Siemens SCALANCE W1750D CLI Function Manual

___________________
___________________
___________________
___________________
___________________
SIMATIC NET
Industrial Wireless LAN
SCALANCE W1750D CLI
Function Manual
03/2019
C7
About this guide
1
Security recommendations
2
SCALANCE W CLI
3
CLI Commands
4
Appendix A
A
9000-G8976-C452-04

Siemens AG
Division Process Industries and Drives
Postfach 48 48
90026 NÜRNBERG
GERMANY
Document order number: C79000-G8976-C452
Ⓟ
Copyright © Siemens AG 2016 - 2019.
All rights reserved
DANGER
indicates that death or severe personal injury will result if proper precautions are not taken.
WARNING
indicates that death or severe personal injury may result if proper precautions are not taken.
CAUTION
indicates that minor personal injury can result if proper precautions are not taken.
NOTICE
indicates that property damage can result if proper precautions are not taken.
WARNING
Siemens products may only be used for the applications described in the catalog and in the relevant technical
ambient conditions must be complied with. The information in the relevant documentation must be observed.
Legal information
Warning notice system
This manual contains notices you have to observe in order to ensure your personal safety, as well as to prevent
damage to property. The notices referring to your personal safety are highlighted in the manual by a safety alert
symbol, notices referring only to property damage have no safety alert symbol. These notices shown below are
graded according to the degree of danger.
If more than one degree of danger is present, the warning notice representing the highest degree of danger will
be used. A notice warning of injury to persons with a safety alert symbol may also include a warning relating to
property damage.
Qualified Personnel
The product/system described in this documentation may be operated only by personnel qualified for the specific
task in accordance with the relevant documentation, in particular its warning notices and safety instructions.
Qualified personnel are those who, based on their training and experience, are capable of identifying risks and
avoiding potential hazards when working with these products/systems.
Proper use of Siemens products
Note the following:
documentation. If products and components from other manufacturers are used, these must be recommended
or approved by Siemens. Proper transport, storage, installation, assembly, commissioning, operation and
maintenance are required to ensure that the products operate safely and without any problems. The permissible
Trademarks
All names identified by ® are registered trademarks of Siemens AG. The remaining trademarks in this publication
may be trademarks whose use by third parties for their own purposes could violate the rights of the owner.
Disclaimer of Liability
We have reviewed the contents of this publication to ensure consistency with the hardware and software
described. Since variance cannot be precluded entirely, we cannot guarantee full consistency. However, the
information in this publication is reviewed regularly and any necessary corrections are included in subsequent
editions.
03/2019 Subject to change

Table of contents
1 About this guide .................................................................................................................................... 13
2 Security recommendations .................................................................................................................... 15
3 SCALANCE W CLI ................................................................................................................................ 19
3.1 Saving Configuration Changes ............................................................................................... 22
3.2 Command Line Editing............................................................................................................ 23
3.3 Specifying Addresses and Identifiers in Commands .............................................................. 24
3.4 Typographic Conventions ....................................................................................................... 25
3.5 Industry Online Support .......................................................................................................... 26
4 CLI Commands ..................................................................................................................................... 27
4.1 A .............................................................................................................................................. 27
4.1.1 a-channel ................................................................................................................................ 27
4.1.2 aaa dns-query-interval ............................................................................................................ 28
4.1.3 aaa radius-attributes ............................................................................................................... 29
4.1.4 aaa radius modifier ................................................................................................................. 30
4.1.5 aaa test-server ........................................................................................................................ 31
4.1.6 a-ant-pol .................................................................................................................................. 31
4.1.7 advanced-zone ....................................................................................................................... 32
4.1.8 aeroscout-rtls .......................................................................................................................... 33
4.1.9 airgroup ................................................................................................................................... 34
4.1.10 airgroupservice ....................................................................................................................... 36
4.1.11 airwave-rtls .............................................................................................................................. 37
4.1.12 ale-report-interval .................................................................................................................... 38
4.1.13 ale-server ................................................................................................................................ 39
4.1.14 alg ........................................................................................................................................... 40
4.1.15 allowed-ap ............................................................................................................................... 41
4.1.16 allow-new-aps ......................................................................................................................... 42
4.1.17 a-max-clients ........................................................................................................................... 42
4.1.18 ams-backup-ip ........................................................................................................................ 43
4.1.19 ams-identity ............................................................................................................................. 44
4.1.20 ams-ip ..................................................................................................................................... 45
4.1.21 ams-key .................................................................................................................................. 45
4.1.22 ap1x ........................................................................................................................................ 46
4.1.23 ap1x-peap-user ....................................................................................................................... 47
4.1.24 ap-frequent-scan ..................................................................................................................... 48
4.1.25 ap-installation .......................................................................................................................... 49
4.1.26 apply........................................................................................................................................ 49
4.1.27 arm .......................................................................................................................................... 50
8 attack....................................................................................................................................... 56
4.1.2
4.1.29 auth-failure-blacklist-time ........................................................................................................ 57
4.1.30 auth-survivability cache-time-out ............................................................................................ 58
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
3

Table of contents
4.2 B ............................................................................................................................................. 59
4.2.1 banner .................................................................................................................................... 59
4.2.2 blacklist-client ......................................................................................................................... 60
4.2.3 blacklist-time .......................................................................................................................... 60
4.2.4 ble .......................................................................................................................................... 61
4.3 C ............................................................................................................................................. 64
4.3.1 calea ....................................................................................................................................... 64
4.3.2 cellular-uplink-profile .............................................................................................................. 65
4.3.3 clarity ...................................................................................................................................... 68
4.3.4 clear ....................................................................................................................................... 69
4.3.5 clear airgroup state statistics ................................................................................................. 70
4.3.6 clear-dhcpoption82 ................................................................................................................ 70
4.3.7 clear-cert ................................................................................................................................ 71
4.3.8 clock set ................................................................................................................................. 72
4.3.9 clock summer-time ................................................................................................................. 73
4.3.10 clock timezone ....................................................................................................................... 75
4.3.11 cluster-security ....................................................................................................................... 75
4.3.12 cluster-security logging .......................................................................................................... 77
4.3.13 commit .................................................................................................................................... 78
4.3.14 configure terminal................................................................................................................... 79
4.3.15 console ................................................................................................................................... 79
4.3.16 content-filtering....................................................................................................................... 80
4.3.17 convert-aos-ap ....................................................................................................................... 81
4.3.18 copy ........................................................................................................................................ 82
4.3.19 custom_var ............................................................................................................................. 84
4.4 D ............................................................................................................................................. 85
4.4.1 debug-rtls-logs ....................................................................................................................... 85
4.4.2 deny-inter-user-bridging ......................................................................................................... 85
4.4.3 deny-local-routing................................................................................................................... 86
4.4.4 device-id ................................................................................................................................. 87
4.4.5 dhcp ....................................................................................................................................... 88
4.4.6 disable-prov-ssid .................................................................................................................... 89
4.4.7 disconnect-user ...................................................................................................................... 89
4.4.8 dot-11a-radio-disable ............................................................................................................. 90
4.4.9 dot-11g-radio-disable ............................................................................................................. 91
4.4.10 download-cert ......................................................................................................................... 91
4.4.11 download-dhcpopt82 .............................................................................................................. 93
4.4.12 dpi .......................................................................................................................................... 94
4.4.13 dpi-error-page-url ................................................................................................................... 95
4.4.14 dynamic-cpu-mgmt ................................................................................................................ 95
4.4.15 dynamic-dns ........................................................................................................................... 96
4.4.16 dynamic-dns-ap...................................................................................................................... 98
4.4.17 dynamic-dns-interval .............................................................................................................. 99
4.4.18 dynamic-radius-proxy ........................................................................................................... 100
4.4.19 dynamic-tacacs-proxy .......................................................................................................... 100
SCALANCE W1750D CLI
4 Function Manual, 03/2019, C79000-G8976-C452-04

