Page 1

Hardware and Software User Manual
Revision Date: 3/14/2017
Page 2

TELEDYNE LECROY
Copyright © 2017 Teledyne LeCroy, Inc.
Frontline, Frontline Test System, ComProbe Protocol Analysis System and ComProbe are registered
trademarks of Teledyne LeCroy, Inc.
The following are trademarks of Teledyne LeCroy, Inc.
l BPA 600™
l Audio Expert System™
l Audio Rating Metric™
l ProbeSync™
The Bluetooth SIG, Inc. owns the Bluetooth® word mark and logos, and any use of such marks by Teledyne
LeCroy, Inc. is under license.
All other trademarks and registered trademarks are property of their respective owners.
i Frontline BPA 600 Hardware & Software User Manual
Page 3

TELEDYNE LECROY
Contents
Chapter 1 Frontline Hardware & Software 1
1.1 What is in this manual 2
1.2 Computer Minimum System Requirements 2
1.3 Software Installation 2
Chapter 2 Getting Started 3
2.1 BPA 600 Hardware 3
2.1.1 Attaching Antennas 3
2.1.2 Connecting/Powering the Frontline BPA 600 Hardware 4
2.1.3 BPA 600 ProbeSync 4
2.2 Data Capture Methods 5
2.2.1 Opening Data Capture Method 5
2.2.2 Frontline BPA 600 Data Capture Methods 7
2.2.3 Frontline ProbeSync™ for Coexistence and Multiple Frontline Device Capture 8
2.2.4 Virtual Sniffing 8
2.3 Control Window 9
2.3.1 Control Window Toolbar 9
2.3.2 Configuration Information on the Control Window 10
2.3.3 Status Information on the Control Window 10
2.3.4 Frame Information on the Control Window 11
2.3.5 Control Window Menus 11
2.3.6 Minimizing Windows 15
Chapter 3 Configuration Settings 16
3.1 BPA 600 Configuration and I/O 16
3.1.1 BPA 600 - Update Firmware 16
3.1.2 BPA 600 IO Datasource Settings 17
3.2 Decoder Parameters 40
3.2.1 Decoder Parameter Templates 42
3.2.2 Selecting A2DP Decoder Parameters 44
3.2.3 AVDTP Decoder Parameters 44
3.2.4 L2CAP Decoder Parameters 48
3.2.5 RFCOMM Decoder Parameters 50
3.3 Mesh Security 53
3.4 Conductive Testing 58
Frontline BPA 600 Hardware & Software User Manual ii
Page 4

TELEDYNE LECROY
3.4.1 Classic Bluetooth Transmitter Classes 58
3.4.2 Bluetooth low energy Transmitter 59
3.4.3 BPA 600 Conductive Testing 59
3.4.4 Bluetooth Conductive Test Process 60
Chapter 4 Capturing and Analyzing Data 62
4.1 Capture Data 62
4.1.1 Air Sniffing: Positioning Devices 62
4.1.2 Capturing Data with BPA 600 Analyzer 65
4.1.3 Combining BPA 600, 802.11, and HSU with ProbeSync 68
4.1.4 Extended Inquiry Response 70
4.2 Protocol Stacks 71
4.2.1 Protocol Stack Wizard 71
4.2.2 Creating and Removing a Custom Stack 72
4.2.3 Reframing 73
4.2.4 Unframing 73
4.2.5 How the Analyzer Auto-traverses the Protocol Stack 74
4.2.6 Providing Context For Decoding When Frame Information Is Missing 74
4.3 Analyzing Protocol Decodes 75
4.3.1 The Frame Display 75
4.3.2 Bluetooth Timeline 111
4.3.3 low energy Timeline 126
4.3.4 Coexistence View 143
4.3.5 Message Sequence Chart (MSC) 172
4.4 Packet Error Rate Statistics 182
4.4.1 Packet Error Rate - Channels (Classic and low energy) 183
4.4.2 Packet Error Rate - Pie Chart and Expanded Chart 185
4.4.3 Packet Error Rate - Legend 186
4.4.4 Packet Error Rate - Additional Statistics 187
4.4.5 Packet Error Rate - Sync Selected Packets With Other Windows 187
4.4.6 Packet Error Rate - Export 188
4.4.7 Packet Error Rate - Scroll Bar 188
4.4.8 Packet Error Rate - Excluded Packets 190
4.5 Bluetooth Audio Expert System™ 190
4.5.1 Supported Codec Parameters 192
iii Frontline BPA 600 Hardware & Software User Manual
Page 5

TELEDYNE LECROY
4.5.2 Starting the AudioExpert System (BPA 600 only) 192
4.5.3 Operating Modes 193
4.5.4 Audio Expert System™ Event Type 200
4.5.5 Audio Expert System™ Window 208
4.5.6 Frame, Packet, and Protocol Analysis Synchronization 222
4.6 Bluetooth Protocol Expert System 223
4.6.1 Starting the Bluetooth Protocol Expert System 223
4.6.2 Bluetooth Protocol Expert System Window 224
4.7 Analyzing Byte Level Data 232
4.7.1 Event Display 232
4.7.2 The Event Display Toolbar 232
4.7.3 Opening Multiple Event Display Windows 234
4.7.4 Calculating CRCs or FCSs 234
4.7.5 Calculating Delta Times and Data Rates 234
4.7.6 Switching Between Live Update and Review Mode 235
4.7.7 Data Formats and Symbols 235
4.8 Data/Audio Extraction 239
Chapter 5 Navigating and Searching the Data 243
5.1 Find 243
5.1.1 Searching within Decodes 244
5.1.2 Searching by Pattern 246
5.1.3 Searching by Time 247
5.1.4 Using Go To 249
5.1.5 Searching for Special Events 251
5.1.6 Searching by Signal 252
5.1.7 Searching for Data Errors 254
5.1.8 Find - Bookmarks 257
5.1.9 Changing Where the Search Lands 258
5.1.10 Subtleties of Timestamp Searching 258
5.2 Bookmarks 259
5.2.1 Adding, Modifying or Deleting a Bookmark 259
5.2.2 Displaying All and Moving Between Bookmarks 260
Chapter 6 Saving and Importing Data 262
6.1 Adding Comments to a Capture File 262
Frontline BPA 600 Hardware & Software User Manual iv
Page 6

TELEDYNE LECROY
6.2 Confirm Capture File (CFA) Changes 262
6.3 Loading and Importing a Capture File 263
6.3.1 Loading a Capture File 263
6.3.2 Importing Capture Files 263
6.4 Printing 264
6.4.1 Printing from the Frame Display/HTML Export 264
6.4.2 Printing from the Event Display 266
6.5 Exporting 267
6.5.1 Frame Display Export 267
6.5.2 Exporting a File with Event Display Export 268
Chapter 7 General Information 271
7.1 System Settings and Progam Options 271
7.1.1 System Settings 271
7.1.2 Changing Default File Locations 274
7.1.3 Side Names 276
7.1.4 Timestamping 277
7.2 Technical Information 279
7.2.1 Performance Notes 279
7.2.2 BTSnoop File Format 280
7.2.3 Ring Indicator 282
7.2.4 Progress Bars 283
7.2.5 Event Numbering 283
7.2.6 Useful Character Tables 283
7.2.7 DecoderScript Overview 285
7.2.8 Bluetooth low energy ATT Decoder Handle Mapping 286
Contacting Frontline Technical Support 287
Appendicies 289
Appendix A: Application Notes 290
A.1 Audio Expert System: aptX 'hiccup' Detected 291
A.1.1 Background 291
A.1.2 Test Setup 291
A.1.3 Discussion 292
A.1.4 Conclusions 295
A.2 Getting the Android Link Key for Classic Decryption 297
v Frontline BPA 600 Hardware & Software User Manual
Page 7

TELEDYNE LECROY
A.2.1 What You Need to Get the Android Link Key 297
A.2.2 Activating Developer options 297
A.2.3 Retrieving the HCI Log 298
A.2.4 Using the ComProbe Software to Get the Link Key 299
A.3 Decrypting Encrypted Bluetooth®data with ComProbe BPA 600 303
A.3.1 How Encryption Works in Bluetooth 303
A.3.2 Legacy Pairing (Bluetooth 2.0 and earlier) 303
A.3.3 Secure Simple Pairing (SSP) (Bluetooth 2.1 and later) 305
A.3.4 How to Capture and Decrypt Data (Legacy Pairing) 305
A.3.5 How to tell if a device is in Secure Simple Pairing Debug Mode 307
A.4 Decrypting Encrypted Bluetooth® low energy 311
A.4.1 How Encryption Works in Bluetooth low energy 311
A.4.2 Pairing 311
A.4.3 Pairing Methods 312
A.4.4 Encrypting the Link 313
A.4.5 Encryption Key Generation and Distribution 313
A.4.6 Encrypting The Data Transmission 314
A.4.7 Decrypting Encrypted Data Using Frontline® BPA 600 low energy Capture 314
A.5 Bluetooth® low energy Security 321
A.5.1 How Encryption Works in Bluetooth low energy 322
A.5.2 Pairing 322
A.5.3 Pairing Methods 323
A.5.4 Encrypting the Link 324
A.5.5 Encryption Key Generation and Distribution 324
A.5.6 Encrypting The Data Transmission 325
A.5.7 IRK and CSRK Revisited 325
A.5.8 Table of Acronyms 326
A.6 Bluetooth Virtual Sniffing 327
A.6.1 Introduction 327
A.6.2 Why HCI Sniffing and Virtual Sniffing are Useful 327
A.6.3 Bluetooth Sniffing History 328
A.6.4 Virtual Sniffing—What is it? 328
A.6.5 The Convenience and Reliability of Virtual Sniffing 329
A.6.6 How Virtual Sniffing Works 329
Frontline BPA 600 Hardware & Software User Manual vi
Page 8

TELEDYNE LECROY
A.6.7 Virtual Sniffing and Bluetooth Stack Vendors 329
A.6.8 Case Studies: Virtual Sniffing and Bluetooth Mobile Phone Makers 330
A.6.9 Virtual Sniffing and You 330
vii Frontline BPA 600 Hardware & Software User Manual
Page 9

Chapter 1 Frontline Hardware & Software
Frontline Test Equipment family of protocol analyzers work with the following technologies.
l Classic Bluetooth
l Bluetooth low energy
l Dual Mode Bluetooth (simultaneous Classic and low energy)
l Bluetooth Coexistence: Bluetooth with 802.11 Wi-Fi
l Bluetooth HCI (USB, SD, High Speed UART)
l NFC
l 802.11 (Wi-Fi)
l SD
l HSU (High Speed UART)
The Frontline hardware interfaces with your computer that is running our robust software engine called the
ComProbe Protocol Analysis System or Frontline software. Whether you are sniffing the air or connecting
directly to the chip Frontline analyzers use the same powerful Frontline software to help you test,
troubleshoot, and debug communications faster.
Frontline software is an easy to use and powerful protocol analysis platform. Simply use the appropriate
Frontline hardware or write your own proprietary code to pump communication streams directly into the
Frontline software where they are decoded, decrypted, and analyzed. Within the Frontline software you see
packets, frames, events, coexistence, binary, hex, radix, statistics, errors, and much more.
This manual is a user guide that takes you from connecting and setting up the hardware through all of the
Frontline software functions for your Frontline hardware. Should you have any questions contact the
Frontline Technical Support Team.
Frontline BPA 600 Hardware & Software User Manual 1
Page 10

TELEDYNE LECROY Chapter 1 Frontline Hardware & Software
1.1 What is in this manual
The Frontline User Manual comprises the following seven chapters. The chapters are organized in the
sequence you would normally follow to capture and analyze data: set up, configure, capture, analyze, save.
You can read them from beginning to end to gain a complete understanding of how to use the Frontline
hardware and software or you can skip around if you only need a refresher on a particular topic. Use the
Contents, Index, and Glossary to find the location of particular topics.
l Chapter 1 Frontline Hardware and Software. This chapter will describe the minimum computer
requirements and how to install the software.
l Chapter 2 Getting Started. Here we describe how to set up and connect the hardware, and how to apply
power. This chapter also describes how to start the Frontline software in Data Capture Methods. You will
be introduced to the Control window that is the primary operating dialog in the Frontline software.
l Chapter 3 Configuration Settings. The software and hardware is configured to capture data. Configuration
settings may vary for a particular Frontline analyzer depending on the technology and network being
sniffed. There are topics on configuring protocol decoders used to disassemble packets into frames and
events.
l Chapter 4 Capturing and Analyzing Data. This Chapter describes how to start a capture session and how
to observe the captured packets, frames, layers and events.
l Chapter 5 Navigating and Searching the Data. Here you will find how to move through the data and how
to isolate the data to specific events, often used for troubleshooting device design problems.
l Chapter 6 Saving and Importing Data. When a live capture is completed you may want to save the
captured data for future analysis, or you may want to import a captured data set from another developer
or for use in interoperability testing. This chapter will explain how to do this for various data file formats.
l Chapter 7 General Information. This chapter provides advanced system set up and configuration
information, timestamping information, and general reference information such as ASCII, baudot, and
EBCDIC codes. This chapter also provides information on how to contact Frontline's Technical Support
team should you need assistance.
1.2 Computer Minimum System Requirements
Frontline supports the following computer systems configurations:
l Operating System: Windows 7/8/10
l USB Port: USB 2.0 High-Speed or or later
The Frontline software must operate on a computer with the following minimum characteristics.
l Processor: Core i5 processor at 2.7 GHz
l RAM: 4 GB
l Free Hard Disk Space on C: drive: 20 GB
1.3 Software Installation
Download the installation software from FTE.com. Once downloaded, double-click the installer and follow the
directions.
Use this link: http://www.fte.com/bpa600-soft.
2 Frontline BPA 600 Hardware & Software User Manual
Page 11

Chapter 2 Getting Started
In this chapter we introduce you to the Frontline hardware and show how to start the Frontline analyzer
software and explain the basic software controls and features for conducting the protocol analysis.
2.1 BPA 600 Hardware
2.1.1 Attaching Antennas
When you remove the Frontline BPA 600 hardware from the box, the first step is to attach the antennas
(Figure 2.1).
Figure 2.1 - BPA 600 Antenna Connectors
1. Attach antennas to the SMA connectors.
Figure 2.2 - Frontline BPA 600 with both antennas attached
Frontline BPA 600 Hardware & Software User Manual 3
Page 12

TELEDYNE LECROY Chapter 2 Getting Started
2.1.1.1 Status LED
The Frontline BPA 600 has two Status LEDs on the RF panel. In the front panel center are the LOW ENERGY
and BR/EDR LEDs.
Figure 2.3 - BPA 600 Hardware LEDs
Table 2.1 - Frontline BPA 600 LED Status
LED Color Frontline BPA 600 Activity
LED Off Frontline BPA 600 device is idle.
Green Frontline BPA 600 is actively sniffing waiting for configured devices to connect.
Blue The configured devices have connected (Asynchronous Connectionless Link (ACL)).
Intermittent
Blue
Configured devices are in "Sniff mode" (slave is listening at a reduced rate, conserving
device power).
2.1.2 Connecting/Powering the Frontline BPA 600 Hardware
Once you have attached the antennas, the next step is to power up and connect the Frontline BPA 600
hardware to the computer.
1. Insert the USB cable into the USB port on the Frontline BPA 600 hardware. The Frontline BPA 600
analyzer requires no external power (Figure 2.4).
Figure 2.4 - BPA 600 USB Connector
2. Insert the other end of the USB cable into the PC.
The next thing to do is to turn on the devices that you will be testing.
2.1.3 BPA 600 ProbeSync
Any Frontline hardware with ProbeSync™ can be connected together to run off of a common clock, ensuring
precise timestamp synchronization.
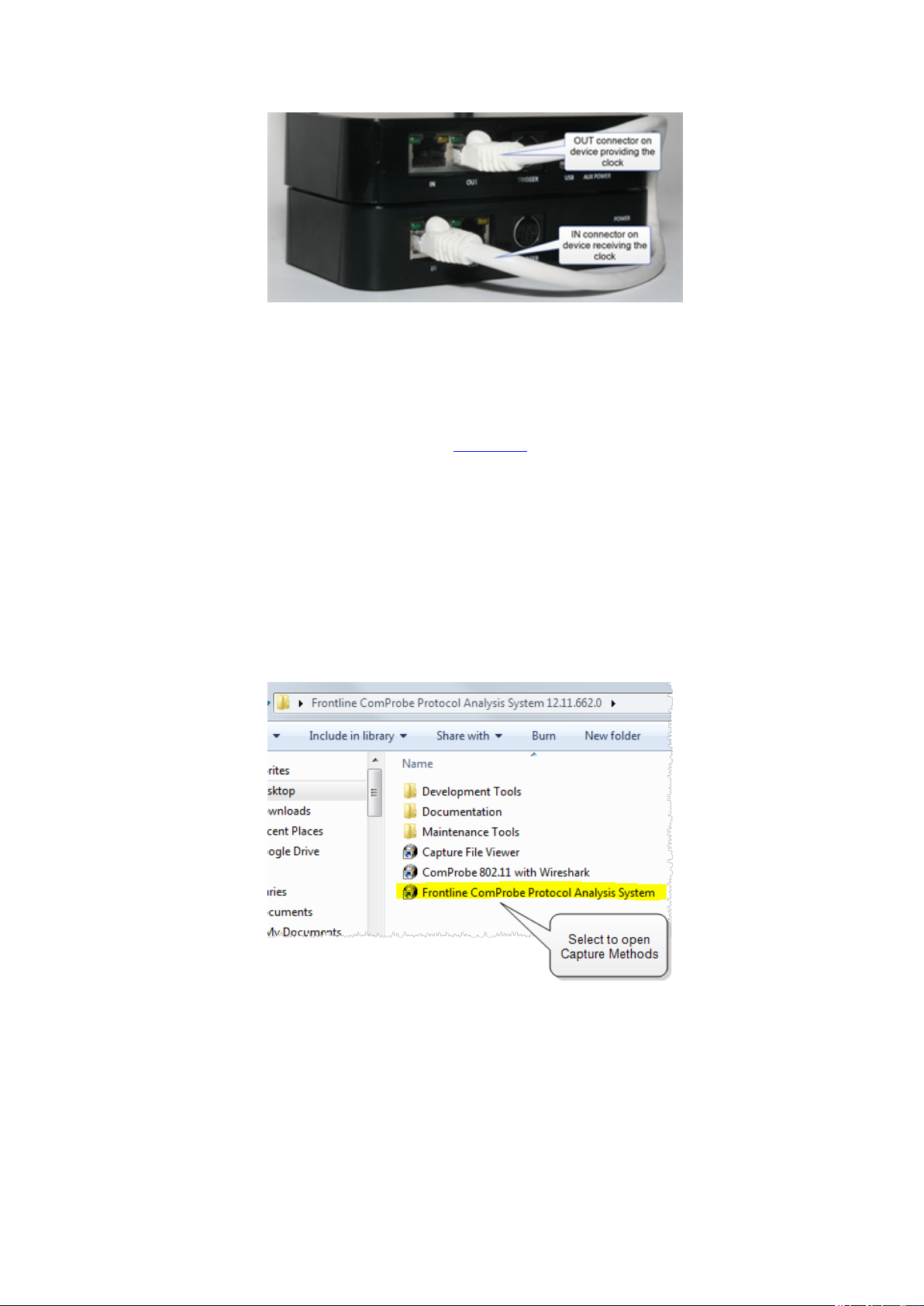
Simply plug the supplied Cat 5 cable into the OUT connector on the sniffer that will be supplying the clock
and connect the other end to the IN connector on the sniffer receiving the clock. ( Figure 2.5 - ). If using a
BPA 600 analyzer with a different Frontline analyzer, the BPA 600 analyzer must provide the clock. Combined
cable length of all the ProbeSync cables connected at a given time should not exceed 1.5 meters (4.5 feet).
4 Frontline BPA 600 Hardware & Software User Manual
Page 13
Chapter 2 Getting Started TELEDYNE LECROY
Figure 2.5 - BPA 600 Hardware ProbeSync connection
Connect the CAT 5 cable before connecting the USB cable to the BPA 600 hardware. If you must change the
ProbeSync connections it may be necessary to cycle the power to the devices to ensure proper
synchronization.
Should the CAT5 cable be connected incorrectly, that is OUT to OUT or IN to IN, an error message will
appear when the BPA 600 software is run. Refer to on page 67
2.2 Data Capture Methods
This section describes how to load TELEDYNE LECROY Frontline Protocol Analysis System software, and how
to select the data capture method for your specific application.
2.2.1 Opening Data Capture Method
On product installation, the installer creates a folder on the windows desktop labeled "Frontline <version #>".
1. Double-click the " Frontline <version #>" desktop folder
This opens a standard Windows file folder window.
Figure 2.6 - Desktop Folder Link
2. Double-click on Frontline ComProbe Protocol Analysis System and the system displays the Select
Data Capture Method... dialog.
Frontline BPA 600 Hardware & Software User Manual 5
Page 14

TELEDYNE LECROY Chapter 2 Getting Started
Note: You can also access this dialog by selecting Start > All Programs > Frontline
(Version #) > Frontline ComProbe Protocol Analysis System
Figure 2.7 - Example: Select Data Capture Method..., BPA 600
Three buttons appear at the bottom of the dialog; Run, Cancel, and Help.
Select Data Capture Method dialog buttons
Button Description
Becomes active when a capture method is selected. Starts the selected capture
method.
Closes the dialog and exits the user back to the computer desktop.
Opens Frontline Help. Keyboard shortcut: F1.
3. Expand the folder and select the data capture method that matches your configuration.
4. Click on the Run button and the Frontline Control Window will open configured to the selected
capture method.
Note: If you don't need to identify a capture method, then click the Run button to start the
analyzer.
Creating a Shortcut
A checkbox labeled Create Shortcut When Run is located near the
bottom of the dialog. This box is un-checked by default. Select this
checkbox, and the system creates a shortcut for the selected method, and
6 Frontline BPA 600 Hardware & Software User Manual
Page 15
Chapter 2 Getting Started TELEDYNE LECROY
places it in the "Frontline ComProbe Protocol Analysis System <version#>" desktop folder and in the start
menu when you click the Run button. This function allows you the option to create a shortcut icon that can be
placed on the desktop. In the future, simply double-click the shortcut to start the analyzer in the associated
protocol.
Supporting Documentation
The Frontline <version #>directory contains supporting documentation for development (Automation,
DecoderScript™, application notes), user documentation (Quick Start Guides and the Frontline User Manual),
and maintenance tools.
2.2.2 Frontline BPA 600 Data Capture Methods
Frontline Protocol Analysis System has different data capture methods to accommodate various applications.
Figure 2.8 - BPA 600 Data Capture Dialog
l BR/EDR - low energy Air Sniffing
l This method requires one Frontline BPA 600 and is used to capture combined BR/EDR and Bluetooth® low
energy data.
l Used for typical applications to capture Classic Bluetooth and Bluetooth low energy data.
l Modes include:
l LE Only - Bluetooth low energy only
l Classic Only Single Connection
l Dual Mode - Classic Bluetooth and Bluetooth low energy.
l Classic Only Multiple Connections
Frontline BPA 600 Hardware & Software User Manual 7
Page 16

