernet unit does not support Auto-negotiation.
Jumbo frames - Jumbo frame is the name given to frames larger than the standard Ethernet
MTU of 1500 bytes. The Datacryptor Ethernet encryptor does not have an MTU limit and will
therefore allow Jumbo frames. Frame size is only limited if fragmentation is enabled.
Multiprotocol Label Switching – MPLS is a solution to the question of many of the earlier
network problems such as speed, scalability and quality of service. This is achieved by the
defining of paths across the network by the addition of label information to a packet to aid
routing etc. It is referred to as multi-protocol because it supports a number of communication
methods such as IP, Frame Relay and ATM. The Datacryptor Ethernet unit is transparent to this
operation as long as the equipment is being deployed in a point-to-point environment.
Page 18 THALES

Datacryptor Ethernet User Manual Installation
5 Installation
This section will detail the installation of the hardware and software. Hardware installation is
discussed first.
Hardware Installation
There are four steps in installing the unit:
• Unpack the Shipping Carton
• Mount the Unit
• Connect the Cables
• Power on the Datacryptor
Unpack the Shipping Carton
Remove all product components from the shipping carton and compare the contents to the
packing list. Keep all packaging in case it is necessary to return the appliance. The Datacryptor
is packaged with the following items:
• Datacryptor Ethernet, with the Datacryptor firmware and software factory-installed on
the appliance.
• 115v, 240v or DC Power Supply cables (as appropriate).
• RS-232 cable.
• Element Manager CD-ROM (includes User Manual).
• Release Notes.
• Quick Start Guide.
Note:
Interface transceivers (if ordered) will be shipped separately from the Datacryptor unit
(1 Gig and 10 Gig Ethernet units only).
Rack-Mounting Instructions
The Datacryptor can be mounted in a standard 19-inch rack using the front mounting
brackets, or simply placed on a rack shelf or solid surface.
Preparation
Before installing the Datacryptor in a 19-inch rack, consider the following rack-mounting
guidelines:
Ambient temperature
Install the Datacryptor in an environment compatible with the 105ºF (40ºC) maximum
recommended ambient temperature. Extra clearance above or below the unit on the rack
is not required; however, be aware that equipment placed in the rack beneath the
Datacryptor can add to the heat load. Therefore, avoid installing in an overly congested
rack. Air flowing to or from other equipment in the rack might interfere with the normal
flow of cooling air through the Datacryptor, increasing the potential for overheating.
1270A450-005 - June 2008 Page 19

Installation Datacryptor Ethernet User Manual
Airflow
Make sure that there is sufficient flow of air around the Datacryptor so that safe operation
is not compromised. Maintain a clearance of at least 3 inches (7.62 cm) at the sides of the
Datacryptor to ensure adequate air intake and exhaust. If installing in an enclosed rack,
make sure the rack has adequate ventilation or an exhaust fan. An enclosed rack with a
ventilation system that is too powerful can prevent proper cooling by creating negative air
pressure around the Datacryptor.
Mechanical Loading
Keep the center of gravity in the rack as low as possible. This ensures that the weight of
the Datacryptor will not make the rack unstable. Make sure that the rack is secured and
use the proper mounting hardware to secure the Datacryptor to the rack.
Circuit Loading
Consider the connection of the Datacryptor to the supply circuit and the effect that
overloading of circuits might have on over current protection and supply wiring. Consult
the voltage and amperage ratings on the UL label affixed to the unit’s rear panel when
addressing this concern. As the 1 Gig and 10 Gig Ethernet units are fitted with two hot
swappable power supply units, consideration could be given to these types of
Datacryptors using a different supply phase for each of the power supply units.
Disconnection
Power disconnection is achieved by removal of the plugs from the mains outlet sockets.
Ensure that the socket-outlets are close to the unit, and can be easily identified and
accessed.
Grounding
Maintain reliable grounding of a rack-mounted Datacryptor. Pay particular attention to
supply connections other than direct connections to the branch circuit, such as the use of
power strips.
Maintenance
Allow at least 19 inches (48.3 cm) of clearance at the front of the rack for maintenance.
Use a cable-management system to help keep cables organized, out of the way, and free
from kinks or bends that degrade cable performance.