Table of contents
4.5 E ............................................................................................................................................ 102
4.5.1 enet-vlan ............................................................................................................................... 102
4.5.2 enet0-bridging ....................................................................................................................... 103
4.5.3 enet0-port-profile ................................................................................................................... 103
4.5.4 enet1-port-profile ................................................................................................................... 104
4.5.5 enet3-port-profile ................................................................................................................... 105
4.5.6 enet2-port-profile ................................................................................................................... 105
4.5.7 enet4-port-profile ................................................................................................................... 106
4.5.8 enhanced-mesh-role-detect .................................................................................................. 107
4.5.9 extended-ssid ........................................................................................................................ 108
4.6 F ............................................................................................................................................ 109
4.6.1 facebook ............................................................................................................................... 109
4.6.2 factory-ssid-enable ................................................................................................................ 109
4.6.3 firewall ................................................................................................................................... 110
4.6.4 firewall-external-enforcement ............................................................................................... 111
4.7 G ........................................................................................................................................... 113
4.7.1 g-channel .............................................................................................................................. 113
4.7.2 g-ant-pol ................................................................................................................................ 113
4.7.3 g-max-clients ......................................................................................................................... 114
4.7.4 gre ......................................................................................................................................... 115
4.8 H ............................................................................................................................................ 118
4.8.1 hash-mgmt-password ........................................................................................................... 118
4.8.2 hash-mgmt-user .................................................................................................................... 118
4.8.3 help ....................................................................................................................................... 120
4.8.4 hostname .............................................................................................................................. 121
4.8.5 hotspot anqp-3-gpp-profile .................................................................................................... 122
4.8.6 hotspot anqp-domain-name-profile ....................................................................................... 123
4.8.7 hotspot-anqp-ip-addr
-avail-profile ......................................................................................... 124
4.8.8 hotspot anqp-nai-realm-profile .............................................................................................. 126
4.8.9 hotspot anqp-nwk-auth-profile .............................................................................................. 130
4.8.10 hotspot anqp-roam-cons-profile ............................................................................................ 132
4.8.11 hotspot anqp-venue-name-profile ......................................................................................... 133
4.8.12 hotspot h2qp-conn-cap-profile .............................................................................................. 137
4.8.13 hotspot h2qp-oper-class-profile ............................................................................................ 138
4.8.14 hotspot-h2qp-oper-name-profile ........................................................................................... 140
4.8.15 hotspot h2qp-osu-provider-profile ......................................................................................... 141
4.8.16 hotspot h2qp-wan-metrics-profile ......................................................................................... 145
4.8.17 hotspot hs-profile .................................................................................................................. 147
4.8.18 hs2-osu-icon-delete .............................................................................................................. 157
4.8.19 hs2-osu-icon-download ......................................................................................................... 158
4.9 I ............................................................................................................................................. 160
4.9.1 iap-master ............................................................................................................................. 160
4.9.2 ids.......................................................................................................................................... 160
4.9.3 ignore-image-check .............................................................................................................. 168
4.9.4 inactivity-ap-timeout .............................................................................................................. 169
4.9.5 inbound-firewall ..................................................................................................................... 170
4.9.6 internal-domains ................................................................................................................... 172
4.9.7 iot transportProfile ................................................................................................................. 173
4.9.8 iot usetransportProfile ........................................................................................................... 177
4.9.9 ip-address ............................................................................................................................. 178
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
5

Table of contents
4.9.10 ip dhcp .................................................................................................................................. 179
4.9.11 ip dhcp pool .......................................................................................................................... 185
4.9.12 ip-mode ................................................................................................................................ 187
4.9.13 ipm ....................................................................................................................................... 188
4.9.14 ip radius ................................................................................................................................ 189
4.10 L ........................................................................................................................................... 190
4.10.1 l3-mobility ............................................................................................................................. 190
4.10.2 lacp-mode ............................................................................................................................ 191
4.10.3 led-off ................................................................................................................................... 192
4.10.4 loginsession ......................................................................................................................... 193
4.10.5 logout ................................................................................................................................... 194
4.11 M .......................................................................................................................................... 195
4.11.1 mas-integration .................................................................................................................... 195
4.11.2 managed-mode-profile ......................................................................................................... 196
4.11.3 managed-mode-sync-server ................................................................................................ 198
4.11.4 mesh .................................................................................................................................... 198
4.11.5 mesh-cluster ......................................................................................................................... 200
4.11.6 mesh-disable ........................................................................................................................ 201
4.11.7 mgmt-accounting.................................................................................................................. 201
4.11.8 mgmt-auth-server ................................................................................................................. 202
4.11.9 mgmt-auth-server-load-balancing ........................................................................................ 203
4.11.10 mgmt-auth-server-local-backup ........................................................................................... 204
4.11.11 mgmt-user ............................................................................................................................ 205
4.11.12 mtu ....................................................................................................................................... 206
4.12 N ........................................................................................................................................... 207
4.12.1 name .................................................................................................................................... 207
4.12.2 ntp-server ............................................................................................................................. 207
4.13 O .......................................................................................................................................... 209
4.13.1 opendns ............................................................................................................................... 209
4.13.2 openflow
-server.................................................................................................................... 210
4.13.3 organization .......................................................................................................................... 211
4.13.4 out-of-service-hold-on-time .................................................................................................. 212
4.14 P ........................................................................................................................................... 213
4.14.1 pcap ..................................................................................................................................... 213
4.14.2 per-ap-ssid ........................................................................................................................... 214
4.14.3 per-ap-vlan ........................................................................................................................... 214
4.14.4 pin-enable ............................................................................................................................ 215
4.14.5 pin-puk ................................................................................................................................. 216
4.14.6 pin-renew ............................................................................................................................. 216
4.14.7 ping ...................................................................................................................................... 217
4.14.8 pppoe-uplink-profile ............................................................................................................. 218
4.14.9 proxy .................................................................................................................................... 219
4.15 R ........................................................................................................................................... 221
4.15.1 radius-vsa-redirect-url .......................................................................................................... 221
4.15.2 reload ................................................................................................................................... 222
4.15.3 remove-blacklist-client ......................................................................................................... 223
4.15.4 reset drt ................................................................................................................................ 224
4.15.5 restrict-corp-access .............................................................................................................. 224
4.15.6 restrict-mgmt-access ............................................................................................................ 225
SCALANCE W1750D CLI
6 Function Manual, 03/2019, C79000-G8976-C452-04

