
/ Gateway User Manual
Model: SR700ac
501 SE Columbia Shores Boulevard, Suite 500
Vancouver, Washington 98661 USA
+1 360 859 1780 / smartrg.com
Release 1.0 March 2017

Table of Contents
Welcome! 3
Purpose & Scope 3
Intended Audience 3
Getting Assistance 3
Copyright and Trademarks 3
Disclaimer 4
Getting Familiar with your Gateway 5
LED Status Indicators 5
Connections 6
DSL 6
WAN 6
LAN 7
USB 7
POWER 7
External Buttons 7
WPS Button 7
WiFi or WLAN Button 8
Reset Button 8
Installing your SR700ac Gateway 8
Logging into your Gateway's UI 8
Device Info 10
Summary 10
WAN 11
Statistics 12
LAN 12
WAN Service 13
xTM 13
xDSL 15
References 17
Route 17
ARP 18
DHCP 19
CPU & Memory 20
Advanced Setup 20
Layer2 Interface 20
ATM Interface 21
PTM Interface 23
ETH Interface 24
WAN Service 26
xPPP over Ethernet 26
IP over Ethernet 33
Bridging 39
LAN 43
IPv6 Autoconfig 45
Ethernet Config 47
NAT 49
Virtual Servers 49
Port Triggering 51
DMZ Host 52
Security 53
IP Filtering - Outgoing 53
IP Filtering - Incoming 54
MAC Filtering 56
Add a MAC Filtering Rule 57
Parental Control 57
Time Restriction 58
URL Filter 59
Quality Of Service 59
QoS Config 60
Supported DSCP Values 61
QoS Queue Config 61
WLAN Queue 63
QoS Classification 63
QoS Port Shaping 66
Routing 67
Default Gateway 67
Static Route 67
Policy Routing 68
RIP (Routing Information Protocol) 69
DNS 71
DNS Server 71
Dynamic DNS 72
Static DNS 73
DSL 74
UPnP 76
DNS Proxy 77
Interface Grouping 78
80
IP Tunnel 80
IPv6inIPv4 80
IPv4inIPv6 81
IPSec 82
Advanced IKE Settings 83
Certificate 84
Local 84
Trusted CA 86
Multicast 88
LTE WAN Service 91
Status Information 91
Network Settings 92
Wireless 93
Basic 93
Security 95
Open & Shared Authentication 97
802.1X Authentication 98
WPA2 & Mixed WPA2/WPA Authentication 100
WPA2-PSK & Mixed WPA2/WPA-PSK Authentication 101
MAC Filter 102
Wireless Bridge 103
Advanced 104
Station Info 108
Wifi Insight 109
Site Survey 111
Channel Statistics 112
Metrics 113
Diagnostics 114
Diagnostics 114
Ethernet OAM 115
Ping Host 117
Trace Route to Host 118
Management 118
Settings 118
Backup 118
Update 120
Restore Default 121
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2016 1

Table of Contents
System Log 122
Security Log 124
SNMP Agent 125
Management Server 126
TR-069 Client 126
STUN Config 129
Internet Time 131
Access Control 132
Accounts 133
Add an Account 133
Modify or Delete an Account 134
Default Passwords 136
Services 136
Passwords 137
Access List 138
Logout Timer 139
Update Software 140
Reboot 140
Logging Out 141
Appendix: Compliance Statements 141
FCC Interference Statement 141
FCC Radiation Exposure Statement 142
FCC - PART 68 142
Ringer Equivalency Number Statement 142
IC CS-03 statement 143
Canada Statement 143
5GHz 144
Revision History 144
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2016 2

Welcome!
Thank you for purchasing this SmartRG product.
SmartRG offers solutions that simplify the complex Internet ecosystem. Our solutions include hardware, software, applications,
enhanced network insights, and security delivered via a future-proof operating system. Based in the USA, SmartRG provides local,
proactive software development and customer support. We proudly offer the best, most innovative broadband gateways available.
Learn more at www.SmartRG.com.
Purpose & Scope
This Gateway User Manual provides SmartRG customers with installation, configuration and monitoring information for their SR700ac
gateway.
Intended Audience
The information in this document is intended for Network Architects, NOC Administrators, Field Service Technicians and other networking professionals responsible for deploying and managing broadband access networks. Readers of this manual are assumed to
have a basic understanding of computer operating systems, networking concepts and telecommunications.
Getting Assistance
Frequently asked questions are provided at the bottom of the Subscribers page of the SmartRG Web site.
Subscribers: If you require further help with this product, please contact your service provider.
Service providers: if you require further help with this product, please open a support request.
Copyright and Trademarks
Copyright © 2017 by SmartRG, Inc. Published by SmartRG, Inc. All rights reserved.
The contents of this publication may not be reproduced in any part or as a whole, transcribed, stored in a retrieval system, translated into any language, or transmitted in any form or by any means, electronic, mechanical, magnetic, optical, chemical, photocopying, manual, or otherwise, without the prior written permission of SmartRG, Inc.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 3

Disclaimer
SmartRG does not assume any liability arising out of the application or use of any products, or software described herein. Neither
does it convey any license under its patent rights nor patent rights of others. SmartRG further reserves the right to make changes to
any products described herein without notice. This publication is subject to change without notice.
Any trademarks mentioned in this publication are used for identification purposes only and may be properties of their respective
owners.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 4
Getting Familiar with your Gateway
This section contains a quick description of the Gateway's lights, ports, and buttons. SmartRG produces several models that vary
slightly in capabilities (See Appendix B for details) but the basic scheme of lights, ports and buttons represented in this section
exists on each model.
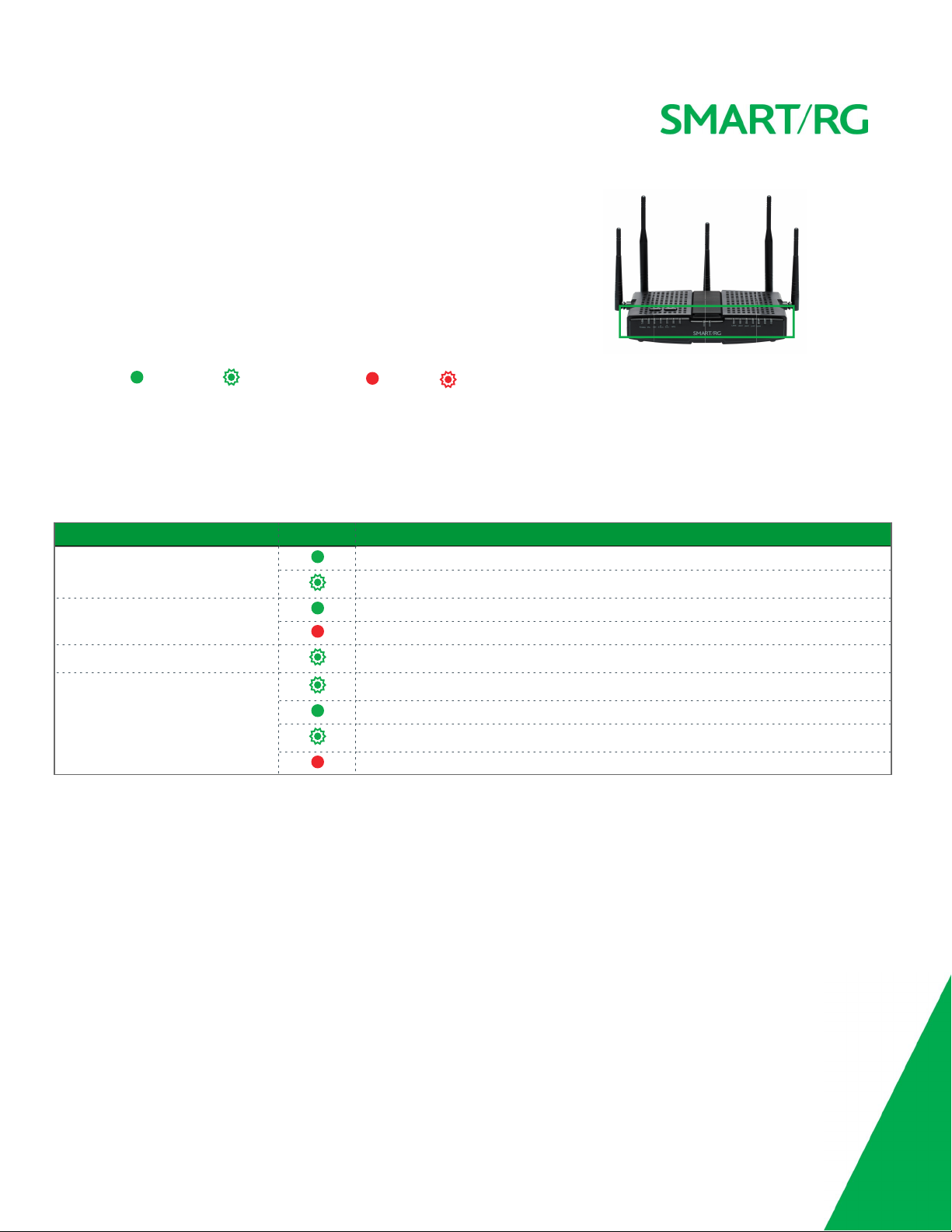
LED Status Indicators
Your SmartRG gateway has several indicator lights (LEDs) on its exterior. The following table explains the actions of the LEDs located on the front of the SR700ac
gateway.
Legend: Green Green blinking Red Red blinking
LED Action Explanation
All LEDs except those listed below Connection enabled.
Data being transferred.
POWER DSL sync acquired and device online.
Power up test.
DSL DSL sync in progress.
WPS WPS setup procedure in progress.
WPS connection completed.
Session overlap detected. Possible security risk.
Failed to find any partner with which to pair.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 5
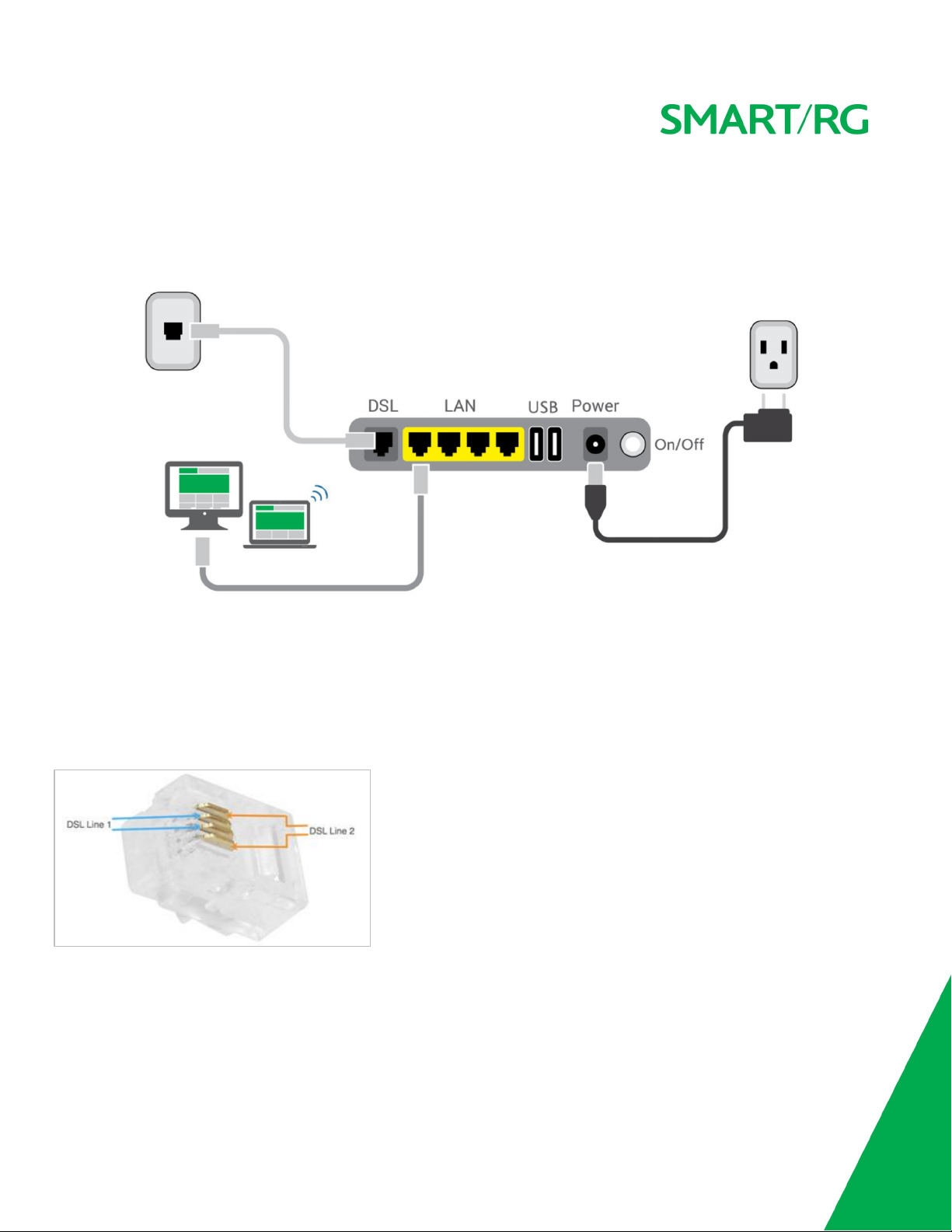
Connections
Below is a generic representation of a SmartRG gateway, Your specific model may have more or fewer ports and controls. Refer to
the Quick Start Guide enclosed with your gateway for specifics regarding installation of your particular model.
The ports depicted in this example are described below.
DSL
The grey RJ12 port labeled DSL is specifically intended for connection to an internet provider via a DSL (Digital Subscriber Line) service. The center pair carries the first DSL line. For models like the SR550n equipped with two DSL ports and bonded DSL capability,
the outer pair carries the second line.
WAN
A stand-alone RJ45 port labeled WAN enables your SmartRG gateway to be hard-wired to another network device with a RJ45/Ethernet output such as a cable, fiber, or DSL modem.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 6

For models with a stand-alone, RJ45, WAN port and a DSL port, the WAN port can be re-purposed to function as an additional LAN
port when your internet connection is via DSL.
For instructions to enable this SmartPortTMfeature, see the Ethernet Configuration section in this manual.
LAN
The four (yellow) RJ45 ports across the back of your gateway labeled LAN1, LAN2, LAN3, LAN4 are the means to connect client
devices such as computers and printers to your gateway.
On some models, one of these four ports may be labeled as WAN indicating SmartPortTMsupport. SmartPort allows a LAN port to be
re-purposed to function as an Ethernet WAN port (described above). When this port is serving as a LAN port, the corresponding LED
on the face of the unit is labeled "WAN"
For instructions to enable this SmartPortTMfeature, see the Ethernet Configuration section in this manual.
USB
USB ports on SmartRG products currently provide +5 DC volts.
POWER
Use only the power supply included with your gateway. Intended for indoor use only.
External Buttons
SmartRG gateways provide push-button controls on the exterior for critical features. These buttons provide a convenient way to trigger WPS mode, toggle the WiFi radio on and off, or reset the gateway. Their presence and locations vary by model.
WPS Button
The WPS button triggers WPS (Wi-Fi Protected Setup™) mode. WPS is a standard means for creating a secure connection between
your gateway and various wireless client devices. It is designed to simplify the pairing process between devices.
This button is located on the top of the gateway. If you have client devices that support WPS, use this button to automatically configure wireless security for your network.
WPS configures one client device at a time. You can repeat the steps as necessary for each additional WPS-compliant device you
wish to connect.
For specific instructions, refer to the Quick Start Guide included with your gateway. Also see the "Basic" section of this manual.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 7

WiFi or WLAN Button
The button labeled WiFi or WLAN (depending on model) toggles the WiFi radio on and off. The WLAN LED indicator on the gateway displays the current state of the Wi-Fi radio. This button is located on the top of the gateway.
To activate the Wi-Fi radio, press and hold the WiFi (WLAN) button for 3-5 seconds and then release. Expect a 1-3 second delay
before the WiFi (WLAN) LED turns on. Repeat this step to deactivate the Wi-Fi radio.
Reset Button
The Reset button is a small hole in the gateway's enclosure with the actual button mounted behind the surface. This style of pushbutton prevents the gateway from being inadvertently reset during handling. Reset must be actuated with a paper clip or similar
implement. This button is located on the back of the gateway.
This pin-hole sized reset button has three functions. The duration for which the button is held dictates which function is carried
out.
!!!ASKSME: Are the hold durations correct?
Hold Duration Effect
Less than 6
seconds
6-20 seconds Performs the software equivalent to the
20 or more seconds Changes the POWER LED to red and the gateway enters CFE mode which is a state associated with performing
Performs a modem reset that is equivalent to the
Restore Defaults
firmware updates via Internet browser.
Reboot
function in the gateway software.
function in the gateway software.
Installing your SR700ac Gateway
1. Connect one end of the phone cable to the DSL port on the gateway and connect the other end to the phone jack on the
wall installed by your provider.
2. Connect one end of the Ethernet cable to a LAN port on the gateway and connect the other end to your computer.
3. Plug the power adapter to the wall outlet and then connect the other end of it to the Power port of the gateway. Turn on
the unit by pressing the On/Off button on the back of the gateway.
Your gateway is now automatically being set up to connect to the Internet. This process may take a few minutes to complete before
you can begin using your Internet applications (browser, email, etc.). If you are unable to connect to the Internet, verify that all
cable connections are in place and the gateway’s power is turned on.
Logging into your Gateway's UI
To manually configure the SmartRG Gateway, you must access the gateway's embedded web UI.
1. Open a browser and enter the gateway's default address (usually http://192.168.1.1; may also be http://192.168.0.1) in the
address bar.
2. For some models, the Network status page appears. If so, click the Manage gateway (advanced) link (usually located in the
upper right corner). The Authentication Required dialog box appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 8
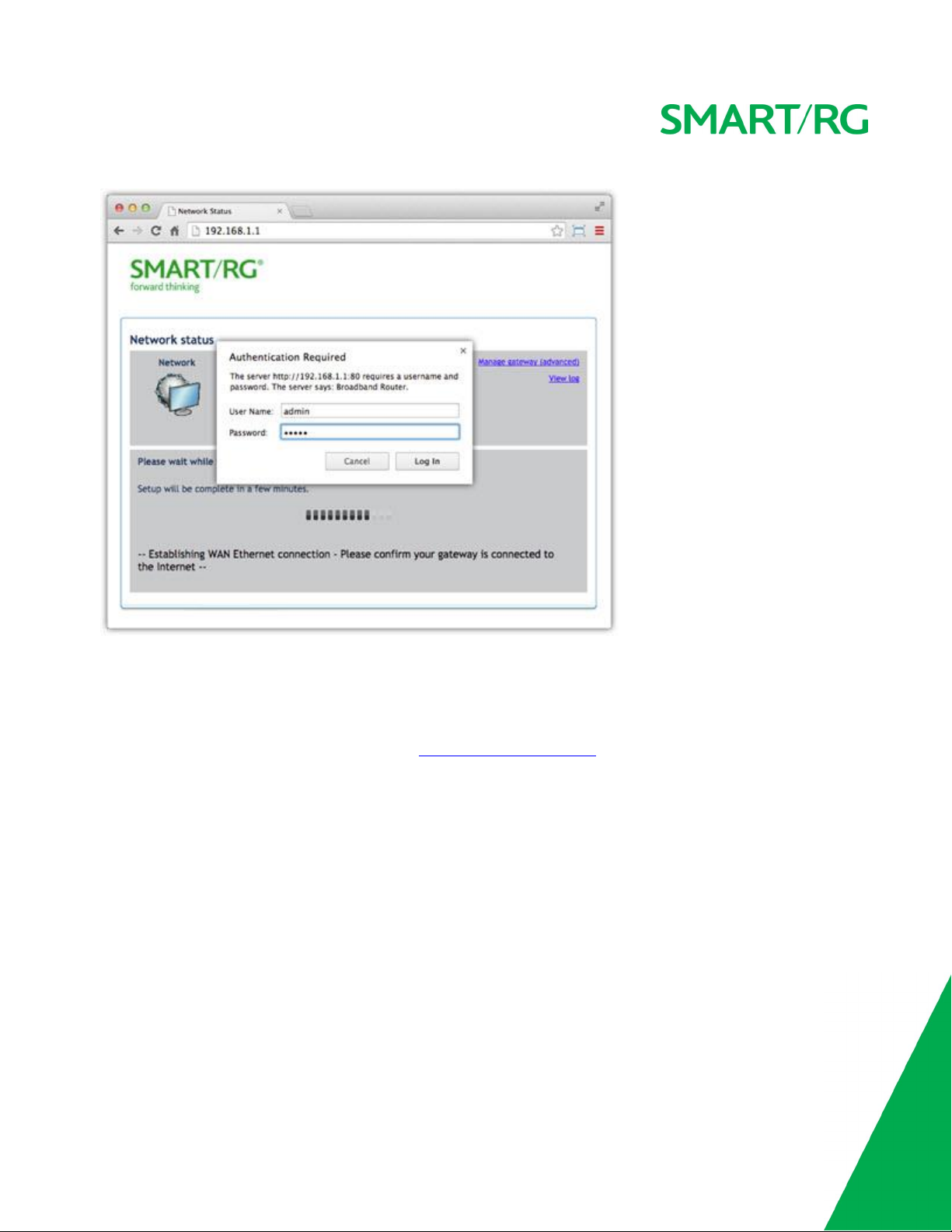
3. For all models, enter the default username and password (usually admin/admin) and click Login or OK to display the default
landing page. For many models, this is the Device Info page.
Note: The gateway's UI can be accessed via the WAN connection by entering the WAN IP address in your browser's address bar and
entering the default username and password: support/support. WAN HTTP access control MUST be enabled to access the gateway's
UI via the WAN connection. For more information, see the Management Access Control section.
If your SmartRG gateway is configured for "bridge mode" (modem) operation, your PC will NOT be able to acquire an address via CPE
DHCP. Instead, manually configure your PC's interface with an IP address on the default network (e.g., 192.168.1.100).
The remainder of this guide is dedicated to a sequential walk-through of the gateway user interface. Screen captures are provided
along with descriptions of the options available on the pictured page. Where applicable, valid values are provided.
For in-depth "how-to" information for specific scenarios, go to the knowledge base found on our support web site. Access to this site is
restricted to SmartRG customers and partners. Do not share links to this site with your subscribers.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 9