TELEDYNE LECROY Chapter 2 Getting Started
l Classic/low energy/802.11 Air Sniffing (optional)
l Two 802.11 and One BPA600
l This method requires one Frontline BPA 600 and two Frontline 802.11 hardware.
l An Frontline 802.11 hardware is included with the Wi-Fi Option.
l Used for Bluetooth Classic/low energy/802.11 coexistence analysis.
l Captures Bluetooth Classic, low energy, and 802.11 data and displays in the Frame Display and
Coexistence View.
l 802.11/Classic/low energy Coexistence
l This method requires one Frontline BPA 600 and one Frontline 802.11 hardware.
l Captures Bluetooth Classic, low energy, and 802.11 data and displays in the Frame Display and
Coexistence View.
2.2.3 Frontline ProbeSync™ for Coexistence and Multiple Frontline Device Capture
ProbeSync™ allows multiple Frontline analyzers to work seamlessly together and to share a common clock.
Clock sharing allows the analyzers to precisely synchronize communications streams and to display resulting
packets in a single shared or coexistent view.
l Classic and low energy Bluetooth sniffing, and 802.11
l ProbeSync configurations include
o
Two BPA 600 units
o
One BPA 600 unit and one 802.11 unit.
o
One BPA 600 unit and one HSU unit.
o
One BPA 600 unit, one HSU unit, one 802.11 unit
Refer to the Frontline product for specific information on using ProbeSync.
2.2.4 Virtual Sniffing
The Virtual Sniffer is a live import facility within Frontline®software that makes it possible to access any layer
in a stack that the programmer has access to and feed this data into the Virtual Sniffer. Please refer to the
“Show Live Import Information“button on the Virtual Sniffer Datasource window in Frontline software. More
information is available in the Live Import Developer's Kit located in the Development Tools folder in Frontline
Protocol Analysis System desktop folder, and a white paper is available at Bluetooth Virtual Sniffing
l FTS Side
o
No hardware required.
o
Frontline software acquires data via user-developed software.
l IEEE 11073+
o
No hardware required
o
for sniffing data virtually from the continua Enabling Software Library (CESL) IEEE 11073 tester.
8 Frontline BPA 600 Hardware & Software User Manual
Page 17
Chapter 2 Getting Started TELEDYNE LECROY
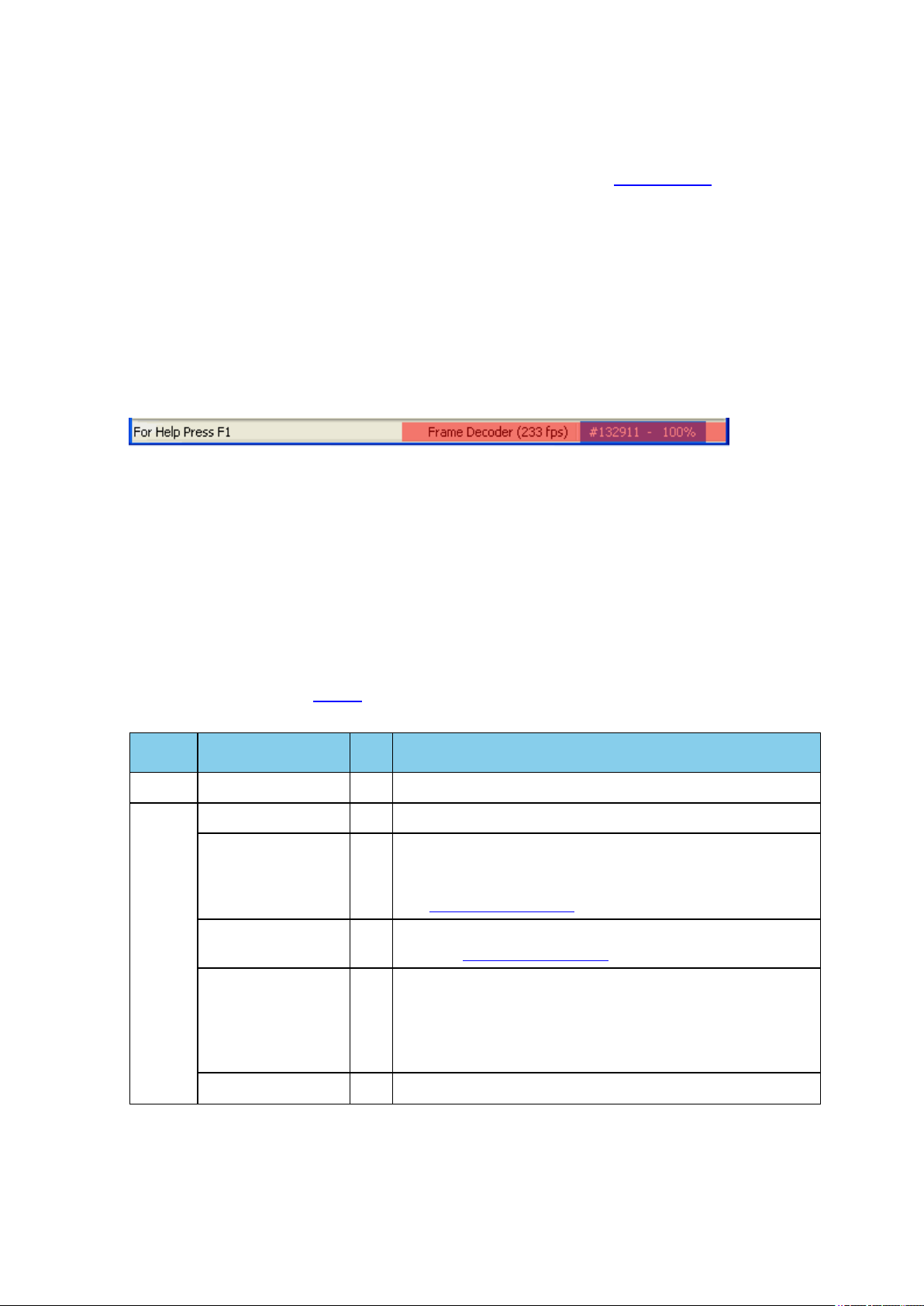
2.3 Control Window
The analyzer displays information in multiple windows, with each window presenting a different type of
information. The Control window opens when the Run button is clicked in the Select Data Capture
Method window. The Control window provides access to each Frontline analyzer functions and settings as
well as a brief overview of the data in the capture file. Each icon on the toolbar represents a different data
analysis function. A sample Control Window is shown below.
Figure 2.9 - Control Window
Because the Control window can get lost behind other windows, every window has a Home icon that
brings the Control window back to the front. Just click on the Home icon to restore the Control window.
When running the Capture File Viewer, the Control window toolbar and menus contain only those
selections needed to open a capture file and display the About box. Once a capture file is opened, the
analyzer limits Control window functions to those that are useful for analyzing data contained in the current
file. Because you cannot capture data while using Capture File Viewer, data capture functions are
unavailable. For example, when viewing Ethernet data, the Signal Display is not available. The title bar of the
Control window displays the name of the currently open file. The status line (below the toolbar) shows the
configuration settings that were in use when the capture file was created.
2.3.1 Control Window Toolbar
Toolbar icon displays vary according to operating mode and/or data displayed. Available icons appear in color,
while unavailable icons are not visible. Grayed-out icons are available for the Frontline hardware and software
configuration in use but are not active until certain operating conditions occur. All toolbar icons have
corresponding menu bar items or options.
Table 2.2 - Control Window Toolbar Icons
Icon Description
Open File - Opens a capture file.
I/O Settings - Opens settings
Save - Saves the capture file.
Clear - Clears or saves the capture file.
Event Display - (framed data only) Opens a Event Display, with the currently selected bytes
highlighted.
Frontline BPA 600 Hardware & Software User Manual 9
Page 18

