Siemens SIMATIC NET SCALANCE WLC711, SCALANCE WLC711 Getting Started

SCALANCE WLC711
___________________
___________________
___________________
___________________
___________________
___________________
___________________
___________________
SIMATIC NET
Industrial Wireless LAN
SCALANCE WLC711
Getting Started
04/2016
C7900
Preface
Security recommendations
1
Description
2
Getting started
3
Basic configuration with the
wizard
4
Managing access points
5
Configuring specific use
cases with the wizard
6
Optional configuration
7
0-G8976-C269-07

Siemens AG
Division Process Industries and Drives
Postfach 48 48
90026 NÜRNBERG
GERMANY
Document order number: C79000-G8976-C269-06
Ⓟ
Copyright © Siemens AG 2011 - 2016.
All rights reserved
Legal information
Warning notice system
DANGER
indicates that death or severe personal injury will result if proper precautions are not taken.
WARNING
indicates that death or severe personal injury may result if proper precautions are not taken.
CAUTION
indicates that minor personal injury can result if proper precautions are not taken.
NOTICE
indicates that property damage can result if proper precautions are not taken.
Qualified Personnel
personnel qualified
Proper use of Siemens products
WARNING
Siemens products may only be used for the applications described in the catalog and in the relevant technical
maintenance are required to ensure that the products operate safely and without any problems. The permissible
ambient conditions must be complied with. The information in the relevant documentation must be observed.
Trademarks
Disclaimer of Liability
This manual contains notices you have to observe in order to ensure your personal safety, as well as to prevent
damage to property. The notices referring to your personal safety are highlighted in the manual by a safety alert
symbol, notices referring only to property damage have no safety alert symbol. These notices shown below are
graded according to the degree of danger.
If more than one degree of danger is present, the warning notice representing the highest degree of danger will
be used. A notice warning of injury to persons with a safety alert symbol may also include a warning relating to
property damage.
The product/system described in this documentation may be operated only by
task in accordance with the relevant documentation, in particular its warning notices and safety instructions.
Qualified personnel are those who, based on their training and experience, are capable of identifying risks and
avoiding potential hazards when working with these products/systems.
Note the following:
documentation. If products and components from other manufacturers are used, these must be recommended
or approved by Siemens. Proper transport, storage, installation, assembly, commissioning, operation and
All names identified by ® are registered trademarks of Siemens AG. The remaining trademarks in this publication
may be trademarks whose use by third parties for their own purposes could violate the rights of the owner.
We have reviewed the contents of this publication to ensure consistency with the hardware and software
described. Since variance cannot be precluded entirely, we cannot guarantee full consistency. However, the
information in this publication is reviewed regularly and any necessary corrections are included in subsequent
editions.
for the specific
11/2016 Subject to change

Preface
Introduction
Who is this document intended for?
Purpose of this document
Validity of this document
By using the Industrial Wireless LAN controller SCALANCE WLC711 along with controllerbased access points, it is possible to set up a single wireless infrastructure for the entire
company. This achieves a high degree of flexibility since mobile subscribers (for example a
laptop) move both in the office and in the automation network and can change over
seamlessly between these networks (roaming). This means that data can be accessed from
anywhere in the company over wireless.
Thanks to the use of a centralized security mechanism for each user group, data is protected
from unauthorized access and manipulation.
The controller-based access points SCALANCE W78xC support the WLAN standards IEEE
802.11a/b/g ad 802.11n and are connected to the IWLAN controller SCALANCE WLC via
gigabit Ethernet. The same applies to the access points SCALANCE W786C, with which a
connection via fiber-optic is possible depending on the version. The controller-based access
points SCALANCE W786-2HPW support the WLAN standards IEEE 802.11a/b/g and are
connected to the IWLAN controller SCALANCE WLC via fast Ethernet or fiber-optic cable.
One requirement for operation is always the use of the IWLAN controller SCALANCE WLC
which makes the group configuration of access points possible. This allows a widespread
IWLAN infrastructure to be represented clearly. The central management with the IWLAN
controller also allows the recording of disruptions, monitoring and documentation of
statistics.
The Getting Started is intended for system administrators who want to configure the wireless
LAN controller SCALANCE Industrial Wireless LAN controller WLC711 and the access
points with the Web Based Management (WBM) of the SCALANCE Industrial Wireless LAN
controller and access points.
This document provides you with a general overview of the functions of the WBM
SCALANCE Industrial Wireless LAN controller and access points. The Getting Started will
quickly help you to learn about configuring the devices.
We recommend that you read the Getting Started not selectively but rather from front to
back. You will get to know the important components that can help you during configuration.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
This document is valid for the SCALANCE IWLAN controller WLC711 and the controllerbased SCALANCE W78xC access points as of firmware version V 9.21.
3
Preface
SIMATIC NET glossary
Security messages
Note
Siemens offers IT security mechanisms for its automation and drive product portfolio in order
to support the safe operation of the plant/machine. Our products are also continuously
developed further with regard to IT security. We therefore recommend that
check for updates of our products and that you only use the latest versions. You will find
information in:
Here, you can register for a product
For the safe operation of a plant/machine, however, it is also necessary to integrate the
automation components into an overall IT security concept for the entire plant/machine,
whic
Products from
Explanations of many of the specialist terms used in this documentation can be found in the
SIMATIC NET glossary.
You will find the SIMATIC NET glossary here:
● SIMATIC NET Manual Collection or product DVD
The DVD ships with certain SIMATIC NET products.
● On the Internet under the following address:
50305045 (https://support.industry.siemens.com/cs/ww/en/view/50305045)
you regularly
http://www.siemens.com/industrialsecurity. (http://www.siemens.com/industrialsecurity.)
-specific newsletter.
h corresponds to the state-of-the-art IT technology. You will find information on this in:
https://support.industry.siemens.com (https://support.industry.siemens.com/cs/de/en/)
other manufacturers that are being used must also be taken into account.
SCALANCE WLC711
4 Getting Started, 04/2016, C79000-G8976-C269-07

Table of contents
Preface ................................................................................................................................................... 3
1 Security recommendations ...................................................................................................................... 7
2 Description ............................................................................................................................................ 13
3 Getting started ...................................................................................................................................... 17
4 Basic configuration with the wizard ........................................................................................................ 23
5 Managing access points ........................................................................................................................ 35
6 Configuring specific use cases with the wizard ...................................................................................... 61
7 Optional configuration ........................................................................................................................... 79
1.1 General information .................................................................................................................. 7
1.2 Security recommendations ....................................................................................................... 8
2.1 General ................................................................................................................................... 13
2.2 Requirement for configuration ................................................................................................ 15
2.3 LED display ............................................................................................................................. 16
3.1 Sequence ................................................................................................................................ 17
3.2 Logon ...................................................................................................................................... 19
3.3 Shutting down and turning off ................................................................................................. 21
4.1 Procedure - "Basic Installation Wizard" page ......................................................................... 25
4.2 Procedure - "Management" page ........................................................................................... 28
5.1 Commissioning access points ................................................................................................ 35
5.2 Registering access points ....................................................................................................... 39
5.3 Configuring access points ....................................................................................................... 45
5.3.1 Single configuration ................................................................................................................ 45
5.3.2 Multiple configuration .............................................................................................................. 58
6.1 Use case: Bridged at WLC ..................................................................................................... 61
6.2 Use case: Bridged at AP ......................................................................................................... 70
7.1 Expanding the number of manageable access points ............................................................ 79
7.2 Access using the Command Line Interface (CLI) ................................................................... 82
7.3 Data backup ............................................................................................................................ 84
7.4 Using reports ........................................................................................................................... 87
7.5 Using policies .......................................................................................................................... 89
7.6 Authentication via RADIUS server .......................................................................................... 91
7.7 User configuration ................................................................................................................... 94
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
5

