Page 1
SonicWALL Secure Remote Access Appliances
SECURE REMOTE ACCESS
SRA 1200/4200 Getting Started Guide
Getting Started Guide
Page 2

SonicWALL
SRA 1200/4200
Getting Started Guide
This Getting Started Guide contains installation procedures and
configuration guidelines for deploying a SonicWALL SRA 1200/4200
appliance into an existing or new network. This document addresses the
most common use-case scenarios and network topologies in which the
SonicWALL SRA 1200/4200 appliance can be deployed.
Document Contents
This document contains the following sections:
Setting Up Your Network - page 3
1
Connecting Your Appliance - page 11
2
Registering Your Appliance - page 21
3
Network Configuration - page 27
4
Support and Training Options - page 41
5
Safety and Regulatory Information - page 49
6
SonicWALL SRA 1200/4200 Getting Started Guide Page 1
Page 3

Page 2 Document Contents
Page 4

Setting Up Your Network
In this Section:
This section provides pre-configuration information. Review this section before setting up your SonicWALL SRA 1200/4200 appliance.
• SRA 1200 System Requirements - page 4
• SRA 4200 System Requirements - page 5
• Selecting a Deployment Scenario - page 7
• Applying Power to the SonicWALL SRA - page 9
1
SonicWALL SRA 1200/4200 Getting Started Guide Page 3
Page 5
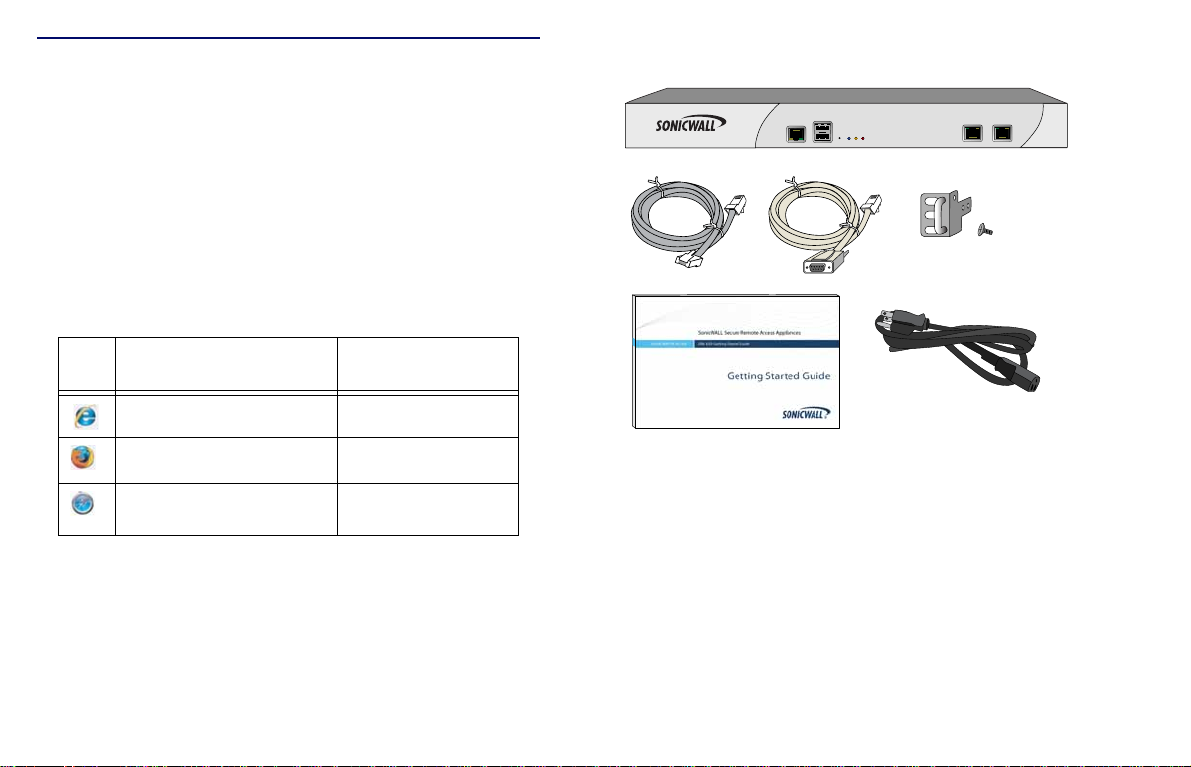
SRA 1200 System Requirements
(x6)
(x2)
(Power cord inlucded
in North America only)
1200
SRA
Secure Remote Access
X0X1
CONSOLE
PWR TEST ALARM
Before you begin the setup process, verify that your package
contains the following parts:
• One SonicWALL SRA 1200 appliance
• One SonicWALL SRA 1200/4200 Getting Started Guide
• One straight-through Ethernet cable
• One serial CLI cable
• One rack-mount kit
• One power cord*
• A Web browser supporting Java Script and HTTP uploads.
Supported browsers include the following:
Supported Browsers Browser Version
Number
Internet Explorer 8.0 or higher
Package Contents for the SonicWALL SRA 1200
Firefox 3.5 or higher
Safari 4.0 or higher
for MacOS
*Power cord intended for use in North America only . For other areas,
please refer to your product reseller.
Page 4 SRA 1200 System Requirements
Missing Items?
If any items are missing from your package, contact
SonicWALL Support:
Web: http://www.sonicwall.com/us/Support.html
Email: customer_service@sonicwall.com
Page 6
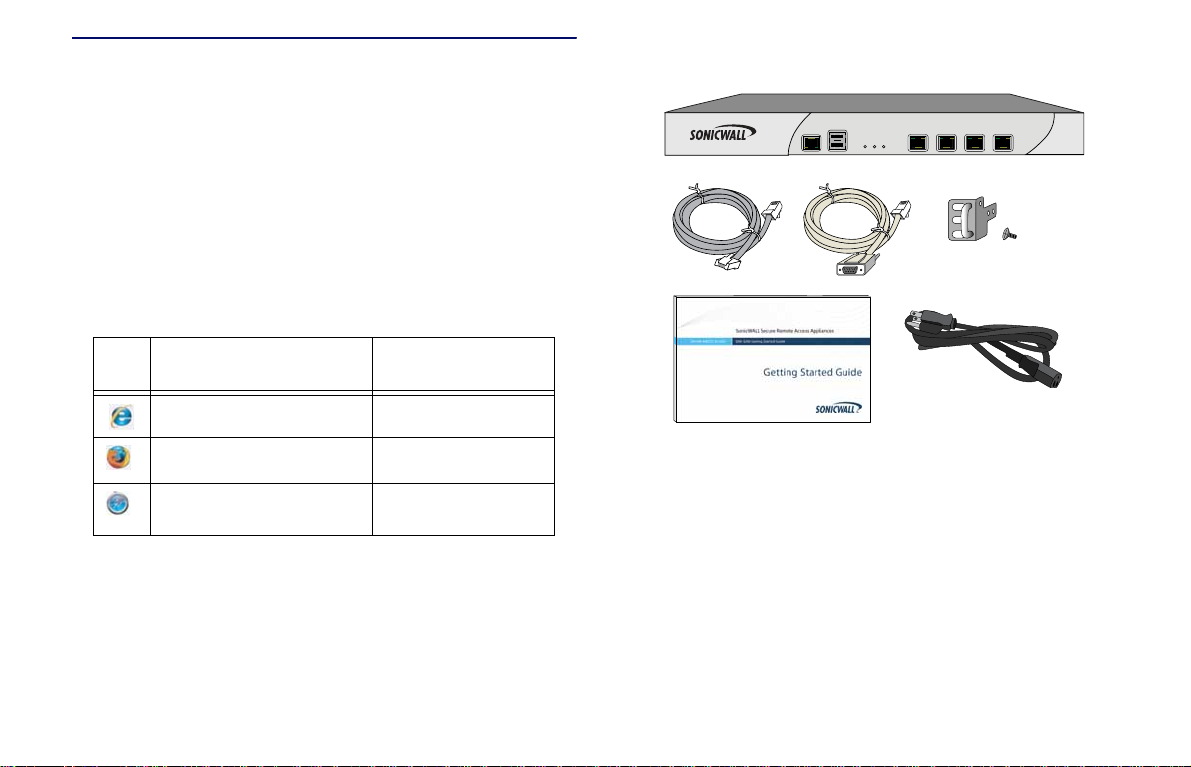
SRA 4200 System Requirements
Secure Remote Access
SRA 4200
(x6)
(x2)
(Power cord inlucded
in North America only)
Before you begin the setup process, verify that your package
contains the following parts:
• One SonicWALL SRA 4200 appliance
• One SonicWALL SRA 1200/4200 Getting Started Guide
• One straight-through Ethernet cable
• One serial CLI cable
• One rack-mount kit
• One power cord*
• A Web browser supporting Java Script and HTTP uploads.
Supported browsers include the following:
Supported Browsers Browser Version
Number
Internet Explorer 8.0 or higher
Package Contents for the SonicWALL SRA 4200
Firefox 3.5 or higher
Safari 4.0 or higher
for MacOS
*Power cord intended for use in North America only . For other areas,
please refer to your product reseller.
Missing Items?
If any items are missing from your package, contact
SonicWALL Support:
Web: http://www.sonicwall.com/us/Support.html
Email: customer_service@sonicwall.com
SonicWALL SRA 1200/4200 Getting Started Guide Page 5
Page 7
What You Need to Begin
• Administrative access to the network gateway device
• A Windows, Linux, or MacOS computer to use as a
management station for initial configuration of the
SonicWALL SRA 1200/4200
• A Web browser supporting Java Script and HTTP uploads
(See previous pages for supported Web browsers)
• An Internet connection
Recording Configuration Information
Record the following setup information to use during the setup
process and for future reference:
Registration Information
Serial Number:
Authentication Code:
Administrator Information
Admin Name:
Admin Password:
Network Configuration Information
Collect the following information about your current network
configuration:
Primary DNS:
Secondary DNS (optional):
DNS Domain:
Record the serial number found on the
bottom panel of your SonicWALL
appliance.
Record the authentication code found on
the bottom panel of your SonicWALL
appliance.
Select an administrator account name.
(default is admin)
Select an administrator password.
(default is password)
Page 6 What You Need to Begin
WINS server(s) (optional):
Page 8
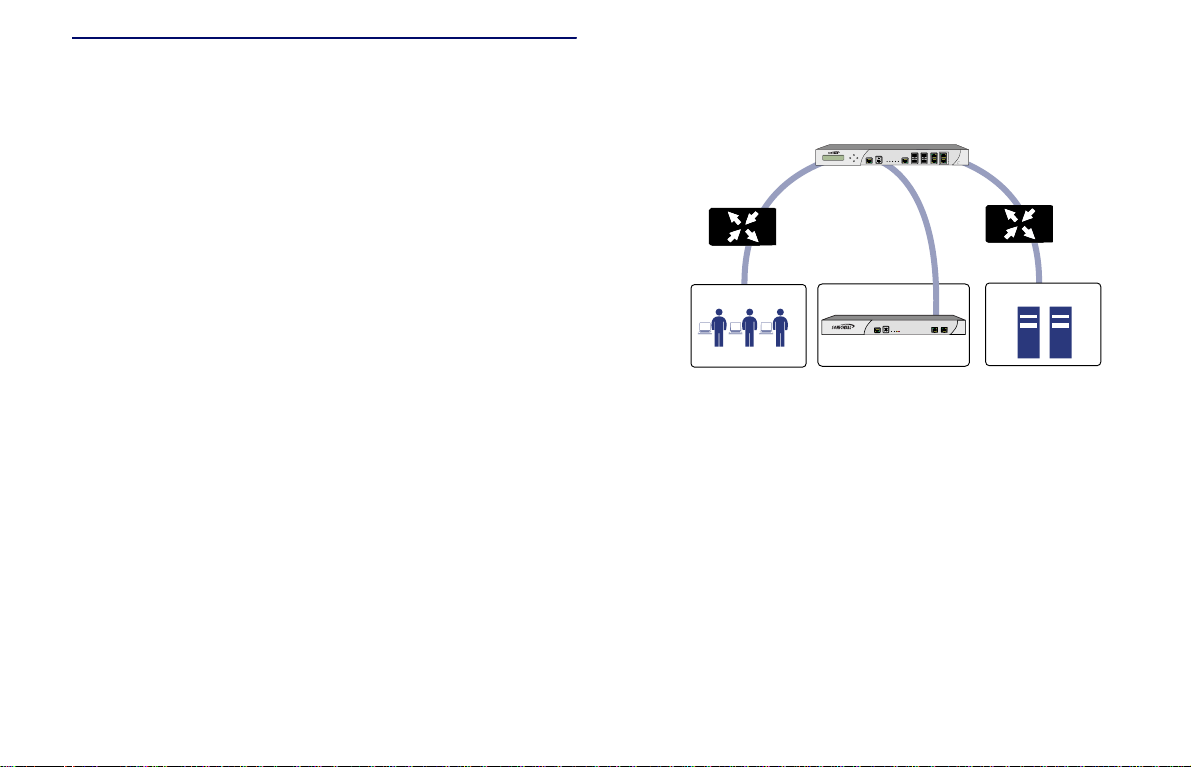
Selecting a Deployment Scenario
The deployment scenarios described in this section are based
on actual customer deployments and are SonicWALLrecommended deployment best practices for SRA appliances .
A SonicWALL SRA appliance is commonly deployed in “onearm” mode over the DMZ or Opt interface on an accompanying
gateway appliance, such as a SonicWALL NSA E7500. This
method of deployment offers additional layers of security
control, plus the ability to use SonicWALL’s UTM services,
including Gateway Anti-Virus, Anti-Spyware, Content Filtering,
Intrusion Prevention Service, and Comprehensive Anti-Spam
Service, to scan all incoming and outgoing NetExtender traffic.
The primary interface (X0) on the SonicWALL SRA connects to
an available segment on the gateway device. The encrypted