Table of contents
4.15.7 rf-band ................................................................................................................................... 226
4.15.8 rf-zone ................................................................................................................................... 227
4.15.9 rf dot11g-radio-profile............................................................................................................ 227
4.15.10 rf dot11a-radio-profile............................................................................................................ 232
4.15.11 routing-profile ........................................................................................................................ 236
4.16 S ............................................................................................................................................ 238
4.16.1 show 1xcert ........................................................................................................................... 238
4.16.2 show aaa ............................................................................................................................... 238
4.16.3 show about ............................................................................................................................ 239
4.16.4 show access-rule .................................................................................................................. 240
4.16.5 show access-rule-all ............................................................................................................. 242
4.16.6 show acl ................................................................................................................................ 243
4.16.7 show airgroup ....................................................................................................................... 244
4.16.8 show airgroupservice ............................................................................................................ 254
4.16.9 show aigroupservice-ids ....................................................................................................... 257
4.16.10 show ale ................................................................................................................................ 258
4.16.11 show ale stats ....................................................................................................................... 260
4.16.12 show alert global ................................................................................................................... 261
4.16.13 show alg ................................................................................................................................ 263
4.16.14 show all monitor .................................................................................................................... 264
4.16.15 show allowed-aps ................................................................................................................. 265
4.16.16 show a-max-clients ............................................................................................................... 266
4.16.17 show amp-audit ..................................................................................................................... 267
4.16.18 show ap allowed-channels .................................................................................................... 272
4.16.19 show ap allowed-max-EIRP .................................................................................................. 273
4.16.20 show ap arm ......................................................................................................................... 275
4.16.21 show ap association.............................................................................................................. 283
4.16.22 show ap bss-table ................................................................................................................. 284
4.16.23 show ap cacert ...................................................................................................................... 286
4.16.24 show ap mesh cluster ........................................................................................................... 288
4.16.25 show ap mpskcache ............................................................................................................. 290
4.16.26 show ap checksum ............................................................................................................... 291
4.16.27 show ap client-match-live ..................................................................................................... 292
4.16.28 show ap client-match-history ................................................................................................ 293
4.16.29 show ap client-match-refused ............................................................................................... 294
4.16.30 show ap client-match-ssid-table radio-mac .......................................................................... 296
4.16.31 show ap client-match-triggers ............................................................................................... 297
4.16.32 show ap client-probe-report .................................................................................................. 298
4.16.33 show ap client-view ............................................................................................................... 299
4.16.34 show ap debug airwave ........................................................................................................ 300
4.16.35 show ap debug airwave-config-received .............................................................................. 311
4.16.36 show ap debug airwave-data-sent ........................................................................................ 312
4.16.37 show ap debug airwave-events-pending .............................................................................. 313
4.16.38 show ap debug airwave-restore-status ................................................................................. 314
4.16.39 show ap debug airwave-signon-key ..................................................................................... 314
4.16.40 show ap debug airwave-state ............................................................................................... 315
4.16.41 show ap debug airwave-stats ............................................................................................... 317
4.16.42 show ap debug am-config ..................................................................................................... 319
4.16.43 show ap debug auth-trace-buf .............................................................................................. 320
4.16.44 show ap debug ble-config ..................................................................................................... 321
4.16.45 show ap debug ble-counters ................................................................................................. 323
4.16.46 show ap debug ble-daemon ................................................................................................. 323
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
7

Table of contents
4.16.47 show ap debug ble-relay ...................................................................................................... 324
4.16.48 show ap debug ble-table ...................................................................................................... 327
4.16.49 show ap debug ble-table assettags ..................................................................................... 328
4.16.50 show ap debug client-frame-history ..................................................................................... 329
4.16.51 show ap debug client-match ................................................................................................ 330
4.16.52 show ap debug client-stats .................................................................................................. 331
4.16.53 show ap debug client-table .................................................................................................. 337
4.16.54 show ap debug core-info ...................................................................................................... 339
4.16.55 show ap debug crash-info .................................................................................................... 340
4.16.56 show ap debug dhcp-packets .............................................................................................. 340
4.16.57 show ap debug dot1x-statistics ............................................................................................ 342
4.16.58 show ap debug driver-config ................................................................................................ 343
4.16.59 show ap debug lldp .............................................................................................................. 348
4.16.60 show ap debug lldp neighbor ............................................................................................... 350
4.16.61 show ap debug lldp state ..................................................................................................... 351
4.16.62 show ap debug mgmt-frames .............................................................................................. 352
4.16.63 show ap debug network-bssid ............................................................................................. 353
4.16.64 show ap debug persistent-clients......................................................................................... 354
4.16.65 show ap debug power-table ................................................................................................. 355
4.16.66 show ap debug radio-stats ................................................................................................... 356
4.16.67 show ap debug radius-statistics ........................................................................................... 359
4.16.68 show ap debug rfc3576-radius-statistics ............................................................................. 360
4.16.69 show ap debug shaping-table .............................................................................................. 362
4.16.70 show ap debug spanning-tree .............................................................................................. 364
4.16.71 show ap debug stm-config ................................................................................................... 365
4.16.72 show ap debug stm-role ....................................................................................................... 366
4.16.73 show ap debug stystem-status ............................................................................................ 366
4.16.74 show ap debug tacas-statistics ............................................................................................ 367
4.16.75 show ap dot11k-beacon-report ............................................................................................ 368
4.16.76 show ap dot11k-nbrs ............................................................................................................ 369
4.16.77 show ap flash-config ............................................................................................................
370
4.16.78 show ap mesh counters ....................................................................................................... 371
4.16.79 show ap mesh link ............................................................................................................... 373
4.16.80 show ap mesh neighbors ..................................................................................................... 375
4.16.81 show ap monitor ................................................................................................................... 377
4.16.82 show ap pmkcache .............................................................................................................. 389
4.16.83 show ap virtual-beacon-report ............................................................................................. 390
4.16.84 show ap1x ............................................................................................................................ 392
4.16.85 show ap1xcert ...................................................................................................................... 392
4.16.86 show ap-alert ........................................................................................................................ 393
4.16.87 show ap-env ......................................................................................................................... 394
4.16.88 show aps .............................................................................................................................. 395
4.16.89 show app-services ............................................................................................................... 398
4.16.90 show arm config ................................................................................................................... 400
4.16.91 show arm-channels .............................................................................................................. 402
4.16.92 show arp ............................................................................................................................... 404
4.16.93 show attack .......................................................................................................................... 405
4.16.94 show audit-trail ..................................................................................................................... 407
4.16.95 show auth-surviveability ....................................................................................................... 408
4.16.96 show backup-config ............................................................................................................. 409
4.16.97 show banner ......................................................................................................................... 411
4.16.98 show blacklist-client ............................................................................................................. 412
SCALANCE W1750D CLI
8 Function Manual, 03/2019, C79000-G8976-C452-04

Table of contents
4.16.99 show ble-config ..................................................................................................................... 413
4.16.100 show calea config ................................................................................................................. 414
4.16.101 show calea statistics ............................................................................................................. 415
4.16.102 show cellular ......................................................................................................................... 416
4.16.103 show cert all .......................................................................................................................... 419
4.16.104 show clarity ........................................................................................................................... 421
4.16.105 show clearpassca ................................................................................................................. 423
4.16.106 show clients .......................................................................................................................... 423
4.16.107 show clock ............................................................................................................................ 427
4.16.108 show cluster-security ............................................................................................................ 430
4.16.109 show config-status ................................................................................................................ 436
4.16.110 show configuration ................................................................................................................ 437
4.16.111 show console-setttings.......................................................................................................... 443
4.16.112 show country-codes .............................................................................................................. 444
4.16.113 show cpcert ........................................................................................................................... 447
4.16.114 show cpu ............................................................................................................................... 448
4.16.115 show datapath ....................................................................................................................... 450
4.16.116 show ddns ............................................................................................................................. 471
4.16.117 show delta-config .................................................................................................................. 472
4.16.118 show derivation-rules ............................................................................................................ 473
4.16.119 show dhcp-allocation ............................................................................................................ 474
4.16.120 show dhcps config ................................................................................................................ 475
4.16.121 show dhcpc-opts ................................................................................................................... 477
4.16.122 show dhcp ............................................................................................................................. 478
4.16.123 show distributed-dhcp-branch-counts ................................................................................... 480
4.16.124 show domain-names ............................................................................................................. 482
4.16.125 show dpi ................................................................................................................................ 482
4.16.126 show dpi-error-page-urls ....................................................................................................... 489
4.16.127 show dpi-stats ....................................................................................................................... 490
4.16.128 show drt state ........................................................................................................................ 494
4.16.129 show election ........................................................................................................................ 495
4.16.130 show esl
................................................................................................................................ 497
4.16.131 show esl-radio ....................................................................................................................... 497
4.16.132 show facebook ...................................................................................................................... 498
4.16.133 show fault .............................................................................................................................. 499
4.16.134 show fiewall ........................................................................................................................... 500
4.16.135 show g-max-clients ............................................................................................................... 501
4.16.136 show gre config ..................................................................................................................... 502
4.16.137 show gre status ..................................................................................................................... 503
4.16.138 show ids ................................................................................................................................ 505
4.16.139 show ids-detection config ..................................................................................................... 507
4.16.140 show ids-protection config .................................................................................................... 509
4.16.141 show inbound-firewall-rules .................................................................................................. 510
4.16.142 show interface counters ........................................................................................................ 511
4.16.143 show image ........................................................................................................................... 512
4.16.144 show iot transportProfile ....................................................................................................... 513
4.16.145 show ip dhcp database ......................................................................................................... 514
4.16.146 show ip igmp ......................................................................................................................... 515
4.16.147 show ip interface ................................................................................................................... 517
4.16.148 show ip route ......................................................................................................................... 518
4.16.149 show ipv6 interface ............................................................................................................... 519
4.16.150 show ipv6 route ..................................................................................................................... 520
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
9