Table of contents
Index .................................................................................................................................................... 97
SCALANCE WLC711
6 Getting Started, 04/2016, C79000-G8976-C269-07

1
1.1
General information
Note
Note the information in the SCALANCE WLC711 user guide and the compact operating
instructions SCALANCE WLC711.
Notes on secure network design
Use WPA2/ WPA2-PSK with AES
Protect your network against man-in-the-middle attacks
Use SNMPv3
To protect your network from attacks, note the following points:
●
To prevent misuse of a password, use only WPA2/AES. WPA2/ WPA2-PSK with AES
provides the highest security.
●
To protect your network from man-in-the-middle attacks, a network topology is
recommended, that makes it more difficult for an attacker to tap into the communications
path between two end devices.
– You can, for example, protect WLAN devices by arranging so that the management
port is accessible only via a separate management VLAN.
– You can also install a separate HTTPS certificate on a WLAN client / access point.
The HTTPS certificate checks the identity of the device and controls the encrypted
data exchange. You can install the HTTPS certificate via HTTP.
●
SNMPv3 provides you with highest possible security when accessing the WLAN devices
via SNMP.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
7

Security recommendations
1.2
Security recommendations
General
Physical access
Software (security functions)
1.2 Security recommendations
To prevent unauthorized access, note the following security recommendations.
● You should make regular checks to make sure that the device meets these
recommendations and/or other security guidelines.
● Evaluate your plant as a whole in terms of security. Use a cell protection concept with
suitable products.
● When confidential zones are used, the internal and external network are disconnected, an
attacker cannot access the data from the outside.
● Operate the device only within a protected network area.
● Use additional devices with VPN functionality (e.g. SCALANCE S) to encrypt and
authenticate communication from and to the devices.
● For data transfer via a non-secure network, use an encrypted VPN tunnel (IPsec) by
using additional devices with VPN functionality (e.g. SCALANCE S).
● For operation of the device in a non-secure infrastructure no product liability will be
accepted.
● Separate connections correctly (WBM. Telnet, SSH etc.).
● Restrict physical access to the device to qualified personnel.
● Lock unused physical ports on the device. Unused ports can be used to gain forbidden
access to the plant.
● Keep the software up to date. Check regularly for security updates of the product.
You will find information on this on the Internet pages "Industrial Security
(http://www.siemens.com/industrialsecurity".
● Inform yourself regularly about security advisories and bulletins published by Siemens
ProductCERT (http://www.siemens.com/cert/en/cert-security-advisories.htm).
● Only activate protocols that you really require to use the device.
● Use the security functions such as address translation with NAT (Network Address
Translation) or NAPT (Network Address Port Translation) to protect receiving ports from
access by third parties.
● Restrict access to the device with a firewall or rules in an access control list (ACL -
Access Control List).
● If RADIUS authentication is via remote access, make sure that the communication is
within the secured network area or is via a secure channel.
● The option of VLAN structuring provides good protection against DoS attacks and
unauthorized access. Check whether this is practical or useful in your environment.
SCALANCE WLC711
8 Getting Started, 04/2016, C79000-G8976-C269-07

Security recommendations
Passwords
Keys and certificates
1.2 Security recommendations
● Enable logging functions. Use the central logging function to log changes and access
attempts centrally. Check the logging information regularly.
● Configure a Syslog server to forward all logs to a central location.
● Use WPA2/ WPA2-PSK with AES to protect the WLAN.
● Define rules for the use of devices and assignment of passwords.
● Regularly update passwords and keys to increase security.
● Change all default passwords for users before you operate the device.
● Only use passwords with a high password strength. Avoid weak passwords for example
password1, 123456789, abcdefgh.
● Make sure that all passwords are protected and inaccessible to unauthorized personnel.
● Do not use the same password for different users and systems or after it has expired.
This section deals with the security keys and certificates you require to set up HTTPS (
HyperText Transfer Protocol Secured Socket Layer).
● We strongly recommend that you create your own HTTPS certificates and make them
● Handle user-defined private keys with great caution if you use user-defined SSH or SSL
● Use the certification authority including key revocation and management to sign the
● Verify certificates and fingerprints on the server and client to avoid "man in the middle"
● We recommend that you use certificates with a key length of 2048 bits.
● Change keys and certificates immediately, if there is a suspicion of compromise.
available.
There are preset certificates and keys on the device. The preset and automatically
created HTTPS certificates are self-signed.
We recommend that you use HTTPS certificates signed either by a reliable external or by
an internal certification authority. The HTTPS certificate checks the identity of the device
and controls the encrypted data exchange. You can install the HTTPS certificate via the
WBM (System > Load and Save).
keys.
certificates.
attacks.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
9

Security recommendations
Secure/non-secure protocols
1.2 Security recommendations
● Avoid and disable non-secure protocols, for example Telnet and TFTP. For historical
reasons, these protocols are still available, however not intended for secure applications.
Use non-secure protocols on the device with caution.
● The following protocols provide secure alternatives:
– SNMPv1/v2 → SNMPv3
Check whether use of SNMPv1 is necessary. SNMPv1 is classified as non-secure.
Use the option of preventing write access. The product provides you with suitable
setting options.
If SNMP is enabled, change the community names. If no unrestricted access is
necessary, restrict access with SNMP.
Use SNMPv3 in conjunction with passwords.
– HTTP → HTTPS
– SNTP → NTP
● Use secure protocols when access to the device is not prevented by physical protection
measures.
● To prevent unauthorized access to the device or network, take suitable protective
measures against non-secure protocols.
● If you require non-secure protocols and services, operate the device only within a
protected network area.
● Restrict the services and protocols available to the outside to a minimum.
SCALANCE WLC711
10 Getting Started, 04/2016, C79000-G8976-C269-07