Connect the Cables
Before beginning, make sure the necessary cables are available. See the
Requirements section below for more information.
Cabling
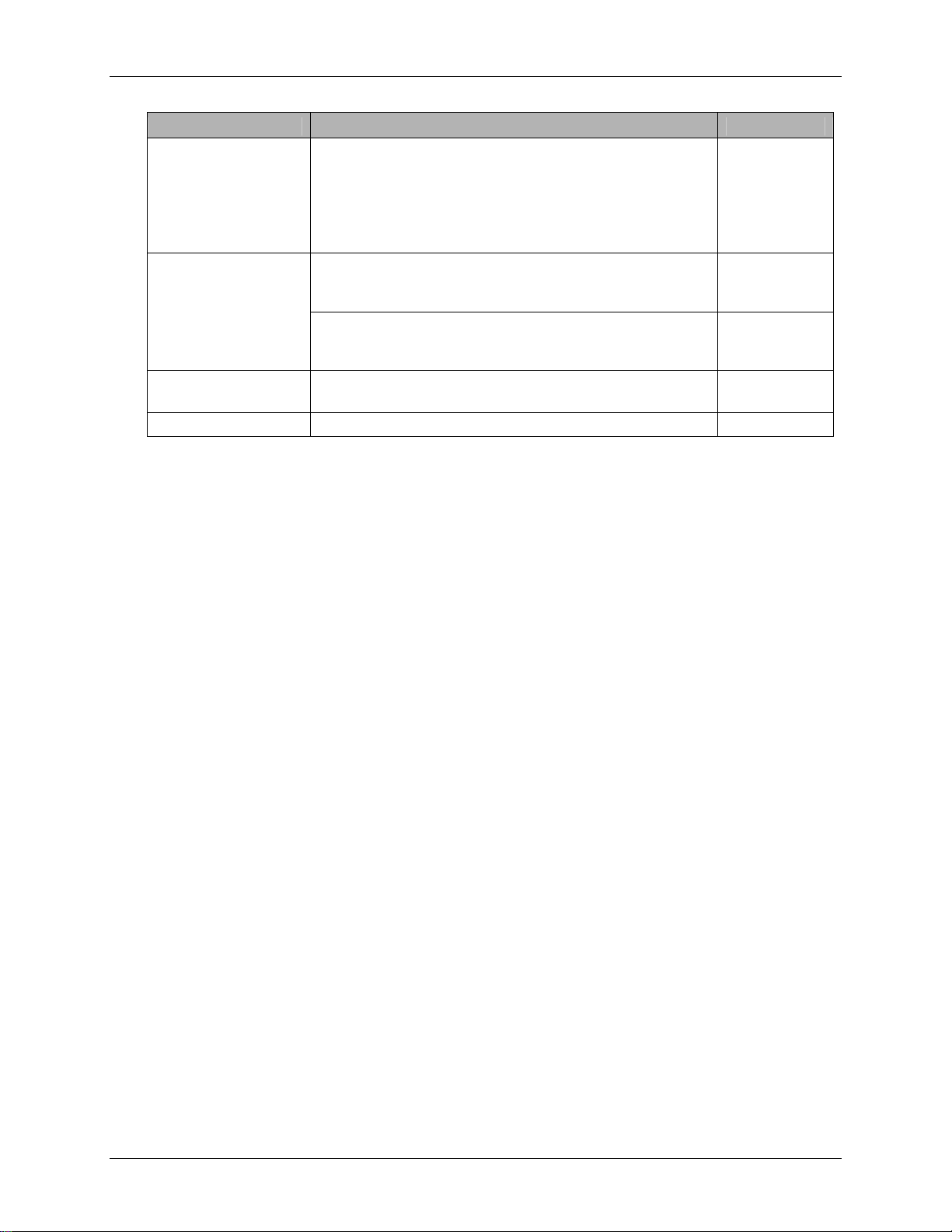
Cabling Requirements
The following table outlines the cabling requirements for each port on the Datacryptor Ethernet.
The connector type listed indicates only what is required to connect to the Datacryptor’s port,
and may or may not be the same connector type required for the other end of the cable.