Table of contents
4.16.151 show l3-mobility.................................................................................................................... 521
4.16.152 show lacp status................................................................................................................... 526
4.16.153 show ldap-servers ................................................................................................................ 527
4.16.154 show lhm .............................................................................................................................. 528
4.16.155 show log ap-debug ............................................................................................................... 530
4.16.156 show log apifmgr .................................................................................................................. 531
4.16.157 show log convert .................................................................................................................. 531
4.16.158 show log debug .................................................................................................................... 531
4.16.159 show log drive ...................................................................................................................... 532
4.16.160 show log kernel .................................................................................................................... 532
4.16.161 show log l3-mobility .............................................................................................................. 533
4.16.162 show log network ................................................................................................................. 534
4.16.163 show log openflow ............................................................................................................... 535
4.16.164 show log papi-handler .......................................................................................................... 535
4.16.165 show log pppd ...................................................................................................................... 535
4.16.166 show log rapper.................................................................................................................... 536
4.16.167 show log rapper-brief ........................................................................................................... 536
4.16.168 show log rapper-counter ...................................................................................................... 537
4.16.169 show log sapd ...................................................................................................................... 538
4.16.170 show log scd ........................................................................................................................ 539
4.16.171 show log security.................................................................................................................. 540
4.16.172 show log system................................................................................................................... 540
4.16.173 show log upgrade ................................................................................................................. 541
4.16.174 show log user ....................................................................................................................... 541
4.16.175 show log user-debug ............................................................................................................ 542
4.16.176 show log vpn-tunnel-primary ................................................................................................ 542
4.16.177 show log vpn-tunnel-backup ................................................................................................ 543
4.16.178 show log vpn-tunnel ............................................................................................................. 544
4.16.179 show log wireless ................................................................................................................. 545
4.16.180 show memory ....................................................................................................................... 545
4.16.181 show mgmt-user................................................................................................................... 547
4.16.182 show network ....................................................................................................................... 548
4.16.183 show network-summary
....................................................................................................... 550
4.16.184 show openflow ..................................................................................................................... 551
4.16.185 show opendns ...................................................................................................................... 552
4.16.186 show out-of-service .............................................................................................................. 553
4.16.187 show pppoe .......................................................................................................................... 554
4.16.188 show port status ................................................................................................................... 555
4.16.189 show process ....................................................................................................................... 557
4.16.190 show proxy config ................................................................................................................ 558
4.16.191 show radio config ................................................................................................................. 559
4.16.192 show radio profile ................................................................................................................. 561
4.16.193 show radius-redirect-url ....................................................................................................... 563
4.16.194 show radius-servers support ................................................................................................ 564
4.16.195 show radius status ............................................................................................................... 565
4.16.196 show radseccert ................................................................................................................... 567
4.16.197 show rlts-logs ....................................................................................................................... 568
4.16.198 show rlts-tags ....................................................................................................................... 569
4.16.199 show running-config ............................................................................................................. 569
4.16.200 show snmp-configuration ..................................................................................................... 573
4.16.201 show snmp trap-queue ........................................................................................................ 574
4.16.202 show ssh .............................................................................................................................. 575
SCALANCE W1750D CLI
10 Function Manual, 03/2019, C79000-G8976-C452-04

Table of contents
4.16.203 show spectum-alert ............................................................................................................... 576
4.16.204 show speed-test .................................................................................................................... 577
4.16.205 show stats ............................................................................................................................. 578
4.16.206 show subscription-aps .......................................................................................................... 586
4.16.207 show summary ...................................................................................................................... 587
4.16.208 show supported-cert-formats ................................................................................................ 588
4.16.209 show swarm .......................................................................................................................... 588
4.16.210 show syslog-level .................................................................................................................. 590
4.16.211 show tacas-servers ............................................................................................................... 591
4.16.212 show tech-support ................................................................................................................. 592
4.16.213 show time-profile ................................................................................................................... 593
4.16.214 show time-range ................................................................................................................... 594
4.16.215 show tspec-calls .................................................................................................................... 595
4.16.216 show usb status .................................................................................................................... 596
4.16.217 show uncommitted-config ..................................................................................................... 598
4.16.218 show upgrade info ................................................................................................................. 598
4.16.219 show uplink ........................................................................................................................... 599
4.16.220 show uplink-vlan ................................................................................................................... 601
4.16.221 show url-visibility ................................................................................................................... 602
4.16.222 show user .............................................................................................................................. 604
4.16.223 show valid-channels .............................................................................................................. 605
4.16.224 show vlan .............................................................................................................................. 607
4.16.225 show version ......................................................................................................................... 607
4.16.226 show vpn ............................................................................................................................... 608
4.16.227 show vpn tunnels .................................................................................................................. 611
4.16.228 show walled-garden .............................................................................................................. 612
4.16.229 show wifi-uplink ..................................................................................................................... 613
4.16.230 show wired-port ..................................................................................................................... 615
4.16.231 show wired-port-settings ....................................................................................................... 617
4.16.232 show wispr config .................................................................................................................. 619
4.16.233 show xml-api-server
.............................................................................................................. 620
4.16.234 sesimagotag-esl-channel ...................................................................................................... 621
4.16.235 sesimagotag-esl-profile ......................................................................................................... 621
4.16.236 snmp-server .......................................................................................................................... 622
4.16.237 speed test ............................................................................................................................. 623
4.16.238 speed test <server> .............................................................................................................. 625
4.16.239 ssh......................................................................................................................................... 627
4.16.240 subscription-ap ...................................................................................................................... 627
4.16.241 subscription-ap-enable.......................................................................................................... 628
4.16.242 swarm-mode ......................................................................................................................... 629
4.16.243 syslog-level ........................................................................................................................... 630
4.16.244 syslocation ............................................................................................................................ 631
4.16.245 syslog-server ......................................................................................................................... 632
4.17 T ............................................................................................................................................ 633
4.17.1 telnet ..................................................................................................................................... 633
4.17.2 telnet-server .......................................................................................................................... 633
4.17.3 terminal-access ..................................................................................................................... 634
4.17.4 tftp-dump-server .................................................................................................................... 635
4.17.5 traceroute .............................................................................................................................. 636
4.17.6 time-range ............................................................................................................................. 636
4.18 U ............................................................................................................................................ 639
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
11