Security recommendations
Port list
Component
Protocol
Soruce
Port
Destination Port
Service
Remark
Require
Firewall
to open
Source
Destination
(TCP/UDP)
Ports for AP/Controller Communication
Management and Data Tunnel
Management and Data Tunnel
between AP and Controller
WASSP
AP and Controller
WASSP
AP and Controller
Access Point
Controller
UDP
Any
13907
WASSP
AP Registration to Controller
Yes
Server
for AP
Access Point
Controller
UDP
Any
427
SLP
AP Registration to Controller
Optional
Controller
Access Point
TCP/UDP
Any
69
TFTP
AP image transfer
Yes 1
Access Point
Controller
TCP/UDP
Any
69
TFTP
AP image transfer
Yes 1
Controller
Access Point
TCP/UDP
Any
22
SCP
AP traces
Yes
2003
Any
Access Point
TCP/UDP
Any
22
SSH
Remote AP login (if enabled)
Optional
Ports for Controller Management
Any
Controller
TCP/UDP
Any
5825
HTTPS
Controller GUI access
Yes
Any
Controller
TCP/UDP
Any
161
SNMP
Controller SNMP access
Yes
Trap
Ports for Inter Controller Mobility and Availability
nel
Controller
Controller
TCP
Any
427
SLP
SLP Directory
Yes
Controller
Controller
TCP
Any
20506
Langley
Remote Langley Secure
Yes
Controller
Controller
TCP
Any
60606
Mobility
VN MGR
Yes
Controller
Controller
TCP
Any
123
NTP
Availability time sync
Yes
DA
for SLP DA request
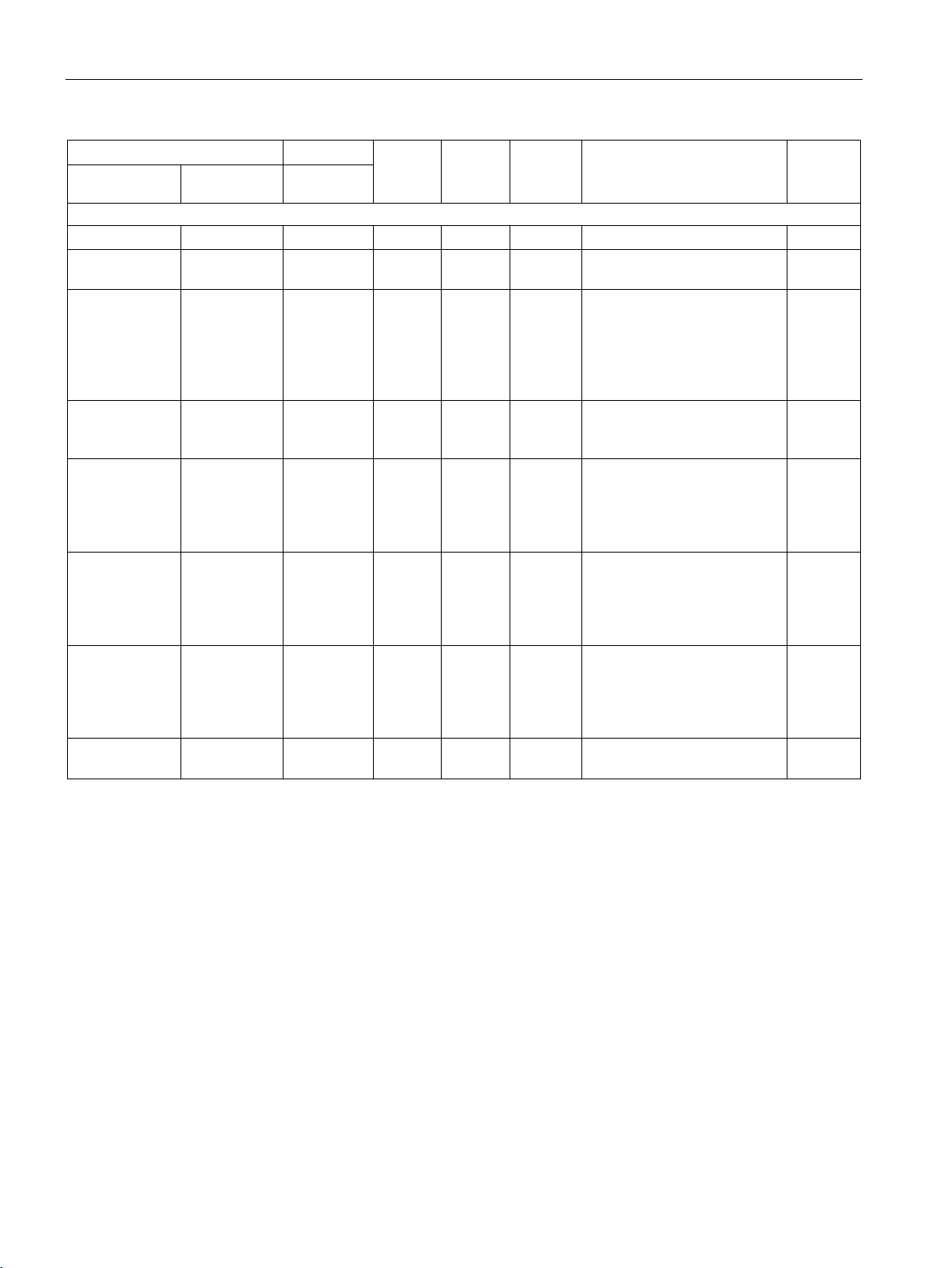
1.2 Security recommendations
The following table provides an overview of the ports through which the IWLAN
controller/access point communicate. Ports may need to be opened for correct working in the
network. Keep this in mind when configuring a firewall.
Controller Access Point UDP Any 13910 WASSP
between AP and Controller
Access Point Controller UDP Any 13910 WASSP
Controller Access Point UDP 4500 Any Secured
Access Point Controller UDP Any 4500 Secured
Access Point Controller UDP Any 67 DHCP
Any Access Point TCP Any 2002,
Any Controller TCP/UDP Any 22 SSH Controller CLI access Yes
RCAPD AP Real Capture (if enabled) Optional
Management Tunnel between
Management Tunnel between
If Controller is DHCP Server
Yes
Yes
Optional
Optional
Optional
Any Controller TCP/UDP Any 162 SNMP
Controller Controller UDP Any 13911 WASSP Mobility and Availability Tun-
Controller DHCP Server UDP Any 67 SLP Asking DHCP Server for SLP
DHCP Server Controller UDP Any 68 SLP Response from DHCP Server
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
Controller SNMP access Yes
Yes
Yes
Yes
11
Security recommendations
Component
Protocol
Soruce
Port
Destination Port
Service
Remark
Require
Firewall
to open
Source
Destination
(TCP/UDP)
Core Back-End Communication
syslog server
zation
ing
(DAS)
(lbs)
point
er
1
control tunnel is enabled TFTP exchanges take place within the secure tunnel and port 69 is not used
1.2 Security recommendations
Controller DNServer UDP Any 53 DNS If using DNS Optional
Controller Syslog Server UDP Any 514 Syslog If Controller logs to external
Optional
Controller RADIUS
Server
UDP Any 1812 RADIUS
Authentication
and
Authori-
Controller RADIUS
Server
Dynamic Au-
Controller UDP Any 3799 Dynamic
thorization
Client (typically
NAC)
Controller AeroScout
Server
UDP Any 1813 RADIUS
Account-
Authorization
Server
UDP 1144 12092 Location-
Based
Service
Proxy
(lbs)
AeroScout
Server
Controller UDP 12092 1144 Location-
Based
Service
Proxy
Controller Check Point UDP Any 18187 Check-
If using RADIUS AAA Optional
If enabled RADIUS account-
Optional
ing
Request from Dynamic Au-
Optional
thorization Client to disconnect a specific client
AeroScout Location-Based
Optional
Service
AeroScout Location-Based
Optional
Service
Logging to Check Point Serv-
Optional
TFTP uses port 69 only when the secure control tunnel is NOT enabled between the AP and controller. If the secure
SCALANCE WLC711
12 Getting Started, 04/2016, C79000-G8976-C269-07