Page 20 THALES
Datacryptor Ethernet User Manual Installation
Port Cabling Supplied By
Network and Host
Port
Management Port
RS-232 Craft Port Shielded copper serial cable, RS-232 DB9 connector
Power receptacles Power supply cables Thales
For the 100 Mb Ethernet unit: Category 5 or above
RJ-45 connector.
For the 1 Gig and 10 Gig Ethernet units:
the SFPs or XFPs ordered with the unit. The options are
Category 5 or above RJ 45 connector. 850nm Multi-mode
fiber. 1310nm or 1550nm Single mode fiber.
Shielded Category 5 straight through cable (STP), RJ-45
connector.
Used when connecting through a LAN.
Category 5 crossover cable with RJ-45 connector.
Required for a direct connection between the management
station and the Datacryptor.
(female to male)
Dependant on
Customer
Customer 10/100 Ethernet
Customer
Thales
To meet the requirements of FCC Part 15 and the Directive 89/336/EEEU EMC C, use only
shielded cables (DB-9 null modem cables and Category 5 STP cables).
To Cable the Datacryptor
The Host and Network interface transceivers that are used with the 1 Gig and 10 Gig Ethernet
units are shipped separately from the Datacryptor unit, and therefore must be inserted before
proceeding with the cabling operation.
The connections are the same when using any of the three types of Ethernet unit. The
illustration below shows a 1 Gig Ethernet unit – please note that the management ports of the
100 Mb Ethernet unit are on its front panel.
• Either connect the RS-232 craft port directly to a PC or workstation using the supplied DB-9
null modem cable, or
• Connect the 10/100 Ethernet management port for management access:
− If connecting to a LAN, use a Category 5 STP straight-through cable with an RJ-45
connector.
− If connecting directly to a PC, use a shielded Category 5 crossover cable and make
sure that the PC and management port IP addresses are on the same subnet.
1270A450-005 - June 2008 Page 21

Installation Datacryptor Ethernet User Manual
Figure 5-1: Datacryptor Panel Connectors
(The 100 Mb Ethernet unit’s management ports are located on the front panel)
WARNING: (1 Gig and 10 Gig Ethernet units only) Infra-red radiation is emitted
from aperture ports of single mode or multi-mode transceivers when no cable is
connected. Avoid exposure and do not stare into the open apertures. Apertures
should be covered when not in use.
Power on the Datacryptor
The Datacryptor software is factory-installed on the appliance. The bootable image is stored on
compact flash. Applying power to the Datacryptor initializes the system, which includes:
• Initializing the components
• Performing hardware diagnostics
• Loading the software
• Diagnostic Boot sequence
To power on the Datacryptor
1. The 1 Gig and 10 Gig Ethernet Datacryptor appliances are supplied with two separate hot
swappable power supply units. The 100 Mb Ethernet units have a single fixed power
supply unit. The power supply units for all models of Datacryptor can be either AC or DC
(-48 V).
2. The AC power supplies are auto-sensing 100 to 240 Volts 50 to 60 Hz.
3. Before applying power to the Datacryptor verify that the voltage shown on the UL label
affixed to the unit’s back panel is appropriate for your site.
CAUTION: If the voltage of the Datacryptor is inappropriate for
your site, do not apply power to the appliance. Contact Customer
Support immediately.
Page 22 THALES
Datacryptor Ethernet User Manual Installation
4. On the Datacryptor’s rear panel, plug the power cords into the power receptacles. Attach
the opposite ends to a power source.