Device Info
There are several selections under Device Info in the left navigation bar. Each of them shows a different element of the gateway's
setup, status or nature of its connection with the provider and also with LAN devices. Device Info pages are read-only. You cannot
interact with or change the settings in this section.
Summary
When you log into the gateway interface, the Device Info summary page is the first to appear. This page displays details about the
hardware and software associated with your gateway. In addition, the current status of the WAN connection (if present) is shown.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 10
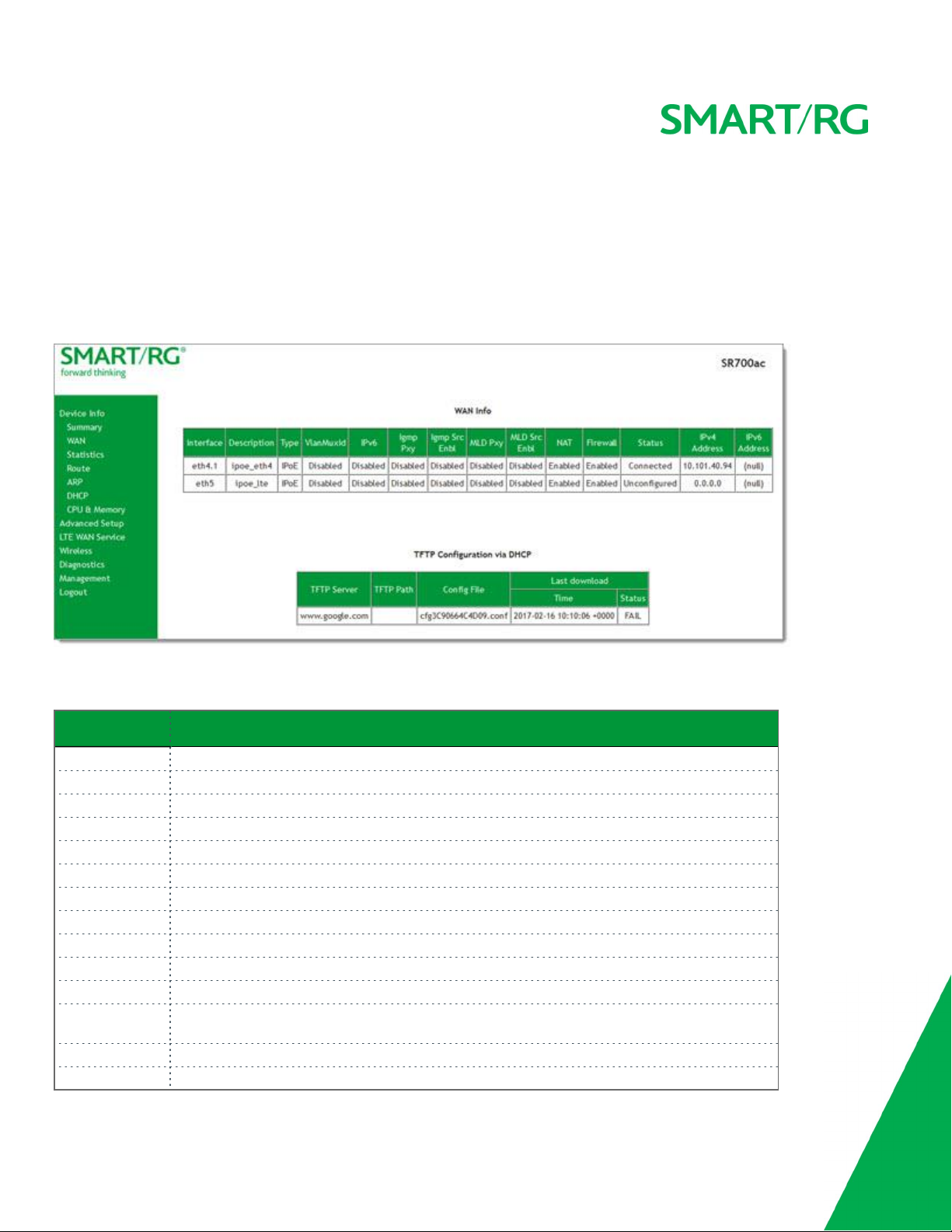
WAN
On this page, you can view information about the connection between your ISP and your gateway. The WAN interface can be DSL or
Ethernet and supports a number of Layer 2 and above configuration options (explained later in this document). Some features are
supported only on specific SmartRG models. Those exceptions are specified in this guide.
In the left navigation bar, click Device Info > WAN. The following page appears.
The fields on this page are explained in the following table.
Field Name Description
Interface The connection interface (Layer 2 interface) through which the gateway handles the traffic.
Description The service description such ipoe_0_0_1, showing the type of WAN and its ID.
Type The service type. Options are
VlanMuxId The VLAN ID. Options are
IPv6 The state of IPv6. Options are
Igmp Pxy The IGMP proxy. Options are
Igmp Src Enbl The IGMP source option. Options are
MLD Pxy The MLD proxy.
MLD Src Enbl The MLD source option. Options are
NAT The state of NAT. Options are
Firewall The state of the Firewall. Options are
Status The status of the WAN connection. Options are
IPv4 Address The obtained IPv4 address.
IPv6 Address The obtained IPv6 address.
Connected
.
PPPoE,IPoE
Disabledor0-4094
Enabled
Enabled
Enabled
and
and
Enabled
Enabled
and
Enabled
Bridge
, and
.
Disabled
Disabled
and
and
Disabled
.
.
.
Disabled
Disabled
Disabled
and
Disconnected,Unconfigured,Connecting
.
.
.
.
, and
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 11

Statistics
In this section, you can view network interface information for LAN, WAN Service, xTM and xDSL. All data is updated in 15-minute
intervals.
LAN
On this page, you can view the received and transmitted bytes, packets, errors and drops for each LAN interface configured on your
gateway. All local LAN Ethernet ports, Ethernet WAN ports and wireless Interfaces are included. For some models, statistics are
provided for multicast, unicast and broadcast traffic.
In the left navigation bar, click Device Info > Statistics. The Statistics -- LAN page appears where you can view detailed information
about the status of your LAN.
To reset the counters, click Reset Statistics near the bottom of the page.
The fields on this page are explained in the following table.
Field Name Description
Interface Available LAN interfaces. Options are
(Wireless LAN-side interface), and
Received&Transmitted
Bytes Total number of packets in bytes.
Pkts Total number of packets.
Errs Total number of error packets.
Drops Total number of dropped packets.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 12
columns
LAN1-LAN4,WAN
2.4 GHz
and
5 GHz
(if configured on your device), and
.
Wl0
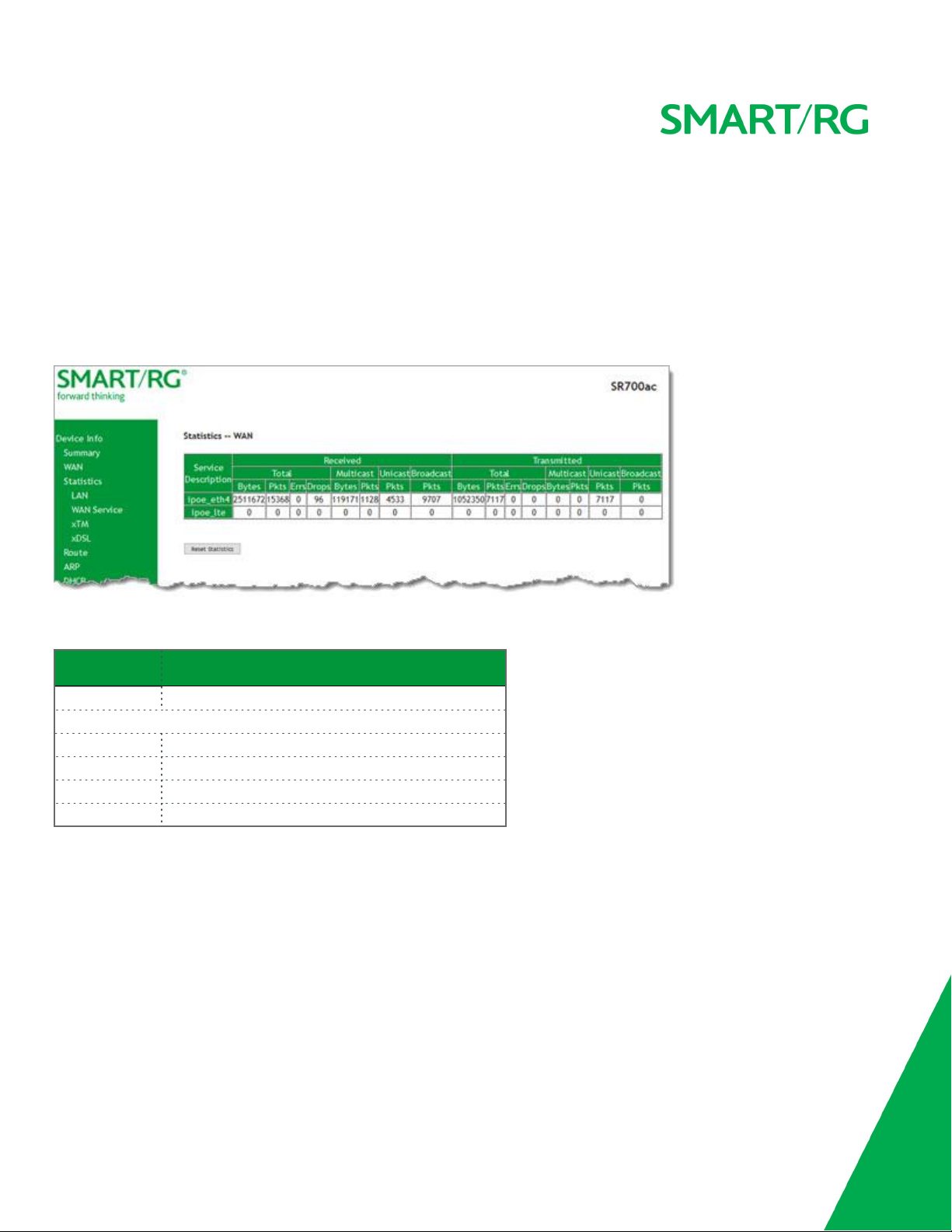
WAN Service
On this page, you can view the received and transmitted bytes, packets, errors and drops for each WAN interface for your SmartRG
Gateway. All WAN interfaces configured for your gateway are included.
In the left navigation bar, click Device Info > Statistics > WAN Service. The Statistics -- WAN page appears where you can view
detailed information about the status of your WAN.
To reset the counters, click Reset Statistics near the bottom of the page.
The fields on this page are explained in the following table.
Field Name Description
Description Service description. Options are:
Received&Transmitted
Bytes Total quantity of packets in bytes.
Pkts Total quantity of packets.
Errs Total quantity of error packets.
Drops Total quantity of dropped packets.
columns
pppoe,ipoe
, andb.
xTM
On this page, you can view the ATM/PTM statistics for your gateway. All WAN interfaces configured for your SmartRG gateway are
included.
In the left navigation bar, click Device Info > Statistics > xTM. The Interface Statistics page appears.
To reset these counters, click Reset Statistics near the bottom of the page.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 13
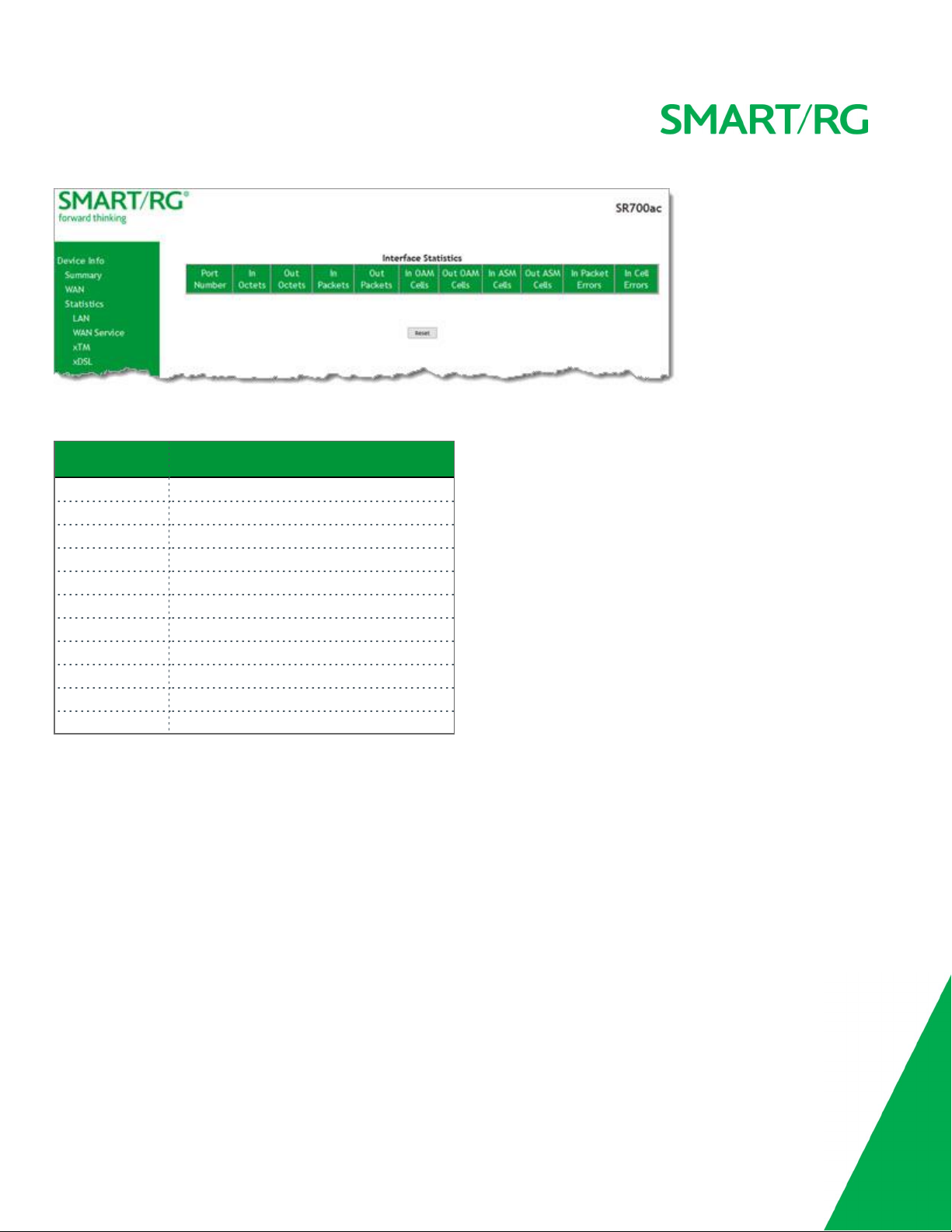
The fields on this page are explained in the following table.
Field Name Description
Port Number Statistics for Port 1, or both ports if bonded.
In Octets Total quantity of received octets.
Out Octets Total quantity of transmitted octets.
In Packets Total quantity of received packets.
Out Packets Total quantity of transmitted packets.
In OAM Cells Total quantity of received OAM cells.
Out OAM Cells Total quantity of transmitted OAM cells.
In ASM Cells Total quantity of received ASM cells.
Out ASM Cells Total quantity of transmitted ASM cells.
In Packet Errors Total quantity of received packet errors.
In Cell Errors Total quantity of received cell errors.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 14

xDSL
On this page, you can view the DSL statistics for your gateway. All xDSL (VDSL or ADSL) interfaces configured for your SmartRG gateway are included. The terms and their explanations are derived from the relevant ITU-T standards and referenced accordingly.
1. In the left navigation bar, click Device Info > Statistics > xDSL. The Statistics - xDSL page appears.
2. To run an xDSL Bit Error Rate (BER) test (to determine the quality of the xDSL connection):
a. Scroll to the bottom of the page and click xDSL BER Test. The ADSL BER Test dialog box appears.
b. In the Tested Time field, select the duration in seconds and click Start. Options range from 1 second to 360 seconds.
The test transfers idle cells containing a known pattern and compares the received data with this known pattern.
Comparison errors are tabulated and displayed.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 15

