Page 1

COMPREHENSIVE INTERNET SECURIT Y
SSSS SSo n i c WALL Security Ap p l i a n c e
SonicOS Standard 3.0
™
Administrator's Guide
Page 2

Chapter : Table of Content s
Table of Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . i
Preface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xi
Copyright Notice. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xi
Trademarks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xi
Limited Warranty . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xii
About this Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xiii
Organization of this Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xiv
Guide Conventions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xvi
Icons Used in this Manual . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xvi
SonicWALL Technical Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xvii
More Information on SonicWALL Products and Services . . . . . . . . . . . . . . . . . . . . . . . . . xvii
PART 1: Introduction
Chapter 1: Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3
What’s New in SonicOS Standard 3.0. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
SonicWALL Management Interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
Navigating the Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
Status Bar. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
Applying Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
Navigating Tables. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
Common Icons in the Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Getting Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7
Logging Out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Chapter 2: Basic SonicWALL Security Appliance Setup. . . . . . . . . . . . . . . . .9
Collecting Required ISP Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Internet Service Provider (ISP) Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Other Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10
Accessing the SonicWALL Security Appliance Management Interface. . . . . . . . . . . . . . . . 11
Using the SonicWALL Setup Wizard. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
SonicWALL TZ 170 SP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless. . . . . . . . . . . . . . . . . . . . 12
Configuring a Static IP Address Internet Connection. . . . . . . . . . . . . . . . . . . . . . . . . . . .12
Configuring a DHCP Internet Connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
Configuring a PPPoE Internet Connection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Configuring PPTP Internet Connectivity. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Configuring the TZ 170 SP using the Setup Wizard. . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
Configuring the TZ 50 Wireless/TZ 150 Wireless/170 Wireless using the Setup Wizard.18
Configuring the TZ 50 Wireless/TZ 150 Wireless/170 Wireless as an Office Gateway . . 18
Configuring the TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless
as a Secure Access Point. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Configuring the TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless
as a Guest Internet Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Configuring the TZ 170 Wireless as a Secure Wirele ss Bridge . . . . . . . . . . . . . . . . . . . .22
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
i
Page 3

Table of Contents
Registering Your SonicWALL Security Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Before You Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Creating a mySonicWALL.com Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Registering Your SonicWALL Security Appliance. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
PART 2: System
Chapter 3: Viewing System Status Information . . . . . . . . . . . . . . . . . . . . . . 29
System > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Wizards . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
System Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
System Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Security Services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Latest Alerts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Network Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Chapter 4: System > Licenses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
System > Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Node License Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Node License Exclusion List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Security Services Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Manage Security Services Online . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Manual Upgrade . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Manual Upgrade for Closed Environments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Chapter 5: Using System Administration . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
System > Administration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Firewall Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Name/Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Login Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Web Management Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Advanced Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Chapter 6: Setting System Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
System > Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Set Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
NTP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Chapter 7: Configuring System Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
System > Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Firmware Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
SafeMode - Rebooting the SonicWALL Security Appliance . . . . . . . . . . . . . . . . . . . . . . 49
Chapter 8: Performing Diagnostic Tests
and Restarting the SonicWALL Security Appliance51
System > Diagnostics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Tech Support Report. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Diagnostic Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Active Connections Monitor. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
CPU Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
DNS Name Lookup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Find Network Path. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Packet Trace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
ii
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 4

Ping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57
Process Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Reverse Name Resolution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
System > Restart. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
PART 3: Network
Chapter 9: Configuring Network Settings . . . . . . . . . . . . . . . . . . . . . . . . . . .61
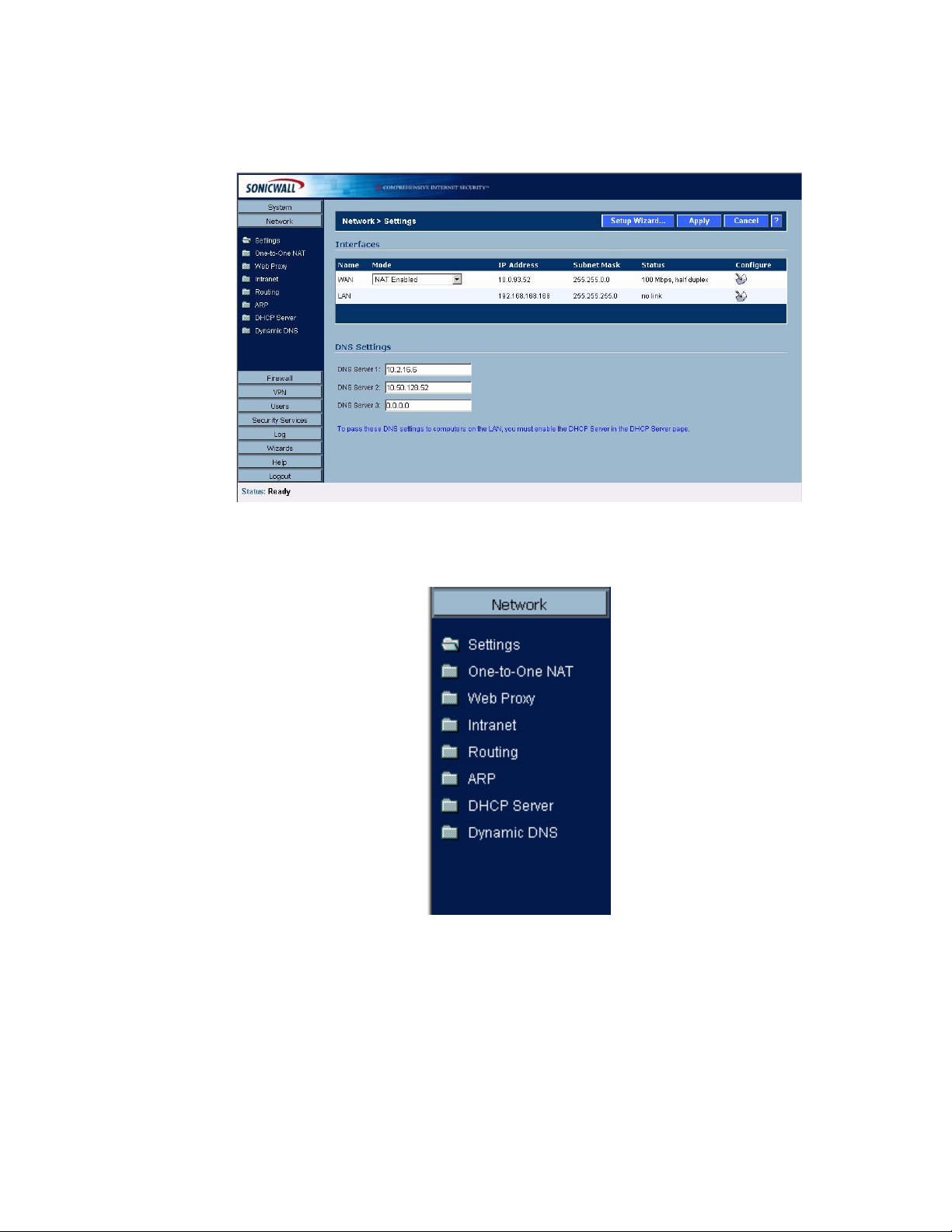
Network > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .61
Setup Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
DNS Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
Configuring the WAN Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Configuring Transparent Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Configuring NAT Enabled. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Configuring NAT with DHCP Client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Configuring NAT with PPPoE Client. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
Configuring NAT with L2TP Client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Configuring NAT with PPTP Client. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .68
Configuring Ethernet Settings in WAN Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Configuring the LAN Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Basic LAN Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Configuring Multiple LAN Subnets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Configuring Ethernet Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Configuring the OPT Interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Configuring Transparent Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Configuring NAT Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Configuring the DMZ Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Configuring Transparent Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Configuring NAT Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
Configuring the Modem Interface
(TZ 170 SP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .75
Failover. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
Advanced . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
Activating the Modem. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Configuring WLAN Properties
(TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless) . . . . . . . . . . . . . . . . . . . . . . . . . . . .79
Chapter 10:Configuring One-to-One NAT . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Network > One-to-One NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
One-to-One NAT Configuration Example. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .82
Chapter 11:Configuring Web Proxy Settings . . . . . . . . . . . . . . . . . . . . . . . . .85
Network > Web Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Configuring Automatic Web Proxy Forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Bypass Proxy Servers Upon Proxy Failure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Forward OPT/DMZ/WLAN Client Requests to Proxy Server . . . . . . . . . . . . . . . . . . . . . . 86
Chapter 12:Configuring Intranet Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . .87
Network > Intranet. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .87
Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
Intranet Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
iii
Page 5

Table of Contents
Chapter 13:Configuring Static Routes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Network > Routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Static Routes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Route Advertisement. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Routing Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Chapter 14:Configuring Address Resolution Protocol Settings. . . . . . . . . . . 93
Network > ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Static ARP Entries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Secondary Subnets with Static ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Prohibit Dynamic ARP Entries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Navigating and Sorting the ARP Cache Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Flushing the ARP Cache. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Chapter 15:Configuring the DHCP Server . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Network > DHCP Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
DHCP Server Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
DHCP Server Lease Scopes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Configuring DHCP Server for Dynamic Ranges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Configuring Static DHCP Entries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Current DHCP Leases. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Chapter 16:Configuring Dynamic DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Network > Dynamic DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Supported DDNS Providers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Configuring Dynamic DNS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Dynamic DNS Settings Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
PART 4: Modem
Chapter 17:Viewing Modem Status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Modem > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Modem Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Chapter 18:Configuring Modem Settings . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Modem > Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Configuring Profile and Modem Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Chapter 19:Configuring Modem Failover . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Modem > Failover. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Modem Failover Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Configuring Modem Failover . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Chapter 20:Configuring Advanced Modem Settings. . . . . . . . . . . . . . . . . . 117
Modem > Advanced . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Chapter 21:Configuring Modem Dialup Properties . . . . . . . . . . . . . . . . . . . 119
Modem > Dialup Profiles. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Dial-Up Profiles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Configuring a Dialup Profile. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Modem > Dialup Profiles > Modem Profile Configuration. . . . . . . . . . . . . . . . . . . . . . . . . 120
Configuring a Dialup Profile. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Chat Scripts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
iv
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 6

PART 5: Wireless
Chapter 22:Setting Up the WLAN Using the Wireless Wizard
and Monitoring Your WLAN127
Considerations for Using Wireless Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Optimal Wireless Performance Recommendations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Adjusting the TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless Antennas. . . . . . . . . . 129
Wireless Guest Services (WGS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Wireless Node Count Enforcement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .130
MAC Filter List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .130
WiFiSec Enforcement. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Using the Wireless Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Wireless > Status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .135
WLAN Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
WLAN Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Station Status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Chapter 23:Configuring Wireless Settings . . . . . . . . . . . . . . . . . . . . . . . . . .139
Wireless > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Wireless Radio Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Wireless Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .140
Secure Wireless Bridging (TZ 170 Only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .141
Configuring a Secure Wireless Bridge . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Chapter 24:Configuring WEP and WPA Encryption. . . . . . . . . . . . . . . . . . .147
Wireless > WEP/WPA Encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .147
WEP Encryption Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
WEP Encryption Keys . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
WPA Encryption Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Chapter 25:Configuring Advanced Wireless Settings. . . . . . . . . . . . . . . . . .151
Wireless > Advanced. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Beaconing & SSID Controls. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Wireless Client Communications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Advanced Radio Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .152
Chapter 26:Configuring the MAC Filter List . . . . . . . . . . . . . . . . . . . . . . . . .155
Wireless > MAC Filter List. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .155
Chapter 27:Configuring Wireless IDS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .157
Wireless > IDS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .157
PART 6: Wireless Guest Services
Chapter 28:Viewing Wireless Guest Services Status. . . . . . . . . . . . . . . . . .163
WGS > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .163
Chapter 29:Configuring Wireless Guest Services . . . . . . . . . . . . . . . . . . . .165
WGS > Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .165
Bypass Guest Authentication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .166
Bypass Filters for Guest Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Enable Dynamic Address Translation (DAT) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .166
Enable SMTP Redirect. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Enable URL Allow List for Authenticated Users. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .167
Enable IP Address Deny List for Authenticated Users. . . . . . . . . . . . . . . . . . . . . . . . . . 167
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
v
Page 7

Table of Contents
Customize Login Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
Custom Post Authentication Redirect Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Maximum Concurrent Guests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
WGS Account Profiles. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Chapter 30:Managing Wireless Guest Accounts . . . . . . . . . . . . . . . . . . . . 171
WGS > Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Working with Guest Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Automatically Generating Guest Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
Manually Configuring Wireless Guests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Flexible Default Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Secure Access Point with Wireless Guest Services . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
PART 7: Firewall
Chapter 31:Configuring Network Access Rules . . . . . . . . . . . . . . . . . . . . . 179
Network Access Rules Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Using Bandwidth Management with Access Rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Firewall > Access Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Restoring Default Network Access Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Adding Rules using the Network Access Rule Wizard . . . . . . . . . . . . . . . . . . . . . . . . . 181
Configuring a Public Server Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Configuring a General Network Access Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
Adding Rules Using the Add Rule Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
Rule Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Chapter 32:Configuring Advanced Rule Options . . . . . . . . . . . . . . . . . . . . 189
Access Rules > Advanced . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
Windows Networking (NetBIOS) Broadcast Pass Through. . . . . . . . . . . . . . . . . . . . . . 189
Detection Prevention . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Source Routed Packets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
TCP Connection Inactivity Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
TCP Checksum Validation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Access Rule Service Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Chapter 33:Configuring Custom Services. . . . . . . . . . . . . . . . . . . . . . . . . . 191
Firewall > Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
User Defined (Custom) Services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Predefined Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Chapter 34:Configuring VoIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Firewall > VoIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
VoIP Protocols. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Configuring the VoIP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Chapter 35:Monitoring Active Firewall Connections . . . . . . . . . . . . . . . . . . 197
Firewall > Connections Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
Setting Filter Logic. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
Using Group Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
PART 8: VPN
Chapter 36:Configuring VPN Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
SonicWALL VPN Options Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
vi
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 8

VPN > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .202
VPN Global Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .202
VPN Policies. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .202
Currently Active VPN Tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Configuring GroupVPN Policy on the SonicWALL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .203
Configuring IKE Preshared Secret. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Configuring GroupVPN with IKE 3rd Party Certificates . . . . . . . . . . . . . . . . . . . . . . . . . 208
Export a GroupVPN Client Policy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Site to Site VPN Configurations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Site-to-Site VPN Deployments. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
VPN Planning Sheet for Site-to-Site VPN Policies. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 214
Configuring Site to Site VPN Policies Using the
VPN Policy Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .215
Creating a Typical IKE Preshared Secret VPN Policy . . . . . . . . . . . . . . . . . . . . . . . . . .216
Creating a Custom VPN Policy IKE with Preshared Secret . . . . . . . . . . . . . . . . . . . . . .217
Creating a Manual Key VPN Policy with the VPN Policy Wizard. . . . . . . . . . . . . . . . . . 218
Configuring IKE 3rd Party Certificates with the VPN Policy Wizard. . . . . . . . . . . . . . . . 219
Creating Site-to-Site VPN Policies Using the VPN Policy Window . . . . . . . . . . . . . . . . 220
Chapter 37:Configuring Advanced VPN Settings. . . . . . . . . . . . . . . . . . . . .229
VPN > Advanced. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .229
Advanced VPN Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .229
VPN User Authentication Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
VPN Bandwidth Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Chapter 38:Configuring DHCP Over VPN . . . . . . . . . . . . . . . . . . . . . . . . . .233
VPN > DHCP over VPN. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
DHCP Relay Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
Configuring the Central Gateway for DHCP Over VPN . . . . . . . . . . . . . . . . . . . . . . . . . 234
Configuring DHCP over VPN Remote Gateway. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .235
Device Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Current DHCP over VPN Leases. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Chapter 39:Configuring L2TP Server Settings. . . . . . . . . . . . . . . . . . . . . . .237
VPN > L2TP Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .237
L2TP Server Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .238
IP Address Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Adding L2TP Clients to the SonicWALL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .238
Currently Active L2TP Sessions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .239
Chapter 40:Managing Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .241
Digital Certificates Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .241
SonicWALL Third-Party Digital Certificate Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
VPN > Local Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .242
Importing Certificate with Private Key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Certificate Details. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .242
Generating a Certificate Signing Request . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
VPN > CA Certificates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .244
Importing CA Certificates into the SonicWALL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
Certificate Details. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .244
Certificate Revocation List (CRL). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .245
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
vii
Page 9

Table of Contents
PART 9: Users
Chapter 41:Viewing User Status and Configuring User Authentication. . . . 249
User Level Authentication Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
Users > Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
Active User Sessions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
Users > Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
Authentication Method. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
Global User Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
Internet Authentication Exclusions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
Acceptable Use Policy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Configuring RADIUS Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
Chapter 42:Configuring Local Users. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Users > Local Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Adding a Local User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
PART 10: Security Services
Chapter 43:Managing SonicWALL Security Services. . . . . . . . . . . . . . . . . 261
SonicWALL Security Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
mySonicWALL.com. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
Activating Free Trials. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
Security Services > Summary. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Security Services Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Manage Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
If Your SonicWALL Security Appliance is Not Registered. . . . . . . . . . . . . . . . . . . . . . . 264
Security Services Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Security Services Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Chapter 44:Configuring SonicWALL Content Filtering Service. . . . . . . . . . 265
SonicWALL Content Filtering Service. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Security Services > Content Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Content Filter Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Activating SonicWALL Content Filtering Service. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Activating a SonicWALL Content Filtering Service
FREE TRIAL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Content Filter Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Restrict Web Features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Trusted Domains. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 269
Message to Display when Blocking. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 269
Configuring SonicWALL Filter Properties. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 269
Custom List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271
Consent. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 272
Mandatory Filtered IP Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Chapter 45:Managing SonicWALL Network Anti-Virus and E-Mail Filter Services275
SonicWALL Network Anti-Virus Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Security Services > Anti-Virus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Activating SonicWALL Network Anti-Virus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Activating a SonicWALL Network Anti-Virus FREE TRIAL . . . . . . . . . . . . . . . . . . . . . . 277
Security Services > E-Mail Filter. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 278
viii
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 10

