Page 1

Sun Java™ System
Portal Server 6
Deployment Planning Guide
2005Q1
Sun Microsystems, Inc.
4150 Network Circle
Santa Clara, CA 95054
U.S.A.
Part No: 817-7697
Page 2

Copyright © 2005 Su n Mi cr osy stems, Inc., 4150 Netw or k Circle, Santa Clar a, California 95054, U. S . A. All rights reserved.
Sun Microsystems, Inc. has intellectual property rights relating to technology embodied in th e p r oduct that is described in this document. In
particular, and without limitation, these intellectual property rights may include one or more of the U.S. patents listed at
http://www.sun.com/patents
and one or more additional patents or pending patent applications in the U.S. and in other countries.
THIS PRODUCT CONTAINS CONFIDENTIAL INFORMATION AND TRADE SECRETS OF SUN MICROSYSTEMS, INC. USE, DISCLOSURE
OR REPRODUCTION IS PROHIBITED WITHOUT THE PRIOR EXPRESS WRITTEN PERMISSION OF SUN MICROSYSTEMS, INC.
U.S. Government Rights - Commercial software. Government users are subject to the Sun Microsystems, Inc. standard license agreement and
applicable provisions of the FAR and its supplements.
This distribution may include materials de ve lo ped by third parties.
Parts of the product may be derived from Berkeley BSD systems, li censed from the Un iversity of Californ ia. UNIX is a registe red tr ademar k in the
U.S. and in other c ountries, exclusively licensed through X/ Open Company, Ltd.
Sun, Sun Microsystems, the Sun logo, Java, Solaris, JDK, Java Naming and Directory Interface, JavaMail, JavaHelp, J2SE, iPlanet, the Duke logo,
the Java Coffee Cup logo, the Solaris logo, the SunTone Certified logo and the Sun ONE logo are trademarks or registered trademarks of Sun
Microsystems, Inc. in the U.S. and other countries.
All SPARC trademar k s ar e u s e d under license and ar e tr ademarks or registered trademarks o f SPARC Internatio nal, Inc. in the U.S . a n d other
countries. Products bearing SPARC trademarks are based upon architecture developed by Sun Microsystems, Inc.
Legato and the Legato logo are registered trademarks, and Legato NetWorker, are trademarks or registered trademarks of Legato Systems, Inc .
The Netscape Communications Corp logo is a trademark or registered trademark of Netscape Communications Corporation.
The OPEN LOOK and Sun(TM) Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges
the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. Sun
holds a non-exclusive license from Xerox to the Xer ox Gr aphi c al User Interface, which li cense also covers Sun's license e s w ho implement O P EN
LOOK GUIs and otherwise comply with Sun's written license agreements.
Products covered by and information contained in this service manual are controlled by U.S. Export Control laws and may be subject to the
export or import laws in other countries. Nuclear, missile, chemical biological weapons or nuclear maritime end uses or end users, whether direct
or indirect, are strictly prohibited. Export or reexport to countries subject to U.S. embargo or to entities identified on U.S. export exclusion lists,
including, but not limited to, th e de nie d persons a nd spe cially designated nationals lists is strictly prohibited.
DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES,
INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE O R NON-INFRINGEMENT,
ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
_______________________________________________________________________________________________________________
Copyright © 2005 Su n Mi c r osy stems, Inc., 4150 Ne tw or k C ir c le , S anta Clara, Calif or nia 95054, Etats-Unis. Tous droits rése r vé s.
Sun Microsystems, Inc. détient les droits de propriété intellectuels relatifs à la technologie incorporée dans le produit qui est décrit dans ce
document. En particulier, et ce sans limitation, ces droits de propriété intellectuelle peuvent inclure un ou plus des brevets américains listés à
http://www.sun.com/patents
l'adresse
et un ou les brevets supplémentaires ou les applications de brevet en attente aux Etats - Unis et dans les
autres pays.
CE PRODUIT CONTIENT DES INFORMATI ONS CONFIDENTIEL LES ET DES SECRETS COMMERCIAUX DE SUN MICR O S Y S TEMS, INC.
SON UTILISATION, SA DIVULGATION ET SA REPRODUCTION SONT INTERDITES SANS L AUTORISATION EXPRESSE, ECRITE ET
PREALABLE DE SUN MICROSYSTEMS, INC.
Cette distribution peut comprendre des composants développés par des tierces parties.
Des parties de ce produit pourront être dérivées des systèmes Berkeley BSD licenciés par l'Université de Californie. UNIX est une marque
déposée aux Etats-Unis et dans d'autres pays et licenciée exclusivement par X/Open Company, Ltd.
Sun, Sun Microsystems, le logo Sun, Java, Solaris, JDK, Java Naming and Directory Interface, JavaMail, JavaHelp, J2SE, iPlanet, le logo Duke, le
logo Java Coffee Cup, le logo Solaris, le logo SunTone Certified et le logo Sun[tm] ONE sont des marques de fabrique ou des marques déposées
de Sun Microsystems, Inc. aux Etats-Unis et dans d'autres pays.
Toutes les marques SPARC sont utilisées sous licence et sont des marques de fabriq ue ou des marques déposées de SPARC International, Inc. aux
Etats-Unis et dans d'autres pays . Les produits po rtant l es marques SPARC sont basés sur un e archi tecture déve loppée p ar Sun Microsystems, Inc.
Legato, le logo Legato, et Legato NetWorker sont des marques de fabrique ou des marques déposées de Legato Systems, Inc. Le logo Netscape
Communications Corp est une marque de fabrique ou une marque déposée de Netscape Communications Corporation.
L'interface d'utilisation graphique OPEN LOOK et Sun(TM) a été développée par Sun Microsystems, Inc. pour ses utilisateurs et licenciés. Sun
reconnaît les efforts de pionniers de Xerox pour la recherche et le développement du concept des interfaces d'utilisation visuelle ou graphique
pour l'industrie de l'informatique. Sun détient une license non exclusive de Xerox sur l'interface d'utilisation graphique Xerox, cette licence
couvrant également les licenciés de Sun qui mettent en place l'interface d'utilisation graphique OPEN LOOK et qui, en outre, se conforment aux
licences écrites de Sun.
Les produits qui font l'objet de ce manuel d'entretien et les infor ma tions qu'il contient sont regis par la legisla tion americaine en matiere de
controle des exportations et peuvent etre soumis au droit d'autres pays dans le domaine des exportations et importations. Les utilisations finales,
ou utilisateurs f inaux, pour des arme s nu c leaires, des mis s iles, des armes biolo g iq u e s et c himiques ou du nucleaire maritime, directement ou
indirectement, sont strictement interdites. Les exportations ou reexportations vers des pays sous embargo des Etats-Unis, ou vers des entites
figurant sur les li ste s d' exclusion d'exportation americaines, y c om pr is, mais de maniere n on exclusive, la liste de pe r sonnes qui fon t ob jet d'un
ordre de ne pas participer, d'une facon directe ou indirecte, aux exportations des produits ou des services qui sont regi par la legislation
americaine en matiere de controle des exportations e t l a l ist e de ress orti ssa nts specifiquement designes, sont rigoureusement interdites.
LA DOCUMENTATION EST FOURNIE "EN L'ETAT" ET TOUTES AUTRES CONDI TI ONS, DECLARATIONS ET GARANTI ES E XPRESSES
OU TACITES SONT FORMELLEMENT EXCLUES, DANS LA MESURE AUTORISEE PAR LA LOI APPLICABLE, Y COMPRIS NOTAMMENT
TOUTE GARANTIE IMPLICITE RELATIVE A LA QUALITE MARCHANDE, A L'APTITUDE A UNE UTILI SATI ON PARTI CULIE RE OU A
L'ABSENCE DE CONTREFACON.
Page 3

Contents
List of Figures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
List of Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Before You Read This Book . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Who Should Read This Book . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
How This Book Is Organized . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Typographic Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Related Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Books in This Documentation Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Other Portal Server Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Other Server Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Accessing Sun Resources Online . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Contacting Sun Te chnical Suppor t . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Related Third-Party Web Site References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Sun Welcomes Your Comments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Chapter 1 Portal Server Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
What is a Portal? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Types of Portals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Collaborative Portals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Business Intelligence Portals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Portal Server Capabilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Sun Java System Portal Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Secure Remote Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Portal Sever in Open Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Portal Server in Secure Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Security, Encryption, and Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Portal Server Deployment Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
3
Page 4

Portal Server Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Identity Manag e m ent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Portal Server Software Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Software Packaging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Software Categories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Compatibility With Java Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
A Typical Portal Server Installati on . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Chapter 2 Portal Server Secure Remote Access Architecture . . . . . . . . . . . . . . . . . . . . . . . . 37
SRA Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Multiple Gateway Instances . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Multiple Portal Server Instances . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Proxy Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Gateway and HTTP Basic Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Gateway and SSL Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Gateway Access Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Gateway Logg ing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Using Accelerators with the Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Netlet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Static and Dynamic Port Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Netlet and Application Integration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Split Tunneling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Netlet Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
NetFile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Initialization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Validating Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Access Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Special Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
NetFile and Multithreading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Rewriter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Rewriter Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Proxylet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Chapter 3 Identifying and Evaluating Your Business and Technical Requirements . . . . . . 51
Business Objectives . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Technical Goals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Mapping Portal Server Features to Your Business Needs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Identity Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
SRA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Search Engine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
4 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 5

Personalization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Aggregation and Integration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Understanding User Behaviors and Patterns . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Chapter 4 Pre-Deployment Considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Determine Your Tuning Goals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Portal Sizing Tips . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Establish Performance Methodology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Portal Sizing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Establish Baseline Sizi ng Fig ur es . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Customize the Baseline Sizing Figures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Validate Baseline Sizing Fig ures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Refine Baseline Sizing Figures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Validate Your Final Figures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
SRA Sizing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Identifying Gateway Key Performance Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Advanced Gatewa y Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
SRA Gateway and SSL Hardware Accelerators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
SRA and Sun Enterprise Midframe Line . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
Chapter 5 Creating Your Portal Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Portal Design Approach . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Overview of High-Level Portal Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Overview of Low-Level Portal Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Logical Portal Architectu re . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Portal Server and Scalability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Vertical Scaling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Horizontal Scaling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Portal Server and High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
System Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Degrees of High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Achieving High Availability for Portal Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Portal Server System Communication Links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Working with Portal Server Building Modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Building Modules and High Availability Scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Building Module Constraints . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Deploying Your Building Module Solution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Designing Portal Use Case Scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Elements of Portal Use Cases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Example Use Case: Authenticate Portal User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Designing Portal Security Strategies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Securing the Operating Environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Contents 5
Page 6

Using Platform Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Using a Demilitarized Zone (DMZ) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Portal Server and Access Manager on Different Nodes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Designing SRA Deployment Scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Basic SRA Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Disable Netlet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Proxylet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Multiple Gateway Instances . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Netlet and Rewriter Proxies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Netlet and Rewriter Proxies on Separate Nodes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Using Two Gateways and Netlet Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Using an Accelerator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Netlet with 3rd Party Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Reverse Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Designing for Localization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Content and Design Implementation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Integration Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
Identity and Directory Structure Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Implementing Single Sign-On . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Portal Desktop Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Client Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Chapter 6 The Production Environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Moving to a Production Environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Monitoring and Tuning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Documenting the Portal . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Monitoring Portal Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Memory Consumption and Garbage Collection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
CPU Utiliza tion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
Access Manager Cache and Session s . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Thread Usage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Portal Usage Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Appendix A Installed Product Layout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Directories Installed for Portal Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Directories Installed for SRA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Appendix B Analysis Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
mpstat . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
iostat . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
netstat . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
6 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 7

Tuning Parameters for
/etc/system
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Appendix C Portal Server and Application Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Introduction to Application Server Support in Portal Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Portal Server on an Application Server Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
Overview of Application Server Enterprise Edition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Overview of BEA WebLogic Server Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Overview of IBM WebSphere Application Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Appendix D Troubleshooting Your Portal Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Troubleshooting Portal Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
UNIX Processes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Recovering the Search Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Working with the Display Profile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
High CPU Utilization for Portal Server Instance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Configuring a Sun Java System Portal Server Instance to Use an HTTP Proxy . . . . . . . . . . . . . . . 162
Troubleshooting SRA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
Debugging the Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
Introduction to
Using
shooter
shooter
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
SRA Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
Appendix E Portal Deployment Worksheets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Portal Assessment Worksheets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Portal Design Task List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Appendix F Portal Server on the Linux Platform . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Limitations Using Linu x . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Comparison of Solaris and Linux Path Names . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Contents 7
Page 8

8 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 9

List of Figures
Figure 1-1 Portal Server in Open Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Figure 1-2 Portal Server in Secure Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Figure 1-3 High-level Architecture for a Busines s -t o-Emp loye e Portal . . . . . . . . . . . . . . . . . . . . . . 34
Figure 1- 4 SRA Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Figure 5-1 Portal Server Communication Links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Figure 5-2 Portal Server Building Module Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Figure 5-3 Best Effort Scenario . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Figure 5-4 No Single Point of Failure Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Figure 5-5 Transparent Failover Example Scenario . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Figure 5-6 Portal Server and Access Manager on Different Nodes . . . . . . . . . . . . . . . . . . . . . . . . 106
Figure 5-7 Two Portal Servers and One Access Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Figure 5-8 One Portal Server and Two Access Managers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Figure 5-9 Two Portal Servers and Two Access Managers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Figure 5-10 Basic SRA Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Figure 5-11 Disable Netlet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Figure 5-12 Proxylet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Figure 5-13 Multiple Gateway Instances . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Figure 5-14 Netlet and Rewriter Proxies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Figure 5-15 Proxies on Separate Nodes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Figure 5-16 Two Gat eways and Netl et Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Figure 5-17 SRA Gateway with External Accelerator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Figure 5-18 Netlet and Third-Party Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Figure 5-19 Using a Reverse Proxy in Front of the Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
List of Figures 9
Page 10

10 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 11

List of Tables
Table 1 Typographical Conventions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Table 3-1 Identity Management Features and Benefits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Table 3-2 SRA Features and Benefits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Table 3-3 Search Features and Benefits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Table 3-4 Personalization Features and Benefits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Table 3-5 Aggregation Featur es and Bene fits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Table 5-1 Portal Server High Av ailability Scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Table 5-2 Use Case: Authenticate Po rtal User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Table A-1 Portal Server Directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Table A-2 Portal Server, SRA Directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Table B-1 Performance Analysis Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Table B-2 /etc/system Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Table B-3 TCP/IP Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Table E-1 General Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Table E-2 Organizational Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
Table E-3 Business Service-level Expectations Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Table E-4 Content Management Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Table E-5 User Management and Security Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Table E-6 Business Intelligence Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Table E-7 Architecture Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Table E-8 Design Task List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Table F-1 Comparison of Solaris and Linux Path Names . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
List of Tables 11
Page 12

12 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 13

This Administration Guide explains how to plan for and deploy Sun Java™ System
Portal Server 6 2005Q1 software. Portal Server Secure Remote Access provides a
platform to create portals for your organizatio n’s integrated data, knowledge
management, and applications. The Portal Server platform offers a complete
infrastructure solution for building and deploying all types of portals, including
business-to-business, business-to-employee, and business-to-consumer.
Before You Read This Book
Portal Server Secure Remote Access is a component of Sun Java Enterprise System,
a software infrastructure that supports enterprise applications distributed across a
network or Internet environment. You should be familiar wi th the documentation
provided with Sun Java Enterprise System, which can be accessed online at
http://docs.sun.com/coll/entsys_05q1
Preface
.
Who Should Read This Book
This Administration Guide is intended for use by those responsible for deploying
Portal Server at your site.
Before you deploy Portal Server, you must be familiar with the following
technologies:
• Sun Java Enterprise System
• Solaris™ Operating System administrative procedures
• Sun Java System Access Manager
• Sun Java System Directory Server
13
Page 14