3. To reset the counters, click Reset Statistics at the bottom of the page.
The fields on this page are explained in the following table.
Field Name Description
Mode xDSL mode that the modem has trained under, such as ADSL2+, G.DMT, etc.
Traffic Type Connection type. Options are:
ATM,PTM
Status Status of the connection. Options are:Up,
ETH
and
.
Disabled,NoSignal
, and
Initializing
.
Link Power State Current link power management state (e.g., L0, L2, L3).
Downstream
Line Coding (Trellis) State of theTrellis Coded Modulation. Options areOnand
and
Upstream
columns
Off
.
SNR Margin (0.1 db) The signal-to-noise ration margin (SNRM) is the maximum increase (in dB) of the
received noise power, such that the modem can still meet all of the target BERs
over all the frame bearers. [2]
Attenuation (0.1 db)
Output Power (0.1
The signal attenuation is defined as the difference in dB between the power
received at the near-end and that transmitted from the far-end. [2]
Transmit power from the gateway to the DSL loop relative to one Milliwatt (dBm).
dBm)
Attainable Rate (Kbps) The typically obtainable sync rate, i.e., the attainable net data rate that the
receive PMS-TC and PMD functions are designed to support under the following conditions:
l Single frame bearer and single latency operation
l Signal-to-Noise Ratio Margin (SNRM) to be equal or above the SNR Target Mar-
gin
l BER not to exceed the highest BER configured for one (or more) latency
paths
l Latency not to exceed the highest latency configured for one (or more)
latency paths
l Accounting for all coding gains available (e.g., trellis coding, RS FEC) with
latency bound
l Accounting for the loop characteristics at the instant of measurement [2]
Rate (Kbps) The current net data rate of the xDSL link. Net data rate is defined as the sum of all
frame bearer data rates over all latency paths. [2]
Super Frames The number of xDSL Super Frames transmitted/received.
Super Frame Errors The number of xDSL Super Frames transmitted/received with errors.
RS Words The number of Reed-Solomon-based Forward Error Correction (FEC) codewords trans-
mitted/received.
RS Correctable Errors The number of Reed-Solomon-based FEC codewords received with errors that have
been corrected.
RS Uncorrectable
Errors
The number of Reed-Solomon-based FEC codewords received with errors that were
not correctable.
HEC Errors A count of ATM HEC errors detected. As per ITU-T G.992.1 and G.992.3, a1-byte HEC
is generated for each ATM cell header. Error detection is implemented as defined in
ITU-T I.432.1 with the exception that any HEC error shall be considered as a mul-
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 16

Field Name Description
tiple bit error, and therefore, HEC Error Correction is not performed. [1],[2]
OCD Errors Total number of Out-of-Cell Delineation errors. ATM Cell delineation is the process
which allows identification of the cell boundaries. The HEC field is used to achieve
cell delineation. [4] An OCD Error is counted when the cell delineation process trans-
itions from the SYNC state to the HUNT state. [2]
LCD Errors Total number of Loss of Cell Delineation errors. An LCD Error is counted when at
least one OCD error is present in each of four consecutive overhead channel periods
and SEF (Severely Errored Frame) defect is present. [2]
Total Cells The total number of cells (OAM and Data cells) transmitted/received.
Data Cells The total number of data cells transmitted/received.
Bit Errors The total number of Idle Cell Bit Errors in the ATM Data Path. [3]
Total ES Total number of Errored Seconds. This parameter is a count of 1-second intervals
with one or more CRC-8 anomalies. [4]
Total SES Total number of Severely Errored Seconds. An SES is declared if, during a 1-second
interval, there are 18 or more CRC-8 anomalies in one or more of the received
bearer channels, or one or more LOS (Loss of Signal) defects, or one or more SEF
(Severely Errored Frame) defects, or one or more LPR (Loss of Power) defects. [4]
Total UAS
Total number of Unavailable Seconds. This parameter is a count of 1-second inter-
vals for which the xDSL line is unavailable. The xDSL line becomes unavailable at
the onset of 10 contiguous SESs. These 10 SES’s shall be included in the unavailable
time. Once unavailable, the xDSL line becomes available at the onset of 10 con-
tiguous seconds with no SESs. These 10 seconds with no SES’s shall be excluded from
unavailable time. [4]
References
[1] ITU-T Recommendation G.992.1 (1999), Asymmetric digital subscriber line (ADSL) transceivers.
[2] ITU-T Recommendation G.992.3 (2005), Asymmetric digital subscriber line transceivers 2 (ADSL2).
[3] ITU-T Recommendation G.997.1 (2006), Physical layer management for digital subscriber line (DSL) transceivers.
[4] ITU-T Recommendation I.432.1 (1999), B-ISDN user-network interface – Physical layer specification: General characteristics.
Route
On this page, you can view the LAN and WAN route table information configured in your SmartRG Gateway for both IPv4 and IPv6
implementation.
In the left navigation bar, click Device Info > Route. The following page appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 17
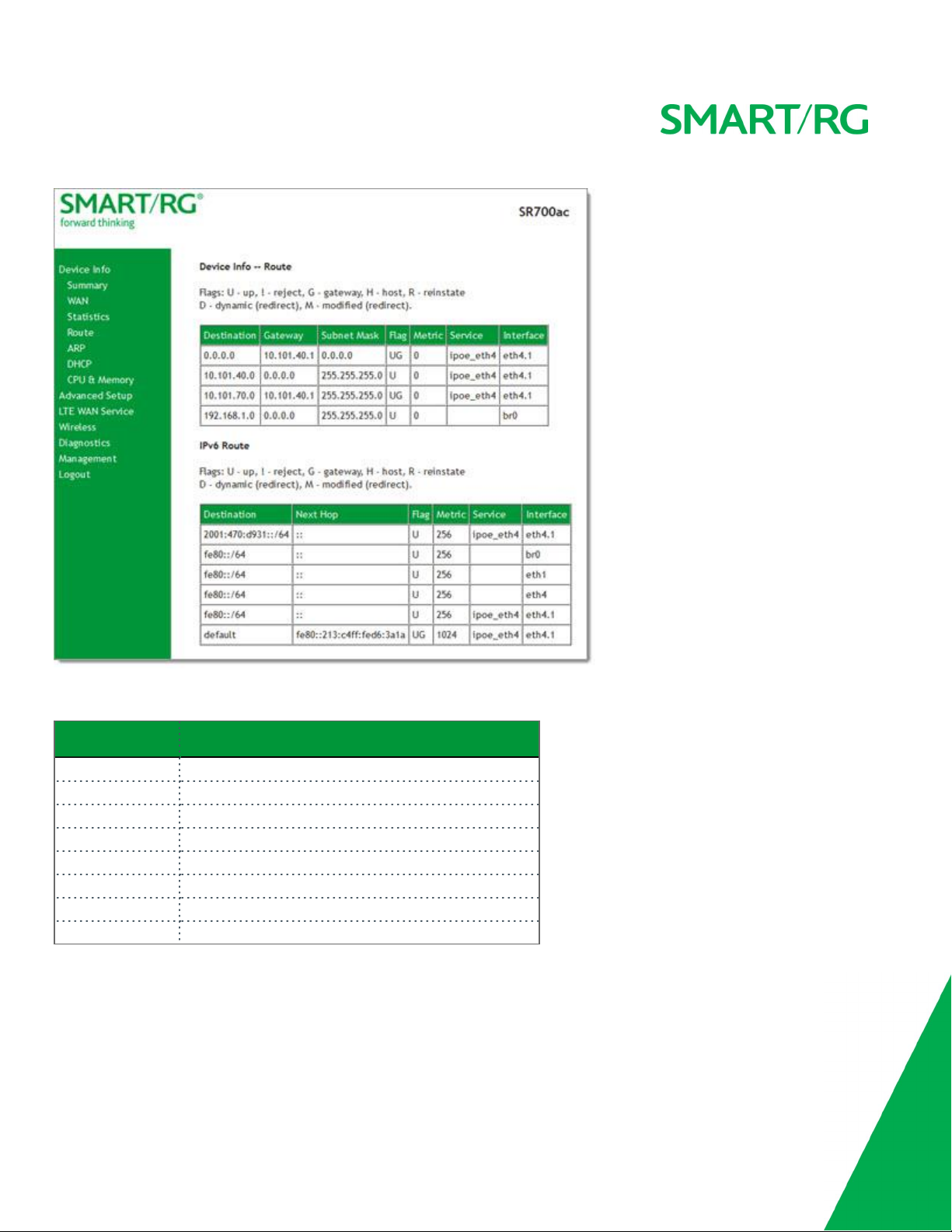
The fields on this page are explained in the following table.
Field Description
Destination Destination IP addresses.
Gateway Gateway IP address.
Subnet Mask Subnet Masks.
Flag Status of the flags.
Metric Number of hops required to reach the default gateway.
Service Service type.
Interface WAN/LAN interface.
Next Hop (
For IPv6 Route only
) Next hop IP address.
ARP
On this page, you can view the host IP addresses and their hardware (MAC) addresses for each LAN Client connected to the gateway
via a LAN Ethernet port or wireless LAN.
In the left navigation bar, click Device Info > ARP. The following page appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 18
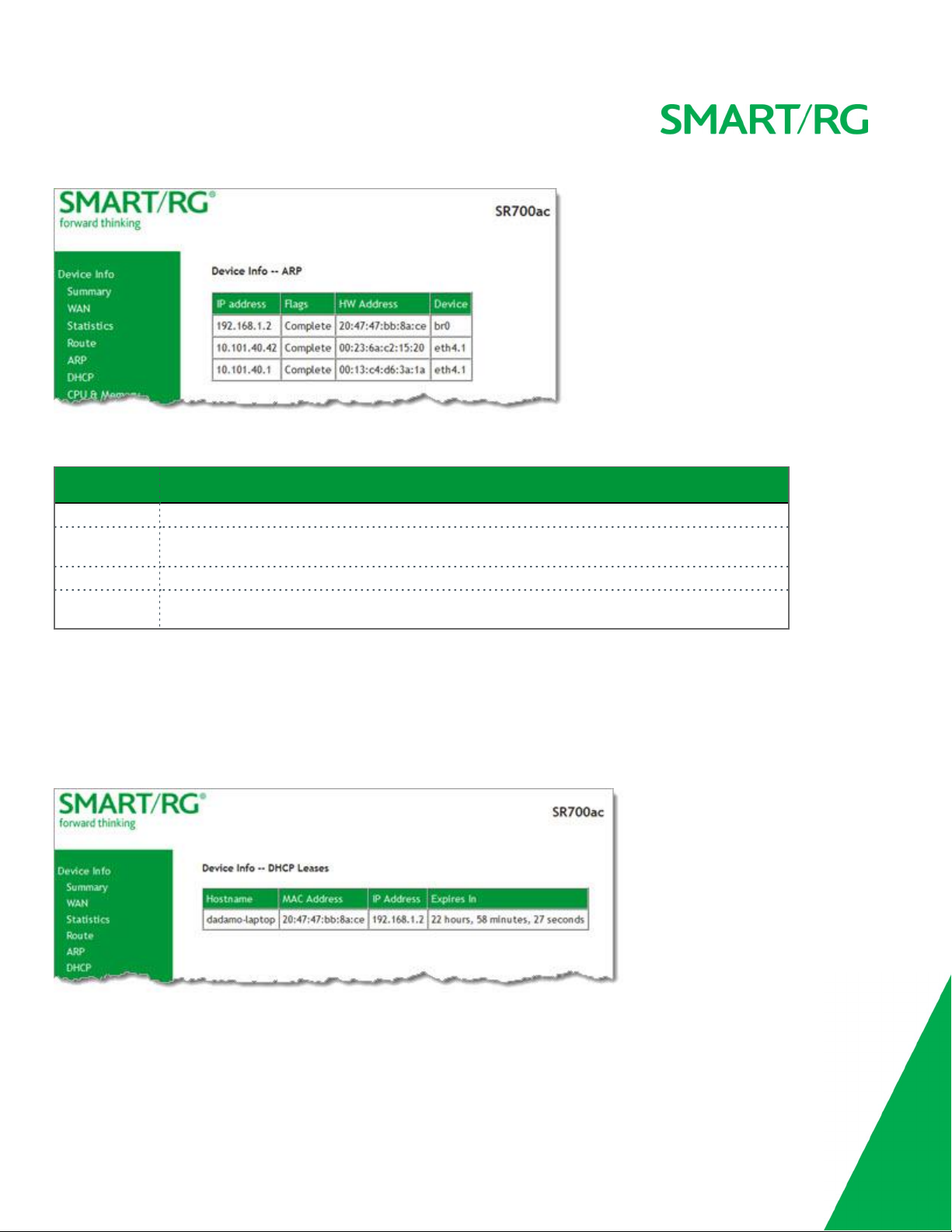
The fields on this page are explained in the following table.
Field Name Description
IP address The IP address of the host.
Flags Each entry in the ARP cache will be marked with one of these flags. Options are:
HW Address The hardware (MAC) address of the host.
Device The system level interface by which the host is connected. Options are:
manent
atm(n)
and
, and
Published
.
.
br(n),atm(n),eth(n)
Complete,Per-
,
DHCP
The DHCP page displays a list of locally connected LAN hosts and their DHCP lease status, which are directly connected to the
SmartRG Gateway via a LAN Ethernet port or Wireless LAN.
In the left navigation bar, select Device Info > DHCP. The following page appears.
The fields on this page are explained in the following table.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 19
Field Name Description
Hostname The host name of each connected LAN device.
MAC Address The MAC Address for each connected LAN device.
IP Address The IP Address for each connected LAN device.
Expires In The time until the DHCP lease expires for each LAN device.
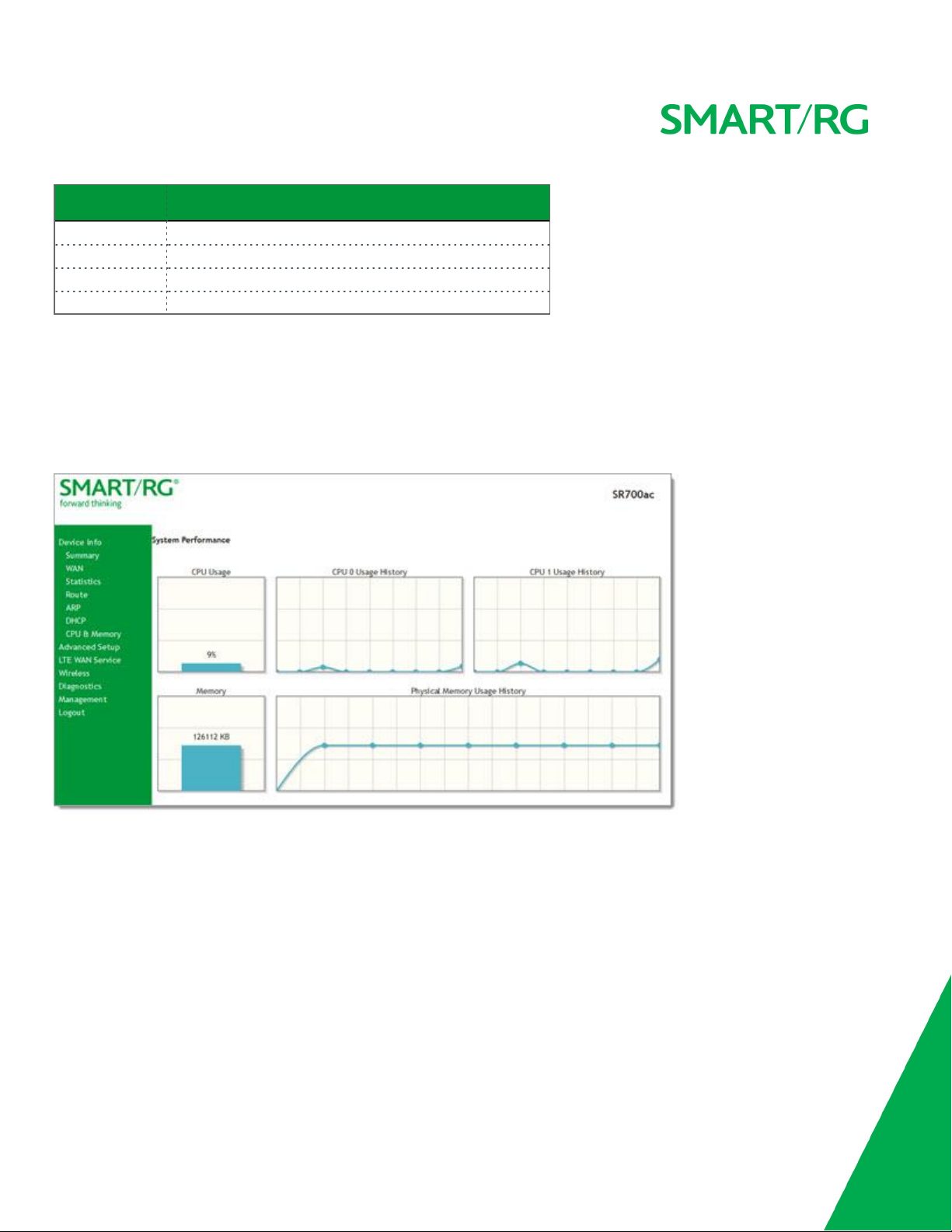
CPU & Memory
On this page, you can view the CPU and memory data for the gateway.
In the left navigation bar, click Device Info > CPU & Memory. The following page appears, showing the current usage and history.
The information refreshes automatically.
Advanced Setup
In this section, you can configure network interfaces, security, quality of service settings, and many other settings for your gateway
and network.
Layer2 Interface
In this section, you can configure interfaces for ATM, PTM and Ethernet interfaces. Generally you can accept the settings configured
by default. If your network is highly customized, you may need to modify some of the settings, such as Username and Password.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 20

ATM Interface
On this page, you can configure Asynchronous Transfer Mode / Permanent Virtual Conduit (ATM/PVC) settings for your gateway. You
can customize latency options, link type, encapsulation mode and more.
Note: Devices (routers) on both ends of the connection must support ATM / PVC.
1. In the left navigation bar, click Advanced Setup > Layer2 Interface > ATM Interface and then click Add. The following page
appears.
2. Modify the settings as desired, using the information provided in the table below.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
VPI Enter a Virtual Path Identifier. A VPI is an 8-bit identifier that uniquely identifies a network
path for ATM cell packets to reach its destination. A unique VPI number is required for each
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 21

Field Name Description
ATM path. This setting works with the VCI. Each individual DSL circuit must have a unique
VPI/VCI combination. String limits are:0-
255
.
VCI Enter a Virtual Channel Identifier. A VCI is a 16-bit identifier that has a unique channel.
65535
.
Select DSL
Latency
Options are:32Select the level of DSL latency. Options are:
l Path0 Fast: No error correction and can provide lower latency on error free lines.
l Path1 Interleaved: Error checking that provides error free data which increases
latency.
l Path0&1 Both: Fast & Interleaved.
Select Link Type Select the linking protocol.
EoA
is the most popular with
PPPoA
a close second (used with
many legacy ISPs). Options are:
l EoA: Ethernet over ATM.
l PPPoA: Point-to-Point Protocol over ATM.
l IPoA: Internet Protocol over ATM.
Encapsulation
Mode
Select whether multiple protocols or only one protocol is carried per PVC (Permanent Virtual Circuit). Options are:
l LLC/ENCAPSULATION: (Available when PPPoA is selected as the Link Type) Logical
Link Control (LLC) encapsulation protocols used with multiple PVCs.
l LLC/SNAP-BRIDGING: (Available when EoA is selected as the Link Type) LLC used to
carry multiple protocols in a single PVC.
l LLC/SNAP-ROUTING: (Available when IPoA is selected as the Link Type) LLC used to
carry one protocol per PVC.
l VC/MUX: Virtual Circuit Multiplexer creates a virtual connection used to carry one
protocol per PVC.
Service Category Select the bit rate protocol. Options are:
l UBR without PCR: Unspecified Bit Rate with no Peak Cell Rate, flow control or time
synchronization between the traffic source and destination. Commonly used with
applications that can tolerate data / packet loss.
l UBR with PCR: Same as above but with a Peak Cell Rate.
l CBR: Constant Bit Rate relies on timing synchronization to make the network traffic
predictable. Used commonly in Video and Audio traffic network applications.
l NON Realtime VBR: Non Realtime Variable Bit Rate used for connections that trans-
port traffic at a Variable Rate. This category requires a guaranteed bandwidth and
latency. It does not rely on timing synchronization between the destination and
source.
l Realtime VBR: Realtime Variable Bit Rate. Same as the above option but relies on tim-
ing and synchronization between the destination and source. This category is commonly used in networks with compressed video traffic.
Minimum Cell
Rate
Minimum allowable rate (cells per second) at which cells can be sent on a ATM network. For
no shaping, enter-1.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 22