2
2.1
General
Information
Siemens Customer Support
Related information can be found on the accompanying SIMATIC NET IWLAN CD:
Which access points can be used?
Note
Detection of W788C-2 M12 EEC devices
During detection of devices, the devices of the
W788C
How is data transferred?
If you have questions or problems, contact Siemens Customer Support at the following
address:
● https://support.industry.siemens.com
● BAK W78xC
● BAK W786-2HPW
● SCALANCE W-700 configuration manual
To achieve an optimum WLAN, the following SCALANCE wireless LAN access points are
ideal:
● SCALANCE wireless LAN W78xC access points
● SCALANCE Wireless LAN access points W788C-2 RJ-45
● SCALANCE Wireless LAN access points W788C-2 M12
● SCALANCE Wireless LAN access points W788C-2 M12 EEC
● SCALANCE Wireless LAN access points W786-2HPW
-2 M12
To transfer the data, the SCALANCE WLC711 has the following RJ-45 Ethernet connectors:
● Management port: "admin" interface. The configuration data is transferred at this port at
10/100/1000 Mbps.
● Data port: "esa0" interface. At this port, the data is transferred at 10/100/1000 Mbps.
You will find further information in the compact operating instructions SCALANCE WLC711.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
W788C-2 M12 EEC variant are shown as
13

Description
Where is the configuration data stored?
What can the WBM do?
2.1 General
Your configuration data is stored directly on the WLC. It is, however, possible to store this
data as a backup and to transfer it to other WLCs. How to create backups is explained in the
SCALANCE WLC711 User Guide.
All access points connected to a WLC are centrally monitored and managed to achieve
better administrative control. When necessary, each AP can be configured, enabled or
disabled separately. APs can be managed using the WLC. Alarms, traps and reporting
statistics are generated and can be evaluated by the network manager. The APs also send
data about performance, security and use to the WLC that can then be put together in
detailed reports.
With the WBM, you have the following options:
● Central configuration, administration and monitoring of several access points by the
SCALANCE Industrial Wireless LAN controller.
● Configuration of filter functions.
● Making the settings:
– Bridge traffic locally at WLC.
The data coming from the access points is forwarded centrally via the WLC.
– Bridge traffic locally at AP:
The data coming from the access points us forwarded directly by the access points to
the wired network.
SCALANCE WLC711
14 Getting Started, 04/2016, C79000-G8976-C269-07

Description
2.2
Requirement for configuration
2.2 Requirement for configuration
To be able to configure the SCALANCE Industrial Wireless LAN controller and the access
points with the WBM, the following conditions must be met:
● Correct connection of the hardware.
● A correct connection between the management port of the SCALANCE WLC711 and a
PC.
You will find information about setting up in the compact operating instructions SCALANCE
WLC711.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
15
Description
2.3
LED display
Introduction
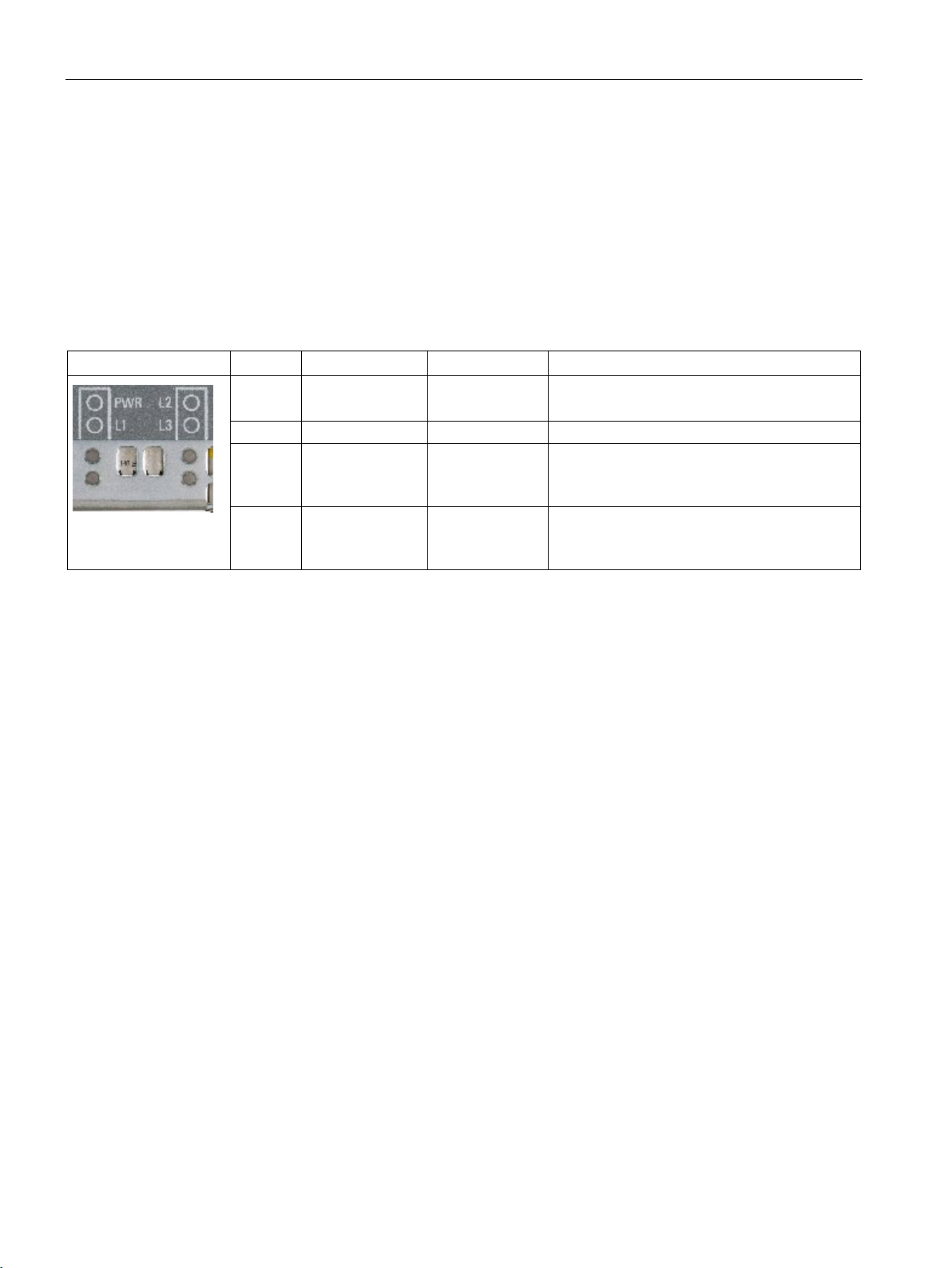
LED display
Status displays
LED
Meaning
LED
Description
GREEN
Supply voltage is applied.
RED
flashing GREEN
2.3 LED display
This section contains information explaining how the LED displays work. This means you
can make sure that the wireless LAN controller has started up completely.
PWR Power supply OFF
L1 - - L2 Battery display flashing RED
L3 RUN/STOP Flashing
YELLOW
Standby mode
Battery low (remaining life less than 1 month).
Battery empty.
System is starting up.
System running.
The L2 and L3 LEDs each flash at 1 second intervals.
If the L2 and L3 LEDs flash yellow together at an interval of 2 seconds, an upgrade or the
import of a configuration following an upgrade is being performed.
SCALANCE WLC711
16 Getting Started, 04/2016, C79000-G8976-C269-07