Configuring SonicWALL Network
Anti-Virus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .278
Chapter 46:Managing SonicWALL Gateway Anti-Virus Service. . . . . . . . . .279
SonicWALL Gateway Anti-Virus Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
Configuring SonicWALL Gateway
Anti-Virus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .283
Chapter 47:Managing SonicWALL Intrusion Prevention Service . . . . . . . . .285
SonicWALL Intrusion Prevention Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .285
SonicWALL IPS Features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .285
SonicWALL Deep Packet Inspection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 286
How SonicWALL’s Deep Packet Inspection Architecture Works . . . . . . . . . . . . . . . . . .287
Security Services > Intrusion Prevention. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .288
Activating SonicWALL IPS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .288
Activating the SonicWALL IPS FREE TRIAL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .289
Chapter 48:Managing SonicWALL Global Security Client . . . . . . . . . . . . . .291
SonicWALL Global Security Client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291
Global Security Client Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .292
How SonicWALL Global Security Client Works . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
SonicWALL Global Security Client Activation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .292
Activating SonicWALL Global Security Client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .293
PART 11: Log
Chapter 49:Viewing Log Events. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .297
SonicOS Log Event Messages Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .297
Log > View. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 298
Navigating and Sorting Log View Table Entries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 298
SonicOS Log Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
Chapter 50:Specifying Log Categories. . . . . . . . . . . . . . . . . . . . . . . . . . . . .301
Log > Categories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .301
Log Categories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 301
Alerts & SNMP Traps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .302
Chapter 51:Configuring Log Automation . . . . . . . . . . . . . . . . . . . . . . . . . . .303
Log > Automation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
E-mail. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .304
Syslog Servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .304
Chapter 52:Configuring Name Resolution . . . . . . . . . . . . . . . . . . . . . . . . . .307
Log > Name Resolution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .307
Selecting Name Resolution Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 308
Specifying the DNS Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 308
Chapter 53:Generating and Viewing Log Reports . . . . . . . . . . . . . . . . . . . .309
Log > Reports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .309
Data Collection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
View Data. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .310
Log > ViewPoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .311
SonicWALL ViewPoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 311
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
ix
Page 11

Table of Contents
Appendix A:Using the SonicSetup Diagnostic and Recovery Tool . . . . . . . 313
SonicSetup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 313
Introduction and Discovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 314
Device Selection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 314
Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315
Diagnostic Results. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 316
SonicROM Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 316
SonicOS Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 317
Restoring Factory Defaults . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 318
Address Synchronization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 319
Appendix B:Resetting the SonicWALL Security Appliance Using SafeMode321
SonicWALL SafeMode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 321
Upgrading SonicOS Firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 323
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 325
x
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 12

Copyright Notice
© 2004 SonicWALL, Inc.
All rights reserved.
Under the copyright laws, this manual or the software described within, can no t be copied, in whole or
part, without the written consent of the manufacturer, except in the normal use of the software to
make a backup copy. The same proprietary and copyright notices must be affixed to any permitted
copies as were affixed to the original. This exception does not allow copies to be made for others,
whether or not sold, but all of the material purchased (with all backup copies) can be sold, given, or
loaned to another person. Under the law, copying includes translatin g into another language or
format.
Preface
Chapter :
Chapter :
Specifications and descriptions subject to change without notice.
Trademarks
SonicWALL is a registered trademark of SonicWALL, Inc.
Microsoft Windows 98, Windows NT, Windows 2000, Windows XP, Windows Server 2003, Internet
Explorer, and Active Directory are trademarks or registered trademarks of Microsoft Corporation.
Netscape is a registered trademark of Netscape Communications Corporation in the U.S. and other
countries. Netscape Navigator and Netscape Communicator are also trademarks of Netscape
Communications Corporation and may be registered outside the U.S.
Adobe, Acrobat, and Acrobat Reader are either registered trademarks or trademarks of Adobe
Systems Incorporated in the U.S. and/or other countries.
Other product and company names mentioned herein may be trademarks and/or registered
trademarks of their respective companies and are the sole prope rty of their respective manufacture rs.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
xi
Page 13

Preface
Limited Warranty
SonicWALL, Inc. warrants that commencing from the delivery date to Customer (but in any case
commencing not more than ninety (90) days after the original shipment by SonicWALL), and
continuing for a period of twelve (12) months, that the product will be free from defects in materials
and workmanship under normal use. This Limited War ra nty is not transferable and applie s only to the
original end user of the product. SonicWALL and its suppliers' entire liability and Customer's sole and
exclusive remedy under this limited warranty will be shipment of a replacement product. At
SonicWALL's discretion the replacement product may be of eq ual or g rea ter fu nctiona lity and may be
of either new or like-new quality. SonicWALL's obligations under this warranty ar e contingent upon the
return of the defective product according to the terms of SonicWALL's then-current Support Services
policies.
This warranty does not apply if the product has been subjected to abnormal electrical stress,
damaged by accident, abuse, misuse or misapplication, or has been modified without the written
permission of SonicWALL.
DISCLAIMER OF WARRANTY. EXCEPT AS SPECIFIED IN THIS WARRANTY, ALL EXPRESS OR
IMPLIED CONDITIONS, REPRESENTATIONS, AND WARRANTIES INCLUDING, WITHOUT
LIMITATION, ANY IMPLIED WARRANTY OR CONDITION OF MERCHANTABILITY, FITNESS FOR
A PARTICULAR PURPOSE, NONINFRINGEMENT, SATISFACTORY QUALITY OR ARISING
FROM A COURSE OF DEALING, LAW, USAGE, OR TRADE PRACTICE, ARE HEREBY
EXCLUDED TO THE MAXIMUM EXTENT ALLOWED BY APPLICABLE LAW. TO THE EXTENT AN
IMPLIED WARRANTY CANNOT BE EXCLUDED, SUCH WARRANTY IS LIMITED IN DURATION
TO THE WARRANTY PERIOD. BECAUSE SOME STATES OR JURISDICTIONS DO NOT ALLOW
LIMITATIONS ON HOW LONG AN IMPLIED WARRANTY LASTS, THE ABOVE LIMITATION MAY
NOT APPLY TO YOU. THIS WARRANTY GIVES YOU SPECIFIC LEGAL RIGHTS, AND YOU MAY
ALSO HAVE OTHER RIGHTS WHICH VARY FROM JURISDICTION TO JURISDICTION. This
disclaimer and exclusion shall apply even if the express warranty set forth above fails of its essential
purpose.
DISCLAIMER OF LIABILITY. SONICWALL'S SOLE LIABILITY IS THE SHIPMENT OF A
REPLACEMENT PRODUCT AS DESCRIBED IN THE ABOVE LIMITED WARRANTY. IN NO EVENT
SHALL SONICWALL OR ITS SUPPLIERS BE LIABLE FOR ANY DAMAGES WHATSOEVER,
INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF PROFITS, BUSINESS
INTERRUPTION, LOSS OF INFORMATION, OR OTHER PECUNIARY LOSS ARISING OUT OF
THE USE OR INABILITY TO USE THE PRODUCT, OR FOR SPECIAL, INDIRECT,
CONSEQUENTIAL, INCIDENTAL, OR PUNITIVE DAMAGES HOWEVER CAUSED AND
REGARDLESS OF THE THEORY OF LIABILITY ARISING OUT OF THE USE OF OR INABILITY TO
USE HARDWARE OR SOFTWARE EVEN IF SONICWALL OR ITS SUPPLIERS HAVE BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. In no event shall SonicWALL or its suppliers'
liability to Customer, whether in contract, tort (including negligence), or otherwise, exceed the price
paid by Customer. The foregoing limitations shall apply even if the above-stated warranty fails of its
essential purpose. BECAUSE SOME STATES OR JURISDICTIONS DO NOT ALLOW LIMITATION
OR EXCLUSION OF CONSEQUENTIAL OR INCIDENTAL DAMAGES, THE ABOVE LIMITATION
MAY NOT APPLY TO YOU.
xii
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 14

About this Guide
Welcome to the SonicWALL SonicOS Standard 3.0 Administrator’s Guide. This manual provides the
information you need to successfully activate, configure, and administer SonicOS Standard 3.0 on the
following SonicWALL security appliance:
SonicWALL TZ 50
SonicWALL TZ 50 Wireless
SonicWALL TZ 150
SonicWALL TZ 150 Wireless
SonicWALL TZ 170
SonicWALL TZ 170 SP
SonicWALL TZ 170 Wireless
SonicWALL PRO 1260
SonicWALL PRO 2040
SonicWALL PRO 3060
Note: For the latest version of this manual as well as other SonicWALL product documentation, refer
to <http//:www.sonicwall.com/services/documentation.html>.
About this Guide
9
Tip: The Getting Start Guide for your SonicWALL security appliance provides instructions for
installing and configuring your SonicWALL security appliance for connecting your network through the
SonicWALL security appliance for secure Internet connectivity.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
xiii
Page 15

Preface
Organization of this Guide
The SonicOS Standard 3.0 Administrator’s Guide organization is structured into the following parts
that parallel the top-level menu items of SonicWALL Web-based mana gement in terface. Within thes e
parts, individual chapters correspond to the specific configuration pages listed as submenu items in
the management interface.
Part 1 Introduction
This part provides an overview of the SonicWALL management interface conventions, explains how
to get your network securely connected to the Internet with the SonicWALL security appliance using
the Setup Wizard, and registering your SonicW AL L sec ur ity ap plia n ce .
Part 2 System
This part covers the configuration of a variety SonicWALL security appliance controls for managing
system status information, registering the SonicWALL security appliance, activating and managing
SonicWALL Security Services licenses, configuring SonicWALL security appliance local and remote
management options, managing firmware versions and preferences, and using included diagnostics
tools for troubleshooting.
Part 3 Network
This part provides instructions for configuring the SonicWALL security appliance for your network
environment. It explains configuring network interface settings manually, setting up a DHCP server,
configuring the Web proxy requests to a network proxy server, configuring static routes and ARP
settings, and configuring dynamic DNS.
Part 4 Modem (TZ 170 SP)
This part explains how to configure the SonicWALL TZ 170 SP’s built-in mo dem for use as the pr imary
Internet connection or as a dial-up failover for the primary broadband Internet connection.
Part 5 Wireless (TZ 150 Wireless/TZ 170 Wireless)
This part explains how to set up the SonicWALL TZ 150 Wireless/TZ 170 Wir eless for secure WiFiSec
or WEP/WPA Internet access, configure wireless intrusion detection settings, and configure wireless
clients for secure wireless and remote access via the SonicWALl Global VPN Client.
Part 6 Wireless Guest Services (TZ 150 Wireless/TZ 170 Wireless)
This part explains how configure wireless guest accounts for th e SonicWALL TZ 150 Wireless/TZ 170
Wireless to securely support wireless network guests.
Part 7 Firewall
This part explains how to configure and manage firewall access po licies to deny o r pe rm it traf fic, how
to configure Voice over IP (VoIP) traffic to pass through, and monitor active firewall connections.
Part 8 VPN
This part covers how to create VPN policies on the SonicWALL security appliance to support
SonicWALL Global VPN Clients for remote client access, as well as site-to-site VPN policies for
connecting Loans between offices running SonicWALL security appliances.
xiv
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 16

Part 9 Users
This part explains how to create and manage a user database on the So nicWALL secu rity ap plian ce.
and how to integrate the SonicWALL security appliance with a RADIUS server for user auth entication.
Part 10 Security Services
This part includes an overview of optional SonicWALL security services. When combined with
network security features of the SonicWALL security appliance, these services provide
comprehensive protection against a wid e rang e of thre a ts, inc l ud in g viru se s, wo rm s, Tr o jan s,
spyware, peer-to-peer and instant mess ag in g ap plic atio n exp loits , ma licio us co de , an d ina p pr opria te
or unproductive web sites.
These subscription-based services include SonicWALL Content Filtering Service, SonicWALL
Network Anti-Virus, Gateway Anti-Virus, SonicWALL Intrusion Prevention Service, and SonicWALL
Global Security Client. FREE trials of many of these these securit y service s ubscriptions are available
after you register your SonicWALL security appliance.
Part 11 Log
This part covers managing the SonicWALL security appliance’s enhanced logging, alerting, and
reporting features. The SonicWALL security appliance’s logging features provide a comprehensive
set of log categories for monitoring security and network activities.
About this Guide
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
xv
Page 17

Preface
Guide Conventions
The following Conventions used in this guide are as follows:
Convention Use
Bold Highlights items you can select on the SonicWALL
management interface.
Italic Highlights a value to enter into a field. For example, “type
192.168.168.168 in the IP Address field.”
Menu Item > Menu Item Indicates a multiple step management interface menu
choice. For example, Security Services > Content Filter
means select Security Services, then select Content
Filter.
Icons Used in this Manual
These special messages refer to noteworthy information, and include a symbol for quick identification:
Alert: Important information that cautions about features affecting firewall performance, security
S
features, or causing potential problems with your SonicWALL security appliance.
9
Â
Tip: Useful information about security features and configurations on your SonicWALL security
appliance.
Note: Important information on a feature that requires callout for special attention.
Cross Reference: Pointer to related or more detailed information on the topic.
xvi
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 18

SonicWALL Technical Support
For timely resolution of technical support questions, visit SonicWALL on the Internet at
<http://www.sonicwall.com/services/support.html>. Web-based resources are available to help you
resolve most technical issues or contact SonicWALL Technical Support.
To contact SonicWALL telephone support, see the telephone numbers listed below:
North America Telephone Support
U.S./Canada - 888.777.1476 or +1 408.752.7819
International Telephone Support
Australia - + 1800.35.1642
Austria - + 43(0)820.400.105
EMEA - +31(0)411.617.810
France - + 33(0)1.4933.7414
SonicWALL Technical Support
Germany - + 49(0)1805.0800.22
Hong Kong - + 1.800.93.0997
India - + 8026556828
Italy - +39.02.7541.9803
Japan - + 81(0)3.5460.5356
New Zealand - + 0800.446489
Singapore - + 800.110.1441
Spain - + 34(0)9137.53035
Switzerland - +41.1.308.3.977
UK - +44(0)1344.668.484
Note: Please visit <http://www.sonicwall.com/services/contact.html> for the latest technical support
telephone numbers.
More Information on SonicWALL Products
and Services
Contact SonicWALL, Inc. for information about SonicWALL products and services at:
Web: http://www.sonicwall.com
E-mail: sales@sonicwall.com
Phone: (408) 745-9600
Fax: (408) 745-9300
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
xvii
Page 19
Preface
Current Documentation
Check the SonicWALL documentation Web site for that latest versions
of this manual and all other SonicWALL product documentation.
http://www.sonicwall.com/services/documentation.html
xviii
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 20

P
ART
1
Part 1Introduction
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
1
Page 21

2
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 22

C
HAPTER
Chapter 1: Introduction
What’s New in SonicOS Standard 3.0
• Real-time Gateway Anti Virus (GAV) - Provides per packet virus scanning using a Deep Packet
Inspection version 2.0 engine. The Real-time GAV feature provides over 4,500 signatures on the SonicWALL TZ series security appliances and over 24,000 signatures on the SonicWALL PRO series
governing gateway appliances. The Real-time GAV feature supports zip and gzip data compression.
The Real-time GAV feature supports scanning the following message delivery protocols:
HyperText Transport Protocol (HTTP)
Simple Mail Transfer Protocol (SMTP)
Internet Message Access Protocol (IMAP)
Post Office Protocol 3 (POP3)
File Transfer Protocol (FTP)
Transmission Control Protocol (TCP) packet streams
• IPS 2.0 - Includes an updated Data Packet Inspection (DPI) engine that powers Intrusion Prevention
Services (IPS) and GAV. The IPS version 2.0 engine includes the following feature enhancements:
IP Fragmentation - Provides the ability to either disallow IP fragments or to reassemble IP
fragments for full application layer inspection.
Checksum Validation - Provides the ability to detect and prevent invalid IP, ICMP, TCP, and
UDP checksums.
Global IP Exclusion List - Provides the ability to configure a range of IP addresses to exclude
specified network traffic from IPS evaluation.
Log Redundancy - Provides the ability to configure per-category and per-signature log
redundancy filter settings.
Dynamic Categorization - Groups and displays signatures automatically in expandable category
views. Category maintenance is performed through automated signature updates.
• Enhanced VoIP Support - Adds comprehensive support for third-party VoIP equipment, including
products from Cisco, Mitel, Pingtel, Grandstream, Polycom, D-Link, Pulver, Apple iChat, and softphones from Yahoo, Microsoft, Ubiquity, and OpenPhone. Enhanced VoIP support adds the ability to
handle SIP, H.323v1, H.323v2, H.323v3, and H.323v4. The internal DHCP Server capability in SonicOS Standard 2.6 allows any SIP endpoint to receive addressing information into the DHCP scope
information, this enables any SIP endpoint to receive SIP Proxy addresses when they issue a DHCP
request on the network.
1
3
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 23