TELEDYNE LECROY Chapter 2 Getting Started
Table 2.2 - Control Window Toolbar Icons (continued)
Icon Description
Frame Display - (framed data only) Opens a Frame Display, with the frame of the currently
selected bytes highlighted.
Notes - Opens the Notes dialog.
Cascade - Arranges windows in a cascaded display.
Bluetooth Packet Timeline - Opens the Packet Timeline dialog.
Coexistence View - Opens the Coexistence View dialog.
Low energy - Opens the low energy Timeline dialog.
Extract Data/Audio - Opens the Extract Data/Audio dialog.
MSC Chart - Opens the Message Sequence Chart
Bluetooth low energy Packet Error Rate Statistics - Opens the Packet Error Rate Statistics
window.
Bluetooth Classic Packet Error Rate Statistics - Opens the Packet Error Rate Statistics
window.
Protocol Expert System - Opens Bluetooth Protocol Expert System window
Audio Expert System - Opens Audio Expert System window
2.3.2 Configuration Information on the Control Window
The Configuration bar (just below the toolbar) displays the hardware configuration and may include I/O
settings. It also provides such things as name of the network card, address information, ports in use, etc.
2.3.3 Status Information on the Control Window
The Status bar located just below the Configuration bar on the Control window provides a quick look at
current activity in the analyzer.
l
o
Not Active means that the analyzer is not currently capturing data.
o
Paused means that data capture has been suspended.
o
Running means that the analyzer is actively capturing data.
l
% Used
10 Frontline BPA 600 Hardware & Software User Manual
Page 19
Chapter 2 Getting Started TELEDYNE LECROY
The next item shows how much of the buffer or capture file has been filled. For example, if you are
capturing to disk and have specified a 200 Kb capture file, the bar graph tells you how much of the
capture file has been used. When the graph reaches 100%, capture either stops or the file begins to
overwrite the oldest data, depending on the choices you made in the System Settings.
l
Utilization/Events
The second half of the status bar gives the current utilization and total number of events seen on the
network. This is the total number of events monitored, not the total number of events captured. The
analyzer is always monitoring the circuit, even when data is not actively being captured. These graphs
allow you to keep an eye on what is happening on the circuit, without requiring you to capture data.
2.3.4 Frame Information on the Control Window
Frame Decoder information is located just below the Status bar on the Control window. It displays two pieces
of information.
l Frame Decoder (233 fps) displays the number of frames per second being decoded. You can toggle this
display on/off with Ctrl-D, but it is available only during a live capture.
l #132911 displays the total frames decoded.
l 100% displays the percentage of buffer space used.
2.3.5 Control Window Menus
The menus appearing on the Control window vary depending on whether the data is being captured live or
whether you are looking at a .cfa file. The following tables describe each menu.
Table 2.3 - Control Window File Menu Selections
Mode Selection
Live
Capture
File
Close
Go Live
Reframe
Unframe
Recreate
Companion File
Hot
Key
Description
Closes Live mode.
Returns to Live mode
If you need to change the protocol stack used to interpret a
capture file and the framing is different in the new stack, you
need to reframe in order for the protocol decode to be correct.
Reframing on page 73
See
Removes start-of-frame and end-of-frame markers from your
data. See
Unframing on page 73
This option is available when you are working with decoders. If
you change a decoder while working with data, you can
recreate the ".frm file", the companion file to the ".cfa file".
Recreating the ".frm file" helps ensure that the decoders will
work properly.
Reload Decoders
The plug-ins are reset and received frames are decoded again.
Frontline BPA 600 Hardware & Software User Manual 11
Page 20
TELEDYNE LECROY Chapter 2 Getting Started
Table 2.3 - Control Window File Menu Selections (continued)
Mode Selection
Live &
Capture
File
Open Capture File
Hot
Key
Ctrl--OOpens a Windows Open file dialog. at the default location
"...\Public Documents\Frontline Test Equipment\My Capture
Files\". Capture files have a .cfa extension.
Description
Save
Exit ComProbe
Protocol Analysis
System
Recent capture files A list of recently opened capture files will appear.
The View menu selections will vary depending on the Frontline analyzer in use.
Table 2.4 - Control Window View Menu Selections
Mode Selection Hot key Description
Live &
Capture
File
Event Display
Frame Display
Bluetooth Timeline
Coexistence View
Ctrl-SSaves the current capture or capture file. Opens a Windows
Save As dialog at the default location "...\Public
Documents\Frontline Test Equipment\My Capture Files\".
Shuts down the ComProbe Protocol Analysis System and all
open system windows.
CtrlShift-E
CtrlShift-M
Opens the Event Display window for analyzing byte level
data.
Opens the Frame Display window for analyzing protocol
level data
Opens the
protocol level data in a packet chronological format and in
packet throughput graph.
Opens the
simultaneously display Classic
energy, and 802.11 packets and thourghput.
Bluetooth Timeline window
Coexistence View window
for analyzing
that can
Bluetooth,Bluetooth
low
Bluetooth low
energy Timeline
Extract Data Audio...
Bluetooth low
energy Packet Error
Rate Statistics
Classic Bluetooth
Packet Error Rate
Statistics
Bluetooth Protocol
Expert
Audio Expert
System
Opens the
analyzing protocol level data in a packet chronological
format and in packet throughput graph.
Opens the
from decoded
Opens the
show a dynamic graphical representation of the error rate
for each low energy channel.
Opens the Classic
a dynamic graphical representation of the error rate for
each channel.
Opens the
assist in the analysis of Bluetooth protocol issues.
Opens the
of detecting and reporting audio impairments.
Bluetooth low energy Timeline window
Data/Audio Extraction
Bluetooth
Bluetooth
Bluetooth Protocol Expert System window
Audio Expert System window
protocols.
low energy
Bluetooth PER Stats window
dialog for pulling data
PER Stats window
for the purpose
for
to show
to
to
12 Frontline BPA 600 Hardware & Software User Manual
Page 21
Chapter 2 Getting Started TELEDYNE LECROY
Table 2.5 - Control Window Edit Menu Selections
Mode Selection
Capture
File
Mode Selection
The following two rows apply to all Frontline products except Set in Target.
Notes
Table 2.6 - Control Window Live Menu Selections
Hot-
key
CtrlShiftO
Hot-
Key
Description
Opens the
comments to a capture file.
Notes window
Description
that allows the user to add
Live
The following rows apply to all Frontline products
Live Clear Shift-
Start Capture
Stop Capture
Shift-F5Begins data capture from the configured wireless devices.
F10 Stops data capture from the configured wireless devices.
Clears or saves the capture file.
F10
Frontline BPA 600 Hardware & Software User Manual 13
Page 22
TELEDYNE LECROY Chapter 2 Getting Started
Table 2.6 - Control Window Live Menu Selections (continued)
Mode Selection
Live &
Capture
File
Hardware Settings
I/O Settings
Hot-
Key
Description
0 - Classic
1 - Bluetooth low energy
0 - Classic
1 - Bluetooth low energy
System Settings
Directories...
Check for New
Releases at Startup
Side Names...
Protocol Stack...
Set Initial Decoder
Parameters...
AltEnter
Opens the System Settings dialog for configuring capture
files.
Opens the
the default file locations.
When this selection is enabled, the program automatically
checks for the latest Frontline protocol analyzer software
releases.
Opens the
names of the slave and master wireless devices.
Opens the
protocol stack they want the analyzer to use when
decoding frames.
Opens the
may be times when the context for decoding a frame is
missing. For example, if the analyzer captured a response
frame, but did not capture the command frame, then the
decode for the response may be incomplete. The Set Initial
Decoder Parameters dialog provides a means to supply the
context for any frame. The system allows the user to define
any number of parameters and save them in templates for
later use.Each entry in the window takes effect from the
beginning of the capture onward or until redefined in the Set
Subsequent Decoder Parameters dialog. This selection is
not present if no decoder is loaded that supports this
feature.
File Locations dialog
Side Names dialog
Select a Stack dialog
Set Initial Decoder Parameters window
where the user can change
used to customize the
where the user defines the
. There
Set Subsequent
Decoder
Parameters...
Automatically
Request Missing
Decoder
Information
Enable/Disable
Bluetooth Protocol
Expert
14 Frontline BPA 600 Hardware & Software User Manual
Opens the
where the user can override an existing parameter at any
frame in the capture. Each entry takes effect from the
specified frame onward or until redefined in this dialog on a
later frame. This selection is not present if no decoder is
loaded that supports this feature.
When checked, this selection opens a dialog that asking for
missing frame information. When unchecked, the analyzer
decodes each frame until it cannot go further and it stops
decoding. This selection is not present if no decoder is loaded
that supports this feature.
When enabled, the
otherwise it is not available. Only available when a
Bluetooth Protocol Expert licensed device is connected.
Set Subsequent Decoder Parameters dialog
Bluetooth Protocol Expert
is active,
Page 23
Chapter 2 Getting Started TELEDYNE LECROY
Table 2.6 - Control Window Live Menu Selections (continued)
Mode Selection
Enable/Disable
Audio Expert
System
The Windows menu selection applies only to the Control window and open analysis windows: Frame
Display, Event Display, Message Sequence Chart, Bluetooth Timeline, Bluetooth low energy
Timeline, and Coexistence View. All other windows, such as the datasource, are not affected by these
selections.
Table 2.7 - Control Window Windows Menu Selections
Mode Selection
Live &
Capture
File
Cascade
Close All Views
Hot-
Key
When enabled, the
wise it is not available. Only available when an Audio
Expert System licensed device is connected.
HotKey
Ctrl-W Arranges open analysis windows in a cascaded view with
window captions visible.
Closes Open analysis windows.
Description
Audio Expert System
Description
is active, other
Minimize Control
Minimizes All
Frame Display
Event Display
Mode Selection Hot-Key Description
Live &
Capture
File
Help Topics
About Frontline
Protocol Analysis
System
Support on the Web
and
Table 2.8 - Control Window Help Menu Selections
When checked, minimizing the Control window also
minimizes all open analysis windows.
When these windows are open the menu will display these
selections. Clicking on the selection will bring that window
to the front.
Opens the Frontline Help window.
Provides a pop-up showing the version and release
information, Frontline contact information, and copyright
information.
Opens a browser to
fte.com
technical support page.
2.3.6 Minimizing Windows
Windows can be minimized individually or as a group when the Control window is minimized. To minimize
windows as a group:
1.
Go to the Window menu on the Control window.
2. Select Minimize Control Minimizes All. The analyzer puts a check next to the menu item,
indicating that when the Control window is minimized, all windows are minimized.
3. Select the menu item again to deactivate this feature.
4. The windows minimize to the top of the operating system Task Bar.
Frontline BPA 600 Hardware & Software User Manual 15
Page 24
Chapter 3 Configuration Settings
In this section the Frontline software is used to configure an analyzer for capturing data .
3.1 BPA 600 Configuration and I/O
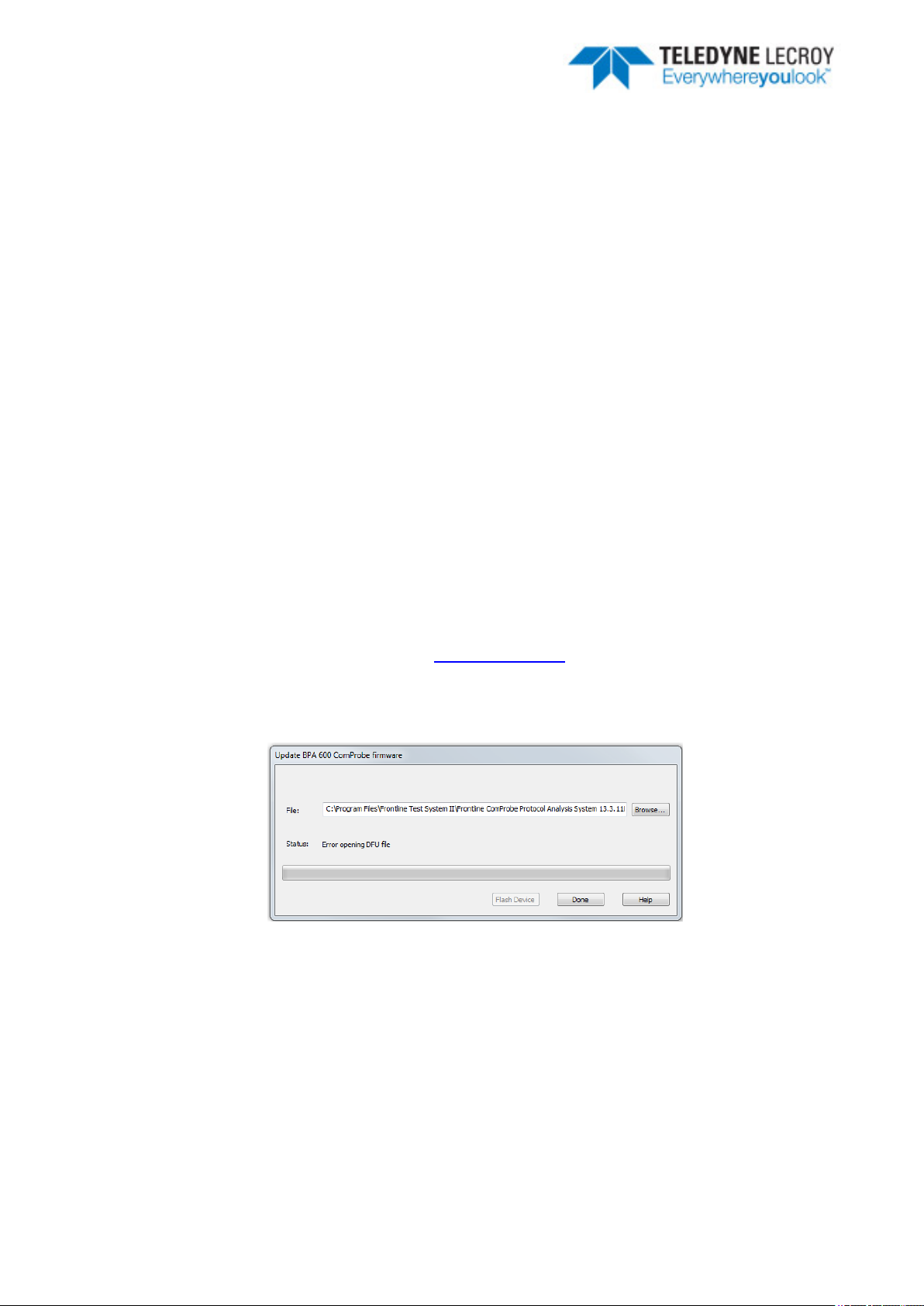
3.1.1 BPA 600 - Update Firmware
When you select the Update Firmware on the BPA 600 Information, the Update ComProbe BPA 600
firmware dialog appears. You use this dialog to update your ComProbe hardware with the latest firmware.
It is very important that you update the firmware. If the firmware versions are not the same, you will not be
able to start sniffing.
Figure 3.1 - BPA 600 Update Firmware Dialog
1. Make sure the cabling is attached to the ComProbe hardware.
2. Select Flash Device.
The download begins, with the Status bar displaying the progress. When the download is complete,
you can check the firmware version by checking the Status dialog.
Frontline BPA 600 Hardware & Software User Manual 16
Page 25
TELEDYNE LECROY Chapter 3 Configuration Settings
3.1.2 BPA 600 IO Datasource Settings
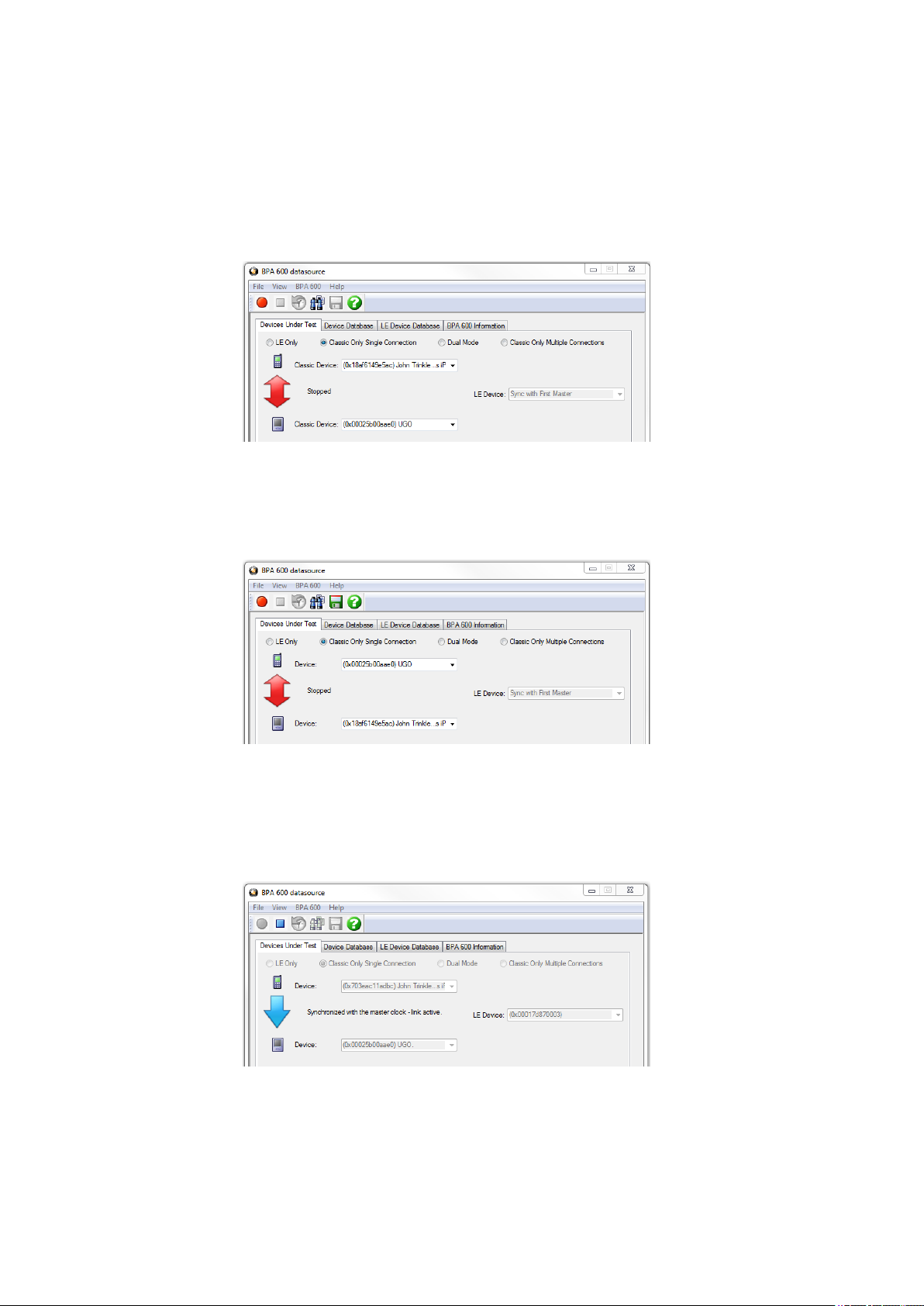
3.1.2.1 Classic Bluetooth® Roleless Connection
When configuring the ComProbe BPA 600 devices for a Classic Bluetooth connection it is no longer necessary
to assign a “Master” or “Slave” role to each of the devices. All Classic connection are “roleless”. For example,
suppose you have a phone and a speaker as shown below:
Figure 3.2 - Example of BPA 600 "roleless" Connection
Alternatively, you can enter the devices as follows where Classic Device drop down controls have
reversed the devices under test shown in the previous image.
Figure 3.3 - Example BPA 600 "roleless" Connection - Switching DUT
It does not matter which position you enter the device. After you have started sniffing and a connection is
made, the arrow will indicate the direction of the connection. In the following screen shot the phone has
connected as the “Master” to the speaker as the “Slave”.
Figure 3.4 - Arrow Shows master-slave Relationship
17 Frontline BPA 600 Hardware & Software User Manual
Page 26
Chapter 3 Configuration Settings TELEDYNE LECROY
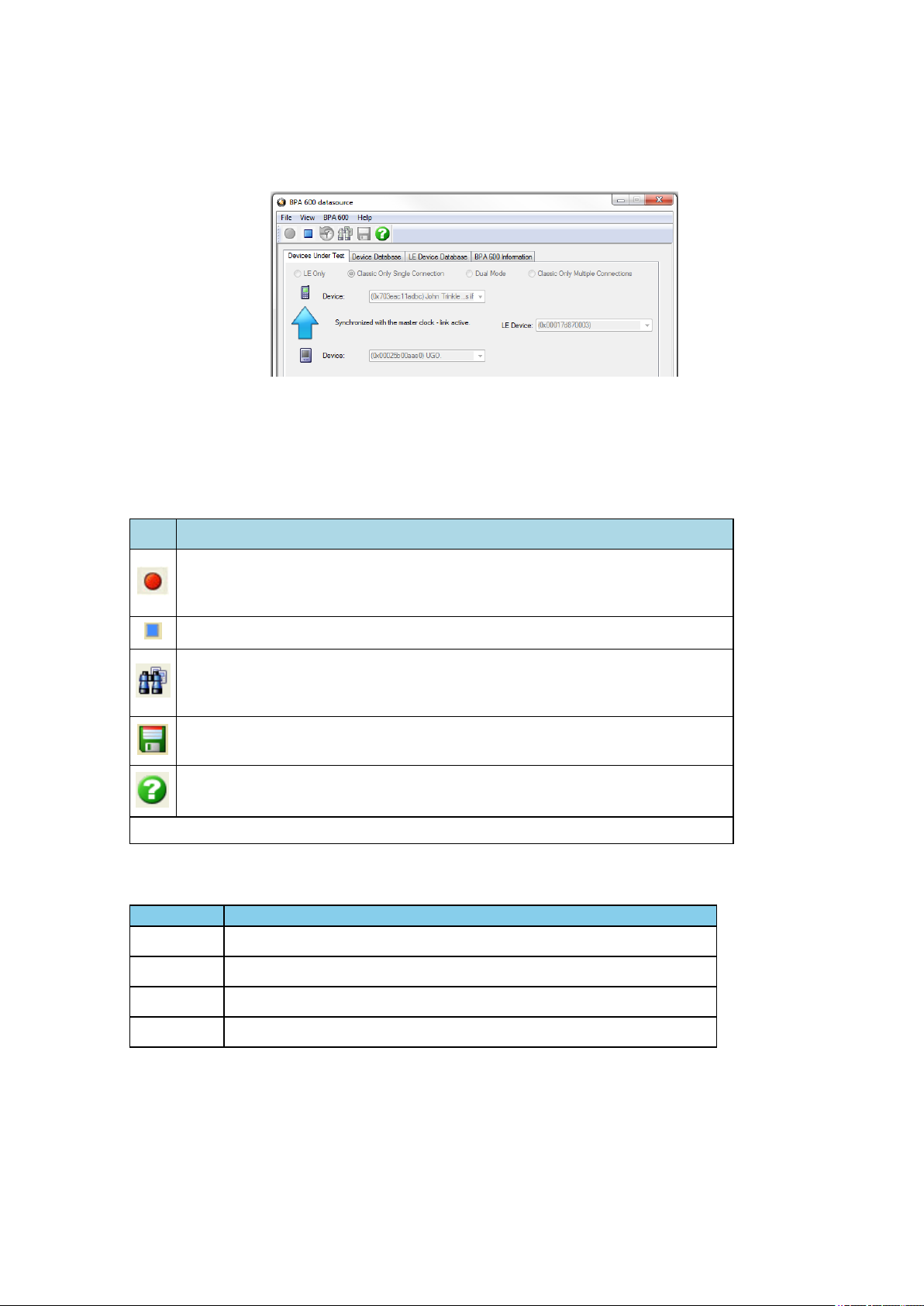
Should the roles change during the connection the arrow will change to show the new "Master/Slave"
connection. In the following screen shot the speaker has connected as the “Master” to the phone as the
“Slave”.
Figure 3.5 - Arrow Showing Results of Role Switch
3.1.2.2 Datasource Toolbar/Menu
The Datasource dialog toolbar and menu options are listed below.
Table 3.1 - BPA 600 datasource Toolbar
Icon Description
Start Sniffing button to begin sniffing. All settings are saved automatically when
you start sniffing. Selection of devices is disabled during sniffing. To select
another device stop sniffing.
Pause button to stop sniffing
When you select the Discover Devices button, the software lists all the
discoverable Bluetooth devices on the Device Database and LE Device
Database tabs.
Save button to save the configuration if you made changes but did not begin
sniffing. All settings are saved automatically when you start sniffing.
Help button opens the help file.
Grayed-out icons are inactive and do not apply to ComProbe BPA 600
Table 3.2 - BPA 600 datasource Menu
Menu Item Description
File
View
BPA 600 Start Sniffing,Stop Sniffing,Discover Devices
Save and Exit options, self explanatory.
Hides or displays the toolbar.
Help
Opens ComProbe
Help
About BPA 600
, and
.
3.1.2.3 Selecting BPA 600 Devices Under Test
The Devices Under Test dialog has all the setup information the analyzer needs in order to synchronize
with the piconet and capture data. The analyzer requires information on the clock synchronization method
and the device address of the device to initially sync to. You must also choose what to sniff.
Frontline BPA 600 Hardware & Software User Manual 18
Page 27
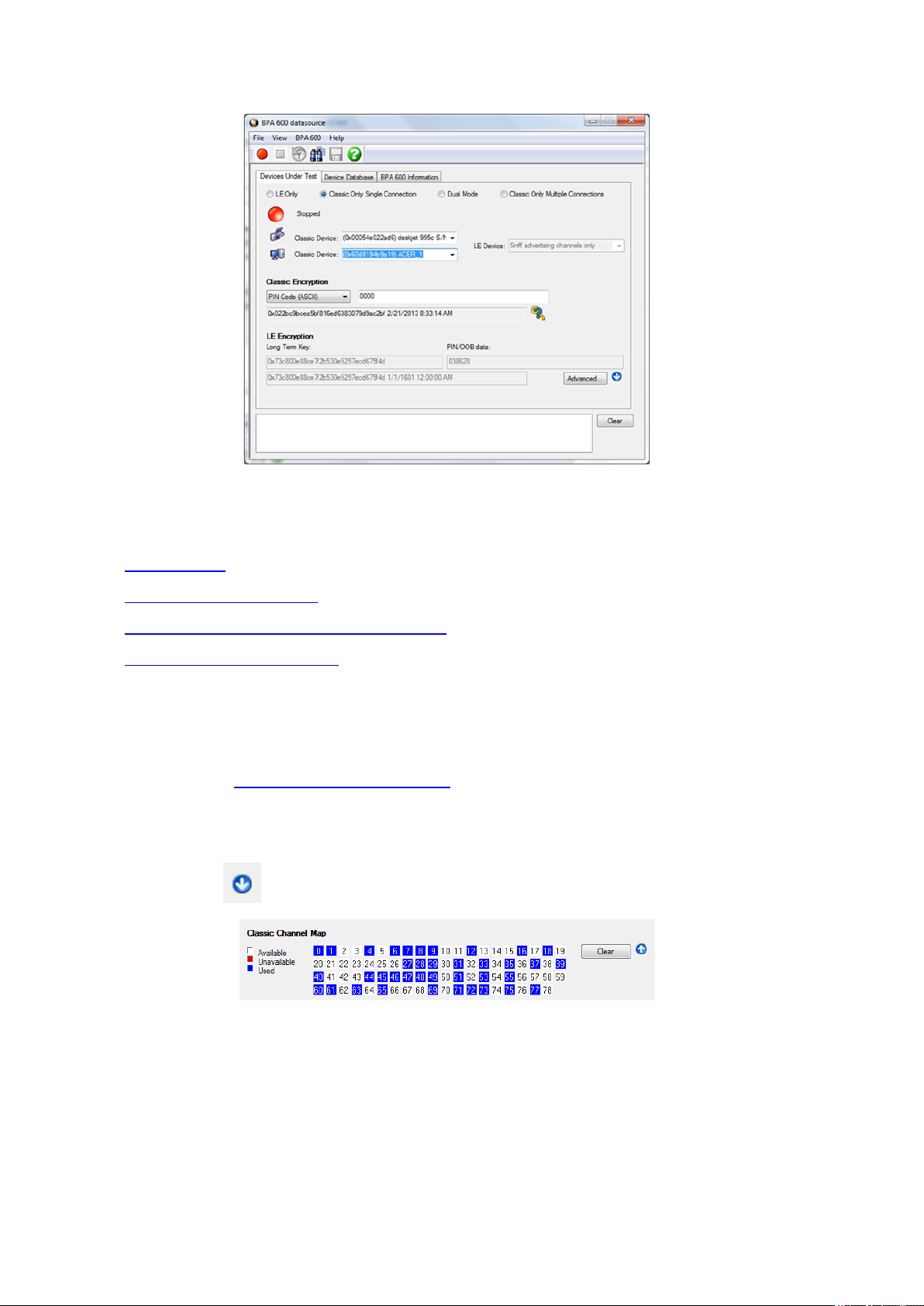
TELEDYNE LECROY Chapter 3 Configuration Settings
Figure 3.6 - BPA 600 Datasource Devices Under Test Dialog
You can choose to capture data using:
l low energy only
l Classic Only, Single Connection
l Dual Mode - Combination of Classic and low energy
l Classic Only, Multiple Connections
Select one of these links above for explanations on how to configure each option.
There are a couple of other functions on the dialog that you need to understand.
Advanced
Click here to see the BPA 600 Advanced Classic Settings.
Channel Map (Classic Bluetoot h)
The Channel Map shows which channels are available for Adaptive Frequency Hopping.
l
Channel Map Click this button to toggle on/off the display of the Channel Map.
Figure 3.7 - Classic Bluetooth Channel Map
This display is used to determine which channels are available with
19 Frontline BPA 600 Hardware & Software User Manual
Page 28

Chapter 3 Configuration Settings TELEDYNE LECROY
Table 3.3 - BPA 600 Channel Map Color Codes
Channel
Color
White Channel is currently available for use.
Description
Red
Blue
The Clear button resets each indicator back to the White state. The indicators are also reset whenever a
new Channel Map goes into effect.
Status Window
A status window at the bottom of the dialog displays information about recent activity.
When Adaptive Frequency Hopping is in use, red indicates that the channel is marked
as unavailable
Indicates that a packet was captured on the channel.
Note: Channel Map is not available for LE Only.
3.1.2.4 BPA 600 Devices Under Test
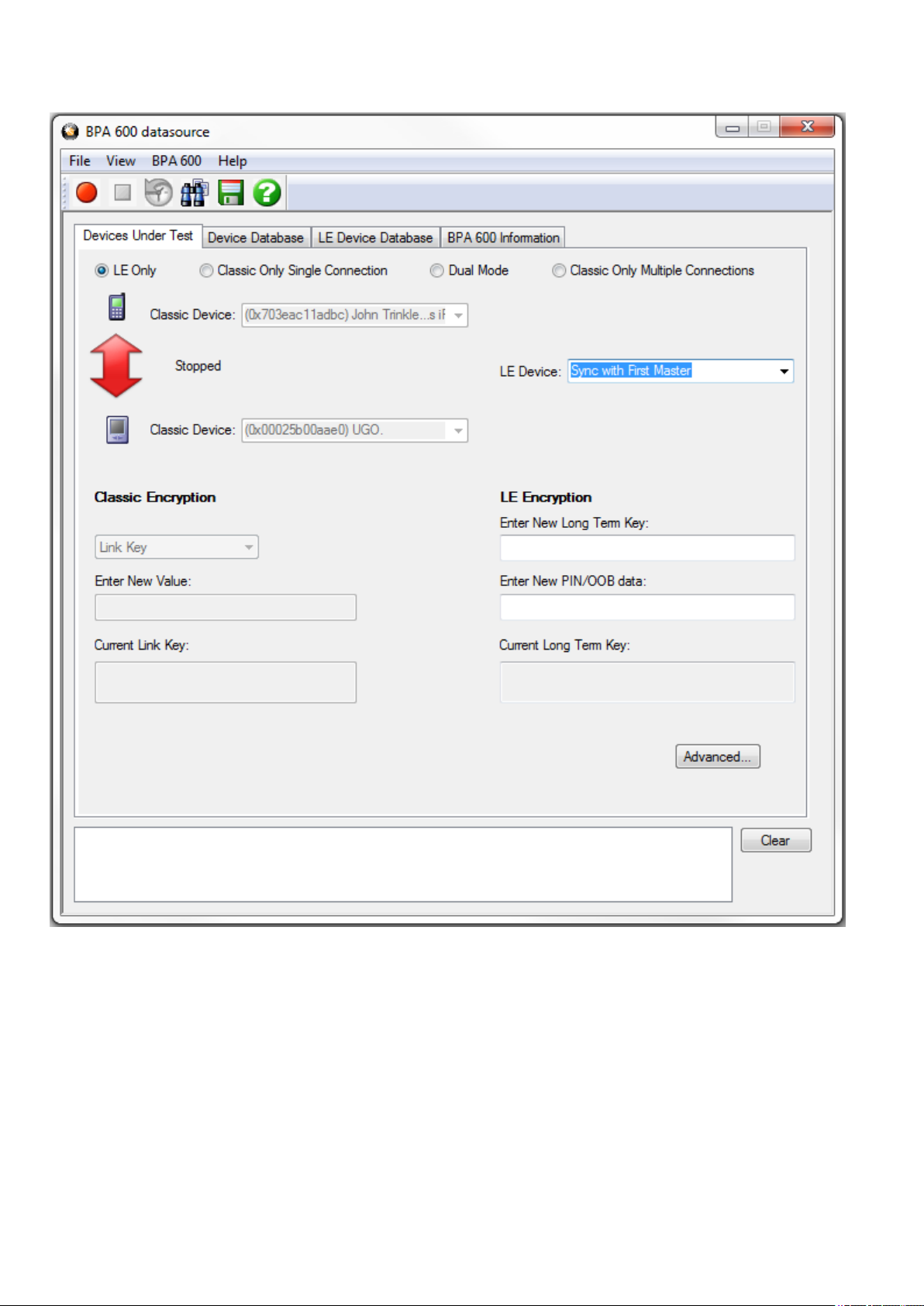
3.1.2.4.1 BPA 600 Devices Under Test - LE Only
By selecting the "LE Only" radio button under the "Devices Under Test" tab you can configure the BPA 600
protocol analyzer for sniffing Bluetooth low energy communications.
Frontline BPA 600 Hardware & Software User Manual 20
Page 29
TELEDYNE LECROY Chapter 3 Configuration Settings
Figure 3.8 - BPA 600 Devices Under Test - low energy
The default value in the LE Device drop down is Sync with First Master. To begin sniffing Bluetooth low
energy simply click the red button to start. The analyzer will capture packets from the first Master that makes
a connection . To capture the advertising traffic and the connection(s), you must specify a device address.
Specifying the LE Device Address and Encryption
21 Frontline BPA 600 Hardware & Software User Manual
Page 30
Chapter 3 Configuration Settings TELEDYNE LECROY
1. If you would like you may specify the LE device
you are testing by typing in or choosing its
address (BD_ADDR). You can type it directly into
the drop down, or choose it from the existing
previous values list in the drop down.
To enter the device manually type the address 12 digit hex number (6 octets). The "0x" is automatically typed in the drop down control.
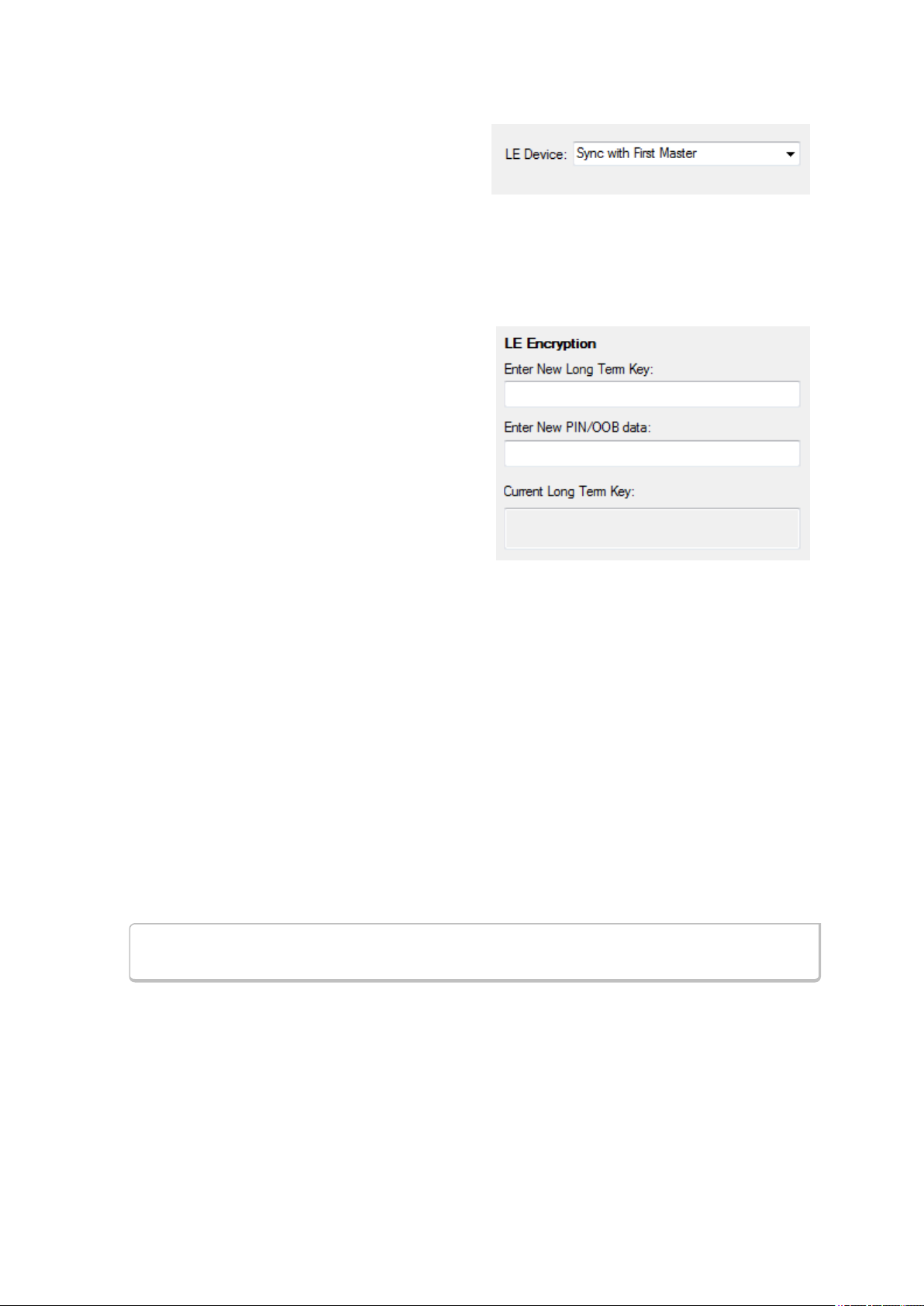
Once you have the devices address identified, the next step is to identify the Encryption.
2. Enter the Long Term Key for the LE Encryption.
The Long Term Key is similar to the Link key in Classic. It
is a persistent key that is stored in both devices and used
to derive a fresh encryption key each time the devices
go encrypted.
Learn more about the Long Term Key.
The Long Term Key is similar to the Link key in Classic; it
is a persistent key that is stored in both devices and used
to derive a fresh encryption key each time the devices
go encrypted.
There are a few differences though:
In Classic the Link key is derived from inputs from both
devices and is calculated in the same way independently by both devices and then stored persistently. The
link key itself is never transmitted over the air during pairing.
In LE, the long term key is generated solely on the slave device and then, during pairing, is distributed to a
master device that wants to establish an encrypted connection to that slave in the future. Thus the long term
key is transmitted over the air, albeit encrypted with a one-time key derived during the pairing process and
discarded afterwards (the so called short term key).
Unlike the link key, this long term key is directional, i.e. it is only used to for connections from the master to
the slave (referring to the roles of the devices during the pairing process). If the devices also want to connect
the other way round in the future, the device in the master role (during the pairing process) also needs to
send its own long term key to the device in the slave role during the pairing process (also encrypted with the
short term key of course), so that the device which was in the slave during the pairing process can be a
master in the future and connect to the device which was master during the pairing process (but then would
be in a slave role).
Since most simple LE devices are only ever slave and never master at all, the second long term key exchange
is optional during the pairing process.
Note: If you use Copy/Paste to insert the Long Term Key , Frontline will auto correct
(remove invalid white spaces) to correctly format the key.
3. Enter a PIN or out-of-band (OOB) value for Pairing.
This optional information offers alternative pairing methods.
One of two pieces of data allow alternative pairing:
Frontline BPA 600 Hardware & Software User Manual 22
Page 31