Field Name Description
Scheduler for
Queues of Equal
Precedence as
the Default
Queue
The algorithm used to schedule the queue behavior. VC scheduling is unique from Default
Queues. Options are:
l WRR: Weighted Round Robin packets are accessed in a round robin style and classes
can be given.
l WFQ: Weighted Fair Queuing packets are assigned in a specific queue.
l Default Queue Weight: The default weight of the specified queue. Options are: 1-
63.
l Default Queue Precedence: The precedence of the specified group. Options are: 1-8
PTM Interface
The SmartRG gateway's VDSL2 standards support Packet Transfer Mode (PTM). An alternative to ATM mode, PTM transports packets
(IP, PPP, Ethernet, MPLS, and others) over DSL links. For more information, refer to the IEEE802.3ah standard for Ethernet in the First
Mile (EFM). Some 500 series gateways have a PTM interface configured by default.
On this page, you can configure a PTM interface for your gateway.
1. In the left navigation bar, click Advanced Setup > Layer2 Interface > PTM Interface and then click Add. The following page
appears.
2. Modify the settings as desired.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 23

Field Name Description
Select DSL Latency Select the level of DSL latency. Options are:
l Path0 Fast: No error correction and can provide lower latency on error-free
lines.
l Path1 Interleaved: Error checking that provides error-free data which
increases latency.
Select Scheduler for
Queues of Equal Precedence as the
Default Queue
Select an algorithm for applying queue data priority. Options are:
l Weighted Round Robin: Time slices are assigned to each process in equal por-
tions and in circular order, handling all processes without priority (also known
as cyclic executive).
l Weighted Fair Queuing: A data packet scheduling technique allowing dif-
ferent scheduling priorities to be assigned to statistically multiplexed data
flows. Since each data flow has its own queue, an ill-behaved flow (that sent
larger packets or more packets per second than the others since it became
active) will only affect itself and not other sessions.
Default Queue
Enter a default weight of the specified queue. Options are:1-63.
Weight
Default Queue Pre-
Enter a precedence for the specified queue. Options are:1-8.
cedence
ETH Interface
If you are using a gateway that is Ethernet-specific (non-DSL), you may want to configure an ETH interface to manage communication.
Most models support Ethernet and can be configured for Ethernet and DSL at the same time. Your gateway has four LAN ports. One
of them can be re-purposed to become an RJ45 WAN port when needed.
On this page, you can configure an Ethernet interface for your gateway.
1. In the left navigation bar, click Advanced Setup > Layer2 Interface > ETH Interface.
2. If no WAN port is configured, the Add button appears. Click Add.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 24

3. If a WAN port is already configured or you clicked Add, the following page appears.
Note: If a WAN port it is already configured, you must remove it before you can define a new one. Before you can remove the
existing port, you must first modify or delete any WAN service that uses it. The Add button does not appear until the existing
port is removed.
4. Select the LAN port you wish to act as a WAN port.
5. Click Apply/Save to commit your changes.
6. To remove the WAN interface, click the Remove checkbox and then click the Remove button.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 25

WAN Service
In this section, you can configure WAN services for:
l "xPPP over Ethernet"
l "IP over Ethernet"
l "Bridging"
A sample configuration scenario is provided for each variation.
xPPP over Ethernet
There are several parts to configuring a PPP over Ethernet WAN service. You will progress through several pages to complete the
configuration.
1. In the left navigation bar, click Advanced Setup > WAN Service and then click Add. The following page appears.
2. Select the Layer2 interface to use for the WAN service.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 26

3. Click Next. The following page appears.
4. Accept the default of PPP over Ethernet (PPPoE) WAN service type.
5. Modify the other settings as needed.
The fields on this page are explained in the following table.
Field Name Description
Enter Service
Enter a name to describe this configuration.
Description
Enter 802.1P Priority Options are0-7. The default is0.
For tagged service, enter values in this field and the 802.1Q VLAN ID field.
For untagged service, enter -1 (disabled) in this field and the 802.1Q VLAN ID field.
Enter 802.1Q VLAN ID Options are0-
4094
. The default is-1(disabled).
For tagged service, enter values in this field and the 802.1P Priority field.
For untagged service, enter -1 (disabled) in this field and the 802.1P Priority field.
Select VLAN TPID Select the TPID for this VLAN. Options are
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 27
0x8100,0x88A8
, and
0x9100
.

Field Name Description
Internet Protocol
Selection
Different scheduling priorities can be applied to statistically multiplexed data flows. Since each data
flow has its own queue, an ill-behaved flow (which has sent larger packets or more packets per
second than the others) will only punish itself and not other sessions. Options are
IPv4&IPv6
(Dual Stack), and
IPv6 Only
.
IPv4 Only
,
Note: When you select IPV4&IPV6 or IPV6, the subsequent options presented will change accordingly.
6. Click Next. The following page appears where you will configure the PPP Username, Password and related information.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 28

7. Modify the fields as needed.
The fields on this page are explained in the following table.
Field Name Description
PPP Username Enter the username required for authentication to the PPP server.
PPP Password Enter the password required for authentication to the PPP server.
PPPoE Service Name (
Optional
) Enter a description for this service.
Authentication Method Select a means for authentication. Options are:
l AUTO: Attempt to automatically detect handshake protocols
(listed below). This is the default.
l PAP: Password Authentication Protocol (plaintext pass-
words).
l CHAP: Challenge Handshake Authentication Protocol. (MD5
hashing scheme on passwords).
l MSCHAP: Microsoft Challenge Handshake Authentication Pro-
tocol. (Microsoft encrypted password authentication protocol).
LCP Keepalive Period The frequency at which the keepalive packet is sent by the gateway
to the PPP server.
LCP Retry Threshold Enter the number of additional attempted packets that the gateway
will send (in the event that the PPP server does not respond to the
Keepalive) before giving up and declaring the connection as Failed.
PPP IP Extension Select whether to forward all traffic to the advanced DMZ IP spe-
cified in the next field.
Advanced DMZ (
Available when PPP IP Extension is selected
) Specify the IP
address and net mask to which PPPoE traffic is forwarded.
Use Static IPv4 Address Specify the IPv4 Address to apply for this WAN service in the
Address
field that appears.
Use Static IPv6 Address Specify the IPv6 Address to apply for this WAN service in the
Enable IPv6 Unnumbered
Model
Address
Click to enable IP processing on a serial interface without assigning it
an explicit IP address. The IP address of another interface can be
field that appears.
can "borrow" the IP address of another interface already configured
on the router, which conserves network and address space.
Launch Dhcp6c for Address
Assignment (IANA)
Launch Dhcp6c for Prefix
Delegation (IAPD)
Available only for IPv6 environments
(
) Select this option for the CPE
to receive the WAN IP from the ISP.
Available only for IPv6 environments
(
) This option is enabled by
default. The CPE generates the WAN IP's prefix from the server's
REST by MAC address. Click the checkbox to disable this option.
Retry PPP password on
authentication error>
Enter the maximum number of PPP authentication retries on failure
Max PPP authentication retries
in the
The default is
65536
(unlimited retries).
field. Options are1-
IPv4
IPv6
65536
.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 29

Field Name Description
Enable PPP Debug Mode Select to have the system put more PPP connection information into
the system log of the device. This is for debugging errors and not for
normal usage.
Bridge PPPoE Frames
Between WAN and Local
Select to enable PPPoE passthrough to relay PPPoE connections from
behind the modem. Also known as Half-Bridged mode.
Ports
Enable Firewall
This option enables functions in the
enabled by default. Click the checkbox to disable this option.
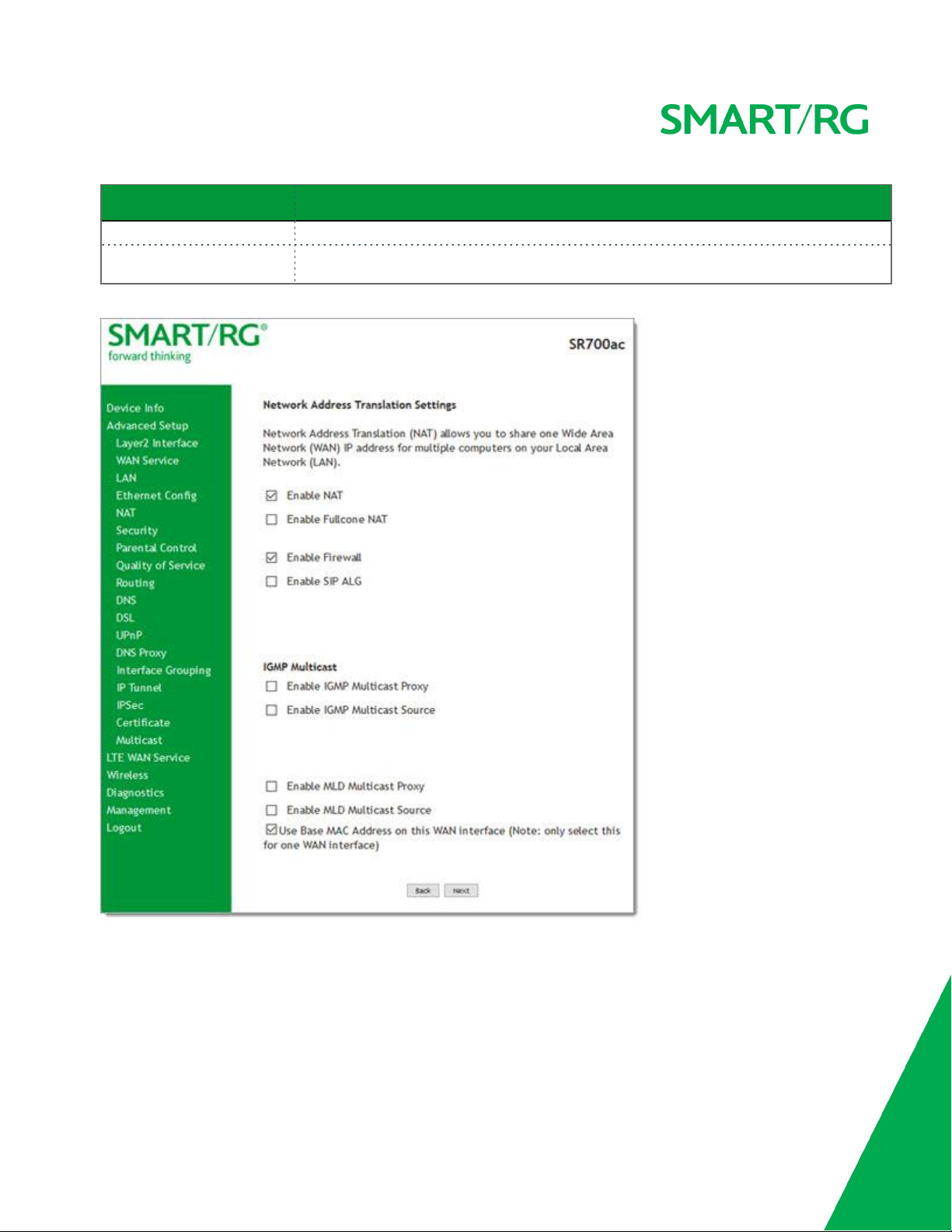
Network Address Translation Settings
section
Security
sub-menu and is
Enable NAT This option is selected by default and enables sharing the WAN inter-
face across multiple devices on the LAN. Click the checkbox to disable NAT.
Enable Fullcone NAT (
Available only when Enable NAT is selected
) Click to enable one-
to-one NAT.
Enable SIP ALG (
Available only when Enable NAT is selected
) Click to enable Session Initiation Protocol (SIP) pass-through NAT. Used for Voice over IP
(VOIP) applications.
IGMP Multicast
Enable IGMP Multicast
Proxy
section
Click to enable Internet Group Membership Protocol (IGMP) multicast. Used by IPv4 hosts to report multicast group memberships to
any neighboring multicast routers.
Enable IGMP Multicast
Select to enable this service to act as an IGMP multicast source.
Source
MLD Multicast
section
Enable MLD Multicast Proxy Click to enable Multicast Listener Discovery (MLD) multicast. Used by
IPv4 hosts to report multicast group memberships to any neighboring
multicast routers.
Enable MLD Multicast
Select to enable this service to act as an MLD multicast source.
Source
MTU size Enter the MTU (Maximum Transmission Unit) size for SmartRG gate-
1370
) Enter the
Use Base MAC Address on
this WAN interface
Enable MAC Clone (
ways supporting a gigabit-capable WAN interface. Options are
1492 bytes
. The default is
1492
bytes.
Use the SmartRG Devices Base (Primary) MAC address. When
unchecked, a unique MAC is assigned for each service.
Appears when Use Base MAC Address is NOT selected
MAC address to be used as the close address.
-
8. Click Next. The following page appears where you will select the interface used as a default gateway used for the PPP service being created.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 30
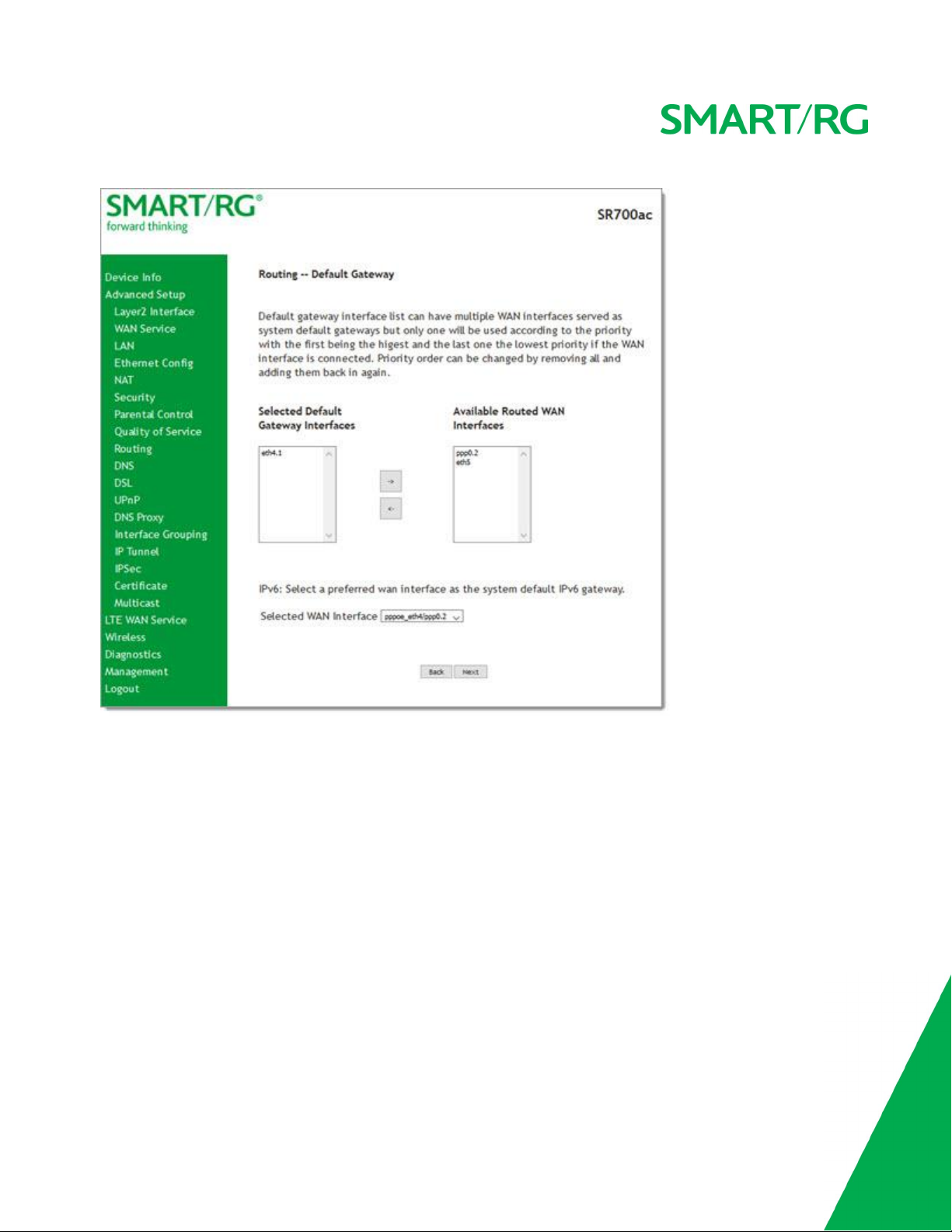
9. Click the arrows to move your selection from left to right or from right to left.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 31
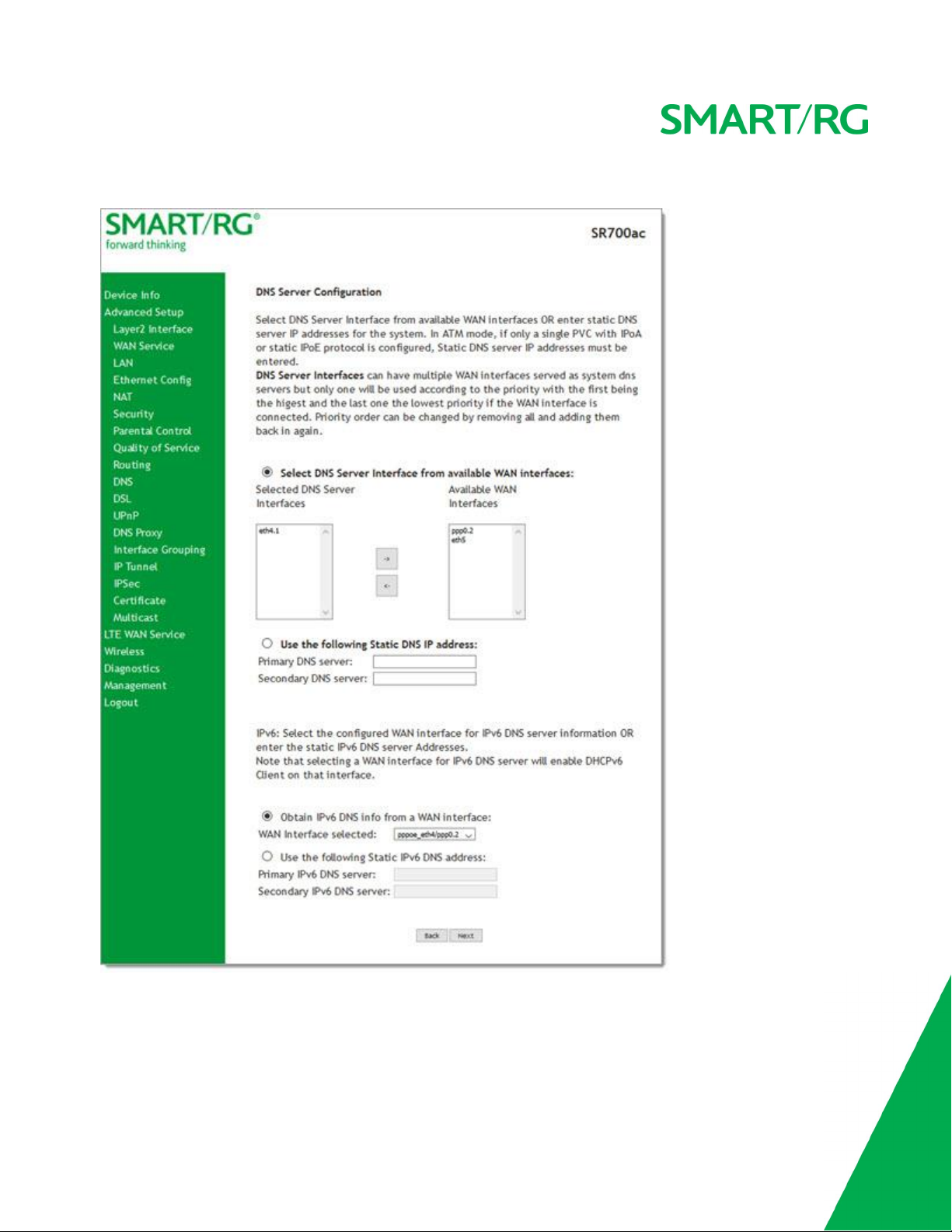
10. Click Next. The following page appears where you will select DNS Server settings.
11. Select the DNS server interface from the available WAN interfaces.
12. Click the arrows to move your selection from left to right or from right to left.
13. Alternatively, you can enter static DNS IP addresses in the Use the following Static DNS IP address section.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 32