3
3.1
Sequence
Step 1 - Prior to configuration
Data
Note
PNIO
For complex plants requiring PROFINET IO communication, stand
points with iPCF support are recommended.
Voice
Captive portal
Step 2 - Setting up the network
Below you will find an overview of the best way to configure access points.
Decide which WLAN service you want to use. The following are available:
●
This WLAN service is recommended if your WLAN is used mainly for normal data traffic,
for example intranet. This WLAN service can be suitable for PROFINET IO if WLAN
clients move within the range of one access point (no roaming of WLAN clients between
several access points). Possible topologies for the WLAN service are as follows:
– Bridge at AP (requirement for PNIO)
– Bridge at WLC
– Routed
●
This WLAN service is recommended if your WLAN is used mainly for voice and video
communication, for example VoIP.
Possible topologies for this WLAN type are as follows:
– Bridged at WLC
– Routed
●
With this WLAN service, you can set up a WLAN specifically for guests.
-alone access
Make sure that the external servers such as DHCP and RADIUS are available and
adequately configured. Make sure that the data port between the Industrial Ethernet switch
(IE Switch) and WLC and the IE switch and APs have the identical subnet configuration.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
17

Getting started
Step 3 - Installing hardware
3.1 Sequence
Install the SCALANCE Industrial Wireless LAN controller and the access points. You will find
further information in the compact operating instructions SCALANCE WLC711.
SCALANCE WLC711
18 Getting Started, 04/2016, C79000-G8976-C269-07
Getting started
3.2
Logon
Prerequisite
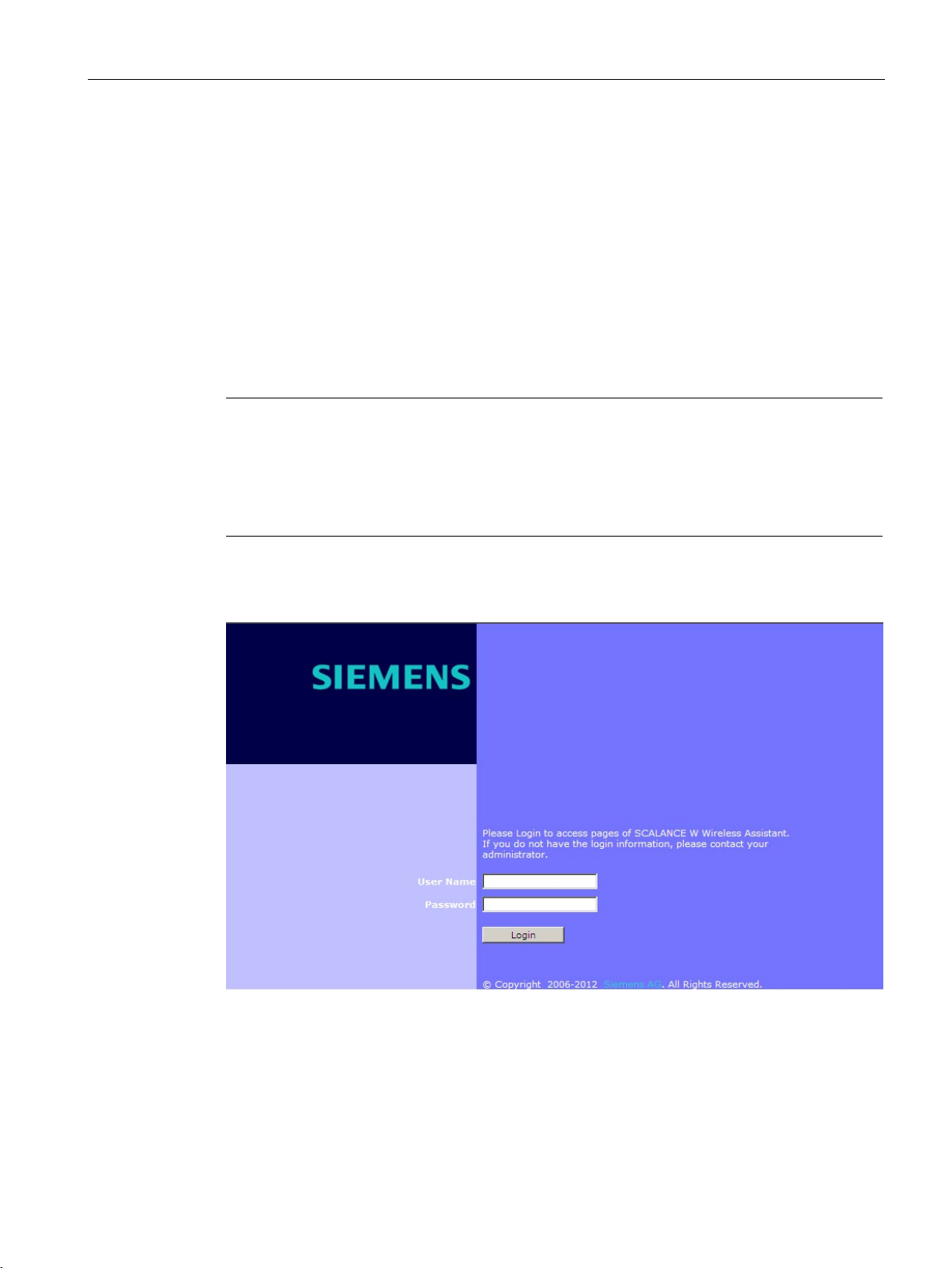
Calling up the logon page
Note
Display of a security message
If a security message is displayed in the Web browser, confirm this to continue the download
of the Web page. The secu
It is possible to install your own certificate. You will find more detailed information in the
SCALANCE WLC711 user guide.
3.2 Logon
To log on with the WBM, a connection must exist between the management port ("admin"
interface) of the WLC and the configuration PC.
To call up the logon page, open a Web browser and enter the default IP address
https://192.168.10.1:5825 in the address line.
rity message results from the pre-installed, self-signed certificate.
This default IP address can be changed using the WBM. The logon page of the WBM
SCALANCE Industrial Wireless LAN controller and access points opens:
Figure 3-1 Logon page
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
19