TELEDYNE LECROY Chapter 3 Configuration Settings
1. PIN is a six-digit (or less if leading zeros are omitted) decimal number.
2. Out-of-Band (OOB) data is a 16-digit hexadecimal code which the devices exchange via a
channel that is different than the le transmission itself. This channel is called OOB. For off-theshelf devices we cannot sniff OOB data, but in the lab you may have access to the data
exchanged through this channel.
3.1.2.4.2 BPA 600 Devices Under Test - Classic Single Connection
Figure 3.9 - BPA 600 Devices Under Test - Classic Only Single Connection
Specifying the Bluetooth Device Address (BD_ADDR)
Select the Bluetooth device address (BD_ADDR) form
the Classic Device: drop down list or from the Device
Database. You can also type in the address as a 12 digit
hex number (6 octets). The "0x" is automatically typed
in by the control. Any devices entered this way is
added to the Device Database
In single connection mode, the analyzer needs to
know the Bluetooth® Device Address (BD_ADDR) for
each device, but it does not need to know which is
master or slave, ComProbe analyzercan figure that
23 Frontline BPA 600 Hardware & Software User Manual
Page 32

Chapter 3 Configuration Settings TELEDYNE LECROY
out for you through roleless connection. You can also manually specify the Bluetooth Device Address.
Classic Encryption
Once you have the devices address identified, the next step is to identify the Encryption.
1. Select an Encryption option.
2. Enter a value for the encryption.
The Current Link Key field displays the currently
provided Link Key and the date and time the key
was provided. The status of the Link Key is
displayed with the following icons:
Icon Link Key Status
Valid
Not Valid
Connection
Attempted But
Failed
Bluetooth devices can have their data encrypted when they communicate. Bluetooth devices on an encrypted
link share a common link key in order to exchange encrypted data. How that link key is created depends
upon the pairing method used.
There are three encryption options in the I/O Settings dialog.
a.
PIN Code (ASCII)
b.
PIN Code (Hex)
c. Link Key
You are able to switch between these methods in the I/O Settings window. When you select a method, a
note appears at the bottom of the dialog reminding you what you need to do to successfully complete the
dialog.
l The first and second options use a PIN Code to generate the Link Key. The devices generate link Keys
during the Pairing Process based on a PIN Code. The Link Key generated from this process is also based on
a random number so the security cannot be compromised. If the analyzer is given the PIN Code it can
determine the Link Key using the same algorithm. Since the analyzer also needs the random number, the
analyzer must catch the entire Pairing Process or else it cannot generate the Link Key and decode the
data.
Example:
If the ASCII character PIN Code is ABC and you choose to enter the ASCII characters, then select PIN
Code (ASCII) from the Encryption drop down list and enter ABC in the field below.
If you choose to enter the Hex equivalent of the ASCII character PIN Code ABC, then select PIN Code
(Hex) from the Encryption drop down list and enter 0x414243 in the field. Where 41 is the Hex
Frontline BPA 600 Hardware & Software User Manual 24
Page 33

TELEDYNE LECROY Chapter 3 Configuration Settings
equivalent of the letter A, 42 is the Hex equivalent of the letter B, and 43 is the Hex equivalent of the
letter C.
Note: When PIN Code (Hex) is selected from the Encryption drop down list, the 0x prefix is entered
automatically.
l Third, if you know the Link Key in advance you may enter it directly. Select Link Key in the Encryption list
and then enter the Link Key in the edit box. If the link key is already in the database, the Link Key is
automatically entered in the edit box after the Master and Slave have been selected. You can also select a
Master, Slave and Link Key from the Device Database.
Note: When the devices are in the Secure Simple Pairing (SSP) Debug Mode, SSP is
automatically supported regardless of encryption configuration.
o
If any one of the Bluetooth devices is in SSP Debug Mode then the BPA 600 analyzer can automatically
figure out the Link Key, and you do not have to do anything.
o
If the Bluetooth devices do not allow Debug Mode activation, enter the Link Key as described above or
import the Link Key using the procedure in Programmatically Update Link Key from 3rd Party
Software.
3.1.2.4.3 BPA 600 Devices Under Test- Dual Mode
Note: When selecting and using either "Dual Mode" or "Classic Only Multiple Connection"
you must connect both antennas (LE and Classic) to the ComProbe BPA 600 hardware.
25 Frontline BPA 600 Hardware & Software User Manual
Page 34

Chapter 3 Configuration Settings TELEDYNE LECROY
Figure 3.10 - BPA 600 Devices Under Test - Dual Mode
Specifying the Bluetoot h Device Address (BD_ADDR)
In Dual Mode, the analyzer needs to know the Bluetooth Device Address (BD_ADDR) for each device, but it
does not need to know which is master or slave for the Classic Bluetooth connection, ComProbe analyzser can
figure that out for you through roleless connection.
Frontline BPA 600 Hardware & Software User Manual 26
Page 35

TELEDYNE LECROY Chapter 3 Configuration Settings
1. You can manually select Select the Bluetooth
device address (BD_ADDR) form the Classic
Device: drop down list or from the Device
Database. You can also type in the address as a
12 digit hex number (6 octets). The "0x" is
automatically typed in by the control. Any
devices entered this way is added to the
Device Database.
2. Specify the "BD_ADDR for the LE Device" by selecting "Sync
with Classic Devices Only". By doing this, the low energy
device will follow connections from or to the specified
device, or from or to the first Classic device that connects
over LE.
Classic Encryption
Bluetooth devices can have their data encrypted when they communicate. Bluetooth devices on an encrypted
link share a common link key in order to exchange
encrypted data. How that link key is created
depends upon the pairing method used.
There are three
encryption options in
the I/O Settings dialog.
a.
PIN Code
(ASCII)
b.
PIN Code (Hex)
c.
Link Key
l The first and second options use a PIN Code to
generate the Link Key. The devices generate link Keys during the Pairing Process based on a PIN Code. The
second Link Key generated from this process is also based on a random number so the security cannot be
compromised. If the analyzer is given the PIN Code it can determine the Link Key using the same
algorithm. Since the analyzer also needs the random number, the analyzer must catch the entire Pairing
Process or else it cannot generate the Link Key and decode the data.
Example:
If the ASCII character PIN Code is ABC and you choose to enter the ASCII characters, then select PIN
Code (ASCII) from the Encryption drop down list and enter ABC in the field below.
If you choose to enter the Hex equivalent of the ASCII character PIN Code ABC, then select PIN Code
(Hex) from the Encryption drop down list and enter 0x414243 in the field. Where 41 is the Hex
equivalent of the letter A, 42 is the Hex equivalent of the letter B, and 43 is the Hex equivalent of the
letter C.
Note: When PIN Code (Hex) is selected from the Encryption drop down list, the 0x
prefix is entered automatically.
27 Frontline BPA 600 Hardware & Software User Manual
Page 36

Chapter 3 Configuration Settings TELEDYNE LECROY
l Third, if you know the Link Key in advance you may enter it directly. Select Link Key in the Encryption list
and then enter the Link Key in the edit box. If the link key is already in the database, the Link Key is
automatically entered in the edit box after the Master and Slave have been selected. You can also pick
Choose Pair from Device Database to select a Master, Slave and Link Key from the Device Database.
1. Select an Encryption option.
2. Enter a value for the encryption.
The Current Link Key field displays the currently provided Link Key and the date and time the key
was provided. The status of the Link Key is displayed with the following icons:
Icon Link Key Status
Valid
Not Valid
Connection
Attempted But
Failed
LE Encryption
1. Enter the New Long Term Key for the LE
Encryption.
The long term key is similar to the Link key in
Classic. It is a persistent key that is stored in both
devices and used to derive a fresh encryption
key each time the devices go encrypted.
Learn more about the Long Term Key.
The Long Term Key is similar to the Link key in
Classic; it is a persistent key that is stored in both
devices and used to derive a fresh encryption
key each time the devices go encrypted.
There are a few differences though:
In Classic the Link key is derived from inputs from both devices and is calculated in the same way
independently by both devices and then stored persistently. The link key itself is never transmitted
over the air during pairing.
In LE, the long term key is generated solely on the slave device and then, during pairing, is distributed
to a master device that wants to establish an encrypted connection to that slave in the future. Thus the
long term key is transmitted over the air, albeit encrypted with a one-time key derived during the
pairing process and discarded afterwards (the so called short term key).
Unlike the link key, this long term key is directional, i.e. it is only used to for connections from the
master to the slave (referring to the roles of the devices during the pairing process). If the devices also
want to connect the other way round in the future, the device in the master role (during the pairing
process) also needs to send its own long term key to the device in the slave role during the pairing
process (also encrypted with the short term key of course), so that the device which was in the slave
Frontline BPA 600 Hardware & Software User Manual 28
Page 37

TELEDYNE LECROY Chapter 3 Configuration Settings
during the pairing process can be a master in the future and connect to the device which was master
during the pairing process (but then would be in a slave role).
Since most simple LE devices are only ever slave and never master at all, the second long term key
exchange is optional during the pairing process.
Note: If you use Copy/Paste to insert the Long Term Key , Frontline will auto correct
(remove invalid white spaces) to correctly format the key.
2. Enter a PIN or out-of-band (OOB) value for Pairing.
This optional information offers alternative pairing methods.
One of two pieces of data allow alternative pairing:
1. PIN is a six-digit (or less if leading zeros are omitted) decimal number.
2. Out-of-Band (OOB) data is a 16-digit hexadecimal code which the devices exchange via
a channel that is different than the le transmission itself. This channel is called OOB.
For off-the-shelf devices we cannot sniff OOB data, but in the lab you may have access
to the data exchanged through this channel.
3.1.2.4.4 BPA 600 Devices Under Test - Classic Only Multiple Connection
Note: When selecting and using either Dual Mode or Classic Only Multiple
Connection you must connect both antennas (LE and Classic) to the ComProbe BPA
600 hardware.
29 Frontline BPA 600 Hardware & Software User Manual
Page 38

Chapter 3 Configuration Settings TELEDYNE LECROY
Figure 3.11 - BPA 600 Devices Under Test - Classic Only Multiple Connections
Specifying the Bluetoot h Device Address (BD_ADDR)
Multiple connection refers to connecting one master with two slave Bluetooth devices. The analyzer needs to
know the Bluetooth Device Address (BD_ADDR) for the Slaves and the Master. The analyzer needs to know
the Bluetooth Device Address (BD_ADDR) for each device, but it does not need to know which is master or
slave as the ComProbe analyzer can figure that out for you through roleless connection. You can also manually
specify the Bluetooth Device Address.
Select the Bluetooth device address (BD_ADDR) form the Classic Device: drop down list or from the Device
Database. You can also type in the address as a 12 digit hex number (6 octets). The "0x" is automatically typed
in by the control. Any devices entered this way is added to the Device Database.
Frontline BPA 600 Hardware & Software User Manual 30
Page 39

TELEDYNE LECROY Chapter 3 Configuration Settings
Using the Device drop down list, elect the Bluetooth Device
Address (BD_ADDR) : from a list of available devices from the
Device Database. You can also type in the address as a 12 digit
hex number (6 octets). The "0x" is automatically typed in by the
control. Any devices entered this way is added to the Device
Database.
Classic Encryption
Bluetooth devices can have their data encrypted when they
communicate. Bluetooth devices on an encrypted link share a
common link key in order to exchange encrypted
data. How that link key is created depends upon the
pairing method used.
There are three encryption options in the I/O
Settings dialog.
a.
PIN Code (ASCII)
b.
PIN Code (Hex)
c. Link Key
You are able to switch between these methods in
the I/O Settings window. When you select a
method, a note appears at the bottom of the dialog
reminding you what you need to do to successfully
complete the dialog.
l The first and second options use a PIN Code to generate the Link Key. The
devices generate link Keys during the Pairing Process based on a PIN Code.
The Link Key generated from this process is also based on a random
number so the security cannot be compromised. If the analyzer is given the
PIN Code it can determine the Link Key using the same algorithm. Since the
analyzer also needs the random number, the analyzer must catch the entire Pairing Process or else it
cannot generate the Link Key and decode the data.
Example:
If the ASCII character PIN Code is ABC and you choose to enter the ASCII characters, then select PIN
Code (ASCII) from the Encryption drop down list and enter ABC in the field below.
If you choose to enter the Hex equivalent of the ASCII character PIN Code ABC, then select PIN Code
(Hex) from the Encryption drop down list and enter 0x414243 in the field. Where 41 is the Hex
equivalent of the letter A, 42 is the Hex equivalent of the letter B, and 43 is the Hex equivalent of the
letter C.
Note: When PIN Code (Hex) is selected from the Encryption drop down list, the 0x
prefix is entered automatically.
l Third, if you know the Link Key in advance you may enter it directly. Select Link Key in the Encryption list
and then enter the Link Key in the edit box. If the link key is already in the database, the Link Key is
automatically entered in the edit box after the Master and Slave have been selected. You can also select a
Master, Slave and Link Key from the Device Database.
31 Frontline BPA 600 Hardware & Software User Manual
Page 40

Chapter 3 Configuration Settings TELEDYNE LECROY
Note: When the devices are in the Secure Simple Pairing (SSP) Debug Mode, SSP is
automatically supported regardless of encryption configuration.
o
If any one of the Bluetooth devices is in SSP Debug Mode then the BPA 600 analyzer can automatically
figure out the Link Key, and you do not have to do anything.
o
If the Bluetooth devices do not allow Debug Mode activation, enter the Link Key as described above or
import the Link Key using the procedure in Programmatically Update Link Key from 3rd Party
Software.
1. Select an Encryption option.
2. Enter a value for the encryption.
The Current Link Key field displays the currently provided Link Key and the date and time the key
was provided. The status of the Link Key is displayed with the following icons:
Icon Link Key Status
Valid
Not Valid
Connection
Attempted But
Failed
3.1.2.4.5 SSP Debug Mode
Bluetooth Core Version 2.1 and later specifications require Bluetooth compliant chip manufactures to include
Secure Simple Pairing (SSP) Debug Mode in the Host Controller. Debug Mode allows developers to debug and
analyze data without exposing any information that is intended to be kept secret. SSP Debug Mode uses a
different Link Key for encryption than is used during normal Bluetooth device operation. Debug Mode is
activated in the Host Controller to allow for data analysis. Once the analysis is complete Debug Mode can be
switched off.
While Bluetooth device 2.1 compliance applies to chip manufacturers, device manufacturers do not have the
same obligation to support SSP Debug Mode therefore some devices may not have this feature enabled.
Debug Mode enables interoperability testing and analysis at all development stages, decreasing time to
market.
3.1.2.4.6 Programmatically Update Link Key from 3rd Party Software
Now the BPA 600 protocol analyzer user can update the link keys for either of the classic links using a very
common Windows message WM_COPYDATA. The mechanism is to send a WM_COPYDATA message to the
BPA 600 datasource.
The best scenario for doing this is when the devices are doing SSP and they are NOT in debug mode. The
following is a snippet of code that gives an example of programmatically sending link key to the ComProbe
Protocol Analysis System software. In order to do this the user needs to know both addresses of the devices
in the link for which they wish to update the link key. Also, the Datasource expects the master and slave
addresses in LSB to MSB format.
Frontline BPA 600 Hardware & Software User Manual 32
Page 41

TELEDYNE LECROY Chapter 3 Configuration Settings
If the link key is sent to ComProbe software after encryption has been turned on over the air, ComProbe
software will flag an error on the Start Encryption packet. Depending on when the link key has been sent
down, ComProbe software may however still be able to sniff the link successfully. In order to guarantee that
ComProbe software is able to sniff the link the link key should be sent to ComProbe software as soon as it is
available and before encryption has been turned on over the air.
Use the following code for BPA 600:
#define HCI_LINK_KEY 1000
HWND nHandle = ::FindWindow(NULL,"BPA 600 datasource");
if(nHandle != 0)
{
COPYDATASTRUCT ds;
enum
{
EncryptionKeySize = 16,
sizeAddressDevice = 6
};
BYTE abytAddressDevice1[sizeAddressDevice] = { 0x12, 0x34, 0x56, 0x78, 0x9a, 0xbc };
//LSB->MSB
BYTE abytAddressDevice2[sizeAddressDevice] = { 0x21, 0x43, 0x65, 0x87, 0xa9, 0xcb };
BYTE abytLinkKey[EncryptionKeySize] = { 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff,
0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff };
ds.cbData = sizeAddressDevice + sizeAddressDevice + EncryptionKeySize;
ds.dwData = HCI_LINK_KEY;
BYTE bytData[sizeAddressDevice + sizeAddressDevice + EncryptionKeySize];
memcpy(&bytData,&abytAddressDevice1,sizeAddressDevice);
memcpy(&bytData[sizeAddressDevice],&abytAddressDevice2,sizeAddressDevice);
memcpy(&bytData
[sizeAddressDevice+sizeAddressDevice],&abytLinkKey,EncryptionKeySize);
ds.lpData = &bytData;
::SendMessage(nHandle, WM_COPYDATA, (WPARAM)GetSafeHwnd(), (LPARAM)&ds);
}
3.1.2.5 BPA 600 Device Database
The Device Database contains information about all the Classic Bluetooth® and Bluetooth low energy devices
that have been discovered or entered by the user.
33 Frontline BPA 600 Hardware & Software User Manual
Page 42

Chapter 3 Configuration Settings TELEDYNE LECROY
BPA 600 Datasource Device Database Tab
The Device Database is automatically updated when you perform certain operation such as entering
encryption information from the Devices Under Test dialog.
l
When you select Discover Device on the toolbar, BPA 600 analyzer lists all the discoverable
Bluetooth® devices.
l When you select a device from the list, then click Select, the information is transferred to the Devices
Under Test dialog.
l You can delete records one at a time by selecting the record, then selecting Delete.
l You can also delete all the records by selecting Delete All.
l The Help opens this help topic.
In the Device Database table the following columns appear.
Table 3.4 - BPA 600 Datasource Device Database Fields
Column Description
BD_ADDR
Friendly Name
Services
The address of the
If available the friendly name of the device
An attribute of the Class of Device (COD) such as Networking, Rendering,
Bluetooth
device
Audio, etc. Data provided from devices supporting Extended Inquiry
Response (EIR).during discovery. Service Class identifies a particular
type of service/functionality provided by the device. Multiple services can
occur. If the device does not support EIR the field will be empty.
Class of Device
A particular type of device such as phone, laptop, wearable, etc. Data
provided from devices supporting Extended Inquiry Response (EIR).during
discovery. COD is a value which identifies a particular type of functionality
provided by the device. For example, there would be a Service Class to
identify a printer, and another Service Class to identify a stereo headset. If
the device does not support EIR the field will be empty.
Frontline BPA 600 Hardware & Software User Manual 34
Page 43