14. Click Next. The summary page appears indicating that your PPPoE WAN setup is complete.
15. Review the summary and either click Apply/Save to commit your changes or click Back to step through the pages in reverse
order to make any necessary alterations.
IP over Ethernet
There are several parts to configuring a IP over Ethernet WAN service. You will progress through several pages to complete the configuration.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 33

1. In the left navigation bar, click Advanced Setup > WAN Service and then click Add. The following page appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 34

2. Select the Layer2 interface to use for the WAN service and click Next. The following page appears.
3. Select the IP over Ethernet WAN service type.
4. Modify the other fields as needed.
The fields on this page are explained in the following table.
Field Name Description
Enter Service
Optional
(
) Enter a name to describe this configuration.
Description
Enter 802.1P Pri-
ority
Enter a priority for this WAN service. Options are0-7. The default is0.
For tagged service, enter values in this field and the 802.1Q VLAN ID field.
For untagged service, enter -1 (disabled) in this field and the 802.1Q VLAN ID field.
Enter 802.1Q VLANIDEnter the VLAN ID for this WAN service. Options are0-
4094
. The default is-1(dis-
abled).
For tagged service, enter values in this field and the 802.1P Priority field.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 35
Field Name Description
For untagged service, enter -1 (disabled) in this field and the 802.1P Priority field.
Select VLAN TPID Select the TPID for this VLAN. Options are
Internet Protocol
Selection
This data packet scheduling technique allows different scheduling priorities to be
applied to statistically multiplexed data flows. Since each data flow has its own
queue, an ill-behaved flow (which has sent larger packets or more packets per
second than the others since it became active) will only punish itself and not other
sessions. Options are
IPv4 Only
is
.
IPv4 Only,IPv4&IPv6 (Dual Stack)
Note: When you select IPV4&IPV6 or IPV6, the options presented on the following
screens change accordingly.
5. Click Next. The following page appears.
0x8100,0x88A8
, and
0x9100
, and
IPv6 Only
.
. The default
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 36

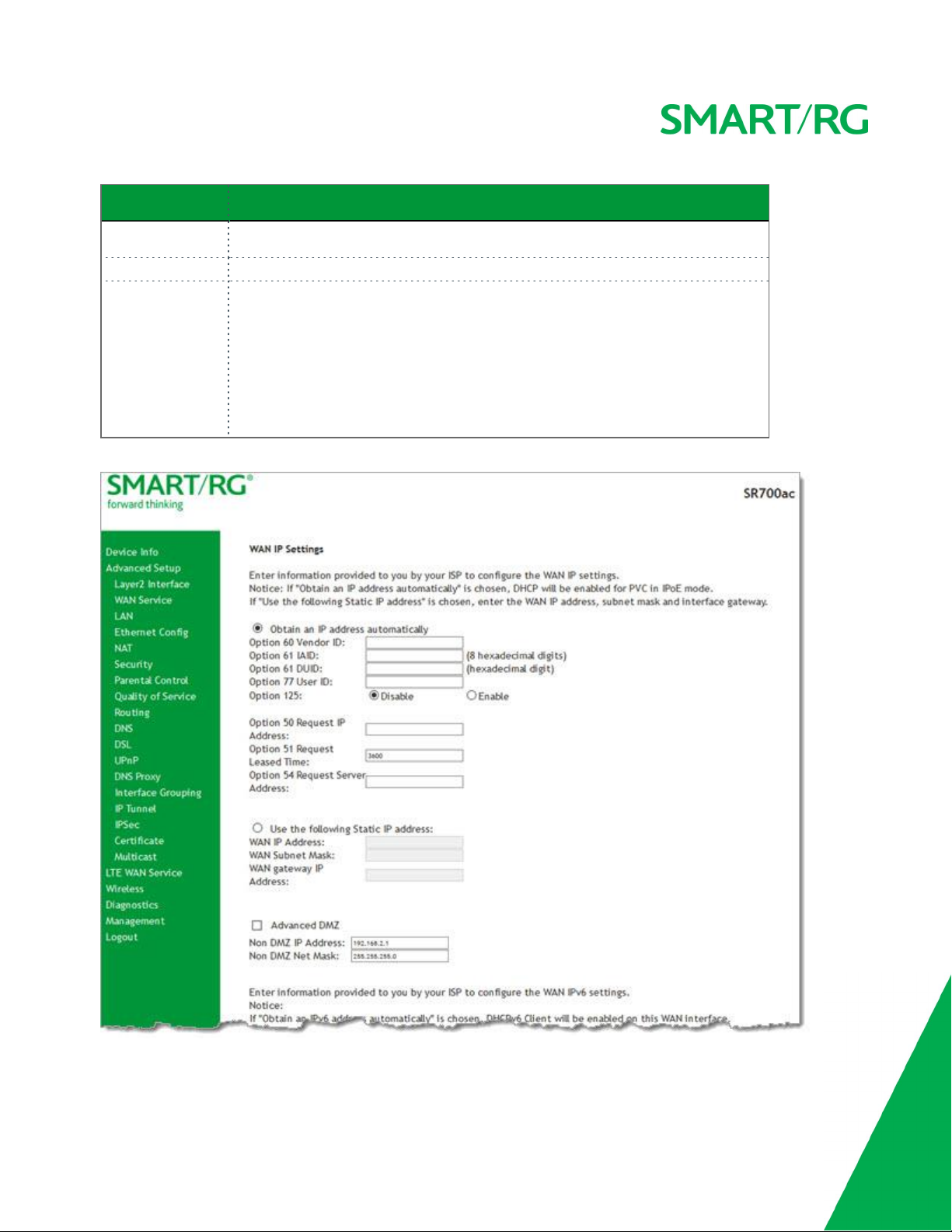
6. Enter the relevant WAN IP Settings.
The fields on this page are explained in the following table.
Field Name Description
Obtain an IP address auto-
When you wish the ISP to automatically assign the WAN IP to the gateway.
matically
Option 60 Vendor ID (
Option 61 IAID (
Optional
Optional
) Broadcast a specific vendor ID for the DHCP server to accept the device.
) Interface Association Identifier (IAID). A unique identifier for an IA, chosen by the
client.
Option 61 DUID (
Optional
) DHCP Unique Identifier (DUID) is used by the client to get an IP address from the
DHCP server.
Option 77 User ID (
Option 125 (
Optional
Optional
) Enter the user class ID that should be used to filter traffic.
) Select whether to enable local devices to automatically receive DHCP options
from the server.
Option 50 Request IP Address Select to request a specific IP address when sending messages. If the address is not avail-
able, the DHCP server assigns the next allowed IP address.
Option 51 Request Leased
Select to request the maximum lease time defined for the client.
Time
Option 54 Request Server
Select to request the IP address of the source server.
Address
Use the following Static IP
Select this option to manually declare the static IP information provided by your ISP.
address
WAN IP Address If using a static IP address, enter the static WAN IPV4 Address.
WAN Subnet Mask If using a static IP address, enter the static Subnet Mask.
WAN gateway IP Address If using a static IP address, enter the static Gateway IP address.
Advanced DMZ (
Optional
) Select this option to enable Advanced DMZ on the WAN service.
Non DMZ IP Address If using the Advanced DMZ feature, you can enter a specific vendor ID that will be broadcast
for the DHCP server to accept the device, y. e.g., 192.168.2.1..
Non DMZ Net Mask If using the Advanced DMZ feature, you can enter a secondary LAN IP address for the gate-
255.255.255.0
.
IPv6 settings
way. The default is
section
The following fields appear when either IPv6 Only or IPv4&IPv6 (Dual Stack) network protocol values is selected on the
WAN Service Configuration page.
Obtain an IPv6 address automatically
Dhcpv6 Address Assignment
Enables the DHCPv6 Client on this WAN interface. Select this option when you want the ISP
to automatically assign the WAN IP to the gateway.
Select this option for the CPE to receive WAN IP from ISP.
(IANA)
Dhcpv6 Prefix Delegation
(IAPD)
Use the following Static IPv6
address
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 37
This option is selected by default and enables the CPE to generate the WAN IP's prefix from
the server's REST by MAC address.
Select this option to manually declare the v6 Static IP information provided by your ISP. In
WAN IPv6 Address/Prefix Length
the
field, enter the IP address / prefix length. If you do
Field Name Description
not specify a prefix length, the default of
Specify the Next-Hop IPv6
address
In the
This address can be either a local link or a global unicast IPv6 address.
7. Click Next. The following page appears.
WAN Next Hop IPv6 Address
/64
is used.
field, enter the IP address of the next WAN in the group.
8. Modify the settings if desired. All settings are optional.
Network Address Translation (NAT) allows you to share one Wide Area Network (WAN) IP address for multiple computers on
your Local Area Network (LAN). If you do not want to enable NAT (atypical) and wish the user of this gateway to access the
Internet normally, you need to add a route on the uplink equipment. Failure to do so will cause access to the Internet to fail.
The fields on this page are explained in the following table.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 38

Field Name Descriptopn
Enable NAT This option is enabled by default and supports sharing the WAN interface
across multiple devices on the LAN. Also enables the functions in the NAT
sub-menu and addition PPPoE NAT features to select. Click the checkbox to
disable NAT.
Enable Fullcone NAT Enables one-to-one NAT.
Enable Firewall This option is enabled by default and enables functions in the
sub-menu.
Enable SIP ALG Click to enable Session Initiation Protocol (SIP) pass-through NAT. Used for
Voice over IP (VOIP) applications.
IGMP Multicast
Enable IGMP Multicast
Proxy
Enable IGMP Multicast
Source
MLD Multicast
Enable MLD Multicast
Proxy
Enable MLD Multicast
Source
Use Base MAC Address
on this WAN interface
Enable MACClone (
section
Click to enable Internet Group Membership Protocol (IGMP) multicast.
Used by IPv4 hosts to report multicast group memberships to any neigh-
boring multicast routers.
Click to enable this service to act as an IGMP multicast source.
section
Click to enable multicast filtering. Used by IPv4 hosts to report multicast
group memberships to any neighboring multicast routers.
Click to enable this service to act as a multicast source.
Click to use the gateway's base (Primary) MAC address. Otherwise, a unique
MAC is assigned for each service.
Appears when Use Base MAC Address is NOT selected
address to be used as the close adddress.
Security
) Enter the MAC
9. For the remaining WAN Service configuration pages, use the instructions provided in the default gateway step in the PPP
over Ethernet section.
Bridging
Before you can configure a bridge WAN service, you must create the related ATM interface.
Note: This feature is available for SR515ac models only.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 39

1. In the left navigation bar, click Advanced Setup > WAN Service and then click Add. The following page appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 40

2. Select an ATM interface for the WAN service and then click Next. The following page appears.
3. Select Bridging. The multicast source fields appear.
4. Modify the fields as needed, using the information in the following table.
Field Name Description
Allow as IGMP Multicast
Select to enable this service to act as an IGMP multicast source.
Source
Allow as MLD Multicast
Select to enable this service to act as an MLD multicast source.
Source
Enter Service Descrip-
Optional
(
) Enter a name to describe this configuration.
tion
Enter 802.1P Priority Enter the priority for this WAN service. Options are0-7. The default is-1(disabled).
For tagged service, enter values in this field and the 802.1Q VLAN ID field.
For untagged service, accept the default of -1 in this field and in the 802.1Q VLAN ID
field.
Enter 802.1Q VLAN ID Enter the VLAN ID for this WAN service. Options are0-
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 41
4094
. The default is-1(disabled).

Field Name Description
For tagged service, enter values in this field and the 802.1P Priority field.
For untagged service, enter -1 (disabled) in this field and in the 802.1P Priority field.
Select VLAN TPID (
Optional
) Select the TPID for this VLAN. Options are
0x8100,0x88A8
5. Click Next. The summary page appears indicating that your Bridging WAN setup is complete.
, and
0x9100
.
6. Review the summary and either click Apply/Save to commit your changes or click Back to step through the pages in reverse
order to make any necessary alterations.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 42

LAN
On the Local Area Network (LAN) Setup page, you can configure the router’s local IP addresses, subnet mask, DHCP behavior and
other related LAN side settings for your gateway.
1. In the left navigation bar, click Advanced Setup > LAN. The following page appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 43

2. Customize the fields as desired.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
GroupName Select an interface group from the list of available groups (defined on the Interface
Grouping page).
IP Address Enter the LAN IP address to be used by LAN devices connecting to this gateway.
Subnet Mask Enter the subnet mask to be used by LAN devices connecting to this gateway.
Enable IGMP Snooping Select to enable your gateway to listen to IGMP network traffic between hosts and
routers. By listening to these conversations, the gateway maintains a map of which
links need which IP multicast streams.
Standard Mode Allows multicast traffic will flood to all bridge ports when there is no client sub-
scribed to any multicast group.
Blocking Mode Blocks multicast data traffic, preventing it from flooding to all bridge ports when no
client subscriptions to a multicast group are present. This option is enabled by
default.
Enable IGMP LAN to
LAN Multicast
Enable LAN Side Fire-
Allows multicast traffic between LANs. Options are
Disable
is
.
Enables the restriction of traffic between LAN hosts.
Disable
and
Enable
. The default
wall
Disable DHCP Server Prevents the DHCP functionality of your gateway from automatically assigning LAN
IPaddresses to host devices as they connect with the gateway.
Enable DHCP Server Allows the DHCP functionality of your gateway to automatically assign LAN IP
addresses to host devices as they connect with the gateway. This option is selected
by default.
Fill in the next three fields to configure this action.
Start IP Address Enter the beginning of the class C IP address range to be assigned by the DHCP
server.
End IP Address Enter the end of the class C IP address range to be assigned by the DHCP server.
Leased Time (hour) Enter the number of hours for which an IP address will be leased. The default is
hours
.
Static IP Lease List Specify a static
your LAN host devices. Click
Apply/Save
click
Automatically create
static IP leases from
the following OUIs
Configure DHCP
Options
For LAN hosts, IP addresses can be assigned manually or by using DHCP. Click
OUI
. Enter the OUI and click
entries that you need.
Enter information for the following three DHCP options:
l Option 66: For some devices that also require access to a TFTP server (device
IP address
to be associated with a
Add Entries
. Enter the MAC address and IP address and
. Repeat this step to create any additional entries that you need.
Apply/Save
. Repeat this step to create any additional
specific MAC Address
of one of
24
Add
configuration name filesare in .cnf file format), which enables the device to
communicate with other infrastructure, select this option to specify the
name of the TFTP server. Option 66 is an IEEE standard.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 44

Field Name Description
l Option 150: Enter a comma-separated list of TFTP IPv4 server addresses. The
maximum allowed is 2.
l Option 43: Enter the loopback address of the master controller in ASCII
format.
Configure the second
IP address and subnet mask for LAN
interface
When you select this option, the
you can enter a second IP address and Subnet mask to support a second, sim-
ultaneous LAN.
For example, the primary LAN might be defined as 192.168.0.1 and this secondary LAN
IP Address
defined as 192.168.2.1.
IPv6 Autoconfig
On this page, you can configure your gateway's IPv6 environment.
Subnet Mask
and
fields appear where
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 45

1. In the left navigation bar, click Advanced Setup > LAN > IPv6 Autoconfig . The following page appears.
2. Modify the fields as needed, using the information in the table below.
3. Click Save/Apply to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Interface Address IPV6 address to assign as the gateways Local LAN IPV6 address and prefix length. Prefix length is required.
IPv6 LAN Applications
Enable DHCPv6
section
This option is selected by default. Click to disable the DHCPv6 feature on the LAN.
Server
Stateless This option is selected by default. Click to stop inheriting IPV6 address assignments from the WAN IPV6 inter-
face.
Stateful Click this option to identify the DHCPv6 server given by the LAN IPV6 network as configured with additional
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 46

Field Name Description
options. Zero compression is not supported. Make sure to enter zeros between the colons, that is, do not
use shorthand notation (::2). Options are:
l Start interface ID: Enter the beginning IPv6 available addresses for DHCP to assign to LAN devices.
l End interface ID: Enter the ending IPv6 available addresses for DHCP to assign to LAN devices.
l Leased Time (hour): Amount of time before a new IPv6 lease is requested by the LAN client.
Enable RADVD (
Optional
) This option is enabled by default. It enables Router Advertisement Daemon (RADVD) service that
sends router advertisements to LAN clients. Clear the check box to disable RADVD. Options are:
l Randomly Generate: This option is selected by default. The prefix is generated automatically.
l Enable ULA Prefix Advertisement: Check this option to enable unique local address (ULA) advert-
isement on the LAN. When you select this option, the Randomly Generate option is selected and the
gateway can generate a random IPv6 prefix.
l Statically Configure: Select this option to configure the IPv6 prefix, and enter values in the Prefix,
Preferred Life Time, and Valid Life Time fields (in hours). The default value for the Time fields is -1
(no limit).
Enable MLD Snooping (
Optional
) This option is enabled by default. It enables Multicast Listener Discovery (MLD) snooping to man-
age IPV6 multicast traffic. Options are:
l Standard Mode: Multicast traffic will flood to all bridge ports when no client subscribes to a mul-
ticast group even if IGMP snooping is enabled.
l Blocking Mode: The multicast data traffic will be blocked and not flood to all bridge ports when
there are no client subscriptions to any multicast group. This is the default.
Enable MLD LAN to
LAN Multicast
Optional
(
) This option is enabled by default. It enables LAN-to-LAN Multicast until the first WAN service is
connected. Options are
Disable
and
Enable
. The default is
Disable
.
Ethernet Config
On this page, you can set the speed and duplex mode for the Ethernet ports and the WAN port, if configured,
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 47

1. In the left navigation bar, click Advanced Setup > Ethernet Config . The following page appears.
2.
In the Configure column, select an option (Auto, 100 Full, 100 Half, 10 Full or 10 Half) for each of the four Ethernet ports
on your gateway.
These options represent 100 megabits or 10 megabits using half or full duplex transmission protocols. When you have a specific device with a known limited transmission speed capability, select one of the latter four options. If you select Auto, your
gateway will automatically select an appropriate setting based on Ethernet auto negotiation with the NIC of the LAN host.
Note: Always select Auto for 1000 BaseT connections.
3. Click Apply/Save to commit your changes.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 48

NAT
In this section, you can configure the settings for Network Address Translation including setting up virtual servers, port triggering
and a DMZ host. There is seldom need to customize these settings as the default settings manage the related features sufficiently
for most environments.
Virtual Servers
Virtual Servers (more commonly known as Port Forwards) is a technique used to facilitate communications by external hosts with services provided within a private local area network.
On this page, you can configure the virtual server settings for your gateway.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 49

1. In the left navigation bar, select Advanced Setup > NAT and then click Add. The following page appears.
2. Customize the fields to create your port forwarding entry.
3. Click Apply/Save to commit your changes. The servers for the selected service appear on the NAT Virtual Servers Setup
page.
The fields on this page are explained in the following table.
Field Name Description
Use Interface Select the WAN interface to which this NAT rule will apply.
Select a Service Select from a list of application that typically require port forwards configured. The
port ranges and protocol fields will be pre-populated.
Custom Service If your application does not appear in the
Select a Service
list, you can enter a unique
name for the application in this field.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 50