user session is passed through the gateway to the SonicWALL
SRA appliance. The SonicWALL SRA appliance decrypts the
session and determines the requested resource.
The session traffic then traverses the gateway appliance to
reach the internal network resources. The gateway appliance
applies security services, such as Intrusion Prevention,
Gateway Anti-Virus, and Anti-Spyware inspection as data
traverses the gateway. The internal network resource then
returns the requested content to the SonicWALL SRA appliance
through the gateway, where it is encrypted and sent to the
client.
Scenario Overviews
Scenario A: SRA on a New DMZ
SonicWALL UTM Appliance
Network Security Appliance
X1
OPT, X2, etc
Router
Remote Users
CONSOLE
Secure Remote Access
WAN DMZ LAN
PWRTESTALARM
SRA Appliance
X0
X0X1
E7500
X0
1200
SRA
Switch
Network Nodes
SonicWALL SRA 1200/4200 Getting Started Guide Page 7
Page 9
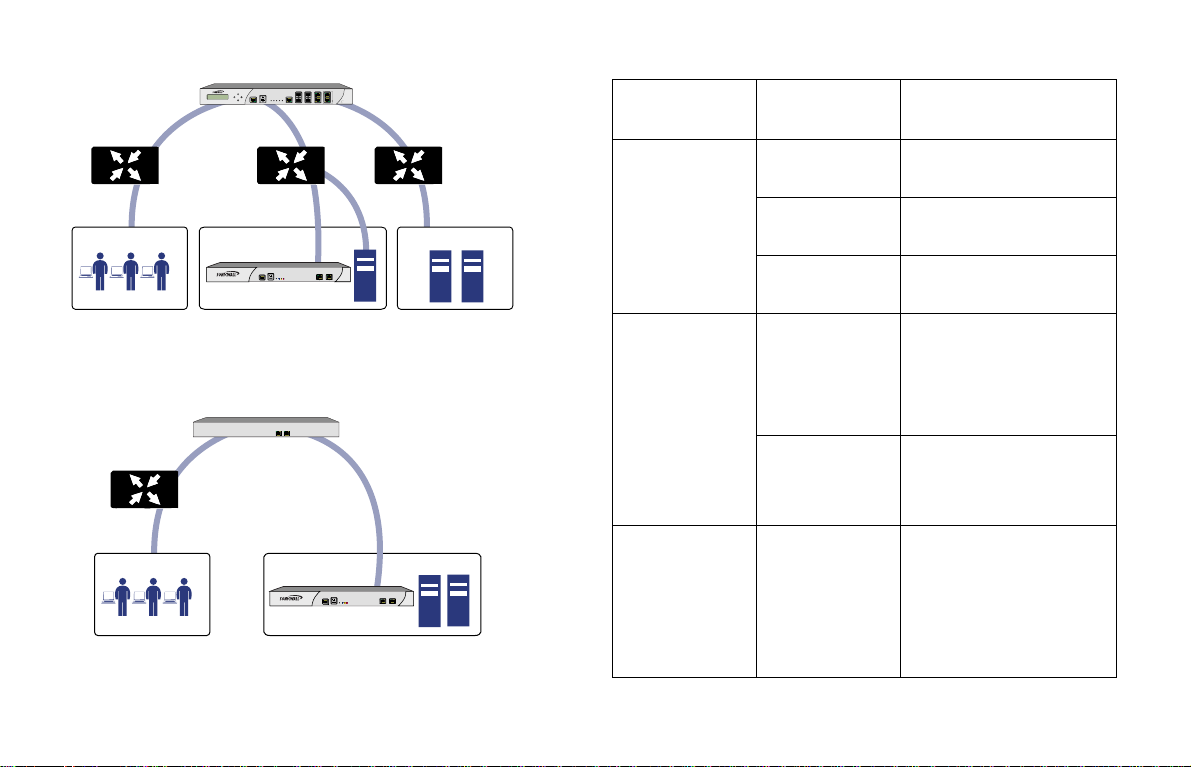
Scenario B: SRA on an Existing DMZ
SonicWALL UTM Appliance
Network Security Appliance
X1
OPT, X2, etc
Router
Remote Users
CONSOLE
Secure Remote Access
SRA Appliance
X0
PWRTESTALARM
Scenario C: SRA on the LAN
Existing Gateway Device
or Switch / Hub
Internet
Router
Remote Users
CONSOLE
Secure Remote Access
SRA Appliance
WAN
X0X1
SRA
E7500
1200
DMZ
LAN Port
X0
PWRTESTALARM
X0
SwitchSwitch
X0X1
SRA
Network Nodes
1200
LAN
SonicWALL SRA 1200/4200 Deployment Scenarios
Gateway
Device
SonicOS Enhanced
3.1 or higher:
• TZ Series
•PRO Series
• NSA E-Class
(SonicOS
5.0+)
•NSA Series
(SonicOS
5.0+)
LANWAN
SonicOS Standard
3.1 or higher:
• TZ Series
• PRO Series
SonicOS Standard
3.1 or higher:
• TZ Series
•PRO Series
SonicWALLs with
legacy firmware
Third-Party Gateway
Device
Deployment
Scenario
SRA on a New DMZ • OPT or unused interface
SRA on Existing
DMZ
Conditions or
Requirements
• New DMZ configured for
NAT or Transparent Mode
• No unused interfaces
• One dedicated interface in
use as an existing DMZ
SRA on the LAN • No unused interfaces
• No dedicated interface for
a DMZ
SRA on a New DMZ • Open OPT or X2 interface
• New DMZ configured for
either NAT or Transparent
Mode
• Provide SonicWALL deep
packet inspection security
services (optional)
SRA on Existing
DMZ
SRA on the LAN • Not planning to use
• OPT or X2 interface in use
with an existing DMZ
• Provide SonicWALL deep
packet inspection security
services (optional)
SonicWALL deep packet
inspection security
services
• Interoperability with a
third-party gateway device
Page 8 Selecting a Deployment Scenario
Page 10
Applying Power to the SonicWALL SRA
1. Plug one end of the power cord into the
SonicWALL SRA 1200/4200 and the other into an
appropriate power outlet.
2. Turn on the power switch located on the rear of the
appliance next to the power cord.
The 'Pwr' LED on the front panel lights up blue when the
appliance is turned on. The 'Test' LED lights up yellow and may
blink for up to a minute while the appliance performs a series of
diagnostic tests. When the 'Test' LED is no longer lit, the
SonicWALL SRA 1200/4200 is ready for configuration.
PWR TEST ALARM
Accessing the Management Interface
To access the Web-based mana gement interface of the
SonicWALL SRA 1200/4200:
1. Connect one end of an Ethernet cable into the ‘X0’ port of
your SonicWALL SRA 1200/4200. Connect the other end
of the cable into the computer you are using to manage the
SonicWALL SRA 1200/4200.
2. Set the computer you use to manage the
SonicWALL SRA 1200/4200 to have a static IP address in
the 192.168.200.x/24 subnet, such as 192.168.200.20.
However, do not use 192.168.200.1, as this address will
conflict with the appliance.
3. Open a Web browser, and enter http://192.168.200.1 (the
default X0 management IP address) in the Location or
Address field.
If the 'Test' or 'Alarm' LEDs remain lit, or if the 'Test' LED blinks
red after the SonicWALL SRA 1200/4200 has booted, restart
the appliance. For more troubleshooting information, refer to the
SonicWALL SSL VPN Administrator’s Guide.
Note: A security warning may appear. Click Continue to this
website or OK to accept the certificate and continue.
SonicWALL SRA 1200/4200 Getting Started Guide Page 9
Page 11
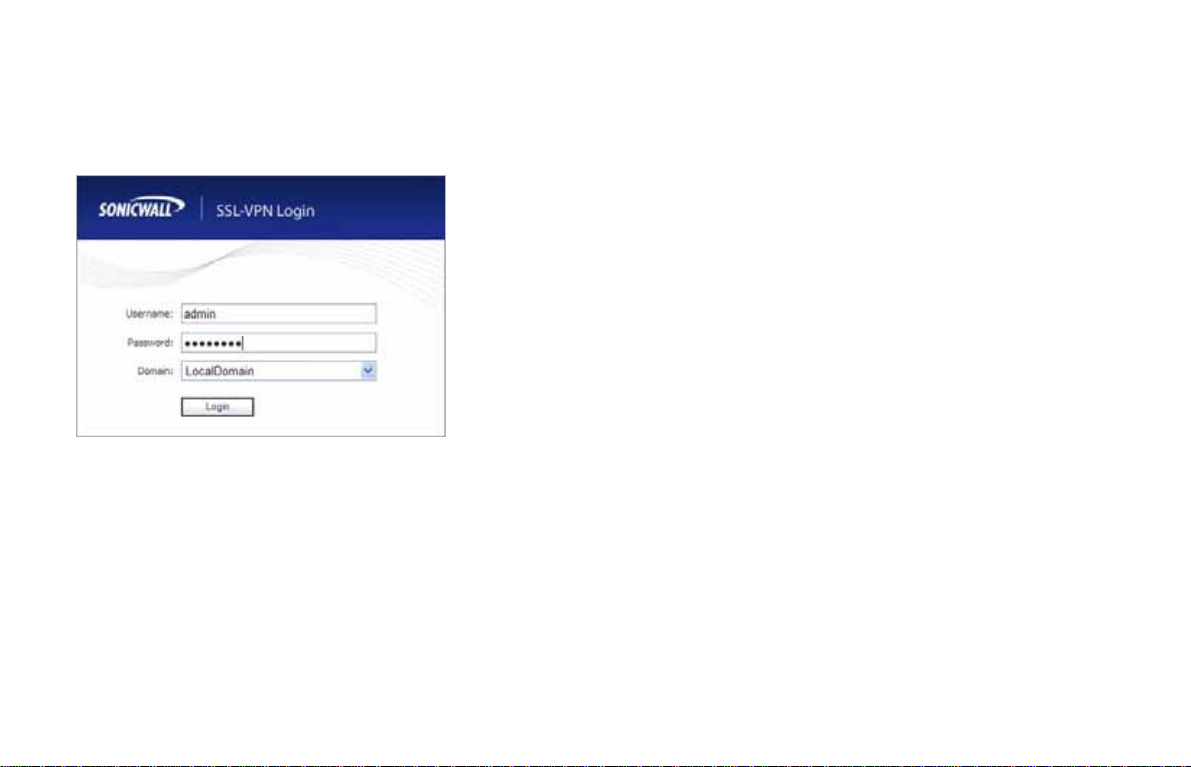
4. The ‘SonicWALL SRA Management Interface Login’
displays and prompts you to enter your user name and
password. Enter “admin” in the User Name field,
“password” in the Password field, select “LocalDomain”
from the Domain drop-down list, and click the Login
button.
Troubleshooting
If you cannot connect to the SonicWALL SRA 1200/4200, verify
the following configurations:
• Did you plug your management workstation into the
interface X0 on the SonicWALL SRA appliance?
Management can only be performed through X0.
• Is the link light illuminated on both the management
station and the SonicWALL SRA appliance?
• Did you correctly enter the SonicWALL SRA 4200
management IP address in your Web browser?
• Is your computer set to a static IP address of
192.168.200.20?
• Is your Domain set to LocalDomain on the login
screen?
If you are still unable to connect to the SonicWALL SRA
appliance, contact SonicWALL Support:
You are now successfully connected to the SRA Management
Interface.
Page 10 Applying Power to the SonicWALL SRA
Web: http://www.sonicwall.com/us/Support.html
Email: customer_service@sonicwall.com
Page 12