Getting started
Initial logon
Access protection of the system - changing passwords
Entering the wrong user name or password
3.2 Logon
Default user data is set in the factory. When you log on the first time, follow the steps below:
1. Enter the user name
2. Enter the password
admin in the "User Name" input box.
abc123 in the "Password" input box.
3. Click the "Login" button. The page for basic configuration with the wizard opens.
When you have completed the basic configuration the start page of the WBM SCALANCE
Industrial Wireless LAN controller and access points is displayed immediately after a new
logon.
We recommend that you protect the system from unauthorized access. To do this, change
the factory-set default administrator password. The procedure is described during basic
configuration with the wizard.
If you enter an unconfigured user name or an incorrect password, an error message is
displayed.
SCALANCE WLC711
20 Getting Started, 04/2016, C79000-G8976-C269-07
Getting started
3.3
Shutting down and turning off
Introduction
Note
Data loss
Remember that data on the hard disk can be lost if you do not shut down the SCALANCE
WLC711 correctly. Make sure that you
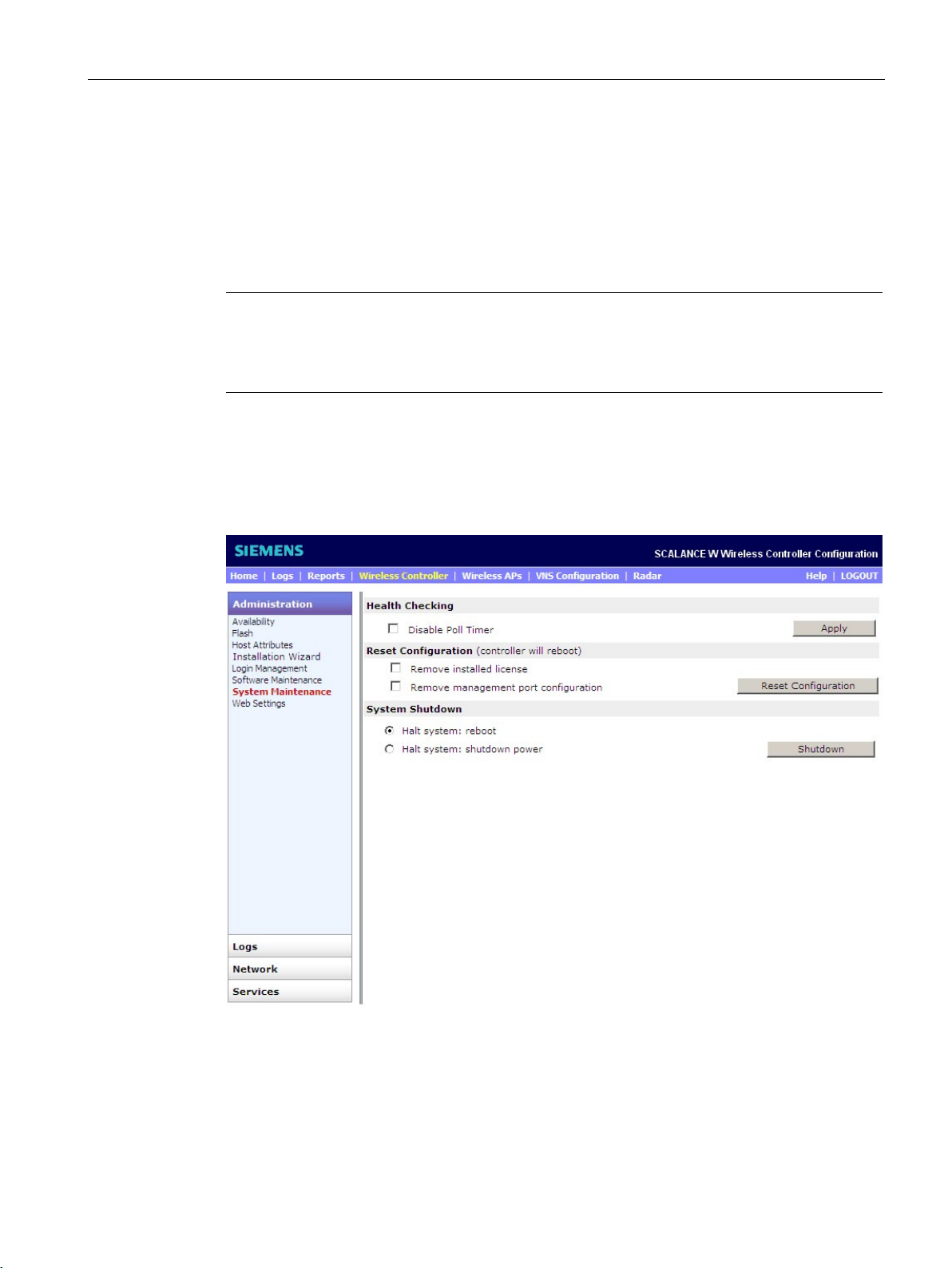
"System Maintenance" configuration page
3.3 Shutting down and turning off
To avoid loss of data, it is advisable to shut down and turn off the SCALANCE WLC711
using the operator interfaces.
use the procedure in this section.
To open the configuration page, select the "Wireless Controller > Administration > System
Maintenance" menu command. The following window opens:
Figure 3-2 "System Maintenance" configuration page
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
21

Getting started
Procedure
Halt system: reboot
Halt system: shutdown power
3.3 Shutting down and turning off
To turn off the SCALANCE WLC711 correctly, follow the steps below:
1. Select from the following options in the "System Shutdown" section:
–
The system is shut down and restarted.
–
The system is shut down safely. All services and applications are stopped.
2. To shut down the system with the APs that belong to it and that are connected to it, click
the "Shutdown" button. A warning appears. To confirm the action, click the "Yes to
continue" button.
As an alternative, you can also shut down the WLC with CLI commands. You will find further
information in the manual SCALANCE WLC711 CLI Reference Guide.
SCALANCE WLC711
22 Getting Started, 04/2016, C79000-G8976-C269-07