Field Name Description
Server IP Address Enter the IP address of the LAN client where the service is hosted.
External Port Start Enter the first external port for this server.
External Port End Enter the last external port for this server.
Protocol Select the protocol to be used with this range of ports. Options are:
Internal Port Start Enter the first internal port for this server.
Internal Port End Enter the last internal port for this server.
TCP/UDP
.
TCP,UDP
, or
Port Triggering
Some applications require that specific ports in the gateway's firewall be opened for access by remote parties. The Port Trigger feature dynamically opens up the open ports in the firewall when an application on the LAN initiates a TCP/UDP connection to a remote
party using the triggering ports. The gateway allows the remote party from the WAN side to establish new connections back to the
application on the LAN side using the Open Ports.
1. In the left navigation bar, click Advanced Setup > NAT > Port Triggering and then click Add. The following page appears.
2. Customize the fields as needed for the firewall pinholes you wish to establish. A maximum 96 entries can be configured.
3. Click Save/Apply to commit your changes. The selected service appears on the NAT Port Triggering Setup page.
The fields on this page are explained in the following table.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 51

Field Name Description
Use Interface Select the interface for which the port triggering rule will apply.
Select an Application Select the application which requires a port trigger entry. The
fields are populated.
Custom Application If the application you want does not appear in the selection list, enter a unique name
for the application for which you are creating a port trigger entry.
Trigger Port Start Enter the starting number of the range of available outgoing trigger ports. Options
are:1-
Trigger Port End Enter the end number of the range of available outgoing trigger ports. Options are:1-
65535
Trigger Protocol Select the protocol required by the application that will be using the ports in the spe-
cified range. Options are:
Open Port Start Enter the starting number of the range of available incoming ports. Options are:1-
65535
Open Port End Enter the end number of the range of available incoming ports. Options are:1-
65535
Open Protocol Select the protocol for the open port. Options are:
65535
.
.
.
.
TCP,UDP
, and
TCP/UDP
.
TCP,UDP
Port
, and
Protocol
and
TCP/UDP
.
DMZ Host
The Broadband Router will forward IP packets from the WAN that do not belong to any of the applications configured in the Virtual
Servers table to the DMZ host computer. If you want to route all internet traffic to a specific LAN device with no filtering or security,
add the IP address of that device to this page.
1. In the left navigation bar, click Advanced Setup > NAT > DMZ Host. The following page appears.
2. Enter the DMZ Host IP Address.
3. Click Save/Apply to commit the new or changed address.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 52

Security
In this section, you can configure filtering for IP and MAC.
IP Filtering - Outgoing
On this page, you can add an outgoing filter when refusal of data from the LAN to the WAN is desired.
1. In the left navigation bar, click Advanced Setup > Security and then click Add. The following page appears.
2. Fill in the fields, using the information in the table below.
3. Click Apply/Save to commit the completed entry.
The fields on this page are explained in the following table.
Field Name Description
Filter Name Enter a descriptive name for this filter. This is a free-form text field.
IP Version For the filter to be configured and effective for IPV6 , the gateway must be installed on a net-
work that is either a pure IPV6 network (with that protocol enabled) or is both IPV4 and IPV6
dual protocol enabled/configured. Options are
If you select IPV6, both the Source and Destination IP address must be specified in IPV6 format.
The following is an IPV6-compliant, hexadecimal address:
2001:0DB8:AC10:FE01:0000:0000:0000:0001.
Protocol Select the protocol profile for the filter you are defining. TCP/UDP is most commonly used.
The options are
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 53
TCP/UDP,TCP,UDP
, and
ICMP
IPv4
].
and
IPv6
. The default is
IPv4
.

Field Name Description
Source IP
address [/prefix
length]
Source Port (port
or port:port)
Destination IP
address
estination Port
(port or port:port)
Enter the source IP address of a LAN side host for which you wish to filter/block outgoing traffic
for the specified protocol(s).
Note: The address specified here can be a particular address or a block of IP addresses on a
given network subnet. This is done by appending the associated routing "/prefix" length
decimal value (preceded with the slash) to the addresses. A valid decimal routing prefix is
required for defining the subnet mask per CIDR notation.
Set the outgoing host port (or range of ports) for the above host (or range of hosts defined by
optional routing or "/prefix" subnet mask) to define the ports profile for which egress traffic
will be filtered from reaching the specified destination(s).
Enter the destination IP address of a LAN side host for which you wish to filter/block outgoing
traffic for the specified protocol(s).
Note: The address specified here can be a particular address or a block of IP address on a given
network subnet. This is done through appending the address with the routing " /prefix " length
decimal value (preceded with the slash) associated. A valid decimal routing prefix is required
for defining the subnet mask per CIDR notation.
Set the destination host port (or range of ports) for the above host (or range of hosts) to define
the destination port profile for which the filtered host egress traffic will be filtered from reaching the otherwise intended destination(s), e.g., to block the traffic to those ports on, say, a
computer external to the local network.
IP Filtering - Incoming
On this page, you can add an incoming filter when refusal of data from the WAN to the LAN is desired.
Note: This option is not available in the SR515ac model.
1. In the left navigation bar, click Advanced Setup > Security > IP Filtering > Incoming and then click Add. The following page
appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 54

2. Fill in the fields, using the information in the table below.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Filter Name A free-form text field. Enter a descriptive name for this filter.
IP Version Select the IP version for this filter. Options are
IPv4
.
IPv4
and
IPv6
. The default is
Protocol Select the protocol to be associated with this incoming filter. Options are:
Source IP address [/pre-
TCP/UDP,TCP,UDP
Enter the source IP address for rule. For IPv6, enter the prefix as well.
, or
ICMP
.
fix length]
Source Port (port or
Enter source port number or range (xxxxx:yyyyy).
port:port)
Destination IP address
Enter the destination IP address for rule. For IPv6, enter the prefix as well.
[/prefix length]
Destination Port (port or
Enter destination port number or range (xxxxx:yyyyy).
port:port)
WAN Interfaces Select the WAN interfaces to which this rule will be applied. Options are
All
or the interfaces defined for your network. The default is
Select All
Select
.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 55
MAC Filtering
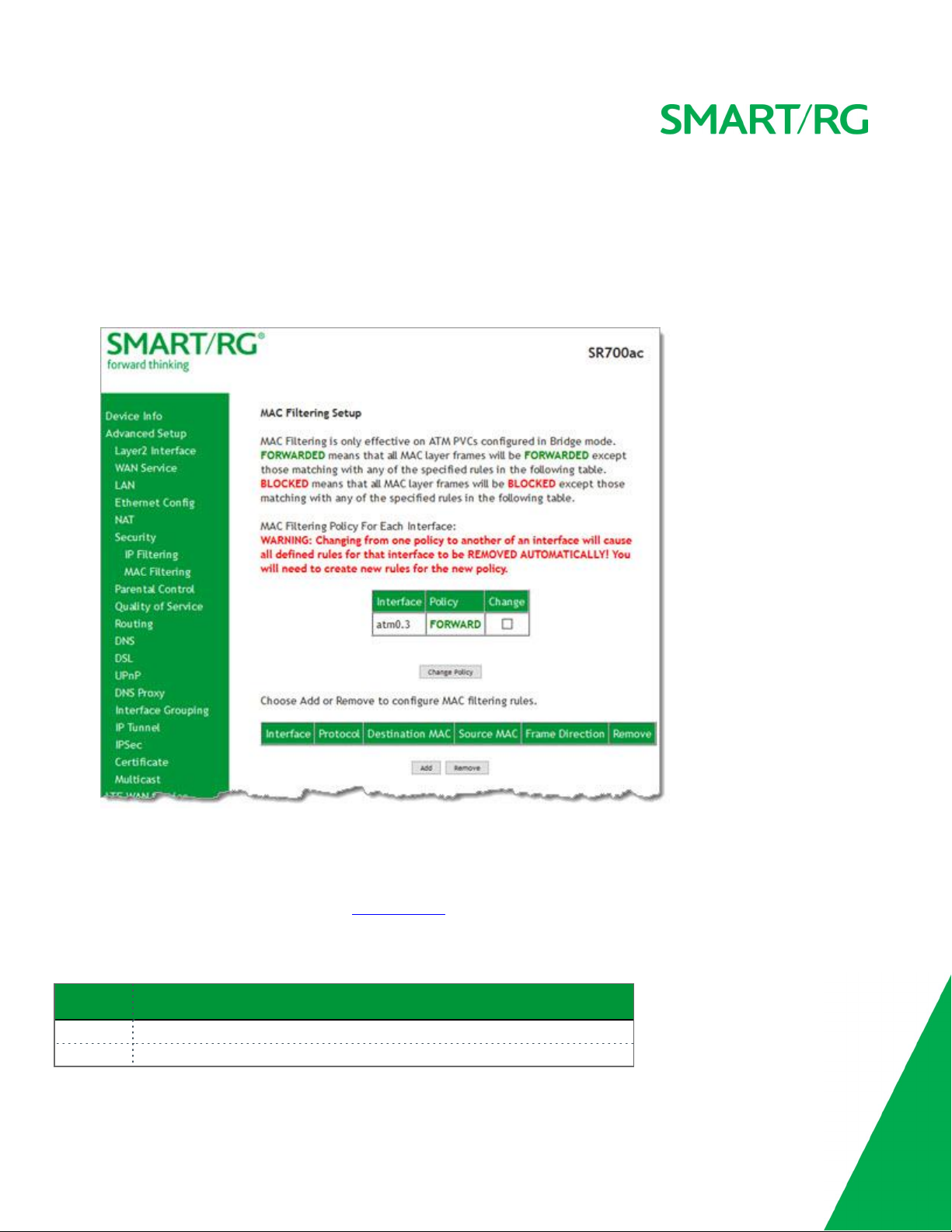
Your SmartRG gateway can block or forward packets based on the originating device. This MAC filtering feature is available only in
Bridge mode. For other modes, similar functionality is available via IP Filtering. On this page, you can manage MAC filtering for your
gateway.
1. In the left navigation bar, click Advanced Setup > Security > MAC Filtering. The following page appears.
2. To modify policy settings:
a. Review the information on the page.
b. Once you understand the consequences of changing the policy, click the Change checkbox, and then click Change
Policy. The policy is switched to FORWARD or BLOCKED.
3. To add a rule, follow the instructions in "MAC Filtering".
4. To remove a rule, click the Remove checkbox next to the rule and click the Remove button.
The fields on this page are explained in the following table.
Field Name Description
Interface The interface associated with an established policy rule.
Policy The policy type that is currently active. Options are
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 56
FORWARD
and
BLOCKED
.

Add a MAC Filtering Rule
You cannot edit rules but you can add new ones and then remove the obsolete ones.
1. On the MAC Filtering page, click Add. The following page appears.
2. Fill in the fields, using the information provided in the following table.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Protocol Type Select the protocol associated with the device at the destination MAC
address. Options are
Destination MAC Address Enter the MAC address of the hardware you wish to associate with this filter.
Source MAC Address Enter the MAC address of the device that is originating requests intended for
the device associated with the Destination MAC address.
Frame Direction Select the incoming/outgoing packet interface. Options are
WAN Interfaces Select the interface to which this filter is applied.
WAN=>LAN
, and
PPPoE,IPv4,IPv6,AppleTalk,IPX,NetBEUI
LAN=>WAN
. The default is
LAN <=> WAN
IGMP
, and
LAN<=>WAN
.
.
,
Parental Control
In this section, you can configure the Parental Control features of your SmartRG gateway to restrict Internet access to certain hours
and to certain URLS.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 57

Time Restriction
On this page, you can restrict Internet access to particular days and specific times for each device that accesses your gateway.
1. In the left navigation bar, click Advanced Setup > Parental Control > Time Restriction and then click Add. The following
page appears.
2. Fill in the fields using the information in the table below.
3. Click Apply/Save.
The fields on this page are explained in the following table.
Field Name Description
User Name Enter a descriptive name for this restriction. This is a free-form text
field.
Browser's MAC Address The MAC address of the connected device. This option is selected by
default.
Other MAC Address Select this option to restrict access to another device. You can view a
list of the connected devices and MAC addresses on the
ARP
page.
Days of the week Select the days
Start Blocking Time / End
Blocking Time
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 58
Enter the range of time that the devices listed above are restricted
from access to the Internet. Use 24-hour clock notation (
(Mon-Sun
) for which the restrictions apply.
Device Info
00:00-24:00
>
).

URL Filter
On this page, you can exclude and include URLs as desired to control access to them. Each list can include up to 100 addresses.
Note: Only one Exclude list and one Include list are supported for each gateway. Unique lists are not supported for connecting
devices.
1. In the left navigation bar, click Advanced Setup > Parental Control > Url Filter.
2. To block a URL:
a. Select Exclude List.
b. Click Add. The following page appears.
c. Click Apply/Save to save your settings. You are returned to the Url Filter page.
3. To create a list of URLs to allow, select Include and repeat the steps 2b and 2c.
The fields on this page are explained in the following table.
Field Name Description
URL Address Enter the URL address to be included in the list.
Port Number (
Optional
) Enter the port number associated with the URL. The default is80.
Quality Of Service
Quality of Service (QoS) enables prioritization of Internet content to help ensure the best possible performance. This is particularly
useful for streaming video and audio content with minimized potential for drop-outs. QoS becomes significant when the sum of all
traffic (audio, vid"QoS Classification", data) exceeds the capacity of the line.
In this section, you can configure QoS settings including traffic queues, classifications (rules) and port shaping.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 59

QoS Config
On this page, you can enable QoS and set the DSCP Mark classification.
The maximum number of queues that can be configured vary by mode, as shown below.
Mode Maximum # of queues
ATM 16
Ethernet 4 per interface
PTM 8
Note: Wireless queues (e.g., the WMM Voice Priority queue) are shown only when wireless is enabled. If the WMM Advertise func-
tion on the Wireless Basic Setup page is disabled, assigning classifications to wireless traffic has no effect.
1. In the left navigation bar, click Advanced Setup > Quality Of Service > QoS Config. The following page appears. QoS is
enabled by default.
2. To disable this feature, click the Enable QoS checkbox.
3. (Optional) In the Select Default DSCP Mark field, select the default Differentiated Services Code Point (DSCP) Mark clas-
sification value to be used. For a list of supported values, see "Supported DSCP Values". The default is No Change(-1).
Warning: If this option was already enabled and you clear the checkbox, QoS will be disabled for ALL interfaces.
4. Click Apply/Save to save your settings.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 60

Supported DSCP Values
The DSCP marking QoS Queue Management Configuration marking on ingress packets is based on the selection you make in the Select
Default DSCP Mark field. The selected default marking is applied automatically to all incoming packets without reference to a par-
ticular classification.
Note: A default DSCP mark value of Default(000000) will mark all egress packets that do NOT match any classification.
The following values are supported. For more information about commonly used DSCP values, refer to RFC 2475.
No Change(-1) CS1(001000) AF32(011100) CS4(100000)
Auto Marking(-2) AF23(010110) AF31(011010) EF(101110)
Default(000000) AF22(010100) CS3(011000) CS5(101000)
AF13(001110) AF21(010010) AF43(100110) CS6(110000)
AF12(001100) CS2(010000) AF42(100100) CS7(111000)
AF11(001010) AF33(011110) AF41(100010)
QoS Queue Config
On this page you can configure a queue and add it to a selected Layer2 interface.
1. In the left navigation bar, click Advanced Setup > Quality Of Service > QoS Queue Config and then click Add. The following
page appears.
2. In the Name field, enter a brief descriptive name for this queue.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 61

3. In the Interface field, select the Layer 2 interface to be associated with this queue. Options include Dynamic WAN and the
interfaces defined for your gateway. When you select an interface, additional fields appear. If you select Dynamic WAN,
they appear once for each defined WAN interface.
4. Fill in the other fields, using the information in the table below.
5. Click Apply/Save to save your settings.
The fields on this page are explained in the following table.
Field Name Description
Name Enter a descriptive name for this configuration. This is a free-form text field.
Enable Select to enable or disable a given QoS queue configured on the selected inter-
face.
Note: Only one queue can be defined for any one interface/precedence pair,
resulting in a maximum of three queues per interface.
Queue Precedence
Select the priority value to be associated with QoS queue defined. Options
include levels for SP and SP|WRR|WFQ.
Note: Lower value = higher priority.
Scheduler Algorithm (
Appears when you select SP|WRR|WFQ in the Queue Precedence field
Select an algorithm for data priority in queues. Options are:
l Strict Priority: Allows shaping of rate and burst size for packets in
queue.
l Weighted Round Robin: Applies a fair round robin scheme weighting
that is effective for networks with fixed packet sizes, e.g., ATM networks.
l Weighted Fair Queuing: Applies a fair queuing weighting scheme via
allowing different sessions to have different service shares for
improved data packets flow in networks with variable packet size, e.g.,
PTM/IP networks.
The following options appear only when the
Scheduler Algorithm
field is set to
Strict Priority
Queue Precedence
.
field is set to
SP|WRR|WFQ
and the
Minimum Rate Enter the minimum shaping rate for packets in QoS queues. Options are1-
100000
Kbps.
To specify no minimum shaping, enter -1.
Shaping Rate Enter the shaping rate for packets in QoS queues. Options are1-
100000
To specify no minimum shaping, enter -1.
)
Kbps.
Shaping Burst Size Enter the shaping burst size to be applied to packets in the defined queue.
Options are
Queue Weight (
Appears when you select either of the Weighted options in the Scheduler
Algorithm field
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 62
1600 bytes
or greater.
) Enter a weight for prioritizing this queue. Options are1-63.
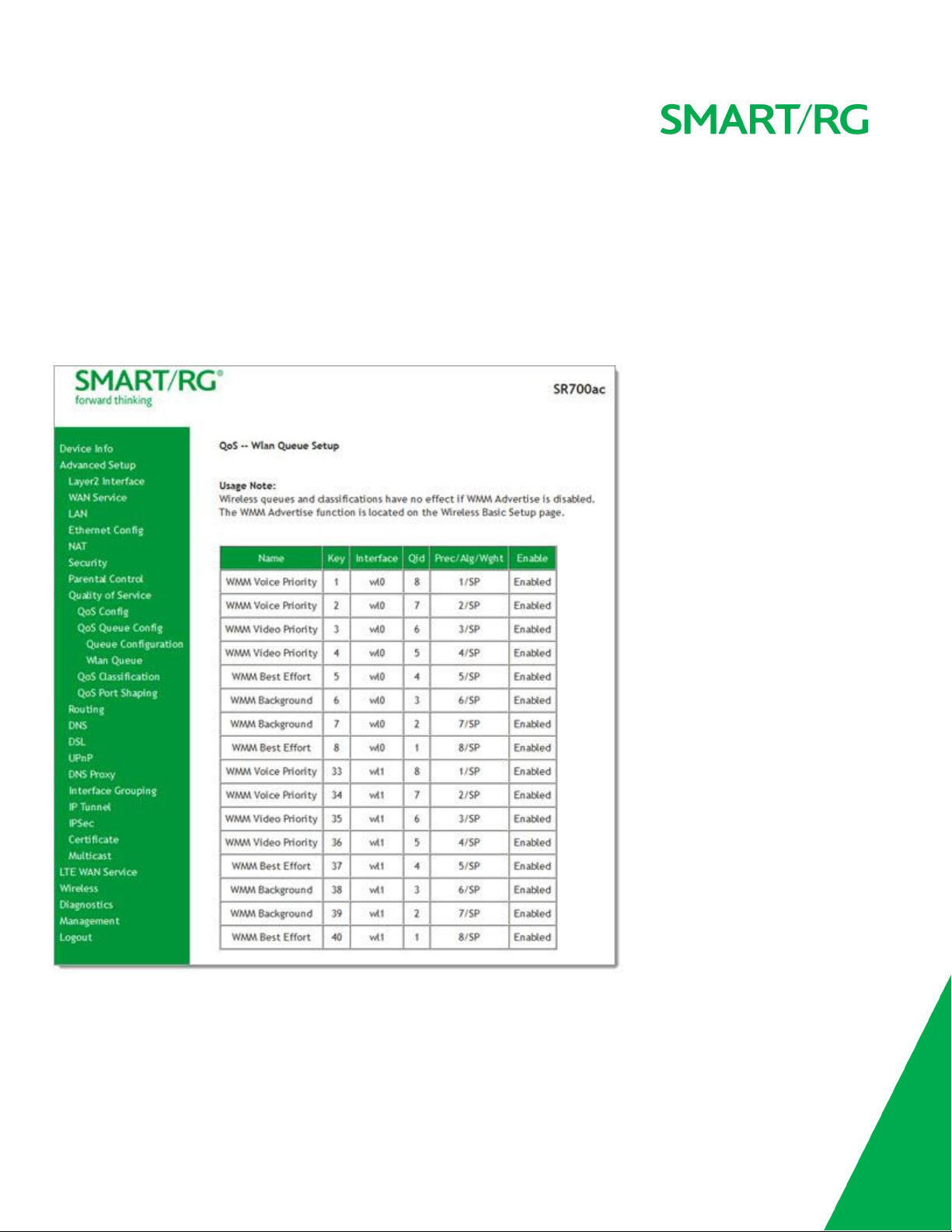
WLAN Queue
On this page, you can view the wireless queues and classifications.
Note: The WMM Advertise option must be enabled before these classifications will function. This option is enabled by default. If you
have disabled it, go to the Wireless > Basic page and clear the Disable WMM Advertise checkbox.
In the left navigation bar, click Advanced Setup > Quality Of Service > QoS Queue Config > Wlan Queue. The following page
appears.
QoS Classification
On this page, you can create traffic class rules for classifying the ingress traffic into a priority queue. You can also mark the DSCP or
Ethernet priority of the packet.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 63