Connecting Your Appliance
In this Section:
This section provides procedures for connecting your SonicWALL SRA 1200/4200 appliance.
• Configuring Your SRA 1200/4200 - page 12
• Connecting Your SRA 1200/4200 - page 18
2
SonicWALL SRA 1200/4200 Getting Started Guide Page 11
Page 13
Configuring Your SRA 1200/4200
Once your SonicWALL SRA 1200/4200 is connected to a
computer through the management port (X0), it can be
configured through the Web-based management interface.
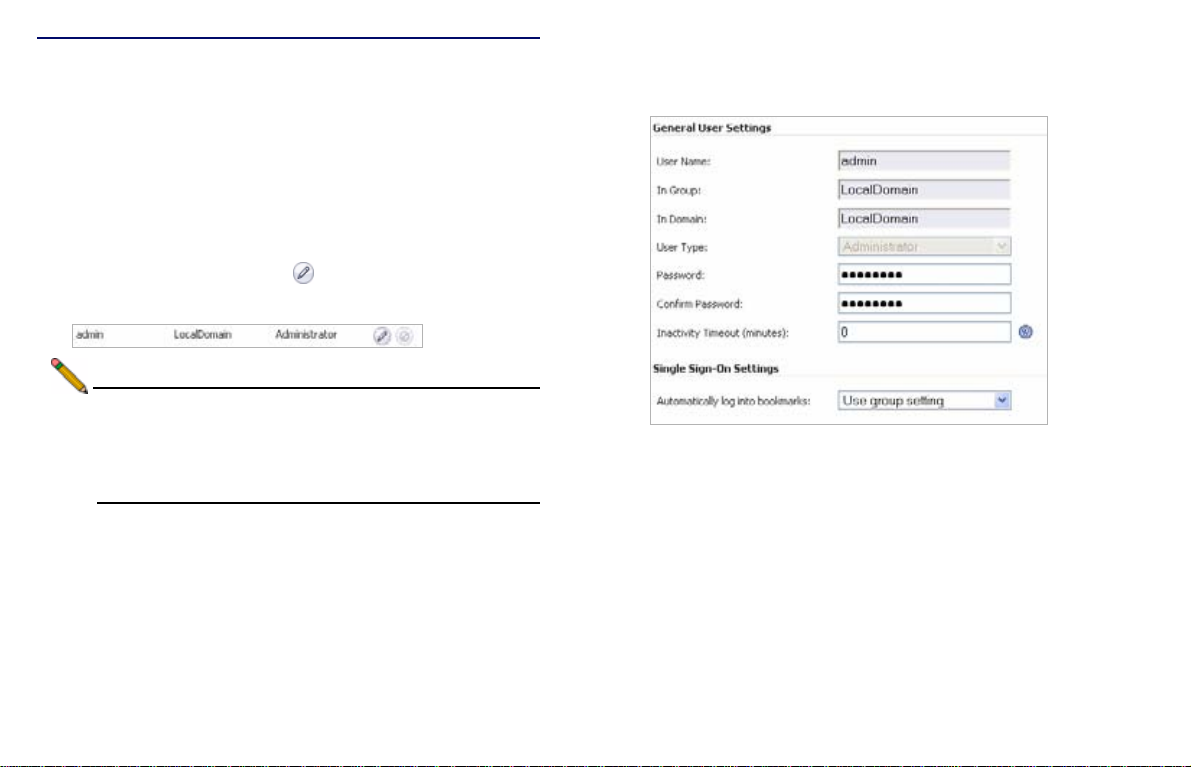
Setting Your Administrator Password
1. From the management interface, select the Users > Local
Users page.
2. Click the Configure button corresponding to the
“admin” account.
Note: Changing your password from the factory default is
strongly recommended. If you change your password,
be sure to keep it in a safe place. If you lose your
password, you will have to reset the SonicWALL SRA
to factory settings losing your configuration.
3. Enter a password for the “admin” account in the Password
field. Re-enter the password in the Confirm Password
field.
4. Click OK to apply changes.
Page 12 Configuring Your SRA 1200/4200
Page 14
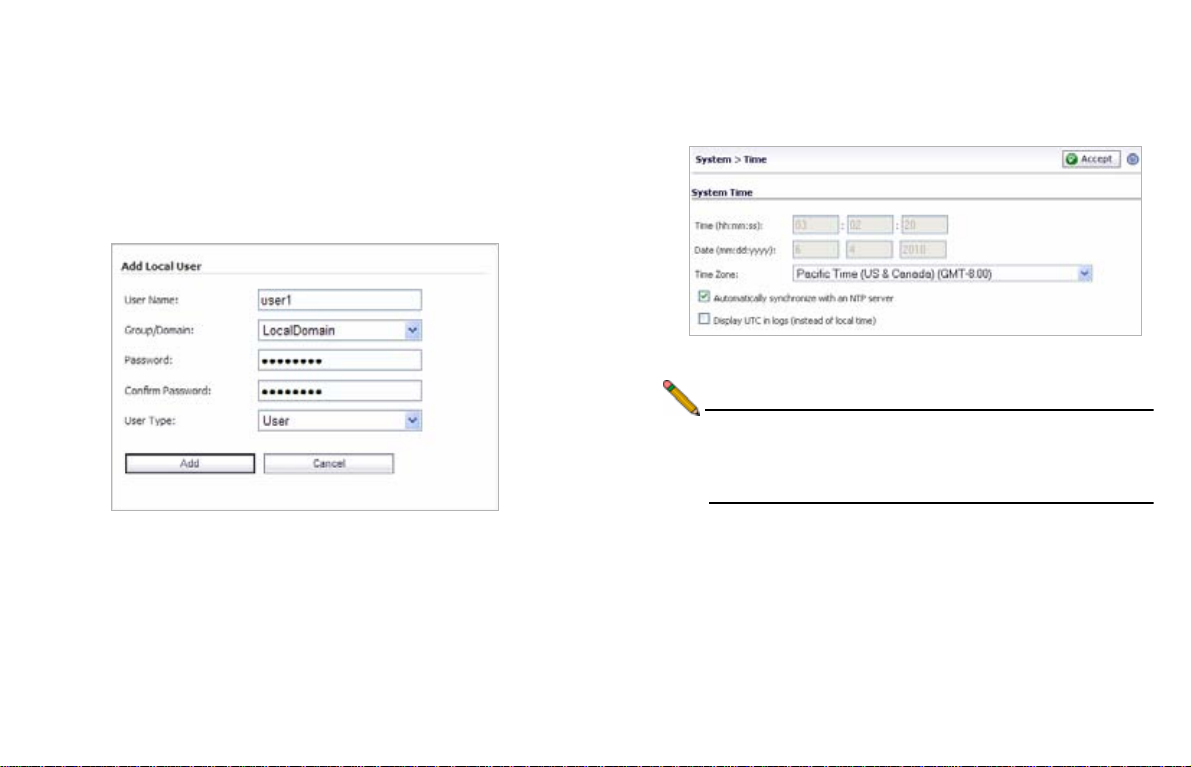
Adding a Local User
1. Navigate to Users > Local Users page.
2. Click the Add User button.
3. Enter a User Name.
4. Select LocalDomain from the Group/Domain drop-down
menu.
5. Enter a Password for the user. Confirm the new password.
6. Select User from the User Type drop-down menu.
7. Click Add to finish adding a local user.
Setting the Time Zone
1. Navigate to the System > Time page.
2. Select the appropriate Time Zone from the drop-down
menu.
3. Click Accept to save changes to the time settings.
Note: Setting the correct time is essential to operations of the
SonicWALL SRA 1200/4200. Be sure to set the time
zone correctly. Automatic synchronization with an NTP
server (default setting) is encouraged for accuracy.
SonicWALL SRA 1200/4200 Getting Started Guide Page 13
Page 15
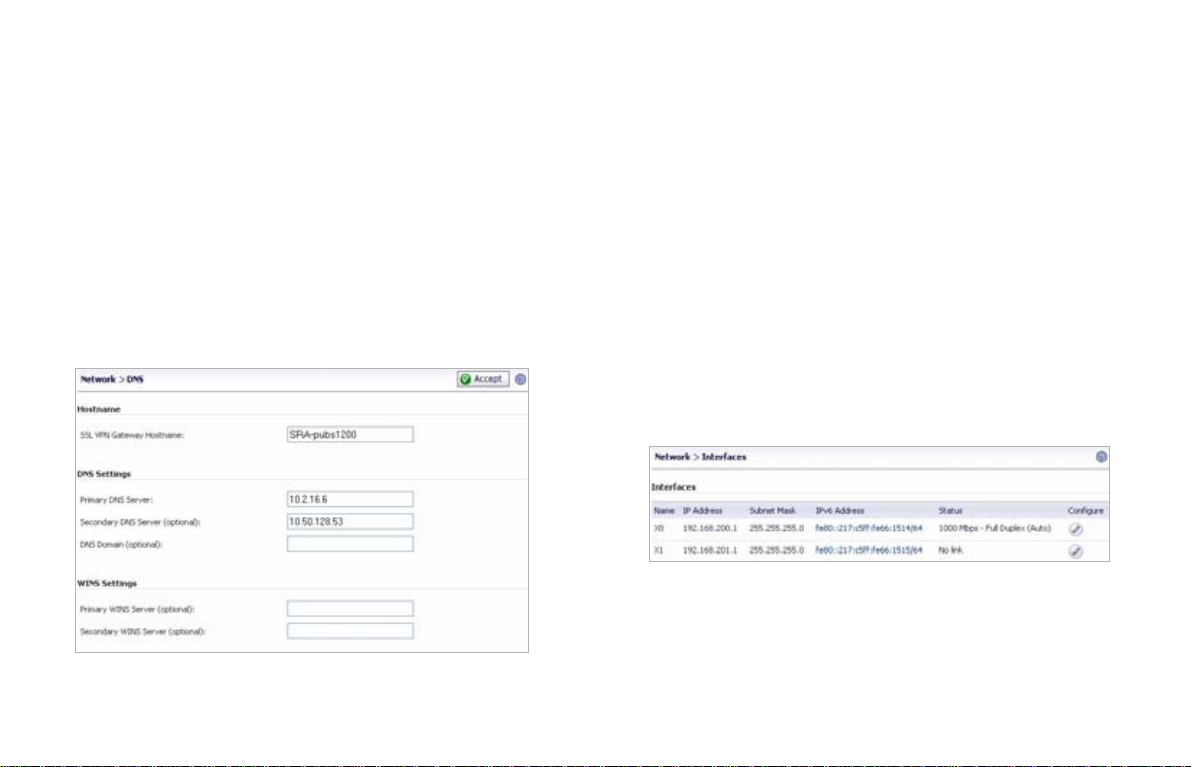
Configuring SRA Network Settings
You will now configure your SRA 1200/4200 network settings.
Refer to the notes you took in the “Recording Configuration
Information” on page 6 to complete this section.
Configuring DNS / WINS
1. Navigate to the Network > DNS page in the management
interface.
2. Enter a unique name for your SonicWALL SRA in the
SSL-VPN Gateway Hostname field.
3. Enter your Primary DNS Server information.
4. (Optional) Enter a secondary DNS server in the
Secondary DNS Server field.
5. (Optional) Enter your DNS Domain.
6. (Optional) Enter your WINS servers in the Primary WINS
Server and Secondary WINS Server fields.
7. Click Accept.
Configuring the X0 IP Address for Scenario B and Scenario C
If you are deploying the SRA in either Scenario B, SRA on an
Existing DMZ or Scenario C, SRA on the LAN, you need to
reset the IP address of the X0 interface on the SRA to an
address within the range of the existing DMZ or the existing
LAN.
To configure the X0 IP address for either of these scenarios:
1. Navigate to the Network > Interfaces page.
2. Click the Configure icon for the X0 interface from the
Interfaces table.
Page 14 Configuring Your SRA 1200/4200
Page 16
3. In the Interface Settings dialog box, set the IP address
and subnet mask to:
If you are using scenario: Set the X0 interface to:
B - SRA on an Existing DMZ IP Address: An unused
address within your DMZ
subnet, for example:
10.1.1.240
Subnet Mask: Must match
your DMZ subnet mask
Configuring a Default Route
Refer to the following table to correctly configure your default
route. If you do not know your scenario, refer to “Selecting a
Deployment Scenario” on page 7.
If you are using scenario: Your upstream gateway device
will be:
A - SRA on a New DMZ The DMZ interface you will
create
C - SRA on the LAN IP Address: An unused
address within your LAN
subnet, for example:
192.168.168.200
Subnet Mask: Must match
your LAN subnet mask
4. Click OK. Note that you will lose connection to the SRA.
5. Reset the management computer to have a static IP
address in the range you just set for the X0 interface, for
example, 10.1.1.20 or 192.168.200.20.
6. Log into the SRA management interface again, using the
IP address you just configured for the X0 interface. For
example, point your browser to
http://192.168.168.200.
B - SRA on an Existing DMZ The existing DMZ interface
C - SRA on the LAN The LAN gateway
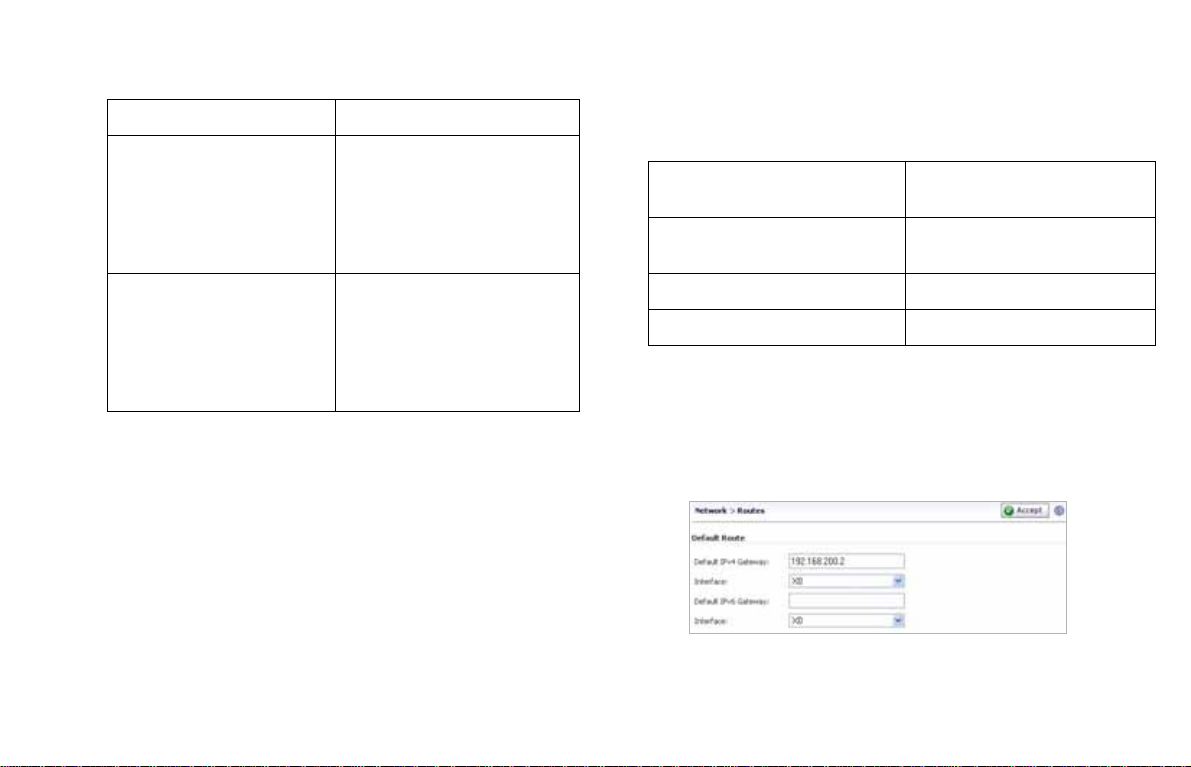
To configure a default route:
1. Navigate to the Network > Routes page.
2. Enter the IP address of your upstream gateway device
in the Default Gateway field.
3. Select X0 in the Interfaces drop-down list.
4. Click Accept.
SonicWALL SRA 1200/4200 Getting Started Guide Page 15
Page 17
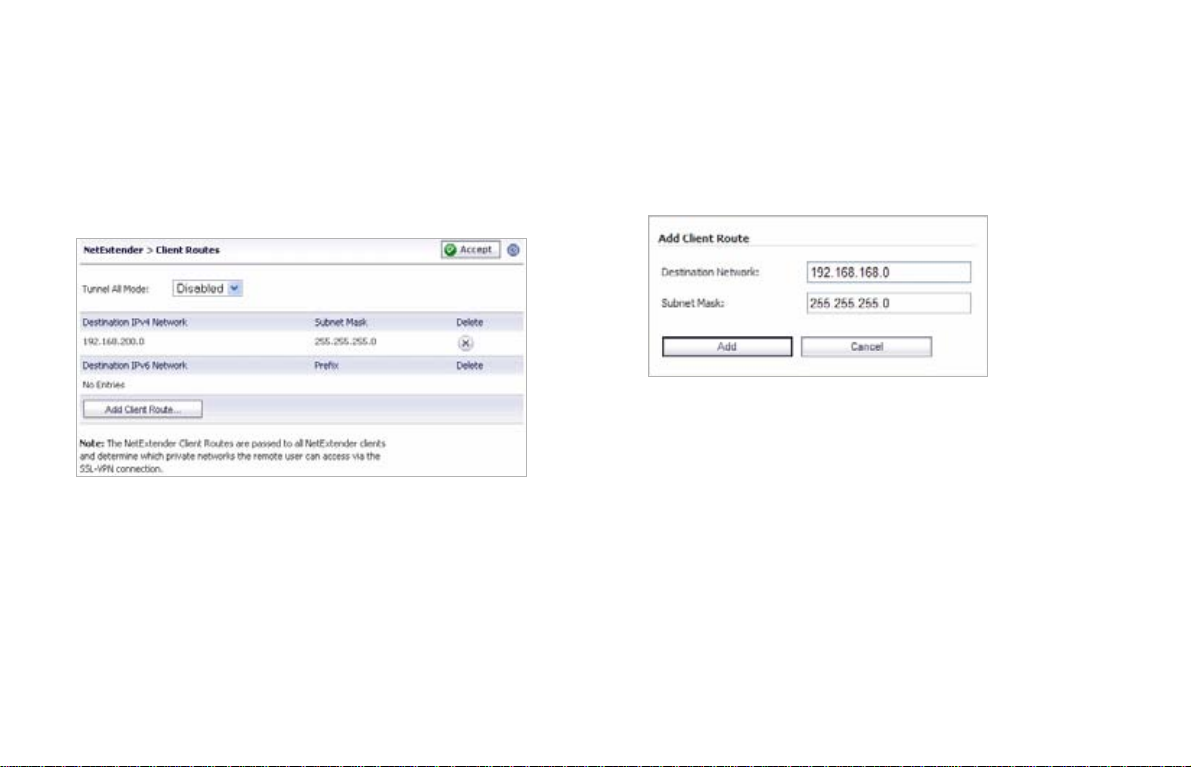
Adding a NetExtender Client Route
NetExtender allows remote clients to have seamless access to
resources on your local network. You can also enable Tunnel
All Mode so that, when NetExtender clients connect, all the
traffic will be tunneled through the NetExtender connection.
To configure a NetExtender client route:
1. Navigate to the NetExtender > Client Routes page.
2. To force all SRA client traffic to pass through the
NetExtender tunnel, select Enabled from the Tunnel All
Mode drop-down list.
3. Click Add Client Route.
4. Enter the IP address of the trusted network to which
you would like to provide access with NetExtender in
the Destination Network field. For example, if you are
connecting to an existing DMZ with the network
192.168.50.0/24 and you want to provide access to your
LAN network 192.168.168.0/24, you would enter
192.168.168.0.
5. Enter your subnet mask in the Subnet Mask field.
6. Click Add to finish adding this client route.
Page 16 Configuring Your SRA 1200/4200
Page 18
Setting Your NetExtender Address Range
The NetExtender IP range defines the IP address pool from
which addresses will be assigned to remote users during
NetExtender sessions. The range needs to be large enough to
accommodate the maximum number of concurrent NetExtender
users you wish to support.
The range should fall within the same subnet as the interface to
which the SonicWALL SRA appliance is connected, and in
cases where there are other hosts on the same segment as the
SonicWALL SRA appliance, it must not overlap or collide with
any assigned addresses. Y ou can determine the correct subnet
based on your network scenario selection:
Scenario A Use the default NetExtender range:
192.168.200.100 to 192.168.200.200
Scenario B Select a range that falls within your existing DMZ
subnet. For example, if your DMZ uses the
192.168.50.0/24 subnet, and you want to support up
to 30 concurrent NetExtender sessions, you could
use 192.168.50.220 to 192.168.50.249, providing
they are not already in use.
Scenario C Select a range that falls within your existing LAN
subnet. For example, if your LAN uses the
192.168.168.0/24 subnet, and you want to support up
to 10 concurrent NetExtender sessions, you could
use 192.168.168.240 to 192.168.168.249, providing
they are not already in use.
To set your NetExtender address range in the management
interface:
1. Navigate to the NetExtender > Client Settings page.
2. Enter an address range for your clients in the Client
Address Range Begin and Client Address Range End
fields.
Scenario A 192.168.200.100 to 192.168.200.200
(default range)
Scenario B An unused range within your DMZ subnet
Scenario C An unused range within your LAN subnet
If you do not have enough available addresses to support your
desired number of concurrent NetExtender users, you may use
a new subnet for NetExtender. This condition may occur if your
existing DMZ or LAN is configured in NAT mode with a small
subnet space, such as 255.255.255.224, or more commonly if
your DMZ or LAN is configured in Transparent mode and you
have a limited number of public addresses from your ISP. In
either case, you may assign a new, unallocated IP range to
NetExtender (such as 192.168.10.100 to 192.168.10.200) and
configure a route to this range on you r gateway appliance.
For example, if your current Transparent range is 67.1 15.1 18.75
through 67.115.118.80, and you wish to support 50 concurrent
NetExtender clients, configure your SRA X0 interface with an
available IP address in the Transparent range, such as
67.115.118.80, and configure your NetExtender range as
192.168.10.100 to 192.168.10.200. Then, on your gateway
device, configure a static route to 192.168.10.0/255.255.255.0
using 67.115.118.80.
SonicWALL SRA 1200/4200 Getting Started Guide Page 17
Page 19