Table of contents
4.18.1 upgrade-drt ........................................................................................................................... 639
4.18.2 upgrade-image ..................................................................................................................... 639
4.18.3 uplink .................................................................................................................................... 641
4.18.4 uplink-vlan ............................................................................................................................ 644
4.18.5 usb-port-disable ................................................................................................................... 645
4.18.6 user ...................................................................................................................................... 645
4.18.7 url-visibility ............................................................................................................................ 647
4.19 V ........................................................................................................................................... 649
4.19.1 version .................................................................................................................................. 649
4.19.2 virtual-controller.................................................................................................................... 649
4.19.3 vlan ....................................................................................................................................... 651
4.19.4 vlan-name ............................................................................................................................ 652
4.19.5 vpn backup ........................................................................................................................... 652
4.19.6 vpn fast-failover .................................................................................................................... 653
4.19.7 vpn gre-outside .................................................................................................................... 654
4.19.8 vpn hold-time ........................................................................................................................ 655
4.19.9 vpn ikepsk ............................................................................................................................ 656
4.19.10 vpn monitor-pkt-lost-cnt ....................................................................................................... 656
4.19.11 vpn monitor-pkt-send-freq .................................................................................................... 657
4.19.12 vpn reconnect-user-on-failover ............................................................................................ 658
4.19.13 vpn reconnect-time-on-failure .............................................................................................. 659
4.19.14 vpn preemption .................................................................................................................... 660
4.19.15 vpn primary .......................................................................................................................... 660
4.20 W .......................................................................................................................................... 662
4.20.1 wlan walled-garden .............................................................................................................. 662
4.20.2 web-server ........................................................................................................................... 663
4.20.3 wlan captive-portal ............................................................................................................... 664
4.20.4 wlan ssid-profile ................................................................................................................... 667
4.20.5 wlan-external-captive-portal ................................................................................................
. 690
4.20.6 wlan auth-server................................................................................................................... 693
4.20.7 wlan access-rule .................................................................................................................. 696
4.20.8 wifi1-mode ............................................................................................................................ 701
4.20.9 wificall-dns-pattern ............................................................................................................... 702
4.20.10 wlan wispr-profile ................................................................................................................. 703
4.20.11 wifi0-mode ............................................................................................................................ 704
4.20.12 wlan ldap-server ................................................................................................................... 705
4.20.13 write ...................................................................................................................................... 708
4.20.14 wired-port-profile .................................................................................................................. 708
4.20.15 wlan sta-profile ..................................................................................................................... 717
4.20.16 wlan tacacs-server ............................................................................................................... 718
4.21 X ........................................................................................................................................... 721
4.21.1 xml-api-server ...................................................................................................................... 721
4.22 Z ........................................................................................................................................... 723
4.22.1 zeroize-tpm-keys .................................................................................................................. 723
4.22.2 zonenmane .......................................................................................................................... 724
A Appendix A .......................................................................................................................................... 725
A.1 Glossary of Terms ................................................................................................................ 725
Index ................................................................................................................................................... 757
SCALANCE W1750D CLI
12 Function Manual, 03/2019, C79000-G8976-C452-04
1
This document describes the CLI command syntax and provides the following information for
each command:
● Command Syntax—The complete syntax of the command.
● Description—A brief description of the command.
● Syntax—A description of the command parameters, the applicable ranges and default
values, if any.
● Usage Guidelines—Information to help you use the command, including prerequisites,
prohibitions, and related commands.
● Example—An example of how to use the command.
● Command Information—This table describes command modes and platforms for which
this command is applicable.
The commands are listed in alphabetical order.
Security information
Siemens provides products and solutions with industrial security functions that support the
secure operation of plants, systems, machines and networks.
In order to protect plants, systems, machines and networks against cyber threats, it is
necessary to implement – and continuously maintain – a holistic, state-of-the-art industrial
security concept. Siemens’ products and solutions constitute one element of such a concept.
Customers are responsible for preventing unauthorized access to their plants, systems,
machines and networks. Such systems, machines and components should only be
connected to an enterprise network or the internet if and to the extent such a connection is
necessary and only when appropriate security measures (e.g. firewalls and/or network
segmentation) are in place.
For additional information on industrial security measures that may be implemented, please
visit https://www.siemens.com/industrialsecurity.
Siemens’ products and solutions undergo continuous development to make them more
secure. Siemens strongly recommends that product updates are applied as soon as they are
available and that the latest product versions are used. Use of product versions that are no
longer supported, and failure to apply the latest updates may increase customers’ exposure
to cyber threats.
To stay informed about product updates, subscribe to the Siemens Industrial Security RSS
Feed under https://www.siemens.com/industrialsecurity.
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
13

About this guide
SCALANCE W1750D CLI
14 Function Manual, 03/2019, C79000-G8976-C452-04
2
General
To prevent unauthorized access, note the following security recommendations.
● You should make regular checks to make sure that the device meets these
recommendations and/or other security guidelines.
● Evaluate your plant as a whole in terms of security. Use a cell protection concept with
suitable products (https://www.industry.siemens.com/topics/global/en/industrial-
security/pages/default.aspx).
● When the internal and external network are disconnected, an attacker cannot access
internal data from the outside. Therefore operate the device only within a protected
network area.
● For communication via non-secure networks use additional devices with VPN functionality
to encrypt and authenticate the communication.
● Terminate management connections correctly (WBM. Telnet, SSH etc.).
Physical access
● Restrict physical access to the device to qualified personnel.
Software (security functions)
● Keep the software up to date. Check regularly for security updates of the product. You will
find information on this on the Internet pages "Industrial Security
(https://www.siemens.com/industrialsecurity)" .
● Inform yourself regularly about security advisories and bulletins published by Siemens
ProductCERT (https://www.siemens.com/cert/en/cert-security-advisories.htm).
● Only activate protocols that you really require to use the device.
● Use the security functions such as address translation with NAT (Network Address
Translation) or NAPT (Network Address Port Translation) to protect receiving ports from
access by third parties.
● Restrict access to the device with a firewall or rules in an access control list (ACL -
Access Control List).
● If RADIUS authentication is via remote access, make sure that the communication is
within the secured network area or is via a secure channel.
● The option of VLAN structuring provides good protection against DoS attacks and
unauthorized access. Check whether this is practical or useful in your environment.
● Enable logging functions. Use the central logging function to log changes and access
attempts centrally. Check the logging information regularly.
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
15

Security recommendations
● Configure a Syslog server to forward all logs to a central location.
● Use WPA2/ WPA2-PSK with AES to protect the WLAN.
Software (security functions)
● Restrict physical access to the device to qualified personnel
Passwords
● Define rules for the use of devices and assignment of passwords.
● Regularly update passwords and keys to increase security.
● Change all default passwords for users before you operate the device.
● Only use passwords with a high password strength. Avoid weak passwords for example
password1, 123456789, abcdefgh.
● Make sure that all passwords are protected and inaccessible to unauthorized personnel.
● Do not use the same password for different users and systems or after it has expired.
Keys and certificates
● This section deals with the security keys and certificates you require to set up HTTPS (
Hypertext Transfer Protocol Secured Socket Layer).
● We strongly recommend that you create your own HTTPS certificates and make them
available. There are preset certificates and keys on the device. The preset and
automatically created HTTPS certificates are self-signed. We recommend that you use
HTTPS certificates signed either by a reliable external or by an internal certification
authority. The HTTPS certificate checks the identity of the device and controls the
encrypted data exchange. You can install the HTTPS certificate via the Configuration
Manual “SCALANCE W UI”, see "Uploading Certificate".
● Handle user-defined private keys with great caution if you use user-defined SSH or SSL
keys.
● Use the certification authority including key revocation and management to sign the
certificates.
● Verify certificates and fingerprints on the server and client to avoid "man in the middle"
attacks.
● We recommend that you use certificates with a key length of 2048 bits.
● Change keys and certificates immediately, if there is a suspicion of compromise.
SCALANCE W1750D CLI
16 Function Manual, 03/2019, C79000-G8976-C452-04