4
Introduction
Note
Reconfiguration of the network topology with the wizard is not possible.
You cannot reconfigure the network topology with the wiza
system reset. You can only modify the network topology later using the "Wireless Controller
> Topologies" menu command.
After you log on the first time, the WBM provides you with a wizard for the basic
configuration of the WLC.
You can call up the wizard at any time using the "Wireless Controller > Installation Wizard"
menu command.
rd, but only configure following a
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
23
Basic configuration with the wizard
Example
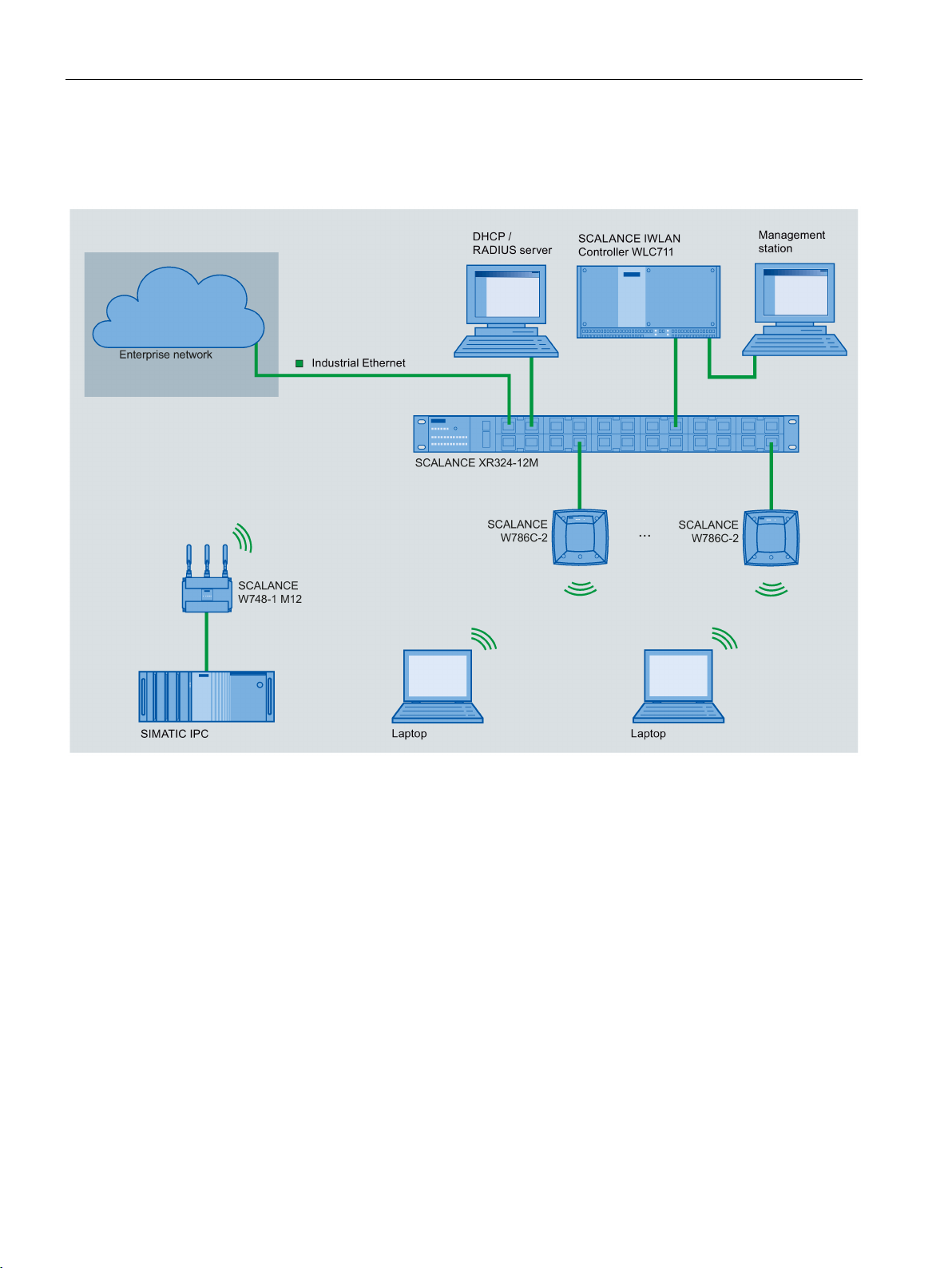
The following graphic shows you a typical WLC-based configuration of a WLAN:
Figure 4-1 Example: Typical WLC-based configuration of a WLAN
SCALANCE WLC711
24 Getting Started, 04/2016, C79000-G8976-C269-07
Basic configuration with the wizard
4.1
Procedure - "Basic Installation Wizard" page
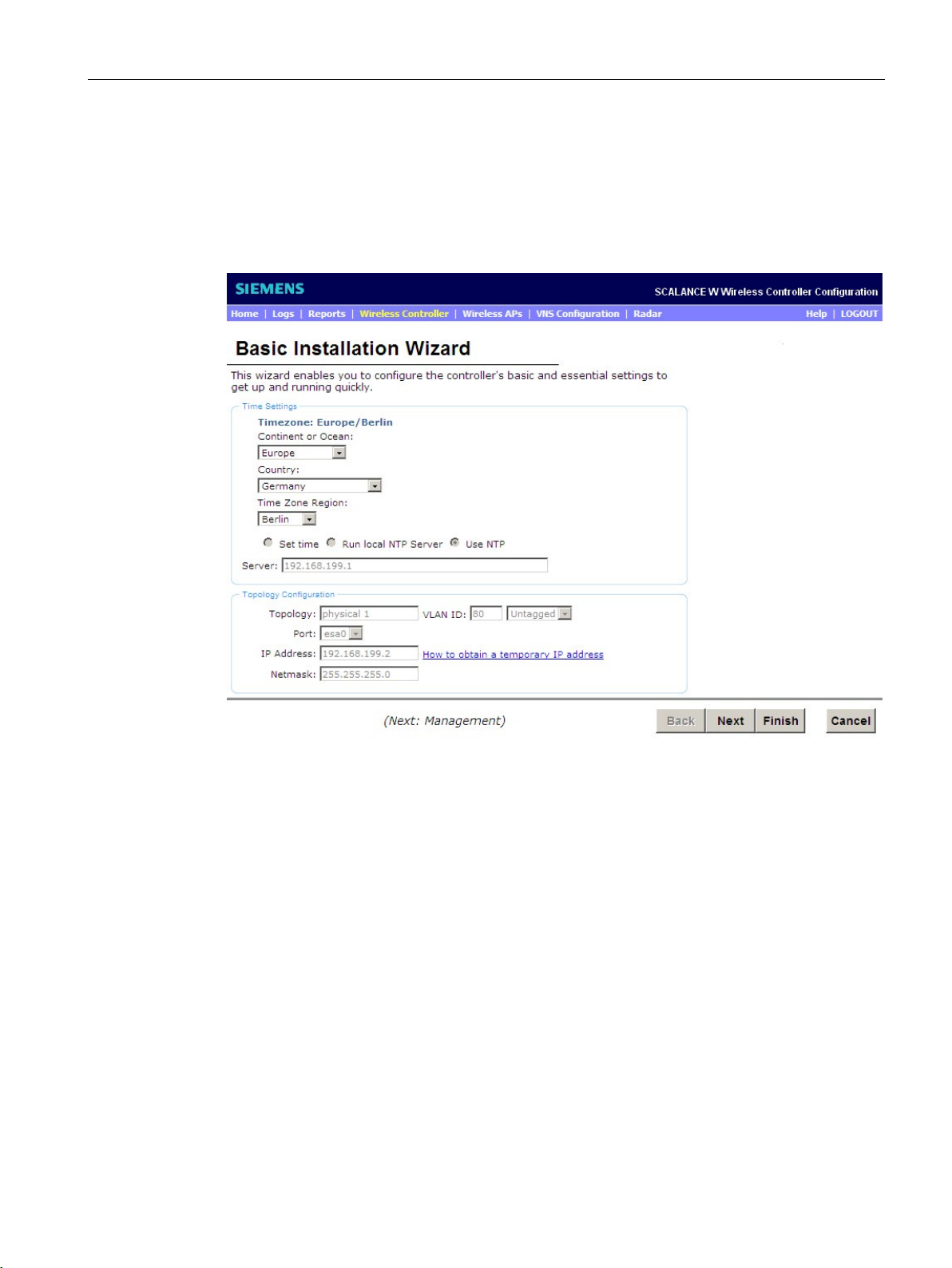
"Basic Installation Wizard" configuration page
Time Settings
4.1 Procedure - "Basic Installation Wizard" page
When you log on for the first time, the following window opens:
Figure 4-2 "Basic Installation Wizard" configuration page
To use the basic installation with the wizard correctly, follow the steps below:
In this section, you configure the time zone of the WLC.
From the drop-down lists, select the continent or ocean, the country and the region of the
time zone in which the WLC is located.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
25

Basic configuration with the wizard
Meaning of the "Time Zone Region" options:
Set time
Run local NTP Server
Use NTP
Topology Configuration
Topology
VLAN ID
Note
VLAN ID 1 is the default internal VLAN ID of the WLC and can therefore only be used after
conf
VLAN ID and Multicast Support".
4.1 Procedure - "Basic Installation Wizard" page
●
With this option, you set the year, the month, the day, the minutes and the seconds
manually using drop-down lists.
●
If you select this option, the WLC functions as an NTP server and provides other devices
with the opportunity of synchronizing their time with the time of the WLC.
●
If you select this option, an external NTP server is used for time-of-day synchronization.
In this input box, enter the IP address of an NTP time server that has a connection to the
network.
In this section, you configure the physical interface of the WLC that is assigned as data port.
Enter the required values in the input boxes:
Using the assigned logical names, topologies are linked to a VNS (Virtual Network Service).
The wizard proposes the predefined name "Physical 1". On completion of the basic
configuration, you can change the name using the "Wireless Controller > Topologies" menu
command.
A VNS is the logical linking of all components required to operate a WLAN. This includes:
● WLAN service
● Policy
● Class of Service
● Topology
Using the VLAN ID, you assign a broadcast domain to the WLC data port. In this area, the
VLAN ID is configured for the WLC. Make sure that the data port of the WLC, the access
points and the connecting network are assigned to the same broadcast domain. Use the
following range for the VLAN ID: 1 to 4094. Enter the VLAN ID you want to work with in the
"VLAN ID" input box.
iguration. You will find further information in the user guide, section "Setting Up Internal
SCALANCE WLC711
26 Getting Started, 04/2016, C79000-G8976-C269-07