Connecting Your SRA 1200/4200
Before continuing, reference the diagrams on the following
pages to connect the SonicWALL SRA 1200/4200 to your
network.
Refer to the options in “Selecting a Deployment Scenario” on
page 7 to determine the proper scenario for your network
configuration:
Scenario A: Connecting Your Network Interfaces
Scenario A: SRA on a New DMZ
SonicWALL UTM Appliance
Network Security Appliance
X1
OPT, X2, etc
E7500
X0
• Scenario A: Connecting Your Network Interfaces - page 18
• Scenario B: Connecting Your Network Interfaces - page 19
• Scenario C: Connecting Your Network Interfaces - page 19
Page 18 Connecting Your SRA 1200/4200
Router
Remote Users
Secure Remote Access
SRA Appliance
CONSOLE
PWRTESTALARM
Switch
1200
SRA
Network Nodes
X0
X0X1
WAN DMZ LAN
To connect the SonicWALL SRA 1200/4200 using Scenario A,
perform the following steps:
1. Connect one end of an Ethernet cable to the OPT, X2,
or other unused port on your existing SonicWALL security
appliance.
2. Connect the other end of the Ethernet cable to the X0
port on the front of your SonicWALL SRA 1200/4200. The
X0 Port LED lights up green indicating an active
connection.
Continue to Chapter
Page 20