C
HAPTER
1:
Introduction
Note: Registration Admission Status (RAS) and Internet Locator Service (ILS) LDAP for H.323 is not
supported on SonicOS Standard 3.0. For H.323 RAS and ILS LDAP support on the SonicWALL TZ
170 Series, upgrade your firmware to SonicOS Enhanced 3.0 (or greater). For H.323 RAS and ILS
LDAP support on the SonicWALL PRO 2040 or SonicWALL PRO 3060, upgrade your firmware to
SonicOS Enhanced 2.5 (or greater).
• Dynamic DNS - Enables the SonicWAL L security device to dynamically register its WAN IP
address with a Dynamic Domain Name Server (DDNS) service prov ide r.
• Lightweight Hotspot Messaging - Pr ovide s Hotspot users authentication between a SonicW ALL
wireless access device (such as a SonicWALL TZ 170 Wireless, or a SonicPoint with a SonicWALL PRO series governing gateway appliance) and an Authentication Back-End (ABE) for parametrically bound network access.
• Wireless Radio Operating Schedule - Provides the ability to create a schedule to control the
operation of the wireless radio for SonicWALL wireless access devices (such as the SonicWALL
TZ 170 Wireless or SonicPoint).
• WiFiSec Exception List - Provides wireless users the flexibility to bypass WiFiSec enforcement.
The WiFiSec Exception List enables you to allow NT Domain logons to occur prior to Global VPN
Client (GVC) tunnel establishment.
• Real-time Monitoring - Includes the following monitoring tools:
CPU Monitor allows you to generate CPU utilization reports in a customizable histogram
format.
Process Monitor allows you to generate reports on current running process es .
Active Connections Monitor allows you to generate reports on current active network
connections.
• DHCP Server Enhancements - Includes expanded hash tables for resource management, accelerated duplicate-address detection, and improved Dynamic Host Config uration Protocol (DHCP)
Server internal-database maintenance management.
• Expanded Logging - Includes additional logging capabilities to provide expanded flexibility. You
can export the log into plain text or CSV values. Logging categories are dramatically expanded,
the logs conform to Syslog severity levels so you can set the SonicWALL security appliance to only
log alerts and messages of specified levels. And you can independently specify which categories
are logged to the internal log. When dire cting logs to external Syslog servers, you can rate -limit the
messages based on events-per-second or maximum bytes-per-second, so that external Syslog
servers do not become overwhelmed.
• Static ARP Support - Enables you to create static Address Resolution Protocol (ARP) entries,
create MAC address to IP address bindings, and to publish static ARP entries for use in a secondary network subnet.
• Virtual Adapter St atic IP Support - Provides support for static IP addr essing of Global VPN Client
(GVC) virtual adapters.
SonicWALL Management Interface
The SonicWALL security appliance’s Web-based management interface provides a easy-to-use
graphical interface for configuring your SonicWALL security appliance. The following provides an
overview of the key management interface objects.
4
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 24
Navigating the Management Interface
Navigating the SonicWALL management interface includes a hierarchy of menu buttons on the
navigation bar (left side of your browser window).
SonicWALL Management Interface
When you click a menu button, related manage ment functions are displayed as submenu items in th e
navigation bar.
To navigate to a submenu page, click the link. When you click a menu button, the first submenu item
page is displayed. The first submenu page is automatically displaye d when you click the menu button.
For example, when you click the Network button, the Network > Settings page is displayed.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
5
Page 25
C
HAPTER
1:
Introduction
Status Bar
The Status bar at the bottom of the management interface window displays the status of actions
executed in the SonicWALL management interface.
Applying Changes
Click the Apply button at the top right corner of the SonicWALL management interface to save any
configuration changes you made on the page.
If the settings are contained in a secondary window within the management interface, when you click
OK, the settings are automatically applied to the SonicWALL security appliance.
Navigating Tables
Navigate tables in the management interface with large number of entries by using the navigation
buttons located on the upper right top corner of the table.
6
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 26

SonicWALL Management Interface
The table navigation bar includes buttons for moving through table pages.
Common Icons in the Management Interface
The following describe the functions of common icons used in the SonicWALL mana gement interface:
Clicking on the edit icon displays a window for editing the settings.
Clicking on the delete icon deletes a table entry
Moving the pointer over the comment icon displays text from a Comment field entry.
Getting Help
Each SonicWALL security appliance includes Web-based on-line help av ailable from the
management interface.
Clicking the question mark ? button on the top-right corner of every page accesses the
context-sensitive help for the page.
Alert: Accessing the SonicWALL security appliance online help requires an active Internet
S
connection.
Logging Out
The Logout button at the bottom of the menu bar terminates the management interface session and
displays the authentication page for logging into the SonicWALL security appliance.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
7
Page 27

C
HAPTER
1:
Introduction
8
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 28

Chapter 2: Basic SonicWALL Security
Appliance Setup
SonicWALL Security Appliance Configuration Steps
C
HAPTER
2
The chapter provides instructions for basic installation of the SonicWALL security appliance running
SonicOS Standard 3.0. After you complete this chapter, computers on your LAN will have secure Internet
Internet access.
• “Collecting Required ISP Information” on page 9
• “Accessing the SonicWALL Security Appliance Management Interface” on page 11
• “Using the SonicWALL Setup Wizard” on page 11
• “Registering Your SonicWALL Security Appliance” on page 24
Collecting Required ISP Information
Before you configure your SonicWALL security appliance for Internet connectivity for your computers,
make sure you have any information required for your type of Internet connection available.
Internet Service Provider (ISP) Information
If You Have a Cable Modem
Your ISP is probably using DHCP to dynamically assign an address to your computer.
You do not need any Internet connection information.
9
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 29
C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
If You Have DSL
Your ISP is probably using PPPoE to dynamically authenticate your login and assign an address to
your computer. You will need:
User Name:
Note: Your ISP may require your user name to include the “@” symbol and the domain name, for
example, “Joe@sonicwall.com”
Password:
If You Have a Static IP Address
Your ISP may have assigned you a static IP address for your computer. If so, the paperwork or e-mail
confirmation from your ISP should contain the following configuration information:
IP Address:
Subnet Mask:
Default Gateway:
Primary DNS:
Secondary DNS (optional):
If Your ISP Provided You With a Server IP Address, User Name, and Password
Your ISP may be using PPTP to establish a secure connection between your computer and a server.
You will need:
Server Address:
User Name:
Password:
If you are unsure what kind of connection you have, the paperwork or e-mail confirmation message
from your ISP should contain the information. If you cannot find the information, you can rely on the
SonicWALL security appliance to automatically detect the correct settings during setup.
Other Information
SonicWALL Management Interface
To access the SonicWALL security appliance Web-based management interface. These are the
default settings, which you can change:
User Name:
Password: password
Note: If you are not using one of the network configurations above, refer to Chapter 3, Configuring
Network Settings.
admin
10
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 30

Accessing the SonicWALL Security Appliance Management Interface
Accessing the SonicWALL Security
Appliance Management Interface
To access the Web-based management interf ace of the SonicWALL security appliance:
1
On the computer you have connected to a network port, start your Web browser.
Alert: Your Web browser must support Java and HTTP uploads. Internet Explorer 5.0 or higher or
S
9
Netscape Navigator 4.7 or higher are recommended.
2
Enter 192.168.168.168 in the Location or Address field. The first time you access the
SonicWALL management interface, the SonicWALL Setup Wizard launches and guides you
through the configuration and setup of your SonicWALL security appliance.
3
If the Setup Wizard does not display, the System > Status page is displayed. Click the Setup
Wizard button on the Network > Settings page.
4
Proceed to one of the following configuration options for your type of Internet connection:
• “Configuring a Static IP Address Internet Connection” on page 12
• “Configuring a DHCP Internet Connection” on page 14
• “Configuring a PPPoE Internet Connection” on page 14
• “Configuring PPTP Internet Connectivity” on page 15
Tip: If you do not know what kind of Internet connection you have, the SonicWALL Setup Wizard will
attempt to detect your connection settings.
Using the SonicWALL Setup Wizard
The SonicWALL Setup Wizard provides user-guided instructions for configuring your SonicWALL
security appliance. If the Setup Wizard does not launch when yo u access the management interface,
you can launch the Setup Wizard using one of the following methods:
• Select the Network > Settings and then click on the Setup Wizard button.
• Select the System > Status page and then click the Wizards button. The SonicWALL
Configuration Wizard is displayed. Select Setup Wizard and click Next.
•Select Wizards on the left-navigation bar. The SonicWALL Configuration Wizard is displayed.
Select Setup Wizard and click Next.
Note: Make sure you have any required ISP information to complete the configuration before using
9
SonicWALL TZ 170 SP
the Setup Wizard.
Tip: You can also configure all your WAN and network settings on the Network > Settings page of
the SonicWALL management interface.
If you are configuring the SonicWALL TZ 70 SP, the Setup Wizard includes two additional modem
configuration pages for configuring the modem as the primary WAN connection or as a failover for the
primary Internet connection. See “Configuring the TZ 170 SP using the Setup Wizard” on page 17.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
11
Page 31
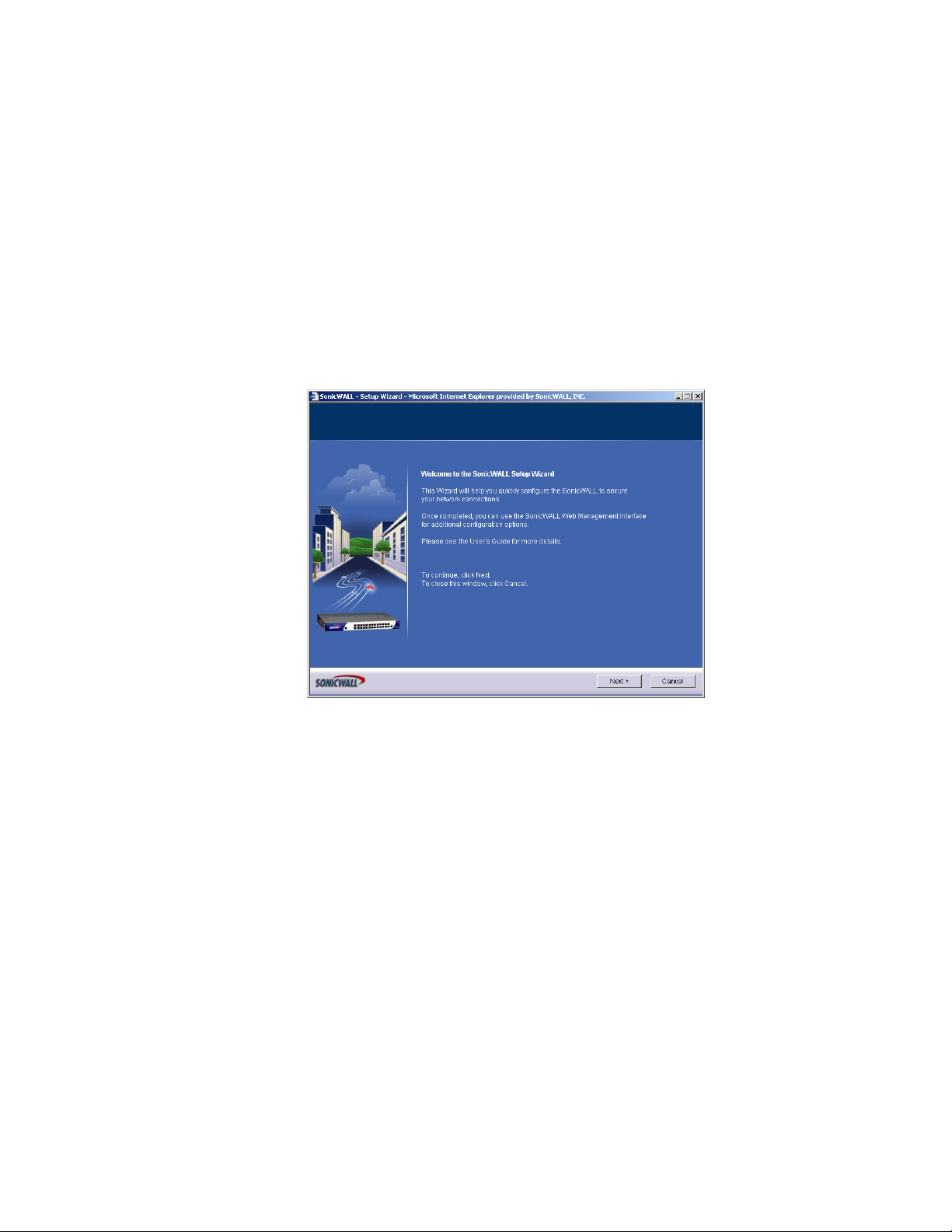
C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170
Wireless
If you are configuring the SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 70 Wireless, the Setup
Wizard includes additional modem configuration pages for configuring the WLAN interface and
setting up WiFISec security.
Configuring a Static IP Address Internet Connection
If you are assigned a single IP address by your ISP, perform the instructions below.
Tip: Be sure to have your network information including your WAN IP address, subnet mask, and
9:
DNS settings ready. This information is obtained from your ISP.
1
Click the Setup Wizard button on the Network > Settings page. The Welcome to the
SonicWALL Setup Wizard page is displayed. Click Next.
12
2
To set the password, enter a new password in the New Password and Confirm New Password
fields. Click Next.
Note: Remember your password. You will need it to access the SonicWALL security appliance
management interface after the initial configuration.
3
Select your local time zone from the Time Zone menu. Click Next.
Note: Set the time zone correctly before you register your SonicWALL security appliance.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 32

Using the SonicWALL Setup Wizard
4
Choose Static IP and click Next.
5
Enter the information provided by your ISP in the following fields: SonicWALL WAN IP Address,
WAN Subnet Mask, WAN Gateway (Router) Address, and DNS Server Addresses. Click Next.
6
The LAN Settings page allows the configuration of the SonicWALL LAN IP Addresses and the
LAN Subnet Mask. The SonicWALL LAN IP Addresses are the private IP address assigned to
the LAN port of the SonicWALL security appliance. The LAN Subn et Mask defines the range o f IP
addresses on the LAN. The default values provided by the SonicWALL security appliance work for
most networks. If you do not use the default settings, enter your preferred private IP address and
subnet mask in the fields.
7
Click Next. The LAN DHCP Server page configures the SonicWALL security appliance DHCP
Server. If enabled, the SonicWALL security appliance automatically configures the IP settings of
computers on the LAN. To enable the DHCP server, select Enable DHCP Server, and specify the
range of IP addresses that are assigned to computers on the LAN.
If Disable DHCP Server is selected, you must configure each computer on your network with a
static IP address on your LAN. Click Next.
8
The Configuration Summary page displays the configuration defined using the Installation
Wizard. To modify any of the settings, click Back to return to any previous page. If the
configuration is correct, click Apply. The SonicWALL security appliance stores the network
settings and then displays the Setup Wizard Complete page.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
13
Page 33

C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
Tip: The SonicWALL security appliance LAN IP address, displayed in the URL field of the Setup
9
Wizard Complete page, is used to log in and manage the SonicWALL security appliance.
9
Click Restart to restart the SonicWALL security appliance. The SonicWALL security appliance
takes approximately 90 seconds or longer to restart. During this time, the yellow Test LED is lit.
Configuring a DHCP Internet Connection
DHCP Internet connections are a common network configuration for customers with cable Internet
service. You are not assigned a specific IP address by your ISP.
1
Click the Setup Wizard button on the Network>Settings page. The Welcome to the
SonicWALL Setup Wizard page is displayed. Click Next.
2
To set the password, enter a new password in the New Password and Confirm New Password
fields. Click Next.
Note: Remember your password. You will need it to access the SonicWALL security appliance
management interface after the initial configuration.
3
Select your local time zone from the Time Zone menu. Click Next.
9
Note: Set the time zone correctly before you register your SonicWALL security appliance.
4
Select DHCP. Click Next. A page is displayed describing an DHCP Internet connection.
5
Click Next.
6
The LAN Settings page allows the configuration of SonicWALL security appliance LAN IP
Addresses and Subnet Masks. SonicWALL security appliance LAN IP Addresses are the private
IP addresses assigned to the LAN of the SonicWALL security appliance. The LAN Subnet Mask
defines the range of IP addresses on the networks. The default values provided by the SonicWALL
security appliance are useful for most networks. Click Next.
7
The LAN DHCP Server window configures the SonicWALL security appliance DHCP Server. If
enabled, the SonicWALL automatically assigns IP settings to computers on the LAN. To enable
the DHCP server, select Enable DHCP Server, and specify the range of IP addresses assigned to
computers on the LAN.
If Disable DHCP Server is selected, the DHCP Server is disabled. Click Next to continue.
8
The Configuration Summary window displays the configuration defined using the Installation
Wizard. To modify any of the settings, click Back to return to any previous page. If the
configuration is correct, click Apply. The SonicWALL security appliance stores the network
settings and then displays the Setup Wizard Complete page.
Tip: The new SonicWALL security appliance LAN IP address, displayed in the URL field of the Setup
Wizard Complete page, is used to log in and manage the SonicWALL security appliance.
9
Click Restart to restart the SonicWALL security appliance. The SonicWALL security appliance
takes 90 seconds to restart. During this time, the yellow Test LED is lit.
Configuring a PPPoE Internet Connection
PPPoE is typically used for DSL In tern et se rvice using a DSL modem. The ISP requires a user name
and password to log into the remote server.
1
Click the Setup Wizard button on the Network > Settings page. The Welcome to the
SonicWALL Setup Wizard page is displayed. Click Next.
2
To set the password, enter a new password in the New Password and Confirm New Password
fields. Click Next.
Note: Remember your password. You will need it to access the SonicWALL security appliance
14
management interface after the initial configuration.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 34