The power LED illuminates when the unit is powered up. The Diagnostic Boot sequence
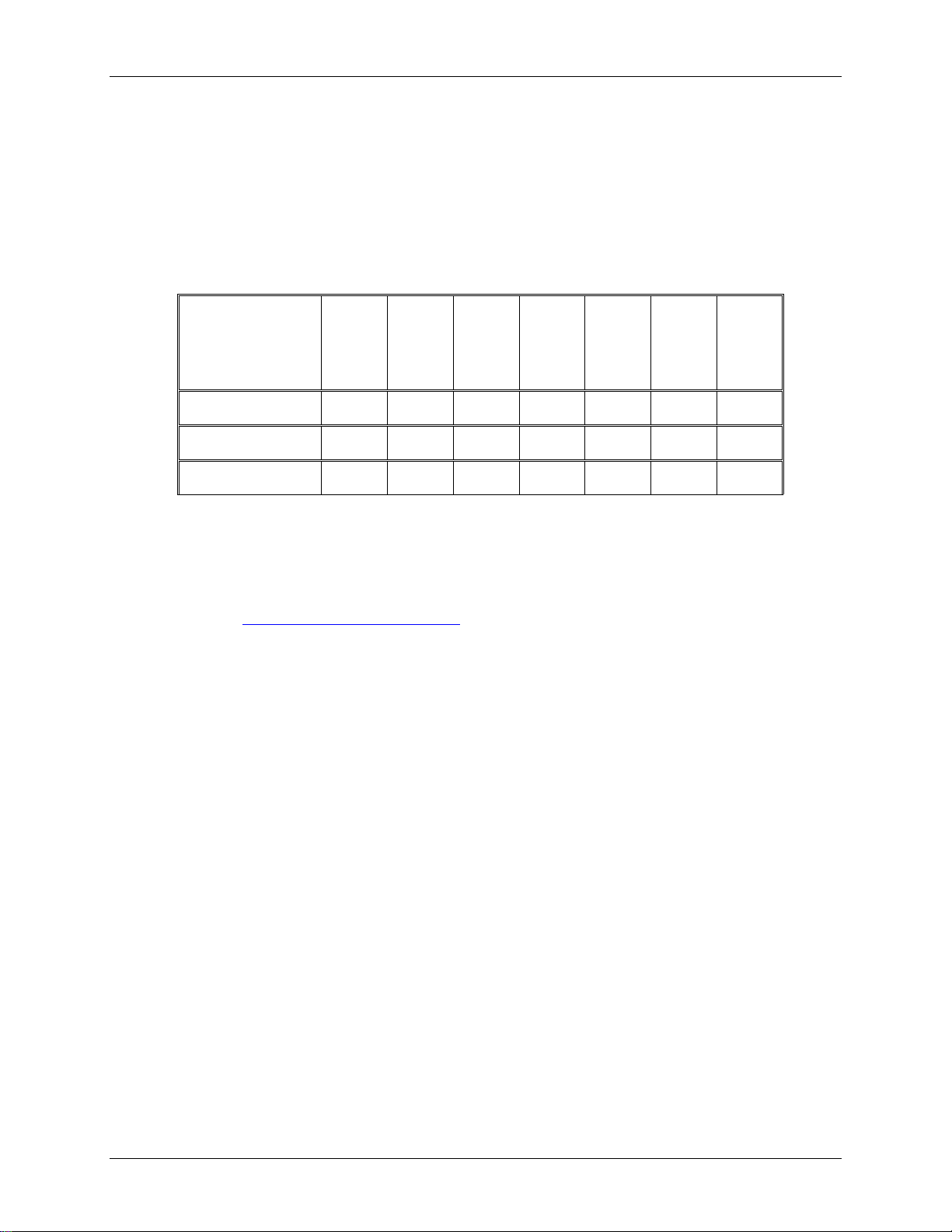
allows the LEDs to be checked and the unit type to be verified. The sequence follows this
pattern:
− All LEDs on for one second.
− A pattern which indicates the unit type for one second.
− All LEDs on for one second.
Unit Type
100 Mb Ethernet
1 Gig Ethernet
10 Gig Ethernet
Where, X is LED on, and _ is LED off.
During the boot process the Datacryptor discards all traffic on its data ports.
If the boot process fails the Error LED illuminates and the Datacryptor generates a critical Error
trap. If you experience a problem during the system initialization, see the troubleshooting
information in
Appendix G: Troubleshooting.
Network
_ X _ _ X X _
_ X _ _ X _ _
_ X _ _ X _ X
Error
Loopback
Alarm
Encrypt
Plain
Host
Software Installation
There are two software programs, the firmware resident in the Datacryptor Ethernet unit and
the Element manager software.
The firmware provides the units functionality and is pre-installed. The unit has the ability to
upgrade with new firmware, offering new features, without the requirement of returning the
unit to Thales. Instructions on the Firmware Upgrade ability will be provided with any upgrade.