TELEDYNE LECROY Chapter 3 Configuration Settings
Table 3.4 - BPA 600 Datasource Device Database Fields (continued)
Column Description
Service/COD
Universally Unique Identifier (UUID) of the Services and COD. 128 bits,
shown in hexadecimal format. If the device does not support EIR the field
will be empty.
Paired BD_ADDR
Paired Friendly Name
Link Key
Last Updated
The address of the
The friendly name of the device this device is paired with.
The Link Key in Classic
low energy used for encrypted data sent between paired devices.
The date the device was entered into the database.
Bluetooth
Bluetooth
device this device is paired with.
or the Long Term Key (LTK) in
Bluetooth
3.1.2.6 BPA 600 low enegy Device Database
The LE Device Database contains information about Bluetooth® low energy devices that have been
discovered or entered by the user. These devices are also listed in the Device Database, but this dataabase
list contains additional information specific only to Bluetooth low energy technology.
Figure 3.12 - BPA 600 Datasource LE Device Database Tab
The LE Device Database is automatically updated when you perform certain operation such as entering
encryption information from the Devices Under Test dialog.
When you select Discover Device on the toolbar, BPA 600 analyzer adds to the lists any new discovered
Bluetooth low energy devices. The list is cumulative and will contain all Bluetooth low energy devices
previously add to the list.
Device Control Menu
Right-clicking anywhere in
the device list will display the
device control menu that will
Select, Delete, or Add a
device.. Clicking on one of
these menu items will
perform the following
actions.
35 Frontline BPA 600 Hardware & Software User Manual
Page 44

Chapter 3 Configuration Settings TELEDYNE LECROY
Table 3.5 - LE Device Database Control Menu
Menu
Item
Select
Will place this device into the
Device Under Test
this menu selection. If multiple devices have been selected/highlighted in the list, the first
device in the list is placed in the Device Under Test.
tab. The device must be selected/highlighted in the list prior to making
LE Device
Action
field in the
LE OnlyorDual Mode
options of the
Delete
Add
Editing a Device
Any device entry can be edited by double-clicking in the field. An edit box will open and new device
information can be typed in.
When editing the BD_Addr Type field "<Tab to toggle>" appears. Press the keyboard Tab key until your
selected device address type appears.
LE Device Database Fields
Will deleted the selected/highlighted device from the database. Selecting/highlighting multiple
devices in the list will delete all of those devices.
Used for manual entry of a device into the database. A new device entry will append to the
end of the device list. To enter data double click on the field and type in the data. For the BD_
Addr Type field, double click and tab to select available types. See the following image.
Figure 3.13 - Add Menu Option Fields Display
Figure 3.14 - Editing IRK Field
In the LE Device Database table the following columns appear.
Table 3.6 - BPA 600 Datasource LE Device Database Fields
Column Description
BD_Add
BD_Addr Type
Identity Resolving Key
(IRK)
Nickname
r The address of the
May be either "Public" or "Random". "Public"addresses are set to BD_
Addr. "Random" is either a 'static" or "private" address. "Static" address
is a 48 bit randomly generated address. "Private" address is a 48 bit
"non-resolvable" address or "resolvable' address. A "resolvable" address
is generated using an IRK.
Will appear when BD_Addr Type is Random, Private, and Resolvable. A
host device with a list of IRKs can search the list to identify a peer
device that has previously authenticated with the host. This field can be
used to identify Bluetooth low energy devices that have previously
authenticated.
A user-added name for the device, often used to make device
identification easier during the analysis. Can be any alpha-numeric
string.
Bluetooth
low energy device
Frontline BPA 600 Hardware & Software User Manual 36
Page 45

TELEDYNE LECROY Chapter 3 Configuration Settings
3.1.2.7 BPA 600 - Information
The BPA 600 Information dialog is one of the four tabs that appear when you first start ComProbe BPA 600
analyzer.
Figure 3.15 - BPA 600 Information Tab
You can also access these tabs by selecting I/O Settings or Hardware Settings from the Options menu on
the Control window toolbar.
There are several pieces of information on this display:
l Displayed in the text window is the serial number of the connected BPA 600 devices. To update the
device list click Refresh Device List.
l If you want to load the latest ComProbe BPA 600 hardware firmware, you select the Update Firmware
button..
l The current firmware is displayed under Firmware Version.
3.1.2.8 BPA 600 Advanced Classic Settings
The Advanced Classic Settings dialog contains additional options for synchronizing the analyzer with the link to
capture data.
37 Frontline BPA 600 Hardware & Software User Manual
Page 46

Chapter 3 Configuration Settings TELEDYNE LECROY
Figure 3.16 - BPA 600 Advanced Classic Settings
1.
ComProbe
Some packet types can be so numerous that they may make it more difficult to locate data packets in
the Frame Display window. You have several options to exclude certain types of packets.
l Filter out ID packets - When this is checked, all ID packets are filtered out.
l Filter out Nulls and Polls - When this is checked, Nulls and Polls packets are filtered out.
l Filter out SCO/eSCO - When this is checked, SCO/eSCO packets are filtered out.
l Prioritized Decryption can be selected if you are having trouble establishing the correct
decryption. This option adjusts the data capture to give priority to establishing the proper
decryption over receiving frames. If you select this option, some frames may be dropped, but
establishing the decryption key will be more efficient.
l Sniffer Diagnostics - When this is checked, some diagnostic data from the ComProbe are
captured and stored in the .cfa file. This is useful when a .cfa file is sent to Frontline for analysis and
diagnosis. Technical Support may ask you to check this option when you are experiencing issues
with BPA 600.
l Single Link Filtering - When this is checked, only packets from the specific Master and Slave
selected in Devices Under Test are displayed. Data from other devices that may be connected to
the Master will be filtered out.
2.
Frame Slicing Settings
l Frame Slicing Settings allows you to enter the size of the largest frame allowed to pass the
analyzer without having any bytes removed. The second field tells the analyzer the number of
Frontline BPA 600 Hardware & Software User Manual 38
Page 47

TELEDYNE LECROY Chapter 3 Configuration Settings
bytes you would like to capture if the frame is larger than the allowable value indicated in the first
field.
3.
Channel Map
l Clear on Resync -used to clear the map each time a re-synchronization occurs
l Send with Data - allows you to send a map each time data is sent instead of just sending a map
when changes occur.
4.
Other Features
l Directed Classic Connection - Applies to Classic Only Multiple Connections
The default configuration for Classic Only Multiple Connections is one master and two slaves.
The Directed Classic Connection allows for simultaneous sniffing of up to three masters and
three slaves in any combination. For example you can have one master with one slave along with a
second master with two slaves, or three one-master one-slave connections.
1. Click to place a check in the Directed Classic Connection check box.
2. Click OK. The Advance Classic Settings dialog will close.
3. In the Devices Under Test tab click on Classic Only Single Connection.
4. In the Classic Device drop-down lists
select the address of the devices to be
in your first link. Then right-click
anywhere in the dialog. A link selector
pop-up will appear. Click on Save to
Link #1. The pop-up will close.
5. Repeat the link selection process for
each additional link.
6. To review your saved links right-click
and select View Directed
Connecctions. All of your selections
will appear in the Directed
Connections pop-up window.
7. Click on OK to close the pop-up.
8. Selecting the Classic Only Multiple
Connections will display the same
information.
9. To reset the Classic Only Multiple
Connections to its default mode,
select any other datasource
configuration radio button and click on
the Advanced button. Click on the
Dircted Classic Connection check
box to remove the check. Click on OK.
The Classic Only Multiple
39 Frontline BPA 600 Hardware & Software User Manual
Page 48

Chapter 3 Configuration Settings TELEDYNE LECROY
Connections dialog will return to its default one master two slave configuration.
Figure 3.17 - Classic Only Multiple Connections in Directed Classic Connections configuration
3.2 Decoder Parameters
Some protocol decoders have user-defined parameters. These are protocols where some information cannot
be discovered by looking at the data and must be entered by the user in order for the decoder to correctly
decode the data. For example, such information might be a field where the length is either 3 or 4 bytes, and
which length is being used is a system option.
There may be times when the context for decoding a frame is missing. For example, if the analyzer captures a
response frame but does not capture the command frame, then the decode for the response may be
incomplete. The Set Initial Decoder Parameters window allows you to supply the context for any frame.
The dialog allows you to define any number of parameters and save them in a template for later use
The decoder template function provides the capacity to create multiple templates that contain different
parameters. This capability allows you to maintain individual templates for each Bluetooth® network
monitored. Applying a template containing only those parameters necessary to decode transmissions
particular to an individual network, enhances the efficiency of the analyzer to decode data.
If you have decoders loaded which require decoder parameters, a window with one tab for every decoder
that requires parameters appears the first time the decoder is loaded.
Frontline BPA 600 Hardware & Software User Manual 40
Page 49

TELEDYNE LECROY Chapter 3 Configuration Settings
For help on setting the parameters, click the Help button on each tab to get help information specific to that
decoder.
If you need to change the parameters later,
l Choose Set Initial Decoder Parameters... from the Options menu on the Control and Frame
Display windows.
Figure 3.18 - Select Set Initial Decoder Parameters... from Control window
The Set Initial Decoder Parameters window opens with a tab for each decoder that requires
parameters.
Figure 3.19 - Tabs for each decoder requiring parameters.
l Each entry in the Set Initial Decoder Parameters window takes effect from the beginning of the
capture onward or until redefined in the Set Subsequent Decoder Parameters dialog.
Override Existing Parameters
The Set Subsequent Decoder Parameters dialog allows the user to override an existing parameter at any
frame in the capture where the parameter is used.
If you have a parameter in effect and wish to change that parameter
l Select the frame where the change should take effect
l Select Set Subsequent Decoder Parameters... from the Options menu, and make the needed
changes. You can also right-click on the frame to select the same option.
41 Frontline BPA 600 Hardware & Software User Manual
Page 50

Chapter 3 Configuration Settings TELEDYNE LECROY
Figure 3.20 - Set Subsequent Decoder Parameters... from Control window
Figure 3.21 - Example: Set Subsequent Decode for Frame #52, RFCOMM
l Each entry in the Set Subsequent Decoder Parameters dialog takes effect from the specified frame
onward or until redefined in this dialog on a later frame.
l The Remove Override button will remove the selected decode parameter override.
l The Remove All button will remove all decoder overrides.
If you do not have decoders loaded that require parameters, the menu item does not appear and you don't
need to worry about this feature.
3.2.1 Decoder Parameter Templates
3.2.1.1 Select and Apply a Decoder Template
1.
Select Set Initial Decoder Parameters... from the Options menu on the Control window
or the Frame Display window.
Frontline BPA 600 Hardware & Software User Manual 42
Page 51

TELEDYNE LECROY Chapter 3 Configuration Settings
2.
Click the Open Template icon in the toolbar and select the
desired template from the pop up list. The system displays the
content of the selected template in the Initial Connections list at
the top of the dialog
3. Click the OK button to apply the selected template and decoders'
settings and exit the Set Initial Decoder Parameters dialog.
3.2.1.2 Adding a New or Saving an Existing Template
Add a Template
A template is a collection of parameters required to completely decode communications between multiple
devices. This procedure adds a template to the system and saves it for later use:
1.
Click the Save button at the top of the Set Initial
Decoder Parameters dialog to display the Template
Manager dialog.
2. Enter a name for the new template and click OK.
The system saves the template and closes the Template
Manager dialog.
3. Click the OK button on the Set Initial Decoder
Parameters window to apply the template and close the
dialog.
Save Changes to a Template
This procedure saves changes to parameters in an existing template.
1.
After making changes to parameter settings in a user defined template, click the Save button at
the top of the Set Initial Decoder Parameters window to display the Template Manager dialog.
2. Ensure that the name of the template is listed in the Name to Save Template As text box and click
OK.
3. The system displays a dialog asking for confirmation of the change to the existing template. Click the
Yes button.
The system saves the parameter changes to the template and closes the Save As dialog.
4. Click the OK button on the Set Initial Decoder Parameters window to apply the template and
close the window.
3.2.1.3 Deleting a Template
1.
After opening the Set Initial Decoder Parameters window click the Delete button in the
toolbar.
The system displays the Template Manager dialog with a list of saved templates.
43 Frontline BPA 600 Hardware & Software User Manual
Page 52

Chapter 3 Configuration Settings TELEDYNE LECROY
2. Select (click on and highlight) the template marked for deletion and click the Delete button.
The system removes the selected template from the list of saved templates.
3. Click the OK button to complete the deletion process and close the Delete dialog.
4. Click the OK button on the Set Initial Decoder Parameters window to apply the deletion and
close the dialog.
3.2.2 Selecting A2DP Decoder Parameters
Decoding SBC frames in the A2DP decoder can be slow if the analyzer decodes all the parts (the header, the
scale factor and the audio samples) of the frame. You can increase the decoding speed by decoding only the
header fields and disregarding other parts. You can select the detail-level of decoding using the Set Initial
Decoder Parameters window.
Note: By default the decoder decodes only the header fields of the frame.
1. Select Set Initial Decoder Parameters from the Options menu on the Control window or the
Frame Display window.
2. Click on the A2DP tab.
3. Choose the desired decoding method.
Figure 3.22 - A2DP Decoder Settings
4. Follow steps to save the template changes or to save a new template.
5. Click the OK button to apply the selection and exit the Set Initial Decoder Parameters window.
3.2.3 AVDTP Decoder Parameters
3.2.3.1 About AVDTP Decoder Parameters
Each entry in the Set Initial Decoder Parameters window takes effect from the beginning of the capture
onward or until redefined in the Set Subsequent Decoder Parameters window.
Frontline BPA 600 Hardware & Software User Manual 44
Page 53

TELEDYNE LECROY Chapter 3 Configuration Settings
Figure 3.23 - AVDTP parameters tab
The AVDTP tab requires the following user inputs to complete a parameter:
l Piconet (Data Source (DS) No.) - When only one data source is employed, set this parameter to 0
(zero), otherwise, set to the desired number of data sources.
l Role - This identifies the role of the device initiating the frame (Master or Slave)
l L2CAP Channel - The channel number 0 through 78.
o
L2CAP channel is Multiplexed - when checked indicates that L2CAP is multiplexed with upper
layer protocols.
l AVDTP is carrying - Select the protocol that AVDTP traverses to from the following:
o
AVDTP Signaling
o
AVDTP Media
o
AVDTP Reporting
o
AVDTP Recovery
o
-Raw Data-
Adding, Deleting, and Saving AVDTP Parameters
1. From the Set Initial Decoder Parameters window, click on the AVDTP tab.
2. Set or select the AVDTP decoder parameters.
3. Click on the ADD button. The Intial Connection window displays the added parameters.
Figure 3.24 - Parameters Added to Decoder
4. To delete a parameter from the Initial Connections window, select the parameter and click on the
Delete button.
5. Decoder parameters cannot be edited. The only way to change a parameter is to delete the original as
described above, and recreate the parameter with the changed settings and selections and then click
on the Add button.
6. AVDTP parameters are saved when the template is saved as described in on page 1 on page 1
45 Frontline BPA 600 Hardware & Software User Manual
Page 54

Chapter 3 Configuration Settings TELEDYNE LECROY
3.2.3.2 AVDTP Missing Decode Information
The analyzer usually determines the protocol carried in an AVDTP payload by monitoring previous traffic.
However, when this fails to occur, the Missing Decoding Information Detected dialog appears and
requests that the user supply the missing information.
The following are the most common among the many possible reasons for a failure to determine the
traversal:
l The capture session started after transmission of the vital information.
l The analyzer incorrectly received a frame with the traversal information.
l The communication monitored takes place between two players with implicit information not included in
the transmission.
In any case, either view the AVDTP payload of this frame (and other frames with the same channel) as hex
data, or assist the analyzer by selecting a protocol using this dialog.
Note: You may use the rest of the analyzer without addressing this dialog. Additional
information gathered during the capture session may help you decide how to respond to
the request for decoding information.
If you are not sure of the payload carried by the subject frame, look at the raw data shown “data” in the
Decoder pane on the Frame Display. You may notice something that hints as to the profile in use.
In addition, look at some of the frames following the one in question. The data may not be recognizable to the
analyzer at the current point due to connection setup, but might be discovered later on in the capture.
Figure 3.25 - Look in Decoder pane for profile hints
3.2.3.3 AVDTP Override Decode Information
The Set Subsequent Decoder Parameters dialog allows the user to override an existing parameter at any
frame in the capture where the parameter is used.
If you have a parameter in effect and wish to change that parameter:
1. Select the frame where the change should take effect.
2. Select Set Subsequent Decoder Parameters from the Options menu, or by selecting a frame in
the frame display and choosing from the right-click pop-up menu, and make the needed changes.
Frontline BPA 600 Hardware & Software User Manual 46
Page 55

TELEDYNE LECROY Chapter 3 Configuration Settings
3. Select the rule you wish to modify from the list of rules.
4. Choose the protocol the selected item carries from the drop-down list, and click OK.
If you do not have any previously overridden parameters, you may
set parameters for the current frame and onwards by rightclicking the desired frame and choosing Provide AVDTP
Rules... from the right-click pop-up menu.
If you have a parameter in effect and wish to change it, there are
two parameters that may be overridden for AVDTP: Change the
Selected Item to Carry, and if AVDTP Media is selected. the
codec type. Because there are times when vital AVDTP
configuration information may not be transferred over the air, we
give users the ability to choose between the four AVDTP channel
types for each L2CAP channel carrying AVDTP as well as codec
type. We attempt to make our best guess at codec information
when it is not transferred over the air, but we realize we may not
always be correct. When we make a guess for codec type, we
specify it in the summary and decode panes by following the
codec with the phrase '(best guess by analyzer). This is to let you
know that this information was not obtained over the air and that
the user may wish to alter it by overriding AVDTP parameters.
Figure 3.26 - AVDTP Override of Frame Information, Item to Carry
47 Frontline BPA 600 Hardware & Software User Manual
Page 56

Chapter 3 Configuration Settings TELEDYNE LECROY
Figure 3.27 - AVDTP Override of Frame Information, Media Codec Selection
Each entry in the Set Subsequent Decoder Parameters dialog takes effect from the specified frame
onward or until redefined in this dialog on a later frame. If you are unhappy with your changes, you can undo
them by simply choosing your override from the dialog box and pressing the 'Remove Override' button. After
pressing 'OK,' the capture file will recompile as if your changes never existed, so feel free to experiment with
desired changes if you are unsure of what configuration to use.
Note: If the capture has no user defined
overrides, then the system displays a dialog
stating that no user defined overrides exist.
3.2.4 L2CAP Decoder Parameters
3.2.4.1 About L2CAP Decoder Parameters
Each entry in the Set Initial Decoder Parameters dialog takes effect from the beginning of the capture onward
or until redefined in the Set Subsequent Decoder Parameters dialog.
Figure 3.28 - L2CAP Decoder parameters tab
The L2CAP Set Initial Decoder Parameters dialog requires the following user inputs to complete a
Parameter :
l Stream - This identifies the role of the device initiating the frame (master or slave)
l Channel ID - The channel number 0 through 78
Frontline BPA 600 Hardware & Software User Manual 48
Page 57

TELEDYNE LECROY Chapter 3 Configuration Settings
l Address - This is the physical connection values for the devices. Each link in the net will have an address.
A piconet can have up to seven links. The Frame Display can
provide address information.
l Data Source (DS) No. -When only one data source is employed,
set this parameter to 0 (zero), otherwise, set to the desired data
source number.
Carries (PSM) - Select the protocol that L2CAP traverses to from the
following:
l AMP Manager
l AMP Test Manager
l SDP
l RFCOMM
l TCS
l LPMP
l BNEP
l HCRP Control
l HCRP Data
l HID
l AVCTP
l AVDTP
l CMTP
l MCAP Control
l IEEE P11073 20601
l -Raw Data-
Adding, Deleting, and Saving L2CAP Parameters
1. From the Set Initial Decoder Parameters window, click on the L2CAP tab.
2. Set or select the L2CAP decoder parameters.
3. Click on the ADD button. The Initial Connection window displays the added parameters.
Figure 3.29 - Parameters Added to Decoder
4. To delete a parameter from the Initial Connections window, select the parameter and click on the
Delete button.
49 Frontline BPA 600 Hardware & Software User Manual
Page 58

Chapter 3 Configuration Settings TELEDYNE LECROY
5. Decoder parameters cannot be edited. The only way to change a parameter is to delete the original as
described above, and recreate the parameter with the changed settings and selections and then click
on the Add button.
6. L2CAP parameters are saved when the template is saved.
3.2.4.2 L2CAP Override Decode Information
The Set Subsequent Decoder Parameters dialog allows the user to override an existing parameter at any
frame in the capture where the parameter is used.
If you have a parameter in effect and wish to change that parameter:
1. Select the frame where the change should take effect
2. Select Set Subsequent Decoder Parameters from
the Options menu, or by selecting a frame in the frame
display and choosing from the right-click pop-up menu,
and make the needed changes. Refer to
3. Change the L2CAP parameter by selecting from the rule
to change, and click on the listed parameters.
4. If you wish to remove an overridden rule click on
Remove Override button. If you want to remove all
decoder parameter settings click on Remove All.
5. Click OK.
Each entry in the Set Subsequent Decoder Parameters
dialog takes effect from the specified frame onward or until
redefined in this dialog on a later frame.
Note: If the capture has no user defined overrides, then the
system displays a dialog stating that no user defined
overrides exist.
3.2.5 RFCOMM Decoder Parameters
3.2.5.1 About RFCOMM Decoder Parameters
Each entry in the Set Initial Decoder Parameters dialog takes effect from the beginning of the capture
onward or until redefined in the Set Subsequent Decoder Parameters dialog.
Figure 3.30 - RFCOMM parameters tab
Frontline BPA 600 Hardware & Software User Manual 50
Page 59

TELEDYNE LECROY Chapter 3 Configuration Settings
The RFCOMM Set Initial Decoder Parameters tab requires the following user inputs to complete a
parameter:
l Stream - Identifies the role of the device initiating the frame (master or slave)
l Server Channel - The Bluetooth® channel number 0 through 78
l DLCI - This is the Data Link Connection Identifier, and identifies the ongoing connection between a client
and a server
l Data Source (DS) No.- When only one data source is employed, set this parameter to 0 (zero),
otherwise, set to the desired data source
l Carries (UUID) - Select from the list to apply the Universal Unique Identifier (UUID) of the application
layer that RFCOMM traverses to from the following:
o
OBEX
o
SPP
o
encap asyncPPP
o
Headset
o
FAX
o
Hands Free
o
SIM Access
o
VCP
o
UDI
o
-Raw Data-
Adding, Deleting, and Saving RFCOMM Parameters
1. From the Set Initial Decoder Parameters window, click on the RFCOMMtab.
2. Set or select the RFCOMMdecoder parameters.
3. Click on the ADD button. The Initial Connection window displays the added parameters.
Figure 3.31 - Parameters Added to Decoder
4. To delete a parameter from the Initial Connections window, select the parameter and click on the
Delete button.
5. Decoder parameters cannot be edited. The only way to change a parameter is to delete the original as
described above, and recreate the parameter with the changed settings and selections and then click
on the Add button.
6. RFCOMM parameters are saved when the template is saved as described in on page 1
3.2.5.2 RFCOMM Missing Decode Information
ComProbe software usually determines the protocol carried in an RFCOMM payload by monitoring previous
traffic. However, when this fails to occur, the Missing Decoding Information Detected dialog appears
51 Frontline BPA 600 Hardware & Software User Manual
Page 60