Scenario B: Connecting Your Network
LAN
WAN
LAN Port
X0
Remote Users
Existing Gateway Device
or Switch / Hub
Internet
Router
1200
SRA
Secure Remote Access
X0X1
CONSOLE
PWRTESTALARM
SRA Appliance
Interfaces
Scenario C: Connecting Your Network Interfaces
Scenario B: SRA on an Existing DMZ
SonicWALL UTM Appliance
Router
Remote Users
X1
Network Security Appliance
OPT, X2, etc
Secure Remote Access
SRA Appliance
CONSOLE
PWRTESTALARM
E7500
X0
SwitchSwitch
DMZ
Network Nodes
LANWAN
X0
X0X1
1200
SRA
To connect the SonicWALL SRA 1200/4200 using Scenario B,
perform the following steps:
1. Connect one end of an Ethernet cable to an unused
port on your DMZ, either directly to the OPT or X2 on your
existing SonicWALL security appliance, or to a hub or
switch on your DMZ.
2. Connect the other end of the Ethernet cable to the X0
port on your SonicWALL SRA 1200/4200. The X0 Port
LED lights up green indicating an active connection.
Continue to Chapter
Scenario C: SRA on the LAN
To connect the SonicWALL SRA 1200/4200 using Scenario C,
perform the following steps:
1. Connect one end of an Ethernet cable to an unused
port on your LAN hub or switch.
2. Connect the other end of the Ethernet cable to the X0
port on the front of your SonicWALL SRA 1200/4200. The
X0 Port LED lights up green indicating an active
connection.
Continue to Chapter
SonicWALL SRA 1200/4200 Getting Started Guide Page 19
Page 21

Page 20 Connecting Your SRA 1200/4200
Page 22

Registering Your Appliance
In this Section:
This section provides instructions for registering your SonicWALL SRA 1200/4200 appliance.
• Creating a MySonicWALL Account - page 22
• Registering Your SonicWALL SRA - page 22
• Services and Licensing - page 23
Note: Registration is an important part of the setup process and is necessary to receive the benefits of SonicWALL services,
user-licensing, firmware updates, and technical support.
3
SonicWALL SRA 1200/4200 Getting Started Guide Page 21
Page 23

Creating a MySonicWALL Account
Registering Your SonicWALL SRA
A MySonicWALL account is required for product registration. If
you already have an account, continue to the following section.
Perform the following steps to create a MySonicWALL account:
1. In your browser, navigate to www. mysonicwall.com.
2. In the login screen, click the Not a registered user? link.
3. Complete the Registration form and click Register.
4. Verify that the information is correct and click Submit.
5. In the screen confirming that your account was created,
click Continue to finish creating your MySonicWALL
account.
This section contains the following subsections:
• Before You Register - page 22
• Product Registration - page 22
Before You Register
Verify that the time, DNS, and default route settings on your
SonicWALL SRA 1200/4200 are correct before you register
your appliance. T o verify or configure these settings, navigate to
the ‘System > Time’, ‘Network > DNS’, or ‘Network > Routes’
pages, respectively.
Product Registration
Register your SonicWALL SRA on MySonicWALL to enable full
functionality.
1. Login to your MySonicW ALL account. If you do not have
an account, you can create one at www.mysonicwall.com.
2. On the main page, enter the appliance serial number in
the Register A Product field. Click Next.
3. On the My Products page, under Add New Product, enter
the friendly name for the appliance, select the Product
Group if any, enter the authentication code into the
appropriate text boxes, and then click Register.
4. On the Product Survey page, fill in the requested
information and click Continue.
Page 22 Creating a MySonicWALL Account
Page 24

Services and Licensing
This section contains the following subsections:
• Service Management - page 23
• Flexible Per-User Licensing - page 24
• Activating Services and Software - page 24
• Trying or Purchasing Services - page 25
Service Management
The Service Management page in MySonicWALL lists services,
support options, and software, such as Web Application Firewall
and ViewPoint, that you can purchase or try with a free trial. For
details on a product or service, click the Info arrow icon next
to the desired item.
If you purchased an appliance that is pre-licensed, you may be
required to enter your activation key here unless current
licenses are already indicated in th e S t atus column wi th either a
license key or an expiration date.
SonicWALL SRA 1200/4200 Getting Started Guide Page 23
Page 25