Basic configuration with the wizard
Tagged
Untagged
"Port" drop-down list
IP Address
Netmask
4.1 Procedure - "Basic Installation Wizard" page
Select the required option from the drop-down list:
●
If you want to forward tagged packets, select this option. Make sure that your devices are
capable of reading tagged packets.
●
If you want to forward untagged packets, select this option. This is the default selection.
From the drop-down list, select the data port "esa0" of the WLC.
Enter the IP address of the data port "esa0" of the WLC. Use the IP address range of your IP
subnet.
If you require information about obtaining a temporary IP address, click on the link "How to
obtain a temporary IP address".
Enter the netmask of the data port "esa0" of the WLC.
To move to the next page of the wizard, click the "Next" button.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
27
Basic configuration with the wizard
4.2
Procedure - "Management" page
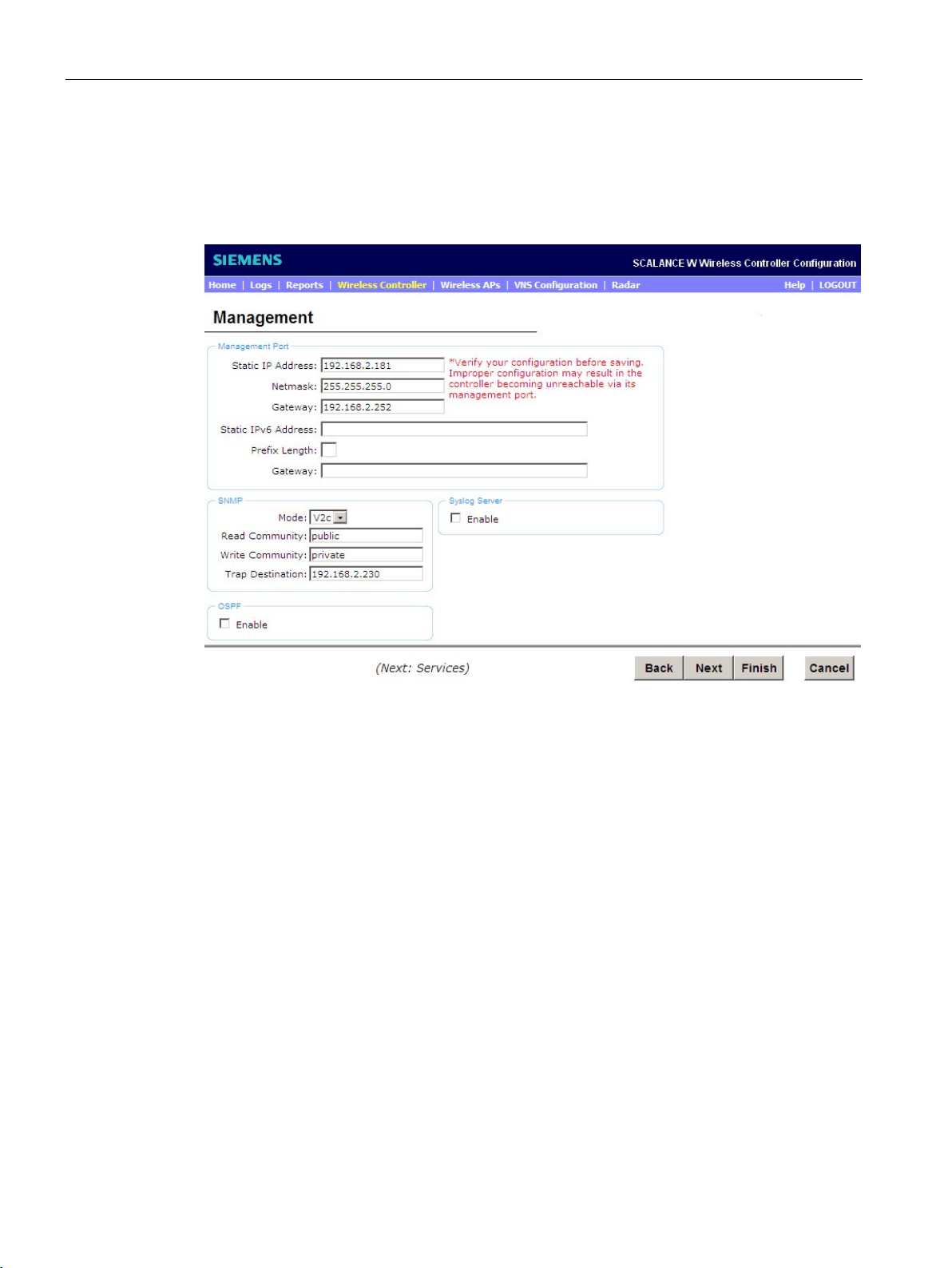
"Management" configuration page
Management port
IP Address
Netmask
4.2 Procedure - "Management" page
Figure 4-3 "Management" configuration page
In this section, you configure the management port of the WLC via which the configuration
data is transferred.
If necessary, adapt the factory setting to your network environment:
Shows the IP address of the management port of the WLC.
To separate the range of the network from the range of the hosts, the corresponding subnet
mask of the IP address is displayed. Enter the netmask of the data port "esa0" of the WLC.
SCALANCE WLC711
28 Getting Started, 04/2016, C79000-G8976-C269-07

Basic configuration with the wizard
Gateway
Note
Check that the contents are correct
Check that your entries are corre
configuration, it will not be possible to establish the connection to the SCALANCE Industrial
Wireless LAN access point.
SNMP
"Mode" drop-down list
OFF
V2c
V3
Note
In this version, some SNMP objects only have
4.2 Procedure - "Management" page
Shows the standard gateway of the network.
ct before saving the settings. If there are errors in the
In this section, the monitoring, control and error detection of the network components is set
using the "Simple Network Management Protocol".
SNMP is a network protocol with which network components can be monitored and
controlled from a central station. The following settings are available:
Select from the following options:
●
If you select this option, you disable SNMP.
●
If you select this option, you allow SNMP version 2. The following input boxes appear for
SNMP communication:
– Read Community
Enter the password to be used for the read mode of SNMP communication.
– Write Community
Here, enter the password to be used for the write mode of SNMP communication.
– Trap Destination
Enter the IP address of the server you are using that will receive the SNMP messages
as network manager.
●
If you select this option, you allow SNMP version 3. Following the basic installation, you
can create users and configure them manually with the " Wireless Controller > SNMP"
menu command.
read permissions.
SCALANCE WLC711
Getting Started, 04/2016, C79000-G8976-C269-07
29

Basic configuration with the wizard
Syslog server
OSPF
Port
Area ID
4.2 Procedure - "Management" page
The syslog server is configured in this section.
Syslog is a protocol used for the transfer of event notification messages via networks.
To use the syslog protocol for the WLC, select the "Enable" check box. The "IP Address"
input box appears in which you enter the IP address of the syslog server.
In this section, you enable the "Open Shortest Path First" protocol. OSPF is a dynamic
routing protocol for medium sized to large IP networks. This protocol allows data streams to
be split up over various routes. If you select OSPF, the WLC uses "Dynamic Route
Selection". This means that subnets are set up.
Select the "Enable" check box. The following options appear:
Click on the topology name of the WLC you want to configure.
Define the area of OSPF. If necessary, adapt the factory setting to your network
environment.
To move to the next page of the wizard, click the "Next" button.
SCALANCE WLC711
30 Getting Started, 04/2016, C79000-G8976-C269-07
 Loading...
Loading...