Chapter 3 Configuration Settings TELEDYNE LECROY
and requests that the user supply the missing information.
The following are the most common among the many possible reasons for a failure to determine the
traversal:
l The capture session started after transmission of the vital information
l The analyzer incorrectly received a frame with the traversal information
l The communication monitored takes place between two players with implicit information not included in
the transmission
In any case, either view the RFCOMM payload of this frame (and other frames with the same channel) as hex
data, or assist the analyzer by selecting a protocol using this dialog.
Note that you may use the rest of the analyzer without addressing this dialog. Additional information gathered
during the capture session may help you decide how to respond to the request for decoding information.
If you are not sure of the payload carried by the subject frame, look at the raw data shown under data in the
Decode pane in the Frame Display. You may notice something that hints as to the profile in use.
In addition, look at some of the frames following the one in question. The data may not be recognizable to the
analyzer at the current point due to connection setup, but might be discovered later on in the capture.
3.2.5.3 RFCOMM Override Decode Information
The Set Subsequent Decoder Parameters dialog allows the user to override an existing parameter at any
frame in the capture where the parameter is used.
If you have a parameter in effect and wish to change that parameter:
1. Select the frame where the change should take effect,
and select Set Subsequent Decoder Parameters
from the Options menu, or by selecting a frame in the
frame display and choosing from the right-click pop-up
menu, and make the needed changes.
2. Change the RFCOMM parameter by selecting from the
Change the Selected Item to Carry drop down list.
3. If you wish to remove an overridden rule click on
Remove Override button. If you want to remove all
decoder parameter settings click on Remove All.
4. Choose the protocol the selected item carries from the
drop-down list, and click OK.
Each entry in the Set Subsequent Decoder Parameters
dialog takes effect from the specified frame onward or until
redefined in this dialog on a later frame.
Frontline BPA 600 Hardware & Software User Manual 52
Page 61

TELEDYNE LECROY Chapter 3 Configuration Settings
Figure 3.32 - Set Subsequent Decoder Parameters selection list
Note: If the capture has no user defined overrides, then the system displays a dialog
stating that no user defined overrides exist.
3.3 Mesh Security
Note: The Bluetooth SIG is currently in the process of developing specifications for use of
Bluetooth technology with mesh networking. Any reference to "Smart Mesh" contained
herein is only in the context of Frontline software and does not represent SIG approved
terminology.
Decryption of Bluetooth low energy using mesh networking requires a key or key sets. This information must
be manually entered into the MeshOptions.ini file located in the system My Decoders folder. Refer to
Changing Default File Locations on page 274 for information on folder locations.
Open a text editor program, such as Windows Notepad, and make the following changes to the
MeshOptions.ini file.
For Bluetooth technology using mesh networking,
Table 3.7 - Bluetooth technology using mesh networking Keys Format
Name Enter as Description
Technology Identifier [mesh] Identifies the beginning of a set of mesh keys.
Friendly Name string, 2 word maximum.
IV Index 8 bytes, hexadecimal
Application Key 16 bytes, hexadecimal
Network Key
Device Key (Optional) 16 bytes, hexadecimal
Note: The Application Key will be substituted for the Device Key when the AFK bit is not
set and the Device Key is absent in the MeshOptions.ini file. AKF is the Application Key
Flag and is a single bit.
16 bytes, hexadecimal
Enter the fields in the order shown and separated by commas. The following code is an example of Bluetooth
technology using mesh networking decryption key entry. Three mesh keys shown. Note that "Sample5" and
"Sample6" keys do not use the optional Device Key.
[mesh]
// Key Format - FriendlyName, IV-Index, App Key, Net Key, Dev Key (Optional)
53 Frontline BPA 600 Hardware & Software User Manual
Page 62

Chapter 3 Configuration Settings TELEDYNE LECROY
Sample1, 00000002, 63964771734fbd76e3b40519d1d94a48,
7dd7364cd842ad18c17c2b820c84c3d6, 63964771734fbd76e3b40519d1d9
Sample5, 01020304, f1a24abea9b86cd33380a24c4dfbe743, efb2255e6422d330088e09bb015ed707
Sample6, 01020304, f1a24abea9b86cd33380a24c4dfbe744, efb2255e6422d330088e09bb015ed708
The Friendly Name is displayed in the summary column of the Mesh tab in the Frame Display. This will help
the user to filter based on the Friendly Name.
Note: "Unknown Network" will be displayed when the given key set(s) defined in
MeshOptions.ini is unable to decrypt a certain frame.
For CSRmesh,
Table 3.8 - CSRmesh Key Set Format
Name Enter as Description
Technology Identifier
Tag
[CSRmesh]
Required to differentiate from [mesh].
Software will only look for keys after this tag, ignoring
comments.
Case insensitive within the brackets.
Key set Name,
passphrase
The following code is an example of CSRmesh decryption key set entry.
[csrmesh]
// Format: My Network, My Password //My Comments
MySampleHome, Password
test
Test Home 1, test1
TestHome2, test2
BT, bluetooth
BT1, bluetooth1
BT2, bluetooth2
Comma separated:
Name = the network name.
passphrase = the network key. If not present a key is not
necessary.
Loading keys or key sets
When the Frontline software is initially loaded, keys or
the key sets will be automatically read from the
MeshOptions.ini file. If the keys or the key sets are
modified while the Frontline software is running,
decoders must be reloaded and the companion files
must be recreated for the change to take effect. Follow
these steps to reload the decoders.
1. In the Frame Display, click on the Reload
Decoders icon , or select Reload
Decoders from the File menu.
2. From the File menu, select Recreate Companion Files.
CSRmesh in BPA 600
Frontline BPA 600 Hardware & Software User Manual 54
Page 63

TELEDYNE LECROY Chapter 3 Configuration Settings
BPA 600 will automatically capture any Bluetooth low energy Advertising packets. CSRmesh packets
transmitted over random Non Resolvable Private Address will be captured and displayed in the Frame
Display.
CSRmesh over GATT
ATT maintains a database which maps handles & UUIDs. When there is a connection request the mappings
will be loaded to the initiator and/or advertiser sides of the database.
Phones can bypass pairing process for pre-paired devices. In this case, handle/UUID can be mapped by brute
force using ATT_Handle_UUID_PreLoad.ini file. This file is to be placed in the root of My Decoders Folder.
For additional information refer to Bluetooth low energy ATT Decoder Handle Mapping on page 286.
Mesh in the Frame Display
In the Frame Display Summary pane, Mesh tabs appear for MTP, MASP, and MCP. The CSRMesh MTP tab
displays the MASP and MCP protocols in the Summary pane.
Figure 3.33 - CSRMesh MTP tab Summay pane display
The bearer can be "ATT" or "LE", and the protocols detected can be "MASP", "MCP", or "Unknown". When the
MTP tab displays "Unknown" in the Protocol column it means
l that the Generated MAC does not match the Received MAC in the packet,
l that there is not a key set to decrypt the payload.
The CSRMesh MASP tab is shown in CSRMesh MSRP tab with Decoder pane inset on page 56 shows the
Decoder pane (inset) with the "Network Info" passphrase and network key shown but there is no network
name.
55 Frontline BPA 600 Hardware & Software User Manual
Page 64

Chapter 3 Configuration Settings TELEDYNE LECROY
Figure 3.34 - CSRMesh MSRP tab with Decoder pane inset
The CSRMesh MCP tab is shown in CSRMesh MCP tab with Decoder pane inset on page 56 shows the Decoder
pane (inset) with the "Network Info" passphrase and network key and network name shown. The network
name appears in the Network column of the Summary pane.
Figure 3.35 - CSRMesh MCP tab with Decoder pane inset
Troubleshooting Tips
MeshOptions.ini Errors
Frontline BPA 600 Hardware & Software User Manual 56
Page 65

TELEDYNE LECROY Chapter 3 Configuration Settings
Table 3.9 - Errors Associated with MeshOptions.ini
Error Displayed Descripton
Error: IV Index should be 8 bytes The IV Index read from MeshOptions.ini is not 8
bytes.
Error: App Key should be 16 bytes The App Key read from MeshOptions.ini is not 16
bytes
Error: Net Key should be 16 bytes The Net Key read from MeshOptions.ini is not 16
bytes
Error: Bad Format. Expected (Name, IVI, App,
Net, Dev)
Something is wrong with formatting (Can be
missing Friendly Name or missing IV Index,
missing App Key,r missing Net key, or missing
commas ‘,’).
Error: MeshOptions.ini file not found The file cannot be located
CSRmesh Errors
a. Incorrect key set
l When the key set entered in MeshOptions.ini is incorrect, most of the Mesh Transport Protocol
frames will contain Mesh Protocol Detected: Error.
l The term “Most” is used because it excludes Mesh Association Protocol (MASP) packets. MASP
packets use a constant Passphrase of 0x00 || MASP.
Figure 3.36 - CSRmesh Bad MAC
l An error message will also be displayed, saying “MAC doesn’t match MASP or MCP”.
This error simply means that the generated MAC does not match the received MAC. This error will
also be generated in the case of a bad packet
b. Decryption Error
l The error message associated with a decryption error will say "Decryption Error".
c. Payload Size
l MTL payload<=9 bytes (MAC+TTL)
o
This error is implying that the Mesh Transport Layer (MTL or MTP) has a payload of less than 9
bytes.
o
Message Authentication Code (MAC) is 8 bytes and Time to live (TTL) is 1 byte.
l HML payload is not available
o
This error indicates that MTP payload contains MAC and TTL but HLM payload is missing or is 0
bytes.
57 Frontline BPA 600 Hardware & Software User Manual
Page 66

Chapter 3 Configuration Settings TELEDYNE LECROY
l MCP data has no encrypted payload
o
This error indicates that the MCP payload contains the nonce (sequence number and source
address) but encrypted payload is missing from the packet.
Bluetooth technology using mesh networking Errors
Table 3.10 - Errors: Bluetooth technology using mesh networking
Error Description
"Reserved"
Opcode
Possible error in
This is most likely the scenario when incorrect keys have been entered. Correct
the keys in the MeshOptions.ini file and reload decoders.
Possible error in net decryption
net decryption
Possible error in
Possible error in app decryption
app decryption
3.4 Conductive Testing
Conductive testing could be used for many reasons, but the most common use is to isolate the Set in Target
test setup from the surrounding environment. Interference from radio frequency (RF) sources is the most
common reason for isolating the test from the environment. This is especially important when the
environment contains RF sources using the industrial, scientific, and medical (ISM) radio bands from 2.4 to
2.485 GHz that are the bands used for Set in Target.
“Conductive” in this context means that you are not “air sniffing”, that is, capturing Set in Target transmissions
on the Frontline analyzer's antenna. The conductive test setup uses coaxial cable to directly connect the
Device Under Test (DUT) to the analyzer's antenna connectors. The coaxial cable provides the isolation from
the environment through shielding.
3.4.1 Classic Bluetooth Transmitter Classes
Classic Bluetooth transmitters are categorized by power classes, that is, by the amount of RF power output. A Bluetooth Class maximum operating range is directly related to the power output. The class is important in
conductive testing because the DUTs and the Frontline unit are connected directly to each other, usually over
small distances. The absence of power loss , which occurs during over-the-air transmission, means that larger
than normal power levels may be present at the receiving port. Attenuation may be necessary to protect both
the DUT and the Frontline unit from excessive power input and to ensure reliable operation.
Classic Bluetooth Power Classes below lists the maximum power and operating range for each Classic
Bluetooth Class.
Table 3.11 - Classic Bluetooth Power
Classes
Class Maximum Power Operating Range
1 100 mW (20 dBm) 100 meters
2 2.5 mW (4 dBm) 10 meters
3 1 mW (0 dBm) 1 meter
Caution: Good engineering judgment is essential to protecting both the Frontline low
energy protocol analyzer and the devices under test from power levels that could
cause damage. The procedures contained here are general guidelines for connecting
the equipment for conductive testing.
Frontline BPA 600 Hardware & Software User Manual 58
Page 67

TELEDYNE LECROY Chapter 3 Configuration Settings
3.4.2 Bluetooth low energy Transmitter
A Bluetooth low energy device maximum operating range is directly related to the power output. The power
output is important in conductive testing because the DUTs and the Frontline unit are connected directly to
each other, usually over small distances. The absence of power loss, which occurs during over-the-air
transmission, means that larger than normal power levels may be present at the receiving port. Attenuation
may be necessary to protect both the DUT and the Frontline unit from excessive power input and to ensure
reliable operation.
Bluetooth low energy Transmitter below lists the maximum power and operating range for Bluetooth low
energy transmitters.
Table 3.12 - Bluetooth low energy Transmitter
Bluetooth SIG
Specification
Up to 4 10 dBm (5 mW) 50 meters
Caution: Good engineering judgment is essential to protecting both the Frontline low
energy protocol analyzer and the devices under test from power levels that could
cause damage. The procedures contained here are general guidelines for connecting
the equipment for conductive testing.
Maximum
Power
Operating
Range
3.4.3 BPA 600 Conductive Testing
Test Equipment
While exact conductive test setups are dependent on the specific circumstances surrounding the DUT RF
interface, the following equipment is required for all test setups.
l Coaxial cable with adapter for connecting to DUT 1.
l Coaxial cable with adapter for connecting to DUT 2.
l 2 Coaxial T-connectors.
l 2 SMA adapters for connecting coaxial cable or attenuators to the BPA 600 antenna connectors.
l Attenuators depending on the Bluetooth Class being tested.
l Frontline BPA 600 Dual Mode Bluetooth Protocol Analyzer
l Personal computer for running Frontline software.
Test Set Up
BPA 600 Conductive Test Setup on page 60 shows the test setup.
59 Frontline BPA 600 Hardware & Software User Manual
Page 68

Chapter 3 Configuration Settings TELEDYNE LECROY
Figure 3.37 - BPA 600 Conductive Test Setup
Both ComProbe BPA 600 antennas must be connected as shown.
The AT1 through AT4 attenuator values will depend on the DUT1 and DUT2 transmitter Class. At higher power
levels all four attenuators may be needed. In all cases, use good engineering practices to protect the devices
under test and the ComProbe hardware from damage, and to ensure reliable operation.
Assuming that there is no attenuation in the test setup:
l At each T-connector the power will split in half. Therefore the power reaching the BPA 600 protocol
analyzer will be one-fourth the transmitted power. For example if DUT1 is a Class 1 device transmitting
+20 dBm (100 mW), at the first T-connector it will split with +17 dBm (50 mW) going to DUT2 and +17dBm
(50 mW) going to the ComProbe analyzer.
l The +17dBm (50 mW) going to the ComProbe analyzer splits again. Each coaxial cable going to a
ComProbe analyzer antenna connector carries +14 dBm (25 mW).
l If DUT1 or DUT2 is a Class 2 device, +8 dBm (6.25 mW) will reach each ComProbe analyzer antenna
connector. If they are Class 3 devices, -6 dBm (0.25 mW) will reach each antenna connector.
l Attenuation should be selected to limit the received power levels to prevent equipment damage, and to
provide sufficient power to reliably operate the equipment. If using attenuation follow these
recommendations:
l If the devices are of the same class, the attenuators AT1 and AT2 should be of equal value.
l Attenuators AT3 and AT4 should be of equal value.
l Determine the maximum power received at the ComProbe antenna jacks. Then select an appropriate
attenuator value to limit the input power to -20 dBm (10 μW) maximum.
3.4.4 Bluetooth Conductive Test Process
After connecting DUT1, DUT2, and the Frontline Bluetooth protocol analyzer hardware, follow these steps to
capture Bluetooth data.
Frontline BPA 600 Hardware & Software User Manual 60
Page 69

TELEDYNE LECROY Chapter 3 Configuration Settings
1. Pair DUT 1 and DUT 2.
2. Establish data transmission between DUT 1 and DUT 2.
3. Begin capture of the data with the Frontline protocol analyzer.
4. Conduct protocol analysis with the Frontline software on the personal computer or save the capture
file for future analysis.
61 Frontline BPA 600 Hardware & Software User Manual
Page 70

Chapter 4 Capturing and Analyzing Data
The following sections describe the various ComProbe software functions that capture and display data
packets.
4.1 Capture Data
4.1.1 Air Sniffing: Positioning Devices
When capturing over the air packets, proper positioning of the Frontline hardware and the Devices Under
Test (DUTs) will result in the best possible captures and will mitigate sources of path loss and interference.
The following procedures will help optimize the capture process especially if you are have problems
obtaining reliable …captures.
Problems with indoor radio propagation
Even in free space, it is well understood that radio frequencies attenuate over distance. The free-space ruleof-thumb dictates that radio energy decreases in strength by 20 dB by each 10-to-1 increase in range. In the
real-world, the effects of objects in an outdoor environment cause reflection, diffraction, and scattering
resulting in greater signal losses. Indoors the situation can be worse. Reflections occur from walls and other
large flat surfaces. Diffraction occurs from objects with sharp edges. Scattering is produced from objects with
rough surfaces and from small objects. Also any object directly in the path of the radiation can present a hard
or soft partition depending on the partition's material properties. Path losses from partitions are difficult to
estimate.
Estimating indoor propagation loss
One estimate of indoor path loss, based on path loss data from a typical building, provides a power
rule. At 2.4 GHz, the following relationship provides an approximate estimate of indoor path loss:
This approximation is expected to have a variance of 13 dB.
Frontline BPA 600 Hardware & Software User Manual 62
Page 71

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Mitigating path loss and interference
Bluetooth device design contributes to mitigating environmental effects on propagation through spread
spectrum radio design, for example. However, careful planning of the testing environment can also
contribute to reliable data capture process.
The first step to ensuring reliable air-sniffing data capture is to understand the RF characteristics of the
Devices Under Test (DUTs). The Bluetooth Class, antenna types, and radiation patterns are all important factors
that can affect the placement of the DUTs and the Frontline hardware. Radiation patterns are rarely spherical,
so understanding your device's radiation patterns can greatly enhance successful data capture. Position
devices to avoid radiation attenuation by the surroundings.
This step is optional: Consider conductive testing to establish a baseline capture. Conductive testing isolates
the DUTs and analyzer from environmental effects.
The next step is to ensure that the testing environment is as clutter-free as possible.
l Line-of-sight obstructions should be eliminated between the Frontline hardware and the DUTs because
they cause a reduction in signal strength. Obstructions include, but are not limited to: water bottles,
coffee cups, computers, computer screens, computer speakers, and books. A clear, unobstructed line-ofsight is preferred for DUT and Frontline hardware positioning.
l If using an analyzer connected to a computer, position the computer on an adjacent table or surface away
from the analyzer and DUTs, taking advantage of the cables' length. If this is not possible, position the
computer behind the analyzer as far away as possible. If using the Frontline FTS4BT, which is a dongle,
either use an extension USB cable or position the computer such that the dongle is positioned towards the
DUTs.
l The preferred placement is positioning the DUTs and the Frontline hardware at the points of an
equilateral triangle in the same horizontal plane, i.e. placed on the same table or work surface. The sides
of the triangle should be between 1 and 2 meters for Bluetooth transmitter classes 1 and 2. The distance
for transmitter class 3 should be 1/2 meter.
Figure 4.1 - Devices Equally Spaced in the Same Horizontal Plane
Finally, eliminate other RF sources.
63 Frontline BPA 600 Hardware & Software User Manual
Page 72

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
l Wi-Fi interference should be minimized or eliminated. Bluetooth shares the same 2.4 GHz frequency
bands as Wi-Fi technology. Wi-Fi interference can cause loss of packets and poor captures. In a laboratory
or testing environment do not place the DUTs and Frontline hardware in close proximity with Wi-Fi
transmitting sources such as laptops or routers. Turning off Wi-Fi on the computer running the Frontline
software is recommended.
Positioning for audio capture
The Bluetooth Audio Expert System provides analysis of audio streams and can assist in identifying problems
with capture methods including positioning and environment because it will point out missing frames. For
hands-free profile data captures both DUTs send and receive data. Therefore, position the devices following
the equilateral triangle arrangement as mentioned above.
However, in A2DP data capture scenario, the equilateral positioning of devices is not optimum because,
normally, only one device is sending data to the other. It is recommended that the Frontline hardware be
positioned closer to the device receiving data so that Frontline better mimics the receiving DUT. Position the
DUTs 1 -2 meters apart for Class 1 and 2 transmitters, and 1/2 meter apart for Class 3 transmitters.
Figure 4.2 - For Audio A2DP, Position Closer to SINK DUT
Poor Placement
A poor test configuration for the analyzer is placing the DUTs very close to each other and the analyzer far
away. The DUTs, being in close proximity to each other, reduce their transmission power and thus make it
hard for the analyzer to hear the conversation. If the analyzer is far away from DUTs, there are chances that
the analyzer may miss those frames, which could lead to failure in decryption of the data.
Obstacles in close proximity to or in between the analyzer and the DUTs can interfere and cause reduction in
signal strength or interference. Even small objects can cause signal scattering.
Frontline BPA 600 Hardware & Software User Manual 64
Page 73

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Figure 4.3 - Example: Poor Capture Environment
4.1.2 Capturing Data with BPA 600 Analyzer
So, now we have our ComProbe BPA600 analyzer installed, devices under test turned on and identified in
BPA600 datasource; it is time to sniff the communication between the devices and capture data.
Once you have completed the Devices Under Test selection, you are ready to capture data.
1. Select Start Sniffing on the Datasource dialog from the toolbar (Figure 4.4) .
Figure 4.4 - Start Sniffing from Datasource Toolbar.
2. Begin the pairing process between the devices (Only if you are using Classic or Classic/low energy.
Low energy by itself does not require that devices be paired.)
As data is being captured, the Capture Status message in the Control window indicates the synchronization
status of the ComProbe BPA600 analyzer as well as the Master-Slave relationship. The colored arrows change
depending on the synchronization state and the direction of the arrow points from Master (arrow tail) to Slave
(arrow head). There are five states:
Table 4.1 - BPA 600 Roleless Arrows
Arrow Description
Blue = synchronized with the Master clock - link active.
65 Frontline BPA 600 Hardware & Software User Manual
Page 74