The following products and services are available for the
SonicWALL SRA 1200/4200 appliance:
• Gateway Service Bundles:
• Per-user license upgrades in flexible block increments
• Desktop and Server Software:
• Virtual Assist
• Web Application Firewall
•ViewPoint
• Support Services:
• Dynamic Support 8x5
• Dynamic Support 24x7
• Software and Firmware Updates
Flexible Per-User Licensing
Your SonicWALL SRA comes standard with a set number of
user licenses. However, as the needs of your organization
change, SonicWALL offers flexible options when it comes to
adding additional licenses.The ability to purchase a convenient
number of additional licenses allows you to plan sensibly for the
future, or provide immediate scalability when you need it most.
Appliance SRA 1200 SRA 4200
Initial User Licenses 525
Additional Per-User
License Packages
Maximum Concurrent
User Sessions Allowed
1 - 5 - 10 10 - 25 - 100
50 500
Activating Services and Software
If you purchase a service subscription or upgrade from a sales
representative, you will receive an activation key. This key is
emailed to you after online purchases, or is on the front of the
certificate that was included with your purchase.
To activate existing licenses, perform the following tasks:
1. Navigate to the 'My Products' page and select the
registered product you want to manage.
2. Locate the product on the 'Service Management' page and
click Enter Key in that row.
3. In the 'Activate Service' page, type or paste your key into
the Activation Key field and then click Submit.
Once the service is activated, you will see an expiration
date or a license key string in the Status column on the
Service Management page.
Page 24 Services and Licensing
Page 26

Trying or Purchasing Services
To try a free trial of a service, click Try in the 'Service
Management' page.
T o purchase a product or service, click Buy Now in the 'Service
Management' page to complete your purchase.
When activation is complete, MySonicWALL displays an
activation screen with service status and expiration information.
The service management screen also displays the product you
licensed.
You have successfully registered your SonicWALL appliance.
SonicWALL SRA 1200/4200 Getting Started Guide Page 25
Page 27

Page 26 Services and Licensing
Page 28

Network Configuration
4
In this Section:
This section provides detailed overviews of deployment scenarios, as well as configuration instructions for connecting your SonicWALL
SRA to various network devices, including gateway appliances.
• Scenario A: SRA on a New DMZ - page 28
• Scenario B: SRA on an Existing DMZ - page 32
• Scenario C: SRA on the LAN - page 36
• Testing Your Remote Connection - page 39
Tip: Before completing this section, fill out the information on "Recording Configuration Information" on page 6.
SonicWALL SRA 1200/4200 Getting Started Guide Page 27
Page 29

Scenario A: SRA on a New DMZ
This section provides procedu res to configure your gateway
appliance based on Scenario A. This section contains the
following subsections:
• Connecting to a SonicWALL Security Appliance - page 28
• Adding a New SRA Custom Zone - page 28
• Allowing a WAN -> SRA Connection - page 29
• Allowing an SRA -> LAN Connection - page 30
Connecting to a SonicWALL Security Appliance
1. Using a computer connected to your LAN, launch your
Web browser and enter the IP address of your existing
SonicWALL security appliance in the Location or
Address field.
2. When the management interface displays, enter your
user name and password in the appropriate fields and
click Login.
Note: Remember that you are logging into your SonicWALL
security appliance, not the SonicWALL SRA.
Adding a New SRA Custom Zone
1. Navigate to the Network > Interfaces page, click
Configure for the X2 interface (or any other available
interface).
2. Select Create New Zone in Zone field. The 'Add Zone'
window opens.
3. Enter SRA in the Name field.
4. Select Public from the Security Type drop-down menu.
5. Un-select the Allow Interface Trust checkbox.
Page 28 Scenario A: SRA on a New DMZ
Page 30

6. Select the Gateway AV, Intrusion Prevention Service
and Anti-Spyware checkboxes. Click OK.
7. On the 'Edit Interface' window, enter the IP address for
this interface in the IP Address field. (For example,
“192.168.200.2”. This should be the same address you
created in "Configuring the X0 IP Address for Scenario B
and Scenario C" on page 14).
8. Enter your Subnet Mask.
9. On the 'Management' area, enable the desired
management options.
10. Click OK to apply changes.
Allowing a WAN -> SRA Connection
To create a public server access rule for HTTP and HTTPS
traffic:
1. Click the Wizards icon in the top right corner of the
management interface.
2. On the 'Welcome' page, select the Public Server Wizard,
and then click Next.
3. On the 'Public Server Type' page, select:
Server Type Other
Services Create new group
The 'Add Service Group' dialog box appears.
4. In the 'Add Service Group' dialog box, create a service
group for HTTP and HTTPS:
• Enter a name for the service.
• Select both HTTP and HTTPS and click .
• Click OK when both the HTTP and HTTPS are in the
right column.
SonicWALL SRA 1200/4200 Getting Started Guide Page 29
Page 31

5. On the 'Server Private Network Configuration' page, enter
the following, and click Next:
Server Name Name for the SonicWALL SRA
Server Private
IPAddress
Server Comment Brief description of the server
SonicWALL SRA’s 'X0' IP address,
192.168.200.1 by default
6. On the 'Server Public Information' page, accept the
default IP address, or enter an IP address in your
allowed public IP range. Click Next.
Note: The default IP address is the WAN IP address of your
SonicWALL security appliance. If you accept this
default, all HTTP and HTTPS traffic to this IP address
will be routed to your SonicWALL SRA.
7. The 'Public Server Configuration Summary' page displays
all the configuration actions that will be performed to create
the public server. Click Apply to create the configuration
and allow access from the WAN to the SRA on the DMZ.
Allowing an SRA -> LAN Connection
When users have connected to the SRA, they need to be able
to connect to resources on the LAN. To allow an SRA to LAN
connection, perform the following steps:
1. Navigate to the Network > Address Objects page.
2. In the 'Address Objects' section, click .
3. In the 'Add Address Object' dialog box, create an address
object for the X0 interface IP address of your SonicWALL
SRA:
Name Name for the SonicWALL SRA
Zone Assignment SRA
Type Host
IP Address SonicWALL SRA’s 'X0' IP address,
4. Click Add to create the object. Once done, click Close.
5. Click again to create an address object for
the NetExtender range.
192.168.200.1 by default
Page 30 Scenario A: SRA on a New DMZ
Page 32

6. In the 'Add Address Object' dialog box, create an address
object for the X0 interface IP address of the SonicWALL
SRA:
Name Name for NetExtender
Zone Assignment SRA
Type Range
Starting IP Address Start of the NetExtender IP
Ending IP Address End of the NetExtender IP
address range,
192.168.200.100 by default
address range,
192.168.200.200 by default
7. Click Add to create the object. Once done, click Close.
8. On the 'Network > Address Objects' page, in the ‘Address
Groups’ section, click .
9. In the 'Add Address Object Group' dialog box, create a
group for the X0 interface IP address of your SonicWALL
SRA and the NetExtender IP range:
• Enter a name for the group.
• In the left column, select the two groups you created
and click the right arrow button .
• Click OK to create the group when both objects are in
the right column.
10. In the administrative interface, navigate to the Firewall >
Access Rules page.
11. On the 'Firewall > Access Rules' page, in the matrix view,
click the SRA > LAN icon.
12. On the resulting 'Firewall > Access Rules' page, click
.
SonicWALL SRA 1200/4200 Getting Started Guide Page 31
Page 33

13. In the 'Add Rule' window, create a rule to allow access to
the LAN for the address group you just created:
Scenario B: SRA on an Existing DMZ
Action Allow
From Zone SRA
To Zone LAN
Service Any
Source The address group you just created,
Destination Any
Users Allowed All
Schedule Always on
Enable Logging Selected
Allow Fragmented Packets Selected
such as SonicWALL_SRA_Group
14. Click OK to create the rule.
Continue to "Te s ting Your Remote Connection" on page 39
This section provides procedures to configure your gateway
appliance based on Scenario B. This section contains the
following subsections:
Prerequisites
• Connecting to a SonicWALL Security Appliance - page 32
• Allowing WAN -> DMZ Connection - page 33
• Allowing DMZ -> LAN Connection - page 34
Connecting to a SonicWALL Security Appliance
1. Using a computer connected to your LAN, launch your
Web browser, and enter the IP address of your existing
SonicWALL security appliance in the Location or Address
field.
2. When the management interface displays, enter your
User Name and Password in the appropriate fields and
click Login.
Note: Remember that you are logging into your SonicWALL
firewall, not the SonicWALL SRA.
Page 32 Scenario B: SRA on an Existing DMZ
Page 34

Allowing WAN -> DMZ Connection
If you are already forwarding HTTP or HTTPS to an internal
server, and you only have a single public IP address, you will
need to select different (unique) ports of operation for either the
existing servers or for the SonicWALL SRA appliance, because
both cannot concurrently use the same IP address and port
combinations.
To create a public server access rule for HTTPS traffic:
1. Click the Wizards icon at the top right of the interface.
2. On the 'Welcome' page, select the Public Server Wizard
and then click Next.
3. On the 'Public Server Type' page, select:
Server Type Other
Services Create new group
The 'Add Service Group' dialog box is displays.
4. In the 'Add Service Group' dialog box, create a service
group for HTTP and HTTPS:
• Enter a name for the service.
• Select both HTTP and HTTPS and click .
• Click OK when HTTP and HTTPS are in the right
column.
5. On the 'Public Server Type' page, click Next.
6. On the 'Server Private Network Configuration' page, enter
the following and click Next:
Server Name Name for the SonicWALL SRA
Server Private IPAddress 'X0' IP address of the SRA appliance
Server Comment Brief description of the server
within your DMZ range, such as
10.1.1.200
7. On the 'Server Public Information' page, accept the
default IP address or enter an IP address in your allowed
public IP range. Click Next.
Note: The default IP address is the WAN IP address of your
SonicWALL firewall. If you accept this default, all HTTP
and HTTPS traffic to this IP address will be routed to
your SonicWALL SRA.
8. The 'Public Server Configuration Summary' page displays
all configuration actions that will be performed to create the
public server. Click Apply to create the configuration and
allow access from the WAN to the SonicWALL SRA on the
DMZ.
SonicWALL SRA 1200/4200 Getting Started Guide Page 33
Page 35