Security recommendations
Secure/non-secure protocols
● Avoid and disable non-secure protocols, for example Telnet and TFTP. For historical
reasons, these protocols are still available, however not intended for secure applications.
Use non-secure protocols on the device with caution.
● The following protocols provide secure alternatives:
– SNMPv1/v2 → SNMPv3
Check whether use of SNMPv1 is necessary. SNMPv1 is classified as non-secure.
Use the option of preventing write access. The product provides you with suitable
setting options. If SNMP is enabled, change the community names. If no unrestricted
access is necessary, restrict access with SNMP. Use SNMPv3 in conjunction with
passwords.
– HTTP → HTTPS
– Telnet → SSH
– SNTP → NTP
– Use secure protocols when access to the device is not prevented by physical
protection measures.
● To prevent unauthorized access to the device or network, take suitable protective
measures against non-secure protocols.
● If you require non-secure protocols and services, operate the device only within a
protected network area.
● Restrict the services and protocols available to the outside to a minimum.
Available protocols per port
The following list provides you with an overview of the open ports on this device. The table
includes the following columns:
● Protocol
All protocols that the device supports
● Port number
Port number assigned to the protocol
● Port status
– Open: The port is always open and cannot be closed.
● Factory setting
– Open: The factory setting of the port is "Open".
– Closed: The factory setting of the port is "Closed".
● Authentication
Specifies whether or not the protocol is authenticated.
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
17
Security recommendations
Protocol
Port number
Port status
Factory setting of the
port
Authentication
Air Monitor
UDP/1144
Open
Open
Yes
slave
Captive portal
TCP/8080
Open
Open
Yes
UDP/1067
Open
Open
No
UDP/4011
Open
Open
No
DTLS
UDP/4433
Open
Open
Yes
TCP/80
Open
Open
No
TCP/4343
Open
Open
Yes
TCP/4343
Open
Open
Yes
TCP/443
Open
Open
Yes
mDNS
UDP/5353
Open
Open
No
NTP
UDP/123
Open
Open
No
UDP/8209
Open
Open
No
UDP/8211
Open
Open
No
(dTable)
UDP/1616
Open
Open
No
UDP/1892
Open
Open
No
SNMPv1
UDP/161
Open
Open
No
TCP/22
Open
Open
Yes
TCP/2322
Open
Open
Yes
Syslog
UDP/514
Open
Open
No
Telnet
TCP/23
Open
Open
Yes
Airgroup UDP/53536 Open Open Yes
Airgroup Master to
Bootps UDP/67 Open Open No
DHCP
HTTP (redirect
4343)
HTTPS
UDP/53535 Open Open No
Proprietary
Proprietary
RADIUS
SNMPv3 UDP/161 Open Open Yes
SSH
UDP/8612 Open Open No
SCALANCE W1750D CLI
18 Function Manual, 03/2019, C79000-G8976-C452-04

3
Note
Although automatic completion is supported for some commands such as configure terminal,
the complete exit
end
execution.
SCALANCE W supports the use of CLI for scripting purposes. You can access the
SCALANCE W CLI through a SSH.
To enable the SSH access to the SCALANCE CLI:
1. From the SCALCNCE W UI, navigate to
2. Select
3. Click
Enabled from the Terminal access drop-down list.
OK.
Connecting to a CLI Session
On connecting to a CLI session, the system displays its host name followed by the login
prompt. Use the administrator credentials to start a CLI session. For example:
(scalance)
User: admin
Password: *****
If the login is successful, the privileged command mode is enabled and a command prompt
is displayed. For example:
(scalance)#
The privileged mode provides access to
commands. The configuration commands are available in the configuration (config) mode.
To move from privileged mode to the configuration mode, enter the following command at
the command prompt:
(scalance)# configure terminal
System > Show advanced options.
show, clear, ping, traceroute, and commit
The configure terminal command allows you to enter the basic configuration mode and the
command prompt is displayed as follows:
(scalance)(config)#
The SCALANCE W CLI allows CLI scripting in several other sub-command modes to allow
the users to configure individual interfaces, SSIDs, access rules, and security settings.
You can use the question mark (?) to view the commands available in a privileged mode,
configuration mode, or sub-mode
and
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
commands must be entered at command prompt for successful
19

SCALANCE W CLI
Applying Configuration Changes
Each command processed by the Virtual Controller is applied on all the slave APs in a
cluster. When you make configuration changes on a master AP in the CLI, all associated
APs in the cluster inherit these changes and subsequently update their configurations. The
changes configured in a CLI session are saved in the CLI context.
The CLI does not support the configuration data exceeding the 4K buffer size in a CLI
session: therefore, SCALANCE W recommends that you configure fewer changes at a time
and apply the changes at regular intervals.
To apply and save the configuration changes at regular intervals, use the following command
in the privileged mode:
(scalance)# commit apply
To apply the configuration changes to the cluster, without saving the configuration, use the
following command in the privileged mode:
(scalance)# commit apply no-save
To view the changes that are yet to be applied, use the following command in the privileged
mode:
(scalance)# show uncommitted-config
To revert to the earlier configuration, use the following command in the privileged mode.
(scalance)# commit revert
Example:
(scalance)(config)# rf dot11a-radio-profile
(scalance)# show uncommitted-config
Configuration Sub-modes
Some commands in configuration mode allow you to enter into a sub-mode to configure the
commands specific to that mode. When you are in a configuration sub-mode, the command
prompt changes to indicate the current sub-mode.
You can exit a sub-command mode and return to the basic configuration mode or the
privileged Exec (enable) mode at any time by executing the
exit or end command.
SCALANCE W1750D CLI
20 Function Manual, 03/2019, C79000-G8976-C452-04

SCALANCE W CLI
Sequence-Sensitive Command
Corresponding no command
opendns <username> <password>
no opendns
rule <dest> <mask> <match> <protocol>
<port>}}[<option1…option9>]
no rule <dest> <:mask> <match> <protocol>
mgmt-auth-server <auth-profile-name>
no mgmt-auth-server <auth-profilename>
set-role <attribute>{{equals| not-equals|
no set-role <attribute>{{equals| not-
with| contains}
no set-role
set-vlan <attribute>{{equals| not-equals|
no set-vlan <attribute>{{equals| not-
with| contains}
no set-vlan
auth-server <name>
no auth-server <name>
Deleting Configuration Settings
Use the no command to delete or negate previously-entered configurations or parameters.
● To view a list of no commands, type
followed by the question mark. For example:
(scalance)(config) # no?
● To delete a configuration, use the
following command removes a configured user role:
(scalance)(config) # no user <username>
● To negate a specific configured parameter, use the
For example, the following command deletes the PPPoE user configuration settings:
(scalance)(config) # pppoe-uplink-profile
(scalance)(pppoe_uplink_profile)# no pppoe-username
Using Sequence Sensitive Commands
The SCALANcE W CLI does not support positioning or precedence of sequence-sensitive
commands. Therefore, Siemens recommends that you remove the existing configuration
before adding or modifying the configuration details for sequence-sensitive commands. You
can either delete an existing profile or remove a specific configuration by using the
commands.
The following table lists the sequence-sensitive commands and the corresponding
command to remove the configuration.
no at the prompt in the relevant mode or sub-mode
no form of a configuration command. For example, the
no parameter within the command.
no…
no
Table 3- 1
<start-port> <end-port> {permit |deny |
src-nat | dst-nat {<IPaddress> <port>|
startswith| ends-with| contains} <operator> <role>| valueof}
startswith| ends-with| contains} <operator> <VLAN-ID>| value-of}
Sequence-Sensitive Commands
<start-port> <end-port> {permit | deny |
src-nat | dst-nat}
equals| starts-with| ends<operator>| value-of}
equals| starts-with| ends<operator>| value-of}
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
21