How This Book Is Organized
•Java™ Web Server
• JavaServer Pages™ technology
• Lightweight Directory Access Protocol (LDAP)
• Hypertext Markup Language (HTML)
• Extensible Markup Language (XML)
How This Book Is Organized
Chapters 1 through 5 provide information on Portal Server Secure Remote Access
deployment. The following table summarizes the content of this book..
Chapter Description
Chapter 1, “Portal Server
Architecture” on page 21
Chapter 2, “Portal Server
Secure Remote Access
Architecture” on page 37
Chapter 3, “Identifying and
Evaluating Your Business
and Technical
Requirements” on page 51
Chapter 4,
“Pre-Deployment
Considerations” on page 61
Chapter 5, “Creating Your
Portal Design” on page 79
Chapter 6, “The Production
Environment” on page 133
Appendix A, “Installed
Product Layout” on
page 139
Appendix B, “Analysis
Tools” on page 143
This chapter describes types of portals servers, Sun Java System
Portal Server in open and secure mode, the Portal Server
components.
This chapter describes the Portal Server Secure Remote Access
architecture, including the key components of Secure Remote
Access with respect to their role in providing secure remote access
to corporate intranet resources from outside the intranet.
This chapter describes how to analyze your organization’s needs
and requirements that lead to designing your portal deployment.
This chapter describes how to establish a baseline sizing figure for
your portal. With a baseline figure established, you can then refine
that figure to account for scalability, high availability, reliability, and
good performance.
This chapter describes how to create your high-level and low-level
portal design and provides information on creating specific sections
of your design plan.
This chapter describes how to tune and monitor your portal.
This appendix describes the directories and configuration files fo r
Portal Server and
Remote Access (SRA).
This appendix describes analysis tools for tuning the operating
system.
Sun Java System Portal Server Secure
14 Portal Server Secure Remote Access 6 2005Q1 • Administration Guide
Page 15

Chapter Description
Appendix C, “Portal Server
and Application Servers” on
page 153
Appendix D,
“Troubleshooting Your
Portal Deployment” on
page 159
Appendix E, “Portal
Deployment Worksheets”
on page 167
Appendix F, “Portal Server
on the Linux Platform” on
page 179
Glossary Glossary
This appendix describes the support for application servers.
This appendix describes how to troubleshoot the Portal Server
software and the Portal Server Secure Remote Access (SRA)
product.
This appendix provides various worksheets to help in the
deployment process.
This appendix contains notes on running Portal Server on a Linux
platform.
Conventions Used in This Book
The tables in this section describe the conventions used in this book.
How This Book Is Organized
Typographic Conventions
The following table describes the typographic conventions used in this book
Table 1 Typographical Conventions.
Typeface Meaning Examples
AaBbCc123
(Monospace)
AaBbCc123
(Monospace
bold)
API and language elements, HTML
tags, web site URLs, command
names, file names, directory path
names, onscreen computer output,
sample code.
What you type, when contrasted
with onscreen computer output.
Edit your
Use
ls -a
.login
to list all files.
% You have mail
% su
Password:
file.
.
Preface 15
Page 16
Related Documentation
Typeface Meaning Examples
AaBbCc123
(Italic)
Book titles, new terms, words to be
emphasized.
A placeholder in a command or path
name to be replaced with a real
name or value.
Related Documentation
The
http://docs.sun.com
documentation online. You can brow se the archive or search for a specific book
title or subject.
Books in This Documentation Set
web site enables you to access Sun technical
Read Chapter 6 in the User’s
Guide.
These are called class options.
Do not save the file.
The file is located in the
install-dir
/bin directory.
The following table summarizes the books included in the Portal Server Secure
Remote Access core documentation set..
Book Title Description
Portal Server Administration Guide
http://docs.sun.com/db/doc/817-7691
Portal Server Secure Remote Access Administration
Guide
http://docs.sun.com/db/doc/817-7693
Portal Server Releas e Not es
http://
docs.sun.com/db/doc/817-7699
16 Portal Server Secure Remote Access 6 2005Q1 • Administration Guide
Describes how to administer Portal Server 6 using
the Access Manager administration console and
the command line.
Describes how to administer Portal Server 6
Secure Remote Access.
Available after the product is released. Contains
last-minute information, including a description of
what is new in this current release, known
problems and limitations, installation notes, and
how to report issues with the software or the
documentation.
Page 17

Book Title Description
Portal Server Tech nic al Re fe re nce G uid e
http://docs.sun.com/db/doc/817-7696
Provides detailed information on the Portal Server
technical concepts (such as Display Profile,
Rewriter), command line utilities, tag libraries (in
the software), and files (such as templates and
JSPs). This guide serves as a single source for
such essential background information.
Other Portal Server Documentation
Other Portal Server books include:
• Portal Server Desktop Customiz ation Guide
http://docs.sun.com/doc/817-5318
• Portal Server Developer's Guide
http://docs.sun.com/doc/817-5319
• Portal Server Mobile Access Deve loper' s Guide
Related Documentation
http://docs.sun.com/doc/817-6258
• Portal Server Mobile Access Developer' s Re ference
http://docs.sun.com/doc/817-6259
• Portal Server Mobile Access Deployme nt Pla nning Guide
http://docs.sun.com/doc/817-6257
• Portal Server Mobile Access Tag Librar y Refe rence
http://docs.sun.com/doc/817-6260
Other Server Documentation
For other server documentation, go to the following:
•Directory Server documentation
http://docs.sun.com/coll/DirectoryServer_04q2
• Web Server documentation
http://docs.sun.com/coll/S1_websvr61_en
Preface 17
Page 18

Accessing Sun Resources Online
• Application Server documentation
http://docs.sun.com/coll/s1_asseu3_en
• Web Proxy Server documentation
http://docs.sun.com/prod/s1.webproxys#hic
Accessing Sun Resources Online
For product downloads, professional services, patches and support, and additional
developer information, go to the following:
•Download Center
http://wwws.sun.com/software/download/
• Professional Services
http://www.sun.com/service/sunps/sunone/index.html
• Sun Enterprise Services, Solaris patches, and Support
http://sunsolve.sun.com/
• Developer Information
http://developers.sun.com/prodtech/index.html
Contacting Sun Technical Support
If you have technical questions about this product that are no t answered in the
product documentation, go to
http://www.sun.com/service/contacting
Related Third-Party Web Site References
Sun is not responsible for the availability of third-party web sites mentioned in this
document. Sun does not endorse and is not responsible or liable for any content,
advertising, products, or other materials that are available on or through such sites
or resources. Sun will not be responsible or liable for any actual or alleged damage
or loss caused or alleged to be caused by or in connection with use of or reliance on
any such content, goods, or services that a r e available on or through such sites or
resources.
18 Portal Server Secure Remote Access 6 2005Q1 • Administration Guide
.
Page 19

Sun Welcomes Your Comments
Sun is interested in improving its documentation and welcomes your comments
and suggestions.
Sun Welcomes Your Comments
To share your comments, go to
the online form, provide the document title and part number. The part n umber is a
seven-digit or nine-digit number that can be found on the title page of the book or
at the top of the document. For example, the title of this book is Sun Java System
Portal Server Secure R emo te Access 2005Q1 Adminis tration Guide, and the part
number is 817-7693.
http://docs.sun.com
and click Send Comments. In
Preface 19
Page 20

Sun Welcomes Your Comments
20 Portal Server Secure Remote Access 6 2005Q1 • Administration Guide
Page 21

Portal Server Architecture
This chapter contains the following s e ctions:
• What is a P o rtal?
• Types of Portals
• Portal Server Capabilities
• Sun Java System Portal Server
• Secure Remote Access
Chapter 1
• Security, Encryption, and Authentication
• Portal Server Deployment Components
• Portal Server Architecture
• Identity Management
• A Typical Portal Server Installation
What is a Portal?
Portals provide the user with a single point of access to a wide variety of content,
data, and services throughout an enterprise. The content displayed through portal
providers, channels, and portlets on the portal page can be personalized based on
user preferences, user role or department within an organization, site design, and
marketing campaigns for customers as end-users.
21
Page 22

Types of Portals
Portals serve as a unified access point to web applications. Portals a lso provide
valuable functions like security, search, collaboration, and workflow. A portal
delivers integrated content and applications, plus a unified, collaborative
workplace. Indeed, portals are the next-generation desktop, delivering e-business
applications over the web to all kinds of client de vices. A complete portal solution
should provide users with access to everything users need to get their tasks
done—any time, anywhere, in a secure manner.
Types of Portals
With many new portal products being announced, the marketpla ce has become
very confusing. Indeed, any product or application that provides a web interface to
business content cou ld be classified as a porta l. For this reason port als have many
different uses and can be classified as one of the following:
• Collaborative Portals
• Business Intelligence Po rtals
Collaborative Portals
Collaborative portals help busi ne ss users organize, find, and share unstructured
office content—for example, e-mail, discussion group material, office documents,
forms, memos , me e ti ng minutes, web d o c u ments, and some s u p p ort for live feeds.
Collaborative portals differ from Internet and intranet portals not only in
supporting a wider range of information, but also by providing a set of content
management and collaborative services.
Content management services include the following:
• Text mining (the discovery of new, previously unknown information)
• Clustering of related unstructured information
• Information categorization
• Summarization to generate abstracts for documents,
• Publishing and subscribing
• Finding people
• Tracking expertise
Collaborative portals are mainly used interna lly as a corporate facility.
22 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 23

Portal Server Capabilities
Collaborative services allow users to do the following:
•Chat
• Organize meetings
• Share calendaring information
• Define user communities
• Participate in net meetings
• Share information in discussion groups and on white boards
Business Intelligence Portals
Business intelligence portals provide executives, managers, and business analysts
with access to business intelligence for making business decisions. This type of
portal typically indexes business intelligence reports, analyses, and predefined
queries, and are associated with financial management, customer relationship
management, and supply chain performa nce management. Business intelligence
portals also provide access to business intelligence tools (reporting, OLAP, data
mining), packaged analytic applications, alerting, publishing and subscribing.
Peoplesoft is a typical vendor provider of bu siness intelligence types of portal.
Types of business intelligence portals include:
• Procurement portal
• Self-service portal
• Business portal
• e-Commerce portal
• Sales support
• Customer relationship management, operations, and employee portals
• Consumer portal
Portal Server Capabilities
Sun Java™ System Portal Server 6 2005Q1 software provides the following
capabilities to your organization:
Chapter 1 Portal Server Architecture 23
Page 24

Sun Java System Portal Server
• Secure access and authorized connectivity, optio na lly using encryption
• Authentication of users before allowing access to a set of resource s that are
• Support for abstractions that provide the ability to pull content from a variety
• A search engine infrastructure to enable intranet content to be organized and
• Ability to store user- and service-specific persistent d ata
• Access to commonly needed applications for accessing services such as mail,
• An administration interface enabling delegated and remote administration
• Single sign-on and security features, enabling standard access to enterprise
• Personalization through the use of portal providers, portlet and web service
between the user’s browser and the enterprise
specific for each user
of sources and aggregate and personalize it into an output format suitable for
the user’s device
accessed from the portal
calendar, and file storage
applications and content
remote portlet.
• Publishing and managing content (provided by third-party applications such
as FatWire)
Sun Java System Portal Server
Portal Server is a component of the Sun Java™ Enterprise System technology. Sun
Java Enterprise System technology supports a wide range of enterprise computing
needs, such as creating a secure intranet portal to provide the employees of an
enterprise with secure access to email and in-house business applications.
The Portal Server product is an identity-enabled portal server solution. It provides
all the user, policy, and identity management to enforce security, web application
single sign-on (SSO), and access capabilities to end user communities. In addition,
Portal Server combines portal services, such as person alization, aggregation,
security, integration, and search. Unique capabilities that enable secure remote
access to inter nal resources and applications round out a complete portal platform
for deploying business-to-employee, business-to-business, and
business-to-consumer portals. The Sun Java System Portal Server Secure Remote
Access (SRA) provides additional secure remote access capabilities to access weband non-web enabled resources.
24 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 25

Each enterprise assesses its own needs and plans its own deplo yment of Java
Enterprise System technology. The optimal deployment for each enterprise
depends on the type of applications that Java Enterprise System technology
supports, the number of users, the kind of hardware that is available, and other
considerations of this type.
Portal Server is able to work with previously installed software components. In this
case, Portal Server uses the installed software when the software is an appropriate
version.
Secure Remote Access
Sun Java System Portal Server Secure Remote Access (SRA) offers browser-based
secure access to portal content and services from any remote browser enabled with
Java technology.
SRA is accessible to users from any Java technology-enabled browser, eliminating
the need for client software. Integration with Portal Server software ensures that
users receive secure encrypted access to the content and services that users have
permission to access.
Secure Remote Access
SRA is targeted toward enterprises deploying highly secure remote access portals.
These portals emphasize security, protection, and privacy of intranet resources.
The SRA services–Access List, the Gateway, NetFile, Netlet, and Proxylet– ena ble
users to securely access intranet resources through the Internet without exposing
these resources to the Internet.
Portal Server runs in open mode and secure mode, that is, either without SRA or
with SRA.
Portal Sever in Open Mode
In open mode, Portal Server is installed without SRA. The typical public portal
runs without secure access using only th e HTTP protocol. Although you can
configure Portal Server to use the HTTPS protocol in open mode (either during or
after installation), secure remot e access is not possible. This means tha t users
cannot access remote file systems and applications.
The main difference between an open portal and a secure portal is that the services
presented by the open portal typically reside within the demilitarized zone (DMZ)
and not within the secured intranet.
Chapter 1 Portal Server Architecture 25
Page 26

Secure Remote Access
If the portal does not contain sensitive information ( d eploying public information
and allowing access to free applications), then responses to access requests by a
large number of users is faster than secure mode.
Figure 1-1 shows Portal Server configured for open mode. In this figure, Portal
Server is installed on a single server behind the firewall. Multiple clients access the
Portal Server system across the Internet through the single firewall, or from a web
proxy server that sits behind a firewall.
NOTE You can provide secure access to users of web-enabled resources by
running Portal Server in open mode with the HTTPS protocol.
However, without SRA, you cannot provide secure remote access to
file systems or TCP/IP applications.
Figure 1-1 Portal Server in Open Mode
Firewall
Client
Internet
Client
Portal Server in Secure Mode
In secure mode, Portal Server is installed with SRA. Secure mode provides users
with secure remote access to required intra ne t file systems and applications.
26 Portal Server 6 2005Q1 • Deployment Planning Guide
intranet
Portal Server
Applications
Page 27
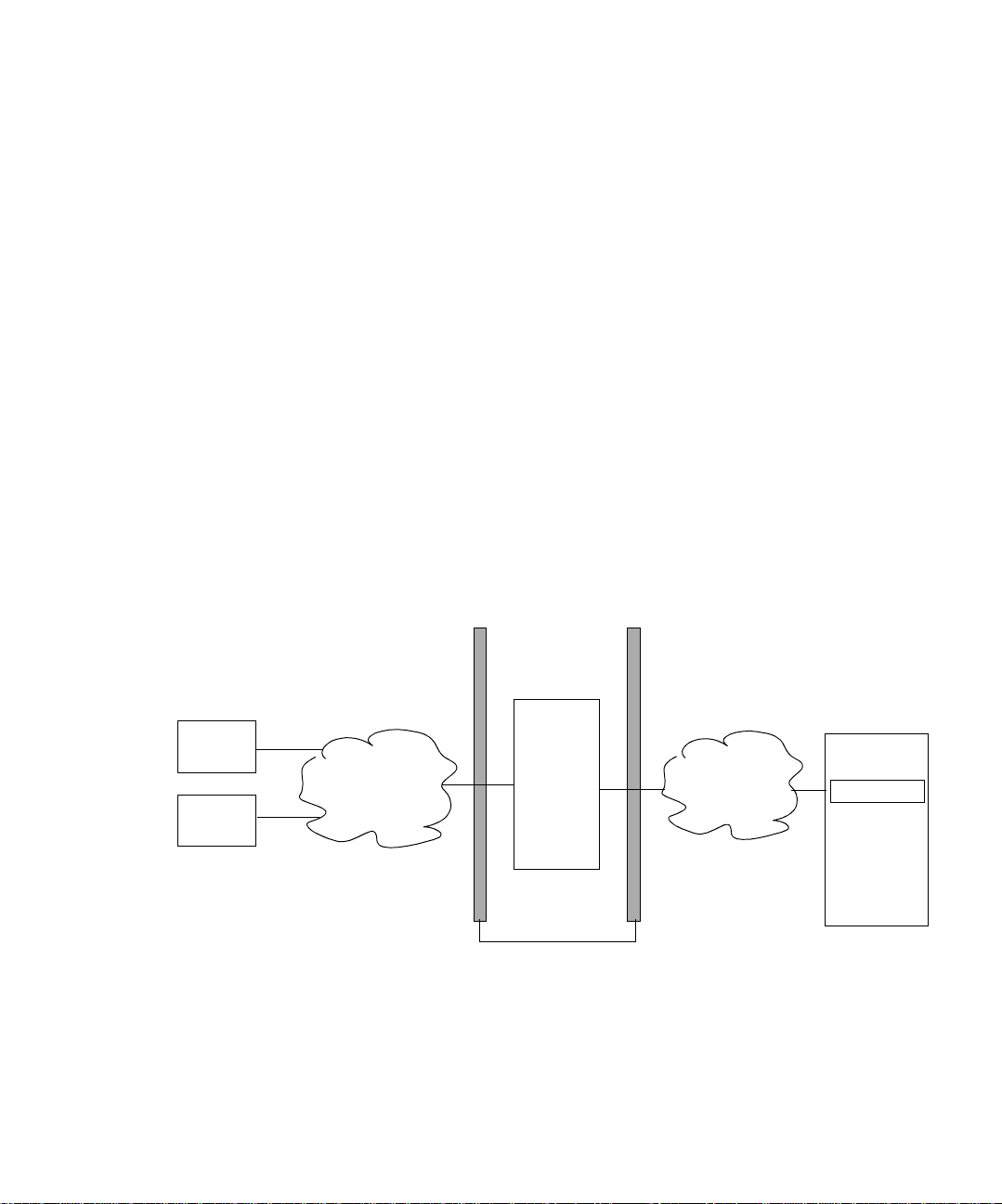
Secure Remote Access
The main advantage of SRA is that only the IP address of the Gateway is published
to the Internet. All other services and their IP addresses are hidden and never
published to a Domain Name Service (DNS) that is running on the public ne twork
(such as the Internet).
The Gateway resides in the demilitarized zone (DMZ). The Gateway provides a
single secure access point to all intranet URL s a nd applications, thus reducing the
number of ports to be opened in the firewall. All other Sun Java System services
such as Session, Authentication, and Portal Desktop, reside behind the DMZ in the
secured intranet. Communication from the client browser to the Gateway is
encrypted using HTTP over Secure Sockets Layer (SSL). Communication fro m th e
Gateway to the server and intranet resources can be either HTTP or HTTPS.
Figure 1-2 shows Portal Server installed with SRA. SSL is used to encrypt the
connection between the client and the Gateway over the Internet. SSL can also be
used to encrypt the connection between the Gateway and the Portal Server system.
The presence of a Gateway between the intranet and the Internet extends the
secure path between the client and the Portal Server system.
Figure 1-2 Portal Server in Secure Mode
Client
Client
Firewall
Internet
Firewall
Gateway
DMZ
Firewall
Portal Server
intranet
Chapter 1 Portal Server Architecture 27
Applications
Page 28