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
Table 4.1 - BPA 600 Roleless Arrows (continued)
Arrow Description
Green = running and waiting for Master to connect to the Slave. A double headed arrow
means that the master and slave have yet to be determined.
Red = initializing or halted. A double headed arrow means that the master and slave have
yet to be determined.
Yellow = waiting for the Master to resume transmission.
Gray = synchronized with the Master clock - link inactive.
When you are capturing data, there are several important concepts to consider.
l Files are placed in My Capture Files by default and have a .cfa extension. Choose Directories from the
Options menu on the Control window to change the default file location.
l Watch the status bar on the Control window to monitor how full the file is. When the file is full, it begins
to wrap , which means the oldest data will be overwritten by new data.
l
Click the Stop icon to temporarily stop data capture. Click the Start Capture icon again to resume
capture. Stopping capture means no data will be added to the capture file until capture is resumed, but
the previously captured date remains in the file.
l
To clear captured data, click the Clear icon .
l If you select Clear after selecting Stop, a dialog appears asking whether you want to save the data.
o
You can click Save File and enter a file name when prompted .
o
If you choose Do Not Save, all data will be cleared.
o
If you choose Cancel, the dialog closes with no changes to the data.
l If you select the Clear icon while a capture is occurring:
o
The capture stops.
o
A dialog appears asking if you want to save the capture
o
You can select Yes and save the capture or select No and close the dialog. In either case, the existing
capture file is cleared and a new capture file is started.
o
If you choose Cancel, the dialog closes with no changes to the data.
l The link key/pin code can be changed while sniffing and the changes will be automatically saved in the
configuration file.
Frontline BPA 600 Hardware & Software User Manual 66
Page 75

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
o
While the device is sniffing click in the Classic Encryption link key/pin code field. This action
places the focus on that window.
o
Change the link key/pin code.
o
The Status window at the bottom of the page will inform the user to move focus away from the
link key/pin code window.
o
Click the mouse outside the link key/pin code field or press the Tab key. This action will remove
the focus from the link key/pin code window.
o
The link key/pin
code changes are
automatically saved
to the configuration file.
4.1.2.1 BPA 600 Capture with ProbeSync
ProbeSync™ allows multiple ComProbe analyzers to work seamlessly together and to share a common clock.
Clock sharing allows the analyzers to precisely synchronize communications stream and to display resulting
packets in a single shared view.
If two ComProbe BPA 600 hardware are connected in a ProbeSync configuration, two to four links can be
synchronized. Four links result when each BPA 600 analyzer is configured for Classic Only Multiple
Connections with two links per BPA 600 device.
When configured for synchronization through ProbeSync one BPA 600 device provides the clock to the other
device. The clock is provided by a CAT 5 cable between the master BPA 600 OUT connector—sending the
synchronizing clock—to the BPA 600 hardware IN connector—receiving the clock.
When the BPA 600 software runs in ProbeSync one Control window opens with two BPA 600 datasource
windows, one for each connected device. Each device datasource is setup individually to sniff their respective
link. Should the hardware be connected incorrectly, that is IN to IN or OUT to OUT, an error message will
appear. Follow the instructions in error message. To continue click on the OK button. The BPA 600
datasource Status window will also display a warning message suggesting information sources.
Figure 4.5 - Incorrect ProbeSync Hardware Connection Error
67 Frontline BPA 600 Hardware & Software User Manual
Page 76

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
Figure 4.6 - Incorrect ProbeSync Hardware Connection Message In Datasource Status
In the device providing the clock, the BPA 600 datasource dialog the Start Sniffing button initiates
the capture for both devices. On the device receiving the clock—cable connected to IN— the BPA 600
datasource dialog Start Sniffing button is disabled when using ProbeSync. In the both device's status
window in the BPA 600 Datasource dialog will announce the synchronizing function of each.
Figure 4.7 - BPA 600 ProbeSync Synchronizing Device Status Message
Figure 4.8 - BPA 600 ProbeSync Synchronized Device Status Message
Data captured in the synchronized device will appear in the Frame Display, Event Display, Bluetooth
Timeline, Bluetooth low energy Timeline, and Coexistence View. Data saved as a capture file will
include data captured on both devices.
BPA 600 hardware can also be connected via ProbeSync to ComProbe 802.11 hardware, but the BPA 600
device must be connected to provide the clock—the CAT5 cable connected to the BPA 600 OUT jack.
4.1.3 Combining BPA 600, 802.11, and HSU with ProbeSync
ProbeSync™ allows multiple ComProbe analyzers to work seamlessly together and to share a common clock.
Clock sharing allows the analyzers to precisely synchronize communications stream and to display resulting
packets in a single shared view.
The ComProbe BPA 600, ComProbe 802.11, and ComProbe HSU analyzers have ProbeSync capability allowing
timestamp synchronization of captured data. Synchronizing the clock for these ComProbe devices used in
combination requires attention to the sequence of hardware connection. It is important to remember the
following key points.
l ComProbe devices are connected serially in a daisy-chain fashion. The combined length of all cables in the
chain cannot exceed 1.5 meters (4.5 ft.).
l The "master" ComProbe device provides the clock to the other devices. All other ComProbe devices are
"slaves" and received the clock from the "master" device.
l On ComProbe devices with an OUT and IN connector, the function of these connectors is dependent on
if they are a "master" or a "slave".
o
"master" device: OUT connector provides the clock to all "slave" devices. IN connector is not used.
o
"slave" device: IN connector receives the clock from the OUT connector of the prior device in the
chain. The OUT connector is just a pass-through connector on a "slave" device.
l BPA 600 is always the "master" device and the first device in the chain, if being used.
l HSU is always the last "slave" device in the chain, if being used.
l HSU maximum capture data rate is 6 Mbit/sec.
Frontline BPA 600 Hardware & Software User Manual 68
Page 77

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Connecting ComProbe BPA 600, ComProbe 802.11, and ComProbe HSU devices in ProbeSync takes place in
the following steps.
1. Connect the ComProbe BPA 600 OUT connector to the ComProbe 802.11 IN connector.
2. Connect the ComProbe HSU Cat 5 cable to the ComProbe 802.11 OUT connector.
Each device datasource is setup individually to sniff their respective link. That is, you will see a separate
datasource window for the BPA 600 device, the 802.11 device, and the HSU device.
Data saved as a capture file will include data captured on each device.
Should the hardware be connected incorrectly, that is IN to IN or OUT to OUT, an error message will
appear. Follow the instructions in error message. To continue click on the OK button. The ComProbe device
datasource Status window will also display a warning message suggesting information sources.
Figure 4.9 - Incorrect ProbeSync Hardware Connection Error
Figure 4.10 - Incorrect ProbeSync Hardware Connection Message In Datasource Status
The BPA 600 datasource dialog Start Sniffing button initiates the capture for all connected
ComProbe 802.11 and HSU devices. On the 802.11 and HSU receiving the clock—cable connected to IN—
the Start Sniffing button is disabled when using ProbeSync. In each ComProbe device's Control window
status window will announce the synchronizing function.
69 Frontline BPA 600 Hardware & Software User Manual
Page 78

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
Figure 4.11 - ProbeSync Synchronizing Device Status Message
Figure 4.12 - ProbeSync Synchronized Device Status Message
Data captured in the synchronized device will appear in the Frame Display, Event Display, Bluetooth
Timeline, Bluetooth low energy Timeline, and Coexistence View.
4.1.4 Extended Inquiry Response
Extended Inquiry Response (EIR) is a tab that appears automatically on the Frame Display window
when you capture data.
Figure 4.13 - Frame Display Extended Inquire Response
EIR displays extensive information about the Bluetooth® devices that are discovered as data is being captured.
EIR provides more information during the inquiry procedure to allow better filtering of devices before
connection; and sniff subrating, which reduces the power consumption in low-power mode.Before the EIR
tab was created, this type of information was not available until a connection was made to a device.
Therefore, EIR can be used to determine whether a connection can/should be made to a device prior to
making the connection.
Frontline BPA 600 Hardware & Software User Manual 70
Page 79

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Note: If a Bluetooth device does not support Extended Inquiry Response, the tab
displays Received Signal Strength Indication (RSSI) data, which is less extensive
than EIR data.
4.2 Protocol Stacks
4.2.1 Protocol Stack Wizard
The Protocol Stack wizard is where you define the
protocol stack you want the analyzer to use when
decoding frames.
To start the wizard:
1. Choose Protocol Stack from the Options
menu on the Control window or click the
Protocol Stack icon on the Frame
Display.
2. Select a protocol stack from the list, and
click Finish.
Most stacks are pre-defined here. If you have
special requirements and need to set up a custom
stack, see Creating and Removing a Custom Stack
on page 72.
1. If you select a custom stack (i.e. one that was defined by a user and not included with the analyzer),
the Remove Selected Item From List button becomes active.
2. Click the Remove Selected Item From Listbutton to remove the stack from the list. You cannot
remove stacks provided with the analyzer. If you remove a custom stack, you need to define it again in
order to get it back.
If you are changing the protocol stack for a capture file, you may need to reframe. See Reframing on page 73
for more information.
You cannot select a stack or change an existing one for a capture file loaded into the Capture File Viewer (the
Capture File Viewer is used only for viewing capture files and cannot capture data). Protocol Stack changes
can only be made from a live session.
71 Frontline BPA 600 Hardware & Software User Manual
Page 80

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
4.2.2 Creating and Removing a Custom Stack
To create a custom stack:
1. Choose Protocol Stack from the
Options menu on the Control
window or click the Protocol Stack
icon on the Frame Display
toolbar.
2. Select Build Your Own from the
list and click Next.
3. The system displays an information
screen that may help you decide if
you need to define your own
custom stack. Defining a custom
stack means that the analyzer uses
the stack for every frame. Frames
that do not conform to the stack
are decoded incorrectly. Click
Next to continue.
Select Protocols
1. Select a protocol from the list on
the left.
2. Click the right arrow button to
move it to the Protocol Decode
Stack box on the right, or doubleclick the protocol to move it to the
right.
3. To remove a protocol from the
stack, double-click it or select it
and click the left arrow button.
4. If you need to change the order of the protocols in the stack, select the protocol you want to move,
and click on the Move Up and Move Down buttons until the protocol is in the correct position.
5. The lowest layer protocol is at the top of the list, with higher layer protocols listed underneath.
Auto-traversal (Have the analyzer Determine Higher Layers)
If you need to define just a few layers of the protocol stack, and the remaining layers can be determined
based on the lower layers:
1. Click the All additional stack layers can be determined automatically button.
2. If your protocol stack is complete and there are no additional layers, click the There are no
additional stack layers button.
3. If you select this option, the analyzer uses the stack you defined for every frame. Frames that do use
this stack are decoded incorrectly.
Frontline BPA 600 Hardware & Software User Manual 72
Page 81

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Save the Stack
1. Click the Add To Predefined List button.
2. Give the stack a name, and click Add.
In the future, the stack appears in the Protocol Stack List on the first screen of the Protocol Stack wizard.
Remove a Stack
1. Select it in the first screen and click Remove Selected Item From List.
2. If you remove the stack, you must to recreate it if you need to use it again.
Note: If you do not save your custom stack, it does appear in the predefined list, but
applies to the frames in the current session. However, it is discarded at the end of the
session.
4.2.3 Reframing
If you need to change the protocol stack used to interpret a capture file and the framing is different in the
new stack, you need to reframe in order for the protocol decode to be correct. You can also use Reframe to
frame unframed data. The original capture file is not altered during this process.
Note: You cannot reframe from the Capture File Viewer .
To reframe your data, load your capture file, select a protocol stack, and then select Reframe from the File
menu on the Control window. Reframe is only available if the frame recognizer used to capture the data is
different from the current frame recognizer.
In addition to choosing to Reframe, you can also be prompted to Reframe by the Protocol Stack Wizard.
1. Load your capture file by choosing Open from the File menu on the Control window, and select the
file to load.
2. Select the protocol stack by choosing Protocol Stack from the Options menu on the Control
window, select the desired stack and click Finish.
3. If you selected a protocol stack that includes a frame recognizer different from the one used to
capture your data, the Protocol Stack Wizard asks you if you want to reframe your data. Choose
Yes.
4. The analyzer adds frame markers to your data, puts the framed data into a new file, and opens the
new file. The original capture file is not altered.
See Unframing on page 73for instructions on removing framing from data.
4.2.4 Unframing
This function removes start-of-frame and end-of-frame markers from your data. The original capture file is
not altered during this process. You cannot unframe from the Capture File Viewer (accessed by selecting
Capture File Viewer or Load Capture File to start the software and used only for viewing capture files).
To manually unframe your data:
1. Select Unframe from the File menu on the Control window. Unframe is only available if a
protocol stack was used to capture the data and there is currently no protocol stack selected.
In addition to choosing to Unframe, you can also be prompted to Unframe by the Protocol Stack Wizard.
73 Frontline BPA 600 Hardware & Software User Manual
Page 82

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
1. Load your capture file by choosing Open from the File menu on the Control window.
2. Select the file to load.
3. Choose Protocol Stack from the Options menu on the Control window
4. Select None from the list
5. Click Finish. The Protocol Stack Wizard asks you if you want to unframe your data and put it into a
new file.
6. Choose Yes.
The system removes the frame markers from your data, puts the unframed data into a new file, and opens
the new file. The original capture file is not altered.
See Reframing on page 73 for instructions on framing unframed data.
4.2.5 How the Analyzer Auto-traverses the Protocol Stack
In the course of doing service discovery, devices ask for and receive a Protocol Descriptor List defining which
protocol stacks the device supports. It also includes information on which PSM to use in L2CAP, or the channel
number for RFCOMM, or the port number for TCP or UDP. The description below talks about how the
analyzer auto-traverses from L2CAP using a dynamically assigned PSM, but the principle is the same for
RFCOMM channel numbers and TCP/UDP port numbers.
The analyzer looks for SDP Service Attribute Responses or Service Search Attribute Responses carrying
protocol descriptor lists. If the analyzer sees L2CAP listed with a PSM, it stores the PSM and the UUID for the
next protocol in the list.
After the SDP session is over, the analyzer looks at the PSM in the L2CAP Connect frames that follow. If the
PSM matches one the analyzer has stored, the analyzer stores the source channel ID and destination channel
ID, and associates those channel IDs with the PSM and UUID for the next protocol. Thereafter, when the
analyzer sees L2CAP frames using those channel IDs, it can look them up in its table and know what the next
protocol is.
In order for the analyzer to be able to auto-traverse using a dynamically assigned PSM, it has to have seen the
SDP session giving the Protocol Descriptor Lists, and the subsequent L2CAP connection using the PSM and
identifying the source and channel IDs. If the analyzer misses any of this process, it is not able to auto-traverse.
It stops decoding at the L2CAP layer.
For L2CAP frames carrying a known PSM (0x0001 for SDP, for example, or 0x0003 for RFCOMM), the analyzer
looks for Connect frames and stores the PSM along with the associated source and destination channel IDs. In
this case the analyzer does not need to see the SDP process, but does need to see the L2CAP connection
process, giving the source and destination channel IDs.
4.2.6 Providing Context For Decoding When Frame Information Is Missing
There may be times when you need to provide information to the analyzer because the context for decoding
a frame is missing. For example, if the analyzer captured a response frame, but did not capture the command
frame indicating the command.
The analyzer provides a way for you to supply the context for any frame, provided the decoder supports it.
(The decoder writer has to include support for this feature in the decoder, so not all decoders support it.
Note that not all decoders require this feature.)
If the decoder supports user-provided context, three items are active on the Options menu of the Control
window and the Frame Display window. These items are Set Initial Decoder Parameters,
Automatically Request Missing Decoding Information, and Set Subsequent Decoder Parameters.
(These items are not present if no decoder is loaded that supports this feature.)
Frontline BPA 600 Hardware & Software User Manual 74
Page 83

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Set Initial Decoder Parameters is used to provide required information to decoders that is not context
dependent but instead tends to be system options for the protocol.
Choose Set Initial Decoder Parameters in order to provide initial context to the analyzer for a decoder. A
dialog appears that shows the data for which you can provide information.
If you need to change this information for a particular frame :
1. Right-click on the frame in the Frame Display window
2. Choose Provide <context name>.
Alternatively, you can choose Set Subsequent Decoder Parameter from the Options menu.
3. This option brings up a dialog showing all the places where context data was overridden.
4. If you know that information is missing, you can't provide it, and you don't want to see dialogs asking
for it, un-check Automatically Request Missing Decoding Information.
5. When unchecked, the analyzer doesn't bother you with dialogs asking for frame information that you
don't have. In this situation, the analyzer decodes each frame until it cannot go further and then simply
stop decoding.
4.3 Analyzing Protocol Decodes
4.3.1 The Frame Display
To open this window
Click the Frame Display icon on the Control window toolbar, or select Frame Display from the
View menu.
75 Frontline BPA 600 Hardware & Software User Manual
Page 84

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
Figure 4.14 - Frame Display with all panes active
Frame Display Panes
The Frame Display window is used to view all frame related information. It is composed of a number of
different sections or "panes", where each pane shows a different type of information about a frame.
l Summary Pane - The Summary Pane displays a one line summary of each frame for every protocol
found in the data, and can be sorted by field for every protocol. Click here for an explanation of the
symbols next to the frame numbers.
l Decode Pane - The Decode Pane displays a detailed decode of the highlighted frame. Fields selected in
the Decode Pane have the appropriate bit(s) or byte(s) selected in the Radix, Binary, Character , and
Event panes
l Radix Pane - The Radix Pane displays the logical data bytes in the selected frame in either hexadecimal,
decimal or octal.
l Binary Pane - The Binary Pane displays a binary representation of the logical data bytes.
Frontline BPA 600 Hardware & Software User Manual 76
Page 85

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
l Character Pane - The Character Pane displays the character representation of the logical data bytes in
either ASCII, EBCDIC or Baudot.
l Event Pane - The Event Pane displays the physical data bytes in the frame, as received on the network.
By default, all panes except the Event Pane are displayed when the Frame Display is first opened.
Protocol Tabs
Protocol filter tabs are displayed in the Frame Display above the Summary pane.
l These tabs are arranged in separate color-
coded groups. These groups and their
colors are General (white), Classic
Bluetooth (blue), Bluetooth low energy
(green), 802.11 (orange), USB (purple),
NFC (brown) and SD (teal). The General
group applies to all technologies. The
other groups are technology-specific.
l Clicking on a protocol filter tab in the General group filters in all packets containing that protocol
regardless of each packet’s technology.
l Clicking on a protocol filter tab in a technology-specific group filters in all packets containing that protocol
on that technology.
l A protocol filter tab appears in the General group only if the protocol occurs in more than one of the
technology-specific tab groups. For example, if L2CAP occurs in both Classic Bluetooth and Bluetooth low
energy , there will be L2CAP tabs in the General group, the Classic Bluetooth group, and the Bluetooth
low energy group.
Select the Unfiltered tab to display all packets.
There are several special tabs that appear in the Summary Pane when certain conditions are met. These
tabs appear only in the General group and apply to all technologies. The tabs are:
l Bookmarks appear when a bookmark is first seen.
l Errors appear when an error is first seen. An error is a physical error in a data byte or an error in the
protocol decode.
l Info appears when a frame containing an Information field is first seen.
The tabs disappear when the capture buffer is cleared during live capture or when decoders are reloaded,
even if one of the tabs is currently selected. They subsequently reappear as the corresponding events are
detected.
Comparing Frames
If you need to compare frames, you can open additional Frame Display windows by clicking on the
Duplicate View icon . You can have as many Frame Display windows open at a time as you wish.
Frame Wrapping and Display
In order to assure that the data you are seeing in Frame Display are current, the following messages appear
describing the state of the data as it is being captured.
l All Frame Display panes except the Summary pane display "No frame selected" when the selected
frame is in the buffer (i.e. not wrapped out) but not accessible in the Summary pane. This can happen
when a tab is selected that doesn’t filter in the selected frame.
77 Frontline BPA 600 Hardware & Software User Manual
Page 86

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
l When the selected frame wraps out (regardless of whether it was accessible in the Summary pane) all
Frame Display panes except the Summary pane display "Frame wrapped out of buffer".
l When the selected frame is still being captured, all Frame Display panes except the Summary pane
display "Frame incomplete".
4.3.1.1 Frame Display Toolbar
The buttons that appear in the Frame Display window vary according to the particular configuration of the
analyzer. For controls not available the icons will be grayed-out.
Table 4.2 - Frame Display Toolbar Icons
Icon Description
Control – Brings the Control window to
the front.
Open File - Opens a capture file.
I/O Settings - Opens the I/O Settings
dialog.
Save - Save the currently selected bytes
or the entire buffer to file.
Clear- Discards the temporary file and
clears the display.
Event Display – Brings the Event Display
window to the front.
Show Message Sequence Chart Message Sequence Chart (MSC)
displays information about the messages
passed between protocol layers.
Duplicate View - Creates a second Frame
Display window identical to the first.
Apply/Modify Display Filters - Opens the
Display Filter dialog.
Quick Protocol Filter - brings up a dialog
box where you can filter or hide one or
more protocol layers.
Protocol Stack - brings up the Protocol
Stack Wizard where you can change the
stack used to decode framed data
Reload Decoders - When Reload
Decoders is clicked, the plug-ins are
reset and received frames are redecoded. For example, If the first frame
occurs more than 10 minutes in the past,
the 10-minute utilization graph stays
blank until a frame from 10 minutes ago or
less is decoded.
Frontline BPA 600 Hardware & Software User Manual 78
Page 87

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Table 4.2 - Frame Display Toolbar Icons(continued)
Icon Description
Find - Search for errors, string patterns,
special events and more.
Display Capture Notes - Brings up the
Capture Notes window where you can
view or add notes to the capture file.
Add/Modify Bookmark - Add a new or
modify an existing bookmark.
Display All Bookmarks - Shows all
bookmarks and lets you move between
bookmarks.
Bluetooth Timeline - Opens the Bluetooth
Timeline
Coexistence View - Opens the
Coexistence View
low energy Timeline- Opens the low
energy Timeline
Extract Data - Opens the Extract Data
dialog.
Bluetooth low energy Packet Error Rate
Statistics Opens the Packet Error Rate
Statistics display
Bluetooth Classic Packet Error Rate
Statistics - Opens the Packet Error Rate
Statistics display.
Bluetooth Expert System - Opens
Bluetooth Expert System window
Audio Expert System - Opens Audio
Expert System Window
Reload Decoders - When Reload Decoders is clicked, the plug-ins are reset
and received frames are re-decoded. For example, If the first frame occurs
more than 10 minutes in the past, the 10-minute utilization graph stays blank
until a frame from 10 minutes ago or less is decoded.
Filter: Text giving the filter currently in
use. If no filter is being used, the text
reads "All Frames" which means that
nothing is filtered out. To see the text of
the entire filter, place the cursor over the
text and a ToolTip pops up with the full
text of the filter.
The following icons all change how the panes are arranged on the Frame
Display. Additional layouts are listed in the View menu.
79 Frontline BPA 600 Hardware & Software User Manual
Page 88