SCALANCE W CLI
3.1 Saving Configuration Changes
3.1 Saving Configuration Changes
The
running-config
are yet to be saved. To view the running-config of an AP, use the following command:
(scalance) # show running-config
When you make configuration changes through the CLI, the changes affect the current
running configuration only. To save your configuration changes, use the following command
in the privileged Exec mode:
(scalance)# write memory
Commands that Reset the AP
If you use the CLI to modify a currently provisioned radio profile, the changes take place
immediately. A reboot of the AP is not required to apply the configuration changes. Certain
commands, however, automatically force AP to reboot. Verify the current network loads and
conditions before executing the commands that enforce a reboot of the AP, as they may
cause a momentary disruption in service as the unit resets.
reload command resets an AP.
The
holds the current AP configuration, including all pending changes which
SCALANCE W1750D CLI
22 Function Manual, 03/2019, C79000-G8976-C452-04
SCALANCE W CLI
Key
Effect
Description
Ctrl A
Home
Move the cursor to the beginning of the line.
Ctrl B
row
Ctrl D
Delete Right
Delete the character to the right of the cursor.
Ctrl E
Ctrl F
arrow
Ctrl K
Delete Right
Delete all characters to the right of the cursor.
Ctrl N
arrow
Ctrl P or up arrow
Previous
Display the previous command in the command history.
Ctrl T
ter to the right of the cursor.
Ctrl U
Clear
Clear the line.
Ctrl W
the first space encountered.
Ctrl X
Delete Left
Delete all characters to the left of the cursor.
3.2 Command Line Editing
3.2 Command Line Editing
The system records your most recently entered commands. You can review the history of
your actions, or reissue a recent command easily, without having to retype it.
To view items in the command history, use the
down
and the
arrow key to move forward. To reissue a specific command, press Enter when
up
arrow key to move back through the list
the command appears in the command history. You can also use the command line editing
feature to make changes to the command prior to entering it. The command line editing
feature allows you to make corrections or changes to a command without retyping. The
following table lists the editing controls. To use key shortcuts, press and hold the
Ctrl button
while you press a letter key.
Table 3- 2 Line Editing Keys
or the left ar-
End Move the cursor to the end of the line.
or the right
or the down
Transpose Swap the character to the left of the cursor with the charac-
Back Move the cursor one character left.
Forward Move the cursor one character right.
Next Display the next command in the command history.
Delete Word Delete the characters from the cursor up to and including
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
23

SCALANCE W CLI
Address/Identifier
Description
dotted decimal notation (for example, 192.0.2.1).
notation (for example, 255.255.255.0).
00:05:4e:50:14:aa).
sensitive (for example, WLAN-01).
used from the AP. Use the same format as for a MAC address.
ESSID includes spaces, enclose the name in quotation marks.
3.3 Specifying Addresses and Identifiers in Commands
3.3 Specifying Addresses and Identifiers in Commands
This section describes addresses and other identifiers that you can reference in CLI
commands.
Table 3- 3 Addresses and Identifiers
IP address For any command that requires entry of an IP address to specify a
network entity, use IPv4 network address format in the conventional
Netmask address For subnet addresses, specify a subnet mask in dotted decimal
MAC address For any command that requires entry of a device’s hardware ad-
dress, use the hexadecimal format (for example,
SSID A unique character string (sometimes referred to as a network
name), consisting of no more than 32 characters. The SSID is case-
BSSID This entry is the unique hard-wireless MAC address of the AP. A
unique BSSID applies to each frequency— 802.11a and 802.11g—
ESSID Typically the unique logical name of a wireless network. If the
SCALANCE W1750D CLI
24 Function Manual, 03/2019, C79000-G8976-C452-04
SCALANCE W CLI
Type Style
Description
mark the titles of books.
Boldface
Commands
amples of commands and command output.
<angle brackets>
Do not type the angle brackets.
[square brackets]
optional. Do not type the brackets.
{Item_A|Item_B}
braces or bars.
{ap-name <ap-name>}|{ipaddr <ip-
the braces or bars.
Note
NOTICE
WARNING
3.4 Typographic Conventions
3.4 Typographic Conventions
The following conventions are used throughout this document to emphasize important
concepts:
Table 3- 4 Typographical Conventions
Italics
This style is used for emphasizing important terms and to
This style is used for command names and parameter
options when mentioned in the text.
This fixed-width font depicts command syntax and ex-
In the command syntax, text within angle brackets represents items that you should replace with information
appropriate to your specific situation.
For example, ping <ipaddr>
In this example, you would type “ping” at the system
prompt exactly as shown, followed by the IP address of
the system to which ICMP echo packets are to be sent.
In the command syntax, items enclosed in brackets are
In the command examples, single items within curled
braces and separated by a vertical bar represent the
available choices. Enter only one choice. Do not type the
addr>}
Two items within curled braces indicate that both parameters must be entered together. If two or more sets of
curled braces are separated by a vertical bar, like in the
example to the left, enter only one choice. Do not type
The following informational icons are used throughout this guide:
Indicates helpful suggestions, pertinent information, and important things to remember.
Indicates a risk of damage to your hardware or loss of data.
Indicates a risk of personal injury or death.
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
25