Security, Encryption, and Authentication
You can add additional servers and Gateways for site expansion. You can also
configure the components of SRA in various ways based on your business
requirements.
Security, Encryption, an d Au the ntica tio n
Portal Server system security relies on the HTTPS encryption protocol, in addition
to UNIX system security, for protecting the Portal Server system software.
Security is provided by the web container, which yo u can configure to use SSL, if
desired. Portal Server also supports SSL for authentication and end-user
registration. By enabling SSL certificates on the web server, the Portal Desktop and
other web applications can also be accessed securely. You can use the Access
Manager policy to enforce URL-based access policy.
Portal Server depends on the authentication service provided by Sun Java System
Access Manager and suppo rts sing le si gn-on (S SO) wi th any produc t that al so us es
the Access Manager SSO mechanism. The SSO mechanism uses encoded cookies to
maintain session state.
Another layer of security is provided by SRA. It uses HTTPS by default for
connecting the client browser to the intranet. The Gateway uses Rewriter to enable
all intranet web sites to be accessed without exposing them directly to the Internet.
The Gateway also provides URL-based access policy enforcement without having
to modify the web servers being accessed.
Communication from the Gateway to the server and intranet resources can be
HTTPS or HTTP. Communication within the Portal Server system, for example
between web applications and the directory server, does not use encryption by
default, but it can be configured to use SSL.
Portal Server Deployment Components
Portal Server deployment consists of the following components:
• IAccess Manager
Access Manager provides user and service management, authentication and
single sign-on services, policy management, logging service, debug utility, the
administration console, and client support interfaces for Portal Server. This
consists of:
28 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 29

Portal Server Architecture
❍ Java Development Kit™ (JDK™)--Java Developm ent Kit software provides
the Java run-time environment for all Java software in Portal Server and its
underlying components. Portal Server depends on the JDK software in the
web container.
❍ Network Security Services for Java software
❍ Sun Java System Web Server
❍ Java API for XML Processing (JAXP),
• Sun Java System Directory Server
Directory Server provides the primary config uration and user profile data
repository for Portal Server. The Directory Server is LDAP compliant and
implemented on an extensible, open schema.
•Web Containers
❍ Sun Java System Web Server
❍ Sun Java System Application Server Enterprise Edition
The following web containers can be used in place of the Web Server and
Application Server software:
❍ BEA WebLogic Server™
❍ IBM WebSphere® Application Server
See the Sun Java System In stallation Guide for information on deploying Portal
Server in various web containers.
NOTE See the Portal Server 6 Release Notes for specific versions of products
supported by P ortal Server.
Portal Server Architecture
Usually, but not always, you deploy Portal Server software on th e following
different portal nodes (servers) that work together to implement the portal:
• Portal Server node. The web server where Portal Server resides. You can also
install the Search component on this node if desired. Access Manager can
reside here.
Chapter 1 Portal Server Architecture 29
Page 30

Identity Management
• Access Manager node.The server where Access Manager can reside. Access
Manager does not have to reside on the same node as Portal Server.
• Search node. Optional. The server you use for the Portal Server Search service.
You can install the Portal Server Search service on its own server for
performance, scalability and availability reasons.
• Gateway nodes. Optional. The server where the SRA Gateway resides. You
can install the Gateway on the portal n ode . Beca use you locate the Gateway in
the DMZ, the Gateway is installed on a separate, non-portal node.
• Netlet Proxy node. Optional. The server used to run applications securely
between users’ remote desktops and the servers running applications on your
intranet.
• Rewriter Proxy node. Optional. The server used to run applications securely
between users’ remote desktops and the servers running applications on your
intranet.
• Directory Server node. The server running Directory Server software. You can
install Directory Server on a non-portal nod e .
• Other servers. These servers, such as mail, file, and legacy servers, provide
backend support, data, and applications to portal users.
Identity Management
Portal Server uses the Access Manager to control many users spanning a variety of
different roles across the organization and sometimes outside the organization
while accessing content, applications and services. The challenges include: Who is
using an application? In what capacity do users serve the organ ization or
company? What do users need to do, and what should users be able to access?
How can others help with the administrative work?
Access Manager software consists of the following components:
• Java software APIs used to access SSO Token, user profiles, logging, and
debugging
• Command line tools such as amadmin, amserver, and ampassword
• Web application services such as session, authentication, logging, and naming
• Administration console web application
• Access Manager SDK
30 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 31

• Access Manager console SDK
• Authentication daemons that support the web applications
See the Access Manager Deploymen t Planning Guide for more information.
Portal Server Software Deployment
This section provides information on sof tware deployed on Portal Server.This
section provides information on the sof tware packaging mechanism, the software
categories within the system, and compatibility with Java software.
Software Packaging
Portal Server uses a “dynamic WAR file” approa ch to deploy software to the
system. Portal Server is installed using Solaris™ packages, which consist of
individual files that comprise web application s, f or exam ple, JAR , JSP, template,
and HTML files. The packages do not contain WAR or EAR files. The packages do
contain
installation time. This dynamically constructed file is then deployed to the web
application container. As additional packages are added to the system, for
example, for localization, the web application file is reb uilt a nd red e ployed.
web.xml fragments that are used to construct the Portal Server WAR file at
Portal Server Software Deployment
NOTE The WAR file packaging and deployment mechanism is for use only
by Portal Server products. Customer modifications to the WAR file
or any files used to build it are currently not supported.
Software Categories
Portal Server distinguishes between the following kinds of software that it installs
onto the Portal Server node:
• Dynamic web applications. These include servlets r unning on a Java platform,
JSP files, content providers, and other items that the web container processe s
when accessed by the user’s browser. For Portal Server, these files are installed
in the Web Server.
Chapter 1 Portal Server Architecture 31
Page 32

Portal Server Software Deployment
• Static web content. These include static HTML files, images, applet JAR files,
and other items that can be served up directly by the web server without using
the Web Server container. For Portal Server, these files are also installed in the
web server.
NOTE Static web content and dynamic web app lications are all grouped
• Configuration data. These include data that is installed into the directory, that
is, the Access Manager service definitions and any other data that modifies the
directory at installation time. This includes modifications to the console
configuration data to connect in the Port al Server extensions. Configuration
data is installed only once no matter how many Portal Server nodes there are.
• SDK. This is the JAR file or files that contain the Java APIs that are made
available by a component. Developers need to install this package on a
development system so that they can compile classes that use the API. If a
component does not export any public Java APIs, it would not have this
package.
together into a single WAR file.
Compatibilit y W ith Ja v a Sof twa re
Portal Server software falls into three categories:
• Applets. Applets used in Portal Server are compatible with Java 1.1, which is
supported by most browsers.
• Web applications. Web applications are intended to be compatible with the
Java 2 Enterprise Edition (J2EE™) we b container based on the ser vlets interface
except where uses of special interfaces are identified. This includes
compatibility with Java 2 and later.
• Stand-alone Java processes. Stand-alone Java software processes are
compatible with Java 2 and later. Some Portal Server software, specifically in
SRA, use Java™ Native Interface (JNI) to call C application programming
interfaces (APIs). These calls are necessary to enable the system to run as the
user
nobody.
32 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 33

A Typical Portal Server Installation
Figure 1-3 on page 34 illustrates some of the components of a portal deployment
but does not address the actual physical network design, single points of failure,
nor high availability. See Chapter 5, “Creating Your Portal Design”, for more
detailed information on portal design.
This illustration shows the high-level architecture of a typical installation at a
company site for a business-to-employee portal. In this figure, the Gateway is
hosted in the company’s DMZ along with other systems accessible from the
Internet, including proxy/cache servers, web servers, and mail Gateways. The
portal node, portal search node, and directory server, are hosted on the internal
network where users have access to systems and services ranging from individual
employee desktop systems to legacy systems.
NOTE If you are designing an ISP hosting deployment, which hosts
separate Portal Server instances for business customers who each
want their own p ort al, cont ac t your Sun Ja va Sy stem rep res enta tiv e.
Portal Server requires customizations to provide ISP hos ting
functionality.
A Typical Portal Server Installation
In Figure 1-3 on page 34, users on the Internet access the Gateway from a browser.
The Gateway connects the user to the IP address and port for the portal users are
attempting to access. For example, a B2B portal would usually allow access to only
port 443, the HTTPS port. Depending on the authorized use, the Gateway forwards
requests to the portal node, or directly to the service on the enterprise internal
network.
Chapter 1 Portal Server Architecture 33
Page 34

A Typical Portal Server Installation
Figure 1-3 High-level Architecture for a Business-to-Employee Portal
Gateway
Telecommuter
PCs/
Workstations
Proxy/
Cache
Airport/Hotel
Kiosks
Internet
Web
Server
Branch Offices
Remote Offices
Customers/Suppliers
Behind Firewall
Mail
Gateway
Portal
Server
Portal
Server
Search
PCs
Desktops
Directory
Server
Mail
Server
Legacy
Server
34 Portal Server 6 2005Q1 • Deployment Planning Guide
DMZ
Page 35

Figure 1-4 shows a Portal Server deployment with SRA services. See Chapter 2,
“Portal Server Secure Remote Access Architecture” for details.
Figure 1-4 SRA Deployment
A Typical Portal Server Installation
Portal
Server
Rewriter
Proxy
Client
Proxylet
Netlet
Gateway
Netlet
Proxy
Web
Server
Host
Application
Host
Application
Chapter 1 Portal Server Architecture 35
Page 36

A Typical Portal Server Installation
36 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 37

Chapter 2
Portal Server Secure Remote Access
Architecture
This chapter describes the Sun Java™ System Portal Server Secure Remote Access
(SRA) architecture.
You administer the configuration information through the Access Manager
administration console.
This chapter describes the following SRA components:
• SRA Gateway
• Netlet
• Netlet Proxy
• NetFile
• Rewriter
• Rewriter Proxy
• Proxylet
SRA Gateway
The SRA Gateway is a standalone Java process that can be considered to be
stateless, since state information can be rebuilt transparently to the end user. The
Gateway listens on configured ports to accept HTTP and HTTPS requests. Upon
receiving a request, the Gateway checks session validity and header information to
determine the type of request. Depending on the type of request, the Gateway
performs the following:
37
Page 38

SRA Gateway
• Netlet request. Routes the request (traffic) to the server specified in the Netlet
rule that the user clicked in the Portal Desktop.
• HTTP(S) traffic. Routes the request to the server as specified by the HTTP
header. Upon receiving a response from the server, the Gateway translates the
response so that all intranet links within the response work on the extranet.
All the Gateway configuration info rmation is stored in the Access Manager’s
LDAP database as a profile. A gateway profile consists of all the configuration
information related to the Gateway except .
All machine-specific information, su ch as machine-specific information such as
host name and IP address, is stored in a configuration file in the local file system
where the Gateway is installed. This enables one gateway profile to be shared
between Gateways that are running on mult iple machines.
As mentioned previously, you can configure the Gateway to run in both HTTP and
HTTPS modes, simultaneously. This helps both intranet and extranet users to
access the same Gateway: extranet users over HTTPS, and intranet users over
HTTP (without the overhead of SSL).
You can also run the Gateway in
Remote Access 6 Administration Guide for more information.
chroot environments. See the Portal Server Secure
Multiple Gateway Instances
If desired, you can run multiple Gateway insta nces on a single machine—this is
referred as a multihomed Gateway. Each Gateway instance listens on separate
port(s). You can configure Gateway instances to contact the same Portal Server
instance, or different Portal Server instances. When running multiple instances of a
Gateway on the same machine, you can associate an independent certificate
database with each instance of the Gateway, and bind that Gateway to a domain. In
essence, this provides the flexibility of having a different Gateway server certificate
for each domain.
Multiple Portal Server Instances
When you configure the Gateway with multiple instances of Portal Server, the
Gateway automatically performs round-robin load balancing by logging in users
with the different servers, alternately. The Gateway also keep s a list of active
servers to avoid trying to login users to an inactive server. This mechanism helps to
avoid single points of failure with Portal Server.
38 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 39

SRA Gateway
NOTE Session stickiness is not required in fr ont of a Gateway (unless you
are using Netlet), however performance is improved with session
stickiness. On the other hand, session stickiness to the Portal Server
instances is enforced by SRA.
Proxy Configuration
The Gateway uses proxies that are specified in its profile to retrieve contents from
various web servers within the intranet and extranet. You can dedicate proxies for
hosts and DNS subdomains and domai ns . Depending on the proxy configuration,
the Gateway uses the appropriate proxy to fetch the required contents. If the proxy
requires authentication, the proxy name is stored as part of the gateway prof ile,
that the Gateway uses automatically, when connecting to the proxy.
Gateway and HTTP Basic Authentication
The Gateway supports basic authentication, that is, prompting for a user ID and
password but not protecting those credentials during transm ission from the user’s
computer to the site’s web server. Such protection usually requires the
establishment of a secure HTTP connection, typically through the use of SSL.
If a web server requires basic authentication the client prompts for user name and
password and sends the information back to the requesting server. With the
Gateway enabled for HTTP basic authentication, it captures the user name and
password information and stores a copy in the user’s profile in the Access Manager
for subsequent authentications and login attempts. The original data is passed by
the Gateway to the destination web server for basic authentication. The web server
performs the validation of the user name an d pass word.
The Gateway also enables fine cont rol of denying and allowing th is capability on
an individual host basis.
Gateway and SSL Support
The Gateway supports both SSL v2 and SSL v3 encryption while running in HTTPS
mode. You can use the Access Manager administration console to enable or disable
specific encryption. The Gateway also supports Transport Layer Security (TLS).
SSL v3 has two authentication modes:
Chapter 2 Portal Server Secure Remote Access Architecture 39
Page 40