Using the SonicWALL Setup Wizard
3
Select your local time zone from the Time Zone menu. Click Next.
Note: Set the time zone correctly before you register your SonicWALL security appliance.
4
Select PPPoE. Click Next.
5
Enter the user name and password provided by your ISP into the User Name and Password
fields. Click Next.
6
The LAN Settings page allows the configuration of SonicWALL security appliance LAN IP
Addresses and LAN Subnet Mask.The SonicWALL security appliance LAN IP Address is the
private IP address assigned to the LAN port of the SonicWALL security appliance. The LAN
Subnet Mask defines the range of IP addresses on the LAN. The default values provided by the
SonicWALL security appliance are useful for most networks. If you do not use the default settings,
enter your preferred IP addresses in the fields. Click Next.
7
The LAN DHCP Server window configures the SonicWALL security appliance DHCP Server. If
enabled, the SonicWALL security appliance automatica lly assigns IP settings to computers on the
LAN. To enable the DHCP server, select Enable DHCP Server, and specify the range of IP
addresses that are assigned to computers on the LAN.
If Disable DHCP Server is selected, you must configure each computer on your network with a
static IP address on your LAN. Click Next.
8
The Configuration Summary window displays the configuration defined using the Installation
Wizard. To modify any of the settings, click Back to return to any previous page. If the
configuration is correct, click Apply. The SonicWALL security appliance stores the network
settings and then displays the Setup Wizard Complete page.
Tip: The new SonicWALL security appliance LAN IP address, displayed in the URL field of the Setup
9
Wizard Complete page, is used to log in and manage the SonicWALL security appliance.
9
Click Restart to restart the SonicWALL security appliance. The SonicWALL security appliance
takes 90 seconds to restart. During this time, the yellow Test LED is lit.
Configuring PPTP Internet Connectivity
PPTP is used to connect to a remote serv er via an Internet connection. It supports older Microsoft
implementations requiring tunneling connectivity.
1
Click the Setup Wizard button on the Network > Settings page. The Welcome to the
SonicWALL Setup Wizard page is displayed. Click Next.
2
To set the password, enter a new password in the New Password and Confirm New Password
fields. Click Next.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
15
Page 35

C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
3
Select your local time from the Time Zone menu. Click Next.
4
Select PPTP. Click Next.
5
Enter the PPTP server IP address in the PPTP Server IP Address field.
6
Enter the user name and password provided by your ISP into the PPTP User Name and PPTP
Password fields. Click Next.
7
The LAN Settings page allows the configuration of SonicWALL security appliance LAN IP
Addresses and LAN Subnet Mask.The SonicWALL security appliance LAN IP Address is the
private IP address assigned to the LAN port of the SonicWALL security appliance. The LAN
Subnet Mask defines the range of IP addresses on the LAN. The default values provid ed by the
SonicWALL security appliance are useful for most networks. If you do not use th e default settings,
enter your preferred IP addresses in the fields. Click Next.
8
The LAN DHCP Server window configures the SonicWALL security appliance DHCP Server. If
enabled, the SonicWALL security appliance automatically assigns IP settings to computers on the
LAN. To enable the DHCP server, select Enable DHCP Server, and specify the range of IP
addresses that are assigned to computers on the LAN.
If Disable DHCP Server is selected, you must configure each computer on your network with a
static IP address on your LAN. Click Next.
9
The Configuration Summary window displays the configuration defined using the Installation
Wizard. To modify any of the settings, click Back to return to any previous page. If the
configuration is correct, click Apply. The SonicWALL security appliance stores the network
settings and then displays the Setup Wizard Complete page.
16
9
Tip: The new SonicWALL security appliance LAN IP address, displayed in the URL field of the Setup
Wizard Complete page, is used to log in and manage the SonicWALL security appliance.
10
Click Restart to restart the SonicWALL security appliance. The SonicWALL security appliance
takes 90 seconds to restart. During this time, the yellow Test LED is lit.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 36

Using the SonicWALL Setup Wizard
Configuring the TZ 170 SP using the Setup Wizard
Configuring the SonicWALL TZ 170 SP security appliance using the Setup Wizard includes two
additional pages for configuring the SonicWALL TZ 170 SP’s modem. Theses pages are displayed
after the Change Time Zone page. Perform the following steps to configure the modem, and then
return to the Setup Wizard instructions.
1
Select the way you will be using the built-in modem on the TZ 17 0 SP.
Yes - I will use a dialup account as a backup for the WAN ethernet connection: This
setting uses the modem dial-up connection as an automatic backup to the WAN ethernet
connection. Use this if you have a DSL or Cable modem, and have dialup access to your ISP.
Yes - Dialup up is my only connection to the Internet: This setting uses the modem dial-up
connection as the only internet connection.
No - I will not use the modem at this time: This setting does not use the modem.
2
Click Next.
3
If you selected to use the modem, enter the phone number, username and passwor d for the dialup connection. Click Next.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
17
Page 37

C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
Configuring the TZ 50 Wireless/TZ 150 Wireless/170
Wireless using the Setup Wizard
The Setup Wizard provides the following four wireless deployment scenarios for the SonicWALL TZ
50 Wireless/TZ 150 Wireless/TZ 170 Wireless security appliances:
Office Gateway - Provides secure access for wired and wireless users on yo ur network.
Secure Access Point - Add secure wireless access to an existing wireless network.
Guest Internet Gateway - Provide guests controlled wireless access to the Internet only.
Secure Wireless Bridge - Operate in wireless bridge mode to securely bridge two networks with
WiFiSec.
Configuring the TZ 50 Wireless/TZ 150 Wireless/170
Wireless as an Office Gateway
Log into the SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless using your administrator’s
name and password. Click Wizards in the top right corner of the System > Status page.
Welcome to the SonicWALL Setup Wizard
1
To begin configuration, select Setup Wizard and click Next.
Selecting the Deployment Scenario
2
Select Office Gateway as the deployment scenario.
To view a description of each type of deployment scenario, click the name of the scenario.
Click Next.
Changing the Password
3
Type a new password in the New Password field. The password should be a uniqu e comb inatio n
of letters, or number, or symbols, or a combination of all three for the most se cure password. Avoid
names, birthdays, or any obvious words. Retyp e th e pa ssw or d in th e Confirm field. Click Next.
Selecting Your Time Zone
4
Select your Time Zone from the Time Zone menu. The security appliance uses an inte rnal clock to
timestamp logs and other functions requ ir in g time . Click Next.
Configuring the WAN Network Mode
5
Confirm that you have the proper network information necessary to configure the SonicWALL
security appliance to access the Internet. Click the hyperlinks for definitions of the networking
terms.
You can choose:
•Static IP, if your ISP assigns you a specific IP address or group of addresses.
•DHCP, if your ISP automatically assigns you a dynamic IP address.
•PPPoE, if your ISP provided you with client software, a user name, and a password.
•PPTP, if your ISP provided you with a server IP address, a user name, and password.
6
Choose the correct networking mode and click Next.
18
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 38

Configuring WAN Settings
7
If you selected Static IP address, you must have your IP address information from your ISP to fill
in the WAN Network Mode fields: Enter the public IP address provided by your ISP in the
SonicWALL WAN IP Address, then fill in the rest of the fields: WAN Subnet Mask, Gateway
(Router) Address, and the primary and secondary DNS Server Addresses. Click Next.
Configuring LAN Settings
8
Type a private IP address in the SonicWALL LAN IP Address field. The default private IP
address is acceptable for most configurations. Type the subnet in the Subnet Mask field. The
Enable Windows Networking Support checkbox is checked to allow Window networking
support. If you do not want to allow Windows networking support, uncheck this setting. Click Next.
Configuring LAN DHCP Settings
9
If you want to use the SonicWALL security appliance’s DHCP Server, check the Enable DHCP
Server on LAN checkbox and enter a range of IP addr esses to assign network d evices in the LAN
Address Range fields. The default entries work for most network configurations. Click Next.
Configuring WLAN 802.11b/g Settings
10
The Service Set ID (SSID) identifies your wireless network. It can be up to 32 alphanumeric
characters long and is case-sensitive. Select the desired channel for your wireless port. Channel
11 is selected by default and is the most commonly used channel. Select a radio mode from the
Radio Mode menu. The default 2.4GHz 802.11b/g Mixed option allows the SonicWALL TZ 50
Wireless/TZ 150 Wireless/TZ 170 Wireless to support b and g. Select United States - US or
Canada - CA from the Country Code menu. Use the default AutoChannel setting in the Chan nel
menu. Click Next.
Using the SonicWALL Setup Wizard
Configuring WiFiSec - VPN Client User Authentication
11
WiFiSec and GroupVPN are automatically enabled on the security appliance using the default
settings associated with each feature. To add a user with VPN Client privileges, type a user name
and password in the User Name and Password fields, and confirm your password in the Confirm
Password field. When users access the security appliance using the VPN client, they are
prompted for a user name and password. Click Next.
Configuring Wireless Guest Services
12
When Enable Wireless Guest Services is selected, guests on your WLAN are permitted access
only to the WAN and are required to log in when accessing the Internet. Up to 10 users by default
can use the same guest account. Type in the account name and password in the Account Name
and Password fields. Configure the Account Lifetime and the Session Timeout times.
Configuration Summary
13
The Configuration Summary page displays all of the settings configured using the Deployment
Scenario Wizard. To change any of the settings, click Back until you see the settings you want to
change. To use this configuration on the security appliance, click Apply.
Storing Configuration
14
Wait for the settings to take effect on the security appliance.
Congratulations
15
!When the settings are applied to the security appliance, the Congratulations pag e is di splayed.
Click Restart to complete the configuration.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
19
Page 39

C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
Configuring the TZ 50 Wireless/TZ 150 Wireless/TZ 170
Wireless as a Secure Access Point
Use the SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless as a secure access point to add
secure wireless access to an existing wireless network.
Log into the SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless using your administrator’s
name and password. Click Wizards in the top right corner of the System > Status page.
Welcome to the SonicWALL Setup Wizard
1
To begin configuration, select Setup Wizard and click Next.
Selecting the Deployment Scenario
2
Select Secure Access Point as the deployment scenario. Click Next.
Changing the Password
3
Type a new password in the New Password field. The password should be a uniqu e comb inatio n
of letters, or number, or symbols, or a combination of all three for the most se cure password. Avoid
names, birthdays, or any obvious words. Retyp e th e pa ssw or d in th e Confirm field. Click Next.
Selecting Your Time Zone
4
Select your Time Zone from the Time Zone menu. The security appliance uses an inte rnal clock to
timestamp logs and other functions requ ir in g time . Click Next.
Configuring the LAN Settings
5
The LAN page allows the configuration of the SonicWALL LAN IP Addresses and the LAN
Subnet Mask.The SonicWALL LAN IP Addresses are the private IP address assigned to the
LAN port of the SonicWALL security appliance. The LAN Subnet Mask defines the range of IP
addresses on the LAN. The default values pro vided by the SonicWALL se curity appliance work for
most networks. If you do not use the default settings, enter your preferred private IP address and
subnet mask in the fields. Fill in the Gateway (Router) Address and the primary and secondary
DNS Server Addresses. Click Next.
Configuring the LAN DHCP Settings
6
The LAN DHCP Settings window configures the SonicWALL security appliance DHCP Server. If
enabled, the SonicWALL security appliance automatically configures the IP settings of computers
on the LAN. To enable the DHCP server, select Enable DHCP Server on LAN, and specify the
range of IP addresses that are assigned to computers on the LAN.
If Enable DHCP Server on LAN is not selected, you must configure each computer on your
LAN with a static IP address. Click Next.
Configuring WLAN 802.11b Settings
7
The Service Set ID (SSID) identifies your wireless network. It can be up to 32 alphanumeric
characters long and is case-sensitive. Select the desired channel for your wireless port. Channe l
11 is selected by default and is the most commonly used channel. Select a radio mode from the
Radio Mode menu. The default 2.4GHz 802.11b /g Mix ed option allows the SonicWALL TZ 50
Wireless/TZ 150 Wireless/TZ 170 Wireless to support b and g. Select United States - US or
Canada - CA from the Country Code menu. Use the default AutoChannel setting in the Channel
menu. Click Next.
20
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 40

Using the SonicWALL Setup Wizard
Configuring WiFiSec - VPN Client User Authentication
8
WiFiSec and Group VPN are automatically enabled on the security appliance using the default
settings associated with each feature. To add a user with VPN Client privileges, type a user name
and password in the User Name and Password fields. When users access the security appliance
using the VPN client, they are prompted for a user name and password. Click Next.
Configuration Summary
9
The Configuration Summary page displays all of the settings configured using the Deployment
Scenario Wizard. To change any of the settings, click Back until you see the settings you want to
change. To apply the current settings to the security appliance, click Apply.
Storing Configuration
10
Wait for the settings to take effect on the security appliance.
Congratulations!
When the settings are applied to the security appliance, th e Congratulations page is displayed. Click
Restart to complete the configuration.
Configuring the TZ 50 Wireless/TZ 150 Wireless/TZ 170
Wireless as a Guest Internet Gateway
Configure your wireless security appliance to provide guests controlled wireless access to the Internet
only.
Log into the SonicWALL TZ 50 Wireless/TZ 150 Wi reless/TZ 170 Wireless using your administrator’s
name and password. Click Wizards in the top right corner of the System > Status page.
Welcome to the SonicWALL Setup Wizard
1
To begin configuration, select Setup Wizard and click Next.
Selecting the Deployment Scenario
2
Select Guest Internet Gateway as the deployment scenario. Click Next.
Changing the Password
3
Type a new password in the New Password field. The password should be a unique combination
of letters, or number, or symbols, or a combination of all three for the most secure password. Avoid
names, birthdays, or any obvious words. Retype the password in the Confirm field. Click Next.
Selecting Your Time Zone
4
Select your Time Zone from the Time Zone menu. The security appliance uses an internal clock to
timestamp logs and other functions requiring time. Click Next.
Configuring the WAN Network Mode
5
Confirm that you have the proper network information necessary to configure the SonicWALL
security appliance to access the Internet. Click the hyperlinks for definitions of the networking
terms.
You can choose:
Static IP, if your ISP assigns you a specific IP address or group of addresses.
DHCP, if your ISP automatically assigns you a dynamic IP address.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
21
Page 41

C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
PPPoE, if your ISP provided you with client software, a user name, and a password.
PPTP, if your ISP provided you with a server IP address, a user name, and password.
6
Choose the correct networking mode and click Next.
Configuring WAN Settings
7
If you selected Static IP address, you must have your IP address information from your ISP to fill
in the WAN Network Mode fields: Enter the public IP address provided by your ISP in the
SonicWALL WAN IP Address, then fill in the rest of the fields: WAN Subnet Mask, Gateway
(Router) Address, and the primary and secondary DNS Server Addresses. Click Next.
Configuring WLAN 802.11b Settings
8
The Service Set ID (SSID) identifies your wireless network. It can be up to 32 alphanumeric
characters long and is case-sensitive. Select the desired channel for your wireless port. Channe l
11 is selected by default and is the most commonly used channel. Select a radio mode from the
Radio Mode menu. The default 2.4GHz 802.11b /g Mix ed option allows the SonicWALL TZ 50
Wireless/TZ 150 Wireless/TZ 170 Wireless to support b and g. Select United States - US or
Canada - CA from the Country Code menu. Use the default AutoChannel setting in the Channel
menu. Click Next.
Configuring Wireless Guest Services
9
When Wireless Guest Services is selected, guests on your WLAN are permitted acce ss only to the
WAN and are required to log in when accessing the Internet. Up to 10 users by defa ult can use the
same guest account. Type in the account na me an d pa ss wor d in the Account Name and
Password fields. Configure the Account Lifetime and the Session Timeout times.
Configuration Summary
10
The Configuration Summary page displays all of the settings configured using the Deployment
Scenario Wizard. To change any of the settings, click Back until you see the settings you want to
change. To apply the current settings to the security appliance, click Apply.
Storing Configuration
11
Wait for the settings to take effect on the security appliance.
Congratulations!
When the settings are applied to the security appliance, the Congratulations page is displayed. Click
Restart to complete the configuration.
Configuring the TZ 170 Wireless as a Secure Wireless
Bridge
Set up the TZ 170 Wireless as a Secure Wireless Bridge to securely bridge two networks with WiFiSec.
Log into the TZ 170 Wireless using your administrator’s name and passwor d. Click Wizards in the top
right corner of the System > Status page.
Welcome to the SonicWALL Setup Wizard
1
To begin configuration, select Setup Wizard and click Next.
Selecting the Deployment Scenario
2
Select Secure Wireless Bridge as the deployment scenario. Click Next.
22
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 42

Changing the Password
3
Type a new password in the New Password field. The password should be a unique combination
of letters, or number, or symbols, or a combination of all three for the most secure password. Avoid
names, birthdays, or any obvious words. Retype the password in the Confirm field. Click Next.
Selecting Your Time Zone
4
Select your Time Zone from the Time Zone menu. The security appliance uses an internal clock to
timestamp logs and other functions requiring time. Click Next.
Configuring LAN Settings
5
Type a private IP address in the SonicWALL LAN IP Address field. The default private IP
address is acceptable for most configurations. Type the subnet in the Subnet Mask field.
If you have Windows devices in both the LAN and WAN zones, you might want to enable win dows
networking between zones. However, this opens a potential security risk.
6
Click Next.
Configuring LAN DHCP Settings
7
If you want to use the security appliance’s built-in DHCP server to assign dynamic IP Addresses
within your LAN, check Enable DHCP Server on LAN and enter the range of addresse s available
to the DHCP Server. Click Next.
Using the SonicWALL Setup Wizard
Configuring WLAN 802.11b Settings
8
The Service Set ID (SSID) identifies your wireless network. It can be up to 32 alphanumeric
characters long and is case-sensitive. Select the desired channel for your wireless port. Channel
11 is selected by default and is the most commonly used channel. Select a radio mode from the
Radio Mode menu. The default 2.4GHz 802.11b/g Mixed option allows the SonicWALL TZ 170
Wireless to support b and g. Select United States - US or Canada - CA from the Country Code
menu. Use the default AutoChannel setting in the Channel menu. Click Next.
Configuring WLAN Network Setting
9
Enter the appropriate network configuration for the security appliance to work in your bridged
network environment. Type a private IP address in the SonicWALL WLAN IP Address field. Type
the subnet in the Subnet Mask field. Enter that address of the Gateway (Router) Address and
the DNS Server Address. If you have a secondary DNS server you can enter its address.
10
Click Next.
Configuring Secure Wireless Bridge Settings
Complete the VPN Security Policy information to configure the Secure Wireless Bridge. Enter the VPN
Policy Name, the Peer IPSec Gateway Address, and th e IKE Shared Secret. Click Next to continue.
Configuration Summary
11
The Configuration Summary page displays all of the settings configured using the Deployment
Scenario Wizard. To change any of the settings, click Back until you see the settings you want to
change. To apply the current settings to the security appliance, click Apply.
Storing Configuration
12
Wait for the settings to take effect on the security appliance.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
23
Page 43