The Element Manager software is provided on the supplied CD-ROM and must be installed as
directed below.
Requirements
The PC to be used for running the Element Manager must meet these minimum requirements:
• The PC must be an IBM PC or compatible that meets the minimum requirements for
running the following version of Microsoft Windows:
− Microsoft Windows XP, Service Pack 2 or higher (32 and 64 bit versions).
− Note: The software may install and run on older Windows platforms, but due to
Microsoft’s Support Lifecycle policy, we may be unable to support installation and
runtime issues on these older platforms. Please refer to the Microsoft Support
Lifecycle support web page at: http://support.microsoft.com/gp/lifecycle.
1270A450-005 - June 2008 Page 23

Installation Datacryptor Ethernet User Manual
• The PC must have a pointing device (mouse), a CD ROM drive, a free serial port, and at
least 228 Mb hard disk space (for the software and data files). If you want to install the
Adobe Acrobat reader (included on the CD to view the manuals) this will require a
further 10 MB of hard disk space.
• The user should ensure that there is at least 5Mb of memory for each copy of the Front
Panel Viewer being run concurrently.
• The PC must be able to reach the Datacryptor on the Ethernet network, or alternatively
be connected to the unit via a serial cable to the unit’s control port.
Installation Procedure
To install the Element Manager on the PC:
• Insert the CD-ROM containing the Element Manager software into your PC.
• This will auto-start the installation page. Select the "Install the Datacryptor Element
Manager Software" link OR run the program ‘setup.exe’ from the root directory on the
CD.
• Follow the instructions displayed by the installation manager.
Page 24 THALES

Datacryptor Ethernet User Manual Connecting to Datacryptor Ethernet Units
6 Connecting to Datacryptor Ethernet Units
There are three methods of connecting to the Datacryptor Ethernet units: Element Manager,
serial connection to CLI, and SNMP.
The Element Manager GUI application is used to manage and configure the Datacryptor Ethernet
device(s). It connects to the Datacryptor via the 10/100 Ethernet Management port.
A serial connection can be made to the Datacryptor Ethernet to interface to a text-based
Command Line Interface (CLI). This serial interface can also be used to access the element
manager software.
A third-party SNMP Version 1, Version 2c, or Version 3 compliant network management
application can collect and display performance monitoring data, but may not alter any system
level parameters. The only supported configuration tasks are those associated with SNMPv3
user and view based access control. SNMP traps are issued as Version 3 and authentication and
encryption are supported.
Users
The Datacryptor Ethernet will encrypt everything passed to it from the host network and place it
onto the public network. Because of this there is no need to create secure users for the
Datacryptor Ethernet, as anyone sending information will automatically use the Datacryptor
Ethernet unit.
The people who administrate and configure the Datacryptor Ethernet do need to be secure and
need to be authenticated using secure methods. Certificates are loaded into the Datacryptor
Ethernet units that have keys used to sign messages between the PC used for configuration and
the units themselves. The AES keys used to encrypt and decrypt the data being passed between
Datacryptor units are automatically generated using Diffie Hellman and the supplied Diffie
Hellman parameters.
When first installing the Datacryptor, use the default password. Thales strongly recommends
that the Administrator changes the password before the unit is put in service and changes from
the Universal CA to their own custom CA to ensure maximum security (see the
Password dialog section). Passwords are case-sensitive.
Change
IP Parameter Configuration via a Serial Connection
When shipped, a Datacryptor Ethernet device has the following port settings:
Port IP address Net Mask
Control 2.2.2.2 255.0.0.0
Ethernet management 255.0.0.0 255.255.255.255
Network 1.n.n.n 255.0.0.0
To change the parameters follow the steps below:
1. Connect the Datacryptor’s RS-232 craft port directly to the terminal’s serial port using
the supplied DB-9 serial cable.
1270A450-005 - June 2008 Page 25
Connecting to Datacryptor Ethernet Units Datacryptor Ethernet User Manual
2. Open a terminal session through a VT-100 terminal emulation program such as
HyperTerminal. Enter the connection name, the appropriate serial port (usually COM1 or
COM2), and the following serial port parameters:
Serial Port Parameter Value
Baud Speed 115,200
Parity None
Data Bits 8
Stop Bits 1
Flow Control None
3. Switch on the Datacryptor unit.
4. As the unit boots the message CONFIG STARTUP Y/N will be shown and all the units
LEDs will be lit.