SRA Gateway
• Mandatory server authentication. The client must authenticate the server.
• Optional authentication. The server is configured to authenticate the client.
Personal Digital Certificate (PDC) authentication is a mechanism that authenticates
a user through SSL client authentication. The Gatewa y supports PDC
authentication with the support of Access Manager authentication modules. With
SSL client authentication, the SSL handshake ends at the Gateway. This PDC-based
authentication is integrated along with the Access Manager’s certificate-based
authentication. Thus, the client certificate is handled by Access Manager and not by
the Gateway.
If the session information is not found as part of the HTTP or HTTPS request, the
Gateway directly takes the user to the authentication page by obtaining the login
URL from Access Manager. Similarly, if the Gateway finds that the session is not
valid as part of a request, it takes the user to the login URL and at successful login,
takes the user to the requested destination.
After the SSL session has been established, the Gateway continues to receive the
incoming requests, checks session validity, and then forwards the request to the
destination web server.
The Gateway server handles all Netlet traffic. If an incoming client request is Netlet
traffic, the Gateway checks for session validity, decrypts the traffic, and forwards it
to the application server. If Netlet Proxy is enabled, the Gateway checks for session
validity and forwards it to Netlet Proxy. The Netlet Proxy then decrypts and
forwards it to the application server.
NOTE Because 40-bit encryption is very insecure, the Gateway provides an
option that enables you to reject connections from a 40-bit
encryption browser.
Gateway Access Control
The Gateway enforces access control by using Allowed U RLs and Denied URLs
lists. Even when URL access is allowed, the Gate way checks the validly of the
session against the Access Manager session server. URLs that are designated in the
Non Authenticated URL list bypass session validation, as well as the Allowed and
Denied lists. Entries in the Denied URLs list take precedence over entries in the
Allowed URLs list. If a particular URL is not part of any list, then access is denied
to that URL. The wildcard character,
either the Allow or Deny list.
40 Portal Server 6 2005Q1 • Deployment Planning Guide
*
, can also be used as a part of the URL in
Page 41

Netlet
Netlet
Gateway Logging
You can monitor the complete user behavior by enabling logging on the Gateway.
The Gateway uses the Access Manager logging API for crea ting logs.
Using Accelerators with the Gateway
You can configure accelerators, which are dedicated hardware co-processors, to
off-load the SSL functions from a server's CPU. Using accelerators frees the CPU to
perform other tasks and increases the processing speed for SSL transactions.
Netlet can provide secure access to fixed port applications and some dynamic port
applications that are available o n the intranet from outside the intranet. The client
can be behind a remote firewall and SSL proxy, or directly connected to the
Internet. All the secure connections made from outside the intranet to the intran et
applications through the Netlet are controlled by Netlet rules.
A Netlet applet running on the browser sets up an encrypted TCP/IP tunnel
between the remote client machine and intranet applications on the remote hosts.
Netlet listens to and accepts connections on preconfigured ports, and routes both
incoming and outgoing traffic between the client and the destination server. Both
incoming and outgoing traffic is encrypted using an encryption algorithm selected
by the user, or configured by the administrator. The Netlet rule contains the details
of all servers, ports, and encryption algorithms used in a connection.
Administrators create Netlet rules by using the Access Manager admi nistration
console.
Static and Dynamic Port Application s
Static port applications run on known or sta tic ports. Examples include IMAPand
POP servers, Telnet daemons, and jCIFS. For static port applications, the Netlet
rule includes the destination server port so that requests can be routed directly to
their destinations.
Chapter 2 Portal Server Secure Remote Access Architecture 41
Page 42

Netlet
Dynamic applications agree upon a port for communication as part of the
handshake. You can include the destination server port as part of the Netlet rule.
The Netlet needs to understand the protocol and examine the data to find the port
being used between the client and the server. FTP is a dynamic port application. In
FTP, the port for actual data transfer between the client and server is specified
through the
PORT command. In this case, the Netlet parses the traffic to obtain the
data channel port dynamically.
Currently, FTP and Microsoft Exchange are the only d ynamic port applications
that Portal Server supports.
NOTE Although Microsoft Exchange 2000 is supported with Netlet, the
following constraints apply:
• You must configure Exchange to use STATIC ports.
• Netlet does not work with Windows 2000 and XP because
Windows 2000 and XP clients reserve the Exchange port (port
135) for the RPC Portmapper, which Active Directory uses.
Previous versions of Windows did not reserve this port. Because
the port is reserved, you cannot assign Netlet to it, and thus the
port cannot provide the necessary tunneling.
• The Outlook 2000 client has the limitation that it does not enable
you to change the port on which you want to connect to the
Exchange server.
42 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 43

Netlet
Netlet and Application Integration
Netlet works with many third parties such as Graphon, Citrix, and pcAnywhere.
Each of these products provides secure access to the user’s Portal Desktop from a
remote machine using Netlet.
Split Tunneling
Split tunneling allows a VPN client to connect to both secure sites and non-secure
sites, without having to connect or disconnect the VPN—in this case, the
Netlet—connection. The client determines whether to send the information over
the encrypted path, or to send it by using the non-encrypted path. The concern
over split tunneling is that you could have a direct connection from the non-secure
Internet to your VPN-secured network, via the client. Turning off split tunneling
(not allowing both connections si multaneously) reduces the vulnerability of the
VPN (or in the case of Netlet) connection to Internet intrusion.
Though Portal Server does not prohibit nor shut down multiple network
connections while attached to the portal site, it does prevent unauthorized users
from “piggybacking” on other us ers’s sessions in the following ways:
• Netlet is an application specific VPN and n ot a general purpose IP router.
Netlet only forwards packets that have been defined by a Netlet rule. This
differs from the standard VPN approach that gives you complete LAN access
once you’ve connected to the network.
• Only an authenticated portal user can run the Netlet. No portal application can
be run until the user has been successfully authenticated, and no new
connections can be made if an authenticated session does not exist.
• All access controls in place on the application side are still in effect so that an
attacker would also have to break in to the back-end application.
• Every Netlet connection results in a dialog box posted by the Netlet (running
in the authenticated user’s JVM™) to the authenticated user’s display. The
dialog box asks for verification and acknowledgement to permit the new
connection. For attackers to be able to utilize a Netlet connection, attackers
would need to know that the Netlet was running, the port number it was
listening on, how to break the back-end applica tion, and convince the user to
approve the connection.
Chapter 2 Portal Server Secure Remote Access Architecture 43
Page 44

Netlet Proxy
Netlet Proxy
A Netlet Proxy helps reduce the number of open ports needed in the firewall to
connect the Gateway and the destination hosts.
For example, consider a configuration where users need Netlet to connect with a
large number of Telnet, FTP, and Microsoft Exchange servers within the intranet.
Assume that the Gateway is in a DMZ. If it routes the traff ic to a ll the destination
servers, a large number of ports would need to be open in the second firewall. To
alleviate this problem, you can use a Netlet Proxy behind the second firewall and
configure the Gateway to forward the traffic to the Netlet Proxy. The Netlet Proxy
then routes all the traffic to the destination servers in the intranet and you reduce
the number of open ports required in the second firewall. You can also deploy
multiple Netlet Proxies behind the second firewall to avoid a single point of failure.
You could also use a third-party proxy to use only one port in the second firewall.
NOTE Installing the Netlet Proxy on a separate node can help with Portal
Server response time by offloading Netlet traffic to a separate node.
NetFile
NetFile enables remote access and operation of file systems that reside within the
corporate intranet in a secure manner.
NetFile uses standard protocols such as NFS, jCIFS, and FTP to conn ect to any of
the UNIX® or Windows file systems that are permissible for the user to access.
NetFile enables most file operations that are typica l to f ile manager applications.
See the Portal Server Secu re Remote Access 6 Administration Guide for more
information.
Components
To provide access to various file systems, Ne tFile has three components:
• NetFile Java 1 Applet. Has an AWT-based user interface. For use with older
browsers that cannot support Java 2.
• NetFile Java 2 Applet. Has a Swing-based user interface. For use with
browsers that support Java plug-ins.
44 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 45

NetFile
• NetFile servlet(s). Two NetFile servlets are present in the web container, one
for each kind of NetFile applet. The servlets are responsible for connecting to
different types of file systems, carrying out the operations that NetFile is
configured to handle, and sending the informatio n back to the applets for
display.
NetFile is internationalized and provides access to file systems irrespective of their
locale (character encodings).
NetFile uses Access Manager to store its own profile, as well as user settings and
preferences. You administer NetFile through the Access Manager administration
console.
Initialization
When a user selects a NetFile link in the Portal Server Desktop, the NetFile servlet
checks if the user has a valid SSO token and permission to execute NetFile. If so, the
applet is rendered to the browser. The NetFile applet connects back to the servlet to
get its own configuration such as siz e , locale, resource bundle, as well as user
settings and preferences. NetFile obtains the locale information and other user
information (such as user name, mail ID, and mail server) using the user’s SSO
token. The user settings include any settings tha t the user has inherited from an
organization or role, settings that are customized by the user, and settings that the
user has stored upon exit from a previous NetFile session.
Validating Credentia ls
NetFile uses the credentials supplied by users to authenticate users before granting
access to the file systems.
The credentials include a user name, password, and Windows or Novell domain
(wherever applicable). Each share can have an independent password, therefore,
users need to enter their credentials for every share (exce pt fo r co mmon hosts) th at
you add.
NetFile uses UNIX Authentication from the Access Manager to grant access to NFS
file systems. For file systems that are accessed over FTP and jCIFs protocols,
NetFile uses the methods provided by the protocol itself to validate the credentials.
Chapter 2 Portal Server Secure Remote Access Architecture 45
Page 46

NetFile
Access Control
NetFile provides various means of file system access control. You can deny access
to users to a particular file system based on the protocol. For example, you can
deny a particular user, role, or organization access to file systems that are accessible
only over NFS.
You can configure NetFile to allow or deny access to file systems at any level, from
organization, to suborganization, to user. You can also allow or deny access to
specific servers. Access can be allowed or denied to file systems f or use r s
depending on the type of host, including Windows, FTP, NFS, and FTP over
NetWare. For example, you can deny access for Windows hosts to all users of an
organization. You can also specify a set of common hosts at an organization or role
level, so that all users in that organization or role can access the common hosts
without having to add them for each and every member of the organization or role.
As part of the NetFile service, you can configure the Allowed URLs or D enied
URLs lists to allow or deny access to servers at the organization, role, or user level.
The Denied URLs list takes precedence over the Allowed URLs. The Allowed URLs
and Denied URLs lists can contain the * wildcard to allow or deny access to a set of
servers under a single domain or subdomain.
Security
When you use NetFile with SRA configured for SSL, all connections made from
NetFile applets to the underlying file system happen over the SSL connection
established between the Gateway and the browser. Because you typically install
the Gateway in a DMZ, and open a limit ed number of ports (usually only one) in
the second firewall, you do not compromise security while providing access to the
file systems.
Special Operations
NetFile is much like a typical file manager application with a set of features that are
appropriate for a remote file manager application. NetFile enables users to upload
and download files between the loca l and remote file systems (shares). You can
limit the size of the upload file (from the local to the remo te file system) through
the Access Manager administra tion console.
46 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 47

Rewriter
NetFile also enables users to select multiple files and compress them by using GZIP
and ZIP compression. Users can select multiple files and send them in a single
email as multiple attachments. NetFile also uses the SSO token of Access Manager
to access the user’s email settings (such as IMAP server, user name, password, and
reply-to address) for sending email.
Double-clicking a file in the NetFile window launches the application
corresponding to the MIME type and opens the file. NetFile provides a d e f ault
MIME types configuration file that has mappings for most popular file types
(extensions) and MIME-types that you can edit for adding new mappings.
You can search for files and display the list in a separate window using NetFile.
The results of each search are displayed in a new window while maintaining the
previous search result windows. The type of character encoding to be used for a
particular share is user configurable, and is part of the share’s setting. If no
character encoding is specified, NetFile uses ISO -88 59 - 1 while working with the
shares. The ISO-8859-1 encoding is ca pable of handling most common languages.
ISO-8859-1 encoding gives NetFile the capability to list files in any language and to
transferring files in any language without damaging the file contents.
NetFile creates temporary files only when mailing f iles (in both NetFile Java 1 and
Java 2). Tempo rary files are no t created during u ploading and downloading files
between Windows file systems and the local file systems over the jCIFS protocol.
Rewriter
NOTE NetFile supports deletion of directories and remote files. A ll the
contents of remote directories are deleted recursively.
NetFile and Multithreading
NetFile uses multithreading to provide the flexibility of running multiple
operations simultaneously. For example, users can launch a search operation, start
uploading files, then send files by using em ail. NetFile performs all three
operations simultaneously and still perm it the user to browse through the file
listing.
Rewriter is an independent co mpon en t th at tra ns lat es al l UR Is (i n both HT ML and
JavaScript code) to ensure that the intranet content is always fetched through the
Gateway. You define a ruleset (a collection of rules) tha t id entifies all URLs that
need to be rewritten in a page. The ruleset is an XML fragment that is written
Chapter 2 Portal Server Secure Remote Access Architecture 47
Page 48

Rewriter Proxy
according to a Document Type Definition (DTD). Using the generic ruleset that
ships with the Rewriter, you can rewrite mos t URLs (but not all) without any
additional rules. Yo u can also associate rulesets with domains for domain-b ased
translations. See the Porta l Server Secure Rem ote Ac cess 6 Admi nistrat ion Guide for
more information.
An external ruleset identifies the URI in the content. Any request that needs to be
served by SRA follows this route:
1. From the request, SRA identifies the URI of the intranet page or Internet page
that needs to be served.
2. SRA uses the proxy settings to connect to the identified URI.
3. The domain of the URI is used to identify the ruleset to be used to rewrite this
content.
4. After fetching the content and ruleset, SRA inputs these to the Rewriter where
identified URIs are translated.
5. The original URI is replaced with the rewritten URI.
6. This process is repeated until the end of the document is reached.
7. The resultant Rewriter output is routed to the browser.
Rewriter Proxy
To minimize the number of open ports in the firewall, use the Rewriter Proxy.
When you install the Rewriter Proxy, HTTP requests are redirected to the Rewriter
Proxy instead of directly to the destination host. The Rewriter Proxy in turn sends
the request to the destination server.
Using the Rewriter Proxy enables secure HTTP traffic between the Gateway an d
intranet computers and offers two advantages:
• If a firewall is between the Gateway and server, the firewall needs to open only
two ports. One firewall is between the Gateway and the Rewriter Proxy and
another is between the Gateway and the Portal Server.
• You can use a third-party proxy to use only one port in the second firewall to
read the Rewriter Proxy.
• HTTP traffic is now secure between the Gateway and the intranet even if the
destination server only supports HTTP protocol (not HTTPS).
48 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 49

Proxylet
Proxylet
NOTE You can run multiple Rewriter Proxies to avoid a single point of
failure and achieve load balancing.
Proxylet is a dynamic proxy server that runs on a client machine. Proxylet redirects
a URL to the Gateway. It does this by reading and modif ying the proxy settings of
the browser on the client machine so that the settings point to the local proxy server
or Proxylet.
It supports both HTTP and SSL, inheriting the transport mode from the Gateway. If
the Gateway is configured to run on SSL, Proxylet establishes a secure channel
between the client machine and the Gateway. Proxylet uses the JSSE API if the
client JVM is 1.4 or higher or if the required jar files reside on the client machine.
Otherwise it uses the KSSL API.
Proxylet is enabled from the Access Manager administration console where the
client IP address and port are specified.
Unlike Rewriter, Proxylet is an out-of-the-box solution with very little or no
post-installation changes. Also Gateway performance improves because Proxylet
does not deal with web content.
Chapter 2 Portal Server Secure Remote Access Architecture 49
Page 50

Proxylet
50 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 51

Chapter 3
Identifying and Evaluat ing Your Business
and Technical Requirements
The first step in planning your deployment is identifying your Sun Java™ System
Portal Server business and technical requirements.. You need to gather both
business and technical requirements before you can address architecture and
design issues.
This chapter contains the following sections:
• Business Objectives
• Technical Goals
• Mapping Portal Server Features to Your Business Needs
• Understanding User Behaviors and Patterns
Business Objectives
Your business requirements address your organization’s problems and
opportunities, and include such factors as:
•Services
• Service availability
•Future growth
• New technologies
• Capital investment
To be useful in formulating design requirements, the business requirements must
address detailed goals and objectives.
51
Page 52