1. In the left navigation bar, click Advanced Setup > Quality Of Service > QoS Classification and then click Add. The following
page appears. A maximum of 32 entries can be configured.
2. Fill in the fields, using the information in the table below.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Traffic Class Name Enter a descriptive name for this rule. This is a free-form text field.
Rule Order Select whether this rule is processed next or last in the list of classification
rules. The only option is Last and cannot be changed.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 64

Field Name Description
Rule Status Select whether this rule is active or inactive. Options are:
able
. The default is
Specify Classification Criteria
section
Ingress Interface Select an interface. Options are
Enable
.
LAN,WAN
and any interface already con-
Enable
and
Dis-
figured for your gateway.
Ether Type Select the Ethernet interface type for this classification. Options include:
Source MAC Address
IP,ARP,IPV6,8855,8856
Enter the source MAC address and mask for this classification.
,and
8021Q
.
Source MAC Mask
Destination MAC Address
Enter the destination MAC address and mask for this classification.
Destination MAC Mask
Source IP Address/Mask
Vendor Class ID
User Class ID
Destination IP
Appear when you select IP or IPv6 in the Ether Type field
(
) Select an
option and enter the appropriate value, i.e, the source IP address and
Source IP mask, vendor class ID, or user class ID.
Enter the destination IP Address and Mask for this classification.
Address/Mask
Differentiated Service
Select the DSCP code that must be present in the queue identifiers.
Code Point (DSCP) Check
Protocol Enter the protocol specified for this classification. Options are
UDP/TCP Source Port (
ICMP
Appears when TCP or UDP is selected in the Protocol field
, and
IGMP
.
TCP,UDP
) Enter the
,
source port for this classification. You can enter a single port or a range of
ports (port:port).
UDP/TCP Destination Port (
Appears when TCP or UDP is selected in the Protocol field
) Enter the destination port for this classification. You can enter a single port or a range of
ports (port:port).
802.1p Priority Check (Appears when
8021Q
is selected in the
Ether Type
field) Select priority
level. Options are 1 - 7.
Specify Classification Results
section
Specify Egress Interface Select the egress interface for this rule. Options are the interfaces already
configured.
Specify Egress Queue Select the egress queue for this rule. Options are the queues already con-
figured.
Mark Differentiated Ser-
Select the desired DSCP code.
vice Code Point
Mark 802.1P priority This value is inserted into the Ethernet frame and used to differentiate
traffic. Lower values assign higher priorities. Options are:1-7.
Set Rate Limit (Kbps) Enter the data traffic rate limit applied for this classification.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 65

QoS Port Shaping
QoS Port Shaping facilitates setting a fixed rate (Kbps) for each of the Ethernet ports.
1. In the left navigation bar, click Advanced Setup > Quality Of Service > QoS Port Shaping. The following page appears.
2. Fill in the fields, using the information in the table below.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Interface Each entry in this column represents one of the Ethernet LAN ports on
the gateway.
Type Each entry in this column identifies the function for which each physical
port is configured on the gateway.
Egress Shaping Rate (Kbps) Enter the data rate for packets on the specified Interface. Options are:
Egress Burst Size (bytes Enter the burst size to be applied to packets in the defined queue.
Ingress Policing Rate (Kbps) Enter data rate for policing incoming packets in the defined queue. The
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 66
1-1,000,000
Options are
If you enter a value of -1 (disabled) in the Egress Shaping Rate field, the
value in this field is ignored.
default is-1(no policing).
Kbps. The default is-1(no shaping).
1600 bytes
or greater. The default is0(no size limit).

Routing
In this section, you can configure default gateways, static routing, policy routing and RIP settings.
Default Gateway
On this page, you can configure the default gateway interface list to establish access priority, that is, iInterfaces are accessed in the
order listed in the Selected Default Gateway Interfaces column.
1. In the left navigation bar, select Advanced Setup > Routing. The following page appears.
2. Select the interfaces that you want used as default gateway interfaces. Click the arrows to move your selection between the
columns. Move the highest priority interface first, followed by the next highest priority interface, and so on.
3. (Optional) In the Selected WAN Interface field, select an IPv6 interface. You must configure the IPv6 interface before it
appears in this field.
4. Click Apply/Save to commit your changes.
Static Route
On this page, you can configure static routes for your network. A static route is a manually configured, fixed route for IP data. You
can enter a maximum of 32 entries.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 67

1. In the left navigation bar, click Advanced Setup > Routing > Static Route and then click Add. The following page appears.
2. Fill in the fields, using the information in the table below.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
IP Version Select the IP version associated with the static route you wish to create.
Options are:
Destination IP address/prefix length
Interface Select the WAN Interface for this route. This list filtered by the selected IP
Gateway IP Address Enter the destination IP address for this route. If needed, include the /prefix
Metric (
Enter the destination network address / subnet mask for route.
version.
length.
Optional
zero(>
than
IPv4
) Establishes traffic priority/weighting. Must be equal to or greater
0).
and
IPv6
.
Policy Routing
Policy routing makes somewhat automated routing choices based on policies defined by a network administrator. For example, a network administrator might want to deviate from standard routing based on destination markers in the packet and, instead, forward a
packet based on the source address.
On this page, you can configure similar policies.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 68

1. In the left navigation bar, click Advanced Setup > Routing > Policy Routing and then click Add. The following page appears.
2. Fill in the fields, using the information in the table below.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Policy Name Enter a descriptive name for this entry to the policy routing table. This is a free-form text field.
Physical LAN Port Select a physical LAN interface for the policy route.
Source IP Enter the IP address for the source of this policy route.
Use Interface Select the WAN Interface for this policy route.
Default Gateway IP Enter the IP address of the default gateway.
RIP (Routing Information Protocol)
RIP is a type of distance-vector routing protocol, which leverages hop count as a metric for routing. RIP puts a limit on the number of
hops (maximum of 15) allowed in order to prevent routing loops. This can sometimes limit the size of networks where RIP can be successfully employed.
On this page, you can configure the RIP settings.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 69

1. In the left navigation bar, click Advanced Setup > Routing > RIP, and then click Add. The following page appears.
2. Fill in the fields, using the information in the table below.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Interface Available WAN interfaces.
Version Select the applicable Routing Interface Protocol version. Options are:1,2, and
default is2.
Operation Select the operation mode. Options are:
l Active: This mode listens and advertises routes.
l Passive: This mode listens only. It does not advertise routes. This is the default.
Enabled Click the checkbox to employ RIP on the displayed interface.
Both
. The
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 70

DNS
In this section, you can configure a DNS server, dynamic DNS and static DNS.
DNS Server
On this page, you can input the Domain Name Server (DNS) information supplied by your service provider.
1. In the left navigation bar, click Advanced Setup > DNS. The following page appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 71

2. Modify the settings as needed, using the information supplied by your provider and that supplied in the table below.
3. Click Apply/Save.
The fields on this page are explained in the following table.
Field Name Description
Select DNS Server Interface
from available WAN interfaces
Use the following Static DNS
IP address
Obtain IPv6 DNS info from a
WAN interface
Use the following Static
IPv6 DNS IP address
Select entries in the
Interfaces
least one entry must remain in the
column.
Click to use static DNS IP addresses. Then, enter the IP addresses of the
primary and secondary DNS servers.
This option is selected by default. Change the value in the
selected
Click to use static DNS IP addresses. Then, enter the IP addresses of the
primary and secondary IPv6 DNS servers.
columns and click the arrows to move them left or right. At
field only for IPv6 environments.
Selected DNS Server Interfaces
Selected DNS Server Interfaces
Available WAN
and
WAN Interface
Dynamic DNS
Dynamic DNS (DDNS) automatically updates a name server in the DNS with the active DNS configuration of its configured hostnames,
addresses or other data. Often this update occurs in real time. On this page, you can configure the settings for this feature.
1. In the left navigation bar, click Advanced Setup > DNS > Dynamic DNS and then click Add. The following page appears.
2. Enter your desired settings.
3. Click Apply/Save to commit your changes.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 72

The fields on this page are explained in the following table.
Field Name Description
D-DNS provider Select a dynamic Domain Name Server provider.
Hostname Enter the hostname of the dynamic DNS server.
Interface Select the gateway WAN interface whose traffic will be pointed at the specified Dynamic DNS provider.
Username Enter the username for the dynamic DNS server.
Password Enter the password for the dynamic DNS server.
Static DNS
The Static DNS service allows you to resolve DNS queries on the Broadband Router by adding a static host name to the IP Address
mappings.
On this page, you can configure up to 10 static DNS entries.
1. In the left navigation bar, click Advanced Setup > DNS > Static DNS and then click Add. The following page appears.
2. In the Host Name field, enter the name of the client computer.
3. In the IP Address field, enter the IP address of the DNS server client used to assist in resolving domain names.
4. Click Apply/Save to commit your changes.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 73

DSL
On this page, you can configure settings for the DSL interface.
Caution: Altering these settings unnecessarily can result in the gateway being unable to attain DSL synchronization.
1. In the left navigation bar, click Advanced Setup > DSL. The following page appears.
2. Modify the fields as needed.
3. Click Apply/Save to commit your changes.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 74

The fields on this page are explained in the following table.
Modulation Data Transmission Rate Max Downstream
(Mbps)
G.Dmt ITU-T G.992.1 standard. 12 1.3
G.lite ITU-T G.991.2 standard. 4 0.5
T1.413 ANSI T1.413 Issue 2 standard. 8 1.0
ADSL2 ITU-T G.992.3 standard. 12 1.0
AnnexL Annex L of ITU-T G.992.3 standard which supports longer loops but with
reduced transmission rates.
ADSL2+ ITU-T G.992.5 standard. 28 1.0
AnnexM Annex L of ITU-T G.992.5 standard which supports extended upstream
24 3
bandwidth.
VDSL2 ITU-T G.993.2 standard. 100 60
The following table explains the maximum transaction power for each profile supported for SRG gateways.
Parameter 8a 8b 8c 8d 12a 12b 17a
Max DS Tx Power (dBm) +17.5 +20.5 +11.5 +14.5
Max US Tx Power (dBm) +14.5
Min bidirectional net data rate 50Mbps 68Mbps 100Mbps
Max
Upstream
(Mbps)
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 75

UPnP
On this page, you can enable UPnP when 3rd party devices on your LAN support this Universal Plug and Play standard. Common client devices include gaming consoles, IP cameras, printers and others. This feature is enabled by default.
1. In the left navigation bar, select Advanced Setup > UPnP. The following page appears.
2. To disable this option, click Enable UPnP to clear the box.
3. Click Apply/Save to commit your changes.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 76

DNS Proxy
On this page, you can configure the DNS proxy settings. A DNS proxy improves domain look-up performance for clients by creating a
historical cache of look-ups.
1. In the left navigation bar, click Advanced Setup > DNS Proxy. The following page appears. This feature is enabled by default.
2. To disable the DNS proxy feature, click the Enable DNS Proxy checkbox to clear it. The Host name and Domain Name fields
are hidden.
3. Click Apply/Save to commit your changes.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 77

Interface Grouping
On this page, you can create an interface group to map local interfaces to WAN interfaces. A typical application for this feature is
assigning IPTV set-top boxes to a WAN interface.
1. In the left navigation bar, click Advanced Setup > Interface Grouping and then click Add (below the table). The following
page appears. (The instructions that display at the top of this page are not shown below).
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 78

2. To create a new interface group, enter a unique Group Name, then proceed with either step 3 (dynamic) or step 4 (static)
below.
3. If this new grouped interface is to share the WAN interface, click Shared WAN Interface. Not selecting this option this will
cause the WAN interface you select to be removed from any other interface groups.
Important: If a vendor ID is configured for a specific client device, make sure to reboot the client device attached to the gate-
way to allow it to obtain an appropriate IP address.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 79

4. In the Available WAN Interfaces list, select the interface(s) that you want to group and click the left arrow to move it to the
Grouped WAN Interfaces list. Hold down the CTRL key or Shift key to select multiple interfaces.
Note: Depending on the WAN interface configuration, these clients may obtain public IP addresses.
5. Do the same in the Grouped and Available LAN Interfaces lists for any applicable LAN interfaces.
6. To automatically add LAN clients (such as set-top boxes) to a WAN Interface in the new group, enter the DHCP vendor ID
string. You can add up to 16 vendor IDs.
When you configure a DHCP vendor ID string, any DHCP client request that includes this vendor ID is denied an IP address
from the local DHCP server (DHCP option 60).
7. Click Apply/Save. Your changes take effect immediately.
8. To remove a grouping, select the grouping and click Remove. You can only remove groupings that you create.
IP Tunnel
IP Tunneling is typically used as a means to establish a path between two independent networks. Your SmartRG gateway supports
connecting islands of IPv6 networks across the IPv4 internet or IPv4 in IPv6 as well.
In this section, you can configure IP tunnel settings.
Note: For IPv6inIPv4, only 6rd configuration is supported. For IPv4inIPv6, only DS-Lite configuration is supported.
IPv6inIPv4
On this page, you can configure the IPv6inIP4 settings.
1. In the left navigation bar, click Advanced Setup > IP Tunnel > IPv6inIPv4 and then click Add. The following page appears.
2. Enter a Tunnel Name.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 80

3. Select the WAN and LAN interfaces associated with the tunnel you wish to establish. The Manual button is selected by
default.
4. Enter the appropriate values in the IPv4 Mask Length, 6rd Prefix with Prefix Length and Border Relay IPv4 Address fields.
5. Click Apply/Save to commit your changes.
IPv4inIPv6
On this page, you can configure the IPv4inIP6 settings.
1. In the left navigation bar, click Advanced Setup > IP Tunnel > IPv6inIPv4 and then click Add. The following page appears.
Note: Currently, only the DS-Lite mechanism is supported.
2. Enter a brief descriptive Tunnel Name.
3. Select the LAN and WAN interfaces associated with the tunnel you wish to establish.
4. In the AFTR field, enter the Address Family Transition Router remote address.
5. Click Apply/Save to commit your changes.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 81
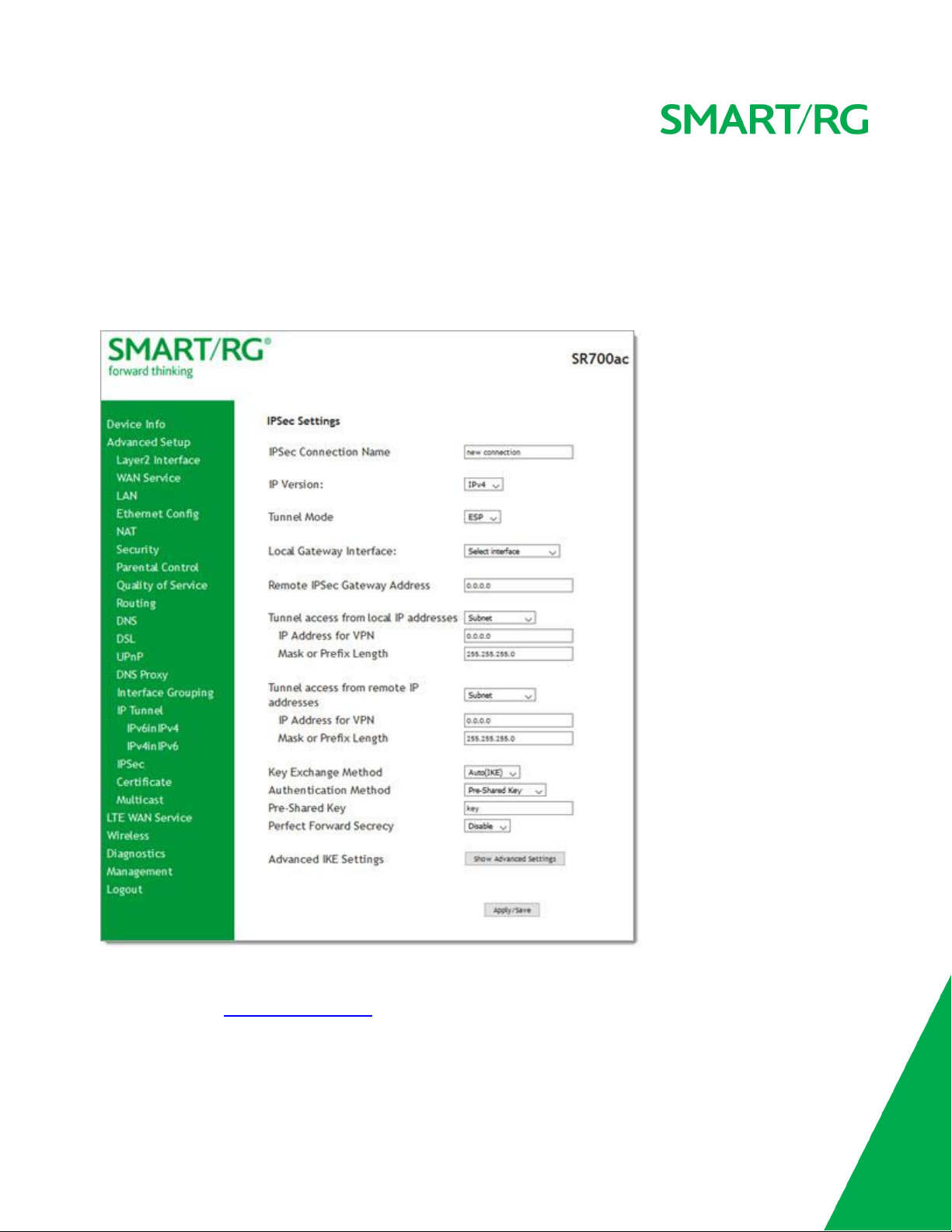
IPSec
Internet Protocol Security is a protocol for securing communications by packet level encryption and authentication.
On this page, you can enable and remove connections, or edit existing connections.
1. In the left navigation bar, click Advanced Setup > IP Sec and then click Add New Connection. The following page appears.
2. Enter your connection details by completing the appropriate fields.
3. If desired, click Advanced IKE Settings to select Phase 1 and Phase 2 specific parameters. For detailed information about
these settings, see "Advanced IKE Settings".
4. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 82