SCALANCE W CLI
3.5 Industry Online Support
3.5 Industry Online Support
In addition to the product documentation, also check out the comprehensive online
information platform of Siemens Industry Online Support at the following Internet address:
https://support.industry.siemens.com/cs/en/
Apart from news, there you will also find:
● Project information: Manuals, FAQs, downloads, application examples etc.
● Contacts, Technical Forum
● The option submitting a support query:
https://support.industry.siemens.com/My/ww/en/requests
● Our service offer:
Right across our products and systems, we provide numerous services that support you in
every phase of the life of your machine or system - from planning and implementation to
commissioning, through to maintenance and modernization.
You will find contact data on the Internet at the following address:
https://www.automation.siemens.com/aspa_app/?ci=yes&lang=en
SCALANCE W1750D CLI
26 Function Manual, 03/2019, C79000-G8976-C452-04
4
Parameter
Description
Range
0.1 dBm and negative values.
AP Platform
Command Mode
All platforms
Privileged EXEC mode
4.1 A
4.1.1 a-channel
Description
This command configures 5 GHz radio channels for a specific AP.
Syntax
a-channel <channel> <tx-power>
<channel> Configures the specified 5 GHz channel The valid channels for a band are
<tx-power> Configures the specified
Usage Guidelines
Use this command to configure radio channels for the 5 GHz band for a specific AP.
Example
The following example configures the 5 GHz radio channel:
(scalance)# a-channel 44 18
Command Information
determined by the AP regulatory
domain.
-51 dBm to 51 dBm
transmission power values. It also supports
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
27
CLI Commands
Parameter
Description
Range
Default
<interval>
val is ranged in minutes.
AP Platform
Command Mode
All platforms
Configuration mode
4.1 A
4.1.2 aaa dns-query-interval
Description
This command configures the interval at which the dns server sends out a query.
Syntax
aaa dns-query-interval <interval>
no aaa dns-query-interval
Usage Guidelines
Use this command to configure the time interval for sending out dns queries.
Example
The following example shows the output of the aaa dns-query-interval command:
20:4c:03:24:89:18 (config) # aaa dns-query-interval 15
Command Information
The time interval at which the
query must be sent. The inter-
0 - 60 mins 15 mins
SCALANCE W1750D CLI
28 Function Manual, 03/2019, C79000-G8976-C452-04
CLI Commands
Parameter
Description
add <attribute>
attribute ID (integer), and type (date, integer, IP address, or string).
date
integer
Adds an integer attribute
ipaddr
string
Adds a date attribute
vendor
(Optional) Display attributes for a specific vendor name and vendor ID.
AP Platform
Command Mode
All platforms
Configuration mode
4.1 A
4.1.3 aaa radius-attributes
Description
This command configures RADIUS attributes to statically configure values to be included in
RADIUS Access- Requests and Accounting-Requests.
Syntax
aaa radius-attributes add <attribute> <attribute-id> {date|integer|ipaddr|string}
[vendor <name> <vendor-id>]
<attribute-id>
Usage Guidelines
Add RADIUS attributes for use in SDRs. Use the show aaa radius-attributes command to
display a list of the current RADIUS attributes recognized by the Mobility Master. To add a
RADIUS attribute to the list, use the
Example
The following command adds the VSA-User-Role:
(scalance) (config)# aaa radius-attributes add User-Role 1 string vendor Siemens 4239
Command Information
Adds the specified attribute name (alphanumeric string), associated
Adds a date attribute
Adds an ip address attribute
aaa radius-attributes command.
SCALANCE W1750D CLI
Function Manual, 03/2019, C79000-G8976-C452-04
29
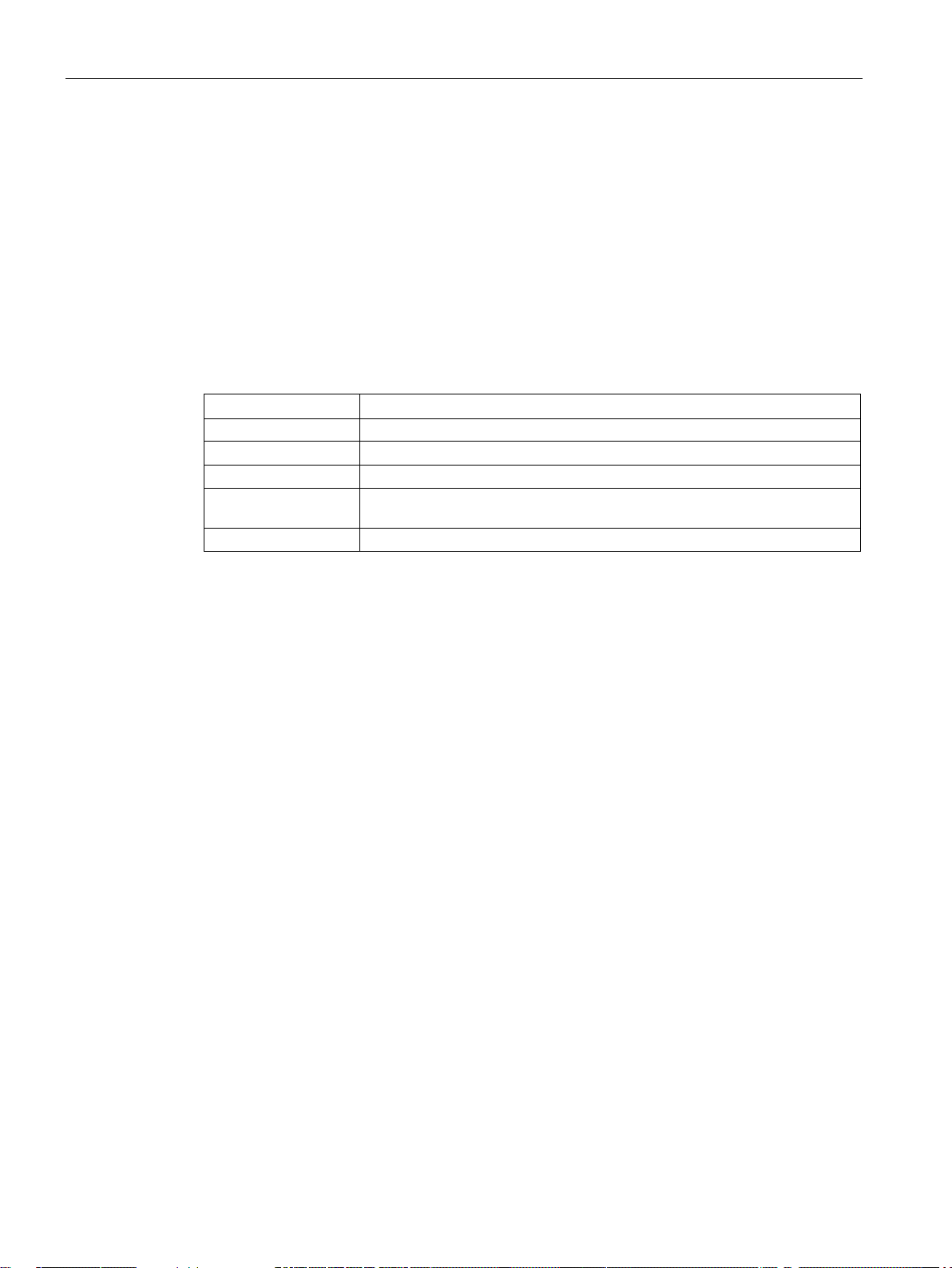
CLI Commands
Parameter
Description
<profile_name>
The specified RADIUS modifier profile name
clone
exclude
Attribute to be excluded in RADIUS request.
include
no
Delete Command
4.1 A
4.1.4 aaa radius modifier
Description
This command configures the RADIUS modifier profile to customize the attributes that are
included, excluded and modified in the RADIUS request before it is sent to the authentication
server.
Syntax
aaa radius-attributes modifier <profile_name>
Copy data from another Radius Modifier Profile.
Authentication protocol type. Use PAP as the authentication typeAttribute/Value to be included in RADIUS request.
Usage Guidelines
Example
Use the show aaa radius modifier command to display a list of RADIUS modifier profiles. To
create a RADIUS modifier profile with customized attributes, use the
aaa radius-attributes
command.
Example for Included attribute
(scalance) [md](config) #aaa radius-attributes add BW-Area-Code 18 integer vendor
Boingo 22472
(scalance) [md](Radius Modifier Profile "radmodifier1") # include BW-Area-Code static
"212"
(scalance) [md](Radius Modifier Profile "radmodifier1") # no include BW-Area-Code
Example for excluded attribute
(scalance) (config) #aaa radius-attributes add BW-Area-Code 18 integer vendor Boingo
22472
(scalance) (Radius Modifier Profile "radmodifier1") # exclude BW-Area-Code
(scalance) (Radius Modifier Profile "radmodifier1") # no exclude BW-Area-Code
Example for modified attribute
Default attributes to carry to radius server can be modified with include option.
(scalance) Radius Modifier Profile "radmodifier1") # include "Siemens -location-id"
static "Shim- office"
SCALANCE W1750D CLI
30 Function Manual, 03/2019, C79000-G8976-C452-04
 Loading...
Loading...