Business Objectives
The business goals of your portal affect deployment decision. Understand your
objectives. If you do not understand your business requirements, you can easily
make erroneous assumptions that could affect the accuracy of your deployment
estimates.
Use these questions to help you identify your business objectives:
• What are the business goals of this portal? (For example, do you want to
enhance customer service? Increase employee productivity? Reduce the cost of
doing business?)
• What kind of portal do you need? (For example, business-to-business,
business-to-consumer , business-to-enterprise, or a hybrid?)
• Who is your target audience?
• What services or functions will the portal deliver to users?
• How will the target audience benefit from the portal?
• What are the priorities for the portal? (If you plan to deploy your portal in
phases, identify priorities for each phase.)
(Optional) Use these questions to help identify your business objectives if you are
deploying a secure portal:
• Do you need to increase employee productivity (by ma king your intranet
applications and servers accessible over the Internet)?
• Do you need to provide secure access to your portal?
• Do you need to reduc e c os t of ownership of an existi ng Vi rt u al Private
Network (VPN) solution?
• Do you want employees to access intranet applications such as Citrix and
pcAnywhere from the Internet?
• Do you want your employees to explore intranet servers or machines from the
Internet?
• Who is your target audience (all portal users, employees, or customers)?
52 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 53

Technical Goals
Your technical requirement (often called functional requirement) discuss the
details of your organization’s system needs and desired results, and include such
factors as:
•Performance
•Security
• Reliability
• Expected performance criteria of the portal
The technical requirements define all functions required of an architecture and
provide guidelines for how each component works and integrates to form an entire
system. Your organization needs technical requirements to formulate the best
design approaches and apply the appropriate technologies to accomplish the
desired architectural solution for your portal.
The reasons you are offering your portal have a direct affect on how you
implement your portal. You must define target population, performance
standards, and other factors related to your goals.
Technical Goals
Use these questions to help you identify the goals of your portal:
• What is your portal’s biggest priority?
• What applications will the portal deliver?
• What is your target population?
• What performance standard is necessary?
• What transaction volume do you expect? What transaction volume do you
expect during peak use?
• What response time is acceptable during peak use?
• What is the necesary level of concurrency? Concurrency is the number of users
who can be connected at any given time?
• Should access to the portal be through intranet or Internet?
• Will your portal be deployed in one phase, or many phases? (Describe each
phase and what will change from phase to phase.)
Chapter 3 Identifying and Evaluating Your Business and Technical Requirements 53
Page 54

Mapping Portal Server Features to Your Business Needs
Mapping Portal Server Fea tures to Your Business
Needs
The previous sections posed questions to you about the various areas of the Portal
Server system from a high-level perspective of business and technical needs. This
section reviews specific technology features with the goal of determining which
technologies are most important for your organization. Review these features
while keeping in mind your organiza tion’s short-, mid-, and long-term plans.
Use the following sections and tables to assess the benefits of the list ed features and
determine their relative priority for your organiza tion. This information will assist
you in developing a deployment plan in a timely and cost effective manner.
NOTE In all likelihood, your Sun Java System sales representative has
previously discussed these topics with you. Thus, this section serves
as a review of that process.
Identity Management
Portal Server uses identity management to control many users spanning a variety
of different roles across the organization and sometimes outside the organization
while accessing content, applications and services. The challenges include: Who is
using an application? In what capacity do users serve the organ ization or
company? What do users need to do, and what should users be able to access?
How can others help with the administrative work?
Table 3-1 shows the identity management features and their benefits.
Table 3-1 Identity Manage m ent Fe at u res and Benefits
Feature Description Benefit
Directory service Portal Server uses Access Manager and
Directory Server
54 Portal Server 6 2005Q1 • Deployment Planning Guide
Portal Server uses an LDAP directory for
storing user profiles, roles, and identity
information for the purpose of authentication,
single sign-on (SSO), delegated
administration, and personalizatio n
Portal Server uses an open schema that can
reside in a centralized user directory, thereby
leveraging an enterprise or service provider’s
investment in the Access Manager and
Directory Server products.
Page 55

Mapping Portal Server Features to Your Business Needs
Table 3-1 Identity Management Features and Benefits (Continued)
Feature Description Benefit
User, policy, and
provisioning
management
Single sign-on
(SSO)
Delegated
administration
Security Provides single sign-on for aggregated
Access Manager enables you to manage
many users spanning a variety of different
roles across the organization and sometimes
outside the organization while accessing
content, applications, and services.
Access Manager integrates user
authentication and single sign-on through an
SSO API. Once the user is authenticated, the
SSO API takes over. Each time the
authenticated user tries to access a protected
page, the SSO API determines if the user has
the permissions required based on their
authentication credentials. If the user is valid,
access to the page is given without additional
authentication. If not, the user is prompted to
authenticate again.
The Access Manager administration console
provides role-based delegated administration
capabilities to different kinds of administrators
to manage organizations, users, policy, roles,
channels, and Portal Desktop providers
based on the given permissions.
applications to the portal.
Provides a centralized identity management
solution for storing and managing identity
information, which is integrated with a policy
solution to enforce access rights, greatly
simplifying these challenges . Extends a
common identity to handle new applications,
enables applications to share ad ministrative
work, and simplifies tasks normally
associated with building these services from
scratch.
Consolidates management of users and
applications. Personalizes content and
service delivery. Simplifies and streamlines
information and service acc e ss. Reduces
costs associated with managing access and
delivery.
Provides secure policy-b a sed access to
applications. Ensures secure access as portal
deployments expand beyond employee LAN
access.
Enhances user productivity by providing a
consistent, centralized mechanism to manage
authentication and single sign-on, while
enabling employees, partners and customers
access to content, applications, and services.
Enables IT to delegate portal administrative
duties to free up valuable IT resources and
administration.
Security is an important functionality in
portals. Security can address many different
needs within the portal, including
authentication into the portal, encryption of
the communications between the portal and
the end user, and authorization of the content
and applications to only users that are
allowed access.
Chapter 3 Identifying and Evaluating Your Business and Technical Requirements 55
Page 56

Mapping Portal Server Features to Your Business Needs
SRA
Table 3-2 shows the Sun Java System Portal Server Se cure Remote Access (SRA)
features and their benefits
Table 3-2 SRA Features and B enefits
Feature Description Benefit
Integrated security Extranet or Virtual Private Network
capabilities “on demand” while providing user,
policy, and authentication services. The
Gateway component provides the interface
and security barrier between remote user
sessions originating from the Internet, and
your corporate intranet.
SRA core Users achieve remote access through four
components:
• Gateway
• NetFile
• Netlet
• Proxylet
Universal access Enables web browser based universal access
with no client software installation or
maintenance necessary.
Netlet Proxy Provides an optional component that ex tends
the secure tunnel from the client, through the
Gateway to the Netlet Proxy that resides in
the intranet.
Extends an enterprise’s content, applications,
files, and services located behind firewalls to
authorized suppliers, business partners, and
employees.
To prevent denial of service attacks, you can
use both internal and external DMZ-based
Gateways.
This component has four parts:
• Gateway—Controls communication
between the Portal Server and the various
Gateway instances.
• NetFile—Enables remote access and
operation of file systems and directories.
• Netlet—Ensures secure communication
between the Netlet applet on the client
browser, the Gateway, and the
application servers.
• Proxylet—Redirects a URL to the
Gateway.
Simplifies the IT administration and
maintenance overhead while dramatically
reducing the time and cost of deployment
Restricts the number of open ports in a
firewall between the demilitarized zone (DMZ)
and the intranet.
56 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 57

Mapping Portal Server Features to Your Business Needs
Feature Description Benefit
Rewriter Proxy Redirects HTTP requests to the Rewriter
Proxy instead of directly to the destination
host. The Rewriter Proxy in turn sends the
request to the destination server.
Using the Rewriter Proxy enables secure
HTTP traffic between the Gateway and
intranet computers and offers two
advantages:
• If a firewall exists between the Gateway
and server, the firewall needs to open
only two ports—one between th e
Gateway and the Rewriter Proxy, and
another between the Gateway and the
Portal Server.
• HTTP traffic is now secure between the
Gateway and the intranet even if the
destination server only supports HTTP
protocol (no HTTPS).
Search Engine
The Search Engine service is used in the following cha nn e ls:
• Subscription channel to summarize the number of hits (relevant information)
that match each profile entry defined by the user for categorized documents
and discussions.
• Discussion channel to
individually search contents and rate the importance for
comments.
Table 3-3 shows the Search features and their benefits.
Table 3-3 Search Features and Benefits
Feature Description Benefit
Search Engine Enables the retrieval of documents based on
criteria specified by the end user.
Categorization Organizes documents into a hierarchy. This
categorization is often referred to as
taxonomy.
Robot The Search Engine robot is an agent that
crawls and indexes information across your
intranet or the Internet.
Discussions A forum for multiple threaded discussions. Contents are individually searchable and
Chapter 3 Identifying and Evaluating Your Business and Technical Requirements 57
Saves users time by providing access to
content.
Provides a different view of documents that
enables browsing and retrieval.
Automatically searches and extracts links to
resources, describes those resources, and
puts the descriptions in the Search database
(also called generation or indexing).
importance rating are given for of all
comments
Page 58

Mapping Portal Server Features to Your Business Needs
Table 3-3 Search Features and Benefits (Continued)
Feature Description Benefit
Subscriptions Enables the user to track new or changed
material in different areas of interest.
Discussions, search categories, and free-form
searches (saved searches) can be tracked.
Personalization
Personalization is the ability to deliver content based on selective criteria and offer
services to a user.
Table 3-4 shows the personalization features and their benefits.
Table 3-4 Personalization Features and Benefits
Feature Description Benefit
Deliver content
based on user’s role
Enable users to
customize content
Aggregate and
personalize content
for multiple users
Portal Server includes the ability to
automatically choose which applications
users are able to access or to use, based on
their role within the organization.
Portal Server enables end users to choose
what content they are interested in seeing.
For example, users of a personal finance
portal choose the stock quotes they would like
to see when viewing their finan cial portfolio.
Portal Server enables an enterprise or service
provider to aggregate and deliver
personalized content to multiple communities
of users simultaneously.
Increases employee productivity , improves
customer relationships, and streamlines
business relationships by providing quick and
personalized access to content and services.
The information available in a portal is
personalized for each individual. In addition,
users can then customize this information
further to their individual tastes. A portal puts
control of the web experience in the hands of
the people using the web, not the web site
builders.
This enables a company to deploy multiple
portals to multiple audiences from one
product and manage them from a central
management console. Also, new content and
services can be added and delivered on
demand without the need to restart Portal
Server. All of this saves time and money, and
ensures consistency in an IT organization.
Aggregation and Integration
One of the most important aspects of a portal is its ability to aggregate and
integrate information, such as applicatio ns, services, and content. This
functionality includes the ability to embed non-persistent information, such as
stock quotes, through the portal, and to run applications within, or deliver them
through, a portal.
58 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 59

Table 3-5 shows the aggregation and integration features and their benefits.
Table 3-5 Aggregation Features and Benefits
Feature Description Benefit
Aggregated
information
Consistent set of
tools
Collaboration Portal Server provides control and access to
Integration Portal Server enables you to use the Portal
The Portal Desktop provides the primary
end-user interface for Portal Server and a
mechanism for extensible content
aggregation through the Provider Application
Programming Interface (PAPI). The Portal
Desktop includes a variety of providers that
enable container hierarchy and the basic
building blocks for building some types of
channels.
Users get a set of tools like web-based email
and calendaring software that follows them
through their entire time at the company.
data as a company-wide resource.
Desktop as the sole place for users to gain
access to or launch applications and access
data.
Users no longer have to search for the
information. Instead, the information finds
them.
Users do not have to use one tool for one
project, another tool for another location.
Also, because these tools all work within the
portal framework, the tools have a co nsistent
look and feel and work similarly, reducing
training time.
In many companies, data is seen as being
owned by individual departments, instead of
as a company-wide resource. The portal can
act as a catalyst for breaking down these silos
and making the data available in a controlled
way to the people who need to use it. This
broader, more immediate access can improve
collaboration.
Iintegration with existing email, calendar,
legacy, or web applications enables the portal
to serve as a unified access point, enabling
users—be that employees, partners, or
customers—to access the inform ation users
need quickly and easily.
Understanding User Behaviors and Patterns
Understanding User Behaviors and Patterns
Study the people who will use your portal. Factors such as when users will use the
portal and how users have used predecessor systems are keys to identifying your
requirements. If your organization’s experience cannot provide these patterns, you
can study the experience of other organizations and estimate them.
Use these questions to help you understand users:
• How many end users will you have? What is the size of your target audience?
Chapter 3 Identifying and Evaluating Your Business and Technical Requirements 59
Page 60

Understanding User Behaviors and Patterns
• Will users login to the portal at the same time each day? Will they use the
portal at work or somewhere else?
• Are users in the same time zone or in different time zones?
• How long do you expect the typical user to be connected, or have a valid portal
session open? What use statistics do you have for existing applications? Do you
have web traffic analysis figures for an existing portal?
• How many visitor sessions, or num b er of single-visitor visits, are likely within
a predefined period of time?
• Is portal use likely to increase over time? Or stay sta b le?
• How fast will your user base grow?
• How have your users used an application that the porta l will deliver to them?
• What portal channels do you expect users to use regularly?
• What expectations about your portal content do your users have? How have
users used predecessor web-based information or other resources that your
portal will offer?
60 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 61

Pre-Deployment Considerations
This chapter contains the following sections:
• Determine Your Tuning Goals
• Portal Sizing Tips
• Establish Performance Methodology
• Portal Sizing
• SRA Sizing
Chapter 4
Determine Your Tuning Goals
Before tuning you portal, work with portal system administrators and portal
developers to set the portal performance objectives based upon the projected
requirements of your portal. Objectives include the number of users, the number of
concurrent users at peak load time and their usage pattern in accessing Sun Java™
System Portal Server.
You need to determine these two factors:
• Are you tuning for portal applications rapid response?
• Are you tuning for a large number of user concurrency?
As the number of users concurrently connected to the portal increase, the
response time decreases given the same hardware and same set of parameters.
Hence, gather information about the level of usage expected on your Su n J ava
System Portal Server, the anticipated number of concurrent users at any given
61
Page 62

Portal Sizing Tips
time, the number of Portal desktop activity requests, the amount of portal
channel usage, acceptable response time for the end-user which is determined
by your organization, and an optimal hard ware configuration to meet the
criteria.
Portal Sizing Tips
This section contains a few tips to help you in the sizing process.
• A business-to-consumer portal requires that you deploy SRA to use the
Gateway and SSL. Make sure you take this into account for your sizing
requirements. Once you turn on SSL, the performance of the portal can be up
to ten times slower than without SSL.
• For a business-to-employee portal, make sure that you have a user profile that
serves as a baseline.
• For any portal, build in headroom for growth. This means not just sizing for
today’s needs, but future needs and capacity. This includes usual peaks after
users return from a break, such as a weekend or holiday, or if usage is
increased over time because the portal is more “sticky.”
• If you are deploying your portal solution across multiple geographic sites, you
need to fully understand the layout of your networks and data centers
• Decide what type of redundancy you need. Consider items such as production
down time, upgrades, and maintenance work. In general, when you take a
portal server out of production, the impact to your capacity should be no more
than one quarter (1/4) of the overall capacity.
• In general, usage concurrencies for a business- to-employee portal are higher
than a business-to-consumer portal.
Establish Performance Methodology
Once you have established your performance goals, follow the steps below to tune
your portal environment.
1. Identify and remove obvious bottlenecks in the processor, memory, network,
and disk.
62 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 63

Portal Sizing
2. Setup a controlled environment to minimize the margin of error (defined as
less than ten percent variation between identical runs).
By knowing the starting data measurement baseline, you can measure the
differences in data performance between sample gathering runs. Be sure
measurements are taken over an adequate period of time and that you are able
to capture and evaluate the results of these tests.
Plan to have a dedicated machine for generating load simulation which is
separate from the Portal Server machine. A dedicated machine helps you to
uncover the origin of performance problems.
See “Portal Sizing ” on page 63.
3. Develop and refine the prototype workload that closely simulates the
anticipated production environment agreed between you and the portal
administrators and portal developers.
See “Analysis Tools” on page 143
4. Monitor customized portal applications such as portlets.
Portal Sizing
You need to establish a baseline sizing figure for your Portal Server. With a
baseline figure established, you can then validate and refine that figure to account
for scalability, high availability, reliability, and good performance.
The portal sizing process consists of the following step s:
1. Establish Baseline Sizing Figures
2. Customize the Baseline Sizing Figures
3. Validate Baseline Sizing Figures
4. Refine Baseline Sizing Figures
5. Validate Your Final Figures
The following sections describe these steps.
Chapter 4 Pre-Deploy men t Consi de ra tions 63
Page 64