C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
Congratulations!
When the settings are applied to the security appliance, the Congratulations page is displayed. Click
Restart to complete the configuration.
Registering Your SonicWALL Security
Appliance
Once you have established your Internet connection, it is recommended you register your SonicWALL
security appliance. Registering your SonicWALL security appliance provides the following benefits:
• Try a FREE 30-day trial of SonicWALL Intrusion Prevention Service, SonicWALL Gateway
Anti-Virus, Content Filtering Service, and Network Anti-Virus.
• Activate SonicWALL security services and upgrades
• Access SonicOS firmware updates
• Get SonicWALL technical support
Before You Register
If your SonicWALL security appliance is not registered, the following message is displayed in the
Security Services folder on the System > Status page in the SonicWALL management interface:
Your SonicWALL is not registered. Click here to Register
mySonicWALL.com account to register the SonicWALL security appliance.
your SonicWALL. You need a
If your SonicWALL security appliance is connected to the Internet, you can create a
mySonicWALL.com account and register your SonicWALL security appliance directly from the
SonicWALL management interface. If you already have a mySonicWALL.com account, you can
register the SonicWALL security appliance directly from the management interface.
Your mySonicWALL.com account is accessible from any Internet connection by pointing your Web
browser to <https://www.mysonicwall.com>. mySonicWALL. co m us es the HTT PS
(Hypertext Transfer Protocol Secure) protocol to protect your sensitive information.
Alert: Make sure the Time Zone and DNS settings on your SonicWALL security appliance are correct
S
when you register the device. See SonicWALL Setup Wizard instructions for instructions on using the
Setup Wizard to set the Time Zone and DNS settings.
Note: mySonicWALL.com registration information is not sold or shared with any other company.
You can also register your security appliance at the <https://www.mysonicwall.com> site by using the
Serial Number and Authentication Code displayed in the Security Services section. Click the
SonicWALL
after you have registered your security appliance. Enter the registration code in the field below the
You will be given a registration code, which you should enter below heading, then click Update.
Creating a mySonicWALL.com Account
Creating a mySonicWALL.com account is fast, simple, and FREE. Simply complete an online
registration form in the SonicWALL management interface.
link to access your mySonicWALL.com account. You will be given a registration code
24
To create a mySonicWALL.com account from the SonicWALL management interface:
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 44

Registering Your SonicWALL Security Appliance
1
In the Security Services section on the System > Status page, click the Register link in Your
SonicWALL is not registered. Click here to Register
2
Click the here link in If you do not have a mySonicWALL account, please click here to cre ate
one on the mySonicWALL Login page.
3
In the MySonicWALL Account page, enter in your information in the Account Information,
Personal Information and Preferences fields in the mySonicWALL.com account form. All fields
marked with an * are required fields.
your SonicWALL.
Note: Remember your username and password to access your mySonicWALL.com account.
4
Click Submit after completing the MySonicWALL Account form.
5
When the mySonicWALL.com server has finished processing your account, a page is displayed
confirming your account has been created. Click Continue.
6
Congratulations! Your mySonicWALL.com account is activated. Now you need to log into
mySonicWALL.com from the management appliance to register your SonicWALL security
appliance.
Registering Your SonicWALL Security Appliance
If you already have a mySonicWALL.com account, follow these steps to register your security
appliance:
1
In the Security Services section on the System > Status page, click the Register link in Your
SonicWALL is not registered. Click here to Register
Login page is displayed.
your SonicWALL. The mySonicWALL
2
In the mySonicWALL.com Login page, enter your mySonicWALL.com username and password
in the User Name and Password fields and click Submit.
3
The next several pages inform you about free trials available to you for SonicWALL’s Security
Services:
Gateway Anti-Virus - protects your entire network from viruses
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
25
Page 45

C
HAPTER
2:
Basic SonicWALL Security Appliance Setup
Network Anti-Virus - protects computers on your network from viruses
Premium Content Filtering Service - protects your network and improves productivity by
limiting access to unproductive and inappr opr i ate Web sites
Intrusion Prevention Service - protects your network from Trojans, wo rms, and application
layer attacks.
Click Continue on each page.
4
At the top of the Product Survey page, enter a friendly name for your SonicWALL security
appliance in the Friendly name field, and complete the optional product survey.
5
Click Submit.
6
When the mySonicWALL.com server has finished processing your registration, a page is
displayed confirming your SonicWALL security appliance is registered.
7
Click Continue. The Manage Services Online table on the System > Licenses page displayed.
Â
Cross Reference: Refer to Part 7, Security Services for information on SonicWALL security services
and activating FREE trials.
26
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 46

P
ART
2
Part 2System
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
27
Page 47

28
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 48

System > Status
System > Status
C
HAPTER
3
Chapter 3: Vi ewing System Status
Information
The Status page contains five sections: System Messages, System Information, Latest Alerts,
Security Services, and Network Interfaces.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
29
Page 49

C
HAPTER
3:
Viewing System Status Information
Wizards
The Wizards button on the System > Status page provides access to the SonicWALL Configuration
Wizard.
This wizard allows you to easily configure the SonicWALL security appliance using the following
wizards:
• Setup Wizard - This wizard helps you quickly configure the SonicWALL security appliance to se-
cure your Internet (WAN) and LAN connections.
• Network Access Rules Wizard - This wizard helps you quickly configure the SonicWALL security
appliance to provide public access to an internal server, such as a Web or E-mail server or create
a general firewall rule.
• VPN Wizard - This wizard helps you create a new site-to-site VPN Policy or configure the WAN
GroupVPN to accept VPN connections from SonicWALL Global VPN Clients.
System Messages
Any information considered relating to possible problems with configurations on the SonicWALL
security appliance such as password, log messages, etc.
System Information
The following information is displayed in this section:
• Model - type of SonicWALL security appliance
• Serial Number - also the MAC address of the SonicWALL security appliance
• Authentication Code - the alphanumeric code used to authenticate th e SonicWALL security
appliance on the registration database at <https://www.mysonicwall.com>.
• Firmware Version - the firmware version loaded on the SonicWALL security appliance.
• ROM Version - indicates the ROM version.
• CPU - displays the percent usage and the type of the SonicWALL security appliance processor.
• Total Memory - indicates the amount of RAM and flash memory.
• Up Time - the length of time, in days, hours, minutes, and seconds the SonicWALL security appliance is active.
• Current Connections - the number of network connections currently existing on the
SonicWALL security appliance.
• Last Modified By- the IP address the administrator connected from and the time of the last modi-
fication.
30
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 50

• Registration Code - the registration code is generated when your SonicWALL security appliance
is registered at <https://www.mysonicwall.com>.
Security Services
If your SonicWALL security appliance is not registered at mySonicWALL.com, the following message
is displayed in the Security Services folder: Your SonicWALL security appliance is not
registered. Click here
mySonicWALL.com account to register your SonicWALL security appliance or activate security
services. You can create a mySonicWALL.com account directly from the SonicWALL management
interface.
Cross Reference: Refer to Chapter 2, Basic SonicWALL Security Appliance Setup for complete
Â
registration instructions.
System > Status
to Register your SonicWALL security appliance. You need a
If your SonicWALL security appliance is registered a list of availa ble Son icWAL L Se curi ty Services
are listed in this section with the status of Licensed or Not Licensed. If Licensed, the Status column
displays the number of licenses and the number of licenses in use. Clicking the Arrow icon displays
the System > Licenses page in the SonicWALL Web-based management interface. SonicWALL
Security Services and SonicWALL security appliance registration is ma naged by mySonicWALL.com.
Cross Reference: Refer to Part 7, Security Services for more information on SonicWALL Security
Â
Services and activating them on the SonicWALL security appliance.
Latest Alerts
Any messages relating to system errors or attacks are displayed in this section. Attack messages
include AV Alerts, forbidden e-mail attachments, fraudulent certificates, etc. System errors include
WAN IP changed and encryption errors. Clicking the blue arrow displays the Log > Log View page.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
31
Page 51

C
HAPTER
3:
Viewing System Status Information
Network Interfaces
The Network Interfaces displays the IP address and link information for interfaces on your SonicWALL
security appliance. The available interfaces displayed in this section depends on the SonicWALL
security appliance model. Clicking the arrow displays the Network > Settings page.
SonicWALL Security
Appliance Model Interfaces
SonicWALL TZ 50 WAN, LAN
SonicWALL TZ 50 Wireless WAN, LAN, WLAN
SonicWALL TZ 150 WAN, LAN
SonicWALL TZ 150 Wireless WAN, LAN, WLAN
SonicWALL TZ 170 WAN, LAN, OPT
SonicWALL TZ 170 SP WAN, LAN, Modem
SonicWALL TZ 170 Wireless WAN, LAN, WLAN
SonicWALL PRO 1260 WAN, LAN, OPT
Â
SonicWALL PRO 2040 WAN, LAN, DMZ
SonicWALL PRO 3060 WAN, LAN, DMZ
Cross Reference: Refer to Chapter 9, Configuring Network Sett ings for more information on
configuring Network Interfaces.
32
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 52

System > Licenses
The System > Licenses page provides links to activate, upgrade, or renew SonicWALL Security
Services and upgrades.
System > Licenses
C
HAPTER
4
Chapter 4: System > Licenses
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
33
Page 53

C
HAPTER
4:
System > Licenses
Node License Status
Node licensing can be monitored and controlled from the System > Licenses pa ge. The Node
License Status section displays the number of licensed nodes, and the number of node s currently in
use. To prevent nodes from consuming licenses (such as for network printers that do not require
Internet access) a facility is provided to construct an exclusion list.
If your SonicWALL security appliance supports an unlimited number of nodes, the Node License
Status section does not include Currently Licensed Nodes and Node License Exclusion List
settings.
Currently Licensed Nodes
On node restricted devices, node usage is calculated by the number of active hosts on local interfa ces
attempting to traverse the WAN interface. After a 5 minute period of inactivity, hosts are no longer
considered active, and are removed from the Currently Licensed Nodes list. Subsequent activity will
add them back to the list.
When the node license limit has been reached, an over-limit host will be denied access to the WAN,
and if the traffic the host is attempting is HTTP, the host is redirected to the License Exceed page on
the SonicWALL security appliance.
Node License Exclusion List
IP Addresses can be added to the Node License Exclusion List by clicking the Add button. The
Add/Edit License Exclusion Node window is displayed.
34
Enter the node IP address in the Node IP Address field and an optional comment in the Comment
field.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 54

You can clicking on the icon in the Exclude column of the Currently Licensed Nodes table to
automatically add the entry to the Node License Exclusion List. Clicking the icon displays an alert
explaining that the host to be excluded and added to the exclusion list, and the node will be prohibited
from accessing the WAN. Clicking OK. The Node License Exclusion List is updated to reflect the
change.
The delete icon can be used to remove entries from the list, and to restore WAN access to the
referenced host. The edit icon allows for a comment to be added or changed on the entry.
The Node License Exclusion List table is also be updated to reflect the change:
Clicking the Auto Firewall Access Rule redirects the management session to the Firewall > Access
Rules page, where the auto-created, non-editable rule can be viewed.
Security Services Summary
System > Licenses
The Security Services Summary table lists the available and activated security services on the
SonicWALL security appliance. The Security Service column lists all the available SonicWALL
security services and upgrades available for the SonicWALL security appliance. The Status column
indicates is the security service is activated (Licensed), available for activation (Not Licensed), or no
longer active (Expired). The number of nodes/users allowed for the license is displayed in the Count
column.
The information listed in the Security Services Summary table is updated from your
mySonicWALL.com account the next time the SonicWALL security appliance automatically
synchronizes with your mySonicWALL.com account (once a day) or you can click the link in To
synchronize licenses with mySonicWALL.com click here in the Manage Security Services
Online section.
Note: Refer to Chapter 8, Setting Up Security Services for more information on SonicWALL Security
Services and activating them on the SonicWALL security appliance.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
35
Page 55

C
HAPTER
4:
System > Licenses
Manage Security Services Online
To activate, upgrade, or renew services, click the link in To Activate, Upgrade, or Renew services,
click here. Click the link in To synchronize licenses with mySonicWALL.com click here to
synchronize your mySonicWALL.com account with the Security Services Summary table.
You can also get free trial subscriptions to SonicWALL Content Filter Service and Network Anti-Virus
by clicking the For Free Trials click here link. When you click these links, the mySonicWALL.com
Login page is displayed. Enter your mySonicWALL.com account username and password in the
User Name and Password fields and click Submit. The Manage Services Online page is displayed
with licensing information from your mySonicWALL.com account.
Manual Upgrade
Manual Upgrade allows you to activate your services by typing the service activation key supplied
with the service subscription not activated on mySonicWALL.com. Type the activation key from the
product into the Enter upgrade key field and click Submit.
Tip: You must have a mysonicwall.com account to upgrade and activate services through the
9
SonicWALL security appliance.
Manual Upgrade for Closed Environments
If your SonicWALL security appliance is deployed in a high security environment that does not allow
direct Internet connectivity from the SonicWALL security appliance, you can enter the encrypted
license key information from http://www.mysonicwall.com manually on the System > Licenses page
in the SonicWALL Management Interface.
Note: Manual upgrade of the encrypted License Keyset is only for Closed Environments. If your
SonicWALL security appliance is connected to the Internet, it is recommended you use the automatic
registration and Security Services upgrade features of your SonicWALL security appliance.
36
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 56

System > Licenses
From a Computer Connected to the Internet
1
Make sure you have an account at http://www.mysonicwall.com and your SonicWALL security
appliance is registered to the account before proceeding.
2
After logging into www.mysonicwall.com, click on your registered SonicWALL security appliance
listed in Registered SonicWALL Products.
3
Click the View License Keyset link. The scrambled text displayed in the text box is the License
Keyset for the selected SonicWALL security appliance and activated Security Services. Copy the
Keyset text for pasting into the System > Licenses page or print the page if you plan to manually
type in the Keyset into the SonicWALL security appliance.
From the Management Interface of the SonicWALL Security Appliance
4
Make sure your SonicWALL security appliance is running SonicOS Standard or Enhanced 2.1 (or
higher).
5
Paste (or type) the Keyset (from the step 3) into the Keyset field in the Manual Upgrade section of
the System > Licenses page (SonicOS).
6
Click the Submit or the Apply button to update your SonicWALL security appliance. The status
field at the bottom of the page displays The configuration has been updated.
7
You can generate the System > Diagnostics > Tech Support Report to verify the upgrade
details.
After the manual upgrade, the System > Licenses page does not contain any registration and
upgrade information. The warning message: SonicWALL Registration Update Needed. Please
update your registration
registered your SonicWALL security appliance. Ignore this message.
information remains on the System > Status page after you have
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
37
Page 57

C
HAPTER
4:
System > Licenses
38
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 58

Chapter 5: Using System Administration
System > Administration
The System > Administration page provides settings for the configuration of SonicWALL security
appliance for secure and remote management. You can manage the SonicWALL security appliance
using a variety of methods, including HTTPS, SNMP or SonicWALL Global Management System
(SonicWALL GMS).
System > Administration
C
HAPTER
5
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
39
Page 59

C
HAPTER
5:
Using System Administration
Firewall Name
The Firewall Name uniquely identifies the SonicWALL security appliance and defaults to the serial
number of the SonicWALL security appliance. The serial number is also the MAC address of the unit.
The Firewall Name is mainly used in e-mailed log files. To change the Firewall Name, enter a unique
alphanumeric name in the Firewall Name field. It must be at least 8 characters in length.
Name/Password
Administrator Name
The Administrator Name can be changed from the default setting of admin to any word using
alphanumeric characters up to 32 characters in length. To create an new administrator name, enter
the new name in the Administrator Name field. Click Apply for the changes to take effect on the
SonicWALL security appliance.
Changing the Administrator Password
To set the password, enter the old password in the Old Password field, and the new password in the
New Password field. Enter the new password again in the Confirm New Password field and click
Apply. Once the SonicWALL security appliance has been updated, a message confirming the update
is displayed at the bottom of the browser window.
Login Security
The Log out the Administrator after inactivity of (minutes) setting allows you to set the length of
inactivity time that elapses before you are automatically logged out of the management interface. By
default, the SonicWALL security appliance logs out the administrator after 5 minutes of inactivity.
9
Enable Administrator/User Lockout
S
Tip: If the Administrator Inactivity Timeout is extended beyond 5 minutes, you should end every
management session by clicking Logout to prevent unauthorized access to the SonicWALL Web
Management Interface.
Enter the desired number of minutes in the Log out the Administrator after inactivity of (minutes)
setting and click Apply. The time range can be from 1 to 99 minutes. Click Apply, and a message
confirming the update is displayed at the bottom of the browser window.
You can configure the SonicWALL security appliance to lockout an administrator or a user if the login
credentials are incorrect. Select the Ena ble Administrator/User Lockout check box to prevent users
from attempting to log into the SonicWALL security appliance without proper authentication
credentials. Enter the number of failed attempts before the user is locked out in the Failed login
attempts per minute before lockout field. Enter the length of time that must elapse before the user
attempts to log into the SonicWALL security appliance again in the Lockout Period (minutes) field.
Alert: If the administrator and a user are logging into the SonicWALL security appliance using the
same source IP address, the administrator is also locked out of the SonicWALL security appliance.
The lockout is based on the source IP address of the user or ad min istr ator .
40
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 60