5. Press Y the unit will respond by displaying a short banner and the prompt IPCONFIG>.
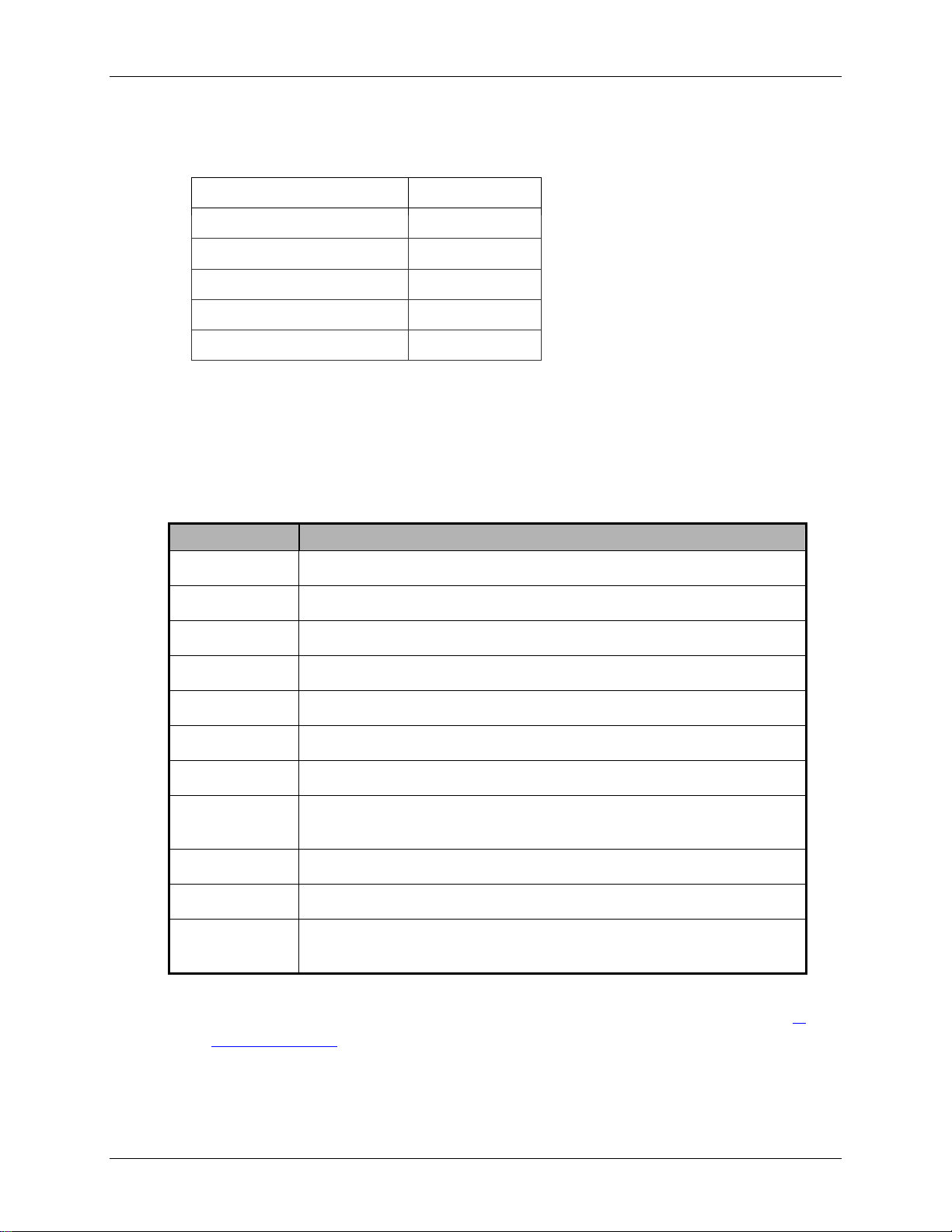
6. At the command prompt, type Help for a list of commands available.
Command Description
HELP Display help for a command
HELPKEYS List of keyboard usage in this command interface
DEFAULT Return all IP address and net mask settings to defaults.