Portal Sizing
Establish Base line Sizing Figu re s
Once you have identified your business and technical requirements, and mapped
Portal Server features to your needs, your sizing requirements emerge as you plan
your overall Portal Server deployment. Your design decisions help you make
accurate estimates regarding Portal Server user sessions and concurrency.
NOTE Sizing requirements for a secure portal deployment using Sun Java
System Portal Server Secure Remote Access (SRA) software are
covered in “SRA Sizing” on page 72.
Your Sun Java System technical representative can provide you with an automated
sizing tool to calculate the estimated number of CPUs your Portal Server
deployment requires. You need to gather the following metrics for input to the
sizing tool:
• Peak Numbers
• Average Time Between Page Requests
• Concurrent Users
• Average Session Time
• Search Engine Factors
Other performance metrics that affect the number of CPUs a Portal Server
deployment requires, but are not used by the sizing tool, are:
• Portal Desktop Configuration
• Hardware and Applications
• Back-end Servers
•Transaction Time
• Workload Conditions
A discussion of the these performance factors follows.
Peak Numbers
Maximum number of concurrent se ssions defines how many connected user s a Portal
Server deployment can handle.
To calculate the maximum number of concurrent sessions, use this formula:
64 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 65

Portal Sizing
maximum number of concurre nt sessions =
expected percent of users onl ine * user base
To identify the size of the user base or pool of potential users for an enterprise
portal, here are some suggestions:
• Identify only users who are active. Do not include users who are, for example,
away on vacation, or on leave.
• Use a finite figure for user base. For an anonymous portal, estimate this
number conservatively.
• Study access logs.
• Identify the geographic locations of your user base.
• Remember what your business plan states regarding who your users are.
Average Time Between Page Requests
Average time between page requests is how often, on average, a user requests a page
from the Portal Server. Pages could be the initial login page to the portal, or a w e b
site or web pages accessed through the Portal Desktop. A page view is a single call
for a single page of information no matter how many items are contained on the
page.
Though web server logs record page requests, using the log to calcu late the
average time between requests on a user basis is not feasible. To calculate the
average time between page requests, you would probably need a commercially
available statistics tool, such as the WebLoad performance testing tool. You can
then use this figure to determine the number of concurrent users.
NOTE Page requests more accurately measure web server traffic than
“hits.” Every time any file is requested from the web server counts
as a hit. A single page call can record many hits, as every item on the
page is registered. For example, a page containing 10 graphic files
records 11 “hits”—one for the HTML page itself and one for each of
the 10 graphic files. For this reason, page requests gives a more
accurate determination of web server traffic.
Concurrent Users
A concurrent user is one connected to a running w e b brows e r process a nd
submitting requests to or receiving results of requests from Portal Server. The
maximum number of concurrent users is the highest possible number of concurrent
users within a predefined period of time.
Chapter 4 Pre-Deploy men t Consi de ra tions 65
Page 66

Portal Sizing
Calculate maximum number of concurrent users after you calculate maximum number
of concurrent sessions. To calculate the maximum number of concurrent users, use
this formula:
concurrent users =
number of concurr ent se ssions / ave rage t ime be tween hits
For example, consider an intranet Portal Server example of 50,000 users. The
number of connected sess ions under its peak loads is estimated to be 80% of its
registered user base. On average, a user accesses the Portal Desktop once every 10
minutes.
The calculation for this example is:
40000 / 10 = 4000
The maximum number of concurrent users during the peak hours for this Portal
Server site should be 4,000.
Average Session Time
Average session time is the time between user login and logout averaged over a
number of users. The length of the session time is inversely proportional to the
number of logins occurring (that is, the longer the session duration, the fewer
logins per second are generated against Portal Server for the same concurrent users
base). Session time is the time between user login and user logout.
How the user uses Portal Server often affects average session time. For example, a
user session involving interactive appl ications typically has a longer sess ion time
than a user session involving inform ation only.
Search Engine Factors
If your portal site will offer a Search channel, you need to include sizing factors for
the Search Engine in your sizing calculations. Search Engine sizing requirements
depend on the foll owing factors:
• The size of index partitions on the active list of the in dex directo ry
Partition size is directly proportional to the size and number of indexed and
searchable terms.
• Average disk space requirement of a resource description (RD)
To calculate this, use this formula:
average disk spac e requ iremen t =
database size / number of RDs in datab ase
66 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 67

The average size adjusts for variations in sizes of RDs. A collection of long,
complex RDs with many indexed terms and a list of short RDs with a few
indexed terms require different search times, even if the complex RDs have the
same number of RDs.
RDs are stored in a hierarch i cal databa se format, where the intrin sic s i ze o f the
database must be accounted for, even when no RD is stored.
• The number of concurrent users who perform search-related activities
To calculate this, use this formula:
number of concurr ent us ers / average time be tween search hits
Use the number of concurrent users value calculated in “Average Time
Between Page Requests” on page 140.
• The type of search operators used
Types of search functions include basic, combining, proximity, passage and
field operator, and wildcard scans. Each function uses different search
algorithms and data structures. Because differences in search algorithms and
data structures increase as the number of search and indexed terms increase,
the type of search function affects times for search result return trips.
Portal Sizing
TIP You can now give the above figures to your technical representative
and ask that the sizing tool be run to identify your estimated number
of CPUs.
Portal Desktop Configuration
Portal Desktop configuration explici tly d e termines the amount of data held in
memory on a per-session basis.
The more channels on the Portal Desktop, the bigger data session size, and the
lesser the throughput of Portal Server.
Another factor is how much interactivity the Po rt al Desktop offers. For example,
channel clicks can generate load on Portal Server or on some other external server.
If channel selections generate load on Portal Server, a higher user activity profile
and higher CPU overhead occur on the node that hosts the Portal Desktop than on
a node that hosts some other external server.
Chapter 4 Pre-Deploy men t Consi de ra tions 67
Page 68

Portal Sizing
Hardware and Applicatio ns
CPU speed and size of the virtual machine for the Java™ platform (Java™ Virtual
Machine or JVM™ software) memory heap affect Portal Server performance.
The faster the CPU speed, the higher the throughput. The JVM memory heap size,
along with the heap generations tuning parameters, can also affect Portal Server
performance.
Back-End Servers
Portal Server aggregates content from external sources. If external content
providers cannot sustain the necessary bandwidth for Portal Server to operate at
full speed, Portal Desktop rendering and throughput request times will not be
optimum. The Portal Desktop waits until all channels are completed (or timed out)
before it returns the request response to the browser.
Plan your back-end infrastructure carefully when you use chann els that:
• Scrape their content from external sources
• Access corporate databases, which typically have slow response times
• Provide email content
• Provide calendar content
Transaction Time
Transaction time, which is the delay taken for an HTTP or HTTPS operation to
complete, aggregates send time, processing time, and response time figures.
You must plan for factors that can affect transaction time. These include:
• Network speed and latency.
You need to especially examine latency over a Wide Area Network (WAN).
Latency can significantly increase retrieval times for large amounts of data.
• The complexity of the Portal Desktop.
• The browser’s connection speed.
For example, a response time delay is longer with a connection speed of 33.6
kilobytes per second than with a LAN connection speed. However, processing
time should remain constant. Transaction time through a dial-up connection
should be faster than transaction time displayed by a load generation tool
because it performs data compression.
68 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 69

Portal Sizing
When you calculate transaction time, size your Portal Server so that processing
time under regular or peak load conditions does not exceed your performance
requirement threshold and so that you can sustain processing time over time.
Workload Conditions
Workload conditions are the most predominantly used system and JVM software
resources on a system. These conditions largely d e pend on user behavior and the
type of portal you deploy.
The most commonly encountered workload conditions on Portal Server software
affect:
•System performance
Portal Server performance is impacted when a large number of concurrent
requests are handled ( such as a hi gh activit y profile). Fo r example, during peak
hours in a business-to-enterprise portal, a significant numbe r of company
employees connect to the portal at the same time. Such a scenario creates a
CPU-intensive workload. In addition, the ratio of concurrent users to
connected users is high.
• System capacity
Portal Server capacity begins to be impacted when large numbers of users log
in. As more users login, users use more of the available memory, and
subsequently, less memory is available to process requests made to the server.
For example, in a business-to-consumer web portal, a large number of
logged-in users are redirected to external web sites once the initial Po rtal
Desktop display is loaded. However, as more users continue to login, users
create the need for more memory, even though the ratio of users submitting
requests to Portal Server and the users merely logged-in is low.
Depending on the user’s behavior at certain times of the day, week, or month,
Portal Server can switch between CPU-intensive and memory-intensive
workloads. The portal site administrator must determine the most important
workload conditions to size and tune the site to meet the enterprise’s business
goals.
Customize the Baseline Sizing Figures
Establishing an appropriat e sizing estimate fo r your Portal Server depl oyment is an
iterative process. You might wish to change the inputs to generate a range of sizing
results. Customizing your Portal Server depl oyment can greatly affect its
performance.
Chapter 4 Pre-Deploy men t Consi de ra tions 69
Page 70

Portal Sizing
After you have an estimate of your sizing, consider:
• LDAP Transaction Numbers
• Application Server Requirements
LDAP Transaction Numbers
Use the following LDAP transactio n numbers for an out-of-the-box portal
deployment to understand the impact of the service demand on the LDAP master
and replicas. These numbers change once you begin customizing the system.
• Access to authless anonymous portal - 0 ops
• Login by using the Login channel - 2 BINDS, 2 SRCH
• Removing a channel from the Portal Desktop - 8 SRCH, 2 MOD
• Reloading the Portal Desktop - 0 ops
Application Serv e r Requirements
One of the primary uses of Portal Server installed on an application server is to
integrate portal providers with Enterprise JavaBeans™ architecture and other
J2EE™ technology stack constructs, such as JDBC and JCA, running on the
application server. These other application s a nd modules can consume resources
and affect your portal sizing.
Validate Baseline Sizing Figures
Now that you have an estimate of the number of CPUs for your portal deployment,
use a trial deployment to measure the performance of the portal. Use load
balancing and stress tests to determine:
• Throughput, the amount of data processed in a specified amount of time
• Latency, the period of time that one component is waiting for another
component
• Maximum number of concurrent sessions
Portal samples are provided with the Portal Server. You can use them, with
channels similar to the ones you will use, to create a load on the system. The
samples are located on the Portal Desktop.
70 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 71

Portal Sizing
Use a trial deployment to determine your final sizing estimates. A trial deployment
helps you to size back-end integration, to avoid potential bottlenecks wit h Portal
Server operations.
Refine Baseline Sizing Figures
Your next step is to refine your sizing figure. In this section, you build in the
appropriate amount of headroom so that you can deploy a portal site that features
scalability, high availability, reliability and good performance.
NOTE Refining baseline sizing requirements for a secure portal
deployment using SRA is covered in “SRA Sizing” on pa ge 72.
Because your baseline sizing figure is based on so many estimates, do not use this
figure without refining it.
When you refine your baseline sizing figure:
• Use your baseline sizing figure as a reference point.
• Expect variations from your baseline sizing figure.
• Learn from the experience of others.
• Use your own judgement and knowledge.
• Examine other factors in your deployme nt.
If the Portal Server deployment involves multiple data centers on several
continents and even traffic, you need a higher final sizing figure than if you
have two single data centers on one continent w ith heavy traffic.
• Plan for changes.
A portal site is likely to experience various changes after you launch it.
Changes you might encounter include the following:
❍ An increase in the number of channels
❍ Growth in the user base
❍ Modification of the portal site’s purpose
❍ Changes in security needs
❍ Power failures
Chapter 4 Pre-Deploy men t Consi de ra tions 71
Page 72

SRA Sizing
❍ Maintenance demands
Considering these factors enables you to develop a sizing figure that is flexible and
enables you to avoid risk when your assumptions regarding your portal change
following deployment.
The resulting figure ensures that your portal site has the following:
• Scalability high availability, reliability and high performance
• Room for whatever you want to provide
• Flexibility for adjusting to changes
Validate Your Final Figures
Use a trial deployment to verify that the portal deployment satisfies your business
and technical requirements.
SRA Sizing
Use this section only if your organizati on is implementing a secure portal by
installing SRA. As you did for portal, for SRA, you must first establish your
Gateway instances baseline sizing estimate (A single machine can have one
Gateway installation but multiple instances. SRA enables you to insta ll multiple
Gateways, each running multiple instances.) Your design decisions help you make
accurate estimates regarding SRA user sessions and concurrency.
You must first establish your Gateway instances bas e line sizing estimate. This
baseline figure represents what you must have to satisfy your Gateway user
sessions and concurrency needs.
Establishing an appropriate sizing estimate for your SRA deployment is an
iterative process. You might wish to change the inputs to generate a range of sizing
results. Test these results against your original requirements. You can avoid most
performance problems by formulating your requirements correctly and setting
realistic expectations of SRA performance.
This section explains the following types of performance factors that the Gateway
instances baseline sizing process involves:
• Identifying Gateway Key Performance Requirements
• Advanc ed Gateway Settings
72 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 73

SRA Sizing
Identifying Gateway Key Performance Requirements
Key performance factors are metrics that your technical representative uses as
input to an automated sizing tool. The sizing tool ca lculates the estimated number
of Gateway instances your SRA deployment requires.
Identifying these key performance factors and giving them to your technical
representative is the first step in formulating your baseline siz ing figure.
NOTE Properly sizing the Gateway is difficult, and using the Gateway
sizing tool is only the beginning. Ga teway performance depends
more on throughput then on the number of users, active users, or
user sessions. Any sizing information for the Gateway has to be
based on a set of assumptions. See “Secure Remote Access Example”
on page 152 fore more information.
These are the key performance factors:
• Session Characteristics
• Netlet Usage Characteristics
NOTE After you calculate these key performance factors, give the figures to
your technical representative. Ask that the Gateway sizing tool be
run to identify the estimated number of Gateway instances.
Session Characteristics
The session characteristics of the Gateway inclu de:
• Total number of SRA (Gateway) users
This represents the size of your user base or pool of potential users for the
secure portal. See “Concurrent Sessions” on page 139 for more information on
estimating this number.
• Expected percentage of total users using the Gateway (at maximum load)
Apply a percentage to your total number of users to determine this figure.
• Average time between page hits
This is how often on average a user requests a page from the portal server.
Chapter 4 Pre-Deploy men t Consi de ra tions 73
Page 74

SRA Sizing
• Sessio n average time
This determines how many log ins per second that the Gateway must sustain
for a given number of concurrent users.
Netlet Usage Characteristics
Consider the following Netlet characteristics of the Gatew ay , whi c h can have a
impact in calculating the number of Gateway instances:
• Netlet is enabled in the Access Manager administration console.
If Netlet is enabled, the Gateway needs to determine whether the incoming
traffic is Netlet traffic or Portal Server traffic. Disabling Netlet reduces this
overhead since the Gateway assumes that all incoming traffic is either HTTP or
HTTPS traffic. Disable Netlet only if you are sure you do not want to use any
remote applications with Portal Server.
• Expected percentage of total users using Netlet
Apply a percentage to your total number of users to determine this figure.
• Expected throughput
Determine the expected throughput of your Gateway, expressed in kilobits per
second (Kbps).
• Netlet Cipher (encryption) being used
Choices include Native VM and Java software plugin ciphers.
74 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 75

SRA Sizing
Advanced Gateway Settings
Use the settings in this section to obtain more accurate results when estimating the
number of Gateway instances for your deployment. These advanced Gateway
settings are used as input to the automated sizing tool.
These are the advanced Gateway settings:
• Page Configuration
•Scalability
• Secure Portal Pi lot Measured Numbers
NOTE After your technical representative has given you a f igure for your
estimated number of CPUs, consider how these related performance
factors affect this figure.
Page Configuration
If you are using an authenticated portal, you must specify both Login Type and
Desktop Type in the page configuration section of the a utomated sizing tool
• Login Type. Describes the type of portal page (content configuration and
delivery method) that end users initially see after submitting user name and
password. This process s typically taxing on the system because the process
involves checking credentials, initializing the session, and delivering initial
content.
The Measured CPU Performance char acterist ic as sociat ed with the Logi n Type
is the Initial Desktop Display variable.
• Desktop Type. Describes the type of portal pages (content configuration and
delivery method) that end users see after the initial portal page. These pages
are displayed with each subsequent interaction with the portal, or on Desktop
refresh. Because the session has already been established and cached content
can be exploited, less system resources are typically required and the pages are
delivered more rapidly.
The Measured CPU Performance characteristic associated with the Desktop
Type is the Desktop Reload variable.
For both Login Type and Desktop Type, select the appropriate content
configuration:
• Light-JSP. Describes a configuration of two tabs with five channels each.
Chapter 4 Pre-Deploy men t Consi de ra tions 75
Page 76