Web Management Settings
The SonicWALL security appliance can be managed using HTTP or HTTPS and a Web browser.
Both HTTP and HTTPS are enabled by default. The default port for HTTP is port 80, but you can
configure access through another port. Enter the number of the desired port in th e Port field, and click
Update. However, if you configure another port for HTTP management, you must include the port
number when you use the IP address to log into the SonicWALL security appliance. For example, if
you configure the port to be 76, then you must enter <LAN IP Address>:76 into the Web browser, i.e.
<http://192.168.168.1:76>
The default port for HTTPS management is 443, the standard port. You can add another layer of
security for logging into the SonicWALL security appliance by changing the default port. To configure
another port for HTTPS management, enter the preferred port number into the Port field, and click
Update. For example, if you configure the HTTPS Manage ment Port to be 700, then you must log into
the SonicWALL security appliance using the port number as well as the IP address, for example,
<https://192.168.168.1:700> to access the SonicWALL security appliance.
System > Administration
The Certificate Selection menu allows you to use a self-signed certificate (Use Self-signed
Certificate), which allows you to continue using a certificate without downloading a new one each
time you log into the SonicWALL security appliance. You can also choose Import Certificate to
select an imported certificate from the VPN > Local Certificates page to use for authentication to the
Management Interface.
The Enable Ping from LAN to management interface setting allows a LAN user to ping the
SonicWALL to verify it is online.
Changing the Default Size for SonicWALL Management Interface Tables
The SonicWALL Management Interface allows you to control the d isplay of large tables of information
across all tables in the management Interface; for example the table on the Firewall > Access Rules
page.
You can change the default table page size in all tables displayed in the SonicWALL Management
Interface from the default 50 items per page to any size ranging from 1 to 5,000 items.
To change the default table size:
1
Enter the maximum table size number in the Table Size field.
2
Click Apply.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
41
Page 61

C
HAPTER
5:
Using System Administration
Advanced Management
Enable SNMP
SNMP (Simple Network Management Protocol) is a network protocol used over User Datagram
Protocol (UDP) that allows network administr at ors to monitor the status of the SonicWALL security
appliance and receive notification of critical events as they occur on the network. The SonicWALL
security appliance supports SNMP v1/v2c and all relevant Management Information Base II (MIB)
groups except egp and at. The SonicWALL security appliance replies to SNMP Get commands for
MIBII via any interface and supports a custom SonicWALL MIB for generating trap messages. The
custom SonicWALL MIB is available for download from the SonicWALL Web site and can be loaded
into third-party SNMP management software such as HP Openview, Tivoli, or SNMPC.
To enable SNMP on the SonicWALL security appliance, select the Enable SNMP check box, and
then click Configure in the System > Administrat ion page.
Note: v1 traps are not supported on the SonicWALL security appliance.
1
Enter the host name of the SonicWALL security ap plia nc e in th e System Name field.
2
Enter the network administrator’s name in the System Contact field.
3
Enter an e-mail address, telephone number, or pager number in the System Location field.
4
Enter a name for a group or community of administrators who can view SNMP data in the Get
Community Name field.
5
Enter a name for a group or community of administrators who can view SNMP traps in the Trap
Community Name field.
6
Enter the IP address or host name of the SNMP manage ment system receiving SNMP traps in the
Host 1 through Host 4 fields. You must configure at least one IP address or host name, but up to
four addresses or host names can be used.
7
Click OK.
42
Trap messages are generated only for the alert message categories normally sent by th e SonicWALL
security appliance. For example, attacks, system errors, or blocked Web sites generate trap
messages. If none of the categories are selected on the Log > Settings page, then no trap messages
are generated.
By default, the SonicWALL security appliance responds only to Get SNMP messages received on its
LAN interface. Appropriate rules must be configured to allow SNMP traffic to and from the WAN
interface. SNMP trap messages can be sent via the LAN or WAN.
Note: Refer to Chapter 4, Configuring Firewall Settings for in structions on add ing services and ru les
to the SonicWALL security appliance.
If your SNMP management system supports discovery, the SonicWALL agent automatically discover
the SonicWALL security appliance on the network. Otherwise, you must add the SonicWALL security
appliance to the list of SNMP-managed devices on the SNMP management system.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 62

Enable Management Using SonicWALL GMS
To enable the SonicWALL security appliance to be managed by SonicWALL Global Management
System (GMS). Select the Enable Management using GMS checkbox, then click Configure. The
Configure GMS Settings window is displayed.
To configure the SonicWALL security appliance for GMS management:
1
Enter the host name or IP address of the GMS Console in the GMS Host Name or IP Address
field.
2
Enter the port in the GMS Syslog Server Port field. The default value is 514.
3
Select Send Heartbeat Status Messages Only to send only heartbeat status instead of log
messages.
4
Select GMS behind NAT Device if the GMS Console is placed behind a device using NAT on the
network. Type the IP address of the NAT device in the NAT Device IP Address field.
5
Select one of the following GMS modes from the Management Mode menu.
IPSEC Management Tunnel - Use the IPSec management tunnel included with the SonicWALL
security appliance. The default IPSec VPN settings are displayed.
Existing Tunnel - Use an existing tunnel for GMS management of the SonicWALL security
appliance.
HTTPS - Use HTTPS for GMS management of the SonicWALL security appliance. The following
configuration settings for HTTPS management mode are displayed:
Send Syslog Messages in Cleartext Format - Sends Syslog messages as cleartext.
Send Syslog Messages to a Distributed GMS Reporting Server - Sends Syslog Messages
to a GMS Reporting Server separated from the GMS management server.
GMS Reporting Server IP Address - Enter the IP address of the GMS Repor ting Server, if the
server is separate from the GMS management server.
GMS Reporting Server Port - Enter the port for the GMS Repo rting Se rver. The de fa ult value
is 514
6
Click OK.
System > Administration
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
43
Page 63

C
HAPTER
5:
Using System Administration
44
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 64

System > Time
The System > Time page defines the time and date settings to time stamp log events, to
automatically update SonicWALL Security Services, and for other internal purposes.
System > Time
C
HAPTER
6
Chapter 6: Setting System Time
By default, the SonicWALL security appliance uses an internal list of public NTP servers to
automatically update the time. Network Time Protocol (NTP) is a protocol used to synchronize
computer clock times in a network of computers. NTP uses Coordinated Universal Time (UTC) to
synchronize computer clock times to a millisecond, and sometimes to a fraction of a millisecond.
Set Time
The SonicWALL security appliance uses the time and date settings to time stamp log events, to
automatically update filtering subscription services, and for other internal purposes. By default, the
SonicWALL security appliance uses an internal list of public NTP servers to automatically update the
time. Network Time Protocol (NTP) is a protocol used to synchronize computer clock times in a
network of computers. NTP uses Coordinated Universal Time (UTC) to synchronize computer clock
times to a millisecond, and sometimes to a fraction of a millisecond.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
45
Page 65

C
HAPTER
6:
Setting System Time
Setting the SonicWALL Security Appliance Time
To select your time zone and automatically update the time, choose the time zone from the Time
Zone menu. The Set time automatically using NTP setting is activated by default to use the NTP
(Network Time Protocol) to set time automatically. If you want to set your time manually, uncheck this
setting. Select the time in the 24-hour format using the Time (hh:mm:ss) menus and the date from
the Date menus. Automatically adjus t clock for daylight savin g changes is activated by default to
enable automatic adjustments for daylight savings time.
Selecting Display UTC in logs (instead of local time) specifies the use universal time (UTC) rather
than local time for log events.
Selecting Display time in International format displays the date in International format, with the day
preceding the month.
After selecting your system time settings, click Apply.
NTP Settings
Network Time Protocol (NTP) is a protocol used to synchronize computer clock times in a network of
computers. NTP uses Coordinated Universal Time (UTC) to synchronize computer clock times to a
millisecond, and sometimes, to a fraction of a millisecond. The SonicWALL security appliance use an
internal list of NTP servers so manually entering a NTP server is optional.
Select Use NTP to set time automatically if you want to use your local server to se t the SonicWALL
security appliance clock. You can also configure Update Interval (minutes) for the NTP server to
update the SonicWALL security appliance. The default value is 60 minutes.
To add an NTP server to the SonicWALL security appliance configuration, click Add. The Add NTP
Server window is displayed. Type the IP address of an NTP server in the NTP Server field. Click Ok.
Then click Apply on the System > Time page to update the SonicWALL security appliance. To delete
an NTP server, highlight the IP address and click Delete. Or, click Delete All to delete all servers.
46
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 66

Chapter 7: Configuring System Settings
System > Settings
The System > Settings page includes features for managing the SonicWALL security appliance
firmware and your custom preferences.
System > Settings
C
HAPTER
7
Settings
Import Settings
To import a previously saved preferences file into the SonicWALL security appliance, follow these
instructions:
1
Click Import Settings to import a previously exported preferences file into the SonicWALL
security appliance. The Import Settings window is displayed.
2
Click Browse to locate the file which has a *.exp file name extension.
3
Select the preferences file.
4
Click Import, and restart the firewall.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
47
Page 67

C
HAPTER
7:
Configuring System Settings
Export Settings
To export configuration settings from the SonicWALL security appliance, use the instructions below:
1
Click Export Settings.
2
Click Export.
3
Click Save, and then select a loca tion to save the file. The file is named “sonicwall.ex p” but can be
renamed.
4
Click Save. This process can take up to a minute. The exported preferences file can be imported
into the SonicWALL security appliance if it is necessary to reset the firmware.
Firmware Management
The Firmware Management section provides settings that allow for easy firmware upgrade and
preferences management. The Firmware Management section allows you to:
• Upload and download firmware images and system settings.
• Boot to your choice of firmware and system settings.
• Manage system backups.
• Return your SonicWALL security appliance to the previous system state.
Note: SonicWALL security appliance SafeMode, which uses the same settings used in the Firmware
Management section, provides quick recovery from uncertain states.
New Firmware
To receive automatic notification of new firmware, select the Notify me when new firmware is
available check box. If you enable this feature, the SonicWALL security appliance sends a status
message to the SonicWALL security appliance firmware server daily with the following information:
• SonicWALL Serial Number
• Product Type
• Current Firmware Version
• Language
• Currently Available Memory
• ROM Version
• Options and Upgrades
Alert: After the initial 90 days from purchase, firmware updates are available only to registered users
S
with a valid support contract. You must register your SonicWALL security appliance at
<https://www.mysonicwall.com>.
Updating Firmware Manually
Click Upload New Firmware to load new firmware in the SonicWALL security appliance. A dialogue
box is displayed warning you that your current firmware version is overwritten by the uploaded
version. You should export your current SonicWALL security appliance settings to a preferences file
before uploading new firmware. Click Browse to locate the new firmware version. Once you locate
the file, click Upload to load the new firmware onto the SonicWALL security appliance.
48
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 68

Firmware Management Settings
The Firmware Management table has the following columns:
• Firmware Image - In this column, types of firmware images are listed:
Current Firmware, firmware currently loaded on the SonicWALL security appliance.
Current Firmware with Factory Default Settings, rebooting using this firmware image resets
the SonicWALL security appliance to its default IP addresses, user name, and password
Current Firmware with Backup Settings, a firmware image created by clicking Create
Backup Settings. This only displays after you create a backup image.
Uploaded Firmware, the last version uploaded from mysonicwall.com. This only displays after
you upload new firmware.
Uploaded Firmware with Factory Default Settings, rebooting using this firmware image
resets the SonicWALL security appliance to its default IP addresses, user name, and
password. This only displays after you upload new firmware.
Uploaded Firmware with Backup Settings, a firmware image created by clicking Create
Backup Settings. This only displays if you upload new firmware after you create a backup
image.
• Version - The firmware version is listed in this column.
• Date - The day, date, and time of downloading the firmware.
• Size - The size of the firmware file in Megabytes (MB).
• Download - Clicking the icon saves the firmware file to a new location on your
computer or network. Only uploaded firmware can be saved to a different location.
• Boot - Clicking the icon reboots the SonicW ALL security app liance with the firmware version listed
in the same row.
System > Settings
S
Alert: When uploading firmware to the SonicWALL securi ty appliance, you must not interrupt the Web
browser by closing the browser, clicking a link, or loading a new page. If the browser is inter rupt ed ,
the firmware may become corrupted.
Note: Clicking Boot next to any firmware image overwrites the existing current firmware image
making it the Current Firmware image. On the PRO 5060, the uploaded firmware images are
removed from the table after rebooting the SonicWALL security appliance.
SafeMode - Rebooting the SonicW ALL Security Appliance
SafeMode allows easy firmware and preferences management as well as quick recovery from
uncertain configuration states. Pressing the Reset button for one second launches the SonicWALL
security appliance into SafeMode. SafeMode allows you to select the firmware version to load and
reboot the SonicWALL security appliance. To access the SonicWALL security appliance using
SafeMode, press the Reset button for 1 second. After the SonicWALL security appliance reboots,
open your Web browser and enter the current IP ad dr ess of th e SonicWALL se curity applian ce or the
default IP address: 192.168.168.168. The SafeMode page is displayed:
SafeMode allows you to do any of the following:
• Upload and download firmware images to the SonicWALL security appliance.
• Upload and download system settings to the SonicWALL security appliance.
• Boot to your choice of firmware options.
• Create a system backup file.
• Return your SonicWALL security appliance to a previous system state.
System Information
System Information for the SonicWALL security appliance is retained and displayed in this section.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
49
Page 69

C
HAPTER
7:
Configuring System Settings
Firmware Management
The Firmware Management table has the following columns:
• Firmware Image - In this column, five types of firmware images are listed:
Current Firmware, firmware currently loaded on the SonicWALL security appliance
Current Firmware with Factory Default Settings, rebooting using this firmware image resets
the SonicWALL security appliance to its default IP addresses, user name, and password
Current Firmware with Backup Settings, a firmware image created by clicking Create
Backup Settings. This only displays after you create a backup image.
Uploaded Firmware, the last version uploaded from mysonicwall.com
Uploaded Firmware with Factory Default Settings, rebooting using this firmware image
resets the SonicWALL security appliance to its default IP addresses, user name, and passwor d
Uploaded Firmware with Backup Settings, a firmware image created by clicking Create
Backup Settings. This only displays after you create a backup image.
• Version - The firmware version is listed in this column.
• Size - The size of the firmware file in Megabytes (MB).
• Download - Clicking the icon saves the firmware file to a new location on your
computer or network. Only uploaded firmware can be saved to a different location.
• Boot - Clicking the icon reboots the SonicW ALL security applian ce with the firmware version liste d
in the same row.
Note: Clicking Boot next to any firmware image overwrites the existing current firmware image
making it the Current Firmware image.
Click Boot in the firmware row of your choice to restart the SonicWALL security appliance.
50
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 70

System > Diagnostics
C
HAPTER
8
Chapter 8: Performing Diagnostic Tests
and Restarting the SonicWALL
Security Appliance
System > Diagnostics
The System > Diagnostics page provides several diagnostic tools which help troubleshoot network
problems as well as CPU and Process Monitors.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
51
Page 71

C
HAPTER
8:
Performing Diagnostic Tests and Restarting the SonicWALL Security Appliance
Tech Support Report
The Tech Support Report generates a detailed report of the SonicWALL security appliance
configuration and status, and saves it to the local hard disk using the Download Report button. This
file can then be e-mailed to SonicWALL Technical Support to help assist with a pro blem.
Alert: You must register your SonicWALL security appliance on mySonicWALL.com to receive
S
Generating a Tech Support Report
technical support.
Before e-mailing the Tech Support Report to the SonicWALL Technical Support team, complete a
Tech Support Request Form at <https://www.mysonicwall.com>. After the form is submitted, a unique
case number is returned. Include this case number in all correspondence, as it allows SonicWALL
Technical Support to provide you with better service.
1
In the Tech Support Report section, select any of the following four report options:
• VPN Keys - saves shared secrets, encryption, and authentication keys to the report.
• ARP Cache - saves a table relating IP addresses to the corresponding MAC or physical
addresses.
• DHCP Bindings - saves entries from the SonicWALL security appliance DHCP server.
• IKE Info - saves current information about active IKE configurations.
2
Click Download Report to save the file to your system. When you click Download Report, a
warning message is displayed.
3
Click OK to save the file. Attach the report to your Tech Support Request e-mail.
52
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 72

Diagnostic Tools
You select the diagnostic tool from the Diagnostic Tools menu in the Diagnostic Tool se ction of th e
System > Diagnostics page. The following diagnostic tools are available:
• Active Connections Monitor
•CPU Monitor
• DNS Name Lookup
• Find Network Path
• Packet Trace
•Ping
• Process Monitor
• Reverse Name Resolution
Active Connections Monitor
The Active Connections Monitor displays real-time, exportable (plain text or CSV), filterable views
of all connections to and through the SonicWALL security appliance.
System > Diagnostics
Active Connections Monitor Settings
You can filter the results to display only connections matching certai n criteria. You can filter by
Source IP, Destination IP, Destination Port, Protocol, Src Interface, and Dst Interface. Enter
your filter criteria in the Active Connections Monitor Settings table.
The fields you enter values into are combined into a search string with a lo gical AND. For example , if
you enter values for Source IP and Destination IP, the search string will look for connections
matching:
Source IP AND Destination IP
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
53
Page 73