DISPLAY Display current IP address and net mask settings
IPFORWARD Enable or disable IP forwarding
ROUTE Add, delete, or display IP routing data
SET Set an IP address and net mask settings
SETTIME Display or set the unit time (Un-commissioned Datacryptor
Ethernet unit)
SHOWLOG Basic display of log contents
VERSIONS Display version numbers of application and bootstrap
EXIT Exit the process and reboot the unit if a parameter has been
changed, or just exit if no changes have been made.
Note: Before setting the Management port’s parameters, you may want to read the IP
Management tab section for some background knowledge on their values.
Page 26 THALES

Datacryptor Ethernet User Manual Connecting to Datacryptor Ethernet Units
7. At the IPCONFIG> prompt, type:
SET <port> <ip address> <subnet mask>
where: <port> identifies the port to be set and is one of the following:
− NETWORK (public network port),
− CONTROL (serial control port),
− ETHERNET (Ethernet management port).
<ipaddr> is IP address of a subnet to be added or deleted.
<netmask value> is netmask of the subnet.
Examples
Set Control 2.2.2.2 255.255.0.0
Sets the Control (serial port) IP Address to 2.2.2.2
Set network 3.4.5.6 255.255.0.0
Sets the network port IP Address to 3.4.5.6
255.255.0.0
Note: - No two IP addresses should be the same
- IP addresses of 127.x.x.x are not allowed.
- Net masks of 0.0.0.0 and 255.255.255.255 are not allowed.
- Public and Private port addresses must be valid Class A, B or C addresses. For
this reason subnet masks must comprise of consecutive
side when represented in binary, for example 255.255.1.0 is invalid.
To make the unit request an Ethernet Management Port IP address from a DHCP/BOOTP server
on the LAN, set its Ethernet Management Port IP address to 255.0.0.0 and net mask to
255.255.255.255 (this is an exception to the rule mentioned in the note above).
To reset the addresses to factory defaults, use the DEFAULT command.
The above section details the steps necessary to connect via the Ethernet management port.
1s from the left hand
Dial Up Networking
It is also possible to connect and run the Element Manager program via the serial Control port
using Dial up Networking.
1. Ensure a serial cable is connected between your PC and the Datacryptor Ethernet unit.
2. Use the Networking wizard for your operating system to generate a Dial up connection;
the following parameters should be used for the settings:
− Set up an advanced connection
− Connect directly to another computer
− Guest
− Connection Name
− Select the Com port to which you have connected the serial cable
− All users
− User Name and Password
3. Select the option for Desktop shortcut.
4. Select Finish.
1270A450-005 - June 2008 Page 27
Connecting to Datacryptor Ethernet Units Datacryptor Ethernet User Manual
5. Click on the shortcut to launch the connection.
6. Select the Properties button.
7. On the General tab confirm correct connection.
8. Click Configure button and use the menu to set the maximum connection speed of
115200 bps. Set the flow control to none; the Ethernet and SONET do not support flow
control.
9. On the Network tab, select TCP/IP and click Properties - enter the address 2.2.2.1.
10. Close down the Properties and click Connect.
11. A connection with the Datacryptor Ethernet will be made. Ensure the connection is made
then disconnect.
Adding a Unit to Element Manager
Once the Management or Dial up connection is set up, you can connect to each Datacryptor
Ethernet unit by adding an icon in the Element Manager. The Dial Up connection created earlier
must be running if a serial connection is to be used.