Allowing DMZ -> LAN Connection
When users have connected to the SRA, they need to be able
to connect to resources on the LAN.
1. Navigate to the Network > Address Objects page.
2. In the 'Address Objects' section, click .
3. In the 'Add Object' dialog box, create an address object
for the X0 interface IP address of your SonicWALL SRA,
then click OK.
Name Name for the SonicWALL SRA
Zone Assignment DMZ
Type Host
IP Address 'X0' IP address of the SRA appliance
4. Click again to create an address object for
the NetExtender range.
within your DMZ range, such as
10.1.1.200
5. In the 'Add Object' dialog box, create an address object
for the X0 interface IP address of your SonicWALL SRA,
then click OK.
Name Name for NetExtender
Zone Assignment DMZ
Type Range
Starting IP Address Start of the NetExtender IP address
Ending IP Address End of the NetExtender IP address
range within your DMZ range, e.g.,
10.1.1.220
range within your DMZ range, e.g.,
10.1.1.250
6. In the 'Address Groups' section, click .
Page 34 Scenario B: SRA on an Existing DMZ
Page 36

7. In the 'Add Address Object Group' dialog box, create a
group for the X0 interface IP address of your SonicWALL
SRA and the NetExtender IP range, then click OK.
• Enter a name for the group.
• In the left column, select the two groups you created
and click the arrow button .
8. Navigate to the Firewall > Access Rules page.
9. On the 'Firewall > Access Rules' page in the matrix view,
click the DMZ > LAN icon.
10. On the resulting 'Firewall > Access Rules' page, click
.
11. In the 'Add Rule' window, create a rule to allow acces s to
the LAN for the address group you just created:
Action Allow
From Zone DMZ
To Zone LAN
Service Any
Source Address group you just created,
Destination Any
Users Allowed All
Schedule Always on
Enable Logging Selected
Allow Fragmented Packets Selected
such as SonicWALL_SRA_Group
12. Click OK to create the rule.
Continue to "Testing Your Remote Connection" on page 39
SonicWALL SRA 1200/4200 Getting Started Guide Page 35
Page 37

Scenario C: SRA on the LAN
This section provides procedu res to configure your gateway
appliance based on Scenario C. This section contains the
following subsections:
• Connecting to a SonicWALL Security Appliance - page 36
• Configuring SRA -> LAN Connectivity - page 36
• Setting Public Server Access - page 38
Connecting to a SonicWALL Security Appliance
1. Using a computer connected to your LAN, launch your
Web browser and enter the IP address of your existing
SonicWALL security appliance in the Location or Address
field.
2. When the management interface displays, enter your
User Name and Password in the appropriate fields and
click Login.
Configuring SRA -> LAN Connectivity
In order for users to access local resources through the
SonicWALL SRA, you must configure your gateway device to
allow an outside connection through the SRA into your LAN.
1. Navigate to the Network > Address Objects page.
2. In the 'Address Objects' section, click .
3. In the 'Add Object' dialog box, create an address object
for the X0 interface IP address of your SonicWALL SRA,
then click OK.
Name Name for the SonicWALL SRA
Zone Assignment SRA
Type Host
IP Address SonicWALL SRA’s X0 IP address,
192.168.200.1 by default
Note: Remember that you are logging into your SonicWALL
security appliance, not the SonicWALL SRA.
Page 36 Scenario C: SRA on the LAN
4. Click OK to create the object.
5. Click again to create an address object for
the NetExtender range.
Page 38

6. In the 'Add Object' dialog box, create an address object
for the X0 interface IP address of your SonicWALL SRA,
then click OK.
Name Name for NetExtender
Zone Assignment SRA
Type Range
Starting IP Address Start of the NetExtender IP address
Ending IP Address End of the NetExtender IP address
range, 192.168.200.100 by default
range, 192.168.200.200 by default
7. On the 'Network > Address Objects' page, in the 'Address
Groups' section, click .
8. In the 'Add Address Object Group' dialog box, create a
group for the X0 interface IP address of your SRA and the
NetExtender IP range, then click OK.
9. Navigate to the Firewall > Access Rules page, set the
page to matrix view, and click the SRA > LAN icon.
10. On the resulting 'Firewall > Access Rules' page, click
.
SonicWALL SRA 1200/4200 Getting Started Guide Page 37
Page 39

11. In the 'Add Rule' window, create a rule to allow access to
the LAN for the address group you just created:
Action Allow
From Zone SRA
To Zone LAN
Service Any
Source Address group just created, such as
Destination Any
Users Allowed All
Schedule Always on
Enable Logging Selected
Allow Fragmented Packets Selected
SonicWALL_SRA_Group
12. Click OK to finish creating the rule.
Setting Public Server Access
1. Click the Wizards icon in the top right corner of the
SonicOS management interface.
2. Select the Public Server Wizard option and click Next.
3. Select Web Server from the Server Type drop-down menu.
4. Select HTTP and HTTPS checkboxes, and click Next.
5. Enter SRA in the Server Name field.
6. Enter 192.168.168.200 (or the address you have
configured to the SRA’s X0 interface) in the Private IP field.
7. Enter a comment, such as “WAN to SRA” to describe your
connection, and click Next.
8. Verify the Public Server field contains the correct IP
address and click Next.
9. Click Apply to finish setting public server access.
Page 38 Scenario C: SRA on the LAN
Page 40

Testing Your Remote Connection
You have now configured your SonicWALL security appliance
and SonicWALL SRA for secure SSL-VPN remote access.This
section provides instructions to verify your connection using a
remote client on the WAN.
Verifying a User Connection from the Internet
1. From a WAN connection outside of your corporate network,
launch a Web browser and enter the following:
https://<WAN_IP_address_of_gateway_device>
2. When prompted, enter the User Name and Password
created in "Adding a Local User" on page 13 of this guide.
3. Select LocalDomain from the drop-down menu and click
Login. The SonicWALL Virtual Office screen appears in
your Web browser.
4. Click NetExtender to start the NetExtender client
installation.
5. If prompted, click Install to complete the client installation.
6. Ping a host on your corporate LAN to verify your remote
connection.
You have now successfully set up your SonicWALL SRA.
Tip: It is easier for remote users to access the SonicWALL
SRA appliance using an a fully qualified domain name
(FQDN) rather than an IP address. It is recommended
that you create a DNS record to allow for FQDN access
to your SonicWALL SRA. If you do not manage your
own public DNS servers, contact your ISP for
assistance.
SonicWALL SRA 1200/4200 Getting Started Guide Page 39
Page 41

Page 40 Testing Your Remote Connection
Page 42

Support and Training Options
In this Section:
This section provides overviews of customer support and training options for SonicWALL SRA appliances.
• Customer Support - page 42
• Knowledge Base - page 42
• User Forums - page 43
• Training - page 44
• Related Documentation - page 45
• SonicWALL Live Product Demos - page 46
• SonicWALL Secure Wireless Network Integrated Solutions Guide - page 47
5
SonicWALL SRA 1200/4200 Getting Started Guide Page 41
Page 43

Customer Support
Knowledge Base
SonicWALL’s customer support Web site is where you will find
featured support topics, tutorials, and more. If you need further
assistance, SonicWALL offers telephone, email, and Webbased support to customers with valid Warranty Support or a
purchased support contract. Please review our Warranty
Support Policy for product coverage.
For answers to support questions, visit:
<http://www.sonicwall.com/us/Support.html>
The Knowledge Base allows users to search for SonicWALL
documents based on the following types of search tools:
•Browse
• Search for keywords
• Full-text search
For further information, visit:
<http://www.sonicwall.com/us/support/kb.asp>
Page 42 Customer Support
Page 44

User Forums
The SonicWALL User Forums is a resource that provides users
the ability to communicate and discuss a variety of security and
appliance subject matters. Categories include:
• SSL-VPN topics
• VPN Client topics
• Continuous Data Protection topics
• Email Security topics
• Network Anti-Virus topics
• SonicPoint and Wireless topics
For further information, visit:
<https://forum.sonicwall.com/>
SonicWALL SRA 1200/4200 Getting Started Guide Page 43
Page 45

Training
SonicWALL offers an extensive sales and technical training
curriculum for Network Administrators, Security Experts and
SonicWALL Medallion Partners who need to enhance their
knowledge and maximize their investment in SonicWALL
Products and Security Applications. SonicWALL Training
provides the following resources for its customers:
• E-Training
• Instructor-Led Training
• Custom Training
• Technical Certification
• Authorized Training Partners
For further information, visit:
<http://www.sonicwall.com/us/training.html>
Page 44 Training
Page 46

Related Documentation
See the following related documents for more information:
• SonicOS SSL-VPN Administrator’s Guide
• SonicOS SSL-VPN User’s Guide
• SonicOS SSL-VPN Release Notes
• SonicOS SSL-VPN Feature Modules
• SonicOS Administrator’s Guide
• SonicOS Feature Modules
• SonicWALL GMS Administrator’s Guide
• SonicWALL ViewPoint Administrator’s Guide
• SonicWALL GAV Administrator’s Guide
• SonicWALL IPS Administrator’s Guide
• SonicWALL Anti-Spyware Administrator’s Guide
• SonicWALL Comprehensive Anti-Spam Services Guide
• SonicWALL CFS Administrator’s Guide
• SonicWALL GVC Administrator’s Guide
For further information, visit:
<http://www.sonicwall.com/us/support/289.html>
SonicWALL SRA 1200/4200 Getting Started Guide Page 45
Page 47

SonicWALL Live Product Demos
Get the most out of your appliance with the complete line of
SonicWALL products. The SonicWALL Live Demo Site provides
free test drives of SonicWALL security products and services
through interactive live product installations:
• SSL-VPN Secure Remote Access
• Unified Threat Management Platform
• Secure Cellular Wireless
• Continuous Data Protection
• Content Filtering
• Secure Wireless Solutions
• Email Security
• GMS and ViewPoint
For further information, visit:
<http://livedemo.sonicwall.com/>
Page 46 SonicWALL Live Product Demos
Page 48

SonicWALL Secure Wireless Network
Integrated Solutions Guide
Looking to go wireless? Have questions about what it takes to
build a truly “secure” wireless network? Check out the
SonicWALL Secure Wireless Network Integrated Solutions
Guide. This book is the official guide to SonicWALL’s marketleading wireless networking and security devices.
This title is available in hardcopy at fine book retailers
everywhere, or by ordering directly from Elsevier Publishing at:
<http://www.elsevier.com>
SonicWALL SRA 1200/4200 Getting Started Guide Page 47
Page 49

Page 48 SonicWALL Secure Wireless Network Integrated Solutions Guide
Page 50

Safety and Regulatory Information
In this Section:
This section provides safety and regulatory information for the SonicWALL SRA 1200/4200 appliances.
• SonicWALL SRA 1200/4200 Appliance Regulatory Statement and Safety Instructions - page 50
• Copyright Notice - page 54
• Trademarks - page 54
6
SonicWALL SRA 1200/4200 Getting Started Guide Page 49
Page 51