SRA Sizing
• Regular-JSP. Describes a configuration of two tabs with seven channels each.
• Heavy—JSP. Describes a configuration of three tabs with seventeen channels
each.
Scalability
You can choose between one, two, and four CPUs per Gateway instance. The
number of CPUs bound to a Gateway instance determines the number of Gateway
instances required for the deployment.
Secure Portal Pilot Measured Numbers
If you have numbers from a pilot of the SRA portal, you can use these numbers in
the Gateway sizing tool to arrive at more accurate results. You would fill in the
following:
• Measured CPU Performance. The values used to help calculate the number of
Gateway instances include:
❍ Initial Portal Desktop Dis play, hits per second per CPU
❍ Portal Desktop Reloads, hits per second per CPU
• Netlet Applications Block Size. This value specif ies the Netlet application byte
size. The Netlet dynamically determines the block size based on the application
that is used. Block size determined by Netlet for a Telnet is based on the
amount of data transferred.
NOTE You do not need to specify the Page Configuration and Sca lability
options if you are using trial depl oyment numbers.
SRA Gateway and SSL Hardware Accelerators
SSL-intensive servers, such as the SRA Gateway, require large amounts of
processing power to perform the encryption required for each secure transaction.
Using a hardware accelerator in the Gateway speeds up the execution of
cryptographic algorithms, thereby increasing the performance speed.
The Sun Crypto Accelerator 1000 board is a short PCI board that functions as a
cryptographic co-processor to accelerate public key and symmetric cryptography.
This product has no external interfaces. The board communicates with the host
through the internal PCI bus interface. The purpose of this board is to accelerate a
variety of computationally intensive cryptographic algorithms for security
protocols in e-commerce applications.
76 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 77

SRA Sizing
See the Portal Server Secure Remote Access 6 Administration Guide for more
information on the Sun Crypto Accelerator 1000 board and other accelerators.
NOTE The Sun Crypto Accelerator 1000 board supports only SSL
handshakes and not symmetric key algorithms. This is not generic to
all other cryptographic accelerators. Other cryptographic
accelerators are on the market and some of them can support
symmetric key encryption. See the following URL for more
information:
http://www.zeus.co m/prod ucts/zw s/secu rity/h ardwar e.html
You could use a hardware accelerator on the Netlet Proxy and Rewriter Proxy
machine and derive some performance improvement.
SRA and Sun Enterprise Midframe Line
Normally, for a production environment, you would deploy Portal Server and SRA
on separate machines. However, in the case of the Sun Enterprise™ midframe
machines, which support multiple hardwa re domains, you can install both Porta l
Server and SRA in different domains on the same Sun Enterprise midframe
machine. The normal CPU and memory requirements that pertain to Portal Server
and SRA still apply; you would impl ement the requirements for each in the
separate domains.
In this type of configuration, pay attention to security issues. For example, in most
cases the Portal Server domain is located on the intranet, while the SRA domain is
in the DMZ.
Chapter 4 Pre-Deploy men t Consi de ra tions 77
Page 78

SRA Sizing
78 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 79

Chapter 5
Creating Your Portal Design
This chapter describes how to create your high-level and low-level portal design
and provides information on creating specific sections of your design plan.
This chapter contains the following sections:
• Portal Design Approach
• Portal Server and Scalability
• Portal Server and High Availability
• Portal Server System Communication Links
• Working with Portal Server Building Modules
• Designing Portal Use Case Scenarios
• Designing Portal Security Strategies
• Portal Server and Access Manager on Different Nodes
• Designing SRA Deployment Scenarios
• Designing for Localization
• Content and Design Implementation
• Identity and Directory Structure Design
Portal Design Approach
At this point in the Sun Java™ System Portal Server deployment process, you’ve
identified your business and technical requirements, and communicated these
requirements to the stakeholders for their approval. Now you are ready to begin
the design phase, in which you develop your high- and low-level designs.
79
Page 80

Portal Design Approach
Your high-level portal design communicates the architecture of the system and
provides the basis for the low-level design of your solution. Further, the high-level
design needs to describe a logical architecture that meets the business and technical
needs that you previously established. The logical architecture is broken down
according to the various applications that comprise the system as a whole and the
way in which users interact with it. In general, the logical architecture includes
Portal Server Secure Remote Access (SRA) , high availability, security (including
Access Manager, and Directory Server architectural components. See “Logical
Portal Architecture” on page 81 for more information.
The high- and low-level designs also need to a ccount for any factors beyond the
control of the portal, including your network, hardware failures, and improper
channel design.
Once developed, the high-level design leads toward the creation of the low-level
design. The low-level design specifies such items as the physical architecture,
network infrastucture, Po rt al De skto p cha nn el an d co nta in er d e sig n an d the act ual
hardware and software components. Once you have completed the high- and
low-level designs, you can begin a trial deployment for testing within your
organization.
Overview of High-Level Portal Design
The high-level design is your first iteration of an architecture approach to support
both the business and technical requirements. The high-level design addresses
questions su ch as:
• Does the proposed architecture support both the business a nd tech nical
requirements?
• Can any modifications strengthen this design?
• Are there alternative architectures that might accomplish this ?
• What is the physical layout of the system?
• What is the mapping of various components and connectivity?
• What is the logical definition describing the different categories of users and
the systems and applications users have access to?
• Does the design account for adding more hardware to the system as required
by the increase in web traffic over time?
80 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 81

Portal Design Approach
Overview of Low-Level Portal Design
The low-level design focuses on specifying the processes and standards you use to
build your portal solution, and specif ying the actual hardware and software
components of the solution, includ ing:
• The Portal Server complex of servers.
• Network connectivity, describing how the portal complex attaches to the
“outside world.” Within this topic, you need to take into accou nt security
issues, protocols, speeds, and connections to other applications or remote sites.
• Information architecture, including user interfaces, content presentation and
organization, da ta sources, and feeds .
• Access Manager architecture, including the strategy and design of
organizations, suborganizations, roles, groups, and users, which is critical to
long-term success.
• Integration strategy, includ ing how the portal acts as an integration point for
consolidating and integrating various information, an d bringing people
together in new ways.
Logical Portal Architecture
Your logical portal architecture defines all the components that make up the portal,
including (but not limited to) the f ollowing:
• Portal Server itself
•Contents from RDBMs
• Third-party content providers
• Custom developed providers and content
• Integration with back-end systems such as messaging and calendaring systems
• Web container for deployment
• Role of the Content Management System
• Customer Resource Management
• Whether the portal runs in open or secure mode (requires Secure Remote
Access)
Chapter 5 Creating Your Portal Design 81
Page 82

Portal Design Approach
• Usage estimates, which include your assumptions on the total number of
registered users, average percentage of registered users logged in per day,
average concurrent users that are logged in per day, average login tim e,
average number of content channels that a logged in user has selected, and
average number of application channels that a logged in user has selected.
Additionally, you need to consider how the following three network zones fit into
your design:
• Internet. The public Internet is any network outside of the intranet and DMZ.
Users portal server and securely access the Gateway and from here.
• Demilitarized Zone (DMZ). A secure area between two firewalls, enabling
access to internal resources while limiting potential for unauthorized entry.
The Gateway resides here where it can securely direct traffic from the
application and content servers to the Internet.
• Intranet. Contains all resource servers. This includes intranet applications, web
content servers, and application servers. The Portal Server and Directory
Server reside here.
The logical architecture describes the Portal Desktop look and feel, including
potential items such as:
• Default page, with its default banner, logo, channels; total page weight, that is,
total number of bytes of all the components of the page, including HTML, style
sheet, JavaScript™, and image files; total number of HTTP requests for the
page, that is, how many HTTP requests are required to complete downloading
the page.
• Personalized pages, with channels that users can conceivably display and what
preferences are available.
The logical architecture is where you also develop a caching strategy, if your site
requires one. If the pages returned to your users contain references to large
numbers of images, Portal Server can deliver these images f or all users. However, if
these types of requests can be offloaded to a reverse proxy type of caching
appliance, you can free up system resources so that Portal Server can service
additional users. Additionally, by pl acing a caching appliance closer to end users,
these images can be delivered to end users somewhat more quickly, thus
enhancing the overall end user experience.
82 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 83

Portal Server and Scalability
Scalability is a system’s ability to accommodate a growing user population, without
performance degradation, by the addition of processing resources. The two general
means of scaling a system are vertica l and horizontal scaling. The subject of this
section is the application of scaling techn iques to the Portal Server product.
Benefits of scalable sy stems include:
•Improved response time
• Fault tolerance
• Manageability
• Expendability
• Simplified application development
• Building modules
Vertical Scaling
Portal Server and Scalabi lit y
In vertical scaling, CPUs, memory, multiple instances of Portal Server, or other
resources are added to one machine. This enables more process instances to run
simultaneously. In Portal Server, you want to make use of this by planning and
sizing to the number of CPUs you need. See Chapter 4, “Pre-Deployment
Considerations” for more information.
Horizontal Scaling
In horizontal scaling, machines are added. This also enables multiple simultaneous
processing and a distributed work load. In Portal Server, you make use of
horizontal scaling because you can run the Portal Server, Directory Server and
Access Manager on different nodes. Horizonta l sca ling can also make use of
vertical scaling, by adding more CPUs, for example.
Additionally, you can scale a Porta l Server installation horizontally by installing
server component instances on multiple machin es. E ach installed server
component instance executes an HTTP process, which listens on a TCP/IP port
whose number is determined at ins tallation time. Gateway components use a
round-robin algorithm to assign new session requests to se rve r instances. While a
session is established, an HTTP cook ie, stored on the client, indicates the session
server. All subsequent requests go to that server.
Chapter 5 Creating Your Portal Design 83
Page 84

Portal Server and High Availability
The section “Working with Portal Server Building Modules” on page 89, discusses
an approach to a specific type of configurati on that provides optimum
performance an d horizontal sc alability.
Portal Server and High Availability
High Availability ensures that your po rtal platform is accessible 24 hours a day,
seven days a week. Today , orga niza tions require t hat da ta an d applicat ions alwa ys
be available. High availability has become a requirement that applies not on ly to
mission-critical applications, but also to the whole IT infrastructure.
System availability is affected not only by computer ha rd ware and software, but
also by people and processes, which can account for up to 80 percent of syst e m
downtime. Availability can be improved through a systemati c appro ach to system
management and by using industry best practices to minimize the impact of
human error.
One important issue to consider is that not al l systems have the same level of
availability requirements. Most applications can be categorized into the following
three groups:
• Task critical. Affects limited number of users; not visible to customers; small
impact on costs and profits
• Business critical. Affects significant number of users; might be visible to some
customers; significant impact on costs and profits
• Mission critical. Affects a large number of users; visible to customers; major
impact on costs and profits
The goals of these levels are to improve the following:
• Processes by reducing human error, automating procedures, and reducing
planned downtime
• Hardware and software availability by eliminating single-point-of-failure
configurations and balancing processing load
The more mission critical the application, the more you need to focus on
availability to eliminate any sing le point of failure (SPOF), and resolve people and
processes issues.
Even if a system is always available, ins ta nces of f ailure recovery might not be
transparent to end users. Depending on the kind of failure, users can lose the
context of their portal application, and might have to login again to get access to
their Portal Desktop.
84 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 85

Portal Server and High Availability
System Availability
System availability is often expressed as a percentage of the system uptime. A basic
equation to calculate system availability is:
Availability = up time / (upti me + d owntim e) * 1 00
For instance, a service level agreement uptime of four digits (99.99 percent) means
that in a month the system can be u n avail abl e fo r about s even h ours . F urth ermo re,
system downtime is the total time the system is not available for use. This total
includes not only unplanned downtime, such as hardware failures and network
outages, but also planned downtime, preventive maintenan ce, softwa re upgrade,
and patches.
If the system is supposed to be available seven days a week, 24 hours a day, the
architecture needs to include redundancy to avoid planned and unplanned
downtime to ensure high availability.
Degrees of High Availability
High availability is not jus t a switch that you can turn on and off. V ario us degrees
of high availability refer to the ability of the system to recover from failures and
ways of measuring system availabil ity. The d e gree of high availability depends on
your specific organization’s fault tolerance requirements and ways of measuring
system availability.
For example, your organization might tolerate the need to reauthenticate after a
system failure, so that a request resulting in a redirection to another login screen
would be considered successful. For other organizations, this might be considered
a failure, even though the service is still being provided by the system.
Session failover alone is not the ultimate answer to trans p aren t failover, because
the context of a particular portal application can be lost after a failover. For
example, consider the case where a user is composing a message in NetMail Lite,
has attached several documents to the email, then the server fails. The user is
redirected to another server and NetMail Lite will have lost the user’s session a nd
the draft message. Other providers, which store contextual data in the current
JVM™, have the same problem.
Achieving High Availabil ity for Portal Server
Making Portal Server highly available involves ensuring high availability on each
of the following com ponents:
Chapter 5 Creating Your Portal Design 85
Page 86

Portal Server System Communication Links
• Gateway. A load balancer used with th e Gateway detects a failed Gateway
component and routes new requests to other Gateways. A load balancer also
has the ability to intelligently distribute the workload across the server pool.
Routing is restored when the failed Gateway recovers. Gateway components
are stateless (session information is stored on the client in an HTTP cookie) so
rerouting around a failed Gateway is transparent to users.
• Portal Server. In open mode, you can use a load balancer to detect a failed
server component and redirect requests to other servers. In secure mode,
Gateway components can detect the presence of a failed server co mponent and
redirect requests to other servers. (This is valid as long as the web container is
the Web Server.)
• Directory Server. A number of options make the LDAP directory highly
available. See “Building Modules and High Availability Scenarios” on page 90
for more information.
• Netlet and Rewriter Proxies. In the case of a software crash, a watchdog
process automatically restarts the proxies. In addition, the Gateway perfor ms
load balancing and failure detection failover for the proxies.
Portal Server System Communication Links
Figure 5-1 on page 87 shows the processes and communication links of a Portal
Server system that are critical to the availability of the solution.
86 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 87

Figure 5-1 Portal Server Communication Links
Browser Gateway
Portal Server System Communication Links
HTTP(s)
Authentication
Service
(servlet)
LDAP
Module
Access Manager
Access Manager
SSO SDK
SSO SDK
LDAP
LDAP
Authentication
Server
In this figure, the box encloses the Portal Server instance running on Web Server
technology. Within the instance are five servlets (Authen tication, Access Manager
administration console, Portal Desktop, Communication Channel, and Search), and
the three SDKs (Access Manager SSO, Access Manager Logging, and Access
Manager Management). The Authentication service servlet also makes use of an
LDAP service provider module.
Access Manager
Admin Console
(servlet)
Portal Server instance running on a web container
Portal Desktop
Service
(servlet)
Logging SDK
LDAP
User/Policy/Service
Profile Database Server
Directory Server (LDAP)
Server
Comm Channel
Service
(servlet)
Search
Service
(servlet)
Access ManagerAccess Manager
Mgmt SDK
SMTP/IMAP
Messaging
Server
A user uses either a browser or the Gateway to communicate with Portal Server.
This traffic is directed to the appropriate servlet. Communication occurs between
the Authentication service’s LDAP module and the LDAP authenticatio n server;
between the Communications channel servlet an d the SMTP/IMAP messaging
server; between the Access Manager SSO SDK and the LDAP server; and between
the Access Manager Management SDK and the LDAP server.
Chapter 5 Creating Your Portal Design 87
Page 88