C
HAPTER
8:
Performing Diagnostic Tests and Restarting the SonicWALL Security Appliance
Check the Group box next to any two or more criteria to combine them with a logical OR. For
example, if you enter values for Source IP, Destination IP, and Protocol, and check Group next to
Source IP and Destination IP, the search string will look for connections matching:
(Source IP OR Destination IP) AND Protocol
Click Apply Filter to apply the filter immediately to the Active Connections Monitor table. Click
Reset Filters to clear the filter and display the unfiltered results again.
You can export the list of active connections to a file. Click Export Results, and select if you want the
results exported to a plain text file, or a Comma Separated Value (CSV) file for importing to a
spreadsheet, reporting tool, or database. If you are prompted to Open or Save the file, select Save.
Then enter a filename and path and click OK.
The connections are listed in the Active Connections Monitor table. The table lists:
• Source IP
• Source Port
• Destination IP
• Destination Port
• Protocol
• Tx Bytes
• Rx Bytes
Click on a column heading to sort by that column.
CPU Monitor
The CPU Monitor diagnostic tool shows real-time CPU utilization in second, minute, hour, and day
intervals (historical data does not persist across reboots).
Note: High CPU utilization is normal during Web-management page rendering, and while saving
preferences to flash. Utilization by these tasks is an indication that available resources are being
efficiently used rather than sitting idle. Traf fic ha nd lin g an d ot he r crit ica l, per fo rma nce-oriented and
system tasks are always prioritized by the scheduler, and never experience starvation.
DNS Name Lookup
The SonicWALL security appliance has a DNS lookup tool that returns the IP address of a domain
name. Or, if you enter an IP address, it returns the domain name for that address.
1
Enter the host name or IP address in the Look up name field. Do not add http to the host name.
54
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 74

2
The SonicWALL security appliance queries the DNS Server and displays the result in the Result
section. It also displays the IP address of the DNS Server used to perform the query.
The DNS Name Lookup section also displays the IP addresses of the DNS Servers configured on
the SonicWALL security appliance. If there is no IP address or IP addres ses in the DNS Server fields,
you must configure them on the Network > Settings page.
Find Network Path
Find Network Path indicates if an IP host is located on the LAN or WAN ports. This can diagnose a
network configuration problem on the SonicWALL security appliance. For example, if the SonicWALL
security appliance indicates that a computer on the Internet is located on the LAN, then the network or
Intranet settings may be misconfigured.
System > Diagnostics
Find Network Path can be used to determine if a target device is located behind a network router
and the Ethernet address of the target device. It also displays the gateway the device is using and
helps isolate configuration problems.
Packet Trace
The Packet Trace tool tracks the status of a communications stream as it moves from source to
destination. This is a useful tool to determine if a communications stream is being stopped at the
SonicWALL security appliance, or is lost on the Internet.
To interpret this tool, it is necessary to understand the three-way handshake that occurs for every
TCP connection. The following displays a typical three-way handshake initiated by a host on the
SonicWALL security appliance LAN to a remote host on the WAN.
1
TCP received on LAN [SYN]
From 192.168.168.158 / 1282 (00:a0:4b:05:96:4a)
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
55
Page 75

C
HAPTER
8:
Performing Diagnostic Tests and Restarting the SonicWALL Security Appliance
To 204.71.200.74 / 80 (02:00:cf:58:d3:6a)
The SonicWALL security appliance receives SYN from LAN client.
2
TCP sent on WAN [SYN]
From 207.88.211.116 / 1937 (00:40:10:0c:01:4e)
To 204.71.200.74 / 80 (02:00:cf:58:d3:6a)
The SonicWALL security appliance forwards SYN from LAN client to remote host.
3
TCP received on WAN [SYN,ACK]
From 204.71.200.74 / 80 (02:00:cf:58:d3:6a)
To 207.88.211.116 / 1937 (00:40:10:0c:01:4e)
The SonicWALL security appliance receives SYN,ACK from remote host.
4
TCP sent on LAN [SYN,ACK]
From 204.71.200.74 / 80 (02:00:cf:58:d3:6a)
To 192.168.168.158 / 1282 (00:a0:4b:05:96:4a)
The SonicWALL security appliance forwards SYN,ACK to LAN client.
5
TCP received on LAN [ACK]
From 192.168.168.158 / 1282 (00:a0:4b:05:96:4a)
To 204.71.200.74 / 80 (02:00:cf:58:d3:6a)
9
Client sends a final ACK, and waits for start of data transfer.
6
TCP sent on WAN [ACK]
From 207.88.211.116 / 1937 (00:40:10:0c:01:4e
To 204.71.200.74 / 80 (02:00:cf:58:d3:6a)
The SonicWALL security appliance forwards the client ACK to the remote host and waits for the data
transfer to begin.
When using packet traces to isolate network connectivity problems, look for the location where the
three-way handshake is breaking down. This helps to determine if the problem resides with the
SonicWALL security appliance configuration, or if there is a problem on the Internet.
Select Packet Trace from the Diagnostic tool menu.
Tip: Packet Trace requires an IP address. The SonicWALL security appliance DNS Name Lookup
tool can be used to find the IP address of a host.
7
Enter the IP address of the remote host in the Trace on IP address field, and click Start. You
must enter an IP address in the Trace on IP address field; do not enter a host name, such as
“www.yahoo.com”. The Trace is off turns from red to green with Trace Active displayed.
8
Contact the remote host using an IP application such as Web, FTP, or Telnet.
9
Click Refresh and the packet trace information is displayed.
10
Click Stop to terminate the packet trace, and Reset to clear the results.
56
The Captured Packets table displays the packet number and the content of the packet, for instance,
ARP Request send on WAN 42 bytes.
Select a packet in the Captured Packets table to display packet details. Packet details include the
packet number, time, content, source of the IP address, and the IP address destination.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 76

Ping
The Ping test bounces a packet off a machine on the Internet and returns it to the sender. This test
shows if the SonicWALL security appliance is able to co ntact the remote host. If users on the LAN are
having problems accessing services on the Internet, try pinging the DNS server, or another machine
at the ISP location. If the test is unsuccessful, try pinging devices outside the ISP. If you can ping
devices outside of the ISP, then the problem lies with the ISP connection.
1
Select Ping from the Diagnostic Tool menu.
2
Enter the IP address or host name of the target device and click Go.
3
If the test is successful, the SonicWALL security appliance returns a message saying the IP
address is alive and the time to return in milliseconds (ms).
Process Monitor
Process Monitor shows individual system processes, their CPU utilization, and their system time.
System > Diagnostics
Reverse Name Resolution
The Reverse Name Resolution tool is similar to the DNS name lookup tool, except that it looks up a
server name, given an IP address.
Enter an IP address in the Reverse Lookup the IP Address field, and it checks all DNS servers
configured for your security appliance to resolve the IP address into a server name.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
57
Page 77

C
HAPTER
8:
Performing Diagnostic Tests and Restarting the SonicWALL Security Appliance
System > Rest art
Click Restart to display the System > Restart page.
The SonicWALL security appliance can be restarted from the Web Management interface. Click
Restart SonicWALL and then click Yes to confirm the restart.
The SonicWALL security appliance takes approximately 60 seconds to restart, and the yellow Test
light is lit during the restart. During the restart time, Internet access is momentarily interrupted on the
LAN.
58
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 78

P
ART
3
Part 3Network
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
59
Page 79

60
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 80

Chapter 9: Configuring Network Settings
Network > Settings
The Network > Settings page allows you to configure the your network and Internet connectivity
settings in the Interface table.
Network > Settings
C
HAPTER
9
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
61
Page 81

C
HAPTER
9:
Configuring Network Settings
Setup Wizard
The Setup Wizard button accesses the SonicWALL Setup Wizard. offers a easy-to-use method for
configuring your SonicWALL security appliance for the most common Internet connectivity options. If
you are unsure about configuring network settings manually, use SonicWALL Setup Wizard.
Interfaces
The Interfaces section displays the available network interfaces for your SonicWALL security
appliance model. The Interfaces table lists the following information about the interfaces:
• Name - the name of the interface
• Mode - the network addressing mode (the WAN) interface
• IP Address - IP address assigned to the interface or whether ranges are defined for the Opt interface in Transparent mode.
• Subnet Mask - the network mask assigned to the subnet
• Status - the link status and speed
• Configure - click the edit icon to display the properties window for configuring the interface.
62
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 82

Interface Options by SonicWALL Security Appliance
SonicWALL Security
Appliance Model Interfaces
SonicWALL TZ 50 WAN, LAN
SonicWALL TZ 50 Wireless WAN, LAN, WLAN
SonicWALL TZ 150 WAN, LAN
SonicWALL TZ 150 Wireless WAN, LAN, WLAN
SonicWALL TZ 170 WAN, LAN, OPT
SonicWALL TZ 170 SP WAN, LAN, Modem
SonicWALL TZ 170 Wireless WAN, LAN, WLAN
SonicWALL PRO 1260 WAN, LAN, OPT
SonicWALL PRO 2040 WAN, LAN, DMZ
SonicWALL PRO 3060 WAN, LAN, DMZ
Network > Settings
DNS Settings
DNS (Domain Name System) is a hierarchical system for identifying hosts on the Internet or on a
private, corporate TCP/IP internetwork. It is a method for identifying hosts with friendly names instead
of IP addresses as well as a method for locating hosts. Hosts are located by resolving their names
into their associated IP addresses so network communication can be initiated with the host computer.
The DNS Settings setting information is automatically entered when you configure your WAN
interface settings. Although, you can enter up to three IP addresses in the DNS Settings section if
your WAN Internet connection using static IP addressing. However, at least one IP address of a DNS
Server is required to resolve host names to IP addresses or IP addresses to host names.
Note: It is strongly recommended to have at least two DNS IP addresses configured on the
SonicWALL security appliance. This provides redundancy in the event one DNS server is unavaila ble.
1
Enter the IP address in the DNS Server 1 field.
2
Enter the second IP address in the DNS Server 2 field.
3
Click Apply for the changes to take effect on the SonicWALL security appliance.
To pass DNS settings to computers on the LAN, you must enable the SonicWALL security appliance
DHCP server on the Network > DHCP Server page.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
63
Page 83

C
HAPTER
9:
Configuring Network Settings
Configuring the WAN Interface
The Mode menu in the Interfaces table for the WAN interface determines the network address
scheme of your SonicWALL security appliance. It includes six options:
• Transparent Mode enables the SonicWALL securi ty appliance to bridge the WAN subnet onto the
LAN interface. It requires valid IP addresses for all computers on your network, but allows remote
access to authenticated users. Your public WAN IP address is visible to the Internet.
• NAT Enabled mode translates the private IP addresses on the network to the single, valid IP
address of the SonicWALL security appliance. Select NAT Enabled if your ISP assigned you only
one or two valid IP addresses.
• NA T with DHCP Client mode co nfigures th e So nicWALL security appliance to request IP settings
from a DHCP server on the Internet. NAT with DHCP Client is a typical network addressing mode
for cable and DSL customers.
• NAT with PPPoE mode uses PPPoE to connect to the Internet. If desktop software and a user
name and password is required by your ISP, select NAT with PPPoE.
• NAT with L2TP Client mode uses IPSec to connect a L2TP server and encrypts all data transmitted from the client to the server. However, it does not encrypt network traffic to other destinations.
• NAT with PPTP Client mode uses Point to Point Tunneling Protocol (PPTP) to connect to a
remote server. It su pports older Microsoft implementations requiring tunneling connectivity.
Configuring Transparent Mode
Transparent Mode requires valid IP addresses for all computers on your network, and allows remote
access to authenticated users. Your public WAN IP address is visible to the Internet. To enable
Transparent Mode, select Transparent M ode from the Mode menu. The WAN and LAN IP addresses
are now identical. To complete the configuration, click Intranet in the Network menu list.
1
Select Specified address ranges are attached to the LAN link.
2
Click Add in the From Address table.
3
Enter the range of network IP addresses on th e LAN.
4
Click OK and then click Apply.
5
Click Restart in the Status bar of the management interface. The SonicWALL security appliance
restarts and updates the configuration.
64
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 84

Configuration Example
Your ISP has given you a public IP address of 66.217.71.191 and a range of public IP address from
66.217.71.192 to 66.217.71.200. To configure the SonicWALL security appliance in Transparent
Mode, select Transparent Mode from the Mode menu. Then follow these steps:
1
Click the icon in the Configure column to display the WAN Settings window.
2
Enter your IP address, 66.217.71.191, in the WAN IP Address field. Complete the rest of the
fields in the WAN Settings window using information provided by the ISP.
3
Click OK.
4
Click Intranet in the Network menu list.
5
Select Specified address ranges are attached to the LAN link.
6
Click Add in the LAN/WAN Client Address Ranges table.
7
Enter your IP address, 66.217.71.192, in the IP Address From fiel d.
8
Enter the IP address, 66.217.71.200, in the IP Address To field and click OK.
9
Click Apply, and then Restart in the Status bar. The SonicWALL security appliance restarts and
updates the configuration.
Configuring the WAN Interface
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
65
Page 85

C
HAPTER
9:
Configuring Network Settings
Configuring NAT Enabled
If your ISP provides a static IP address for your Internet connection, use the NAT Enabled.
1
Select NAT Enabled from the drop-down menu in the Mode column of the Interfaces table.
2
Click on the edit icon in the Configure column of the WAN interface. The WAN Properties
window is displayed.
3
In the WAN Settings section, enter a valid public IP address in the SonicWALL WAN IP (NAT
Public) Address field.
4
Enter the subnet mask in the WAN Subnet Mask field.
5
Enter the IP address of the router in the WAN Gateway (Router) Address field.
6
Click OK.
Configuring NAT with DHCP Client
If your ISP did not provide you with a public IP address, the SonicWALL security appliance can obtain
an IP address from a DHCP server at the ISP. NAT with DHCP Client is typically used with cable and
DSL connections. To configure NAT with DHCP Client, log into the SonicWALL security appliance
and click Network.
1
Select NAT with DHCP Client from the drop-down menu in the Mode column of the Interfaces
table.
2
Click the edit icon in the WAN entry of the Interfaces table. The WAN Properties window is
displayed.
3
Enter the host name assigned to you by your ISP in the Host Name field. (Optional)
4
Click Renew to obtain new IP address settings for the SonicWALL security applia nce.
5
Click Release to remove the IP address settings from the SonicWALL security appliance. Click
Refresh to reload the current settings into the SonicWALL security appliance.
6
Click OK.
66
Note: DNS Settings are obtained automatically when the SonicWALL security appliance receives its
IP address information from the DHCP Server.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 86

Configuring NAT with PPPoE Client
The SonicWALL security appliance can use Point-to-Point Protocol over Ethernet to connect to the
Internet. If your ISP requires the installation of desktop software as well as a user name and
password to access the Internet, enable NAT with PPPoE Client.
1
Select NAT with PPPoE Client from the drop-down menu in the Mode column of the Interfaces
table.
2
Click the edit icon in the WAN entry of the Interfaces table. The WAN Properties window is
displayed.
3
Select Obtain an IP Address Automatically if you do not have a p ublic IP address from your ISP.
If you have an IP address from your ISP, select Use the following Address, and enter the IP
address in the IP address field.
4
Click the PPPoE tab.
5
Enter your user name and password provided by your ISP in the User Name and User Password
fields.
6
Select Inactivity Disconnect (minutes) to end the connection after a specified time of inactivity.
10 minutes is the default value.
7
Click OK.
Configuring the WAN Interface
Configuring NAT with L2TP Client
If your Internet connection is provided through a L2TP server, you must configure the SonicWALL
security appliance to use NAT with L2TP Client. L2TP (Layer 2 Tunneling Protocol) provides
interoperability between VPN vendors that protocols such as Point-to-Point Tunneling Protocol
(PPTP) and Layer 2 Forwarding (L2F) do not have.
1
Log into the SonicWALL security appliance, and click Network.
2
Select NAT with L2TP Client from the Network Addressing Mode menu.
3
Click the edit icon in the WAN entry of the Interfaces table. The WAN Properties window is
displayed.
4
Obtain an IP Address Automatically is selected by default. Enter your host name in the Host
Name field. Click Renew to obtain new IP addressing information. Click Release to discard IP
addressing information. Click Refresh to reload the IP addressing information.
5
If you have IP addressing information, select Use the following IP Address.
6
Enter your public IP address in the SonicWALL WAN IP (NAT Public) Address field.
7
Enter the WAN Subnet information in the WAN Subnet Mask field.
8
Enter the WAN Gateway IP address in the WAN Gateway (Router) Address field.
9
Click on the L2TP tab.
10
Enter your user name in the User Name field.
11
Enter your password in the User Password field.
12
Enter the IP address of the L2TP Server in the L2TP Server IP Address field.
13
Enter the host name of the L2TP Server in the L2TP Host Name field.
14
Select Inactivity Disconnect (minutes) to end the connection after a specified time of inactivity.
15
Once a connection is established, the SonicWALL security appliance WAN IP address, the
Gateway address and the DNS Server IP addresses are displayed in the Settings Acquired via
L2TP section.
16
Click OK.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
67
Page 87