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
Table 4.2 - Frame Display Toolbar Icons(continued)
Icon Description
Show Default Panes - Returns the panes
to their default settings.
Show Only Summary Pane - Displays
only the Summary pane.
Shall All Panes Except Event Pane Makes the Decode pane taller and the
Summary pane narrower.
Toggle Display Lock - Prevents the
display from updating.
Go To Frame
First Frame - Moves to the first frame in
the buffer.
Previous Frame - Moves to the previous
frame in the buffer.
Next Frame - Moves to the next frame in
the buffer.
Last Frame - Moves to the last frame in
the buffer.
Find on Frame Display only searches the
Decode Pane for a value you enter in the
text box.
Find Previous Occurrence - Moves to the
previous occurrence of the value in the
Frame Display Find.
Find Next Occurrence - Moves to the next
occurrence of the value in the Frame
Display Find.
Cancel Current Search - Stops the
current Frame Display Find.
Frontline BPA 600 Hardware & Software User Manual 80
Page 89

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Table 4.2 - Frame Display Toolbar Icons(continued)
Icon Description
Summary Drop Down Box: Lists all the
protocols found in the data in the file. This
box does not list all the protocol decoders
available to the analyzer, merely the
protocols found in the data. Selecting a
protocol from the list changes the
Summary pane to display summary
information for that protocol. When a low
energy predefined Named Filter (like
Nulls and Polls) is selected, the
Summary drop-down is disabled.
Text with Protocol Stack: To the right of the Summary Layer box is some text
giving the protocol stack currently in use.
Note: If the frames are sorted in other than ascending frame number order, the order of the
frames in the buffer is the sorted order. Therefore the last frame in the buffer may not have
the last frame number.
4.3.1.2 Frame Display Status Bar
The Frame Display Status bar appears at the bottom of the Frame Display. It contains the following
information:
l Frame #s Selected: Displays the frame number or numbers of selected (highlighted) frames, and the
total number of selected frames in parentheses
l Total Frames: The total number of frames in the capture buffer or capture file in real-time
l Frames Filtered In: The total number of frames displayed in the filtered results from user applied filters
in real-time
4.3.1.3 Hiding and Revealing Protocol Layers in the Frame Display
Hiding protocol layers refers to the ability to prevent a layer from being displayed on the Decode pane.
Hidden layers remain hidden for every frame where the layer is present, and can be revealed again at any
time. You can hide as many layers as you wish.
Note: Hiding from the Frame Display affects only the data shown in the Frame Display and not any
information in any other window.
There are two ways to hide a layer.
1. Right-click on the layer in the Decode pane, and choose Hide [protocol name] Layer In All
Frames.
2. Click the Set Protocol Filtering button on the Summary pane toolbar. In the Protocols to Hide
box on the right, check the protocol layer(s) you want hidden. Click OK when finished.
To reveal a hidden protocol layer:
81 Frontline BPA 600 Hardware & Software User Manual
Page 90

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
1. Right-click anywhere in the Decode pane
2. Choose Show [protocol name] Layer from the right-click menu, or click the Set Protocol Filtering
button and un-check the layer or layers you want revealed.
4.3.1.4 Physical vs. Logical Byte Display
The Event Display window and Event Pane in the Frame Display window show the physical bytes. In
other words, they show the actual data as it appeared on the circuit. The Radix, Binary and Character panes in
the Frame Display window show the logical data, or the resulting byte values after escape codes or other
character altering codes have been applied (a process called transformation).
As an example, bytes with a value of less than 0x20 (the 0x indicates a hexadecimal value) cannot be
transmitted in Async PPP. To get around this, a 0x7d is transmitted before the byte. The 0x7d says to take the
next byte and subtract 0x20 to obtain the true value. In this situation, the Event pane displays 0x7d 0x23,
while the Radix pane displays 0x03.
4.3.1.5 Sorting Frames
By default, frames are sorted in ascending numerical sequence by frame number. Click on a column header
in the Summary pane to sort the frames by that column. For example, to sort the frames by size, click on the
Frame Size column header.
An embossed triangle next to the header name indicates which column the frames are sorted by. The
direction of the triangle indicates whether the frames are in ascending or descending order, with up being
ascending.
Note that it may take some time to sort large numbers of frames.
4.3.1.6 Frame Display - Find
Frame Display has a simple Find function that you can use to search the Decode Pane for any alpha
numeric value. This functionality is in addition to the more robust Search/Find dialog.
Frame Display Find is located below the toolbar on the Frame Display dialog.
Figure 4.15 - Frame Display Find text entry field
Where the more powerful Search/Find functionality searches the Decode, Binary, Radix, and Character
panes on Frame Display using TImestamps, Special Events, Bookmarks, Patterns, etc.,
Frontline BPA 600 Hardware & Software User Manual 82
Page 91

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Figure 4.16 - Search/Find Dialog
Find on Frame Display only searches the Decode Pane for a value you enter in the text box.
To use Find:
1. Select the frame where you want to begin the search.
2. Enter a value in the Find text box.
Note: The text box is disabled during a live capture.
Select Find Previous Occurrence to begin the search on frames prior to the frame you
3.
selected, or Find Next Occurrence to begin the search on frames following the frame you
selected.
The next occurrence of the value (if it is found) will be
highlighted in the Decode Pane.
4. Select Find Previous Occurrence or Find Next Occurrence
to continue the search.
There are several important concepts to remember with Find.
l When you enter a search string and select Enter, the search moves forward.
l If you select Find Previous Occurrence, when the search reaches the first frame it will then cycle to
the last frame and continue until it reaches the frame where the search began.
l Shift + F3 is a shortcut for Find Previous Occurrence.
83 Frontline BPA 600 Hardware & Software User Manual
Page 92

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
l If you select Find Next Occurrence, when the search reaches the last frame it will then cycle to the first
frame and continue until it reaches the frame where the search began.
l F3 is a shortcut for Find Next Occurrence.
l You cannot search while data is being captured.
l After a capture is completed, you cannot search until Frame Display has finished decoding the frames.
l Find is not case sensitive.
l The status of the search is
displayed at the bottom of the
dialog.
l The search occurs only on the
protocol layer selected.
l To search across all the protocols on the Frame Display, select the Unfiltered tab.
l A drop-down list displays the search values entered during the current
session of Frame Display.
l The search is cancelled when you select a different protocol tab during
a search.
l You can cancel the search at any time by selecting the Cancel Current
Search button.
4.3.1.7 Synchronizing the Event and Frame Displays
The Frame Display is synchronized with the Event Display. Click on a frame in the Frame Display and
the corresponding bytes is highlighted in the Event Display. Each Frame Display has its own Event
Display.
As an example, here's what happens if the following sequence of events occurs.
1.
Click on the Frame Display icon in Control window toolbar to open the Frame Display.
2.
Click on the Duplicate View icon to create Frame Display #2.
3.
Click on Event Display icon in Frame Display #2. Event Display #2 opens. This Event
Display is labeled #2, even though there is no original Event Display, to indicate that it is
synchronized with Frame Display #2.
4. Click on a frame in Frame Display #2. The corresponding bytes are highlighted in Event Display
#2.
5. Click on a frame in the original Frame Display. Event Display #2 does not change.
4.3.1.8 Working with Multiple Frame Displays
Multiple Frame Displays are useful for comparing two frames side by side. They are also useful for comparing
all frames against a filtered subset or two filtered subsets against each other.
Frontline BPA 600 Hardware & Software User Manual 84
Page 93

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
l
To create a second Frame Display, click the Duplicate View icon on the Frame Display toolbar.
This creates another Frame Display window. You can have as many Frame Displays open as you
wish. Each Frame Display is given a number in the title bar to distinguish it from the others.
l
To navigate between multiple Frame Displays, click on the Frame Display icon in the Control
window toolbar.
A drop-down list appears, listing all the currently open Frame Displays.
l Select the one you want from the list and it comes to the front.
Note: When you create a filter in one Frame Display, that filter does not automatically
appear in the other Frame Display. You must use the Hide/Reveal feature to display a
filter created in one Frame Display in another.
Note: When you have multiple Frame Display windows open and you are capturing data,
you may receive an error message declaring that "Filtering cannot be done while receiving
data this fast." If this occurs, you may have to stop filtering until the data is captured.
4.3.1.9 Working with Panes on Frame Display
When the Frame Display first opens, all panes are displayed except the Event pane (To view all the panes,
select Show All Panes from the View menu).
l
The Toggle Expand Decode Pane icon makes the decode pane longer to view lengthy decodes
better.
l
The Show Default Panes icon returns the Frame Display to its default settings.
l
The Show only Summary Pane icon displays on the Summary Pane.
To close a pane, right-click on the pane and select Hide This Pane from the pop-up menu, or de-select
Show [Pane Name] from the View menu.
To open a pane, right-click on the any pane and select Show Hidden Panes from the pop-up menu and
select the pane from the fly-out menu, or select Show [Pane Name] from the View menu.
To re-size a pane, place the cursor over the pane border until a double-arrow cursor appears. Click and drag
on the pane border to re-size the pane.
4.3.1.10 Frame Display - Byte Export
The captured frames can be exported as raw bytes to a text file.
85 Frontline BPA 600 Hardware & Software User Manual
Page 94

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
1. From the Frame Display File menu select Byte Export....
Figure 4.17 - Frame Display File menu, Byte Export
2. From the Byte Export window specify the frames to export.
l All Frames exports all filtered-in frames including those scrolled off the Summary pane. Filtered-
in frames are dependent on the selected Filter tab above the Summary pane. Filtered-out
frames are not exported.
l Selected Frames export is the same as All Frames export except that only frames selected in the
Summary pane will be exported.
Figure 4.18 - Byte Export dialog
Click the OK button to save the export. Clicking the Cancel button will exit Byte Export.
3. The Save As dialog will open. Select a directory location and enter a file name for the exported
frames file.
Frontline BPA 600 Hardware & Software User Manual 86
Page 95

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
Figure 4.19 - Save As dialog
Click on the Save button.
The exported frames are in a text file that can be opened in any standard text editing application. The header
shows the export type, the capture file name, the selected filter tab, and the number of frames. The body
shows the frame number, the timestamp in the same format shown in the Frame Display Summary pane,
and the frame contents as raw bytes.
Figure 4.20 - Sample Exported Frames Text File
4.3.1.11 Panes in the Frame Display
4.3.1.11.1 Summary Pane
The Summary pane displays a one-line summary of every frame in a capture buffer or file, including
frame number, timestamp, length and basic protocol information. The protocol information included for each
frame depends on the protocol selected in the summary layer box (located directly below the main toolbar).
On a two-channel circuit, the background color of the one-line summary indicates whether the frame came
from the DTE or the DCE device. Frames with a white background come from the DTE device, frames with a
gray background come from the DCE device.
The ComProbe USB Summary pane in displays a one-line summary of every transaction in a capture buffer
or file. Whenever there is a transaction it is shown on a single line instead of showing the separate messages
that comprise the transaction. The Msg column in that case says “Transaction”.
Each message in a transaction contains a packet identifier (PID). All of the PIDs in a transaction are shown in
the transaction line.
87 Frontline BPA 600 Hardware & Software User Manual
Page 96

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
All "IN" transactions (i.e. transactions that contain an IN token message) are shown with a purple background.
All other transactions and all non-transactions are shown with a white background. "IN" transactions have
special coloring because that is the only place where the primary data flow is from a device to the Host.
The protocol information included for each frame depends on the protocol selected in the summary layer
box (located directly below the main toolbar).
Frame numbers in red indicate errors, either physical (byte-level) or frame errors. If the error is a frame
error in the displayed protocol layer, the bytes where the error occurred is displayed in red. The Decode
Pane gives precise information as to the type of error and where it occurred.
The Summary pane is synchronized with the other panes in this window. Click on a frame in the Summary
pane, and the bytes for that frame is highlighted in the Event pane while the Decode pane displays the full
decode for that frame. Any other panes which are being viewed are updated accordingly. If you use one pane
to select a subset of the frame, then only that subset of the frame is highlighted in the other panes.
Protocol Tabs
Protocol filter tabs are displayed in the Frame Display above the Summary pane.
l These tabs are arranged in separate color-coded groups. These groups and their colors are General
(white), Classic Bluetooth (blue), Bluetooth low energy (green), 802.11 (orange), USB (purple), and SD
(brown). The General group applies to all technologies. The other groups are technology-specific.
Figure 4.21 - Example Protocol Tags
l Clicking on a protocol filter tab in the General group filters in all packets containing that protocol
regardless of each packet’s technology.
l Clicking on a protocol filter tab in a technology-specific group filters in all packets containing that protocol
on that technology.
l A protocol filter tab appears in the General group only if the protocol occurs in more than one of the
technology-specific tab groups. For example, if L2CAP occurs in both Classic Bluetooth and Bluetooth low
energy , there will be L2CAP tabs in the General group, the Classic Bluetooth group, and the Bluetooth low
energy group.
Select the Unfiltered tab to display all packets.
There are several special tabs that appear in the Summary pane when certain conditions are met. These
tabs appear only in the General group and apply to all technologies. The tabs are:
l Bookmarks appear when a bookmark is first seen.
l Errors appear when an error is first seen. An error is a physical error in a data byte or an error in the
protocol decode.
l Info appears when a frame containing an Information field is first seen.
The tabs disappear when the capture buffer is cleared during live capture or when decoders are reloaded,
even if one of the tabs is currently selected. They subsequently reappear as the corresponding events are
detected.
Frontline BPA 600 Hardware & Software User Manual 88
Page 97

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
The tabs disappear when the capture buffer is cleared during live capture or when decoders are reloaded,
even if one of the tabs is currently selected. They subsequently reappear as the corresponding events are
detected.
Use the navigation icons, keyboard or mouse to move through the frames. The icons and move
you to the first and last frames in the buffer, respectively. Use the Go To icon to move to a specific
frame number.
Placing the mouse pointer on a summary pane header with truncated text displays a tooltip showing the full
header text.
Figure 4.22 - Summary pane (right) with Tooltip on Column 5 (Tran ID)
Sides in Bluetooth low energy
A Bluetooth low energy data connection consists of connection events, which are a series of transmissions on
the same channel. In each connection event the master transmits first, then the slave, and then the devices
take turns until the connection event is finished.
When the data connection is encrypted and the packets are successfully decrypted, the sniffer can determine
exactly who sent which packet (only non-empty, encrypted packets – empty packets are never encrypted).
These packets are labeled either ‘M’ for master or ‘S’ for slave.
When the data connection is unencrypted or when encrypted packets are not successfully decrypted by the
sniffer, the sniffer cannot distinguish the two devices’ (master and slave) packets by their content, just by the
packet timing. In those cases we label each device as side ‘1’ or ‘2’, not as master or slave. In each connection
event, packets sent by the device which transmitted first in the connection event are labeled ‘1’, and packets
sent by the device which transmitted second are labeled ‘2’.
If no packets in the connection event are missed by the sniffer, the device labeled ‘1’ is the master and the
device labeled ‘2’ is the slave. However, if we do not capture the very first packet in a connection event (i.e.
the packet sent by the master) but do capture the packet sent by the slave, we label the slave as side ‘1’ since
it is the first device we heard in the connection event. Because there is potential clock drift since the last
connection event, we cannot use the absolute timing to correct this error; there would still be cases where
we get it wrong. Therefore we always assign ‘1’ to the first packet in a connection event. So even though it is
rare, there are connection events where packets sent by the slave device are labeled ‘1’ and packets sent by
the master are labeled ‘2’.
Finally, in a noisy environment it is also possible that the sniffer does not capture packets in the middle of a
connection event. If this occurs and the sniffer cannot determine the side for the remaining packets in that
connection event, the side is labeled ‘U’ for “unknown”.
89 Frontline BPA 600 Hardware & Software User Manual
Page 98

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
4.3.1.11.2 Bluetooth low energy Data Encryption/Master and Slave
Assignment
A Bluetooth low energy data connection consists of connection events, which are a series of transmissions on
the same channel. In each connection event the master transmits first, then the slave, and then the devices
take turns until the connection event is finished.
When the data connection is encrypted and the packets are successfully decrypted, the sniffer can determine
exactly who sent which packet (only non-empty, encrypted packets – empty packets are never encrypted).
These packets are labeled either ‘M’ for master or ‘S’ for slave.
When the data connection is unencrypted or when encrypted packets are not successfully decrypted by the
sniffer, the sniffer cannot distinguish the two devices’ (master and slave) packets by their content, just by the
packet timing. In those cases we label each device as side ‘1’ or ‘2’, not as master or slave. In each
connection event, packets sent by the device which transmitted first in the connection event are labeled ‘1’,
and packets sent by the device which transmitted second are labeled ‘2’.
If no packets in the connection event are missed by the sniffer, the device labeled ‘1’ is the master and the
device labeled ‘2’ is the slave. However, if we do not capture the very first packet in a connection event (i.e.
the packet sent by the master) but do capture the packet sent by the slave, we label the slave as side ‘1’ since
it is the first device we heard in the connection event. Because there is potential clock drift since the last
connection event, we cannot use the absolute timing to correct this error; there would still be cases where
we get it wrong. Therefore we always assign ‘1’ to the first packet in a connection event. So even though it is
rare, there are connection events where packets sent by the slave device are labeled ‘1’ and packets sent by
the master are labeled ‘2’.
Finally, in a noisy environment it is also possible that the sniffer does not capture packets in the middle of a
connection event. If this occurs and the sniffer cannot determine the side for the remaining packets in that
connection event, the side is labeled ‘U’ for “unknown”.
4.3.1.11.3 Bluetooth low energy Decryption Status
Occasionally you may have a packet with an event status of “received without errors,” but a decryption status
of “unable to decrypt.” There are three main causes for this, and in order of likelihood they are:
1. Wrong Long-Term Key – having the wrong long-term key will cause this error, so the first thing to
check is that your long term key is entered correctly in the datasource settings.
2. Dropped Packets – Too much interference with a ComProbe device will cause dropped packets and
may cause this error. As a rule of thumb, it is always a good idea to ensure the ComProbe device is
positioned away from sources of interference, and is placed in between the two devices being sniffed.
3. Faulty Device – although the chances of this are low, it is possible that a device is not encrypting
packets properly. This is likely to happen only if you are a firmware developer working on encryption.
4.3.1.11.4 Customizing Fields in the Summary Pane
You can modify the Summary Pane in Frame Display.
Summary pane columns can be reordered by dragging any column to a different position.
Fields from the Decode pane can be added to the summary pane by dragging any Decodepane field to the
desired location in the summary pane header. If the new field is from a different layer than the summary
pane a plus sign (+) is prepended to the field name and the layer name is added in parentheses. The same
field can be added more than once if desired, thus making it possible to put the same field at the front and
back (for example) of a long header line so that the field is visible regardless of where the header is scrolled
to.
An added field can be removed from the Summary pane by selecting Remove New Column from the
right-click menu.
Frontline BPA 600 Hardware & Software User Manual 90
Page 99

TELEDYNE LECROY Chapter 4 Capturing and Analyzing Data
The default column layout (both membership and order) can be restored by selecting Restore Default
Columns from the Format or right-click menus.
Changing Column Widths
To change the width of a column:
1. Place the cursor over the right column divider until the cursor changes to a solid double arrow.
2. Click and drag the divider to the desired width.
3. To auto-size the columns, double-click on the column dividers.
Hiding Columns
To hide a column:
1. Drag the right divider of the column all the way to the left.
2. The cursor changes to a split double arrow when a hidden column is present.
3. To show the hidden column, place the cursor over the divider until it changes to a split double arrow,
then click and drag the cursor to the right.
4. The Frame Size, Timestamp, and Delta columns can be hidden by right-clicking on the header and
selecting Show Frame Size Column, Show Timestamp Column, or Show Delta Column.
Follow the same procedure to display the columns again.
Moving Columns - Changing Column Order
To move a column :
1. Click and hold on the column header
2. Drag the mouse over the header row.
3. A small white triangle indicates where the column is moved to.
4. When the triangle is in the desired location, release the mouse.
Restoring Default Column Settings
To restore columns to their default locations, their default widths, and show any hidden columns
1. Right-click on any column header and choose Restore Default Column Widths, or select Restore
Default Column Widths from the Format menu.
4.3.1.11.5 Frame Symbols in the Summary Pane
Table 4.3 - Frame Symbols
Symbol Description
A green dot means the frame was decoded successfully, and the protocol listed in the Summary
Layer drop-down box exists in the frame. No dot means the frame was decoded successfully, but
the protocol listed in the Summary Layer drop-down box does not exist in the frame.
91 Frontline BPA 600 Hardware & Software User Manual
Page 100

Chapter 4 Capturing and Analyzing Data TELEDYNE LECROY
Table 4.3 - Frame Symbols (continued)
Symbol Description
A green circle means the frame was not fully decoded. There are several reasons why this might
happen.
l One reason is that the frame compiler hasn't caught up to that frame yet. It takes some time
for the analyzer to compile and decode frames. Frame compilation also has a lower priority
than other tasks, such as capturing data. If the analyzer is busy capturing data, frame
compilation may fall behind. When the analyzer catches up, the green circle changes to either
a green dot or no dot.
l Another reason is if some data in the frame is context dependent and we don't have the
context. An example is a compressed header where the first frame gives the complete
header, and subsequent frames just give information on what has changed. If the analyzer
does not capture the first frame with the complete header, it cannot decode subsequent
frames with partial header information.
A magenta triangle indicates that a bookmark is associated with this frame. Any comments
associated with the bookmark appear in the column next to the bookmark symbol.
4.3.1.11.6 Decode Pane
The Decode pane (aka detail pane) is a post-process display that provides a detailed decode of each
frame transaction (sometimes referred to as a frame). The decode is presented in a layered format that can
be expanded and collapsed depending on which layer or layers you are most interested in. Click on the plus
sign to expand a layer. The plus sign changes to a minus sign. Click on the minus sign to collapse a layer. Select
Show All or Show Layers from the Format menu to expand or collapse all the layers. Layers retain their
expanded or collapsed state between frames.
Protocol layers can be hidden, preventing them from being
displayed on the Decode pane. Right-click on any protocol
layer and choose Hide [protocol name] from the right-click
menu.
In a USB transaction, all messages that comprise the
transaction are shown together in the detail pane. The color
coding that is applied to layers when the detail pane displays a single message is applied to both layers and
messages when the detail pane displays a transaction. To keep the distinction between layers and messages
clear, each header of each message in the detail pane ends with the word “Message” or “Messages”. The
latter is used because data and handshake messages are shown as a single color-coded entry
Each protocol layer is represented by a color, which is used to highlight the bytes that belong to that protocol
layer in the Event, Radix, Binary and Character panes. The colors are not assigned to a protocol, but are
assigned to the layer.
The Event, Radix, Binary, Character and Decode panes are all synchronized with one another. Clicking on
an element in any one of the panes highlights the corresponding element in all the other panes.
Click the Toggle Expand Decode Pane icon to make the Decode pane taller. This allows for more of
a lengthy decode to be viewed without needing to scroll.
Frontline BPA 600 Hardware & Software User Manual 92
 Loading...
Loading...