Portal Server System Communication Links
• Figure 5-1 on page 87 shows that if the fol lowing processes or communication
links fail, the portal solution become s unavailable to end users: Portal Server
Instance. Runs in the context of a web container. Components within an
instance communicate through the JVM™ using Java™ APIs. An instance is a
fully qualified dom ain name and a TCP port number . Portal Server services are
web applications that are implemented as serv lets or J SP™ files.
Portal Server is built on top of Access Mana ger fo r authentication single
sign-on (session) management, policy, and profile database access. Thus, Portal
Server inherits all the benefits (and constraints) of Access Manager with
respect to availability and fault tolerance.
By design, Access Manager’s services are either stateless or the services can
share context data. Services can recover to the previous state in case of a service
failure.
Within Portal Server, Portal Desktop and NetMail services do not share state
data among instances. This means that an instance redirect causes the user
context to be rebuilt for the enabled services. Usually, redirected users do not
notice this because Portal Server services can rebuild a user context from the
user’s profile, and by using contextual data stored in the request. While this
statement is generally true for out-of-the-box services, it might not be true for
channels or custom code. Developers need to be careful to not design stateful
channels to avoid loss of context upon instance failover.
• Profile Database Server. The profile database server is implemented by
Directory Server software. Although this server is not strictly part of Portal
Server, availability of the server and integrity of the database are fundamental
to the availability of the system.
• Authentication Serv er. This is the directory server for LDAP authentication
(usually, the same server as the profile database server). You can apply the
same high availability techniques to this server as for the profi le database
server.
• SRA Gateway and Proxies. The SRA Gateway is a standalone Java technology
process that can be considered stateless, because state information can be
rebuilt transparently to end users. The Gateway profile maintains a list of
Portal Server instances and does round robin load balancing across the
Gateway instances. Session stickiness is not required in front of a Gateway, but
with session stickin ess, performance is bet t er. On the other hand, session
stickiness to Portal Server instances is enforced by SRA.
88 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 89

Working with Portal Server Bu ildi ng Mo dule s
SRA includes other Java technology processes ca lled Netlet Proxy and
Rewriter Proxy. You use these proxies to extend the security perimeter from
behind the firewall, and limit the number of holes in the DMZ. You can install
these proxies on separate nodes.
Working with Portal Server Building Modules
Because deploying Portal Server is a complex process invo lving many other
systems, this section describes a specific configuration that provides optimum
performance and horizontal scalability. This configuration is known as a Portal
Server building module.
A Portal Server building module is a hardware and software construct with limited
or no dependencies on shared services. A typical deployment uses multiple
building modules to achieve optimum performance and horizontal scalability.
Figure 5-2 shows the building module architecture.
Figure 5-2 Portal Server Building Module Architecture
Portal
Server
Instance
Search
Engine
Se
s
Database
SSe
Directory
Server
Master
Replica
SSe
NOTE The Portal Server building module is simply a recommended
configuration. In some cas es, a different configuration mi ght result
in slightly better throughput (usually at the cos t of added
complexity). For example, adding another instance of Portal Server
to a four CPU system might result in up to ten percent additional
throughput, at the cost of requiring a load balancer even when using
just a single system.
Chapter 5 Creating Your Portal Design 89
Page 90

Working with Portal Server Bu ildi ng Mo dule s
Building Modules and High Availab ilit y Sc enarios
Portal Server provides three scenarios for high availability:
• Best Effort
The system is available as long as the hardware does not fail and as long as the
Portal Server processes can be restar ted by the watchdog process.
• No Single Point of Failure
The use of hardware and software replication creates a deployment with no
single point of failure (NSPOF). The system is always available, as long as no
more than one failure occurs consecutively anywhere in the chain of
components. However, in the case of failures, user sessi ons are lost.
• Transparent Failover
The system is always available but in ad d ition to NSPOF, failover to a backup
instance occurs transparently to end users. In most cases, users do not notice
that they have been redirected to a different node or instance. Sessions are
preserved across nodes so that users do not have to reauthenticate. Portal
Server services are stateless or use checkpointing mechanisms to rebuild the
current execution contex t up to a certain point.
Possible supported architectures include the following:
• Using Sun™ Cluster software on components that support Sun Cluster agents
• Multi-master Directory Server techniques
This section explains implementing these architectures and leverages the building
module concept, from a high-availability standpoint.
90 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 91

Table 5-1 summarizes these high availability scenarios along with their supporting
techniques.
Table 5-1 Portal Server Hig h Availability Sce narios
Component
Requirements
Hardware Redundancy Yes Yes Yes
Portal Server Building
Modules
Multi-master Configuration No Yes Yes
Load Balancing Yes Y es Yes
Stateless Applications and
Checkpointing
Mechanisms
Session Failover No No Yes.
Directory Server Clustering No No Y es
Necessary for Best
Effort Deployment?
No Yes Yes
No No Yes
Necessary for NSPOF
Deployment?
Necessary for Transparent
Failover Deployment?
Working with Portal Server Bu ildi ng Mo dule s
NOTE Load balancing is not provided out-of-the-box with the Web Server
product.
Chapter 5 Creating Your Portal Design 91
Page 92

Working with Portal Server Bu ildi ng Mo dule s
Best Effort
In this scenario, you install Portal Server and Directory Server on a single node that
has a secured hardware configuration for continuous availability, such as Sun Fire
UltraSPARC® III machines. (Securing a Solaris™ Op erating Environment system
requires that changes be made to its default configuration.)
This type of server features full hardware redundancy, including: redundant
power supplies, fans, system controllers; dynamic reconfiguration; CPU hot-plug;
online upgrades; and disks rack that can be configured in RAID 0+1 (striping plus
mirroring), or RAID 5 using a volume management system, which prevents loss of
data in case of a disk crash. Figure 5-3 shows a small, best effort deployment using
the building module architecture.
Figure 5-3 Best Effort Scenario
Browser
Portal
Server
Search
Engine
Se
s
Database
SSe
Directory
Server
In this scenario, for memory allocation, four CPUs by eight GB RAM (4x8) of
memory is sufficient for one building module. The Access Manager console is
outside of the building module so that it can be shared with other resources. (Your
actual sizing calculations might result in a different al location amount.)
This scenario might suffice for task critical requirements. Its major weakness is that
a maintenance action ne ce ssitating a system shutdown results in service
interruption.
When SRA is used, and a software crash occurs, a watchdog process automatically
restarts the Gateway, Netlet Proxy, and Rewriter Proxy.
92 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 93

No Single Point of Failure
Portal Server natively supports the no single point of failure (NSPOF) scenario.
NSPOF is built on top of the best effort scenario, and in addition, introduces
replication and load balancing.
Figure 5-4 No Single Point of Failure Example
Building Module 1
Portal
Load
Balancer
Client
Server
Instance
Working with Portal Server Bu ildi ng Mo dule s
Directory
Server
Master
Replica
Search
Engine
Se
s
Database
SSe
Building Module 2
Portal
Server
Search
Engine
Se
s
Database
SSe
Multi-Master
Replication
Directory
Server
Master
Replica
Chapter 5 Creating Your Portal Design 93
Page 94

Working with Portal Server Bu ildi ng Mo dule s
As stated earlier, a building module consists of a a Portal Server instance, a
Directory Server master replica for profile reads and a search engine database. As
such, at least two building modules are necessary to achieve NSPOF, thereby
providing a backup if one of the building modules fails. These building modules
consist of four CPUs by eight GB RAM.
When the load balancer detects Portal Server failures, it redirects users’ requests to
a backup building module. Accuracy of failure detection varies among load
balancing products. Some products are ca pable of checking the availability of a
system by probing a service involving several functional areas of the server, such
as the servlet engine, and the JVM. In particular, mo st vendor solutions from
Resonate, Cisco, Alteon, and others enable you to create arbitrary scripts for server
availability. As the load balancer is not part of the Portal Server software, you must
acquire it separately from a third- party vendor.
NOTE The Access Manager product requires that you set up load
balancing to enforce sticky sessions. This means that once a session is
created on a particular instance, the load balancer needs to always
return to the same instance for that session. The load balancer
achieves this by binding the session cookie with the instance name
identification. In principle, that binding is reestablished when a
failed instance is decommissioned. Sticky sessi ons are also
recommended for performance reasons.
Multi-master replication (MMR) takes places betw een the building modules. The
changes that occur on each directory are replicated to the other, which means that
each directory plays both roles of supplier and consumer. For more information on
MMR, refer to the Directory Server 6 De ployment Guide.
NOTE In general, the Directory Server instance in each building module is
configured as a replica of a master directory, which runs elsewhere.
However, nothing prevents you from using a master directory as
part of the building module. The use of masters on dedicated nodes
does not improve the availability of the solution. Use dedicated
masters for performance reasons.
94 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 95

Working with Portal Server Bu ildi ng Mo dule s
Redundancy is equally important to the directory master so that profile changes
through the administration console or the Portal Desktop, along with consumer
replication across building modules, can always be maintained. Portal Server and
Access Manager support MMR. The NSPOF scenario uses a multi-master
configuration. In this configuration, two suppliers can accept updates, synchronize
with each other, and update all consumers. The consumers can refer update
requests to both masters.
SRA follows the same replication and load balancing pattern as Portal Server to
achieve NSPOF. As such, two SRA Gateways and pair of proxies are necessary in
this scenario. The SRA Gateway detects a Portal Server instance failure when the
instance does not respond to a request after a certain time-out value. When this
occurs, the HTTPS request is routed to a backup server. The SRA Gateway
performs a periodic check for availability until the first Portal Server instance is up
again.
The NSPOF high availability scena r io is suitable to business critical deployments.
However, some high availability limitations in this scenario might not fulfill the
requirements of a mission critical d e ployment.
Chapter 5 Creating Your Portal Design 95
Page 96

Working with Portal Server Bu ildi ng Mo dule s
Transparent Failover
Transparent failover uses the same replication model as the NSPOF scenario but
provides additional high availability features, which make the failover to a backup
server transparent to end users.
Figure 5-5 on page 96 shows a transparent failover scenario. Two building modules
are shown, consisting of four CPUs by eight GB RAM. Load balancing is
responsible for detecting Portal Server failures and redirecting users’ requests to a
backup Portal Server in the building module. Building Module 1 stores sessions in
the sessions repository. If a crash occurs, the application server retrieves sessions
created by Building Module 1 from the sessions repository.
Figure 5-5 Transparent Failover Example Scenario
Browser
Load
Balancer
Building Module 1
Portal
Server
Instance
Search
Engine
Se
s
Database
SSe
Building Module 2
Portal
Server
Instance
Search
Engine
Se
s
Database
SSe
Directory
Server
Master
Replica
Multi-Master
Replication
Sessions
Repository
Directory
Server
Master
Replica
96 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 97

Working with Portal Server Bu ildi ng Mo dule s
The session repository is provided by the application server software. Portal Server
is running in an application server. Porta l Server supports transparent failover on
application servers that support HttpS es sion failover. See Appendix C, “Portal
Server and Application Servers” for more information.
With session failover, users do not need to reauthenticate after a crash. In addition,
portal applications can rely on session persistence to store context data used by the
checkpointing. You configure session failover in the
setting the
The Netlet Proxy cannot support the transparent failover scenario because of the
limitation of the TCP protocol. The Netlet Proxy tunnels TCP connections, and you
cannot migrate an open TCP connection to another server. A Netlet Proxy crash
drops off all outstanding connections th at w ould have to be reestablished.
com.iplanet.am.session.failover.enabled property to
AMConfig.properties file by
true
.
Building Module Constraints
The constraints on the scalability of building modules are given by the number of
LDAP writes resulting from profile updates a nd the maximum size of the LDAP
database. For more information, see “Directory Server Requirements” on page 98.
NOTE If the LDAP server crashes with the
the files are lost when the server restarts. This improves
performance but also affects availability.
If the analysis at your specific site indicates that the number of LDAP write
operations is indeed a constraint, some of the possible solutions include creating
building modules that replicate only a specific branch of the directory and a layer
in front that directs incoming requests to the appropriate instance of portal.
_db files in the /tmp directory,
Deploying Your Building Module Solution
This section describes guidelines for deploying your building module solution.
Deployment Guidel ines
How you construct your building modue affects performance. Consider the
following recommendations to deploy your building module properly:
• Deploy a building module on a single machine.
Chapter 5 Creating Your Portal Design 97
Page 98

Working with Portal Server Bu ildi ng Mo dule s
• If you use multiple machines, or if your Portal Server machine is running a
large number of instances, use a fast network interconnect.
• On servers with more than eight CPUs, create processor sets or domains with
either two or four CPUs. For example, if you choose to install two instances of
Portal Server on an eight CPU server, create two four-CPU processor sets.
Directory Server Requirements
Identify your Directory Server requirements for your building module
deployment. For specific information on Directory Server deployme nt, see the
Directory Server Deployment Guide.
Consider the following Directory Server guidelines when you plan your Portal
Server deployment:
• The amount of needed CPU in the Directory Server consumer replica processor
set depends on the number of Portal Server instances in the building module as
well as performance and capacity considerations.
• If possible, dedicate a Directory Server instance for the sole use of the Portal
Server instances in a building module. (See Figure 5-2 on page 89.)
• Map the entire directory database indexes and cache in memory to avoid disk
latency issues.
• When deploying multiple building modules, use a multi-master configuratio n
to work around bottlenecks caused by the profile updates a nd replication
overhead to the Directory Server supplier.
Search Engine Structure
When you deploy the Search Engine as part of your building module solution,
consider the following:
• In each building module, make sure only one Portal Server instance has the
Search Engine database containing the RDs. The remaining Portal Server
instances have default empty Search Engine databases.
• Factors that influence whether to use a building module for the portal Search
database include the intensity of search activities in a Portal Server
deployment, the range of search hits, and the average number of search hits for
all users, in addition to the number of concurrent searches. For example, the
load generated on a server by the Search Engine can be both memory and CPU
intensive for a large index and heavy query load.
98 Portal Server 6 2005Q1 • Deployment Planning Guide
Page 99

Designing Portal Use Case Scen ario s
• You can install Search on a machine separate from Portal Server, to keep the
main server dedicated to portal activity. When you do so, you use the
searchURL property of the Se arch provider to point to the second machine
where Search is installed. The Search instance is a normal portal instance. You
install the Search instance just as you do the portal instance, but use it just for
Search functionality.
• The size of the Search database dictates whether more than one machine needs
to host the Search database by replicating it across machines or building
module. Consider using high-end disk a rrays.
• Use a proxy server for caching the search hit results. When doing so, you need
to disable the document level security. See the Portal Server 6 Admin i stration
Guide for more information on document level security.
Designing Portal Use Case Scenarios
Use case scenarios are written scenarios used to test and present the system’s
capabilities and form an important part of your high-level design. Though you
implement use case scenarios toward the end of the project, formulate them early
on in the project, once you have established your requirements.
When available, use cases can provide valuable insight into how the system is to be
tested. Use cases are beneficial in identifying how you need to design the user
interface from a navigational perspective. When designing use cases, compare
them to your requirements to get a thorough view of their completeness and how
you are to interpret the test results.
Use cases provide a method for organizing your requirements. Instead of a
bulleted list of requirements, you organize them in a way that tells a story of how
someone can use the system. This provides for greater completeness and
consistency, and also gives you a better unde rstanding of the importance of a
requirement from a user perspective.
Use cases help to identify and clarify the functional requirements of the portal. Use
cases capture all the different ways a portal would be used, including the set of
interactions between the user and the portal as well as the services, tasks, and
functions the portal is required to perform.
A use case defines a goal-oriented set of interactions between external actors and
the portal system. (Actors are parties outside the system that interact with the
system, and can be a class of use rs, roles users can play, or othe r systems.)
Chapter 5 Creating Your Portal Design 99
Page 100

Designing Portal Use Case Scenarios
Use case steps are written in an easy-to-understand structured narrative using the
vocabulary of the domain.
Use case scenarios are an instance of a use case, representing a single path through
the use case. Thus, there may be a scenario for the main flow through the use case
and other scenarios for each possible variation of flow through the use case (for
example, representing each option).
Elements of Por tal Us e Ca s es
When developing use cases for your portal, keep the following elements in mind:
• Priority. Describes the priority, or ranking of the use case. For example, this
could range from High to Medium to Low.
• Context of use. Describes the setting or environment in which the use case
occurs.
• Scope. Describes the conditions and limits of the use case.
• Primary user. Describes what kind of user this applies to, for example, an end
user or an administrator.
• Special requirements. Describes any other conditions that apply.
•Stakeholders. Describes the people who have a "vested interest" in how a
product decision is made or carried ou t.
• Precondition. Describes the prerequisites that must be met for the use case to
occur.
• Minimal guarantees. Describes the minimum that must occur if the use case is
not successfully completed.
• Success guarantees. Describes what happens if the use case is successfully
completed.
• Trigger. Describes the particular item in the system that causes the event to
occur.
• Description. Provides a step-by-step account of the use case, from start to
finish.
100 Portal Server 6 2005Q1 • Deployment Planning Guide
 Loading...
Loading...