C
HAPTER
9:
Configuring Network Settings
Configuring NAT with PPTP Client
If your Internet connection is provided through a PPTP server, you must configure the SonicWALL
security appliance to use NAT with PPTP Client.
Log into the SonicWALL security appliance, and click Network.
1
Select NAT with PPTP Client from the Network Addressing Mode menu.
2
Click the edit icon in the WAN entry of the Interfaces table. The WAN Properties window is
displayed.
3
Obtain an IP Address Automatically is selected by default. Enter your host name in the Host
Name field. Click Renew to obtain new IP addressing information. Click Release to discard IP
addressing information. Click Refresh to reload the IP addressing infor matio n.
4
If you have IP addressing information, select Use the following IP Address.
5
Enter the WAN IP address in the SonicWALL WAN IP (NAT Public) Address field.
6
Enter the WAN Subnet information in the WAN Subnet Mask field.
7
Enter the WAN Gateway IP address in the WAN Gateway (Router) Address field.
8
Click on the PPTP tab.
9
Enter your user name in the User Name field.
10
Enter your password in the User Password field.
11
Enter the IP address of the PPTP Server in the PPTP Server IP Address field.
12
Enter the host name of the PPTP Client in the PPTP (Client) Host Name field.
13
Select Inactivity Disconnect (minutes) to end the connection after a specified time of inactivity.
14
Once a connection is established, the SonicWALL security appliance WAN IP address, the
Gateway address and the DNS Server IP addresses are displayed in the Settings Acquired via
PPTP section.
15
Click OK.
Configuring Ethernet Settings in WAN Properties
The Ethernet tab in the WAN Properties window allows you to manage the Ethernet settings of the
WAN interface. For most networks, you do not need to make any changes on this page.
68
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 88

9
Configuring the WAN Interface
The WAN Interface Settings information at the top of the Ethernet page is the Ethernet address of
the WAN interface on the SonicWALL security appliance.
Auto Negotiate is selected by default because the Ethernet links automatically negotiate the speed
and duplex mode of the Ethernet connection. If you select Force, you must force the connection
speed and duplex from the Ethernet card to the SonicWALL security appliance as well.
If you select Force, an information dialog is displayed with the following message:
Note: Disabling Auto Negotiate on this interface will also disable AutoMDIX on this interface. You
may need to switch from a straight-through Ethernet cable to a cross over Ethernet cable, or viceversa. Click OK to proceed.
Select Proxy management workstation Ethernet address on WAN if you are managing the
Ethernet connection from the LAN side of your netwo rk. The SonicWALL se curity appliance takes the
Ethernet address of the computer managing the SonicWALL security appliance and proxies that
address onto the WAN port of the SonicWALL security appliance. For instance, if your ISP is using
the MAC address of your network card for identification, you can pr oxy the MAC address of your
network card onto the SonicWALL WAN port.
Tip: If you are not managing the Ethernet connection from the LAN, the SonicWALL security
appliance looks for a random computer on the network creating a lengthy search process.
Note: If you enable this feature, it may take the SonicWALL a lengthy period of time to locate the
management station.
S
Fragment non-VPN outbound packets larger than WAN MTU is selected by default with a default
WAN MTU value of 1500 based on the Ethernet standard MTU. Specifies all non-VPN outbound
packets larger than this Interface’s MTU be fragmented. The minimum value is 68. Decreasing the
packet size can improve network performance as large packets require more network transmissions
when a router cannot handle the packet size. Specifying the fragmenting of VPN outbound packets is
set in the VPN > Advanced page.
Ignore Don’t Fragment (DF) Bit - Overrides DF bits in packets.
Select Enable Bandwidth Management to allocate bandwidth resources to critical applications on
the your network. Enter the total bandwidth available in th e Ava ila ble WAN Ba ndwidt h (K bps ) field.
20.00 Kbps is the default available WAN bandwidth.
Alert: Bandwidth management is only available on outbound network tr affic.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
69
Page 89

C
HAPTER
9:
Configuring Network Settings
Configuring the LAN Interface
Basic LAN Configuration
1
Click on the edit icon in the Configure column of the LAN information. The LAN Properties
window is displayed.
2
In the General Settings section, enter a valid private IP address in the SonicWALL LAN IP field.
3
Enter the subnet mask in the LAN Subnet Mask field.
4
Click OK.
Configuring Multiple LAN Subnets
This multiple LAN subnet feature supports legacy networks incorporating the SonicWALL security
appliance, as well as enable you to add more nodes if the original subnet is full. To configure this
feature, you must have an additional IP address assigned to the SonicWALL security appliance. All
users on the subnet must use this address as their default router/gateway address.
1
Click on the edit icon in the Configure column of the LAN information. The LAN Properties
window is displayed.
2
Click Add. The Add LAN Subnet Entry window is displayed.
3
Enter the additional LAN IP address in the IP Address field.
4
Enter the subnet in the Subnet Mask field. You can edit or delete any LAN subnet entries.
Select an entry and click Edit to change the information.
Select an entry and click Delete to remove the entry from the table.
Click Delete All to remove all the entries in the table.
5
Click OK.
70
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 90

Configuring Ethernet Settings
The Ethernet tab in the LAN Properties window allows you to manage the Ethernet settings of LAN
interface. For most networks, you do not need to make any changes on this page.
Configuring the OPT Interface
The LAN Interface Settings information at the top of the Ethernet page is the Ethernet address of
the LAN interface on the SonicWALL security appliance.
Auto Negotiate is selected by default because the Ethernet links automatically negotiate the speed
and duplex mode of the Ethernet connection. If you select Force, you must force the connection
speed and duplex from the Ethernet card to the SonicWALL security appliance as well.
If you select Force, an information dialog is displayed with the following message:
Note: Disabling Auto Negotiate on this interface will also disable AutoMDIX on this interface. You
may need to switch from a straight-through Ethernet cable to a cross over Ethernet cable, or viceversa. Click OK to proceed.
Configuring the OPT Interface
You can configure the OPT interface in either Tran sp ar e nt Mod e or NAT Mo d e:
• Transparent Mode enables the SonicWALL security appliance to bridge the OPT sub net onto the
WAN interface. It requires valid IP addresses for all computers connected to the OPT interface on
your network, but allows remote access to authenticated users. You can use the OPT interface in
Transpar ent mode for public se rvers and devices with st atic IP a ddresses you want visible ou t side
your SonicWALL security appliance-protected network.
• NAT Mode translates the pr iva te IP addr es se s of de vice s conn ected to the OPT interface to a sin-
gle, static IP address.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
71
Page 91

C
HAPTER
9:
Configuring Network Settings
Configuring Transparent Mode
Transparent Mode requires valid IP addresses for all computers on your network, and allows remote
access to authenticated users.
To enable Transparent Mode:
1
Click the Edit Icon in the line for the OPT interface in the Interfaces table. The OPT Properties
window displays.
2
Select OPT in Transparent Mode. The OPT and WAN IP addresses are now identical.
3
To add an address or range of addresses, click Add below the address range list. The
Add Opt Entry dialog box displays.
4
Enter a single IP address or the beginning of a range of IP addresses in the IP Address From
field.
Note: The address or range of addresses must be within the a vailable r ange of IP addre sses for your
WAN interface.
5
For a range of IP addresses, enter the ending address in the IP Address To field.
6
Click OK and then click Apply.
72
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 92

Configuring NAT Mode
NAT Enabled mode gives the OPT interface a single IP address an d a su bn et of ava ilab le IP
address. The IP addresses of devices connecting to the OPT interface are translated to the single
OPT interface IP address.
1
Click the Edit Icon in the line for the OPT interface in the Interfaces table. The OPT Properties
window displays.
Configuring the DMZ Interface
2
Select OPT in NAT Mode.
3
Enter an IP address in the OPT Private Address field.
4
Enter the subnet mask in the OPT Subnet Mask field.
5
If you want to use the OPT interface as a DMZ, enter a publicly visible IP address in the
DMZ NAT Many-to-One Public Address field. This address will be visible to the internet for
public servers in your network.
6
Click OK.
Configuring the DMZ Interface
You can configure the DMZ interface in either Transparent Mode or NAT Mode:
• Transparent Mode enables the SonicWALL security appliance to bridge the DMZ subnet onto the
WAN interface. It requires valid IP ad dresses for all computers connected to the DMZ interface on
your network, but allows remote access to authenticated users. You can use the DMZ interface in
Transpar ent mode for public se rvers and devices with st atic IP a ddresses you want visible ou t side
your SonicWALL security appliance-protected network.
• NAT Mode translates the private IP addresses of devices connected to the DMZ interface to a sin-
gle, static IP address.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
73
Page 93

C
HAPTER
9:
Configuring Network Settings
Configuring Transparent Mode
Transparent Mode requires valid IP addresses for all computers on your network, and allows remote
access to authenticated users.
To enable Transparent Mode:
1
Click the Edit Icon in the line for the DMZ interface in the Interfaces table. The DMZ
Properties window displays.
2
Select DMZ in Transparent Mode. The OPT and WAN IP addresses are now identical.
3
To add an address or range of addresses, click Add below the address range list. The Add DMZ
Entry dialog box displays.
4
Enter a single IP address or the beginning of a range of IP addresses in the IP Address From
field.
Note: The address or range of addresses must be within the a vailable r ange of IP addre sses for your
WAN interface.
5
For a range of IP addresses, enter the ending address in the IP Address To field.
6
Click OK and then click Apply.
74
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 94

Configuring the Modem Interface (TZ 170 SP)
Configuring NAT Mode
NAT Mode gives the DMZ interface a single IP address and a subnet of available IP address. The IP
addresses of devices connecting to the DMZ interface are translated to the single DMZ interface IP
address.
1
Click the edit icon in the line for the DMZ interface in the Interfaces table. The DMZ
Properties window displays.
2
Select DMZ in NAT Mode.
3
Enter an IP address in the DMZ Private Address field.
4
Enter the subnet mask in the DMZ Subnet Mask field.
5
To use the DMZ interface as a DMZ, enter a publicly visible IP address in the DMZ NAT Many-toOne Public Address field. This address will be visible to the Internet for public servers in your
network.
6
Click OK.
Configuring the Modem Interface
(TZ 170 SP)
The SonicWALL TZ 170 SP includes the Modem interface in the Interfaces table on the
Network > Settings page.
Clicking the edit icon for the Modem interface displays the Modem Settings window for configuring
the modem properties.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
75
Page 95

C
HAPTER
9:
Configuring Network Settings
Settings
Modem Settings
Profiles
Speaker Volume - choose On or Off for your modem speaker volume. The default is On.
Modem Initialization - You can specify the country to initialize your modem by choosing Initialize
Modem For Use In and specifying the country from the menu or specify the initialization of your
modem using AT commands by selecting Initialize Modem Using AT Commands and entering your
AT Commands in the text field.
Select your primary profile from the Primary Profile menu. You create th e profiles for this menu in the
Modem > Dialup Profiles page. If you have more than one dial-up ISP account, you can specify a
secondary profile from the Secondary Profile menu.
76
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 96

Failover
The Failover page in the Modem Setting window includes the same settings on the Modem >
Failover page. If you configured the failover settings on the Modem > Failover page, they are
displayed in the Failover page. If you have not configured Failover settings, use the following
instructions to configure the Failover Settings:
1
2
3
4
5
Configuring the Modem Interface (TZ 170 SP)
Select Enable WAN Failover.
Select Enable Preempt Mode if you want the primary WAN Ethernet interface to take over from
the secondary modem WAN interface when it becomes active after a failure. If you do not enable
Pre-empt Mode, the secondary WAN modem interface remains active as the WAN interface until
you click Disconnect.
Select Enable Probing. Probing for WAN connectivity occurs over the Ethernet connection, the
dial-up connection, or both. When probing is disabled on the Ethernet link, the SonicWALL
security appliance only performs link detection. If the Ethernet connection is lost for a duration of
5-9 seconds, the SonicWALL security applianc e co nsiders the Ethernet connection to be
unavailable. If the Ethernet link is lost for 0-4 seconds, the SonicWALL security appliance do es not
consider the connection to be lost. If you are swapping cables quickly, unnecessary WAN failover
does not occur on the SonicWALL security appliance. If probing is enabled and the cable is
unplugged, the 5-9 seconds link detection does not occur. Instead, the probing rules apply to the
connection using the parameters configured for Probe Interval (seconds) and Failover Trigger
Level (missed probes) settings. If probing is enabled on dialup, the dialup connection is
terminated and re-established when probing fails over the modem.
Select an option from the Probe through menu. Select Ethernet Only to probe the Ethernet WAN
connection and failover to the modem when the connection is lost. Select Modem Only to probe a
dial-up connection and have the modem redial when the dial-up co nnection is lost. Select Modem
and Ethernet to enable both types of probing on the SP.
Enter the IP address for the probe target in the Probe Target (IP Address) field. The Probe IP
address is a static IP address on the WAN. If this field is left blank, or 0.0.0.0 is entered as the
address, the Probe Target is the WAN Gateway IP address.
Note: The probe is a ping sent to the specified IP address to determine Internet connectivity.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
6
Select ICMP Probing or TCP Probing from the Probe Type options. If you select TCP Probing,
enter the TCP port number in the TCP port field.
7
In the Probe Interval (seconds) field, enter the amount of time between probes to the Probe
Target. The default value is 5 seconds. To deactivate the Probe Detection feature, enter 0 as the
77
Page 97

C
HAPTER
9:
Configuring Network Settings
value. In this case, the WAN failover only occurs when loss of the physical WAN Ethernet
connection occurs on the SonicWALL security appliance.
8
Enter the number of missed probes required for the WAN failo ver to occur in the Failover Trigger
Level (missed probes) field.
9
Enter a value for the number of successful probes required to reactivate the primary connection in
the Successful Probes to Reactivate Primary field. The default value is five (5). By requiring a
number of successful probes before the SonicWALL security appliance returns to its primary
connection, you can prevent the SonicWALL security appliance from returning to the primary
connection before the primary connection becomes stable.
Advanced
The Advanced page allows you remotely trigger the modem to dial-out to establish an WAN
connection. Selecting Enable Remotely Triggered Dial-out configures the modem to accept
remotely triggered dial-out.
If you check Requires Authentication, enter a password in the Password and Confirm Password
fields. You will be prompted for a password before being allowed to trigger a dial-out.
Activating the Modem
If the modem is inactive, an inactive link and Connect button are displayed in the Status column of
the Interfaces table on the Network>Settings page. Clicking the Connect button establishes your
modem connection. Once the connection is established, the inactive
to active
and Disconnect.
link and Connect button change
78
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 98

Configuring WLAN Properties (TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless)
Configuring WLAN Properties
(TZ 50 Wireless/TZ 150 Wireless/TZ 170
Wireless)
The SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170 Wireless includes the WLAN interface in
the Interfaces table on the Network>Settings page.
Clicking the Edit icon for the WLAN interface displays the WLAN Settings window for configuring the
WLAN properties.
•The Enable WLAN setting is checked by default to activate the WLAN interface on the
SonicWALL security appliance.
•Select WiFiSec Enforcement to require that all traffic that enters into the WLAN interface be
either IPSec traffic, WPA traffic, or both. With WiFiSec Enforcement enabled, all non-guest wireless clients are required to use the strong security of IPSec. The VPN connection inherent in
WiFiSec terminates at the GroupVPN Policy, which you can configure on the VPN > Settings
page.
• If you have not selected WiFiSec Enforcement, you can select Require WiFiSec for Site-to-Site
VPN T unnel Traversal to require WiFiSec security for all wireless conn ections thr ough the WLAN
zone that are part of a site-to-site VPN.
• Click Trust WPA traffic to accept WPA as an allowable alternative to IPSec. The SonicWALL TZ
50 Wireless/TZ 150 Wireless/TZ 170 Wireless supports both WPA-PSK (Pre-shared key) and
WPA-EAP (Extensible Authentication Protocol using an external 802.1x/EAP capable RADIUS
server).
• WLAN IP Address: The IP address of the SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170
Wireless WLAN interface.
• WLAN Subnet Mask: The subnet of the SonicWALL TZ 50 Wireless/TZ 150 Wireless/TZ 170
Wireless WLAN interface.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
79
Page 99

C
HAPTER
9:
Configuring Network Settings
• SSID: Enter a recognizable string for the SSI D for the SonicWALL TZ 50 Wireless/TZ 150
Wireless/TZ 170 Wireless security appliance. This is the name that will appear in clients’ lists of
available wireless connections.
• Radio Mode: The default 2.4GHZ 802.11b/g mixed enables the SonicWALL TZ 50 Wireless/TZ
150 Wireless/TZ 170 Wireless to support both 802.11b and 802.11g wireless card clients.
• Country Code: Select the country where you are operating the SonicWALL TZ 50 Wireless/TZ
150 Wireless/TZ 170 Wireless. The country code determines wh ich Regulatory Domain the r adio
operation falls under.
• Channel: Select the channel the radio will operate on. The default is AutoChannel, which automatically selects the channel with the least interference. Use AutoChannel unless you have a
specific reason to use or avoid specific channels.
80
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
Page 100

Chapter 10: Configuring One-to-One NAT
Network > One-to-One NAT
One-to-One NAT maps valid, external addresses to private addresses hidden by NAT. Computers on
your private LAN or OPT interface are accessed on the Internet at the corresponding public IP
addresses.
Network > One-to-One NAT
C
HAPTER
10
You can create a relationship between internal and external addresses by defining internal and
external address ranges. Once the relat ion sh ip is defined, the computer with the first IP address of
the private address range is accessible at the first IP address of the external address range, the
second computer at the second external IP address, etc.
To configure One-to-One NAT, select the Network > One-to-One NAT page.
To configure One-to-One NAT, complete the following instructions.
1
Select the Enable One-to-One NAT check box.
2
Click Add. The Add NAT Entry window is displayed.
3
Enter the beginning IP address of the private address range being mapped in the Private Range
Start field. This is the IP address of the first machine that is accessible from the Internet.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
81
 Loading...
Loading...