SonicWALL SRA 1200/4200 Appliance
Regulatory Statement and Safety
Instructions
Regulatory Model/Type Product Name
1RK23-088
1RK23-07C
This regulatory information can also be found in the electronic file,
“SonicWALL_SRA_Regulatory_Statement.pdf,” located on the
SonicWALL Web site: <
The above SonicWALL appliances are designed to be mounted in a
standard 19-inch rack mount cabinet. The following conditions are
required for proper installation:
• Use the mounting hardware recommended by the rack
manufacturer and ensure that the rack is adequate for the
application.
• Four mounting screws, compatible with the rack design, must be
used and hand tightened to ensure secure installation. Choose a
mounting location where all four mounting holes line up with those
of the mounting bars of the 19-inch rack mount cabinet.
• Mount in a location away from direct sunlight and sources of heat.
A maximum ambient temperature of 104º F (40º C).
• Route cables away from power lines, fluorescent lighting fixtures,
and sources of noise such as radios, transmitters and broadband
amplifiers.
• The included power cord is intended for use in North America only.
For European Union (EU) customers, a power cord is not included.
• Ensure that no water or excessive moisture can enter the unit.
http://www.sonicwall.com>.
SonicWALL SRA 1200
SonicWALL SRA 4200
• Allow unrestricted airflow around the unit and through the vents on
the side of the unit. A minimum of 1 inch (25.44mm) clearance is
recommended.
• Mount the SonicWALL appliances evenly in the rack in order to
prevent a hazardous condition caused by uneven mechanical
loading.
• If installed in a closed or multi-unit rack assembly, the operating
ambient temperature of the rack environment may be greater than
room ambient temperature. Therefore, consideration should be
given to installing the equipment in an environment compatible
with the maximum recommended ambient temperature shown
above.
• Consideration must be given to the connection of the equipment to
the supply circuit. The effect of overloading the circuits has
minimal impact on overcurrent protection and supply wiring.
Appropriate consideration of equipment nameplate ratings must
be used when addressing this concern.
• Reliable grounding of rack-mounted equipment must be
maintained. Particular attention must be given to power supply
connections other than direct connections to the branch circuits
such as power strips.
Lithium Battery Warning
The Lithium Battery used in the SonicWALL Internet security appliance
may not be replaced by the user. The SonicWALL must be returned to a
SonicWALL authorized service center for replacement with the same or
equivalent type recommended by the manufacturer. If, for any reason,
the battery or SonicWALL Internet security appliance must be disposed
of, do so following the battery manufacturer's instructions.
Cable Connections
All Ethernet and RS232 (Console) cables are designed for intra-building
connection to other equipment. Do not connect these ports directly to
communication wiring or other wiring that exits the building where the
SonicWALL is located.
Page 50 SonicWALL SRA 1200/4200 Appliance Regulatory Statement and Safety Instructions
Page 52

Weitere Hinweise zur Montage
Das SonicWALL Modell ist für eine Montage in einem standardmäßigen
19-Zoll-Rack konzipiert. Für eine ordnungsgemäße Montage sollten die
folgenden Hinweise beachtet werden:
• Vergewissern Sie sich, dass das Rack für dieses Gerät geeignet
ist und verwenden Sie das vom Rack-Hersteller empfohlene
Montagezubehör.
• Verwenden Sie für eine sichere Montage vier passende
Befestigungsschrauben, und ziehen Sie diese mit der Hand an.
Wählen Sie einen Ort im 19-Zoll-Rack, wo alle vier Befestigungen
der Montageschien verwendet werden.
• Wählen Sie für die Montage einen Ort, der keinem direkten
Sonnenlicht ausgesetzt ist und sich nicht in der Nähe von
Wärmequellen befindet. Die Umgebungstemperatur darf nicht
mehr als 40 °C betragen.
• Achten Sie darauf, das sich die Netzwerkkabel nicht in der
unmittelbaren Nähe von Stromleitungen, Leuchtstoffröhren und
Störquellen wie Funksendern oder Breitbandverstärkern befinden.
• Das beigefügte Netzkabel ist nur für den Gebrauch in
Nordamerikas Vorgesehen. Für Kunden in der Europaïschen
Union (EU) ist ein Netzkabel nicht im Lieferumfang enthalten.
• Stellen Sie sicher, dass das Gerät vor Wasser und höher
Luftfeuchtigkeit geschützt ist.
• Stellen Sie sicher, dass die Luft um das Gerät herum zirkulieren
kann und die Lüftungsschlitze an der Seite des Gehäuses frei
sind. Hier ist ein Belüftungsabstand von mindestens 26 mm
einzuhalten.
• Wenn das Gerät in einem geschlossenen 19”-Gehäuse oder mit
mehreren anderen Geräten eingesetzt ist, wird die Temperatur in
der Gehäuse höher sein als die Umgebungstemperatur. Achten
Sie darauf, daß die Umgebungstemperatur nicht mehr als 40 °C
beträgt.
• Bringen Sie die SonicWALL waagerecht im Rack an, um mögliche
Gefahren durch ungleiche mechanische Belastung zu vermeiden.
• Prüfen Sie den Anschluss des Geräts an die Stromversorgung,
damit der Überstromschutz sowie die elektrische Leitung nicht von
einer eventuellen Überlastung der Stromversorgung beeinflusst
werden. Prüfen Sie dabei sorgfältig die Angaben auf dem
Aufkleber des Geräts.
• Eine sichere Erdung der Geräte im Rack muss gewährleistet sein.
Insbesondere muss auf nicht direkte Anschlüsse an Stromquellen
geachtet werden wie z. B. bei Verwendung von
Mehrfachsteckdosen.
Hinweis zur Lithiumbatterie
Die in der Internet Security Appliance von SonicWALL verwendete
Lithiumbatterie darf nicht vom Benutzer ausgetauscht werden. Zum
Austauschen der Batterie muss die SonicWALL in ein von SonicWALL
autorisiertes Service-Center gebracht werden. Dort wird die Batterie
durch denselben oder entsprechenden, vom Hersteller empfohlenen
Batterietyp ersetzt. Beachten Sie bei einer Entsorgung der Batterie oder
der SonicWALL Internet Security Appliance die diesbezüglichen
Anweisungen des Herstellers.
Kabelverbindungen
Alle Ethernet- und RS232-C-Kabel eignen sich für die Verbindung von
Geräten in Innenräumen. Schließen Sie an die Anschlüsse der
SonicWALL keine Kabel an, die aus dem Gebäude in dem sich das
Gerät befindet, herausgeführt werden.
SonicWALL SRA 1200/4200 Getting Started Guide Page 51
Page 53

FCC Part 15 Class A Notice
Declaration of Conformity
NOTE: This equipment was tested and found to comply with the
limits for a Class A digital device, pursuant to Part 15 of the
FCC Rules. These limits are designed to provide reasonable
protection against harmful interference when the equipment is
operated in a commercial environment. This equipment
generates, uses, and can radiate radio frequency energy. And if
not installed and used in accordance with the instruction
manual, the device may cause harmful interference to radio
communications. Operation of this equipment in a residential
area is likely to cause harmful interference in which case the
user is required to correct the interference at his own expense.
Canadian Radio Frequency Emissions Statement
This Class A digital apparatus complies with Canadian ICES-
003. Cet appareil numérique de la classe A conforme à toute la
norme NMB-003 du Canada.
Complies with EN 55022 Class A and CISPR22 Class A
Warning: This is a class A product. In a domestic environment,
this product may cause radio interference in which case the
user may be required to take adequate measures.
Caution: Modifying this equipment or using this equipment for
purposes not shown in this manual without the written consent
of SonicWALL, Inc. could void the user's authority to operate
this equipment.
Application of council Directive 2004/108/EC (EMC) and 2006/
95/EC (LVD)
Standards to which conformity is declared
EN 55022 (2006) +A (2007) Class A
EN 55024 (1998) +A1 (2001), +A2 (2003)
EN 61000-3-2 (2006)
EN 61000-3-3 (1995) +A1 (2001), +A2 (2005)
EN 60950-1 (2006)
National Deviations: AR, AT, AU, BE, BR, CA, CH, CN, CZ, DE,
DK, FI, FR, GB, GR, HU, IL, IN, IT, JP , KE, KR, MY, NL, NO, PL,
SE, SG, SI, SK, US
Page 52 SonicWALL SRA 1200/4200 Appliance Regulatory Statement and Safety Instructions
Page 54

BMSI Statement (Class A) Regulatory Information for Korea
Ministry of Information and T elecommunication
Certification Numbers SWL-1RK23-07C and
SWL-1RK23-088
All products with country code “” (blank) and “A” are made
in the USA.
All products with country code “B” are made in China.
All products with country code “C” or “D” are made in
T aiwan R.O.C.
All certificates held by Secuwide, Corp.
SonicWALL SRA 1200/4200 Getting Started Guide Page 53
Page 55

Copyright Notice
Trademarks
© 2010 SonicWALL, Inc.
All rights reserved.
Under the copyright laws, this manual or the software described
within, can not be copied, in whole or part, without the written
consent of the manufacturer, except in the normal use of the
software to make a backup copy. The same proprietary and
copyright notices must be affixed to any permitted copies as
were affixed to the original. This exception does not allow
copies to be made for others, whether or not sold, but all of the
material purchased (with all backup copies) can be sold, given,
or loaned to another person. Under the law, copying includes
translating into another language or format.
Specifications and descriptions subject to change without
notice.
SonicWALL is a registered trademark of SonicWALL, Inc.
Microsoft Windows Vista, Windows XP, Windows 2000,
Windows NT, Windows Server 200, Internet Explorer, and
Active Directory are trademarks or registered trademarks of
Microsoft Corporation.
Netscape is a registered trademark of Netscape
Communications Corporation in the U.S. and other countries.
Netscape Navigator and Netscape Communicator are also
trademarks of Netscape Communications Corporation and may
be registered outside the U.S.
Adobe, Acrobat, and Acrobat Reader are either registered
trademarks or trademarks of Adobe Systems Incorporated in
the U.S. and/or other countries.
Firefox is a trademark of the Mozilla Foundation.
Other product and company names mentioned herein may be
trademarks and/or registered trademarks of their respective
companies and are the sole property of their respective
manufacturers.
Page 54 Copyright Notice
Page 56

Notes
SonicWALL SRA 1200/4200 Getting Started Guide Page 55
Page 57

Notes
Page 56 Notes
Page 58

SonicWALL, Inc.
2001 Logic Drive T+1408.745.9600
San Jose, CA 95124-3452 F+1408.745.9300
www.sonicwall.com
P/N 2 32-001815-50
Rev A 6/2 010
©2010SonicWALL,Inc.is aregisteredtrademarkofSonicWALL,Inc.Otherproductnamesmentionedhereinmaybetrademarksand/orregisteredtrademarks of their respective companies. Specications and descriptionssubjec t tochange without notice.
 Loading...
Loading...