Field Name Description
IPSec Connection Name A free form text field. Enter a descriptive name for this connection
IP Version Select the IP version environment associated with your infrastructure. Options are
IPv4
and
IPv6
.
Tunnel Mode Select the encapsulation method to be used. Options are:
l ESP: Use this mode to encapsulate a packet with ESP and IP headers. An ESP trailer is added to
the packet for authentication and integrity.
l AH: Use this mode to encapsulate a packet with AH and IP headers. For authentication, the
entire packet is signed.
Local Gateway Interface Select the WAN connection to be associated with this tunnel.
Remote IPSec Gateway
Enter the WAN IP for this tunnel.
Address
Tunnel Access From Local
IP Addresses
Select IP information for site A and B. Options are:
l Subnet: Allows access to the entire LAN.
l Single Address: For single host, select this option.
IP Address for VPN Enter the IP address for local access.
Mask or Prefix Length Enter the subnet mask or prefix length for IP address entered for local access, e.g., 255.255.255.0.
Tunnel Access From
Remote IP Addresses
Select IP information for site A and B. Options are:
l Subnet: Allows access to the entire LAN.
l Single Address: For single host, select this option.
IP Address for VPN Enter the IP address for remote access.
Mask or Prefix Length Enter the subnet mask or prefix length for IP address entered for remote access, e.g., 255.255.255.0.
Key Exchange Method The key-exchange method to be used for IPSec. Options are:
l Auto(IKE): This method uses the negotiated key-exchange method for IPSec. This is the default
and recommended for best results.
l Manual: This method requires that you configure the details.
Authentication Method Select the method by which the remote end will authenticate. Options are:
l Pre-Shared Key: A key is distributed to authorized users for logging into the system. Enter the
key in the Pre-shared Key field.
l Certificate (x.509): A certificate is used for authentication. Select the certificate file in the
Certificate field that appears.
Perfect Forward Secrecy This setting determines whether a session key derived from a set of long-term keys is compromised if
one of the long-term keys in the set is compromised.
l Enable: Prevents long-term key from being compromised.
l Disable: Permits long-term keys to be compromised.
Advanced IKE Settings
You can configure advanced IKE settings if desired.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 83

1. On the IPSec Settings page, click Show Advanced IKE Settings to display the Phase 1 and Phase 2 fields.
2. Fill in the fields, using the information in the table below.
Field Name Description
Mode Select a mode. Options are
Encryption Algorithm Select the encryption algorithm. Options are
Integrity Algorithm Select the integrity algorithm. Options are
Select Diffie-Hellman Group for
Key Exchange
Key Life Time Enter the number of seconds that a key is valid. The default
3. Click Apply/Save to commit your changes.
128,AES-192
Select the D-H group. Options are
default is
3600
is
1024bit
seconds.
, and
AES-256
.
Main
.
Aggressive
and
3DES,AES -
MD5
768bit-8192bit
.
and
SHA1
. The
.
Certificate
On this page, you can configure certificates for the gateway. You can use Local and Trusted CA certificates on this gateway.
Local
Local certificates are used to identify the gateway to other users.
On this page, you can create a new certificate request locally and have it signed by a certificate authority, or you can import an existing certificate.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 84

1. In the left navigation bar, click Advanced Setup > Certificate > Local and then click Create Certificate Request. The following page appears.
2. Enter your connection details by completing the appropriate fields. For more information about certificates, refer to the ITU
X.509 standard.
3. Click Apply to complete the request.
The fields on this page are explained in the following table.
Field Name Description
Certificate Name A free-form text field used to describe the intended use of the certificate.
Common Name Enter the IP address (in dotted decimal notation), domain name or email address in
the field provided. The domain name or email address is for identification purposes
and is a free-form text field.
Organization Name Enter the organization for which this certificate is requested. Typically, this is the
name of the company creating the request.
Country/Region Select the country or region in which this certificate will be employed.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 85

4. To import a certificate and the corresponding private key, click Import Certificate. The following page appears.
5. In the Certificate Name field, type "cpecert".
6. Paste the Certificate details between the BEGIN and END markers.
7. Paste the Private Key information between the BEGIN and END markers.
8. Click Apply to implement this certificate.
Trusted CA
On this page, you import and store up to four trusted certificates. Trusted Certificates are used to identity other gateways to your
gateway as a trusted source.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 86

1. In the left navigation bar, click Advanced Setup > Certificate > Trusted CA and then click Import Certificate. The following
page appears.
2. In the Certificate Name field, type "acscert", and then paste the certificate details between the BEGIN and END markers.
3. Click Apply to commit this certificate.
After you add one certificate, a Remove button appears on the Trusted CA landing page. Click this button to remove the current
certificate and replace it with a new one.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 87

Multicast
Multicast methodology is used for applications shipping information simultaneously to multiple destinations. The most common scenario is Internet television and other streaming media. In IP Multicast, the implementation occurs at the IP routing level, where
routers create the most efficient distribution paths for packets sent to a destination.
On this page, you can configure the multicast settings.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 88

1. In the left navigation bar, select Advanced Setup > Multicast. The following page appears.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 89

2. In the Multicast Precedence field, select whether IGMP packets are given priority handling and at what level. Options are:
l Disable: IGMP packets are not prioritized. This is the default.
l Enable: IGMP packets are prioritized using the multicast precedence value. The lower the multicast precedence
value, the higher that IGMP packets will be placed in the queue.
3. In the Multicast Strict Grouping Enforcement field, select whether grouping is stricly enforced. Options are Disable and
Enable. The default is Disable.
4. Modify the other fields as needed, using the information in the table below. The same fields are provided for both IGMP and
MLD configuration.
5. To add an IPaddress to a group exception list, type the IP address and mask/mask bits in the appropriate fields and click Add.
6. Click Apply/Save to commit your changes.
7. To remove an IP addresses from a group exception list, click the Remove checkbox next to the address and then click
Remove Checked Entries.
The fields on this page are explained in the following table.
Field Name Description
Default Version Enter the supported IGMP version. Options are:1-3.
Query Interval The interval at which the multicast router sends a query messages to hosts,
expressed in seconds.
If you enter a number below 128, the value is used directly. If you enter a number
128, it is interpreted as an exponent and mantissa.
Query Response Interval
Upon receiving a query packet, a host begins counting down seconds, from a random number. When the timer expires, the host sends its report.
Enter the maximum number of seconds that a host can pick to count down from.
The value must be greater than the Query Interval. If using IGMP v1, this value is
fixed at 10 seconds.
Last Member Query
Interval
Enter the maximum response time within which the host must respond to the Out
of Sequence query from the router. The default is
1000ms
.
IGMP uses this value when the router receives an IGMPv2 Leave report indicating
at least one host wants to leave the group. Upon receiving the Leave report, the
router verifies whether the interface is configured for IGMP Immediate Leave. If
not, the router sends the out-of-sequence query.
Robustness Value Enter the value representing the complexity of the query. The greater the value,
the more robust the query. Options are:2-7.
Maximum Multicast
Enter the maximum number of groups allowed.
Groups
Maximum Multicast
Enter the maximum number of data sources allowed. Options are:1-24.
Data Sources
Maximum Multicast
Group Members
Enter the maximum number of multicast groups that can be joined on a port or
group of ports.
Fast Leave Enable Select whether the IGMP proxy removes group members immediately without
sending a query. Options are:
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 90

Field Name Description
l Enabled: Group members are removed immediately.
l Disabled: Group members are removed after a query is sent and a
response received.
LTE WAN Service
In this section, you can view LTE WAN status and configure the related network settings.
Status Information
On this page, you can view information about the LTE connection between your provider and your gateway.
In the left menu, click LTE WAN Service > Status Information. The following page appears.
The fields on this page are explained in the following table.
Field Name Description
SIM status
SIM State of the SIM card if inserted into the SIM slot on the rear of the SR700ac. Options are READY and
LTE Module Info
Manufacturer Manufacturer of the LTE Module.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 91
section
NA.
section

Field Name Description
Model Model of the LTE Module.
Firmware Version Firmware version of the LTE Module
IMEI International Mobile Equipment Identity is a unique 15-digit number used to identify valid equip-
ment on a network provider.
IMSI International Mobile Subscriber Identity is a unique number stored on the SIM Card used to identify
the subscriber of the network provider.
LTE Information
Network Connected Status State of the LTE connection. Options are
Signal Quality Quality of the LTE signal. Options are
RSSI Received Signal Strength Indicator. The measured dBm level of the received radio signal with the
IPv4 Address IPv4 Address for the LTE connection.
section
4G Connected,3G Connected,Disconnected,Not
Attached
network provider. If no signal is found, “No Signal” appears in this field.
SIM Card not detected
, and
.
Excellent,Average,Poor
, and
No Signal
.
Network Settings
On this page, you can configure the Network Settings of the LTE connection between your provider and your gateway.
1. Insert the SIM card received from your network provider into the SIM card slot on the back of the SR700ac with the gold contacts facing up.
Note: The SIM card slot is located beneath the black WAN Ethernet port on the back of the gateway.
2. In the left navigation bar, click LTE WAN Service > Network Settings. The following page appears.
3. Modify the settings as needed, using the information provided in the table below.
4. Click Save to commit your changes.
Note: The settings take up to 90 seconds to save.
The fields on this page are explained in the following table.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 92

Field
Name
Network Mode
Network
Dial
Mode
APN Settings
APN
Name
Description
section
Select the Network Dial Mode. Options are 4G/3G Auto, 4G Only, and 3G Only.
section
Enter the Access Point Name for your network provider.
Wireless
In this section, you can configure the wireless interface settings for your gateway, including basic and advanced settings, MAC filtering, and wireless bridging.
Note: While separate pages are provided for both wireless bands (2.4 Ghz and 5 Ghz), the fields are the same for both bands.
Basic
On this page, you can configure basic features of the Wi-Fi LAN interface. You can enable or disable the Wi-Fi LAN interface, hide the
network from active scans, set the Wi-Fi network name (also known as SSID) and restrict the channel set based on country requirements.
1. In the left navigation bar, click Wireless. The following page appears.
Note: Menu options appear for both wireless channels. Click the wireless channel that you want to configure and proceed
with configuration. The same fields are available for both channels.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 93

2. Modify the settings as desired, using the information provided in the table below. The table at the bottom of the page lists
the guest/virtual access points defined for your gateway. If desired, you can define up to three virtual access points for guest
use.
3. Click Apply/Save to commit your settings.
The fields on this page are explained in the following table.
Field Name Description
Enable WiFi Button This option is enabled by default. To disable the gateway's Wi-Fi button, click
the checkbox to clear it.
Enable Wireless This option is enabled by default. To disable the gateway's Wi-Fi radio, click
the checkbox to clear it.
Hide Access Point Click to hide the access point SSID from end users.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 94

Field Name Description
Clients Isolation Click to prevent LAN client devices from communicating with one another on
the wireless network.
Disable WMM Advertise Click to stop the wireless from advertising Wireless Multimedia (WMM) func-
tionality. WMM provides basic Quality of Service (QOS) for applications.
Enable Wireless Multicast
Forwarding
SSID Enter the Wi-Fi SSID.
BSSID Enter the Basic Service Set Identifier (BSSID) to provide the MAC address
Country Select the country in which the gateway is deployed.
Country RegRev Enter the revision number of the regulations being followed for the selected
Max Clients Enter the maximum number of clients that can access the route wirelessly.
Wireless - Guest/Virtual Access Points
Enabled Click to enable a virtual wireless access point for guest access.
SSID Enter your wireless SSID.
Hidden Click to hide the SSID from being broadcast publicly.
Isolate Clients Click to prevent client PCs from communicating with one another.
Disable WMM Advertise Click to stop the wireless from advertising Wireless Multimedia (WMM) func-
Enable WMF Click to enable Wireless Multicast Forwarding (WMF).
Max Clients Enter the maximum number of clients allowed for this wireless channel.
BSSID Displays the Basic Service Set Identifier or
Click to enable Wireless Multicast Forwarding (WMF). Multicast traffic is forwarded across wireless clients.
assigned to the wireless router.
country. The default is0.
table
tionality.
N/A
.
Security
On this page, you can configure security features of the wireless LAN interface, either manually or via Wi-Fi Protected Setup (WPS).
Note: When WPS is enabled, the STA PIN and Authorized MAC fields appear. If both of these fields are empty, PBC becomes the
default value. If Hide Access Point is enabled or the MAC filter list is empty with "Allow" selected, WPS2 will be disabled.
1. In the left navigation bar, click Wireless > Security. The Security page appears for the 5 GHz band page. To configure the 2.4
GH band, click 2.4 Ghz Band in the left menu.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 95
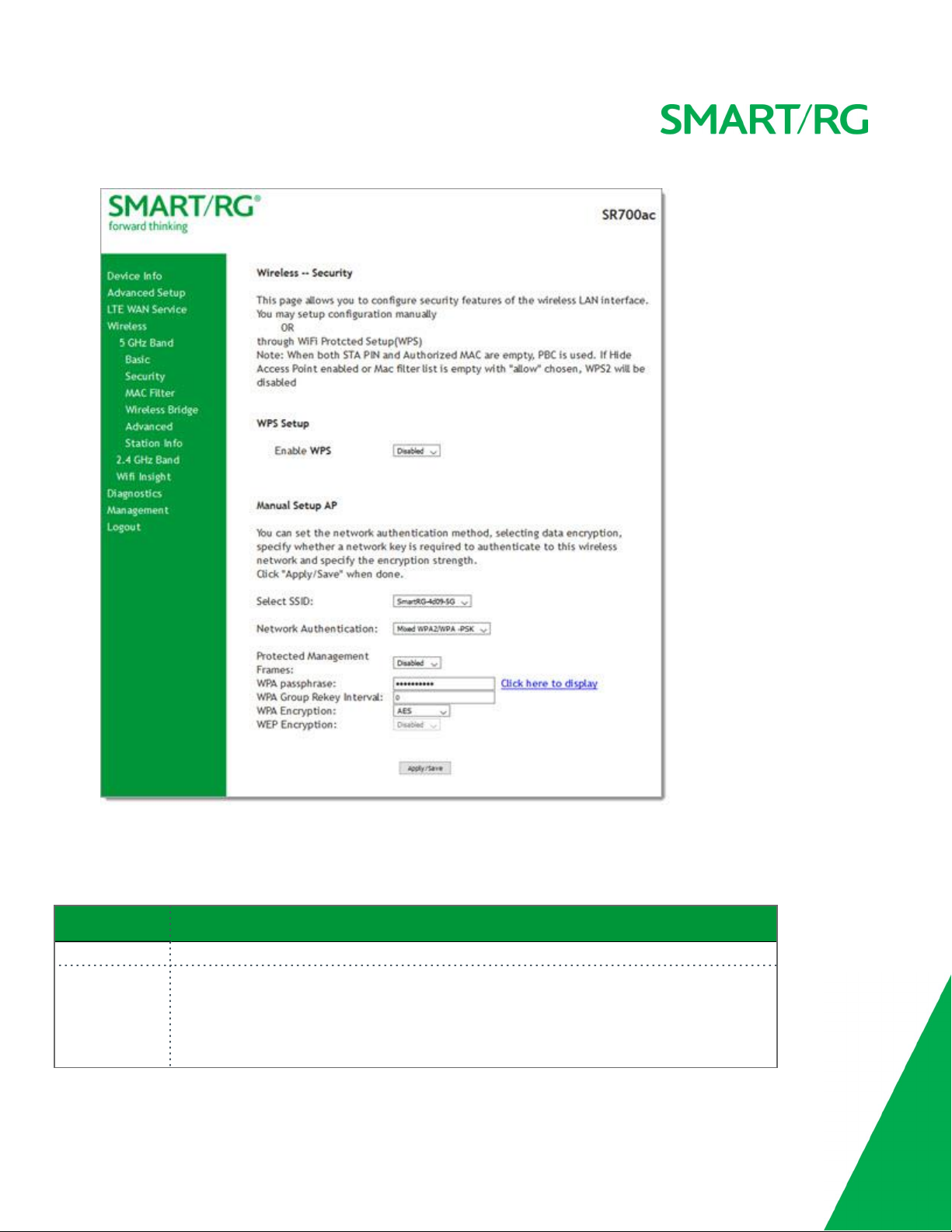
2. Modify the settings as needed, using the information provided in the field description table.
3. Click Apply/Save to commit your changes.
The fields on this page are explained in the following table.
Field Name Description
Enable WPS Select to enable Wi-Fi Protected Setup. Options are:
Add Client (
Appears when WPS is enabled
Enter STA PIN
Use AP PIN
and
) Select the method for generating the WPS PIN. Options are:
.
Enabled
and
Disabled
.
To add an enrollee station, click Add Enrollee.
Note: If the PIN and Set Authorized Station MAC fields are left blank, the PBC (push-button)
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 96

Field Name Description
mode is automatically made active.
Set WPS AP Mode (
Device PIN (
Appears when WPS is enabled
l Configured: The gateway assigns security settings to clients.
l Unconfigured: An external client assigns security settings to the gateway.
Appears when WPS is enabled
) Select how security is assigned to clients.
) The PIN for the gateway. This value is generated by the access
point.
Manual Setup AP
section
Select SSID Select the SSID of the wireless network to which this security configuration will apply.
Network
Authentication
Select the desired network security authentication type. Options are:
WPA2,WPA2-PSK,Mixed WPA2/WPA
Mixed WPA2/WPA-PSK
, and
Open,Shared,802.1X
.
,
The fields shown in the Manual Setup AP section of the page vary based on the network authentication method that you select. The
variations are explained in the following sections:
l "Open & Shared Authentication"
l "802.1X Authentication"
l "WPA2 & Mixed WPA2/WPA Authentication"
l "WPA2-PSK & Mixed WPA2/WPA-PSK Authentication"
Open & Shared Authentication
The same configuration fields apply for both Open and Shared authentication types. However, WPS may not be used with the Shared
method.
1. On the Wireless > Security page for the band that you want to configure, select Open or Shared in the Network Authentic-
ation field.
2. For Open authentication, in the Enable WPS field, select Enabled. The following fields appear.
Note: For Shared authentication, this option is set to Disabled and cannot be changed.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 97

3. Fill in the fields, using the information in the field description table below.
4. Click Apply/Save to save the settings.
The fields on this page are explained in the following table.
Field Name Description
Select SSID Select the SSID of the wireless network to which this security configuration will
apply.
WEP Encryption Select to enable Wired Equivalent Privacy (WEP) mode. Options are
Encryption Strength (
Current Network Key (
Network Key 1-4 (
Disabled
Appears when WEP Encryption is set to Enabled
tion method. Options are
security.
Appears when WEP Encryption is set to Enabled
presently in effect.
Appears when WEP Encryption is set to Enabled
keys using the on-screen instructions to achieve the desired security strength (128bit or 64-bit).
.
128-bit
and
64-bit
) Select the length of the encryp-
. 128-bit is the more robust option for
) Select which of the four keys is
) Enter up to four encryption
Enabled
and
802.1X Authentication
1. On the Wireless > Security page for the band that you want to configure, select 802.1X in the Network Authentication field.
The following fields appear.
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 98

2. Fill in the fields, using the information in the field description table below.
3. Click Apply/Save to save the settings.
The fields on this page are explained in the following table.
Field Name Description
RADIUS Server IP
address
RADIUS Port Enter the port number for the RADIUS server. Port
RADIUS Key (
Enter the IP address of the RADIUS (Remote Authentication Dial In User Service) server associated with your network.
1812
is the current standard for RADIUS
authentication per the IETF RFC 2865. Older servers may use port
Optional
) Enter the encryption key (if required) needed to authenticate to the specified
1645
. Options are1-
65535
.
RADIUS Server.
WEP Encryption Wired Equivalent Privacy (WEP) encryption mode is enabled by default and cannot be
changed.
Encryption
Strength
Current Network
Select the length of the encryption method. Options are
more robust option for security.
Select which of the four keys is presently in effect.
128-bit
and
64-bit
. 128-bit is the
Key
Network Key 1-4 Enterone or two encryption keys using the on-screen instructions to achieve the desired secur-
ity strength (128-bit or 64-bit).
SMAR TRG INC. PROPRIETAR Y AND CONFIDENTIAL. ALL RIGHTS RESERVED. COPYRIGHT © 2017 99
 Loading...
Loading...