1. Start the Element Manager, e.g. by double-clicking its icon:
2. The Element Manager Main Window will be displayed:
3. Add a new Datacryptor Ethernet unit by clicking on the New Unit icon
the New Unit option from the File menu. This will launch the Add a New Unit Wizard:
or selecting
Page 28 THALES
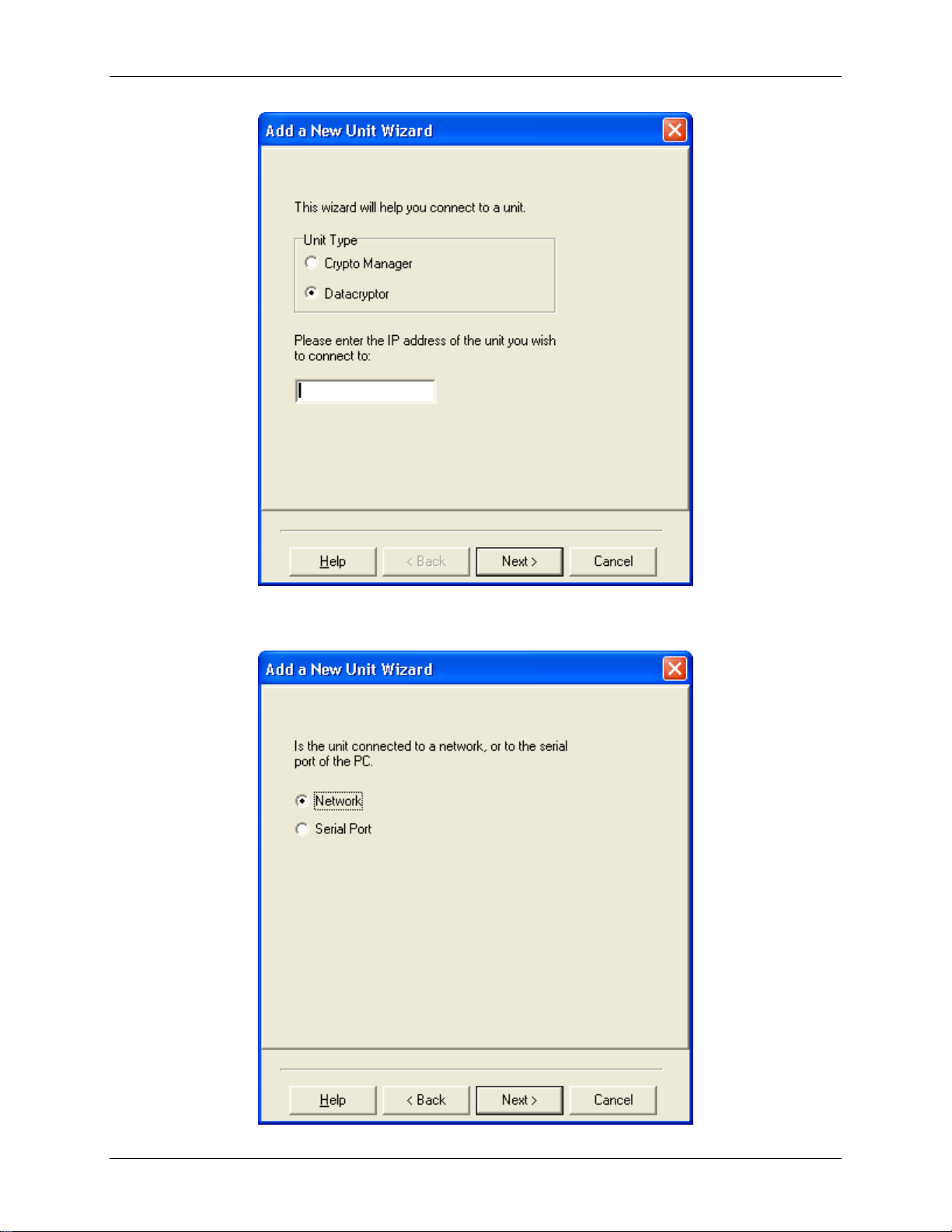
Datacryptor Ethernet User Manual Connecting to Datacryptor Ethernet Units
4. Select the unit type as Datacryptor and enter the IP address of the Datacryptor Ethernet
unit. Press Enter or select Next to continue.
1270A450-005 - June 2008 Page 29

Connecting to Datacryptor Ethernet Units Datacryptor Ethernet User Manual
5. Select the connection type for the Datacryptor Ethernet unit; press Enter or click on Next
to continue.
6. The application will attempt to connect to the specified IP address and - if successful -
display the unit's Unit Name by way of confirmation, as above. Type a descriptive name
for the connection in the edit box (this will be shown in the main window below its icon).
7. Click Finish or press Enter to finish adding the new connection and Datacryptor icon,
which will be displayed as a new icon in the main window like this:
Page 30 THALES
 Loading...
Loading...